Page 1

Intel® Active Management Technology v4.0
Administrator's Guide
Overview
Product Overview
Operational Modes
Setup and Configuration Overview
Provisioning Methods
Menus and Defaults
MEBx Settings Overview
ME Configuration Menu
AMT Configuration Menu
MEBx Defaults
Setup and Configuration
Methods Overview
Configuration Service
MEBx Interface (Enterprise Mode)
MEBx Interface
System Deployment
Operating System Drivers
(SMB Mode)
Management
Intel AMT Web GUI
AMT Redirection (SOL/IDE-R)
AMT Redirection Overview
Troubleshooting
Troubleshooting
If you purchased a DELL™ n Series computer, any references in this document to Microsoft
are not applicable.
Information in this document is subject to change without notice.
© 2008 Dell Inc. All rights reserved.
Reproduction of these materials in any manner whatsoever without the written permission of Dell Inc. is strictly forbidden.
Trademarks used in this text: Dell, Latitude, and the DELL logo are trademarks of Dell Inc.; Intel is a registered trademark of Intel Corporation in
the U.S. and other countries; Microsoft and Windows are either trademarks or registered trademarks of Microsoft Corporation in the United States
and/or other countries.
Other trademarks and trade names may be used in this document to refer to either the entities claiming the marks and names or their products.
Dell Inc. disclaims any proprietary interest in trademarks and trade names other than its own.
August 2008 Rev. A00
®
Windows® operating systems
Page 2
Back to Contents Page
Overview
Intel® Active Management Technology (Intel AMT) allows companies to easily manage their networked computers in the
following ways:
Discover computing assets on a network regardless of whether the computer is turned on or off – Intel AMT uses
information stored in nonvolatile system memory to access the computer. The computer can even be accessed while it
is powered off (also called out-of-band or OOB access).
Remotely repair systems even after operating system failures – In the event of a software or operating system failure,
Intel AMT can be used to access the computer remotely for repair purposes. IT administrators can also detect computer
system problems easily with the assistance of Intel AMT's out-of-band event logging and alerting.
Protect networks from incoming threats while easily keeping software and virus protection up to date across the
network.
Software Support
Several independent software vendors (ISVs) are building software packages to work with Intel AMT features. This provides IT
administrators many options when it comes to remotely managing the networked computer assets within their company.
Features and Benefits
Intel AMT
Features Benefits
Out-of-band (OOB) access
Remote troubleshooting and recovery Significantly reduces desk side visits, increasing the efficiency of IT technical staff
Proactive alerting Decreases downtime and minimizes repair times
Remote hardware and software asset
tracking
Third-party nonvolatile storage
*
Information on this page provided by Intel.
The Intel® Management Engine BIOS Extension (MEBx) is an optional ROM module provided to Dell™ from Intel that is
included in the Dell BIOS. The MEBx has been customized for Dell computers.
Back to Contents Page
Allows remote management of platforms regardless of system power or operating
system state
Increases speed and accuracy over manual inventory tracking, reducing asset
accounting costs
Increases speed and accuracy over manual inventory tracking, reducing asset
accounting cost
Page 3

Back to Contents Page
Operational Modes
Intel® AMT can be set up for either Enterprise or Small and Medium Business operational modes (also called provisioning
models). Both operational modes support dynamic and static IP networking.
If you use dynamic IP networking (DHCP), the Intel AMT host name and the operating system host name must match. You
must also configure both the operating system and Intel AMT to use DHCP as well.
If you use static IP networking, the Intel AMT IP address must be different from the operating system's IP address.
Additionally, the Intel AMT hostname must be different from the operating system's hostname.
Enterprise mode – This mode is for large organizations. This is an advanced networking mode that supports
Transport Layer Security (TLS) and requires a configuration service. Enterprise mode allows IT administrators to set up
and configure Intel AMT securely for remote management. The Dell™ computer is defaulted to Enterprise mode when it
leaves the factory. The mode can be changed during the setup and configuration process.
Small Medium Business (SMB) mode – This mode is a simplified operational mode that does not support TLS and
does not require a setup application. SMB mode is for customers who do not have independent software vendor (ISV)
management consoles or the necessary network and security infrastructures to use encrypted TLS. In SMB mode, Intel
AMT setup and configuration is a manual process completed through the Intel ME BIOS Extension (MEBx). This mode is
the easiest to implement since it does not require much infrastructure, but it is the least secure since all network traffic
is not encrypted.
Intel AMT Configuration sets up all other Intel AMT options not covered in Intel AMT Setup, such as enabling the computer for
Serial-Over-LAN (SOL) or IDE-Redirect (IDE-R).
You can change the settings modified in the configuration phase many times over the course of a computer's life span. You
can make changes to the computer locally or through a management console.
Back to Contents Page
Page 4

Back to Contents Page
Setup and Configuration Overview
The following is a list of important terms related to the Intel® AMT setup and configuration.
Setup and configuration — The process that populates the Intel AMT-managed computer with usernames,
passwords, and network parameters that enable the computer to be administered remotely.
Provisioning — The act of setting up and configuring Intel AMT.
Configuration service — A third-party application that completes the Intel AMT provisioning.
Intel AMT WebGUI — A Web browser-based interface for limited remote computer management.
You must set up and configure Intel AMT in a computer before using it. Intel AMT setup readies the computer for Intel AMT
mode and enables network connectivity. This setup is generally performed only once in the lifetime of a computer. When Intel
AMT is enabled, it can be discovered by management software over a network.
Once Intel AMT is set up in Enterprise mode, it is ready to initiate configuration of its own capabilities. When all required
network elements are available, simply connect the computer to a power source and the network, and Intel AMT automatically
initiates its own configuration. The configuration service (a third-party application) completes the process for you. Intel AMT is
then ready for remote management. This configuration typically takes only a few seconds. When Intel AMT is set up and
configured, you can reconfigure the technology as needed for your business environment.
Once Intel AMT is set up in SMB mode, the computer does not have to initiate any configuration across the network. It is set
up manually and is ready to use with the Intel AMT Web GUI.
Intel AMT Setup and Configuration States
The act of setting up and configuring Intel AMT is also known as provisioning. An Intel AMT capable computer can be in one
of three setup and configuration states:
The factory-default state is a fully unconfigured state in which security credentials are not yet established and Intel
AMT capabilities are not yet available to management applications. In the factory-default state, Intel AMT has the
factory-defined settings.
The setup state is a partially configured state in which Intel AMT has been set up with initial networking and transport
layer security (TLS) information: an initial administrator password, the provisioning passphrase (PPS), and the
provisioning identifier (PID). When Intel AMT has been set up, Intel AMT is ready to receive enterprise configuration
settings from a configuration service.
The provisioned state is a fully configured state in which the Intel Management Engine (ME) has been configured with
power options, and Intel AMT has been configured with its security settings, certificates, and the settings that activate
the Intel AMT capabilities. When Intel AMT has been configured, the capabilities are ready to interact with management
applications.
Back to Contents Page
Page 5

Back to Contents Page
The act of setting up and configuring Intel® AMT is known as provisioning. There are two methods of provisioning a computer
with Enterprise mode:
Legacy
IT TLS-PSK
Legacy
If you want Transport Layer Security (TLS), execute the legacy method of Intel AMT setup and configuration on an isolated
network separate from the corporate network. A setup and configuration server (SCS) requires a secondary network
connection to a certification authority (an entity which issues digital certificates) for TLS configuration.
Initially the computers are shipped in the factory-default state with Intel AMT ready for configuration and provisioning. These
computers must go through Intel AMT setup in order to go from the factory-default state to the setup state. Once the
computer is in the setup state, you can continue to configure it manually or connect it to a network where it connects with an
SCS and begin Enterprise Mode Intel AMT configuration.
IT TLS-PSK
IT TLS-PSK Intel AMT setup and configuration is usually performed in a company's IT department. The following are required:
Setup and configuration server
Network and security infrastructure
Intel AMT capable computers in the factory-default state are given to the IT department, which is responsible for Intel AMT
setup and configuration. The IT department can use any method to input Intel AMT setup information, after which the
computers are in Enterprise Mode and in the In-Setup phase. An SCS must generate PID and PPS sets.
Intel AMT configuration must occur over a network. The network can be encrypted using the Transport Layer Security PreShared Key (TLS-PSK) protocol. Once the computers connect to an SCS, Enterprise Mode Configuration occurs.
Back to Contents Page
Page 6
Back to Contents Page
MEBx Settings Overview
The Intel® Management Engine BIOS Extension (MEBx) provides platform-level configuration options for you to configure the
behavior of Management Engine (ME) platform. Options include enabling and disabling individual features and setting power
configurations.
This section provides details about MEBx configuration options and constraints, if any.
All the ME Platform Configuration setting changes are not cached in MEBx. They are committed to ME non-volatile memory
(NVM) until you exit MEBx. Hence, if MEBx crashes, the changes made until that point are NOT going to be committed to ME
NVM.
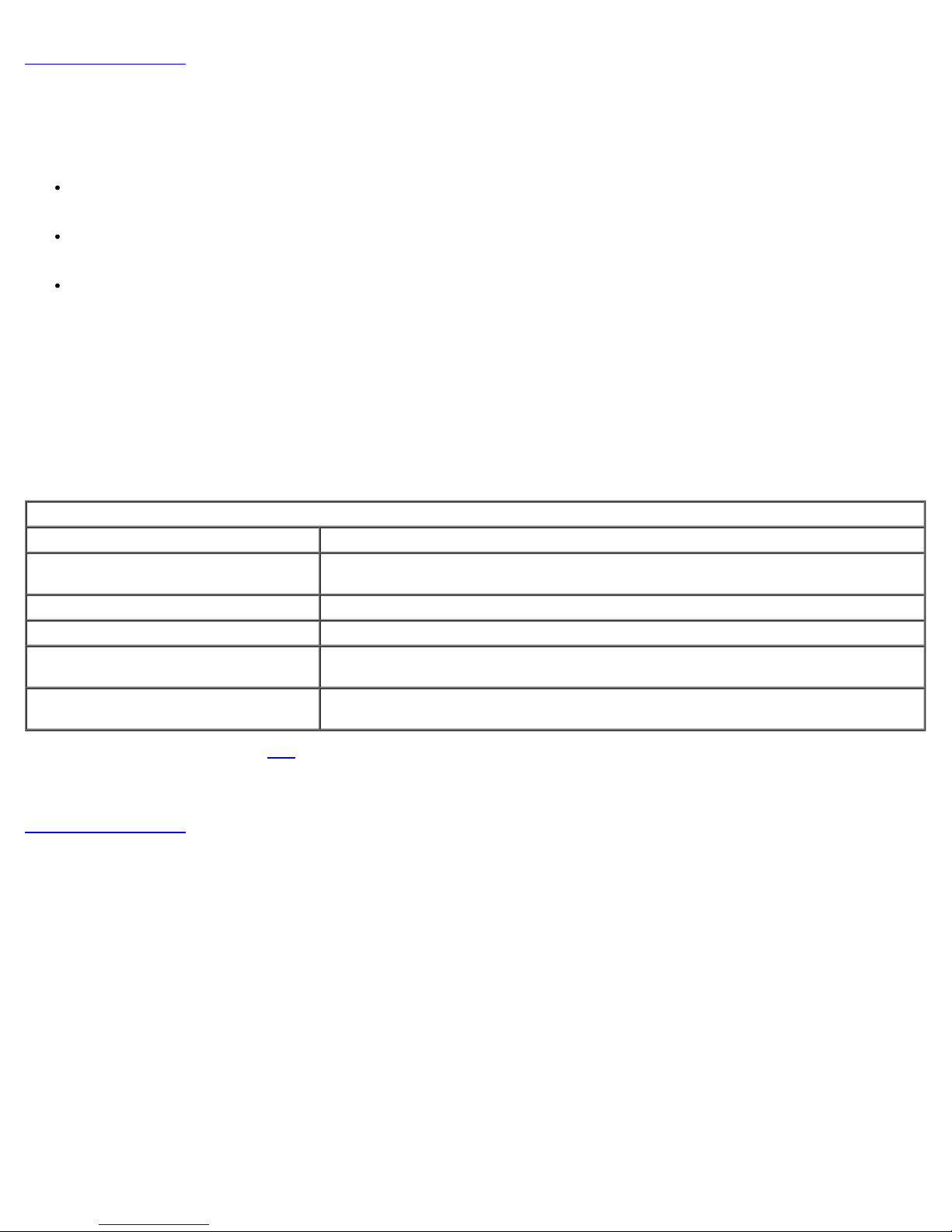
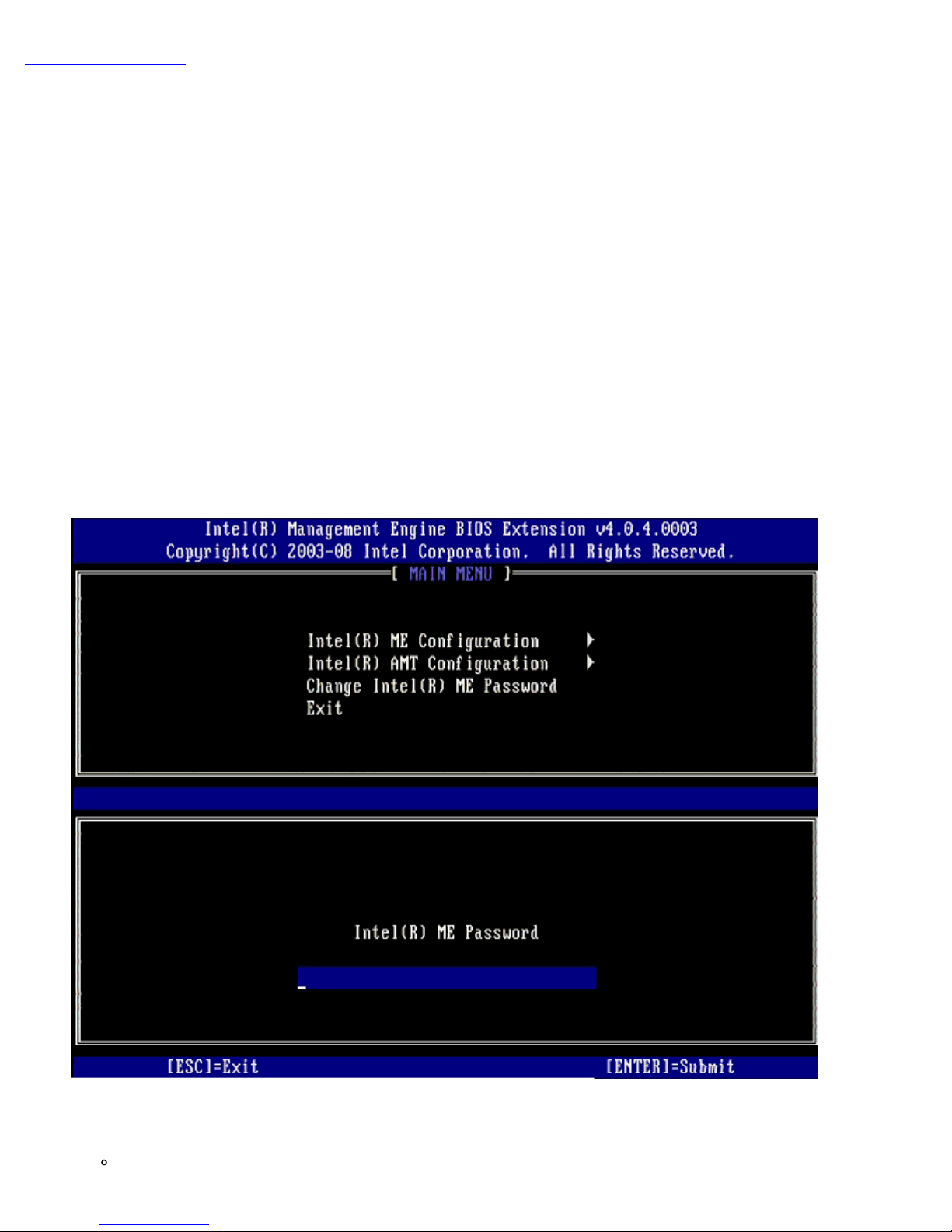
Access MEBx Configuration User Interface
The MEBx configuration user interface can be accessed on a computer through the following steps:
1. Turn on (or restart) your computer.
2. When the blue DELL™ logo appears, press <Ctrl><p> immediately.
If you wait too long and the operating system logo appears, continue to wait until you see the Microsoft® Windows®
desktop. Then shut down your computer and try again.
3. Type the ME password. Press <Enter>.
The MEBx screen appears as shown below.
The main menu presents three function selections:
Intel ME Configuration
Page 7

Intel AMT Configuration
Change Intel ME Password
The Intel ME Configuration and Intel AMT Configuration menus are discussed on the following pages. First, the password must
be changed in order to proceed through these menus.
Changing the Intel ME Password
The default password is admin and is the same on all newly deployed platforms. You must change the default password before
changing any feature configuration options.
The new password must include the following elements:
Eight characters
One uppercase letter
One lowercase letter
A number
A special (nonalphanumeric) character, such as !, $, or ; excluding the :, ", and , characters.)
The underscore ( _ ) and spacebar are valid password characters but do NOT add to the password complexity.
*
Information on this page provided by Intel.
Back to Contents Page
Page 8
Back to Contents Page
ME Configuration Menu
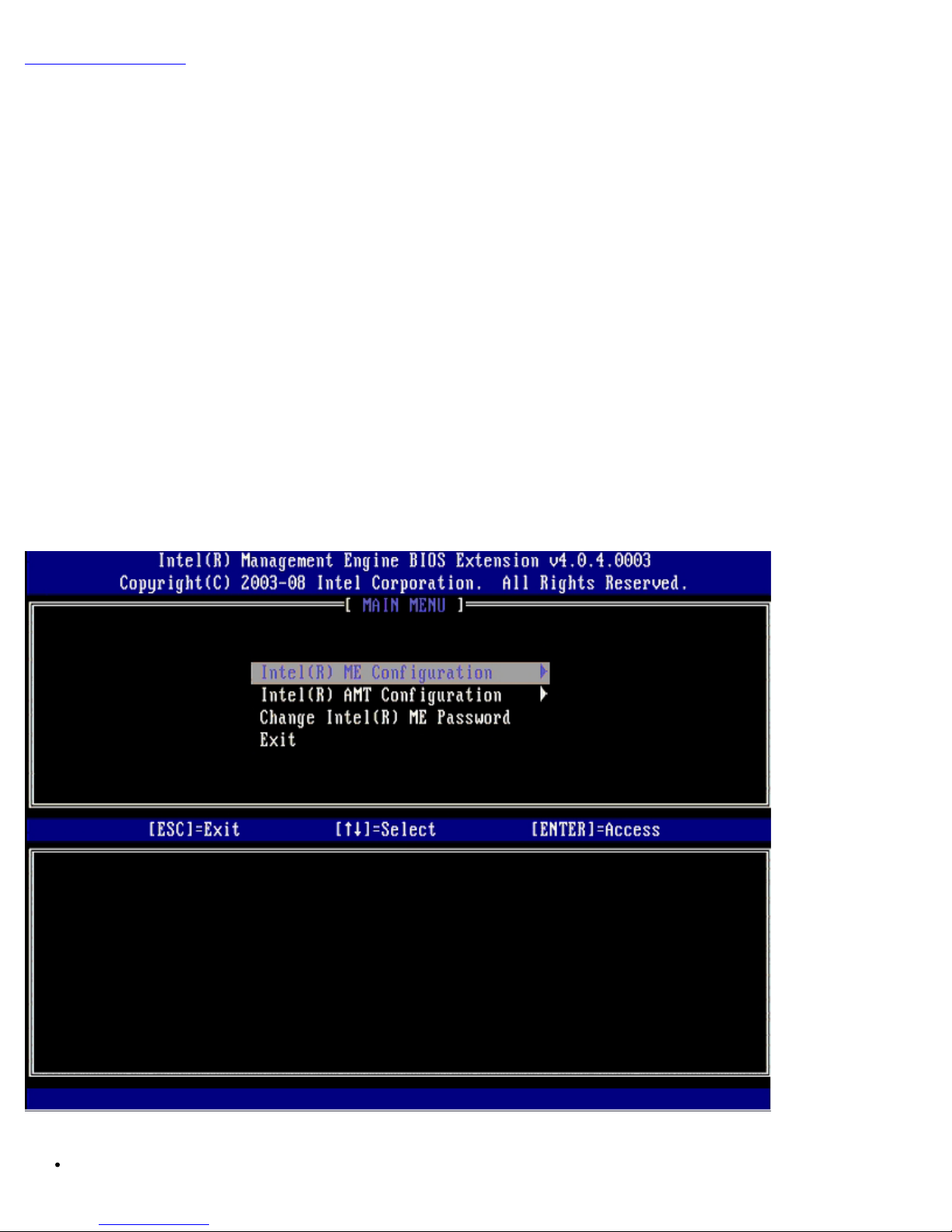
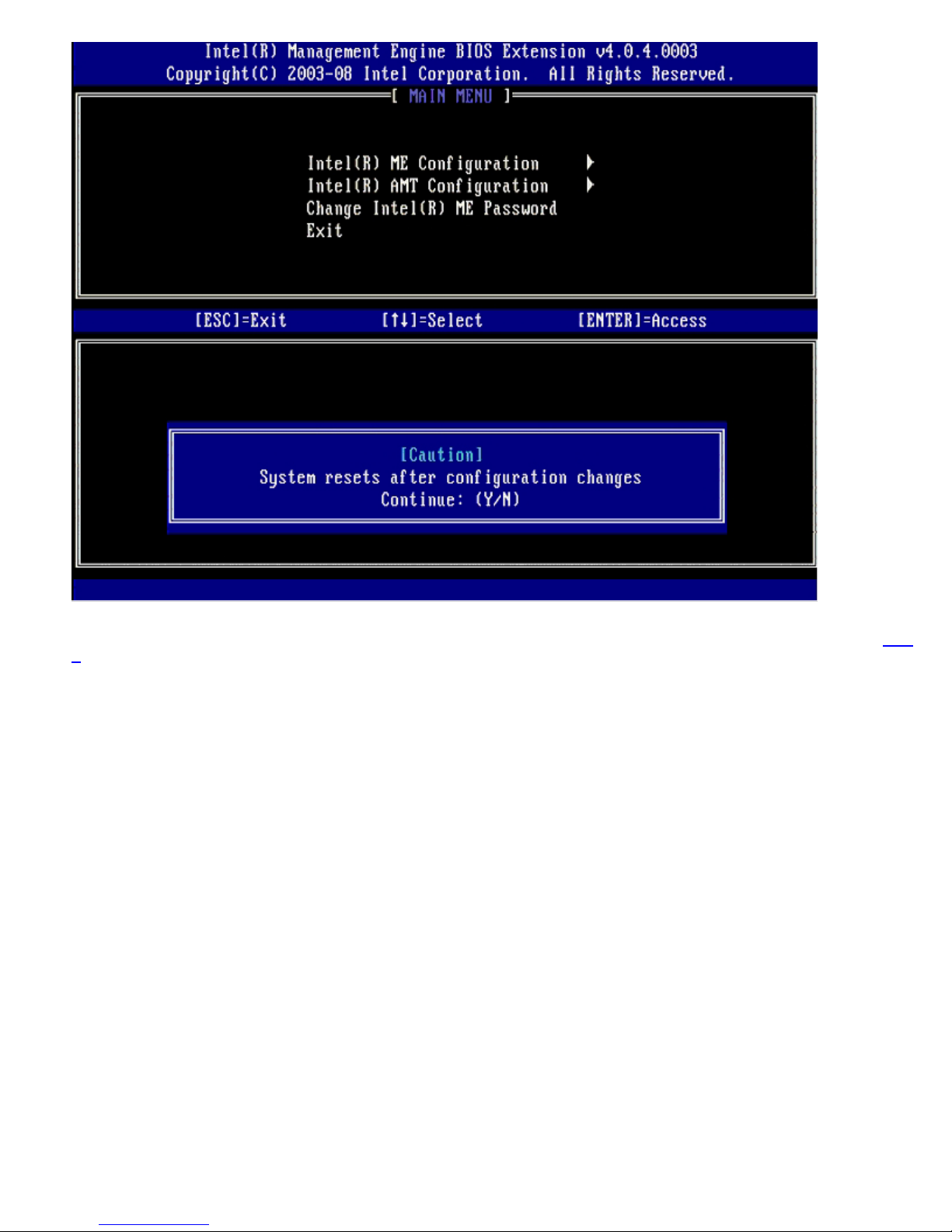
To reach the Intel® Management Engine (ME) Platform Configuration page, follow these steps:
1. Under the Management Engine BIOS Extension (MEBx) main menu, select ME Configuration. Press <Enter>.
2. The following message appears:
System resets after configuration changes. Continue: (Y/N)
3. Press <Y>.
The ME Platform Configuration page opens. This page allows you to configure the specific functions of the ME such as
features, power options, and so on. Below are quick links to the various sections.
Intel ME State Control
Intel ME Firmware Local Update
Intel ME Features Control
Manageability Feature Selection
Intel ME Power Control
Intel ME ON in Host Sleep States
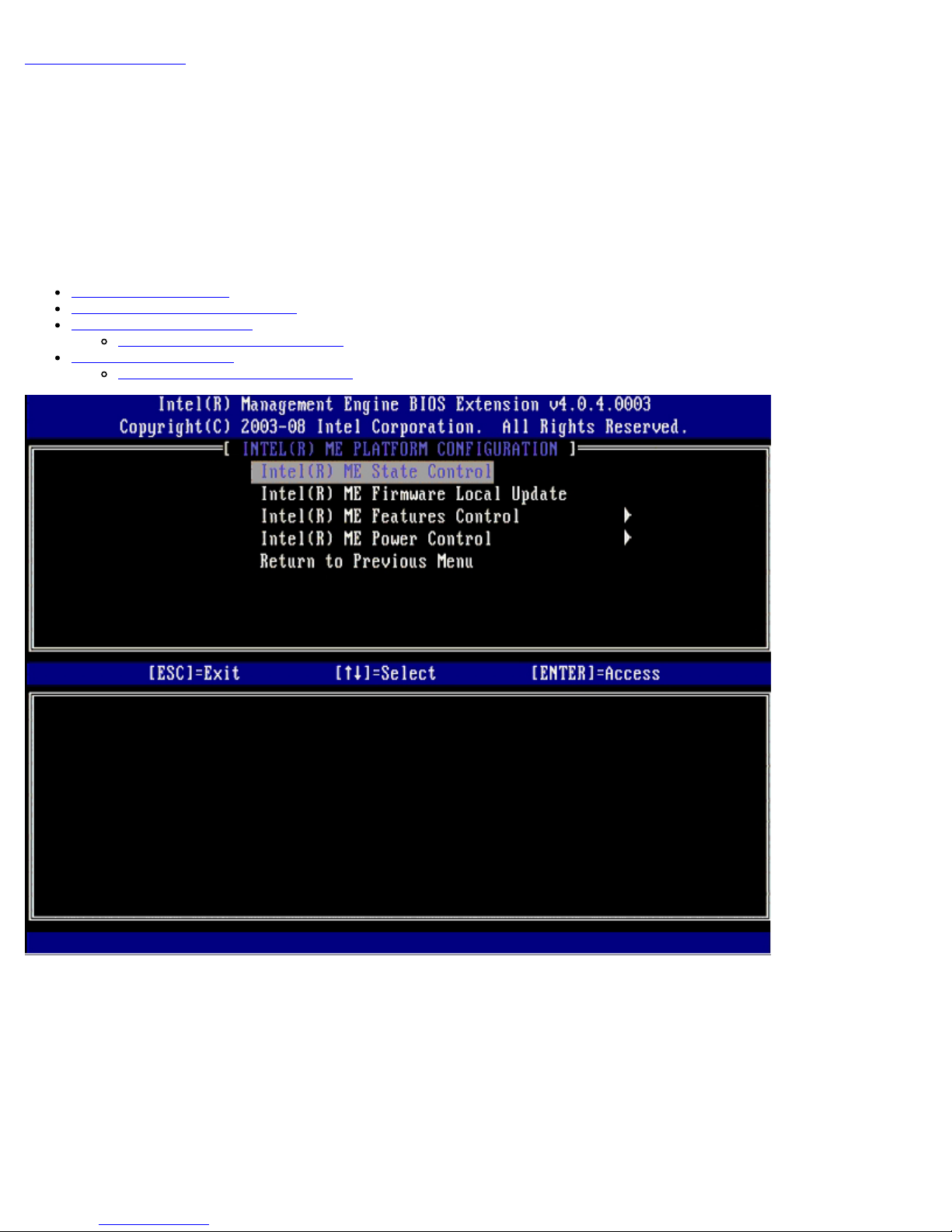
Intel ME State Control
When the ME State Control option is selected on the ME Platform Configuration menu, the ME State Control menu
appears. You can disable ME to isolate the ME computer from main platform until the end of the debugging process.
Page 9
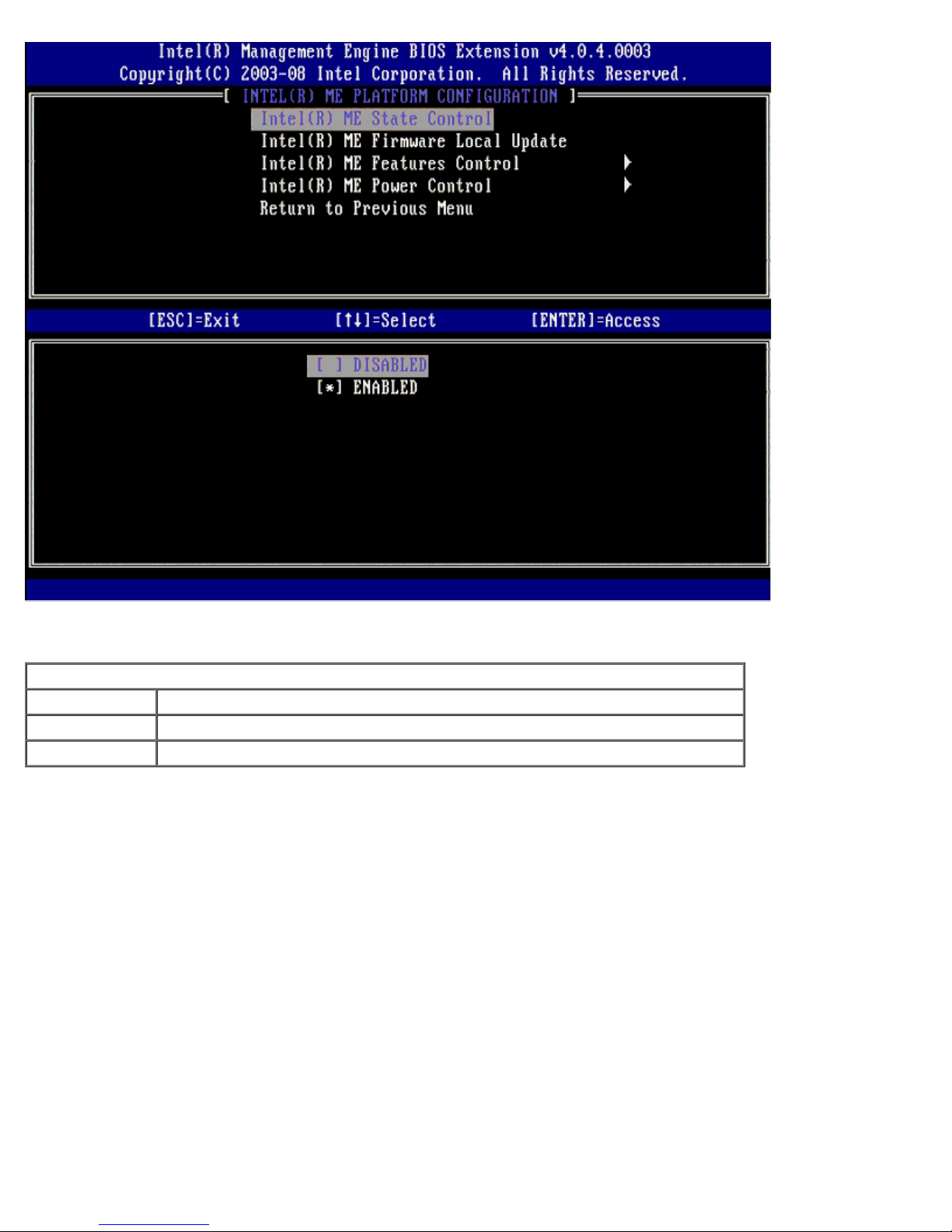
When enabled, the ME State Control option lets you disable ME to isolate the ME computer from the main platform while
debugging a field malfunction. The table below illustrates the details of the options.
ME Platform State Control
Option Description
Enabled Enable the Management Engine on the platform
Disabled Disable the Management Engine on the platform
In fact, the ME is not really disabled with the Disabled option. Instead, it is paused at the very early stage of its booting so
the computer has no traffic originating from the ME on any of its busses, ensuring that an you can debug a computer problem
without worrying about any role the ME might have played in it.
Intel ME Firmware Local Update
This option on the ME Platform Configuration menu sets the policy for allowing the MEBx to be updated locally. The default
setting is Disabled. The other setting available is Enabled. Enabled allows local ME firmware updates. Disable does not
allow local ME firmware updates.
Page 10
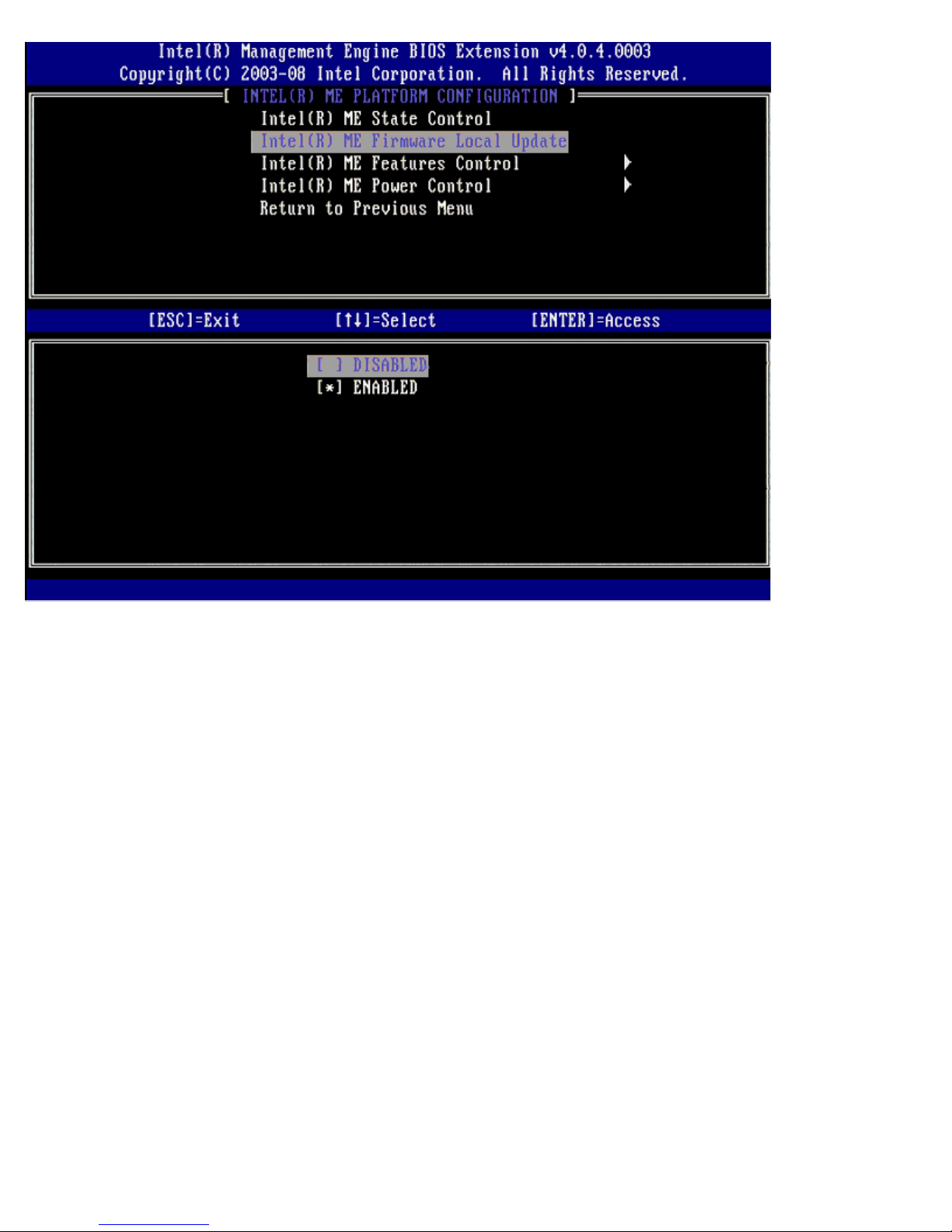
Intel ME Features Control
The ME Features Control menu contains the following configuration selection.
Manageability Feature Selection
When you select the Manageability Feature Selection option on the ME Features Control menu, the ME Manageability
Feature menu appears.
Page 11
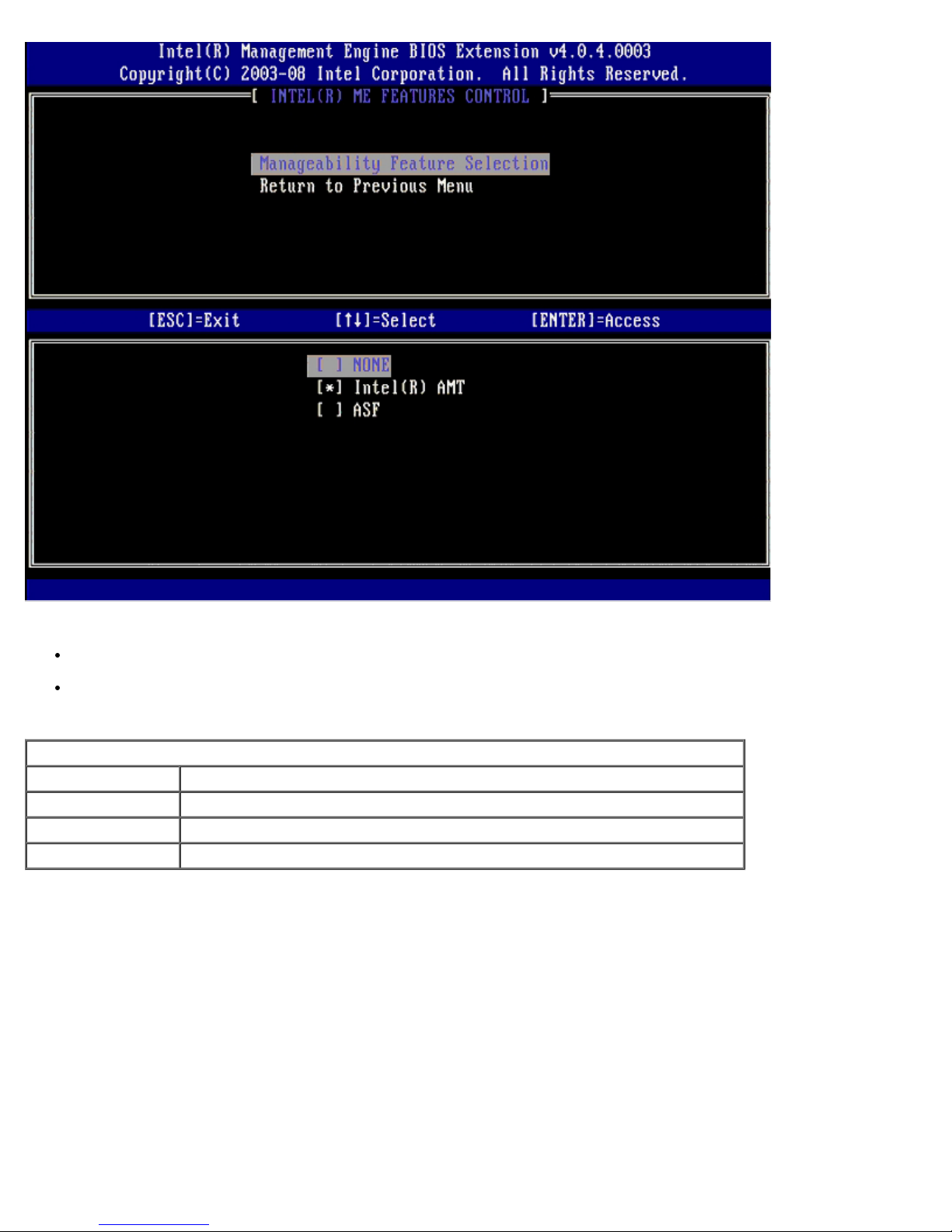
You can use this option to determine which manageability feature is enabled.
ASF — Alert Standard Format. ASF is a standardized corporate assets management technology. The Intel ICH9
platform supports ASF specification 2.0.
Intel AMT — Intel Active Management Technology. Intel AMT is an improved corporate assets management technology.
The table below explains these options.
Management Feature Select Option
Option Description
None Manageability Feature is not selected
Intel AMT Intel AMT manageability feature is selected
ASF ASF manageability feature is selected
When you change the option from Intel AMT to None, a warning that Intel AMT un-provisions automatically if you accept the
change appears.
The None option has no manageability feature provided by the ME computer. In this case, the firmware is loaded (i.e., ME is
still enabled) but the management applications remain disabled.
Intel ME Power Control
To comply with ENERGY STAR requirements, the Intel Management Engine can be turned off in various sleep states. Intel ME
Power Control menu configures Intel ME platform power policies.
ME On in Host Sleep States
When the ME ON in Host Sleep States option is selected on the ME Power Control menu, the ME in Host Sleep States
Page 12
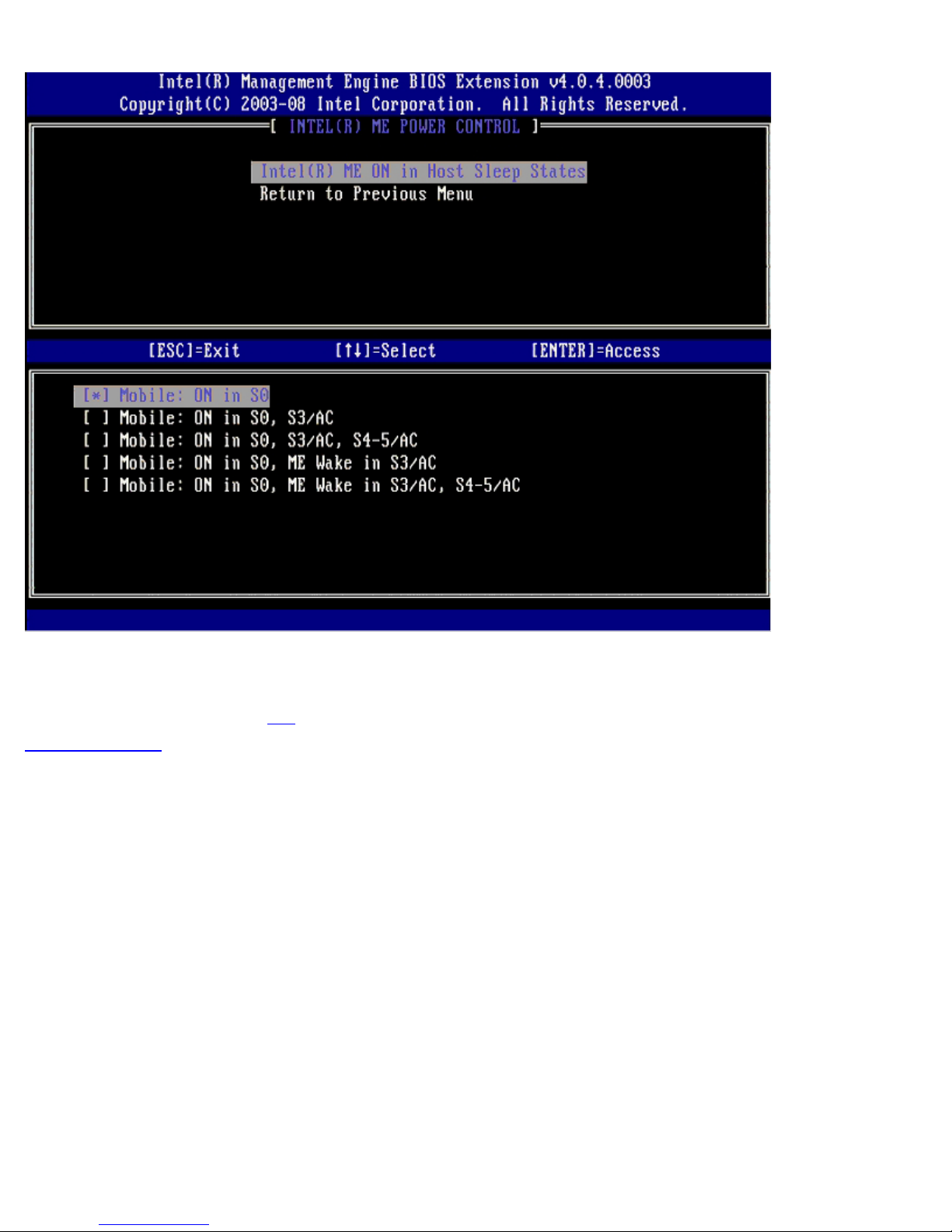
menu loads.
The power package selected determines when the ME is turned ON. The default power package is Mobile: ON in S0. The end
user administrator can choose which power package is used depending on computer usage. The power package selection page
can be seen above.
*
Information on this page provided by Intel.
Back to Contents Page
Page 13
Back to Contents Page
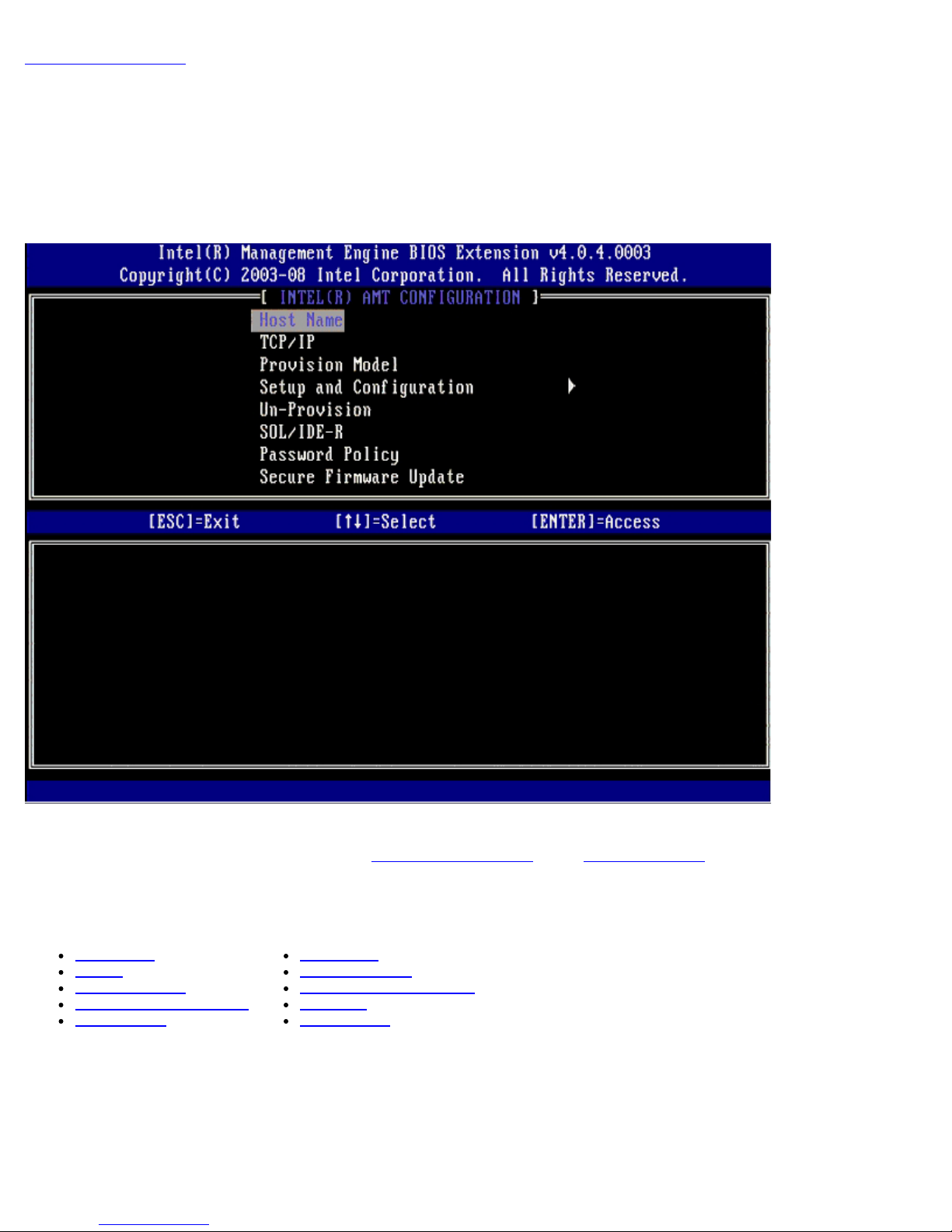
AMT Configuration Menu
After you completely configure the Intel® Management Engine (ME) feature, you must reboot before configuring the Intel AMT
for a clean system boot. The image below shows the Intel AMT configuration menu after a user selects the Intel AMT
Configuration option from the Management Engine BIOS Extension (MEBx) main menu. This feature allows you to
configure an Intel AMT capable computer to support the Intel AMT management features.
You need to have a basic understanding of networking and computer technology terms, such as TCP/IP, DHCP, VLAN, IDE,
DNS, subnet mask, default gateway, and domain name. Explaining these terms is beyond the scope of this document.
The Intel AMT Configuration page contains the user-configurable options listed below.
For images of these menu options, refer to the "Enterprise Mode Setup
" and "SMB Mode Setup" pages of this document.
Menu Options
Host Name
TCP/IP
Provision Model
Setup and Configuration
Un-Provision
Host Name
A hostname can be assigned to the Intel AMT capable computer. This is the host name of the Intel AMT-enabled computer. If
Intel AMT is set to DHCP, the host name MUST be identical to the operating system machine name.
SOL/IDE-R
Password Policy
Secure Firmware Update
Set PRTC
Idle Timeout
Page 14

TCP/IP
Allows you to change the following TCP/IP configuration of Intel AMT.
Network interface – ENABLE** / DISABLED
If the network interface is disabled, all the TCP/IP settings are no longer needed.
DHCP Mode – ENABLE** / DISABLED
If DHCP Mode is enabled, TCP/IP settings are configured by a DHCP server.
If DHCP mode is disabled, the following static TCP/IP settings are required for Intel AMT. If a computer is in static mode it
needs a separate MAC address for the Intel Management Engine. This extra MAC address is often called the Manageability
MAC (MNGMAC) address. Without a separate Manageability MAC address, the computer can NOT be set to static mode.
IP address – Internet address of the Intel Management Engine.
Subnet mask – The subnet mask used to determine what subnet IP address belongs to.
Default Gateway address – The default gateway of the Intel Management Engine.
Preferred DNS address – Preferred domain name server address.
Alternate DNS address – Alternate domain name server address.
Domain name – Domain name of the Intel Management Engine.
Provision Model
The following provisioning models are available:
Provisioning Mode – Enterprise** / Small Business
This allows you to select between small business and enterprise mode. Enterprise mode may have different security
settings than small business mode. Because of the different security settings, each of these modes requires a different
process to complete the setup and configuration process.
Setup and Configuration
The menu contains the parameters for the setup and configuration server. This menu also contains the security settings for
PSK and PKI configurations.
Page 15
Current Provisioning Mode – Displays the current provisioning TLS Mode: None, PKI, or PSK. This configuration is
only shown in Enterprise Provision Model.
Provisioning Record – Displays the provision PSK/PKI record data of the computer. If the data has not been entered,
the MEBX displays a message that states "Provision Record not present". If the data is entered, the Provision Record
displays the following:
TLS provisioning mode – Displays the current configuration mode of the computer: None, PSK or PKI.
Provisioning IP – The IP of the setup and configuration server.
Date of Provision – Displays the date and time of the provisioning in the format MM/DD/YYYY at HH:MM.
DNS – Displays if Secure DNS is being used or not. 0 indicates DNS is not in use, 1 indicates secure DNS is
being used (PKI only).
Host Initiated – Displays if the setup and configuration process was initiated by the host: 'No' indicates the
setup and configuration process was not host initiated; 'Yes' indicates the setup and configuration process was
host initiated (PKI only).
Hash Data – Displays the 40 character certificate hash data (PKI only).
Hash Algorithm – Describes the hash type. Currently only SHA1 is supported (PKI only).
IsDefault – Displays 'Yes' if the Hash algorithm is the default algorithm selected. Displays 'No' if the hash
algorithm is not the default algorithm used (PKI only).
FQDN – FQDN of the provisioning server mentioned in certificate (PKI only).
Serial Number – The 32 character that indicate the Certificate Authority serial numbers.
Time Validity Pass – Indicates whether the certificate passed the time validity check.
Provisioning Server – The IP address and port number (0 – 65535) for an Intel AMT provisioning server. This
configuration is only shown for the enterprise provision model. The default port number is 9971.
TLS PSK – Contains the settings for TLS PSK configuration settings.
Set PID and PPS – Sets the provisioning identifier (PID) and provisioning passphrase (PPS). Enter the PID and
PPS in the dash format. (Ex. PID: 1234-ABCD ; PPS: 1234-ABCD-1234-ABCD-1234-ABCD-1234-ABCD) NOTE A PPS value of ' '0000-0000-0000-0000-0000-0000-0000-0000' does not change the setup configuration state.
If this value is used the setup and configuration state stays as 'Not-started'.
Delete PID and PPS – Deletes the current PID and PPS stored in ME. If there is no PID and PPS entered, the
MEBX returns an error message. Using this option does NOT set the setup and configuration process parameter
to "Not Started." This option sets the setup and configuration process parameter to "In Process."
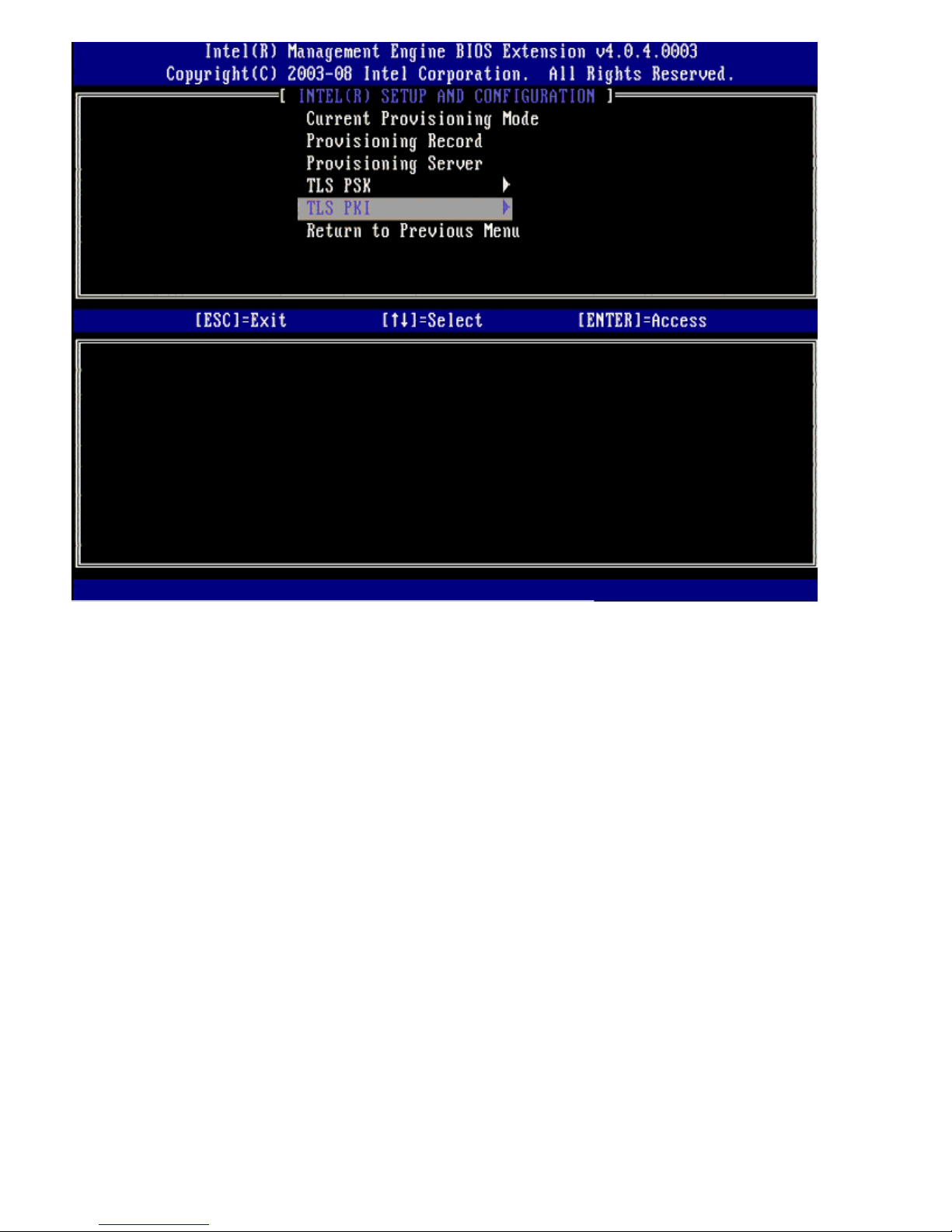
TLS PKI – Contains the settings for the TLS PKI configuration settings.
Remote Configuration Enable/Disable – Disables or enables remote configuration. If this option is not
enabled, remote configuration cannot occur.
Manage Certificate Hashes – Displays the list of hashes that are currently stored and the current status. To
Page 16
change the active status of the certificate press the <+> key. To delete the hash press the <del> key. To add
another key press the <ins> key.
Set FQDN – Sets the fully qualified domain name for the computer.
Set PKI DNS suffix – Sets the PKI DNS suffix.
TLS PSK
The submenu contains the settings for TLS PSK configuration settings. Setting or deleting the PID/PPS causes a partial unprovision if the setup and configuration is "In-process".
Set PID and PPS – Sets the PID and PPS. Enter the PID and PPS in the dash format. (Ex. PID: 1234-ABCD ; PPS:
1234-ABCD-1234-ABCD-1234-ABCD-1234-ABCD) A PPS value of '0000-0000-0000-0000-0000-0000-0000-0000'
does not change the setup configuration state. If this value is used the setup and configuration state stays as "Notstarted."
Delete PID and PPS – Deletes the current PID and PPS stored in ME. If there is no PID and PPS entered, the MEBX
returns an error message.
TLS PKI – Remote Configuration Settings
The remote configuration options are contained under the TLS PKI sub menu. There are four remote configuration items:
Remote Configuration Enable/Disable
Manage Certificate Hashes
Set FQDN
Set PKI DNS Suffix
Page 17
Remote Configuration Enable/Disable
The selectable options are Enable and Disable. If Remote Configuration is disabled, the menu options underneath are still
displayed, but are not be used until Remote Configuration is enabled.
This option cannot be modified once the setup and configuration process is in process. This parameter can only be modified
while the computer is in the factory default or un-provisioned state.
Enabling/disabling remote configuration causes a partial un-provision if the setup and configuration is In-process.
Manage Certificate Hashes
Select the Manage Certificate Hashes option under the Remote Configuration menu to display the Manage Certificate
Hashes menu. Four default hashes are available from the factory. Hashes can be deleted or added per customer needs.
Page 18
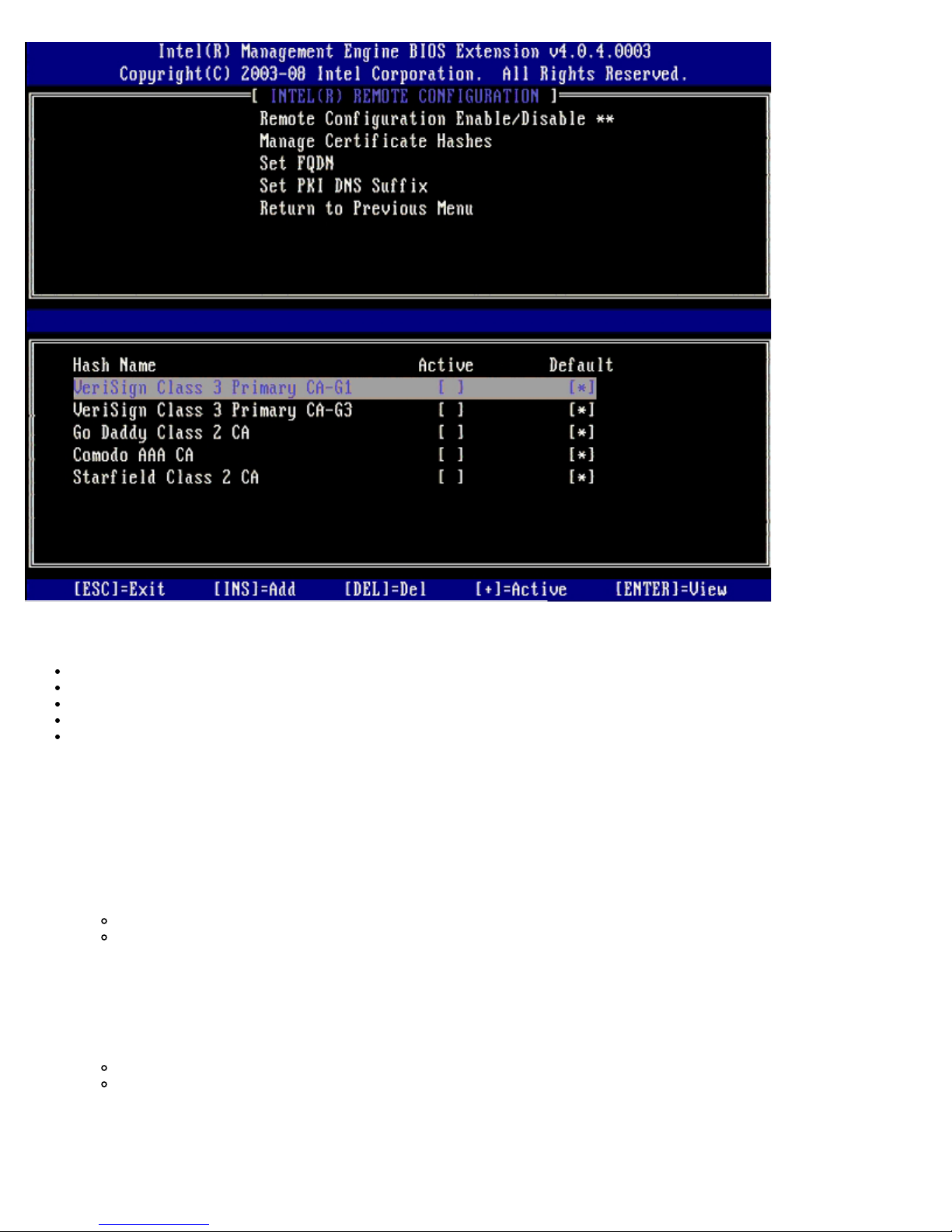
The Manage Certificate Hash screen has several keyboard controls available to you to manage the hashes on the computer.
The following keys are valid when in the Manage Certificate Hash menu:
Escape key – Exits from the menu
Insert key – Adds a customized certificate hash to the computer
Delete key – Deletes the currently selected certificate hash from the computer
<+> key – Changes the active state of the currently selected certificate hash
Enter key – Displays the details of the currently selected certificate hash
Adding a Customized Hash
1. Press <Insert> in the Manage Certificate Hash screen. A text field is displayed requesting the hash name.
2. You must enter the hash name. The hash name must be a maximum of 32 characters. Upon pressing <Enter> you are
prompted to enter the certificate hash value.
3. The certificate hash value is a 20 byte hexadecimal number. You must enter the hash data in the correct format or the
message Invalid Hash Certificate Entered - Try Again is displayed. Upon pressing <Enter> you are asked
about setting the active state of the hash.
4. This query allows for setting the active state of the customized hash.
Yes – The customized hash is be marked as active.
No (Default) – VA_Hash is be maintained within EPS.
Deleting a Hash
1. Press <Delete> in the Manage Certificate Hash screen to display the
Delete this certificate hash? (Y/N)
prompt.
2. This option allows deleting of the selected certificate hash.
Yes – MEBx shall send the message to FW to delete the selected hash.
No – MEBx shall not delete the selected hash and returns to the Remote Configuration.
Changing the Active State
Press the <+> key in the Manage Certificate Hash screen to display the
Page 19
Change the active state of this hash? (Y/N)
prompt. Answering yes to this question toggles the active state of the currently selected certificate hash. Setting a hash as
active indicates that the hash is available to use when during PSK provisioning.
Viewing a Certificate Hash
Press <Enter> in the Manage Certificate Hash screen. The details of the selected certificate hash are displayed to include:
the hash name, the certificate hash data, and the active and default states.
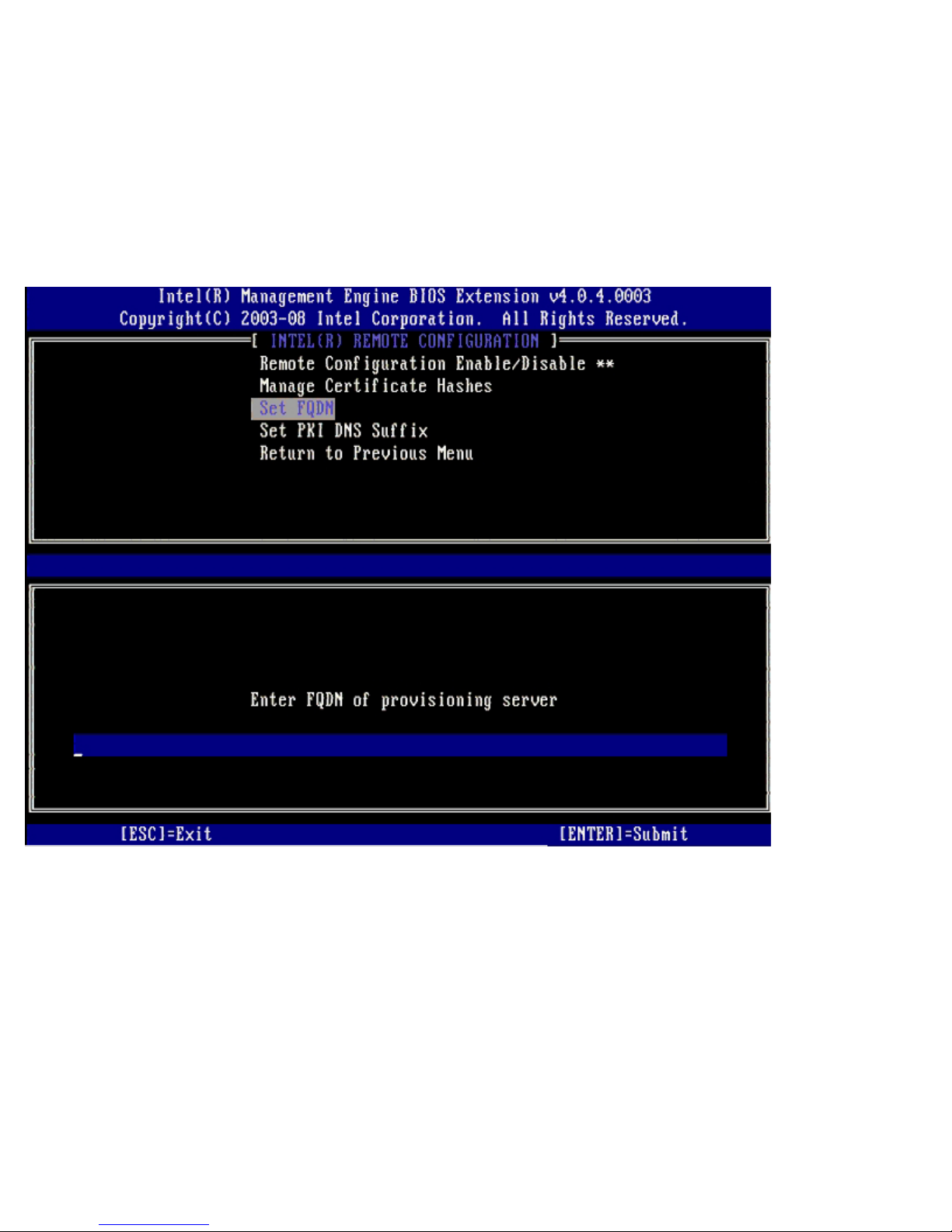
Set FQDN
When the Set FQDN option is selected under the Remote Configuration menu, you are prompted to enter the Fully
Qualified Domain Name (FQDN) of the Provisioning Server.
Set PKI DNS Suffix
When the Set PKI DNS Suffix option is selected under the Remote Configuration menu, you are prompted to enter the
PKI DNS Suffix of the Provisioning Server. The Key Value is maintained in EPS.
Page 20
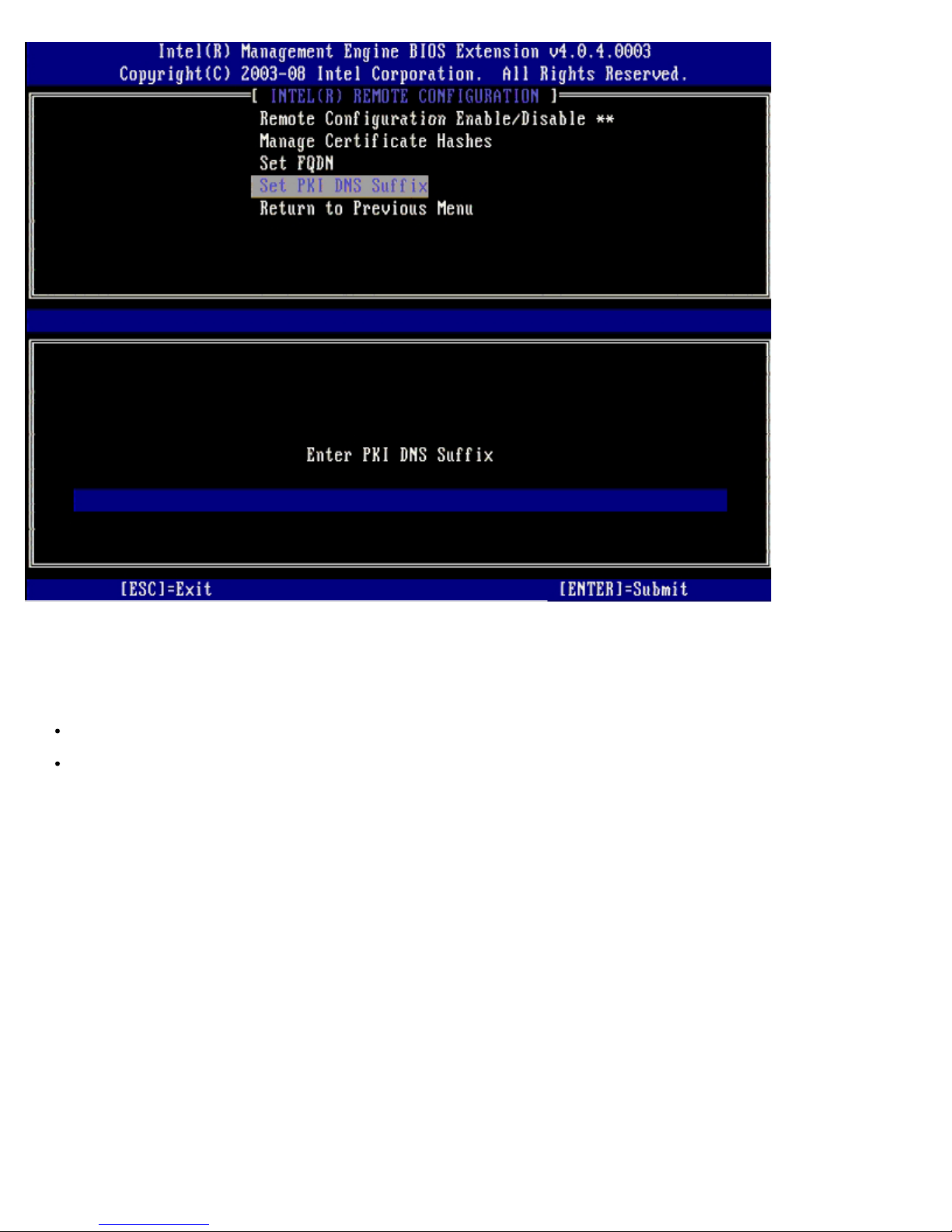
Un-provision
The Un-Provision option allows you to reset the Intel AMT configuration to factory defaults. There are two types of unprovision:
Full Un-provision – This option resets all of the Intel AMT settings to their default values. If a PID/PPS value is
present, both values are lost. The MEBx password remains untouched.
CMOS clear – This un-provision option is not available in the MEBx. This option clears all values to their default values.
If a PID/PPS is present, both values are lost. The MEBx password resets to the default value (admin). To invoke this
option, you need to clear the CMOS (i.e. system board jumper).
Page 21
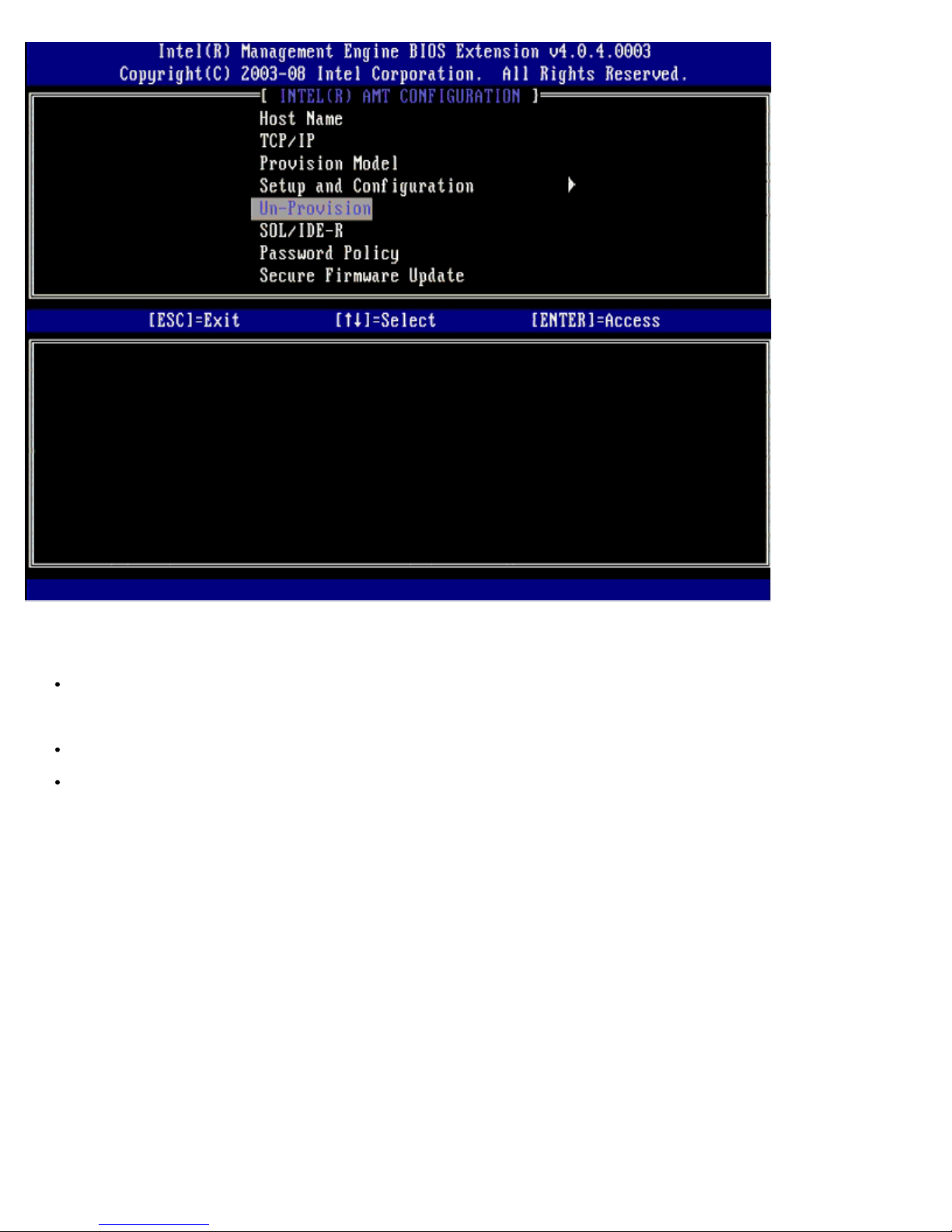
SOL/IDE-R
Username and Password – DISABLED** / ENABLED
This option provides the user authentication for SOL/IDER session. If the Kerberos protocol is used, set this option to
Disabled and set the user authentication through Kerberos. If Kerberos is not used, you have the choice to enable or
disable user authentication on the SOL/IDER session.
Serial-Over-LAN (SOL) – DISABLED** / ENABLED
SOL allows the Intel AMT managed client console input/output to be redirected to the management server console.
IDE Redirection (IDE-R) – DISABLED** / ENABLED
IDE-R allows the Intel AMT managed client to be booted from remote disk images at the management console.
Page 22
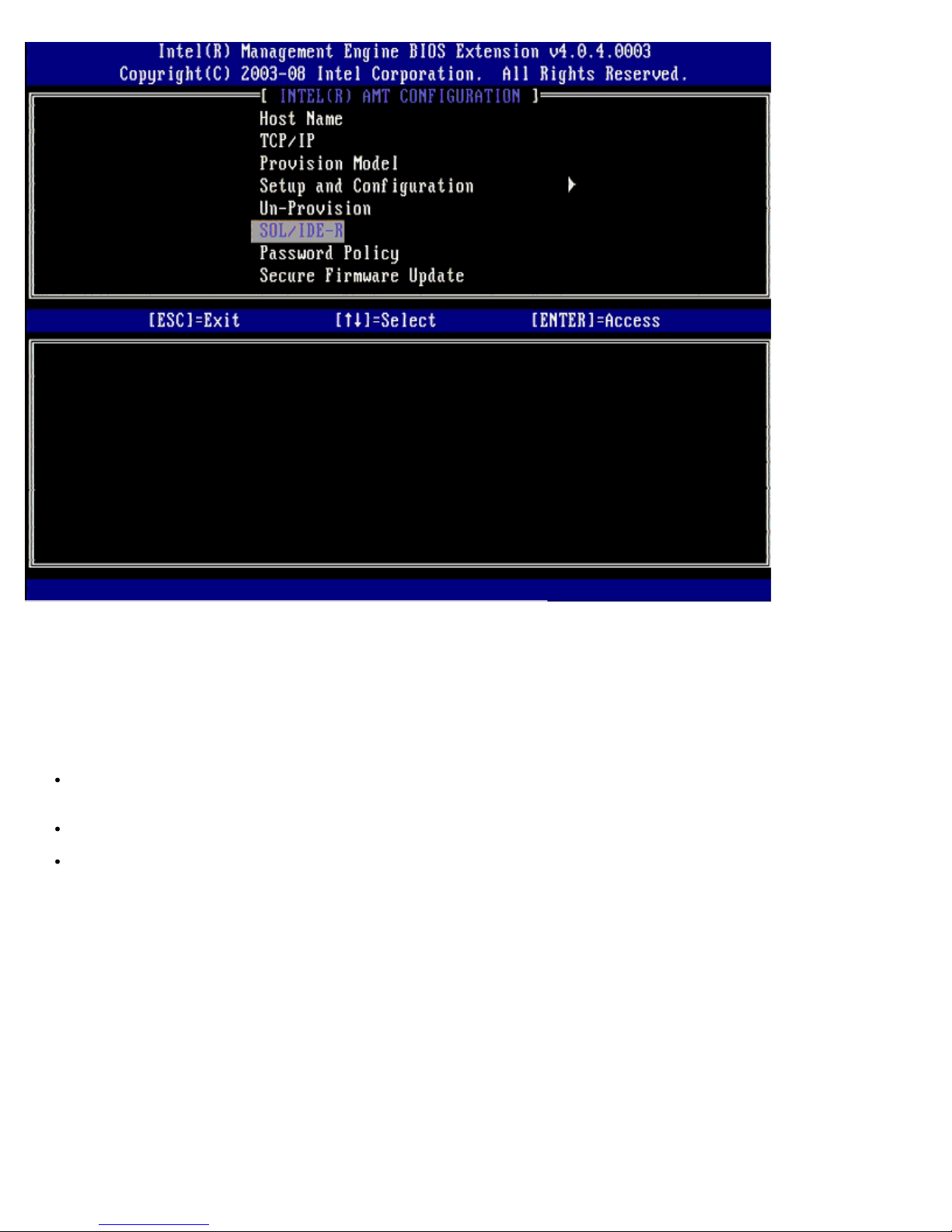
Password Policy
There are two passwords present for the firmware. The MEBX password is the password that is entered when a user is
physically at the system. The network password is the password that is entered when accessing an ME enabled system
through the network. This option determines when network password and the MEBX password will be synched. The MEBX
password can still be modified by users directly in front of the system. However, depending on the option selected below, the
network password and the MEBX password may be different. The settings are:
Default Password Only – MEBX password and the network password will only be synched when the password is
changed from the default password. After the MEBX password is changed from the default value, the network password
and the MEBX password maybe different.
During Setup and Configuration – MEBX password and the network password will be synched during the setup and
configuration state. After the setup and configuration process is complete, the passwords maybe different.
Anytime – MEBX password and network password will be synched when either the MEBX password or the network
password is changed.
Page 23
Secure Firmware Update
This option allows you to enable/disable secure firmware updates. Secure firmware update requires an administrator user
name and password. If the administrator user name and password are not supplied, the firmware cannot be updated.
When the secure firmware update feature is enabled, you are able to update the firmware using the secure method.
Secure firmware updates pass through the LMS driver. If secure and local firmware update is disabled, the user must enable
secure firmware update or local firmware update to allow the firmware updates.
Page 24
Set PRTC
Enter PRTC in GMT (UTC) format (YYYY:MM:DD:HH:MM:SS). Valid date range is 1/1/2004 – 1/4/2021. Setting PRTC value is
used for virtually maintaining PRTC during power off (G3) state. This configuration is only displayed for the Enterprise
Provision Model.
Page 25
Idle Timeout
Use this setting to define the ME WOL idle timeout. When this timer expires, the ME enters a low-power state. This timeout
only takes affect when one of the ME WOL power policies is selected. Enter the value in minutes.
Page 26
Intel AMT in DHCP Mode Settings Example
The table below shows a basic field settings example for the Intel AMT Configuration menu page to configure the computer
in DHCP mode.
Intel AMT Configurations Example in DHCP Mode
Intel AMT Configuration Parameters Values
Intel AMT Configuration Select and press <Enter>.
Host Name
Example: IntelAMT
This is the same as the operating system machine name.
Set the parameters as follows:
TCP/IP
Provision Model
SOL/IDE-R
Remote FW Update Enabled
Save and exit MEBx and then boot the computer to the Windows® operating system.
Enable Network interface
Enable DHCP Mode
Set a domain name (e.g., amt.intel.com)
Intel AMT 4.0 Mode
Small Business
Enable SOL
Enable IDE-R
Intel AMT in Static Mode Settings Example
Page 27
The table below shows a basic field settings example for the Intel AMT Configuration menu page to configure the computer
in static mode. The computer requires two MAC addresses (GBE MAC address and Manageability MAC Address) to operate in
static mode. If there is no Manageability MAC address, Intel AMT cannot be set in static mode.
Intel AMT Configurations Example in Static Mode
Intel AMT Configuration Parameters Values
Intel AMT Configuration Select and press <Enter>
Host Name Example: IntelAMT
Set the parameters as follows:
Enable Network interface
Disable DHCP Mode
Set an IP address (e.g., 192.168.0.15)
TCP/IP
Set a subnet mask (e.g., 255.255.255.0)
The default gateway address is optional
The preferred DNS address is optional
The Alternate DNS address is optional
Set the domain name (e.g., amt.intel.com)
Provision Model
Small Business
Enable SOL
Intel AMT 4.0 Mode
SOL/IDE-R
Enable IDE-R
Remote FW Update Enabled
Save and exit MEBx and then boot computer to the Windows operating system.
*
Information on this page provided by Intel.
Back to Contents Page
Page 28

Back to Contents Page
MEBx Defaults
The table below lists all the default settings for the Intel® Management Engine BIOS Extension (MEBx).
Password admin
Intel ME Platform Configuration
Intel ME Platform State Control
Intel ME Firmware Local Update
Intel ME Features Control
Manageability Feature Selection
Intel ME Power Control
Intel ME ON in Host Sleep States
Intel AMT Configuration Default Settings
Host Name
TCP/IP
DHCP Enabled. Disable? N
Domain Name
Provision Model
Enterprise. Change to Small Business? N
Setup and Configuration
Current Provisioning Mode Provisioning Mode: PKI
Provisioning Record Displays the provision PSK/PKI record data
Provisioning Server
Provisioning Server Address 0.0.0.0
Port Number (0-65535) 0
TLS PSK
Set PID and PPS ** blank (format ABCD-1234)
Delete PID and PPS **
TLS PKI
Remote Configuration Enable/Disable ** Disabled
Manage Certificate Hashes Five default hashes active
Set FQDN blank
Set PKI DNS Suffix blank
Un-Provision
SOL/IDE-R
Username & Password
Serial Over LAN
IDE Redirection
Password Policy
3
1
Enabled *
Disabled
Enabled *
Disabled
None
Intel AMT *
ASF
Mobile: ON in S0 *
Mobile: ON in S0, S3/AC
Mobile: ON in S0, S3/AC, S4-5/AC
Mobile: ON in S0; ME WoL in S3/AC
Mobile: ON in S0; ME WoL in S3/AC, S4-5/AC
2
blank
of the computer.
Disabled
Enabled *
Disabled
Enabled *
Disabled
Enabled *
Default Password Only *
During Setup and Configuration
Page 29

Anytime
Secure Firmware Update
Set PRTC blank
Disabled
Enabled *
Idle Timeout
Timeout Value (0x0-0xFFFF) 1
*Default setting
**May cause Intel AMT partial unprovision
1
Intel ME Platform State Control is only changed for Management Engine (ME) troubleshooting.
2
In Enterprise mode, DHCP automatically loads the domain name.
3
Un-provision setting only seen if the box is provisioned.
Back to Contents Page
Page 30

Back to Contents Page
Setup and Configuration Methods Overview
As discussed in the Setup and Configuration Overview section, the computer has to be configured before the Intel AMT
capabilities are ready to interact with management application. There are two methods to complete the provisioning process
(in order from least complex to most complex):
Configuration service — A configuration service allows you to complete the provisioning process from a GUI console
on their server with only one touch on each of the Intel AMT capable computers. The PPS and PID fields are completed
using a file created by the configuration service saved to a USB mass storage device.
MEBx interface — The IT administrator manually configures the Management Engine BIOS Extension (MEBx) settings
on each Intel AMT ready computer. The PPS and PID fields are completed by typing the 32 character and 8 character
alpha-numeric keys created by the configuration service into the MEBx interface.
Details on using these various methods are available in the next few sections.
Back to Contents Page
Page 31

Back to Contents Page
Configuration Service
This section discusses Intel® AMT setup and configuration using a USB storage device. You can set up and locally configure
password, provisioning ID (PID), and provisioning passphrase (PPS) information with a USB drive key. This is also called USB
provisioning. USB provisioning allows you to manually set up and configure computers without the problems associated with
manually typing in entries.
USB provisioning only works if the MEBx password is set to the factory default of admin. If the password has been changed,
reset it to the factory default by clearing the CMOS.
The following is a typical USB drive key setup and configuration procedure. For a detailed walk-through using Altiris® Dell™
Client Manager (DCM), refer to the USB device procedure
1. An IT technician inserts a USB drive key into a computer with a management console.
2. The technician requests local setup and configuration records from a setup and configuration server (SCS) through the
console.
3. The SCS does the following:
1. Generates the appropriate passwords, PID, and PPS sets
2. Stores this information in its database
3. Returns the information to the management console
4. The management console writes the password, PID, and PPS sets to a setup.bin file in the USB drive key.
5. The technician takes the USB drive key to the staging area where new Intel AMT capable computers are located. The
technician then does the following:
1. Unpacks and connects computers, if necessary
2. Inserts the USB drive key into a computer
3. Turns on that computer
6. The computer BIOS detects the USB drive key.
If found, the BIOS looks for a setup.bin file at the beginning of the drive key. Go to step 7.
If no USB drive key or setup.bin file is found, then restart the computer. Ignore the remaining steps.
7. The computer BIOS displays a message that automatic setup and configuration will occur.
1. The first available record in the setup.bin file is read into memory. The process accomplishes the following:
Validates the file header record
Locates the next available record
If the procedure is successful, the current record is invalidated so it cannot be used again
2. The process places the memory address into the MEBx parameter block.
3. The process calls MEBx.
8. MEBx processes the record.
9. MEBx writes a completion message to the display.
10. The IT technician turns off the computer. The computer is now in the setup state and is ready to be distributed to
users in an Enterprise mode environment.
11. Repeat step 5 if you have more than one computer.
page.
Refer to the management console supplier for more information on USB drive key setup and configuration.
USB Drive Key Requirements
The USB drive key must meet the following requirements to be able to set up and configure Intel AMT:
It must be greater than 16 MB.
It must be formatted with the FAT16 file system.
The sector size must be 1 KB.
The USB drive key is not bootable.
The setup.bin file must be the first file landed on the USB drive key. The USB key must not contain any other files
whether hidden, deleted, or otherwise.
Back to Contents Page
Page 32
Back to Contents Page
MEBx Interface (Enterprise Mode)
The Intel® Management Engine BIOS Extension (MEBx) is an optional ROM module that Intel provides to Dell™ to be included
in the Dell BIOS. The MEBx has been customized for Dell computers.
Enterprise mode (for large corporate customers) requires a setup and configuration server (SCS). An SCS runs an application
over a network that performs Intel AMT setup and configuration. The SCS is also known as a provisioning server as seen in
the MEBx. An SCS is typically provided by independent software vendors (ISVs) and is contained within the ISV management
console product. Consult with the management console supplier for more information.
Follow the steps below to set up and configure Intel AMT in the Enterprise mode.
ME Configuration
To enable Intel Management Engine (ME) on the target platform:
1. Press <Ctrl><p> at the Dell logo screen to enter the MEBx screens.
2. Type admin in the Intel ME Password field. Press <Enter>.
Passwords are case sensitive.
You must change the default password before making changes to the MEBx options.
3. Select Change Intel ME Password. Press <Enter>. Type the new password twice for verification.
The new password must include the following elements:
Eight characters
Page 33

One uppercase letter
One lowercase letter
A number
A special (nonalphanumeric) character, such as !, $, or ; excluding the :, ", and , characters.)
The underscore ( _ ) and spacebar are valid password characters but do NOT add to the password complexity.
4. Change the password to establish Intel AMT ownership. The computer then goes from the factory-default state to the
setup state.
5. Select Intel ME Configuration, and then press <Enter>.
ME Platform Configuration allows you to configure ME features such as power options, firmware update capabilities,
and so on.
Page 34

6. Press <y> when the following message appears:
System resets after configuration change. Continue (Y/N).
Page 35
Intel ME State Control is the next option. The default setting for this option is Enabled. Do not change this setting
to Disabled. If you want to disable Intel AMT, change the Manageability Feature Selection option to None in step
9.
Page 36

7. Select Intel ME Firmware Local Update. Press <Enter>.
8. Then, select either Enabled or Disabled, and press <Enter>.
The default setting for this option is Disabled.
Page 37

9. Select Intel ME Features Control, and then press <Enter>.
Page 38

Manageability Feature Selection is the next option. This feature sets the platform management mode. The default
setting is Intel AMT.
Selecting the None option disables all remote management capabilities.
Page 39

10. Select Return to Previous Menu, and then press <Enter>.
Page 40

11. Select Intel ME Power Control, and then press <Enter>.
Page 41

Intel ME ON in Host Sleep States is the next option. The default setting is Mobile: ON in S0.
Page 42

12. Select Return to Previous Menu, and then press <Enter>.
Page 43

13. Select Return to Previous Menu, and then press <Enter>.
Page 44

14. Exit the MEBx Setup and save the ME configuration.
The computer displays an Intel ME Configuration Complete message and then restarts. After the ME configuration is
complete, you can configure the Intel AMT settings.
Intel AMT Configuration
To enable Intel AMT Configuration settings on the target platform, perform the following steps:
1. At the initial boot screen, press <Ctrl><p> to re-enter the MEBx screens as seen in step 1
Engine for Enterprise Mode."
2. When a prompt for the password appears, enter the new Intel ME password.
3. Select Intel AMT Configuration, and then press <Enter>.
of "Enabling Management
Page 45

4. Select Host Name, and then press <Enter>.
5. Type in a unique name for this Intel AMT machine, and then press <Enter>.
Spaces are not accepted in the host name. Make sure there is not a duplicate host name on the network. Host names
can be used in place of the computer's IP for any applications requiring the IP address.
Page 46

6. Select TCP/IP. Press <Enter>.
7. Press <n>when the following message appears:
[DHCP Enable] Disable DHCP (Y/N)
Page 47

8. Type the domain name into the Domain name field.
Page 48

9. Select Provision Model from the menu, and then press <Enter>.
10. Press <n>when the following message appears:
[Enterprise] change to Small Business: (Y/N)
Page 49

11. Select Setup and Configuration from the menu, and then press <Enter>.
Page 50

12. Select Current Provisioning Mode to display the current mode, and then press <Enter>.
The current provisioning mode is displayed. Press <Enter> or <Esc> to exit.
Page 51

13. Select Provisioning Record from the menu, and then press <Enter>.
The screen displays the provision PSK/PKI record data of the computer. If the data has not been entered, the MEBX
displays a message that states
Provision Record not present
If the data is entered, the Provision Record displays one of several messages
.
Page 52

14. Select Provisioning Server from the menu, and then press <Enter>.
Page 53

15. Type the provisioning server IP in the Provisioning server address field and press <Enter>.
The default setting is 0.0.0.0. This default setting works only if the DNS server has an entry that can resolve the
provision server to the IP of the provisioning server.
Page 54

16. Type the port in the Port number field and press <Enter>.
The default setting is 0. If left at the default setting of 0, the Intel AMT attempts to contact the provisioning server on
port 9971. If the provisioning server is listening on a different port, enter it here.
Page 55

17. Select TLS PSK from the menu, and then press <Enter>.
Page 56

18. Set PID and PPS is the next option.
The PID and PPS can be input manually or by using a USB key once the SCS generates the codes.
This option is for entering the provisioning ID (PID) and provisioning passphrase (PPS). PIDs are eight characters and
PPS are 32 characters. There are dashes between every set of four characters, so including dashes, PIDs are nine
characters and PPS are 40 characters. An SCS must generate these entries.
Page 57

Skip the Delete PID and PPS option. This option returns the computer to factory defaults. See the "Return to Default"
section for more information about unprovisioning.
19. Select Return to Previous Menu, and then press <Enter>.
Page 58

20. Select TLS PKI from the menu, and then press <Enter>.
Page 59
21. Select Remote Configuration Enable/Disable from the menu, and then press <Enter>.
This option is Disabled by default and can be Enabled if the network infrastructure does not support a Certificate
Authority (CA).
Page 60

22. If Enabled, refer to steps 19 through 21. If not Enabled, skip to step 22.
Page 61

Manage Certificate Hashes option is the next option. Four hashes are configured by default. Hashes can be deleted
or added per customer needs.
Page 62

23. Select Set FQDN from the menu, and then press <Enter>.
24. Type the FQDN of the provisioning server in the text field and press <Enter>.
Page 63

25. Select Set PKI DNS Suffix from the menu. Press <Enter>.
26. Type the PKI DNS Suffix in the text field and press <Enter>.
Page 64

27. Select Return to Previous Menu, and press <Enter>.
Page 65

28. Select Return to Previous Menu, and then press <Enter>.
This returns you to the Intel AMT Configuration menu.
Page 66

Skip the Un-Provision option. This option returns the computer to factory defaults. See the "Return to Default"
section for more information about unprovisioning.
Page 67

29. Select SOL/IDE-R, and then press <Enter>.
Page 68

30. Press <y> when the following message appears:
[Caution] System resets after configuration changes. Continue: (Y/N)
.
Page 69

User name & Password
31. Select Enabled and then press <Enter>.
This option allows you to add users and passwords from the WebGUI. If the option is disabled, then only the
administrator has MEBx remote access.
Page 70

32. For Serial Over LAN (SOL/IDE-R), select Enabled and then press <Enter>.
Page 71

33. For IDE Redirection<, select Enabled and then press <Enter>.
Page 72

Secure Firmware Update is the next option. The default setting is Enabled.
Page 73

Skip Set PRTC.
Page 74

Idle Timeout is the next option. The default setting is 1. This timeout is applicable only when a WoL option is selected
for enabling ME for the Enterprise operating mode.
Page 75

34. Select Return to Previous Menu, and then press <Enter>.
Page 76

35. Select Exit, and then press <Enter>.
Page 77

36. Press <y> when the following message appears:
Are you sure you want to exit? (Y/N):
Page 78
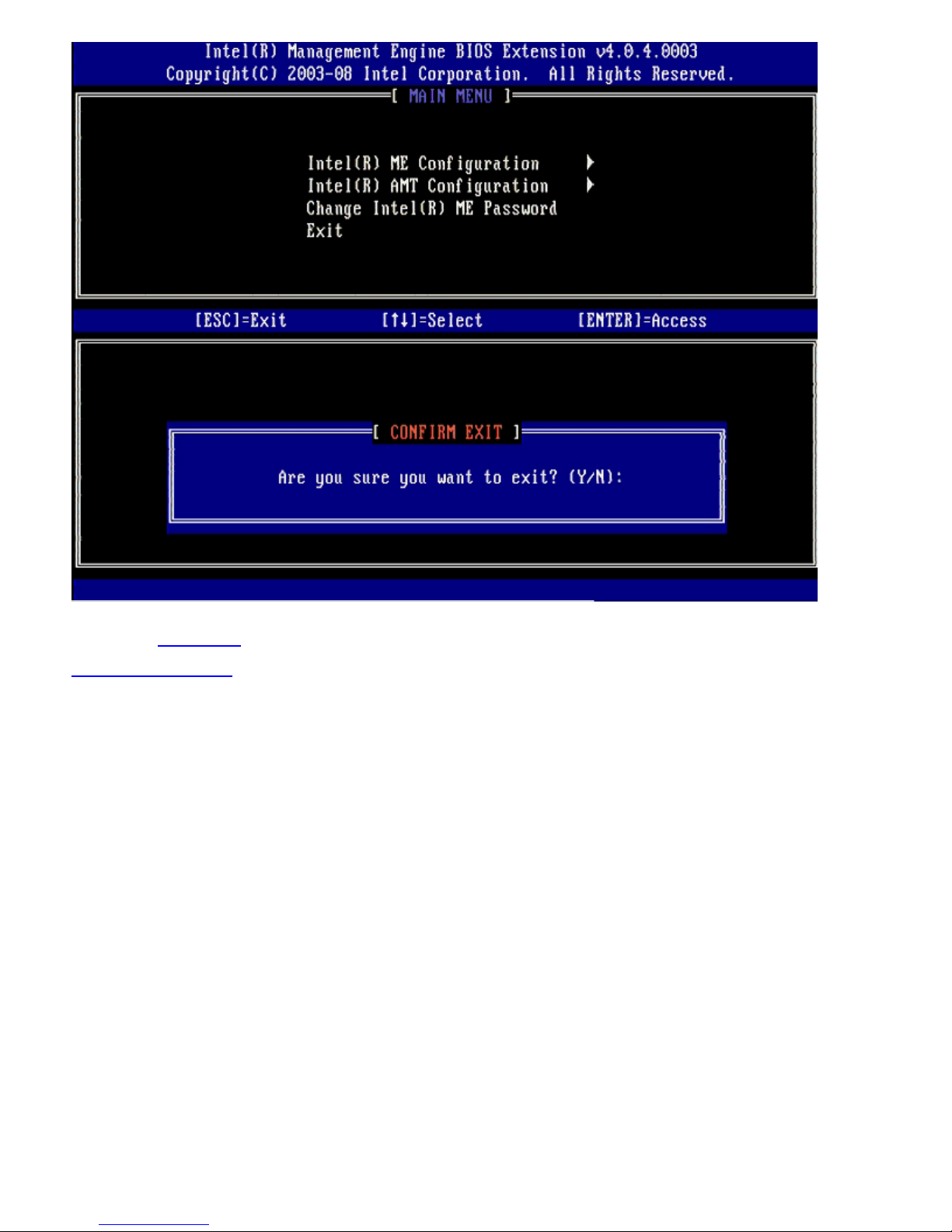
The computer restarts. Turn off the computer and disconnect the power cable. The computer is now in setup state and
is ready for deployment
.
Back to Contents Page
Page 79

Back to Contents Page
MEBx Interface (SMB Mode)
The Intel® Management Engine BIOS Extension (MEBx) is an optional ROM module that Intel provides to Dell™ to be included
in the Dell BIOS. The MEBx has been customized for Dell computers.
Dell also supports setup and configuration of Intel AMT in the small and medium business (SMB) mode. The only setting not
required in the SMB mode is the Set PID and PPS option. Also, the Provision Model option is set to Small Business
instead of Enterprise.
Follow the steps below to set up and configure Intel AMT in the SMB mode.
ME Configuration
To enable Intel Management Engine (ME) on the target platform, perform the following steps:
1. Press <Ctrl><p> at the Dell logo screen to enter the MEBx screens.
2. Type admin in the Intel ME Password field. Press <Enter>. Passwords are case sensitive.
You must change the default password before making changes to the MEBx options.
3. Select Change Intel ME Password, and then press <Enter>.
4. Type the new password twice for verification.
The new password must include the following elements:
Eight characters
One uppercase letter
One lowercase letter
Page 80

A number
A special (nonalphanumeric) character, such as !, $, or ; excluding the :, ", and , characters.)
The underscore ( _ ) and spacebar are valid password characters but do NOT add to the password complexity.
5. Change the password to establish Intel AMT ownership.
The computer then goes from the factory-default state to the setup state.
6. Select Intel ME Configuration, and then press <Enter>.
ME Platform Configuration allows you to configure ME features such as power options, firmware update capabilities,
and so on.
Page 81

7. Press <y> when the following message appears:
System resets after configuration change. Continue (Y/N).
Page 82

Intel ME State Control is the next option. The default setting for this option is Enabled. Do not change this setting
to Disabled. If you want to disable Intel AMT, change the Manageability Feature Selection option to None later in
this procedure.
Page 83

8. Select Intel ME Firmware Local Update and then press <Enter>.
9. Select either Enabled or Disabled, and then press <Enter>.
The default setting for this option is Disabled.
Page 84

10. Select Intel ME Features Control, and then press <Enter>.
Page 85

Manageability Feature Selection is the next option. This feature sets the platform management mode. The default
setting is Intel AMT. Selecting the None option disables all remote management capabilities.
Page 86

11. Select Return to Previous Menu, and then press <Enter>.
Page 87

12. Select Intel ME Power Control, and then press <Enter>.
Page 88

Intel ME ON in Host Sleep States is the next option. The default setting is Mobile: ON in S0.
Page 89

13. Select Return to Previous Menu and then press <Enter>.
Page 90

14. Select Return to Previous Menu, and then press <Enter>.
Page 91

15. Exit the MEBx Setup and save the ME configuration.
The computer displays an Intel ME Configuration Complete message and then restarts. After the ME configuration is
complete, you can configure the Intel AMT settings.
Intel AMT Configuration
Enabling Intel AMT for SMB Mode
1. At the initial boot screen, press <Ctrl><p> to re-enter the MEBx screens.
2. When a prompt for the password appears, enter the new Intel ME password.
3. Select Intel AMT Configuration, and then press <Enter>.
Page 92

4. Select Host Name, and then press <Enter>.
5. Type in a unique name for this Intel AMT machine, and then press <Enter>.
Spaces are not accepted in the host name. Make sure there is not a duplicate host name on the network. Host
names can be used in place of the computer's IP for any applications requiring the IP address.
Page 93

6. Select TCP/IP, and then press <Enter>.
7. Press <n> when the following message appears:
[DHCP Enable] Disable DHCP (Y/N)
Page 94

8. Type the domain name into the field.
Page 95

9. Select Provision Model from the menu, and then press <Enter>.
10. Press <y> when the following message appears:
[Enterprise] change to Small Business: (Y/N)
Page 96

11. Skip the Un-Provision option. This option returns the computer to factory defaults. See the "Return to Default"
section for more information about unprovisioning.
12. Select SOL/IDE-R. Press <Enter>.
Page 97

13. Press <y> when The following message appears:
[Caution] System resets after configuration changes. Continue: (Y/N)
Page 98

14. Select Enabled for Username & Password, and then press <Enter>.
This option allows you to add users and passwords from the WebGUI. If the option is disabled, then only the
administrator has MEBx remote access.
Page 99

15. For Serial Over LAN, select Enabled and then press <Enter>.
Page 100

16. For IDE Redirection, select Enabled and then press <Enter>.
 Loading...
Loading...