Page 1

Multi-Homing Security Gateway User’s Manual
Multi-Homing Security
Gateway
MH-2000, MH-4000
User’s Manual
Page 2

Multi-Homing Security Gateway User’s Manual
Copyright
Copyright (C) 2005 PLANET Technology Corp. All rights reserved.
The products and programs described in this User’s Manual are licensed products of PLANET Technology, This User’s
Manual contains proprietary information protected by copyright, and this User’s Manual and all accompanying hardware,
software, and documentation are copyrighted.
No part of this User’s Manual may be copied, photocopied, reproduced, translated, or reduced to any electronic medium
or machine-readable form by any means by electronic or mechanical. Including photocopying, recording, or information
storage and retrieval systems, for any purpose other than the purchaser's personal use, and without the prior express
written permission of PLANET Technology.
Disclaimer
PLANET Technology does not warrant that the hardware will work properly in all environments and applications, and
makes no warranty and representation, either implied or expressed, with respect to the quality, performance,
merchantability, or fitness for a particular purpose.
PLANET has made every effort to ensure that this User’s Manual is accurate; PLANET disclaims liability for any
inaccuracies or omissions that may have occurred.
Information in this User’s Manual is subject to change without notice and does not represent a commitment on the part of
PLANET. PLANET assumes no responsibility for any inaccuracies that may be contained in this User’s Manual. PLANET
makes no commitment to update or keep current the information in this User’s Manual, and reserves the right to make
improvements to this User’s Manual and/or to the products described in this User’s Manual, at any time without notice.
If you find information in this manual that is incorrect, misleading, or incomplete, we would appreciate your comments and
suggestions.
CE mark Warning
This is a class B device, in a domestic environment; this product may cause radio interference, in which case the user
may be required to take adequate measures.
To avoid the potential effects on the environment and human health as a result of the presence of hazardous
substances in electrical and electronic equipment, end users of electrical and electronic equipment should
understand the meaning of the crossed-out wheeled bin symbol. Do not dispose of WEEE as unsorted
municipal waste and have to collect such WEEE separately.
Trademarks
The PLANET logo is a trademark of PLANET Technology.
This documentation may refer to numerous hardware and software products by their trade names. In most, if not all cases,
these designations are claimed as trademarks or registered trademarks by their respective companies.
Customer Service
For information on customer service and support for the Multi-Homing Security Gateway, please refer to the following
Website URL:
http://
www.planet.com.tw
Before contacting customer service, please take a moment to gather the following information:
♦ Multi-Homing Security Gateway serial number and MAC address
♦ Any error messages that displayed when the problem occurred
♦ Any software running when the problem occurred
♦ Steps you took to resolve the problem on your own
Revision
User’s Manual for PLANET Multi-Homing Security Gateway
Model: MH-2000, MH-4000
Rev: 4.0 (September, 2005)
Page 3

Multi-Homing Security Gateway User’s Manual
Table of Contents
CHAPTER 1: INTRODUCTION ........................................................................................................................ 1
1.1 FEATURES................................................................................................................................................................1
1.2 PACKAGE CONTENTS .............................................................................................................................................. 2
1.3 MH-2K/4K FRONT VIEW.........................................................................................................................................2
1.4 MH-2K/4K REAR PANEL.........................................................................................................................................3
1.5 SPECIFICATION ........................................................................................................................................................4
CHAPTER 2: HARDWARE INSTALLA TION.................................................................................................... 5
2.1 INSTALLATION REQUIREMENTS ...............................................................................................................................5
2.2 OPERATION MODE...................................................................................................................................................5
2.2.1 Transparent Mode Connection Example...................................................................................................6
2.2.2 NAT Mode Connecting Example................................................................................................................ 6
CHAPTER 3: GETTING STARTED .................................................................................................................. 7
3.1 WEB CONFIGURATION .............................................................................................................................................7
3.2 CONFIGURE WAN 1 INTERFACE ............................................................................................................................. 8
3.3 CONFIGURE WAN 2 INTERFACE ........................................................................................................................... 10
3.4 CONFIGURE DMZ INTERFACE ...............................................................................................................................10
3.5 CONFIGURE POLICY ..............................................................................................................................................10
CHAPTER 4: WEB CONFIGURATION .......................................................................................................... 13
4.1 SYSTEM .................................................................................................................................................................14
4.1.1 Admin ...........................................................................................................................................................16
4.1.2 Settings........................................................................................................................................................18
4.1.3 Date/Time.................................................................................................................................................... 24
4.1.4 Multiple Subnet...........................................................................................................................................25
4.1.5 Hacker Alert.................................................................................................................................................29
4.1.6 Blaster Alert.................................................................................................................................................31
4.1.7 Route Table .................................................................................................................................................31
4.1.8 DHCP........................................................................................................................................................... 33
4.1.9 Dynamic DNS..............................................................................................................................................35
4.1.10 Host Table..................................................................................................................................................37
4.1.11 SNMP (MH-4000 only).............................................................................................................................39
4.1.12 Permitted IPs.............................................................................................................................................40
4.1.13 Language...................................................................................................................................................42
4.1.14 Logout........................................................................................................................................................42
4.1.15 Software Update....................................................................................................................................... 43
Page 4

Multi-Homing Security Gateway User’s Manual
4.2 INTERFACE.............................................................................................................................................................44
4.2.1 LAN...............................................................................................................................................................44
4.2.2 WAN............................................................................................................................................................. 45
4.2.3 DMZ..............................................................................................................................................................50
4.3 ADDRESS ...............................................................................................................................................................52
4.3.1 LAN...............................................................................................................................................................52
4.3.2 LAN Group...................................................................................................................................................55
4.3.3 WAN............................................................................................................................................................. 58
4.3.4 WAN Group.................................................................................................................................................60
4.3.5 DMZ..............................................................................................................................................................63
4.3.6 DMZ Group..................................................................................................................................................66
4.4 SERVICE ................................................................................................................................................................69
4.4.1 Pre-defined..................................................................................................................................................69
4.4.2 Custom.........................................................................................................................................................70
4.4.3 Group............................................................................................................................................................73
4.5 SCHEDULE .............................................................................................................................................................76
4.6 QOS.......................................................................................................................................................................79
4.7 AUTHENTICATION ...................................................................................................................................................81
4.7.1 Auth Setting................................................................................................................................................. 81
4.7.2 Auth User.....................................................................................................................................................82
4.7.3 Auth User Group......................................................................................................................................... 86
4.7.4 Radius Server (MH-4000 Only)................................................................................................................89
4.7.5 POP3 (MH-4000 only)................................................................................................................................89
4.7.6 LDAP (MH-4000 only)................................................................................................................................90
4.8 CONTENT FILTERING..............................................................................................................................................92
4.8.1 URL Blocking...............................................................................................................................................92
4.8.2 Script Blocking............................................................................................................................................ 94
4.8.3 P2P Blocking...............................................................................................................................................95
4.8.4 IM Blocking..................................................................................................................................................96
4.8.5 Download Blocking..................................................................................................................................... 97
4.9 VIRTUAL SERVER...................................................................................................................................................99
4.9.1 Mapped IP .................................................................................................................................................100
4.9.2 Virtual Server.............................................................................................................................................102
4.10 POLICY ..............................................................................................................................................................108
4.10.1 Outgoing.................................................................................................................................................. 108
4.10.2 Incoming.................................................................................................................................................. 114
4.10.3 WAN To DMZ & LAN To DMZ............................................................................................................... 118
4.10.4 DMZ To WAN & DMZ To LAN...............................................................................................................122
4.11 VPN ...................................................................................................................................................................127
Page 5

Multi-Homing Security Gateway User’s Manual
4.11.1 IPSec Autokey.........................................................................................................................................127
4.11.2 PPTP Server............................................................................................................................................ 172
4.11.3 PPTP Client............................................................................................................................................. 176
4.12 INBOUND BALANCE (MH-4000 ONLY) .............................................................................................................. 180
4.13 LOG ...................................................................................................................................................................203
4.13.1 T raf fic Log................................................................................................................................................203
4.13.2 Event Log ................................................................................................................................................205
4.13.3 Connection Log.......................................................................................................................................208
4.13.4 Log Backup.............................................................................................................................................210
4.14 ALARM ...............................................................................................................................................................213
4.14.1 Blaster Alarm...........................................................................................................................................213
4.14.2 T raf fic Alarm............................................................................................................................................214
4.14.3 Event Alarm............................................................................................................................................. 215
4.15 ACCOUNTING REPORT (MH-4000 ONLY) ......................................................................................................... 217
4.15.1 Setting......................................................................................................................................................217
4.15.2 Outbound Accounting Report...............................................................................................................217
4.15.3 Inbound Accounting Report..................................................................................................................222
4.16 STATI STICS ........................................................................................................................................................226
4.16.1 Interface Statistics..................................................................................................................................226
4.16.2 Policy Statistics....................................................................................................................................... 227
4.17 STATU S ..............................................................................................................................................................230
4.17.1 Interface Status.......................................................................................................................................230
4.17.2 System Info (MH-4000 only).................................................................................................................230
4.17.3 Auth Status..............................................................................................................................................231
4.17.4 ARP Table................................................................................................................................................232
4.17.5 DHCP Clients..........................................................................................................................................233
Page 6

Multi-Homing Security Gateway User’s Manual
Chapter 1: Introduction
As Internet become essential for your business, the only way to prevent your Internet connection from failure
is to have more than one connection. PLANET’s Multi-Homing Security Gateways (MH-2K/4K, in the
following section) reduce the risk of potential shutdown if one of the Internet connections should fail. In
addition, they allow you to perform load-balancing by distributing the traffic through two WAN connections.
With embedded DNS server of MH-4000, connections from Internet are given the IP address of two WAN
ports to balance the traffic over the links.
Not only a multi-homing device, PLANET’s MH-2K/4K also provides a complete security solution in a box.
The policy-based firewall, Intrusion detection and prevention, content filtering function and VPN connectivity
with 3DES and AES encryption make it a perfect product for your network security. No more complex
connection and settings for integrating different security products on the network is required.
Bandwidth management function is also supported on MH-2K/4K to offers network administrators an easy
yet powerful means to allocate network resources based on business priorities, and to shape and control
bandwidth usage.
1.1 Features
♦ WAN Backup: MH-2K/4K can monitor the each WAN link status and automatically activate backup links
when a failure is detected. The detection is based on the configurable target Internet addresses.
♦ Outbound Load Balancing: The network sessions are assigned based on the user configurable load
balancing mode, including “Auto”, “Round-Robin”, “By Traffic”, “By Session” and “By Packet”. User can
also configure which IP or TCP/UDP type of traffic use which WAN port to connect.
♦ Inbound Load Balancing with Embedded DNS Server: In order to direct traffic to hosted servers
through two links and provide inbound loading balancing, the MH-4000 provides a built-in DNS server for
the hosted servers.
♦ Policy-based Firewall: The built-in policy-based firewall prevents many known hacker attack, including
SYN attack, ICMP flood, UDP flood, Ping of Death, etc. The access control function allowed only
specified WAN or LAN users to use only allowed network services on specified time.
♦ VPN Connectivity: The security gateway supports PPTP and IPSec VPN. With DES, 3DES and AES
encryption and SHA-1 / MD5 authentication, the network traffic over public Internet is secured.
♦ Content Filtering: The security gateway can block network connection based on URLs, Scripts (The
Pop-up, Java Applet, cookies and Active X), P2P (eDonkey, Bit Torrent and WinMX), Instant Messaging
(MSN, Yahoo Messenger, ICQ, QQ and Skype) and Download blocking.
♦ Dynamic Domain Name System (DDNS): The Dynamic DNS service allows you to alias a dynamic IP
address to a static hostname.
♦ Multiple NAT: Multiple NAT allows local port to set multiple subnetworks and connect with the Internet
through different WAN IP Addresses.
- 1 -
Page 7

Multi-Homing Security Gateway User’s Manual
♦ Server Load Balancing: Up to 4 group virtual servers are supported for server load balancing
♦ Dynamic Host Control Protocol (DHCP) client and server: In the WAN site, the DHCP client can get
an IP address from the Internet Server Provider (ISP) automatically. In the LAN site, the DHCP server
can allocate up to 253 client IP addresses and distribute them including IP address, subnet mask as well
as DNS IP address to local computers. It provides an easy way to manage the local IP network.
♦ Web based GUI: supports web based GUI for configuration and management. It also supports multiple
language including English, Traditional Chinese and Simplified Chinese.
♦ Bandwidth Management: Network packets can be classified based on IP address, IP subnet and
TCP/UDP port number and give guarantee and burst bandwidth with three levels of priority.
♦ User Authentication: User database can be configured on the devices, MH-4000 also supports the
authenticated database through external RADIUS, POP3 and LDAP server.
1.2 Package Contents
The following items should be included:
MH-2000
Multi-Homing Security Gateway
User’s Manual CD-ROM
This Quick Installation Guide
Power Adapter
MH-4000
Multi-Homing Security Gateway
User’s Manual CD-ROM
This Quick Installation Guide
Power Cord
Rack-mounting kit
RS-232 console cable
If any of the contents are missing or damaged, please contact your dealer or distributor immediately.
1.3 MH-2K/4K Front View
MH-2000 Front Panel
- 2 -
Page 8

Multi-Homing Security Gateway User’s Manual
LED Description
PWR Power is supplied to this device.
STATUS Blinks to indicate this devise is being turned on
and booting. After one minute, this LED indicator
will stop blinking, it means this device is now
ready to use.
WAN1,
WAN2, LAN,
DMZ
MH-4000 Front Panel
LED Description
PWR Power is supplied to this device.
WAN1,
WAN2, LAN,
DMZ
Steady on indicates the port is connected to
other network device.
Blink to indicates there is traffic on the port
Green Steady on indicates the port is
connected to other network device.
Blink to indicates there is traffic on the
port
Orange Steady on indicates the port is
connected at 100Mbps speed
1.4 MH-2K/4K Rear Panel
MH-2000 Rear Panel
Port or button Description
RESET Press this button to restore to factory default
settings.
WAN 1,
WAN2
LAN Connect to your local PC, switch or other
DMZ Connect to your server or other network
Connect to your xDSL/Cable modem or other
Internet connection devices
local network device
device
- 3 -
Page 9

Multi-Homing Security Gateway User’s Manual
MH-4000 Rear Panel
1.5 Specification
Product Multi-homing Security Gateway
Model MH-2000 MH-4000
Hardware
Ethernet
LED POWER, STATUS, 10/100 and LNK/ACT for each LAN and WAN port
Power 5VDC, 2.4A 100~240 VAC, 50~60Hz
Operating Environment Temperature: 0~50°C
Dimension W x D x H, mm 220 x 149 x 37 431 x 254 x 44
Regulatory FCC, CE Mark
Software
Management Web Web, SNMP
Network Connection Transparent mode (WAN to DMZ), NAT, Multi-NAT, Static Route, RIPv2
Outbound Load Balancing Policy-based routing
Inbound Load Balancing Built-in DNS for inbound
Firewall Policy-based firewall rule with schedule
VPN Tunnels 200 1000
VPN Functions PPTP, IPSec
Bandwidth Management Policy-based bandwidth management
Content Filtering URL blocking
User authentication Built-in user database Built-in user database with up to 500 entries
Log and Alarm Log and alarm for event and traffic
Statistics Traffic statistic for interface (WAN 1/2) and policies
Others Dynamic DNS
LAN 1 x 10/100Mbps RJ-45
WAN 2 x 10/100Mbps RJ-45
DMZ 1 x 10/100Mbps RJ-45
Relative Humidity: 10%~90%
Load-balancing by Round-Robin, traffic, session and packet
NAT/ NAPT
SPI firewall
Prevention of SYN attack, ICMP Flood, UDP flood, Ping of Death, Tear Drop, IP
Spoofing, IP route, Port Scan and Land attack
DES, 3DES and AES encrypting
SHA-1 / MD5 authentication algorithm
Remote access VPN (Client-to-Site) and Site to Site VPN
Guarantee and maximum bandwidth with 3 priority levels
Classify traffics based on IP, IP subnet, TCP/UDP port
Blocks Popup, Java Applet, cookies and Active X
P2P blocking
IM blocking
Download blocking
Support RADIUS authentication
Log can be saved from web, sent by e-mail or sent to syslog server
Graphic display
Record up to 30 day
NTP support
DHCP server
Mapping IP (DMZ)
Server load balancing
- 4 -
Page 10

Multi-Homing Security Gateway User’s Manual
Chapter 2: Hardware Installation
2.1 Installation Requirements
Before installing MH-2K/4K, make sure your network meets the following requirements.
- Mechanical Requirements
MH-2K/4K is installed between your Internet connection and local area network. You can place it on the
table or rack, and locate the unit near the power outlet.
- Electrical Requirements
MH-2K/4K is a power-required device, that means, it will not work until it is powered. If your network PCs
will need to transmit data all the time, please consider use an UPS (Uninterrupted Power Supply) for your
MH-2K/4K. It will prevent you from network data loss. In some area, installing a surge suppression device
may also help to protect your device from being damaged by unregulated surge or current to the
MH-2K/4K.
- Network Requirements
In order for MH-2K/4K to secure your network traffic, the traffic must pass through the device at a useful
point in a network. In most situations, MH-2K/4K should be placed behind the Internet connection device.
2.2 Operation Mode
MH-2K/4K DMZ port supports three operation modes, Disable, NAT and Transparent. In Disable mode, the
DMZ port is not active. In transparent mode, MH-2K/4K works as proxy with forward DMZ packet to WAN
and forward WAN packet to DMZ. The DMZ and WAN side IP addresses are in the same subnet. In NAT
mode, DMZ side user will share one public IP address of WAN port to make Internet connection. Please
find the following two pictures for example.
- 5 -
Page 11
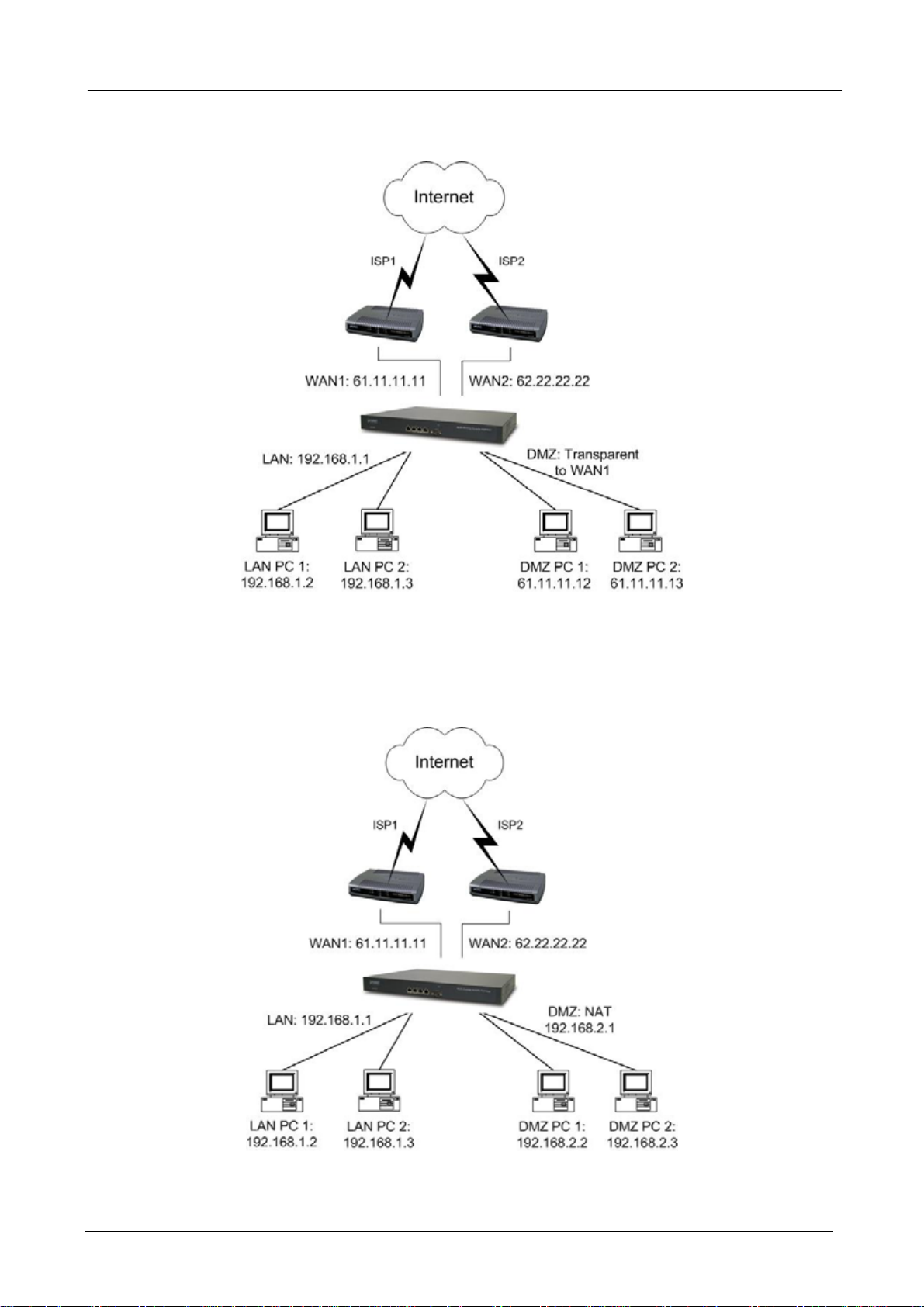
2.2.1 Transparent Mode Connection Example
Multi-Homing Security Gateway User’s Manual
The WAN1 and DMZ side IP addresses are on the same subnet. This application is suitable if you have a
subnet of IP addresses and you do not want to change any IP configuration on the subnet.
2.2.2 NAT Mode Connecting Example
DMZ and WAN1 IP addresses are on the different subnet. This provides higher security level then
transparent mode.
- 6 -
Page 12
Multi-Homing Security Gateway User’s Manual
Chapter 3: Getting Started
3.1 Web Configuration
STEP 1:
Connect the Administrator’s PC and the LAN port of MH-2K/4K to a hub or switch. Make sure there is a link
light on the hub/switch for both connections. MH-2K/4K has an embedded web server used for management
and configuration. Use a web browser to display the configurations of MH-2K/4K (such as Internet Explorer
4(or above) or Netscape 4.0(or above) with full java script support). The default IP address of MH-2K/4K is
192.168.1.1 with a subnet mask of 255.255.255.0. Therefore, the IP address of the Administrator PC must be
in the range between 192.168.1.2– 192.168.1.254
If the company’s LAN IP Address is not subnet of 192.168.1.0, (i.e. LAN IP Address is 172.16.0.1), then the
Administrator must change his/her PC IP address to be within the same range of the LAN subnet (i.e.
172.16.0.2). Reboot the PC if necessary.
By default, MH-2K/4K is shipped with its DHCP Server function enabled. This means the client computers on
the LAN network including the Administrator PC can set their TCP/IP settings to automatically obtain an IP
address from the device.
The following table is a list of private IP addresses. These addresses may not be used as a WAN IP address.
10.0.0.0 ~ 10.255.255.255
172.16.0.0 ~ 172.31.255.255
192.168.0.0 ~ 192.168.255.255
STEP 2:
Once the Administrator PC has an IP address on the same network as the Multi-Homing Security Gateway,
open up an Internet web browser and type in
A pop-up screen will appear and prompt for a username and password. A username and password is required
to connect to MH-2K/4K. Enter the default login username and password of Administrator (see below).
Username: admin
Password: admin
Click OK.
http://192.168.1.1 in the address bar.
- 7 -
Page 13
Multi-Homing Security Gateway User’s Manual
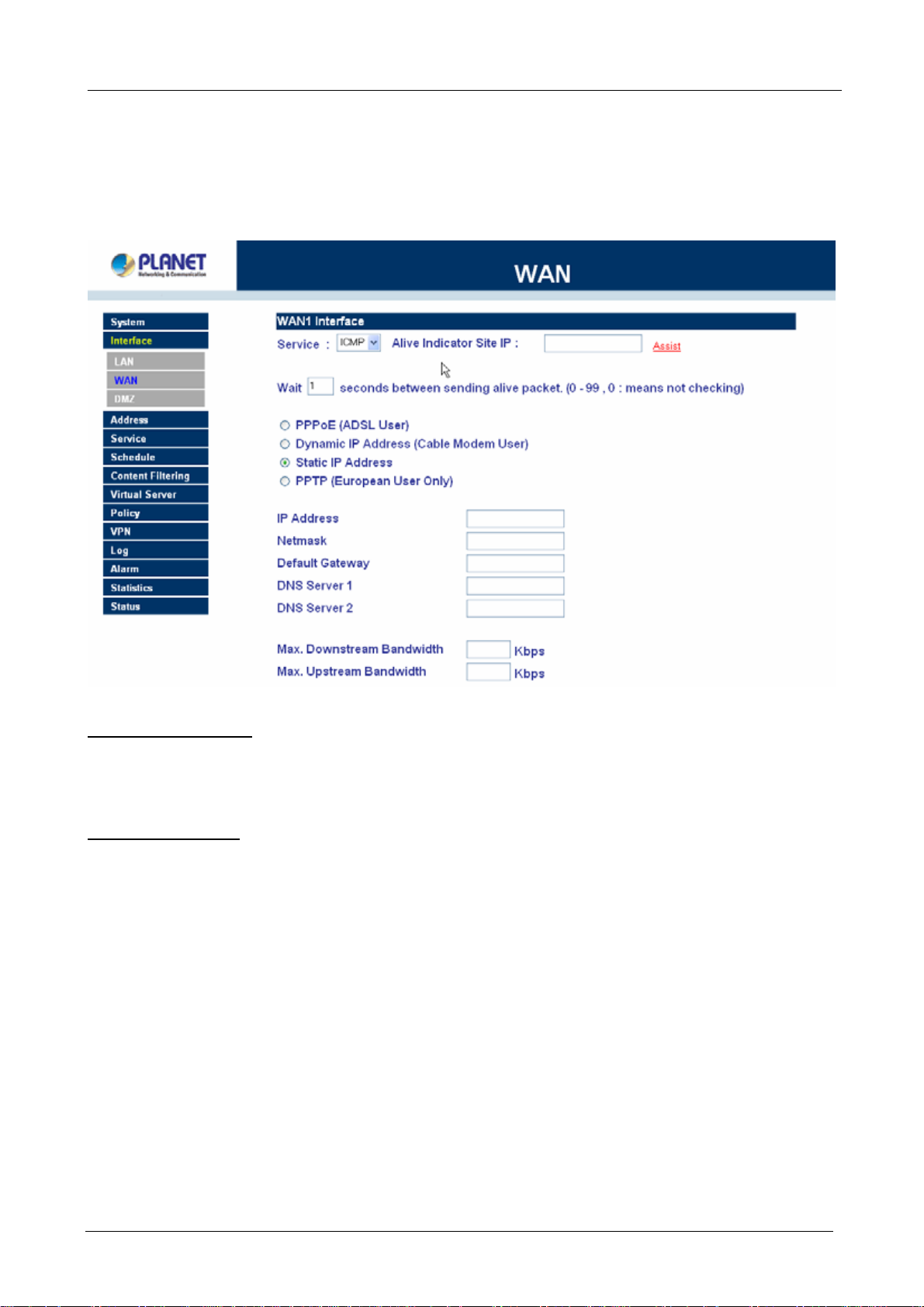
3.2 Configure WAN 1 interface
After entering the username and password, MH-2K/4K WebUI screen will display. Select the Interface tab on
the left menu then click on WAN below it.
Click on Modify button of WAN NO.1. The following page is shown.
Alive Indicator Site IP: This feature is used to ping an address for detecting WAN connection status.
Service: ICMP You can select an IP address by Assist, or type an IP address manually.
Service: DNS You can select a DNS IP and Domain name by Assist, or type the related data manually.
PPPoE (ADSL User): This option is for PPPoE users who are required to enter a username and password in
order to connect.
Username: Enter the PPPoE username provided by the ISP.
Password: Enter the PPPoE password provided by the ISP.
IP Address provided by ISP:
Dynamic: Select this if the IP address is automatically assigned by the ISP.
Fixed: Select this if you were given a static IP address. Enter the IP address that is given to you by
your ISP.
Max. Upstream/Downstream Bandwidth: The bandwidth provided by ISP.
Service-On-Demand:
The PPPoE connection will automatically disconnect after a length of idle time (no activities). Enter in
the amount of idle minutes before disconnection. Enter ‘0’ if you do not want the PPPoE connection to
disconnect at all.
- 8 -
Page 14
Multi-Homing Security Gateway User’s Manual
For Dynamic IP Address (Cable Mod em User): This option is for users who are automatically assigned an
IP address by their ISP, such as cable modem users. The following fields apply:
MAC Address: This is the MAC Address of the device. Some ISPs require specified MAC address. If the
required MAC address is your PC’s, click Clone MAC Address.
Hostname: This will be the name assign to the device. Some cable modem ISP assigns a specific
hostname in order to connect to their network, please enter the hostname here. If not
required by your ISP, you do not have to enter a hostname.
Domain Name: You can specify your own domain name or leave it blank.
User Name: The user name is provided by ISP.
Password: The password is provided by ISP.
Max. Upstream/Downstream Bandwidth: The bandwidth provided by ISP.
For Static IP Address: This option is for users who are assigned a static IP Address from their ISP. Your ISP
will provide all the information needed for this section such as IP Address, Netmask, Gateway, and DNS.
IP Address: Enter the static IP address assigned to you by your ISP. This will be the public IP address of
the WAN 1 port of the device.
Netmask: This will be the Netmask of the WAN 1 network. (i.e. 255.255.255.0)
Default Gateway: This will be the Gateway IP address.
Domain Name Server (DNS): This is the IP Address of the DNS server.
Max. Upstream/Downstream Bandwidth: The bandwidth provided by ISP.
For PPTP (European User Only): This is mainly used in Europe. You need to know the PPTP Server
address as well as your name and password.
User Name: The user name is provided by ISP.
Password: The password is provided by ISP.
IP Address: Enter the static IP address assigned to you by your ISP, or obtain an IP address
automatically from ISP.
PPTP Gateway: Enter the PPTP server IP address assigned to you by your ISP.
Connect ID: This is the ID given by ISP. This is optional.
Max. Upstream/Downstream Bandwidth: The bandwidth provided by ISP.
BEZEQ-ISRAEL: Select this item if you are using the service provided by BEZEQ in Israel.
Service-On-Demand: The PPTP connection will automatically disconnect after a length of idle time (no
activities). Enter the amount of idle minutes before disconnection. Enter ‘0’ if you
do not want the PPTP connection to disconnect at all.
NOTE: This function is not supported on MH-4000.
Ping: Select this to allow the WAN network to ping the IP Address of MH-2K/4K This will allow people from
the Internet to be able to ping MH-2K/4K WAN IP. If set to enable, the device will respond to echo request
packets from the WAN network.
- 9 -
Page 15
Multi-Homing Security Gateway User’s Manual
WebUI: Select this to allow the device WebUI to be accessed from the WAN network. This will allow the
WebUI to be configured from a user on the Internet. Keep in mind that the device always requires a username
and password to enter the WebUI.
3.3 Configure WAN 2 interface
If you want to connect WAN 2 to another ISP connection, click Modify button of WAN No. 2 then repeat above
procedures to setup.
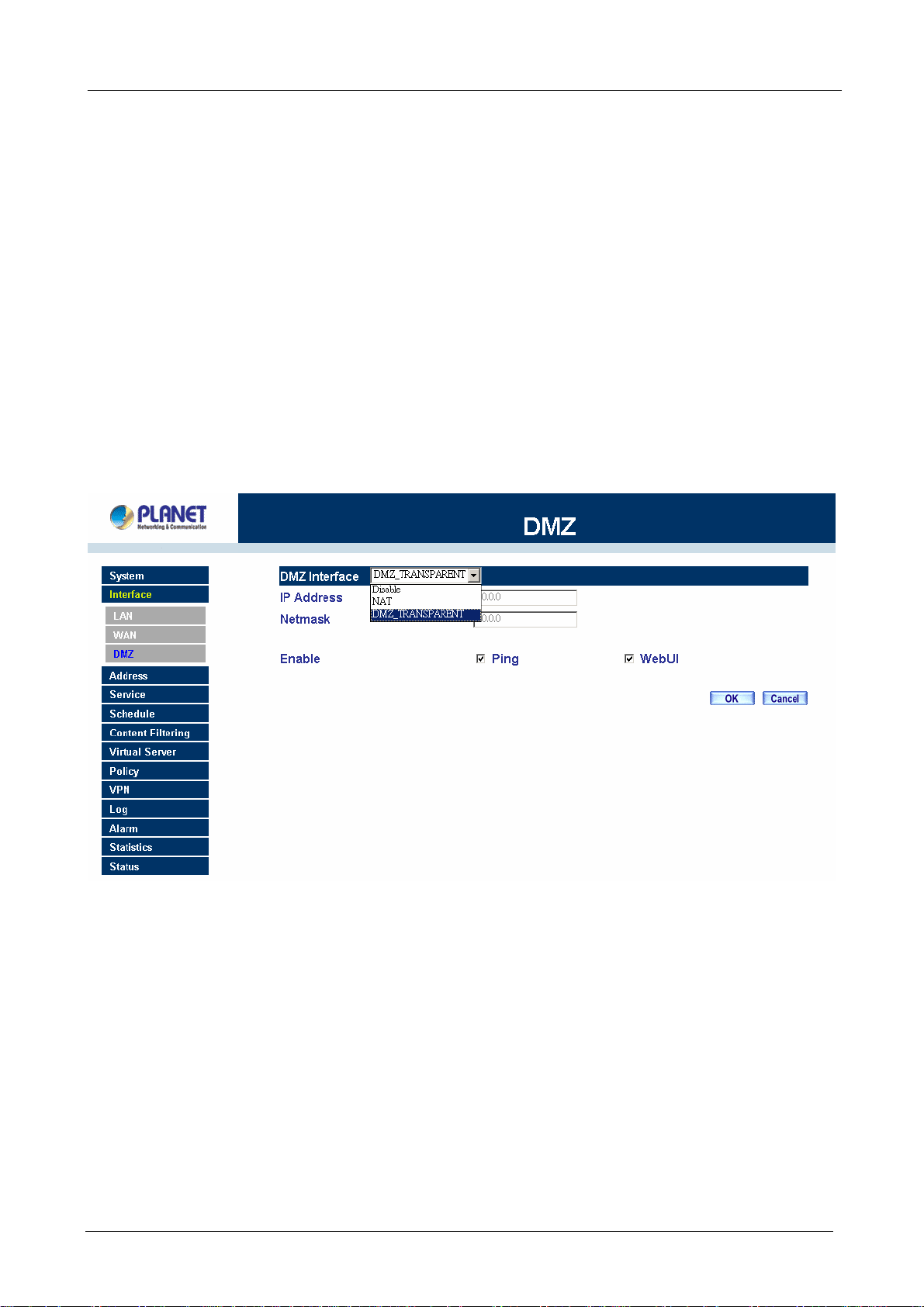
3.4 Configure DMZ interface
Depends on your network requirement, you can disable the DMZ port, make DMZ port transparent to WAN 1 or
enable NAT function on it.
To configure the DMZ port, select the Interface tab on the left menu, then click on DMZ, the following page is
shown.
Please refer to section 3 for select the mode you need and configure relative IP parameters.
3.5 Configure Policy
STEP 1:
Click on the Policy tab from the main function menu, and then click on Outgoing (LAN to WAN) from the
sub-function list.
STEP 2:
Click on New Entry button.
STEP 3:
When the New Entry option appears, enter the following configuration:
Source Address – select “Inside_Any”
- 10 -
Page 16
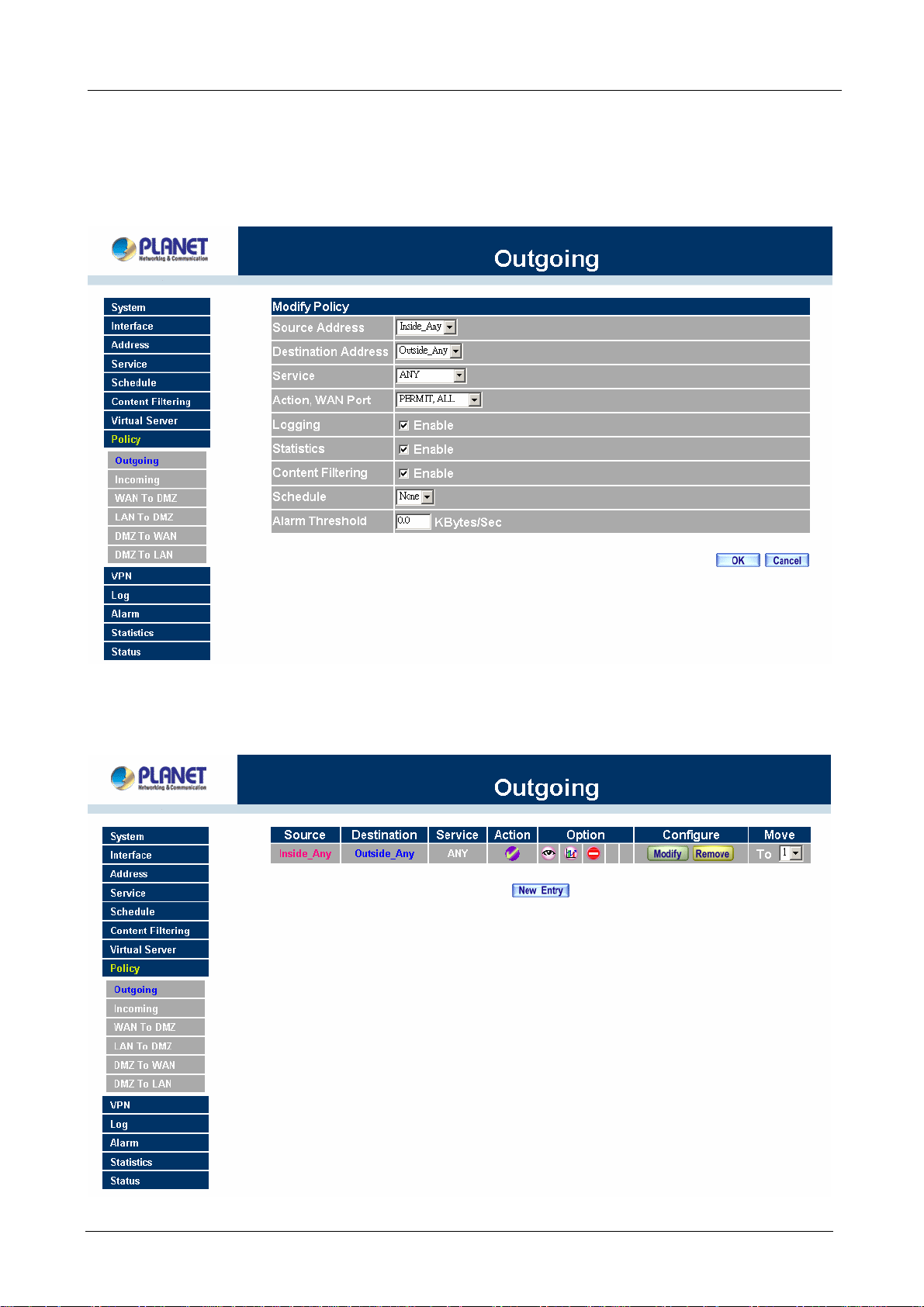
Destination Address – select “Outside_Any”
Service - select “ANY”
Action - select “Permit, ALL”
Click on OK to apply the changes.
Multi-Homing Security Gateway User’s Manual
STEP 4:
The configuration is successful when the screen below is displayed.
- 11 -
Page 17

Multi-Homing Security Gateway User’s Manual
Please make sure that all the computers that are connected to the LAN port have their Default Gateway IP
Address set to MH-2K/4K’s LAN IP Address (i.e. 192.168.1.1). At this point, all the computers on the LAN
network should gain access to the Internet immediately. If MH-2K/4K filter function is required, please refer to
the Policy section in chapter 4.
- 12 -
Page 18
Multi-Homing Security Gateway User’s Manual
Chapter 4: Web Configuration
The functions of MH-2000 and MH-4000 have some differences. MH-4000 support more functions then
MH-2000. Please find the following table for a list of their functions comparison.
Menu items MH-2000 MH-4000
System
Admin V V
Setting V V
Date/Time V V
Multiple Subnet V V
Hacker Alert V V
Blaster Alert V V
Route Table V V
DHCP V V
Host Table V V
SNMP N/A V
Dynamic DNS V V
Language V V
Permitted IP V V
Logout V V
Software Update V V
Interface V V
LAN V V
WAN V V
DMZ V V
Address V V
LAN V V
LAN Group V V
WAN V V
WAN Group V V
DMZ V V
DMZ Group V V
Service V V
Pre-defined V V
Custom V V
Group V V
Schedule V V
QoS V V
Authentication V V
Auth User V V
Auth User Group V V
RADIUS N/A V
Content Filter V V
URL Blocking V V
Script Blocking V V
P2P Blocking V V
IM Blocking V V
Download Blocking V V
Virtual Server V V
Mapped IP V V
Virtual Server1 V V
Virtual Server2 V V
Virtual Server3 V V
- 13 -
Page 19
Multi-Homing Security Gateway User’s Manual
Virtual Server4 V V
Policy V V
Outgoing V V
Incoming V V
WAN to DMZ V V
LAN to DMZ V V
DMZ to WAN V V
DMZ to LAN V V
VPN V V
IPSec Autokey V V
PPTP Server V V
PPTP Client V V
Inbound Balance N/A V
Log V V
Traffic Log V V
Event Log V V
Connection Log V V
Log Backup V V
Alarm V V
Traffic Alarm V V
Event Alarm V V
Accounting Report N/A V
Outbound N/A V
Inbound N/A V
Statistics V V
Interface Statistics V V
Policy Statistics V V
Status V V
Interface Status V V
System Info. N/A V
Auth. Status V V
ARP Table V V
DHCP Clients V V
4.1 System
MH-2K/4K Administration and monitoring configuration is set by the System Administrator. The System
Administrator can add or modify System settings and monitoring mode. The sub Administrators can only read
System settings but not modify them. In System, the System Administrator can:
1. Add and change the sub Administrator’s names and passwords;
2. Back up all MH-2K/4K settings into local files;
3. Set up alerts for Hackers invasion.
“System” is the managing of settings such as the privileges of packets that pass through MH-2K/4K and
monitoring controls. Administrators may manage, monitor, and configure MH-2K/4K settings. All
configurations are “read-only” for all users other than the Administrator; those users are not able to change
any settings for MH-2K/4K.
Admin: Control of user access to MH-2K/4K. He/she can add/remove users and change passwords.
- 14 -
Page 20

Multi-Homing Security Gateway User’s Manual
Setting: The Administrator may use this function to backup MH-2K/4K configurations and export (save) them
to an “Administrator” computer or anywhere on the network; or restore a configuration file to the device; or
restore MH-2K/4K back to default factory settings. Under Setting, the Administrator may enable e-mail alert
notification. This will alert Administrator(s) automatically whenever MH-2K/4K has experienced unauthorized
access or a network hit (hacking or flooding). Once enabled, an IP address of a SMTP (Simple Mail Transfer
protocol) Server is required. Up to two e-mail addresses can be entered for the alert notifications.
Date/Time: This function enables MH-2K/4K to be synchronized either with an Internet Server time or with the
client computer’s clock.
Multiple Subnet: This function allows local port to set multiple subnet works and connect with the internet
through different WAN 1 IP Addresses.
Hacker Alert: When abnormal conditions occur, MH-2K/4K will send an e-mail alert to notify the Administrator,
and also display warning messages in the Event window of Alarm.
Blaster Alert: This function is to protect your network from blaster worm. When abnormal network access on
RPC port occur, MH-2K/4K will block the access on specified time, send an e-mail alert or SNMP trap to notify
the Administrator, and also display warning messages in the Event window of Alarm.
Route Table: Use this function to enable the Administrator to add static routes for the networks when the
dynamic route is not efficient enough.
DHCP: Administrator can configure DHCP (Dynamic Host Configuration Protocol) settings for the LAN (LAN)
network.
Host Table: MH-2K/4K Administrator may use the Host Table function to make the device act as a DNS
Server for the LAN and DMZ network. All DNS requests to a specific Domain Name will be routed to
MH-2K/4K’s IP address. For example, an organization has their mail server (i.e., mail.planet.com.tw) in the
DMZ network (i.e. 192.168.10.10). The outside Internet world may access the mail server of the organization
easily by its domain name, providing that the Administrator has set up Virtual Server or Mapped IP settings
correctly. However, for the users in the LAN network, their WAN DNS server will assign them a public IP
address for the mail server. So for the LAN network to access the mail server (mail.planet.com.tw), they would
have to go out to the Internet, then come back through MH-2K/4K to access the mail server. Essentially, the
LAN network is accessing the mail server by a real public IP address, while the mail server serves their
request by a NAT address and not a real one. This odd situation occurs when there are servers in the DMZ
network and they are bound to real IP addresses. To avoid this, set up Host Table so all the LAN network
computers will use MH-2K/4K as a DNS server, which acts as the DNS Proxy.
- 15 -
Page 21
Multi-Homing Security Gateway User’s Manual
Dynamic DNS: The Dynamic DNS (require Dynamic DNS Service) allows you to alias a dynamic IP address
to a static hostname, allowing your device to be more easily accessed by specific name. When this function is
enabled, the IP address in Dynamic DNS Server will be automatically updated with the new IP address
provided by ISP.
SNMP (MH-4000 only): Provide the System Administrator enabling SNMP Trap Alert Notification for sending
email to the setting SNMP Trap receiver IP address when the network is disconnected/ connected and being
attacked by hackers or when emergency conditions occur.
Language: Both Chinese and English are supported in MH-2K/4K.
Permitted IP: Enables the Administrator to authorize specific internal/external IP address(es) for Managing
Gateway.
Logout: Administrator logs out the Multi-Homing Security Gateway. This function protects your system while
you are away.
Software Update: The administrator can update the device’s software with the latest version. Administrators
may visit distributor’s web site to download the latest firmware. Administrators may update the device
firmware to optimize its performance and keep up with the latest fixes for intruding attacks.
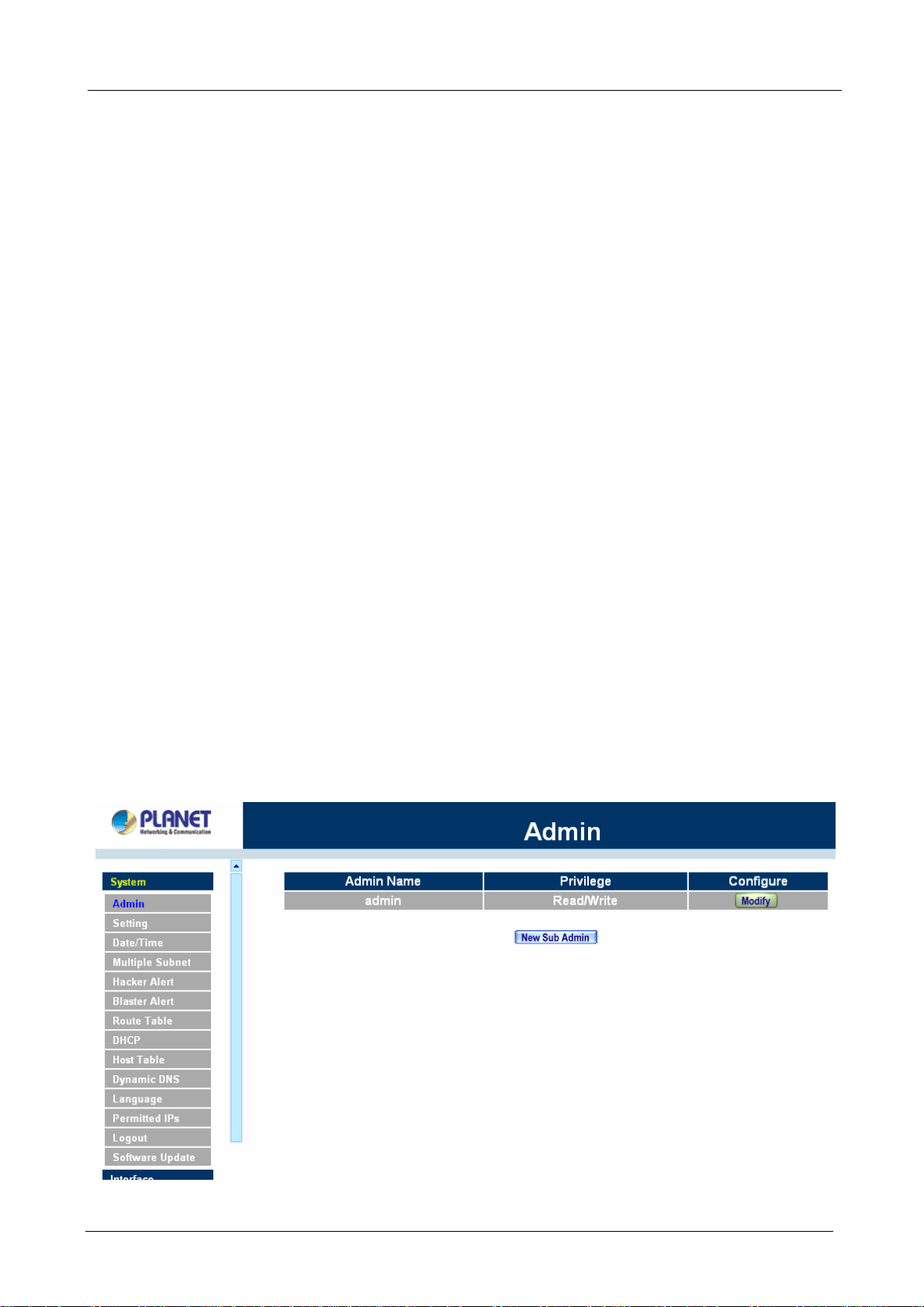
4.1.1 Admin
On the left hand menu, click on Setup, and then select Admin below it. The current list of Administrator(s)
shows up.
ÍÍ
- 16 -
Page 22
Multi-Homing Security Gateway User’s Manual
Settings of the Administration table
Administrator Name: The username of Administrators for MH-2K/4K. The user admin cannot be removed.
Privilege: The privileges of Administrators (Admin or Sub Admin)
The username of the main Administrator is Administrator with read / write privilege.
Sub Admins may be created by the Admin by clicking
New Sub Admin
. Sub Admins have read only
privilege.
Configure: Click Modify to change the “Sub Administrator’s” password and click Remove to delete a “Sub
Administrator.”
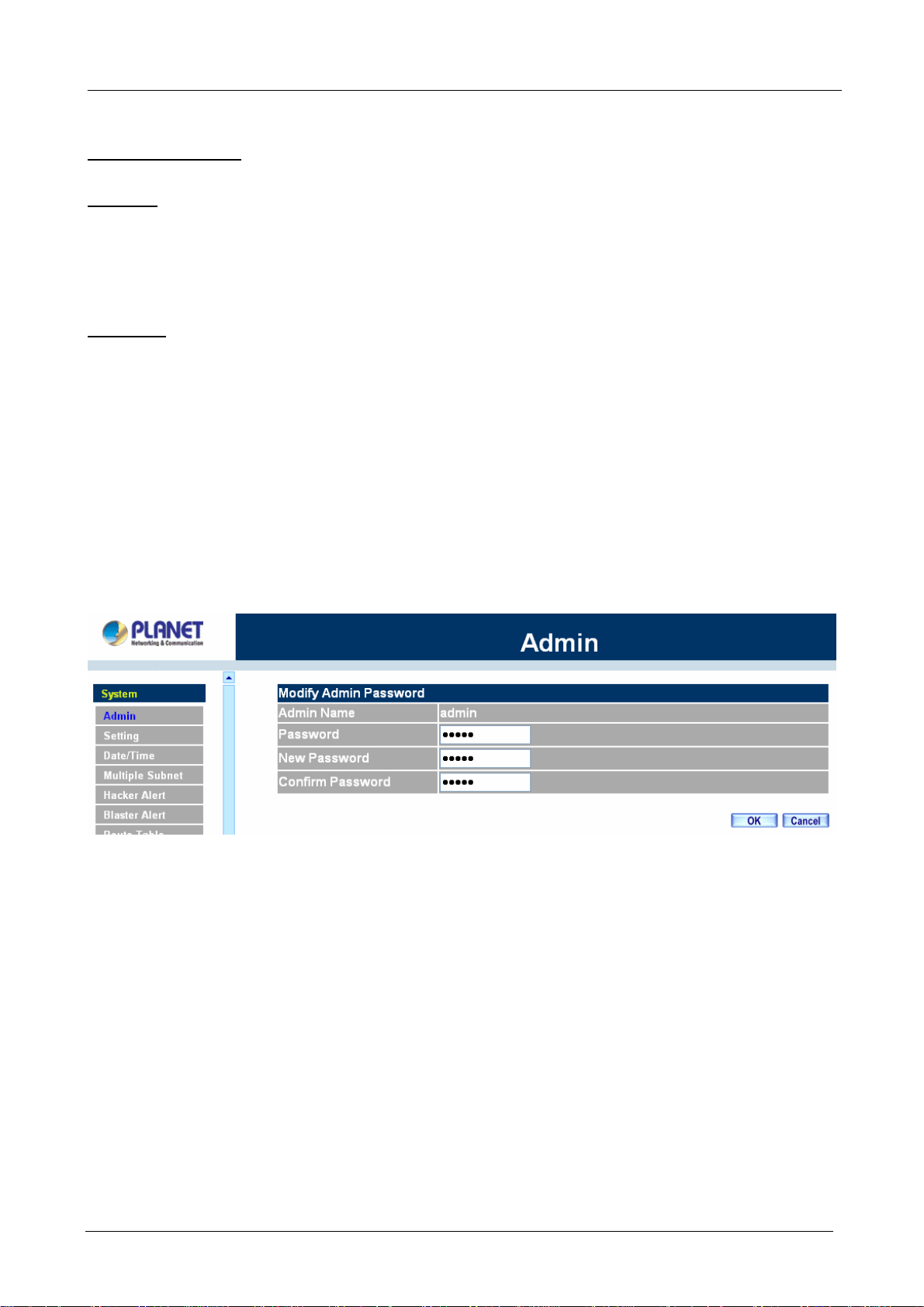
Changing the Main/Sub-Administrator’s Password
Step 1. The Modify Administrator Password window will appear. Enter in the required information:
Password: enter original password.
New Password: enter new password
Confirm Password: enter the new password again.
Step 2. Click OK to confirm password change or click Cancel to cancel it.
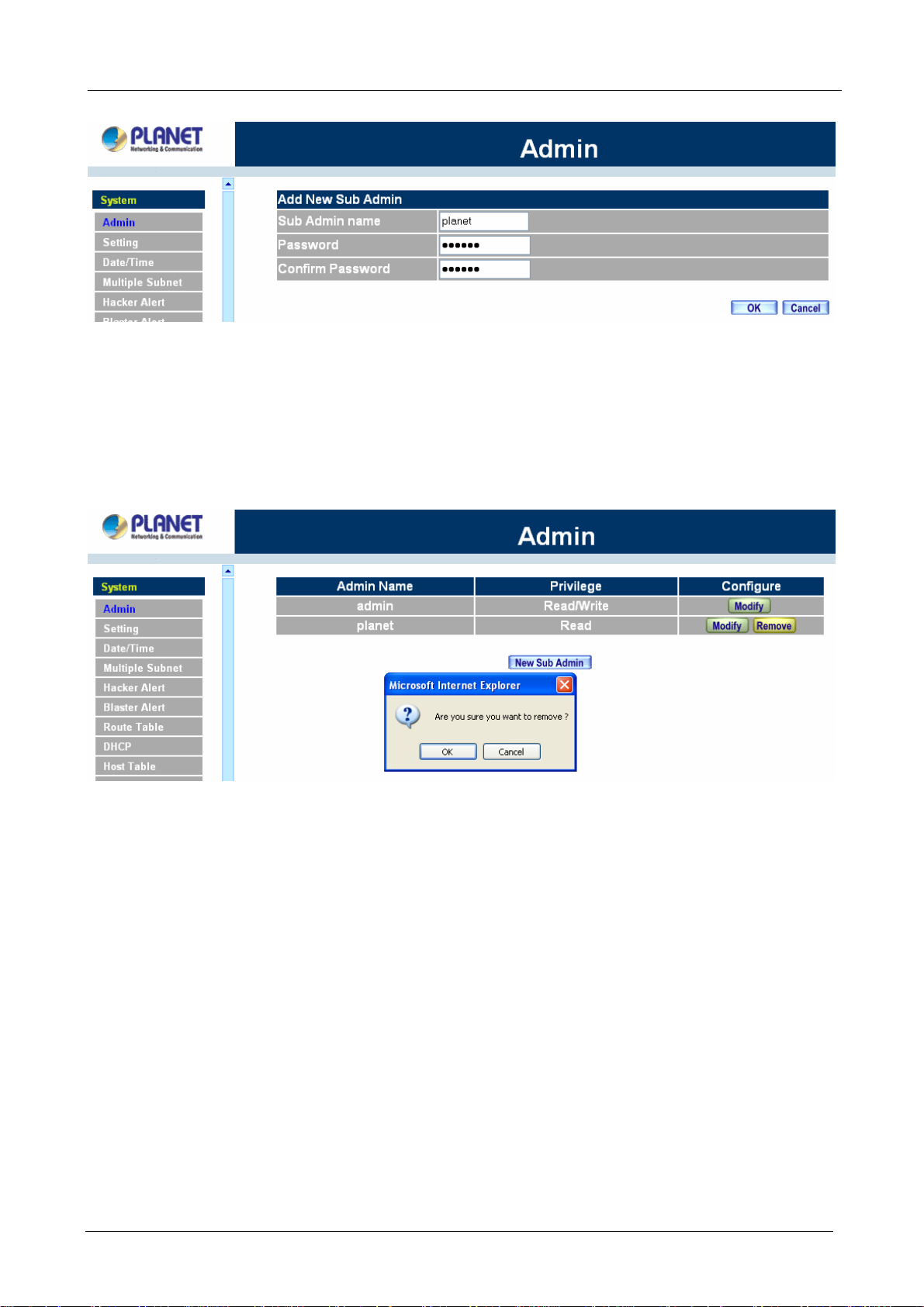
Adding a new Sub Administrator
Step 1. In the Add New Sub Administrator window:
Sub Admin Name: enter the username of new Sub Admin.
Password: enter a password for the new Sub Admin.
Confirm Password: enter the password again.
Step 2. Click OK to add the user or click Cancel to cancel the addition.
- 17 -
Page 23
Multi-Homing Security Gateway User’s Manual
Removing a Sub Administrator
Step 1. In the Administration table, locate the Administrator name you want to edit, and click on the
Remove option in the Configure field.
Step 2. The Remove confirmation pop-up box will appear. Click OK to remove that Sub Admin or click
Cancel to cancel.
4.1.2 Settings
The Administrator may use this function to backup MH-2K/4K configurations and export (save) them to an
“Administrator” computer or anywhere on the network; or restore a configuration file to the device; or restore
MH-2K/4K back to default factory settings.
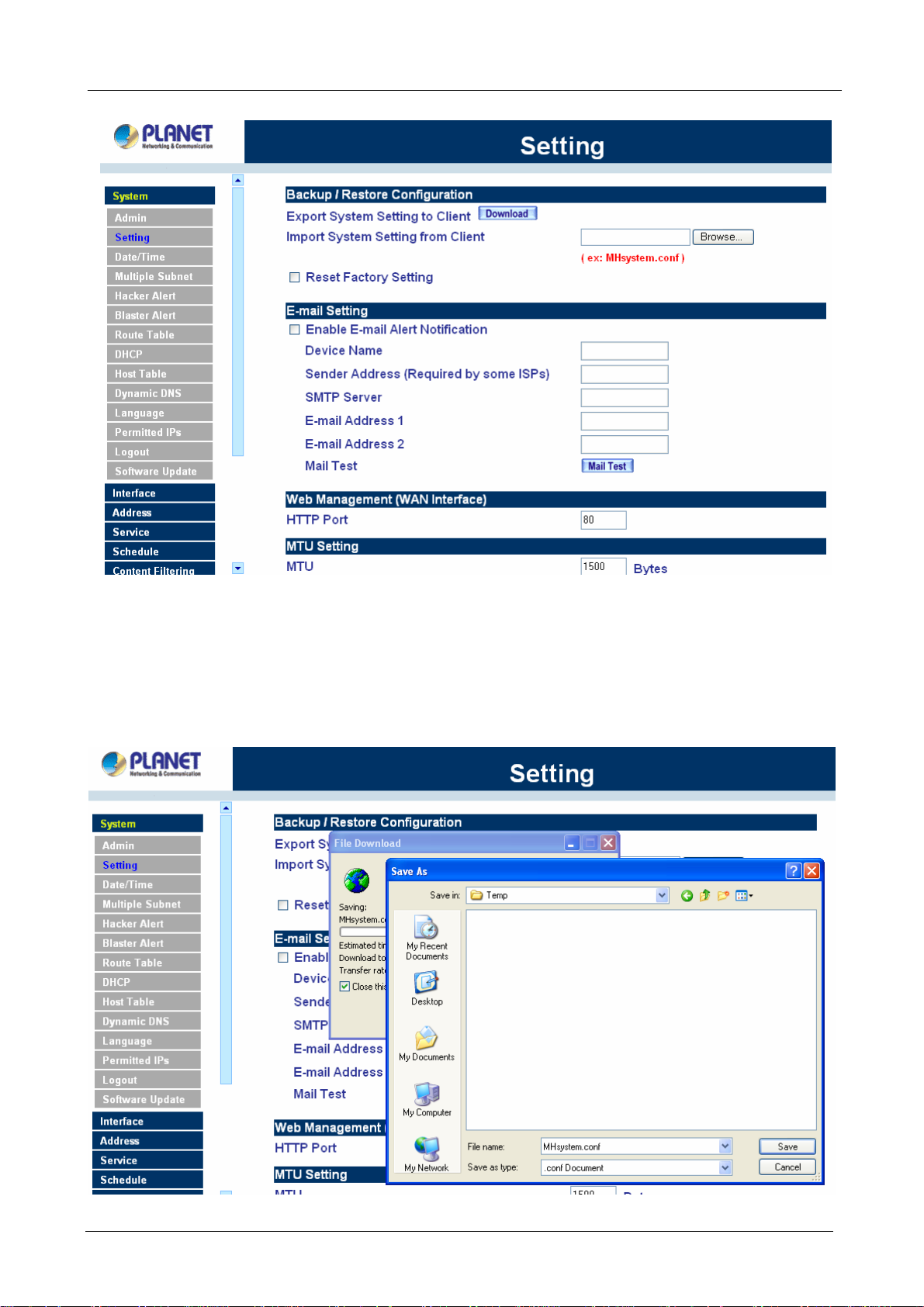
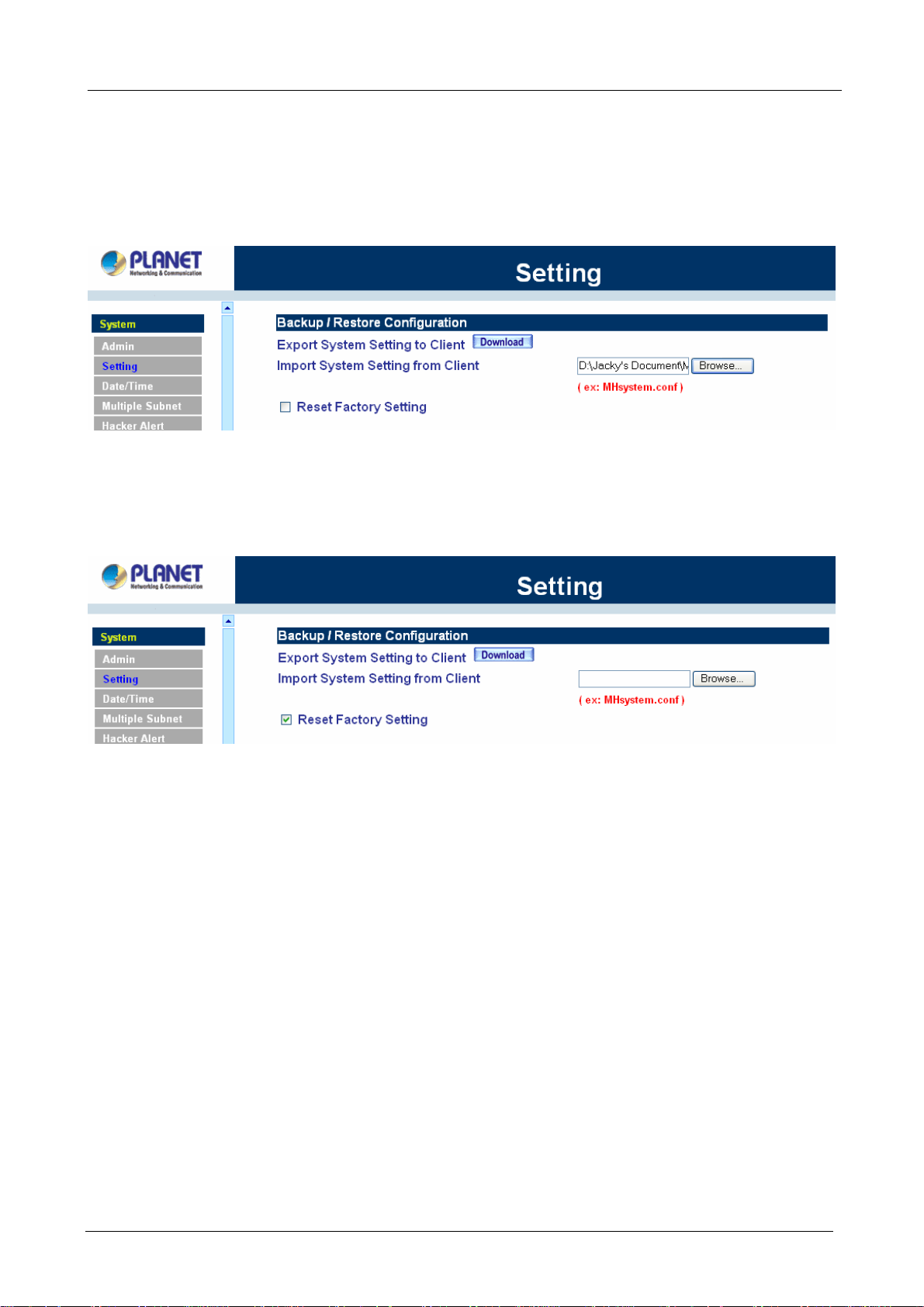
Entering the Settings window
Click Setting in the System menu to enter the Settings window. MH-2K/4K Configuration settings will be
shown on the screen.
- 18 -
Page 24
ÍÍ
Multi-Homing Security Gateway User’s Manual
Exporting MH-2K/4K settings
Step 1. Under Configuration, click on the Download button next to Export Sy stem Settings to Client.
Step 2. When the File Download pop-up window appears, choose the destination place to save the
exported file. The Administrator may choose to rename the file if preferred.
- 19 -
Page 25
Multi-Homing Security Gateway User’s Manual
Importing MH-2K/4K settings
Under Configuration, click on the Browse button next to Import System Settings. When the Choose File
pop-up window appears, select the file which contains the saved MH-2K/4K Settings, then click OK.
Click OK to import the file into MH-2K/4K or click Cancel to cancel importing.
Restoring Factory Default Settings
Step 1. Select Reset Factory Settings under Configuration.
Click OK at the bottom-right of the screen to restore the factory settings.
Enabling E-mail Alert Notification
Step 1. Select Enable E-mail Alert Notification under E-Mail Settings. This function will enable the
Multi-Homing Security Gateway to send e-mail alerts to the System Administrator when the
network is being attacked by hackers or when emergency conditions occur.
Step 2. SMTP Server IP: Enter SMTP server’s IP address.
Step 3. E-Mail Address 1: Enter the first e-mail address to receive the alarm notification.
Step 4. E-Mail Address 2: Enter the second e-mail address to receive the alarm notification. (Optional)
Click OK on the bottom-right of the screen to enable E-mail alert notification.
- 20 -
Page 26
Multi-Homing Security Gateway User’s Manual
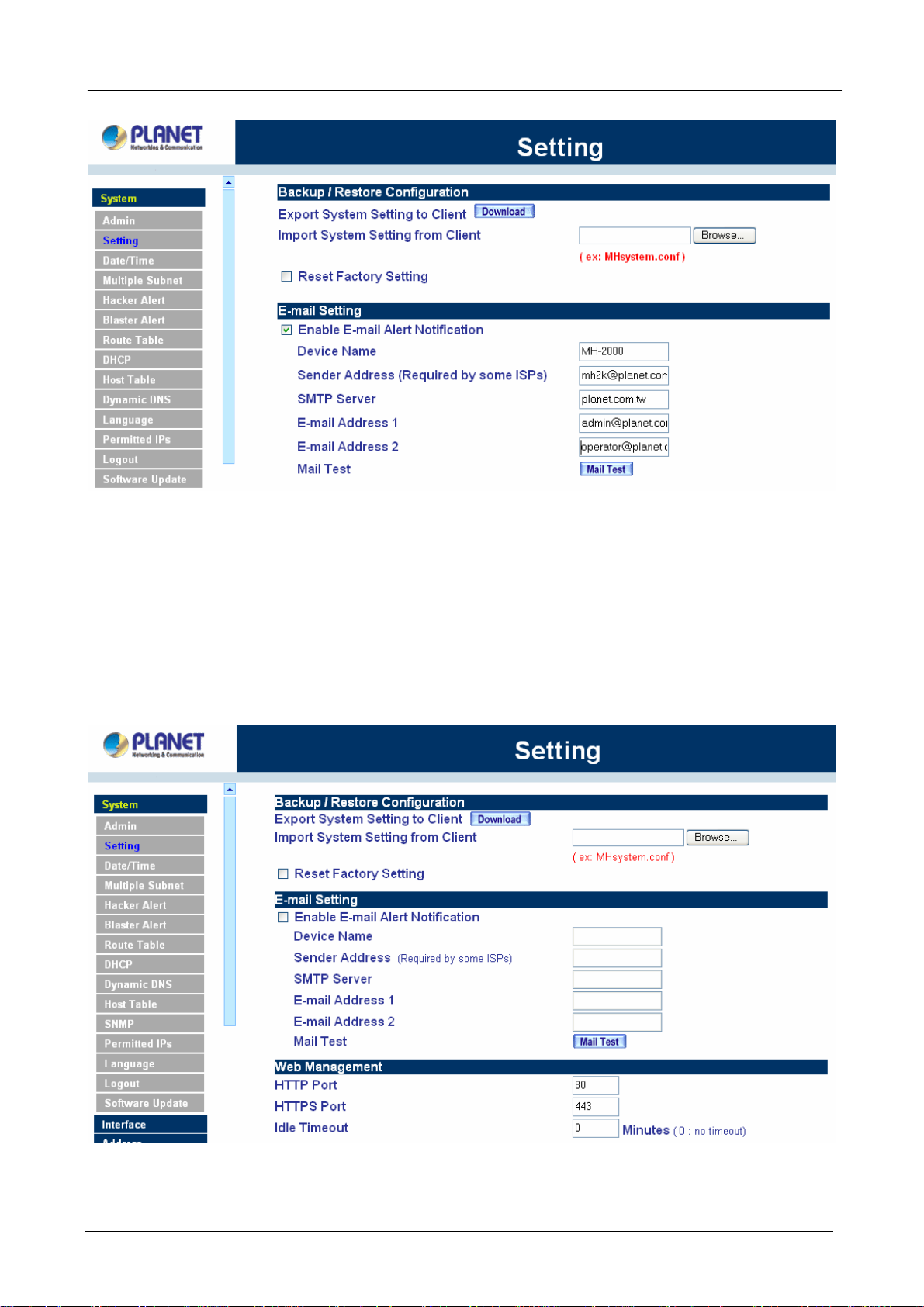
Web Management (WAN Interface)
The administrator can change the port number used by HTTP or HTTPS port anytime. (HTTPS only
supports with MH-4000)
Step 1. Set Web Management (WAN Interface). The administrator can change the port number used
by HTTP or HTTPS port anytime.
Step 2. Idle Timeout. Fill in the Idle Timeout setting, when time is up, the remote user will be logout
automatically. 0 means no timeout. (Idle Timeout only supports with MH-4000)
- 21 -
Page 27
Multi-Homing Security Gateway User’s Manual
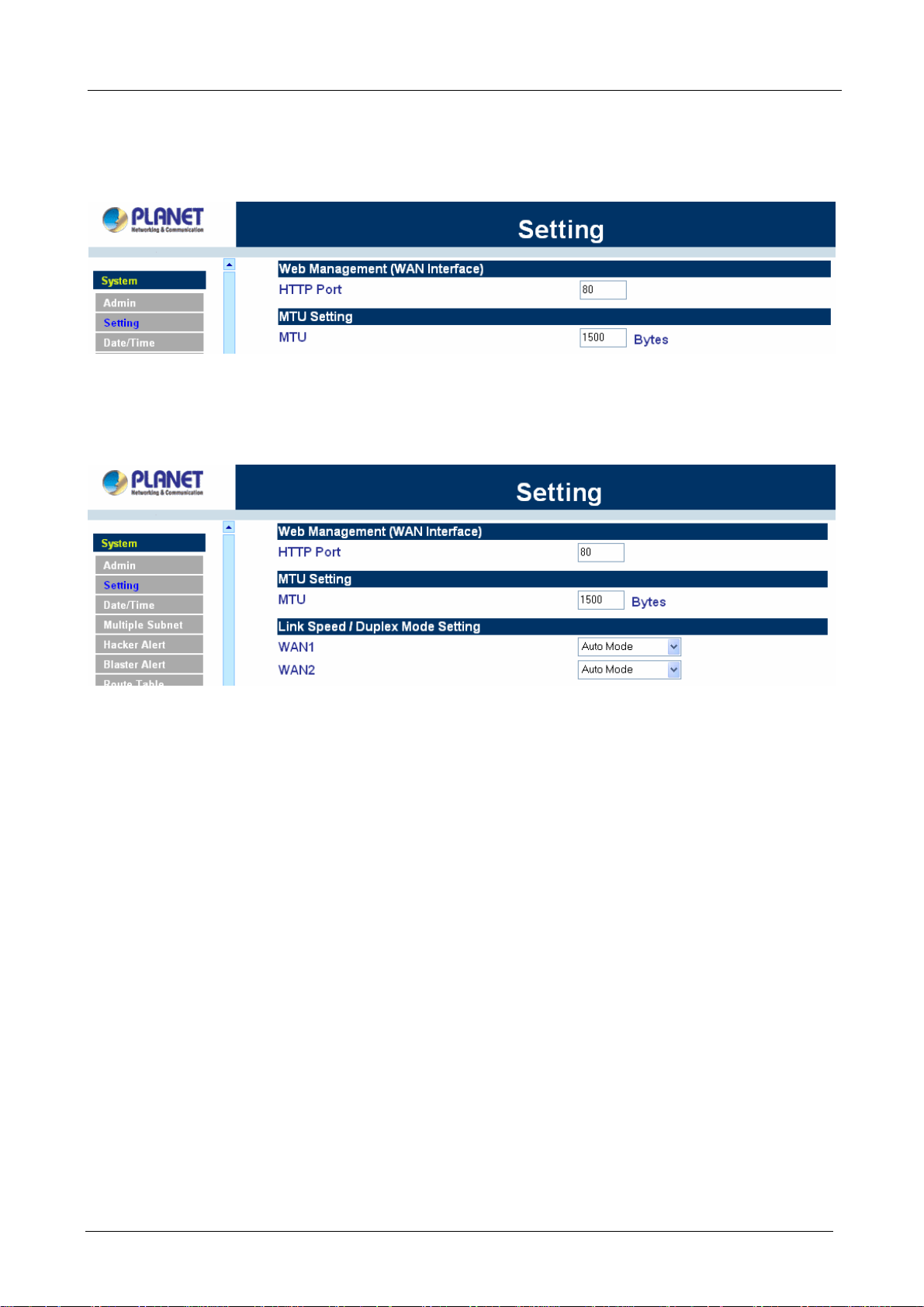
MTU (set networking packet length)
The administrator can modify the networking packet length.
Step 1. MTU Setting. Modify the networking packet length.
Link Speed / Duplex Mode Setting
This function allows administrator to set the transmission speed and mode of WAN Port. This feature is only
available with MH-2000.
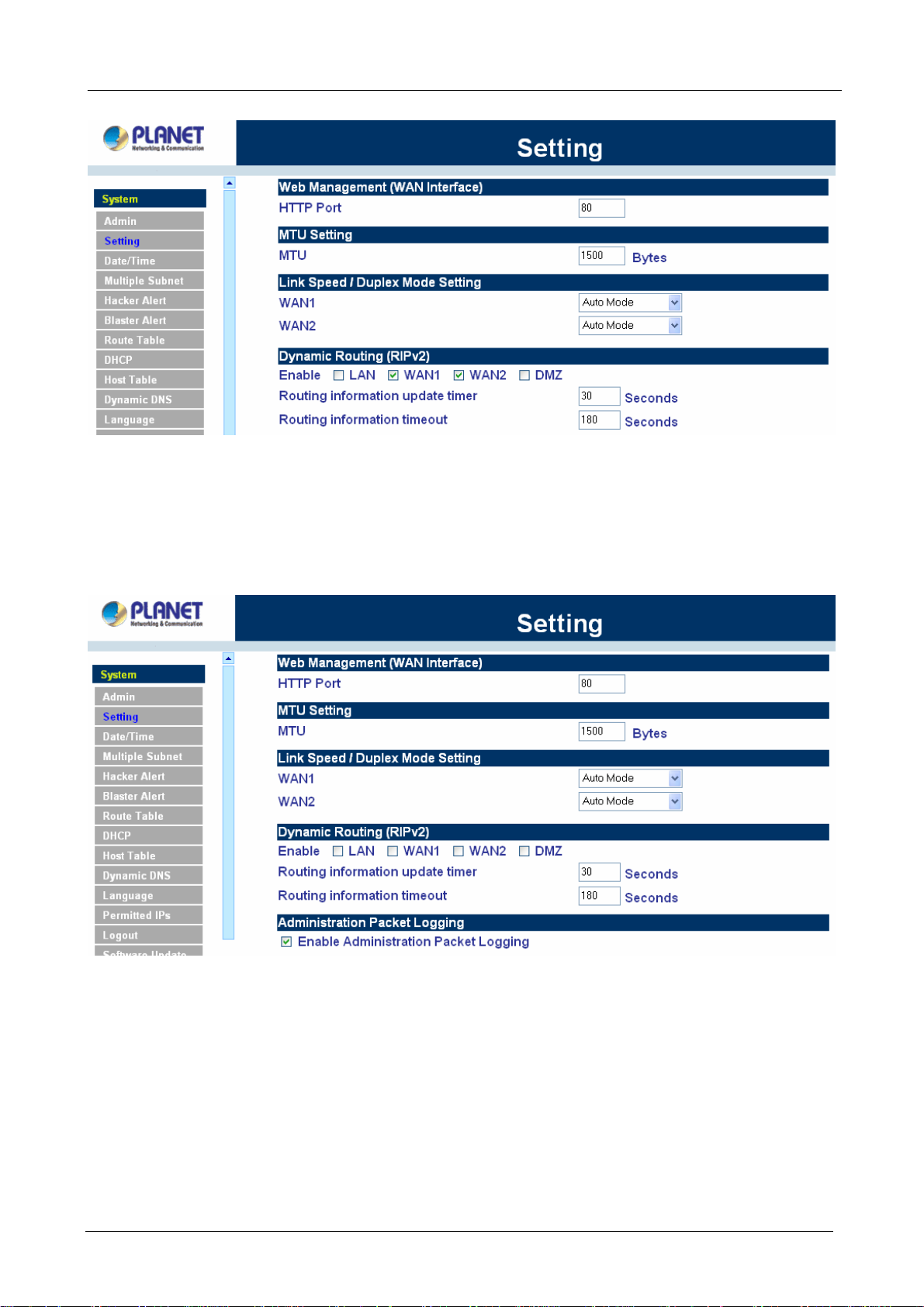
Dynamic Routing (RIPv2)
Enable Dynamic Routing (RIPv2), MH-2K/4K will advertise an IP address pool to the specific network so that
the address pool can be provided to the network. You can choose to enable LAN, WAN or DMZ interface to
allow RIP protocol supporting.
Routing information update timer: MH-2K/4K will send out the RIP protocol in a period of time to update the
routing table, the default timer is 30 seconds.
Routing information timeout: If MH-2K/4K does not receive the RIP protocol from the other router in a
period of time, MH-2K/4K will cut off the routing automatically until it receives RIP protocol again. The default
timer is 180 seconds.
- 22 -
Page 28
Multi-Homing Security Gateway User’s Manual
Administration Packet Logging
Step 1. Select this option to the device’s Administration Packet Logging. Once this function is
enabled, every packet to this appliance will be recorded for system administrator to trace.
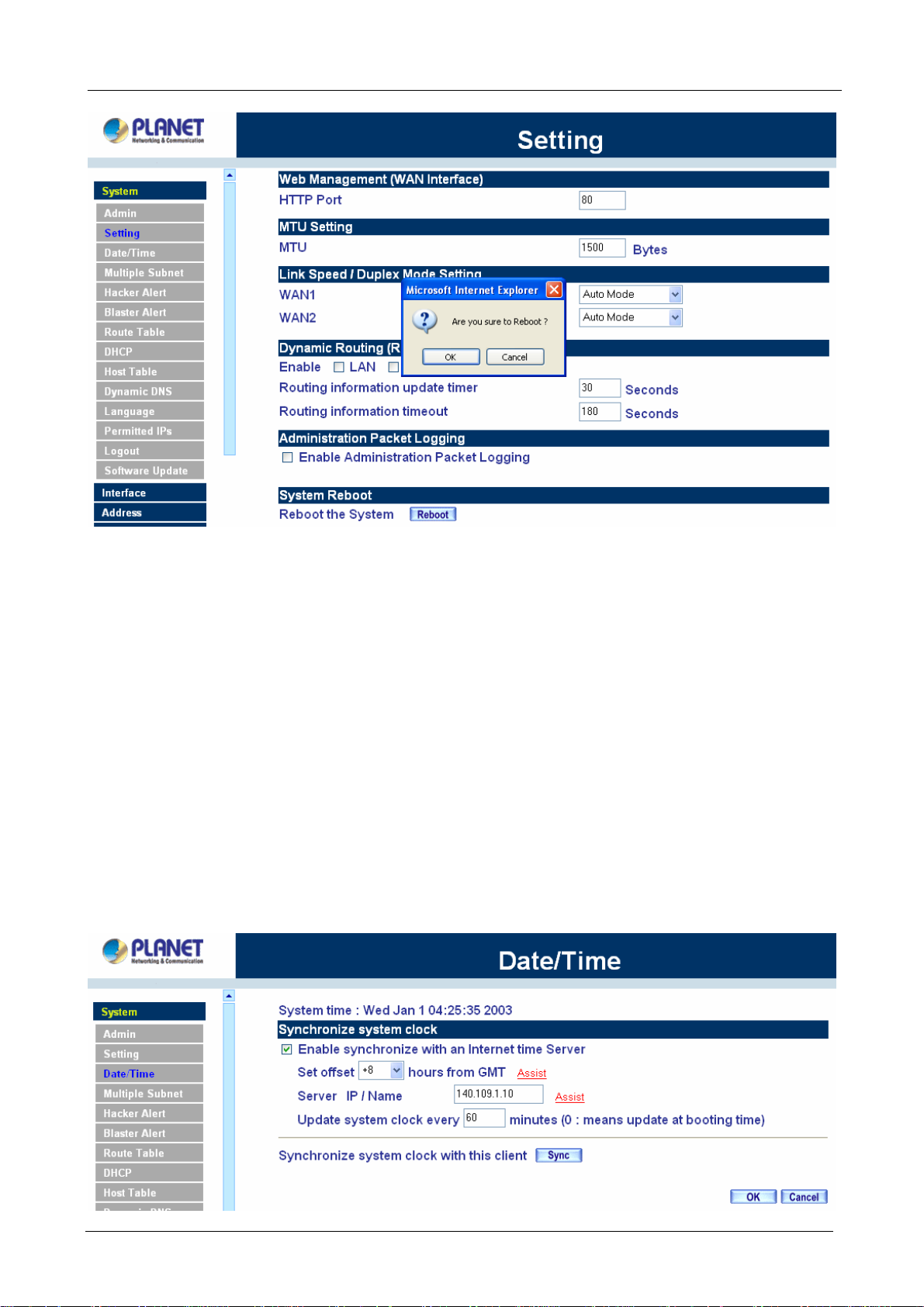
System Reboot
Once this function is enabled, MH-2K/4K will be rebooted.
Reboot Appliance: Click Reboot.
A confirmation pop-up box will appear. Follow the confirmation pop-up box, click OK to restart MH-2K/4K or
click Cancel to discard changes
- 23 -
Page 29
Multi-Homing Security Gateway User’s Manual
4.1.3 Date/Time
Synchronizing the MH-2K/4K with the System Clock
Administrator can configure MH-2K/4K’s date and time by either syncing to an Internet Network Time Server
(NTP) or by syncing to your computer’s clock.
Follow these steps to sync to an Internet Ti me Server
Step 1. Enable synchronization by checking the box.
Step 2. Click the down arrow to select the offset time from GMT.
Step 3. Enter the Server IP Address or Server name with which you want to synchronize.
Step 4. Update system clock every 5 minutes You can set the interval time to synchronize with outside
servers. If you set it to 0, it means the device will not synchronize automatically.
Follow this step to sync to your computer’s clock.
Step 1. Click on the Sync button. Click OK to apply the setting or click Cancel to discard changes.
- 24 -
Page 30
Multi-Homing Security Gateway User’s Manual
4.1.4 Multiple Subnet
NA T mode
Multiple Subnet allows local port to set multiple subnet works and connect with the internet through different
WAN 1 IP Addresses.
For instance: The lease line of a company applies several real IP Addresses 168.85.88.0/24, and the
company is divided into R&D department, service, sales department, procurement department, accounting
department, the company can distinguish each department by different subnet works for the purpose of
convenient management. The settings are as the following:
1. R&D department sub-network: 192.168.1.11/24(LAN ) ÅÆ 168.85.88.253(WAN 1)
2. Service department sub-network: 192.168.2.11/24(LAN ) ÅÆ 168.85.88.252(WAN 1)
3. Sales department sub-network: 192.168.3.11/24(LAN ) ÅÆ 168.85.88.251(WAN 1)
4. Procurement department sub-network: 192.168.4.11/24(LAN ) ÅÆ 168.85.88.250(WAN 1)
5. Accounting department sub-network: 192.168.5.11/24(LAN ) ÅÆ 168.85.88.249(WAN 1)
The first department(R&D department) was set while setting interface IP, the other four ones have to be added
in Multiple Subnet, after completing the settings, each department use the different WAN IP Address to
connect to the internet. The settings of LAN computers on service department are as the following
Service IP Address: 192.168.2.1
Subnet Mask: 255.255.255.0
Default Gateway: 192.168.2.11
The other departments are also set by groups, this is the function of Multiple Subnet.
Multiple Subnet settings
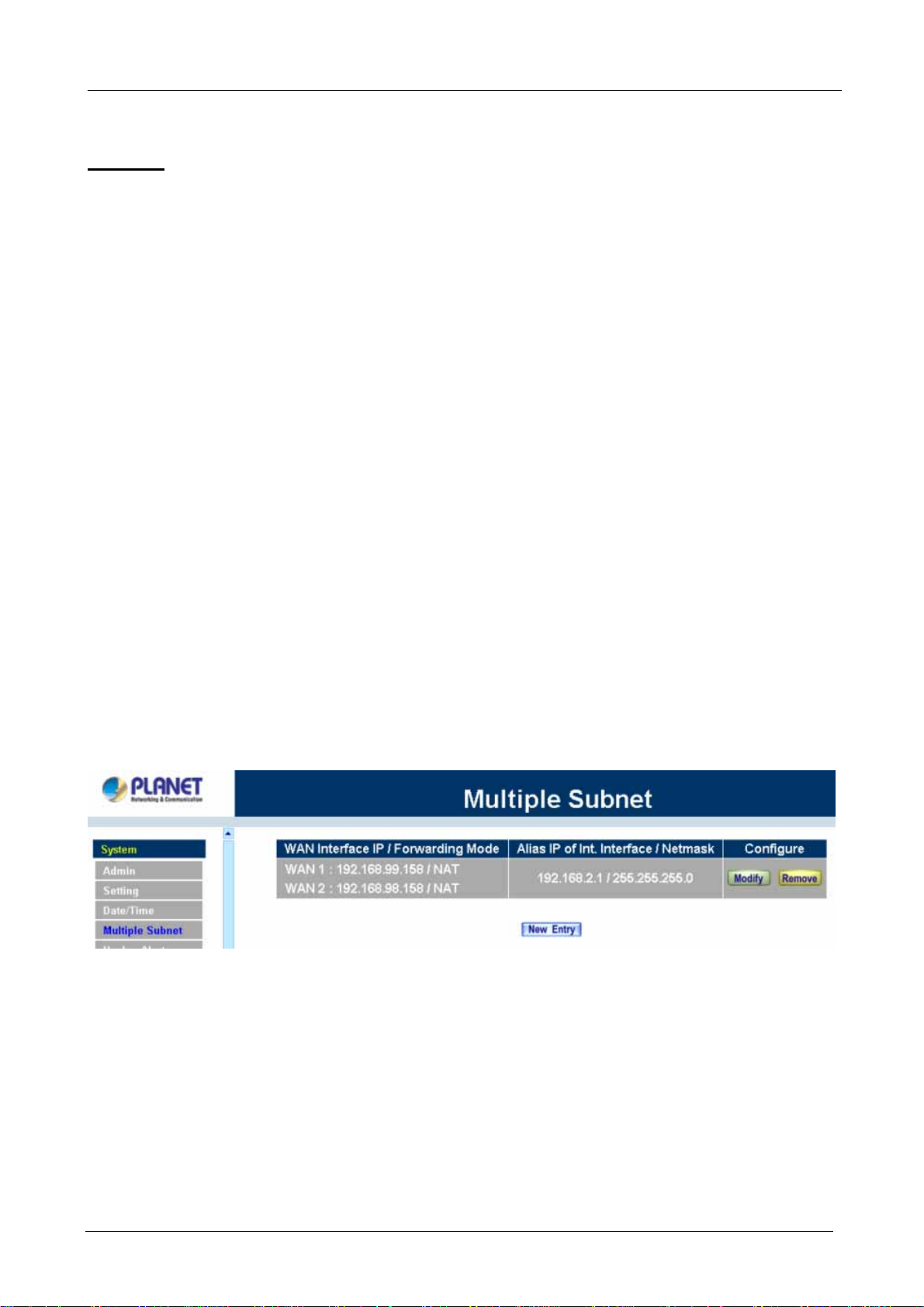
Click Multiple Subnet in the System menu to enter Multiple Subnet window.
Multiple Subnet functions:
WAN Interface IP / Forwarding Mode: Display WAN Port IP Address and Forwarding Mode.
Alias IP of Int. Interface / Netmask: Local port IP Address and subnet Mask.
Configure: Modify the settings of Multiple Subnet. Click Modify to modify the parameters of Multiple Subnet
or click Delete to delete settings.
Add a Multiple Subnet NAT Mode:
Step 1: Click the New Entry button below to add Multiple Subnet.
- 25 -
Page 31

Multi-Homing Security Gateway User’s Manual
Step 2: Enter the IP Address in the website name column of the new window.
Alias IP of LAN Interface: Enter Local port IP Address.
Netmask: Enter Local port subnet Mask.
WAN Interface IP: Add WAN 1 or WAN 2 IP.
Forwarding Mode: Click the NAT button below to setup.
Step 3: Click OK to add Multiple Subnet or click Cancel to discard changes.
Modify a Multiple Subnet:1
Step 1: Find the IP Address you want to modify and click Modify.
Step 2: Enter the new IP Address in Modify Multiple Subnet window.
Step 3: Click the OK button below to change the setting or click Cancel to discard changes.
Removing a Multiple Subnet:
Step 1: Find the IP Address you want to delete and click Delete.
Step 2: A confirmation pop-up box will appear, click OK to delete the setting or click Cancel to discard
changes.
Routing Mode
Multiple Subnet allows local port to set Multiple Subnet Routing Mode and connect with the internet through
different WAN IP Addresses.
- 26 -
Page 32

Multi-Homing Security Gateway User’s Manual
For example, the leased line of a company applies several real IP Addresses 168.85.88.0/24 and the
company is divided into R&D, Customer Service, Sales, Procurement, and Accounting Department. The
company can distinguish each department by different sub-network for the purpose of convenient
management.
The settings are as the following:
R&D: Alias IP of LAN interface - 168.85.88.1, Netmask: 255.255.255.192
Sales: Alias IP of LAN interface - 168.85.88.65, Netmask: 255.255.255.192
Procurement: Alias IP of LAN interface - 168.85.88.129, Netmask: 255.255.255.192
Accounting: Alias IP of LAN interface - 168.85.88.193, Netmask: 255.255.255.192
Click System Configuration on the left side menu bar, then click Multiple Subnet below it. Enter Multiple
Subnet window.
Multiple Subnet functions
WAN Interface IP / Forwarding Mode: Display WAN Port IP Address and Forwarding Mode which is NAT
Mode or Routing Mode.
Alias IP of Int. Interface / Subnet Mask: Local port IP Address and subnet Mask.
Modify: Modify the settings of Multiple Subnet. Click Modify to modify the parameters of Multiple Subnet or
click Remove to delete settings.
Adding a Multiple Subnet Routing Mode
Step 1: Click the Add button below to add Multiple Subnet.
Step 2: Enter the IP Address in Add Multiple Subnet window.
Alias IP of LAN Interface: Enter Local port IP Address.
Netmask: Enter Local port subnet Mask.
WAN Interface IP: Add WAN1 or WAN2 IP
Forwarding Mode: Click the Routing button below to setup.
Step 3: Click OK to add Multiple Subnet or click Cancel to discard changes.
- 27 -
Page 33

Multi-Homing Security Gateway User’s Manual
Step 4: Adding a new WAN to LAN Policy. In the Incoming window, click the New Entry button.
Modify a Multiple Subnet Routing Mode
Step 1: Find the IP Address you want to modify in Multiple Subnet menu, then click Modify button, on the right
side of the service providers, click OK.
Step 2: Enter the new IP Address in Modify Multiple Subnet window.
Step 3: Click the OK button below to change the setting or click Cancel to discard changes.
Removing a Multiple Subnet Routing Mode
Step 1: Find the IP Address you want to delete in Multiple Subnet menu, then click Delete button, on the right
side of the service providers, click OK.
Step 2: A confirmation pop-up box will appear, click OK to delete the setting or click Cancel to discard
- 28 -
Page 34

changes.
4.1.5 Hacker Alert
Multi-Homing Security Gateway User’s Manual
The Administrator can enable the device’s auto detect functions for hacker attacking this section. When
abnormal conditions occur, MH-2K/4K will send an e-mail alert to notify the Administrator, and also display
warning messages in the Event window of Alarm.
ÍÍ
Auto Detect functions
Some worms will attack your MS system in accordance with their weakness, such as
Sasser, Blaster, Code Red and Nimda. Select the blocking function of MH-4000 will
prevent you to be attacking by these worms (MH-4000 only).
Detect SYN Attack: Select this option to detect TCP SYN attacks that hackers send to
server computers continuously to block or cut down all the connections of the servers.
These attacks will prevent valid users from connecting to the servers. After enabling this
function, the System Administrator can enter the number of SYN packets per second that is
- 29 -
Page 35

Multi-Homing Security Gateway User’s Manual
allowed to enter MH-2K/4K. Once the SYN packets exceed this limit, the activity will be
logged in Alarm and an email alert is sent to the Administrator. The default SYN flood
threshold is set to 200 Pkts/Sec .
Detect ICMP Flood: Select this option to detect ICMP flood attacks. When hackers
continuously send PING packets to all the machines of the LAN networks or to the
MH-2K/4K, your network is experiencing an ICMP flood attack. This can cause traffic
congestion on the network and slows the network down. After enabling this function, the
System Administrator can enter the number of ICMP packets per second that is allowed to
enter the network or MH-2K/4K. Once the ICMP packets exceed this limit, the activity will be
logged in Alarm and an email alert is sent to the Administrator. The default ICMP flood
threshold is set to 1000 Pkts/Sec.
Detect UDP Flood: Select this option to detect UDP flood attacks. A UDP flood attack is
similar to an ICMP flood attack. After enabling this function, the System Administrator can
enter the number of UDP packets per second that is allow to enter the network MH-2K/4K.
Once the UDP packets exceed this limit, the activity will be logged in Alarm and an email
alert is sent to the Administrator. The default UDP flood threshold is set to 1000 Pkts/Sec .
Detect Ping of Death Attack: Select this option to detect the attacks of tremendous trash
data in PING packets that hackers send to cause System malfunction. This attack can cause
network speed to slow down, or even make it necessary to restart the computer to get a
normal operation.
Detect Tear Drop Attack: Select this option to detect tear drop attacks. These are packets
that are segmented to small packets with negative length. Some Systems treat the negative
value as a very large number, and copy enormous data into the System to cause System
damage, such as a shut down or a restart.
Detect IP Sp oofing Attack: Select this option to detect spoof attacks. Hackers disguise
themselves as trusted users of the network in Spoof attacks. They use a fake identity to try
to pass through MH-2K/4K System and invade the network.
Filter IP Source Route O ption: Each IP packet can carry an optional field that specifies the
replying address that can be different from the source address specified in packet’s header.
Hackers can use this address field on disguised packets to invade LAN networks and send
LAN networks’ data back to them.
Detect Port Scan Attack: Select this option to detect the port scans hackers use to
continuously scan networks on the Internet to detect computers and vulnerable ports that
are opened by those computers.
Detect Land Attack: Some Systems may shut down when receiving packets with the same
source and destination addresses, the same source port and destination port, and when
SYN on the TCP header is marked.
- 30 -
Page 36

Multi-Homing Security Gateway User’s Manual
Enable this function to detect such abnormal packets.
After enabling the needed detect functions, click OK to activate the changes.
4.1.6 Blaster Alert
The Administrator can enable the device’s auto detect functions for blaster worm attacking the local network.
When abnormal conditions occur, MH-2K/4K will send an e-mail alert and/or SNMP trap to notify the
Administrator, and also display warning messages in the Blaster window of Alarm.
Blaster Alerts Settings
After enabling the needed options, click OK to activate the changes.
ÍÍ
Enable Blaster Blocking: Select this option to enable the blaster blocking function. Once
the blaster worm is detected, it will block the TCP port 135 for user-drefined blocking time.
Enable E-mail Alert Notification: When Blaster worm is detected, send alert e-mail to
administrator by using e-mail address defined on System -> Setting.
Enalbe SNMP Trap Alert Notification: When Blaster worm is detected, send SNMP trap to
user-defined SNMP trap receiver IP address defined on System -> SNMP (MH-4000 only).
Enable NetBIOS Alert Notification: When Blaster worm is detected, send alart message
to administrator by using “Net send” command (MH-4000 only).
4.1.7 Route Table
In this section, the Administrator can add static routes for the networks.
Entering the Route Table screen
Step 1. Click System on the left side menu bar, then click Route Table below it. The Route Table
window appears, in which current route settings are shown.
- 31 -
Page 37

Multi-Homing Security Gateway User’s Manual
ÍÍ
Route Table functions
Interface: Destination network, LAN or WAN 1 networks.
Destination IP: IP address of destination network.
NetMask: Netmask of destination network.
Gateway: Gateway IP address for connecting to destination network.
Configure: Change settings in the route table.
Adding a new Static Route
Step 1. In the Route Table window, click the New Entry button.
Step 2. In the Add New Static Route window, enter new static route information.
Step 3. In the Interface field’s pull-down menu, choose the network to connect (LAN, WAN1, WAN2,
DMZ).
Step 4. Click OK to add the new static route or click Cancel to cancel.
Modifying a Static Route:
Step 1. In the Route Table menu, find the route to edit and click the corresponding Modify option in the
Configure field.
Step 2. In the Modify Static Route window, modify the necessary routing addresses.
Step 3. Click OK to apply changes or click Cancel to cancel it.
- 32 -
Page 38

Multi-Homing Security Gateway User’s Manual
Removing a Static Route
Step 1. In the Route Table window, find the route to remove and click the corresponding Remove option
in the Configure field.
Step 2. In the Remove confirmation pop-up box, click OK to confirm removing or click Cancel to cancel
it.
4.1.8 DHCP
In the section, the Administrator can configure DHCP (Dynamic Host Configuration Protocol) settings for the
LAN (LAN) network.
Entering the DHCP window
Click System on the left hand side menu bar, then click DHCP below it. The DHCP window appears in which
current DHCP settings are shown on the screen.
- 33 -
Page 39

ÍÍ
Multi-Homing Security Gateway User’s Manual
Dynamic IP Address functions
Subnet: LAN network’s subnet
NetMask: LAN network’s netmask
Gateway: LAN network’s gateway IP address
Broadcast: LAN network’s broadcast IP address
Enabling DHCP Support
Step 1. In the Dynamic IP Address window, click Enable DHCP Support.
Domain Name: The Administrator may enter the name of the LAN network domain if preferred.
Automatically Get DNS: Check this box to automatically detect DNS server.
DNS Server 1 : Enter the distributed IP address of DNS Server 1.
DNS Server 2 : Enter the distributed IP address of DNS Server 2.
WINS Server 1 : Enter the distributed IP address of WINS Server 1.
WINS Server 2 : Enter the distributed IP address of WINS Server 2.
LAN interface:
Client IP Address Range 1: Enter the starting and the ending IP address dynamically
assigning to DHCP clients.
Client IP Address Range 2: Enter the starting and the ending IP address dynamically
assigning to DHCP clients. (Optional)
DMZ interface:
Client IP Address Range 1: Enter the starting and the ending IP address dynamically
assigning to DHCP clients.
Client IP Address Range 2: Enter the starting and the ending IP address dynamically
assigning to DHCP clients. (Optional)
- 34 -
Page 40

Multi-Homing Security Gateway User’s Manual
Leased Time: Enter the leased time for DHCP.
Step 2. Click OK to enable DHCP support.
4.1.9 Dynamic DNS
The Dynamic DNS (require Dynamic DNS Service) allows you to alias a dynamic IP address to a static
hostname, allowing your device to be more easily accessed by specific name. When this function is enabled,
the IP address in Dynamic DNS Server will be automatically updated with the new IP address provided by
ISP.
ÍÍ
Click Dynamic DNS in the System menu to enter Dynamic DNS window.
The icons in Dynamic DNS window:
!: Update Status,
Domain name: Enter the password provided by ISP.
WAN IP Address: IP Address of the WAN port.
Configure: Modify dynamic DNS settings. Click Modify to change the DNS parameters; click Delete to delete
the settings.
How to use dynamic DNS:
MH-2K/4K provides many service providers, users have to register prior to use this function. For the usage
regulations, see the providers’ websites.
How to register:
Firstly, Click Dynamic DNS in the System menu to enter Dynamic DNS window, then click Add button,on the
right side of the service providers, click Register, the service providers` website will appear, please refer to
Connecting; Update succeed; Update fail; Unidentified error.
the website for the way of registration.
- 35 -
Page 41

Multi-Homing Security Gateway User’s Manual
Click to link to the website selected on the left.
Add Dynamic DNS settings
Step 1. Click Add button.
Step 2. Click the information in the column of the new window.
Service providers: Select service providers.
Sign up: to the service providers’ website.
WAN IP Address: IP Address of the WAN port.
Automatically : Check to automatically fill in the WAN IP.。
User Name: Enter the registered user name.
Password: Enter the password provided by ISP (Internet Service Provider).
Domain name: Your host domain name provided by ISP.
Click OK to add dynamic DNS or click Cancel to discard changes.
Modify dynamic DNS
Step 1. Find the item you want to change and click Modify.
Step 2. Enter the new information in the Modify Dynamic DNS window.
Click OK to change the settings or click Cancel to discard changes.。
- 36 -
Page 42

Multi-Homing Security Gateway User’s Manual
Remove Dynamic DNS
Step 1. Find the item you want to change and click Remove.
Step 2. A confirmation pop-up box will appear, click OK to delete the settings or click Cancel to discard
changes.
4.1.10 Host Table
The Multi-Homing Security Gateway’s Administrator may use the Host Table function to make the MH-2K/4K
act as a DNS Server for the LAN and DMZ network. All DNS requests to a specific Domain Name will be
routed to MH-2K/4K’s IP address. For example, let’s say an organization has their mail server (i.e.,
mail.planet.com.tw) in the DMZ network (i.e. 192.168.10.10). The outside Internet world may access the mail
server of the organization easily by its domain name, providing that the Administrator has set up Virtual Server
or Mapped IP settings correctly. However, for the users in the LAN network, their WAN DNS server will assign
them a public IP address for the mail server. So for the LAN network to access the mail server
(mail.planet.com.tw), they would have to go out to the Internet, then come back through MH-2K/4K to access
the mail server. Essentially, the LAN network is accessing the mail server by a real public IP address, while
the mail server serves their request by a NAT address and not a real one.
This odd situation occurs when there are servers in the DMZ network and they are bound to real IP addresses.
To avoid this, set up Host Table so all the LAN network computers will use MH-2K/4K as a DNS server, which
acts as the DNS Proxy.
- 37 -
Page 43

Multi-Homing Security Gateway User’s Manual
If you want to use the Host Table function of the device, the end user’s main DNS server IP address
should be the same IP Address as the device.
Click on System in the menu bar, then click on Host Table below it. The Host Table window will appear.
Below is the information needed for setting up the Host Table:
• Host Name: The domain name of the server
• Virtual IP Address: The virtual IP address respective to Host Table
• Configure: modify or remove each Host table policy
Adding a new Host Table
Step 1: Click on the New Entry button and the Add New Host Table window will appear.
Step 2: Fill in the appropriate settings for the domain name and virtual IP address.
Step 3: Click OK to save the policy or Cancel to cancel.
Modifying a Host Table
Step 1: In the Host Table window, find the policy to be modified and click the corresponding Modify option in
the Configure field.
- 38 -
Page 44

Multi-Homing Security Gateway User’s Manual
Step 2: Make the necessary changes needed.
Step 3: Click OK to save changes or click on Cancel to cancel modifications.
Removing a Host Table
Step 1: In the Host Table window, find the policy to be removed and click the corresponding Remove option
in the Configure field.
Step 2: A confirmation pop-up box will appear, click OK to remove the DNS Proxy or click Cancel.
4.1.11 SNMP (MH-4000 only)
The administrator could send the information to SNMP by enabling SNMP Agent.
NOTE: This function is not supported on MH-2000.
Step 1: Enable SNMP Agent.
Step 2: Enter Appliance Name.
Step 3: Enter Appliance Location.
Step 4: Enter Community.
Step 5: Enter Contact Person.
Step 6: Enter Description or not.
- 39 -
Page 45

SNMP Trap Settings
Multi-Homing Security Gateway User’s Manual
Allow the System Administrator to enable SNMP Trap Alert Notification for sending trap message to the set
SNMP Trap receiver IP address when the network is disconnected/ connecting and being attacked by hackers
or when emergency conditions occur.
Step 1: Enable SNMP Trap Alert Notification.
Step 2: SNMP Trap Receiver Address : Set the SNMP Trap Receiver Address.
Step 3: SNMP Trap Port : Set the SNMP Trap Receiver Port.
Step 4: SNMP Trap Test : Click the [Trap Test] button to test if you can receive the SNMP Trap Alert
Notification.
4.1.12 Permitted IPs
Only the authorized IP address is permitted to manage MH-2K/4K.
ÍÍ
- 40 -
Page 46

Multi-Homing Security Gateway User’s Manual
Add Permitted IP Address
Step 1. Click New Entry button.
Step 2. In IP Address field, enter the LAN IP address or WAN IP address.
IP address: Enter the LAN IP address or WAN IP address.
Netmask: Enter the netmask of LAN/WAN.
Ping: Select this to allow the external network to ping the IP Address of the Firewall.
HTTP/HTTPS: Check this item, Web User can use HTTP or HTTPS to connect to the Setting
window of MH-2K/4K (HTTPS is only available with MH-4000).
Step 3. Click OK to add Permitted IP or click Cancel to discard changes.
Modify Permitted IP Address
Step 1. In the table of Permitted IPs, highlight the IP you want to modify, and then click Modify.
Step 2. In Modify Permitted IP, enter new IP address.
Step 3. Click OK to modify or click Cancel to discard changes.
Remove Permitted IP addresses
Step 1. In the table of Permitted IPs, highlight the IP you want to remove, and then click Remove.
- 41 -
Page 47

Multi-Homing Security Gateway User’s Manual
Step 2. In Remove Permitted IP, enter new IP address.
Step 3. In the confirm window, click OK to remove or click Cancel to discard changes.
4.1.13 Language
Administrator can configure MH-2K/4K to select the Language version
Step 1. Select the Language version (English Version, Traditional Chinese Version or Simplified
Chinese Ver sion).
Step 2. Click [OK] to set the Language version or click Cancel to discard changes.
ÍÍ
4.1.14 Logout
Step 1. Select this option to the device’s Logout MH-2K/4K. This function protects your system while
you are away.
Step 2. Click Logout MH-2K/4K.
Step 3. Click OK to logout or click Cancel to discard the change.
- 42 -
Page 48

Multi-Homing Security Gateway User’s Manual
ÍÍ
4.1.15 Software Update
Under Software Update, the admin may update the device’s software with a newer software.
You may acquire the current version number of software in Version Number. Administrators may visit
distributor’s web site to download the latest version and save it in server’s hard disc.
Step 1. Click Browse to select the latest version of Software.
Step 2. Click OK to update software.
ÍÍ
NOTE: It takes three minutes to update the software. The system will restart automatically after updating the
software.
- 43 -
Page 49

Multi-Homing Security Gateway User’s Manual
4.2 Interface
In this section, the Administrator can set up the IP addresses for the office network. The Administrator may
configure the IP addresses of the LAN network, the WAN 1/2 network, and the DMZ network. The netmask
and gateway IP addresses are also configured in this section.
4.2.1 LAN
Entering the Interface menu:
Click on Interface in the left menu bar. Then click on LAN below it. The current settings of the interface
addresses will appear on the screen.
Configuring the Interface Settings
Using the LAN Interface, the Administrator sets up the LAN network. The LAN network will use a private IP
scheme. The private IP network will not be routable on the Internet.
IP Address: The private IP address of MH2000/MH4000’s LAN network is the IP address of the LAN port of
the device. The default IP address is 192.168.1.1. If the new LAN IP Address is not 192.168.1.1, the
Administrator needs to set the IP Address on the computer to be on the same subnet as MH-2K/4K and
restart the System to make the new IP address effective. For example, if MH-2K/4K’s new LAN IP Address is
172.16.0.1, then enter the new LAN IP Address 172.16.0.1 in the URL field of browser to connect to
MH-2K/4K.
NetMask: This is the subnet mask of the LAN network. The default netmask of the device is 255.255.255.0.
Ping: Select this to allow the LAN network to ping the IP Address of MH-2K/4K. If set to enable, the device will
respond to ping packets from the LAN network.
HTTP/HTTPS: Select this to allow the device WEBUI to be accessed from the LAN network (HTTPS is only
available with MH-4000).
- 44 -
Page 50

Multi-Homing Security Gateway User’s Manual
4.2.2 WAN
Entering the Interface menu
Click on Interface in the left menu bar. Then click on WAN below it. The current settings of the interface
addresses will appear on the screen.
Balance Mode:
Auto: MH-2K/4K distributes the WAN 1/2 download by proportion automatically according to the WAN
download bandwidth. (For users who are using various download bandwidth)
Round-Robin: MH-2K/4K distributes the WAN 1/2 download bandwidth 1:1, in other words, it selects
the agent by order. (For users who are using same download bandwidths)
By Traffic: MH-2K/4K distributes the WAN 1/2 download bandwidth by traffic. (For users who are
connected to the Internet via a fixed WAN IP address)
By Session: MH-2K/4K distributes the WAN 1/2 download bandwidth by session. (For users who are
connected to the Internet via a fixed WAN IP address)
By Packet: MH-2K/4K distributes the WAN 1/2 download bandwidth by packet and saturated
connection. (For users who are connected to the Internet via a fixed WAN IP address)
WAN No: WAN port 1 or 2.
Connect Mode: Display the current connection mode: PPPoE, Dynamic IP Address (Cable Modem User) or
Static IP Address.
IP Address: Display the current WAN IP Address.
Saturated Connections: Set the number for saturation whenever session numbers reach it, the MH-2K/4K
switches to the next WAN port on the list. This function is only applicable for By Session mode.
Ping / HTTP/ HTTPS: Display Ping/HTTP/HTTPS functions of WAN 1/2 to show if they are enabled or
disabled. (HTTPS is only available with MH-4000)
Configure: Click Modify to modify WAN 1/2 settings.
Priority: Set priority of WAN 1/2 for Internet Access.
WAN 1/2 Interfac e
- 45 -
Page 51

Multi-Homing Security Gateway User’s Manual
Using the WAN 1/2 Interface, the Administrator can sets up the WAN 1/2 network. These IP Addresses are
real public IP Addresses, and are routable on the Internet.
Alive Indicator Site IP: This feature is used to ping an address for detecting WAN connection status.
Service: ICMP You can select an IP address by Assist, or type an IP address manually.
Service: DNS You can select a DNS IP and Domain name by Assist, or type the related data manually.
For PPPoE (ADSL User): This option is for PPPoE users who are required to enter a username and
password in order to connect, such as ADSL users.
Current Status: Displays the current line status of the PPPoE connection.
IP Address: Displays the IP Address of the PPPoE connection
Username: Enter the PPPoE username provided by the ISP.
Password: Enter the PPPoE password provided by the ISP.
IP Address provided by ISP:
Dynamic: Select this if the IP address is automatically assigned by the ISP.
Fixed: Select this if you were given a static IP address. Enter the IP address that is given to you by
your ISP.
Max. Upstream/Downstream Bandwidth: The bandwidth provided by ISP.
Service-On-Demand:
Auto Disconnect: The PPPoE connection will automatically disconnect after a length of idle time (no
activities). Enter in the amount of idle minutes before disconnection. Enter ‘0’ if you do not want the
PPPoE connection to disconnect at all.
Ping: Select this to allow the WAN 1 network to ping the IP Address of MH-2K/4K. This will allow people
from the Internet to be able to ping MH-2K/4K. If set to enable, the device will respond to echo request
packets from the WAN 1/2 network.
HTTP/HTTPS: Select this to allow the device WebUI to be accessed from the WAN 1 network. This will
allow the WebUI to be configured from a user on the Internet. Keep in mind that the device always
requires a username and password to enter the WebUI. (HTTPS is only available with MH-4000)
- 46 -
Page 52

Multi-Homing Security Gateway User’s Manual
For Dynamic IP Address (Cable Mod em User): This option is for users who are automatically assigned an
IP address by their ISP, such as cable modem users. The following fields apply:
IP Address: The dynamic IP address obtained by MH-2K/4K from the ISP will be displayed here. This
is the IP address of the WAN 1 (WAN 2 ) port of the device.
MAC Address: This is the MAC Address of the device.
Hostname: This will be the name assign to the device. Some cable modem ISP assign a specific
hostname in order to connect to their network. Please enter the hostname here. If not required by
your ISP, you do not have to enter a hostname.
Domain Name: You can specify your own domain name or leave it blank.
User Name: The user name is provided by ISP.
Password: The password is provided by ISP.
Max. Upstream/Downstream Bandwidth: The bandwidth provided by ISP.
Ping: Select this to allow the WAN 1 network to ping the IP Address of MH-2K/4K. This will allow
people from the Internet to be able to ping MH-2K/4K. If set to enable, the device will respond to echo
request packets from the WAN 1 network.
HTTP/HTTPS: Select this to allow the device WEBUI to be accessed from the WAN 1 network. This
- 47 -
Page 53

Multi-Homing Security Gateway User’s Manual
will allow the WebUI to be configured from a user on the Internet. Keep in mind that the device always
requires a username and password to enter the WebUI. (HTTPS is only available with MH-4000)
For Static IP Address: This option is for users who are assigned a static IP Address from their ISP. Your ISP
will provide all the information needed for this section such as IP Address, Netmask, Gateway, and DNS.
Use this option also if you have more than one public IP Address assigned to you.
IP Address: Enter the static IP address assigned to you by your ISP. This will be the public IP
address of the WAN 1 port of the device.
Netmask: This will be the subnet mask of the WAN 1 network. (i.e. 255.255.255.0)
Default Gateway: This will be the Gateway IP address.
Domain Name Server (DNS): This is the IP Address of the DNS server.
Max. Upstream/Downstream Bandwidth: The bandwidth provided by ISP.
Ping: Select this to allow the WAN 1 network to ping the IP Address of MH-2K/4K. This will allow
people from the Internet to be able to ping MH-2K/4K. If set to enable, the device will respond to echo
request packets from the WAN 1 network.
HTTP/HTTPS: Select this to allow the device WEBUI to be accessed from the WAN 1 network. This
will allow the WebUI to be configured from a user on the Internet. Keep in mind that the device always
requires a username and password to enter the WebUI. (HTTPS is only available with MH-4000)
- 48 -
Page 54

Multi-Homing Security Gateway User’s Manual
For PPTP (European User Only): This is mainly used in Europe. You need to know the PPTP Server
address as well as your name and password.
User Name: The user name is provided by ISP.
Password: The password is provided by ISP.
IP Address: Enter the static IP address assigned to you by your ISP, or obtain an IP address
automatically from ISP.
PPTP Gateway: Enter the PPTP server IP address assigned to you by your ISP.
Connect ID: This is the ID given by ISP. This is optional.
Max. Upstream/Downstream Bandwidth: The bandwidth provided by ISP.
BEZEQ-ISRAEL: Select this item if you are using the service provided by BEZEQ in Israel.
Service-On-Demand: The PPPoE connection will automatically disconnect after a length of idle time
(no activities). Enter in the amount of idle minutes before disconnection. Enter ‘0’ if you do not want the
PPPoE connection to disconnect at all.
Ping: Select this to allow the WAN 1 network to ping the IP Address of MH-2K/4K.This will allow people
from the Internet to be able to ping MH-2K/4K. If set to enable, the device will respond to echo request
packets from the WAN 1 network.
HTTP: Select this to allow the device WEBUI to be accessed from the WAN 1 network. This will allow
the WebUI to be configured from a user on the Internet. Keep in mind that the device always requires a
username and password to enter the WebUI.
- 49 -
Page 55

NOTE: This function is not supported on MH-4000.
Multi-Homing Security Gateway User’s Manual
4.2.3 DMZ
The Administrator uses the DMZ Interface to set up the DMZ network. The DMZ network consists of server
computers such as FTP, SMTP, and HTTP (web). These server computers are put in the DMZ network so they
can be isolated from the LAN (LAN) network traffic. Broadcast messages from the LAN network will not cross
over to the DMZ network to cause congestions and slow down these servers. This allows the server computers
to work efficiently without any slowdowns.
- 50 -
Page 56

Multi-Homing Security Gateway User’s Manual
DMZ Interface: Display DMZ NAT Mode /DMZ TRANSPARENT Mode functions of DMZ to show if they are
enabled or disabled.
IP Address: The private IP address of MH-2K/4K’s DMZ interface. This will be the IP address of the DMZ port.
If it is in NAT mode, the IP address the Administrator chooses will be a private IP address and cannot use the
same network as the WAN or LAN network.
NetMask: This will be the subnet mask of the DMZ network.
Ping: Select this to allow the DMZ network to ping the IP Address of MH-2K/4K. This will allow people from
the Internet to be able to ping MH-2K/4K. If set to enable, the device will respond to echo request packets
from the DMZ network.
HTTP/HTTPS: Select this to allow the device WEBUI to be accessed from the WAN 1 network. This will allow
the WebUI to be configured from a user on the Internet. Keep in mind that the device always requires a
username and password to enter the WebUI. (HTTPS is only available with MH-4000)
- 51 -
Page 57

Multi-Homing Security Gateway User’s Manual
4.3 Address
MH-2K/4K allows the Administrator to set addresses of the LAN network, LAN network group, WAN network,
WAN group, DMZ network and DMZ group. These settings are to be used for policy editing.
What is the Address Table?
An IP address in the Address Table can be an address of a computer or a sub network. The Administrator can
assign an easily recognized name to an IP address. Based on the network it belongs to, an IP address can be
LAN IP address, WAN IP address and DMZ IP address. If the Administrator needs to create a control policy
for packets of different IP addresses, he can first add a new group in the LAN Network Group or the WAN
Network Group and assign those IP addresses into the newly created group. Using group addresses can
greatly simplify the process of building control policies.
How to use Address Table
With easily recognized names of IP addresses and names of address groups shown in the address table, the
Administrator can use these names as the source address or destination address of control policies. The
address table should be built before creating control policies, so that the Administrator can pick the names of
correct IP addresses from the address table when setting up control policies.
4.3.1 LAN
Entering the LAN window
Step 1. Click LAN under the Address menu to enter the LAN window. The current setting information
such as the name of the LAN network, IP and Netmask addresses will show on the screen.
ÍÍ
Definition
Name: Name of LAN network address.
IP: IP address of LAN network
Netmask: subnet mask of LAN network.
MAC Address: MAC address corresponded with LAN IP address.
Configure: You can configure the settings in LAN network. Click Modify to change the parameters in LAN
- 52 -
Page 58

Multi-Homing Security Gateway User’s Manual
network. Click Remove to delete the settings.
In the LAN window, if one of the members has been added to Policy or LAN Group, the Configure column
will show the message – In Use. In this case, you are not allowed to modify or remove the setting.
Adding a new LAN Address
Step 1. In the LAN window, click the New Entry button.
Step 2. In the Add New Address window, enter the settings of a new LAN network address.
Step 3. Click OK to add the specified LAN network or click Cancel to cancel the changes.
If you want to enable Get Static IP address from DHCP Server function, enter the MAC Address then check
the Get Static IP address from DHCP Server.
Modifying an LAN Address
Step 1. In the LAN window, locate the name of the network to be modified. Click the Modify option in its
corresponding Configure field. The Modify Address window appears on the screen
immediately.
Step 2. In the Modify Address window, fill in the new addresses.
Step 3. Click OK to save changes or click Cancel to discard changes.
- 53 -
Page 59

Multi-Homing Security Gateway User’s Manual
Removing a LAN Address
Step 1. In the LAN window, locate the name of the network to be removed. Click the Remove option in
its corresponding Configure field.
Step 2. In the Remove confirmation pop-up box, click OK to remove the address or click Cancel to
discard changes.
- 54 -
Page 60

Multi-Homing Security Gateway User’s Manual
4.3.2 LAN Group
Entering the LAN Group window
The LAN Addresses may be combined together to become a group.
Step 1. Click LAN Group under the Address menu to enter the LAN Group window. The current setting
information for the LAN network group appears on the screen.
ÍÍ
Definitions (LAN group):
Name: Name of the LAN group.
Member: Members of the group.
Configure: Configure the settings of LAN group. Click Modify to change the settings of LAN group. Click
Remove to delete the group.
In the LAN Group window, if one of the LAN Group has been added to Policy, the Configure column will
show the message – In Use. In this case, you are not allowed to modify or remove the LAN group. You have
to delete the Group in Policy window, and then you are allowed to configure the LAN Group.
Adding a LAN Group
Step 1. In the LAN Group window, click the New Entry button to enter the Add New Address Group
window.
Step 2. In the Add New Address Group window:
A vailable Address: list the names of all the members of the LAN network.
- 55 -
Page 61

Multi-Homing Security Gateway User’s Manual
Selected Address: list the names to be assigned to the new group.
Name: enter the name of the new group in the open field.
Step 3. Add members: Select names to be added in Available Address list, and click the Add>> button
to add them to the Selected Address list.
Step 4. Remove members: Select names to be removed in the Selected Address list, and click the
<<Remove button to remove these members from Selected Address list.
Step 5. Click OK to add the new group or click Cancel to discard changes.
Modifying a LAN Group
Step 1. In the LAN Group window, locate the network group desired to be modified and click its
corresponding Modify option in the Configure field.
Step 2. A window displaying the information of the selected group appears:
Available Address: list names of all members of the LAN network.
Selected Address: list names of members which have been assigned to this group.
Step 3. Add members: Select names in Available Address list, and click the Add>> button to add
them to the Selected Address list.
Step 4. Remove members: Select names in the Selected Address list, and click the <<Remove
button to remove these members from the Selected Address list.
Click OK to save changes or click Cancel to discard changes.
- 56 -
Page 62

Multi-Homing Security Gateway User’s Manual
Removing a LAN Group
Step 1. In the LAN Group window, locate the group to be removed and click its corresponding Remove
option in the Configure field.
Step 2. In the Remove confirmation pop-up box, click OK to remove the group or click Cancel to
discard changes.
- 57 -
Page 63

Multi-Homing Security Gateway User’s Manual
4.3.3 WAN
Entering the WAN window
Step 1. Click WAN under the Address menu to enter the WAN window. The current setting information,
such as the name of the WAN network, IP and Netmask addresses will show on the screen.
ÍÍ
Definitions
Name: Name of WAN network address.
IP/Netmask: IP address/Netmask of WAN network.
Configure: Configure the settings of WAN network. Click Modify to change the settings of WAN network.
Click Remove to delete the setting of WAN network.
NOTE: In the WA N Network window, if one of the members has been added to Policy or LAN Group, the
Configure column will show the message – In Use. In this case you are not allowed to modify or remove the
settings.
Adding a new WAN Address
Step 1. In the WAN window, click the New Entry button.
Step 2. In the Add New Address window, enter the settings for a new WAN network address.
Step 3. Click OK to add the specified WAN network or click Cancel to discard changes.
- 58 -
Page 64

Multi-Homing Security Gateway User’s Manual
Modifying an WAN Address
Step 1. In the WAN table, locate the name of the network to be modified and click the Modify option in
its corresponding Configure field.
Step 2. The Modify Address window will appear on the screen immediately. In the Modify Address
window, fill in new addresses.
Step 3. Click OK to save changes or click Cancel to discard changes.
- 59 -
Page 65

Multi-Homing Security Gateway User’s Manual
Removing an WAN Address
Step 1. In the WAN table, locate the name of the network to be removed and click the Remove option in
its corresponding Configure field.
Step 2. In the Remove confirmation pop-up box, click OK to remove the address or click Cancel to
discard changes.
4.3.4 WAN Group
Entering the WAN Group window
Step 1. Click the WAN Group under the Address menu bar to enter the WAN window. The current
settings for the WAN network group(s) will appear on the screen.
ÍÍ
- 60 -
Page 66

Multi-Homing Security Gateway User’s Manual
Definitions:
Name: Name of the WAN group.
Member: Members of the group.
Configure: Configure the settings of WAN group. Click Modify to change the parameters of WAN group Click
Remove to delete the selected group.
NOTE: In the WAN Group window, if one of the members has been added to the Policy, “In Use” message
will appear in the Configure column. You are not allowed to modify or remove the settings. Go to the Policy
window to remove the setting, and then you can configure.
Adding an WAN Group
Step 1. In the WAN Group window, click the New Entry button and the Add New Address Group
window will appear.
Step 2. In the Add New Address Group window the following fields will appear:
Name: Enter the name of the new group.
Available Address: List the names of all the members of the WAN network.
Selected Address: List the names to assign to the new group.
Add members: Select the names to be added in the Available Address list, and click the
Add>> button to add them to the Selected Address list.
Remove members: Select the names to be removed in the Selected Address list, and click
the <<Remove button to remove them from the Selected Address list.
Step 3. Click OK to add the new group or click Cancel to discard changes.
- 61 -
Page 67

Multi-Homing Security Gateway User’s Manual
Modifying a WAN Gr oup
Step 1. In the WAN Group window, locate the network group to be modified and click its corresponding
Modify button in the Configure field.
Step 2. A window displaying the information of the selected group appears:
Available Address: list the names of all the members of the WAN network.
Selected Address: list the names of the members that have been assigned to this group.
Step 3. Add members: Select the names to be added in the Available Address list, and click the
Add>> button to add them to the Selected Address list.
Step 4. Remove members: Select the names to be removed in the Selected Address list, and click the
<<Remove button to remove them from the Selected Address list.
Step 5. Click OK to save changes or click Cancel to discard changes.
Removing a W AN Group
Step 1. In the WAN Group window, locate the group to be removed and click its corresponding Modify
option in the Configure field.
Step 2. In the Remove confirmation pop-up box, click OK to remove the group or click Cancel to discard
changes.
- 62 -
Page 68

Multi-Homing Security Gateway User’s Manual
4.3.5 DMZ
Entering the DMZ window:
Click DMZ under the Address menu to enter the DMZ window. The current setting information such as the
name of the LAN network, IP, and Netmask addresses will show on the screen.
- 63 -
Page 69

Multi-Homing Security Gateway User’s Manual
Adding a new DMZ Address:
Step 1. In the DMZ window, click the New Entry button.
Step 2. In the Add New Address window, enter the settings for a new DMZ address.
Step 3. Click OK to add the specified DMZ or click Cancel to discard changes.
Modifying a DMZ Address:
Step 1. In the DMZ window, locate the name of the network to be modified and click the Modify option in
its corresponding Configure field.
Step 2. In the Modify Address window, fill in new addresses.
Step 3. Click OK on save the changes or click Cancel to discard changes.
- 64 -
Page 70

Multi-Homing Security Gateway User’s Manual
Removing a DMZ Address:
Step 1. In the DMZ window, locate the name of the network to be removed and click the Remove option in
its corresponding Configure field.
Step 2. In the Remove confirmation pop-up box, click OK to remove the address or click Cancel to discard
changes.
- 65 -
Page 71

Multi-Homing Security Gateway User’s Manual
4.3.6 DMZ Group
Entering the DMZ Group window
Click DMZ Group under the Address menu to enter the DMZ window. The current settings information for the
DMZ group appears on the screen.
Adding a DMZ Group:
Step 1. In the DMZ Group window, click the New Entry button.
Step 2. In the Add New Address Group window:
Available Address: list names of all members of the DMZ.
Selected Address: list names to assign to a new group.
Step 3. Name: enter a name for the new group.
Step 4. Add members: Select the names to be added from the Available Address list, and click the
Add>> button to add them to the Selected Address list.
Step 5. Remove members: Select names to be removed from the Selected Address list, and click the
<<Remove button to remove them from the Selected Address list.
Step 6. Click OK to add the new group or click Cancel to discard changes.
- 66 -
Page 72

Multi-Homing Security Gateway User’s Manual
Modifying a DMZ Group:
Step 1. In the DMZ Group window, locate the DMZ group to be modified and click its corresponding
Modify button in the Configure field.
Step 2. A window displaying information about the selected group appears:
Available Address: list the names of all the members of the DMZ.
Selected Address: list the names of the members that have been assigned to this group.
Step 3. Add members: Select names to be added from the Available Address list, and click the Add>>
button to add them to the Selected Address list.
Step 4. Remove members: Select names to be removed from the Selected Address list, and click the
<<Remove button to remove them from Selected Address list.
Step 5. Click OK to save changes or click Cancel to cancel editing.
- 67 -
Page 73

Multi-Homing Security Gateway User’s Manual
Removing a DMZ Group:
Step 1. In the DMZ Group window, locate the group to be removed and click its corresponding Remove
option in the Configure field.
Step 2. In the Remove confirma tion pop-up box, click OK to remove the group.
- 68 -
Page 74

Multi-Homing Security Gateway User’s Manual
4.4 Service
In this section, network services are defined and new network services can be added. There are three sub
menus under Service which are: Pre-defined, Custom, and Group. The Administrator can simply follow the
instructions below to define the protocols and port numbers for network communication applications. Users
then can connect to servers and other computers through these available network services.
What is Service?
TCP and UDP protocols support varieties of services, and each service consists of a TCP Port or UDP port
number, such as TELNET(23), SMTP(21), POP3(110),etc. MH-2K/4K defines two services: pre-defined
service and custom service. The common-use services like TCP and UDP are defined in the pre-defined
service and cannot be modified or removed. In the custom menu, users can define other TCP port and UDP
port numbers that are not in the pre-defined menu according to their needs. When defining custom services,
the client port ranges from 1024 to 65535 and the server port ranges from 0 to 1023.
How do I use Service?
The Administrator can add new service group names in the Group option under Service menu, and assign
desired services into that new group. Using service group the Administrator can simplify the processes of
setting up control policies. For example, there are 10 different computers that want to access 5 different
services on a server, such as HTTP, FTP, SMTP, POP3, and TELNET. Without the help of service groups, the
Administrator needs to set up 50 (10x5) control policies, but by applying all 5 services to a single group name
in the service field, it takes only one control policy to achieve the same effect as the 50 control policies.
4.4.1 Pre-defined
Entering a Pre-defined window
Step 1. Click Pre-defined under it. A window will appear with a list of services and their associated IP
addresses. This list cannot be modified.
ÍÍ
- 69 -
Page 75

Icons and Descriptions
Figur
Description
TCP services, i.g. AFP over TCP, FTP, FINGER, HTTP, HTTPS, IMAP, SMTP,
POP3, ANY, AOL, BGP, GOPHER, InterLocator, IRC, L2TP, LDAP,
NetMeeting, NNTP, PPTP, Real Media, RLOGIN, SSH, TCP ANY, TELNET,
VDO Live, WAIS, WINFRAME, X-WINDOWS, MSN, etc.
UDP services, i.g. IKE, DNS, NTP, RIP, SNMP, SYSLOG, TALK, TFTP,
UDP-ANY, UUCP, NFS, PC Anywhere, etc.
ICMP services, i.g. PING, TRACEROUTE, etc.
4.4.2 Custom
Multi-Homing Security Gateway User’s Manual
Entering the Custom window
Step 1. Click Custom under it. A window will appear with a table showing all services currently defined
by the Administrator.
ÍÍ
Definitions:
Service name: The defined service name.
Protocol: Network protocol used in the basic setting. Such as TCP、UDP or others.
Client port: The range of Client port in defined service. If the number of ports entered in the two fields of
Client port is different, it means that the port numbers between these two numbers are opened. If the number
of ports entered in the two fields of Client port is identical, it means that the entered port number is opened.
- 70 -
Page 76

Multi-Homing Security Gateway User’s Manual
Service port: The range of Service port in defined service.
If the number of ports entered in the two fields of Service port is different, it means that the port numbers
between these two numbers are opened. If the number of ports entered in the two fields of Service port is
identical, it means that the entered port number is opened.
Configure: Configure the settings in Service table. Click Modify to change the parameters in Service table.
Click Remove to delete the selected setting.
NOTE: In the Custom window, if one of the services has been added to Policy or Group, ”In Use” message
will appear in the Configure column. In this case you are not allowed to modify or remove the settings. Go to
the Policy or Group window to delete the setting, and then you can configure the settings.
Adding a new Service
In the Custom window, click the New Entry button and a new service table appears.
In the new service table:
New Service Name: This will be the name referencing the new service.
Protocol: Enter the network protocol type to be used, such as TCP, UDP, or Other (please
enter the number for the protocol type).
Client Port: enter the range of port number of new clients.
Server Port: enter the range of port number of new servers.
The client port ranges from 1024 to 65535 and the server port ranges from 0 to 1023.
Step 1. Click OK to add new services, or click Cancel to cancel.
Step 2. Click OK to accept editing; or click Cancel.
- 71 -
Page 77

Multi-Homing Security Gateway User’s Manual
Modifying Custom Services
Step 1. A table showing the current settings of the selected service appears on the screen
Step 2. Enter the new values.
Step 3. Click OK to accept editing; or click Cancel.
Removing Custom Services
Step 1. Click its corresponding Remove option in the Configure field.
Step 2. In the Remove confirmation pop-up box, click OK to remove the selected service or click
Cancel to cancel action.
- 72 -
Page 78

Multi-Homing Security Gateway User’s Manual
4.4.3 Group
Accessing the Group window
Step 1. Click Group under it. A window will appear with a table displaying current service group settings
set by the Administrator.
ÍÍ
Definitions:
Group name: The Group name of the defined Service.
Service: The Service item of the Group.
Configure: Configure the settings of Group. Click Modify to change the parameters of the Group. Click
Remove to delete the Group.
NOTE: In the Group window, if one of the Service Groups has been added to Policy. “In Use” message will
appear in the Configure column. You are not allowed to modify or remove the settings. Go to the Policy
window, remove the Service group first, and then you are allowed to configure the setting.
Adding Service Groups
Step 1. In the Group window, click the New Entry button.
Step 2. In the Add Service Group window, the following fields will appear:
Available Services: list all the available services.
Selected Services: list services to be assigned to the new group.
Step 3. Enter the new group name in the group Name field. This will be the name referencing the
created group.
Step 4. To add new services: Select the services desired to be added in the Available Services list
and then click the Add>> button to add them to the group.
- 73 -
Page 79

Multi-Homing Security Gateway User’s Manual
Step 5. To remove services: Select services desired to be removed in the Available Services, and
then click the <<Remove button to remove them from the group.
Step 6. Click OK to add the new group.
Modifying Service Groups
Step 1. In the Mod (modify) group window the following fields are displayed:
Available Services: lists all the available services.
Selected Services: list services that have been assigned to the selected group.
Step 2. Add new services: Select services in the Available Services list, and then click the Add>>
button to add them to the group.
Step 3. Remove services: Select services to be removed in the Selected Services list, and then click
the <<Remove button to remove theses services from the group.
Step 4. Click OK to save editing changes.
- 74 -
Page 80

Multi-Homing Security Gateway User’s Manual
Removing Service Groups
In the Remove confirmation pop-up box, click OK to remove the selected service group or click Cancel to
cancel removing.
- 75 -
Page 81

Multi-Homing Security Gateway User’s Manual
4.5 Schedule
MH2K/4K allows the Administrator to configure a schedule for policies to take affect. By creating a schedule,
the Administrator is allowing MH2K/4K policies to be used at those designated times only. Any activities
outside of the scheduled time slot will not follow MH2K/4K policies therefore will likely not be permitted to pass
through MH2K/4K. The Administrator can configure the start time and stop time, as well as creating 2 different
time periods in a day. For example, an organization may only want MH2K/4K to allow the LAN network users
to access the Internet during work hours. Therefore, the Administrator may create a schedule to allow
MH2K/4K to work Monday-Friday, 8AM - 5PM only. During the non-work hours, MH2K/4K will not allow
Internet access.
Accessing the Schedule window
Step 1. Click on Schedule on the menu bar and the schedule window will appear displaying the active
schedules.
ÍÍ
The following items are displayed in this window:
Name: the name assigned to the schedule
Configure: modify or remove
Adding a new Schedule
Step 1. Click on the New Entry button and the Add New Schedule window will appear.
Schedule Name: Fill in a name for the new schedule.
Period: Configure the start and stop time for the days of the week that the schedule will be
active.
Step 2. Click OK to save the new schedule or click Cancel to cancel adding the new schedule.
- 76 -
Page 82

Multi-Homing Security Gateway User’s Manual
NOTE: In setting a Schedule, the value in Start time must be less than the value in Stop Time, or you cannot
add or configure the setting.
Modifying a Schedule
Step 1. In the Schedule window, find the policy to be modified and click the corresponding Modify option
in the Configure field. Make needed changes.
Step 2. Click OK to save changes.
- 77 -
Page 83

Multi-Homing Security Gateway User’s Manual
Removing a Schedule
Step 1. In the Schedule window, find the policy to be removed and click the corresponding Remove
option in the Configure field.
Step 2. A confirmation pop-up box will appear, click on OK to remove the schedule.
- 78 -
Page 84

Multi-Homing Security Gateway User’s Manual
4.6 QoS
By configuring the QoS, you can control the outbound Upstream/downstream Bandwidth.
The administrator can configure the bandwidth according to the WAN bandwidth.
Downstream Bandwidth: To configure the Guaranteed Bandwidth and Maximum Bandwidth.
Upstream Bandwidth: To configure the Guaranteed Bandwidth and Maximum Bandwidth.
QoS Priority: To configure the priority of distributing Upstream/Downstream and unused bandwidth.
MH2K/4K configures the bandwidth by different QoS , and selects the suitable QoS through Policy to control
and efficiently distribute bandwidth. MH2K/4K also makes it convenient for the administrator to use MH2K/4K
with the best Utility.
Configuration of QoS
Click QoS in the menu bar on the left hand side.
ÍÍ
Definitions:
Name: The name of the QoS you want to configure.
WAN: Display WAN 1 or WAN 2.
Downstream Bandwidth: To configure the Guaranteed Bandwidth and Maximum Bandwidth.
Upstream Bandwidth: To configure the Guaranteed Bandwidth and Maximum Bandwidth.
Priority: To configure the priority of distributing Upstream/Downstream and unused bandwidth.
Add New QoS
Step 1. Click QoS in the menu bar on the left hand side.
Step 2. Click the New Entry button to add new QoS.
- 79 -
Page 85

Multi-Homing Security Gateway User’s Manual
Definition
Name: The name of the QoS you want to configure.
Downstream Bandwidth: To configure the Guarateed Bandwidth and Maximum Bandwidth.
Upstream Bandwidth: To configure the Guarateed Bandwidth and Maximum Bandwidth.
QoS Priority: To configure the priority of distrubuting Upstream/Downstream and unused bandwidth.
Click the OK button to add new QoS.
Modify QoS
Step 1. Click QoS in the menu bar on the left hand side.
- 80 -
Page 86

Multi-Homing Security Gateway User’s Manual
Click the Modify button to modify QoS.
Definition:
Name: The name of the QoS you want to configure.
Downstream Bandwidth: To configure the Guarateed Bandwidth and Maximum Bandwidth.
Upstream Bandwidth: To configure the Guarateed Bandwidth and Maximum Bandwidth.
QoS Priority: To configure the priority of distrubuting Upstream/Downstream and unused bandwidth.
Click the OK button to modify QoS.
Delete QoS
Step 1. In the QoS window, find the QoS you want to change, and click Delete in the Configure column.
Step 2. In the Delete QoS window, click OK to delete the QoS or click Cancel to discard the change.
4.7 Authentication
By configuring the Authentication, you can control the user’s access right time of LAN to WAN. The
administrator can configure the authentication according to the authentication account and password.
MH2K/MH4K configures the authentication of LAN’s user by setting account and password to identify the
privilege.
4.7.1 Auth Setting
The administrator can specify the port number and authentication time of authentication management system
for LAN user to access WAN network.
Configuration of Authentication
Click Authentication in the menu bar on the left hand side and click Auth Setting.
- 81 -
Page 87

Multi-Homing Security Gateway User’s Manual
Authentication Port: The port number used for user login page. When user want to access WAN network
and the authentication (Policy -> Outgoing) is enabled, the user has to send http request with this port number.
MH-2K/MH-4K will send a User Login page for user to input user name and password. For example, if the
gateway IP address is 192.168.1.1 and authentication port is 82, user have to open a web browser and input
http://192.168.1.1:82 on the address file to have the user login page.
Re-Login if Idle: When the LAN user access to WAN network and do not use for a while, the connection will
be time-out. User has to re-login again. The default time is 30 minutes and you can configure this time by
“System”-> “Setting” page.
Re-Login after user login successfully: When user login authentication page successfully access WAN for
a while, MH-2K/MH-4K will asking user login again. The default time is unlimited time.
Disallow Re-Login auth user has login: when the user login authentication page, can not login same
account again on other web page.
URL to redirect when authentication succeed: You can set up the default webpage to force user to access
it first when user passes the authentication.
Messages to display when user login: You can specify a message to display at user’s login page when
user passes the authentication.
4.7.2 Auth User
Click Authentication in the menu bar on the left hand side and click Auth User.
- 82 -
Page 88

Definitions:
Multi-Homing Security Gateway User’s Manual
Name:The name of the Authentication you want to configure.
Configure: modify settings or remove users.
Adding a new Auth User
Step 1. In the Authentication window, click the New User button to create a new Auth User.
Step 2. In the Auth-User window:
Auth-User Name: enter the username of new Authentication.
Password: enter a password for the new Authentication.
Con firm Password: enter the password again.
Step 3. Click OK to add the user or click Cancel to cancel the addition.
- 83 -
Page 89

Multi-Homing Security Gateway User’s Manual
NOTE: When the LAN user access to WAN network and do not use for a while, the connection will be
time-out. User has to re-login again. The default time is 30 minutes and you can configure this time by
“Authentication”-> “Auth Setting” page.
In the form of controlling the [Outgoing] Policy, enable the Authentication-User Function.
NOTE: If Outgoing Policy only has configured one rule with Authentication feature enabled, please add
another rule to allow DNS protocol passing through Internet. After that, when each LAN user tries to browse
website, the Authentication page will pop up automatically.
User Login Page Definitions:
- 84 -
Page 90

User Name: The name of the Authentication you want to configure.
Password: The input carries on the authentication the password
Modifying the Authentication User
Multi-Homing Security Gateway User’s Manual
Step 1. In the Authentication window, locate the Auth-User name you want to edit, and click on Modify
in the Configure field.
Step 2. The Modify Auth-User Password window will appear. Enter in the required information:
Auth-User: show original authentication user.
Password: show original password.
New Pa ssword: enter new password
Confirm Password: enter the new password again.
Step 3. Click OK to confirm authentication user change or click Cancel to cancel it.
- 85 -
Page 91

Multi-Homing Security Gateway User’s Manual
Removing a Authentication User
Step 1. In the Authentication table, locate the Auth-User name you want to edit, and click on the Remove
option in the Configure field.
Step 2. The Remove confirmation pop-up box will appear.
Step 3. Click OK to remove that Authentication User or click Cancel to cancel.
4.7.3 Auth User Group
Accessing the Auth User Group window
Click Authentication in the menu bar on the left hand side of the window. Click Auth User Group under it.
A window will appear with a table displaying current Auth User Group settings by the Administrator.
- 86 -
Page 92

Multi-Homing Security Gateway User’s Manual
Adding Auth User Group
Step 1. In the Auth User Group window, click the New Entry button.
In the Auth User Group window, the following fields will appear:
Name: Enter the new Auth User group name.
Available auth user: List all the available Auth User.
Selected auth user: List Auth User to be assigned to the new group.
Step 2. Enter the new group name in the group Name field. This will be the name referencing the created
group.
Step 3. To add new Auth User: Select the Auth User desired to be added in the Available auth user list,
and then click the Add>> button to add them to the group.
Step 4. To remove Auth User: Select Auth User desired to be removed in the Available auth user list, and
then click the <<Remove button to remove them from the group.
Step 5. Click OK to add the new group.
Modifying Auth User Group
Step 1. In the Auth User Group window, locate the Auth User Group to be edited. Click its corresponding
Modify option in the Configure field.
Step 2. In the Modify Auth group window the following fields are displayed::
- 87 -
Page 93

Multi-Homing Security Gateway User’s Manual
Name: Enter the new Auth User group name .
Available auth user: List all the available Auth User.
Selected auth user: List Auth User to be assigned to the new group.
Step 3. To add new Auth User: Select the Auth User desired to be added in the Available auth user list,
and then click the Add>> button to add them to the group.
Step 4. To remove Auth User: Select Auth User desired to be removed in the Available auth user list, and
then click the <<Remove button to remove them from the group.
Step 5. Click OK to modify the Group.
Removing Auth User Group
Step 1. In the Auth User Group window, locate the Auth User Group to be removed and click its
corresponding Remove option in the Configure field.
Step 2. In the Remove confirmation pop-up box, click OK to remove the selected service group or click
Cancel to cancel removing.
- 88 -
Page 94

Multi-Homing Security Gateway User’s Manual
4.7.4 Radius Server (MH-4000 Only)
Click Authentication on the left side menu bar, then click Radius Server below it. The following window is
shown.
Definition
♦ Enable RADIUS Server: Enable RADIUS Server Authentication.
♦ RADIUS Server IP: Enter RADIUS Server IP address.
♦ RADIUS Server Port: Enter RADIUS Server Port. The default port is 1812.
♦ Shared Secret: The Password for MH-4000 to access RADIUS Server.
♦ Enable 802.1x RADIUS Server Authentication: Enable 802.1x RADIUS Server Authentication.
4.7.5 POP3 (MH-4000 only)
Click Authentication on the left side menu bar, then click POP3 below it. The following window is shown.
- 89 -
Page 95

Multi-Homing Security Gateway User’s Manual
Definition
♦ Enable POP3 Server: Enable POP3 Server Authentication.
♦ POP3 Server : Enter POP3 Server IP address or domain name.
♦ POP3 Server Port: Enter POP3 Server Port. The default port is 110.
4.7.6 LDAP (MH-4000 only)
Click Authentication on the left side menu bar, then click LDAP below it. The following window is shown.
Definition
♦ Enable LDAP Server: Enable LDAP Server Authentication.
♦ LDAP Server: Enter LDAP Server IP address or domain name.
♦ LDAP Server Port: Enter LDAP Server Port. The default port is 389
- 90 -
Page 96

Multi-Homing Security Gateway User’s Manual
♦ Search Distinguished Name: The Distinguished Name will be used to search by LDAP server. (ex:
dc=mydomain,dc=com)
♦ LDAP Filter: Input the object located at the range of Distinguished Name. (ex: (objectClass=*))
♦ User Distinguished Name: The user Distinguished Name of LDAP server. (ex:
cn=users,dc=mydomain,dc=com)
♦ Password: The password of the user Distinguished Name
- 91 -
Page 97

Multi-Homing Security Gateway User’s Manual
4.8 Content filtering
Content Filtering includes “URL Blocking” , “Script Blocking”, “P2P Blocking”, “IM Blocking” and
“Download Blocking”.
URL Blocking: The administrator can use a complete domain name or key word to make rules for specific
websites.
Script Blocking: To let Popup、ActiveX、Java、Cookie in or keep them out.
P2P Blocking: Block P2P program, include “eDonkey”, “Bit Torrent “ and “WinMX”.
IM Blocking: Block Internet Message program, include “MSN”, “Yahoo Messenger”, “ICQ”, “QQ” and
“Skype”.
Download Blocking: Block download connection, audio and video transferring from web page. You can
select to block which type of extension name or all type of the file.
4.8.1 URL Blocking
The Administrator may setup URL Blocking to prevent LAN network users from accessing a specific website
on the Internet. Any web request coming from an LAN network computer to a blocked website will receive a
blocked message instead of the website.
Entering the URL blocking window
Step 1. Click on URL Blocking under the Configuration menu bar.
Step 2. Click on New Entry.
ÍÍ
Definition:
URL String: The domain name that is blocked to enter by MH-2K/4K.
Configure: To change the settings of URL Blocking, click Modify to change the parameters; click Delete to
delete the settings.
Adding a URL Blocking policy
Step 1. After clicking New Entry, the Add New Block String window will appear.
Step 2. Enter the URL of the website to be blocked.
- 92 -
Page 98

Multi-Homing Security Gateway User’s Manual
Step 3. Click OK to add the policy. Click Cancel to discard changes.
Modifying a URL Blocking Policy
Step 1. In the URL Blocking window, find the policy to be modified and click the corresponding Modify
option in the Configure field.
Step 2. Make the necessary changes needed.
Step 3. Click on OK to save changes or click on Cancel to discard changes.
Removing a URL Blocking policy
Step 1. In the URL Blocking window, find the policy to be removed and click the corresponding
Remove option in the Configure field.
Step 2. A confirmation pop-up box will appear, click on OK to remove the policy or click on Cancel to
discard changes.
- 93 -
Page 99

Multi-Homing Security Gateway User’s Manual
Note: After finishing Content Filtering setting, you must enable it at Outgoing Policy, or Content Filtering will
not be workable.
4.8.2 Script Blocking
To let Popup, ActiveX, Java, or Cookies in or keep them out.
Step 1: Click Content Filtering in the menu.
Step 2: Script Blocking detective functions.
Popup: Prevent pop-up boxes from appearing.
ActiveX: Prevent ActiveX packets.
Java: Prevent Java packets.
Cookie: Prevent Cookie packets.
Step 3: After selecting each function, click the OK button below.
- 94 -
Page 100

Multi-Homing Security Gateway User’s Manual
ÍÍ
When the system detects the setting, MH-2K/4K will spontaneously work.
Note: After finishing Content Filtering setting, you must enable it at Outgoing Policy, or Content Filtering will
not be workable.
4.8.3 P2P Blocking
Step 1: Click Content Filtering in the menu.
Step 2: Select P2P Blocking and configure the setting.
eDonkey Block: Prevent eDonkey connection built up.
Bit Torrent Block: Prevent Bit Torrent connection built up.
WinMX: Prevent WinMX connection built up.
Step 3: After selecting each function, click the OK button below.
- 95 -
 Loading...
Loading...