Page 1
Application Note
Renesas RA Family
Installing and Utilizing the Cryptographic User
Keys using SCE9
Introduction
Cryptography is important becaus e it provides the tools to implement solutions for authenticity,
confidentiality, and integrity, which are vital aspects of any security solution. In modern cryptographic
systems, the security of the system no longer depends on the secrecy of the algorithm used but rather on the
secrecy of the keys. Renesas RA Family cryptographic key installation provides several options for
minimizing the exposure of the user keys and providing optimal production and field key management
support.
This application project explains these key installation methods and provides examples for the currently
available methods supported via the Renesas Flexible Software Package.
An AES plaintext key installation example is provided for the Renesas RA Family RA6M4 MCU group.
Required Resources
Development tools and software
• The e
• Renesas Flexible Software Package (FSP) v2.2.0 or later
• SEGGER J-link
The above three software components: the FSP, J-Link USB drivers and e2 studio are bundled in a
downloadable platform installer available on the FSP webpage at renesas.com/ra/fsp
2
studio ISDE v2020-10 or greater
®
USB driver
.
Hardware
• EK-RA6M4, Evaluation Kit for RA6M4 MCU Group (http://www.renesas.com/ra/ek-ra6m4
• Workstation running Windows® 10 and Tera Term console, or similar application
• Two USB device cables (type-A male to micro-B male)
)
Prerequisites and Intended Audience
This application note assumes you have some experience with the Renesas e2 studio IDE and Arm®
TrustZone® based development models with e
have some knowledge of RA Family MCU security features. See chapter 49, Security Features in the
Renesas RA6M4 Group MCU User’s Manual: Hardware for background knowledge preparation for the
cryptographic key installation.
The intended audience are product developers, product manufacturers, product support, or end users who
are involved with any stage of the MCU user key management of the RA Family MCUs with Arm TrustZone.
2
studio. In addition, the application note assumes that you
R11AN0473EU0110 Rev.1.10 Page 1 of 17
Dec.20.2020
Page 2

Renesas RA Family Installing and Utilizing the Cryptographic User Keys using SCE9
Contents
1. Root of Trust and its Protection ............................................................................................... 3
1.1 What is Root of Trust ............................................................................................................................... 3
1.2 Protecting the Root of Trust .................................................................................................................... 3
2. Introduction to SCE9 and Associated Keys .............................................................................. 3
2.1 Secure Crypto Engine (SCE9) ................................................................................................................ 3
2.2 SCE9 Associated Keys ........................................................................................................................... 4
3. Cryptographic User Key Installation ......................................................................................... 4
3.1 Plaintext User Key Installation Features ................................................................................................. 4
3.2 Key Wrapping with SCE9 ........................................................................................................................ 5
3.3 Advantages of Key Wrapping .................................................................................................................. 5
3.3.1 Advantages of Key Wrapping over Key Encryption .............................................................................. 5
3.3.2 Advantages of Key Wrapping using MCU HUK .................................................................................... 6
3.4 Plaintext User Key Installation Use Cases .............................................................................................. 6
4. Example Project with AES User Key Handling ......................................................................... 8
4.1 Import and Compile the Example Project ................................................................................................ 9
4.2 Setting up the Hardware ........................................................................................................................ 10
4.3 Running the Example Project ................................................................................................................ 11
5. Appendix ............................................................................................................................... 15
5.1 Glossary ................................................................................................................................................ 15
6. References ............................................................................................................................ 15
7. Website and Support ............................................................................................................. 16
Revision History ............................................................................................................................ 17
R11AN0473EU0110 Rev.1.10 Page 2 of 17
Dec.20.2020
Page 3
Renesas RA Family Installing and Utilizing the Cryptographic User Keys using SCE9
1. Root of Trust and its Protection
1.1 What is Root of Trust
Roots of trust are highly-reliable hardware, firmware, and software components that perform specific, critical
security functions (https://csrc.nist.gov/projects/hardware-roots-of-trust
typically consists of identity and cryptographic keys rooted in the hardware of a device. It establishes a
unique, immutable, and unclonable identity to authorize a device in the IoT network.
• Secure boot is part of the services provided in the Root of Trust in many security systems. Authentication
of the application utilizes Public Key Encryption. The associated keys are part of the Root of Trust of the
system.
• Device Identity, which consists of Device Private Key and Device Certificate, is part of the Root of Trust
for many IoT devices.
). In an IoT system, a root of trust
1.2 Protecting the Root of Trust
From the above Root of Trust discussion, we can realize that leakage of the cryptographic user keys can
bring the secure system into a risky state. Protection of the Root of Trust involves key accessibility within the
cryptographic boundary only and keys that are unclonable. Root of Trust should be locked from read and
write access from unauthorized parties.
Renesas user key management system can provide all the above desired protection. In addition, Renesas
user key installation services provide several options from which user can pick and choose the installation
methods which fits their existing architecture.
2. Introduction to SCE9 and Associated Keys
Next generation RA Family MCUs expand Renesas’ strong security offerings with the new SCE9 secure
crypto engine and authenticated Device Lifecycle Management (DLM). This application project focuses on
the security feature brought by SEC9. For the security features brought by DLM, please reference the
application note Renesas Device Lifecycle Management Key Installation
for details.
2.1 Secure Crypto Engine (SCE9)
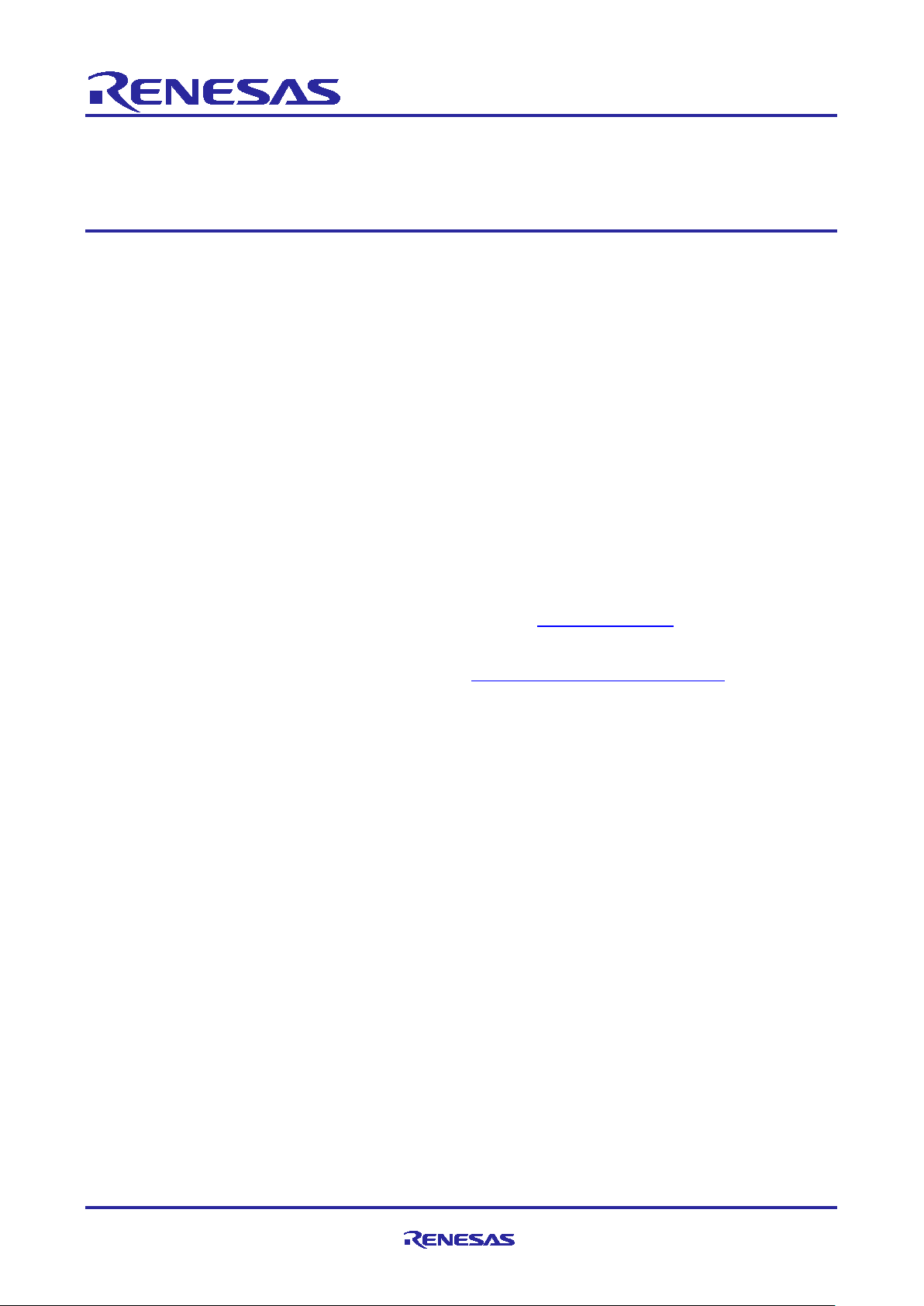
Figure 1. Secure Crypto Engine 9
The Secure Crypto Engine 9 is an isolated subsystem within the MCU.
• The crypto engine contains hardware accelerators for both symmetric and asymmetric cryptographic
algorithms, as well as various hashes and message authentication codes.
• It also contains a True Random Number Generator, providing an entropy source for the cryptographic
operations.
• The Secure Crypto Engine is protected by an Access Management Circuit, which shuts down the crypto
engine in the event of an illegal external access attempt.
R11AN0473EU0110 Rev.1.10 Page 3 of 17
Dec.20.2020
Page 4
Renesas RA Family Installing and Utilizing the Cryptographic User Keys using SCE9
Lifecycle Transition Keys
AES
RSA
ECC
HMAC
2.2 SCE9 Associated Keys
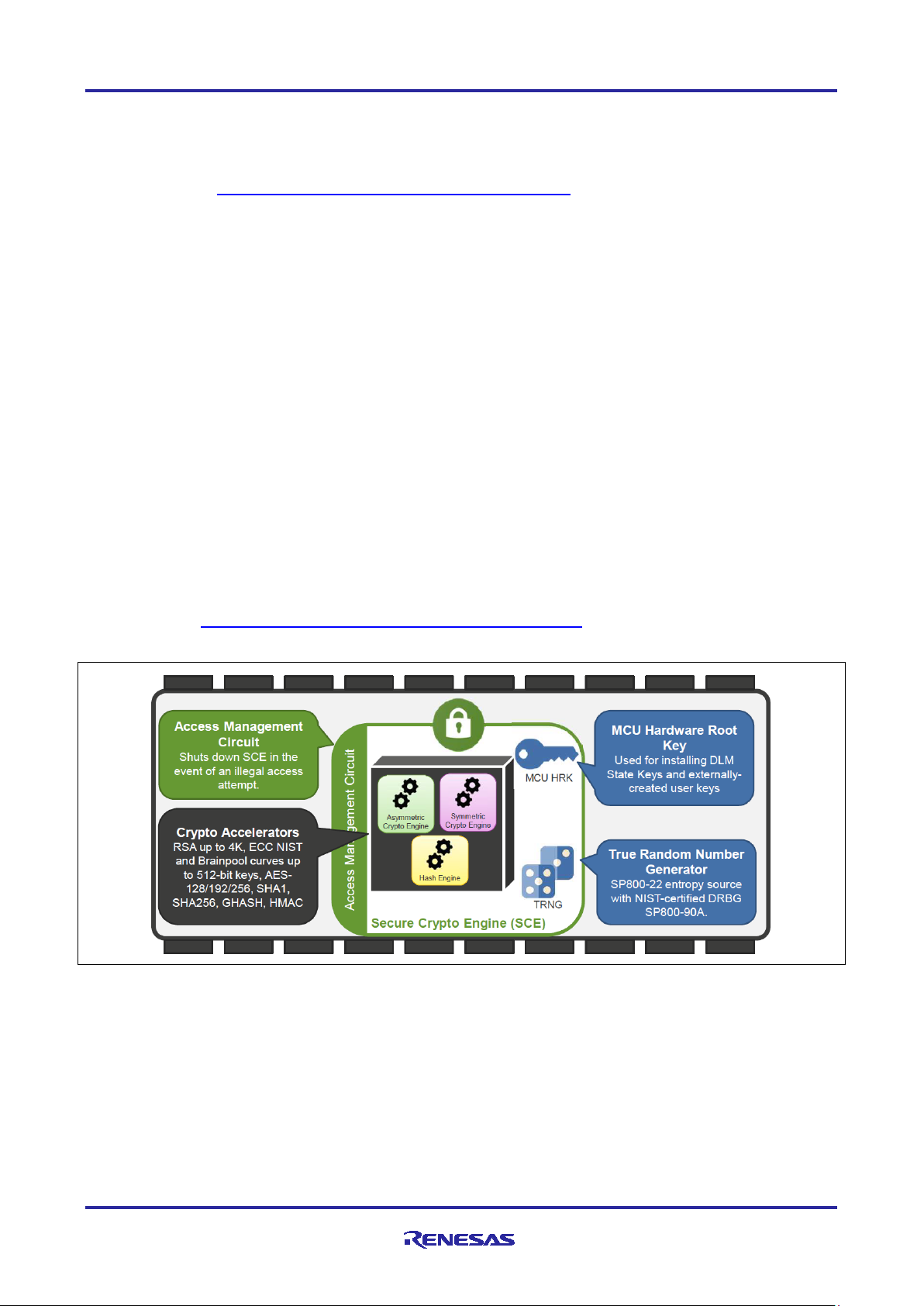
Figure 2. Security Keys
RA Family MCUs with the SCE9 crypto engine is associated with two new types of keys compared with
SCE7.
• The first is an MCU-u niq ue Hardware Unique Key (HUK), a 256-bit random key that is preprogrammed in
the Renesas factory.
• This key is stored in unmapped flash, ass ess able only by the SCE9, not to application code. It is
further protected by being stored not in plaintext, but rather wrapped by the HRK (Hardware Root Key)
and MCU unique ID.
• The SCE9 can access this HUK to perform user key wrapping.
• Since the HUK is stored in an MCU-uniquely wrapped format, even if an attacker was able to extract
the stored key, another MCU won’t be able to use it.
• The second type of keys are associated with the Renesas Device Lifecycle Management (DLM) system.
• For the installation and usage of the DLM Keys, please reference application note
Renesas Device
Lifecycle Management Key Installation.
The HRK and HUK are used in the user key Installation process.
3. Cryptographic User Key Installation
The table below summarizes the key types that can be installed into Renesas RA MCUs with the SCE9
Secure Crypto Engine, for example, RA6M4 and RA4M3. Installed keys will be stored wrapped by the MCU’s
HUK.
Table 1 Supported Key Types
SECDBG_KEY, NONSECDBG_KEY, RMA_KEY
AES-128, AES-192, AES-256
RSA-1024, RSA-2048, RSA-3072, RSA-4096 (Public and Private)
NIST P-192, P-224, P-256, and P-384
Brainpool P256r1, P384r1, and P512r1 (Public and Private)
HMAC-SHA224, HMAC-SHA256
3.1 Plaintext User Key Installation Features
Plaintext user key refers to the fact that the user keys can be provided in plaintext format to SCE9. When the
plaintext key is installed, the SCE9 wraps the plaintext key with HUK and provides the wrapped key outside
SCE9 for storage.
R11AN0473EU0110 Rev.1.10 Page 4 of 17
Dec.20.2020
Page 5
Renesas RA Family Installing and Utilizing the Cryptographic User Keys using SCE9
Figure 3. Plaintext Key Installation
This plaintext key installation process gives all security control of the keys to the product developer, which
enables the developer to benefit from any existing secure key provisioning infrastructure. However, we do
not recommend long-term storage of plaintext keys on the MCU. Therefore, the RA Family MCUs have the
capability to install and securely store a plaintext key in wrapped format by wrapping the key with the MCU
HUK.
Plaintext key installation is supported with FSP 2.0.0 or later. How to get the plaintext user key into the MCU
RAM or flash in preparation for installation is out of scope for this application project. Product developers can
use their existing infrastructure to interface to the MCU based on their specific environment.
Note: This plaintext key installation procedure is recommended to be performed in a secure environment.
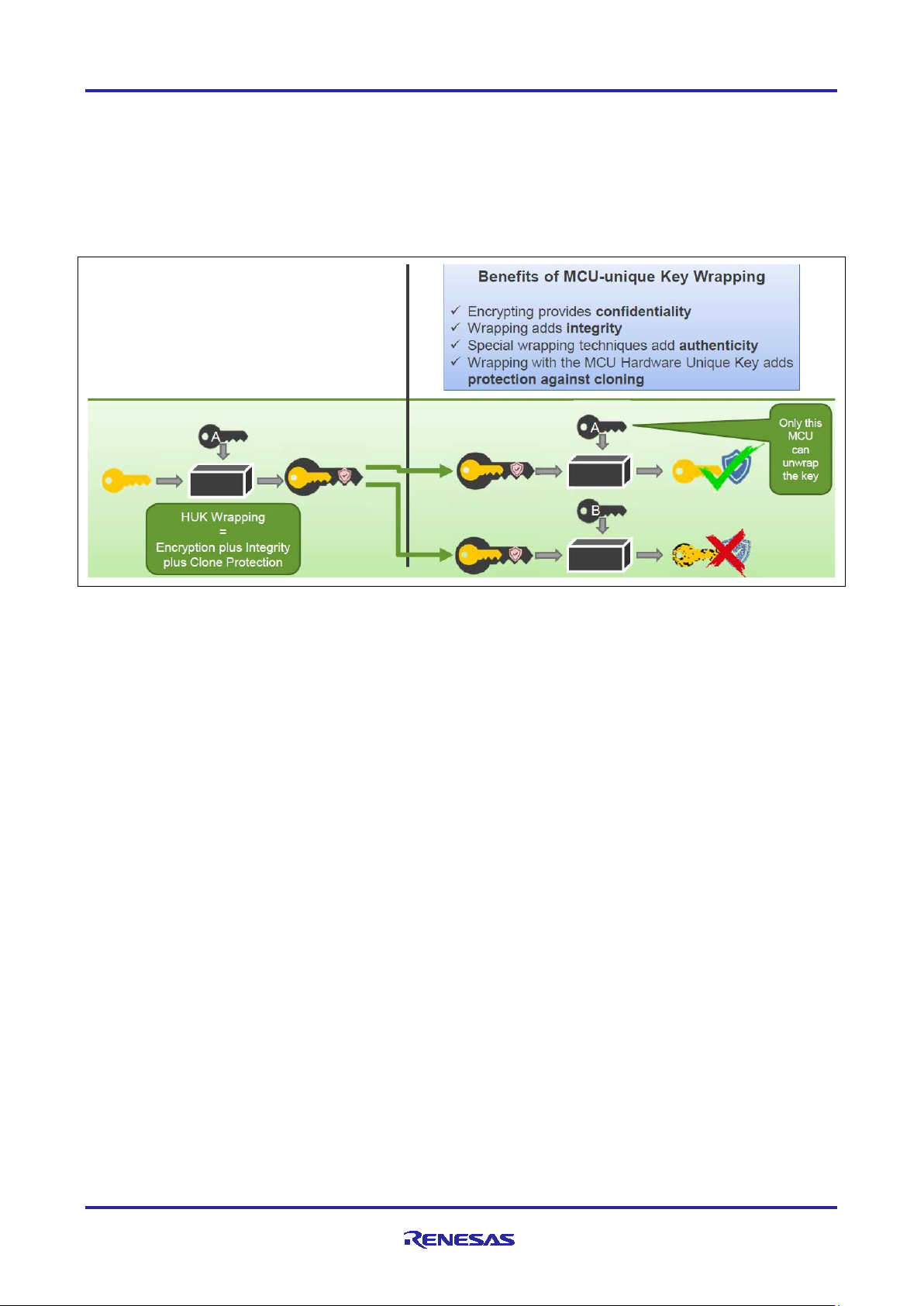
3.2 Key Wrapping with SCE9
Key wrapping with SCE9 involves encryption using the MAC of the MCU unique ID and user key encrypted
with the HUK. The encryption aspect provides confidentiality of the key. Wrapping with MAC code adds
integrity and authenticity. Finally, wrappi ng with the MCU HUK adds clone protection. Advantages of Key
Wrapping
3.2.1 Advantages of Key Wrapping over Key Encryption
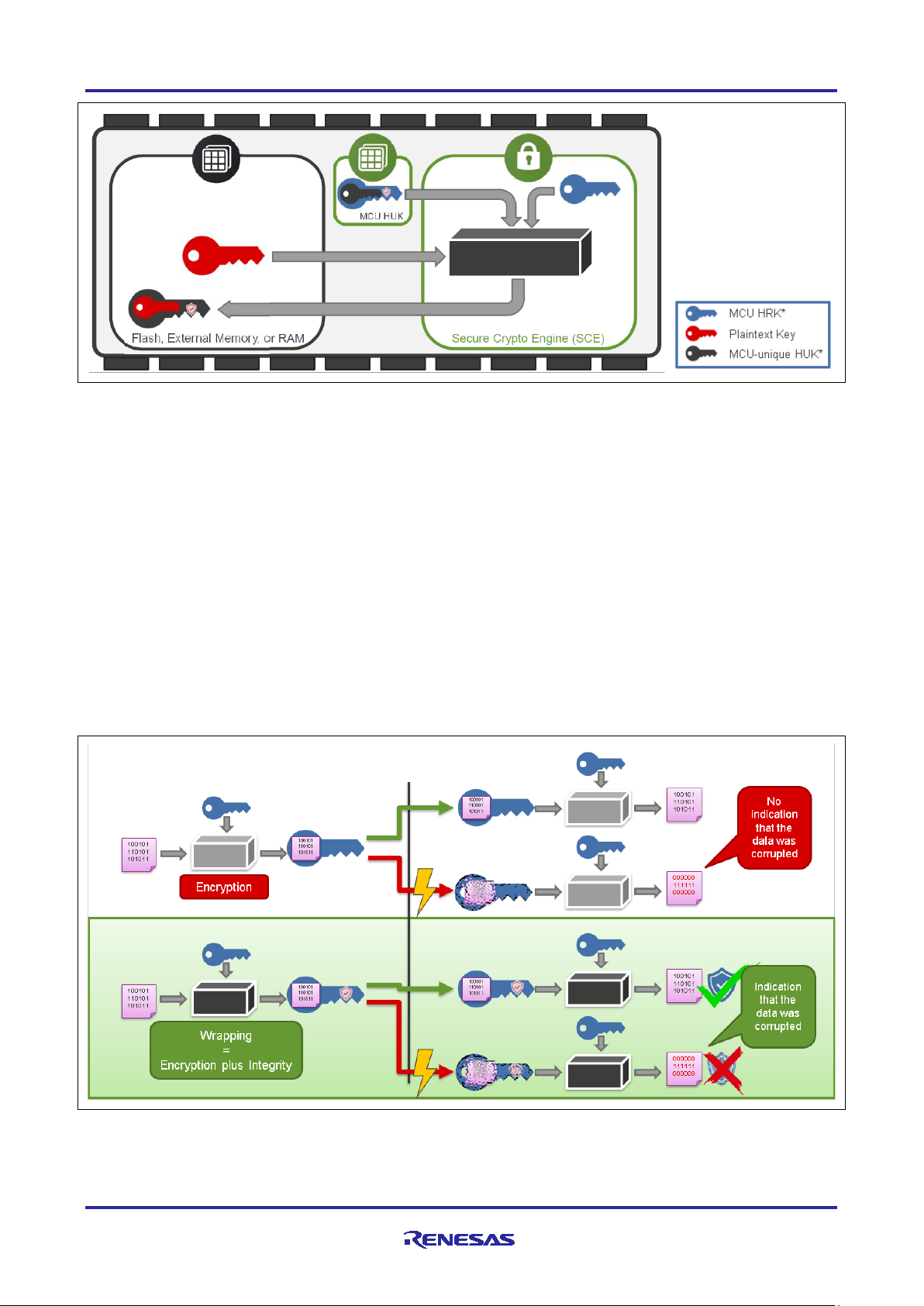
Figure 4. Key Wrapping vs. Key Encryption
It is important to understand the difference between wrapping and encrypting for secure asset storage. We
will use symmetric encryption here to demonstrate.
R11AN0473EU0110 Rev.1.10 Page 5 of 17
Dec.20.2020
Page 6
Renesas RA Family Installing and Utilizing the Cryptographic User Keys using SCE9
• When data is encrypted and sent to another recipient, if that recipient has the same key, they can
decrypt the data. This results in a confidential exchange of information. However, what if there was a
problem with the transmission of the encrypted data? If the recipient unknowingly receives corrupted
information, the decryption algorithm will generate garbage data, with no indication that the original data
has been corrupted.
• Wrapping solves this problem for us by adding an integrity checking mechanism to the encrypted output.
3.2.2 Advantages of Key Wrapping using MCU HUK
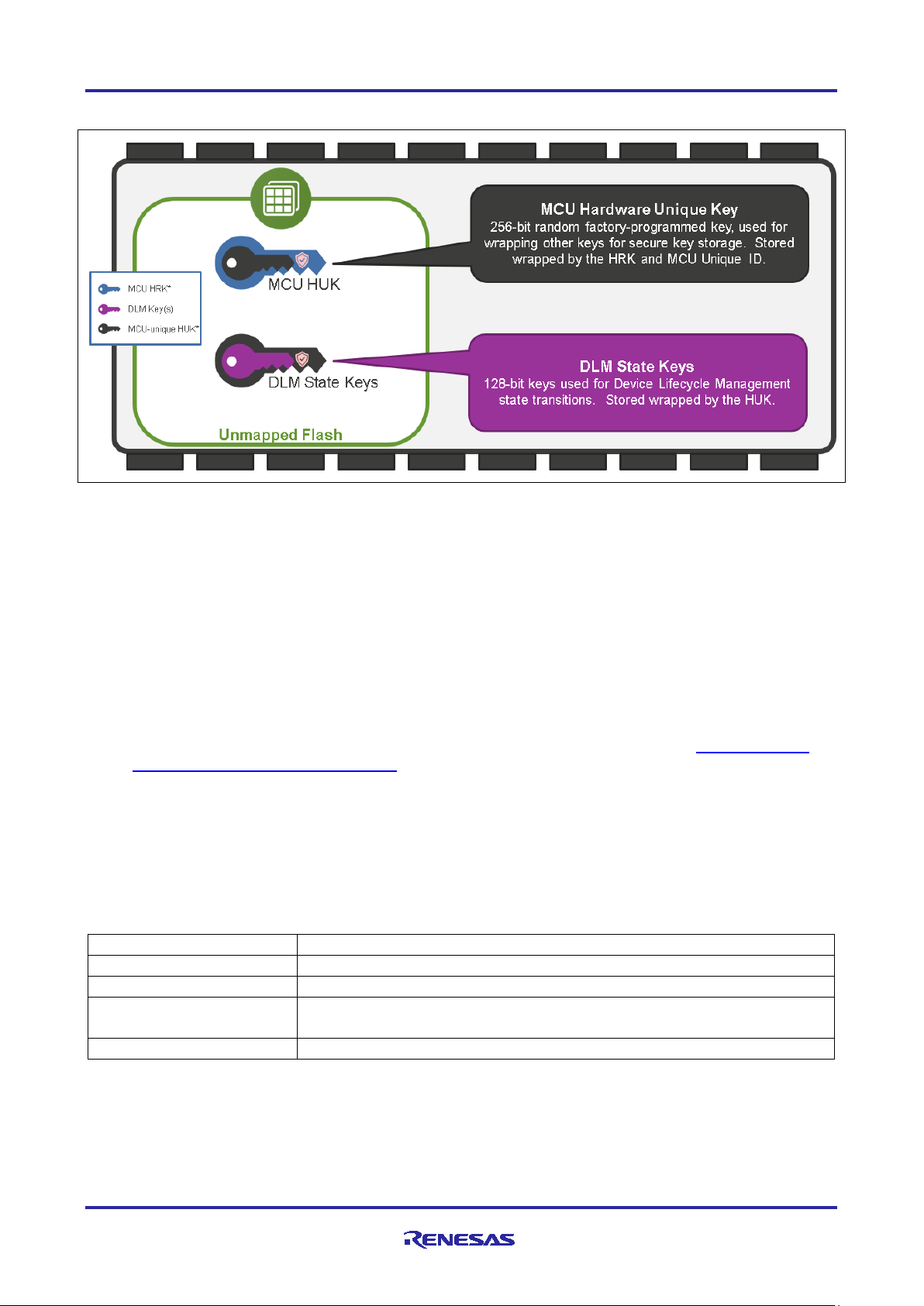
Figure 5. Key Wrapping using the HUK
Using the MCU Hardware Uniq ue Key to wrap the stored keys adds another protection feature – clone
protection.
• If the wrapped key is transmitted or copied to another MCU, that MCU’s HUK will not be able to unwrap
nor decrypt the information, maintaining the security of the key.
• MCU-wrapped keys can only be unwrapped by the MCU that wrapped them
• The MCU’s HUK is used as part of the wrapping algorithm
• Since the HUK is unique, no other MCU can unwrap the key
• Benefits
• Wrapped keys can be stored in non-secure memory
• Even if the entire MCU contents are copied onto another device, the keys cannot be utilized nor
exposed
3.3 Plaintext User Key Installation Use Cases
This section summaries several common use cases for key installation.
Case 1: Plaintext Key Installation During Production Provisioning/Programming
In this case, user keys are injected to the MCU based on customer’s existing or preferred method. The
injected plaintext key is then installed by MCU application-level code using the Renesas RA Family FSP.
This use case enables installation of pre-generated keys, which should be performed in a secure
environment. Solutions for this use case are supported by FSP 2.0.0 or later. The FSP APIs used are
demonstrated in the example project included in this application project.
R11AN0473EU0110 Rev.1.10 Page 6 of 17
Dec.20.2020
Page 7

Renesas RA Family Installing and Utilizing the Cryptographic User Keys using SCE9
Plaintext Key Injection
MCU Key Generation (Wrapped Key)
Mass Production
Provides scalability, Faster
Provides scalability, Slower
Secure Environment
Recommended
Not required
Device Identity
Supported
Supported
Figure 6. Plaintext Key Installation During Production
Case 2: Plaintext Key Installation Over Secure Communication Path
It is possible to provide a secure communication path for plaintext key installation. In this use case, the
plaintext key is securely transmitted and injected to the MCU. The MCU secure application software then
installs the plaintext key, storing the key in wrapped format. Solutions to support this use case are dependent
on the communication path implementation. Customers can leverage the MCU operations provided for Case
1 to implement this solution.
Figure 7. Plaintext Key Installati on Over Secure Communication Path
Comparing Key Installation and MCU Key Generation
The following table summarizes the use case comparison between Key Injection and MCU Key Generation:
Table 2 Use Case Comparison with MCU Generated Keys
R11AN0473EU0110 Rev.1.10 Page 7 of 17
Dec.20.2020
Page 8

Renesas RA Family Installing and Utilizing the Cryptographic User Keys using SCE9
4. Example Project with AES User Key Handling
The hardware features of SCE9 are accesed via the FSP driver r_sce. For most application development,
developers can use the middleware PSA Crypto layer to interface with the SCE9. However, some SCE9
functionality does not map to PSA Crypto APIs; therefore, r_sce key installation related AP Is must be used
directly.
Figure 8. Crypto stacks
Using PSA Crypto with TrustZone needs some special handling compared with other drivers. Unlike other
FSP drivers, the PSA Crypto module cannot be added as a Non-Secure-Callable module. The reason for
this is that to achieve the security objective of controlling access to protected keys, both the PSA Crypto
code as well as the keys must be placed in the secure region. The PSA Crypto API requires access to the
keys directly during initializ atio n and later via a k e y handle. Therefore, the PSA Crypto module should
reside in the secure region.
To provide services to the Non-Secure region, you need to create application-specific user defined NonSecure Callable (NSC) APIs in the secure region. Proper security considerations can be implemented in the
Non-Secure Callable API to limit access to the NSC APIs.
The need for the Non- Secure region accessing cryptographic service in the secure region varies from
application to application. You need to adjust the Non-Secure Callable API provided in this example project
based on your specific application. It is not advised to use the example as-is for a real-world secure
application.
Below is the high-level software block diagram of the example project provided in this application project.
R11AN0473EU0110 Rev.1.10 Page 8 of 17
Dec.20.2020
Page 9

Renesas RA Family Installing and Utilizing the Cryptographic User Keys using SCE9
Figure 9. Software Block Diagram
The Non-Secure Callable APIs are defined in aes_functions.h file. These APIs are explained below:
• BSP_CMSE_NONSECURE_ENTRY bool init_lfs(void);
Initializes the LittleFS system: formatted and mounted.
• BSP_CMSE_NONSECURE_ENTRY bool create_aes_key(aes_creation_args_t *args);
Allows the Non-Secure project to initiate new AES key creation by installing a 256-bit AES plaintext key
(generated as a random number using the MCU’s TRNG) as a wrapped key. Once the plaintext user key
is injected into the MCU, the SCE9 driver is used to convert the plaintext key into wrapped key format by
wrapping the plaintext ke y using the HUK. The plaintext key will be erased immediately after the
conversion. The wrapped AES key is further imported into the PSA key storage system and stored in the
data flash for user application usage.
• BSP_CMSE_NONSECURE_ENTRY bool destroy_the_key(void);
Removes the key from the key management system.
• BSP_CMSE_NONSECURE_ENTRY bool
encryption_operation(non_secure_encryption_args_t *args);
Encrypts user data using the created AES key.
• BSP_CMSE_NONSECURE_ENTRY bool
decryption_operation(non_secure_decryption_args_t *args);
Decrypts user data using the created AES key.
4.1 Import a nd Compile the Example Project
Follow the FSP User’s Manual section, Importing an Existing Pro ject into e2 studio to import the Secure and
Non-Secure Projects into the workspace and compile in the order instructed below.
R11AN0473EU0110 Rev.1.10 Page 9 of 17
Dec.20.2020
Page 10

Renesas RA Family Installing and Utilizing the Cryptographic User Keys using SCE9
1. Expand the secure project installing_utilizing_user_keys_ra6m4_s, and double-click the
configuration.xml to launch the configurator. Click Generate Project Content and then build the
Secure project. Project should build with no errors.
Note that there are third party software warn ings .
2. Expand the non-secure project installing_utilizing_user_keys_ra6m4_ns, double-click the
configuration.xml to launch the configurator. Click Generate Project Content and then build the
Non-Secure project.
4.2 Setting up the Hardware
Establish the following connections:
• EK-RA6M4 jumper setting: J6 closed, J9 open. Other jumpers keep out-of-box setting.
• USB cable connected between J10 and development PC to provide power and debugging capability
using the on-board debugger
Initialize the MCU using Renesas Device Partition Manager
This step is optional but recommended. Prior to downloaing the example application, we recommend
initializing the device to SSD state. Flash content not permanently locked down will be erased during this
process. This is particularly helpful if the device was previously used in NSECSD state or have certain flash
block locked up temporarily.
Note: You need to power cycle the board prior to working with Renesas Device Part itio n Man ager after a
debug session if using J-Link as connection interface.
2
Open the Renesas Device Partition Manager. With the e
Renesas Device Partition Manager.
studio IDE, click the Run tab and then select
Figure 10. Open Renesas Device Partition Manager
Next, check Initialize device back to factory default, choose J-Link as the connection method, and then
click Run.
R11AN0473EU0110 Rev.1.10 Page 10 of 17
Dec.20.2020
Page 11

Renesas RA Family Installing and Utilizing the Cryptographic User Keys using SCE9
Figure 11. Initialize RA6M4 using Renesas Device Partition Manager
4.3 Running the Example Project
To run the application, right-click on installing_utilizing_user_keys_ra6m4_ns and select Debug
As > Renesas GDB Hardware Debugging.
R11AN0473EU0110 Rev.1.10 Page 11 of 17
Dec.20.2020
Page 12

Renesas RA Family Installing and Utilizing the Cryptographic User Keys using SCE9
Figure 12. Running the Application
Note that prior to the application execution, the IDAU regions will be set up to assume the values via the
debugger interaction with t he MCU boot loa der .
Both the secure and non-secure projects are now loaded, and the debugger should be paused in the
Reset_Handler() at the SystemInit() call in the Secure project.
Figure 13. Secure Project Reset Handler
R11AN0473EU0110 Rev.1.10 Page 12 of 17
Dec.20.2020
Page 13

Renesas RA Family Installing and Utilizing the Cryptographic User Keys using SCE9
Click Switch if the Confirm Perspective Swit ch window pops up. Click twice to run the project.
Next, launch J-Link RTT Viewer V6.86 or later.
Figure 14. Launch J-Link RTT Viewer
Select Existing Session as connection type. Click on the button and scroll down to Renesas to find the
correct device R7FA6M4AF. Also set up the RTT Control Block to Search Range. Set the search range to
0x20000000 0x10000 and then click OK to start the RTT Viewer.
Note: This Search Size 0x10000 is based on this example applicatio project, if your application uses RTT
viewer in Non-Secure region and there is a large secure binary, user needs to increase the Search
Size to cover the Non-Secure project SRAM regions.
If the host PC has more than one J-Link debugger connected to the PC, set the Serial No (by default Serial
No is set to 0).
Figure 15. Launch SEGGER RTT Viewer
Click OK and follow the steps below to walkthrough the functions provided by the system:
Step 1: The main menu items are printed on the RTT Viewer Terminal 0.
Figure 16. Main Menu
R11AN0473EU0110 Rev.1.10 Page 13 of 17
Dec.20.2020
Page 14

Renesas RA Family Installing and Utilizing the Cryptographic User Keys using SCE9
Input 1 to create Wrapped Key from Plaintext key input. The AES plaintext key is generated by using PSA
API psa_generate_random.
Figure 17. Creating the Wrapped Key from plaintext input
Input 2 to encrypt the user data using the generated wrapped AES key.
Figure 18. Encrypt user data using the Wrapped AES key
Input 3 to decrypt the encrypted data.
Figure 19. Decrypt the Encrypted Data using the Same AES Key
Input 4 to compare decrypted user data with original unencrypted data.
Figure 20. Check whether the decrypted data matches the original
Input 5 to remove the AES key from system.
Note: No TrustZone secure fault is generated in this case.
Figure 21. Destroy the created AES Key
R11AN0473EU0110 Rev.1.10 Page 14 of 17
Dec.20.2020
Page 15
Renesas RA Family Installing and Utilizing the Cryptographic User Keys using SCE9
Term
Meaning
HSM
A hardware security module (HSM) is a physical computing device that safeguards
signatures, strong authentication, and other cryptographic functions.
HRK
Hardware Root Key is a secret key resides in the SEC9 module which is used to wrap
the HUK for secure storage.
Unique ID
A Unique IDentification value, unique to each individual RA Family MCU, that is stored
inside the MCU. The unique ID is used by the SCE9 when it wraps a key.
MAC
Message Authentication Code is a short piece of information used to authenticate a
changes to the message content.
5. Appendix
5.1 Glossary
and manages digital keys, performs encryption and decryption functions for digital
message to confirm that the message came from the stated sender (its authenticity) and
has not been changed. The MAC value protects both a message's data integrity as well
as its authenticity, by allowing verifiers (who also possess the secret key) to detect any
6. References
1. Renesas Device Lifecycle Management Key Installation
R11AN0473EU0110 Rev.1.10 Page 15 of 17
Dec.20.2020
Page 16

Renesas RA Family Installing and Utilizing the Cryptographic User Keys using SCE9
7. Website and Support
Visit the following URLs to learn about the RA family of microcontrollers, download tools and documentation,
and get support.
EK-RA6M4 Resources renesas.com/ra/ek-ra6m
RA Product Information renesas.com/ra
Flexible Software Package (FSP) renesas.com/ra/fsp
RA Product Support Forum renesas.com/ra/forum
Renesas Support renesas.com/support
4
R11AN0473EU0110 Rev.1.10 Page 16 of 17
Dec.20.2020
Page 17

Renesas RA Family Installing and Utilizing the Cryptographic User Keys using SCE9
Rev.
Date
Description
Page
Summary
1.10
Dec.20.2020
-
Added missing graph
1.00
Dec.2.2020
-
First release document
Revision History
R11AN0473EU0110 Rev.1.10 Page 17 of 17
Dec.20.2020
Page 18

Corporate Headquarters
Contact information
www.renesas.com
Trademarks
of their respective owners.
Notice
1. Descriptions of circuits, software and other related information in this document are provided only to illustrate the operation of semiconductor products
and application examples. You are fully responsible for the incorporation or any other use of the circuits, software, and information in the design of your
product or system. Renesas Electronics disclaims any and all liability for any losses and damages incurred by you or third parties arising from the use
of these circuits, software, or information.
2. Renesas Electronics hereby expressly disclaims any warranties against and liability for infringement or any other claims involving patents, copyrights,
or other intellectual property rights of third parties, by or arising from the use of Renesas Electronics products or technical information described in this
document, including but not limited to, the product data, drawings, charts, programs, algorithms, and application examples.
3. No license, express, implied or otherwise, is granted hereby under any patents, copyrights or other intellectual property rights of Renesas Electronics
or others.
4. You shall not alter, modify, copy, or reverse engineer any Renesas Electronics product, whether in whole or in part. Renesas Electronics disclaims any
and all liability for any losses or damages incurred by you or third parties arising from such alteration, modification, copying or reverse engineering.
5. Renesas Electronics products are classified according to the following two quality grades: “Standard” and “High Quality”. The intended applications for
each Renesas Electronics product depends on the product’s quality grade, as indicated below.
"Standard": Computers; office equipment; communications equipment; test and measurement equipment; audio and visual equipment; home
"High Quality": Transportation equipment (automobiles, trains, ships, etc.); traffic control (traffic lights); large-scale communication equipment; key
Unless expressly designated as a high reliability product or a product for harsh environments in a Renesas Electronics data sheet or other Renesas
Electronics document, Renesas Electronics products are not intended or authorized for use in products or systems that may pose a direct threat to
human life or bodily injury (artificial life support devices or systems; surgical implantations; etc.), or may cause serious property damage (space
system; undersea repeaters; nuclear power control systems; aircraft control systems; key plant systems; military equipment; etc.). Renesas Electronics
disclaims any and all liability for any damages or losses incurred by you or any third parties arising from the use of any Renesas Electronics product
that is inconsistent with any Renesas Electronics data sheet, user’s manual or other Renesas Electronics document.
6. When using Renesas Electronics products, refer to the latest product information (data sheets, user’s manuals, application notes, “General Notes for
Handling and Using Semiconductor Devices” in the reliability handbook, etc.), and ensure that usage conditions are within the ranges specified by
Renesas Electronics with respect to maximum ratings, operating power supply voltage range, heat dissipation characteristics, installation, etc. Renesas
Electronics disclaims any and all liability for any malfunctions, failure or accident arising out of the use of Renesas Electronics produ cts outs i de of s uc h
specified ranges.
7. Although Renesas Electronics endeavors to improve the quality and reliability of Renesas Electronics products, semiconductor products have specific
characteristics, such as the occurrence of failure at a certain rate and malfunctions under certain use conditions. Unless designated as a high reliability
product or a product for harsh environments in a Renesas Electronics data sheet or other Renesas Electronics document, Renesas Electronics
products are not subject to radiation resistance design. You are responsible for implementing safety measures to guard against the possibility of bodily
injury, injury or damage caused by fire, and/or danger to the public in the event of a failure or malfunction of Renesas Electronics products, such as
safety design for hardware and software, including but not limited to redundancy, fire control and malfunction prevention, appropriate treatment for
aging degradation or an y othe r app ropriate measures. Because the evaluation of microcomputer software alone is very difficult and impractical, you are
responsible for evaluating the safety of the final products or systems manufactured by you.
8. Please contact a Renesas Electronics sales office for details as to environmental matters such as the environmental compatibility of each Renesas
Electronics product. You are responsible for carefully and sufficiently investigating applicable laws and regulations that regulate the inclusion or use of
controlled substances, including without limitation, the EU RoHS Directive, and using Renesas Electronics products in compliance with al l these
applicable laws and regulations. Renesas Electronics disclaims any and all liability for damages or losses occurring as a result of your noncompliance
with applicable laws and regulations.
9. Renesas Electronics products and technologies shall not be used for or incorporated into any products or systems whose manufacture, use, or sale is
prohibited under an y appli cable domestic or foreign laws or regulations. You shall comply with any applicable export control laws and regulations
promulgated and administered by the governments of any countries asserting jurisdiction over the parties or transactions.
10. It is the responsibility of the buyer or distributor of Renesas Electronics products, or any other party who distributes, disposes of, or otherwise sells or
transfers the product to a third pa rty, to notify such third party in advance of the contents and conditions set forth in this document.
11. This document shall not be reprinted, reproduced or duplicated in any form, in whole or in part, without prior written consent of Renesas Electronics.
12. Please contact a Renesas Electronics sales office if you have any questions regarding the information contained in this document or Renesas
Electronics products.
(Note1) “Renesas Electronics” as used in this document means Renesas Electronics Corporation and also includes its directly or indirectly contr oll ed
subsidiaries.
(Note2) “Renesas Electronics product(s)” means any product developed or manufactured by or for Renesas Electronics.
electronic appliances; machine tools; personal electronic equipment; industrial robots; etc.
financial terminal systems; safety control equipment; etc.
Rev.4.0-1 November 2017)
TOYOSU FORESIA, 3-2-24 Toyosu,
Koto-ku, Tokyo 135-0061, Japan
Renesas and the Renesas logo are trademarks of Renesas Electronics
Corporation. All trademarks and registered trademarks are the property
For further information on a product, technology, the most up-to-date
version of a document, or your ne are s t sales office, please visit:
www.renesas.com/contact/
.
© 2020 Renesas Electronics Corporation. All rights reserved.
 Loading...
Loading...