Nortel Networks WEB OS 212777 User Manual

Web OS Switch Software
10.0 Application Guide
Part Number: 212777, Revision A, Febru ar y 2002
50 Great Oaks Boulevard
San Jose, California 95119
408-360-5500 Main
408-360-5501 Fax
www.nortelnetworks.com

Web OS 10.0 Application Guide
Copyright 2002 Nortel Networks, Inc., 50 Great Oaks Boulevard, San Jose, California 95119, USA. All
rights reserved. Part Number: 212777, Revision A.
This document is protected by copyright and distributed under licenses restricting its use, copying,
distribution, and decompilation. No part of this document may be reproduced in any form by any means
without prior written authoriza tion of Nortel Networks, Inc. Doc umentation is provided “as is” without
warranty of any kind, either express or implied, including any kind of implied or express warranty of noninfringement or the implied warrant ies of merchantability or fi tness for a particular purpose.
U.S. Government End Users: This document is provided with a “commercial item” as defined by FAR
2.101 (Oct 1995) and contains “commercial technical data” and “commercial software documentation” as
those terms are used in FAR 12.21 1-12.212 (Oct 1995). Government End Users are authorized to use this
documentation only in accordance with those rights and restrictions set forth herein, consistent with FAR
12.211- 12.212 (Oct 1995), DFARS 227.7202 (JUN 1995) and DFARS 252.227-7015 (Nov 1995).
Nortel Networks, Inc. reserves the right to change any products described herein at any time, and without
notice. Nortel Networks, Inc. assumes no re sponsibility or liability arising from the use of prod ucts
described herein, except a s expressly agreed to in writing by Nortel Ne tworks, Inc. The use and purchase of
this product does not convey a license under any patent rights, trademark rights, or any other intellectual
property righ ts of Nortel Ne tworks, Inc.
Web OS, Alteon 180, Alteon 180e, Alteon 184, Alteon AD3, Alteon AD4, and ACEswitch are trademarks
of Nortel Networks, Inc. in the Unite d States and certain other countries. Cisco
registered trademarks of Cisco Systems, Inc. in the United States and certain other countries. Check Point
and FireW all-1
®
are trademarks or registered trademarks of Check Point Software T echnologies Ltd. Any
®
and EtherChannel® are
other trademarks appearing in this manual are owned by their respective companies.
®
2
212777-A, February 2002

Contents
Preface 21
Who Should Use This Guide 21
What You’ll Find in This Guide 21
Typographic Conventions 23
Contacting Us 24
Part 1: Basic Switching & Routing
Chapter 1: Basic IP Routing 27
IP Routing Benefits 28
Routing Between IP Subnets 28
Example of Subnet Routing 31
Defining IP Address Ranges for the Local Route Cache 35
Border Gateway Protocol (BGP) 36
Internal Routing Versus Exte rnal Routing 36
Forming BGP Peer Routers 37
BGP Failover Configuration 37
DHCP Relay 41
DHCP Overview 41
DHCP Relay Agent Configuration 42
Chapter 2: VLANs 43
VLAN ID Numbers 44
VLAN Tagging 44
VLANs and the IP Interfaces 45
VLAN Topologies and Design Issues 45
212777-A, February 2002
Example 1: Multiple VLANS with Tagging Adapters 46
Example 2: Parallel Links with VLANs 48
3

Web OS 10.0 Application Guide
VLANs and Spanning Tree Protocol 49
Bridge Protocol Data Units (BPDUs) 50
Multiple Spanning Trees 51
VLANs and Default Gateways 58
Segregating VLAN Traffic 58
Configuring the Local Network 60
Configuring Default Gateways per VLAN 60
VLANs and Jumbo Frames 63
Isolating Jumbo Frame Traffic using VLANs 63
Routing Jumbo Frames to Non-Jumbo Frame VLANs 64
Chapter 3: Port Trunking 65
Overview 65
Statistical Load Distribution 66
Built-In Fau lt Tolerance 66
Port Trunking Example 67
Chapter 4: OSPF 69
OSPF Overview 69
Types of OSPF Areas 70
Types of OSPF Routing Devices 71
Neighbors and Adjacencies 72
The Link-State Database 72
The Shortest Path First Tree 73
Internal Versus External Routing 73
OSPF Implementation in Web OS 74
Configurable Parameters 74
Defining Areas 75
Interface Cost 77
Electing the Designated Router and Backup 77
Summarizing Routes 77
Default Routes 78
Virtual Links 79
Router ID 80
Authentication 80
Host Routes for Load Balancing 82
OSPF Features Not Supported in This Release 82
n
Contents
4
212777-A, February 2002

OSPF Configuration Examples 83
Example 1: Simple OSPF Domain 84
Example 2: Virtual Links 86
Example 3: Summarizing Routes 90
Example 4: Host Routes 92
Verifying OSPF Configuration 98
Chapter 5: Secure Switch Management 99
Setting Allowable Source IP Address Ranges 100
Secure Switch Management 101
Authentication and Authorization 101
Requirements 102
RADIUS Authentication and Authorization 103
RADIUS Authentication Features in Web OS 104
Web Switch User Accounts 105
Secure Shell and Secure Copy 107
Encryption of Management Messages 108
SCP Services 108
RSA Host and Server Keys 109
Radius Authentication 110
SecurID Support 110
Port Mirroring 113
Web OS 10.0 Application Guide
Part 2: Web Switching Fundamentals
Chapter 6: Server Load Balancing 117
Understanding Server Load Balancing 118
Implementing Basic Server Load Balancing 121
Extending SLB Topologies 136
212777-A, February 2002
Identifying Your Network Needs 118
How Server Load Balancing Works 119
Network Topology Requirements 122
Configuring Server Load Balancing 124
Additional Server Load Balancing Options 128
Proxy IP Addresses 136
Mapping Ports 139
Direct Server Interacti on 142
Delayed Binding 146
Contents
n
5

Web OS 10.0 Application Guide
Load Balancing Special Services 149
IP Server Load Balancing 149
FTP Server Load Balancing 150
Domain Name Server (DNS) Load Balancing 151
Real Time Streaming Protocol SLB 155
Wireless Application Protocol SLB 158
Intrusion Detection System Server Load Balancing 163
WAN Link Load Balancing 166
Chapter 7: Filtering 169
Overview 170
Filtering Benefits 170
Filtering Criteria 170
Stacking Filters 172
Overlapping Filters 172
The Default Filter 173
VLAN-based Filtering 174
Optimizing Filter Performance 176
Filter Logs 176
IP Address Ranges 178
Cache-En abled versus Cache-Di sabled Filters 1 78
TCP Rate Limiting 179
Configuring TCP Rate Limiting Filters 180
Tunable Hash for Filter Redirection 184
Filter-based Security 185
Network Address Translation 191
Static NAT 191
Dynamic NAT 193
FTP Client NAT 195
Matching TCP Flags 197
Matching ICMP Message Types 201
n
Contents
6
212777-A, February 2002

Chapter 8: Application Redirection 203
Overview 204
Web Cache Redirection Environment 204
Additional Application Redirection Options 205
RTSP Web Cache Redirection 211
IP Proxy Addresses for NAT 213
Excluding Noncacheable Sites 215
Chapter 9: Virtual Matrix Architecture 217
Chapter 10: Health Checking 219
Real Server Health Checks 221
DSR Health Checks 222
Link Health Checks 223
Configuring the Switch for Link Health Checks 223
TCP Health Checks 224
ICMP Health Checks 224
Script-Based Health Checks 225
Configuring the Switch for Script-Based Health Checks 225
Script Format 226
Scripting Guidelines 227
Script Configuration Examp les 227
Application-Specific Health Checks 230
HTTP Health Checks 231
UDP-Based DNS Health Checks 233
FTP Server Health Checks 234
POP3 Server Health Checks 235
SMTP Server Health Checks 236
IMAP Server Health Checks 237
NNTP Server Health Checks 238
RADIUS Server Health Checks 239
HTTPS/SSL Server Health Checks 240
WAP Gateway Health Checks 240
LDAP Health Checks 243
ARP Health Checks 245
Failure Types 246
Service Failure 246
Server Failure 246
Web OS 10.0 Application Guide
212777-A, February 2002
Contents
n
7

Web OS 10.0 Application Guide
Chapter 11: High Availability 247
VRRP Overview 248
VRRP Components 248
VRRP Operation 251
Selecting the Master VRRP Router 251
Active-Standby Failover 252
Failover Methods 253
Active-Standby Redundancy 254
Active-Active Redundancy 255
Hot-Standby Redundancy 256
Synchronizing Configurations 258
Web OS Extensions to VRRP 259
Virtual Server Routers 259
Sharing/Active-Active Failover 260
Tracking VRRP Router Priority 261
High Availability Configurations 263
Active-Standby Virtual Server Router Configuration 263
Active-Active VIR and VSR Configuration 265
Active/Active Server Load Balancing Configuration 267
VRRP-Based Hot-Standby Configuration 275
Virtual Router Deployment Considerations 277
Mixing Active-Standby and Active-Active Virtual Routers 277
Synchronizing Active/Active Failover 277
Eliminating Loops with STP and VLANs 278
Assigning VRRP Virtual Router ID 280
Configuring the Switch for Tracking 280
Synchronizing Configurations 282
Stateful Failover of Layer 4 and Layer 7 Persistent Sessions 283
What Happens When a Switch Fails 284
Viewing Statistics on P ersistent Port Sessions 286
n
Contents
8
212777-A, February 2002

Part 3: Advanced Web Switching
Chapter 12: Global Server Load Balancing 289
GSLB Overview 290
Benefits 290
Compatibil ity with Other Web OS Features 290
How GSLB Works 291
Configuring GSLB 293
IP Proxy for Non-HTTP Redirects 304
How IP Proxy Works 305
Configuring Proxy IP Addresses 307
Verifying GSLB Operation 308
Configuring Client Site Preferences 308
Using Border Gateway Protocol for GSLB 312
Chapter 13: Firewall Load Balancing 313
Firewall Overview 314
Basic FWLB 316
Basic FWLB Implementation 317
Configuring Basic FWLB 319
Four-Subnet FWLB 326
Four-Subnet FWLB Implementation 327
Configuring Four-Subnet FWLB 329
Advanced FWLB Concepts 346
Free-Metric FWLB 346
Adding a Demilitarized Zone (DMZ) 349
Firewall Health Checks 351
Web OS 10.0 Application Guide
Chapter 14: Virtual Private Network Load Balancing 353
Overview 354
VPN Load-Balancing Configuration 356
212777-A, February 2002
Virtual Private Networks 354
How VPN Load Balancing Works 354
Requirements 356
VPN Load-Balancing Configuration Example 356
Contents
n
9

Web OS 10.0 Application Guide
Chapter 15: Content Intelligent Switching 371
Overview 372
Parsing Content 373
HTTP Header Inspection 374
Buffering Content with Multiple Frames 374
Content Intelligent Ser ver Load Balancing 375
URL-Based Server Load Balancing 375
Virtual Hos ting 380
Cookie-Based Preferent i al Load Bala nci n g 383
Browser-Smart Load Balancing 386
URL Hashing for Server Load Balancing 387
Header Hash Load Balancing 389
DNS Load Balancing 390
Layer 7 RTSP Load Balancing 392
Content Inte lligent Web Cac he Redirection 394
URL-Based Web Cache Redirection 395
HTTP Header-Based Web Cache Redirection 403
Browser-Based Web Cache Redirection 405
URL Hashing for Web Cache Redirection 406
Layer 7 RTSP Streaming Cache Redirection 409
Exclusionary String Matching for Real Servers 410
Configuring for Exclusionary URL String Matching 410
Regular Expression Matching 412
Standard Regular Expression Characters 412
Configuring Regular Expressions 413
Content Precedence Lookup 414
Requirements 415
Using the or and and Operators 415
Assigning Multiple Strings 416
Layer 7 Deny Filter 417
10
n
Contents
212777-A, February 2002

Chapter 16: Persistence 421
Overview of Persistence 422
Using Source IP Address 422
Using Cookies 423
Using SSL Session ID 423
Cookie-Based Persiste nce 424
Permanent and Temporary Cookies 425
Cookie Formats 425
Cookie Properties 426
Client Browsers that Do Not Accept Cookies 426
Cookie Modes of Operation 427
Configuring Cookie-Based Persistence 430
Server-Side Multi-Response Cookie Search 436
SSL Session ID-Based Persistence 437
How SSL Session ID-Based Persistence Works 437
Chapter 17: Bandwidth Management 441
Overview 442
Bandwidth Policies 444
Rate Limits 445
Bandwidth Policy Configuration 445
Data Pacing 446
Classifica tion Criteria 447
Server Output Bandwidth Control 447
Application Bandwidth Control 447
Combinations 448
Precedence 448
Bandwidth Classification Configuration 448
Frame Discard 449
URL-Based Bandwidth Management 449
HTTP Header-Based Bandwidth Management 451
Cookie-Based Bandwidth Management 451
Bandwidt h Statistics and History 452
Statistics Maintained 452
Statistics and Management Information Bases 452
Packet Colo ring (TOS bits) for Burst Limit 4 53
Operational Keys 453
Web OS 10.0 Application Guide
212777-A, February 2002
Contents
n
11

Web OS 10.0 Application Guide
Configuring Bandwidth Management 454
Additional Configuration Examples 457
Preferential Services Examples 460
Glossary 471
Index 475
12
n
Contents
212777-A, February 2002

Figures
Figure 1-1: The Router Legacy Network 29
Figure 1-2: Switch-Based Routing Topology 30
Figure 1-3: iBGP and eBGP 37
Figure 1-4: BGP Failover Configuration Example 38
Figure 1-5: DHCP Relay Agent Configuration 42
Figure 2-1: Example 1: Multiple VLANs with Tagging Gigabit Adapters 46
Figure 2-2: Example 2: Parallel Links with VLANs 48
Figure 2-3: Using Multiple Instances of Spanning Tree Protocol 51
Figure 2-4: VLAN 3 Isolated in a Single Spanning Tree Group 52
Figure 2-5: Implementing Multiple Spanning Tree Groups 53
Figure 2-6: Default Gateways per VLAN 58
Figure 2-7: Jumbo Frame VLANs 64
Figure 3-1: Port Trunk Group 65
Figure 3-2: Port Trunk Group Configuration Example 67
Figure 4-1: OSPF Area Types 70
Figure 4-2: OSPF Domain and an Autonomous System 71
Figure 4-3: Injecting Default Routes 78
Figure 4-4: OSPF Authentication 80
Figure 4-5: A Simple OSPF Domain 84
Figure 4-6: Configuring a Virtual Link 86
Figure 4-7: Summarizing Routes 90
Figure 4-8: Configuring OSPF Host Routes 92
Figure 5-1: Authentication and Authorization: How It Works 103
Figure 5-2: Monitoring Ports 113
212777-A, February 2002
13

Web OS 10.0 Application Guide
Figure 6-1: Traditional Versus SLB Network Configurations 119
Figure 6-2: Web Hosting Configuration Without SLB 121
Figure 6-3: Web Hosting with SLB Solutions 121
Figure 6-4: SLB Client/Server Traffic Routing 122
Figure 6-5: Example Network for Client/Server Port Configuration 123
Figure 6-6: Basic Virtual Port to Real Port Mapping Configuration 140
Figure 6-7: Direct Server Return 143
Figure 6-8: Mapped and Nonmapped Server Access 144
Figure 6-9: DoS SYN Attacks without Delayed Binding 146
Figure 6-10: Repelling DoS SYN Attacks With Delayed Binding 147
Figure 6-11: Layer 4 DNS Load Balancing 151
Figure 7-1: Assigning Filters According to Range of Coverage 172
Figure 7-2: Assigning Filters to Overlapping Ranges 172
Figure 7-3: Assigning a Default Filter 173
Figure 7-4: VLAN-based Filtering 174
Figure 7-5: Configuring Clients with Different Rates 180
Figure 7-6: Limiting User Access to Server 183
Figure 7-7: Security Topology Example 185
Figure 7-8: Static Network Address Translation 192
Figure 7-9: Dynamic Network Address Translation 193
Figure 7-10: Active FTP for Dynamic NAT 195
Figure 7-11: TCP ACK Matching Network 197
14
n
Figures
Figure 8-1: Traditional Network Without Web Cache Redirection 204
Figure 8-2: Network with Web Cache Redirection 205
Figure 11-1: Example 1: VRRP Router 250
Figure 11-2: Example 2: VRRP Router 252
Figure 11-3: A Non-VRRP, Hot-Standby Configuration 253
Figure 11-4: Active-Standby Redundancy 254
Figure 11-5: Active-Active Redundancy 255
Figure 11-6: Hot-Standby Redundancy 256
Figure 11-7: Active-Active High Availability 260
Figure 11-8: Active-Standby High-Availability Configuration 263
Figure 11-9: Active-Active High-Availability Configuration 265
Figure 11-10: Hot-Standby Configuration 275
Figure 11-11: Loops in Active-Active Configuration 278
Figure 11-12: Cross-Redundancy Creates Loops, But STP Resolves Them 279
Figure 11-13: Using VLANs to Create Non-Looping Topologies 279
Figure 11-14: Stateful Failover Example when the Master Switch Fails 284
212777-A, February 2002

Web OS 10.0 Application Guide
Figure 12-1: DNS Resolution with Global Server Load Balancing 291
Figure 12-2: GSLB Topology Example 294
Figure 12-3: HTTP and Non-HTTP Redirects 304
Figure 12-4: POP3 Request Fulfilled via IP Proxy 305
Figure 12-5: GSLB Proximity Tables: How They Work 309
Figure 12-6: Configuring Client Proximity Table 310
Figure 13-1: Typical Firewall Configuration Before FWLB 314
Figure 13-2: Basic FWLB Topology 316
Figure 13-3: Basic FWLB Process 317
Figure 13-4: Basic FWLB Example Network 319
Figure 13-5: Four-Subnet FWLB Topology 326
Figure 13-6: Four-Subnet FWLB Process 327
Figure 13-7: Four-Subnet FWLB Example Network 329
Figure 13-8: Basic FWLB Example Network 346
Figure 13-9: Four-Subnet FWLB Example Network 347
Figure 13-10: Typical Firewall Load-Balancing Topology with DMZ 349
Figure 14-1: Basic Network Frame Flow and Operation 355
Figure 14-2: VPN Load-Balancing Configuration Example 356
Figure 14-3: Checkpoint Rules for Both VPN Devices as Seen in the Policy
Editor 368
Figure 15-1: Content Intelligent Load Balancing Example 372
Figure 15-2: URL-Based Server Load Balancing 376
Figure 15-3: Balancing Nontransparent Caches 387
Figure 15-4: Load Balancing DNS Queries 390
Figure 15-5: URL-Based Web Cache Redirection 396
Figure 15-6: URL Hashing for WCR 408
Figure 15-7: Content Precedence Lookup Protectors Example 415
Figure 15-8: Content Precedence Lookup Multiple Strings Example 416
Figure 15-9: Configuring Layer 7 Deny Filter 417
Figure 16-1: Cookie-Based Persistence: How It Works 424
Figure 16-2: Insert Cookie Mode 427
Figure 16-3: Passive Cookie Mode 428
Figure 16-4: Rewrite Cookie Mode 429
Figure 16-5: SSL Session ID-Based Persistence 438
212777-A, February 2002
Figures
n
15

Web OS 10.0 Application Guide
Figure 17-1: Bandwidth Management: How It Works 442
Figure 17-2: Bandwidth Rate Limits 444
Figure 17-3: Virtual Clocks and TDT 446
Figure 17-4: URL-Based Bandwidth Management 450
Figure 17-5: URL-B ased Bandwidth Mana gement with Web Cache Redir ection 450
Figure 17-6: Cookie-Based Bandwidth Management 451
Figure 17-7: Cookie-Based Preferential Services 467
16
n
Figures
212777-A, February 2002

Tables
Table 1-1: Subnet Routing Example: IP Address Assignments 31
Table 1-2: Subnet Routing Example: IP Interface Assignments 31
Table 1-3: Subnet Routing Example: Optional VLAN Ports 33
Table 1-4: Local Routing Cache Address Ranges 35
Table 2-1: Ports, Trunk Groups, and VLANs 49
Table 2-2: Multiple Spanning Tree Groups per VLAN 54
Table 2-3: Route Cache Example 59
Table 5-1: User Access Levels 105
Table 5-2: Web OS Alteon Levels 106
Table 6-1: Web Host Example: Real Server IP Addresses 124
Table 6-2: Web Host Example: Port Usage 126
Table 6-3: Well-Known Application Ports 128
Table 6-4: Proxy Example: Port Usage 137
Table 7-1: Well-Known Protocol Types 171
Table 7-2: Well-Known Application Ports 171
Table 7-3: Filtering IP Address Ranges 178
Table 7-4: Web Cache Example: Real Server IP Addresses 186
Table 7-5: TCP Flags 197
Table 7-6: ICMP Message Types 201
Table 8-1: Web Cache Example: Real Server IP Addresses 206
Table 11-1: Active Standby Configuration 252
Table 11-2: Sharing Active-Active Failover 260
Table 11-3: VRRP Tracking Parameters 261
212777-A, February 2002
17

Web OS 10.0 Application Guide
Table 12-1: GSLB Example: California Real Server IP Addresses 296
Table 12-2: GSLB Example: California Alteon 180 Port Usage 297
Table 12-3: Denver Real Server IP Addresses 300
Table 12-4: Web Host Example: Alteon 180 Port Usage 301
Table 12-5: HTTP Versus Non-HTTP Redirects 305
Table 15-1: Standard Regular Expression Special Characters 412
Table 15-2: Real Server Content 416
Table 16-1: Comparison Among the Three Cookie Modes 427
Table 17-1: Bandwidth Rate Limits 445
Table 17-2: Bandwidth Policy Limits 445
18
n
Tables
212777-A, February 2002

New Features
The following table lists the new features in Web OS 10.0 and the supported platforms:
Feature Alteon Web Switches
AD3/180e
Vlan-based default gateway No Yes
Vlan Filtering No Yes
Multiple Instances of Spanning Tree Yes Yes
Layer 7 deny filter Yes Yes
Increase real server support to 1024 No Yes
SYN Attack Detection/Protection Yes Yes
Enhanced Port Mirroring Yes Yes
Reporting Classification Manager: SYSLOG and
SNMP
Reporting Classification Manager: Ability to fil-
ter SYSLOG based on seve rity
Reporting Classif ication Manager: SNMP traps
defined for VRRP state changes
Reporting Classif ication Manager: SNMP traps
defined for failed login
Selectable Hash Parameters Yes Yes
No Yes
No Yes
No Yes
No Yes
Alteon Web Switches
AD4/184
Layer 4 DNS Load Bala ncing (UDP and TCP
ports)
L7 DNS Load Balancing Yes Yes
Enhanced DNS Health Check Yes Yes
TCP Rate Limiting Yes Yes
212777-A, February 2002
Yes Yes
19

Web OS 10.0 Application Guide
Feature Alteon Web Switches
AD3/180e
Alteon Web Switches
AD4/184
Hash on any HTTP header Yes Yes
Increase support of 16 r port to vport No Yes
Increased number of scripted health check to 16 No Yes
Descriptive names for filters Yes Yes
OSPF No Yes
LDAP health check Yes Yes
Streaming Cache Redirection Yes Yes
L7 Parsing of RTSP SLB Yes Yes
ARP health check Yes Yes
Telnet client Yes Yes
Increase logging buffer Yes Yes
Support of OPER command on Web OS BBI and
No Yes
SNMP
Enhanced Web OS Browser-based Interface
No Yes
support
n
New Features
20
Configurable prompt name Yes Yes
Bandwidth management No Yes
212777-A, February 2002

Preface
This Application Guide describes how to configure and use the Web OS software on the Alteon
Web switches. For documentation on installing the switches physically, see the Hardware
Installation Guide for your particular switch model.
Who Should Use This Guide
This Application Guide is intended for network installers and system administrators engaged in
configuring and maintaining a network. The administrator should be familiar with Ethernet
concepts, IP addressing, Spanning Tree Protocol, and SNMP configuration parameters.
What You’ll Find in This Guide
This guide will help you plan, implement, and administer Web OS software. Where possible,
each section provides feature overviews, usage examples, and configuration instructions.
Part 1: Basic Switching & Routing
n Chapter 1, “Basic IP Routing,” describes how to configure the Web switch for IP routing
n Chapter 2, “VLANs,” describes how to configure Virtual Local Area Networks (VLANs)
n Chapter 3, “Port Trunking,” describes how to group multiple physical ports together to
n Chapter 4, “OSPF,” describes OSPF concepts, how OSPF is implemented in Web OS, and
212777-A, February 2002
using IP subnets, Border Gateway Protocol (BGP), or DHCP Relay.
for creating separate network segments, including how to use VLAN tagging for devices
that use multiple VLANs. This chapter also describes how Jumbo frames can be used to
ease server processing overhead.
aggregate the bandwidth between large-scale network devices.
four examples of how to configure your switch for OSPF support.
21

Web OS 10.0 Application Guide
n Chapter 5, “Secure Switch Management,” describes how to manage the switch using spe-
cific IP addresses, RADIUS authentication, Secure Shell (SSH), and Secure Copy (SCP).
Part 2: Web Switching Fundamentals
n Chapter 6, “Server Load Balancing,” describes how to configure the Web switch to bal-
ance network traffic among a pool of available servers for more efficient, robust, and scal-
able network services.
n Chapter 7, “Filtering,” describes how to configure and optimize network traffic filters for
security and Network Address Translation purposes.
n Chapter 8, “Application Redirection,” describes how to use filters for redirecting traffic to
such network streamlining devices as Web caches.
n Chapter 9, “Virtual Matrix Architecture,” describes how to optimize system resources by
distributing the workload to multiple processors.
n Chapter 10, “Health Checking,” describes how to configure the Web switch to recognize
the availability of the various network resources used with the various load-balancing and
application redirection features.
n Chapter 11, “High A v ailability,” descr ibes ho w to use the Virtual Router Redundan cy Pro -
tocol (VRRP) to ensure that network resources remain available if one Web switch fails.
22
n
Preface
Part 3: Advanced Web Switching
n Chapter 12, “Global Server Load Balancing,” describes configuring Server Load Balanc-
ing across multiple geographic sites.
n Chapter 13, “Firewall Load Balancing,” describes how to combine features to provide a
scalable solution for load balancing multiple firewalls.
n Chapter 14, “Virtual Private Network Load Balancing,” describes using your Web switch
to load balance secure point-to-point links.
n Chapter 15, “Content Intelligent Switching,” describes how to perform load balancing and
application redirection based on Layer 7 packet content in for mation (such as URL, HTTP
Header, browser type, and cookies).
n Chapter 16, “Persistence,” describes how to ensure that all connections from a specific cli-
ent session reach the same server. Persistence can be based on cookies or SSL session ID.
n Chapter 17, “Bandwidth Management,” describes how to configure the Web switch for
allocating specific portions of the available bandwidth for specific users or applications.
212777-A, February 2002

Web OS 10.0 Application Guide
Typographic Conventions
The following table describes the typographic styles used in this book.
Table 1 Typographic Conventions
Typeface or
Symbol
AaBbCc123 This type is used for names of commands,
AaBbCc123 This bold type appears i n command exam-
<AaBbCc123> This italicized type appears in command
[ ] Command items shown inside brackets are
Meaning Example
files, and directories used within the text.
It also depict s on -sc re en co mput er ou tput a nd
prompts.
ples. It shows text that must be typed in
exactly as shown.
examples as a parameter placeholder. Replace
the indicated text with the appropriate real
name or value when using the command. Do
not type the brackets.
This also shows book titles, special terms, or
words to be emphasized .
optional and can be used or excluded as the
situation demands. Do not type the bracke ts.
View the readme.txt file.
Main#
Main# sys
T o establish a Telnet session, enter:
host# telnet <IP address>
Read your User’s Guide thoroughly.
host# ls [-a]
212777-A, February 2002
Preface
n
23

Web OS 10.0 Application Guide
Contacting Us
For complete product support and sales information, visit the Nortel Networks website at the
following URL:
http://www.nortelnetworks.com
See the contact information on this site for regional support and sales phone numbers an d
e-mail addresses.
n In North America, dial toll-free 1-800-4NORTEL.
n Outside North America, call 987-288-3700.
24
n
Preface
212777-A, February 2002

Part 1: Basic Switching &
Routing
This section discusses basic Layer 1 through Layer 3 switching and routing functions. In addition to switching traffic at near line rates, the Web switch can perform multi-protocol routing.
This section includes the following basic switching and routing topics:
n Basic IP Routing
n VLANs
n Jumbo Frames
n Port Trunking
n Border Gateway Protocol (BGP)
n Open Shortest Path First (OSPF)
n Secure Switch Management
212777-A, February 2002
25

Web OS 10.0 Application Guide
n
Basic Switching & Routing
26
212777-A, February 2002

CHAPTER 1
Basic IP Routing
This c ha pt er pro vides confi guration back ground and ex amples for usi ng the Alte on Web switch
to perform IP routing functions. The following topics are addressed in this chapter:
n “IP Routing Benefits” on page 28
n “Routing Between IP Subnets” on page 28
n “Example of Subnet Routing” on page 31
n “Defining IP Address Ranges for the Local Route Cache” on page 35
n “Border Gateway Protocol (BGP)” on page 36
n “DHCP Relay” on page 41
212777-A, February 2002
27

Web OS 10.0 Application Guide
IP Routing Benefits
The Alteon W eb switch us es a combination of configur able IP switch interfaces and IP routing
options. The switch IP routing capabilities provide the following benefits:
n Connects the server IP subnets to the rest of the backbone network.
n Performs server load balancing (using both Layer 3 and Layer 4 switching in combina-
tion) to server subnets that are separate from backbone subnets.
n Provides another means to invisibly introduce Jumbo frame technology into the server-
switched network by automatically fragmenting UDP Jumbo frames when routing to non-
Jumbo frame VLANs or subnets.
n Provides the ability to route IP traffic between multiple Virtual Local Area Networks
(VLANs) configured on the switch.
Routing Between IP Subnets
The physical layout of most corporate networks has evolved over time. Classic hub/router
topologies have given way to faster switched topologies, particularly now that switches are
increasingly intelligent. Alteon Web switches are intelligent and fast enough to perform routing functions on a par with wire speed Layer 2 switching.
The combination of faster routing and switching in a single device provides another service—
it allows you to build versatile topologies that account for legacy configurations.
n
Chapter 1: Basic IP Routing
28
212777-A, February 2002
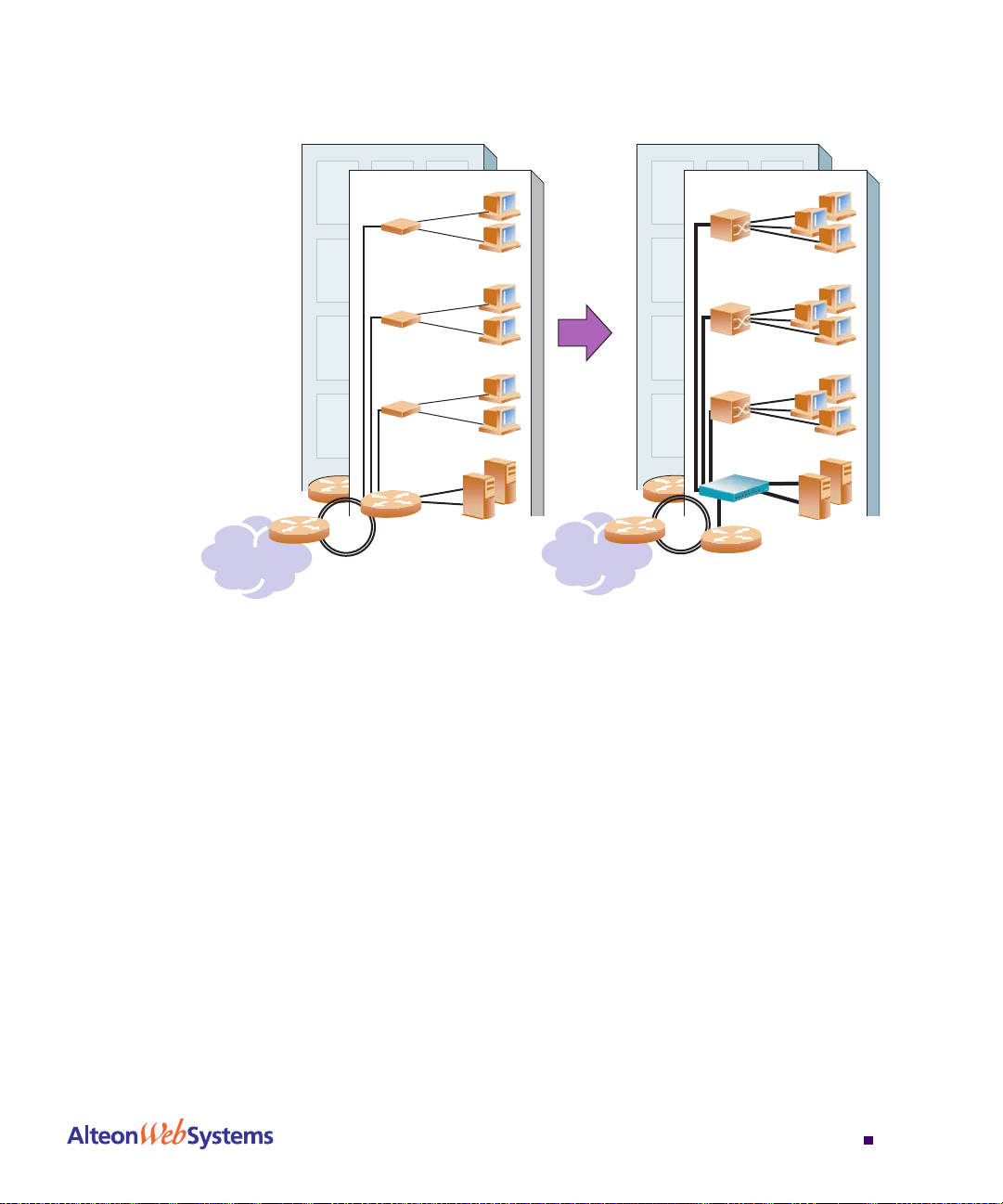
For example, consider the following topology migration:
Web OS 10.0 Application Guide
Internet
FDDI
Admin. Subnet
Hub
Eng. Subnet
Hub
Staff Subnet
Hub
Server
Subnet
Router
Internet
Admin/Sales
Switch
Eng/Staff2/Sales
Switch
Staff/Eng2
Switch
Server
Subnet
Web Switch
FDDI
Router
Figure 1-1 The Router Legacy Network
In this example, a corporate campus has migrated from a router-centric topology to a faster,
more powerful, switch-based topology. As is often the case, the legacy of network growth and
redesign has left the system with a mix of illogically distributed subnets.
This is a situation that switching alone cannot cure. Instead, the router is flooded with crosssubnet communication. This compromises efficiency in two ways:
n Routers can be slower than switches. The cross-subnet side trip from the switch to the
n Traffic to the router increases, increasing congestion.
Even if every end-station could be moved to better logical subnets (a daunting task), competition for access to common server pools on different subnets still burdens the routers.
This problem is solved by using Alteon Web switches with built-in IP routing capabilities.
Cross-subnet LAN tra ffic can now be routed within t he Web swi tc hes wi th wi re s peed Layer 2
switching performance. This not only eases the load on the router but saves the network
administrators from reconfiguring each and every end-station with new IP addresses.
212777-A, February 2002
router and back again adds two hops for the data, slowing throughput considerably.
Chapter 1: Basic IP Routing
n
29
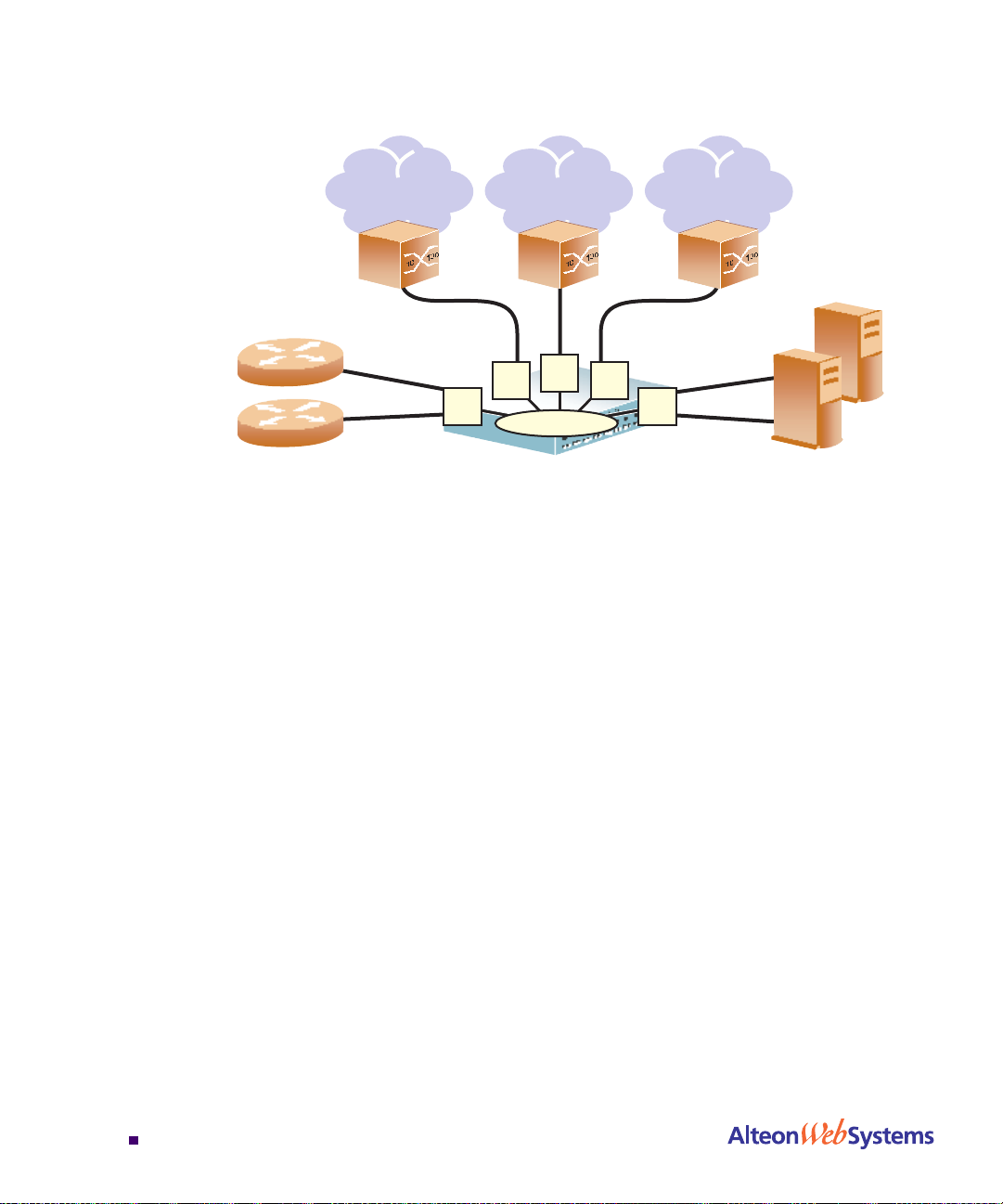
Web OS 10.0 Application Guide
Take a closer look at the Alteon Web switch in the following configuration example:
10/100 Client Subnet
100.20.10.1-254
Primary Default
Router: 205.21.17.1
1000 Mbps
Secondary Default
Router: 205.21.17.2
First Floor
Second Floor
10/100 Client Subnet
131.15.15.1-254
1000 Mbps
IF#3
IF#2 IF#4
IF#1 IF#5
IP Routing
Alteon Web Switch
Third Floor
10/100 Client Subnet
208.31.177.1-254
1000 Mbps
Server Subnet:
206.30.15.1-254
Figure 1-2 Switch-Based Routing Topology
The Alteon Web switch connects the Gigabit Ethernet and Fast Ethernet trunks from various
switched subnets throughout one building. Common servers are placed on another subnet
attached to the switch. A primary and backup router are attached to the switch on yet another
subnet.
Without Layer 3 IP routing on the switch, cross-s ubnet communicatio n is relayed to the defau lt
gateway (in this case, the router) for the next level of routing intelligence. The router fills in the
necessary address information and sends the data back to the switch, which then relays the
packet to the proper destination subnet using Layer 2 switching.
With Layer 3 IP routing in place on the Alteon Web switch, routing between different IP subnets can be accomplished entirely within the switch. This leaves the routers free to handle
inbound and outbound traffic for this group of subnets.
T o mak e imp lementation even eas ier, UDP Jumbo frame traffi c is auto matically fr agmen ted to
regular Ethernet frame sizes when routing to non-Jumbo frame VLANS or subnets. This automatic frame conversion allows servers to communicate using Jumbo frames, all transparently
to the user.
n
Chapter 1: Basic IP Routing
30
212777-A, February 2002
 Loading...
Loading...