Page 1

RSA SecurID Ready Implementation Guide
Last Modified: September 30, 2005
Partner Information
Product Information
Partner Name
Web Site www.nortelnetworks.com
Product Name
Version & Platform
Product Description
Product Category
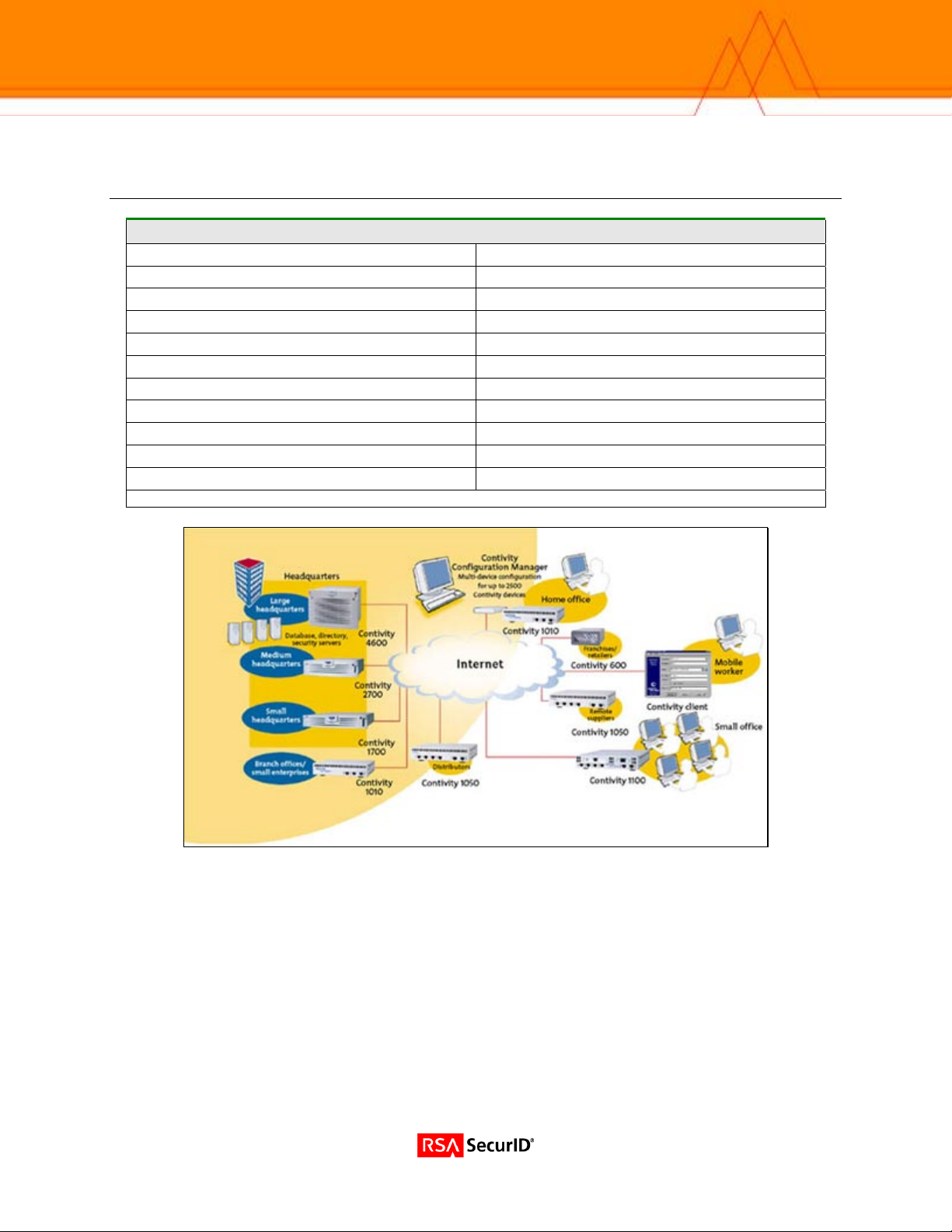
Nortel Networks
Nortel VPN Router
1050, 1740, 2700, 5000 Series
Each Nortel VPN Router is a single hardware device that provides routing,
firewall, bandwidth management, encryption, authentication, and data
integrity for secure tunneling across managed IP networks and the Internet.
With Contivity VPN Switches, you can connect remote users, branch
offices, suppliers, and customers with the cost and performance
advantages of shared IP networks and the security and control you would
expect from private networks.
Virtual Private Networking
1
Page 2
Solution Summary
Partner Integration Overview
Authentication Methods Supported
List Library Version Used
RSA Authentication Manager Name Locking
RSA Authentication Manager Replica Support
Secondary RADIUS Server Support
Location of Node Secret on Agent
RSA Authentication Agent Host Type
RSA SecurID User Specification
RSA SecurID Protection of Administrative Users
RSA Software Token API Integration
Use of Cached Domain Credentials
RADIUS
N/A
No
No
Yes (3)
‘None stored’
Communication Server
Designated users
No
Yes
No
2
Page 3

Product Requirements
Partner Product Requirements: Nortel VPN Router
Firmware Version
Partner Product Requirements: Nortel VPN Client
Operating System Required Patches
Windows XP
Windows 2000
Windows 98
Windows ME
Note: Nortel VPN Client Version 4.86 is the last release that provides
support for the Windows NT operating system.
Version 4.91 will be the last release that provides support for Windows 98
and Windows ME operating systems.
V05_05.202
3
Page 4

Agent Host Configuration
To facilitate communication between the Nortel VPN Router and the RSA Authentication Manager / RSA
SecurID Appliance, an Agent Host record must be added to the RSA Authentication Manager database.
The Agent Host record identifies the
about communication and encryption.
To create the Agent Host record, you will need the following information.
• Hostname
• IP Addresses for all network interfaces
• RADIUS Secret (When using RADIUS Authentication Protocol)
When adding the Agent Host Record, you should configure the Nortel VPN Router as Communication
Server.
the
Please refer to the appropriate RSA Security documentation for additional information about Creating,
Modifying and Managing Agent Host records.
This setting is used by the RSA Authentication Manager to determine how communication with
Nortel VPN Router will occur.
Note: Hostnames within the RSA Authentication Manager / RSA SecurID
Appliance must resolve to valid IP addresses on the local network.
Nortel VPN Router within its database and contains information
4
Page 5
Partner Authentication Agent Configuration
Before You Begin
This section provides instructions for integrating the Nortel VPN Router with RSA SecurID Authenticatio n.
This document is not intended to suggest optimum installations or configurations.
It is assumed that the reader has both working knowledge of all products involved, and the ability to
perform the tasks outlined in this section. Administrators should have access to the product
documentation for all products in order to install the required components.
All vendor products/components must be installed and working prior to the integration. Perf orm the
necessary tests to confirm that this is true before proceeding.
Nortel VPN Router Configuration
Enabling Support for RSA SecurID Authentication
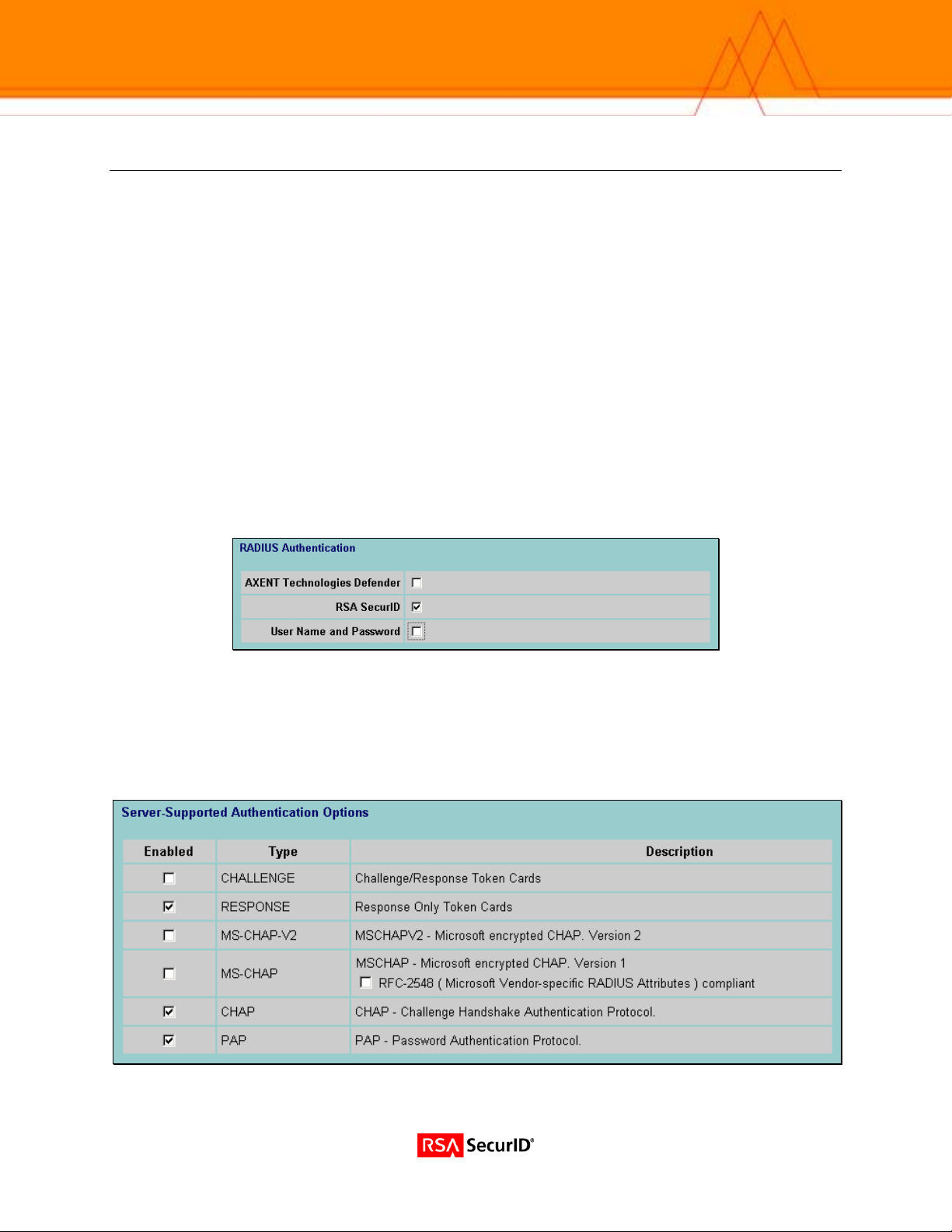
1. Using your Internet Browser, connect and login to your Nortel Contivity Switch Administration Console.
2. Enable RSA SecurID authentication via RADIUS
(Services > IPSec > RADIUS Authentication).
VPN Router Supported Authentication Types
1. The Nortel VPN Router supports RSA ACE/Server authentication of users via Radius only. This is configured in
the (Servers > Radius Auth) page of the CES Web management interface.
2. Check the box at the top of the screen that says ‘Enable Access to RADIUS Authentication’.
3. Under the ‘Server-Supported Authentication Options’ section, click the checkbox to enable support for Response
Only authentication. This configuration is used for RSA SecurID Authentication.
5
Page 6
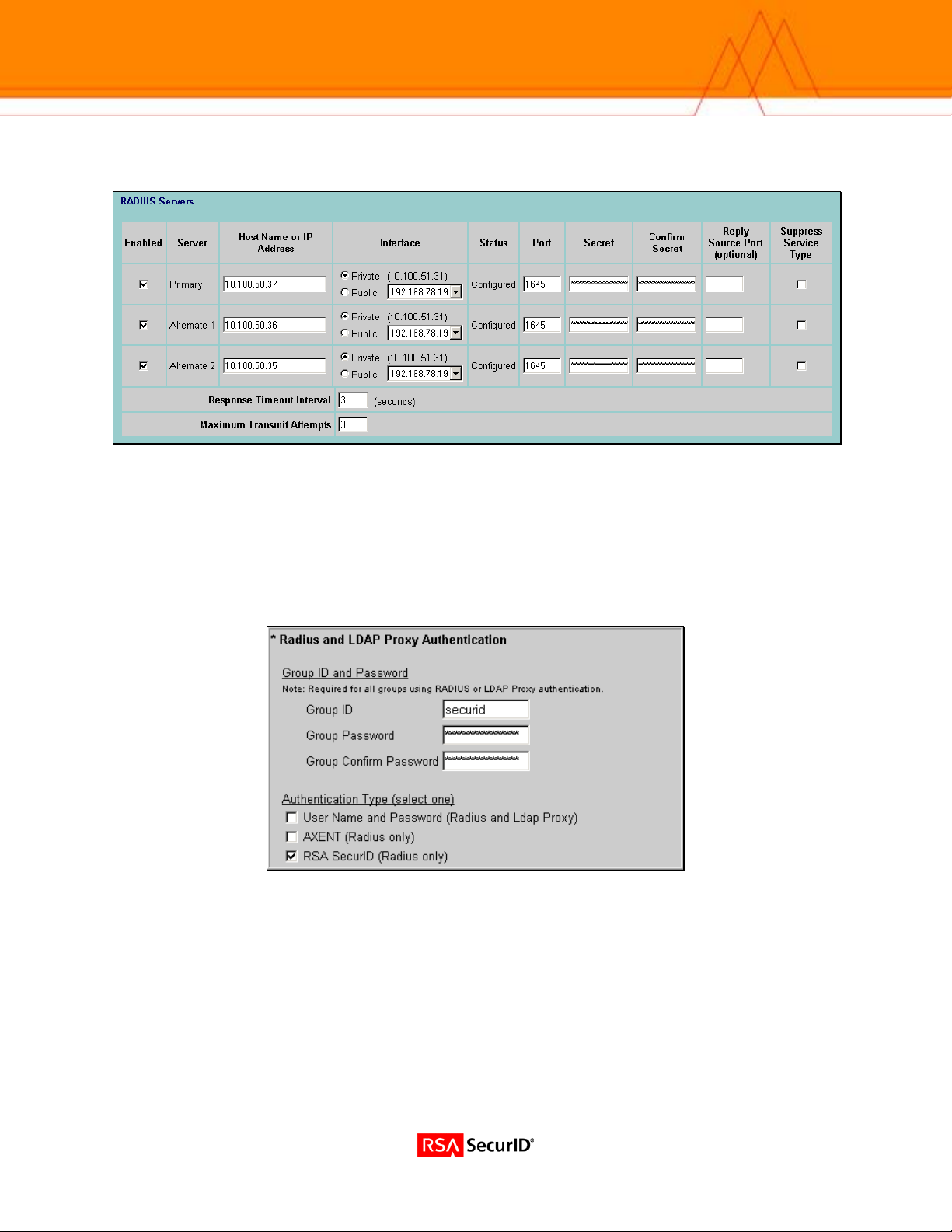
4. In the ‘RADIUS Servers’ section, fill out the info required. The Secret information for these servers should match
the encryption key assigned in the Agent Host configuration.
RADIUS Group Configuration
Any user seeking RADIUS authentication must belong to a group specified by a group ID and password,
configured in the Profiles > Groups > Edit > IPSec > Authentication > Configure page. This is a two-step
process where (1) the Switch authenticates the remote user with RSA SecurID tokens, and (2) the client
uses the Group ID and Group Password to authenticate the Switch's identity.
1. Click to enable the RSA SecurID token security authentication.
2. Enter the Group ID and Password, which provide access to the switch.
6
Page 7

IPSec Client configuration
Upon first run of the Contivity VPN Client, you will be prompted to create a connection profile via the
Connection Wizard.
Use the screenshots below as a guide to setting up your connection for RSA SecurID authentication. For
a detailed explanation of each configuration parameter, please reference the manuals from Nortel that
comes with the client software.
Connection Wizard
Authentication type
Connection Profile name and description
Token card type
7
Page 8

User ID for RSA SecurID Authentication
Name/IP Address of switch
Do you need to initiate a dial up connection first or are you
already connected to the internet/network?
Login screen
Setup complete!
8
Page 9
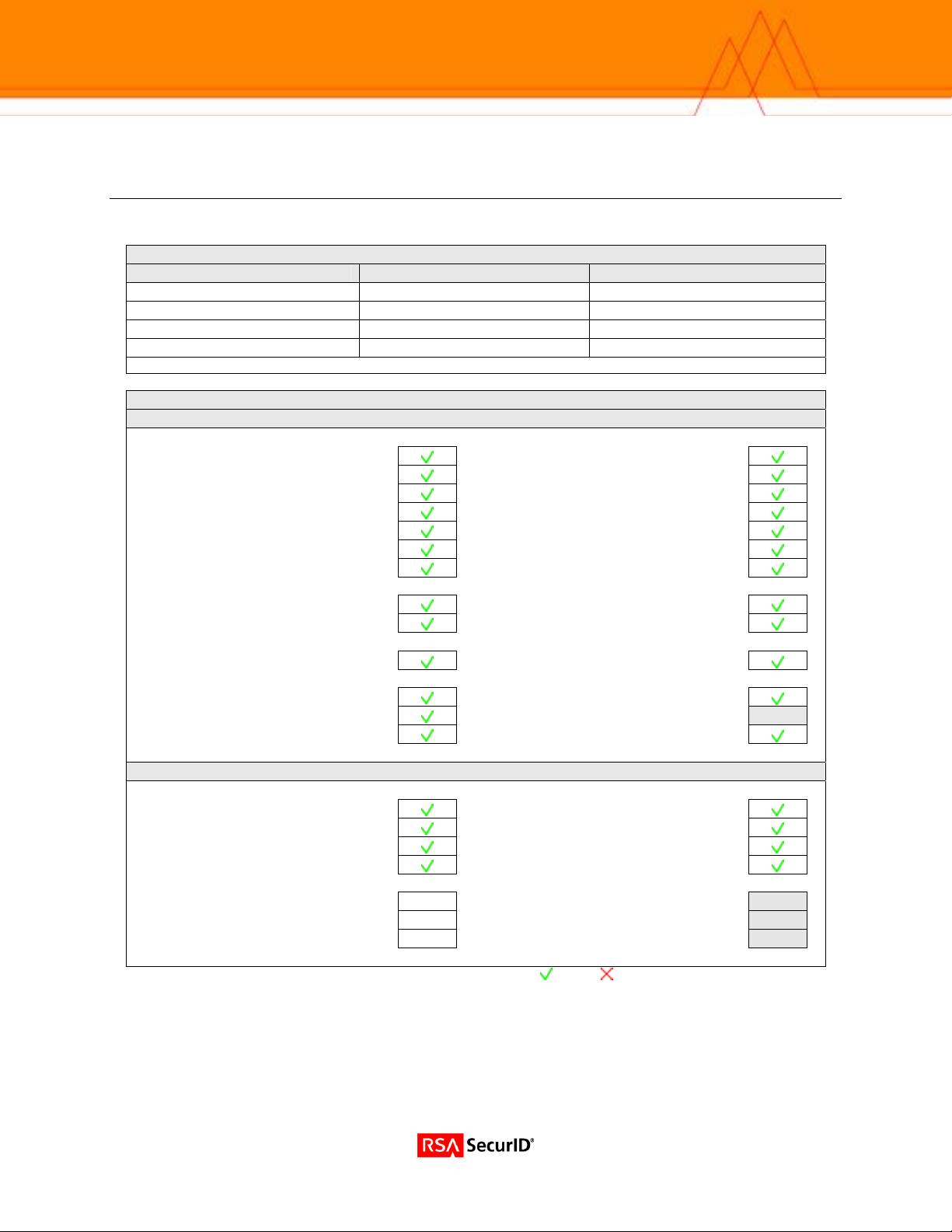
Certification Checklist
Date Tested: September 30, 2005
Certification Environment
Product Name Version Information Operating System
RSA Authentication Manager
RSA Software Token
RSA Authentication Utility
Nortel VPN Router
RSA Native Protocol RADIUS Protocol
New PIN Mode
Force Authentication After New PIN
System Generated PIN
User Defined (4-8 Alphanumeric)
User Defined (5-7 Numeric)
User Selectable
Deny 4 and 8 Digit PIN
Deny Alphanumeric PIN
PASSCODE
16 Digit PASSCODE
4 Digit Password
Next Tokencode Mode
Next Tokencode Mode
Load Balancing / Reliability Testing
Failover (3-10 Replicas)
Name Locking Enabled
No RSA Authentication Manager
RSA Software Token API Functionality
System Generated PIN
User Defined (8 Digit Numeric)
User Selectable
Next Tokencode Mode
Domain Credential Functionality
Determine Cached Credential State N/A
Set Domain Credential N/A
Retrieve Domain Credential N/A
EF = Pass = Fail N/A = Non-Available Function
6.1 Windows 2003 Server (SP1)
3.0.5 Windows XP Professional (SP2)
1.0 Build 25 Windows XP Professional (SP2)
1050 Firmware V05_05.202
Mandatory Functionality
Force Authentication After New PIN
System Generated PIN
User Defined (4-8 Alphanumeric)
User Defined (5-7 Numeric)
User Selectable
Deny 4 and 8 Digit PIN
Deny Alphanumeric PIN
16 Digit PASSCODE
4 Digit Password
Next Tokencode Mode
Failover
Name Locking Enabled
No RSA Authentication Manager
Additional Functionality
System Generated PIN
User Defined (8 Digit Numeric)
User Selectable
Next Tokencode Mode
Determine Cached Credential State
Set Domain Credential
Retrieve Domain Credential
9
Page 10
Known Issues
RSA Software Token
The Contivity VPN Client can be configured to detect the installation of the RSA Software Token through
the presence of stauto32.dll. Users will then be prompted for their Pin only. The Tokencode displayed on
the Software Token is automatically coupled with the Pin and passed along to the RSA ACE/Server.
This functionality is configured within the Contivity VPN Client under (Options > Authentication Options >
Response Only Token > Options > Use Installed SoftID Software Token)
New Pin mode
RSA SecurID Software Token integration with the Contivity VPN Client supports basic authentication
functionality. When the user is in New Pin Mode, they need to enter ‘0000’ in the PIN window to initiate
the authentication process. Also, once the PIN is created, they will have to wait for the “Tokencode to
change” before successfully logging in.
10
Page 11

Alphanumeric PINS
The Contivity VPN Client does not allow alphabetic characters to be entered in the Passcode field of the
connection dialog box.
There is a workaround for instances where alphanumeric PINs are allowed for SecurID users, the
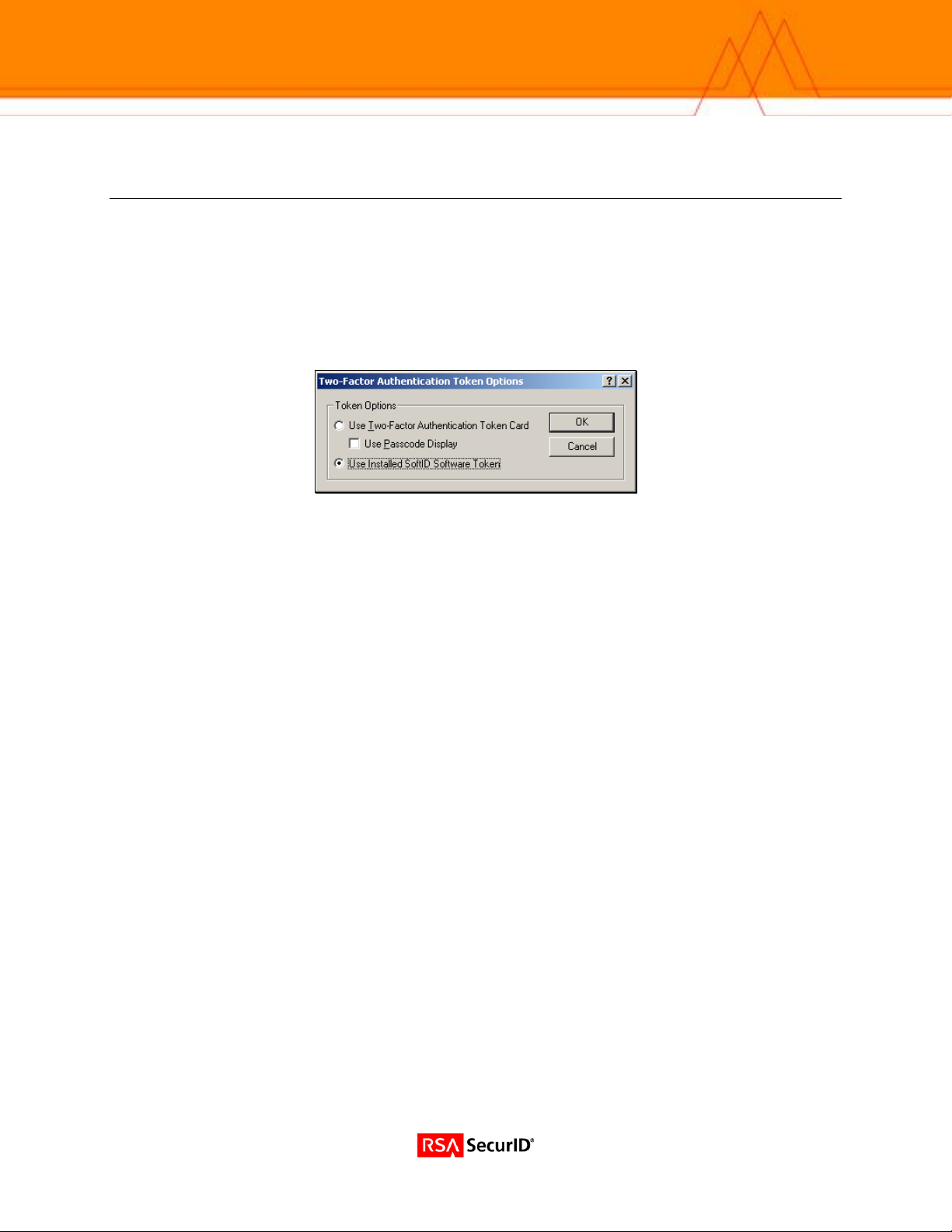
Contivity VPN Client must be configured to display separate Tokencode and PIN fields.
This is achieved by clearing the Use Passcode Display checkbox in the Two-Factor Authentication Token
Options dialog. The user can then enter an alphanumeric PIN in the separate PIN field.
Response Only Token Options
Authentication Options
RSA Software Updates
RSA Software Token 3.0.5
Certification Testing was completed with a point release build of the RSA Software Token Application. In
order to ensure a successful integration, please verify that the build of the utility is correct prior to
beginning the integration.
For the updated build of the RSA Security Software Token, please contact RSA Security Customer
Support or login to RSA SecureCare Online for download instructions.
RSA Authentication Utility 1.0 Build 25
Certification Testing was completed with a point release build of the RSA Authentication Utility. In order to
ensure a successful integration, please verify that the build of the utility is correct prior to beginning the
integration.
For the updated build of the RSA Authentication Utility, please contact RSA Security Customer Support or
login to RSA SecureCare Online for download instructions.
11
Page 12

RSA Authentication Utility (SID800 Integration)
Authentication fails if user enters 0000 as permanent SecurID PIN.
A user may not be able to authenticate when completing the New PIN procedure if the user enters four
zeros (0000) as the permanent PIN. You cannot use 0000 as a permanent PIN.
System-generated RSA SecurID SID800 PIN with VPN Client
If your USB token is in New PIN mode during authentication to a VPN client, and the RSA Authentication
Manager requires that you accept a system-generated SecurID PIN, a delay occurs once you accept the
SecurID PIN. You then are prompted to enter the new SecurID PIN with the next Tokencode to complete
authentication. This does not happen if the RSA Authentication Manager specifies a user-generated
SecurID PIN.
12
 Loading...
Loading...