Page 1

User’s Guide
Intel PRO/100 Family
Packet Protect
Enabling the IPSec Protocol on
Microsoft Windows NT 4.0
®
®
Page 2

Intel® Packet Protect User’s Guide
Where to Go for More Information
Readm e Files
For more information ab out installation and general information about
the product, see the readme text file. To view the files, view the root
folder on the Intel CD-ROM. Open readme.txt with any text editor.
Online Services
You can use the Internet to download soft ware updates, and to view
troubleshooting tips, installation notes, and more. Online services are
on the World Wide Web at:
http://support.intel.com
Copyright © 2000, In tel Corporati on. All rights reserved.
Intel Corporation, 5200 N.E. Elam Y oung Parkway, Hillsboro, OR 97124-6497
Intel Corporation assumes no responsibility for errors or omissions in this document. Nor does Intel
make any commitment to update the information contained herein.
* Other product and corporate names may be trademarks of other companies and are used only for
explanation and to the own er s’ benefit, without intent to infringe.
ii
Page 3

Contents
Where to Go for More Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . ii
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . iii
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1
What is I n tel
Packet Protect Features 2
Complete Your Security Solution 2
Hardware Accelera tion 2
Domestic and Export Versions 2
Additional Information 3
How Packet Protect Works . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4
What is IP Security? 4
What is Internet Key Exchange? 4
The Process 5
Packet Protect? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2
Contents
Get Started . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6
Installing Packet Protect . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
Developing Your Deployment Model . . . . . . . . . . . . . . . . . . . . . . . . . . 8
Review Your Network Architecture and
Corporate Security Guidelines . . . . . . . . . . . . . . . . . . . . . . . . . . 8
Assign security behavior roles to computers that you want to use
Packet Protect 9
Develop a strategy for handling pre-shared keys 10
Understand the Default Rule 11
Consider exceptions to the Default Rule 11
What are the Trade-offs? 12
Conclusion 14
Set Up Intel Adapters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
Install Intel Adapters 15
Configure Intel Adapters 15
Install Packet Protect . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
System Require me nts 17
Licensing 17
Install Packet Protect 17
View Your Security Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
iii
Page 4

Intel® Packet Protect User’s Guide
Configuring Security Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
Understand Default Security Behavior . . . . . . . . . . . . . . . . . . . . . . . . 22
Default Behaviors in Packet Protect 22
Set up Your System Policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
What is a Policy? 25
What is a Rule? 25
The Default Rule 26
Importance of Rule Order 27
How Does the System Policy Work? 28
Add Rules to the System Policy 28
Making Changes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
Modify the System Policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Modify Destina tion Workgroups or Security Actions 41
Delete a Rule 41
Restore the System Policy 42
Monitor Packet Protect Computers . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
View Status at a Packet Protect Client 44
Set Up Compatible Policies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
Work with Other Security Products . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
Turn Security On for a Computer . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
Install Security for a New Computer 47
Turn Security on Manually for an Existing Computer 47
Turn Security Off for a Computer . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48
Shut Down Packet Protect at a Computer 48
Uninstall Packet Prote ct from a Computer 48
Troubleshooting and FAQs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
Troubleshooting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
Frequently Asked Questions (FAQs) . . . . . . . . . . . . . . . . . . . . . . . . . . 52
Appendix A — IKE and IPSec . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
IKE and IPSec Work Together . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
How Packet Protect Uses IKE . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
Identity Negotiation Settings 55
IPSec Settings 57
iv
Page 5

Contents
Examples 58
How Packet Protect Uses IPSec . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59
Security Associ ations 59
Security Association Lifetimes 59
How IPSec Protects Packets 60
Appendix B — Interoperability with Microsoft Windows* 2000 . 63
Interoperability with Windows* 2000 . . . . . . . . . . . . . . . . . . . . . . . . . 64
Appendix C — Network Software Li c ense Agreement . . . . . . . . . 65
Network Software License Agreement . . . . . . . . . . . . . . . . . . . . . . . . 66
Intel Automated Customer Support . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
Readme Files on Your Product Disk 67
Web and Inter net Sites 67
Customer S upport Technicians 67
Glossary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 73
v
Page 6

Intel® Packet Protect User’s Guide
vi
Page 7
1
Introduction
Wi th the growing amount of information that travels on your local area network
(LAN), confidential information has become a target for intruders bo th ins ide
and outside your company. These intruders may be employees, visitors to your
company, or a hacker who breaks through your firewall.
Intel® Packet Prot ect helps protect Internet P rotocol (IP) traffic as it travels
betwe en computers on your LA N . This protects confidential data from being
retrieved by intruders.
In this chapter, you’ll find information about:
• Packet Protect overview
• How Packet Protect works
• Getting started
1
Page 8

Intel® Packet Protect User’s Guide
What is Intel
Packet Protect is designed to protec t the confidentiality and authenticity of IP
traffic on your LAN.
Packet Protect can assist you in creating a departmental solution fo r your security concerns.
Many data compromises are attempted from within a company firewall. Unless
you protect informati on as it travels on th e network, it can be received by
unwanted users.
For example, employees retrieving confidential designs from a Research &
De velopment department server use Packet Protect to encrypt the inform ation
while it travels on the LAN. Encryption protects the confi dentiality of the information. Each employee’s computer can also verify the integrity of the information upon receipt.
Pa cket P r ote ct?
Packet Protect Features
Packet Protect enables you to:
• Protect confidentiality and authenticity of IP traffic on your LAN using
Internet Protocol Security (IPSec), including Internet Key Exchange (IKE).
• Offlo a d se cu r ity task s to an Int el PRO/100 S Management or Server
Adapt er to optimize network performance.
Complete Your Security Solution
If you need to protect data stored on a computer, u se operating syst em features
comb in e d w ith Pack et Prote ct. Pack et Prot ec t protects da ta t rave ling between
comput ers, not while it ’s store d on a com puter. You should use your operating
system features or network infrast ructure element to provide access control to
certain areas of the computers on the network.
Hardware Acceleration
Imple menti ng an I PSec solut io n can increa se CPU uti lizat i on fo r comp uter s th at
use the IPSec software. This is common when implementing any IPSec solution
because of the intense computation required to encrypt, decrypt, and validate
packets. Howe ver, there is a way to offload secur ity tasks from the CP U .
You can combine Packet Protect with the use of an Intel PRO/100 S Management o r Serv er Adap ter t o reduc e CP U ut iliz at io n. Th is fr ee s CPU ut il i zati on fo r
other tasks, while reducing the impact to network performance.
Domestic and Export Ve rsions
Packet Protect i s availabl e in both domestic and export v ersions. The export version supports DES (56-bit) encryption only. The domestic version, available in
the United States and Canada, supports DES and 3DES (168-bit) encryption.
2
Page 9

Additional Information
This Packet Protect User’s Guide in Adobe Acrobat* format can be found in the
Packet Protect directory on the product CD-ROM. Packet Protect help can be
found in the Help directory on the product CD-ROM.
Introduction
3
Page 10

Intel® Packet Protect User’s Guide
How Pac k et Protect Works
Packet Protect hel ps you protect network traffic that is sent from one server or
client to another. Packet Protect uses these steps to protect informa tion traveling
on the ne tw ork:
1. Activate IKE (Internet Key Ex ch ange ). Neg ot iates par am e ters fo r se cu re
communication.
2. Activate IPSec (Internet Protocol Security). Protects the communication
using the security par am eters it negotiated successfully using IKE.
What is IP Security?
Internet Protocol (IP) Securit y (commonly called IPSec) is a set of standa rd protocols used to protect t h e confidentiality and authenticity of IP communicati ons.
IPSec accomplishes this using the following:
• Encryption. Protects confidentiality of inform ation traveling on the network . Each packet is encrypted so that unwanted recipient s can’t interpret
it. Packet Protect uses DES 56-bit and 3DES 168-b it encrypti on algorithms
(3DE S in U .S . and Ca na d a versio n only) .
•Integrity. Protects the authenticity of the information traveling on the network by verifying that each packet was unchanged in transport. Packet Protect uses MD5 and SHA-1 authentication algorithms for bot h ESP and AH
auth entication.
• An ti-re pl a y protection. Protects the network by preventi ng an intruder
from successfully repeatedly sending an identical packet in an attempt to
confuse the system.
For more information about IPSec, see “Appendix A — IKE and IPSec” on
page 53.
What is Internet Key E xch ang e?
Inter net K ey Exc han ge ( IKE) is a s ta nda rd pro toc ol use d t o ne go tiat e a pro tect ed
communication. Ne gotiation is the first pha se in setting u p a secure communi cation. IKE verifies the identity of the computers using pre-shared keys. Then it
negotiates a set of se curity settings to protect the communication.
IKE is a pro to col t hat ope rate s i ns ide a f ra me wo rk def i ne d by I SAK MP ( Inter net
Security Associati on Key Management Protocol) and is used to support the
establishment of Security Associations.
For mo re information about IKE, see “Appendix A — IKE and IPSec” on
page 53.
4
Page 11
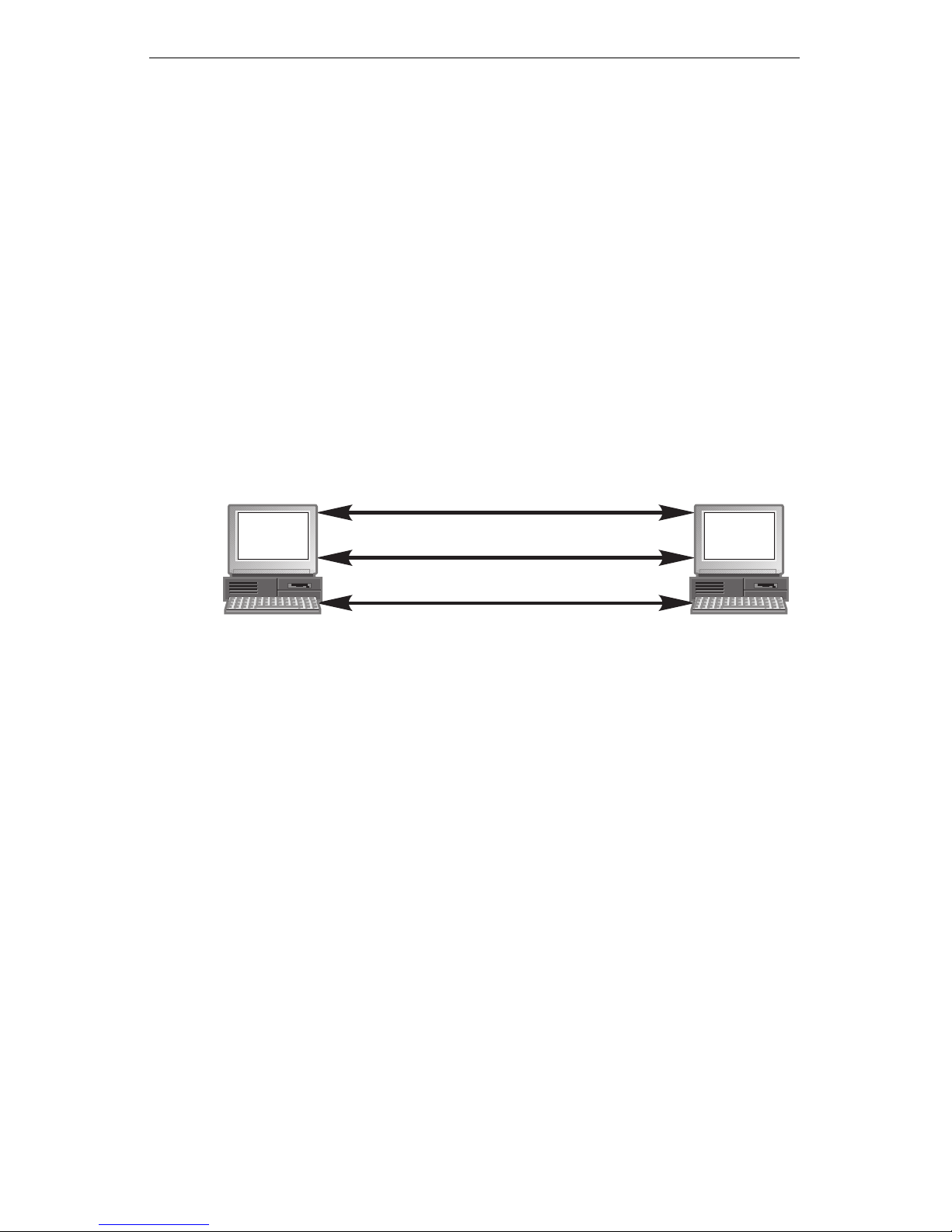
The Process
If two com puters require security, each time they attempt to communicate wit h
each o ther Packet Protect foll ows these steps to attempt a protected comm unication:
1. Ea ch co mput er uses IK E to ver i fy that the oth er is th e comp ute r i t clai ms to
2. I f i den tit y v erif i ca tion i s s ucces sf ul i n Step 1, the tw o com p uters use IKE t o
3. If the agreement is successful in Step 2, both computers will use the agreed
As long as the protected communication is active, the two computers can
exchange information, without repeating Steps 1 and 2 (up to the pre-defined
time and size limits — se e Table 6 on page 34 for more information).
The following diagram shows the roles of IKE and IPSec.
Introduction
be.
agree upon the IPSec sett ings to use.
upon IPSec settings to protect the data as it travels.
Step 1: IKE Verif ies Pre-shared Key
Step 2: I KE Negotiates IPSec Settings
Step 3: IPSec Protect s the Communication
5
Page 12

Intel® Packet Protect User’s Guide
Get Started
To start using Pac ket Protect
1. Evaluate your network arch itecture and decide which areas require Packet
Protect. For details, see “Developing Your Depl oyment Model” on pag e 8.
2. Install Packet Protect on those computer s that require security. For deta ils,
see “Install Packet Protect” on page 17.
3. Set up security settings for each computer where you installed Packet Protect. For details, see Chapter 3, “Configuring Securi ty S ettings” on
page 21.
6
Page 13
2
Installi ng Packet Prote ct
To set up yo u r netwo rk in prepa ra tion fo r deploy ing se cu rity, there ar e several
things to cons ider. This cha pter gui de s you th rough th e set up process so you can
begin deplo ying se cu rity m os t effe ctively.
In this chapter, you’ll find information about:
• De veloping your deployment model.
• Setting up Intel
• Installing Packet Protect.
network adapters.
7
Page 14

Intel® Packet Protect User’s Guide
Developing Your Deployment Model
In order to use Packet Protect successfully, you must develop a deployment
model that fulfills your s ecurity needs on your ne twork. There are sev eral stages
to consider in deve loping your deployment model.
• Review your network architecture and corporate security guidelines.
• Assign security behavior roles to computers that you want to use Packet
Protect.
• Develop a strategy for using pre-shared keys.
• Under stand the Default Rule.
• Consi der exceptions to the Default Rule.
This discussion represents only an overview of some of the issues that should be
considered when deploying Packet Protect in your enterprise. For more detailed
information about depl oyment models , please refer t o “Scalable Deployment of
IPSec in Corporate I ntranets”white paper from t he Intel Architecture Labs Internet Building Blocks Initiative. This white paper can be found at:
ftp://download. intel.com/ ial/home/ibbi/ipsec_122.pdf
Review Your Network Arch itecture and
Corporate Security Guidelines
The amount of confide ntial information traveling on your net work grows as
more employees use your corporate network. This poses a security risk if som eone breaks through your firewal l, or someone already behind your f irewall has
access to the network—those people can access confidential information. For
example, an intruder can mimic an IP address and receive inform ation that was
intended for someo ne else at that IP address. Or, an intruder can use software to
view data as it travels on your LAN.
You can deploy Packet Protect in the areas of your network that transmit sensi tive informati on. Some areas of your network might require the additional protection provided b y Packet Protect, while other areas might not. Use your
corp orate security guidelines to help determine w h ich areas of your network
require Packet Protect.
Perhaps you have a server that stores hi ghly confidential information, such as
corporate financial figures or e-comm erce transact ions. You can use your o perating system’s tools to help protect data stored on the server’ s hard disk, but
what ab out when other computers access that information? Use Pac k et Protect
8
Page 15
Installing Packet Protect
to protect your highly confidential in formation as it travels t o and from the
server.
Assign security behavior roles to computers that you wan t to use
Packet Protect
Packet Protect use s default secur ity behavior t o determine how a com puter will
communicate with other computers on the network. There are three default
behaviors: Secure Responder, Secure Initiator and Lockdown.
Secure Responder
A computer with the default behavior of Secure Responder alw ays initiates and
accep t s tra ffi c th at is not secu red. H ow ever, it wil l accep t a secur e co m m u nication if it is initiated by another computer. Of course, the negotiation will succeed
only if one th e pr opos als in the li st of f ere d b y the ini t iator can be matc hed by the
respond er.
Secure Responder is a likely behavior for the majority of workstations in a network. Communicati ons will always be allowed in the clear between computers
that are Secure Responders or Secure Initiators, but will communicate securely
with a computer (usually a server) with Lockdown default behavior.
Secure Initiator
A computer with the default behavior of Secure Initiator will always attemp t to
initiate secure communications on all outbound traffic. Even if an inbound communi ca ti on flow is ini tiated in th e cl ea r, the respon se da ta flow wi ll ca u se the
comput er to initiate a secure session. Ho w ever, if a secure session cannot be in itiated, the computers will fallb ack to communicat ing in the clear.
Secure Initiator behavior is appropriate for both workstations and servers . Compute rs who wish to use peer-to-peer secure communications can use S ecure Ini-
9
Page 16

Intel® Packet Protect User’s Guide
tiator behavior. Also, many servers can use this behavior as well, as long as the
fallback behavi or is acceptable for your network.
Secure Initiator is similar to Secure Responder, exc ept that all outb ound traffic
will result in an attempt to negotiate parameters for security.
Lockdown
A computer with Lockdown behavior will alw ays initiate and respond securely
to all data flows. If the negotiatio n fails on either computer, then traf fic will be
denied.
Lockdown behavior is used for serv ers with high content value, as it requires
security for all data transmissions.
Communicat ing with non-Packet Protect computers
It is comm on to not use Packet Protect on all the computers in your network.
While the secur it y th at P acke t Pro te ct can provi de is ben ef ici al , th ere are se v er al
reasons to limit the computers on your netw ork that use Packet Protect, such as:
• Only a limited number of com puters on your network require se cure communications.
• In order to minimize CPU utilization, you want to limit use of Packet Protect to computers that already have PRO /100S Management or Server
adapters.
Comput ers tha t use the defa ul t beha vio r of Sec ur e Responde r or Sec ur e Initi at or
will always be able to communicate in the clear with computers in your network
that do not use Packet Protect.
Comput ers that use the default behavior of Lockdown will not be able to co mmunicate with computers in your network that do not use Packet Protect.
Develop a strategy for handling pre-shared keys
When two computers attempt secure communication, they negotiate parameters
for the communicati on. In addition to using their default behavior, described in
the previous section, they also exchange a st ring of characters known as a p reshared key.
When the computers begin to negotiate parameters, they compare their preshared ke y s. If bo th comp ute rs hav e th e s ame p re -s hared ke y, th en the co mput er s
will go ahead and negotiate parameters for the session. If the comput ers have a
different pre- shared key, then the negotiati on for secure communication will
cease.
Once the pre-shared keys have been compared and matched between the two
comput ers, the IKE protocol generates secure, secret session keys. N o one can
find out what these session keys are, even if the y know what the pre-shared ke y
is. Although pre-shared keys are sometimes called passwords, they do not ac t
like p ass wor ds. Ev e n when you k no w wha t t he pre- sh ared k e y is , y ou canno t us e
that key to intercept or decrypt the information that is being transmitted.
10
Page 17

Installing Packet Protect
Sharing keys
It’s importa nt when yo u are developing your depl oyment model that you decide
how to handle the distribution of the pre-shared key. Some networks use a
widely-published key, known as a “group key” or the “pre-shared key on the
wall.” In this strategy, you make the pre-shared available to everyone. This way,
all com puters will be configured to use the same key. This ensures that when
secure communications are requested, then IK E will be able to negotiate secure
communications when the keys are matc hed between two co m puters.
In addition to “group key,” some enterprises may want to u se additional, more
private pre-shared keys in cert ain instances. For example, the president and the
chief financial officer of a corporation may wish to send secured tr ansmissions
to each other. In this instanc e, each of these computers would use the gr oup key
as part of their standa rd Syst em P olicy, but would create a special rule to cov e r
communications just between them. (See “Consider exceptions to the Default
Rule” for more information on implementing this scenario.) In this case, they
might li k ely cho ose a more sec ret pr e- sh ared k e y th at just t he t wo comput er s u se
with each other.
Understand the Default Rule
Every computer that uses Packet Pro tect has a single Sys tem Policy. Each System Policy initially contains a single Default Rule. The Default Rule is quite
simple:
For Everybody, use the De fa u lt Se c ur ity Act io n . If the rule fails, Allow
Communication without Security.
Note: For computers that use the Lockdown behavior wth the
Default Rule, if the rule fails then
fallback action.
See “The D efault Rule” on page 26 for more information .
Note:
See “What is a Rule?” on page 25 for more information about rules in Packet
Protect.
If you want to have secure communication between a Packet
Protect computer and a Windows 2000* computer, you must
use the Default Rule. Intel recommends that yo u do not
delete the Default Rule.
Deny Communication
is the
Consider exceptions to the Default Rule
Many enterprises may find that b y careful consideration of th e default behavior
roles, a widely publis hed pre-shared key, and the Default Rule, they can meet
their security requirements without extra effo rt. This model is quite workable
and provides adequate security. It is also simple to deploy and maintain.
11
Page 18
Intel® Packet Protect User’s Guide
Some enterprises may wish to create additional rules that govern communications between two spe c ific computers.
Earlier, we introduced a scenario where the president and chief financial officer
of a company wished to implement extra security for their communications. For
this scenario, a new rule is needed. Let’s compare a possible rule for this scenario to the S ys te m Po li cy ’s Defau lt Rule :
Property New Rule Default Rule
Table 1: Rule Comparison
Destination
Workgroup
Security Action New Security Action: Up
Rule Failure Deny Communication. Allow communication in
Authentication Use a new pre-shared
President and CFO only Everybody
Default Sec ur ity Action:
to 15 m inutes or 50 MB,
whichever occurs first.
Then, a new security
association is negotiated.
key, known only to these
two comput ers.
Up to 8 h ours , then a n ew
security association is
negotiated.
the clear.
Use the System Policy’s
settings
In addition to these rules, both the president and the Chief Financial Officer
woul d hav e the Sec ure In it ia to r de faul t beha vio r. The ru le mi ght al so wan t t o us e
more se cure options, such as perfect forward secrecy , whic h provides a very
secure neg otiation of session keys. There are many oth er security options that
can be chosen when you create a security action for this rule. See “Customize
Security Actions” on page 33 for more infor mation on optio ns for security
actions.
By compar ing the new ru le and the default rule, you can see how the new rule
provides an extra m easure of security. The new security action is much more
limited. Longer time and/or size limi ts on a security action can give an intr uder
an opportunity to intercept and possibly corrupt pack ets. By denying c om m unication in case of rul e failure, you ensure that communication between these t w o
computers will never occur in the clear.
What are the Trade-offs?
A very important part of developing your deployment model is to consider not
only the initial deployment, but maintaining the System Policies on all the computers that use Packet Protect in your network.
Clearly, the simplest model we discussed will be the easiest to deplo y and maintain. When all computers u se the same defa ults—Default Rule, security action,
12
Page 19

Installing Packet Protect
fallback to clear communicatio n, same pre-shared key—then you’ll be able to
gain adequate security with minimum impact to your network.
If you decide on a more complex deployment model, you should consider the
benefits of the extra security that you have against the costs of maintaining and
running the mod el. There are two ar eas that you should evaluate—maintenance
and CPU utilization.
Maintenance
If you are considering a deployment model with many customizations and speciali zed rules , be aw are of t he t ime a nd ef for t requir ed f or on going m aint ena nce.
Becau se each computer with Packet Protect must be configured individually,
custom izations require more effort to keep each computer up-t o -date.
Let’s consider the previous example of the special rule for the president and
Chief Financial Officer of the corporation. In ord er for this rule to work as
designe d, all a sp ect s of t he rul e mus t ma tch, or commun ic ation wil l b e de nied. I f
the president’s computer uses a different setting in the security action from the
CFO’s computer, then a secur ity association cannot be negotiated and there fore
all com m unication is denied. Consider then that it might take several days for
the president and CFO to even discover that their communications haven’t been
taking place, as assumed.
Even a new computer for the president could prevent secure communication
from happening. For example, when you set up this special rule, you identified
the two computers to Packet Protect by the names of the com puters. The president’s new computer has a ne w nam e. When the pres ident and the CFO attempt
to communicate the next time, th e rule will fail, because of the computer name.
You c an imagine how difficult it can bec o me to maintain specialized rules, desti nation workgro ups, and security actions in your network. Intel recommends that
you begin by using the simple, default model for secure communications. Over
time, you may consider customizations to enhance secure communications in
spec ial cases.
CPU Utilization
Anoth er ve ry impo rt ant f ac to r to co nsi der i s t he eff ec t of I PSec on y our net wo rk ,
as well as the individual computers using Packet Protect . Generally, you can
assume that when you choose most sophisticated security options, there will be
impac t on your network.
One example is choosing to use ESP (Encapsulation Security Payload) and AH
(Authen ti cat ion H eade r) aut hen tica ti on t ogeth er. While th is combi na tion a f fo rds
extra protecti on, you must consider that when you use both of these methods,
you cannot offload any processing to the adapter, and thus CPU utilization
incre ases. H owever, if you use jus t ES P au th en tication wi t h th e ap p ropri ate
adapter, you can take adv antage of the hardware of fload and get better CPU util itzation.
You must also consider the adap ters that are installed in you r Packet Protect
comput ers. Only the Intel PRO /100 S Server Adapter and Intel PRO/ 100 S Man-
13
Page 20

Intel® Packet Protect User’s Guide
agemen t A dapter can perform hardware offloading. If you ha ve other Intel PRO/
100 Ada pters in Packet Protect computers, you won’t be able to offload any processing, thus i ncreasing CPU utilization and potent ially slo w ing that co mputer’s
netw ork performance.
Other security opti ons are considered “costly” as well. Perfect Forward Secrecy
is very secure, but if used widely throughout the network, there can be a significant effect on servers that have a lot of secure traffic.
Conclusion
Hopefully, this section provided some guidelines for you to consider as you
develop your deployment model. There are no hard-and-fast rules that you must
follo w. However , Inte l r eco mmends tha t you be gin your use of IPSe c an d Pa ck et
Protect slowly in your enterprise. You should consid er starting with a small
group that use t he same pre-shared key and default System Policy. When you’ve
had a chance to evaluate this first implementation phase, you can then decide
how to expand your use of Packet Prote ct.
14
Page 21

Set Up Intel Adapters
Before you install Packet Protect, install the necessary Intel adapters on your
servers and client s that will use Packet Protect. Packet Protect only operates
with Intel adapters that are configured to use Intel drivers.
Inst a ll Intel Ad apte r s
Packet Protect works with Intel adapters that are designed to offload CPU-intensive tasks to the adapter. This helps reduce the impact to network perform ance
and CPU utilization. Intel adapters that support the offload capab ilities include
the following:
• Intel PRO/100 S Server Adapter
• Intel PRO/100 S Managem ent Adapter
Installing Packet Protect
Note:
Note:
Although Intel adapters can be installed on var ious operating
syste ms , P a cket Protect suppo rts only Windo ws NT* 4.0 with
Service Pack 5.
Packet Protect also works with the following Intel adapters,
but security tasks will not offload to these adapters, and network performance will be affected.
PR O/10+ PCI LAN adapter
PRO/10 0B LAN ad ap t e r
PRO/100B T4 LAN adapter
PRO/100+ LAN adapter
PRO/100+ Management adapter
PRO/100+ Server adapter
PRO/100+ Dual Port Server adapter
PRO/100 CardBus II
PRO/100 RealPort
PRO/100 LAN+Modem56 CardBus II
PRO/100 LAN+Modem56 RealPort
TM
CardBus II
TM
Cardbus II
Install Intel adap ters for the servers and clients that use Pa cket Protect.
T o install Intel adapters
1. Refer to the Installation Guide that came with the adapters for information
about installati on
2. After installation, verify network access for each compute r that will use
Packe t Pr otect b y che cking t he Link a nd Act i vit y LEDs o n the ada pter. You
can also double-click Network Neighborhood on a computer’s desk top to
verify that ot her are as of the net wo rk are vi sible.
Configure Intel Adapters
Afte r you install adapters in the com puters that will use Packet Protect, configure them, as necessary, before you install Packet Protect. For e xam ple, you
15
Page 22

Intel® Packet Protect User’s Guide
migh t in stall m ultipl e adapt ers on a se rve r. Then you mi gh t te am tho se ad ap ters
together to take advantage of adapter fault tolerance or adaptive load balancing.
Mult ip le A d apters
If you install multiple adapters in one computer, note the following:
• Install multiple adapters before installing Packet Protect.
• Each co m puter has only one sec urity policy. This me ans that the same
security settings will apply to all of the adapters in one computer.
• If you use at least one Intel PRO/100 S Server or Management adapter in a
comput er, Packet Protect will be able to off load encryption and authentication tasks to that ad apter.
• If you need to add or remove an adapter f rom a team after you install
Packet Protect, you must uninstall Packet Protect from that computer, add
or remo ve the necessary adapters, and then reinstall Packet Protect.
When you uninstall Packet Protect, you lose all of your customized information, including rules and security actions. When you reinstall Packet
Protect, you will only have the single Default Rule in your System Policy.
Adapter Teaming
Adapter Teaming and Packet Protect work together only for computers with
Wi ndows NT operating system installed. If you set up Adapter Teamin g for multiple adapters, keep the following in mind:
• Conf igure Adapter Teami ng before installing Packet Protect.
• Refer to the previous page to make sure all adapters in the team are either
offload-enabled Intel adapt ers, or appear in the list of compat ible Intel
adapters on the previous page.
• If you need to add or remove an adapter from a team after you install
Packet Protect, you must uninstall Packet Protect from that computer, add
or remo ve the necessary adapters, and then re-install Packet Protec t.
• Consi der using high-speed adapters to limit upgrading.
16
Page 23
Install Packet Protect
Before you insta ll Packet Protect on your computer, make sure the computer
meets the following system requirements . Packet Protect computers can be servers or workstations.
System Requirements
Befor e installing Packet Protect, make sure your computers meet these requirements:
• Windows NT 4.0 with Service Pack 5 or 6a (or higher)
• 40 MB available disk space
• 32 MB RAM minimu m, 64M B RA M re commended
®
• 200 MHz Pentium
• Intel adapter (PRO/100 family)
Note
: See “Install Intel Adapters” on page 15 for information on
choosi ng an Intel ada pter.
processor performance level or higher recomm ended
Installing Packet Protect
Licensing
All installations are subject t o the end user’s acceptance of the applicable In tel
Softw are License Agr eement.
Install Packet Protect
You wil l need the information detailed in the follo w ing table during Packet Protect installati on at each compute r. To complete the installa tion most efficiently,
gather the foll owing information before you begin.
Information
You N eed
Default
behavior
Table 2: Required Information
Description
Decide how you want the computer to communicate
with other computers on the network:
• Secure Responder
• Secure Initiator
•Lockdown
For more information about these settings, see
“Default Behaviors for Packet Protect Computers” on
page 22.
Pre-shared key Enter a pre-shared key the computer will use to
communicate securely with other IPSec computers. A
pre-shared key is similar to a secret password.
17
Page 24

Intel® Packet Protect User’s Guide
To install Packet Protect
1. Verify that the computer you have chosen meets the minimum requirements detailed under “Sy stem Requiremen ts” on page 17.
2. Insert th e pr oduct C D- R OM in to the CD-ROM driv e at the comput er wher e
you want to install Packet Protect.
3. Browse to the CD-ROM using Windows Explorer.
4. Doubl e-click d:\packet protect\setup.exe, where d:\ is t he drive of your CDROM drive.
5. Follow the dialog bo x instructions on the screen.
Ke ep a confidential record of the information you enter. If you need to reinstall
Pac ket Protect lat er, you will need to re-ent er this information.
Notes:
If the static IP address or the DNS name of the computer
changes, you must re store t he S yste m Policy. Yo u wi ll lose all
your customizations when you restore the System Policy.
Also, if there are other computers in the network that have
rules that apply to the computers whose IP address or DNS
name changes, the rules of those computers need to be
changed. For information on restoring the System Policy, see
“Restore t he Syst em Policy” on page 42.
You can also install from a mapped drive where you have
stored the Packet Protect installation file s.
If you already have adapter teaming installed on the system,
there’s no need to re-enter the TCP/IP settings during Packet
Protect installation (you are not prom pted for this information).
To verify that Packet Protect is installed and running on a computer:
1. At the taskbar on the computer, select Settings > Contro l Panel.
2. Doub le -c lick Se r vi ces and ver ify that Int el Polic y A ge n t is st arted .
If Intel Policy Agent doesn’t appear in the list, Packet Protect has b een shut
dow n or is not function ing properly. See “Turn Security on Manually for an
Existing Computer” on page 47 for detai ls about restarting P acket Protect .
See the chapter “Troubleshooting and FAQs” on page 49 for general troubleshooting guidelines and a list of common Packet Protect installation problems
and their solutions.
18
Page 25
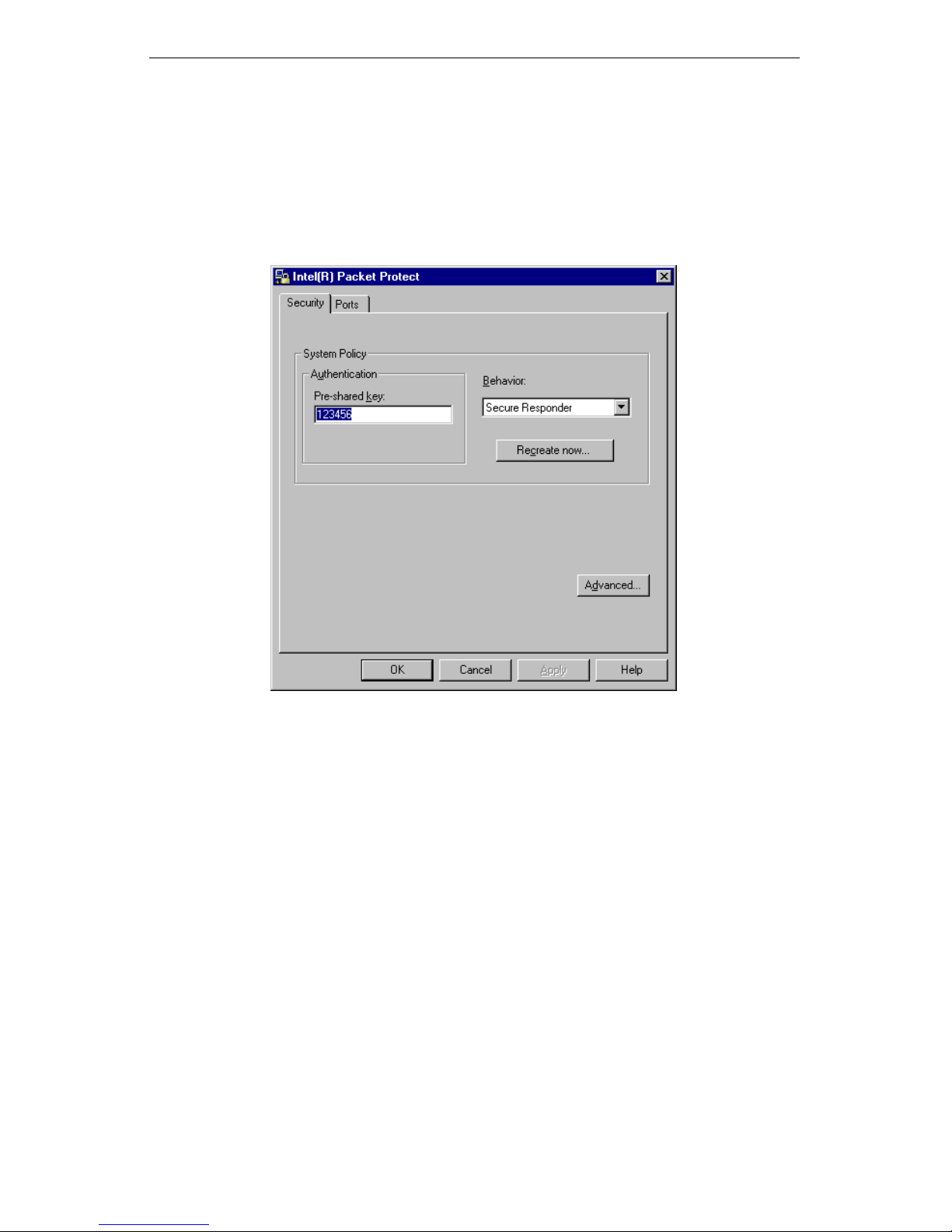
View Your Security Settings
Duri ng installation, you set up basic security settings for the computer—the
authent i cati on meth od and the de faul t be ha vior for t he clie nt . To view your secu rity settings, double-click Intel(R) Packet Protect at the Control Panel. The
authentication setting and default behavior you chose during installation appear
in the Security tab.
Installing Packet Protect
See the next chapter for information on editing basic settings and configuring
advanc ed secu r ity sett ings.
19
Page 26

Intel® Packet Protect User’s Guide
20
Page 27
3
Configuring Security Settings
If you have install ed Pac ket Protect, you have already set up basic security settings for the computer. You may view or edit these settings using Packet Protect.
Optionally, you may als o use the Advanced setti ngs in Packet Protect, if you are
familiar with encryption and authentication settings, to configure the security
poli cy tha t co m e s w ith Pack et Protect.
In this chapter, you’ll find information about:
• Understanding default security behavior (basic settings).
• Setting up your System Policy (adva nced settings).
21
Page 28

Intel® Packet Protect User’s Guide
Understand Default Security Behavior
Duri ng installat ion, you selected a default beha vior for your computer to use for
all comm unications. You also entered a pre- shared key that matches the
pre-shared key on other computers in the netw ork so the com puter can communicate securely with other computers possessing the same pre-shared key.
Default Behaviors in Packet Protect
In order to operate with security settings, your computer needs to know how to
communicate with other IPSec-enabled computers. In the absence of a rule that
match es a s pe ci fic co mmuni cat io n need , Pa ck et Pr ot ect us es de fa ult beh a viors t o
determine how IPSec computers use security. If a matching rule exists on the
two co mput ers th at are attem ptin g to c omm unicat e, th e defa ult beh a vior w ill not
be used. The table below describes the default beh aviors available with Packet
Protect.
: You can set up specific security policies with rules to apply to
Notes
specific types of comm unications using advanced security
settings. See “Set up Your System Policy” on page 25 for
more information.
You cannot make any changes to Packet Protect on a computer unless you are logged on as
users cannot modify Packet Protect settings.
administrator
. Individual
Table 3: Default Behaviors for Packet Protect Computers
Default
Behavior Description
Secure
Responder
(Example:
workstations)
Computers with this behavior initiate communication
without security (in the clear), but will attempt to
negotiate a secure communication if one is
requested. For example, if a Secure Responder
workstation attempts to a ccess a file server and tha t
file server requ e s ts a secure communication, the
workstation will resp ond in a secure manner.
If two worksta tions are configured with this setting
and they atte mpt to communicate with each other,
the communication is allowed without security (in
the cle ar) . Als o, Secure Resp ond ers a nd computers
that are not IPSec-enabled communicate without
security .
22
Page 29

Configuring Security Settings
Table 3: Default Behaviors for Packet Protect Computers
Default
Behavior Description
Secure Initiato r
(Example:
servers)
Lockdown
(Example : servers
that require strict
security)
Compute rs with this behavi o r req uest security for all
commun ica ti ons , but don’t requ ire it. For exam pl e , a
Secure Initiato r server always initiates
communications by requesting security. If the
negotiation for a secure communication is
unsuccessful, the Secure Initiator server
com m unic ates with out se cur ity (in the clea r).
Computers with this behavior
communication. Lockdown computers do not
communicate withou t s ecurity, that is, they do not
communicate in the clear.
Only use Lockdown if a computer will be accessed
by a very limited number of computers, and those
computers are all properly set up with Packet
Protect. If a backup to another comp uter on the
network is scheduled auto matically, it will fail unless
the other computer is also security-enabled.
require
security for
all
23
Page 30

Intel® Packet Protect User’s Guide
To change the default behavior for a Packe t Protect computer
1. Click Start > Settings > Control Panel.
2. Clic k Intel
Packet Protect. The Packet Protect Security tab appears:
3. To change the behavior for your computer, use the Behavior drop-do w n list
to choose one of these behavior s: Secure Responder, Secure Initiator, or
None.
4. To change the pre-shared ke y, type a new key in Pre-Shared key bo x.
5. When you ar e finished viewing and making changes in the Security tab,
click OK.
24
Page 31

Set up Your System Policy
You set up basic security settings when you install Pack et Protect. If you are
familiar with encry ption and authentication settings you can use the advanced
settings in Packet Protect to configure specific security settings to apply to different types of communi cation. Packet Protect comes with a system policy that
contains advanced security settings.
What is a Policy?
A policy helps determine how the computers you manage communicat e w ith
each other and with other computers on the network. Policies contain one or
more ru les and use rul es to specify how computers on the LAN com municate in
a protected way. Your Packet Protect policy comes with pre-defined rules. Each
rule has its own set of conditions that, if matched, apply defined security settings. You can edit the pre-defined rules or create new rules for your policy.
What is a Rule?
Configuring Security Settings
A rule defines how you want to communicate with other computers on the network. For example, one rule can define how to communicate with a file server
using sp eci fi c se cur ity s et tings . An oth er can d ef i ne an enti re g roup of comput er s
for which communication will always be allowed “in the clear ” (without security).
The rules in your system policy are listed in the Policy Editor. To view the Policy Editor, cli ck Ad va nc ed on th e Secur i t y Tab.
25
Page 32

Intel® Packet Protect User’s Guide
Every rule contains the information described in the following tab le.
Rule Setting Description
Table 4: Rule Settings
Destination
workgroup
Security acti on Colle ction of security se t tings used when ne goti a ti ng a
Rule failure Definition of what happens when the rule is applied,
Authentication Definition of how your computer verifies the other
: All rule s s pecify All IP f or the Traffi c Gr oup. If a rul e is applied,
Note
Collection of computers with which a computer
communicates.
commun ication.
but the communication is not negotiated successfully.
You can allow the communication to occur unsecured,
or deny the communication.
computer’s pre-shared key when the rule is applied.
You can use the authentication settings already
specified for your computer (on the Security tab), or
use custom settings for th e rul e (p rop ose a pre-shared
key).
the security settings apply to all IP traffic between the two
computers communicating. Refer to the readme file on the
product CD-ROM for a list of ports and protocols that are
always sent unprotected in order for Packet Protect to function.
The Default Rule
When you install Packet Protect, the default rule is created . The Def ault Rule
has these properties:
• Destination Workgroup Everybody.
• Security Action Default Action.
26
Applies to every computer in the LAN.
The sta ndar d se curity ac tion, w hich us e s a
time limit of 8 hours. Refe r to “Customize
Security Actions” on page 33 for detailed
inform ation about security actio ns.
Page 33

• If rule fails Allow Communication without Security.
• Rule authentication Use Sys tem Po licy’s settings.
Importance of Rule Order
Configuring Security Settings
If the computers cannot negotiate a secure
communication, then communication is
allowed without any security. For comp uters
that use the Lockdown behavior—if the rule
fails, then communication is denied.
When Packet Protect was installed, each
computer was set up to use a pre-shared key.
When two computers attempt to communicate
securely using a pre-shared key, each
computer must have the same key entered. If
these keys do not match, the rule cannot be
authenticated by the computers and it will fail.
The System Policy typically contains one or m ore rules. Place the rules in the
order you want them applie d. If you have one general rule and also an exception
to that ru le, pla ce the excepti o n be fore th e g en eral ru le ; otherw i se , the spe ci fic
rule is never applied.
It is cr iti cal tha t you or der rules appr opria te ly to en sure t he y beh av e as ex pec ted.
The following example shows what might happen if the rules are not in the correct order.
Example of rule ordering
Suppose you have created a destination workgroup for the finance managers at
your co m p a ny. You ne ed to send sen s itive information to th e m a na gers, so yo u
have created a rule with hig h security settings. You decide tha t if one of the
finance managers does not meet the security action settings, you do not want to
transmit information. Y ou also have the Default Rule with security settings to
use when communicating with everyone on the LAN. However, if the settings
fail to be negotiated, you will still allow the communication to take plac e w ithout security. The rules you have created appear in the table below.
Table 5 : Correct Ord ering for Rules
Rule Name
To Finance
Management
Default Rule Everybody DES+MD5+None Allow
Destination
Workgroup
Finance
Managers
Security Action If rule fails
3DES+SHA1+None Deny
27
Page 34

Intel® Packet Protect User’s Guide
The rule ordering abov e requires the Finance Managers workgroup to have a
rule listing your computer and the 3DES +SHA1+None security action in or der
to negotiate secur e com munication. If the Finance Managers workgroup does
not ha ve a matchin g rule, communica tion will be denied.
Notice the importance of rule order. If the Default Rule was ordered before the
To Finance Management rule, communication with Finance manager worksta tions would be allowed “in the clear” (with no security) even if the Finance
Managers workgroup does not have a mat ching rule for communication with
R&D using the 3DES+ SHA1+None algorithms. In this case, the general rule
woul d be applied first, and the spec ific rule would never be applied.
For ins tr uc tions on ho w t o order rul es, see “ Ste p 3: O rder t he Rul es ” on page 31.
The next section explains more about how Packet Protect computers use rules.
For information about security algorithms and about their notation, see “About
algorithm notation” on page 36.
How Does the System Policy Work?
The System Policy defines a collection of rules that describes the security settings to enforce under certain situations. When a comput er attempts communication, Packet Protect evaluates a number of things before allowing the
communication.
The following example describes how the policy w orks:
1. MyComputer attempts to communica te with MyServ er with a rule using
the 3DES+SHA1+None encryption algorithms.
2. If a rule match is found, MyComputer proposes the security action settings and authentica tion settings that you defined for that rule. The two
comput ers negotiate the securit y settings. If that security settings negotiation is successful, the two comput ers communicate using the agreed upon
settings. If that negotiation fails, the communication fails or is allowed
unsecured, depending on the if rule fails specification.
If a rule match isn’t found, the system proposes the pre-shared key
assigned for that computer’s w orkgroup. It the n proposes pre-de fined security settings such as default settings that are used for all communications.
See “Appendix A — IKE and IPSec” on page 53 for more information.
Note:
If the destination computer uses Packet Protect, it also
searches its policy for a rule with settings that ma tch. If your
computer and the destination computer have matching rules,
the communication is allowed secure according to the specified security action settings.
Add Rules to the System Policy
Addin g rules to your policy is optional. If you are unsure whether you need new
new rules, see “What is a Policy?” on page 25 for more information.
Crea ting a new rule involves several steps:
28
Page 35

Configuring Security Settings
1. Viewing the System Policy.
2. Defining a new rule for the System Policy.
3. Ordering the rules.
In gen eral, follow these guid elines when you make rules:
• When you add a rule to comput er A’s policy for secur e communication
with computer B, you mus t add a matching rule in computer B’s policy for
secure communication with computer A . Otherwise, the rule w ill fail and
communication will be denied or allo we d unsecure (depending on the If
rule fails setting for both workgroups’ rules).
• If you add two rules that include some of the same computers (for example,
one ru les lists computer A as the destination workgroup, and another rule
lists Everybody – all computers on the network – as the destination workgroup), you must order the specific rule before t he general rule. Otherwise,
the specific rule will never be applied. See “Imp ortance of Rule Order” on
page 27 for more information.
Step 1: View the System Policy
1. At the Control Panel, click Intel Packet Protect.
2. On the Security tab, click Advanced... . The Policy Editor dialog box
appears:
29
Page 36

Intel® Packet Protect User’s Guide
Step 2: Define a new rule for t he policy
1. Click New Rule. The New Rule dialog box appears.
2. In the Rule Name text box, type a name for the rule.
3. In the D estination workgroup text box, sel ect the group of com puters for
which you want this rule to apply.
The list includes destination workgroups that are already created (either as
part of the Default Rule or that you crea ted). If you want to view, edit, or
create a destination workgr oup, see “Customize Destination Workg roups”
on pag e 31 fo r m ore info r m ation .
4. In the Sec uri t y acti on te x t bo x, sel ect the gro up of sec ur ity se tt in gs th at you
want to define for this rule.
The list includes sec urity actions you have already created and p re-defined
security actions that come with Packet Protect. I f you want to view, edit, or
create a secu rity ac tion, se e “Cu stom iz e Securi ty Ac tions ” on page 33 fo r
more i nformation.
5. In the If rule fails text bo x, select whether to deny or allow a com m unication if this rule is matched, but the comm unication fails to negotiate.
6. In the Authenticatio n area, decide whether you want to use the default settings or propose custom authentication settings.
You spec ified the default settings when you installed Packet Protect (displayed on the Security tab).
7. Click OK.
8. Repeat steps 2 through 7 to ad d m ore rules to the System Policy.
30
Page 37

Configuring Security Settings
Step 3: Order the Rules
1. On the Policy Editor dialog box, click a rule.
2. Click Move Up or Move Down to move t he rule up or down one line. You
can also select a rule and drag it up or down.
The rules are applied in the order in which they are listed. The rule at the
top of th e lis t is appl ie d befor e al l ru les bel ow it , for example.
See “Im portance of Rule Order” on page 27 for more information about ordering rules.
T o modify a rule
In order to apply your rule to a communication, the computer with which you
are attempting commun ication must have a rule with mat ching settings . If you
have already coordinated rules with the other computers with which you wish to
communicate, modifying your rule will require modi fication to rules for other
comput ers.
1. Before you modify a rule, check the fol lowing:
• If you have already set up matching rules for other IPSec computers,
DO NOT follow the steps below .
• If you have not set up matching rules for other IPSec compu ters, con-
tinue with the steps bel ow.
2. In the Policy Editor dialog box, select rule you want to modify.
3. Click Edi t Rule. The Edit Rule dial og box appears.
4. Make changes, as neces sary, then click OK.
Customize Destination Workgroups
A destina ti on work gro up is a col le ctio n of co mput er s with w hich you r co mput er
communicates. For example, if your computer requires specific security when
communicating with the Research & Dev elopment Workgroup, your policy
must include a rule with security settings that specifies th e R esearch & Development Workgr oup as the destination workgroup, and Research & Develo pm ent
comput ers must have a rule specifyi ng the same security settings and your computer as the destination workgroup.
The following destination workgrou ps are available:
• Eve rybody: Use this destination workgroup when you wan t the rule to
apply to communication with all computers on your LAN.
• Destination workgroups you create.
If a comp uter or group of computers you need is not in the destination workgroup list, create a new destination workgroup.
To create a new destination workgroup
1. On the Policy Editor dialog box, select the rule for which you want a new
destination workgroup.
31
Page 38

Intel® Packet Protect User’s Guide
2. Click Edi t Rule. The Edit Rule dial og box appears.
3. Click Customize Destination. The Customize Destination Workgroups dialog box appears.
4. Click New.
5. In the Destination workgroup box, type a new name for the destination
workgroup.
6. To add computers to the destination workgroup, in the Add computers by
text box, sel ect how you want to identify computers for addition to the destinat ion workgroup: by IP addre ss or by computer name.
: Check with your network administrator to determine how to
Note
add computers to a workgroup. If the computer you want to
add to this workgroup has a permanent (or static) IP
addresses, you should probably add computers to the workgroup by IP address. If the computer you want to add uses s
dynamic IP addresses (where a temporary IP address is
assigned to a computer for each session), then you should
probably add computers to the workgroup by computer name.
7. Type the computer name or IP address for a computer you want to add to
the wo rkgroup.
8. Click Add>>.
9. Repeat st eps 5 through 8 for eac h computer you want to add.
10. If you need to del ete a com p uter fr om th e des tinat i on wor kgrou p, se le ct the
comput er from the list on the righ t, then click <<Re m ove.
11. If desired, continu e adding destinat ion workgroups by clicking New again
and repeating Steps 4-7 .
12. Click OK. The s elec te d de stin at io n w ork group app ear s aut omat i call y i n the
Edit Rule dialog box.
32
Page 39

Configuring Security Settings
Destination workgroups can be used in multiple rules. If you modify a desti nation workgroup, other rules may be affected.
Before you modif y a destination w orkgroup, check the followin g :
• If you have used the destination workgroup in any other rules, do not
follow the steps below. See “M odify Destination Workgroups or Security Actions” on page 41 for more information.
• If you have not used the desti nation workgroup in any other rule, con-
tinue with the steps bel ow.
To modify a destination wor kgroup
1. In the Cus tomize Des ti na tion Workgro ups dial og box , sel ec t the de st in atio n
work group you want to mod ify.
2. Make changes, as neces sary, then click OK.
Customize Security Actions
You must specify a security action for each rule. This sectio n defines the security settings you can apply when two comput ers communicate .
Packet Protect pro vides six pre-defined security actions, described below. Se e
“Available Setti ngs for Security Actions ” on page 34 for detailed information
about the security settings listed here.
•Clear
Use to co m municate completely in the cl ear, without any security.
• Default Action
Use to get an act i on th at pro vid es a high level of secu rity, alon g wit h a high
level of int erope ra b ility. The default acti o n is a rich se t of IPS e c propo s als
that includes var ious levels of ESP (Encapsula tion Security P ayload)
encryption, ESP authen tication, and AH authentication. It provide s a maximum level of interoperabili ty with non-Packet Protect implem entations of
IPSec.
•Deny
Use to deny any communications between two computers.
• Initiate Clear, Secure Responder
Use when you want to initiate communications in the clear and will attempt
to negotiate a secure connection if requested. This security action is most
appropriate for workstations.
• Secure Initiator, Fallback Clear
Use when you wan t to request security for all communi cations, but do not
require it. If a secur e connection cannot be negotiated, then the co m munication will be in the clear. This security action is appropriate fo r servers.
• Secure Initiator, Fallback Deny
Use when you wan t to require security for all communications. If a sec ure
33
Page 40

Intel® Packet Protect User’s Guide
connection cannot be negotiated, then the communication request is
denied. This security action is approp riate for serv ers.
Remember that two computers att em p ting to commun icate must agree on cer-
tain settings in order to communicate using IPSec.
The Requires Matc h? colum n in the table below indicates whether the source
and destination comput ers must have the same security setting..
Table 6: Available Settings for Security Ac tions
Security
Setting Description
Time lim it The length of time (in minutes or hours) the
protected communication can be active
before the system renegotiates. To increase
protection, lower the time limit (to a minimum
of 10 minutes). Th is makes the system renegotiate a new security association more
often, but increases network traffic. You may
specify a time limit, size limit, or both. This
setting is optional.
If two computers re quire different time lim its,
the communication is re-negotiated w hen the
lower tim e limit is re ach ed. If a tim e l imit is not
defined, the default is 8 hours.
Size limit The amount of data (in MB) that can be
transferred during a security association
before the system renegotiates. To increase
protection, lower the size limit (to a minimum
of 20 MB). This make s the sys tem ren egoti ate
a new security association more often, but
increases network traffic. You may specify a
time limit, size limit, or both. This setting is
optional.
Requires
Match?
No
No
34
If two computers attempting to communicate
require different size limits, the security
association expires when it reaches the lower
size limit. If you specify a size limit only, an 8hour time limit is appli ed auto matically. The
default is no size limit. There is no maximu m
size limit for a security association.
Page 41
Configuring Security Settings
Table 6: Available Settings for Security Ac tions
Security
Setting Description
Perfect
forward
secrecy
The sys t em p ropo ses a second set of keys for
the security association (instead of using the
first set of keys used to verify identific ation).
Packet Protect is designe d to agree on any of
the settings (including none), but it proposes
the setting yo u select.
: DO NOT use per fect forward se c rec y if
Note
your computers will need to co mmunicate
securely with Windows* 2000 I PSec computers or any other non-Packet Protect IPSec
comp uters. Th is setting is not compatible with
non-Packet Protect IPSec computers and may
caus e communication to fail.
Anti-r eplay
protection
The system does not accept repeated
packets; that is, packets that the system
already received. This helps protect against
an intruder sending the same packets
repeatedly in an attempt to confuse an
application. Always use this option because it
increases the le ve l of prot ectio n with v ery littl e
impact on network traffic.
Requires
Match?
No
No
Use
algorithms in
order of
preference
Note:
Combinations of algorithms a computer must
Yes
use for a com m uni cati on: ESP en cry ption,
ESP authentication, and AH authentication.
Packet Protect proposes the algorithm list (in
order of preference) to the destination
computer du ring negot iat ion.
T wo compu ters
attemptin g to com municate securely m u st
agree on an algorithm combination
.
If your computer needs to communicate securely to a mixed
domesti c and e xport group of computer s, make su re your policies have compatible encryption settings. Computers using
the export version can use DES encryption only . If computers
using the export version re ceive a policy specifying 3DES
encryption, they will actually use DES encryption for the communication. Consider including both DES (56-Bit) and 3DES
(168-Bit) encryption in your security actions.
35
Page 42

Intel® Packet Protect User’s Guide
About algori thm notation
Each security action can specify algorit hms to use for encr yption and authenticatio n. Ther e ar e three cat ego ries (E n cr yptio n , ES P [En caps ul a tion Se cu ri ty
Payload] Authentication, and AH [Authentication H eader] Authentication.
At least one of these categories must be used in a security action, or you can use
two or even all three.
IPSec and Packet Protect use a kind of “shorthand” notati on for describing the
algorithms used in a security action—Encryptio n value + ESP val u e + A H
value. For example, i f you create a security action that uses DES for Encryptio n,
SHA1 for ES P, and do not use AH, this would be shown as DES+ SH A 1+None.
To create a new security action
1. On the Policy Editor dialog box, select the rule for which you want a new
security action.
2. Click Edi t Rule. The Edit Rule dial og box appears.
3. Click Cust om ize Security. The Customize Security Actions dialog box
appears.
4. Click New.
5. In the Se c ur ity acti on list bo x , ty pe a new nam e fo r th e secur it y ac tion.
6. Specify a time and/or size limit for the security association. Refer to
Table 6, “Available Settings for Security Actions,” on page 34 for detailed
infor m ation abo u t th ese item s .
7. If applicable, select the Perfect Forward Secrecy check box.
: DO NOT use Perfect Forward Secrecy if your computers will
Note
need to communicate securely with W indows 2000 IPSec
computers or any other non-Packet P r otec t I PSec computers .
8. Select Anti-replay protection. (Always select th is setting because it
increases network pr otection with very little impact on network tr affic—
see Table 6 on page 34 for details.)
9. Add alg orithms to the preference list for the securi ty action:
• In the Encryption, ESP Authentication, and AH Authentication list
box es, select which algorithms you want to propose for the security
action. You must select at least one algorit hm from any of the lists.
• Click Add.
Repeat this step for each algorithm combi nation you want to add.
10. If you n eed to rem o ve an algorithm combination from the preference list,
select the combination from the list on the right, then click Remove.
11. To indicate your order of preference, move the algorithm combinations to
the correct location on the list by selecting an algorithm combination and
clicking Move Up or Move Down. Move the most important selection to
the top of the list and continue in descending order of importance.
36
Page 43

Configuring Security Settings
12. To continue adding s ecurity actions, click New again and repeat Steps 5-11.
13. When you f inish, clic k OK. The selected security action appears automatically in the New Rule dialog box.
To modify a security action
Security actions can be used in m ultiple rules. If you modify a security action,
other rules may be af fected.
1. Before you modify a security acti on, check the foll owing:
• If you have used the security action in any other rules, DO NOT fol-
low t he s tep s below . See “ Modi fy De st inat ion Workgrou ps o r Secur it y
Acti ons” on page 41 for instructions.
• If you have not used the security action in any other rule, continue
with th e steps below.
2. In the Customize Sec urity Action dialog box, select the security act ion you
want to modify.
3. Make changes, as neces sary, then click OK.
37
Page 44

Intel® Packet Protect User’s Guide
38
Page 45

4
Making Changes
Be carefu l whe n you mak e ch ang es t o your pol ic y. The sett in gs yo u modi fy may
be used for more than one rule in your policy. This means changes you make
may affect other rules in your policy, a nd m ay even require changes to policies
for other Packet Protect computers.
In this chapter, you’ll find information about:
• Modif ying rules.
• Modif ying custom destination workgroups and custom sec urity actions.
• Deleting rules.
• Rest oring the system policy.
39
Page 46

Intel® Packet Protect User’s Guide
Modify the System Policy
Modif ying a computer’s Sys tem Policy may impact policies that belong to other
clients with which your computer communicates using Packet Protect. In order
to apply your rule to a security association, the co mputer with which you are
attem pting communication must have a rule with matching settings. If you have
already coordinate d rules with these ot her computers, m odifying your rul e w ill
require modificat ion to the rules f or the other computers. Contact the network
admin istr ato r if you ha ve an y que st ions o r co nce rns abo ut modif yi ng rul es i n the
System Policy.
You may edi t the Default Rul e that comes with your Packet Protect System Policy (see “The Defau lt Rule” on page 26 for a descri ption of the Defa ult Rule).
Notes:
You should car efully consider the possibl e e ffects of c han gi ng
the Def ault Rule . If y ou modif y the De fau lt Rule ext ensiv el y on
a computer, then you run the risk of that computer not being
able to successfully negotiate a secure transmission with
another computer in your network.
If y ou ha ve to re-ins tal l Packet Pro tec t f or any reaso n, or need
to recreate the Default Rule, y ou will lose y our customizations
and will have to specify them again.
T o modify a rule
1. Dete rm ine which of the other computers on the LAN have a matching rule
for the rul e yo u wil l edit. You need this in fo r m at ion lat er.
2. On the Policy Editor dia log box, select the rule you w ant to modify.
3. Click Edi t Rule. The Edit Rule dial og box appears.
4. Make changes as necessary.
5. If you cli ck any of the Customize buttons to make cha nges, see “Modify
Destination Workgroups or Security Actions” for mo re information.
6. Click OK.
7. Go to the other computers that have a matching rule for the rule you just
modified (if you do not administer the other computers, coordinate the
needed rule changes with the other administrator). Complete steps 2-6 on
each of the other computers to update the settings so the rules have matching settings.
Note:
40
You must change matching rules on other computers when
you modify your rules. Otherwise, when the computers
attempt to communica te, the rule may fail and the security
settings are not us ed.
Page 47

Modi fy Destination Workgroups or Sec urity Act ions
Destination workgroups and security actions can be used in multiple rules. If
you modi fy these items, other rul es may be affected. Follow these steps to
ensu re that you address other affected ru les.
Dete rmine which other computers on the LAN have a matching rule for the rule
you will edit. You will need this information later.
To edit destination workgroups or security act ions:
1. Dete rm ine which o ther rules that use the destination workgroup or security
action you wish to modify. You will need this information late r.
2. On the Policy Editor dia log box, select the rule containing the des tination
work group or security actio n you w ant to edit.
3. Click Edi t Rule. The Edit Rule dial og box appears.
4. Click Cust om ize Destination or Customize Secur ity, de pending on what
you wan t to edit. The appropriate dialog box appears.
5. Selec t th e item yo u wa nt to m od i fy.
Making Changes
6. Make changes as necessary.
7. When you are finished, click OK.
Any rule that uses the destination workgroup or security actio n y ou just
modified will also use the modified settings.
8. Administer the other computers that have a rule matching any of the rules
that use the modified destin ation workgroup or secur ity action. (If you do
not administer the other computers, coordinate the needed rule changes
with the other adm inistrator.) Compl e te steps 2-7 to update the settings in
the ma tc hi n g ru le .
Note
Delete a Rule
Caution:
To de le te a ru le:
: You must change matching rules on other computers when
you modify your rules. Otherwise, when the computers
attempt to communica te, the rule fails and the security settings are not used.
After you delete a rule, you cannot recover its information.
1. On the Policy Editor dialog box, select the rule you want to delete.
2. Click Delete Rule.
3. Click Yes to confirm the deletion.
Note
: If other computers have a rule that matches the one you just
deleted, you should delete the m atching rule in the System
Policy of those computers.
41
Page 48

Intel® Packet Protect User’s Guide
Restore the System Policy
If the System Policy on your computer has been extensively modified, you may
find that your computer can not always negotiate a secure communic ation with
another computer on the LAN.
When thi s occurs, you shoul d consider removing your customi zations and
returning to the original System Policy, with its Default Rule. You will lose all
of your customizations, including customized desti nation workgroups and security actions.
To restore the System Policy
1. Disp la y th e Intel Pa ck et Pro tect Se c ur i t y Tab.
2. Click Recreate Now. All your customizatio ns are removed and you now
have the default System Policy on your computer.
42
Page 49

5
Maintaining Packet Protect
You need to perform certain tasks to ensure that Packet Protect is running
smoothly on their network.
In this chapter, you’ll find information about:
• Monito ring Packet Protect computers.
• Setting Up Compatible Policies
• Installing a new adapter for a Packet Protect c om puter.
• Working with other security products.
• Turning security on.
• Turning securit y off.
43
Page 50

Intel® Packet Protect User’s Guide
Monitor Packet Protect Computers
View Status at a Packet Protect Client
At each computer, you can verify if Packet Protect is running.
To verify whether Packet Protect is runni ng
1. At the taskbar on the computer, select Settings > Contro l Panel.
2. Doub le -c lick Se r vi ces and ver ify that Int el Polic y A ge n t is st arted .
If Intel Policy Agent doesn’t appear in the list, Packet Protect has b een shut
dow n or is not function ing properly. See “Turn Security on Manually for an
Existing Computer” on page 47 for detai ls about restarting P acket Protect .
44
Page 51

Set Up Compatible Policies
Two Packet Protect-enabled computers m ust agree on certain settings in order to
communicate in a protected way. These settin gs m u st be agreed upon by both
comput ers. I t beco mes i nc rea singl y d if f i cult to set up an IPSe c s ecuri ty sy stem if
there is a different network administrator who manages computers with which
you need to communicate using Packet Protect.
Cont act the ot h er netw or k admi ni strato r w h o is also us ing Pac ke t Prote ct to
coordinate the management of Packet Protect compute rs. One of you may need
to updat e your cl i ent ’ s Sys tem Pol ic y to be com pati bl e wi th th e o the r com pu ter’s
System Policy.
Two computers must use compatible settings for the following:
• Authe ntication. Both computers mus t use the same method to authenticate
each other’s i d entity (e.g., both computers must use the same pre-shared
key)
• IPSec. Both computers must use compatible IPSec settings. See “Customize Security Actions” on page 33 and “How Packet Protect Uses IPSec” on
page 59 fo r a lis t o f the requ ir ed sett in g s.
45
Page 52

Intel® Packet Protect User’s Guide
Work with Other Security Products
On your ne twork, there may be installations of an IPSec product othe r than
Pac ket Protect. If this is the case, make sure that the security settings used by
your com puters match the security settings used by the other IPSec compute rs.
This is because two IPSec-enabled com puters must agree on these security settings in order to communicate in a protected way.
You migh t be m anaging both security product deployments, in which case you
can verify the settings that need to match. If another network administrator manages th e secur ity com p u ters usi ng a different pro duct, contac t th at netw or k
admi ni strato r to verify th e se tting s.
: If the other network adm inistrator manages Windows* 2000
Note
IPSec computers, you will need to create a separate destination w orkg roup for each Windows 2000 IPSe c co mpu t er. This
will maximize IPS ec interoperability.
In order to communicate with a Packet Protect computer using IPS ec, the two
computers must use compatible settings for the following:
• Authentication. Bot h com p uters must use pr e-shared keys (the pr e-shared
key must be th e same for both computers ) to authenticate each other’s identity.
• IKE. Both computers mu st use compatible IKE set tings. See “How Packet
Protect Uses IKE” on page 55 for a list of settings.
• IPSec. Both computers must use compatible IPSec settings. See “Customize Security Actions” on page 33 and “How Packet Protect Uses IPSec” on
page 59 fo r a lis t o f the requ ir ed sett in g s.
Note:
If you decide to install Packet Protect for a computer that currently uses a different IPSec product, uninstall the other product, then install Packet Protect. For more information about
installation, see “Install Security for a New Com puter” on
page 47.
46
Page 53

Turn Security On for a Computer
After general deployment of Packet Protect, you might need to turn security on
for a computer if the computer is new and hasn’t had Packet Protect installed
befo re. Or, you might need to manual ly turn Packet Protect on for an existing
comp u te r if Packet Pro tect was turne d o ff prev io usly.
Install Security for a New Computer
If a new computer requires Packet Protect, follo w the instruct ions under “Install
Packet Protect” on page 17.
Turn Security on Manually for an Existing Computer
Afte r installation, Packet P rotect is desig n ed to start automatically upon system
startup. If for some reason Packet Protect isn’t running, you can re start it.
If you turned off security for a client and are now turning it back on, make sure
you reverse whatever method you used to turn it off. See “Turn Security Off for
a Comput er” on page 48 for details about the ways you can turn o ff Packet Pr otect at a client.
T o manually turn Packet Protect on
1. At the taskbar on the computer, select Settings > Contro l Panel.
2. Doub le-cl ick Ser vices.
3. Select Intel Policy Agent and click Start.
47
Page 54

Intel® Packet Protect User’s Guide
Turn Security Off for a Computer
There ma y be cases when you need to remove security from a client. For example, when the compute r no longer requi res protected traffic. There are tw o w ays
you can remove secur ity from a client:
1. Shut down Packet Protect at the computer
2. Uninstall Packet Protect at the computer
Shut Down Packet P rotect at a Computer
Pac ket Protect is de signed to run automatically every time the computer starts.
You can shut down Packet Protect for the current session, or you can change the
computer setup so Packet Protect doesn’t run each time the computer starts.
To shut down Packet Protect for the current comp uter session
1. At the taskbar on the computer, select Settings > Contro l Panel.
2. Doub le-cl ick Ser vices.
3 Select Inte l Po licy Ag e nt and cl ick Sto p.
Note:
If you want to turn security on later, man ually restart Packet
Protect. See “Turn Security on Manually for an Existing Computer” for more information.
Uninstall Packet Protect from a Computer
Uninstalling Pack et Protect from a computer permanently removes all Packet
Protect-related files, including IPSec, IKE, policies, and related Packet Protect
program files.
To uninstall Packet Protect
1. At the taskbar on the computer, select Settings > Contro l Panel.
2. Double-click Add/Remove Programs.
3. On the Install/Uninstall tab, Select Packet Protect and click Add/Remove.
Follow the prompts to uninstall Packet Protect.
Caution:
When you uninstall Packet Protect, you lose all your customizations.
48
Page 55
6
Troubleshooting and FAQs
This ch apter details tips for troubleshooting Packet Protec t. This chapter also
provides a list of frequently asked questions about the product.
49
Page 56

Intel® Packet Protect User’s Guide
Troubleshooting
Communica ti on fails
If a Packet Pr otect computer cannot comm unicate with another co m puter, c heck
the following:
• Verify that each computer’s basic security settings are set to allow communication. If the computers are using advanced securit y settings, ve rify that
the com puters have matching rules. The rules must allow for a match
betw ee n ESP and AH se tting s fo r th e se curity ac tion.
• If usin g pr e-s ha red ke ys , v er ify t hat ea ch com puter is s et up to use the sam e
pre-shared key when communicating with each another. Note that
pre-shared keys ar e case-sensitive.
• At the client, verify that Packet Protect is running. Click the Start button on
the taskbar, se lect Settings > Control Panel. Double-click Services and verify that Intel Policy Agent is started.
Communicat ion fails when passing through a firewall
Depend ing on the type of firewall, IPSec ma y affect the deployment in different
ways:
• Some f i re wa ll s b lock o uts id e- in traffic wi tho ut per fo rmi ng n etw ork a ddr es s
translation (NAT). These firewalls can sometimes be configured to allow
IPSec traffic to flow from within the network.
• Proxying firewalls use HTTP, Telnet, FTP and other application proxies or
SOCKS to forward traffic. With these f irewalls, IPSec cannot be used to
protect traff ic end-to-end. IPSec can be used within the local LAN, but all
outside traffic will remain unprotected .
• If a gateway or firewall is pre sent doing network address translat ion, IPSec
cannot be applied since IPSec packets are encrypted and integrity-protected, making address and port substitution impossible.
The ef fe ct s of IP Sec o n f irewall pol ic ies v a ry g reatl y o n th e type a nd g oal s o f the
firewalls. Refer to your firewall vendor for information on IPSec support.
Packet Protect doesn’t start automatically upon startup
At the computer, make sure that Packe t Protect is s tarted as a s ervice. See “Turn
Security On for a Compute r” on page 47.
Multicast, Broadcast , and IGMP traffic isn’t protected
Multicast traffic is always unprotected when you use Packet Protect because of
IPSec standards. In addition, IGMP traffic is unprotected.
50
Page 57

Troubleshoot ing and FAQs
I changed the IP address or DNS name of a computer, now it can’t
communicate on the network
If you have custom rules, there may be other computers in t he network that have
an old IP address or DNS nam e of a computer in their rules. These rules must be
modified to reflect the IP address/DNS name change.
I think som e transmi tted i nfor mati on is unp rote cted and it shouldn’t
be
• Check the security action settings of both computers to make sure they
match . Also try to determine which rule is being applied t o the communication . If the rule is set to a llow the commu nication if the rule fa ils, the compute rs will transmit data “in the clear” (without security).
• Check the default behavior. If both computers use Secure Respond er or No
Security, they will always communicate in the clear. If none of the rules
applies to the communication, the communication is unprotected if the
default behavior is Secure Initiator or Secure Responder.
• When a computer begins co m munication with another computer, the first
few seconds are allowed in the clear if the rule be ing used as a fallback
clear setting or if there are no matching rules and the behavior is Secure
Initia to r or Secu r e R es p on d er.
• The fol lowing por ts al w ays allow t raffic to pass in the clear:
• UDP port 53 (for DNS traffic)
• UDP port 68 to UDP port 67 (for DHCP)
• UDP port 137 to UDP port 137 (NetBIOS nam e service)
• UDP port 138 to UDP po rt 138 (Ne tBIOS datagram serive)
• TCP any port to TCP port 389 (LDAP directory access)
51
Page 58

Intel® Packet Protect User’s Guide
Frequently Asked Questions (FAQs)
What is Packet Protect?
Packet Protect hel ps protect Internet Protocol (IP) traffic as it travels between
computers on your LAN.
What is IPSec?
Internet Protocol (IP) Security is a set of protocols used to help secure the
exchange of IP data. For more information about IPSec, see “Appendix A — IKE
and IPSec” on page 53.
What is IK E ?
Internet Key Exchange is a protocol used to verify the identity of computers and
negotiate a protected communication. For more information about IKE, see
“Appendix A — IKE and IPSec” .
How does Packet Protect work with multiple adapters?
Pac ket Protect can work with multiple adapters that you inst all in one computer.
If you use an Intel
offloads encryption tasks to an y of these adapters. For more information, see
“Mul tiple A d ap ters” on pa ge 16.
PRO/100 S Management or Server adapter, Packet Protect
How does Packet Protect work with Adapter Teaming?
Adapter Teaming and Packet Protect work together only for computers with
Windows NT
*
operating systems installed. For more informati on, see “Adapter
Teaming” on page 16.
How does implementing Packet Protect affect my network performance?
Like an y I PSec solut ion , Pac ke t Pr otect dec rease s ne tw ork per form ance be cau se
of the intense computation required to encrypt, decrypt , and v alidate packets.
Use Pa cket Protect wit h an Intel PRO/100 S Management or Server Adapter to
reduce the impact on processor utilization and networ k traffic . Packet Prote ct is
designed to offloa d processor-intensive tasks (ESP and AH algorithm calculations) to these Intel adapters tha t are installe d in a computer. This frees up the
comput er’s processor util ization for othe r tasks, reducing the impact to the network performance.
How can I tell if Packet Protect is running?
From th e Start menu, se le ct Se ttin gs > Contro l P ane l. Double- cl ic k Serv ices and
verify that Intel Policy Agent is started.
Why isn’t Multicast, Broadcast, and IGMP traff ic protected
Multicast traffic is always unprotected when you use Packet Protect because of
IPSec standards. In addition, IGMP traffic is unprotected.
52
Page 59
A
Appendix A — IKE and IPSec
A protected communication using Packet Protect involves I n ternet Key
Exchange (I KE) and In terne t Pro tocol Sec ur ity ( IPS ec). Thi s a ppendi x d esc ribe s
details about IKE and IPSec, and how the technologies work together to protect
information as it travels on your network.
In this appe ndix, you’ll find the following information:
• An overview of IKE and IPSec.
• How Packet Protect uses IKE.
• How Packet Prote ct uses IPSec.
For mo re information ab out IKE and IPSec, including applicable RFCs, see
Internet Engineering Task Force IPSec Working Gr oup Web site at
http://www.ietf.org.
53
Page 60

Intel® Packet Protect User’s Guide
IKE and IPSec Work Together
Packet Protect use s IK E and IPSec to protect packets tr aveling on the network:
• IKE — Negotiates the security settings to be used by IPSec for protection
of the communication.
• IPSec — Protects the packets traveli ng between two computers that ar e
attem pting to communicate.
The following diagram illustrates how Packet Protect uses IKE and IPSec
together to protect a communi cation between two computers
Step 1: IKE ve rifies pre-sha red keys
Step 2: I KE Negotiates IPSec Settings
Step 3: IPSec Protect s Packets
.
54
Page 61

How Pac k et Protect Uses IKE
IKE is a set of standard protocols developed by the Internet Engineering Task
Force (IETF). IKE is used to authenticate a nd negotiate a pr otected communication. Using IK E is a tw o step pr oc ess:
1 IK E v erifies t he pre-shared keys of the two comp uters that ar e attempting
to communicate.
2 IKE negotiates a set of security settings to be used by IPSec.
Each com puter must agree upon the secur ity settings before IKE can establish a
protected communication for IPSec.
Identity Negotiation Settings
When IKE negotiates security for two computers, it requires that the following
be compatible:
• IKE se ttings
• Authentication method
IKE Settings
IKE settings are agreed upon by the tw o computers that are attempt ing to verify
each other’s pre-shared key. They are used to protect the IKE negotiation transactions. Th i s allows th e tw o computers to negotia te with ou t comp ro m i sing
secret key or password informati on.
The diagram below shows the steps that Packet Protect performs to protect a
communication. The IKE settings are used during Steps 1 and 2.
IKE settings protect IKE pre-shared
key verification and n eg otiati o n steps
Step 1: I KE Verifies Pre-shared Keys
Step 2: I KE Negotiates IPSec Settings
Step 3: IPSec Protect s Packets
Packet Protect use s pre-define d IK E settings, des igned for maximum compatibility with computers that us e Packet Protec t and other IPSec products.
If two Packet Protect computers attempt to communicate, the y use the same
default IKE settings. If one of the computers is managed by a different IPSec
product, make sure that the IKE settings match. If necessary, make changes to
55
Page 62
Intel® Packet Protect User’s Guide
the IKE settings in the other IPSec product. The following table describes the
pre-defined IKE set tings for each computer that uses P acket Protect.
Table 7: Pre-Defined IKE Settings
Preferred
Order
Encryption Hashing
Diffie-
Hellman
1 DES (56-bit) MD5 768-Bit
2 DES (56-bit) SHA-1 768-Bit
3 3DES (168-bit)
MD5 1024-Bit
Domestic v ersion only
4 3DES (168-bit)
SHA-1 1024-Bit
Domestic v ersion only
A compute r th at requ est s a prot ect ed communi cat ion pro pos es i ts lis t of IKE set tings to the computer with which it is trying to communicate. The IKE settings
are proposed in order of preference, but the responding computer can agree on
any of the proposed comb inations. The responding comput er must ha ve one of
the com b inations defined, or the co mmunication is not allowed using IPSec.
So urce compu ter
Propose s defined IK E
settings
NOTE:
Authentication Method
IKE re qu ir es that two co m pu t ers use th e sam e au th entic ation method to verify
each other’s identity. Packet Protect supports the following:
• Pre- sh ared ke ys — If using pre- shared keys, the two computers attempting to communicate must propose the same pre-shared key, otherw ise they
cannot communicate us ing IPSec. If you change the pre-shared key for a
workgroup, remember that this changes the pre-shared key used for all
56
Destination computer
Picks which IKE settings to use
from the s ource computer’s list
The IKE settings used by Packet Protect cannot be customized. If you
require different settings for a communication with a computer that
uses a different IPSec product, change the IKE settings in the other
product to match one of the IKE setting combin ations used by Pa cket
Protect (as noted in the above table).
Page 63
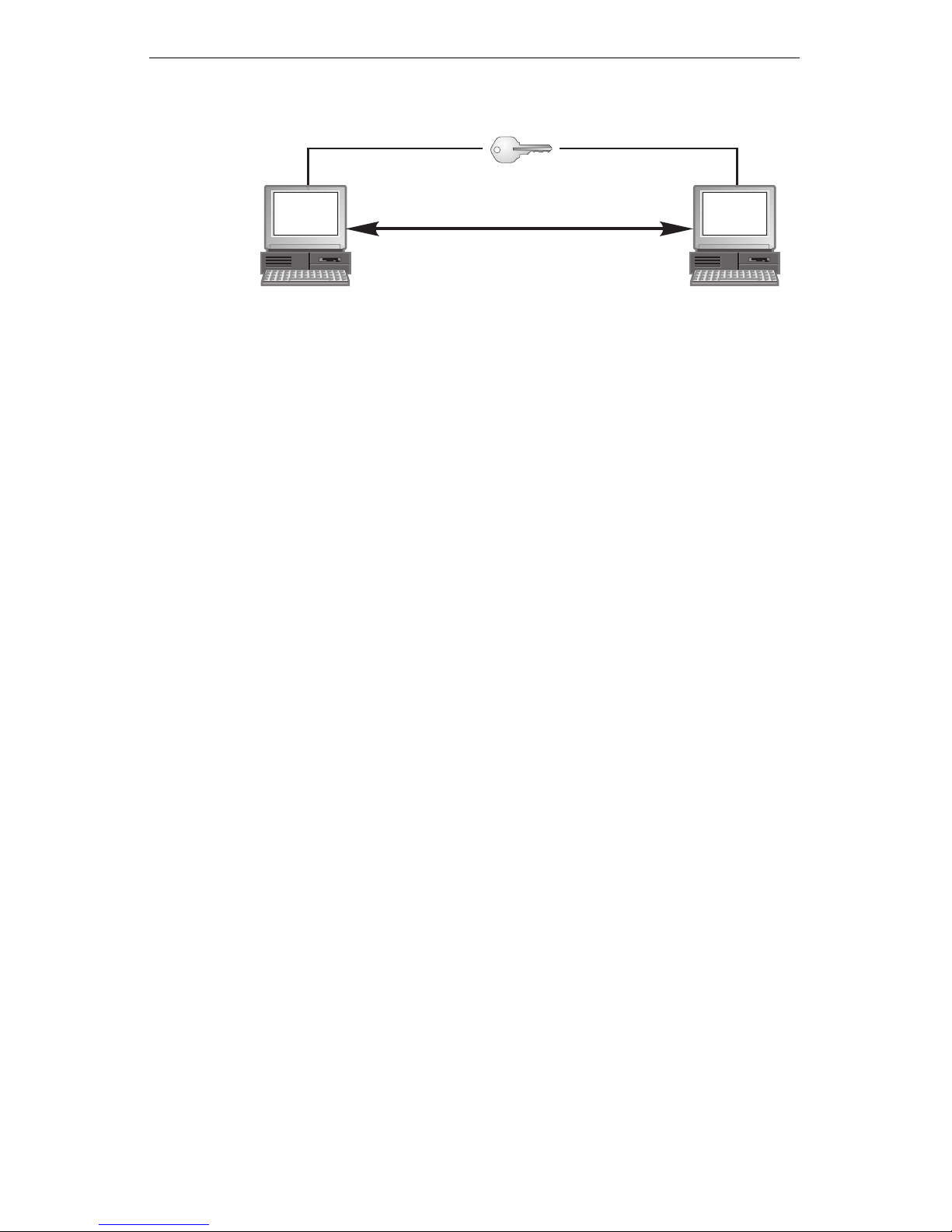
communications for all computers in the workgroup.
IPSec Settings
Afte r IKE verifies the ident ity of each computer, it negotiates w hich IPSec set tings to use to protect the communication after negotiation. Packet Protect
comes with pre-defined IPSec options, or you can create your own.
Each com puter must agree upon the IPSec setti ngs to use before IKE can establish a protected communication for data transfer.
Secure communication using the
same pre-shared key
Pre-defined IPSec Settings
Packet Protect comes with pre-defined IPSec settings, called security actions.
These security actio ns are designed for maximum compatibility between computers using Packet Protect and other IPSec products.
A compute r th at requ est s a prote ct ed co mmunic at io n propos es it s IPSec set tings
to the computer with which it is trying to communicate. The IPSec settings
include a list of algorithm combinations that appear i n order of prefere nce. The
other computer must al low one of the se defined algorithm combin ations, otherwise, the communication is not allowed using IPSec.
For a description of t he individual IPSec settin gs and how you might use them,
see “Available Settin gs for Security A ctions” on pag e 34.
Custom IPSec Settings
Although it is recommended that you use the pre-defined IPSec settings (security a ct ions) th at com e with P ac ke t Prot ec t, you can al so c reat e yo ur ow n to m eet
your custom corp orate security guidelines. If you create your own, keep in mind
that t wo c omput er s mus t agr ee o n ce rtai n se ttin gs i n o rde r to c omm unicat e u sing
IPSec.
For more information about creating your own IP Sec security actions, see “Customiz e Securi ty Ac tions ” on page 33.
57
Page 64

Intel® Packet Protect User’s Guide
Examples
The following diagram illustrates failed IKE negotiations due to mismatched
settings.
Pre-shared key = 123456
Default IKE s e ttings
/SHA-1
DES
Pre-shared key = 777777
Default IKE s e ttings
/SH A-1
3DES
The following diagram illustrates successful IKE negotiations due to matched
settings
Pre-shared key = 12345 6
Def aul t IKE se ttin g s
/SHA-1
3DES
Pre-shared key = 12345 6
Def aul t IKE se ttin g s
/SHA-1
3DES
58
Page 65

How Pac k et Protect Uses IPSec
IPSec is a set of standard protocols developed by the Internet Engineering Task
Force (IETF). IPSec is used to protect the privacy and integrity of IP communications. It protects IP communications using algorithms that perform encryption
and authentication tasks, as well as other features that enfor ce additional protection.
If IKE successfully negotiates a pr otected communication, it passes the agreed
upon information to the IPSec driver used by Packet Protect. Then, the IPSec
driver uses that information to determine how to protect the IP com m unication.
Security Associations
IP com munications use a security contract or security association when they are
protected using IPSec . After a security association is set up between two com puters, the computers can exchange data and IPSec will protect that data using
one or more of ESP encryption, ESP authentication, or AH authentication algorithms
The diagram below shows the steps that Packet Protect performs to protect a
communication. The security association is establi shed in Step 3.
Step 1: IKE Verif ies Pre-shared Key
Step 2: I KE Negotiates IPSec Settings
Step 3: IPSec Protects Packets
Security association
For mor e infor mat io n abou t eac h IPSec set t ing, se e “IP Sec Settin gs” on page 57
and “Customize Security Actions” on page 33.
Security Association Lifetimes
Securi ty a ss ociat i ons expi re if th ey re ac h th e max imum thr es hol d de fi ned for the
communic at ion. Pac ke t P ro tect is de signe d to au to m a ticall y re-neg o tia te t h e
security association when it is about to expire ( usually when it reaches approximately 80% of its lifetime), if one of the following is true:
• The security action is currently in use, that is, data is being transferred currently.
• The security action has been used recently, that is, data was transferred
using that security association.
59
Page 66
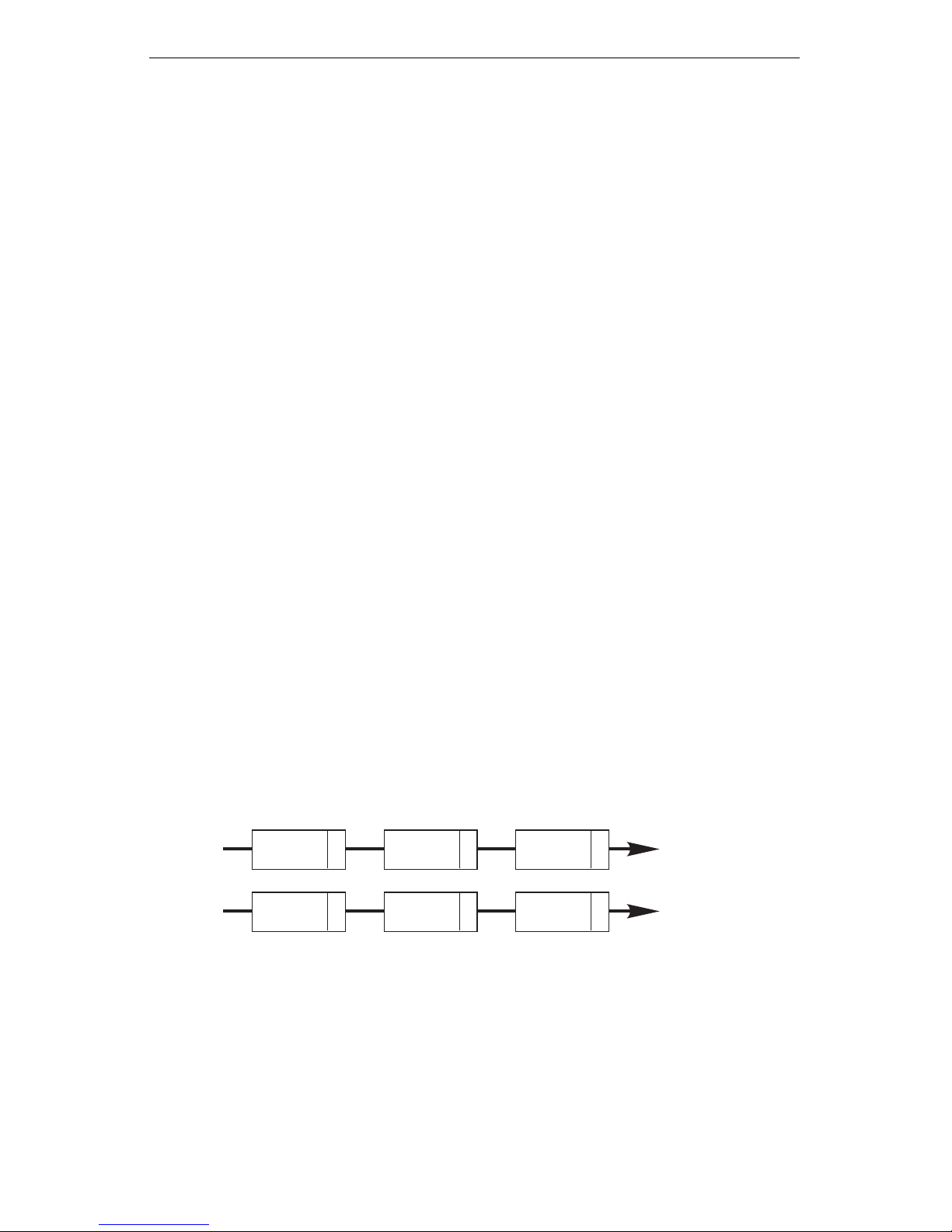
Intel® Packet Protect User’s Guide
Packet Protect re-negotiates the IPSec settings only; it doesn’t need to re-verify
the identity of the computers because it is already known. This helps reduce network traf fic by reducing extra key generation.
If the security association is not renewed automatically and consequently
exp ires, a securi ty association between the same computers will requi re both
IKE steps: pre-shared key verification and IPSec negotiation.
How IPSec Protects Packets
IPSec applies the sele cted algorithms to each packet that is protected by IPSec.
The algorithms provide one of the following protection features:
• Encryption and privacy
• Integrity
• T im e and size limits
• Anti-replay protection
The following secti ons describe some technical det ail about encryption and
integrity protection. The other features of IPSec ar e described in “Customize
Security Actions” on page 33.
Encryption
Use enc ryption to prote ct the confidentiality of packets. Encryption encodes
packets so they are unreadable unless the receiver has the proper key to decode
the packets.
If a packet is encrypt ed using ESP encryption (DES or 3DES algorithms), it is
unreadable while in transit. Other types of encryption can protect the confidentiality of information while stored on a computer – Pac ket Protect is designed to
protect the co nfid e ntiali ty of infor m at io n whil e tr avel ing on th e ne t wo rk . The
following diagram shows unencrypted and encrypted pack ets traveling on the
network.
*&e# x2q%z k4!ht68
pear apple banana
Encrypted packets
Packets “in the
clear”
If the packets pass th rough any routers or switches, the encrypted packets ar e
relayed without requi ring IPSec on those devices.
Integrity
Data integrity verifies that the packet was unch anged during transport over the
netw ork. It also verifies that other packets where not inserted into the packet
flow. This helps prevent a computer from accepting packets from an intruder
who is attempting to send packets on the netw ork.
60
Page 67

Use in tegrity features to prote ct the authenticity of packets, that is, verify that
the packet was unchanged during transport over the network. Inte grity featur es
also verify that no other packets we re inserted into the packet flow.
Packet Protect uses ESP and AH algorithms (MD5 or SHA-1) to protect the
integrity of packets.
The following diagram shows two sets of packets traveling on the network. The
first set uses integrity protection; the second set does not.
Verified
packets
Unverifi ed packets
Intruder
XX
changes packets
61
Page 68

Intel® Packet Protect User’s Guide
62
Page 69

Appendix B — Interoperability
B
with Microsoft Windows* 2000
An ov erview of interoperabil ity between Windows 2000 comp uters and Packet
Protect computers.
63
Page 70

Intel® Packet Protect User’s Guide
Interoperability with Windows* 2000
By default, IPSec is not enabled in Windows 2000. W indows 2000 is installed
with “N o Security” as the IPSec default a ction. You can use the IP Security Pol icy Ma nagement tool to activate IPSec in Wind ows 2000.
Windows 2000 has three IPSec default behaviors—Server, Secure Server, and
Client— that you can choose from when you configure the computer.
Currently, Packet Protect interoperates with Windows 2000 using a pre-shared
key. How ever, because Windows 2000 default authentication mechanism is Kerbero s, whic h is not su pported by Packet Protect, the authentication must be
changed to use pre-shared keys. Be sure to use the same pre-shared keys on
Wi ndows 2000 computers as Packet Protect-enabled co mp uters for proper
interoperability.
Tips: If you have Windows 2000 computers and want them to communicate
securely with Packet Protect-enabled computers, you must use the
Default Rule that is set up with the Packet Protect System Policy. Do
not erase or modify the Default Rule for best results.
For maximum interoperability, be sure to place each Windows 2000
computers in its own Destination Workgroup.
Creating P olicies
To create custom IPSec policies in Windows 2000
1. On t h e taskbar, click Start and select Settings > Control Panel.
2. Double-click Network and Dial-up Connections.
3. Right-click Local A rea Connection and select Properties.
4. Click Advanced and select the Options tab.
5. Under Optional settings, click IP security.
6. Click Properties.
7. Clic k Use thi s IP secur it y poli c y, and then s el ect the I PSec pol icy y ou wa nt to
use.
You can also use the IPSecurity Policies snap-in in the Microsoft Management
Console ( MMC) . Set it to use th e l oca l co mput er , right - click th e pol ic y you wan t
to use, and then click Assign.
You must be a me mber of the Adminis trators group to set IPSec polici es. If a
comput er par ti cipa te s in a Windows 2 000 do mai n, the comput er may r ecei v e t he
IPSec policy from Active Directory, overriding the local IPSec policy. In this
case, the options are disabled and you cannot change them from t he local computer.
64
Page 71

Appendix C — Network
C
Software License Agreement
This appendix details the following:
• Network Sof tware License Agre ement
• Intel Automated Customer Support
65
Page 72

Intel® Packet Protect User’s Guide
Network Software License Agreement
IMPORTANT - READ BEFORE COPYING, INSTALLING OR USING.
Do not use or load this software and any associated materials (collectively, the “Software”) until you
have carefully read the following terms and conditions. By loading or using the Software, you agree to
the terms of this Agreement. If you do not wish to so agree, do not install or use the Software.
LICENSE
and you may make one back-up copy of the Software, subject to these conditions:
1. This Software is li cen se d for use only in conjunction with Intel component products. Use of the
Software in conjunction with non-Intel component products is not licensed hereunder.
2. You may not copy, modify, rent, sell, distribute or transfer any part of the Software except as
provided in this Agreement, and you agree to prevent unauthorized copying of the Software.
3. You may not reverse engineer, decom pile, or disassemble the Software.
4. You may not sublicense or permit simultaneous use of the Software by more than one user.
5. The So ftw are ma y c ontai n th e sof tw are or othe r prope rty of th ird par t y supp li ers , some of wh ich may
be identified in, and licensed in accordance with, any enclosed “license.txt” file or other text or fil e.
OWNERSHIP OF SOFTWARE AND COPYRIGHTS
with Intel or its suppliers. The Software is copyrighted and protected by the laws of the United States
and other countries, and international treaty provisions. You may not remove any copyright notices
from the Software. Intel may make changes to the Softwar e, or to items referenced therein , at an y time
without notice, but is not obligated to support or update the Software. Except as otherwise expressly
provided, Intel grants no express or implied right under Intel patents, copyrights, trademarks, or other
intellectual property rights. You may transfer the Software only if the recipient agrees to be fully bound
by these terms and if you retain no copies of the Software.
LIMITED MEDIA WARRANTY
Intel warrants the media to be free from material physical defects for a period of ninety (90) days after
deliver y b y Intel. If such a defect is found, return the media to Intel for replacement o r alternate de li very of the Software as Intel may select.
EXCLUSION OF OTHER WARRANTIES
WARE IS PROVIDED "AS IS" WITHOUT ANY EXPRESS OR IMPLIED WARRANTY OF
ANY KIND INCLUDING W ARRANTIES OF MERCHANTABILITY, NON-INFRINGEMENT,
OR FITNESS FOR A PART ICULAR PURPOSE. Intel does not warrant or assume responsibility
for the accuracy or completeness of any informatio n, text, graphics, links or other items contained
within the Software.
. Y ou may copy the Software onto a single computer for your personal, non-commercial use,
. Title to all copies of the Software remains
. If the Software has been delivered by Intel on physical media,
. EXCEPT AS PROVIDED ABOVE, TH E SOFT-
LIMITATION OF LIABILITY
FOR ANY DAMAGES WHATSOEVER (INCLUDING, WITHOUT LIMITATION, LOST PROFITS,
BUSINESS INTERRUPTION, OR LOST INFORMATION) ARISING OUT OF THE USE OF OR
IN A BILITY TO USE THE SOFTWARE, EVEN IF IN TEL HAS BEEN ADVISED O F THE POSSIBILITY OF SUCH DAMAGES. SOME JURISDICTIONS PROHIBIT EXCLUSION OR LIMITATION OF LIABILITY FOR IMPLIED WARR ANTIES OR CONSEQUENTIAL OR INCIDENTAL
DAMA GES, SO THE ABOVE LIMIT ATION MA Y NOT APPLY TO YOU. YOU MA Y ALSO HAVE
OTHER LEGAL RIGHTS THAT VARY FROM JURISDICTI ON TO JURISDICTION.
TERMINATIO N O F THIS AGREEMENT
violate its terms. Upon termination, you will immediately destroy the Software or return all copies of
the Software to Intel.
66
. IN NO EVENT SHALL INTEL OR ITS SUPPLIERS BE LIABLE
. Intel may terminate this Agreement at any time if you
Page 73

Appen di x C — N etw ork S of tw are Li ce nse
Intel Automated Customer Support
You can reach Intel’s automated support service s 24 hours a day, every da y at no charge.
The services contain the most up-to-date informati on about Intel products. You can access
installation instructions, troubleshooting information, and general product information.
Readme Files on Your Product Disk
To review the readme topics, insert the PRO /100 S Server or Management adapter disk in
a disk drive, switch to that dri ve, and type:
SETUP /README and then press Enter.
Web and Internet Sites
Support: http://support.intel.com
Network Products: http://www.intel.com/ network
Corporate: http://www.intel.com
FTP Host: download.intel.com
FTP Directory: /support/network/adapter/
Customer Support Technicians
US and Canad a: 1-916-377-7000 (7:00 - 17:00 M-F Pacific Time)
Worldwide access: Intel has technical suppo rt centers worldwide. Many of the cen ters are
staffed by t echnicians who speak the local languages. For a list of a ll Intel support centers,
the telephone numbers, and the ti m es they are open, go to:
http://support. intel.com/support/9089.htm.
67
Page 74

Intel® Packet Protect User’s Guide
68
Page 75
G
Glossary
3DES
Triple Data Encryption Standard, or
Triple DES. An encryption standard used
to encode data w h ile it trav els on a network . 3DES uses 168-bit keys to encrypt
data.
3DES is avai la bl e only in the do m estic
version of Packet Protect.
AH
Authentication Header. A protocol of verifying the integrity of packets, that is, the
packets are known to be from th e originating computer. Packet Protect uses MD5
and SHA-1 to authenticate packets.
anti-replay
Protection against receiving repeat data
trans m itted on th e netwo rk . T hi s he lps
prevent an intruder from successfully
sending the same data in an attempt to
confu se the sy s t e m (fo r examp le , th e computer could repeat the task of restarting a
server).
authentication
The process of verifying the id entity of a
compute r. Packet Protect authenticates a
computer using pre-shared keys. It helps
verify that a computer is who it claims to
be.
cryptography
The science of protecting the privacy of
data by encoding the data so it is unreadable to anyone who doesn’t have a secr et
key to decode it .
CPU utilizati on
A measurement of the average load on a
compute r’s processor. As processor usage
increases due to security tasks, users may
notice slower performance. Intel
PRO/100 S Management and Server
Adapters are designed to offload the security o v er head f ro m P ack et Prot ec t by us in g
a special on-board processor, thereby
redu cing pr ocess o r utiliz ation.
decryption
The un-en cod ing of e ncr ypt ed da ta us in g a
secret password or k ey.
69
Page 76

Intel® Packet Protect User’s Guide
DES
Data Encryption Standard. A n encryption
standard used to protect data confidentiality by encoding the data before it travels
on a network.Packet Protect supports 56bit DE S an d 16 8- bit 3D ES (3 D E S available in the United States and Canada
only).
destinat ion workgroup
A logical collection of comput ers (server s
and clients) that you define in Packet Protect. Destination workgroups contain lists
of computers with which a computer in the
source workgroup may want to communicate using IPSec.
Dest ination workgroups in Packet Protect
are dif fe rent fro m workgr oups i n Wi ndows
operating syst ems.
default behavior
The setting for a workgroup specified in
Packet Protect that determines how a computer communicates using IPSec.
Diffie-Hellman
A method of sharing a secret key between
two computers.
DNS
Domain Name Se rver. The network of
Domain Name Serv ers that resolve fully
qualified domain names (FQDNs) to their
corresponding IP addresses.
encryption
The process of protecting data confidentiality by encoding the data so it is unreadable t o a ny one who doesn’t hav e the se cre t
key to decode it. You can read data if it
isn’t encrypted, but you can’t read data
while it’s encrypted.
ESP
Encapsulation Security Payload. A
method of protecting the confidentiality
and/or inte grity of data. ESP can be used
to protect data confidentiality by encrypting the data using DES or 3DES. ESP can
also be used to verify the origination of
data by au the nt icat ing the dat a us ing MD5
or SHA-1.
FQDN
Full y Q ualifie d D omai n N ame. Th e
unique name given to a computer or
device. When addres sing information or
requests, it’s often easier to remember a
fully q ual ified domai n na me rat he r t ha n a n
IP address. Because computers communicate using IP addresses, DNS software
matche s the fully quali fied domain name
to its corresponding IP address so users
can communicate using the domain name
and the IP address.
ICMP
Interne t Co ntr ol M essage Pr oto col. A ty pe
of IP protocol used to transmit data that
typically contains error or expla natory
information. For example, the ping command uses ICMP to transmit data about
network connectivity.
IETF
Internet Engineering Task Force. The
organization that is developi ng and standardizing IKE and IPSec.
IKE
Internet Key Exchange. A protocol b uilt
on standards that is used to negotiate a
protected communication.
IKE is a subset profile of ISAKMP/Oakley. It is bei ng developed by the Internet
Engineering Task Force (IETF).
intruder
An unwanted visitor fr om inside or outside your company who may try to stea l
inform ation or harm your network.
IP
Internet Protocol. A set of rules that
70
Page 77

Glossary
describe how computers transmit data
with a destination address.
IP address
A seri es of numbe rs that identifies a connection point or dev ice on an IP network.
Each connection point and device needs a
uniq ue IP address to communicate using
IP. For example, 192. 168.1.1 is a sample
IP address.
IPSec
Internet Protocol (IP) Security. A set of
protoc ols us ed to he lp se cur e th e e xc han ge
of IP da ta . IPSe c i s bei ng d e vel ope d b y the
Internet Engineering Task Force (IETF).
key
A set of bytes tha t enc ry pt or dec ryp t da ta.
Ke ys allow y ou to protect data from being
read by an intruder on the network. Keys
can be symm etric or asymmetric and
asymmetric keys can be either public or
private.
LAN
Local Area Network. A communications
network usually located within a building
or sma ll n um b er of buildin gs . Fo r exa m ple, com puters and printers at many com panies are connected to a LAN.
lockdown
A description of a defau lt behavior fo r a
computer that uses Packet Protect. A
Lockd own computer initiates an d replies
to all communications by request ing security; it on ly com munic at es usin g IPS e c
(requires that the other c omputer also uses
IPSec). A common use for this setting is a
server that requires very restricted access.
MD5
Message Digest Algorithm. An algorithm
often used to verify the integrity of packets traveling on a network. The algorithm
transforms any numb e r of bytes into a
fixed number of bytes; no other set of
bytes produces the same result.
network
One or more compu te rs tha t ar e conne ct ed
together for communication purpose s.
offload
The assignment of algorit hm computations from software to hardware. Packet
Protect offl o ad s secur it y tasks to In te l
PRO/100 S Managem ent and Server
adapters to speed proces sing and increase
network performance.
packet
A piece of data th at tra vels on th e networ k.
Each packet contains the data being transmitted, along with a destination address.
Packet Protect protects packets as they
travel on the network using IPSec.
perfect f orward secrecy
The generation of an additional key pair to
be used during data transf er. This he lps
guarantee that no keys are re-used. Using
perfect forward secrecy increases protection, but generates more CPU utilization.
policy
A colle ction of security settings an d rules
that are applied to a group of compu ters.
port
A connection point used by IP applications. For example, a Web server typically
sends and re ce i v es inf or mat ion on por t 8 0.
pre-shared key
A secret password that a computer presents to help verify its identity. Pre-shared
keys are used during negotiation of a
secure com m unication. Each computer
must pre sent the same pre -shared key in
order to communication using IPSec.
protocol
A set of guidelines that describe how net-
71
Page 78

Intel® Packet Protect User’s Guide
works or applications communicate. If the
set of rules are followed, information can
be processed correct ly. This allo w s compute rs and hardware devices to communicate with one another e ven if they’re
different from one another.
rule
A definition of the security settings to
apply when a computer communicates
with a de stina tion co m p uter us in g a speci fied protocol.
secure initiator
A description of a defau lt behavior fo r a
computer that uses Packet Protect. A
Secure Initiator computer initiates communications by requesting security and
responds to communication request s w ithout security (“in the clear”). A common
use for this setting is a server that doesn’t
require the strict control of the Lockdown
setting.
secure responder
A description of a defau lt behavior fo r a
computer that uses Packet Protect. A
Secure R e sponder compu ter initiates communications without security (“in the
clear” ), b u t can re spo nd t o com muni ca tion
requests with security. A common use for
this setting is a w orkstation.
the existing security association).
security assoc iation lifetime
The duration of a security association. A
lifetime can be limited by t im e or by the
amount of d ata transmitted.
SHA-1
Secure Hash Algorithm. An algorithm
often used to verify the integrit y of packets traveling on a network. The algo rithm
transforms any number of bytes into a
fixed number of bytes.
traff ic
Packets travel ing on the network.
workgrou p
A logica l collection of computers (servers
and clients) that you define in Packet Protect.
W o rkgro ups i n Pac ke t Pro tect ar e di f f erent
from wor kgroups in Wi ndows operating
system s.
security action
A collection of IPSec settings that are propose d wh en two computers attempt to
communi ca te. P a ck et Pr ote ct uses se cur ity
actions when a rule is matched for a communication.
security association
A secur ity contract between two computers. Wh ile the security association is
active (8 ho u rs is the de fa ult), th e tw o
comput ers can send data without re-ne gotiating a communication (as long as the
data being sent uses a pr otocol defined in
72
Page 79

Index
A
adapters
installing 15
teaming and 16
use multip le 16
algorithms and securit y actions 35
Anti-replay protection 4
anti-replay protection 35
authentication
of rules 26
C
clients
failed communication between 50
turn off security for 48
turn o n se c u ri ty for 4 7
uninsta ll ing Packet Protect from 48
configu re adapters for Packet Protect 15
customize
destina tion workgroups 31
Index
D
Data Encrypt ion Standard 60
data integrity 60
DES. See Data Encryption Standard
destina ti on workgroups
customize 31
modify 33
modify after policy distribution 41
domestic ver sion of Packet Protect 2
E
Encapsulat ion Security Payload 60
encryption algorithms 35
encryption of data packets 4, 60
ESP. See Encapulation Securi ty Payload
export version of Packet Protect 2
F
FAQs. See Frequent ly Asked Questi ons
firewall
using Packet Protect with 50
firewa lls 5 0
Frequentl y Asked Question s 49
73
Page 80

Intel® Packet Protect User’s Guide
G
gateway 50
glossary 69
H
hardware
acceler ati on 2
hardware acceleration 2
help file for Packe t P rotect 3
I
IKE. See Internet Key Exchange
installation
more information ii
notes ii
integr it y of data packets 4
Interne t Key Exchange
authentication 56
definition 4
how it works with IPSec 54
how Packet Protect uses 55
settings 55
Internet Protocol Security
data integrity and 60
definition 4
encryption of data packets 60
how it protects packets 59, 60
how it works with IKE 54
how Packet Protect uses 59
securit y associations and 59
settings 57
Internet Protocol traffic
protect ion of 1
traffic not protected by Packet Protect 50, 52
interoper ability with other security products 46
introduction 1–6
intruder s 1
IP. See Internet Protcol
IPSec. See Internet Protocol Security
L
LAN. See Local Area Network
Local Area Network 1
Lockdown workgroup behavior 23
74
Page 81

N
network addr ess transl ati on 50
O
ordering rules 27
other security products
inter ope rability with 43
overview 2
overvie w of Packet Protect 2
P
Packet Protect
administrator and client versions 3
domestic and export versi ons 2
features 2
frequently asked questions 49
get started 6
getting started 6
how it works 4
HTML help 3
introduction 1
prepari ng for installation 8
purpose 2
troubl eshooting 49
work with other IPSec products 46
perfect forward secrecy 35
policy
definition of 25
modifyi ng aft er distribution 40
set up compatible policies 45
Index
R
readme fil es ii
rules
authentication setting 26
definition of 25
delete after policy distribution 41
If rule fails 26
importance of order 25, 27
ordering 31
S
Secure Initiator workgroup behavior 23
Secure Responder workgroup behavior 22
security action
customize 33
75
Page 82

Intel® Packet Protect User’s Guide
security actions
create new 36
customize 33
definition of 26
modify after policy distribution 41
service s on the Worl d Wide Web ii
size limit and security actions 34
support ser vices 67
T
time limi t and security actions 34
troubl eshooting 49
more information ii
U
uninstalling
Packet Protect at clients 48
V
view
status at cli ents 44
W
workgroups
customize security actions 33
modify dest ination workgroups 31
76
 Loading...
Loading...