Page 1

Disk Wiper™ 8.5
User Manual
Page 2

Disk Wiper™ 8.5 2 User Manual
CONTENTS
1 Introduction................................................................................................................... 4
2 Key Features.................................................................................................................. 4
3 Disk Wiper Editions...................................................................................................... 5
4 Installation ..................................................................................................................... 6
4.1 Package Contents................................................................................................................................. 6
4.2 Minimum System Requirements ........................................................................................................ 6
4.3 Installation Procedure ......................................................................................................................... 6
5 Basic Concepts............................................................................................................... 8
5.1 Data Sanitization..................................................................................................................................8
5.2 Data Security Standards......................................................................................................................8
5.3 64-bit Support.......................................................................................................................................9
5.4 Scheduling...........................................................................................................................................10
6 Interface Overview...................................................................................................... 11
6.1 General Layout...................................................................................................................................11
6.2 Main Menu .........................................................................................................................................12
6.3 Tool Bar ..............................................................................................................................................13
6.4 Virtual Operations Bar......................................................................................................................13
6.5 Common Tasks Bar ...........................................................................................................................14
6.6 Disk Map............................................................................................................................................. 15
6.7 Explorer Bar.......................................................................................................................................15
6.8 Legend Bar .........................................................................................................................................16
6.9 Status Bar ...........................................................................................................................................16
7 Settings Overview........................................................................................................ 18
7.1 General Options ................................................................................................................................. 18
7.2 Wipe Options......................................................................................................................................19
7.3 Partitioning Options ..........................................................................................................................19
7.4 E-Mail Options................................................................................................................................... 20
7.5 Virtual Mode Options........................................................................................................................ 21
7.6 Operation Dependency Options........................................................................................................22
8 Getting Information about Disks............................................................................... 24
9 Wipe Tasks................................................................................................................... 26
9.1 Wipe Hard Disk/Partition .................................................................................................................26
9.2 Clear Free Space ................................................................................................................................30
9.3 Build Wiping Media...........................................................................................................................31
10 Scheduling Operations................................................................................................ 34
10.1 Save to Scheduler ...............................................................................................................................36
11 Scripting.......................................................................................................................37
12 Partition Management................................................................................................ 39
12.1 Create Partition..................................................................................................................................39
12.2 Format Partition ................................................................................................................................41
12.3 Delete Partition...................................................................................................................................43
13 Hard Disk Management ............................................................................................. 45
13.1 Update MBR.......................................................................................................................................45
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 3

Disk Wiper™ 8.5 3 User Manual
14 Extra Functionality ..................................................................................................... 46
14.1 View Partition/Hard Disk Properties............................................................................................... 46
14.2 Mount Partition..................................................................................................................................46
14.3 Test Surface ........................................................................................................................................48
14.4 Check File System Integrity.............................................................................................................. 48
14.5 Edit/View Sectors............................................................................................................................... 49
14.6 Send Log Files ....................................................................................................................................50
15 Glossary........................................................................................................................52
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 4

Disk Wiper™ 8.5 4 User Manual
1 Introduction
Data security nowadays is the burning issue not only for companies and government agencies, but rank and
file people as well. Our personality is now fully embedded in computer technology. It is computer you apply
to when at work, it is also computer you use at home for entertainment or as a reservoir for containing some
valuable data such as personal correspondence, banking account information, credit card numbers, financial
records, whatever… It is obvious that this kind of data should in no way be available to others. That is why,
when disposing of a storage device (a hard disk or a flash memory drive), the crucial thing is to make sure it
does not contain any information, because simple deletion, or even reformatting do not guarantee data
security at all. To do that, you need a specially designed tool.
Our program is a fast, convenient and reliable solution providing irreversible destruction of data on separate
partitions or entire hard disks (IDE, SCSI, SATA, USB, etc.) as well as any type of flash memory devices.
The key features of the program are listed in the special chapter
Setting up any operation is accomplished by using practical wizards. Each step of the wizard includes indepth information in order to allow the user to make the right choice. Graphical representations of the data
help the user to gain a better understanding.
In this manual you will find the answers to many of the technical questions which might arise while using
the program.
.
2 Key Features
Let us list some of the key features:
User friendly interface. Easily understood icons accompany all functions of the program.
Previewing the resulting layout of hard disks before actually executing operations (so-called virtual
operations).
Support of major national government and military data erasure standards as well as the possibility to
create a customized algorithm.
Wipe Wizard that enables to successfully destroy all on-disk information including standard
bootstrap code and other system service structures, thus providing high level of security, and that
even beginners may understand.
Wiping Media Builder that helps the user to create bootable media with the DOS-based version of
the program to boot from and destroy all on-disk information even when the current operating
system cannot boot anymore. The DOS-based version can boast the same interface as the Windows
version does, providing a unique possibility to enjoy XP-like environment and functionality under
DOS.
Clear Free Space function to destroy any remnants of deleted files/directories left on disk without
affecting the used data.
Schedule the operation. The user can set a convenient time for the program to perform the operation
automatically.
Basic functions for initializing, partitioning and formatting hard disks. Instead of the standard
Windows disk tools, the program supports all file systems.
Shutdown After Apply function enables to set the computer to automatically switch off on the
successful accomplishment of any scheduled operation.
Some features may be unavailable in the version of the product you have. To learn more
about it please consult the Disk Wiper Editions chapter.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 5

Disk Wiper™ 8.5 5 User Manual
3 Disk Wiper Editions
The product is being released in several editions, Personal and Professional, which vary in price and
provided functionality:
The Personal edition does not enable to use national government and military data erasure standards,
but two wipe algorithms (Paragon’s and customized).
The Personal edition does not support scripting, i.e. it cannot perform batch tasks in the unattended
mode.
Generate Script and Save to Scheduler program’s dialogs are unavailable in the Personal edition.
There is no possibility to send notifications by e-mail on the carried out operations in the Personal
edition.
Supported Operating Systems
OS
Windows 95
Windows 98
Windows Me
Windows NT
Windows NT Server Family
Windows 2000 Professional
Windows XP Home Edition
Windows XP Professional/ 64-bit
Windows 2000 Server Family
Windows Storage Server 2003
Windows Server 2003 Web
Windows Server 2003 Standard
Windows Server 2003 Standard 64-bit
Windows Server 2003 Enterprise
Windows Server 2003 Enterprise 64-bit/
Itanium
Windows Server 2003 Datacenter
Windows Server 2003 Datacenter 64bit/ Itanium
Windows Small Business Server 2003
Standard/ Premium
Windows Vista
Personal Professional
Yes Yes
Yes Yes
Yes Yes
Yes Yes
Yes Yes
Yes Yes
Yes Yes
Yes Yes
Yes Yes
Yes Yes
Yes Yes
Yes Yes
No No
Yes Yes
No No
Yes Yes
No No
Yes Yes
Yes Yes
Please take into consideration the mentioned above peculiarities of the certain versions when
working with the program.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 6

Disk Wiper™ 8.5 6 User Manual
4 Installation
This chapter provides information which is needed to perform the correct installation of the program, and in
addition, checks if the current installation is working correctly.
4.1 Package Contents
The installation package includes the following components:
Launcher (with an embedded HTML browser)
Wipe Wizard
Wiping Media Builder
Partition Management
Hard Disk Management
Scheduler with Task Editor
Extra Functionality
4.2 Minimum System Requirements
To use the program on a computer satisfactorily, ensure that it meets the following minimum system
requirements:
Operating systems: Windows 95/98/ME/NT/2000/XP/2003 Server/Vista and XP 64-bit
Internet Explorer 5.0 or higher
Intel Pentium CPU or its equivalent, with 300 MHz processor clock speed
128 MB of RAM
Hard disk drive with 40 MB of available space
SVGA video adapter and monitor
Mouse
4.3 Installation Procedure
The installation process consists of the following steps:
1. Run Setup Application
From the folder, where the setup files are kept, run the SETUP.EXE file. This application will guide the user
through the process of the program installation. The setup utility is compiled with the InstallShield SDK,
hence it contains the standard user interface and set of installation steps.
In case there is some previous version of the program installed on the computer, the program
will offer the user to uninstall it first.
2. Starting Setup
The Welcome page informs that the application is being installed. Click the Next button to continue.
3. Confirm License Agreement
The License Agreement page displays the Paragon License Agreement. Read the agreement and then click
the Yes button to accept. If the user does not agree with any conditions stated there, the installation process
will be interrupted.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 7
Disk Wiper™ 8.5 7 User Manual
4. Select an Installation Folder
The Destination Location page allows the user to choose the folder where the program will be installed. By
default, the installation folder will be created as:
C:\Program Files\Paragon Software\Paragon Disk Wiper. To select another folder, click the Browse
button.
After you have selected the required folder, click the Next button to continue.
Do not install the program on network drives. Do not use Terminal Server sessions to install
and run the program. In both cases, the program functionality will be limited
5. Select a Program Group
The Program Folder page enables the user to select the application's program group for the Start Menu. By
default, it will be the program group:
Start > Programs > Paragon Disk Wiper.
Click the Next button to continue.
6. Verify Setup Settings
The Start Copying page allows the user to verify settings, which have already been made and correct them if
necessary. Press the Back button to return to the previous page and modify the installation settings. Click the
Next button to complete the installation process.
7. Copying Files
The Setup Status page shows the overall progress of the installation. Click the Cancel button to abort the
setup.
8. Finishing the Installation
The Final page reports the end of the setup process.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 8

Disk Wiper™ 8.5 8 User Manual
5 Basic Concepts
This chapter explains terms and ideas that show how the program works. To understand these helps to obtain
a general notion of the operation performance and makes it easier for the user to operate the program.
5.1 Data Sanitization
Data security is a two-sided problem. It is to be made clear, that providing confidentiality implies not only
information to be stored properly, but also be destroyed according to certain rules. The first step to
protecting yourself is to know exactly which security precautions work and which do not.
Many people believe the misconception that repartitioning a disk will result in complete destruction of its
contents. Actually that is not quite so. Repartitioning the drive only alters references to partitions in the
Partition Table, leaving all file data intact. In fact, there are a number of programs available to successfully
recover previously deleted partitions.
Formatting a drive also does not guarantee data destruction. Formatting procedure implies modification of
the Master File Table (MFT) that keeps track of where file contents are stored on the disk and verification of
each sector for consistency. Even a low-level format does not actually erase the file contents for good, since
they can still be resurrected from their deleted state with minimal effort by using the popular today Magnetic
Force Microscopy technology.
The only way to make sure that all the data has been erased from a hard drive is to overwrite all on-disk
sectors with random patterns of ones and zeros. Although this sounds complex, there is an easy way to do
this.
The process of deliberately, irreversibly removing or destroying the data stored on a memory device
(magnetic disks, flash memory drives, etc.) is generally known as Data Sanitization. A device that has been
sanitized has no usable residual data and even advanced forensic tools should not ever be able to recover it,
thus providing maximum level of security.
5.2 Data Security Standards
To irreversibly destroy all on-disk information there have been developed a number of disk sanitizing
standards. They are distinguished by wiping patterns and number of passes:
1. US DoD 5220.22-M. US Department of Defense recommends to overwrite all addressable locations
with a character, its complement and then a random character. Finally, the target data area is to be
verified;
2. US Navy standards NAVSO P-5239-26.
NAVSO P-5239-26 for RLL encoded drives. At first to write the fixed value (0xffffffff) to
the target data area, then the fixed value (0x27ffffff), and then random values. Finally, the
target data area is to be verified;
NAVSO P-5239-26 for MFM encoded drives. At first to write the fixed value (0xffffffff) to
the target data area, then the fixed value (0xbfffffff), and then random values. Finally, the
target data area is to be verified;
3. British HMG Infosec Standard No.5. At first to write a single character pattern, then its
complement and then a random character. Finally, the target data area is to be verified;
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 9
Disk Wiper™ 8.5 9 User Manual
4. German VSItR Standard. Overwrite the deleted information 7 times, consistently filling it with the
following patterns: 0x00, 0xFF, 0x00, 0xFF, 0x00, 0xFF, 0xAA. Finally, the target data area is to be
verified;
5. Australian ASCI 33. Overwrite with a character (C), then verify. Overwrite with –C (the first pass
character’s inverse), then verify again. Overwrite everything with both C and –C once again but
without verification. Fill everything with random characters.
6. Russian GOST R 50739-95. Destroy information by a single pass with writing random characters
into each sector byte.
7. Peter Gutmann's algorithm. A whopping 35 passes, with 27 random-order passes using specific
patterns combined with eight passes using random patterns;
8. Bruce Schneier's algorithm. Two passes of specific patterns followed by five passes using a
cryptographically secure pseudo-random sequence;
9. Paragon's algorithm.
Overwrite each sector with a forcefully randomized 512-byte string, new for each sector,
using CSPRNG (cryptographically secure pseudo-random number generator).
Overwrite each erased sector with its complement.
Overwrite each sector with a 512-byte string (CSPRNG), again forcefully randomized and
different from the first pass, and new for each sector.
Fill each erased sector with 0xAA value. Finally, the target data area is to be verified.
Military and government standards always require 100 percent residual data verification. It
is necessary to make sure that the operation has been properly accomplished. Besides
corrupted sectors discovered during the operation are to be logged to keep the user informed,
since these sectors may contain classified information.
All of the above-mentioned data erasure standards are implemented in the program. Besides the user has the
possibility to create a customized algorithm, defining up to 4 wiping patterns, number of passes for each
wiping pattern and for the group of patterns, thus providing the maximum possible security level.
Some features may be unavailable in the version of the product you have. To learn more
about it please consult the Disk Wiper Editions chapter.
5.3 64-bit Support
The bulk of software today is written for a 32-bit processor. It can meet the requirements of almost any end
user. However that is not the case when dealing with servers processing large amounts of data with complex
calculations of very large numbers. That is where 64-bit architecture comes into play.
It can boast improved scalability for business applications that enables to support more customer databases
and more simultaneous users on each server. Besides a 64-bit kernel can access more system resources, such
as memory allocation per user. A 64-bit processor can handle over 4 billion times more memory addresses
than a 32-bit processor. With these resources, even a very large database can be cached in memory.
Although many business applications run without problems on 32-bit systems, others have grown so
complex that they use up the 4 GB memory limitation of a 32-bit address space. With this large amount of
data, fewer memory resources are available to meet memory needs. On a 64-bit server, most queries are able
to perform in the buffers available to the database.
Some 32-bit applications make the transition to the 64-bit environment seamlessly others do not. For
instance, system-level utilities and programs that provide direct hardware access are likely to fail. Our
program offers a full-fledged support of the 64-bit architecture providing fault-tolerant work for system
dependent modules.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 10
Disk Wiper™ 8.5 10 User Manual
5.4 Scheduling
The automation of the program’s operations is particularly effective when the user has to repeat a sequence
of actions on a regular basis. For example, when a specific project is being developed on a computer on a
day-to-day basis and a clear free space operation is made every evening so as to destroy any remnants of
deleted files/directories left on disk, thus maintaining confidentiality, it should be possible to simplify
certain routine operations.
Another aspect of any automation process is that it runs automatically without the user having to be present.
The program is able to execute operations without the user being involved. In addition, it allows an
optimization of your computer’s work-load. This is especially important when operations require a
considerable amount of computer resources – processor time, memory and more. A number of operations,
which can decrease the performance, can be run during the night or whenever the computer has the least
work-load to perform.
The program has a special tool for scheduling
example, some operations may be performed daily, others - weekly and so on. The scheduled operation
starts at a specified time without interrupting the user's current activity.
. The user can set out a timetable for various operations. For
Some features may be unavailable in the version of the product you have. To learn more
about it please consult the Disk Wiper Editions chapter.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 11
Disk Wiper™ 8.5 11 User Manual
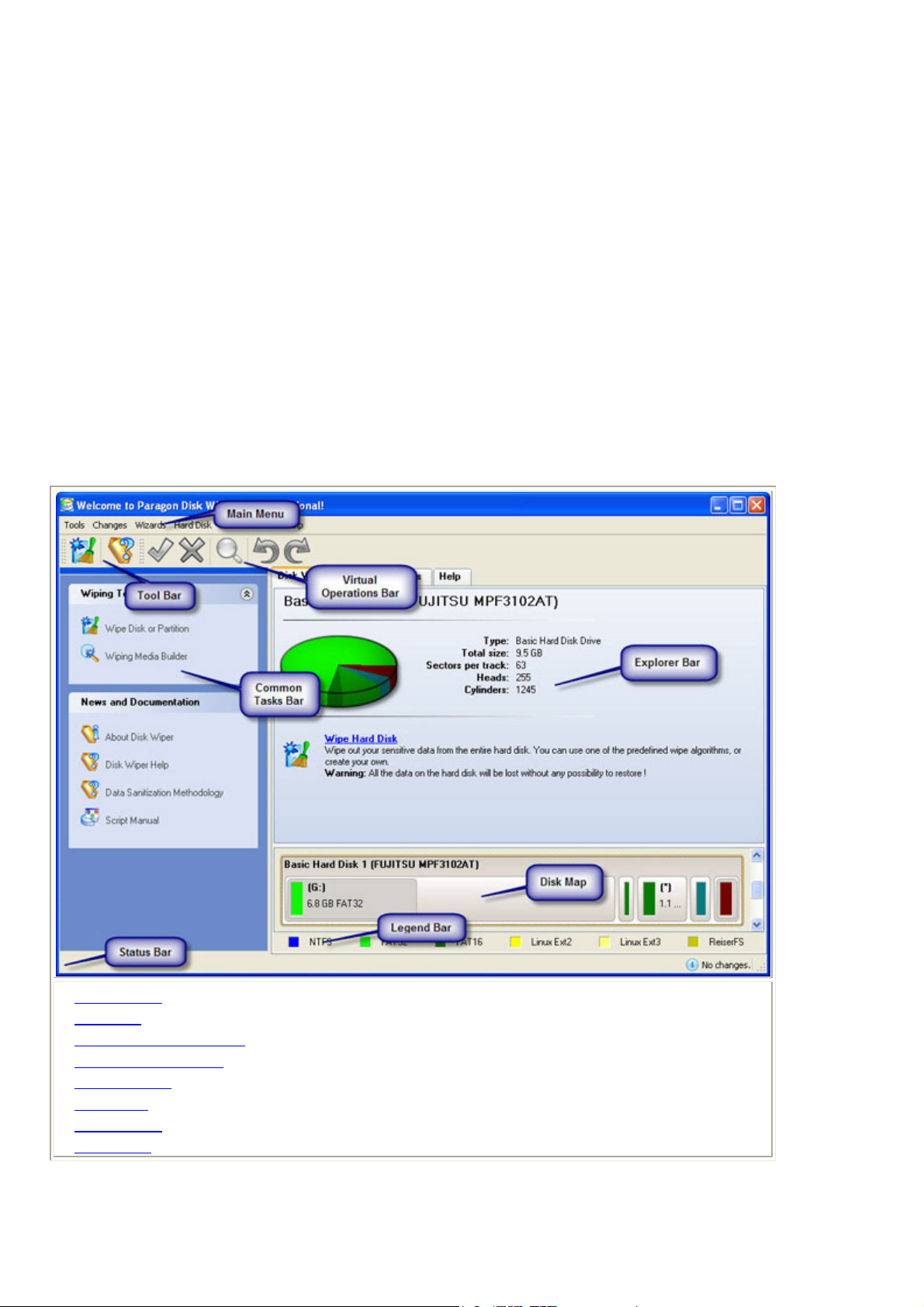
6 Interface Overview
This chapter introduces the graphical interface of the program to the user. The design of the interface
precludes any mistake being made on the part of the user. Most operations are performed through the system
of wizards. Buttons and menus are accompanied by easy understandable icons. Nevertheless, any problems
that might occur while managing the program can be tackled by reading this very chapter.
6.1 General Layout
When the user starts the program, the first component that is displayed is called the Launcher. It enables the
user to run wizards and utilities, to specify program settings, to visualize the operating environment and the
hard disk configuration.
The Launcher’s window can be conditionally subdivided into several sections that differ in their purpose and
functionality:
1. Main Menu
2. Tool Bar
3. Virtual Operations Bar
4. Common Tasks Bar
5. Explorer Bar
6. Disk Map
7. Legend Bar
8. Status Bar
Some of the panels have similar functionality with a synchronized layout. The program enables the user to
conceal some of the panels to simplify the interface management.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 12

Disk Wiper™ 8.5 12 User Manual
All panels are separated by vertical and horizontal expandable sliders, allowing the user to customize the
screen layout.
6.2 Main Menu
The Main Menu provides access to the entire functionality of the program. The available functions are as
listed below:
MENU ITEM FUNCTIONALITY
Tools
Generate Script… Generate a script for the task
Save to Scheduler… Schedule pending operations
Send Log Files Compress and send the log to the Paragon Support Team
Wiping Media
Builder…
Create the DOS-based version of the program to boot from and destroy all ondisk information even when the current operating system cannot boot anymore
Settings... Edit the general settings of the program
Exit Exit the program
Changes
Undo "the last virtual
operation"
Redo "the last virtual
operation"
Cancel the last virtual operation on the List of Pending Operations
Cancel the last undo virtual operation on the List of Pending Operations
View Changes… Display the List of Pending Operations
Apply Changes Launch the real execution of virtual operations
Discard All Changes Cancel all virtual operations on the List of Pending Operations
Reload Disk Info Refresh the current information about disks
Wizards
Wipe Hard Disk or
Partition...
Hard Disk
Destroy all on-disk information including standard bootstrap code and other
system service structures
Update MBR Update MBR (Master Boot Record) of the selected hard disk
Edit/View Sectors… View/edit sectors of the selected hard disk
Properties… Get in-depth information on the properties of selected hard disk
Partition
Create Partition… Create a partition of any file system with the Create Partition dialog
Format Partition… Format a partition of any file system Format Partition dialog
Delete Partition… Delete a partition of any file system Delete Partition dialog
Assign Drive Letter… Assign drive letter to the selected partition
Remove Drive
Letter…
Clear Free Space…
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Remove drive letter for the selected partition
Destroy any remnants of deleted files/directories left on disk without affecting
the used data
Page 13
Disk Wiper™ 8.5 13 User Manual
Test Surface… Test surface of the selected partition/block of free space
Check File System
Integrity…
Edit/View Sectors… View/edit sectors of the selected partition
Properties… Get in-depth information on the properties of selected partition
View
Toolbar
Status Bar Display the Status bar
Common Tasks Bar Display the Common tasks bar
Disk Map Legend Display the Disk map legend
Disk Map Location
Help
Help Open the Help system
About Open the dialog with information about the program
The Main Menu contents available at the moment may vary depending on the selected object.
Some features may be unavailable in the version of the product you have. To learn more
about it please consult the Disk Wiper Editions chapter.
Check the selected partition for possible file system errors
Manage the Tool Bar representation: show / hide standard and navigation
buttons, text labels and large icons.
Select whether the Disk map will be located on the top of the main window or
at the bottom
6.3 Tool Bar
The Toolbar provides fast access to the most frequently used operations:
BUTTON FUNCTIONALITY
Wipe a hard disk or
partition
Open the Help system
6.4 Virtual Operations Bar
The program supports previewing the resulting layout of hard disks before actually executing operations (socalled virtual mode of execution). In fact, when the virtual mode is enabled
accomplish operations immediately, but places them on the List of Pending Operations for later
accomplishment.
The Virtual Operations Bar enables to manage pending operations.
, the program does not
BUTTON FUNCTIONALITY
Cancel the last virtual operation on the List
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
of Pending Operations
Page 14
Disk Wiper™ 8.5 14 User Manual
Cancel the last undo virtual operation on
the List of Pending Operations
Display the List of Pending Operations
Launch the real execution of virtual
operations
Cancel all virtual operations on the List of
Pending Operations
Virtual mode is an effective way of protection from any troubles, since no operations will be
executed until clicking the Apply button for confirmation, thus giving a second chance to
weigh all pros and cons of this or that particular operation. The program politely reminds the
user that there are unsaved changes by showing the following window:
6.5 Common Tasks Bar
The Common Tasks Bar is located on the left side of the main window. It is intended for easy access to the
program's wizards that provide all the functionality needed to manage copy operations.
The bar contains two tabs named Wiping Tools and News and Documentation. Each of these contains a
separate button bar which can be folded by clicking it.
Wiping Tools
Starting the Wipe Wizard. The Wipe Wizard assists the
user with destroying all on-disk information.
Starting the Wiping Media Builder Wizard that helps to
create bootable media with the DOS-based version of the
program.
News and Documentation
Opening the page which contains information about the
program. This page will be displayed in the Explorer bar.
Launching the Help system.
Opening a brief review on the Data Sanitization issue.
Opening a brief review on the Paragon Scripting
Language.
Some features may be unavailable in the version of the product you have. To learn more
about it please consult the Disk Wiper Editions chapter.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 15
Disk Wiper™ 8.5 15 User Manual
6.6 Disk Map
The Disk Map is displayed in the Explorer bar when the Disk View tab is selected. It is located either at the
top or at the bottom of the window, depending on the state of the Disk Map Location option (Main menu:
View > Disk Map Location). The user can change the current location of the map with this option.
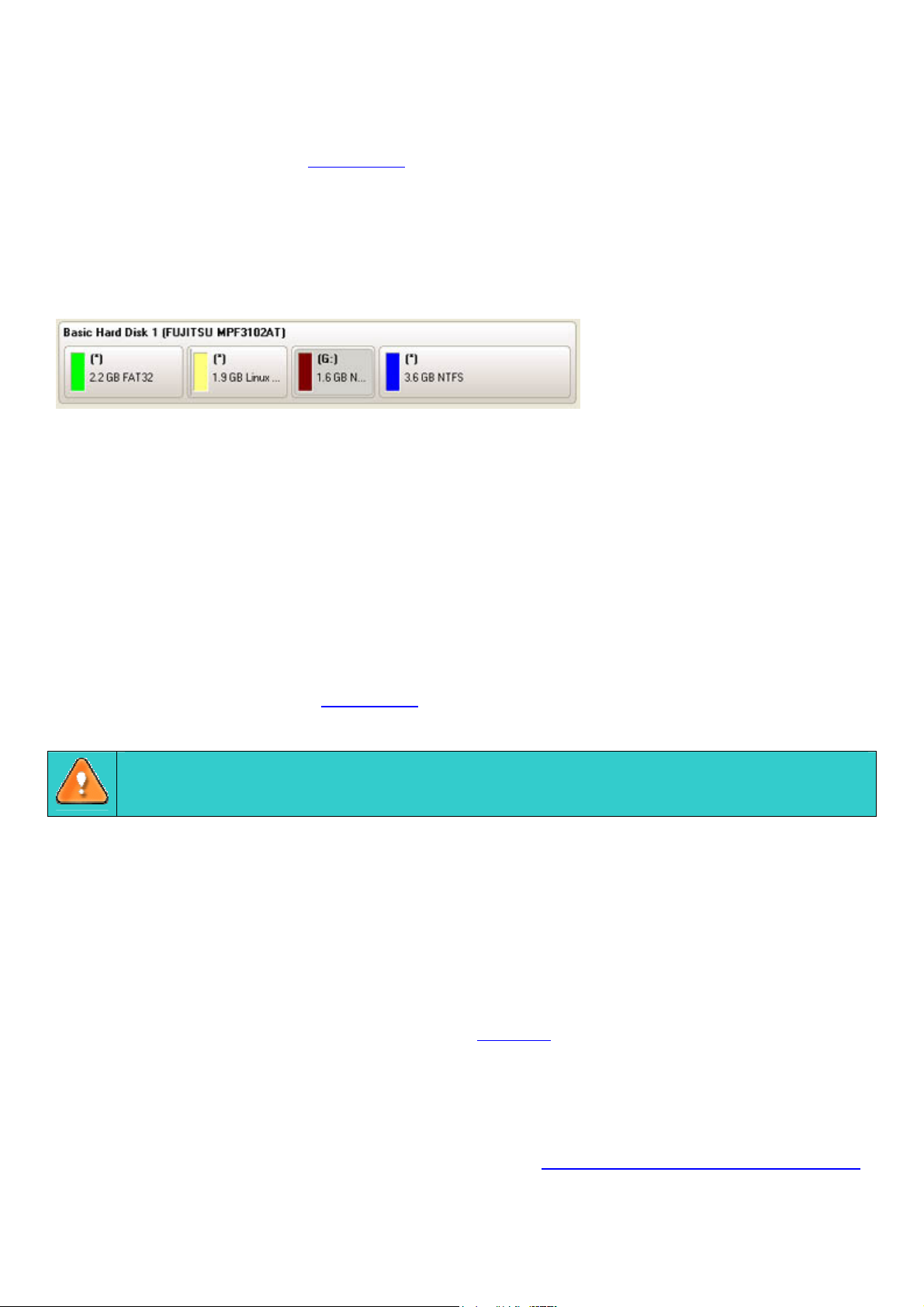
As the name infers, the Disk Map displays the layout of physical and logical disks. Physical disks are
represented with rectangle bars that contain small-sized bars. These small-sized bars represent logical disks.
Their color depends on the file system of the appropriate partition.
Large-sized bars display the following information about physical disks:
Manufacturer,
Model.
Small-sized bars display the following information about logical disks:
Serial number,
Drive letter,
Total size,
File system.
Furthermore, it is possible to estimate the used disk space by looking at the size of the bar’s shaded area.
Disk Map is synchronized with the Explorer bar
bar displays detailed information of the selected disk.
The user can click a large-sized bar to display information about the appropriate physical
disk in the Explorer bar. A click on a small-sized bar will lead to displaying information
about the appropriate logical disk.
. When the user selects a disk on the Disk Map the Explorer
6.7 Explorer Bar
The Explorer Bar is located in the center of the main window which emphasizes its importance. The bar
displays reference information including:
User Manual,
Information about the program consisting of the product's name, the version of the program and a list
of helpful links,
Detailed information about disks selected on the Disk Map,
List of scheduled operations,
According to these categories the Explorer bar has five tabs:
Disk View, which allows the user to view detailed information about any of the disks.
Scheduled Tasks, which gives the user the possibility of browsing and editing scheduled operations.
Help System, which contains the User Manual and information about the program.
The user is able to access the desired information by clicking on the appropriate tab.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 16
Disk Wiper™ 8.5 16 User Manual
The Explorer Bar is a fully-functional embedded HTML browser, which enables the user to address, for
example, our company's website to look through important technical notes or download the latest updates
without having to close the program. The Help System of the program is HTML-oriented. The user can read
the user manual and follow external links from to get additional information.
To easily navigate through browsed pages, the program provides the following functionality:
BUTTON FUNCTIONALITY
Return to the previously browsed page
Open the next browsed page
Stop loading the current page
Refresh the contents of the current page
6.8 Legend Bar
The Legend Bar explains the color scheme used for disk and partition presentation. The user can hide (or
show) the bar with the appropriate Main menu item: View > Disk Map Legend. When it is activated it can be
found at the bottom of the Explorer bar
The program distinguishes between the following types of known file systems:
- FAT16/32,
- NTFS,
- Linux Ext2/3,
- Linux ReiserFS.
.
6.9 Status Bar
This is the bottom part of the main window. The status bar displays menu hints, for each item the cursor
points to.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 17

Disk Wiper™ 8.5 17 User Manual
The user can hide (or show) the bar with the appropriate Main menu item: View > Status bar.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 18

Disk Wiper™ 8.5 18 User Manual
7 Settings Overview
The Settings dialog is available from the Main menu: Tools > Settings. All the settings are grouped into
several sections of which the functions are described in the following paragraphs. The list of sections is
placed on the left side of the dialog. By selecting a section from the list, the user opens a set of options.
7.1 General Options
This section contains a set of general options that will be taken into account during all the operations carried
out with the program. The user can switch between the following modes:
Verify data written. If this option is marked, every write-to-disk action is followed by the
read-and-compare action. This feature may be helpful in case of running an unstable hard
disk, however it will negatively affect the overall performance.
Enable data loss protection. Activate the option to force the program to work in the fail-safe
mode (also referred to as data-loss protection mode), which ensures more safety for
operations by maintaining the special journal of operations’ progress. In case of hardware
malfunction, power outages or operating system failure, the modified partition may become
corrupted and non-operable. However, the program will be able to complete the interrupted
operation, thus "reviving" the partition.
If the system has crashed during the operation in the fail-safe mode, insert the bootable
Recovery CD and restart the computer. The program will automatically detect the journal of
the interrupted operation and complete the operation.
It is strongly recommended to enable this option.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 19

Disk Wiper™ 8.5 19 User Manual
Try to access non-BIOS disk cylinders. The option works only under Windows 95, 98, ME.
When activated, the program performs a special procedure to define the disk capacity and
does not use the value that is returned by BIOS.
7.2 Wipe Options
Here the user can select a wipe method from the pull down list to be used by default during wipe operations.
The user can switch between the following modes:
US DoD 5220.22-M
NAVSO P-5239-26 for RLL encoded drives
NAVSO P-5239-26 for MFM encoded drives
British HMG Infosec Standard No.5
German VSItR Standard
Australian ASCI 33
Russian GOST R 50739-95
Peter Gutmann's algorithm
Bruce Schneier's algorithm
Paragon's algorithm
To know more about various erasure algorithms, please consult the Data Security Standards
chapter.
7.3 Partitioning Options
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 20

Disk Wiper™ 8.5 20 User Manual
This section contains a set of options that will be taken into account during partitioning operations. The user
can activate the following modes:
64 KB cluster size for FAT16 partitions. Only Windows NT 4.0/2000/XP/2003 support 64 KB
clusters.
Request confirmation before partition deletion.
Request confirmation when converting FAT16 to FAT32 during such partitioning operations as
copy disk/partition, restore disk/partition.
Surface test level. The option affects the following operations: format partition, copy partition,
restore partition, retest the surface. While performing the surface test, the program detects corrupted
sectors and marks them as unusable.
7.4 E-Mail Options
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 21

Disk Wiper™ 8.5 21 User Manual
This section contains a set of options that will be taken into account during the Send log files and Send email notification operations. The user can define:
Outgoing mail server (SMTP). To send messages by using the built-in mail client, it is necessary to
have access to a computer running an SMTP (Simple Mail Transfer Protocol) server. All outgoing
messages are first sent to the SMTP server, which in its turn delivers them to the required recipients.
The address may be represented as a traditional Internet host name (e.g.: mail.com) or as an IP
numeric address (e.g. xxx.xxx.xxx.xx).
User e-mail address. Specify an e-mail address that has been assigned by the Internet Service
Provider or organization's e-mail administrator.
My outgoing server requires authentication. Activate the option to allow the program to make
authentication on the server before sending messages.
- User name. Enter the name that will be used to log in to the e-mail account.
- Password. Enter the password that will be used to access the mail server.
Send e-mail notification on apply. Specify an e-mail to send notifications on the carried out
operations.
- Send mail in HTML format. Activate the option to create messages in the HTML format instead
of plain text.
- Send complete report after applying operations. Activate the option to create an in-depth report
on the carried out operations and send it after performing the last operation.
- Send graphical view of the disk sub-system before and after apply. Activate the option to allow
the program to attach two pictures of the disk layout made before and after the operation is
completed.
Some features may be unavailable in the version of the product you have. To learn more
about it please consult the Disk Wiper Editions chapter.
7.5 Virtual Mode Options
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 22

Disk Wiper™ 8.5 22 User Manual
Allow virtual mode. In this section the user can choose whether to allow operations to carry out
immediately or to place them on the List of Pending Operations for later execution. Just mark the
option to enable virtual operations.
Close progress dialog automatically. Mark the option to automatically close the progress dialog
when the required operation(s) is completed.
Virtual mode can be particularly beneficial for such operations as Generate script… or Save
to scheduler…
7.6 Operation Dependency Options
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 23

Disk Wiper™ 8.5 23 User Manual
This section contains a set of options that will be taken into account when the Send e-mail notification on
apply function is enabled. By marking the appropriate operations the user can choose whether to receive an
e-mail notification after the particular operation is completed or not. However, the user will not be notified
by e-mail in case operations (if any) require the system reboot.
Some features may be unavailable in the version of the product you have. To learn more
about it please consult the Disk Wiper Editions chapter.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 24

Disk Wiper™ 8.5 24 User Manual
8 Getting Information about Disks
The user is able to view in-depth information on the properties of hard disks. The main tool to extract this
information is the Disk Map. It represents the actual state of the computer’s hard disks. The Disk Map
chapter is a detailed description on this topic.
Generally the hard disks are represented on the map by rectangular bars, which also contain small-sized
bars. The small-sized bars represent logical disks (partitions). When the user selects a large-sized bar, the
Explorer bar
displays information about the disk in a bright, graphical form.
The model and serial number of the disk serve as the title of the browsed page. The disk layout is shown in
form of a circular graph, where the color of a sector corresponds to a file system of an appropriate partition.
On the right the user may see a table, which contains the following information:
Type of hard disk (basic or dynamic),
Total size (in GB),
Information on geometry of the disk (amount of sectors per track, heads and cylinders).
Below there is a list of wizards available for the user. If the user clicks a corresponding record the
appropriate wizard will be started. All default values for the operation parameters will correspond to the
disk’s settings. The list of wizards contains a detailed description of tasks that can be performed by the
wizard. This nullifies the possibility of selecting the wrong wizard.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 25

Disk Wiper™ 8.5 25 User Manual
When the user selects a small-sized bar (i.e. corresponding to a logical disk), the Explorer bar will display
information on it as well. The page title will contain a drive letter, which is assigned to the disk. The disk
layout graph will be colored in accordance with the volume ratio of the used space to the free space (the
light colored sector). The table on the right will contain the following information:
Volume label (if available),
Type of the logical disk,
File system (represented by the color of the graph and the selected bar),
Total size, used space and free space (in GB or MB).
Below there is a list of wizards, which may be called for this disk. All default values of parameters will
correspond to the disk settings.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 26

Disk Wiper™ 8.5 26 User Manual
9 Wipe Tasks
This chapter lists various scenarios of wipe operations which may be accomplished by the program. This has
already been reviewed in the Basic concepts chapter
and descriptions of operations.
9.1 Wipe Hard Disk/Partition
The program provides the ability to wipe hard disks/partitions of any file system. During the wiping process,
the program destroys all on-disk information including standard bootstrap code and other system service
structures, thus providing high level of security. The program offers support of major national government
and military data erasure standards as well as the possibility to create a customized algorithm. This operation
cannot be substituted by simply deleting or formatting of a hard disk/partition.
The operation can be accomplished with the Wipe Wizard. The wizard is so well designed that the user
simply needs to follow its easy instructions to carry out the operation.
. Here the user will find more useful recommendations
9.1.1 Starting
There are several ways to start the Wipe Wizard:
In the Main menu: select Wizards > Wipe Hard Disk or Partition…
On the Common Tasks bar: click the Wipe Disk or Partition item of the Wizards menu.
In the Toolbar: click the Wipe Wizard button.
Select a hard disk or partition on the Disk map and click the Wipe Hard Disk item if a hard
disk was selected or Wipe Partition item if a partition was selected on the page that appears
in the Explorer bar.
After following one of the above mentioned actions, the Welcome page of the wizard is displayed.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 27

Disk Wiper™ 8.5 27 User Manual
9.1.2 Settings
The Wipe Wizard allows the user to configure the settings and then start the operation in accordance with
the entered parameters. Here the user sets the parameters of the operation defining:
The hard disk/partition to wipe. Select a hard disk/partition the data of which you want to
destroy.
Wipe mode. This section enables to switch between two options:
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 28

Disk Wiper™ 8.5 28 User Manual
- Wipe out all data. Mark the option to irreversibly destroy all on-disk data of the selected
object.
- Clear (wipe) free space. Mark the option to destroy any remnants of deleted
files/directories left on disk without affecting the used data.
The Clear Free Space operation is available only for Logical and Primary partitions of
known file systems.
Wipe method. Here the user can select a specific data erasure algorithm from the pull down
list or create a customized method by marking the appropriate option.
- In case the user preferred to use a specific algorithm, the next page of the wizard enables
to get detailed information on the selected algorithm, choose whether to carry out residual
data verification or not specifying the percentage of sectors to check and estimate the time
required to accomplish the operation.
Some features may be unavailable in the version of the product you have. To learn more
about it please consult the Disk Wiper Editions chapter.
- In case the user preferred to create a customized algorithm, the next page of the wizard
enables to define up to 4 wiping patterns, number of passes for each wiping pattern and
for the group of patterns. The Mask spinner control allows the user to set a two-figure
hexadecimal character value ("00" by default). The available range is from "00" to "FF".
The user can also choose whether to carry out residual data verification or not specifying
the percentage of sectors to check.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 29

Disk Wiper™ 8.5 29 User Manual
Revise your changes. This page informs the user on all the actions to be made in the wizard
in a bright, graphical form.
9.1.3 Results
Depending on the user’s choice the Wipe Wizard:
starts the operation
reconsiders it
By clicking the More options button during the operation execution the user can set up a
number of additional parameters:
Shutdown system on complete. Mark the option to automatically switch off the
After the operation is completed the user can see a well informative summary page, providing structurally
divided in-depth information on all the actions made in the wizard.
computer on the successful accomplishment of the operation.
Minimize to system tray. Click it to minimize the window to the Windows system tray.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 30

Disk Wiper™ 8.5 30 User Manual
The program also enables to store the resulted report. To do that, just press the Save button and choose the
exact location in the opened dialog.
To make sure that all on-disk data is irreversibly destroyed call the Disk Viewer dialog by clicking the
appropriate tab and see it for yourself.
The Summary page will be available only when the Virtual operations are disabled.
9.2 Clear Free Space
The program allows the user to destroy any remnants of deleted files/directories left on disk without
affecting the used data by overwriting contents of unused clusters with certain patterns. Besides providing
high level of data protection this function can be particularly useful when dealing with certain non-standard
protection/registration/deactivation hidden marks made by some software.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 31

Disk Wiper™ 8.5 31 User Manual
In order to start the operation the user should take the following steps:
1. Select a partition on the Disk Map.
2. Call the Clear Free Space dialog selecting in the Main menu: Partition > Clear Free Space…
3. Define parameters of the operation with the Clear Free Space dialog. Initially the program suggests some
consistent values for all parameters. In most cases, the user may just press the Wipe button to confirm the
operation.
HEX value. The Hex value spinner control allows the user to set a two-figure hexadecimal character
value ("00" by default). The available range is from "00" to "FF". It is synchronized with the ASCII
value.
ASCII value. The ASCII value spinner control enables to set the symbolic presentation of the
character to use according to the 7-bit American Standard Code for Information Interchange ("#0" by
default). It is synchronized with the Hex value.
Number of passes. The user can choose number of passes for the wiping pattern (1 by default). The
available range is from 1 to 100.
Verify wipe results. The user can also choose whether to carry out residual data verification or not
specifying the percentage of sectors to check.
The Clear Free Space operation is only available for Logical and Primary partitions of
known file systems.
By clicking the More options button during the operation execution the user can set up a
number of additional parameters:
Close progress dialog automatically. Mark the option to automatically close the
progress dialog after the operation is completed.
Shutdown system on complete. Mark the option to automatically switch off the
computer on the successful accomplishment of the operation.
Minimize to system tray. Click it to minimize the window to the Windows system tray.
9.3 Build Wiping Media
The program provides the possibility to create the DOS-based version of the program on external media
(CD, DVD or floppy disks) to boot from and destroy all on-disk information even when the current
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 32

Disk Wiper™ 8.5 32 User Manual
operating system cannot boot anymore. The operation can be accomplished with the Wiping Media Builder
Wizard.
9.3.1 Starting
There are several ways to start the Wiping Media Builder Wizard:
In the Main menu: select Tools > Wiping Media Builder…
On the Common Tasks bar: click the Wiping Media Builder item of the Wizards menu.
After following one of the above mentioned actions, the Welcome page of the wizard is displayed.
9.3.2 Settings
The Wiping Media Builder Wizard allows the user to make proper settings and then start the operation in
accordance with the entered parameters. In our case we set parameters of the future bootable media defining:
Type of the wiping media the user is creating. The program can be placed either on a
CD/DVD disc or on a floppy disk.
Contents of the wiping media. The bootable media may include the standard Wiping Media
image (it is a part of the installation package) or software, defined by the user. In the last case
the user can record a beforehand-prepared image setting the path to the image file on the disk.
A recording device. Appropriate external media (CD/DVD or a floppy disk) should be
inserted into the selected device.
CD/DVD writing parameters (in case the user selects this kind of media). Writing
parameters include writing speed (maximum or minimum) and the ability of ejecting the
recorded disc after completing the operation.
The program supports CD-R, CD-RW, DVD-R, DVD+R, DVD-RW, DVD+RW and also DVD-R, DVD+R
double layer discs. If the inserted disc is not empty the Wizard suggests erasing its contents. If the user
confirms the operation the program erases the re-writable disc's contents and starts recording.
9.3.3 Results
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 33

Disk Wiper™ 8.5 33 User Manual
The Wiping Media Builder Wizard starts the operation after completing the settings mentioned above. As a
result the user receives bootable media with the DOS-based version of the program.
It can boast the same interface as the Windows version does, providing a unique possibility to enjoy XP-like
environment and functionality under the DOS environment.
The Summary page will be available only when the Virtual operations are disabled.
Some features may be unavailable in the version of the product you have. To learn more
about it please consult the Disk Wiper Editions chapter.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 34

Disk Wiper™ 8.5 34 User Manual
10 Scheduling Operations
The program allows the user to automate operations. The utility for this purpose is referred to as the
embedded Scheduler, which is used to specify the time for the execution of any operation. There are two
categories for time settings (these correspond to appropriate items in the Schedule type menu):
Initiating operation by an event:
- One time only (i.e. the Once item)
- When system starts (i.e. the At System Startup item)
- When the user logs on (i.e. the At Logon item).
Initiating operation periodically (i.e. Daily, Weekly, Monthly).
The user needs to select one of the variants. Depending on the choice, the scheduler will display a form that
allows the user to set the schedule.
To run the task in the log-off mode, please specify administering login info by following the
appropriate link in the left lower corner of the page.
The Shutdown System on Complete option enables to automatically switch off the computer on
the successful accomplishment of the operation.
All scheduled tasks are placed in a separate list, which can be retrieved by clicking the Scheduled Tasks tab
in the Explorer bar
:
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 35

Disk Wiper™ 8.5 35 User Manual
On every task the user can get in-depth information, including:
The task name
The full path to the generated script of the task
Scheduled time of launch
Statistics on the last launch
Scheduled time of the next launch
Used account information
Comments to the task
To easily manage tasks, the program enables to arrange them according to a certain characteristic just by
clicking on the required property.
This feature can be particularly beneficial when the Scheduled Tasks list contains too many
items.
It is also possible to enable/disable, rename, delete, refresh or modify additional properties of the selected
task.
To modify additional properties of the selected task with the Task Editor, the user should select the
Properties item of the context menu, which can be called by a right-click on the appropriate task.
The dialog window has two tabs - General and Schedule. The General tab contains:
The full path to the program-interpreter of the macro-commands which describes the scheduled task
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 36

Disk Wiper™ 8.5 36 User Manual
The line of parameters for starting the interpreter (i.e. the task described in macro-language)
Comments referring to the task
The option of enabling/disabling the task.
The Schedule
tab contains the timetable of the task, which the user can modify. In order to apply the
changes, the user needs to click the Apply button at the foot of the dialog.
10.1 Save to Scheduler
The program provides the ability to schedule any virtual operation placed on the List of Pending Operations.
In order to start the operation the user should take the following steps:
1. Call the Save to Scheduler dialog in the Main menu: Tools > Save to Scheduler…
2. Specify the time for the execution of operations on the List of Pending Operations.
This command is unavailable if there are no operations on the List of Pending Operations.
To learn more about how to set a timetable for execution please consult the Scheduling
Operations chapter.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 37

Disk Wiper™ 8.5 37 User Manual
11 Scripting
The program actions can also be represented in form of a script. The script describes the appropriate
operation with macro-language commands. There is an interpreter utility - SCRIPTS.exe, which is included
in the program installation package. This utility works in the unattended mode, which allows the user to
automate operations.
11.1.1 Starting
The user may not write a script since the program has a convenient interface for such a task. In order to
generate a script on the base of the entered parameters of the required operation, the user should take the
following steps:
Select in the Main menu: Tools > Generate Script…
This command is unavailable if there are no operations on the List of Pending Operations.
11.1.2 Settings
Define script generation options with the Generate script dialog.
Script file destination. The program allows saving script files to local drives. Press the Browse
button to define destination and a filename for a new script file. The default file extension that is
reserved for scripting files is .psl. However, a script can be saved under any filename.
In addition, there is the possibility to make further detailed settings (although the default values will do in
most cases). To activate the advance mode, the user needs to click the More options button at the foot of the
dialog page. The following options become available:
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 38

Disk Wiper™ 8.5 38 User Manual
Interaction with the user. Mark the option to pause the script interpreter during the execution to
prompt the user’s confirmation or other input. Otherwise the program will not stop using default
values for parameters if needed.
Commit after each operation. Mark the option to commit changes after each operation.
Check for errors after each operation. Mark the option to insert a special code in script, which
checks the status of the last executed operation and stops the script processing if there are errors of
any kind.
11.1.3 Results
After the operation is completed the user receives a new script file. It is placed into the specified destination,
its features defined in the dialog.
To learn more about scripts please consult the Paragon Scripting Language manual.
Some features may be unavailable in the version of the product you have. To learn more
about it please consult the Disk Wiper Editions chapter.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 39

Disk Wiper™ 8.5 39 User Manual
12 Partition Management
In this chapter you will find all the information necessary to carry out partitioning operations supported by
the program.
12.1 Create Partition
The program provides the ability to create new partitions by using the DOS partitioning scheme.
12.1.1 Restrictions
1. Do not use the Create Partition function in order to undelete the last deleted partition.
2. The program cannot create new partitions on Dynamic Disks. The current version of the program supports
only hard disks that use the DOS partitioning scheme (in Windows 2000 and XP these disks are named
Basic Disks).
3. According to the rules of the DOS partitioning scheme, the following combinations of partitions cannot be
created:
Two Extended Partitions on one hard disk
Five or more Primary partitions on one hard disk
If there is an Extended Partition on the disk, only three Primary partitions are allowed
4. The program allows creating new partitions only within blocks of unpartitioned space. It cannot convert a
free space on an existing partition to a new partition.
12.1.2 Starting
In order to start the operation the user should take the following steps:
1. Select a block of free space on the Disk Map.
2. Call the Create Partition dialog to define appropriate settings. There are several ways to do it:
Select in the Main menu: Partition > Create Partition.
Call the popup menu for the selected partition (right click of the mouse button) on the Disk Map,
then select the menu item: Create Partition.
12.1.3 Settings
Define the future partition parameters with the Create Partition dialog. Initially the program suggests some
consistent values for all parameters. In most cases, the user can just press the Yes button to confirm the
operation.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 40

Disk Wiper™ 8.5 40 User Manual
Define whether the partition will be Primary, Extended or Logical. Select the desired type of the
new partition from this pull-down list. As a matter of fact, the available alternatives fundamentally
depend on the type of the selected block of free space - within the Logical free space, only Logical
partitions can be created; Within the Primary free space, both Primary partitions or the Extended
Partition can be created.
Partition Size. Define the size (in MB) of the new partition.
Free space before. Define the position (in MB) of the new partition relative to the beginning of the
block of free space.
Free space after. Define the amount of trailing free space (in Mb) at the end of the new partition.
Partition size and position may also be defined by using the drag-and-drop technique. To do
that, just carry out the required operation on the Disk Map. The virtual operations are to be
available.
File system for new partition. From the pull-down list select a file system the newly created
partition will be formatted to, otherwise the partition will remain unformatted (so that it will not be
ready to use).
In addition, there is the possibility to make further detailed settings (although the default values will do in
most cases). To activate the advance mode, the user needs to click the More options button at the foot of the
dialog page. Depending on the file system, the following options become available:
Whether the surface test will be performed. Mark the option to make the program perform the
surface test on the formatted partition. In this case, the program will find bad and unstable sectors
and mark them unusable in the file system metadata.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 41

Disk Wiper™ 8.5 41 User Manual
The amount of sectors per boot. This parameter is available exclusively for FAT16 and FAT32 file
systems. Set the number of sectors to be reserved for the boot area on the partition with this spinner
control.
The amount of root entries. This parameter is available exclusively for FAT16 file system. Set the
maximum amount of files/directories to be placed in the Root Directory on the FAT16 partition.
The amount of sectors per cluster. Define the Cluster Size for the formatted partition with this
spinner control.
12.1.4 Results
After the operation is completed the user receives a fully functional partition.
By clicking the More options button during the operation execution the user can set up a
number of additional parameters:
Close progress dialog automatically. Mark the option to automatically close the
progress dialog after the operation is completed.
Shutdown system on complete. Mark the option to automatically switch off the
computer on the successful accomplishment of the operation.
Minimize to system tray. Click it to minimize the window to the Windows system tray.
12.2 Format Partition
Any partition should contain some file system to be used for keeping data. The process of installing a file
system is commonly known as formatting. A huge variety of file systems have been developed these days.
The program provides the ability to format existing or newly created partitions of the following file systems:
- FAT12 & FAT16
- FAT32
- NTFS
- Ext2
- Ext3
- ReiserFS
- Linux Swap v. 2
- HPFS
12.2.1 Starting
In order to start the operation the user should take the following steps:
1. Select a block of free space on the Disk Map.
2. Call the Format Partition dialog to define appropriate settings. There are the following ways to do it:
Select in the Main menu: Partition > Format Partition.
Call the popup menu for the selected partition (right click of the mouse button) on the Disk Map,
then select the menu item: Format Partition.
12.2.2 Settings
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 42

Disk Wiper™ 8.5 42 User Manual
prog
Define parameters of the formatting operation with the Format Partition dialog. Initially the program
suggests some consistent values for all parameters. In most cases, the user can just press the Format button
to confirm the operation.
File system. Select the desired file system type from this pull-down list. In fact, the program displays
only file systems that can be correctly placed to the selected partition, taking the capacity of the
selected partition into account.
Volume label. Enter a label for the selected partition in this textual field. The Volume label is an
irrelevant parameter of a logical drive that can be used for drive identification.
In addition, there is the possibility to make further detailed settings (although the default values will do in
most cases). To activate the advance mode, the user needs to click the More options button at the foot of the
dialog page. Depending on the file system, the following options become available:
Use OS built-in routine. Mark the option to restrict the available values according to the used OS.
Whether the surface test will be performed. Mark the option to make the program perform the
surface test on the formatted partition. In this case, the program will find bad and unstable sectors
and mark them unusable in the file system metadata.
The amount of sectors per boot. This parameter is available exclusively for FAT16 and FAT32 file
systems. Set the number of sectors to be reserved for the boot area on the partition with this spinner
control.
The amount of root entries. This parameter is available exclusively for FAT16 file system. Set the
maximum amount of files/directories to be placed in the Root Directory on the FAT16 partition.
The amount of sectors per cluster. Define the Cluster Size for the formatted partition with this
spinner control.
12.2.3 Results
After the operation is completed the user receives a fully functional partition formatted to the file system
specified.
By clicking the More options button during the operation execution the user can set up a
number of additional parameters:
Close
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
ress dialog automatically. Mark the option to automatically close the
Page 43

Disk Wiper™ 8.5 43 User Manual
progress dialog after the operation is completed.
Shutdown system on complete. Mark the option to automatically switch off the
computer on the successful accomplishment of the operation.
Minimize to system tray. Click it to minimize the window to the Windows system tray.
12.3 Delete Partition
The program allows the user to delete partitions on hard disks partitioned with the DOS partitioning scheme.
The program removes references to the partition from the Partition Table, so that the information from the
deleted partition becomes inaccessible. The resulted disk space can be used to create new partitions.
Contents of the deleted partition do not disappear from the disk but merely are unavailable for the operating
system.
12.3.1 Starting
In order to start the operation the user should take the following steps:
1. Select a block of free space on the Disk Map.
2. Call the Delete Partition dialog to define appropriate settings. There are several ways to do it:
Select in the Main menu: Partition > Delete Partition.
Call the popup menu for the selected partition (right click of the mouse button) on the Disk Map,
then select the menu item: Delete Partition.
12.3.2 Settings
Despite different work algorithms, both the Delete Partition Wizard and the Delete Partition dialog provide
the same level of functionality, thus let us just take as an example the dialog version of the operation.
Define parameters of the delete operation with the Delete Partition dialog.
Enter the volume label to confirm deleting. To confirm the deletion of the selected partition, enter
its Volume Label. The actual Volume Label value is displayed above.
Do not ask volume label next time. Mark the option to inhibit confirmation of the partition deletion.
In addition, there is the possibility to wipe partition data as well. To do that, just click the More options
button at the foot of the dialog page. When it is marked, the following options become available:
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 44

Disk Wiper™ 8.5 44 User Manual
Select the byte mask…. The HEX value spinner control allows the user to set a two-figure
hexadecimal character value ("00" by default). The available range is from "00" to "FF". It is
synchronized with the ASCII value.
Specify the number of wiping passes. The user can choose number of passes for the wiping pattern.
Verify wipe results. The user can also choose whether to carry out residual data verification or not
specifying the percentage of sectors to check.
12.3.3 Results
The deletion of a partition takes only a fraction of a second. However, the program waits until Windows
completes the modification of the disk layout.
By clicking the More options button during the operation execution the user can set up a
number of additional parameters:
Close progress dialog automatically. Mark the option to automatically close the
progress dialog after the operation is completed.
Shutdown system on complete. Mark the option to automatically switch off the
computer on the successful accomplishment of the operation.
Minimize to system tray. Click it to minimize the window to the Windows system tray.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 45

Disk Wiper™ 8.5 45 User Manual
13 Hard Disk Management
This chapter lists various scenarios of hard disk operations which may be accomplished by the program.
13.1 Update MBR
The program allows the user to overwrite the current bootable code in the MBR (Master Boot Record) by
the standard bootstrap code.
This feature can repair corrupted bootable code on a hard disk as a result of boot virus attacks or
malfunction in the boot managing software.
In order to start the operation the user should take the following steps:
1. Select a hard disk on the Disk Map.
2. There are several ways to run the operation:
Select in the Main menu: Hard Disk > Update MBR.
Call the popup menu for the selected hard disk (right click of the mouse button) on the Disk Map,
then select the menu item: Update MBR.
3. The operation will be performed immediately after confirmation.
By clicking the More options button during the operation execution the user can set up a
number of additional parameters:
Close progress dialog automatically. Mark the option to automatically close the
progress dialog after the operation is completed.
Shutdown system on complete. Mark the option to automatically switch off the
computer on the successful accomplishment of the operation.
Minimize to system tray. Click it to minimize the window to the Windows system tray.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 46

Disk Wiper™ 8.5 46 User Manual
14 Extra Functionality
This chapter describes the supplementary functionality available in the program.
14.1 View Partition/Hard Disk Properties
The program enables to obtain in-depth information on the properties of hard disks/partitions. Besides the
general information, such as capacity, used space or file system type it provides the possibility to get info on
a hard disk geometry, cluster size, exact partition location, etc.
In order to view properties of a partition/hard disk the user should take the following steps:
1. Select a partition/hard disk on the Disk Map.
2. Call the popup menu for the selected partition/hard disk (right click of the mouse button) on the Disk
Map, then select the menu item: Properties…
3. The provided information is grouped according to its properties, thus select the required tab and get the
information you need.
14.2 Mount Partition
The program allows the user to assign or remove drive letters of existing formatted partitions.
14.2.1 Assign Drive Letter
In order to mount a partition the user should take the following steps:
1. Select a partition on the Disk Map.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 47

Disk Wiper™ 8.5 47 User Manual
2. Call the Add Drive Letter dialog to define appropriate settings. There are several ways to do it:
Select in the Main menu: Partition > Assign Drive Letter…
Call the popup menu for the selected partition (right click of the mouse button) on the Disk Map,
then select the menu item: Assign Drive Letter…
3. Define a drive letter for the selected partition with the Add Drive Letter dialog. Initially the program
suggests some consistent value for this parameter. So the user may just press the Yes button to confirm the
operation.
Assign the following drive letter. The pull-down list contains vacant drive letters that can be associated
with the selected partition. Assign a drive letter to a non-mounted partition, or change the existed drive letter
for already mounted partition.
4. The operation will be performed immediately after confirmation.
14.2.2 Remove Drive Letter
In order to unmount a partition the user should take the following steps:
1. Select a partition on the Disk Map.
2. Call the Remove Drive Letter dialog to define appropriate settings. There are several ways to do it:
Select in the Main menu: Partition > Remove Drive Letter.
Call the popup menu for the selected partition (right click of the mouse button) on the Disk Map,
then select the menu item: Remove Drive Letter.
Modifying drive letter of the system partition will result in inability to boot the operating
system.
After having processed partitions with installed software, some programs may not run
properly.
3. The operation will be performed immediately after confirmation.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 48

Disk Wiper™ 8.5 48 User Manual
By clicking the More options button during the operation execution the user can set up a
number of additional parameters:
Close progress dialog automatically. Mark the option to automatically close the
progress dialog after the operation is completed.
Shutdown system on complete. Mark the option to automatically switch off the
computer on the successful accomplishment of the operation.
Minimize to system tray. Click it to minimize the window to the Windows system tray.
14.3 Test Surface
The program allows performing additional surface tests on existing partitions and blocks of free space.
In order to start the surface test the user should take the following steps:
1. Select a partition or a block of free space on the Disk Map.
2. Call the Test Surface dialog to define appropriate settings. There are several ways to do it:
Select in the Main menu: Partition > Test Surface…
Call the popup menu for the selected partition (right click of the mouse button) on the Disk Map,
then select the menu item: Test Surface…
Surface test level. Choose the level of the test procedure.
3. The operation will be performed immediately after confirmation.
By clicking the More options button during the operation execution the user can set up a
number of additional parameters:
Close progress dialog automatically. Mark the option to automatically close the
progress dialog after the operation is completed.
Shutdown system on complete. Mark the option to automatically switch off the
computer on the successful accomplishment of the operation.
Minimize to system tray. Click it to minimize the window to the Windows system tray.
14.4 Check File System Integrity
The program can check the file system integrity on existing partitions. This function can be used for
detecting file system errors before performing operations on a partition.
Most useful operations require the targeted partition to have a valid file system to be processed.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 49

Disk Wiper™ 8.5 49 User Manual
In order to start the system integrity check the user should take the following steps:
1. Select a partition on the Disk Map or on the List of Partitions.
2. Call the Check File System Integrity dialog to define appropriate settings. There are several ways to do it:
Select in the Main menu: Partition > Check File System Integrity.
Call the popup menu for the selected partition (right click of the mouse button) on the Disk Map,
then select the menu item: Check File System Integrity.
3. The operation will be performed immediately after confirmation.
By clicking the More options button during the operation execution the user can set up a
number of additional parameters:
Close progress dialog automatically. Mark the option to automatically close the
progress dialog after the operation is completed.
Shutdown system on complete. Mark the option to automatically switch off the
computer on the successful accomplishment of the operation.
Minimize to system tray. Click it to minimize the window to the Windows system tray.
14.5 Edit/View Sectors
With the built-in Edit/View Sectors tool the program enables to view/edit sectors on existing partitions/hard
disks providing the possibility to directly access and modify sectors, save and restore sectors from specified
files, navigate through the system metadata, etc.
In order to start the Edit/View Sectors operation the user should take the following steps:
1. Select a hard disk/partition on the Disk Map or on the List of Partitions.
2. Call the Edit/View Sectors dialog to define appropriate settings. There are several ways to do it:
Select in the Main menu: Partition/Hard Disk > Edit/View Sectors.
Call the popup menu for the selected partition/hard disk (right click of the mouse button) on the Disk
Map, then select the menu item: Edit/View Sectors.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 50

Disk Wiper™ 8.5 50 User Manual
Careless use of the Edit Sectors function may result in the irreversible data corruption.
14.6 Send Log Files
The program allows the user to simplify the procedure of sending support requests to the Paragon Support
Team. In case of having difficulties with handling the program, the user, with the help of this very function,
can address the company support engineers and provide them with all the information they need such as disk
layout, performed operations, etc. in order to tackle the encountered problem. Information of that kind is
stored in Log files.
In order to start the operation the user should take the following steps:
1. Call the Send Log Files dialog in the Main menu: Tools > Send Log Files
2. Give a detailed description on the encountered problem.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 51

Disk Wiper™ 8.5 51 User Manual
By clicking the Send button the built-in mail client will generate a template request with attached
compressed log files and then send it to the Paragon Support Team.
14.6.1 Log Files
Log files are simple textual files that can be opened by any text editor. There are several log files
automatically generated by the program:
Contains in-depth information on parameters and
Stubact.log
performance of all operations carried out by the
program
Pwlog.txt
Cdb.log
BioNTlog.txt
or
Bio95log.txt
Log files do not contain any confidential information on the operating system settings or the
user documents.
The Send Log Files function is only available when outgoing mail server (SMTP) and the user
e-mail address are properly set. To learn more about it please consult the Settings Overview
chapter.
Besides brief overview on operations it also contains
detailed information about the state of all hard disks
Contains low-level information on the CD/DVD devices
used in the system
It is an OS-dependent supplementary log file derived
from Bioxx.dll. It may contain valuable information on
Windows family operating systems
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
Page 52

Disk Wiper™ 8.5 52 User Manual
15 Glossary
Magnetic Force Microscopy (MFM) is an effective tool to magnetic investigations on submicron scale.
Image obtained by MFM is the space distribution of some parameter characterizing magnetic probe-sample
interaction, i.e. interaction force, amplitude of vibrating magnetic probe, etc. The MFM technology can be
successfully used to resurrect deleted information.
Master File Table (MFT) is a relational database that consists of rows of file records and columns of file
attributes. It contains at least one entry for every file on an NTFS volume, including the MFT itself. MFT is
similar to a FAT table in a FAT file system.
Partitioning scheme is a set of rules, constraints and the format of on-disk structures that keep information
of the partitions that are located on the hard disk. There are several partitioning schemes, which can be used.
The most popular partitioning scheme is the so-called DOS partitioning scheme. It was introduced by IBM
and Microsoft to use multiple partitions in the disk subsystems on IBM PC compatible computers.
Another popular partitioning scheme is the so-called LDM (Logical Disks Model) that originates from UNIX
mainframe systems. The Veritas Executive accommodates the simplified version of LDM to the Windows
2000 operating system.
Windows 2000 and XP support two quite different partitioning schemes: the old DOS partitioning scheme
and the new Dynamic Disk Management (DDM). The problem is that older versions of Windows do not
support DDM. In addition, most hard disk utilities do not support it as well.
Copyright© 1994-2007 Paragon Software Group. All rights reserved.
 Loading...
Loading...