Page 1

RAM
Security Systems
OPERATING INSTRUCTIONS
EN
Page 2

Operating instructions
RFID Access Management
This work is protected by copyright. Any rights derived from the copyright shall be reserved for SICK AG.
Reproduction of this document or parts of this document is only permissible within the limits of the legal
determination of Copyright Law. Alteration or abridgment of the document is not permitted without the explicit
written approval of SICK AG.
2 Operating instructions | SICK 8018582/2015-11-03
Subject to change without notice
Page 3

Operating instructions
Contents
RFID Access Management
Contents
1 About these operating instructions ............................................................................... 6
1.1 Function of this document .................................................................................... 6
1.2 Target group .......................................................................................................... 6
1.3 Information depth ................................................................................................. 7
1.4 Abbreviations used ............................................................................................... 7
1.5 Symbols used ........................................................................................................ 8
2 Safety ............................................................................................................................... 9
2.1 Qualified safety personnel .................................................................................... 9
2.2 Application of the system ...................................................................................10
2.3 Intended use .......................................................................................................10
2.4 General safety notes and protective measures ....................................................11
2.4.1 Safety notes and symbols.................................................................11
2.4.2 General safety notes .........................................................................12
2.4.3 Potential sources of danger .............................................................12
2.5 Protection of the environment ............................................................................14
2.5.1 Power consumption ..........................................................................14
2.5.2 Disposal after final decommissioning ..............................................14
3 System description ...................................................................................................... 15
3.1 Scope of delivery .................................................................................................15
3.2 Specific features .................................................................................................17
3.2.1 An overview of the system components ..........................................17
3.2.2 Operating principle of the management software ..........................20
3.2.3 Notes on the tags ..............................................................................23
3.3 Status indicators .................................................................................................24
3.3.1 RFU62x RFID interrogator .................................................................24
3.3.2 RFU63x RFID interrogator .................................................................25
3.3.3 CDB650 connection module ............................................................26
3.3.4 CMC600 cloning module ..................................................................27
4 Setup and mounting .................................................................................................... 28
4.1 RFU62x configuration device .............................................................................28
4.2 RFID interrogators at the access points ............................................................28
4.2.1 Notes on mounting the RFID interrogators ......................................28
4.2.2 RFU62x RFID interrogator .................................................................30
4.2.3 RFU63x RFID interrogator .................................................................31
4.2.4 Mounting the connection module ....................................................31
5 Electrical installation .................................................................................................. 32
5.1 Connecting the RFU62x configuration device ...................................................32
5.2 Connecting RFU6xx RFID interrogators ..............................................................33
5.2.1 Connecting the power supply/switching output ..............................34
5.2.2 Connection to the network ...............................................................35
5.3 Connecting RFID interrogators via a connection module .................................35
5.3.1 Connecting an RFID interrogator to a connection module .............35
5.3.2 Connecting the power supply/switching output in the
connection module ...........................................................................36
5.3.3 Inserting the cloning module ............................................................37
5.3.4 Connecting the additional switching output of the
connection module ...........................................................................38
8018582/2015-11-03 Operating instructions| SICK 3
Subject to change without notice
Page 4

Operating instructions
Contents
RFID Access Management
5.4 Connecting the configuration PC to the network .............................................. 38
5.5 SICK connection accessories ............................................................................. 39
6 Commissioning RFID Access Management ............................................................... 40
6.1 Switching on the system .................................................................................... 40
6.2 Installing ECS on the configuration PC .............................................................. 40
6.2.1 Installing ECS .................................................................................... 41
6.2.2 Installing the SOPAS configuration software .................................. 42
6.3 Altering the IP addresses of the RFID interrogators ......................................... 43
6.3.1 Connecting the configuration PC to RFID interrogators ................. 44
6.3.2 Altering the default IP address ........................................................ 46
6.3.3 Displaying devices in the project tree ............................................. 48
6.4 Inserting the microSD card into access point RFID interrogators ................... 49
6.5 Setting the transmitting power of the RFID interrogators at the access
points ................................................................................................................... 51
6.5.1 Loading the device in the project tree ............................................. 51
6.5.2 Setting the device parameters......................................................... 52
6.5.3 Testing RFU transmitting power ....................................................... 52
6.6 Changing the password to log in to devices ...................................................... 53
6.7 Saving the device configuration ........................................................................ 54
6.8 Launching ECS .................................................................................................... 54
6.8.1 Logging in as an Integrator .............................................................. 54
6.8.2 Program overview ............................................................................. 55
6.9 Making central settings ...................................................................................... 56
6.9.1 Information about the tag ................................................................ 57
6.9.2 Information about the time server ................................................... 58
6.9.3 Storing the password for communication with the RFID
interrogators ..................................................................................... 58
6.9.4 Configuring the RFID interrogator indicators .................................. 58
6.9.5 Saving settings .................................................................................. 58
6.10 Recording access points .................................................................................... 59
6.10.1 Recording the configuration device ................................................. 60
6.10.2 Recording RFID interrogators for the access control system ......... 61
6.10.3 The access points in the System Overview ..................................... 63
6.10.4 Modifying an access point ............................................................... 64
6.11 Creating access profiles ..................................................................................... 65
6.12 Creating a participant with access profiles ....................................................... 68
6.13 Assigning tags to participants ............................................................................ 71
6.14 Participants and registered tags in the System Overview ................................ 73
6.15 Testing access control ........................................................................................ 73
4 Operating instructions | SICK 8018582/2015-11-03
Subject to change without notice
7 Working with RFID Access Management ................................................................... 74
7.1 Modifying an access profile ............................................................................... 75
7.2 Editing access authorizations ............................................................................ 75
7.2.1 Sorting/filtering the participant list ................................................. 75
7.2.2 Adding participants ........................................................................... 77
7.2.3 Deleting participants who leave the company ................................ 77
7.2.4 Deactivating a lost tag ...................................................................... 78
7.2.5 Displaying the access authorization for a tag ................................. 80
7.2.6 Modifying the access authorization of a participant ...................... 81
7.2.7 Checking the access authorization validity ..................................... 82
7.3 Reading the update status of the access points .............................................. 83
Page 5

Operating instructions
Contents
RFID Access Management
7.4 Viewing access logs ............................................................................................85
7.4.1 Opening the list of access logs .........................................................85
7.4.2 Filtering the list of access logs .........................................................86
7.4.3 Closing the access control display ...................................................87
7.5 Managing RFID Access Management ................................................................88
7.5.1 Performing a data backup/restoring the database ........................88
7.5.2 Changing passwords for user roles ..................................................89
7.5.3 Changing the user language .............................................................90
7.5.4 Defining the access of the Information Security Officer to
access logs using the four eyes principle ........................................91
8 Maintenance and repairs ............................................................................................ 92
8.1 Maintenance tasks .............................................................................................92
8.2 Replacing components .......................................................................................92
8.2.1 Replacing the RFU62x configuration device ...................................92
8.2.2 Replacing the RFID interrogator at the access point ......................93
9 Fault diagnosis ............................................................................................................. 95
9.1 Response to faults ..............................................................................................95
9.2 Fault situations ....................................................................................................95
9.3 SICK support........................................................................................................96
9.4 Fault indication on the RFID interrogator ..........................................................96
9.5 System logs in RFID Access Management ........................................................97
9.6 Fault diagnosis in SOPAS ....................................................................................98
10 Technical data .............................................................................................................. 99
10.1 Data sheets .........................................................................................................99
10.1.1 RFID Access Management................................................................99
10.1.2 RFU63x RFID interrogator data sheet ........................................... 100
10.1.3 RFU62x RFID interrogator data sheet ........................................... 101
10.1.4 CDB650 connection module data sheet ...................................... 102
10.1.5 CMC600-101 cloning module data sheet .................................... 102
10.1.6 Configuration PC system requirements ........................................ 103
10.2 Dimensional drawings ..................................................................................... 104
10.2.1 RFU63x dimensional drawing ........................................................ 104
10.2.2 RFU62x dimensional drawing ........................................................ 105
10.2.3 CDB620 connection box dimensional drawing ............................ 106
11 Annex .......................................................................................................................... 107
11.1 List of tables ..................................................................................................... 107
11.2 List of figures .................................................................................................... 108
11.3 Keywords index ................................................................................................ 109
8018582/2015-11-03 Operating instructions| SICK 5
Subject to change without notice
Page 6
Chapter 1 Operating instructions
About these operating
instructions
RFID Access Management
1 About these operating instructions
Please read this chapter carefully before you begin working with this documentation and
RFID Access Management (RAM for short).
1.1 Function of this document
These operating instructions are designed to give technical personnel instructions on
the safe mounting, configuration, electrical installation, commissioning, operation, and
maintenance of RFID Access Management.
1.2 Target group
These operating instructions are intended for people who plan, mount, connect,
commission, operate, and maintain the access control systems.
Activities Target group
Mounting, electrical installation,
maintenance, and replacement of
system components
Commissioning and configuration Qualified personnel, such as service technicians
Tab. 1: Target group
Qualified personnel, such as service technicians
or industrial electricians
or engineers
6 Operating instructions | SICK 8018582/2015-11-03
Subject to change without notice
Page 7
Operating instructions Chapter 1
About these operating
instructions
RFID Access Management
1.3 Information depth
Note
These operating instructions contain information on the following topics:
• System description
• Setup and mounting
• Electrical installation
• Commissioning and operation
• Maintenance and repairs
• Fault diagnosis and troubleshooting
• Technical data and dimensioned drawings
When planning and using RFID systems, technical skills are required that are not covered
by this document.
The official and legal regulations for operating the RFMS Access Management must always
be complied with.
The IP addresses are assigned using the SICK SOPAS configuration software.
Please also refer to the information concerning RFID and building security that is available
on the Internet at www.sick.com.
There, you can find sample applications and a list of frequently asked questions about
RFID and building security.
1.4 Abbreviations used
ECS
EMS
LED
RFID
RFU
RAM
SOPAS
Entry Exit Configuration Software = System components for managing the access rights
of persons and vehicles and for assigning tags.
Entry Exit Management Software = System components for communication between RFID
Access Management and the RFID interrogators at the access points
Light Emitting Diode
Radio Frequency Identification = Identification of objects by means of electromagnetic
waves
Radio Frequency Unit = Writer and reader for RFID system
RFID Access Management = System for managing access rights based on RFID
SICK OPEN PORTAL for APPLICATION and SYSTEMS Engineering Tool = SICK configuration
software
8018582/2015-11-03 Operating instructions| SICK 7
Subject to change without notice
Page 8

Chapter 1 Operating instructions
About these operating
instructions
RFID Access Management
1.5 Symbols used
Recommendation
Note
1. / 2. ...
Recommendations are designed to assist you in the decision-making process with respect
to the use of a certain function or technical measure.
Notes provide information about the features of a device, application tips, or other
information that may come in useful.
Instructions that must be carried out in the described order are referred to as step-by-step
instructions and are indicated by numbered lists. Carefully read and follow the instructions
for action.
Instructions for taking action are indicated by an arrow. Carefully read and follow the
instructions for action.
8 Operating instructions | SICK 8018582/2015-11-03
Subject to change without notice
Page 9
Operating instructions Chapter 2
Safety
•
RFID Access Management
2 Safety
This chapter concerns your own safety and the safety of the system operator.
Please read this chapter carefully before you begin working with RFID Access
Management.
2.1 Qualified safety personnel
RFID Access Management must only be mounted, commissioned, and maintained by
properly qualified personnel.
The following qualifications are necessary for the various tasks:
Activities Qualification
Mounting and
maintenance
Electrical installation and
replacement
Commissioning, operation,
and configuration
• Practical technical training
• Knowledge of the current safety regulations in the
workplace
Practical electrical training
• Knowledge of current electrical safety regulations
• Knowledge of device control and operation in the
particular application concerned (e.g., logistics gate
(lock))
• Knowledge of the mechanical and electrical parameters
of the access control that relate to operation and use
• Knowledge of the software and hardware environment
in the particular application
• Basic knowledge of the Windows operating system
used
• Basic knowledge of data transmission
• Basic knowledge of the design and setup (addressing)
of Ethernet connections when connecting the RFID
interrogators to the Ethernet
• Basic knowledge of how to use an HTML browser
(e.g., Internet Explorer) to access the online help
Tab. 2: Qualified safety personnel
8018582/2015-11-03 Operating instructions| SICK 9
Subject to change without notice
Page 10

Chapter 2 Operating instructions
Safety
RFID Access Management
2.2 Application of the system
RFID Access Management is a system for the flexible management and configuration of
access rights in an access control system based on RFID.
Rights are assigned and revoked quickly and conveniently directly at the PC with the aid
of Entry Exit Configuration Software. The tabletop RFU62x RFID interrogator allows tags
to be managed with ease.
The permissions are passed on to the RFID interrogators of the access points via Ethernet
and saved there. RFID interrogators from the RFU6xx device families can be used as
readers.
2.3 Intended use
RFID Access Management may only be used as described in section 2.2 Application of
the system. It may only be used by qualified personnel in the environment in which it was
mounted and initially commissioned by qualified safety personnel in accordance with
these operating instructions.
The equipment may only be operated in an industrial environment.
RFID Access Management must not be used in an explosion-protected environment.
If used in any other way or if alterations are made to the system or the devices are opened
– including in the context of mounting and installation – this will void any warranty claims
directed to SICK AG.
10 Operating instructions | SICK 8018582/2015-11-03
Subject to change without notice
Page 11

Operating instructions Chapter 2
Safety
RFID Access Management
2.4 General safety notes and protective measures
2.4.1 Safety notes and symbols
The following safety and hazard symbols are used for your own safety, for the safety of
third parties, and for the safety of the system. You must therefore observe these symbols
at all times.
HAZARD
Denotes an immediate hazard that may result in severe to fatal injuries.
The symbol shown on the left-hand side of the note refers to the type of hazard in question
(the example here shows a risk of injury resulting from electrical current).
WARNING
Denotes a potentially dangerous situation that may result in severe to fatal injuries.
The symbol shown on the left-hand side of the note refers to the type of hazard in question
(the example here shows a risk of injury resulting from falling components).
CAUTION
Caution note
Denotes a potentially dangerous situation that may result in minor personal injury or
possible material damage.
The symbol shown on the left-hand side of the note refers to the type of hazard in question
(the example here shows a risk of damage to the eye by laser beams).
NOTE
Denotes a potential risk of damage or functional impairment to the device or the devices
connected to it.
This symbol includes a reference to supplementary technical documentation.
8018582/2015-11-03 Operating instructions| SICK 11
Subject to change without notice
Page 12

Chapter 2 Operating instructions
Safety
RFID Access Management
2.4.2 General safety notes
General, recognized safety-related rules and regulations were taken into account in the
design and manufacture of the system. Risks for the user resulting from the system cannot
however be completely ruled out. The safety notes below must therefore be strictly
observed.
WARNING
Safety notes
Observe the following to ensure the safe use of the system as intended.
• The notes in these operating instructions (e.g., regarding use, mounting, installation,
and commissioning) must be observed.
• All official and statutory regulations governing the operation of the system must be
complied with.
• National and international legal specifications apply to the installation and use of the
system, to its commissioning, and to recurring technical inspections, in particular:
– The work safety regulations and safety regulations.
– Any other relevant safety regulations.
• The manufacturer and user of the system are responsible for coordinating and
complying with all applicable safety specifications and regulations in cooperation with
the relevant authorities.
• The checks must be carried out by qualified safety personnel or specially qualified and
authorized personnel, and must be recorded and documented to ensure that the tests
can be reconstructed and retraced at any time.
• These operating instructions must be made available to the operator of the system.
The system operator has to be instructed by qualified safety personnel and has to read
the operating instructions.
RFID Access Management is intended solely for use in industrial environments. Radio
interference may result when used in residential areas.
2.4.3 Potential sources of danger
RFID Access Management has been designed and implemented in a way that allows for
safe operation. Potential hazards are virtually eliminated. However, a certain level of risk
will always remain.
Awareness of potential sources of danger in the system will help you to work in a safer
manner and thus prevent accidents.
To avoid risks, please also observe the special warnings in each of the individual chapters.
WARNING
12 Operating instructions | SICK 8018582/2015-11-03
Subject to change without notice
Page 13

Operating instructions Chapter 2
Safety
RFID Access Management
Risks during electrical installation
HAZARD
Risk of injury due to electrical current
Standard safety requirements must be met when working on electrical systems.
The power supply must be disconnected when attaching and detaching electrical
connections.
Select and implement wire cross-sections and their correct fuse protection in
accordance with the applicable standards.
HAZARD
Risk of injury and damage caused by electrical current
Improper handling of live devices may lead to severe personal injury or death by electric
shock.
Electrical installation and maintenance work must always be carried out by personnel
authorized to do so.
Do not touch any live components.
In the event of danger, immediately disconnect the system from the power supply.
Always use original fuses with the specified current rating.
Report any damaged cables to the maintenance team without delay.
Risks during commissioning and configuration
WARNING
Risk resulting from incorrect commissioning and configuration
Do not commission without testing by qualified safety personnel!
Before you operate the system or a device for the first time, you must have it checked and
approved by qualified safety personnel.
WARNING
Risk of ground potential equalization currents
The RFID interrogators are designed to be operated in a system with professional
grounding of all connected devices and mounting surfaces to the same ground potential.
Due to equipotential bonding currents between the RFID interrogator and other grounded
devices in the system, incorrect grounding of the RFID interrogator can charge the metal
housing to a dangerous voltage, cause malfunction and destruction of devices as well as
damage to the cable shielding through heating, and thus cause cable fires.
8018582/2015-11-03 Operating instructions| SICK 13
Subject to change without notice
Page 14

Chapter 2 Operating instructions
Safety
RFID Access Management
Risks during maintenance and repair work
HAZARD
Disconnect the power to the system
Make sure the power supply for the entire system is disconnected throughout the entire
time that you are carrying out maintenance and repair work.
HAZARD
Risk of injury due to electrical current
Only a qualified electrician or trained person working under the guidance and supervision
of a qualified electrician is permitted to work on electrical systems or equipment and they
must comply with the electrical regulations.
NOTE
Claims under the warranty rendered void
Do not open the housing of the RFID interrogator. The device is sealed.
If the device is opened, any warranty claims against SICK AG will be void.
The cover on the card slot can be removed to insert the microSD card.
2.5 Protection of the environment
RFID Access Management has been designed to minimize its environmental impact.
It consumes very little power.
Always act in an environmentally responsible manner at work. For this reason, please note
the following information regarding disposal.
2.5.1 Power consumption
At full transmitting power, an RFU62x RFID interrogator consumes approx. 8 watts of
power; an RFU63x RFID interrogator approx. 20 watts.
2.5.2 Disposal after final decommissioning
Always dispose of unusable or irreparable devices in an environmentally safe manner in
accordance with the relevant national waste disposal regulations.
Dispose of all electronic assemblies as hazardous waste. The electronic assemblies are
easy to dismantle.
See also section 7.2 Disposal.
Note
SICK AG does not take back devices that are unusable or irreparable.
14 Operating instructions | SICK 8018582/2015-11-03
Subject to change without notice
Page 15

Operating instructions Chapter 3
System description
for Europe/South Africa)
for short
1 Adapter for microSD card
1 Sample tag
1 Operating instructions
for USA/Canada)
for short
1 Adapter for microSD card
1 Sample tag
1 Operating instructions
RFID Access Management
3 System description
This chapter provides information on the special features of RFID Access Management. It
describes the design and operating principle of the system solution.
3.1 Scope of delivery
RFID Access Management is available in various system configurations.
RAM620-10x01
The RAM620-10x01 system variant is used to monitor one access point.
Fig. 1: RAM620-10x01 scope of delivery
Part no. Quantity Description
1077596 RAM620-10001
1 RFU620-10100 RFID interrogator (radio equipment approval
1 microSD card with system components ECS610-10000
(Entry Exit Configuration Software) – ECS for short, and
EMS610-00000 (Entry Exit Management Software) – EMS
1077598 RAM620-10101
1 RFU620-10101 RFID interrogator (radio equipment approval
1 microSD card with system components ECS610-10000
(Entry Exit Configuration Software) – ECS for short, and
EMS610-00000 (Entry Exit Management Software) – EMS
8018582/2015-11-03 Operating instructions| SICK 15
Subject to change without notice
Page 16

Chapter 3 Operating instructions
System description
for Europe/South Africa)
for short
1 Adapter for microSD card
1 Sample tag
1 Operating instructions
for USA/Canada)
for short
1 Adapter for microSD card
1 Sample tag
1 Operating instructions
RFID Access Management
RAM630-10x01
The RAM630-10x01 system variant is used to monitor one access point.
Fig. 2: RAM630-10x01 scope of delivery
The RAM630-10x01 system variant is used to monitor one access point.
Part no. Quantity Description
1077597 RAM630-10001
1 RFU630-13100 RFID interrogator (radio equipment approval
1 microSD card with system components ECS610-10000
(Entry Exit Configuration Software) – ECS for short, and
EMS610-00000 (Entry Exit Management Software) – EMS
1077599 RAM630-10101
1 RFU630-13101 RFID interrogator (radio equipment approval
1 microSD card with system components ECS610-10000
(Entry Exit Configuration Software) – ECS for short, and
EMS610-00000 (Entry Exit Management Software) – EMS
16 Operating instructions | SICK 8018582/2015-11-03
Subject to change without notice
Additional components required
To manage the access points and access rights, you will need the following components:
• An RFU62x RFID interrogator configuration device to read the tags.
• A configuration PC with Entry Exit Configuration Software to manage the access rights
of persons and vehicles and to assign tags.
• An Ethernet switch.
Page 17
Operating instructions Chapter 3
System description
RFID Access Management
Additional accessories
• Mounting kits for mounting the RFID interrogators (see chapter 4 Setup and mounting).
• Network device for connecting the RFU62x configuration device and connecting cables
(see chapter 5.5 SICK connection accessories).
• CDB650 connection module for each RFID interrogator to cover extended distances
between the RFID interrogator and the connections.
• CMC600 cloning module for enhanced protection against tampering in the CDB650
connection module.
Thorough check for completeness
Important note
It is recommended that you carefully check for and report transport damage of
any kind as soon as possible after receiving the components you have ordered.
Also verify that the delivery includes all components listed on the delivery note.
3.2 Specific features
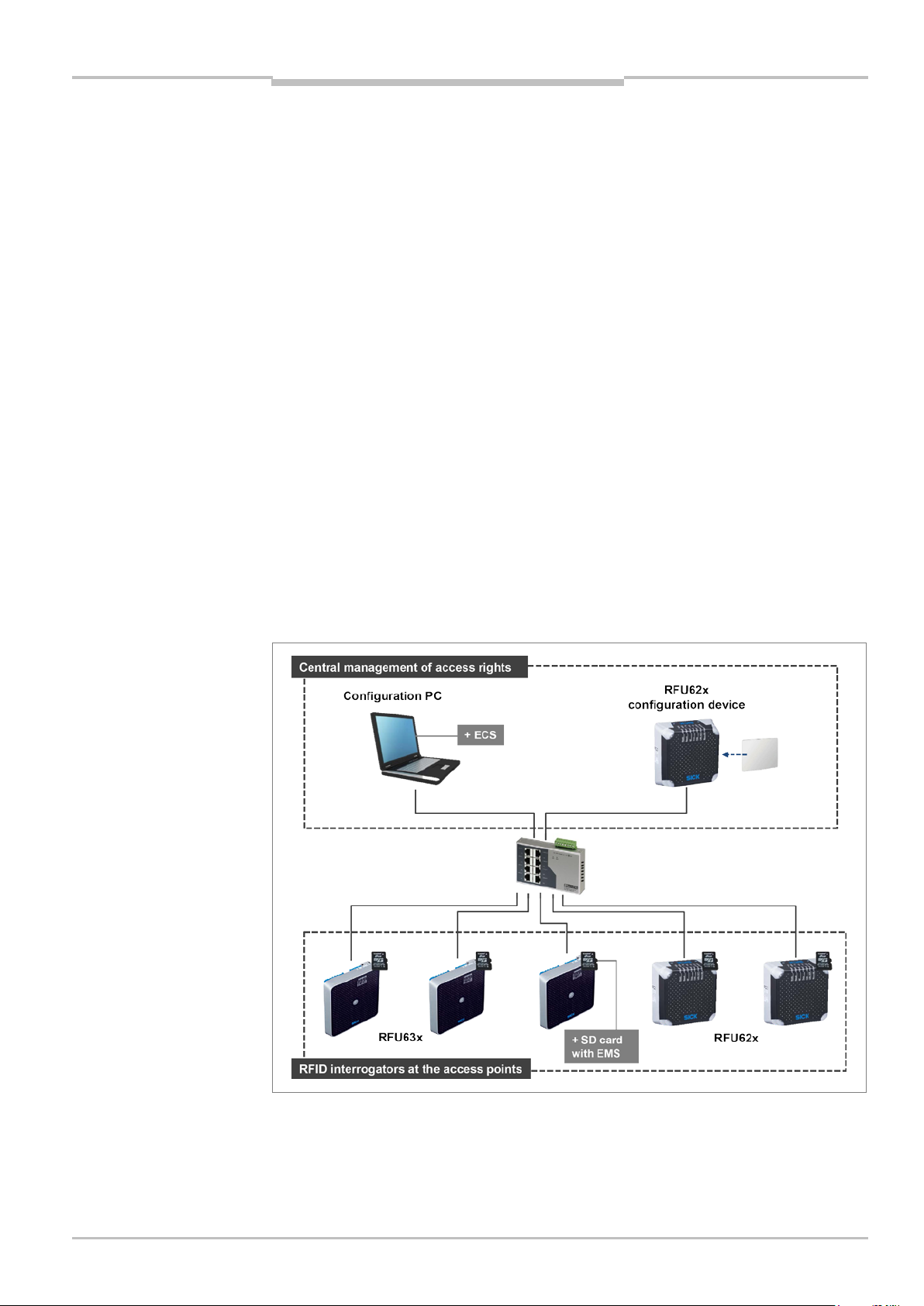
3.2.1 An overview of the system components
To manage and configure access rights, RFID Access Management requires
a commercially available configuration PC and a type RFU62x RFID interrogator.
Type RFU62x and RFU63x RFID interrogators are used at the access points of the
access control system. Communication between the devices takes place via an
Ethernet connection.
8018582/2015-11-03 Operating instructions| SICK 17
Subject to change without notice
Fig. 3: System components
Page 18

Chapter 3 Operating instructions
System description
RFID Access Management
The RFID interrogators at the access points are connected to the power supply and, via I/O
connection, to the access control system.
Fig. 4: Operation without connection module
Managing access rights
The Entry Exit Configuration Software system component is installed on the configuration
PC. This manages the access rights of persons and vehicles as well as the assignment of
tags. It communicates with the RFID interrogators at the access points and configures the
switching operations for the controlling the access points.
The configuration device for reading the tags is a type RFU62x RFID interrogator with
integrated antenna and a scanning range of up to 1 m. The tag that has been read in is
assigned to a participant in the configuration software. Existing assignments are displayed
in the software's Tag Management view.
Transferring access rights
The access rights managed in ECS are transferred to the RFID interrogators of the access
points via Ethernet and saved there. Communication between the configuration PC and
RFID interrogators takes place via the EMS system component. This is installed as
a counterpart to the ECS management software in the relevant RFID interrogator via
a microSD card.
If the RFID interrogator delivers a positive read result, this is reported to the access control
system via a digital switching output.
Note
The microSD card also acts as a form of copy protection. It must be inserted into each
RFID interrogator that is managed with RFID Access Management.
Tags
The RFU62x and RFU63x RFID interrogators used in RFID Access Management process all
standard passive tags in accordance with ISO-/IEC-18000-6C and EPCglobal UHF C1G2 in
the regional UHF carrier frequency range.
18 Operating instructions | SICK 8018582/2015-11-03
Subject to change without notice
Page 19

Operating instructions Chapter 3
System description
RFID Access Management
Using a CDB650 connection module (optional)
Optionally, the RFU6xx RFID interrogators can be operated at the access points via
a connection module. The connection module connects the RFID interrogator to the
power supply and, via a digital switching output, to the electronic access control system.
It helps to bridge extended distances between the RFID interrogator and the connections.
The RFID interrogator is connected to the connection module via a pre-assembled cable.
The connection module is wired to the power supply and control system via corresponding
terminals inside the housing.
Tamper protection
Fig. 5: Operation with connection module
As the connection module is generally mounted at a location that is not accessible to
outsiders, it is also ideally protected against tampering.
If the switching operations are not to take place directly in the RFID interrogator, but in the
connection module instead in order to provide increased protection against tampering, the
CMC600-101 cloning module must also be connected there. The cloning module supports
the connected RFID interrogator with two additional inputs and outputs.
8018582/2015-11-03 Operating instructions| SICK 19
Subject to change without notice
Fig. 6: Operation with connection module and cloning module
Page 20

Chapter 3 Operating instructions
System description
RFID Access Management
3.2.2 Operating principle of the management software
The ECS management software is responsible for managing all parameters that are
relevant for access control and for transferring these to the RFID interrogators of the
access points.
Managing the access points
All points at which only authorized persons or vehicles are to be admitted access to
a defined area are recorded in RFID Access Management as access points.
An access point is how an RFID interrogator is shown in the ECS management software.
Note
Fig. 7: Managing the access points
Access authorizations for up to 20 access points can be managed in one RFID Access
Management.
Managing the access profiles
Access authorizations are defined in ECS as access profiles. An access profile is created
for one or more access points. The period during which access is permitted is stored by
means of corresponding time frames. Access profiles are initially defined without reference
to persons or vehicles.
20 Operating instructions | SICK 8018582/2015-11-03
Subject to change without notice
Page 21

Operating instructions Chapter 3
System description
RFID Access Management
Fig. 8: Managing the access profiles
Managing authorized participants and tags
All persons or vehicles that are to be admitted access to a defined area are referred
to as participants in RFID Access Management.
A participant is granted access authorization by being assigned an access profile.
One participant may have several access profiles. Participants with the same access
profiles have the same access rights for the specified period.
A tag is assigned to each authorized participant. The tag is read by the RFU62x
configuration device.
The tag grants a person or vehicle access to the relevant area for the defined time frame.
8018582/2015-11-03 Operating instructions| SICK 21
Subject to change without notice
Fig. 9: Managing authorized participants and tags
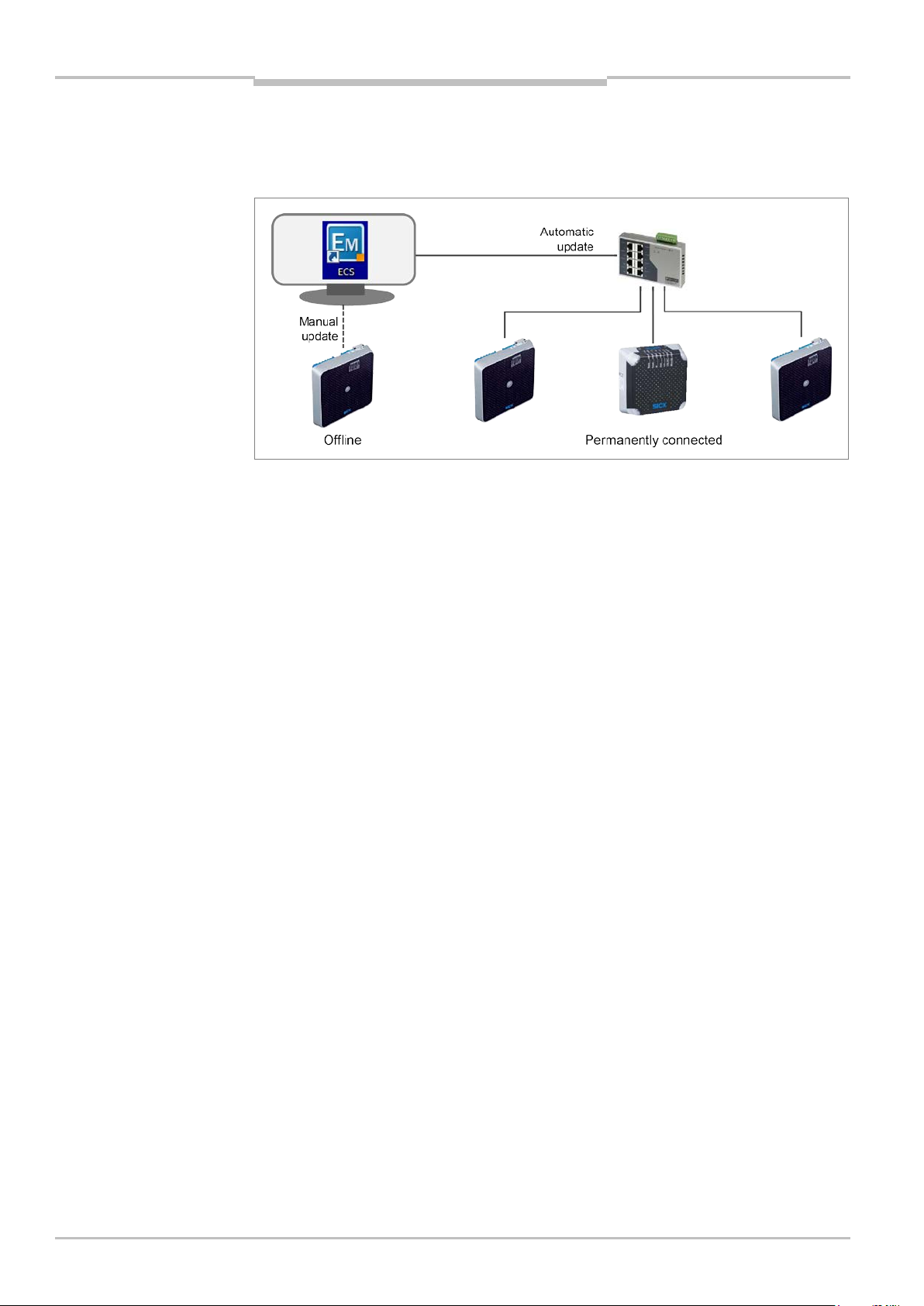
Updating access rights
All access-related information about the participant is transferred to the corresponding
RFID interrogators. The transfer takes place automatically for all RFID interrogators
connected to the configuration PC.
Page 22
Chapter 3 Operating instructions
System description
RFID Access Management
RFID interrogators that are not permanently connected to the configuration PC have to be
updated manually by means of a direct connection between the configuration PC and RFID
interrogator.
Fig. 10: Updating access rights
22 Operating instructions | SICK 8018582/2015-11-03
Subject to change without notice
Page 23

Operating instructions Chapter 3
System description
RFID Access Management
3.2.3 Notes on the tags
The system uses tags that are certified to ISO/IEC 18000-6C, IPC Class 1 Gen 2.
Adjacent UHF tags and HF tags should be avoided on vehicles; otherwise, there is a risk
of frequency interference.
The tags are not included with delivery. Therefore, please observe the notes below when
selecting tags.
Recommended tags
Fig. 11: Recommended tags
No. Type Explanation SICK part no. No.
1 ISO card tag For use as a personnel badge 6051820
2 On-metal tag For mounting on the metal surface
6052346
of the vehicle
Tab. 3: Recommended tags
Sample tag
RFID Access Management is supplied with an empty ISO card tag. This is used to set up
and test the configuration.
8018582/2015-11-03 Operating instructions| SICK 23
Subject to change without notice
Page 24

Chapter 3 Operating instructions
System description
RFID Access Management
3.3 Status indicators
3.3.1 RFU62x RFID interrogator
The RFU62x RFID interrogator has the following status indicators:
Fig. 12: Status indicators on the RFU62x RFID interrogator
No. LED
1 LEDs for indicating the status
2 LEDs for indicating the read response in the four corners of the antenna
cover
LEDs for indicating the status
LED Color Meaning
Ready Green Device ready
Red Hardware fault
Result Green Read or write successful
RF Green UHF field activated
Data Green Data output via host interface
CAN Green Data traffic via CAN bus
LNK TX Green Data traffic via Ethernet
microSD Green microSD card inserted and ready for operation
(not with RFU62x configuration device)
Tab. 4: Status indicators on the RFU62x RFID interrogator
LEDs for indicating the read response
In the default configuration, the light output of the four LEDs in the corners of the
antenna cover indicates whether a UHF field is present and tags have been detected.
The LED indicators can be set via RFID Access Management (see chapter
6.9.4 Configuring the RFID interrogator indicators).
24 Operating instructions | SICK 8018582/2015-11-03
Subject to change without notice
Page 25

Operating instructions Chapter 3
System description
RFID Access Management
3.3.2 RFU63x RFID interrogator
The RFU63x RFID interrogator has the following status indicators:
Fig. 13: Status indicators on the RFU63x RFID interrogator
No. LED
1 LEDs for indicating the status
2 LED in the center of the RFID interrogator for indicating the read response
LEDs for indicating the status
LED Color Meaning
Ready Green Device ready
Red Hardware fault
Result Green Read or write successful
RF Green UHF field activated
Data Green Data output via host interface
CAN Green Data traffic via CAN bus
LNK TX Green Data traffic via Ethernet
microSD Green microSD card inserted and ready for operation
Tab. 5: Status indicators on the RFU63x RFID interrogator
LEDs for indicating the read response
In the default configuration, the light output of the four LEDs in the corners of the
antenna cover indicates whether a UHF field is present and tags have been detected.
The LED indicators can be set via RFID Access Management (see chapter
6.9.4 Configuring the RFID interrogator indicators).
8018582/2015-11-03 Operating instructions| SICK 25
Subject to change without notice
Page 26
Chapter 3 Operating instructions
System description
EXT.IN 2
EXT.OUT 2
IN
OFF: Volt-free
RFID Access Management
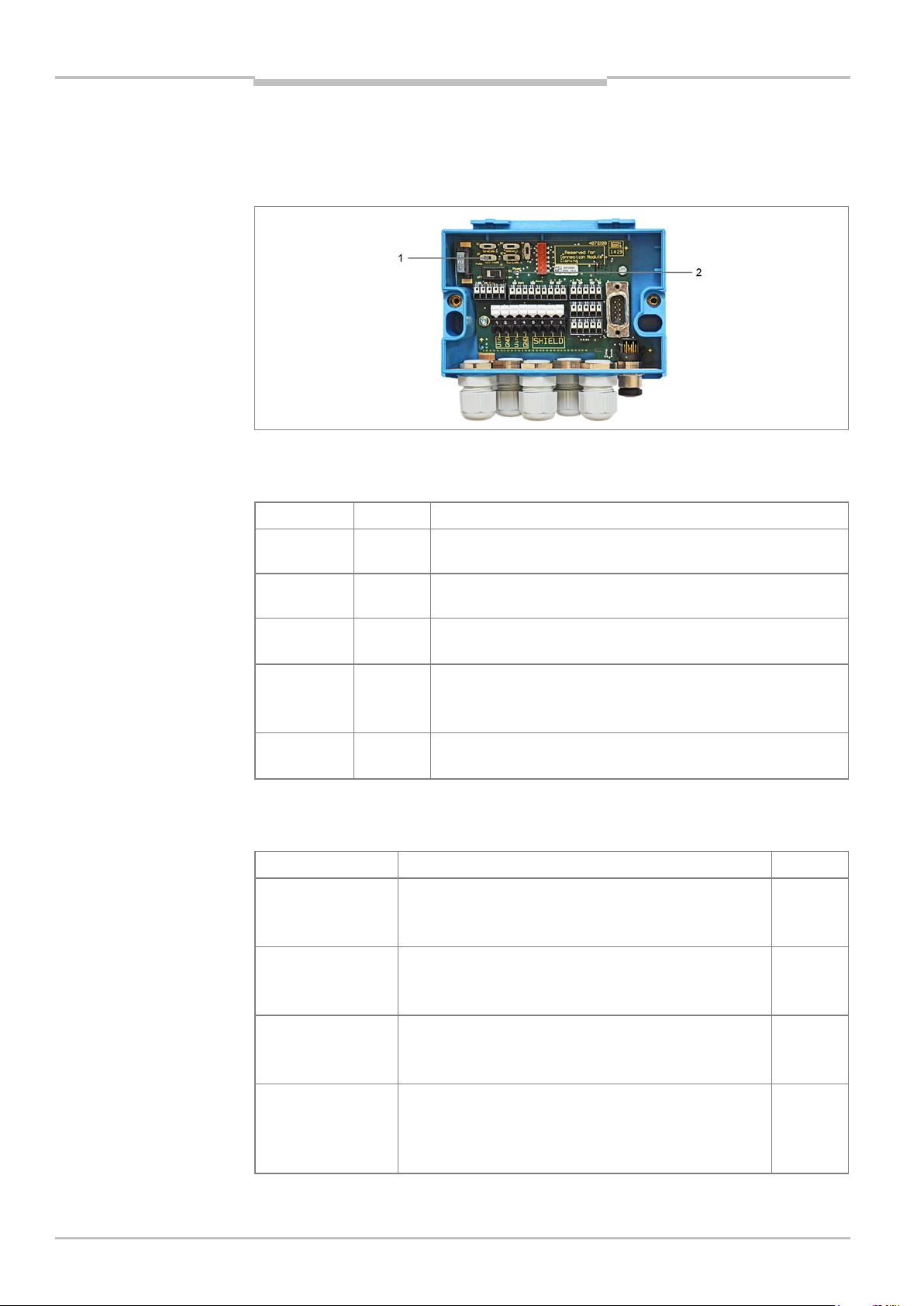
3.3.3 CDB650 connection module
All configuration switches (1) and LEDs (2) on the CDB650 connection module are visible
through the cover.
Fig. 14: Status indicators on the CDB650 connection module
LEDs
LED Color Function
Power UIN Green
Lights up if the CDB650 has a supply voltage and switch S1
is set to ON.
SENS/IN 1
SENS/IN 2
EXT.IN 1
Green
Green
Lights up if the corresponding input of the RFID interrogator
is activated.
Lights up if the corresponding, additional input of the RFID
interrogator (via CMC600) is activated.
RES/OUT 1
…
Orange
Lights up if the corresponding output of the RFID interrogator
is present and activated.
RES/OUT 4
EXT.OUT 1
Orange
Lights up if the corresponding, additional output of the RFID
interrogator (via CMC600) is activated.
Tab. 6: Status indicators on the CDB650 connection module
Relevant configuration switches
Switch Function Default
S1 (Power) S1 (Power) supply voltage present
ON: Supply voltage U
OFF: Supply voltage U
IN
on
off
S2 (Term CAN) CAN bus termination
ON
OFF
ON: 120 ohm resistor connected
OFF: No termination
S3 (SGND - GND) Reference potential for sensor GND
OFF
ON: Connected to ID sensor GND
26 Operating instructions | SICK 8018582/2015-11-03
Subject to change without notice
S4 (CMC) Integration of the CMC600
YES: CMC600 connected in cable for AUX interface of
the ID sensor
NO: No CMC600 inserted
Tab. 7: Configuration switches in the CDB650 connection module
NO
Page 27

Operating instructions Chapter 3
System description
RFID Access Management
3.3.4 CMC600 cloning module
The cloning module has the following configuration switches and status indicators:
Fig. 15: Status indicators on the cloning module
No. Meaning
1 Switch for network address
2 Switch for operating mode
3 Write protection switch
4 Monitoring LEDs
Tab. 8: Configuration switches and status indicators in the cloning module
Behavior of the yellow monitoring LED
Behavior Meaning
Flashing slowly The cloning module has launched and is waiting for commands
from the RFID interrogator.
Flashing rapidly The cloning module was switched to transparent (mode 0).
The RFID interrogator cannot access the cloning module.
Tab. 9: Yellow monitoring LED in the cloning module
Behavior of the green monitoring LED
Behavior Meaning
Flashing
(briefly on, mainly off)
Flashing
(briefly on, mainly off)
The RFID interrogator is importing parameter values from the
cloning module.
The RFID interrogator is copying parameter values to the
cloning module.
Permanently on The cloning module is operational. The RFID interrogator has
successfully accessed the cloning module.
8018582/2015-11-03 Operating instructions| SICK 27
Subject to change without notice
Tab. 10: Green monitoring LED in the cloning module
Page 28

Chapter 4 Operating instructions
Setup and mounting
RFID Access Management
4 Setup and mounting
4.1 RFU62x configuration device
Only the RFU62x RFID interrogator is used as a device to configure the access control
system.
The device can be placed on an even surface, e.g., on a table.
It does not require mounting.
4.2 RFID interrogators at the access points
Type RFU62x and RFU63x RFID interrogators can be mounted at the access points.
Use the brackets available as accessories for the mounting process.
4.2.1 Notes on mounting the RFID interrogators
The mounting procedure and position depend on the antenna field of the RFID interrogator
and the tags used.
Mounting position
• The RFID radio field must point in the direction of the tag.
• Ideally, you should mount the RFID interrogator on the side where the tags are
identified.
• Alternatively, the RFID interrogator can be mounted above the entry lane of a gate.
The RFID interrogator must be mounted at an angle so that it points to the center of
the reading positions that the object passes.
Unobstructed view of the tag
• Ensure that there is an unobstructed view from the RFID interrogator to the tag.
No objects (including persons) must be positioned between the RFID interrogator
and the tag during the read process.
This would attenuate and reflect the generated UHF field and thereby reduce the
scanning range and processing speed of the RFID interrogator.
28 Operating instructions | SICK 8018582/2015-11-03
Subject to change without notice
Page 29

Operating instructions Chapter 4
Setup and mounting
RFID Access Management
Scanning range of the reading field
Ensure that the distance from the RFID interrogator to the tag is as short as possible.
Please note that the RFID interrogator has a lobar send and receive characteristic.
This means that there are a number of small zones where the send and receive signals
are weaker because of the physical principles involved.
Fig. 16: Lobar send and receive characteristic of the internal antenna
• For optimum reading accuracy and, in turn, reliability, the tag should be located in the
axis of the RFID interrogator in front of the read area, and the tag should be parallel to
the RFID interrogator (i.e., the angle should be as small as possible).
Fig. 17: Ideal positions for tag/RFID interrogator
Approach angle in the case of a large metal surface on the front
If an RFU63x is mounted in front of any metal surfaces at the front, then an approach
angle of approx. 5° must be observed. With a RFU62x, the recommended approach angle
is 10°.
8018582/2015-11-03 Operating instructions| SICK 29
Subject to change without notice
Fig. 18: Selecting the approach angle of the RFID interrogators in the case of a large metal surface
on the front
Page 30

Chapter 4 Operating instructions
Setup and mounting
RFID Access Management
4.2.2 RFU62x RFID interrogator
Mount the RFU62x where shocks and vibrations are minimized.
For the purposes of mounting, five SICK mounting kits are available as accessories.
The mounting kits can also be combined.
1. Mount the mounting kit on the RFU62x.
2. Use the mounting kit to mount the RFU62x at the designated point.
3. Align the RFU62x so that it points to the center of the anticipated reading position.
For further details on mounting, please refer to the operating instructions for the RFU62x.
Order no. Description
2061737 Mounting bracket incl. mounting material for attaching to the
RFU62x
2071773 Frame bracket incl. mounting material for attaching to the RFU62x
2016110 Quick-action lock system in combination with 2071067 mounting
bracket for attaching to the RFU62x
2071862 VESA adapter plate incl. mounting material for attaching to the
RFU62x
Individual bracket made of pipe elements and clamps with
2071862 VESA adapter plate for the RFU62x
2068919 Link clamp with 4 M6 x 12 cylinder head screws
5327612 Cross clamp
30 Operating instructions | SICK 8018582/2015-11-03
Subject to change without notice
5327613 Sealing plug, ∅ 30 mm
Page 31

Operating instructions Chapter 4
Setup and mounting
RFID Access Management
5327610 Pipe, ∅ 30 mm, length 1 m
5327611 Base clamp
Tab. 11: Mounting kits for the 62x RFID interrogator
4.2.3 RFU63x RFID interrogator
Mount the RFU63x where shocks and vibrations are minimized.
For the purposes of mounting, three SICK mounting kits are available as accessories.
The mounting kits can also be combined.
1. Mount the mounting kit on the RFU63x.
2. Use the mounting kit to mount the RFU63x at the designated point.
3. Align the RFU63x so that it points to the center of the anticipated reading position.
For further details on mounting, please refer to the operating instructions for the RFU63x.
Order no. Description
2060912 Mounting kit 1 incl. mounting material for wall mounting the
2071862 VESA adapter plate incl. mounting material for attaching to the
2061737 Pivot mounting bracket incl. mounting material for attaching to
Tab. 12: Mounting kits for the 63x RFID interrogator
4.2.4 Mounting the connection module
When mounting the CDB650 connection module, select a location that offers optimum
protection against sabotage.
When selecting the mounting location, ensure that length of cable between the connection
module and the RFID interrogator is no more than 3 m.
For further details on mounting, please refer to the operating instructions for the
respective connection module.
RFU63x
RFU63x
the RFU63x
8018582/2015-11-03 Operating instructions| SICK 31
Subject to change without notice
Page 32

Chapter 5 Operating instructions
Electrical installation
RFID Access Management
5 Electrical installation
HAZARD
Risk of injury due to electrical current
Only a qualified electrician or trained person working under the guidance and supervision
of a qualified electrician is permitted to work on electrical systems or equipment and they
must comply with the electrical regulations.
HAZARD
Disconnect the power to the system
Make sure that all devices are disconnected from the power supply during the electrical
installation work.
HAZARD
Risk of injury due to electrical current
If the wall plug is used, the RFU62x configuration device is connected directly to the power
supply (AC 100 ... 264 V/50 ... 60 Hz).
Standard safety requirements must be met when working on electrical systems.
The power supply must be disconnected when attaching and detaching electrical
connections.
Select and implement wire cross-sections and their correct fuse protection in
accordance with the applicable standards.
5.1 Connecting the RFU62x configuration device
Only the RFU62x RFID interrogator is used as a device to configure the access control
system. The connections are located on the rear of the housing.
Fig. 19: Connection of the RFU62x configuration device
Connection to power supply
The connection to the power supply is established conveniently via the power supply unit
with a 17-pin pre-assembled connecting cable with M12 female connector. This power
supply unit is available as SICK accessory (see chapter 5.5 SICK connection accessories).
1. Connect the female connector of the connecting cable to the PWR, AUX, CAN I/O
connection and screw together the plug connector.
2. Plug the power supply unit into a suitable fused power outlet.
32 Operating instructions | SICK 8018582/2015-11-03
Subject to change without notice
Page 33

Operating instructions Chapter 5
Electrical installation
RFID Access Management
Connection to the network
The configuration device is also connected to the Ethernet switch via an Ethernet cable.
1. Connect the M12 male connector of the Ethernet cable to the Ethernet female
connector and screw together the plug connector.
2. Route the Ethernet cable from the RFID interrogator to the Ethernet switch.
3. There, insert the RJ45 male connector into an open female connector.
5.2 Connecting RFU6xx RFID interrogators
Type RFU6xx RFID interrogators are used at the access points of the access control
system.
If the devices are operated without a connection module, connection to the power supply
and digital switching output is established via a connecting cable with an M12 plug
connector and one open end. The connection to the configuration PC is established via
a pre-assembled Ethernet cable.
Fig. 20: Connection of the RFID interrogators (overview)
Note
The switching output is configured via ECS.
Note
If you download the Entry Exit Configuration Software system component from the SICK
website, you can insert the microSD card straight into the device. The microSD card must
only be used when the power to the RFID interrogator has been disconnected. For further
information, also read chapter 6.4 Inserting the microSD card into access point RFID
interrogators.
In all other cases, you must install Entry Exit Configuration Software on the configuration
PC before inserting the microSD card.
8018582/2015-11-03 Operating instructions| SICK 33
Subject to change without notice
Page 34

Chapter 5 Operating instructions
Electrical installation
Pin
Signal
Function
Wire color *
1 Ground
Brown
2 Supply voltage
Blue
3 CAN bus (IN/OUT)
White
4 CAN bus (IN/OUT)
Green
5 Host interface (receiver+)
Pink
6
Host interface (receiver–)
Yellow
7 AUX interface (sender)
Black
8 AUX interface (receiver)
Gray
9 Common ground for all inputs
Red
10 Switching input 1
Violet
11 Host interface (receiver+)
Gray-pink
12
Host interface (receiver–)
Red-blue
13 Switching output 1
White-green
14 Switching output 2
Brown-green
15 Switching input 2
White-yellow
16
Yellow-brown
17
White-gray
* The color codes are valid for cables with part no. 6042772 (3 m) and part no. 6042773
(5 m).
RFID Access Management
5.2.1 Connecting the power supply/switching output
Establish the connection to the power supply and connect the switching output to the
access control mechanism.
1. Connect the M12 female connector of the connecting cable on the RFID interrogator to
the PWR, AUX, CAN I/O connection (RFU62x) or to connection 1 (RFU63x) and screw
together the plug connector.
Fig. 21: Connecting RFID interrogators to the power supply/switching output
2. Connect the wires of the open cable end as per the following pin assignment:
34 Operating instructions | SICK 8018582/2015-11-03
Subject to change without notice
Page 35

Operating instructions Chapter 5
Electrical installation
RFID Access Management
5.2.2 Connection to the network
The connection of the RFID interrogator to the configuration PC is established directly via
the Ethernet connection on the device.
1. Connect the male connector of the Ethernet cable to the Ethernet female connector
and screw together the plug connector.
2. Route the Ethernet cable from the RFID interrogator to the switch.
3. There, insert the RJ45 male connector into an open female connector.
Note
If the device cannot be permanently connected to the configuration PC due to space
restrictions, the device must be manually configured later on via a direct connection to
the PC.
5.3 Connecting RFID interrogators via a connection module
The connection between the RFID interrogator and connection module is established via
a 17-pin connecting cable. All other cables (power supply, switching outputs, etc.) are
connected to the terminals via cable glands. For details of the terminal pin assignment,
see the cover of the connection module.
The connection of the RFID interrogator to the configuration PC is established directly via
the Ethernet connection on the device.
5.3.1 Connecting an RFID interrogator to a connection module
8018582/2015-11-03 Operating instructions| SICK 35
Subject to change without notice
Fig. 22: Connecting RFID interrogators via a connection module
1. Connect the female connector of the connecting cable to the M12 male connector of
the connection module and screw together the plug connector.
2. Run the cable to the connection module.
3. Connect the male connector of the connecting cable to the M12 female connector of
the connection module and screw together the plug connector.
Page 36
Chapter 5 Operating instructions
Electrical installation
RFID Access Management
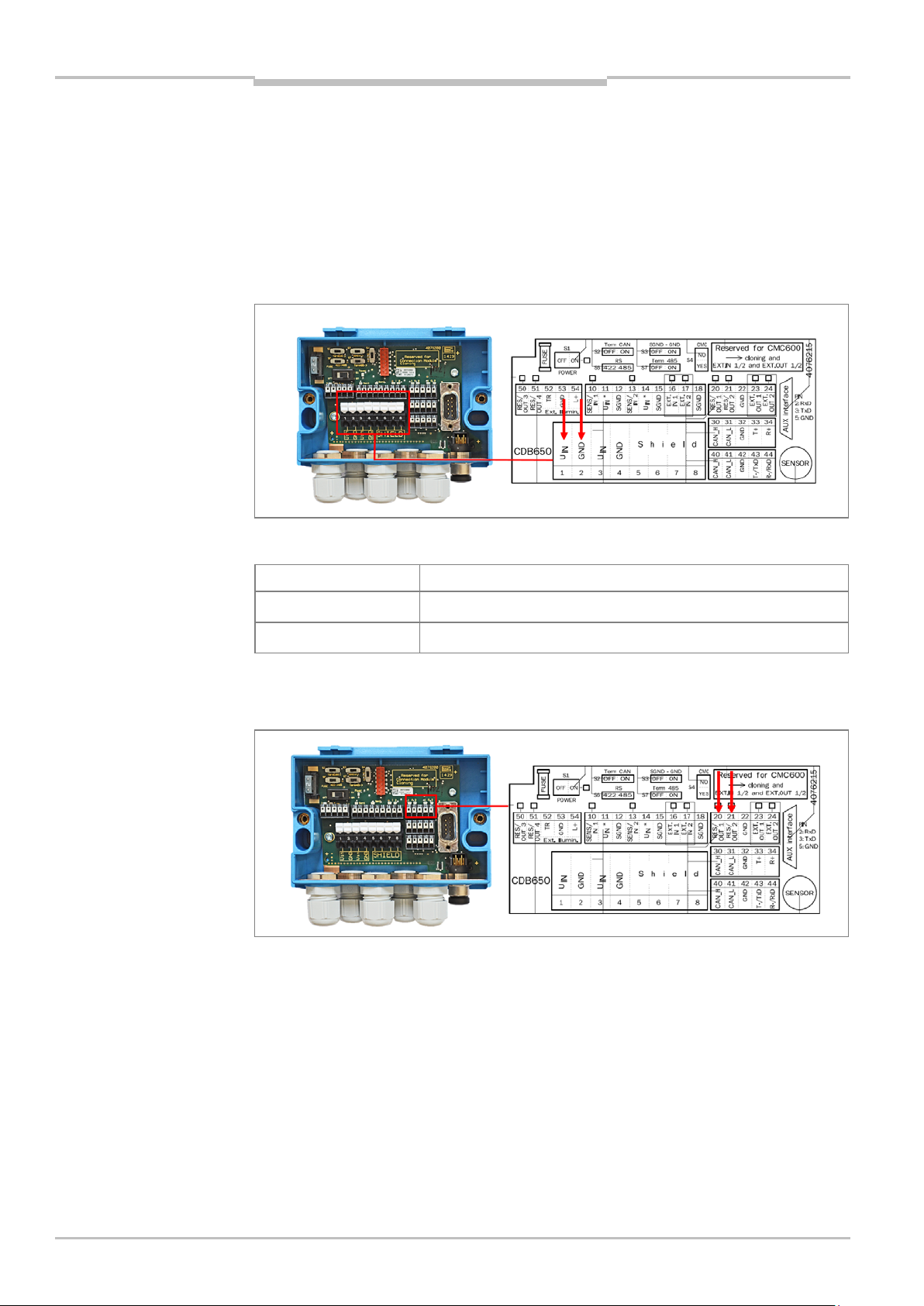
5.3.2 Connecting the power supply/switching output in the connection module
The following chapter describes the terminal pin assignment if you are using the
connection module without a cloning module.
1. Undo the screws on the cover and remove it from the CDB650 connection module.
2. Run the supply cable through the PG connector into the inside of the CDB650 housing
and connect the wires of the power supply to terminals 1 and 2.
Fig. 23: Connection of the power supply in the connection module
Terminal strip Connection
1 U IN Supply voltage for RFID interrogator
2 GND GND for RFID interrogator
Tab. 13: Terminals for power supply in the connection module
3. For the digital switching output connection, use terminals 20 or 21.
Fig. 24: Connection of the digital switching output in the connection module
36 Operating instructions | SICK 8018582/2015-11-03
Subject to change without notice
Page 37

Operating instructions Chapter 5
Electrical installation
RFID Access Management
5.3.3 Inserting the cloning module
Insert the cloning module into the slot on the CDB650 connection module.
NOTE
Disconnecting the connection module
Mounting may only take place when the power to the connection module has been
disconnected.
1. Undo the screws on the cover and remove it from the connection module.
2. Set switch S1 (Power) to OFF to ensure that the connection module is isolated from
the supply voltage.
3. In the connection module, set switch S4 (CMC) to the bottom position to operate the
CMC600.
4. Insert the cloning module into the connection module at the designated slot.
The housing nose of the CMC600 then automatically interlocks the S4 (CMC) switch.
Fig. 25: Inserting the cloning module in the connection module
5. Set the write protection switch of the CMC600 to the top position (OFF) if you wish
to describe the CMC600 memory.
Fig. 26: Write protection switch in the cloning module
6. Set the S1 (Power) switch back to ON.
8018582/2015-11-03 Operating instructions| SICK 37
Subject to change without notice
Page 38

Chapter 5 Operating instructions
Electrical installation
RFID Access Management
5.3.4 Connecting the additional switching output of the connection module
If you are using the additional switching outputs of the connection module,
use terminals 23 or 24 for the connection.
Fig. 27: Connection of the additional digital switching outputs in the connection module
5.4 Connecting the configuration PC to the network
In general, the configuration PC containing the management software is connected to
the RFID interrogators via a network switch.
Fig. 28: Connecting the configuration PC to the network
Connection via Ethernet switch
Connect the PC to the Ethernet switch.
Direct network connection between the PC and RFID interrogator
A direct network connection between the RFID interrogator and the configuration PC is
required in the following cases:
• Setting the transmitting power of the RFID interrogators with SOPAS (see 6.5.3 Testing
RFU transmitting power).
• Configuring RFID interrogators that are not permanently connected to the configuration
PC.
38 Operating instructions | SICK 8018582/2015-11-03
Subject to change without notice
Fig. 29: Direct connection between the configuration PC and RFID interrogator
Page 39

Operating instructions Chapter 5
Electrical installation
Accessory
Description
Part number
Power supply unit
Power supply unit with pre-assembled M12
2062249
Connecting cable for
Connecting cable with M12 male connector,
6042773
Ethernet connecting
Connecting cable with M12 male connector,
6034414
Ethernet connecting
Connection type with RJ45/RJ45 male
6026083
CDB650-204
Basic connection module for connecting
1064114
Connecting cable for
Connecting cable for connecting the CDB650
6051194
CMC-101 cloning
External parameter memory with 2 additional
1042259
RFID Access Management
5.5 SICK connection accessories
female connector, 17-pin for connecting the
RFID interrogator to the power outlet
Power/I/O, etc.
cable
cable
connection module
the RFU interrogator
4-pin/17-pin for connecting the interrogator
to customer-specific connection box (Power,
SerialData/CAN/I/O)
- 03 m
- 05 m
4-pin/RJ45
connector
- 03 m
a sensor with 2 A fuse, 5 cable glands, and
RS-232 interface to the sensor via M12,
17-pin female connector
All outputs connected to terminal
connection module and RFID interrogator,
M12, 17-pin
- 03 m
6042772
module
inputs and outputs for integration in the
CDB650 connection module
8018582/2015-11-03 Operating instructions| SICK 39
Subject to change without notice
 Loading...
Loading...