Page 1

REV1.0.0
1910020676
LevelOne
FGS-2800
Web Smart Switch
24 ports RJ-45 Fast Ethernet, 4 ports RJ-45
Gigabit Ethernet with 2 ports shared SFP
fiber optical
User Manual
Page 2

CONTENTS
Package Contents ............................................................................................................................ 1
Chapter 1 About this Guide ............................................................................................................ 2
1.1 Intended Readers ........................................................................................................... 2
1.2 Conventions ................................................................................................................... 2
1.3 Overview of This Guide .................................................................................................. 2
Chapter 2 Introduction .................................................................................................................... 5
2.1 Overview of the Switch ................................................................................................... 5
2.2 Main Features ................................................................................................................ 5
2.3 Appearance Description ................................................................................................. 5
2.3.1 Front Panel .......................................................................................................... 5
2.3.2 Rear Panel .......................................................................................................... 6
Chapter 3 Login to the Switch ........................................................................................................ 8
3.1 Login ............................................................................................................................... 8
3.2 Configuration .................................................................................................................. 8
Chapter 4 System ......................................................................................................................... 10
4.1 System Info .................................................................................................................. 10
4.1.1 System Summary .............................................................................................. 10
4.1.2 Device Description ............................................................................................. 11
4.1.3 System Time ...................................................................................................... 12
4.1.4 Daylight Saving Time ........................................................................................ 13
4.1.5 System IP .......................................................................................................... 14
4.2 User Management ........................................................................................................ 15
4.2.1 User Table ......................................................................................................... 15
4.2.2 User Config ....................................................................................................... 15
4.3 System Tools ................................................................................................................ 17
4.3.1 Config Restore .................................................................................................. 17
4.3.2 Config Backup ................................................................................................... 17
4.3.3 Firmware Upgrade............................................................................................. 18
4.3.4 System Reboot .................................................................................................. 19
4.3.5 System Reset .................................................................................................... 19
4.4 Access Security ............................................................................................................ 19
4.4.1 Access Control .................................................................................................. 19
Chapter 5 Switching ..................................................................................................................... 22
5.1 Port ............................................................................................................................... 22
5.1.1 Port Config ........................................................................................................ 22
5.1.2 Port Mirror.......................................................................................................... 23
I
Page 3

5.1.3 Port Security ...................................................................................................... 25
5.1.4 Port Isolation ..................................................................................................... 26
5.2 LAG .............................................................................................................................. 27
5.2.1 LAG Table .......................................................................................................... 28
5.2.2 Static LAG.......................................................................................................... 29
5.3 Traffic Monitor ............................................................................................................... 30
5.3.1 Traffic Summary ................................................................................................ 30
5.3.2 Traffic Statistics ................................................................................................. 32
5.4 MAC Address ............................................................................................................... 33
5.4.1 Address Table .................................................................................................... 34
5.4.2 Static Address .................................................................................................... 35
5.4.3 Dynamic Address .............................................................................................. 36
5.4.4 Filtering Address ................................................................................................ 37
Chapter 6 VLAN............................................................................................................................ 39
6.1 802.1Q VLAN ............................................................................................................... 40
6.1.1 VLAN Config ...................................................................................................... 41
6.1.2 Port Config ........................................................................................................ 44
6.2 Application Example for 802.1Q VLAN ........................................................................ 45
Chapter 7 Spanning Tree .............................................................................................................. 47
7.1 STP Config ................................................................................................................... 52
7.1.1 STP Config ........................................................................................................ 52
7.1.2 STP Summary ................................................................................................... 54
7.2 Port Config ................................................................................................................... 54
7.3 MSTP Instance ............................................................................................................. 56
7.3.1 Region Config .................................................................................................... 56
7.3.2 Instance Config ................................................................................................. 57
7.3.3 Instance Port Config .......................................................................................... 58
7.4 STP Security ................................................................................................................ 60
7.4.1 Port Protect ....................................................................................................... 60
7.4.2 TC Protect ......................................................................................................... 63
7.5 Application Example for STP Function ........................................................................ 63
Chapter 8 Multicast ....................................................................................................................... 67
8.1 IGMP Snooping ............................................................................................................ 69
8.1.1 Snooping Config ................................................................................................ 70
8.1.2 Port Config ........................................................................................................ 71
8.1.3 VLAN Config ...................................................................................................... 72
8.1.4 Multicast VLAN .................................................................................................. 74
II
Page 4

8.2 Multicast IP ................................................................................................................... 77
8.2.1 Multicast IP Table .............................................................................................. 77
8.2.2 Static Multicast IP .............................................................................................. 78
8.3 Multicast Filter .............................................................................................................. 79
8.3.1 IP-Range ........................................................................................................... 79
8.3.2 Port Filter ........................................................................................................... 80
8.4 Packet Statistics ........................................................................................................... 81
Chapter 9 QoS .............................................................................................................................. 83
9.1 DiffServ ......................................................................................................................... 86
9.1.1 Port Priority ........................................................................................................ 86
9.1.2 Schedule Mode ................................................................................................. 87
9.1.3 802.1P Priority ................................................................................................... 87
9.1.4 DSCP Priority .................................................................................................... 88
9.2 Bandwidth Control ........................................................................................................ 90
9.2.1 Rate Limit .......................................................................................................... 90
9.2.2 Storm Control .................................................................................................... 91
Chapter 10 SNMP........................................................................................................................... 93
10.1 SNMP Config ................................................................................................................ 95
10.1.1 Global Config ..................................................................................................... 95
10.1.2 SNMP View ....................................................................................................... 96
10.1.3 SNMP Group ..................................................................................................... 97
10.1.4 SNMP User ........................................................................................................ 98
10.1.5 SNMP Community ........................................................................................... 100
10.2 Notification .................................................................................................................. 101
10.3 RMON......................................................................................................................... 103
10.3.1 History Control ................................................................................................. 104
10.3.2 Event Config .................................................................................................... 105
10.3.3 Alarm Config .................................................................................................... 105
Chapter 11 Maintenance .............................................................................................................. 108
11.1 System Monitor .......................................................................................................... 108
11.1.1 CPU Monitor .................................................................................................... 108
11.1.2 Memory Monitor .............................................................................................. 109
11.2 Log .............................................................................................................................. 109
11.2.1 Log Table .......................................................................................................... 110
11.2.2 Local Log .......................................................................................................... 110
11.2.3 Remote Log ...................................................................................................... 111
11.2.4 Backup Log ...................................................................................................... 112
III
Page 5

11.3 Device Diagnostics ...................................................................................................... 112
11.3.1 Cable Test ......................................................................................................... 112
11.3.2 Loopback .......................................................................................................... 113
11.4 Network Diagnostics ................................................................................................... 114
11.4.1 Ping .................................................................................................................. 114
11.4.2 Tracert .............................................................................................................. 115
Appendix A: Specifications ........................................................................................................... 117
Appendix B: Configuring the PCs ................................................................................................. 118
Appendix C: Glossary .................................................................................................................. 120
IV
Page 6

Package Contents
The following items should be found in your box:
FGS-2800
power cord
19" Rackmount Kit
Quick Installation Guide
Resource CD (User Manual)
Note:
Make sure that the package contains the above items. If any of the listed items are damaged or
missing, please contact your distributor.
1
Page 7
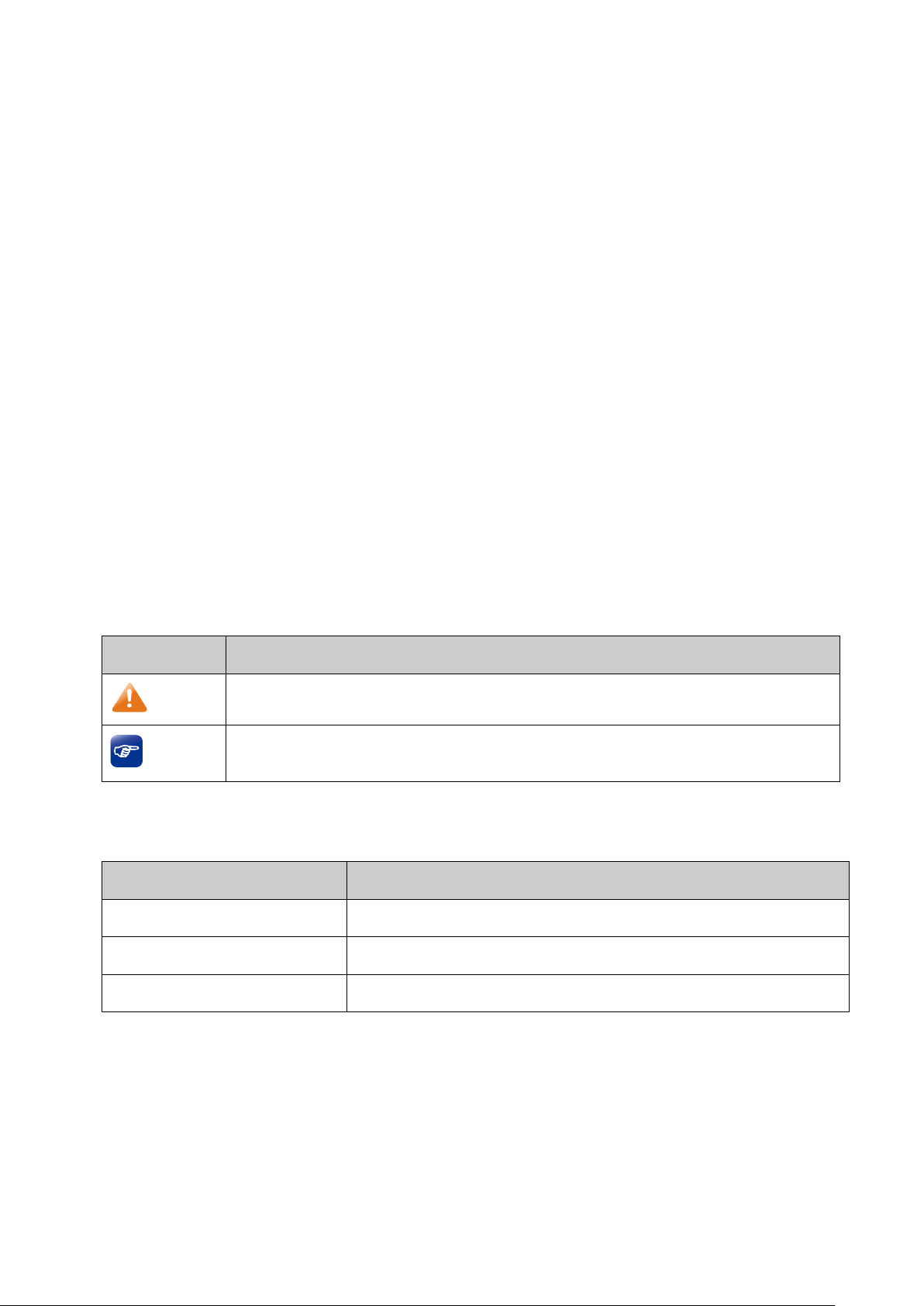
Symbol
Description
Note:
Ignoring this type of note might result in a malfunction or damage to the device.
Tips:
This format indicates important information that helps you make better use of your
device.
Chapter
Introduction
Chapter 1 About This Guide
Introduces the guide structure and conventions.
Chapter 2 Introduction
Introduces the features, application and appearance of FGS-2800.
Chapter 3 Login to the Switch
Introduces how to log on to the Web management page.
Chapter 1 About this Guide
This user guide contains information for setup and management of FGS-2800 24+4G Gigabit Web
Smart Switch with 2 Combo SFP Slots. Please read this guide carefully before operation.
1.1 Intended Readers
This guide is intended for network managers familiar with IT concepts and network terminologies.
1.2 Conventions
In this guide the following conventions are used:
The switch or FGS-2800 mentioned in this guide stands for FGS-2800 24+4G Gigabit Web
Smart Switch with 2 Combo SFP Slots without any explanation.
Menu Name→Submenu Name→Tab page indicates the menu structure. System→System
Info→System Summary means the System Summary page under the System Info menu
option that is located under the System menu.
Bold font indicates a button, a toolbar icon, menu or menu item.
Symbols in this guide:
1.3 Overview of This Guide
2
Page 8
Chapter
Introduction
Chapter 4 System
This module is used to configure system properties of the switch.
Here mainly introduces:
System Info: Configure the description, system time and network
parameters of the switch.
User Management: Configure the user name and password for
users to log on to the Web management page with a certain
access level.
System Tools: Manage the configuration file of the switch.
Access Security: Provide different security measures for the
login to enhance the configuration management security.
Chapter 5 Switching
This module is used to configure basic functions of the switch. Here
mainly introduces:
Port: Configure the basic features for the port.
LAG: Configure Link Aggregation Group. LAG is to combine a
number of ports together to make a single high-bandwidth data
path.
Traffic Monitor: Monitor the traffic of each port
MAC Address: Configure the address table of the switch.
DHCP Filtering: Monitor the process of the host obtaining the IP
address from DHCP server.
Chapter 6 VLAN
This module is used to configure VLANs to control broadcast in
LANs. Here mainly introduces:
802.1Q VLAN: Configure port-based VLAN.
Chapter 7 Spanning Tree
This module is used to configure spanning tree function of the
switch. Here mainly introduces:
STP Config: Configure and view the global settings of spanning
tree function.
Port Config: Configure CIST parameters of ports.
MSTP Instance: Configure MSTP instances.
STP Security: Configure protection function to prevent devices
from any malicious attack against STP features.
Chapter 8 Multicast
This module is used to configure multicast function of the switch.
Here mainly introduces:
IGMP Snooping: Configure global parameters of IGMP Snooping
function, port properties, VLAN and multicast VLAN.
Multicast IP: Configure multicast IP table.
Multicast Filter: Configure multicast filter feature to restrict users
ordering multicast programs.
Packet Statistics: View the multicast data traffic on each port of
the switch, which facilitates you to monitor the IGMP messages
in the network.
3
Page 9
Chapter
Introduction
Chapter 9 QoS
This module is used to configure QoS function to provide different
quality of service for various network applications and
requirements. Here mainly introduces:
DiffServ: Configure priorities, port priority, 802.1P priority and
DSCP priority.
Bandwidth Control: Configure rate limit feature to control the
traffic rate on each port; configure storm control feature to filter
broadcast, multicast and UL frame in the network.
Voice VLAN: Configure voice VLAN to transmit voice data
stream within the specified VLAN so as to ensure the
transmission priority of voice data stream and voice quality.
Chapter 10 ACL
This module is used to configure match rules and process policies
of packets to filter packets in order to control the access of the
illegal users to the network. Here mainly introduces:
ACL Config: ACL rules.
Policy Config: Configure operation policies.
Policy Binding: Bind the policy to a port/VLAN to take its effect on
a specific port/VLAN.
Chapter 11 SNMP
This module is used to configure SNMP function to provide a
management frame to monitor and maintain the network devices.
Here mainly introduces:
SNMP Config: Configure global settings of SNMP function.
Notification: Configure notification function for the management
station to monitor and process the events.
RMON: Configure RMON function to monitor network more
efficiently.
Chapter 12 Maintenance
This module is used to assemble the commonly used system tools
to manage the switch. Here mainly introduces:
System Monitor: Monitor the memory and CPU of the switch.
Log: View configuration parameters on the switch.
Device Diagnostics: Test the connection status of the cable
connected to the switch, test if the port of the switch and the
connected device are available.
Network Diagnostics: Test if the destination is reachable and the
account of router hops from the switch to the destination.
Appendix A Specifications
Lists the hardware specifications of the switch.
Appendix B Configure the PCs
Introduces how to configure the PCs.
Appendix C Glossary
Lists the glossary used in this manual.
4
Return to CONTENTS
Page 10

Chapter 2 Introduction
Thanks for choosing the FGS-2800 24+4G Gigabit Web Smart Switch with 2 Combo SFP Slots!
2.1 Overview of the Switch
Designed for workgroups and departments, FGS-2800 provides wire-speed performance and full
set of layer 2 management features. It provides a variety of service features and multiple powerful
functions with high security.
The EIA-standardized framework and smart configuration capacity can provide flexible solutions
for a variable scale of networks. QoS and IGMP snooping/filtering optimize voice and video
application. Link aggregation(LACP) increases aggregated bandwidth, optimizing the transport of
business critical data. SNMP, RMON, WEB/Telnet Log-in bring abundant management policies.
FGS-2800 switch integrates multiple functions with excellent performance, and is friendly to
manage, which can fully meet the need of the users demanding higher networking performance.
2.2 Main Features
Resiliency and Availability
+ Link aggregation (LACP) increases aggregated bandwidth, optimizing the transport of
business critical data.
+ IEEE 802.1s Multiple Spanning Tree provides high link availability in multiple VLAN
environments.
+ Multicast snooping automatically prevents flooding of IP multicast traffic.
+ Root Guard protects root bridge from malicious attack or configuration mistakes
Layer 2 Switching
+ Supports up to 512 VLANs simultaneously (out of 4K VLAN IDs).
Quality of Service
+ Supports L2/L3 granular CoS with 4 priority queues per port.
+ Rate limiting confines the traffic flow accurately according to the preset value.
Security
+ L2/L3/L4 Access Control Lists restrict untrusted access to the protected resource.
+ Provides SSHv1/v2, SSL 2.0/3.0 and TLS v1 for access encryption.
Manageability
+ Supports Telnet, SNMP v1/v2c/v3, RMON and web access.
+ Port Mirroring enables monitoring selected ingress/egress traffic.
2.3 Appearance Description
2.3.1 Front Panel
Figure 2-1 Front Panel
5
Page 11
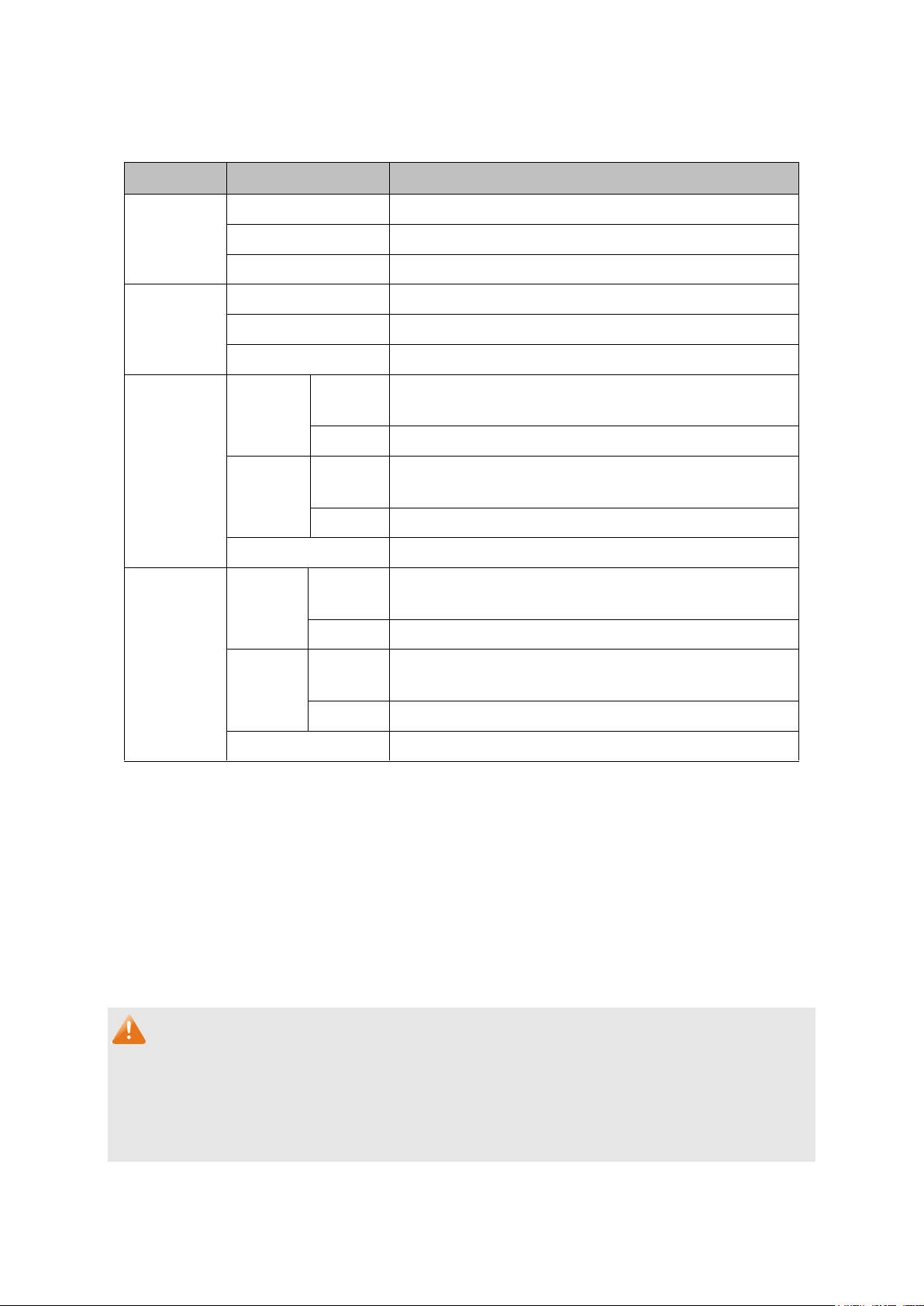
Name
Status
Indication
Power
On
Power is on.
Flashing
Power supply is abnormal.
Off
Power is off or power supply is abnormal.
System
On
The switch is working abnormally.
Flashing
The switch is working normally.
Off
The switch is working abnormally.
10/100M
Green
On
A 100Mbps device is connected to the corresponding
port, but no activity.
Flashing
Data is being transmitted or received.
Yellow
On
A 10Mbps device is connected to the corresponding
port, but no activity.
Flashing
Data is being transmitted or received.
Off
No device is connected to the corresponding port.
1000M
Green
On
A 1000Mbps device is connected to the corresponding
port, but no activity.
Flashing
Data is being transmitted or received.
Yellow
On
A 10/100Mbps device is connected to the
corresponding port, but no activity.
Flashing
Data is being transmitted or received.
Off
No device is connected to the corresponding port.
The following parts are located on the front panel of the switch:
LEDs
10/100Mbps Ports: Designed to connect to the device with a bandwidth of 10Mbps or
100Mbps. Each has a corresponding 10/100M LED.
10/100/1000Mbps Ports: Designed to connect to the device with a bandwidth of 10Mbps,
100Mbps or 1000Mbps. Each has a corresponding 10/100/1000M LED.
SFP Ports: Designed to install the SFP module. FGS-2800 features 2 Combo SFP Slots. Port
27F shares the same LED with Port 27 and Port 28F shares the same LED with Port 28. The
Port 27F (28F) and Port 27 (28) are referred to as ―combo‖ ports, which means they cannot be
used simultaneously, otherwise only SFP ports work. The SFP module supports hot-plugging.
Note:
When using the SFP port with a 100M module or a gigabit module, you need to configure its
corresponding Speed and Duplex mode on Switching → Port → Port Config page. For 100M
module, please select 100MFD while select 1000MFD for gigabit module. By default, the Speed
and Duplex mode of SFP port is 1000MFD.
6
Page 12
Reset: Press this button for five seconds or above to reset the software setting back to factory
default settings.
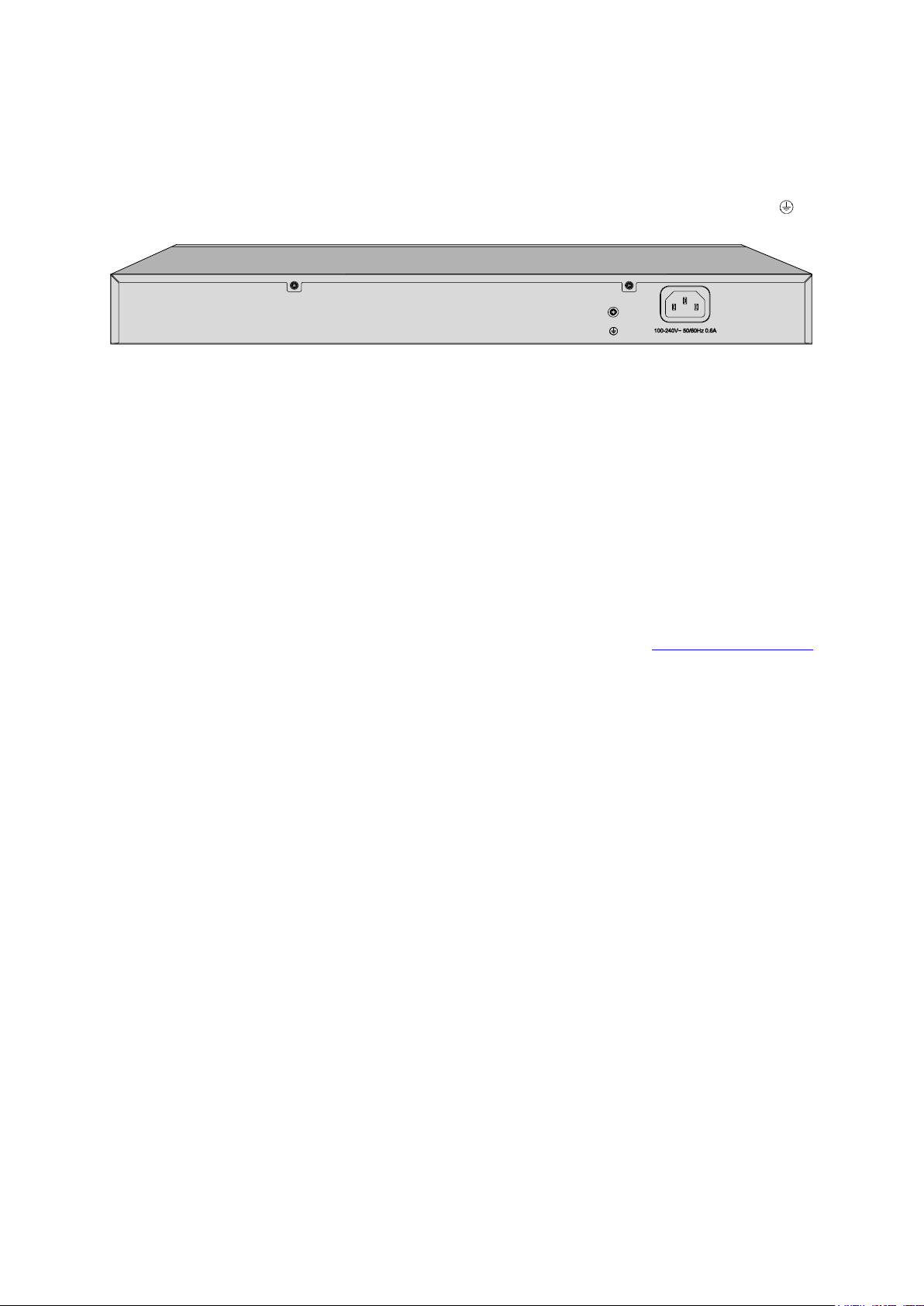
2.3.2 Rear Panel
The rear panel of FGS-2800 features a power socket and a Grounding Terminal (marked with ).
Figure 2-2 Rear Panel
Grounding Terminal: FGS-2800 already comes with Lightning Protection Mechanism. You can
also ground the switch through the PE (Protecting Earth) cable of AC cord or with Ground
Cable.
AC Power Socket: Connect the female connector of the power cord here, and the male
connector to the AC power outlet. Please make sure the voltage of the power supply meets the
requirement of the input voltage (100-240V~ 50/60Hz 0.6A).
Return to CONTENTS
7
Page 13
Chapter 3 Login to the Switch
3.1 Login
1) To access the configuration utility, open a web-browser and type in the default address
http://192.168.1.1 in the address field of the browser, then press the Enter key.
Figure 3-1 Web-browser
Tips:
To log in to the switch, the IP address of your PC should be set in the same subnet addresses of
the switch. The IP address is 192.168.1.x ("x" is any number from 2 to 254), Subnet Mask is
255.255.255.0. For the detailed instructions as to how to do this, please refer to Appendix B.
2) After a moment, a login window will appear, as shown in Figure 3-2. Enter admin for the User
Name and Password, both in lower case letters. Then click the Login button or press the Enter
key.
Figure 3-2 Login
3.2 Configuration
After a successful login, the main page will appear as Figure 3-3, and you can configure the
function by clicking the setup menu on the left side of the screen.
8
Page 14
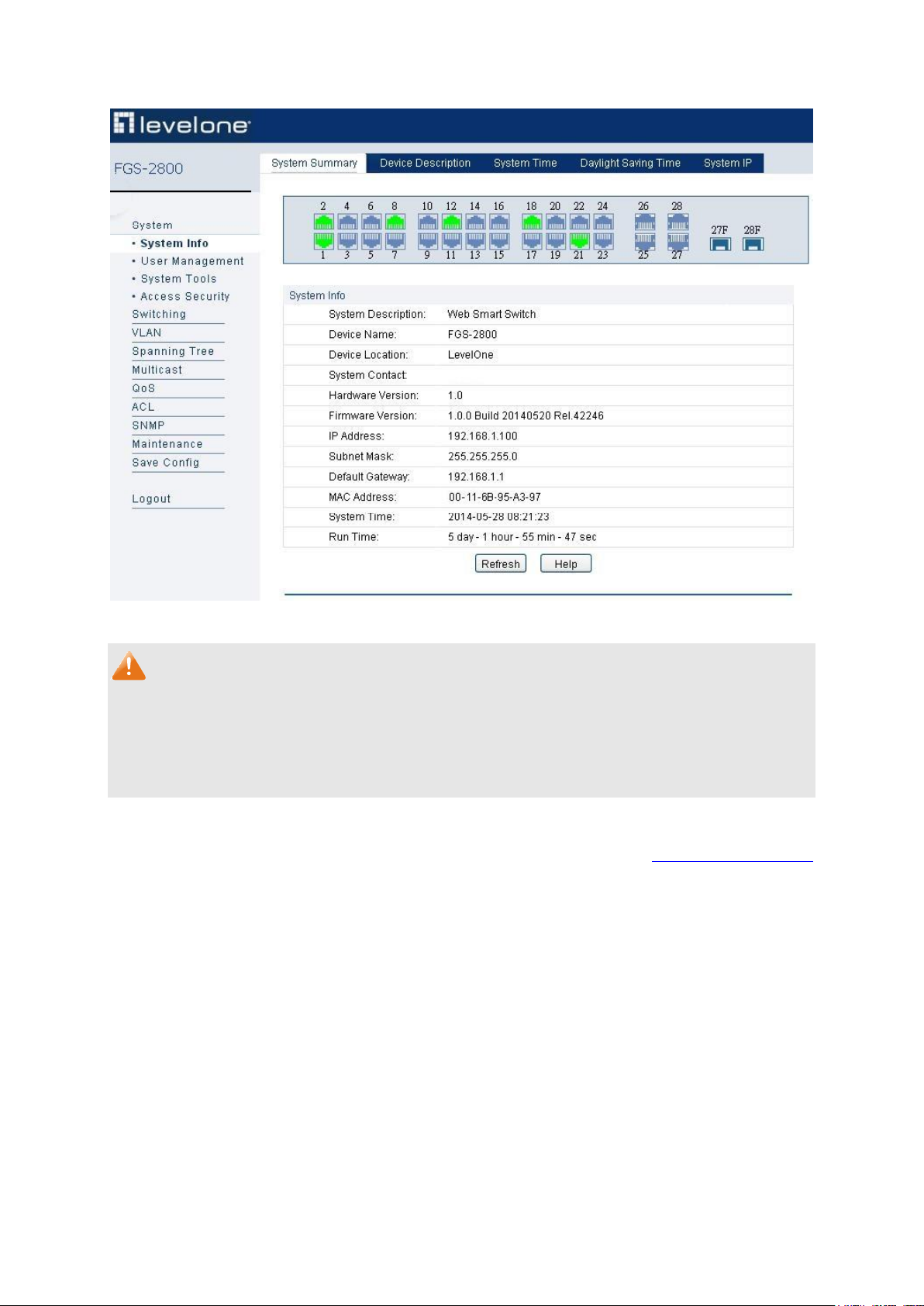
Figure 3-3 Main Setup-Menu
Note:
Clicking Apply can only make the new configurations effective before the switch is rebooted. If
you want to keep the configurations effective even the switch is rebooted, please click Saving
Config. You are suggested to click Saving Config before cutting off the power or rebooting the
switch to avoid losing the new configurations.
Return to CONTENTS
9
Page 15
Indicates the 100Mbps port is not connected to a device.
Chapter 4 System
The System module is mainly for system configuration of the switch, including four submenus:
System Info, User Management, System Tools and Access Security.
4.1 System Info
The System Info, mainly for basic properties configuration, can be implemented on System
Summary, Device Description, System Time, Daylight Saving Time and System IP pages.
4.1.1 System Summary
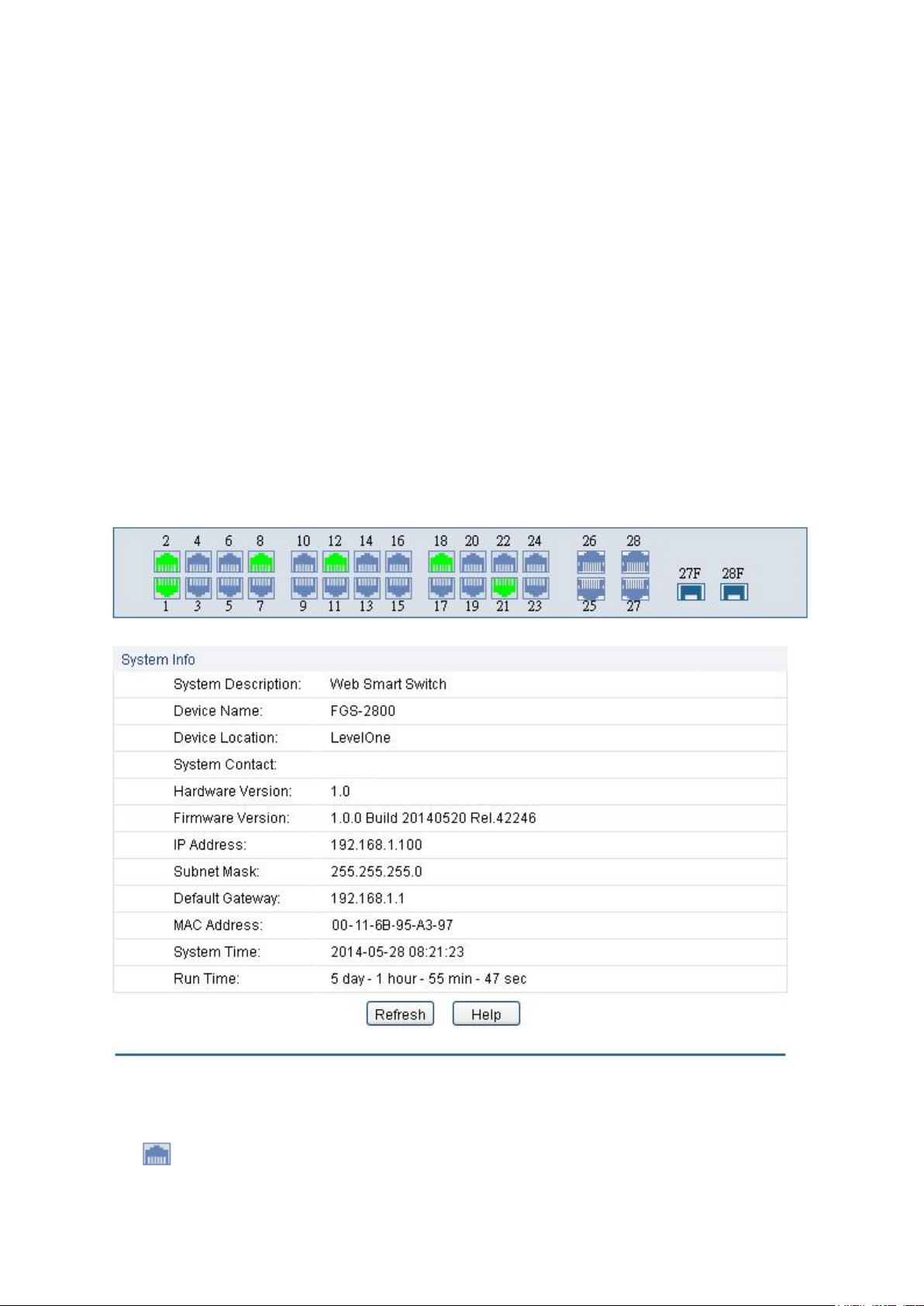
On this page you can view the port connection status and the system information.
The port status diagram shows the working status of 24 10/100Mbps RJ45 ports and 4
10/100/1000Mbps RJ45 ports and 2 SFP ports of the switch. Ports 1 to 24 are 10/100Mbps ports.
Ports 25-28 are 10/100/1000Mbps ports, among which ports 27 and 28 are Combo ports with SFP
ports labeled 27F and 28F.
Choose the menu System→System Info→System Summary to load the following page.
Figure 4-1 System Summary
Port Status
10
Page 16
Indicates the 100Mbps port is at the speed of 100Mbps.
Indicates the 100Mbps port is at the speed of 10Mbps.
Indicates the 1000Mbps port is not connected to a device.
Indicates the 1000Mbps port is at the speed of 1000Mbps.
Indicates the 1000Mbps port is at the speed of 10Mbps or 100Mbps.
Indicates the SFP port is not connected to a device.
Indicates the SFP port is at the speed of 1000Mbps.
Indicates the SFP port is at the speed of 100Mbps.
Port:
Displays the port number of the switch.
Type:
Displays the type of the port.
Rate:
Displays the maximum transmission rate of the port.
Status:
Displays the connection status of the port.
When the cursor moves on the port, the detailed information of the port will be displayed.
Figure 4-2 Port Information
Port Info
Click a port to display the bandwidth utilization on this port. The actual rate divided by theoretical
maximum rate is the bandwidth utilization. The following figure displays the bandwidth utilization
monitored every four seconds. Monitoring the bandwidth utilization on each port facilitates you to
monitor the network traffic and analyze the network abnormities.
11
Page 17
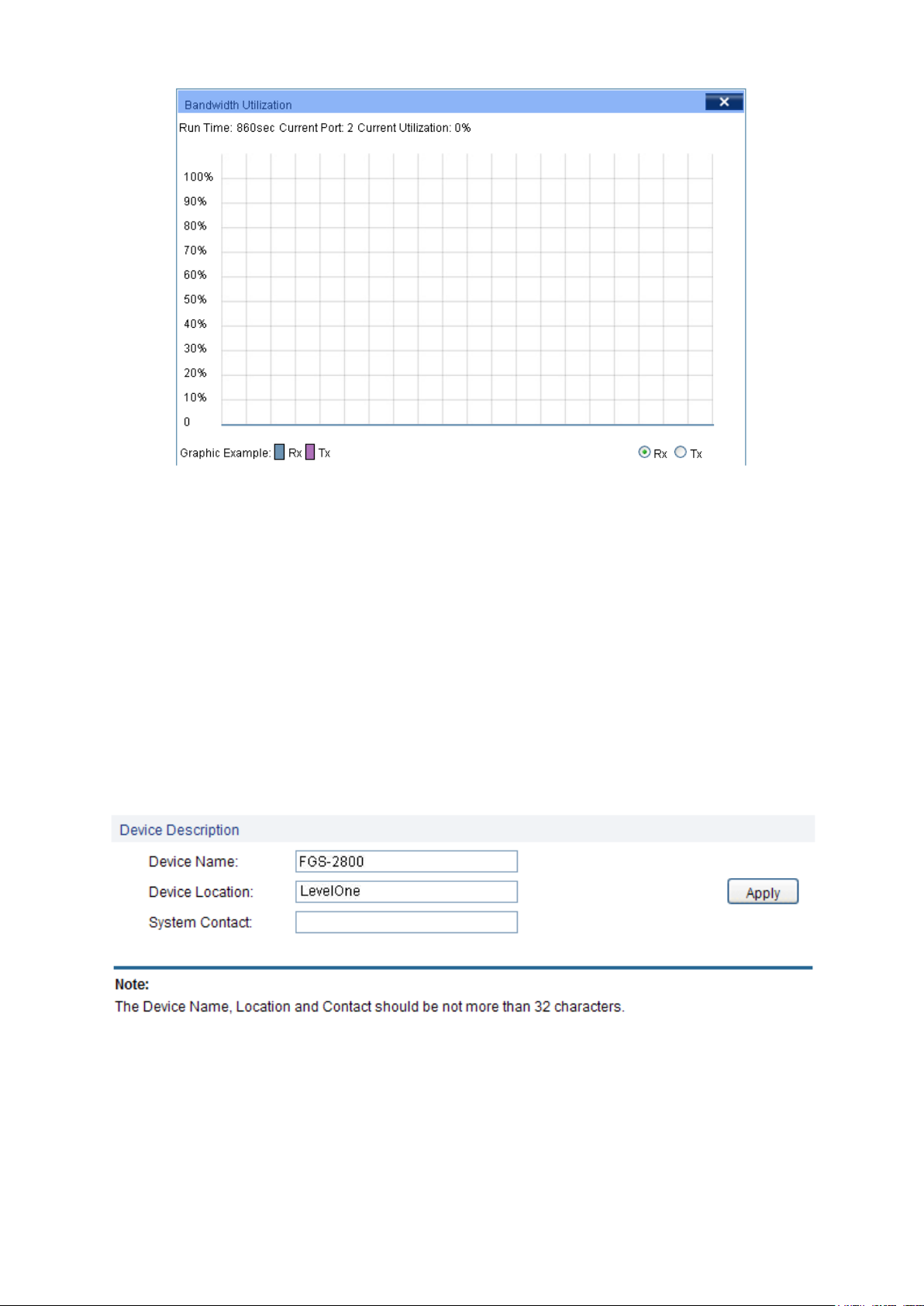
Rx:
Select Rx to display the bandwidth utilization of receiving packets
on this port.
Tx:
Select Tx to display the bandwidth utilization of sending packets
on this port.
Device Name:
Enter the name of the switch.
Device Location:
Enter the location of the switch.
Figure 4-3 Bandwidth Utilization
Bandwidth Utilization
4.1.2 Device Description
On this page you can configure the description of the switch, including device name, device location
and system contact.
Choose the menu System→System Info→Device Description to load the following page.
Figure 4-4 Device Description
The following entries are displayed on this screen:
Device Description
12
Page 18
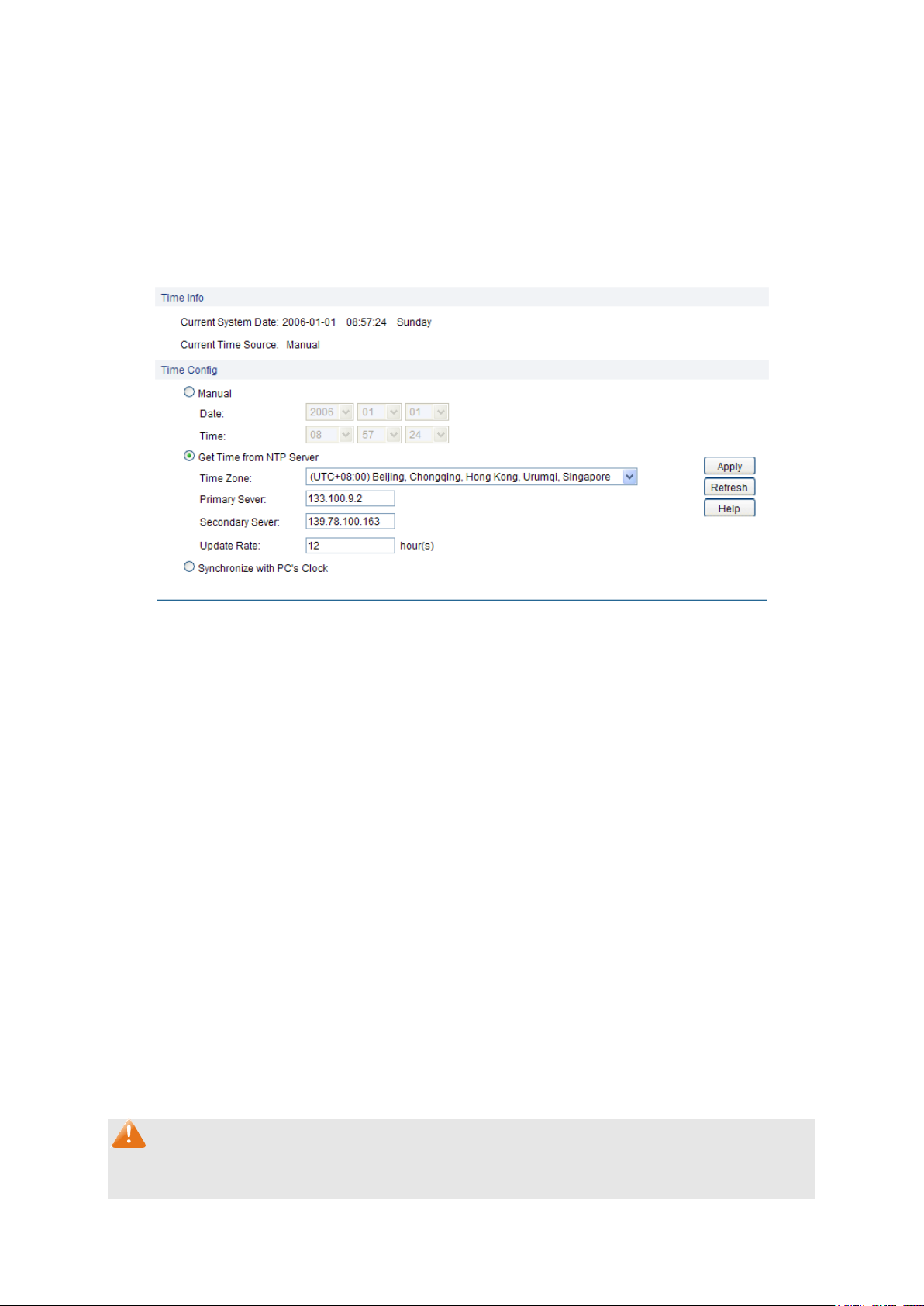
System Contact:
Enter your contact information.
Current System
Date:
Displays the current date and time of the switch.
Current Time
Source:
Displays the current time Source of the switch.
Manual:
When this option is selected, you can set the date and time
manually.
Get Time from NTP
Server:
When this option is selected, you can configure the time zone and
the IP Address for the NTP Server. The switch will get time
automatically if it has connected to a NTP Server.
Time Zone: Select your local time.
Primary/Secondary NTP Server: Enter the IP Address for
the NTP Server.
Update Rate: Specify the rate fetching time from NTP server.
Synchronize with
PC’S Clock:
When this option is selected, the administrator PC’s clock is
utilized.
4.1.3 System Time
System Time is the time displayed while the switch is running. On this page you can configure the
system time and the settings here will be used for other time-based functions.
You can manually set the system time or synchronize with PC’s clock as the system time.
Choose the menu System→System Info→System Time to load the following page.
Figure 4-5 System Time
The following entries are displayed on this screen:
Time Info
Time Config
Note:
1. The system time will be restored to the default when the switch is restarted and you need to
reconfigure the system time of the switch.
13
Page 19
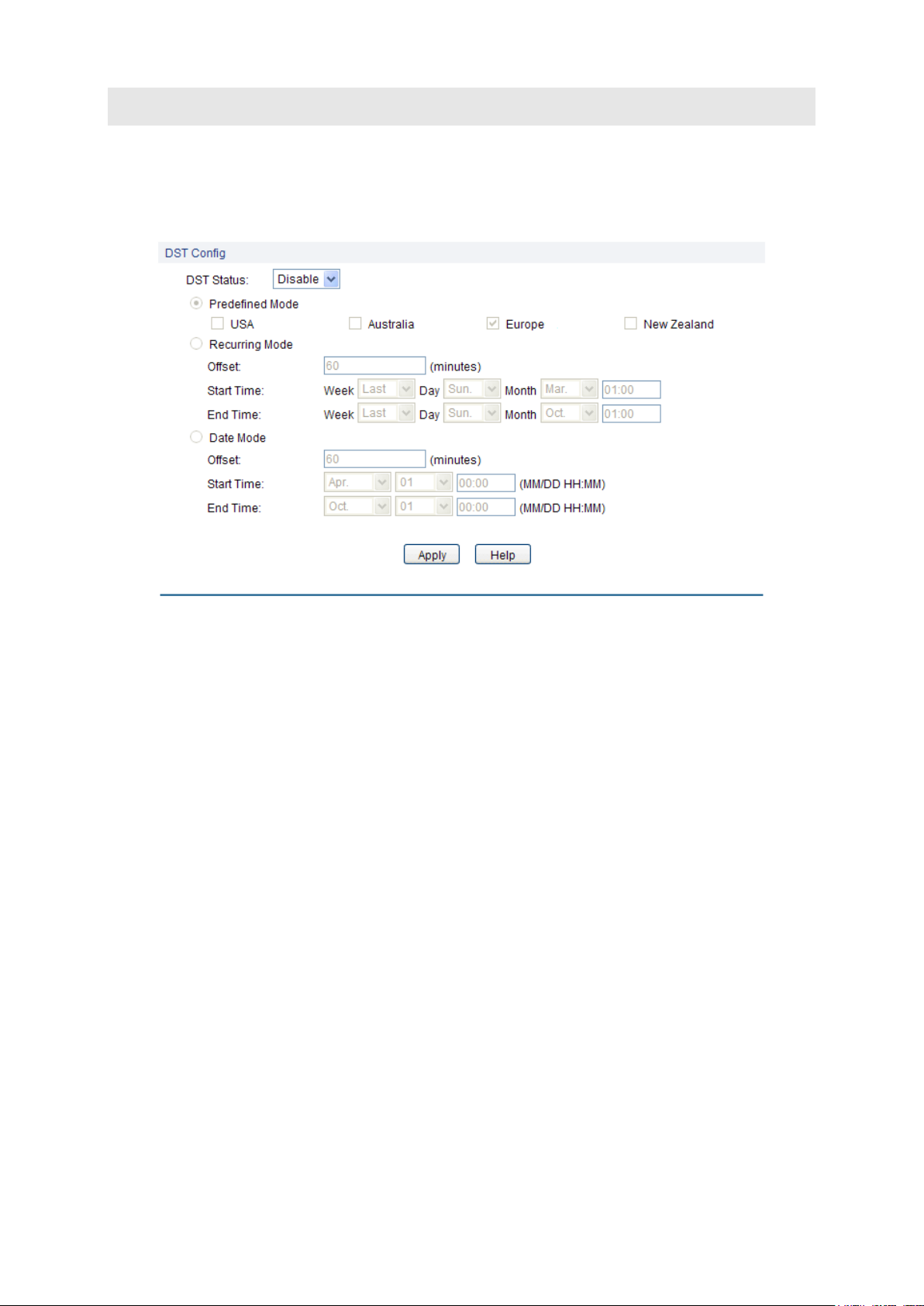
DST Status:
Enable or disable the DST.
Predefined Mode:
Select a predefined DST configuration.
USA: Second Sunday in March, 02:00 ~ First Sunday in
November, 02:00.
Australia: First Sunday in October, 02:00 ~ First Sunday in
April, 03:00.
Europe: Last Sunday in March, 01:00 ~ Last Sunday in
October, 01:00.
New Zealand: Last Sunday in September, 02:00 ~ First Sunday
in April, 03:00.
Recurring Mode:
Specify the DST configuration in recurring mode. This
configuration is recurring in use.
Offset: Specify the time adding in minutes when Daylight
Saving Time comes.
Start/End Time: Select starting time and ending time of Daylight
Saving Time.
2. When Get Time from NTP Server is selected and no time server is configured, the switch will
get time from the time server of the Internet if it has connected to the Internet.
4.1.4 Daylight Saving Time
Here you can configure the Daylight Saving Time of the switch.
Choose the menu System→System Info→Daylight Saving Time to load the following page.
Figure 4-6 Daylight Saving Time
The following entries are displayed on this screen:
DST Config
14
Page 20
Date Mode:
Specify the DST configuration in Date mode. This configuration is
recurring in use.
Offset: Specify the time adding in minutes when Daylight
Saving Time comes.
Start/End Time: Select starting time and ending time of Daylight
Saving Time.
MAC Address:
Displays MAC Address of the switch.
IP Address Mode:
Select the mode to obtain IP Address for the switch.
Static IP: When this option is selected, you should enter IP
Address, Subnet Mask and Default Gateway manually.
DHCP: When this option is selected, the switch will obtain
network parameters from the DHCP Server.
BOOTP: When this option is selected, the switch will obtain
network parameters from the BOOTP Server.
Note:
1. When the DST is disabled, the predefined mode, recurring mode and date mode cannot be
configured.
2. When the DST is enabled, the default daylight saving time is of Europe in predefined mode.
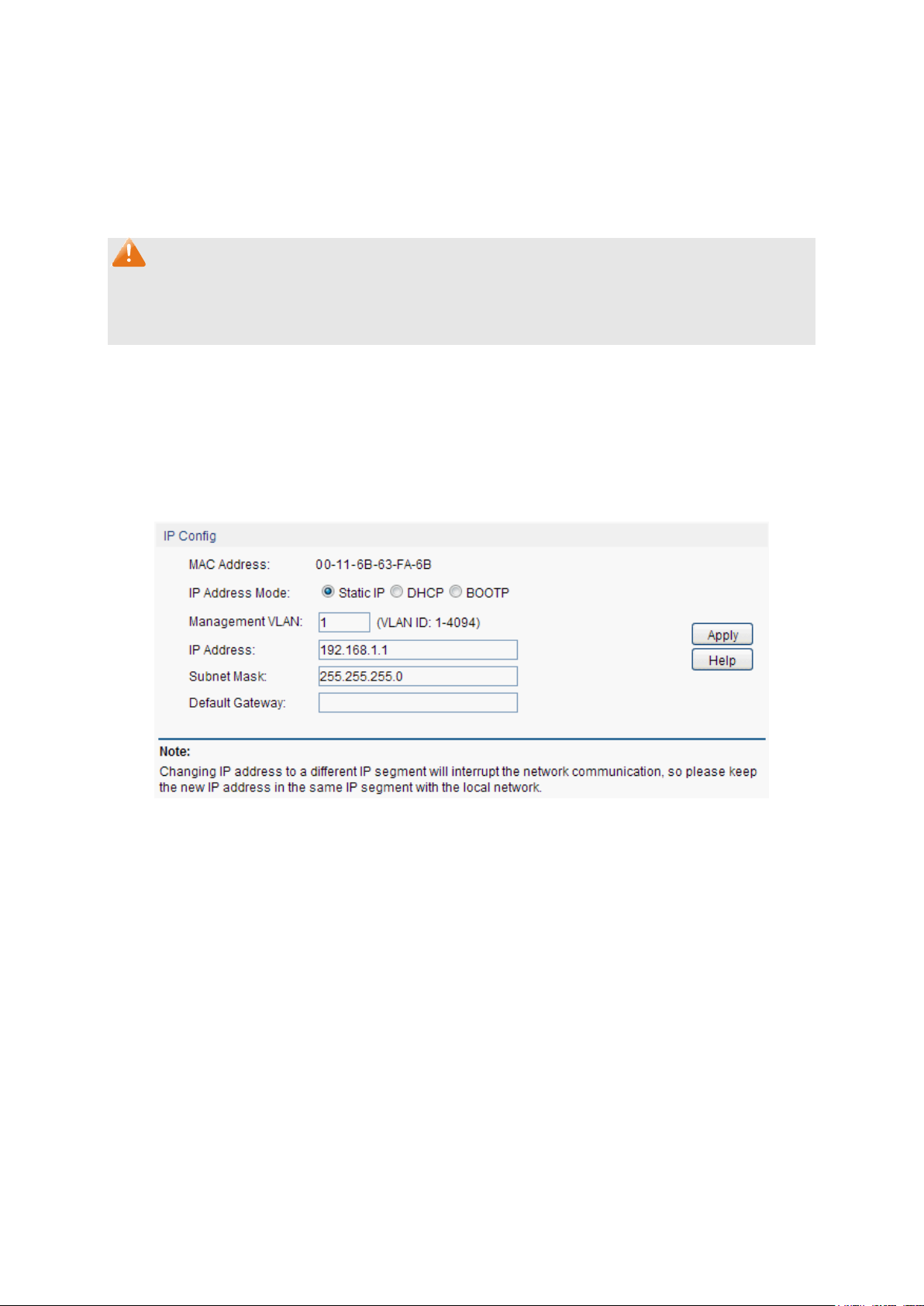
4.1.5 System IP
Each device in the network possesses a unique IP Address. You can log on to the Web
management page to operate the switch using this IP Address. The switch supports three modes
to obtain an IP address: Static IP, DHCP and BOOTP. The IP address obtained using a new mode
will replace the original IP address. On this page you can configure the system IP of the switch.
Choose the menu System→System Info→System IP to load the following page.
Figure 4-7 System IP
The following entries are displayed on this screen:
IP Config
15
Page 21
Management VLAN:
Enter the ID of management VLAN, the only VLAN through which
you can get access to the switch. By default VLAN1 owning all the
ports is the Management VLAN and you can access the switch via
any port on the switch. However, if another VLAN is created and
set to be the Management VLAN, you may have to reconnect the
management station to a port that is a member of the
Management VLAN.
IP Address:
Enter the system IP of the switch. The default system IP is
192.168.1.1 and you can change it appropriate to your needs.
Subnet Mask:
Enter the subnet mask of the switch.
Default Gateway:
Enter the default gateway of the switch.
Note:
1. Changing the IP address to a different IP segment will interrupt the network communication,
so please keep the new IP address in the same IP segment with the local network.
2. The switch only possesses an IP address. The IP address configured will replace the original
IP address.
3. If the switch gets the IP address from DHCP server, you can see the configuration of the
switch in the DHCP server; if DHCP option is selected but no DHCP server exists in the
network, a few minutes later, the switch will restore the setting to the default.
4. If DHCP or BOOTP option is selected, the switch will get network parameters dynamically
from the Internet, which means that its IP address, subnet mask and default gateway can not
be configured.
5. By default, the IP address is 192.168.1.1.
4.2 User Management
User Management functions to configure the user name and password for users to log on to the
Web management page with a certain access level so as to protect the settings of the switch from
being randomly changed.
The User Management function can be implemented on User Table and User Config pages.
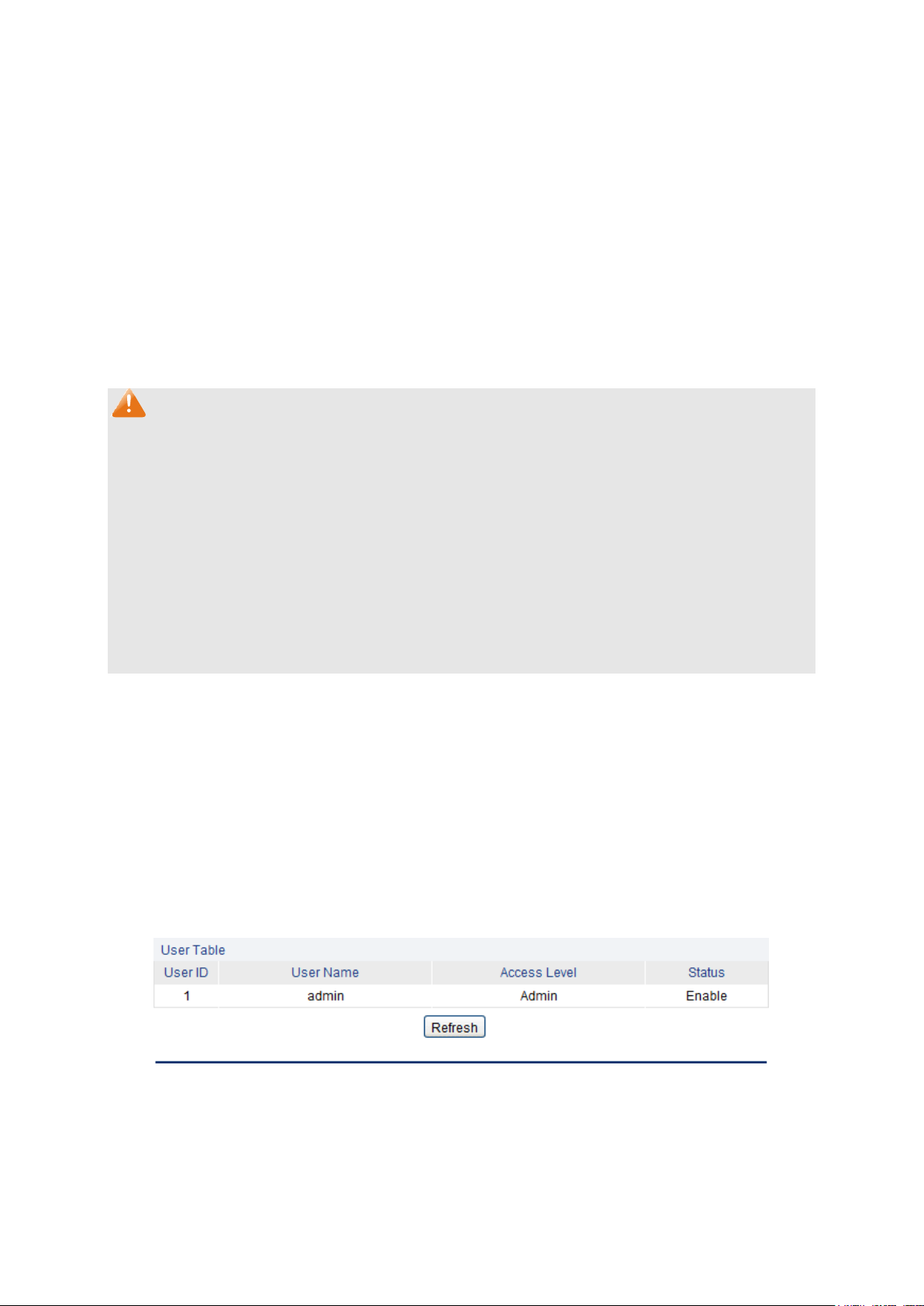
4.2.1 User Table
On this page you can view the information about the current users of the switch.
Choose the menu System→User Management→User Table to load the following page.
Figure 4-8 User Table
4.2.2 User Config
On this page you can configure the access level of the user to log on to the Web management
page. The switch provides two access levels: Guest and Admin. The guest only can view the
settings without the right to configure the switch; the admin can configure all the functions of the
16
Page 22
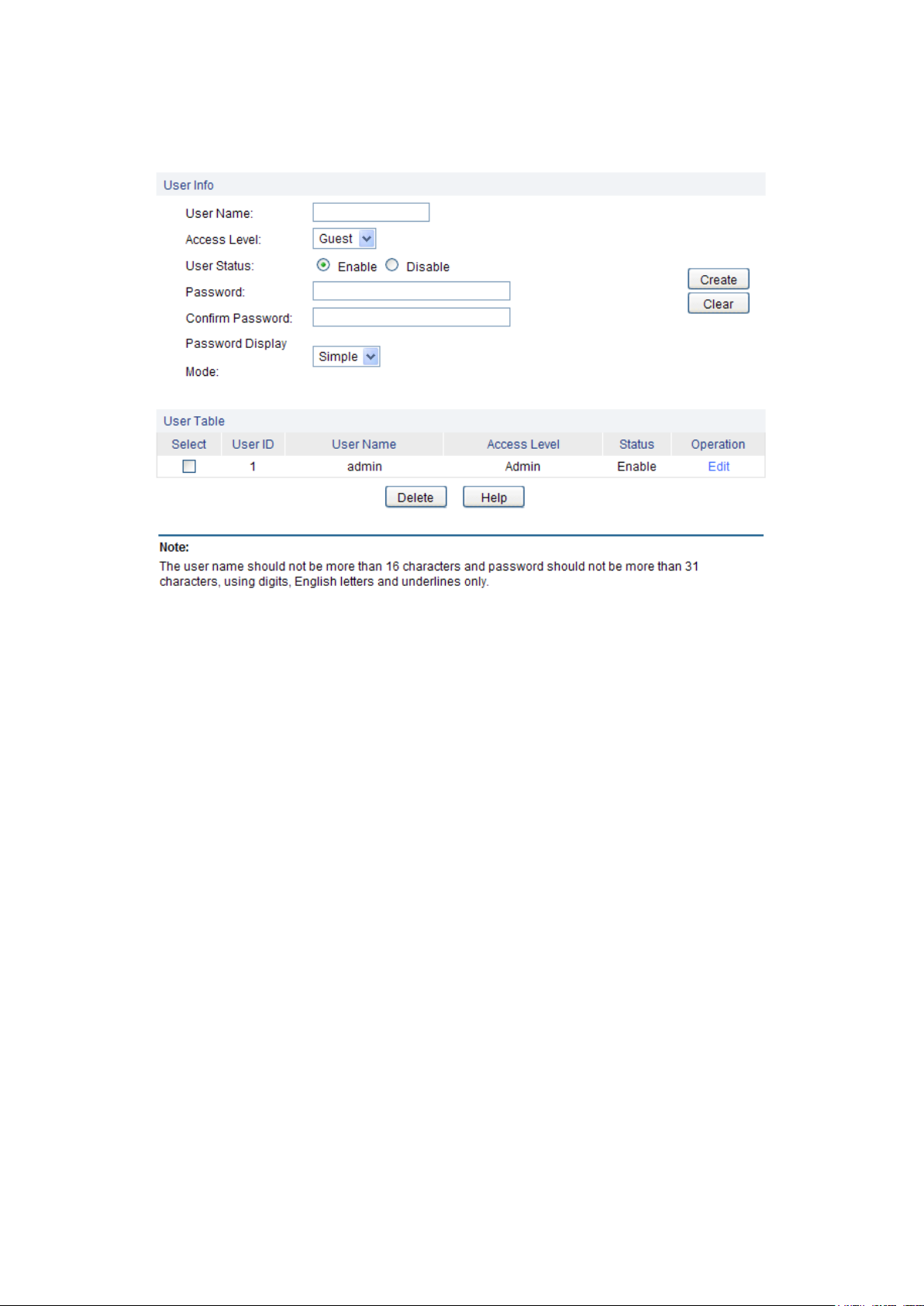
User Name:
Create a name for users’ login.
Access Level:
Select the access level to login.
Admin: Admin can edit, modify and view all the settings of
different functions.
Guest: Guest only can view the settings without the right to edit
and modify.
User Status:
Select Enable/Disable the user configuration.
Password:
Type a password for users’ login.
Confirm Password:
Retype the password.
Password Display
Mode:
Select password display mode.
Simple: Displays the password with plaintext in configure file.
Cipher: Displays the password with ciphertext in configure
file.
Select:
Select the desired entry to delete the corresponding user
information. It is multi-optional The current user information can’t
be deleted.
switch. The Web management pages contained in this guide are subject to the admin’s login without any
explanation.
Choose the menu System→User Management→User Config to load the following page.
Figure 4-9 User Config
The following entries are displayed on this screen:
User Info
User Table
17
Page 23
User ID, Name,
Access Level and
status:
Displays the current user ID, user name, access level and user
status.
Operation:
Click the Edit button of the desired entry, and you can edit the
corresponding user information. After modifying the settings,
please click the Modify button to make the modification effective.
Access level and user status of the current user information can’t
be modified.
Restore Config:
Click the Restore Config button to restore the backup
configuration file. It will take effect after the switch automatically
reboots.
4.3 System Tools
The System Tools function, allowing you to manage the configuration file of the switch, can be
implemented on Config Restore, Config Backup, Firmware Upgrade, System Reboot and
System Reset pages.
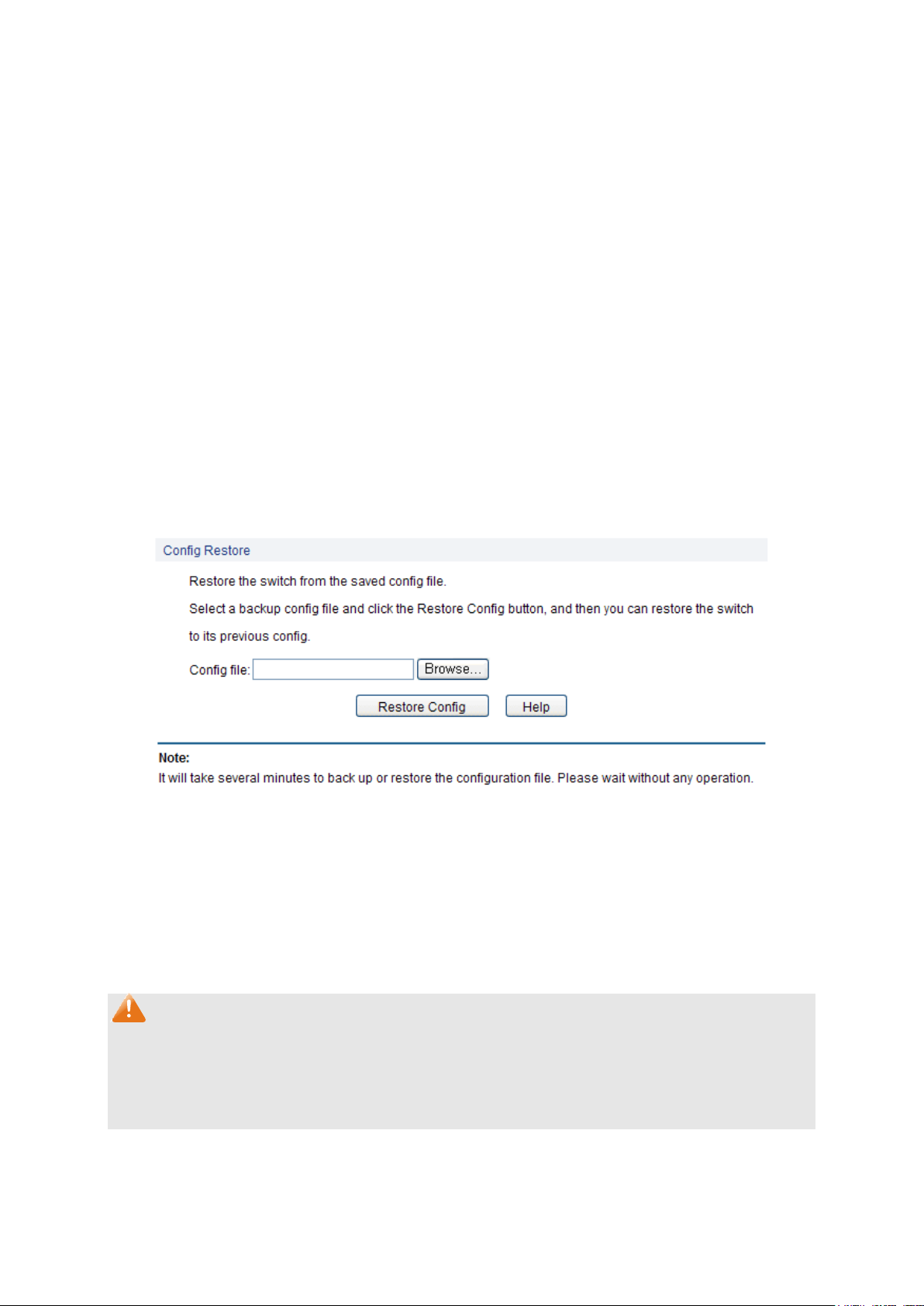
4.3.1 Config Restore
On this page you can upload a backup configuration file to restore your switch to this previous
configuration.
Choose the menu System→System Tools→Config Restore to load the following page.
Figure 4-10 Config Restore
The following entries are displayed on this screen:
Config Restore
Note:
1. It will take a few minutes to restore the configuration. Please wait without any operation.
2. To avoid any damage, please don’t power down the switch while being restored.
3. After being restored, the current settings of the switch will be lost. Wrong uploaded
configuration file may cause the switch unmanaged.
18
Page 24
Backup Config:
Click the Backup Config button to save the current configuration
as a file to your computer. You are suggested to take this measure
before upgrading.
4.3.2 Config Backup
On this page you can download the current configuration and save it as a file to your computer for
your future configuration restore.
Choose the menu System→System Tools→Config Backup to load the following page.
Figure 4-11 Config Backup
The following entries are displayed on this screen:
Config Backup
Note:
It will take a few minutes to backup the configuration. Please wait without any operation.
4.3.3 Firmware Upgrade
The switch system can be upgraded via the Web management page. To upgrade the system is to
get more functions and better performance.
Choose the menu System→System Tools→Firmware Upgrade to load the following page.
Figure 4-12 Firmware Upgrade
Note:
1. Don’t interrupt the upgrade.
19
Page 25
2. Please select the proper software version matching with your hardware to upgrade.
3. To avoid damage, please don't turn off the device while upgrading.
4. After upgrading, the device will reboot automatically.
5. You are suggested to backup the configuration before upgrading.
4.3.4 System Reboot
On this page you can reboot the switch and return to the login page. Please save the current
configuration before rebooting to avoid losing the configuration unsaved.
Choose the menu System→System Tools→System Reboot to load the following page.
Figure 4-13 System Reboot
Note:
To avoid damage, please don't turn off the device while rebooting.
4.3.5 System Reset
On this page you can reset the switch to the default. All the settings will be cleared after the switch
is reset.
Choose the menu System→System Tools→System Reset to load the following page.
Figure 4-14 System Reset
Note:
After the system is reset, the switch will be reset to the default and all the settings will be cleared.
4.4 Access Security
Access Security provides different security measures for the remote login so as to enhance the
configuration management security. It can be implemented on Access Control, SSL Config and
SSH Config pages.
4.4.1 Access Control
On this page you can control the users logging on to the Web management page to enhance the
configuration management security. The definitions of Admin and Guest refer to 4.2 User
Management.
20
Page 26
Control Mode:
Select the control mode for users to log on to the Web
management page.
Disable:Disable the access control function.
IP-based: Select this option to limit the IP-range of the users
for login.
MAC-based: Select this option to limit the MAC address of the
users for login.
Port-based: Select this option to limit the ports for login.
IP Address&Mask
These fields can be available for configuration only when IP-based
mode is selected. Only the users within the IP-range you set here
are allowed for login.
MAC Address:
The field can be available for configuration only when MAC-based
mode is selected. Only the user with this MAC Address you set
here are allowed for login.
Port:
The field can be available for configuration only when Port-based
mode is selected. Only the users connected to these ports you set
here are allowed for login.
Choose the menu System→Access Security→Access Control to load the following page
Figure 4-15 Access Control
The following entries are displayed on this screen:
Access Control Config
21
Page 27

Session Timeout:
If you do nothing with the Web management page within the
timeout time, the system will log out automatically. If you want to
reconfigure, please login again.
Number Control;
Select Enable/Disable the Number Control function.
Admin Number:
Enter the maximum number of the users logging on to the Web
management page as Admin.
Guest Number:
Enter the maximum number of the users logging on to the Web
management page as Guest.
Session Config
Access User Number
4.4.2 SSL Config
SSL (Secure Sockets Layer), a security protocol, is to provide a secure connection for the
application layer protocol (e.g. HTTP) communication based on TCP. SSL is widely used to secure
the data transmission between the Web browser and servers. It is mainly applied through
ecommerce and online banking.
SSL mainly provides the following services:
1. Authenticate the users and the servers based on the certificates to ensure the data are
transmitted to the correct users and servers;
2. Encrypt the data transmission to prevent the data being intercepted;
3. Maintain the integrality of the data to prevent the data being altered in the transmission.
Adopting asymmetrical encryption technology, SSL uses key pair to encrypt/decrypt information. A
key pair refers to a public key (contained in the certificate) and its corresponding private key. By
default the switch has a certificate (self-signed certificate) and a corresponding private key. The
Certificate/Key Download function enables the user to replace the default key pair.
After SSL is effective, you can log on to the Web management page via https://192.168.1.1. For
the first time you use HTTPS connection to log into the switch with the default certificate, you will
be prompted that ―The security certificate presented by this website was not issued by a trusted
certificate authority‖ or ―Certificate Errors‖. Please add this certificate to trusted certificates or
continue to this website.
On this page you can configure the SSL function.
22
Page 28
SSL:
Select Enable/Disable the SSL function on the switch.
Certificate File:
Select the desired certificate to download to the switch. The
certificate must be BASE64 encoded.
Key File:
Select the desired SSL key to download to the switch. The key
must be BASE64 encoded.
Choose the menu System→Access Security→SSL Config to load the following page.
Figure 4-16 SSL Config
The following entries are displayed on this screen:
Global Config
Certificate Download
Key Download
Note:
1. The SSL certificate and key downloaded must match each other; otherwise the HTTPS
connection will not work.
2. The SSL certificate and key downloaded will not take effect until the switch is rebooted.
3. To establish a secured connection using https, please enter https:// into the URL field of the
browser.
4. It may take more time for https connection than that for http connection, because https
connection involves authentication, encryption and decryption etc.
4.4.3 SSH Config
As stipulated by IFTF (Internet Engineering Task Force), SSH (Secure Shell) is a security protocol
established on application and transport layers. SSH-encrypted-connection is similar to a telnet
connection, but essentially the old telnet remote management method is not safe, because the
password and data transmitted with plain-text can be easily intercepted. SSH can provide
information security and powerful authentication when you log on to the switch remotely through
an insecure network environment. It can encrypt all the transmission data and prevent the
information in a remote management being leaked.
23
Page 29
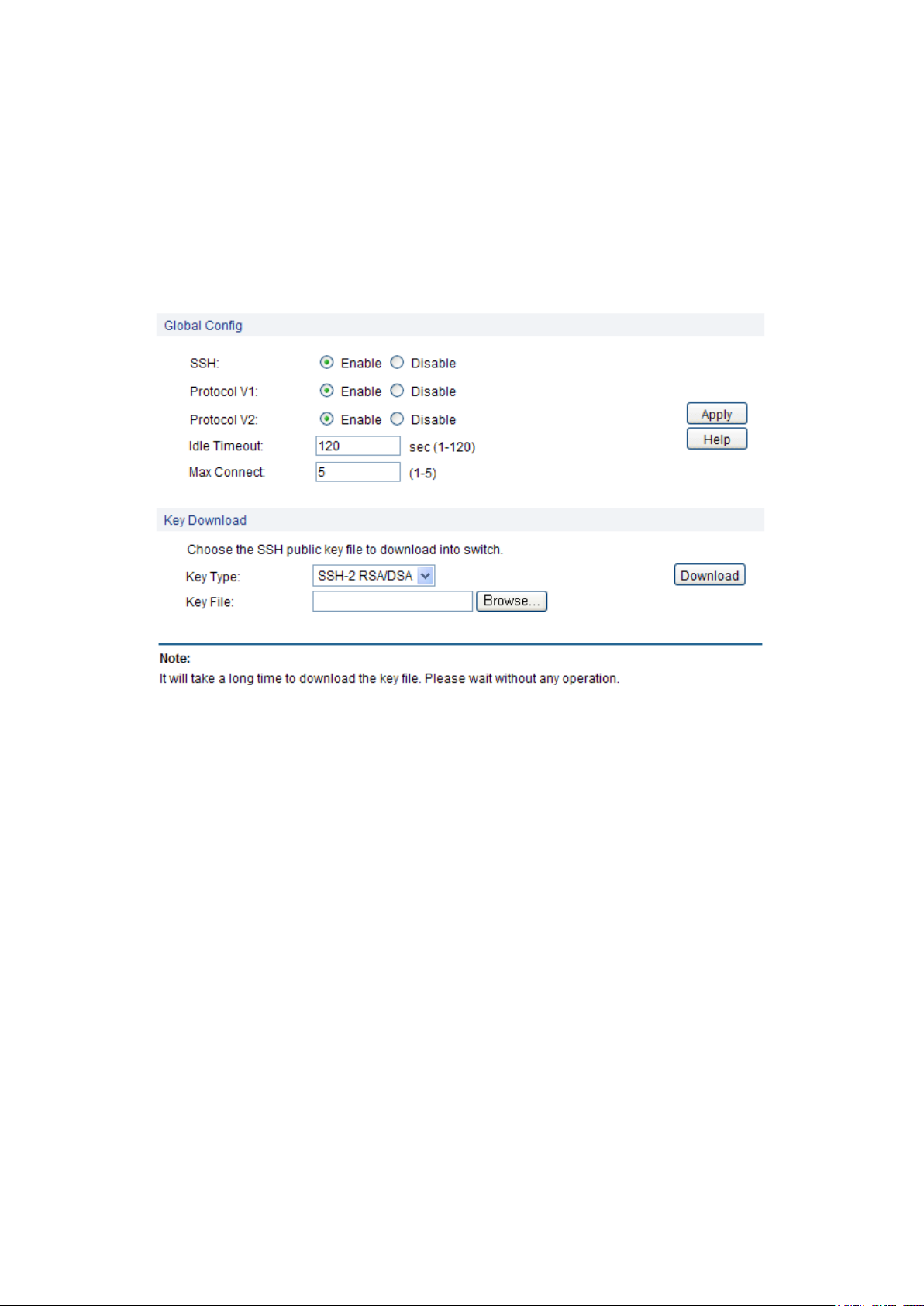
SSH:
Select Enable/Disable SSH function.
Protocol V1:
Select Enable/Disable SSH V1 to be the supported protocol.
Protocol V2:
Select Enable/Disable SSH V2 to be the supported protocol.
Idle Timeout:
Specify the idle timeout time. The system will automatically
release the connection when the time is up. The default time is
120 seconds.
Max Connect:
Specify the maximum number of the connections to the SSH
server. No new connection will be established when the number
of the connections reaches the maximum number you set. The
default value is 5.
Key Type:
Select the type of SSH key to download. The switch supports
three types: SSH-1 RSA, SSH-2 RSA and SSH-2 DSA.
Key File:
Select the desired key file to download.
Comprising server and client, SSH has two versions, V1 and V2 which are not compatible with
each other. In the communication, SSH server and client can auto-negotiate the SSH version and
the encryption algorithm. After getting a successful negotiation, the client sends authentication
request to the server for login, and then the two can communicate with each other after successful
authentication. This switch supports SSH server and you can log on to the switch via SSH
connection using SSH client software.
SSH key can be downloaded into the switch. If the key is successfully downloaded, the certificate
authentication will be preferred for SSH access to the switch.
Choose the menu System→Access Security→SSH Config to load the following page.
Figure 4-17 SSH Config
The following entries are displayed on this screen:
Global Config
Key Download
24
Page 30
Download:
Click the Download button to down the desired key file to the
switch.
Note:
1. Please ensure the key length of the downloaded file is in the range of 256 to 3072 bits.
2. After the key file is downloaded, the user’s original key of the same type will be replaced. The
wrong uploaded file will result in the SSH access to the switch via Password authentication.
Application Example 1 for SSH:
Network Requirements
1. Log on to the switch via password authentication using SSH and the SSH function is enabled
on the switch.
2. PuTTY client software is recommended.
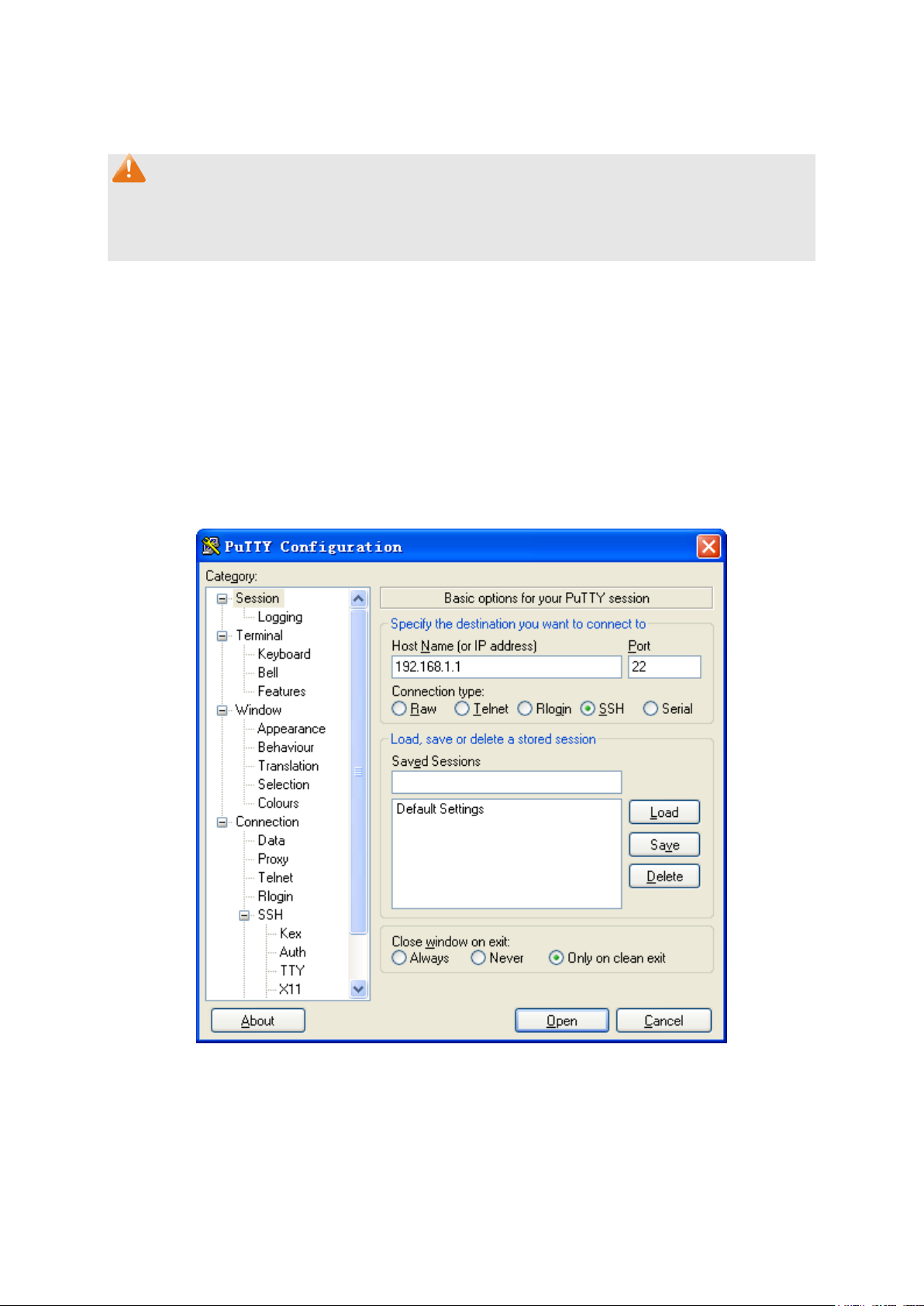
Configuration Procedure
1. Open the software to log on to the interface of PuTTY. Enter the IP address of the switch into
Host Name field; keep the default value 22 in the Port field; select SSH as the Connection
type.
2. Click the Open button in the above figure to log on to the switch. Enter the login user name and
password, and then you can continue to configure the switch.
25
Page 31

Application Example 2 for SSH:
Network Requirements
1. Log on to the switch via key authentication using SSH and the SSH function is enabled on the
switch.
2. PuTTY client software is recommended.
Configuration Procedure
1. Select the key type and key length, and generate SSH key.
Note:
1. The key length is in the range of 256 to 3072 bits.
2. During the key generation, randomly moving the mouse quickly can accelerate the key
generation.
2. After the key is successfully generated, please save the public key and private key to the
computer.
26
Page 32

3. On the Web management page of the switch, download the public key file saved in the
computer to the switch.
Note:
1. The key type should accord with the type of the key file.
2. The SSH key downloading can not be interrupted.
4. After the public key is downloaded, please log on to the interface of PuTTY and enter the IP
address for login.
27
Page 33

5. Click Browse to download the private key file to SSH client software and click Open.
After successful authentication, please enter the login user name. If you log on to the switch
without entering password, it indicates that the key has been successfully loaded.
28
Page 34

Note:
Following the steps above, you have already entered the User EXEC Mode of the switch. However,
to configure the switch, you need a password to enter the Privileged EXEC Mode first. For a switch
with factory settings, the Privileged EXEC Mode password can only be configured through the
console connection. For how to configure the Privileged EXEC Mode password, please refer to the
1.1.2 Configuring the Privileged EXEC Mode Password in CLI Reference Guide.
Return to CONTENTS
29
Page 35

Port Select:
Click the Select button to quick-select the corresponding port
based on the port number you entered.
Select:
Select the desired port for configuration. It is multi-optional.
Port:
Displays the port number.
Chapter 5 Switching
Switching module is used to configure the basic functions of the switch, including four submenus:
Port, LAG, Traffic Monitor, MAC Address and DHCP Filtering.
5.1 Port
The Port function, allowing you to configure the basic features for the port, is implemented on the
Port Config, Port Mirror, Port Security, Port Isolation and Loopback Detection pages.
5.1.1 Port Config
On this page, you can configure the basic parameters for the ports. When the port is disabled, the
packets on the port will be discarded. Disabling the port which is vacant for a long time can reduce
the power consumption effectively. And you can enable the port when it is in need.
The parameters will affect the working mode of the port, please set the parameters appropriate to
your needs.
Choose the menu Switching→Port→Port Config to load the following page.
Figure 5-1 Port Config
The following entries are displayed on this screen:
Port Config
30
Page 36

Description:
Give a description to the port for identification.
Status:
Allows you to Enable/Disable the port. When Enable is
selected, the port can forward the packets normally.
Speed and Duplex:
Select the Speed and Duplex mode for the port. The device
connected to the switch should be in the same Speed and
Duplex mode with the switch. When ―Auto‖ is selected, the
Speed and Duplex mode will be determined by
auto-negotiation. For the SFP port, this switch does not support
auto-negotiation.
Flow Control:
Allows you to Enable/Disable the Flow Control feature. When
Flow Control is enabled, the switch can synchronize the speed
with its peer to avoid the packet loss caused by congestion.
LAG:
Displays the LAG number which the port belongs to.
Note:
1. The switch can not be managed through the disabled port. Please enable the port which is
used to manage the switch.
2. The parameters of the port members in a LAG should be set as the same.
3. When using the SFP port with a 100M module or a gigabit module, you need to configure its
corresponding Speed and Duplex mode. For 100M module, please select 100MFD while
select 1000MFD for gigabit module. By default, the Speed and Duplex mode of SFP port is
1000MFD.
5.1.2 Port Mirror
Port Mirror, the packets obtaining technology, functions to forward copies of packets from
one/multiple ports (mirrored port) to a specific port (mirroring port). Usually, the mirroring port is
connected to a data diagnose device, which is used to analyze the mirrored packets for monitoring
and troubleshooting the network.
Choose the menu Switching→Port→Port Mirror to load the following page.
Figure 5-2 Mirroring Port
31
Page 37

The following entries are displayed on this screen:
Group:
Displays the mirror group number.
Mirroring:
Displays the mirroring port number.
Mode:
Displays the mirror mode.
Mirrored Port:
Displays the mirrored ports.
Operation:
Click Edit to configure the mirror group.
Number:
Select the mirror group number you want to configure.
Mirroring Port:
Select the mirroring port number.
Mirror Group List
Click Edit to display the following figure.
The following entries are displayed on this screen:
Mirror Group
Mirroring Port
Figure 5-3 Mirroring Port
32
Page 38

Port Select:
Click the Select button to quick-select the corresponding port
based on the port number you entered.
Select:
Select the desired port as a mirrored port. It is multi-optional.
Port:
Displays the port number.
Ingress:
Select Enable/Disable the Ingress feature. When the Ingress is
enabled, the incoming packets received by the mirrored port will
be copied to the mirroring port.
Egress:
Select Enable/Disable the Egress feature. When the Egress is
enabled, the outgoing packets sent by the mirrored port will be
copied to the mirroring port.
LAG:
Displays the LAG number which the port belongs to. The LAG
member can not be selected as the mirrored port or mirroring
port.
Mirrored Port
Note:
1. The LAG member can not be selected as the mirrored port or mirroring port.
2. A port can not be set as the mirrored port and the mirroring port simultaneously.
3. The Port Mirror function can take effect span the multiple VLANs.
5.1.3 Port Security
MAC Address Table maintains the mapping relationship between the port and the MAC address of
the connected device, which is the base of the packet forwarding. The capacity of MAC Address
Table is fixed. MAC Address Attack is the attack method that the attacker takes to obtain the
network information illegally. The attacker uses tools to generate the cheating MAC address and
quickly occupy the MAC Address Table. When the MAC Address Table is full, the switch will
broadcast the packets to all the ports. At this moment, the attacker can obtain the network
information via various sniffers and attacks. When the MAC Address Table is full, the packets
traffic will flood to all the ports, which results in overload, lower speed, packets drop and even
breakdown of the system.
Port Security is to protect the switch from the malicious MAC Address Attack by limiting the
maximum number of MAC addresses that can be learned on the port. The port with Port Security
feature enabled will learn the MAC address dynamically. When the learned MAC address number
reaches the maximum, the port will stop learning. Thereafter, the other devices with the MAC
address unlearned can not access to the network via this port.
Choose the menu Switching→Port→Port Security to load the following page.
33
Page 39

Select:
Select the desired port for Port Security configuration. It is
multi-optional.
Port:
Displays the port number.
Max Learned MAC:
Specify the maximum number of MAC addresses that can be
learned on the port.
Learned Num:
Displays the number of MAC addresses that have been learned
on the port.
Learn Mode:
Select the Learn Mode for the port.
Dynamic: When Dynamic mode is selected, the learned
MAC address will be deleted automatically after the aging
time.
Static: When Static mode is selected, the learned MAC
address will be out of the influence of the aging time and
can only be deleted manually. The learned entries will be
cleared after the switch is rebooted.
Permanent: When Permanent mode is selected, the
learned MAC address will be out of the influence of the
aging time and can only be deleted manually. The learned
entries will be saved even the switch is rebooted.
Status:
Select Enable/Disable the Port Security feature for the port.
Figure 5-4 Port Security
The following entries are displayed on this screen:
Port Security
34
Page 40

Port:
Select the port number to set its forwardlist.
Forward Portlist:
Select the port that to be forwarded to.
Note:
The Port Security function is disabled for the LAG port member. Only the port is removed from the
LAG, will the Port Security function be available for the port.
5.1.4 Port Isolation
Port Isolation provides a method of restricting traffic flow to improve the network security by
forbidding the port to forward packets to the ports that are not on its forward portlist.
Choose the menu Switching→Port→Port Isolation to load the following page.
The following entries are displayed on this screen:
Port Isolation Config
Figure 5-5 Port Isolation Config
35
Page 41

Port:
Display the port number.
Forward Portlist:
Display the forwardlist.
Loopback Detection
Status:
Here you can enable or disable loopback detection function
globally.
Detection Interval:
Set a loopback detection interval between 1 and 1000 seconds.
By default, it’s 30 seconds.
Port Isolation List
5.1.5 Loopback Detection
With loopback detection feature enabled, the switch can detect loops using loopback detection
packets. When a loop is detected, the switch will display an alert or further block the corresponding
port according to the port configuration.
Choose the menu Switching→Port→Loopback Detection to load the following page.
Figure 5-6 Loopback Detection Config
The following entries are displayed on this screen:
Global Config
36
Page 42
Automatic Recovery
Time :
Time allowed for automatic recovery when a loopback is detected.
It can be set as intergral multiple of detection interval.
Web Refresh Status:
Here you can enable or disable web automatic refresh.
Web Refresh Interval:
Set a web refresh interval between 3 and 100 seconds. By default,
it’s 3 seconds.
Port Config
Port Select:
Click the Select button to quick-select the corresponding port
based on the port number you entered.
Select:
Select the desired port for loopback detection configuration. It is
multi-optional.
Port:
Displays the port number.
Status:
Enable or disable loopback detection function for the port.
Operation Mode:
Select the mode how the switch processes the detected loops.
Alert: When a loop is detected, displays an alert.
Port based: When a loopback is detected, displays an alert
and blocks the port.
Recovery Mode:
Select the mode how the blocked port recovers to normal status.
Auto: Block status can be automatically removed after
recovery time.
Manual: Block status only can be removed manually.
Loop Status:
Displays the port status whether a loopback is detected.
Block Status:
Displays the port status about block or unblock.
LAG:
Displays the LAG number the port belongs to.
Manual Recover:
Manually remove the block status of selected ports.
Note:
1. Recovery Mode is not selectable when Alert is chosen in Operation Mode.
2. Loopback Detection must coordinate with storm control.
5.2 LAG
LAG (Link Aggregation Group) is to combine a number of ports together to make a single
high-bandwidth data path, so as to implement the traffic load sharing among the member ports in
the group and to enhance the connection reliability.
For the member ports in an aggregation group, their basic configuration must be the same. The
basic configuration includes STP, QoS, VLAN, port attributes, MAC Address Learning mode
and other associated settings. The further explains are following:
If the ports, which are enabled for the 802.1Q VLAN, STP, QoS and Port Configuration
(Speed and Duplex, Flow Control), are in a LAG, their configurations should be the same.
The ports, which are enabled for the Port Security, Port Mirror and MAC Address Filtering,
can not be added to the LAG.
37
Page 43

Hash Algorithm:
Select the applied scope of Aggregate Arithmetic, which
results in choosing a port to transfer the packets.
SRC MAC + DST MAC: When this option is selected,
the Aggregate Arithmetic will apply to the source and
destination MAC addresses of the packets.
SRC IP + DST IP: When this option is selected, the
Aggregate Arithmetic will apply to the source and destination
IP addresses of the packets.
Select:
Select the desired LAG. It is multi-optional.
Group Number:
Displays the LAG number here.
If the LAG is needed, you are suggested to configure the LAG function here before configuring the
other functions for the member ports.
Tips:
1. Calculate the bandwidth for a LAG: If a LAG consists of the four ports in the speed of
1000Mbps Full Duplex, the whole bandwidth of the LAG is up to 8000Mbps (2000Mbps * 4)
because the bandwidth of each member port is 2000Mbps counting the up-linked speed of
1000Mbps and the down-linked speed of 1000Mbps.
2. The traffic load of the LAG will be balanced among the ports according to the Aggregate
Arithmetic. If the connections of one or several ports are broken, the traffic of these ports will
be transmitted on the normal ports, so as to guarantee the connection reliability.
The LAG function is implemented on the LAG Table, Static LAG and LACP Config configuration
pages.
5.2.1 LAG Table
On this page, you can view the information of the current LAG of the switch.
Choose the menu Switching→LAG→LAG Table to load the following page.
Figure 5-6 LAG Table
The following entries are displayed on this screen:
Global Config
LAG Table
38
Page 44

Description:
Displays the description of LAG.
Member:
Displays the LAG member.
Operation:
Allows you to view or modify the information for each LAG.
Edit: Click to modify the settings of the LAG.
Detail: Click to get the information of the LAG.
Click the Detail button for the detailed information of your selected LAG.
Figure 5-7 Detail Information
5.2.2 Static LAG
On this page, you can manually configure the LAG.
Choose the menu Switching→LAG→Static LAG to load the following page.
Figure 5-8 Manually Config
39
Page 45

Group Number:
Select a Group Number for the LAG.
Description:
Displays the description of the LAG.
Member Port:
Select the port as the LAG member. Clearing all the ports of
the LAG will delete this LAG.
The following entries are displayed on this screen:
LAG Config
Member Port
Tips:
1. The LAG can be deleted by clearing its all member ports.
2. A port can only be added to a LAG. If a port is the member of a LAG, the port number will be
displayed in gray and can not be selected.
5.2.3 LACP Config
LACP (Link Aggregation Control Protocol) is defined in IEEE802.3ad and enables the dynamic link
aggregation and disaggregation by exchanging LACP packets with its partner. The switch can
dynamically group similarly configured ports into a single logical link, which will highly extend the
bandwidth and flexibly balance the load.
With the LACP feature enabled, the port will notify its partner of the system priority, system MAC,
port priority, port number and operation key (operation key is determined by the physical
properties of the port, upper layer protocol and admin key). The device with higher priority will lead
the aggregation and disaggregation. System priority and system MAC decide the priority of the
device. The smaller the system priority, the higher the priority of the device is. With the same
system priority, the device owning the smaller system MAC has the higher priority. The device with
the higher priority will choose the ports to be aggregated based on the port priority, port number
and operation key. Only the ports with the same operation key can be selected into the same
aggregation group. In an aggregation group, the port with smaller port priority will be considered
as the preferred one. If the two port priorities are equal, the port with smaller port number is
preferred. After an aggregation group is established, the selected ports can be aggregated
together as one port to transmit packets.
On this page, you can configure the LACP feature of the switch.
Choose the menu Switching→LAG→LACP Config to load the following page.
40
Page 46

System Priority:
Specify the system priority for the switch. The system priority and
MAC address constitute the system identification (ID). A lower system
priority value indicates a higher system priority. When exchanging
information between systems, the system with higher priority
determines which link aggregation a link belongs to, and the system
with lower priority adds the proper links to the link aggregation
according to the selection of its partner.
Port Select:
Click the Select button to quick-select the corresponding port based
on the port number you entered.
Select:
Select the desired port for LACP configuration. It is multi-optional.
Port:
Displays the port number.
Admin Key:
Specify an admin key for the port. The member ports in a dynamic
aggregation group must have the same admin key.
Figure 5-10 LACP Config
The following entries are displayed on this screen:
Global Config
LACP Config
41
Page 47
Port Priority:
Specify a Port Priority for the port. This value determines the priority
of the port to be selected as the dynamic aggregation group
member. The port with smaller Port Priority will be considered as the
preferred one. If the two port priorities are equal; the port with
smaller port number is preferred.
Mode:
Specify LACP mode for your selected port.
Status:
Enable/Disable the LACP feature for your selected port.
LAG:
Displays the LAG number which the port belongs to.
5.3 Traffic Monitor
The Traffic Monitor function, monitoring the traffic of each port, is implemented on the Traffic
Summary and Traffic Statistics pages.
5.3.1 Traffic Summary
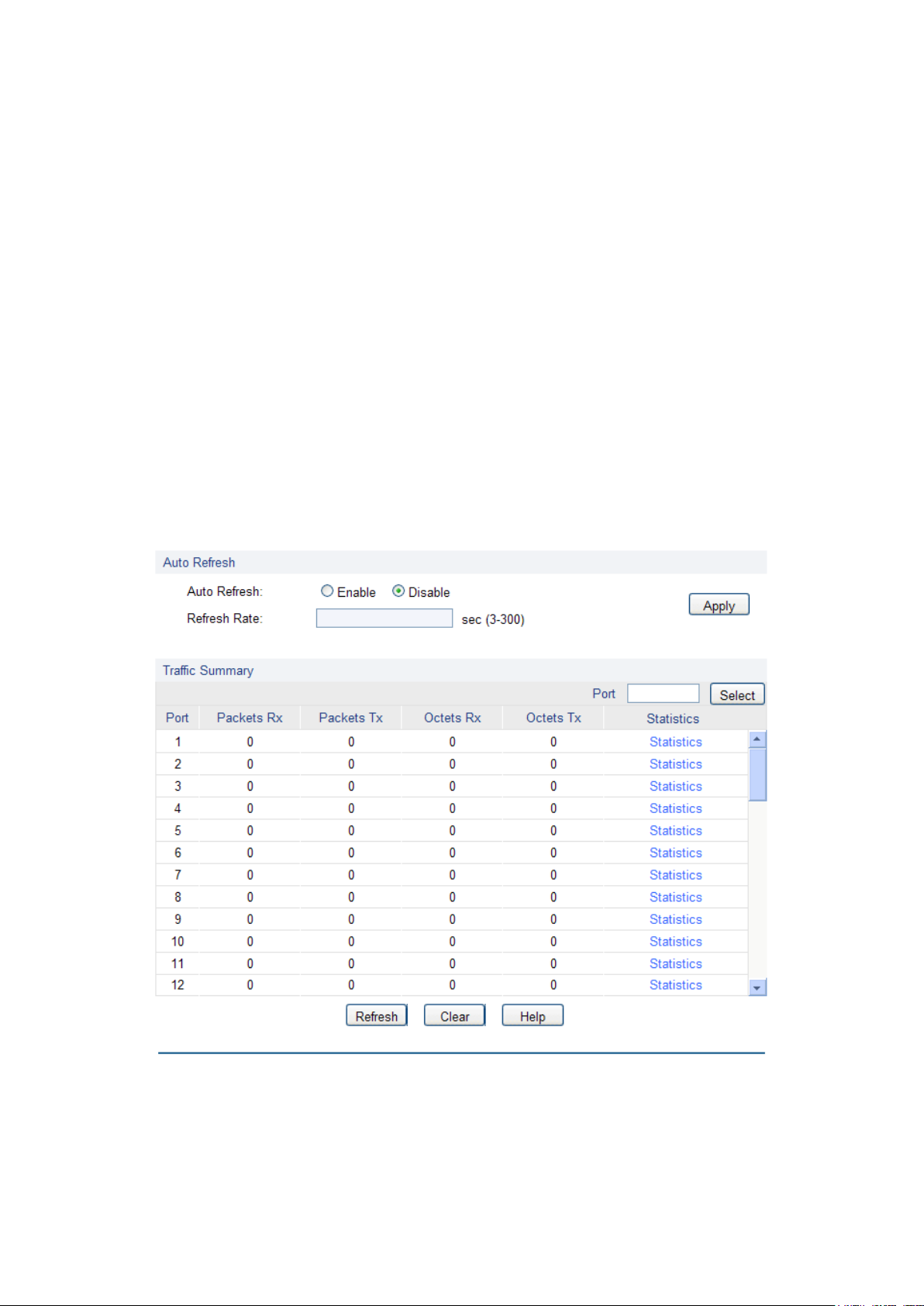
Traffic Summary screen displays the traffic information of each port, which facilitates you to
monitor the traffic and analyze the network abnormity.
Choose the menu Switching→Traffic Monitor→Traffic Summary to load the following page.
Figure 5-9 Traffic Summary
42
Page 48

The following entries are displayed on this screen:
Auto Refresh:
Allows you to Enable/Disable refreshing the Traffic Summary
automatically.
Refresh Rate:
Enter a value in seconds to specify the refresh interval.
Port Select:
Click the Select button to quick-select the corresponding port based
on the port number you entered.
Port:
Displays the port number.
Packets Rx:
Displays the number of packets received on the port. The error
packets are not counted in.
Packets Tx:
Displays the number of packets transmitted on the port.
Octets Rx:
Displays the number of octets received on the port. The error octets
are counted in.
Octets Tx:
Displays the number of octets transmitted on the port.
Statistics:
Click the Statistics button to view the detailed traffic statistics of the
port.
Auto Refresh
Traffic Summary
5.3.2 Traffic Statistics
Traffic Statistics screen displays the detailed traffic information of each port, which facilitates you to
monitor the traffic and locate faults promptly.
Choose the menu Switching→Traffic Monitor→Traffic Statistics to load the following page.
43
Page 49

Auto Refresh:
Allows you to Enable/Disable refreshing the Traffic Summary
automatically.
Refresh Rate:
Enter a value in seconds to specify the refresh interval.
Port:
Enter a port number and click the Select button to view the traffic
statistics of the corresponding port.
Received:
Displays the details of the packets received on the port.
Sent:
Displays the details of the packets transmitted on the port.
Broadcast:
Displays the number of good broadcast packets received or
transmitted on the port. The error frames are not counted in.
Multicast:
Displays the number of good multicast packets received or
transmitted on the port. The error frames are not counted in.
Unicast:
Displays the number of good unicast packets received or
transmitted on the port. The error frames are not counted in.
Alignment Errors:
Displays the number of the received packets that have a bad Frame
Check Sequence (FCS) . The length of the packet is from 64 bytes
to maximal bytes of the jumbo frame(usually 10240 bytes).
Figure 5-10 Traffic Statistics
The following entries are displayed on this screen:
Auto Refresh
Statistics
44
Page 50

UndersizePkts:
Displays the number of the received packets (excluding error
packets) that are less than 64 bytes long.
Pkts64Octets:
Displays the number of the received packets (including error
packets) that are 64 bytes long.
Pkts65to127Octets:
Displays the number of the received packets (including error
packets) that are between 65 and 127 bytes long.
Pkts128to255Octets:
Displays the number of the received packets (including error
packets) that are between 128 and 255 bytes long.
Pkts256to511Octets:
Displays the number of the received packets (including error
packets) that are between 256 and 511 bytes long.
Pkts512to1023Octets:
Displays the number of the received packets (including error
packets) that are between 512 and 1023 bytes long.
PktsOver1023Octets:
Displays the number of the received packets (including error
packets) that are over 1023 bytes.
Collisions:
Displays the number of collisions experienced by a port during
packet transmissions.
Type
Configuration
Way
Aging out
Being kept after
reboot
(if the configuration
is saved)
Relationship between the
bound MAC address and
the port
Static
Address Table
Manually
configuring
No
Yes
The bound MAC address
can not be learned by the
other ports in the same
VLAN.
Dynamic
Address Table
Automatically
learning
Yes
No
The bound MAC address
can be learned by the other
ports in the same VLAN.
Filtering
Address Table
Manually
configuring
No
Yes
-
5.4 MAC Address
The main function of the switch is forwarding the packets to the correct ports based on the
destination MAC address of the packets. Address Table contains the port-based MAC address
information, which is the base for the switch to forward packets quickly. The entries in the Address
Table can be updated by auto-learning or configured manually. Most the entries are generated and
updated by auto-learning. In the stable networks, the static MAC address entries can facilitate the
switch to reduce broadcast packets and enhance the efficiency of packets forwarding remarkably.
The address filtering feature allows the switch to filter the undesired packets and forbid its
forwarding so as to improve the network security.
The types and the features of the MAC Address Table are listed as the following:
Table 5-1 Types and features of Address Table
45
Page 51

MAC Address:
Enter the MAC address of your desired entry.
VLAN ID:
Enter the VLAN ID of your desired entry.
Port:
Select the corresponding port number of your desired entry.
Type:
Select the type of your desired entry.
All: This option allows the address table to display all the
address entries.
Static: This option allows the address table to display the static
address entries only.
Dynamic: This option allows the address table to display the
dynamic address entries only.
Filtering: This option allows the address table to display the
filtering address entries only.
MAC Address:
Displays the MAC address learned by the switch.
VLAN ID:
Displays the corresponding VLAN ID of the MAC address.
Port:
Displays the corresponding Port number of the MAC address.
Type:
Displays the Type of the MAC address.
This function includes four submenus: Address Table, Static Address, Dynamic Address and
Filtering Address.
5.4.1 Address Table
On this page, you can view all the information of the Address Table.
Choose the menu Switching→MAC Address→Address Table to load the following page.
Figure 5-11 Address Table
The following entries are displayed on this screen:
Search Option
Address Table
46
Page 52

Aging Status:
Displays the Aging status of the MAC address.
MAC Address:
Enter the static MAC Address to be bound.
VLAN ID:
Enter the corresponding VLAN ID of the MAC address.
Port:
Select a port from the pull-down list to be bound.
Search Option:
Select a Search Option from the pull-down list and click the Search
button to find your desired entry in the Static Address Table.
MAC: Enter the MAC address of your desired entry.
VLAN ID: Enter the VLAN ID number of your desired entry.
Port: Enter the Port number of your desired entry.
5.4.2 Static Address
The static address table maintains the static address entries which can be added or removed
manually, independent of the aging time. In the stable networks, the static MAC address entries
can facilitate the switch to reduce broadcast packets and remarkably enhance the efficiency of
packets forwarding without learning the address. The static MAC address learned by the port with
Port Security enabled in the static learning mode will be displayed in the Static Address Table.
Choose the menu Switching→MAC Address→Static Address to load the following page.
Figure 5-12 Static Address
The following entries are displayed on this screen:
Create Static Address
Search Option
47
Page 53

Select:
Select the entry to delete or modify the corresponding port number. It
is multi-optional.
MAC Address:
Displays the static MAC Address.
VLAN ID:
Displays the corresponding VLAN ID of the MAC address.
Port:
Displays the corresponding Port number of the MAC address. Here
you can modify the port number to which the MAC address is bound.
The new port should be in the same VLAN.
Type:
Displays the Type of the MAC address.
Aging Status:
Displays the Aging Status of the MAC address.
Static Address Table
Note:
1. If the corresponding port number of the MAC address is not correct, or the connected port (or
the device) has been changed, the switch can not be forward the packets correctly. Please
reset the static address entry appropriately.
2. If the MAC address of a device has been added to the Static Address Table, connecting the
device to another port will cause its address not to be recognized dynamically by the switch.
Therefore, please ensure the entries in the Static Address Table are correct and valid.
3. The MAC address in the Static Address Table can not be added to the Filtering Address Table
or bound to a port dynamically.
4. This static MAC address bound function is not available if the 802.1X feature is enabled.
5.4.3 Dynamic Address
The dynamic address can be generated by the auto-learning mechanism of the switch. The
Dynamic Address Table can update automatically by auto-learning or aging out the MAC address.
To fully utilize the MAC address table, which has a limited capacity, the switch adopts an aging
mechanism for updating the table. That is, the switch removes the MAC address entries related to
a network device if no packet is received from the device within the aging time.
On this page, you can configure the dynamic MAC address entry.
Choose the menu Switching→MAC Address→Dynamic Address to load the following page.
48
Page 54

Auto Aging:
Allows you to Enable/Disable the Auto Aging feature.
Aging Time:
Enter the Aging Time for the dynamic address.
Search Option:
Select a Search Option from the pull-down list and click the Search
button to find your desired entry in the Dynamic Address Table.
MAC: Enter the MAC address of your desired entry.
VLAN ID: Enter the VLAN ID number of your desired entry.
Port: Enter the Port number of your desired entry.
LAG ID:Enter the LAG ID of your desired entry.
Select:
Select the entry to delete the dynamic address or to bind the MAC
address to the corresponding port statically. It is multi-optional.
MAC Address:
Displays the dynamic MAC Address.
VLAN ID:
Displays the corresponding VLAN ID of the MAC address.
Port:
Displays the corresponding port number of the MAC address.
Type:
Displays the Type of the MAC address.
Aging Status:
Displays the Aging Status of the MAC address.
Figure 5-13 Dynamic Address
The following entries are displayed on this screen:
Aging Config
Search Option
Dynamic Address Table
49
Page 55

Bind:
Click the Bind button to bind the MAC address of your selected entry to
the corresponding port statically.
MAC Address:
Enter the MAC Address to be filtered.
VLAN ID:
Enter the corresponding VLAN ID of the MAC address.
Tips:
Setting aging time properly helps implement effective MAC address aging. The aging time that is
too long or too short results decreases the performance of the switch. If the aging time is too long,
excessive invalid MAC address entries maintained by the switch may fill up the MAC address table.
This prevents the MAC address table from updating with network changes in time. If the aging time
is too short, the switch may remove valid MAC address entries. This decreases the forwarding
performance of the switch. It is recommended to keep the default value.
5.4.4 Filtering Address
The filtering address is to forbid the undesired packets to be forwarded. The filtering address can
be added or removed manually, independent of the aging time. The filtering MAC address allows
the switch to filter the packets which includes this MAC address as the source address or
destination address, so as to guarantee the network security. The filtering MAC address entries
act on all the ports in the corresponding VLAN.
Choose the menu Switching→MAC Address→Filtering Address to load the following page.
Figure 5-14 Filtering Address
The following entries are displayed on this screen:
Create Filtering Address
50
Page 56

Search Option
Search Option:
Select a Search Option from the pull-down list and click the Search
button to find your desired entry in the Filtering Address Table.
MAC: Enter the MAC address of your desired entry.
VLAN ID: Enter the VLAN ID number of your desired entry.
Select:
Select the entry to delete the corresponding filtering address. It is
multi-optional.
MAC Address:
Displays the filtering MAC Address.
VLAN ID:
Displays the corresponding VLAN ID.
Port:
Here the symbol ―__‖ indicates no specified port.
Type:
Displays the Type of the MAC address.
Aging Status:
Displays the Aging Status of the MAC address.
Filtering Address Table
Note:
The MAC address in the Filtering Address Table can not be added to the Static Address Table or
bound to a port dynamically.
5.5 DHCP Filtering
Nowadays, the network is getting larger and more complicated. The amount of the PCs always
exceeds that of the assigned IP addresses. The wireless network and the laptops are widely used
and the locations of the PCs are always changed. Therefore, the corresponding IP address of the
PC should be updated with a few configurations. DHCP (Dynamic Host Configuration Protocol)
functions to solve the above mentioned problems.
However, during the working process of DHCP, generally there is no authentication mechanism
between Server and Client. If there are several DHCP servers in the network, network confusion
and security problem will happen. To protect the switch from being attacked by illegal DHCP
servers, you can configure the desired ports as trusted ports and only the clients connected to the
trusted ports can receive DHCP packets from DHCP severs. Here the DHCP Filtering function
performs to monitor the process of hosts obtaining IP addresses from DHCP servers.
DHCP Working Principle
DHCP works via the ―Client/Server‖ communication mode. The Client applies to the Server for
configuration. The Server assigns the configuration information, such as the IP address, to the
Client, so as to reach a dynamic employ of the network source. A Server can assign IP address for
several Clients, which is illustrated in the following figure.
51
Page 57

Figure 5-17 Network diagram of DHCP
For different DHCP clients, DHCP server provides three IP address assigning methods:
(1) Manually assign the IP address: Allows the administrator to bind the static IP address to a
specific client (e.g.: WWW Server) via the DHCP server.
(2) Automatically assign the IP address: DHCP server assigns the IP address without an
expiry time limitation to the clients.
(3) Dynamically assign the IP address: DHCP server assigns the IP address with an expiry
time. When the time for the IP address expired, the client should apply for a new one.
Most clients obtain IP addresses dynamically, which is illustrated in the following figure.
Figure 5-18 Interaction between a DHCP client and a DHCP server
(1) DHCP-DISCOVER Stage: The Client broadcasts the DHCP-DISCOVER packet to find
the DHCP server.
(2) DHCP-OFFER Stage: Upon receiving the DHCP-DISCOVER packet, the DHCP server
selects an IP address from the IP pool according to the assigning priority of the IP
addresses and replies to the client with DHCP-OFFER packet carrying the IP address and
other information.
52
Page 58

(3) DHCP-REQUEST Stage: In the situation that there are several DHCP servers sending the
DHCP-OFFER packets, the client will only respond to the first received DHCP-OFFER
packet and broadcast the DHCP-REQUEST packet which includes the assigned IP
address of the DHCP-OFFER packet.
(4) DHCP-ACK Stage: Since the DHCP-REQUEST packet is broadcasted, all DHCP servers
on the network segment can receive it. However, only the requested server processes the
request. If the DHCP server acknowledges assigning this IP address to the client, it will
send the DHCP-ACK packet back to the client. Otherwise, the Server will send the
DHCP-NAK packet to refuse assigning this IP address to the client.
DHCP Cheating Attack
During the working process of DHCP, generally there is no authentication mechanism between
Server and Client. If there are several DHCP servers in the network, network confusion and
security problem will happen. The common cases incurring the illegal DHCP servers are the
following two:
(1) It’s common that the illegal DHCP server is manually configured by the user by mistake.
(2) Hacker exhausted the IP addresses of the normal DHCP server and then pretended to be
a legal DHCP server to assign the IP addresses and the other parameters to Clients. For
example, hacker used the pretended DHCP server to assign a modified DNS server
address to users so as to induce the users to the evil financial website or electronic trading
website and cheat the users of their accounts and passwords. The following figure
illustrates the DHCP Cheating Attack implementation procedure.
Figure 5-19 DHCP Cheating Attack Implementation Procedure
DHCP Filtering feature allows only the trusted ports to forward DHCP packets and thereby
ensures that users get proper IP addresses. DHCP Filtering is to monitor the process of hosts
obtaining the IP addresses from DHCP servers, and record the IP address, MAC address, VLAN
and the connected Port number of the Host for automatic binding. DHCP Filtering feature prevents
the network from the DHCP Server Cheating Attack by discarding the DHCP packets on the
distrusted port, so as to enhance the network security.
Choose the menu Switching → DHCP Filtering to load the following page.
53
Page 59

DHCP Filtering:
Enable/Disable the DHCP Filtering function globally.
Figure 5-20 DHCP Filtering
The following entries are displayed on this screen:
DHCP Filtering
Trusted Port
Here you can select the desired port(s) to be Trusted Port(s). Only the Trusted Port(s) can
receive DHCP packets from DHCP Servers. Click All button to select all ports. Click Clear
button to select none.
Return to CONTENTS
54
Page 60

Chapter 6 VLAN
The traditional Ethernet is a data network communication technology based on CSMA/CD (Carrier
Sense Multiple Access/Collision Detect) via shared communication medium. Through the
traditional Ethernet, the overfull hosts in LAN will result in serious collision, flooding broadcasts,
poor performance or even breakdown of the Internet. Though connecting the LANs through
switches can avoid the serious collision, the flooding broadcasts can not be prevented, which will
occupy plenty of bandwidth resources, causing potential serious security problems.
A Virtual Local Area Network (VLAN) is a network topology configured according to a logical
scheme rather than the physical layout. The VLAN technology is developed for switches to control
broadcast in LANs. By creating VLANs in a physical LAN, you can divide the LAN into multiple
logical LANs, each of which has a broadcast domain of its own. Hosts in the same VLAN
communicate with one another as if they are in a LAN. However, hosts in different VLANs cannot
communicate with one another directly. Therefore, broadcast packets are limited in a VLAN. Hosts
in the same VLAN communicate with one another via Ethernet whereas hosts in different VLANs
communicate with one another through the Internet devices such as Router, the Layer3 switch, etc.
The following figure illustrates a VLAN implementation.
Figure 6-1 VLAN implementation
Compared with the traditional Ethernet, VLAN enjoys the following advantages.
(1) Broadcasts are confined to VLANs. This decreases bandwidth utilization and improves
network performance.
(2) Network security is improved. VLANs cannot communicate with one another directly. That
is, a host in a VLAN cannot access resources in another VLAN directly, unless routers or
Layer 3 switches are used.
(3) Network configuration workload for the host is reduced. VLAN can be used to group
specific hosts. When the physical position of a host changes within the range of the VLAN,
you do not need to change its network configuration.
A VLAN can span across multiple switches, or even routers. This enables hosts in a VLAN to be
dispersed in a looser way. That is, hosts in a VLAN can belong to different physical network
segments. This switch supports 802.1Q VLAN to classify VLANs. VLAN tags in the packets are
necessary for the switch to identify packets of different VLANs.
55
Page 61

6.1 802.1Q VLAN
VLAN tags in the packets are necessary for the switch to identify packets of different VLANs. The
switch works at the data link layer in OSI model and it can identify the data link layer encapsulation
of the packet only, so you can add the VLAN tag field into the data link layer encapsulation for
identification.
In 1999, IEEE issues the IEEE 802.1Q protocol to standardize VLAN implementation, defining the
structure of VLAN-tagged packets. IEEE 802.1Q protocol defines that a 4-byte VLAN tag is
encapsulated after the destination MAC address and source MAC address to show the information
about VLAN.
As shown in the following figure, a VLAN tag contains four fields, including TPID (Tag Protocol
Identifier), Priority, CFI (Canonical Format Indicator), and VLAN ID.
Figure 6-2 Format of VLAN Tag
(1) TPID: TPID is a 16-bit field, indicating that this data frame is VLAN-tagged. By default, it is
0x8100 in this switch.
(2) Priority: Priority is a 3-bit field, referring to 802.1p priority. Refer to section ―QoS & QoS
profile‖ for details.
(3) CFI: CFI is a 1-bit field, indicating whether the MAC address is encapsulated in the
standard format in different transmission media. This field is not described in detail in this
chapter.
(4) VLAN ID: VLAN ID is a 12-bit field, indicating the ID of the VLAN to which this packet
belongs. It is in the range of 0 to 4,095. Generally, 0 and 4,095 is not used, so the field is in
the range of 1 to 4,094.
VLAN ID identifies the VLAN to which a packet belongs. When the switch receives an untagged
packet, it will encapsulate a VLAN tag with the default VLAN ID of the inbound port for the packet,
and the packet will be assigned to the default VLAN of the inbound port for transmission.
In this user guide, the tagged packet refers to the packet with VLAN tag whereas the untagged
packet refers to the packet without VLAN tag, and the priority-tagged packet refers to the packet
with VLAN tag whose VLAN ID is 0.
Link Types of ports
When creating the 802.1Q VLAN, you should set the link type for the port according to its
connected device. The link types of port including the following two types: Untagged and Tagged.
(1) Untagged: The untagged port can be added in multiple VLANs. If a VLAN-tagged packet
arrives at a port and the VLAN ID in its VLAN tag does not match any of the VLAN the
ingress port belongs to, this packet will be dropped. The packets forwarded by the
untagged port are untagged.
(2) Tagged: The tagged port can be added in multiple VLANs. If a VLAN-tagged packet
arrives at a port and the VLAN ID in its VLAN tag does not match any of the VLAN the
ingress port belongs to, this packet will be dropped. When the VLAN-tagged packets are
forwarded by the Tagged port, its VLAN tag will not be changed.
56
Page 62

Port Type
Receiving Packets
Forwarding Packets
Untagged Packets
Tagged Packets
Untagged
Packets
Tagged
Packets
Untagged
When untagged
packets are received,
the port will add the
default VLAN tag, i.e.
the PVID of the
ingress port, to the
packets.
If the VID of packet is
allowed by the port,
the packet will be
received.
If the VID of packet is
forbidden by the port,
the packet will be
dropped.
The packet
will be
forwarded
unchanged.
The packet
will be
forwarded
after
removing its
VLAN tag
Tagged
The packet
will be
forwarded
with the
PVID of
egress port
as its VLAN
tag.
The packet
will be
forwarded
with its
current
VLAN tag.
PVID
PVID (Port Vlan ID) is the default VID of the port. When the switch receives an untagged packet, it
will add a VLAN tag to the packet according to the PVID of its received port and forward the
packets.
When creating VLANs, the PVID of each port, indicating the default VLAN to which the port
belongs is an important parameter with the following two purposes:
(1) When the switch receives an untagged packet, it will add a VLAN tag to the packet
according to the PVID of its received port
(2) PVID determines the default broadcast domain of the port, i.e. when the port receives UL
packets or broadcast packets, the port will broadcast the packets in its default VLAN.
Different packets, tagged or untagged, will be processed in different ways, after being received by
ports of different link types, which is illustrated in the following table.
IEEE 802.1Q VLAN function is implemented on the VLAN Config page.
6.1.1 VLAN Config
On this page, you can configure the 802.1Q VLAN and its ports.
Choose the menu VLAN→802.1Q VLAN→VLAN Config to load the following page.
Table 6-1 Relationship between Port Types and VLAN Packets Processing
57
Page 63

VLAN ID:
Enter the VLAN ID you want to create. It ranges from 2 to 4094.
Name:
Give a name to the VLAN for identification.
VLAN ID Select:
Click the Select button to quick-select the corresponding VLAN
based on the VLAN ID you entered.
Select:
Select the desired port for configuration.
VLAN ID:
Displays the VLAN ID.
Name:
Displays the name of the specific VLAN.
Untagged Ports:
Show the untagged ports of the specific VLAN.
Tagged Ports:
Show the tagged ports of the specific VLAN.
Operation:
You can delete the specific VLAN when you click the word
"Delete".
VLAN ID:
Displays the VLAN ID you choose.
VLAN Name:
Here you can set the name of the VLAN you choose.
Figure 6-3 VLAN Table
To ensure the normal communication of the factory switch, the default VLAN of all ports is set to
VLAN1. VLAN1 can not be modified or deleted.
The following entries are displayed on this screen:
VLAN Create
VLAN Table
VLAN Membership
58
Page 64

Port:
Displays the port number.
Untagged:
The port will be an untagged member of the specific VLAN if you
select it.
Tagged:
The port will be an tagged member of the specific VLAN if you
select it.
NotMember:
The port will not be a member of the specific VLAN if you select
it.
PVID:
Here you can change the PVID of the specific port.
LAG:
Displays the LAG to which the port belongs to.
6.2 Application Example for 802.1Q VLAN
Network Requirements
Switch A is connecting to PC A and Server B;
Switch B is connecting to PC B and Server A;
PC A and Server A is in the same VLAN;
PC B and Server B is in the same VLAN;
PCs in the two VLANs cannot communicate with each other.
Network Diagram
59
Page 65

Configuration Procedure
Step
Operation
Description
1
Configure the
Link Type of the
ports
Required. On VLAN→802.1Q VLAN→VLAN Config page, configure
the link type of Port 2, Port 3 and Port 4 as Untagged, Tagged and
Untagged respectively
2
Create VLAN10
Required. On VLAN→802.1Q VLAN→VLAN Config page, create a
VLAN with its VLAN ID as 10, owning Port 2 and Port 3.
3
Create VLAN20
Required. On VLAN→802.1Q VLAN→VLAN Config page, create a
VLAN with its VLAN ID as 20, owning Port 3 and Port 4.
Step
Operation
Description
1
Configure the
Link Type of the
ports
Required. On VLAN→802.1Q VLAN→VLAN Config page, configure
the link type of Port 7, Port 6 and Port 8 as Untagged, Tagged and
Untagged respectively.
2
Create VLAN10
Required. On VLAN→802.1Q VLAN→VLAN Config page, create a
VLAN with its VLAN ID as 10, owning Port 6 and Port 8.
3
Create VLAN20
Required. On VLAN→802.1Q VLAN→VLAN Config page, create a
VLAN with its VLAN ID as 20, owning Port 6 and Port 7.
Configure Switch A
Configure Switch B
Return to CONTENTS
60
Page 66

Chapter 7 Spanning Tree
STP (Spanning Tree Protocol), subject to IEEE 802.1D standard, is to disbranch a ring network in
the Data Link layer in a local network. Devices running STP discover loops in the network and block
ports by exchanging information, in that way, a ring network can be disbranched to form a
tree-topological ring-free network to prevent packets from being duplicated and forwarded endlessly
in the network.
BPDU (Bridge Protocol Data Unit) is the protocol data that STP and RSTP use. Enough
information is carried in BPDU to ensure the spanning tree generation. STP is to determine the
topology of the network via transferring BPDUs between devices.
To implement spanning tree function, the switches in the network transfer BPDUs between each
other to exchange information and all the switches supporting STP receive and process the
received BPDUs. BPDUs carry the information that is needed for switches to figure out the
spanning tree.
STP Elements
Bridge ID(Bridge Identifier): Indicates the value of the priority and MAC address of the bridge.
Bridge ID can be configured and the switch with the lower bridge ID has the higher priority.
Root Bridge: Indicates the switch has the lowest bridge ID. Configure the best PC in the ring
network as the root bridge to ensure best network performance and reliability.
Designated Bridge: Indicates the switch has the lowest path cost from the switch to the root
bridge in each network segment. BPDUs are forwarded to the network segment through the
designated bridge. The switch with the lowest bridge ID will be chosen as the designated bridge.
Root Path Cost: Indicates the sum of the path cost of the root port and the path cost of all the
switches that packets pass through. The root path cost of the root bridge is 0.
Bridge Priority: The bridge priority can be set to a value in the range of 0~61440. The lower value
priority has the higher priority. The switch with the higher priority has more chance to be chosen as
the root bridge.
Root Port: Indicates the port that has the lowest path cost from this bridge to the Root Bridge and
forwards packets to the root.
Designated Port: Indicates the port that forwards packets to a downstream network segment or
switch.
Port Priority: The port priority can be set to a value in the range of 0~240. The lower value priority
has the higher priority. The port with the higher priority has more chance to be chosen as the root
port.
Path Cost: Indicates the parameter for choosing the link path by STP. By calculating the path cost,
STP chooses the better links and blocks the redundant links so as to disbranch the ring-network to
form a tree-topological ring-free network.
The following network diagram shows the sketch map of spanning tree. Switch A, B and C is
connected together in order. After STP generation, switch A is chosen as Root Bridge, the path
from port 2 to port 6 is blocked.
Bridge: Switch A is the root bridge in the whole network; switch B is the designated bridge of
switch C.
Port: Port 3 is the root port of switch B and port 5 is the root port of switch C; port 1 is the
designated port of switch A and port 4 is the designated port of switch B; port 6 is the blocked
port of switch C.
61
Page 67

Figure 7-1 Basic STP diagram
STP Timers
Hello Time:
Hello Time ranges from 1 to 10 seconds. It specifies the interval to send BPDU packets. It is used
to test the links.
Max. Age:
Max. Age ranges from 6 to 40 seconds. It specifies the maximum time the switch can wait without
receiving a BPDU before attempting to reconfigure.
Forward Delay:
Forward Delay ranges from 4 to 30 seconds. It specifies the time for the port to transit its state
after the network topology is changed.
When the STP regeneration caused by network malfunction occurs, the STP structure will get
some corresponding change. However, as the new configuration BPDUs cannot be spread in the
whole network at once, the temporal loop will occur if the port transits its state immediately.
Therefore, STP adopts a state transit mechanism, that is, the new root port and the designated
port begins to forward data after twice forward delay, which ensures the new configuration BPDUs
are spread in the whole network.
BPDU Comparing Principle in STP mode
Assuming two BPDUs: BPDU X and BPDU Y
If the root bridge ID of X is smaller than that of Y, X is superior to Y.
If the root bridge ID of X equals that of Y, but the root path cost of X is smaller than that of Y, X is
superior to Y.
If the root bridge ID and the root path cost of X equal those of Y, but the bridge ID of X is smaller
than that of Y, X is superior to Y.
If the root bridge ID, the root path cost and bridge ID of X equal those of Y, but the port ID of X is
smaller than that of Y, X is superior to Y.
STP Generation
In the beginning
In the beginning, each switch regards itself as the root, and generates a configuration BPDU for
each port on it as a root, with the root path cost being 0, the ID of the designated bridge being that
of the switch, and the designated port being itself.
62
Page 68

Step
Operation
1
If the priority of the BPDU received on the port is lower than that of the BPDU of
the port itself, the switch discards the BPDU and does not change the BPDU of
the port.
2
If the priority of the BPDU is higher than that of the BPDU of the port itself, the
switch replaces the BPDU of the port with the received one and compares it with
those of other ports on the switch to obtain the one with the highest priority.
Step
Operation
1
For each switch (except the one chosen as the root bridge) in a network, the port
that receives the BPDU with the highest priority is chosen as the root port of the
switch.
2
Using the root port BPDU and the root path cost, the switch generates a
designated port BPDU for each of its ports.
Root ID is replaced with that of the root port;
Root path is replaced with the sum of the root path cost of the root port and
the path cost between this port and the root port;
The ID of the designated bridge is replaced with that of the switch;
The ID of the designated port is replaced with that of the port.
3
The switch compares the resulting BPDU with the BPDU of the desired port
whose role you want to determine.
If the resulting BPDU takes the precedence over the BPDU of the port, the
port is chosen as the designated port and the BPDU of this port is replaced
with the resulting BPDU. The port regularly sends out the resulting BPDU;
If the BPDU of this port takes the precedence over the resulting BPDU, the
BPDU of this port is not replaced and the port is blocked. The port only can
receive BPDUs.
Comparing BPDUs
Each switch sends out configuration BPDUs and receives a configuration BPDU on one of its ports
from another switch. The following table shows the comparing operations.
Table 7-1 Comparing BPDUs
Selecting the root bridge
The root bridge is selected by BPDU comparing. The switch with the smallest root ID is chosen as
the root bridge.
Selecting the root port and designate port
The operation is taken in the following way:
Table 7-2 Selecting root port and designated port
Tips:
In a STP with stable topology, only the root port and designated port can forward data, and the
other ports are blocked. The blocked ports only can receive BPDUs.
RSTP (Rapid Spanning Tree Protocol), evolved from the 802.1D STP standard, enable Ethernet
ports to transit their states rapidly. The premises for the port in the RSTP to transit its state rapidly
are as follows.
63
Page 69

The condition for the root port to transit its port state rapidly: The old root port of the switch
stops forwarding data and the designated port of the upstream switch begins to forward
data.
The condition for the designated port to transit its port state rapidly: The designated port is
an edge port or connecting to a point-to-point link. If the designated port is an edge port, it
can directly transit to forwarding state; if the designated port is connecting to a
point-to-point link, it can transit to forwarding state after getting response from the
downstream switch through handshake.
RSTP Elements
Edge Port: Indicates the port connected directly to terminals.
P2P Link: Indicates the link between two switches directly connected.
MSTP (Multiple Spanning Tree Protocol), compatible with both STP and RSTP and subject to IEEE
802.1s standard, not only enables spanning trees to converge rapidly, but also enables packets of
different VLANs to be forwarded along their respective paths so as to provide redundant links
with a better load-balancing mechanism.
Features of MSTP:
MSTP combines VLANs and spanning tree together via VLAN-to-instance mapping table. It
binds several VLANs to an instance to save communication cost and network resources.
MSTP divides a spanning tree network into several regions. Each region has several
internal spanning trees, which are independent of each other.
MSTP provides a load-balancing mechanism for the packets transmission in the VLAN.
MSTP is compatible with both STP and RSTP.
MSTP Elements
MST Region (Multiple Spanning Tree Region): An MST Region comprises switches with the same
region configuration and VLAN-to-Instances mapping relationship.
IST (Internal Spanning Tree): An IST is a spanning tree in an MST.
CST (Common Spanning Tree): A CST is the spanning tree in a switched network that connects all
MST regions in the network.
CIST (Common and Internal Spanning Tree): A CIST, comprising IST and CST, is the spanning
tree in a switched network that connects all switches in the network.
The following figure shows the network diagram in MSTP.
64
Page 70

Figure 7-2 Basic MSTP diagram
MSTP
MSTP divides a network into several MST regions. The CST is generated between these MST
regions, and multiple spanning trees can be generated in each MST region. Each spanning tree is
called an instance. As well as STP, MSTP uses BPDUs to generate spanning tree. The only
difference is that the BPDU for MSTP carries the MSTP configuration information on the switches.
Port States
In an MSTP, ports can be in the following four states:
Forwarding: In this status the port can receive/forward data, receive/send BPDU packets as
well as learn MAC address.
Learning: In this status the port can receive/send BPDU packets and learn MAC address.
Blocking: In this status the port can only receive BPDU packets.
Disconnected: In this status the port is not participating in the STP.
Port Roles
In an MSTP, the following roles exist:
Root Port: Indicates the port that has the lowest path cost from this bridge to the Root Bridge
and forwards packets to the root.
Designated Port: Indicates the port that forwards packets to a downstream network segment
or switch.
Master Port: Indicates the port that connects a MST region to the common root. The path
from the master port to the common root is the shortest path between this MST region and
the common root.
Alternate Port: Indicates the port that can be a backup port of a root or master port.
Backup Port: Indicates the port that is the backup port of a designated port.
Disabled: Indicates the port that is not participating in the STP.
65
Page 71

The following diagram shows the different port roles.
Figure 7-3 Port roles
The Spanning Tree module is mainly for spanning tree configuration of the switch, including four
submenus: STP Config, Port Config, MSTP Instance and STP Security.
7.1 STP Config
The STP Config function, for global configuration of spanning trees on the switch, can be
implemented on STP Config and STP Summary pages.
7.1.1 STP Config
Before configuring spanning trees, you should make clear the roles each switch plays in each
spanning tree instance. Only one switch can be the root bridge in each spanning tree instance. On
this page you can globally configure the spanning tree function and related parameters.
Choose the menu Spanning Tree→STP Config→STP Config to load the following page.
Figure 7-4 STP Config
66
Page 72

STP:
Select Enable/Disable STP function globally on the switch.
Version:
Select the desired STP version on the switch.
STP: Spanning Tree Protocol.
RSTP: Rapid Spanning Tree Protocol.
MSTP: Multiple Spanning Tree Protocol.
CIST Priority:
Enter a value from 0 to 61440 to specify the priority of the switch
for comparison in the CIST. CIST priority is an important criterion
on determining the root bridge. In the same condition, the switch
with the highest priority will be chosen as the root bridge. The
lower value has the higher priority. The default value is 32768 and
should be exact divisor of 4096.
Hello Time
Enter a value from 1 to 10 in seconds to specify the interval to
send BPDU packets. It is used to test the links. 2*(Hello Time + 1)
≤ Max Age. The default value is 2 seconds.
Max Age:
Enter a value from 6 to 40 in seconds to specify the maximum
time the switch can wait without receiving a BPDU before
attempting to reconfigure. The default value is 20 seconds.
Forward Delay:
Enter a value from 4 to 30 in seconds to specify the time for the
port to transit its state after the network topology is changed.
2*(Forward Delay-1) ≥ Max Age. The default value is 15 seconds.
TxHold Count:
Enter a value from 1 to 20 to set the maximum number of BPDU
packets transmitted per Hello Time interval. The default value is
5pps.
Max Hops:
Enter a value from 1 to 40 to set the maximum number of hops
that occur in a specific region before the BPDU is discarded. The
default value is 20 hops.
The following entries are displayed on this screen:
Global Config
Parameters Config
Note:
1. The forward delay parameter and the network diameter are correlated. A too small forward
delay parameter may result in temporary loops. A too large forward delay may cause a
network unable to resume the normal state in time. The default value is recommended.
2. An adequate hello time parameter can enable the switch to discover the link failures occurred
in the network without occupying too much network resources. A too large hello time
parameter may result in normal links being regarded as invalid when packets drop occurred in
the links, which in turn result in spanning tree being regenerated. A too small hello time
parameter may result in duplicated configuration being sent frequently, which increases the
network load of the switches and wastes network resources. The default value is
recommended.
3. A too small max age parameter may result in the switches regenerating spanning trees
frequently and cause network congestions to be falsely regarded as link problems. A too large
max age parameter result in the switches unable to find the link problems in time, which in
turn handicaps spanning trees being regenerated in time and makes the network less
adaptive. The default value is recommended.
67
Page 73

4. If the TxHold Count parameter is too large, the number of MSTP packets being sent in each
hello time may be increased with occupying too much network resources. The default value is
recommended.
7.1.2 STP Summary
On this page you can view the related parameters for Spanning Tree function.
Choose the menu Spanning Tree→STP Config→STP Summary to load the following page.
Figure 7-5 STP Summary
7.2 Port Config
On this page you can configure the parameters of the ports for CIST
Choose the menu Spanning Tree→Port Config to load the following page.
68
Page 74

Port Select:
Click the Select button to quick-select the corresponding port based
on the port number you entered.
Select:
Select the desired port for STP configuration. It is multi-optional.
Port:
Displays the port number of the switch.
Status:
Select Enable /Disable STP function for the desired port.
Priority:
Enter a value from 0 to 240 divisible by 16. Port priority is an important
criterion on determining if the port connected to this port will be chosen
as the root port. The lower value has the higher priority.
ExtPath:
ExtPath Cost is used to choose the path and calculate the path costs
of ports in different MST regions. It is an important criterion on
determining the root port. The lower value has the higher priority.
IntPath:
IntPath Cost is used to choose the path and calculate the path costs of
ports in an MST region. It is an important criterion on determining the
root port. The lower value has the higher priority.
Edge Port:
Select Enable/Disable Edge Port. The edge port can transit its state
from blocking to forwarding rapidly without waiting for forward delay.
P2P Link:
Select the P2P link status. If the two ports in the P2P link are root port
or designated port, they can transit their states to forwarding rapidly to
reduce the unnecessary forward delay.
MCheck:
Select Enable to perform MCheck operation on the port. Unchange
means no MCheck operation.
STP Version:
Displays the STP version of the port.
Figure 7-6 Port Config
The following entries are displayed on this screen:
Port Config
69
Page 75

Port Role:
Displays the role of the port played in the STP Instance.
Root Port: Indicates the port that has the lowest path cost from
this bridge to the Root Bridge and forwards packets to the root.
Designated Port: Indicates the port that forwards packets to a
downstream network segment or switch.
Master Port: Indicates the port that connects a MST region to the
common root. The path from the master port to the common root
is the shortest path between this MST region and the common
root.
Alternate Port: Indicates the port that can be a backup port of a
root or master port.
Backup Port: Indicates the port that is the backup port of a
designated port.
Disabled: Indicates the port that is not participating in the STP.
Port Status:
Displays the working status of the port.
Forwarding: In this status the port can receive/forward data,
receive/send BPDU packets as well as learn MAC address.
Learning: In this status the port can receive/send BPDU packets
and learn MAC address.
Blocking: In this status the port can only receive BPDU packets.
Disconnected: In this status the port is not participating in the STP.
LAG:
Displays the LAG number which the port belongs to.
Note:
1. Configure the ports connected directly to terminals as edge ports and enable the BPDU
protection function as well. This not only enables these ports to transit to forwarding state
rapidly but also secures your network.
2. All the links of ports in a LAG can be configured as point-to-point links.
3. When the link of a port is configured as a point-to-point link, the spanning tree instances
owning this port are configured as point-to-point links. If the physical link of a port is not a
point-to-point link and you forcibly configure the link as a point-to-point link, temporary loops
may be incurred.
7.3 MSTP Instance
MSTP combines VLANs and spanning tree together via VLAN-to-instance mapping table
(VLAN-to-spanning-tree mapping). By adding MSTP instances, it binds several VLANs to an
instance to realize the load balance based on instances.
Only when the switches have the same MST region name, MST region revision and
VLAN-to-Instance mapping table, the switches can be regarded as in the same MST region.
The MSTP Instance function can be implemented on Region Config, Instance Config and
Instance Port Config pages.
7.3.1 Region Config
On this page you can configure the name and revision of the MST region
Choose the menu Spanning Tree→MSTP Instance→Region Config to load the following page.
70
Page 76

Region Name:
Create a name for MST region identification using up to 32 characters.
Revision:
Enter the revision from 0 to 65535 for MST region identification.
Instance ID Select:
Click the Select button to quick-select the corresponding Instance ID
Figure 7-7 Region Config
The following entries are displayed on this screen:
Region Config
7.3.2 Instance Config
Instance Configuration, a property of MST region, is used to describe the VLAN to Instance
mapping configuration. You can assign VLAN to different instances appropriate to your needs.
Every instance is a VLAN group independent of other instances and CIST.
Choose the menu Spanning Tree→MSTP Instance→Instance Config to load the following page.
Figure 7-8 Instance Config
The following entries are displayed on this screen:
Instance Table
71
Page 77

based on the ID number you entered.
Select:
Select the desired Instance ID for configuration. It is multi-optional.
Instance:
Displays Instance ID of the switch.
Status:
Select Enable/Disable the instance.
Priority:
Enter the priority of the switch in the instance. It is an important
criterion on determining if the switch will be chosen as the root bridge
in the specific instance.
VLAN ID:
Enter the VLAN ID which belongs to the corresponding instance ID.
After modification here, the previous VLAN ID will be cleared and
mapped to the CIST.
Clear:
Click the Clear button to clear up all VLAN IDs from the instance ID.
The cleared VLAN ID will be automatically mapped to the CIST.
VLAN-Instance Mapping
VLAN ID:
Enter the desired VLAN ID. After modification here, the new VLAN ID
will be added to the corresponding instance ID and the previous VLAN
ID won’t be replaced.
Instance ID:
Enter the corresponding instance ID.
7.3.3 Instance Port Config
A port can play different roles in different spanning tree instance. On this page you can configure
the parameters of the ports in different instance IDs as well as view status of the ports in the
specified instance.
Choose the menu Spanning Tree→MSTP Instance→Instance Port Config to load the following
page.
72
Page 78

Instance ID:
Select the desired instance ID for its port configuration.
Port Select:
Click the Select button to quick-select the corresponding port based
on the port number you entered.
Select:
Select the desired port to specify its priority and path cost. It is
multi-optional.
Port:
Displays the port number of the switch.
Priority:
Enter the priority of the port in the instance. It is an important criterion
on determining if the port connected to this port will be chosen as the
root port.
Path Cost:
Path Cost is used to choose the path and calculate the path costs of
ports in an MST region. It is an important criterion on determining the
root port. The lower value has the higher priority.
Port Role:
Displays the role of the port played in the MSTP Instance.
Port Status:
Displays the working status of the port.
LAG:
Displays the LAG number which the port belongs to.
Figure 7-9 Instance Port Config
The following entries are displayed on this screen:
Port Config
Note:
The port status of one port in different spanning tree instances can be different.
73
Page 79

Step
Operation
Description
1
Make clear roles the switches
play in spanning tree
instances: root bridge or
designated bridge
Preparation.
2
Globally configure MSTP
parameters
Required. Enable Spanning Tree function on the switch
and configure MSTP parameters on Spanning
Tree→STP Config→STP Config page.
3
Configure MSTP parameters
for ports
Required. Configure MSTP parameters for ports on
Spanning Tree→Port Config→Port Config page.
4
Configure the MST region
Required. Create MST region and configure the role the
switch plays in the MST region on Spanning
Tree→MSTP Instance→Region Config and Instance
Config page.
5
Configure MSTP parameters
for instance ports
Optional. Configure different instances in the MST region
and configure MSTP parameters for instance ports on
Spanning Tree→MSTP Instance→Instance Port
Config page.
Global configuration Procedure for Spanning Tree function:
7.4 STP Security
Configuring protection function for devices can prevent devices from any malicious attack against
STP features. The STP Security function can be implemented on Port Protect and TC Protect
pages.
Port Protect function is to prevent the devices from any malicious attack against STP features.
7.4.1 Port Protect
On this page you can configure loop protect feature, root protect feature, TC protect feature,
BPDU protect feature and BPDU filter feature for ports. You are suggested to enable
corresponding protection feature for the qualified ports.
Loop Protect
In a stable network, a switch maintains the states of ports by receiving and processing BPDU
packets from the upstream switch. However, when link congestions or link failures occurred to the
network, a down stream switch does not receive BPDU packets for certain period, which results in
spanning trees being regenerated and roles of ports being reselected, and causes the blocked
ports to transit to forwarding state. Therefore, loops may be incurred in the network.
The loop protect function can suppresses loops. With this function enabled, a port, regardless of
the role it plays in instances, is always set to blocking state, when the port does not receive BPDU
packets from the upstream switch and spanning trees are regenerated, and thereby loops can be
prevented.
74
Page 80

Root Protect
A CIST and its secondary root bridges are usually located in the high-bandwidth core region.
Wrong configuration or malicious attacks may result in configuration BPDU packets with higher
priorities being received by the legal root bridge, which causes the current legal root bridge to lose
its position and network topology jitter to occur. In this case, flows that should travel along
high-speed links may lead to low-speed links, and network congestion may occur.
To avoid this, MSTP provides root protect function. Ports with this function enabled can only be set
as designated ports in all spanning tree instances. When a port of this type receives BDPU
packets with higher priority, it transits its state to blocking state and stops forwarding packets (as if
it is disconnected from the link). The port resumes the normal state if it does not receive any
configuration BPDU packets with higher priorities for a period of two times of forward delay.
TC Protect
A switch removes MAC address entries upon receiving TC-BPDU packets. If a user maliciously
sends a large amount of TC-BPDU packets to a switch in a short period, the switch will be busy
with removing MAC address entries, which may decrease the performance and stability of the
network.
To prevent the switch from frequently removing MAC address entries, you can enable the TC
protect function on the switch. With TC protect function enabled, if the account number of the
received TC-BPDUs exceeds the maximum number you set in the TC threshold field, the switch
will not performs the removing operation in the TC protect cycle. Such a mechanism prevents the
switch from frequently removing MAC address entries.
BPDU Protect
Ports of the switch directly connected to PCs or servers are configured as edge ports to rapidly
transit their states. When these ports receive BPDUs, the system automatically configures these
ports as non-edge ports and regenerates spanning trees, which may cause network topology jitter.
Normally these ports do not receive BPDUs, but if a user maliciously attacks the switch by sending
BPDUs, network topology jitter occurs.
To prevent this attack, MSTP provides BPDU protect function. With this function enabled on the
switch, the switch shuts down the edge ports that receive BPDUs and reports these cases to the
administrator. If a port is shut down, only the administrator can restore it.
BPDU Filter
BPDU filter function is to prevent BPDUs flood in the STP network. If a switch receives malicious
BPDUs, it forwards these BPDUs to the other switched in the network, which may result in
spanning trees being continuously regenerated. In this case, the switch occupying too much CPU
or the protocol status of BPDUs is wrong.
With BPDU filter function enabled, a port does not receive or forward BPDUs, but it sends out its
own BPDUs. Such a mechanism prevents the switch from being attacked by BPDUs so as to
guarantee generation the spanning trees correct.
Choose the menu Spanning Tree→STP Security→Port Protect to load the following page.
75
Page 81

Port Select:
Click the Select button to quick-select the corresponding port based
on the port number you entered.
Select:
Select the desired port for port protect configuration. It is
multi-optional.
Port:
Displays the port number of the switch.
Loop Protect:
Loop Protect is to prevent the loops in the network brought by
recalculating STP because of link failures and network congestions.
Root Protect:
Root Protect is to prevent wrong network topology change caused by
the role change of the current legal root bridge.
TC Protect:
TC Protect is to prevent the decrease of the performance and stability
of the switch brought by continuously removing MAC address entries
upon receiving TC-BPDUs in the STP network.
BPDU Protect:
BPDU Protect is to prevent the edge port from being attacked by
maliciously created BPDUs
BPDU Filter:
BPDU Filter is to prevent BPDUs flood in the STP network.
LAG:
Displays the LAG number which the port belongs to.
Figure 7-10 Port Protect
The following entries are displayed on this screen:
Port Protect
76
Page 82

TC Threshold:
Enter a number from 1 to 100. It is the maximum number of the
TC-BPDUs received by the switch in a TC Protect Cycle. The
default value is 20.
TC Protect Cycle:
Enter a value from 1 to 10 to specify the TC Protect Cycle. The
default value is 5.
7.4.2 TC Protect
When TC Protect is enabled for the port on Port Protect page, the TC threshold and TC protect
cycle need to be configured on this page.
Choose the menu Spanning Tree→STP Security→TC Protect to load the following page.
Figure 7-11 TC Protect
The following entries are displayed on this screen:
TC Protect
7.5 Application Example for STP Function
Network Requirements
Switch A, B, C, D and E all support MSTP function.
A is the central switch.
B and C are switches in the convergence layer. D, E and F are switches in the access layer.
There are 6 VLANs labeled as VLAN101-VLAN106 in the network.
All switches run MSTP and belong to the same MST region.
The data in VLAN101, 103 and 105 are transmitted in the STP with B as the root bridge. The
data in VLAN102, 104 and 106 are transmitted in the STP with C as the root bridge.
Network Diagram
77
Page 83

Configuration Procedure
Step
Operation
Description
1
Configure ports
On VLAN→802.1Q VLAN page, configure the link type
of the related ports as Trunk, and add the ports to VLAN
101-VLAN 106. The detailed instructions can be found
in the section 802.1Q VLAN.
2
Enable STP function
On Spanning Tree→STP Config→STP Config page,
enable STP function and select MSTP version.
On Spanning Tree→STP Config→Port Config page,
enable MSTP function for the port.
3
Configure the region name and
the revision of MST region
On Spanning Tree→MSTP Instance→Region Config
page, configure the region as PS-G and keep the
default revision setting.
4
Configure VLAN-to-Instance
mapping table of the MST region
On Spanning Tree→MSTP Instance→Instance
Config page, configure VLAN-to-Instance mapping
table. Map VLAN 101, 103 and 105 to Instance 1; map
VLAN 102, 104 and 106 to Instance 2.
Step
Operation
Description
1
Configure ports
On VLAN→802.1Q VLAN page, configure the link type
of the related ports as Trunk, and add the ports to VLAN
101-VLAN 106. The detailed instructions can be found
in the section 802.1Q VLAN.
2
Enable STP function
On Spanning Tree→STP Config→STP Config page,
enable STP function and select MSTP version.
On Spanning Tree→STP Config→Port Config page,
enable MSTP function for the port.
3
Configure the region name and
the revision of MST region
On Spanning Tree→MSTP Instance→Region Config
page, configure the region as PS-G and keep the
default revision setting.
4
Configure VLAN-to-Instance
mapping table of the MST region
On Spanning Tree→MSTP Instance→Instance
Config page, configure VLAN-to-Instance mapping
table. Map VLAN 101, 103 and 105 to Instance 1; map
VLAN 102, 104 and 106 to Instance 2.
5
Configure switch B as the root
bridge of Instance 1
On Spanning Tree→MSTP Instance→Instance
Config page, configure the priority of Instance 1 to be 0.
6
Configure switch B as the
designated bridge of Instance 2
On Spanning Tree→MSTP Instance→Instance
Config page, configure the priority of Instance 2 to be
4096.
Configure Switch A:
Configure Switch B:
78
Page 84

Configure Switch C:
Step
Operation
Description
1
Configure ports
On VLAN→802.1Q VLAN page, configure the link type
of the related ports as Trunk, and add the ports to VLAN
101-VLAN 106. The detailed instructions can be found
in the section 802.1Q VLAN.
2
Enable STP function
On Spanning Tree→STP Config→STP Config page,
enable STP function and select MSTP version.
On Spanning Tree→STP Config→Port Config page,
enable MSTP function for the port.
3
Configure the region name and
the revision of MST region
On Spanning Tree→MSTP Instance→Region Config
page, configure the region as PS-G and keep the
default revision setting.
4
Configure VLAN-to-Instance
mapping table of the MST region
On Spanning Tree→MSTP Instance→Instance
Config page, configure VLAN-to-Instance mapping
table. Map VLAN 101, 103 and 105 to Instance 1; map
VLAN 102, 104 and 106 to Instance 2.
5
Configure switch C as the root
bridge of Instance 1
On Spanning Tree→MSTP Instance→Instance
Config page, configure the priority of Instance 1 to be
4096.
6
Configure switch C as the root
bridge of Instance 2
On Spanning Tree→MSTP Instance→Instance
Config page, configure the priority of Instance 2 to be 0.
Step
Operation
Description
1
Configure ports
On VLAN→802.1Q VLAN page, configure the link type
of the related ports as Trunk, and add the ports to VLAN
101-VLAN 106. The detailed instructions can be found
in the section 802.1Q VLAN.
2
Enable STP function
On Spanning Tree→STP Config→STP Config page,
enable STP function and select MSTP version.
On Spanning Tree→STP Config→Port Config page,
enable MSTP function for the port.
3
Configure the region name and
the revision of MST region
On Spanning Tree→MSTP Instance→Region Config
page, configure the region as PS-G and keep the
default revision setting.
4
Configure VLAN-to-Instance
mapping table of the MST region
On Spanning Tree→MSTP Instance→Instance
Config page, configure VLAN-to-Instance mapping
table. Map VLAN 101, 103 and 105 to Instance 1; map
VLAN 102, 104 and 106 to Instance 2.
Configure Switch D:
The configuration procedure for switch E and F is the same with that for switch D.
The topology diagram of the two instances after the topology is stable
For Instance 1 (VLAN 101, 103 and 105), the red paths in the following figure are connected
links; the gray paths are the blocked links.
79
Page 85

For Instance 2 (VLAN 102, 104 and 106), the blue paths in the following figure are connected
links; the gray paths are the blocked links.
Suggestion for Configuration
Enable TC Protect function for all the ports of switches.
Enable Root Protect function for all the ports of root bridges.
Enable Loop Protect function for the non-edge ports.
Enable BPDU Protect function or BPDU Filter function for the edge ports which are connected to
the PC and server.
Return to CONTENTS
80
Page 86

Chapter 8 Multicast
Multicast Overview
In the network, packets are sent in three modes: unicast, broadcast and multicast. In unicast, the
source server sends separate copy information to each receiver. When a large number of users
require this information, the server must send many pieces of information with the same content to
the users. Therefore, large bandwidth will be occupied. In broadcast, the system transmits
information to all users in a network. Any user in the network can receive the information, no
matter the information is needed or not.
Point-to-multipoint multimedia business, such as video conferences and VoD (video-on-demand),
plays an important part in the information transmission field. Suppose a point to multi-point service
is required, unicast is suitable for networks with sparsely users, whereas broadcast is suitable for
networks with densely distributed users. When the number of users requiring this information is
not certain, unicast and broadcast deliver a low efficiency. Multicast solves this problem. It can
deliver a high efficiency to send data in the point to multi-point service, which can save large
bandwidth and reduce the network load. In multicast, the packets are transmitted in the following
way as shown in Figure 8-1.
Figure 8-1 Information transmission in the multicast mode
Features of multicast:
1. The number of receivers is not certain. Usually point-to-multipoint transmission is needed;
2. Multiple users receiving the same information form a multicast group. The multicast
information sender just need to send the information to the network device once;
3. Each user can join and leave the multicast group at any time;
4. Real time is highly demanded and certain packets drop is allowed.
81
Page 87

Multicast IP address range
Description
224.0.0.0~224.0.0.255
Reserved multicast addresses for routing protocols
and other network protocols
224.0.1.0~224.0.1.255
Addresses for video conferencing
239.0.0.0~239.255.255.255
Local management multicast addresses, which are
used in the local network only
Multicast Address
1. Multicast IP Address:
As specified by IANA (Internet Assigned Numbers Authority), Class D IP addresses are used as
destination addresses of multicast packets. The multicast IP addresses range from
224.0.0.0~239.255.255.255. The following table displays the range and description of several
special multicast IP addresses.
Table 8-1 Range of the special multicast IP
2. Multicast MAC Address:
When a unicast packet is transmitted in an Ethernet network, the destination MAC address is the
MAC address of the receiver. When a multicast packet is transmitted in an Ethernet network, the
destination is not a receiver but a group with uncertain number of members, so a multicast MAC
address, a logical MAC address, is needed to be used as the destination address.
As stipulated by IANA, the high-order 24 bits of a multicast MAC address begins with 01-00-5E
while the low-order 23 bits of a multicast MAC address are the low-order 23 bits of the multicast IP
address. The mapping relationship is described as Figure 8-2.
Figure 8-2 Mapping relationship between multicast IP address and multicast MAC address
The high-order 4 bits of the IP multicast address are 1110, identifying the multicast group. Only 23
bits of the remaining low-order 28 bits are mapped to a multicast MAC address. In that way, 5 bits
of the IP multicast address is not utilized. As a result, 32 IP multicast addresses are mapped to the
same MAC addresses.
Multicast Address Table
The switch is forwarding multicast packets based on the multicast address table. As the
transmission of multicast packets can not span the VLAN, the first part of the multicast address
table is VLAN ID, based on which the received multicast packets are forwarded in the VLAN
owning the receiving port. The multicast address table is not mapped to an egress port but a group
port list. When forwarding a multicast packet, the switch looks up the multicast address table
based on the destination multicast address of the multicast packet. If the corresponding entry can
not be found in the table, the switch will broadcast the packet in the VLAN owning the receiving
port. If the corresponding entry can be found in the table, it indicates that the destination address
82
Page 88

VLAN ID
Multicast IP
Port
should be a group port list, so the switch will duplicate this multicast data and deliver each port one
copy. The general format of the multicast address table is described as Figure 8-3 below.
Figure 8-3 Multicast Address Table
IGMP Snooping
In the network, the hosts apply to the near Router for joining (leaving) a multicast group by sending
IGMP (Internet Group Management Protocol) messages. When the up-stream device forwards
down the multicast data, the switch is responsible for sending them to the hosts. IGMP Snooping is
a multicast control mechanism, which can be used on the switch for dynamic registration of the
multicast group. The switch, running IGMP Snooping, manages and controls the multicast group via
listening to and processing the IGMP messages transmitted between the hosts and the multicast
router, thereby effectively prevents multicast groups being broadcasted in the network.
The Multicast module is mainly for multicast management configuration of the switch, including
four submenus: IGMP Snooping, Multicast IP, Multicast Filter and Packet Statistics.
8.1 IGMP Snooping
IGMP Snooping Process
The switch, running IGMP Snooping, listens to the IGMP messages transmitted between the host
and the router, and tracks the IGMP messages and the registered port. When receiving IGMP
report message, the switch adds the port to the multicast address table; when the switch listens to
IGMP leave message from the host, the router sends the Group-Specific Query message of the
port to check if other hosts need this multicast, if yes, the router will receive IGMP report message;
if no, the router will receive no response from the hosts and the switch will remove the port from
the multicast address table. The router regularly sends IGMP query messages. After receiving the
IGMP query messages, the switch will remove the port from the multicast address table if the
switch receives no IGMP report message from the host within a period of time.
IGMP Messages
The switch, running IGMP Snooping, processes the IGMP messages of different types as follows.
1. IGMP Query Message
IGMP query message, sent by the router, falls into two types, IGMP general query message and
IGMP group-specific-query message. The router regularly sends IGMP general message to query
if the multicast groups contain any member. When receiving IGMP leave message, the receiving
port of the router will send IGMP group-specific-query message to the multicast group and the
switch will forward IGMP group-specific-query message to check if other members in the multicast
group of the port need this multicast.
When receiving IGMP general query message, the switch will forward them to all other ports in the
VLAN owning the receiving port. The receiving port will be processed: if the receiving port is not a
router port yet, it will be added to the router port list with its router port time specified; if the
receiving port is already a router port, its router port time will be directly reset.
When receiving IGMP group-specific-query message, the switch will send the group-specific query
message to the members of the multicast group being queried.
2. IGMP Report Message
IGMP report message is sent by the host when it applies for joining a multicast group or responses
to the IGMP query message from the router.
83
Page 89

When receiving IGMP report message, the switch will send the report message via the router port
in the VLAN as well as analyze the message to get the address of the multicast group the host
applies for joining. The receiving port will be processed: if the receiving port is a new member port,
it will be added to the multicast address table with its member port time specified; if the receiving
port is already a member port, its member port time will be directly reset.
3. IGMP Leave Message
The host, running IGMPv1, does not send IGMP leave message when leaving a multicast group,
as a result, the switch can not get the leave information of the host momentarily. However, after
leaving the multicast group, the host does not send IGMP report message any more, so the switch
will remove the port from the corresponding multicast address table when its member port time
times out. The host, running IGMPv2 or IGMPv3, sends IGMP leave message when leaving a
multicast group to inform the multicast router of its leaving.
When receiving IGMP leave message, the switch will forward IGMP group-specific-query message
to check if other members in the multicast group of the port need this multicast and reset the
member port time to the leave time. When the leave time times out, the switch will remove the port
from the corresponding multicast group. If no other member is in the group after the port is
removed, the switch will send IGMP leave message to the router and remove the whole multicast
group.
IGMP Snooping Fundamentals
1. Ports
Router Port: Indicates the switch port directly connected to the multicast router.
Member Port: Indicates a switch port connected to a multicast group member.
2. Timers
Router Port Time: Within the time, if the switch does not receive IGMP query message from the
router port, it will consider this port is not a router port any more. The default value is 300 seconds.
Member Port Time: Within the time, if the switch does not receive IGMP report message from the
member port, it will consider this port is not a member port any more. The default value is 260
seconds.
Leave Time: Indicates the interval between the switch receiving a leave message from a host and
the switch removing the host from the multicast groups. The default value is 1 second.
The IGMP Snooping function can be implemented on Snooping Config, Port Config, VLAN
Config and Multicast VLAN pages.
8.1.1 Snooping Config
To configure the IGMP Snooping on the switch, please firstly configure IGMP global configuration
and related parameters on this page.
If the multicast address of the received multicast data is not in the multicast address table, the
switch will broadcast the data in the VLAN. When Unknown Multicast Discard feature is enabled,
the switch drops the received unknown multicast so as to save the bandwidth and enhance the
process efficiency of the system. Please configure this feature appropriate to your needs.
Choose the menu Multicast→IGMP Snooping→Snooping Config to load the following page.
84
Page 90

IGMP Snooping:
Select Enable/Disable IGMP Snooping function globally on the
switch.
Unknown Multicast:
Select the operation for the switch to process unknown multicast,
Forward or Discard.
Description:
Displays IGMP Snooping status.
Member:
Displays the member of the corresponding status.
Figure 8-4 Basic Config
The following entries are displayed on this screen:
Global Config
IGMP Snooping Status
8.1.2 Port Config
On this page you can configure the IGMP feature for ports of the switch.
Choose the menu Multicast→IGMP Snooping→Port Config to load the following page.
Figure 8-5 Port Config
85
Page 91

Port Select:
Click the Select button to quick-select the corresponding port
based on the port number you entered.
Select:
Select the desired port for IGMP Snooping feature configuration. It
is multi-optional.
Port:
Displays the port of the switch.
IGMP Snooping:
Select Enable/Disable IGMP Snooping for the desired port.
Fast Leave:
Select Enable/Disable Fast Leave feature for the desired port. If
Fast Leave is enabled for a port, the switch will immediately
remove this port from the multicast group upon receiving IGMP
leave messages.
LAG:
Displays the LAG number which the port belongs to.
The following entries are displayed on this screen:
Port Config
Note:
1. Fast Leave on the port is effective only when the host supports IGMPv2 or IGMPv3.
2. When both Fast Leave feature and Unknown Multicast Discard feature are enabled, the
leaving of a user connected to a port owning multi-user will result in the other users
intermitting the multicast business.
8.1.3 VLAN Config
Multicast groups established by IGMP Snooping are based on VLANs. On this page you can
configure different IGMP parameters for different VLANs.
Choose the menu Multicast→IGMP Snooping→VLAN Config to load the following page.
Figure 8-6 VLAN Config
The following entries are displayed on this screen:
VLAN Config
86
Page 92

VLAN ID:
Enter the VLAN ID to enable IGMP Snooping for the desired
VLAN.
Router Port Time:
Specify the aging time of the router port. Within this time, if the
switch doesn’t receive IGMP query message from the router port,
it will consider this port is not a router port any more.
Member Port Time:
Specify the aging time of the member port. Within this time, if the
switch doesn’t receive IGMP report message from the member
port, it will consider this port is not a member port any more.
Leave Time:
Specify the interval between the switch receiving a leave
message from a host and the switch removing the host from the
multicast groups.
Static Router Port:
Select the static router port which is mainly used in the network
with stable topology.
VLAN Table
VLAN ID Select:
Click the Select button to quick-select the corresponding VLAN
ID based on the ID number you entered.
Select:
Select the desired VLAN ID for configuration. It is multi-optional.
VLAN ID:
Displays the VLAN ID.
Router Port Time:
Displays the router port time of the VLAN.
Member Port Time:
Displays the member port time of the VLAN.
Leave Time:
Displays the leave time of the VLAN.
Router Port:
Displays the router port of the VLAN.
Step
Operation
Description
1
Enable IGMP Snooping
function
Required. Enable IGMP Snooping globally on the switch
and for the port on Multicast→IGMP
Snooping→Snooping Config and Port Config page.
2
Configure the multicast
parameters for VLANs
Optional. Configure the multicast parameters for VLANs on
Multicast→IGMP Snooping→VLAN Config page.
If a VLAN has no multicast parameters configuration, it
indicates the IGMP Snooping is not enabled in the VLAN,
thus the multicast data in the VLAN will be broadcasted.
Note:
The settings here will be invalid when multicast VLAN is enabled.
Configuration procedure:
8.1.4 Multicast VLAN
In old multicast transmission mode, when users in different VLANs apply for join the same
multicast group, the multicast router will duplicate this multicast information and deliver each
VLAN owning a receiver one copy. This mode wastes a lot of bandwidth.
87
Page 93

Multicast VLAN:
Select Enable/Disable Multicast VLAN feature.
VLAN ID:
Enter the VLAN ID of the multicast VLAN.
Router Port Time:
Specify the aging time of the router port. Within this time, if the
switch doesn’t receive IGMP query message from the router port,
it will consider this port is not a router port any more.
Member Port Time:
Specify the aging time of the member port. Within this time, if the
switch doesn’t receive IGMP report message from the member
port, it will consider this port is not a member port any more.
Leave Time:
Specify the interval between the switch receiving a leave message
from a host, and the switch removing the host from the multicast
groups.
Static Router Port:
Select the static router port which is mainly used in the network
with stable topology.
The problem above can be solved by configuring a multicast VLAN. By adding switch ports to the
multicast VLAN and enabling IGMP Snooping, you can make users in different VLANs share the
same multicast VLAN. This saves the bandwidth since multicast streams are transmitted only
within the multicast VLAN and also guarantees security because the multicast VLAN is isolated
from user VLANS.
Before configuring a multicast VLAN, you should firstly configure a VLAN as multicast VLAN and
add the corresponding ports to the VLAN on the 802.1Q VLAN page. If the multicast VLAN is
enabled, the multicast configuration for other VLANs on the VLAN Config page will be invalid, that
is, the multicast streams will be transmitted only within the multicast VLAN.
Choose the menu Multicast→IGMP Snooping→Multicast VLAN to load the following page.
Figure 8-7 Multicast VLAN
The following entries are displayed on this screen:
Multicast VLAN
Note:
1. The router port should be in the multicast VLAN, otherwise the member ports can not receive
multicast streams.
88
Page 94

Step
Operation
Description
1
Enable IGMP Snooping
function
Required. Enable IGMP Snooping globally on the switch
and for the port on Multicast→IGMP
Snooping→Snooping Config and Port Config page.
2
Create a multicast VLAN
Required. Create a multicast VLAN and add all the member
ports and router ports to the VLAN on the VLAN→802.1Q
VLAN page.
Configure the link type of the router ports as Tagged.
3
Configure parameters for
multicast VLAN
Optional. Enable and configure a multicast VLAN on the
Multicast→IGMP Snooping→Multicast VLAN page.
It is recommended to keep the default time parameters.
4
Look over the configuration
If it is successfully configured, the VLAN ID of the multicast
VLAN will be displayed in the IGMP Snooping Status table
on the Multicast→IGMP Snooping→Snooping Config
page.
2. The Multicast VLAN won't take effect unless you first complete the configuration for the
corresponding VLAN owning the port on the 802.1Q VLAN page.
3. It is recommended to choose GENERAL as the link type of the member ports in the multicast
VLAN.
4. After a multicast VLAN is created, all the IGMP packets will be processed only within the
multicast VLAN.
Configuration procedure:
Application Example for Multicast VLAN:
Network Requirements
Multicast source sends multicast streams via the router, and the streams are transmitted to user A
and user B through the switch.
Router: Its WAN port is connected to the multicast source; its LAN port is connected to the switch.
The multicast packets are transmitted in VLAN3.
switch: Port 3 is connected to the router and the packets are transmitted in VLAN3; port 4 is
connected to user A and the packets are transmitted in VLAN4; port 5 is connected to user B and
the packets are transmitted in VLAN5.
User A: Connected to Port 4 of the switch.
User B: Connected to port 5 of the switch.
Configure a multicast VLAN, and user A and B receive multicast streams through the multicast
VLAN.
89
Page 95

Network Diagram
Step
Operation
Description
1
Create VLANs
Create three VLANs with the VLAN ID 3, 4 and 5 respectively,
and specify the description of VLAN3 as Multicast VLAN on
VLAN→802.1Q VLAN page.
2
Configure ports
On VLAN→802.1Q VLAN function pages.
For port 3, configure its link type as Tagged, and add it to VLAN3,
VLAN4 and VLAN5.
For port 4, configure its link type as Untagged, and add it to
VLAN3 and VLAN 4.
For port 5, configure its link type as Untagged, and add it to
VLAN3 and VLAN 5.
3
Enable IGMP
Snooping function
Enable IGMP Snooping function globally on Multicast→IGMP
Snooping→Snooping Config page. Enable IGMP Snooping
function for port 3, port 4 and port 5 on Multicast→IGMP
Snooping→Port Config page.
4
Enable Multicast
VLAN
Enable Multicast VLAN, configure the VLAN ID of a multicast
VLAN as 3 and keep the other parameters as default on
Multicast→IGMP Snooping→Multicast VLAN page.
5
Check Multicast VLAN
3-5 and Multicast VLAN 3 will be displayed in the IGMP
Snooping Status table on the Multicast→IGMP
Snooping→Snooping Config page.
Configuration Procedure
8.2 Multicast IP
In a network, receivers can join different multicast groups appropriate to their needs. The switch
forwards multicast streams based on multicast address table. The Multicast IP can be
implemented on Multicast IP Table, Static Multicast IP page.
90
Page 96

Multicast IP:
Enter the multicast IP address the desired entry must carry.
VLAN ID:
Enter the VLAN ID the desired entry must carry.
Port:
Select the port number the desired entry must carry.
Type:
Select the type the desired entry must carry.
All: Displays all multicast IP entries.
Static: Displays all static multicast IP entries.
Dynamic: Displays all dynamic multicast IP entries.
Multicast IP
Displays multicast IP address.
VLAN ID:
Displays the VLAN ID of the multicast group.
Forward Port
Displays the forward port of the multicast group.
Type:
Displays the type of the multicast IP.
8.2.1 Multicast IP Table
On this page you can view the multicast IP table on the switch.
Choose the menu Multicast→Multicast IP→Multicast IP Table to load the following page.
Figure 8-8 Multicast IP Table
The following entries are displayed on this screen:
Search Option
Multicast IP Table
Note:
If the configuration on VLAN Config page and multicast VLAN page is changed, the switch will
clear up the dynamic multicast addresses in multicast address table and learn new addresses.
8.2.2 Static Multicast IP
Static Multicast IP table, isolated from dynamic multicast group and multicast filter, is not learned
by IGMP Snooping. It can enhance the quality and security for information transmission in some
fixed multicast groups.
Choose the menu Multicast→Multicast IP→Static Multicast IP to load the following page.
91
Page 97

Multicast IP:
Enter static multicast IP address.
VLAN ID:
Enter the VLAN ID of the multicast IP.
Forward Port:
Enter the forward port of the multicast group.
Search Option:
Select the rules for displaying multicast IP table to find the desired
entries quickly.
All: Displays all static multicast IP entries.
Multicast IP: Enter the multicast IP address the desired entry
must carry.
VLAN ID: Enter the VLAN ID the desired entry must carry.
Port: Enter the port number the desired entry must carry.
Select:
Select the desired entry to delete the corresponding static
multicast IP. It is multi-optional.
Multicast IP:
Displays the multicast IP.
VLAN ID:
Displays the VLAN ID of the multicast group.
Forward Port:
Displays the forward port of the multicast group.
Figure 8-9 Static Multicast IP Table
The following entries are displayed on this screen:
Create Static Multicast
Search Option
Static Multicast IP Table
8.3 Multicast Filter
When IGMP Snooping is enabled, you can specified the multicast IP-range the ports can join so as
to restrict users ordering multicast programs via configuring multicast filter rules.
When applying for a multicast group, the host will send IGMP report message. After receiving the
report message, the switch will firstly check the multicast filter rules configured for the receiving
92
Page 98

IP Range ID:
Enter the IP-range ID.
Start Multicast IP:
Enter start multicast IP of the IP-range you set.
End Multicast IP:
Enter end multicast IP of the IP-range you set.
IP-Range ID Select:
Click the Select button to quick-select the corresponding IP-range
ID based on the ID number you entered.
Select:
Select the desired entry to delete or modify the corresponding
IP-range. It is multi-optional.
IP-Range ID:
Displays IP-range ID.
Start Multicast IP:
Displays start multicast IP of the IP-range.
End Multicast IP:
Displays end multicast IP of the IP-range.
port. If the port can be added to the multicast group, it will be added to the multicast address table;
if the port can not be added to the multicast group, the switch will drop the IGMP report message.
In that way, the multicast streams will not be transmitted to this port, which allows you to control
hosts joining the multicast group.
8.3.1 IP-Range
On this page you can figure the desired IP-ranges to be filtered.
Choose the menu Multicast→Multicast Filter→IP-Range to load the following page.
Figure 8-10 Multicast Filter
The following entries are displayed on this screen:
Create IP-Range
IP-Range Table
8.3.2 Port Filter
On this page you can configure the multicast filter rules for port. Take the configuration on this
page and the configuration on IP-Range page together to function to implement multicast filter
function on the switch.
93
Page 99

Port Select:
Click the Select button to quick-select the corresponding port
based on the port number you entered.
Select:
Select the desired port for multicast filtering. It is multi-optional.
Port:
Displays the port number.
Filter:
Select Enable/Disable multicast filtering feature on the port.
Action Mode:
Select the action mode to process multicast packets when the
multicast IP is in the filtering IP-range.
Permit: Only the multicast packets whose multicast IP is in
the IP-range will be processed.
Deny: Only the multicast packets whose multicast IP is not in
the IP-range will be processed.
Bound IP-Range (ID):
Enter the IP-rang ID the port will be bound to.
Max Groups:
Specify the maximum number of multicast groups to prevent some
ports taking up too much bandwidth.
LAG:
Displays the LAG number which the port belongs to.
Choose the menu Multicast→Multicast Filter→Port Filter to load the following page.
Figure 8-11 Port Filter
The following entries are displayed on this screen:
Port Filter Config
Note:
1. Multicast Filter feature can only have effect on the VLAN with IGMP Snooping enabled and
Unknown Multicast disabled.
2. Multicast Filter feature has no effect on static multicast IP.
94
Page 100

Step
Operation
Description
1
Configure IP-Range
Required. Configure IP-Range to be filtered on
Multicast→Multicast Filter→IP-Range page.
2
Configure multicast filter
rules for ports
Optional. Configure multicast filter rules for ports on
Multicast→Multicast Filter→Port Filter page.
Auto Refresh:
Select Enable/Disable auto refresh feature.
Refresh Period:
Enter the time from 3 to 300 in seconds to specify the auto refresh
period.
3. Up to 5 IP-Ranges can be bound to one port.
Configuration Procedure:
8.4 Packet Statistics
On this page you can view the multicast data traffic on each port of the switch, which facilitates you
to monitor the IGMP messages in the network.
Choose the menu Multicast→Packet Statistics to load the following page.
Figure 8-12 Packet Statistics
The following entries are displayed on this screen:
Auto Refresh
IGMP Statistics
95
 Loading...
Loading...