Panasonic CF-19KHRL6AM, CF-19KJRAGAM, CF-19KJRAX2M, CF-19KJRC62M, CF-19KJRCXAM Supplementary Instructions Manual
...
Contents
Supplementary Instructions
for Fingerprint Reader
Personal Computer
Model No. CF-19 / CF-30 Series
Names and Function of Parts ..................................... 2
Overview ....................................................................... 4
Installation.................................................................... 6
More Advanced Security ........................................... 9
Useful Information ....................................................10
Troubleshooting .......................................................14
Specifications............................................Back cover
Terms and illustrations in this Manual
NOTE: Useful and helpful information.
CAUTION: Condition that may result in minor or moderate injury.
[start] - [Run]: Click [start], and then click [Run].
You may need to double-click in some cases.
Î : Page in these Supplementary Instructions or in the Reference
Manual for the computer.
Some of the illustrations in this manual may differ slightly in shape from the
actual items in order to make the explanation easier to understand.
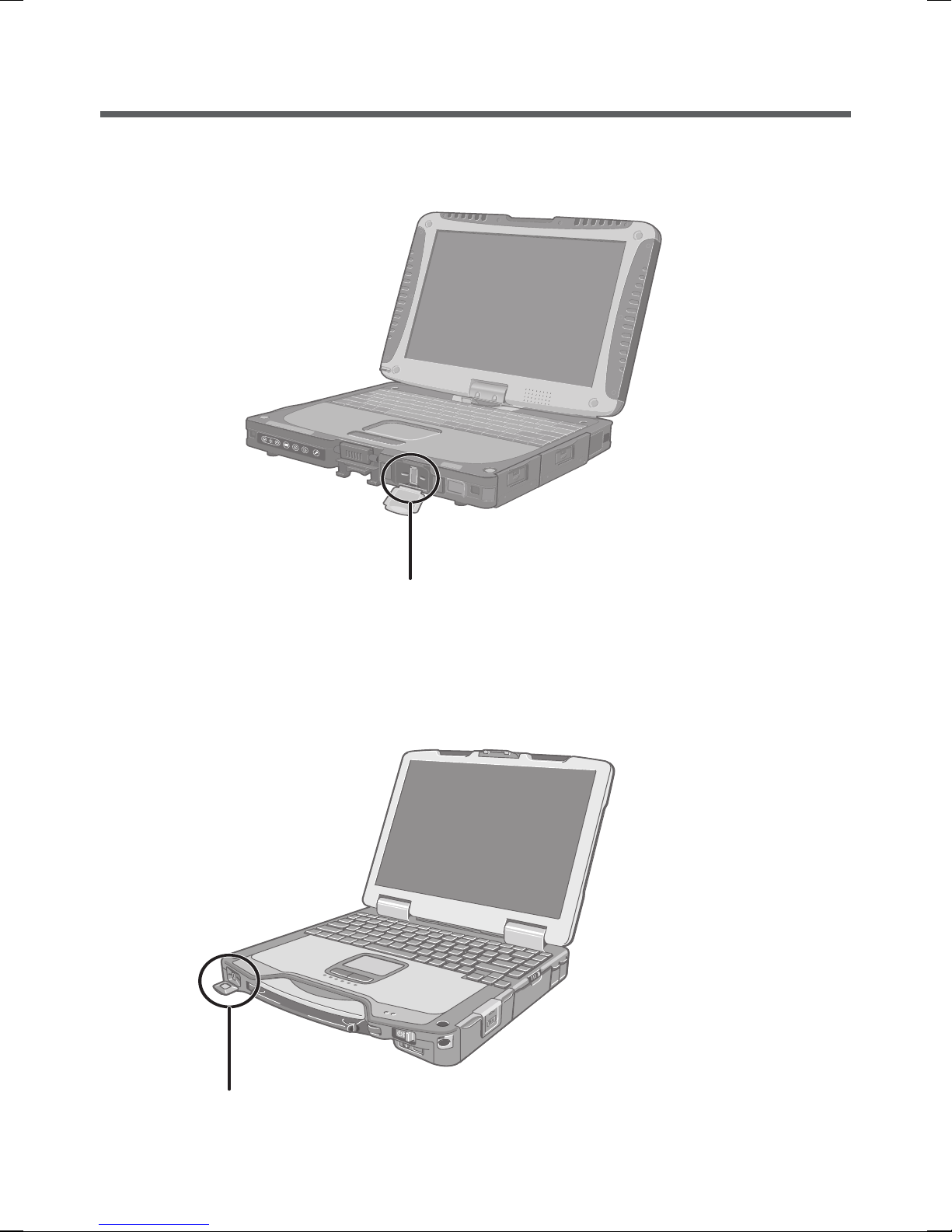
Names and Functions of Parts
Except the following, refer to the Operating Instructions for the computer.
<CF-19 Series>
<CF-30 Series>
Fingerprint Reader
(Appearance may differ, depending on specifications.)
Fingerprint Reader
(Appearance may differ, depending on specifications.)
2

How to Use the Fingerprint Reader
This section explains how your fingerprints are enrolled and authenticated.
1 Slide your finger to the right or
left.
To prevent a reading error.
A Set the first joint of your finger on the
sensor as illustrated to the right.
B Slide your finger to the right or left while
keeping it in contact with the fingerprint sensor.
C Slide your finger to the right or left until
the sensor is visible.
When the fingerprint sensor does not
enroll or authenticate your fingerprint properly:
· You slid your finger too fast or too slow.
· Your finger was soiled or it has a scar on the surface.
· Your finger was wet or extremely dry.
· Your fingerprint does not have sufficient data for personal identification.
For further information, refer to “Troubleshooting (For Devices)”. (Î page 14)
or
Fingerprint sensor
Fingerprint sensor
CAUTION
To protect the fingerprint sensor, be sure to close the cover when not
using the fingerprint reader.
We shall not be liable for any loss or damage whatsoever resulting from
your Fingerprint device or neglect of Fingerprint device use, or any data
loss resulting from such developments as Fingerprint authentication
device malfunctioning.
3
Overview
Fingerprint’s Outline
The conventional security systems use ID/passwords and token devices such as IC
cards to authenticate users. Therefore the passwords and token devices are exposed to the risk of being lost, stolen and hacking.
The Fingerprint authentication method uses user’s fingerprints instead of passwords
for security authentication. You can use your fingerprints to start up your computer
and log on Windows.
We recommend you use the Fingerprint Reader in combination with the TPM (Trusted
Platform Module) to increase the security level of your computer.
Recommended Installation Procedure
Performed by the Computer Administrator
Step 1
TPM Installation ( “Installation Manual of TPM”)
(If the TPM is not being used, skip this step.)
Step 2
Fingerprint Utility Installation
Step 3
TPM Fingerprint Utility Initialization
(If the TPM is not being used, skip this step.)
User Fingerprint Enrollment
Performed by each user
Step 4
User’s Data
• Windows Logon Password
• Fingerprint
• Fingerprint Backup Password
• Power-on Password
This manual describes Steps 2, 3 and the initial part of Step 4.
For further steps, refer to the UPEK Protector Suite QL Help menu. (Click [start] - [All
Programs] - [Protector Suite QL] - [Help].)
Precautions
Security Functions
Fingerprint Authentication Technology does not guarantee complete authentication and
individual identification. Please acknowledge we shall not be liable for any loss or damage whatsoever resulting from the use of, or inability to use your Fingerprint device.
The Fingerprint authentication method uses multiple fingerprints, encryption keys,
credentials data and passwords. You might not be able to use your data if you
lose fingerprints, keys, credentials and passwords, so keep them in a safe place.
For further information, refer to “Backup”. (Îpage 10)
General interaction with third-party applications: There is no guarantee
that there will not be any negative interaction with any third-party software,
and will not accept any responsibility for such an interaction.
4
You cannot use this function at the same time as the SD security function
is being used. When SD security is set, disable SD security function in the
following order before initial setting of fingerprint authentication.
A Log on to Windows as an Administrator.
B Click [start] - [All Programs] - [Panasonic] - [SD Card Setup].
C Add a check mark for [Use the SD card when starting the computer].
D Click [OK].
· Follow the on-screen instructions.
· SD security is disabled and all registered SD memory cards become unavailable when your computer starts up.
5
Installation
Step1 TPM Installation
Refer to on-screen manuals “Installation Manual Trusted Platform Module (TPM)”.
(Click [start] - [Run], enter [C:\util\drivers\tpm\README.pdf], and click [OK].)
If the TPM is not being used, skip this step.
Step2 Fingerprint Utility Installation
Performed by the Computer Administrator.
Preparation
[Only CF-19 series with Windows XP Tablet PC Edition]
Move Tablet PC Input Panel from upper right to the bottom right or bottom left .
If this procedure is skipped, the “Please swipe you finger” message may overlap
the Tablet PC Input Panel.
1 Log on to Windows as an Administrator.
2 Close all other programs.
3 Click [start] - [Run], enter [C:\util\drivers\fngprint\psql\
setup.exe], and click [OK].
The “Protector Suite QL ∗.∗ Setup” screen appears.
4 Click [Next].
Installation starts. Carefully read the License Agreement, select “I accept the
license agreement”, and click [Next]. Follow the on-screen instructions.
∗∗
5 When the “Protector Suite
message appears, click [Finish] - [OK].
The computer restarts.
∗∗
∗.
∗ has been successfully installed.”
∗∗
∗∗
6 Log on to Windows as an Administrator.
The “Protector Suite QL Icon” appears in the notification area.
Step 3 TPM Fingerprint Utility Initialization
Performed by the Computer Administrator.
The “Invalid TPM status” message is displayed by the “Protector Suite QL Icon”
in the notification area.
If the TPM is not being used, skip this step.
6
 Loading...
Loading...