Page 1

PGP® Whole Disk Encryption
Deployment Guide
Page 2

Version Information
PGP Whole Disk Encryption Deployment Guide. Version 9.6.1. Released May 2007.
Copyright Information
Copyright © 1991–2007 by PGP Corporation. All Rights Reserved. No part of this document can be reproduced or transmitted in any form or by any
means, electronic or mechanical, for any purpose, without the express written permission of PGP Corporation.
Trademark Information
PGP, Pretty Good Privacy, and the PGP logo are registered trademarks and Rest Secured is a trademark of PGP Corporation in the US and other
countries. IDEA is a trademark of Ascom Tech AG. Windows and ActiveX are registered trademarks of Microsoft Corporation. AOL is a registered
trademark, and AOL Instant Messenger is a trademark, of America Online, Inc. Red Hat and Red Hat Linux are trademarks or registered trademarks of
Red Hat, Inc. Linux is a registered trademark of Linus Torvalds. Solaris is a trademark or registered trademark of Sun Microsystems, Inc. AIX is a
trademark or registered trademark of International Business Machines Corporation. HP-UX is a trademark or registered trademark of Hewlett-Packard
Company. SSH and Secure Shell are trademarks of SSH Communications Security, Inc. Rendezvous and Mac OS X are trademarks or registered
trademarks of Apple Computer, Inc. Symantec, the Symantec logo, and LiveUpdate are registered trademarks of Symantec Corporation. All other
registered and unregistered trademarks in this document are the sole property of their respective owners.
Licensing and Patent Information
The IDEA cryptographic cipher described in U.S. patent number 5,214,703 is licensed from Ascom Tech AG. The CAST encryption algorithm is licensed
from Northern Telecom, Ltd. PGP Corporation has secured a license to the patent rights contained in the patent application Serial Number 10/655,563
by The Regents of the University of California, entitled Block Cipher Mode of Operation for Constructing a Wide-blocksize block Cipher from a
Conventional Block Cipher. Some third-party software included in PGP Universal Server is licensed under the GNU General Public License (GPL). PGP
Universal Server as a whole is not licensed under the GPL. If you would like a copy of the source code for the GPL software included in PGP Universal
Server, contact PGP Support (http://www.pgp.com/support). PGP Corporation may have patents and/or pending patent applications covering subject
matter in this software or its documentation; the furnishing of this software or documentation does not give you any license to these patents.
Acknowledgments
This product includes or may include:
• The Zip and ZLib compression code, created by Mark Adler and Jean-Loup Gailly, is used with permission from the free Info-ZIP implementation,
developed by zlib (http://www.zlib.net
under the MIT License found at http://www.opensource.org/licenses/mit-license.html
freely available high-quality data compressor, is copyrighted by Julian Seward, © 1996-2005. • Application server (http://www.jakarta.apache.org/
server (http://www.apache.org/
HTML, developed by the Apache Software Foundation. The license is at www.apache.org/licenses/LICENSE-2.0.txt
binding framework for moving data from XML to Java programming language objects and from Java to databases, is released by the ExoLab Group
under an Apache 2.0-style license, available at http://www.castor.org/license.html
Foundation that implements the XSLT XML transformation language and the XPath XML query language, is released under the Apache Software
License, version 1.1, available at http://xml.apache.org/xalan-j/#license1.1
(JMX), is released under an Apache-style license, available at http://mx4j.sourceforge.net/docs/ch01s06.html
the work of the Independent JPEG Group. (http://www.ijg.org/
MIT License http://www.opensource.org/licenses/mit-license.html
University of Cambridge. ©1997-2006. The license agreement is at http://www.pcre.org/license.txt
Name System (DNS) protocols developed and copyrighted by Internet Systems Consortium, Inc. (http://www.isc.org
daemon developed by The FreeBSD Project, © 1994-2006. • Simple Network Management Protocol Library developed and copyrighted by Carnegie
Mellon University © 1989, 1991, 1992, Networks Associates Technology, Inc, © 2001- 2003, Cambridge Broadband Ltd. © 2001- 2003, Sun
Microsystems, Inc., © 2003, Sparta, Inc, © 2003-2006, Cisco, Inc and Information Network Center of Beijing University of Posts and
Telecommunications, © 2004. The license agreement for these is at http://net-snmp.sourceforge.net/about/license.html
by Network Time Protocol and copyrighted to various contributors. • Lightweight Directory Access Protocol developed and copyrighted by OpenLDAP
Foundation. OpenLDAP is an open-source implementation of the Lightweight Directory Access Protocol (LDAP). Copyright © 1999-2003, The
OpenLDAP Foundation. The license agreement is at http://www.openldap.org/software/release/license.html
developed by OpenBSD project is released by the OpenBSD Project under a BSD-style license, available at http://www.openbsd.org/cgi-
bin/cvsweb/src/usr.bin/ssh/LICENCE?rev=HEAD. • PC/SC Lite is a free implementation of PC/SC, a specification for SmartCard integration is released
under the BSD license. • Postfix, an open source mail transfer agent (MTA), is released under the IBM Public License 1.0, available at
http://www.opensource.org/licenses/ibmpl.php
BSD-style license, available at http://www.postgresql.org/about/licence
specified programs at scheduled times. Copyright © 1993, 1994 by Paul Vixie; used by permission.
). • Libxml2, the XML C parser and toolkit developed for the Gnome project and distributed and copyrighted
. Copyright © 2007 by the Open Source Initiative. • bzip2 1.0, a
), web
), Jakarta Commons (http://jakarta.apache.org/commons/license.html) and log4j, a Java-based library used to parse
. • Castor, an open-source, data-
. • Xalan, an open-source software library from the Apache Software
. • mx4j, an open-source implementation of the Java Management Extensions
. • jpeglib version 6a is based in part on
) • libxslt the XSLT C library developed for the GNOME project and distributed under the
. • PCRE version 4.5 Perl regular expression compiler, copyrighted and distributed by
. • BIND Balanced Binary Tree Library and Domain
) • Free BSD implementation of
. • NTP version 4.2 developed
. • Secure shell OpenSSH version 4.2.1
. • PostgreSQL, a free software object-relational database management system, is released under a
. • 21.vixie-cron is the Vixie version of cron, a standard UNIX daemon that runs
Export Information
Export of this software and documentation may be subject to compliance with the rules and regulations promulgated from time to time by the Bureau
of Export Administration, United States Department of Commerce, which restricts the export and re-export of certain products and technical data.
Limitations
The software provided with this documentation is licensed to you for your individual use under the terms of the End User License Agreement provided
with the software. The information in this document is subject to change without notice. PGP Corporation does not warrant that the information meets
your requirements or that the information is free of errors. The information may include technical inaccuracies or typographical errors. Changes may be
made to the information and incorporated in new editions of this document, if and when made available by PGP Corporation.
Page 3

Contents
Overview 3
Who Should Read This Guide 3
Other Relevant Resources 4
Understanding PGP Whole Disk Encryption 5
About PGP Whole Disk Encryption 5
Components of a Typical PGP WDE Deployment 6
How Does PGP Whole Disk Encryption Work? 7
About PGP Universal Server 7
Major Steps 9
Preparation 11
Placing the PGP Universal Server in Your Network 12
Adding the PGP Universal Server to your Network 12
Deployment Options 12
Configuring your Firewall 13
Understanding Enrollment 14
Understanding the Two Enrollment Paths 14
Understanding the LDAP Directory Synchronization Feature 15
Understanding Policies 15
Preparing End-User Systems 16
Installation and Configuration 17
Before You Install 17
Installing the Server Software 17
Configuring the PGP Universal Server 19
Removing Unneeded Services 19
Setting Up Administrators 20
Establishing Backups 21
Securing your PGP Universal Server 21
Configuring Policies 22
Configuring the LDAP Directory Synchronization Feature 23
Configuring Enrollment 24
Email Enrollment 25
LDAP Directory Synchronization Enrollment 26
i
Page 4

PGP® Whole Disk Encryption Contents
Establishing PGP WDE Client Settings 27
Key Settings for Your PGP WDE Clients 28
Key Generation Settings 28
Key Mode Settings 29
Options Settings 31
Establishing PGP Desktop Settings for Your PGP WDE Clients 33
The General Tab 33
The File & Disk Tab 36
The Licensing Tab 39
Other Internal User Policy Settings 40
Creating the PGP WDE Client Installer 41
Creating an Installer with Auto-Detect Policy 42
Creating an Installer with Preset Policy 43
Creating an Installer with No Policy Settings 45
Testing the PGP WDE Client Installer 47
Deploying the PGP WDE Client Installer 49
Assisting Your PGP WDE Users 51
The End-User Experience 53
During the Installation Process 53
During WDE Setup 54
During Normal Usage 55
Glossary 56
ii
Page 5

1
Overview
This Guide describes how to create, deploy, and manage the PGP Whole Disk
Encryption (WDE) product in an enterprise environment, using the PGP
Universal Server product as the management server.
Some of the information in this Guide also applies to deploying any PGP
Desktop client product.
In This Chapter
Who Should Read This Guide.................................................................... 3
Other Relevant Resources ........................................................................ 3
Who Should Read This Guide
This Guide assumes you are an IT or messaging support professional who will
be performing one or more of the following deployment tasks:
Setting up and configuring the PGP Universal Server as the management
server.
Understanding and configuring PGP WDE client options.
Creating, testing, and distributing the PGP WDE client installers.
Preparing your end users for a successful installation.
This Guide assumes you have already read the PGP Universal Server
Administrator's Guide and have installed and used a PGP Universal Server in a
lab environment.
Note: PGP Corporation strongly recommends you take the time to
understand your goals for the software products available from PGP
Corporation and your organization's plans for them, both now and in the
future. The decisions you make now in deploying PGP WDE affect how you
can do things in the future. For example, your choice of key mode now will
impact decisions you make later.
3
Page 6

PGP® Whole Disk Encryption Overview
Other Relevant Resources
Note: This document focuses on details surrounding deployment of the PGP
WDE product. However, the first step in deploying PGP WDE is to install and
configure the PGP Universal Server product, which you will use to manage
your PGP WDE clients. Deployment of the PGP Universal Server itself is
described at a very high level in this document. Refer to the PGP Universal
Administrator's Guide for detailed deployment information.
Use this PGP WDE Deployment Guide in conjunction with the following
resources:
PGP Universal Administrator's Guide: The Administrator's Guide explains all
aspects of the PGP Universal Server you will be using as a management
server. Specifically, the PGP Universal Administrator's Guide describes
setting up and configuring your PGP Universal Server, using the server to
configure options for your PGP WDE clients, and creating PGP WDE client
installers.
PGP WDE Quick Start Guide (QSG): The Quick Start Guide introduces you
to the features of the PGP WDE product. Consider distributing the PGP
WDE QSG to your end users to introduce them to the product.
PGP Desktop User's Guide: The User's Guide explains all aspects of the
PGP WDE product. If you want more information about the PGP WDE
product than is provided in the PGP WDE QSG, consult the PGP Desktop
User's Guide.
Online help: Both the PGP Universal Server and PGP WDE include built-in
online help.
PGP Corporation Support forums: Visit the PGP Support forum
(http://forums.pgpsupport.com) for answers to frequently asked questions
about PGP WDE and PGP Universal.
4
Page 7

Understanding PGP Whole
2
Disk Encryption
This chapter tells you about PGP WDE and shows a typical PGP WDE
deployment.
In This Chapter
About PGP Whole Disk Encryption............................................................ 5
Components of a Typical PGP WDE Deployment..................................... 6
How Does PGP Whole Disk Encryption Work?......................................... 7
About PGP Universal Server...................................................................... 7
About PGP Whole Disk Encryption
PGP WDE is a software product from PGP Corporation that secures files stored
on protected drives with transparent full disk encryption. If a protected system
is lost or stolen, data stored on the protected drive is completely inaccessible
without the proper authentication. For more information about the PGP WDE
product, see the PGP Desktop User's Guide.
The PGP WDE product also provides the following functionality for your users:
Use part of your hard drive space as an encrypted virtual disk volume with
its own drive letter.
Create secure, encrypted Zip archives.
Put files and folders into a single encrypted, compressed archive that can
be opened on Windows systems that do not have PGP WDE or PGP
Desktop installed.
Completely destroy files and folders so that even file recovery software
cannot recover them.
Securely erase free space on your drives so that deleted data is truly
unrecoverable.
5
Page 8

PGP® Whole Disk Encryption Understanding PGP Whole Disk Encryption
PGP WDE is both a product sold by PGP Corporation and a feature in several
PGP Corporation products.
When this Guide refers to "PGP WDE," it refers to the PGP WDE product. Bear
in mind, however, that "whole disk encryption" is only one feature of the PGP
WDE product.
Components of a Typical PGP WDE Deployment
The following are elements of a typical PGP WDE deployment:
1 PGP Whole Disk Encryption is a licensed component of the PGP Desktop
product. To deploy PGP WDE, you must install the PGP WDE software on
a client system via a customized installer you create using the PGP
Universal Server.
2 PGP Universal Server is a platform for creation and management of PGP
Corporation encryption applications, including PGP WDE. The PGP
Universal Server must be able to communicate with your PGP WDE clients
so that it can:
provide a pre-configured installer for the system.
enroll and bind the client to the server.
provide and enforce policies.
provide recovery options.
3 Directory/LDAP Server (for example, Active Directory). An LDAP server:
provides an authentication mechanism during PGP WDE client
enrollment/installation.
enables you to synchronize groups for policy application.
leverages existing information about the user (email, DN, user certs,
and so on).
4 Your DNS server needs to be configured to support your PGP Universal
Server; be sure to coordinate with your IT group to ensure a successful
installation.
6
Page 9
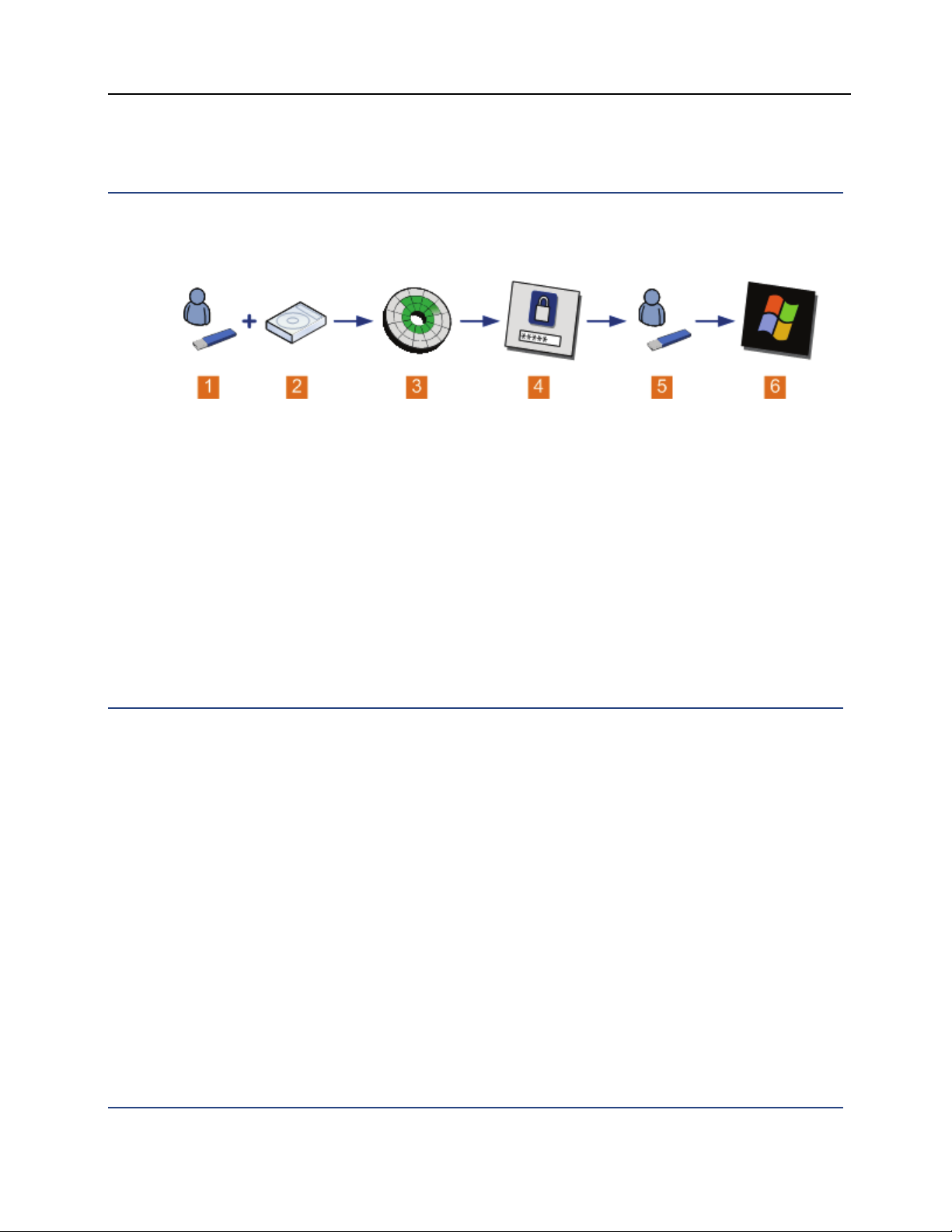
PGP® Whole Disk Encryption Understanding PGP Whole Disk Encryption
How Does PGP Whole Disk Encryption Work?
The following is an overview of the PGP WDE encryption process and
subsequent user experience.
1 The PGP WDE passphrase or token user...
2 ... encrypts the boot drive on their system automatically or manually.
3 The drive is transparently encrypted sector by physical sector.
4 Once encryption begins, and thereafter, the PGP WDE user must
authenticate via the BootGuard screen.
5 To access the system, the user enters a passphrase or inserts the USB
token and then authenticates.
6 If the Single Sign-On feature is enabled, the system automatically logs in to
Microsoft Windows.
System behavior is the same as it was prior to encryption.
About PGP Universal Server
PGP Universal Server is a platform for central management and deployment of
PGP Corporation encryption applications, including PGP WDE. You use the PGP
Universal Server to configure PGP WDE client options, provide custom policies
and settings for your PGP WDE users, create the client installers, and manage
the clients after installation (including Whole Disk Recovery Tokens for each
managed client, for example).
7
Page 10

Page 11

3
Major Steps
This Guide is organized into sections that correspond with the order PGP
Corporation recommends you use to deploy PGP WDE. Depending on your
environment, you may perform some of these tasks in a slightly different order.
This Guide covers the steps to take to configure and deploy PGP WDE clients
using a PGP Universal Server as the management server:
1 Preparation. Learn what you need to do before you install the PGP
Universal Server, including:
where to put your PGP Universal Server in your network.
what you need to know to add the PGP Universal Server to your
network.
how to configure your firewall to support the PGP Universal Server.
how to choose the enrollment method your PGP WDE users will use.
how to set up LDAP directory synchronization (if applicable).
2 Installation and configuration. Describes the process of installing the
PGP Universal Server software and steps you through the configuration
wizard. All PGP Universal setups go through this process, but there are
some things specific to deployments.
3 Configuring the PGP Universal Server. Describes the features of your
PGP Universal Server that impact your deployment:
directory synchronization
enrollment
administrative user email setup
automated backups
removal of unneeded services
other desirable services
policies
4 Setting PGP WDE client options. Summarizes the PGP WDE options you
control so that you can appropriately configure them to reflect your
organization's security requirements.
5 Creating the PGP WDE client installer. Describes the process of creating
the actual client installer executable.
6 Testing the client installer. Lists ways you can test your client installer
before full deployment.
9
Page 12

PGP® Whole Disk Encryption Major Steps
7 Deploying the client installer to end users. Provides options for
deploying the client installer executable to your end users.
8 Assisting your users. Discusses some of the things you can do to help
prepare your end users for the new software they will be receiving.
10
Page 13

4
Preparation
Preparation consists of things you need to do or to understand before you begin
installing your PGP Universal Server as your management server:
Where to put your PGP Universal Server in your network.
What you need to know to add the PGP Universal Server to your network.
How to configure your firewall to support the PGP Universal Server.
Understanding the LDAP Directory Synchronization feature.
Understanding policy options.
Understanding enrollment methods.
Making sure the systems on which PGP WDE will be installed are
appropriately prepared.
In This Chapter
Placing the PGP Universal Server in Your Network................................. 12
Adding the PGP Universal Server to your Network................................. 12
Configuring your Firewall......................................................................... 13
Understanding Enrollment....................................................................... 14
Understanding the Two Enrollment Paths .............................................. 14
Understanding the LDAP Directory Synchronization Feature ................. 15
Understanding Policies ............................................................................ 15
Preparing End-User Systems................................................................... 16
11
Page 14

PGP® Whole Disk Encryption Preparation
Placing the PGP Universal Server in Your Network
As a best practice, PGP Corporation recommends placing the PGP Universal
Server in your DMZ for use as a management server for your PGP WDE
deployment.
This allows both internal and external users access to the server (for example, if
you have laptop users who travel, you cannot count on them being on the VPN
when they install the PGP WDE client).
For details on the tasks involved in placing your server, see the PGP Universal
Administrator’s Guide.
Adding the PGP Universal Server to your Network
Once you have determined a network location for your PGP Universal Server,
you must do the following:
Note: You may need to consult with your network and/or system engineering
teams to support the deployment of your PGP Universal Server.
Assign an appropriate IP address to the PGP Universal Server.
Configure the appropriate subnet and gateway.
Configure the appropriate hostname and DNS.
Deployment Options
There are other options to consider at this point:
Do you want to replace the default self-signed server SSL certificate with a
Note: The use of forward and reverse DNS is required; using a host files
is not sufficient.
Make sure the DNS includes appropriate A and PTR records that are in
place prior to installation of the PGP Universal Server.
Also make sure the DNS is reachable by the PGP Universal Server in the
DMZ.
real SSL certificate?
PGP Corporation strongly recommends that you obtain a valid SSL/TLS
certificate for each of your PGP Universal Servers from a public Certificate
Authority (CA), such as GeoTrust, available at the PGP Online Store
(https://store.pgp.com/). This ensures that clients will have confidence in
establishing secure communications with your servers. An in-house CA will
not be recognized by the PGP WDE client.
12
Page 15

PGP® Whole Disk Encryption Preparation
Are you going to use DNS round robin or a load balancer with your PGP
Universal Server?
If so, acquire the proper number of IP addresses or VIP addresses required
for each machine in the cluster as well as proper DNS forward and reverse
pointers. Getting this information in advance will help to ensure a smooth
implementation.
Configuring your Firewall
The PGP WDE clients you are deploying will be in contact with your PGP
Universal Server management server on a regular basis. They must be able to
communicate with each other; otherwise, many aspects of your deployment
will not work. Also, the management server needs certain ports open on your
firewall for a variety of purposes.
Firewall changes should be done before you install the PGP Universal Server.
Specifically:
Clients must be able to access the management server via HTTPS on port
443; allow traffic in both directions.
The management server must be able to make LDAP and LDAPS queries
on ports 389 and 636, respectively, to the LDAP server you are using for
directory synchronization.
If you are using email enrollment, no LDAP connectivity is required
internally, but external LDAP access may be required to support other PGP
WDE functionality; key lookups or file/folder encryption, for example.
The management server needs Internet access on port 80 for updates and
licensing. Only outbound access on port 80 is required.
Licensing can be done manually without Internet connectivity, but requires
pre-authorization from PGP Customer Support (support.pgp.com).
The management server needs FTP or SCP access on ports 21 or 22,
respectively, for delivery of backups to an appropriate location.
Regular backups are important to support the ability to recover from
unexpected failure of the PGP Universal Server. PGP Corporation strongly
recommends you set up regular schedule of backups of the data on your
PGP Universal Server.
You will be configuring the PGP Universal Server you are using as a
management server via its web-based administrative interface using
HTTPS on port 9000, so this port needs to be open.
Enabling SSH access to the management server on port 22 will give you
access should web-based access be down for some reason.
13
Page 16

PGP® Whole Disk Encryption Preparation
Notification emails from the management server to administrators of the
PGP Universal Server are sent via SMTP on port 25, so that port should be
open between the PGP Universal Server and the mail server that will
accept email from administrators.
Understanding Enrollment
PGP WDE clients synchronize with their PGP Universal Server during installation
via the PGP client enrollment process. Once enrolled with their PGP Universal
Server, clients receive encryption keys, policies, and management updates from
the PGP Universal Server. The enrollment process establishes the relationship
between the client and the server, binding the managed client to the specific
PGP Universal Server.
There are two methods for enrolling your PGP WDE users:
LDAP Directory Synchronization: Requires that the LDAP Directory
Synchronization feature be enabled (and correctly configured) and the
Enroll clients using directory synchronization checkbox be selected on
the Directory Synchronization screen in the PGP Universal Server's
management interface. To enroll, the client will provide authentication
credentials to the LDAP directory specified in the LDAP Directory
Synchronization feature.
Email: Requires only that the PGP WDE client and the management server
are able to communicate via SMTP email. This method is available for all
client installations, provided there is a usable email account on the client
system. This method is available even if the PGP Universal Server is not
performing email encryption. To enroll with a server, the client sends an
email to the PGP Universal Server. The PGP Universal Server will process
the email message and then send an email message back to the PGP WDE
client, which will use the return email to finalize the enrollment process,
and then continue with the installation.
Understanding the Two Enrollment Paths
There are two basic "paths" for deciding how to configure the LDAP Directory
Synchronization feature, policies, and enrollment methods:
If you have an up-to-date LDAP directory server in your organization, you
will probably want to enable the LDAP Directory Synchronization feature
(and turn enrollment on), select Auto detect policies, and use the LDAP
Directory Synchronization feature for enrollment. This leverages the
information in your LDAP directory and simplifies the job of the
administrator.
14
Page 17
PGP® Whole Disk Encryption Preparation
If you do not have an up-to-date LDAP directory server in your organization,
you will want to keep the LDAP Directory Synchronization feature disabled,
select Preset policy, and use email enrollment.
Understanding the LDAP Directory Synchronization Feature
LDAP Directory Synchronization is a feature of PGP Universal which, if enabled
(it is disabled by default), can be used with your PGP WDE deployment.
Enabling this feature lets your PGP Universal Server query your organization's
LDAP directory server for information about users and import the appropriate
users, thus taking advantage of existing information about users and their
authentication credentials.
Note: Proper LDAP syntax must be used when you work with the LDAP
Directory Synchronization feature.
There are three LDAP Directory Synchronization configuration options:
LDAP Directory Synchronization enabled, enrollment on. The specified
LDAP directory will be used to determine which users are in what groups
for the purposes of applying the appropriate policy and for enrollment.
LDAP Directory Synchronization enabled, enrollment off. The specified
LDAP directory will be used to determine which users are in what groups
for the purposes of applying the appropriate policy, but not for enrollment
purposes. (Email enrollment will be used).
Disabled. LDAP Directory Synchronization is disabled; the PGP Universal
Server will not check any LDAP directories in your organization either for
users to be imported or for enrollment. (Email enrollment will be used).
Understanding Policies
There are three methods available to determine how your PGP WDE users will
receive internal user policies from the PGP Universal Server; which one you
choose depends on your particular circumstances.
The three policy methods are:
No policy. Your PGP WDE users can do anything their license allows; they
will not receive any policies from the PGP Universal management server.
Auto detect policy. Your PGP WDE users are constrained by the policy
that applies to the LDAP directory group they are in. (This option requires
that you enable the LDAP Directory Synchronization feature.) Using this
policy option means that the most appropriate policy will be selected
automatically and applied for the LDAP directory group your users are in.
Users could have a different policy applied in the future if a new policy is
created that is more appropriate for their LDAP directory group.
15
Page 18

PGP® Whole Disk Encryption Preparation
Preset policy. Your PGP WDE users are constrained by the settings of the
selected preset policy , either default policy or a custom policy you create.
You can change the settings of the selected preset policy in the future and
the new settings will apply to the users constrained by the policy, with the
exception of actions taken at installation.
Preparing End-User Systems
PGP Corporation strongly recommends you check the PGP Desktop
Release Notes and PGP Universal Release Notes to make sure the systems
in your deployment environment are ready for installation of both the
server and WDE client.
Make sure clients meet the listed minimum system requirements.
Determine whether the email clients used in your environment are
supported clients.
Verify that your anti-virus and firewall software is compatible.
Review the list of known software conflicts and ensure you will not
encounter these in your deployment.
Ensure that target client systems include scandisk (Windows chkdsk.exe,
for example, or SpinRite or Norton Disk Doctor, if available) and
defragmentation (Windows defrag.exe, for example, or PerfectDisk, if
available) software, for preparing their drives for installation of PGP WDE.
16
Page 19

Installation and
5
Configuration
This section describes the installation process at a high level. For a more
detailed description of each activity, see the PGP Universal Administrator's
Guide.
In This Chapter
Before You Install .................................................................................... 17
Installing the Server Software ................................................................. 17
Before You Install
Before you install the software, ensure you have the following available to you:
The appropriate hardware on which to install the PGP Universal Server
software. The current PGP Universal Server Certified Hardware List is
located in the most recent version of the PGP Universal Release Notes.
The most recent version of the PGP Universal Server software.
The most recent version of the PGP Universal Administrator's Guide.
To view the most recent version of the PGP Universal Release Notes and PGP
Universal Administrator's Guide , please go to the PGP Support Portal and view
the Knowledge Base article PGP User Guides, Administrator Guides, Quick Start
Guides, and Release Notes (https://support.pgp.com/?faq=589).
Installing the Server Software
To install the server software:
1 Perform the standard installation of the PGP Universal Server software, as
described in Chapter 6 of the PGP Universal Administrator's Guide.
17
Page 20

PGP® Whole Disk Encryption Installation and Configuration
2 Configure the server using the Setup Assistant. Connect to the PGP
Universal Server when the standard installation is complete, as described in
Chapter 7 of the PGP Universal Administrator's Guide.
3 On the Welcome screen, read the text, then click the Forward arrow.
4 On the End User License Agreement screen, read the text of the License
Agreement, then click the I Agree button.
5 On the Setup Type screen, select Primary, then click the Forward arrow
to continue.
6 On the Date & Time screen, enter the appropriate information, then click
the Forward arrow to continue.
7 On the Network Setup screen, verify that the information you entered in
the Standard installation is correct, and then click the Forward arrow.
8 On the Confirmation screen, verify that the information is correct, and
then click Done.
9 When the Licensing screen appears, enter the appropriate licensing
information for the PGP Universal Server you are using as a management
server, and click Save.
10 On the Administrator Name & Passphrase screen, enter the appropriate
information, and then continue.
11 On the Mail Processing screen, select Gateway Placement, and then
continue.
12 On the Mail Server Selection screen, enter the appropriate information,
and then continue.
13 On the Directory Server screen, do one of the following:
If you will be enabling the LDAP Directory Synchronization feature,
enter the IP address or hostname of the LDAP directory server you
want to use, then continue.
If you are not going to be enabling the LDAP Directory
Synchronization feature, click Skip.
14 On the Ignition Keys screen, make the desired selection, then continue.
15 On the Ignition Keys screen that appears, enter the appropriate
information, and then continue.
16 On the Backup Organization Key screen, enter a passphrase to protect
your Organization Key, then click Backup Key. An Organization Key will be
generated. This key allows you to restore your PGP Universal Server from a
backup, should that be necessary. (The other use of an Organization Key,
to sign the keys created by the PGP Universal Server, does not apply if you
are using the PGP Universal Server only as a management server.)
17 When the Confirmation screen appears, check to make sure the settings
are correct, and then click Done.
18
Page 21

Configuring the PGP
6
Universal Server
There are multiple aspects of the PGP Universal Server that you should
configure to get it ready for use as a management server:
Removing unneeded services.
Setting up administrators.
Establishing settings for backups.
Securing the server.
Configuring policies.
Configuring the LDAP Directory Synchronization feature (if applicable).
Configuring enrollment.
In This Chapter
Removing Unneeded Services ................................................................ 19
Setting Up Administrators ....................................................................... 20
Establishing Backups ............................................................................... 21
Securing your PGP Universal Server ....................................................... 21
Configuring Policies ................................................................................. 22
Configuring the LDAP Directory Synchronization Feature....................... 22
Configuring Enrollment............................................................................ 24
Removing Unneeded Services
Some services provided by the PGP Universal Server are unnecessary if the
server is being used only as a management server for PGP Desktop clients.
PGP Corporation recommends modifying the default settings of these services,
as described below, for optimal operation of your management server.
Do the following:
Navigate to Mail > Proxies and delete the SMTP proxy; it is not needed.
19
Page 22

PGP® Whole Disk Encryption Configuring the PGP Universal Server
Navigate to Mail > Mail Routes. Delete all existing entries and add a new
entry with an asterisk (*) as the domain name and the IP address of the
mail server that will accept mail for delivery from the PGP Universal Server.
This will force the PGP Universal Server not to use DNS for mail queries;
instead, it will send all mail to the specified mail route.
Navigate to Services > Web Messenger. Click Disable to deactivate the
service.
Navigate to Services > Keyserver. Click Disable to deactivate the service.
Your PGP Universal Server offers a number of other services that you may or
may not want to activate if you are using the server only as a management
server. For more information about these services, see the PGP Universal
Administrator's Guide
Setting Up Administrators
PGP Universal Servers allow multiple administrators and supports different roles
for administrators. You can set up an administrator whose access would be
limited to handling just Whole Disk Recovery Tokens, for example.
During installation, you create one administrator; this administrator is a
superuser, which means they have access to all PGP Universal functionality.
To create additional administrators:
1 From the Users > Administrators card, click Add Administrator.
2 In the Login Name field, enter a login name for the new administrator.
3 In the Passphrase field, enter a passphrase for this administrator.
4 In the Confirm field, enter the same passphrase again.
5 In the Email field, enter the email address of the new administrator.
6 Select the Send Daily Status Email checkbox if you want the new
administrator to receive a daily status email for your system.
7 From the Role list, select the role for the new administrator. The privileges
for the selected role appear.
8 Click Save. The new administrator is added.
For more information about administrators, see the PGP Universal
Administrator's Guide.
20
Page 23

PGP® Whole Disk Encryption Configuring the PGP Universal Server
Establishing Backups
PGP Universal Server provides two ways to back up your data: scheduled
backups and on-demand backups. Backup files can be stored on the PGP
Universal Server, or they can be automatically sent to a location you specify.
To establish automatic backups
1 Navigate to the System > System Backups screen of the administrative
interface, and click Backup Schedule. The Backup Schedule dialog
appears.
2 Click Enable Scheduled Backups.
3 Select the boxes representing the names of the days of the week on which
you want backups performed.
4 Specify a time for the backups to begin in the Start backups at field.
5 Click Save.
To perform an on-demand backup
1 Navigate to the System > System Backups screen.
2 Click Backup Now.
A backup of your data is performed immediately. When the backup is complete,
it displays in the Backups list.
For more information, see the PGP Universal Administrator's Guide.
Securing your PGP Universal Server
You can use hardware or software Ignition Keys to protect the data on your PGP
Universal Server:
Hardware Token Ignition Keys. When you insert a PKCS#11 token in the
PGP Universal Server, the PGP Universal Server will detect it and allow you
to use it as an Ignition Key. The token must contain a single key, which
must be protected by a PIN. You can cache the token’s PIN so that you do
not need to enter the PIN at restart, just have the token present.
Soft-Ignition Passphrase Ignition Keys. A passphrase you specify
protects the PGP Universal Server.
For more information, see the PGP Universal Administrator's Guide.
21
Page 24

PGP® Whole Disk Encryption Configuring the PGP Universal Server
Configuring Policies
As administrator, you control a variety of settings on the PGP WDE software
your end users will be using, including key settings, PGP WDE client settings,
directory services, client updates, and proxy server settings.
These policies are called internal user policies, and are for your internal PGP
WDE end users only. They have nothing to do with the mail processing policies
that can be configured on a PGP Universal Server.
To begin configuring internal user policies for your PGP WDE end users, select
the Policy tab and then click Internal User Policy. The Internal User Policy
card appears.
By default, one internal user policy is always created: Internal Users: Default.
You have several options at this point:
Configure the default Internal Users: Default policy so that it conforms to
your organization's security policies and use that policy for your PGP WDE
users.
Create a new internal user policy, configure that policy so that it conforms
to your organization's security policies, use the new policy for your PGP
WDE users.
Create multiple new internal user policies, configure them appropriately,
use them for your PGP WDE users. For example, if your organization's
security policies calls for stronger security for executives or certain
departments, you could create multiple internal user policies to support
this.
The settings you can configure for internal user policies are described below.
For more information about these settings, refer to the PGP Universal
Administrator's Guide.
22
Page 25

PGP® Whole Disk Encryption Configuring the PGP Universal Server
Configuring the LDAP Directory Synchronization Feature
If you have an up-to-date LDAP directory server in your organization, you will
probably want to enable the LDAP Directory Synchronization feature on your
PGP Universal Server so that you can use your LDAP server for auto-detecting
polices and enrollment. This both leverages the information in your LDAP
directory and simplifies the job of the administrator.
To enable the LDAP Directory Synchronization feature
1 Navigate to the Policy > Internal User Policy screen in the administrative
interface. The Internal User Policy card appears.
2 Click Directory Synchronization. The Directory Synchronization card
appears.
3 Select Enable Directory Synchronization.
4 From the Protocol menu, select LDAP or LDAPS. Note that LDAPS may
place a higher load on the LDAP directory.
5 Enter the fully qualified domain name or IP address of the LDAP directory
server in the Hostname field.
6 Keep the default value of 389 for LDAP or 636 for LDAPS, or enter a
preferred value in the Port field.
7 If desired, enter a value in the Base DN field; this narrows the search for
users and certificates to that portion of the directory. While this is an
optional field, using a Base DN generally improves performance. Refer to
PGP Universal Administrator's Guide for more information.
8 Enter an appropriate value in the Bind DN field. This value will be used to
initially bind (or log in) to the directory server. Binding determines the
permission level granted for the duration of a connection. If you are using
the Bind DN field, enter the passphrase used for authentication in the
Passphrase field. Note: All PGP WDE users that you want to be managed
by your PGP Universal management server must have query access.
9 If you are working on the Primary server in a cluster, select Use this
directory for the entire cluster if this is the only directory server you want
searched for users, and you want all of the PGP Universal Servers in the
cluster to access this same directory. Additionally, if you enable this
setting, all Directory Synchronization settings will be automatically copied
to the Secondary servers in the cluster. You do not need to enable
Directory Synchronization on Secondary servers. This checkbox is only
available on the Primary server in a cluster.
23
Page 26
PGP® Whole Disk Encryption Configuring the PGP Universal Server
10 Select Enroll clients using directory authentication if you want PGP
WDE user enrollment authentication through Directory Synchronization
instead of through email. If you do not choose this enrollment option, users
will be enrolled through email. User enrollment through LDAP allows you to
deploy PGP WDE to your end users without requiring email processing.
11 Select Enable LDAP Referrals to allow the PGP Universal Server to query
referred LDAP directories for user information. The LDAP directory you
choose for Directory Synchronization can respond to PGP Universal Server
queries with a referral or reference to another LDAP directory. If you allow
PGP Universal Server to query referred LDAP directories, the search can
take a long time. If you do not allow referred queries, PGP Universal Server
will disable users not found in the named directory, even if user information
is available in the referred directory.
12 Set the LDAP Cache Timeout (in minutes). The default is 10 minutes.
The LDAP cache contains timestamps that record when the PGP Universal
Server last queried user information. The user information itself is stored in
the PGP Universal Server database, not in the cache. The time stamp in the
cache prevents another search on the user within the cache timeout limit,
to keep LDAP queries from overloading the system.
13 Select your LDAP directory type. Choose Active Directory or OpenLDAP
(RFC 1274). Active Directory is the default setting. Microsoft Active
Directory uses the sAMAccountName attribute for user information, where
OpenLDAP-based directories use the attribute uid for user information.
PGP Universal Server queries user information using only the necessary
attributes, providing faster results when querying user information.
14 Click Save.
Configuring Enrollment
As described previously, there are two methods available for enrollment:
Email (the default). Requires only that the PGP WDE client and the PGP
Universal management server be able to communicate via SMTP email.
This method is available for all client installations, as long as there is a
usable email account on the client system, even if the PGP Universal
Server is not performing email encryption or is out of the mailflow.
LDAP Directory Synchronization. Requires that the LDAP Directory
Synchronization feature be enabled (and correctly configured) and that the
“Enroll clients using directory synchronization” option be selected on the
Directory Synchronization card. To enroll, the client will provide
authentication credentials to the LDAP directory specified in the LDAP
Directory Synchronization feature.
24
Page 27

PGP® Whole Disk Encryption Configuring the PGP Universal Server
The following information is common to both methods of enrollment:
Port 443 must be open between your PGP WDE clients and the PGP
Universal Server. This is the port the PGP WDE clients use to get policy
and receive encryption keys. Enrollment will fail if port 443 is blocked.
On the Organization > Managed Domains screen, make sure that your
managed domain matches up with the domain you use for email. You
must do this even if you are not using the messaging functionality of
the PGP Universal Server. For example, if you have an email address of
jsmith@eng.example.com
and the managed domain configured on your
PGP Universal Server is example.com, enrollment will not work because
the domain does not exactly match what is configured on the PGP
Universal Server. It is possible to configure multiple email domains on the
PGP Universal Server; configuring eng.example.com as an additional
domain would solve the problem.
Make sure you have DNS properly configured, including pointer records, or
enrollment may fail.
Email Enrollment
To configure email enrollment:
Navigate to the Mail > Mail Routes screen on your PGP Universal Server
and add a route from the protected domain to the hostname of your mail
server. For example, you could use the domain name eng.example.com
and the hostname/IP mail.eng.example.com (or whatever your mail server
address is).
If you have already configured a mail route using an asterisk (*) as the
domain name and the IP address of the mail server that will accept mail for
delivery from the PGP Universal Server, you do not need to configure
another mail route.
Make sure port 25 is open between your PGP Universal Server and your
mail server and make sure your mail server accepts SMTP (Domino servers
might not by default, for example).
25
Page 28

PGP® Whole Disk Encryption Configuring the PGP Universal Server
When your PGP WDE users install PGP WDE on their systems, an Enrollment
Assistant will appear, asking them to open their email client, check for new
messages, and open the enrollment email message the management server
sends them. It is critical that your users open the message, as it puts a cookie
onto their system. This cookie is required for the successful completion of the
enrollment process.
LDAP Directory Synchronization Enrollment
You may want to use tools such as ADSIedit (from the Windows Support tools
section of your Server OS CD) or SoftTerra's ldapbrowser from
ldapbrowser.com to facilitate LDAP Directory Synchronization enrollment. This
ensures that proper LDAP syntax is used.
Your directory schema must contain certain attributes for you to use LDAP
Directory Synchronization enrollment. Every user is required to have an email
address in the attribute mail.
Other settings to check include:
cn, mail
smtpProxyAddress (or proxyAddress SMTP:)
uid
sAMAccountName
Usercertificate
binary
All these attributes (except Usercertificate and binary) need to be present in the
directory. The attribute of your LDAP filter needs to be present as well.
When your PGP WDE users install PGP WDE on their systems, they will be
prompted for their username and password on the LDAP directory. Ensure that
they do this, as it is required for the successful completion of the enrollment
process.
26
Page 29

Establishing PGP WDE
7
Client Settings
The PGP WDE client is the component that must be installed on each system in
your deployment.
Consider the following topics when planning to configure PGP WDE clients:
Specifying the appropriate key settings.
Setting up administrators.
Establishing settings for backups.
Securing the server.
Configuring policies.
Configuring the LDAP Directory Synchronization feature (if applicable).
Configuring enrollment.
In This Chapter
Key Settings for Your PGP WDE Clients ................................................. 28
Establishing PGP Desktop Settings for Your PGP WDE Clients ............. 33
Other Internal User Policy Settings ......................................................... 40
27
Page 30
PGP® Whole Disk Encryption Establishing PGP WDE Client Settings
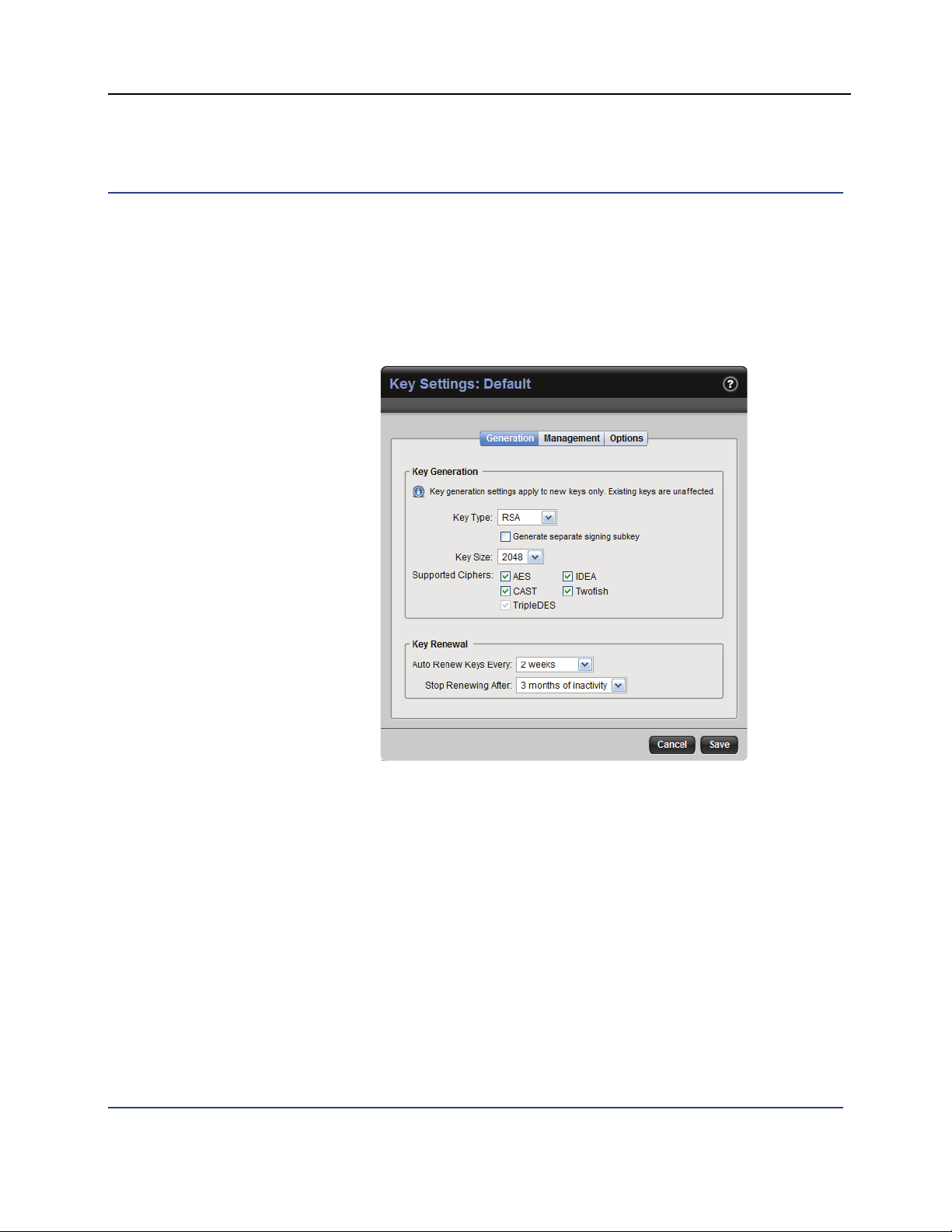
Key Settings for Your PGP WDE Clients
These settings apply to the PGP keys that your PGP WDE users can create. The
settings are found on the three tabs of the PGP Universal Server management
console (Policy > Internal User Policy > [policy] > Key Settings).
Key Generation Settings
The settings on the Generation tab:
Key Type: Select the default key type for your PGP WDE users, either RSA
or DH/DSS. The default is RSA.
Generate a separate signing subkey: Check if you want your PGP WDE
users to be able to generate separate signing subkeys.
Key Size: Select the default key size for your PGP WDE users. Available
options are 1024, 1536, 2048, 3072, and 4096.
Supported Ciphers: Deselect any cipher type you do not want your end
users to be able to use. TripleDES is the default cipher, used if none of the
other ciphers are chosen or available; it cannot be deselected.
28
Page 31

PGP® Whole Disk Encryption Establishing PGP WDE Client Settings
Auto-Renew Keys Every: Select an auto-renewal time frame for the keys
of your PGP WDE users. Internal keys will automatically be renewed in the
time frame you specify unless they have exceeded the inactivity threshold
in Stop Renewing After. Select Never renew if you want your internal keys
never to renew; this means the keys will never expire, regardless of
inactivity.
Stop Renewing After: Specify a period of inactivity after which a key will
not be automatically renewed. Select Never stop renewing if you want
keys of your PGP WDE users to be continually renewed. The question you
should ask yourself here is how long a period of inactivity for a given user
should be before you reasonably conclude that the user account is no
longer in use.
It is generally a good idea to set the auto-renewal time to be fairly short.
This helps ensure that the PGP Universal Server manages itself without
you needing to delete a user manually in the event someone leaves your
organization.
Key Mode Settings
The options on the Management tab let you select which key modes your PGP
WDE users will be able to select when they create keys. You must allow at
least one key mode.
Note: The decisions you make now in deploying PGP WDE, including
selecting a key mode, affect how you can deploy and use other PGP
Corporation products in the future.
29
Page 32

PGP® Whole Disk Encryption Establishing PGP WDE Client Settings
Available options are:
Server Key Mode (SKM). Select this option if you want the PGP Universal
Server to generate and manage the keys of your PGP WDE users. Giving
your PGP WDE users no key mode options other than SKM means there
will be restrictions on what PGP WDE features your PGP WDE users can
use, as they do not have control over their PGP keypair. They will not be
able to sign PGP Zip archives, encrypt PGP Virtual Disk volumes to their
key, and would have to switch key modes if your organization later wants
them to use PGP NetShare or PGP Messaging.
PGP Corporation recommends that PGP WDE users not be restricted to
SKM, so that they have access to the full range of PGP WDE features.
Client Key Mode (CKM). Select this option if you want your PGP WDE
users to be able to generate and manage their own PGP keys.
Guarded Key Mode (GKM). Select this option if you want your PGP WDE
users to be able to generate and manage their own keys, and you also
want encrypted copies of users’ private keys stored on the PGP Universal
Server as a backup for the end user.
Server Client Key Mode (SCKM). Select this option if you want private
encryption keys shared between your PGP WDE users and the PGP
Universal Server, and private signing keys stored only on the clients. SCKM
supports PGP WDE, PGP NetShare, and PGP Messaging users.
For more information, see the PGP Universal Administrator's Guide.
30
Page 33
PGP® Whole Disk Encryption Establishing PGP WDE Client Settings
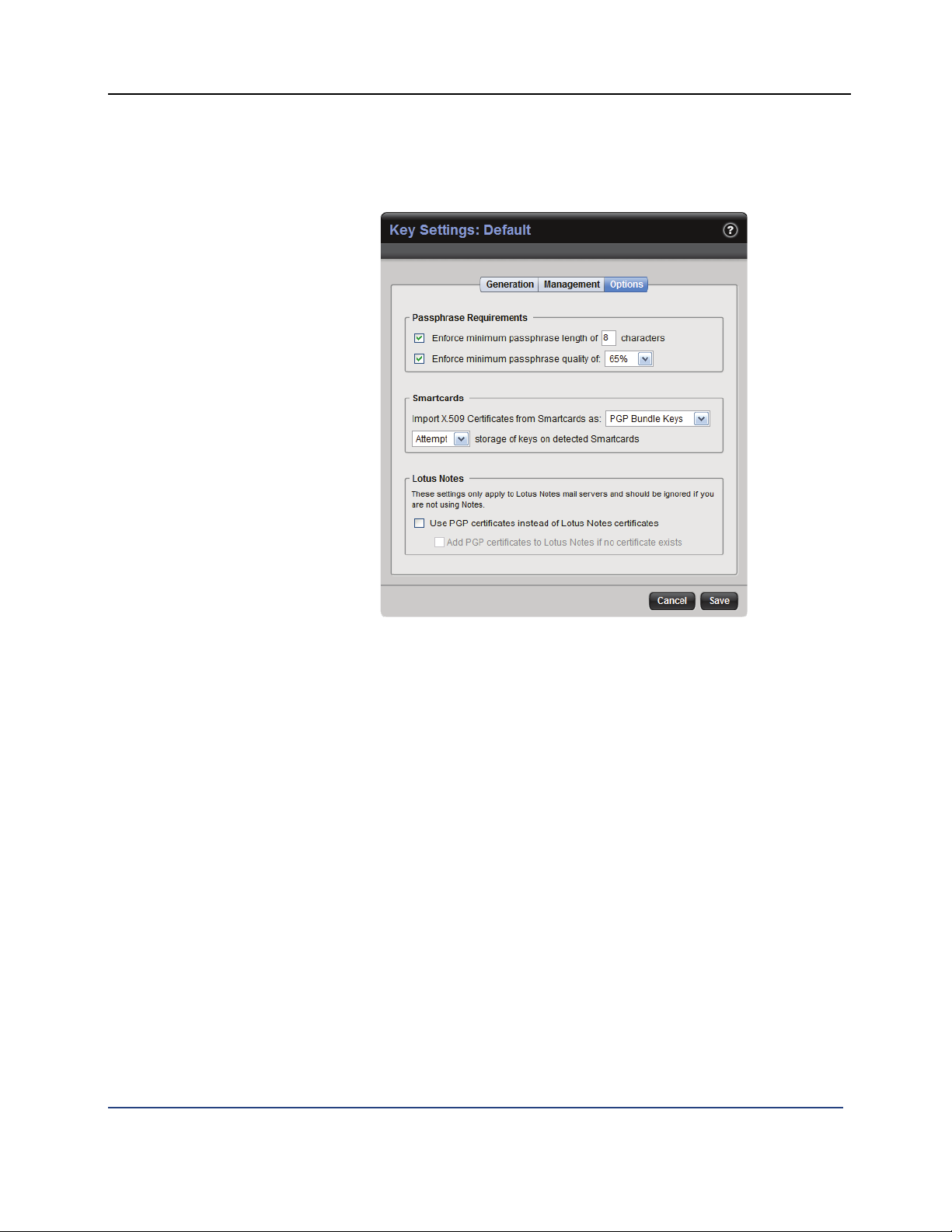
Options Settings
The settings on the Options tab:
Enforce minimum passphrase length of X characters. Enable if you
want to require a minimum number of characters in passphrases for new
keys created by your PGP WDE users. The default is eight characters.
Enforce minimum passphrase quality of X%. Enable if you want to
require a minimum passphrase quality level for new keys created by your
PGP WDE users.
Import X.509 certificates from smartcards as: Select PGP Bundle Keys,
PGP Wrapper Keys, or User selectable.
PGP Bundle Keys bundles user X.509 signing and encryption
certificates into a single identity. This is the recommended option.
PGP Wrapper Keys allows user X.509 signing and encryption
certificates to be imported as separate identities. This option is not
recommended because it only functions in an exclusively S/MIME
environment.
User selectable allows your PGP WDE users to choose how to import
their smartcard X.509 certificates.
31
Page 34

PGP® Whole Disk Encryption Establishing PGP WDE Client Settings
Storage of keys on detected Smartcards. Select Attempt or Require.
Attempt means that PGP WDE will attempt to store new keys
created by your PGP WDE users on supported smartcards that are
detected, but will not require a supported smartcard in order to create
a new key.
Require means that new keys your PGP WDE users create must be
stored on a supported smartcard. They will not be able to create a key
unless it can be stored on a smartcard.
Use PGP certificates instead of Lotus Notes certificate. Select if you are
using a Lotus Notes mail server but you want your PGP WDE users to use
a PGP x.509 certificate as the user's active certificate in Lotus Notes, but
only if the user is already using a non-PGP X.509 certificate. The Lotus
Notes certificate is suppressed.
Lotus Notes users without PGP client software will be able to find PGP
X.509 certificates in the Domino Directory and use them to encrypt mail. If
someone using both PGP WDE and Lotus Notes turns off PGP WDE email
proxying, the user can still decrypt incoming mail and sign outgoing mail.
The Lotus Notes full-text indexer can index PGP-encrypted content; MIMEformatted mail becomes searchable, but Lotus Notes Rich Text mail does
not.
Add PGP certificates to Lotus Notes if no certificate exists. Select if you
want the PGP certificates to be inserted into the Lotus Notes certificate
directory, whether the user has another certificate or not. Only available if
Use PGP certificates instead of Lotus Notes certificate is selected.
32
Page 35
PGP® Whole Disk Encryption Establishing PGP WDE Client Settings
Establishing PGP Desktop Settings for Your PGP WDE Clients
These settings are found on the three tabs of the PGP Universal Server
management console (Policy > Internal User Policy > [policy] > PGP Desktop
Settings).
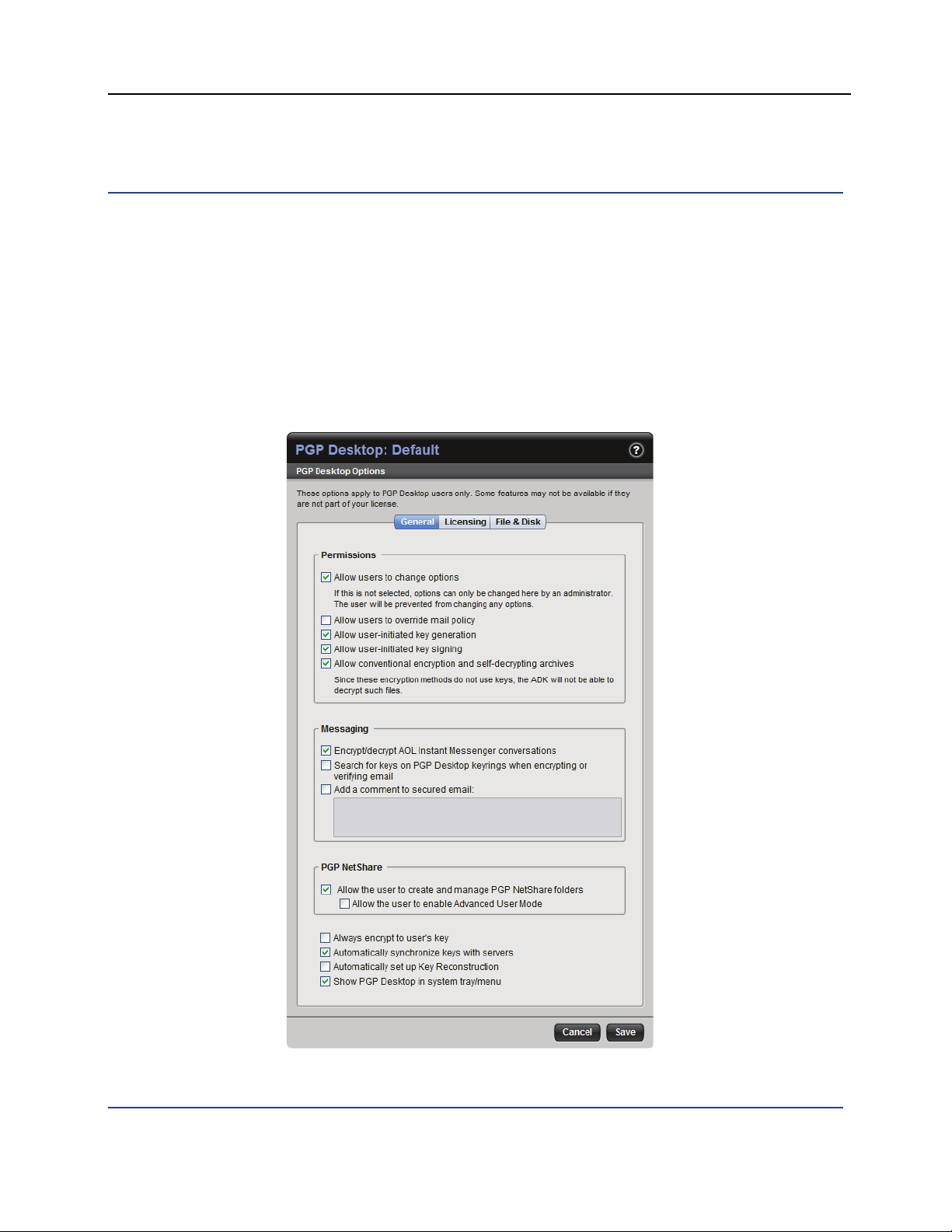
The General Tab
The settings on the General tab control Permissions, Messaging, and PGP
NetShare; they also include some general settings. For detailed descriptions of
these settings, see the PGP Universal Administrator's Guide.
33
Page 36

PGP® Whole Disk Encryption Establishing PGP WDE Client Settings
The settings on the General tab are:
Allow users to change options. When selected, lets your PGP WDE
users change the settings that you, their administrator, have established.
Deselect this option to prevent them from changing these settings.
Allow users to override mail policy. When selected, lets your PGP WDE
users take actions that override the mail policy of the PGP Universal Server.
This setting allows users to create messaging policies that could make
their messaging less secure. Deselect to prevent users from overriding
mail policy.
Allow user-initiated key generation. When selected, lets your PGP WDE
users create new keys and subkeys—in addition to the key created during
installation. Deselect to prevent them from creating new keys after
installation and from making certain changes to their keypairs, such as
adding and removing ADKs, appointing and removing third-party key
revokers, or creating and using subkeys.
Allow user-initiated key signing. When selected, lets your PGP WDE
users sign keys. Deselect to prevent them from signing keys. You may
need to do this to enforce centralized control over the validity of keys in
your organization.
Allow conventional encryption and self-decrypting archives. When
selected, lets your PGP WDE users conventionally encrypt files using a
passphrase instead of a key, or create self-decrypting archives (SDAs).
Note that conventionally encrypted and self-decrypting files cannot be
decrypted by your organization's ADK, which may conflict with your data
recovery policy. Deselect to prevent users from conventionally encrypting
files or creating SDAs.
Encrypt/Decrypt AOL Instant Messenger conversations. When
selected, the instant messages (IMs) between your PGP WDE users and
other PGP Desktop users are protected. Note that IMs will be protected
only if both users are running PGP WDE or PGP Desktop software with this
setting enabled. Deselect if you do not want these IM sessions to be
protected.
Search for keys on PGP Desktop keyrings when encrypting or
verifying email. When selected, lets your PGP WDE users import keys
into their keyring so that they can encrypt or verify messages without
needing to refer to the PGP Universal Server for key information. This
allows your PGP WDE users to operate as if they were not bound to the
PGP Universal Server, even if they are. Deselect to prevent them from
searching for keys on their own keyring when encrypting or verifying email.
Add a comment to secured email. When selected, appends the text in
the box to clear-signed PGP blocks, including exported key files, and
encrypted files and text. Deselect and leave the box empty if you do not
want a comment to be appended to these messages.
34
Page 37

PGP® Whole Disk Encryption Establishing PGP WDE Client Settings
Note: The two PGP NetShare settings (Allow the user to create and manage
PGP NetShare folders and Allow the user to enable Advanced User Mode) do
not apply to PGP WDE users.
Always encrypt to user’s key. When selected, every message your PGP
WDE users send will be encrypted to their key. This is in addition to any
other user- or system-specified key; for example, the ADK. Deselect if you
do not want messages to be automatically encrypted to the user’s key.
Users can still manually encrypt their messages to their key.
Automatically synchronize keys with servers. When selected, PGP
WDE will automatically keep your users’ keys synchronized with configured
servers (when enabled, user key data synchronizes every 24 hours with the
data on the PGP Universal Server). Deselect this option to prevent
automatic synchronization of keys.
Automatically set up Key Reconstruction. When selected, key
reconstruction is set up automatically for your PGP WDE users when new
keys are created. The key reconstruction data is stored on the PGP
Universal Server. Keys created on smartcards and tokens are not
compatible with key reconstruction. For information on key reconstruction,
see the PGP Desktop User’s Guide and the Inside PGP Key Reconstruction
White Paper on the PGP Corporation website.
Show PGP Desktop in system tray/menu. When selected, the PGP
WDE padlock icon appears in the system tray of your PGP WDE users
when PGP WDE is active on their systems. The icon provides access to
some PGP WDE features without requiring users to launch the whole
application. Deselect to hide the icon.
35
Page 38

PGP® Whole Disk Encryption Establishing PGP WDE Client Settings
The File & Disk Tab
The settings on the File & Disk tab control File Shredding, PGP Virtual Disk, and
PGP Whole Disk; they also include some general settings. Refer to the PGP
Universal Administrator's Guide for detailed descriptions of these settings.
The settings on the File & Disk tab are:
Number of shredder passes. Enter the number of shredder passes your
PGP WDE users will use when they shred. The default is 3. The larger the
number, the more secure the shred, but the longer the shred process
takes.
Warn user before shredding files. When selected, your PGP WDE users
will be warned before files on their system are shredded. Deselect to
suppress this warning.
36
Page 39

PGP® Whole Disk Encryption Establishing PGP WDE Client Settings
Automatically shred when emptying the Recycle Bin/Trash. When
selected, your PGP WDE users will have files they delete from their
system shredded instead of just deleted. Deselect to prevent deleted files
from being shredded.
Automatically create PGP Virtual Disk upon installation. When
selected, a PGP Virtual Disk volume will be created automatically for your
PGP WDE users. Refer to the PGP Universal Administrator's Guide for
more information about this option.
Unmount when inactive for X minutes. When selected, the PGP Virtual
Disk volumes of your PGP WDE users will be automatically unmounted
after the specified number of minutes of inactivity on their systems. This
could prevent the protected data on a PGP Virtual Disk volume from being
available to unauthorized persons if you leave work without unmounting
the volume, for example. Deselect to prevent PGP Virtual Disk volumes
from being automatically unmounted because of inactivity.
Unmount on system sleep. When selected, the PGP Virtual Disk volumes
of your PGP WDE users will automatically unmount if the system goes to
sleep. Some systems do not support sleep mode, so this option would not
apply. Deselect to prevent unmount on sleep.
Prevent sleep if disk(s) cannot be unmounted. When selected, the
systems of your PGP WDE users will not sleep if, for some reason, a PGP
Virtual Disk volume cannot be unmounted. Using this option could prevent
loss of data. Deselect to permit sleep even if a volume cannot be
unmounted.
Allow user-initiated whole disk encryption and decryption. When
selected, your PGP WDE users will be able to whole disk encrypt drives on
their system. Deselect to prevent your users from whole disk encrypting
drives on their system.
Encrypt disks to existing Windows password (Single Sign-On). When
selected, your PGP WDE users will be able to log into PGP WDE at the
same time they log into their Windows system. Deselect to prevent your
users from using the single sign-on feature of PGP WDE.
Note: Using the Single Sign-On feature is both a popular feature and it can be
leveraged to enforce PGP WDE passphrase quality alignment with your
corporate passphrase quality requirements.
Maximum CPU Usage. When selected, makes the process of whole disk
encrypting a drive faster by using more CPU cycles. Deselect to prevent
extra CPU cycles from going to the whole disk encryption process. Some
systems may experience lag during usage when Maximum CPU Usage is
enabled.
Force encryption of removable USB disks. When selected, requires that
any removable USB drives on the system be whole disk encrypted.
Deselect to disable this requirement. This feature requires that userinitiated encryption (and decryption) be enabled.
37
Page 40

PGP® Whole Disk Encryption Establishing PGP WDE Client Settings
When selected, if one of your PGP WDE users attaches a portable drive to
their system, they are prompted to either accept whole disk encryption of
the drive or unmount the drive. This prevents protected data from being
copied onto an unprotected drive. This feature is only available for
Microsoft Windows clients. Refer to the PGP Desktop User's Guide for
more information.
Power failure safety. When selected, in the event of a power failure
during whole disk encryption of a drive, the system can recover the data
and restart encryption. Deselect to disable this feature. Initial encryption
may take longer when Power failure safety is enabled.
Enable administrators to recover disks remotely. When selected, PGP
administrators can remotely regain access to a drive that has been whole
disk encrypted if the usual authentication method is unavailable. Deselect
to disable this option.
Warning: If this option is disabled, and one of your PGP WDE users whole
disk encrypts a drive, then only that user will be able to access the data on
that drive. If the user forgets their passphrase, the data will be lost.
Automatically encrypt book disk upon installation. When selected,
forces whole disk encryption of the book disk when PGP WDE is installed.
Deselect to disable this feature.
Require Aladdin eToken Pro for hardware security. When selected,
requires that your PGP WDE users who whole disk encrypt their boot drive
have an Aladdin eToken Pro installed to access the data. Users will not be
able to complete the installation of PGP WDE without setting up the
Aladdin eToken. Note that if the Aladdin eToken is lost, the encrypted drive
is inaccessible. Deselect this option to disable this requirement.
Before a user can install PGP WDE with this option enabled, they must
already have the Aladdin eToken drivers installed on their computer. You
can find the drivers on the Aladdin website
(www.aladdin.com/support/default.asp).
38
Page 41

PGP® Whole Disk Encryption Establishing PGP WDE Client Settings
The Licensing Tab
You enter your PGP WDE license information on the License tab; this
information will be integrated in the PGP WDE client installers. You can enter
information for multiple versions of PGP WDE.
On the Licensing tab, click the Enter License button.
When the Enter License Information dialog appears, fill in the following fields:
Licensee Name. Enter the name of the person under which the licenses
were purchased.
Licensee Organization. Enter the name of the organization that purchased
the licenses.
Licensee Email. Enter the email address of the person to contact regarding
the license.
39
Page 42

PGP® Whole Disk Encryption Establishing PGP WDE Client Settings
Other Internal User Policy Settings
These settings are found on the three tabs at the bottom of the Policy Options
card (Policy > Internal User Policy > [policy]).
The Directory Services tab of the Policy Options card is different depending on
whether you are editing the Internal Users: Default policy or a policy you
created.
If you are editing the Internal Users: Default policy, select Exclude non-
matching users by default if you want your the policies of your PGP WDE
users to be able to include some users from your LDAP directory using
Directory Synchronization but exclude others. Checking this box means
that if none of the custom user policies you configure apply to a user, that
user will be automatically treated as an excluded user. If you do not check
this box, and if none of the custom user policies apply to a user, then the
default internal user policy applies.
If you are editing a user-created policy, you can assign policies to internal
users based on their directory attributes, if the LDAP Directory
Synchronization feature is enabled. Refer to the PGP Universal
Administrator's Guide for more information.
The setting on the Client Updates tab of the Policy Options card is:
Notify users of software updates and automatically download. Select
if you want your PGP WDE users to be automatically notified of software
updates; available updates will be downloaded automatically. Deselect to
prevent automatic download of new PGP WDE client software.
The settings on the Proxy Server tab of the Policy Options card are:
Use an HTTPS Proxy Server for PGP client communications. Select if
your PGP WDE clients connect to the PGP Universal Server through a
proxy server.
Hostname. Enter the hostname of the HTTPS proxy server.
Port. Enter the port used to access the HTTPS proxy server.
40
Page 43

Creating the PGP WDE
8
Client Installer
Once you have configured the settings for your PGP WDE client installers, there
are three ways to actually create the PGP WDE client installer:
with auto-detect policy.
with preset policy.
with no policy settings.
In This Chapter
Creating an Installer with Auto-Detect Policy.......................................... 42
Creating an Installer with Preset Policy ................................................... 43
Creating an Installer with No Policy Settings .......................................... 44
41
Page 44

PGP® Whole Disk Encryption Creating the PGP WDE Client Installer
Creating an Installer with Auto-Detect Policy
This option for creating your PGP WDE client installers uses your organization's
LDAP directory and requires that the LDAP Directory Synchronization feature
already be enabled and appropriately configured on the PGP Universal Server.
To create a PGP Desktop installer with auto-detect policy
1 Create the custom user policies you want to be linked to your PGP WDE
users. If you do not create any custom user policies, then your PGP WDE
users will automatically be linked to the Internal Users: Default policy. You
can, however, create custom user policies in the future that may be linked
to your PGP WDE users, depending on the settings in the custom policies.
2 Configure the settings on the PGP Desktop screen appropriately for these
custom user policies. Refer to your PGP Universal Administrator's Guide
for specific instructions.
3 Click Save. The Policy Options card for the custom policy appears.
4 Click Save. The Internal User Policy card appears.
5 On the Internal User Policy card, click Download Client. The Download
PGP Clients card appears.
6 In the Client field, select PGP Desktop.
7 In the Platform field, select Windows (Vista, XP, 2000) or Mac OS X, as
appropriate.
42
Page 45

PGP® Whole Disk Encryption Creating the PGP WDE Client Installer
8 Make sure the Customize checkbox is selected. If it is not selected, select
it.
9 Select Auto-detect Policy.
10 In the PGP Universal Server field, enter the PGP Universal Server you
want the application to interact with. The PGP Universal Server you are
using to create the installer is listed by default.
11 In the Mail Server Binding field, enter the name of the mail server you
want bound to the PGP Universal Server. You must enter this information
unless your users read mail directly from this PGP Universal Server.
Customized client installations will not work without mail server binding.
You can use the * wildcard character to bind automatically to any mail
server. Mail policy will be enforced for any mail server to which the client
connects. You can use the wildcard as follows: *, *.example.com, and
example.*.com. If you are creating a binding for an internal MAPI email
client, you must use the WINS name of the Exchange Server. If you are
creating a binding for an internal Lotus Notes email client, you must use
the fully qualified domain name of the Domino server.
12 Click Download. The PGP WDE client installer is created and downloaded
to your system.
Creating an Installer with Preset Policy
This option for creating your PGP WDE client installers does not use an LDAP
directory nor the LDAP Directory Synchronization feature.
To create a PGP WDE client installer with preset policy
1 Create the custom user policy you want to be linked to your PGP WDE
users. If you do not create a custom user policy, then the Internal Users:
Default policy will be the only policy with which you can link your PGP
WDE users.
2 Configure the settings on the PGP Desktop screen appropriately for the
custom user policy.
3 Click Save. The Policy Options card for the custom policy appears.
4 Click Save. The Internal User Policy card appears.
5 On the Internal User Policy card, click Download Client. The Download
PGP Clients card appears.
6 In the Client field, select PGP Desktop.
7 In the Platform field, select Windows (Vista, XP, 2000) or Mac OS X, as
appropriate.
43
Page 46

PGP® Whole Disk Encryption Creating the PGP WDE Client Installer
8 Make sure the Customize checkbox is selected. If it is not selected, select
it.
9 Select Preset Policy, then select the policy you want your PGP WDE users
to be linked to from the drop-down list. If you have not created any custom
user policies, then the drop-down list will have Default as the only entry.
10 You can also select to embed policy and license information into the
installer for offline use. Offline use means no connection between PGP
WDE and PGP Universal Server. The client will not receive any updated
policy information from the PGP Universal management server, even if the
policy is updated on the server side.
11 In the PGP Universal Server field, enter the PGP Universal Server you
want the PGP WDE to interact with. The PGP Universal Server you are
using to create the installer is listed by default.
12 In the Mail Server Binding field, enter the name of the mail server you
want bound to that PGP Universal Server. You must enter this information
unless your users read mail directly from the PGP Universal Server via POP
or IMAP. Customized client installations will not work without mail server
binding. You can use the * wildcard character to bind automatically to any
mail server. Mail policy will be enforced for any mail server to which the
client connects. You can use the wildcard as follows: *, *.example.com,
and example.*.com. If you are creating a binding for an internal MAPI email
client, you must use the WINS name of the Exchange Server. If you are
creating a binding for an internal Lotus Notes email client, you must use
the fully qualified domain name of the Domino server.
13 Click Download. The PGP WDE client installer is created and downloaded
to your system.
44
Page 47

PGP® Whole Disk Encryption Creating the PGP WDE Client Installer
Creating an Installer with No Policy Settings
You have the option of creating your PGP WDE client installer with no policy
settings, which means that your PGP WDE users can do anything their license
allows; they will not receive any policies from the PGP Universal management
server. Note that this option is virtually the same as standalone usage, and
defeats the purpose of using a PGP Universal Server to manage your PGP WDE
users.
To create a PGP Desktop installer with no associated policy
1 On the Internal User Policy card, click Download Client. The Download
PGP Clients card appears.
2 In the Client field, select PGP Desktop.
3 In the Platform field, select Windows (Vista, XP, 2000) or Mac OS X, as
appropriate.
4 Make sure the Customize checkbox is deselected. If it is selected,
deselect it.
5 Click Download. The PGP Desktop installer is created and downloaded to
your system.
45
Page 48

Page 49

Testing the PGP WDE
9
Client Installer
Once you have created a PGP WDE client installer with the desired settings for
your PGP WDE users, PGP Corporation strongly recommends that you not
immediately deploy it. Instead, test your client installer on as many
representative machines as you can; you will save yourself a lot of time by
finding and solving problems with the installer before your full deployment.
Naturally, if any of these tests have unexpected results, you will need to fix the
problems and, if necessary, create an updated client installer.
Ways of testing your PGP WDE client installer include:
Install it on a network that is separate from your production environment.
Install it on a system configured with your standard corporate image.
Install it on a system with your standard corporate image plus other
software common in your organization, allowed or not.
Run a pilot deployment to a small number of users or a single department.
47
Page 50

Page 51

Deploying the PGP WDE
10
Client Installer
How you deploy the PGP WDE client installer to your users depends on your
unique circumstances. Note that the PGP Universal Server, which manages
your PGP WDE clients, cannot be used to deploy the client installer.
Some common methods include:
Using an enterprise software distribution system such as SMS or Tivoli.
Downloaded from a Web/file server.
Distributed on CD, DVD, or thumb drive.
49
Page 52

Page 53

Assisting Your PGP WDE
11
Users
There are a number of things that PGP Corporation recommends you do to help
support your PGP WDE users:
Provide your PGP WDE users with a document, created by your
organization, that talks about PGP WDE: this document could include what
PGP WDE is, what they are expected to use it for, what it does to their
system, and what to do if they have problems with PGP WDE. For more
information about what information you could include in such a document,
refer to The End-User Experience.
Tell them about steps they should take to make sure their drives are in
good condition before they whole disk encrypt them, especially checking
the drive for errors. PGP Corporation recommends a third-party scandisk
utility such as SpinRite or Norton Disk Doctor, for example. Tell them that
defragmenting the drive is also a good idea; recommend the built-in
Windows utility or an third-party utility, such as PerfectDisk.
Even if you do not provide your PGP WDE users with a document that talks
about PGP WDE, you should definitely give them a written statement
about what PGP WDE should be used for and what it must be used for.
Include a summary of your official corporate security policies and how they
can use PGP WDE to conform to those policies.
Give them a copy of the PGP Whole Disk Encryption Quick Start Guide and
the PGP Desktop User's Guide. Strongly encourage them to read the Quick
Start Guide before installing PGP WDE on their systems.
Tell them about the other resources that are available to them: the built-in
online help, the PGP Support Portal (https://support.pgp.com), and the PGP
Support forum (http://forums.pgpsupport.com).
Tell them about steps they should take to make sure their drives are in
good condition before they whole disk encrypt them, especially checking
the drive for errors. PGP Corporation recommends a third-party scandisk
utility such as SpinRite or Norton Disk Doctor, for example. Tell them that
defragmenting the drive is also a good idea; recommend the built-in
Windows utility or an third-party utility, such as PerfectDisk.
Give them a phone number to call or an email address to write to in case
they experience problems.
Set up a system so that each user can report a successful installation.
51
Page 54

Page 55

12
The End-User Experience
Your PGP WDE users will notice changes to how they use their computer both
during the installation of PGP WDE and afterwards. You can help ensure a
successful end-user experience with PGP WDE by preparing your end users for
these changes.
If you decide to provide your PGP WDE users with a document created by your
organization, you may want to include some or all of the following points.
Depending on configuration, some of these points may not apply to your PGP
WDE users.
In This Chapter
During the Installation Process................................................................ 53
During WDE Setup .................................................................................. 54
During Normal Usage .............................................................................. 54
During the Installation Process
The following items may impact your PGP WDE users during installation:
The installation process begins by double-clicking the PGP WDE client
installer. A reboot of the system is required when the installation process is
complete.
During the installation process, PGP WDE will coordinate with the PGP
Universal Server and link to the most appropriate user policy. This linkage is
based on how closely the settings for the particular user in the LDAP
directory match the settings of the available user policies (if LDAP Directory
Synchronization is being used). If you later add a more appropriate policy,
the affected PGP WDE users will automatically become linked to the new,
more appropriate policy. Note that the MSIE proxy setting of the user must
be correct if they are enrolling from outside your corporate network.
Unless Server Key Mode is the only allowed key mode, the installation
process will prompt your PGP WDE users to create a PGP keypair. If you
are allowing them to select between two or more keys modes, you should
provide them with guidance regarding what is the best choice based on
how they will be using the product.
53
Page 56

PGP® Whole Disk Encryption The End-User Experience
If you are not using encrypted email, have your PGP WDE users leave the
email field blank when they are creating their PGP keypair and have them
skip adding their public key to the PGP Global Directory. This will ensure
that they do not get encrypted email that they cannot decrypt.
Part of the installation process includes a "cookie" being placed onto the
systems of your PGP WDE users. This is required for communications
between the system and the PGP Universal Server.
During WDE Setup
The following items may impact your PGP WDE users during setup:
You can configure whole disk encryption of the boot drive on the systems
of your PGP WDE users to begin automatically or you can let them start the
process manually sometime after installation.
Whole disk encryption of a drive is a background process; your PGP WDE
users can continue to use their systems while the drive is being encrypted.
The process of whole disk encrypting a drive can be paused, either
manually or if the system is shut down or restarted, goes into standby
mode, or on laptops if the system goes to battery power (you can only
being whole disk encrypting a drive on a laptop if the system is on AC
power).
On rare occasions, the whole disk encryption of a drive stops and displays
the "Unable to instrument disk" error message. This usually occurs when
there is not enough contiguous space available on the drive being
encrypted, there are disk errors on the drive, or if Windows is reserving
some of the space being used to encrypt the drive. The solution is to have
the user check the drive for errors and defragment it, then try again to
whole disk encrypt it.
54
Page 57

PGP® Whole Disk Encryption The End-User Experience
During Normal Usage
The following items may impact your PGP WDE users during usage:
On startup, the BootGuard screen will appear, requiring appropriate
authentication before allowing access to any data on the system.
The PGP Tray icon will appear in the Windows System Tray, providing easy
access to many PGP WDE features.
The Notifier screen will appear above the Windows System Tray when PGP
WDE performs certain actions, providing information about the action being
taken.
PGP WDE functionality may change from time to time if the policies that
apply to a user changes. PGP WDE checks with the PGP Universal Server it
is enrolled with for policy changes at startup, every 24 hours after startup,
when email messages are sent (if email proxying is enabled).
55
Page 58

PGP® Whole Disk Encryption Glossary
Glossary
enrollment: A process during installation of PGP WDE client software where
the PGP WDE client synchronizes with the PGP Universal Server. The
enrollment process establishes the relationship between the client and the
server, binding the managed client to the specific PGP Universal Server. During
enrollment, and when appropriate afterwards, the PGP WDE client receives
encryption keys, policies, and management updates from the PGP Universal
Server.
full disk encryption: A security industry term for encryption of all data on a
drive below the application layer.
key mode: One of the four "modes" in which a PGP keypair can be created.
Different key modes are more appropriate for different configurations.
LDAP directory synchronization: an optional feature of PGP Universal that lets
your PGP Universal Server query your organization's LDAP directory server (A
Microsoft Active Directory server, for example), thus taking advantage of
existing information about configured users and their authentication credentials.
PGP Universal Server: A software/hardware product from PGP Corporation
used for configuration and management of PGP Corporation encryption
applications, including PGP WDE.
PGP Whole Disk Encryption: A software product from PGP Corporation that
secures files stored on protected drives with transparent full disk encryption. It
also includes other encryption features.
Whole Disk Recovery Token: A feature of PGP WDE where a recovery token
is created that can later be used to recover access to a drive if the normal
authentication method is no longer available.
56
 Loading...
Loading...