Page 1
Part No. 209321-A
August 2000
4401 Great America Parkway
Santa Clara, CA 95054
Getting Started with the Business Policy Switch 2000 Management Software
Page 2

2
Copyright © 2000 Nortel Networks
All rights reserved. August 2000.
The information in this document is subjectto change without notice. The statements, configurations, technical
data, and recommendations in this document are believed to be accurate and reliable, but are presentedwithout
expressor implied warranty. Users must take full responsibility for their applications of any products specified in
this document. The information in this document is proprietary to Nortel Networks NA Inc.
The software described in this document is furnished under a license agreement and m ay be used only in
accordance with the terms of that license. The software licenseagreement is included in this document.
Trademarks
NORTEL NETWORKS is a trademark of Nortel Networks.
Microsoft, MS, MS-DOS, Windows, and WindowsNT are registered trademarksof Microsoft Corporation.
All other trademarks and registered trademarks are the property of their respective owners.
Restricted rights legend
Use, duplication, or disclosure by the UnitedStates Government is subject to restrictions as set forth in
subparagraph (c)(1)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013.
Notwithstanding any other license agreement that may pertain to, or accompany the delivery of, this computer
software, the rights of the United States Government regardingits use, reproduction, and disclosure are as set forth
in the Commercial Computer Software-Restricted Rights clause at FAR 52.227-19.
Statement of conditions
In the interest of improving internaldesign,operational f unction, and/or reliability, Nortel Networks NA Inc.
reserves the right to make changes to the products described in this document without notice.
Nortel Networks NA Inc. does not assume any liability that may occur due to the use or application of the
product(s) or circuit layout(s) describedherein.
Portions of the code in thissoftware product may be Copyright © 1988, Regents of the University of California. All
rightsreserved. Redistribution and use in source and binary forms of such portions are permitted,provided that the
above copyright notice and this paragraphare duplicated in all such forms and that any documentation, advertising
materials, and other materials related to such distribution and use acknowledgethat such portions of the software
were developed by the University of California, Berkeley. The name of the University may not be used to endorse
or promote products derived from such portions of the software without specific prior written permission.
SUCH PORTIONS OF THE SOFTWARE ARE PROVIDED “AS IS” AND WITHOUT ANY EXPRESS OR
IMPLIED WARRANTIES, INCLUDING, W ITHOUT LIMITATION, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE.
In addition, the program and information contained herein are licensed only pursuant to a license agreement that
containsrestrictions on use and disclosure (that may incorporate by reference certain limitations and notices
imposed by third parties).
209321-A
Page 3

Nortel Networks NA Inc. software license agreement
NOTICE: Please carefully read this license agreement before copying or using the accompanying softwareor
installing the hardware unit with pre-enabled software(each of which is referredto as “Software” in this
Agreement). BY COPYING OR USING THE SOFTWARE, YOU ACCEPT ALL OF THE TERMS AND
CONDITIONS OF THIS LICENSE AGREEMENT. THE TERMS EXPRESSED IN THIS AGREEMENT ARE
THE ONLY TERMS UNDER WHICH NORTEL NETWORKS WILL PERMIT YOU TO USE THE
SOFTWARE. If you do not accept these terms and conditions, return the product, unused and in the original
shippingcontainer, within 30 days of purchase to obtain a credit for the full purchase price.
1. License grant. Nortel Networks NA Inc. (“NortelNetworks”) grants the end user of the Software (“Licensee”) a
personal, nonexclusive,nontransferablelicense: a) to use the Software eitheron a singlecomputeror, if applicable,
on a single authorized device identified by hostID, for which it was originally acquired; b) to copy the Software
solely for backup purposes in support of authorized use of the Software; and c) to use and copy the associated user
manualsolely in supportof authorized use of the Softwareby Licensee. This license applies to the Software only
and does not extend to Nortel Networks Agent software or other Nortel Networks software products. Nortel
NetworksAgent software or other Nortel Networks software products are licensed for use under the terms of the
applicable Nortel Networks NA Inc. Software License Agreement that accompanies such software and upon
paymentby the end user of the applicable license fees for such software.
2. Restrictions on use; reservationof rights.The Software and user manuals are protected under copyright laws.
NortelNetworks and/orits licensors retain all title and ownership in both the Software and user manuals,including
any revisionsmade byNortelNetworks or its licensors. The copyright notice must be reproduced and includedwith
any copy of any portion of the Software or user manuals. Licensee may not modify, translate, decompile,
disassemble, use for any competitiveanalysis,reverseengineer, distribute, or create derivative works from the
Software or user manuals or any copy, in whole or in part. Except as expressly provided in this Agreement,
Licensee maynot copy or transfer the Softwareor user manuals,in whole or in part. The Softwareand usermanuals
embody Nortel Networks’ and its licensors’confidential and proprietary intellectual property. Licensee shall not
sublicense, assign, or otherwisedisclose to any third party the Software, or any information about the operation,
design,performance, or implementation of the Software and user manuals that is confidential to Nortel Networks
and its licensors; however, Licensee may grant permission to its consultants, subcontractors, and agents to use the
Software at Licensee’sfacility, providedthey have agreed to use the Software only in accordance with the terms of
this license.
3. Limited warranty. Nortel Networks warrants each item of Software, as delivered by Nortel Networks and
properly installed and operated on Nortel Networks hardware or other equipment it is originally licensedfor,to
functionsubstantially as described in itsaccompanying user manual during its warranty period,which beginsonthe
date Softwareis first shipped to Licensee. If any item of Software fails to so function during its warranty period,as
the sole remedyNortel Networks will at its discretion provide a suitable fix, patch, or workaround for the problem
that may be included in a future Software release. Nortel Networks further warrants to Licensee that the media on
which the Software is provided will be free from defects in materials and workmanship under normal use for a
periodof 90 days from the date Software is first shipped to Licensee. Nortel Networks will replace defective media
at no charge if it is returnedto NortelNetworksduring the warranty periodalongwithproofof the date of shipment.
This warrantydoes not apply if the media has been damaged as a result of accident,misuse, or abuse. The Licensee
assumesall responsibility for selection of the Software to achieve Licensee’s intended results and for the
installation, use, and results obtained from the Software. Nortel Networks does not warrant a) that the functions
contained in the software will meet the Licensee’s requirements, b) that the Software will operate in the hardware or
software combinations that the Licensee may select, c) that the operation of the Software will be uninterrupted or
error free, or d) that all defects in the operation of the Software will be corrected. Nortel Networks is not obligated
to remedy any Software defect that cannot be reproduced with the latest Software release. These warranties do not
apply to the Softwareif it has been (i) altered, except by NortelNetworksor in accordance with its instructions;(ii)
used in conjunction w ith another vendor’sproduct, resulting in the defect; or (iii) damaged by improper
environment, abuse, misuse, accident, or negligence. THE FOREGOING WARRANTIES AND LIMITATIONS
ARE EXCLUSIVE REMEDIES AND ARE IN LI EU OF ALL OTHER WARRANTIES EXPRESS OR IMPLIED,
3
Getting Started with the Business Policy Switch 2000 Management Software
Page 4

4
INCLUDING WITHOUT LIMITATION ANY WARRANTY OF MERCHANTABILITY OR FITNESS FOR A
PARTICULAR PURPOSE. Licensee is responsible for the security of its own data and information and for
maintaining adequate procedures apart from the Software to reconstruct lost or altered files, data, or programs.
4.Limitationof liability. IN NO EVENT WILL NORTEL NETWORKS OR ITS LICENSORS BE LIABLE FOR
ANY COST OF SUBSTITUTE PROCUREMENT; SPECIAL, INDIRECT, I NCIDENTAL, OR
CONSEQUENTIAL DAM AGES; OR ANY DAMAGES RESULTING FROM INACCURATE OR LOST DATA
OR LOSS OF USE OR PROFITS ARISING OUT OF OR IN CONNECTION WITH THE PERFORMANCE OF
THE SOFTWARE, EVEN IF NO RTEL NETWORKS HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH
DAMAGES. IN NO EVENT SHALL THE LIABILITY OF NORTEL NETWORKS RELATING TO THE
SOFTWARE OR THIS AGREEMENT EXCEED THE PRICE PAID TO NORTEL NETW ORKS FOR THE
SOFTWARE LICENSE.
5. Government licensees. This provision applies to all Software and documentation acquireddirectly or indirectly
by or on behalf of the United States Government. The Software and documentation are commercialproducts,
licensedon the open marketat market prices,and were developed entirelyat private expense and without the use of
any U.S. Government funds. The license to the U.S. Government is granted only with restricted rights, and use,
duplication, or disclosure by the U.S. Government is subject to the restrictions set forth in subparagraph(c)(1) of
the Commercial Computer Software––Restricted Rights clause of FAR 52.227-19 and the limitations set out in this
licensefor civilian agencies, and subparagraph (c)(1)(ii)of the Rights in Technical Data and Computer Software
clause of DFARS 252.227-7013,for agencies of the Department of Defense or their successors,whicheveris
applicable.
6. Use of software i n the European Community. This provision appliesto all Softwareacquiredfor use within the
European Community. If Licensee uses the Software within a country in the European Community, the Software
Directive enacted by the Council of European Communities Directive dated 14 May, 1991, will apply to the
examination of the Software to facilitate interoperability. Licensee agrees to notify Nortel Networks of any such
intended examinationof the Software and may procure support and assistancefrom Nortel Networks.
7. Termand termination. This license is effective until terminated; however, all of the restrictions with respect to
Nortel Networks’copyright in the Software and user manuals will cease being effective at the date of expirationof
the Nortel Networks copyright; those restrictions relatingto use and disclosure of Nortel Networks’ confidential
information shall continue in effect. Licensee may terminate this license at any time. The license will automatically
terminate if Licensee fails to comply with any of the terms and conditions of the license. Upon termination for any
reason,Licensee will immediately destroy or return to Nortel Networks the Software,user manuals, and all copies.
Nortel Networks is not liable to Licensee for damagesin any form solely by reason of the terminationof this
license.
8. Export and re-export.Licensee agrees not to export,directly or indirectly, the Software or related technicaldata
or information without first obtaining any required export licenses or other governmental approvals. Without
limiting the foregoing, Licensee, on behalf of itself and its subsidiaries and affiliates, agrees that it will not, without
firstobtainingall export licenses and approvals required by the U.S. Government: (i) export, re-export, transfer, or
divertany such Softwareor technical data, or any direct product thereof, to any country to which such exports or
re-exports are restrictedor embargoedunder United States exportcontrol lawsand regulations, or to any nationalor
resident of such restricted or embargoed countries; or (ii) provide the Software or relatedtechnical data or
information to any military end user or for any military end use, including the design, development, or production
of any chemical, nuclear, or biological weapons.
209321-A
Page 5

9. General. If any provision of this Agreement is held to be invalid or unenforceable by a court of competent
jurisdiction,the remainderof the provisionsof this Agreementshallremain in full forceand effect. This Agreement
will be governed by the laws of the state of California.
Should you have any questions concerningthis Agreement,contact Nortel Networks, 4401 Great America
Parkway, P.O. Box 58185, Santa Clara, California 95054-8185.
LICENSEE ACKNOWLEDGES THATLICENSEE HAS READ THIS AGREEMENT, UNDERSTANDS IT,
AND AGREES TO BE BOUND BY ITS TERMS AND CONDITIONS. LICENSEE FURTHER AGREES THAT
THIS AGREEMENT IS THE ENTIRE AND EXCLUSI VE AGREEMENT BETWEEN NORTEL NETWORKS
AND LI CENSEE, WHICH SUPERSEDES ALL PRIOR ORAL AND WRITTEN AGREEMENTS AND
COMMUNICATIONS BETWEEN THE PARTIES PERTAINING TO THE SUBJECT MATTER OF THIS
AGREEMENT. NO DIFFERENT OR ADDITIONAL TERMS WILL BE ENFORCEABLE AGAINST NORTEL
NETWORKS UNLESS NORTEL NETWORKS GIVES ITS EXPRESS WRITTEN CONSENT, INCLUDING AN
EXPRESS WAIVER OF THE TERMS OF THIS AGREEMENT.
5
Getting Started with the Business Policy Switch 2000 Management Software
Page 6

6
209321-A
Page 7

Contents
Preface ......................................................13
Before you begin .....................................................13
Textconventions......................................................14
Relatedpublications...................................................15
Howtogethelp ......................................................16
Chapter 1
Managementbasics............................................17
Management tools ....................................................17
DeviceManager...................................................17
Web management interface . . ........................................18
SettingtheswitchIPparameters .........................................18
Accesslevelsandpasswords ...........................................20
Chapter 2
Installing Device Manager software. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
7
AccessingtheNortelNetworksWebsite...................................21
Windowsinstallation...................................................21
UNIXinstallation......................................................22
InstallingthesoftwareinaSolarisenvironment ..........................23
InstallingthesoftwareinanHP-UXenvironment .........................25
InstallingthesoftwareinanIBMAIXenvironment ........................26
Chapter 3
DeviceManagerbasics.........................................29
Starting Device Manager . ..............................................29
Setting t he Device Manage r properties . . . .................................30
Openingadevice .....................................................32
Getting Started with the Business Policy Switch 2000 Management Software
Page 8

8 Contents
Device Manager window . ..............................................34
Editingobjects .......................................................43
Working with statistics and graphs ........................................43
Telnetingtoaswitch...................................................51
Traplog ............................................................51
OnlineHelp .........................................................52
Menubar ........................................................35
Toolbar..........................................................36
Deviceview ......................................................36
Selectingobjects...............................................37
Selectingasingleobject .........................................37
Selectingmultipleobjects ........................................38
Viewing information about an MDA .................................38
LEDsandports ................................................39
Shortcut menus ...................................................40
Statusbar .......................................................42
Using the buttons in Device Manager dialog boxes . . . .....................42
Typesofstatistics .................................................44
Typesofgraphs ...................................................44
Statisticsforsingleandmultipleobjects ................................47
Viewingstatisticsasgraphs..........................................49
209321-A
Chapter 4
Webmanagementinterfacebasics ...............................53
Requirements . . . .....................................................53
AccessingtheWebinterface ............................................54
Web page layout .....................................................56
Menu ...........................................................57
Contentarea .....................................................59
Icons ...........................................................59
Settingupsecurity ....................................................60
Settingconsole,Telnet,andWebpasswords ............................61
Settingremotedial-inaccesssecurity..................................62
Index........................................................63
Page 9

Figures
Figure1 Mainmenu ................................................19
Figure2 IPConfiguration/Setupmenu ..................................19
Figure 3 Device Manager window ......................................30
Figure4 Propertiesdialogbox ........................................31
Figure5 OpenDevicedialogbox ......................................33
Figure6 Deviceview................................................34
Figure 7 Parts of the Device Manager window . ...........................35
Figure8 Objectsinthedeviceview ....................................37
Figure9 MDAdialogbox ............................................39
Figure 10 Port color legend ............................................40
Figure11 Switchunitshortcutmenu ....................................40
Figure12 Portshortcutmenu ..........................................41
Figure13 MDAshortcutmenu .........................................41
Figure14 Linegraph.................................................45
Figure15 Areagraph ................................................45
Figure16 Bargraph .................................................46
Figure17 Piegraph .................................................46
Figure18 Interfacestatisticsforasingleport..............................47
Figure19 Interfacestatisticsformultipleports .............................48
Figure20 Statisticsdialogboxforaport .................................49
Figure 2 1 System Information home page ................................55
Figure 22 Login pa ge . . ..............................................55
Figure 23 Parts of the Web management page . ...........................57
Figure24 Menu.....................................................57
Figure25 Consolepasswordpage ......................................61
Figure 26 Radius m anagement page . . . .................................62
9
Getting Started with the Business Policy Switch 2000 Management Software
Page 10

10 Figures
209321-A
Page 11

Tables
Table1 Propertiesdialogboxitems ...................................31
Table2 SNMPcommunitystringdefaultvalues ..........................32
Table3 OpenDevicedialogboxitems .................................33
Table4 Menubarcommands ........................................35
Table5 Toolbarbuttons .............................................36
Table 6 Port color codes ............................................39
Table 7 Switch unit shortcut menu commands ...........................40
Table8 Portshortcutmenucommands.................................41
Table9 DeviceManagerbuttons......................................42
Table10 Typesofstatistics ...........................................44
Table11 Graphdialogboxbuttons .....................................50
Table12 Helpfilelocations ...........................................52
Table13 UserlevelsintheWebmanagementinterface .....................56
Table14 Menuheadingsandoptions ...................................58
Table15 Pageicons ................................................59
11
Getting Started with the Business Policy Switch 2000 Management Software
Page 12

12 Tables
209321-A
Page 13

Preface
13
Business Policy Switch 2000 management software provides the m eans to
configure and monitor the operation of your Business Policy Switches.
Management software includes the console interface resident in each Business
Policy Switch; Java-based Device Manager software, which you install on a
management station in the network; and a Web-based management interface
accessible through a Web browser.
This guide provides instructions for installing the Device Manager software and
summarizes procedures for using Device Manager and the Web interface. For
information a bout using the console interface, refer to Using the Business Policy
Switch 2000.
This guide includes the following information:
• A summary of management options for the switch
• Instructions to install Device Manager software
• A summary of navigation procedures for D evice Manager and initial setup
procedures using Device Manager
• An overview of the Web management interface
• Common startup problems and how to troubleshoot them
Before you begin
This guide is intended for network administrators with the following background:
• Basic knowledge of networks, Ethernet bridging, and IP and IPX routing
• Familiarity with networking concepts and terminology
• Basic knowledge of network topologies
• Experience with windowing systems, graphical user interfaces (GU Is), or
Web browsers
Getting Started with the Business Policy Switch 2000 Management Software
Page 14

14 Preface
Text conventions
This guide uses the following text conventions:
angle brackets (< >) Indicate that you choose the text to enter based on the
description inside the brackets. Do not type the
brackets when entering the command.
Example: If the command syntax is
ping
<ip_address>
ping 192.32.10.12
, you enter
bold Courier text
Indicates command names and options and text that
you need to enter.
Example: Enter
# chmod 755 ./install_dmvm.
italic text Indicates new terms, book titles, and variables in
command syntax descriptions. Where a variable is two
or more words, the words are connected by an
underscore.
Example: If the command syntax is
install_dmvm <
target_directory>,target_directory
<
filename
>
variable and you substitute one value for it.
plain Courier
text
Indicates command syntax and system output, for
example, prompts and system messages.
Example:
% JDM
separator ( > ) Shows menu paths.
Example: Edit > File System identifies the File System
option on the Edit menu.
is one
209321-A
Page 15

Related publications
For more information about using the Business Policy Switch, r efer to the
following publications:
• Using the Business Policy Sw itch 2000 (part number 208700-A)
Describes how to install and use the Business P olicy Switch 2000; includes
instructions to use the console interface to configure the switch.
• Business Policy Switch 2000 Installation Instructions (part number
209319-A)
Provides installation instructions for the switch in English and five other
languages.
• Installing Media De pendent Adapters (MDAs) (part number 302403-D)
Provides installation instructions for media dependent adapters in the
Business Policy Switch; includes descriptions of the available MDAs.
• Reference for the Business Policy Switch 2000 Management Software
Operations (part number 209322-A)
Preface 15
Describes how to use Device Manager software to manage the switch.
• Installation and Reference for the 100 Watt DC -DC Converter Module (part
number 209132-A)
Describes how to install and connect the BayStack DC-DC Converter.
• Installing the BayStack 400-ST1 Cascade Module (part number 304433-B)
Describes how to install cascade modules in the switch and connect up to
eight such switches into a stack configuration.
• Using Web-Based Management for the Business Policy Switch 2000 (part
number 209570-A)
Describes how to use the Web-based management interface to configure and
monitor switch operations.
Getting Start ed with the Business Policy Switch 2000 Management Software
Page 16

16 Preface
You can print selected technical m anuals and release notes free, directly from the
Internet. Go to the support.baynetworks.com/library/tpubs/URL. Find the product
for which you need documentation. Then locate the specific c ategory a nd model
or version for your hardware or software product. Use Adobe Acrobat Reader to
open the manuals and release notes, search for the sections you need, and print
them on most standard printers. Go to Adobe Systems at www.adobe.com to
download a free copy of Acrobat Reader.
You can purchase selected doc umentation sets, CDs, and technical publications
though the Internet at the www1.fatbrain.com/documentation/nortel/ URL.
Howtogethelp
If you purchased a service contract for your Nortel Networks product from a
distributor or authorized reseller, contact the technical support staff for that
distributor or reseller for assistance.
If you purchased a NortelNetworks service program, contact one of the following
Nortel Networks Technical S olutions Centers:
209321-A
Technical Solutions Center Telephone
EMEA (33) (4) 92-966-968
North America (800) 2LANWAN or (800) 252-6926
Asia Pacific (61) (2) 9927-8800
China (800) 810-5000
An Express Routing Code (ERC) is available for many Nortel Ne tworks products
and services. When you use an ERC, your call is routed to a technical support
person who specializes in supporting that product or service. To locate a n ERC for
your product or service, go to the www12.nortelnetworks.com/ URL and c lick
ERC at the bottom of the page.
Page 17

Chapter 1
Management basics
This chapter summarizes basic operational procedures in a Business Policy
Switch and provides an overview of switch management options. Topics in this
chapter include the following information:
• Overview of management tools (next)
• Setting IP parameters for management access to the switch ( page 18)
• Access levels and passwords (page 20)
Management tools
You can use three management tools to monitor a nd manage your Business Policy
Switch:
• Device Manager software (next)
• Web m anagement interface (page 18)
• Console port interface (Refer to Using the Business Policy Switch 2000.)
17
Device Manager
The Java-based Device Manager for the Business P olicy Switches is a graphical
user interface (GUI) that allows you to manage a standalone switch or a single
switch stack. Device Manager provides the options found in other m anagement
tools, as well as the ability to manage VLANs and MultiLink Trunks. You can
display or print statistics and other data in one of three graph formats. To use
Device Manager, you must have network connectivity to a management station
running Device Manager on one of the supported platforms. You must also assign
an IP address to the switch, as described in “Setting the switch IP parameters” on
page 18.”
Getting Started with the Business Policy Switch 2000 Management Software
Page 18

18 Chapter 1 Management bas ics
Web management interface
The Business Policy Switch Web management interface is a Web-based graphical
user interface that you use with a Web browser to manage a standalone switch or
switch stack. You can access devices on your network from various locations
within the network.
To access the Web interface, you need a Web browser and an IP a ddress for the
switch or switch stack. Toassign the IP a ddress to the switch, refer to “Settingthe
switch IP parameters” next.
Setting the switch IP parameters
To allow management access to the switch, you must assign I P parameters for the
switch.
To set the IP parameters:
1 Connect a terminal to the Console port on the switch.
209321-A
2 Set the terminal protocol as follows:
• 9600 baud
• No parity
• 8 bits
• 1 stop bit
• Flow control set to Xon/Xoff
• Window Terminal Emulator option set to no
• Terminal Preferences: Function, Arrow, and Control keys active
• Buffer size set to 24
3 Connect the switch to power.
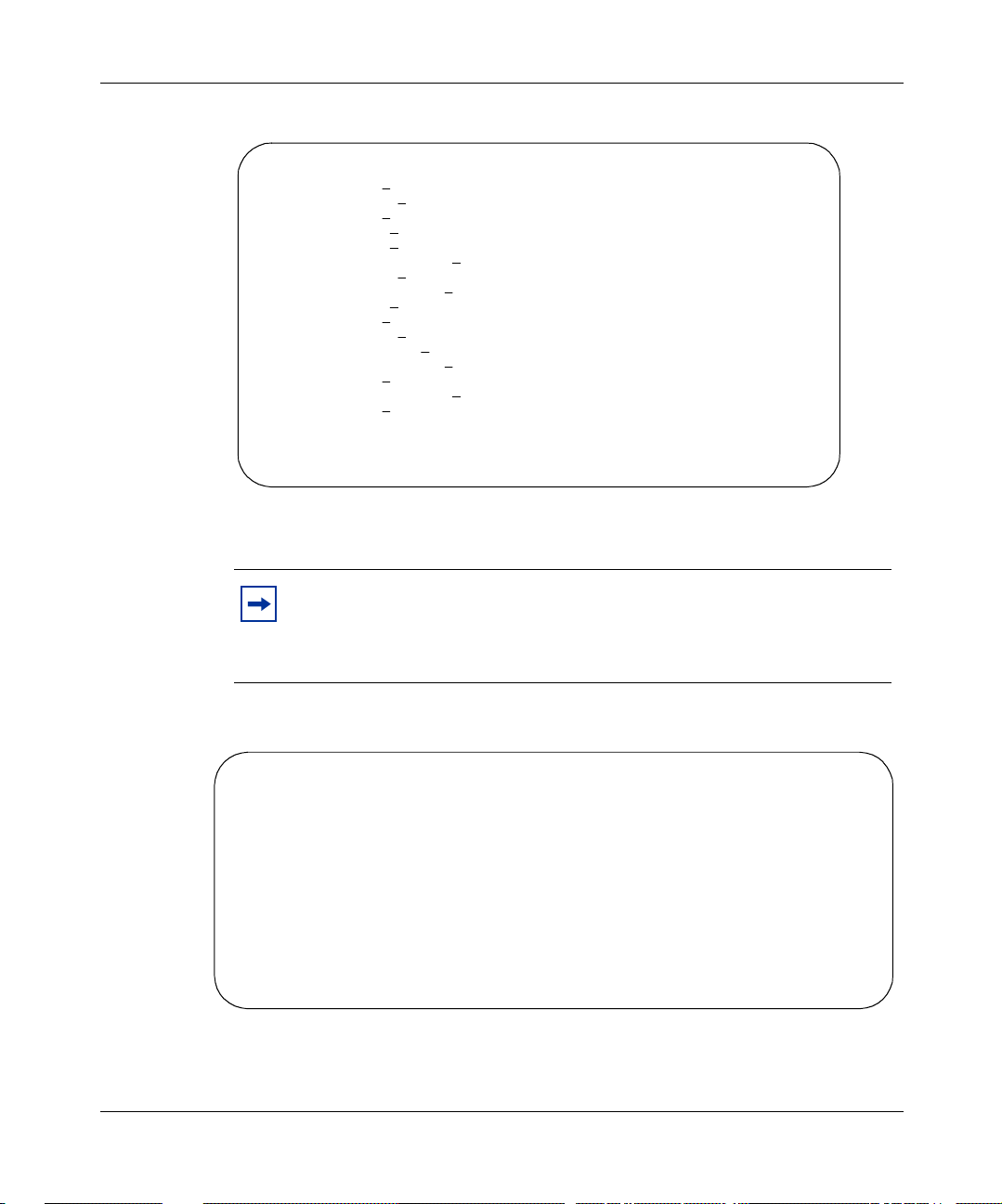
4 After the Nortel Networks logo is displayed, press [Ctrl]-Y to display the
Main Menu (Figure 1).
At first the screen displays the Main Menu for a standalone switch. The n, if
the switch is part of a stack configuration, the screen is refreshed within 20
secondsto show the Main Menu f or a stack configuration. The Main Menu for
a stack configuration includes stack features (bold text in Figure 1).
Page 19
Chapter 1 Management basics 19
Figure 1 Main menu
Business Policy Switch Main Menu
I
P Configuration/Setup...
P Configuration...
SNM
S
ystem Characteristics...
Sw
itch Configuration...
nsole/Comm Port Configuration...
Co
Identify U
Ren
Display H
Sp
anning Tree Configuration...
T
ELNET Configuration...
Sof
Config
Display E
R
eset
Reset to D
ogout
L
Use arrow keys to highlight option, press <Return> or <Enter> to
select option. Press Ctrl-R to return to previous menu. Press Ctrl-C
to return to Main Menu.
nit Numbers...
umber Stack Units...
ardware Units...
tware Download...
uration File...
vent Log
efault Settings
5 Select IP Configuration/Setup (or press i) to display the I P
Configuration/Setup m enu (Figure 2).
Note: The default management VLAN in the B usiness Policy Switch is
VLAN 1. To manage the switch, m ake sure the network management
station is on the managementVLAN or is connected to the management
VLAN through routers.
Figure 2 IP Configuration/Set up menu
IP Configuration/Setup
BootP Request Mode: [ BootP Disabled ]
Configurable In Use Last Boot
In-Band Stack IP Address: [xx.xx.xx.xxx] xx.xx.xx.xxx 0.0.0.0
In-Band Switch IP Address: [xx.xx.xx.xxx] 0.0.0.0
In-Band Subnet Mask: [255.255.255.0] 255.255.255.0 0.0.0.0
Default Gateway: 0.0.0.0 0.0.0.0 0.0.0.0
Use space bar to display choices, press <Return> or <Enter> to select
choice. Press Ctrl-R to return to previous menu. Press Ctrl-C to
return to Main Menu.
------------------ ----------------- -------------
Getting Start ed with the Business Policy Switch 2000 Management Software
Page 20

20 Chapter 1 Management bas ics
6 Do one of the following,based on your configuration:
• For a standalone switch, e nter the IP address of the switch in the In-Band
Switch IP Address field.
Note: If the In-Band Subnet Mask field does not already contain a value
when you e nter the IP address in the In-Band Switch IP Address field,
the switch software provides an in-use default value for the In-Band
Subnet Mask field, based on the class of the entered IP address.
• For a stack configuration, enter the Stack IP address in the In-Band Stack
IP Address field.
Note: The In-Band Switch IP Address fieldallows this switch to operate
as a standaloneswitch. However, this field is not required for the
operation of the stack. You c annot enter the same IP address in both
fields.
7 In the In-Band Subnet Mask field, enter the IP subnet mask address.
8 In the Default Gateway field, enter the default gateway address.
Access levels and passwords
Access to m anagement f unctions for Business P olicy Switches is controlled by
passwords and community strings. Different passwords or community strings
allow access to different levels of m anagement functions.
Access to Device Manager requires entering community strings. Access to the
Web interface requires a user identification and a password.
209321-A
Page 21

Chapter 2
Installing Device Manager software
Device Manager software is available on the Nortel Networks Services and
Support Web site as a self-extracting executable file. This chapter provides
instructions to install the Device Manager software in a Windows or UNIX
environment.
Accessing the Nortel Networks Web site
To access the Nortel Networks Services and Support Web site:
1 Go to the following URL:
www12.nortelnetworks.com/software
2 Under Switching Products, choose Business Policy S witch 2000, and
click Go.
21
3 Scroll down to Business Policy Switch Device Manager.
4 Follow the instructions in one of the next sections, depending on the platform
on which you will install the software.
Windows installation
The minimum system requirements for installing Device Manager on Microsoft
Windows NT®, Windows®95, or Windows 98 are:
• 75 MHz Pentium or 100 MHz 486 processor
• 16 MB DRAM
• 100 MB space on the hard disk
Getting Started with the Business Policy Switch 2000 Management Software
®
Page 22

22 Chapter 2 Installing D evice Manager software
To install the management software on a Windows platform:
➨ On the Business Policy Switch software Web page, click jdm_xxx.exe.
Note: In the f ile name, xxx represents the current version of the Device
Manager software.
The file uncompresses and installs the Java Runtime Environment (JRE) and
the Device Manager software into the appropriate directories on your system.
To run the Device Manager software:
➨ From the Windows Start menu, choose Programs > Nortel F rame Switch
Management Software > Device Manager.
UNIX installation
The minimum system requirements for installing Device Manager in a UNIX
environment are:
209321-A
• SPARC workstation running the Sun Solaris 2.5.x (or higher) operating
system
— 120 MB space on the hard disk
— 4 MB available in a temporary directory
— 60 MB freein the directory where you want to installthe Device Manager
software
— 32 MB DRAM
or
• HP workstation running the HP/UX 10.20 or 11.x operating system
— 120 MB space on the hard disk
— 4 MB available in a temporary directory
— 60 MB freein the directory where you want to install the Device Manager
software
— 32 MB DRAM
or
Page 23

Chapter 2 Installing Device Manager s oftware 23
• AIX workstation running the IBM AIX 4.1 operating system
— 120 MB space on the hard disk
— 4 MB available in a temporary directory
— 60 MB freein the directory where you want to installthe Device Manager
software
— 32 MB DRAM
Installing the Device Ma nager software in a UNIX environment requires two or
three steps, depending on the specific platform:
1 In a Solaris environment, install Solaris patches (next).
2 In all three environments, install the Java Runtime Environment (JRE):
• For a Solaris environment, the JRE is available on the Nortel Networks
Services and Support Web site (page 23).
• For an HP-UX or IBM AIX environment, go to the HP or IBM Web site
to obtain the JRE (page 25 or page 26).
3 Install the Device M anager software.
You only need to install the Solaris patches and JRE once. After they are installed,
you can upgrade your system to later versions of Device M anager without
installing the patches and JRE again.
Installing the software in a Solaris environment
To install the Device Manager software in a Solaris e nvironment:
1 Install Solaris patches. Nortel Networks provides the necessary patches for
Solaris 5.5.1 and Solaris 5.6.
a Use the
installed on your workstation.
b On the Business Policy SwitchUNIX software Web page, click one of the
following links to download the correct pa tches for your Solaris version:
— 1.1.8_09a_patches_sparc_5.5.1.tar for Solaris 5.5.1
— 1.1.8_09a_patches_sparc_5.6.tar f or Solaris 5.6
c For instructions to install the patches, click README.sparc_1.1.8_09a.
Getting Start ed with the Business Policy Switch 2000 Management Software
uname -a command to determine the version of Solaris that is
Page 24

24 Chapter 2 Installing D evice Manager software
2 Install the Java Runtime Environment f or Solaris systems:
a On the Business Policy Switch UNIX software Web Page, click
Solaris_JRE_1.1.8_09a_sparc.bin.
b For instructions to install the Solaris JRE, click install_jre.txt.
3 Install the Device Manager software:
On the Business Policy Switch UNIX software Web page, click jdm_xxx.tar.
Note: In the f ile name, xxx represents the current version of the Device
Manager software.
The file uncompresses and installs the Device Manager software into the
appropriate directories on your system.
Before you run the Device Manager software, you must se t the following UNIX
environment variables:
setenv JAVA_HOME
setenv PATH${JAVA_HOME}/bin:${PATH}
setenv LD_LIBRARY_PATH [JAVA_HOME}/lib/sparc/
native_thread:${LD_LIBRARY_PATH}
setenv CLASSPATH ${JAVA_HOME}/lib/rt.jar:${CLASSPATH}
<JRE installed path>
To start Device Manager:
➨ Enter:
% JDM a.b.c.d
where
a.b.c.d
is the I P address of the device.
209321-A
Page 25

Chapter 2 Installing Device Manager s oftware 25
Installing the software in an HP-UX environment
Nortel Ne tworks does not directly provide the JRE for HP-UX systems. However,
you can download the JRE from the HP corporate Web site.
To install the Device Manager software in an HP-UX environment:
1 Install the JRE for HP-UX:
a Go to one of the following UR Ls, depending on your version of HP-UX:
— http://unixsolutions.hp.com/products/java/jre_os10118_content.html
for HP-UX 10.20
— http://unixsolutions.hp.com/products/java/jre_os10118_content.html
for HP-UX 11.x
b Follow the prompts to download and install the JR E for your HP-UX
system.
2 Install the Device Manager software:
On the Business Policy Switch UNIX software Web page, click jdm_xxx.tar.
Note: In the f ile name, xxx represents the current version of the Device
Manager software.
The file uncompresses and installs the Device Manager software into the
appropriate directories on your system.
Before you run the Device Manager software, you must se t the following UNIX
environment variables:
setenv JAVA_HOME
setenv PATH${JAVA_HOME}/bin:${PATH}
setenv LD_LIBRARY_PATH [JAVA_HOME}/lib/sparc/
native_thread:${LD_LIBRARY_PATH}
setenv CLASSPATH ${JAVA_HOME}/lib/rt.jar:${CLASSPATH}
Getting Start ed with the Business Policy Switch 2000 Management Software
<JRE installed path>
Page 26

26 Chapter 2 Installing D evice Manager software
To start Device Manager:
➨ Enter:
% JDM a.b.c.d
where
a.b.c.d
is the IP address of the device.
Installing the software in an IBM AIX environment
Nortel Networks does not directly provide the JRE for IBM AIX systems.
However, you can download the JRE from the IBM corporate Web site.
To install the management software in an IBM AIX environment:
1 Install the JRE for IBM AIX:
a Go to the http://www6.software.ibm.com/dl/dka/dka-p URL.
b Follow the prompts to download and install the JRE for your IBM AIX
system.
2 Install the Device Manager software:
On the Business Policy Switch UNIX software Web page, click jdm_xxx.tar.
Note: In the f ile name, xxx represents the current version of the Device
Manager software.
209321-A
The file uncompresses and installs the Device Manager software into the
appropriate directories on your system.
Before you run the Device Manager software, you must se t the following UNIX
environment variables:
setenv JAVA_HOME
setenv PATH${JAVA_HOME}/bin:${PATH}
setenv LD_LIBRARY_PATH [JAVA_HOME}/lib/sparc/
native_thread:${LD_LIBRARY_PATH}
setenv CLASSPATH ${JAVA_HOME}/lib/rt.jar:${CLASSPATH}
<JRE installed path>
Page 27

To start Device Manager:
➨ Enter:
Chapter 2 Installing Device Manager s oftware 27
% JDM
where
a.b.c.d
a.b.c.d
is the IP address of the device.
Getting Start ed with the Business Policy Switch 2000 Management Software
Page 28

28 Chapter 2 Installing D evice Manager software
209321-A
Page 29

Chapter 3
Device Manager basics
This chapter describes basic procedures f or using the Device Manager software.
The chapter includes the following information:
• Instructions to start Device Ma nager, set the Device Manager properties, and
open a device (next)
• A summary of the Device Manager user interface features and how to use
them (starting on page 34)
• Instructions to view statistics and display graphs (page 43)
• Instructions to use Device Manager to Telnet to a switch ( pa ge 51)
• Information about the trap log (page 51)
• Information about online Help (page 52)
Starting Device Manager
29
To start Device Manager:
➨ Do one of the following, depending upon your operating system environment:
• In a Microsoft®Windows®environment, from the Windows taskbar
choose Start > Programs > Nortel F rame Switch Management Software >
Device Manager.
• In a UNIX environment, verify that the Device Manager installation
directory is in your search path; then enter:
JDM
Getting Started with the Business Policy Switch 2000 Management Software
Page 30

30 Chapter 3 Device Manager basics
The initial Device Manager window opens (Figure 3).
Note: On startup, Device M anager performs a DNS lookup for the
machine on which it is running. If the DNS lookup is slow or fails, the
initial Device Manager window may take up to 30 seconds to open.
Figure 3 Device Manager window
Setting the Device Manager properties
Device Manager communicates with the B usiness P olicy Switch using S imple
Network Management Protocol (SNMP). The software is shipped with default
values set for important communication parameters, such as the polling interval,
timeout, and retry count. You may want to set the parameters before you open a
device to manage.
To se t the Device M anager properties:
1 Choose Device > Properties.
The Properties dialog box opens (Figure 4).
209321-A
Page 31

Chapter 3 Device Manager basics 31
Figure 4 Properties dialog box
2 Type information and select check boxes.
3 Click OK.
Table 1 describes items in the P r operties dialog box.
Table 1 Properties dialog box items
Area Item Description
Polling Status Interval Interval at which statistics and status information are gathered (default is
300 seconds).
(Iftraps,Status
Interval)
HotswapDetect
every
Enable Enables (checked) or disables (not checked) periodic pollingof the device
Intervalat whichstatistics and statusinformation are gathered when traps
are enabled (default is 300 seconds).
The interval at which Device Manager polls for module information
(default is 600 seconds).
for updated status. If polling is disabled, the switch or stackstatus is
updated only when youclick Refresh in thechassis window.
Getting Start ed with the Business Policy Switch 2000 Management Software
Page 32

32 Chapter 3 Device Manager basics
Table 1 Properties dialog box items (continued)
Area Item Description
SNMP Retry Count Number of times Device Manager retransmits polling information.
Timeout Length of each retry of each polling waiting period. When accessing the
device through a slow link, you may want to increase the timeout interval
and then change the Retransmission Strategy to super linear.
Trace Enables (checked) or disables (not checked)SNMP tracing. When Trace
is selected, SNMP protocoldata units (PDUs) are displayed in the
Device > Log dialog box.
Register for Traps Specifies whether or not Device Manager should automatically register to
receive traps when Device Manager is launched against a switch.
Max Traps in Log The specified number of traps that can existin the trap log (default is
Trap Port Specifies the UDP port that Device Manager will listen on to receive
Confirm row
deletion
500).
SNMP traps.
When this check box is selected, a confirmation dialog box is displayed
when you try to delete a row from a Device Manager table.
Opening a device
209321-A
“Opening” a device displays the device view, a picture of the device. To open the
device view, you must enter community strings that determine the access level
granted to the device. Table 2 shows the default a ccess community strings for the
Device Manager software.
Table 2 SNMP community string default values
Access level Description
Read-only public
Read-write private
Read-write-all secret
Page 33

Chapter 3 Device Manager basics 33
To display the device view:
1 Do one of the following:
• Choose Device > Open.
• Choose Device > Open Last, and select an IP address from the list.
• Click the folder icon in the Device Manager window.
• Press [Ctrl] + O.
The Open Device dialog box opens (Figure 5).
Figure 5 Open Device dialog box
Table 3 describes the items in the Open Device dialog box.
Table 3 Open Device dialog box items
Item Description
Device Name Either an IP address or a DNS name for the device, entered by the
user.
Read Community SNMP read community string for the device. Default is
(displayed as ******). The entryis case-sensitive.
Write Community SNMP write community string for the device. Default is
(displayed as *******).The entry is case-sensitive.
public
private
2 In the Device Name text box, type the DNS name or IP address of the device.
Getting Start ed with the Business Policy Switch 2000 Management Software
Page 34

34 Chapter 3 Device Manager basics
3 In the Read Community and Write Community text boxes, type the proper
community strings (Table2onpage32).
Note: To gain Read-Write-All access to a device in Device Manager,
you must e nter the Read-Write-All c ommunity string for both the Read
Community and Write Community strings.
4 Click Open.
Device Manager automatically determines what version of software the
selected device is running and displays the appropriate Device Manager
dialog boxes. The Device Manager window opens, showing a picture of the
device (Figure 6) that r epresents the physical features of the device.
Figure 6 Device view
Device M anager window
The Device Manager w indow (Figure 7) has the following parts:
•Menubar
• Toolbar
• Device view
• Status bar
209321-A
Page 35

Figure 7 Parts of the Device Manager window
Menu bar
Toolbar
Device view
Status bar
Menu bar
Use the menu bar to set up and operate Device M anager (Table 4).
Table 4 Menu bar commands
Chapter 3 Device Manager basics 35
Command Description
Device Opens the Open Device dialog box.
Edit Opens edit dialog boxes for selected objects in the device view (refer to
Graph Opens statistics dialog boxesfor the selected object.
VLAN Opensdialog boxes for managing VLANs, spanning tree groups (STGs),
Rmon Opens RMON configuration and m onitoring dialog boxes.
Actions Provides quick opening of a Telnet session without going through other
Help Opens online Help topics for Device Manager and provides a legend for
“Selecting objects” on page 37). This command also opens dialog boxes
for managing files and running diagnostic tests.
and Multi-Link Trunks.
dialog boxes.
the port colors in the device view.
Getting Start ed with the Business Policy Switch 2000 Management Software
Page 36

36 Chapter 3 Device Manager basics
Toolbar
The toolbar contains buttons that provide quick a ccess to commonly used
commands and some additional actions (Table 5).
Table 5 Toolbar buttons
Button Name Description Menu bar equivalent
Open Device Opens the Open Device dialog
box.
Refresh
Device
Status
Trap Log Opens the trap log. Device> Trap Log
Help Opens online Help in a Web
Edit Selected Displays configuration data f or
Graph
Selected
Telnet Opens a Telnet session. Actions > Telnet
Alarm
Manager
Refreshes the device view
information.
browser.
the selected chassis object.
Opens statistics and graphing
dialog boxes for the selected
object
Opens t he Rmon Alarm
Manager.
1
Device > Open
Device > Refresh Status
Help > Device
Edit > Unit
Edit > Chassis
Edit > Port
Graph > Chassis
Graph > Port
Rmon > Alarm Manager
209321-A
1 If the online Help does not launch, refer to page 52.
Device view
The device view (Figure 8) allows you to determine at a glance the operating
status of the various units and ports in your hardware c onfiguration. You also use
the device view to pe rform m anagement tasks on specific objects.
Page 37

Selecting objects
The types of objects contained in the device view a r e:
• A standalone switch ( called a unit in the menus and dialog boxes)
• A switch stack (called a chassis in the menus and dialog boxes)
• A media dependent a dapter ( MDA) (called a unit in the menus and dialog
boxes)
• A port
Figure 8 Objects in the deviceview
Switch unit or
chassisobject
Port object
Chapter 3 Device Manager basics 37
MDA object
Selecting a single object
To select a single object:
➨ Click the edge of the object.
The object is outlined in yellow, indicating that it is selected. Subsequent
activities in Device Manager refer to the selected object.
Getting Start ed with the Business Policy Switch 2000 Management Software
Page 38

38 Chapter 3 Device Manager basics
Selecting multiple objects
To select m ultiple objects of the same type (such as ports or switches of the same
type):
➨ Do one of the following:
• For a block of contiguous ports, dr ag to select the group of ports.
• For multiple ports, MDAs, or switches in the stack, [Ctrl]-click on the
objects.
Note: In a switch stack that c ontains B usiness Policy S witches and
BayStack switches, you can select only one type of switch at a time.
To select all the ports in a standalone switch or in a switch stack:
➨ Choose Edit > Select > Ports.
To select all the “units” (switches and MDAs, but not ports):
209321-A
➨ Choose Edit > Select > Units.
To select an entire stack:
➨ Choose Edit > Select > Chassis.
Viewing information about an MDA
To view information about an MDA:
1 Select the MDA.
2 Choose Edit > Unit.
The Edit > Unit dialog box opens for the MDA (Figure 9). The Edit > Unit
dialog box describes the M DA installed in the switch.
Page 39

Chapter 3 Device Manager basics 39
Figure 9 MDA dialog box
LEDs and ports
The color of LEDs in the device view is the same as the c olors of the LEDs on the
physical switch. However, the device view does not show blinking activity of the
LEDs.
For a full description of the LEDs for the Business P olicy S witch, r efer to Using
the Business Policy Switch 2000.
The ports on the device view are color coded to show port status. Table 6 shows
the status assigned to each color.
Table 6 Port color codes
Color Description
Green Port is operating.
Red Port has been manually disabled.
Orange Port has no link.
Light Blue Port is in standby mode.
Dark Blue Port is being tested.
Gray Port is unmanageable.
In addition, the Help m enu provides a legend that identifies the port colors and
their meanings (Figure 10).
Getting Start ed with the Business Policy Switch 2000 Management Software
Page 40

40 Chapter 3 Device Manager basics
Figure 10 Port color legend
Shortcut menus
Each object in the device view has a shortcut menu that opens when you
right-click a selected object. The switch shortcut menu (Figure 11) provides
access to basic hardware information about the switch and to the graphing dialog
boxes for the switch.
Figure 11 Switch unit shortcut menu
209321-A
Table 7 describes the c ommands on the switch unit shortcut m enu.
Table 7 Switch unit shortcut menu commands
Command Description
Edit Opens a read-only dialog box that provides
basic hardware information about the switch.
Graph Opens a dialog box that displays statistics for
theswitchandallowsyoutodisplaythe
statisticsas a graph.
Page 41

Chapter 3 Device Manager basics 41
The port shortcutmenu (Figure 12)provides a faster path for editing and graphing
a single port; however, you can access the same options using the menu bar or the
toolbar.
Figure 12 Port shortcut menu
Table 8 describes the c ommands on the port shortcut menu.
Table 8 Port shortcut menu commands
Command Descriptions
Edit Opens a dialog box that allows youto set operating parameters
for the port.
Graph Opens a dialog box that displays statistics for the por t and
Enable Administratively brings a port up.
Disable Administratively shuts down a port. The color of the por t
allows you to display the statistics as a graph.
changes t o red in the device view.
The MDA shortcut menu (Figure 13) contains a single command, Edit, thatopens
a read-only dialog box with basic hardware information about the MDA.
Figure 13 MDA shortcut menu
Getting Start ed with the Business Policy Switch 2000 Management Software
Page 42

42 Chapter 3 Device Manager basics
Status bar
The status bar displays error and informational messages f rom the software
application. These messages are not related to the device being m anaged.
Using the buttons in Device Manager dialog boxes
Table 9 describes buttons in D evice Manager dia log boxes. Not all buttons appear
in all dialog boxes.
Table 9 Device Manager buttons
Button Name Description
Insert Opensa dialog box to create a new entr y for a table; then
Copy Copies selected cells from a table.
Paste Pastes copied values to a currently selected table cell.
from the dialog box, inser ts thenew entry in the table.
209321-A
Reset
Changes
Print Table or
Print Graph
Stop Stopsthe current action (compiling,saving,and so forth).
Export Data Exports information to a file you specify. You can then
Causes changed (but not applied) fields to revert to their
previousvalues.
Prints the table or graph that is displayed.
If you ar e updating or compiling a large data table, the
Refreshbutton changes to a Stop button while t his action
is taking place. Clicking t he Stopbutton interrupts the
polling process.
import this file into a text editor or spreadsheet for further
analysis.
Page 43

Editing objects
You can edit objects and values in the Device Manager device view in the
following ways:
• Select an object and, on the toolbar, click the Edit Selected button.
The edit dialog box opens for that object.
• From a switch or port shortcut menu, choose Edit. The edit dialog box opens
for that object.
When you change the value in a box, the changed value is displayed in bold.
However, changes are not applied to the running configuration until you click
Apply.
Chapter 3 Device Manager basics 43
Note: Many dialog boxes contain a Refresh button. After you apply
changes to fields, click Refresh to display the new information in the
dialog box.
Working with statistics and graphs
Device Manager tracks a wide range of statistics for each switch, the stack
(chassis), and each port. You can view and graph statistics for a single object or
multiple objects. For information about the statistics tracked for the switch and
ports, refer to Using the Business Policy Switch 2000.
This se ction describes the types of statistics and gr aphs available, the graph dialog
boxes, and the procedure for creating a graph.
Getting Start ed with the Business Policy Switch 2000 Management Software
Page 44

44 Chapter 3 Device Manager basics
Types of statistics
The data tables in the statistics dialog boxes list the c ounters, or categories of
statistics being gathered, for the specified object. For example, the categories for
ports include Interface, Ethernet Errors, Bridge, and R m on. Each category can be
associated with six types of statistics (Table 10).
Table 10 Types of statistics
Statistic Description
AbsoluteValue The total count since the last time counters were reset. A system
reboot resets all counters.
Cumulative The total count since the statistics window was first opened. The
Average The cumulative count divided by the cumulative elapsed time.
Minimum The minimum average for the counter for a given polling interval over
Maximum The maximum average for the counter for a given polling interval over
LastValue The average for the counter over the last polling interval.
elapsed time for the cumulative counter is displayed at the bottom of
the graph window.
the cumulative elapsed time.
the cumulative elapsed time.
209321-A
Types of graphs
With Device Manager, you can create line, area, bar, and pie gr aphs. Figure 14,
Figure 15, Figure 16,andFigure 17 illustrate the different graph styles,
respectively.
Page 45

Figure 14 Line graph
Chapter 3 Device Manager basics 45
Figure 15 Area graph
Getting Start ed with the Business Policy Switch 2000 Management Software
Page 46

46 Chapter 3 Device Manager basics
Figure 16 Bar graph
209321-A
Figure 17 Pie graph
Page 47

Chapter 3 Device Manager basics 47
Statistics for single and multiple objects
Statistics for a selected object or objects a re displayed in the statistics dialog box.
The dialog box for a single object shows all six types of statistics for each counter
(Figure 18).
Figure 18 Interface statistics for a single port
The statistics dialog box for multiple objects shows a single type of statistics
(Table 10) for the selected objects. For example, Figure 19 shows LastValue
statistics for the selected ports.
Getting Start ed with the Business Policy Switch 2000 Management Software
Page 48

48 Chapter 3 Device Manager basics
Figure 19 Interface statistics for multiple ports
To change the type of statistics displayed, selecta different type from the show list
at the bottom of the dialog box.
Statistics type
209321-A
The statistics are updated based on the poll interval shown at the bottom of the
dialog box. You can select a different polling interval.
Buttons for bar, pie, and line graphs are located at the bottom of a statistics dialog
box. See the next section, “Viewing statistics as graphs,” for instructions to use
these buttons.
You can export the statistics to a tab-separated file format and import the file into
other applications. To export the information, use the Export Data button below
the table.
Page 49

Viewing statistics as graphs
To create a graph for an object:
1 Select the object or objects to be graphed (see “Selecting objects” on
page 37).
2 Do one of the following:
• On the toolbar, click Graph Selected.
• From the shortcut menu for the object, choose Graph.
• From the main menu, choose Graph > Chassis or Graph > P ort.
A statistics dialog box opens with tabs for different categories of statistics for
the selected object (Figure 20).
Figure 20 Statistics dialog box for a port
Chapter 3 Device Manager basics 49
3 Select a tab for the gr oup of statistics you want to view.
4 On the displayed da ta table, drag to select the cells you want to graph. (They
must be in the same row or column.)
Getting Start ed with the Business Policy Switch 2000 Management Software
Page 50

50 Chapter 3 Device Manager basics
5 Click one of the graph buttons at the bottom of the dialog box (see “Types of
graphs” on page 44).
A graph dialog box opens for the se lected graph type.
6 To pr int a copy of the graph, click Print.
Buttons at the top of the gr aph dialog boxes for line, area, and bar graphs allow
you to change the orientation of the graph, change the scale, or change the graph
type. Table 11 describes the buttons in the graph dialog boxes.
Table 11 Graph dialog box buttons
Button Name Description
Stacked “Stacks”data quantities instead of displaying them
Horizontal Rotates the graph 90 degrees.
side-by-side.
209321-A
Log Scale Changesthe scaleof t he x-axis (of an unrotatedgraph)
from numeric to logarithmic.
Line Chart Converts an area graph or bar graph to a line graph.
Area Chart Converts a line graph or bar graph to an area graph.
Bar Chart Converts a line graph or area graph to a bar graph.
Page 51

Telnetingtoaswitch
From Device Manager, you can initiate a Telnet session to the console interface
for the switch or stack you are currently accessing.
To Telnet to a switch:
➨ Do one of the following:
• From the Device Manager main menu, choose Actions > Telnet.
• On the toolbar, click the Telnet button.
A Telnet w indow to the switch opens.
Trap log
Chapter 3 Device Manager basics 51
You can configure a Business Policy Switch to send SNMP generic traps. When
Device Manager is running, any traps r eceived are recorded in the trap log.You
set the maximum number of entries in the trap log using the Properties window
(page 30). The default number of trap log entries is 500.
To view the trap log:
➨ Do one of the following:
• On the toolbar, click the Trap Log button.
• From the Device Manager Main Menu, choose Device > Trap Log.
Note: When you operate Device Manager from a UNIX platform, you
must be logged in as root in order to receive traps.
Getting Start ed with the Business Policy Switch 2000 Management Software
Page 52

52 Chapter 3 Device Manager basics
By default, traps are sent in SNMP V2c format. However, if you are using an
older network management system (NMS), one that supports only SNMP V1
traps (HP OpenView), you can specify that the traps be sent in V1 format.
Management stations operating with Device Manager are automatically added to
trap receivers.
For more information about traps and trap receivers, refer to Using the Business
Policy Switch 2000.
Online Help
Online Help in Device Manager is context-sensitive. You use a Web browser to
display online Help. The Web browser should launch automatically when you
click the Help button. If the Help topic you are accessing is not displayed in your
browser, exit the existing browser session and click the Help button a gain. I f, for
some reason, the Web browser does not launch, the default locations of the Help
files are the directories listed in Table 12.
209321-A
Table 12 Help file locations
Platform Default path
Windows 95, Windows 98, or Windows NT
UNIX
c:\jnm\help\dm\dm.html
DM-UNIX/DM/help/dm/dm.html
Page 53

Chapter 4
Web management interface basics
A Business Policy Switch includes a Web management interface that lets you
monitor your switch through a World Wide Web browser from anywhere on the
network. The Web interface provides many of the same monitoring and
configuration features a s the Device Manager software.
This chapter provides an overview of the Web management interface and its
navigation f eatures. For information about spec ific Web management pages,
check the online Help in the Web management interface. For information about
using the Web m anagement interface to configure and ma nage the switch,refer to
Using Web-Based Management for the Business Policy Switch 2000.
This chapter contains information about the following topics:
• Requirements (this page)
• Accessing your switch through the Web interface (page 54)
• Security (page 60)
53
Requirements
To use the Web-based management interface you need:
• A computer connected to any of the network ports
• Oneof the following Web browsers installed on the computer:
— Microsoft Internet Explorer, version 4.0 or later
— Netscape Navigator, version 4.51 or la ter
• TheIP address of the switch or switch stack
Getting Started with the Business Policy Switch 2000 Management Software
Page 54

54 Chapter 4 Web management interface basics
Note: As long as you ha ve a route to the switch and there are no filters or
access policies in effect, you should be able to m onitor the switch using the
Web interface.
For instructions to set the IP address of the switch, refer to “Setting the switch IP
parameters” on page 18.
Access to the Web management interface must also be enabled for the switch (the
default setting) using the console interface. For information about enabling Web
access, refer to Using the Business Policy Switch 2000.
Accessing the Web interface
Before you log in to the Web management interface, use the console interface to
verify the VLAN port assignments and to make sure that the switch CPU and your
computer are assigned to the same VLAN. If the devices are not connected to the
same VLAN, the IP address of the switch will not open the home page.
209321-A
To access the Web interface:
1 Start your Web browser.
2 Inthe Web address field of yourWebbrowser,type the switchIP address, and
press [Enter].
If this is the first time you are logging in to the Web management interface,
the System Information home page opens (Figure 21).
Page 55

Chapter 4 W eb management interface basics 55
Figure 21 System Information home page
Network security does not yet exist the first time you access the Web
management interface. As the system a dministrator, you must create access
parameters and passwords. For more information about setting access
parameters and system passwords, refer to “Setting up security” on page 60.
3 If passwords have already been set, the login page opens (Figure 22).
Figure 22 Login page
4 Inthe Username text box, type ro for read-only access or rw for read-write
access.
Getting Start ed with the Business Policy Switch 2000 Management Software
Page 56

56 Chapter 4 Web management interface basics
5 In the Password text box, type your password.
6 Click Log On.
The System Information home page opens.
With Web access enabled, the switch can support up to four concurrent Web page
users. Two pre-defined user levels are available, and each user level has a
corresponding user name and password.
Table 13 shows the two pre-defined user levels available and their corresponding
access levels in the Web management interface.
Table 13 User levels in the Web management interface
User level User name Password Access level
Read-only ro XXXXXXXX Read-only
Read-write rw XXXXXXXX Full read/write access
Information is available online about the Web management interface. To access
more information about the Web management interface:
➨ Do one of the following:
• Click Support > Help to view the e ntire Help f ile.
• For context-sensitive Help, click the Help button on any page to view
information specifically about that page.
Web page layout
All the Web management pages for the Business Policy Switch have a common
layout (Figure 23). Each is divided into two sections: the menu and the content
area. All Web pages are optimized for an 800 x 600 pixel screen size.
209321-A
Page 57

Figure 23 Parts o f the Web management page
Web browser toolbar
Administration > System Information
Menu
Summary
Configuration
Fault
Statistics
Application
Administration
System Info(option)
Security
Logout
Reset
Support
Business Policy Switch 2000
sysDescription
sysUpTime 35 Minutes, 29 Seconds
sysName
sysLocation
sysContact
BayStack 460 HW:AB3 FW:V0.2E
SW:v1.0.0.33
Menu
The menu (Figure 24) is the same for all pages. I t contains a list of seven main
headings.
Chapter 4 W eb management interface basics 57
?
Help button
Content
area
9794EA
Figure 24 Menu
Getting Start ed with the Business Policy Switch 2000 Management Software
Page 58

58 Chapter 4 Web management interface basics
The first six headings provide options for viewing and configuring switch
parameters. The Support heading provides options to open the online Help file
and the Nortel Networks Web site. Table 14 lists the main menu headings and
their associated options. For detailed information about managing the switch
using the Web management interface, refer to Using Web-Based Management for
the Business Policy Switch 2000.
Table 14 Menu headings and options
Heading Option
Summary Stack Information
Configuration IP
Fault RMON Threshold
Statistic Port
Application Port Mirroring
SwitchInformation
Switch View
Identify Unit Numbers (only for a stack configuration)
Stack Numbering (only f or a stack configuration)
System
SNMPv1
SNMPv3
SNMP Trap
MAC Address Table
Find MAC Address
Port Management
High Speed Flow Control
Software Download
ConfigurationFile
Console/Comm Port
Stack OperationalMode
RMON Event Log
System Log
Interface
Ethernet Errors
TransparentBridging
RMON Ethernet
RMON History
Rate Limiting
IGMP
VLAN
Spanning Tree
MultiLink Trunk
QoS
COPS
209321-A
Page 59

Chapter 4 W eb management interface basics 59
Table 14 Menu headings and options (cont inued)
Heading Option
Administration System Information
Support Help
Content area
The content area displays tables of information with buttons that you use to
configure a nd monitor the switch. Some tables may be too big to fit the displayed
page area. In these cases, use the scroll bars at the side and bottom to view the
entire table.
Icons
Some pages c ontain icons that allow you to modify information in a statistical
table or to display statistics in chart format. Table 15 describes the icons.
Table 15 Page icons
Security
Logout
Reset
Reset to Defaults
Release Notes
Manuals
Upgrade
Icon Name Description
Modify Modifiesthe row.
Help Opens online Help.
Delete Deletes a row.
Pie chart Displays the statistics as a pie chart.
Getting Start ed with the Business Policy Switch 2000 Management Software
Page 60

60 Chapter 4 Web management interface basics
Table 15 Page icons (continued)
Icon Name Description
Bar graph Displaysstatistics as a bar graph.
Line graph Displays statistics as a line graph.
Setting up security
To set passwords a nd RADIUS (Remote Authentication Dial In User Service)
authentication settings for the for the switch or stack, use the Security pages.
These pages allow you to create or modify the passwords of a standalone switch
or any switches within the stack framework, and allow you to set the security
parameters for remote dial access users.
Note: Nortel Ne tworks recommends that when you install the switch,
you set the initial system passwords using the console interface. After
that, you can update them using the Web management interface. For
information a bout using the console interface, refer to Using the
Business Policy Switch 2000.
209321-A
To set console, Web, and Telnet passwords and R ADIUS authentication settings:
➨ From the main menu, choose Administration > Security.
Four options are displayed:
•Web
Allows you to define Web password settings in switch or stack mode.
• Telnet
Allows you to define Telnet password settings in switch or stack mode.
• Console
Allows you to define console password settings in switch (stand alone) or
stack mode.
Page 61

Chapter 4 W eb management interface basics 61
•Radius
Allows you to set the server parameters that will provide authentication,
authorization, and accounting for RADIUS.
Note: For information on setting switch (standalone) or stack
operational m odes, refer to Using Web-Based Management for the
Business Policy Switch 2000.
Setting console, Telnet, and Web passwords
1 From the main menu, se lect Adm inistration > Security.
2 On the Security page list, click Console, Telnet, or Web.
The selected pa ssword management page opens (Figure 25).
Note: The title of the page indicateswhich type of access you are setting
the password for. In Figure 25, the network administrator selected
Administration > Security > Console.
Figure 25 Console pas sword page
3 Choose the type of password:
• None—specifies no password f or this type of access
• Local Password—sets a password for access through direct network
connection or a direct C onsole port connection
Getting Start ed with the Business Policy Switch 2000 Management Software
Page 62

62 Chapter 4 Web management interface basics
• RADIUS Authentication—sets a password for remote dial-in. If you
select this password type, you must also set up RADIUS authentication
from the Radius management page.
4 Type the password for read-only and read-write user access.
5 Click S ubmit to save the c hanges.
Setting remote dial-in access security
To set the parameters for remote dial-in access security:
1 From the main menu, se lect Administration > Security > Radius.
The Radius management pa ge opens (Figure 26).
Figure 26 Radius management page
209321-A
2 Type the IP addresses of the primary and secondary RADIUS servers.
3 Type the number of the user datagram protocol (UDP) port for the RADIUS
server. The default value is 1645.
4 Type a character string for the RADIUS Shared Secret. This parameter is a
special switch security code that provides authentication to the RADIUS
server. The value can be any contiguous ASCII string that contains at least
one printable character, up to a m aximum of 35.
5 Click S ubmit.
Page 63

Index
63
A
AbsoluteValue statistics 44
access levels 20, 32, 56
Actions menu 35
AIX installation of Device Manager 26
Alarm Manager button 36
Area Chart button 50
area graph example 45
Average statistics 44
B
Bar Chart button 50
bar graph example 46
blinking LEDs 39
buttons
dialog boxes 42
toolbar 36
C
color-coded ports 39
communicationparameters, setting for Device
Manager 30
community strings
default 32
entering 33
Confirm row deletion parameter 32
console passwords 60
content area, Web page 59
conventions, text 14
Copy button 42
Cumulative statistics 44
customer s upport 16
D
data, exporting 48
default access community strings 32
Device Manager
installing on UNIX 22
installing on Windows 21
requirements 17
setting properties 30
starting 29
summary 17
Device Manager window 30
Device menu 35
Device Name pa rameter 33
device view
displaying 33
summary 36
device, opening 33
Disable command 41
disabled port, color 39
E
Edit command 40, 41
Edit menu 35
Edit Selected button 36
Enable c ommand 41
Export Data button 42, 48
Getting Started with the Business Policy Switch 2000 Management Software
Page 64

64 Index
G
graph
creating 49
modifying 50
Graph command 40, 41
graph dialog box 50
Graph menu 35
GraphSelectedbutton36,49
graph types 44
H
Help button 36
Help menu 35
Help, Device Manager 52
Horizontal button 50
Hotswap Detect every parameter 31
HP/UX installation of Device Manager 25
I
If traps,status interval parameter 31
Insert button 42
installation, Device Manager 21
IP parameters, setting 18
J
JRE (Java Runtime Environment)
installing for HP-UX 25
installing for IBM AIX 26
installing for Solaris 24
L
LastValue statistics 44
layout, Web page 56
LEDs in device view 39
legend, port color 35, 39
Line Chart button 50
line graph example 45
link, lacking,color 39
Log Scale button 50
login window 55
M
Main Menu, console 19
MaxTrapsinLogfield32
Maximum statistics 44
MDA
shortcut menu 41
viewing 38
media dependent adapter. See MDA
menu bar, Device Manager 35
menu, Web 57
menus. See individual menu names
Microsoft Internet Explore, software version 53
Minimum statistics 44
multiple objects, selecting 38
N
Netscape Navigator, software version 53
network security
at first login 55
setting up 60
new table entry, creating 42
O
object types 37
objects
editing 43
selecting37
online Help 35, 52
Open Device button 33, 36
Open Device dialog box 33, 35
operating port, color 39
209321-A
Page 65

Index 65
P
password management pages 61
passwords 20, 56, 60
Paste button 42
patches,Solaris 23
pie graph example 46
polling interval 48
polling interval, setting 31
polling waiting period 32
port color legend 39
port shortcut menu 41
ports
color-coded 39
disabled 39
selecting 38
Print button 42
product support 16
Properties dialog box 30
publications
hard copy 16
related15
R
Radius authentication 61
Radius management page 62
Read Community parameter 33
Read Community, SNMP 34
read-only access 62
read-write a ccess 62
Read-Write-All access34
Refresh Device Status button 36
Register for Traps parameter 32
release notes, obtaining 58
remote dial-in access 62
requirements
Device Manager 17
UNIX installation of Device Manager 22
Web management interface 18, 53
Windows installation of Device Manager 21
Reset C hanges button 42
Retry Count parameter 32
Rmon menu 35
S
shortcut menus
MDA 41
port 41
switch unit 40
single object, selecting 37
SNMP tracing 32
SNMP traps 5 1
software installation
AIX 26
HP/UX 23
Solaris 23
UNIX 22
Windows 21
Solaris installation of Device Manager 23
Solaris patches, installing 23
Stackedbutton50
standalone switch, setting IP parameters 20
standby port, color 39
statistics
for a single object 47
for multiple objects 48
graphing 43
types 44
statistics dialog box
multiple objects 48
single object 47
statisticsdialog boxes 35
Status Interval parameter 31
Status Poll Enable parameter 31
Getting Start ed with the Business Policy Switch 2000 Management Software
Page 66

66 Index
status polling 31
Stop button 42
Support heading 58
support Web site 21
support, Nortel Networks 16
switch stack, s electing 38
switch stack, setting IP parameters 20
switch unit shortcut menu 40
switch, selecting 37
System Information home page 54
T
technical publications 16
technical support 16
Telnet button 36, 51
Telnet passwords 60
Telnet session 35, 36, 51
tested port, color 39
text conventions 14
Timeout parameter 32
timeout, setting 32
toolbar, Device Ma nager 36
Trace parameter 32
trap log 51
TrapLogbutton36
Trap Port parameter 32
troubleshooting
adjusting polling waiting period 32
locations of Help files 52
opening the Web home page 54
receiving traps 51
selecting switches in device view 38
setting UNIX environment variables 25
types of objects 37
U
UNIX
installing Device Manager 22
receiving traps 51
UNIX environment variables25
UNIX environment variables for DeviceManager
24
unmanageable port, color 39
user levels 56
V
value, changed 43
versions, Web browsers 53
VLAN menu 35
W
WebHelpfile,accessing58
Web management interface
description 18
opening 54
requirements 18
Web management interface requirements 53
Web management options 58
Web passwords 60
Web site, Services and Support 21
window, Device Manager 30, 34
Windows installation for Device Manager 21
Write Community parameter 33
Write Community, SNMP 34
209321-A
 Loading...
Loading...