Page 1

GEP-1070
L2 Managed Gigabit PoE Switch, 802.3at PoE+,
8 PoE Outputs, 2 x SFP
User Manual
V1.0
Digital Data Communications Asia Co., Ltd.
http://www.level1.com
1
Page 2

About This Manual
Purpose
Audience
Conventions
This manual gives specific information on how to operate and use the
management functions of the Gigabit PoE Ethernet Switch.
The Manual is intended for use by network administrators who are
responsible for operating and maintaining network equipment.
Consequently, it assumes a basic working knowledge of general switch
functions, the Internet Protocol (IP), and Simple Network Management
Protocol (SNMP).
The following conventions are used throughout this manual to show
information.
NOTE: Emphasizes important information or calls your attention to
related features or instructions.
C
AUTION
data, or damage the system or equipment.
:
Alerts you to a potential hazard that could cause loss of
Warranty
Disclaimer
W
ARNING
personal injury.
A copy of the specific warranty terms applicable to your products and
replacement parts can be obtained from your local Sales and Service
Office or authorized dealer.
Manufacturer does not warrant that the hardware will work properly in
all environments and applications, and marks no warranty and
representation, either implied or expressed, with respect to the quality,
performance, merchantability, or fitness for a particular purpose.
Manufacturer disclaims liability for any inaccuracies or omissions that
may have occurred. Information in this User’s Manual is subject to
change without notice and does not represent a commitment on the part
of Manufacturer. It assumes no responsibility for any inaccuracies that
may be contained in this User’s Manual, makes no commitment to
update or keep current the information in this User’s Manual, and
reserves the right to make improvements to this User’s Manual and/or to
the products described in this User’s Manual, at any time without notice.
:
Alerts you to a potential hazard that could cause
FCC Statement
This equipment has been tested and found to comply with the limits
2
Page 3

for a Class A digital device, pursuant to Part 15 of the FCC Rules. These
limits are designed to provide reasonable protection against harmful
interference when the equipment is operated in a commercial
environment. This equipment generates, uses, and can radiate radio
frequency energy and, if not installed and used in accordance with the
instruction manual, may cause harmful interference to radio
communications. Operation of this equipment in a residential area is likely
to cause interference, in which case the user, at his or her own expense
will be required to take whatever measures to correct the interference.
FCC Caution
To assure continued compliance (example-use only shielded
interface cables when connection to computer or peripheral devices). Any
changes or modifications not expressly approved by the party
responsible for compliance could void the user’s authority to
operate the equipment. This device complies with Part 15 of the FCC
Rules. Operation is subject to the Following two conditions: (1) This
device may not cause harmful interference, and (2) this device must
accept any interference received, including interference that may
cause undesired operation.
CE Warning This is a Class A device, In a residential environment, this product may
cause radio interference, in which case the user may be required to take
adequate measures.
RELATED PUBLICATIONS
The following publication details the hardware features of the switch, including the physical and
performance-related characteristics, and how to install the switch:
The Installation Guide
As part of the switch’s software, there is an online web-based help that describes all
management related features.
Information furnished by Yoda Communications, Inc. is believed to be accurate and reliable.
However, no responsibility is assumed by Yoda Communications for its use, nor for any
infringements of patents or other rights of third parties which may result from its use. No license
is granted by implication or otherwise under any patent or patent rights of Yoda Communications.
Yoda Communications reserves the right to change specifications at anytime without notice.
Copyright (C) 2013 by Digital Data Communications Asia Co., Ltd
Taiwan, R.O.C.
All rights reserved.
3
Page 4

Table of Content
SECTION I GETTING STARTED .................................................................................. 9
1. INTRODUCTION ......................................................................................................... 10
1.1. Key Features .................................................................................................. 10
1.2. Description of Software Features .................................................................... 12
1.3. Reset Button & LED Indicators ....................................................................... 16
1.4. System Defaults ............................................................................................. 17
2. INITIAL SWITCH CONFIGURATION .......................................................................... 20
SECTION II WEB CONFIGURATION ......................................................................... 21
3. USING THE WEB INTERFACE .................................................................................. 22
3.1. Navigating the Web Browser Interface............................................................ 22
Home Page .................................................................................................... 22
Configuration Options ..................................................................................... 22
Panel Display ................................................................................................. 23
Main Menu ..................................................................................................... 23
4. CONFIGURING THE SWITCH .................................................................................... 34
4.1. System ........................................................................................................... 34
System Information Configuration ................................................................... 34
IP Configuration .............................................................................................. 35
IPV6 Configuration ......................................................................................... 37
NTP Configuration .......................................................................................... 39
System Log Configuration .............................................................................. 40
4.2. Power Reduction ............................................................................................ 42
Controlling LED Intensity ................................................................................ 42
Reducing Power for EEE ................................................................................ 43
4.3. Thermal Protection ......................................................................................... 45
4.4. Ports ............................................................................................................... 46
4.5. Security .......................................................................................................... 49
Switch Security ............................................................................................... 49
Network Security ............................................................................................ 77
Authentication Servers (AAA) ....................................................................... 112
4
Page 5

4.6. Aggregation .................................................................................................. 114
Static Trunks Configuration .......................................................................... 115
LACP Configuration ...................................................................................... 117
4.7. Loop Protection ............................................................................................ 119
4.8. Spanning Tree .............................................................................................. 120
Bridge Settings ............................................................................................. 123
Multiple Spanning Trees Instance (MSTI) Mapping ...................................... 126
Multiple Spanning Tree Instance (MSTI) Priorities ........................................ 128
CIST Ports .................................................................................................... 129
MSTI Ports ................................................................................................... 133
4.9. Multicast VLAN Registration (MVR) .............................................................. 134
4.10. IPMC Configurations .................................................................................... 138
IGMP Snooping ............................................................................................ 138
MLD Snooping .............................................................................................. 145
4.11. Link Layer Discovery Protocol (LLDP) .......................................................... 152
LLDP Configuration ...................................................................................... 152
LLDP-MED Configuration ............................................................................. 155
4.12. Power over Ethernet (PoE) ........................................................................... 160
PoE Configuration ........................................................................................ 161
PoE Scheduling ............................................................................................ 163
PoE Auto Checking ...................................................................................... 164
4.13. MAC Address Table ..................................................................................... 166
4.14. IEEE 802.1Q VLANs .................................................................................... 169
VLAN Membership ....................................................................................... 170
VLAN Ports .................................................................................................. 170
4.15. Private VLANs .............................................................................................. 173
PVLAN Membership ..................................................................................... 173
Port Isolation ................................................................................................ 174
4.16. VCL Configuration ........................................................................................ 175
MAC-based VLAN ........................................................................................ 175
Protocol-based VLAN ................................................................................... 176
4.17. Voice VLAN ................................................................................................ .. 180
Configuring VoIP Traffic ............................................................................... 180
5
Page 6

Configuring Telephony OUI .......................................................................... 183
4.18. Quality of Service (QoS) ............................................................................... 184
Configuring Port Classification ...................................................................... 184
Configuring Port Policing .............................................................................. 186
Configuring Egress Port Scheduler ............................................................... 187
Configuring Egress Port Shaper ................................................................... 190
Configuring Port Tag Remarking Mode......................................................... 191
Configuring Port DSCP Translation and Rewriting ........................................ 193
Configuring DSCP-Based QOS ................................................................ .... 194
Configuring DSCP Translation ...................................................................... 195
Configuring DSCP Classification .................................................................. 197
Configuring QOS Control Lists ..................................................................... 197
Configuring Storm Control ............................................................................ 201
4.19. Configuring Port Mirroring............................................................................. 203
4.20. Configuring UPnP ......................................................................................... 204
4.21. sFlow Agent.................................................................................................. 206
5. MONITORING THE SWITCH .................................................................................... 208
5.1. System ......................................................................................................... 208
Displaying System Information ..................................................................... 208
Displaying CPU Load ................................................................................... 210
Displaying Log Messages ............................................................................. 210
Displaying Detailed Log ................................................................................ 212
5.2. Displaying Thermal Protection ...................................................................... 213
5.3. Ports ............................................................................................................. 214
Displaying Port Status .................................................................................. 214
Displaying Traffic Overview .......................................................................... 215
Displaying QOS Statistics ............................................................................. 216
Displaying QCL Status ................................................................................. 216
Displaying Detailed Port Statistics ................................................................ 218
5.4. Security ........................................................................................................ 219
Displaying Access Management Statistics .................................................... 220
Network Security .......................................................................................... 221
AAA for RADIUS Servers ............................................................................. 235
6
Page 7

Switch Security ............................................................................................. 240
5.5. Link Aggregation Control Protocol (LACP) .................................................... 246
Displaying LACP System Status ................................................................... 246
Displaying LACP Port Status ........................................................................ 247
Displaying LACP Port Statistics .................................................................... 248
5.6. Loop Protection ............................................................................................ 250
5.7. Spanning Tree .............................................................................................. 251
Displaying STP Bridge Status ....................................................................... 251
Displaying STP Port Status .......................................................................... 253
Displaying STP Port Statistics ...................................................................... 254
5.8. MVR ............................................................................................................. 256
Displaying MVR Statistics ............................................................................. 256
Displaying MVR Channel Group ................................................................... 257
Displaying MVR SFM Information ................................................................. 257
5.9. IPMC ............................................................................................................ 259
IGMP SNOOPING ........................................................................................ 259
MLD SNOOPING ......................................................................................... 262
5.10. Link Layer Discovery Protocol (LLDP) .......................................................... 266
Displaying LLDP Neighbour .......................................................................... 266
Displaying LLDP-MED Neighbour ................................................................. 267
Displaying LLDP Neighbour PoE Information ............................................... 270
Displaying LLDP Neighbour EEE Information ............................................... 271
Displaying LLDP Port Statistics .................................................................... 273
5.11. Displaying PoE Status .................................................................................. 275
PoE Configuration Status ............................................................................. 275
PoE Scheduling Status ................................ ................................................. 276
PoE Auto Checking Status ........................................................................... 277
5.12. Displaying MAC Address Table .................................................................... 279
5.13. VLANs Member ............................................................................................ 280
Displaying VLAN Membership ...................................................................... 280
Displaying VLAN Port Status ........................................................................ 281
5.14. MAC-based VLANs (VCL) ............................................................................ 283
Displaying MAC-based VLANs ..................................................................... 283
7
Page 8

5.15. sFlow Statistics ............................................................................................. 284
6. DIAGNOSTICS ................................ ................................................................ ......... 286
6.1. Pinging ......................................................................................................... 286
6.2. ICMPv6 Pinging ............................................................................................ 288
6.3. Running Cable Diagnostics .......................................................................... 290
7. MAINTENANCE ........................................................................................................ 291
7.1. Restarting the Switch .................................................................................... 291
7.2. Restoring Factory Defaults ........................................................................... 292
7.3. Software ....................................................................................................... 293
Software Upload ........................................................................................... 293
Software Image Select ................................................................................. 293
7.4. Configuration ................................................................................................ 295
Saving Configuration Settings ...................................................................... 295
Upload Configuration Settings ...................................................................... 295
SECTION III APPENDICES ...................................................................................... 297
A. SOFTWARE SPECIFICATIONS .............................................................................. 298
A.1. Software Features ........................................................................................ 298
A.2. Management Features ................................................................................. 299
A.3. Standards ..................................................................................................... 299
A.4. Management Information Bases (MIB) ......................................................... 300
B. TROUBLESHOOTING ............................................................................................. 302
B.1. Accessing the Management Interface ........................................................... 302
B.2. Accessing the Web Page.............................................................................. 303
B.3. Factory Default Reset ................................................................................... 306
B.4. Using System Logs....................................................................................... 306
C. LICENSE INFORMATION ....................................................................................... 307
D. GLOSSARY ............................................................................................................. 313
8
Page 9

SECTION I GETTING STARTED
The Section I provides an overview of the GEP-1070 Layer-2 managed Gigabit PoE
Switch, and introduces some basic concepts about switching network management. It also
describes the basic settings required to access the management interfaces.
This section includes these chapters:
◆ “1. Introduction” on page 10
◆ “2. Initial Switch Configurations” on page 20
9
Page 10

Feature
Description
Configuration Backup
and Restore
Backup to management station using Web interface
1. INTRODUCTION
The GEP-1070 is a Layer-2 managed Gigabit PoE Switch with 8-port UTP for Gigabit
Ethernet cable plus 2-port SFP for Gigabit fiber link. It provides a broad range of
management features for Layer 2 switching to deliver high levels of performance that are
commensurate with Gigabit Ethernet networking. With the Power over Ethernet (PoE)
features, it simplifies power installation in an environment where remote PoE devices are
required.
The Gigabit PoE switch provides 10/100/1000Mbps Gigabit Ethernet connections with many
networking capabilities per port basis including Security, QoS service, Bandwidth Control,
Spanning Tree Protocol, VLAN, IGMP, SNMP settings, PoE time scheduling functions,
keep-alive autochecking, etc.
The default configuration can be used for most of the features provided by this switch.
However, there are many options that you should configure to maximizes the switch
performance for your particular network environment.
The Gigabit PoE switch is equipped with a power supply to operate under 100~240 VAC,
50~60 Hz. The AC power cord connector is at the rear panel next to the power on/off switch.
Turning on the power, the switch will first perform “self-diagnostic” test, and take about 510 seconds to complete the process.
1.1. Key Features
The Managed Gigabit PoE Ethernet Switch is equipped with an 8-port RJ45 connector for
10/100/1000M Ethernet, plus 2-port SFP connectors for Gigabit Fiber modules. The 8-port
Gigabit RJ45 connectors are with IEEE802.3af/at PoE+ 30W capability to provide high
Power over Ethernet (PoE) to the connected PD devices. In addition to the LED indicators
for each port, a built-in push button is also provided for switch reset.
The key features are as the following table;
Table 1: Key Features
10
Page 11

Feature
Description
Authentication
Telnet, Web – user name/password, RADIUS, TACACS+
Web – HTTPS
Telnet – SSH
SNMP v1/2c - Community strings
SNMP version 3 – MD5 or SHA password
Port – IEEE 802.1X, MAC address filtering
General Security
Measures
Private VLANs
Port Authentication
Port Security
DHCP Snooping (with Option 82 relay information)
IP Source Guard
Access Control Lists
Supports up to 256 rules
DHCP
Client
DNS
Client and Proxy service
Port Configuration
Speed, duplex mode, flow control, MTU, response to excessive
collisions, power saving mode
Rate Limiting
Input rate limiting per port (manual setting or ACL)
Port Mirroring
1 sessions, up to 10 source ports to one analysis port per session
Port Trunking
Supports up to 5 trunks – static or dynamic trunking (LACP)
Congestion Control
Throttling for broadcast, multicast, unknown unicast storms
Address Table
8K MAC addresses in the forwarding table, 1000 static MAC
addresses, 1K L2 IGMP multicast groups and 128 MVR groups
IP Version 4 and 6
Supports IPv4 and IPv6 addressing, management, and QoS
IEEE 802.1D Bridge
Supports dynamic data switching and addresses learning
Store-and-Forward
Switching
Supported to ensure wire-speed switching while eliminating
bad frames
Spanning Tree
Algorithm
Supports standard STP, Rapid Spanning Tree Protocol
(RSTP), and Multiple Spanning Trees (MSTP)
Virtual LANs
Up to 4K using IEEE 802.1Q, port-based, protocol-based,
private VLANs, and voice VLANs, and QinQ tunnel
Traffic Prioritization
Queue mode and CoS configured by Ethernet type, VLAN ID,
TCP/ UDP port, DSCP, ToS bit, VLAN tag priority, or port
Qualify of Service
Supports Differentiated Services (DiffServ), and DSCP
remarking
Link Layer
Discovery Protocol
Used to discover basic information about neighboring devices
Power over Ethernet
Supports PoE Time scheduling, and Keep-alive autochecking
11
Page 12

Feature
Description
Multicast Filtering
Supports IGMP snooping and query, MLD snooping, and
MulticastVLAN Registration
1.2. Description of Software Features
CONFIGURATION BACKUP AND RESTORE
You can save the current configuration settings to a file on the management station (using
the web interface) or a TFTP server (using the console interface through Telnet), and later
download this file to restore the switch configuration settings.
AUTHENTICATION
This switch authenticates management access via a web browser. User names and
passwords can be configured locally or can be verified via a remote authentication server
(i.e., RADIUS or TACACS+). Port-based authentication is also supported via the IEEE
802.1X protocol. This protocol uses Extensible Authentication Protocol over LANs (EAPOL)
to request user credentials from the 802.1X client, and then uses the EAP between the
switch and the authentication server to verify the client’s right to access the network via an
authentication server (i.e., RADIUS or TACACS+ server).
Other authentication options include HTTPS for secure management access via the web,
SSH for secure management access over a Telnet-equivalent connection, SNMP Version 3,
IP address filtering for SNMP/Telnet/web management access, and MAC address filtering
for port access.
ACCESS CONTROL LISTS
ACLs provide packet filtering for IP frames (based on protocol, TCP/UDP port number or
frame type) or layer 2 frames (based on any destination MAC address for unicast, broadcast
or multicast, or based on VLAN ID or VLAN tag priority). ACLs can by used to improve
performance by blocking unnecessary network traffic or to implement security controls by
restricting access to specific network resources or protocols. Policies can be used to
differentiate service for client ports, server ports, network ports or guest ports. They can
also be used to strictly control network traffic by only allowing incoming frames that match
the source MAC and source IP on specific port.
PORT CONFIGURATION
You can manually configure the speed and duplex mode, and flow control used on specific
ports, or use auto-negotiation to detect the connection settings used by the attached device.
12
Page 13

Use the full-duplex mode on ports whenever possible to double the throughput of switch
connections. Flow control should be enabled to control network traffic during periods of
congestion and prevent the loss of packets when port buffer thresholds are exceeded. The
switch supports flow control based on the IEEE 802.3x standard (incorporated in IEEE
802.3-2002).
RATE LIMITING
This feature controls the maximum rate for traffic transmitted or received on an interface.
Rate limiting is configured on interfaces at the edge of a network to limit traffic into or out of
the network. Traffic that falls within the rate limit is transmitted, while packets that exceed
the acceptable amount of traffic are dropped.
PORT MIRRORING
The switch can unobtrusively mirror traffic from any port to a monitor port. You can then
attach a protocol analyzer or RMON probe to this port to perform traffic analysis and verify
connection integrity.
PORT TRUNKING
Ports can be combined into an aggregate connection. Trunks can be manually set up or
dynamically configured using Link Aggregation Control Protocol (LACP – IEEE 802.3-2005).
The additional ports dramatically increase the throughput across any connection, and
provide redundancy by taking over the load if a port in the trunk should fail. The switch
supports up to 5 trunks.
STORM CONTROL
Broadcast, multicast and unknown unicast storm suppression prevents traffic from
overwhelming the network. When enabled on a port, the level of broadcast traffic passing
through the port is restricted. If broadcast traffic rises above a pre-defined threshold, it will
be throttled until the level falls back beneath the threshold.
STATIC ADDRESSES
A static address can be assigned to a specific interface on this switch.
Static addresses are bound to the assigned interface and will not be moved. When a static
address is seen on another interface, the address will be ignored and will not be written to
the address table. Static addresses can be used to provide network security by restricting
access for a known host to a specific port.
13
Page 14

IEEE 802.1D BRIDGE
The switch supports IEEE 802.1D transparent bridging. The address table facilitates data
switching by learning addresses, and then filtering or forwarding traffic based on this
information. The address table supports up to 16K addresses.
STORE-AND-FORWARD SWITCHING
The switch copies each frame into its memory before forwarding them to another port. This
ensures that all frames are a standard Ethernet size and have been verified for accuracy
with the cyclic redundancy check (CRC). This prevents bad frames from entering the
network and wasting bandwidth.
To avoid dropping frames on congested ports, the switch provides 8 MB for frame buffering.
This buffer can queue packets awaiting transmission on congested networks.
SPANNING TREE ALGORITHM
The switch supports these spanning tree protocols:
◆ Spanning Tree Protocol (STP, IEEE 802.1D) – Supported by using the STP backward
compatible mode provided by RSTP. STP provides loop detection. When there are
multiple physical paths between segments, this protocol will choose a single path and
disable all others to ensure that only one route exists between any two stations on the
network. This prevents the creation of network loops. However, if the chosen path
should fail for any reason, an alternate path will be activated to maintain the connection.
◆ Rapid Spanning Tree Protocol (RSTP, IEEE 802.1w) – This protocol reduces the
convergence time for network topology changes to about 3 to 5 seconds, compared to
30 seconds or more for the older IEEE 802.1D STP standard. It is intended as a
complete replacement for STP, but can still interoperate with switches running the older
standard by automatically reconfiguring ports to STP-compliant mode if they detect STP
protocol messages from attached devices.
◆ Multiple Spanning Tree Protocol (MSTP, IEEE 802.1s) – This protocol is a direct
extension of RSTP. It can provide an independent spanning tree for different VLANs. It
simplifies network management, provides for even faster convergence than RSTP by
limiting the size of each region, and prevents VLAN members from being segmented
from the rest of the group (as sometimes occurs with IEEE 802.1D STP).
VIRTUAL LANS
The switch supports up to 4096 VLANs. A Virtual LAN is a collection of network nodes that
share the same collision domain regardless of their physical location or connection point in
the network. The switch supports tagged VLANs based on the IEEE 802.1Q standard.
Members of VLAN groups can be manually assigned to a specific set of VLANs. This allows
the switch to restrict traffic to the VLAN groups to which a user has been assigned. By
segmenting your network into VLANs, you can:
14
Page 15

◆ Eliminate broadcast storms which severely degrade performance in a flat network.
◆ Simplify network management for node changes/moves by remotely configuring VLAN
membership for any port, rather than having to manually change the network connection.
◆ Provide data security by restricting all traffic to the originating VLAN.
◆ Use private VLANs to restrict traffic to pass only between data ports and the uplink ports,
thereby isolating adjacent ports within the same VLAN, and allowing you to limit the total
number of VLANs that need to be configured.
◆ Use protocol VLANs to restrict traffic to specified interfaces based on protocol type.
IEEE 802.1Q TUNNELING (QINQ)
This feature is designed for service providers carrying traffic for multiple customers across
their networks. QinQ tunneling is used to maintain customer-specific VLAN and Layer 2
protocol configurations even when different customers use the same internal VLAN IDs.
This is accomplished by inserting Service Provider VLAN (SPVLAN) tags into the
customer’s frames when they enter the service provider’s network, and then stripping the
tags when the frames leave the network.
TRAFFIC PRIORITIZATION
This switch prioritizes each packet based on the required level of service, using four priority
queues with strict or Weighted Round Robin queuing. It uses IEEE 802.1p and 802.1Q tags
to prioritize incoming traffic based on input from the end-station application. These functions
can be used to provide independent priorities for delay-sensitive data and best-effort data.
This switch also supports several common methods of prioritizing layer 3/4 traffic to meet
application requirements. Traffic can be prioritized based on the priority bits in the IP
frame’s Type of Service (ToS) octet or the number of the TCP/UDP port. When these
services are enabled, the priorities are mapped to a Class of Service value by the switch,
and the traffic then sent to the corresponding output queue.
QUALITY OF SERVICE
Differentiated Services (DiffServ) provides policy-based management mechanisms used for
prioritizing network resources to meet the requirements of specific traffic types on a per-hop
basis. Each packet is classified upon entry into the network based on access lists, DSCP
values, or VLAN lists. Using access lists allows you select traffic based on Layer 2, Layer 3,
or Layer 4 information contained in each packet. Based on network policies, different kinds
of traffic can be marked for different kinds of forwarding.
POWER OVER ETHERNET (PoE)
PoE supports IEEE802.3af/at auto-detection for 15W/30W power provision. Different priority
can be assigned to each port in case of exceeding power budget. The PoE status will
15
Page 16
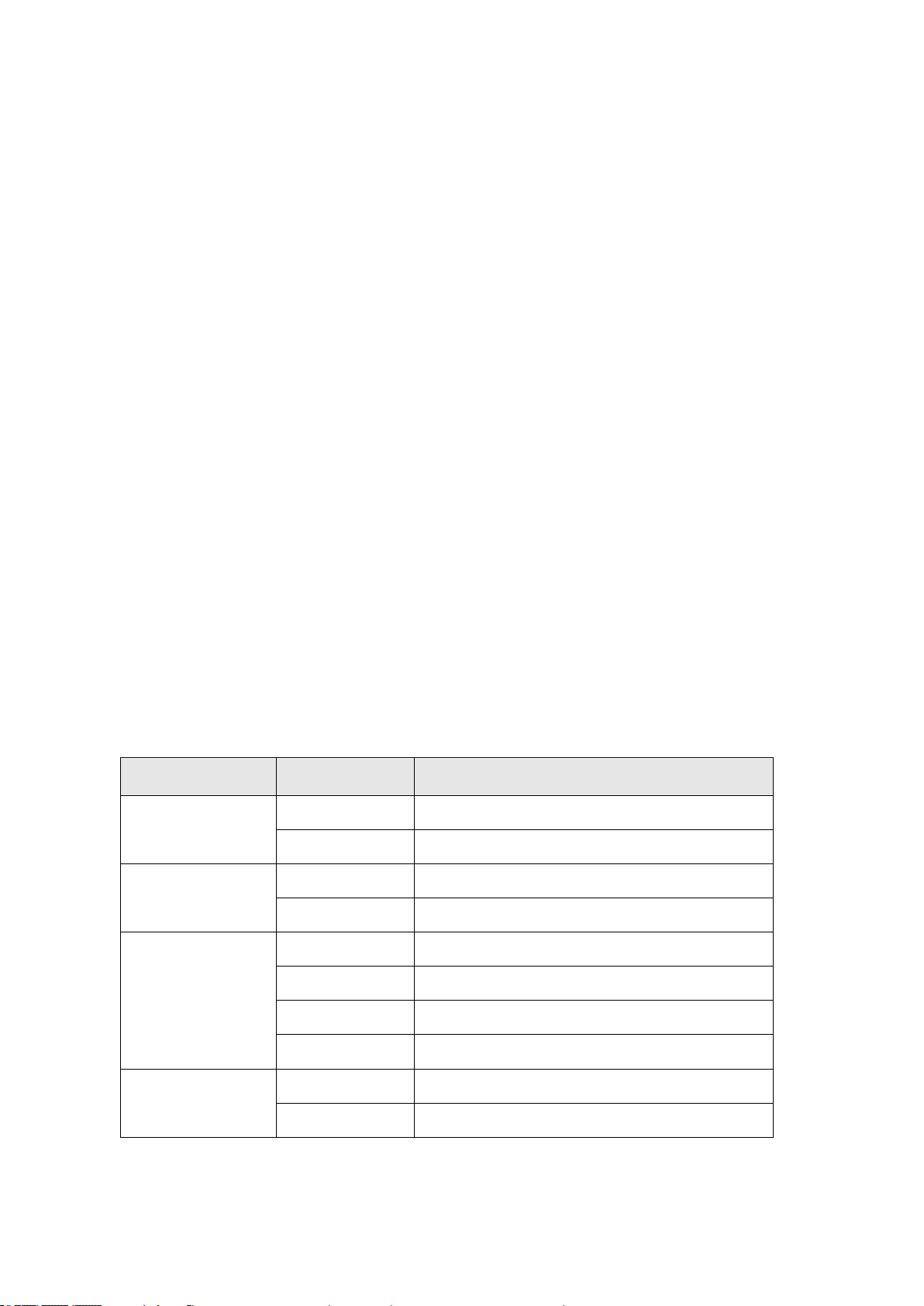
LED
Status
Descriptions
CPU
ON
System is ready.
OFF
System is not ready.
PWR
ON
System power is on.
OFF
System power is off.
LAN
Green ON
LAN Port is in connection of 1000Mbps.
Yellow ON
LAN Port is in connection of 10/100Mbps.
Flashing
Data is transmitting or receiving
OFF
No Ethernet connection.
PoE
ON
Power over Ethernet is ON.
OFF
Power over Ethernet is OFF.
show the PoE class and wattage for each port. PoE Time Scheduling can be configured for
ON/OFF in each port for 24-hour/7-days weekly basis. In addition, the keep-alive IP autochecking can be enabled to ping the connected powered IP device. It can reboot and reset
the power when the connected IP device fails to respond to the ping checking.
MULTICAST FILTERING
Specific multicast traffic can be assigned to its own VLAN to ensure that it does not interfere
with normal network traffic and to guarantee real-time delivery by setting the required
priority level for the designated VLAN. The switch uses IGMP Snooping and Query to
manage multicast group registration for IPv4 traffic, and MLD Snooping for IPv6 traffic. It
also supports Multicast VLAN Registration (MVR) which allows common multicast traffic,
such as television channels, to be transmitted across a single network-wide multicast VLAN
shared by hosts residing in other standard or private VLAN groups, while preserving
security and data isolation for normal traffic.
1.3. Reset Button & LED Indicators
The Reset button on the front panel can be used to reset the switch, and the Etherent
connections will restart again. Note that all the settings will remain unchanged.
The descriptions of LED indicators per port basis are as the following table:
Table 2: LED Status and Descriptions
16
Page 17
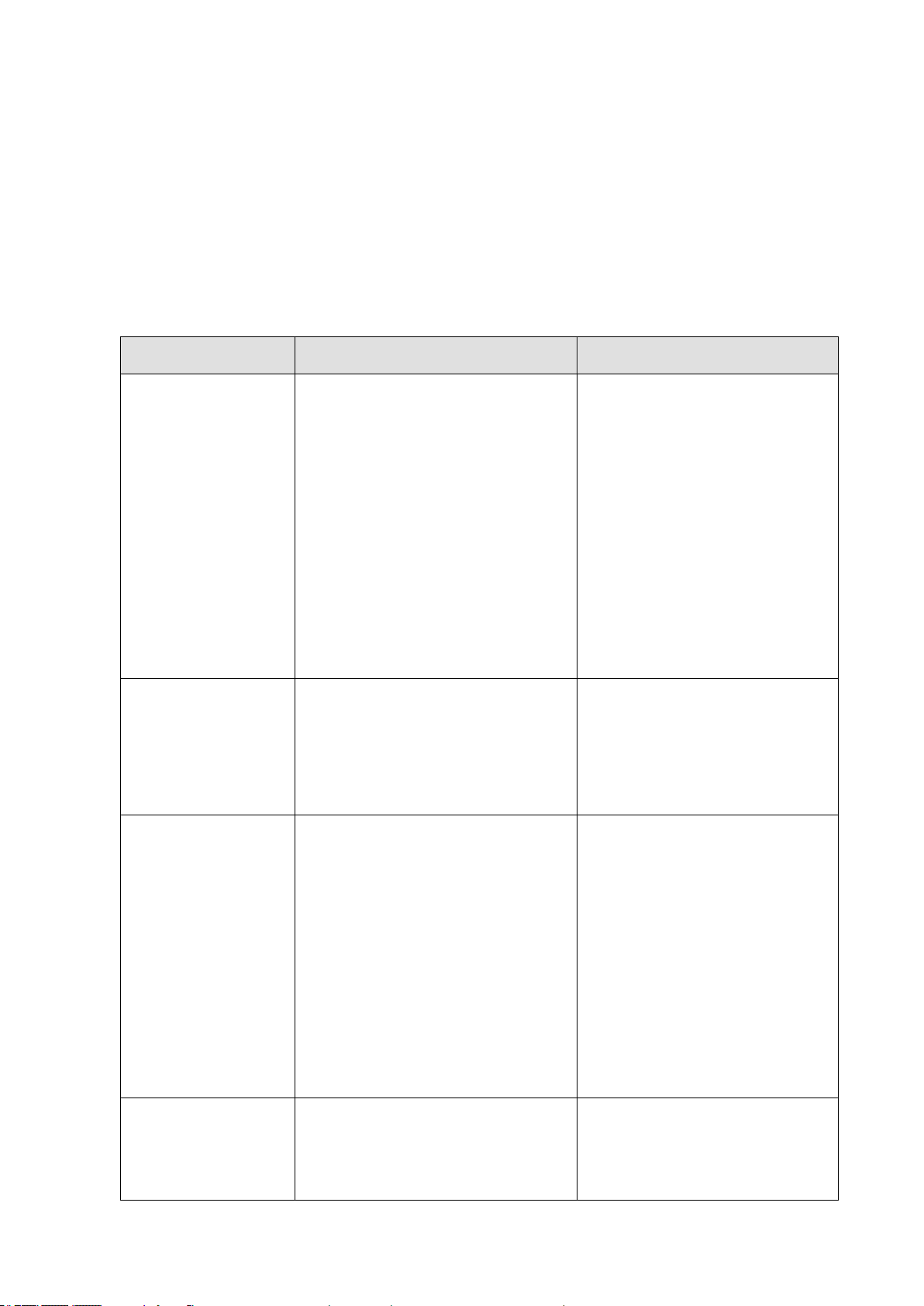
Function
Parameter
Default
Authentication
User Name
Password
RADIUS Authentication
TACACS+ Authentication
802.1X Port Authentication
HTTPS
SSH
Port Security
IP Filtering
“admin”
“ ”
Disabled
Disabled
Disabled
Enabled
Enabled
Disabled
Disabled
Web
Management
HTTP Server
HTTP Port Number
HTTP Secure Server
HTTP Secure Server Redirect
Enabled
80
Enabled
Disabled
SNMP
SNMP Agent
Community Strings
Traps
SNMP V3
Disabled
“public” (read only)
“private” (read/write)
Global: disabled
Authentication traps:
enabled
Link-up-down events:
enabled
View:default_view
Group: default_rw_group
Port
Configuration
Admin Status
Auto-negotiation
Flow Control
Enabled
Enabled
Disabled
1.4. System Defaults
The system defaults are provided in the configuration file “Config.xml.” To reset the switch
defaults, this file should be set as the startup configuration file.
The following table lists some of the basic system defaults.
Table 3: System Defaults
17
Page 18
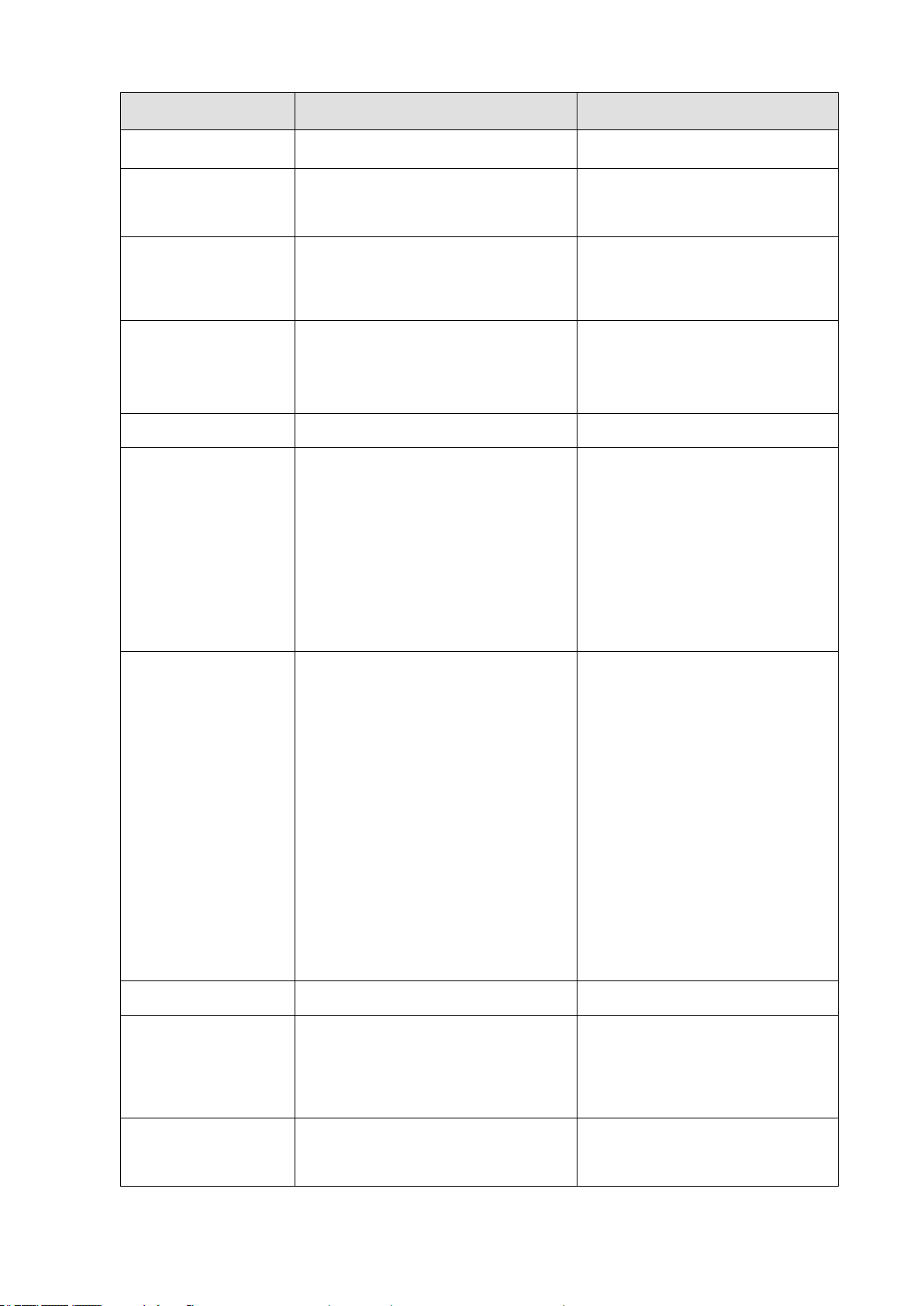
Function
Parameter
Default
Rate Limiting
Input and output rate limits
Disabled
Port Trunking
Static Trunks
LACP (all ports)
None
Disabled
Storm Protection
Status
Broadcast: Enabled (1 kpps)
Multicast: disabled
Unknown unicast: disabled
Spanning Tree
Algorithm
Status
Edge Ports
Enabled, RSTP
(Defaults: RSTP standard)
Enabled
Address Table
Aging Time
300 seconds
Virtual LANs
Default VLAN
PVID
Acceptable Frame Type
Ingress Filtering
Switchport Mode (Egress
Mode)
1
1
All
Disabled
Access
Traffic
Prioritization
Ingress Port Priority
Queue Mode
Weighted Round Robin
Ethernet Type
VLAN ID
VLAN Priority Tag
ToS Priority
IP DSCP Priority
TCP/UDP Port Priority
0
Strict
Queue: 0 1 2 3 4 5 6 7
Weight: Disabled in strict mode
Disabled
Disabled
Disabled
Disabled
Disabled
Disabled
LLDP
Status
Enabled
PoE
Configurations
Time Scheduling
IP Autochecking
Enabled
Disabled
Disabled
IP Settings
Management. VLAN
IP Address
VLAN 1
192.168.1.1
18
Page 19
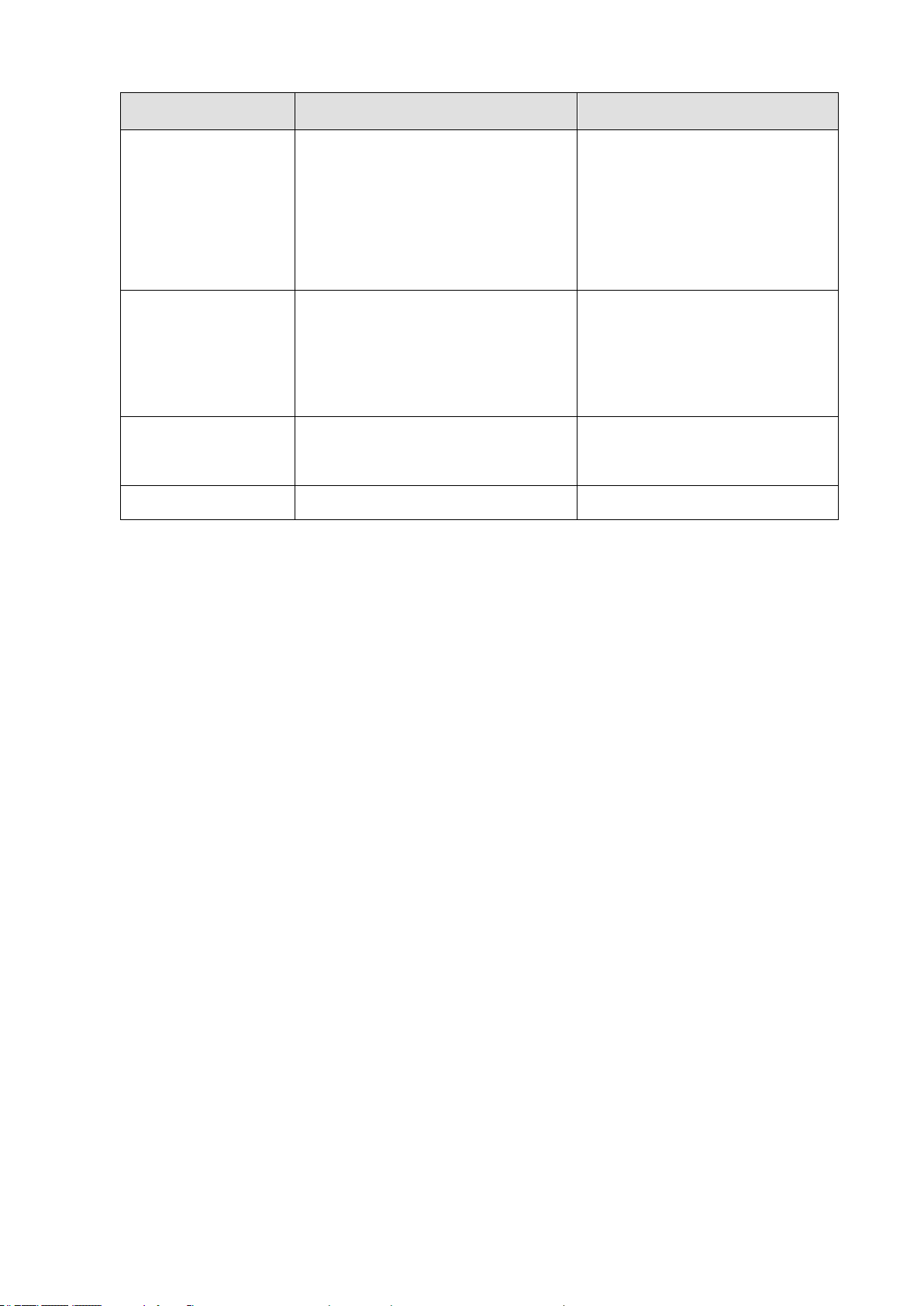
Function
Parameter
Default
Subnet Mask
Default Gateway
DHCP
DNS
255.255.255.0
0.0.0.0
Client: Disabled
Snooping:Disabled
Proxy service: Disabled
Multicast
Filtering
IGMP Snooping
MLD Snooping
Multicast VLAN Registration
Snooping: Disabled
Querier: Disabled
Disabled
Disabled
System Log
(console only)
Status
Messages Logged to Flash
Disabled
All levels
NTP
Clock Synchronization
Disabled
19
Page 20

2. INITIAL SWITCH CONFIGURATION
This chapter includes information on installations of the switch and basic configuration
procedures.
To make use of the management features of your switch, you must first configure it with an
IP address that is compatible with the network in which it is being installed. This should be
done before you permanently install the switch in the network.
Follow this procedure:
1. Place the switch close to the PC that you intend to use for configuration. It helps if you
can see the front panel of the switch while working on your PC.
2. Connect the Ethernet port of your PC to any port on the front panel of the switch. Connect
power to the switch and verify that you have a link by checking the front panel LEDs.
3. Check that your PC has an IP address on the same subnet as the switch. The default IP
address of the switch is 192.168.1.1 and the subnet mask is 255.255.255.0.. The PC
and switch are on the same subnet if they both have addresses starting with 192.168.1.x.
If the PC and switch are not on the same subnet, you must manually set the PC’s IP
address to 192.168.1.x (where “x” is any number from 2 to 254, except 1).
4. Open your web browser and enter the address http://192.168.1.1. If your PC is properly
configured, you will see the login page of the switch. If you do not see the login page,
repeat step 3 or refer to Appendix B.2 “Accessing the Web page”.
5. Enter “admin” for the user name and password, and then click on the Login button.
6. From the menu, click System, and then IP. To request an address from a local DHCP
Server, mark the DHCP Client check box. To configure a static address, enter the new IP
Address, IP Mask, and other optional parameters for the switch, and then click on the
Save button.
If you need to configure an IPv6 address, select IPv6 from the System menu, and either
submit a request for an address from a local DHCPv6 server by marking the Auto
Configuration check box, or configure a static address by filling in the parameters for an
address, network prefix length, and gateway router.
No other configuration changes are required at this stage, but it is recommended that you
change the administrator’s password before logging out. To change the password, click
Security and then Users. Select “admin” from the User Configuration list, fill in the Password
fields, and then click Save.
20
Page 21

SECTION II WEB CONFIGURATION
This section describes the basic switch features, along with a detailed description of how to
configure each feature via a web browser.
This section includes these chapters:
◆ "3. Using the Web Interface" on page 22
◆ "4. Configuring the Switch" on page 34
◆ "5. Monitoring the Switch" on page 208
◆ "6. Diagnostics" on page 286
◆ "7. Maintenance" on page 291
21
Page 22
3. USING THE WEB INTERFACE
This switch provides an embedded HTTP web agent. Using a web browser you can
configure the switch and view statistics to monitor network activity. The web agent can be
accessed by any computer on the network using a standard web browser (Internet Explorer
5.0, Netscape 6.2, Mozilla Firefox 2.0.0.0, or more recent versions).
3.1. Navigating the Web Browser Interface
To access the web-browser interface you must first enter a user name and password. The
administrator has Read/Write access to all configuration parameters and statistics. The
default user name for the administrator is “admin” and for password.
Home Page
When your web browser connects with the switch’s web agent, the home page is displayed
as shown below. The home page displays the Main Menu on the left side of the screen and
an image of the front panel on the right side. The Main Menu links are used to navigate to
other menus, and display configuration parameters and statistics.
Figure 1: Home Page
Configuration Options
Configurable parameters have a dialog box or a drop-down list. Once a configuration
change has been made on a page, be sure to click on the Save button to confirm the new
setting. The following table summarizes the web page configuration buttons.
22
Page 23
Button
Action
Save
Sets specified values to the system
Reset
Cancels specified values and restores current values prior to pressing
“Save.”
Logs out of the management interface
Displays help for the selected page
Table 4: Web Page Configuration Buttons
NOTE:
To ensure proper screen refresh, be sure that Internet Explorer is configured so that the
setting “Check for newer versions of stored pages” reads “Every visit to the page.”
Internet Explorer 6.x and earlier: This option is available under the menu “Tools / Internet
Options / General / Temporary Internet Files / Settings.”
Internet Explorer 7.x: This option is available under “Tools / Internet Options / General /
Browsing History / Settings / Temporary Internet Files.”
Panel Display
The web agent displays an image of the switch’s ports. The refresh mode is disabled by
default. Click Auto-refresh to refresh the data displayed on the screen approximately once
every 5 seconds, or click Refresh to refresh the screen right now. Clicking on the image of a
port opens the Port State page as described on page 210.
Figure 2: Front Panel Indicators
Main Menu
Using the onboard web agent, you can define system parameters, manage and control the
switch, and all its ports, or monitor network conditions. The following table briefly describes
the selections available from this program.
23
Page 24

Menu
Description
Page
Configuration
34
System
34
Information
Configures system contact, name and location
34
IP
Configures IPv4 and SNTP settings
35
IPv6
Configures IPv6 and SNTP settings
37
NTP
Enables NTP, and configures a list of NTP servers
39
Log
Configures the logging of messages to a remote
logging process, specifies the remote log server, and
limits the type of system log messages sent
40
Power Reduction
42
LED
Reduces LED intensity during specified hours
42
EEE
Configures Energy Efficient Ethernet for specified
queues, and specifies urgent queues which are to
transmit data after maximum latency expires
regardless queue length
43
Thermal Protection
Configures temperature priority levels, and assigns
those priorities for port shut-down if exceeded
45
Ports
Configures port connection settings
46
Security
49
Switch
49
Users
Configures user names, passwords, and access levels
49
Privilege Levels
Configures privilege level for specific functions
51
Auth Method
Configures authentication method for management
access via local database, RADIUS or TACACS+
52
SSH
Configures the Secure Shell server
55
HTTPS
Configures secure HTTP settings
56
Access
Management
Sets IP addresses of clients allowed management
access via HTTP/HTTPS, and SNMP, and Telnet/SSH
58
SNMP
Simple Network Management Protocol
59
System
Configures read-only and read/write community
strings for SNMP v1/v2c, engine ID for SNMP v3, and
trap parameters
60
Table 5: Main Menu
24
Page 25

Menu
Description
Page
Communities
Configures community strings
64
Users
Configures SNMP v3 users on this switch
65
Groups
Configures SNMP v3 groups
66
Views
Configures SNMP v3 views
68
Access
Assigns security model, security level, and read / write
views to SNMP groups
69
Network
76
Limit Control
Configures port security limit controls, including secure
address aging; and per port security, including
maximum allowed MAC addresses, and response for
security breach
76
NAS
Configures global and port settings for IEEE 802.1X
78
ACL
Access Control Lists
89
Ports
Assigns ACL, rate limiter, and other parameters to
ports
89
Rate Limiters
Configures rate limit policies
91
Access
Control List
Configures ACLs based on frame type, destination
MAC type, VLAN ID, VLAN priority tag; and the action
to take for matching packets
92
DHCP
Dynamic Host Configuration Protocol
98
Snooping
Enables DHCP snooping globally; and sets the trust
mode for each port
98
Relay
Configures DHCP relay information status and policy
100
IP Source Guard
Filters IP traffic based on static entries in the IP
Source Guard table, or dynamic entries in the DHCP
Snooping table
102
Configuration
Enables IP source guard and sets the maximum
number of clients that can learned dynamically
102
Static Table
Adds a static addresses to the source-guard binding
table
104
ARP Inspection
Address Resolution Protocol Inspection
105
Configuration
Enables inspection globally, and per port
105
25
Page 26

Menu
Description
Page
Static Table
Adds static entries based on port, VLAN ID, and
source MAC address and IP address in ARP request
packets
108
AAA
Configures RADIUS authentication server, RADIUS
accounting server, and TACACS+ authentication
server settings
109
Aggregation
111
Static
Specifies ports to group into static trunks
112
LACP
Allows ports to dynamically join trunks
114
Loop Protection
116
Spanning Tree
117
Bridge Settings
Configures global bridge settings for STP, RSTP and
MSTP; also configures edge port settings for BPDU
filtering, BPDU guard, and port error recovery
119
MSTI Mapping
Maps VLANs to a specific MSTP instance
123
MSTI Priorities
Configures the priority for the CIST and each MISTI
125
CIST Ports
Configures interface settings for STA
126
MSTI Ports
Configures interface settings for an MST instance
130
MVR
Configures Multicast VLAN Registration, including
global status, MVR VLAN, port mode, and immediate
leave
131
IPMC
IP Multicast
134
IGMP Snooping
Internet Group Management Protocol Snooping
134
Basic
Configuration
Configures global and port settings for multicast
filtering
135
VLAN
Configuration
Configures IGMP snooping per VLAN interface
138
Port Group
Filtering
Configures multicast groups to be filtered on specified
port
140
MLD Snooping
Multicast Listener Discovery Snooping
141
Basic
Configuration
Configures global and port settings for multicast
filtering
141
VLAN
Configures MLD snooping per VLAN interface
144
26
Page 27

Menu
Description
Page
Configuration
Port Group
Filtering
Configures multicast groups to be filtered on specified
port
146
LLDP
Link Layer Discovery Protocol
148
LLDP
Configures global LLDP timing parameters, and portspecific TLV attributes
148
LLDP-MED
Configures LLDP-MED attributes, including device
location, emergency call server, and network policy
discovery
151
PoE
Configures Power-over-Ethernet settings for each port
156
Configuration
To disable/enable PoE with priority, and power limit
157
Time Scheduling
To set the scheduling date and hourly period.
159
Auto Checking
To set the checking IP address, and time intervals.
160
MAC Table
Configures address aging, dynamic learning, and
static addresses
162
VLANs
Virtual LANs
164
VLAN
Membership
Configures VLAN groups
165
Ports
Specifies default PVID and VLAN attributes
166
Private VLANs
168
PVLAN
Membership
Configures PVLAN groups
168
Port Isolation
Prevents communications between designated ports
within the same private VLAN
169
VCL
VLAN Control List
170
MAC-based
VLAN
Maps traffic with specified source MAC address to a
VLAN
170
Protocol-based
VLAN
172
Protocol to
Group
Creates a protocol group, specifying supported
protocols
172
Group to
VLAN
Maps a protocol group to a VLAN for specified ports
174
Voice VLAN
175
27
Page 28

Menu
Description
Page
VoIP Traffic
Configures global settings, including status, voice
VLAN ID, VLAN aging time, and traffic priority; also
configures port settings, including the way in which a
port is added to the Voice VLAN, and blocking nonVoIP addresses
176
Telephony OUI
Maps the OUI in the source MAC address of ingress
packets to the VoIP device manufacturer
178
QoS
179
Port
Classification
Configures default traffic class, drop priority, user
priority, drop eligible indicator, classification mode for
tagged frames, and DSCP-based QoS classification
179
Port Policing
Configures Policing setting for all the switch ports
including packet rate, and flow control
181
Port Scheduler
Provides overview of QoS Egress Port Schedulers,
including the queue mode and weight; also configures
egress queue mode, queue shaper (rate and access
to excess bandwidth), and port shaper
183
Port Shaping
Provides overview of QoS Egress Port Shapers,
including the rate for each queue and port; also
configures egress queue mode, queue shaper (rate
and access to excess bandwidth), and port shaper
185
Port Tag
Remarking
Provides overview of QoS Egress Port Tag
Remarking; also sets the remarking mode (classified
PCP/DEI values, efault PCP/DEI values, or mapped
versions of QoS class and drop priority)
186
Port DSCP
Configures ingress translation and classification
settings and egress re-writing of DSCP values
188
DSCP-Based
QoS
Configures DSCP-based QoS ingress classification
settings
189
DSCP
Translation
Configures DSCP translation for ingress traffic or
DSCP remapping for egress traffic
190
DSCP
Classification
Maps DSCP values to a QoS class and drop
precedence level
192
QoS Control List
Configures QoS policies for handling ingress packets
based on Ethernet type, VLAN ID, TCP/UDP port,
DSCP, ToS, or VLAN priority tag
193
28
Page 29

Menu
Description
Page
Storm Control
Sets limits for broadcast, multicast, and unknown
unicast traffic
196
Mirroring
Sets source and target ports for mirroring
198
UPnP
Enables UPnP and defines timeout values
199
Monitor
204
System
204
Information
Displays basic system description, switch’s MAC
address, system time, and software version
204
CPU Load
Displays graphic scale of CPU utilization
206
Log
Displays logged messages based on severity
206
Detailed Log
Displays detailed information on each logged message
208
Thermal Protection
Shows the current chip temperature
209
Ports
210
State
Displays a graphic image of the front panel indicating
active port connections
210
Traffic Overview
Shows basic Ethernet port statistics
211
QoS Statistics
Shows the number of packets entering and leaving the
egress queues
212
QCL Status
Shows the status of QoS Control List entries
212
Detailed Statistics
Shows detailed Ethernet port statistics
214
Security
215
Access
Management
Statistics
Displays the number of packets used to manage the
switch via HTTP, HTTPS, and SNMP, Telnet, and
SSH
215
Network
217
Port Security
Shows the entries authorized by port security services,
including MAC address, VLAN ID, the service state,
time added to table, age, and hold state
217
NAS
Shows global and port settings for IEEE 802.1X
220
Switch
Shows port status for authentication services, including
802.1X security state, last source address used for
authentication, and last ID
220
29
Page 30

Menu
Description
Page
Port
Displays authentication statistics for the selected port –
either for 802.1X protocol or for the remote
authentication server depending on the authentication
method
221
ACL Status
Shows the status for different security modules which
use ACL filtering, including ingress port, frame type,
and forwarding action
225
DHCP
Dynamic Host Configuration Protocol
227
Snooping
Statistics
Shows statistics for various types of DHCP protocol
packets
227
Relay
Statistics
Displays server and client statistics for packets
affected by the relay information policy
228
ARP Inspection
Displays entries in the ARP inspection table, sorted
first by port, then VLAN ID, MAC address, and finally
IP address
230
IP Source
Guard
Displays entries in the IP Source Guard table, sorted
first by port, then VLAN ID, MAC address, and finally
IP address
230
AAA
Authentication, Authorization and Accounting
231
RADIUS Overview
Displays status of configured RADIUS authentication
and accounting servers
231
RADIUS Details
Displays the traffic and status associated with each
configured RADIUS server
233
Switch Security
Shows information about MAC address learning for
each port, including the software module requesting
port security services, the service state, the current
number of learned addresses, and the maximum
number of secure addresses allowed
236
LACP
Link Aggregation Control Protocol
242
System Status
Displays administration key and associated local ports
for each partner
242
Port Status
Displays administration key, LAG ID, partner ID, and
partner ports for each local port
244
Port Statistics
Displays statistics for LACP protocol messages
245
Loop Protection
246
30
Page 31

Menu
Description
Page
Spanning Tree
247
Bridge Status
Displays global bridge and port settings for STA
247
Port Status
Displays STA role, state, and uptime for each port
249
Port Statistics
Displays statistics for RSTP, STP and TCN protocol
packets
251
MVR
Multicast VLAN Registration
252
Statistics
Shows statistics for IGMP protocol messages used by
MVR
252
Group Information
Shows information about the interfaces associated
with multicast groups assigned to the MVR VLAN
253
IPMC
IP Multicast
254
IGMP Snooping
254
Status
Displays statistics related to IGMP packets passed
upstream to the IGMP Querier or downstream to
multicast clients
254
Group
Information
Displays active IGMP groups
255
IPv4 SFM
Information
Displays IGMP Source-Filtered Multicast Information
including group, filtering mode (include or exclude),
source address, and type (allow or deny)
256
MLD Snooping
Multicast Listener Discovery Snooping
257
Status
Displays MLD querier status and protocol statistics
257
Group
Information
Displays active MLD groups
259
IPv6 SFM
Information
Displays MLD Source-Filtered Multicast Information
including group, filtering mode (include or exclude),
source address, and type (allow or deny)
260
LLDP
Link Layer Discovery Protocol
261
Neighbors
Displays LLDP information about a remote device
connected to a port on this switch
261
LLDP-MED
Neighbors
Displays information about a remote device connected
to a port on this switch which is advertising LLDP-MED
TLVs, including network connectivity device, endpoint
device, capabilities, application type, and policy
263
31
Page 32

Menu
Description
Page
PoE
Displays status of all LLDP PoE neighbors, including
power device type (PSE or PD), source of power,
power priority, and maximum required power
265
EEE
Displays Energy Efficient Ethernet information
advertised through LLDP messages
266
Port Statistics
Displays statistics for all connected remote devices, and
statistics for LLDP protocol packets crossing each port
268
PoE
Displays the status for all PoE ports, including the PD
class, requested power, allocated power, power and
current used, and PoE priority
270
MAC Table
Displays dynamic and static address entries associated
with the CPU and each port
273
VLANs
Virtual LANs
275
VLAN
Membership
Shows the current port members for all VLANs
configured by a selected software module
275
VLAN Port
Shows the VLAN attributes of port members for all VLANs
configured by a selected software module which uses
VLAN management, including PVID, VLAN aware, ingress
filtering, frame type, egress filtering, and PVID
276
VCL
VLAN Control List
278
MAC-based VLAN
Displays MAC address to VLAN map entries
278
Diagnostics
279
Ping
Tests specified path using IPv4 ping
279
Ping6
Tests specified path using IPv6 ping
281
VeriPHY
Performs cable diagnostics for all ports or selected port to
diagnose any cable faults (short, open etc.) and report the
cable length
283
Maintenance
284
Restart Device
Restarts the switch
284
Factory Defaults
Restores factory default settings
285
Software Upload
Updates software on the switch with a file specified on the
management station
286
Configuration
288
32
Page 33

Menu
Description
Page
Save
Saves configuration settings to a file on the management
station
288
Upload
Restores configuration settings from a file on the
management station
289
33
Page 34

4. CONFIGURING THE SWITCH
This chapter describes all of the basic configuration tasks for the switch management.
4.1. System
System Information Configuration
Use the System Information Configuration page to identify the system by configuring contact
information, system name, location of the switch, and time zone offset.
PATH
Configuration / System / Information
Figure 3: System Information Configuration
PARAMETERS
These parameters are displayed:
◆ System Contact – Administrator responsible for the system. (Maximum length: 255
characters)
◆ System Name – Name assigned to the switch system. (Maximum length: 255 characters)
◆ System Location – Specifies the system location. (Maximum length: 255 characters)
34
Page 35

WEB INTERFACE
To configure System Information:
1. Click Configuration, System, Information.
2. Specify the contact information for the system administrator, as well as the name and
location of the switch. Also indicate the local time zone by configuring the appropriate
offset.
3. Click Save.
IP Configuration
This section describes how to configure an IP interface for management access to the
switch over the network. This switch supports both IP Version 4 and Version 6, and can be
managed simultaneously through either of these address types. You can manually configure
a specific IPv4 or IPv6 address or direct the switch to obtain an IPv4 address from a DHCP
server when it is powered on. An IPv6 address can be either manually configured or
dynamically generated.
Setting an IPV4 Address
Use the IP Configuration page to configure an IPv4 address for the switch. The IP address
for the switch is obtained via DHCP by default for VLAN 1. To manually configure an
address, you need to change the switch's default settings to values that are compatible with
your network. You may also need to establish a default gateway between the switch and
management stations that exist on another network segment.
Note: An IPv4 address for this switch is obtained via DHCP by default. If the switch does not
receive a response from a DHCP server, it will default to the IP address 192.168.1.1 and
subnet mask 255.255.255.0.
You can manually configure a specific IP address, or direct the device to obtain an address
from a DHCP server. Valid IPv4 addresses consist of four decimal numbers, 0 to 255,
separated by periods. Anything other than this format will not be accepted.
PATH
Configuration / System / IP
35
Page 36

Figure 4: IP Configuration
PARAMETERS
These parameters are displayed:
IP Configuration
◆ DHCP Client – Specifies whether IP functionality is enabled via Dynamic Host
Configuration Protocol (DHCP). If DHCP is enabled, IP will not function until a reply has
been received from the server. Requests will be broadcasted periodically by the switch for
an IP address. DHCP values can include the IP address, subnet mask, and default
gateway. (Default: Enabled)
◆ IP Address – Address of the VLAN specified in the VLAN ID field. This should be the
VLAN to which the management station is attached. Valid IP addresses consist of four
numbers, 0 to 255, separated by periods. (Default: 192.168.1.1)
◆ IP Mask – This mask identifies the host address bits used for routing to specific subnets.
(Default: 255.255.255.0)
◆ IP Router – IP address of the gateway router between the switch and management
stations that exist on other network segments.
◆ VLAN ID – ID of the configured VLAN. By default, all ports on the switch are members of
VLAN 1. However, the management station can be attached to a port belonging to any
VLAN, as long as that VLAN has been assigned an IP address. (Range: 1-4095; Default:
1)
◆ DNS Server – A Domain Name Server to which client requests for mapping host names to
IP addresses are forwarded.
36
Page 37

IP DNS Proxy Configuration
◆ DNS Proxy – If enabled, the switch maintains a local database based on previous
responses to DNS queries forwarded on behalf of attached clients. If the required
information is not in the local database, the switch forwards the DNS query to a DNS
server, stores the response in its local cache for future reference, and passes the
response back to the client.
WEB INTERFACE
To configure an IP address:
1. Click Configuration, System, IP.
2. Specify the IPv4 settings, and enable DNS proxy service if required.
3. Click Save.
IPV6 Configuration
Use the IPv6 Configuration page to configure an IPv6 address for management access to
the switch.
IPv6 includes two distinct address types - link-local unicast and global unicast. A link-local
address makes the switch accessible over IPv6 for all devices attached to the same local
subnet. Management traffic using this kind of address cannot be passed by any router
outside of the subnet. A link-local address is easy to set up, and may be useful for simple
networks or basic troubleshooting tasks. However, to connect to a larger network with
multiple segments, the switch must be configured with a global unicast address. A link-local
address must be manually configured, but a global unicast address can be either manually
configured or dynamically assigned.
PATH
Configuration / System / IPv6
37
Page 38

Figure 5: IPv6 Configuration
USAGE GUIDELINES
◆ All IPv6 addresses must be formatted according to RFC 2373 “IPv6 Addressing
Architecture,” using 8 colon-separated 16-bit hexadecimal values. One double colon may
be used in the address to indicate the appropriate number of zeros required to fill the
undefined fields.
◆ When configuring a link-local address, note that the prefix length is fixed at 64 bits, and
the host portion of the default address is based on the modified EUI-64 (Extended
Universal Identifier) form of the interface identifier (i.e., the physical MAC address). You
can manually configure a link-local address by entering the full address with the network
prefix FE80.
◆ To connect to a larger network with multiple subnets, you must configure a global unicast
address. There are several alternatives to configuring this address type:
■ The global unicast address can be automatically configured by taking the network prefix
from router advertisements observed on the local interface, and using the modified EUI-64
form of the interface identifier to automatically create the host portion of the address. This
option can be selected by enabling the Auto Configuration option.
■ You can also manually configure the global unicast address by entering the full address
and prefix length.
◆ The management VLAN to which the IPv6 address is assigned must be specified on the
IP Configuration page.
PARAMETERS
These parameters are displayed:
38
Page 39

◆ Auto Configuration – Enables stateless autoconfiguration of IPv6 addresses on an
interface and enables IPv6 functionality on the interface. The network portion of the
address is based on prefixes received in IPv6 router advertisement messages, and the
host portion is automatically generated using the modified EUI-64 form of the interface
identifier; i.e., the switch's MAC address. (Default: Disabled)
◆ Address – Manually configures a global unicast address by specifying the full address
and network prefix length (in the Prefix field). (Default: 192.168.1.1)
◆ Prefix – Defines the prefix length as a decimal value indicating how many contiguous bits
(starting at the left) of the address comprise the prefix; i.e., the network portion of the
address. (Default: 96 bits) Note that the default prefix length of 96 bits specifies that the
first six colon-separated values comprise the network portion of the address.
◆ Router – Sets the IPv6 address of the default next hop router. An IPv6 default gateway
must be defined if the management station is located in a different IPv6 segment.
An IPv6 default gateway can only be successfully set when a network interface that directly
connects to the gateway has been configured on the switch.
WEB INTERFACE
To configure an IPv6 address:
1. Click Configuration, System, IPv6.
2. Specify the IPv6 settings. The information shown below provides a example of how to
manually configure an IPv6 address.
3. Click Save.
NTP Configuration
Use the NTP Configuration page to specify the Network Time Protocol (NTP) servers to
query for the current time. NTP allows the switch to set its internal clock based on periodic
updates from an NTP time server. Maintaining an accurate time on the switch enables the
system log to record meaningful dates and times for event entries. If the clock is not set, the
switch will only record the time from the factory default set at the last bootup.
When the NTP client is enabled, the switch periodically sends a request for a time update to
a configured time server. You can configure up to five time server IP addresses. The switch
will attempt to poll each server in the configured sequence.
PATH
Configuration \ System \ NTP
39
Page 40

Figure 6: NTP Configuration
PARAMETERS
These parameters are displayed:
◆ Mode – Enables or disables NTP client requests.
◆ Server – Sets the IPv4 or IPv6 address for up to five time servers. The switch attempts to
update the time from the first server, if this fails it attempts an update from the next server
in the sequence. The polling interval is fixed at 15 minutes.
WEB INTERFACE
To configure the NTP servers:
1. Click Configuration, System, NTP.
2. Enter the IP address of up to five time servers.
3. Click Save.
System Log Configuration
Use the System Log Configuration page to send log messages to syslog servers or other
management stations. You can also limit the event messages sent to specified types.
PATH
Configuration \ System \ Log
40
Page 41

Figure 7: Configuring Settings for Remote Logging of Error Messages
COMMAND USAGE
When remote logging is enabled, system log messages are sent to the designated server.
The syslog protocol is based on UDP and received on UDP port 514. UDP is a
connectionless protocol and does not provide acknowledgments. The syslog packet will
always be sent out even if the syslog server does not exist.
PARAMETERS
These parameters are displayed:
◆ Server Mode – Enables/disables the logging of debug or error messages to the remote
logging process. (Default: Disabled)
◆ Server Address – Specifies the IPv4 address or alias of a remote server which will be
sent syslog messages.
◆ Syslog Level – Limits log messages that are sent to the remote syslog server for the
specified types. Messages options include the following:
■ Info – Send informations, warnings and errors. (Default setting)
■ Warning – Send warnings and errors.
■ Error – Send errors.
WEB INTERFACE
To configure the logging of error messages to remote servers:
1. Click Configuration, System, Log.
41
Page 42

2. Enable remote logging, enter the IP address of the remote server, and specify the type of
syslog messages to send.
3. Click Apply.
4.2. Power Reduction
The switch provides power saving methods including controlling the intensity of LEDs, and
powering down the circuitry for port queues when not in use.
Controlling LED Intensity
Use the LED Power Reduction Configuration page to reduces LED intensity during specified
hours.
PATH
Configuration \ Power Reduction \ LED
Figure 8: Configuring LED Power Reduction
COMMAND USAGE
◆ The LEDs power consumption can be reduced by lowering the intensity. LED intensity
could for example be lowered during night time, or turned completely off. It is possible to
set the LEDs intensity for each of the 24 hours of the day.
◆ When a network administrator performs maintenance of the switch (e.g., adding or moving
42
Page 43

users) he might want to have full LED intensity during the maintenance period. Therefore
it is possible to specify set the LEDs at full intensity for a specific period of time.
Maintenance time is the number of seconds that the LEDs are set to full intensity after a
port changes link state.
PARAMETERS
These parameters are displayed:
LED Intensity Timers
◆ Time – Time at which LED intensity is set.
◆ Intensity – LED intensity (Range: 0-100%, in increments of 10%, where 0% means off
and 100% means full power)
Maintenance
◆ On time at link change – LEDs set at full intensity for a specified period when a link
change occurs. (Default: 10 seconds)
◆ On at errors – LEDs set at full intensity when a link error occurs.
WEB INTERFACE
To configure LED intensity:
1. Click Configuration, Power Reduction, LED.
2. Set LED intensity for any required hour of the day. Click Add Time to set additional entries.
3. Set the duration of full intensity when a link change occurs.
4. Specify whether or not to use full intensity when a link error occurs.
5. Click Apply.
Reducing Power for EEE
Use the EEE Configuration page to configure Energy Efficient Ethernet (EEE) for specified
queues, and to specify urgent queues which are to transmit data after maximum latency
expires regardless of queue length.
PATH
Configuration \ Power Reduction \ EEE
43
Page 44

Figure 9: Configuring EEE Power Reduction
COMMAND USAGE
◆ EEE works by powering down circuits when there is no traffic. When a port gets data to be
transmitted all relevant circuits are powered up. The time it takes to power up the circuits
is call the wakeup time. The default wakeup time is 17 μs for 1 Gbps links and 30 μs for
other link speeds. EEE devices must agree upon the value of the wakeup time in order to
make sure that both the receiving and transmitting devices have all circuits powered up
when traffic is transmitted. The devices can exchange information about the device
wakeup time using LLDP protocol.
To maximize power savings, the circuit is not started as soon as data is ready to be
transmitted from a port, but instead waits until 3000 bytes of data is queued at the port. To
avoid introducing a large delay when the queued data is less then 3000 bytes, data is
always transmitted after 48 μs, giving a maximum latency of 48 μs plus the wakeup time.
◆ If required, it is possible to minimize the latency for specific frames by mapping the frames
to a specific queue (EEE Urgent Queues). When an urgent queue gets data to be
transmitted, the circuits will be powered up at once and the latency will be reduced to the
wakeup time.
PARAMETERS
These parameters are displayed:
◆ Port – Port identifier.
◆ EEE Enabled – Enables or disables EEE for the specified port.
◆ EEE Urgent Queues – Specifies which are to transmit data after the maximum latency
expires regardless queue length.
44
Page 45

WEB INTERFACE
To configure the power reduction for idle queue circuits:
1. Click Configuration, Power Reduction, EEE.
2. Select the circuits which will use EEE.
3. If required, also specify urgent queues which will be powered up once data is queued and
the default wakeup time has passed.
4. Click Save.
4.3. Thermal Protection
Use the Thermal Protection Configuration page to set temperature priority levels, and
assign those priorities for port shut-down if exceeded.
PATH
Configuration / Thermal Protection
Figure 10: Configuring Thermal Protection
COMMAND USAGE
Thermal protection is used to protect the switch ASIC from overheating. When the internal
temperature of the switch exceeds a specified protection level, ports can be turned off to
45
Page 46

decrease power consumption. Port shut down can be prioritized based on assigned
temperatures.
PARAMETERS
These parameters are displayed:
Temperature settings for priority groups
◆ Priority – A priority assigned to a specific temperature. (Range: 0-3)
◆ Temperature – The temperature at which the ports with the corresponding priority will be
turned off. (Range: 0-255° C)
Port priorities
◆ Port – Port identifier.
◆ Priority – The priority level at which to shut down a port. (Range: 0-3)
WEB INTERFACE
To configure the thermal protection:
1. Click Configuration, Thermal Protection.
2. Select the circuits which will use EEE.
3. Set the temperature threshold for each priority, and then assign a priority level to each of
the ports.
4. Click Save.
4.4. Ports
Use the Port Configuration page to configure the connection parameters for each port. This
page includes options for enabling auto-negotiation or manually setting the speed and
duplex mode, enabling flow control, setting the maximum frame size, specifying the
response to excessive collisions, or enabling power saving mode.
PATH
Configuration \ Ports
46
Page 47

Figure 11: Port Configuration
PARAMETERS
These parameters are displayed:
◆ Link – Indicates if the link is up or down.
◆ Speed – Sets the port speed and duplex mode using auto-negotiation or manual selection.
The following options are supported:
■ Disabled - Disables the interface. You can disable an interface due to abnormal
behavior (e.g., excessive collisions), and then re-enable it after the problem has been
resolved. You may also disable an interface for security reasons.
■ Auto - Enables auto-negotiation. When using auto-negotiation, the optimal settings will
be negotiated between the link partners based on their advertised capabilities.
■ 1Gbps FDX - Supports 1 Gbps full-duplex operation
■ 100Mbps FDX - Supports 100 Mbps full-duplex operation
■ 100Mbps HDX - Supports 100 Mbps half-duplex operation
■ 10Mbps FDX - Supports 10 Mbps full-duplex operation
■ 10Mbps HDX - Supports 10 Mbps half-duplex operation
(Default: Autonegotiation enabled; Advertised capabilities for RJ-45: 1000BASE-T -
10half, 10full, 100half, 100full, 1000full; SFP: 1000BASE-SX/LX/LH - 1000full)
Note: The 1000BASE-T standard does not support forced mode. Auto- negotiation should
always be used to establish a connection over any 1000BASE-T port or trunk. If not used,
the success of the link process cannot be guaranteed when connecting to other types of
switches.
47
Page 48

◆ Flow Control – Flow control can eliminate frame loss by “blocking” traffic from end
stations or segments connected directly to the switch when its buffers fill. When enabled,
back pressure is used for half- duplex operation and IEEE 802.3-2005 (formally IEEE
802.3x) for full- duplex operation. (Default: Disabled)
When auto-negotiation is used, this parameter indicates the flow control capability
advertised to the link partner. When the speed and duplex mode are manually set, the
Current Rx field indicates whether pause frames are obeyed by this port, and the Current
Tx field indicates if pause frames are transmitted from this port.
Avoid using flow control on a port connected to a hub unless it is actually required to solve
a problem. Otherwise back pressure jamming signals may degrade overall performance
for the segment attached to the hub.
◆ Maximum Frame Size – Sets the maximum transfer unit for traffic crossing the switch.
Packets exceeding the maximum frame size are dropped. (Range: 9600-1518 bytes;
Default: 9600 bytes)
◆ Excessive Collision Mode – Sets the response to take when excessive transmit
collisions are detected on a port.
■ Discard - Discards a frame after 16 collisions (default).
■ Restart - Restarts the backoff algorithm after 16 collisions.
◆ Power Control – Adjusts the power provided to ports based on the length of the cable
used to connect to other devices. Only sufficient power is used to maintain connection
requirements.
EEE 802.3 defines the Ethernet standard and subsequent power requirements based on
cable connections operating at 100 meters. Enabling power saving mode can significantly
reduce power used for cable lengths of 20 meters or less, and continue to ensure signal
integrity.
The following options are supported:
■ Disabled – All power savings mechanisms disabled (default).
■ Enabled – Both link up and link down power savings enabled.
■ ActiPHY – Link down power savings enabled
■ PerfectReach – Link up power savings enabled.
WEB INTERFACE
To configure port connection settings:
1. Click Configuration, Ports.
2. Make any required changes to the connection settings.
3. Click Save.
48
Page 49

4.5. Security
You can configure this switch to authenticate users logging into the system for management
access or to control client access to the data ports.
Management Access Security (Switch menu) – Management access to the switch can be
controlled through local authentication of user names and passwords stored on the switch, or
remote authentication of users via a RADIUS or TACACS+ server. Additional authentication
methods includes Secure Shell (SSH), Secure Hypertext Transfer Protocol (HTTPS) over the
Secure Socket Layer (SSL), static configuration of client addresses, and SNMP.
General Security Measures (Network menu) – This switch supports many methods of
segregating traffic for clients attached to each of the data ports, and for ensuring that only
authorized clients gain access to the network. Private VLANs and port-based authentication
using IEEE 802.1X are commonly used for these purposes. In addition to these methods,
several other options of providing client security are supported by this switch. These include
limiting the number of users accessing a port. The addresses assigned to DHCP clients can
also be carefully controlled using static or dynamic bindings with DHCP Snooping and IP
Source Guard commands.
ARP Inspection can also be used to validate the MAC address bindings for ARP packets,
providing protection against ARP traffic with invalid MAC to IP address bindings, which forms
the basis for “man-in-the- middle” attacks.
Switch Security
Users Configuration
Use the User Configuration page to control management access to the switch based on
manually configured user names and passwords.
PATH
Configuration \ Security \ Switch \ Users
Figure 12: Configuring User Accounts
49
Page 50

COMMAND USAGE
◆ The default administrator name is “admin” without the password.
◆ The guest only has read access for most configuration parameters. However, the
administrator has write access for all parameters governing the onboard agent. You
should therefore assign a new administrator password as soon as possible, and store it in
a safe place.
◆ The administrator has a privilege level of 15, with access to all process groups and full
control over the device. If the privilege level is set to any other value, the system will refer
to each group privilege level. The user's privilege should be same or greater than the
group privilege level to have the access of a group. By default, most of the group privilege
levels are set to 5 which provides read-only access and privilege level 10 which also
provides read/write access. To perform system maintenance (software upload, factory
defaults, etc.) the user’s privilege level should be set to 15. Generally, the privilege level
15 can be used for an administrator account, privilege level 10 for a standard user
account, and privilege level 5 for a guest account.
PARAMETERS
These parameters are displayed:
◆ User Name – The name of the user. (Maximum length: 8 characters; maximum number
of users: 16)
◆ Password – Specifies the user password. (Range: 0-8 characters plain text, case
sensitive)
◆ Password (again) – Re-type the string entered in the previous field to ensure no errors
were made. The switch will not change the password if these two fields do not match.
◆ Privilege Level – Specifies the user level. (Options: 1 - 15)
Access to specific functions are controlled through the Privilege Levels configuration page.
The default settings provide four access levels:
■ 1 – Read access of port status and statistics.
■ 5 – Read access of all system functions except for maintenance and debugging
■ 10 – read and write access of all system functions except for maintenance and
debugging
■ 15 – read and write access of all system functions including maintenance and debugging.
WEB INTERFACE
To configure a user account:
1. Click Configuration, System, Switch, Users.
50
Page 51

2. Click “Add new user.”
3. Enter the user name, password, and privilege level.
4. Click Save.
Privilege Levels Configuration
Use the Privilege Levels page to set the privilege level required to read or configure specific
software modules or system settings.
PATH
Configuration \ Security \ Switch \ Privilege Levels
Figure 13: Configuring Privilege Levels
PARAMETERS
These parameters are displayed:
◆ Group Name – The name identifying a privilege group. In most cases, a privilege group
51
Page 52

consists of a single module (e.g., LACP, RSTP or QoS), but a few groups contains more
than one module. The following describes the groups which contain multiple modules or
access to various system settings:
■ System: Contact, Name, Location, Timezone, Log
■ Security: Authentication, System Access Management, Port (contains Dot1x port, MAC
based and the MAC Address Limit), ACL, HTTPS, SSH, ARP Inspection, and IP source
guard.
■ IP: Everything except for ping.
■ Port: Everything except for VeriPHY.
■ Diagnostics: ping and VeriPHY.
■ Maintenance: CLI - System Reboot, System Restore Default, System Password,
Configuration Save, Configuration Load and Firmware Load. Web - Users, Privilege
Levels and everything in Maintenance.
■ Debug: Only present in CLI.
◆ Privilege levels – Every privilege level group can be configured to access the following
modules or system settings: Configuration Read- only, Configuration/Execute Read-write,
Status/Statistics Read-only, and Status/Statistics Read-write (e.g., clearing statistics).
The default settings provide four access levels:
■ 1 – Read access of port status and statistics.
■ 5 – Read access of all system functions except for maintenance and debugging
■ 10 – read and write access of all system functions except for maintenance and
debugging
■ 15 – read and write access of all system functions including maintenance and
debugging.
WEB INTERFACE
To configure privilege levels:
1. Click Configuration, Security, Switch, Privilege Levels.
2. Set the required privilege level for any software module or functional group.
3. Click Save.
Authentication Method Configuration
Use the Authentication Method Configuration page to specify the authentication method for
controlling management access through the console, Telnet, SSH or HTTP/HTTPS. Access
can be based on the (local) user name and password configured on the switch, or can be
52
Page 53

controlled with a RADIUS or TACACS+ remote access authentication server. Note that the
RADIUS servers used to authenticate client access for IEEE 802.1X port authentication are
also configured on this page.
Remote Authentication Dial-in User Service (RADIUS) and Terminal Access Controller
Access Control System Plus (TACACS+) are logon authentication protocols that use
software running on a central server to control access to RADIUS-aware or TACACS-aware
devices on the network. An authentication server contains a database of multiple user
name/password pairs with associated privilege levels for each user that requires
management access to the switch.
Figure 14: Authentication Server Operation
PATH
Configuration \ Security \ Switch \ Auth Method
Figure 15: Authentication Method for Management Access
USAGE GUIDELINES
53
Page 54

◆ The switch supports the following authentication services:
■ Authorization of users that access the Telnet, SSH, the web, or console management
interfaces on the switch.
■ Accounting for users that access the Telnet, SSH, the web, or console management
interfaces on the switch.
■ Accounting for IEEE 802.1X authenticated users that access the network through the
switch. This accounting can be used to provide reports, auditing, and billing for services
that users have accessed.
◆ By default, management access is always checked against the authentication database
stored on the local switch. If a remote authentication server is used, you must specify the
authentication method and the corresponding parameters for the remote authentication
protocol on the Network Access Server Configuration page. Local and remote logon
authentication can be used to control management access via Telnet, SSH, a web
browser, or the console interface.
◆ When using RADIUS or TACACS+ logon authentication, the user name and password
must be configured on the authentication server. The encryption methods used for the
authentication process must also be configured or negotiated between the authentication
server and logon client. This switch can pass authentication messages between the
server and client that have been encrypted using MD5 (Message-Digest 5), TLS
(Transport Layer Security), or TTLS (Tunneled Transport Layer Security).
Note: This guide assumes that RADIUS and TACACS+ servers have already been
configured to support AAA. The configuration of RADIUS and TACACS+ server software
is beyond the scope of this guide. Refer to the documentation provided with the RADIUS
and TACACS+ server software.
PARAMETERS
These parameters are displayed:
◆ Client – Specifies how the administrator is authenticated when logging into the switch via
Telnet, SSH, a web browser, or the console interface.
◆ Authentication Method – Selects the authentication method.
(Options: None, Local, RADIUS, TACACS+; Default: Local)
Selecting the option “None” disables access through the specified management interface.
◆ Fallback – Uses the local user database for authentication if none of the configured
authentication servers are alive. This is only possible if the Authentication Method is set to
something else than “none” or “local.”
WEB INTERFACE
To configure authentication for management access:
54
Page 55

1. Click Configuration, Security, Switch, Auth Method.
2. Configure the authentication method for management client types, and specify whether or
not to fallback to local authentication if no remote authentication server is available.
3. Click Save.
SSH Configuration
Use the SSH Configuration page to configure access to the Secure Shell (SSH) management
interface. SSH provides remote management access to this switch as a secure replacement
for Telnet. When the client contacts the switch via the SSH protocol, the switch generates a
public-key that the client uses along with a local user name and password for access
authentication. SSH also encrypts all data transfers passing between the switch and SSHenabled management station clients, and ensures that data traveling over the network arrives
unaltered.
PATH
Configuration \ Security \ Switch \ SSH
Figure 16: SSH Configuration
USAGE GUIDELINES
◆ You need to install an SSH client on the management station to access the switch for
management via the SSH protocol. The switch supports both SSH Version 1.5 and 2.0
clients.
55
Page 56

◆ SSH service on this switch only supports password authentication. The password can be
authenticated either locally or via a RADIUS or TACACS+ remote authentication server,
as specified on the Auth Method menu (page 52).
To use SSH with password authentication, the host public key must still be given to the
client, either during initial connection or manually entered into the known host file.
However, you do not need to configure the client's keys.
◆ The SSH service on the switch supports up to four client sessions. The maximum number
of client sessions includes both current Telnet sessions and SSH sessions.
PARAMETERS
These parameters are displayed:
◆ Mode - Allows you to enable/disable SSH service on the switch.
(Default: Enabled)
WEB INTERFACE
To configure SSH:
1. Click Configuration, Security, Switch, SSH.
2. Enable SSH if required.
3. Click Save.
HTTPS Configuration
Use the HTTPS Configuration page to enable the Secure Hypertext Transfer Protocol
(HTTPS) over the Secure Socket Layer (SSL). HTTPS provides secure access (i.e., an
encrypted connection) to the switch's web interface.
PATH
Configuration \ Security \ Switch \ HTTPS
Figure 17: HTTPS Configuration
56
Page 57

Web Browser
Operating System
Internet Explorer 5.0 or
later
Windows 98,Windows NT (with service pack 6a)
Windows 2000, Windows XP, Windows Vista,
Windows 7
Netscape 6.2 or later
Windows 98,Windows NT (with service pack 6a),
Windows 2000, Windows XP, Windows Vista, Solaris
2.6
Mozilla Firefox 2.0.0.0 or
later
Windows 2000, Windows XP, Windows Vista,
Linux
USAGE GUIDELINES
◆ If you enable HTTPS, you must indicate this in the URL that you specify in your browser:
https://device[:port-number]
◆ When you start HTTPS, the connection is established in this way:
■ The client authenticates the server using the server's digital certificate.
■ The client and server negotiate a set of security protocols to use for the connection.
■ The client and server generate session keys for encrypting and decrypting data.
■ The client and server establish a secure encrypted connection.
A padlock icon should appear in the status bar for Internet Explorer 5.x or above,
Netscape 6.2 or above, and Mozilla Firefox 2.0.0.0 or above.
◆ The following web browsers and operating systems currently support HTTPS:
Table 6: HTTPS System Support
57
Page 58

PARAMETERS
These parameters are displayed:
◆ Mode - Enables HTTPS service on the switch. (Default: Enabled)
◆ Automatic Redirect - Sets the HTTPS redirect mode operation. When enabled,
management access to the HTTP web interface for the switch are automatically
redirected to HTTPS. (Default: Disabled)
WEB INTERFACE
To configure HTTPS:
1. Click Configuration, HTTPS.
2. Enable HTTPS if required and set the Automatic Redirect mode.
3. Click Save.
Access Management Configuration
Use the Access Management Configuration page to create a list of up to 16 IP addresses or
IP address groups that are allowed management access to the switch through the web
interface, or SNMP, or Telnet.
The management interfaces are open to all IP addresses by default. Once you add an entry
to a filter list, access to that interface is restricted to the specified addresses. If anyone tries
to access a management interface on the switch from an invalid address, the switch will
reject the connection.
PATH
Configuration \ Security \ Switch \ Access Management
Figure 18: Access Management Configuration
58
Page 59

PARAMETERS
These parameters are displayed:
◆ Mode – Enables or disables filtering of management access based on configured IP
addresses. (Default: Disabled)
◆ Start IP Address – The starting address of a range.
◆ End IP Address – The ending address of a range.
◆ HTTP/HTTPS – Filters IP addresses for access to the web interface over standard HTTP,
or over HTTPS which uses the Secure Socket Layer (SSL) protocol to provide an
encrypted connection.
◆ SNMP – Filters IP addresses for access through SNMP.
◆ TELNET / SSH – Filters IP addresses for access through Telnet, or through Secure Shell
which provides authentication and encryption.
WEB INTERFACE
To configure addresses allowed access to management interfaces on the switch:
1. Click Configuration, Security, Switch, Access Management.
2. Set the Mode to Enabled.
3. Click “Add new entry.”
4. Enter the start and end of an address range.
59
Page 60

Model
Level
Community
String
Group
Read
View
Write
View
Security
v1
noAuth
NoPriv
public
default_
ro_group
default_vi
ew
none
Community string
only
5. Mark the protocols to restrict based on the specified address range.
6. Click Save.
SNMP Configuration
Simple Network Management Protocol (SNMP) is a communication protocol designed
specifically for managing devices on a network. Equipment commonly managed with SNMP
includes switches, routers and host computers. SNMP is typically used to configure these
devices for proper operation in a network environment, as well as to monitor them to evaluate
performance or detect potential problems.
Managed devices supporting SNMP contain software, which runs locally on the device and is
referred to as an agent. A defined set of variables, known as managed objects, is maintained
by the SNMP agent and used to manage the device. These objects are defined in a
Management Information Base (MIB) that provides a standard presentation of the information
controlled by the agent. SNMP defines both the format of the MIB specifications and the
protocol used to access this information over the network.
The switch includes an onboard agent that supports SNMP versions 1, 2c, and 3. This agent
continuously monitors the status of the switch hardware, as well as the traffic passing through
its ports. A network management station can access this information using software such as
HP OpenView. Access to the onboard agent from clients using SNMP v1 and v2c is
controlled by community strings. To communicate with the switch, the management station
must first submit a valid community string for authentication.
Access to the switch using from clients using SNMPv3 provides additional security features
that cover message integrity, authentication, and encryption; as well as controlling user
access to specific areas of the MIB tree.
The SNMPv3 security structure consists of security models, with each model having it's own
security levels. There are three security models defined, SNMPv1, SNMPv2c, and SNMPv3.
Users are assigned to “groups” that are defined by a security model and specified security
levels. Each group also has a defined security access to set of MIB objects for reading and
writing, which are known as “views.” The switch has a default view (all MIB objects) and
default groups defined for security models v1 and v2c. The following table shows the security
models and levels available and the system default settings.
Table 7: SNMP Security Models and Levels
60
Page 61

v1
noAuth
NoPriv
private
default_
rw_group
default_
view
default_
view
Community string
only
v1
noAuth
NoPriv
user
defined
user
defined
user
defined
user
defined
Community string
only
v2c
noAuth
NoPriv
public
default_r
o_group
default_
view
none
Community string
only
v2c
noAuth
NoPriv
private
default_rw
_group
default_
view
default
_view
Community string
only
v2c
noAuth
NoPriv
user
defined
user
defined
user
defined
user
defined
Community string
only
v3
noAuth
NoPriv
user
defined
default_r
w_group
default
_view
default_vi
ew
A user name
match only
v3
Auth
NoPriv
user
defined
user
defined
user
defined
user
defined
Provides user
authentication via
MD5 or SHA
algorithms
v3
Auth Priv
user
defined
user
defined
user
defined
user
defined
Provides user
authentication via MD5
or SHA algorithms
and data privacy using
DES 56-bit encryption
Note: The predefined default groups and view can be deleted from the system. You can then
define customized groups and views for the SNMP clients that require access.
Configuring SNMP System and Trap Settings
Use the SNMP System Configuration page to configure basic settings and traps for SNMP.
To manage the switch through SNMP, you must first enable the protocol and configure the
basic access parameters. To issue trap messages, the trap function must also be enabled
and the destination host specified.
PATH
Configuration \ Security \ Switch \ SNMP \ System
Figure 19: SNMP System Configuration
61
Page 62

PARAMETERS
These parameters are displayed:
SNMP System Configuration
◆ Mode – Enables or disables SNMP service. (Default: Disabled)
◆ Version – Specifies the SNMP version to use. (Options: SNMP v1, SNMP v2c, SNMP v3;
Default: SNMP v2c)
◆ Read Community – The community used for read-only access to the SNMP agent.
(Range: 0-255 characters, ASCII characters 33-126 only; Default: public) This parameter
only applies to SNMPv1 and SNMPv2c. SNMPv3 uses the User-based Security Model
(USM) for authentication and privacy. This community string is associated with SNMPv1
or SNMPv2 clients in the SNMPv3 Communities table (page 60).
◆ Write Community – The community used for read/write access to the SNMP agent.
(Range: 0-255 characters, ASCII characters 33-126 only; Default: private) This parameter
only applies to SNMPv1 and SNMPv2c. SNMPv3 uses the User-based Security Model
(USM) for authentication and privacy. This community string is associated with SNMPv1
or SNMPv2 clients in the SNMPv3 Communities table (page 60).
◆ Engine ID – The SNMPv3 engine ID. (Range: 10-64 hex digits, excluding a string of all 0’s
or all F’s; Default: 800007e5017f000001) An SNMPv3 engine is an independent SNMP
agent that resides on the switch. This engine protects against message replay, delay, and
redirection. The engine ID is also used in combination with user passwords to generate
the security keys for authenticating and encrypting SNMPv3 packets. A local engine ID is
automatically generated that is unique to the switch. This is referred to as the default
engine ID. If the local engine ID is deleted or changed, all local SNMP users will be
62
Page 63

cleared. You will need to reconfigure all existing users.
SNMP Trap Configuration
◆ Trap Mode - Enables or disables SNMP traps. (Default: Disabled) You should enable
SNMP traps so that key events are reported by this switch to your management station.
Traps indicating status changes can be issued by the switch to the specified trap manager
by sending authentication failure messages and other trap messages.
◆ Trap Version - Indicates if the target user is running SNMP v1, v2c, or v3. (Default: SNMP
v1)
◆ Trap Community - Specifies the community access string to use when sending SNMP
trap packets. (Range: 0-255 characters, ASCII characters 33-126 only; Default: public)
◆ Trap Destination Address - IPv4 address of the management station to receive
notification messages.
◆ Trap Destination IPv6 Address - IPv6 address of the management station to receive
notification messages. An IPv6 address must be formatted according to RFC 2373 “IPv6
Addressing Architecture,” using 8 colon-separated 16-bit hexadecimal values. One double
colon may be used to indicate the appropriate number of zeros required to fill the
undefined fields.
◆ Trap Authentication Failure - Issues a notification message to specified IP trap
managers whenever authentication of an SNMP request fails. (Default: Enabled)
◆ Trap Link-up and Link-down - Issues a notification message whenever a port link is
established or broken. (Default: Enabled)
◆ Trap Inform Mode - Enables or disables sending notifications as inform messages. Note
that this option is only available for version 2c and 3 hosts. (Default: traps are used)
The recipient of a trap message does not send a response to the switch. Traps are
therefore not as reliable as inform messages, which include a request for
acknowledgement of receipt. Informs can be used to ensure that critical information is
received by the host. However, note that informs consume more system resources
because they must be kept in memory until a response is received. Informs also add to
network traffic. You should consider these effects when deciding whether to issue
notifications as traps or informs.
◆ Trap Inform Timeout - The number of seconds to wait for an acknowledgment before
resending an inform message. (Range: 0-2147 seconds; Default: 1 second)
◆ Trap Inform Retry Times - The maximum number of times to resend an inform message
if the recipient does not acknowledge receipt. (Range: 0-255; Default: 5)
◆ Trap Probe Security Engine ID (SNMPv3) - Specifies whether or not to use the engine
ID of the SNMP trap probe in trap and inform messages. (Default: Enabled)
◆ Trap Security Engine ID (SNMPv3) - Indicates the SNMP trap security engine ID.
SNMPv3 sends traps and informs using USM for authentication and privacy. A unique
engine ID for these traps and informs is needed. When “Trap Probe Security Engine ID” is
63
Page 64

enabled, the ID will be probed automatically. Otherwise, the ID specified in this field is
used. (Range: 10-64 hex digits, excluding a string of all 0’s or all F’s)
Note: The Trap Probe Security Engine ID must be disabled before an engine ID can be
manually entered in this field.
◆ Trap Security Name (SNMPv3) - Indicates the SNMP trap security name. SNMPv3 traps
and informs use USM for authentication and privacy. A unique security name is needed
when SNMPv3 traps or informs are enabled.
Note: To select a name from this field, first enter an SNMPv3 user with the same Trap
Security Engine ID in the SNMPv3 Users Configuration menu (see "Configuring SNMPv3
Users" on page 65).
WEB INTERFACE
To configure SNMP system and trap settings:
1. Click Configuration, Security, Switch, SNMP, System.
2. In the SNMP System Configuration table, set the Mode to Enabled to enable SNMP
service on the switch, specify the SNMP version to use, change the community access
strings if required, and set the engine ID if SNMP version 3 is used.
3. In the SNMP Trap Configuration table, enable the Trap Mode to allow the switch to send
SNMP traps. Specify the trap version, trap community, and IP address of the
management station that will receive trap messages either as an IPv4 or IPv6 address.
Select the trap types to issue, and set the trap inform settings for SNMP v2c or v3 clients.
For SNMP v3 clients, configure the security engine ID and security name used in v3 trap
and inform messages.
4. Click Save.
64
Page 65

Setting SNMPV3 Community Access Strings
Use the SNMPv3 Community Configuration page to set community access strings. All
community strings used to authorize access by SNMP v1 and v2c clients should be listed in
the SNMPv3 Communities Configuration table. For security reasons, you should consider
removing the default strings.
PATH
Configuration \ Security \ Switch \ SNMP \ Communities
Figure 20: SNMPv3 Community Configuration
PARAMETERS
These parameters are displayed:
◆ Community – Specifies the community strings which allow access to the SNMP agent.
(Range: 1-32 characters, ASCII characters 33-126 only; Default: public, private) For
SNMPv3, these strings are treated as a Security Name, and are mapped as an SNMPv1
or SNMPv2 community string in the SNMPv3 Groups Configuration table.
◆ Source IP – Specifies the source address of an SNMP client.
◆ Source Mask – Specifies the address mask for the SNMP client.
WEB INTERFACE
To configure SNMP community access strings:
1. Click Configuration, Security, Switch, SNMP, Communities.
2. Set the IP address and mask for the default community strings. Otherwise, you should
consider deleting these strings for security reasons.
3. Add any new community strings required for SNMPv1 or v2 clients that need to access the
65
Page 66

switch, along with the source address and address mask for each client.
4. Click Save.
Configuring SNMPV3 Users
Use the SNMPv3 User Configuration page to define a unique name and remote engine ID for
each SNMPv3 user. Users must be configured with a specific security level, and the types of
authentication and privacy protocols to use.
Note: Any user assigned through this page is associated with the group assigned to the USM
Security Model on the SNMPv3 Groups Configuration page, and the views assigned to that
group in the SNMPv3 Access Configuration page.
PATH
Configuration \ Security \ Switch \ SNMP \ Users
Figure 21: SNMPv3 User Configuration
PARAMETERS
These parameters are displayed:
◆ Engine ID - The engine identifier for the SNMP agent on the remote device where the
user resides. (Range: 10-64 hex digits, excluding a string of all 0’s or all F’s)
To send inform messages to an SNMPv3 user on a remote device, you must first specify
the engine identifier for the SNMP agent on the remote device where the user resides.
The remote engine ID is used to compute the security digest for authenticating and
encrypting packets sent to a user on the remote host.
SNMP passwords are localized using the engine ID of the authoritative agent. For informs,
the authoritative SNMP agent is the remote agent. You therefore need to configure the
66
Page 67

remote agent's SNMP engine ID before you can send proxy requests or informs to it. (See
"Configuring SNMP System and Trap Settings" on page 60.)
◆ User Name - The name of user connecting to the SNMP agent. (Range: 1-32 characters,
ASCII characters 33-126 only)
◆ Security Level - The security level assigned to the user:
■ NoAuth, NoPriv - There is no authentication or encryption used in SNMP
communications. (This is the default for SNMPv3.)
■ Auth, NoPriv - SNMP communications use authentication, but the data is not encrypted.
■ Auth, Priv - SNMP communications use both authentication and encryption.
◆ Authentication Protocol - The method used for user authentication. (Options: None,
MD5, SHA; Default: MD5)
◆ Authentication Password - A plain text string identifying the authentication pass phrase.
(Range: 1-32 characters for MD5, 8-40 characters for SHA)
◆ Privacy Protocol - The encryption algorithm use for data privacy; only 56-bit DES is
currently available. (Options: None, DES; Default: DES)
◆ Privacy Password - A string identifying the privacy pass phrase. (Range: 8-40 characters,
ASCII characters 33-126 only)
WEB INTERFACE
To configure SNMPv3 users:
1. Click Configuration, Security, Switch, SNMP, Users.
2. Click “Add new user” to configure a user name.
3. Enter a remote Engine ID of up to 64 hexadecimal characters
4. Define the user name, security level, authentication and privacy settings.
5. Click Save.
Configuring SNMPV3 Groups
Use the SNMPv3 Group Configuration page to configure SNMPv3 groups. An SNMPv3
group defines the access policy for assigned users, restricting them to specific read and write
views as defined on the SNMPv3 Access Configuration page. You can use the pre-defined
default groups, or create a new group and the views authorized for that group.
PATH
Configuration \ Security \ Switch \ SNMP \ Groups
67
Page 68

Figure 22: SNMPv3 Group Configuration
PARAMETERS
These parameters are displayed:
◆ Security Model - The user security model. (Options: SNMP v1, v2c, or the User-based
Security Model – usm).
◆ Security Name - The name of a user connecting to the SNMP agent. (Range: 1-32
characters, ASCII characters 33-126 only)
The options displayed for this parameter depend on the selected Security Model. For
SNMP v1 and v2c, the switch displays the names configured on the SNMPv3
Communities Configuration menu. For USM (or SNMPv3), the switch displays the names
configured with the local engine ID in the SNMPv3 Users Configuration menu. To modify
an entry for USM, the current entry must first be deleted.
◆ Group Name - The name of the SNMP group. (Range: 1-32 characters, ASCII characters
33-126 only)
WEB INTERFACE
To configure SNMPv3 groups:
1. Click Configuration, Security, Switch, SNMP, Groups.
2. Click “Add new group” to set up a new group.
3. Select a security model.
4. Select the security name. For SNMP v1 and v2c, the security names displayed are based
on the those configured in the SNMPv3 Communities menu. For USM, the security names
displayed are based on the those configured in the SNMPv3 Users Configuration menu.
68
Page 69

5. Enter a group name. Note that the views assigned to a group must be specified on the
SNMP Accesses Configuration menu.
6. Click Save.
Configuring SNMPV3 Views
Use the SNMPv3 View Configuration page to define views which restrict user access to
specified portions of the MIB tree. The predefined view “default_view” includes access to the
entire MIB tree.
PATH
Configuration \ Security \ Switch \ SNMP \ Views
Figure 23: SNMPv3 View Configuration
PARAMETERS
These parameters are displayed:
◆ View Name – The name of the SNMP view. (Range: 1-32 characters, ASCII characters
33-126 only)
◆ View Type – Indicates if the object identifier of a branch within the MIB tree is included or
excluded from the SNMP view. Generally, if the view type of an entry is “excluded,”
another entry of view type “included” should exist and its OID subtree should overlap the
“excluded” view entry.
◆ OID Subtree – Object identifiers of branches within the MIB tree. Note that the first
character must be a period (.). Wild cards can be used to mask a specific portion of the
69
Page 70

OID string using an asterisk. (Length: 1-128)
WEB INTERFACE
To configure SNMPv3 views:
1. Click Configuration, Security, Switch, SNMP, Views.
2. Click “Add new view” to set up a new view.
3. Enter the view name, view type, and OID subtree.
4. Click Save.
Configuring SNMPV3 Group Access Rights
Use the SNMPv3 Access Configuration page to assign portions of the MIB tree to which each
SNMPv3 group is granted access. You can assign more than one view to a group to specify
access to different portions of the MIB tree.
PATH
Configuration \ Security \ Switch \ SNMP \ Access
Figure 24: SNMPv3 Access Configuration
70
Page 71

PARAMETERS
These parameters are displayed:
◆ Group Name – The name of the SNMP group. (Range: 1-32 characters, ASCII characters
33-126 only)
◆ Security Model – The user security model. (Options: any, v1, v2c, or the User-based
Security Model – usm; Default: any)
◆ Security Level – The security level assigned to the group:
■ NoAuth, NoPriv – There is no authentication or encryption used in SNMP
communications. (This is the default for SNMPv3.)
■ Auth, NoPriv – SNMP communications use authentication, but the data is not
encrypted.
■ Auth, Priv – SNMP communications use both authentication and encryption.
◆ Read View Name – The configured view for read access. (Range: 1-32 characters, ASCII
characters 33-126 only)
◆ Write View Name – The configured view for write access. (Range: 1-32 characters, ASCII
characters 33-126 only)
WEB INTERFACE
To configure SNMPv3 group access rights:
1. Click Configuration, Security, Switch, SNMP, Access.
2. Click Add New Access to create a new entry.
3. Specify the group name, security settings, read view, and write view.
4. Click Save.
71
Page 72

RMON Configuration
RMON Statistics
Use the RMON Statistics Configuration page for configurations.
PATH
Configuration \ Security \ Switch \ RMON \ Statistics
Figure 25: RMON Statistics Configuration
PARAMETERS
These parameters are displayed:
◆ Delete – Check to delete the entry after the next save.
◆ ID – Indicates the index of the entry. The range is from 1 to 65,535.
◆ Data Source – Indicates the port ID which wants to be monitored. If in stacking switch, the
value must add 1000*(switch ID-1), for example, if the port is switch 3 port 5, the value is
2005.
WEB INTERFACE
To configure RMON Statistics table:
1. Click Configuration, Security, Switch, RMON, Statistics.
2. Click Add New Entry to create a new entry. The entry index key is ID.
3. Specify the ID, Data Source settings.
4. Click Save.
72
Page 73

RMON History
Use the RMON History Configuration page for configurations.
PATH
Configuration \ Security \ Switch \ RMON \ History
Figure 26: RMON History Configuration
PARAMETERS
These parameters are displayed:
◆ Delete – Check to delete the entry after the next save.
◆ ID – Indicates the index of the entry. The range is from 1 to 65,535.
◆ Data Source – Indicates the port ID which wants to be monitored. If in stacking switch, the
value must add 1000*(switch ID-1), for example, if the port is switch 3 port 5, the value is
2005.
◆ Interval – Indicates the interval in seconds for sampling the history statistics data. The
range is from 1 to 3600, default value is 1800 seconds.
◆ Buckets – Indicates the maximum data entries associated this History control entry stored
in RMON. The range is from 1 to 3600, default value is 50.
◆ Buckets Granted – The number of data shall be saved in the RMON.
WEB INTERFACE
To configure RMON History table:
1. Click Configuration, Security, Switch, RMON, History.
2. Click Add New Entry to create a new entry. The entry index key is ID.
3. Specify the ID, Data Source, interval settings.
4. Click Save.
73
Page 74

RMON Alarm
Use the RMON Alarm page for configurations.
PATH
Configuration \ Security \ Switch \ RMON \ Alarm
Figure 27: RMON Alarm Configuration
PARAMETERS
These parameters are displayed:
◆ Delete – Check to delete the entry after the next save.
◆ ID – Indicates the index of the entry. The range is from 1 to 65,535.
◆ Interval – Indicates the interval in seconds for sampling and comparing the rising and
falling threshold. The range is from 1 to 2^31-1.
◆ Variable – Indicates the particular variable to be sampled, the possible variables are:
■ InOctets: The total number of octets received on the interface, including framing
characters.
■ InUcastPkts: The number of uni-cast packets delivered to a higher-layer protocol.
■ InNUcastPkts: The number of broad-cast and multi-cast packets delivered to a
higher-layer protocol.
■ InDiscards: The number of inbound packets that are discarded even the packets are
normal.
■ InErrors: The number of inbound packets that contained errors preventing them from
being deliverable to a higher-layer protocol.
■ InUnknownProtos: the number of the inbound packets that were discarded because
of the unknown or un-support protocol.
■ OutOctets: The number of octets transmitted out of the interface , including framing
characters.
74
Page 75

■ OutUcastPkts: The number of uni-cast packets that request to transmit.
■ OutNUcastPkts: The number of broad-cast and multi-cast packets that request to
transmit.
■ OutDiscards: The number of outbound packets that are discarded event the packets
is normal.
■ OutErrors: The number of outbound packets that could not be transmitted because of
errors.
■ OutQLen: The length of the output packet queue (in packets).
◆ Sample Type – The method of sampling the selected variable and calculating the value to
be compared against the thresholds, possible sample types are:
■ Absolute: Get the sample directly.
■ Delta: Calculate the difference between samples (default).
◆ Value – The value of the statistic during the last sampling period.
◆ Startup Alarm – The method of sampling the selected variable and calculating the value
to be compared against the thresholds, possible sample types are:
■ RisingTrigger alarm when the first value is larger than the rising threshold.
■ FallingTrigger alarm when the first value is less than the falling threshold.
■ RisingOrFallingTrigger alarm when the first value is larger than the rising threshold
or less than the falling threshold (default).
◆ Rising Threshold – Rising threshold value (-2147483648 ~ 2147483647).
◆ Rising Index – Rising event index (1-65535).
◆ Falling Threshold – Falling threshold value (-2147483648 ~ 2147483647).
◆ Falling Index – Falling event index (1-65535).
WEB INTERFACE
To configure RMON Alarm table:
1. Click Configuration, Security, Switch, RMON, Alarm.
2. Click Add New Entry to create a new entry. The entry index key is ID.
3. Specify the ID, Interval, Variable, Sample Type, Value, and other settings.
4. Click Save.
75
Page 76

RMON Event
Use the RMON Event page for configurations.
PATH
Configuration \ Security \ Switch \ RMON \ Event
Figure 28: RMON Event Configuration
PARAMETERS
These parameters are displayed:
◆ Delete – Check to delete the entry after the next save.
◆ ID – Indicates the index of the entry. The range is from 1 to 65,535.
◆ Desc – Indicates this event, the string length is from 0 to 127, default is a null string.
◆ Type – Indicates the notification of the event, the possible types are:
■ none: The total number of octets received on the interface, including framing characters.
■ log: The number of uni-cast packets delivered to a higher-layer protocol.
■ snmptrap: The number of broad-cast and multi-cast packets delivered to a higher-layer
protocol.
■ logandtrap: The number of inbound packets that are discarded even the packets are
normal.
◆ Community – Specify the community when trap is sent, the string length is from 0 to 127,
default is "public".
◆ Event Last Time – Indicates the value of sysUpTime at the time this event entry last
generated an event.
76
Page 77

WEB INTERFACE
To configure RMON Event table:
1. Click Configuration, Security, Switch, RMON, Event.
2. Click Add New Entry to create a new entry. The entry index key is ID.
3. Specify the ID, Data Source, Desc, Type, Community settings.
4. Click Save.
Network Security
Limit Controls
Use the Port Security Limit Control Configuration page to limit the number of users accessing
a given port. A user is identified by a MAC address and VLAN ID. If Limit Control is enabled
on a port, the maximum number of users on the port is restricted to the specified limit. If this
number is exceeded, the switch makes the specified response.
PATH
Configuration \ Security \ Network \ Limit Control
Figure 29: Port Limit Control Configuration
PARAMETERS
The following parameters are displayed on the Port Limit Control
77
Page 78

System Configuration
◆ Mode – Enables or disables Limit Control is globally on the switch. If globally disabled,
other modules may still use the underlying functionality, but limit checks and
corresponding actions are disabled.
◆ Aging Enabled – If enabled, secured MAC addresses are subject to aging as discussed
under Aging Period. With aging enabled, a timer is started once the end-host gets
secured. When the timer expires, the switch starts looking for frames from the end-host,
and if such frames are not seen within the next Aging Period, the end-host is assumed to
be disconnected, and the corresponding resources are freed on the switch.
◆ Aging Period – If Aging Enabled is checked, then the aging period is controlled with this
parameter. If other modules are using the underlying port security for securing MAC
addresses, they may have other requirements for the aging period. The underlying port
security will use the shortest requested aging period of all modules that use this
functionality. (Range: 10-10,000,000 seconds; Default: 3600 seconds)
Port Configuration
◆ Port – Port identifier.
◆ Mode – Controls whether Limit Control is enabled on this port. Both this and the global
Mode must be set to Enabled for Limit Control to be in effect. Notice that other modules
may still use the underlying port security features without enabling Limit Control on a
given port.
◆ Limit – The maximum number of MAC addresses that can be secured on this port. This
number cannot exceed 1024. If the limit is exceeded, the corresponding action is taken.
The switch is “initialized” with a total number of MAC addresses from which all ports draw
whenever a new MAC address is seen on a Port Security-enabled port. Since all ports
draw from the same pool, it may happen that a configured maximum cannot be granted if
the remaining ports have already used all available MAC addresses.
◆ Action – If Limit is reached, the switch can take one of the following actions:
■ None: Do not allow more than the specified Limit of MAC addresses on the port, but
take no further action.
■ Trap: If Limit + 1 MAC addresses is seen on the port, send an SNMP trap. If Aging is
disabled, only one SNMP trap will be sent, but with Aging enabled, new SNMP traps will
be sent every time the limit is exceeded.
■ Shutdown: If Limit + 1 MAC addresses is seen on the port, shut down the port. This
implies that all secured MAC addresses will be removed from the port, and no new
addresses will be learned. Even if the link is physically disconnected and reconnected on
the port (by disconnecting the cable), the port will remain shut down. There are three ways
to re-open the port:
■ Boot the switch,
78
Page 79

■ Disable and re-enable Limit Control on the port or the switch,
■ Click the Reopen button.
■ Trap & Shutdown: If Limit + 1 MAC addresses is seen on the port, both the “Trap” and
the “Shutdown” actions described above will be taken.
◆ State – This column shows the current state of the port as seen from
the Limit Control's point of view. The state takes one of four values:
■ Disabled: Limit Control is either globally disabled or disabled on the port.
■ Ready: The limit is not yet reached. This can be shown for all Actions.
■ Limit Reached: Indicates that the limit is reached on this port. This state can only be
shown if Action is set to None or Trap.
■ Shutdown: Indicates that the port is shut down by the Limit Control module. This state
can only be shown if Action is set to Shutdown or Trap & Shutdown.
◆ Re-open – If a port is shut down by this module, you may reopen it by clicking this button,
which will only be enabled if this is the case. For other methods, refer to Shutdown in the
Action section. Note, that clicking the Reopen button causes the page to be refreshed, so
non-committed changes will be lost.
WEB INTERFACE
To configure port limit controls:
1. Click Configuration, Security, Network, Limit Control.
2. Set the system configuration parameters to globally enable or disable limit controls, and
configure address aging as required.
3. Set limit controls for any port, including status, maximum number of addresses allowed,
and the response to a violation.
4. Click Save.
Network Access Servers (NAS)
Network switches can provide open and easy access to network resources by simply
attaching a client PC. Although this automatic configuration and access is a desirable feature,
it also allows unauthorized personnel to easily intrude and possibly gain access to sensitive
network data.
Use the Network Access Server Configuration page to configure IEEE 802.1X port-based
and MAC-based authentication settings. The 802.1X standard defines a port-based access
control procedure that prevents unauthorized access to a network by requiring users to first
submit credentials for authentication. Access to all switch ports in a network can be centrally
controlled from a server, which means that authorized users can use the same credentials for
79
Page 80

authentication from any point within the network.
80
Page 81

Figure 30: Using Port Security
This switch uses the Extensible Authentication Protocol over LANs (EAPOL) to exchange
authentication protocol messages with the client, and a remote RADIUS authentication server
to verify user identity and access rights. These backend servers are configured on the AAA
menu (see page 109).
When a client (i.e., Supplicant) connects to a switch port, the switch (i.e., Authenticator)
responds with an EAPOL identity request. The client provides its identity (such as a user
name) in an EAPOL response to the switch, which it forwards to the RADIUS server. The
RADIUS server verifies the client identity and sends an access challenge back to the client.
The EAP packet from the RADIUS server contains not only the challenge, but the
authentication method to be used. The client can reject the authentication method and
request another, depending on the configuration of the client software and the RADIUS
server. The encryption method used by IEEE 802.1X to pass authentication messages can
be MD5 (Message-Digest 5), TLS (Transport Layer Security), PEAP (Protected Extensible
Authentication Protocol), or TTLS (Tunneled Transport Layer Security). However, note that
the only encryption method supported by MAC-Based authentication is MD5. The client
responds to the appropriate method with its credentials, such as a password or certificate.
The RADIUS server verifies the client credentials and responds with an accept or reject
packet. If authentication is successful, the switch allows the client to access the network.
Otherwise, network access is denied and the port remains blocked.
The operation of 802.1X on the switch requires the following:
◆ The switch must have an IP address assigned (see page 35).
◆ RADIUS authentication must be enabled on the switch and the IP address of the RADIUS
server specified. Backend RADIUS servers are configured on the Authentication
Configuration page (see page 109).
◆ 802.1X / MAC-based authentication must be enabled globally for the switch.
◆ The Admin State for each switch port that requires client authentication must be set to
802.1X or MAC-based.
◆ When using 802.1X authentication:
81
Page 82

■ Each client that needs to be authenticated must have dot1x client software installed and
properly configured.
■ When using 802.1X authentication, the RADIUS server and 802.1X client must support
EAP. (The switch only supports EAPOL in order to pass the EAP packets from the server
to the client.)
■ The RADIUS server and client also have to support the same EAP authentication type MD5, PEAP, TLS, or TTLS. (Native support for these encryption methods is provided in
Windows 7, Windows Vista, Windows XP, and in Windows 2000 with Service Pack 4. To
support these encryption methods in Windows 95 and 98, you can use the AEGIS dot1x
client or other comparable client software.)
MAC-based authentication allows for authentication of more than one user on the same
port, and does not require the user to have special 802.1X software installed on his
system. The switch uses the client's MAC address to authenticate against the backend
server. However, note that intruders can create counterfeit MAC addresses, which makes
MAC-based authentication less secure than 802.1X authentication.
PATH
Configuration / Security / Network / NAS
Figure 31: Network Access Server Configuration
82
Page 83

USAGE GUIDELINES
When 802.1X is enabled, you need to configure the parameters for the authentication
process that runs between the client and the switch (i.e., authenticator), as well as the client
identity lookup process that runs between the switch and authentication server. These
parameters are described in this section.
PARAMETERS
These parameters are displayed:
System Configuration
◆ Mode - Indicates if 802.1X and MAC-based authentication are globally enabled or
disabled on the switch. If globally disabled, all ports are allowed to forward frames.
◆ Reauthentication Enabled – Sets clients to be re-authenticated after an interval specified
by the Re-authentication Period. Re-authentication can be used to detect if a new device
is plugged into a switch port. (Default: Disabled)
For MAC-based ports, reauthentication is only useful if the RADIUS server configuration
has changed. It does not involve communication between the switch and the client, and
therefore does not imply that a client is still present on a port (see Age Period below).
◆ Reauthentication Period – Sets the time period after which a connected client must be
re-authenticated. (Range: 1-3600 seconds; Default: 3600 seconds)
◆ EAPOL Timeout – Sets the time the switch waits for a supplicant response during an
authentication session before retransmitting a Request Identify EAPOL packet. (Range: 1255 seconds; Default: 30 seconds)
◆ Aging Period – The period used to calculate when to age out a client allowed access to
the switch through Single 802.1X, Multi 802.1X, and MAC-based authentication as
described below. (Range: 10-1000000 seconds; Default: 300 seconds)
When the NAS module uses the Port Security module to secure MAC addresses, the Port
Security module needs to check for activity on the MAC address in question at regular
intervals and free resources if no activity is seen within the given age period.
If reauthentication is enabled and the port is in a 802.1X-based mode, this is not so critical,
since supplicants that are no longer attached to the port will get removed upon the next
reauthentication, which will fail. But if reauthentication is not enabled, the only way to free
resources is by aging the entries.
For ports in MAC-based Auth. mode, reauthentication does not cause direct
communication between the switch and the client, so this will not detect whether the client
is still attached or not, and the only way to free any resources is to age the entry.
◆ Hold Time – The time after an EAP Failure indication or RADIUS timeout that a client is
not allowed access. This setting applies to ports running Single 802.1X, Multi 802.1X, or
83
Page 84

MAC-based authentication. (Range: 10-1000000 seconds; Default: 10 seconds)
If the RADIUS server denies a client access, or a RADIUS server request times out
(according to the timeout specified on the AAA menu on page 109), the client is put on
hold in the Unauthorized state. In this state, the hold timer does not count down during an
on-going authentication.
In MAC-based Authentication mode, the switch will ignore new frames coming from the
client during the hold time.
◆ RADIUS-Assigned QoS Enabled - RADIUS-assigned QoS provides a means to centrally
control the traffic class to which traffic coming from a successfully authenticated
supplicant is assigned on the switch. The RADIUS server must be configured to transmit
special RADIUS attributes to take advantage of this feature.
The RADIUS-Assigned QoS Enabled checkbox provides a quick way to globally
enable/disable RADIUS-server assigned QoS Class functionality. When checked, the
individual port settings determine whether RADIUS-assigned QoS Class is enabled for
that port. When unchecked, RADIUS-server assigned QoS Class is disabled for all ports.
When RADIUS-Assigned QoS is both globally enabled and enabled for a given port, the
switch reacts to QoS Class information carried in the RADIUS Access-Accept packet
transmitted by the RADIUS server when a supplicant is successfully authenticated. If
present and valid, traffic received on the supplicant’s port will be classified to the given
QoS Class. If (re-)authentication fails or the RADIUS Access-Accept packet no longer
carries a QoS Class or it's invalid, or the supplicant is otherwise no longer present on the
port, the port's QoS Class is immediately reverted to the original QoS Class (which may
be changed by the administrator in the meanwhile without affecting the RADIUSassigned setting).
This option is only available for single-client modes, i.e. port-based 802.1X and Single
802.1X.
RADIUS Attributes Used in Identifying a QoS Class
The User-Priority-Table attribute defined in RFC4675 forms the basis for identifying the QoS
Class in an Access-Accept packet.
Only the first occurrence of the attribute in the packet will be considered. To be valid, all 8
octets in the attribute's value must be identical and consist of ASCII characters in the range
'0' -'3', which translates into the desired QoS Class in the range 0-3.
QoS assignments to be applied to a switch port for an authenticated user may be configured
on the RADIUS server as described below:
■ The “Filter-ID” attribute (attribute 11) can be configured on the RADIUS server to pass
the following QoS information:
84
Page 85

Profile
Attribute Syntax
Example
DiffServ
service-policy-in=policy-map-name
service-policy-in=p1
Rate
Limit
rate-limit-input=rate
rate-limit-input=100
(in units of Kbps)
802.1p
switchport-priority-default=value
switchport-prioritydefault=2
Table 8: Dynamic QoS Profiles
■ Multiple profiles can be specified in the Filter-ID attribute by using a semicolon to
separate each profile.
For example, the attribute “service-policy-in=pp1;rate-limitinput=100” specifies that the
diffserv profile name is “pp1,” and the ingress rate limit profile value is 100 kbps.
■ If duplicate profiles are passed in the Filter-ID attribute, then only the first profile is
used.
For example, if the attribute is “service-policy-in=p1;service-policyin=p2”, then the switch
applies only the DiffServ profile “p1.”
■ Any unsupported profiles in the Filter-ID attribute are ignored.
For example, if the attribute is “map-ip-dscp=2:3;service-policyin=p1,” then the switch
ignores the “map-ip-dscp” profile.
■ When authentication is successful, the dynamic QoS information may not be passed
from the RADIUS server due to one of the following conditions (authentication result
remains unchanged):
■ The Filter-ID attribute cannot be found to carry the user profile.
■ The Filter-ID attribute is empty.
■ The Filter-ID attribute format for dynamic QoS assignment is unrecognizable (can not
recognize the whole Filter-ID attribute).
■ Dynamic QoS assignment fails and the authentication result changes from success to
failure when the following conditions occur:
■ Illegal characters found in a profile value (for example, a nondigital character in an 802.1p profile value).
■ Failure to configure the received profiles on the authenticated port.
■ When the last user logs off on a port with a dynamic QoS assignment, the switch
restores the original QoS configuration for the port.
■ When a user attempts to log into the network with a returned dynamic QoS profile that
is different from users already logged on to the same port, the user is denied access.
■ While a port has an assigned dynamic QoS profile, any manual QoS configuration
85
Page 86

changes only take effect after all users have logged off the port.
◆ RADIUS-Assigned VLAN Enabled - RADIUS-assigned VLAN provides a means to
centrally control the VLAN on which a successfully authenticated supplicant is placed on
the switch. Incoming traffic will be classified to and switched on the RADIUS-assigned
VLAN. The RADIUS server must be configured to transmit special RADIUS attributes to
take advantage of this feature.
The “RADIUS-Assigned VLAN Enabled” checkbox provides a quick way to globally
enable/disable RADIUS-server assigned VLAN functionality. When checked, the
individual port settings determine whether RADIUS- assigned VLAN is enabled for that
port. When unchecked, RADIUS-server assigned VLAN is disabled for all ports.
When RADIUS-Assigned VLAN is both globally enabled and enabled for a given port, the
switch reacts to VLAN ID information carried in the RADIUS Access-Accept packet
transmitted by the RADIUS server when a supplicant is successfully authenticated. If
present and valid, the port's Port VLAN ID will be changed to this VLAN ID, the port will
be set to be a member of that VLAN ID, and the port will be forced into VLAN- unaware
mode. Once assigned, all traffic arriving on the port will be classified and switched on the
RADIUS-assigned VLAN ID.
If (re-)authentication fails or the RADIUS Access-Accept packet no longer carries a VLAN
ID or it's invalid, or the supplicant is otherwise no longer present on the port, the port's
VLAN ID is immediately reverted to the original VLAN ID (which may be changed by the
administrator in the meanwhile without affecting the RADIUS-assigned setting).
This option is only available for single-client modes, i.e. port-based 802.1X and Single
802.1X.
Note: For trouble-shooting VLAN assignments, use the Monitor > VLANs > VLAN
Membership and VLAN Port pages. These pages show which modules have (temporarily)
overridden the current Port VLAN configuration.
RADIUS Attributes Used in Identifying a VLAN ID
RFC 2868 and RFC 3580 form the basis for the attributes used in identifying a VLAN ID in an
Access-Accept packet. The following criteria are used:
■ The Tunnel-Medium-Type, Tunnel-Type, and Tunnel-Private-Group- ID attributes must all
be present at least once in the Access-Accept packet.
■ The switch looks for the first set of these attributes that have the same Tag value and fulfil
the following requirements (if Tag == 0 is used, the Tunnel-Private-Group-ID does not need
to include a Tag):
■ Value of Tunnel-Medium-Type must be set to “IEEE-802” (ordinal 6).
■ Value of Tunnel-Type must be set to “VLAN” (ordinal 13).
■ Value of Tunnel-Private-Group-ID must be a string of ASCII characters in the range 0-9,
86
Page 87

which is interpreted as a decimal string representing the VLAN ID. Leading '0's are discarded.
The final value must be in the range 1-4095.
The VLAN list can contain multiple VLAN identifiers in the format “1u,2t,3u” where “u”
indicates an untagged VLAN and “t” a tagged VLAN.
◆ Guest VLAN Enabled – A Guest VLAN is a special VLAN - typically with limited network
access - on which 802.1X-unaware clients are placed after a network administratordefined timeout. The switch follows a set of rules for entering and leaving the Guest VLAN
as listed below.
The “Guest VLAN Enabled” checkbox provides a quick way to globally enable/disable
Guest VLAN functionality. When checked, the individual port settings determine whether
the port can be moved into Guest VLAN. When unchecked, the ability to move to the
Guest VLAN is disabled for all ports.
When Guest VLAN is both globally enabled and enabled for a given port, the switch
considers moving the port into the Guest VLAN according to the rules outlined below. This
option is only available for EAPOL-based modes, i.e. Port-based 802.1X, Single 802.1X,
and Multi 802.1X
NOTE: For trouble-shooting VLAN assignments, use the Monitor > VLANs > VLAN
Membership and VLAN Port pages. These pages show which modules have (temporarily)
overridden the current Port VLAN configuration.
Guest VLAN Operation
When a Guest VLAN enabled port's link comes up, the switch starts transmitting EAPOL
Request Identity frames. If the number of transmissions of such frames exceeds Max. Reauth.
Count and no EAPOL frames have been received in the meanwhile, the switch considers
entering the Guest VLAN. The interval between transmission of EAPOL Request Identity
frames is configured with EAPOL Timeout. If Allow Guest VLAN if EAPOL Seen is enabled,
the port will now be placed in the Guest VLAN. If disabled, the switch will first check its
history to see if an EAPOL frame has previously been received on the port (this history is
cleared if the port link goes down or the port's Admin State is changed), and if not, the port
will be placed in the Guest VLAN. Otherwise it will not move to the Guest VLAN, but continue
transmitting EAPOL Request Identity frames at the rate given by EAPOL Timeout.
Once in the Guest VLAN, the port is considered authenticated, and all attached clients on the
port are allowed access on this VLAN. The switch will not transmit an EAPOL Success frame
after entering the Guest VLAN.
While in the Guest VLAN, the switch monitors the link for EAPOL frames, and if one such
frame is received, the switch immediately takes the port out of the Guest VLAN and starts
authenticating the supplicant according to the port mode. If an EAPOL frame is received, the
port will never be able to go back into the Guest VLAN if the “Allow Guest VLAN if EAPOL
Seen” is disabled.
87
Page 88

◆ Guest VLAN ID – This is the value that a port's Port VLAN ID is set to if a port is moved
into the Guest VLAN. It is only changeable if the Guest VLAN option is globally enabled.
(Range: 1-4095)
◆ Max. Reauth. Count - The number of times that the switch transmits an EAPOL Request
Identity frame without receiving a response before adding a port to the Guest VLAN. The
value can only be changed if the Guest VLAN option is globally enabled. (Range: 1-255)
◆ Allow Guest VLAN if EAPOL Seen – The switch remembers if an EAPOL frame has
been received on the port for the lifetime of the port. Once the switch considers whether to
enter the Guest VLAN, it will first check if this option is enabled or disabled. If disabled (the
default), the switch will only enter the Guest VLAN if an EAPOL frame has not been received
on the port for the lifetime of the port. If enabled, the switch will consider entering the Guest
VLAN even if an EAPOL frame has been received on the port for the lifetime of the port. The
value can only be changed if the Guest VLAN option is globally enabled.
Port Configuration
◆ Port – Port identifier.
◆ Admin State – If NAS is globally enabled, this selection controls the port's authentication
mode. The following modes are available:
■ Force Authorized – The switch sends one EAPOL Success frame when the port link
comes up. This forces the port to grant access to all clients, either dot1x-aware or
otherwise. (This is the default setting.)
■ Force Unauthorized – The switch will send one EAPOL Failure frame when the port
link comes up. This forces the port to deny access to all clients, either dot1x-aware or
otherwise.
■ Port-based 802.1X – Requires a 802.1x-aware client to be authorized by the
authentication server. Clients that are not 802.1x-aware will be denied access.
■ Single 802.1X – At most one supplicant can get authenticated on the port at a time. If
more than one supplicant is connected to a port, the one that comes first when the port's
link comes up will be the first one considered. If that supplicant doesn't provide valid
credentials within a certain amount of time, another supplicant will get a chance. Once a
supplicant is successfully authenticated, only that supplicant will be allowed access. This
is the most secure of all the supported modes. In this mode, the Port Security module is
used to secure a supplicant's MAC address once successfully authenticated.
■ Multi 802.1X – One or more supplicants can get authenticated on the same port at the
same time. Each supplicant is authenticated individually and secured in the MAC table
using the Port Security module.
In multi 802.1X it is not possible to use the multicast BPDU MAC address as the destination
MAC address for EAPOL frames sent from the switch towards the supplicant, since that
88
Page 89

would cause all supplicants attached to the port to reply to requests sent from the switch.
Instead, the switch uses the supplicant's MAC address, which is obtained from the first
EAPOL Start or EAPOL Response Identity frame sent by the supplicant. An exception to this
is when no supplicants are attached. In this case, the switch sends EAPOL Request Identity
frames using the BPDU multicast MAC address as the destination - to wake up any
supplicants that might be on the port.
The maximum number of supplicants that can be attached to a port can be limited using the
Port Security Limit Control functionality.
■ MAC-based Auth. – Enables MAC-based authentication on the port. The switch does
not transmit or accept EAPOL frames on the port. Flooded frames and broadcast traffic
will be transmitted on the port, whether or not clients are authenticated on the port,
whereas unicast traffic from an unsuccessfully authenticated client will be dropped.
Clients that are not (or not yet) successfully authenticated will not be allowed to transmit
frames of any kind.
The switch acts as the supplicant on behalf of clients. The initial frame (any kind of frame)
sent by a client is snooped by the switch, which in turn uses the client's MAC address as both
user name and password in the subsequent EAP exchange with the RADIUS server. The 6byte MAC address is converted to a string on the following form “xx-xx-xx-xx-xx-xx”, that is, a
dash (-) is used as separator between the lower-cased hexadecimal digits. The switch only
supports the MD5-Challenge authentication method, so the RADIUS server must be
configured accordingly.
When authentication is complete, the RADIUS server sends a success or failure indication,
which in turn causes the switch to open up or block traffic for that particular client, using the
Port Security module. Only then will frames from the client be forwarded on the switch. There
are no EAPOL frames involved in this authentication, and therefore, MAC-based
Authentication has nothing to do with the 802.1X standard.
The advantage of MAC-based authentication over port-based 802.1X is that several clients
can be connected to the same port (e.g. through a 3rd party switch or a hub) and still require
individual authentication, and that the clients don't need special supplicant software to
authenticate. The advantage of MAC-based authentication over 802.1X-based authentication
is that the clients don't need special supplicant software to authenticate. The disadvantage is
that MAC addresses can be spoofed by malicious users - equipment whose MAC address is
a valid RADIUS user can be used by anyone. Also, only the MD5-Challenge method is
supported. The maximum number of clients that can be attached to a port can be limited
using the Port Security Limit Control functionality. Further Guidelines for Port Admin State:
■ Port Admin state can only be set to Force-Authorized for ports participating in the
Spanning Tree algorithm (see page 117).
■ When 802.1X authentication is enabled on a port, the MAC address learning function
for this interface is disabled, and the addresses dynamically learned on this port are
removed from the common address table.
89
Page 90

■ Authenticated MAC addresses are stored as dynamic entries in the switch's secure
MAC address table. Configured static MAC addresses are added to the secure address
table when seen on a switch port. Static addresses are treated as authenticated without
sending a request to a RADIUS server.
■ When port status changes to down, all MAC addresses are cleared from the secure
MAC address table. Static VLAN assignments are not restored.
◆ RADIUS-Assigned QoS Enabled – Enables or disables this feature for a given port.
Refer to the description of this feature under the System Configuration section.
◆ RADIUS-Assigned VLAN Enabled – Enables or disables this feature for a given port.
Refer to the description of this feature under the System Configuration section.
◆ Guest VLAN Enabled – Enables or disables this feature for a given port. Refer to the
description of this feature under the System Configure section.
◆ Port State – The current state of the port:
■ Globally Disabled – 802.1X and MAC-based authentication are globally disabled. (This is
the default state.)
■ Link Down – 802.1X or MAC-based authentication is enabled, but there is no link on the
port.
■ Authorized – The port is in Force Authorized mode, or a single- supplicant mode and the
supplicant is authorized.
■ Unauthorized – The port is in Force Unauthorized mode, or a single-supplicant mode and
the supplicant is not successfully authorized by the RADIUS server.
■ X Auth/Y Unauth – The port is in a multi-supplicant mode. X clients are currently
authorized and Y are unauthorized.
◆ Restart – Restarts client authentication using one of the methods described below. Note
that the restart buttons are only enabled when the switch’s authentication mode is globally
enabled (under System Configuration) and the port's Admin State is an EAPOL-based or
MAC-Based mode. Clicking these buttons will not cause settings changed on the page to
take effect.
■ Reauthenticate – Schedules reauthentication to whenever the quiet-period of the port
runs out (EAPOL-based authentication). For MAC-based authentication, reauthentication
will be attempted immediately. The button only has effect for successfully authenticated
clients on the port and will not cause the clients to get temporarily unauthorized.
■ Reinitialize – Forces a reinitialization of the clients on the port and thereby a
reauthentication immediately. The clients will transfer to the unauthorized state while the
reauthentication is in progress.
90
Page 91

WEB INTERFACE
To configure 802.1X Port Security:
1. Click Configuration, Security, Network, NAS.
2. Modify the required attributes.
3. Click Save.
Access Control List (ACL)
An Access Control List (ACL) is a sequential list of permit or deny conditions that apply to IP
addresses, MAC addresses, or other more specific criteria. This switch tests ingress packets
against the conditions in an ACL one by one. A packet will be accepted as soon as it
matches a permit rule, or dropped as soon as it matches a deny rule. If no rules match, the
frame is accepted. Other actions can also be invoked when a matching packet is found,
including rate limiting, copying matching packets to another port or to the system log, or
shutting down a port.
Assigning ACL Polocies and Responses
Use the ACL Port Configuration page to define a port to which matching frames are copied,
enable logging, or shut down a port when a matching frame is seen. Note that rate limiting
(configured with the Rate Limiter menu, page 91) is implemented regardless of whether or
not a matching packet is seen.
PATH
Configuration \ Security \ Network \ ACL \ Ports
Figure 32: ACL Port Configuration
91
Page 92

PARAMETERS
These parameters are displayed:
◆ Port – Port Identifier.
◆ Policy ID – An ACL policy configured on the ACL Entry (ACE) Configuration page. (Range:
1-8; Default: 1, which is undefined)
◆ Action – Permits or denies a frame based on whether it matches a rule defined in the
assigned policy. (Default: Permit)
◆ Rate Limiter ID – Specifies a rate limiter (page 91) to apply to the port. (Range: 1-15;
Default: Disabled)
◆ Redirect to – Defines a port to which matching frames are re-directed. (Range: 1-28;
Default: Disabled)
To use this function, Action must be set to Deny for the local port.
◆ Mirror - Mirrors matching frames from this port. (Default: Disabled) To use this function,
the destination port to which traffic is mirrored must be configured on the Mirror Configuration
page (see "Configuring Port Mirroring" on page 198).
ACL-based port mirroring set by this parameter and port mirroring set on the general Mirror
Configuration page are implemented independently. To use ACL-based mirroring, enable the
Mirror parameter on the ACL Ports Configuration page. Then open the Mirror Configuration
page, set the “Port to mirror on” field to the required destination port, and leave the “Mode”
field Disabled.
92
Page 93

◆ Logging - Enables logging of matching frames to the system log. (Default: Disabled)
Open the System Log Information menu to view any entries stored in the system log for this
entry. Related entries will be displayed under the “Info” or “All” logging levels.
◆ Shutdown - Shuts down a port when a macthing frame is seen.
(Default: Disabled)
◆ Counter - The number of frames which have matched any of the rules defined in the
selected policy.
WEB INTERFACE
To configure ACL policies and responses for a port:
1. Click Configuration, ACL, Ports.
2. ssign an ACL policy configured on the ACE Configuration page, specify the responses to
invoke when a matching frame is seen, including the filter mode, copying matching frames to
another port, logging matching frames, or shutting down the port. Note that the setting for
rate limiting is implemented regardless of whether or not a matching packet is seen.
3. Repeat the preceding step for each port to which an ACL will be applied.
4. Click Save.
Configuring Rate Limiters
Use the ACL Rate Limiter Configuration page to define the rate limits applied to a port (as
configured either through the ACL Ports Configuration menu or the Access Control List
Configuration menu.
PATH
Configuration \ Security \ Network \ ACL \ Rate Limiters
Figure 33: ACL Rate Limiter Configuration
93
Page 94

PARAMETERS
These parameters are displayed:
◆ Rate Limiter ID - Rate limiter identifier. (Range: 0-14; Default: 1)
◆ Rate - The threshold above which packets are dropped. (Options: 0-100 pps, or 0, 100,
2*100, 3*100, ... 1000000 kbps)
Due to an ASIC limitation, the enforced rate limits are slightly less than the listed options.
For example: 1 Kbps translates into an enforced threshold of 1002.1 pps.
◆ Unit - Unit of measure. (Options: pps or kbps; Default: pps)
WEB INTERFACE
To configure rate limits which can be applied to a port:
1. Click Configuration, Security, Network, ACL, Rate Limiters.
2. For any of the rate limiters, select the maximum ingress rate that will be supported on a
port once a match has been found in an assigned ACL.
3. Click Save.
Configuring Access Control Lists
Use the Access Control List Configuration page to define filtering rules for an ACL policy, for
a specific port, or for all ports. Rules applied to a port take effect immediately, while those
defined for a policy must be mapped to one or more ports using the ACL Ports Configuration
menu (page 89).
PATH
94
Page 95

Configuration \ Security \ Network \ ACL \ Access Control List
Figure 34: Access Control List Configuration
USAGE GUIDELINES
◆ Rules within an ACL are checked in the configured order, from top to bottom. A packe will
be accepted as soon as it matches a permit rule, or dropped as soon as it matches a deny
rule. If no rules match, the frame is accepted.
◆ The maximum number of ACL rules that can be configured on the switch is 128.
◆ The maximum number of ACL rules that can be bound to a port is 10.
◆ ACLs provide frame filtering based on any of the following criteria:
■ Any frame type (based on MAC address, VLAN ID, VLAN priority)
■ Ethernet type (based on Ethernet type value, MAC address, VLAN ID, VLAN priority)
■ ARP (based on ARP/RARP type, request/reply, sender/target IP, hardware address
matches ARP/RARP MAC address, ARP/RARP hardware address length matches
protocol address length, matches this entry when ARP/RARP hardware address is equal to
Ethernet, matches this entry when ARP/RARP protocol address space setting is equal to
IP (0x800)
■ IPv4 frames (based on destination MAC address, protocol type, TTL, IP fragment, IP
option flag, source/destination IP, VLAN ID, VLAN priority)
PARAMETERS
These parameters are displayed:
ACCESS CONTROL LIST CONFIGURATION
◆ Ingress Port – Any port, port identifier, or policy.
◆ Frame Type – The type of frame to match.
◆ Action – Shows whether a frame is permitted or denied when it matches an ACL rule.
95
Page 96

Button
Description
Inserts a new ACE before the current row.
Edits the ACE.
Moves the ACE up the list.
Moves the ACE down the list.
Deletes the ACE.
The lowest plus sign adds a new entry at the bottom of the list.
◆ Rate Limiter – Shows if rate limiting will be enabled or disabled when matching frames
are found.
◆ Port Copy – Shows the port to which matching frames are copied.
◆ Mirror – Mirrors matching frames from this port. (Default: Disabled) See "Configuring Port
Mirroring" on page 198.
◆ Logging – Shows if logging of matching frames to the system log is enabled or disabled.
Open the System Log Information menu to view any entries stored in the system log for
this entry. Related entries will be displayed under the “Info” or “All” logging levels.
◆ Shutdown – Shows if a port is shut down when a macthing frame is found.
◆ Counter – Shows he number of frames which have matched any of the rules defined for
this ACL.
The following buttons are used to edit or move the ACL entry (ACE):
Table 9: QCE Modification Buttons
ACE CONFIGURATION
Ingress Port and Frame Type
◆ Ingress Port – Any port, port identifier, or policy. (Options: Any port, Port 1-10, Policy 1-8;
Default: Any)
◆ Frame Type – The type of frame to match. (Options: Any, Ethernet, ARP, IPv4; Default:
Any)
Filter Criteria Based on Selected Frame Type
◆ Ethernet:
MAC Parameters
■ SMAC Filter – The type of source MAC address. (Options: Any, Specific - user defined;
Default: Any)
■ DMAC Filter – The type of destination MAC address. (Options: Any, MC - multicast, BC broadcast, UC - unicast, Specific - user defined; Default: Any)
96
Page 97

Ethernet Type Parameters
■ EtherType Filter – This option can only be used to filter Ethernet II formatted packets.
(Options: Any, Specific (600-ffff hex); Default: Any)
A detailed listing of Ethernet protocol types can be found in RFC 1060. A few of the more
common types include 0800 (IP), 0806 (ARP), 8137 (IPX).
◆ ARP:
MAC Parameters
■ SMAC Filter – The type of source MAC address. (Options: Any, Specific - user defined;
Default: Any)
■ DMAC Filter – The type of destination MAC address. (Options: Any, MC - multicast, BC broadcast, UC - unicast; Default: Any)
ARP Parameters
■ ARP/RARP – Specifies the type of ARP packet. (Options: Any - no ARP/RARP opcode
flag is specified, ARP - frame must have ARP/ RARP opcode set to ARP, RARP - frame
must have ARP/RARP opcode set to RARP, Other - frame has unknown ARP/RARP
opcode flag; Default: Any)
■ Request/Reply – Specifies whether the packet is an ARP request, reply, or either type.
(Options: Any - no ARP/RARP opcode flag is specified, Request -frame must have ARP
Request or RARP Request opcode flag set, Reply - frame must have ARP Reply or RARP
Reply opcode flag; Default: Any)
■ Sender IP Filter – Specifies the sender’s IP address. (Options: Any - no sender IP filter
is specified, Host - specifies the sender IP address in the SIP Address field, Network specifies the sender IP address and sender IP mask in the SIP Address and SIP Mask
fields; Default: Any)
■ Target IP Filter – Specifies the destination IP address. (Options: Any - no target IP filter
is specified, Host -specifies the target IP address in the Target IP Address field, Network specifies the target IP address and target IP mask in the Target IP Address and Target IP
Mask fields; Default: Any)
■ ARP SMAC Match – Specifies whether frames can be matched according to their
sender hardware address (SHA) field settings. (0ptions: Any - any value is allowed, 0 ARP frames where SHA is not equal to the SMAC address, 1 - ARP frames where SHA is
equal to the SMAC address; Default: Any)
■ RARP DMAC Match – Specifies whether frames can be matched according to their
target hardware address (THA) field settings. (Options: Any - any value is allowed, 0 RARP frames where THA is not equal to the DMAC address, 1 -RARP frames where THA
is equal to the DMAC address; Default: Any)
■ IP/Ethernet Length – Specifies whether frames can be matched according to their
ARP/RARP hardware address length (HLN) and protocol address length (PLN) settings.
(Options: Any - any value is allowed, 0 -ARP/RARP frames where the HLN is equal to
97
Page 98

Ethernet (0x06) and the (PLN) is equal to IPv4 (0x04) must not match this entry, 1 ARP/RARP frames where the HLN is equal to Ethernet (0x06) and the (PLN) is equal to
IPv4 (0x04) must match this entry; Default: Any)
■ IP – Specifies whether frames can be matched according to their ARP/RARP hardware
address space (HRD) settings. (Options: Any any value is allowed, 0 - ARP/RARP frames
where the HRD is equal to Ethernet (1) must not match this entry, 1 -ARP/RARP frames
where the HRD is equal to Ethernet (1) must match this entry; Default: Any)
■ Ethernet – Specifies whether frames can be matched according to their ARP/RARP
protocol address space (PRO) settings. (Options: Any - any value is allowed, 0 ARP/RARP frames where the PRO is equal to IP (0x800) must not match this entry, 1 ARP/ RARP frames where the PRO is equal to IP (0x800) must match this entry; Default:
Any)
◆ IPv4:
MAC Parameters
■ DMAC Filter – The type of destination MAC address. (Options: Any, MC - multicast, BC -
broadcast, UC - unicast; Default: Any)
IP Parameters
■ IP Protocol Filter – Specifies the IP protocol to filter for this rule. (Options: Any, ICMP,
UDP, TCP, Other; Default: Any)
The following additional fields are displayed when these protocol filters are selected.
ICMP Parameters
■ ICMP Type Filter – Specifies the type of ICMP packet to filter for this rule. (Options: Any,
Specific: 0-255; Default: Any)
■ ICMP Code Filter – Specifies the ICMP code of an ICMP packet to filter for this rule.
(Options: Any, Specific (0-255); Default: Any)
UDP Parameters
■ Source Port Filter – Specifies the UDP source filter for this rule. (Options: Any, Specific
(0-65535), Range (0-65535); Default: Any)
■ Dest. Port Filter – Specifies the UDP destination filter for this rule. (Options: Any,
Specific (0-65535), Range (0-65535); Default: Any)
TCP Parameters
■ Source Port Filter – Specifies the TCP source filter for this rule. (Options: Any, Specific
(0-65535), Range (0-65535); Default: Any)
■ Dest. Port Filter – Specifies the TCP destination filter for this rule. (Options: Any,
Specific (0-65535), Range (0-65535); Default: Any)
■ TCP FIN – Specifies the TCP “No more data from sender” (FIN) value for this rule.
(Options: Any - any value is allowed, 0 - TCP frames where the FIN field is set must not
match this entry, 1 - TCP frames where the FIN field is set must match this entry; Default:
98
Page 99

Any)
■ TCP SYN – Specifies the TCP “Synchronize sequence numbers” (SYN) value for this
rule. (Options: Any - any value is allowed, 0 - TCP frames where the SYN field is set must
not match this entry, 1 -TCP frames where the SYN field is set must match this entry;
Default: Any)
■ TCP RST – Specifies the TCP “Reset the connection” (RST) value for this rule. (Options:
Any - any value is allowed, 0 - TCP frames where the RST field is set must not match this
entry, 1 - TCP frames where the RST field is set must match this entry; Default: Any)
■ TCP PSH – Specifies the TCP “Push Function” (PSH) value for this rule. (Options: Any -
any value is allowed, 0 -TCP frames where the PSH field is set must not match this entry, 1
-TCP frames where the PSH field is set must match this entry; Default: Any)
■ TCP ACK – Specifies the TCP “Acknowledgment field significant” (ACK) value for this
rule. (Options: Any - any value is allowed, 0 - TCP frames where the ACK field is set must
not match this entry, 1 -TCP frames where the ACK field is set must match this entry;
Default: Any)
■ TCP URG – Specifies the TCP “Urgent Pointer field significant” (URG) value for this rule.
(Options: Any - any value is allowed, 0 - TCP frames where the URG field is set must not
match this entry, 1 - TCP frames where the URG field is set must match this entry; Default:
Any)
■ IP TTL – Specifies the time-to-Live settings for this rule. (Options: Any - any value is
allowed, Non-zero - IPv4 frames with a TTL field greater than zero must match this entry,
Zero -IPv4 frames with a TTL field greater than zero must not match this entry; Default:
Any)
■ IP Fragment – Specifies the fragment offset settings for this rule. This involves the
settings for the More Fragments (MF) bit and the Fragment Offset (FRAG OFFSET) field
for an IPv4 frame. (Options: Any - any value is allowed, Yes - IPv4 frames where the MF
bit is set or the FRAG OFFSET field is greater than zero must match this entry, No -IPv4
frames where the MF bit is set or the FRAG OFFSET field is greater than zero must not
match this entry; Default: Any)
■ IP Option – Specifies the options flag setting for this rule. (Options: Any - any value is
allowed, Yes - IPv4 frames where the options flag is set must match this entry, No -IPv4
frames where the options flag is set must not match this entry; Default: Any)
■ SIP Filter – Specifies the source IP filter for this rule. (Options: Any - no source IP filter is
specified, Host - specifies the source IP address in the SIP Address field, Network specifies the source IP address and source IP mask in the SIP Address and SIP Mask
fields; Default: Any)
■ DIP Filter – Specifies the destination IP filter for this rule. (Options: Any - no destination
IP filter is specified, Host - specifies the destination IP address in the DIP Address field,
Network - specifies the destination IP address and destination IP mask in the DIP Address
and DIP Mask fields; Default: Any)
Response to take when a rule is matched
99
Page 100

◆ Action – Permits or denies a frame based on whether it matches an ACL rule. (Default:
Permit)
◆ Rate Limiter – Specifies a rate limiter (page 91) to apply to the port. (Range: 1-16; Default:
Disabled)
◆ Port Copy – Defines a port to which matching frames are copied. (Range: 1-10; Default:
Disabled)
◆ Mirror – Mirrors matching frames from this port. (Default: Disabled) See "Configuring Port
Mirroring" on page 198.
ACL-based port mirroring set by this parameter and port mirroring set on the general Mirror
Configuration page are implemented independently. To use ACL-based mirroring, enable the
Mirror parameter on the ACE Configuration page. Then open the Mirror Configuration page,
set the “Port to mirror on” field to the required destination port, and leave the “Mode” field
Disabled.
◆ Logging – Enables logging of matching frames to the system log. (Default: Disabled)
Open the System Log Information menu to view any entries stored in the system log for this
entry. Related entries will be displayed under the “Info” or “All” logging levels.
◆ Shutdown – Shuts down a port when a macthing frame is seen. (Default: Disabled)
◆ Counter – Shows he number of frames which have matched any of the rules defined for
this ACL.
VLAN Parameters
◆ 802.1Q Tagged – Specifies whether or not frames should be 802.1Q tagged. (Options:
Any, Disabled, Enabled; Default: Any)
◆ VLAN ID Filter – Specifies the VLAN to filter for this rule. (Options: Any, Specific (1-4095);
Default: Any)
◆ Tag Priority – Specifies the User Priority value found in the VLAN tag (3 bits as defined
by IEEE 802.1p) to match for this rule. (Options: Any, Specific (0-7); Default: Any)
WEB INTERFACE
To configure an Access Control List for a port or a policy:
1. Click Configuration, Security, Network, ACL, Access Control List.
2. Click the button to add a new ACL, or use the other ACL modification buttons to specify
the editing action (i.e., edit, delete, or moving the relative position of entry in the list).
3. When editing an entry on the ACE Configuration page, note that the items displayed
depend on various selections, such as Frame Type and IP Protocol Type. Specify the
relevant criteria to be matched for this rule, and set the actions to take when a rule is
matched (such as Rate Limiter, Port Copy, Logging, and Shutdown).
4. Click Save.
100
 Loading...
Loading...