Page 1
User Guide
SMART SWITCH
LGS3XX
1
Page 2

Contents
Chapter 1 – Getting Started ............................................................................... 5
Chapter 2 – System Status ................................................................................. 9
System Summary .................................................................................................................................... 9
RMON ........................................................................................................................................................ 10
Interface Statistics .............................................................................................................................. 17
Chapter 3 – Quick Start ..................................................................................... 19
Chapter 4 – System Management ................................................................. 20
System Information ............................................................................................................................. 20
Management Session Timeout ........................................................................................................ 21
Time ........................................................................................................................................................... 21
SNMP ........................................................................................................................................................ 27
Logs ........................................................................................................................................................... 44
Chapter 5 – Port Management ........................................................................ 50
Ports .......................................................................................................................................................... 50
Link Aggregation ................................................................................................................................... 52
Green Ethernet ...................................................................................................................................... 56
PoE ............................................................................................................................................................. 59
Discovery - LLDP .................................................................................................................................. 65
Chapter 6 – VLAN Management ..................................................................... 77
VLANs ....................................................................................................................................................... 77
Interfaces ................................................................................................................................................ 81
VLAN Memberships ............................................................................................................................. 84
VLAN Groups.......................................................................................................................................... 85
Voice VLAN ............................................................................................................................................. 88
Chapter 7 - Spanning Tree Management .................................................... 93
Spanning Tree ........................................................................................................................................ 94
STP Interfaces ....................................................................................................................................... 96
RSTP Interfaces .................................................................................................................................... 97
2
Page 3

MSTP Properties ................................................................................................................................... 99
MSTP Instance Status ..................................................................................................................... 102
MSTP Instance Interface ................................................................................................................ 103
Chapter 8 - MAC Address Management .................................................. 106
Dynamic MAC Addresses ............................................................................................................... 106
Static MAC Addresses .................................................................................................................... 107
Reserved MAC Addresses ............................................................................................................. 108
Chapter 9 – Multicast ...................................................................................... 110
Feature Configuration ..................................................................................................................... 112
IGMP Snooping ................................................................................................................................... 114
MLD Snooping .................................................................................................................................... 115
Multicast Router Ports .................................................................................................................... 116
Forward All ........................................................................................................................................... 117
Unregistered Multicast ................................................................................................................... 118
IGMP/MLD IP Group Addresses ................................................................................................... 120
MAC Group Address FDB ............................................................................................................... 121
IP Group Address FDB ..................................................................................................................... 123
Chapter 10 - IP Interface ............................................................................... 125
IPv4 ......................................................................................................................................................... 125
IPv6 ......................................................................................................................................................... 128
Chapter 11 - IP Network Operations .......................................................... 135
Domain Name System ...................................................................................................................... 135
DHCP ...................................................................................................................................................... 136
DHCP Snooping Binding Database ............................................................................................. 141
Interface Settings ............................................................................................................................. 143
Chapter 12 – Security ..................................................................................... 144
Management Security ..................................................................................................................... 144
RADIUS ................................................................................................................................................. 152
Network Access Control ................................................................................................................. 155
Port Security ....................................................................................................................................... 165
Storm Control ..................................................................................................................................... 167
3
Page 4

Chapter 13 - Access Control List ............................................................... 169
MAC-Based ACL ................................................................................................................................ 170
MAC-Based ACE ................................................................................................................................ 171
IPv4-Based ACL ................................................................................................................................. 173
IPv4-Based ACE................................................................................................................................. 174
IPv6-Based ACL ................................................................................................................................. 176
IPv6-Based ACE................................................................................................................................. 176
ACL Binding ......................................................................................................................................... 178
Chapter 14 - Quality of Service ................................................................... 180
Feature Configuration ..................................................................................................................... 182
Queue Scheduling ............................................................................................................................. 183
CoS/802.1p to Queue ..................................................................................................................... 184
DSCP to Queue ................................................................................................................................... 186
Bandwidth Control ............................................................................................................................ 187
Egress Shaping .................................................................................................................................. 188
Basic QoS ............................................................................................................................................. 189
QoS Statistics .................................................................................................................................... 191
Chapter 15 - Maintenance ............................................................................ 193
Reboot ................................................................................................................................................... 193
File Management ............................................................................................................................... 193
Diagnostics .......................................................................................................................................... 201
Chapter - 16 Support ...................................................................................... 208
4
Page 5

Chapter 1 – Getting Started
There are two ways to configure the device: through the graphical user interface and through the
menu command line interface.
Starting the Web-based Configuration Utility
This section describes how to navigate the Web-based switch configuration utility. If you are
using a pop-up blocker, make sure it is disabled. The following browsers are supported:
• Firefox (versions 16 and latest)
• IE version (versions 10 and latest)
• Chrome (versions 35 and latest)
Browser Restrictions
If you are using IPv6 interfaces on your management station, use the IPv6 global address and not
the IPv6 link local address to access the device from your browser.
Launching the Configuration Utility
To open the Web-based configuration utility, do the following:
1. Open a Web browser.
2. Enter the IP address of the device you are configuring in the address bar on the browser,
and then press Enter.
NOTE—When the device is using the factory default IP address of 192.168.1.251, its
power LED flashes continuously. When the device is using a DHCP assigned IP address or
an administrator-configured static IP address, the power LED is on solid.
3. On the login page, enter the username/password.
ASCII characters. The default username is “admin” and the default password is “admin”.
The password can contain up to 64
5
Page 6
Logging Out
By default, the application logs out after ten minutes of inactivity.
CAUTION
Unless the Running Configuration is copied to the Startup Configuration, rebooting the
device will remove all changes made since the last time the file was saved. Save the
Running Configuration to the Startup Configuration before logging off to preserve any
changes you made during this session.
When you click Quick Start > Save Your Configurations, the Configuration File Copy page
appears. Save the Running Configuration file by copying it to the Startup Configuration
file.
To log out, click Logout in the top right corner of any page. The system logs out of the device.
NOTE—When a timeout occurs or you intentionally log out of the system, a message appears,
and the login page appears with a message indicating the logged-out state.
Interface Naming Conventions
Within the GUI, interfaces are denoted by linking the following elements:
•
Type of interface: The following types of interfaces are found on the switch:
o
Gigabit Ethernet ports (displayed as GE).
o
LAG (Port Channel) (displayed as LAG).
o
VLAN
•
Interface Number: Port, LAG or VLAN ID
Window Navigation
This section describes the features of the Web-based switch configuration utility.
Application Header
The Application Header appears on every page. It provides the following application links:
Application Link Name Description
Logout Click to log out of the Web-based switch configuration utility.
Firmware Version Display the device version number.
Help Click for the link to this administration guide.
6
Page 7
Management Buttons
The following table describes the commonly used buttons that appear on various pages in the
system.
Button Name Description
Add
Apply
Close
Clear All
Clear
Click to display the related Add page and add an entry to a table.
Enter the information and click Apply to save it to the Running
Configuration. Click Close to return to the main page. Click
Save to display the Configuration File Copy page and save the
Running Configuration to the Startup Configuration file type
on the device.
Click to apply changes to the Running Configuration on the
device. If the device is rebooted, the Running Configuration is
lost unless it is saved to the Startup Configuration file type or
another file type. Click Save to display the Configuration File
Copy page and save the Running Configuration to the Startup
Configuration file type on the device.
Click to return to the previous page. Any changes not applied
are cleared.
Click to clear the statistic counters for all interfaces.
Click to clear information, such a counters of an interface, all
interface, or log files.
Delete
Edit
Search
Refresh
Test or Start
View or View All
After selecting an entry in the table, click Delete to remove.
Select the entry and click Edit.
1. Click Apply to save the changes to the Running
Configuration.
2. Click Close to return to the main page.
Enter the query filtering criteria and click Search.
Click Refresh to refresh the counter values.
Click Test/Start to perform the related tests.
Click View to display details associated with the entry
selected or for all entries (respectively).
7
Page 8
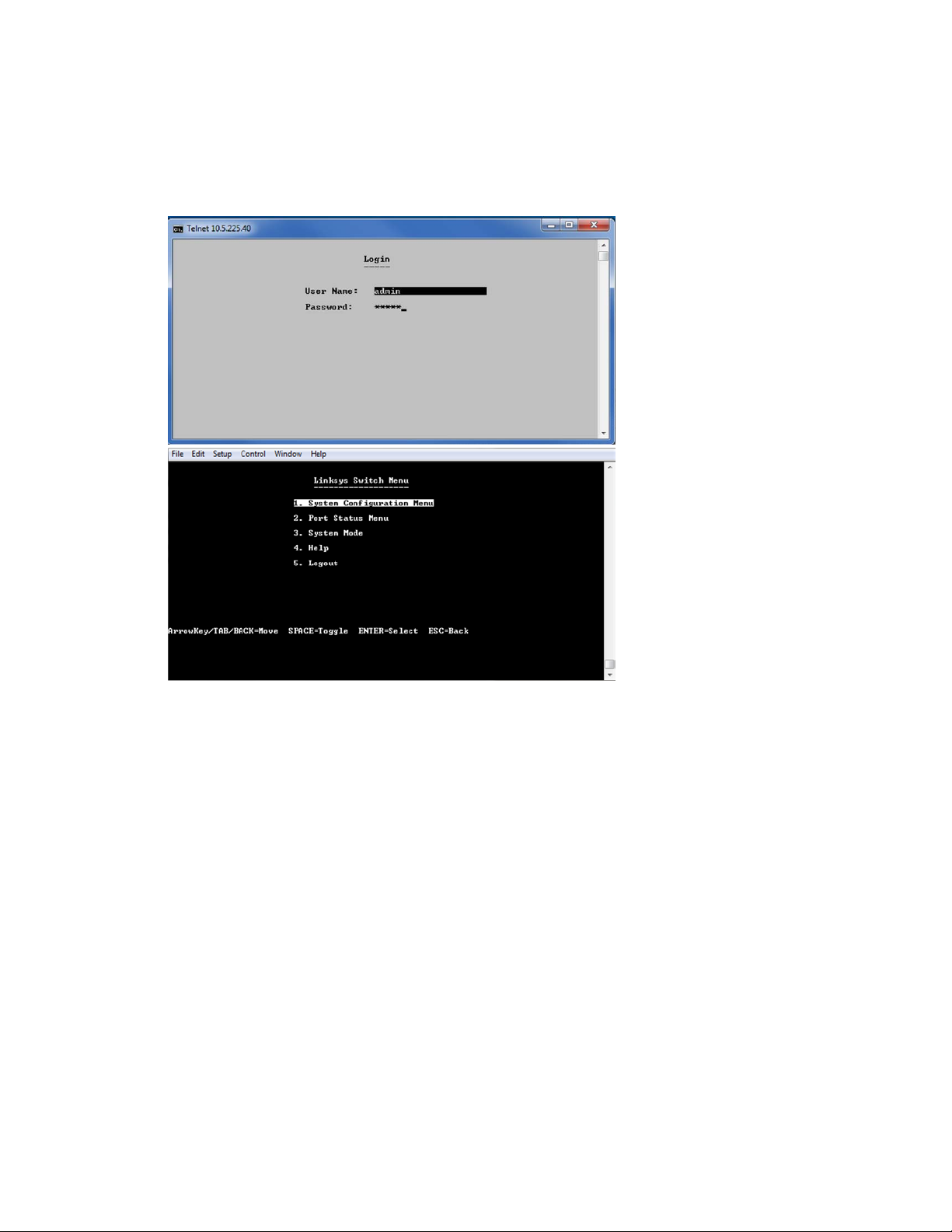
Configuring with Menu Command Line Interface
To configure with the device through the menu CLI:
1. Log on to the device through telnet.
2. Configure the device.
3. Click Logout.
8
Page 9

Chapter 2 – System Status
System Summary
The System Summary page provides a graphic view of the device, and displays device status,
hardware information, firmware version information, general PoE status, and other items.
To view system information, click System Status > System Summary.
contains system and hardware information.
•
System Mode—Specifies whether the system is operating in Layer 2 system mode.
•
System Description—A description of the system.
•
System Location—Physical location of the device.
System Management > System Information.
•
System Contact—Name of a contact person.
System Management > System Information.
•
Host Name—Name of the device.
word “switch” followed by the three least significant bytes of the device base MAC address
(the six furthest right hexadecimal digits).
•
Base MAC Address—Device MAC address.
•
SNMP Object ID—Unique vendor identification of the network management subsystem.
By default, the device host name is composed of the
To edit this field, go to Configuration >
To edit this field, go to Configuration >
The System Summary page
9
Page 10
•
Firmware Version—Firmware version number.
•
Boot Code Version—Boot version number.
•
Hardware Version —Hardware version number of the device.
•
Serial Number—Serial number. Device Status
•
Fan Status—Applicable only to models that have fans. The following values are possible:
o
OK—Fan is operating normally.
o
Fail—Fan is not operating correctly.
•
Date & Time—System date and time.
•
System Uptime—Length of time since last reboot.
RMON
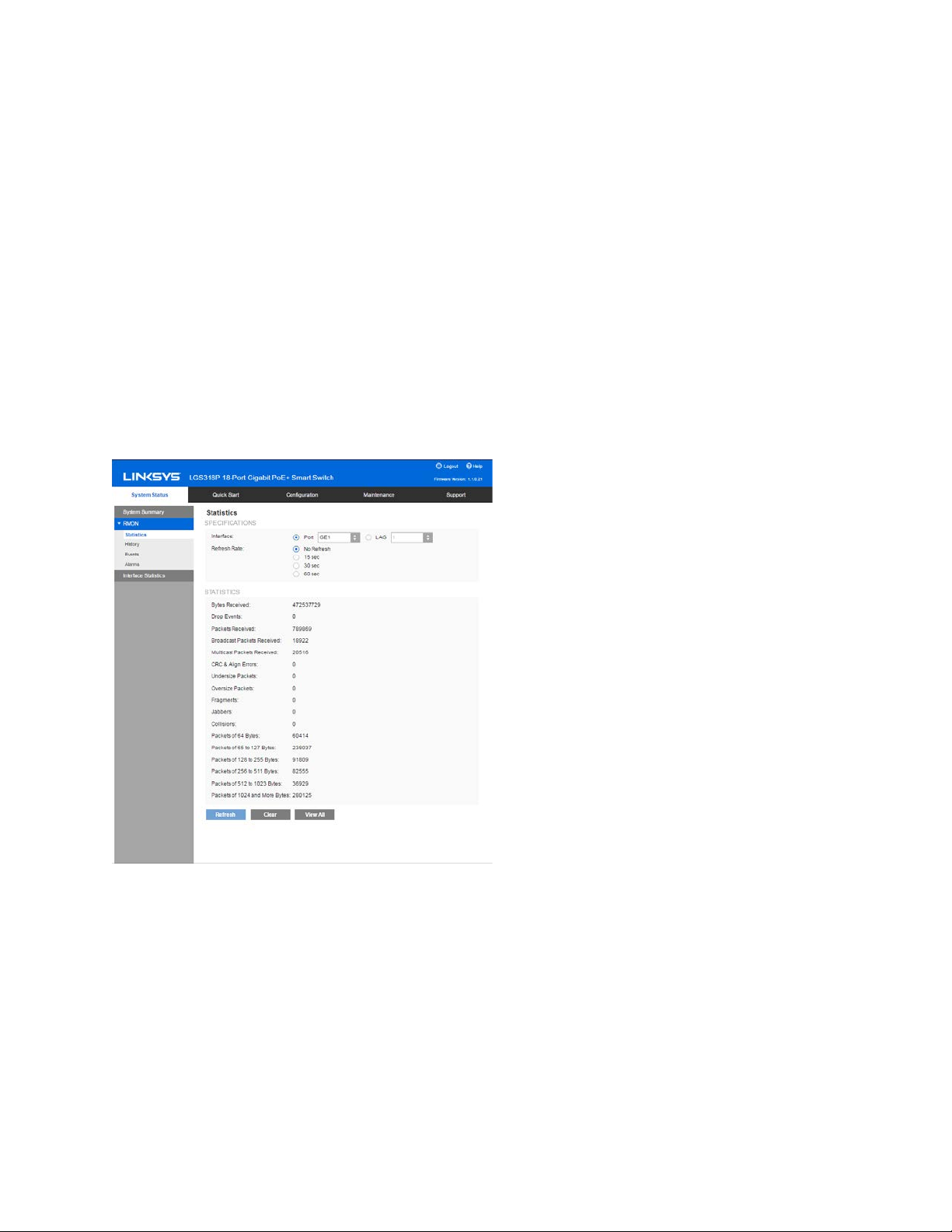
RMON Statistics
The Statistics page displays detailed information regarding packet sizes and information
regarding physical layer errors. The information displayed is according to the RMON (Remote
Network Monitoring) standard. An oversized packet is defined as an ethernet frame with the
following criteria:
•
Packet length is greater than MRU byte size.
•
Collision event has not been detected.
•
Late collision event has not been detected.
•
Received (Rx) error event has not been detected.
•
Packet has a valid CRC.
10
Page 11

To view RMON statistics and/or set the refresh rate:
1. Click System Status > RMON > Statistics.
2. Select the Interface for which statistics are to be displayed.
3. Select the Refresh Rate, the time period that passes before the interface statistics are
refreshed.
The statistics are displayed for the selected interface.
•
Bytes Received—Number of octets received, including bad packets and FCS octets, but
excluding framing bits.
•
Drop Events—Number of packets dropped.
•
Packets Received—Number of good packets received, including Multicast and Broadcast
packets.
•
Broadcast Packets Received—Number of good Broadcast packets received. This number
does not include Multicast packets.
•
Multicast Packets Received—Number of good Multicast packets received.
•
CRC & Align Errors—Number of CRC and Align errors that have occurred.
•
Undersize Packets—Number of undersized packets (less than 64 octets) received.
•
Oversize Packets—Number of oversized packets (over 2000 octets) received.
•
Fragments—Number of fragments (packets with less than 64 octets, excluding framing
bits, but including Frame Check Sequence octets) received.
•
Jabbers—Total number received packets that were longer than 1632 octets. This number
excludes frame bits, but includes FCS octets that had either a bad FCS with an integral
number of octets (FCS Error) or a bad FCS with a non-integral octet (Alignment Error)
number. A jabber packet is defined as an Ethernet frame that satisfies the following
criteria:
•
Packet data length is greater than MRU.
•
Packet has an invalid CRC.
•
Received (Rx) Error Event has not been detected.
•
Collisions—Number of collisions received. If Jumbo Frames are enabled, the threshold of
Jabber Frames is raised to the maximum size of Jumbo Frames.
•
Frames of 64 Bytes—Number of frames, containing 64 bytes that were received.
•
Frames of 65 to 127 Bytes—Number of frames, containing 65-127 bytes that were
received.
•
Frames of 128 to 255 Bytes—Number of frames, containing 128-255 bytes that were
received.
•
Frames of 256 to 511 Bytes—Number of frames, containing 256-511 bytes that were
received.
11
Page 12
•
Frames of 512 to 1023 Bytes—Number of frames, containing 512-1023 bytes that
were received.
•
Packets of 1024 and More Bytes—Number of frames, containing 1024- 2000 bytes,
and Jumbo Frames, that were received.
To clear or view statistics counters:
•
Click Refresh to refresh the counters on the page.
•
Click Clear to clear the selected interfaces counters.
•
Click View All to see all ports on a single page.
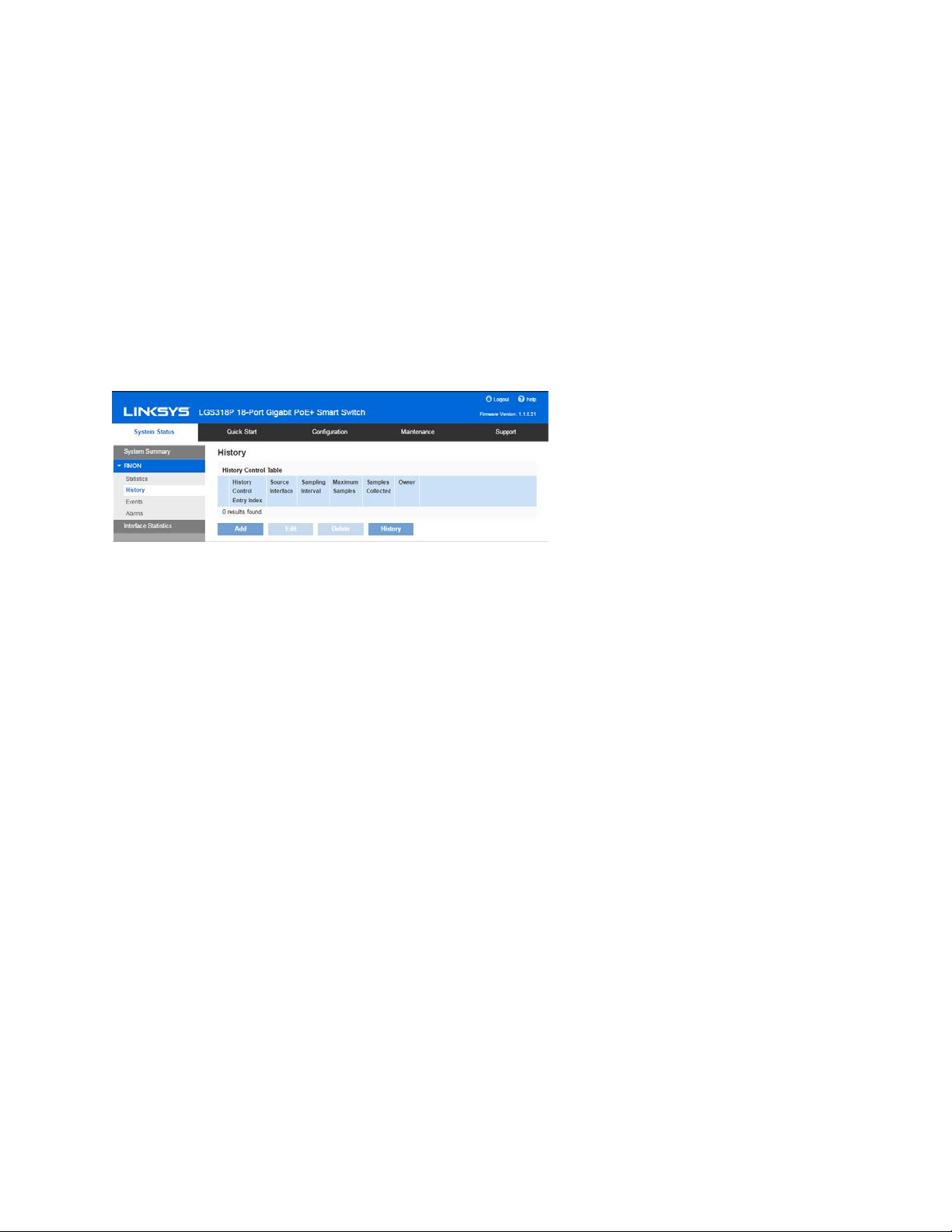
RMON History
The RMON feature enables monitoring statistics per interface.
The History Control Table page defines the sampling frequency, amount of samples to store and
the port from which to gather the data.
After the data is sampled and stored, it appears in the History Table page that can be viewed by
clicking the History button.
To enter RMON control information:
1. Click System Status > RMON > History.
2. Click Add.
3. Enter the parameters.
•
New History Control Entry Index—Displays the number of the new History table
entry.
•
Source Interface—Select the type of interface from which the history samples are
to be taken.
•
Maximum Samples—Enter the number of samples to store.
•
Samples Collected—RMON is allowed by the standard to not grant all requested
samples, but rather to limit the number of samples per request. Therefore, this
field represents the sample number actually granted to the request that is equal or
less than the requested maximum sample.
•
Sampling Interval—Enter the time in seconds that samples are collected from the
ports. The field range is 1-3600.
•
Owner—Enter the RMON station or user that requested the RMON information.
12
Page 13
4. Click Apply. The entry is added to the History Control Table page, and the Running
Configuration file is updated.
5. Click the History button (described below) to view the actual statistics.
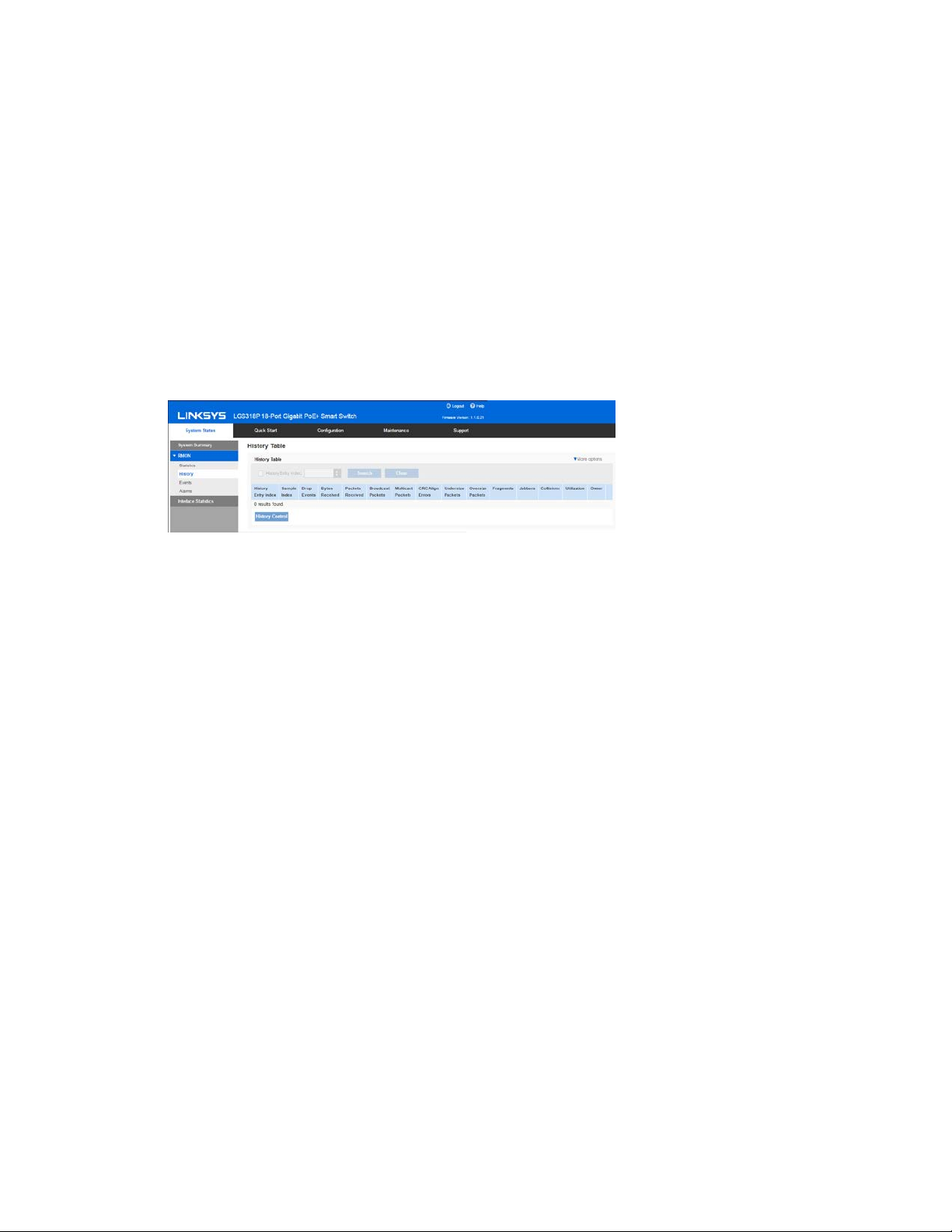
RMON History Table
The History Table page displays interface-specific statistical network samplings. The samples
were configured in the History Control table described above.
To view RMON history statistics:
1. Click System Status > RMON > History.
2. Click History.
3. From the History Entry Index drop down menu, optionally select the entry number of the
sample to display.
The fields are displayed for the selected sample.
•
Owner—History table entry owner.
•
Sample No.—Statistics were taken from this sample.
•
Drop Events—Dropped packets due to lack of network resources during the
sampling interval. This may not represent the exact number of dropped packets,
but rather the number of times dropped packets were detected.
•
Bytes Received—Octets received including bad packets and FCS octets, but
excluding framing bits.
•
Packets Received—Packets received, including bad packets, Multicast, and
Broadcast packets.
•
Broadcast Packets—Good Broadcast packets excluding Multicast packets.
•
Multicast Packets—Good Multicast packets received.
•
CRC Align Errors—CRC and Align errors that have occurred.
•
Undersize Packets—Undersized packets (less than 64 octets) received.
•
Oversize Packets—Oversized packets (over 2000 octets) received.
•
Fragments—Fragments (packets with less than 64 octets) received, excluding
framing bits, but including FCS octets.
13
Page 14
•
Jabbers—Total number of received packets that were longer than 2000 octets.
This number excludes frame bits, but includes FCS octets that had either a bad
FCS (Frame Check Sequence) with an integral number of octets (FCS Error) or a
bad FCS with a non-integral octet (Alignment Error) number.
•
Collisions—Collisions received.
•
Utilization—Percentage of current interface traffic compared to maximum traffic
that the interface can handle.
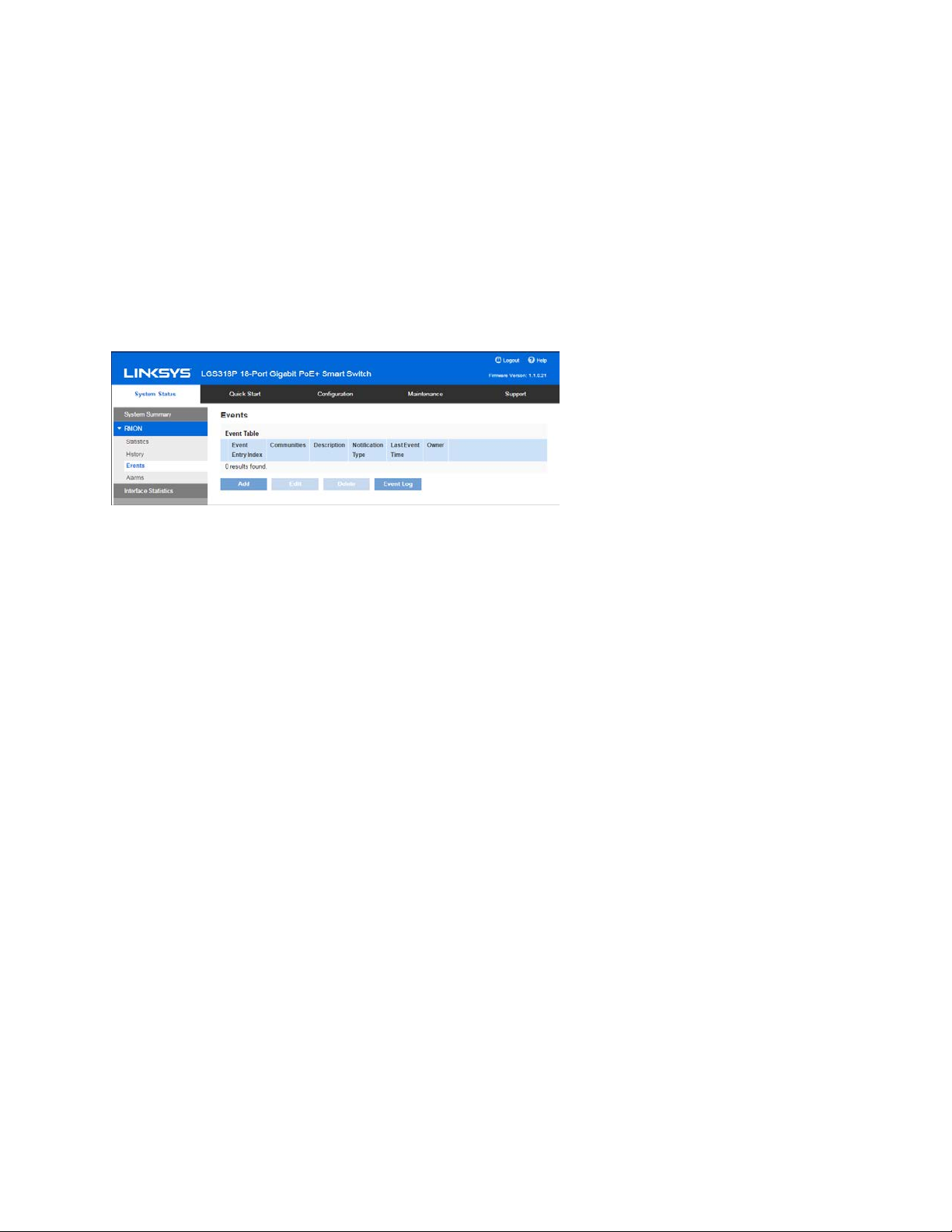
RMON Events
You can control the occurrences that trigger an alarm and the type of notification that occurs.
•
Events Page—Configures what happens when an alarm is triggered. This can be any
combination of logs and traps.
•
Alarms Page—Configures the occurrences that trigger an alarm.
To define RMON events:
1. Click System Status > RMON > Events.
This page displays previously defined events.
2. Click Add.
3. Enter the parameters.
•
Event Entry Index —Displays the event entry index number for the new entry.
•
Community—Enter the SNMP community string to be included when traps are sent
(optional). Note that the community must be defined using the Defining SNMPv1
and v2 Notification Recipients or Defining SNMPv3 Notification Recipients pages
for the trap to reach the Network Management Station
•
Description—Enter a name for the event. This name is used in the Add RMON
Alarm page to attach an alarm to an event.
•
Notification Type—Select the type of action that results from this event.
o
None—No action occurs when the alarm goes off.
o
Log (Event Log Table)—Add a log entry to the Event Log table when the
alarm is triggered.
14
Page 15
o
Trap (SNMP Manager and SYSLOG Server)—Send a trap to the remote log
server when the alarm goes off.
o
Log and Trap—Add a log entry to the Event Log table and send a trap to the
remote log server when the alarm goes off.
•
Last Event Time—Displays the time of the event. (This is a read-only table in the
parent window and cannot be defined).
•
Owner—Enter the device or user that defined the event.
4. Click Apply. The RMON event is saved to the Running Configuration file.
5. Click Event Log to display the log of alarms that have occurred and that have been logged
(see description below).
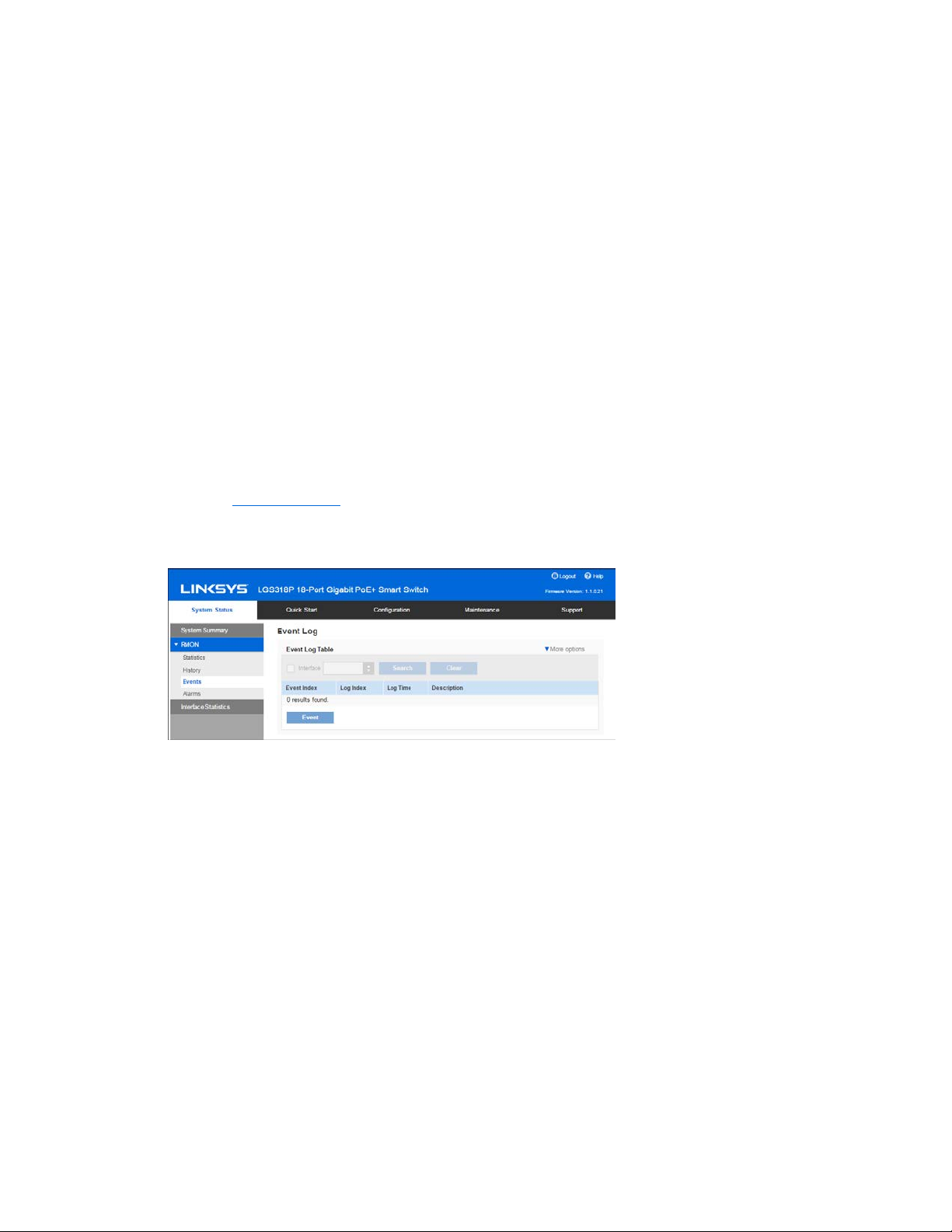
RMON Events Logs
The Event Log Table page displays the log of events (actions) that occurred. Two types of events
can be logged: Log or Log and Trap. The action in the event is performed when the event is bound
to an alarm (see RMON Alarms
•
Click System Status > RMON > Events.
•
Click Event Log.
) and the conditions of the alarm have occurred.
o
Event Index—Event’s log entry number.
o
Log Index.—Log number (within the event).
o
Log Time—Time that the log entry was entered.
o
Description—Description of event that triggered the alarm.
15
Page 16

RMON Alarms
RMON alarms provide a mechanism for setting thresholds and sampling intervals to generate
exception events on counters or any other SNMP object counter maintained by the agent. Both
the rising and falling thresholds must be configured in the alarm. After a rising threshold is
crossed, no rising events are generated until the companion falling threshold is crossed. After a
falling alarm is issued, the next alarm is issued when a rising threshold is crossed.
One or more alarms are bound to an event, which indicates the action to be taken when the alarm
occurs.
Alarm counters can be monitored by either absolute values or changes (delta) in the counter
values.
To enter RMON alarms:
1. Click System Status > RMON > Alarms. All previously-defined alarms are displayed. The
fields are described in the Add RMON Alarm page below.
•
Counter Value—Displays the value of the statistic during the last sampling period.
2. Click Add.
3. Enter the parameters.
•
Alarm Entry Index—Displays the alarm entry number.
•
Interface—Select the type of interface for which RMON statistics are displayed.
•
Counter Name—Select the MIB variable that indicates the type of occurrence
measured.
•
Sample Type—Select the sampling method to generate an alarm. The options are:
o
Absolute—If the threshold is crossed, an alarm is generated.
o
Delta—Subtracts the last sampled value from the current value. The
difference in the values is compared to the threshold. If the threshold was
crossed, an alarm is generated.
o
Interval—Enter the alarm interval time in seconds.
•
Rising Event—Select an event to be performed when a rising event is triggered.
Events are created in the Events page.
•
Rising Threshold—Enter the value that triggers the rising threshold alarm
•
Falling Event—Select an event to be performed when a falling event is triggered.
16
Page 17

•
Falling Threshold—Enter the value that triggers the falling threshold alarm.
•
Startup Alarm—Select the first event from which to start generation of alarms.
Rising is defined by crossing the threshold from a low-value threshold to a highervalue threshold.
o
Rising Alarm—A rising value triggers the rising threshold alarm.
o
Falling Alarm—A falling value triggers the falling threshold alarm.
o
Rising and Falling—Both rising and falling values trigger the alarm.
•
Owner—Enter the name of the user or network management system that receives
the alarm.
4. Click Apply. The RMON alarm is saved to the Running Configuration file.
Interface Statistics
The Interface Statistics page displays traffic statistics per port. The refresh rate of the
information can be selected.
This page is useful for analyzing the amount of traffic that is both sent and received and its
dispersion (Unicast, Multicast, and Broadcast).
17
Page 18

To display Ethernet statistics and/or set the refresh rate:
1. Click System Status > Interface Statistics.
2. Enter the parameters.
o
Interface—Select the specific interface for which Ethernet statistics are to be
displayed.
o
Refresh Rate—Select the time period that passes before the interface Ethernet
statistics are refreshed. The available options are as follows:
-
No Refresh—Statistics are not refreshed.
-
15 Sec—Statistics are refreshed every 15 seconds.
-
30 Sec—Statistics are refreshed every 30 seconds.
-
60 Sec—Statistics are refreshed every 60 seconds.
o
Total Octets—Octets received, including bad packets and FCS octets, but excluding
framing bits.
o
Unicast Packets—Good Unicast packets received.
o
Multicast Packets—Good Multicast packets received.
o
Broadcast Packets—Good Broadcast packets received.
o
Error Packets—Packets with errors received.
o
Total Octets—Octets transmitted, including bad packets and FCS octets, but
excluding framing bits.
o
Unicast Packets—Good Unicast packets transmitted.
o
Multicast Packets—Good Multicast packets transmitted.
o
Broadcast Packets—Good Broadcast packets transmitted.
To clear or view statistics counters:
•
Click Refresh to refresh the counters on the page.
•
Click Clear to clear the selected interfaces counters.
•
Click View All to see all ports on a single page.
18
Page 19
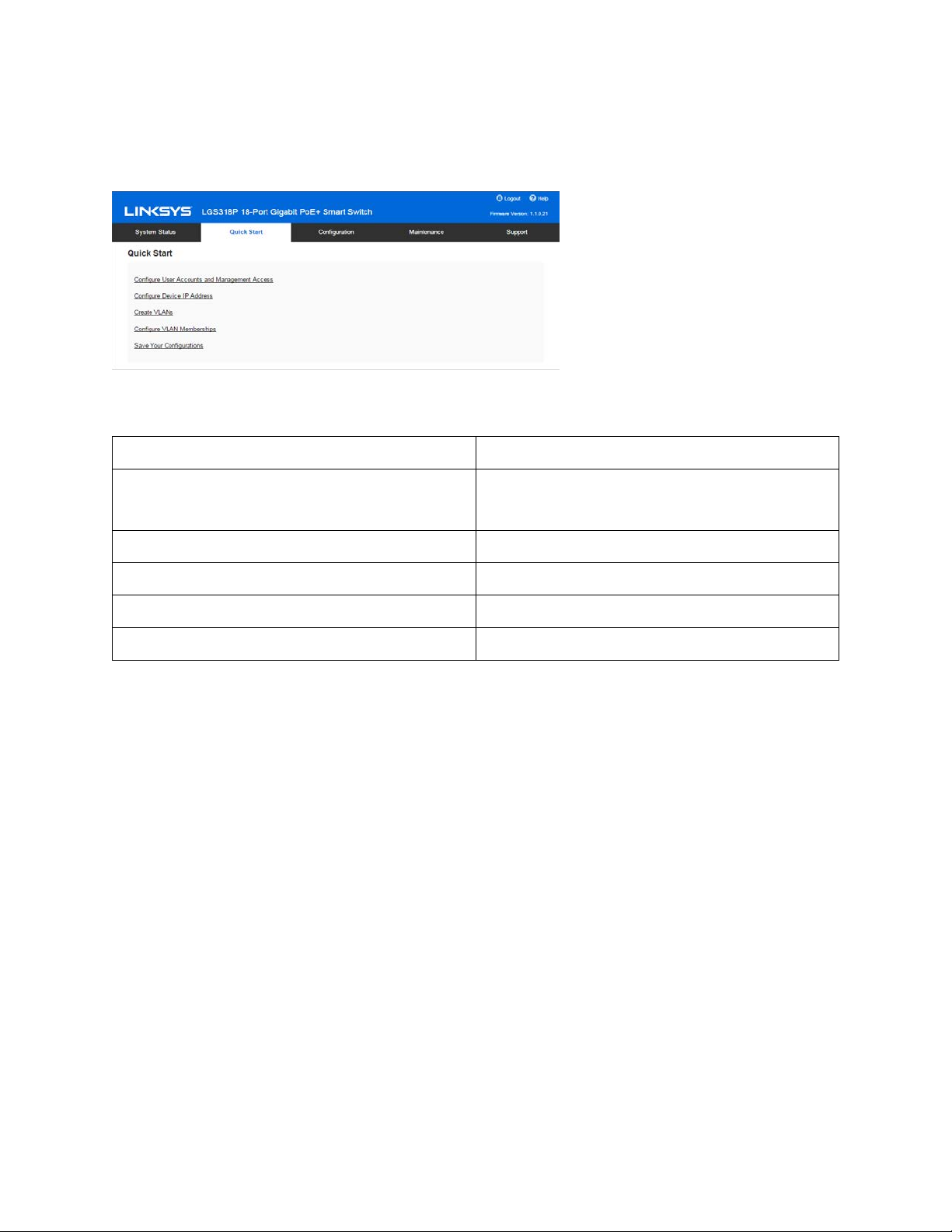
Chapter 3 – Quick Start
To simplify device configuration through quick navigation, the Quick Start page provides links to
the most commonly used pages.
Link Name (on the Page) Linked Page
Configure User Accounts and
Management Access
Configure Device IP Address IPv4 Interface
Create VLANs VLANs
Configure VLAN Memberships VLAN Memberships
Save Your Configuration Configuration File Copy
Clicking on the Support link takes you to the device product support page.
User Access & Accounts
19
Page 20

Chapter 4 – System Management
System Information
To enter system information:
1. Click Configuration > System Management > System Information.
2. View or modify the system settings.
•
System Description—Displays a description of the device.
•
System Location—Enter the location where the device is physically located.
•
System Contact—Enter the name of a contact person.
•
System Host Name—Select the host name of this device.
o
Default—The default host name (System Name) of these switches is
switch123456, where 123456 represents the last three bytes of the
device MAC address in hex format.
o
User Defined—Enter the host name. Use only letters, digits, and hyphens.
Host names cannot begin or end with a hyphen. No other symbols,
punctuation characters, or blank spaces are permitted (as specified in
RFC1033, 1034, 1035).
3. Click Apply to save the values in the Running Configuration file.
20
Page 21
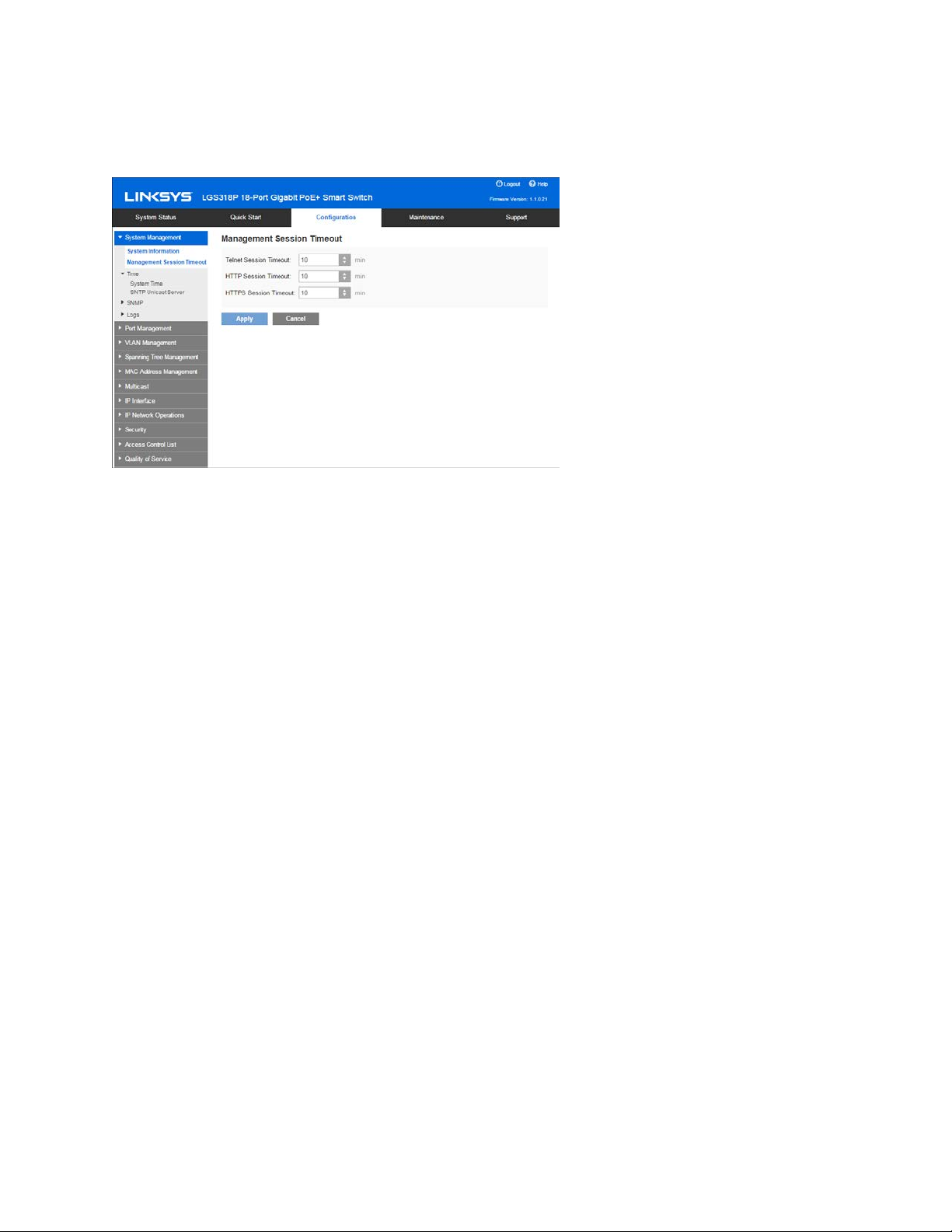
Management Session Timeout
The Management Session Timeout configures the time intervals that the management sessions
can remain idle before they timeout and you must log in again to reestablish the session.
To set the idle session timeout for various types of sessions:
1. Click Configuration > System Management > Management Session Timeout.
2. Select the timeout for the following sessions from the corresponding list. The default
timeout value is 10 minutes.
•
Telnet Session Timeout—Select the timeout for a Telnet session.
•
HTTP Session Timeout—Select the timeout for an HTTP session.
•
HTTPs Session Timeout—Select the timeout for an HTTPS session.
3. Click Apply to set the configuration settings on the device.
Time
Network time synchronization is critical because every aspect of managing, securing, planning,
and debugging a network involves determining when events occur. Without synchronized clocks,
accurately correlating log files between devices when tracking security breaches or network
usage is impossible.
Synchronized time also reduces confusion in shared file systems, as it is important for the
modification times to be consistent, regardless of the machine on which the file systems reside.
For these reasons, it is important that the time configured on all of the devices on the network is
accurate.
Note—The device supports Simple Network Time Protocol (SNTP) and when enabled, the device
dynamically synchronizes the device time with time from an SNTP server. The device operates
only as an SNTP client, and cannot provide time services to other devices.
21
Page 22

Clock Source
System time can be set manually by the user, or dynamically from an SNTP server. If an SNTP
server is chosen, the manual time settings are overwritten when communications with the server
are established.
As part of the boot process, the device always configures the time, time zone, and DST. These
parameters are obtained from SNTP, values set manually, or if all else fails, from the factory
defaults.
•
Manual—User must manually set the time.
•
SNTP—Time can be received from SNTP time servers. SNTP ensures accurate network
time synchronization of the device up to the millisecond by using an SNTP server for the
clock source. When specifying an SNTP server, if choosing to identify it by hostname,
three suggestions are given in the GUI:
o
time-a.timefreq.bldrdoc.gov
o
time-b.timefreq.bldrdoc.gov
o
time-c.timefreq.bldrdoc.gov
Note—SNTP is the recommended method for time setting.
SNTP Modes
The device can receive system time from an SNTP server in one of the following ways:
•
Client Broadcast Reception (passive mode)—SNTP servers broadcast the time,
and the device listens to these broadcasts. When the device is in this mode, there
is no need to define a Unicast SNTP server.
•
Client Broadcast Transmission (active mode)—The device, as an SNTP client,
periodically requests SNTP time updates. This mode works in either of the
following ways:
o
SNTP Anycast Client Mode—The device broadcasts time request packets
to all SNTP servers in the subnet, and waits for a response.
o
Unicast SNTP Server Mode—The device sends Unicast queries to a list of
manually-configured SNTP servers, and waits for a response.
The device supports having all of the above modes active at the same time and selects the
best system time received from an SNTP server, according to an algorithm based on the
closest stratum (distance from the reference clock).
Time Zone and Daylight Savings Time (DST)
The Time Zone and DST can be set on the device in the following ways:
•
Dynamic configuration of the device through a DHCP server, where:
•
Dynamic DST, when enabled and available, always takes precedence over the manual
configuration of DST.
22
Page 23
•
If the server supplying the source parameters fails, or dynamic configuration is disabled
by the user, the manual settings are used.
•
Dynamic configuration of the time zone and DST continues after the IP address lease time
has expired.
•
Manual configuration of the time zone and DST becomes the Operational time zone and
DST, only if the dynamic configuration is disabled or fails.
Note—The DHCP server must supply DHCP option 100 in order for dynamic time zone
configuration to take place.
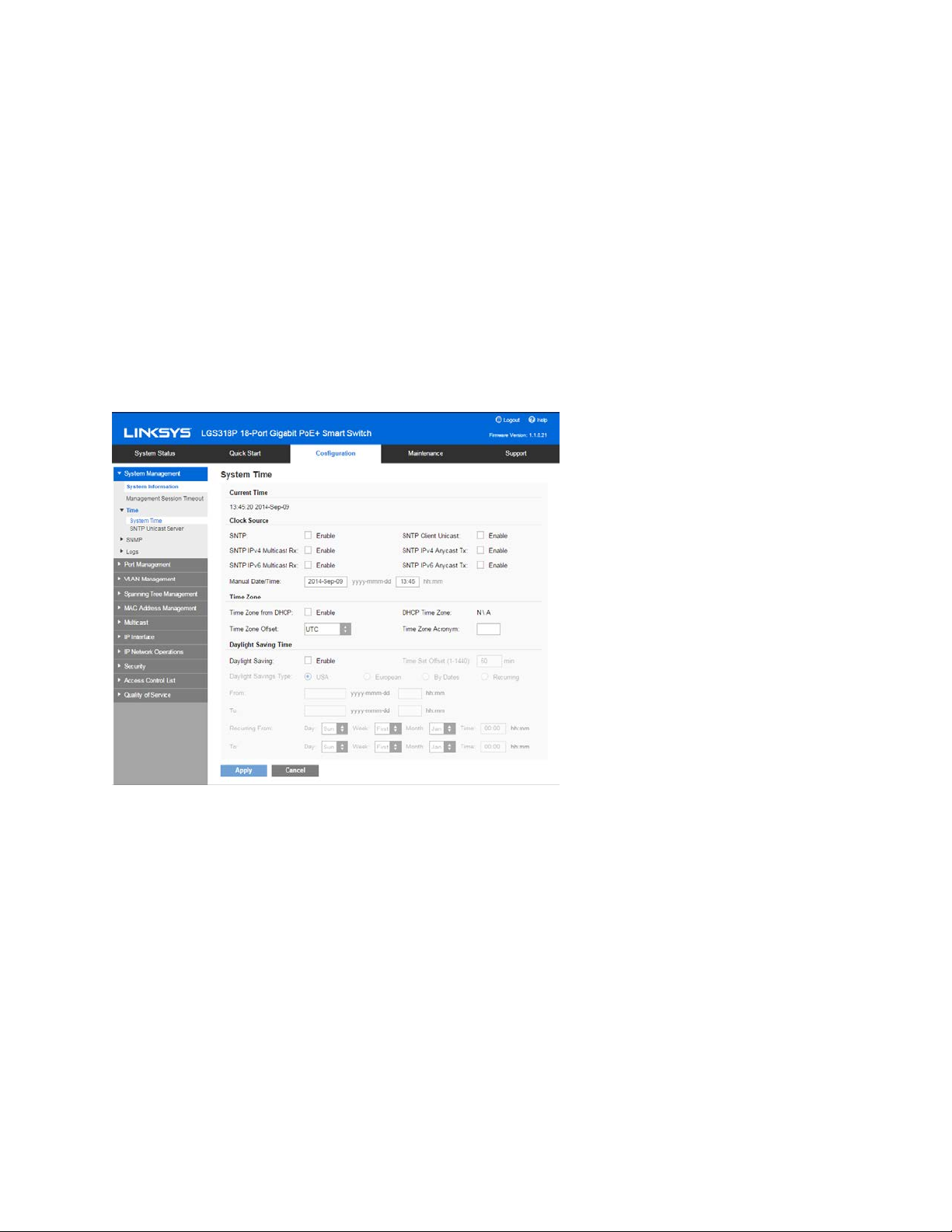
System Time
Use the System Time page to select the system time source. If the source is manual, you can
enter the time here.
Caution—If the system time is set manually and the device is rebooted, the manual time settings
must be reentered.
To define system time:
1. Click Configuration > System Management > Time > System Time.
The current time is displayed. This shows the DHCP time zone or the acronym for the userdefined time zone if these were defined.
23
Page 24

2. Enter these parameters:
Clock Source
•
SNTP-If you enable this, the system time is obtained from an SNTP server.
To use this feature, you must also configure a connection to an SNTP server in the
SNTP Unicast Server page.
•
SNTP Client Unicast-Select to enable client Unicast mode.
•
SNTP IPv4 Multicast Rx-Select to receive SNTP IPv4 Multicast synchronization
packets requesting system time information. The packets are transmitted to all
SNTP servers on the subnet.
•
SNTP IPv4 Anycast Tx-Select to transmit SNTP IPv4 Anycast synchronization
packets requesting system time information. The packets are transmitted from
any SNTP servers on the subnet.
•
SNTP IPv6 Multicast Rx-Select to receive SNTP IPv6 Multicast synchronization
packets requesting system time information. The packets are transmitted to all
SNTP servers on the subnet.
•
SNTP IPv6 Anycast Tx-Select to transmit SNTP IPv6 Anycast synchronization
packets requesting system time information. The packets are transmitted from
any SNTP servers on the subnet.
•
Manual Date/Time-Set the date and time manually. The local time is used when
there is no alternate source of time, such as an SNTP server.
Time Zone
•
Time Zone from DHCP-Select to enable dynamic configuration of the time zone
and the DST from the DHCP server. Whether one or both of these parameters can
be configured depends on the information found in the DHCP packet. If this option
is enabled, you must also enable DHCP client on the device. The DHCP Client
supports Option 100 providing dynamic time zone setting.
•
DHCP Time Zone-Displays the acronym of the time zone configured from the
DHCP server. This acronym appears in the Actual Time field.
•
Time Zone Offset-Select the difference in hours between Greenwich Mean Time
(GMT) and the local time. For example, the Time Zone Offset for Paris is GMT +1,
while the Time Zone Offset for New York is GMT - 5.
•
Time Zone Acronym-Enter a user-defined name that represents the time zone you
have configured. This acronym appears in the Actual Time field.
Daylight Savings Time
Select to enable Daylight Saving Time.
•
Time Set Offset-Enter the number of minutes offset from GMT ranging from1-
1440. The default is 60.
24
Page 25
•
Daylight Savings Type
o
USA - DST is set according to the dates used in the USA.
o
European - DST is set according to the dates used by the European Union
and other countries that use this standard.
o
By Dates - DST is set manually, typically for a country other than the USA
or a European country. This allows customization of the start and stop of
DST.
-
From - Date and time that DST starts.
-
To - Date and time that DST ends.
o
Recurring From / Recurring To) - DST occurs on the same date every year.
This allows customization of the start and stop of DST
-
Day - Day of the week on which DST begins every year.
-
Week - Week within the month from which DST begins every year.
-
Month - Month of the year in which DST begins every year.
-
Time - The time at which DST begins every year.
3. Click Apply. The system time values are written to the Running Configuration file.
SNTP Unicast Server
Up to 16 Unicast SNTP servers can be configured.
Note—To specify a Unicast SNTP server by name, you must first configure DNS server(s) on the
device (see
enabled (in the System Time page).
Domain Name System
). To add a Unicast SNTP server, SNTP Client Unicast must be
25
Page 26

To add a Unicast SNTP server:
1. Click Configuration > System Management > Time > SNTP Unicast Server.
This page displays the following information for each Unicast SNTP server:
•
SNTP Server—SNTP server IP address. The preferred server, or hostname, is
chosen according to its stratum level.
•
SNTP Server Status—SNTP server status. The possible values are:
-
Up—SNTP server is currently operating normally.
-
Down—SNTP server is currently not available.
-
Unknown—SNTP server is currently being searched for by the device.
-
In Process—Occurs when the SNTP server does not fully trust its own time
server (i.e. when first booting up the SNTP server).
•
Stratum Level—Distance from the reference clock expressed as a numerical value.
An SNTP server cannot be the primary server (stratum level 1) unless polling
interval is enabled.
•
Offset—Estimated offset of the server's clock relative to the local clock, in
milliseconds. The host determines the value of this offset using the algorithm
described in RFC 2030.
•
Delay—Estimated round-trip delay of the server's clock relative to the local clock
over the network path between them, in milliseconds. The host determines the
value of this delay using the algorithm described in RFC 2030.
•
Poll Interval—Displays whether polling is enabled or disabled.
•
Authentication Key ID—Key Identification used to communicate between the
SNTP server and device.
•
Last Response Time—Last date and time a response was received from this SNTP
server.
2. To add a Unicast SNTP server, enable SNTP Client Unicast.
3. Click Add.
4. Enter the following parameters:
•
SNTP Server—Select if the SNTP server is going to be identified by its IP address
or if you are going to select a well-known SNTP server by name from the list.
Note—To specify a well-known SNTP server, the device must be connected to the
internet and configured with a DNS server or configured so that a DNS server is
identified by using DHCP. (See
•
IP Version—Select the version of the IP address: Version 6 or Version 4.
•
IPv6 Address Type—Select the IPv6 address type (if IPv6 is used). The options are
Domain Name System
in Chapter 11.)
26
Page 27

•
Link Local—The IPv6 address uniquely identifies hosts on a single network link. A
link local address has a prefix of FE80, is not routable, and can be used for
communication only on the local network. Only one link local address is supported.
If a link local address exists on the interface, this entry replaces the address in the
configuration.
•
Link Local Interface—Select the link local interface (if IPv6 AddressType Link
Local is selected) from the list.
•
Global—The IPv6 address is a global Unicast IPV6 type that is visible and
reachable from other networks.
•
SNTP Server IP Address—Enter the SNTP server IP address. The format depends
on which address type was selected.
•
SNTP Server Name—Select the name of the SNTP server from a list of well-known
NTP servers. If other is chosen, enter the name of an SNTP server in the adjacent
field.
•
Poll Interval—Select to enable polling of the SNTP server for system time
information. All NTP servers that are registered for polling are polled, and the clock
is selected from the server with the lowest stratum level (distance from the
reference clock) that is reachable. The server with the lowest stratum is
considered to be the primary server. The server with the next lowest stratum is a
secondary server, and so forth. If the primary server is down, the device polls all
servers with the polling setting enabled, and selects a new primary server with the
lowest stratum.
5. Click Apply. The STNP server is added, and you are returned to the main page.
SNMP
This section describes the Simple Network Management Protocol (SNMP) feature that provides a
method for managing network devices.
SNMP Versions
The device functions as an SNMP agent and supports SNMPv1, v2, and v3. It also reports system
events to trap receivers using the traps defined in the supported MIBs (Management Information
Base).
•
SNMPv1 and v2
To control access to the system, a list of community entries is defined. Each community
entry consists of a community string and its access privilege. The system responds only to
SNMP messages specifying the community which has the correct permissions and correct
operation.
SNMP agents maintain a list of variables that are used to manage the device. These
variables are defined in the Management Information Base (MIB).
27
Page 28

Note—Due to the security vulnerabilities of other versions, it is recommended to use
SNMPv3.
•
SNMPv3
In addition to the functionality provided by SNMPv1 and v2, SNMPv3 applies access
control and new trap mechanisms to SNMPv1 and SNMPv2 PDUs. SNMPv3 also defines a
User Security Model (USM) that includes:
o
Authentication—Provides data integrity and data origin authentication.
o
Privacy—Protects against disclosure message content. Cipher Block- Chaining
(CBC-DES) is used for encryption. Either authentication alone can be enabled on an
SNMP message, or both authentication and privacy can be enabled on an SNMP
message. However, privacy cannot be enabled without authentication.
o
Timeliness—Protects against message delay or playback attacks. The SNMP
agent compares the incoming message time stamp to the message arrival time.
SNMP Workflow
Note—For security reasons, SNMP is disabled by default. Before you can manage the device via
SNMP, you must turn on SNMP in the SNMP > Feature Configuration page.
If you decide to use SNMPv1 or v2:
1. Navigate to the SNMP -> Communities page and click Add. The community can be
associated with access rights and a view in Basic mode or with a group in Advanced mode.
There are two ways to define access rights of a community:
•
Basic mode—The access rights of a community can configure with Read Only,
Read Write, or SNMP Admin. In addition, you can restrict the access to the
community to only certain MIB objects by selecting a view (defined in the Views
page).
•
Advanced Mode—The access rights of a community are defined by a group
(defined in the Groups page). You can configure the group with a specific security
model. The access rights of a group are Read, Write, and Notify.
2. Choose whether to restrict the SNMP management station to one address or allow SNMP
management from all addresses. If you choose to restrict SNMP management to one
address, then input the address of your SNMP Management PC in the IP Address field.
3. Input the unique community string in the Community String field.
4. Optionally, enable traps by using the Trap Settings page.
5. Optionally, define a notification filter(s) by using the Notification Filter page.
6. Configure the notification recipients on the Notification Recipients SNMPv1, v2 page.
28
Page 29

If you decide to use SNMPv3:
1. Define the SNMP engine by using the Engine ID page. Either create a unique Engine ID or
use the default Engine ID. Applying an Engine ID configuration clears the SNMP database.
2. Optionally, define SNMP view(s) by using the Views page. This limits the range of Object
IDs available to a community or group.
3. Define groups by using the Groups page.
4. Define users by using the SNMP Users page, where they can be associated with a group. If
the SNMP Engine ID is not set, then users may not be created.
5. Optionally, enable or disable traps by using the Trap Settings page.
29
Page 30

6. Optionally, define a notification filter(s) by using the Notification Filter page.
7. Define a notification recipient(s) by using the Notification Recipients SNMPv3 page.
Device Model Object IDs (OIDs):
Mode Name Description Object ID
LGS308
LGS318
LGS326
LGS308P
LGS318P
LGS326P
Private OIDs are placed under: enterprises(1).linksys(3955).smb(1000).switch01(201).
8-Port Smart Gigabit Switch enterprises(1) . linksys(3955) .
smb(1000).3.8.1
18-Port Smart Gigabit Switch
26-Port Smart Gigabit Switch
8-Port Smart Gigabit PoE+ Switch
18-Port Smart Gigabit PoE+ Switch
26-Port Smart Gigabit PoE+ Switch
enterprises(1) . linksys(3955) .
smb(1000).3.18.1
enterprises(1) . linksys(3955) .
smb(1000).3.26.1
enterprises(1) . linksys(3955) .
smb(1000).3.8.2
enterprises(1) . linksys(3955) .
smb(1000).3.18.2
enterprises(1) . linksys(3955) .
smb(1000).3.26.
30
Page 31

Feature Configuration
The Engine ID is used by SNMPv3 entities to uniquely identify them. An SNMP agent is considered
an authoritative SNMP engine. This means that the agent responds to incoming messages (Get,
GetNext, GetBulk, Set) and sends trap messages to a manager. The agent's local information is
encapsulated in fields in the message.
Each SNMP agent maintains local information that is used in SNMPv3 message exchanges. The
default SNMP Engine ID is composed of the enterprise number and the default MAC address. This
engine ID must be unique for the administrative domain, so that no two devices in a network have
the same engine ID.
Local information is stored in four MIB variables that are read-only (snmpEngineId,
snmpEngineBoots, snmpEngineTime, and snmpEngineMaxMessageSize).
Caution—When the engine ID is changed, all configured users and groups are erased.
To configure SNMP:
1. Click Configuration > System Management > SNMP > Feature Configuration.
2. Enter the following fields:
•
SNMP—Select to enable SNMP.
•
Authentication Notification—Select to enable SNMP authentication failure
notification.
•
SNMP Notification—Select to enable SNMP notifications.
•
Local SNMPv3 Engine ID—Configure the engine. The options:
31
Page 32

o
Use Default—Select to use the device-generated engine ID. The default
engine ID is based on the device MAC address, and is defined per standard
as:
-
First 4 octets—First bit = 1, the rest is the IANA enterprise number.
-
Fifth octet—Set to 3 to indicate the MAC address that follows.
-
Last 6 octets—MAC address of the device.
-
None—No engine ID is used.
o
User Defined—Enter the local device engine ID. The field value is a
hexadecimal string (range: 10 - 64). Each byte in the hexadecimal
character strings is represented by two hexadecimal digits.
All remote engine IDs and their IP addresses are displayed in the Remote
Engine ID table.
3. Click Apply. The Running Configuration file will be updated.
The Remote Engine ID table shows the mapping between IP addresses of the engine and
Engine ID. To add the IP address of an engine ID:
4. Click Add. Enter the following fields:
•
Remote Engine IP Address—Select whether to specify the Engine ID server by IP
address or name.
•
IP Version—Select the supported IP format.
•
IPv6 Address Type—Select the IPv6 address type (if IPv6 is used). The options are:
o
Link Local—The IPv6 address uniquely identifies hosts on a single network
link. A link local address has a prefix of FE80, is not routable, and can be
used for communication only on the local network. Only one link local
address is supported. If a link local address exists on the interface, this
entry replaces the address in the configuration.
o
Global—The IPv6 address is a global Unicast IPV6 type that is visible and
reachable from other networks.
•
Remote Engine IP Address—Enter the IP address of the log server.
•
Remote Engine IP Name—Enter the domain name of the log server.
•
Engine ID—Enter the Engine ID.
5. Click Apply. The Running Configuration file is updated.
32
Page 33
Views
A view is a user-defined label for a collection of MIB subtrees. Each subtree ID is defined by the
Object ID (OID) of the root of the relevant subtrees. Either well- known names can be used to
specify the root of the desired subtree or an OID can be entered (see Device Model Object IDs
).
Each subtree is either included or excluded in the view being defined.
The Views page enables creating and editing SNMP views. The default views (Default,
DefaultSuper) cannot be changed.
Views can be attached to groups in the Groups page or to a community which employs basic
access mode through the Communities page.
To define SNMP views:
1. Click Configuration > System Management > SNMP > Views.
2. Click Add to define new views.
3. Enter the parameters.
•
View Name—Enter a view name between 0-30 characters.
•
View Object—Select the node in the MIB tree that is included or excluded in the
selected SNMP view. The options to select the object are as follows:
o
Object ID—Enter an OID not offered in the Object ID Selection List option.
o
Object ID Selection List—Enables you to navigate the MIB tree. Press the
Up arrow to go to the level of the selected node's parent and siblings; press
the Down arrow to descend to the level of the selected node's children.
Click nodes in the view to pass from one node to its sibling. Use the
scrollbar to bring siblings in view.
33
Page 34

4. Include or exclude the MIB object from the view. If Include Object is selected, the MIB
objects are included in the view, otherwise they are excluded.
5. Click Apply.
6. In order to verify your view configuration, select the user-defined views from the View
Name list. The following views exist by default:
•
Default—Default SNMP view for read and read/write views.
•
DefaultSuper—Default SNMP view for administrator views. Other views can be
added.
•
Object ID—Displays the Object ID and its subtree to be included or excluded in the
SNMP view.
•
Object View—Displays whether the defined object and its subtree are included or
excluded in the selected SNMP view.
Groups
In SNMPv1 and SNMPv2, a community string is sent along with the SNMP frames. The community
string acts as a password to gain access to an SNMP agent. However, neither the frames nor the
community string are encrypted. Therefore, SNMPv1 and SNMPv2 are not secure.
In SNMPv3, the following security mechanisms can be configured:
•
Authentication—The device checks that the SNMP user is an authorized system
administrator. This is done for each frame.
•
Privacy—SNMP frames can carry encrypted data. Thus, in SNMPv3, there are three levels
of security:
•
No security (No authentication and no privacy)
•
Authentication (Authentication and no privacy)
•
Authentication and privacy
34
Page 35

SNMPv3 provides a means of controlling the content each user can read or write and the
notifications they receive. A group defines read/write privileges and a level of security. It becomes
operational when it is associated with an SNMP user or community.
Note—To associate a non-default view with a group, first create the view in the Views page.
To create an SNMP group:
1. Click Configuration > System Management>SNMP > Groups.
This page displays the existing SNMP groups and their security levels. The following fields
are displayed for each SNMP group (only the fields not explained in the Add page):
•
No Authentication Read View—No authentication is needed, and anyone is able to
read the view.
•
No Authentication Write View—No authentication is needed, and anyone is able to
write the view.
•
No Authentication Notify View—No authentication is needed, and anyone is able to
receive notification of the view.
•
Authentication Read View—Only authenticated users are allowed to read the view.
By default, all users or community of a group can access all the MIB objects. A
group can be limited to specific view(s) based on the read, write, notify,
authentication and/or privacy configurations.
•
Authentication Write View—Only authenticated users are able to write the view.
Management access is write for the selected view.
•
Authentication Notify View—Only authentication users are allowed to received
notification.
•
Privacy Read View— When reading the objects in the view, the SNMP messages
are encrypted.
•
Privacy Write View—When writing the object in the view, the SNMP messages are
encrypted.
•
Privacy Notify View - Notification on the objects in the view are encrypted.
2. Click Add.
3. Enter the parameters.
•
Group Name—Enter a new group name.
•
Security Model—Select the SNMP version attached to the group, SNMPv1, v2, or
v3.
Three types of views with various security levels can be defined. For each security
level, select the views for Read, Write and Notify by entering the following fields:
o
Enable—Select this field to enable the Security Level.
35
Page 36

o
Security Level—Define the security level attached to the group. SNMPv1
and SNMPv2 support neither authentication nor privacy. If SNMPv3 is
selected, select to enable one of the following:
o
No Authentication and No Privacy—Neither the Authentication nor the
Privacy security levels are assigned to the group.
o
Authorized View—Select the Read, Write and Notify views associated with
this group and with the above security level.
o
Authentication and No Privacy—Authenticates SNMP messages, and
ensures the SNMP message origin is authenticated but does not encrypt
them.
o
Authorized View—Select the Read, Write and Notify views associated with
this group and with the above security level.
o
Authentication and Privacy—Authenticates SNMP messages, and encrypts
them.
o
Authorized View—Select the Read, Write and Notify views associated with
this group and with the above security level.
4. Click Apply. The SNMP group is saved to the Running Configuration file.
Users
An SNMP user is defined by the login credentials (username, passwords, and authentication
method) and by the context and scope in which it operates by association with a group and an
Engine ID.
The configured user has the attributes of its group, and the access privileges configured within
the associated view.
36
Page 37

Groups enable network managers to assign access rights to a group of users instead of to a single
user.
A user can only belong to a single group.
To create an SNMPv3 user, the following must first exist:
An engine ID must first be configured on the device. This is done in the Engine ID page.
An SNMPv3 group must be available. An SNMPv3 group is defined in the Groups page.
To display SNMP users and define new ones:
1. Click Configuration > System Management>SNMP > Users.
This page contains existing users.
2. Click Add.
This page provides information for assigning SNMP access control privileges to SNMP
users.
3. Enter the parameters.
•
User Name—Enter a name for the user.
•
Engine ID—Select either the local or remote SNMP entity to which the user is
connected. Changing or removing the local SNMP Engine ID deletes the SNMPv3
User Database. To receive inform messages and request information, you must
define both a local and remote user.
o
Local—User is connected to the local device.
o
Engine—User is connected to a different SNMP entity besides the local
device. If the remote Engine ID is defined, remote devices receive inform
messages, but cannot make requests for information.
Select the remote engine ID.
•
Group Name—Select the SNMP group to which the SNMP user belongs. SNMP
groups are defined in the Add Group page.
Note—Users, who belong to groups which have been deleted, remain, but they are
inactive.
•
Authentication Method—Select the Authentication method that varies according
to the Group Name assigned. If the group does not require authentication, then the
user cannot configure any authentication. The options are:
o
None—No user authentication is used.
o
MD5—A password that is used for generating a key by the MD5
authentication method.
o
SHA—A password that is used for generating a key by the SHA (Secure
Hash Algorithm) authentication method.
37
Page 38

•
Authentication Password—If authentication is accomplished by either a MD5 or a
SHA password, enter the local user password in either Encrypted or Plaintext.
Local user passwords are compared to the local database, and can contain up to
32 ASCII characters.
•
Privacy Method—Select one of the following options:
o
None—Privacy password is not encrypted.
o
DES—Privacy password is encrypted according to the Data Encryption
Standard (DES).
•
Privacy Password—16 bytes are required (DES encryption key) if the DES privacy
method was selected. This field must be exactly 32 hexadecimal characters. The
Encrypted or Plaintext mode can be selected.
4. Click Apply to save the settings.
Communities
Access rights in SNMPv1 and SNMPv2 are managed by defining communities in the Communities
page. The community name is a type of shared password between the SNMP management station
and the device. It is used to authenticate the SNMP management station.
Communities are only defined in SNMPv1 and v2 because SNMPv3 works with users instead of
communities. The users belong to groups that have access rights assigned to them.
The Communities page associates communities with access rights, either directly (Basic mode) or
through groups (Advanced mode):
•
Basic Mode—The access rights of a community can configure with Read Only, Read Write,
or SNMP Admin. In addition, you can restrict the access to the community to only certain
MIB objects by selecting a view (defined in the SNMP Views page).
38
Page 39

•
Advanced Mode—The access rights of a community are defined by a group (defined in the
Groups page). You can configure the group with a specific security model. The access
rights of a group are Read, Write, and Notify.
To define SNMP communities:
1. Click Configuration > System Management>SNMP > Communities.
This page contains a table of configured SNMP communities and their properties.
2. Click Add.
This page enables network managers to define and configure new SNMP communities.
3. Enter the following fields:
•
SNMP Management Station—Select User Defined to enter the management
station IP address that can access the SNMP community. Select All to indicate
that any IP device can access the SNMP community.
•
IP Version—Select either IPv4 or IPv6.
•
IPv6 Address Type—Select the supported IPv6 address type if IPv6 is used. The
options are:
o
Link Local—The IPv6 address uniquely identifies hosts on a single network
link. A link local address has a prefix of FE80, is not routable, and can be
used for communication only on the local network. Only one link local
address is supported. If a link local address exists on the interface, this
entry replaces the address in the configuration.
o
Global—The IPv6 address is a global Unicast IPV6 type that is visible and
reachable from other networks.
o
Interface—If the IPv6 address type is Link Local, select whether it is
received through a VLAN or ISATAP.
•
IP Address—Enter the SNMP management station IP address.
•
Community—Enter the community name used to authenticate the management
station to the device.
•
Access Control—Select one of the following:
o
Basic—In this mode, there is no connection to any group. You can only
choose the community access level (Read Only, Read Write, or SNMP
Admin) and, optionally, further qualify it for a specific view. By default, it
applies to the entire MIB.
o
Advanced—In this mode, access is controlled by group configurations.
•
Access Mode—Configure the community:
o
Read Only—Management access is restricted to read-only. Changes
cannot be made to the community.
39
Page 40

o
Read Write—Management access is read-write. Changes can be made to
the device configuration, but not to the community.
o
SNMP Admin—User has access to all device configuration options, as well
as permissions to modify the community. SNMP Admin is equivalent to
Read Write for all MIBs except for the SNMP MIBs. SNMP Admin is
required for access to the SNMP MIBs.
o
View Name—Select an SNMP view (a collection of MIB subtrees to which
access is granted).
o
Group Name—Select an SNMP group that determines the access rights in
Advanced mode.
4. Click Apply. The SNMP Community is defined, and the Running Configuration is updated.
Notification Filters
The Notification Filter page enables configuring SNMP notification filters and Object IDs (OIDs)
that are checked. After creating a notification filter, it is possible to attach it to a notification
recipient in the Notification Recipients SNMPv1/v2 page, and Notification Recipients SNMPv3
page.
The notification filter enables filtering the type of SNMP notifications that are sent to the
management station based on the OID of the notification to be sent.
To define a notification filter:
1. Click Configuration > System Management>SNMP > Notification Filter.
The Notification Filter page contains notification information for each filter. The table is
able to filter notification entries by Filter Name.
2. Click Add.
40
Page 41

3. Enter the parameters.
•
Filter Name—Enter a name between 0-30 characters.
•
Filter Object—Select the node in the MIB tree that is included or excluded in the
selected SNMP filter. The options to select the object are as follows:
o
Selection List—Enables you to navigate the MIB tree. Press the Up arrow
to go to the level of the selected node's parent and siblings; press the Down
arrow to descend to the level of the selected node's children. Click nodes in
the view to pass from one node to its sibling. Use the scrollbar to bring
siblings in view.
o
If Object ID is used, the object identifier is included in the view if the Include
in filter option is selected.
4. Include or exclude in Object Filter. If this is selected, the selected MIBs are included in the
filter, otherwise they are excluded.
5. Click Apply. The SNMP views are defined and the running configuration is updated.
V1/V2 Notification Recipients
Trap messages are generated to report system events, as defined in RFC 1215. The system can
generate traps defined in the MIB that it supports.
Trap receivers (aka Notification Recipients) are network nodes where the trap messages are sent
by the device. A list of notification recipients are defined as the targets of trap messages.
A trap receiver entry contains the IP address of the node and the SNMP credentials
corresponding to the version that is included in the trap message. When an event arises that
requires a trap message to be sent, it is sent to every node listed in the Notification Recipient
Table.
41
Page 42

The Notification Recipients SNMPv1/v2 page and the Notification Recipients SNMPv3 page
enable configuring the destination to which SNMP notifications are sent, and the types of SNMP
notifications that are sent to each destination (traps or informs). The Add/Edit pop-ups enable
configuring the attributes of the notifications.
An SNMP notification is a message sent from the device to the SNMP management station
indicating that a certain event has occurred, such as a link up/ down.
It is also possible to filter certain notifications. This can be done by creating a filter in the
Notification Filter page and attaching it to an SNMP notification recipient. The notification filter
enables filtering the type of SNMP notifications that are sent to the management station based
on the OID of the notification that is about to be sent.
To define a recipient in SNMPv1/v2:
1. Click Configuration > System Management >SNMP > Notification Recipients.
This page displays the currently-defined SNMP recipients.
2. Enter the parameters.
•
Recipient—Select whether to specify the remote log server by IP address or
server name.
•
IP Version—Select either IPv4 or IPv6.
•
IPv6 Address Type—Select either Link Local or Global.
o
Link Local—The IPv6 address uniquely identifies hosts on a single network
link. A link local address has a prefix of FE80, is not routable, and can be
used for communication only on the local network. Only one link local
address is supported. If a link local address exists on the interface, this
entry replaces the address in the configuration.
o
Global—The IPv6 address is a global Unicast IPV6 type that is visible and
reachable from other networks.
o
Interface—If the IPv6 address type is Link Local, select whether it is
received through a VLAN or ISATAP.
•
Recipient IP Address—Enter the IP address of where the traps are sent.
•
Recipient IP Name—Enter the server name of where the traps are sent.
•
UDP Port—Enter the UDP port used for notifications on the recipient device.
•
Notification Type—Select whether to send Traps or Informs. If both are required,
two recipients must be created.
•
Notification Version—Select the trap SNMP version 1 or 2.
•
Community—Select from the pull-down the community string of the trap manager.
Community String names are generated from those listed in the Community page.
•
Notification Filter—Select to enable filtering the type of SNMP notifications sent
to the management station. The filters are created in the Notification Filter page.
42
Page 43

•
Filter Name—Select the SNMP filter that defines the information contained in
traps (defined in the Notification Filter page).
3. Click Apply. The SNMP Notification Recipient settings are written to the Running
Configuration file.
V3 Notification Recipients
To define a recipient in SNMPv3:
1. Click SNMP > Notification Recipients SNMPv3.
This page displays recipients for SNMPv3.
2. Enter the fields:
•
IP Version—Select either IPv4 or IPv6.
•
IPv6 Address Type—Select the IPv6 address type (if IPv6 is used). The options are:
o
Link Local—The IPv6 address uniquely identifies hosts on a single network
link. A link local address has a prefix of FE80, is not routable, and can be
used for communication only on the local network. Only one link local
address is supported. If a link local address exists on the interface, this
entry replaces the address in the configuration.
o
Global—The IPv6 address is a global Unicast IPV6 type that is visible and
reachable from other networks.
•
Link Local Interface—Select the link local interface (if IPv6 Address Type Link
Local is selected) from the pull-down list.
•
Recipient IP Address/Name—Enter the IP address or server name of where the
traps are sent.
•
UDP Port—Enter the UDP port used to for notifications on the recipient device.
43
Page 44

•
Notification Version—Select SNMP v3.
•
Notification Type—Select whether to send traps or informs. If both are required,
two recipients must be created.
•
Timeout—Enter the amount of time (seconds) the device waits before re- sending
informs/traps. Timeout: Range 1-300, default 15.
•
Retries—Enter the number of times that the device resends an inform request.
Retries: Range 1-255, default 3.
•
User Name—Select from the drop-down list the user to whom SNMP notifications
are sent. In order to receive notifications, this user must be defined on the SNMP
User page, and its engine ID must be remote.
•
Security Level—Select how much authentication is applied to the packet.
Note—The Security Level here depends on which User Name was selected. If this
User Name was configured as No Authentication, the Security Level is No
Authentication only. However, if this User Name has assigned Authentication and
Privacy on the User page, the security level on this screen can be either No
Authentication, or Authentication Only, or Authentication and Privacy.
The options are:
o
No Authentication—Indicates the packet is neither authenticated nor
encrypted.
o
Authentication—Indicates the packet is authenticated but not encrypted.
o
Privacy—Indicates the packet is both authenticated and encrypted.
•
Notification Filter—Select to enable filtering the type of SNMP notifications sent
to the management station. The filters are created in the Notification Filter page.
•
Filter Name—Select the SNMP filter that defines the information contained in
traps (defined in the Notification Filter page).
3. Click Apply. The SNMP Notification Recipient settings are written to the Running
Configuration file.
Logs
Each log is a set of messages describing system events. The device generates the following local
logs:
•
Log sent to the console interface.
•
Log written into a cyclical list of logged events in the RAM and erased when the device
reboots.
•
Log written to a cyclical log-file saved to the Flash memory and persists across reboots.
44
Page 45

In addition, you can send messages to remote SYSLOG servers in the form of SNMP traps and
SYSLOG messages.
You can configure the messages that are written to each log by severity, and a message can go to
more.
Log Management
You can select the events by severity level. Each log message has a severity level marked with the
first letter of the severity level separated by dashes (-) on each side (except for Emergency that is
indicated by the letter F). For example, the log message “%INIT-I-InitCompleted: … “ has a
severity level of I, meaning Informational.
The event severity levels are listed from the highest severity to the lowest severity:
1. Emergency—System is not usable.
2. Alert—Action is needed.
3. Critical—System is in a critical condition.
4. Error—System is in error condition.
5. Warning—System warning has occurred.
6. Notice—System is functioning properly, but a system notice has occurred.
7. Informational—Device information.
8. Debug—Detailed information about an event.
You can select different severity levels for RAM and Flash logs. These logs are displayed in the
RAM Log page and Flash Memory Log page, respectively.
Selecting a severity level to be stored in a log causes all of the higher severity events to be
automatically stored in the log. Lower severity events are not stored in the log.
45
Page 46

For example, if Warning is selected, all severity levels that are Warning and higher are stored in
the log (Emergency, Alert, Critical, Error, and Warning). No events with severity level below
Warning are stored (Notice, Informational, and Debug).
To set global log parameters:
1. Click Configuration > System Management > Logs > Log Management.
2. Enter the parameters:
•
System Log
o
Logging—Select to enable message logging.
o
Originator Identifier—Enables adding an origin identifier to SYSLOG
messages. The options:
o
None—Do not include the origin identifier in SYSLOG messages.
o
Hostname—Include the system hostname in SYSLOG messages.
o
IPv4 Address—Include the IPv4 address of the sending interface
inSYSLOG messages.
o
IPv6 Address—Include the IPv6 address of the sending interface
inSYSLOG messages.
o
User Defined—Enter a description to be included in SYSLOG messages.
•
Log Settings
o
Severity—Select the severity levels of the messages to be logged to the
following:
o
RAM Memory Logging—Severity levels of the messages to be logged to
the RAM.
o
Flash Memory Logging—Severity levels of the messages to be logged to
the Flash memory.
3. Click Apply. The Running Configuration file is updated.
46
Page 47

Remote Log Servers
The Remote Log Servers page enables defining remote SYSLOG servers where log messages are
sent (using the SYSLOG protocol). For each server, you can configure the severity of the
messages that it receives.
To define SYSLOG servers, do the following:
1. Click Configuration > System Management > Logs > Remote Log Servers.
2. Click Add.
3. Enter the parameters.
•
Enter New Server
o
Remote Log Server—Select whether to identify the remote log server
by IP address or name.
o
IP Version—Select the supported IP version.
o
IPv6 Address Type—Select the IPv6 address type (if IPv6 is used). The
options:
-
Global—The IPv6 address is a global Unicast IPV6 type that
is visible and reachable from other networks.
-
Link Local—The IPv6 address uniquely identifies hosts on a
single network link. A link local address has a prefix of
FE80, is not routable, and can be used for communication
only on the local network. Only one link local address is
supported. If a link local address exists on the interface, this
entry replaces the address in the configuration.
-
Interface—Select the link local interface (if IPv6 Address
Type Link Local is selected) from the list.
47
Page 48

o
Log Server IP Address—Enter the IP address of the log server if it is to
be identified by address.
o
Log Server Name—Enter the domain name of the log server if it is to be
identified by name.
•
Server Settings
o
UDP Port—Enter the UDP port to which the log messages are sent.
o
Facility—Select a facility value from which system logs are sent to the
remote server. Only one facility value can be assigned to a server. If a
second facility code is assigned, the first facility value is overridden.
o
Description—Enter a server description.
o
Minimum Logging Level—Select the minimum level of system log
messages to be sent to the server.
4. Click Apply. The SYSLOG server is added, and the Running Configuration file is updated.
RAM Log
The RAM Log page displays all messages that were saved in the RAM (cache) in chronological
order. Entries are stored in the RAM log according to the configuration in the Log Management
page.
Click Configuration > System Management > Logs > RAM Log.
•
Log Index—Log entry number.
•
Log Time—Time when message was generated.
48
Page 49

•
Severity—Event severity.
•
Description—Message text describing the event.
To clear the log messages, click Clear.
Flash Memory Log
The Flash Memory Log page displays the messages that were stored in the Flash memory, in
chronological order. The minimum severity for logging is configured in the Log Management page.
Flash logs remain when the device is rebooted. You can clear the logs manually.
Click Configuration > System Management > Logs > Flash Memory Log.
•
Log Index—Log entry number.
•
Log Time—Time when message was generated.
•
Severity—Event severity.
•
Description—Message text describing the event.
To clear the messages, click Clear.
49
Page 50

Chapter 5 – Port Management
Ports
To configure port settings:
1. Click Configuration > Port Management > Ports.
2. Select Enable to support jumbo packets of up to 10 KB in size. If Jumbo Frames is not
enabled (default), the system supports packet size up to 2,000 bytes. For Jumbo Frames
to take effect, the device must be rebooted after the feature is enabled.
3. To update the port settings, select the desired port, and click Edit.
•
Select Your Port
o
Port—Select the port number from the drop-down menu.
•
Port settings
o
Operational Status—Displays whether the port is up or down. If the
port is down because of an error, the description of the error is
displayed.
o
Administrative Mode—Select to change the operational status.
o
Suspended Port—Select to reactivate a port that has been suspended.
The reactivate operation brings the port up without regard to why the
port was suspended.
50
Page 51

o
Protected Port—Select to make this a protected port. (A protected port
is also referred to as a Private VLAN Edge.)
Features of a protected port:
-
Protected Ports provide Layer 2 isolation between interfaces
(Ethernet ports and LAGs) that share the same VLAN.
-
Packets received from protected ports can be forwarded only
to unprotected egress ports. Protected port filtering rules are
also applied to packets that are forwarded by software, such as
snooping applications.
-
Port protection is not subject to VLAN membership. Devices
connected to protected ports are not allowed to communicate
with each other, even if they are members of the same VLAN.
-
Both ports and LAGs can be defined as protected or
unprotected.
-
Protected LAGs are described in the LAGs section.
o
Auto Negotiation—Select to enable auto-negotiation on the port. Auto
negotiation enables a port to advertise its transmission speed, duplex
mode, and flow control abilities to the port link partner.
o
Port Speed—Port type determines available speeds. You can designate
this field only when port Auto Negotiation is disabled.
o
Duplex Mode—Select the port duplex mode. This field is configurable
only when Auto Negotiation is disabled, and the port speed is set to
10M or 100M. At port speed of 1G, the mode is always full duplex.
-
Half—The interface supports transmission between the device
and the client in only one direction at a time.
-
Full—The interface supports transmission between the device
and the client in both directions simultaneously.
o
Auto Advertisement—Select the capabilities advertised by Auto
Negotiation when it is enabled.
-
Max Capability—All port speeds and duplex mode settings can
be accepted.
-
10 Full Duplex—10 Mbps speed and Full Duplex mode.
-
10 Half Duplex—10 Mbps speed and Half Duplex mode.
-
100 Full Duplex—100 Mbps speed and Full Duplex mode.
-
100 Half Duplex—100 Mbps speed and Half Duplex mode.
-
1000 Full Duplex—1000 Mbps speed and Full Duplex mode.
51
Page 52

Click Apply.
4.
o
Back Pressure—Used with Half Duplex mode to slow down the packet
reception speed when the device is congested. It disables the remote
port, preventing it from sending packets by jamming the signal.
o
Flow Control—Enable or disable 802.3x Flow Control, or enable the
Auto Negotiation of flow control on the port (only when in Full Duplex
mode).
o
MDI/MDIX—Media Dependent Interface/Media Dependent
o
Interface with Crossover status on the port.
-
MDIX—Select to swap the port’s transmit and receives pairs.
-
MDI—Select to connect this device to a station by using a
straight-through cable.
-
Auto—Select to configure this device to automatically detect
the correct pinouts for the connection to another device.
o
Description—Enter a port description.
Link Aggregation
Link Aggregation Control Protocol (LACP) is part of the IEEE specification (802.3ad) that enables
you to bundle several physical ports together to form a single logical channel (LAG). LAGs multiply
the bandwidth, increase port flexibility, and provide link redundancy between two devices.
This switch supports two kinds of LAG.
•
Static—A LAG is static if the LACP is disabled. The ports assigned to a static LAG are
always active members. After a LAG is manually created, the LACP option cannot be
added or removed until the LAG is edited and a member is removed (which can be added
prior to applying), then the LACP button becomes available for editing.
•
Dynamic—A LAG is dynamic if LACP is enabled. The ports assigned to dynamic LAG are
candidate ports. LACP determines which candidate ports are active member ports. The
non-active candidate ports are standby ports ready to replace any failing active member
ports.
Load Balancing
Traffic forwarded to a LAG is load-balanced across the active member ports, thus achieving an
effective bandwidth close to the aggregate bandwidth of all the active member ports of the LAG.
Traffic load balancing over the active member ports of a LAG is managed by a hash-based
distribution function that distributes Unicast and Multicast traffic based on Layer 2 or Layer 3
packet header information.
52
Page 53

This switch supports two modes of load balancing.
•
By MAC Addresses—(Default) Based on the destination and source MAC addresses of all
packets.
•
By IP and MAC Addresses—Based on the destination and source IP addresses for IP
packets, and destination and source MAC addresses for non-IP packets.
LAG Management
In general, a LAG is treated by the system as a single logical port. In particular, the LAG has port
attributes similar to a regular port, such as state and speed.
The device supports four LAGs. Each LAG has the following characteristics:
•
All ports in a LAG must be of the same media type.
•
To add a port to the LAG, it cannot belong to any VLAN except the default VLAN.
•
Ports in a LAG must not be assigned to another LAG.
•
No more than eight ports are assigned to a static LAG and no more than 16 ports can be
candidates for a dynamic LAG.
•
All the ports in a LAG must have auto-negotiation disabled, although the LAG can have
auto-negotiation enabled.
•
When a port is added to a LAG, the configuration of the LAG is applied to the port. When
the port is removed from the LAG, its original configuration is reapplied.
•
Protocols, such as Spanning Tree, consider all the ports in the LAG to be one port.
Default Settings and Configuration
Ports are not members of a LAG and are not candidates to become part of a LAG.
Static and Dynamic LAG Workflow
After a LAG has been manually created, LACP cannot be added or removed until the LAG is edited
and a member is removed. Only then the LACP field is activated.
•
To configure a static LAG:
1. Disable LACP on the LAG to make it static. Assign up to eight member ports to the
static LAG in the Port List to the LAG Port Member list. Perform these actions in
the LAGs page.
2. Configure various aspects of the LAG, such as speed and flow control by using the
Edit LAG page.
•
To configure a dynamic LAG:
1. Enable LACP on the LAG. Assign up to 16 candidates ports to the dynamic LAG by
selecting and moving the ports from the Port List to the LAG Port Member List by
using the LAGs page.
2. Configure various aspects of the LAG, such as speed and flow control by using the
LAGs page.
53
Page 54

LAGs
The LAGs page enables you to configure the global settings, and to select and edit the desired
LAG on the Edit LAG Membership page.
To define the member or candidate ports in a LAG:
1. Click Configuration > Port Management > Link Aggregation > LAGs.
2. Select the Load Balance Method
•
by MAC Address—(Default) Based on the destination and source MAC addresses
of all packets.
•
by IP and MAC Address—Based on the destination and source IP addresses for IP
packets, and destination and source MAC addresses for non-IP packets.
3. Select the LAG to be configured, and click Edit.
•
Select Your LAG
o
LAG—Select the LAG from the drop-down menu.
•
LAG Settings
o
Operational Status—Whether the LAG is up or down.
o
Port List—Move those ports that are to be assigned to the LAG from the
Port List to the LAG Port Member list. Up to eight ports per static LAG can
be assigned, and 16 ports can be assigned to a dynamic LAG.
o
LAG Mode—Displays whether the LAG is up or down.
o
Suspended LAG—Select to reactivate the LAG.
o
Protected LAG—Select to make the LAG a protected port for Layer 2
isolation. See Port settings
LAGs.
o
LACP—Select to enable LACP on the selected LAG. This makes it a
for details regarding protected ports and
dynamic LAG. This field can only be enabled after moving a port to the LAG
in the next field.
54
Page 55

o
Auto Negotiation—Select to enable auto-negotiation on the LAG. Autonegotiation is a protocol between two link partners that enables a LAG to
advertise its transmission speed and flow control to its partner (the Flow
Control default is disabled). It is recommended to keep auto-negotiation
enabled on both sides of an aggregate link, or disabled on both sides, while
ensuring that link speeds are identical.
o
Port Speed—Configure the speed of the LAG. The port types determine the
available speeds. You can designate this field only when port autonegotiation is disabled.
o
Auto Advertisement—Select the capabilities to be advertised by the LAG.
-
Max Capability—All LAG speeds and both duplex modes are
available.
-
10 Full Duplex—The LAG advertises a 10 Mbps speed and the
mode is full duplex.
-
100 Full Duplex—The LAG advertises a 100 Mbps speed and the
mode is full duplex.
-
1000 Full Duplex—The LAG advertises a 1000 Mbps speed and
the mode is full duplex.
o
Flow Control—Set Flow Control to either Enable or Disable or AutoNegotiation.
o
Description—Enter the LAG name or a comment.
4. Click Apply. LAG membership is saved to the Running Configuration file.
55
Page 56

Green Ethernet
Green Ethernet is a common name for a set of features that is designed to be environmentally
friendly, and to reduce the power consumption of a device. Green Ethernet is different from EEE
in that Green Ethernet energy-detect is enabled on all devices where only the gigabyte ports are
enabled with EEE.
The Green Ethernet feature can reduce overall power usage in the following ways.
•
Short-Reach Mode—Provides for power savings on a short length of cable. After cable
length is analyzed, the power usage is adjusted for various cable lengths. If the cable is
shorter than 50 meters, the device uses less power to send frames over the cable, thus
saving energy. This mode is only supported on RJ45 GE ports; it does not apply to Combo
ports. This mode is globally disabled by default. It cannot be enabled if EEE mode is
enabled (see below).
802.3 Energy Efficient Ethernet (EEE)—Reduces power consumption when there is no traffic on
the port. See Energy Efficient Ethernet
On a given port, if EEE is enabled, short reach mode will be disabled. If Short Reach Mode is
enabled, EEE is grayed out.
for more information. EEE is enabled globally by default.
These modes are configured per port, without taking into account the LAG membership of the
ports.
56
Page 57

Power savings, current power consumption and cumulative energy saved can be monitored. The
total amount of saved energy can be viewed as a percentage of the power that would have been
consumed by the physical interfaces had they not been running in Green Ethernet mode.
The saved energy displayed is only related to Green Ethernet. The amount of energy saved by
EEE is not displayed.
Energy Efficient Ethernet
EEE is designed to save power when there is no traffic on the link. In Green Ethernet, power is
reduced when the port is down. With EEE, power is reduced when the port is up, but there is no
traffic on it.
When using 802.3 EEE, systems on both sides of the link can disable portions of their
functionality and save power during periods of no traffic. 802.3 EEE supports IEEE 802.3 MAC
operation at 100 Mbps and 1000 Mbps.
LLDP is used to select the optimal set of parameters for both devices. If LLDP is not supported by
the link partner, or is disabled, 802.3 EEE will still be operational, but it might not be in the optimal
operational mode.
The 802.3 EEE feature is implemented using a port mode called Low Power Idle (LPI) mode. When
there is no traffic and this feature is enabled on the port, the port is placed in the LPI mode, which
reduces power consumption dramatically.
Both sides of a connection (device port and connecting device) must support 802.3 EEE for it to
work. When traffic is absent, both sides send signals indicating that power is about to be reduced.
When signals f s (and not in Down status), and power is reduced.
For ports to stay in LPI mode, the Keep Alive signal must be received continuously from both
sides.
Power Saving by Disabling Port LEDs
Use the Green Ethernet feature to disable port LEDs (link, speed, and PoE) when they are not
needed. Enable them if needed (debugging, connecting additional devices, etc.).
Advertise Capabilities Negotiation
802.3 EEE support is advertised during the Auto-Negotiation stage. Auto-Negotiation provides a
linked device with the capability to detect the abilities (modes of operation) supported by the
device at the other end of the link, determine common abilities, and configure itself for joint
operation. Auto-Negotiation is performed at the time of link-up, on command from management,
or upon detection of a link error. During the link establishment process, both link partners
exchange their 802.3 EEE capabilities. Auto- Negotiation functions automatically without user
interaction when it is enabled on the device.
57
Page 58

Note—If Auto-Negotiation is not enabled on a port, the EEE is disabled. The only exception is if the
link speed is 1GB, then EEE will still be enabled even though Auto-Negotiation is disabled.
Default Configuration
By default, 802.3 EEE is enabled globally and per port.
Interactions Between Features
802.3 EEE interactions with other features:
•
If auto-negotiation is not enabled on the port, the 802.3 EEE operational status is
disabled. The exception to this rule is that if the link speed is 1gigabit, EEE will still be
enabled even though Auto-Negotiation is disabled.
•
If 802.3 EEE is enabled and the port is going up, it commences to work immediately in
accordance with the maximum wake time value of the port.
•
On the GUI, the EEE field for the port is not available when the Short Reach Mode option
on the port is checked.
•
If the port speed on the GE port is changed to 10Mbit, 802.3 EEE is disabled. This is
supported in GE models only.
802.3 EEE Configuration Workflow
This section describes how to configure the 802.3 EEE feature and view its counters.
1. Ensure that auto-negotiation is enabled on the port by opening the Ports page.
•
Select a port and open the Edit Ports page.
•
Select Auto Negotiation field to ensure that it is enabled.
2. Ensure that 802.3 Energy Efficient Ethernet (EEE) is globally enabled in the Green
Ethernet page (it is enabled by default). This page also displays how much energy has been
saved.
3. Ensure that 802.3 EEE is enabled on a port by opening the Green Ethernet page.
•
Select a port, open the Edit Ports page.
•
Check the 802.3 Energy Efficient Ethernet (EEE) mode on the port (it is enabled by
default).
Configuring Green Ethernet
To configure Green Ethernet globally and on a port:
1. Click Configuration > Port Management > Green Ethernet.
•
Energy Detect Mode—Select to globally enable.
•
Port LEDs—Select to disable port LEDs. When disabled, ports do not display link
status, activity, etc.
•
Short Reach—Select to globally enable Short Reach mode if there are Green
Ethernet ports on the device.
58
Page 59

Note—If Short Reach is enabled, EEE must be disabled.
•
802.3 Energy Efficient Ethernet (EEE)—Select to globally enable EEE.
2. Click Apply to set the global settings.
•
Power Savings—The percentage of power saved by running Green Ethernet and
Short Reach. The power savings displayed is only relevant to the power saved by
Short Reach and Energy Detect modes. The EEE power savings is dynamic by
nature since it is based on port utilization and is therefore not taken into
consideration. The power saving calculation is performed by comparing the
maximum power consumption without power savings to the current consumption.
•
Cumulative Energy Saved—The amount of energy saved from the last device
reboot in watt hours. This value is updated each time there is an event that affects
power saving.
3. Select a port and click Edit.
•
Select Your Port
o
Port—Select a port from the drop-down menu.
•
Port Settings
o
Energy Detect Mode—Select to enable.
o
Short Reach Mode—Select to enable.
o
802.3 EEE Mode—Select to enable.
o
EEE LLDP Mode—Select to enable.
•
EEE Status—Whether EEE is currently operating on the local port. This is a
function of whether it has been enabled (Administrative Status), whether it has
been enabled on the local port and whether it is operational on the local port.
Note—The Green Ethernet Table displays the Short Reach, Energy Detect and
EEE settings for each port; however, they are not enabled on any port unless they
are also enabled globally.
PoE
A Power over Ethernet (PoE) device is PSE (Power Sourcing Equipment) that delivers electrical
power to connected PD (Powered Devices) over existing copper cables without interfering with
the network traffic, updating the physical network or modifying the network infrastructure. The
PoE feature is only available on PoE-based devices.
59
Page 60

PoE capabilities:
•
Eliminates the need to run 110/220 V AC power to all devices on a wired LAN.
•
Removes the necessity for placing all network devices next to power sources.
•
Eliminates the need to deploy double cabling systems in an enterprise, significantly
decreasing installation costs.
Power over Ethernet can be used in any enterprise network that deploys relatively lowpowered devices connected to the Ethernet LAN:
•
IP phones
•
Wireless access points
•
IP gateways
•
Audio and video remote monitoring devices
PoE Operation
PoE implementation stages:
•
Detection—Sends special pulses on the copper cable. When a PoE device is located at the
other end, that device responds to these pulses.
•
Classification—Negotiation between the Power Sourcing Equipment (PSE) and the
Powered Device (PD) commences after the Detection stage. During negotiation, the PD
specifies its class, which is the amount of maximum power that the PD consumes.
•
Power Consumption—After the classification stage completes, the PSE provides power to
the PD. If the PD supports PoE, but without classification, it is assumed to be class 0 (the
maximum). If a PD tries to consume more power than permitted by the standard, the PSE
stops supplying power to the port.
Power Modes
Power per port can be limited depending on the Power Mode:
•
Port Limit—Power is limited to a specified wattage. For these settings to be active, the
system must be in PoE Port Limit mode. That mode is configured in the PoE Feature
Configuration page. When the power consumed on the port exceeds the port limit, the port
power is turned off.
•
Class Limit—Power is limited based on the class of the connected PD. For these settings
to be active, the system must be in PoE Class Limit mode. That mode is configured in the
PoE Feature Configuration page. When the power consumed on the port exceeds the class
limit, the port power is turned off.
60
Page 61

PoE Priority Example
A 48-port device is supplying a total of 375 watts.
The administrator configures all ports to allocate up to 30 watts each. This results in 48 times 30
ports equaling 1440 watts, which is too much. The device cannot provide enough power to each
port, so it provides power according to the priority.The administrator sets the priority for each
port, allocating how much power it can be given.
These priorities are entered in the PoE Port Limit Mode or Class Limit Power Mode pages.
PoE Configuration Considerations
There are two factors to consider in PoE configuration:
•
The amount of power that the PSE can supply
•
The amount of power that the PD is attempting to consume
You can decide the following:
•
Maximum power a PSE is allowed to supply to a PD
•
POE mode—To change the mode from Class Power Limit to Port Limit, and vice versa,
during device operation. The power values per port that were configured for the Port Limit
mode are retained.
Note—Changing the mode from Class Limit to Port limit, and vice versa, when the device
is operational forces the Powered Device to reboot.
•
Maximum port limit allowed as a per-port numerical limit in mW (Port Limit mode).
The PoE-specific hardware automatically detects the PD class and its power limit according to
the class of the device connected to each specific port (Class Limit mode).
If at any time during the connectivity an attached PD requires more power from the device than
the configured allocation allows (no matter if the device is in Class Limit or Port Limit mode), the
device maintains the up/down status of the PoE port link, turns off power delivery to the PoE port,
and logs the reason for turning off power.
Caution—Consider the following when connecting switches capable of supplying PoE.
o
The PoE model of the device is PSE (Power Sourcing Equipment) that is capable of
supplying DC power to attaching PD (Powered Devices). These devices include
VoIP phones, IP cameras, and wireless access points.
o
Even though the PoE switches are PSE, and as such should be powered by AC,
they could be powered up as a legacy PD by another PSE due to false detection.
When this happens, the PoE device may not operate properly and may not be able
to properly supply power to its attaching PDs.
61
Page 62

o
To prevent false detection, you should disable PoE on the ports on the PoE
switches that are used to connect to PSEs. You should also first power up a PSE
device before connecting it to a PoE device. When a device is being falsely
detected as a PD, you should disconnect the device from the PoE port and power
cycle the device with AC power before reconnecting its PoE ports.
Feature Configuration
The Feature Configuration page enables selecting either the Port Limit or Class Limit PoE mode.
These settings are entered in advance. When the PD actually connects and is consuming power, it
might consume much less than the maximum power allowed.
Output power is disabled during power-on reboot, initialization, and system configuration to
ensure that PDs are not damaged.
To configure PoE on the device and monitor current power usage:
1. Click Configuration > Port Management > PoE > Feature Configuration.
2. Enter values for:
•
Power Mode—Select one of the following options:
•
Port Limit—The maximum power limit per each port is configured by the user.
•
Class Limit—The maximum power limit per port is determined by the class of the
device, which results from the Classification stage.
Note—When you change from Port Limit to Class Limit, or vice versa, you must disable
PoE ports, and enable them after changing the power configuration.
The following counters are displayed for the device:
•
Nominal Power —The total amount of power in watts that the device can supply to
all the connected PDs.
62
Page 63

•
Consumed Power—Amount of power in watts that is currently being consumed by
the PoE ports.
•
Available Power—Nominal power in watts minus the amount of consumed power.
3. Click Apply to save the PoE properties.
Port Limit Power Mode
To configure port limit power mode:
1. Click Configuration > Port Management > PoE > Port Limit Power Mode. The list of fields
below is for Port Limit Power Mode.
•
PoE Status—Enable or disable PoE on the port.
•
Power Priority Level—Port priority is low, high, or critical, for use when the power
supply is low. For example, if the power supply is running at 99% usage and port 1
is prioritized as high, but port 3 is prioritized as low, port 1 receives power and port
3 might be denied power.
•
Power Allocation Limit (mW)—Power in milliwatts allocated to the port.
•
Max Power Allocation (mW)—Maximum amount of power permitted on this port.
•
Power Consumption (mW)—Amount of power assigned to the powered device
connected to the selected interface.
•
Class—Power class of device.
•
Operational Status—Displays whether Power Limit mode is enabled or disabled on
the port.
2. Select a port and click Edit. Enter the fields as described above.
3. Click Apply. The PoE settings for the port are written to the Running Configuration file.
63
Page 64

Class Limit Power Mode
To configure class limit power mode:
1. Click Configuration > Port Management > PoE > Class Limit Power Mode.
•
PoE Status—Enable or disable PoE on the port.
•
Power Priority Level—Port priority is low, high, or critical, for use when the power
supply is low. For example, if the power supply is running at 99% usage and port 1
is prioritized as high, but port 3 is prioritized as low, port 1 receives power and port
3 might be denied power.
•
Class—Class configured on this port. The classes are shown in the following:
Class
0 15.4 watt
1 4.0 watt
2 7.0 watt
3 15.4 watt
4 30.0 watt
•
Max Power Allocation (mW)—Maximum amount of power permitted on this port.
The switch hardware may actually supply 5-10% more power than Max Power
Allocation to accommodate the power loss over the wire.
•
Power Consumption (mW)—Amount of power assigned to the powered device
connected to the selected interface.
•
Operational Status—Whether the Class Limit mode is enabled or disabled on the
port.
Maximum Power Delivered by Device Port
64
Page 65

2. Select a port and click Edit. Enter the fields as described above.
3. Click Apply. The PoE settings for the port are written to the Running Configuration file.
Discovery - LLDP
Link Layer Discovery Protocol (LLDP) is a link layer protocol for directly-connected LLDP-capable
neighbors to advertise themselves and their capabilities. LLDP enables network managers to
troubleshoot and enhance network management in multi-vendor environments. LLDP
standardizes methods for network devices to advertise themselves to other systems, and to store
discovered information.
By default, the device sends an LLDP advertisement periodically to all its interfaces and
processes incoming LLDP packets as required by the protocols. In LLDP, advertisements are
encoded as TLV (Type, Length, Value) in the packet.
The information learned is stored in the data in a Management Information Base (MIB). The
network management system models the topology of the network by querying these MIB
databases.
By default, the device terminates and processes all incoming LLDP packets as required by the
protocol.
The LLDP protocol has an extension called LLDP Media Endpoint Discovery (LLDP-MED) that
provides and accepts information from media endpoint devices such as VoIP phones and video
phones.
Some notes about LLDP configuration:
•
LLDP can be enabled or disabled globally or per port. The LLDP capability of a port is
relevant only if LLDP is globally enabled.
•
If LLDP is globally enabled, the device filters out incoming LLDP packets from ports that
are LLDP-disabled.
•
If LLDP is globally disabled, the device can be configured to discard, VLAN- aware
flooding, or VLAN-unaware flooding of all incoming LLDP packets. VLAN-aware flooding
floods an incoming LLDP packet to the VLAN where the packet is received excluding the
ingress port. VLAN-unaware flooding floods an incoming LLDP packet to all the ports
excluding the ingress port. The default is to discard LLDP packets when LLDP is globally
disabled. You can configure the discard/flooding of incoming LLDP packets from the LLDP
Feature Configuration page.
•
LLDP end devices, such as IP phones, learn the voice VLAN configuration from LLDP
advertisements. By default, the device is enabled to send out LLDP advertisement based
on the voice VLAN configured at the device. Refer to the Voice VLAN for details.
Note—LLDP does not distinguish if a port is in a LAG. If there are multiple ports in a LAG, LLDP
transmit packets on each port without taking into account the fact that the ports are in a LAG.
65
Page 66

The operation of LLDP is independent of the STP status of an interface.
If 802.1x port access control is enabled at an interface, the device transmits and receives LLDP
packets to and from the interface only if the interface is authenticated and authorized.
If a port is the target of mirroring, then LLDP considers it down.
Note—LLDP are link layer protocols for directly-connected LLDP capable devices to advertise
themselves and their capabilities. In deployments where the LLDP-capable devices are not
directly connected and are separated with LLDP-incapable devices, the LLDP-capable devices
may be able to receive the advertisement from other devices only if the LLDP-incapable devices
flood the LLDP packets they receive. If the LLDP-incapable devices perform VLAN-aware
flooding, then LLDP-capable devices can hear each other only if they are in the same VLAN. An
LLDP-capable device may receive advertisements from more than one device if the LLDPincapable devices flood the LLDP packets.
Workflows
Following are examples of actions that can be performed with the LLDP feature and in a
suggested order. You can refer to the LLDP section for additional guidelines on LLDP
configuration. LLDP configuration pages are accessible under the Configuration > Port
Management > Discovery - LLDP menu.
1. Enter LLDP global parameters, such as LLDP Frames Handling using the LLDP Feature
Configuration page.
2. Configure LLDP per port by using the LLDP Feature Configuration page. On this page,
interfaces can be configured to receive/transmit LLDP PDUs, send SNMP notifications,
specify which TLVs to advertise, and advertise the device's management address.
3. Create LLDP MED network policies by using the LLDP MED Network Policy page.
4. Associate LLDP MED network policies and the optional LLDP-MED TLVs to the desired
interfaces by using the LLDP MED Port Settings page.
Feature Configuration
66
Page 67

The LLDP-MED TLVs to be advertised can be selected in the LLDP MED Port Settings page, and
the management address TLV of the device may be configured to be advertised.
To configure the LLDP port settings:
1. Click Configuration > Port Management > Discovery – LLDP > Feature Configuration.
The following fields are displayed (only fields that do not appear in the Edit page are
described):
•
Interface—The port to edit.
•
LLDP MED Status—Enabled or disabled.
•
Number of neighbors—Number of neighbors discovered.
•
Neighbor Capability—Displays the primary functions of the neighbor; for example:
Bridge or Router.
•
Local PoE—Local PoE information advertised.
o
power priority—Port power priority
o
power value—Port power value
•
Neighbor PoE—PoE information advertised by the neighbor.
o
power priority—Port power priority
o
power value—Port power value
2. Enter the following fields.
•
LLDP Status—Select to enable LLDP on the device (enabled by default).
•
LLDP Frame Handling—If LLDP is not enabled, select the action to be taken if a
packet that matches the selected criteria is received:
o
Filtering—Delete the packet.
o
Flooding—Forward the packet to all VLAN members.
3. Select a port and click Edit.
•
Port—Select the port to edit.
•
LLDP Status—Select the LLDP publishing option for the port. The values are:
o
Tx Only—Publishes but does not discover.
o
Rx Only—Discovers but does not publish.
o
Tx & Rx—Publishes and discovers.
o
Disable—Indicates that LLDP is disabled on the port.
•
Available Optional TLVs—Information to be published by the device.
•
Advertise Optional TLVs—Select the information to be published by the device by
moving the TLV from the Available Optional TLVs list. The available TLVs contain
the following information:
67
Page 68

o
Port Description—Information about the port, including manufacturer,
product name and hardware/software version.
o
System Name—System's assigned name (in alpha-numeric format). The
value equals the sysName object.
o
System Description—Description of the network entity (in alpha-numeric
format). This includes the system's name and versions of the hardware,
operating system, and networking software supported by the device. The
value equals the sysDescr object.
o
System Capabilities—Primary functions of the device, and whether or not
these functions are enabled on the device. The capabilities are indicated by
two octets. Bits 0 through 7 indicate Other, Repeater, Bridge, WLAN AP,
Router, Telephone, DOCSIS cable device, and station respectively. Bits 8
through 15 are reserved.
o
802.3 MAC-PHY—Duplex and bit rate capability and the current duplex
and bit rate settings of the sending device. It also indicates whether the
current settings are due to auto-negotiation or manual configuration.
o
802.3 Link Aggregation—Whether the link (associated with the port on
which the LLDP PDU is transmitted) can be aggregated. It also indicates
whether the link is currently aggregated, and if so, provides the aggregated
port identifier.
o
802.3 Maximum Frame—Maximum frame size capability of the MAC/PHY
Management Address TLV—Select one of the following ways to advertise
the IP management address of the device:
o
Auto Advertise—Specifies that the software automatically chooses a
management address to advertise from all the IP addresses of the device.
In case of multiple IP addresses, the software chooses the lowest IP
address among the dynamic IP addresses. If there are no dynamic
addresses, the software chooses the lowest IP address among the static IP
addresses.
o
None—Do not advertise the management IP address.
o
Manual Advertise—Select this option and the management IP address to
be advertised.
•
Management IP Address—If Manual Advertise was selected, select the
Management IP address from the addresses provided.
4. Enter the relevant information, and click Apply. The port settings are written to the
Running Configuration file.
68
Page 69

LLDP MED Ports
The LLDP MED Ports page enables the selection of the LLDP MED TLVs and/or the network
policies to be included in the outgoing LLDP advertisement for the desired interfaces. Network
Policies are configured using the LLDP MED Network Policy page.
To configure LLDP MED on each port:
1. Click Configuration > Port Management > Discovery – LLDP > LLDP MED Ports.
This page displays the following LLDP MED settings for all ports (only fields not described
in the Edit page are listed):
•
Location—Whether Location TLV is transmitted.
•
PoE—Whether POE-PSE TLV is transmitted.
•
Inventory—Whether Inventory TLV is transmitted.
2. The message at the top of the page indicates whether the generation of the LLDP MED
Network Policy for the voice application is automatic or not. Click on the link to change the
mode.
3. To associate additional LLDP MED TLV and/or one or more user-defined LLDP MED
Network Policies to a port, select it, and click Edit.
4. Enter the parameters:
•
Port—Select the interface to configure.
•
LLDP MED Status—Enable/disable LLDP MED on this port.
•
Available Optional TLVs—Select the TLVs that can be published by the device by
moving them from the Advertise Optional TLVs list.
69
Page 70

•
Available Network Policies—Select the LLDP MED policies to be published by
LLDP by moving them from the Available Network Policies list. These were created
in the LLDP MED Network Policy page. To include one or more user-defined
network polices in the advertisement, you must also select Network Policy from
the Available Optional TLVs.
Note—The following fields must be entered in hexadecimal characters in the exact
data format that is defined in the LLDP-MED standard (ANSI-TIA1057_final_for_publication.pdf):
•
Location Coordinate—Enter the coordinate location to be published by LLDP.
•
Location Civic Address—Enter the civic address to be published by LLDP.
•
Location (ECS) ELIN—Enter the Emergency Call Service (ECS) ELIN location to
be published by LLDP.
5. Click Apply. The LLDP MED port settings are written to the Running Configuration file.
LLDP Local Information
70
Page 71

To view the LLDP local port status advertised on a port:
1. Click Configuration > Port Management Discovery - LLDP > LLDP Local Information.
2. Select the desired port from the Port list.
This page displays the following groups of fields (the actual fields displayed depend on the
optional TLVs selected to be advertised):
•
Global
o
Chassis ID Subtype—Type of chassis ID. (For example, the MAC address.)
o
Chassis ID—Identifier of chassis. Where the chassis ID subtype is a MAC
address, the MAC address of the device appears.
o
System Name—Name of device.
o
System Description—Description of the device (in alpha-numeric format).
o
Supported System Capabilities—Primary functions of the device, such as
Bridge, WLAN AP, or Router.
o
Enabled System Capabilities—Primary enabled function(s) of the device.
o
Port ID Subtype—Type of the port identifier that is shown.
o
Port ID—Identifier of port.
o
Port Description—Information about the port, including manufacturer,
product name and hardware/software version.
•
Management Address
o
Displays the table of addresses of the local LLDP agent. Other remote
managers can use this address to obtain information related to the local
device. The address consists of the following elements:
o
Address Subtype—Type of management IP address that is listed in the
o
Management Address field; for example, IPv4.
o
Address—Returned address most appropriate for management use.
o
Interface Subtype—Numbering method used for defining the interface
number.
o
Interface Number—Specific interface associated with this management
address.
•
MED Information
o
Capabilities Supported—MED capabilities supported on the port.
o
Current Capabilities—MED capabilities enabled on the port.
o
Device Class—LLDP-MED endpoint device class. The possible device
classes are:
o
Endpoint Class 1—Generic endpoint class, offering basic LLDP services.
71
Page 72

o
Endpoint Class 2—Media endpoint class, offering media streaming
capabilities, as well as all Class 1 features.
o
Endpoint Class 3—Communications device class, offering all Class 1 and
Class 2 features plus location, 911, Layer 2 device support, and device
information management capabilities.
o
PoE Device Type—Port PoE type; for example, powered.
o
PoE Power Source—Port power source.
o
PoE Power Priority—Port power priority.
o
PoE Power Value—Port power value.
o
Hardware Revision—Hardware version.
o
Firmware Revision—Firmware version.
o
Software Revision—Software version.
o
Serial Number—Device serial number.
o
Manufacturer Name—Device manufacturer name.
o
Model Name—Device model name.
o
Asset ID—Asset ID.
•
Location Information
o
Civic—Street address.
o
Coordinates—Map coordinates: latitude, longitude, and altitude.
o
ECS ELIN—Emergency Call Service (ECS) Emergency Location
Identification Number (ELIN).
•
Network Policy
o
Application Type—Network policy application type; for example, Voice.
o
VLAN ID—VLAN ID for which the network policy is defined.
o
VLAN Type—VLAN type for which the network policy is defined. The
possible field values are:
-
-
o
User Priority—Network policy user priority.
o
DSCP—Network policy DSCP.
Tagged—Indicates the network policy is defined for tagged VLANs.
Untagged—Indicates the network policy is defined for untagged
VLANs.
72
Page 73

LLDP Neighbor Information
The LLDP Neighbors Information page contains information that was received from neighboring
devices. After timeout (based on the value received from the neighbor Time To Live TLV during
which no LLDP PDU was received from a neighbor), the information is deleted.
To view the LLDP neighbor information:
Click Configuration>Port Management > Discovery - LLDP > LLDP Neighbor Information.
•
Local Port—Number of the local port to which the neighbor is connected
•
Global
o
Local Port—Port number. (Ron- Gina Please confirm the Global items.)
o
MSAP Entry—Device Media Service Access Point (MSAP) entry number.
•
Basic Details
o
Chassis ID Subtype—Type of chassis ID (for example, MAC address).
o
Chassis ID—Identifier of the 802 LAN neighboring device chassis.
o
Port ID Subtype—Type of the port identifier that is shown.
o
Port ID—Identifier of port.
o
Port Description—Information about the port, including manufacturer, product
name and hardware/software version.
o
System Name—Name of system that is published.
o
System Description—Description of the network entity (in alpha-numeric format).
This includes the system name and versions of the hardware, operating system,
and networking software supported by the device. The value equals the sysDescr
object.
73
Page 74

o
Supported System Capabilities—Primary functions of the device. The capabilities
are indicated by two octets. Bits 0 through 7 indicate Other, Repeater, Bridge,
WLAN AP, Router, Telephone, DOCSIS cable device, and station, respectively. Bits
8 through 15 are reserved.
o
Enabled System Capabilities—Primary enabled function(s) of the device.
•
Management Address
o
Address Subtype—Managed address subtype; for example, MAC or IPv4.
o
Address—Managed address.
o
Interface Subtype—Port subtype.
o
Interface Number—Port number.
•
MED Information
o
Capabilities Supported—MED capabilities enabled on the port.
o
Current Capabilities—MED TLVs advertised by the port.
o
Device Class—LLDP-MED endpoint device class. The possible device classes are:
-
-
-
o
PoE Device Type—Port PoE type, for example, powered.
o
PoE Power Source—Port’s power source.
o
PoE Power Priority—Port’s power priority.
o
PoE Power Value—Port’s power value.
o
Hardware Revision –Hardware version.
o
Firmware Revision—Firmware version.
o
Software Revision—Software version.
o
Serial Number—Device serial number.
o
Manufacturer Name—Device manufacturer name.
o
Model Name—Device model name.
o
Asset ID—Asset ID.
Endpoint Class 1—Indicates a generic endpoint class, offering basic LLDP
services.
Endpoint Class 2—Indicates a media endpoint class, offering media
streaming capabilities as well as all Class 1 features.
Endpoint Class 3—Indicates a communications device class, offering all
Class 1 and Class 2 features plus location, 911, Layer 2 switch support
and device information management capabilities.
•
Location Information
Enter the following data structures in hexadecimal as described in section 10.2.4 of the
ANSI-TIA-1057 standard:
74
Page 75

o
Civic—Civic or street address.
o
Coordinates—Location map coordinates—latitude, longitude, and altitude.
o
ECS ELIN—Device’s Emergency Call Service (ECS) Emergency Location
Identification Number (ELIN).
o
Unknown—Unknown location information.
•
Network Policy
o
Application Type—Network policy application type, for example, Voice.
o
VLAN ID—VLAN ID for which the network policy is defined.
o
VLAN Type—VLAN type, Tagged or Untagged, for which the network policy is
defined.
o
User Priority—Network policy user priority.
o
DSCP—Network policy DSCP.
LLDP MED Network Policy
LLDP Media Endpoint Discovery (LLDP-MED) is an extension of LLDP that provides the following
additional capabilities to support media endpoint devices:
•
Enables the advertisement and discovery of network polices for real-time applications
such as voice and/or video.
•
Enables discovery of the device location to allow creation of location databases and, in the
case of Voice over Internet Protocol (VoIP), Emergency Call Service (E-911) by using IP
Phone location information.
•
Troubleshooting information. LLDP MED sends alerts to network managers upon:
o
Port speed and duplex mode conflicts
o
QoS policy misconfigurations
75
Page 76

Setting LLDP MED Network Policy
An LLDP-MED network policy is a related set of configuration settings for a specific real-time
application such as voice, or video. A network policy, if configured, can be included in the outgoing
LLDP packets to the attached LLDP media endpoint device. The media endpoint device must send
its traffic as specified in the network policy it receives. For example, a policy can be created for
VoIP traffic that instructs VoIP phone to:
•
Send voice traffic on VLAN 10 as tagged packet and with 802.1p priority 5.
•
Send voice traffic with DSCP 46.
Network policies are associated with ports by using the LLDP MED Port Settings page. An
administrator can manually configure one or more network policies and the interfaces where the
policies are to be sent. It is the administrator's responsibility to manually create the VLANs and
their port memberships according to the network policies and their associated interfaces.
In addition, an administrator can instruct the device to automatically generate and advertise a
network policy for voice application based on the voice VLAN maintained by the device. Refer the
Auto Voice VLAN section for details on how the device maintains its voice VLAN.
To define an LLDP MED network policy:
1. Click Configuration > Port Management > Discovery – LLDP > LLDP MED Network.
This page contains previously-created network policies.
2. When Network Policy for Voice Application is enabled, the device automatically generates
and advertises a network policy with the current voice VLAN configuration. Go to Voice
VLAN > Feature Configuration page to configure the voice VLAN.
3. Click Apply to add this setting to the Running Configuration file.
4. To define a new policy, click Add.
5. Enter the values:
•
Network Policy Number—Select the number of the policy to be created.
•
Application—Select the type of application (type of traffic) for which the network
policy is being defined.
•
VLAN ID—Enter the VLAN ID to which the traffic must be sent.
•
VLAN Tag—Select whether the traffic is Tagged or Untagged.
•
Layer 2 Priority—Select the traffic priority applied to traffic defined by this
network policy. This is the CoS value.
•
DSCP Value—Select the DSCP value to associate with application data sent by
neighbors. This informs them how they must mark the application traffic they send
to the device.
6. Click Apply. The network policy is defined.
Note—You must manually configure the interfaces to include the desired manually-defined
network policies for the outgoing LLDP packets using the LLDP MED Port Settings.
76
Page 77
Chapter 6 – VLAN Management
VLANs
A VLAN is a logical group of ports that enables devices associated with it to communicate with
each other over the Ethernet MAC layer, regardless of the physical LAN segment of the bridged
network to which they are connected.
Each VLAN is configured with a unique VLAN ID (VID) with a value from 1 to 4094. A port on a
device in a bridged network is a member of a VLAN if it can send data to and receive data from the
VLAN. A port is an untagged member of a VLAN if all packets destined for that port into the VLAN
have no VLAN tag. A port is a tagged member of a VLAN if all packets destined for that port into
the VLAN have a VLAN tag. A port can be a member of only one untagged VLAN but can be a
member of multiple tagged VLANs.
A port in VLAN Access mode can be part of only one VLAN. If it is in General or Trunk mode, the
port can be part of one or more VLANs.
VLANs address security and scalability issues. Traffic from a VLAN stays within the VLAN, and
terminates at devices in the VLAN. It also eases network configuration by logically connecting
devices without physically relocating those devices.
If a frame is VLAN-tagged, a four-byte VLAN tag is added to each Ethernet frame. The tag
contains a VLAN ID between 1 and 4094, and a VLAN Priority Tag (VPT) between 0 and 7. See
QoS Operation
When a frame enters a VLAN-aware device, it is classified as belonging to a VLAN, based on the
four-byte VLAN tag in the frame.
If there is no VLAN tag in the frame or the frame is priority-tagged only, the frame is classified to
the VLAN based on the PVID (Port VLAN Identifier) configured at the ingress port where the frame
is received.
for details about VPT.
77
Page 78

The frame is discarded at the ingress port if Ingress Filtering is enabled and the ingress port is not
a member of the VLAN to which the packet belongs. A frame is regarded as priority-tagged only if
the VID in its VLAN tag is 0.
Frames belonging to a VLAN remain within the VLAN. This is achieved by sending or forwarding a
frame only to egress ports that are members of the target VLAN. An egress port may be a tagged
or untagged member of a VLAN.
The egress port:
•
Adds a VLAN tag to the frame if the egress port is a tagged member of the target VLAN,
and the original frame does not have a VLAN tag.
•
Removes the VLAN tag from the frame if the egress port is an untagged member of the
target VLAN, and the original frame has a VLAN tag.
VLAN Roles
All VLAN traffic (Unicast/Broadcast/Multicast) remains within its VLAN. Devices attached to
different VLANs do not have direct connectivity to each other over the Ethernet MAC layer.
Device VLANs can only be created statically. Some VLANs can have additional roles, including:
•
Voice VLAN: For more information refer to the Voice VLAN section.
•
Guest VLAN: Set in the Edit VLAN Authentication page.
•
Default VLAN: For more information refer to the Configuring Default VLAN Settings
section.
•
Management VLAN: For more information refer to the Configuring IP Information section.
VLAN Configuration
To configure VLANs:
1. If required, change the default VLAN as described in the Default VLAN Settings section.
2. Create the required VLANs as described in the VLANs - Creating VLANs section.
3. Set the desired VLAN-related configuration for ports, as described in the Interface
Settings section.
4. Assign interfaces to VLANs as described in the Port to VLAN section or the VLAN
Memberships section.
5. View the current VLAN port membership for all the interfaces as described in the VLAN
Memberships section.
6. If required, configure VLAN groups as described in the MAC-based Groups section.
78
Page 79

Default VLAN Settings
When using factory default settings, the device automatically creates VLAN 1 as the default
VLAN, the default interface status of all ports is Trunk, and all ports are configured as untagged
members of the default VLAN.
The default VLAN has the following characteristics:
•
It is distinct, non-static/non-dynamic, and all ports are untagged members by default.
•
It cannot be deleted.
•
It cannot be given a label.
•
It cannot be used for any special role, such as unauthenticated VLAN or Voice VLAN. This
is only relevant for OUI-enabled voice VLAN.
•
If a port is no longer a member of any VLAN, the device automatically configures the port
as an untagged member of the default VLAN. A port is no longer a member of a VLAN if the
VLAN is deleted or the port is removed from the VLAN.
When the VID of the default VLAN is changed, the device performs the following on all the ports in
the VLAN, after saving the configuration and rebooting the device:
•
Removes VLAN membership of the ports from the original default VLAN (takes effect
after reboot).
•
Changes the PVID (Port VLAN Identifier) of the ports to the VID of the new default VLAN.
•
The original default VLAN ID is removed from the device. To be used, it must be recreated.
•
Adds the ports as untagged VLAN members of the new default VLAN.
To change the default VLAN:
1. Click Configuration > VLAN Management > VLANs.
2. Enter the value for the following field:
•
Current Default VLAN ID—Displays the current default VLAN ID.
•
Default VLAN ID After Reboot—Enter a new VLAN ID to replace the default VLAN
ID after reboot.
3. Click Apply.
4. Click Save and save the Running Configuration to the Startup Configuration.
The Default VLAN ID After Reset becomes the Current Default VLAN ID after you reboot the
device.
Creating VLANs
You can create a VLAN, but this has no effect until the VLAN is attached to at least one port,
either manually or dynamically. Ports must always belong to one or more VLANs.
79
Page 80

The Smart device supports up to 128 VLANs, including the default VLAN. Each VLAN must be
configured with a unique VID with a value from 1 to 4094. The device reserves VID 4095 as the
Discard VLAN and VID 4094 for 802.1x. All packets classified to the Discard VLAN are discarded
at ingress, and are not forwarded to a port. The VLANs page enables you to change the default
VLAN and create a new VLAN.
To change or add a VLAN:
1. Click Configuration > VLAN Management > VLANs.
2. Click Add to add one or more new VLANs.
The page enables the creation of either a single VLAN or a range of VLANs.
3. Enter the following fields for the new VLANs.
•
VLAN—Select one of the following options:
-
Single VLAN—Select to create a single VLAN.
-
Range of VLANs—Select to create a range of VLANs and specify the range
of VLANs to be created by entering the Starting VID and Ending VID,
inclusive. When using the Range function, the maximum number of VLANs
you can create at one time is 100.
•
VLAN ID—Enter a VLAN ID.
•
VLAN Name—Enter a VLAN name.
•
VLAN ID Range—Enter a range of VLANs.
4. Click Apply to create the VLAN(s).
80
Page 81

Interfaces
The Interface Settings page displays and enables configuration of VLAN-related parameters for
all interfaces.
To configure the interface settings:
1. Click VLAN Management > Interface Settings.
2. Select an interface type (Port or LAG), and click Search. Ports or LAGs and their VLAN
Membership are displayed.
3. To configure a Port or LAG, select it and click Edit.
Note—To add a port or LAG to a VLAN, click Join VLAN. The Join VLAN page is displayed.
4. Enter the values for the following fields:
•
Interface—Select a Port/LAG.
•
Interface VLAN Mode—Select the interface mode for the VLAN. The options are:
-
Access—The interface is an untagged member of a single VLAN. A port
configured in this mode is known as an access port.
-
Trunk—The interface is an untagged member of one VLAN at most, and is a
tagged member of zero or more VLANs. A port configured in this mode is
known as a trunk port.
-
General Port—The interface can support all functions as defined in the
IEEE 802.1q specification. The interface can be a tagged or untagged
member of one or more VLANs.
81
Page 82

•
PVID—Enter the Port VLAN ID (PVID) of the VLAN to which incoming untagged and
priority tagged frames are classified. The possible values are 1 to 4094.
•
Acceptable Frame Type—Select the type of frame that the interface can receive.
Frames that are not of the configured frame type are discarded at ingress. These
frame types are only available in General mode. Possible values are:
-
Admit All—The interface accepts all types of frames: untagged frames,
tagged frames, and priority tagged frames.
-
Admit Tagged Only—The interface accepts only tagged frames.
-
Admit Untagged Only—The interface accepts only untagged and priority
frames.
•
Ingress Filtering—(Available only in General mode) Select to enable ingress
filtering. When an interface is ingress filtering enabled, the interface discards all
incoming frames that are classified as VLANs of which the interface is not a
member. Ingress filtering can be disabled or enabled on general ports. It is always
enabled on access ports and trunk ports.
5. Click Apply. The parameters are written to the Running Configuration file.
Join VLAN
When a port is forbidden default VLAN membership, that port is not allowed membership in any
other VLAN. An internal VID of 4095 is assigned to the port.
To forward packets properly, intermediate VLAN-aware devices that carry VLAN traffic along the
path between end nodes must be manually configured.
Untagged port membership between two VLAN-aware devices with no intervening VLAN-aware
devices, must be to the same VLAN. In other words, the PVID on the ports between the two
devices must be the same if the ports are to send and receive untagged packets to and from the
VLAN. Otherwise, traffic might leak from one VLAN to another.
Frames that are VLAN-tagged can pass through other network devices that are VLAN-aware or
VLAN-unaware. If a destination end node is VLAN-unaware, but is to receive traffic from a VLAN,
then the last VLAN-aware device (if there is one), must send frames of the destination VLAN to
the end node untagged.
To add a port to a VLAN:
1. Click VLAN Management > Interface Settings.
2. Select an interface type (Port or LAG), and click Search.
3. To add a Port or LAG to a VLAN, select it and click Join VLAN.
82
Page 83

4. Enter the following fields:
•
VLAN Mode
-
Access—The interface is an untagged member of a single VLAN. A port
configured in this mode is known as an access port.
-
Trunk—The interface is an untagged member of one VLAN at most, and is a
tagged member of zero or more VLANs. A port configured in this mode is
known as a trunk port.
-
General Port—The interface can support all functions as defined in the
IEEE 802.1q specification. The interface can be a tagged or untagged
member of one or more VLANs.
•
Tagging
-
Forbidden—The interface is not allowed to join the VLAN. When a port is
not a member of any other VLAN, enabling this option on the port makes
the port part of internal VLAN 4095 (a reserved VID).
-
Excluded—The interface is currently not a member of the VLAN. This is the
default for all the ports and LAGs when the VLAN is newly created.
-
Tagged—The interface is a tagged member of the VLAN.
-
Untagged—The interface is an untagged member of the VLAN. Frames of
the VLAN are sent untagged to the interface VLAN.
-
PVID—Port PVID is set to this VLAN. If the interface is in access mode or
trunk mode, the device automatically makes the interface an untagged
member of the VLAN. If the interface is in general mode, you must manually
configure VLAN membership.
5. Click Apply. The port is added to the VLAN and the settings are written to the Running
Configuration file.
83
Page 84

VLAN Memberships
The VLAN Memberships page displays the VLAN memberships of the ports in various
presentations. You can use them to add memberships to or remove memberships from the VLANs.
When a port is forbidden default VLAN membership, that port is not allowed membership in any
other VLAN. An internal VID of 4095 is assigned to the port.
To forward packets properly, intermediate VLAN-aware devices that carry VLAN traffic along the
path between end nodes must be manually configured.
Untagged port membership between two VLAN-aware devices with no intervening VLAN-aware
devices, must be to the same VLAN. In other words, the PVID on the ports between the two
devices must be the same if the ports are to send and receive untagged packets to and from the
VLAN. Otherwise, traffic might leak from one VLAN to another.
Frames that are VLAN-tagged can pass through other network devices that are VLAN-aware or
VLAN-unaware. If a destination end node is VLAN-unaware, but is to receive traffic from a VLAN,
then the last VLAN-aware device (if there is one), must send frames of the destination VLAN to
the end node untagged.
Use the VLAN Memberships page to display and configure the ports within a specific VLAN.
To assign a port to one or more VLANs:
1. Click Configuration > VLAN Management > VLAN Memberships.
2. Select VLAN ID and interface type (Port or LAG), and click Search.
84
Page 85

•
Interface—Port/LAG ID.
•
PVID—Port PVID is set to this VLAN. If the interface is in access mode or trunk
mode, the device automatically makes the interface an untagged member of the
VLAN. If the interface is in general mode, you must manually configure VLAN
membership.
•
Access—Select to make the interface an access interface on this VLAN.
•
Trunk—Select to make the interface a trunk interface on this VLAN.
•
General Port—The interface can support all functions as defined in the IEEE
802.1q specification. The interface can be a tagged or untagged member of one or
more VLANs.
•
Forbidden—The interface is not allowed to join the VLAN. When a port is not a
member of any other VLAN, enabling this option on the port makes the port part of
internal VLAN 4095 (a reserved VID).
•
Excluded—The interface is currently not a member of the VLAN. This is the default
for all the ports and LAGs when the VLAN is newly created.
•
Tagged—The interface is a tagged member of the VLAN. This is not relevant for
Access ports.
•
Untagged—The interface is an untagged member of the VLAN. Frames of the
VLAN are sent untagged to the interface VLAN. This is not relevant for Access
ports.
3. Click Apply. The settings are modified and written to the Running Configuration file.
VLAN Groups
This section describes how to configure Mac-based VLAN groups.
VLAN groups classify packets into VLANs based on their MAC addresses.
VLAN groups can be used to separate traffic into different VLANs for security and/or load
balancing.
If several classifications schemes are defined, packets are assigned to a VLAN in the following
order:
•
TAG—If the packet is tagged, the VLAN is taken from the tag.
•
MAC-Based VLAN—If a MAC-based VLAN has been defined, the VLAN is taken from the
source MAC-to-VLAN mapping of the ingress interface.
•
PVID—VLAN is taken from the port default VLAN ID.
85
Page 86

MAC-Based Group
MAC-based VLAN classification enables packets to be classified according to their source MAC
address. You can then define MAC-to-VLAN mapping per interface.
You can define several MAC-based groups, which each group containing different MAC
addresses.
These MAC-based groups can be assigned to specific ports/LAGs. MAC-based groups cannot
contain overlapping ranges of MAC addresses on the same port.
The following table describes the availability of MAC-based groups in various SKUs:
Table 1 MAC-Based Group Availability
SKU System Mode MAC-Based Groups
Smart Layer 2
Layer 3
Managed Layer 2
Layer 3
To define a MAC-based group:
1. Assign a MAC address to a VLAN group ID (using the MAC-Based Groups page).
2. For each required interface:
•
Assign the VLAN group to a VLAN (using the Mac-Based VLAN page). The
interfaces must be in General mode.
•
If the interface does not belong to the VLAN, manually assign it to the VLAN using
the VLAN Membership page.
Yes
No
Yes
No
86
Page 87

To assign a MAC address to a VLAN Group:
1. Click Configuration > VLAN Management > MAC-Based Group.
2. Click Add.
3. Enter the values for the following fields:
•
Group ID—Enter a user-created VLAN group ID number.
•
MAC Address—Enter a MAC address to be assigned to a VLAN group.
Note—This MAC address cannot be assigned to any other VLAN group.
•
Prefix Mask—Enter one of the following:
-
Host—Source host of the MAC address
-
Length—Prefix of the MAC address
4. Click Apply. The MAC address is assigned to a VLAN group.
MAC-Based VLAN per interface
See Table 1 for a description of the availability of this feature. Ports/LAGs must be in General
mode.
To assign a MAC-based VLAN group to a VLAN on an interface:
1. Click Configuration > VLAN Management > MAC-Based VLAN.
2. Click Add.
3. Enter the values for the following fields:
•
Interface—Enter a general interface (port/LAG) through which traffic is received.
•
Group ID—Select a VLAN group, defined in the MAC-Based Groups page.
•
VLAN ID—Select the VLAN to which traffic from the VLAN group is forwarded.
87
Page 88

4. Click Apply to set the mapping of the VLAN group to the VLAN. This mapping does not
bind the interface dynamically to the VLAN; the interface must be manually added to the
VLAN.)
Voice VLAN
In a LAN, voice devices, such as IP phones, VoIP endpoints, and voice systems are placed into the
same VLAN. This VLAN is referred as the voice VLAN. If the voice devices are in different voice
VLANs, IP (Layer 3) routers are needed to provide communication.
Auto Voice VLAN
The device supports the Telephony OUI (Organization Unique Identifier) voice VLAN mode. The
two modes affect how voice VLAN and/or voice VLAN port memberships are configured.
In Telephony OUI mode, the voice VLAN must be a manually-configured VLAN, and cannot be the
default VLAN.
When the device is in Telephony OUI mode and a port is manually configured as a candidate to join
the voice VLAN, the device dynamically adds the port to the voice VLAN if it receives a packet
with a source MAC address matching one of the configured telephony OUIs. An OUI is the first
three bytes of an Ethernet MAC address. For more information about Telephony OUI, see
Telephony OUI Interfaces
.
Voice End-Points
To have a voice VLAN work properly, the voice devices, such as IP phones and VoIP endpoints,
must be assigned to the voice VLAN where it sends and receives its voice traffic.
Two possible scenarios:
•
A phone/endpoint may be statically configured with the voice VLAN.
•
A phone/endpoint may obtain the voice VLAN in the boot file it downloads from a TFTP
server. A DHCP server may specify the boot file and the TFTP server when it assigns an IP
address to the phone.
You can create a network policy manually or enable the device to automatically generate a
network policy, based on a voice VLAN configuration.
The device expects the attaching voice devices to send voice VLAN, tagged packets. On ports
where the voice VLAN is the native VLAN or that is configured with auto voice VLAN by Telephony
OUI, voice VLAN untagged packets are possible.
88
Page 89

Voice VLAN CoS
The device can advertise the CoS/802.1p and DSCP settings of the voice VLAN by using LLDPMED Network policies. You can create your network policy manually or enable the device to
automatically generate the network policy based on your voice VLAN configuration. MEDsupported devices must send their voice traffic with the same CoS/802.1p and DSCP values, as
received with the LLDP- MED response.
You can disable the automatic update between Voice VLAN and LLDP-MED and use his own
network policies.
Working with the OUI mode, the device can additionally configure the mapping and remarking
(CoS/802.1p) of the voice traffic based on the OUI.
By default, all interfaces are CoS/802.1p trusted. The device applies the quality of service based
on the CoS/802.1p value found in the voice stream.
For Telephony OUI voice streams, you can override the class of service and optionally remark the
802.1p of the voice streams by specifying the desired CoS/802.1p values and using the
remarking option under Telephony OUI.
Voice VLAN Constraints
The following constraints exist:
•
Only one Voice VLAN is supported.
•
A VLAN that is defined as a Voice VLAN cannot be removed.
In addition the following constraints are applicable for Telephony OUI:
•
The Voice VLAN cannot be VLAN1 (the default VLAN).
•
The Voice VLAN QoS decision has priority over any other QoS decision, except for the
Policy decision.
•
A new VLAN ID can be configured for the Voice VLAN only if the current Voice VLAN does
not have candidate ports.
•
The interface VLAN of a candidate port must be in General or Trunk mode.
•
The Voice VLAN QoS is applied to candidate ports that have joined the Voice VLAN, and to
static ports.
•
The voice flow is accepted if the MAC address can be learned by the Forwarding Database
(FDB). (If there is no free space in FDB, no action occurs).
89
Page 90
Feature Configuration
To configure Auto Voice VLAN:
1. Click Configuration > VLAN Management > Voice VLAN > Feature Configuration.
2. Enter the following to configure Voice VLAN:
•
Voice VLAN ID—Enter the identifier of the current voice VLAN
•
CoS/802.1p—Select the CoS/802.1p value to be used by the LLDP-MED as a
voice network policy.
3. Enter the following to configure telephone OUI voice VLAN:
•
Telephone OUI Voice VLAN—Check to enable automatically adding ports to voice
VLAN when OUI packets are received.
•
Remark CoS/802.1p—Select the enable remarking packets with the CoS/802.1p
value.
•
Aging Time—Enter the time delay to remove a port from the voice VLAN after all of
the MAC addresses of the phones detected on the ports have aged out.
4. Click Apply to save the settings to the Running Configuration file.
Refer to Administration > Discovery > LLDP > LLDP MED Network Policy to enable automatic
generation of network policy for voice.
To view or add a new OUI:
1. Click Configuration > VLAN Management > Voice VLAN > Feature Configuration.
2. Click Add to add a new OUI.
90
Page 91

3. Enter the values for the following fields:
•
Telephony OUI—First six digits of the MAC address that are reserved for OUIs.
•
Description—User-assigned OUI description.
Note—Click Restore to delete all of the user-created OUIs, and leave only the default
OUIs in the table. The OUI information may not be accurate until the restoration is
completed. This may take several seconds. After several seconds have passed, refresh
the page by exiting it and re-entering it.
To delete all the OUIs, select the top checkbox. All the OUIs are selected and can be
deleted by clicking Delete. If you then click Restore, the system recovers the known OUIs.
4. Click Apply. The OUI is added to the Telephony OUI Table.
Telephony OUI Interfaces
QoS attributes can be assigned per port to the voice packets in one of two modes:
•
All—Quality of Service (QoS) values configured to the Voice VLAN are applied to all of the
incoming frames that are received on the interface and are classified to the Voice VLAN.
•
Telephony Source MAC Address (SRC)—The QoS values configured for the Voice VLAN
are applied to any incoming frame that is classified to the Voice VLAN and contains an OUI
in the source MAC address that matches a configured telephony OUI.
Use the Telephony OUI Interface page to add an interface to the voice VLAN on the basis of the
OUI identifier and to configure the OUI QoS mode of voice VLAN.
91
Page 92

To configure Telephony OUI on an interface:
1. Click Configuration > VLAN Management > Voice VLAN > Telephony OUI Interfaces.
2. To configure an interface to be a candidate port of the telephony OUI-based voice VLAN,
click Edit.
3. Enter the values for the following fields:
•
Interface—Select an interface.
•
Telephony OUI VLAN—If enabled, the interface is a candidate port of the
telephony OUI based voice VLAN. When packets that match one of the configured
telephony OUI are received, the port is added to the voice VLAN.
•
QoS Mode—Select one of the following options:
o
All—QoS attributes are applied on all packets that are classified to the
Voice VLAN.
o
Telephony Source MAC Address—QoS attributes are applied only on
packets from IP phones.
4. Click Apply.
92
Page 93

Chapter 7 - Spanning Tree Management
Spanning Tree Protocol protects a Layer 2 Broadcast domain from Broadcast storms by
selectively setting links to standby mode to prevent loops. In standby mode, these links
temporarily stop transferring user data. After the topology changes so that the data transfer is
made possible, the links are automatically reactivated.
Loops occur when alternate routes exist between hosts. Loops in an extended network can cause
switches to forward traffic indefinitely, resulting in increased traffic load and reduced network
efficiency.
STP provides a tree topology for any arrangement of switches and interconnecting links, by
creating a unique path between end stations on a network, and thereby eliminating loops.
Spanning Tree Protocol versions:
•
Classic STP – Provides a single path between any two end stations, avoiding and
eliminating loops.
•
Rapid STP (RSTP) – Detects network topologies to provide faster convergence of the
spanning tree. This is most effective when the network topology is naturally treestructured, and therefore faster convergence might be possible. RSTP is enabled by
default.
•
Multiple STP (MSTP) – Classic STP and Rapid STP detect Layer 2 loops, and attempt to
mitigate them by preventing the involved port from transmitting traffic. Since loops exist
on a per-Layer 2-domain basis, there can be a loop in VLAN A and no loop in VLAN B. If
both VLANs are on Port X, Classic STP and Rapid STP will mitigate the loop by stopping
traffic on the entire port, including VLAN B traffic.
MSTP solves this problem by enabling several STP instances, so that it is possible to
detect and mitigate loops separately in each instance. By associating instances to VLANs,
each instance is associated with the Layer 2 domain on which it performs loop detection
and mitigation. This enables a port to be stopped in one instance, such as traffic from
VLAN A that is causing a loop, while traffic can remain active in another domain where no
loop was seen, such as on VLAN B.
93
Page 94

Spanning Tree
To set the STP status and global settings:
1. Click Configuration > Spanning Tree Management > Spanning Tree.
2. Enter the parameters.
Global Settings:
•
Spanning Tree—Select to enable on the device.
•
Spanning Tree Mode—Select an STP mode - Classic STP, Rapid STP or Multiple
STP.
•
Path Cost Default Values—Selects the method used to assign default path costs
to the STP ports. The default path cost assigned to an interface varies according
to the selected method.
o
Short—Specifies the range 1 through 65,535 for port path costs.
o
Long—Specifies the range 1 through 200,000,000 for port path costs.
•
BPDU Handling—Select how Bridge Protocol Data Unit (BPDU) packets are
managed when STP is disabled on the port or the device. BPDUs are used to
transmit spanning tree information.
o
Filtering—Filters BPDU packets when Spanning Tree is disabled on an
interface.
o
Flooding—Floods BPDU packets when Spanning Tree is disabled on an
interface.
94
Page 95

Bridge Settings:
•
Priority—Sets the bridge priority value. After exchanging BPDUs, the device with
the lowest priority becomes the Root Bridge. In the case that all bridges use the
same priority, then their MAC addresses are used to determine the Root Bridge.
The bridge priority value is provided in increments of 4096. For example, 4096,
8192, 12288, and so on.
•
Hello Time—Set the interval (in seconds) that a Root Bridge waits between
configuration messages.
•
Max Age—Set the interval (in seconds) that the device can wait without receiving a
configuration message, before attempting to redefine its own configuration.
•
Forward Delay—Set the interval (in seconds) that a bridge remains in a learning
state before forwarding packet.
Designated Root:
•
Bridge ID—The bridge priority concatenated with the MAC address of the device.
•
Root Bridge ID—The Root Bridge priority concatenated with the MAC address of
the Root Bridge.
•
Root Port—The port that offers the lowest cost path from this bridge to the Root
Bridge. (This is significant when the bridge is not the root.)
•
Root Path Cost—The cost of the path from this bridge to the root.
•
Topology Changes Counts—The total number of STP topology changes that have
occurred.
•
Last Topology Change—The time interval that elapsed since the last topology
change occurred. The time appears in a days/hours/minutes/seconds format.
3. Click Apply. The STP Global settings are written to the Running Configuration file.
95
Page 96

STP Interfaces
The STP Interface page enables you to configure STP on a per-port basis, and to view the
information learned by the protocol, such as the designated bridge. The defined configuration
entered is valid for all flavors of the STP protocol.
To configure STP on an interface:
1. Click Configuration > Spanning Tree Management > STP Interfaces.
2. Select an interface type and click Edit.
3. Enter the parameters.
•
STP—Select to enable STP on the port.
•
BPDU Handling—Select how BPDU packets are managed when STP is disabled on
the port or the device. BPDUs are used to transmit spanning tree information.
o
Use Global Settings—Select to use the settings defined in the Spanning
Tree page.
o
Filtering—Filters BPDU packets when Spanning Tree is disabled on an
interface.
o
Flooding—Floods BPDU packets when Spanning Tree is disabled on an
interface.
•
Path Cost—Set the port contribution to the root path cost or use the default cost
generated by the system.
•
Priority—Select the priority value of the port. The priority value influences the port
choice when a bridge has two ports connected in a loop. The priority is a value from
0 to 240, set in increments of 16.
96
Page 97

•
Port State—Displays the current STP state of a port.
o
Disabled—STP is currently disabled on the port. The port forwards traffic
while learning MAC addresses.
o
Blocking—The port is currently blocked, and cannot forward traffic (with
the exception of BPDU data) or learn MAC addresses.
o
Listening—The port is in Listening Mode. The port cannot forward traffic,
and cannot learn MAC addresses.
o
Learning—The port is in Learning Mode. The port cannot forward traffic,
but it can learn new MAC addresses.
o
Forwarding—The port is in Forwarding Mode. The port can forward traffic
and learn new MAC addresses.
•
Designated Bridge ID—Displays the priority and interface of the selected port.
•
Designated Port ID—Displays the priority and interface of the selected port.
•
Designated Cost—Displays the cost of the port participating in the STP topology.
Ports with a lower cost are less likely to be blocked if STP detects loops.
4. Click Apply. The interface
RSTP Interfaces
settings are written to the Running Configuration file.
Rapid Spanning Tree Protocol (RSTP) enables a faster STP convergence without creating
forwarding loops.
The RSTP Interface Settings page enables you to configure RSTP per port. Any configuration that
is done on this page is active when the global STP mode is set to RSTP or MSTP.
97
Page 98

To configure RSTPs:
1. Click Configuration > Spanning Tree Management > Spanning Tree.
2. Select Rapid STP on the Spanning Tree Mode line.
3. Click Configuration > Spanning Tree Management > Spanning Tree > RSTP Interfaces.
4. Select an interface, and click Edit.
5. Enter the interface settings:
•
Point to Point Mode - Define the point-to-point link status. Ports defined as full
duplex are considered point-to-point port links.
o
Enable - This port is an RSTP edge port when this feature is enabled, and is
brought to Forwarding Mode quickly (usually within 2 seconds).
o
Disable - The port is not considered point-to-point for RSTP purposes,
which means that STP works on it at regular speed, as opposed to high
speed.
o
Auto - Automatically determines the device status by using RSTP BPDUs
•
Edge Port Mode - Enables or disables Fast Link on the port. If Fast Link Mode is
enabled on a port, the port is automatically set to forwarding state when the port
link is up. Fast Link optimizes the STP protocol convergence.
The options:
o
Enable - Enables Fast Link immediately.
o
Disable - Disables Fast Link.
o
Auto - Enables Fast Link a few seconds after the interface becomes active.
This allows STP to resolve loops before enabling Fast Link.
Note—It is recommended to set the value to Auto so that the device sets the port
to fast link mode if a host is connected to it, or sets it as a regular STP port if
connected to another device. This helps avoid loops.
•
STP Mode - Select either STP or RSTP.
•
Point to Point Status-Displays the point-to-point operational status if the Point to
Point Administrative Status is set to Auto.
•
Port Role - Displays the role of the port that was assigned by STP to provide STP
paths. Possible roles:
o
Root - Lowest cost path to forward packets to the root bridge.
o
Designated - The interface through which the bridge is connected to the
LAN, which provides the lowest cost path from the LAN to the root bridge.
o
Alternate - Provides an alternate path to the root bridge from the root
interface.
98
Page 99

o
Backup - Provides a backup path to the designated port path toward the
spanning tree leaves. This provides a configuration in which two ports are
connected in a loop by a point-to-point link. Backup ports are also used
when a LAN has two or more established connections to a shared segment.
o
Disabled - The port is not participating in spanning tree.
•
Port Status - Displays the RSTP status on the specific port.
o
Disabled - STP is currently disabled on the port.
o
Blocking - The port is currently blocked, and it cannot forward traffic or
learn MAC addresses.
o
Listening - The port is in Listening Mode. The port cannot forward traffic,
and cannot learn MAC addresses.
o
Learning - The port is in Learning Mode. The port cannot forward traffic,
however it can learn new MAC addresses.
o
Forwarding - The port is in Forwarding Mode. The port can forward traffic
and learn new MAC addresses.
6. Click Apply. The Running Configuration file is updated.
MSTP Properties
Multiple Spanning Tree Protocol (MSTP) is used to separate the STP port state between various
domains (on different VLANs). For example, while port A is blocked in one STP instance due to a
loop on VLAN A, the same port can be placed in the Forwarding State in another STP instance.
The MSTP Properties page enables you to define the global MSTP settings.
Each MSTP instance calculates and builds a loop free topology to bridge packets from the VLANs
that map to the instance. Refer to the MSTP Properties page.
99
Page 100

Decide which MSTP instance be active in what VLAN, and associate these MSTP instances to
VLAN(s) accordingly.
Configure MSTP attributes on the following pages:
•
MSTP Properties
•
MSTP Instance Status
•
MSTP Instance Interface
MSTP Interfaces
The global MSTP configures a separate Spanning Tree for each VLAN group and blocks all but one
of the possible alternate paths within each spanning tree instance. MSTP enables formation of
MST regions that can run multiple MST instances (MSTI). Multiple regions and other STP bridges
are interconnected using one single common spanning tree (CST).
MSTP is fully compatible with RSTP bridges, in that an MSTP BPDU can be interpreted by an
RSTP bridge as an RSTP BPDU. This not only enables compatibility with RSTP bridges without
configuration changes, but also causes any RSTP bridges outside of an MSTP region to see the
region as a single RSTP bridge, regardless of the number of MSTP bridges inside the region itself.
Up to three MST instances (predefined from 1-3) can be defined on Smart switches, in addition to
instance zero.
VLAN to MSTP Instance Mapping
For two or more switches to be in the same MST region, they must have the same VLANs to MST
instance mapping, the same configuration revision number, and the same region name. Switches
intended to be in the same MST region are never separated by switches from another MST region.
If they are separated, the region becomes two separate regions.
The VLAN to MSTP instance mapping is done in the MSTP Properties page. Each VLAN can be
mapped to a MSTP instance. For devices to be in the same region, they must have the same
mapping of VLANs to MSTP instances.
Configuration on this page (and all of the MSTP pages) applies if the system STP mode is MSTP.
Note—The same MSTI can be mapped to more than one VLAN, but each VLAN can only have one
MST Instance attached to it.
For those VLANs that are not explicitly mapped to one of the MST instances, the device
automatically maps them to the CIST (Core and Internal Spanning Tree) instance. The CIST
instance is MST instance 0.
To configure MSTP:
1. Click Configuration > Spanning Tree Management > Spanning Tree.
2. Select Multiple STP on the Spanning Tree Mode line.
3. Click Configuration > Spanning Tree Management> MSTP Properties.
100
 Loading...
Loading...