Page 1

Intel® Blade Server Ethernet Switch
Modules SBCEGBESW1 and
SBCEGBESW10 CLI Guide
A Guide for System Administrators of Intel® Server Products
Intel Order Number D67145-002
Page 2

Disclaimer
Information in this document is provided in connection with Intel® products. No license, express or implied, by
estoppel or otherwise, to any intellectual property rights is granted by this document. Except as provided in Intel's
Terms and Conditions of Sale for such products, Intel assumes no liability whatsoever, and Intel disclaims any
express or implied warranty, relating to sale and/or use of Intel products including liability or warranties relating to
fitness for a particular purpose, merchantability, or infringement of any patent, copyright or other intellectual property
right. Intel products are not intended for use in medical, life saving, or life sustaining applications.
Intel may make changes to specifications and product descriptions at any time, without notice.
Intel and Intel Xeon are trademarks or registered trademarks of Intel Corporation or its subsidiaries in the United
States and other countries.
Other names and brands may be claimed as the property of others.
Copyright © 2006, Intel Corporation. All Rights Reserved.
This product includes software developed by the OpenSSL Project for use in the Open SSL Toolkit (http://
wwww.openssl.org/).
This product includes software developed by the NetBSD Foundation, Inc., and its contributors.
This product includes crytographic software written by Eric Young (eay@cryptsoft.com).
This product includes software written by Tim Hudson (tjh@cryptsoft.com).
SECURE SOCKETS LAYER DELIVERABLE: The Secure Sockets Layer shall constitute “OpenSSL Deliverables”
hereunder. The OpenSSL Deliverables are provided to Licensee under the terms of this Agreement and the
OpenSSL License Agreement (the “OpenSSL License”), and any use of such OpenSSL Deliverables shall comply
with the terms and conditions of the OpenSSL License and this Agreement. A copy of the OpenSSL License is
available in the license.txt file accompanying the Deliverables and at http://www.openssl.org/source/license.html.
SSH PROTOCOL SUITE OF NETWORK CONNECTIVITY TOOLS DELIVERABLES: The SSH protocol suite of
network connectivity tools shall constitute “Open SSH Deliverables” hereunder. The OpenSSH Deliverables are
provided to Licensee under the terms of this Agreement and the BSD License (the “BSD License”), and any use of
such OpenSSH Deliverables shall comply with the terms and conditions fo the BSD License and this Agreement. A
copy of the BSD License is set forth as below:
Copyright © Marvell International Ltd. and its affiliates.
All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the
following conditions are met:
1. Redistribution of source code must retain the above copyright notice, this list of conditions and the following
disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software must display the following acknowledgement:
This product includes software developed by the NetBSD Foundation, Inc. and its contributors.
4. Neither the name of Marvell nor the names of its contributors may be used to endorse or promote products derived
from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS “AS IS” AND ANY
EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL
THE COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT,
STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE
USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
ii Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 3

Safety Information
Important Safety Instructions
Read all caution and safety statements in this document before performing any of the
instructions.
Wichtige Sicherheitshinweise
Lesen Sie zunächst sämtliche Warnund Sicherheitshinweise in diesem Dokument, bevor
Sie eine der Anweisungen ausführen.
Consignes de sécurité
Lisez attention toutes les consignes de sécurité et les mises en garde indiquées dans ce
document avant de suivre toute instruction.
Instrucciones de seguridad importantes
Lea todas las declaraciones de seguridad y precaución de este documento antes de realizar
cualquiera de las instrucciones.
重要安全指导
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide iii
在执行任何指令之前,请阅读本文档中的所有注意事项及安全声明。 和/或
http://support.intel.com/support/motherboards/server/sb/CS-010770.htm
Server Boards and Server Chassis Safety Information(《Intel
服务器主板与服务器机箱安全信息》)。
上的 Intel
Page 4

Warnings
Heed safety instructions: Before working with your server product, whether you are
using this guide or any other resource as a reference, pay close attention to the safety
instructions. You must adhere to the assembly instructions in this guide to ensure and
maintain compliance with existing product certifications and approvals. Use only the
described, regulated components specified in this guide. Use of other products /
components will void the UL listing and other regulatory approvals of the product and
will most likely result in noncompliance with product regulations in the region(s) in which
the product is sold.
System power on/off: The power button DOES NOT turn off the system AC power. To
remove power from system, you must unplug the AC power cord from the wall outlet.
Make sure the AC power cord is unplugged before you open the chassis, add, or remove
any components.
Hazardous conditions, devices and cables: Hazardous electrical conditions may be
present on power, telephone, and communication cables. Turn off the server and
disconnect the power cord, telecommunications systems, networks, and modems attached
to the server before opening it. Otherwise, personal injury or equipment damage can
result.
Electrostatic discharge (ESD) and ESD protection: ESD can damage disk drives,
boards, and other parts. We recommend that you perform all procedures in this chapter
only at an ESD workstation. If one is not available, provide some ESD protection by
wearing an antistatic wrist strap attached to chassis ground any unpainted metal surface on
your server when handling parts.
iv Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 5

Preface
About this Manual
Thank you for purchasing and using an Intel® Blade Server Ethernet Switch Module
SBCEGBESW1 or SBCEGBESW10.
This manual is written for System Administrators who have knowledge of device
management through Command Line Interface (CLI) commands.This document provides
the basic rules for understanding how the commands are presented in this guide. The
Guide also provides command by command information of all available CLI commands,
inclusive of the command description, command syntax, any parameters, other relevant
command information, and a basic example. For the latest version of this manual, see
http://support.intel.com.
Manual Organization
Chapter 1 Using CLI
Chapter 2 AAA Commands
Chapter 3 Address Table Commands
Chapter 4 ACL Commands
Chapter 5 Clock Commands
Chapter 6 Configuration and Image File Commands
Chapter 7 Ethernet Configuration Commands
Chapter 8 GVRP Commands
Chapter 9 IGMP Snooping Commands
Chapter 10 IP Address Commands
Chapter 11 LACP Commands
Chapter 12 Line Commands
Chapter 13 Management ACL Commands
Chapter 14 PHY Diagnostics Commands
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide v
Page 6

Chapter 15 Port Channel Commands
Chapter 16 Port Monitor Commands
Chapter 17 QoS Commands
Chapter 18 RMON Commands
Chapter 19 RADIUS Commands
Chapter 20 Web Server Commands
Chapter 21 SNMP Commands
Chapter 22 Spanning-Tree Commands
Chapter 23 SSH Commands
Chapter 24 Syslog Commands
Chapter 25 System Management Commands
Chapter 26 TACACS+ Commands
Chapter 27 User Interface Commands
Chapter 28 VLAN Commands
Chapter 29 802.1x Commands
Appendix A: Getting Help
vi Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 7

Contents
Important Safety Instructions ................................................................................................ iii
Wichtige Sicherheitshinweise ............................................................................................... iii
Consignes de sécurité .......................................................................................................... iii
Instrucciones de seguridad importantes ............................................................................... iii
Warnings ............................................................................................................................... iv
About this Manual .................................................................................................................. v
Manual Organization ..............................................................................................................v
Chapter 1: Using CLI ..................................................................................................1
Overview ................................................................................................................................1
Chapter 2: AAA Commands ...................................................................................... 9
aaa authentication login .........................................................................................................9
aaa authentication enable ....................................................................................................10
login authentication ..............................................................................................................11
enable authentication ...........................................................................................................12
ip http authentication ............................................................................................................13
ip https authentication ..........................................................................................................14
show authentication methods ..............................................................................................15
password .............................................................................................................................16
enable password ..................................................................................................................17
username .............................................................................................................................18
Chapter 3: Address Table Commands ................................................................... 21
bridge address .....................................................................................................................21
bridge multicast filtering .......................................................................................................22
bridge multicast address ......................................................................................................23
bridge multicast forbidden address ......................................................................................24
bridge multicast forward-all ..................................................................................................25
bridge multicast forbidden forward-all ..................................................................................26
bridge aging-time .................................................................................................................27
clear bridge ..........................................................................................................................28
port security .........................................................................................................................28
port security mode ...............................................................................................................29
port security routed secure-address ....................................................................................30
show bridge address-table ...................................................................................................31
show bridge address-table static .........................................................................................32
show bridge address-table count .........................................................................................33
show bridge multicast address-table ...................................................................................34
show bridge multicast filtering ..............................................................................................36
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide vii
Page 8

show ports security .............................................................................................................. 37
show ports security addresses ............................................................................................ 38
Chapter 4: ACL Commands .....................................................................................41
ip access-list ........................................................................................................................ 41
permit (ip) ............................................................................................................................ 42
deny (IP) .............................................................................................................................. 44
mac access-list .................................................................................................................... 46
permit (MAC) ....................................................................................................................... 47
deny (MAC) ......................................................................................................................... 48
service-acl ........................................................................................................................... 50
show access-lists ................................................................................................................ 50
show interfaces access-lists ................................................................................................ 51
Chapter 5: Clock Commands ...................................................................................53
clock set .............................................................................................................................. 53
clock source ........................................................................................................................ 54
clock timezone ..................................................................................................................... 54
clock summer-time ..............................................................................................................55
sntp authentication-key ....................................................................................................... 57
sntp authenticate ................................................................................................................. 58
sntp trusted-key ................................................................................................................... 59
sntp client poll timer ............................................................................................................. 59
sntp broadcast client enable ................................................................................................ 60
sntp anycast client enable ................................................................................................... 61
sntp client enable (Interface) ............................................................................................... 62
sntp unicast client enable .................................................................................................... 63
sntp unicast client poll ......................................................................................................... 63
sntp server ........................................................................................................................... 64
show clock ........................................................................................................................... 65
show sntp configuration ....................................................................................................... 66
show sntp status .................................................................................................................. 67
Chapter 6: Configuration and Image File Commands ...........................................69
copy ..................................................................................................................................... 69
delete ................................................................................................................................... 71
boot system ......................................................................................................................... 72
show running-config ............................................................................................................73
show startup-config ............................................................................................................. 74
show backup-config .............................................................................................................75
show bootvar ....................................................................................................................... 76
Chapter 7: Ethernet Configuration Commands .....................................................79
interface ethernet ................................................................................................................ 79
interface range ethernet ...................................................................................................... 79
viii Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 9

shutdown .............................................................................................................................80
description ...........................................................................................................................81
speed ...................................................................................................................................82
duplex ..................................................................................................................................83
negotiation ...........................................................................................................................84
flowcontrol ............................................................................................................................85
mdix .....................................................................................................................................86
back-pressure ......................................................................................................................87
port jumbo-frame .................................................................................................................87
clear counters ......................................................................................................................88
set interface active ...............................................................................................................89
show interfaces advertise ....................................................................................................90
show interfaces configuration ..............................................................................................91
show interfaces status .........................................................................................................92
show interfaces description .................................................................................................93
show interfaces counters .....................................................................................................94
show ports jumbo-frame ......................................................................................................97
port storm-control include-multicast (GC) ............................................................................98
port storm-control include-multicast (IC) ..............................................................................98
port storm-control broadcast enable ....................................................................................99
port storm-control broadcast rate .......................................................................................100
show ports storm-control ...................................................................................................101
Chapter 8: GVRP Commands ................................................................................ 103
gvrp enable (Global) ..........................................................................................................103
gvrp enable (Interface) .......................................................................................................103
garp timer ...........................................................................................................................104
gvrp vlan-creation-forbid ....................................................................................................105
gvrp registration-forbid .......................................................................................................106
clear gvrp statistics ............................................................................................................107
show gvrp configuration .....................................................................................................108
show gvrp statistics ............................................................................................................109
show gvrp error-statistics ...................................................................................................110
Chapter 9: IGMP Snooping Commands ............................................................... 111
ip igmp snooping (Global) ..................................................................................................111
ip igmp snooping (Interface) ..............................................................................................111
ip igmp snooping mrouter learn-pim-dvmrp .......................................................................112
ip igmp snooping host-time-out ..........................................................................................113
ip igmp snooping mrouter-time-out ....................................................................................114
ip igmp snooping leave-time-out ........................................................................................115
show ip igmp snooping mrouter .........................................................................................116
show ip igmp snooping interface .......................................................................................117
show ip igmp snooping groups ..........................................................................................118
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide ix
Page 10

Chapter 10: IP Address Commands ......................................................................121
ip address .......................................................................................................................... 121
ip address dhcp ................................................................................................................. 122
ip default-gateway .............................................................................................................123
show ip interface ............................................................................................................... 124
arp ................................................................................................................................... 125
arp timeout ........................................................................................................................ 126
clear arp-cache .................................................................................................................. 127
show arp ............................................................................................................................ 127
ip domain-lookup ...............................................................................................................128
ip domain-name .................................................................................................................129
ip name-server .................................................................................................................. 130
ip host ................................................................................................................................ 131
clear host ........................................................................................................................... 131
clear host dhcp .................................................................................................................. 132
show hosts ........................................................................................................................ 133
Chapter 11: LACP Commands ...............................................................................135
lacp system-priority ...........................................................................................................135
lacp port-priority ................................................................................................................. 135
lacp timeout ....................................................................................................................... 136
show lacp ethernet ............................................................................................................ 137
show lacp port-channel ..................................................................................................... 139
Chapter 12: Line Commands .................................................................................141
Line ................................................................................................................................... 141
show line ........................................................................................................................... 141
Chapter 13: Management ACL Commands ..........................................................145
management access-list .................................................................................................... 145
Chapter 14: PHY Diagnostics Commands ............................................................153
test copper-port tdr ............................................................................................................ 153
show copper-ports tdr ........................................................................................................ 154
show copper-ports cable-length ........................................................................................ 155
................................................................................................................................... 155
Chapter 15: Port Channel Commands ..................................................................157
................................................................................................................................... 157
interface port-channel ........................................................................................................ 157
interface range port-channel ............................................................................................. 158
channel-group ................................................................................................................... 158
show interfaces port-channel ............................................................................................ 159
Chapter 16: Port Monitor Commands ...................................................................161
port monitor vlan-tagging ................................................................................................... 162
x Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 11

show ports monitor ............................................................................................................163
Chapter 17: QoS Commands .................................................................................165
qos ....................................................................................................................................165
show qos ............................................................................................................................166
show qos aggregate-policer ...............................................................................................166
show qos interface .............................................................................................................167
show qos map ....................................................................................................................169
class-map ..........................................................................................................................170
show class-map .................................................................................................................171
match .................................................................................................................................172
policy-map .........................................................................................................................173
class ...................................................................................................................................174
show policy-map ................................................................................................................175
trust cos-dscp ....................................................................................................................176
set ....................................................................................................................................177
police .................................................................................................................................178
service-policy .....................................................................................................................179
qos aggregate-policer ........................................................................................................180
show qos aggregate-policer ...............................................................................................181
police aggregate ................................................................................................................182
wrr-queue cos-map ............................................................................................................183
wrr-queue bandwidth .........................................................................................................184
priority-queue out num-of-queues ......................................................................................185
traffic-shape .......................................................................................................................186
show qos interface .............................................................................................................187
qos wrr-queue threshold ....................................................................................................189
qos map policed-dscp ........................................................................................................190
qos map dscp-queue .........................................................................................................191
qos trust (Global) ...............................................................................................................192
qos trust (Interface) ............................................................................................................193
qos cos ..............................................................................................................................194
qos dscp-mutation .............................................................................................................195
qos map dscp-mutation .....................................................................................................196
Chapter 18: RMON Commands ............................................................................. 199
show rmon statistics ..........................................................................................................199
rmon collection history .......................................................................................................201
show rmon collection history ..............................................................................................202
show rmon history ..............................................................................................................203
rmon alarm .........................................................................................................................206
show rmon alarm-table ......................................................................................................208
show rmon alarm ...............................................................................................................209
rmon event .........................................................................................................................210
show rmon events ..............................................................................................................211
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide xi
Page 12

show rmon log ................................................................................................................... 212
rmon table-size .................................................................................................................. 214
Chapter 19: RADIUS Commands ...........................................................................215
radius-server host .............................................................................................................. 215
radius-server key ............................................................................................................... 216
radius-server retransmit .................................................................................................... 217
radius-server source-ip ...................................................................................................... 218
radius-server timeout ......................................................................................................... 219
radius-server deadtime ...................................................................................................... 220
show radius-servers .......................................................................................................... 220
Chapter 20: Web Server Commands .....................................................................223
ip http server ...................................................................................................................... 223
ip http port ......................................................................................................................... 223
ip http exec-timeout ...........................................................................................................224
ip https server .................................................................................................................... 225
ip https port ........................................................................................................................ 226
ip https exec-timeout ......................................................................................................... 226
crypto certificate generate ................................................................................................. 227
crypto certificate request ................................................................................................... 228
crypto certificate import ..................................................................................................... 230
ip https certificate .............................................................................................................. 231
show crypto certificate mycertificate .................................................................................. 232
show ip http ....................................................................................................................... 233
show ip https ..................................................................................................................... 234
Chapter 21: SNMP Commands ..............................................................................237
snmp-server community .................................................................................................... 237
snmp-server view .............................................................................................................. 238
snmp-server group ............................................................................................................ 239
snmp-server user .............................................................................................................. 241
snmp-server engineID local ............................................................................................... 242
snmp-server enable traps .................................................................................................. 244
snmp-server filter ............................................................................................................... 245
snmp-server host ...............................................................................................................246
snmp-server v3-host .......................................................................................................... 247
snmp-server trap authentication ........................................................................................ 248
snmp-server contact .......................................................................................................... 249
snmp-server location ......................................................................................................... 250
snmp-server set ................................................................................................................. 251
show snmp ........................................................................................................................ 252
show snmp engineid .......................................................................................................... 253
show snmp views .............................................................................................................. 254
show snmp groups ............................................................................................................ 255
xii Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 13

show snmp filters ...............................................................................................................256
show snmp users ...............................................................................................................257
Chapter 22: Spanning-Tree Commands ............................................................... 259
spanning-tree .....................................................................................................................259
spanning-tree mode ...........................................................................................................259
spanning-tree forward-time ................................................................................................260
spanning-tree max-age ......................................................................................................262
spanning-tree priority .........................................................................................................263
spanning-tree disable ........................................................................................................264
spanning-tree cost .............................................................................................................264
spanning-tree port-priority ..................................................................................................265
spanning-tree portfast ........................................................................................................266
spanning-tree link-type ......................................................................................................267
spanning-tree pathcost method .........................................................................................268
spanning-tree bpdu ............................................................................................................269
clear spanning-tree detected-protocols .............................................................................270
spanning-tree mst priority ..................................................................................................270
spanning-tree mst max-hops .............................................................................................271
spanning-tree mst port-priority ...........................................................................................272
spanning-tree mst cost ......................................................................................................273
spanning-tree mst configuration ........................................................................................274
instance (mst) ....................................................................................................................275
name (mst) .........................................................................................................................276
revision (mst) .....................................................................................................................276
show (mst) .........................................................................................................................277
exit (mst) ............................................................................................................................278
abort (mst) .........................................................................................................................279
spanning-tree guard root ...................................................................................................279
show spanning-tree ...........................................................................................................280
Chapter 23: SSH Commands .................................................................................295
ip ssh port ..........................................................................................................................295
ip ssh server ......................................................................................................................295
crypto key generate dsa ....................................................................................................296
crypto key generate rsa .....................................................................................................297
ip ssh pubkey-auth .............................................................................................................298
crypto key pubkey-chain ssh .............................................................................................299
user-key .............................................................................................................................300
key-string ...........................................................................................................................301
show ip ssh ........................................................................................................................302
show crypto key mypubkey ................................................................................................303
show crypto key pubkey-chain ssh ....................................................................................304
Chapter 24: Syslog Commands ............................................................................ 307
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide xiii
Page 14

logging on .......................................................................................................................... 307
logging ............................................................................................................................... 308
logging buffered ................................................................................................................. 309
logging buffered size ......................................................................................................... 310
clear logging ...................................................................................................................... 310
logging file ......................................................................................................................... 311
clear logging file ................................................................................................................ 312
aaa logging ........................................................................................................................ 313
file-system logging ............................................................................................................. 313
management logging ......................................................................................................... 314
show logging ..................................................................................................................... 315
show logging file ................................................................................................................ 317
show syslog-servers .......................................................................................................... 318
Chapter 25: System Management Commands .....................................................321
ping ................................................................................................................................... 321
traceroute .......................................................................................................................... 322
telnet .................................................................................................................................. 325
resume .............................................................................................................................. 328
reload ................................................................................................................................ 328
hostname ........................................................................................................................... 329
show users ........................................................................................................................ 330
show sessions ................................................................................................................... 331
show system ...................................................................................................................... 332
show system id .................................................................................................................. 333
show system flowcontrol ................................................................................................... 334
show system mode ............................................................................................................ 335
show version ..................................................................................................................... 335
service cpu-utilization ........................................................................................................336
show cpu utilization ...........................................................................................................337
Chapter 26: TACACS+ Commands .......................................................................339
tacacs-server host .............................................................................................................339
tacacs-server key ..............................................................................................................340
tacacs-server timeout ........................................................................................................ 341
tacacs-server source-ip ..................................................................................................... 342
show tacacs ....................................................................................................................... 342
Chapter 27: User Interface Commands .................................................................345
enable ................................................................................................................................ 345
disable ............................................................................................................................... 345
login ................................................................................................................................... 346
configure ............................................................................................................................ 347
exit (Configuration) ............................................................................................................ 348
exit ................................................................................................................................... 348
xiv Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 15

end ....................................................................................................................................349
help ....................................................................................................................................350
terminal datadump .............................................................................................................350
show history .......................................................................................................................351
show privilege ....................................................................................................................352
do ....................................................................................................................................353
Chapter 28: VLAN Commands .............................................................................. 355
vlan database ....................................................................................................................355
vlan ....................................................................................................................................355
interface vlan .....................................................................................................................356
interface range vlan ...........................................................................................................357
name ..................................................................................................................................358
switchport protected ...........................................................................................................359
switchport mode .................................................................................................................360
switchport access vlan .......................................................................................................360
switchport trunk allowed vlan .............................................................................................361
switchport trunk native vlan ...............................................................................................362
switchport general allowed vlan .........................................................................................363
switchport general pvid ......................................................................................................364
switchport general ingress-filtering disable ........................................................................365
switchport general acceptable-frame-type tagged-only .....................................................366
switchport forbidden vlan ...................................................................................................366
ip internal-usage-vlan ........................................................................................................367
show vlan ...........................................................................................................................368
show vlan internal usage ...................................................................................................369
show interfaces switchport .................................................................................................370
map protocol protocols-group ............................................................................................373
switchport general map protocols-group vlan ....................................................................374
map mac macs-group ........................................................................................................375
switchport general map macs-group vlan ..........................................................................376
map subnet subnets-group ................................................................................................377
switchport general map subnets-group vlan ......................................................................377
show vlan protocols-groups ...............................................................................................378
show vlan macs-groups .....................................................................................................379
show vlan subnets-groups .................................................................................................380
Chapter 29: 802.1x Commands ............................................................................. 383
aaa authentication dot1x ....................................................................................................383
dot1x system-auth-control .................................................................................................384
dot1x port-control ...............................................................................................................384
dot1x re-authentication ......................................................................................................386
dot1x timeout re-authperiod ...............................................................................................386
dot1x re-authenticate .........................................................................................................387
dot1x timeout quiet-period .................................................................................................388
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide xv
Page 16

dot1x timeout tx-period ...................................................................................................... 389
dot1x max-req ................................................................................................................... 390
dot1x timeout supp-timeout ............................................................................................... 391
dot1x timeout server-timeout ............................................................................................. 392
show dot1x ........................................................................................................................ 393
show dot1x users .............................................................................................................. 395
show dot1x statistics ......................................................................................................... 397
ADVANCED FEATURES .................................................................................................. 398
dot1x auth-not-req .............................................................................................................398
dot1x multiple-hosts .......................................................................................................... 399
dot1x single-host-violation ................................................................................................. 400
dot1x guest-vlan ................................................................................................................ 401
dot1x guest-vlan enable .................................................................................................... 402
show dot1x advanced ........................................................................................................ 403
Appendix A: Getting Help ......................................................................................405
World Wide Web ............................................................................................................... 405
Telephone ......................................................................................................................... 405
xvi Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 17

1 Using CLI
Overview
This document describes the Command Line Interface (CLI) used to manage the Intel®
Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10. The
switches can operate as standalone systems, or can be stacked together in the same
system.
Most of the CLI commands are applicable to both switch modules.
This chapter describes how to start using the CLI and the CLI command editing features.
CLI Command Modes
Introduction
The Command Line Interface (CLI) is divided into different command modes. Each
command mode has its own set of specific commands. Entering a question mark ? at the
system prompt (console prompt) displays a list of commands available for that particular
command mode.
From each command mode a specific command is used to navigate from one command
mode to another. The order for mode access is as follows: User EXEC mode, Privileged
EXEC mode, Global Configuration mode, and Interface Configuration mode.
When starting a session, the initial mode is the User EXEC mode. Only a limited subset of
commands are available in User EXEC mode. This task level does not change the
configuration. To enter the next level, the Privileged EXEC mode, a password is required.
The Privileged EXEC mode gives access to commands that displays device configuration
and provides access to the device Configuration mode.
The Global Configuration mode manages the device configuration on a global level.
The Interface Configuration mode configures specific interfaces in the device.
User EXEC Mode
After logging into the device, the user is automatically in User EXEC command mode
unless the user is defined as a privileged user. In general, the User EXEC commands allow
the user to perform basic tests, and list system information.
The user-level prompt consists of the device host name followed by the angle bracket (>).
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 1
Page 18
Using CLI
The default host name is Console unless it has been changed using the hostname
Console>
command in the Global Configuration mode.
Privileged EXEC Mode
Privileged access is password protected to prevent unauthorized use because many of the
Privileged commands set operating system parameters. The password is not displayed on
the screen and is case sensitive.
Privileged users enter directly into the Privileged EXEC mode. To enter the Privileged
EXEC mode from the User EXEC mode, perform the following steps:
At the prompt enter the enable command and press <Enter>. A password prompt is
displayed.
Enter the password and press <Enter>. The password is displayed as *. The Privileged
EXEC mode prompt is displayed. The Privileged EXEC mode prompt consists of the
device host name followed by #.
Console#
To return from the Privileged EXEC mode to the User EXEC mode, use the disable
command. The following example illustrates how to access the Privileged EXEC mode
and return to the User EXEC mode:
Console> enable
Enter Password: ******
Console#
Console# disable
Console>
The exit command is used to return from any mode to the previous mode except when
returning to the User EXEC mode from the Privileged EXEC mode. For example, the exit
command is used to return from the Interface Configuration mode to the Global
Configuration mode.
Global Configuration Mode
Global Configuration mode commands apply to features that affect the system as a whole,
rather than just a specific interface. The configure Privileged EXEC mode command is
used to enter the Global Configuration mode.
To enter the Global Configuration mode perform the following steps:
1. At the Privileged EXEC mode prompt enter the configure command and press
<Enter>. The Global Configuration mode prompt is displayed. The Global
2 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 19

Using CLI
Configuration mode prompt consists of the device host name followed by (config)
and #.
2. To return from the Global Configuration mode to the Privileged EXEC mode, the
user can use one of the following commands:
exit
end
Ctrl+Z
The following example illustrates how to access the Global Configuration mode and
return to the Privileged EXEC mode:
Console#
Console# configure
Console(config)# exit
Console#
Interface Configuration and Specific Configuration Modes
Interface Configuration mode commands modify specific interface operations. The
following are the Interface Configuration modes:
• Line Interface — Contains commands to configure the management connections.
These include commands such as line timeout settings, etc. The line Global
Configuration mode command is used to enter the Line Configuration command
mode.
• VLAN Database — Contains commands to create a VLAN as a whole. The vlan
database Global Configuration mode command is used to enter the VLAN Database
Interface Configuration mode.
• Management Access List — Contains commands to define management access-lists.
The management access-list Global Configuration mode command is used to enter the
Management Access List Configuration mode.
• Ethernet — Contains commands to manage port configuration. The interface ethernet
Global Configuration mode command is used to enter the Interface Configuration
mode to configure an Ethernet type interface.
• Port Channel — Contains commands to configure port-channels, for example,
assigning ports to a port-channel. Most of these commands are the same as the
commands in the Ethernet interface mode, and are used to manage the member ports
as a single entity. The interface port-channel Global Configuration mode command is
used to enter the Port Channel Interface Configuration mode.
• SSH Public Key-chain — Contains commands to manually specify other device SSH
public keys. The crypto key pubkey-chain ssh Global Configuration mode command
is used to enter the SSH Public Key-chain Configuration mode.
• QoS — Contains commands related to service definitions. The qos Global
Configuration mode command is used to enter the QoS services configuration mode.
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 3
Page 20

Using CLI
• MAC Access-List — Configures conditions required to allow traffic based on MAC
addresses. The mac access-list Global Configuration mode command is used to enter
the MAC access-list configuration mode.
Starting the CLI
The device can be managed over a direct connection via a Telnet connection. The device
is managed by entering command keywords and parameters at the prompt. Using the
device command-line interface (CLI) is very similar to entering commands on a UNIX
system.
If access is via a Telnet connection, ensure that the device has a defined IP address,
corresponding management access is granted, and the workstation used to access the
device is connected to the device prior to using CLI commands.
1. Enter the following commands to begin the configuration procedure:
Console> enable
Console# configure
Console(config)#
2. Configure the device and enter the necessary commands to complete the required
tasks.
3. When finished, exit the session with the exit command.
When a different user is required to log onto the system, use the login Privileged EXEC
mode command. This effectively logs off the current user and logs on the new user.
Editing Features
Entering Commands
A CLI command is a series of keywords and arguments. Keywords identify a command,
and arguments specify configuration parameters. For example, in the command show
interfaces status ethernet Ext.1, show, interfaces and status are keywords, ethernet is an
argument that specifies the interface type, and Ext.1 specifies the port.
To enter commands that require parameters, enter the required parameters after the
command keyword. For example, to set a password for the administrator, enter:
Console(config)# username admin password alansmith
When working with the CLI, the command options are not displayed. The command is not
selected from a menu, but is manually entered. To see what commands are available in
each mode or within an Interface Configuration, the CLI does provide a method of
displaying the available commands, the command syntax requirements and in some
instances parameters required to complete the command. The standard command to
request help is ?.
4 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 21

Using CLI
There are two instances where help information can be displayed:
• Keyword lookup — The character ? is entered in place of a command. A list of all
valid commands and corresponding help messages are is displayed.
• Partial keyword lookup — If a command is incomplete and or the character ? is
entered in place of a parameter. The matched keyword or parameters for this
command are displayed.
To assist in using the CLI, there is an assortment of editing features. The following
features are described:
• Terminal Command Buffer
• Command Completion
• Nomenclature
• Keyboard Shortcuts
• Terminal Command Buffer
Every time a command is entered in the CLI, it is recorded on an internally managed
Command History buffer. Commands stored in the buffer are maintained on a First In
First Out (FIFO) basis. These commands can be recalled, reviewed, modified, and
reissued. This buffer is not preserved across device resets.
By default, the history buffer system is enabled, but it can be disabled at any time. For
information about the command syntax to enable or disable the history buffer, see “show
history”.
There is a standard default number of commands that are stored in the buffer. The standard
number of 10 commands can be increased to 216. By configuring 0, the effect is the same
as disabling the history buffer system. For information about the command syntax for
configuring the command history buffer, see history size.
To display the history buffer, see “show history”.
Negating the Effect of Commands
For many configuration commands, the prefix keyword no can be entered to cancel the
effect of a command or reset the configuration to the default value. This guide describes
the negation effect for all applicable commands.
Command Completion
If the command entered is incomplete, invalid or has missing or invalid parameters, then
the appropriate error message is displayed. This assists in entering the correct command.
By pressing the <Tab> button, an incomplete command is entered. If the characters
already entered are not enough for the system to identify a single matching command,
press ? to display the available commands matching the characters already entered.
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 5
Page 22

Using CLI
Nomenclature
When referring to an Ethernet port in a CLI command, the following format is used:
For an Ethernet port on a standalone device: Ethernet_type port_number
For an Ethernet port on a stacked device: unit_number/Ethernet_type port number
The Ethernet type may be Gigabit Ethernet (indicated by “g”).
For example, g3 stands for Gigabit Ethernet port 3 on a stand-alone device, whereas 1/3
stands for Gigabit Ethernet port 3 on stacking unit.
The ports may be described on an individual basis or within a range. Use format port
number-port number to specify a set of consecutive ports and port number, port number to
indicates a set of non-consecutive ports. For example, g1-3 stands for Gigabit Ethernet
ports 1, 2 and 3, and g1,5 stands for Gigabit Ethernet ports 1 and 5.
Keyboard Shortcuts
The CLI has a range of keyboard shortcuts to assist in editing the CLI commands. The
following table describes the CLI shortcuts.
Keyboard KeyDescription
The following list provides a description of keyboard shortcuts:
• Up-arrow key — Recalls commands from the history buffer, beginning with the most
recent command. Repeat the key sequence to recall successively older commands.
• Down-arrow key — Returns the most recent commands from the history buffer after
recalling commands with the up arrow key. Repeating the key sequence will recall
successively more recent commands.
• Ctrl+A — Moves the cursor to the beginning of the command line.
• Ctrl+E — Moves the cursor to the end of the command line.
• Ctrl+Z / End — Returns back to the Privileged EXEC mode from any configuration
mode.
• Backspace key — Deletes one character left to the cursor position.
6 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 23
CLI Command Conventions
When entering commands there are certain command entry standards that apply to all
commands. The following table describes the command conventions.
ConventionDescription
[ ]In a command line, square brackets indicates an optional entry.
{ }In a command line, curly brackets indicate a selection of compulsory parameters
separated by the | character. One option must be selected. For example: flowcontrol
{auto|on|off} means that for the flowcontrol command either auto, on or off must be
selected.
Italic fontIndicates a parameter.
<Enter> Indicates an individual key on the keyboard. For example, <Enter> indicates
the Enter key.
Ctrl+F4Any combination keys pressed simultaneously on the keyboard.
Using CLI
all — When a parameter is required to define a range of ports or parameters and all is
an option, the default for the command is all when no parameters are defined. For
example, the command interface range port-channel has the option of either entering a
range of channels, or selecting all. When the command is entered without a parameter,
it automatically defaults to all.
Copying and Pasting Text
Up to 1000 lines of text (or commands) can be copied and pasted into the device.
It is the user’s responsibility to ensure that the text copied into the device consists of legal
commands only.
This feature is dependent on the baud rate of the device.
When copying and pasting commands from a configuration file, make sure that the
following conditions exist:
A device Configuration mode has been accessed.
The commands contain no encrypted data, like encrypted passwords or keys. Encrypted
data cannot be copied and pasted into the device.
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 7
Page 24

Using CLI
8 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 25

2 AAA Commands
aaa authentication login
The aaa authentication login Global Configuration mode command defines login
authentication. To restore defaults, use the no form of this command.
Syntax
aaa authentication login {default | list-name} method1 [method2...]
no aaa authentication login {default | list-name}
Parameters
• default — Uses the listed authentication methods that follow this argument as the
default list of methods when a user logs in.
• list-name — Character string used to name the list of authentication methods activated
when a user logs in. (Range: 1-12 characters)
• method1 [method2...] — Specify at least one method from the following list:
Keyword Description
enable Uses the enable password for authentication.
line Uses the line password for authentication.
local Uses the local username database for authentication.
none Uses no authentication.
radius Uses the list of all RADIUS servers for authentication.
tacacs Uses the list of all TACACS+ servers for authentication.
Default Configuration
The local user database is checked. This has the same effect as the command aaa
authentication login list-name local.
Command Mode
Global Configuration mode
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 9
Page 26
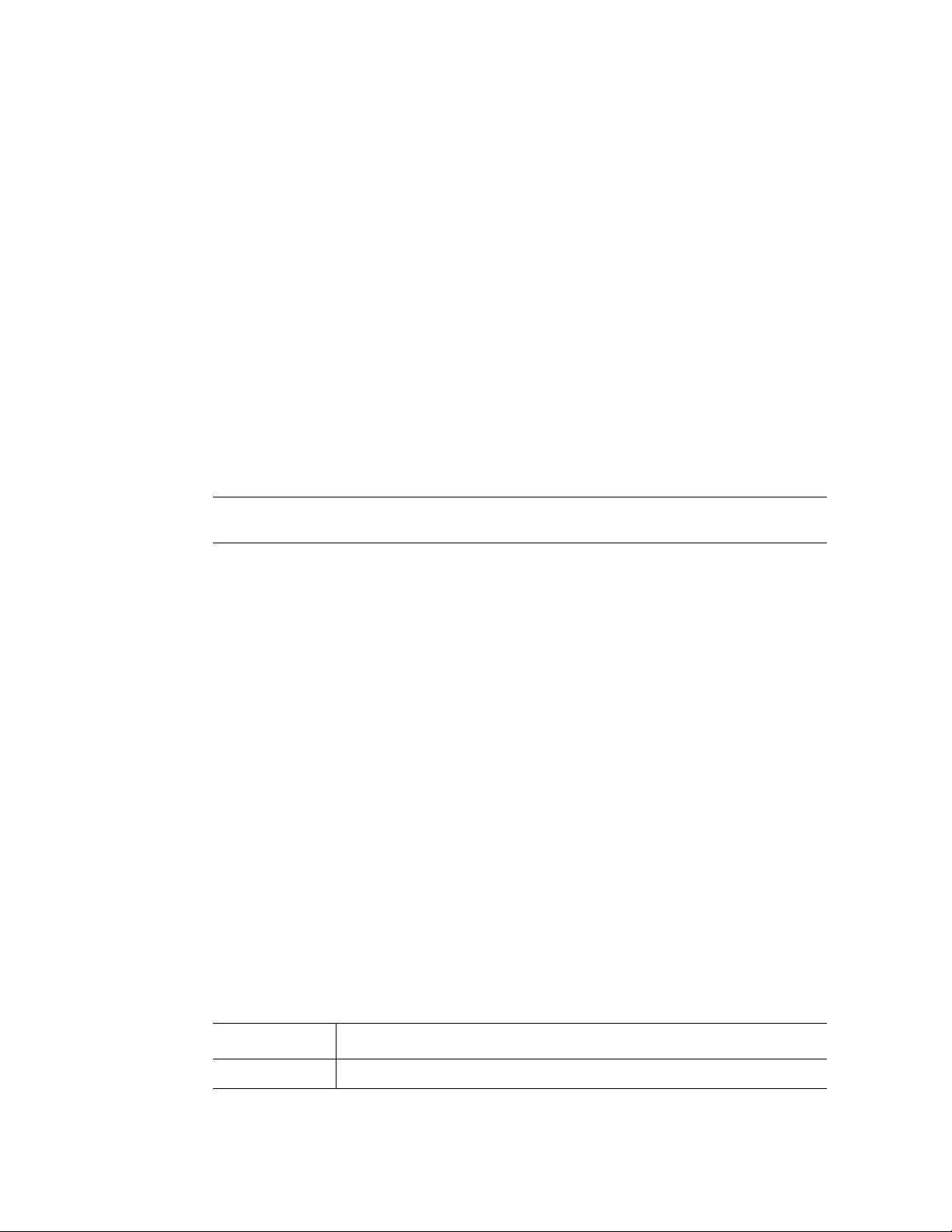
AAA Commands
User Guidelines
The default and optional list names created with the aaa authentication login command
are used with the
login authentication command.
Create a list by entering the
particular protocol, where list-name is any character string used to name this list. The
method argument identifies the list of methods that the authentication algorithm tries, in
the given sequence.
The additional methods of authentication are used only if the previous method returns an
error, not if it fails. To ensure that the authentication succeeds even if all methods return
an error, specify none as the final method in the command line.
aaa authentication login list-name method command for a
Example
The following example configures the authentication login.
Console(config)# aaa authentication login default radius tacacs enable
line local none
aaa authentication enable
The aaa authentication enable Global Configuration mode command defines
authentication method lists for accessing higher privilege levels. To restore defaults, use
the no form of this command.
Syntax
aaa authentication enable {default | list-name} method1 [method2...]
no aaa authentication enable {default | list-name}
Parameters
• default — Uses the listed authentication methods that follow this argument as the
default list of methods, when using higher privilege levels.
• list-name — Character string used to name the list of authentication methods
activated, when using access higher privilege levels. (Range: 1-12 characters)
• method1 [method2...] — Specify at least one method from the following list:
Keyword Description
enable Uses the enable password for authentication.
10 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 27

Keyword Description
line Uses the line password for authentication.
none Uses no authentication.
radius Uses the list of all RADIUS servers for authentication. Uses username
tacacs Uses the list of all TACACS+ servers for authentication. Uses username
Default Configuration
If the default list is not set, only the enable password is checked. This has the same effect
as the command
Command Mode
Global Configuration mode
AAA Commands
$enabx$., where x is the privilege level.
"$enabx$." where x is the privilege level.
aaa authentication enable default enable.
User Guidelines
The default and optional list names created with the aaa authentication enable command
are used with the
The additional methods of authentication are used only if the previous method returns an
error, not if it fails. To ensure that the authentication succeeds even if all methods return
an error, specify none as the final method in the command line.
aaa authentication enable default requests sent by the device to a RADIUS or
All
TACACS+ server include the username $enabx$., where x is the requested privilege level.
enable authentication command.
Example
The following example sets the enable password for authentication when accessing higher
privilege levels.
Console(config)# aaa authentication enable default enable
login authentication
The login authentication Line Configuration mode command specifies the login
authentication method list for a remote telnet or console. To restore the default
configuration specified by the
command.
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 11
aaa authentication login command, use the no form of this
Page 28

AAA Commands
Syntax
login authentication {default | list-name}
no login authentication
Parameters
• default — Uses the default list created with the aaa authentication login command.
• list-name — Uses the indicated list created with the aaa authentication login
command.
Default Configuration
Uses the default set with the command aaa authentication login.
Command Mode
Line Configuration mode
User Guidelines
To change (or rename) an authentication method, use the negate command and create a
new rule with the new method name.
Example
The following example specifies the default authentication method for a console.
Console(config)# line console
Console(config-line)# login authentication default
enable authentication
The enable authentication Line Configuration mode command specifies the
authentication method list when accessing a higher privilege level from a remote Telnet or
console. To restore the default configuration specified by the
command, use the no form of this command.
Syntax
aaa authentication enable
enable authentication {default | list-name}
no enable authentication
12 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 29

Parameters
• default — Uses the default list created with the aaa authentication enable command.
• list-name — Uses the indicated list created with the aaa authentication enable
command.
Default Configuration
Uses the default set with the aaa authentication enable command.
Command Mode
Line Configuration mode
User Guidelines
There are no user guidelines for this command.
AAA Commands
Example
The following example specifies the default authentication method when accessing a
higher privilege level from a Telnet.
Console(config)# line console
Console(config-line)# enable authentication default
ip http authentication
The ip http authentication Global Configuration mode command specifies
authentication methods for HTTP server users. To restore the default configuration, use
the no form of this command.
Syntax
ip http authentication method1 [method2...]
no ip http authentication
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 13
Page 30
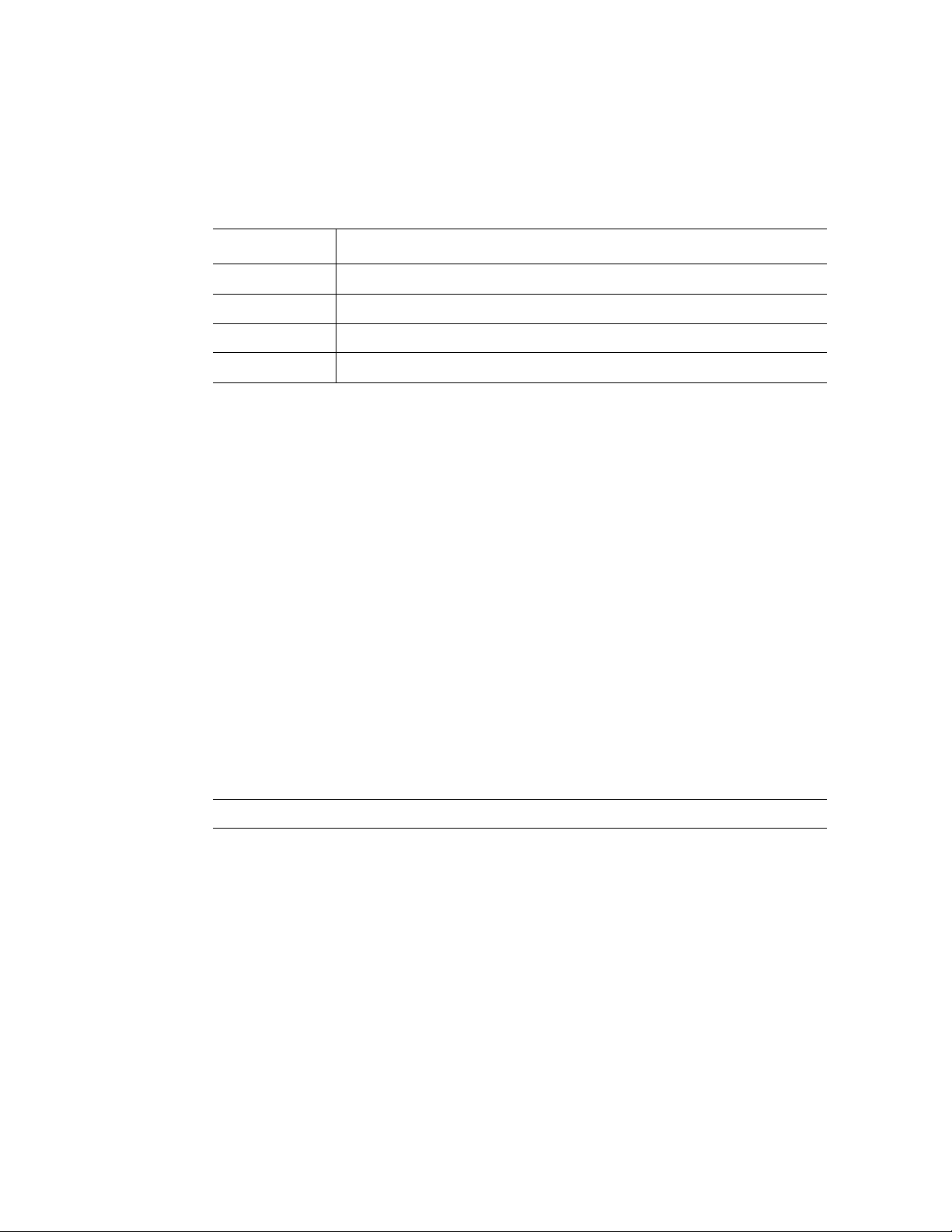
AAA Commands
Parameters
• method1 [method2...] — Specify at least one method from the following list:
Keyword Description
local Uses the local username database for authentication.
none Uses no authentication.
radius Uses the list of all RADIUS servers for authentication.
tacacs Uses the list of all TACACS+ servers for authentication.
Default Configuration
The local user database is checked. This has the same effect as the command ip http
authentication
Command Mode
local.
Global Configuration mode
User Guidelines
The additional methods of authentication are used only if the previous method returns an
error, not if it fails. To ensure that the authentication succeeds even if all methods return
an error, specify
none as the final method in the command line.
Example
The following example configures the HTTP authentication.
Console(config)# ip http authentication radius tacacs local none
ip https authentication
The ip https authentication Global Configuration mode command specifies
authentication methods for HTTPS server users. To restore the default configuration, use
the no form of this command.
Syntax
ip https authentication method1 [method2...]
no ip https authentication
14 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 31

Parameters
• method1 [method2...] — Specify at least one method from the following list:
Keyword Description
local Uses the local username database for authentication.
none Uses no authentication.
radius Uses the list of all RADIUS servers for authentication.
tacacs Uses the list of all TACACS+ servers for authentication.
Default Configuration
The local user database is checked. This has the same effect as the command ip https
authentication
Command Mode
AAA Commands
local.
Global Configuration mode
User Guidelines
The additional methods of authentication are used only if the previous method returns an
error, not if it fails. To ensure that the authentication succeeds even if all methods return
an error, specify none as the final method in the command line.
Example
The following example configures HTTPS authentication.
Console(config)# ip https authentication radius tacacs local none
show authentication methods
The show authentication methods Privileged EXEC mode command displays
information about the authentication methods.
Syntax
show authentication methods
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 15
Page 32

AAA Commands
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Example
The following example displays the authentication configuration.
Console# show authentication methods
login Authentication Method Lists
---------------------------------
Default: Local
Enable Authentication Method Lists
----------------------------------
Default: Radius, Enable
Console_Enable: Enable, None
Line Login Method List Enable Method List
-----------------------------------------
Console Default Default
Telnet Default Default
SSH DefaultDefault
http: Local
https: Local
dot1x:
password
The password Line Configuration mode command specifies a password on a line. To
remove the password, use the no form of this command.
Syntax
password password [encrypted]
no password
16 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 33

Parameters
• password — Password for this level. (Range: 1-159 characters)
• encrypted — Encrypted password to be entered, copied from another device
configuration.
Default Configuration
No password is defined.
Command Mode
Line Configuration mode
User Guidelines
If a password is defined as encrypted, the required password length is 32 characters.
AAA Commands
Example
The following example specifies the password called `secret' on a Telnet.
Console(config)# line console
Console(config-line)# password secret
enable password
The enable password Global Configuration mode command sets a local password to
control access to user and privilege levels. To remove the password requirement, use the
no form of this command.
Syntax
enable password [level level] password [encrypted]
no enable password [level level]
Parameters
• password — Password for this level. (Range: 1-159 characters)
• level — Level for which the password applies. If not specified the level is 15 (Range:
1-15).
• encrypted — Encrypted password entered, copied from another device configuration.
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 17
Page 34

AAA Commands
Default Configuration
No enable password is defined.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
The following example sets a local level 15 password called `secret' to control access to
user and privilege levels.
Console(config)# enable password secret level 15
username
The username Global Configuration mode command creates a user account in the local
database. To remove a user name, use the no form of this command.
Syntax
username name [password password] [level level] [encrypted]
no username name
Parameters
• name — The name of the user. (Range: 1-20 characters)
• password — The authentication password for the user. (Range: 1-159 characters)
• level — The user level (Range: 1-15). If a level is not specified, the level is
automaically set to 1.
• encrypted — Encrypted password entered, copied from another device configuration.
Default Configuration
No user is defined.
18 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 35

Command Mode
Global Configuration mode
User Guidelines
User account can be created without a password.
Example
The following example configures user called bob with password `lee' and user level 15 to
the system.
Console(config)# username bob password lee level 15
AAA Commands
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 19
Page 36

AAA Commands
20 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 37

3 Address Table Commands
bridge address
The bridge address Interface Configuration (VLAN) mode command adds a MAC-layer
station source address to the bridge table. To delete the MAC address, use the no form of
this command.
Syntax
bridge address mac-address {ethernet interface | port-channel port-channel-number}
[permanent | delete-on-reset | delete-on-timeout | secure]
no bridge address [mac-address]
Parameters
• mac-address — A valid MAC address.
• interface — A valid Ethernet port.
• port-channel-number — A valid port-channel number.
• permanent — The address can only be deleted by the no bridge address command.
• delete-on-reset — The address is deleted after reset.
• delete-on-timeout — The address is deleted after "age out" time has expired.
• secure — The address is deleted after the port changes mode to unlock learning (no
port security command). This parameter is only available when the port is in the
learning locked mode.
Default Configuration
No static addresses are defined. The default mode for an added address is permanent.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
Using the no form of the command without specifying a MAC address deletes all static
MAC addresses belonging to this VLAN).
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 21
Page 38

Address Table Commands
Example
The following example adds a permanent static MAC-layer station source address
3aa2.64b3.a245 on port 1 to the bridge table.
Console(config)#
Console(config-if)#
interface vlan
bridge address
bridge multicast filtering
The bridge multicast filtering Global Configuration mode command enables filtering
multicast addresses. To disable filtering multicast addresses, use the no form of this
command.
Syntax
• bridge multicast filtering
• no bridge multicast filtering
Default Configuration
Filtering multicast addresses is disabled. All multicast addresses are flooded to all ports.
Command Mode
2
3aa2.64b3.a245
ethernet
ext.1
permanent
Global Configuration mode
User Guidelines
If multicast devices exist on the VLAN, do not change the unregistered multicast
addresses state to drop on the switch ports.
If multicast devices exist on the VLAN and IGMP-snooping is not enabled, the bridge
multicast forward-all command should be used to enable forwarding all multicast packets
to the multicast switches.
Example
In the folowing example, bridge multicast filtering is enabled.
Console(config)#
22 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
bridge multicast filtering
Page 39

bridge multicast address
The bridge multicast address Interface Configuration (VLAN) mode command registers a
MAC-layer multicast address in the bridge table and statically adds ports to the group. To
unregister the MAC address, use the no form of this command.
Syntax
bridge multicast address {mac-multicast-address | ip-multicast-address}
bridge multicast address {mac-multicast-address | ip-multicast-address} [add | remove]
{ethernet interface-list | port-channel port-channel-number-list}
no bridge multicast address {mac-multicast-address | ip-multicast-address}
Parameters
• add — Adds ports to the group. If no option is specified, this is the default option.
Address Table Commands
• remove — Removes ports from the group.
• mac-multicast-address — A valid MAC multicast address.
• ip- multicast-address — A valid IP multicast address.
• interface-list — Separate nonconsecutive Ethernet ports with a comma and no spaces;
a hyphen is used to designate a range of ports.
• port-channel-number-list — Separate nonconsecutive port-channels with a comma
and no spaces; a hyphen is used to designate a range of ports.
Default Configuration
No multicast addresses are defined.
Command Mode
Interface Configuration (VLAN) mode
User Guidelines
If the command is executed without add or remove, the command only registers the group
in the bridge database.
Static multicast addresses can only be defined on static VLANs.
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 23
Page 40

Address Table Commands
Example
The following example registers the MAC address:
Console(config)#
Console(config-if)#
interface vlan
bridge multicast address
8
01:00:5e:02:02:03
The following example registers the MAC address and adds ports statically.
Console(config)#
Console(config-if)#
ext.1, ext.2
interface vlan
bridge multicast address
8
01:00:5e:02:02:03
bridge multicast forbidden address
The bridge multicast forbidden address Interface Configuration (VLAN) mode command
forbids adding a specific multicast address to specific ports. Use the no form of this
command to restore the default configuration.
Syntax
bridge multicast forbidden address {mac-multicast-address | ip-multicast-address} {add |
remove} {ethernet interface-list | port-channel port-channel-number-list}
no bridge multicast forbidden address {mac-multicast-address | ip-multicast-address}
add ethernet
Parameters
• add — Adds ports to the group.
• remove — Removes ports from the group.
• mac-multicast-address — A valid MAC multicast address.
• ip- multicast-address — A valid IP multicast address.
• interface-list — Separate nonconsecutive Ethernet ports with a comma and no spaces;
hyphen is used to designate a range of ports.
• port-channel-number-list — Separate nonconsecutive valid port-channels with a
comma and no spaces; a hyphen is used to designate a range of port-channels.
Default Configuration
No forbidden addresses are defined.
24 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 41

Command Modes
Interface Configuration (VLAN) mode
User Guidelines
Before defining forbidden ports, the multicast group should be registered.
Example
In this example, MAC address 0100.5e02.0203 is forbidden on port 2 within VLAN 8.
Address Table Commands
Console(config)#
Console(config-if)#
Console(config-if)#
ext.2
interface vlan
bridge multicast address
bridge multicast forbidden address
8
0100.5e.02.0203
bridge multicast forward-all
The bridge multicast forward-all Interface Configuration (VLAN) mode command
enables forwarding all multicast packets on a port. To restore the default configuration,
use the no form of this command.
Syntax
bridge multicast forward-all {add | remove} {ethernet interface-list | port-channel portchannel-number-list}
no bridge multicast forward-all
Parameters
• add — Force forwarding all multicast packets.
0100.5e02.0203
add ethernet
• remove — Do not force forwarding all multicast packets.
• interface-list — Separate nonconsecutive Ethernet ports with a comma and no spaces;
a hyphen is used to designate a range of ports.
• port-channel-number-list — Separates nonconsecutive port-channels with a comma
and no spaces; a hyphen is used to designate a range of port-channels.
Default Configuration
This setting is disabled.
Command Mode
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 25
Page 42
Address Table Commands
Interface Configuration (VLAN) mode
User Guidelines
There are no user guidelines for this command.
Example
In this example, all multicast packets on port 1 are forwarded.
Console(config)#
Console(config-if)#
ethernet ext.1
interface vlan 2
bridge multicast forward-all add
bridge multicast forbidden forward-all
The bridge multicast forbidden forward-all Interface Configuration (VLAN) mode
command forbids a port to be a forward-all-multicast port. To restore the default
configuration, use the no form of this command.
Syntax
bridge multicast forbidden forward-all {add | remove} {ethernet interface-list | portchannel port-channel-number-list}
no bridge multicast forbidden forward-all
Parameters
• add — Forbids forwarding all multicast packets.
• remove — Does not forbid forwarding all multicast packets.
• interface-list — Separates nonconsecutive Ethernet ports with a comma and no
spaces; a hyphen is used to designate a range of ports.
• port-channel-number-list — Separates nonconsecutive port-channels with a comma
and no spaces; a hyphen is used to designate a range of port-channels.
Default Configuration
This setting is disabled.
Command Mode
Interface Configuration (VLAN) mode
26 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 43

User Guidelines
IGMP snooping dynamically discovers multicast device ports. When a multicast device
port is discovered, all the multicast packets are forwarded to it unconditionally.
This command prevents a port from becoming a multicast device port.
Example
In this example, forwarding all multicast packets to 1 with VLAN 2 is forbidden.
Address Table Commands
Console(config)#
Console(config-if)#
interface vlan
bridge multicast forbidden forward-all add ethernet ext.1
bridge aging-time
The bridge aging-time Global Configuration mode command sets the address table aging
time. To restore the default configuration, use the no form of this command.
Syntax
bridge aging-time seconds
no bridge aging-time
Parameters
• seconds — Time in seconds. (Range: 10-630 seconds)
Default Configuration
2
The default setting is 300 seconds.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 27
Page 44

Address Table Commands
Example
In the following example, the bridge aging time is set to 250 seconds.
Console(config)#
clear bridge
The clear bridge Privileged EXEC mode command removes any learned entries from the
forwarding database.
Syntax
clear bridge
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
bridge aging-time
250
User Guidelines
There are no user guidelines for this command.
Example
In the following example, the bridge tables are cleared.
Console#
port security
The port security Interface Configuration mode command locks the port to block
unknown traffic and prevent the port from learning new addresses. To restore the default
configuration, use the no form of this command.
Syntax
port security [forward | discard | discard-shutdown] [trap seconds] [max]
clear bridge
28 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 45

no port security
Parameters
• forward — Forwards packets with unlearned source addresses, but does not learn the
address.
• discard — Discards packets with unlearned source addresses. This is the default if no
option is indicated.
• discard-shutdown — Discards packets with unlearned source addresses. The port is
also shut down.
• seconds — Sends SNMP traps and defines the minimum amount of time in seconds
between consecutive traps. (Range: 1-1000000)Default Configuration
This setting is disabled.
Command Mode
Interface Configuration (Ethernet, port-channel) mode
Address Table Commands
User Guidelines
There are no user guidelines for this command.
Example
In this example, port 1 forwards all packets without learning addresses of packets from
unknown sources and sends traps every 100 seconds if a packet with an unknown source
address is received.
Console(config)#
Console(config-if)#
interface ethernet
port security forward trap
port security mode
The port security mode Interface Configuration mode command configures the port
security mode. To restore the default configuration, use the no form of this command.
Syntax
port security mode {lock | mac-addresses}
ext.1
100
no port security mode
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 29
Page 46

Address Table Commands
Parameters
• lock — Saves the current dynamic MAC addresses associated with the port and
disables learning, relearning and aging.
• mac-addresses — Deletes the current dynamic MAC addresses associated with the
port and learns up to the maximum number addresses allowed on the port. Relearning
and aging are enabled.
Default Configuration
This setting is disabled.
Command Mode
Interface Configuration (Ethernet, port-channel) mode
User Guidelines
There are no user guidelines for this command.
Example
In this example, port security mode is set to dynamic for Ethernet interface 1.
Console(config)#
Console(config-if)#
interface ethernet
port security mode mac-addresses
ext.1
port security routed secure-address
The port security routed secure-address Interface Configuration (Ethernet, port-channel)
mode command adds a MAC-layer secure address to a routed port. Use the no form of this
command to delete a MAC address.
Syntax
port security routed secure-address mac-address
no port security routed secure-address mac-address
Parameters
mac-address — A valid MAC address.
30 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 47

Default Configuration
No addresses are defined.
Command Mode
Interface Configuration (Ethernet, port-channel) mode. Cannot be configured for a range
of interfaces (range context).
User Guidelines
The command enables adding secure MAC addresses to a routed port in port security
mode. The command is available when the port is a routed port and in port security mode.
The address is deleted if the port exits the security mode or is not a routed port.
Example
In this example, the MAC-layer address 66:66:66:66:66:66 is added to port 1.
Address Table Commands
Console(config)#
Console(config-if)#
interface ethernet
port security routed secure-address
show bridge address-table
The show bridge address-table Privileged EXEC mode command displays all entries in
the bridge-forwarding database.
Syntax
show bridge address-table [vlan vlan] [ethernet interface | port-channel port-channelnumber | address mac address]
Parameters
• vlan — Specifies a valid VLAN, such as VLAN 1.
• interface — A valid Ethernet port.
• port-channel-number — A valid port-channel number.
• mac address — A valid MAC address.
ext.1
66:66:66:66:66:66
Default Configuration
This command has no default configuration.
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 31
Page 48

Address Table Commands
Command Mode
Privileged EXEC mode
User Guidelines
Internal usage VLANs (VLANs that are automatically allocated on ports with a defined
Layer 3 interface) are presented in the VLAN column by a port number and not by a
VLAN ID.
"Special" MAC addresses that were not statically defined or dynamically learned are
displayed in the MAC address table. This includes, for example, MAC addresses defined
in ACLS.
Example
In this example, all classes of entries in the bridge-forwarding database are displayed.
Console#
Aging time is 300 sec
interface mac address Port Type
--------- -------------- ---- -------
1 00:60:70:4C:73:FF 5 dynamic
1 00:60:70:8C:73:FF 5 dynamic
200 00:10:0D:48:37:FF 5 static
show bridge address-table
show bridge address-table static
The show bridge address-table static Privileged EXEC mode command displays statically
created entries in the bridge-forwarding database.
Syntax
show bridge address-table static [vlan vlan] [ethernet interface | port-channel portchannel-number]
Parameters
• vlan — Specifies a valid VLAN, such as VLAN 1.
• interface — A valid Ethernet port.
32 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 49

• port-channel-number — A valid port-channel number.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Example
In this example, all static entries in the bridge-forwarding database are displayed.
Address Table Commands
Console#
Aging time is 300 sec
vlan mac address port type
---- ----------------- ---- -----------------
1 00:60:70:4C:73:FF 8 Permanent
1 00:60.70.8C.73:FF 8 delete-on-timeout
200 00:10:0D:48:37:FF 9 delete-on-reset
show bridge address-table static
show bridge address-table count
The show bridge address-table count Privileged EXEC mode command displays the
number of addresses present in the Forwarding Database.
Syntax
show bridge address-table count [vlan vlan] [ethernet interface-number | port-channel
port-channel-number]
Parameters
• vlan — Specifies a valid VLAN, such as VLAN 1.
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 33
Page 50

Address Table Commands
• interface — A valid Ethernet port.
• port-channel-number — A valid port-channel number.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Example
In this example, the number of addresses present in all VLANs are displayed.
Console#
Capacity: 8192
Free: 8083
Used: 109
Secure addresses: 2
Static addresses: 1
Dynamic addresses: 97
Internal addresses: 9
show bridge address-table count
show bridge multicast address-table
The show bridge multicast address-table Privileged EXEC mode command displays
multicast MAC address or IP address table information.
Syntax
show bridge multicast address-table [vlan vlan-id] [address mac-multicast-address | ipmulticast-address] [format ip | format mac]
34 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 51

Parameters
• vlan-id — Indicates the VLAN ID. This has to be a valid VLAN ID value.
• mac-multicast-address — A valid MAC multicast address.
• ip-multicast-address — A valid IP multicast address.
• format ip / mac — Multicast address format. Can be ip or mac. If the format is
unspecified, the default is mac.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
Address Table Commands
A MAC address can be displayed in IP format only if it is in the range of 0100.5e00.0000-
0100.5e7f.ffff.
Example
In this example, multicast MAC address and IP address table information is displayed.
Console#
Vlan MAC Address Type Ports
---- -------------- ------- ----------
1 01:00:5e:02:02:03 static 1, 2
19 01:00:5e:02:02:08 static 1-8
19 00:00:5e:02:02:08 dynamic 9-11
Forbidden ports for multicast addresses:
Vlan MAC Address Ports
---- -------------- -----
1 01:00:5e:02:02:03 8
19 01:00:5e:02:02:08 8
show bridge multicast address-table
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 35
Page 52

Address Table Commands
Console#
Vlan IP/MAC Address Type Ports
---- ----------------- ------ ---------
1 224-239.130|2.2.3 static 1, 2
19 224-239.130|2.2.8 static 1-8
19 224-239.130|2.2.8 dynamic 9-11
Forbidden ports for multicast addresses:
Vlan IP/MAC Address Ports
---- ----------------- ------
1 224-239.130|2.2.3 8
19 224-239.130|2.2.8 8
show bridge multicast address-table format ip
A multicast MAC address maps to multiple IP addresses as shown above.
show bridge multicast filtering
The show bridge multicast filtering Privileged EXEC mode command displays the
multicast filtering configuration.
Syntax
show bridge multicast filtering vlan-id
Parameters
• vlan-id — Indicates the VLAN ID. This has to be a valid VLAN ID value.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
36 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 53

Example
Address Table Commands
In this example, the multicast configuration for VLAN 1 is displayed.
Console#
Filtering: Enabled
VLAN: 1
Port Static Status
---- --------- ---------
1 Filter
2 Filter
3 - Filter
show bridge multicast filtering
show ports security
The show ports security Privileged EXEC mode command displays the port-lock status.
Syntax
1
show ports security [ethernet interface | port-channel port-channel-number]
Parameters
• interface — A valid Ethernet port.
• port-channel-number — A valid port-channel number.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 37
Page 54

Address Table Commands
Example
In this example, all classes of entries in the port-lock status are displayed:
Console#
Port Status Learning Action Maximum Trap Frequency
---- ------- -------- ------- ------- ------- ---------
1 Locked Dynamic Discard 3 Enable 100
2 Unlocked Dynamic - 28 - -
3 Locked Disabled Discard,
show ports security
8 Disable -
Shutdown
The following table describes the fields shown above.
Field Description
Port The port number.
Status The values are: Locked/Unlocked.
Learning The learning mode.
Action Action on violation.
Maximum The maximum number of addresses that can be associated on this port in
Trap Sends traps in case of a violation.
Frequency The minimum time interval between consecutive traps.
theStatic Learning mode or in the Dynamic Learning mode.
show ports security addresses
The show ports security addresses Privileged EXEC mode command displays the current
dynamic addresses in locked ports.
Syntax
show ports security addresses [ethernet interface | port-channel port-channel-number]
Parameters
• interface — A valid Ethernet port.
• port-channel-number — A valid port-channel number
Default Configuration
This command has no default configuration.
38 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 55

Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Example
This example displays dynamic addresses in all currently locked ports.
Address Table Commands
Console#
Port Status Learning Current Maximum
---- -------- -------- ------- -------
1 Disabled Lock - 1
2 Disabled Lock - 1
3 Enabled Max-addresses 0 1
4 Port is a member in port-channel ch1
5 Disabled Lock - 1
6 Enabled Max-addresses 0 10
ch1 Enabled Max-addresses 0 50
ch2 Enabled Max-addresses 0 128
show ports security addresses
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 39
Page 56

Address Table Commands
40 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 57

4 ACL Commands
ip access-list
The ip access-list Global Configuration mode command enables the IP-Access
Configuration mode and creates Layer 3 ACLs. To delete an ACL, use the
command.
Syntax
ip access-list name
no form of this
no ip access-list
Parameters
• name — Specifies the name of the ACL. (Range: 0-32 characters)
Default Configuration
The default for all ACLs is deny-all.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
The following example shows how to create an IP ACL.
name
Console(config)#
Console(config-ip-al)#
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 41
ip access-list
ip-acl1
Page 58

ACL Commands
permit (ip)
The permit IP-Access List Configuration mode command permits traffic if the conditions
defined in the permit statement match.
Syntax
permit {any | protocol} {any | {source source-wildcard}} {any | {destination
destination-wildcard
permit-icmp {any | {source source-wildcard}} {any | {destination destination-
wildcard
permit-igmp {any | {source source-wildcard}} {any | {destination destination-
wildcard
permit-tcp {any | {source source-wildcard}} {any | source-port} {any |{destination
destination-wildcard
number] [flags list-of-flags]
}} [dscp dscp number | ip-precedence ip-precedence]
}} {any | icmp-type} {any | icmp-code} [dscp number | ip-precedence number]
}} {any | igmp-type} [dscp number | ip-precedence number]
}} {any | destination-port} [dscp number | ip-precedence
permit-udp {any | {source source-wildcard}} {any | source-port} {any | {destination
destination-wildcard
}} {any | destination-port} [dscp number | ip-precedence number]
Parameters
• source — Specifies the source IP address of the packet. Specify any to indicate IP
address 0.0.0.0 and mask 255.255.255.255.
• source-wildcard — Specifies wildcard to be applied to the source IP address. Use 1s
in bit positions to be ignored. Specify
255.255.255.255.
• destination — Specifies the destination IP address of the packet. Specify any to
indicate IP address 0.0.0.0 and mask 255.255.255.255.
• destination-wildcard — Specifies wildcard to be applied to the destination IP address.
Use 1s in bit positions to be ignored. Specify
mask 255.255.255.255.
• protocol — Specifies the abbreviated name or number of an IP protocol. (Range: 0-
255)
The following table lists the protocols that can be specified:
IP Protocol Abbreviated Name Protocol Number
Internet Control Message Protocol icmp 1
Internet Group Management Protocol igmp 2
IP in IP (encapsulation) Protocol ipinip 4
Transmission Control Protocol tcp 6
Exterior Gateway Protocol egp 8
any to indicate IP address 0.0.0.0 and mask
any to indicate IP address 0.0.0.0 and
42 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 59

IP Protocol Abbreviated Name Protocol Number
Interior Gateway Protocol igp 9
User Datagram Protocol udp 17
Host Monitoring Protocol hmp 20
Reliable Data Protocol rdp 27
Inter-Domain Policy Routing Protocol idpr 35
Ipv6 protocol ipv6 41
Routing Header for IPv6 ipv6-route 43
Fragment Header for IPv6 ipv6-frag 44
Inter-Domain Routing Protocol idrp 45
Reservation Protocol rsvp 46
General Routing Encapsulation gre 47
Encapsulating Security Payload (50) esp 50
Authentication Header ah 51
ICMP for IPv6 ipv6-icmp 58
EIGRP routing protocol eigrp 88
Open Shortest Path Protocol ospf 89
Protocol Independent Multicast pim 103
Layer Two Tunneling Protocol l2tp 115
ISIS over IPv4 isis 124
(any IP protocol) any (25504)
ACL Commands
• dscp — Indicates matching the dscp number with the packet dscp value.
• ip-precedence — Indicates matching ip-precedence with the packet ip-precedence
value.
• icmp-type — Specifies an ICMP message type for filtering ICMP packets. Enter a
value or one of the following values:
quench, redirect, alternate-host-address, echo-request, router-advertisement,
router-solicitation, time-exceeded, parameter-problem, timestamp, timestampreply, information-request, information-reply, address-mask-request, addressmask-reply, traceroute, datagram-conversion-error, mobile-host-redirect, ipv6where-are-you, ipv6-i-am-here, mobile-registration-request, mobile-registrationreply, domain-name-request, domain-name-reply, skip
255)
echo-reply, destination-unreachable, source-
and photuris. (Range: 0-
• icmp-code — Specifies an ICMP message code for filtering ICMP packets. ICMP
packets that are filtered by ICMP message type can also be filtered by the ICMP
message code. (Range: 0-255)
• igmp-type — IGMP packets can be filtered by IGMP message type. Enter a number or
one of the following values:
0-255)
dvmrp, host-query, host-report, pim or trace. (Range:
• destination-port — Specifies the UDP/TCP destination port. (Range: 0-65535)
• source-port — Specifies the UDP/TCP source port. (Range: 0-65535)
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 43
Page 60

ACL Commands
• list-of-flags — Specifies a list of TCP flags that can be triggered. If a flag is set, it is
prefixed by “+”.
If a flag is not set, it is prefixed by “-”. The possible values are:
+rst, +syn, +fin, -urg, -ack, -psh, -rst, -syn
one string. For example:
Default Configuration
No IPv4 ACL is defined.
Command Mode
IP-Access List Configuration mode
User Guidelines
Use the ip access-list Global Configuration mode command to enable the IP-Access List
Configuration mode.
+urg, +ack, +psh,
and -fin. The flags are concatenated into
+fin-ack.
Before an Access Control Element (ACE) is added to an ACL, all packets are permitted.
After an ACE is added, an implied
and those packets that do not match the conditions defined in the permit statement are
denied.
Example
The following example shows how to define a permit statement for an IP ACL.
Console(config)#
Console(config-ip-al)#
deny (IP)
The deny IP-Access List Configuration mode command denies traffic if the conditions
defined in the deny statement match.
Syntax
deny [disable-port] {any | protocol} {any | {source source-wildcard}} {any |
{
destination destination-wildcard}} [dscp dscp number | ip-precedence ip-precedence]
[
in-port port-num | out-port port-num]
deny-any-any condition exists at the end of the list
ip access-list
permit
rsvp 192.1.1.1 0.0.0.0
ip-acl1
any dscp
56
deny-icmp
deny-igmp
44 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 61

Parameters
ACL Commands
deny-tcp
deny-udp
• disable-port — Specifies that the port is disabled.
• source — Specifies the IP address or host name from which the packet was sent.
Specify
any to indicate IP address 0.0.0.0 and mask 255.255.255.255.
• source-wildcard — (Optional for the first type) Specifies wildcard bits by placing 1s
in bit positions to be ignored. Specify
255.255.255.255.
any to indicate IP address 0.0.0.0 and mask
• destination — Specifies the IP address or host name to which the packet is being sent.
Specify
any to indicate IP address 0.0.0.0 and mask 255.255.255.255.
• destination-wildcard — (Optional for the first type) Specifies wildcard bits by placing
1s in bit positions to be ignored. Specify
255.255.255.255.
any to indicate IP address 0.0.0.0 and mask
• protocol — Specifies the abbreviated name or number of an IP protocol. The
following table lists protocols that can be specified:
IP Protocol Abbreviated Name Protocol Number
Internet Control Message Protocol icmp 1
Internet Group Management Protocol igmp 2
IP in IP (encapsulation) Protocol ip 4
Transmission Control Protocol tcp 6
Exterior Gateway Protocol egp 8
Interior Gateway Protocol igp 9
User Datagram Protocol udp 17
Host Monitoring Protocol hmp 20
Reliable Data Protocol rdp 27
Inter-Domain Policy Routing Protocol idpr 35
Ipv6 protocol ipv6 41
Routing Header for IPv6 ipv6-route 43
Fragment Header for IPv6 ipv6-frag 44
Inter-Domain Routing Protocol idrp 45
Reservation Protocol rsvp 46
General Routing Encapsulation gre 47
Encapsulating Security Payload (50) esp 50
Authentication Header ah 51
ICMP for IPv6 ipv6-icmp 58
EIGRP routing protocol eigrp 88
Open Shortest Path Protocol ospf 89
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 45
Page 62

ACL Commands
IP Protocol Abbreviated Name Protocol Number
IP-within-IP Encapsulation Protocol ipip 94
Protocol Independent Multicast pim 103
Layer Two Tunneling Protocol l2tp 115
ISIS over IPv4 isis 124
(any IP protocol) any (25504)
• in-port port-num — (Optional) Specifies the input port of the devise. In case of
egress classification this port will be devise input port.
• out-port port-num — (Optional) Specifies the output port of the devise.
• dscp — Indicates matching the dscp number with the packet dscp value.
• ip-precedence — Indicates matching ip-precedence with the packet ip-precedence
value.
Default Configuration
This command has no default configuration
Command Mode
IP-Access List Configuration mode
User Guidelines
Use the ip access-list Global Configuration mode command to enable the IP-Access List
Configuration mode.
Before an Access Control Element (ACE) is added to an ACL, all packets are permitted.
After an ACE is added, an implied
and those packets that do not match the defined conditions are denied.
Example
The following example shows how to define a permit statement for an IP ACL.
Console(config)#
Console(config-ip-al)#
mac access-list
deny-any-any condition exists at the end of the list
ip access-list
deny
rsvp 192.1.1.1 0.0.0.255
ip-acl1
any
The mac access-list Global Configuration mode command enables the MAC-Access List
Configuration mode and creates Layer 2 ACLs. To delete an ACL, use the
no form of this
command.
46 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 63

Syntax
mac access-list name
no mac access-list name
Parameters
• name — Specifies the name of the ACL. (Range: 0-32 characters)
Default Configuration
The default for all ACLs is deny all.
Command Mode
Global Configuration mode
ACL Commands
User Guidelines
There are no user guidelines for this command.
Example
The following example shows how to create a MAC ACL.
Console(config)#
Console(config-mac-al)#
permit (MAC)
The permit MAC-Access List Configuration mode command defines permit conditions
of an MAC ACL.
Syntax
permit {any | {host source source-wildcard} any | {destination destination-wildcard}}
[
vlan vlan-id] [cos cos cos-wildcard] [ethtype eth-type]
mac access-list
macl-acl1
Parameters
• source — Specifies the source MAC address of the packet.
• source-wildcard — Specifies wildcard bits to be applied to the source MAC address.
Use 1s in bit positions to be ignored.
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 47
Page 64

ACL Commands
• destination — Specifies the MAC address of the host to which the packet is being
sent.
• destination-wildcard — Specifies wildcard bits to be applied to the destination MAC
address. Use 1s in bit positions to be ignored.
• vlan-id — Specifies the ID of the packet vlan. (Range: 0-4095)
• cos — Specifies the Class of Service (CoS) for the packet. (Range: 0-7)
• cos-wildcard — Specifies wildcard bits to be applied to the CoS.
• eth-type — Specifies the Ethernet type of the packet .(Range: 0-65535)
Default Configuration
No MAC ACL is defined.
Command Mode
MAC-Access List Configuration mode
User Guidelines
Before an Access Control Element (ACE) is added to an ACL, all packets are permitted.
After an ACE is added, an implied
and those packets that do not match the conditions defined in the permit statement are
denied.
If the VLAN ID is specified, the policy map cannot be connected to the VLAN interface.
Example
The following example shows how to create a MAC ACL with permit rules.
Console(config)#
Console(config-mac-al)#
deny (MAC)
The deny MAC-Access List Configuration mode command denies traffic if the conditions
defined in the deny statement match.
deny-any-any condition exists at the end of the list
mac access-list
permit 6:6:6:6:6:6 0:0:0:0:0:0 any vlan 6
macl-acl1
Syntax
deny [disable-port] {any | {source source-wildcard} {any | {destination destination-
wildcard
48 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
}}[vlan vlan-id] [cos cos cos-wildcard] [ethtype eth-type]
Page 65

Parameters
• disable-port — Indicates that the port is disabled if the statement is deny.
• source — Specifies the MAC address of the host from which the packet was sent.
• source-wildcard — (Optional for the first type) Specifies wildcard bits by placing 1s
in bit positions to be ignored.
• destination — Specifies the MAC address of the host to which the packet is being
sent.
• destination-wildcard — (Optional for the first type) Specifies wildcard bits by placing
1s in bit positions to be ignored.
• vlan-id — Specifies the ID of the packet vlan.
• cos — Specifies the packets’s Class of Service (CoS).
• cos-wildcard — Specifies wildcard bits to be applied to the CoS.
• eth-type — Specifies the packet’s Ethernet type.
Default Configuration
ACL Commands
This command has no default configuration.
Command Mode
MAC-Access List Configuration mode
User Guidelines
MAC BPDU packets cannot be denied.
This command defines an Access Control Element (ACE). An ACE can only be removed
by deleting the ACL, using the
Alternatively, the Web-based interface can be used to delete ACEs from an ACL.
Before an Access Control Element (ACE) is added to an ACL, all packets are permitted.
After an ACE is added, an implied
and those packets that do not match the conditions defined in the permit statement are
denied.
If the VLAN ID is specified, the policy map cannot be connected to the VLAN interface.
Example
no mac access-list Global Configuration mode command.
deny-any-any condition exists at the end of the list
The following example shows how to create a MAC ACL with deny rules on a device.
Console(config)#
Console (config-mac-acl)#
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 49
mac access-list
deny
6:6:6:6:6:6:0:0:0:0:0:0
macl1
any
Page 66

ACL Commands
service-acl
The service-acl Interface Configuration mode command applies an ACL to the input
interface. To detach an ACL from an input interface, use the no form of this command.
Syntax
service-acl {input acl-name}
no service-acl {input}
Parameters
• acl-name—Specifies the ACL to be applied to the input interface.
Default Configuration
This command has no default configuration.
Command Mode
Interface (Ethernet, port-channel) Configuration mode.
User Guidelines
In advanced mode, when an ACL is bound to an interface, the port trust mode is set to
trust 12-13 and not to 12.
Example
The following example binds (services) an ACL to VLAN 2.
Console(config)#
Console(config-if)#
interface vlan
show access-lists
The show access-lists Privileged EXEC mode command displays access control lists
(ACLs) defined on the device.
2
service-acl input
macl1
Syntax
show access-lists [name]
50 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 67

Parameters
• name — The name of the ACL.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Example
ACL Commands
The following example displays access lists defined on a device.
Console#
IP access list ACL1
permit ip host 172.30.40.1 any
permit rsvp host 172.30.8.8 any
show access-lists
show interfaces access-lists
The show interfaces access-lists Privileged EXEC mode command displays access lists
applied on interfaces.
Syntax
show interfaces access-lists [ethernet interface | port-channel port-channel-number]
Parameters
• interface — Valid Ethernet port. (Full syntax: unit/port)
• port-channel-number — Valid port-channel number.
Default Configuration
This command has no default configuration.
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 51
Page 68

ACL Commands
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Example
The following example displays ACLs applied to the interfaces of a device:
Console#
Interface Input ACL
--------- ---------
1 ACL1
1 ACL3
show interfaces access-lists
52 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 69

5 Clock Commands
clock set
The clock set Privileged EXEC mode command manually sets the system clock.
Syntax
clock set hh:mm:ss day month year
or
clock set hh:mm:ss month day year
Parameters
• hh:mm:ss — Current time in hours (military format), minutes, and seconds. (hh: 0-23,
mm: 0-59, ss: 0-59
• day — Current day (by date) in the month. (Range: 1-31)
)
• month — Current month using the first three letters by name. (Range: Jan, …, Dec)
• year — Current year. (Range: 2000-2097)
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Example
The following example sets the system time to 13:32:00 on March 7th, 2005.
Console# clock set 13:32:00 7 Mar 2005
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 53
Page 70

Clock Commands
clock source
The clock source Global Configuration mode command configures an external time
source for the system clock. Use
Syntax
clock source {sntp}
no clock source
Parameters
• sntp — SNTP servers
Default Configuration
No external clock source
no form of this command to disable external time source.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
The following example configures an external time source for the system clock.
Console(config)# clock source sntp
clock timezone
The clock timezone Global Configuration mode command sets the time zone for display
purposes. To set the time to the Coordinated Universal Time (UTC), use the
this command.
no form of
Syntax
clock timezone hours-offset [minutes minutes-offset] [zone acronym]
54 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 71

no clock timezone
Parameters
• hours-offset — Hours difference from UTC. (Range: –12 hours to +13 hours)
• minutes-offset — Minutes difference from UTC. (Range: 0-59)
• acronym — The acronym of the time zone. (Range: Up to 4 characters)
Default Configuration
Clock set to UTC.
Command Mode
Global Configuration mode
User Guidelines
Clock Commands
The system internally keeps time in UTC, so this command is used only for display
purposes and when the time is manually set.
Example
The following example sets the timezone to 6 hours difference from UTC.
Console(config)# clock timezone -6 zone CST
clock summer-time
The clock summer-time Global Configuration mode command configures the system to
automatically switch to summer time (daylight saving time). To configure the software not
to automatically switch to summer time, use the
Syntax
clock summer-time recurring {usa | eu | {week day month hh:mm week day month
hh:mm
clock summer-time date date month year hh:mm date month year hh:mm [offset offset]
[
}} [offset offset] [zone acronym]
zone acronym]
no form of this command.
clock summer-time date month date year hh:mm month date year hh:mm [offset offset]
[
zone acronym]
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 55
Page 72

Clock Commands
no clock summer-time recurring
Parameters
• recurring — Indicates that summer time should start and end on the corresponding
specified days every year.
• date — Indicates that summer time should start on the first specific date listed in the
command and end on the second specific date in the command.
• usa — The summer time rules are the United States rules.
• eu — The summer time rules are the European Union rules.
• week — Week of the month. (Range: 1-5, first, last)
• day — Day of the week (Range: first three letters by name, like sun)
• date — Date of the month. (Range:1-31)
• month — Month. (Range: first three letters by name, like Jan)
• year — year - no abbreviation (Range: 2000-2097)
• hh:mm — Time in military format, in hours and minutes. (Range: hh: 0-23, mm:0-59)
• offset — Number of minutes to add during summer time. (Range: 1-1440)
• acronym — The acronym of the time zone to be displayed when summer time is in
effect. (Range: Up to 4 characters)
Default Configuration
Summer time is disabled.
offset — Default is 60 minutes.
acronym — If unspecified default to the timezone acronym.
If the timezone has not been defined, the default is UTC.
Command Mode
Global Configuration mode
User Guidelines
In both the date and recurring forms of the command, the first part of the command
specifies when summer time begins, and the second part specifies when it ends. All times
are relative to the local time zone. The start time is relative to standard time. The end time
is relative to summer time. If the starting month is chronologically after the ending month,
the system assumes that you are in the southern hemisphere.
USA rule for daylight savings time:
56 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 73

Example
Clock Commands
Start: First Sunday in April
End: Last Sunday in October
Time: 2 am local time
EU rule for daylight savings time:
Start: Last Sunday in March
End: Last Sunday in October
Time: 1.00 am (01:00)
The following example sets summer time starting on the first Sunday in April at 2 am and
finishing on the last Sunday in October at 2 am.
Console(config)# clock summer-time recurring first sun apr 2:00 last sun oct
2:00
sntp authentication-key
The sntp authentication-key Global Configuration mode command defines an
authentication key for Simple Network Time Protocol (SNTP). To remove the
authentication key for SNTP, use the
Syntax
sntp authentication-key number md5 value
no sntp authentication-key number
Parameters
• number — Key number (Range: 1-4294967295)
• value — Key value (Range: 1-8 characters)
Default Configuration
No authentication key is defined.
no form of this command.
Command Mode
Global Configuration mode
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 57
Page 74

Clock Commands
User Guidelines
Multiple keys can be generated.
Example
The following example defines the authentication key for SNTP.
Console(config)#
sntp authentication-key
sntp authenticate
The sntp authenticate Global Configuration mode command grants authentication for
received Simple Network Time Protocol (SNTP) traffic from servers. To disable the
feature, use the
Syntax
sntp authenticate
no sntp authenticate
Default Configuration
No authentication
Command Mode
no form of this command.
8
md5
ClkKey
Global Configuration mode
User Guidelines
The command is relevant for both unicast and broadcast.
Example
The following example defines the authentication key for SNTP and grants authentication.
Console(config)#
Console(config)#
58 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
sntp authentication-key
sntp trusted-key
8
8
md5
ClkKey
Page 75

sntp trusted-key
The sntp trusted-key Global Configuration mode command authenticates the identity of
a system to which Simple Network Time Protocol (SNTP) will synchronize. To disable
authentication of the identity of the system, use the
Syntax
sntp trusted-key key-number
no sntp trusted-key key-number
Parameters
• key-number — Key number of authentication key to be trusted. (Range: 1-
4294967295)
Default Configuration
Clock Commands
no form of this command.
No keys are trusted.
Command Mode
Global Configuration mode
User Guidelines
The command is relevant for both received unicast and broadcast.
If there is at least 1 trusted key, then unauthenticated messages will be ignored.
Example
The following example authenticates key 8.
Console(config)#
Console(config)#
sntp authentication-key
sntp trusted-key
sntp client poll timer
8
8
md5
ClkKey
The sntp client poll timer Global Configuration mode command sets the polling time for
the Simple Network Time Protocol (SNTP) client. To restoreTo restoreTo restore default
configuration, use the
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 59
no form of this command.
Page 76

Clock Commands
Syntax
sntp client poll timer seconds
no sntp client poll timer
Paramethers
• seconds — Polling interval in seconds. (Range: 60-86400)
Default Configuration
Polling interval is 1024 seconds.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
The following example sets the polling time for the SNTP client to 120 seconds.
Console(config)#
sntp client poll timer
sntp broadcast client enable
The sntp broadcast client enable Global Configuration mode command enables Simple
Network Time Protocol (SNTP) broadcast clients. To disable SNTP broadcast clients, use
the
no form of this command.
Syntax
sntp broadcast client enable
no sntp broadcast client enable
120
Default Configuration
The SNTP broadcast client is disabled.
60 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 77

Command Mode
Global Configuration mode
User Guidelines
Use the sntp client enable (Interface) Interface Configuration mode command to enable
the SNTP client on a specific interface.
Example
The following example enables the SNTP broadcast clients.
Clock Commands
Console(config)#
sntp broadcast client enable
sntp anycast client enable
The sntp anycast client enable Global Configuration mode command enables SNTP
anycast client. To disable the SNTP anycast client, use the
Syntax
sntp anycast client enable
no sntp anycast client enable
Default Configuration
The SNTP anycast client is disabled.
Command Mode
Global Configuration mode
no form of this command.
User Guidelines
Polling time is determined by the sntp client poll timer Global Configuration mode
command.
Use the
the SNTP client on a specific interface.
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 61
sntp client enable (Interface) Interface Configuration mode command to enable
Page 78

Clock Commands
Example
The following example enables SNTP anycast clients.
console(config)#
sntp anycast client enable
sntp client enable (Interface)
The sntp client enable Interface Configuration (Ethernet, port-channel, VLAN) mode
command enables the Simple Network Time Protocol (SNTP) client on an interface. This
applies to both receive broadcast and anycast updates. To disable the SNTP client, use the
no form of this command.
Syntax
sntp client enable
no sntp client enable
Default Configuration
The SNTP client is disabled on an interface.
Command Mode
Interface Configuration (Ethernet, port-channel, VLAN) mode
User Guidelines
Use the sntp broadcast client enable Global Configuration mode command to enable
broadcast clients globally.
Use the
anycast clients globally.
sntp anycast client enable Global Configuration mode command to enable
Example
The following example enables the SNTP client on Ethernet port 3.
Console(config)#
Console(config-if)#
62 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
interface ethernet
sntp client enable
ext.3
Page 79

sntp unicast client enable
The sntp unicast client enable Global Configuration mode command enables the device
to use the Simple Network Time Protocol (SNTP) to request and accept SNTP traffic from
servers. To disable requesting and accepting SNTP traffic from servers, use the
this command.
Syntax
sntp unicast client enable
no sntp unicast client enable
Default Configuration
The SNTP unicast client is disabled.
Command Mode
Clock Commands
no form of
Global Configuration mode
User Guidelines
Use the sntp server Global Configuration mode command to define SNTP servers.
Example
The following example enables the device to use the Simple Network Time Protocol
(SNTP) to request and accept SNTP traffic from servers.
Console(config)#
sntp unicast client enable
sntp unicast client poll
The sntp unicast client poll Global Configuration mode command enables polling for the
Simple Network Time Protocol (SNTP) predefined unicast servers. To disable the polling
for SNTP client, use the
Syntax
no form of this command.
sntp unicast client poll
no sntp unicast client poll
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 63
Page 80

Clock Commands
Default Configuration
Polling is disabled.
Command Mode
Global Configuration mode
User Guidelines
Polling time is determined by the sntp client poll timer Global Configuration mode
command.
Example
The following example enables polling for SNTP predefined unicast clients.
Console(config)#
sntp server
The sntp server Global Configuration mode command configures the device to use the
Simple Network Time Protocol (SNTP) to request and accept SNTP traffic from a
specified server. To remove a server from the list of SNTP servers, use the
command.
Syntax
sntp server {ip-address | hostname}[poll] [key keyid]
no sntp server host
Parameters
• ip-address — IP address of the server.
• hostname — Hostname of the server. (Range: 1-158 characters)
• poll — Enable polling.
sntp unicast client poll
no form of this
• keyid — Authentication key to use when sending packets to this peer. (Range:1-
4294967295)
Default Configuration
No servers are defined.
64 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 81

Command Mode
Global Configuration mode
User Guidelines
Up to 8 SNTP servers can be defined.
Clock Commands
Use the
predefined unicast clients globally.
To enable polling you should also use the
mode command for global enabling.
Polling time is determined by the
command.
Example
The following example configures the device to accept SNTP traffic from the server on
192.1.1.1.
Console(config)#
show clock
The show clock Privileged EXEC mode command displays the time and date from the
system clock.
sntp unicast client enable Global Configuration mode command to enable
sntp unicast client poll Global Configuration
sntp client poll timer Global Configuration mode
sntp server
192.1.1.1
Syntax
show clock [detail]
Parameters
• detail — Shows timezone and summertime configuration.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 65
Page 82

Clock Commands
User Guidelines
The symbol that precedes the show clock display indicates the following:
Symbol Description
* Time is not authoritative.
(blank) Time is authoritative.
. Time is authoritative, but SNTP is not synchronized.
Example
The following example displays the time and date from the system clock.
Console# show clock
15:29:03 PDT(UTC-7) Jun 17 2005
Time source is SNTP
Console#
15:29:03 PDT(UTC-7) Jun 17 2005
Time source is SNTP
show clock detail
Time zone:
Acronym is PST
Offset is UTC-8
Summertime:
Acronym is PDT
Recurring every year.
Begins at first Sunday of April at 2:00.
Ends at last Sunday of October at 2:00.
Offset is 60 minutes.
show sntp configuration
The show sntp configuration Privileged EXEC mode command shows the configuration
of the Simple Network Time Protocol (SNTP).
Syntax
show sntp configuration
Default Configuration
This command has no default configuration.
66 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 83

Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Example
The following example displays the current SNTP configuration of the device.
Clock Commands
Console#
Polling interval: 1024 seconds
MD5 Authentication keys: 8, 9
Authentication is required for synchronization.
Trusted Keys: 8, 9
Unicast Clients Polling: Enabled
Server Polling Encryption Key
----------- ------- --------------
176.1.1.8 Enabled 9
176.1.8.179 Disabled Disabled
Broadcast Clients: Enabled
Anycast Clients: Enabled
Broadcast Interfaces: 1, 3
show sntp configuration
show sntp status
The show sntp status Privileged EXEC mode command shows the status of the Simple
Network Time Protocol (SNTP).
Syntax
show sntp status
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 67
Page 84

Clock Commands
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Example
The following example shows the status of the SNTP.
Console# show sntp status
Clock is synchronized, stratum 4, reference is 176.1.1.8, unicast
Reference time is AFE2525E.70597B34 (00:10:22.438 PDT Jul 5 1993)
Unicast servers:
Server Status Last response Offset
[mSec]
----------- ------- ---------------------------- ------ ------
176.1.1.8 Up 19:58:22.289 PDT Feb 19 2005 7.33 117.79
176.1.8.179 Unknown 12:17.17.987 PDT Feb 19 2005 8.98 189.19
Anycast server:
Server Interface Status Last response Offset Delay
[mSec] [mSec]
--------- ------- ----- ----------------------------- ------ -----
176.1.11.8 VLAN 118 Up 9:53:21.789 PDT Feb 19 2005 7.19 119.89
Broadcast:
Interface IP Address Last response
--------- --------- ----------------------------
13 0.0.0.0 00:00:00.0 Feb 19 2005
vlan 1 16.1.1.200 15:15:16.0 LLBG Feb 19 2006
Delay
[mSec]
68 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 85

6 Configuration and Image File
Commands
copy
The copy Privileged EXEC mode command copies files from a source to a destination.
Syntax
copy source-url destination-url
Parameters
• source-url — The source file location URL or reserved keyword of the source file to
be copied.
(Range: 1-160 characters)
• destination-url — The destination file URL or reserved keyword of the destination
file.
(Range: 1-160 characters)
The following table displays keywords and URL prefixes.
Keyword Source or Destination
flash: Source or destination URL for flash memory. It’s the default in case a URL is
specified without a prefix.
running-config Represents the current running configuration file.
startup-config Represents the startup configuration file.
image If the source file, represents the active image file. If the destination file,
represents the non-active image file.
boot Boot file.
tftp:// Source or destination URL for a TFTP network server. The syntax for this alias
xmodem: Source for the file from a serial connection that uses the Xmodem protocol.
unit://member/
image
unit://member/
boot
null: Null destination for copies or files. A remote file can be copied to null to
is tftp://host/[directory]/filename. The host can be represented by its IP
address or hostname.
Image file on one of the units. To copy from the master to all units, specify * in
the member field.
Boot file on one of the units. To copy from the master to all units, specify * in
the member field.
determine its size.
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 69
Page 86

Configuration and Image File Commands
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
The location of a file system dictates the format of the source or destination URL.
The entire copying process may take several minutes and differs from protocol to protocol
and from network to network.
*.prv and *.sys files cannot be copied.
Understanding Invalid Combinations of Source and Destination
Some invalid combinations of source and destination exist. Specifically, you cannot copy
if one of the following conditions exist:
The source file and destination file are the same file.
xmodem: is the destination file. The source file can be copied to image, boot and null:
only.
tftp:// is the source file and destination file on the same copy.
The following table describes copy characters:
Character Description
! For network transfers, indicates that the copy process is taking place. Each exclamation
point indicates successful transfer of ten packets (512 bytes each).
. For network transfers, indicates that the copy process timed out. Generally, many
periods in a row means that the copy process may fail.
Copying an Image File from a Server to Flash Memory
To copy an image file from a server to flash memory, use the copy source-url image
command.
Copying a Boot File from a Server to Flash Memory
To copy a boot file from a server to flash memory, enter the copy source-url boot
command.
Copying a Configuration File from a Server to the Running Configuration File
70 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 87

Configuration and Image File Commands
To load a configuration file from a network server to the running configuration file of the
device, enter the
copy source-url running-config command. The commands in the loaded
configuration file are added to those in the running configuration file as if the commands
were typed in the command-line interface (CLI). Thus, the resulting configuration file is a
combination of the previous running configuration and the loaded configuration files with
the loaded configuration file taking precedence.
Copying a Configuration File from a Server to the Startup Configuration
To copy a configuration file from a network server to the startup configuration file of the
device, enter
copy source-url startup-config. The startup configuration file is replaced by
the copied configuration file.
Storing the Running or Startup Configuration on a Server
Use the copy running-config destination-url command to copy the current configuration
file to a network server using TFTP. Use the
copy startup-config destination-url
command to copy the startup configuration file to a network server.
Saving the Running Configuration to the Startup Configuration
To copy the running configuration to the startup configuration file, enter the copy
running-config startup-config
command.
Example
The following example copies system image file1 from the TFTP server 172.16.101.101
to a non-active image file.
Console#
Accessing file 'file1' on 172.16.101.101...
Loading file1 from 172.16.101.101:
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! [OK]
Copy took 0:01:11 [hh:mm:ss]
copy tftp://
172.16.101.101/file1
image
delete
The delete Privileged EXEC mode command deletes a file from a flash memory device.
Syntax
delete url
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 71
Page 88

Configuration and Image File Commands
Parameters
• url — The location URL or reserved keyword of the file to be deleted. (Range: 1-160
characters)
The following table displays keywords and URL prefixes:
Keyword Source or Destination
flash: Source or destination URL for flash memory. It’s the default in case a URL is specified
without a prefix.
startup-config Represents the startup configuration file.
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
*.sys, *.prv, image-1 and image-2 files cannot be deleted.
Example
The following example deletes the file called ‘test’ from the flash memory.
Console#
Delete flash:test? [confirm]
boot system
The boot system Privileged EXEC mode command specifies the system image that the
device loads at startup.
Syntax
boot system {image-1 | image-2}
delete flash:
test
Parameters
• image-1 — Specifies image 1 as the system startup image.
• image-2 — Specifies image 2 as the system startup image.
72 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 89

Default Configuration
If the unit number is unspecified, the default setting is the master unit number.
Command Mode
Privileged EXEC mode
User Guidelines
Use the show bootvar command to find out which image is the active image.
Example
The following example loads the system image 1 at device startup.
Configuration and Image File Commands
Console#
boot system image-1
show running-config
The show running-config Privileged EXEC mode command displays the contents of the
currently running configuration file.
Syntax
show running-config
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 73
Page 90

Configuration and Image File Commands
Example
The following example displays the contents of the running configuration file.
Console#
hostname device
interface ethernet ext.1
ip address 176.242.100.100 255.255.255.0
duplex full
speed 1000
interface ethernet ext.2
ip address 176.243.100.100 255.255.255.0
duplex full
speed 1000
show running-config
show startup-config
The show startup-config Privileged EXEC mode command displays the contents of the
startup configuration file.
Syntax
show startup-config
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
74 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 91

Example
Configuration and Image File Commands
The following example displays the contents of the running configuration file.
Console#
hostname device
interface ethernet ext.1
ip address 176.242.100.100 255.255.255.0
duplex full
speed 1000
interface ethernet ext.2
ip address 176.243.100.100 255.255.255.0
duplex full
speed 1000
show startup-config
show backup-config
The show backup-config Privileged EXEC mode command displays the contents of the
backup configuration file.
Syntax
show backup-config
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 75
Page 92
Configuration and Image File Commands
Example
The following example displays the contents of the backup configuration file.
Console#
software version 1.1
hostname device
interface ethernet ext.1
ip address 176.242.100.100 255.255.255.0
duplex full
speed 1000
interface ethernet ext.2
ip address 176.243.100.100 255.255.255.0
duplex full
speed 1000
show backup-config
show bootvar
The show bootvar Privileged EXEC mode command displays the active system image
file that is loaded by the device at startup.
Syntax
show bootvar
Default Configuration
This command has no default configuration.
Command Mode
Privileged EXEC mode
User Guidelines
There are no user guidelines for this command.
76 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 93

Example
Configuration and Image File Commands
The following example displays the active system image file that is loaded by the device
at startup.
Console#
Unit Active Image Selected for next boot
---- ------------ ----------------------
1 image-1 image-1
show bootvar
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 77
Page 94

Configuration and Image File Commands
78 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 95

7 Ethernet Configuration
Commands
interface ethernet
The interface ethernet Global Configuration mode command enters the interface
configuration mode to configure an Ethernet type interface.
Syntax
interface ethernet interface
Parameters
• interface — Valid Ethernet port. (Full syntax: unit/port)
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
There are no user guidelines for this command.
Example
The following example enables configuring Ethernet port 8
Console(config)#
interface ethernet
interface range ethernet
The interface range ethernet Global Configuration mode command configures multiple
Ethernet type interfaces at the same time.
ext.8
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 79
Page 96

Ethernet Configuration Commands
Syntax
interface range ethernet {port-list | all}
Parameters
• port-list — List of valid ports. Where more than one port is listed, separate the
nonconsecutive ports with a comma and no spaces, use a hyphen to designate a range
of ports and group a list separated by commas in brackets.
• all — All Ethernet ports.
Default Configuration
This command has no default configuration.
Command Mode
Global Configuration mode
User Guidelines
Commands under the interface range context are executed independently on each active
interface in the range. If the command returns an error on one of the active interfaces, it
does not stop executing commands on other active interfaces.
Example
The following example shows how ports 10 to 12 and 1 to 14 are grouped to receive the
same command.
Console(config)#
Console(config-if)#
shutdown
The shutdown Interface Configuration (Ethernet, port-channel) mode command disables
an interface. To restart a disabled interface, use the
Syntax
interface range ethernet
10-12,1-14
no form of this command.
shutdown
no shutdown
80 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 97

Default Configuration
The interface is enabled.
Command Mode
Interface Configuration (Ethernet, port-channel) mode
User Guidelines
There are no user guidelines for this command.
Example
The following example disables Ethernet port 5 operations.
Ethernet Configuration Commands
Console(config)#
Console(config-if)#
The following example restarts the disabled Ethernet port.
Console(config)#
Console(config-if)#
description
The description Interface Configuration (Ethernet, port-channel) mode command adds a
description to an interface. To remove the description, use the
Syntax
description string
no description
Parameters
interface ethernet
shutdown
interface ethernet
no shutdown
ext.5
ext.5
no form of this command.
• string — Comment or a description of the port to enable the user to remember what is
attached to the port. (Range: 1-64 characters)
Default Configuration
The interface does not have a description.
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 81
Page 98

Ethernet Configuration Commands
Command Mode
Interface Configuration (Ethernet, port-channel) mode
User Guidelines
There are no user guidelines for this command.
Example
The following example adds a description to Ethernet port 5.
speed
Syntax
Parameters
Console(config)#
Console(config-if)#
The speed Interface Configuration (Ethernet, port-channel) mode command configures
the speed of a given Ethernet interface when not using auto-negotiation. To restore the
default configuration, use the
speed {10 | 100 | 1000| 10000}
no speed
interface ethernet
description
no form of this command.
"RD SW#3"
ext.5
• 10 — Forces10 Mbps operation.
• 100 — Forces 100 Mbps operation.
• 1000 — Forces 1000 Mbps operation.
• 10000 — Forces 10000 Mbps operation.
Default Configuration
Maximum port capability
Command Mode
Interface Configuration (Ethernet, port-channel) mode
82 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
Page 99

User Guidelines
The no speed command in a port-channel context returns each port in the port-channel to
its maximum capability.
Example
The following example configures the speed operation of Ethernet port 5 to 100 Mbps
operation.
Ethernet Configuration Commands
duplex
Syntax
Parameters
Console(config)#
Console(config-if)#
The duplex Interface Configuration (Ethernet) mode command configures the full/half
duplex operation of a given Ethernet interface when not using auto-negotiation. To restore
the default configuration, use the
duplex {half | full}
no duplex
interface ethernet
speed 100
no form of this command.
ext.5
• half — Forces half-duplex operation
• full — Forces full-duplex operation
Default Configuration
The interface is set to full duplex.
Command Mode
Interface Configuration (Ethernet) mode
User Guidelines
When configuring a particular duplex mode on the port operating at 10/100 Mbps, disable
the auto-negotiation on that port.
Half duplex mode can be set only for ports operating at 10 Mbps or 100 Mbps.
Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide 83
Page 100

Ethernet Configuration Commands
Example
The following example configures the duplex operation of Ethernet port 1 to full duplex
operation.
Console(config)#
Console(config-if)#
negotiation
The negotiation Interface Configuration (Ethernet, port-channel) mode command enables
auto-negotiation operation for the speed and duplex parameters of a given interface. To
disable auto-negotiation, use the
Syntax
negotiation [capability1 [capability2…capability5]]
no negotiation
Parameters
• capability — Specifies the capabilities to advertise. (Possible values: 10h, 10f,
100h,100f, 1000f)
interface ethernet ext.
duplex full
no form of this command.
1
Default Configuration
Auto-negotiation is enabled.
If unspecified, the default setting is to enable all capabilities of the port.
Command Mode
Interface Configuration (Ethernet, port-channel) mode
User Guidelines
If capabilities were specified when auto-negotiation was previously entered, not
specifying capabilities when currently entering auto-negotiation overrides the previous
configuration and enables all capabilities.
84 Intel® Blade Server Ethernet Switch Modules SBCEGBESW1 and SBCEGBESW10 CLI Guide
 Loading...
Loading...