Nokia IP60 User Manual

Part No. N450000643 Rev 001
Published February 2008
Nokia IP60 Security Appliance
User Guide

2 Nokia IP60 Security Appliance User Guide
COPYRIGHT
©2008 Nokia. All rights reserved.
Rights reserved under the copyright laws of the United States.
RESTRICTED RIGHTS LEGEND
Use, duplication, or disclosure by the United States Government is subject to restrictions as set forth in subparagraph
(c)(1)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013.
Notwithstanding any other license agreement that may pertain to, or accompany the delivery of, this computer software,
the rights of the United States Government regarding its use, reproduction, and disclosure are as set forth in the
Commercial Computer Software-Restricted Rights clause at FAR 52.227-19.
IMPORTANT NOTE T O USERS
This software and hardware is provided by Nokia Inc. as is and any express or implied warranties, including, but not
limited to, implied warranties of merchantability and fitness for a particular purpose are disclaimed. In no event shall
Nokia, or its affiliates, subsidiaries or suppliers be liable for any direct, indirect, incidental, special, exemplary, or
consequential damages (including, but not limited to, procurement of substitute goods or services; loss of use, data, or
profits; or business interruption) however caused and on any theory of liability, whether in contract, strict liability, or tort
(including negligence or otherwise) arising in any way out of the use of this software, even if advised of the possibility of
such damage.
Nokia reserves the right to make changes without further notice to any products herein.
TRADEMARKS
Nokia is a registered trademark of Nokia Corporation. Other products mentioned in this document are trademarks or
registered trademarks of their respective holders.
080101

Nokia IP60 Security Appliance User Guide 3
Nokia Contact Information
Corporate Headquarters
Regional Contact Information
Nokia Customer Support
Web Site http://www.nokia.com
Telephone 1-888-477-4566 or
1-650-625-2000
Fax 1-650-691-2170
Mail
Address
Nokia Inc.
313 Fairchild Drive
Mountain View, California
94043-2215 USA
Americas Nokia Inc.
313 Fairchild Drive
Mountain View, CA 94043-2215
USA
Tel: 1-877-997-9199
Outside USA and Canada: +1 512-437-7089
email: info.ipnetworking_americas@nokia.com
Europe,
Middle East,
and Africa
Nokia House, Summit Avenue
Southwood, Farnborough
Hampshire GU14 ONG UK
Tel: UK: +44 161 601 8908
Tel: France: +33 170 708 166
email: info.ipnetworking_emea@nokia.com
Asia-Pacific 438B Alexandra Road
#07-00 Alexandra Technopark
Singapore 119968
Tel: +65 6588 3364
email: info.ipnetworking_apac@nokia.com
Web Site: https://support.nokia.com/
Email: tac.support@nokia.com
Americas Europe
Voice: 1-888-361-5030 or
1-613-271-6721
Voice: +44 (0) 125-286-8900
Fax: 1-613-271-8782 Fax: +44 (0) 125-286-5666
Asia-Pacific
Voice: +65-67232999
Fax: +65-67232897
050602

4 Nokia IP60 Security Appliance User Guide

Contents
Contents
About This Guide ................................................................................................................................ 11
Introduction ......................................................................................................................................... 13
About Your Nokia IP60 Appliance ................................................................................................... 13
Nokia IP60 Products ......................................................................................................................... 13
Security ................................................................................................................................................ 29
Introduction to Information Security ................................................................................................. 29
The Nokia IP60 Firewall ................................................................................................................... 32
Installing and Setting Up the Nokia IP60 Appliance ....................................................................... 39
Before You Install the Nokia IP60 Appliance ................................................................................... 39
Nokia IP60 and Nokia IP60 Wireless Installation ............................................................................. 50
Cascading Your Appliance ............................................................................................................... 54
Connecting the Appliance to Network Printers ................................................................................. 55
Setting Up the IP60 Appliance .......................................................................................................... 55
Getting Started .................................................................................................................................... 59
Initial Login to the Nokia IP60 Portal ............................................................................................... 59
Logging on to the Nokia IP60 Portal ................................................................................................ 60
Accessing the Nokia IP60 Portal Remotely Using HTTPS ............................................................... 61
Using the Nokia IP60 Portal.............................................................................................................. 63
Logging off ....................................................................................................................................... 65
Configuring the Internet Connection ................................................................................................ 67
Overview ........................................................................................................................................... 67
Using the Internet Wizard ................................................................................................................. 68
Using Internet Setup .......................................................................................................................... 76
Setting Up Dialup Modems ............................................................................................................... 96
Viewing Internet Connection Information ...................................................................................... 102
Enabling/Disabling the Internet Connection ................................................................................... 105
Using Quick Internet Connection/Disconnection ............................................................................ 105
Configuring a Backup Internet Connection ..................................................................................... 105
Configuring WAN Load Balancing ................................................................................................ 106
Managing Your Network .................................................................................................................. 109
Configuring Network Settings ........................................................................................................ 109
Using Network Objects ................................................................................................................... 134
Configuring Network Service Objects ............................................................................................ 142
Contents 5

Contents
Using Static Routes ......................................................................................................................... 144
Managing Ports ............................................................................................................................... 148
Using Bridges ..................................................................................................................................... 157
Overview ......................................................................................................................................... 157
Workflow ........................................................................................................................................ 162
Adding and Editing Bridges ................................ ............................................................................ 162
Adding Internal Networks to Bridges ............................................................................................. 165
Adding Internet Connections to Bridges ......................................................................................... 168
Deleting Bridges ............................................................................................................................. 172
Configuring High Availability ......................................................................................................... 173
Overview ......................................................................................................................................... 173
Configuring High Availability on a Gateway ................................................................................. 175
Sample Implementation on Two Gateways ..................................................................................... 178
Using Traffic Shaper ......................................................................................................................... 181
Overview ......................................................................................................................................... 181
Setting Up Traffic Shaper ............................................................................................................... 182
Predefined QoS Classes .................................................................................................................. 182
Adding and Editing Classes ............................................................................................................ 184
Viewing and Deleting Classes......................................................................................................... 187
Restoring Traffic Shaper Defaults ................................................................................................... 187
Working with Wireless Networks .................................................................................................... 189
Overview ......................................................................................................................................... 189
Configuring Wireless Networks ...................................................................................................... 194
Troubleshooting Wireless Connectivity .......................................................................................... 215
Viewing Reports ................................................................................................................................ 217
Viewing the Event Log ................................................................................................................... 217
Using the Traffic Monitor ............................................................................................................... 219
Viewing Computers ........................................................................................................................ 222
Viewing Connections ...................................................................................................................... 224
Viewing Wireless Statistics ............................................................................................................. 226
Viewing the Routing Table ............................................................................................................. 229
Setting Your Security Policy ............................................................................................................ 231
The Nokia IP60 Firewall Security Policy........................................................................................ 232
Default Security Policy ................................................................................................................... 233
Setting the Firewall Security Level ................................................................................................. 233
6 Nokia IP60 Security Appliance User Guide

Contents
Configuring Servers ........................................................................................................................ 236
Using Rules ..................................................................................................................................... 238
Using Port-Based Security .............................................................................................................. 247
Using Secure HotSpot ..................................................................................................................... 251
Using NAT Rules ............................................................................................................................ 255
Using Web Rules ............................................................................................................................ 261
Using SmartDefense .......................................................................................................................... 269
Overview ......................................................................................................................................... 269
Configuring SmartDefense .............................................................................................................. 269
SmartDefense Categories ................................................................................................................ 274
Resetting SmartDefense to its Defaults ........................................................................................... 308
Using VStream Antivirus ................................................................................................................. 309
Overview ......................................................................................................................................... 309
Enabling/Disabling VStream Antivirus................................................................ ........................... 311
Viewing VStream Antivirus Signature Database Information ........................................................ 311
Configuring VStream Antivirus ...................................................................................................... 312
Updating VStream Antivirus ........................................................................................................... 324
SMART Management and Subscription Services .......................................................................... 325
Connecting to a Service Center ....................................................................................................... 325
Viewing Services Information ........................................................................................................ 330
Refreshing Your Service Center Connection .................................................................................. 330
Configuring Your Account ............................................................................................................. 332
Disconnecting from Your Service Center ....................................................................................... 332
Web Filtering .................................................................................................................................. 333
Email Filtering ................................................................................................................................ 337
Automatic and Manual Updates ...................................................................................................... 340
Working with VPNs .......................................................................................................................... 343
Overview ......................................................................................................................................... 343
Setting Up Your Nokia IP60 Appliance as a VPN Server .............................................................. 347
Adding and Editing VPN Sites ........................................................................................................ 359
Viewing and Deleting VPN Sites .................................................................................................... 383
Enabling/Disabling a VPN Site ....................................................................................................... 383
Logging on to a Remote Access VPN Site ...................................................................................... 384
Logging off a Remote Access VPN Site ......................................................................................... 385
Installing a Certificate ..................................................................................................................... 386
Contents 7

Contents
Uninstalling a Certificate ................................................................................................................ 392
Viewing VPN Tunnels .................................................................................................................... 392
Viewing IKE Traces for VPN Connections .................................................................................... 395
Viewing VPN Topology ................................................................................................................. 396
Managing Users ................................................................................................................................. 397
Changing Your Login Credentials .................................................................................................. 397
Adding and Editing Users ............................................................................................................... 399
Adding Quick Guest HotSpot Users ............................................................................................... 402
Viewing and Deleting Users ........................................................................................................... 403
Setting Up Remote VPN Access for Users ..................................................................................... 404
Using RADIUS Authentication ....................................................................................................... 404
Configuring RADIUS Attributes .................................................................................................... 408
Using Remote Desktop ...................................................................................................................... 411
Overview ......................................................................................................................................... 411
Workflow ........................................................................................................................................ 411
Configuring Remote Desktop.......................................................................................................... 412
Configuring the Host Computer ...................................................................................................... 415
Accessing a Remote Computer's Desktop ....................................................................................... 417
Maintenance ...................................................................................................................................... 419
Viewing Firmware Status ................................................................................................................ 420
Updating the Firmware ................................................................................................................... 421
Upgrading Your License ................................................................................................................. 423
Configuring Syslog Logging ................................ ................................ ........................................... 424
Controlling the Appliance via the Command Line .......................................................................... 425
Configuring HTTPS ........................................................................................................................ 429
Configuring SSH ............................................................................................................................. 431
Configuring SNMP ......................................................................................................................... 432
Setting the Time on the Appliance .................................................................................................. 436
Using Diagnostic Tools ................................................................................................................... 439
Backing Up the Nokia IP60 Appliance Configuration .................................................................... 451
Resetting the Nokia IP60 Appliance to Defaults ............................................................................. 453
Running Diagnostics ....................................................................................................................... 455
Rebooting the Nokia IP60 Appliance .............................................................................................. 456
Using Network Printers .................................................................................................................... 457
Overview ......................................................................................................................................... 457
8 Nokia IP60 Security Appliance User Guide

Contents
Setting Up Network Printers ........................................................................................................... 457
Configuring Computers to Use Network Printers ........................................................................... 459
Viewing Network Printers ............................................................................................................... 470
Changing Network Printer Ports ..................................................................................................... 471
Resetting Network Printers ............................................................................................................. 472
Troubleshooting ................................................................................................................................ 473
Connectivity .................................................................................................................................... 473
Service Center and Upgrades .......................................................................................................... 475
Other Problems ............................................................................................................................... 476
Specifications ..................................................................................................................................... 477
Technical Specifications ................................................................................................................. 477
CE Declaration of Conformity ........................................................................................................ 479
Federal Communications Commission Radio Frequency Interference Statement .......................... 481
Glossary of Terms ............................................................................................................................. 483
Index ................................................................................................................................................... 487
Contents 9

About Your Nokia IP60 Appliance
Note: Notes are denoted by indented text and preceded by the Note icon.
Warning: Warnings are denoted by indented text and preceded by the Warning icon.
If this icon appears...
You can perform the task using these products...
Nokia IP60
Nokia IP60 Wireless
All products with USB ports, specifically, Nokia IP60 Wireless
Only products without ADSL. Note: Nokia IP60 appliances do not
provide ADSL.
About This Guide
To make finding information in this manual easier, some types of information are marked with special
symbols or formatting.
Boldface type is used for command and button names.
Each task is marked with an icon indicating the Nokia IP60 product required to perform the task, as
follows:
Chapter 1: About This Guide 11


About Your Nokia IP60 Appliance
This chapter includes the following topics:
About Your Check Point Nokia IP60 Nokia IP60 Appliance ..................... 13
The Nokia IP60 Series and Nokia IP60 Wireless Series ............................ 13
Contacting Technical Support .................................................................... 28
Feature
Nokia IP60
Concurrent Users
8 / 16 / 32 / Unrestricted
Introduction
Chapter 1
This chapter introduces the Nokia IP60 appliance and this guide.
About Your Nokia IP60 Appliance
The Nokia IP60 appliance is a Unified Threat Management (UTM) appliance that delivers proven, tightly
integrated security features to provide the perfect blend of simplicity and security. Based on the same
Check Point technologies that secure the Fortune 100, IP60 appliances deliver uncompromising security,
while streamlining deployment and administration.
IP60 appliances integrate a complete set of security features into a single, easy-to-install unit, including
firewall, VPN, intrusion prevention, antivirus, antispam, Web filtering, reporting & monitoring, and
Network Access Control (NAC). In addition, IP60 appliances offer powerful networking capabilities,
including advanced routing, traffic shaping, high availability, redundant Internet connections, and extensive
VLAN support.
All IP60 appliances can be integrated into an overall enterprise security policy for maximum security.
Check Point's Security Management Architecture (SMART) delivers a single enterprise-wide security
policy that you can centrally manage and automatically deploy to an unlimited number of Nokia IP60
gateways.
Nokia IP60 Products
The Nokia IP60 appliance incorporates the following product families.
Nokia IP60 Internet Security Appliance, which corresponds with the Nokia IP60.
Nokia IP60 Wireless Security Appliance, which corresponds with the Nokia IP60 Wireless.
Nokia IP60 Features
Table 1: Nokia IP60 Features
Chapter 1: Introduction 13
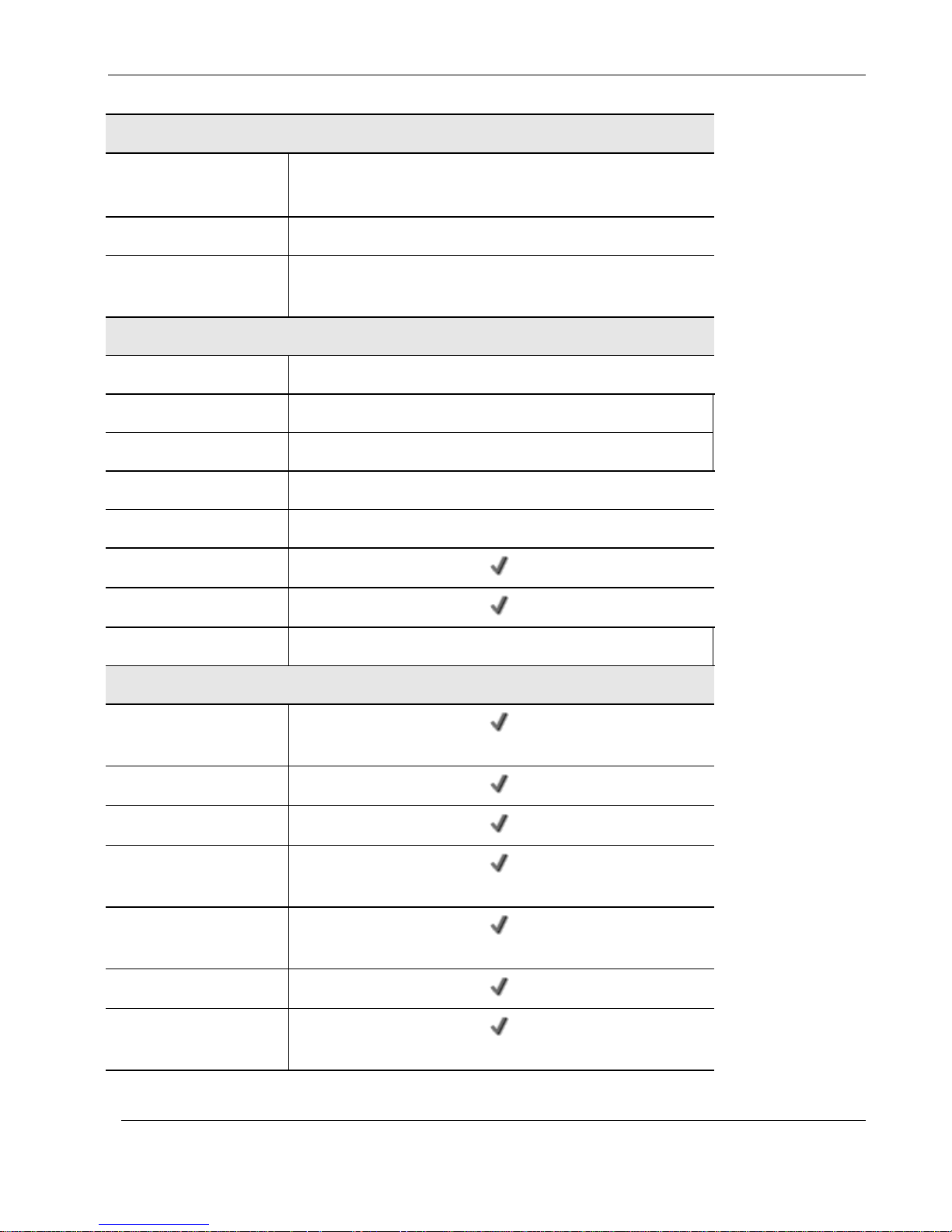
Nokia IP60 Products
Capacity
Firewall Throughput
(Mbps)
190Mbps
VPN Throughput (Mbps)
35Mbps
Concurrent Firewall
Connections
8,000
Hardware Features
4-Port LAN Switch
10/100 Mbps
WAN Port
Ethernet, 10/100 Mbps
ADSL Standards
—
DMZ/WAN2 Port
10/100 Mbps
Dialup Backup
With external serial / USB modem
Console Port (Serial)
Print Server
USB 2.0 Ports
—
Firewall & Security Features
Check Point Stateful
Inspection Firewall
Application Intelligence
SmartDefense™ (IPS)
Network Address
Translation (NAT)
Four Preset Security
Policies
Anti-spoofing
Voice over IP (H.323)
Support
14 Nokia IP60 Security Appliance User Guide
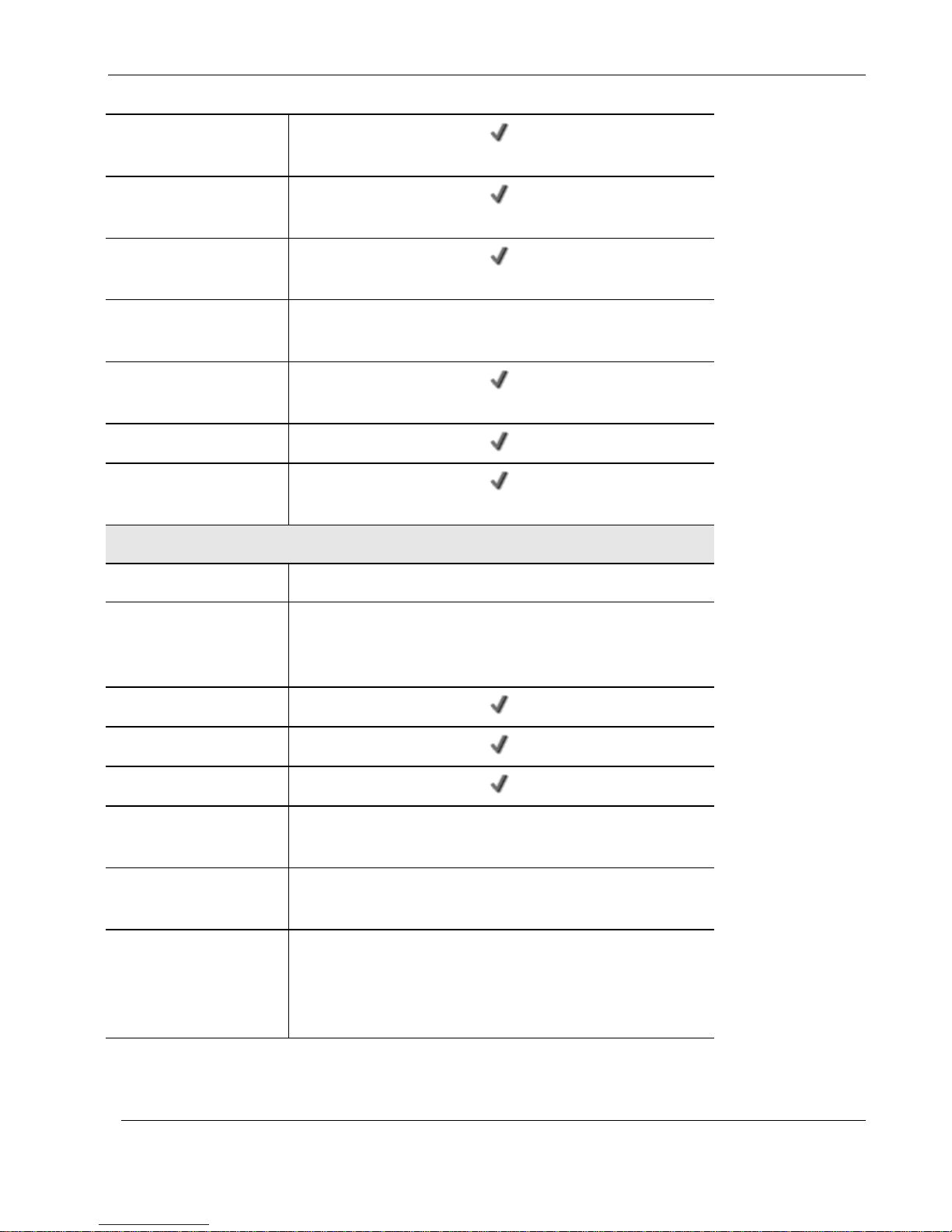
Nokia IP60 Products
Unlimited INSPECT Policy
Rules
Instant Messenger
Blocking / Monitoring
P2P File Sharing Blocking
/ Monitoring
Port-based and Tag-based
VLAN
32 (XU) / 10 (Other Models)
Port-based Security
(802.1x)
Web Rules
Secure HotSpot (Guest
Access)
VPN
Remote Access Users
1/10/15/25
VPN Server with
OfficeMode and RADIUS
Support
SecuRemote, L2TP
Site-to-Site VPN Gateway
Route-based VPN
Backup VPN Gateways
Remote Access VPN
Client
SecuRemote (Included)
Site-to-Site VPN Tunnels
(Managed)
100
IPSEC Features
Hardware-accelerated DES, 3DES, AES, MD5, SHA-1, Hardware
Random Number Generator (RNG), Internet Key Exchange (IKE),
Perfect Forward Secrecy (PFS), IPSEC Compression, IPSEC
NAT Traversal (NAT-T), IPSEC VPN Pass-through
Chapter 1: Introduction 15
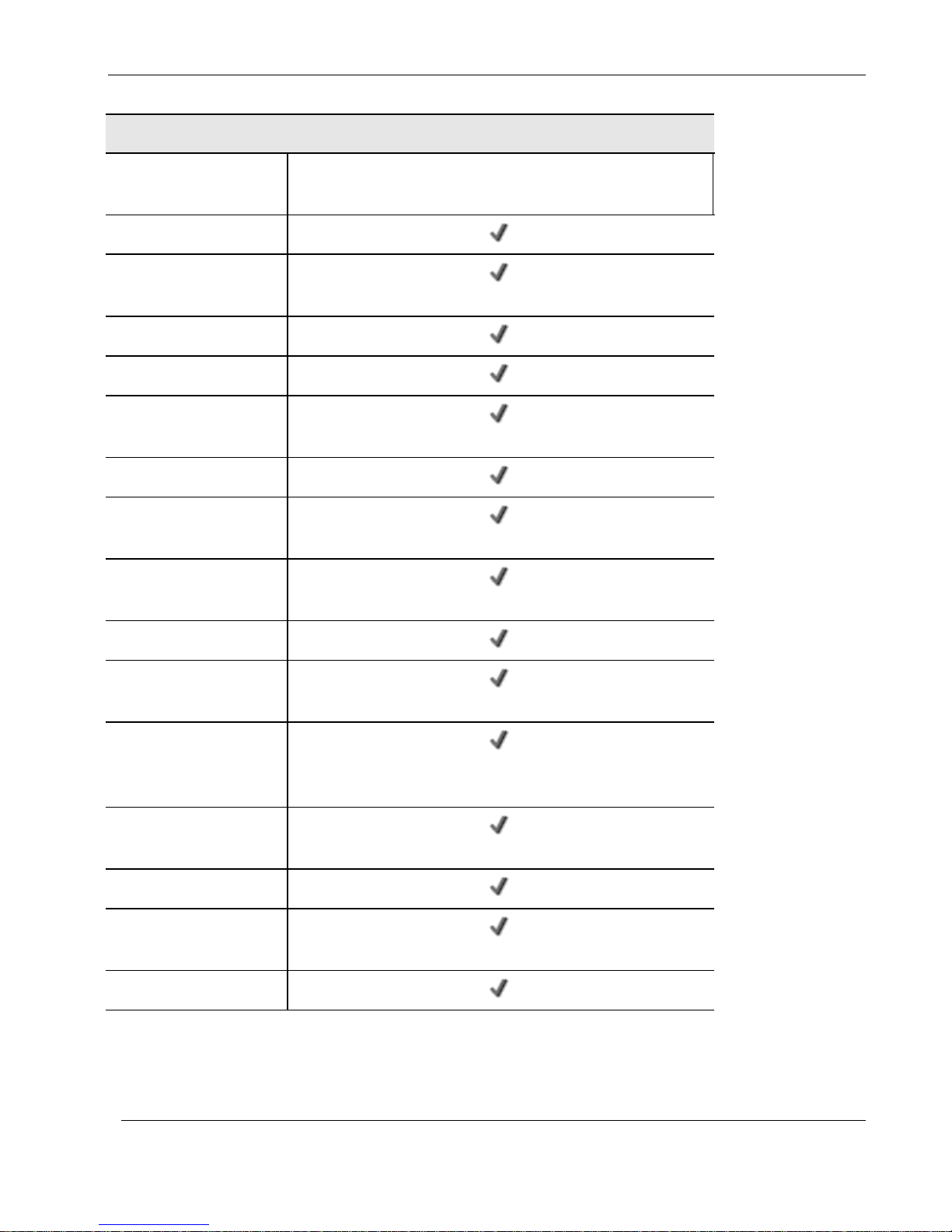
Nokia IP60 Products
Networking
Supported Internet
Connection Methods
Static IP, DHCP, PPPoE, PPTP, Telstra, Cable, Dialup
Transparent Bridge Mode
Spanning Tree Protocol
(STP)
Traffic Shaper (QoS)
Traffic Monitoring
Dead Internet Connection
Detection (DCD)
WAN Load Balancing
Backup Internet
Connection
DHCP Server, Client, and
Relay
MAC Cloning
Network Address
Translation (NAT) Rules
Static Routes, Source
Routes, and ServiceBased Routes
Ethernet Cable Type
Recognition
DiffServ Tagging
Automatic Gateway
Failover (HA)
Dynamic Routing
16 Nokia IP60 Security Appliance User Guide

Nokia IP60 Products
Management
Central Management
Check Point SmartCenter, Check Point SmartLSM, Check Point
SmartUpdate, CheckPoint Provider-1, SofaWare SMP
Local Management
HTTP / HTTPS / SSH / SNMP / Serial CLI
Remote Desktop
Integrated Microsoft Terminal Services Client
Local Diagnostics Tools
Ping, WHOIS, Packet Sniffer, VPN Tunnel Monitor, Connection
Table Monitor, My Computers Display, Routing Table Display,
Local Logs
NTP Automatic Time
Setting
TFTP Rapid Deployment
Hardware Specifications
Power
100/110/120/210/220/230VAC (Linear Power Adapter) or
100~240VAC (Switched Power Adapter)
Mounting Options
Desktop, Wall, or Rack Mounting*
Warranty
1 Year Hardware
Feature
Nokia IP60 Wireless
Concurrent Users
8 / 16 / 32 / Unrestricted
Capacity
Firewall Throughput (Mbps)
190 Mbps
VPN Throughput (Mbps)
35Mbps
Concurrent Firewall Connections
8,000
Hardware Features
4-Port LAN Switch
10/100 Mbps
* Rack mounting requires the optional rack mounting kit (sold separately).
Nokia IP60 Wireless Features
Table 2: Nokia IP60 Wireless Series Features
Chapter 1: Introduction 17
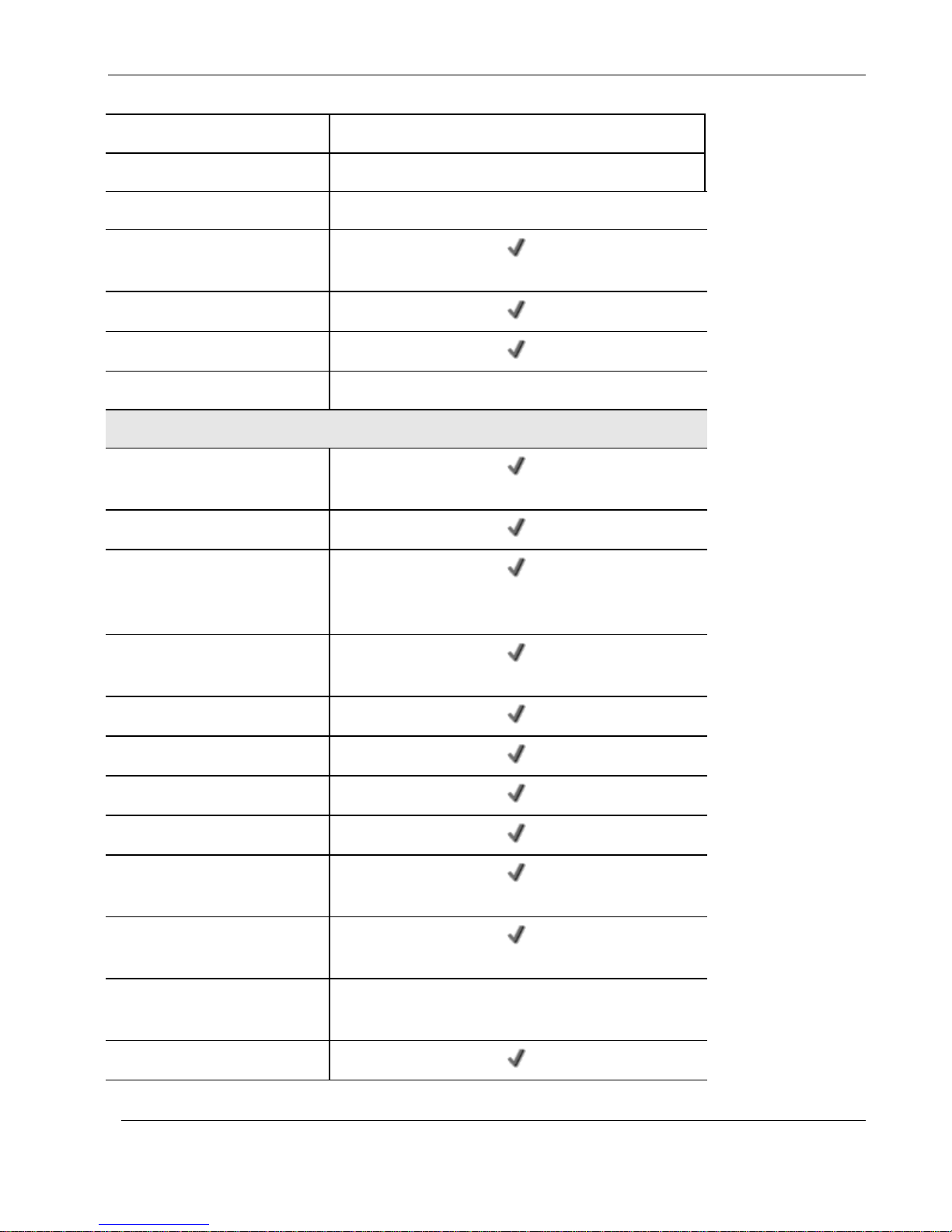
Nokia IP60 Products
WAN Port
10/100 Mbps
ADSL Standards
—
DMZ/WAN2 Port
10/100 Mbps
Dialup Backup (Req. Ext.
Modem)
Console Port (Serial)
Print Server
USB 2.0 Ports
2
Firewall & Security Features
Check Point Stateful Inspection
Firewall
Application Intelligence (IPS)
Intrusion Detection and
Prevention using Check Point
SmartDefense
Network Address Translation
(NAT)
Four Preset Security Policies
Anti-spoofing
Voice over IP (H.323) Support
Unlimited INSPECT Policy Rules
Instant Messenger Blocking /
Monitoring
P2P File Sharing Blocking /
Monitoring
Port-based, Tag-based, and
Other VLAN
32 (WU) / 10 (Other Models)
Port-based Security (802.1x)
18 Nokia IP60 Security Appliance User Guide
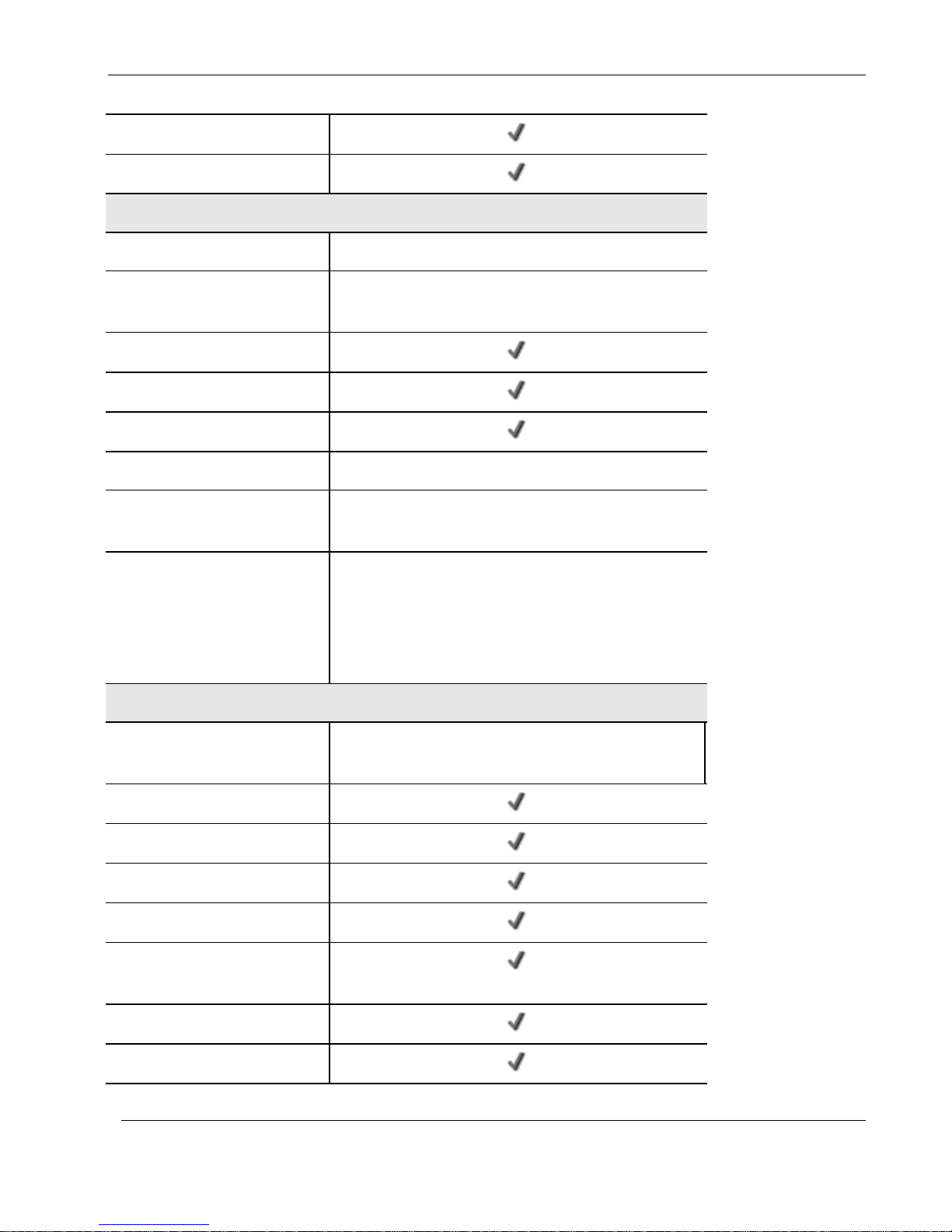
Nokia IP60 Products
Web Rules
Secure HotSpot (Guest Access)
VPN
Remote Access Users
1/10/15/25
VPN Server with OfficeMode and
RADIUS Support
SecuRemote, L2TP
Site-to-Site VPN Gateway
Route-based VPN
Backup VPN Gateways
Remote Access VPN Client
SecuRemote (Included)
Site-to-Site VPN Tunnels
(Managed)
100
IPSEC Features
Hardware-accelerated DES, 3DES, AES, MD5, SHA-1,
Hardware Random Number Generator (RNG), Internet
Key Exchange (IKE), Perfect Forward Secrecy (PFS),
IPSEC Compression, IPSEC NAT Traversal (NAT-T),
IPSEC VPN Pass-through
Networking
Supported Internet Connection
Methods
Static IP, DHCP, PPPoE, PPTP, Telstra, Cable, Dialup
Transparent Bridge Mode
Spanning Tree Protocol (STP)
Traffic Shaper (QoS)
Traffic Monitoring
Dead Internet Connection
Detection (DCD)
WAN Load Balancing
Backup Internet Connection
Chapter 1: Introduction 19
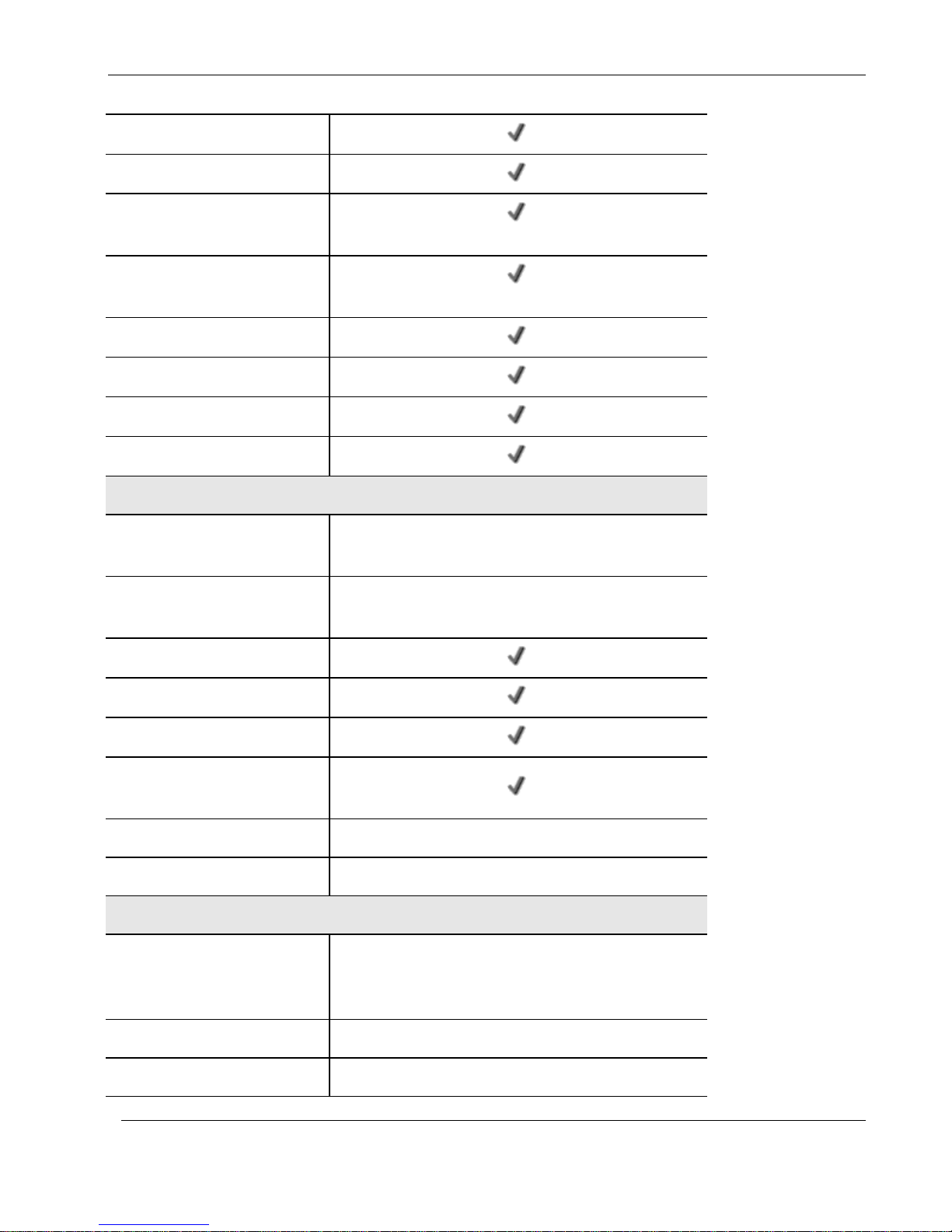
Nokia IP60 Products
DHCP Server, Client, and Relay
MAC Cloning
Network Address Translation
(NAT) Rules
Static Routes, Source Routes,
and Service-Based Routes
Ethernet Cable Type Recognition
DiffServ Tagging
Automatic Gateway Failover (HA)
Dynamic Routing
Wireless
Wireless Protocols
802.11b (11 Mbps), 802.11g (54 Mbps), Super G* (108
Mbps)
Wireless Security
VPN over Wireless, WEP, WPA2 (802.11i), WPA-
Personal, WPA-Enterprise, 802.1x
Wireless QoS (WMM)
Dual Diversity Antennas
Virtual Access Points (VAP)
Wireless Distribution System
(WDS) Links
Wireless Range (Standard Mode)
Up to 100 m Indoors and 300 m Outdoors
Wireless Range (XR Mode)*
Up to 300 m Indoors and 1 km Outdoors
Management
Central Management
Check Point SmartCenter, Check Point SmartLSM, Check
Point SmartUpdate, CheckPoint Provider-1, SofaWare
SMP
Local Management
HTTP / HTTPS / SSH / SNMP / Serial CLI
Remote Desktop
Integrated Microsoft Terminal Services Client
20 Nokia IP60 Security Appliance User Guide

Nokia IP60 Products
Local Diagnostics Tools
Ping, WHOIS, Packet Sniffer, VPN Tunnel Monitor,
Connection Table Monitor, Wireless Monitor, My
Computers Display, Routing Table Display, Local Logs
NTP Automatic Time Setting
TFTP Rapid Deployment
Hardware Specifications
Power
100/110/120/210/220/230VAC (Linear Power Adapter) or
100~240VAC (Switched Power Adapter)
Mounting Options
Desktop, Wall, or Rack Mounting**
Warranty
1 Year Hardware
* Super G and XR mode are only available with select wireless network adapters. Actual ranges are subject
to change in different environments.
* Rack mounting requires the optional rack mounting kit (sold separately).
Optional Security Services
The following subscription security services are available to IP60 owners by connecting to a Service
Center:
Firewall Security and Software Updates
Web Filtering
Email Antivirus and Antispam Protection
VStream Embedded Antivirus Updates
Dynamic DNS Service
VPN Management
Security Reporting
Vulnerability Scanning Service
These services require an additional purchase of subscription. For more information, contact your Check
Point reseller.
Software Requirements
One of the following browsers:
Microsoft Internet Explorer 6.0 or higher
Netscape Navigator 6.0 and higher
Mozilla Firefox
Chapter 1: Introduction 21

Nokia IP60 Products
Note: For proper operation of the IP60 Portal, disable any pop-up blockers for
http://my.firewall.
Getting to Know Your Nokia IP60 Appliance
Package Contents
The Nokia IP60 package includes the following:
Nokia IP60 Internet Security Appliance
Power supply
CAT5 Straight-through Ethernet cable
Getting Started Guide
Documentation CDROM
Wall mounting kit
RS232 serial adaptor (RJ45 to DB9); model SBX-166LHGE-5 only
22 Nokia IP60 Security Appliance User Guide

Nokia IP60 Products
Label
Description
PWR
A power jack used for supplying power to the unit. Connect the supplied power
supply to this jack.
RESET
A button used for rebooting the IP60 appliance or resetting the IP60 appliance to
its factory defaults. You need to use a pointed object to press this button.
Short press. Reboots the IP60 appliance
Long press (7 seconds). Resets the IP60 appliance to its factory defaults,
and resets your firmware to the version that shipped with the IP60
appliance. This results in the loss of all security services and
passwords and reverting to the factory default firmware. You will have
to re-configure your IP60 appliance.
Do not reset the unit without consulting your system administrator.
Serial
A serial (RS-232) port used for connecting computers in order to access the
Nokia IP60 CLI (Command Line Interface), or for connecting an external dialup
modem.
Depending on the appliance model, this port may have either a DB9 RS232
connector, or an RJ-45 connector. In models with an RJ-45 connector, an RJ-45
to DB9 converter is supplied for your convenience.
Warning: Do not connect an Ethernet cable to the RJ-45 serial port.
Figure 1: Nokia IP60 Appliance Rear Panel
Network Requirements
10BaseT or 100BaseT Network Interface Card installed on each computer
CAT 5 STP (Category 5 Shielded Twisted Pair) Straight Through Ethernet cable for each
attached device
A broadband Internet connection via cable or DSL modem with Ethernet interface (RJ-45)
Rear Panel
All physical connections (network and power) are made via the rear panel of your IP60 appliance.
The following table lists the Nokia IP60 appliance's rear panel elements.
Table 3: Nokia IP60 Appliance Rear Panel Elements
Chapter 1: Introduction 23

Nokia IP60 Products
Label
Description
WAN
Wide Area Network: An Ethernet port (RJ-45) used for connecting your
broadband modem, a wide area network router, or a network leading to the
Internet
DMZ/
WAN2
A dedicated Ethernet port (RJ-45) used to connect a DMZ (Demilitarized Zone)
computer or network. Alternatively, can serve as a secondary WAN port or as a
VLAN trunk.
LAN 1-4
Local Area Network switch: Four Ethernet ports (RJ-45) used for connecting
computers or other network devices
LED
State
Explanation
PWR/SEC
Off
Power off
Flashing quickly (Green)
System boot-up
Flashing slowly (Green)
Establishing Internet connection
Flashing (Red)
Hacker attack blocked
On (Green)
Normal operation
On (Red)
Error
LAN 14/WAN/
DMZ/WAN2
LINK/ACT Off, 100 Off
Link is down
Figure 2: Nokia IP60 Appliance Front Panel
Front Panel
The Nokia IP60 appliance includes several status LEDs that enable you to monitor the appliance’s
operation.
For an explanation of the Nokia IP60 appliance’s status LEDs, see the table below.
Table 4: Nokia IP60 Appliance Status LEDs
24 Nokia IP60 Security Appliance User Guide

Nokia IP60 Products
LED
State
Explanation
LINK/ACT On, 100 Off
10 Mbps link established for the
corresponding port
LINK/ACT On, 100 On
100 Mbps link established for the
corresponding port
LNK/ACT Flashing
Data is being transmitted/received
VPN
Off
No VPN activity
Flashing (Green)
VPN activity
On (Green)
VPN tunnels established, no activity
Serial
Off
No Serial port activity
Flashing (Green)
Serial port activity
Getting to Know Your Nokia IP60 Wireless Appliance
Package Contents
The Nokia IP60 Wireless package includes the following:
Nokia IP60 Wireless Internet Security Appliance
Power supply
CAT5 Straight-through Ethernet cable
Getting Started Guide
Documentation CDROM
Wall mounting kit
RS232 serial adaptor (RJ45 to DB9)
Two antennas
USB extension cable
Chapter 1: Introduction 25

Nokia IP60 Products
Label
Description
PWR
A power jack used for supplying power to the unit. Connect the supplied power
supply to this jack.
RESET
A button used for rebooting the IP60 appliance or resetting the IP60 appliance to
its factory defaults. You need to use a pointed object to press this button.
Short press. Reboots the IP60 appliance
Long press (7 seconds). Resets the IP60 appliance to its factory defaults,
and resets your firmware to the version that shipped with the IP60
appliance. This results in the loss of all security services and
passwords and reverting to the factory default firmware. You will have
to re-configure your IP60 appliance.
Do not reset the unit without consulting your system administrator.
USB
Two USB 2.0 ports used for connecting USB-based printers or modems
Figure 3: Nokia IP60 Wireless Appliance Rear Panel
Figure 4: Nokia IP60 Wireless Appliance Rear Panel
Network Requirements
10BaseT or 100BaseT Network Interface Card installed on each computer
CAT 5 STP (Category 5 Shielded Twisted Pair) Straight Through Ethernet cable for each
attached device
An 802.11b, 802.11g or 802.11 Super G wireless card installed on each wireless station
A broadband Internet connection via cable or DSL modem with Ethernet interface (RJ-45)
Rear Panel
All physical connections (network and power) are made via the rear panel of your IP60 appliance.
The following table lists the Nokia IP60 Wireless appliance's rear panel elements.
Table 5: Nokia IP60 Wireless Appliance Rear Panel Elements
26 Nokia IP60 Security Appliance User Guide

Nokia IP60 Products
Label
Description
Serial
A serial (RS-232) port used for connecting computers in order to access the
Nokia IP60 CLI (Command Line Interface), or for connecting an external dialup
modem.
Depending on the appliance model, this port may have either a DB9 RS232
connector, or an RJ-45 connector. In models with an RJ-45 connector, an RJ-45
to DB9 converter is supplied for your convenience.
Warning: Do not connect an Ethernet cable to the RJ-45 serial port.
WAN
Wide Area Network: An Ethernet port (RJ-45) used for connecting your
broadband modem, a wide area network router, or a network leading to the
Internet.
DMZ/
WAN2
A dedicated Ethernet port (RJ-45) used to connect a DMZ (Demilitarized Zone)
computer or network. Alternatively, can serve as a secondary WAN port or as a
VLAN trunk.
LAN 1-4
Local Area Network switch: Four Ethernet ports (RJ-45) used for connecting
computers or other network devices.
ANT 1/
ANT 2
Antenna connectors, used to connect the supplied wireless antennas .
LED
State
Explanation
PWR/SEC
Off
Power off
Flashing quickly (Green)
System boot-up
Figure 5: Nokia IP60 Wireless Appliance Front Panel
Front Panel
The Nokia IP60 Wireless appliance includes several status LEDs that enable you to monitor the appliance’s
operation.
For an explanation of the Nokia IP60 Wireless appliance’s status LEDs, see the table below.
Table 6: Nokia IP60 Wireless Appliance Status LEDs
Chapter 1: Introduction 27

Nokia IP60 Products
LED
State
Explanation
Flashing slowly (Green)
Establishing Internet connection
Flashing (Red)
Hacker attack blocked
On (Green)
Normal operation
On (Red)
Error
Flashing (Orange)
Software update in progress
LAN 1-4/
WAN/
DMZ/WAN2
LINK/ACT Off, 100 Off
Link is down
LINK/ACT On, 100 Off
10 Mbps link established for the
corresponding port
LINK/ACT On, 100 On
100 Mbps link established for the
corresponding port
LNK/ACT Flashing
Data is being transmitted/received
VPN
Off
No VPN activity
Flashing (Green)
VPN activity
On (Green)
VPN tunnels established, no activity
Serial
Off
No Serial port activity
Flashing (Green)
Serial port activity
USB
Off
No USB port activity
Flashing (Green)
USB port activity
WLAN
Off
No WLAN activity
Flashing (Green)
WLAN activity
Contacting Technical Support
If there is a problem with your IP60 appliance, see http://support.nokia.com.
You can also download the latest version of this guide from the Nokia Support site.
28 Nokia IP60 Security Appliance User Guide

Introduction to Information Security
This chapter includes the following topics:
Introduction to Information Security .......................................................... 29
The Nokia IP60 Firewall ............................................................................ 32
Security
Chapter 2
This chapter explains the basic security concepts.
Introduction to Information Security
Network security is but a small part of information security, which in turn is only a fraction of general
security. In order to understand why the IP60 appliance is the best product for securing the business
network, we must first examine information security requirements in general.
Information is Valuable!
The most valuable asset an organization has is its information. The type of information maintained by an
organization depends on the organization's type and purpose. For example:
Almost every organization stores information about its operations, such as employees' names and
other personal details, salaries, and so on.
Depending on the role of different governmental offices, they may store personal information
about citizens, residential addresses, car licenses registration, and so on.
The army stores information about its soldiers, weapons inventory, and intelligence information
about other armies. Much of this information is confidential.
A bank stores information about its customers' accounts, their money transactions, ATM machine
access codes, and so on. Much of this information is confidential.
Commercial companies store information about their revenues, business and marketing plans,
current and future product lines, information about competitors, and so on.
Just as the type of information may differ from organization to organization, the form in which it is stored
may vary. For example, some forms of information are:
Information recorded in written media, such as paper documents, books, and files
Knowledge that is stored in a person's mind and can be exchanged verbally
Information stored on electronic media, such as computers' hard drives, CDs, and tapes
The form in which an organization stores its information may make the information more or less accessible
to people outside the organization.
Why Protect Business Information?
There are various reasons why it is necessary to protect business information:
Chapter 2: Security 29

Introduction to Information Security
To prevent the theft, abuse, misuse, or any form of damage to crucial information
For example, no business wants to find its customer list or future secret product line plans in the hands
of the competition.
To comply with local laws
Local laws may enforce the protection, integrity, and availability of specific information, such as an
individual's personal details, in order to respect the individual's right to privacy. Local laws may also
enforce the security requirements made in the Health Insurance Portability and Accountability Act of
1996 (HIPAA).
To comply with another organization's security requirements
Some organizations require their business partners to comply with international standards of security.
Information Security Challenges
The challenges of information security can be divided into the following areas:
Confidentiality and Privacy - Ensuring that only the intended recipients can read certain
information
Authentication - Ensuring that information is actually sent by the stated sender
Integrity - Ensuring that the original information was not altered and that no one tampered with it
Availability - Ensuring that important information can be accessed at all times and places
The Security Policy
In order to meet these challenges, an organization must create and enforce a security policy. A security
policy is a set of rules that defines how and by whom sensitive information should be accessed, handled,
and distributed, both within and outside of the organization. For example, a security policy may include the
following rules regarding visitors who arrive at an enterprise building's lobby:
Visitors must sign in at the entrance desk.
Visitors must wear a visitor badge and be escorted while in the building.
Visitors cannot use their badge to open electronic doors.
Other types of security policy rules and measures might be:
Only the executive manager has access to financial reports.
Visitors must open their bags for a security check.
Surveillance cameras should be positioned in the area of the building.
Passwords must be changed on a daily basis.
Confidential papers must be shredded after use.
An organization's security policy is usually designed by a person who is in charge of handling all security
matters for the organization. This person is called a security manager.
30 Nokia IP60 Security Appliance User Guide
 Loading...
Loading...