Page 1

Administrator Guide
PGP Endpoint 4.4 SR1
02_108P 4.4 SR1 Administrator Guide
Page 2

- 2 -
Page 3

Notices
Version Information
PGP Endpoint Administrator Guide - PGP Endpoint Version 4.4 SR1 - Released: August 2009
Document Number: 02_108P_4.4 SR1_092322120
Copyright Information
Copyright© 1991-2009 by PGP Corporation. All Rights Reserved. No part of this document can be
reproduced or transmitted in any form or by any means, electronic or mechanical, for any purpose, without
the express written permission of PGP Corporation.
Trademark Information
PGP, Pretty Good Privacy, and the PGP logo are registered trademarks of PGP Corporation in the
US and other countries. IDEA is a trademark of Ascom Tech AG. Windows and ActiveX are registered
trademarks of Microsoft Corporation. AOL is a registered trademark, and AOL Instant Messenger is a
trademark, of America Online, Inc. Red Hat and Red Hat Linux are trademarks or registered trademarks
of Red Hat, Inc. Linux is a registered trademark of Linus Torvalds. Solaris is a trademark or registered
trademark of Sun Microsystems, Inc. AIX is a trademark or registered trademark of International Business
Machines Corporation. HP-UX is a trademark or registered trademark of Hewlett-Packard Company. SSH
and Secure Shell are trademarks of SSH Communications Security, Inc. Rendezvous and Mac OS X
are trademarks or registered trademarks of Apple Computer, Inc. All other registered and unregistered
trademarks in this document are the sole property of their respective owners.
Licensing and Patent Information
The IDEA cryptographic cipher described in U.S. patent number 5,214,703 is licensed from Ascom Tech
AG. The CAST-128 encryption algorithm, implemented from RFC 2144, is available worldwide on a royaltyfree basis for commercial and non-commercial uses. PGP Corporation has secured a license to the patent
rights contained in the patent application Serial Number 10/655,563 by The Regents of the University of
California, entitled Block Cipher Mode of Operation for Constructing a Wide-blocksize block Cipher from a
Conventional Block Cipher. Some third-party software included in PGP Universal Server is licensed under
the GNU General Public License (GPL). PGP Universal Server as a whole is not licensed under the GPL.
If you would like a copy of the source code for the GPL software included in PGP Universal Server, contact
PGP Support (http://www.pgp.com/support). PGP Corporation may have patents and/or pending patent
applications covering subject matter in this software or its documentation; the furnishing of this software or
documentation does not give you any license to these patents.
Acknowledgements
This product includes or may include:
• The Zip and ZLib compression code, created by Mark Adler and Jean-Loup Gailly, is used with
permission from the free Info-ZIP implementation, developed by zlib (http://www.zlib.net). • Libxml2,
the XML C parser and toolkit developed for the Gnome project and distributed and copyrighted under
the MIT License found at http://www.opensource.org/licenses/mit-license.html. Copyright © 2007 by
the Open Source Initiative. • bzip2 1.0, a freely available high-quality data compressor, is copyrighted
by Julian Seward, © 1996-2005. • Application server (http://jakarta.apache.org/), web server (http://
- 3 -
Page 4

PGP Endpoint
www.apache.org/), Jakarta Commons (http://jakarta.apache.org/commons/license.html) and log4j, a
Java-based library used to parse HTML, developed by the Apache Software Foundation. The license
is at www.apache.org/licenses/LICENSE-2.0.txt. • Castor, an open-source, databinding framework for
moving data from XML to Java programming language objects and from Java to databases, is released
by the ExoLab Group under an Apache 2.0-style license, available at http://www.castor.org/license.html.
• Xalan, an open-source software library from the Apache Software Foundation that implements the
XSLT XML transformation language and the XPath XML query language, is released under the Apache
Software License, version 1.1, available at http://xml.apache.org/xalan-j/#license1.1. • Apache Axis is
an implementation of the SOAP (“Simple Object Access Protocol”) used for communications between
various PGP products is provided under the Apache license found at http://www.apache.org/licenses/
LICENSE-2.0.txt. • mx4j, an open-source implementation of the Java Management Extensions (JMX),
is released under an Apache-style license, available at http://mx4j.sourceforge.net/docs/ch01s06.html.
• jpeglib version 6a is based in part on the work of the Independent JPEG Group. (http://www.ijg.org/)
• libxslt the XSLT C library developed for the GNOME project and used for XML transformations is
distributed under the MIT License http://www.opensource.org/licenses/mit-license.html. • PCRE version
4.5 Perl regular expression compiler, copyrighted and distributed by University of Cambridge. ©1997-2006.
The license agreement is at http://www.pcre.org/license.txt. • BIND Balanced Binary Tree Library and
Domain Name System (DNS) protocols developed and copyrighted by Internet Systems Consortium,
Inc. (http://www.isc.org) • Free BSD implementation of daemon developed by The FreeBSD Project, ©
1994-2006. • Simple Network Management Protocol Library developed and copyrighted by Carnegie
Mellon University © 1989, 1991, 1992, Networks Associates Technology, Inc, © 2001- 2003, Cambridge
Broadband Ltd.© 2001- 2003, Sun Microsystems, Inc., © 2003, Sparta, Inc, © 2003-2006, Cisco, Inc and
Information Network Center of Beijing University of Posts and Telecommunications, © 2004. The license
agreement for these is at http://net-snmp.sourceforge.net/about/license.html. • NTP version 4.2 developed
by Network Time Protocol and copyrighted to various contributors. • Lightweight Directory Access Protocol
developed and copyrighted by OpenLDAP Foundation. OpenLDAP is an open-source implementation of
the Lightweight Directory Access Protocol (LDAP). Copyright © 1999-2003, The OpenLDAP Foundation.
The license agreement is at http://www.openldap.org/software/release/license.html. • Secure shell
OpenSSH version 4.2.1 developed by OpenBSD project is released by the OpenBSD Project under
a BSD-style license, available at http://www.openbsd.org/cgibin/cvsweb/src/usr.bin/ssh/LICENCE?
rev=HEAD. • PC/SC Lite is a free implementation of PC/SC, a specification for SmartCard integration is
released under the BSD license. • Postfix, an open source mail transfer agent (MTA), is released under
the IBM Public License 1.0, available at http://www.opensource.org/licenses/ibmpl.php. • PostgreSQL,
a free software object-relational database management system, is released under a BSD-style license,
available at http://www.postgresql.org/about/licence. • PostgreSQL JDBC driver, a free Java program
used to connect to a PostgreSQL database using standard, database independent Java code, (c)
1997-2005, PostgreSQL Global Development Group, is released under a BSD-style license, available
at http://jdbc.postgresql.org/license.html. • PostgreSQL Regular Expression Library, a free software
object-relational database management system, is released under a BSD-style license, available at
http://www.postgresql.org/about/licence. • 21.vixie-cron is the Vixie version of cron, a standard UNIX
daemon that runs specified programs at scheduled times. Copyright © 1993, 1994 by Paul Vixie; used
by permission. • JacORB, a Java object used to facilitate communication between processes written in
Java and the data layer, is open source licensed under the GNU Library General Public License (LGPL)
available at http://www.jacorb.org/lgpl.html. Copyright © 2006 The JacORB Project. • TAO (The ACE
ORB) is an open-source implementation of a CORBA Object Request Broker (ORB), and is used for
communication between processes written in C/C++ and the data layer. Copyright (c) 1993-2006 by
Douglas C. Schmidt and his research group at Washington University, University of California, Irvine, and
Vanderbilt University. The open source software license is available at http://www.cs.wustl.edu/~schmidt/
ACEcopying. html. • libcURL, a library for downloading files via common network services, is open source
- 4 -
Page 5

software provided under a MIT/X derivate license available at http://curl.haxx.se/docs/copyright.html.
Copyright (c) 1996 - 2007, Daniel Stenberg. • libuuid, a library used to generate unique identifiers, is
released under a BSD-style license, available at http://thunk.org/hg/e2fsprogs/?file/fe55db3e508c/lib/uuid/
COPYING. Copyright (C) 1996, 1997 Theodore Ts’o. • libpopt, a library that parses command line options,
is released under the terms of the GNU Free Documentation License available at http://directory.fsf.org/
libs/COPYING.DOC. Copyright © 2000-2003 Free Software Foundation, Inc. • gSOAP, a development
tool for Windows clients to communicate with the Intel Corporation AMT chipset on a motherboard, is
distributed under the GNU Public License, available at http://www.cs.fsu.edu/~engelen/soaplicense.html.
• Windows Template Library (WRT) is used for developing user interface components and is distributed
under the Common Public License v1.0 found at http://opensource.org/licenses/cpl1.0.php. • The Perl Kit
provides several independent utilities used to automate a variety of maintenance functions and is provided
under the Perl Artistic License, found at http://www.perl.com/pub/a/language/misc/Artistic.html.
Export Information
Export of this software and documentation may be subject to compliance with the rules and regulations
promulgated from time to time by the Bureau of Export Administration, United States Department of
Commerce, which restricts the export and re-export of certain products and technical data.
Limitations
The software provided with this documentation is licensed to you for your individual use under the terms of
the End User License Agreement provided with the software. The information in this document is subject
to change without notice. PGP Corporation does not warrant that the information meets your requirements
or that the information is free of errors. The information may include technical inaccuracies or typographical
errors. Changes may be made to the information and incorporated in new editions of this document, if and
when made available by PGP Corporation.
Notices
- 5 -
Page 6

PGP Endpoint
- 6 -
Page 7

Table of Contents
Preface: About This Document................................................................11
Typographical Conventions.......................................................................................... 11
Getting Assistance........................................................................................................11
Chapter 1: PGP Endpoint System Architecture..................................... 13
About Application Control and Device Control Architecture.........................................13
The Database............................................................................................................... 15
The Administration Server............................................................................................15
The Management Server Console............................................................................... 16
The Client..................................................................................................................... 17
Chapter 2: Understanding Cryptography................................................21
About Encryption...........................................................................................................21
Advanced Encryption Standard....................................................................................22
RSA Encryption.............................................................................................................23
Chapter 3: Device Control Encryption Methodology............................. 25
Encrypting Removable Storage Devices......................................................................25
Easy Exchange Encryption................................................................................... 26
Encrypting Media...................................................................................................26
Centralized Encryption...........................................................................................29
Decentralized Encryption.......................................................................................29
Chapter 4: Application Control Methodology.........................................31
About File, Macro, and Script Execution Control.........................................................32
Identifying DLL Dependencies......................................................................................32
Maintaining Application Control....................................................................................33
Operating System Updates and Patches..............................................................33
Frequently Changing Software Use...................................................................... 33
Software Updates..................................................................................................34
New Software Installations....................................................................................34
- 7 -
Page 8

Table of Contents
Chapter 5: Understanding Administration Server-Client Communications37
Chapter 6: Deploying the Client...............................................................45
Macros and Other Changing Files........................................................................ 34
Deleting Local Authorization Files.........................................................................35
About Administration Server-Client Communications...................................................37
Administration Server Communications................................................................ 38
Changing Licenses for the Administration Server.................................................39
Changing the SysLog Server................................................................................39
About Administration Server-Client Communication Encryption...................................40
Digital Signatures and Certificate Authorities (CA)............................................... 40
Digital Signatures...................................................................................................40
About Administration Server-Client Proxy Communications.........................................41
Configuring Administration Server-Client Proxy Communication.......................... 42
About PGP Endpoint Client Deployment......................................................................45
Deploying the Client with a Ghost Image.....................................................................46
Deploying the Client with Windows Group Policy........................................................47
Deploying the Client with Other Tools..........................................................................48
Chapter 7: Controlling Administrative Rights........................................ 51
About PGP Endpoint Access Control Rights................................................................51
Defining User Access...................................................................................................52
Using the Access Control Visual Basic Script..............................................................53
Chapter 8: Using File Tools..................................................................... 57
About File Tools............................................................................................................57
Using the PGP Endpoint Authorization Service Tool...................................................57
Using the PGP Endpoint Application Control File Tool................................................61
Using the SXDomain Tool............................................................................................64
Chapter 9: Managing Registry Keys........................................................67
Database Connection Loss Registry Key.....................................................................67
Authorization Service Registry Key..............................................................................68
Debugging Registry Key...............................................................................................69
- 8 -
Page 9

Table of Contents
General Registry Keys................................................................................................ 70
Security Registry Keys................................................................................................. 71
Configure MaxSockets...........................................................................................73
Configuring MaxSockets and TLSMaxSockets.....................................................74
Command & Control Registry Key............................................................................... 74
Client Kernel Registry Key........................................................................................... 75
Software Registry Key..................................................................................................76
Administration Server Registry Key..............................................................................77
Authorization Wizard Registry Key...............................................................................77
- 9 -
Page 10

Table of Contents
- 10 -
Page 11

Preface
About This Document
This Administrator Guide is a resource written for all users of PGP Endpoint 4.4 SR1. This
document defines the concepts and procedures for installing, configuring, implementing, and
using PGP Endpoint 4.4 SR1.
Tip:
PGP documentation is updated on a regular basis. To acquire the latest version of this or
any other published document, please refer to the PGP Support Portal Web Site (https://
support.pgp.com).
Typographical Conventions
The following conventions are used throughout this documentation to help you identify various
information types.
Convention Usage
bold Buttons, menu items, window and screen objects.
bold italics Wizard names, window names, and page names.
italics New terms, options, and variables.
UPPERCASE SQL Commands and keyboard keys.
monospace File names, path names, programs, executables, command
syntax, and property names.
Getting Assistance
Getting Product Information
Unless otherwise noted, the product documentation is provided as Adobe Acrobat PDF files
that are installed with PGP Endpoint. Online help is available within the PGP Endpoint product.
Release notes are also available, which may have last-minute information not found in the
product documentation.
- 11 -
Page 12

Preface
Contacting Technical Support
• To learn about PGP support options and how to contact PGP Technical Support, please visit
the PGP Corporation Support Home Page (http://www.pgp.com/support).
• To access the PGP Support Knowledge Base or request PGP Technical Support, please visit
PGP Support Portal Web Site (https://support.pgp.com).
Note:
You may access portions of the PGP Support Knowledge Base without a support agreement;
however, you must have a valid support agreement to request Technical Support.
• For any other contacts at PGP Corporation, please visit the PGP Contacts Page (http://
www.pgp.com/company/contact/index.html).
• For general information about PGP Corporation, please visit the PGP Web Site (http://
www.pgp.com).
• To access the PGP Support forums, please visit PGP Support (http://
forums.pgpsupport.com). These are user community support forums hosted by PGP
Corporation.
- 12 -
Page 13
Chapter
1
PGP Endpoint System Architecture
In this chapter:
• About Application Control
and Device Control
Architecture
• The Database
• The Administration Server
• The Management Server
Console
• The Client
Application Control and Device Control architecture is a
3-tier structure composed of an Administration Server,
database, and one or more clients. A Management Server
Console provides the administrative interface between the
system administrator and Administration Server.
About Application Control and Device Control Architecture
PGP Endpoint architecture is a multi-tier system composed of a database, an Administration
Server, and a client.
The three primary components that form the basis of PGP Endpoint system architecture interact
as follows. The Administration Server component runs as a service that:
• Keeps track of the connected clients and their status.
• Coordinates data flow between the Administration Server(s) and the SQL database.
The database component serves as the central repository of the authorization and permission
policies. The client component stores file authorization and device permission policies locally,
and controls user access from the endpoint to software applications and all connected devices.
To change authorization and permission policies, an administrator uses a Management Server
Console to interface with the Administration Server(s), which then communicate with the
database and the client(s).
PGP Endpoint system architecture is scalable to meet the needs of any enterprise. You can use
multiple Administration Server(s) and clients.
- 13 -
Page 14
PGP Endpoint
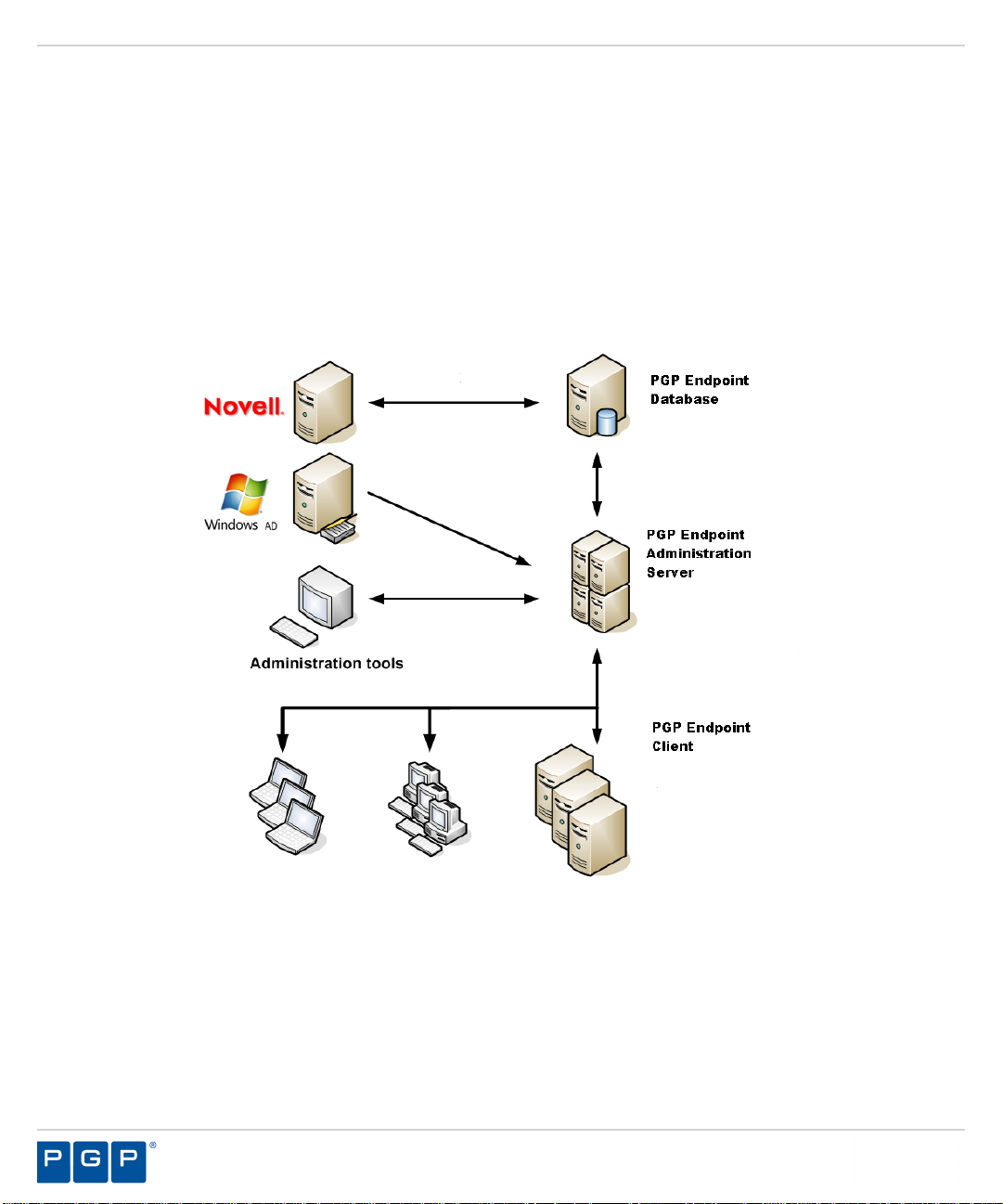
The Application Control and Device Control architecture components are:
• The database which serves as the central repository of authorization information for devices
and applications.
• One or more Administration Servers that communicate between the database, the protected
clients, and the Management Server Console.
• The client (installed on each computer, endpoint or server that you want to protect).
• The Management Server Console, which provides the administrative user interface for the
Administration Server.
The following figure illustrates the relationships between the components.
Figure 1: Application and Device Control Architecture
- 14 -
Page 15

PGP Endpoint System Architecture
The Database
The database serves as the central repository of software and device permission data.
Administrator and user access logs are also stored in the database.
The database uses one of the following Microsoft® SQL® Server products:
• Microsoft SQL Server 2005
• Microsoft SQL Server 2008
• Microsoft SQL Server 2005 Express
• Microsoft SQL Server 2008 Express
For evaluations and test environments Microsoft SQL Server 2005 Express and Microsoft SQL
Server 2005 Express are sufficient. Enterprise implementation must use the Microsoft SQL
Server 2005 or 2008 edition.
The Administration Server
The Administration Server runs as a Windows® service that coordinates and tracks data flow
between Administration Server(s), connected clients, and the SQL® database.
The Administration Server service runs under any domain account capable of reading domain
users, user groups, and computer accounts from the domain controller. The Administration
Server performs the following functions:
• Retrieves user access and device permission policies from the database which are stored in
the Administration Server cache.
• Signs and/or encrypts the user access and/or device permission list, compresses the list,
and communicates updated user access and/or device permission lists to client servers and
computers, where the permission policies are stored locally. Permission policy updates only
communicate changes to the existing user access and device permission policies, rather
than retransmitting entire policies.
• Saves a log of administrator actions and, optionally, users actions including information about
when application or device access is denied.
Each PGP Endpoint product installation requires at least one Administration Server and a
corresponding DataFileDirectory (DFD). The DFD can reside on the same computer or a shared
network resource, to store log information. All servers can write to a shared DataFileDirectory or
to a different directory for each Administration Server, depending upon the unique architecture
of your network environment.
Up to three Administration Servers can be defined during client installation. Additional servers
can be assigned by:
• Changing the Server Address default option in the Management Server Console Tools
menu, as outlined in the Application Control User Guide or Device Control User Guide
(https://support.pgp.com).
• Modifying the Server parameter for the Command & Control Registry Key on page 74
- 15 -
Page 16

PGP Endpoint
The Administration Server sends user access and device permission changes to users when:
• A user logs in.
• An administrator sends updated information to all computers, specific computers, or export
changes to a file.
• A user requests updated information from a client computer.
An administrator uses the Management Server Console to interact with Administration Server.
The Management Server Console
The Management Server Console is the administrative interface for the Administration Server.
This product component is used to configure Application Control and Device Control.
You can install the console on one or more computers, including the database or Administration
Server hosts.
The Management Server Console does not connect directly to the database. All communication
with the database is conducted via the Administration Server(s). The Management Server
Console and Administration Server use Remote Procedure Call (RPC) protocol authenticate
encrypted communications.
You use the console to:
• Define administrator roles.
• Monitor system administrator and user activity logs and options.
• Define default settings for administrative tools.
• Generate standard or custom reports.
When you are using Device Control, you can:
• Manage access to removable storage devices.
• Authorize user access to specific CD/DVD media for use with CD/DVD drives.
• Encrypt removable media and devices.
• View lists of files and data transferred using authorized media.
• View the content of files transferred using authorized removable storage devices.
• View information about user attempts to access or connect unauthorized removable storage
devices.
When you are using Application Control, you can:
• Build and manage centrally authorized lists of executable files, scripts, and macros.
• Organize authorized application software files into logical file groups.
• Assign file groups to users and user groups.
• Manage and maintain the software authorization database.
- 16 -
Page 17

PGP Endpoint System Architecture
The Client
The client is installed on each client computer to enforce file authorization and device
permissions policies.
You can install the client on the same computer as the Management Server Console when
you are using Device Control. Each protected computer can maintain local authorization and
device permission files, so that routine application requests do not have to traverse the network.
Only log files and periodic differential updates are sent from client computers to the using the
Management Server Console.
When a client requests a connection to the Administration Server listed by DNS name, the
name is resolved and the first IP address returned is selected, as required by round-robin DNS
conventions for a server-client connection attempt. This behavior is controlled by the FirstServer
registry key.
If the connection attempt fails, the client selects the next server name from the list and repeats
the process. After reaching the end of the list and no server-client connection is established,
the client uses the locally cached user access and device permission list. The first connected
server receives client logs and shadow files in a compressed format that is stored in the
DataFileDirectory (DFD) defined during installation.
When you are using Device Control, the client:
• Ensures that only removable storage devices and media that the user is authorized for can
be accessed. Any attempt to access unauthorized devices or media is denied, regardless of
the computer the user logs into.
When you are using Application Control, the client performs the following:
• Calculates the digital signature, or hash, for files requiring authorization.
• Checks the digital signature against the locally stored authorization list for a matching digital
signature.
• Denies and logs any user attempts to run unauthorized files.
• Allows, when expressly permitted, a user to locally authorize a denied file.
• Generates log records of all application access attempts, approved and denied. The Log
Access Denied option is enabled by default.
- 17 -
Page 18
PGP Endpoint
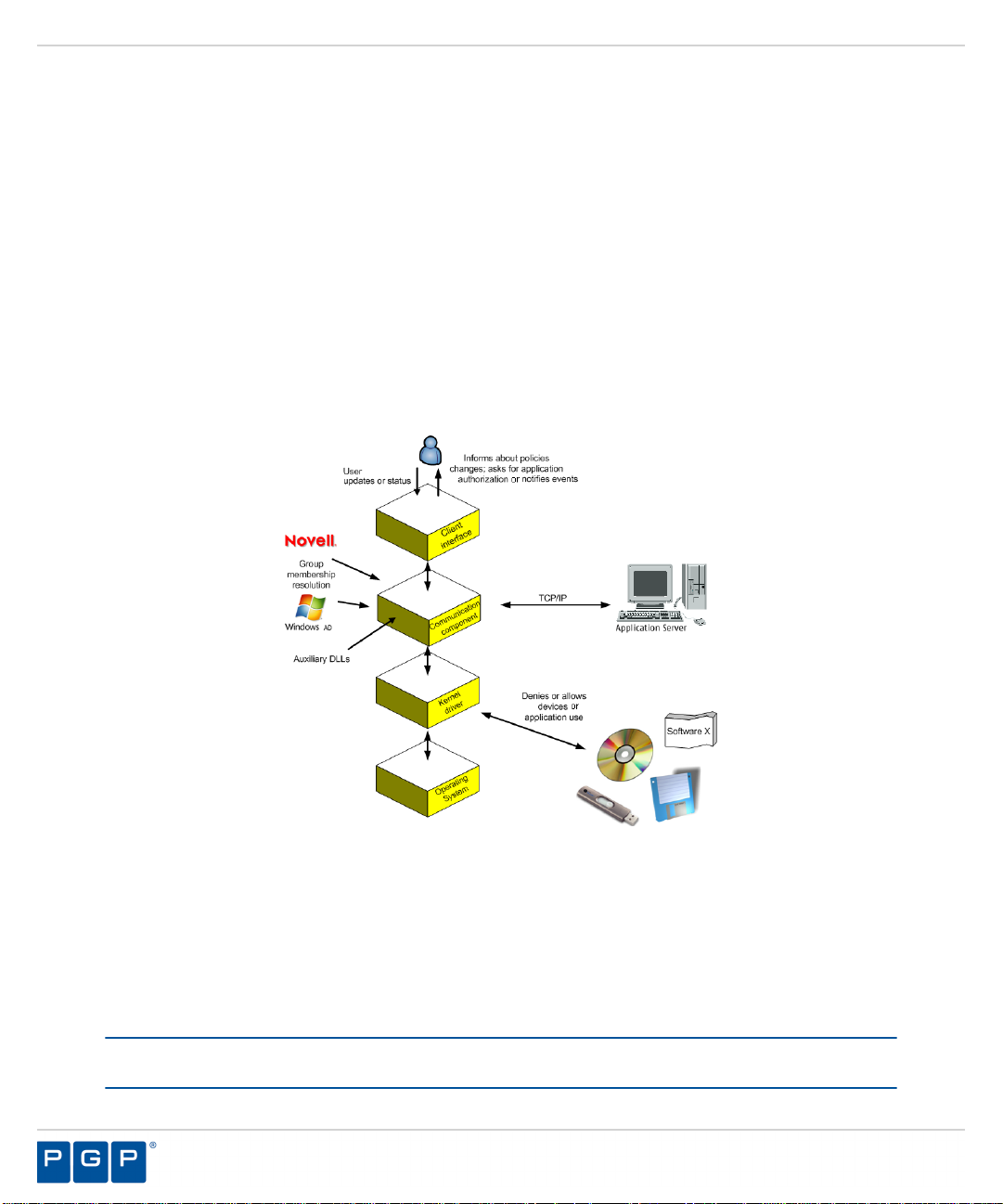
The client is composed of the following components:
• Kernel driver (Sk.sys), that runs on supported operating systems to enforce defined policies
for determining which applications and/or devices users can access.
• Communication service (scomc.exe), which provides communication with the Administration
Server(s). This component, PGP Endpoint Command & Control (SCC), runs as a service,
that sends log data to the Administration Server that can be viewed via the Management
Server Console.
• User interface (RtNotify), which informs the user of updated policy changes completed by
the administrator (these messages can be deactivated). RtNotify is used by the client to
retrieve user certificates on demand.
• Auxiliary dynamically linked library (DLL) files, which provide additional features to the
core components. These files contain support for RtNotify localization information, 16-bit
application control, and macro and script protection.
The following illustrates the relationships between the client component layers.
Figure 2: Client Component Layers
After the client is installed, RTNotify appears as an icon in the system tray. Through RTNotify
the user receives information about permission changes via pop-up messages. End-users can
interact with the client to:
• Locally authorize software application files
• Manage user access to removable storage devices
• Update permissions changes when the client receives event notifications
.
Important: A user cannot change any Application Control or Device Control administrative
settings or permissions.
- 18 -
Page 19

PGP Endpoint System Architecture
The administrator can query the client to obtain the salt value used for endpoint maintenance,
when the computer is not connected to the network and this value cannot be obtained using the
Management Server Console.
When an Administration Server is unavailable at login, the client uses the locally cached
permission list from the last successful Administration Server connection. If no permission list
exists, the client denies user access to all device and application requests. Permissions lists
can be imported to a computer, as necessary, when no server connection is available or the
computer is disconnected from the network.
A key security principle of Application Control or Device Control is that, even when the
communication service or user interface is disabled, the kernel driver always protects the
client computer. Protection remains in force and the least privilege principle applies. This
principle denies user access to applications or devices that are not expressly permitted. Client
components use client hardening functionality as described in the Application Control User
Guide (https://support.pgp.com) to protect against user tampering.
- 19 -
Page 20

PGP Endpoint
- 20 -
Page 21
Chapter
2
Understanding Cryptography
In this chapter:
• About Encryption
• Advanced Encryption
Standard
• RSA Encryption
Encryption transforms a plain text message using an
algorithm, or cipher, into a coded message called ciphertext.
Only designated users possessing special knowledge,
usually referred to as a key, can access the data.
Cryptography involves two processes:
• Encryption
• Decryption
Encryption can be used to protect computer data, such
as files on computers and removable storage devices.
The purpose of encryption is to prevent third parties from
accessing the sensitive information. This is particularly
important for sensitive data. Encrypting such data helps
protect it, should physical security measures fail.
Decryption is the process of decoding data that is encrypted
using a secret key or password. If the password is not
correct, it will be impossible to get the encryption key and
subsequently decrypt the encoded information.
About Encryption
The Application Control and Device Control applications use two encryption algorithms to secure
data in transit and data at rest.
The encryption algorithms used are:
• Advanced Encryption Standard (AES) 256-bit encryption
• RSA (for Rivest, Shamir, and Adleman)
- 21 -
Page 22

PGP Endpoint
Using these algorithms Application Control and Device Control accomplish the primary criteria
used measure the effectiveness of a cryptographic method:
• Confidentiality (privacy), only an authorized recipient can extract the original data from the
encrypted message.
• Integrity, a recipient can determine whether the data was altered during the transmission.
• Authentication, a recipient can unmistakably identify the sender and verify who actually sent
the data.
• Non-repudiation, a sender cannot deny sending the data.
Advanced Encryption Standard
Device Control uses the Advanced Encryption Standard (AES) 256-bit encryption standard,
which provides a powerful, unbreakable encryption method to ensure data is always protected.
AES is based on a design principle known as a substitution permutation network and has a fixed
block size of 128 bits and a key size of 128, 192, or 256 bits. The AES cipher is specified as
a number of repetitions of transformation rounds that convert the input plain text into the final
output of cipher text.
Assuming one byte equals 8 bits, the fixed block size of 128 bits is 128 ÷ 8 = 16 bytes. AES
operates on a 4×4 array of bytes, termed the state. Each turn generates a new state from the
previous state. The final state after all rounds contains the ciphered text.
Each round consists of several processing steps, including one that depends on the encryption
key. A set of reverse rounds is applied to transform cipher text back into the original plain text
using the same encryption key. PGP works with a 256-bit block. In this case, the algorithm uses
8x6 matrices as states and sub keys. The 256-bit algorithm executes 14 rounds.
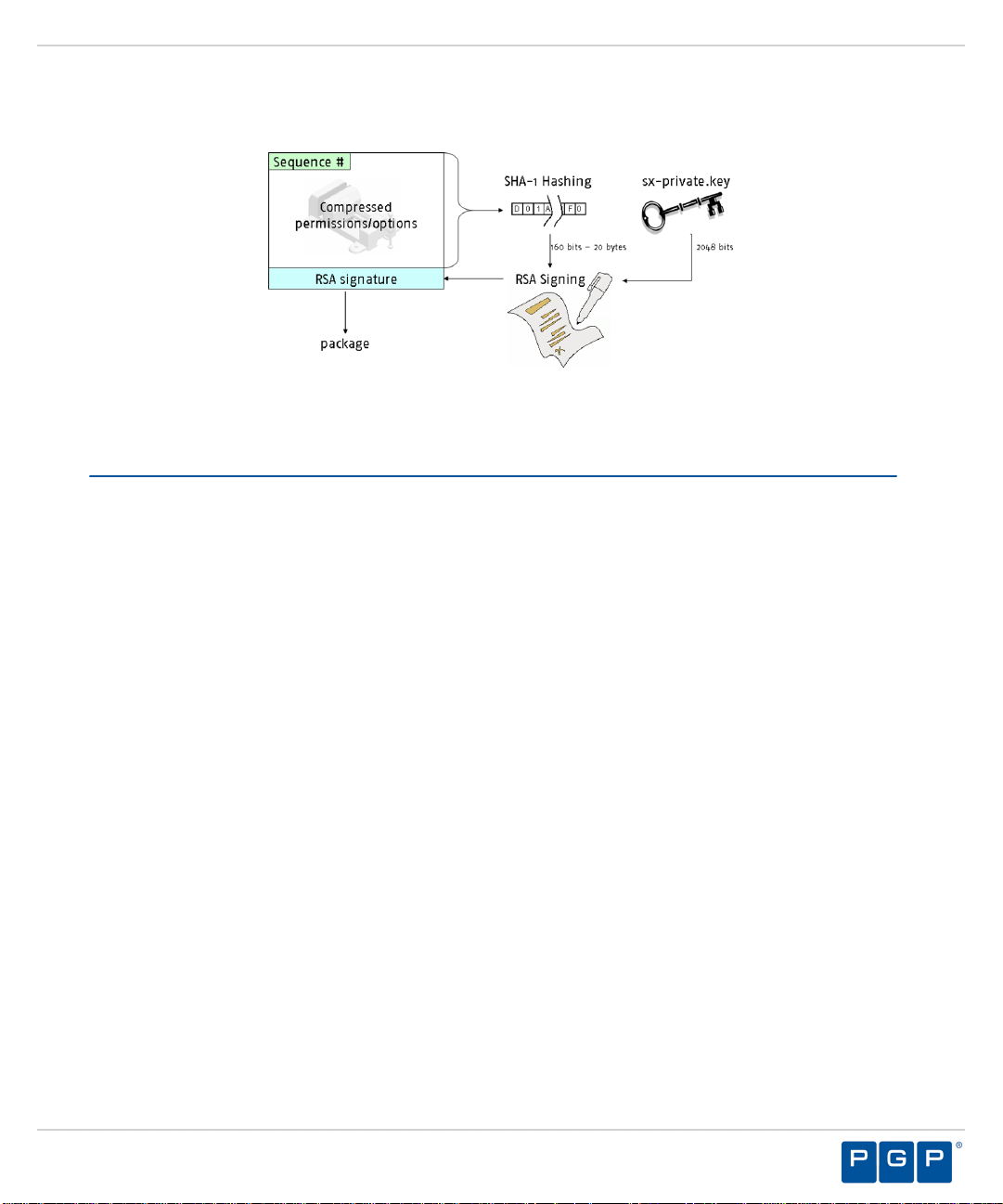
To ensure that the symmetric AES key is not visible when stored in the database, and cannot be
read by anyone who has access to the database, Device Control uses public-private key pairbased encryption to encode a symmetric encryption key. This algorithm uses the same key for
encryption and decryption.
The Administration Server and kernel clients contain a default embedded encryption key
pair that is only used for software evaluation purposes. You create your own key pair before
deploying the client in your environment using the Key Pair Generator tool. If a higher level
of protection is required, PGP strongly recommends storing the private key external to the
- 22 -
Page 23
Understanding Cryptography
Administration Server. Only the public key should be available to the clients. The private key
should only be available to the Administration Server, internally or externally.
Figure 3: Device Control Key Encryption
RSA Encryption
In cryptography, RSA (named after its developers, Rivest, Shamir, and Adelman) is an algorithm
for public-key cryptography. It is an algorithm known to be suitable for signing messages, as well
as encryption. RSA is believed to be secure given sufficiently long keys.
RSA involves a public key and a private key. The public key can be known to everyone and is
used for encrypting messages. Messages encrypted with the public key can only be decrypted
using the private key.
The RSA algorithm bases its security on the difficulty of factoring large prime numbers. RSA
keys are typically 1024–2048 bits long. In cryptography, key size or key length is the size,
usually measured in bits or bytes, of the key used in a cryptographic algorithm. PGP Endpoint
uses the RSA algorithm with a key size of 2048 bits, making it very difficult to compromise. It is
extremely important to use a strong random number generator for the symmetric key, otherwise
an eavesdropper wanting to see a message could bypass RSA by guessing the symmetric key.
- 23 -
Page 24

PGP Endpoint
- 24 -
Page 25

Chapter
3
Device Control Encryption Methodology
In this chapter:
• Encrypting Removable
Storage Devices
Device Control supports several encryption methods
depending upon the needs of users and the policies
established for your enterprise network. Each method uses
the Advanced Encryption Standard (AES) 256-bit encryption
standard. Device Control encryption can be performed
centrally, by a network administrator using the Management
Server Console, or decentrally, by a user with permitted
access using the client.
Encrypting Removable Storage Devices
Device Control creates encrypted files in virtual memory, and then writes the files to physical
media available in various formats, such as removable storage devices and CD/DVDs.
Centralized and decentralized encryption provide an administrator with the flexibility to centrally
encrypt removable media, enable users to encrypt removable media using the client, and
enforce the use of encrypted media.
Device Control supports centralized (from the Management Server Console) and decentralized
(from the client) encryption methods for ciphering data copied to removable storage media. The
following methods are available for encrypting removable storage devices and CD/DVD media
using:
• Easy Exchange encryption, which encrypts devices for portable use. Portable use means
that a user can use the encrypted device with a password and the encryption key, without
having to connect to the network through a computer running the client.
• Full and slow encryption, which encrypts devices for non-portable use. Non-portable use
means that a user can only use the encrypted device with a password when connected to the
network through a computer running the client.
- 25 -
Page 26

PGP Endpoint
Easy Exchange Encryption
Easy Exchange encryption is volume-based. The entire volume of the removable storage media
is used for ciphering existing data and all sectors on the volume and installing the Secure
Volume Browser (SVolBro.exe) deciphering program.
Devices encrypted using the Easy Exchange method do not require a password or encryption
key when attached to a computer running the client. These encrypted devices are transparently
deciphered when users attach the device to a computer running the client, and there is a
Microsoft® Certificate Authority (CA) available from the network for authentication.
Important: When there is no Microsoft Enterprise CA installed in the network, users can only
access encrypted data using a password and a public encryption key.
When a user is working outside your network, they must use the installed Secure Volume
Browser to access encrypted data. The Secure Volume Browser does not require local
administrative rights, however a password and a public encryption key are required. The Secure
Volume Browser program is automatically copied on to the media when it is encrypted.
The administrator also has an option during encryption to export the public key to the media or
to an external file, depending on enterprise network security policies and procedures.
Important: If the encryption key is not exported to the encrypted media, then an administrator
must send the key in a separate file to the user before the decryption process can start.
The Easy Exchange encryption method is used for centralized and decentralized encryption
because this method uses the Secure Volume Browser to unlock the medium for user access.
Encrypting Media
Encrypting media from the client uses the Encrypt Medium dialog. The rules governing the
behavior of the encryption options depend upon the Export permissions assigned by the
administrator for user access.
Encryption from the client offers both Easy Exchange (portable) and Extended Capacity
Encryption (non-portable) options. You can also centralize medium encryption with out using
- 26 -
Page 27

Device Control Encryption Methodology
the Management Server Console. All of these options offer control over exporting the medium
encryption key.
Figure 4: Encrypt Medium Dialog
Standard User Options Rules
The default behavior for the Encrypt Medium dialog options are governed by the following
rules.
• When a user selects Easy Exchange, the Erase unused space on media option is enabled
and selected by default. A user may choose to deselect this option.
• When a user selects Extended Capacity, the PGP user and Windows user options are
disabled when selecting Add to add users, user can only have one passphrase.
• When a user selects Extended Capacity, the Erase unused space and Retain existing
data on device options are enabled and selected by default, unless Erase unused space
on media is forced by the administrator through the Management Server Console. When
selecting an options, the remaining option is deselected.
• When a user selects Retain existing data on device is selected, the erase unused space
on media is deselected regardless of the option set by the administrator in the Management
Server Console.
• When a user has Export permission, Central Encryption enabled and deselected by
default.
• When a user selects Central Encryption, the current user is automatically added to the
users list as centralized user.
• When a user deselects Central Encryption, the centralized user is automatically removed
from the list of users granted access to the media.
• When a user does not have Export permission, the Add and Remove controls are disabled.
• When a user has Export permission, the Add and Remove controls are enabled; however,
the Remove control remains disabled until a user is selected.
• A user may remove a multiple users from the list using SHIFT or CTRL.
- 27 -
Page 28

PGP Endpoint
For the list of users granted access:
• When a user does not have valid certificate, the user name is displayed in red and disabled.
• When a user is added, its domain and account name are displayed to distinguish between
users having similar names in different contexts.
• When a user selects Extended Capacity the user can add only one passphrase user.
When a user selects Easy Exchange:
• User can add any number of Passphrase users.
• User can add any number of Windows users.
• User can add any number of PGP users.
When a user selects Extended Capacity:
• A user may add one Passphrase user.
• A user may not add certain Windows users.
• A user may not add certain PGP users.
The Encrypt option remains disabled until the valid user is added to list of users granted
access.
Advanced Options Rules
The default behavior for the Advanced Options in the Encrypt Medium dialog are governed by
the following rules.
List of users granted access the current user is added by default as a:
• Centralized user when no Export permission is available.
• Windows user when Export permission is available.
Note: The number of user or machine certificates is shown for the Windows user.
• The current user is added by default as a PGP user when Export permission is available.
• The user list is disabled when a user, other than the current user, does not have Export
permission.
Encryption options for Easy Exchange are:
• Enabled when the device size is less than 128GB.
• Disabled when the device size is greater than or equal to 128GB.
Encryption options for Extended Capacity Encryption are:
• Enabled when the device size is 128GB.
• Disabled when the device size is greater than or equal 128GB.
Central encryption options are:
• Disabled when a user does not have Export permission.
• Enabled when a user has Export permission.
- 28 -
Page 29

Device Control Encryption Methodology
Data options are set as follows:
• The Retain existing data on device is not selected and is disabled if no recognized file
system has been found on the media.
Note: When Retain existing data on device option is selected, the erase unused space on
media is disabled regardless of the option set in the Management Server Console.
• The Erase unused space on media option is selected and disabled if this option is set by
the administrator in the Management Server Console.
The Add and Remove controls are:
• Disabled when a user does not have Export permission.
• Enabled when Export permission is available, however, Remove remains disabled until a
user is selected.
Centralized Encryption
Centralized encryption is encryption performed at the Management Server Console by a
network administrator. Centralized encryption offers users that have a Microsoft Enterprise
Certificate Authority installed transparent device use within the network.
A user encrypting a removable storage device, ciphered using centralized encryption does not
perceive that the device is encrypted. Users can freely use their removable storage device with
any computer on the enterprise network, with delegated permission. There is no need for the
user to have the encryption key or know the password. Authentication automatically takes place
in the background, between the client and the certification authority. Even if the user loses the
device, data protection is ensured.
Decentralized Encryption
Decentralized encryption enables a user to perform device encryption at a computer workstation
without requiring network administrator rights. The user is forced to cipher and administer their
removable storage devices, based on user access and device permissions established centrally
by the network administrator.
Decentralized encryption is defined by an administrator using a central rule that establishes
which users have access to removable storage devices, whether a user is forced to encrypt
their removable storage devices, and whether they are allowed to access unencrypted devices.
Depending upon the rule, a user may be able to:
• Read and/or write data to a removable storage device.
• Encrypt a device.
• Format a device.
Users encrypt their devices using the Easy Exchange method, where all existing data is erased
and the remaining storage volume is encrypted. Removable storage devices encrypted using
decentralized encryption can also be used outside the enterprise network, when necessary.
When a user has the necessary permissions formats or modifies an encrypted removable
storage device, the Security Identification (SID) changes. The new SID that is not recognized
- 29 -
Page 30

PGP Endpoint
by the Administration Server because there is no matching record in the database. Therefore,
access to the new device is restricted. This ensures that no data, encrypted or not, can leave
the enterprise network using unauthorized removable storage devices. As an additional security
measure when a removable storage device is used outside the network, an administrator can
choose to export the public key to an external file that can be sent separately to the user,
instead of storing the public key on the removable storage device.
Encryption from the client provides several options:
• Passphrase users can use encrypted media with an encryption key stored on the device at
the time of encryption.
• Passphrase users can use encrypted media with an encryption key accessed from a file that
is stored separately from the media at the time of encryption.
• Windows Active Directory users can use encrypted media with an encryption key protected
by a Certificate Authority.
• PGP key users can use encrypted media with an encryption key protected by a PGP Desktop
keyring password.
- 30 -
Page 31

Chapter
4
Application Control Methodology
In this chapter:
• About File, Macro, and
Script Execution Control
• Identifying DLL
Dependencies
• Maintaining Application
Control
Application Control is an operating system software
application extension that enforces strict control over
which executable files, scripts, and macros can be run.
An administrator initially creates, and then maintains, a
centralized list of authorized applications that users or user
groups are explicitly designated to run. This ensures that
only applications that have been previously identified and
authorized by a network administrator can be run by users.
Any unauthorized software application, known or unknown,
cannot run.
The initial central Application Control authorization list can
be constructed using a combination of tools available in the
Management Server Console including:
• Authorization Wizard
• Scan Explorer templates
• Standard File Definitions
However, there are other types of executable files,
scripts, and macros that have unique Application Control
authorization requirements, including embedded macros,
scripts, and Dynamic-Link Library (DLL) executable files.
- 31 -
Page 32

PGP Endpoint
About File, Macro, and Script Execution Control
You can specify which executable files, scripts, and macros a user is permitted to use.
Application Control recognizes the following types of scripts and macros:
• VBScript (short for Visual Basic Scripting Edition) that runs within a host environment,
including Windows Script Host (WSH) and Internet Explorer (IE) Internet Information
Services (IIS). The script file must have the .vbs file extension to be recognized by
Application Control.
• JScript (short for JavaScript) that runs as a Windows Script engine plugged into any
application that supports Windows Script, such as Internet Explorer, Active Server Pages,
and Windows Script Host. The script file must have the .js file extension to be recognized by
Application Control.
• Visual Basic for Applications (VBA) macros that may be embedded and run from many
Microsoft® Office formats, such as .doc,.dot, .xls, and .ppt files. A hash is created for the
whole file, not just the macro content. VBA is closely related to Visual Basic, but generally
only runs code within a host application rather than as a standalone application.
Identifying DLL Dependencies
Dynamic-Link Libraries (DLLs) are executable software applications that cannot run
independently. These libraries usually have the file extension .dll, .ocx (for libraries containing
ActiveX controls), or .drv (for legacy system drivers). A dependency is the degree to which a
program module depends on another to run. When one program depends on another, both of
them must be installed and authorized to work together.
You must independently identify all DLL dependencies to authorize the DLLs required for your
software applications to work. The Authorization Wizard and Standard File Definitions (SFD)
import tools do not identify software DLL dependencies for authorization. After you identify DLL
- 32 -
Page 33

Application Control Methodology
dependencies, you can identify and assign all required files to the corresponding application file
group.
Danger: You must identify and authorize DLLs separately for Application Control, rather than
scanning for these files with Scan Explorer templates or using the Authorization Wizard,
because malicious software applications can be hidden in DLLs.
DLLs require independent identification because applications automatically load DLL files:
• Listed in an application DLL/EXE import table before loading a software application, to
resolve DLL references.
• Explicitly by the application at run time.
• As dependencies of DLLs that use other DLLs.
Maintaining Application Control
Administrators must perform frequent maintenance tasks for operating system patches and
service packs, software updates, new software installations, and frequently changing software
application uses in any network environment. These tasks also require frequent updates to the
Application Control central file authorization list.
Application Control provides different tools that address:
• Operating System Updates and Patches on page 33
• Frequently Changing Software Use on page 33
• Software Updates on page 34
• New Software Installations on page 34
• Macros and Other Changing Files on page 34
Operating System Updates and Patches
Operating systems are subject to continual updates and upgrades.
Microsoft® provides Windows® Server Update Services (WSUS) for downloading, approving,
and managing the distribution of Windows Operating System (OS) updates for all computers
in your network. You can use the PGP Endpoint Authorization Service tool to monitor and
authorize OS changes and create updates for the central authorization list using Microsoft SUS
or WSUS, thereby minimizing the network administration burden.
Frequently Changing Software Use
Some software applications must be updated daily, such as antivirus, antispam, or antispyware
applications; other applications only receive periodic upgrades or updates. Using the Path
- 33 -
Page 34

PGP Endpoint
Rules feature in the Management Server Console, combined with trusted ownership, you can
allow software updates and modifications of frequently updated applications.
When software application updates are automatically allowed by your network administration
policies, you can create specific path rules for each application that is frequently updated.
Instead of individually authorizing application files using file groups, you can administer file
authorization updates using path rules, if all of the following policies are true:
• You trust the source of the file updates.
• You are confident the update mechanisms can be trusted.
Finally, you can combine the path rules with trusted ownership verification to complete the
Application Control authorization schema.
Software Updates
Periodic or single instance software application updates can modify a few application files or
constitute a completely new installation. The methods for authorizing these types of software
application updates vary, depending upon the source of the update and the computers and
users targeted for the update.
Depending on the type of update and the targeted computers you can:
• Create an application-specific template to assign authorized users and user groups, using
the Scan Explorer.
• Use the Log Explorer to identify the software application and assign users and user groups
to corresponding authorized file groups.
• Use the Authorization Wizard.
New Software Installations
All enterprise network systems routinely deploy new software installations. For planned, known,
and trusted source installations of new application software, the Authorization Wizard is the
most administratively efficient method for authorizing new software application installations.
New software application installations are generally deployed from the following locations:
• Deployment from a central file server repository.
• Using Microsoft Systems Management Server (SMS) packages.
• Directly on a client computer using a CD/DVD source.
Regardless of the new software application deployment method, you can use the Authorization
Wizard to scan, identify, and authorize the new application software executable files.
Macros and Other Changing Files
As an administrator you may be constantly challenged with authorizing files containing
embedded macros. The content of such files may change frequently because any user can edit
the macro content stored in the file.
Macros embedded in files with a previously calculated hash, for example Microsoft Word or
Microsoft Excel files, are unique. These are legal files that are authorized to run. However,
- 34 -
Page 35

Application Control Methodology
after a file is modified and re-saved in the system, the file no longer corresponds with the hash
calculated when the file was initially authorized.
The next time a user attempts to run the modified file, access will be denied because the hash
does not match the hash originally calculated. A good practice is to discourage modifying the
macro content embedded in files and assign these types of files Windows® Read-Only file
permission.
Deleting Local Authorization Files
Local authorization should only be granted to trusted users. Depending upon your security
policies, you may need to periodically delete local user authorization lists.
You can delete locally authorized software applications when:
• An application is locally authorized by numerous users and merits control by central
authorization, instead of local authorization.
• Policy changes require that all file authorizations must be centrally controlled.
• A user can no longer be considered trusted.
• A user mistakenly authorizes an application file.
Local authorizations are stored in a local file on the client. To remove local authorization files,
delete the .locauth files stored in %WINDOWS%\system32\sxdata folder. You can perform local
authorization file maintenance on a per-user basis or delete file batches at startup by defining a
task in the Windows Scheduler.
Globally Disable Local Authorization
You can disable locally authorized executable files, scripts, or macros using file group
assignments.
When you do not want to delete local authorization files, you can still disable access to locally
authorized files through user file group assignments.
1. Create a file group named Not Allowed.
2. Add all applications that are not allowed to run to the Not Allowed file group.
Do not assign this file group to any user/user group.
3. Send updates to all computers.
- 35 -
Page 36

PGP Endpoint
- 36 -
Page 37

Chapter
5
Understanding Administration Server-Client Communications
In this chapter:
• About Administration
Server-Client
Communications
• About Administration
Server-Client
Communication Encryption
• About Administration
Server-Client Proxy
Communications
The Administration Server uses a TCP/IP server. When the
Administration Server is not reachable because of a firewall
on the client, the client can initiate communication through a
proxy server.
About Administration Server-Client Communications
PGP Endpoint is based on standard TCP/IP protocols for all communication between clients and
servers.
TCP/IP was chosen due to its pervasive implementation throughout most IT infrastructures.
They are the most widely used open-system (non-proprietary) protocols since they are equally
well suited for LAN or WAN communication. Using the TCP/IP protocol offers some clear
advantages over other protocols, including the following:
• Allows enterprise networking connectivity between Windows and non-Windows based
computers.
• Can be used to create client-server applications.
Currently PGP Endpoint uses only two configurable ports for full two-way communication
between the client and server components. As with other TCP-based services, Administration
- 37 -
Page 38

PGP Endpoint
Servers cannot handle clients connecting through a firewall or proxy unless the required ports
are opened. By default:
• The server uses port 65129 or 65229 (for the TLS protocol) to listen to clients or other
Administration Server requests.
• Clients use port 33115 by default to receive information and respond if the Administration
Server initiated the communication.
These three ports are required for full two-way communication. You can configure these ports as
required by your environment.
Figure 5: Administration Server-Client Communication
Administration Server Communications
The Administration Server consists internally of two distinct subsystems. The first subsystem
handles requests from administrative clients and exposes services via a secure, authenticated
Remote Procedure Call (RPC). The second subsystem communicates with the clients.
The Administration Server RPC is used to expose administrative functionality (the interfaces
required to browse and manage the hashes and file groups in the database) and to offer control
over driver behavior. Internally, the Administration Server uses a thread pool to perform mass
updates. It connects to each client individually according to the driver state. The database
keeps track of drivers and users that are on-line. This is more than broadcasting, but offers the
advantage of guaranteed delivery, a feature not found in broadcast-capable protocols.
- 38 -
Page 39

Understanding Administration Server-Client Communications
The Administration Server uses a TCP/IP server based on Microsoft Windows Input Output
Completion Ports (IOCP). The most important server tasks are responding to login and log off
notification messages from the clients, such as processing start (boot) and stop (shutdown)
messages from clients, and creating and dispatching hash-lists requested by clients.
The TCP/IP client built into the Administration Server serves primarily to push updates to clients.
When an administrator makes changes to options or permissions, clients may need immediate
updates. For permission changes, this typically invalidates the existing hash-list cache.
Forced updates create a need for multiple Administration Server instances to communicate
intra-server. In particular, when an administrator requests an immediate hash-list update, the
instruction to flush the hash-list cache must be relayed to every server to keep the caches
coherent. Since all servers share a common database, they register themselves in the
database. Intra-server notifications are sent through the respective TCP/IP channel.
Changing Licenses for the Administration Server
When you need to change the license for the Administration Server, you must stop the server,
change the license, then restart the server.
1. Select Start > Run.
2. Type cmd in the Open: field.
3. On the command line, type: net stop sxs.
4. Copy the new PGP Endpoint license file to the \\Windows\System32 or \\Windows
\SysWOW64 folder, and rename the file to Endpoint.lic.
5. Select Start > Run .
6. Type cmd in the Open: field.
7. On the command line, type: net start sxs.
Result: The Administration Server restarts with the new license information.
Changing the SysLog Server
During the SXS installation you can enter a SysLog server address specify whether you want to
log audit events, system events, client events, or some combination thereof. You may change
the SysLog server address and specifications after installation.
You can modify the following Administration Serverregistry keys as described by the General
Registry Keys on page 70 section.
1. Select Start > Run.
2. Type regedit in the Open: field.
3. Select HKEY_LOCAL_MACHINE > SYSTEM > CurrentControlSet > Services > sxs >
parameters from the registry keys.
Step Result: The Registry Editor window opens.
- 39 -
Page 40

PGP Endpoint
4. Select any one or all of the following registry key parameters:
• SysLogServerAddress - specifies the name of the SysLog server.
• SysLogGenerateMsg - specifes the type of log event(s) sent to the SysLog server.
5. Close the Registry Editor window.
Result: SysLog behaviour changes based on the registry key data values that you specify.
About Administration Server-Client Communication Encryption
The Administration Server uses a symmetric encryption system to communicate with the client.
There are several methods that generate symmetrical public-private key pairs. The most well
known method is based on the RSA algorithm. The security this algorithm provides relies on
the difficulty of factoring large prime numbers. Device Control uses the RSA algorithm with
a key size of 2048 bits, making it extremely difficult to compromise. The security of a strong
cryptographic system depends on the secrecy of the key and key size.
The need for strong cryptographic security underscores the importance of generating your
own key pair during installation and using a long seed value, before deploying Device Control
clients in your environment. The private key should not be communicated to the clients and
should reside on the Administration Server computer or stored on an external medium for added
security.
Digital Signatures and Certificate Authorities (CA)
For complete data security, digital signatures are combined with digital certificates that
authenticate the identity of a sender.
Using a digital signature ensures, to a certain extent, the authenticity of the sender. Since
only the public key of the sender can decrypt the digital signature, this only ensures that the
sender has the private key corresponding to the public key used to decrypt the digital signature.
To confirm the authenticity of the sender, a digital certificate is used. A digital certificate is an
electronic document that certifies that a particular user owns a certain public key. A third party,
called the certificate authority (CA), signs this document. You need to install the Microsoft CA
service to create your own CA to use with Device Control encryption.
Digital Signatures
Device Control uses digital signatures to ensure the integrity of the private and public key pair.
A digital signature is a stamp attached to a data transmission that can be used to determine
whether an intervening malicious user tampered with the transmission.
The digital signature for a message is generated as follows:
1. A message digest or hash is generated using a set of hashing algorithms. A message digest
is:
• A summary of the data transmitted.
- 40 -
Page 41

Understanding Administration Server-Client Communications
• Always smaller than the message.
• Detects even the slightest change in the data that produces a different hash.
2. The private key of the sender is used to encrypt the message hash that is the digital
signature.
3. The digital signature is attached to the message which is then sent to the recipient.
The recipient then performs the following:
1. Uses the public key of the sender to decrypt the digital signature and obtain the message
hash generated by the sender.
2. Uses the same message hash algorithm as the sender to generate a message hash for the
received message.
3. Compares the two message hashes. If the message hashes are not exactly the same, a
third-party tampered with the message or there was a problem with the data transmission.
You can be assured that the digital signature was originated by the sender, not by a malicious
user, because only the public key of the sender can decrypt the digital signature. If the
decryption using the public key renders a faulty signature hash, either the signature, or the data,
is not exactly what the sender originally transmitted.
About Administration Server-Client Proxy Communications
The client communicates with the Administration Server using Fully Qualified Domain Name
(FQDN) address(es) configured during the client setup. The FQDN addresses may not be
reachable when the client initiates communication, particularly when using remote clients via
a Virtual Private Network (VPN) connection that does not have a physical connection to the
Administration Server or a firewall is blocking the required ports when they should not be open
for security reasons.
A client may use a proxy configured for the Internet Explorer to reach the Administration Server,
when the client cannot establish communication using a defined fully qualified domain name
(FQDN).
When the Administration Server is not reachable for the aforementioned reasons, all
communication is accomplished using the Internet through a proxy that acts as a barrier
between the internal network and the Internet. Many enterprises use proxy servers to manage
a variety of communication protocols and add a higher level of security to their network
- 41 -
Page 42
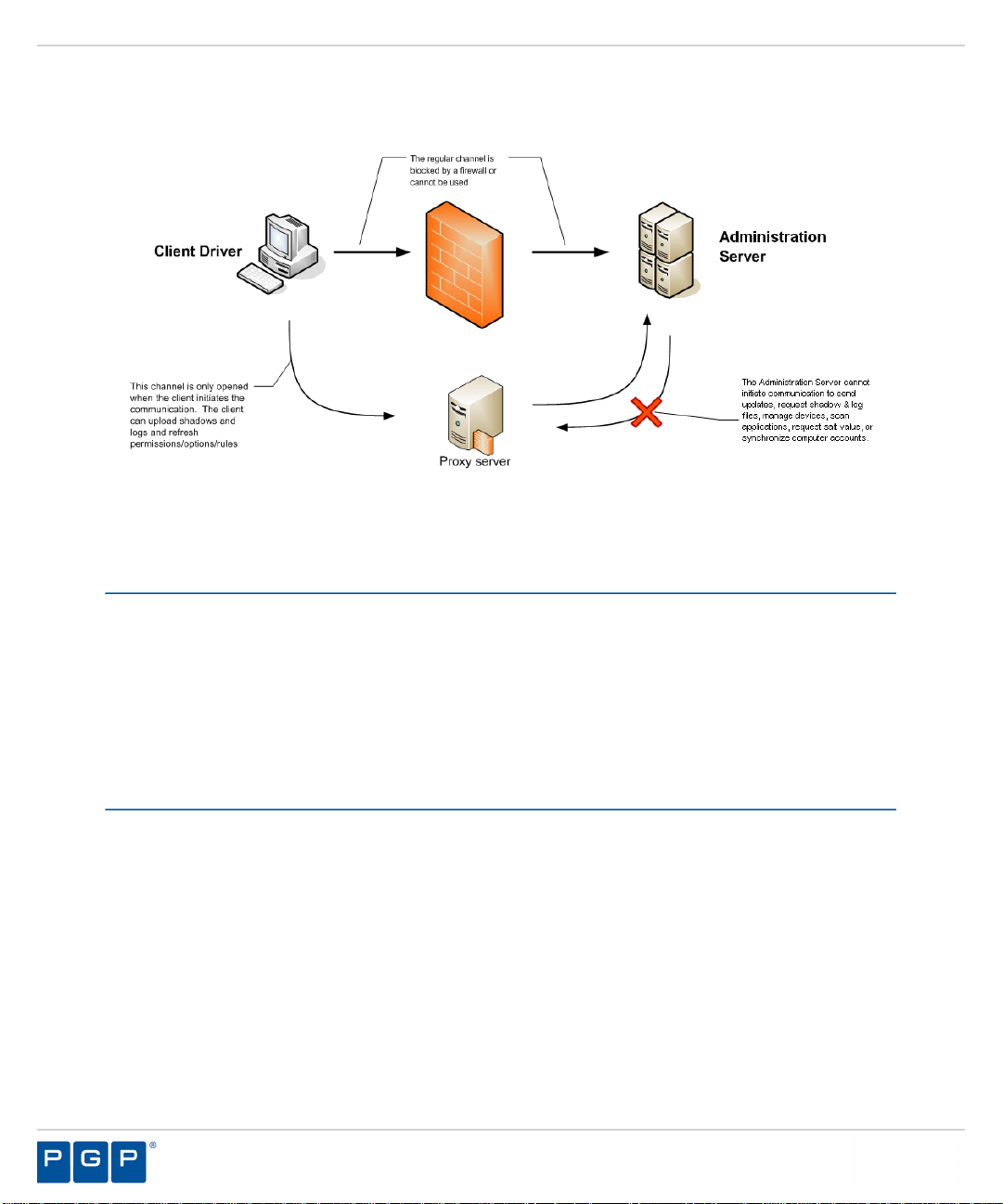
PGP Endpoint
environment. Data transferred via proxy connections is very resistant to eavesdropping and
interception.
Figure 6: Administration Server-Client Proxy Communications
Configuring Administration Server-Client Proxy Communication
When using a proxy, the client mimics a Microsoft® Internet Explorer proxy configuration.
Prerequisites:
Before configuring proxy communication for the client, you must :
• Install the client on a support operating system using the TLS encryption protocol.
• Set the Administration Server TLS port registry key value to 443. This port is used for secure
web browser communications and should be configured for the client, Administration Server,
and proxy.
• Install a valid certificate authority.
• Use a supported version of Microsoft Internet Explorer (IE).
Proxy communication can be established in one of the following modes:
• Automatically by detecting settings or using an automatic configuration script with Web
Proxy Automatic Discovery (WPAD). Automatic proxy configuration uses a Dynamic Host
Configuration Protocol (DHCP) server.
• Manually using a proxy server for your LAN with a secure Hypertext Transfer Protocol
Secure (HTTPS) address.
1.
Open Microsoft Internet Explorer®.
- 42 -
Page 43

Understanding Administration Server-Client Communications
2. Select Tools > Internet Options > Connections > LAN Settings.
Step Result: The Local Area Network (LAN) Settings dialog opens.
Figure 7: Local Area Network (LAN) Settings
3. To define a new WPAD option, select the applicable DHCP server in the DHCP console tree.
4. From the Action menu, select Set Predefined Options.
Step Result: The Predefined Options and Values dialog opens.
Figure 8: Predefined Options and Values
5. Click Add.
6. Select the Options class you want to modify from the drop-down list.
7. Type an Option name.
8. Click OK.
9. Right-click the Server Options branch, in the DHCP console tree.
10.Select New Scope.
11.Select Configure Options, select the WPAD value.
12.Type the proxy address in the String Value field.
13.After creating the Scope, right-click Scope Options.
- 43 -
Page 44

PGP Endpoint
14.Select Configure Options.
Step Result: The Scope Options dialog opens.
Figure 9: Scope Options Dialog
15.Click the Advanced tab.
16.Select the Option name you created in a previous step.
17.Click OK.
Result: The proxy server is defined.
- 44 -
Page 45

Chapter
6
Deploying the Client
In this chapter:
• About PGP Endpoint
Client Deployment
• Deploying the Client with a
Ghost Image
• Deploying the Client with
Windows Group Policy
• Deploying the Client with
Other Tools
The PGP Endpoint Client Deployment tool is generally
used to silently deploy the client to a group of computers,
after you create deployment packages. Depending
upon unique network environment requirements for your
organization, you can perform unattended client installations
using alternate deployment methods. For information
regarding the use of the PGP Endpoint Client Deployment
tool, refer to the Device Control User Guide or Application
Control User Guide (https://support.pgp.com).
About PGP Endpoint Client Deployment
You can deploy the client using methods other than the PGP Endpoint Client Deployment
tool, depending upon your environment and company policies.
Client deployment methods, in addition to the PGP Endpoint Client Deployment tool, include
using:
• A ghost image.
• Windows Group Policy.
• Third-party software deployment tools.
- 45 -
Page 46

PGP Endpoint
Deploying the Client with a Ghost Image
Network administrators commonly deploy standard computer images for new computers and
computer upgrades using General Hardware-Oriented System Transfer (Ghost) software.
Prerequisites:
Before you can create and deploy a ghost image of the client, you must:
• Install the client.
• Disable the Client Hardening default option according to the Device Control User Guide or
Application Control User Guide.
Ghost Imaging is the process of copying the contents of one computer hard disk to another disk
or to an image file. Provisioning with a standard set of software allows a new user to begin with
a complete application suite and eliminates the need to install individual applications. Using the
following procedure, the client can be deployed with ghost imaging.
1. Change all drivers to start in demand mode, by selecting Windows Start > Run.
2. Type regedit in the Open box.
3. Select the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services/scomc registry
key.
4. Set the Start parameter value REG_DWORD to 4.
5. Select the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services/sk-ndis registry
key.
6. Edit the Start parameter value REG_DWORD to 4.
7. Select Start > Control Panel > Network Connections > Local Area Connection >
Properties.
8. On the General tab, disable the SK-NDIS filter.
9. Select Windows Start > Run > Regedit.
10.Select the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control
\VirtualDeviceDrivers registry key.
11.Delete the C:\WINDOWS\system32\sxd-vdd.dll value from the registry key.
12.Restart the computer.
13.Create the ghost image from the computer hosting the client.
14.Change the unique SID and name of the computer.
15.Select Windows Start > Run > Regedit .
16.Select the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services/scomc registry
key.
- 46 -
Page 47

Deploying the Client
17.Set the Start parameter value REG_DWORD to 2.
18.Select the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services/sk-ndis registry
key.
19.Edit the Start parameter value REG_DWORD to 0.
20.Select the HKEY_LOCAL_MACHINE\SYSTEM\SOFTWARE\Microsoft\Windows
\CurrentVersion\Run registry key.
21.Add the %SYSTEMROOT%\System32\sxd-vdd.dll value to the VDD registry key.
22.Restart the computer.
23.Select Start > Control Panel > Network Connections > Local Area Connection >
Properties.
24.On the General tab, enable the SK-NDIS filter.
Result: The client ghost image is created on the client computer hosting the client.
Deploying the Client with Windows Group Policy
You can implement a computer-based group policy for all computers in a domain. Group
policies can be applied to sites, domains, or Active Directory organizational units (OU), based
on individual system requirements and the types of computers in the groups. The Group Policy
Management Console (GPMC) has superseded the Active Directory Users and Computers
dialog for Windows XP®.
Prerequisites:
Before using a third-party software deployment tool to deploy clients, you must:
1. Create a deployment package using the PGP Endpoint Client Deployment tool. Refer to
the Device Control User Guide or Application Control User Guide (https://support.pgp.com)
for instructions about creating deployment packages.
2. Copy the entire deployment package folder to a local directory on the server that will be
used to deploy the client. This directory should include the *.msi installation file and the sx-
public.key public key file.
The following procedure demonstrates how to apply Windows® group policy for deploying
clients.
Note: Execution of this procedure may vary according to individual operating system
requirements. For the purposes of this example, the operating system reference is Windows
2003 Server.
1. Select Start > All Programs > Administrative Tools > Active Directory Users and
Computers.
Step Result: The Active Directory Users and Computers dialog opens.
- 47 -
Page 48

PGP Endpoint
2. In the console tree, right-click the DomainName, where the DomainName is the name of
your domain.
3. Click Properties.
4. Select the Group Policy tab.
5. Click New to create a new group policy.
6. Click Edit.
7. Under Computer Configuration, expand the Software Settings folder.
8. Right-click Software Installation.
9. Select New > Package .
10.In the Open dialog, type the full Universal Naming Convention (UNC) path of the shared
installer package that you want to install using the \\file server\share\client.msi format.
Important: Do not use Browse to access the location. Make sure that you use the UNC
path to the shared installer package.
11.Click Open.
12.Click Assigned.
13.Click OK.
Step Result: The package is listed in the right pane of the Group Policy window.
14.Close the Group Policy tab.
15.Click OK.
16.Close the Active Directory Users and Computers dialog.
Result: When the client computer restarts, the managed software package is automatically
installed.
Deploying the Client with Other Tools
You can use a third-party software deployment tool to deploy the PGP Endpoint client for a
group of computers in your network.
Prerequisites:
Before using a third-party software deployment tool to deploy clients, you must:
1. Create a deployment package using the PGP Endpoint Client Deployment tool. Refer to
the Device Control User Guide or Application Control User Guide (https://support.pgp.com)
for instructions about creating deployment packages.
2. Copy the entire deployment package folder to a local directory on the server that will be
used to deploy the client. This directory should include the *.msi installation file and the sx-
public.key public key file.
- 48 -
Page 49

Deploying the Client
1. Open the third-party tool.
2. Run the following command-line in the appropriate entry: Msiexec /i
"PGPEndpointClient.msi" /qn TRANSFORMS="PGPEndpointClient.mst" /L*v %TMP%
\setupcltsu.log
3. Deploy the client using the third-party tool.
Result: The third-party software deployment tool installs the client on the specified target
computers.
- 49 -
Page 50

PGP Endpoint
- 50 -
Page 51

Chapter
7
Controlling Administrative Rights
In this chapter:
• About PGP Endpoint
Access Control Rights
• Defining User Access
• Using the Access Control
Visual Basic Script
Access privileges are set in the system to allow or restrict
administrative privileges. Administrative privileges are
shown in the Connection panel of the Management
Server Console.The system recognizes two types of
administrators:
• Enterprise administrators, who have complete,
unrestricted administrative privileges.
• Administrators, who have restricted administrative
privileges.
About PGP Endpoint Access Control Rights
You can use the ctrlacx.vbs script to manage and show the user access control rights defined in
the Active Directory hierarchy.
You can use the Visual Basic® script file, ctrlacx.vbs, to set, view, or modify the Manage PGP
Endpoint Settings control rights in the Active Directory. This script allows Active Directory
administrators to delegate administrative access to computers, users, user groups, and
organizational units without allowing other task management, which is required by default, to the
administrators.
- 51 -
Page 52

PGP Endpoint
Defining User Access
The Management Server Console can only be accessed by authorized network administrators.
To control user access to the Management Server Console, you can define two types of
administrators:
• An Enterprise Administrator has full access to all management functions.
Note: Initially, any member of the Windows Administrators group for a Administration
Server has the privileges of a Enterprise Administrator. After an Enterprise Administrator is
designated, administrative privileges are automatically restricted for the members of the local
Administrators group.
• An Administrator has restricted access to Management Server Console functions as defined
by the Enterprise Administrator.
An Enterprise Administrator can delegate administrative rights to other administrators using
Active Directory Organizational Units. These rights are described in the following table.
Table 1: PGP Endpoint Administrator Rights
Administrative
Rights
View all device
permissions and
file authorizations
Modify file
authorizations
device permissions
level device
permissions
Administrator Type Limitations PGP Endpoint
Application
All PGP Endpoint
administrators
Enterprise
Administrators
Enterprise
Administrators
Members of the
Settings (Device
Control) role
Enterprise
Administrators
Members of the
Settings (Device
Control) role
NA Application
Control; Device
Control
NA Application
Control
NAModify global-level
Only users the
administrator is allowed
to manage
NAModify computer-
Only for the computers
that the administrator is
allowed to manage
Device Control
Device Control
- 52 -
Page 53

Controlling Administrative Rights
Administrative
Rights
group device
permissions
Manage builtin accounts
(Everyone,
LocalSystem, and
so forth)
Initially, any administrator with password access to a Administration Server and the
Management Server Console can use the Management Server Console.
Before using PGP Endpoint, PGP recommends setting up administrators who have access to
the Management Server Console. You can assign different roles to administrators, but you must
define at least one Enterprise Administrator.
The following rules apply to administrative user roles:
Administrator Type Limitations PGP Endpoint
Application
Enterprise
Administrators
Members of the
Settings (Device
Control) role
Enterprise
Administrators
NAModify computer-
Only if the administrator
is allowed to manage
all the computers in the
computer group for all
accounts
NA Application
Device Control
Control; Device
Control
• You must always designate one Enterprise Administrator before you modify the list of
administrators.
• All Administration Servers share the same database, so some administrative rights set for an
administrator can be used for other Administration Servers.
• Local computer users cannot manage the Management Server Console, even if assigned as
an Enterprise Administrator, because they cannot connect to an Administration Server.
Using the Access Control Visual Basic Script
You use the Visual Basic® script file, ctrlacx.vbs, to set, view, or modify the Manage PGP
Endpoint Settings control rights in the Active Directory.
Prerequisites:
•
Install the Windows® Script Host (WSH) interpreter. See Script Host (http://
msdn.microsoft.com/en-us/library/ec0wcxh3(VS.85).aspx) for additional information about
the Windows Script Host.
• Schedule domain synchronization.
- 53 -
Page 54

PGP Endpoint
When ctrlacx.vbs runs, the script creates a special entry in the permissions list of the AD
organization unit named Manage PGP Endpoint Settings. This entry only affects Device
Control software administrator users and the devices they control permissions for. If you
assign this setting to a specific user, who is also an Administrator defined using the User
Access Manager dialog in the Management Server Console, this Administrator can only
manage, directly from the Management Server Console, the designated users, user groups,
and computers that the Administrator is assigned rights for. Administrator access rights are
described by Defining User Access in the Application Control or Device Control User Guide
(http://support.pgp.com/).
1. Select Start > Run.
2. Type: cscript ctrlacx.vbs [parameter from following list]>filename.txt
3. Add any of the following optional parameters, individually or in combination, to the
parameters list command line:
Parameter Description
- Shows a brief description for each available parameter.
-e Lists all access control rights, with condensed output.
-v Lists all access control rights, with detailed output.
-q cn Shows control rights by canonical name.
-s Shows PGP Manage PGP Endpoint Settings rights.
-create Creates or updates PGP Manage PGP Endpoint
Settings rights.
-delete Deletes PGP Manage PGP Endpoint Settings rights.
4. Click OK.
Result: The delegation rights you create can be assigned to Active Directory organizational
units (OUs).
- 54 -
Page 55

Controlling Administrative Rights
Example:
To list all control access rights in condensed mode redirecting the output to
MyFile.txt file, type:
cscript ctrlacx.vbs –e > MyFile.txt
To show the Manage PGP Endpoint Settings rights interactively, type:
ctrlacx.vbs -s
After Completing This Task:
You can assign the delegation rights by using the Windows Management Services and MMC
when you run the script with -create parameter. See Windows Management Services and MMC
(http://technet.microsoft.com/en-us/library/bb742441.aspx#XSLTsection123121120120) for
additional information about assigning delegation rights.
- 55 -
Page 56

PGP Endpoint
- 56 -
Page 57

Chapter
8
Using File Tools
In this chapter:
• About File Tools
• Using the PGP Endpoint
Authorization Service Tool
• Using the PGP Endpoint
Application Control File
Tool
• Using the SXDomain Tool
As you work with the Application Control and Device Control
products, the number of files in the database increases
over time, increasing the administrative burden associated
with managing large volumes of files. PGP Endpoint
provides several administrative functions that allow an
administrator to manage multiple files automatically or in a
single instance.
About File Tools
PGP Endpoint provides tools for administrators to manage large volumes of files in the PGP
Endpoint Application Control database.
You can use the following tools to manage large volumes of files for Application Control,
including the:
• Authorization Service
• Versatile File Processor
• File Import/Export
• SXDomain
Using the PGP Endpoint Authorization Service Tool
You can use the PGP Endpoint Application Control Authorization Service Tool to monitor
approved and synchronized changes to executable file authorization policies using Microsoft
Update Services (SUS) and Windows® Server Update Services (WSUS).
The PGP Endpoint Authorization Service Tool service authorizes all approved Microsoft
updates and fixes, creates corresponding hash files, and updates the database.
- 57 -
®
®
Page 58

PGP Endpoint
1. From the location where you saved the PGP Endpoint application software, run the \server
\authsrv\setup.exe file.
Step Result: The Welcome page opens.
2. Click Next.
Step Result: The License Agreement page opens.
Figure 10: License Agreement Page
3. Review the license agreement and, if you agree, select I accept the terms in the license
agreement.
4. Click Next.
5. From the PGP Endpoint Administration Server dialog, enter an Administration Server IP
address in the corresponding field.
- 58 -
Page 59

6. Click Next.
Step Result: The Software Update Services dialog opens.
Figure 11: Software Update Services Dialog
Using File Tools
7. Select one of the following options:
• Microsoft Software Update Services (SUS version 1.0)
• Microsoft Windows Server Update Services (WSUS version 2.0 and greater)
8. Select any of the following PGP Endpoint Authorization Service Options.
• Provide information on each scan by e-mail
• Use verbose report mode
• Do not automatically start PGP Endpoint Authorization Service when Setup is
finished
Step Result: If you choose to Provide information on each scan by e-mail, the E-mail
configuration dialog opens. The PGP Endpoint Authorization Service
tool does not support Outlook Express or Internet Information Server
(IIS) as clients for sending email messages. If there is already an account for
- 59 -
Page 60

PGP Endpoint
Figure 12: E-mail Configuration Dialog
these types of clients, the SMTP IP address is transferred directly to the PGP
Endpoint Authorization Service configuration.
Note: If you select Do not automatically start PGP Endpoint Authorization
Service when Setup is finished, the service will automatically start when one
of the following events occurs:
• A change is made by WSUS in the default update folder.
• An administrator approves the SUS updates using the PGP Endpoint
Management Server Console.
• One hour elapses after installing the PGP Endpoint Authorization Service.
9. Click Next.
10.From the Destination Folder dialog, click Change to choose an installation destination
folder other than the default folder C:\Program Files\PGP Corporation\PGP Endpoint.
11.Click Next.
Step Result: The Ready to Install the Program dialog opens.
12.Click Install.
A progress bar runs on the page, showing installation progress.
Step Result: The Completed page opens.
- 60 -
Page 61

Using File Tools
13.Click Finish.
Result: The PGP Endpoint Database Explorer window shows the specified installation
directory(s) in the Files tab.
After Completing This Task:
After installing the PGP Endpoint Application Control Authorization Service Tool you
must configure and synchronize WSUS. See Configure and Synchronize WSUS (http://
technet.microsoft.com/en-us/library/cc708455.aspx) for more information about configuring
WSUS or SUS.
You can modify PGP Endpoint Authorization Service Tool by rerunning the Authorization
Service Tool.
Using the PGP Endpoint Application Control File Tool
You use the Versatile File Processor tool to scan files in specific locations.
The PGP Endpoint Application Control File Tool tool consists of two files:
• The filetool.dll that provides the underlying functionality. This file is used by other PGP tools,
such as the Authorization Service Tool.
• The filetool.exe command line executable file that uses the filetool.dll.
The PGP Endpoint Application Control File Tool tool works in one of two modes depending
on the parameters you select. The operation modes are:
• Online mode - The online mode is used to scan specific files. The PGP Endpoint
Application Control File Tool connects, by default, to the local Administration Server using
the login identity of the current user and scans file locations to assign the scanned files to file
groups. The files can be assigned automatically, using Administration Server suggestions.
Note: You can override the user login default using the command line parameters –s
<server> and –u <user/password>. After the assignment, and if the –p option is specified, the
tool can request Administration Server to notify all the clients (drivers).
• Offline mode - The offline mode produces scan files. Even though the scan files have
exactly the same format as the scan files produced by the driver, these cannot be used
directly. Offline mode requires an output file name only if using the –o parameter. File
assignments cannot be made in offline mode. You can copy the resulting scan files, from the
directory that you specified in the command line instruction, to the Administration Server %/
DataFleDirectory/% to compare your results with previously scanned files.
Note: The PGP Endpoint Application Control File Tool tool can scan files contained in
archives files with the following extensions:.cab,.zip,.rar,.ace,.jar, and .cs. However, some.cab
archives do not have a standard cabinet structure despite having a.cab extension so it may not
be possible to scan them correctly.
1. Select Start > Run .
2. Browse to the location where you saved the PGP Endpoint application software, and select
\bin\tools\FileTool.exe file.
- 61 -
Page 62

PGP Endpoint
3. Add any of the following optional parameters, individually or in combination, to the
parameters list command line.
Tip: If you execute the PGP Endpoint Application Control File Tool without parameters,
help output is displayed.
Parameter Description
-s Administration Server (The default is the current
Administration Server).
-u User/password to connect to the Administration Server.
(The default is the current user).
-o Offline mode; generate a scan
-d0 Delta mode off. (This is the default value).
-d1 Delta mode on, avoid rescanning files already scanned.
-d2 Delta mode on, clear the list then memorize files already
scanned.
-f Access failure, retry (n) times with a least (m) seconds
between attempts. Example: -f 10,3 (10 retry attempts with
3 seconds) between attempts.
-v Verbose report; generate an xml report that you save
to a location you specify in the command line after the
parameter.
-r Report; generate an xml report, errors only, that you save
to a location you specify in the command line after the
parameter.
-i Ignore archive contents.
target File or directory to scan.
Tip: To avoid recursive scan on directory, terminate the
target entry with \\.The target may also be entered using
one of the following keywords in brackets:
• [drives] (All hard drives)
• [media] (All removable media)
• [all] (All hard drives and removable media)
-e An option wildcard mask.
- 62 -
Page 63

Using File Tools
Parameter Description
-c0 File group creation, use only existing groups.
-c1 File group creation, create if necessary. (This is the
default value).
-a0 Keep existing assignment, automatically assign new files
to existing groups, and assign remaining files to groups
you select.
Tip: Accepts a list of file groups using the format
FileGroup1,FileGroup2...FileGroup
n
-a1 Keep existing assignment, assign new files to groups you
select.
-a2 Assign existing and new files to group.
-x0 Process all files.
Tip: Be very cautious when using this parameter because
all files are scanned, even if the files are not executable.
-x1 Only process executable files.
-x2 Only process executable files having a valid digital
signature.
-p Push updates to all online clients.
Result: The specified file locations are scanned and the files designated by the parameters
are assigned to file groups.
- 63 -
Page 64

PGP Endpoint
Using the SXDomain Tool
The SXDomain utility provides a method to automatically schedule domain synchronization,
using the Windows Task Scheduler.
You can schedule domain synchronizations with a task scheduler, such as the Windows Task
Scheduler. You create a batch file that contains a list domains to synchronize.
Figure 13: Synchronization Script Process
1. Navigate to C:\Program Files\PGP Corporation\PGP Endpoint\SXTools.
2. Create a batch file named sxsync.bat containing the following command line: CMD/C
SXDOMAIN- s SXS_Server -i -e <mydomains.txt> error_list.txt.
3. Navigate to the Windows Control Panel, select Scheduled Tasks.
- 64 -
Page 65

4. Select Add Scheduled Tasks.
Step Result: The Scheduled Task Wizard dialog opens.
Using File Tools
Figure 14: Scheduled Task Wizard
5. Click Next.
6. Select the sxsynch.bat file from files shown.
7. Click Next.
8. Type a name for your scheduled task at the prompt.
9. Select a schedule frequency from the options listed from Perform this task.
10.Click Next.
11.Select the day and time you want to perform the task.
12.Click Next.
Step Result: A user name and password information dialog opens.
13.Type the user name in the User Name field.
14.Type the associated password in the Password and Confirm Password fields.
15.Click Next.
Step Result: A dialog opens showing the name of the scheduled task and the date and time
the task is scheduled to perform.
- 65 -
Page 66

PGP Endpoint
16.Click Finish.
Result: Domain synchronization is scheduled to perform according to your specifications.
- 66 -
Page 67

Chapter
9
Managing Registry Keys
In this chapter:
• Database Connection
Loss Registry Key
• Authorization Service
Registry Key
• Debugging Registry Key
• General Registry Keys
• Security Registry Keys
• Command & Control
Registry Key
• Client Kernel Registry Key
• Software Registry Key
• Administration Server
Registry Key
• Authorization Wizard
Registry Key
Registry keys can be used to adapt Application Control and
Device Control according to enterprise-specific network
environment policies and requirements.Registry keys that
can be modified include:
• Administration Server keys
• Client keys
• Management Server Console keys
Database Connection Loss Registry Key
The database connection registry key parameters allow you to define Administration Server
behavior during periods of database connectivity loss. The Administration Server can run
with intermittent database connectivity, ignoring the lack of database connection for specified
periods. During these periods, the Administration Server retries connecting to the database.
After repeatedly attempting to establish database connectivity, the Administration Server
- 67 -
Page 68

PGP Endpoint
declines further connectivity requests from the client and console, until database connectivity is
restored.
The following table describes the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet
\Services\sxs registry key parameters for the Administration Server. All registry key entries are
of the type: REG_SZ (= string value), unless designated otherwise.
Table 2: Database Connection Loss Registry Key Parameters
Parameter Name Description Default Value
DbConnectionCount Shows the number of database
connections in the connection
pool.
DbConnectionString Shows the driver, server,
database, and trusted
connection or user name and
password.
DbInitializationDelay Shows the period in seconds
that the Administration Server
waits before contacting the SQL
server.
20
Provider=sqloledb;
DataSource= ;
InitialCatalog=sx;
Trusted_Connection=yes
300
Authorization Service Registry Key
The parameters for the PGP Endpoint Authorization Service tool registry key parameters are
shown in the following table.
Table 3: Authorization Service Tool Registry Key Parameters
Key Name Description Default Values
CmdLineBlockParams Allows user to setup assignment
mode, group name(s), and filters
in the FileTool.exe command line
parameters.
-a1 = Microsoft
Update Files
Log file name Depends upon the Log to file value. authSrvHlpr.log
Log to file Sends debug message to the log
file
yes=1
- 68 -
no = 0
Page 69

Managing Registry Keys
Key Name Description Default Values
OutputDirectory Directory path where output XML
reports are located.
SendMail The service sends e-mail at the
end of the scan, which includes the
command line and attached XML
report.
SXSServer Name or IP address of the
Administration Server.
VerboseReport Report mode.
no=normal report mode
WSUSContentDirectory Absolute directory path where
WSUS files are located.
C:\Program
Files\PGP
\PGP Endpoint
\ Authorization
Service\Logs\
no = 0
Not applicable.
yes = verbose
report mode
C:\
Debugging Registry Key
You can use the debugging registry key parameters to specify the behavior for debugging the
Administration Server.
The following table describes the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet
\Services\sxs registry key parameters for the Administration Server. All registry key entries are
of the type: REG_SZ (= string value), unless designated otherwise.
Table 4: Debugging Registry Key Parameters
Key Name Description Default
Value
Debug For the Administration Server running as a service, a
debugger will launch and attach to the server when the
value is set to yes = 1.
Log file name Shows the name of the log file written when Log to file
= yes .
Log to console Sends debug messages to the console when the value
is set to yes = 1.
Log to dbwin Sends debug messages to the DBwin32 when the
value is set to yes = 1.
- 69 -
no = 0
sxs.log
no = 0
no = 0
Page 70

PGP Endpoint
Key Name Description Default
Value
Log to file Sends debug messages to the log file when the value
is set to yes = 1.
VerboseSyncLogging The Administration Server logs the important object
attributes retrieved during domain synchronization.
no = 0
no = 0
General Registry Keys
The general registry key parameters govern the general behavior of the Administration Server.
The following table describes the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet
\Services\sxs registry key parameters for the Administration Server. All registry key entries are
of the type: REG_SZ (= string value), unless designated otherwise.
Table 5: General Registry Key Parameters
Parameter Name Description Default Value
AdoVersion Specifies a string representing the version of
Active Directory objects used.
Concurrency Shows how many running threads are
allowed for the input/output connection port
(IOCP). Zero is equivalent to one thread per
central processing unit (CPU). Maximum
number equals MaxThreads.
No value.
0=auto
DataFileDirectory Shows the name of the base directory where
the Administration Server stores data files.
SysLogGenerateMsg Determines what type of logs are sent to the
SysLog server.
1 = Audit logs only
2 = System logs only
SysLogServerAddress The SysLog server that the Administration
Server sends server and audit log events to.
- 70 -
C:\DataFileDirectory
3 = Audit and system
logs
Specified during
initial client
installation.
Page 71

Managing Registry Keys
Security Registry Keys
The security registry key parameters govern the security configuration for the Administration
Server.
The following table describes the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet
\Services\sxs registry key parameters for the Administration Server. All registry key entries are
of the type: REG_SZ (= string value), unless designated otherwise.
Table 6: Security Registry Key Parameters
Parameter Name Description Default
Value
CommVer
MaxSockets Specifies the maximum number of TCP
Port
Specifies the client-server communication
protocol that the Administration Server uses
as follows:
0 = Client version lower than 3.1
1 = Client versions 3.1 or 3.2
2 = Client version 4.0
3 = Client version 4.1 or higher
connections allowed at any time.
Specifies the TCP port where the socket-
based Administration Server listens for new
connections.
Minimum value = 1
Maximum value = 65534
3
5000
65129
- 71 -
Page 72

PGP Endpoint
Parameter Name Description Default
Value
RpcProtectionLevel
SecureInterSxs Specifies that inter-PGP Endpoint
Specifies whether the RPC server requires
RPC clients to authenticate.
0 = OS selects protection level
1 = No protection
2 = Client identify is verified when connecting
to the PGP Endpoint Administration Server
3 = Examines client credentials for TCP
connection.
4 = Examines client credentials for TCP
connection, adds cryptographic signature to
every packet.
5 = Examines client credentials for TCP
connection, adds additional cryptographic
signature to every packet.
6 = Examines client credentials for TCP
connection, adds cryptographic signature
to every packet, and encrypts data in both
directions
Administration Server communication use the
TLS protocol.
6
no
SndPort
SxdConnectTimeoutMSec Specifies the time in milliseconds that the
Specifies the TCP where the PGP Endpoint
client listens for new connections.
Minimum value = 1
Maximum value = 65534
Administration Server waits to accept a TCP
connection for the client. The value should be
between 500 and 120000 ms.
- 72 -
33115
5000
Page 73

Managing Registry Keys
Parameter Name Description Default
Value
SxdPort
TLSMaxSockets Specifies the maximum number of TCP
TLSPort
Specifies the TCP port where the built-in
client server listens for new connections.
Minimum value = 1
Maximum value = 65534
connections allowed when using the TLS
protocol.
Specifies the TLS port where the socketbased Administration Server listens for new
connections.
Minimum value = 1
Maximum value = 65534
33115
0
65229
Configure MaxSockets
When certain security registry key parameters interact, some of the combinations formed are not
valid as shown in the following table.
Table 7: Configure MaxSockets
Secure
InterSxs
CommVer TLSMax
Sockets
MaxSockets Combined
Result
No
<3
3
0 0 Not valid
0 >0 Valid
>0 0 Not valid
>0 >0 Valid
0 0 Not valid
0 >0 Not valid
>0 0 Not valid
>0 >0 Valid
0 0 Not validYes <3
0 >0 Not valid
- 73 -
Page 74

PGP Endpoint
Secure
InterSxs
CommVer TLSMax
Sockets
>0 0 Valid
>0 >0 Valid
3
0 0 Not valid
0 >0 Not valid
>0 0 Valid
>0 >0 Valid
MaxSockets Combined
Result
Configuring MaxSockets and TLSMaxSockets
The following table describes the parameters used for the MaxSockets and TLSMaxSockets
configuration rules.
Table 8: Configuring MaxSockets and TLSMaxSockets
TLSMaxSockets and MaxSockets Values Description
TLSMaxSockets>0 AND MaxSockets=0 Only TLS connections are available for
PGP Endpoint Administration Server-client
communication using the TLSPort port
specification.
TLSMaxSockets=0 AND MaxSockets>0 Only non-TLS connections are available
for PGP Endpoint Administration Serverclient communication using the Port port
specification.
TLSMaxSockets>0 AND MaxSockets>0 Both TLS and non-TLS connections are
available for PGP Endpoint Administration
Server-client communication using the
TLSPort and Port port specifications.
Command & Control Registry Key
The registry key parameters for PGP Endpoint Command & Control (SCC) that govern the
behavior for all communication between the server, the client(s), and the Certificate Authority
(CA) server are shown in the following table.
The following table describes the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet
\Services\scomc registry key parameters for the PGP Endpoint Command & Control module. All
registry key entries are of the type: REG_SZ (= string value), unless designated otherwise.
- 74 -
Page 75

Managing Registry Keys
Table 9: PGP Endpoint Command and Control (SCC) Registry Key Parameters
Key Name Description Default Value
CertGeneration
ImportDir Shows the directory used import the policies file. C:\Program Files
Log file name Shows the name of the log file. scomc.log
Log to console
Log to dbwin
Log to file
Servers Shows a list of PGP Endpoint Administration
TicketDir Shows directory where endpoint maintenance
Yes=Client is in automatic mode and requests CA
certificate.
No=Client is in manual mode and a user certificate
must be generated manually.
Yes=Sends debug message to console.
No=No debug messages sent to console.
Yes=Sends debug message to dbwin.
No=No debug messages sent to dbwin.
Yes=Sends debug message to log file.
No=No debug messages sent to log file.
Server names by FDQN or IP address.
tickets are stored.
Defined during client
install.
\PGP\ PGP Endpoint
\Import
No default value.
No
No
Defined during server
install.
Cannot modify this
key.
UseTLS
Yes=TLS protocol used
No=TLS protocol not used
Defined during server
install.
Client Kernel Registry Key
The client kernel parameter subentries are shown in the following table.
The following table describes the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet
\Services\sk registry key parameters for the client kernel. All registry key entries are of the type:
REG_SZ (= string value), unless designated otherwise.
- 75 -
Page 76

PGP Endpoint
Table 10: Client Kernel Registry Key Parameters
Parameter Name Description Default Value
EncryptionMode EncryptionMode which SK runs one of the
following masks:
encLpc = 1
encFips = 2
encPgp = 4
NDISInstallation Specifies how SCOMC installs SK-NDIS .
1 = Uninstall only an existing SK-NDIS driver.
2 = Uninstall an existing SK-NDIS driver, then
install a new SK-NDIS driver.
encDefault = 0
None.
Software Registry Key
The registry key parameters that govern the application software configuration are shown in the
following table.
The following table describes the HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft
\Windows NT\RPC registry key parameters for the Management Server Console module. All
registry key entries are of the type: REG_SZ (= string value), unless designated otherwise.
Table 11: Software Registry Key Parameters
Parameter Name Description Default Value
EnableAuthEpResolution Sets the
RestrictRemoteClients
functionality status for the
RPC interface. Remote and
anonymous RPC call is
available only if:
• RPC registry key and
EnableAuthEpResolution
value described are
created during setup.
• The
EnableAuthEpResolution
registry value is set to 0.
- 76 -
0
Page 77

Managing Registry Keys
Administration Server Registry Key
The Administration Server registry key parameters allow you to define default server and
number of servers connected to the database and console.
The following table describes the HKEY_USERS\Software\PGP\PGP Endpoint\Server registry
key parameters for the Administration Server module. All registry key entries are of the type:
REG_SZ (= string value), unless designated otherwise.
Table 12: Administration Server Registry Key Parameters
Parameter Name Description Default Value
DefaultServer Name of the last Administration Server
that the Management Server Console
connected to.
Server List Lists the names of the Administration
Servers that the Management Server
Console connected to. Server names
are separated by commas.
None.
None.
Authorization Wizard Registry Key
The Authorization Wizard registry key parameters allow you to define the behavior for
communication between theAdministration Server and the wizard.
The following table describes the HKEY_USERS\Software\PGP\SecureEXE\AuthWiz
\Parameters registry key parameters for the Authorization Wizard module. All registry key
entries are of the type: REG_SZ (= string value), unless designated otherwise.
Table 13: Authorization Wizard Registry Key Parameters
Parameter Name Description Default Value
AutoAssign Specifies whether the Administration
Server should assign the hashed files
to a file group.
Yes
DefaultServer The Administration Server that the
Authorization Wizard sends a result
to. The value is the Administration
Server IP address.
- 77 -
127.0.0.1
Page 78

PGP Endpoint
Parameter Name Description Default Value
DefaultTemDir The file location where the
Authorization Wizard stores results
before uploading to an Administration
Server.
%TEMP%
- 78 -
 Loading...
Loading...