Page 1

Notices
1.0
No part of this publication may be reproduced, stored in a retrieval system, or
transmitted, in any form or by any means, mechanical photocopying, recording or
otherwise, without the prior written permission of the manufacturer.
The information within this manual is subject to change without notice.
The manufacturer shall not be held liable for technical or editorial errors or omissions
contained in herein; nor for incidental or consequential damages resulting from the
furnishing, performance or use of this material.
Microsoft Windows is a registered trademark of the Microsoft Corporation.
Product names mentioned herein are for identification purposes only, and may be
trademarks and/or registered trademarks of their respective companies.
Macrovision Statement
If your computer has a DVD drive and an analog TV Out port, the following
paragraph applies:
This product incorporates copyright protection technology that is protected by method
claims of certain U.S. patents and other intellectual property rights owned by
Macrovision Corporation and other rights owners. Use of this copyright protection
technology must be authorized by Macrovision Corporation, and is intended for home
and other limited viewing uses only unless otherwise authorized by Macrovision
Corporation. Reverse engineering or disassembly is prohibited.
Copyright 2003 All rights are reserved
Notices i
Page 2

Important Safety Information
Safety Instructions
Your system is designed and tested to meet the latest standards for safety of
information technology equipment. However, to ensure safe use of this product, it is
important that the safety instructions marked on the product and in the documentation
are followed.
Always follow these instructions to help guard against personal injury and
damage to your system.
i
Setting Up your System
• Read and follow all instructions marked on the product and in the
documentation before you operate your system. Retain all safety and operating
instructions for future use.
• Do not use this product near water or a heat source such as a radiator.
• Set up the system on a stable work surface.
• The product should be operated only with the type of power source indicated on
the rating label.
• Ensure that the electrical outlet you are using to power your equipment is easily
accessible in case of fire or short circuit.
• If your computer has a voltage selector switch, make sure that the switch is in
the proper position for your area.
• Openings in the computer case are provided for ventilation. Do not block or
cover these openings. Make sure you provide adequate space, at least 6 inches
(15 cm), around the system for ventilation when you set up your work area.
Never insert objects of any kind into the computer ventilation openings.
• Ensure that the fan vents on the bottom of the casing are clear at all times. Do
not place the computer on a soft surface, doing so will block the bottom vents.
• If you use an extension cord with this system, make sure that the total ampere
rating on the products plugged into the extension cord does not exceed the
extension cord ampere rating.
ii Users Manual
Page 3
Care During Use
• Do not walk on the power cord or allow anything to rest on it.
• Do not spill anything on the system. The best way to avoid spills is to not eat or
drink near your system.
• Some products have a replaceable CMOS battery on the system board. There is
a danger of explosion if the CMOS battery is replaced incorrectly. Replace the
battery with the same or equivalent type recommended by the manufacturer.
Dispose of batteries according to the manufacturer’s instructions. If the CMOS
battery requires replacement insure that a qualified technician performs the task
• When the computer is turned off, a small amount of electrical current still flows
through the computer. To avoid electrical shock, always unplug all power
cables, remove the battery and modem cables from the wall outlets before
cleaning the system.
• Unplug the system from the wall outlet and refer servicing to qualified
personnel if:
– The power cord or plug is damaged.
– Liquid has been spilled into the system.
– The system does not operate properly when the operating instructions are
followed.
– The system was dropped or the casing is damaged.
– The system performance changes.
Replacement Parts and Accessories
Use only replacement parts and accessories recommended by manufacturer.
To reduce the risk of fire, use only No. 26 AWG or larger telecommunications
line cord.
Do not use this product in areas classified as hazardous. Such areas include
patient care areas of medical and dental facilities, oxygen rich environments,
Writtenby:DarylL. Osden
or industrial areas.
Battery Disposal
Do not put rechargeable batteries or products powered by non-removable
rechargeable batteries in the garbage.
Contact the Samsung Helpline for information on how to dispose of batteries that you
cannot use or recharge any longer.
Follow all local regulations when disposing of old batteries.
Important Safety Information iii
Page 4

Laser Safety
All systems equipped with CD or DVD drives comply with the appropriate safety
standards, including IEC 825. The laser devices in these components are classified as
“Class 1 Laser Products” under a US Department of Health and Human Services
(DHHS) Radiation Performance Standard. Should the unit ever need servicing, contact
an authorized service location.
Laser Safety Note:
Use of controls or adjustments or performance of procedures other than those
specified in this manual may result in hazardous radiation exposure. To
prevent exposure to laser beams, do not try to open the enclosure of a CD or
DVD drive.
Power Cord Requirements
The power cord set (wall plug, cable and AC adapter plug) you received with your
computer meets the requirements for use in the country where you purchased your
equipment.
Power cord sets for use in other countries must meet the requirements of the country
where you use the computer. For more information on power cord set requirements,
contact your authorized dealer, reseller, or service provider.
General Requirements
The requirements listed below are applicable to all countries:
• The length of the power cord set must be at least 6.00 feet (1.8m) and a
maximum of 9.75 feet (3.0m).
• All power cord sets must be approved by an acceptable accredited agency
responsible for evaluation in the country where the power cord set will be used.
• The power cord set must have a minimum current capacity of 7 A and a
nominal voltage rating of 125 or 250 volts AC, as required by each country’s
power system.
• The appliance coupler must meet the mechanical configuration of an EN 60
320/IEC 320 Standard Sheet C7 connector, for mating with appliance inlet on
the computer.
iv Users Manual
Page 5

Regulatory Compliance Statements
Wireless Guidance
Low power, Radio LAN type devices (radio frequency (RF) wireless communication
devices), operating in the 2.4 GHz Band, may be present (embedded) in your notebook
system. The following section is a general overview of considerations while operating
a wireless device.
Additional limitations, cautions, and concerns for specific countries are listed in the
specific country sections (or country group sections). The wireless devices in your
system are only qualified for use in the countries identified by the Radio Approval
Marks on the system rating label. If the country you will be using the wireless device
in, is not listed, please contact your local Radio Approval agency for requirements.
Wireless devices are closely regulated and use may not be allowed.
The power output of the wireless device or devices that may be embedded in your
notebook is well below the RF exposure limits as known at this time. Because the
wireless devices (which may be embedded into your notebook) emit less energy than
is allowed in radio frequency safety standards and recommendations, manufacturer
believes these devices are safe for use. Regardless of the power levels, care should be
taken to minimize human contact during normal operation.
As a general guideline, a separation of 20 cm (8 inches) between the wireless device
and the body, for use of a wireless device near the body (this does not include
extremities) is typical. This device should be used more than 20 cm (8 inches) from the
body when wireless devices are on and transmitting.
This transmitter must not be collocated or operate in conjunction with any other
antenna or transmitter.
Some circumstances require restrictions on wireless devices. Examples of common
restrictions are listed below:
Radio frequency wireless communication can interfere with equipment on
commercial aircraft. Current aviation regulations require wireless devices to be
turned off while traveling in an airplane. 802.11B (also known as wireless
Ethernet or Wifi) and Bluetooth communication devices are examples of
devices that provide wireless communication.
Regulatory Compliance Statements v
Page 6

In environments where the risk of interference to other devices or services is
harmful or perceived as harmful, the option to use a wireless device may be
restricted or eliminated. Airports, Hospitals, and Oxygen or flammable gas
laden atmospheres are limited examples where use of wireless devices may
be restricted or eliminated. When in environments where you are uncertain of
the sanction to use wireless devices, ask the applicable authority for
authorization prior to use or turning on the wireless device.
Every country has different restrictions on the use of wireless devices. Since
your system is equipped with a wireless device, when traveling between
countries with your system, check with the local Radio Approval authorities
prior to any move or trip for any restrictions on the use of a wireless device in
the destination country.
If your system came equipped with an internal embedded wireless device, do
not operate the wireless device unless all covers and shields are in place and
the system is fully assembled.
Wireless devices are not user serviceable. Do not modify them in any way.
Modification to a wireless device will void the authorization to use it. Please
contact manufacturer for service.
Only use drivers approved for the country in which the device will be used. See
the manufacturer System Restoration Kit, or contact manufacturer Technical
Support for additional information.
vi Users Manual
Page 7

United States of America
Unintentional Emitter per FCC Part 15
This device complies with Part 15 of the FCC Rules. Operation is subject to the
following two conditions:(1) this device may not cause harmful interference, and (2)
this device must accept any interference received, including interference that may
cause undesired operation.
This equipment has been tested and found to comply with the limits for a Class
B digital device pursuant to Part 15 of the FCC Rules. These limits are
Writtenby:DarylL. Osden
If necessary, the user should consult the dealer or an experienced radio/television
technician for additional suggestions. The user may find the following booklet helpful:
“Something About Interference.” This is available at FCC local regional offices. Our
company is not responsible for any radio or television interference caused by
unauthorized modifications of this equipment or the substitution or attachment of
connecting cables and equipment other than those specified by our company. The
correction will be the responsibility of the user. Use only shielded data cables with this
system.
designed to provide reasonable protection against harmful interference in a
residential installation. This equipment generate uses and can radiate radio
frequency energy and if not installed and used in accordance with the
instructions may cause harmful interference will not occur in a particular
installation. If this equipment does cause harmful interference to radio or
television reception, which can be determined by turning the equipment off
and on, the user is encouraged to try to correct the interference by one or more
of the following measures:
• Reorient or relocate the receiving antenna.
• Increase the separation between the equipment and receiver.
• Connect the equipment into an outlet on a circuit different from that
to which the receiver is connected.
• Consult the dealer or an experienced radio/TV technician for help.
Intentional emitter per FCC Part 15
Low power, Radio LAN type devices (radio frequency (RF) wireless communication
devices), operating in the 2.4 GHz Band, may be present (embedded) in your notebook
system. This section is only applicable if these devices are present. Refer to the system
label to verify the presence of wireless devices.
Wireless devices that may be in your system are only qualified for use in the United
States of America if an FCC ID number is on the system label.
Regulatory Compliance Statements vii
Page 8
The FCC has set a general guideline of 20 cm (8 inches) separation between the device
and the body, for use of a wireless device near the body (this does not include
extremities). This device should be used more than 20 cm (8 inches) from the body
when wireless devices are on. The power output of the wireless device (or devices),
which may be embedded in your notebook, is well below the RF exposure limits as set
by the FCC.
This transmitter must not be collocated or operate in conjunction with any other
antenna or transmitter.
Operation of this device is subject to the following two conditions: (1) This device may
not cause harmful interference, and (2) this device must accept any interference
received, including interference that may cause undesired operation of the device.
Wireless devices are not user serviceable. Do not modify them in any way.
Modification to a wireless device will void the authorization to use it. Contact
manufacturer for service.
FCC Statement for Wireless LAN use:
“While installing and operating this transmitter and antenna combination the
radio frequency exposure limit of 1mW/cm2 may be exceeded at distances
close to the antenna installed. Therefore, the user must maintain a minimum
distance of 20cm from the antenna at all times. This device can not be
colocated with another transmitter and transmitting antenna.”
FCC Part 68
This equipment compiles with part of the FCC rules. On the back of this equipment is
a label that contains, among other information, the FCC registration number and ringer
equivalence number (REN) for this equipment. If requested, this information must be
provided to the telephone company.
This equipment uses the following USOC jacks : RJ11C
An FCC compliant telephone cord and modular plug is provided with this equipment.
This equipment is designed to be connected to the telephone network or promises
wiring using a compatible modular jack which is Part 68 compliant. See Installation
Instructions for details.
The REN is used to determine the quantity of devices which may be connected to
telephone line. Excessive RENs on the telephone line may result in the devices not
ringing in response to an incoming call. In most, but not all areas, the sum of RENs
should not exceed five (5.0). To be certain of the number of devices that may be
connected to a line, as determined by total RENs, contact the local telephone company
to determine the maximum REN for the calling area.
viii Users Manual
Page 9

If the terminal equipment causes harm to the telephone network, the Telephone
Company will notify you in advance that temporary discontinuance of service may be
required. But if advance notice is not practical, the telephone company will notify the
customer as soon as possible. Also, you will be advised of your right to file a complaint
with the FCC if you believe it is necessary.
The telephone company may make changes in its facilities, equipment, operations, or
procedures that could affect the operation of the equipment. If this happens, the
telephone company will provide advanced notice in order for you to make necessary
modifications to maintain uninterrupted service.
If trouble is experienced with this equipment (Modem) for repair or warranty
information, please contact your local distributor. If the equipment is causing harm to
the telephone network, the telephone company may request that you disconnect the
equipment until the problem is resolved.
The user must use the accessories and cables supplied by the manufacturer to get
optimum performance from the product.
No repairs may be done by the customer.
This equipment cannot be used on public coin phone service provided by the telephone
company. Connection to party line service is subject to state tariffs.
The Telephone Consumer Protection Act of 1991 makes it unlawful for any person to
use a computer or other electronic device, including fax machines, to send any message
unless such message clearly contains in a margin at the top or bottom of each
transmitted page or on the first page of the transmission, the date and time it is sent and
an identification of the business or other entity, or other individual sending the message
and the telephone number of the sending machine or such business, other entity, or
individual. (The telephone number provided may not be any number for which charges
exceed local or long-distance transmission charges.)
In order to program this information into your fax machine, refer to your
communications software user manual.
Regulatory Compliance Statements ix
Page 10
Canada
Unintentional Emitter per ICES-003
This digital apparatus does not exceed the Class B limits for radio noise emissions from
digital apparatus as set out in the radio interference regulations of Industry Canada.
Le présent appareil numérique n’émet pas de bruits radioélectriques dépassant les
limitesapplicables aux appareils numériques de Classe B prescrites dans le règlement
sur le brouillage radioélectrique édicté par Industrie Canada.
Intentional Emitter per RSS 210
Low power, Radio LAN type devices (radio frequency (RF) wireless communication
devices), operating in the 2.4 GHz Band, may be present (embedded) in your notebook
system. This section is only applicable if these devices are present. Refer to the system
label to verify the presence of wireless devices.
Wireless devices that may be in your system are only qualified for use in Canada if an
Industry Canada ID number is on the system label.
As a general guideline, a separation of 20 cm (8 inches) between the wireless device
and the body, for use of a wireless device near the body (this does not include
extremities) is typical. This device should be used more than 20 cm (8 inches) from the
body when wireless devices are on.
The power output of the wireless device (or devices), which may be embedded in your
notebook, is well below the RF exposure limits as set by Industry Canada.
This transmitter must not be collocated or operate in conjunction with any other
antenna or transmitter.
Operation of this device is subject to the following two conditions: (1) This device may
not cause harmful interference, and (2) this device must accept any interference
received, including interference that may cause undesired operation of the device.
x Users Manual
To prevent radio interference to licensed service, this device is intended to be
operated indoors and away from windows to provide maximum shielding.
Equipment (or its transmit antenna) that is installed outdoors is subject to
licensing.
Wireless devices are not user serviceable. Do not modify them in any way.
Modification to a wireless device will void the authorization to use it. Contact
manufacturer for service.
Page 11
Telecommunications per DOC notice (for products fitted with an IC-compliant modem)
The Industry Canada label identifies certified equipment. This certification means that
the equipment meets certain telecommunications network protective, operation, and
safety requirements. The Department does not guarantee the equipment will operate to
the users’ satisfaction.
Before installing this equipment, users should make sure that it is permissible to be
connected to the facilities of the local telecommunications company. The equipment
must also be installed using an acceptable method of connection. In some cases, the
inside wiring associated with a single-line individual service may be extended by
means of a certified connector assembly. The customer should be aware that
compliance with the above conditions may not prevent degradation of service in some
situations.
Repairs to certified equipment should be made by an authorized Canadian maintenance
facility designated by the supplier. Any repairs or alterations made by the user to this
equipment, or equipment malfunctions, may give the telecommunications company
cause to request the user to disconnect the equipment.
Users should make sure, for their own protection, that the electrical ground connections
of the power utility, telephone lines, and internal metallic water pipe system, if present,
are connected together. This precaution may be particularly important in rural areas.
To avoid electrical shock or equipment malfunction do not attempt to make
electrical ground connections by yourself. Contact the appropriate inspection
authority or an electrician, as appropriate.
The Ringer Equivalence Number (REN) assigned to each terminal device provides
an indication of the maximum number of terminals allowed to be connected to a
telephone interface. The termination on an interface may consist of any combination of
devices subject only to the requirement that the sum of the Ringer Equivalence
Numbers of all the devices does not exceed 5.
Regulatory Compliance Statements xi
Page 12

European Union
The following information is only applicable to systems labeled with the CE mark .
European Directives
This Information Technology Equipment has been tested and found to comply with the
following European directives:
• EMC Directive 89/336/EEC with amending directives 92/31/EEC & 93/68/
EEC as per
– EN 55022 Class B
– EN 61000-3-2
– EN 61000-3-3
– EN 55024
• Low Voltage Directive (Safety) 73/23/EEC as per EN 60950(A1/A2/A3/A4/
A11)
• Radio and Telecom Terminal Equipment Directive 199/5/EC as per
– CTR21 (if fitted with a modem device)
– ETS 300 328 (if fitted with a 2.4 GHz band embedded wireless device)
– ETS 301 489-1 (if fitted with a 2.4 GHz band embedded wireless device)
– ETS 301 489-17 (if fitted with a 2.4 GHz band embedded wireless device)
European Radio Approval Information (for products fitted with EU-approved radio devices)
This Product is a Notebook computer; low power, Radio LAN type devices (radio
frequency (RF) wireless communication devices), operating in the 2.4 GHz band, may
be present (embedded) in your notebook system which is intended for home or office
use. This section is only applicable if these devices are present. Refer to the system
label to verify the presence of wireless devices.
Wireless devices that may be in your system are only qualified for use in the European
Union or associated areas if a CE mark with a Notified Body Registration Number
and the Alert Symbol is on the system label.
The power output of the wireless device or devices that may be embedded in you
notebook is well below the RF exposure limits as set by the European Commission
through the R&TTE directive.
xii Users Manual
Page 13
European States qualified under wireless approvals:
EU
Austria, Belgium, Denmark, Finland, France (with frequency
restrictions),
Germany, Greece, Ireland, Italy, Luxembourg, The
Netherlands, Portugal, Spain, Sweden and the United Kingdom.
Accept EU
Iceland, Liechtenstein, Norway and Switzerland
European States with restrictions on use:
EU
In France, the frequency range is restricted to 2446.5-2483.5 MHz for
devices above 10 mW transmitting power such as wireless LAN.
Accept EU No limitations at this time.
European Telecommunication Information (for products fitted with EU-approved modems)
Marking by the symbol indicates compliance of this equipment to the Radio and
Telecom Terminal Equipment Directive 1999/5/EC. Such marking is indicative that
this equipment meets or exceeds the following technical standards:
CTR 21 – Attachment requirements for pan-European approval for connection to the
analogue Public Switched Telephone Networks (PSTNs) of TE (excluding TE
supporting voice telephony services) in which network addressing, if provided, is by
means of Dual Tone Multi-Frequency (DTMF) signaling.
Although this equipment can use either loop disconnect (pulse) or DTMF
(tone) signaling, only the performance of the DTMF signaling is subject to
regulatory requirements for correct operation. It is therefore strongly
recommended that the equipment is set to use DTMF signaling for access to
public or private emergency services. DTMF signaling also provides faster call
setup.
This equipment has been approved to Council Decision 98/482/EEC—“CTR 21” for
Pan-European single terminal connection to the Public Switched Telephone Network
(PSTN).
However, due to differences between the individual PSTNs provided in different
countries, the approval does not, of itself, give an unconditional assurance of
successful operation on every PSTN termination point. In the event of problems, you
should contact manufacturer Technical Support.
Regulatory Compliance Statements xiii
Page 14
Using Your Documentation
Congratulations on your purchase of a notebook computer with the Windows® XP
operating system. Whether you are new to using a portable computer or are an
experienced user, this user’s manual can help you get the most from your computer.
Manual Documentation Conventions
Information Icons
Three icons and their associated messages appear in this manual. The information
icons are placed before the step/information they apply to:
Warning:
Indicates the possibility of personal injury.
Caution:
Warns you of possible damage to equipment or data.
Note:
Informs you of special circumstances.
Technical Information:
Informs you of special requirements or limitations for use of item(s).
Keyboard Conventions
Keys that you need to press to perform certain functions are displayed in the manual in
brackets. For example:
<Ctrl> indicates the control key (Ctrl on the keyboard).
If you need to press two keys at the same time, the key names are shown joined by a
plus sign. For example:
<Fn+F8> means that you should press the Fn key and hold it and then press the F8
key.
Using Your Documentation 1
Page 15
CD-ROM Device Naming Convention
In many installation programs you will have to get a program from the CD-ROM
device. The program installation sequence assumes that the CD is drive d:\, however
this is not always the case. The name of the CD-ROM drive is the letter following the
letter assigned to your last HDD. For instance, if you have one HDD with two
partitions, the HDD is drives C: and D: and the CD-ROM drive is then drive E.
Touchpad Conventions
You may be asked to click or double-click on items on the display screen. As a general
note the touchpad actions act much in the same way as a wheel mouse, any differences
are explained fully.
The object that needs to be clicked upon will be displayed in Bold text or shown in a
small figure such as the “Start Button” shown on the right =>.
Table 1. Touchpad Click Conventions
Action Process
Click Depress the touchpad left button and release
Double-click Quickly click the left touchpad button two times
Windows Conventions:
Almost all “Windows” programs will display the name/function of a button or
icon if you place the touchpad pointer on the item you want information about.
Software User Documentation
Your computer is shipped from the factory with several software programs installed.
The software may include its own online or printed documentation. Refer to the
documentation or the Help options in the software for more information.
The figures and illustrations in this manual may not be identical to those on
your system.
General Icon Note:
Some of the Icons used in Windows XP may be placed on the taskbar by
selecting (ex: Place the volume icon in the taskbar) in the properties dialog
box.
2 Users Manual
Page 16

Getting Started
Introducing Your Computer
Front View
LCD Latch
LCD Panel
Power Button
Speakers
Wireless LAN/
Bluetooth Key (p17)
Keyboard (p11)
Touchpad (p14)
Touchpad Button
Status Lights (LED)
(p19)
Getting Started 3
Page 17

Right View
Left View
Modem port
Modem port
(p41)
Back View
LAN Port
(p42)
DC-In Port
USB Port
(2.0)
Fan Vent
1394 Port
(6 Pin)
Microphone
Infrared Port
Headphone
Jack
Jack
USB Port
(p62)
PCMCIA Slot
(2.0)
Monitor Port
Memory Card Slot
(p37)
(p38)
4 Users Manual
Security Lock Port (p84)
Page 18

Bottom View
Battery Latches
Wireless LAN module (optional) or Bluetooth module (optional) is intalled in
the mini PCI compartment.
Battery (p76)
Docking Connector
Memory and Mini
PCI Module
Compartment
Getting Started 5
Page 19

Introducing the Docking Station (Optional)
Docking station is an extension device that connects with the computer and allows you
to use additional functions including CD drive and various types of ports.
You cannot use the LAN port and monitor port on your computer when it is
connected to the docking station. Use the ports on the docking station instead.
Top View
Computer Connector
CD Drive Latch
Hook
Front View
CD Drive*
(p29)
* The type the CD drive installed on your computer varies according to your option. (p81)
Undock Button
Floppy Disk Drive
(p28)
FDD Latch
6 Users Manual
Page 20

Right View
Left View
Speaker Computer Release Lever
Computer Release Lever
Back View
Security Lock Port Lever
PS/2 Port
USB Ports
(1.1)
1394 Port
(4 Pin)
Serial Port
S/PDIF Jack
(p34)
Parallel Port
Speaker
Monitor Port
LAN port
Security Lock Port
(p84)
DC-In Port
Getting Started 7
Page 21

Docking station only supports USB 1.1.
To use the USB port (1.1) of the docking station
1. Start the computer and press <F2> to enter Setup.
2. Change USB 2.0 Controller value in Advanced menu to Disabled.
3. Press <F10> to save changes and exit setup.
Bottom View
Using Q10’s docking station
Q10’s docking station is compatible with Q20 model. You cannot use the
memory card slot when you are using Q10's docking station.
Woofer (Bass Speaker)
8 Users Manual
Page 22

Turning the Computer On and Off
To turn on the computer
1. Insert the battery and connect the AC adapter according to the Installation Guide.
2. Slide the LCD latch to the right and open the LCD panel.
3. Press the power button.
To turn off the computer
1. Click the start button ( ) on the taskbar.
2. Click Turn Off Computer.
3. Click Turn Off.
Getting Started 9
Page 23

If the computer is not turned off properly due to a system error, press
<Ctrl>+<Alt>+<Delete>. When [Windows Task Manager] dialog box appears,
click Shut Down > Turn Off to turn off the computer. Your unsaved work may
be lost/damaged.
If <Ctrl>+<Alt>+<Delete> keys do not operate either, press the power button
for more than 4 seconds to turn off the computer. Your unsaved work may be
lost/damaged. When you turn on the computer next time, it will perform a disk
checking process.
10 Users Manual
Page 24

Using the Keyboard
Your computer has an 82-key keyboard. By pressing designated key combinations, you
can have access to all the key functions of a full-sized keyboard.
Function & Special Purpose Keys
Function
Key
Embedded Numeric Keypad
Although the layout of the keys on your computer’s keyboard is different from
that on a desktop computer’s keyboard, the keyboard feels like a full-sized
keyboard when you use it.
Windows
Key
Cursor/Screen
Control Keys
The keys on the keyboard can be grouped into the following categories:
• Full-sized Alphanumeric typewriter keys are arranged like a standard
typewriter keyboard and are used for text entry. The Windows keys on either
side of the spacebar open Windows menus and perform other special functions.
• Function keys, when pressed together with the <Fn> key, enable special
functions.
• Cursor and Screen control keys move the cursor. They may perform other
functions, depending on your software.
To clean the computer keyboard, use slightly damp cotton swabs. Scrub the keys and
the surface around the keys.
Getting Started 11
Page 25
Do not allow liquid to drip into the keyboard or you may damage the keyboard.
Using the Numeric Keypad
Your keyboard includes a numeric keypad, which is a group of keys that you can set to
type numbers and mathematical symbols, such as the plus sign. A number or symbol
on the corner of each keypad key shows its numeric function.
Num Lock LED
Press <Fn+Num Lock> to turn on the embedded numeric keypad. The numeric
functions of the keypad are enabled and the Num Lock LED turns on. (See ”Reading
the Status Indicators” on page 19 for the location of the Num Lock LED.)
While the numeric functions are enabled, you can temporarily return a key to its normal
function by pressing the key and the <Fn> key. For example to type the letter m, press
<Fn+M>, this operation displays the letter m.
To turn the numeric keypad off, press <Fn+Num Lock> again. The Num Lock LED
turns off.
12 Users Manual
Page 26

Using Special Function Keys
The function key activates special functions when it is pressed in combination with
another keys.
<Fn> Key
Combinations
<F1/Prt Sc> Print Screen Saves an image of the current screen in clipboard.
<F2/Sys Rq> System Request In DOS mode, calls another operating system. It does not have specific
<F4/ > User Launches a user-defined program. Calculator program is launched as
<F5/ CRT/LCD> CRT/LCD Switches the display between the LCD and external display device
<F6/Mute> Mute Turns the audio output on and off.
<F7/ > Volume Down Decreases the audio volume.
<F8/ > Volume Up Increases the audio volume.
<F9/Rest> Rest Puts the computer into suspended mode. (p72)
<F10/ > Brightness Down Makes the LCD screen dimmer.
<F11/ > Brightness Up Makes the LCD screen brighter.
<F12/Scroll> Scroll Lock Scrolls the screen up and down while the cursor position does not
<Num Lock> Number Lock Enables the numeric keypad. (p12)
<Insert/
Pause/Brk>
</PgUp> Page Up Move to the above screen.
</PgDn> Page Down Move to the below screen.
Key Name Key Function
function in Windows, and executes pre-defined function in some
programs.
default. (p17)
when an external display device is connected. (p70)
change in some applications.
Pause/Break In DOS mode, pauses the scroll of the screen or exits a running
program.
When you press a function key combination, the system sound may be
temporarily muted.
Getting Started 13
Page 27
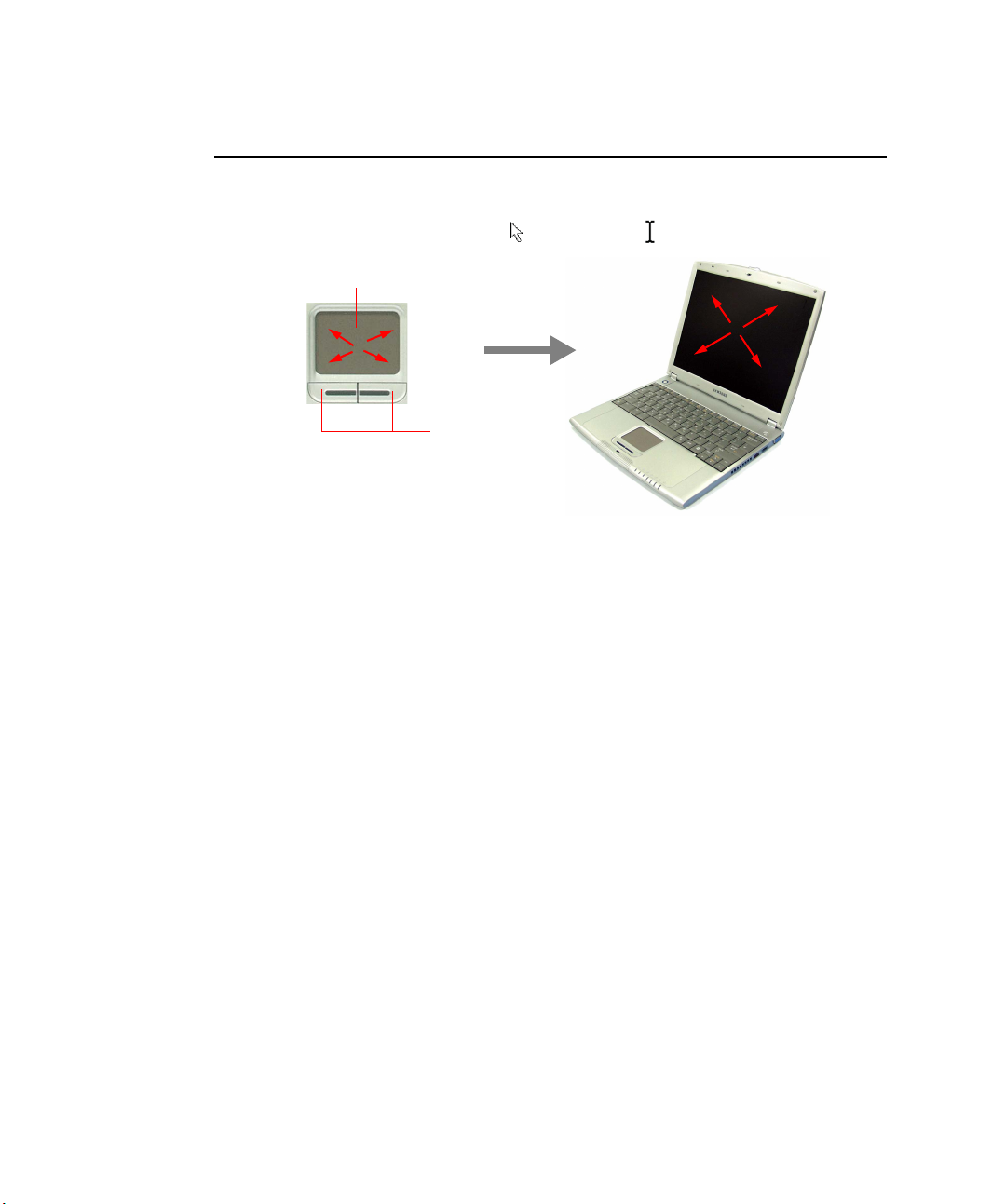
Using the Touchpad
In Windows, you always see a small graphical image on the screen that indicates the
location where you can take the next action. This image is called a pointer, and is
usually displayed in arrow shape ( ) or ‘I’ shape ( ).
Touchpad
Touchpad Buttons
The touchpad on your computer allows you to move the pointer on the LCD screen,
just like a mouse that is used with a desktop computer. The touchpad buttons allow you
to take actions with the pointer, such as selecting an item or executing a command.
14 Users Manual
Page 28
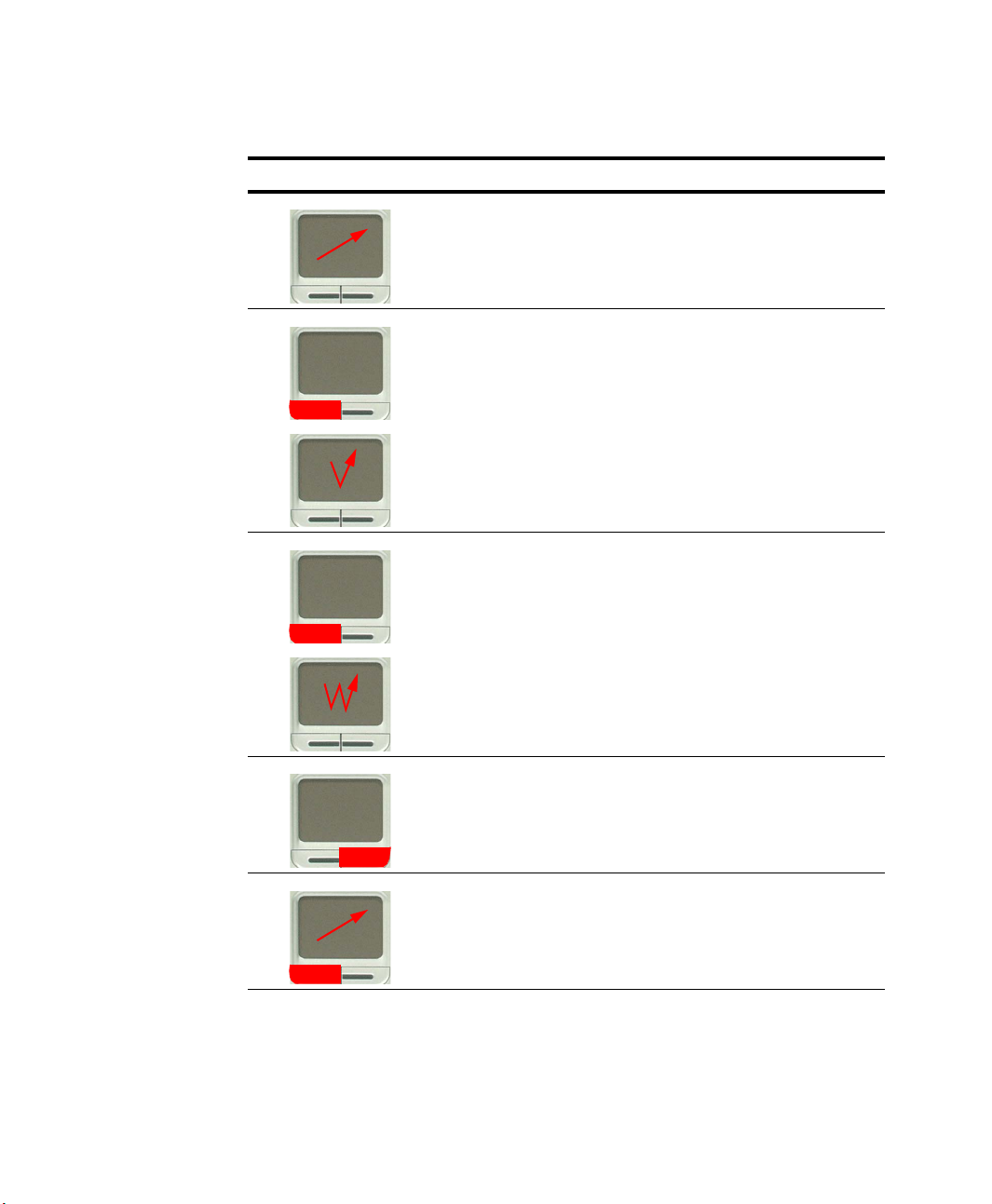
You can use various actions with your touchpad as described below.
d
Action Function Process
Move Move the pointer Place your finger on the touchpad
and slide your finger to a
destination.
Click Select an object, open a menu, or
Double-Click Launch a program or open a file Place the pointer over an object,
Right-Click Display a short cut menu Place the pointer over an object,
execute a button
Place the pointer over an object,
then press left touchpad button
once.
Or, place the pointer over an
object, then tap the touchpad once
with your finger.
then quickly press left touchpad
button twice.
Or, place the pointer over an
object, then quickly tap the
touchpad twice with your finger.
then press right touchpad button
once.
Drag
Move an object, or select an area
or multiple objects
Place the pointer over an object or
on a starting location.
While pressing the left touchpad
button, press down on the
touchpad and slide your finger to a
destination or ending location.
Getting Started 15
Page 29
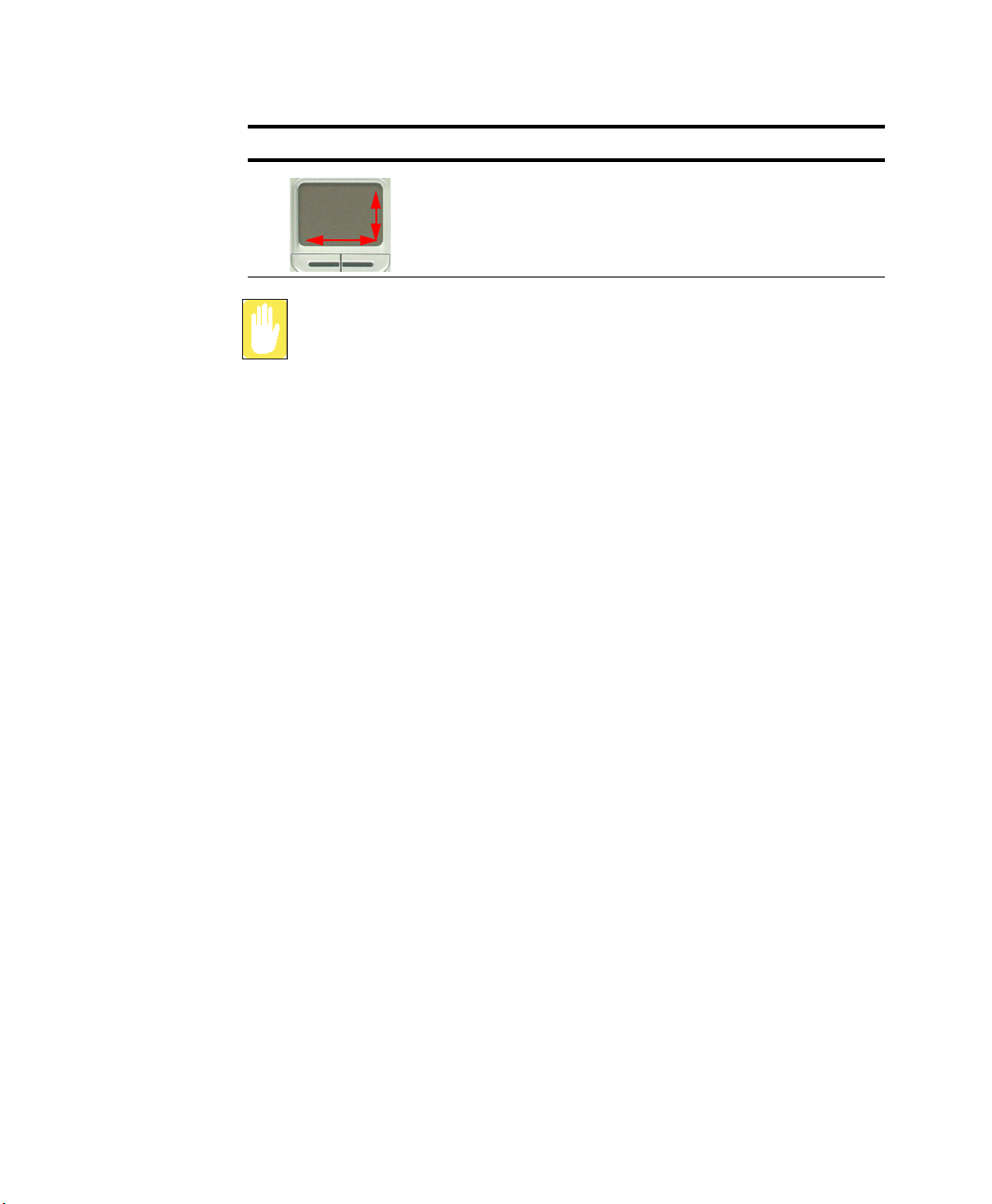
Action Function Process
Scroll Display upper/lower/left/right part
of the content within a window
(Applicable to certain programs
only)
Place your finger on the right edge
or bottom edge of the touchpad
and move vertically or horizontally.
Make sure to use your finger to move the pointer with the touchpad. Do not
use any sharpened tool because it may damage your touchpad.
16 Users Manual
Page 30
Hot Keys
Wireless LAN/Bluetooth Key<F4> Key
Wireless LAN/
Bluetooth Key
Turns on and off the wireless LAN/Bluetooth function for the models with
wireless LAN/Bluetooth function.
Launches Internet Explorer for the models without wireless LAN/Bluetooth
function.
What is Bluetooth?
Bluetooth is a worldwide standard for the wireless exchange of data between
two devices.
Using Wireless LAN/Bluetooth Key
Loading or unloading wireless LAN/Bluetooth driver takes about 5 seconds.
Therefore, if you turn wireless LAN/Bluetooth on/off using the wireless LAN/
Bluetooth key, the button does not work for 5 seconds. (For wireless LAN/
Bluetooth installed models)
Getting Started 17
Page 31

Changing the Hot Key Setting
You can change the configuration of the wireless LAN/Bluetooth key (when no
wireless LAN/Bluetooth module is installed on your computer) and <Fn>+<F4> key
so that another program is launched by pressing the key. Following example shows you
how to change the <Fn>+<F4> key setting.
1. Double-click the SENS Keyboard icon ( ) on the taskbar.
2. Click Browse in the User item.
Internet field is not displayed on a computer with wireless LAN/Bluetooth
module.
3. Select the desired program in [Open] dialog, and click Open. (Example: Paint)
4. Click OK on [Key Settings] dialog to save the changes.
18 Users Manual
Page 32

Reading the Status Indicators
Status indicators show the status of computer functions.
Num Lock Turns on when the numeric keypad is activated.
Caps Lock Turns on when all alphabet characters you type will be in upper case.
Scroll Lock Turns on when it is set to scroll the screen up and down while the cursor
Power Turned green - when the computer is turned on.
Hard disk drive Blinks when the hard disk drive is in operation.
Battery Turned green - when the battery is fully charged, or when the battery is not
position does not change in some applications.
Blinks - when the computer is in Standby mode.
installed.
Turns amber - when the battery is being charged.
Blinks - when the battery is not properly installed.
Wireless LAN/
Bluetooth
Turns on when Wireless LAN/Bluetooth function is enabled.
(This light does not operate for the models without wireless LAN/Bluetooth
function.)
Getting Started 19
Page 33

Adjusting LCD Brightness
There are 8 levels of LCD brightness (1: Dimmest ~ 8: Brightest).
Press <Fn>+<F10/ > or <Fn>+<F11/ > keys from the keyboard to adjust LCD
brightness. When changed, the current LCD brightness is displayed on the top left
corner of the LCD screen for a few seconds. Once the LCD brightness is changed, the
changed settings will be maintained after restarting the computer.
If the power source is changed
If the power source is changed (AC to battery or battery to AC) during
operation, the following default brightness settings will be restored.
- when operating on AC power: Level 6
- when operating on battery power: Level 4
To save the battery charge
When your computer is operating on battery power, adjusting the LCD
brightness level to dimmer diminishes the battery power consumption.
20 Users Manual
Bad pixels in the LCD
The limits of the LCD manufacturing technology allow a maximum of 10
abnormal or bad pixels, which do not affect system performance. This system
may have the same level of abnormal or bad pixels as any other company’s
products.
Maintenance Instructions
When cleaning the LCD panel, use only computer specific cleaners on a soft
cloth, and lightly wipe in one direction.
Page 34

Adjusting the Volume
To adjust using keyboard
Press <Fn>+<F7/ > or <Fn>+<F8/ > from the keyboard.
To adjust using volume adjustment program
Click the Volume icon( ) on the taskbar, and move the Volume slider to a desired
level.
For advanced volume control options, double-click the Volume icon( ), and adjust
the volume level in the volume control program.
To display the Volume icon on the taskbar
Click Start > Control Panel > Sound, Speech, and Audio Devices >
Sounds and Audio Devices. On the Volume tab, select “Place volume icon
in the taskbar” check box and click OK.
Getting Started 21
Page 35

Introducing Windows
Understanding the Desktop
The desktop is the working area on the computer. It consists of the large workspace and
a taskbar at the bottom.
Shortcut
Icons
Start Menu
Start Button
Recycle Bin
Language Bar
Start Button
Taskbar
Recycle Bin
Language Bar
22 Users Manual
Taskbar
Opens the Start menu.
Displays programs that are currently running. Frequently used
icons can be placed here.
Deleted files or folders are sent here.
Switches text input language.
System Tray withClock
Page 36

Understanding the Start Menu
The Start menu includes everything that is required to start Windows. From the Start
menu it is possible to run a program, open a file, assign system users with Control
Panel, receive support by clicking Help and Support, and search desired items from the
computer or Internet by clicking Search.
My Computer
Frequently used programs
All Programs
Start Button
Control Panel
Help and Support
My Computer
Control Panel
Help and
Support
Search
Run
Displays the contents of the hard disk, the CD-ROM drive, the network
drive, and floppy disks. It can also be used to search and open files and
folders.
Enables users to configure settings on the computer.
Provides on-line help, information on Windows and troubleshooting.
Enables users to search for information in files or the Internet.
Run programs or documents.
Introducing Windows 23
Page 37

Understanding a Window
A window is the basic component in working with the computer. The My Computer
window, which is a window for the computer's hard drive, will be used as an example
here to show the basic composition of a window.
Click Start > My Computer.
Folder Icon
Title Bar
Menu Bar
Close Button
Maximize Button
Minimize Button
Quick Task Window
Double-click the hard drive (local disk) to view internal folders and files stored in it. If
the contents do not appear, click Show the contents of this folder.
Folders
Files
Double-click
Shared
Documents or
Local Disk.
You can see files
and folders.
What is a drive?
A storage device in which files and folders are saved in, and read from.
What is a folder?
A folder is used to group and manage files systematically, and may include
files in sub-folders. It is similar to a bookshelf.
What is a file?
A file is a document or various kinds of material that is generated as a result
of program operation. It is also called data.
To view the entire structure of the drive
Click the Folder icon in the taskbar to view the entire structure. Click again to
return to the Quick Task Window.
24 Users Manual
Page 38

Help and Support Center
Help and Support Center provides references and troubleshooting information
regarding computer use.
Click Start > Help and Support.
Windows XP Tour
You can tour elementary functions provided by Windows XP.
Click Start > Tour Windows XP.
Or click Start > All Programs > Accessories > Tour Windows XP.
Click on the topics to find out about important functions of Windows XP.
Introducing Windows 25
Page 39

Using the Computer
Using the Docking Station (Optional)
To dock your computer
You can dock your computer anytime whether your computer is turned on or off.
You cannot use the LAN port and monitor port on your computer when it is
connected to the docking station. Disconnect the cables before docking your
computer.
1. Place the front part of the computer on the hooks of the docking station.
1
2
2. Press the back part of the computer down until the computer clicks into the
26 Users Manual
docking station fully.
Page 40

To undock your computer
To undock your computer with the power off
1. Turn off the computer.
2. Grab the two computer release levers on the docking station and pull them
outward.
3. Separate the computer from the docking station.
To undock your computer with the power on
1. Push the undock button on the docking station or click Start > Undock
Computer.
2. After docking release complete message is displayed on the screen, wait about 10
seconds, and separate the system.
If you push the undock button when the remaining battery charge is under
20%, the computer automatically goes into standby mode.
Always separate the computer from the docking station after pushing
the undock button on the docking station.
If you push the undock button and do not separate the computer, there will be
no sound output.
Using the Computer 27
Page 41

Using the Floppy Disk Drive
To insert a floppy disk
To use the floppy disk drive, install the appropriate driver in the FDD
installation CD provided with your floppy disk drive.
Push in a floppy disk with the label facing up until the eject button pops up.
Eject Button
To eject a floppy disk
1. Stop any process that accesses the floppy disk drive.
2. Push the eject button and the floppy disk pops out. Remove the floppy disk.
28 Users Manual
Page 42

Using the CD Drive
One of the following CD drives is installed in the docking station. You can purchase
other CD drives additionally, and replace the existing one. (Refer to ”Replacing the CD
Drive in the Docking Station” (p 81).)
CD-ROM drive Reads a CD.
CD-RW drive Reads and writes a CD.
DVD-ROM drive Reads a CD/DVD.
CD-RW/DVD-ROM Combo drive Reads a CD/DVD and writes a CD.
To insert a CD
1. Push the eject button on the CD drive.
2. When the tray slides out, place a CD onto the tray with the label facing up, and
push the CD down until it clicks.
Emergency Eject Hole
Eject Button
CD Access LED
3. Push the tray in gently until it clicks.
To eject a CD
1. Stop any process that accesses the CD drive and ensure the CD access LED is
turned off.
2. Press the eject button on right side of the CD drive.
3. When the tray slides out, remove the CD from the tray.
4. Push the tray in gently until it clicks.
Using the Computer 29
Page 43

If you remove the CD when the CD access LED is on, the disk and the data in
it may be damaged.
Emergency Eject Hole
To eject a CD when the CD drive is not working or the computer is turned off,
unfold a paper clip, and insert the unfolded end of the clip into the emergency
eject hole and press until the CD tray opens.
To clean a CD or DVD title
Clean the disc with a soft clean cloth by wiping from the center outwards.
To play a DVD
You have to install the DVD software provided on a separate CD to view a
DVD title.
To use the Windows Media Player
The Windows Media Player allows you to play audio and video files from the computer
or the Internet.
To launch the Windows Media Player, click Start > All Programs > Accessories >
Entertainment > Windows Media Player.
Features
Playback Control Area
30 Users Manual
Playlist
Page 44

Windows Media Player tour
For more information about using the Windows Media Player, run the
Windows Media Player and click Help > Help Topics > Windows Media
Player tour.
To play a video CD
If a video CD does not run automatically, follow these steps.
1. Insert a video CD into the CD drive.
2. When the CD drive window appears, double-click the MPEGAV folder.
3. Double-click the .dat file.
4. When the [Caution] dialog appears, click Open With.
5. Select “Select the program from a list” and click OK.
6. Select the Windows Media Player, and click OK. The video starts playing.
Above procedure applies only to the video CDs that has a .dat file as the
execution file. Playing procedure may be different according to video CDs.
Using the Computer 31
Page 45

To write data on a CD (Option)
If your computer has CD-RW functionality, you can copy data to a blank CD or create
an audio CD.
An additional CD writing program is supplied in an additional CD. For
information about use, refer to the supplied manual.
You cannot write to a CD that already has data in it.
1. Insert a blank CD into the CD drive.
2. On the [CD Drive] dialog, select Open Writable CD Folder and click OK. The
CD drive window appears.
3. Click Start > My Computer.
4. In My Computer window, select files and folders to copy, then drag and drop them
onto the CD drive window.
My Computer window
32 Users Manual
4. Drag and drop folders or
files to copy.
5. Click Write these files to CD.
CD drive window
Page 46

5. Click Write these files to CD in the CD drive window.
6. When the CD Writing Wizard appears, enter the CD label, and click Next. The
data begins copying.
7. When copying is completed, a ‘completed’ message appears and the CD drive
window opens automatically.
For more information on writing CDs
Click Start > Help and Support. Type “CD copy” in the search field, and click
the Search icon ( ).
For more information on creating an audio CD
Run the Windows Media Player program, click the Help > Help Topics. Click
Using Windows Media Player > Using CDs > Creating your own CDs > To
create your own CD.
Using the Computer 33
Page 47

Enjoying Home Theater (S/PDIF Port)
Your computer supports 5.1 channel output, which is a basic function for home theater
systems, and DVD drives. It provides 3D surrounding sound and vivid screen.
What is a home theater system?
Home theater system usually consists of a TV, DVD, 5.1 channel speaker, and
digital amp and provides a high-resolution screen (MPEG2) and 3D
surrounding sound (Dolby 5.1 or DTS). With a home theater system, you can
enjoy a vivid screen and sound in your home as if you are in a movie theater.
The following devices are required to enjoy a home theater system.
S/PDIF port on the docking station Optional
5.1 channel speaker system (amplifier, speakers, connection cables) Purchased separately
DVD drive and DVD playing program on the computer Optional
DVD title that supports 5.1 channel Purchased separately
To use home theater system, complete the following procedures:
• Step 1. Connect 5.1 channel speaker system to your computer.
• Step 2. Configure digital sound output on the computer.
• Step 3. Enable S/PDIF output on the DVD program.
34 Users Manual
Page 48

Step 1. Connect 5.1 channel speaker system to your computer
1. Connect amplifier to docking station’s S/PDIF jack.
2. Connect speakers to the amplifier. (Refer to speaker system’s manual.)
TV
Digital Amplifier
Front Left Speaker
Surround Left Speaker Surround Right Speaker
Computer
Center
Speaker
You need a TV that supports VGA port to display through a TV.
Sub
Woofer
Front Right Speaker
Step 2. Configure digital sound output on the computer
1. Click Start > Control Panel > Sounds, Speech and Audio Devices > Sounds
and Audio Devices.
2. In the Device volume field on the Volume tab, click Advanced.
3. In the [Master Volume] dialog, click Option > Advanced Controls. Then
Advanced button is displayed on the bottom of the dialog.
4. Click Advanced, select “1 SPDIF”, then click Close.
Using the Computer 35
Page 49

Step 3. Enable S/PDIF output on the DVD program
To use 5.1 channel speakers, you need to install the Power DVD program from the
DVD Installation CD provided with your computer, then change the settings as per the
following.
1. Run Power DVD program and click the Settings icon ( ).
2. On the Audio tab, set the Audio Output setting to “Use SPDIF” and click OK.
Now, you can enjoy home theater using DVD titles.
36 Users Manual
To control volume for your 5.1 channel speaker, use the control on the digital
amp. (Please refer to the speaker manual.)
Page 50

Using the PCMCIA Card Slot
Various different functions can be added by inserting PCMCIA cards into the system.
This system supports 16/32 bit, type I or II PCMCIA card types.
The PCMCIA card slot does not support a ZV card or a PCMCIA III card.
To insert a PCMCIA card
Before using the PCMCIA slot, remove the slot protector.
Push the eject button of the PCMCIA card slot once to pop it out. Push the
button again to eject the slot protector.
1. Insert a PCMCIA card into the PCMCIA card slot on the side of the computer.
Eject Button
2. Windows automatically installs the necessary driver for the card. If there is no
available driver found by Windows, you have to install the driver using a disk
supplied with the card.
To remove a PCMCIA card
1. Double-click Safely Removes Hardware icon ( ) on the taskbar.
2. On the [Safely Remove Hardware] dialog, select the appropriate PCMCIA card
and click Stop.
3. When [Stop a Hardware Device] dialog appears, click OK.
4. Click Close to close the [Safely Remove Hardware] dialog.
5. Push eject button of the PCMCIA card slot once, then the button pops out.
6. Push the button again to eject the PCMCIA card.
Using the Computer 37
Page 51

Using Memory Card Slot
Through the memory card slot, you can use memory cards such as memory stick, SD
(Secure Digital) memory card, and MMC (Multi Media Card). You can use the
memory cards as a removable disk, and use them to exchange data between your
computer and digital devices such as a digital camera.
Memory Stick
Restriction in Using Memory Stick
Your computer supports a maximum Memory Stick size of 128 MB. Please
check the amount of memory of Memory Stick in advance when you purchase
a Memory Stick. The MagicGate Memory Stick has a storage function and a
security function. This computer does not support the security function, only
the storage function.
SD (Secure Digital) Memory Card /
To insert and use a memory card
Before using the memory card slot, remove the slot protector.
Press the end of the slot protector softly to pop it outward, then remove it.
You should insert the memory card upside down.
Inserting wrong side up may cause damage in the memory card and the
computer.
MMC (Multi Media Card)
38 Users Manual
Page 52

1. Turn the memory card upside down and insert the card into the memory card slot.
2. Click Start > My Computer. The inserted memory card is displayed.
Memory Stick
SD (Secure Digital) Memory Card /
MMC (Multi Media Card)
3. You can write data to the memory card. If the memory card is not formatted yet,
format the memory card before use.
To remove a memory card
1. Press the end of the memory card softly to pop it outward.
2. Remove the memory card.
Do not remove a memory card for about 20 seconds after format, write, or
delete operation in Windows 2000, Me, or 98SE. Removing a memory card
immediately after the operations may cause damage to the memory card
caused by the inherent problem of the Windows operating system.
Using the Computer 39
Page 53

To format a memory card
You can use a memory card after the format operation. The procedures to format a
memory card are described below.
Since format operation deletes all data in the memory card, please make sure
that there is no important data in the memory card before formatting.
To protect the data in the memory card
Set the write protection tab of the Memory Stick or SD memory card to the
Lock position.
1. Click Start > My computer.
2. Press the right touchpad button on the memory card drive, and select Format from
the pop-up menu.
3. Click Start to start the format operation.
To use a memory card in both the computer and other digital device such as
digital camera, it is recommended to format the memory card in the digital
device. If you format the memory card in the computer, you may have to format
the memory card in other digital device again to use the memory card in the
digital device.
To format a Memory Stick in Windows 2000, Me, or 98SE, install the Memory
Stick Formatter software included in the system software CD.
40 Users Manual
Page 54

Connecting to the Internet
Connecting with a Modem
Before Start:
• Prepare a telephone line that is not digital.
• Contact an internet service provider (ISP) for instructions on how to connect to
and disconnect from the Internet.
1. Connect a telephone line to the computer’s modem port.
2. Connect to the Internet according to the instructions provided by your ISP.
If the Internet connection is not disconnected properly, additional telephone
charges may be imposed.
Connecting to the Internet 41
Page 55

Connecting Through a Wired LAN
1. Connect a LAN cable to the computer’s LAN port.
2. Click Start > Control Panel.
3. Click Network and Internet Connections in the [Control Panel] window.
4. Click Network Connections in the [Network and Internet Connections] window.
5. Right-click the Local Area Connection icon and click Properties.
42 Users Manual
Page 56

6. On the General tab, select “Internet Protocol(TCP/IP)” and click Properties.
7. To use DHCP:
On the General tab, select “Obtain an IP address automatically” and “Obtain DNS
server address automatically”. Click OK.
To use a static IP:
On the General tab, select “Use the following IP address” and fill in the IP
address, Subnet mask, Default gateway, Preferred DNS server, and Alternative
DNS server fields. Click OK.
To use both DHCP and static IP simultaneously:
On the Alternate Configuration tab, click User configured and fill in the fields.
Click OK.
Connecting to the Internet 43
Page 57

Connecting Through a Wireless LAN (Option)
A wireless network (Wireless LAN) environment is a network environment that
enables communication between multiple computers at home or a small-size office
through wireless LAN devices.
Using the wireless network connections between the systems, you can use normal
network functions such as sharing of files, folders and printers. Using computer-tocomputer network (ad hoc) connections, you can access the Internet through a
computer connected directly to the Internet even if your computer is not directly
connected to the Internet. For details, see “Using Network Services” on page 55.
The information provided in this section only applies to models equipped with
an optional wireless LAN device.
To turn off the Wireless LAN
If the wireless LAN is turned on, the computer consumes much power,
therefore shortening the amount of time you can run on battery. Therefore, if
you are not using the WLAN or if you are in an environment that does not
provided WLAN, you are recommended to turn off the WLAN by pushing the
WLAN/Bluetooth button (p17) on the computer.
Wireless network connections can be classified into two categories.
1) Access Point
You can connect to an AP to use the network. This is possible only in an environment
equipped with an AP. For details, see “Connecting to an Access Point (AP)” on page
45.
2) Computer-to-computer (ad hoc)
This is also called a peer-to-peer or ad hoc network.
In computer-to-computer wireless networks, you can wirelessly connect 2 or more
computers that have wireless LAN modules. Using computer-to-computer wireless
44 Users Manual
What is an Access Point (AP)?
An AP is a network device that bridges wired and wireless LANs, and
corresponds to a wireless hub in a wired network. You can connect multiple
wireless LAN installed computers to an AP.
Page 58

networks, you can access the Internet through a computer that is connected to the
Internet even if your computer is not directly connected to the Internet. For details, see
“Connecting to computer-to-computer networks (peer-to-peer or ad hoc)” on page 46.
Connecting to an Access Point (AP)
This section describes how to connect to an AP. You can use the network when you are
connected to an AP.
In this section, the configuration procedures are described for Windows XP
installed computers. For information on the configuration procedures for other
operating systems, see “Using Wireless Networks in Other Operating
Systems” on page 51. Please ask your network administrator about detailed
configuration information such as the network key (encryption key).
1. Right-click on the Wireless Network Connection ( ) icon on the taskbar, and
select View Available Wireless Networks.
2. Select your desired AP (e.g. Test) to connect, and enter the encryption key for the
AP in the Network key field, and click Connect.
Connecting to the Internet 45
Page 59

If the network key is not configured for the desired AP, select 'Allow me to
connect to the selected wireless network, even though it is not secure’.
Now you are connected to the AP, and you can access the network.
Checking the connection status
Move the mouse pointer over the Wireless Network Connection ( ) icon on
the taskbar, and the connection status is displayed.
Connecting to computer-to-computer networks (peer-to-peer or
ad hoc)
In computer-to-computer wireless networks, you can wirelessly connect 2 or more
computers that have wireless LAN modules.
You can connect by completing the following steps:
• Step 1. Set up a computer-to-computer network on a computer.
• Step 2. Connect to the configured computer from other computers.
46 Users Manual
In this section, the configuration procedures are described for Windows XP
installed computers. For information on the configuration procedures for other
operating systems, see “Using Wireless Networks in Other Operating
Systems” on page 51.
Page 60

Step 1. Setting up a computer-to-computer network
1. Right-click on the Wireless Network Connection ( ) icon on the taskbar, and
select View Available Wireless Networks.
2. Click Advanced.
3. On the Wireless Network tab, click Advanced.
4. Clear 'Automatically connect to non-default network' check box, if it is selected.
Select 'Computer-to-computer (ad hoc) networks only', and click Close.
5. In the Wireless Networks tab, click Add.
Connecting to the Internet 47
Page 61

6. Enter the network name (e.g. samsung), and unselect 'The key is provided for me
automatically'. Enter the encryption key in the Network key field, and click OK.
To prevent a network connection from an unauthorized user, it would be better
to configure a network key (encryption key). A network key consists of 5 or 13
alphanumeric characters (e.g. magic), or of 10 or 26 hexadecimal numbers (a
hexadecimal number is represented by numbers '0' to '9' or letters 'a' to 'f').
48 Users Manual
Page 62
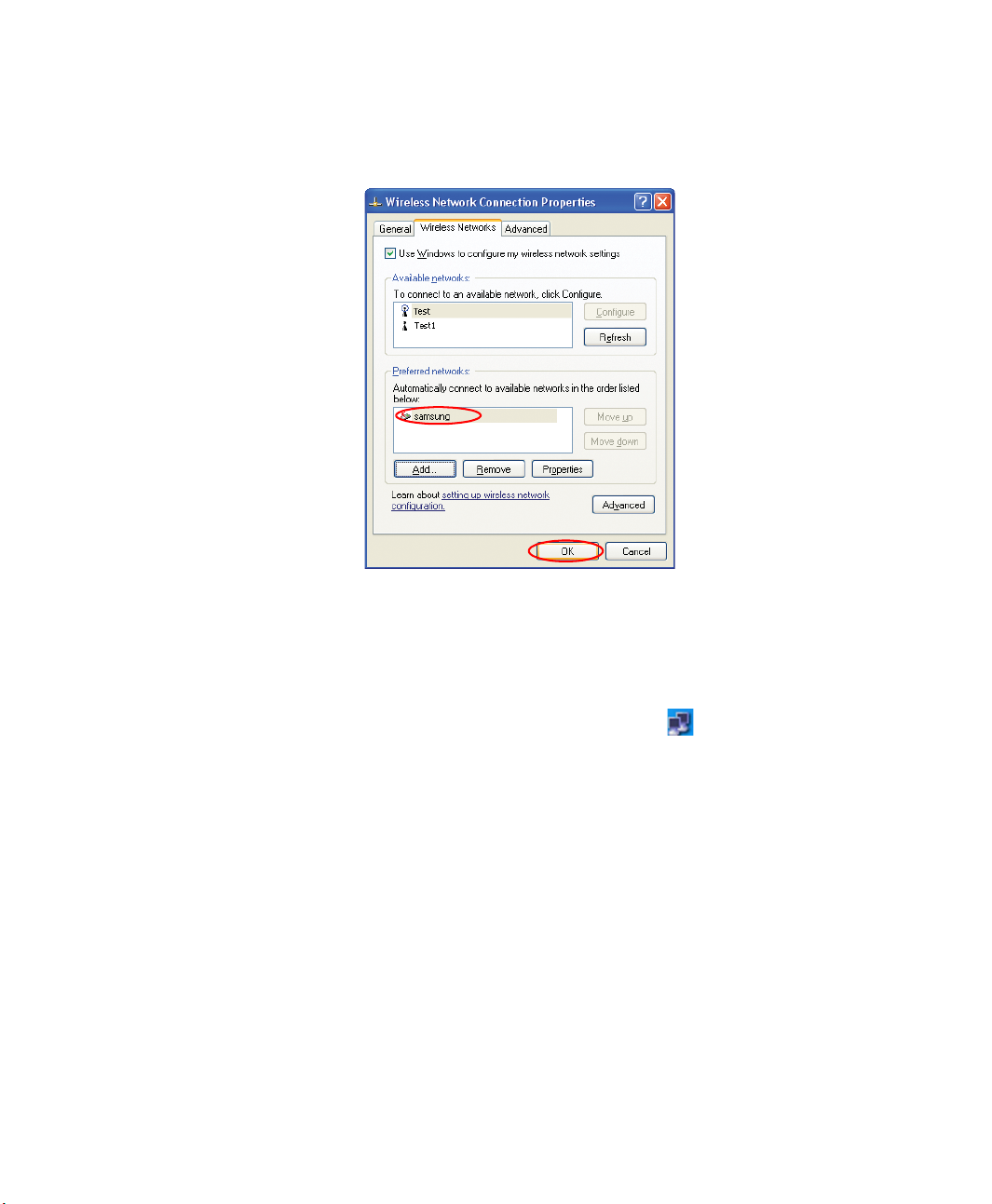
7. Check that the configured network name (e.g. samsung) is in the ’Preferred
networks’ item, and click OK.
Now your wireless network setup has been completed.
Step 2. Connecting to the configured computer
1. Right-click on the Wireless Network Connection ( ) icon on the taskbar, and
select View Available Wireless Networks.
2. Select the wireless network name (e.g. samsung) specified in ”Connecting to
computer-to-computer networks (peer-to-peer or ad hoc)” on page 46, enter the
encryption key in the Network key field, and then click Connect.
Connecting to the Internet 49
Page 63

If the network key is not configured in ”Connecting to computer-to-computer
networks (peer-to-peer or ad hoc)” on page 46, select 'Allow me to connect to
the selected wireless network, even though it is not secure'.
The two computers are connected and are able to communicate with each other. When
the computers are connected, the 'Wireless Network Connection' message is displayed
for a short time over the Wireless Network Connection icon of the two computers.
Checking the connection status
Move the mouse pointer over the Wireless Network Connection ( ) icon on
the taskbar, and the connection status is displayed.
50 Users Manual
Page 64

Using Wireless Networks in Other Operating Systems
In a operating system other than Windows XP, you have to install additional wireless
LAN configuration program, and configure wireless network settings.
To use wireless network connection, complete the following procedures.
• Step1. Install the wireless LAN configuration program (PROSet).
• Step2. Configure wireless network settings through the wireless LAN
configuration program.
Step 1. Installing the wireless LAN configuration program (PROSet)
You can install the wireless LAN client administrator program following the
instruction displayed automatically when you insert the system software CD. Insert the
system software CD into the CD-ROM drive, and install the wireless LAN
configuration program.
To disable the 'Intel Configuration Service' window afterward
After installing the wireless LAN configuration program, select "Do not show
this again." check box, then click Close.
Step 2. Using the wireless LAN configuration program (PROSet)
Double-click the wireless LAN program ( ) icon on the taskbar.
(Or, click Start > All Programs > Intel Network Adapters > Intel(R) PROSet.)
In some languages, some buttons on the window may not be displayed. If this
is the case, resize the window to use the program.
Configure wireless network settings in PROSet following the procedures below.
Connecting to the Internet 51
Page 65

To connect to an Access Point:
To connect to an access point or existing computer-to-computer (Ad Hoc) network,
refer to the following procedures. (To create a new computer-to-computer network,
refer to the following "To create computer-to-computer (Ad Hoc) network" section.)
1. Click Scan in the Networks tab.
2. Select the name of desired access point or computer-to-computer network to
connect from the searched available networks list, and click Connect.
If your desired network does not appear, click Refresh.
An access point is represented by the ( ) icon, and a computer-to-computer
network is represented by the ( ) icon. An ( ) icon is displayed in front of
an access point or a computer-to-computer network with configured security
settings.
3. Select "Yes, create a profile for this Network.", and click OK.
4. Enter Profile Name and click Next.
5. Enter the network authentication, data encryption (WEP), key index, and
password configured for the target access point or computer-to-computer network
in the Security Settings window, and click Finish.
52 Users Manual
The network authentication, data encryption (WEP), key index, and password
of a access point are configured in the access point management program.
For information on the security information, check the security settings of the
access point or ask your wireless network administrator.
To connect to an existing computer-to-computer (Ad Hoc) network, enter the
password configured when creating the computer-to-computer network for the
first time. You do not need to enter network authentication or key index.
Security Settings
- Network authentication: Network authentication has two options of Open
System and Shared Key. If you select Open, no authentication procedure is
used. If you select Shared, the WEP key is used as the authentication
procedure. The default option setting is Open.
Page 66

- Data encryption (WEP): IEEE 802.11 WEP (Wired Equivalent Privacy)
standard has two security levels of 64-bit key (40-bit key for some cases) and
128-bit key.
- Key index: Select the current encryption key index used by the access point
out of 1 to 4.
- To use pass phrase: Click Use pass phrase to activate, and enter 5 (for 64bit) or 13 (for 128-bit) alphanumeric characters (represented by 0-9, a-z, or AZ).
- To use WEP key: Click Use WEP keys to activate, and enter a hexadecimal
number (represented by 0-9 and A-F) of 10 (for 64-bit) or 26 (for 128-bit) digits
in the WEP key field.
When a wireless connection to an access point is established, the connection icon
( ) appears in front of the name of the connected profile.
To create a computer-to-computer (Ad Hoc) network:
To create a new computer-to-computer (Ad Hoc) network or to connect to a hidden
access point (Stealth/Closed Mode), refer to the following procedures.
A hidden access point is an access point that exists, but is configured not to
be detected by the scan operation to prevent access attempts from
unauthorized users.
1. Click Add in the Networks tab.
2. Enter Profile Name and Network name (SSID), select Operating Mode, then
click Next.
What is a network name (SSID)?
Network name (SSID) is a name that a wireless adapter uses for identifying
connection. Enter the name of computer-to-computer network to create (e.g.,
P2P) or the name of access point to connect. The network name identifies
cases. (capital and lowercase) For the name of access point, check the
settings of the access point, or ask your wireless network administrator.
Operating Mode:
- Infrastructure - Connect to an Access Point - Select to connect to an
access point.
- Ad hoc - Connect directly to other computers - Select to create a
computer-to-computer (Ad Hoc) network.
Connecting to the Internet 53
Page 67

3. Configure password setting to be used for computer-to-computer network
connection in the Security Settings window.
To connect to an access point, enter the network authentication, data encryption
(WEP), key index, and password configured in the access point.
It is recommended to configure data encryption for security purposes when
creating a computer-to-computer network connection profile. For more
information on security settings refer to the security settings in Connecting to
an AP or Help.
When you are creating a computer-to-computer network connection profile,
the network authentication setting is disabled.
4. When a profile creation is completed, the new created profile appears in the
profiles list in the Networks tab. Select corresponding profile, and click Connect
to connect to the created profile.
When a wireless connection to the created profile is established, the connection
icon ( ) appears in front of the name of the connected profile.
54 Users Manual
Page 68

Using Network Services
While the computer is connected to the network, you can use network services to share
files, folders, and printers. Using computer-to-computer wireless networks, you can
access the Internet through a computer that is connected to the Internet even if your
computer is not directly connected to the Internet.
Network services are provided for the computers that are connected to the
network through wired or wireless network connections. For details, see
“Connecting Through a Wired LAN” on page 42 and see “Connecting Through
a Wireless LAN (Option)” on page 44.
Sharing files or folders
This section describes how to share files and folders between computers connected to
the network.
To share files, complete the following procedures:
• Step 1. Configuring the sharing of files and folders on a computer.
• Step 2. Accessing shared files and folders from another computer.
When a file or folder is shared, anyone connected to the network can open and
delete the shared file or folder.
Configure a file sharing network only when the network is secure, and do not
share important data.
Connecting to the Internet 55
Page 69

Step 1. Configuring Sharing
1. Right-click the target file or folder to share in My Computer, and select Sharing
and Security.
2. Click 'IF you understand the security risks but want to share files without running
the wizard, click here'.
It has the same security effect as that of the 'Network Setup Wizard'.
This screen does not appear if Internet Sharing Network Wizard has been
installed in the computer-to-computer wireless network environment.
3. Select 'Just enable file sharing', and click OK.
4. In the 'Network sharing and security' field, select 'Share this folder on the network',
The file and folder sharing configuration has been completed.
56 Users Manual
enter the share name, and click OK.
Be cautious when selecting 'Allow network users to change my files' since
other network users can change the files in the shared folder.
Page 70

Step 2. Using Shared Files or Folders
This section describes how to access shared files or folders if your computer is a
member of the same workgroup.
1. Click Start > My Computer. Under Other Places, click My Network Places in
your computer.
2. Click 'View workgroup computers', and click the desired computer to access the
shared file.
If your computer is a member of another workgroup:
1. Click Other Places > Microsoft Windows Network.
2. Click the desired workgroup.
3. Click the desired computer to display the shared files or folders.
Sharing Printers
This section describes how to share a printer between computers connected to a
network.
To share a printer, complete the following procedures:
• Step 1. Configure printer sharing in the computer connected to the printer.
• Step 2. Add and use the shared printer in other computers on the network.
Connecting to the Internet 57
Page 71

Step 1. Configuring Printer Sharing
1. From the computer connected to the printer, click Start > Printers and Faxes.
2. Right-click the printer you want to share, and click Sharing.
3. Select 'Share this printer', enter a share name for the shared printer, and click OK.
4. In the Printers and Faxes window, you will find the printer icon has been changed
to another icon on a hand.
Step 2. Adding and Using a Shared Printer.
1. From a different computer that wants to use the shared printer, click Start >
2. Click Add a printer.
3. In the Add Printer Wizard, click Next.
4. Select 'A network printer, or a printer attached to another computer', and click
58 Users Manual
Printers and Faxes.
Next.
Page 72

5. Select 'Browse for a printer', and click Next.
6. Select the workgroup or computer, select the desired printer, and click Next.
If you cannot find the desired printer, try again after a while.
7. Read the warning about a shared printer, and click Yes to install the shared printer.
8. Select Yes for 'Do you want to use this printer as a default printer?', and click Next.
9. Click Finish.
10. When the printer sharing configuration has been completed, the shared printer
appears in the Printers and Faxes window.
Now you can print using the shared printer even if your computer is not directly
connected to a printer.
Connecting to the Internet 59
Page 73

Sharing an Internet Connection
Using computer-to-computer (peer-to-peer) network connections, you can access the
Internet through a computer connected to the Internet even if your computer is not
directly connected to the Internet.
To share an Internet connection, the computers should be connected to a
computer-to-computer (peer-to-peer) wireless network. For details, see
“Connecting to computer-to-computer networks (peer-to-peer or ad hoc)” on
page 46.
Also, one of the computers has to be connected to the Internet (external
network).
The configuration procedure to share an Internet connection are described for
Windows XP installed computers.
To share an Internet connection, complete the following procedures:
• Step 1. Configuring a Internet connection sharing from the computer connected
to the Internet.
• Step 2. After completing the shared Internet connection configuration, check
that the other computers can access the Internet through the shared Internet
connection.
Step 1. Configuring Internet Sharing.
Configuring a shared Internet connection on the computer connected to the Internet.
1. Click Start > Control Panel > Network and Internet Connections > Network
2. Right-click on the device connected to the Internet, the external network, and
60 Users Manual
Connections.
select Properties.
Page 74

If the computer is connected to the Internet through a wired LAN, select 'Local
Area Connection'.
3. On the Advanced tab, select 'Allow other network users to connect through this
computer's Internet connection', and click OK.
Step 2. Checking the Shared Internet Connection.
When the Internet connection sharing configuration has been completed, the network
icon in the Network Connections window is displayed as follows:
Click Start > Control Panel > Network and Internet Connections > Network
Connections.
– A computer connected to the Internet.
– A computer sharing the remote Internet connection (other computer).
If the icon does not appear after a long time, restart the computer.
Computers on the network can access the Internet through the shared Internet
connection only when the computer connected to the Internet is turned on.
Connecting to the Internet 61
Page 75

Infrared Communication (Optional)
Your computer may have infrared port. Using the infrared port, you can transfer data
to computer, printer, camera and other devices through infrared communication.
Restrictions in Use
For infrared communication, the devices should have infrared communication
capability, and should be located within 1 m of each other. In addition, there
should be no obstacle between the infrared ports of the target devices.
To establish infrared connection
The procedures to communicate with another computer through infrared port are
described below.
1. Locate the target computers so that the infrared ports face each other.
2. When infrared communication is available, a beep sounds and Send files to
another computer icon ( ) appears on the desktop.
You can now transfer data through infrared communication.
To transmit data through infrared communication
The procedures to transmit files to another computer are described below.
1. Connect the target computers through infrared communication.
2. Drag a file over the Send files to another computer icon in one of the computer.
3. [Wireless Link] dialog appears on the other computer screen. Click Yes.
4. When the file transmission is completed, click Close to close the [Receiving Files]
62 Users Manual
dialog.
To change infrared communication configuration
To change the folder to save the received files, or to receive images from a
digital camera, click Start > Control Panel > Printers and Other Hardware
> Wireless Link and change the configuration.
Page 76

If you cannot use infrared communication
1. Check BIOS setup.
a. Start the computer, and press <F2> to enter System Setup.
b. Select I/O Device Configuration in the Advanced menu, and press
<Enter>.
c. Select Infrared, and set the item to Enabled by pressing <F5> or <F6>.
d. Save the configuration, and exit the Setup.
2. Check Windows configuration.
a. Click Start > Control Panel > Performance and Management > System
> Hardware tab > Device Manager.
b. Double-click the “Infrared device”, and then double-click “IrDA Fast Infrared
Port” item.
c. On the Advanced tab, select “Infrared Transceiver A” in the Properties field,
then select “Vishay TFDS-6500” in the Value field.
d. Click OK.
Connecting to the Internet 63
Page 77

Customizing Your Computer
Using System Setup
The System Setup (BIOS) program enables you to configure your computer hardware
and set security and power-savings options. The settings you choose are stored in
battery-maintained CMOS memory that saves the information even when the
computer’s power is turned off. When your computer is turned back on, it is configured
with the values found in this memory.
Run System Setup if you get a message prompting you to run the program. You may
also want to run System Setup, particularly the first time you use your computer, to set
the time and date, use security or power-management features, or alter the settings of
other features.
BIOS Caution:
If you are not familiar with BIOS setup and what the parameters mean, seek
help from a person who is knowledgeable. Incorrect settings may cause your
system to malfunction or "Crash”.
Your computer’s version of System Setup may not include all the fields listed
here or may include additional fields. Field names and order of appearance
can vary according to the version of the BIOS (basic input/output system) on
your computer.
64 Users Manual
Page 78

Starting System Setup
To start System Setup, turn on your computer and then press <F2> and hold until the
System Setup screen appears.
Table 2. System Setup Menus
Menu Function
Main Changes the basic system.
Advanced Configures advanced features on your computer.
Security Enables security features, including passwords.
Boot Specifies the order of boot devices and configures boot
Exit Specifies how to exit System Setup.
To open the menu you need to use, use the left or right arrow keys to select the menu
name.
Navigation Key Function
<F1> Displays the General Help window.
<Esc> Exits the current menu.
<> or <> Moves the cursor up and down between fields.
<> or <> Selects different menus. Pressing the <Esc>key at the Main
<F5> Scrolls backwards through the options for the highlighted field.
<F6> Scrolls forward through the options for the highlighted field.
<F9> Sets the parameters for the current menu to their default values.
<F10> Save changes and exit system setup.
<Enter> Executes commands or opens a submenu.
features.
Table 3. System Setup Navigation Keys
menu brings you to the Exit menu.
Customizing Your Computer 65
Page 79

Changing Booting Priority
You can select the booting priority among the devices such as the hard drive, CD-ROM
drive, etc. The following example describes how to configure the hard drive as the first
booting device when the CD-ROM drive is configured as the first booting device by
default.
1. Select the Boot menu in System Setup.
2. Use <> key to move to the Boot Device Priority, and press <Enter>.
3. Use <> key to move to the Hard Drive item, and press <F6> until it is at the
very top.
4. Press <F10> to save the changed configuration, and exit System Setup.
Now you can boot the system with the hard disk drive as the first booting device.
66 Users Manual
Page 80

Configuring the Password
Setting the Supervisor Password
By configuring a supervisor password, you can restrict system access to authorized
users only.
1. Select the Security menu in the System Setup. To enter System Setup, see “Starting
System Setup” on page 65.
2. On the Set Supervisor Password item, press <Enter>.
3. Enter a password, press <Enter>, re-enter the password for confirmation, and
press <Enter> again.
4. When a message confirming the password configuration appears in the [Setup
Notice] window, press <Enter>.
Setting the User Password
You can configure user passwords so that other users can use the system.
Before configuring a user password, a supervisor password must have been
configured.
Users can start the system with their user password, but cannot enter into the
System Setup.
Deactivating the supervisor password also deactivates the user password.
On the Set User Password item, press <Enter>, and complete step 3-4 of "Setting the
Supervisor Password".
Activating the Booting Password
Before activating the booting password, the supervisor password must have
been configured.
Set the Password on boot option to [Enabled].
From now on, system booting will not proceed without the password.
Customizing Your Computer 67
Page 81

Activating the Hard Disk Drive Password
Activating the hard disk drive password prevents the currently installed hard disk drive
from being used in other systems.
Before activating the hard disk drive password, the supervisor password must
have been configured.
On the Set HDD 0 Password item, press <Enter>, and complete step 3-4 of "Setting
the Supervisor Password".
Deactivating the Password
1. On the password to delete, press <Enter>. (e.g. supervisor password)
2. Enter the current configured password, and press <Enter>.
3. Leave the 'Enter New Password' and 'Confirm New Password' field empty, and
press <Enter> to deactivate the password.
68 Users Manual
Page 82

Configuring Resolution and Color Depth
Screen resolution is the number of pixels displayed on the screen. High resolution
makes the overall screen area large, although individual items appear small. Color
quality is determined by the number of bits used to represent a pixel on the screen. High
color quality displays more number of colours on your screen.
1. Select Start > Control Panel > Appearance and Themes > Change the screen
resolution.
2. Make changes on the Settings tab of the [Display Properties] dialog box.
To change your screen
resolution, move the slider
to select an appropriate
resolution.
3. When you have completed configuration, click Apply.
To change the number of
colors displayed on a
monitor, select an
appropriate colour quality.
It is recommended setting the resolution to 1024x768, and the number of
colours to Highest (32bit).
Customizing Your Computer 69
Page 83

Using External Display Devices
Using external display devices such as monitor or projector, you can view the screen
images alternatively or simultaneously. You can extend the screen into two display
devices to use larger workspace.
Using external display devices would be especially useful when you are giving
presentations or watching a video file.
1. Connect a monitor or a projector to the monitor port of the computer or the docking
station.
2. Right-click on the desktop, and select Graphics Options > Graphics Properties.
3. On the Devices tab, select your desired display device, and click OK. (The
displayed device list is determined by the currently connected devices.)
70 Users Manual
Monitor Displays on an external device such as monitor or a projector.
Notebook Displays on the notebook LCD only.
Intel(R) Dual
Display Clone
Extended
Desktop
Displays the same screen on the notebook LCD, and an external device such as
monitor or projector.
Extends the screen into the notebook LCD and an external device such as monitor or
projector to use a 2 times larger workerspace.
Page 84

To switch display devices using shortcut key
You can switch display devices easily by pressing <Fn>+<F5 / LCD/CRT>
shortcut key.
Provided that the CRT monitor is connected, the display order will be LCD >
CRT > LCD+CRT whenever the <Fn>+<F5 / LCD/CRT> key is pressed.
You cannot use the <Fn>+<F5 / LCD/CRT> shortcut key in the full screen
mode DOS prompt.
To change display devices easily
Right-click on the desktop, and select Graphics Options > Output To to change
the current display device easily.
To change the screen resolution and color quality
If the screen does not appear clearly, please try to change the screen
resolution and colour quality. In the figure of step 3, select a device, and
configure the color, screen area, and refresh rate.
Customizing Your Computer 71
Page 85

System Management
Using Power Management Options
Your computer includes Power Management options that can help the battery charge
last longer and extend the life of the battery. Power-management options will slow
down or shut off system components when the components are not being used.
Power management may slow down system performance. Your computer runs fastest
with the power cord attached, when power management is disabled.
In the next sections, basic and advanced methods of power management will be
discussed.
Basic Power Management Schemes
This section discusses the basic schemes of power management when the computer is
operating on battery power or using AC power.
Standby vs. Hibernation
Hibernation is a state where the contents of memory are stored in a special file
on the hard disk, and Standby simply keeps a small holding current through
the memory to keep the data. You are more likely to sustain loss of data in
Standby mode so it is recommended to save all open files before entering
Standby.
To enter the power management window complete the following:
1. Click Start > Control Panel > Performance and Maintenance.
2. Click icon to display the Power Options Properties window.
72 Users Manual
Changing Devices:
Do not change PC Cards while in standby or hibernate modes.
Page 86

3. Click the Power Schemes tab to display the basic power management options.
Power Schemes Tab
4. Select the time that you wish each of the following actions to occur in Battery and
AC power mode.
• Turn off monitor
• Turn off hard disks
• System standby
• System hibernates
Turning off the monitor and HDDs will save a substantial amount of battery power,
therefore when in battery only mode select the shortest time practical.
a Hibernate Mode (Power Management or Manual Method)
When hibernation is used, your computer turns off and when you power up again,
everything is restored exactly as you left it—including programs and documents
you may not have saved or closed. Everything in memory gets saved to the HDD,
and the monitor and hard disk get turned off.
System Management 73
Page 87

If You Reinstall Windows:
You should re-establish hibernate in power options by opening Power
Options Properties window and click on the Hibernate tab then click
“Enable Hibernation”.
Hibernate Tab
Frequent Interruptions:
If you experience frequent interruptions, you might also consider putting your
computer into automatic hibernation after a specified number of minutes using
the power management options.
a Standby Mode (Power Management or Manual Method)
Standby is used mainly for conserving battery power in your notebook computer. It
also gives you the benefit of getting right back to your work without waiting for the
computer to restart. Standby turns off your monitor and hard disks, placing your entire
system in a low-power state. When you return to your computer, restores your desktop
exactly as you left it. It is recommended that you do not enter standby mode with less
than 20% battery power.
5. Click OK to set your power management options and close the window.
74 Users Manual
Rest Key:
The manual <Fn+F9/Rest> key combination will not activate Standby or
Hibernate modes while you are playing a multimedia program or have an
active USB device connected.
Page 88

Advanced Power Management Schemes
This section discusses the advanced power management schemes. There are two
buttons that you can use to manually conserve power.
To enter the power management window complete the following:
1. Click Start > Control Panel > Performance and Maintenance.
2. Click icon to display the Power Options Properties window.
3. Click the Advanced tab to display the advanced power management options.
Advanced Tab
Power & Sleep Button
Programming Windows
4. Select the mode (Do nothing/Ask me what to do/Standby/Hibernate/Shut
down) assigned to the Power button and/or Rest <F9> key. Also select the action
(Do nothing/Standby/Hibernate) associated with closing the computer lid.
The “Rest” key is assigned to the <Fn+F9/Rest> key combination. See ”Basic
Power Management Schemes” on page 72 for a better understanding of
Standby and Hibernate modes.
5. Click OK to set your power management options and close the window.
You can return to normal operation after you have used one of the “Power
Management” buttons by quickly pushing and releasing the Power button.
System Management 75
Page 89

Using the Battery
Your computer uses a smart rechargeable Lithium-ion (Li-ion) battery pack for power
when the AC adapter is not attached to an electrical outlet. The smart battery gives a
accurate measurement of the current battery capacity which helps extend operating
time by enabling effective power management in operating systems that take
advantage of the accurate information supplied by the battery.
Charging the Battery
Your computer’s battery starts charging automatically when you connect the power to
the computer and to an electrical outlet.
Approximate charging time for the standard Li-Ion battery is 1.5 hours when the
computer is turned off. While the battery is charging normally, the battery charge light
on the computer is amber. When the battery is fully charged, the light changes to green.
When you use a new battery pack for the first time or use a battery after a long period
of storage, the initial battery life is shorter than normal. Normal battery life resumes
after a few discharge-recharge cycles.
Follow these rules for charging your battery:
• A battery normally discharges power when not used for long periods of time.
Be sure to recharge the battery every two months when it is not in use.
• Make habit of discharging your battery fully before recharging the battery. This
can help extend the life of the battery.
• Do not attempt to charge the battery in temperatures of under 0
o
C or over 45oC
76 Users Manual
All batteries eventually wear out and lose the ability to hold a charge. You may
need to replace your battery pack after a year of average usage.
Battery charging time may differ depending on system environment or
condition of use.
Page 90

Safely Using the Battery
Follow these guidelines to safely use the battery:
• Turn off your computer and unplug it if you accidentally:
– Expose the equipment to liquid.
– Drop, jar, or damage the computer.
• Use only Samsung approved battery chargers.
• Do not disassemble the battery, heat it above 100°C, or burn it. The battery
used in this computer may cause a fire or chemical burn if mistreated.
• Your computer's rechargeable battery may be considered hazardous waste. If
you replace your battery with a new one:
– Keep the old battery out of the reach of children.
– Dispose of the old battery promptly.
– Make sure that you follow all local requirements when you dispose of the
old battery.
Installing the Battery
To install the battery pack:
1. With the computer’s power off, close the LCD panel and turn the computer over
so the bottom of the unit faces up.
Insert the battery into the battery compartment, ensuring the correct
orientation so that the battery fits in its compartment properly.
System Management 77
Page 91

2. Insert the battery into the battery compartment until the battery latch snaps into
place.
Left Battery Latch
3
Right Battery Latch
2
3. Slide the left battery latch towards the center to lock the battery in place.
Removing the Battery
Your computer comes with the battery pack.
To remove the battery from the computer:
1. Turn the computer’s power off.
2. Close the LCD panel, and turn the computer over so that the bottom of the unit
faces up.
3. Slide the left battery latch outward.
4. While holding the right battery latch outward, slide the battery out of the battery
compartment.
78 Users Manual
Page 92

Monitoring the Battery Charge
To monitor in control panel
Click Start > Control Panel > Performance and Management > Power Options >
Power Meter tab. Power source and remaining battery charge are displayed.
To monitor on the battery
Press the PUSH button on the battery. The amount of remaining battery charge (%) is
displayed.
Using the battery
Battery is an expendable supply, so when you use it for a long time, the
capacity/battery life is shortened. If the battery life is reduced to under half of
the initial time, we recommend that you purchase a new battery to use.
System Management 79
Page 93

Battery Warning
You will hear an alarm when the remaining battery charge is under 10%.
Connect the power cable or turn off the computer and install a fully charged
battery.
When the remaining battery charge is under 3%, the computer automatically
saves current work and turns off. This may be different according to the
settings in Control Panel > Performance and Maintenance > Power
Options > Alarms tab.
Battery Calibration
Calibrating your battery once a month is one of the recommended methods of
increasing your computer’s battery life. To calibrate the battery complete the following
steps:
Calibration Notes:
You should start the battery calibration process with a fully charged battery,
battery status LED is green. The power meter may not show 100%.
Before you commence the battery calibration process you should fully charge,
then fully discharge and finally fully recharge the battery again.
1. Disconnect the AC power adapter after turning off the system.
2. Restart your computer and press <F2> to enter BIOS setup.
3. Using the arrow keys, highlight Smart Battery Calibration in the Boot menu.
4. Press <Enter> to start calibration process. The calibration usually takes 3 to 5
hours depending on the current battery charge.
5. When the calibration process is complete, recharge the battery fully.
80 Users Manual
Page 94

Replacing the CD Drive in the Docking Station
If you want to use another CD drive in the docking station, you can purchase a CD
drive additionally, and replace the existing one as follows.
1. Turn off and detach the computer from the docking station.
2. Slide the CD drive latch in the docking station inward to pop the CD drive outward.
CD drive latch
3. Remove the CD drive.
4. Insert a new CD drive in the CD drive compartment and push in until the latch
clicks.
System Management 81
Page 95
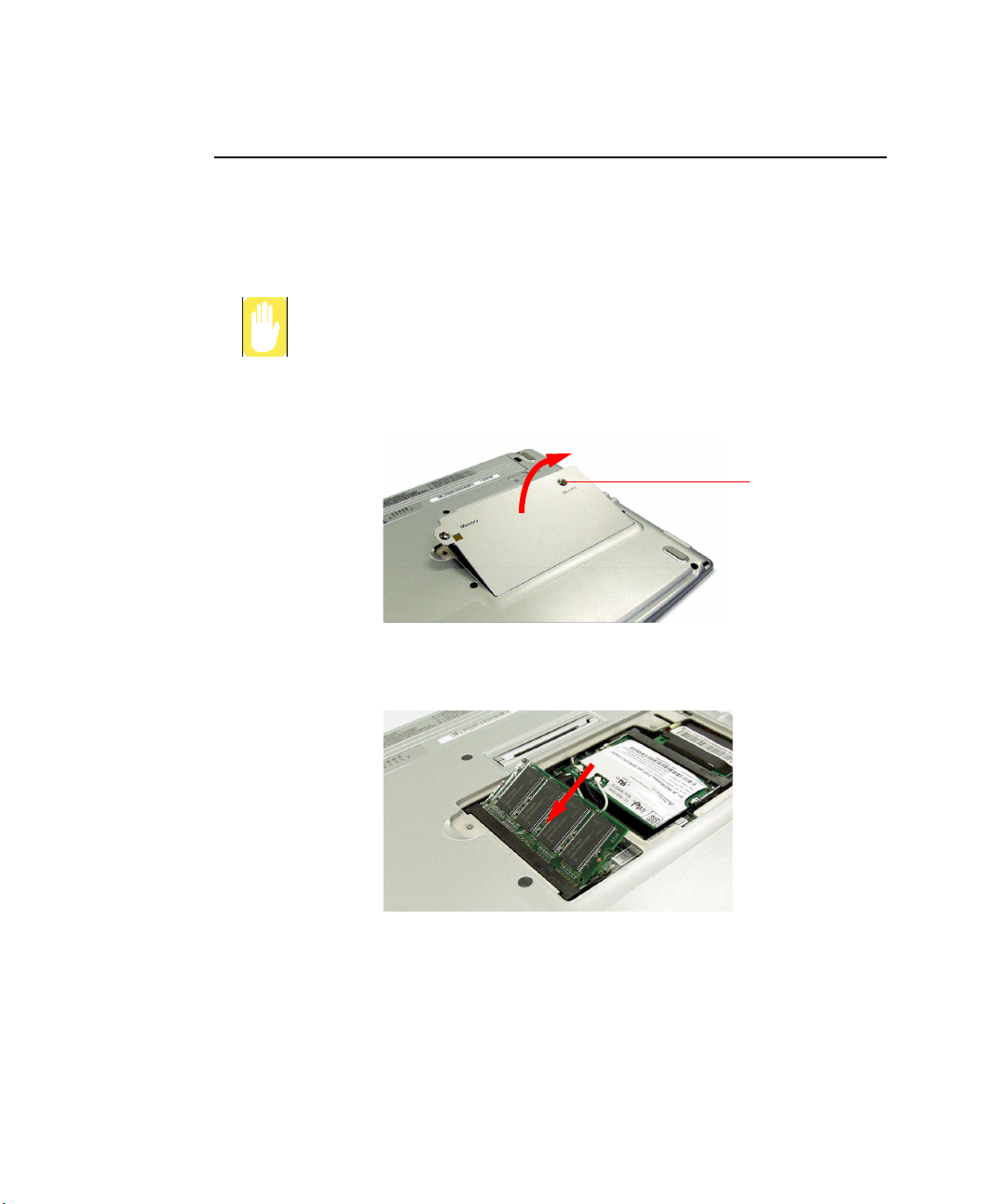
Upgrading Memory Module
Your computer has an installed 128/256 MB memory module depending on your
model. There is an empty slot for an additional memory module in the memory
compartment on the bottom of the computer. To add memory module, complete the
following procedures.
Before installing memory module, turn off the system completely. Do not install
memory module when the system is in suspended mode.
1. Using a screwdriver, open the memory compartment cover on the bottom of the
system.
Screw
2. Align the new memory module connectors accordingly and slide it into the slot at
a 30
° angle.
3. Push the memory module in until the module clicks into place. If the memory
4. Close and fix the memory compartment cover using a screwdriver.
82 Users Manual
module is not fixed completely, push the module while pushing the memory
module latches outward.
Page 96

To remove a memory module
After removing the memory compartment cover, push the memory module
latches outward to pop the memory module outward. Pull out the module at
about 30° angle.
System Management 83
Page 97

Using the Security Lock Port
The security lock is a device used to physically 'fix' the system when using it in a public
place. The locking device needs to be purchased separately. The shape and methods of
use may differ depending on the manufacturer. Please refer to the manual provided
with the security lock for proper use.
1. Connect a security lock cable to a fixed object.
2. While holding the security lock port lever to the left, connect the cable to the
security lock port.
To connect the cable on the security lock port of the docking station, slide the
security lock port lever to the left and connect the cable.
84 Users Manual
When you use the security lock port of the docking station, the computer can
not be separated from the docking station.
Page 98

Using Options
You can select these options at purchase:
• Wireless communication module
(802.11b, bluetooth)
• CD Drive
(CD-ROM drive / CD-RW drive / DVD-ROM drive /
CD-RW/DVD-ROM Combo drive)
You can purchse these options separately:
• Extra battery pack (4 cell/8 cell)
The options that are available may change periodically. Contact your reseller for
updated information on current and new options.
System Management 85
Page 99

Tips for Using Your Computer
The following information helps you avoid potential problems as you use your
computer:
Do not try to disassemble your computer. Opening the system chassis voids
your warranty. Only an authorised manufacturer service center can replace or
add any parts inside the chassis.
• Follow all the instructions and cautions in your computer user documentation.
• The LCD has a polarized surface and can be damaged easily. To prevent
damage, avoid touching the screen.
• Use only approved AC adapters, auto adapters, memory modules and other
options.
• Because a notebook computer is small and has restricted air flow around
components, it is more likely to overheat than a desktop computer. A fan inside
your computer runs when needed to help eliminate heat. Make sure the fan vent
on the left side of your computer is not blocked when you use the computer.
Occasionally check the vents and remove any accumulated dust on the outside.
• Avoid using or storing the computer in extremely hot or cold areas, such as a
car on a hot day. Keep the computer away from heaters and out of direct
sunlight. Exposure to excessive heat may damage computer components. If you
have left your computer in a hot place, let it cool down slowly to room
temperature (with the LCD panel open) before using it.
• Do not remove the memory-module compartment door, or try to install a
memory module when the computer is on. (For information on installing
memory modules, see “Upgrading Memory Module” on page 82.)
• Set up your computer work area to avoid physical strain. Sit with your back
straight and supported by your chair. Adjust your chair or work table so that
your arms and wrists can remain in a relaxed position, parallel with the floor.
Avoid bending or twisting your wrists as you work. Your hands should “float”
slightly above the keyboard. Refer to a book on office ergonomics for more
information on setting up your work area.
• Take frequent breaks from working at the computer to rest your eyes and
stretch your muscles.
• Remember to save your data files frequently and to make backup copies of your
files.
86 Users Manual
Page 100

Travelling with Your Computer
Air Travel
If you are travelling by air, follow these tips:
• Take the computer with you as carry-on luggage. Do not check the computer
with your baggage.
• Allow the computer and disks to go through the X-ray security devices. Do not
hand-carry disks through the walk-through metal detectors, which can cause
loss of data.
• Make sure that the battery is charged or the power cord is easily accessible.
You may be required to turn on the computer for airport security personnel.
• Be prepared to turn off the computer during take off and landing.
Handling Spills
Do not spill anything on your computer. The best way to avoid spills is to avoid eating
and drinking around your computer. If you do spill something on your computer, turn
off your computer, unplug it immediately, and do the following:
• If you spill liquid on the keyboard, drain as much of the liquid from the
keyboard as possible. Be careful not to let the liquid drip onto the LCD panel.
Allow the system to dry for several days before trying to use it.
• If you spill liquid on an external keyboard or keypad, unplug it and drain as
much of the liquid as possible. Allow the keyboard to sit at room temperature
for a full day before trying to use it.
Sweet liquids leave a sticky residue that may jam the keyboard despite your
efforts to dry it.
• If you spill liquid on the LCD panel, clean it immediately with a soft cloth and
denatured alcohol or a proprietary LCD screen cleaner. Do not use water,
window cleaner, acetone, aromatic solvent, or dry, rough towels to clean it.
Some liquids damage the polarized LCD screen. If your screen is damaged,
contact your authorized manufacturer’s service center for a replacement.
System Management 87
 Loading...
Loading...