Page 1

SCSxx05/SCSxx20
Secure Console Server
User Guide
Models SCS3205, SCS4805, SCS820, SCS1620
with Firmware v4.3 and later
Part No. 900-287
Rev. D April 2004
Page 2

Copyright & Trademark
© 2003, Lantronix. All rights reserved. No part of the contents of this book may
be transmitted or reproduced in any form or by any means without the written
permission of Lantronix. Printed in the United States of America.
Lightwave Communications is a Lantronix Inc. Company. Ethernet is a trademark
of XEROX Corporation. UNIX is a registered trademark of The Open Group.
Windows 95, Windows 98, Windows 2000, and Windows NT are trademarks of
Microsoft Corporation. Netscape is a trademark of Netscape Communications
Corporation.
LINUX GPL Compliance
Certain portions of source code for the software supporting the SCSxx05™ and
SCSxx20™
published by the Free Software Foundation and may be redistributed and
modified under the terms of the GNU GPL. A machine readable copy of the
corresponding portions of GPL licensed source code are available at the cost of
distribution.
Such source code is distributed WITHOUT ANY WARRANTY, INCLUDING
ANY IMPLIED WARRANTY OF MERCHANTABILITY OR FITNESS FOR A
PARTICULAR PURPOSE. See the GNU General Public License for more
details.
are licensed under the GNU General Public License (GPL) as
A copy of the GNU General Public License is available on the Lantronix Web Site
at http://www.lantronix.com/
You can also obtain it by writing to the Free Software Foundation, Inc. 59 Temple
Place, Suite 330, Boston, MA 02111-1307 USA.
or by visiting http://www.gnu.org/copyleft/gpl.html
Contacts
Lantronix Corporate Headquarters
15353 Barranca Parkway
Irvine, CA 92618, USA
Phone: 949-453-3990
Fax: 949-453-3995
Technical Support
Phone: 800-422-7044 or 949-453-7198
Fax: 949-450-7226
Fax: 949-450-7226
Online: www.lantronix.com/support
Email: support@lantronix.com
Sales Offices
For a current list of our domestic and international sales offices, go to the
Lantronix web site at http://www.lantronix.com/about/contact/index.html
i
Page 3

Disclaimer & Revisions
Operation of this equipment in a residential area is likely to cause interference in
which case the user, at his or her own expense, will be required to take whatever
measures may be required to correct the interference.
Note: This equipment has been tested and found to comply with the
limits for Class A digital device pursuant to Part 15 of the FCC Rules.
These limits are designed to provide reasonable protection against
harmful interference when the equipment is operated in a commercial
environment. This equipment generates, uses, and can radiate radio
frequency energy and, if not installed and used in accordance with this
User Guide, may clause interference to radio communications. Operation
of this equipment in a residential area is likely to cause interference, in
which case the user will be required to correct the interference at his own
expense.
The user is cautioned that changes and modifications made to the
equipment without approval of the manufacturer could void the user’s
authority to operate this equipment.
Changes or modifications to this device not explicitly approved by Lantronix will
void the user's authority to operate this device.
The information in this guide may change without notice. The manufacturer
assumes no responsibility for any errors that may appear in this guide.
Date Part No Rev. Comments
8/03 900-287 B
10/03 900-287 C
4/04 900-287 D
Combined SCSxx05 and SCSxx20 products (firmware v.4.3
and later) in one user guide. Updated warranty information.
Added safety precautions in English and multiple languages;
revised declarations of conformity.
Removed Web interface.
ii
Page 4

Safety Precautions
Please follow the safety precautions described below when installing and
operating the SCSxx05/SCSxx20 Secure Console Server.
Cover
Do not remove the cover of the chassis. There are no user-serviceable
Refer all servicing to Lantronix.
Service personnel: Dispose of used batteries according to the
Power Plug
When disconnecting the power cable from the socket, pull on the plug,
Always connect the power cord to a properly wired and grounded power
Only use a power cord with a voltage and current rating greater than the
Install the unit near an AC outlet that is easily accessible.
Always connect any equipment used with the product to properly wired
To help protect the product from sudden, transient increases and
Do not connect or disconnect this product during an electrical storm.
Grounding
parts inside. Opening or removing the cover may expose you to
dangerous voltage that could cause fire or electric shock.
instructions. There is a risk of explosion if the battery is replaced with an
incorrect type.
not the cord.
source. Do not use adapter plugs or remove the grounding prong from
the cord.
voltage and current rating marked on the unit.
and grounded power sources.
decreases in electrical power, use a surge suppressor, line conditioner,
or uninterruptible power supply (UPS).
Maintain reliable grounding of this product.
Pay particular attention to supply connections when connecting to power
strips, rather than directly to the branch circuit.
Fuses
For protection against fire, replace the power-input-module fuse with the
same type and rating.
Rack
Do not install the unit in a rack in such a way that a hazardous stability
condition results because of uneven loading. A drop or fall could cause
injury.
Before operating the SCS, make sure the SCS is secured to the rack.
Port Connections
Only connect the network port to an Ethernet network that supports
10Base-T/100Base-TX.
Only connect device ports to equipment with serial ports that support
EIA-232 (formerly RS-232C).
Only connect the terminal port to equipment with serial ports that support
EIA-232 (formerly RS-232C).
iii
Page 5

Precauciones de seguridad
Al instalar y utilizar el servidor seguro de consola SCSxx05/SCSxx20, observe
las precauciones de seguridad que se describen a continuación.
Tapa
No retire la tapa del chasis. En el interior no hay ninguna pieza que el
usuario deba manipular. Abrir o retirar la tapa puede exponer al usuario
a tensiones peligrosas que pueden causar fuego o electrocución. Si la
batería se sustituye por una de tipo incorrecto, puede producirse una
explosión.
Confíe todas las actividades de mantenimiento o reparación a Lantronix.
Personal de mantenimiento: Deshágase de las baterías usadas de
acuerdo con las instrucciones. Si la batería se sustituye por una de tipo
incorrecto, puede producirse una explosión.
Enchufe de alimentación
Al desconectar el cable de alimentación de la toma, tire del enchufe, no
del propio cable.
Conecte siempre el cable de alimentación a una toma eléctrica
correctamente cableada y conectada a tierra. No use adaptadores de
enchufes ni elimine la patilla de toma de tierra del cable.
Use sólo un cable de alimentación adecuado para unos valores de
tensión e intensidad superiores a la tensión y la intensidad indicados en
la unidad.
Instale la unidad cerca de un toma de CA de fácil acceso.
Conecte siempre cualquier equipo que se use con el producto a tomas
eléctricas correctamente cableadas y conectadas a tierra.
Para proteger el producto contra aumentos y descensos transitorios
bruscos de la alimentación eléctrica, use un supresor de sobrecargas
momentáneas, un acondicionador de línea, o una fuente de alimentación
ininterrumpida (UPS).
No conecte ni desconecte este producto durante una tormenta eléctrica.
Toma de tierra
Mantenga este producto conectado en todo momento a una toma de
tierra fiable.
Preste especial atención a las conexiones de alimentación cuando se
conecta a regletas de terminales, en lugar de hacerlo directamente al
circuito derivado.
Fusibles
Para proteger la unidad contra el fuego, cuando sea necesario sustituya
el fusible del módulo de entrada de alimentación por otro del mismo tipo
y capacidad.
Bastidor
No instale la unidad en un bastidor (rack) de manera que quede en un
equilibrio inestable peligroso debido a el reparto irregular del peso. La
caída de la unidad podría causar lesiones.
Antes de utilizar el servidor seguro de consola (SCS), verifique que el
SCS está bien fijado al bastidor.
iv
Page 6

Conexiones de puertos
Conecte el puerto de red solamente a una red Ethernet compatible con
10Base-T/100Base-TX.
Conecte los puertos de dispositivos solamente a equipos con puertos
serie compatibles con EIA-232 (antes, RS-232C).
Conecte el puerto terminal solamente a equipos con puertos serie
compatibles con EIA-232 (antes, RS-232C).
Précautions relatives à la sécurité
Pour des raisons de sécurité, respectez les précautions suivantes lorsque vous
installez et utilisez un équipement de la gamme Secure Console Server
SCSxx05/SCSxx20.
Boîtier
Ne déposez jamais le boîtier du châssis. Aucun élément interne de cet
appareil ne peut être réparé ou remplacé par l’utilisateur. En ouvrant le
boîtier, vous vous exposeriez à un risque d’électrocution ou d’incendie.
Confiez toute opération d'entretien ou de dépannage à du personnel
agréé par Lantronix.
Personnel d’entretien : Respectez les instructions relatives à la mise au
rebut des batteries usagées. Il y a risque d’explosion si la batterie est
remplacée par une autre batterie de type incorrect.
Prise d’alimentation secteur
Pour débrancher le câble d’alimentation électrique, tirez sur la prise, pas
sur le cordon.
Veillez à toujours brancher le câble d’alimentation électrique à une prise
correctement câblée avec mise à la terre. N’utilisez pas d’adaptateur, et
ne démontez pas la fiche de terre du câble.
Utilisez uniquement un câble d’alimentation électrique certifié pour une
tension et une intensité supérieures à la tension et à l’intensité
nominales de l’équipement.
Installez cet équipement à proximité d’une prise électrique aisément
accessible.
Veillez à toujours brancher tout équipement utilisé avec celui-ci à une
prise correctement câblée avec mise à la terre.
Pour protéger ce produit des fluctuations de tension et des transitoires
du courant électrique, il est conseillé d’utiliser une protection contre les
surtensions, un filtre de secteur ou un onduleur avec batterie (UPS).
Veillez à ne pas laisser cet équipement connecté au secteur durant un
orage.
Mise à la terre
Veillez à préserver une mise à la terre fiable de ce produit.
Prêtez particulièrement attention aux connexions d’alimentation si vous
raccordez cet équipement à une prise multiple au lieu de le brancher
directement sur le circuit principal.
v
Page 7

Fusibles
Pour assurer la protection contre l’incendie, remplacez toujours le fusible
du module d’alimentation électrique par un modèle du même type et de
la même capacité.
Rack
N’installez pas cet équipement dans un rack si une mauvaise répartition
des masses risque de provoquer l’instabilité du rack. Toute chute risque
de provoquer des blessures.
Avant de mettre le SCS en service, veillez à ce qu’il soit fermement fixé
dans le rack.
Connexions
Veillez à ne connecter le port réseau qu’un un réseau Ethernet prenant
en charge les standards 10Base-T/100Base-TX.
Veillez à ne connecter les ports pour périphériques qu’à des
équipements prenant en charge le standard EIA-232 (anciennement
dénommé RS-232C).
Veillez à ne connecter le port pour terminal qu’à un équipement doté
d’un port série prenant en charge le standard EIA-232 (anciennement
dénommé RS-232C).
Sicherheitshinweise
Beachten Sie bei der Installation und beim Betrieb des Secure Console Server
SCSxx05/SCSxx20 die nachstehenden Sicherheitshinweise.
Abdeckung
Nehmen Sie nicht die Abdeckung des Gehäuses ab. Im Gerät befinden
sich keine vom Benutzer wartbaren Teile. Durch Öffnen oder Entfernen
der Abdeckung können Sie gefährlichen Spannungen ausgesetzt
werden, die einen Brand verursachen oder einen elektrischen Schlag
bewirken könnten.
Überlassen Sie alle Wartungsarbeiten Lantronix.
Wartungspersonal: Entsorgen Sie alte Batterien gemäß den
Anweisungen. Wird die Batterie durch eine falsche Batterie ersetzt,
besteht Explosionsgefahr.
Netzstecker
Ziehen Sie, um das Gerät vom Netz zu trennen, am Stecker und nicht
am Kabel.
Stecken Sie das Anschlusskabel immer in eine korrekt verdrahtete und
geerdete Steckdose ein. Verwenden Sie keine Adapterstecker und
entfernen Sie nicht den Schutzkontakt vom Stecker.
Verwenden Sie nur ein Anschlusskabel, das für eine höhere Spannung
und einen höheren Strom ausgelegt ist als auf dem Gerät angegeben.
Stellen Sie das Gerät in der Nähe einer frei zugänglichen Steckdose auf.
Schließen Sie Geräte, die in Verbindung mit dem Produkt eingesetzt
werden, nur an korrekt verdrahteten und geerdeten Steckdosen an.
Schützen Sie das Produkt mit einer Überspannungsschutzvorrichtung,
einem Netzentstörgerät oder einer unterbrechungsfreien
Stromversorgung (USV) vor vorübergehenden Spannungsanstiegen und
-abfällen.
vi
Page 8

Während eines Gewitters dürfen Sie das Gerät nicht anschließen oder
vom Netz trennen.
Erdung
Schließen Sie das Gerät an einem zuverlässigen Erdungspunkt an.
Achten Sie besonders auf die einwandfreie Verbindung, wenn der
Anschluss über eine Steckdosenleiste und nicht direkt am Endstromkreis
erfolgt.
Sicherungen
Ersetzen Sie die Netzteilsicherung nur durch eine Sicherung desselben
Typs und derselben Nennstromstärke, um die Gefahr eines Brandes zu
vermeiden.
Rack
Achten Sie beim Einbau des Geräts in ein Rack darauf, dass dieses
gleichmäßig belastet wird, damit die Stabilität gewährleistet ist. Das
herunterfallende Gerät kann beschädigt werden oder Verletzungen
verursachen.
Überprüfen Sie das SCS vor Inbetriebnahme auf festen Sitz im Rack.
Portanschlüsse
Schließen Sie den Netzwerkport nur an eine Ethernet-Netzwerk an, von
dem 10Base-T/100Base-TX unterstützt wird.
Schließen Sie die Geräteports nur an Geräte mit seriellen Ports an, die
EIA-232 (früher RS-232C) unterstützen.
Schließen Sie den Konsolenport nur an Geräte mit seriellen Ports an, die
EIA-232 (früher RS-232C) unterstützen.
Меры предосторожности
При установке и эксплуатации защищенного консольного сервера (Secure
Console Server) SCSxx05/SCSxx20 соблюдайте описанные ниже меры
предосторожности.
Крышка
Не снимайте крышку с рамы. Внутри нет деталей, которые должны
обслуживаться пользователем. При открытии или удалении крышки
вы можете подвергнуть себя опасности воздействия высокого
напряжения, которое способно вызвать пожар или электрический
удар.
По всем вопросам техобслуживания обращайтесь к компании
Lantronix.
Обслуживающий персонал: удаляйте все использованные батареи в
соответствии с инструкциями. Если существующая батарея
заменяется на батарею другого типа, существует риск
возникновения пожара.
Вилка электропитания
При отсоединении силового кабеля из розетки держите его за вилку,
а не за шнур.
Всегда вставляйте силовой шнур в заземленную и снабженную
правильной электропроводкой розетку. Не используйте вилкипереходники или не удаляйте заземляющий штырь со шнура.
vii
Page 9

Используйте только шнур питания, у которого номинальные
значения напряжения и тока превышают номинальные значения
напряжения и тока, указанные на устройстве.
Установите устройство вблизи розетки переменного тока, к которой
имеется легкий доступ.
Всегда подсоединяйте любое оборудование, используемое вместе с
изделием, к заземленным источникам питания с правильной
электропроводкой.
Для защиты изделия от неожиданных неустановившихся
увеличений и уменьшений электрической мощности используйте
ограничитель перенапряжений, устройство защиты от электрических
помех или источник бесперебойного питания.
Не подсоединяйте это изделие во время грозы.
Заземление
Это изделие постоянно должно иметь надежное заземление.
При подсоединении к шинам питания особое внимание обращайте
на соединения питания, а не на ответвление цепи.
Предохранители
Для защиты от пожара, заменяйте предохранитель модуля подвода
питания на предохранитель такого же типа, рассчитанный на
аналогичный номинальный ток.
Стойка
Не устанавливайте устройство на стойку так, чтобы возникала
опасность нарушения стабильности из-за неравномерной нагрузки.
Падение может привести к травме.
До работы с SCS убедитесь в том, что SCS закреплен на стойке.
Соединения портов
Сетевой порт подсоединяйте только к сети Ethernet,
поддерживающей 10Base-T/100Base-TX.
Порты устройства подсоединяйте только к оборудованию с
последовательными портами, поддерживающими EIA-232 (прежнее
название RS-232C).
Терминальный порт подсоединяйте только к оборудованию с
последовательными портами, поддерживающими EIA-232 (прежнее
название RS-232C).
viii
Page 10

ix
Page 11

x
Page 12

xi
Page 13

xii
Page 14

xiii
Page 15

xiv
Page 16

Contents
Safety Precautions _____________________________________________________ iii
1: Introduction ___________________________________________________ 1-1
SCSxx05 and SCSxx20_________________________________________________ 1-1
Hardware Features ____________________________________________________ 1-3
System Features ______________________________________________________ 1-4
Protocol Support ______________________________________________________ 1-4
System Components ___________________________________________________ 1-5
Connection Formats ___________________________________________________ 1-5
Access Control _______________________________________________________ 1-6
Device Port Buffer _____________________________________________________ 1-7
Technical Specifications ________________________________________________ 1-8
Product Information Label _______________________________________________ 1-9
System Resource Information ___________________________________________ 1-10
Copyright & Trademark________________________________________________________ i
LINUX GPL Compliance _______________________________________________________ i
Contacts ___________________________________________________________________ i
Disclaimer & Revisions ________________________________________________________ii
Serial Devices _____________________________________________________________ 1-5
Network __________________________________________________________________ 1-6
Modem (SCSxx20) _________________________________________________________ 1-6
Power Manager____________________________________________________________ 1-6
256K FIFO Buffer __________________________________________________________ 1-7
Port Data Logging __________________________________________________________ 1-7
Logging to File_____________________________________________________________ 1-7
Email Notification __________________________________________________________ 1-7
2: Installation ____________________________________________________ 2-1
Physical Installation____________________________________________________ 2-1
Power ______________________________________________________________ 2-2
AC Input _________________________________________________________________ 2-2
DC Input _________________________________________________________________ 2-2
Connecting a Terminal _________________________________________________ 2-3
Connecting to a Device Port _____________________________________________ 2-4
Connecting the Network Port_____________________________________________ 2-5
Connecting the Modem Port (SCSxx20) ____________________________________ 2-5
Power Manager Interface _______________________________________________ 2-6
3: Quick Start ____________________________________________________ 3-1
Before You Begin _____________________________________________________ 3-1
Method #1 – Using the Front Panel Display _________________________________ 3-2
Navigating ________________________________________________________________ 3-2
Entering the Settings________________________________________________________ 3-2
Method # 2- Using Telnet _______________________________________________ 3-4
4: Configuration __________________________________________________ 4-1
xv
Page 17

Connecting Using Telnet or Your Serial Terminal _____________________________ 4-2
Logging in as System Administrator _______________________________________ 4-2
Accessing the Setup Menu ______________________________________________ 4-2
Navigating ________________________________________________________________ 4-3
Done Option ______________________________________________________________ 4-4
Configuring Hostname and IP Address _____________________________________ 4-4
Configuring Timezone __________________________________________________ 4-6
Configuring DNS ______________________________________________________ 4-8
Configuring Services ___________________________________________________ 4-9
Enabling/Disabling Web Configuration ____________________________________ 4-10
Configuring NTP _____________________________________________________ 4-10
Configuring Email Relay _______________________________________________ 4-11
Configuring Timeouts _________________________________________________ 4-11
Configuring Modem (SCSxx20 Only) _____________________________________ 4-12
Configuring CHAP Secrets _____________________________________________ 4-15
Configuring PAP Secrets_______________________________________________ 4-16
Configuring User Authentication _________________________________________ 4-16
Configuring NIS___________________________________________________________ 4-17
Configuring LDAP _________________________________________________________ 4-18
Configuring RADIUS ________________________________________________________ 4-1
Configuring Global Port Permissions ___________________________________________ 4-1
Done User Authentication ____________________________________________________ 4-2
Configuring NFS Mount_________________________________________________ 4-2
Configuring Firewall (Packet Filtering)______________________________________ 4-4
Configuring Device Ports________________________________________________ 4-5
Device Port Configuration Options _____________________________________________ 4-6
Device Port Menu __________________________________________________________ 4-6
Device Port Names _________________________________________________________ 4-6
Device Port Parameters _____________________________________________________ 4-7
Device Logging Parameters _________________________________________________ 4-10
Done Device Ports ________________________________________________________ 4-14
Updating Software____________________________________________________ 4-14
Using Done _________________________________________________________ 4-16
Saving _____________________________________________________________ 4-17
Rebooting __________________________________________________________ 4-17
5: Web Interface __________________________________________________ 5-1
Accessing the Web Interface_____________________________________________ 5-1
Web Configuration Utility Main Page_______________________________________ 5-2
Configurable Parameters________________________________________________ 5-2
Web Access Delay ____________________________________________________ 5-3
Saving Web Interface Entries ____________________________________________ 5-4
Exiting ______________________________________________________________ 5-4
6: Modem Setup __________________________________________________ 6-1
Installing a Modem Card ________________________________________________ 6-1
Initializing the Modem __________________________________________________ 6-1
xvi
Page 18

7: System Administrator and User Functions __________________________ 7-1
System Administrator Functions __________________________________________ 7-1
Security and Passwords _____________________________________________________ 7-1
Changing the Sysadmin Password _____________________________________________ 7-1
Changing the Root Password _________________________________________________ 7-2
If You Misplace the Sysadmin Password ________________________________________ 7-3
User Access and Functions______________________________________________ 7-3
Network Port Access________________________________________________________ 7-3
Terminal Port Access _______________________________________________________ 7-4
Modem Module ____________________________________________________________ 7-4
Selecting a Device Port______________________________________________________ 7-4
Direct Mode_______________________________________________________________ 7-5
Logging Out_______________________________________________________________ 7-6
8: Commands ____________________________________________________ 8-1
Summary of Commands ________________________________________________ 8-1
System Commands ____________________________________________________ 8-2
SAVE____________________________________________________________________ 8-2
reboot ___________________________________________________________________ 8-2
poweroff _________________________________________________________________ 8-3
help _____________________________________________________________________ 8-3
alias_____________________________________________________________________ 8-3
setup ____________________________________________________________________ 8-3
passwd __________________________________________________________________ 8-4
break ____________________________________________________________________ 8-4
changes__________________________________________________________________ 8-4
config-save _______________________________________________________________ 8-4
config-restore _____________________________________________________________ 8-4
install-modem _____________________________________________________________ 8-4
man _____________________________________________________________________ 8-4
modem-hangup ____________________________________________________________ 8-4
info _____________________________________________________________________ 8-4
reset-modem______________________________________________________________ 8-5
scp______________________________________________________________________ 8-5
sftp _____________________________________________________________________ 8-5
ssh______________________________________________________________________ 8-5
ssh-keygen _______________________________________________________________ 8-5
syslog ___________________________________________________________________ 8-5
timeout __________________________________________________________________ 8-6
unsaved__________________________________________________________________ 8-6
version___________________________________________________________________ 8-6
Device Commands ____________________________________________________ 8-7
devices __________________________________________________________________ 8-7
editdev___________________________________________________________________ 8-7
listdev ___________________________________________________________________ 8-7
connections _______________________________________________________________ 8-8
cat ______________________________________________________________________ 8-8
clear ____________________________________________________________________ 8-8
xvii
Page 19

less _____________________________________________________________________ 8-8
logout ___________________________________________________________________ 8-8
User Management Commands ___________________________________________ 8-9
listusers __________________________________________________________________ 8-9
adduser __________________________________________________________________ 8-9
edituser _________________________________________________________________ 8-10
deluser _________________________________________________________________ 8-11
editbrk __________________________________________________________________ 8-11
editesc__________________________________________________________________ 8-11
passwd _________________________________________________________________ 8-11
User Commands _____________________________________________________ 8-12
select___________________________________________________________________ 8-12
direct ___________________________________________________________________ 8-12
telnetconfig ______________________________________________________________ 8-12
listen ___________________________________________________________________ 8-12
clear ___________________________________________________________________ 8-12
exit_____________________________________________________________________ 8-12
logout __________________________________________________________________ 8-12
Break Sequence __________________________________________________________ 8-12
Escape Sequence_________________________________________________________ 8-12
Advanced Sysadmin Commands ________________________________________ 8-13
Using ssh Keys and keygen Procedures _______________________________________ 8-13
Mounting File Systems During Boot ___________________________________________ 8-14
Mounting File Systems Dynamically Using autofs ________________________________ 8-15
9: Port Access ___________________________________________________ 9-1
Telnet to Serial Port Feature _____________________________________________ 9-1
Accessing Serial Ports ______________________________________________________ 9-1
Assigning an IP Port Number to a Serial Port_____________________________________ 9-3
Testing __________________________________________________________________ 9-4
Saving the Changes to Flash _________________________________________________ 9-4
IP Address per Serial Port Feature ________________________________________ 9-5
Setting the IP Addresses ____________________________________________________ 9-5
Testing __________________________________________________________________ 9-7
Saving the Changes to Flash _________________________________________________ 9-8
Final Testing ______________________________________________________________ 9-8
Bypassing Authentication ____________________________________________________ 9-9
A: Unix Command Help ____________________________________________ A-1
less command_____________________________________________________________ A-1
vi Editor Commands ________________________________________________________ A-3
B: Hexadecimal Conversion Chart ___________________________________ B-1
C: Pinouts and Adapters ___________________________________________ C-1
SCSxx05 ____________________________________________________________C-2
SCSxx05 Pinouts __________________________________________________________C-2
SCSxx05 Adapters _________________________________________________________ C-3
SCSxx20 ___________________________________________________________C-12
SCSxx20 Pinouts _________________________________________________________C-12
xviii
Page 20

SCSxx20 Adapters ________________________________________________________ C-13
D: Compliance and Warranty Information _____________________________ D-1
Compliance Information (1) ______________________________________________D-1
Compliance Information (2) ______________________________________________D-3
Warranty ____________________________________________________________D-4
xix
Page 21

11:: IInnttrroodduuccttiioonn
The Lantronix SCS family of Secure Console Servers enables IT professionals to
remotely and securely configure and administer servers, routers, switches,
telephone equipment, or other devices equipped with a serial port.
This chapter introduces you to the Lantronix SCSxx05 and SCSxx20 products. It
includes the following topics:
Topic Page
SCSxx05 and SCSxx20 1-1
Hardware Features 1-3
System Features 1-4
Protocol Support 1-4
System Components 1-5
Connection Formats 1-5
Access Control 1-6
Device Port Buffer 1-7
Technical Specifications i1-8
Product Information Label 1-9
System Resource Information 1-10
SCSxx05 and SCSxx20
The Lantronix SCSxx05 and SCSxx20 are console servers offering
authentication and secure encryption. These SCS models offer a compact
solution for remote and local management of up to 48 devices (e.g., servers,
routers, and switches) with RS-232C (now EIA-232) compatible serial consoles in
a 1U-tall rack space. You can access the attached devices with keyboard
commands from a local terminal, through a network, or through a dial-up
connection.
1-1
Page 22

SCSxx05/SCSxx20 User Guide 1: Introduction
Figure 1-1. SCS4805 – 48 Device Ports, 1 Network Port, 1 Terminal Port, AC Powered
This User Guide covers the following products:
Model SCS820 - AC or DC Powered 8-Port Secure Console Server
Model SCS1620 - AC or DC Powered 16-Port Secure Console Server
Model SCS3205 - AC Powered 32-Port Secure Console Server
Model SCS4805 - AC Powered 48-Port Secure Console Server
The SCS4805 is depicted above; the other models are similar. The products
differ only in the number of device ports provided and in AC or DC power and
modem availability. The SCSxx20 models have dual entry redundant power
supplies for mission critical applications. They are available in AC or DC powered
versions and can include an optional internal modem. In general, we refer to this
product family as SCS products.
Figure 1-2. SCS3205 - 32 Device Ports, 1 Network Port, 1 Terminal Port, AC Powered
1-2
Page 23

SCSxx05/SCSxx20 User Guide 1: Introduction
Figure 1-3. SCS1620A – 16 Device Ports, 1 Network Port, 1 Terminal Port, AC Powered
Figure 1-4. SCS820 – 8 Device Ports, 1 Network Port, 1 Terminal Port, AC Powered
Hardware Features
1U-tall (1.75 inches) rack-mountable secure console server
One 10Base-T/100Base-TX network port for connection to your IP
network
Up to 48 RS232 serial device ports connected via Category 5 (RJ45)
wiring
One serial terminal port (console port) for VT100 terminal or PC with
emulation
(Optional) One modem module, for analog dial-up connections
(SCSxx20 only)
256KB-per-port buffer memory for device ports; logging supported
Front panel 2-line backlit LCD display and pushbutton controls
128MB flash memory; 128MB RAM; field-upgradeable
Universal AC power input (100-240V, 50/60 Hz)
–48VDC power option (SCSxx20 only)
Convection cooled, silent operation, low power consumption
Support for PCU8 power control unit
1-3
Page 24

SCSxx05/SCSxx20 User Guide 1: Introduction
System Features
Ability to connect up to 48 RS-232 serial consoles
10Base-T/100Base-TX IP network compatible
Buffer logging to file
ID/Password security, configurable access rights
Email notification
Secure shell (SSH) security
Open Lightweight Directory Access Protocol (LDAP)
Network File System (NFS) support
Network Information Service (NIS) capable for centrally managed
permissions
Ability to Telnet to a serial port by IP address per port or by IP address
and TCP port number
Ability to work with an external modem (SCSxx05 and SCSxx20) and
optional internal modem (SCSxx20)
No unintentional break ever sent to attached servers (Solaris Ready
Certified)
Simultaneous access on the same port - "listen" mode
Local access through terminal port
Built-in setup routine for simple setup and administration
Web administration (using any modern browser)
Protocol Support
The SCS supports the TCP/IP network protocol as well as:
SSH, Telnet, and PPP for connections in and out of the SCS
DNS for text-to-IP address name resolution
SNMP for remote monitoring and management
FTP for file transfers and firmware upgrades
TFTP for firmware upgrades
DHCP for IP address assignment
HTTP/HTTPS for easy browser-based configuration
NTP for time synchronization
LDAP, NIS, RADIUS, CHAP, and PAP for user authentication
CHAP (Challenge Handshake Authentication Protocol)
A secure protocol for connecting to a system; more secure than the PAP.
DHCP (Dynamic Host Configuration Protocol)
Internet protocol for automating the configuration of computers that use TCP/IP.
DNS (Domain Name Servers)
A system that allows a network nameserver translate text host names into
numeric IP addresses.
1-4
Page 25

SCSxx05/SCSxx20 User Guide 1: Introduction
LDAP (Lightweight Directory Access Protocol)
A set of protocols for accessing information directories.
NFS (Network File System)
A protocol that allows file sharing across a network.
NIS
(Network Information System)
A network-naming and administration system for smaller networks.
NTP (Network Time Protocol)
A protocol used to synchronize time on networked computers and equipment.
PAP (Password Authentication Protocol)
A method of user authentication in which the username and password are
transmitted over a network and compared to a table of name-password pairs.
PPP (Point to Point Protocol)
A mechanism for creating and running IP and other network protocols over a
serial link.
RADIUS (Remote Authentication Dial-In User Service)
An authentication and accounting system used by many Internet Service
Providers (ISPs).
SNMP (Simple Network Management Protocol)
Commands that allow system administrators to monitor and manage nodes on a
LAN (Local Area Network) and respond to queries from other network hosts. One
community name can be configured with read/write access.
SSH (Secure Shell)
A secure transport protocol based on public-key cryptography.
Telnet
A terminal protocol that provides an easy-to-use method of creating terminal
connections to a network host.
System Components
All system components are enclosed in a rack-mountable metal chassis. The
chassis has 8, 16, 32, or 48 device ports, one terminal port, and one network
port. An optional modem module is available for the SCSxx20 that you can add
at any time. The front panel features an LCD display and pushbuttons for access
to some system information.
Connection Formats
All physical connections to the product are made to the rear panel using industrystandard cabling and connectors. All serial connections and network
connections use conventional Category 5 (Cat5) cabling (RJ45 jacks). Required
cables and adapters for certain servers, switches, and other products are
available from Lantronix (see http://www.lantronix.com/
.)
Serial Devices
1-5
Page 26

SCSxx05/SCSxx20 User Guide 1: Introduction
All devices attached to both the device ports and the terminal port must support
the RS-232C (EIA-232) standard. Category 5 cabling with RJ45 connections is
used for the device port connections and for the terminal port.
Device ports (numbered from port 1 to port 48) support seven baud rate options:
2400, 4800, 9600, 19200, 38400, 57600, and 115200 baud.
Network
The SCS network interface is a 10Base-T/100Base-TX connector, for use with a
conventional TCP/IP network using standard RJ45-terminated Category 5
cables. The system administrator must configure the network parameters before
the SCS can be accessed over the network.
Modem (SCSxx20)
The optional modem module connects to a conventional telephone line using
standard RJ11 modular telephone cable. The analog modem on the card
connects at speeds up to 38,400 baud. Any PPP features require a modem.
With the modem installed, the SCSxx20 supports:
Plain Text TTY
PPP connection, with PAP or CHAP authentication
Callback connection
Note: Both the SCSxx05 and the SCSxx20 can work with an external
modem.
Power Manager
The SCSxx20 has an extra power manager port for connection to the Lantronix
Power Control Unit (PCU8). However, any available device port may be used as
the power manager port on the SCSxx05 and SCSxx20.
Figure 1-5. SCS4805 Rear Panel Connections for Network, Terminal (Console), and Device Ports
Access Control
The system administrator controls access to attached servers or devices by
assigning access rights to up to 128 user profiles. Each user has an assigned ID,
password, and access rights. Other access options may include externally
configured authentication methods such as NIS and LDAP.
1-6
Page 27

SCSxx05/SCSxx20 User Guide 1: Introduction
Device Port Buffer
The SCS products support port data buffering of the messages on the system's
device ports. Port buffers are enabled by default.
256K FIFO Buffer
Each device port stores 256 KB (approximately 400 screens) of I/O data in a true
FIFO buffer. You may view this data while the user is not directly interacting with
the attached device.
Buffered data is not normally stored in memory and will be lost in the event of a
power failure if it is not logged using an NFS mount solution (see Port Data
Logging, below). If the buffer data overflows the buffer capacity, only the oldest
data will be lost, and only in the amount of overrun (not in large blocks of
memory).
Port Data Logging
The SCS supports real-time data logging for each device port. The port can save
the data log to a file, send an email notification of an issue, or take no action.
SAVE (a system administrator command, discussed later) does not affect the
buffer log files. Logging the data to an NFS mount location ensures that the
device port data will be maintained (elsewhere) in the event of a power failure.
Logging to File
Data can be logged either to a file on the SCS or to a file on a remote NFS
server. Data logged to a local SCS file is limited in size by the available space on
the SCS, and may be lost in the event of a power loss. Data logged to a file on
an NFS server does not have these limitations. The system administrator can
define the path for logged data on a port-by-port basis and configure file size and
number of files per port for each logging event.
Email Notification
The system administrator can configure the device log to automatically send an
email alert message to the appropriate parties indicating a particular error. The
email is triggered when a user-defined number of characters in the log from your
server or device is exceeded.
1-7
Page 28

SCSxx05/SCSxx20 User Guide 1: Introduction
Technical Specifications
Table 1-1. SCSxx05 Technical Specifications
CPU, Memory
Serial Interface
(Device)
Serial Interface
(Terminal)
Network Interface
Power Supply
Dimensions
Weight
Temperature
Relative Humidity
Heat Flow Rate
AMD SC520 133 MHz
128 MB FLASH Card Memory (non-volatile)
128MB RAM
256K FIFO Buffer RAM per Device Port
RJ45-type 8-conductor connector (DTE default; configurable)
Speed software selectable (2400 to 115,200 baud)
Software selectable EIA-232 (formerly RS-232C)
RJ45-type 8-pin connector (DTE default)
Speed software selectable (2400 to 115,200 baud)
Software selectable EIA-232 (formerly RS-232C)
10Base-T/100Base-TX RJ45 Ethernet
Universal AC Power input, 100-240VAC 50/60 Hz
IEC-type regional cord set included
SCS3205: 1U, 1.75 in x 17.25 in x 12.25 in (4.45 cm x 43.8 cm x 31.1 cm)
SCS4805: 1U, 1.75 in x 17.25 in x 14.75 in (4.45 cm x 43.8 cm x 37.5 cm)
SCS3205: 4.5 kg (10 lbs)
SCS4805: 5.0 kg (11 lbs)
Operating: 0 to 50 °C (32 to 122 °F), 30 to 90 %RH, non-condensing
Storage: -20 to 70 °C (-4 to 158 °F), 10 to 90 %RH, non-condensing
Operating: 10% to 90% non-condensing; 40% to 60% recommended
Storage: 10% to 90% non-condensing
62 BTU/hr.
1-8
Page 29

SCSxx05/SCSxx20 User Guide 1: Introduction
Table 1-2. SCSxx20 Technical Specifications
CPU, Memory
Serial Interface
(Device)
Serial Interface
(Terminal)
Network Interface
Modem (optional)
Power Supply AC Power:
Dimensions
Weight
Temperature
AMD SC520 133 MHz
128 MB FLASH Card Memory (non-volatile)
128MB RAM (includes 256K FIFO Buffer RAM per device port)
RJ45-type 8-conductor connector (DCE default; configurable)
Speed software selectable (2400 to 115,200 baud)
Software selectable EIA-232 (formerly RS-232C)
RJ45-type 8-pin connector (DCE default)
Speed software selectable (2400 to 115,200 baud)
Software selectable EIA-232 (formerly RS-232C)
10Base-T/100Base-TX RJ45 Ethernet
RJ11C connector; analog POTS format; 38,400 baud max
Universal AC Power input, 100-240VAC 50/60 Hz
IEC-type regional cord set included
DC Power:
-48 VDC only, externally fused
SCS820: 1U, 1.75 in x 17.25 in x 12.25 in (4.45 cm x 43.8 cm x 31.1 cm)
SCS1620: 1U, 1.75 in x 17.25 in x 13.00 in (4.45 cm x 43.8 cm x 33.0 cm)
SCS820: 4.8 kg (10.6 lbs)
SCS1620: 5.0 kg (11 lbs)
Operating: 0 to 50 °C (32 to 122 °F), 30 to 90 %RH, non-condensing
Storage: -20 to 70 °C (-4 to 158 °F), 10 to 90 %RH, non-condensing
Relative Humidity
Heat Flow Rate
Operating: 10% to 90% non-condensing; 40% to 60% recommended
Storage: 10% to 90% non-condensing
75 BTU/hr.
Product Information Label
The product information label on the underside of the unit contains the following
information about your specific unit:
Bar Code
Serial Number/Date Code
Regulatory Certifications and Statements
Manufacturer's Contact Information
1-9
Page 30

SCSxx05/SCSxx20 User Guide 1: Introduction
System Resource Information
The SCS is programmable using OS-level commands and options. The system
administrator configures the product using a command-line interface or one of
several prepared scripts.
Numerous resources on the Internet (and elsewhere) provide information about
security options, programming tools and techniques, and configuration advice. A
few of the Internet sites are listed below:
SSH info: www.openSSH.org
RFC's (the standards and details behind the Internet): www.rfc-editor.org
PuTTY, a free Win32 Telnet/SSH Client (recommended):
http://www.chiark.greenend.org.uk/~sgtatham/putty/
Security: www.bastille-linux.org
An online manual on Linux security:
http://www.linuxdoc.org/LDP/solrhe/Securing-Optimizing-Linux-RHEdition-v1.3/
The following sites have more information about Linux (from basic to advanced):
www.kernel.org
www.tldp.org
http://www.linuxlinks.org/
1-10
Page 31

22:: IInnssttaallllaattiioonn
This chapter provides instructions for installing the SCS. It includes the following
topics:
Topic Page
Physical Installation 2-1
Power 2-2
Connecting a Terminal 2-3
Connecting to a Device Port 2-4
Connecting the Network Port 2-5
Connecting the Modem Port (SCSxx20) 2-5
Power Manager Interface 2-6
Caution: To avoid physical and electrical hazards, please be sure to
read Safety Precautions on page iii before installing the SCS.
Physical Installation
You can install the SCS either in an EIA-standard 19-inch rack (1U tall) or as a
desktop unit. For desktop use, you may remove the rack mount brackets and use
the four rubber feet provided.
Make all physical connections to the rear of the SCS. You may use the backlit
front-panel LCD display during initial setup and to view current network settings.
Figure 2-1. SCS4805 Rear Panel Connections and Labels (with Rack-Mount Brackets)
DEVICES
38
14
434039 4241 4544 4846 47 Cau tion ! Rep lace with s ame ty pe and ra ting fus e .
1917 181615 23 242120 22
100-240V ~, .5A, 50/ 60 Hz T 4A, 2 50 VAC
25NETWORK 2726 302928 3231 353433 3736
CONS OLE 321 87654 12 1311910
The SCS uses convection cooling to dissipate excess heat.
Note: Be careful not to block the air vents on the sides of the unit. If you
mount it in an enclosed rack, we recommended that the rack have a
ventilation fan to provide adequate airflow through the unit.
2-1
Page 32

SCSxx05/SCSxx20 User Guide 2: Installation
Power
The SCS consumes less than 25W of electrical power.
AC Input
The SCS has a universal auto-switching AC power supply. The power supply
accepts AC input voltage between 100 and 240 VAC with a frequency between
50/60 Hz. The power inlet to the chassis uses a conventional IEC-type cord set,
which Lantronix provides. Rear-mounted IEC-type AC power connector(s) are
provided for your universal AC power input. The SCSxx05 has a single
supply/input, while the SCSxx20 has dual inputs and dual supplies. The power
connector also houses a replaceable protective fuse and the on/off switch. In
addition, we provide the SCSxx20 with a “Y” cord.
Figure 2-2. AC Power Input and Power Switch on Rear of SCS4805
DC Input
The DC version of the SCSxx20 accepts standard –48 VDC power. The
SCSxx20 accepts two DC power inputs for supply redundancy. Lantronix
provides the DC power via industry standard Wago connectors. The connectors
are also available separately from Lantronix.
Figure 2-3. DC Power Input and Power Switch on Rear of SCS1620
2-2
Page 33

SCSxx05/SCSxx20 User Guide 2: Installation
Connecting a Terminal
The terminal port is for local access to the SCS and the attached devices. You
may attach a dumb terminal or computer with terminal emulation to the terminal
port. The SCS terminal port uses RS-232C protocol and supports VT100
emulation.
Figure 2-4. SCS3205 Rear Panel Connections and Labels (with Rack-Mount Brackets)
17 1918 20 252321 22 2 4 26 27 2928 30
31 32 NET WO R K
US
entela
C
Certified
Caution! Replac e with sa m e ty pe and rating fuse.
®
4312 97685
DEVIC ES
14131210 11
1615
CONSOLE
10 0-240V ~ , .3A, 50/ 60 Hz
T 4A, 25 0 VAC
The default communication parameters for the terminal port are:
9600 baud
8 data bits
1 stop bit
No parity
XON/XOFF flow control
DCE port type
Adapters from Lantronix may be used to connect the terminal port to the serial
port on your terminal or other DTE device. See http://www.lantronix.com/ .
To connect a terminal:
1. Attach the Lantronix adapter to your terminal (use PN 200.2066A adapter for
the SCSxx05 or PN 200.0066 for the SCSxx20 in most cases) or your PC's
serial port (use PN 200.2070A adapter for the SCSxx05 or PN 200.0070
adapter for the SCSxx20).
2. Connect the Cat 5 cable to the adapter, and connect the other end to the
SCS terminal port.
3. Turn on the terminal or start your computer’s communication program (e.g.,
HyperTerminal for Windows).
4. Once the SCS is running, press Enter to establish connection. You should
see an SCSxxxx and login prompt on your terminal. You are connected.
5. Refer to the Quick Start chapter for instructions on setting up the network
port quickly.
2-3
Page 34

SCSxx05/SCSxx20 User Guide 2: Installation
Connecting to a Device Port
You can connect any device that has a serial console port to the SCS for
consolidated remote administration. You can configure the device ports
individually. The console port must support the RS-232C interface. Additionally,
many servers must either have the serial port enabled as a console, or must
have the keyboard and mouse detached. Consult the server hardware and/or
software documentation for more information.
Figure 2-5. Connections on Rear of SCS4805 (Mostly Device Ports Using RJ45 Connectors)
The default communication parameters for the device ports are:
9600 baud
8 data bits
1 stop bit
No parity
XON/XOFF flow control
DTE port type
You can configure each device port individually with the following values:
Baud rates: 2400, 4800, 9600, 19200, 38400, 57600, or 115200 baud
Note: We recommend using baud rates of 57600 or less for
optimal performance.
Data bits: 6,7, or 8
Stop bits: 1 or 2
Parity: none, odd, even, mark or space
Flow control: XON/XOFF or RTS/CTS
Port type: DTE or DCE; a port may also be disabled
Buffering: may be inhibited on a port-by-port basis
2-4
Page 35

SCSxx05/SCSxx20 User Guide 2: Installation
Connecting the Network Port
The SCS’s network port (10Base-T/100Base-TX) allows remote access to the
attached devices and the system administrative functions.
You must first set up the network parameters for the network port before you can
reach the SCS remotely. You can change the network parameters from the front
panel of the SCS, or you may Telnet to the default address. Refer to the Quick
Start chapter for instructions.
Connecting the Modem Port (SCSxx20)
An optional modem module is available for the SCSxx20. The modem may be
installed at the factory or can be ordered separately for later installation.
Caution: When installing or removing a modem, be extremely careful to avoid
contact with interior components. Contact could cause a short, resulting in fire or
electric shock.
Figure 2-6. SCS1620 Modem Module
The SCSxx20 modem is an analog modem supporting connection rates up to
38,400 baud. The modem has a single RJ11-type analog telephone jack plus five
status LEDs. The user interface to the modem is identical to that found on the
terminal port or the network port. The modem is configured as device port 19 on
the SCS1620 and device port 11 on the SCS820.
The default communication parameters for the modem port are:
38400 baud
8 data bits
1 stop bit
No parity
RTS/CTS flow control
You initially configure the modem using the system’s setup program (see
Configuration). If you are installing a modem into a working SCSxx20 system,
refer to the Commands chapter.
2-5
Page 36

SCSxx05/SCSxx20 User Guide 2: Installation
Power Manager Interface
The SCSxx20 has a dedicated port for the Lantronix PCU8 Power Control Unit.
With the SCSxx05 (and the SCSxx20, if desired), you may use any available
device port. The PCU8 uses a DB9 connector on its serial connector and
requires a Part Number 200.0069 DB9 to RJ45 adapter for that connection.
(Lantronix supplies one such adapter with each PCU8 system).
The required (default of PCU8) communication parameters for a device port for
use as a power manager port are:
9600 baud
8 data bits
1 stop bit
No parity
XON/XOFF flow control
DTE port type
Refer to the PCU8 documentation for baud rate options.
2-6
Page 37

33:: QQuuiicckk SSttaarrtt
This chapter helps you get your IP network port up and running quickly, so you
may administer the SCS using your network. There are two methods to quick
start the network connections:
You may use the front panel display and buttons, or
You may use your existing IP network, accessing the default IP address
Once you have identified your IP network parameters to the SCS, you can use
your IP network connections to configure and administer it.
Note: Be sure to address security issues (access and passwords) first
when administering the system. See the Commands chapter for a list of
the commands, including steps to change the system's passwords.
This chapter includes the following topics:
Topic Page
Before You Begin 3-1
Method #1 – Using the Front Panel Display 3-2
Method # 2- Using Telnet. 3-4
Before You Begin
Before you begin, make sure you know:
An IP address that will be unique and valid on your network (Out of the
box, the IP network port identity has a generic default value of 10.0.0.1.)
Subnet mask (generic default value is 255.0.0.0)
Gateway
DNS settings
Date, time, and time zone
Terminal port settings
Make sure the SCS is plugged in to power and is turned on.
3-1
Page 38

SCSxx05/SCSxx20 User Guide 3: Quick Start
Method #1 – Using the Front Panel Display
You can use the front panel display and pushbuttons to set up the basic network
interface. The system administrator can then access the SCS using your existing
IP network.
Figure 3-1. Front Panel LCD Display and Five Pushbuttons
(Enter, Up, Down, Left and Right)
The front panel display initially shows the server name (e.g., SCS4805) and the
date and time. Using the five pushbuttons, you can change the IP Address,
subnet mask, gateway, and DNS settings; date/time and time zone features; and
terminal port baud rate settings.
Note: Have your information handy as the display will time out without
accepting any unsaved changes if you take more than 30 seconds
between entries.
Once you save the values for your network, the network subsystem restarts (the
front panel display indicates “restarting”), after which the network connection
becomes active.
Navigating
The front panel has one ENTER button and four arrow buttons (up, left, right, and
down). Press the arrow buttons to navigate from one option to another, or to
increment or decrement a numerical entry of the selected feature. Use the
ENTER button to select an option to change or to save your settings.
Note: Some models have a SELECT button instead of an ENTER
button. The instructions are the same for using the SELECT button.
Entering the Settings
1. To change the front panel settings, press the right arrow on the front panel to
enter the display programming mode and to scroll between the available
options. Options include:
Network Settings
Terminal Settings
Release Date
Time/Date Settings
Return to normal display
2. In this example, stop at Network Settings.
3-2
Page 39

SCSxx05/SCSxx20 User Guide 3: Quick Start
Figure 3-2. Front Panel Setup Options with Associated Parameters
Normal Network Terminal Release Dates Time / Date Settings
IP Setting Settings System Timezone
Subnet Mask LCD Calendar
Gateway
DNS1
DNS2
DNS3
3. When the display shows the feature that you wish to edit, press the Enter
key on the keypad to enter the editing mode. In our example, the display
shows Editing Network Settings. A cursor displays below one character of
the existing IP address setting.
4. Enter a new IP address as follows:
a) Use the left or right arrow to move the cursor to the left or to the right
position. Use the up and down arrows to increment or decrement the
numerical value.
b) When you have the complete parameter value as you want it, press the
ENTER button to complete the entry. The system will save your new
value (indicated with an asterisk in the display) after you complete all
required parameters.
>
Note: You must edit the IP Address, the Subnet Mask, and the
Gateway parameters together for a valid IP address
combination.
5. Press the down arrow to move to the next parameter
6. Repeat steps 3-5 to select and complete the remaining options.
7. To save your entries for that group of parameters when you are done:
a) In response to the Save Changes? prompt, press the down arrow button
again. A Yes/No prompt displays.
b) To save the changes, use the left/right arrow buttons to select Yes, and
press the ENTER button.
When network parameters are successfully changed, the front display
indicates Network Restarting. If you do not see this display, there is an
error with your entry, and no network changes were implemented. You
must go back and re-enter the parameters.
8. Repeat steps 3-7 for each menu option.
9. To review the saved settings, press the up or down arrows to step through
the current settings.
When you are done, the front panel returns to the clock display. The network
port resets to the new settings, and you can connect to your IP network for
further administration. You should be able to Telnet or SSH to the SCS with
your network connection.
10. Log in using sysadmin as the user name and the default password, PASS.
11. Continue entering settings using the setup command. (See Configuration.)
3-3
Page 40

SCSxx05/SCSxx20 User Guide 3: Quick Start
Method # 2- Using Telnet
You can use Telnet to connect to the SCS instead of using the terminal port if
your workstation is configured to communicate with the default network settings
of the SCS. The default IP address of the SCS is 10.0.0.1 with a subnet mask of
255.0.0.0. If you temporarily change your workstation to an IP address of
10.X.X.X with a subnet mask of 255.0.0.0, you can Telnet to the SCS using the
following commands:
1. To access the SCS, on the command line type telnet 10.0.0.1 and press
Enter. You should be at the login prompt at this point.
2. Log in using sysadmin as the user name and the default password, PASS.
3. Continue entering settings using the setup command. (See Configuration.)
3-4
Page 41

44:: CCoonnffiigguurraattiioonn
The setup command provides a text-based interface for administering the SCS.
It requires VT100 terminal support using the keyboard (no mouse support).
The setup command prompts the system administrator for appropriate entries to
simplify the configuration process. The setup command runs automatically to
initially configure the SCS; the sysadmin may run it manually at any time
thereafter from a network connection or the terminal port.
Note: The Web-based interface uses the same terms and fields as the
setup user interface for its programming steps. After you have initially
set up the unit using the setup command, you can easily switch from
one administration method to the other if desired. (See Web Interface.)
At default values, SSH is not enabled (encryption keys have not been
generated), so Telnet or the terminal port is used to initially access and configure
the SCS.
When you first install the SCS, the automatic setup script helps you configure the
majority of the system functions and automatically saves the programming
changes to non-volatile memory. Upon completion of this automated script file,
the SCS automatically reboots to ensure that all processes are updated.
This chapter includes the following topics:
Topic Page
Connecting Using Telnet or Your Serial Terminal 4-2
Logging in as System Administrator 4-2
Accessing the Setup Menu 4-2
Configuring Hostname and IP Address 4-4
Configuring Timezone 4-6
Configuring DNS 4-8
Configuring Services 4-9
Enabling/Disabling Web Configuration 4-10
Configuring NTP 4-10
Configuring Email Relay 4-11
Configuring Timeouts 4-11
Configuring Modem (SCSxx20 Only) 4-12
Configuring CHAP Secrets 4-15
Configuring PAP Secrets 4-16
Configuring User Authentication 4-16
Configuring NFS Mount 4-2
Configuring Firewall (Packet Filtering) 4-4
4-1
Page 42

SCSxx05/SCSxx20 User Guide 4: Configuration
Topic Page
Configuring Device Ports 4-5
Updating Software 4-14
Using Done 4-16
Saving 4-17
Rebooting 4-17
Connecting Using Telnet or Your Serial Terminal
If you are not already connected as described in Quick Start, you have two
options:
Connect the terminal port to a VT100 terminal device or computer using
a VT100 terminal emulation program. (See Connecting a Terminal.)
Telnet via your network connection.
Your screen displays the SCS name and a login prompt after power-up.
Logging in as System Administrator
If you are not already logged in as described in Quick Start, follow these steps:
1. Type sysadmin (a predefined user with special privileges) and press Enter.
The Password prompt displays.
SCS4805 login: sysadmin
Password:
sysadmin>
2. Type your password and press Enter. The default password is PASS. (The
password does not display when you type it.) If this is the first time you have
logged in as the system administrator, the setup (configuration) screen
displays.
Accessing the Setup Menu
The following screen displays when the setup program starts, whether
automatically (the first time the sysadmin logs in) or when the system
administrator enters the setup command after logging in.
1. If this is not the first time you have logged in, type setup and press Enter.
4-2
Page 43

SCSxx05/SCSxx20 User Guide 4: Configuration
Figure 4-1. Setup (System Configuration) Program
2. To make changes to the system configuration, select Yes and press Enter.
A setup (configuration) menu, including the available configuration options
and a Done option, displays. (You must scroll down to see all of the menu
options.)
Note: If you select No, the setup program ends, and the command
prompt displays.
Figure 4-2. Setup Menu
Navigating
You can step through the menu and the configuration screens using the arrow,
Tab, and Enter keys.
4-3
Page 44

SCSxx05/SCSxx20 User Guide 4: Configuration
Table 4-1. Setup Menu Navigation
Action Key
To select a menu option Use the up and down arrows on your keyboard
(not on the numeric keypad)
To select Yes or No
To complete an entry and continue
To go to the next area of the screen
To go to the next screen
To go back a screen
To exit free-form text editing mode
Use the up and down arrows to move between
Yes and No.
Press Enter.
Note: Pressing Enter selects the default
operation in most of the screens.
Press Tab.
Use the arrows and the Tab key to select
<Next> and press Enter.
Note: With the exception of multiple choice or
free-form text entries, just pressing Enter will
take you to the next screen.
Use the Tab key and the arrows to select
<Back>, and then press Enter.
Press the Esc key.
Done Option
The last item in the menu list is Done. You must use this option to complete your
entries and to exit the setup script. Done prepares any entries to be written to
flash memory, but it does not write them to flash memory. For more information
about Done, refer to the end of this chapter.
The Configure Device Ports option (second to last menu item) uses Done
differently. For the device port configuration, when you reach the end of a
routine, Done prompts you to save the changes, and if you select Yes, writes
your entries to flash memory. At this point, you can no longer “undo” your entries
during this session.
Note: You can exit setup at any time by selecting Done.
Configuring Hostname and IP Address
While you can set the IP address and other network parameters using the front
panel buttons (see Quick Start), to change all of the IP address parameters, you
must complete the steps in the first option of the setup menu, Configure
Hostname and IP Address. Use this option to specify the following parameters:
DHCP (A DHCP server automatically assigns the IP address and
network settings.)
Hostname (including domain name)
IP address (of the SCS)
Network mask (of the IP address)
Gateway (IP address of the router of this network)
1. Select Configure Hostname and IP Address and press Enter. The DHCP
prompt displays.
4-4
Page 45

SCSxx05/SCSxx20 User Guide 4: Configuration
2. Select Yes to use DHCP to obtain the IP address, netmask, and gateway, or
No to enter your own values.
DHCP
What is the value for BOOTPROTO?
Enable DHCP (Please select ‘dhcp’ or ‘none’)
If you choose ‘none’, you MUST provide values for IPADDR,
NETMASK, and GATEWAY.
Dhcp
none
3. Press Enter. The hostname and IP address prompt displays.
4. Enter a value for the hostname. The default hostname is the SCS model
name (e.g., SCS4805). There is a 64-character limit (contiguous characters).
Hostname and IP Address
What is the value of HOSTNAME?
Name of this Host (including domain, e.g.,
host.company.com).
We need the canonical name here to obtain the DNS domain.
IMPORTANT: The DNS domain name is determined from this
answer.
Answer: SCS4805
Be sure to include the domain name as well. In the following example,
we add lantronix.com to the default factory name of SCS4805 to get
SCS4805.lantronix.com.
Hostname and IP Address
Answer: SCS4805.lantronix.com
Note: After the value is accepted and saved, and you have rebooted the
system, the hostname appears as your command prompt and on the front
panel LCD display.
5. Press Enter. The IP address prompt displays.
6. If you selected DHCP in step 2, press Enter through the IP address,
netmask, and gateway prompts (the system will ignore these values), and
continue with Configuring Timezone.
7. If you did not select DHCP in step 2, enter the network IP address for the
SCS.
Do not use leading zeros in the numeric fields for “dot-quad” numbers less
than 100. For example, if your IP address is 172.20.201.28, do not enter 028
for the last segment.
Hostname and IP Address
What is the value for IPADDR?
4-5
Page 46

SCSxx05/SCSxx20 User Guide 4: Configuration
Ip Address in dot quad notation (e.g., 10.2.3.4)
Answer: 172.20.201.28
8. Press Enter. The netmask prompt displays.
9. Enter the value of the netmask, in dot-quad notation.
Hostname and IP Address
What is the value for NETMASK?
IP Netmask in dot quad notation (e.g., 255.255.255.0)
Answer: 255.0.0.0
10. Press Enter. The gateway prompt displays.
11. Enter the IP address of your gateway.
Hostname and IP Address
What is the value for GATEWAY?
IP Address of the Gateway in dot quad notation (e.g.,
10.2.3.254)
Answer: 172.20.201.254
12. Press Enter. The setup menu returns with Configure Timezone selected.
Configuring Timezone
Use the Configure TImezone option to specify your local time zone.
1. With Configure Timezone selected, press Enter. The timezone prompt
displays.
2. Use the arrow keys to select the local time zone from the list of international
time zones (for example, Africa, America, Brazil), and press Enter.
3. If a sublist displays, select a more specific location (for example US/Hawaii)
and press Enter.
Select your local timezone.
The SCS1620 supports all international timezones.
Select your local Timezone.
..
US/Alaska
US/Aleutian
US/Arizona
US/Central
US/East – Indiana
US/Eastern
US/Hawaii
Note: To go back one level in the Timezone script, select the ".."
line from the top of the Timezone submenu. Select a value, tab to
< Next >, and press Enter to continue.
4-6
Page 47

SCSxx05/SCSxx20 User Guide 4: Configuration
4-7
Page 48

SCSxx05/SCSxx20 User Guide 4: Configuration
4. At the end of the Timezone script, press Enter. The setup menu returns with
Configure DNS selected.
At this point, you may continue with the next setup menu item, you may use
the arrow keys to select another item in the list, or you may arrow down to
Done to exit the setup script. (You can do this for any of the high level menu
items.)
Configuring DNS
Use this option to configure the following parameters:
Primary DNS nameserver (required if you choose to configure DNS
servers).
Secondary DNS nameserver (optional)
Tertiary DNS nameserver (optional)
1. With Configure DNS selected, press Enter. The primary name server
prompt displays.
2. Enter the IP address for the primary nameserver (required) and press Enter.
Note: If you cannot complete this entry now, enter an address of
0.0.0.0 for the primary nameserver. The system will accept this entry
even though it is not a valid nameserver address. You must correct it
later.
Input value for PRI_NAMESERVER
IP Address (in dot quad notation) of the primary nameserver
Answer: 172.20.201.63
3. Enter the IP Address of your secondary nameserver (optional) and press
Enter.
4. Enter the IP Address for the tertiary nameserver (optional) and press Enter.
The system displays the /etc/hosts file for additional hostnames that you
may wish to add. You may edit this list.
Edit hosts?
(Use <Escape> to end edit)
A /etc/hosts file for this host. Based on previous answers, we
have installed an appropriate entry for this host. Please
remove any entries that are not valid. The localhost entry is
required for proper operation.
127.0.0.1 localhost.localdomain localhost
172.19.21.245 SCS1620.support.int.Lantronix.com SCS1620
5. Press the <Esc> key to end the editing, and then press Enter. The setup
menu returns with Configure Services selected.
4-8
Page 49

SCSxx05/SCSxx20 User Guide 4: Configuration
Configuring Services
With this menu option, you enable or disable the following:
Syslog (system logging) (default is enabled)
System logins using SSH (default is disabled)
System logins using Telnet (default is enabled)
Simple Network Management Protocol (SNMP Agent) (default is
disabled)
1. With Configure Services selected, press Enter. The syslog prompt displays.
2. Select Yes to enable or No (default) to disable syslog, and press Enter. The
SSH logins prompt displays.
3. Select Yes to enable or No (default) to disable SSH logins. Most system
administrators enable SSH logins, which are the preferred method of
accessing the system.
Note: If you enable SSH logins, the initial reboot process may take
several minutes while the SCS regenerates SSH keys.
Enable ssh Logins?
Do you want to enable system logins via ssh?
This is the recommended method of login because of its
security.
Yes / No
4. Press Enter. The Telnet logins prompt displays.
For Telnet logins, the default setting is Yes (to allow simple Telnet
connections into the SCS even during its initial configuration). You may
choose to disable Telnet access for security reasons, especially if you intend
to use SSH.
5. Select Yes (default) to enable or No to disable Telnet logins, and press
Enter. The enable SNMP Agent prompt displays.
6. Select Yes to enable or No (default) to disable SNMP agent.
Enable SNMP Agent?
Do you want to enable the Simple Network Management
Protocol Agent?
This will allow reading status and statistics via SNMP.
This is a read-onlyl SNMP agent.
Yes / No
7. Press Enter. The setup menu returns with Web Configuration selected.
4-9
Page 50

SCSxx05/SCSxx20 User Guide 4: Configuration
Enabling/Disabling Web Configuration
The SCS offers a Web-based configuration interface, which you can only access
through your browser using SSL (Secure Sockets Layer) (https://). The Web
interface has most of the same options as the console-based setup routine and
may be useful for updating configuration options after you complete the initial
setup.
This option enables or disables the ability to update the SCS configuration using
the Web interface.
1. With Web Configuration selected, press Enter. The enable Web
configuration prompt displays. By default, the Web interface is disabled.
Many system administrators consider a Web-based interface a security risk,
and choose to disable the Web interface.
Enable Web Configuration?
Do you want to enable the LCI Web Configuration utility?
This will allow using a Web browser to configure the
SCS4805.
This uses https (SSL) only.
Yes / No
2. Select Yes to enable or No (default) to disable Web configuration, and press
Enter. The setup menu returns with Configure NTP selected.
Configuring NTP
This option enables or disables the Network Time Protocol (NTP) function, which
synchronizes the time clock in the SCS with other NTP devices on your network.
The default is disabled.
1. With Configure NTP selected, press Enter. The NTP prompt displays.
Enable NTP Daemon?
Do you want to enable the Network Time Protocol Daemon?
This will cause the SCS4805 system clock to be synchronized
with other machines using NTP
Enable NTP Daemon?
Yes / No
2. Select Yes to enable or No (default) to disable NTP and press Enter.
3. If you selected Yes, enter the IP addresses of up to three NTP servers.
Identify at least two for best results. (Press Enter in between.)
4. Press Enter after the third server prompt displays. The setup menu returns
with Configure Email Relay selected.
4-10
Page 51

SCSxx05/SCSxx20 User Guide 4: Configuration
Configuring Email Relay
The SCS incorporates a mail transport agent for email delivery. Use this option to
identify your network’s SMTP relay server.
1. With Configure Email Relay selected, press Enter.
2. Leave this value blank unless email delivery is not working, in which case
enter the IP address of your network’s SMTP relay server.
Input value for SMART_RELAY
IP Address (in dot quad notation) of your network’s SMTP
relay server.
This should normally be left blank. Enter a relay server
here only if Email delivery is not working and you are
certain that DNS is properly configured.
Input value for SMART_RELAY.
Answer:
3. Press Enter. The setup menu returns with Configure Timeouts selected.
Configuring Timeouts
You can set up the SCS to disconnect from an idle Telnet or terminal connection
after a specified period of time. You can enable or disable the timeout daemon to
configure the disconnection of idle connections for:
Telnet timeout (default is disabled)
PPP timeout (default is disabled)
Terminal port timeout (default is disabled)
You can program each timer in a range of 1 to 30 minutes.
Note: By default, all timers are disabled. Once you enable a timer, you
can disable it by entering 0 (zero).
1. With Configure Timeouts selected, press Enter. The timeout prompt
displays.
2. Select Yes to enable or No (default) to disable the timeout daemon, and
press Enter. If you selected Yes, the Telnet timeout prompt displays.
If you selected No, the setup menu returns with Configure Modem
(SCSxx20) or Configure CHAP Secrets (SCSxx05) selected.
3. To cause an idle Telnet connection to be disconnected after a specified
number of minutes, backspace over the existing value and enter a number
between 1 and 30 (minutes).
Configure Telnet Timeout
Input value for Configure Telnet Timeout
Answer: 15
4-11
Page 52

SCSxx05/SCSxx20 User Guide 4: Configuration
4. Press Enter. The PPP timeout prompt displays.
5. To cause an idle PPP connection to be disconnected after a specified
number of minutes, backspace over the existing value and enter a number
between 1 and 30 (minutes).
Configure PPP Timeout
Input value for Configure PPP Timeout.
Answer: disabled
6. Press Enter. The terminal port timeout prompt displays.
7. To cause an idle terminal port connection to be disconnected after a
specified number of minutes, backspace over the existing value and enter a
number between 1 and 30 (minutes).
Configure Telnet Port Timeout
Input value for Configure Terminal Port Timeout.
Answer: 10
8. Press Enter. The setup menu returns with the next available menu option,
Configure Modem for the SCSxx20 or Configure CHAP Secrets for the
SCSxx05, selected.
Configuring Modem (SCSxx20 Only)
The internal modem is available, but optional, in the SCSxx20 products. The
Configure Modem option does not display on the SCSxx05 setup menu.
Note: You configure an external modem by enabling a port as an operator port
in the Configuring Device Ports option.
If a modem is installed, configure it as follows.
Enable modem logins (to allow PPP and/or TTY) (default is disabled.)
Enable modem TTY logins (default is enabled.)
Enable modem TTY modem callbacks (The default is enabled.)
Enter callback telephone number (if you enable callbacks)
Enable PPP logins (The default is enabled.)
Enter IP address(es) (local and remote) for PPP Link
Enable CHAP for PPP Authentication (default is disabled; PAP will be
used).
If you do not enable the modem, your system skips past the setup entries for
CHAP secrets or PAP secrets, as they are related to operation of the modem.
The system also bypasses steps related to TTY logins and callbacks.
4-12
Page 53

SCSxx05/SCSxx20 User Guide 4: Configuration
1. With Configure Modem selected, press Enter. The enable modem logins
prompt displays.
2. Select Yes to enable or No (default) to disable modem logins.
Enable Modem Logins?
Do you want to enable logins on the Modem?
This will allow PPP and TTY logins.
Enable Modem Logins?
Yes / No
If you selected No, the Configure User Authentication menu displays.
Continue with Configuring User Authentication on page 4-16.
3. Press Enter. The TTY callbacks prompt displays.
4. Select Yes to configure the modem to do a TTY callback or No to bypass this
configuration.
Configure Modem TTY Callbacks?
Do you want to have the Modem do a TTY callback?
If you do, you will next have to edit the callback
configuration.
Configure Modem TTY Callbacks?
Yes / No
5. Press Enter. If you selected Yes, the login configuration prompt displays.
If you selected No, the PPP logins prompt displays. Continue with step 8.
6. Enter the TTY callback number (in xxx-xxx-xxx format) following the –S on
the line beginning with #Modem_cb.
Edit login.config?
(Use <Escape> to end edit)
TTY Callback telephone numbers and callback login pseudo-usernames.
The telephone number the modem should callback to should be inserted
following the ‘-S’ on the line beginning with ‘modem_cb’.
In the telephone number use only digits and any of the following: ,-()
# A login by this user causes a text login callback
#modem_cb - - /usr/sbin/callack -S callback-number-here
7. Press Esc to end the editing mode. The PPP logins prompt displays.
4-13
Page 54
SCSxx05/SCSxx20 User Guide 4: Configuration
8. Select Yes to enable a direct PPP login, or No to disable a direct PPP login.
Enable PPP Logins?
Do you want to enable PPP logins?
This will allow a direct PPP login without having to log
into a user shell.
Yes / No
9. Press Enter. If you selected Yes, the PPP parameters options prompt
displays.
If you selected No, the Configure User Authentication menu displays.
Continue with Configuring User Authentication on page 4-16.
10. Enter the local and remote IP addresses you want to use with the PPP link in
the format: Local_IP_Addr:Remote_IP_ADDR (for example,
192.168.0.1:172.20.101.3). Both entries are optional.
PPP Options
Input value for PPP IP Addresses
Input the IP Address(s) you want to use with the PPP link.
The format is:
Local_IP_Addr:Remote_IP_Addr
Both addresses should be in dot quad notation with no
spaces before or after the ‘:’. Both IP addresses are
optional. Make the line blank if you do not want to
specify any address.
Input value for PPP IP Addresses
Answer:
11. Press Enter. The enable CHAP prompt displays.
If you select Yes, the setup menu returns with Configure CHAP Secrets
selected.
If you select No, the setup menu returns with Configure PAP Secrets
selected.
4-14
Page 55
SCSxx05/SCSxx20 User Guide 4: Configuration
Configuring CHAP Secrets
The SCSxx20 supports either CHAP or PAP, but not both. PAP is the default
authentication method.
The CHAP parameters include:
Client
Server
Secret (password used for authentication; generated by the system
administrator)
IP address (acceptable local IP address)
1. With CHAP Secrets on the setup menu selected, press Enter. The CHAP
secrets prompt displays.
2. Use the arrows to move the cursor to the end of the first line (Secrets for
authentication using CHAP), and press Enter to create a new line.
3. Enter the CHAP secrets information as four separate fields, separating the
entries with a space: client, server, secret, and IP address. (Do not use a
# sign, which indicates a comment.)
Edit chap-secrets?
(Use <Escape> to end edit)
Each line should contain four fields containing:
Client server secret IP-address
The second line usually contains the same info as the first line
# Secrets for authentication using CHAP
#clients server secret IP addresses
#example SCS.localdomain password_1 *
#SCS.localdomain example password_2 *
* * * *
4. Press Esc to exit editing mode. The setup menu returns with Configure PAP
Secrets, selected.
4-15
Page 56

SCSxx05/SCSxx20 User Guide 4: Configuration
Configuring PAP Secrets
PAP is the default authentication method. The parameters include:
Client
Server
Secret (password used for authentication; generated by the system
administrator)
IP address (acceptable local IP address)
1. With PAP Secrets on the setup menu selected, press Enter. The PAP
secrets prompt displays.
2. Use the arrows to move the cursor to the end of the first line (Secrets for
authentication using PAP), and press Enter to create a new line.
3. Enter the PAP secrets information as four separate fields, separating the
entries with a space: client, server, secret, and IP address. (Do not use a
# sign, which indicates a comment.
Edit pap-secrets?
(Use <Escape> to end edit)
Each line should contain four fields containing:
Client server secret IP-address
The second line usually contains the same info as the first line
# Secrets for authentication using PAP
#clients server secret IP addresses
* * * *
* * *
4. Press Enter. The setup menu returns, with Configure User
Authentication, selected.
Configuring User Authentication
This option on the setup menu provides a submenu of user authentication
methods. Only one external authentication method (NIS, LDAP, or RADIUS) may
be enabled at a time. Enabling one method automatically disables the others.
NIS (default is disabled)
LDAP (default is disabled)
RADIUS (default is disabled)
Global port permissions
4-16
Page 57

SCSxx05/SCSxx20 User Guide 4: Configuration
1. With Configure User Authentication selected, press Enter. The User
Authentication menu displays with Configure NIS selected.
Figure 4-3. User Authentication Menu
2. Follow the instructions below for the method (NIS, LDAP, or RADIUS) you
want to use. In addition to the selected method, you may configure global
port permissions.
Configuring NIS
If you are using NIS authentication, you must:
Identity the NIS domain name (often same as hostname).
Enable NIS (default is disabled.)
Identify NIS master server (required if NIS is enabled)
Identify up to five NIS slave servers (optional)
Note: You must not use packet filtering (firewall) if you are using NIS,
because it would filter out the NIS packets.
1. With Configure NIS selected, press Enter. The NIS domain name prompt
displays.
2. Enter the NIS domain name.
NIS Domain Name
What is the value for NIS Domain?
Answer: lantronix.com
3. Press Enter. The enable NIS prompt displays.
4. Select Yes to enable NIS to authenticate users and/or obtain port
permissions.
5. Press Enter. The NIS master server prompt displays.
4-17
Page 58

SCSxx05/SCSxx20 User Guide 4: Configuration
6. Enter the IP Address (in dot quad notation) of at least the NIS master server
(required), and press Enter. The first slave server prompt displays. You may
configure up to five NIS slave servers (SLAVE-1 through SLAVE-5). Slave
server values are optional. There are five similar screens, one for each NIS
slave server.
7. Enter the IP address of the first slave server and press Enter.
8. Repeat step 7 for each slave server, or just press Enter until the User
Authentication menu returns. Continue with Configure Global Port
Permissions or Done User Authentication.
Configuring LDAP
If you are using LDAP (Version 2), you must:
Enable LDAP (version 2) authentication (default is disabled)
Enter the IP address of the LDAP server
Enter the input value for the LDAP base
1. With Configure LDAP selected, press Enter. The LDAP prompt displays.
2. Select Yes to enable LDAP to authenticate users.
3. Press Enter. The LDAP IP address prompt displays.
4. Enter the IP address of the LDAP server and press Enter. The LDAP base
prompt displays.
5. Enter the name of the LDAP search base. There is no default value.
Ldap.conf
Input value for LDAP Base
The distinguished name of the LDAP search base.
(example: dc=company,dc=com)
Answer: dc=lantronix,dc=com
6. Press Enter. The User Authentication menu returns. Continue with
Configure Global Port Permissions or Done User Authentication.
4-18
Page 59

Configuring RADIUS
If you are using the RADIUS option for authenticating users, you must:
Enable RADIUS (default is disabled)
Enter the IP address of a RADIUS server
Enter the shared secret (text string that serves as a password between a
RADIUS client and the SCS)
Enter the timeout (server connection timeout)
1. With Configure RADIUS selected, press Enter. The RADIUS prompt
displays.
2. Select Yes to enable RADIUS to authenticate users, and press Enter.
3. Enter lines containing the IP Address of a RADIUS server, the shared secret,
and the timeout in seconds (optional). You may specify an optional port with
the IP Address (in the form IP Address:Port); if you do not specify an optional
port, the SCS uses the default RADIUS ports, 1812 and 1813.
4. The format for each line is:
server-IP-address[:port] secret [timeout]
RADIUS Servers
Edit RADIUS Servers?
(Use <Escape> to end edit)
Please install lines containing the IP Address (in dot quad
notation) of a RADIUS server, the shared secret, and
optionally the timeout in seconds. Each line shall be of
the form:
# 192.168.0.10:45 secret 1
# radiusserver.domain.com other-secret 3
5. Press Esc. The User Authentication Menu returns with Configure Global
Port Permissions selected. Continue with Configure Global Port
Permissions or Done User Authentication.
Configuring Global Port Permissions
With this option, you can configure global default port permissions for users. This
is useful if you are using NIS, LDAP, or RADIUS to authenticate users and you
have not used “adduser” to create a port permissions file for every user. The
global port permissions will be used for users who do not have their own port
permissions file or do not have port permissions specified in an NIS map.
You can configure the following permissions:
Allow Direct (direct mode default port permissions; users may interact
with a port) See page 7-5 for more information on direct mode.
Allow Listen (listen mode default port permissions; users may only view
the data on a port)
Allow Clear (clear default port permissions; users may clear the port
buffer)
4-1
Page 60

SCSxx05/SCSxx20 User Guide 4: Configuration
1. With Configure Global Port Permissions selected, press Enter. The direct
mode permissions prompt displays.
2. If desired, enter a range and/or list of ports (for example, 1, 3, 5-7) to which
the direct mode permissions will apply.
Default Permissions
What is the value for ALLOW_DIRECT?
Specify the port-direct mode default port permissions. The
ports can be specified using a range and/or list.
Example: 1, 3,
What is the value for ALLOW_DIRECT?
( Press TAB or ENTER to end editing )
Answer: 1-48
3. Press Enter. The listen mode permissions prompt displays.
4. If desired, enter a range and/or list of listen mode permissions.
5. Press Enter. The clear mode permissions prompt displays.
6. If desired, enter a range and/or list of listen mode permissions.
7. Press Enter. The User Authentication Menu returns with Done User
Authentication selected.
Done User Authentication
This option returns you to the main setup menu.
With Done User Authentication selected, press Enter. The setup menu returns
with Configure NFS Mount selected.
Configuring NFS Mount
Here you can configure the NFS server that the SCS can use for port logging to a
file. If you mount a network (shared) disk onto the SCS, device port logging can
be to a file residing on a remote networked disk. This configuration avoids
possible limitations in the amount of disk space available for the file.
Note: You must not use packet filtering (firewall) if you are using NFS
because it would filter out the NFS packets.
You have the following options:
Enable/disable mounting an NFS share (default is disabled)
Identify the NFS server
4-2
Page 61

SCSxx05/SCSxx20 User Guide 4: Configuration
1. With NFS Mount selected, press Enter. The NFS mount prompt displays.
Enable NFS?
Do you want to mount an NFS share from an NFS server?
Do not use packet filtering (firewall) if you are using NFS
or NIS
Enable NFS?
Yes
No
2. Select Yes to install the NFS server information to mount an NFS share, or
No to disable this option. If you answer Yes, the NFS value prompt displays.
If you answer No, the setup menu returns Configure the Firewall, selected.
3. Enter the NFS server path in the format: nfs_server_hostname or
ipaddr:/exported/path
The exported path will be mounted to /nfs on the SCS. If the line begins
with a '#', please remove it.
Note: Exporting an incorrect NFS server path may degrade the
performance of the system.
Input value for NFS mount
Install the NFS server info to mount an NFS share.
The format is:
nfs_server_hostname or ipaddr:/exported/path
The exported path will be mounted to /nfs on the SCS.
If the line begins with a ‘#’, please remove it.
Input value for NFS mount
(Press TAB or ENTER to end editing)
Answer: 172.19.0.60:/home/share
4. Press Enter. The setup menu returns with Configure the Firewall selected.
4-3
Page 62

SCSxx05/SCSxx20 User Guide 4: Configuration
Configuring Firewall (Packet Filtering)
The SCS incorporates a packet filtering option (a "firewall"). (The Web
configuration interface uses the term “Packet Filtering.”)
Note: You must not use packet filtering (firewall) if you are using NFS or
NIS, because it would filter out the NFS or NIS packets.
You may configure the firewall for your site by setting the following parameters.
Enable/disable Firewall (default is disabled)
Reject method (default is Reject; returns a connection denied on blocked
ports.)
Ping response (default is disabled, which makes the SCS visible to
pings)
TCP public services (default is ssh, telnet, and https allowed)
UDP public services (default is ntp allowed)
1. With Configure the Firewall selected, press Enter. The firewall prompt
displays.
2. Select Yes to enable or No (default) to disable packet filtering, and press
Enter. If you selected Yes, the reject method prompt displays.
If you selected No, the setup menu returns with Configure Device Ports
selected.
3. To choose the reject method for attempts to access your site, select Deny or
Reject (default). (The screen explains these responses.)
What is the value for REJECT_METHOD?
Use DENY to ignore connection attempt on blocked ports.
Use REJECT to return connection denied on blocked ports.
DENY / REJECT
4. Press Enter. The ping response prompt displays.
5. Select Yes to enable the SCS to be invisible to ping or traceroute inquiries,
or No (default) to disable this feature.
Enable INVISIBLE_TO_PING?
Do you want the SCS4805 to be invisible to ping and
traceroute?
You will still be able to ping and traceroute outbound from
the SCS4805. Yes is recommended for maximum security.
Yes / No
6. Press Enter. The TCP public services prompt displays.
4-4
Page 63

SCSxx05/SCSxx20 User Guide 4: Configuration
7. To enter the list of TCP Public Services that the SCS should support, edit the
text-entry list from the choices indicated in the Answer field (ftp-data, ftp,
SSH, telnet, www, and https).
Firewall.conf
What is the value for TCP_PUBLIC_SERVICES?
This is the list of ports we allow TCP connections to.
Answer: ssh telnet https
For example, you may choose to remove telnet from this list of services
for security reasons, leaving only ssh and https .
What is the value for TCP_PUBLIC_SERVICES?
This is the list of ports we allow TCP connections to.
Answer: ssh https
8. Press the Esc key to end the editing, and press Enter. The UDP public
services prompt displays
9. To identify the UDP public services to be supported, enter the services
required for your configuration in the Answer field.
What is the value for UDP_PUBLIC_SERVICES?
This is the list of ports we allow UDP connections to.
Answer: ntp
10. Press the Esc key to end text entry, and press Enter to continue. The setup
menu returns with Configure Device Ports selected.
Configuring Device Ports
Note: It is generally not necessary to change the configuration of the
terminal port, other than its data rate. Therefore, no options are available
on the setup menu or Web interface for changing its configuration. If you
need to make a change, use the dtedce command to change the DTE or
DCE setting, and use the buttons on the front panel to change the baud
rate (see Method #1 – Using the Front Panel Display).
The Configure Device Ports option on the setup menu is actually a script
running within the setup script. Therefore, some of its processes are different
from those of other options. Done in the Configure Device Ports routine
causes your changes to be written to the flash memory. This is different from
Done at the end of the setup menu list, which just prepares the entries to be
saved. Also, <Back> navigation is disabled in some places.
4-5
Page 64

SCSxx05/SCSxx20 User Guide 4: Configuration
Device Port Configuration Options
You can configure the device ports for port identity (apply a relevant name) and
for feature access and buffer logging. You can configure device ports (for
departments, for identifying equipment types, or for any other reason) in any
combination; groups can be any individual port number, any range of numbers,
or a combination of both. Device ports remain unique; the groups are not used
for access, but merely to assist in your setup of the device ports.
Device Port Names (change or accept defaults)
Device Port Parameters (by port or group of ports)
Device Logging Parameters (by port or group of ports)
Done Device Ports (writes the device port parameters to flash when
executed)
Device Port Menu
1. Select Configure Device Ports on the setup menu. The system may take a
few seconds to show an intermediate screen and then continue to the Device
Port menu with Device Port Names selected.
2. Continue with Device Port Names, or select one of the other options from
the menu.
Figure 4-4. Configure Device Ports Menu
Device Port Names
The Device Port Names option allows you to assign a meaningful name to each
device port. Default values are DEVICE_01 through DEVICE_48 (for the
SCS4805). You can rename each port individually to have a server name, a
description, or other relevant naming convention.
1. To administer port names, select Device Port Names and press Enter.
2. Enter a port number, and press Enter. You have two options. You can
choose to name the device port or select Done to exit this option.
3. To name the device port, select Set the Name of a Device Port and press
Enter. The existing information for that device port displays. The preset port
names are DEVICE_01 through DEVICE_48 (in SCS4805).
4-6
Page 65

SCSxx05/SCSxx20 User Guide 4: Configuration
4. Backspace over the existing data, and enter your name for this port. The
device name cannot contain a space. Use an underscore if you need an
empty space in the name.
5. Press Enter. You have two options:
To go back and name or rename the same device port, repeat steps 3-5.
To save your name change to flash memory now, select Done and
press Enter: A confirmation screen displays. Continue with step 6.
6. To confirm, select Yes. You cannot undo these name changes after this
point. (If you select No, you return to the previous screens to make changes.)
7. Press Enter. There is a short delay while the system saves the changes to
flash memory. Now you can name a different port of group of ports.
8. You have two options:
To repeat the process of naming ports for a different port or group of
ports, select Yes.
To move on to the next option, Device Port Parameters, select No.
9. Press Enter. If you selected No, the Configure Device Port menu returns
with Device Port Parameters selected.
Device Port Parameters
You can configure the device port parameters on individual ports or in ad hoc
groups. You determine the group and then apply selected features to the ports in
that group.
The device port parameters that you configure include:
Enable/disable operator mode (default is disabled)
Baud rate (default is 9600)
Data bits (default is 8)
Stop bits (default is 1)
Parity (default is None)
Flow control (default is XON/XOFF)
Port type (default is DTE for the SCSxx05 and DCE for the SCSxx20))
Inhibit buffering (default is no)
Define a Group of Ports to Configure
1. Select Device Port Parameters and press Enter.
2. Select Setup the Device Parameters and press Enter. You are prompted to
identify the port or ports that should be configured with these steps.
4-7
Page 66
SCSxx05/SCSxx20 User Guide 4: Configuration
3. In the Answer field, enter the number, range, or combination of ports to be
administered.
What device port do you want to configure?
Input a device number, a device name, or a range.
Examples of ranges:
3,7,9
2-12
1,4,6-9,14
Valid port range is 1-48
What device port do you want to configure?
Answer: 1-3,5,7-9,26
4. Press Enter. The enable operator port prompt displays. This option allows
PPP as well as terminal logins through an external modem.
Note: If you connect a modem, make sure to set the port type to
DTE.
Enable Port 3,7,9 as an operator port?
Do you want to enable system logins on Port 3,7,9?
A modem may be connected to this port and PPP will be
supported as well as TTT logins. If you connect a modem to
this port, make sure the port type is set to DTE.
Enable Port 3,7,9 as an operator port?
Yes / No
5. Select Yes to enable system logins, or No (default) to disable system logins,
and press Enter. The operator port baud rate displays if you enabled an
operator port or group of ports; otherwise the baud rate prompt displays.
Operator Port Baud Rate
You can select from seven device baud rates: 2400, 4800, 9600, 19200, 38400,
57600 and 115,200. The default is 115,200.
1. Use the arrow keys to select the baud rate for the operator port(s) from the
list displayed.
2. Press Enter. The baud rate prompt displays.
Baud Rate
You can select from seven device baud rates: 2400, 4800, 9600, 19200, 38400,
57600 and 115,200. Most devices use 9600 as the terminal/administration port's
baud rate, so the device port defaults to this value. Check the equipment settings
and documentation for the proper baud rate.
1. Use the arrow keys to select the baud rate for the port(s) from the list
displayed.
2. Press Enter. The data bits prompt displays.
4-8
Page 67

SCSxx05/SCSxx20 User Guide 4: Configuration
Data Bits, Stop Bits, and Parity
The format of the bit-wise transmission of data is determined by the data bits,
stop bits, and parity parameters. The default settings are 8 data bits, 1 stop bit,
and no parity. Check your equipment documentation for the proper settings.
1. Use the arrow keys to select the data bits for the port(s) from the list
displayed.
2. Press Enter. The stop bits prompt displays.
3. Select the stop bits (1 or 2) for the port(s).
4. Press Enter. The parity prompt displays.
5. Select the parity for the port(s).
Device xx Parity
NONE
ODD
EVEN
MARK
SPACE
6. Press Enter. The flow control prompt displays.
Flow Control
The device port flow control setting determines the method of flow control.
The two most common settings are XON/XOFF (software) and RTS/CTS
(hardware). The default setting for the device ports is XON/XOFF. Check the
equipment documentation for the correct flow control setting.
1. Select the flow control for the port(s).
Device xx Flow Control
XON/XOFF
RTS/CTS
2. Press Enter. The port type prompt displays.
Port Type
Each SCSxx05 device port is factory configured as a DTE device, ad each
SCSxx20 device port is factory configured as a DCE device.
Note: Make sure to select DTE if you enabled an operator port or group
of ports.
1. Select the Port Type (OFF, DTE, or DCE) for this group of ports. OFF
disables the port.
2. Press Enter. The inhibit buffering prompt displays.
Inhibit Buffering
By default, buffering is enabled (Inhibit Buffering is No). Inhibiting buffering
disables the buffering on a port, including bi-directional traffic that a system
administrator or user may record in direct mode. Therefore, a system
administrator may choose to inhibit buffering temporarily when entering sensitive
data, so the other users cannot view the data. Alert and panic messages from the
attached device are still stored when nobody is connected.
4-9
Page 68

SCSxx05/SCSxx20 User Guide 4: Configuration
1. Select Yes to disable buffering, or select No (default) to enable buffering.
2. Press Enter. You have two options:
To go back and change any of your settings for this port or group of
ports, select the Setup the Device parameters option, or
When you are satisfied with the changes you have made, or you wish to
administer additional ports, select Done.
3. Press Enter. If you selected Done, you now confirm your changes.
Confirm Changes
1. To commit your changes to flash memory now:
a) Select Yes. You cannot undo this group of device parameter changes
after this point. (If you select No, you return to the previous screens to
make changes.)
b) Press Enter. There is a short delay while the system saves the changes
to flash memory. After the changes are confirmed, the system offers the
ability to configure a different port or group of ports.
2. You have two options:
To repeat the process of setting device port parameters, select Yes, or
To move on to the next option, Device Logging, select No.
3. Press Enter. If you selected No, the Configure Device Port menu returns
with Device Logging Parameters selected.
Device Logging Parameters
You can configure logging parameters on individual ports or on ad hoc groups of
ports.
Device logging parameters include:
File logging (default is disabled)
Syslog logging (default is disabled)
Email logging (default is disabled)
1. Define the port or group of ports. (See Define a Group of Ports to Configure
on page 4-7.)
2. Select Device Logging Parameters from the Configure Device Port menu.
3. Press Enter. The Device Logging Parameters menu displays, with File
Logging Port selected.
4-10
Page 69

SCSxx05/SCSxx20 User Guide 4: Configuration
File Logging by Port
This option includes the following parameters:
Enable/disable (default is disabled)
Number of files saved per port
Log file path (can be NFS mounted)
Log file size (in bytes)
1. With File Logging Port selected, press Enter. The log to file flag prompt
displays.
2. Select Enable to enable file logging for the selected device port(s), or select
Disable to disable file logging, and press Enter. The number of files saved
per port prompt displays.
3. Enter the number of files to be logged for the device port(s). These files
keep a history of the data received from the port(s). The default value is two
files (even if no entry is made here); you may keep as many files as you
wish.
If you are specifying a range or a group of ports, remember that each port will
have its own unique files (the log file name(s) contain the port number to
differentiate the similar files in the log file directory).
4. Press Enter. The log file path prompt displays.
5. Enter the log directory path for the log file(s). The system defaults this path to
/var/tmp/ if you make no entry. Ensure that the directory exists and is
writeable.
Set Log File Path for Device Port xx.
Set the Log File Path name (must end in / i.e.
/var/log/tmp/) for Port xx
Answer: /var/tmp/
6. Press Enter. The log file size prompt displays.
4-11
Page 70

SCSxx05/SCSxx20 User Guide 4: Configuration
7. Enter the desired log file size in bytes (2048 = 2K). The default is 2048 bytes.
The amount of available memory limits the maximum size of the log file.
8. Press Enter. the Device Logging Parameters menu returns with Syslog Port
Logging, selected.
Syslog Logging by Port
Next, you configure the following syslog options for the same port(s):
Enable/Disable (default is disabled)
Set Syslog Facility (user, local0, local1, local2, etc....local7)
Set Syslog Level (Emergency, Alert, Critical, Error, Warning, Notice, Info,
Debug)
1. With Syslog Port Logging selected, press Enter. The syslog flag prompt
displays.
2. Select to Enable or Disable (default) syslogging for the port(s), and press
Enter. The syslog facility prompt displays.
3. From the list, select the syslog facility to use for the port(s) and press Enter.
The set syslog level prompt displays.
4. From the list, select the syslog alert level for the port(s). The levels are, from
the top down, most severe to least severe. They classify the importance of
each connected server within your configuration.
5. Press Enter. The Device Logging Parameters menu returns with Email
Logging Port selected.
Email Logging
Email Logging (Email Notification) sends an email message to pre-defined email
addresses when 'alert' criteria have been met. Data received on the SCS device
port(s) trigger the alert. The default is disabled, although some preset values are
entered for the timers.
Email logging provides the following options for a port or group of ports:
Enable/disable (default is disabled)
Alarm byte count (count the number of characters to trigger an alarm)
Alarm timer (how long to capture data after byte count trigger)
Alarm ignore timer (how long, after byte count trigger, to ignore additional
alarms)
Email subject line (put in a message header to be read in the email
subject)
“Send To” email address
“cc:” to email address
1. With Email Logging Port selected, press Enter. The email flag prompt
displays.
2. Select Enable or Disable (default). If enabled, the email flag triggers an
email message to be sent to the defined recipients when the alert condition
has been met. Press Enter. The alarm byte counter prompt displays.
4-12
Page 71

SCSxx05/SCSxx20 User Guide 4: Configuration
3. Enter the number (digits) of bytes of data the port will receive after which the
SCS will capture log data and send an email regarding this port.
In most cases, the terminal (console) port of your device does not send any
data unless there is an alarm condition. After the SCS receives a small
number of bytes, it can perceive that your device needs some attention. The
SCS contacts your technician via email when that point has been passed,
and the email includes the logged data. A threshold preset at 30 characters
means that as soon as the SCS receives 30 bytes of data, it captures log
data and sends an email regarding this port.
Set EMail Alarm Byte Counter Device Port 1,4,5-7.
Input value for Set Email Alarm Byte Counter Device Port
1,4,5-7.
This number represents how many bytes have to come into the
port before an Email is generated.
Answer: 35
4. Press Enter. The email timer prompt displays.
5. Enter the amount of time, in seconds, for the email to capture data after the
initial byte counter trigger is met. The default is 40 seconds.
Email timer is a time limit of how long, in seconds, the device port will capture
data before closing the log file (with a fixed internal buffer maximum capacity
of 1500 bytes) and sending it as an email message. The SCS sends the data
as the body text in the email message to your predefined recipients.
6. Press Enter. The email ignore timer prompt displays.
7. Enter the number of seconds (digits) for the desired ignore time. The default
is 600 seconds (10 minutes).
This is a period of time, after the email message has been sent, for which the
device port will ignore additional characters received. The data will simply be
ignored and not trigger additional alarms until this time elapses.
Note: The email buffer does not collect any additional characters in its buffer
during this ignore time. However, if syslog is also active, the logger still
buffers any data to syslog.
8. Press Enter. The email subject text prompt displays.
9. Delete the default text and enter a subject text appropriate for your site.
The email subject line is pre-defined for each port with its port number. You
can use the email subject to inform the desired recipients of the problem on a
certain server or location (e.g., server location or other classification of your
equipment). This is helpful if the email message goes to the sysadmin's or
service technician's mobile or wireless device (e.g., text messaging via
email).
The message body will contain the ASCII data from the device port for as
long as the sysadmin has indicated the SCS should capture the data.
Set Email Subject Device Port 1,4,5-7.
Answer: This is the subject line for the generated email.
4-13
Page 72

SCSxx05/SCSxx20 User Guide 4: Configuration
10. Press Enter. The email address prompt displays.
11. Enter the complete email address of the message recipient(s) for each
device port(s). Each device port has its own recipient list. If you wish to enter
more than one email address, separate the addresses with a single space.
Set Email Address(es) Device Port 1,4,5-7.
Answer: SiteTech@ServerFarm.com
12. Press Enter. The cc: prompt displays.
13. Enter the email address(es), if any, to which the alert message should be
copied. If entering more than one email address, separate the addresses
with a single space. You may cc: as many parties as you wish.
14. Press Enter. The Device Logging Parameters menu returns with Done
selected. You may select the other options to change you settings, if desired.
15. When you are satisfied with your entries and want to save them, press Enter.
A confirmation prompt displays:
16. To confirm your entries, select Yes. The system saves the entries to flash
memory. You have two options:
To configure additional device ports, select Yes and press Enter.
If you have finished configuring device ports, select No and press Enter.
The Device Logging Parameters menu returns with Done Device Ports
selected.
Note: Email notification changes do not take affect until after the
system reboots.
Done Device Ports
To return to the setup menu when you are satisfied with your device port
settings:
1. Select Done Device Ports.
2. Press Enter. The setup menu displays with Software Updates selected.
Updating Software
Use this option to download the latest firmware for your SCS. You must have an
ftp server set up on your network to perform these actions. You will need to
enter:
Server type: ftp or tftp (tftp is the default)
IP address of the server
FTP or TFTP path
FTP user
FTP password of the user
Software update files (default is none)
4-14
Page 73

SCSxx05/SCSxx20 User Guide 4: Configuration
1. With Software Updates selected, press Enter. The protocol prompt
displays.
What is the value for PROTOCOL?
Please enter ‘tftp’ or ‘ftp’ to select the server type that
will be used to obtain Software update files and as the
server type for configuration save and restore.
tftp
ftp
2. Select the type of server you will use for obtaining updates and saving or
restoring configurations, and press Enter. The server IP address prompt
displays.
What is the value for SERVERIPADDR?
Please enter the IP address in dot quad notation of the
server that will be used to obtain Software update files
and as the server for configuration save and restore.
3. Enter the IP address of the server and press Enter. The default path prompt
displays.
What is the value for FTPPATH?
Please enter the default path on the server that will be
used to obtain Software update files and as the location on
the server to get and put configuration save files.
What is the value for FTPPATH?
Answer: /scs-updates
4. Enter the default path on the server for obtaining software files and getting
and putting configuration save files, and press Enter. The ftp user prompt
displays.
What is the value for FTPUSER?
If you selected ‘ftp’ as the protocol, you will need to
specify an ftp user for the server. The default entry will
work if the ftp server allows anonymous access and the
FTPPATH specified allows anonymous puts.
What is the value for FTPUSER?
Answer: backup
5. Enter the ftp user and press Enter. The ftp password prompt displays.
What is the value for FTPPASSWORD?
If you selected ‘ftp’ as the protocol, you will need to
specify a password for the ftp user of the server. The
default entry will work if the ftp server allows anonymous
access and the FTPPATH specified allows anonymous puts.
What is the value for FTPPASSWORD
Answer: backup
4-15
Page 74

SCSxx05/SCSxx20 User Guide 4: Configuration
6. Enter the ftp user password and press Enter. The install software
updates prompt displays.
Input value for Install Software Update(s)
Enter a space separated list of software update files to
apply.
They will be obtained from the server specified by
SERVERIPADDR.
Unless the filename here is specified with a path, the
files will be obtained from FTPPATH.
Successfully applied updates will appear in the Updates
Applied item below.
Input value for Install Software Update (s)
Answer: upgrade-to-4.3-part1.sh upgrade-to-4.3-part2.sh
7. Enter the software update files (with a space between file names), to obtain
from the server you specified, and press Enter. The edit updates applied
prompt displays.
8. Add, delete, or change any of the listed files, and press Esc to exit editing
mode. The setup menu returns with Done selected.
Note: To save or restore a configuration, use the config-save or
config-restore commands, respectively.
Using Done
After completing the setup menu, use Done, the last option, to finalize and exit
the setup process.
1. Select Done and press Enter. The system asks whether to keep the recent
parameter changes.
2. To save the parameter changes in RAM (volatile memory) in preparation for
using the SAVE command, select Yes. It may take several minutes for the
system to save your changes. Changes that the system accepts are marked
OK in green. Changes that involve disabling an option that was enabled
previously are marked Failed in red.
4-16
Page 75

SCSxx05/SCSxx20 User Guide 4: Configuration
Saving
This SAVE command saves all changes and updates to non-volatile
memory.
The SCS automatically saves the programmed parameters after running the
setup script for the first time only. After that, the system administrator must run
SAVE manually, as follows:
1. To permanently save any parameter changes, type SAVE (all caps) at the
command prompt.
2. Press Enter. It may take a few minutes for the system to save your entries.
The reboot and the poweroff commands check for unsaved data before
execution, just in case a SAVE is required. They prompt you to execute a SAVE,
if necessary.
Note: SAVE does not store the buffered data, which is only maintained
in RAM. If you require the buffered data, you can poll the appropriate
ports and capture the buffered data at any time.
Rebooting
The very first time you log in to the SCS as sysadmin, a special routine runs to
properly set up the system files, read/write operations, and other aspects of the
file system. The SCS automatically reboots after running the setup script for the
first time. All other setup script sessions require you to use the reboot command
to ensure that all configuration changes are made.
1. To make the parameter changes take effect, type reboot at the command
prompt.
2. Press Enter.
3. If file changes have not been saved into non-volatile memory, the reboot
operation includes a prompt, allowing you to SAVE the files if desired.
Note: The system administrator is automatically logged out.
4-17
Page 76

55:: WWeebb IInntteerrffaaccee
The SCS incorporates a browser-based interface for the system administrator.
This interface provides an alternate method of updating most of the parameters
initially set up using the setup command. The Web interface is password
protected, using SSL encryption. Always use the https:// prompt.
This chapter includes the following topics:
Topic Page
Accessing the Web Interface 5-1
Web Configuration Utility Main Page 5-2
Configurable Parameters 5-2
Web Access Delay 5-4
Saving Web Interface Entries 5-4
Exiting 5-4
Accessing the Web Interface
Before using the Web interface, you should have:
Assigned the IP address of the SCS (using either the buttons on the front
of the unit or the setup command)
Initially configured the unit using the setup command.
You must log in using the sysadmin username and password. Cookies must be
enabled in your browser.
1. Launch your Browser, and type https:// followed by the IP Address (URL) of
your SCS.
For example, if the IP address is 172.20.201.245, the login URL is https://
172.20.201.245.
Figure 5-1. IP Address of SCS in URL
An SSL security alert displays.
2. Click Yes.
3. Enter the username sysadmin and your sysadmin password (default is
PASS).
4. Click OK. The Lantronix Web Configuration Utility Main page displays.
5-1
Page 77

SCSxx05/SCSxx20 User Guide 5: Web Interface
Web Configuration Utility Main Page
The Web Configuration Utility allows the system administrator to configure the
SCS, much like the setup script does via a network or terminal connection.
Figure 5-2. The SCS Web Configuration Utility Main Page
This section of the User Guide does not show each window, which are selfexplanatory. Apply, Cancel, and Save buttons are at the bottom of each
parameter window. (See Saving Web Interface Entries on page 5-4.)
Configurable Parameters
To use the Web interface, select any of the tabs near the top of the page. Each
tab allows you to configure a particular parameter or set of parameters. When
you select User Authentication, several sub-tabs display below the first line of
tabs:
Figure 5-3: User Authentication Selection
The same is true for the Device Ports tab:
Figure 5-4: Device Ports Selection
The Configuration chapter explains the parameters in detail. The table below
provides links to these explanations.
5-2
Page 78

SCSxx05/SCSxx20 User Guide 5: Web Interface
Table 5-1. Links to Setup Menu Parameters
Parameter Link Page
Network Configuring Hostname and IP Address 4-4
Timezone Configuring Timezone 4-6
DNS Configuring DNS 4-8
Services Configuring Services 4-9
NTP Configuring NTP 4-10
Email Relay Configuring Email Relay 4-11
Timeouts Configuring Timeouts 4-11
Modem
(SCSxx20 only)
CHAP Secrets Configuring CHAP Secrets 4-15
PAP Secrets Configuring PAP Secrets 4-16
User Auth. Configuring User Authentication 4-16
NFS Mount Configuring NFS Mount 4-2
Packet Filtering Configuring Firewall (Packet Filtering) 4-4
Device Ports Configuring Device Ports 4-5
S/W Updates Updating Software 4-14
Configuring Modem (SCSxx20 Only) 4-12
Some functions cannot be administered using the Web interface:
Users cannot access the system using the Web interface (only the
system administrator can).
You cannot enable or disable the Web interface from the Web interface.
You cannot reboot, power off, or access the command line interface from
the Web interface.
Web Access Delay
The Web interface has a built-in delay of approximately one minute between
sessions to allow the system to write files as required before the next Web
interface session can open. This delay also prohibits two network users from
accessing the system via the Web interface at the same time. After the current
user closes the browser and the timeout expires, click the hostname (in this case
SCS1620) at the top of the page. The login window displays.
Note: If you properly exit the Web interface and then reconnect from the
same IP connection, the delay might not occur.
Figure 5-5. Web Access Delay Message
5-3
Page 79

SCSxx05/SCSxx20 User Guide 5: Web Interface
Saving Web Interface Entries
Figure 5-6. Buttons at Bottom of Web Utility Configuration Page
Apply Changes
Applies the changes for the current page, but does not save them to flash
memory. Closing the Web window does not save or apply any changes.
You must apply changes after completing the changes for a single Web page.
Cancel
Clears changes on a Web page that you don’t want to apply.
Save System Config
Saves the configuration to flash memory, but does not apply or save any entries
that have not been applied.
Can be used at any time, but is really only needed after you have applied all of
the configuration changes.
Exiting
Note: For those entries that require a reboot to function (e.g., network
parameter changes), the system administrator must reboot the system
using the command line interface.
To exit the Web interface:
1. Press the Save System Config button to permanently store your changes in
flash memory. The system implements most settings after you click the Save
System Config button, but some changes may require a reboot to take
effect.
2. To logout, close the browser window.
5-4
Page 80

66:: MMooddeemm SSeettuupp
If your SCSxx20 was shipped with a modem installed, it is not necessary to
perform the modem setup, and you can skip this chapter. This procedure is for
installing a modem in the field.
This chapter includes the following topics:
Topic Page
Installing a Modem Card 6-1
Initializing the Modem 6-1
Installing a Modem Card
Note: It is not necessary to power down the unit before installing the modem
card.
1. Remove the blank metal plate covering the modem slot on the SCSxx20.
2. Insert the modem card into the open slot in the rear of the SCSxx20.
Figure 6-1. Installing a Modem Card in the SCSxx20
3. Tighten the screws on the modem card by hand.
4. Connect the modem to your telephone line using the RJ11 telephone cord.
Initializing the Modem
If a modem card is installed into a working SCS1620, the system administrator
must initialize it for proper operation with the system using the install_modem
command. This command forces a hardware reset of the modem module and
then sends an initialization string that configures the modem for the system. This
string also saves these values into the modem's non-volatile memory.
6-1
Page 81

SCSxx05/SCSxx20 User Guide 6: Modem Setup
To initialize the modem (only needed when first installed):
1. Login as sysadmin
2. Type install_modem at the sysadmin> prompt.
3. When the command has run completely, the sysadmin> prompt displays.
The modem has reset and is ready to use.
SCS1620 login: sysadmin
Password:
sysadmin>install_modem
sysadmin>
4. Check the status LEDs on the modem module.
Figure 6-2. Normal Modem LEDs (Red-Red-Green-Green-Red) for an idle Modem Port
A red LED indicates the “inactive” state, and a green LED indicates the “active”
state. The PWR LED should always be green when the system is on.
6-2
Page 82

77:: SSyysstteemm AAddmmiinniissttrraattoorr aanndd UUsseerr FFuunnccttiioonnss
This chapter describes how the system administrator and users gain access to
the system and the functions permitted for each role. It includes the following
topics.
Topic Page
System Administrator Functions 7-1
User Access and Functions 7-3
System Administrator Functions
The system administrator specifies settings such as user IDs, device
configuration, and terminal and access rights to suit the application. The system
administrator is also responsible for configuring the system to work in your
network.
The system administrator initially uses Telnet or a terminal to access and
configure the SCS, and may choose to use the Web-based interface to update
the configuration.
Note: Please see the Configuration chapter for instructions on logging
on and logging out as the system administrator.
Security and Passwords
The SCS uses Linux/UNIX commands to administer the system. The system
administrator and the users access the system using a shell interface, which
limits what they can affect in the operating system.
Note: This guide discusses applicable Linux commands only.
The shell offers the appropriate level of administration while maintaining the
integrity of the system. The system administrator should change passwords upon
installation to protect the system.
The sysadmin programming level is as close to “root” as is required to administer
the SCS, but it is not the most senior root level. The most senior root level is
intentionally removed from the shell; however, it exists in the system and the
system administrator must change its password to protect against unauthorized
access or changes.
Changing the Sysadmin Password
The system administrator must change the password for the sysadmin level
before connecting the SCS to a network or making it accessible to others. The
passwd command is discussed in the Commands chapter.
7-1
Page 83

SCSxx05/SCSxx20 User Guide 7: System Administrator and User Functions
Changing the Root Password
The system administrator must also change the password for the root level.
Although users do not require root access, the system administrator can access
it using SSH. Make sure to know the root access password and be certain that it
has not been left as the common default value. This is especially important if
SSH is enabled, since SSH can offer the ability for root-level access by a remote
system (depending on sysadmin settings).
To change the root-level password of the SCS, follow the procedure below. It
uses the passwd command but with some changes for root level. The default
root password is root.
1. Log in as sysadmin. The command-line prompt displays.
2. Type bash to start a shell process (notice: sysadmin level = $).
3. su (switch user) to root level; enter the existing root password (default =
root). After the system accepts the password, notice that the root level =
sysadmin@SCSXXYY/#.
4. Type passwd to change the root level password. The “authentication tokens
updated” message displays.
5. Type exit to leave root level (sysadmin@ $).
6. Type exit to leave shell level (sysadmin>).
7. Type logout to log out of the system.
Note: Before you SAVE the system data, verify that your new root password is
correct. Repeat step 3, and when you are prompted for a password, enter the
new password.
7-2
Page 84

SCSxx05/SCSxx20 User Guide 7: System Administrator and User Functions
If You Misplace the Sysadmin Password
You can lock the system down and prevent programming access if you
misplace your password. If this should happen, recover the system as follows:
1. Connect a terminal or PC running terminal software to the terminal port on
the SCS.
2. Power up the SCS.
3. At the boot prompt, type ?.
4. At the second boot prompt, type linux single and press Enter.
5. At the # prompt, type passwd sysadmin and press Enter.
6. Enter the new password and press Enter.
7. At the prompt, enter the new password again and press Enter.
8. Type reboot and press Enter.
9. Once the system reboots, log in using the new sysadmin password.
User Access and Functions
The user can be any person who is assigned a user name and password by the
system administrator. The system may have up to 200 unique users (including
sysadmin, the only default user). For security reasons, users can change their
own password.
For the most part, users access the SCS through the network connection. In
general, only the system administrator uses the terminal port, as it is hardwired to
the chassis.
Network Port Access
To connect to the SCS network port, use a TCP/IP Telnet client to Telnet to the
IP address assigned to the SCS, or use SSH.
OCTANE_65 10# Telnet 172.16.1.31
Trying 172.16.1.31...
Connected to 172.16.1.31
Escape character is ‘^]’.
SCS4805 login: imauser
Password:
imauser>
Once connected, you may access the SCS ports for which you have permission.
7-3
Page 85

SCSxx05/SCSxx20 User Guide 7: System Administrator and User Functions
Terminal Port Access
To form a terminal port connection to the SCS, use a hardwired VT100 terminal
or terminal emulation program that is connected to the terminal connector on the
SCS. The system administrator normally uses this type connection during service
events; however, any user who has access to the VT100 terminal and a
password can log into the system this way.
SCS4805
SCS4805 login:
SCS4805 login: imauser
Password:
imauser>
1. At the SCS login prompt, enter your user name and press Enter.
Note: Always use the Enter key near the alphanumeric keys on
your keyboard.
2. At the Password prompt, enter your password and press Enter. (The system
does not display the characters you type.) The command prompt changes to
the user’s login name (as above).
Modem Module
The SCSxx20 with the optional modem module can support three configurations:
Plain text tty: Provides an interface identical to that of the terminal port
or a telnet-ed user, with the standard login and password prompts.
PPP connection: Allows a remote user to establish a PPP connection
with the SCS. You need a standard SCS user/password pair to
authenticate to the system. IP traffic can then be forwarded through the
SCS to the Ethernet port. This allows standard Internet applications to
communicate to systems, including the SCSxx20, on the network
attached to the Ethernet port of the SCSxx20. These applications include
but are not limited to telnet, ftp, and SSH. CHAP is also supported.
Callback Connection: Allows a remote user to establish a connection
with the SCSxx20 only after the user logs in with a callback pseudo user,
at which time the SCSxx20 drops the connection, delays for a period of
time (30 sec.), and then dials the user back at a pre-assigned phone
number. Callback may be tty or PPP.
Selecting a Device Port
The system administrator assigns permission to connect to specific device ports
in your user profile. If you try to connect, but you do not have access, the
message “NO ACCESS TO DEVICE CHANNEL” displays.
1. To select a server connected to a device port, type select followed by a
device port ID. For example, to connect to a server named Alpha on device
port 2, you may either type select Alpha or select 2.
2. Press Enter.
Monitoring the Buffered Data for a Port
When you select a server, the prompt changes to the server name in the general
form USER_NAME-SERVER_NAME>. For example, if user GEORGE selects
7-4
Page 86

SCSxx05/SCSxx20 User Guide 7: System Administrator and User Functions
Alpha, the prompt would read GEORGE-Alpha>. When this prompt displays, you
are in monitor mode. There is no direct communication between you and the
server.
Note: You may select a server already selected by another user.
The system saves any output from the server to a buffer that you may access
(using cat or less), but you may not issue commands to the server. If you want to
issue commands to the server, you must enter direct mode.
Deselecting a Server
You may exit from the current device port by using the exit command or
selecting another device port.
Direct Mode
If you want to interact directly with a server rather than only monitor its output,
you must enter direct mode.
To enter direct mode using the direct or dir n command:
1. Select a device port.
2. Do one of the following:
To enter direct mode for the currently selected device port only, enter the
direct command.
To select a device port and enter direct mode in one step, enter the dir n
command, where n is the device port number or the name assigned to
the port.
3. Press Enter.
Your terminal directly connects to the server and acts as if the terminal was
physically connected to the server. The SCS displays the last page of the device
buffer along with a system information message indicating the device port
selected.
To escape from direct mode, use the direct mode escape sequence. The direct
mode escape sequence is a series of two to five characters that allow you to
leave direct mode and return to monitor mode. The factory default for the direct
mode escape sequence is Esc+A (escape key, then uppercase "a"); you may
change the sequence by using the editesc command.
Edit Escape Sequence
We recommend that you only change the escape sequence if it causes problems
with your hardware or software. Also, we recommend that you avoid
combinations of the Ctrl key and other keys, as these combinations are usually
for sending and receiving special characters through the terminal. When you
change the escape sequence, a window with the hexadecimal representation of
the old escape sequence displays.
Note: Pressing Esc to exit from the edit prompt does not work; it adds
more Esc characters to the direct mode escape sequence. Use \x to
prefix any hexadecimal characters entered in the escape sequence. (The
default sequence is \x1BA = Esc+A, where 1B is the Hex value for Esc,
and A is the letter A.)
To keep the existing sequence, press Enter.
7-5
Page 87

SCSxx05/SCSxx20 User Guide 7: System Administrator and User Functions
To change the sequence, enter the new sequence and press Enter. If for
some reason the sequence is unacceptable, an error message displays,
and the sequence reverts to the existing character values.
A list of hexadecimal character settings is provided at the end of this User Guide.
Logging Out
Always log out when you are finished with your session activity.
To log out from a user session:
1. Type logout.
2. Press Enter.
If you are logging out from a network, the SCS disconnects the Telnet or SSH
session. If you are logging out from a direct serial session, the SCS returns to the
login prompt.
The system administrator may configure the SCS to automatically log you out if
the terminal connection has been idle for a period of time. This is a security
precaution. Depending on your terminal's settings, you may have an inactive
window open if the SCS has disconnected.
7-6
Page 88

88:: CCoommmmaannddss
This chapter includes the following topics:
Topic Page
Summary of Commands 8-1
System Commands 8-1
Device Commands 8-7
User Management Commands 8-9
User Commands 8-12
Advanced Sysadmin Commands 8-13
Summary of Commands
A summary of the SCS commands is provided below. Some commands only
sysadmin can access, while all defined users can access others.
sysadmin User Command Purpose
x
x x
x
x
x x
x
x x
x
x
x x
x
x x
x
x x
x
x x
x x
x x
x x
x x
x
x x
x x
x x
x
x x
x x
x
Table 8-1. Summary of Commands
adduser
alias
bash
break
cat
changes
clear
config-restore
config-save
connections
deluser
direct
dtedce
editbrk
editdev
editesc
edituser
exit
help
info
install-modem
less
listdev
listen
listusers
logout
man
modem-hangup
Adds a user.
Lists command aliases.
Go to a Linux bash prompt.
Breaks a connection.
Displays the history buffer for a port.
Lists files changed from factory settings
Clears port buffer.
Restores a configuration.
Saves a configuration.
Lists all users in direct mode.
Deletes a user.
Enters direct mode.
Configures the device port type.
Edits user 'send break' sequence.
Edits device settings.
Edits user direct mode 'escape' sequence.
Edits user settings.
Deselects a port.
Displays help.
Shows system information.
Installs internal modem. (SCSxx20 only)
Browses history buffer.
Lists device names.
Listens to a port.
Lists users.
Logs out.
Displays online manual pages.
Hangs up internal modem. (SCSxx20 only)
8-1
Page 89

SCSxx05/SCSxx20 User Guide 8: Commands
sysadmin User Command Purpose
x x
x
x
x
x
x x
x x
x
x x
x x
x x
x x
x
x x
x
x x
passwd
poweroff
reboot
reset-modem
SAVE
select
scp
setup
sftp
ssh
ssh-keygen
Telnet
telnetconfig
timeout
unsaved
version
Sets user password.
Powers-off (shuts down) the SCS.
Reboots the SCS.
Resets the internal modem. (SCSxx20 only)
Commits (saves) programming changes.
Selects a port.
Secures copy.
Initially configures the SCS.
Secures ftp.
Establishes an SSH connection.
Generates SSH keys.
Uses Telnet.
Assigns a unique TCP port or IP address to a
device port.
Sets the timeout timers.
Lists files saved since last save.
Shows version information.
Note: Command-line entries are case sensitive. Some system
commands display the syntax options when you access them. Many OSrelated functions are described in the online MAN pages, accessible from
the bash shell.
System Commands
The following commands (not necessarily in order) are used to set up the
system. All commands are case sensitive.
SAVE
SAVE saves any new system data to the system's non-volatile memory. All
parameters and settings that the sysadmin changes remain in RAM until then.
The sysadmin should run SAVE before powering off or rebooting the system.
SAVE is not required the very first time (only) that the sysadmin sets up the
system using the automated setup script. In this instance, the system
automatically runs the setup program, automatically stores the files properly, and
reboots upon completion of the program.
reboot
To reboot the SCS any time, use the reboot command. The system resets,
disconnects all users, and runs the power-on self-test. Only the system
administrator may issue the reboot command.
sysadmin>reboot
Broadcast message from root (ttyM9) Tue Oct 2 14:24:49
2001...
The system is going down for reboot NOW !!
System reboot is delayed by one minute from the time you enter the command.
Any active network sessions disconnect while the system reboots, and no
network sessions can be established while the system reboots.
Note: Use reboot now to prevent the one-minute delay and to reboot
immediately.
8-2
Page 90

SCSxx05/SCSxx20 User Guide 8: Commands
poweroff
Use the poweroff command to shut the system off. This command allows the
system to properly close any open files and gracefully exit and shut down. If you
turn off the system without using the poweroff command (including power
failure), the system will require some extra self-checks and start-up time the next
time it boots up.
sysadmin>poweroff
Broadcast message from root (ttyterm) Tue Oct 2 14:27:12
2001...
The system is going down for system halt NOW !!
After you enter the poweroff command, the system may take up to two minutes
to close all files and prepare to be shut off.
Turn off the power supply switch (or power off the circuit) only after the front
panel display says "OK to power off". The SCS must be power-cycled to restart.
help
About help files:
? accesses a list of available commands.
Command-specific help is provided for some commands, when you type
' --h' (space, dash, dash, the letter h) after the command.
Other commands use ' -h' (space, dash, letter h).
Some commands offer pop-up help if your entry is in an invalid format.
Some commands do not provide a help file.
q exits help.
Note: Some system commands (e.g., poweroff, reboot) operate
immediately and do not have a help file using --help or -h.
alias
Use alias to get a list of some of the system command aliases.
sysadmin>alias
Command aliases:
dir - direct
devl - listdevice
sel - select
? - help
ver - version
lu - listusers
devices - editdev
dev - editdev
setup
The setup program runs automatically the first time the system administrator logs
into the system. The program steps the system administrator through a majority
of the configuration options for the system. The command does not configure
devices or users.
After the initial running of the system, use the setup command to change system
settings or parameters. Always remember to use SAVE if you are manually
running the setup program.
8-3
Page 91

SCSxx05/SCSxx20 User Guide 8: Commands
passwd
At the first login, the SCS uses the factory default password, PASS (all upper
case). The sysadmin should change this default password as soon as possible to
prevent access by unauthorized personnel.
sysadmin>passwd
Changing password for sysadmin
(current) UNIX password:
New UNIX password:
Retype new UNIX password:
passwd: all authentication tokens updated successfully
sysadmin>
To change the sysadmin factory default password, type passwd (all lower case)
at the sysadmin> prompt. The system prompts you to enter a new password. The
new password must be six or more alphanumeric characters and is casesensitive.
The sysadmin must also change the root password. While root access is not
required in the SCS system; changing the root password from the default
ensures the security of your system. The root password is more senior than the
sysadmin password and is administered differently. (See Changing the Root
Password.)
break
Use this command to break a connection. The syntax is break <port # > (e.g.,
break 1, break 2, break 3).
changes
Use this command to list files that have been changed from factory settings.
config-save
Use this command to place a backup of the system configuration on the ftp or tftp
server configured in the setup process. The sysadmin must first configure the
ftp/tftp server parameters as described in Updating Software.
config-restore
Use this command to load the saved backup of the system configuration from the
ftp or tftp server configured in the setup process. The sysadmin must first
configure the ftp/tftp server parameters as described in Updating Software.
install-modem
Use this command to install an internal modem. (SCSxx20 only)
man
Use man <command name> to search for a help file (online manual pages) or
descriptive information for a Linux/UNIX command.
modem-hangup
Use this command to hang up an internal modem. (SCSxx20 only)
info
The info command displays the shell version.
8-4
Page 92

SCSxx05/SCSxx20 User Guide 8: Commands
sysadmin>
sysadmin>info
SCS4805 Shell V4.00
sysadmin>
reset-modem
Use this command to reset the internal modem. (SCSxx20 only)
scp
Use scp to perform a secure copy, using SSH, between two hosts. The file copy
is encrypted and is therefore secure.
Refer to the man pages for scp for a description and command options.
sftp
Use sftp to perform a secure file transfer transaction, using SSH, between two
servers. It is similar to ftp except that it is encrypted for security.
Refer to the man pages for sftp for a description and command options.
ssh
Use ssh to open up a secure shell connection between two hosts to transfer files
or data between the systems. In this case, the SCS is a client device and is
connected to an SSH host elsewhere. You may need to generate the security
keys for SSH using ssh-keygen, depending on your application of SSH.
Refer to the man pages for SSH for a description and command options.
ssh-keygen
Use ssh-keygen to create the security keys for your client system to interact with
an SSH host elsewhere. After the keys have been generated, the user can
establish a secure shell connection using SSH over a network.
See Advanced Sysadmin Commands later in this chapter for an ssh-keygen
tutorial. Refer to the man pages for SSH for a description and command options.
syslog
The SCS keeps a system log file called /var/log/syslog. The level of logging is
controlled by the file /etc/syslog.conf.
The SCS can log the following:
Warning level events: no events
Notice level events:
− Device settings changed
− Begin and end direct mode
− Device buffer cleared
− Begin and end listen mode
− Begin and end bash shell
Info level events
− User settings modified
− User begin and end of SCS command shell
− Device selected
− Device unselected (exit command)
8-5
Page 93

SCSxx05/SCSxx20 User Guide 8: Commands
− Device buffer examined (less or cat)
− User becomes root
The SCS comes set to log all warnings and higher events. The default file entry
is *.warning, with lower level settings (a lower level generates more messages)
in *.notice and *.info (even more events).
To change the logging level:
1. Log in as sysadmin.
2. Type bash and press Enter.
3. Edit the file /etc/syslog.conf (vi /etc/syslog.conf) and press Enter.
4. Restart the system logger by typing service syslog restart and pressing
Enter.
5. To return to the SCS command shell, type exit and press Enter.
timeout
When a user logs into the system, a timeout clock starts for that connection. It
checks for continuous idle time on that connection. There are three separate
timers in the system for the two possible methods of accessing the system (via
terminal or via network port connection). The system senses periods of “no
activity” on the connection, and if the idle time exceeds the timeout duration, the
system disconnects the port.
Use timeout -h to get a help file for the timeout feature.
Use timeout -c [value = 0, or 1-30] for the terminal port timeout.
Use timeout -t [value = 0, or 1-30] for the Telnet (network) timeout.
You may disable timeout for any or all of the connection ports. The timeout
duration may be from 1 to 30 minutes. Each time is approximate, and may be as
much as 59 seconds longer than the programmed time (e.g., setting a timeout to
3 minutes can take from 3:00 to 3:59 minutes to occur). Setting a timeout to 0
disables that timeout operation.
Type timeout or timeout ? to list the current timeout settings.
unsaved
Use this command to list files that have changed since the last save.
version
Use version to determine the version of the shell. Use version -a to get a
display of the version of the system files.
sysadmin>
sysadmin>ver
ci V3.13
sysadmin>
sysadmin>version -a
SAVE V3.23
break V3.08
ci V3.13
connections V3.04
devices V3.11
direct V3.14
dtedce V3.17
8-6
Page 94
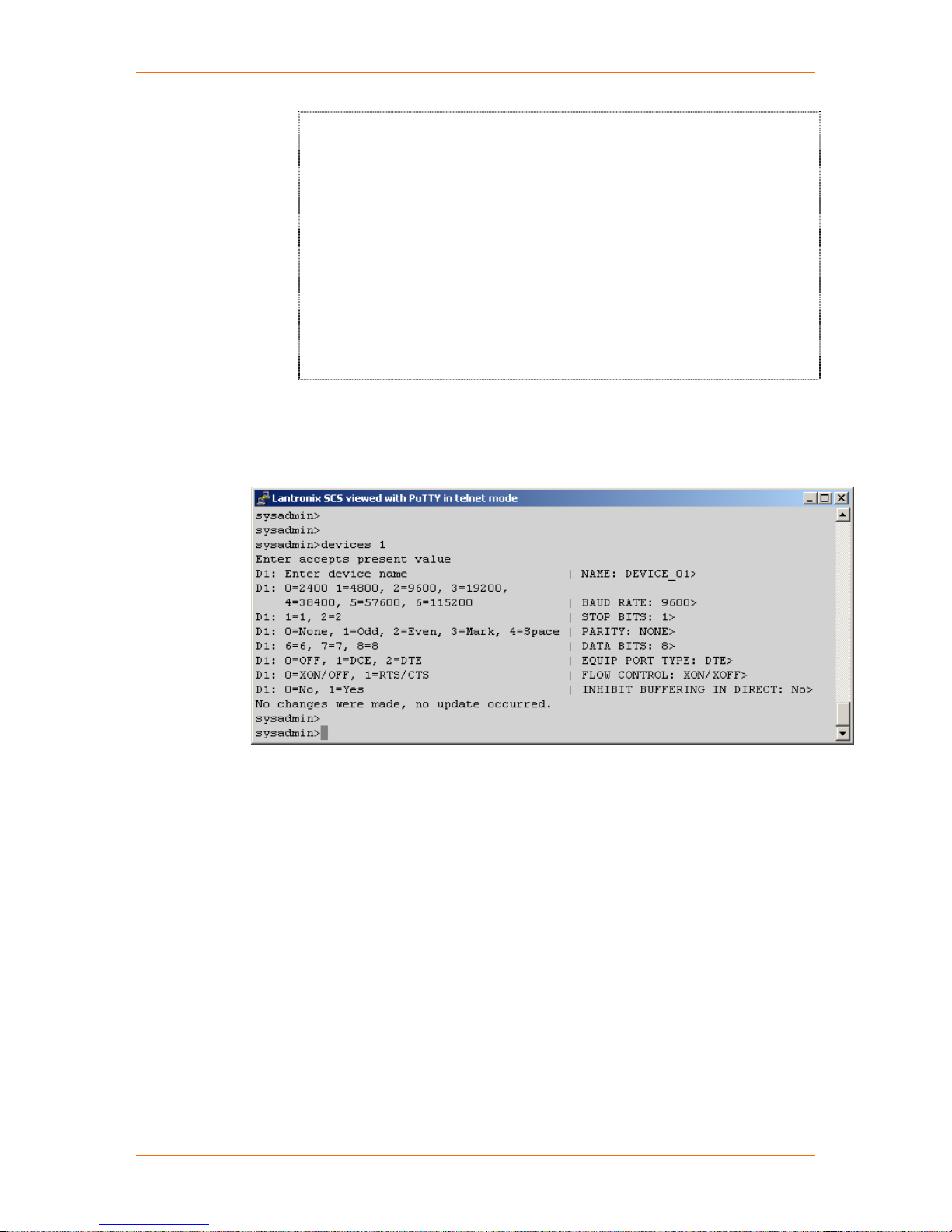
SCSxx05/SCSxx20 User Guide 8: Commands
edituser V3.05
lcd V3.13
lciclear V3.06
lcistty V3.06
listen V3.21
listend V3.22
ltxloggerd V1.17
lu V3.05
modem_reset V3.10
perms V3.09
timeout V3.08
timeoutd V3.06
lci-system-configure V1.22
EXAR-XR16L788 Device Driver V2.8
SCS4805 release date: Thu Sep 19 16:14:49 2002 V4.0
sysadmin>
Device Commands
The system administrator may define the device port parameters using the
devices, editdev, and listdev commands.
devices
Use devices to obtain a list of all options for all device ports. Press the spacebar
to continue the list, and press q when you reach the end prompt.
editdev
Use editdev -u <device number or name> to edit and update the parameter
settings of a device. Step through each device option; when you are done, the
system prompts “Are you sure?” before accepting the changes. Remember to
SAVE.
listdev
Use the listdev command to display a list of device port names and their
corresponding port numbers.
Programmable elements include: device name, baud rate, stop bits, parity, data
bits, DCE/DTE, flow control, and inhibit buffering in direct mode. Pressing Enter
accepts the parameter as is. If you need to make changes, you can edit each
parameter as it comes up after each > prompt.
8-7
Page 95

SCSxx05/SCSxx20 User Guide 8: Commands
Device Name
The device name cannot contain a space. Use an underscore if you need an
empty space in the name.
Baud Rate
Seven device baud rates are offered: 2400, 4800, 9600, 19200, 38400, 57600,
and 115,200. Most devices use 9600 as the terminal/administration port's baud
rate, so the device port defaults to this value. Check the equipment settings and
documentation for the proper baud rate.
Stop Bits, Parity, Data Bits
The stop bits, parity, and data bits parameters determine the format of the bitwise transmission of data. The default settings are 1 stop bit, no parity, and 8
data bits. Check your equipment documentation for the proper settings.
DCE/DTE
The SCSxx05 device and terminal ports are factory configured as DTE devices.
The SCSxx20 device and terminal ports are factory configured as DCE devices.
Flow Control
The device port flow control setting determines the method of flow control.
The two most common settings are XON/XOFF (software) and RTS/CTS
(hardware). The default setting for the device ports is XON/XOFF. Check the
equipment documentation for the correct flow control setting.
Buffering
The Inhibit Buffering in Direct setting allows the administrator to turn off port
buffering while a user is connected to the device and is in direct mode. The
device port buffer still collects data while not in direct mode when this setting is
active. You may disable direct mode buffering so other users cannot view
sensitive data, but the system stores alert and panic messages from the attached
device when nobody is connected. This setting is disabled by default, so buffer
data is collected both in and out of direct mode.
connections
Use connections to display a snapshot list of all users connected in direct mode.
cat
Use cat <port name or number> to display the buffer information for that port.
clear
Use clear <port name or number> to clear the buffer for that port.
less
Use less <port name or number> to browse the buffer for that port. When the
buffer reaches the capacity of the screen, it pauses; press the spacebar to
continue the display. When the buffer reaches the end, it displays "END"; press q
to quit the less program and return to the command line.
logout
Use logout to quit your session with the system.
8-8
Page 96
SCSxx05/SCSxx20 User Guide 8: Commands
User Management Commands
The system administrator uses the following commands to add and delete users
and to add and change settings for system users. The sysadmin is also a user,
although one who cannot be deleted.
listusers
Use listusers to get a list of all assigned users in the SCS.
sysadmin>listusers
test
sysadmin
user1
kevin
ross
bill
anthony
tom
harry
george
adduser
Use adduser <user name> to add a new user profile including the user’s
password, port configuration, and default operational sequences.
sysadmin>
sysadmin>adduser
usage: /lci/bin/adduser name
sysadmin>adduser newuser
Changing password for user newuser
New UNIX password:
Retype new UNIX password:
passwd: all authentication tokens updated successfully
Enter accepts present value
Server number of 0 (zero) will remove all access to servers
ESCAPE_SEQ= \x1bA >
BREAK_SEQ= \x1bB >
ALLOW_CLEAR= 1-9 > 1-8
ALLOW_DIRECT= 1-9 > 1,3,5,7
ALLOW_LISTEN= 1-9 > 1-3,5,7-9
Are you sure? y
sysadmin>
1. Type adduser and press Enter.
2. Type the desired user name (case sensitive) and press Enter. A prompt asks
for a password for the new user.
Note: Passwords should be at least six chara cte rs long. If a
password is less than 6 characters long, the system warns you that it
is “bad password: too short.” However, if you ignore the message
and re-enter the password (to confirm it), the system will accept it.
As soon as you enter the password, the system creates the new user identity and
authenticates and creates the default parameters for it.
When the user logs in for the first time, the system asks for this password. This
password is case-sensitive. Users can change their own passwords using the
passwd command at a later time.
8-9
Page 97

SCSxx05/SCSxx20 User Guide 8: Commands
The system automatically enters the edituser mode for this new user, allowing
the system administrator to change any of the preset parameters.
edituser
Use this command to edit the port configuration and default operational
sequences for that user profile. This command creates user IDs and privileges.
The system prompts the sysadmin to define the device ports that the user will be
allowed to access for direct connections. You can administer ports:
Individually (e.g., 4)
As a range (e.g., 5-7)
As selective ports (e.g., 1,4,5,6,9)
As combinations of the above (e.g., 1-4,6,8)
The ALLOW_CLEAR option determines whether a user may use the clear
command to delete all the data stored in a device port FIFO buffer. The
administrator may want to inhibit this ability to preserve user accountability when
accessing attached devices. Users are allowed to clear buffers by default.
The ALLOW_DIRECT option determines which devices a user may select for
direct access.
The ALLOW_LISTEN option determines which devices a user may select for
listen mode.
1. You have two options:
To edit or change parameters for the sysadmin, enter the command
edituser without a user name.
To edit or change parameters for a particular user after defining that user
ID, use the edituser command.
For example, if the user newuser needed to have more concurrent login
capabilities, the administrator would type edituser newuser on the
command line.
2. As each line comes up, change the settings and press Enter, or press Enter
to accept the current setting.
Note: When editing any group of parameters, press Enter to accept
the current value and move to the next parameter in the list.
If you change any parameters, the system prompts "Are you sure?"
8-10
Page 98

SCSxx05/SCSxx20 User Guide 8: Commands
3. To accept the changes, type y for yes, or to reject the changes, type n or do
not enter anything.
4. Press Enter.
sysadmin>
sysadmin>edituser
Enter accepts present value
Server number of 0 (zero) will remove all access to servers
ESCAPE_SEQ= \x1bA >
BREAK_SEQ= \x1bB >
ALLOW_CLEAR= 1-8 > 1-9
ALLOW_DIRECT= 1-9 >
ALLOW_LISTEN= 1-8 >
Are you sure? y
sysadmin>
sysadmin>
sysadmin>edituser newuser
Enter accepts present value
Server number of 0 (zero) will remove all access to servers
ESCAPE_SEQ= \x1bA >
BREAK_SEQ= \x1bB >
ALLOW_CLEAR= 1-8 >
ALLOW_DIRECT= 1,3,5-7 >
ALLOW_LISTEN= 1-4,8-9 >
sysadmin>
deluser
To delete an existing user ID from the system, use deluser <user name> (all on
the same line).
Note: The deluser command does not verify whether you wish to delete
the user or not. Be careful!
Use the listusers command after deleting a user ID to verify the deletion.
editbrk
Use editbrk <user name> to edit the break sequence for a user. The break
sequence (user key strokes; default is Esc+B) displays to the system
administrator in its ASCII form in the edituser list. See Break Sequence on page
8-12 for more information.
editesc
Use editesc <user name> to edit the escape sequence for a user. The escape
sequence (user key strokes; default is Esc+A) displays to the system
administrator in its ASCII form in the edituser list. See Escape Sequence on
page 8-12 for more information.
passwd
When logged in as sysadmin, use passwd to change the sysadmin password.
Use passwd <user name> to change a user's password. Passwords should be
six characters or longer, and are case-sensitive.
8-11
Page 99

SCSxx05/SCSxx20 User Guide 8: Commands
User Commands
After the user logs in to the system, the user name becomes the command
prompt. For example, ross> displays after Ross logs in.
Users log in to identify themselves to the system and to access the device ports
to which the system administrator has assigned them privileges.
select
Use select <port name or number> to select a port (only applies to ports for
which this user is allowed clear, direct, or listen access).
direct
Use direct <port name or number> to connect to a port (only applies to a port
for which this user is allowed direct access).
telnetconfig
Use telnetconfig < port name or number> or telnetconfig <IP address> to
assign a unique TCP port or IP address to a device port so that Telnet can be
used to connect to the device port. Only the sysadmin user has permission to run
telnetconfig. Users who wish to Telnet to a device port must have must have
direct access rights to use this command.
listen
Use listen <port name or number> to listen to a port (only applies to ports for
which this user is allowed listen access).
clear
Use clear <port name or number> to clear the buffer of a device port (only
applies to ports for which this user is allowed clear access).
exit
Use exit to disconnect from a port that you are connected to. When you are
disconnected, the command line displays.
logout
The user can log out of a port connection by typing logout on the command line.
Break Sequence
The user can send a break signal to the external device using a programmed
break sequence. The preset value for this option is Esc+B (performed quickly but
not simultaneously).
Escape Sequence
The user can disconnect from a port by using a programmed escape sequence.
The preset value for this option is Esc+A (performed quickly but not
simultaneously).
8-12
Page 100

SCSxx05/SCSxx20 User Guide 8: Commands
Advanced Sysadmin Commands
You can access the following features from the command line interface or
administer them using a Linux command line prompt through your network.
Using ssh Keys and keygen Procedures
The following info is taken, with great liberties, from an open source article
discussing ssh and keygen. It is online at:
http://igloo.its.unimelb.edu.au/Webmail/security/msg00010.html.
ssh-agent: Type My Passphrase Once
Ssh-agent makes this all so easy. Basically, it loads my private key into memory once per
session, prompting me for a passphrase to decrypt the key at the time of load. At that
point, I can use this key as if it had no passphrase until I end that session or remove the
key from memory. Since it's never written to disk in its decrypted form, this is pretty darn
safe. Let's see this at work:
[max@miraclehut ~]$ ssh-agent /bin/bash
[max@miraclehut max]$ ssh-add
Need passphrase for /home/max/.ssh/identity (max@miraclehut).
Enter passphrase:
Identity added: /home/max/.ssh/identity (max@miraclehut)
[max@miraclehut jay]$ ssh humperdink@castle
In the first step, I invoke the ssh-agent, giving it a child program to run. The agent gives
access to my key(s) only to its children. I run bash here, so that every program I run in this
new bash shell can have access to my private key. I just as well could have typed "sshagent xterm" or "ssh-agent startx" to give all programs run in a specific xterm or in X
session, respectively, this kind of access.
In the second step, I actually give the agent my key. I decrypt it once, by entering my
passphrase. I won't have to type my passphrase again until I quit bash.
Finally, in the third step, I ssh to my "humperdink" account on the "castle" host. As long as
I have set up that account properly, by appending this account's ~/.ssh/identity.pub to the
end of humperdink@castle ~/.ssh/authorized_keys file, I'll connect with no password
whatsoever! I can keep doing things like this over and over, using scp to copy files, ssh to
login interactively, or ssh user@target "command" to execute commands on a remote
host. When I'm done, I can type exit to kill off the bash shell, and thus the agent.
8-13
 Loading...
Loading...