HCS301
K
EE
L
OQ
Code Hopping Encoder*
FEATURES
Security
• Programmable 28-bit serial number
• Programmable 64-bit encryption key
• Each transmission is unique
• 66-bit transmission code length
• 32-bit hopping code
• 34-bit fixed code (28-bit serial number,
4-bit button code, 2-bit status)
• Encryption keys are read protected
Operating
• 3.5V - 13.0V operation
• Four button inputs
- 15 functions available
• Selectable baud rate
• Automatic code word completion
• Battery low signal transmitted to receiver
• Battery low indication on LED
• Non-volatile synchronization data
Other
• Functionally identical to HCS300
• Easy to use programming interface
• On-chip EEPROM
• On-chip oscillator and timing components
• Button inputs have internal pulldown resistors
• Current limiting on LED
• Low external component cost
output
Typical Applications
The HCS301 is ideal for Remote Keyless Entry (RKE)
applications. These applications include:
• Automotive RKE systems
• Automotive alarm systems
• Automotive immobilizers
• Gate and garage door openers
• Identity tokens
• Burglar alarm systems
DESCRIPTION
The HCS301, from Microchip Technology Inc., is a code
hopping encoder designed for secure Remote Keyless
Entry (RKE) systems. The HCS301 utilizes the K
code hopping technology , which incorporates high security, a small package outline, and low cost, to make this
device a perfect solution for unidirectional remote keyless entry systems and access control systems.
EE
OQ
L
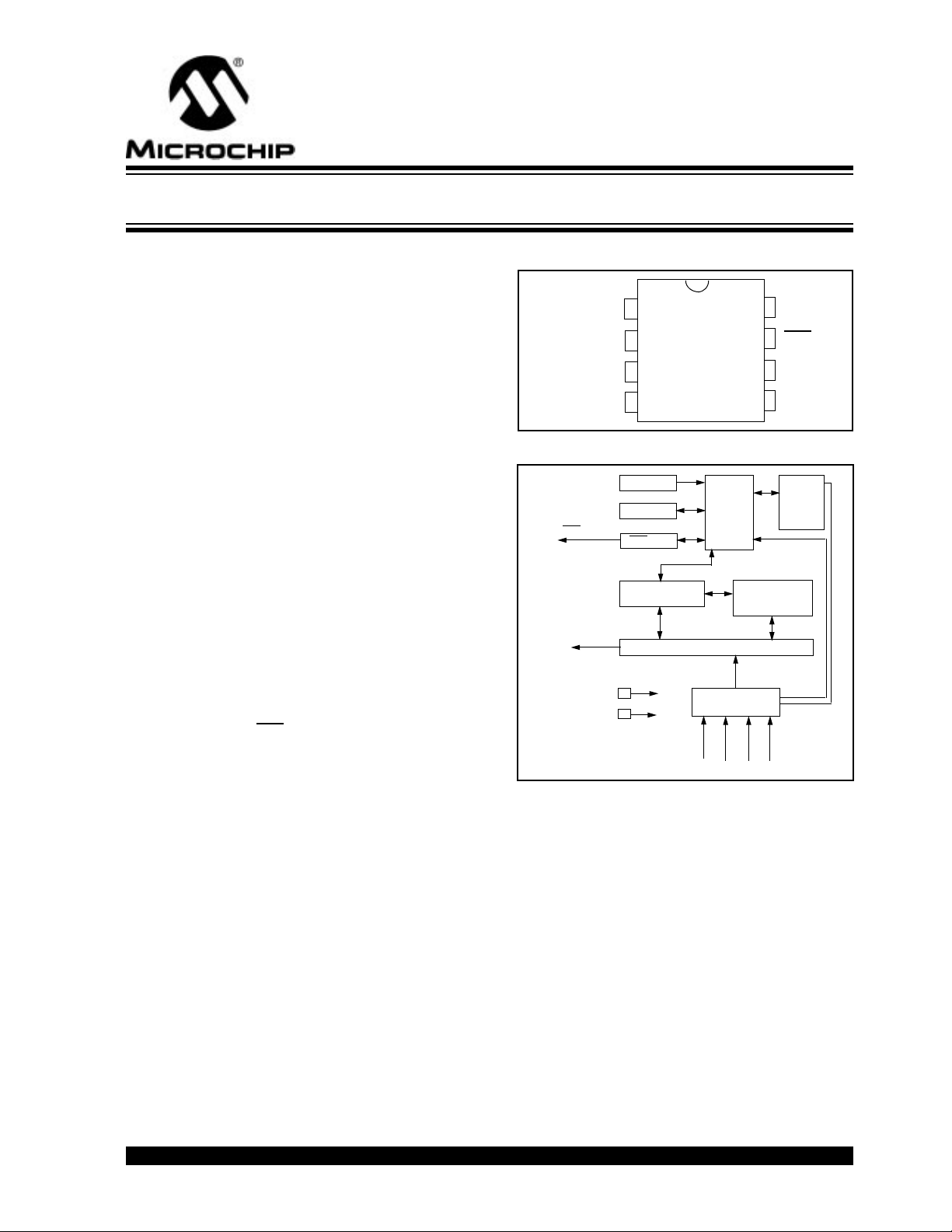
PACKA GE TYPES
PDIP, SOIC
8
DD
S0
S1
S2
S3
1
2
3
4
HCS301
V
LED
7
6
PWM
V
SS
5
HCS301 BLOCK DIAGRAM
Oscillator
Reset circuit
LED
PWM
The HCS301 combines a 32-bit hopping code
generated by a non-linear encryption algorithm, with a
28-bit serial number and six status bits to create a
66-bit transmission stream. The length of the
transmission eliminates the threat of code scanning
and the code hopping mechanism makes each
transmission unique, thus rendering code capture and
resend (code grabbing) schemes useless.
The encryption key, serial number, and configuration
data are stored in EEPROM which is not accessible via
any external connection. This makes the HCS301 a
very secure unit. The HCS301 provides an easy to use
serial interface for programming the necessary security
keys, system parameters, and configuration data.
The encryption keys and code combinations are programmable but read-protected. The keys can only be
verified after an automatic erase and programming
operation. This protects against attempts to gain
access to keys and manipulate synchronization values .
LED driver
EEPROM
VSS
VDD
Controller
32-bit shift register
Button input port
S
S
2
3
Encoder
S1S
0
Power
latching
and
switching
KeeLoq is a registered trademark of Microchip Technology Inc.
*Code hopping encoder patents issued for Europe, U. S. A., and R. S. A.
1996 Microchip Technology Inc.
Preliminary
DS21143A-page 1
HCS301
The HCS301 operates over a wide voltage range of
3.5 volts to 13.0 volts and has four button inputs in an
8-pin configuration. This allo ws the system designer the
freedom to utilize up to 15 functions. The only
components required for device operation are the buttons and RF circuitry, allowing a very low system cost.
1.0 SYSTEM OVERVIEW
ey Terms
K
ufacturer’s code – a 64-bit word, unique to
• Man
each manufacturer, used to produce a unique
encryption key in each transmitter (encoder).
• Encr
yption Key – a unique 64-bit key generated
and programmed into the encoder during the
manufacturing process. The encryption key
controls the encryption algorithm and is stored in
EEPROM on the encoder device.
1.1 Learn
The HCS product family facilitates several learn strategies to be implemented on the decoder. The following
are examples of what can be done. It must be pointed
out that there exists some third-party patents on learning strategies and implementation.
The HCS301 is a code hopping encoder device that is
designed specifically for keyless entry systems,
primarily for vehicles and home garage door openers. It
is meant to be a cost-effective, yet secure solution to
such systems. The encoder por tion of a keyless entry
system is meant to be held by the user and operated to
gain access to a vehicle or restricted area. The
HCS301 requires very few external components
(Figure 2-1).
1.1.1 NORMAL LEARN
The receiver uses the same information that is transmit-
ted during normal operation to derive the transmitter’s
secret key, decrypt the discrimination value and the
synchronization counter.
1.1.2 SECURE LEARN*
The transmitter is activated through a special button
combination to transmit a stored 48-bit value (random
seed) that can be used for key generation or be part of
the key. Transmission of the random seed can be disabled after learning is completed.
Most low-end keyless entry systems transmit the same
code from a transmitter every time a button is pushed.
The relative number of code combinations for a lo w end
system is also a relatively small number. These
shortcomings provide the means for a sophisticated
thief to create a device that ‘grabs’ a transmission and
re-transmits it later, or a device that scans all possible
combinations until the correct one is found.
The HCS301 employs the K
encryption algorithm to achieve a high level of security.
Code hopping is a method by which the code
transmitted from the transmitter to the receiver is
different every time a button is pushed. This method,
coupled with a transmission length of 66 bits, virtually
eliminates the use of code ‘grabbing’ or code
‘scanning’.
As indicated in the block diagram on page one, the
HCS301 has a small EEPROM array which must be
loaded with several parameters before use. The most
important of these values are:
• A 28-bit serial number which is meant to be
unique for every encoder
• An encryption key that is generated at the time of
production
• A 16-bit synchronization value
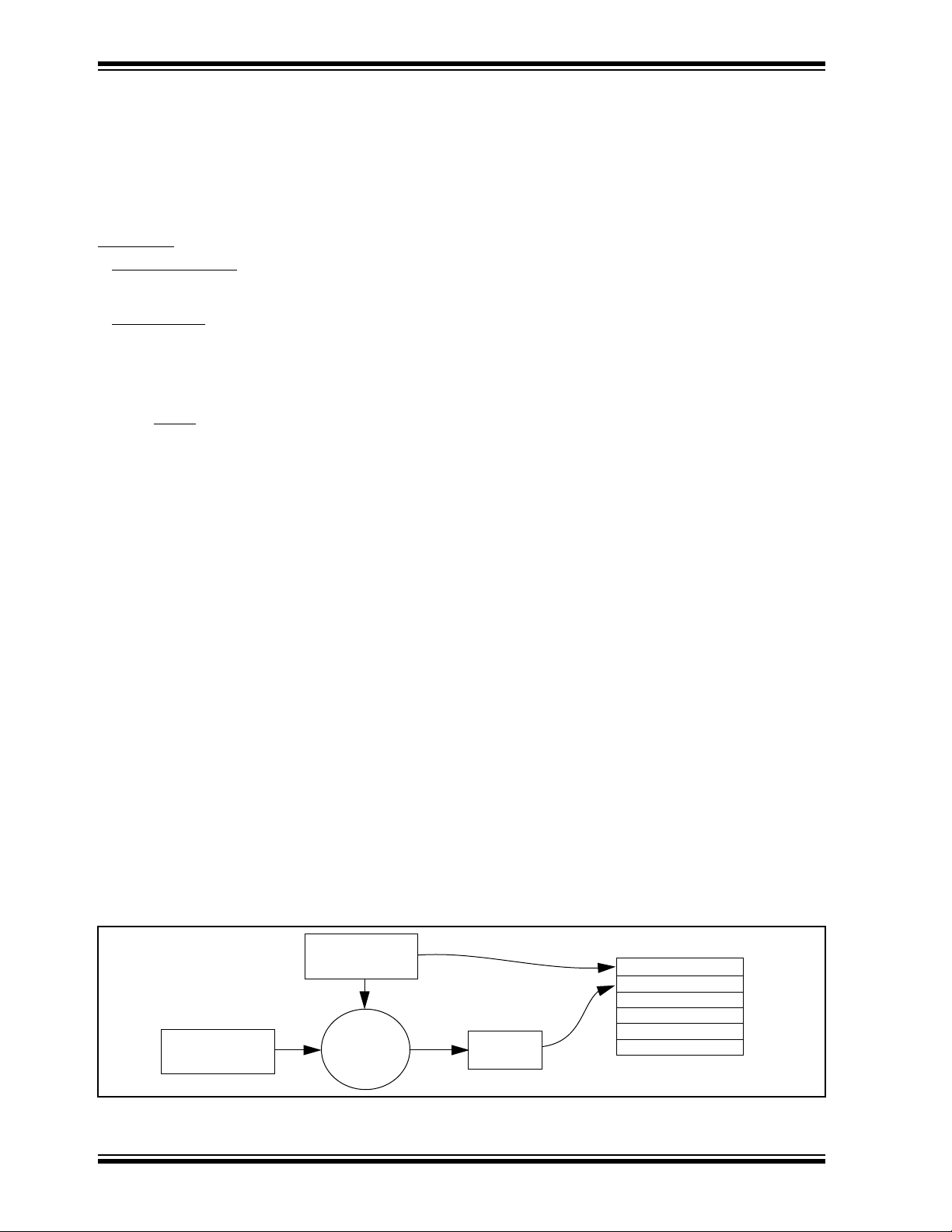
The serial number for each transmitter is programmed
by the manufacturer at the time of production. The
generation of the encryption key is done using a key
generation algorithm (Figure 1-1). Typically, inputs to
the key generation algorithm are the serial number of
the transmitter and a 64-bit manufacturer’s code. The
manufacturer’s code is chosen by the system
manufacturer and must be carefully controlled. The
manufacturer’s code is a pivotal part of the overall
system security.
EE
L
OQ
code hopping
FIGURE 1-1: CREATION AND STORAGE OF ENCRYPTION KEY DURING PRODUCTION
HCS301 EEPROM Array
Serial Number
Encryption Key
Sync Counter
.
.
.
1996 Microchip Technology Inc.
Manufacturer’s
EE
OQ
*K
L
learning patents pending.
DS21143A-page 2
Code
Transmitter
Serial Number
Key
Generation
Algorithm
Encryption
Key
Preliminary
HCS301
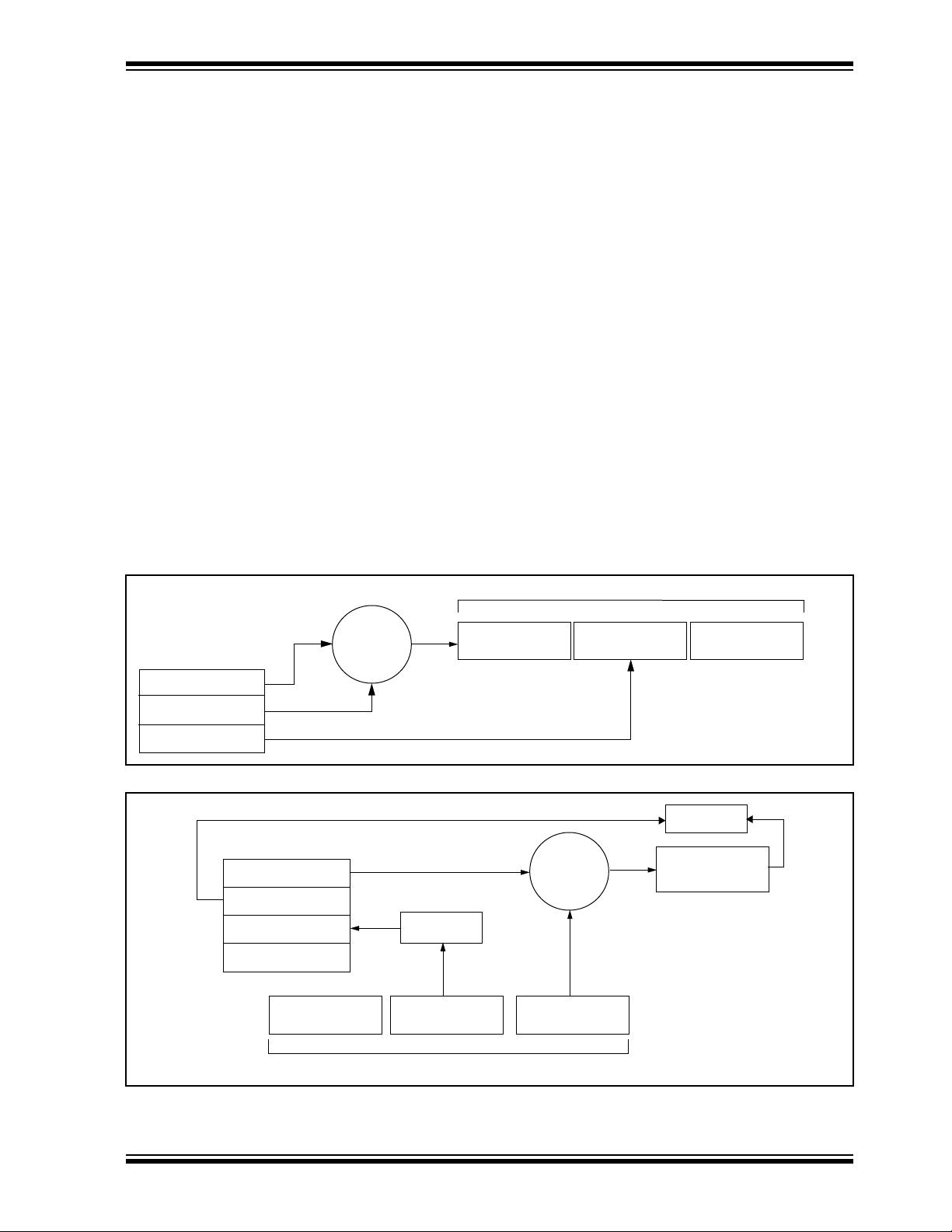
The 16-bit synchronization value is the basis for the
transmitted code changing for each transmission, and
is updated each time a button is pressed. Because of
the complexity of the code hopping algorithm, a change
in one bit of the synchronization value will result in a
large change in the actual transmitted code. There is a
relationship (Figure 1-2) between the key values in
EEPROM and how they are used in the encoder . Once
the encoder detects that a button has been pressed,
the encoder reads the button and updates the synchronization counter. The synchronization value is then
combined with the encryption key in the encryption
algorithm and the output is 32 bits of encrypted information. This data will change with every button press,
hence, it is referred to as the hopping portion of the
code word. The 32-bit hopping code is combined with
the button information and the serial number to form the
code word transmitted to the receiver. The code word
format is explained in detail in Section 4.3.
Any type of controller may be used as a receiver, but it
is typically a microcontroller with compatible firmware
that allows the receiver to operate in conjunction with a
transmitter, based on the HCS301. Section 7.0
provides more detail on integrating the HCS301 into a
total system.
Before a transmitter can be used with a particular
receiver, the transmitter must be ‘learned’ by the
receiver. Upon learning a transmitter, information is
stored by the receiver so that it may track the
transmitter, including the serial number of the
transmitter, the current synchronization value for that
transmitter and the same encryption key that is used on
the transmitter. If a receiv er receives a message of v alid
format, the serial number is checked and, if it is from a
learned transmitter, the message is decrypted and the
decrypted synchronization counter is checked against
what is stored. If the synchronization value is verified,
then the button status is checked to see what operation
is needed. Figure 1-3 shows the relationship between
some of the values stored by the receiver and the values received from the transmitter.
FIGURE 1-2: BASIC OPERATION OF TRANSMITTER (ENCODER)
Transmitted Information
EEPROM Array
Encryption Key
Sync Counter
Serial Number
KEELOQ
Encryption
Algorithm
32 Bits of
Encrypted Data
Serial Number
FIGURE 1-3: BASIC OPERATION OF RECEIVER (DECODER)
EEPROM Array
Encryption Key
Sync Counter
Serial Number
Manufacturer Code
Button Press
Information
Check for
Match
Serial Number
KEELOQ
Encryption
Algorithm
32 Bits of
Encrypted Data
Button Press
Information
Check for
Match
Decrypted
Synchronization
Counter
1996 Microchip Technology Inc.
Received Information
Preliminary
DS21143A-page 3
HCS301
2.0 DEVICE OPERATION
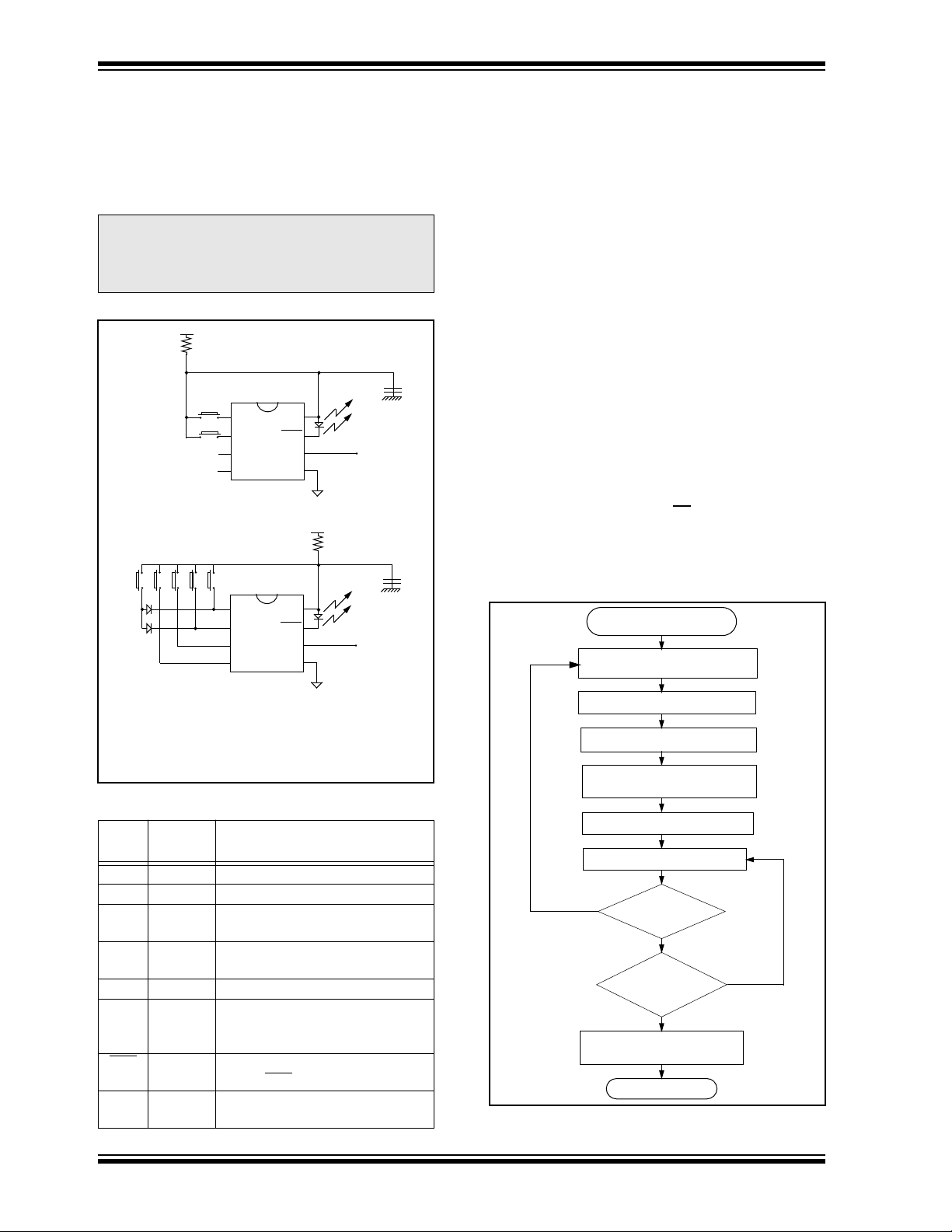
As shown in the typical application circuits (Figure 2-1),
the HCS301 is a simple device to use. It requires only
the addition of buttons and RF circuitry for use as the
transmitter in your security application. A description of
each pin is described in Table 2-1.
Note: When V
loads, a resistor with a minimum value of 50 Ω
should be used in line with V
clamping of PWM at 9.0V in the event of PWM
overshoot.
FIGURE 2-1: TYPICAL CIRCUITS
(Note 2)
B0
B1
B4 B3 B2 B1 B0
DD
> 9.0V and driving low capacitive
DD
. This prevents
+12V
R
VDD
S0
VDD
S1
S2
S3
2 button remote control
LED
PWM
V
SS
(Note 2)
VDD
Tx out
+12V
R
The high security level of the HCS301 is based on the patented K
EE
L
OQ
technology . A b lock cipher based on a b lock
length of 32 bits and a key length of 64 bits is used. The
algorithm obscures the information in such a way that ev en
if the transmission information (before coding) differs by
only 1 bit from the information in the previous transmission, the next coded transmission will be totally different.
Statistically, if only 1 bit in the 32-bit string of information
changes, approximately 50 percent of the coded transmission will change. The HCS301 will wake up upon detecting
a switch closure and then delay approximately 10 ms for
switch debounce (Figure 2-2). The synchronization information, fixed information, and switch information will be
encrypted to form the hopping code. The encrypted or
hopping code portion of the transmission will change every
time, even if the same b utton is pushed again. A code that
has been transmitted will not occur again for more than
64K transmissions. This will provide more than 18 years of
typical use before a code is repeated, based on 10 operations per day. Overflow information sent from the encoder
can be used by the decoder to extend the number of
unique transmissions to more than 192K.
If, in the transmit process, it is detected that a new button(s) has been pressed, a reset will immediately be
forced and the code word will not
be completed. Please
note that buttons removed will not have any effect on the
code word unless no buttons remain pressed. In this case ,
the code word will be completed and the power down will
occur.
S0
VDD
LED
S1
PWM
S2
S3
V
SS
5 button remote control (Note1)
Note 1: Up to 15 functions can be implemented by pressing
more than one button simultaneously or by using a
suitable diode array.
Tx out
2: Resistor (R) is recommended for current limiting.
TABLE 2-1: PIN DESCRIPTIONS
Name
S0 1 Switch input 0
S1 2 Switch input 1
S2 3 Switch input 2/Can also be clock
S3 4 Switch input 3/Clock pin when in
V
SS
PWM 6 Pulse width modulation (PWM)
LED
V
DD
Pin
Number
Description
pin when in programming mode
programming mode
5 Ground reference connection
output pin/Data pin for
programming mode
7 Cathode connection for directly
driving LED
during transmission
8 Positive supply voltage
connection
FIGURE 2-2: ENCODER OPERATION
Power Up
(A button has been pressed)
Reset and Debounce Delay
Load T r ansmit Register
Yes
Word Transmission
(10 ms)
Sample Inputs
Update Sync Info
Encrypt With
Encryption Key
T r ansmit
Buttons
Added?
No
All
Buttons
Released?
Yes
Complete Code
Stop
No
DS21143A-page 4
Preliminary
1996 Microchip Technology Inc.
HCS301
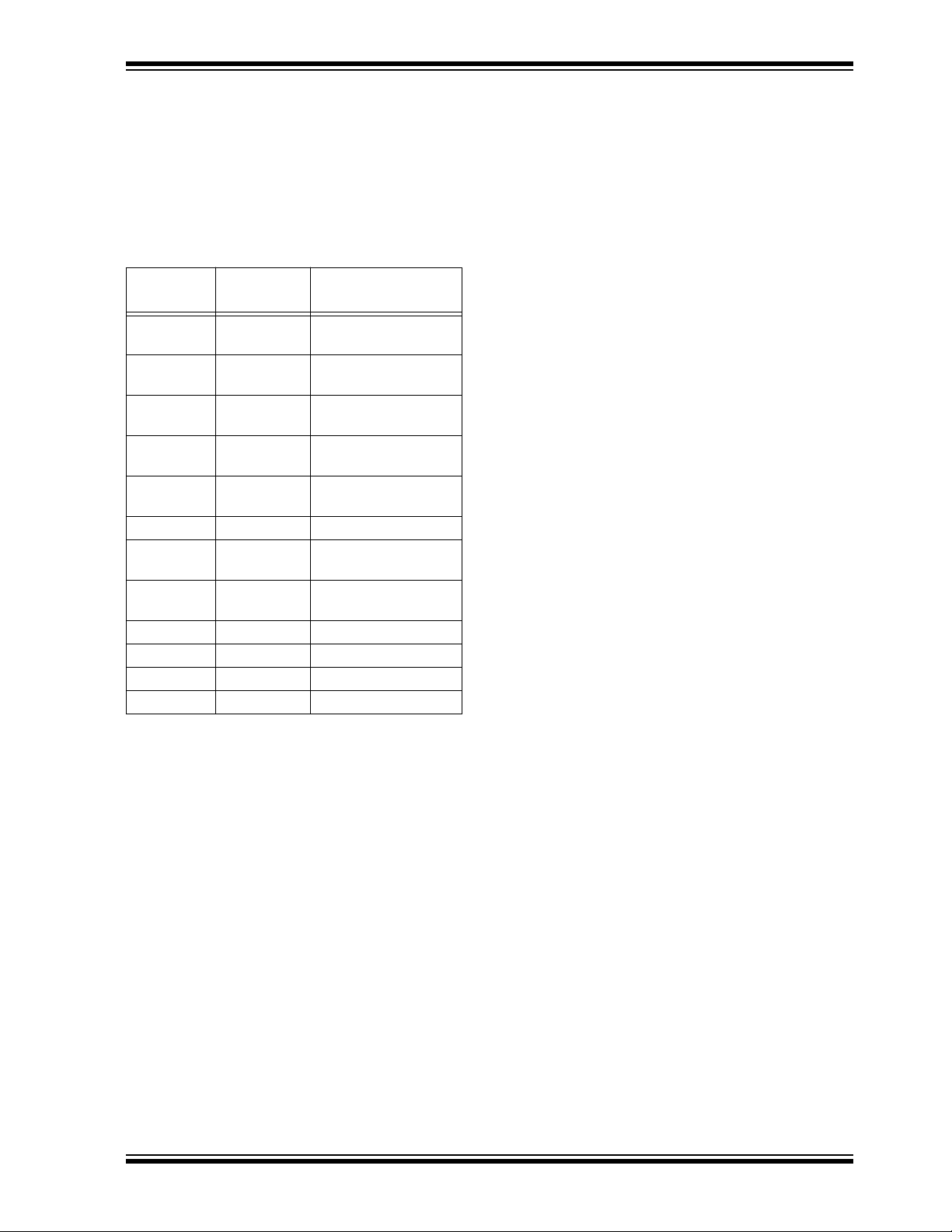
3.0 EEPROM MEMORY ORGANIZATION
The HCS301 contains 192 bits (12 x 16-bit words) of
EEPROM memory (Table 3-1). This EEPROM array is
used to store the encryption key information,
synchronization value, etc. Further descriptions of the
memory array is given in the following sections.
TABLE 3-1: EEPROM MEMORY MAP
WORD
ADDRESS
0 KEY_0 64-bit encryption key
1 KEY_1 64-bit encryption key
2 KEY_2 64-bit encryption key
3 KEY_3 64-bit encryption key
4 SYNC 16-bit synchronization
5 RESERVED Set to 0000H
6 SER_0 Device Serial Number
7 SER_1(Note) Device Serial Number
8 SEED_0 Seed Value (word 0)
9 SEED_1 Seed Value (word 1)
10 EN_KEY 16-bit Envelope Key
11 CONFIG Configuration Word
Note: The MSB of the serial number contains a bit
3.1 Key_0 - Key_3 (64-Bit Encryption Key)
The 64-bit encryption key is used by the transmitter to
create the encrypted message transmitted to the
receiver. This key is created and programmed at the
time of production using a key generation algorithm.
The key generation algorithm is different from the
K
encryption method. Inputs to the key generation
algorithm are the serial number for the particular
transmitter being used and the 64-bit manufacturer’s
code. While the key generation algorithm supplied from
Microchip is the typical method used, a user may elect
to create their own method of key generation. This may
be done providing that the decoder is programmed with
the same means of creating the key for
decryption purposes.
EE
L
OQ
MNEMONIC DESCRIPTION
(word 0)
(word 1)
(word 2)
(word 3)
value
(word 0)
(word 1)
used to select the auto shutoff timer.
algorithm, although it too is a proprietary
3.2 SYNC (Synchronization Counter)
This is the 16-bit synchronization value that is used to
create the hopping code for transmission. This value
will be changed after every transmission.
3.3 SER_0, SER_1 (Encoder Serial Number)
SER_0 and SER_1 are the lower and upper words of
the device serial number, respectively. Although there
are 32 bits allocated for the serial number, only the
lower order 28 bits are transmitted. The serial number
is meant to be unique for every transmitter. The most
significant bit of the serial number (Bit 31) is used to
turn the auto shutoff timer on or off.
3.3.1 AUTO-SHUTOFF TIMER SELECT
The most significant bit of the serial number (Bit 31) is
used to turn the Auto-shutoff timer on or off. This timer
prevents the transmitter from draining the battery
should a button get stuck in the on position for a long
period of time. The time period is approximately
25 seconds, after which the device will go to the
Time-out mode. When in the Time-out mode , the device
will stop transmitting, although since some circuits
within the device are still active, the current dr a w within
the Shutoff mode will be more than Standby mode. If
the most significant bit in the serial number is a one,
then the Auto-shutoff timer is enabled, and a zero in the
most significant bit will disable the timer. The length of
the timer is not selectable.
3.4 SEED_0, SEED_1 (Seed Word)
This is the two-word (32 bits) seed code that will be
transmitted when all four buttons are pressed at the same
time. This allows the system designer to implement the
secure learn feature or use this fixed code word as part of
a different key gener ation/tr ac king process .
3.5 EN_Key (Envelope Encryption Key)
Envelope encryption is a selectable option that
encrypts the portion of the transmission that contains
the transmitter serial number and function code. Selecting this option is done by setting the appropriate bit in
the configuration word (Table 3-2). Normally, the serial
number and function code are transmitted in the clear
(unencrypted), but for an added level of security, the
system designer may elect to implement this option.
The envelope encryption key is used to encrypt the
serial number and function code portion of the transmission, if the envelope encryption option has been
selected. The envelope encryption algorithm is a different algorithm than the key generation or transmit
encryption algorithm. The EN_k e y is typically a random
number and the same for all transmitters in a system.
1996 Microchip Technology Inc.
Preliminary
DS21143A-page 5
HCS301
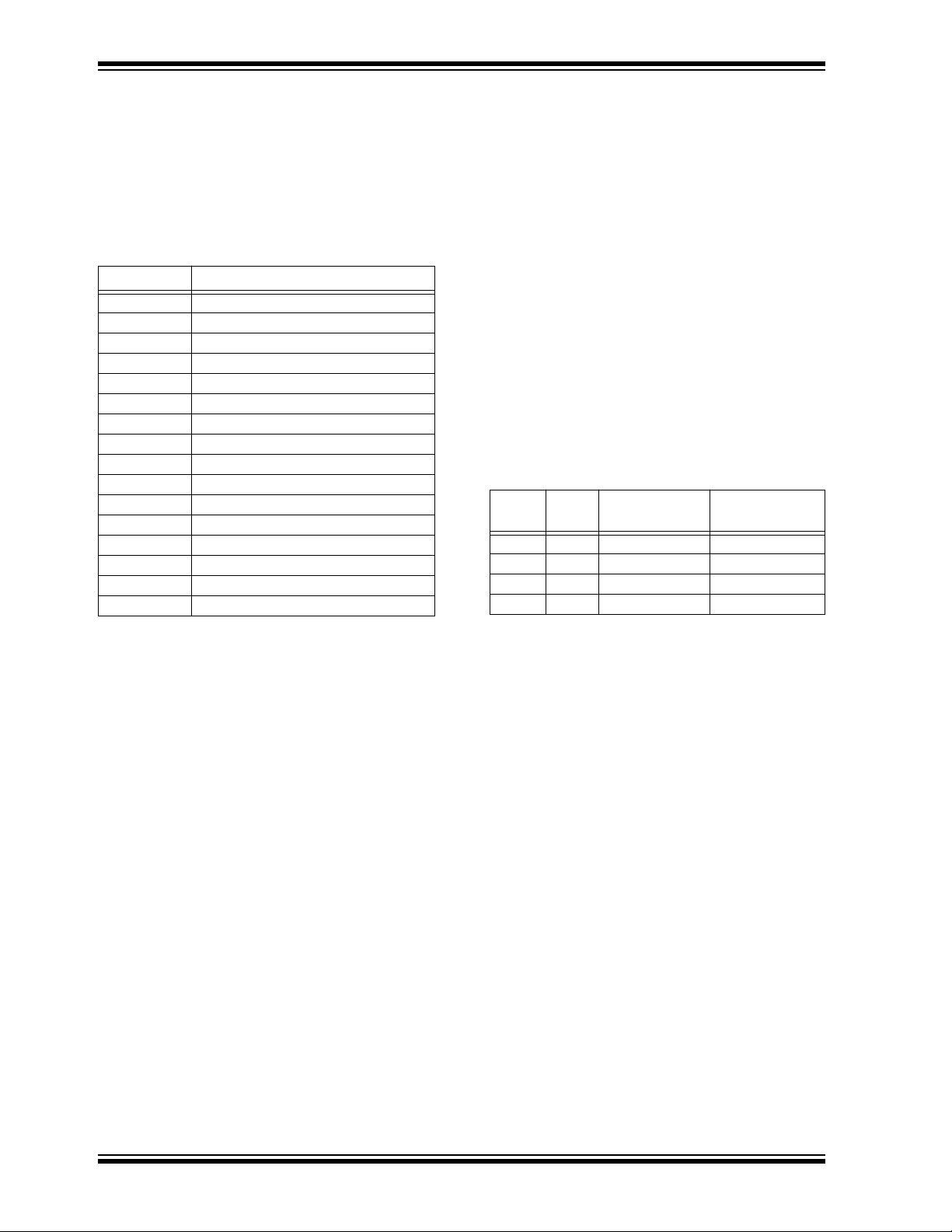
3.6 Configuration Wor d
The configuration word is a 16-bit word stored in
EEPROM array that is used by the device to store
information used during the encryption process, as well
as the status of option configurations. Further
explanations of each of the bits are described in the
following sections.
TABLE 3-2: CONFIGURATION WORD
Bit Number Bit Description
0 Discrimination Bit 0
1 Discrimination Bit 1
2 Discrimination Bit 2
3 Discrimination Bit 3
4 Discrimination Bit 4
5 Discrimination Bit 5
6 Discrimination Bit 6
7 Discrimination Bit 7
8 Discrimination Bit 8
9 Discrimination Bit 9
10 Overflow Bit 0 (OVR0)
11 Overflow Bit 1 (OVR1)
12 Low V oltage Trip Point Select
13 Baudrate Select Bit 0 (BSL0)
14 Baudrate Select Bit 1 (BSL1)
15 Envelope Encryption Select (EENC)
0x0000 and clear OVR1 the second time the counter
wraps. Once cleared, OVR0 and OVR1 cannot be set
again, thereby creating a permanent record of the
counter overflow. This prevents fast cycling of 64K
counter. If the decoder system is programmed to track
the overflow bits, then the effective number of unique
synchronization values can be extended to 196,608.
3.6.3 ENVELOPE ENCRYPTION (EENC)
If the EENC bit is set to a 1, the serial number and func-
tion code will also be encrypted so that it will appear to
be random. The 16-bit en velope k ey and env elope algorithm will be used for encryption.
3.6.4 BAUDRATE SELECT BITS (BSL0, BSL1)
BSL0 and BSL1 select the speed of transmission and
the code word blanking. Table 3-3 shows how the bits
are used to select the different baud rates and
Section 5.2 provides detailed explanation in code word
blanking.
TABLE 3-3: BAUDRATE SELECT
BSL1 BSL0
0 0 400 µ s All
0 1 200 µ s 1 out of 2
1 0 100 µ s 1 out of 2
1 1 100 µ s 1 out of 4
Basic Pulse
Element
Code Wor ds
T ransmitted
3.6.1 DISCRIMINATION VALUE (DISC0 TO DISC9)
The discrimination value can be programmed with any
value to serve as a post decryption check on the
decoder end. In a typical system, this will be
programmed with the 10 least significant bits of the
serial number or a constant value, which will also be
stored by the receiver system after a transmitter has
been learned. The discrimination bits are part of the
information that is to form the encrypted portion of the
transmission. After the receiver has decrypted a transmission, the discrimination bits can be checked against
the stored value to verify that the decryption process
was valid.
3.6.2 OVERFLOW BITS (OVR0 AND OVR1)
The overflow bits are used to e xtend the number of possible synchronization values. The synchronization
counter is 16 bits in length, yielding 65,536 values
before the cycle repeats. Under typical use of
10 operations a day, this will provide nearly 18 years of
use before a repeated value will be used. Should the
system designer conclude that is not adequate, then
the overflow bits can be utilized to e xtend the number of
unique values. This can be done by programming
OVR0 and OVR1 to 1s at the time of production. The
encoder will automatically clear OVR0 the first time that
the synchronization value wraps from 0xFFFF to
DS21143A-page 6
Preliminary
1996 Microchip Technology Inc.

HCS301
3.6.5 LOW VOLTAGE TRIP POINT SELECT
The low voltage trip point select bit is used to tell the
HCS301 what V
level is being used. This information
DD
will be used by the device to determine when to send
the voltage low signal to the receiver. When this bit is
set to a one, the V
from a 9.0 volt or 12.0 volt V
then the V
DD
level is assumed to be 6.0 volts. Refer to
level is assumed to be operating
DD
level. If the bit is set low,
DD
Figure 3-1 for voltage trip point.
The LED current limiting resistor value also affects the
LED current:
•V
LOW
•V
LOW
is tested at 3.5V and 13.0V.
LOW
V
1 (high limiting).
=
0 (low limiting).
=
FIGURE 3-1: TYPICAL VOLTAGE TRIP
POINTS (BY
CHARACTERIZATION)
Volts (V)
5.5
5.0
4.5
4.0
3.5
3.0
2.5
9.0
8.5
8.0
7.5
7.0
-40 20 40 100
-20 0 60 80
VLOW sel = 0
VLOW sel = 1
Temp (C)
V
LOW
Max
Min
Max
Min
4.0 T RANSMITTED W ORD
4.1 Transmission Format
The HCS301 transmission is made up of several parts
(Figure 4-1). Each transmission is begun with a
preamble and a header, followed by the encrypted and
then the fixed data. The actual data is 66 bits which
consists of 32 bits of encrypted data and 34 bits of fixed
data. Each transmission is followed by a guard period
before another transmission can begin. Refer to
Table 8-4 for transmission timing requirements. The
encrypted portion provides up to four billion changing
code combinations and includes the button status bits
(based on which buttons were activated) along with the
synchronization counter value and some discrimination
bits. The fixed portion is compr ised of the status bits,
the function bits and the 28-bit serial number. The fixed
and encrypted sections combined increase the number
of combinations to 7.38 x 10
4.2 Synchronous T ransmission Mode
Synchronous transmission mode can be used to clock
the code word out using an external clock.
T o enter synchronous transmission mode , the programming mode start-up sequence must be executed as
shown in Figure 4-3. If either S1 or S0 is set on the f alling edge of S2 (or S3), the device enters synchronous
transmission mode. In this mode, it functions as a normal transmitter, with the e xception that the timing of the
PWM data string is controlled externally and that 16
extra bits are transmitted at the end with he code word.
The button code will be the S0, S1 value at the falling
edge S2 or S3. The timing of the PWM data str ing is
controlled by supplying a clock on S2 or S3 and should
not exceed 20 KHz. The code word is the same as in
PWM mode with 16 reserved bits at the end of the
word. The reser ved bits can be ignored. When in synchronous transmission mode S2 or S3 should not be
toggled until all internal processing has been completed as shown in Figure 4-4.
19
.
1996 Microchip Technology Inc.
4.3 Code Wor d Organization
The HCS301 transmits a 66-bit code word when a
button is pressed. The 66-bit word is constructed from
a Fixed Code portion and an Encrypted Code por tion
(Figure 4-2).
The Encrypted Data is generated from 4 button bits, 2
overflow counter bits, 10 discrimination bits and the
16-bit sync value (Figure 8-5).
The Fixed Code Data is made up from two status bits,
four button bits and the 28-bit serial number. The four
button bits and the 28-bit serial number may be
encrypted with the Envelope Key if the envelope
encryption is enabled by the user.
Preliminary
DS21143A-page 7

HCS301
FIGURE 4-1: CODE WORD TRANSMISSION FORMAT
LOGIC ‘0’
LOGIC ‘1’
Bit
Period
Preamble
TP
Header
TH
Encrypted Portion
of Transmission
THOP
FIGURE 4-2: CODE WORD ORGANIZATION
Fixed Code Data Encrypted Code Data
Repeat
(1 bit)
VLOW
(1 bit)
1 bit of Status
1 bit Fixed
Button
Status
(4 bits)
28-bit
Serial Number
+
Serial Number and
Button Status (32 bits)
Button
Status
(4 bits)
FIGURE 4-3: SYNCHRONOUS TRANSMISSION MODE
t = 50 ms
PWM
Fixed Portion of
Transmission
+
TFIX
Discrimina-
tion bits
(12 bits)
32 bits of Encrypted Data
Guard
Time
TG
16-bit
Sync Value
66 bits
of Data
Transmitted
S2(S3)
S[1:0]
“01,10,11”
FIGURE 4-4: TRANSMISSION WORD FORMAT DURING SYNCHRONOUS TRANSMISSION MODE
Reserved Padding
Button
Code
Serial Number Data Word Sync Counter
16 2 4 28 16 16
Transmission Direction
DS21143A-page 8
Preliminary
1996 Microchip Technology Inc.

HCS301
5.0 SPECIAL FEATURES
5.1 Code Wor d Completion
Code word completion is an automatic feature that
makes sure that the entire code word is transmitted,
even if the button is released before the transmission is
complete. The HCS301 encoder powers itself up when
a button is pushed and powers itself down after the
command is finished, if the user has already released
the button. If the button is held down beyond the time
for one transmission, then multiple transmissions will
result. If another button is activated during a
transmission, the active transmission will be aborted
and the new code will be generated using the new
button information.
5.2 Blank Alternate Code Word
Federal Communications Commission (FCC) part 15
rules specify the limits on fundamental power and
harmonics that can be transmitted. Power is calculated
on the worst case average power transmitted in a
100ms window. It is therefore advantageous to
minimize the duty cycle of the transmitted word. This
can be achieved by minimizing the duty cycle of the
individual bits and by blanking out consecutive words.
Blank Alternate Code Word (BACW) is used for
reducing the average power of a transmission
(Figure 5-1). This is a selectable feature that is
determined in conjunction with the baudrate selection
bits BSL0 and BSL1. Using the BACW allows the user
to transmit a higher amplitude transmission if the
transmission length is shorter. The FCC puts
constraints on the average power that can be
transmitted by a device, and BA CW eff ectively pre v ents
continuous transmission by only allowing the transmission of every second or every fourth code word. This
reduces the average power transmitted and hence,
assists in FCC approval of a transmitter device.
5.3 Envelope Encryption Option
Envelope Encryption is a user selectable option which
is meant to offer a higher level of security for a code
hopping system. During a normal transmission with the
envelope encryption turned off, the 28-bit serial number
and function code are transmitted in the clear (unencrypted). If envelope encryption is selected, then the
serial number and function code are also encrypted
before transmission. The encryption for the serial number is done using a different algorithm than the transmission algorithm. The envelope encryption scheme is
not nearly as complex as the K
hence, not as secure. When the env elope encryption is
used, the serial number must be decrypted using the
envelope key and envelope decryption. After the serial
number is obtained, the normal decryption method can
be used to decrypt the hopping code.
EELOQ algorithm and,
FIGURE 5-1: BLANK ALTERNATE CODE WORD (BACW)
Amplitude
100ms
Time
BACW Disabled
(All words transmitted)
BACW Enabled
(1 out of 2 transmitted)
BACW Enabled
(1 out of 4 transmitted)
100ms
A
2A
4A
One Code Word
100ms
100ms
1996 Microchip Technology Inc. Preliminary DS21143A-page 9

HCS301
5.4 Secure Learn
In order to increase the level of security in a system, it is
possible for the receiver to implement what is known as
a secure learn function. This can be done b y utilizing the
seed value on the HCS301 which is stored in EEPROM
and can only be transmitted when all four button inputs
are pressed at the same time (Table 5-1). Instead of the
normal key generation method being used to create the
encryption key, this seed value is used.
TABLE 5-1: PIN ACTIVATION TABLE
S3 S2 S1 S0 Notes
10001 1
20010 1
30011 1
40100 1
50101 1
60110 1
70111 1
81000 1
91001 1
10 1 0 1 0 1
11 1 0 1 1 1
12 1 1 0 0 1
13 1 1 0 1 1
14 1 1 1 0 1
15 1 1 1 1 2
Note 1: Transmit generated 32-bit code hopping
word.
2: Transmit 32-bit seed value.
5.6 VLOW: Voltage LOW indicator
The VLOW bit is transmitted with every transmission
(Figure 8-5) and will be transmitted as a one if the
operating voltage has dropped below the low voltage
trip point. The trip point is selectable between two
values, based on the battery voltage being used. See
Section 3.6.5 for a description of how the low voltage
select option is set. This VLOW signal is transmitted so
the receiver can alert the user that the transmitter battery is low.
5.7 RPT: Repeat indicator
This bit will be low for the first transmitted word. If a
button is held down for more than one transmitted code
word, this bit will be set to indicate a repeated code
word and remain set until the button is released.
5.8 LED Output Operation
During normal transmission the LED output is LOW. If
the supply voltage drops below the low voltage trip
point, the LED
5 Hz during the transmission (Section 3.6.5). The limiting resistor is selectable between two nominal values
(Section 3.6.5).
output will be toggled at approximately
5.5 Auto-shutoff
The Auto-shutoff function automatically stops the
device from transmitting if a button inadvertently gets
pressed for a long period of time. This will prevent the
device from draining the battery if a button gets pressed
while the transmitter is in a pocket or purse. This function can be enabled or disabled and is selected by setting or clearing the Auto-shutoff bit (Section 3.3.1).
Setting this bit high will enable the function (turn
Auto-shutoff function on) and setting the bit low will disable the function. Time-out period is approximately 25
seconds.
DS21143A-page 10 Preliminary 1996 Microchip Technology Inc.

HCS301
6.0 PROGRAMMING THE HCS301
When using the HCS301 in a system, the user will have
to program some parameters into the device including
the serial number and the secret key before it can be
used. The programming cycle allows the user to input
all 192 bits in a serial data stream, which are then
stored internally in EEPROM. Programming will be
initiated by forcing the PWM line high, after the S3 line
has been held high for the appropriate length of time
line (Table 6-1 and Figure 6-1). After the program mode
is entered, a delay must be provided to the device for
the automatic bulk write cycle to complete. This will
write all locations in the EEPROM to an all zeros pattern. The device can then be programmed by clocking
in 16 bits at a time, using S3 as the clock line and PWM
FIGURE 6-1: PROGRAMMING WAVEFORMS
S3
(Clock)
PWM
(Data)
Enter Program
Mode
TPS
TPH1
T
PBW
TCLKH
TDS
TCLKL
Bit 0 Bit 1 Bit 2 Bit 3 Bit 14 Bit 15 Bit 16 Bit 17
as the data in line. After each 16-bit word is loaded, a
programming delay is required for the internal program
cycle to complete. This delay can take up to Twc. At the
end of the programming cycle, the device can be verified (Figure 6-2) by reading back the EEPROM. Reading is done by clocking the S3 line and reading the data
bits on PWM. For security reasons, it is not possible to
execute a verify function without first programming the
EEPROM. A verify operation can only be done
immediately following the program cycle.
Note: To ensure that the device does not acci-
dentally enter programming mode (resulting in a bulk erase), PWM should never be
pulled high by the circuit connected to it.
Special care should be taken when driving
PNP RF transistors.
TWC
TDH
TPH2
Data for Word 0 (KEY_0)
Repeat 12 times for each word
Note 1: Unused button inputs to be held ground during the entire programming sequence.
2: The V
DD pin must be taken to ground after a programming/verify cycle.
FIGURE 6-2: VERIFY WAVEFORMS
End of
Programming Cycle
PWM
(Data)
S3
(Clock)
Note: If a verify operation is to be done, then it must immediately follow the program cycle.
Begin Verify Cycle Here
Bit 0Bit191Bit190
TWC
Data in Word 0
Bit 1 Bit 2 Bit 3 Bit 15Bit 14 Bit 16 Bit 17 Bit190 Bit191
TDV
TABLE 6-1: PROGRAMMING/VERIFY TIMING REQUIREMENTS
VDD = 5.0V ± 10%
25° C ± 5 °C
Parameter Symbol Min. Max. Units
Program mode setup time T
Hold time 1 T
Hold time 2 T
Bulk Write time T
Program delay time T
Program cycle time T
Clock low time T
Clock high time T
Data setup time T
Data hold time T
Data out valid time T
PS 3.5 4.5 ms
PH1 3.5 — ms
PH250 — µs
PBW — 2.2 ms
PROG — 2.2 ms
WC —36ms
CLKL 25 — µs
CLKH 25 — µs
DS 0—µs
DH 18 — µs
DV 10 24 µs
Data for Word 1
1996 Microchip Technology Inc. Preliminary DS21143A-page 11

HCS301
7.0 INTEGRATING THE HCS301 INTO A SYSTEM
Use of the HCS301 in a system requires a compatible
decoder. This decoder is typically a microcontroller with
compatible firmware. Microchip will provide (via a
license agreement) firmware routines that accept
transmissions from the HCS301 and decrypt the
hopping code portion of the data stream. These
routines provide system designers the means to
develop their own decoding system.
7.1 Learning a transmitter to a receiver
In order for a transmitter to be used with a decoder , the
transmitter must first be ‘learned’. Several learning
strategies can be followed in the decoder implementation. When a transmitter is lear ned to a decoder, it is
suggested that the decoder stores the serial number
and current synchronization value in EEPROM. The
decoder must keep track of these values for every
transmitter that is learned (Figure 7-1). The maximum
number of transmitters that can be learned is only a
function of how much EEPROM memory storage is
available. The decoder must also store the manufacturer’s code in order to learn a transmission transmitter ,
although this value will not change in a typical system
so it is usually stored as part of the microcontroller
ROM code. Storing the manufacturer’s code as part of
the ROM code is also better for security reasons.
It must be stated that some learning strategies have
been patented and care must be taken not to infringe.
FIGURE 7-1: TYPICAL LEARN SEQUENCE
Enter Learn
Mode
Wait for Reception
of a Valid Code
Generate Key
from Serial Number
Use Generated Key
to Decrypt
Compare Discrimination
Value with Fixed Value
Equal
?
Yes
Wait for Reception
of Second Valid Code
Use Generated Key
to Decrypt
Compare Discrimination
Value with Fixed Value
Equal
?
Yes
No
No
Counters
Sequential
?
Yes
Learn successful Store:
Serial number
Encryption key
Synchronization counter
Exit
No
Learn
Unsuccessful
DS21143A-page 12 Preliminary 1996 Microchip Technology Inc.

HCS301
7.2 Decoder operation
In a typical decoder operation (Figure 7-2), the key generation on the decoder side is done by taking the serial
number from a transmission and combining that with
the manufacturer’s code to create the same secret key
that was used by the transmitter . Once the secret key is
obtained, the rest of the transmission can be decrypted.
The decoder waits for a transmission and immediately
can check the serial number to determine if it is a
learned transmitter. If it is, it tak es the encrypted portion
of the transmission and decrypts it using the stored key .
It uses the discrimination bits to determine if the
decryption was valid. If everything up to this point is
valid, the synchronization value is evaluated.
FIGURE 7-2: TYPICAL DECODER
OPERATION
Start
No
Transmission
Received
?
Yes
No
Decrypt T ransmission
Does
Serial Number
Match
?
Yes
7.3 Synchronization with Decoder
The KEELOQ technology features a sophisticated
synchronization technique (Figure 7-3) which does not
require the calculation and storage of future codes. If
the stored counter value for that particular transmitter
and the counter value that was just decrypted are within
a formatted window of say 16, the counter is stored and
the command is executed. If the counter value was not
within the single operation window, but is within the
double operation window of say 32K window, the transmitted synchronization value is stored in temporary
location and it goes back to waiting for another transmission. When the next valid transmission is received,
it will check the new value with the one in temporary
storage. If the two values are sequential, it is assumed
that the counter had just gotten out of the single operation ‘window’, but is now back in sync, so the new synchronization value is stored and the command
executed. If a transmitter has somehow gotten out of
the double operation window, the transmitter will not
work and must be re-learned. Since the entire window
rotates after each valid transmission, codes that have
been used are part of the ‘block ed’ (32K) codes and are
no longer valid. This eliminates the possibility of grabbing a previous code and re-transmitting to gain entry.
Note: The synchronization method described in
this section is only a typical implementation
and because it is usually implemented in
firmware, it can be altered to fit the needs
of a particular system
FIGURE 7-3: SYNCHRONIZATION WINDOW
No
Decryption
Valid
No
No
Counter
Within 16
Counter
Within 32K
Save Counter
in T emp Location
Is
?
Yes
Is
?
No
Is
?
Yes
Yes
Execute
Command
and
Update
Counter
Entire Window
rotates to eliminate
use of previously
used codes
Blocked 32K
Codes
Open 32K
Codes
Current
Position
Current window
of 16 codes
1996 Microchip Technology Inc. Preliminary DS21143A-page 13

HCS301
8.0 ELECTRICAL CHARACTERISTICS
TABLE 8-1: ABSOLUTE MAXIMUM RATINGS
Symbol Item Rating Units
DD Supply voltage -0.3 to 13.3 V
V
IN Input voltage -0.3 to 13.3 V
V
OUT Output voltage -0.3 to VDD + 0.3 V
V
OUT Max output current 25 mA
I
STG Storage temperature -55 to +125 °C (Note)
T
LSOL Lead soldering temp 300 °C (Note)
T
ESD ESD rating 4000 V
V
Note: Stresses above those listed under “ABSOLUTE MAXIMUM RATINGS” ma y cause permanent damage to the
device.
TABLE 8-2: DC CHARACTERISTICS
Commercial (C): Tamb = 0°C to +70°C
Industrial (I): Tamb = -40°C to +85°C
3.5V < V
DD < 13.0V
Parameter Sym. Min Typ* Max Unit Conditions
Operating current (avg) I
Standby current I
High level Input voltage V
Low level input voltage V
High level output voltage V
Low level output voltage V
sink current ILED 3.5
LED
Resistance; S0-S3 R
Resistance; PWM R
* Typical values are at 25°C.
CC 0.6
CCS 110µA
IH 0.4 VDD VDD+
IL -0.3 0.15 VDD V
OH 0.5VDD VIOH = -2 mA
OL 0.08 VDD VIOL = 2 mA
S0-3 40 60 80 KΩ VIN = 4.0V
PWM 80 120 160 KΩ VIN = 4.0V
2.7
1.5
8.0
4.7
3.7
1.0
3.0
12.0
0.3
5.9
4.6
VDD = 3.5V
mA
V
DD = 6.6V
V
DD = 13.0V
(Figure 8-1)
V
mA VDD = 6.6V, Vlow source = 0
V
DD = 13.0V, Vlow source = 1
DS21143A-page 14 Preliminary 1996 Microchip Technology Inc.

FIGURE 8-1: TYPICAL ICC CURVE OF HCS301 WITH EXTERNAL RESISTORS
50Ω External
12.0
10.0
8.0
6.0
mA
4.0
2.0
0.0
23456789 1112
VBAT [V]
1K External
12.0
10
HCS301
13
mA
mA
10.0
8.0
6.0
4.0
2.0
0.0
2 3 4 5 6 7 8 9 11121310
VBAT [V]
2K External
12.0
10.0
8.0
6.0
4.0
2.0
0.0
2 3 4 5 6 7 8 9 11121310
VBAT [V]
LEGEND
Typical
Maximum
Minimum
1996 Microchip Technology Inc. Preliminary DS21143A-page 15

HCS301
FIGURE 8-2: POWER UP AND TRANSMIT TIMING
Button Press
PWM
Sn
Detect
DB
T
TTD
T
BP
Code
Word
1
TABLE 8-3: POWER UP AND TRANSMIT TIMING REQUIREMENTS
VDD = +3.5 to13.0V
Commercial (C): Tamb = 0°C to +70°C
Industrial (I): Tamb = -40°C to +85°C
Code Word Transmission
Code
Word
2
TTO
Code
Word
3
Code
Word
n
Parameter Symbol Min Max Unit Remarks
Time to second button press T
Transmit delay from button detect T
Debounce delay T
Auto-shutoff time-out period T
Note 1: TBP is the time in which a second button can be pressed without completion of the first code word and the
intention was to press the combination of buttons.
2: The auto shutoff timeout period is not tested.
BP 10 + Code
Word Time
TD 10 25 ms
DB 615ms
TO 20 40 s
25 + Code
Word Time
ms
(Note 1)
(Note 2)
FIGURE 8-3: PWM FORMAT
TE
TE
TE
LOGIC ‘0’
LOGIC ‘1’
TBP
Preamble
TP
Header
TH
Encrypted Portion
of Transmission
THOP
Fixed portion of
Transmission
TFIX
Guard
Time
TG
FIGURE 8-4: PREAMBLE/HEADER FORMAT
Data Word
P0
DS21143A-page 16 Preliminary 1996 Microchip Technology Inc.
Preamble Header
P12
23 TE
10 TE
Transmission
Bit 0 Bit 1

FIGURE 8-5: DATA WORD FORMAT
LSB
LSB
MSB MSB S3 S0 S1 S2 VLOW RPT
HCS301
Serial Number Button Code Status
Header
Bit 0 Bit 1
Hopping Code Word
Bit 30
Bit 31 Bit 32 Bit 33 Bit 58 Bit 59
Bit 60
Bit 61
Fixed Code Word
Bit 62 Bit 63 Bit 64 Bit 65
TABLE 8-4: CODE WORD TRANSMISSION TIMING REQUIREMENTS
VDD = +3.5 to 13.0
Commercial (C): Tamb = 0°C to +70°C
Industrial (I): Tamb = -40°C to +85°C
Symbol Characteristic
Number
of T
Min. Typ. Max. Min. Typ. Max. Min. Typ. Max. Units
E
All 1 out of 2 1 out of 4
TE Basic pulse element 1 280 400 620 140 200 310 70 100 155 µs
BP PWM bit pulse width 3 840 1200 1860 420 600 930 210 300 465 µs
T
P Preamble duration 23 6.4 9.2 14.3 3.2 4.6 7.1 1.6 2.3 3.6 ms
T
H Header duration 10 2.8 4.0 6.2 1.4 2.0 3.1 0.7 1.0 1.6 ms
T
HOP Hopping code duration 96 26.9 38.4 59.5 13.4 19.2 29.8 6.7 9.6 14.9 ms
T
FIX Fixed code duration 102 28.6 40.8 63.2 14.3 20.4 31.6 7.1 10.2 15.8 ms
T
G Guard Time 39 10.9 15.6 24.2 5.5 7.8 12.1 2.7 3.9 6.0 ms
T
— T otal Transmit Time 270 75.6 108.0 167.4 37.8 54.0 83.7 18.9 27.0 41.9 ms
— PWM data rate — 1190 833 538 2381 1667 1075 4762 3333 2151 bps
Note: The timing parameters are not tested but derived from the oscillator clock.
Code Wor ds T ransmitted
Guard
Time
FIGURE 8-6: HCS301 TE VS. TEMP (BY CHARACTERIZATION ONLY)
1.7
1.6
1.5
1.4
1.3
1.2
TE
1.1
1.0
0.9
0.8
0.7
0.6
-50 -40 -30 -20 -10 0 10 20 30 40 50 60 70 80 90
TE Max.
VDD = 3.5V
VDD ≥ 5.0V
TE Max.
VDD = 5.0V
Typical
VDD ≥ 5.0V
TE Min.
TEMPERATURE
1996 Microchip Technology Inc. Preliminary DS21143A-page 17

HCS301
NOTES:
DS21143A-page 18 Preliminary 1996 Microchip Technology Inc.

NOTES:
HCS301
1996 Microchip Technology Inc. Preliminary DS21143A-page 19

HCS301
HCS301 Product Identification System
To order or to obtain information (e.g., on pricing or delivery), please use the listed part numbers, and refer to the factory or the listed
sales offices.
HCS301 - /P
Package: P = Plastic DIP (300 mil Body), 8-lead
SN = Plastic SOIC (150 mil Body), 8-lead
Temperature Blank = 0°C to +70°C
Range: I = -40°C to +85°C
AMERICAS
Corporate Office
Microchip T echnology Inc.
2355 West Chandler Blvd.
Chandler, AZ 85224-6199
Tel: 602 786-7200 Fax: 602 786-7277
Technical Support:
Web:
http://www.microchip.com
Atlanta
Microchip T echnology Inc.
500 Sugar Mill Road, Suite 200B
Atlanta, GA 30350
Tel: 770 640-0034 Fax: 770 640-0307
Boston
Microchip T echnology Inc.
5 Mount Royal Avenue
Marlborough, MA 01752
Tel: 508 480-9990 Fax: 508 480-8575
Chicago
Microchip T echnology Inc.
333 Pierce Road, Suite 180
Itasca, IL 60143
Tel: 708 285-0071 Fax: 708 285-0075
Dallas
Microchip T echnology Inc.
14651 Dallas Parkway, Suite 816
Dallas, TX 75240-8809
Tel: 214 991-7177 Fax: 214 991-8588
Dayton
Microchip T echnology Inc.
Suite 150
Two Prestige Place
Miamisburg, OH 45342
Tel: 513 291-1654 Fax: 513 291-9175
Los Angeles
Microchip T echnology Inc.
18201 Von Karman, Suite 1090
Irvine, CA 92715
Tel: 714 263-1888 Fax: 714 263-1338
New Y ork
Microchip T echnology Inc.
150 Motor Parkway, Suite 416
Hauppauge, NY 11788
Tel: 516 273-5305 Fax: 516 273-5335
602 786-7627
Device:
HCS301
HCS301T
AMERICAS (CON’T)
San Jose
Microchip T echnology Inc.
2107 North First Street, Suite 590
San Jose, CA 95131
Tel: 408 436-7950 Fax: 408 436-7955
Toronto
Microchip T echnology Inc.
5925 Airport Road, Suite 200
Mississauga, Ontario L4V 1W1, Canada
Tel: 905 405-6279Fax: 905 405-6253
ASIA/PACIFIC
Hong Kong
Microchip T echnology
RM 3801B, Tower Two
Metroplaza
223 Hing Fong Road
Kwai Fong, N.T. Hong Kong
Tel: 852 2 401 1200 Fax: 852 2 401 3431
Korea
Microchip T echnology
168-1, Youngbo Bldg. 3 Floor
Samsung-Dong, Kangnam-Ku,
Seoul, Korea
Tel: 82 2 554 7200 Fax: 82 2 558 5934
Singapore
Microchip T echnology
200 Middle Road
#10-03 Prime Centre
Singapore 188980
Tel: 65 334 8870 Fax: 65 334 8850
Taiwan
Microchip T echnology
10F-1C 207
Tung Hua North Road
T aipei, Taiwan, ROC
Tel: 886 2 717 7175 Fax: 886 2 545 0139
Code Hopping Encoder
Code Hopping Encoder (Tape and Reel)
EUROPE
United Kingdom
Arizona Microchip Technology Ltd.
Unit 6, The Courtyard
Meadow Bank, Furlong Road
Bourne End, Buckinghamshire SL8 5AJ
Tel: 44 1628 851077 Fax: 44 1628 850259
France
Arizona Microchip Technology SARL
Zone Industrielle de la Bonde
2 Rue du Buisson aux Fraises
91300 Massy - France
Tel: 33 1 69 53 63 20 Fax: 33 1 69 30 90 79
Germany
Arizona Microchip Technology GmbH
Gustav-Heinemann-Ring 125
D-81739 Muenchen, Germany
Tel: 49 89 627 144 0 Fax: 49 89 627 144 44
Italy
Arizona Microchip Technology SRL
Centro Direzionale Colleoni
Palazzo Pegaso Ingresso No. 2
Via Paracelso 23, 20041
Agrate Brianza (MI) Italy
Tel: 39 39 689 9939 Fax: 39 39 689 9883
JAPAN
Microchip Technology Intl. Inc.
Benex S-1 6F
3-18-20, Shin Yokohama
Kohoku-Ku, Yokohama
Kanagawa 222 Japan
Tel: 81 45 471 6166 Fax: 81 45 471 6122
6/14/96
All rights reserved.
1996, Microchip Technology Inc.,USA., 6/96
Information contained in this publication regarding device applications and the like is intended through suggestion only and may be superseded by updates. No representation or warranty is given and no liability is assumed by Microchip Technology Incorporated with respect to the accuracy or use of such information, or infringement
of patents or other intellectual property rights arising from such use or otherwise. Use of Microchip’s products as critical components in life support systems is not authorized except with express written approval by Microchip . No licenses are conveyed, implicitly or otherwise, under any intellectual property rights. The Microchip logo and
name are registered trademarks of Microchip Technology Inc. All rights reserved. All other trademarks mentioned herein are the property of their respective companies.
DS21143A-page 20 Preliminary 1996 Microchip Technology Inc.
 Loading...
Loading...