Page 1

© 2007-2009, NEC Computers S.A.S. All rights reserved.
NEC® GENERATION N3000
USER’S GUIDE
*Details of the product may vary from those illustrated.
After completing the steps in the Quick Start Guide that comes with your computer, your notebook
computer is ready to go! To get started, do the following:
• Read "Setting Up a Healthy Work Environment" for guidelines that help you use your computer
productively and safely. Information includes how to set up and use your computer to reduce your risk
of developing nerve, muscle, or tendon disorders.
• Read through this on-line documentation to familiarise yourself with the notebook computer.
• Register the service with NEC Computers S.A.S.:
either on line on http://ultracare.nec-computers.com;
or by filling out the UltraCare Registration Card and returning it by mail or fax (contact details on
the UltraCare Registration Card).
• Create your recovery media. See
"Master DVD Creator for Windows Vista®".
Generation N3000 M760s Rev 0.1
1
Page 2

Preface
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Copyright
Preface
Proprietary Notice and Liability Disclaimer
Copyright© 2007-2009 NEC Computers S.A.S. All Rights Reserved.
The information disclosed in this document, including all designs and related materials, is the valuable
property of NEC Computers S.A.S. and/or its licensors. NEC Computers S.A.S. and/or its licensors, as
appropriate, reserve all patent, copyright and other proprietary rights to this document, including all
design, manufacturing, reproduction, use, and sales rights thereto, except to the extent said rights are
expressly granted to others.
The NEC Computers S.A.S. product(s) discussed in this document are warranted in accordance with the
terms of the Warranty Statement accompanying each product. However, actual performance of each such
product is dependent upon factors such as system configuration, customer data, and operator control.
Since implementation by customers of each product may vary, the suitability of specific product
configurations and applications must be determined by the customer and is not warranted by
NEC Computers S.A.S.
T o allow for des ign and specification improvements, the information in this document is subject to change
at any time, without notice. Reproduction of this document or portions thereof without prior written
approval of NEC Computers S.A.S. is prohibited.
Trademark Acknowledgements
NEC®, NEC POWERMATE®, and NEC VERSA® are registered trademarks of NEC Corporation, used
under license.
Celeron®, Intel®, Intel®Centrino®Pro, Intel®Centrino®Duo, Intel®Centrino®Pro, Intel®CoreTM,
Intel®CoreTMDuo, Intel®CoreTMSolo, Intel®CoreTM2 Duo, Intel®CoreTM2Solo,
Intel®CoreTM2 Extreme, Intel®CoreTM2 Quad, Intel SpeedStep®, Intel®ViivTM, Intel®vProTM are
trademarks or registered trademarks of Intel Corporation.
AMD, AMD AthlonTM, AMD DuronTM, AMD SempronTM, AMD TurionTM, AMD K6®, AMD K6®-2,
AMD K6
®
-III, AMD K7TM, AMD K8TM, the AMD logo, and combinations thereof are trademarks of
Advanced Micro Devices, Inc.
Microsoft
®
, Windows®, Windows®XP, Windows Vista®, Windows®Mail,
Microsoft
®
Outlook®Express, Outlook 2007, Microsoft®Internet Explorer®, Excel®, AeroTM are
trademarks or registered trademarks of Microsoft Corporation in the United States and/or other countries.
Microsoft product box shot(s) reprinted with permission from Microsoft Corporation.
Microsoft product screen shot(s) reprinted with permission from Microsoft Corporation.
FreeDos
TM
is a trademark of James F. Hall, founder and coordinator of the 'FreeDOS Project'.
PS/2 is a trademark of International Business Machines, Inc.
The Bluetooth® word mark, figure mark, and combination mark are registered trademarks and are wholly
owned by the Bluetooth SIG.
Other product names mentioned in this manual may be trademarks or registered trademarks of their
respective companies. NEC Computers S.A.S. claims no interest in trademarks other than its own.
2
Page 3

Preface
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Text Set-Up
Preface
To make this guide as easy to use as possible, the text is laid out as follows.
Note: notes give particularly important information about whatever is being described.
Caution: cautions indicate situations that can damage the system hardware or software.
Warning: warnings alert you to situations that could result in serious personal injury or loss
of life.
Eco-friendly: Tips and tricks to help you use your computer in an eco-friendly manner.
• Names of keys are printed as they appear on the keyboard.
For example, Ctrl, Alt, or Enter.
• Text that you must type is printed in bold type.
For example, type dir.
• Window titles, field names, pane names, application names, list box names... are printed in italic type.
For example, the Power Options Properties window.
• Buttons, check box names, tabs, icons, menus, menu choices, key names... are printed in bold type.
For example, click Start, and select Programs.
• Click on the hyperlinked text for more information on the subject.
3
Page 4

Preface
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Safety and Environment Notices
Preface
Information to User of Class B Computer Device
European Notice
Products with the CE marking comply with both the ElectroMagnetic Compatibility Directive (2004/108/
EEC) and the Low Voltage Directive (2006/95/EEC) issued by the Commission of the European
Community.
Compliance with these directives implies conformity to the following European Standards:
• EN55022: Radio Disturbance Characteristics
• EN55024: Immunity Characteristics
• EN60950-1: Product Safety - If your computer includes a telecommunication network board, the input/
output socket is classified as Telecommunication Network Voltage (TNV-3)
• EN61000-3-2: Limitation of harmonic current emissions
• EN61000-3-3: Limitation of voltage fluctuation and flicker in low-voltage supply system
Modem (for models with modem)
The equipment has been approved in accordance with Council Decision 98/482/EC for pan-European
single terminal connection to the Public Switched Telephone Network (PSTN). However, due to
differences between the individual PSTNs provided in different countries, the approval does not, of itself,
give an unconditional assurance of successful operation on every PSTN network termination point.
In the event of problems, you should contact your equipment supplier in the first instance.
Modifications to the product
Preface
CE marking
NEC Computers S.A.S. cannot be held responsible for unauthorized modifications made by the user and
the consequences thereof, which may alter the conformity of the product with the CE Marking.
Radio Frequency Interference Statement
Caution: changes or modifications to this unit not expressly approved by the party responsible
for compliance could void the user's authority to operate the equipment.
Note: this is a Class B Digital Device. This equipment has been tested and found to comply with
the limits for a Class B digital device, pursuant to Part 15 of the FCC Rules. These limits are
designed to provide reasonable protection against harmful interference in a residential installation.
This equipment generates, uses and can radiate radio frequency energy and, if not installed and
used in accordance with the instructions, may cause harmful interference to radio communications.
There is no guarantee, however, that interference will not occur in a particular installation. If this
equipment does cause harmful interference to radio or television reception, which can be determined by
4
Page 5

Preface
© 2007-2009, NEC Computers S.A.S. All rights reserved.
turning the equipment off and on, the user is encouraged to try to correct the interference by one or more
of the following measures.
• Reorient or relocate the receiving antenna.
• Increase the distance between the equipment and receiver.
• Connect the equipment to an outlet on a circuit different from the one to which the receiver is
connected.
To meet FCC standards, shielded cables and power cords are required to connect this device to a personal
computer or other Class B certified device.
Radio-communications Regulations (if applicable)
Specific regulations apply when using wireless radio-communication products.
If your system features Wireless LAN and/or Bluetooth capabilities, follow the links below for more
information on these regulations:
• "802.11x Wireless LAN Regulations", also known as Wireless LAN
• "Bluetooth
®
Regulations"
Note: Hereby, NEC Computers S.A.S., declares that this computer is in compliance with the
essential requirements and other relevant provisions of Directive 1999/5/EC.
Connections and Remote Earths
PELV (Protected Extra Low Voltage)
To ensure the extra-low voltage integrity of the equipment, only connect equipment with mains-protected
electrically-compatible circuits to the external ports.
SELV (Safety Extra Low Voltage)
Every input and output of this product is classified as Safety Extra Low Voltage.
Remote earths
To prevent electrical shock, connect all local (individual office) computers and computer support
equipment to the same electrical circuit of the building wiring. If you are unsure, check the building
wiring to avoid remote earth conditions.
Building supply
Only connect the equipment to a building supply that is in accordance with current wiring regulations in
your country. In the U.K., these are the IEE regulations.
Laser Compliance Statement
The optical devices are tested and certified to be compliant with International Electrotechnical
Commission IEC60825-1 and European EN60825-1 standards for Class 1 laser products.
5
Page 6

Preface
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Class 1 laser products are not considered hazardous. The optical devices are designed such that there is
never human access to laser radiation above a Class 1 level during normal operation or prescribed
maintenance conditions.
The optical devices installed in your computer is designed for use solely as a component of such
electronic product and therefore does not comply with the appropriate requirements of Code of Federal
Regulation Sec. 1040.10 and Sec. 1040.11 for COMPLETE laser products.
Because exposure to laser radiation is extremely hazardous, under no circumstances should the user
attempt to disassemble the laser device.
Safety And Maintenance Precautions
1. Read all of these instructions.
2. Save these instructions for future use.
3. Follow all warnings and instructions marked on the products.
4. Unplug this product from the wall outlet before cleaning. Do not use liquid or aerosol cleaners. Use a
damp cloth for cleaning.
5. Do not use this product near water.
6. Do not place this product on an unstable surface. If the product should fall, it may become seriously
damaged and, more importantly, may cause injury to the user.
7. This product should be operated from the type of power source indicated on the label. If you are not
sure of the type of power available, consult your dealer or local power company.
8. Never push objects of any kind into this product through cabinet slots, as they may touch dangerous
voltage points or cause short circuits, risking the possibility of a fire or electric shock. Never spill
liquid of any kind onto the product.
9. Do not attempt to service this product yourself. If you have the slightest suspicion that the product is
not in proper working order, unplug the unit and seek assistance from qualified service personnel,
especially under the following conditions:
• When the power cord or plug is damaged or frayed.
• If liquid has been spilled onto the product, or if the product has been exposed to water.
• If the product has been dropped or the cabinet has been damaged.
• If the product exhibits a distinct deterioration in performance, indicating a need for service.
If the product does not operate normally when the operating instructions are followed, adjust only those
controls that are covered by the operating instructions, since improper adjustment of other controls may
result in further damage or complications.
Power Supply, AC Adapter and Cables
AC Adapter
You must unplug the AC adapter cord to disconnect the equipment from the power supply. In that aim, the
socket-outlet should be installed near to the equipment and should be easily accessible.
6
Page 7

Preface
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Under no circumstances should the user attempt to disassemble the AC adapter. The AC adapter has no
user-replaceable parts. Inside the AC adapter are hazardous voltages that can cause serious personal
injury. A defective AC adapter must be returned to your dealer.
The AC adapter is intended for use with a computer and meets EN60950 standards.
• Do not cover or place objects on the AC Adapter. Keeping the adapter clear of objects lets the adapter
cool properly during use.
• The AC adapter is intended for use in a protected environment.
• Only use the AC adapter that comes with your system. Although other adapters may look similar, using
them can damage your system.
Power Cables
Warning: Do not hold the power plug with a wet hand.
Do not disconnect/connect the plug while your hands are wet. Failure to follow this warning
may cause an electric shock.
Use the authorized power cord only.
Use only the power cord that comes with your equipment. Using an unauthorized power cord may cause a
fire when the electric current exceeds the rated flow.
Also, observe the following to prevent an electric shock or fire caused by a damaged cord.
• Do not stretch the cord harness.
• Do not alter, modify, or repair the power cord.
• Do not bend the power cord.
• Do not twist the power cord.
• Do not step on the power cord. Keep chemicals away from the power cord.
• Do not bundle power cords.
• Do not place any object on the power cord.
• Do not pinch the power cord.
• Do not secure the power cord with staples or equivalents.
Do not use the attached power cord for any other devices or usage.
The power cord that comes with your equipment is designed to connect with this equipment, and its safety
has been tested. Do not use the attached power cord for any other purpose. Doing so may cause a fire or an
electric shock.
Do not pull the cord harness to disconnect the power cord.
Hold the connector of the power cord and pull it straight. Pulling the cord harness or applying excess force
to the connector may cause a damage to the cable, resulting in a fire or an electric shock.
7
Page 8

Preface
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Replacing the Power Cord
Replace the power cord if it gets damaged. Contact your dealer for an exact replacement. The replacement
must be of the same type and voltage rating as the original cord. Refer to the information indicated on the
original power cord.
The plug must display an international agency approval marking. The cord must be suitable for use in the
end-user country. Consult your dealer or the local electrical authorities if you are unsure of the type of
power cord to use in your country.
Extension Cord
If an extension cord is used with this product, make sure that the sum of the ampere ratings of all the
products plugged into the extension cord does not exceed the extension cord's ampere rating. Also, make
sure that total amperage of all the products plugged into any one outlet at any one time does not exceed 15
amperes.
Cables
The EMC performances of system are guaranteed provided that efficient shields are used on cable’s
interface.
The use of shielded interface cable is required for USB, IEEE1394, serial, printer, game, analogue or
digital audio/video, Ethernet LAN, PS\2, TV or FM antennas, and generally all high speeds cables’
interfaces.
Only Ethernet LAN or RTC modem cable can have length exceeding 3 meters.
For Ethernet LAN cable, use FTP shielded cables only (cat 5).
Batteries
Using the Battery Pack
For battery precautions, please refer to"Battery Precautions".
Replacing Batteries
A lithium battery maintains system configuration information. In the event that the battery fails to
maintain system configuration information, we recommend that you replace the battery.
Please contact your service representative or your T echnical Support Centre if this CMOS battery needs to
be replaced.
For battery disposal, please refer to "Battery Disposal".
Using this Equipment
Do not disassemble, repair, or alter the equipment.
Never attempt to disassemble, repair, or alter the equipment on any occasion other than described in this
manual. Failure to follow this instruction may cause an electric shock or fire as well as malfunctions of the
equipment.
8
Page 9

Preface
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Chassis Cover Removal and Replacement
Before removing the chassis cover to service or modify the equipment, you must disconnect all power and
modem cords (and remove the main battery in portable computers).
Replace the chassis cover and secure it with the screws before plugging in the power cable and turning it
on.
Avoid contact with the equipment during thunderstorms.
In thunderstorm conditions, make sure that you disconnect your modem from the telephone line or your
TV port from the aerial socket. A lightning strike to nearby telephone lines or an aerial could damage your
modem, TV card or even your whole computer system. Please note that the product warranty does not
apply if damage to your computer is the result of a lightning strike.
Excessive sound pressure from earphones and headphones can cause
hearing loss.
Adjustment of the equalizer to other values than the neutral or centre position may increase the earphones
and headphones output voltage and therefore the sound pressure level.
Other influencing factors relevant for the earphones/headphones output and which are specified by the
manufacturer (e.g. operating system, other equalizer software, firmware and drivers) may increase the
earphones and headphones output voltage and therefore the sound pressure level.
Heat Build-Up
The AC adapter and the underside of the computer can become hot after prolonged use. Sustained
physical contact with either should be avoided.
Glass Display
Take care when handling, cleaning transporting or storing the computer. Do not:
• Press against, bend or twist the screen.
• Close the lid with anything on the keyboard.
• Transport in a container with a shard, hard object against the lid.
Any of the above actions may result in damage to the screen.
Air Circulation - System Cooling
Slots and openings in the cabinet are provided for ventilation to ensure reliable operation of the product
and to protect it from overheating. These openings should never be blocked or covered. The openings
should never be blocked by placing the product on a bed, sofa, rug or other similar surfaces. This product
should never be placed near or over any object which produces heat. This product should not be placed in
a built-in installation unless proper ventilation is provided.
Caution: Storing your notebook computer in a low-airflow environment (e.g. a closed briefcase)
while it is running may damage it or cause fire.
9
Page 10
Preface
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Environmental Information
This product is prepared for recycling, and was the subject of restrictions on both chlorinated and
brominated flame retardants and polymers, and heavy metals such as cadmium, mercury and lead.
ENERGY STAR® Compliance
NEC computers bearing the ENERGY STAR® logo are compliant with the
ENERGY STAR® specifications for computers set forth by the Environmental
Protection Agency (EPA). As an ENERGY STAR® Partner,
NEC Computers S.A.S. has determined that the products marked with the
ENERGY STAR® logo meet the ENERGY STAR® guidelines for energy
efficiency.
NEC computers that have earned the ENERGY STAR® logo help save energy
(and then money), through special energy-efficient designs, which allow them to
use less energy to perform regular tasks, and automatically enter a low-power mode when not in use.
ENERGY STAR® power management features place monitors and computers into a low-power mode
after a period of inactivity. They have been set for the ENERGY STAR®-compliant configurations as
follows:
• after 15 minutes of inactivity for the monitor
• after 30 minutes of inactivity for the computer.
Simply touching the mouse or keyboard wakes the computer and monitor in seconds.
By choosing an ENERGY STAR®-compliant computer, you help fight global warming and promote
cleaner air without sacrificing the product quality and performance you expect from an NEC computer.
More information at http://www.energystar.gov.
Product Disposal
The Waste Electrical and Electronic Equipment (WEEE) Directive requires that used
electrical and electronic products must be disposed of separately from normal household
waste in order to promote reuse, recycling, other forms of recovery and to reduce the
quantity of waste to be eliminated with a view to reducing landfill. This includes
accessories such as a keyboard, mouse, remote control, speakers, etc. When you dispose of
such products, please follow the agreement made between you and NEC Computers S.A.S.
and/or your retailer.
Battery Disposal
Warning: there is a danger of explosion if the battery is incorrectly replaced or disposed of in
fire. Replace only with the same or equivalent type recommended by the manufacturer.
Ultimate disposal of the batteries should be handled according to all national laws and regulations. Do not
place used batteries in your regular waste: the incineration, landfilling or mixing of batteries with the
municipal solid waste stream is prohibited by law in most countries. Contact your local waste
management officials for other information regarding the environmentally sound collection, recycling,
and disposal of the batteries.
10
Page 11

Preface
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Lead-free Product
NEC Computers S.A.S. eliminated toxic substances like lead from its products. A lead-free product helps
protect your health and promotes environmentally sound recovery and disposal of waste from electrical
and electronic equipment. NEC Computers S.A.S. complies with the European Community stringent
RoHS Directive mandating restrictions on hazardous substances in electrical and electronic equipment.
For information on the NEC Computers S.A.S. recycling program, refer to:
http://www.nec-eco.com/
11
Page 12

Preface
© 2007-2009, NEC Computers S.A.S. All rights reserved.
802.11x Wireless LAN Regulations
Preface
Note: Due to the evolving state of regulations and standards in the wireless LAN fields
(IEEE802.11 and similar standards), the information provided here is subject to change.
NEC Computers S.A.S. assumes no responsibility for errors or omissions in this document.
Wireless Network Device and Your Health
The wireless network device installed in your system, like other radio devices, emits radio frequency
electromagnetic energy. The level of energy emitted by this device, however, is less than the
electromagnetic energy emitted by other wireless devices such as mobile phones. The wireless network
device operates within the guidelines found in radio frequency safety standards and recommendations.
These standards and recommendations reflect the consensus of the scientific community and result from
deliberations of panels and committees of scientists who continually review and interpret the extensive
research literature. In some situations or environments, the use of the wireless network devices may be
restricted by the proprietor of the building or responsible representatives of the applicable organization.
Examples of such situations include the following:
• Using the wireless network device on board air planes.
• Using it in any other environment where the risk of interference with other devices or services is
perceived or identified as being harmful.
If you are uncertain of the policy that applies to the use of wireless devices in a specific organization or
environment (an airport, for example), you are encouraged to ask for authorization to use the wireless
network device before you turn it on.
European Declaration of Conformity
This equipment complies with the essential requirements and other
relevant provisions of the European Union directive 1999/5/EC.
The wireless network device must be used in strict accordance
with the manufacturer's instructions as described in the user
documentation that comes with the product. NEC Computers S.A.S. is not responsible for any radio or
television interference caused by unauthorized modification of the devices included with the network
connection kit, or the substitution or attachment of connecting cables and equipment other than that
specified by NEC Computers S.A.S. The correction of interference caused by such unauthorized
modification, substitution or attachment is the responsibility of the user. NEC Computers S.A.S. and its
authorized resellers or distributors are not liable for any damage or violation of government regulations
that may arise from the user failing to comply with these guidelines.
Local Restriction of 802.11a, b, g, n Radio Usage
Due to the fact that the frequencies used by 802.11a, 802.11b, 802.11g and 802.11n wireless LAN devices
may not yet be harmonized in all countries, 802.11a, 802.11b, 802.11g and 802.11n products are designed
for use only in specific countries, and are not allowed to be operated in countries other than those listed in
"NEC Generation N3000 Specifications""NEC Versa M580 Specifications".
As a user of these products, you are responsible for ensuring that the products are used only in the
countries for which they were intended and for verifying that they are configured with the correct
selection of frequency and channel for the country of use. Any deviation from permissible settings and
restrictions in the country of use could be an infringement of national law and may be punished as such.
12
Page 13

Preface
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Bluetooth® Regulations
Preface
Bluetooth Device and Your Health
The bluetooth device installed in your system, like other radio devices, emits radio frequency
electromagnetic energy. The level of energy emitted by this device, however, is less than the
electromagnetic energy emitted by other wireless devices such as mobile phones. The bluetooth device
operates within the guidelines found in radio frequency safety standards and recommendations. These
standards and recommendations reflect the consensus of the scientific community and result from
deliberations of panels and committees of scientists who continually review and interpret the extensive
research literature. In some situations or environments, the use of the bluetooth devices may be restricted
by the proprietor of the building or responsible representatives of the applicable organization. Examples
of such situations include the following:
• Using the bluetooth device on board air planes.
• Using it in any other environment where the risk of interference with other devices or services is
perceived or identified as being harmful.
If you are uncertain of the policy that applies to the use of bluetooth devices in a specific organization or
environment (an airport, for example), you are encouraged to ask for authorization to use the bluetooth
device before you turn it on.
European Declaration of Conformity
This product is in compliance with the essential requirements and other relevant provisions of the
European Directive 1999/5/EC.
The bluetooth device must be used in strict accordance with the manufacturer's instructions as described
in the user documentation that comes with the product. NEC Computers S.A.S. is not responsible for any
radio or television interference caused by unauthorized modification of the devices included with the
network connection kit, or the substitution or attachment of connecting cables and equipment other than
that specified by NEC Computers S.A.S. The correction of interference caused by such unauthorized
modification, substitution or attachment is the responsibility of the user. NEC Computers S.A.S. and its
authorized resellers or distributors are not liable for any damage or violation of government regulations
that may arise from the user failing to comply with these guidelines.
Note: In some countries the use of the Bluetooth
®
technology is restricted. Before using it, make
sure you read the restriction information in the "NEC Generation N3000 Specifications".
Note: In some countries the use of the Bluetooth
®
technology is restricted. Before using it, make
sure you read the restriction information in the "NEC Versa M580 Specifications"
13
Page 14

Preface
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Maintenance Safety Precautions
Preface
Observe safety rules when working inside the system and when handling computer components. Avoid
electric shock or personal injury by observing the following warning.
Hazardous Voltage
Warning: before removing the system unit cover, turn off the power and unplug the system
power cable (and remove the main battery in portable computers). Power is removed only when
the power cable is unplugged.
Electrostatic Discharge
Warning: your computer's internal components are highly susceptible to risk of damage from
electrostatic discharge (static electricity, which occurs naturally on your body due to friction).
To avoid damaging your equipment, always earth yourself to your computer system before
opening the computer's chassis or handling any internal component(s).
To do this, use the following procedure:
1. For best results, we strongly recommend you purchase
an anti-static wrist strap (available at electronic supply
stores). To use it, connect the strap's metal “alligator
clip” to an unpainted metal portion of your computer's
chassis.
2. Then connect the elastic wrist band to the strap, and
slide the wrist band onto your wrist.
Note: if you do not have a wrist strap, you can earth yourself by touching (and maintaining
continuous contact with) an unpainted metal part of the computer's chassis while handling any of
your computer's internal components or working inside the system.
Safety Rules
• Select a suitable work space
Avoid carpets in cool, dry areas.
When you work on a carpet where static electricity is likely to be generated, make sure you take
anti-static measures beforehand.
• Cloth
Do not wear a wool or synthetic cloth to work inside the computer.
Wear anti-static shoes to work inside the computer.
Take off any jewels (a ring, bracelet, or wrist watch) before working inside the computer.
• Handling of components
Keep any component in an anti-static bag until you actually install it to the computer.
Hold a component by its edge to avoid touching any terminals or parts.
14
Page 15

Preface
© 2007-2009, NEC Computers S.A.S. All rights reserved.
To store or carry any component, place it in an anti-static bag.
Turn off and disconnect all peripherals.
Do not disassemble parts other than those specified in the procedure.
Label any cable connectors before disconnecting. Note where the connector goes and in what
position it was installed.
Take care when connecting or disconnecting cables. A damaged cable can cause a short in the
electrical circuit.
When installing a cable, route the cable so it is not pinched by other components and is out of the
path of the system unit cover.
Prevent damage to the connectors by aligning connector pins before you connect the cable.
Misaligned connector pins can cause damage to system components at power-on.
When disconnecting a cable, always pull on the cable connector or strain-relief loop, not on the
cable itself.
Chassis Cover Removal and Replacement
When working inside your computer, you must replace the chassis cover and secure it with the screws
before plugging in the power cable and turning it on.
15
Page 16

Preface
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Setting Up a Healthy Work Environment
Preface
Warning: prolonged or improper use of a computer workstation may pose a risk of serious
injury (see "Potential Medical Conditions"). Please note that some people are more susceptible to
developing these disorders due to pre-existing conditions or psychosocial factors (see "Pre-
Existing Conditions and Psychosocial Factors"). To reduce your risk of injury, set up and use
your computer in the manner described in the "Arrange Your Equipment" section. Please note
that precautions can be taken in order to prevent physical discomfort (see "Reducing The Risk of
Injuries").
Potential Medical Conditions
Computers are everywhere. More and more people sit in front of computers for longer periods of time.
Some nerve, tendon and muscle disorders (musculoskeletal disorders) may be associated with repetitive
activities, improper work environments, and incorrect working habits. Examples of musculoskeletal
disorders that may be associated with certain forms of repetitive activities include: carpal tunnel
syndrome, tendinitis, tenosynovitis, de Quervain's tenosynovitis and trigger finger, as well as other nerve,
tendon and muscle disorders.
Although some studies have shown an association between increasing hours of keyboard use and the
development of some musculoskeletal disorders, it is still unclear whether working at a computer causes
such disorders. Some doctors believe that using the keyboard and mouse may aggravate existing
musculoskeletal disorders.
Note: contact a doctor if you experience pain, tenderness, swelling, burning, cramping, stiffness,
throbbing, weakness, soreness, tingling and/or numbness in the hands, wrists, arms, shoulders,
neck, back and/or legs.
Repetitive Strain Injury (RSI)
Repetitive Strain Injury is caused by a constant tension of the muscles in your arms and by making the
same repetitive movements with fingers, wrist and elbow when controlling the mouse. The symptoms of
RSI are pain and stiffness in neck, shoulders, arms, wrists and hands. Other symptoms are cramps,
tingling and exhaustion in these areas.
From Monks to Video Games Users
Repetitive Strain Injury might seem a modern age disease, caused by the increasing use of computers at
work and at home, but monks already caught it in the Middle Ages. In the 16th century the Italian doctor
Ramazini described the same symptoms among monks writing bibles day in day out in cold and dark
rooms. In later centuries similar symptoms like knitting-, telegrapher-, hairdresser- and violin arms
occurred more often. The latest versions of RSI are caused by minor movements of the thumb when
operating the joystick of a game console.
16
Page 17

Preface
© 2007-2009, NEC Computers S.A.S. All rights reserved.
The Three Stages of Repetitive Strain Injury
Real RSI-pain implies that the problems persist for a longer period of time, normally for a minimum of
three months. The development can be divided into three stages:
• Stiffness, numbness, irritation, sometimes in combination with light or sharp pains. These problems
disappear, but return when similar work is done.
• The problems do not disappear overnight. Continuous light pain, also after a period of rest. After a
longer period of rest (holidays) the pain does go away, but returns easily when similar work is done.
• Continuous pain often combined with reduced strength and less accurate control. At work, the pain
intensifies. When rested, the pain remains.
Pre-Existing Conditions and Psychosocial Factors
Pre-existing conditions that may cause or make some people more susceptible to musculoskeletal
disorders include the following: hereditary factors, vascular disorders, obesity, nutritional deficiencies
(e.g., Vi tamin B deficiency), endocrine disorders (e.g., diabetes), hormonal imbalances, connective tissue
disorders (e.g., arthritis), prior trauma (to the hands, wrists, arms, shoulders, neck, back, or legs), prior
musculoskeletal disorders, aging, fluid retention due to pregnancy, poor physical conditioning, dietary
habits and other conditions.
Psychosocial factors associated with these disorders include: workplace stress, poor job satisfaction, lack
of support by management and/or lack of control over one's work.
Reducing The Risk of Injuries
The precautions described below can be taken in order to prevent physical discomfort.
Vary Your Workday
If you use your computer for prolonged periods, follow these instructions.
• Vary your tasks throughout the day.
• Take frequent short breaks that involve walking, standing, and stretching. During these breaks, stretch
muscles and joints that were in one position for an extended period of time (refer to "Practice Some
Stretching Exercises" below). Relax muscles and joints that were active.
• Use a timer or reminder software to remind you to take breaks.
• To enhance blood circulation, alter your sitting posture periodically and keep your hands and wrists
warm.
Practice Some Stretching Exercises
The daily exercises described below can be very effective in stopping Repetitive
Strain Injury development or minimising its effects. They can easily be carried out
behind your PC.
17
Page 18

Preface
© 2007-2009, NEC Computers S.A.S. All rights reserved.
• Bend wrists, stretch and close fingers - stretch your arms and wrists with closed fingers; keep this
pose for 8 seconds. Repeat the exercise 3 times. You can repeat the same exercise with your finger
stretched.
• Lift shoulders - lift your shoulders straight up, hold that pose for 8 seconds and repeat the exercise 3
times.
• Rotate shoulders - rotate both your shoulders clockwise and counter-clockwise for 8 seconds. Repeat
this exercise 3 times.
• Stretch neck and shoulders - bend your head to the left, right, front and back. Keep each position for
8 seconds. Repeat this exercise 3 times.
• Stretch the flexors - fold your hands into a praying position; palms flat against each other in front of
your chest. Pull your hands gently downwards along your chest towards the stomach, keeping the
elbows in the same position. Repeat the exercise 3 times and keep the pose for 8 seconds.
• Stretch the extensors - stretch your arm straightforward. Rotate your hand 90 degrees and keep your
thumb down. Grab your hand with your other hand, and gently pull your hand towards you. Hold this
pose for 8 seconds and repeat this exercise 3 times.
Arrange Your Equipment
You will find below explanations on how to set up your computer to fit your physical needs. This
information is based on ergonomics - the science of making the workplace fit the needs of the worker.
Note: To increase your comfort and safety when using your notebook computer as your
primary computer system at your home or office, note the following recommendations:
• use a separate, external keyboard attached to your notebook computer
• use a separate, external monitor attached to your notebook computer.
Arrange your equipment so that you can work in a natural and relaxed position. Place items that you use
frequently within easy reach. Adjust your workstation set-up to the proper height (as described below) by
lowering the table or stand that holds your computer equipment or raising the seat height of your chair.
Position your computer directly in front of you for increased safety and comfort.
Your Chair
Your chair should be adjustable and stable. Vary your posture throughout the day. Check the following:
• Keep your body in a relaxed yet upright position. The backrest of your
chair should support the inward curve of your back.
• Use the entire seat and backrest to support your body . Tilt the backrest
slightly (90° to 105°). The angle formed by your thighs and back
should be 90° or more.
• Your seat depth should allow your lower back to comfortably contact
the backrest. Make sure that the backs of your lower legs do not press
against the front of the chair.
18
Page 19

Preface
© 2007-2009, NEC Computers S.A.S. All rights reserved.
• Extend your lower legs slightly so that the angle between your thighs and lower legs is 90° or more.
• Place your feet flat on the floor. Only use a footrest when attempts to adjust your chair and workstation
fail to keep your feet flat.
• Be sure that you have adequate clearance between the top of your thighs and the underside of your
workstation.
• Use armrests or forearm supports to support your forearms. If adjustable, the armrests or forearm
supports should initially be lowered while all the other adjustments discussed in this section are made.
Once all these adjustments are completed, raise the armrests or adjust the forearm supports until they
touch the forearms and allow the shoulder muscles to relax.
Yo u r De s k
There is no specific height recommended for your desk. This can vary between 60 to 70 cm, depending
upon your size. The standard workaround is that it should be at approximately your elbow height.
The desktop should be clean and organized in such a way that frequently used objects are close enough
without excessive reaching. If you use a document holder, it should be placed at approximately the same
height as the monitor and at the same distance from the eyes to prevent frequent eye shifts.
The area underneath the desk should be clean to accommodate your legs and allow for stretching.
Your Input Devices
Note the following points when positioning your computer or any external input devices.
• Position your keyboard directly in front of you. Avoid reaching when using your keyboard or mouse.
• If you use a mouse, position it at the same height as the keyboard and next to the keyboard. Keep your
wrists straight and use your entire arm when moving a mouse. Do not grasp the mouse tightly. Grasp
the mouse lightly and loosely.
• Adjust the keyboard height so that your elbows are near your body and your forearms are parallel to the
floor, with your forearms resting on either armrests or forearm supports, in the manner described
previously. If you do not have armrests or forearm supports, your upper arms should hang comfortably
at your sides.
• Adjust the keyboard slope so that your wrists are straight while you are typing.
• Type with your hands and wrists floating above the keyboard. Use a wrist pad only to rest your wrists
between typing. Avoid resting your wrists on sharp edges.
• Type with your wrists straight. Instead of twisting your wrists sideways to press hard-to-reach keys,
move your whole arm. Keep from bending your wrists, hands, or fingers sideways.
• Press the keys gently; do not bang them. Keep your shoulders, arms, hands and fingers relaxed.
19
Page 20

Preface
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Your Screen or Monitor
Correct placement and adjustment of the screen or external monitor can reduce eye, shoulder, and neck
fatigue. Check the following when you position the screen or external monitor.
• Adjust the height of your screen or external monitor so that the top of the screen is at or slightly below
eye level. Your eyes should look slightly downward when viewing the middle of the screen or external
monitor.
• Position your screen or external monitor no closer than 30 cm and no further away than 75 cm from
your eyes. The optimal distance is between 35 cm and 45 cm.
• Rest your eyes periodically by focusing on an object at least 6 metres away. Blink often.
• Position the screen or external monitor at a 90° angle to windows and other light sources to minimise
glare and reflections. Adjust the monitor tilt so that ceiling lights do not reflect on your screen or
external monitor.
• If reflected light makes it hard for you to see your screen or external monitor, use an anti-glare filter.
• Clean your screen or external monitor regularly. Use a lint-free, non-abrasive cloth and a non-alcohol,
neutral, non-abrasive cleaning solution or glass cleaner to minimise dust.
• Adjust the screen or external monitor's brightness and contrast controls to enhance readability.
• Use a document holder placed close to the screen or external monitor.
• Position whatever you are looking at most of the time (the screen or reference material) directly in front
of you to minimise turning your head while you are typing.
• Get regular eye check-ups.
Your Sound Devices
Excessive sound pressure from earphones and headphones can cause hearing loss.
• Keep your computer’s sound level low.
• Get regular hearing check-ups.
20
Page 21

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Around the Front of the System
Discovering Your Computer
Figure 1: Front features
A Integrated Camera (optional) - allows you to create video or to capture pictures. The camera can also
be used for video conferencing.
Note: Please remove the camera lens protection sheet before using it.
B LCD Panel - the notebook computer comes with a colour LCD panel that you can adjust for a
comfortable viewing position.
C Speakers - provide stereo sound for your multimedia presentations or listening pleasure.
D Power Button - refer to the "Buttons" section below for details.
E Keyboard - standard QWERTY-key layout. For more information, refer to "Keyboard".
F Microphone - Allows you to record mono sound with your computer. Refer to "Audio".
G Touchpad - works like a standard computer mouse. Refer to "Touchpad" below for details.
H Status LEDs - refer to "Status LEDs" below for details.
I Buttons - refer to "Buttons" below for details.
J Wireless Antennae - refer to "Wireless Antennae" below for details.
21
Page 22

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Status LEDs
• Power Status LED:
Lights green: the computer is on.
Blinks green: the computer is in a power-saving mode.
• Battery Status LED:
Lights green: the battery is fully charged or empty.
Lights orange: the battery is charging.
Blinks orange rapidly: the battery is almost discharged
Note: If the LED blinks when powering on your computer, there is not enough battery
power to boot up the system. Attach the AC adapter. Refer to "Connecting the AC Adapter".
• Wireless LAN / Bluetooth Status LED:
Off: wireless LAN / Bluetooth feature is off.
lights green: the wireless LAN feature is enabled.
lights orange: the Bluetooth feature is enabled.
lights yellow: the Bluetooth and the wireless LAN features are enabled.
Note: The wireless LAN status LED only lights if your system is equipped with a wireless
LAN board.
• Num Lock LED: lights green when Num Lock is active.
• Disk Drive Access LED: blinks green when the system is accessing the hard disk drive.
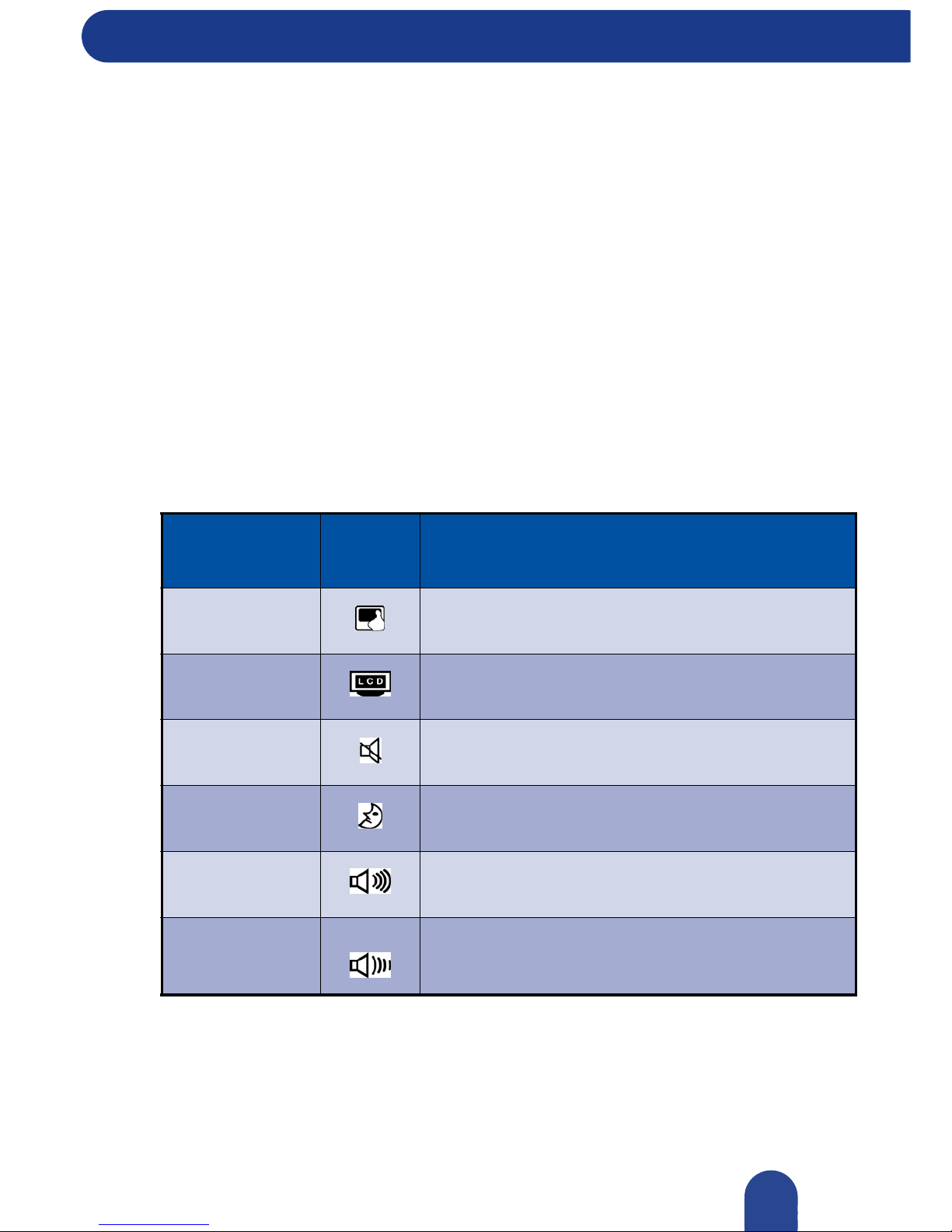
Buttons
Quick Launch Email Button
Press to launch your messaging software.
Quick Launch Web Button
Press to launch your navigating software.
Quick Launch Silent Mode Button
Press to launch the silent mode for power saving.
Note: When enabled, Silent Mode reduces fan noise and saves power consumption. This may
reduce computer performance.
22
Page 23
Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Power Button
The power button defaults are defined as described in the Advanced features of the Power Options
Properties. Refer to:
"Managing System Power (Windows Vista®)".
• Power on or off the system when pressed.
If you modify the Power Button option to a power-saving mode, please note the following:
• Briefly press the power button to put the system in a power-saving mode.
• Press and hold the power button in place for 4 or more seconds to initiate power override (powers off
the system). Only use this option if you cannot power off your system using the normal procedure
described in the tips section relevant to your operating system. Refer to:
"Tips for Using Microsoft® Windows Vista®".
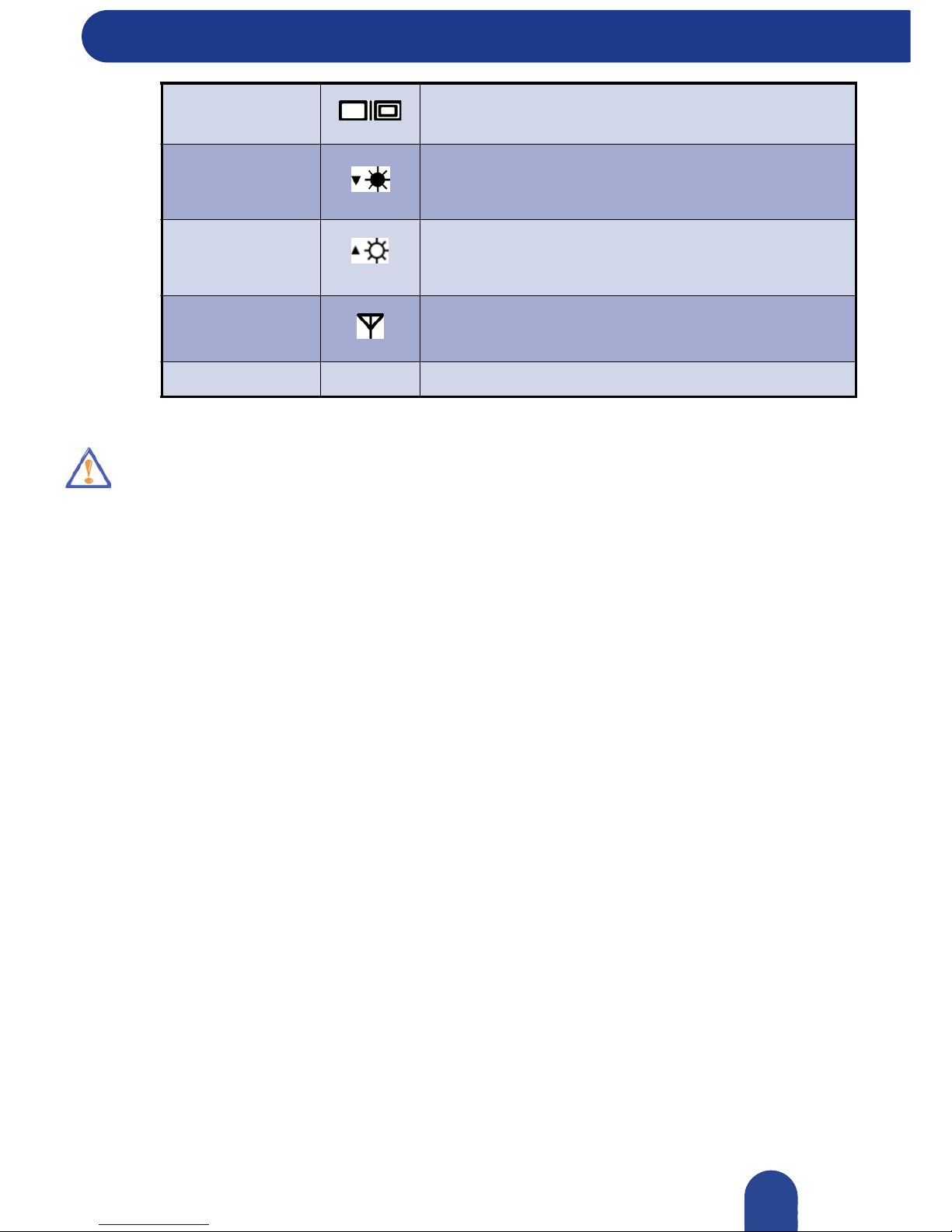
Keyboard
The following function key combinations are pre-programmed for the notebook computer.
Key
Combination
Symbol
on key
Associated Action
Fn-F1 Activates and deactivates the touchpad.
Fn-F2 Turns screen backlight off.
Fn-F3 Sets the internal speakers to mute.
Fn-F4 Puts the computer in a sleep mode.
Fn-F5 Decreases the speaker volume.
Fn-F6 Increases the speaker volume.
Table 1: Key combinations
23
Page 24
Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Caution: When you press Fn-F10, the webcam is disabled and is not visible anymore in the
Device Manager menu. Press Fn-F10 again to turn on the camera.
Refer also to "Using the Keyboard".
Fn-F7
Toggles the video mode between the notebook computer
screen and an external monitor.
Fn-F8
Decreases the LCD brightness. This only affects the display
on your notebook computer, not on monitors connected to
your notebook computer.
Fn-F9
Increases the LCD brightness. This only affects the display
on your notebook computer, not on monitors connected to
your notebook computer.
Fn-F11 Sets the wireless connection.
Fn-F12 Sets the bluetooth connection.
Table 1: Key combinations (continued)
24
Page 25
Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
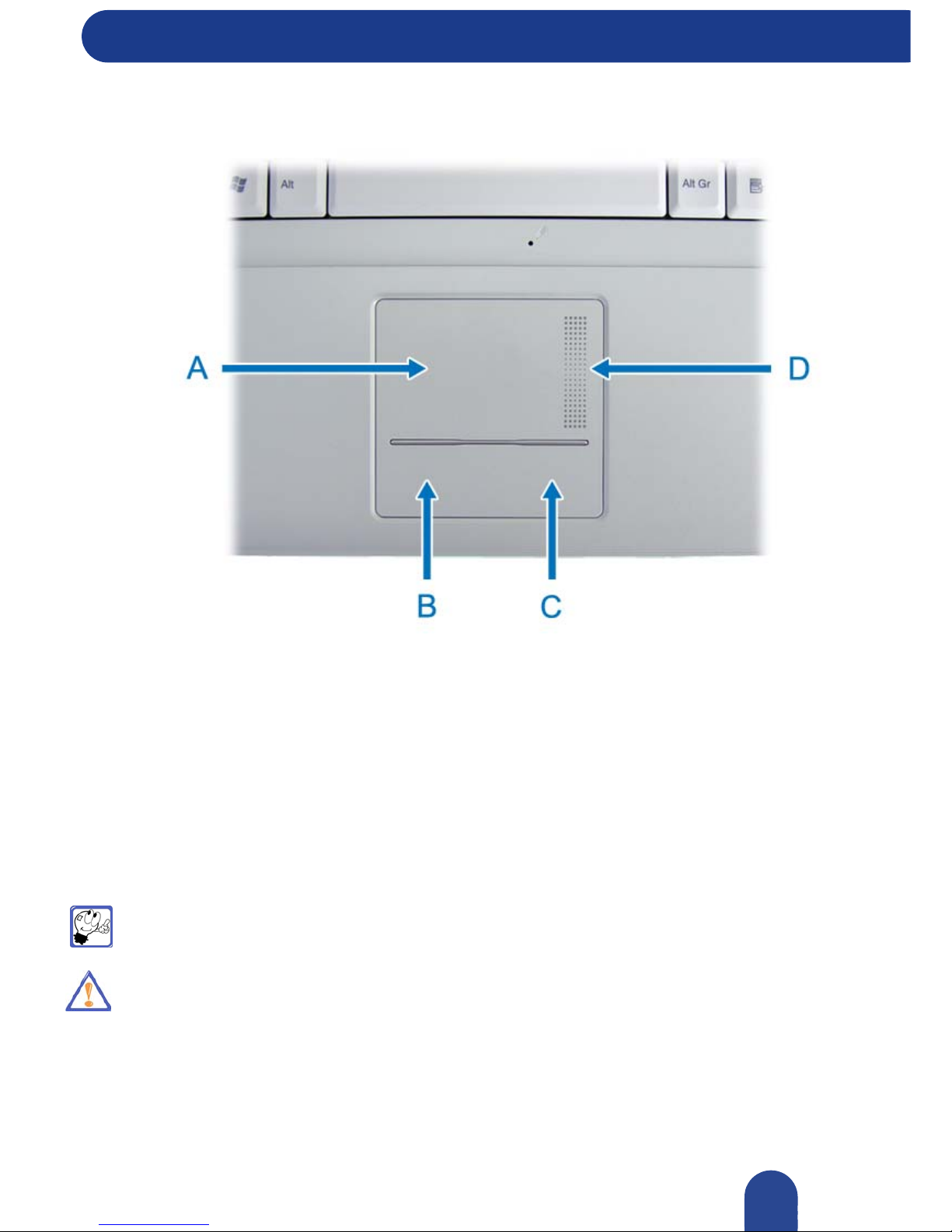
Touchpad
Figure 2: Touchpad
Refer to "Using the Touchpad" for information on how to use and configure the touchpad.
Wireless Antennae
Wireless antennae send and receive signals from the wireless devices installed in your notebook computer.
These antennae are not visible from the outside of the computer.
Note: The computer display panel must be open, and the antennae free from obstruction
before a wireless connection can be established.
Caution: The wireless devices installed in this notebook computer have been designed so that
they do not exceed the limits for exposure to radio frequency recommended by the international
guidelines (ICNIRP). SAR (Specific Absorption Rate) is the rate at which energy is absorbed in
body tissues and it is strongly dependent on the separation distance between the high-frequency
source (antennae) and the body. The wireless devices meet international guidelines for exposure to
radio frequency radiation only if the distance between your body and the antennae is at least a few
centimetres.
A: Touchpad B: Left button
C: Right button D: 2-way scroll button
25
Page 26

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Caution: Specific wireless regulatory notices apply to each country or region. Refer to "802.11x
Wireless LAN Regulations".
26
Page 27

© 2007-2009, NEC Computers S.A.S. All rights reserved.
Around the Back of the System
The back panel of the notebook computer offers the following feature.
A Battery Bay - equipped with a rechargeable battery. Refer to "Replacing the Primary Battery".
Figure 3: Back panel feature
27
Page 28

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Around the Left Side of the System
Discovering Your Computer
The left side of your notebook computer provides the features shown in the figure.
A AC Power Port - lets you attach the notebook computer to the AC power source using the AC adapter
that comes with your system. Keep the system connected to AC power whenever possible to keep the
battery pack and internal CMOS battery charged. Refer to "AC Adapter".
B VGA Port - use this 15-pin port to attach an external monitor to your notebook computer. Refer to
"Connecting an External VGA Monitor".
C LAN Port (C) - a 10/100/1000 Mbps LAN feature is included with your system. Refer to the
"Connecting a Network Cable" section for more information.
D Fan Vents - allow your system to cool properly and maintain a safe operating environment.
Warning: do not block the fan vents while the notebook computer is in use.
E USB Ports - a Universal Serial Bus (USB) port allows you to connect an USB-equipped peripheral
device (for example a printer, a mouse or a keyboard) to your notebook computer. Refer to "USB
Devices".
F USB Ports - a Universal Serial Bus (USB) port allows you to connect an USB-equipped peripheral
device (for example a printer, a mouse or a keyboard) to your notebook computer. Refer to "USB
Devices".
G 7 in 1 Card Reader - allows you to read the following memory cards formats: SD / mini SD / MMC /
RSMMC / MS / MS PRO / MS DUO). Refer to "7 in 1 Flash Memory Card Reader".
H Express Card Slot - you can add hardware capabilities such as memory, wired and wireless
communications cards and security devices by simply inserting these modules into this slot. Refer to
"Express Card".
Figure 4: Left side features
28
Page 29

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Around the Right Side of the System
Discovering Your Computer
The right side of the notebook computer offers the following features.
A Line In - lets you use another audio system, like a home stereo, as an input source. Use a cable to
connect to the Line Out port on the other audio system to record or play. Refer to "Audio".
B Microphone In - allows you to connect an external microphone for monophonic recording or
amplification through the unit. Refer to "Audio".
C Line Out - lets you plug in stereo headphones or external speakers. Refer to "Audio".
D USB Port - a Universal Serial Bus (USB) port allows you to connect an USB-equipped peripheral
device (for example a printer, a mouse or a keyboard) to your notebook computer. Refer to "USB
Devices".
E Optical Disc Drive - refer to "Optical Disc Drive" for more information on the optical disc drive
installed in your notebook computer.
F Release Button - ejects the disc tray. Press this button when power is on to insert a disc into or remove
a disc from the drive.
G Emergency Eject Hole - allows you to manually remove a disc from the drive if the eject function is
disabled by software or a power failure occurs.
H Modem Port (D) - a 56K fax/data modem card is included with your system. Refer to the"Connecting
a Modem Cable" section for more information.
I Security Cable Slot - allows you to attach an antitheft device to your notebook computer. Refer to
"Security Features and Passwords".
Figure 5: Right side features
29
Page 30

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Around the Bottom of the System
Discovering Your Computer
The bottom of the notebook computer offers the following features.
A Battery Security Lock - slide the lock towards the outside to unlock the battery.
B Battery Bay - equipped with a rechargeable battery. Refer to "Replacing the Primary Battery".
C Battery Release Latch - slide and hold the lock to the right to release the battery.
D Memory Bay - refer to "Memory Modules".
E Hard Disk Drive Bay - refer to "Hard Disk Drive".
Caution: Be aware that your system may radiate heat when used for an extended period of time.
Figure 6: Bottom features
30
Page 31

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Using the Keyboard
Discovering Your Computer
Figure 7: Keyboard
Note: Depending on the model, the keyboard layout may be slightly dif ferent from what is shown.
The keyboard is equipped with many features. These include:
A Function Keys - Twelve function keys, F1 through F12, are available on the notebook keyboard. These
keys work together with the Fn key to activate special functions. Some of these keys (printed in blue)
are pre-programmed with dual functions.
Function keys are application-driven. See the specific application's user guide for information about
how each function key works within the application you are using.
Refer to "Keyboard""Keyboard" for more information about the function key combinations pre-
programmed for your notebook computer.
B Numeric Keypad - Pressing Num Lock (in colour) on the keyboard activates the numeric keypad
numbers and functions printed in blue on the bottom right corner of the keys.
The keypad lets you type numbers and mathematical operands (+, -) as you would on a calculator. The
keypad is ideal for entering long lists of numbers.
When you press Num Lock (in colour) again, the keys revert to their normal functions as typewriter
keys.
C Typewriter Keys - Typewriter keys (also called alphanumeric keys) are used to enter text and
characters. Keys with blue print on them behave differently when combined with control keys or the
Fn key.
D Control Keys - Ctrl, Alt, Fn, Alt Gr and Shift are controls used in conjunction with other keys to
change their functions. To use control keys, press and hold the control key while pressing another key.
For example, "Press Ctrl c" means to hold down the Ctrl key and press the c key . Key combinations are
specific to the application you are running.
31
Page 32

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
The CTRL key is used in conjunction with another key. CTRL key combinations are defined by the
application being used. Look in the help menu of the program that you are using to find a list of the
function keys and their uses.
Like the Control Key, the ALT key is used in combination with other keys. In most Windows
programs, each of the menu choices at the top of the screen has one letter underlined. Holding down
the ALT key while pressing the key corresponding to the underlined letter will open the menu just as
though you had clicked your mouse on that menu choice. For instance, if the menu shows the choice
File, you can open that menu by clicking the mouse on the word File or by pressing the ALT key and
the F key simultaneously. The ALT Gr key present on some keyboards functions like the ALT key. It
also allows you to select the third function marked on a key (Euro symbol for example).
E Cursor Control keys - Cursor control keys let you position the cursor on the screen where you want.
On the screen, the cursor is a blinking underline, block, or vertical bar depending on the application.
The cursor indicates where the next typed text will be inserted.
F Windows keys - Use the following two keys to facilitate your work.
Shortcut/Application key - provides quick access to shortcut menus. (This key acts like a right
mouse button.)
Floating Window key - displays the Start menu.
32
Page 33

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Using the Touchpad
Discovering Your Computer
The touchpad is an easy way to control the cursor with your finger. Lightly glide your finger across the
touchpad and the cursor follows. To use the touchpad, you can:
• Single tap to the touchpad, or single click on the left button, equivalent to a single click of the primary
mouse button.
• Double tap to the touchpad, or double click on the left button, equivalent to a double click of the
primary mouse button.
• Click and hold, then drag your finger across the touchpad, equivalent to a click and drag of the primary
mouse button.
• Press the scroll button up, down, left or right
1
, to scroll your document or screen.
If you find the double tap difficult to use, go to the next section for general directions about adjusting the
touchpad properties.
Note: If you install another mouse driver over the shipping default, the double-tap capability may
be lost.
Making Touchpad Adjustments in Windows
The touchpad offers a number of options that let you customise how it functions. To access these options:
• In Windows Vista, go to Start , Control Panel, and choose Mouse in Hardware and Sound.
The options let you control the size and colour of the cursor, cursor speed, the accepted double-click
speed, and selection button orientation.
Making Touchpad Adjustments in Synaptics Utility
Refer to "Making Touchpad Adjustments in Synaptics".
Touchpad Tips
Follow these basic ergonomic tips while working:
• Use a light touch on the touchpad surface.
• Set up the notebook with your keyboard and touchpad at a comfortable height. Keep your forearms
parallel to the floor. Your wrists should be relaxed and straight.
• While using the keyboard and touchpad, keep your shoulders and arms as relaxed as possible.
• Take regular breaks from the computer to rest your eyes. Perform stretching exercises to relax your
fingers, hands, wrists, forearms and shoulders.
See "Setting Up a Healthy Work Environment" for more information.
1.The left / right scroll feature may not be present on some models.
Refer to "Touchpad" for more information.
Refer to "Touchpad" for more information.
33
Page 34

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Making Touchpad Adjustments in Synaptics
Discovering Your Computer
The Synaptics device driver provides a variety of advanced features for end users. Open the utility by
clicking on the Synaptics icon in the taskbar. According to your model, the following features may be
available.
Touch Sensitivity
The Touch Sensitivity feature allows you to get the best performance from the touchpad. You can
personalize the touch sensitivity settings for your finger size and style of touch.
Tapping
Tapping on the touchpad surface is usually quicker and more convenient than using a mouse or
mechanical buttons, and gives the same result as clicking the primary mouse button. Tapping twice in
rapid succession produces a double-click.
Tap Zones
The Tap Zone feature allows you to configure each of the four corners of the touchpad surface to act as
different buttons when tapped. You can configure the tap zones to perform an action, such as launching an
application. You can also adjust the size of each tap zone.
Virtual Scrolling
The Virtual Scrolling feature allows you to scroll through documents, web pages, and so forth with a
single stroke of the finger. Virtual Scrolling operates the scroll bars automatically so there is no need to
move the pointer away from its current location. Virtual Scrolling works with most scrollable windows
such as word processing documents, spreadsheets, and large digital images. It also works with other
scrollable items such as file lists and font lists. Virtual Scrolling provides smooth and easy scrolling for all
applications.
Corner Taps and Programmable Tap Zones
Corner taps and programmable tap zones allow you to assign button controls or other functions to an area
on the touchpad surface. For example, you can program the right hand corner of the touchpad to perform
the equivalent of a right button mouse click, or program another corner of the touchpad to launch the Start
Menu. The actions are entirely up to you, and are programmable through the Synaptics driver.
PalmCheck
The PalmCheck™ feature guards against unintentional cursor movement and tapping caused by
accidental contact of the palm or hand with the touchpad. PalmCheck allows the touchpad to recognize
when your palm is resting on it or brushing its surface while typing. This helps prevent unwanted pointer
movement or clicks.
EdgeMotion
The EdgeMotion™ feature is designed to simplify long-distance pointer motions. With EdgeMotion, you
are not restricted by the size of the touchpad when dragging an item across the screen or pointing. When
your finger reaches the edge of the touchpad, holding your finger on the edge will cause the cursor to
continue moving in that direction until your finger is lifted.
Programmable Button Assignments
The Programmable Button Assignment feature allows you to configure the action performed when a
button is pressed. For example, you could define the right button to “go to a web page in the default
34
Page 35

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
browser.” Each time that button is clicked, the web browser would automatically open and load the
specified page. However, the factory defaults for mechanical buttons are generally set to emulate primary
and secondary mouse clicks.
Virtual Zooming
The Virtual Zooming feature makes increasing or decreasing the magnification of a document quick and
easy . By holding down the control key and running a finger along the right edge of the touchpad will zoom
in or out, depending on the direction of motion. This feature is available with applications that have a
zoom feature and support the Microsoft IntelliMouse™.
Slow Motion
The Slow Motion feature allows you to reduce the speed of the pointer to improve pointing accuracy for
fine positioning. Activate Slow Motion by pressing and holding a specified key (user-selected) while
moving the pointer.
Constrained Motion
The Constrained Motion feature allows you to force purely horizontal or vertical motion of the pointer on
the screen. This feature is most beneficial when using a drawing program. Constrained Motion is activated
by pressing and holding a specified key (user-selected) while moving the pointer. When the key is pressed,
the initial direction of the pointer’s motion determines the allowed direction of movement for as long as
the finger remains on the touchpad.
Animated Tray Icon
The animated tray icon provides instant visual feedback about taps and finger motion
35
Page 36

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
AC Adapter
Discovering Your Computer
Use the AC adapter and power cable that came with your notebook to run your computer on alternating
current (AC) power, or to recharge the battery pack. Use the AC adapter whenever a wall outlet is nearby.
Keep the adapter connected whenever possible. The AC adapter charges the battery when it is connected,
whether the notebook computer is powered on or off.
Figure 8: AC adapter
Warning: Do not attempt to disassemble the AC adapter. The AC adapter has no user-
replaceable or serviceable parts inside. Dangerous voltage in the AC adapter can cause serious
personal injury or death. The AC adapter is intended for use with a computer and must meet
EN609050 standards.
A: AC Adapter B: Adapter Cable
C: Power Cable
36
Page 37

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Connecting the AC Adapter
Connect the AC adapter as follows:
1. Connect the AC adapter cable to the power port on your notebook computer.
2. Plug one end of the AC power cable into the AC adapter and the other end into a properly grounded
wall outlet. Make sure the power source falls within the system compatible range.
Figure 9: Connecting the AC adapter
Caution:
•
Do not cover or place objects on the AC adapter. Keeping the adapter clear of objects lets
the adapter cool properly during use.
• Only use the AC adapter that comes with your notebook. Although other adapters look
similar, using them can damage your system.
37
Page 38

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Battery Pack
Discovering Your Computer
The NEC notebook computer comes with a rechargeable battery.
Refer to the "NEC Generation N3000 Specifications" chapter for more information.
Note: although the battery is fully charged at the factory, transit and shelf time may reduce the
initial battery charge. We recommend that the first time you use your system, you connect it to AC
power using the AC adapter. This also recharges your battery. For more information, refer to
"Initial Use or After Prolonged Storage Period".
Battery Precautions
To prevent accidental battery ignition, rupture, or explosion, adhere to the following precautions.
Warning: There is a danger of explosion if the battery is incorrectly replaced. Replace only
with the same or equivalent type recommended by the manufacturer. Discard used batteries
according to the manufacturer's instructions.
To avoid personal injury and property damage, read these battery precautions on handling,
charging and disposing batteries.
• Keep the battery away from heat sources incl uding direct sunlight, open fires, microwave
ovens, and high-voltage containers. Temperatures over 60ºC may cause damage.
• Do not drop or impact the battery.
• Do not disassemble the battery.
• Do not solder the battery.
• Do not puncture the battery.
• Do not use a battery that appears damaged or deformed, has any rust on its casing, is
discoloured, overheats, or emits a foul odour.
• Keep the battery dry and away from water.
• Keep metal objects away from battery terminals. Metal objects in contact with the
connectors can cause a short circuit and damage.
If the battery leaks:
• If the battery leaks onto skin or clothing, wash the area immediately with clean water.
Battery fluid can cause a skin rash and damage fabric.
• If battery fluid gets into eyes, DO NOT rub; rinse with clear water immediately and consult
a doctor.
• Take extra precautions to keep a leaking battery away from fire. There is a danger of
ignition or explosion.
38
Page 39

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Using the Battery
Microsoft Windows Power Meter
Move your cursor over the power meter icon on the task bar to see the remaining battery charge. When
the AC adapter is connected to the notebook computer, the power meter icon looks like this . Right-
click the icons to open the Power Meter window or to display power properties.
What to Do on Low Battery
When battery power reaches the low battery alarm percentage defined in the power option properties
(Refer to "Managing System Power (W indows®Vista)"), a notification message is displayed or the system
beeps a warning. Always respond by immediately saving your data, and connect your system to the AC
adapter. If an AC adapter is not available, change the battery using the battery replacement procedure.
See "Replacing the Primary Battery".
If you do not take any action, the system will automatically go into Hibernation (Save To File) mode.
Charging the Battery
Refer to "Charging Lithium-ion Batteries".
Conserving Battery Power
Some operations like the ones listed below significantly reduced battery performance:
• using optical drives,
• using USB devices, wireless communication devices, or Express cards,
• defining display settings to high-brightness,
• running program requiring maximum power such as 3D games.
While on the road, it is important to be aware of the simple things you can do to extend the life of the
system's main battery.
• Turn down the screen brightness.
Refer to "Keyboard".
• Enable the power management features:
"Managing System Power (Windows
®
Vista)".
• Disable the wifi or bluetooth feature if not used ("Keyboard").
• Remove the Express or PC card from its slot if not used.
Refer to "Removing an Express Card".
• Avoid using an external mouse, use the integrated touchpad.
• Avoid animated screen savers, use the standard Windows screen saver.
• Close the programs you are not using.
39
Page 40

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
How to Prolong Lithium-Based Batteries
A lithium-ion battery in use typically lasts between 18-24 months. Follow the below recommendations to
prolong your battery life cycle.
Initial Use or After Prolonged Storage Period
Your new battery comes in a discharged condition and must be charged before use. Upon initial use (or
after prolonged storage period) the battery may require two or three charge/discharge cycles before
achieving maximum capacity. To do so, unplug the AC adapter, turn off power management features
(through BIOS Setup- refer and Windows power management), and turn on the system. Once the battery
is discharged (maximum 95% depth-of-discharge recommended), plug in the AC adapter and recharge the
battery (without interruption).
Calibrating Regularly the Battery
Batteries should be calibrated by applying a deliberate full discharge once every month. Refer to "Initial
Use or After Prolonged Storage Period" for the procedure. If ignored, the fuel gauge will become
increasingly less accurate and in some cases, cut off the device prematurely.
Charging Lithium-ion Batteries
Except in situations described in "Initial Use or After Prolonged Storage Period" and "Calibrating
Regularly the Battery", avoid full discharge. The battery lasts longer with partial rather than full
discharges. It is recommended not to discharge it below 20%.
Note: Under normal conditions, a lithium-ion battery provides 500-800 charge/discharge cycles.
Two 50% charges correspond to a single charge cycle (and not to two charge cycles). Therefore,
you can charge the battery more often; this will not reduce the battery life cycle.
Precautions for Recharging the Battery
Rechargeable batteries can be used under a wide temperature range. But this does not automatically
permit charging at these extreme conditions. The maximum allowable charge temperatures are between
0 °C and 45 °C (32 °F - 113 °F), 20 °C being the optimum one. Temperatures out of this range may
prevent charge or cut off the charge prematurely.
Storing Lithium-ion Batteries
If you do not plan on using the battery for a month or more, we recommend storing it in a clean, dry, cool
place away from heat and metal object. Ensure that it is wrapped protectively and nothing will be dropped
on it.
As a fully discharged battery may turn off its protection circuit, it is recommended to store it at 40%
charge (best by charging it than discharging it.) The battery should be re-installed every 3-4 weeks and
allowed a full discharge (refer to "Initial Use or After Prolonged Storage Period".) Leaving a battery in
storage for longer than this without using could cause the battery to fully discharge as the circuitry of the
battery itself consumes power and then, may cause failure.
Note: Short battery life being mainly caused by heat rather than charge/discharge patterns, cool
storage (between 0 °C -20 °C) is more important than state of charge.
40
Page 41

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Battery and AC Power
Should the battery be removed from the computer when running on AC power? Leaving a battery in a
computer while using an electrical outlet for long periods of time may reduce the life cycle of the battery
because of heat. In that case, remove the battery from the computer and store it according to the
precautions in "Storing Lithium-ion Batteries".
41
Page 42

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Replacing the Primary Battery
Discovering Your Computer
This section describes how to remove and replace the primary battery.
Handling the Battery
Review the following before handling the system battery and read the section about "Battery Pack".
Caution: Use the battery only in the notebook computer for which it is designed. Mixing other
notebook batteries, other manufacturer's batteries, or using a combination of very old and new
batteries can deteriorate battery and equipment performance.
Warning: To prevent accidental battery ignition or explosion, adhere to the following:
• Keep the battery away from extreme heat.
• Keep metal objects away from the battery terminals to prevent a short circuit.
• Make sure the battery is properly installed in the battery bay.
• Read the precautions printed on the battery.
Installing the Battery in your System
Caution: Be sure to save your data before replacing the battery pack or connect the AC adapter.
Failure to do so can result in data loss.
1. Save your files, exit Windows, and turn off system power.
2. Close the LCD panel and turn the system over.
3. Remove the battery as follows:
• Slide the battery security lock (B) towards the unlock position.
• Slide the battery release latch (A) towards the unlock position and hold it.
42
Page 43

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Figure 10: Unlocking the battery
• Pivot the battery pack (C), remove it from its compartment, and set it aside.
4. Insert the new battery as follows:
• Insert the battery pack (C) in its compartment until it locks into place.
• Slide the battery security lock (B) towards the lock position.
5. Turn the system over.
Disposing of the Battery
Before disposing of the battery, put adhesive tape on the connectors. Contact your local waste
management officials for information regarding environmentally sound collection, recycling and disposal
of batteries. Refer to "Environmental Information".
43
Page 44

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
USB Devices
Discovering Your Computer
USB (Universal Serial Bus) is an interface designed to make it easy to connect various devices to your
computer. These peripherals may include a digital camera, scanner, printer, external optical drive, modem,
mouse, keyboard, key, game device, etc. Your computer is equipped with several USB ports that increase
your connectivity choices.
Note: Read the instructions included with the USB de vice. If they contradict the information in
this topic, follow the instructions that came with the device.
1. If your USB device uses a power cord, connect the device to a power source and turn it on before
connecting it.
2. Determine which USB port you want to connect your device to and plug the device into the selected
USB port.
Figure 11: Connecting a USB device
If Windows® is able to install a device driver automatically, you'll be notified that the device is ready
to use. Otherwise, Windows® will prompt you to insert a disc containing the driver for the device.
3. After installation is complete, check the information for your device to see if any additional software
that might have been included with the device should be installed.
Connecting and Disconnecting Devices
Note: USB devices can be hot-swapped or plugged, meaning that you do not need to turn
off your system before plugging or removing USB devices.
The first time you connect a device that plugs into a universal serial bus (USB) port, Windows
®
automatically installs a driver for that device. After a driver is installed, you can disconnect and reconnect
the device without performing any additional steps.
When unplugging storage devices, such as USB flash drives, you should be sure that the computer has
finished saving any information to the device before removing it. If the device has an activity light, wait
for a few seconds after the light has finished flashing before unplugging it.
If you see the Safely Remove Hardware icon in the notification area at the far right of the task bar, you can
use this to ensure that devices have finished all operations in progress and are ready to remove.
44
Page 45

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
1. Click the Safely Remove Hardware icon and you'll see a list of devices.
Figure 12: Safely remove hardware icon (Windows Vista®)
2. In the Safely Remove Hardware window, select the device you wish to remove, and click the Stop
button.
3. When prompted, click OK to confir m.
4. Unplug the connector from the USB port. Pull the connector, not the cable.
45
Page 46

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Connecting a Network Cable
Discovering Your Computer
Your computer features a network adapter that allows you to connect it to a local area network (LAN).
1. "Motherboard Layout and Connectors"Connect the network cable to the network adapter connector as
shown below.
Figure 13: Connecting a network cable
Note: Once the cable connector clicks into place, gently pull on the cable to ensure that it is
securely attached.
2. Connect the other end of the network cable to a network connection device or a network wall
connector.
46
Page 47

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Connecting a Modem Cable
Discovering Your Computer
Your computer features a modem that allows you to connect to the Internet through a telephone line.
Note: When using a modem outside of the country where you purchased it, you might need an
international telephone adapter, available at most electronics supply stores.
1. Connect one end of the cable into a standard telephone wall outlet, using an adapter if necessary.
2. Connect the other end of the cable into the modem port on your computer.
Figure 14: Connecting a modem cable
Setting the Modem’s Dialling Properties
In some instances, your modem may not detect the correct country as your default country settings. In this
case, you will need to change the country settings manually.
• In Windows Vista
®
, select Start, Control Panel, click on Phone and Modem Options.
47
Page 48

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Connecting to a Wireless LAN
The WLAN (Wireless Local Area Network) technology uses radio waves to transmit data to a distance of
up to 30 meters (100 feet). It allows transmission of data between WLAN equipped devices such as
notebook or desktop computers, mobile phones, printers or many other accessories.
Note: Wireless LAN equiped devices cannot communicate with devices equiped with
Bluetooth or 3G wireless devices.
Note: According to the computer equipment, you can use simultaneously different wireless
technologies. For Example, you can receive e-mails through Wireless LAN connection and print a
document through your Bluetooth equipped printer.
Discovering Your Computer
Determining the Wireless Configuration Utility
Depending on the software installed on your computer, different wireless configuration utilities may
manage your network devices:
• Your wireless network card’s client utility:
• The Windows Vista® operating system
To determine which wireless configuration utility is managing your wireless network card:
In Windows Vista®:
1. Click Start, Connect To, then Manage wireless networks.
2. Double-click a profile to open the wireless network properties screen.
Managing the Wireless Network Card Through Windows
®
Note: Press the Wireless LAN button to activate the wireless LAN feature. Refer to "Keyboard".
Connecting to a wireless network in Windows Vista
®
1. Make sure that the Wireless LAN feature is enabled.
2. Click on Start, select Control Panel, and click on Network and Internet Connections.
3. Click on Network and Sharing Center.
4. Click on Connect to a network on the left pane.
5. Select the available network of your choice on the Connect a network window, and click on Connect.
Wireless LAN Regulations
Specific regulations apply when using wireless LAN products. Refer to "802.11x Wireless LAN
Regulations".
48
Page 49

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Setting up a Bluetooth Connection
Discovering Your Computer
Bluetooth is a WPAN (Wireless Personal Area Network) technology that uses radio waves to transmit data
to a distance of up to 9 m (29 feet). It allows the transmission of data between Bluetooth-equipped devices
such as cellular phones, handheld devices, printers, and notebook or desktop computers.
Note: Bluetooth-equipped devices cannot communicate with devices used for Wireless Local
Area Networks (WLAN).
Note: Press the Bluetooth button to activate the Bluetooth feature. Refer to "Keyboard".
Configuring a Bluetooth Connection Using Bluetooth Manager
1. From the lower-right corner of the task bar, right-click the Bluetooth icon in the task bar and
select Add a Bluetooth Device.
The Add Bluetooth Device Wizard displays.
2. Follow the instructions of the wizard.
Connecting to a Bluetooth Personal Area Network (PAN)
1. To connect to a bluetooth device, right-click the Bluetooth icon in the task bar and select Join a
PAN.
2. Select in the list the bluetooth device you want to connect to, and click Connect.
Bluetooth Regulations
Specific regulations apply when using Bluetooth products. See "Bluetooth® Regulations".
49
Page 50

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Integrated Camera (optional)
Discovering Your Computer
Located on the top of the LCD panel and associated with the BisonCap utility software, the integrated
camera allows you to create video or to capture pictures. The camera can also be used for video
conferencing.
Note: You may be prompted to turn on the camera by pressing Fn-F10 if the camera has been
disabled.
Recording Video
1. Click the BisonCap icon on the Desktop.
The BisonCap software utility opens.
2. In the File menu, click Set Capture File, and type a name for your video in File name. Close the
window.
3. To modify the quality of the image, in the Options menu, click Video Capture Filter.
4. To modify the size of the image, in the Options menu, click Video Capture Pin.
5. To start recording, in the Capture menu, click Start Capture., and click OK when prompted.
6. Stop registering by selecting Stop Capture in the Capture menu.
Note: You can define a time limit by selecting Capture, Record Time Limit (before starting the
capture). Check Enable Record Time Limit and define the time in seconds.
Recording Video and Audio
Perform the same process as in "Recording Video" but before starting the capture, select Capture, then
Record Audio. (a check mark appears in front of the option when it is selected.)
Capturing an Image
1. Click on the BisonCap icon on the Desktop.
The BisonCap software utility opens.
2. To modify the quality of the image, in the Options menu, click Video Capture Filter.
3. In the Options menu, click Take Picture.
Your image is saved on the desktop in a Snapshot file.
50
Page 51

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Connecting an External VGA Monitor
Discovering Your Computer
You can add a standard external monitor to your notebook system using a display signal cable (usually
provided with the monitor). One end of the cable must have a 15-pin connector for the system.
Connect an external monitor to your system as follows.
1. Check that the notebook computer is powered off and the monitor power switch is turned off.
2. Attach the 15-pin cable connector to the monitor port on the system. Secure the cable connection with
the screws provided.
Figure 17: Connecting an external VGA monitor
3. Connect the monitor power cable and plug it into a properly grounded wall outlet.
4. Follow any set-up instructions in the monitor's user's guide.
5. Turn on power to the system and device.
6. Press the relevant function key to toggle through the video modes.
Refer to "Keyboard" for more information on the function keys.
More information in "Configuring the Display Settings with SiS VGA Control Center".
51
Page 52

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Optical Disc Drive
Discovering Your Computer
Identifying the Optical Disc Drive Installed in your Computer
Your computer may be equipped with an optical disc drive that varies according to the model purchased.
To know which type of optical disc drive is installed on your computer, follow the instructions below:
1. Click Start, All Programs, Accessories, System Tools, System Information.
2. In the left column of the System Information window, select Components then CD-ROM. The name
of the installed optical drive displays in the right-hand panel.
Technical Specifications (including LEDs and Controls) of the
Optical Disc Drive Installed in your Computer
For more information about the model installed on your computer, refer to the section "NEC Generation
N3000 Specifications""NEC Versa M580 Specifications".
Which Optical Discs to Use with the Optical Disc Drive Installed in
your Computer
Use the following table to know which optical discs to use according to the optical disc drive type.
Note: Due to the variety of CD and DVD standards, recordable discs may not be compatible with
all standard models of optical disc drives.
About Recordable (R), ReWritable (RW) and RAM Formats
•
Recordable (R) format can only record data once and then the data becomes permanent on the disc. The
disc can not be recorded onto a second time.
• With ReWritable (RW) format, data can be erased and recorded over numerous times without
damaging the medium (over 1000 rewrites possible in ideal situations)
• RAM format allows theoretically over 100 000 rewrites.
Optical Discs →
Optical Drives
a
↓
CD-ROM
CD-R
CD-RW
DVD-ROM
DVD-R
DVD-RW
DVD+R
DVD+RW
DVD-RAM
DVD+R9
DVD-R9
CD-ROM drive
R R R
CD-R drive
R R/W R/W
CD-RW drive
R R/W R/W
Table 3: Which optical discs to use with the optical disc drive installed in your computer
52
Page 53

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Caution: Check that the blank discs ar e certified up to the optical drive's maximum writing speed
(e.g. 8x). Each standard that the drive can write to may require a different speed of disc (e.g. a
drive may be able to write to a recordable CD at 24x, but to a recordable DVD at 4x). If you
purchase discs rated to a lower speed you may need to reduce the writing speed manually, or risk
being unable to write to the discs.
NEC Computers S.A.S. cannot guarantee that all recordable media available on the market
provides error-free data storage. There is always a certain risk of failure during the write process.
This type of failure may make the disk unfit for use.
Combo drive
(DVD + CD-RW)
R R/W R/W R R R R R R R
DVD-ROM drive
R R R R R R R R R R R
DVD-R drive
R R/W R/W R R/W R/W R R R R
DVD-RW drive
R R/W R/W R R/W R/W R R R R
DVD+R drive
R R/W R/W R R R R/W R/W R R
DVD+RW drive
R R/W R/W R R R R/W R/W R R
Dual DVD±RW
drive
R R/W R/W R R/W R/W R/W R/W R R
Multi DVD-RW
and RAM drive
R R/W R/W R R/W R/W R R R/W R R
Super multi
DVD±RW and
RAM drive
R R/W R/W R R/W R/W R/W R/W R/W R R
DVD+R9 drive
R R/W R/W R R/W R/W R/W R/W R R/W R
DVD-R9 drive
R R/W R/W R R/W R/W R/W R/W R R R/W
Dual DVD-R9
drive
R R/W R/W R R/W R/W R/W R/W R R/W R/W
a. Logos on the optical disc drive indicate which optical disks to use with the optical disc drive
R = read; W = write
Optical Discs →
Optical Drives
a
↓
CD-ROM
CD-R
CD-RW
DVD-ROM
DVD-R
DVD-RW
DVD+R
DVD+RW
DVD-RAM
DVD+R9
DVD-R9
Table 3: Which optical discs to use with the optical disc drive installed in your computer
53
Page 54

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Disc Loading
To insert a disc into the drive, follow these steps:
1. Press the open/close button. A tray slides out from the reader door.
2. Remove the disc from its protective case.
Note: Hold the disc by its centre hole and outer edges to avoid touching its
surface.
3. Place the disc, printed side up, into the circular area of the tray.
4. Press the open/close button again or push the front of the tray carefully. The tray automatically slides
into the reader.
Disk Removing
To remove a disk from the drive, follow these steps:
1. Press the open/close button, the tray will slide out of the reader.
Note: If the access lamp is orange, the CD is being accessed. Confirm that the access lamp
is not lit before pressing the open/close button.
2. Holding the disk by its centre hole and outer edges, remove it from the tray and place it in its
protective case.
3. Press the open/close button again or push the front of the tray carefully to close the tray.
Emergency Disk Removing
If you fail to eject the disk tray with the open/close button, follow the procedure below:
1. Shut down the computer.
2. Insert a metal pin of approximately 1.2 mm in diameter and 100 mm in length (a straightened large
paper clip will make a substitute) into the emergency hole on the front of the optical drive and gently
push it in until the tray is ejected.
Note: Do not use a toothpick or plastic stick that is easy to break. If the above procedure does not
allow you take out the disk, contact your service representative.
3. Hold the tray and pull it gently out.
4. Take out the disk and place it in its protective case.
5. Push the tray back into position.
Writing CDs or DVDs
A software application for writing CDs or DVDs has been pre-installed on your computer:
"Roxio®Creator®".
Note: it is a criminal offence, under applicable copyright laws, to make unauthorised copies of
copyright-protected material, including computer programs, films, broadcasts and sound
recordings. This equipment should not be used for such purposes.
54
Page 55

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
CD / DVD Burning Tips
T o avoid burning unusable, unplayable, incompatible or defective discs (a.k.a. "coasters"), we recommend
the following:
• Use high quality media. Defects in the media will cause defects in your written disc.
• Keep your hands off the disc... or at least the underside of the disc. Fingerprints or dirt on the bottom of
the disc can cause distortion of the writing or reading laser.
• Keep your discs dust-free.
• Turn off other programs, including screen savers.
• Choose a slow writing speed. While higher speed recording saves time and generally results in great
discs, slower speed recordings may give you your best chance for a higher quality disc, with lower
error rates.
• Keep your hard disks defragmented.
• Do not leave open sessions. Unless you are storing data in increments to a recordable disc (using multi-
session recording), you should "finalise" your recording. This is necessary for compatibility with audio
CD players.
• Keep in mind that some types of players, particularly DVD video players, can not play back certain
recordable disc formats.
Playing DVDs
A software application for playing DVDs has been pre-installed on your computer:
"Cyberlink®PowerDVDTM".
Note: it is not recommended that you use the DVD player while other programs are active.
This will affect the performance of the player, reducing display quality.
Note: when you insert a DVD disc it may take a while before it is recognised and the DVD player
is launched. Please be patient and wait for a few seconds when starting a DVD title.
Region Coding Note
Region coding is a requirement by the DVD specification that prevents DVD content from being played in
areas of the world for which it was not intended. This allows films to be released on DVD in one area,
while still playing in cinemas in others. The region code on DVD discs you purchase should correspond to
the region code of your DVD drive. For European countries this code is 2.
If you purchase a DVD disc from any other region, it will not function on your system. The region code
should be shown on the back of the DVD case. It is represented by a small map of the world, with a
number super-imposed over the top; this number is the region code.
55
Page 56

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
General Information About Optical Discs (CDs/DVDs/CDRWs etc.)
Optical Disc Care
When handling optical discs, keep the following guidelines in mind.
• Do not drop the disk.
• Do not place anything on the disk or bend the disk.
• Do not touch the signal side (nothing is printed on this side) with your hand.
• Only handle discs by the outer and inner edges.
• When a disc becomes dirty, clean it with a soft cloth. Wipe the disc from the centre outwards.
Caution: Avoid using benzene, paint thinner, record cleaner, static repellent, or any other
chemical on the disc. Chemicals and cleaners can damage the disc.
• Avoid scratching or soiling the side of the disc that has no printing or writing on it. This is the data side
of the disc.
• Do not write on or apply labels to either side of the disc. Never write with a ballpoint on the surface of
the disc.
• Keep the disk away from cigarette smoke.
• Do not store a disc in places exposed to high temperature and humidity.
• Do not place a disc under direct sunlight.
• Store discs in their cases to prevent dust contamination, scratches, bending and other damage.
Cleaning an Optical Disk
A dusty optical disk or dust-accumulated tray causes the device to fail to read data correctly.
Follow the procedure below to clean the tray and optical disk regularly:
1. Press the open/close button on the front of the optical drive. The tray comes out.
2. Hold the optical disk lightly and take it out from the tray.
Note: Do not touch the signal side (nothing is printed on this side) of the optical disk with
your hand.
3. Wipe the tray with a dry soft cloth.
Caution: Do not wipe the lens of the optical drive. Doing so may damage the lens and may cause
a malfunction of the drive.
56
Page 57

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
4. Press the open/close button or gently push on the tray front to close the tray.
5. Wipe the signal side of the disk with a dry soft cloth.
Note: Wipe optical disks from the centre to the outside.
Caution: Use only optical disk cleaner if necessary. Cleaning an optical disk with record spray/
cleaner, benzene, or thinner causes damage to the disk contents. At worst, inserting the disk into
the computer may cause malfunction or failure.
57
Page 58

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
7 in 1 Flash Memory Card Reader
Discovering Your Computer
Your computer provides a seven-in-one card reader that can accept the following three types of memory
card.
• Memory Stick™, Memory Stick PRO and Memory Stick Duo card
• MultiMedia (MMC) and Reduced Size MultiMedia (RS-MMC) card
• Secure Digital (SD) and Mini-SD card
All of these memory cards are used in a wide selection of digital cameras, PDAs, MP3 players and mobile
phones. The cards can be used as 'bridge media', transferring files (music, images, presentations, data,
etc...) between your computer and other devices.
Inserting and Removing a Memory Card
1. Align the card so that the connector points towards the port, with the connectors facing down.
Figure 16: Inserting a memory card
2. Carefully slide the card into the port. If you find you need to use any force to insert the card, try
reorientating the card slightly.
Note: The last 3 to 8 mm of the card will extend from beyond the slot, depending on the card
used.
3. If the card contains some files, the Windows Auto Play window may appear (this depends on the
contents of the card) and ask you if you wish to use a program to access the contents of the card. Select
an option here if it is appropriate, otherwise select Cancel. If the card contains no files, or unknown
files, a window will open showing the contents of the card.
Note: If you wish to access the contents of the memory card later; you can do it via 2 icons called
Removable Disk located in the My Computer window in Windows XP, and in the Computer
window in Windows Vista.
4. When you have finished with the card, you can remove it by carefully pulling it out of the port.
58
Page 59

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Caution: Make sure that no programs are using the contents of the card before you remove it. A
program attempting to use a card that is no longer present can cause errors on your computer.
Caution: Always remove any memory cards before moving your computer.
59
Page 60

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Express Card
Discovering Your Computer
You can add hardware capabilities such as memory, wired and wireless
communications cards and security devices by simply inserting these
modules into this slot.
Depending on your computer model, it supports two form factors:
Express Card/34 (34 mm wide) and Express Card/54 (54 mm wide, in an
L-shape) — the connector is the same width (34 mm) on both. Standard
cards are 75 mm long (10.6 mm shorter than CardBus) and 5 mm thick,
but may be thicker on sections that extend outside the standard form
factor — for antennas, sockets, etc.
Refer to the "E xp res sC ard Sl ot "" Ex pre ss Ca rd S l ot " section for more information on the PC card slot(s)
present in your computer.
Inserting an Express Card
1. Align the card so that the connector points towards the slot and the arrow or the label shows on the top
face of the card.
Figure 19: Inserting an Express Card
2. Slide the card into the slot and press firmly until it is completely seated in its connector.
3. Most Express cards are automatically detected and the appropriate device driver is installed. The
system may require to use the manufacturer's drivers. In that case insert the CD shipped with the
Express card.
The computer beeps twice to indicate a successful installation.
Removing an Express Card
Press on the card to eject it.
Note: ExpressCard technology is designed to allow users to install and remove modules at any
time, without having to switch off their systems (hot plug functionality).
60
Page 61

Discovering Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Audio
Discovering Your Computer
Your system may come equipped with the following built-in audio ports that let you record and play
sound.
Line Out or Headphone Port
Lets you plug in stereo headphones or powered speakers.
Note: Plugging in external speakers may disable the built-in speakers.
Line In Port
Lets you use another audio system, like a home stereo or an MP3 player, as an input source. Use a cable to
connect to the Line Out port on the other audio system to record or play.
Microphone In Port
Allows you to connect an external microphone for monophonic recording or amplification through the
unit.
Note: Plugging in an external microphone may disable the built-in microphone.
Audio Connectors on Your Computer
Refer to "Around the Right Side of the System""Around the Right Side of the System".
You can use the"Realtek HD Audio Manager" to configure your audio settings.
Adjusting the Volume
Use any of the following means to adjust the playback volume:
• volume control feature that can be found in the Accessories menu or on the Taskbar,
• volume control located on the external speakers (if applicable).
61
Page 62

Software and Utilities
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Operating System Introduction
Software and Utilities
Microsoft® Windows®Operating Systems
Your computer comes pre-installed with a Microsoft® operating system. This Microsoft® operating
system provides a means of running applications, navigating through your file structure, and using your
computer. Each operating system offers its own look and tools through an easy-to-use graphical interface.
• "Microsoft
®
Windows®Vista Operating System"
FreeDosTM Operating System
FreeDOS aims to be a 100 % MS-DOS compatible operating system. FreeDOS is released under the GNU
General Public License. The GNU license, created by the Free Software Foundation, means you have
access to the source code for all FreeDOS programs.
For more information about FreeDOS, please refer to the http://www.freedos.org internet site.
62
Page 63

Software and Utilities
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Microsoft® Windows Vista® Operating System
Software and Utilities
As previous versions, the Microsoft Windows Vista® operating system includes a desktop with icons, a
task bar for quick access to a variety of system function, a start menu to easily access all applications and
powerful system utilities, with renewed design and organisation.
Windows Vista® also includes brand new features designed to make your computing experience easier,
faster, more pleasant and more efficient.
Among these new features are:
• Security features - Windows Vista
®
features a whole range of security utilities, among which
Windows Firewall, a powerful firewall, Windows Defender, an antispyware, and new functionalities
for Internet Explorer (for more information about Internet Explorer, see "Microsoft®Internet
Explorer® (Windows®Vista)").
Caution: Windows Defender is an antispyware, not an antivirus. It will NOT protect your
computer from viruses. We strongly advise you to use an antivirus.
• Reliability features - Windows Vista
®
makes it easier for you to keep your data and computer safe from
user error, hardware failure, thanks to dif ferent levels of protection and utilities gathered in the Backup
and Restore control panel.
• Organization features - Windows Vista
®
introduces enhanced desktop search and organization that
makes it easier to organize and find your files on your computer. As the best example, the new Instant
Search function, available almost anywhere in Windows Vista®, is an enhanced search function that
helps you locate quickly what you are looking for on your computer.
• Personalization features - Make your computing environment more beautiful and convenient than ever
by using Windows Vista® personalization possibilities and gadgets. Among these, discover the new
Sidebar, a pane on the side of the Windows Vista® desktop where you can keep your gadgets (for
example the weather forecast, a calculator and a sticky note) organized and always available.
You can take a tour of these features and others on Microsoft Vista’s web site at the address:
http://www.microsoft.com/windowsvista/features/default.mspx.
Note: for more information on a specific feature, please search Windows Vista
®
help. To do this,
click the start Start button , and select Help and Support.
Task bar Icons
With Windows Vista®, a number of icons appears on the task bar. Use the cursor to hover over the icon
and display its function. Right-click the icon to display its menu options, or double-click the icon to
launch it.
63
Page 64

Software and Utilities
© 2007-2009, NEC Computers S.A.S. All rights reserved.
The task bar has two icon areas:
Figure 23: Windows Vista® task bar
A: The quick launch (A), i.e. the left hand side of the task bar can be hidden or active.
B: The notification area (B), i.e. the right hand side of the task bar, can be easily configured, for instance,
to hide icons that are not used fr equently. Some hardwar e items or softwar e titles will place a small icon in
this area, allowing you to easily customize and control their settings or status (examples are virus
scanners, printers, PC cards...).You may personalize your task bar. To learn how to do this, please see
"Customizing the Task Bar".
Note: Depending on the version of Windows Vista
®
installed on your computer or if you have
installed or deactivated programs, the icons described here may slightly differ and/or may be
accompanied by others.
Start Menu
The Start menu features a whole new look and feels to be more efficient and comprehensive.
It features an Instant Search box, that can help you to find a specific file, application, or Internet
favourite. As you begin typing, Windows Vista® instantly searches file and application names, metadata,
and the full text of all files, and it displays the search results organized by type.
You can access your installed software and other Windows® programs through the Start menu by
selecting All Programs.
Power Management
Through Windows® you can manage power properties of your system, for example the time before the
computer automatically goes to sleep. To know more about power management, check "Managing System
Power (Windows
®
Vista)".
64
Page 65

Software and Utilities
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Tips for Using Microsoft® Windows Vista
®
Software and Utilities
This section provides various tips that should help you get the most of your Microsoft® Windows Vista
®
operating system.
Note: if you are familiar with previous versions of Microsoft Windows
®
, we advise you to check
out the new features specific to Windows Vista®. To do so, click the Start button , Help and
Support, and pick the What's new topic.
Changing the AutoPlay Setting
Your system may be automatically configured to allow an optical disc to play automatically upon
insertion. Windows Vista® makes this feature very convenient to use by allowing you to match types of
optical discs (music, mixed content, blank) with a specific program.
Follow this example to configure your system to automatically play a music CD with the Windows
®
Media Player upon insertion in the optical drive:
1. Click the Start button , Control Panel, and in Hardware and Sound click AutoPlay.
2. For every type of media or device, select an action to perform. In this case, for Audio CD, choose Play
Audio CD using Windows Media Player.
3. Click Save.
Changing the Display Resolution
1. Click the Start button , Control Panel, and in Appearance and Personalization, click Adjust
screen resolution.
The Display Settings window opens.
2. Adjust the Resolution cursor to the resolution of your choice.
Customizing the Task Bar
The task bar is locked by default; to make any change to the size or content, you first need to unlock it.
1. Right-click the taskbar.
2. Remove the check mark in front of the Lock the Taskbar option.
You may now resize and customize the task bar according to your wishes.
• Right-click the task bar and select Too lb ar s; add a check mark in front of the tool bar you wish to add
to the task bar area.
• Right-click the task bar and select Properties to access the Taskbar and Notification area options.
In the Taskbar tab, uncheck Group similar taskbar buttons if you do not wish to take advantage of
the feature that groups sessions of a same program (for instance several documents opened in the
same word processor) in one single entry in the task bar. Note that all sessions are immediately
accessible by clicking the arrow on the right of the task bar entry.
65
Page 66

Software and Utilities
© 2007-2009, NEC Computers S.A.S. All rights reserved.
In the Taskbar tab, put a check mark in front of Show Quick Launch to add shortcuts to your
favourite software applications or directories in the task bar area located just to the right of the Start
button.
In the Notification area tab, clic k Customize to change the notification area behaviour, for instance,
if you do not wish to take advantage of the feature that hides the seldom used notification icons.
Note: If you wish to restore the Vol um e icon to the notification area, right click the task bar,
unlock it, click Properties and check the Vol um e box in the Notification Area tab of the
Properties window.
Customizing the Desktop
If you were familiar with previous versions of Windows®, note that you can easily restore to the Desktop
the familiar Documents, Computer, and Network icons.
1. Right-click anywhere on the Desktop and select Personalize in the pop-up window.
2. In the Personalization window, click Change desktop icons on the left pane.
3. In the Desktop Icon Settings window, check or uncheck the icons you wish to have on the Desktop.
4. Click Apply and OK to close the window.
Establishing Passwords
To set passwords, you must first set user accounts. Each user can be assigned a different password, or no
password at all.
1. Click the Start button , Control Panel, and in User Accounts and Family Safety, click Add or
remove user accounts
2. Click Create a new account.
3. Type a name for the account.
4. Choose the account type:
• Standard user - Standard account users can use most software and change system settings that do
not affect other users or the security of the computer.
• Administrator - Administrators have complete access to the computer and can make any desired
changes. To help make the computer more secure, administrators are asked to provide their
password or confirmation before making changes that affect other users.
5. Click Create Account.
6. Click the account you just created, and click Create a password.
7. Follow the on screen instructions, and when finished, click Create Password.
You will now be prompted for this password each time you log on to Windows
®
.
To be prompted for this password when you resume from Standby, follow the steps below:
1. Click the Start button , Control Panel, and System and Maintenance.
2. In Power Options, click Require a password on wakeup.
66
Page 67

Software and Utilities
© 2007-2009, NEC Computers S.A.S. All rights reserved.
3. In the System Settings window, check Require a password option. (If the option is greyed out, you
may need to click Change Settings that are currently unavailable).
4. click Save changes.
You can now close the Control Panel.
To be prompted for this password when you resume from the screen saver, follow the steps below:
1. click the Start button , Control Panel, and Appearance and Personalization.
2. click Change screen saver.
3. On the Screen Saver Settings window, check the On resume, display logon screen option.
4. click Apply and OK. You can now close the Control Panel.
Parental Controls
Windows Vista® features an enhanced parental controls utility that will help parents manage which
computer games their children are allowed to play and which applications and web sites they can use. It is
also possible to set specific times when children are allowed to use the computer.
To access the Parental Controls panel, click the Start button , Control panel, in User Accounts and
Family Safety click Set up parental controls for any user. From there, you can manage the settings for
each child's profile to adapt to the age and interests of the child.
Here are the five types of limitations you can set:
• Time limits for the use of the computer: For example, you may want your children to have access to
the computer only from 6 to 8 pm on school days, and from 10 am to 4 pm on week-ends.
• Computer games: You can control which computer games your children are allowed to play by
allowing or restricting games by content, title, or age rating set by an independent rating boards.
• Applications: You can block or allow your children’s access to any program on the computer.
• Web sites: You can place appropriate limits on your children’s access to specific web pages,
downloads, and so on.
• Activity reports: You can choose to receive and review deta iled reports of your children’s computer
use.
Turning Your Computer Off
When you are not using your computer, you have the choice among several actions. To choose one, click
the Start button , then click the arrow on the right of the lock button .
The choices are:
• Sleep, see "Sleep"
• Hibernate, see "Hibernate"
• Shut Down
67
Page 68

Software and Utilities
© 2007-2009, NEC Computers S.A.S. All rights reserved.
To get more information, see "Windows Vista® Power Management Level".Windows Vista
®
Mobility Center
Windows Vista® Mobility Center is a single place where you can quickly view and adjust some essential
settings of your notebook computer.
To access Windows Vista® Mobility Center, click the Start button , Control Panel, Mobile PC and
Mobility Center.
Figure 24: Windows Vista
®
Mobility Center
Note: Click the icon of each feature to make additional adjustments.
68
Page 69

Software and Utilities
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Managing System Power (Windows Vista®)
Software and Utilities
Windows Vista® Power Options
In Windows Vista®, most power management settings are controlled through Windows® Power Options
properties, not through the BIOS setup utility, unless otherwise noted.
Power management is a balance between system performance and energy saving. According to your work
needs or habits, you will prefer high performance and low energy saving, or conversely.
To access Windows® Power Options properties click the Start button , Control Panel, in System
and Maintenance click Power Options.
Windows Vista® proposes you to define the following power management options:
• What the power button does
• What closing the lid does
• Change plan settings:
when to turn off the display
when the computer sleeps. See "Windows Vista® Power Management Level"
the display brightness
• Create a power plan, when pre-defined settings do not meet your requirement.
Windows Vista® Power Management Level
Windows Vista® offers the definition of the power management’s level. This level occurs automatically,
based on the system's default settings, when invoked.
To access Windows Vista® Power Management states, click the Start button , Control Panel, in
System and Maintenance click Power Options, Change Plan Settings, Change Advanced Power
Settings, Sleep.
The Windows Vista
®
power management level corresponds to:
Sleep
Sleep manages power by saving your current working environment to memory and shutting down most
system devices.
Use the Sleep mode, when you want to have a break for few minutes.
Hibernate
Also known as Save-To-Disk (STD) or Save-To-File (STF), Hibernate manages power by saving the
current working environment to an area on your hard disk before turning your system off. It conserves the
most battery power.
Use the Hibernate mode, when you know that you will not use your computer for a while.
69
Page 70

Software and Utilities
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Hybrid Sleep
This power management option gives you the best from Sleep and Hibernate. It saves documents,
applications, and data to both the hard drive and memory , so that you save as much ener gy as in Hibernate,
but still can get up and running as fast as in Sleep.
Note: In case of power failure, your work is restored from the hard drive with the Hybrid
Sleep and Hibernate options, whereas with the Sleep option your work is lost.
70
Page 71

Software and Utilities
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Norton Internet Security
TM
Software and Utilities
• Automatically detects and blocks viruses, spyware, and worms.
• Advanced phishing protection identifies and blocks fraudulent websites.
• Rootkit Protection finds and removes hidden threats in the operating system.
• Smart firewall blocks hackers and stops spyware transmitting unauthorized information.
• Intrusion Prevention automatically shields newly discovered security vulnerabilities.
• Network protection configures security settings when logged on at home, or on public networks.
• Full System Scan performs a deep scan to remove existing viruses, spyware and other threats.
Norton Protection Center provides a central place to easily check overall security settings. Includes
protection updates and new product features as available throughout the renewable service period of 90
days.
Using Norton Internet Security
TM
At the first startup you will be prompted to configure the antivirus software according to your needs. We
advise you to register online your copy of the software application, and to subscribe to the virus definition
service update. To be effective, an antivirus software must be updated often and on a regular basis.
Note: Your Norton Internet Security
TM
comes with a complimentary 90 days subscription to the
virus definition service update. At the end of this 90 days period, you will be proposed to subscribe
to the virus definition service update, we strongly advise you to subscribe.
Getting Help in Norton Internet Security
TM
Online help is available for this software application; on the main window, under Quick Links, click Help
to open the help window, or press the F1 key on your keyboard.
For more information about Norton Intenet Security , please refer to Symantec website at the address http:/
/www.symantec.com/norton/products/overview.jsp?pcid=mp&pvid=nis2008.
You may also download the Norton Internet Security User's Guide from Symantec Support website at the
address
http://www.symantec.com/techsupp/home_homeoffice/products/nis/nis_2008/manuals.html.
Restoring Norton Internet Security
TM
If needed you can uninstall and reinstall Norton Internet SecurityTM via SmartRestore.
• "SmartRestore for Windows Vista
®
"
Note: The availability of the above mentioned feature(s) on your computer may vary according to
the model, the configuration and the country where it has been purchased; it is subject to
modification without any notice.
71
Page 72

Software and Utilities
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Microsoft®Internet Explorer® (Windows Vista®)
Software and Utilities
With an Internet connection and Microsoft®Internet Explorer®, you can find and view information about
anything on the Web, as well as view off-line html pages.
Microsoft®Internet Explorer® makes it easy to get the most from the World Wide Web, whether you are
searching for new information or browsing your favourite web sites. Built-in IntelliSense technology can
save you time completing routine Web tasks, such as automatically completing Web addresses and forms
for you, and automatically detecting your network and connection status.
Accessing Microsoft®Internet Explorer
®
To access Microsoft®Internet Explorer® click the Start button and Internet Explorer.
Using Microsoft®Internet Explorer
®
Microsoft®Internet Explorer® offers the following features:
Figure 25: Microsoft®Internet Explorer®bar features
A Address Bar - allows you to type directly the World Wide Web address of the requested web site, or
to type Find, Go or ? followed by a keyword, web site name or phrase.
B Instant Search Box - allows you to search a keyword or phrase on Internet, linked to one or several
search providers. The result of your search is displayed in a new tab (E).
C Favorites Center - lets you organize your favourite web sites, feeds and history of the visited web
sites.
D Quick Tabs Button - this button is displayed when more than one web page is open. The Quick Tabs
button gives direct access to open web pages through thumbnails or a list.
E Tabbed Browsing - allows you to open several web pages in one window, switching easily from one
tab to another one. You can save single tabs or a group of tabs in your Favorites Center (C).
F Home Page - lets you set up your home web page.
G Feeds - allows you to receive updates of your favorite web sites, news and blogs, without having to
visit them.
H Print Button - lets you preview the appearance of a printed page and modify the layout according to
your preference.
I Page Button - allows you to handle web pages, such as save them on your computer or send them by
e-mail, or to adjust the size view of the page or of the text.
72
Page 73

Software and Utilities
© 2007-2009, NEC Computers S.A.S. All rights reserved.
J Tools Button - main features are to filter phishing scams and add-ons, manage pop-ups and other
Internet options.
Note: You can set parental controls on Internet access to protect your children from violent or
pornographic inappropriate web sites. Please see "Parental Controls" to get more details on how to
use parental controls.
Getting Help in Microsoft®Internet Explorer
®
To access Online Help, press F1, or click Help, then Contents and Index.
Figure 26: Getting help in Microsoft®Internet Explorer
®
Note: The availability of the above-mentioned features may vary according to the model, the
configuration and the country. It is subject to modification without any notice.
73
Page 74

Software and Utilities
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Microsoft® Windows®Mail (Windows Vista®)
Software and Utilities
Sending e-mails is one of the most popular computer-related activities. As e-mail's popularity and
importance have grown over the years, some annoyances and risks have also emerged. Windows®Mail is
designed to help you meet these challenges so your e-mail experience is as productive and fun as possible.
Windows®Mail includes features that help you reduce the risks, while enjoying the many benefits, of e-
mail.
Accessing Windows®Mail
The e-mail client installed on your computer is Windows®Mail. To access it, click the Start button ,
then Windows®Mail. You need to subscribe to an ISP to connect to the Internet before you can use your
Internet browser.
Features of Windows®Mail
Windows®Mail includes features that help you minimize the annoyances and risks associated with using
e-mail while enjoying the benefits of staying in touch with others.
Instant Search
Some of us have thousands of e-mail messages stored in our Inbox, making it challenging to find a
specific message when we need it. To help you, Windows®Mail includes a built-in Instant Search box
that lets you search all of your e-mail messages almost instantaneously without leaving Windows®Mail.
Instant Search is not just confined to e-mail; this feature is available throughout Windows Vista®. And
when you search from Search Explorer in Windows Vista®, you can find documents and other files in
addition to e-mail messages.
Junk mail filter
Unwanted junk e-mail (spam) is annoying and disruptive, forcing you to wade through useless or
offensive messages to find the ones you care about. To help reduce the hassle, Windows
®
Mail includes a
built-in filter which automatically screens e-mail to identify and separate junk e-mail. Unlike other filters
which require you to "train" the filter to correctly identify junk, Windows
®
Mail automatically identifies it
from the first use, without the need for feedback from you. You can choose to adjust the sensitivity of the
filter to block more e-mail, or to block less e-mail, depending on your needs.
Phishing filter
Phishing is a type of fraud designed to steal your identity. In phishing scams, scam artists try to get you to
disclose valuable personal data—like credit card numbers, passwords, account data, or other
information—by convincing you to provide it under false pretenses. Phishing e-mails claim to be from a
trusted financial institution or online service. By including links to fraudulent websites, these e-mail
messages can trick you into providing your personal information. Windows®Mail has a phishing filter
that analyzes e-mail to help detect these fraudulent links and help protect you from these online scams.
74
Page 75

Software and Utilities
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Reliability
In the past, people who used Microsoft®Outlook®Express occasionally had problems opening their large
data files of saved e-mail. Windows®Mail is based on brand new technology for storing e-mail, and is
significantly more reliable so you can have more confidence in your e-mail experience.
Getting Help in Windows®Mail
Want to know more about your e-mail Client? Simply press the F1 key when in Windows®Mail or have a
look at the help accessible from the Help menu.
Note: The availability of the above mentioned feature(s) on your computer may vary according to
the model, the configuration and the country where it has been purchased; it is subject to
modification without any notice.
75
Page 76

Software and Utilities
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Cyberlink®PowerDVD
TM
Software and Utilities
Cyberlink®PowerDVDTMoffers maximum video and audio playback entertainment on the PC. It comes
complete with numerous customisable video/audio controls that can deliver the highest quality viewing
and listening experience. It also offers feature-rich navigation controls, for a more interactive and tailored
DVD experience.
Note: this software application is only available on DVD-ROM drive, DVD-RW drive or DVD/
CD-RW combination drive configurations.
Accessing Cyberlink®PowerDVD
TM
Access Cyberlink®PowerDVDTM by clicking the Start button, All Programs, Multimedia and
PowerDVD.
Features of Cyberlink®PowerDVD
TM
• Enhanced On Screen Display (OSD)
• Dual subtitles and closed caption decoder
• Dolby headphone technology, Dolby digital decoder
• Digital zoom
• Multiple navigation controls
• Express menu
• Dual playback modes for wide screen titles
Getting Help in Cyberlink®PowerDVD
TM
On-line help is available for this software application; click the Question Mark icon at the bottom right
corner to open the help topics, or press the F1 key on your keyboard.
You can also access the help of Cyberlink®PowerDVDTM directly from the Start menu, without starting
Cyberlink®PowerDVDTM, by clicking the Start button, All Programs, Online documentation and
PowerDVD.
Restoring Cyberlink®PowerDVD
TM
If needed you can uninstall and reinstall Cyberlink®PowerDVDTM via SmartRestore:
• "SmartRestore for Windows
®
Vista"
Note: The availability of the above mentioned feature(s) on your computer may vary
according to the model, the configuration and the country where it has been purchased; it is
subject to modification without any notice.
76
Page 77

Software and Utilities
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Roxio®Creator
®
Software and Utilities
Roxio®Creator® is the CD/DVD writer software application that has been preinstalled on your system.
Note: this software application is only available on configurations with an optical disk writer
device.
Warning: It is a criminal offence, under applicable copyright laws, to make unauthorised
copies of copyright-protected material, including computer programs, films, broadcasts and
sound recordings. This equipment should not be used for such purposes.
Accessing Roxio®Creator
®
To access Roxio®Creator® click the Start button, select All Programs, Multimedia and click Creator.
Getting Help in Roxio®Creator
®
When using Roxio®Creator®, you can hold the pointer over a button to see a short description of its
function. Click the Help button on the Toolbar or press the F1 key on your keyboard to open the Help file.
You can also access the help of Roxio®Creator® directly from the Start menu, without starting
Roxio®Creator®, by clicking the Start button, All Programs, Online documentation and Creator.
Restoring Roxio®Creator
®
If needed you can uninstall and reinstall Roxio®Creator® via SmartRestore:
• "SmartRestore for Windows
®
Vista"
Note: The availability of the above mentioned feature(s) on your computer may vary according to
the model, the configuration and the country where it has been purchased; it is subject to
modification without any notice.
77
Page 78

Software and Utilities
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Microsoft® Office Ready 2007 Professional
Software and Utilities
At NEC Computers S.A.S., it is our greatest ambition to
bring you the latest and proven features and technologies.
This is why your computer is provided with Office Ready
2007 Professional.
Office Ready 2007 Professional is a trial version of Office
2007 Professional. It is a complete suite of productivity and
database software that will help you save time and stay
organized. With Office 2007 Professional:
• Work more efficiently and effectively ;
• Manage all your contact and customer information in one place ;
• Create professional marketing materials and campaigns in-house ;
• Find, use, and manage information more effectively.
All this is possible thanks to the software of Office 2007, namely:
• Word
• Excel
• Outlook with Business Contact Manager
• Publisher
• PowerPoint
• Access
You will find more information about each software on their online help.
At the end of the 60-day trial period, you will have to buy one if you want to go on using the software of
the Microsoft Office suite. Please contact Microsoft or your NEC® vendor.
Note: The availability of the above mentioned feature(s) on your computer may vary according to
the model, the configuration and the country where it has been purchased; it is subject to
modification without any notice.
78
Page 79

Software and Utilities
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Plug-Ins
Software and Utilities
NEC Computers S.A.S. has installed on your machine a number of plug-ins you can use to enhance your
browser when you're on the Internet.
What is a Plug-in ?
A plug-in is a component that allows you for example to read specific file formats, listen to sounds or
watch movies over the internet by extending your browser capabilities.
ShockWave Plug-in
ShockWave by Macromedia is one of the industry standards for downloading and experiencing interactive
multimedia, graphics and audio on the web. Companies such as CNN, Warner Bros., Sony, Paramount and
Virgin use ShockWave as an integral part of their own Web sites.
This plug-in allows you to experience high resolution images and graphics, zooming and panning up to
25000 % without losing any of the original picture quality. The plug-in also lets you experience exciting
interactive animations that can include audio from hi-fi to CD quality.
Flash Player Plug-in
The flash plug-in is another plug-in by Macromedia that lets you experience vector based animation over
the web. Flash files are very small, animated graphics and drawings that play on web pages in real time,
even over a low-speed connection. Flash also gives you interactive buttons, anti-aliased graphics, outline
fonts and zooming control for use on web pages.
Note: The availability of the above mentioned feature(s) on your computer may vary according to
the model, the configuration and the country where it has been purchased; it is subject to
modification without any notice.
79
Page 80

Software and Utilities
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Adobe®Acrobat®Reader
Software and Utilities
Adobe®Acrobat®Reader allows you to view, navigate, and print PDF files from your local hard drive,
your local network, or the Internet.
Installing Adobe®Acrobat®Reader
Adobe®Acrobat®Reader is preinstalled on your system.
Accessing Adobe®Acrobat®Reader
Access Adobe®Acrobat®Reader by clicking Start, All Programs and Acrobat Reader or double-click
the icon on the desktop.
Getting Help in Adobe®Acrobat®Reader
For further information on Adobe®Acrobat®Reader, click on Help in the menu bar.
Restoring Adobe®Acrobat®Reader
If needed you can uninstall and reinstall Adobe®Acrobat®Reader via SmartRestore.
• "SmartRestore for Windows
®
Vista"
Note: The availability of the above mentioned feature(s) on your computer may vary according to
the model, the configuration and the country where it has been purchased; it is subject to
modification without any notice.
80
Page 81

Software and Utilities
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Configuring the Display Settings with SiS VGA
Control Center
Software and Utilities
The SiS VGA Control Center allows you to configure your display settings and to select the display
modes.
Correcting Colours
This menu allows you to adjust colour intensity of your notebook computer’screen and the external
monitor, if connected.
1. Open the utility by right-clicking the icon in the task bar, and click Control Center.
2. Select Desktop Gamma Correction.
The following menu displays.
Figure 22: SiS VGA Control Center - Desktop Gamma Correction
81
Page 82

Software and Utilities
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Setting Video Parameters
This menu allows you to adjust colour intensity for videos.
1. Open the utility by right-clicking the icon in the task bar, and click Control Center.
2. Select Video Setting.
The following menu displays.
Figure 23: SiS VGA Control Center - Video Setting
82
Page 83

Software and Utilities
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Configuring Multiple Display
This menu allows you to switch from single mode display to multi-mode or clone mode display.
1. Connect an external monitor to your computer as described in "Connecting an External VGA
Monitor".
2. Open the utility by right-clicking the icon in the task bar, and click Control Center.
3. Select Display Setting.
The following window displays.
Figure 24: SiS VGA Control Center - Display Setting
4. Select your display scheme.
83
Page 84

Software and Utilities
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Realtek HD Audio Manager
Software and Utilities
Note: Depending on your model, the graphical user interface may look different.
Open Realtek Audio Manager by clicking the icon in the System tray as shown below.
Figure 30: Realtek HD Audio Manager icon
The right side of the window contains information about:
• the number of audio connectors in your system as well as whether they are analog or digital
• the internal audio devices in your system, like speakers or an internal microphone.
Figure 31: Realtek HD Audio Manager connector panel
Connecting an Audio Device
When connecting a device to an audio connector, a window may pop up to let you know the type of audio
device supported by the connector. Confirm the selection by clicking OK or select the correct audio
84
Page 85

Software and Utilities
© 2007-2009, NEC Computers S.A.S. All rights reserved.
device in the list. In the displayed tab, define the settings for the connected audio device. For more
information, refer to the below sections for each audio device.
Note: The sample rate and the bit depth can be defined for each audio device. Open the Default
Format tab and select the desired settings.
Speakers
Speaker Configuration Tab
Test your speakers as follows:
1. In the drop-down list next to the picture (A), select the option describing the number of speakers in
your system.
2. Click the arrow icon (B) to test the speakers.
Figure 32: Realtek HD Audio Manager speaker settings
Sound Effect Tab
Click the Sound Effect tab to define the Environment, Equalizer and Karaoke settings.
Environment
Click the arrow of the drop-down box next to Environment to display the sound effects available such as
Stone Corridor or Bathroom.
85
Page 86

Software and Utilities
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Equalizer
Click the arrow of the drop-down box next to Equalizer to display the preset equalizer settings available
such as Pop or Jazz.
Karaoke Mode
This feature allows you to eliminate the vocal of the song or to find a key which better fits your vocal
range.
Microphone - Line In
Click these tabs to define settings for a better recording quality. Two additional options are available for
the microphone:
• Noise suppression,
• Acoustic echo cancellation.
Figure 33: Realtek HD Audio Manager microphone
86
Page 87

Configuring and Upgrading Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Setup Utility
Configuring and Upgrading Your Computer
The Setup program makes it possible to change and store system configuration information, such as the
types of peripherals that are installed, the boot-up sequence for the system, and enabling or disabling
power management features. The Setup information is stored in CMOS RAM, and is backed up by a
battery when system power is turned off.
Note: Make a copy of the original factory settings in the Setup program, along with any changes
you make to those settings. By doing so, you can restore the original factory configuration if the
new settings are not satisfactory.
Warning: this material is intended for experienced users only!
Entering the Setup Utility
Access the BIOS utility at power-on. Just press F2 when the following prompt appears:
Press <F2> to enter Setup.
When you press F2 to enter BIOS Setup, the system interrupts the Power-On Self-Test (POST) and
displays the current CMOS RAM settings.
If the system detects an error during POST, it prompts you with a double beep and a message: "Press
<F1> to resume." If you press F1, the system enters BIOS Setup automatically. If you want to fix the
error, carefully read the error message that appears above the prompt (taking notes if you want), and press
F2.
BIOS Setup Menus
Detailed and up-to-date information about the BIOS menus are available on www.nec-computers.com in
the Support section.
87
Page 88

Configuring and Upgrading Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
General Information About the BIOS
Configuring and Upgrading Your Computer
Your computer system is made up of many different components that work together to keep the system
operating normally. One of them is the system's BIOS (Basic Input Output Syst em), which helps regulate
system operation, using the CMOS (Configuration Memory Operating System) settings that keep a
“record” of your system's configuration.
Generally, you shouldn't have to access the BIOS or change any of its factory settings; for optimum
system performance, it's best to leave them as they are, since an incorrect setting could affect your
system's operation. If necessary, however, you can use your computer's Setup Utility program to make
changes to your system configuration.
When your computer was first assembled, information about its configuration was stored in CMOS RAM,
a special type of memory backed up by a battery. CMOS RAM “remembers” your computer's
configuration even when the computer is switched off.
Occasionally, you may need to change or update the information stored in CMOS RAM, such as:
• When you add or remove an hard disk drive, or change the type of video display;
• If you change your system's hardware configuration (for example, by adding a modem);
• If you want to make certain adjustments (explained in this chapter) that can improve your computer's
performance; or
• If the information in CMOS RAM was accidentally lost.
Note: Usually with Windows
®
operating systems it will not be necessary to configure any devices
due to the operating system's Plug and Play capabilities. However, it may be necessary to configure
certain devices with the Setup program; either due to the addition of IDE or SATA devices,
conflicts with the Plug and Play system or the necessity for a specific configuration - such as for
operating the computer without an operating system or for defining specific memory addresses or
IRQs.
BIOS Upgrades
BIOS upgrades, including certain language options, are available through your authorised service
representative. Please contact them for further details or check at www.nec-computers.com in the Support
section.
88
Page 89

Configuring and Upgrading Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Hard Disk Drive
Configuring and Upgrading Your Computer
For more information about the hard disk drives that can be installed in the notebook computer, refer to
the '"NEC Generation N3000 Specifications".
Follow these steps to replace the hard disk drive.
Warning: Always disc onnect the AC power cord from the wall outlet and the system, remove
the battery and unplug the modem cable when upgrading one of the computer's components.
Observe the "Maintenance Safety Precautions".
1. Power off the system and disconnect the AC power cord from the wall and the system.
Disconnect any other external devices.
2. Close the LCD panel and turn the system over.
3. Remove the two screws (A) securing the bay cover.
Figure 29: Removing the screws of the hard disk drive bay cover
4. Lift the bay cover and set it aside.
89
Page 90

Configuring and Upgrading Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Figure 30: Removing the hard disk drive
5. Pull the hard disk drive straight back (1) until it disengages from the bay connector.
6. Lift the hard disk drive up (2) and remove it from the bay.
7. Slide the new hard disk drive into the bay and push firmly to connect it to the system board.
8. Replace the bay cover and secure it with two screws.
90
Page 91

Configuring and Upgrading Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Memory Modules
Configuring and Upgrading Your Computer
For more information about the type of memory supported by your notebook, refer to "NEC Generation
N3000 Specifications".
Caution: Only install NECC approved memory modules to ensure proper functionality of your
notebook computer.
Follow these steps to upgrade the system memory.
Warning: Always disconnect the AC power cord from the wall outlet and the system, remove
the battery and unplug the modem cable when upgrading one of the computer's components.
Observe the "Maintenance Safety Precautions".
1. Power off the system and disconnect the AC power cord from the wall and the system.
2. Disconnect any other external devices.
3. Close the LCD panel and turn the system over.
4. Remove the battery. See "Replacing the Primary Battery".
5. Remove the three screws (A) securing the bay cover.
Figure 31: Removing the screws securing the memory bay cover
91
Page 92

Configuring and Upgrading Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Figure 32: Disconnecting the fan cable
6. Open the bay cover and carefully disconnect the fan cable (A).
7. Lift the bay cover and set it aside.
8. Locate the free memory slot (B).
Figure 33: Replacing a memory module
9. Align the notch with the notch in the bay connector and install the module as follows:
92
Page 93

Configuring and Upgrading Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
• Hold the SO-DIMM module at a 60-degree angle and align the SO-DIMM connector with the
slot (B) in the system. Push the connector into the slot.
• Press down on the edge of the SO-DIMM module until the locking tabs on the sides (A) snap into
place, securing the module.
Note: To remove a SO-DIMM module (C), press the locking tabs (A) away from the sides
of the module until the module pops up. Then, remove the SO-DIMM module.
10. Replace the bay cover.
11. Secure the three screws that were removed during step 5.
12. Install the battery.
13. Connect the AC adapter to the computer and to the wall outlet and power on the system.
The additional memory is automatically detected and system configuration information are updated.
You can check the amount of memory installed as follows:
• Windows Vista
®
: Start, Control Panel, System and Maintenance, then System.
93
Page 94

Taking Care of Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Security Features and Passwords
Taking Care of Your Computer
The system has software and mechanical security features that offer protection against unauthorised
access to your system and data.
BIOS Security Features
Refer to "Setup Utility" for more information on how to set Supervisor and User passwords.
Security Features in the Windows® Operating Systems
For more information on how to set user accounts and passwords refer to:
• "Tips for Using Microsoft
®
Windows Vista®"
Security Cable
Your computer features a security cable slot. This lock prevents your computer from being moved or
stolen.
To locate this slot, see "Around the Right Side of the System""Around the Left Side of the System".
Note: Your computer does not ship with a security cable lock.
Install an optional security cable as follows:
1. Select the object in the room to which you will secure your computer. Choose an immovable piece of
furniture or fixture (a table or desk leg with a cross bar).
2. Take the looped end of the steel cable (optional) and wrap around an immovable object. Choose an
object that prevents an intruder from slipping the cable out from under the object.
3. Feed the locking device through the looped end of the cable.
4. To install the security cable, make sure that the lock is in the unlocked position. To do so, insert the
key into the lock and, holding the locking device stable, turn the key clockwise to the unlocked
position.
5. Insert the locking device into the security cable slot in your computer. Turn the key 90° counter-
clockwise to lock and remove the key. Check that the security cable is secure by gently pulling on the
locking device.
TPM or Trusted Platform Module
The Trusted Platform Module (TPM) is a component on the motherboard that is specifically designed to
enhance platform security above-and-beyond the capabilities of today's software by providing a protected
space for some security critical tasks. Using both software and hardware, the TPM protects encryption and
signature keys at their most vulnerable stages/operations when the keys are being used in unencrypted
forms. The TPM is specifically designed to shield unencrypted keys as well as platform and user
authentication information from software-based attacks.
For more information refer to "Installing Infineon TPM Professional Package".
Password Procedures
A good password should consist of:
94
Page 95

Taking Care of Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
• At least one upper case letter (A to Z)
• At least one numerical character (0 to 9)
• At least one symbol character (!, @, &, etc.)
.
Note: Avoid using names or dates that can be easily guessed: birthdays, anniversaries,
family member names, pet names, etc.
95
Page 96

Taking Care of Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
System Care
Taking Care of Your Computer
Your system is a durable, dependable computer built for heavy use. With protective measures and proper
care, you can prevent problems and keep your computer many years.
For the environment as well as for you best interest, please follow the rules described below. This
measures apply both to hardware and software elements.
Eco-friendly: Taking care of your system is a first step toward environment protection. To
go even farther, see "Ecological Computer Use".
Protecting Your System
Protecting your Material
• Connect a Back-UPS unit between your computer and the grounded wall outlet. A Back-UPS unit
protects your system from sudden transient increases and decreases in electrical power.
Be sure to connect all peripherals, such as your monitor and printer, to the Back-UPS unit that should
be the only device that you plug into the wall outlet.
• Disconnect your system from telephone and power lines when a electrical storm threatens. If you have
a fax/modem, lightning can travel in on the phone line and can damage both the fax/modem and the
system unit. Lightning can also travel in on power lines and damage your monitor and system unit.
Note: Please note that the product warranty does not apply if damage to your computer is the
result of a lightning strike.
• Avoid repeated power-on cycles. These subject the system components to temperature variations and
stress.
After turning off power, wait about five seconds for the hard disk to spin down before you power on
again.
• Be sure that system power is off before you connect or disconnect a cable. Never make cable changes
when the system power is on. Doing so could damage your system and its peripherals.
• Place your computer away from direct sunlight and extreme temperatures.
Refer to the "NEC Generation N3000 Specifications" for the recommended operating environment.
• Be sure that nothing is placed on top of your system power cables.
• Prevent dust from entering your system by covering it when it is not in use.
Protecting your Data
• Keep your antivirus program updated at all times. This is especially important if you often exchange
data over the Internet. Your system is delivered with an antivirus software pre-installed on your hard
drive. For better security, update the virus definition files as often as possible. An automatic update at
each Internet connection is the best solution.
• Before installing a new program of your computer, check the source in order to make sure the program
is authentic and virus-free.
96
Page 97

Taking Care of Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
• Install only legally obtained programs on your computer.
Warning: It is a criminal offence, under applicable copyright laws, to make unauthorised
copies of copyright-protected material, including computer programs, films, broadcasts and
sound recordings.
• Always check the source of files that you import on your computer, whether you received them by
email, downloaded them from the Internet or got them from another source. Every file that enter your
computer should be legal and virus-free.
• Do not import illegal files on your computer.
Warning: It is a criminal offence, under applicable copyright laws, to make unauthorised
copies of copyright-protected material, including computer programs, films, broadcasts and
sound recordings.
Preparing to all Eventualities
• Back up your BIOS settings: these parameters saved in the CMOS memory define how your
computer works and minor changes to them can modify the way your computer functions. To back up
the BIOS settings, take a piece of paper, enter the BIOS (see "Setup Utility") and note the settings and
their values.
Note: Do not forget to modify what is written on this piece of paper each time you modify the
BIOS settings.
• Create recovery disc(s) as proposed in:
"SmartRestore for Windows®Vista".
• Back up your data on a regular basis. You can use the Microsoft backup tool to save your files from
your computer to media such as a CD, a DVD or a removable hard disk. Refer to the Windows® on-line
help for more information.
Cleaning your System
Cleaning your Material
Warning: For safety, power off and unplug your system, monitor and any external devices
before cleaning them.
• Clean the outside of the computer with a soft clean cloth.
• You can remove stubborn stains with a cloth slightly dampened with a mild detergent. Never use a
strong cleaner or solvent on any part of the system.
• Keep food and liquids away from your computer.
• Periodically clean the keyboard with a vacuum cleaner brush attachment. Do not use any liquid
cleaners on the keyboard as they can damage it.
• Clean the monitor screen with a monitor glass cleaner and wipe it with a clean, lint-free cloth.
97
Page 98

Taking Care of Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Cleaning your Operating System
• Clean up your configuration by deleting the programs you do not use. Check the Windows
®
on-line
help to know how to do this.
• Run system cleanup to delete unnecessary temporary files, temporary internet files and empty your
recycle bin, freeing up hard drive space. Check the Windows® on-line help to know how to do this.
• Clean up your files by putting regularly your files in order, and deleting or archiving the ones you do
not use. This will free up some space on your hard disk.
• Shutdown your computer when you are done using it, so that your computer can initalize itself.
Moving or Shipping Your System Safely
Use these steps to prepare your system for moving or shipping:
1. Back up the files on the hard disk drive to discs or to an external hard disk drive.
2. Remove any CD or DVD from the optical drive.
3. Turn off the system unit and any external options connected to it.
4. Unplug the system unit power cable from the wall outlet or Back-UPS unit, then from the unit itself.
5. Unplug any external options from the wall outlets or Back-UPS unit, then disconnect them from the
computer.
6. Pack the system components in the original shipping materials and cartons. If these are not available,
be sure to use adequate packing materials to protect the components.
98
Page 99

Taking Care of Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Preventive Maintenance
Taking Care of Your Computer
The following checklist will help you to set up a preventive maintenance plan in order to prevent system
problems. Depending on what your computer is being used for, adapt it to your own needs. you will find
all details about the recommended operations in "System Care".
The items are classified according to the recommended frequency.
First Time Use
• Back up your BIOS settings.
• Create recovery disc(s) as proposed in:
"SmartRestore for Windows®Vista".
Every Day
• Update your antivirus definition.
• Shutdown your computer.
Every Week
• Clean up your hard disk.
• Backup your data.
Every Month
• Clean up your computer and the peripherals.
• Clean up the programs and files in your system.
99
Page 100

Taking Care of Your Computer
© 2007-2009, NEC Computers S.A.S. All rights reserved.
Ecological Computer Use
Taking Care of Your Computer
System Care
In order to keep your computer efficient for a long time, you need to devote some time and thought to your
computer care. Respect the instructions given in the "System Care" section. In order to do this, you can
use the preventive maintenance plan proposed in the "Preventive Maintenance" section.
To go even further in the ecological use of your computer, please read the following sections.
Power Savings
Power Management
A computer is electricity-consuming. To keep this consumption as low as possible, make the best use of
your operating system’s power management parameters, according to your needs. You can define for
instance that your computer will go into sleep mode after 10 minutes unused. See
• "Managing System Power (Windows Vista
®
)".
In addition, here are some other helpful power management tips:
• Limit screen-saver use. A screen saver does not save energy. In fact, more often than not, a screen saver
not only will draw power for the monitor, but also will keep the CPU from shutting down. Instead, set
your computer to turn off the monitor first, then go into standby mode after a longer period of
inactivity.
• Keeping your Virtual Private Network (VPN) connected may limit your system's ability to enter
standby mode. We recommend you disconnect your VPN when not actively using your corporate
network.
• Many popular computer games and other third party software packages that run in the background will
not allow the computer to go to sleep – even if they are paused or the active window is minimized.
• Some web sites or pages that have active banners and or animated advertisements will not allow the
computer to sleep on its own and must be closed, or the computer put manually into a sleep state.
• Advanced users may wish to establish multiple power schemes to address different usage models. For
example, you can create a power scheme for playing music CDs that shuts off your hard drive and
monitor immediately, but never puts your system into standby mode.
• To maximize the battery life of your notebook computer, consider setting even more aggressive
monitor, hard drive and standby/sleep settings for battery mode.
Turning Your Computer Off
Turn your computer off if you will not use it for several hours. If you need to keep it on, for example when
you are burning a CD, do not forget to turn off the peripherals (screen, speakers, printer...).
Shutting Your System Down
As some LEDs stay on even when the system is shut down, it might be a good idea to power it down
completely when you don’t use it for a long period, for nights or week-ends for example.
100
 Loading...
Loading...