Page 1

PGP™ Universal Server
Administrator's Guide
3.2
Page 2

Page 3

The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement.
Version 3.2.1. Last updated: April 2012.
Legal Notice
Copyright (c) 2012 Symantec Corporation. All rights reserved.
Symantec, the Symantec Logo, PGP, Pretty Good Privacy, and the PGP logo are trademarks or registered trademarks of Symantec Corporation or its
affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners.
The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering.
No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if
any.
THE DOCUMENTATION IS PROVIDED"AS IS"AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING
ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT
TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR
INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION.
THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE.
The Licensed Software and Documentation are deemed to be commercial computer software as defined in FAR 12.212 and subject to restricted rights
as defined in FAR Section 52.227-19 "Commercial Computer Software - Restricted Rights" and DFARS 227.7202, et seq. “Commercial Computer
Software and Commercial Computer Software Documentation”, as applicable, and any successor regulations. Any use, modification, reproduction
release, performance, display or disclosure of the Licensed Software and Documentation by the U.S. Government shall be solely in accordance with
the terms of this Agreement.
Symantec Corporation
350 Ellis Street
Mountain View, CA 94043
Symantec Home Page (
Printed in the United States of America.
10 9 8 7 6 5 4 3 2 1
http://www.symantec.com)
Page 4

Page 5

Contents
Introduction
What is PGP Universal Server? 1
PGP Universal Server Product Family 2
Who Should Read This Guide 2
Common Criteria Environments 2
Improvements in this Version of PGP Universal Server 2
Using the PGP Universal Server with the Command Line 4
Symbols 4
Getting Assistance 5
Getting product information 5
Technical Support 5
Contacting Technical Support 6
Licensing and registration 6
Customer service 6
Support agreement resources 7
1
The Big Picture 9
Important Terms 9
PGP Products 9
PGP Universal Server Concepts 10
PGP Universal Server Features 11
PGP Universal Server User Types 12
Installation Overview 13
About Integration with Symantec Protection Center 18
Before You Integrate with Protection Center 18
About Open Ports 21
TCP Ports 21
UDP Ports 22
About Naming your PGP Universal Server
How to Name Your PGP Universal Server 23
Naming Methods 24
23
Understanding the Administrative Interface 25
System Requirements 25
Logging In 25
The System Overview Page 26
Managing Alerts 27
Logging In For the First Time 28
Administrative Interface Map 28
Icons 29
Page 6

ii Contents
Licensing Your Software 35
Overview 35
Licensing a PGP Universal Server 35
License Authorization 35
Licensing the Mail Proxy Feature 35
Licensing PGP Desktop 36
Operating in Learn Mode 37
Purpose of Learn Mode 37
Checking the Logs 38
Managing Learn Mode 38
Managed Domains 39
About Managed Domains 39
Adding Managed Domains 40
Deleting Managed Domains 40
Understanding Keys 41
Choosing a Key Mode For Key Management 41
Changing Key Modes 43
How PGP Universal Server Uses Certificate Revocation Lists 44
Key Reconstruction Blocks 44
Managed Key Permissions 45
Managing Organization Keys 47
About Organization Keys 47
Organization Key 47
Inspecting the Organization Key 48
Regenerating the Organization Key 48
Importing an Organization Key 49
Organization Certificate 50
Inspecting the Organization Certificate 50
Exporting the Organization Certificate 51
Deleting the Organization Certificate 51
Generating the Organization Certificate 51
Importing the Organization Certificate 52
Renewing the Organization Certificate 52
Additional Decryption Key (ADK) 53
Importing the ADK 54
Inspecting the ADK 54
Deleting the ADK 54
External User Root Key 55
Generating the External User Root Key 55
Importing the External User Root Key 55
Deleting the External User Root Key 56
Page 7

External User Root Certificate 56
Generating the External User Root Certificate 56
Importing the External User Root Certificate 57
Deleting the External User Root Certificate 57
Verified Directory Key 58
Importing the Verified Directory Key 58
Inspecting the Verified Directory Key 58
Deleting the Verified Directory Key 59
iii Contents
Administering Managed Keys
Viewing Managed Keys 61
Managed Key Information 62
Email Addresses 64
Subkeys 64
Certificates 65
Permissions 65
Attributes 66
Symmetric Key Series 66
Symmetric Keys 68
Custom Data Objects 69
Exporting Consumer Keys 70
Exporting the Managed Key of an Internal User 70
Exporting the Managed Key of an External User 71
Exporting PGP Verified Directory User Keys 71
Exporting the Managed Key of a Managed Device 71
Deleting Consumer Keys 72
Deleting the Managed Key of an Internal User 72
Deleting the Managed Key of an External User 72
Deleting the Key of a PGP Verified Directory User 73
Deleting the Managed Key of a Managed Device 73
Approving Pending Keys 73
Revoking Managed Keys 74
Managing Trusted Keys and Certificates
61
77
Overview 77
Trusted Keys 77
Trusted Certificates 77
Adding a Trusted Key or Certificate 78
Inspecting and Changing Trusted Key Properties 78
Deleting Trusted Keys and Certificates 79
Searching for Trusted Keys and Certificates 79
Managing Group Keys 81
Overview 81
Establishing Default Group Key Settings 81
Adding a Group Key to an Existing Group 82
Creating a New Group with a Group Key 82
Removing a Group Key from a Group 83
Deleting a Group Key 83
Page 8

iv Contents
Revoking a Group Key 84
Exporting a Group Key 84
Setting Mail Policy 85
Overview 85
How Policy Chains Work 85
Mail Policy and Dictionaries 86
Mail Policy and Key Searches 87
Mail Policy and Cached Keys 87
Understanding the Pre-Installed Policy Chains 88
How Upgrading and Updating Affect Mail Policy Settings 89
Mail Policy Outside the Mailflow 89
Using the Rule Interface 90
The Conditions Card 90
The Actions Card 92
Building Valid Chains and Rules 92
Using Valid Processing Order 93
Creating Valid Groups 94
Creating a Valid Rule 95
Managing Policy Chains 96
Mail Policy Best Practices 96
Restoring Mail Policy to Default Settings 96
Editing Policy Chain Settings 96
Adding Policy Chains 97
Deleting Policy Chains 98
Exporting Policy Chains 98
Printing Policy Chains 99
Managing Rules 99
Adding Rules to Policy Chains 99
Deleting Rules from Policy Chains 99
Enabling and Disabling Rules 100
Changing the Processing Order of the Rules 100
Adding Key Searches 100
Choosing Condition Statements, Conditions, and Actions 101
Condition Statements 101
Conditions 102
Actions 106
Working with Common Access Cards 119
Applying Key Not Found Settings to External Users 121
Overview 121
Bounce the Message 121
PDF Messenger 122
PDF Messenger Secure Reply 122
Working with Passphrases 123
Certified Delivery with PDF Messenger 123
Send Unencrypted 124
Smart Trailer 124
PGP Universal Web Messenger 126
Changing Policy Settings 127
Changing User Delivery Method Preference 127
Page 9
Using Dictionaries with Policy 129
Overview 129
Default Dictionaries 130
Editing Default Dictionaries 131
User-Defined Dictionaries 132
Adding a User-Defined Dictionary 132
Editing a User-Defined Dictionary 133
Deleting a Dictionary 134
Exporting a Dictionary 134
Searching the Dictionaries 134
Keyservers, SMTP Archive Servers, and Mail Policy 137
Overview 137
Keyservers 137
Adding or Editing a Keyserver 138
Deleting a Keyserver 140
SMTP Servers 140
Adding or Editing an Archive Server 140
Deleting an Archive Server 141
v Contents
Managing Keys in the Key Cache 143
Overview 143
Changing Cached Key Timeout 143
Purging Keys from the Cache 143
Trusting Cached Keys 144
Viewing Cached Keys 144
Searching the Key Cache 145
Configuring Mail Proxies 147
Overview 147
PGP Universal Server and Mail Proxies 147
Mail Proxies in an Internal Placement 148
Mail Proxies in a Gateway Placement 149
Changes in Proxy Settings from PGP Universal Server 2.0 to 2.5 and later 150
Mail Proxies Page 151
Creating New or Editing Existing Proxies 151
Creating or Editing a POP/IMAP Proxy 151
Creating or Editing an Outbound SMTP Proxy 153
Creating or Editing an Inbound SMTP Proxy 155
Creating or Editing a Unified SMTP Proxy 156
Email in the Mail Queue
Overview 159
Deleting Messages from the Mail Queue 159
159
Page 10

vi Contents
Specifying Mail Routes 161
Overview 161
Managing Mail Routes 162
Adding a Mail Route 162
Editing a Mail Route 162
Deleting a Mail Route 163
Customizing System Message Templates 165
Overview 165
Templates and Message Size 165
PDF Messenger Templates 166
PGP Universal Web Messenger Templates 166
Editing a Message Template 167
Managing Groups 169
Understanding Groups 169
Sorting Consumers into Groups 169
Everyone Group 170
Excluded Group 170
Policy Group Order 170
Migrate Groups from PGP Universal Server 2.12 SP4 171
Setting Policy Group Order 171
Creating a New Group 171
Deleting a Group 172
Viewing Group Members 172
Manually Adding Group Members 172
Manually Removing Members from a Group 173
Group Permissions 174
Adding Group Permissions 174
Deleting Group Permissions 174
Setting Group Membership 175
Searching Groups 176
Creating Group Client Installations 177
How Group Policy is Assigned to PGP Desktop Installers 177
When to Bind a Client Installation 178
Creating PGP Desktop Installers 179
Managing Devices 183
Managed Devices 183
Adding and Deleting Managed Devices 184
Adding Managed Devices to Groups 184
Managed Device Information 186
Deleting Devices from PGP Universal Server 189
Deleting Managed Devices from Groups 190
WDE Devices (Computers and Disks) 191
WDE Computers 191
WDE Disks 192
Page 11

Contents vii
Searching for Devices 194
Administering Consumer Policy 197
Understanding Consumer Policy 197
Managing Consumer Policies 197
Adding a Consumer Policy 197
Editing a Consumer Policy 198
Deleting a Consumer Policy 199
Making Sure Users Create Strong Passphrases 199
Understanding Entropy 200
Enabling or Disabling Encrypted Email 200
Using the Windows Preinstallation Environment 201
X.509 Certificate Management in Lotus Notes Environments 201
Trusting Certificates Created by PGP Universal Server 202
Setting the Lotus Notes Key Settings in PGP Universal Server 203
Technical Deployment Information 204
Offline Policy 205
Using a Policy ADK 206
Out of Mail Stream Support 206
Enrolling Users through Silent Enrollment 208
Silent Enrollment with Windows 208
Silent Enrollment with Mac OS X 208
PGP Whole Disk Encryption Administration 209
PGP Whole Disk Encryption on Mac OS X with FileVault 209
How Does Single Sign-On Work? 209
Enabling Single Sign-On 210
Managing Clients Remotely Using a PGP WDE Administrator Active Directory Group 211
Managing Clients Locally Using the PGP WDE Administrator Key 212
Setting Policy for Clients 215
Client and PGP Universal Server Version Compatibility 215
Serving PGP Admin 8 Preferences 216
Establishing PGP Desktop Settings for Your PGP Desktop Clients 217
PGP Desktop Feature License Settings 218
Enabling PGP Desktop Client Features in Consumer Policies 218
Controlling PGP Desktop Components 219
PGP Portable 220
PGP Mobile 221
PGP NetShare 221
How the PGP NetShare Policy Settings Work Together 221
Multi-user environments and managing PGP NetShare 222
Backing Up PGP NetShare-Protected Files 222
Using Directory Synchronization to Manage Consumers
How PGP Universal Server Uses Directory Synchronization 225
Base DN and Bind DN 226
Consumer Matching Rules 227
Understanding User Enrollment Methods 227
Before Creating a Client Installer 228
225
Page 12

viii Contents
Email Enrollment 229
Directory Enrollment 231
Certificate Enrollment 232
Enabling Directory Synchronization 234
Adding or Editing an LDAP Directory 234
The LDAP Servers Tab 235
The Base Distinguished Name Tab 236
The Consumer Matching Rules Tab 236
Testing the LDAP Connection 237
Using Sample Records to Configure LDAP Settings 237
Deleting an LDAP Directory 237
Setting LDAP Directory Order 238
Directory Synchronization Settings 238
Managing User Accounts
Understanding User Account Types 241
Viewing User Accounts 241
User Management Tasks 241
Setting User Authentication 241
Editing User Attributes 242
Adding Users to Groups 242
Editing User Permissions 242
Deleting Users 243
Searching for Users 243
Viewing User Log Entries 244
Changing Display Names and Usernames 244
Exporting a User’s X.509 Certificate 245
Revoking a User's X.509 Certificate 245
Managing User Keys 246
Managing Internal User Accounts 246
Importing Internal User Keys Manually 247
Creating New Internal User Accounts 247
Exporting PGP Whole Disk Encryption Login Failure Data 248
Internal User Settings 248
Managing External User Accounts 252
Importing External Users 252
Exporting Delivery Receipts 253
External User Settings 254
Offering X.509 Certificates to External Users 255
Managing Verified Directory User Accounts 256
Importing Verified Directory Users 257
PGP Verified Directory User Settings 257
241
Recovering Encrypted Data in an Enterprise Environment 259
Using Key Reconstruction 259
Recovering Encryption Key Material without Key Reconstruction 260
Encryption Key Recovery of CKM Keys 260
Encryption Key Recovery of GKM Keys 260
Encryption Key Recovery of SCKM Keys 260
Encryption Key Recovery of SKM Keys 261
Using an Additional Decryption Key for Data Recovery 262
Page 13
PGP Universal Satellite 263
Overview 263
Technical Information 263
Distributing the PGP Universal Satellite Software 264
Configuration 264
Key Mode 264
PGP Universal Satellite Configurations 265
Switching Key Modes 268
Policy and Key or Certificate Retrieval 268
Retrieving Lost Policies 268
Retrieving Lost Keys or Certificates 269
PGP Universal Satellite for Mac OS X 271
Overview 271
System Requirements 271
Obtaining the Installer 271
Installation 272
Updates 272
Files 272
ix Contents
PGP Universal Satellite for Windows 275
Overview 275
System Requirements 275
Obtaining the Installer 275
Installation 276
Updates 276
Files 277
MAPI Support 277
External MAPI Configuration 277
Lotus Notes Support 278
External Lotus Notes Configuration 278
Configuring PGP Universal Web Messenger 281
Overview 281
PGP Universal Web Messenger and Clustering 282
External Authentication 282
Customizing PGP Universal Web Messenger 284
Adding a New Template 284
Troubleshooting Customization 289
Changing the Active Template 291
Deleting a Template 291
Editing a Template 292
Downloading Template Files 292
Restoring to Factory Defaults 292
Configuring the PGP Universal Web Messenger Service 292
Starting and Stopping PGP Universal Web Messenger 293
Selecting the PGP Universal Web Messenger Network Interface 293
Page 14

x Contents
Setting Up External Authentication 295
Creating Settings for PGP Universal Web Messenger User Accounts 296
Setting Message Replication in a Cluster 297
Configuring the Integrated Keyserver 299
Overview 299
Starting and Stopping the Keyserver Service 299
Configuring the Keyserver Service 299
Configuring the PGP Verified Directory 301
Overview 301
Starting and Stopping the PGP Verified Directory 302
Configuring the PGP Verified Directory 302
Managing the Certificate Revocation List Service 305
Overview 305
Starting and Stopping the CRL Service 305
Editing CRL Service Settings 306
Configuring Universal Services Protocol 307
Starting and Stopping USP 307
Adding USP Interfaces 307
Introducing PGP Remote Disable and Destroy 1
About PGP Remote Disable and Destroy 1
Components of PGP RDD 1
How PGP RDD Works 1
System Graphs 3
Overview 3
CPU Usage 3
Message Activity 3
Whole Disk Encryption 4
System Logs 5
Overview 5
Filtering the Log View 6
Searching the Log Files 6
Exporting a Log File 7
Enabling External Logging 7
Page 15

Configuring SNMP Monitoring 9
Overview 9
Starting and Stopping SNMP Monitoring 10
Configuring the SNMP Service 10
Downloading the Custom MIB File 11
xi Contents
Viewing Server and License Settings and Shutting Down Services
Overview 13
Server Information 13
Setting the Time 13
Licensing a PGP Universal Server 14
Downloading the Release Notes 14
Shutting Down and Restarting the PGP Universal Server Software Services 15
Shutting Down and Restarting the PGP Universal Server Hardware 15
13
Managing Administrator Accounts 17
Overview 17
Administrator Roles 17
Administrator Authentication 19
Creating a New Administrator 19
Importing SSH v2 Keys 20
Deleting Administrators 20
Inspecting and Changing the Settings of an Administrator 21
Configuring RSA SecurID Authentication 22
Resetting SecurID PINs 23
Daily Status Email 24
Protecting PGP Universal Server with Ignition Keys
Overview 25
Ignition Keys and Clustering 26
Preparing Hardware Tokens to be Ignition Keys 26
Configuring a Hardware Token Ignition Key 28
Configuring a Soft-Ignition Passphrase Ignition Key 28
Deleting Ignition Keys 29
25
Backing Up and Restoring System and User Data
Overview 31
Creating Backups 31
Scheduling Backups 32
Performing On-Demand Backups 32
Configuring the Backup Location 32
Restoring From a Backup 33
Restoring On-Demand 34
Restoring Configuration 34
Restoring from a Different Version 35
31
Page 16
xii Contents
Updating PGP Universal Server Software 37
Overview 37
Inspecting Update Packages 38
Setting Network Interfaces 39
Understanding the Network Settings 39
Changing Interface Settings 40
Adding Interface Settings 40
Deleting Interface Settings 40
Editing Global Network Settings 41
Assigning a Certificate 41
Working with Certificates 41
Importing an Existing Certificate 42
Generating a Certificate Signing Request (CSR) 42
Adding a Pending Certificate 43
Inspecting a Certificate 44
Exporting a Certificate 44
Deleting a Certificate 44
Clustering your PGP Universal Servers 45
Overview 45
Cluster Status 46
Creating a Cluster 47
Deleting Cluster Members 49
Clustering and PGP Universal Web Messenger 50
Managing Settings for Cluster Members 50
Changing Network Settings in Clusters 51
About Clustering Diagnostics 51
Monitoring Data Replication in a Cluster 52
Index
55
Page 17

Introduction
1
This Administrator’s Guide describes both the PGP™ Universal Server and Client
software. It tells you how to get them up and running on your network, how to
configure them, and how to maintain them. This section provides a high-level overview
of PGP Universal Server.
What is PGP Universal Server?
PGP Universal Server is a console that manages the applications that provide email,
disk, and network file encryption. PGP Universal Server with PGP Universal Gateway
Email provides secure messaging by transparently protecting your enterprise messages
with little or no user interaction. The PGP Universal Server replaces PGP Keyserver
with a built-in keyserver, and PGP Admin with PGP Desktop configuration and
deployment capabilities.
PGP Universal Server also does the following:
Automatically creates and maintains a Self-Managing Security Architecture
(SMSA) by monitoring authenticated users and their email traffic.
Allows you to send protected messages to addresses that are not part of the SMSA.
Automatically encrypts, decrypts, signs, and verifies messages.
Provides strong security through policies you control.
PGP Universal Satellite, a client-side feature of PGP Universal Server, does the
following:
Extends security for email messages to the computer of the email user.
Allows external users to become part of the SMSA.
If allowed by an administrator, gives end users the option to create and manage
their keys on their computers.
PGP Desktop, a client product, is created and managed through PGP Universal Server
policy and does the following:
Creates PGP keypairs.
Manages user keypairs.
Stores the public keys of others.
Encrypts user email and instant messaging (IM).
Encrypts entire, or partial, hard drives.
Enables secure file sharing with others over a network.
Page 18
2 Introduction
PGP Universal Server Product Family
PGP Universal Server Product Family
PGP Universal Server functions as a management console for a variety of encryption
solutions. You can purchase any of the PGP Desktop applications or bundles and use
PGP Universal Server to create and manage client installations. You can also purchase a
license that enables PGP Universal Gateway Email to encrypt email in the mailstream.
The PGP Universal Server can manage any combination of the following PGP
encryption applications:
PGP Universal Gateway Email provides automatic email encryption in the
gateway, based on centralized mail policy.
This product requires administration by the PGP Universal Server.
PGP Desktop Email provides encryption at the desktop for mail, files, and AOL
Instant Messenger traffic.
This product can be managed by the PGP Universal Server.
PGP Whole Disk Encryption provides encryption at the desktop for an entire disk.
This product can be managed by the PGP Universal Server.
PGP NetShare provides transparent file encryption and sharing among desktops.
This product can be managed by the PGP Universal Server.
Who Should Read This Guide
This Administrator’s Guide is for the person or persons who implement and maintain
your organization’s PGP Universal Server environment. These are the PGP Universal
Server administrators.
This guide is also intended for anyone else who wants to learn about how PGP Universal
Server works.
Common Criteria Environments
To be Common Criteria compliant, see the best practices in PGP Universal Server 2.9
Common Criteria Supplemental. These best practices supersede recommendations made
elsewhere in this and other documentation.
Improvements in this Version of PGP Universal Server
PGP Universal Server 3.2.1 introduces the following new and improved features:
Page 19

Improvements in this Version of PGP Universal Server
This release provides support for VMware VMotion HA Configurations. PGP
Universal Server with VMware VMotion allows virtual machines on failed ESX
server hosts to restart on surviving ESX hosts.
This release contains improvements in the backup process which provides a faster
way to take and restore backups. Users also now have the capability of specifying
encryption and compression with each backup.
Improvements made to streamline the migration process.
PGP Universal Web Messenger users are now notified when their accounts are
about to expire.
PGP Universal Web Messenger has added functionality to prevent a Cross Sites
Request Forge attacks. PGP Universal Server already provides functionality to
prevent CSRF attacks.
The default mail policy includes the following changes:
New default mail policy no longer uses opportunistic encryption. Email is
secured only if the sender specifies (such as by selecting the Encrypt button
in the email client or by marking the email as "Sensitive").
New default mail policy attempts to encrypt the mail if the subject line
contains “PDF”, and should be delivered as a secure PDF message if the key is
not found and PGP Universal Web Messenger/PDF options are enabled.
“Excluded Signed”, and “Excluded Unsigned” rules are removed as they are
now part of opportunistic encryption.
Secure Reply option for PDF Messenger is enabled by default.
PGP NetShare can be integrated with Symantec Data Loss Prevention to provide
automatic encryption of files without end-user intervention. A Data Loss
Prevention administrator defines policies and rules that define the parameters for
identifying sensitive files and provide credentials for the encryption. The
integration is accomplished using an endpoint client-side plug-in. Files under
consideration for sensitive content can be data in motion (DIM) or data at rest
(DAR). For more information, see the PGP NetShare Flex Response Plug-In for Data
Loss Prevention Implementation Guide.
PGP Universal Server 3.2.0 introduces the following new and improved features:
X.509 certificates are available to your external users through the PGP Universal
Web Messenger interface. External users download the certificates, add them to
their mail clients, and use them to communicate securely with users in your
managed domain.
The PGP Universal Server user interface and all end user documentation have
been rebranded to include the Symantec logo and colors. The product name
remains the same.
We improved performance and page load times for many parts of the interface.
You can now allow your external users to securely reply to PDF Messenger
messages.
You can now monitor the how well data is being replicated throughout your
cluster members.
After you migrate to PGP Universal Server 3.2.1, you can verify whether your
backup/restore or PUP update was successful. `
You can now require users to authenticate at the PGP BootGuard screen with their
user name, domain, and passphrase.
3 Introduction
Page 20
4 Introduction
Using the PGP Universal Server with the Command Line
Symantec Patch Distribution Center now provides all software updates, which
replaces PGP update servers. Automatic updates through the PGP update servers
are no longer available.
PGP Universal Server is now integrated with Symantec Protection Center, which
offers a single point of administration and helps you manage PGP Universal
Server and other security products.
PGP Universal Server now supports group keys, which allows you to protect
shared files and folders in PGP NetShare. Group keys allow you to easily add or
remove group members without affecting the PGP NetShare metadata associated
with the protected files and folders.
You can now allow users, who use certificates or smart cards to log in to Microsoft
Windows, to enroll in PGP Desktop using those certificates.
Using the PGP Universal Server with the Command Line
You can use the PGP Universal Server command line for read-only access to, for
example, view settings, services, logs, processes, disk space, query the database, and so
on.
Symbols
Note: If you modify your configuration using the command line, and you do not
follow these procedures, your PGP Support agreement is void.
Changes to the PGP Universal Server using command line must be:
Authorized in writing by PGP Support.
Implemented by PGP's partner, reseller, or internal employee who is certified in
the PGP Advanced Administration and Deployment Training.
Summarized and documented in a text file in /var/lib/ovid/customization
on the PGP Universal Server.
Changes made through the command line may not persist through reboots and may
become incompatible in a future release. When troubleshooting new issues, PGP
Support can require you to revert custom configurations on the PGP Universal Server
to a default state.
Notes, Cautions, and Warnings are used in the following ways.
Note: Notes are extra, but important, information. A Note calls your attention to
important aspects of the product. You can use the product better if you read the
Notes.
Caution: Cautions indicate the possibility of loss of data or a minor security breach. A
Caution tells you about a situation where problems can occur unless precautions are
taken. Pay attention to Cautions.
Page 21

Warning: Warnings indicate the possibility of significant data loss or a major security
breach. A Warning means serious problems will occur unless you take the
appropriate action. Please take Warnings very seriously.
Getting Assistance
For additional resources, see these sections.
Getting product information
The following documents and online help are companions to the PGP Universal Server
Administrator’s Guide. This guide occasionally refers to information that can be found
in one or more of these sources:
Online help is installed and is available in the PGP Universal Server product.
PGP Universal Server Installation Guide—Describes how to install the PGP
Universal Server.
PGP Universal Server Upgrade Guide—Describes the process of upgrading your
PGP Universal Server.
PGP Universal Mail Policy Diagram—Provides a graphical representation of how
email is processed through mail policy. You can access this document via the PGP
Universal Server online help.
You can also access all the documentation by clicking the online help icon in the
upper-right corner of the PGP Universal Server screen.
PGP Universal Satellite for Windows and Mac OS X includes online help.
PGP Universal Server and PGP Satellite release notes are also provided, which may
have last-minute information not found in the product documentation.
Getting Assistance
5 Introduction
Technical Support
Symantec Technical Support maintains support centers globally. Technical Support’s
primary role is to respond to specific queries about product features and functionality.
The Technical Support group also creates content for our online Knowledge Base. The
Technical Support group works collaboratively with the other functional areas within
Symantec to answer your questions in a timely fashion. For example, the Technical
Support group works with Product Engineering and Symantec Security Response to
provide alerting services and virus definition updates.
Symantec’s support offerings include the following:
A range of support options that give you the flexibility to select the right amount
of service for any size organization
Telephone and/or Web-based support that provides rapid response and
up-to-the-minute information
Upgrade assurance that delivers software upgrades
Page 22

6 Introduction
Getting Assistance
Global support purchased on a regional business hours or 24 hours a day, 7 days a
week basis
Premium service offerings that include Account Management Services
For information about Symantec’s support offerings, you can visit our Web site at the
following URL:
www.symantec.com/business/support/
All support services will be delivered in accordance with your support agreement and
the then-current enterprise technical support policy.
Contacting Technical Support
Customers with a current support agreement may access Technical Support
information at the following URL:
www.symantec.com/business/support/
Before contacting Technical Support, make sure you have satisfied the system
requirements that are listed in your product documentation. Also, you should be at the
computer on which the problem occurred, in case it is necessary to replicate the
problem.
When you contact Technical Support, please have the following information available:
Product release level
Hardware information
Available memory, disk space, and NIC information
Operating system
Version and patch level
Network topology
Router, gateway, and IP address information
Problem description:
Error messages and log files
Troubleshooting that was performed before contacting Symantec
Recent software configuration changes and network changes
Licensing and registration
If your Symantec product requires registration or a license key, access our technical
support Web page at the following URL:
www.symantec.com/business/support/
Customer service
Customer service information is available at the following URL:
www.symantec.com/business/support/
Page 23

Customer Service is available to assist with non-technical questions, such as the
following types of issues:
Questions regarding product licensing or serialization
Product registration updates, such as address or name changes
General product information (features, language availability, local dealers)
Latest information about product updates and upgrades
Information about upgrade assurance and support contracts
Information about the Symantec Buying Programs
Advice about Symantec's technical support options
Nontechnical presales questions
Issues that are related to CD-ROMs or manuals
Support agreement resources
If you want to contact Symantec regarding an existing support agreement, please
contact the support agreement administration team for your region as follows:
Getting Assistance
7 Introduction
Asia-Pacific and Japan customercare_apac@symantec.com
Europe, Middle-East, Africa
North America, Latin America
semea@symantec.com
supportsolutions@symantec.com
Page 24

Page 25

The Big Picture
2
This chapter describes some important terms and concepts and gives you a high-level
overview of the things you need to do to set up and maintain your PGP Universal Server
environment.
Important Terms
The following sections define important terms you will encounter throughout the PGP
Universal Server and this documentation.
PGP Products
PGP Universal Server: A device you add to your network that provides secure
messaging with little or no user interaction. The PGP Universal Server
automatically creates and maintains a security architecture by monitoring
authenticated users and their email traffic. You can also send protected messages
to addresses that are not part of the security architecture.
PGP Global Directory: A free, public keyserver hosted by Symantec
Corporation. The PGP Global Directory provides quick and easy access to the
universe of PGP keys. It uses next-generation keyserver technology that
queries the email address on a key (to verify that the owner of the email
address wants their key posted) and lets users manage their own keys. Using
the PGP Global Directory significantly enhances your chances of finding a
valid public key of someone to whom you want to send secured messages.
For external users without encryption keys, PGP Universal Server offers multiple
secure delivery options, leveraging third-party software that is already installed
on typical computer systems, such as a web browser or Adobe Acrobat Reader. For
email recipients who do not have an encryption solution, you can use of of the
following secure delivery options from PGP Universal Server:
PGP Universal Satellite: The PGP Universal Satellite software resides on the
computer of the email user. It allows email to be encrypted end to end, all the
way to and from the desktop (for both internal and external users). Using
PGP Universal Satellite is one of the ways for external users to participate in
the SMSA. It also allows users the option of controlling their keys on their
local computers (if allowed by the administrator).
PGP Universal Web Messenger: The PGP Universal Web Messenger service
allows an external user to securely read a message from an internal user
before the external user has a relationship with the SMSA. If PGP Universal
Web Messenger is available via mail policy for a user and the recipient’s key
cannot be found, the message is stored on the PGP Universal Server and an
unprotected message is sent to the recipient. The unprotected message
includes a link to the original message, held on the PGP Universal Server.
The recipient must create a passphrase, and then can access his encrypted
messages stored on PGP Universal Server.
Page 26

10 The Big Picture
Important Terms
PDF Messenger: PDF Messenger enables sending encrypted PDF messages to
external users who do not have a relationship with the SMSA. In the normal
mode, as with PGP Universal Web Messenger, the user receives a message
with a link to the encrypted message location and uses a PGP Universal Web
Messenger passphrase to access the message. PDF Messenger also provides
Certified Delivery, which encrypts the message to a one-time passphrase,
and creates and logs a delivery receipt when the user retrieves the
passphrase.
PGP Desktop: A client software tool that uses cryptography to protect your data
against unauthorized access. PGP Desktop is available for Mac OS X and Windows.
PGP Whole Disk Encryption: Whole Disk Encryption is a feature of PGP
Desktop that encrypts your entire hard drive or partition (on Windows
systems), including your boot record, thus protecting all your files when you
are not using them.
PGP NetShare: A feature of PGP Desktop for Windows with which you can
securely and transparently share files and folders among selected
individuals. PGP NetShare users can protect their files and folders simply by
placing them within a folder that is designated as protected.
PGP Virtual Disk: PGP Virtual Disk volumes are a feature of PGP Desktop
that let you use part of your hard drive space as an encrypted virtual disk.
You can protect a PGP Virtual Disk volume with a key or a passphrase. You
can also create additional users for a volume, so that people you authorize
can also access the volume.
PGP Zip: A feature of PGP Desktop that lets you put any combination of files
and folders into a single encrypted, compressed package for convenient
transport or backup. You can encrypt a PGP Zip archive to a PGP key or to a
passphrase.
PGP Portable: A separately-licensed feature that enables you to send encrypted
files to users who do not have PGP Desktop software, and to transport files
securely to systems that do not or cannot have PGP software installed.
PGP Universal Server Concepts
keys.<domain> convention: PGP Universal Server automatically looks for valid
public keys for email recipients at a special hostname, if no valid public key is
found locally to secure a message. This hostname is keys.<domain> (where
<domain> is the email domain of the recipient). For example, Example
Corporation’s externally visible PGP Universal Server is named
keys.example.com.
Symantec Corporation strongly recommends you name your externally visible
PGP Universal Server according to this convention because it allows other PGP
Universal Servers to easily find valid public keys for email recipients in your
domain.
For more information, see Naming your PGP Universal Server (see "
your PGP Universal Server" on page
Security Architecture: Behind the scenes, the PGP Universal Server creates and
manages its own security architecture for the users whose email domain it is
securing. Because the security architecture is created and managed automatically,
we call this a self-managing security architecture (SMSA).
About Naming
23).
Page 27

PGP Universal Server Features
Administrative Interface: Each PGP Universal Server is controlled via a
Web-based administrative interface. The administrative interface gives you
control over PGP Universal Server. While many settings are initially established
using the web-based Setup Assistant, all settings of a PGP Universal Server can be
controlled via the administrative interface.
Backup and Restore: Because full backups of the data stored on your PGP
Universal Server are critical in a natural disaster or other unanticipated loss of
data or hardware, you can schedule automatic backups of your PGP Universal
Server data or manually perform a backup.
You can fully restore a PGP Universal Server from a backup. In the event of a
minor problem, you can restore the PGP Universal Server to any saved backup. In
the event that a PGP Universal Server is no longer usable, you can restore its data
from a backup onto a new PGP Universal Server during initial setup of the new
PGP Universal Server using the Setup Assistant. All backups are encrypted to the
Organization Key and can be stored securely off the PGP Universal Server.
Cluster: When you have two or more PGP Universal Servers in your network, you
configure them to synchronize with each other; this is called a “cluster.”
Dictionary: Dictionaries are lists of terms to be matched. The dictionaries work
with mail policy to allow you to define content lists that can trigger rules.
Directory Synchronization: If you have LDAP directories in your organization,
your PGP Universal Server can be synchronized with the directories. The PGP
Universal Server automatically imports user information from the directories
when users send and receive email; it also creates internal user accounts for them,
including adding and using X.509 certificates if they are contained in the LDAP
directories.
Ignition Keys: You can protect the contents of a PGP Universal Server, even if the
hardware is stolen, by requiring the use of a hardware token or a software
passphrase, or both, on start.
Keyserver: Each PGP Universal Server includes an integrated keyserver populated
with the public keys of your internal users. When an external user sends a
message to an internal user, the external PGP Universal Server goes to the
keyserver to find the public key of the recipient to use to secure the message. The
PGP Universal Server administrator can enable or disable the service, and control
access to it via the administrative interface.
Learn Mode: When you finish configuring a PGP Universal Server using the Setup
Assistant, it begins in Learn Mode, where the PGP Universal Server sends
messages through mail policy without taking any action on the messages, and does
not encrypt or sign any messages.
Learn Mode gives the PGP Universal Server a chance to build its SMSA (creating
keys for authenticated users, for example) so that when when Learn Mode is
turned off, the PGP Universal Server can immediately begin securing messages. It
is also an excellent way for administrators to learn about the product.
You should check the logs of the PGP Universal Server while it is in Learn Mode to
see what it would be doing to email traffic if it were live on your network. You can
make changes to the PGP Universal Server’s policies while it is in Learn Mode
until things are working as expected.
Important Terms
11 The Big Picture
Page 28

12 The Big Picture
Important Terms
Mail Policy: The PGP Universal Server processes email messages based on the
policies you establish. Mail policy applies to inbound and outbound email
processed by both PGP Universal Server and client software. Mail policy consists
of multiple policy chains, comprised of sequential mail processing rules.
Organization Certificate: You must create or obtain an Organization Certificate to
enable S/MIME support by PGP Universal Server. The Organization Certificate
signs all X.509 certificates the server creates.
Organization Key: The Setup Assistant automatically creates an Organization Key
(actually a keypair) when it configures a PGP Universal Server. The Organization
Key is used to sign all PGP keys the PGP Universal Server creates and to encrypt
PGP Universal Server backups.
Caution: It is extremely important to back up your Organization Key: all keys the
PGP Universal Server creates are signed by the Organization Key, and all
backups are encrypted to the Organization Key. If you lose your Organization
Key and have not backed it up, the signatures on those keys are meaningless and
you cannot restore from backups encrypted to the Organization Key.
PGP Verified Directory: The PGP Verified Directory supplements the internal
keyserver by letting internal and external users manage the publishing of their
own public keys. The PGP Verified Directory also serves as a replacement for the
PGP Keyserver product. The PGP Verified Directory uses next-generation
keyserver technology to ensure that the keys in the directory can be trusted.
Server Placement: A PGP Universal Server can be placed in one of two locations in
your network to process email.
With an internal placement, the PGP Universal Server logically sits between your
email users and your mail server. It encrypts and signs outgoing SMTP email and
decrypts and verifies incoming mail being picked up by email clients using POP or
IMAP. Email stored on your mail server is stored secured (encrypted).
With a gateway placement, the PGP Universal Server logically sits between your
mail server and the Internet. It encrypts and signs outgoing SMTP email and
decrypts and verifies incoming SMTP email. Email stored on your mail server is
stored unsecured.
For more information, see Configuring Mail Proxies (on page
Universal Server Installation Guide.
Setup Assistant: When you attempt to log in for the first time to the
administrative interface of a PGP Universal Server, the Setup Assistant takes you
through the configuration of that PGP Universal Server.
Group Key: A server-managed keypair shared by a group of users. A Group Key is
assigned to a group based on membership in an Active Directory security group.
This allows membership in the Active Directory security group to be modified
without affecting the metadata associated with the protected data. To create a
Group Key, the Directory Synchronization feature must be enabled and
synchronized with an Active Directory database.
147) and the PGP
PGP Universal Server User Types
Administrators: Any user who manages the PGP Universal Server and its security
configuration from inside the internal network.
Page 29

Installation Overview
Only administrators are allowed to access the administrative interface that
controls PGP Universal Server. A PGP Universal Server supports multiple
administrators, each of which can be assigned a different authority: from
read-only access to full control over every feature and function.
Consumers: Internal, external, and Verified Directory users, and devices.
External Users: External users are email users from other domains (domains
not being managed by your PGP Universal Server) who have been added to
the SMSA.
Internal Users: Internal users are email users from the domains being
managed by your PGP Universal Server.
PGP Universal Server allows you to manage PGP Desktop deployments to your
internal users. The administrator can control which PGP Desktop features are
automatically implemented at install, and establish and update security policy
for PGP Desktop users that those users cannot override (except on the side of
being more secure).
PGP Verified Directory Users: Internal and external users who have
submitted their public keys to the PGP Verified Directory, a Web-accessible
keyserver.
Devices: Managed devices, WDE computers, and WDE disks. Managed
devices are arbitrary objects whose keys are managed by PGP Universal
Server. WDE computers, and WDE disks are devices that are detected when
users enroll.
Other Email Users: Users within your organization can securely send email to
recipients outside the SMSA.
First, the PGP Universal Server attempts to find a key for the recipient. If that
fails, there are four fallback options, all controlled by mail policy: bounce the
message back to the sender (so it is not sent unencrypted), send unencrypted,
Smart Trailer, and PGP Universal Web Messenger mail.
Smart Trailer sends the message unencrypted and adds text giving the recipient
the option of joining the SMSA by installing PGP Universal Satellite, using an
existing key or certificate, or using PGP Universal Web Messenger. PGP Universal
Web Messenger lets the recipient securely read the message on a secure website; it
also gives the recipient options for handling subsequent messages from the same
domain: read the messages on a secure website using a passphrase they establish,
install PGP Universal Satellite, or add an existing key or certificate to the SMSA.
13 The Big Picture
Installation Overview
The following steps are a broad overview of what it takes to plan, set up, and maintain
your PGP Universal Server environment.
Most of the steps described here are described in detail in later chapters. Steps 1 and 4
are described in the PGP Universal Server Installation Guide. Note that these steps
apply to the installation of a new, stand-alone PGP Universal Server.
If you plan to install a cluster, you must install and configure one PGP Universal Server
following the steps outlined here. Subsequent cluster members will get most of their
configuration settings from the initial server by replication.
The steps to install and configure a PGP Universal Server are as follows:
Page 30

14 The Big Picture
Installation Overview
1 Plan where in your network you want to locate your PGP Universal Server(s).
Where you put PGP Universal Servers in your network, how many PGP Universal
Servers you have in your network, and other factors all have a major impact on
how you add them to your existing network.
Create a diagram of your network that includes all network components and
shows how email flows; this diagram details how adding a PGP Universal Server
impacts your network.
For more information on planning how to add PGP Universal Servers to your
existing network, see Adding the PGP Universal Server to Your Network in the
PGP Universal Server Installation Guide.
2 Perform necessary DNS changes.
Add IP addresses for your PGP Universal Servers, an alias to your keyserver,
update the MX record if necessary, add keys.<domain>, hostnames of potential
Secondary servers for a cluster, and so on.
Properly configured DNS settings (including root servers and appropriate reverse
lookup records) are required to support PGP Universal Server. Make sure both
host and pointer records are correct. IP addresses must be resolvable to
hostnames, as well as hostnames resolvable to IP addresses.
3 Prepare a hardware token Ignition Key.
If you want to add a hardware token Ignition Key during setup, install the drivers
and configure the token before you begin the PGP Universal Server setup process.
See Protecting PGP Universal Server with Ignition Keys (on page
25) for
information on how to prepare a hardware token Ignition Key.
Note: In a cluster, the Ignition Key configured on the first PGP Universal Server
in the cluster will also apply to the subsequent members of the cluster.
4 Install and configure this PGP Universal Server.
The Setup Assistant runs automatically when you first access the administrative
interface for the PGP Universal Server. The Setup Assistant is where you can set
or confirm a number of basic settings such as your network settings,
administrator password, server placement option, mail server address and so on.
The details of this process are described in Setting Up the PGP Universal Server in
the PGP Universal Server Installation Guide.
Note: If you plan to configure multiple servers as a cluster, you must configure
one server first in the normal manner, then add the additional servers as cluster
members. You can do this through the Setup Assistant when you install a server
that will join an existing cluster, or you can do this through the PGP Universal
Server administrative interface. For more information see Cluster Member
Configuration in the PGP Universal Server Installation Guide.
5 License your server.
You cannot take a PGP Universal Server out of Learn Mode or install updates until
the product is licensed. Once it is licensed, you should check for product updates
and install them if found. For more information, see Licensing Your Software (on
35).
page
Page 31

Installation Overview
If you want the PGP Universal Server to provide mail proxy services, you must
have a PGP Universal Server license with the mailstream feature enabled, and you
must check the Enable Mail Proxies check box on the System Settings page in the
PGP Universal Server administrative interface. For more information, see
Licensing Your Software (on page
35).
6 If you have a PGP key you want to use as your Organization Key with PGP
Universal Server, import it, then back it up.
Your Organization Key does two important things: it is used to sign all user keys
the PGP Universal Server creates and it is used to encrypt PGP Universal Server
backups. This key represents the identity of your organization, and is the root of
the Web-of-Trust for your users.
If your organization uses PGP Desktop and already has an Corporate Key or
Organization Key, and you want to use that key with PGP Universal Server, you
should import it as soon as you have configured your server, then create a backup
of the key.
If your organization does not have an existing key that you want to use as your
Organization Key, use the Organization Key the Setup Assistant automatically
creates with default values. For more information, see Managing Organization
Keys (on page
47).
No matter which key you use as your Organization Key, it is very important to
make a backup of the key. Since PGP Universal Server’s built-in back-up feature
always encrypts backups to this key, you need to provide a copy of your
Organization Key to restore your data.
For more information, see Organization Certificate (on page
50).
7 If you have a PGP Additional Decryption Key (ADK) that you want to use with
PGP Universal Server, add it.
An ADK is a way to recover an email message if the recipient is unable or unwilling
to do so; every message that is also encrypted to the ADK can be opened by the
holder(s) of the ADK. You cannot create an ADK with the PGP Universal Server,
but if you have an existing PGP ADK (generated by PGP Desktop, an ideal scenario
for a split key; refer to the PGP Desktop User’s Guide for more information), you
can add it to your PGP Universal Server and use it. For more information, see
Additional Decryption Key (ADK) (on page
53).
8 Create a SSL/TLS certificate or obtain a valid SSL/TLS certificate.
You can create a self-signed certificate for use with SSL/TLS traffic. Because this
certificate is self-signed, however, it might not be trusted by email or Web browser
clients. Symantec Corporation recommends that you obtain a valid SSL/TLS
certificate for each of your PGP Universal Servers from a reputable Certificate
Authority.
This is especially important for PGP Universal Servers that are accessed publicly.
Older Web browsers might reject self-signed certificates or not know how to
handle them correctly when they encounter them via PGP Universal Web
Messenger or Smart Trailer.
For more information, see Working with Certificates (on page
41).
9 Configure the Directory Synchronization feature if you want to synchronize an
LDAP directory with your PGP Universal Server.
If you have an existing LDAP server, using the Directory Synchronization feature
gives you more control over which users, keys, and certificates are added to the
PGP Universal Server.
15 The Big Picture
Page 32

16 The Big Picture
Installation Overview
By default, user enrollment is set to Email enrollment. If you elect to use
certificate enrollment or LDAP directory enrollment, you must have an LDAP
directory configured and Directory Synchronization enabled. You can change the
client enrollment setting from the Directory Synchronization Settings page in the
PGP Universal Server administrative interface.
For more information, see Using Directory Synchronization to Manage Consumers
(on page
225).
10 Configure PGP Desktop client features.
The PGP Desktop client basic (default) license is installed along with the PGP
Universal Server, so adding the client license as a separate step is not necessary.
However, the optional features (messaging, PGP Whole Disk Encryption, and PGP
NetShare) are disabled by default. If you have purchased a license for those
features, you must edit your client policy settings to enable them. For more
information about consumer policy settings, see "Establishing PGP Desktop
Settings for Your PGP Desktop Clients (on page
217)".
11 Add trusted keys, configure consumer policy, and establish mail policy.
All these settings are important for secure operation of PGP Universal Server. For
more information on adding trusted keys from outside the SMSA, see Managing
Trusted Keys and Certificates (on page
policy settings, see Administering Consumer Policy (on page
77). For more information about consumer
197). For information
on setting up mail policy, see Setting Mail Policy (on page 85).
Note: When setting policy for Consumers, PGP Universal Server provides an
option called Out of Mail Stream (OOMS) support. OOMS specifies how the email
gets transmitted from the client to the server when PGP Desktop cannot find a
key for the recipient and therefore cannot encrypt the message.
OOMS is disabled by default. With OOMS disabled, sensitive messages that can't
be encrypted locally are sent to PGP Universal Server "in the mail stream" like
normal email. Importantly, this email is sent in the clear (unencrypted). Mail or
Network administrators could read these messages by accessing the mail server's
storage or monitoring network traffic. However, archiving solutions, outbound
anti-virus filters, or other systems which monitor or proxy mail traffic will
process these messages normally.
You can elect to enable OOMS, which means that sensitive messages that can't be
encrypted locally are sent to PGP Universal Server "out of the mail stream." PGP
Desktop creates a separate, encrypted network connection to the PGP Universal
Server to transmit the message. However, archiving solutions, outbound
anti-virus filters, or other systems which monitor or proxy mail traffic will not
see these messages.
During your configuration of your PGP Universal Server you should determine
the appropriate settings for your requirements. This option can be set separately
for each policy group, and is set through the Consumer Policy settings. For more
details on the effects of enabling or disabling OOMS, see Out of Mail Stream
Support.
12 Install and configure additional cluster server members.
Page 33

Installation Overview
You can do this through the Setup Assistant when you install a server that will
join an existing cluster, or you can do this through the PGP Universal Server
administrative interface. Remember that you must configure one server in the
normal manner before you can add and configure additional servers as cluster
members. For more information, see Clustering your PGP Universal Servers (on
45).
page
13 Reconfigure the settings of your email clients and servers, if necessary.
Depending on how you are adding the PGP Universal Server to your network,
some setting changes might be necessary. For example, if you are using a PGP
Universal Server placed internally, the email clients must have SMTP
authentication turned on. For PGP Universal Servers placed externally, you must
configure your mail server to relay SMTP traffic to the PGP Universal Server.
14 Enable SNMP Polling and Traps.
You can configure PGP Universal Server to allow network management
applications to monitor system information for the device on which PGP Universal
Server is installed and to send system and application information to an external
destination. See Configuring SNMP Monitoring (on page
9) for more information.
15 Distribute PGP Universal Satellite and/or PGP Desktop to your internal users, if
appropriate.
If you want to provide seamless, end-to-end PGP message security without the
need for any user training, have them use PGP Universal Satellite.
Exchange/MAPI and Lotus Notes environments also require the use of PGP
Universal Satellite. PGP Desktop provides more features and user control than
PGP Universal Satellite. For more information, see PGP Universal Satellite and
Configuring PGP Desktop Installations.
16 Analyze the data from Learn Mode.
In Learn Mode, your PGP Universal Server sends messages through mail policy
without actually taking action on the messages, decrypts and verifies incoming
messages when possible, and dynamically creates a SMSA. You can see what the
PGP Universal Server would have done without Learn Mode by monitoring the
system logs.
Learn Mode lets you become familiar with how the PGP Universal Server operates
and it lets you see the effects of the policy settings you have established before the
PGP Universal Server actually goes live on your network. Naturally, you can fine
tune settings while in Learn Mode, so that the PGP Universal Server is operating
just how you want before you go live.
For more information, see Operating in Learn Mode (on page
37).
17 Adjust policies as necessary.
It might take a few tries to get everything working just the way you want. For
example, you might need to revise your mail policy.
18 Perform backups of all PGP Universal Servers before you take them out of Learn
Mode.
This gives you a baseline backup in case you need to return to a clean installation.
For more information, see Backing Up and Restoring System and User Data (on
31).
page
19 Take your PGP Universal Servers out of Learn Mode.
17 The Big Picture
Page 34

18 The Big Picture
About Integration with Symantec Protection Center
Once this is done, email messages are encrypted, signed, and decrypted/verified,
according to the relevant policy rules. Make sure you have licensed each of your
PGP Universal Servers; you cannot take a PGP Universal Server out of Learn Mode
until it has been licensed.
20 Monitor the system logs to make sure your PGP Universal Server environment is
operating as expected.
About Integration with Symantec Protection Center
Protection Center helps strengthen the security of your organization by providing easy
access to security metrics and simplified security management. You can log in to PGP
Universal Server and other security products from within Protection Center. This
feature allows for a single point of administration. The tasks you perform within each
product's separate console can now be performed through Protection Center.
Protection Center also aggregates security data from PGP Universal Server and other
Symantec Corporation products and combines that data into cross-product reports,
providing you with a more complete, all-in-one view of the security of your enterprise.
PGP Universal Server sends the following data to be included in aggregated reports:
Internal users
Client computers
Client computer status
Encryption status per client device
PGP Whole Disk Encryption login failure alerts, which Protection Center calls
incident events
Protection Center install agents, which in this case refers only to PGP Universal
Server itself
Before You Integrate with Protection Center
Both Protection Center and PGP Universal Server must be installed and set up before
integration and registration.
For detailed information about how to set up your Protection Center and register PGP
Universal Server, see the Protection Center documentation.
Complete the following tasks to prepare PGP Universal Server for registration with and
discovery by Protection Center.
To register PGP Universal Server on Protection Center, you need the PGP
Universal Server's IP address, as well as the username and passphrase of a
superuser administrator. All other registration information appears automatically
in the Advanced Options section of the registration interface and do not need to be
entered manually.
Best Practice: Create a superuser account to be used only for registration. This
provides stability even when other administrators leave the company.
Page 35

About Integration with Symantec Protection Center
You cannot register with Protection Center using an administrator account that
authenticates using SecurID. You must use an account with a passphrase. The
account used for registration is not related to which administrators can log in to
Protection Center. Any PGP Universal Server administrator, including SecurID
and passphrase administrators, can log in to Protection Center, if you map a new
Protection Center user account to that administrator. For more information, see
the Protection Center documentation.
Make sure that the time settings for PGP Universal Server and Protection Center
match, with less than a minute's difference. The hour and time zone settings do
not have to match, but the minute setting must be the same. If the minute settings
do not match, registration fails and an error message appears.
Register only one PGP Universal Server in a cluster. Because data is replicated
among cluster members, registering more than one cluster member results in
duplicate data sent to Protection Center. For example, if you manage 10 encrypted
devices, it will appear in Protection Center reports as if there are 20. If you have
cluster members located in the DMZ as well as inside your network, register a
cluster member within your network, not one in the DMZ, because cluster
members in the DMZ do not usually store private keys.
19 The Big Picture
Page 36

Page 37
3
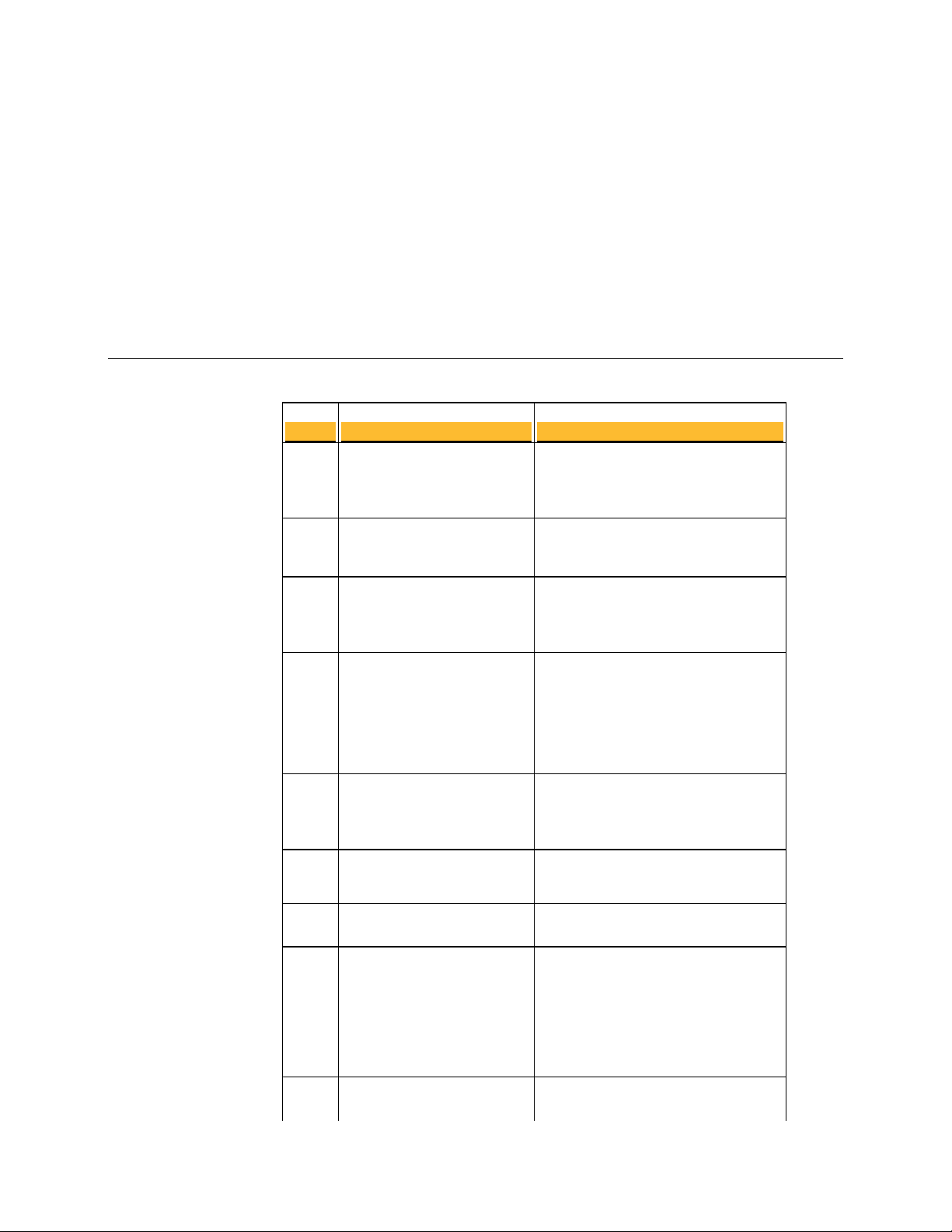
TCP Ports
About Open Ports
This chapter provides information on the ports a PGP Universal Server has open and on
which ports it listens.
Port Protocol/Service Comment
21
File Transfer Protocol (FTP)
Used to transmit encrypted backup
archives to other servers. Data is sent via
passive FTP, so port 20 (FTP Data) is not
used.
22
25
80
110
143
389
443
444
Open Secure Shell (SSH)
Simple Mail Transfer
Protocol (SMTP)
HyperText Transfer
Protocol (HTTP)
Post Office Protocol (POP)
Internet Message Access
Protocol (IMAP)
Lightweight Directory
Access Protocol (LDAP)
HyperText Transfer
Protocol, Secure (HTTPS)
Simple Object Access
Protocol, Secure (SOAPS)
Used for remote shell access to the server
for low-level system administration.
Used to send mail. In a gateway placement,
the PGP Universal Server listens on port
25 for incoming and outgoing SMTP
traffic.
Used to allow user access to the PGP
Verified Directory. If the PGP Verified
Directory is disabled, access on this port is
automatically redirected to port 443 over
HTTPS.
Also used for Universal Services Protocal
(USP) keyserver connection.
Used to retrieve mail by users with POP
accounts in an internal placement. Closed
to gateway placements.
Used to retrieve mail by users with IMAP
accounts in an internal placement. Closed
to gateway placements.
Used to allow remote hosts to look up local
users' public keys.
Used for PGP Desktop and PGP Universal
Satellite policy distribution and PGP
Universal Web Messenger access.
If the Verified Directory is disabled, used
for HTTPS access.
Also used for Universal Services Protocal
(USP)over SSL for keyserver connection.
Used to cluster replication messages.
Page 38

22 About Open Ports
UDP Ports
Port Protocol/Service Comment
21
File Transfer Protocol (FTP)
Used to transmit encrypted backup
archives to other servers. Data is sent via
passive FTP, so port 20 (FTP Data) is not
used.
465
636
993
995
9000
Simple Mail Transfer
Protocol, Secure (SMTPS)
Lightweight Directory
Access Protocol, Secure
(LDAPS)
Internet Message Access
Protocol, Secure (IMAPS)
Post Office Protocol, Secure
(POPS)
HyperText Transfer
Protocol, Secure (HTTPS)
Used to send mail securely in internal
placements. Closed to gateway placements.
This is a non-standard port used only by
legacy mail servers. We recommend,
rather than using this port, you use
STARTTLS on port 25.
Used to securely allow remote hosts to
look up public keys of local users.
Used to retrieve mail securely by users
with IMAP accounts in internal
placements. Closed to gateway placements.
Used to retrieve mail securely by users
with POP accounts in internal placements.
Closed to gateway placements.
Allows access to the PGP Universal Server
administrative interface.
UDP Ports
Port Protocol/Service Comment
53
123
161
Domain Name System (DNS )
Network Time Protocol (NTP )
Simple Network Management
Protocol (SNMP)
Used to look up a Fully Qualified
Domain Name (FQDN ) on the
DNS server and translate to an
IP address.
Used to synchronize the
system’s clock with a reference
time source on a different server.
Used by network management
applications to query the health
and activities of PGP Universal
Server and the computer on
which it is installed.
Page 39

About Naming your PGP Universal Server
4
This chapter describes how and why to name your PGP Universal Server using the
keys.<domain> convention.
How to Name Your PGP Universal Server
Unless a valid public key is found locally, PGP Universal Servers automatically look for
valid public keys for email recipients by attempting to contact a keyserver at a special
hostname, keys.<domain>, where <domain> is the recipient's email domain.
For example, an internal user at example.com sends an email to
susanjones@widgetcorp.com. If no valid public key for Susan is found on the Example
PGP Universal Server, it automatically looks for a valid public key for Susan at
keys.widgetcorp.com, even if there is no domain policy for widgetcorp.com on
Example’s PGP Universal Server. Keys are found locally if they are cached, or if Susan
was an external user who explicitly supplied her key through PGP Universal Web
Messenger. If the Widgetcorp PGP Universal Server is named using the keys.<domain>
convention, the Example Corp. PGP Universal Server can find a valid public key for
susan@widgetcorp.com at keys.widgetcorp.com.
Caution: Symantec Corporation strongly recommends you name your PGP Universal
Server according to this convention, because it allows other PGP Universal Servers
to easily find valid public keys for email recipients in your domain. You must also use
this convention to name your externally visible PGP Universal Server.
If your organization uses email addresses, such as mingp@example.com and
mingp@corp.example.com, your PGP Universal Server must be reachable at
keys.example.com and keys.corp.example.com. If you have multiple PGP Universal
Servers in a cluster that are managing an email domain, only one of those PGP
Universal Servers needs to use the keys.<domain> convention.
Note: Keys that are found using the keys.<domain> convention are treated as valid
and trusted.
Keys.<domain> should be the address of a load-balancing device, which distributes
connections to your PGP Universal Server’s keyserver service. The ports that need to be
load balanced are the ports on which you are running your keyserver service, port 389
for LDAP and 636 for LDAPS. You can also name your PGP Universal Server according
to your company's required naming convention and ensure that the server has a DNS
alias of keys.<domain>.com.
If you are administering multiple email domains, you should establish the
keys.<domain> convention for each email domain. If your PGP Universal Server is
behind your corporate firewall, you must ensure that ports 389 (LDAP) and 636 (LDAPS)
are open to support the keys.<domain> convention.
Page 40

24 About Naming your PGP Universal Server
Naming Methods
Naming Methods
To support the keys.<domain> convention, you can name your PGP Universal Server in
one of the following ways:
In the Setup Assistant, name your PGP Universal Server with the keys.<domain>
convention in the Host Name field on the Network Setup page.
On the Network Settings page, change the host name of your PGP Universal
Server to keys.<domain> .
Create a DNS alias to your PGP Universal Server that uses the keys.<domain>
convention that is appropriate for your DNS server configuration.
Page 41

Understanding the Administrative Interface
5
This section describes the PGP Universal Server’s Web-based administrative interface.
System Requirements
The PGP Universal Server administrative interface has been fully tested with the
following Web browsers:
Logging In
Windows
Mac OS X
Although the administrative interface works with other Web browsers, we recommend
these browsers for maximum compatibility.
A login name and passphrase for the administrative interface were originally
established when you configured the server using the Setup Assistant. In addition, the
original administrator may have created additional administrators, and may have
configured your PGP Universal Server to accept RSA SecurID authentication.
To log in to your server’s administrative interface
1 In a Web browser, type https://
Note: If you see a Security Alert dialog box relating to the security certificate, it
means you need to replace the self-signed certificate created automatically with
a certificate from a public Certificate Authority.
The Login page appears.
2 Type the current login name in the Username field.
3 Type the current passphrase or SecurID passcode in the Passphrase field.
(If SecurID authentication is enabled, a message below the Passphrase field will
indicate that a SecurID passcode can be entered. A given administrator is
configured to use either passphrase or SecurID authentication, not both.)
4 Click the Login button or press Enter.
5 If the login credentials are accepted, the System Overview page appears.
6 If the login credentials do not match, an error is displayed. For passphrase
authentication that fails, an "Invalid Login" error appears. For SecurID
authentication, different events may occur. See the following procedure for more
information.
Internet Explorer 6 and greater
Firefox 3.6 and greater
Safari 5.0 and greater
Firefox 3.6 and greater
<domain name of server>:9000/ and press Enter.
Page 42

26 Understanding the Administrative Interface
The System Overview Page
To log in using RSA SecurID authentication
1 Follow steps 1-4 in the procedure above. If your SecurID passcode is accepted, and
no PIN reset is required, the System Overview page appears.
Note: If PGP Universal Server fails to connect with any RSA Manager server, you
will be presented with the standard "Invalid Login" message. The connection
failure will be logged in the PGP Universal Server Administration log, enabling
you to determine whether this was the cause of the login failure.
2 If the RSA server policy determines that a PIN reset is required, upon successful
login the PIN Reset dialog appears. Depending on the RSA server policy, you may
be able to have the RSA server generate a new PIN for you, or enter a new PIN
manually. When this is done, the System Overview page appears. For more details
see Resetting SecurID PINs (on page
3 If the RSA server detects a problem with the token code portion of your passcode,
you are asked to re-enter your PIN plus the next code shown on your SecurID
token. Type your PIN and the next token code that appears, then click Login or
press Enter.
4 Based on your RSA server policy, you may be given several chances to
authenticate successfully using the next token code. However, eventually
continued failures will result in a failed login.
23).
Note: Log in events are logged in the PGP Universal Server Administration log.
Successful and failed attempts, and next tokencode requests are logged, as are
problems connecting to the RSA Manager servers.
The System Overview Page
The System Overview page is the first page you see when you log in to PGP Universal
Server. You can also view it from Reporting > Overview.
The page provides a general report of system information and statistics. The
information displayed includes:
System alerts, including licensing issues and PGP Whole Disk Encryption login
failures. System alerts appear at the top of the page.
System Graphs for CPU usage, message activity, and Whole Disk Encryption. Click
the buttons to switch the graphs. Click the System Graphs heading to go to the
Reporting > Graphs page. See System Graphs (on page
about system graphs.
Services information, including which services are running or stopped.
Depending on the service, the entry may also include the number of users or
keys handled by the service.
Click the service name link to go to the administrative page for that service.
For a running Web Messenger service, click the URL to go to the Web
Messenger interface.
3) for more information
Page 43

Managing Alerts
For a running Verified Directory service, click the URL to go to the Verified
Directory interface to search for a key, upload your own public key, or
remove your key from the searchable directory.
System Statistics, including software version number, system uptime, total
messages processed, and number of PGP Portable Disks created. Click the
Statistics link to go to the System > General Settings page.
Mail Queue statistics show the number of email messages in the queue waiting to
be processed, if applicable, and the size of the mail queue. Click the Mail Queue
link to go to the Mail > Mail Queue status page for detailed information about the
contents of the mail queue. Estimated Policy Group Membership shows the
number of members in each consumer policy group. Click a policy group name to
go to the page for configuring that policy group.
Clustering provides status information about the cluster configuration, if this
PGP Universal Server is a member of a cluster. This display shows, for each cluster
member, its hostname or IP address, its status, its location (Internal or DMZ) and a
login icon (except for the member on which you are currently logged in). Click the
Clustering heading to go to the System > Clustering page. This display does not
appear if your PGP Universal Server is not a member of a cluster.
Click Refresh (at the top of the System Overview page) to refresh the information
shown on this page.
The Manage Alerts button takes you to the Alerts page where you can configure how
you want to be notified about WDE login failures. For more details, see Managing Alerts
(on page
The Export Data button lets you export statistics for WDE Activity, WDE Login
Failures, PDF Messenger Certified Delivery Receipts, and the Mail Policy Print View
(which provides in a printable format all your mail policy chains and rules). Because the
report can take a long time to generate, you can begin running the report and have an
email notification sent to you when the report is ready to be downloaded.
27).
27 Understanding the Administrative Interface
Managing Alerts
The PGP Universal Server groups failed login attempts into reported login failures. This
feature is intended to make reporting about failed login attempts more useful, because
one or several failed login attempts by a PGP Whole Disk Encryption user does not
necessarily mean an attempted break-in. Use the Alerts dialog box to choose how many
failed login attempts constitutes a login failure. For example, you can specify that an
alert should be triggered after 3 failed login attempts. If 6 failed attempts occur, 2 login
failure alerts appear.
Alerts about PGP Whole Disk Encryption login failures appear on the System Overview
page and in the Daily Status Email. Alerts for devices belonging to specific users appear
on the user's Internal Users dialog box.
Alerts are also sent when a user is locked out of a system because he or she exceeded
the number of allowable login failures set on the Disk Encryption tab of Consumer
Policy.
To specify how you want to be notified of PGP Whole Disk Encryption login failures
1 From the System Overview page, click Manage Alerts.
The Alerts dialog box appears.
Page 44

28 Understanding the Administrative Interface
Logging In For the First Time
2 Specify how many consecutive failed login attempts a single device must report
before the administrator is notified.
3 Choose how long you want login failure alerts to be displayed on the System
Overview page, the Daily Status Email, and the Internal Users page, in hours or
days.
4 Specify how long you want to keep login failure records in the database, in days.
Logging In For the First Time
The first time you log in to the PGP Universal Server, a welcome dialog box appears.
The welcome dialog box provides access to documentation. You can choose to have the
welcome dialog box appear every time you log in.
What’s New—Lists the new features in PGP Universal Server 3.2.
Mail Policy Diagram—Provides a graphical representation of how email is
processed through mail policy.
PGP Universal Upgrade Guide—Provides instructions on how to migrate PGP
Keyserver data, how to upgrade your PGP Universal Server, and how version 2.0.6
settings migrate into the mail policy environment.
You can also access all the documentation by clicking the online help icon in the upper
right corner of the PGP Universal Server page.
Administrative Interface Map
The administrative interface is organized as follows:
Sections Pages
Reporting Overview
Graphs
Logs
Consumers Groups
Users
Devices
Consumer Policy
Managed Domains
Directory Synchronization
Keys Managed Keys
Trusted Keys
Page 45

Organization Keys
Ignition Keys
Keyservers
Key Cache
Mail Mail Policy
Dictionaries
Archive Servers
Proxies
Mail Queue
Mail Routes
Message Templates
Services Web Messenger
Keyserver
Icons
29 Understanding the Administrative Interface
Icons
SNMP
Verified Directory
Certificate Revocation
USP
PGP RDD
System General Settings
Administrators
Backups
Updates
Network
Clustering
The administrative interface uses the following icons.
Type Icon Description
Actions
Add
Remove
Page 46

30 Understanding the Administrative Interface
Icons
Type Icon Description
Connect
Delete
Clear Search
Install/Export
Reinstall/Regenerate
Restore
Revoke
Forward
Back
First
Users
Last
Move priority up
Move priority down
Closed Action
Opened Action
Help
Print
Internal user
Administrative user
Excluded user
Internal user, revoked
Expired internal user
External user, revoked
Page 47

Type Icon Description
External user
External user, pending
Expired external user
Directory user
Expired directory user
Directory user, pending
Icons
31 Understanding the Administrative Interface
Keys and Certificates
Key
Key, expired
Key, revoked
Key reconstruction
Whole Disk Recovery Token
Keypair
Keypair, expired
Keypair, revoked
Group key
Group key, expired
Group key, revoked
Certificate
Expired certificate
Page 48

32 Understanding the Administrative Interface
Icons
Type Icon Description
Revoked certificate
Expired certificate pair
Certificate pair
Revoked certificate pair
ADK (Additional Decryption Key)
Organization Key
Verified Directory Key
Mail Policy
`
User Policy
Default policy chain
Policy chain
Policy rule
Dictionary term
Excluded address
Pending excluded address
Keyserver
Default keyserver
Default policy
Excluded policy
Web Messenger
Default template
Page 49
Type Icon Description
Customized template
Broken template
Icons
33 Understanding the Administrative Interface
Backup
Update
Clustering
Logs
Backup successful
Backup pending
Backup failed
Successful install
Update ready to be installed
Failed install
Cluster
Active cluster
Inactive cluster
Info
Notice
Miscellaneous
Warning
Error
Domain
Mail proxy (SMTP, POP, IMAP)
Inbound mailserver
Outbound mailserver
Page 50

34 Understanding the Administrative Interface
Icons
Type Icon Description
SMTP server
Mail route
Network interface
Learn mode
Access control enabled
Page 51
6
Overview
Licensing Your Software
This section describes how to license your PGP Universal Server.
Your PGP Universal Server must have a valid license to be taken out of Learn Mode. In
other words, without a valid license, your PGP Universal Server will never encrypt or
sign any email messages.
If you licensed your PGP Universal Server using the Setup Assistant, you do not have to
license it again. If you did not, then you can license it at any time afterwards using the
administrative interface.
The PGP Universal Server can provide security for email messaging by inserting itself
into the flow of email traffic in your network, intercepting, or proxying, that traffic, and
processing it (encrypt, sign, decrypt, verify) based on the applicable policies.
The email proxying feature available on the PGP Universal Server can only be used if
you have the PGP Universal Gateway Email license.
Licensing a PGP Universal Server
If you did not install your license when you set up your PGP Universal Server during
the Setup Assistant, you can add a license from the System > General Settings page.
For instructions, see Licensing a PGP Universal Server (on page
License Authorization
When you enter your license information, whether in the Setup Assistant or from the
System > General Settings page, the PGP Universal Server automatically authorizes the
license number. You do not need an internet connection.
Licensing the Mail Proxy Feature
You must have a PGP Universal Gateway Email license or you cannot use the Mail
Proxies feature on the administrative interface. In addition, the Enable Mail Proxies
check box on the System Settings page must be checked. If you installed your license
during system setup (through the Setup Assistant) and checked the Enable Mail
Proxies check box at that time, the check box ont he System Settings page will be
checked.
14).
Page 52

36 Licensing Your Software
Licensing PGP Desktop
You can verify that your license includes the Mail Proxies feature on the System
Settings page
For information about the Mail Proxies feature, see Configuring Mail Proxies (on page
147).(from the System > General Settings tab).
Licensing PGP Desktop
In PGP Universal Server version 3.2.1 and later, managed PGP Desktop client licenses
are built in to the server; you no longer need to add the desktop license as a separate
step.
However, you must still purchase a license to use the PGP Desktop features such as PGP
Whole Disk Encryption, messaging, and PGP NetShare. These separately-licensed
features are disabled by default. Based on your license, you must configure each
consumer policy to enable the PGP Desktop features for which you have a license.
For more information, see Establishing PGP Desktop Settings for Your PGP Desktop
Clients (on page
217).
Page 53
7
Operating in Learn Mode
When you finish configuring a PGP Universal Server using the Setup Assistant, it
begins running in Learn Mode.
In Learn Mode, messages are processed through mail policy, but none of the actions
from the policy are performed. Messages are neither encrypted nor signed. This
functions as a rehearsal, so that you can learn how policies would affect email traffic if
implemented. While running in Learn Mode, the PGP Universal Server also creates keys
for authenticated users so that when Learn Mode is turned off, the server can secure
messages immediately.
After messages go through mail policy, PGP Universal Server decrypts and verifies
incoming messages for which there are local internal or external user keys. Outgoing
messages are sent unencrypted. In Learn Mode, non-RFC compliant email is sent
unprocessed and in the clear. Turn Learn Mode off to process messages through the
mail policy exception chain.
In Learn Mode, the PGP Universal Server:
Creates user accounts with user keys, in accordance with Consumer Policy.
Decrypts messages using internal and external keys stored on the server, but does
not search for keys externally.
Does not encrypt or sign messages.
Will not apply mail policy to messages, and will not take any Key Not Found action
on messages.
Note: Your PGP Universal Server must be licensed before you can take it out of Learn
Mode.
Purpose of Learn Mode
Learn Mode allows you to:
View (by examining the logs) how policies would affect email traffic if
implemented.
Build the SMSA (creating keys for authenticated users, for example) so that when
the server goes live—when Learn Mode is turned off—the server can secure
messages immediately.
Identify mailing lists your users send messages to and add their addresses to the
dictionaries of Excluded Email Addresses. Most likely, users won't send encrypted
messages to a mailing list.
PGP Universal Server decrypts and verifies incoming email while operating in
Learn Mode.
PGP Universal Server still automatically detects mailing lists when Learn Mode is
off, but unless the addresses were retrieved via the Directory Synchronization
feature, they require approval from the PGP Universal Server administrator to be
added to the list of excluded email addresses. For more information, see Using
Dictionaries with Policy (on page
129).
Page 54
38 Operating in Learn Mode
Checking the Logs
Mailing lists are identified per RFC 2919, List-Id: A Structured Field and
Namespace for the Identification of Mailing Lists, as well as by using default
exclusion rules.
Checking the Logs
The effects of your policies can be checked while Learn Mode is on, even though the
server is not actually encrypting or signing messages.
To check the server’s logs
1 Access the administrative interface for the server.
The administrative interface appears.
2 Click Reporting, then Logs.
The System Logs page appears.
3 Check the logs to see what effect your policies are having on email traffic.
Managing Learn Mode
The PGP Universal Server is put into Learn Mode by the Setup Assistant. If your server
is in Learn Mode, you see a yellow icon, the Change Mode button, in the upper-right
corner of your browser page.
To turn off Learn Mode
1 Click the Change Mode button in the upper-right corner of the page.
The Mail Processing Settings dialog box appears.
2 Deselect Operate in Learn Mode.
3 Click Save.
Learn Mode is turned off.
To turn on Learn Mode
1 Click the Change Mode button in the upper-right corner of the page.
The Mail Processing Settings dialog box appears.
2 Select Operate in Learn Mode.
3 Click Save.
Learn Mode is turned on.
Page 55

Managed Domains
8
This section describes how to create and manage the internal domains for which your
PGP Universal Server protects email messages.
About Managed Domains
The Managed Domains page gives you control over the domains for which the PGP
Universal Server is handling email.
Email users from domains being managed by your server are called “internal users.”
Conversely, email users from domains not being managed by your server but who are
part of the SMSA are called “external users.”
For example, if your company is “Example Corporation,” you can have the domain
“example.com” and your employees would have email addresses such as
“jsmith@example.com.”
If this were the case, you would want to establish “example.com” as a domain to be
managed by your server. When you install your PGP Universal Server you have the
opportunity to add a managed domain in the Setup Assistant. If you do not set it up at
that time, you can use the Managed Domains page to add it. You can also add additional
managed domains from the Managed Domains page, if you have users with addresses in
multiple domains that you want to be considered internal users.
Managed domains automatically include sub-domains, so in the example above, users
such as “
Multi-level domain structures as used by some countries are also acceptable: for
example, the domain “example.co.uk.”
The Managed Domains page accepts Internet DNS domain names and Domino domains.
You must have an Internet DNS domain name, and if you have Notes users, you must
also include the Domino domain name. WINS names (for example,
belong here.
Usually, you specify your Internet domain during installation through the Setup
Assistant. If your PGP Universal Server is also managing a Domino server, you must
add your Domino domain name manually through the Managed Domains page.
For example, if you have an Internet domain "example.com" and a Domino domain
"ExDomino," you would add example.com as the managed domain during setup, for
SMTP addressing. You would then add ExDomino as an additional managed domain, for
Domino addressing.
Mail to and from your managed domains is processed according to your mail policy.
You can also create mail policy rules specifically for your managed domains. See the
chapter Setting Mail Policy (on page
Managed domains entered on the Managed Domains page populate the Managed
Domains dictionary. The dynamic Managed Domains dictionary automatically includes
subdomains. See Using Dictionaries with Policy (on page 129) for more information on
dictionaries.
mingp@corp.example.com” would also be considered internal users.
\\EXAMPLE) do not
85) for more information on creating mail policies.
Page 56

40 Managed Domains
Adding Managed Domains
Adding Managed Domains
To add a domain to the list of managed domains
1 Click Add Managed Domain.
The Add Managed Domain dialog box appears.
2 Type a domain name in the Domain field.
Do not type WINS names (for example,
domain names or Domino domain names.
3 Click Save.
Deleting Managed Domains
\\EXAMPLE) here. Type only Internet DNS
If you delete a managed domain, all the user IDs within that domain remain in the
system. Users can still encrypt and sign messages with their keys.
To remove a domain name already on the list of managed domains
1 Click the icon in the Delete column of the domain you want to remove from the
list.
A confirmation dialog box appears.
2 Click OK.
The confirmation dialog box disappears and the selected domain name is removed
from the list of managed domains.
Page 57
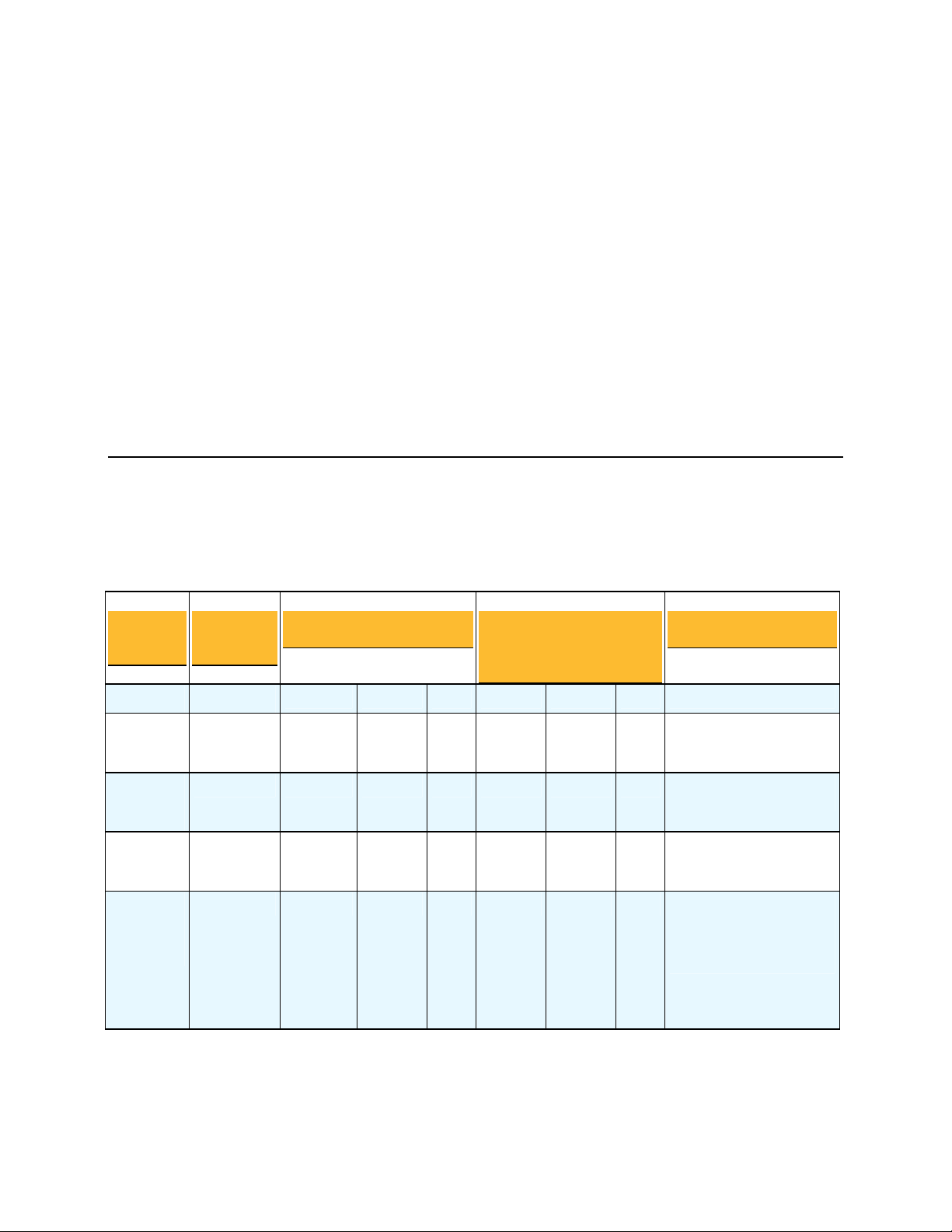
Understanding Keys
9
This chapter introduces some of the concepts related to how Consumer keys are
managed. It introduces the concept of key modes, which are used to control whether
internal and external users can manage their own keys or whether keys should be
managed by PGP Universal Server. It also discusses the use of Certificate Revocation
Lists and key reconstruction blocks.
Choosing a Key Mode For Key Management
When you create PGP Universal Satellite and PGP Desktop installers, you can choose
whether you want internal and external users to be able to manage their own keys, or
whether keys should be managed by the PGP Universal Server. End-to-end email
processing functions refer to encryption, decryption,and signing performed at the
client, rather than on the PGP Universal Server.
PGP PGP Universal Gateway Keys Managed By
NetShare
Support
Email Functions
End-to-end Email
Processing Functions
Server
Client Key
Mode
(CKM)
Guarded
Key Mode
(GKM)
Server Key
Mode
(SKM)
Server
Client Key
Mode
(SCKM)
Encrypt Decrypt Sign Encrypt Decrypt Sign
Yes No No No Yes Yes Yes No
Yes No No No Yes Yes Yes Private keys stored
passphrase-protected
Yes Yes Yes Yes Yes Yes Yes Yes
Yes Yes Yes No Yes Yes Yes Public and private
encryption subkeys stored on
client and PGP Universal
Server, private signing
subkeys stored only on client
Server Key Mode (SKM)—The PGP Universal Server generates and manages user
keys.
Page 58

42 Understanding Keys
Choosing a Key Mode For Key Management
Users cannot manage their own keys.
PGP Universal Server administrators have access to private keys.
If a user has a client installation, the user’s keys are downloaded to the client
at each use.
SKM can also be used without client installations; if there is no client
installation, you must use SKM.
The client stores the private key encrypted to a random passphrase, so users
can read email offline.
In PGP Universal Gateway Email environments, existing users with SKM key
mode keys who install PGP Desktop for the first time will be prompted
automatically to re-enroll and create a CKM, GKM, or SCKM key.
Client Key Mode (CKM)—Users use client software to generate and manage their
own keys.
PGP Universal Server administrators do not have access to private keys.
CKM user email is secure on the mail server.
CKM users are responsible for backing up their keys; if they lose their private
keys, there is no way to retrieve them.
Users who want to be able to read their email offline and unconnected to
PGP Universal Server must use CKM.
PGP NetShare supports CKM; it requires that users control their own keys.
PGP Universal Gateway Email does not support CKM.
Guarded Key Mode (GKM)—Users generate and manage their own keys, and store
their passphrase-protected private keys on the server.
GKM is similar to CKM, except that PGP Universal Server stores protected
copies of private keys.
PGP NetShare supports GKM; it requires that users control their own keys.
PGP Universal Gateway Email does not support GKM.
Server Client Key Mode (SCKM)—Keys are generated on the client. Private
encryption subkeys are stored on both the client and PGP Universal Server, and
private signing subkeys are stored only on the client.
SCKM allows for separate signing and encryption subkeys, comparable to
X.509 signing and encryption keys.
The public and private encryption subkey is on the server, but by default
encryption is not performed on the server.
The public-only signing subkey is on the server. PGP Universal Server
cannot sign email for the user.
Mail processing must take place on the client side to use the SCKM signing
subkey. If you want to use PGP Universal Gateway Email with SCKM keys,
you must be using PGP Universal Server 2.5 or later. PGP Universal Gateway
Email allows email encryption and decryption with SCKM keys, but email
will not be signed.
SCKM is compatible with smart cards, but encryption keys are not generated
on the token. Copy the keys onto the token after generation.
Page 59

Changing Key Modes
Choosing a Key Mode For Key Management
43 Understanding Keys
If an SCKM user resets their key, the entire SCKM key is revoked, including
all subkeys, and remains on the PGP Universal Server as a non-primary key
for the user. This non-primary key can still be used for decryption, and
remain on the PGP Universal Server until manually removed by the
administrator.
SCKM is not supported by legacy PGP Desktop installations before version
9.0.
PGP NetShare supports SCKM; it requires that users control their own keys.
Which key management option you choose depends on what your users need and which
client application they use. Server Key Mode is generally appropriate for PGP Universal
Satellite users. Client Key Mode is more appropriate for PGP Desktop users. If your
security policy requires that a user’s signing key is only in the possession of the user,
but the user’s encryption key must be archived, SCKM is the correct choice.
If you allow PGP Desktop users to change their options and allow user-initiated key
generation, users can switch key modes.
If the user’s policy has changed to permit user-managed keys, then the user is
automatically prompted to create a new key, and no further action is necessary.
However, if the user’s policy has always permitted user key management, and the user
wants to switch key modes, the user should follow this procedure.
To change key mode
1 Open PGP Desktop and select the PGP Messaging service whose key mode you
want to determine.
The account properties and security policies for the selected service appear.
2 Click Key Mode.
The PGP Universal Key Mode page appears, describing your current key
management mode.
3 Click Reset Key.
The PGP Key Setup Assistant appears.
4 Read the text, then click Next.
The Key Management Selection page appears.
5 Select the desired key mode.
Depending on how yourPGP Universal Server administrator configured your copy
of PGP Desktop, some key modes might not be available.
6 Click Next.
The Key Source Selection screen appears.
7 Choose one of the following:
New Key. You are prompted to create a new PGP key, which is used to
protect your messaging.
PGP Desktop Key. You are prompted to specify an existing PGP key to use to
protect your messaging.
Page 60

44 Understanding Keys
How PGP Universal Server Uses Certificate Revocation Lists
Import Key. You are prompted to import a PGP key, which is used to protect
your messaging.
8 Make the desired selection, then click Next.
9 If you selected New Key:
a Type a passphrase for the key, then click Next.
b When the key is generated, click Next.
c Click Finish.
10 If you selected PGP Desktop Key:
a Select the key from the local keyring that you want to use, then click
b Click Finish.
11 If you selected Import Key:
a Locate the file that holds the PGP key you want to import (it must
b Click Finish.
Next.
contain a private key), then click Next.
How PGP Universal Server Uses Certificate Revocation
Lists
A certificate revocation list (CRL) is a list of certificates that have been revoked before
their scheduled expiration date. The PGP Universal Server retrieves CRLs for
certificates from CRL Distribution Points (DP).
The PGP Universal Server checks the CRL DPs automatically before encrypting a
message to a certificate, including certificates for internal and external users, as well as
certificates in the cache. The server also checks the CRL DPs before importing any
internal or external user certificate. It does not check before importing Trusted
Certificates, or before connecting to servers with SSL certificates.
The PGP Universal Server checks the revocation status of just the recipient's
certificate. It does not check the revocation status of the other certificates in the
signing chain.
Once retrieved, certificate revocation status is stored on the parent certificate, so the
Trusted Certificate for each user certificate stores the list of all the associated revoked
certificates. Once the CRL is stored on the Trusted Certificate, the PGP Universal Server
runs future CRL checks based on the “next update” date for that list.
Key Reconstruction Blocks
Key reconstruction blocks allow users to retrieve their private keys if they forget their
passphrases.
Page 61

Managed Key Permissions
Key reconstruction blocks contain several user-defined questions and the user's private
key, which is encrypted with the answers to those questions.
PGP Universal Server stores these questions and answers so that users can get back
their private keys in case they lose their passphrases. For example, if a user writes five
questions and answers, they can be asked three (or more) of the questions to
reconstruct their private key.
If an internal PGP Desktop user has uploaded a key reconstruction block to the PGP
Universal Server, you can delete it. You might want to delete a key reconstruction block
if you have already deleted or revoked the associated key and you do not want the key
to be recoverable. If you delete the key reconstruction block, it is no longer stored on
the PGP Universal Server, although it is possible that the user also has a copy.
Note: Keys created on smart cards and tokens are not compatible with PGP Desktop's
key reconstruction feature.
See Recovering Encrypted Data in an Enterprise Environment (on page 259) for
information on other methods of data recovery.
45 Understanding Keys
Managed Key Permissions
Key permissions determine what actions consumers (users or managed devices) can
perform upon managed keys. Key permissions are set in three ways:
At the group level: permissions can be set that determine how group members can
interact with managed keys. Permissions set for a group are inherited by all
members of the group.
At the consumer level: individual consumers may be granted permissions. These
permissions will exists in addition to the permissions the consumer inherits from
the groups of which it is a member.
At the managed key level: a managed key can have permissions that specify what
actions consumers or groups can take upon it. These are set individually for a
managed key.
Permissions are positive (they allow actions) and are additive: the actions enabled for a
consumer relative to a managed key are combination of the permissions allowed by the
consumer's group membership, plus permissions allowed for the consumer, plus
permissions allowed by the key.
There are no deny permissions.
Page 62

Page 63

Managing Organization Keys
10
This section describes the various keys and certificates you can configure and use with
your PGP Universal Server.
About Organization Keys
There are multiple keys and certificates you can use with your PGP Universal Server:
Organization Key. Used to sign all user keys the PGP Universal Server creates and
to encrypt server backups.
Organization Certificate. Used to generate user S/MIME certificates in an
S/MIME environment.
External User Root Key. Provides the key material used to generate the External
User Root Certificate.
External User Root Certificate. Used to generate X. 509 S/MIME certificates for
download by external users.
Additional Decryption Key (ADK). Used to reconstruct messages if the recipient
is unable or unwilling to do so. Every message encrypted to an external recipient
by an internal user is also encrypted to the ADK, allowing the PGP Universal
Server administrator to decrypt any message sent by internal users, if required to
do so by regulations or security policy.
Verified Directory Key. Used to sign keys submitted to the PGP Verified Directory
by external users.
The Organization Keys page provides access to all of these.
All of these keys should be created on an internal cluster member only, not on a
member located in the DMZ.
Organization Key
Your Organization Key is used to sign all user keys the PGP Universal Server creates
and to encrypt server backups. The Organization Key is what was referred to as the
Corporate Key in the old PGP Keyserver environment.
Warning: You must make a backup of your Organization Key, in case of a problem
with the server. That way, you can restore your server from a backup using the
backup Organization Key.
Each PGP Universal Server is pre-configured with a unique Organization Key generated
by the Setup Assistant. If you would like to use different settings for this key, you can
regenerate the key with the settings you prefer. This should only be done prior to live
deployment of the server or creation of user keys by the server.
The Organization Key automatically renews itself one day before its expiration date. It
renews with all the same settings.
Page 64

48 Managing Organization Keys
Organization Key
If you have multiple PGP Universal Servers in a cluster, the Organization Key is
synchronized.
An Organization Key’s identification is based on the name of the managed domain for
which the key was created. Organization Keys by convention have one ID per managed
domain so that they can be easily found via a directory lookup.
The Organization Key information includes the Public Keyserver URL, as specified on
the Services > Keyserver page. Anytime the Public Keyserver URL changes, that
information on the Organization Key changes immediately.
Inspecting the Organization Key
To inspect the properties of an Organization Key
1 Click the name of the Organization Key.
The Organization Key Info dialog box appears.
2 Inspect the properties of the Organization Key.
3 To export either just the public key portion of the Organization Key or the entire
keypair, click the Export button and save the file to the desired location. Optional:
You can protect your Organization Key with a passphrase when you export it.
When you export the Organization Key you also get the Organization Certificate.
You can use PGP Desktop to extract the Organization Certificate from the
Organization Key.
4 Click OK.
If you are going to regenerate your Organization Key, you should use a fairly high
bit size, such as 2048. However, if you are going to be using X.509 certificates and
S/MIME, be aware that many clients only support up to 1024 bits; thus you may
want to use 1024 bits for maximum compatibility with S/MIME. All clients can be
expected to support at least 4096 bits.
Regenerating the Organization Key
Warning: Changing the Organization Key makes all previous backups undecryptable
and all validity signatures on the keys of internal users are unverifiable until they
are automatically renewed. Only change the Organization Key if you fully understand
the consequences of this action.
Caution: Changing the Organization Key deletes Ignition Keys. If you have hard or
soft token Ignition Keys configured, regenerating the Organization Key deletes them.
Without an Ignition Key, PGP Universal Web Messenger messages are not stored
encrypted.
Note: The Organization Key signs all Trusted Keys and Certificates. If you regenerate
the Organization Key, the signature on the Trusted Keys and Certificates becomes
invalid. You must re-import all Trusted Keys and Certificates to have them signed by
the new Organization Certificate. For more information, see Managing Trusted Keys
and Certificates (on page
77).
Page 65
To regenerate an Organization Key
1 Click Regenerate in the Action column of the Organization Key whose properties
you want to change.
2 The following warning dialog box appears:
Regenerating the Organization Key will cause problems with existing key
signatures and backups. Any existing Ignition Keys and Organization Certificate
will also be removed. Are you sure you want to proceed?
3 Click OK.
The Organization Key Generation dialog box appears.
4 Make the desired changes to the properties of the Organization Key.
5 Click Generate.
Importing an Organization Key
You also have the option of importing an existing PKCS #12 key and using that as your
Organization Key.
Organization Key
49 Managing Organization Keys
Caution: Importing an Organization Key deletes Ignition Keys. If you have hard or
soft token Ignition Keys configured, importing an Organization Key deletes them.
Deleting the Ignition Key stops PGP Universal Web Messenger from being stored
encrypted
To import an Organization Key
1 Click the icon in the Import column of the Organization Key row.
2 The following warning dialog box appears:
Importing a new Organization Key will cause the current key (and Organization
Certificate, if any) to be deleted, and will cause problems with existing key
signatures and backups. Any existing Ignition Keys will also be removed. Are you
sure you want to proceed?
3 Click OK.
The Import Organization Key dialog box appears.
4 Do one of the following:
If you want to import a key that has been saved as a file, click Browse to
locate the file of the key you want to import.
If you want to import a key by cutting and pasting, copy the key you want to
be your Organization Key to the Clipboard and paste it into the Key Block
box.
5 Type the passphrase for the key, if required.
6 Click Import.
The Organization Key you imported appears in the Organization Key row.
Page 66

50 Managing Organization Keys
Organization Certificate
Organization Certificate
An Organization Certificate is required for S/MIME support. You can only have one
Organization Certificate attached to your Organization Key. You cannot restore from a
backup with more than one Organization Certificate associated with your Organization
Key.
The PGP Universal Server will automatically generate certificates as well as keys for
new internal consumers created after you import or generate an Organization
Certificate. All internal consumers receive a certificate added to their keys within a
certain amount of time, between 24 hours to two weeks. However, certificates issued by
the old Organization Certificate remains on users’ keys until the certificate expires.
PGP Universal Server also creates separate signing and encryption certificates for
imported SKM and SCKM internal keys, based on the appropriate subkey. PGP
Universal Server creates single signing and encryption certificates for imported CKM
and GKM keys, based on the user's topkey.
You have several options for dealing with Organization Certificates. You can:
Create a self-signed Organization Certificate. Unfortunately, a self-signed
Organization Certificate will not be universally recognized, so Symantec
Corporation recommends using a certificate from a reputable Certificate Authority
(CA). Self-signed X.509 Organization Certificates are version 3.
Create a Certificate Signing Request for a certificate authorized by an existing CA.
When you receive the certificate back from the CA as a file, you will need to import
that file.
Import an existing certificate to use as your Organization Certificate. Imported
X.509 certificates must be version 3.
To enable S/MIME support, the certificate of the issuing Root CA, and all other
certificates in the chain between the Root CA and the Organization Certificate, are on
the list of trusted keys and certificates on the Trusted Keys and Certificates page.
A self-signed Organization Certificate has the same expiration date as the Organization
Key, unless the Organization Key is set never to expire. If the Organization Key never
expires, the Organization Certificate expires 10 years from the date you generate it. You
must regenerate the Organization Certificate before it expires and distribute the new
Certificate to anyone who uses your old Organization Certificate as a trusted root CA.
This certificate is also required if you want PGP Universal Server to generate X.509
certificates for external users. External users can download and use X.509 certificates
from the PGP Universal Web Messenger interface to communicate securely with users
inside your managed domain. For more information, see Offering X.509 Certificates to
External Users (on page
255).
Inspecting the Organization Certificate
To inspect the settings of an Organization Certificate
1 Click the name of the Organization Certificate.
The Organization Certificate Info dialog box appears.
2 Inspect the settings of the Organization Certificate.
Page 67

3 Click OK.
Exporting the Organization Certificate
To export an Organization Certificate to a file
1 Click on the Organization Certificate.
The Organization Certificate Info dialog box appears.
2 Click Export.
The Export Certificate dialog box appears.
3 Do one of the following:
To export just the public key portion of the certificate, select Export Public
Key.
To export the public and private key portions of the certificate, select Export
Keypair and type a passphrase to protect the private key once it is exported.
The resulting file is in PKCS #12 format.
4 Click Export.
5 At the prompt that appears, click Save.
6 Specify a name and location to save the file, then click Save.
The Organization Certificate Info dialog box appears.
7 Click OK.
Organization Certificate
51 Managing Organization Keys
Deleting the Organization Certificate
To delete an Organization Certificate
1 Click the Delete icon in the Action column of the Organization Certificate.
A confirmation dialog box appears.
2 Click OK.
The Organization Certificate is deleted.
Generating the Organization Certificate
To create a Certificate Signing Request (CSR)
1 Click the icon in the Action column of the Organization Certificate row.
The Generate Organization Certificate dialog box appears.
2 Type a name for the certificate in the Common Name field.
Page 68

52 Managing Organization Keys
Organization Certificate
3 Type an email address in the Contact Email field.
4 Type your organization’s name in the Organization Name field.
5 Type your organization’s unit designation in the Organization Unit field.
6 Type a city or locality, as appropriate, in the City/Locality field.
7 Type a state or province, as appropriate, in the Province/State field.
8 Type a country in the Country field.
9 If you want to generate a self-signed certificate, click Generate Self-signed. PGP
10 Click the Generate CSR button.
11 Copy the entire contents of the CSR dialog box to a file, then click OK.
12 Paste the CSR into the appropriate field on your third-party CA interface.
13 When you receive the certificate from the CA, use the Import feature to import it
Universal Server generates a certificate. To generate a Certificate Signing Request
(CSR) instead, proceed to the next step.
The CSR dialog box appears, showing the certificate signing request (CSR).
The CA sends the certificate back to you when it has approved it.
as your Organization Certificate.
Importing the Organization Certificate
To import a certificate to be your Organization Certificate
1 Click the icon in the Import column of the Organization Certificate row.
The Import Organization Certificate dialog box appears.
2 Copy the certificate you want to be your Organization Certificate.
3 Paste the text into the Certificate Block box.
4 Click Save.
The Organization Certificate you imported appears in the Organization Certificate
row.
Renewing the Organization Certificate
Start the renewal process for an Organization Certificate issued by a certificate
authority before it expires by generating a new Certificate Signing Request. This is not
necessary for self-signed certificates.
To renew an Organization Certificate
1 Click the Add icon in the Action column of the Organization Certificate row.
The Generate Organization Certificate dialog box appears.
2 Type a name for the certificate in the Common Name field.
3 Type an email address in the Contact Email field.
Page 69
4 Type your organization’s name in the Organization Name field.
5 Type your organization’s unit designation in the Organization Unit field.
6 Type a city or locality, as appropriate, in the City/Locality field.
7 Type a state or province, as appropriate, in the Province/State field.
8 Type a country in the Country field.
9 Click the Generate CSR button.
The CSR dialog box appears, showing the certificate signing request (CSR).
10 Copy the entire contents of the CSR dialog box to a file, then click OK.
11 Paste the CSR into the appropriate field on your third-party CA interface.
The CA sends the certificate back to you when it has approved it.
12 When you receive the certificate from the CA, delete the existing Organization
Certificate and import the new one.
Additional Decryption Key (ADK)
Additional Decryption Key (ADK)
53 Managing Organization Keys
An Additional Decryption Key (ADK) is a way to retrieve an email message or other
encrypted data if the recipient is unable or unwilling to do so and if required by
regulation or security policy. Every message sent by an internal user is also encrypted
to the ADK. Messages encrypted to the ADK can be opened by the recipient and/or by
the holder(s) of the ADK. The ADK is also added to disks encrypted with PGP Whole
Disk Encryption.
If you have an Additional Decryption Key uploaded, all outbound email is encrypted to
it when mail policy is applied. This setting appears in the Send (encrypted/signed) action
and the setting cannot be disabled. For more information, see the chapter "Setting Mail
Policy."
You can create an ADK with PGP Desktop, then add it to your PGP Universal Server and
use it.
You can also add an ADK to a consumer policy. Clients with a policy with an ADK have
all messages and other data encrypted to the policy-specific ADK as well as to the
Organization ADK.
Note: S/MIME messages are not encrypted to the ADK.
If you use an ADK, PGP Universal Server adds the ADK to all new keys that it generates
and all outbound email messages are automatically encrypted to it.
If you are going to use an ADK on your PGP Universal Server, you should import it prior
to generating any user keys. You should also try to avoid changing to a different ADK
later on, because doing so results in some keys being associated with the old ADK and
some with the new ADK. If you add or change an ADK, it is only associated with the
keys of new users. Existing users do not get that ADK added to their key.
Only PGP keys can be used as ADKs, and a key with a certificate cannot be used as an
ADK.
For information on using an ADK in a split key scenario, see the PGP Desktop User’s
Guide.
Page 70

54 Managing Organization Keys
Additional Decryption Key (ADK)
Importing the ADK
To import an ADK to your PGP Universal Server
1 Copy the key of the ADK you are adding to the Clipboard using PGP Desktop.
2 Click the Add icon in the Action column of the Additional Decryption Key row.
3 Paste the key of the ADK into the Import Key Block box, or browse to find and
4 Click Import.
Inspecting the ADK
To inspect the properties of an ADK
1 Click the name of the ADK.
2 Inspect the properties of the ADK.
3 To export the ADK, click Export and save the file to the desired location.
4 Click OK.
The Add Additional Decryption Key dialog box appears.
import a key.
The ADK you added appears in the Additional Decryption Key row.
The Additional Decryption Key Info dialog box appears.
Deleting the ADK
To delete an ADK
Note: All keys generated while the ADK was present continue to reference the ADK
even after you delete the ADK. The change applies only to keys that are generated
after the ADK is deleted.
1 Click the delete icon in the Action column of the ADK.
A confirmation dialog box appears.
2 Click OK.
The ADK is deleted.
Page 71

External User Root Key
The External User Root Key provides the key material used to generate the External
User Root Certificate. The External User Root Key and Certificate allow external users
to generate and download X.509 certificates through the PGP Universal Web Messenger
interface to use to securely communicate with users inside your managed domain. For
more information, see Offering X.509 Certificates to External Users (on page
Create this key on an internal cluster member only, not on a member located in the
DMZ.
Generating the External User Root Key
To generate an External User Root Key
1 Click the Generate icon in the Action column of the External User Root Key.
The External User Root Key Generation dialog box appears.
2 Select the size, allowed ciphers, and key expiration period for the key.
3 Click Generate.
External User Root Key
55 Managing Organization Keys
255).
Importing the External User Root Key
To import an External User Root Key
1 Click the icon in the Import column of the External User Root Key row.
The Import Organization Key dialog box appears.
2 Do one of the following:
If you want to import a key that has been saved as a file, click Browse to
locate the file of the key you want to import.
If you want to import a key by cutting and pasting, copy the key you want to
be your Organization Key to the Clipboard and paste it into the Key Block
box.
3 Type the passphrase for the key, if required.
4 Click Import.
The External User Root Key you imported appears in the External User Root Key
row.
Page 72

56 Managing Organization Keys
External User Root Certificate
Deleting the External User Root Key
If you delete the External User Root Key, external users with X.509 certificates
generated by PGP Universal Server will no longer be able to communicate securely with
internal users.
To delete an External User Root Key
1 Click the Delete icon in the Action column of the External User Root Key.
A confirmation dialog box appears.
2 Click OK.
The key is deleted.
External User Root Certificate
The External User Root Certificate generates and signs external user X.509 certificates.
External users can generate and download X.509 certificates through the PGP Universal
Web Messenger interface to use to securely communicate with users inside your
managed domain.
To deliver X.509 certificates to external users, you must have an Organization
Certificate, an External User Root Key, and an External User Root Certificate.
The Organization Certificate and the External User Root Certificate must not expire
before the external user certificates expire. If either expires before the user certificate
does, external users will no longer be able to communicate securely with internal users.
The External User Root Certificate inherits trust from the Organization Certificate.
This mean most internal users automatically trust external user certificates because
they are signed by the External User Root Certificate. Only internal users with
standalone policies do not trust external user certificates, because those PGP Desktop
installations cannot access the External User Root Certificate.
For more information on delivering certificates to external users, see Offering X.509
Certificates to External Users (on page
Create this certificate on an internal cluster member only, not on a member located in
the DMZ.
255).
Generating the External User Root Certificate
To create a Self-Signed Certificate or a Certificate Signing Request (CSR)
1 Click the icon in the Action column of the External User Root Certificate row.
The Generate X509 Certificate dialog box appears.
2 Type a name for the certificate in the Common Name field.
3 Type an email address in the Contact Email field.
4 Type your organization’s name in the Organization Name field.
Page 73

External User Root Certificate
5 Type your organization’s unit designation in the Organization Unit field.
6 Type a city or locality, as appropriate, in the City/Locality field.
7 Type a state or province, as appropriate, in the Province/State field.
8 Type a country in the Country field.
9 If you want to generate a self-signed certificate, click Generate Self-signed. PGP
Universal Server generates a certificate. To generate a Certificate Signing Request
(CSR) instead, proceed to the next step.
10 Click the Generate CSR button.
The CSR dialog box appears, showing the certificate signing request (CSR).
11 Copy the entire contents of the CSR dialog box to a file, then click OK.
12 Paste the CSR into the appropriate field on your third-party CA interface.
The CA sends the certificate back to you when it has approved it.
13 When you receive the certificate from the CA, use the Import feature to import it
as your External User Root Certificate.
57 Managing Organization Keys
Importing the External User Root Certificate
To import a certificate to be your External User Root Certificate
1 Click the icon in the Import column of the External User Root Certificate row.
The Add Certificate to Key dialog box appears.
2 Copy the certificate you want to be your External User Root Certificate.
3 Paste the text into the Certificate Block box.
4 Click Save.
The External User Root Certificate you imported appears in the External User
Root Certificate row.
Deleting the External User Root Certificate
If you delete the External User Root Certificate, external users with X.509 certificates
generated by PGP Universal Server will no longer be able to communicate securely with
internal users.
To delete an External User Root Certificate
1 Click the Delete icon in the Action column of the External User Root Certificate.
A confirmation dialog box appears.
2 Click OK.
The certificate is deleted.
Page 74

58 Managing Organization Keys
Verified Directory Key
Verified Directory Key
The Verified Directory Key is the signing key for PGP Verified Directory users outside
your managed domain. It must consist of both private and public keys. Once you choose
the setting to allow internal and external users to submit their keys through the PGP
Verified Directory, you must upload a Verified Directory Key. Users cannot submit their
keys to PGP Verified Directory until you have added the Verified Directory Key. For
more information, see Configuring the PGP Verified Directory (on page
If you have multiple PGP Universal Servers in a cluster, the Verified Directory Keys are
synchronized.
Importing the Verified Directory Key
To import a Verified Directory Key to your PGP Universal Server
1 Copy the key of the Verified Directory Key you are adding to the Clipboard using
PGP Desktop.
2 Click the Add icon in the Action column of the Verified Directory Key row.
The Add Verified Directory Key dialog box appears.
3 Paste the key of the Verified Directory Key into the Import Key Block box, or
browse to find and import a key.
4 Type the private key Passphrase.
5 Click Import.
The Verified Directory Key you added appears in the Verified Directory Key row.
302).
Inspecting the Verified Directory Key
To inspect the properties of the Verified Directory Key
1 Click the name of the Verified Directory Key.
The Verified Directory Key Info dialog box appears.
2 Inspect the properties of the Verified Directory Key.
3 To export the Verified Directory Key, click Export.
To export just the public key portion of the Verified Directory Key, select
Export Public Key.
To export the public and private key portions of the key, select Export
Keypair and type a passphrase to protect the private key once it is exported.
4 Click OK.
Page 75

Deleting the Verified Directory Key
To delete the Verified Directory Key
1 Click the delete icon in the Action column of the Verified Directory Key.
A confirmation dialog box appears.
2 Click OK.
Verified Directory Key
59 Managing Organization Keys
Page 76

Page 77

11
Administering Managed Keys
PGP Key Management Server (KMS) is new technology that centralizes the
management of multiple kinds of encryption keys for your organization onto a single
server, thus allowing multiple applications in your enterprise to operate against the
same set of keys.
To accommodate this new PGP KMS technology, new terms and concepts are being used
to describe how PGP applications understand keys, users, and servers, and the
relationships between them.
With PGP KMS, a Consumer is an identity associated with a person or a device. A
consumer can be a User, generally identified with a person. A user has a key, can
encrypt things, send and receive email, and so on. One person can have more than one
user identity (for example, they could be the holder of a corporate ADK as one identity
and a PGP Desktop user as a second identity, each identity having a different PGP
keypair).A consumer can also be a Managed Device, such as a web server that handles
credit cards or a bank's automated teller machine. Each consumer has a Managed Key,
which is a keypair managed by PGP KMS for the consumer.
A Managed Key is a PGP keypair with some additional information. A managed key can
be used to encrypt, decrypt, sign, and verify. It is also known as a Managed Asymmetric
Key, or MAK, in the USP API and in PGP Command Line. A managed key may or may
not have associated symmetric keys, symmetric key series, or custom data objects.
Symmetric Keys (also known as Managed Encryption Keys, or MEKs) are always
associated with a managed key. A symmetric key can be used to encrypt and decrypt; it
cannot sign or verify. Any number of symmetric keys can be associated with a managed
key. Symmetric keys can have a Validity Period, allowing them to be valid for a
specified period. At the end of the specified period, the symmetric key expires and a
new symmetric key can be automatically created. The old symmetric key is retained in
an expired state and kept, to decrypt older data if necessary.
A Symmetric Key Series (or MEK series) is series of symmetric keys, each one of which
is automatically created, is valid for the duration of its Validity Period, and then expires
and is replaced by a new symmetric key. Consumers using a symmetric key series can
be automatically notified of a new symmetric key so that they can synchronize to the
series and thus use the correct symmetric key at the correct time. In other cases, no
notification is needed; when you encrypt against the symmetric key series, the active
symmetric key is used automatically.
Custom Data Objects are encrypted data objects stored on a PGP KMS and associated
with a managed key. It is just like a regular encrypted file except it is stored on a PGP
KMS. Custom data objects are also known as Managed Secure Data, or MSDs).
Symmetric Keys and Custom Data Objects can be created, edited, searched for and
deleted by external applications using the USP APIs, or through PGP Command Line
commands. They can be viewed through the PGP Universal Server administrative
interface, but cannot be created or modified by a PGP Universal Server administrator.
Viewing Managed Keys
Managed keys can be associated with several types of consumers: internal, external,
and verified directory users, and managed devices for which keys have been imported.
Page 78

62 Administering Managed Keys
Managed Key Information
There are a number of paths available to view managed keys.
For a User, you can access the Managed Key Information page by clicking the Key
For a Managed Device, you can access the Managed Key Information page by
The organization key and Verified Directory signing keys are also managed keys, but
are discussed in Managing Organization Keys (on page
To view all managed keys
1 Go to the Keys > Managed Keys page.
The Managed Keys Display shows the following information about the keys:
Key ID: click this to view Managed Key Information for this managed key.
Name: the display name and email address of the user, or the display name of the
Key Mode: the key mode type (SKM, CKM, GKM, SCKM)
Key Size and type: key size in bits and the key type (RSA or DH/DSS)
Created: date the key was created.
Expires: date the key will expire (or never if it does not expire
Status: the status of the key (valid, revoked, expired).
Recovery: whether a key reconstruction block has been uploaded
Owner: the owner of the key. For Users, the user is the owner of his/her keys.
Using the icons under the Actions area you can:
Revoke the key
Export the key
Delete the key.
ID from the Managed Key section of the user's User Information page.
clicking the Key ID from the Managed Key section of the Managed Device
Information page.
47).
This displays the list of all managed keys in the PGP Universal Server database.
managed device.
Managed Key Information
The Managed Key Information page shows detailed information about a managed key.
To view detailed information about a specific managed key
1 Click the Key ID of the managed key from any of the following pages:
From the Managed Keys page
From the Managed Key section of a User Information page
From the Managed Key section of a Device Information page The Managed Key
Information page appears for the key you selected.
Page 79

Administering Managed Keys
Managed Key Information
From this page you can view detailed information about the key. You can also add or
change information about the device.
To changed the display name of the key
1 Click Edit Names... and type a new display name for the key.
2 Click Save to save the change or Cancel to close the dialog without making the
change.
To change the owner of the key
1
Click Edit Owner....
This takes you to the Edit Owner page where you can change the owner of this
managed key.
Note: Keys associated with email addresses cannot have their owner modified.
The Edit Owner... key will be disabled in this case.
2 Click Save to save the change or Cancel to close the dialog without making the
change.
63
To revoke the managed key of an SKM key
1 Click Revoke.
A confirmation dialog box appears.
2 Click OK.
The key is revoked.
To Export the managed key
1 Click Export.
If only the public key is available, the text of the key downloads to your system.
If both the public and the private key are available, the Export Key dialog box
appears.
2 Select Export Public Key to export just the public key portion of the keypair.
3 Select Export Keypair to export the entire keypair, the public key and the private
key portions.
4 If you want to protect the exported key file with a passphrase, type it in the
Passphrase field.
If a private key already has an attached passphrase, it is already protected and
there is no need to type another passphrase. When you export the keypair, you
receive a file containing an unencrypted public key and an encrypted private key.
5 Click Export.
The key is exported.
Page 80

64 Administering Managed Keys
Managed Key Information
To delete the managed key
1 Click Delete.
2 Click OK.
Note: When you delete an internal user’s key, the private key material is deleted,
which means messages are no longer decryptable. If you want to retain the private
key material, you can revoke the key instead of deleting it.
To view Symmetric Key Series and the symmetric keys associated with this managed key
Click Symmetric Key Series... to display the Symmetric Key Series associated with
This button is only enabled for managed keys that have associated Symmetric keys.
Symmetric keys, also known as Managed Encryption Keys, or MEKs, can be used to
encrypt or decrypt; it cannot sign or verify.
These keys can only be created by external applications using the USP API or PGP
Command Line. For more information about Symmetric Key Series and Symmetric
Keys, see Symmetric Key Series (on page
A confirmation dialog box appears.
The key of is deleted.
this managed key.
66).
Email Addresses
Subkeys
To view Custom Data Objects associated with this managed key
Click Custom Data Objects... to display the list of custom data objects associated
with this managed key.
This button is only enabled for managed keys that have associated data objects. These
objects can only be created by external applications using the USP API. For more
information about Custom Data Objects, see Custom Data Objects (on page 69).
To view the Email Addresses associated with this key
Expand the Email Addresses section of the Managed Key Information page. This
displays the list of email addresses associated with this managed key.
If this is the managed key of a managed device, no email address will be present.
To view the subkeys associated with this managed key
Expand the Subkeys section of the Managed Key Information page.
This displays any subkeys associated with this managed key.
Page 81

Certificates
Managed Key Information
65 Administering Managed Keys
For each subkey, this section shows the Key ID, the usage flags that are set for the
key, the key size (in bits) and key type (RSA or DH/DSS), the date the key was
create, the date it expires (or Never if it does not expire) and the key status (Valid
or Expired).
To view the certificates associated with this managed key
Expand the Certificates section of the Managed Key Information page.
This displays any certificates that are associated with this managed key.
For each certificate, this section shows Common Name to which the certificate was
issued, the date the certificate was created (meaning when it was imported into
PGP Universal Server), the date on which it expires,and the usage flags that are set
for the certificate.
The Actions section at the end of the row provides icons for revoking, exporting,
and deleting the certificate. You can revoke a certificate attached to any key type if
the certificate was generated by PGP Universal Server. Revoked certificates are
added to the CRL.
Permissions
Managed Key permissions are similar to the permissions that can be granted to a
Consumer or Group, with an important exception: while group and consumer
permissions define the actions a consumer or group member can perform, a Managed
Key permission defines what actions others (Groups or Consumers) can perform upon
the Managed Key.
For example, a Consumer may be given a permission such as:
Can read public key of Managed Key Joe Smith <jsmith@example.com>
while a Managed Key may have a permission such as:
Group Marketing can delete
meaning that any Consumer that is a member of the group Marketing can delete this
key.
To view, set, or delete Permissions for this key
1 Expand the Permissions section of the Managed Key Information page.
If permissions have been added specifically for this device, the permission settings
are listed in this area.
If a listed permission involves a named consumer or a group, you can click the
name to see details about the consumer or group.
2 To add, edit, or delete permissions, click View and Edit Permissions....
The Permissions page for this key appears.
To remove a permission, click the Delete icon.
Page 82

66 Administering Managed Keys
Symmetric Key Series
3 To search for a specific permission, type the relevant string into the Search field at
4 To add, remove or modify permissions, click Add Permissions...
5 Use the drop-down menus to create a new permission.
6 Click the Add icon to create as many permissions as necessary. Use the Remove
Attributes
To view, add, or delete Attributes for this key
1 Expand the Attributes section of the Key Information page.
2 To add, delete, or modify attributes for this device, click Edit Attributes....
3 To add attributes, type the attribute name and its value in the fields provided.
4 To change an attribute name or its value, just retype the information in the field.
5 To remove an attribute, click the Remove icon.
To remove multiple permissions, check the boxes next to the permissions
you want to delete and select Delete Selected from the Options menu. To
remove all permissions, select Delete All from the Options menu.
the top right of the dialog box, and click the search icon.
The permissions list will be filtered to display only permissions that match the
search criterion.
icon to remove individual permission.
If attributes have been added, the attribute/value pairs are listed in this area.
Attributes are arbitrary name/value pairs. Outside applications can make requests
related to attributes through the USP API or using PGP Command Line commands.
To add additional attributes, click the Add icon.
Symmetric Key Series
A KMS license is required to access Symmetric Key Series and Symmetric Keys.
Symmetric keys (also known as Managed Encryption Keys, or MEKs) can be used,
through the USP API or the PGP Command Line commands, to encrypt and decrypt
data. A symmetric key typically has a limited life span, with a specific validity period
that determines how long the key remains valid. At the end of the validity period, the
current key expires and is replaced by a new symmetric key.
The Symmetric Key Series is the set of the current plus expired keys, maintained by
PGP Universal Server. The currently valid key is used to encrypt content during its
validity period, and to decrypt content encrypted during this validity period. The
expired keys are maintained in order to decrypt content that was encrypted in the past;
PGP Universal Server determines which key to use for decryption based on the date the
content was encrypted.
To view the symmetric key series associated with this managed key
1 Go to the Keys > Managed Keys page.
Page 83

Symmetric Key Series
This displays the list of all managed keys in the PGP Universal Server database.
2 Click the Key ID of the managed key.
The Managed Key Information page appears for the key you selected.
3 Click the Symmetric Key Series... button to display a list of Symmetric Key Series
owned by this managed key.
The information shown in this list includes the key series display name, the
validity period, the date at which the key will expire (or never); the date when it
will next be renewed (or never); and the number of symmetric keys in this series.
4 To delete one or more key series, click the delete icon in the key series row, or
check one or more rows and select Delete Selected from the Options menu, or
select the Delete All option.
5 To export one or more keys, check one or more rows and select Export Selected
from the Options menu, or select the Delete All option.
6 Click the key series name to view the list of symmetric keys that are included in
the series.
To view an individual symmetric key series
1 From the Managed Key Information page, click the Symmetric Key Series...
button to display the list of Symmetric Key Series owned by this managed key.
2 Click a key series name to view the list of symmetric keys that are included in that
series.
The Symmetric Key Series Information page appears.
On this page you can see the same basic information about the key series as was
shown in the Symmetric Key Series list. You can also view and set attributes and
permissions for the key, and force a rekey of the series.
3 To view or set attributes for this key series, expand the Attributes section of the
Symmetric Key Series Information page. This shows any attribute/value pairs
defined for this key series.
To add an attribute or to modify existing ones, click Edit Attributes...
4 To view the permissions for this key series, expand the Permissions section of the
Symmetric Key Series Information page. This shows any permissions allowed for
this key.
To add or delete permissions, click View and Edit Permissions....
The Permissions page for this key appears. You can delete permissions by
clicking the delete icon next to a permission.
You can add a new permission by clicking Add Permissions..., which takes you
to a page where you can add permissions.
5 To view the individual Symmetric Keys within this series, click Symmetric Keys....
For details of the pages that show the Symmetric Keys, see Symmetric Keys (on
68).
page
67 Administering Managed Keys
To force replacement of the current valid key
1 Click Force Rekey.
Page 84

68 Administering Managed Keys
Symmetric Keys
Symmetric Keys
Individual Symmetric Keys are contained within a Symmetric Key Series, which is itself
associated with a specific managed key. To view the set of individual Symmetric Keys,
you must navigate through the Symmetric Key Series display.
To view the set of Symmetric Keys in a series
1 From the Managed Key Information page, click the Symmetric Key Series...
2 Click a key series name to view the list of symmetric keys that are included in that
3 Click the Symmetric Keys... button to display the list of Symmetric Keys in the
4 To delete an individual Symmetric Key, click the Delete icon. You can also delete
5 To export one or more individual Symmetric Keys, click their check boxes and
This lets you replace the current valid symmetric key, regardless of its validity
period or when it is due to expire. The current valid symmetric key is marked
expired, and a new symmetric key is created as the valid key.
button to display the list of Symmetric Key Series owned by this managed key.
series.
The Symmetric Key Series Information page appears.
selected key series.
From this list, you can see each Key ID, along with the Validity dates (start and end
dates) for each key.
The key icon at the left of each Key ID indicates whether the key is expired or valid
- normally only the last key in the list will be valid, the others will be expired.
multiple keys by clicking check boxes and selecting Delete Selected from the
Options menu, or by selecting the Delete All option.
select Export Selected from the Options menu. You can export all the keys by
selecting the Export All option.
To view the details of an individual Symmetric Key
1 From the list of symmetric keys, click the individual key ID to display the
Symmetric Key Information page.
This shows the key UUID, the date it was created, and its validity start and end
dates.
2 To view or set attributes for this key, expand the Attributes section of the
Symmetric Key Information page. This shows any attribute/value pairs defined for
this key series.
Note: Attributes of symmetric keys cannot be added or modified through the PGP
Universal Server administrative interface. They can only be manipulated using
PGP Command Line commands or through the USP API.
3 To view the data in this key, click Show Data. This displays the data in a text
field. The administrator can copy the contents for use elsewhere.
Click Hide Data to hide the data display.
Page 85

Custom Data Objects
A KMS license is required to access Custom Data Objects (also known as Managed
Secure Data, or MSDs).
Custom Data Objects are always associated with (owned by) a Managed Key. They can be
used to store arbitrary data objects securely in the PGP Universal Server database. They
are created and manipulated using the USP API or PGP Command Line commands.
Custom Data Objects can be viewed through the PGP Universal Server administrative
interface. The administrator can also add and edit attributes and permissions for a
Custom Data Object.
To view a list of the Custom Data Objects associated with a managed key
1 From the Managed Key Information page, click the Custom Data Objects... button
to display the list of Custom Data Objects owned by this managed key.
For each object in the list, this page shows its name, its size (in kbytes), and its
MIME type.
PGP Universal Server supports the MIME types for image files, plain text, rich
text, and PDF.
2 To delete an individual Custom Data Object, click the Delete icon next to the
object. You can also delete multiple objects by clicking the appropriate check boxes
and selecting Delete Selected from the Options menu, or by selecting the Delete
All option.
3 To view an individual Custom Data Object, click the object ID.
Custom Data Objects
69 Administering Managed Keys
To view the details of an individual Symmetric Key
1 From the list of symmetric keys, click the individual key ID to display the
Symmetric Key Information page.
This shows the key UUID, the date it was created, and its validity start and end
dates.
2 To view or set attributes for this Custom Data Object, expand the Attributes
section of the Custom Data Object Information page. This shows any
attribute/value pairs defined for this key series.
To add an attribute or to modify existing ones, click Edit Attributes... For
details on adding or editing attributes, see Attributes (Managed Keys) (see
"
Attributes" on page 66).
3 To view the permissions for this key series, expand the Permissions section of the
Custom Data Object Information page. This shows any permissions allowed for
this object.
To add or delete permissions, click View and Edit Permissions....
Page 86

70 Administering Managed Keys
Exporting Consumer Keys
The Permissions page for this object appears. You can delete permissions by
clicking the Delete icon next to a permission.
4 You can add a new permission by clicking Add Permissions..., which takes you to a
page where you can add permissions. For details on adding or editing permissions,
see Permissions (Managed Keys) (see "Permissions" on page 65).
5 To view the data in this Custom Data Object as plain text, click Show Data.
If the MIME type of the object is one that PGP Universal Server recognizes, it
attempts to display the data using the appropriate application in a separate
browser window or tab. If it does not recognize the MIME type, it displays the data
in a text field.
Click Hide Data to hide the data display.
Exporting Consumer Keys
The following sections describe how to export keys for users and managed devices.
Exporting the Managed Key of an Internal User
If the user’s key data is stored in Server Key Mode, you can export both public and
private key information. If the private key is stored protected by the user’s passphrase,
you cannot export it unencrypted. If the key data is in Client Key Mode, the private key
is not stored on the server and cannot be exported.
To export the managed key of an internal user
1 From the Consumers > Users page, click the check box for the internal user whose
key you want to export.
2 From the Options menu, select Export Keys for Selected.
If only the public key is available, the text of the key downloads to your local
system.
If both the public and the private key are available, the Export Key dialog box
appears, allowing you to choose to export only the public key, or both public and
private portions of the key.
3 Select Export Public Key to export just the public key portion of the keypair.
4 Select Export Keypair to export the entire keypair, the public key and the private
key portions.
5 If you want to protect the exported key file with a passphrase, type it in the
Passphrase field.
If a private key already has an attached passphrase, it is already protected and
there is no need to type another passphrase at this time. When you export the
keypair, you receive a file containing an unencrypted public key and an encrypted
private key.
6 Click Export.
The key is exported to your local system.
Page 87

Exporting the Managed Key of an External User
To export the managed key of an external user
1 From the Consumers > Users page, click the check box for the external user whose
key you want to export.
2 From the Options menu, select Export Keys for Selected.
If only the public key is available, the text of the key downloads to your system.
If both the public and the private key are available, the Export Key dialog box
appears.
3 Select Export Public Key to export just the public key portion of the keypair.
4 Select Export Keypair to export the entire keypair, the public key and the private
key portions.
5 If you want to protect the exported key file with a passphrase, type it in the
Passphrase field.
If a private key already has an attached passphrase, it is already protected and
there is no need to type another passphrase. When you export the keypair, you
receive a file containing an unencrypted public key and an encrypted private key.
6 Click Export.
The key is exported.
Exporting Consumer Keys
71 Administering Managed Keys
Exporting PGP Verified Directory User Keys
To export the key of directory users
1 From the Consumers > Users page,select the check box for the users whose key
you want to export.
2 From the Options menu, select Export Keys for Selected.
The text of the keys downloads to your local system.
Exporting the Managed Key of a Managed Device
To export the managed key of an external user
1 From the Consumers > Devices page, select the check box for the managed device
whose key you want to export.
The Managed Device Information page for the device appears.
2 From the Managed Keys tab, click the Export icon in the Actions column of the
managed key you want to delete.
If only the public key is available, the text of the key downloads to your system.
Page 88

72 Administering Managed Keys
Deleting Consumer Keys
If both the public and the private key are available, the Export Key dialog box
appears.
3 Select Export Public Key to export just the public key portion of the keypair.
4 Select Export Keypair to export the entire keypair, the public key and the private
key portions.
5 If you want to protect the exported key file with a passphrase, type it in the
Passphrase field.
If a private key already has an attached passphrase, it is already protected and
there is no need to type another passphrase. When you export the keypair, you
receive a file containing an unencrypted public key and an encrypted private key.
6 Click Export.
The key is exported.
Deleting Consumer Keys
The following sections describe how to delete keys for users and managed devices.
Deleting the Managed Key of an Internal User
If you delete a user’s key, the private key material is gone, which means messages are
no longer decryptable. If you want to retain the private key material, you can revoke the
key instead of deleting it. For more information see Revoking Managed Keys (on page
74).
To delete the managed key of an internal user
1 Select the user you want from the Internal Users page.
The Internal User Information dialog box appears.
2 From the Managed Keys tab, click the Delete icon in the Actions column of the
managed key you want to delete.
A confirmation dialog box appears.
3 Click OK.
The key of the internal user is deleted.
Deleting the Managed Key of an External User
To delete the managed key of an external user
1 Select the user you want from the External Users page.
The External User Information dialog box appears.
Page 89

2 From the Managed Keys tab, click the Delete icon for the managed key you want to
delete.
A confirmation dialog box appears.
3 Click OK.
The key of the external user is deleted.
Deleting the Key of a PGP Verified Directory User
To delete the key of a PGP Verified Directory user
1 Select the user you want from the Verified Directory Users page.
The Directory User Information dialog box appears.
2 From the Managed Keys tab, click the Delete icon for the managed key you want to
delete.
A confirmation dialog box appears.
3 Click OK.
The key of the PGP Verified Directory user is deleted.
Approving Pending Keys
73 Administering Managed Keys
Deleting the Managed Key of a Managed Device
To delete the key of a managed device
1 Select the managed device you want from the All Devices or Managed Devices
page.
The Managed Device Information dialog box appears.
2 From the Managed Keys tab, click the Delete icon for the managed key you want to
delete.
A confirmation dialog box appears.
3 Click OK.
The key of the managed device is deleted.
Approving Pending Keys
Internal Users
In addition to automatically creating a key for your email users or manually adding
internal users, you can allow internal users to submit their own keys through the PGP
Verified Directory. Allowing user key submission is useful for internal users who
already have keys, such as existing PGP Desktop users who of course would have their
own PGP key. If the user already has a PGP key, and the new key is approved, the new
key replaces the old key.
Page 90

74 Administering Managed Keys
Revoking Managed Keys
PGP Desktop users upload their public keys through the PGP Verified Directory
interface at the interface and port you configure on the Verified Directory page. They
can also upload keys through the PGP Desktop "Send To" function.
On the Verified Directory page, you can specify how you want these user-submitted
keys approved. If you have set the PGP Verified Directory to require either a
confirmation email from the user or to require you, the administrator, to manually
approve the key, the user’s PGP key status is marked pending. See Configuring the PGP
Verified Directory (on page
To manually approve the key submission
1 From the Internal Users page, click the plus sign icon to approve the key.
2 Click the minus sign icon to deny the submitted key.
3 Click the delete icon to delete the user.
Directory users
If you have set the PGP Verified Directory to require either a confirmation email from
the user or to require you, the administrator, to manually approve the key, the user’s
PGP key status are pending.
302) for information on the PGP Verified Directory.
To manually approve the key submission, choose one of the following
1 To approve a single user key, click the plus sign icon in the Options column to
approve the key.
2 Click the minus sign icon to deny the submitted key.
3 Click the delete icon to delete the user.
Or
1 To approve multiple user keys, click the check box at the far right end of the row
of each of the directory user key you want to approve.
2 Select Approve Selected or Approve All from the Options menu.
Revoking Managed Keys
Revoking a key removes the Organization Key signature from the key. Only keys for
which the PGP Universal Server has the private key can be revoked; that is, only the
keys of SKM users can be revoked. The Revoke button is disabled for all other keys.
If you revoke an internal user's managed key, it continues being published via the LDAP
server, but appears marked as a revoked key, and it appears on the Certificate
Revocation Lists.
Once you revoke a key, you cannot un-revoke it.
Note: Revoking a key is safer than deleting a user because the private key material is
preserved, which means that decryption continues to work.
Page 91

Revoking Managed Keys
To revoke the managed key of an internal user
1 Select the user you want from the Internal Users page.
The Internal User Information dialog box appears.
2 From the Managed Keys tab, click the Revoke icon next to the key you want to
Revoke.
Note: If the key is not an SKM key, the Revoke icon is disabled.
A confirmation dialog box appears.
3 Click OK.
The internal user’s key is revoked.
To revoke the managed key of a managed device
1 Select the managed device you want from the All Devices or Managed Devices
page.
The Managed Device Information dialog box appears.
2 From the Managed Keys tab, click the Revoke icon next to the key you want to
revoke.
A confirmation dialog box appears.
3 Click OK.
The internal user’s key is revoked.
75 Administering Managed Keys
Page 92

Page 93

12
Overview
Trusted Keys
Managing Trusted Keys and Certificates
This section describes how trusted keys and certificates are used with your PGP
Universal Server. You can find the list of trusted keys at Organization > Trusted Keys.
The Trusted Keys and Certificates page lists keys and certificates that are not part of
the SMSA created by PGP Universal Server but which nevertheless you do trust.
In those cases where your PGP Universal Server cannot find a public key for a
particular user on any of the keyservers you have defined as trusted, it also searches
the default directories. If it finds a key in one of the default directories, it trusts (and
therefore can use) that key only if it has been signed by one of the keys in the trusted
keys list.
For example, if your company’s law firm uses a PGP Corporate Signing Key (CSK), you
can add this key as a trusted key. Then, if someone in your firm wants to send a
message to someone at the law firm and the PGP Universal Server finds that person’s
key, signed by the law firm’s CSK, in a default directory, then that key can be used by
the server to securely send the message to the recipient at the law firm.
Trusted Certificates
PGP Universal Server can use S/MIME only if it has the root certificates from the CAs
available to verify the client certificates. These CAs can be in your company or they can
be an outside-managed CA, such as VeriSign.
To enable S/MIME support, the certificate of the issuing Root CA, and all other
certificates in the chain between the Root CA and the Organization Certificate, are on
the list of trusted keys and certificates on the Trusted Keys and Certificates page.
PGP Universal Server comes with information on many public CAs already installed on
the Trusted Keys and Certificates page. Only in-house CAs or new public CAs that issue
user certificates need to be manually imported. You can inspect, export (save on your
computer), or delete the root certificates at any time.
Trusted Certificates can be in any of the following formats: .cer, .crt, .pem and .p7b.
Page 94

78 Managing Trusted Keys and Certificates
Adding a Trusted Key or Certificate
Adding a Trusted Key or Certificate
To add a trusted key or certificate
1 On the Trusted Keys and Certificates page, click Add Trusted Key.
The Add Trusted Key dialog box appears.
2 Do one of the following:
To import a trusted key saved in a file, click Browse and choose the file on
your system that contains the trusted key or certificate you want to add.
To import a key in key block format, paste the key block of the trusted key or
certificate into the Import Key Block box (you need to copy the text of the
trusted key or certificate first to paste it).
3 If desired, select any of the following:
Trust key for verifying mail encryption keys. Enable this option to trust the
key or certificate added to verify signatures on keys from default keyservers.
Trust key for verifying SSL/TLS certificates (only valid if importing X.509
certificate). Enable this option to trust the X.509 certificate added to verify
SSL/TLS certificates presented from remote SMTP/POP/IMAP mail servers.
Trust key for verifying keyserver client certificates (only valid if importing
X.509 certificate). Enable this option to trust the X.509 certificate added to
verify keyserver client authentication certificates.
4 Click Save.
Note: SSL v1.0 certificates are not supported.
Inspecting and Changing Trusted Key Properties
To inspect or change the properties of a trusted key or certificate
1 Click on the User ID (the name) of the trusted key or certificate whose properties
you want to inspect in the list of trusted keys and certificates.
The Trusted Key Info dialog box appears.
2 Inspect the properties of the trusted key or certificate you selected. You can click
more to see all the certificate data, which appears in a pop-up dialog box.
3 To export the trusted key, click Export and save the file to the desired location.
4 To change the properties of the trusted key or certificate, select any of the
following:
Trust key for verifying mail encryption keys. Enable this option to trust the
key or certificate added to verify signatures on keys from default keyservers.
Page 95

Trust key for verifying SSL/TLS certificates. Enable this option to trust the
X.509 certificate added to verify SSL/TLS certificates presented from remote
SMTP/POP/IMAP mail servers.
Trust key for verifying keyserver client certificates. Enable this option to
trust the X.509 certificate added to verify keyserver client authentication
certificates.
5 Click Save.
Deleting Trusted Keys and Certificates
To delete a trusted key or certificate
1 Click the delete icon in the row of the trusted key or certificate you want to delete.
A confirmation dialog box appears.
2 Click OK.
The trusted key or certificate you specified is removed from the list.
Deleting Trusted Keys and Certificates
79 Managing Trusted Keys and Certificates
Searching for Trusted Keys and Certificates
To find keys and certificates using search, enter the criteria for which you want to
search, and click Search. A list of keys and certificates that fit the criteria you specified
appears.
Page 96

Page 97
13
Overview
Managing Group Keys
This section describes how group keys are used with PGP Universal Server. You can
find the list of group keys at Keys > Managed Keys. Group keys have "(Group)"
appended to their name.
A group key is a PGP Universal Server-managed keypair shared by a group of users. A
group key is assigned to a PGP Universal Server group. A group key can be assigned to
one group only; a group can have only one active group group key assigned to it (a
group can have multiple revoked group keys).
Note: In version 3.2 of PGP Universal Server, group keys can only be used with PGP
NetShare.
Group keys can be assigned to any PGP Universal Server group. To use the Generate
AD Group Keys wizard to create a group, however, requires the Directory
Synchronization feature to be enabled and synchronized with an Active Directory
database.
Membership in a group can be modified without affecting the metadata associated with
the data protected by the group key. For groups that are based on membership in an
Active Directory security group, membership in the AD security group can also be
modified without affecting the metadata.
The users of a group key must be in a PGP Universal Server-managed environment;
group keys are not supported in standalone environments.
Once created, normal key lifecycle events (creating, editing, revoking, deleting, logging,
and so on) for group keys are managed by the PGP Universal Server.
Group keys are fully compatible with additional decryption keys (ADKs).
Caution: The Distinguished Name (DN) of an Active Directory security group
associated with a group key should not be changed after creation. This could lead to
loss of access to the private portion of the group key. Additionally, the "memberOf"
attribute for members of a group with an associated group key should be set to the
same value as the Distinguished Name (DN) of the group.
Establishing Default Group Key Settings
To establish default settings for your group keys
1 Navigate to the Consumers > Groups screen, then click the Group Key Settings
button.
2 Select the appropriate Key Generation settings.
Page 98
82 Managing Group Keys
Adding a Group Key to an Existing Group
3 Click Save.
Note: If you change the default group key settings, the new settings apply only to
group keys created after you make the changes; the settings of existing group keys
are not affected.
Adding a Group Key to an Existing Group
To add a group key to an existing group
1 Go to the Consumers > Groups page. The Keys column shows a group key icon for
those groups that already have a group key assigned.
2 Click on the name of the group to which you want to add a group key.
3 In the Keys row, click View.
4 Click Add Group Keys to add a group key to this group.
5 Click Generate to create a new group key or Import to import an existing keypair
as the group key.
When you click Generate, a new group key will be created using the current
default settings for a group key.
When you click Import, the Import Key page appears. Select a key file or paste a
key block, enter the passphrase of the private key, then click Import.
6 Click Save to add the key to the group.
Caution: A group can only have one active group key. If you add a group key to a
group that already has a group key assigned, the existing group key will be
overwritten by the group key you are adding.
Creating a New Group with a Group Key
To create a new group with a group key
1 On the Groups page, click Add Group. The Groups Settings: Add Group page
appears.
2 On the General subtab, type in a Group Name and Description.
3 To apply a consumer policy to members of this group, select Apply Consumer
Policy to members of this group, and choose a consumer policy from the
drop-down menu.
4 To add a group key to this group, click Generate to create a new group key or
Import to import an existing keypair as the group key.
When you click Generate, a new group key will be created using the current
default settings for a group key.
Page 99
When you click Import, the Import Key page appears. Select a key file or paste a
key block, enter the passphrase of the private key, then click Import.
5 On the Membership subtab, enable Match Consumers Via Directory
Synchronization.
6 For LDAP Directory, select the appropriate LDAP directory from the drop-down
menu.
7 Select If all of the following apply, then enter "memberOf" without the quotes in
the Attribute field. In the Value field, check Regular Expression, then enter the
Distinguished Name (DN) of the appropriate Active Directory security group.
8 Click Save to create the group.
Note: To quickly create a new group from an Active Directory security group with an
automatically generated group key, go to Keys > Managed Keys, click on the
Generate AD Group Keys button, and follow the on-screen instructions.
Removing a Group Key from a Group
Removing a Group Key from a Group
83 Managing Group Keys
To remove a group key from a group
1 Go to the Consumers > Groups page. The Keys column shows a keypair icon for
those groups that already have a group key assigned.
2 Click on the name of the group from which you want to delete the group key.
3 In the Keys row, click View.
4 In the Key ID column, click on the key ID of the group key you want to delete.
5 Click Delete.
6 When the confirmation dialog appears, click OK.
7 To confirm that the group key was deleted from the group, go to the Consumers >
Groups page. The Keys column will no longer show a keypair icon for the group
from which you deleted the group key.
Deleting a Group Key
To delete a group key
1 Go to Keys > Managed Keys. In the listing of managed keys, group keys have their
own icon and their names have "(Group)" without the quotes appended to the end
of their name.
2 Click on the key ID of the group key you wish to delete.
3 On the information screen for the group key, click Delete.
4 When the confirmation dialog appears, click OK.
Page 100

84 Managing Group Keys
Revoking a Group Key
Caution: Do not delete a group key that is currently assigned to a group unless you
are adding a new group key to the group.
Revoking a Group Key
To revoke a group key
1 Go to Keys > Managed Keys. In the listing of managed keys, group keys have their
own icon and their names have "(Group)" without the quotes appended to the end
of their name.
2 In the Actions column of the group key you wish to revoke, click the Revoke icon.
3 When the confirmation dialog appears, click OK.
Caution: Do not revoke a group key that is currently assigned to a group unless you
are adding a new group key to the group.
Exporting a Group Key
To export a group key
1 Go to Keys > Managed Keys. In the listing of managed keys, group keys have their
own icon and their names have "(Group)" without the quotes appended to the end
of their name.
2 In the Actions column of the group key you wish to export, click the Export icon.
3 On the Export Key dialog, choose to export just the public key or the entire
keypair. Enter a passphrase and confirm it if you wish to protect the keypair file.
Click Export.
4 Save the file to your local system.
 Loading...
Loading...