Page 1

Nortel Networks
VPN Gateway 3050
RSA SecurID Ready Implementation Guide
Partner Information
Last Modified: March 14, 2008
Product Information
Partner Name
Web Site www.nortelnetworks.com
Product Name
Version & Platform
Product Description
Product Category
Nortel Networks
VPN Gateway 3050
7.0.1.0
The Nortel Networks VPN Gateway 3050 is a remote access
security solution that extends the reach of enterprise applications
and resources to remote users. The gateway performs on-the-fly
content transformation to instantly convert most intranet resour ces
into externally-viewable, secure HTML pages and employs an
advanced network address and port translation (NAPT) utility to
build SSL-secured VPN tunnels for client/server communications
Perimeter Defense (VPN, Firewalls & Intrusion Detection)
Page 2
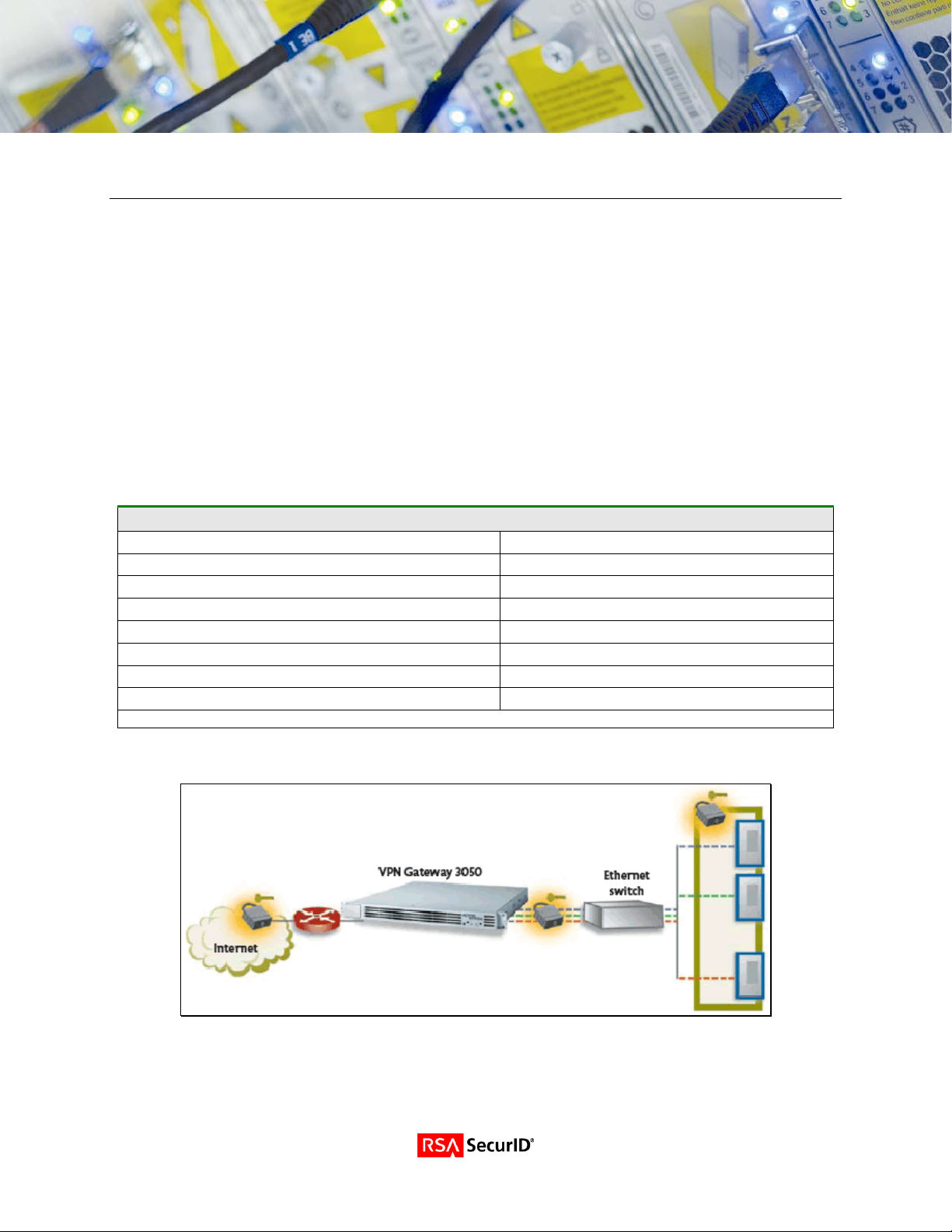
Solution Summary
The Nortel Networks VPN Gateway 3050 is a remote access security solution that extends the reach of
enterprise applications and resources to remote employees, partners, and customers. By using the
native capability of widely deployed Web browsers, the SSL VPN Gateway offers a convenient clientless
alternative for securely provisioning resources for remote users, without the need to install and manage
client tunneling software on their PCs.
Due to the clientless nature of this solution, Strong two factor authentication is essential to ensure the
identity of users connecting to your Enterprise from the internet. For this reason, Nortel Networks VPN
Gateway 3050 provides support for the RSA Authentication Manager as a method of strong
authentication for users using RSA SecurID Authentication.
For enterprises maintaining IPsec VPN environments, the Nortel VPN Gateway 3050 provides a new
level of deployment flexibility and end-user support by incorporating IPsec VPN client termination to
remove the network administrator's challenge of managing multiple devices to deliver both types of
remote access service.
Partner Integration Overview
Authentication Methods Supported
List Library Version Used
RSA Authentication Manager Replica Support *
Secondary RADIUS Server Support
RSA Authentication Agent Host Type
RSA SecurID User Specification
RSA SecurID Protection of Administrative Users
RSA Software Token and RSA SecurID 800 Automation
Native RSA SecurID Authentication, RADIUS
5.0.3
Full Replica Support
Yes Support for 2 Secondary Serves
Communication Server
Designated Users,
Yes via RADIUS. See Known issues.
No
2
Page 3

Product Requirements
Partner Product Requirements: Nortel VPN Gateway 3050
Firmware Version
7.0.1.0
Hardware Platform
Platform Required Patches
VPN 3050, ASA 310, ASA 410, ASA 310 FIPS N/A
Additional Software Requirements
Application Additional Patches
Internet Explorer 5.0, 5.5 and 6.0
RSA SecurID files
RSA SecurID Authentication Files
Files Location
sdconf.rec In Memory
Node Secret In Memory
sdstatus.12 In Memory
sdopts.rec Not implemented
Go to the appendix of this document to get detailed information regarding
these files.
3
Page 4
Agent Host Configuration
Important: “Agent Host” and “Authentication Agent” are synonymous.
“Agent Host” is a term used with the RSA Authentication Manager 6.x
servers and below. RSA Authentication Manager 7.1 uses the term
“Authentication Agent”.
Important: All “Authentication Agent” types for 7.1 should be set to
“Standard Agent”.
To facilitate communication between the Nortel VPN Gateway and the RSA Authentication Manager /
RSA SecurID Appliance, an Agent Host record must be added to the RSA Authentication Manager
database and the RADIUS server database if using RADIUS. The Agent Host record identifies the
VPN Gateway
within its database and contains information about communication and encryption.
To create the Agent Host record, you will need the following information.
• Hostname
• IP Addresses for all network interfaces
When adding the Agent Host Record, you should configure the Nortel VPN Gateway as Communication
. This setting is used by the RSA Authentication Manager to determine how communication with
Server
Nortel VPN Gateway will occur.
the
To create the RADIUS client record, you will need the following information.
• Hostname
• IP Addresses for all network interfaces
• RADIUS Secret
Nortel
Note: Hostnames within the RSA Authentication Manager / RSA SecurID
Appliance must resolve to valid IP addresses on the local network.
Please refer to the appropriate RSA Security documentation for additional information about Creating,
Modifying and Managing Agent Host records.
4
Page 5

Partner Authentication Agent Configuration
Before You Begin
This section provides instructions for integrating the partners’ product with RSA SecurID Auth entication.
This document is not intended to suggest optimum installations or configurations.
It is assumed that the reader has both working knowledge of all products involved, and the ability to
perform the tasks outlined in this section. Administrators should have access to the product
documentation for all products in order to install the required components.
All vendor products/components must be installed and working prior to the integration. Perf orm the
necessary tests to confirm that this is true before proceeding.
Nortel VPN Gateway 3050 Agent configuration
Administrative tasks can be performed in the Command Line Interface (CLI) as well as the Web
Administration GUI. All configuration steps and screenshots in this guide will refer to GUI administration.
Please refer to Nortel Administrative documentation for more complete details on CLI and GUI
Administration tasks.
RSA SecurID Authentication Configuration Overview
1. Create a User Group
2. Configure the RSA Server record
3. Configuring the RSA SecurID Authentication Servers
RADIUS Authentication Configuration Overview
1. Create a User Group
2. Configuring the RADIUS Authentication Servers
5
Page 6

Creating and Configuring a RSA SecurID or RADIUS User Group
1. From the admin console, expand VPN Gateways and click Add to add a VPN Gateway.
2. Click
3. Now click on the VPN Gateway you just created and click on Groups.
4. Click on the button Add New Group.
5. Fill out the form with the desired group name, user type and description.
6. Click Update and then Apply to add the new group to the configuration.
7. From the Groups menu on the administration console, click on the group name.
8. Select the Access List tab.
9. Create an appropriate Access list based on your organizations configuration. In the example b elow you will
Create VPN.
see we have created a generic rule allowing all access for authenticated RSA SecurID or RADIUS users.
10. Click Update to apply the Access rules.
11. Configure the user group for any necessary links or VPN Settings as required.
12. Click Apply to add the new information to the IOS configuration.
6
Page 7

Configure the RSA Server record
1. Open the Management Interface (MIP) of the Nortel VPN Gateway using a web browser. Authenticate with
administrative user account and select the Config tab.
2. From the SSL-VPN admin menu select
3. Click the Add button and complete the form.
4. Click Apply to commit changes to the IOS configuration.
Note: You must Update and Apply the RSA Server Group entry before
you import the sdconf.rec file
5. To import your sdconf.rec file you will return to the RSA Servers menu and modify the entry for the
sdconf.rec file you will be adding.
Administration > RSA Servers item.
6. Click import to upload the sdconf.rec file and then click Apply changes to the IOS configuration.
Configuring the RSA SecurID Authentication Servers
1. From the admin console, select VPN Gateways > Authentication.
2. Click Add.
3. Enter information for the Authentication Server such as Name and Display Name. The Authentication
Mechanism will be RSA. Then click update to complete additional RSA SecurID authentication options.
4. Select the Settings tab and fill in the appropriate information.
• RSA Server IP.Hostname: Select the RSA Authentication Manger server you created.
• Group For RSA Authenticated Users: Select The Group name you created for the.
5. Click Update and then Apply to add the new information to the IOS configuration.
7
Page 8

Configuring the RADIUS Authentication Servers
6. From the admin console, select VPN Gateways > Authentication.
7. Click Add.
8. Enter information for the Authentication Server such as Name and Display Name. The Authentication
Mechanism will be RADIUS. Then click update to complete additional RADIUS authentication options.
9. Select the Servers tab and click Add.
10. Enter the appropriate information for you server and click Update.
Note: You can add a maximum of three RSA RADIUS servers to this
authentication server list.
11. Click Apply to add the new information to the IOS configuration.
8
Page 9

Configuring RADIUS Authentication Servers for Administrative Access
1. From the admin console, select Administration > RADIUS.
2. Click Add.
3. Enter information for the RADIUS Authentication Server.
4. Click update.
5. Enable authentication by selecting
enabled for RADIUS Authentication Status.
6. Click update then Apply.
NEW-PIN mode does not work via the admin console. See the Known
issues section of this guide for more information.
9
Page 10

Testing the configuration
1. Open a web browser and point to the portal address.
2. For user credentials enter a SecurID username and Passcode.
3. From the Login Service list select your RSA SecurID or RSA RADIUS challenge group.
4. Click Login to authenticate and enter the Portal Server.
Note: The user name does not need to exist on the VPN Gateway 3050
in order to be authenticated. The VPN Gateway 3050 will pass off
authentication to the RSA Authentication Manager as a trusted
authentication source.
10
Page 11

Certification Checklist
Date Tested: September 26, 2007
Certification Environment
Product Name Version Information Operating System
RSA Authentication Manager
RSA RADIUS Server
VPN Gateway 3050
RSA Native Protocol RADIUS Protocol
New PIN Mode
Force Authentication After New PIN
System Generated PIN
User Defined (4-8 Alphanumeric)
User Defined (5-7 Numeric)
User Selectable
Deny 4 and 8 Digit PIN
Deny Alphanumeric PIN
PASSCODE
16 Digit Passcode
4 Digit Password
Next Tokencode Mode
Next Tokencode Mode
Load Balancing / Reliability Testing
Failover (3-10 Replicas)
Name Locking Enabled
No RSA Authentication Manager
RSA Software Token Automation
System Generated PIN
User Defined (8 Digit Numeric)
User Selectable
Next Tokencode Mode
RSA SecurID 800 Token Automation
System Generated PIN
User Defined (8 Digit Numeric)
User Selectable
Next Tokencode Mode
Credential Functionality
Determine Cached Credential State
Set Credential
Retrieve Credential
SWA / BSD = Pass = Fail N/A = Non-Available Function
6.1 Windows 2003 Server
6.1 Windows 2003 Server
7.0.1.0 IOS Router
Mandatory Functionality
Force Authentication After New PIN
System Generated PIN
User Defined (4-8 Alphanumeric)
User Defined (5-7 Numeric)
User Selectable
Deny 4 and 8 Digit PIN
Deny Alphanumeric PIN
16 Digit Passcode
4 Digit Password
Next Tokencode Mode
Failover
Name Locking Enabled
No RSA Authentication Manager
Additional Functionality
N/A
N/A
N/A
N/A
N/A
N/A
N/A
N/A
N/A
N/A
N/A
System Generated PIN
User Defined (8 Digit Numeric)
User Selectable
Next Tokencode Mode
System Generated PIN
User Defined (8 Digit Numeric)
User Selectable
Next Tokencode Mode
Determine Cached Credential State
Set Credential
Retrieve Credential
N/A
N/A
N/A
N/A
N/A
N/A
N/A
N/A
11
Page 12

Certification Checklist For RSA Authentication Manager 7.x
Date Tested: March 14, 2008
Certification Environment
Product Name Version Information Operating System
RSA Authentication Manager
RSA RADIUS Server
VPN Gateway 3050
RSA Native Protocol RADIUS Protocol
New PIN Mode
Force Authentication After New PIN
System Generated PIN
User Defined (4-8 Alphanumeric)
User Defined (5-7 Numeric)
Deny 4 and 8 Digit PIN
Deny Alphanumeric PIN
Deny Numeric PIN
PIN Reuse
Passcode
16 Digit Passcode
4 Digit Fixed Passcode
Next Tokencode Mode
Next Tokencode Mode
Load Balancing / Reliability Testing
Failover (3-10 Replicas)
No RSA Authentication Manager
RSA Software Token Automation
System Generated PIN
User Defined (8 Digit Numeric)
PIN Expiration
Next Tokencode Mode
RSA SecurID 800 Token Automation
System Generated PIN
User Defined (8 Digit Numeric)
PIN Expiration
Next Tokencode Mode
SWA = Pass = Fail N/A = Non-Available Function
7.1 Windows 2003
7.1 Windows 2003
7.0.1.0 IOS Router
Mandatory Functionality
System Generated PIN
User Defined (4-8 Alphanumeric)
User Defined (5-7 Numeric)
Deny 4 and 8 Digit PIN
Deny Alphanumeric PIN
Deny Numeric PIN
PIN Reuse
16 Digit Passcode
4 Digit Fixed Passcode
Next Tokencode Mode
Failover
No RSA Authentication Manager
Force Authentication After New PIN
Additional Functionality
N/A
N/A
N/A
N/A
N/A
N/A
N/A
N/A
System Generated PIN
User Defined (8 Digit Numeric)
PIN Expiration
Next Tokencode Mode
System Generated PIN
User Defined (8 Digit Numeric)
PIN Expiration
Next Tokencode Mode
N/A
N/A
N/A
N/A
N/A
N/A
N/A
N/A
12
Page 13

Known Issues
PIN Rejection: When a PIN is rejected by the Authentication Manager Server the user is questioned by
the client to try a different PIN but the program flow is not intuitive.
1. The user first authenticates using either Token or Password. The user is next prompted to create a new PIN.
2. The user must re-enter the new PIN to validate input from the previous step.
3. If rejected, the client displays the question to the user with an empty text box for input.
4. The client will accept any input by the user and then prompt for a new Passcode to restart the authentication
process.
5. The user then inputs a valid Passcode.
13
Page 14

Administration Logon.
NEW-PIN mode does not work via the admin console. The user is prompted to create or accept a PIN
but the PIN never gets sent to the server and the user gets redirected to a blank web page.
14
Page 15

Appendix
Delete Node Secret
1. Navigate to Config > Administration > RSA Servers and click on the link for the RSA Authentication Server
Label you created.
2. Click the button labeled Remove Node Secret.
Remove sdconf.rec and sdstatus.12
1. Navigate to Config > Administration > RSA Servers.
2. Check the box for the RSA Authentication Server Label you created.
3. Click delete.
4. You now need to add a new record for an RSA Authentication Managers for authentication.
15
 Loading...
Loading...