Page 1

BASIC-SO
REFERENCE MANUAL
Manual
Order
No.
9800758-02
I
Intel Corporation,
Copyright © 1978,
3065
Bowers
1979
Intel Corporation
Avenue, Santa Clara, California
95051
r
Page 2

Additional copies of this manual
Literature Department
Intel Corporation
3065
Bowers Avenue
Santa Clara, CA
95051
or
other Intel literature may be obtained from:
The information in this document
Intel Corporation makes no warranty
is
subject to change without notice.
of
any kind with regard to this material, including, but not limited
to, the implied warranties of merchantability and fitness for a particular purpose.. Intel Corporation
assumes no responsibility for any errors that may appear in this document. Intel Corporation makes no
commitment to update nor to keep current the information contained in this document.
Intel Corporation assumes no responsibility for the use
an Intel product.
No
other circuit patent licenses are implied.
Intel software products are copyrighted by and shall remain the property
duplication
or
disclosure
is
subject to restrictions stated in Intel's software license,
of
any circuitry other than circuitry embodied in
of
Intel Corporation. Use,
or
as defined in ASPR
7-104.9(a)(9).
or
No part of this document may be copied
written consent
The following are trademarks
and the combination
of
Intel Corporation.
i
ICE
iCS
Insite
Intel
Intelevision
Intellec
of
Intel Corporation and may be used only to describe Intel products:
of
ICE, iCS, iSBC, MCS,
ii
reproduced in any form or by any means without the prior
iSBC
Library Manager
MCS
Megachassis
Micromap
Multibus
or
RMX and a numerical suffix.
Multirnodule
PROMPT
Prornware
RMX
UPI
~Scope
A108/0979/7500
FL
Page 3

PREFACE
This manual describes and explains the features and conventions
tended
systems using the Intel
Single Board Computer Systems using the Intel Real-Time Multitasking Executive
(RMX-80).
This manual
Intel
and five appendices;
"Introduction" describes the general capabilities of BASIC-80, and its operating en-
vironment.
"Language Elements" describes the ways BASIC-80 represents its instructions, con-
stants, variables, arrays,
"Entering and Editing Programs" shows how you enter text and edit it, at time
entry or after storage.
"Error
error-resolving routines.
"Disk File
files
"Commands and Statements" describes each command and
order.
BASIC-80, as implemented on Intel Intellec
Systems Implementation Supervisor (ISIS-II), and on Intel
is
written for users who require concise, complete information about
BASIC-80 characteristics, and organizes this information into seven chapters
operators, and expressions.
Handling" shows how errors are identified, trapped, and used to initiate
Input/Output"
are created and used.
describes and sh0ws how random and sequential data
microcomp~ter
of
Intel Disk Ex-
development
statem~nt
in alphabetic
of
"Functions" describes each function in alphabetic order.
"Appendix
tions, and codes in tabular format.
"Appendix
variable names.
"Appendix C: BASIC-80 Command Characters" lists BASIC-80 one-character
editing and control characters and their meanings.
"Appendix D:
"Appendix E: Calling Non-BASIC-80 Subroutines" shows how to prepare and call
PL/M-80, FORTRAN-80, and 8080/S085 assembly language subroutines.
"Appendix F: Configuring RMX-80 BASIC-80" shows how to configure BASIC-80
with various hardware systems using
Other Relevant Intel Publications:
The following manuals are required to use
• ISIS-II User's Guide, 9800306, which describes how to operate
Systems Implementation Supervisor" operating system (ISIS-II).
A:
BASIC-80 Error Codes" lists all BASIC-80 error messages, descrip-
B:
BASIC-80 Reserved Words" lists words that cannot be used in
ASCII Codes" lists ASCII codes and their meanings.
RMX-SO.
BASIC-80 with ISIS-Il
or
RMX-80:
the
Intel
iii
Page 4

•
RMX-80
Real-Time Mulitasking Executive
•
RMX-80
operation
The following manuals may be required if you intend to call subroutines written in
other Intel-supported languages:
• 8080/8085
describes the instructions and directives
User's Guide, 9S00522, which describes how to operate the Intel
(RMX-SO).
Installation Guide, 9803087-01, which describes installation and
of
the Intel Real-Time Multitasking Executive.
Assembly
Language Programming Manual, 9800301, which
of
the 8080/8085 assembler.
• 8080/8085 Macro Assembler Operator's Manual, 9800292, which describes how
to assemble (using
•
PL/M-80
conventions,
• ISIS-II
to use the
•
FORTRAN-80
instructions, conventions, and usage
FORTRAN-SO programs.
Programming Manual, 9S00268, which describes the instructions,
PL/M-80
ISIS-II based
• ISIS-II FOR
how to use the
machine code.
The following manuals are required
of
BASIC-80 described in Appendix F:
•
iSBC
80/30 Single Board Computer Hardware Reference Manual, 9S00611,
which describes how
•
iSBC
Manual,
RMX-80 configuration.
•
iSBC
which describes how
configuration.
•
iSBC
016
9800279, which describes how to map memory to fit the sample
204 Flexible Diskette Controller Hardware Reference Manual, 9S00568,
80/10 Hardware Reference Manual, 9S00230.
ISIS-II) a program written in S080/S085 assembly language.
and
usage
of
PL/M-SO,
and
how
to
create
PL/M-80
programs.
Compiler Operator's Manual, 9800300, which describes how
PL/M
compiler to generate executable machine code.
Programming Manual, 9800481, which describes the
of
FORTRAN-80, and how
TRAN-80
Random
Compiler Operator's Manual, 9800480, which describes
ISIS-II based FORTRAN-SO compiler to generate executable
to
implement the RMX-80 sample configuration
to
configure the iSBC 80/30 under RMX-80.
Access
to
configure the iSBC 204 for the sample RMX-80
Memory
Board Hardware Reference
to
create
• iSBCBO/10A Hardware Reference Manual, 9S00230.
•
iSBC
80/20 Hardware Reference Manual, 9S00317.
•
iSBC
80/20-4 Hardware Reference Manual, 9S00317.
iv
Page 5

CONTENTS
CHAPTER!
INTRODUCTION
Operating System Interface . . . . . . . . . . . . . . . . . . . . .
Invoking BASIC-80
Manipulating Files from BASIC-80
Listing the Directory
Renaming a File. . . . . . . . . . . . . . . . . . . . . . . . . . .
Changing File Attributes
Deleting a File . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Loading a
Saving a Program . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
CHAPTER
Program.
2
TO
BASIC-SO
...........................
of
a Disk. . . . . . . . . . . . . . .
..
. . . . . . . . . . . . . . . . . . . . . . . . . . .
..
. . . . . . . . . .
. . . . . . . . . . . . . . . . .
LANGUAGE ELEMENTS
Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Statements.
Functions
Representing
Syntax
.........................................
Numeric
Constants.
Integer Constants
Decimal Integer Constants. . . . . . . . . . . . . . . . . .
Hexadecimal Integer Constants. . . . . . . . . . . . . .
Octal Integer Constants . . . . . . . . . . . . . . . . . . . .
Single-Precision Floating-Point Constants
Double-Precision Floating-Point Constants
Variables
String
String Constants . . . . . . . . . . . . . . . . . . . . . . . . . .
String Variables
Converting
Array Variables
String Arrays
Operators and Precedence
Arithmetic Operators . . . . . . . . . . . . . . . . . . . . .
Relational Operators. . . . . . . . . . . . . . . . . . . . . .
Logical Operators . . . . . . . . . . . . . . . . . . . . . . . .
String
Expressions
Numeric Expressions
String Expressions. . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
....................................
Data
...............................
Data
................
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
....................................
Data
...................................
Data
Operator
....
.....
.............................
. . . . . . . . . . . . . . . . . . . . . . . . . . . .
...............................
..............................
............................
. . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . .
of
Evaluation.
.......................
......
.....
. . . . . .
PAGE
..
1-1
1-1
..
1-2
..
1-3
..
1-3
..
1-3
..
1-3
..
1-4
..
1-4
..
2-1
..
2-1
..
2-1
2-5
2-5
2-5
..
2-5
..
2-6
..
2-6
..
2-6
..
2-6
..
2-7
2-7
2-7
2-7
2-8
..
2-8
2-8
..
2-9
2-9
2-10
..
2-11
..
2-11
..
2-11
..
2-12
2-12
..
2-12
2-12
..
2-12
A Subcommand. . . . . . . . . . . . . . . . . . . . . . . . . . . . .
E
Subcommand.
Carriage Return. . . . . . . . . . . . . . . . . . . . . . . . . . . . .
CHAPTER
ERROR
BASIC-80
Syntax Error Messages. . . . . . . . . . . . . . . . . . . . . . .
Overflow, Underflow, and Divide-by-Zero
Integer
Error
Trace Facility. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Error
Restarting
HANDLING
Error
Overflow
Underflow
Divide-by-Zero . . . . . . . . . . . . . . . . . . . . . . . . . . .
Operations
Trapping
Simulation. . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Program
CHAPTER
DISK FILE
Sequential File
Opening a Sequential File. . . . . . . . . . . . . . . . . . . . .
Writing to a Sequential
Reading from a Sequential
Closing a Sequential File
Random File
I/O
Buffers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Defining a Random
Opening and Closing a Random Disk
Reading from a Random
Writing to a Random
CHAPTER
COMMANDS
. . . . . . . . . . . . . . . . . . . . . . . . . . . .
4
Messages. . . . . . . . . . . . . . . . . . . . . .
..................................
.................................
............................
..
. . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Execution
....................
5
INPUT
I/O
I/O
................................
IOUTPUT
. . . . . . . . . . . . . . . . . . . . . . . . . . . .
File.
. . . . . . . . . . . . . . . . . .
File.
. . . . . . . . . . . . . . .
...
. . . . . . . . . . . . . . . . . .
I/O
Field-FIELD
I/O
I/O
File
File
...................
...........
File.
................
6
AND
STATEMENTS
........
. . . . . .
CHAPTER 7
FUNCTIONS
APPENDIX
A
BASIC-SO ERROR CODES
PAGE
..
3-6
..
3-6
..
3-6
..
4-1
..
4-1
4-1
4-1
4-2
..
4-2
4-2
..
4-2
..
4-3
..
4-4
4-4
..
5-1
..
5-1
..
5-2
..
5-2
..
5-3
5-4
..
5-4
5-4
..
5-6
5-6
5-7
CHAPTER
ENTERING
Entering Instruction
Correcting Entry
Editing
Program
D Subcommand
L Subcommand
I Subcommand
H Subcommand. . . . . . . . . . . . . . . . . . . . . . . . . . . . .
X Subcommand. . . . . . . . . . . . . . . . . . . . . . . . . . . . .
S Subcommand
K Subcommand. . . . . . . . . . . . . . . . . . . . . . . . . . . . .
C Subcommand. . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Q Subcommand
3
AND
EDITING PROGRAMS
Lines.
Errors.
Text.
...............................
...............................
...............................
...............................
...............................
. . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . .
..
..
..
..
..
..
..
3-1
3-1
3-2
3-3
3-4
3-4
3-4
3-4
3-5
3-5
3-6
3-6
APPENDIXB
BASIC-SO RESERVED WORDS
APPENDIXC
BASIC-SO COMMAND CHARACTERS
APPENDIXD
ASCII CODES
APPENDIXE
CALLING NON-BASIC-SO SUBROUTINES
APPENDIXF
RMX/80
BASIC-80
v
Page 6
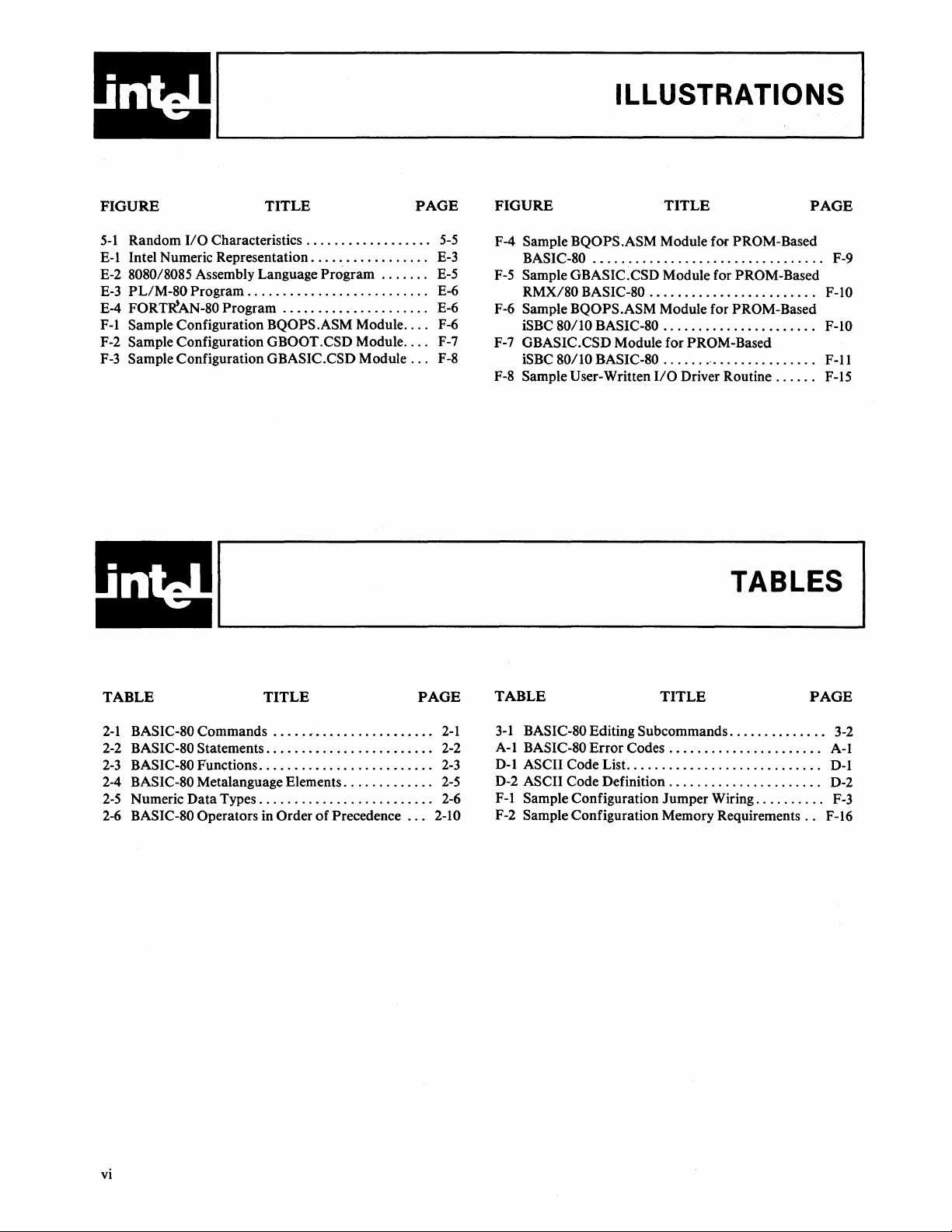
ILLUSTRATIONS
FIGURE
5-1
Random
E-l Intel Numeric Representation
E-2 8080/8085 Assembly Language Program
E-3
PL/M-80
FORT~AN-80
E-4
F-l Sample Configuration
F-2 Sample Configuration
F-3
Sample Configuration GBASIC.CSD Module
1/0
Characteristics
Program.
TITLE
.................
.................
. . . . . . . . . . . . . . . . . . . . . . .
Program
.....................
BQOPS.ASM Module
GBOOT.CSD Module
.......
....
....
PAGE
'
5-5
E-3
E-5
..
E-6
E-6
F-6
F-7
...
F-8
FIGURE
F-4 Sample BQOPS.ASM Module for PROM-Based
BASIC-80
F-5
Sample GBASIC.CSD Module for PROM-Based
RMX/80
F-6 Sample BQOPS.ASM Module for PROM-Based
iSBC
F-7 GBASIC.CSD Module for PROM-Based
iSBC
F-8 Sample User-Written 110 Driver Routine
.................................
BASIC-80
80/10
BASIC-80
80/10
BASIC-80
TITLE
........................
......................
....... ' ...............
......
TABLES
PAGE
F-9
F-IO
F-IO
F-ll
F-15
TABLE
2-1
BASIC-80 Commands
2-2
BASIC-80 Statements. . . . . . . . . . . . . . . . . . . . . .
2-3
BASIC-80 Functions
2-4
BASIC-80 Metalanguage Elements. . . . . . . . . . .
Numeric Data Types
2-5
2-6
BASIC-80 Operators in Order
TITLE
........................
.........................
.........................
of
Precedence
PAGE
..
..
...
2-1
2-2
2-3
2-5
2-6
2-10
TABLE
3-1
BASIC-80 Editing Subcommands
A-I BASIC-80 Error Codes
D-l ASCII Code List. . . . . . . . . . . . . . . . . . . . . . . . . .
D-2 ASCII Code Definition. . . . . . . . . . . . . . . . . . . .
F-l Sample Configuration Jumper Wiring
F-2 Sample Configuration Memory Requirements
TITLE
..............
......................
..........
PAGE
A-I
..
D-l
..
D-2
F-3
..
F-16
3-2
vi
Page 7

CHAPTER 1
INTRODUCTION
BASIC-SO
Series II Microcomputer Development Systems, which use the Intel Systems Implementation Supervisor (ISIS-II), and for Intel Single Board Computers, which use
Intel's Real-Time Multitasking Executive
applying the computational and input! output capabilities
development system to a wide range of business, information handling, numeric
analysis, and data processing applications.
BASIC-SO
quirements for ISIS-II BASIC-80 include an Intellec Microcomputer Development
System with at least
requirements, both hardware and software, are described in Appendix F
manual.
BASIC-SO
capability, and full disk
written functions can be defined, and up to
Intel-supported languages
language) and called from
is
Intel's implementation
can be used with either the ISIS-II or RMX/SO operating systems. Re-
4SK
of memory space, and one disk drive. RMX/SO
includes
21
commands,
I/O
(both sequential and random access). In addition, user-
(FORTRAN-SO, PL/M-SO, and
BASIC-SO.
of
disk extended BASIC for Intellec and Intellec
(RMX/SO).
39
statements,
25
It
offers a quick method
of
4S
functions, a line-editing
subroutines can
TO BASIC-80
of
the microcomputer
BASIC-SO
of
this
be
written in other
SOSO/SOS5
assembly
Intel integer, single-precision floating-point, and double-precision floating-point
arithmetic standards are all supported, offering flexible combinations of processing
16
speed and accuracy (up to
can have virtually as many dimensions as needed; the only limit on the number
dimensions that can be specified
Hexadecimal and octal integer representation, combined with bitwise Boolean
logical operators, make sophisticated mask operations easy. A full range
is
functions
The disk
files, but also the ability to create, rename, change the attributes of, delete, and list
the directory
BASIC-SO
system with at least
available to provide flexibility in manipulating character data.
I/O
features include not only the ability to read from and write to disk
of
disk files without returning to the operating system.
requires
an
4SK
digits in the range ± 2.2 x
is
the 255-character program statement length.
Intellec or Intellec Series II microcomputer development
RAM and ISIS-II operating system (version 3.4 or later).
-308
to ±
1.S x 10
308
).
Arrays
of
of
string
Operating System Interface
You can invoke
for boot loading upon restart. Once BASIC
the disk file-handling functions as well as the ability to load and save programs.
BASIC-SO
from ISIS-II, or configure
is
running, you have access to many
RMX-SO
BASIC-SO
in PROM
of
Invoking BASIC-80
Once you configure RMX/SO BASIC-SO, you
restart.
will
always enter
BASIC-SO
upon
1-1
Page 8

Introduction to BASIC-80
To
invoke BASIC-80 from ISIS-II, enter the name
BASIC interpreter. Options also allow you to specify the name
a program to be loaded after
BASIC-80's work area. The format
BASIC-80
of
the command is:
of
the file that contains the
of
a file that contains
is
running, and upper memory limit for
BAS
IC-80
-BASIC
is
the ISIS-II command prompt.
enter the command.
BASIC
specifies the name
filename
is
an optional parameter
loaded and run after
MEMTOP(address)
is
an
that
number.
interpreter, and less
system.
Examples
[filename] [MEMTOP(address)]
It
is
displayed automatically before you
of
the file that contains the
that
specifies the name
BASIC-SO
is
running.
BASIC-SO
of
optional parameter that specifies the upper bound
BASIC-80 can use. Address can be either a decimal
It
must be greater
than
than
3800H plus the number
OBEBFH in a
48K
system
or
interpreter.
a file that
of
the memory
or
hexadecimal
of
bytes in the
OF6BFH in a
is
to be
64K
1.
If
the interpreter
-BASIC
2.
If
the situation
a disk in drive
-BASIC
3.
If
the
situation
using memory beyond address
-BASIC
If
a fatal ISIS-II error occurs while BASIC-80
initialized and the contents
is
in a file named BASIC
is
the same as
1,
but
you want to run a file named ANLYZE on
1:
:F1
:ANL YZE
is
the same as 2,
but
you also want to prevent BASIC-80 from
54400:
:F1
:ANLYZE MEMTOP(54400)
of
the BASIC-80 work area
on
a disk in drive 0 enter:
is
running, ISIS-II
is
lost, including any
is
re-
program editing you have done since you last entered a save command.
Manipulating Files from BASIC-SO
BASIC-80 lets you list a disk directory, rename a file, change the attributes of a file,
and delete a file. These functions can also be performed using
of course.
ISIS-II
or
RMX-80,
1-2
Page 9
BASIC-SO
Introduction
to
BASIC-SO
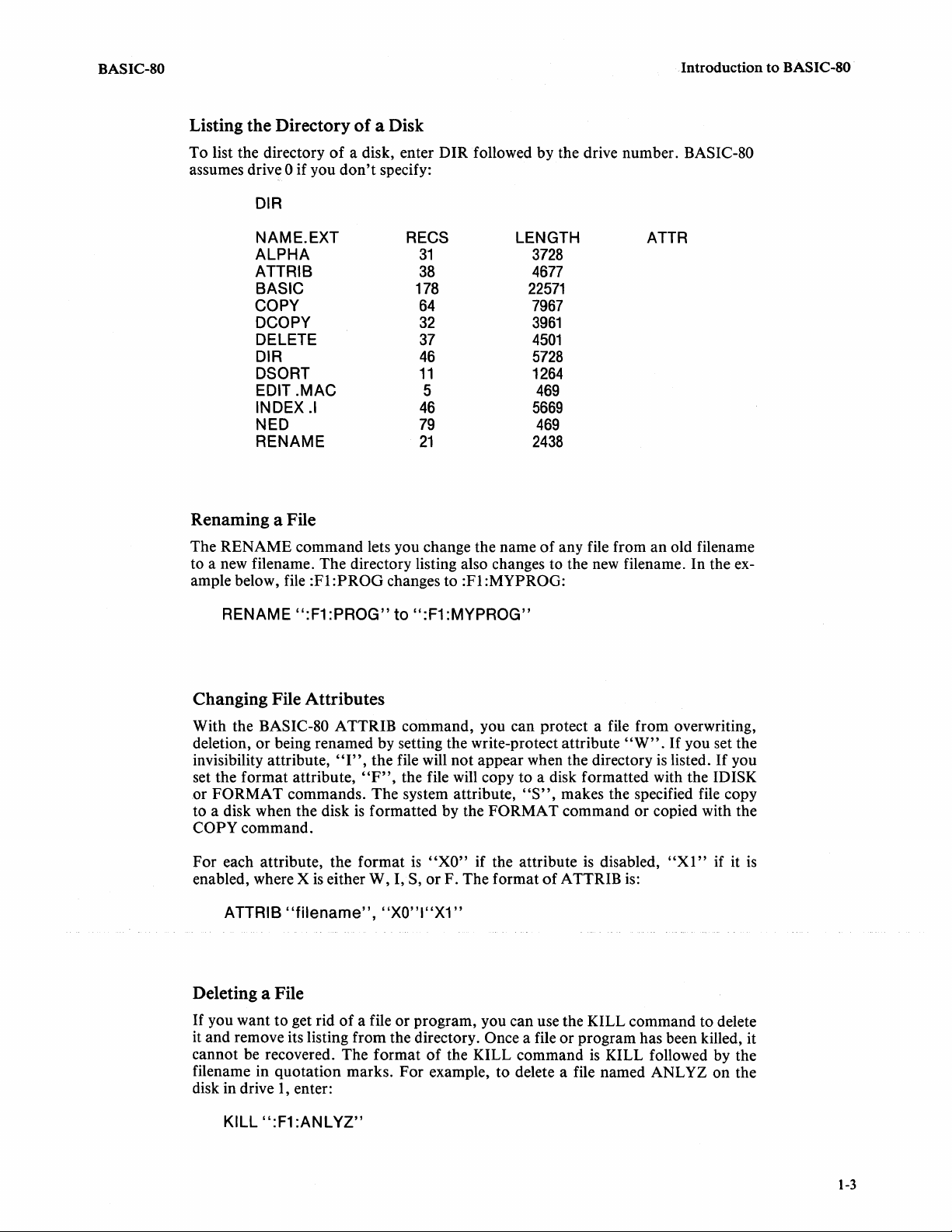
Listing the Directory
To list the directory
assumes drive 0 if you
DIR
NAME.EXT
ALPHA
ATTRIB
BASIC 178
COpy
DCOPY
DELETE
DIR
DSORT
EDIT
.MAC
INDEX
NED
RENAME
of
a Disk
of
a disk, enter DIR followed by the drive number. BASIC-80
don't
specify:
RECS LENGTH
31
38
64
32
37
46
11
5
.I
46
79
21
3728
4677
22571
7967
3961
4501
5728
1264
469
5669
469
2438
ATTR
Renaming a File
The RENAME command lets you change the name
to a new filename. The directory listing also changes to the new filename. In the example below, file
:FI:PROG
changes to :FI:MYPROG:
of
any file from an old filename
RENAME
":F1
:PROG"
to
":F1
:MYPROG"
Changing File Attributes
With the BASIC-80 A TTRIB command, you can protect a file from overwriting,
deletion,
invisibility attribute,
set the format attribute,
or FORMAT commands. The system attribute,
to a disk when the disk
or
being renamed by setting the write-protect attribute
"I",
the file will not appear when the directory
"F",
the file will copy to a disk formatted with the IDISK
"S",
makes the specified file copy
is
formatted by the FORMAT command or copied with the
"W"
.
If
you set the
is
listed.
If
you
COPY command.
For each attribute, the format
enabled, where X
ATTRIB
is
either W, I, S,
"filename",
is
"XO"
or
F. The format
"XO"I"X1"
if the attribute
of
A TTRIB
is
disabled,
is:
"Xl"
if it
Deleting a File
If
you want to get rid
it
and remove its listing from the directory. Once a file or program has been killed, it
cannot be recovered. The format
filename in quotation marks. For example, to delete a file named ANL
disk in drive
1,
enter:
of
a file or program, you can use the KILL command to delete
of
the KILL command
is
KILL followed by the
YZ
on
the
is
KILL
":F1
:ANLYZ"
1-3
Page 10

Introduction
to
BASIC-80
Loading a Program
BASIC-80
The LOAD command loads a
stored in either ASCII
a disk in drive
LOAD ":F1 :ANLYZE"
OK
You can now run, list, or edit the program.
Saving
The SAVE command copies your program from Intellec memory to disk. You must
specify a filename, enclosed in quotation marks:
SAVE ":F1 :ANLYZ"
The SAVE command can also be used to list the contents
printer or other output device. For example, to list the current file on a line printer,
you would enter:
SAVE
1:
a Program
":LP:"
or
,A
BASIC-SO
internal format.
program from disk. The program can be
To
load a program named ANL YZE from
of
the current file on a line
4"4;0"1"
You can only write data to one disk in any disk drive each time you invoke
If
BASIC.
another, and try to write to the new disk, you lose all data on the
The exception to this
ble to change a disk on a drive if that drive has not been written to since
another drive has been written to.
gram writes
another and write on it, the contents
however, your program wrote on a disk in drive 1 between writing on the
different disks in drive
you write to a disk in a given drive, remove that disk and insert
new
disk.
is
on systems with more than one drive.
As
an example, if your
on
a file in drive 0, and you then remove that disk, insert
of
that second disk
0, there would be no problem.
It
is
permissi-
BASIC-SO
will
be lost.
pro-
If,
1-4
There are no restrictions on reading from disks.
Page 11

CHAPTER 2
LANGUAGE ELEMENTS
A BASIC-80 program consists
of
instructions, which tell BASIC-80 what to do, and
data, which gives BASIC-80 the inform.ation necessary to do it. This chapter
describes the different types
of
instructions and data, and shows how to represent
them.
Instructions
BASIC-80 performs work by interpreting user-provided instructions. These instructions are divided into three categories: commands, statements, and functions. These
instruction types are described in the following topics; the individual instructions are
described in detail in Chapters 6 and 7.
Commands
Commands are executed as soon as you enter them; they alter
grams or files. Most commands can be used in program statements, but many
them halt program execution and force variables to zero or null.
2-1
Table
lists the BASIC-80 commands.
Statements
Statements are executed when they are encountered during program execution. They
of
make up most
commands.
the instructions
of
a program. Most statements can be entered as
or
direct entire pro-
of
Table 2-2 lists the BASIC-80 statements.
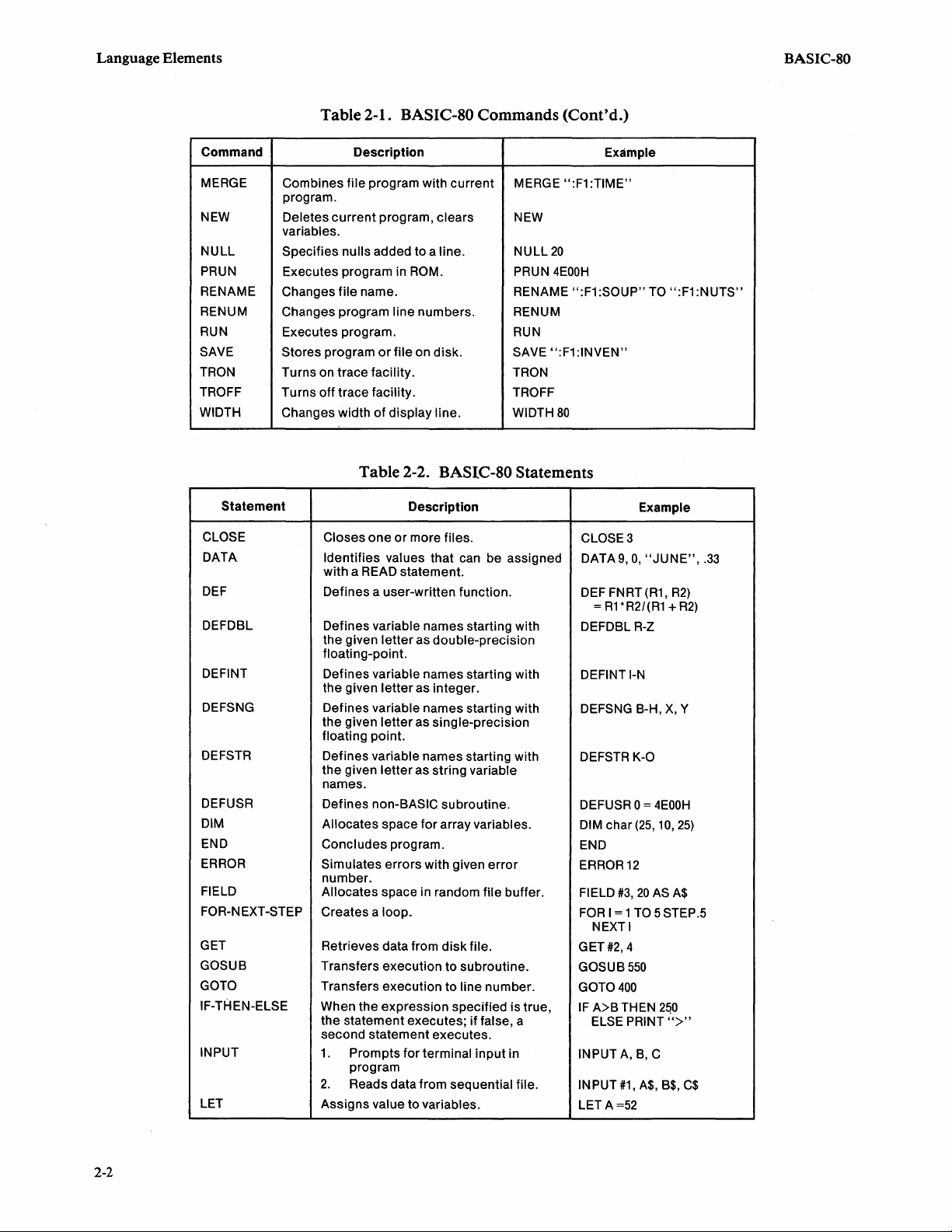
Table
2-1. BASIC-SO
Command
ATTRIB
AUTO
CLEAR
CONT
DELETE
DIR
EDIT
EXIT
KILL
LIST
LOAD
Changes the attributes of a file.
Automatically
statements.
Sets aside memory
Continues execution
Deletes a
program.
Displays a
files
Specifies a program statement
be changed.
Retu rns
Deletes a file from disk.
Displays a
program.
Retrieves a file from disk.
Description
numbers program
line
or
list
on
of
a disk.
to
operating system .
line
or
for
strings.
after
BREAK.
lines
from a
all non-invisible
lines
of
a
Commands
ATTRIB
AUTO
CLEAR
CONT
DELETE
DIR1
to
EDIT
EXIT
KILL ":F1 :STAT"
LIST
LOAD ":F1 :DATES"
"~F1
25,500
2000
700~875
170
300-400
Example
:STAT",
"W1"
Page 12
Language Elements
BASIC-80
Table 2-1. BASIC-80 Commands
Command
MERGE Combines file program with current
NEW
NULL
PRUN
RENAME
RENUM Changes program line numbers. RENUM
RUN
SAVE Stores program
TRON
TROFF
WIDTH
program.
Deletes
variables.
Specifies nulls added to a line. NULL
Executes program in
Changes
Executes program.
Turns on trace facility. TRON
Turns off trace facility. TROFF
Changes width
Description
MERGE
current
program, clears
ROM. PRUN
file
name. RENAME ":F1 :SOUP"
or
file on disk.
of
display line.
NEW
RUN
SAVE ":F1:INVEN"
WIDTH
Table 2-2. BASIC-80 Statements
Statement
CLOSE
DATA
DEF
DEFDBL
DEFINT
DEFSNG
DEFSTR
DEFUSR
DIM
END
ERROR
FIELD
FOR-NEXT-STEP
GET
GOSUB
GOTO
TH
EN-ELSE
IF-
INPUT
LET
Closes
Identifies values that can be assigned
with a READ statement.
Defines a user-written function.
Defines variable names starting with
the given
floating-point.
Defines variable names starting with
the given
Defines variable names starting with
the given
floating point.
Defines variable names starting with
the given
names.
Defines non-BASIC subroutine.
Allocates space for array variables.
Concludes program.
Simulates errors with given
number.
Allocates space in random file buffer.
Creates a loop.
Retrieves data from
Transfers execution to subroutine.
Transfers execution to line number.
When the expression specified is true,
the statement executes;
second statement executes.
1.
Prompts for terminal
program
2.
Reads data from sequential file.
Assigns value to variables.
one
letter
letter
letter
letter
Description
or
more files.
as double-precision
as integer.
as single-precision
as string variable
disk
file.
if
false, a
input
error
in
(Cont'd.)
":F1:TIME"
20
4EOOH
80
CLOSE 3
DATA
DEF
=
DEFDBL
DEFINT
DEFSNG B-H,
DEFSTR
DEFUSR 0 =
DIM
END
ERROR
FIELD #3,20
FOR
NEXTI
GET#2,4
GOSUB
GOT0400
IF
A>B THEN
ELSE PRINT
INPUT
INPUT
LET A=52
Example
TO
":F1
Example
9,0,
"JUNE",
FNRT
(R1,
R-Z
I-N
K-O
12
TO
550
B,
A$,
R2)
R2)
X,
Y
4EOOH
AS
A$
5 STEP.5
2~0
">"
C
B$,
C$
R1
*R2/(R1 +
char (25,10,25)
1=1
A,
#1,
:NUTS"
.33
2-2
Page 13
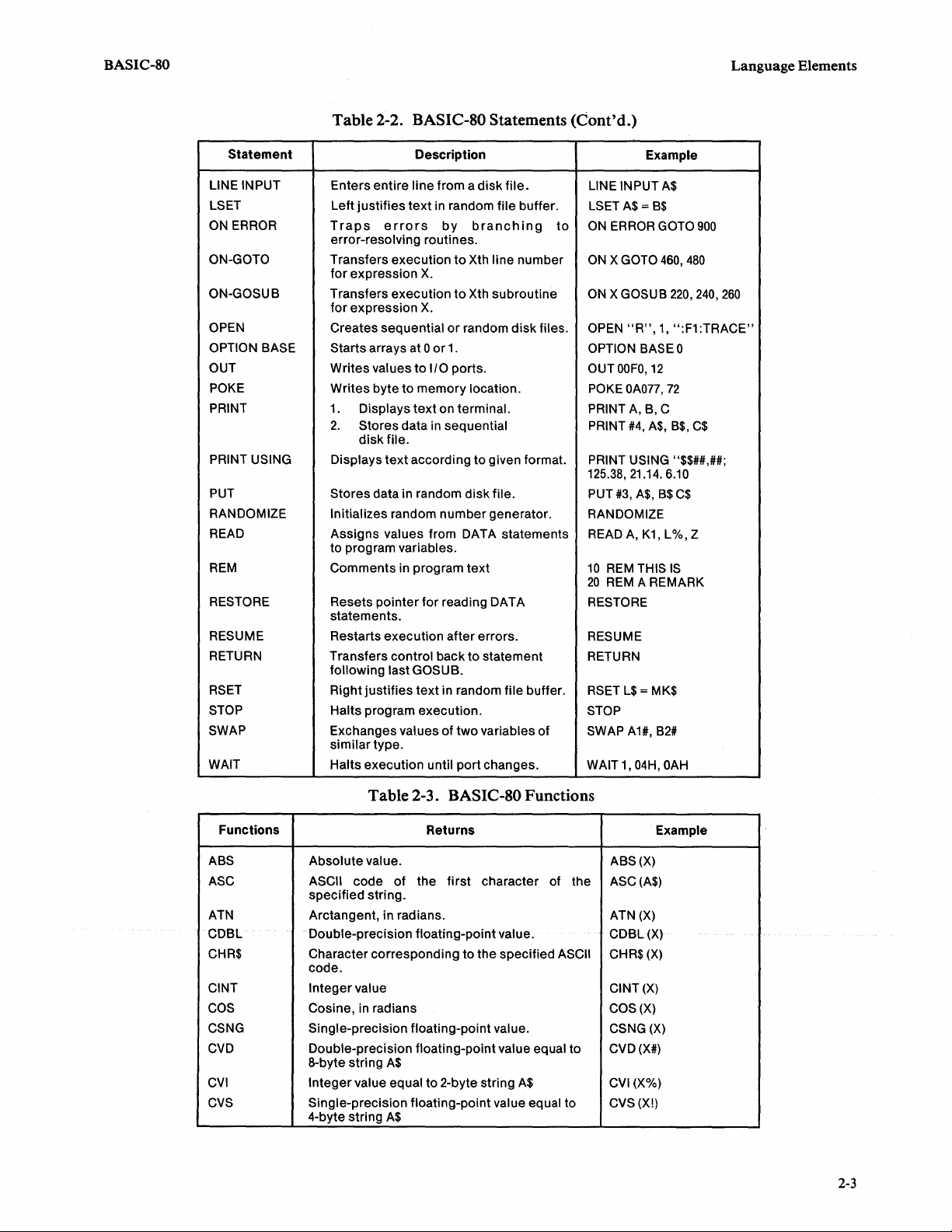
BASIC-SO
Language Elements
Statement
LINE INPUT
lSET
ON
ERROR
ON-GOTO
ON-GOSUB
OPEN
OPTION BASE
OUT
POKE
PRINT
PRINT USING
PUT
RANDOMIZE
READ
REM
RESTORE
RESUME
RETURN
RSET
STOP
SWAP
WAIT
Table 2-2. BASIC-80 Statements
Description
Enters entire line from a disk
left
justifies
Traps
error-resolving routines.
Transfers execution
for expression
Transfers execution
for expression
Creates sequential
Starts arrays at 0
Writes values
Writes byte
1.
Displays
2.
Stores data in sequential
disk file.
Displays
Stores data in random disk file.
Initializes random number generator.
Assigns values from DATA statements
to program variables.
Comments in program
Resets pOinter for reading DATA
statements.
Restarts execution after errors.
Transfers control back
following last GOSUB.
Right
Halts program execution.
Exchanges values of two variables of
similar type.
Halts execution until port changes.
errors
to
text
justifies
text
in random file buffer.
by
to
X.
to
X.
or
or
1.
to
I/O
ports.
memory location.
text
on terminal.
according
text
in random file buffer.
file.
branching
Xth line number
Xth subroutine
random
disk
to
given format.
text
to
statement
files.
(Cont'd.)
Example
LINE INPUT
LSET
A$ = B$
to
ON
ERROR
ON
X GOTO
ON
X GOSUB
OPEN
"R",
OPTION BASEO
OUTOOFO,12
POKE
OA077,
PRINT
A,
B,
PRINT
#4,
A$,
PRINT USING "$$##,##;
125.38,21.14.6.10
PUT
#3,
A$,
RANDOMIZE
READ
A,
K1,
10
REM
REM
l$ = MK$
A1#,
THIS
A REMARK
04H,
20
RESTORE
RESUME
RETURN
RSET
STOP
SWAP
WAIT 1,
A$
GOTO
900
460,
480
220, 240,
1,
":F1:TRACE"
72
C
B$,
C$
B$
C$
l%,
Z
IS
B2#
OAH
260
Functions
ABS
ASC
ATN
COSl
CHR$
CINT
COS
CSNG
CVD
CVI
CVS
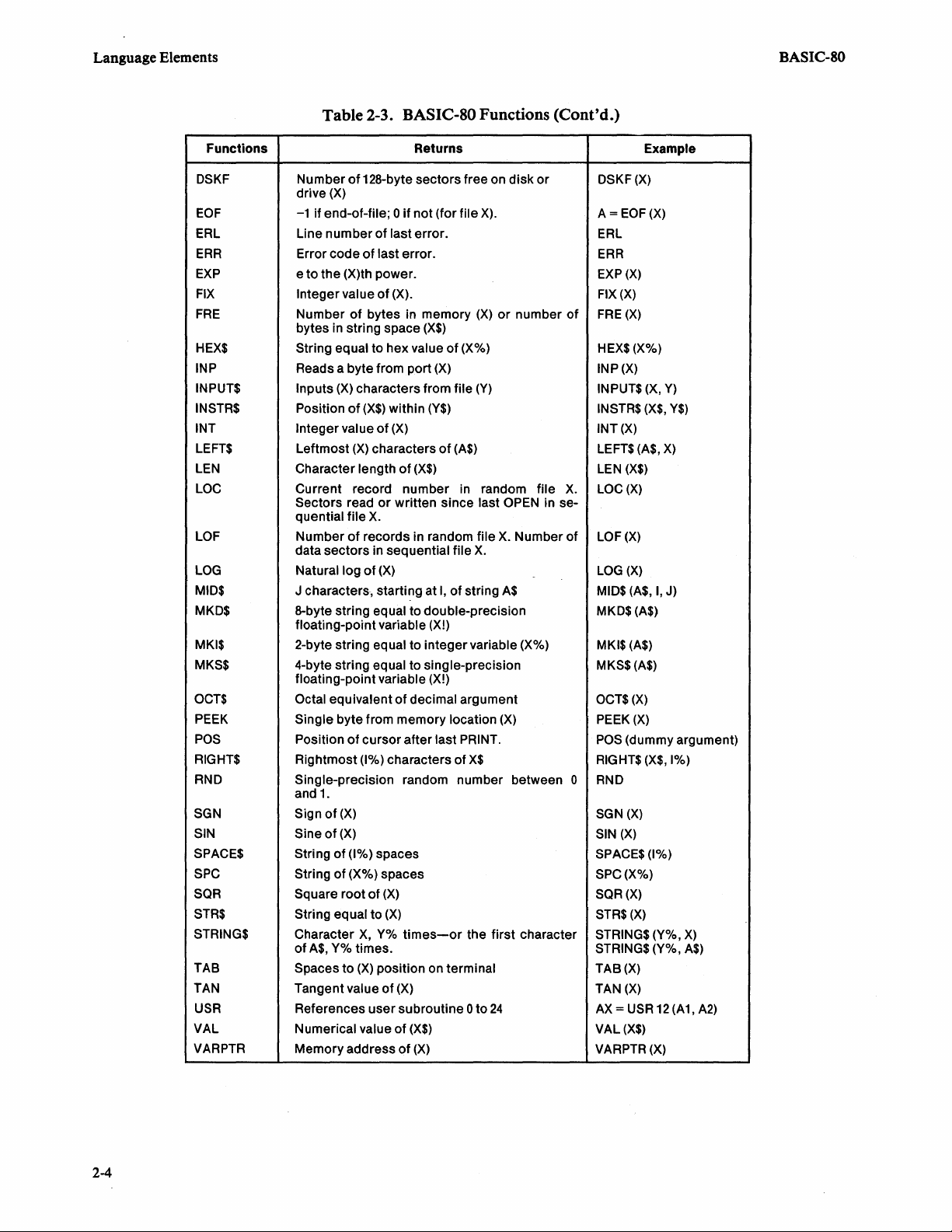
Table 2-3. BASIC-80 Functions
Returns
Absolute value.
ASCII code
specified string.
Arctangent, in radians.
Double-precision floating-point value.
Character corresponding to the specified
code.
Integer value
Cosine,
Single-precision floating-point value.
Double-precision floating-point value equal to
8-byte string
Integer value equal
Single-precision floating-point value equal to
4-byte string
in
radians
of
the first character of the
A$
to
2-byte string
A$
A$
ASCII
ABS(X)
ASC(A$)
ATN(X)
CDSl
(X)
CHR$
(X)
CINT(X)
COS
(X)
CSNG
(X)
CVD(X#)
CVI
(X%)
CVS(X!)
Example
2-3
Page 14
Language Elements
BASIC-80
Table 2-3. BASIC-80 Functions (Cont'd.)
Functions
DSKF
EOF
ERL
ERR
EXP
FIX
FRE
HEX$
INP
INPUT$
INSTR$
INT
LEFT$
LEN
LOC
LOF
LOG
MID$
MKD$
MKI$
MKS$
OCT$
PEEK
POS
RIGHT$
RND
SGN
SIN
SPACES
SPC
SQR
STR$
STRING$
TAB
TAN
USR
VAL
VARPTR
Returns
Number
drive
-1 if end-of-file; 0
Line
Error
e
Integer value
Number
bytes in string space
String equal to hex value
Reads a byte from port (X)
Inputs (X) characters from file
Position
Integer value
Leftmost
Character length
Current record
Sectors read
quential file
Number
data sectors in sequential file
Natural log
J characters, starting at
B-byte string equal to double-precision
floating-point variable (X!)
2-byte string equal to integer variable (X%)
4-byte string equal to single-precision
floating-point variable (X!)
Octal equivalent
Single byte from memory location
Position
Rightmost
Single-precision random number between 0
and
Sign
Sine
String
String
Square root
String equal
Character
of
Spaces
Tangent value
References
Numerical value
Memory address
of
128-byte sectors free on disk
(X)
number
to
the (X)th power.
1.
of
of
A$,
of
code
of
last error.
of
of
bytes in memory
of
(X$)
of
(X)
characters
or
X.
of
records in random file
of
(X)
of
cursor after last PRINT.
(1%)
(X)
(X)
of
(1%)
spaces
of
(X%) spaces
of
to
X,
Y% times.
Y%
to
(X)
position on terminal
user
or
if
not
(for file
X).
last error.
(X).
(X)
or
X.
X$
(Y)
to
X.
A$
(X)
first
24
number
Number
character
(X$)
of
(X%)
within
(Y$)
(X)
of
(A$)
of
(X$)
number
written since last OPEN in se-
of
decimal argument
characters
(X)
(X)
times-or
of
(X)
subroutine 0
of
(X$)
of
(X)
in random file
I,
of
string
of
the
DSKF(X)
A
= EOF(X)
ERL
ERR
EXP
FIX
of
FRE
HEX$(X%)
INP(X)
INPUT$ (X,
INSTR$
INT(X)
LEFT$
LEN
LOC
X.
of
LOF (X)
LOG
MID$
MKD$ (A$)
MKI$ (A$)
MKS$(A$)
OCT$(X)
PEEK
POS
RIGHT$
RND
SGN
SIN
SPACE$(I%)
SPC(X%)
SQR
STR$
STRING$ (Y%,
STRING$ (Y%,
TAB
TAN
AX = USR
VAL
VARPTR(X)
Example
(X)
(X)
(X)
Y)
(X$,
Y$)
(A$,
X)
(X$)
(X)
(X)
(A$,
I,
J)
(X)
(dummy argument)
(X$,
1%)
(X)
(X)
(X)
(X)
X)
A$)
(X)
(X)
12
(A1,
A2)
(X$)
2-4
Page 15

BASIC-SO
Language Elements
Functions
Functions are built-in routines that return a value based on the argument or
arguments supplied. They can be used to form expressions with either commands
statements.
Table
2-3
BASIC-SO
lists the
includes both numeric and string functions.
BASIC-SO
functions. In addition to these, up to
10
user-written
or
functions can be defined with the DEFFN statement.
Representing Data
The instructions described in the previous topics tell BASIC-80 what to do; to carry
out these instructions, you must also provide data in a specific fashion. Intel
BASIC-80 includes constant and variable values, in either numeric or string format;
allows these values to be grouped into arrays; provides for conversion from one data
type to another; and allows these values to be combined into expressions using
arithmetic, relational, and logical operators.
Syntax
BASIC-SO
accepts instructions and data in a specific format. This format, called
syntax, must be followed to obtain useful, predictable results.
of
superset
language elements used to illustrate
ANSI Minimal BASIC syntax. The table below describes the meta-
BASIC-80 syntax.
Table 2-4. BASIC-80 Metalanguage Elements
Condition
An
instruction that requires no argument is
shown by itself in uppercase letters.
If
an
argument must be provided, the descrip-
tion
of
follows the instruction.
If
the argument is enclosed in brackets.
If more than one type of argument can be
specified, the choices are separated by ver-
tical lines.
If
signify repetition.
the argument, in lowercase letters,
an
argument is optional, the description of
an
argument can be repeated, three dots
RESTORE
GOTOline
POKE
address, value
RESUME
SAVE
PRINT
READ
ON
[line number]
"filename"
expressionlvariable
data [,data] ...
variable GOSUB line [,line] ...
Numeric Data
BASIC-SO
categories, there are three types
point, and double-precision floating-point.
accepts numeric values as either constants or variables. Within these two
of
representation: integer, single-precision floating-
BASIC-SO
Example
[,A]
syntax
is
a
Using the DEFINT, DEFSNG, or DEFDBL statements, you can define a range of
letters to signify integer, single-precision floating-point, or double-precision
If
you
don't
floating-point numeric variables.
it with a one-character suffix when you use the variable or constant letter name.
you
don't
specify numeric type, the default
define numeric type, you can specify
is
single-precision floating-point, as if a
If
DEFSNG A-Z instruction had been given.
Table
2-5
summarizes
the
characteristics and methods of specifying numeric data
types.
2-5
Page 16
Language Elements
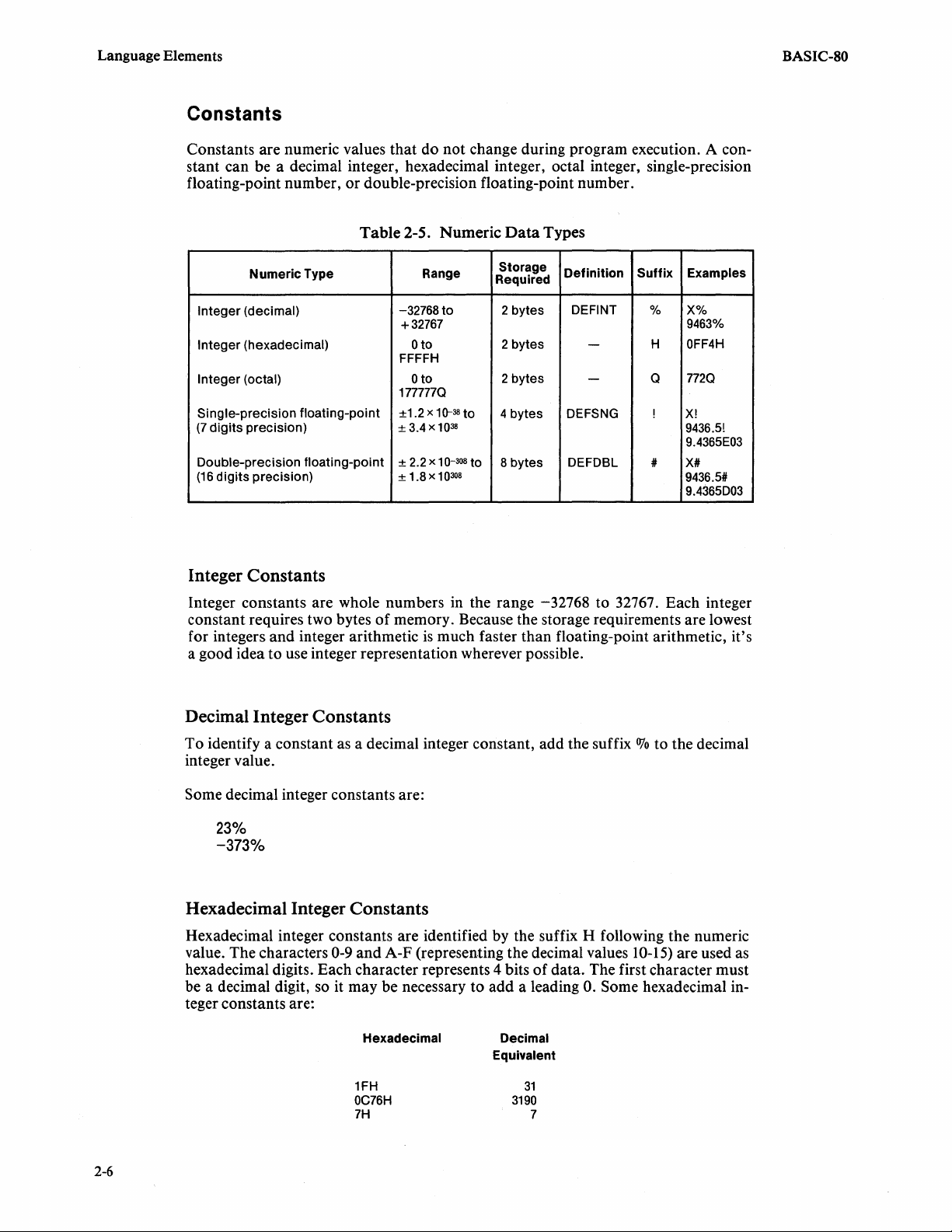
Constants
Constants are numeric values that do not change during program execution. A constant can be a decimal integer, hexadecimal integer, octal integer, single-precision
floating-point number, or double-precision floating-point number.
Table
2-5.
Numeric
Data
BASIC-80
Types
Numeric
Integer
Integer
Integer
Single-precision
(7
Double-precision floating-point
(16
(decimal)
(hexadecimal)
(octal)
digits
precision)
digits
precision)
Type
floating-point
Range
-32768
+32767
Oto
FFFFH
Oto
1777770
±1.2 x
±
3.4 x 10
±
2.2
x 10-
± 1.8 x
10-
10
to
38
308
38
308
Storage
Required
2 bytes
2 bytes -
2
bytes
to
4
bytes
to
8 bytes DEFDBL
Definition
DEFINT % X%
-
DEFSNG
Integer Constants
Integer constants are whole numbers in the range
constant requires two bytes
for integers and integer arithmetic
of
memory. Because the storage requirements are lowest
is
much faster than floating-point arithmetic, it's
a good idea to use integer representation wherever possible.
-32768
to 32767. Each integer
Decimal Integer Constants
To identify a constant as a decimal integer constant, add the suffix
integer value.
Suffix
070
Examples
9463%
H
OFF4H
7720
0
!
X!
9436.5!
9.4365E03
#
X#
9436.5#
9.4365D03
to the decimal
2-6
Some decimal integer constants are:
Hexadecimal Integer Constants
Hexadecimal integer constants are identified by the suffix H following the numeric
value. The characters
0-9 and A-F (representing the decimal values
hexadecimal digits. Each character represents 4 bits
be a decimal digit, so
it
may be necessary to
add
a leading
teger constants are:
Hexadecimal
1FH
OC76H
7H
Decimal
Equivalent
3190
of
data. The first character must
o.
31
7
10-15)
are used as
Some hexadecimal in-
Page 17

BASIC-80
Language Elements
Octal Integer Constants
Octal integer constants are identified by the suffix Q following the numeric value.
The numerals
octal iQteger constants are:
0-7
are
used as octal digits. Each digit represents 3 bits
of
data.
Some
Octal
7720
44440
7Q
Decimal
Equivalent
506
2340
7
Single-Precision Floating-Point Constants
Single-precision floating-point constants are identified by the suffix ! following the
numeric value, by
the presence
point numbers
of
digits
accuracy.
Each single-precision floating-point constant requires
Because this is
stants,
arithmetic,
and
it's
point operators.
Some single-precision floating-point constants are:
142!
-1.414
6.259371
the
letter E identifying the exponent in scientific notation,
of
a decimal point in a number having seven
in
the
range ± 1.2 x
half
the storage required
because single-precision arithmetic
a good idea
to
use single-precision wherever possible for floating-
10-
38
to ± 3.4 x
by
double-precision floating-point con-
is
E-09
or
fewer digits. Floating-
38
10
are represented with seven
four
bytes
of
quicker
than
double-precision
or
by
memory.
Double-Precision Floating-Point Constants
Double-precision floating-point constants are identified by the suffix # following the
numeric value, by
having more
± 1.8 x
10
308
Each double-precision floating-point constant requires eight bytes
the
letter D identifying the exponent in scientific notation,
than
seven digits. Floating-point numbers in the range ± 2.2 x
are represented with
16
digits
of
accuracy.
10-
of
memory. Some
or
308
by
to
double-precision floating-point constants are:
-2.001317921012
11235813213455
24.2#
Variables
Numeric variables represent numeric values
tion. These
can
be
of
three types, like numeric constants: integer, single-precision
floating-point, or double-precision floating-point. Numeric variables are repre-
sented by one
or
two characters followed by
first character must be a letter; the second, which
alphanumeric character.
If
the variable name contains more
besides a type identifier suffix, the rest
No words used as
BASIC-80 instruction words may be used within variable names.
that
can
change during program execu-
an
optional type identifier suffix.
is
optional, may be any
than
two characters
of
the variable name characters are ignored.
The
2-7
Page 18

Language Elements
If
a variable
NEW,
Individual variables can be specified by individual type identifier suffixes, which
override group type identifiers used to specify blocks
these suffixes.
is
referenced before it has been assigned a value, its value
RUN, CLEAR, LOAD, and MERGE instructions set all variables to zero.
of
variables. Table
is
zero. The
2-5
shows
BASIC-80
Blocks
single-precision,
statements. The general form of these statements is: DEFxxx m[-n], where n
letter A through Z,
(Le., the block L-Q
a certain letter or letters may be defined as one type.
The variable default type
at the start
should define them
type identifiers
override any variable block type assignment.
Note that A$,
type for variables beginning with the letter A
the same variable.
To economize on memory space and execution time, you should use integer
representation rather
rather
of
variables beginning with specific characters can be specified as integer,
or
double-precision with the DEFINT, DEFSNG, and DEFDBL
and m is
is
of
a given program.
at
(%
for
AOJo,
A!, and
than
double-precision, when this
any letter A through Z that precedes n in the alphabet,
legal, but Q-L
is
single precision, as if a DEFSNG A-Z had been executed
the start
integer,!
AI
than
single-precision representation,
is
not). In this way, all variables beginning with
If
certain variables should be of another type, you
of
the program to prevent errors. In all cases, the
for single-precision, and I for double-precision)
are four different variables.
is
single precision, then A and
is
possible.
If
the default variable
and
single-precision
is
A!
any
are
String Data
BASIC-80 accepts strings
either constants or variables.
of
characters as data. Like numeric values, strings can be
String Constants
A string constant
marks cannot be used within string constants. String constants can be up to
characters long. Some string constants are:
"This
"48, 23H, 373799"
is
a group
is a string
of
characters, enclosed in quotation marks. Quotation
constant."
255
String Variables
String variables are string values which can change during program execution. A
is
string variable name
followed by
first two are read.
String variables can contain strings
BASIC-80, however, there
command must
some examples of assignments to
A$ = "Enter
B$ = "40
NAMES$ =
$.
If
be
* 1. 7234E +
one or more characters, the first
more
than
two characters are entered as a variable name, onlv the
is
only storage space for 100 characters. The CLEAR
used to increase the amount of available string space. Here are
strip.g variables:
next data
"Warren,
string"
3"
Mark, Evan"
of
from 0-255 characters. When you first invoke
of
which must be a letter,
2-8
Page 19

BASIC-SO
Language Elements
Converting Data
It
is
sometimes useful to convert one type
these conversions with the HEX$, OCT$, CHR$, STR$, VAL, CVD, CVI, CVS,
CDBL, CSNG, CINT, MKS$, MKD$, and MKI$ functions.
of
data into another.
BASIC-SO
suppo. I...,
The HEX$ and
OCT$ functions return a string
respectively, that represent the numeric argument. The
of
string
function returns the numeric value
CHR$ returns the
The CVI,
sion floating-point,
decimal digits that represent the decimal value of the argument. The VAL
of
the string argument, if the string
ASCII equivalent
of
an integer argument, between 0 and 255.
CVS, and CVD functions convert a given string into integer, single- preci-
or
double-precision floating-point numeric values, respectively.
These functions are used to retrieve numeric values from the
when doing random disk
110.
of
hexadecimal and octal digits,
STR$ function returns a
is
a number.
input/
output buffer
The MKI$, MKS$, and MKD$ functions convert integer, single-precision floatingpoint, and double-precision floating-point numeric values, respectively, into a
string. These functions are used to store humeric values in the input/output buffer
when doing random disk
You can convert a numeric variable (integer, single-precision floating-point,
double-precision floating-point) to any
110.
of
these types by using the variable in an
or
ex-
pression with the CINT, CDBL, or CSNG functions:
A# =
CDSl
l4!
= CSNG
VAR5 = CINT (VAR5)
(A%)
(l4)
Array Variables
An array
is
a group
of
variables identified by the same name, specified by subscripts
that define their position in the array. An array variable can have as many dimensions as will fit on a single line. An array variable
is
specified by following a variable
name with as many subscripts as there are dimensions. A subscript must be an integer value, and enclosed within parentheses
square brackets.
If
there
is
more
or
than one subscript, separate them with a comma. Expressions can be used to specify
subscripts; they are rounded to integer form. Here are some array variables:
X
(10)
R1
(5,4)
Y(I,1)
SA(I + 3,X(10))
BASIC-SO
defined as
BASE
normally indexes arrays from zero; that is; the first element in
O.
To start arrays
at
one in BASIC-SO, enter the instruction OPTION
1 in your program before you dimension or reference any arrays.
an
array
is
The DIM statement allocates array space and specifies the maximum allowable
If
subscript for a given dimension.
formally dimensioned,
examples
An attempt
of
the DIM statement:
DIM X(15)
DIM R1(12,8)
DIM K(17,24)
to
specify
BASIC-SO
an
array variable whose subscripts are larger than the dimensioned value, or which exceed
OF
RANGE error
message~
an array variable
allocates
10
in the default mode, causes a SUBSCRIPT OUT
an
index
is
referenced before it has been
of
10
for each dimension. Some
2-9
Page 20
Language Elements
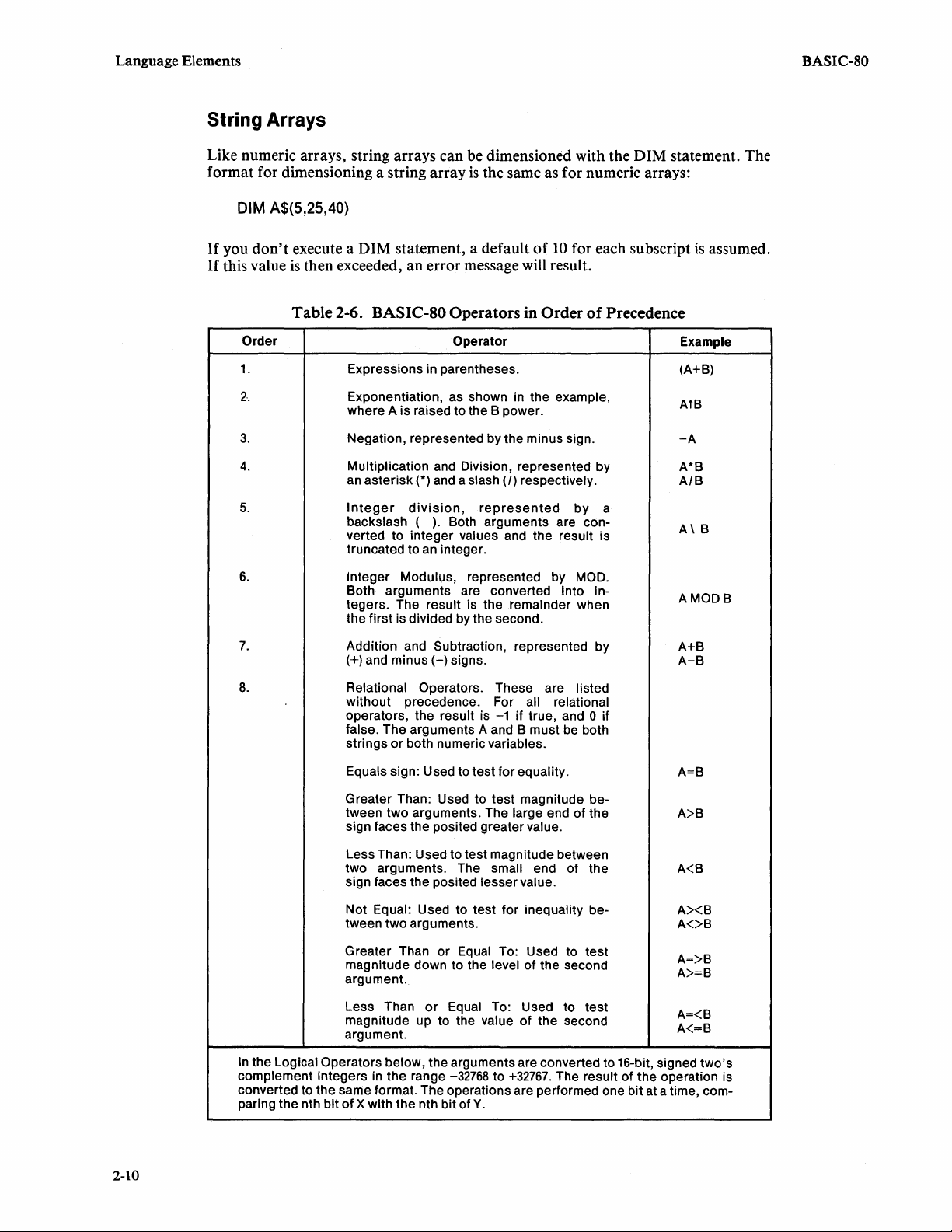
String Arrays
Like numeric arrays, string arrays can be dimensioned with the DIM statement. The
format for dimensioning a string array
If
you
If
this value
DIM A$(5,25,40)
don't
execute a DIM statement, a default
is
then exceeded, an error message will result.
Table
2-6. BASIC-80
is
the same as for numeric arrays:
of
10
for each subscript
Operators
in
Order
of
Precedence
is
assumed.
BASIC-80
Order
1.
2·.
3.
4.
5.
6.
7.
8.
Operator
Expressions in parentheses.
Exponentiation, as shown in the example,
where A is raised to the B power.
Negation, represented by the minus sign.
Multiplication and Division, represented by
an
asterisk
Integer
backslash (
verted to integer
truncated to an integer.
Integer Modulus, represented by MOD.
Both arguments are converted into integers. The
the first is divided by the second.
Addition and Subtraction, represented by
(+) and minus
Relational Operators. These are listed
without precedence. For all relational
operators, the result is -1
false. The arguments A and B must
strings
Equals sign: Used to
(*)
and a slash
division,
).
Both arguments are con-
result is the remainder when
(-)
signs.
or
both numeric variables.
(I)
respectively.
represented
values and the result is
if
true, and 0 if
test
for equality.
be
by
both
Example
(A+B)
AtB
-A
A*B
AlB
a
A\B
AMODB
A+B
A-B
A=B
2-10
Greater Than: Used to test magnitude between two arguments. The
sign faces the posited greater
Less Than: Used to test magnitude between
two arguments. The
sign faces the posited
Not Equal: Used to test for inequality be-
two
tween
Greater Than or
magnitude down to the
argument.
Less Than
magnitude up to the
argument.
In
the Logical Operators below, the arguments are converted to 16-bit, signed
complement integers
converted to the same format. The operations are performed one
paring the nth bit
of
X with the nth bit of
arguments.
Equal To: Used to test
or
Equal To: Used to test
in
the range -32768 to
large end
value.
small end of the
less.er value.
level
of
the second
value
of
the second
+32767.
Y.
The result of the operation is
of
the
bit
at a time, com-
A>B
A<B
A><B
A<>B
A=>B
A>=B
A=<B
A<=B
two's
Page 21
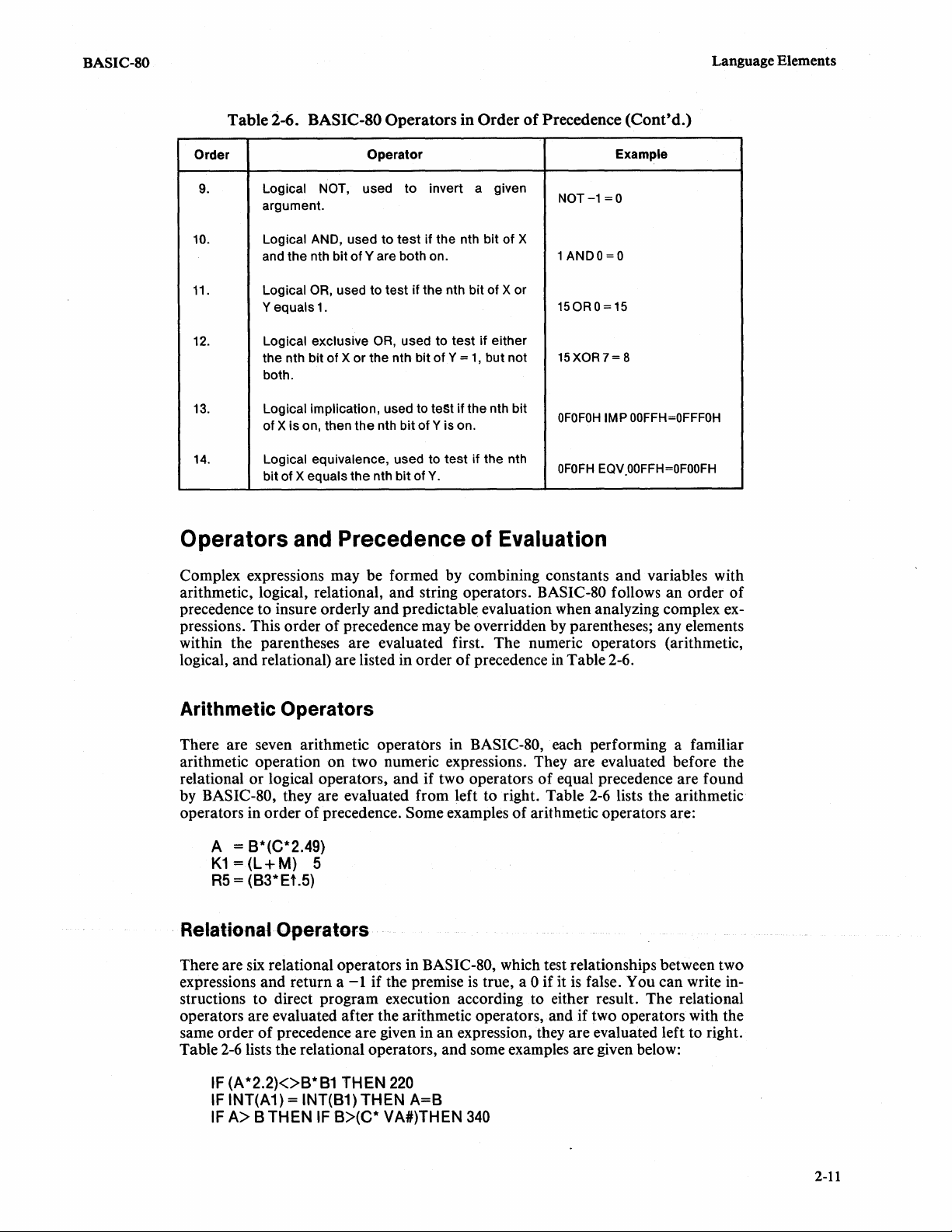
BASIC-80
Table
2-6.
BASIC-SO
Operators
in
Order
of
Precedence
Language Elements
(Cont'd.)
Order
9.
10.
11.
12.
13.
14.
Operator
Logical NOT, used
argument.
Logical
and the nth bit
Logical
Y equals
Logical exclusive OR, used
the nth bit of X or the nth bit
both.
Logical implication, used to test
of
Logical equivalence, used to
bit
AND,
used
of
OR, used to test
1.
X is on, then the nth bit
of X equals
the
to
Yare
nth
to
invert a given
test
if the nth bit
both on.
if
the nth bit of X or
to
of
of
Y is on.
test
bit
of
Y.
test
if
Y =
1,
if
the nth bit
if the nth
of
X
either
but not
NOT-1
1ANDO=O
150RO=15
15XOR7=
OFOFOH
OFOFH
Example
=0
8
IMP
OOFFH=OFFFOH
EQV.OOFFH=OFOOFH
Operators and Precedence of Evaluation
Complex expressions may be formed by combining constants and variables with
arithmetic, logical, relational, and string operators.
precedence to insure orderly and predictable evaluation when analyzing complex
pressions. This order
of
precedence may be overridden
within the parentheses are evaluated first. The numeric operators (arithmetic,
logical, and relational) are listed in order
of
precedence
BASIC-SO
by
in
follows an order of
parentheses; any elements
Table 2-6.
ex-
Arithmetic Operators
There are seven arithmetic operators in
arithmetic operation on two numeric expressions. They are evaluated before the
relational or logical operators, and if two operators
BASIC-SO, they are evaluated from left to right. Table
by
of
operators in order
precedence. Some examples
A = 8*(C*2.49)
K1=(L+M)
RS
= (83*
Et
S
.S)
BASIC-SO,
of
arithmetic operators are:
each performing a familiar
of
equal precedence are found
2-6
lists the arithmetic
Relational Operators
There are six relational operators in
-1
expressions and return a
if the premise
structions to direct program execution according to either result. The relational
operators are evaluated after the arithmetic operators, and if two operators with the
same order
Table
IF
IF
IF
of
precedence are given in an expression, they are evaluated left to right.
2-6
lists the relational operators, and some examples are given below:
(A*2.2)<>8*81
THEN
INT(A1) = INT(81) THEN
A>
B THEN
IF
8>(C*
BASIC-SO,
220
A=B
VA#)THEN
which test relationships between two
is
true, a 0 if it
is
false. You can write in-
340
2-11
Page 22

Language Elements
Logical Operators
The logical operators NOT, AND, OR, XOR, IMP, and EQV are operators that
compare the nth bit
evaluated after the arithmetic and relational operators; therefore, arithmetic expressions resolve to a number which
operator test can be used with logical operations.
of
the same precedence in a single expression, they are evaluated left to right. Table
2-6
lists the logical operators in order of precedence'. Some examples
operators, used in complex expressions, are shown below.
String Operator
The relational operators may be used with strings to compare them according to
ASCII order.
to the first
used with strings: the concatenation operator
two
of
argument X with the nth bit
IF
A>=3.5X
IF
B=1
IF
(A-B) AND
or
more strings joined together.
A$ =
B$+C$
OR
X > 3 THEN
OR B=2 OR B=3 THEN
If
part
(B+3)
strings
of
the longer, then the longer
THEN STOP ELSE
of
unequal length are compared, and the shorter
of
argument
is
compared with another number. A relational
If
there are two logical operators
01=0
2750
ELSE
280u
IF
(A AND
is
greater. There
(+).
This operator defines a string
B)
THEN CLOSE 2
is
Y.
They are
of
the logical
is
identical
one operator only
BASIC-SO
as
Expressions
Except for the command and stateqlent instructions, all of the language elements
previously discussed can be combined to form expressions. Depending on the type of
constants, variables, and operators used, expressions can be classed as numeric or
string.
Numeric Expressions
In BASIC-80, numeric expressions are created with numeric variables, constants,
functions, and operators. Variables are initialized with
values with assignment statements, or with
INPUT statements during program
execution.
Any function which returns a numeric value can be used in a numeric expression.
Strings can only be used if they are converted to a number. Numeric expressions can
use arithmetic, logical,
K(I) = B*SOR(X)
IF
A>12.1 THEN C = C + 1
IF PEEK (2FFFH) AND
or
relational operators. Some numeric expressions:
OCH
THEN PRINT
String Expressions
String expressions can be specified in BASIC-80 using string constants, string
variables, relational operators, and the concatenation operator
If
tion operator combines two strings into one.
characters, execution halts and
an
error message
sions are:
A$ =
"NAME:" + NAME$
IF B1$>R$ THEN 81$ =
R$(I)=R$(I) + S$(I) +
""
"DONE"
the resulting string
0, and may be assigned other
"ON"
(+).
The concatena-
is
longer than
is
displayed. Some string expres-
255
2-12
Page 23

CHAPTER 3
ENTERING
With BASIC-80, you can create new programs by entering statements line by line, or
you can access saved programs from disk storage.
you can use the ISIS-II BASIC-80 Text Editor
RMX/80
The following topics show how to use
ISIS-II BASIC-80 Text Editor to aid program development.
BASIC-80 does not have a Text Editor.
AND
BASIC-80 programming features and the
EDITING PROGRAMS
If
you're using ISIS-II BASIC-80,
to
alter
new
or saved instruction lines.
Entering Instruction Lines
When you invoke BASIC without specifying a file name, there
is
ready
to
The system
sists
of
a line number from 0 to 65529 followed by the language elements (program
statement, constants, variables, operators, functions, etc.).
number alone after a line with that number has been entered with text, that line
deleted.
You can enter statements in any order. To review the statements in a program, use
the
LIST command.
You can have
given increment, by using the
mand,
When you end the statement with a carriage return (CR), it prints the next line
number and again waits. To stop the automatic line numbers, enter a Control-C.
BASIC displays the line number and waits for you to enter the statement.
BASIC-80 provide line numbers, starting
accept commands or program statements. A statement con-
It
displays the statement in numeric order.
AUTO command. After you enter the AUTO com-
is
no program
If
you type a line
at
a given number, with a
to
run.
is
If
AUTO generates a line number that already exists in the program, it prints
asterisk (*) after the line number.
If
the existing statement.
You can use Control-I
is
of each line
Control-I, the cursor or print head moves to the beginning of the next column.
BASIC assumes a width
WIDTH command.
To enter more
If
you want to format the program so that additional statements appear on separate
lines (but are still
(LF) key to move to the beginning
number
doesn't end until you enter CR.
To
BASIC-80 doesn't try to execute such lines,
of
put
a comment in a BASIC-80 'program, enter REM after the line number.
divided into 8-character-wide columns. Each time you press
than
part
times, up to the 255-character line-length limit; the program statement
you enter a Control-C, the existing line
as
a tab key
of
one statement per line, separate each statement with a colon (:).
of
the same numbered program statement), use the Line Feed
If
you enter a statement, what you enter replaces
is
unchanged.
if
you want to format your statements. The width
72
characters. You can change the width with the
of
the next display line. You can do this any
but
they become part
of
the program.
Correcting Entry Errors
If
you make
key
to
pressing CR).
an
error while entering a line, you can correct it by using the RUBOUT
erase characters (as long as you haven't entered the line into memory by
an
3-1
Page 24

Entering
and
Editing
In the Command Mode, the RUBOUT key deletes the last entered character each
time you press it, and backspaces the cursor on a CRT.
RMX/SO
CR, the program statement
BASIC-SO,
RUBOUT echoes the last-entered character.
is
entered without the rubbed-out characters.
On a teletype, or with
If
you then press
enter new characters and then press CR, the new characters appear in the line.
If
BASIC-SO
you
Suppose you enter 52 instead of 55.To erase the
30
A=8*52 •
30
A=8*5
If
you press RUBOUT again, the 5
30
A=8*
To change
30
A=8*52 •
30
A=8*
30
A=8*37 •
52
•
•
to
37,
press RUBOUT twice, then
•
is
deleted:
2,
press RUBOUT:
3,
7:
When using the Edit Mode, RUBOUT works somewhat differently. Refer to the
Editing
Program Text Section for details.
Control-R displays the line as corrected, still waiting for more input:
30
A--=8xx*522537 (Control-R)
A = 8*37
To cancel a line, simply press Control-X.
Editing Program
Intel ISIS-II
or entire lines. The Editing Mode has its own set
3-1
briefly describes each
terminal beeps and the character
BASIC-SO
Text
has an Editing Mode used to change individual characters,
of
subcommands and syntax. Table
of
the subcommands.
is
ignored.
If
an illegal character
is
entered, the
3-2
Table 3-1.
Function
To delete text:
To insert text:
To
delete all characters to the right of the cursor
and insert
To insert characters at the end of the line:
To search for a character:
To
To change next n characters to y characters:
To restore
To restore original line and restart Edit Mode:
To print balance of line and restart Edit Mode: L
To leave Edit Mode and keep changes:
To
edited
To delete unwanted characters:
To place one logical statement line on two
physical lines:
To leave next n characters unchanged:
text:
delete all characters until specified character:
original line and leave Edit Mode:
leave Edit Mode, keep changes, and print the
line:
BASIC-80Editing Subcommands
or
more
Syntax
[integer] 0
I character [character. .. ]
H character [character ... ]
X character [character ... ]
[integer]
[integer] K character
[integer] C character [character ... ]
Q
A
E
Carriage return
Rubout
Line Feed
[integ.er] space
S character
Page 25

BASIC-SO
Entering
and
Editing
Complete editing
variables to zero or null.
editing mode with the
BASIC-80 returns
of
a line replaces the old line with the edited line. This resets all
To
end editing without losing prior variable values, exit the
Q subcommand after the line number has been printed.
to
command level, variable values are unchanged
and
any editing
changes are lost.
There are three ways to enter the Editing Mode:
1)
Type
EDIT
line number, and BASIC-80 returns the line number requested.
you press the space bar, the cursor moves
to
the desired location in the instruc-
tion line.
2)
When entering text, type a Control A instead
of
a carriage return. This causes a
carriage return, a space, and the computer prints an exclamation point. The cur-
at
sor points
ing the space bar.
last line,
3)
If
BASIC-80 encounters an instruction line with a syntax error during program
execution, it will halt
the first character
If
and
you
can't
you use CONTROL-A after listing a program, it edits the
change line numbers.
and
print
of
the sequence, and can be advanced by press-
an
error message
of
the format: SYNTAX ER-
ROR IN (line number). Below the error message, the computer returns the line
and
number,
In the Edit Mode, pressing
deleted. Use the D subcommand to delete characters
In the explanatory sections
edited by each subcommand. The
head,
and
all characters are shown as they appear
the line may be edited.
RUBOUT will echo characters,
b~low,
a typical line
"."
,in
the Edit Mode.
of
program text
indicates the position
on
the terminal. Such editing sub-
but
is
of
the cursor
they are
edited and re-
commands as D, L, Carriage Return, Escape, and so on are represented
theses: (CR), (ESC), (D), (4SE) to avoid confusion.
You should
tryout
other examples to gain facility with the editor.
or
in
these
If
not
print
paren-
or
of
In the following sequence
hypothetical program. Line
edit subcommands,
40 returns a syntax error message, since it needs a
PRINT instruction following ELSE,
40
IF
A>B THEN
120
OR
ELSE
and
should not contain OR:
"NULL
SET"
we
will be editing line 40
of
D Subcommand
The D subcommand
counted as characters.
just the remaining characters are deleted. The argument n
to 255, and the default value
backslashes, i.e.,
The syntax
of
[integer] D
In the example below, line 40 returned a SYNTAX ERROR message when the program ran.
BASIC-SO displays the error message and enters the Edit Mode.
ing the space
incorrect character
40
IF
A>B THEN
40
IF
A>B THEN
The command( 3D) (press 3, then
is
used to delete characters to the right
If
there are less than n characters to the right
is
\characters\
the D subcommand
bar, the text
is
of
line
encountered.
120
OR
ELSE
120.
of
the cursor. Spaces are
of
the cursor,
is
an integer in the range 1
1.
The deleted characters are printed enclosed by
.
is:
By
40
is
displayed character by character until the
"NULL
D)
results in:
SET"
press-
a
40
IF
A>B THEN
120
\OR\
•
3-3
Page 26

Entering
and
Editing
L Subcommand
BASIC-80
The L subcommand prints the rest
subcommands. The cursor
command
to
display previously edited text and restart editing at the beginning
is
of
the original line, and waits for further editing
to the left
of
the first character. You can use the L sub-
of
the
line:
40
IF
A>B
THEN
40.
120
ELSE
"NULL
SET"
I Subcommand
The I subcommand inserts characters after the last character typed. Each character
typed after typing I
ESCAPE key. To end insertion and leave the Editing Mode, press the Carriage
the
Return key. Characters may be deleted when using the I subcommand by pressing
RUBOUT key.
the
The syntax
of
I character [character] ...
Suppose you want
space bar until you reach the proper point:
40
IF
A>B
and then enter:
(I) PRINT (ESC) (L)
And you
40
IF
A>B
is
inserted
at
the I subcommand
to
insert the word
THEN
120
ELSE.
will see:
THEN
120
ELSE PRINT
the current cursor position. To end insertion, press
is:
"PRINT"
"NULL
into the previous example. Press the
SET"
H Subcommand
The H Subcommand deletes all characters to the right
the insertion mode, like the I Subcommand. When through inserting characters,
enter
(ESC) to end insertion
of
The syntax
H Character[Character] ...
If
you want to change the message
"UNDEFINED
the H subcommand
SET",
or
(CR) to end editing.
is:
"NULL
you can use the H Subcommand to do it. Move the cursor to
the proper point with the space bar:
40
IF
A>B
THEN
120
ELSE PRINT
Enter (H) "UNDEFINED
40
IF
A>B
THEN
120
SET"
(ESC) (L):
ELSE PRINT "UNDEFINED
SET"
of
the cursor, and then enters
in the previous example to
SET"
X Subcommand
The X subcommand prints the rest
of
end
command is used
the line, and enters the insertion mode; as for the I subcommand. This sub-
to
add new text
the insertion mode.
of
the line to be edited, moves the cursor to the
at
the end
of
instruction lines. Execution
is
as in
3-4
Page 27

BASIC-SO
Entering
and
Editing
The syntax
Returning to the previous example, if you wish to add text
of
the X subcommand is:
X character [character] ...
at
the end
of
the given in-
struction line, use the X subcommand:
40
•
Enter (X)
40
IF
A>B
Enter new
40
IF A >B
THEN
text
THEN
120
ELSE PRINT "UNDEFINED
at
the
cursor-;A;
120
ELSE PRINT "UNDEFINED
B (ESC) (L):
SET"
•
SET";A;
B
S Subcommand
The S subcommand examines characters to the right of the cursor., to find the nth
occurrence
default
searches, printing all characters encountered. When the nth occurrence
fied character
specified character
The syntax
of
the specified character, where n
is
1.
This subcommand skips the first character to the right of the cursor and
is
an integer in the range 1 to 255; the
of
is
found, the cursor stops
is
not found, the cursor stops at the end
of
the S subcommand
is:
at
the character.
If
the nth occurrence of the
of
the line.
the speci-
[integer] S character
The S subcommand can be used with an example to find the nth occurrence
we
specified character. Suppose
"E"
the 3rd letter
40
•
Enter (3SE):
40
IF
A>B
At
this point, the other editing subcommands may be used.
in line 40:
THEN
120
want to move the cursor to the space occupied by
ELSE •
of
the
K Subcommand
The K subcommand functions like the S subcommand except that it deletes all
of
characters passed over until the nth occurrence
deleted characters are enclosed in backslashes.
The syntax
of
the K subcommand
[integer] K character
is:
The K subcommand may be used on our example.
of
P,
1st occurrence
40
•
Enter
and print backslashes:
(1
KP)
the specified character. The
It
will
eliminate all text up to the
\40\
IF
A>B
THEN
Enter (L)
40
PRINT "UNDEFINED
120
ELSE.
SET";A;
B
3-5
Page 28

Entering
and
Editing
C Subcommand
The C subcommand changes the next n characters to the specified character(s).
of
integer is specified, the character immediately to the right
the cursor
is
changed.
If
BASIC-SO
no
The syntax
of
the C subcommand is:
[integer] C character [character ... ]
In our previous example, line 40 was reduced to:
40
PRINT "UNDEFINED
This can be changed to print
Move
the
cursor to:
40
PRINT.
Enter
(2C)
RE
(L)
40
PRINT "REDEFINED
40
•
SET";A;
"REDEFINED
SET";
8
A;8
SET"
with C:
Q Subcommand
The Q subcommand restores the original line, as it was prior to editing,
the editing mode. Note
This subcommand returns the user
edited command. This subcommand only works when editing program lines.
that
if
an
instruction
to
is
edited with Q, the changes are lost.
the command mode without executing an
and
leaves
A Subcommand
The A subcommand restores the original line and prints the original line number
is
below. Editing
lines.
When the A subcommand
40
PRINT "UNDEFINED
restarted. This subcommand only works when editing program
is
used with the previous example, the result
is:
SET".
Enter (A) (L)
40
IF
A>B THEN
120
ELSE
"NULL
SET"
40.
E Subcommand
The E subcommand exits the editing mode. The edited line replaces the original line.
When the E subcommand
40
PRINT "UNDEFINED SET"
(The E subcommand is entered)
Carriage
A Carriage Return exits the editing mode,
The edited line replaces the original line.
Return
is
used with the previous example, the result
and
prints
the rest
of
the line being edited.
is:
3-6
Page 29

CHAPTER 4
ERROR
If
you enter improper instructions, syntax, or formats, BASIC-80 issues an error
message. This chapter explains what these errors mean, how they may be trapped
with the ON ERROR statement and pinpointed with the TRON, TROFF, ERR, and
ERL instructions, and how errors may be simulated with the ERROR statement.
HANDLING
BASIC-80 Error Messages
When BASIC-80 encounters an error in a program, it displays an error message.
Appendix A lists the error messages and error codes, and describes their meaning.
These errors stop program execution. You can use the
to correct obvious errors, add error-trapping instructions, or use the trace facility.
Syntax
If
message, and enters the Edit Mode:
Error
BASIC-80 detects a syntax error,
10
LET
20
PRINT A
RUN
SYNTAX ERROR
10
•
Messages
A=
IN
10
it
stops program execution, displays an error
BASIC-80 editor at this point
You can now change line 10, as described in Chapter
without making any changes, and to preserve the variable values in the program,
Q.
If
type
variable values are lost.
you enter any other editing subcommands (including Carriage Return)
3.
To leave the Edit Mode
Overflow, Underflow, and Divide-by-Zero
In BASIC-80, the single- and double-precision floating-point overflow, underflow,
and divide-by-zero errors do not halt program execution.
Overflow. Single-precision floating-point overflow occurs when the magnitude of a
(±)
single-precision numeric value exceeds
floating-point overflow occurs when the magnitude
(±)
E20*1
D200*1
1.79 x
E20
D200
1.79769313486231
value exceeds
generated, the message OVERFLOW
ble magnitude for the given representation with the appropriate sign
ex~cution
The following examples show single- and double-precision overflow:
proceeds.
10
A = 1
20
D#
= 1
30
PRINT A;D#
RUN
OVERFLOW
OVERFLOW
3.402824E + 38
308
10
(1.79D308). When a value of this magnitude
3.4 x
is
displayed, a value equal to the largest possi-
D +
308
38
10
(3.4E38). Double-precision
of
a double-precision numeric
is
assigned, and
is
4-1
Page 30

Error
Handling
BASIC-SO
Underflow. Single-precision floating-point underflow occurs when the magnitude
of
a single-precision numeric value
precision floating-point underflow occurs when the magnitude of a double-
is
precision numeric value
is
magnitude
generated, no message
less
than
is
less than
(±)
2.2 x
is
printed, the result
10-
(±)
308
1.2 x
(2.2D-308). When a value of this
10-
is
defined
38
(1.2E-38). Double-
as
zero, and pro-
gram execution continues.
is
Divide-By-Zero. Divide-by-zero
precision overflow protocol, except that the message printed
Integer
Operations
handled identically to single- and double-
is
DIVIDE-BY -ZERO.
Integer overflow and division by zero are treated as normal errors. Program execution halts. Integer overflow occurs when a value greater than 32767.49 or less than
is
-32768.49
Error
converted to integer representation. Integer underflow cannot occur.
Trapping
Error trapping allows you to trap and correct errors. Errors normally halt program
is
execution and return error messages. When given before an error
encountered, the
ON ERROR GOTO statement transfers program execution to a specified line
number when an error occurs, and suppresses any error messages other than those
you specify and write yourself.
specified location to identify and correct errors. In the following example, when
is
entered in response to the INPUT statement, an error occurs and the user-written
You can write an error-service routine at the
-3
error message displays:
10
ON ERROR GOTO
20
INPUT A
30
PRINT SQR{A)
40
GOTO
100
110
120
RUN
20
PRINT
PRINT
RESUME NEXT
"ARGUMENT
"ENTER
100
NEW
CANNOT
VALUE."
BE
NEGATIVE."
? 3
1.732051
?
-3
ARGUMENT CANNOT
ENTER NEW
VALUE
BE
NEGATIVE
?
Suppose there
is
no error routine (made up of lines
10,
100,
110,
and
120)
in
the
above example, and you wish to identify this particular error. The ERR and ERL
A)
functions return the error code number (see Appendix
error occurs in, respectively. In this way, you can identify the kind
and the line number the
of
error and the
line it occurs in and write individual error handling routines for individual errors.
The program below uses ERL and ERR to identify the location and nature of any
error.
In the following example, the
routine at line
100, which identifies one specific error (division by zero) and the line
ON ERROR statement enables the error-service
number in which it occurs:
4-2
Page 31

BASIC-80
10
ON ERROR GOTO 100
20
30
40
GOTO
100
110
120
RUN
?
13
INPUT
PRINT
A
521
A
20
PRINT
IF 11=ERR
RESUME NEXT
"Error";ERR;"at
THEN
PRINT
line";ERL
"Division
by
zero"
4
? 0
Error
11
at
line
30
Division
by
zero
?
Trace Facility
The TRON and TROFF (trace
execution
of
each line. The line number of each program statement executed
displayed in brackets. The preceding example would run like this after entering
TRON and then RUN:
on
and trace off) commands are used to examine the
is
Error Handling
[10]
[20]? • 5 (CR)
[30]
10.4
[40] [20]? •
[30]
7.428571
[40] [20]? • 0 (CR)
[30] [100]
[110]
Division
[120] [40] [20]? •
The ON
ERROR
7 (CR)
Error
11
at
line
30
by
zero
OOTO 0 statement has a special meaning. When entered outside
error handling routines it disables any prior
handled
normally-error
entered inside
an
error handling routine, it allows normal handling of a given error
messages are displayed and execution
or errors, as shown in the example below.
10
ON ERROR GOTO 100
20
30
40
50
100
110
120
130
RUN
INPUT
PRINT
PRINT
STOP
A,B
AlB
SQR(8-A}
IF ERR<>11
8=1
RESUME
ON ERROR GOTO 0
THEN
130
? 2,0
2
Illegal
Ok
function
call
in
40
ON
ERROR OOTO so that errors are
is
lialted. When
of
The error routine (lines 100-130) sets B to 1 when the divide-by-zero error occurs,
but allows other errors to interrupt operation in a conventional way.
The non-fatal floating-point overflow and divide-by-zero errors are trapped like
of
other errors. No messages are displayed in this case, and the results
the calcula-
tions are undefined.
4-3
Page 32

Error Handling
BASIC-SO
Error Simulation
BASIC-SO provides a statement that can simulate any errors which produce
code. When the
ERROR
BASIC-SO acts as if the specified error
demonstrates how
10
ON ERROR GOTO
20
INPUT
30
B = A *
40
PRINT B
50
GOTO
70
IF
11
80
RESUME NEXT
If
line 40
is
replaced with:
40
ERROR
Program
control transfers to line
ERROR
A
.3842
20
= ERR THEN PRINT
11
statement
can be used
70
"Division
70
regardless
is
encountered during program execution,
had
occurred. The example below
to
test
an
error handling routine.
by
zero"
of
the result
of
the operation in line
30.
Restarting Program Execution
You can restart program execution after it has halted with the RUN
instruction, and after
instruction. Remember
an
error in
that
RUN sets all variables
an
ON
ERROR routine with the RESUME
to
zero.
or
an
error
CONT
RUN restarts program execution
number
is
specified, or
at
the specified line number.
CONT restarts execution at the line after a STOP, END,
countered.
CONT will also restart program execution after
at
the lowest-numbered line
It
can be used
of
a program if no line
at
any time.
or
CONTROL-C
an
error, but
it
is
en-
will try to
execute the erroneous line.
RESUME can only be used when the halt occurs in
an
ON ERROR routine.
It
given following the error-resolving routine pointed to by the ON ERROR instruction.
It
can be used three ways: RESUME to begin execution
RESUME NEXT to begin execution
RESUME followed
by
a line number
to
at
the line following the erroneous line;
begin execution
at
the erroneous line;
at
any other line.
is
4-4
Page 33

CHAPTER 5
DISK FILE INPUT/OUTPUT
BASIC-SO
random. Sequential
random
Because
ISIS-II and RMX/80-DFS format (:Fn:name.ext, where n
BASIC-SO
• DIR, which lists the files
• RENAME, which changes the name
• A TTRIB, which changes the attributes
• KILL, which deletes a disk file (it
For more information about
Guide.
Although both sequential and random
on disk, sequential
haven't worked with disk files before, it would probably be better to start with
quential
includes two types
I/O
I/O
lets you specify where in the file you read or write.
BASIC-SO
also gives you access to disk file-handling commands:
the name must be different because
delete lines from a program).
110
to learn the principles.
runs under ISIS-II and RMX/SO, filenames correspond to the
I/O
of
disk file Input/Output operations: sequential and
lets you read or write a file from the beginning to the end;
on
a disk
of
a disk file
of
a disk file
is
actually the system DELETE command,
BASIC-SO
ISIS-II filenames or operations,
I/O
allow you to create, read, and write files
is
somewhat simpler in concepts and operation.
is
the drive number).
includes a DELETE command to
see
the ISIS-II User's
If
but
you
se-
Sequential File
BASIC-SO
numbers and strings
must open the file, execute a series
statements, then close the file.
A sequential file
you must close the file and open it again with the opposite attribute. Any
tion that immediately follows
Sequential
is
1/0
I/O
allows you to build sequential data files containing
of
up to
255
characters. In general, to use sequential
of
INPUT (to read) or PRINT (to write)
open either for input or output. To switch from one to the other,
an
OPEN statement starts at the beginning of the file.
110
110
you
opera-
Opening a Sequential File
You open a sequential file with the OPEN statement.
to be opened for input or output, assigns it a file number, and specifies the filename.
Up to
six
files can be open
specifies output does not exist, it
again without closing it first.
To open an input file named :Fl:DATES and assign
OPEN "1",#1,":F1:DATES"
at
one time.
If
you attempt to do so, an error message results.
If
the file named in an OPEN statement that
is
created. Once a file
It
specifies whether the file
is
open, it cannot be opened
it
file
number
1:
is
5-1
Page 34

Disk File
Input/Output
BASIC-SO
String and numeric expressions can replace any
OPEN M$,FN,
DN$+
"OUTPUT"
This statement opens a file for either input or output, depending
"I"
or
"0")
and
(it must be either
must be from 1 to 6). The name
should be
":FO:"
followed by the
through
six
characters
":F9:",
OUTPUT.
assigns the file number represented by FN (it
of
the file
depending
of
the parameters:
on
the value of M$
is
the value
on
of
the string variable DN$ (it
how many drives you have, or null)
NOTE
Remember that opening a file for output destroys
an
existing file
of
same name.
Writing to a Sequential File
After you open a sequential file for output, you can write data to it with the
statement.
that a
number (preceded by
To
print a series
You can also use the full formatting capabilities of the
PRINT
PRINT
If
you open an existing file for output, its contents are deleted.
statement
of
constants and variables to file 3:
#3,
"Today's
is
being used to write to a sequential disk file, the file
#, followed by a comma) follows the word PRINT.
date is
";MO$;OA;",";YR
PRINT
USING statement:
To
the
PRINT
specify
PRINT
Refer to Chapter 6 for further details of
#3
USING, "###,##;"234.41 ;81.20;4.68
PRINT
USING.
Reading from a Sequential File
After you open a sequential file for input, you can read data from it with the INPUT
and LINE INPUT statements.
read from a sequential disk file, the file number (preceded by
comma) follows the word
The INPUT statement reads the specified number
the disk file. Numeric values (in the disk file) can be separated by a blank, comma,
carriage return, or line feed.
String values can be enclosed in quotation marks, or given as unquoted strings.
Quoted strings terminate
commas, carriage returns, line feeds, or if they exceed
Assume, for example, that disk file
represents a carriage return-line feed pair in the disk file):
"R1"
,200,
"R2"
,2200,
"R4"
,.47
After the file
string value to
is
opened for input, the following INPUT statement would assign a
R$
and the subsequent numeric value to R:
To
specify that these statements are being used to
# and followed by a
INPUT
on
or
LINE INPUT.
of
values (numeric or string) from
the quote marks, while unquoted strings terminate
255
characters in length.
#2
"R3"
contains the following
,10000
data
(a new line
on
5-2
INPUT #2,R$,R
If
executed four times, it would read all eight values.
Page 35

BASIC-80
Disk File
Input/Output
LINE INPUT,
on
the other hand, ignores blanks, commas, and quotation marks,
and reads everything between the current file position and the next carriage returnline feed,
logical line, LINE
line. The string
ample, assume
or
up to
255
characters.
INPUT
is
assigned to the single string variable specified. In the preceding ex-
that
instead
will read to the end
of
If
the last INPUT did not read to the end of a
of
that line before reading the next
the INPUT statement shown, the following statement
was executed:
LINE INPUT #2,R$
The value
This statement
data values, such
ment created with the
The
of
R$
would be:
"R1"
,200,
"R2"
,2200,
"R3"
,10000
is
useful for reading from a file that consists of lines, not individual
as
lines from an ASCII-saved BASIC-80 program file,
ISIS-II text editor.
INPUT$ function reads the specified number
or
a docu-
of
characters from a sequential
file:
10
OPEN
20
PRINT INPUT$ (3,1)
30
CLOSE
40
END
This program reads the first 3 characters from the file
them.
If
you execute line
"1",#1,":F1:MONTHS"
#1
20
again, INPUT$
:Fl
:MONTHS and prints
will
read the next 3 characters.
is
set to
-1.
When you read the last value from a file, an end-of-file flag
can be tested with the
end-of-file flag
tion halts.
To
prevent surprises, you can test for an end-of-file with the EOF func-
EOF
function.
is
set, BASIC-80 issues an INPUT PAST END message and execu-
If
you try to read data from a disk file after the
This flag
tion and then branch to an appropriate routine:
250
IF
EOF
(1)
300
310
CLOSE 1
PRINT
"END
THEN
300
OF INPUT
DATA"
Closing a Sequential File
Once you read or write the desired data from or to a sequential file, you must close
the file. This can be done in several ways.
CLOSE command closes one
The
CLOSE 1,2,5
or
more files:
If
you enter CLOSE with no file number, all open files are closed. The END state-
and
EXIT
ment and the NEW
commands close all disk files. After closing a file, you
can open it again for input or output, with the same or a different file number.
5-3
Page 36

Disk File
Input/Output
BASIC-SO
Random File
Random
flexible because you can move back and forth within a disk file. These are the key
differences:
• To get
• Random
• Because all data in random files
• You must use special assignment statements to
• Unless you simply want to read
I/O
data
must understand how
110
floppy disk sector. You must specify how this 128-byte string
fields and assigned to string variables.
strings
calculations with
dom file, you must first convert it to a string. Special functions are provided
do this.
buffer. This
fixed-length; the special assignment statements accommodate variables
longer
which record you want to read or write.
that
or
shorter than the specified field.
I/O
requires a bit more care and coding than sequential
from random disk files to BASIC-80 variables and vice-versa, you
BASIC-80 uses
operations (GET and PUT) always read or write all
represent numbers into numeric values if you want to
them.· Likewise, if you want to write a numeric value
is
due to the fact that the fields you define in an
110
buffer space.
is
treated as string data, you must convert
put
a string variable into an
or
write records
in
sequence, you .must specify
I/O,
128
is
divided into
I/O
buffer are
but
bytes
is
do
to
that
more
of
any
a ran-
to
110
of
are
a
1/0
Buffers
BASIC-80 reserves space
assigned to each open file (when an OPEN statement
record from a random file using GET, the 128-byte string
a variable.
define what portions
To emphasize: the usual variable and line delimiters
ing. All
than
buffer are set
It
is placed in the 110 buffer assigned to that file, and it
128
bytes from the specified sector are placed
128
bytes were written to the sector, the remaining character positions in the
to
ASCII blanks (hexadecimal
Defining a Random
When a sector has been read into the 110 buffer, it exists as a 128-byte string. You
must define how the string
statement specifies to
to string variables (initially they
treated as a 128-byte string).
The FIELD statement tells
starting with the first, are to be associated with a variable. For example, assume you
have opened a random file, assigned it the file number 3 (the
works just like in sequential
that the first
the string variable N$, enter the following FIELD statement:
20 characters of each sector contain a name. To assign these
for
six
I/O
buffers, each
of
the string are to be assigned to what variable
20)
1/0
Field-FIELD
is
to be assigned to a variable or variables. The FIELD
BASIC-80 what character positions in the buffer correspond
128
bytes long. One buffer
is
executed). When you read a
is
not assigned directly to
is
up to you to
or
variables.
(",
CR) have no special mean-
in
the 110 buffer.
.
If
fewer
must be string variables, because the sector
BASIC-80, for a given file, what character positions,
OPEN
command
110), and read the first sector from the file. You know
20
bytes to
is
is
5-4
FIELD
#3,
20
AS
N$
Page 37
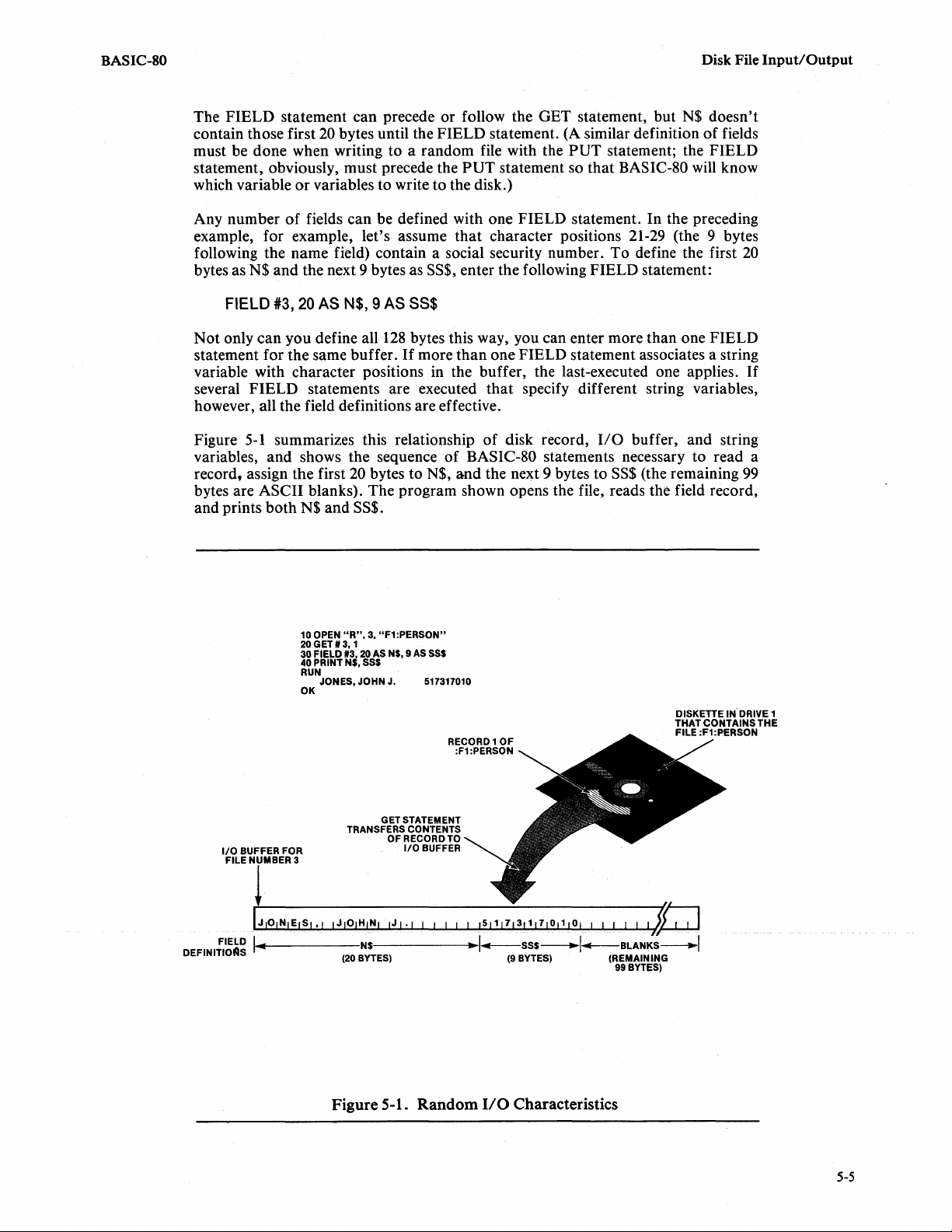
BASIC-SO
Disk File Input/Output
or
The FIELD statement can precede
20
contain those first
bytes until the FIELD statement. (A similar definition
must be done when writing to a random file with the
statement, obviously, must precede the
which variable
Any number
or
variables to write to the disk.)
of
fields
can
be defined with one FIELD statement. In the preceding
example, for example, let's assume
follow the GET statement, but
PUT
statement; the FIELD
PUT
statement so that BASIC-80 will know
that
character positions 21-29 (the 9 bytes
following the name field) contain a social security number. To define the first
N$
doesn't
of
fields
20
bytes as N$ and the next 9 bytes as SS$, enter the following FIELD statement:
#3,
20
AS
N$, 9 AS
Not
FIELD
only
can
you define all
statement for the same buffer.
variable with character positions in the buffer, the last-executed one applies.
several FIELD statements are executed
SS$
128
bytes this way, you can enter more than one FIELD
If
more
than
one FIELD statement associates a string
that
specify different string variables,
If
however, all the field definitions are effective.
5-1
Figure
variables,
summarizes this relationship
and
shows the sequence
record, assign the first
20
bytes to N$,
of
disk record,
of
BASIC-80 statements necessary to read a
and
the next 9 bytes to
110
buffer, and string
SS$
(the remaining
99
bytes are ASCII blanks). The program shown opens the file, reads the field record,
and prints both N$ and
SS$.
10
OPEN
20
GET'3,
30 FIELD
40 PRINT
RUN
JONES, JOHN J. 517317010
OK
1/0
BUFFER FOR
FILE
"rMBER
3
IJ,o,N,E,s,,J
DEFINI~~~~
"""1·1f-------N$------·
IJIOIHINI
"R",
3,
"F1:PERSON"
1
1#3.1
20
AS
N$, 9
AS
N~,
55$
TRANSFERS CONTENTS
(20
BYTES)
55$
GET
STATEMENT
OFRECORDTO
1/0
BUFFER
IJI·I
RECORD
1 OF
:F1:PERSON
11511171311171011101 I I I I I
...
I..--ss$------~BLANKS---+-1
(9
BYTES)
Iltl
(REMAIN ING
99
BYTES)
I I
Figure
5-1.
Random
I/O
Characteristics
5-5
Page 38

Disk File Input/Output
Opening and Closing a Random Disk File
As
with sequential disk files, you must open random disk files before you can write
to them
isn't opened for either input
you can read from
or
read from them, and close them when you're through. A random file
or
output, however; once it's open for random
it
or
write
to
it interchangeably.
BASIC-SO
I/O,
To open the
OPEN
Any
of
OPEN
This opens the file whose name
I/O
and assigns it the file number represented by the numeric variable F.
As
with sequential
numbers);
and EXIT commands close all open files;
Reading from a Random
You can retrieve
entering the GET statement, you must specify the file you want to read.
file
":FI
"R",
:PERSON"
#3,
":F1 :PERSON"
for random
110
and assign it file number
3:
the parameters can be variables:
"R",
F,
FN$
is
represented by the string variable FN$ for random
I/O,
the CLOSE statement can specify a file number (or
CLOSE by itself closes all open files. The END statement and the NEW
STOP does not.
1/0
File
data
formatted and stored on disk with the GET statement. When
You can
also specify the record you wish to read by entering the record number after the file
number.
If
you
don't
specify the record number, BASIC-80 either reads the first
record, if there has been no read operation since the file was opened, or reads the
record that follows the last record read. To read the first record from file I:
GET #3,1
To read the next record:
GET
#3
As
described earlier (in
FIELD), the GET statement reads
dom file by the
OPEN statement. The FIELD statement specifies which portions
the buffer are to be assigned
as
string data).
Assume, for example, you have a file written as a random
SON. The first 20 characters
"110
Buffers" and "Defining Random
128
bytes into the
to
string variables (all data in random
of
each sector contains a name, and the next 9
I/O
110
Fields-
buffer assigned to the ran-
of
I/O
files
is
stored
liD
file named :FI :PER-
characters contain a social security number. The following statements open the file,
define which parts
10
OPEN
20
FIELD
30
GET #3,1
of
the buffer correspond to variables, and read the first sector:
"R",
#3,
":F1 :PERSON"
#3,
20
AS
N$, 9 AS
SS$
To print the name:
40
PRINT
N$
5-6
Page 39

BASIC-SO
Disk
File
It's
not
quite so simple to print
I/O
files, however, because they are represented as strings. You must convert each
string
that
represents a number to its corresponding numeric value, either integer,
single-precision floating-point,
or
do calculations with numeric values from random
or
double-precision floating point. The CVI, CVS,
and CVD functions, respectively, perform this conversion.
is
Assume that there
an additional 2-character field following the 9-character social
security number that represents the number of hours worked in the previous week.
The following statements open the file, define the fields, read the first (or next)
record, and increment the variable
10
OPEN
20
FIELD
30
GET
40
PRINT N$; SS$;
50
HW = HW + CVI (H$)
60
PRINT
"R",
#3,
#3
"TOTAL
#3,
":F1
20
AS N$, 9 AS SS$, 2 AS H$
"HOURS
HOURS
HW
by the number of hours worked:
:PERSON"
=";
=";
HW
CVI (H$)
Input/Output
The two characters defined as H$ are converted to an integer.
To
convert a string to
a numeric variable, the number of string characters must equal the number
required to store the corresponding numeric data type:
Integer
Single-precision value
Double-precision value
If
the number
fewer
than
required,
execution halts.
CVI
CVS
CVD
of
string characters represented by the argument of the function
an
ILLEGAL FUNCTION CALL error message
If
the string variable is longer than required, the extra characters are
2 bytes
4 bytes
8 bytes
is
printed and
ignored.
Writing to a Random
To
store data in a random disk file, you follow the same sequence of
FIELD statements as when reading from a random disk file. The
128
bytes
writes the
The FIELD statement, however, defines fixed-length fields in the
the data to be written to disk into the
statements: LSET and RSET. LSET left-aligns a variable
RSET right-aligns it.
ded with ASCII blanks
of
the
In
both
(20H);
1/0
File
I/O
buffer to the disk file.
I/O
cases, if the variable
if
the variable
OPEN
PUT
I/O
buffer. To get
buffer, there are two special assignment
in
the buffer field, and
is
shorter than the field, it
is
longer than the field, it
is
truncated.
of
bytes
is
and
statement
is
pad-
For
example, assume you have opened a file for random
3, and defined the first
20
characters as N$. You must use LSET
I/O,
assigned it file number
or
RSET to place
values in the buffer:
10 OPEN
20
FIELD
30
LSET N$ =
40
PUT #3,1
"R",
#3,
#3,
20
A$
":F1
AS N$
:PERSON"
This technique may be used for storing variables for use in another program, linked
to
the first program with the RUN statement (see description
of
Whatever the length
is
less
than
20
characters long, the remaining characters
A$, its leftmost
(20H). Statement 40 writes all
128
bytes
20
characters are now identified as N$.
of
the
I/O
buffer to disk file number
of
N are set
of
RUN, chapter 6).
to
ASCII blanks
#3.
If
A$
5-7
Page 40

Disk
File Input/Output
Remember that random disk files are stored as strings. Just as you must convert
that
fields
represent numeric values when you read them (using
eVI,
CVS, or CVD),
so must you convert numeric values to their corresponding strings when writing to a
random file, using the MKI$, MKS$, and MKD$ functions. Again, you must be sure
of
to allow for the number
bytes required
to
store the three numeric data types.
BASIC-SO
Integer
Single-precision value
Double-precision value
MKI$
MKS$
MKD$
2 bytes
4 bytes
8 bytes
For example, assume that you open a random file and define two fields: the first 2
characters as P$ and the next 4 characters as C$; the first field represents a part
number and the second its cost. The following statements open the file, set
to a variable
number
10
20
30
40
50
The part number,
P A and
5:
OPEN
FIELD
LSET
RSET
PUT#5, 1
"R",
#5,
P$
C$
C$
equal to a variable CO, then write the two values to file
#5,
":F1
:PARTS"
2 AS
P$,
4 AS
C$
= MKI$ (PA)
= MKS$ (CO)
of
course, must be between -32768 and 32767, and the cost
P$ equal
will
be
accurate to 7 digits.
Two other functions are related to random disk 110: LOC and LOF. LOF returns
of
the number
was last read
the last sector in the file; LOC returns the number
or
written.
of
the sector that
5~8
Page 41

CHAPTER 6
COMMANDS
AND STATEMENTS
ATTRIB
The A TTRIB command changes certain specified attributes
You can protect any file from writing or deleting or renaming by enabling the 'write
protect' attribute, and you can later disable this attribute to alter or delete the
specified file. The formats for these two operations are given below.
You can also enable
Refer to the
using ATTRIB with system, format, and invisible attributes.
To protect a file from writing, deletion, and renaming:
ATTRIB ":Fdrive number:filename",
To write to, delete,
ATTRIB
ISIS-II
":Fdrive
or
disable other file attributes with the A TTRIB command.
User's Guide, File Control Commands, for information on
"W1"
or
rename a previously protected file:
number:filename", "WO"
of
BASIC-80 disk files.
AUTO
The AUTO command automatically generates a line number
each line when you are entering a program. The first operand specifies the number
of
the first line entered after the AUTO command; the second, which
specifies the increment. Both operands default to
AUTO [first line
To number lines starting with
AUTO
To number lines with an increment
AUTO 300,50
If
AUTO generates a line number that already exists in the program, the generated
is
number
line in the program, enter Control-C to stop the
followed by
J[,
increment]
10
in increments
of
50
starting with line 300:
an
asterisk. To erase the existing line, enter CR; to leave that
10.
of
10:
AUTO process.
at
the beginning of
is
optional,
CLEAR
The CLEAR command sets all variables, arrays, and function definitions to zero,
If
and closes files.
zero and string variables will be null. The first expression
ment, and the value
variables are referenced after a CLEAR, numeric variables
of
this expression becomes the string space,
is
specified as
in
bytes.
an
will
argu-
be
CLEAR [expression[,address]]
6-1
Page 42

Commands and Statements
If
a second expression
to BASIC. This number
highest memory location used
storage space are available.
is
specified, it indicates the highest memory location available
is
similar to the MEMTOP option.
is
unchanged. At sign-on only
If
not specified, the
100
bytes
of
string
BASIC-SO
CLEAR
will
reserve 2000 (decimal) bytes for string space, and
any memory address above
2000,
ODOOOH
ODOOOH.
will
not allow BASIC to use
CLOSE
The CLOSE statement concludes
statement for
an
open file disassociates the file name and the file number used to
open the file, but the file may be opened again under the same or another file
number. Close without options closes all files.
The END, NEW, MERGE,
arguments) statements close all disk files automatically, but
CLOSE [[I]
10
OPEN
20
GETI3,1
30
FIELD #3,20,AS N$, 9 AS SS$
40
PRINT 'N$,SS$
50
CLOSEI3
RUN
JONES,
Ok
file
"R"
JOHN
number
,13,
"F1
J.
I/O
activities for one or more disk files. A CLOSE
LOAD, RUN (without
[,[1]
file
number]
:PERSON"
517317010
... ]
F)
and CLOSE (without
STOP does not.
6-2
CONT
The CONT command continues program execution after a Control-C, a STOP, an
ERROR interruption,
of
an
because
resumes
error, BASIC-80 will try to re-execute the same line again. Execution
at
the statement after the break occurred unless input from the terminal was
interrupted; in this case, the prompt
if the program was modified during the break, but variable values may be changed.
CONT
In the example below, the program expects a numeric input and
Control-C.
ENTER NEXT INTEGER STRING
?41
tC
BREAK
OK
CONT
?
37
IN
240
or
an END statement has been executed.
(1)
is
reprinted. Execution cannot be continued
If
execution halts
is
interrupted with a
Page 43

BASIC-SO
Commands and Statements
DATA
The DATA statement prefaces lines
and
command
may be numeric, strings,
("
")
they may
blanks are ignored.
assigned as values to variables. The data is separated by commas
or
quoted strings.
not
contain commas (,)
DATA
instruction lines may be located anywhere in program
of
data
that are read sequentially by the READ
If
strings are
or
semicolons (;) and leading
text. BASIC maintains a pointer which keeps track
read. This pointer
program
read.
is
RUN.
It
can be moved with the RESTORE command.
DATA
[,
number I string
10
DATA
20
DATA
30
DATA
40
FOR
50
READ X, A$, Y
60
PRINT X; A$; Y
70
NEXT
RUN
10
IS
LESS
44
IS
GREATER
1.71S
Ok
is
It
numbeq
10, IS LESS
44,
1.7,
1=1
TO 3
THAN
EQUAL
set to the first data element
increments
string
IS GREATER
"IS
THAN
TO 1.7
to
subsequent DATA elements when its elements are
literal I quoted
literal I quoted
THAN,
EQUAL
77
-32
77
THAN,
TO
",
string]
-32
1.7EO
of
string
...
and
not
surrounded by quotes
or
trailing
of
the next DATA element
to
be
the first DATA statement when a
DEF FN(X)
The DEF FN(X) statement defines arithmetic or string functions for later use in program text. The name given to the function must be FN followed by a valid variable
name. The variable(s) given are the arguments used within the function. Any oneline expression can be used. User-defined functions can be
string, and any number
parameters must be specified when the function
Functions may
DEF
not
function
be redefined.
name
of
arguments are allowed. The correct number
is
[(variable [,
variable
... ])]=
The rules for function name are the same as for variable name.
10
DEF
FNAC
20
FOR X = 1 TO
30
PRINT FNAC (X),
40
NEXT X
50
END
RUN
.159155
.954931
(X) = (1/(2*3.14159))*X
10
.31831
1.11409 1.27324 1.4324
.477465
.63662
.795776
1.59155
of
any type, arithmetic
or
of
referenced within a program.
expression
6-3
Page 44

Commands and Statements
DEFSNG
DEFDBL
DEFSTR
DEFINT
BASIC-SO
The DEFSNO, DEFDBL, DEFSTR, and
that
a given block
letter
of
variable names.
statements specify single precision floating point, double precision floating point,
string,
according to
in which m represents
Z. These two letters represent the boundaries
If
must
L,
and
DEFXXX m
n
is
not
used, only variables beginning with letter m are specified.
follow m in alphabetic sequence; in other words, blocks may be defined as D
or A to
0,
10
DEFSTR S
20
DEFDBL D
30
DEFINT I-N
of
letters will designate a specific
The
DEFSNO, DEFDBL, DEFSTR,
integer representation, respectively. Blocks
the
syntactic
[-n][,m[-n]]
but
not
format
any
letter, A through Z, and n represents any letter B through
as P to A
given below:
...
or
Z to M.
DEFINT
of
a block
statements are used to specify
data
type when used as the first
and
DEFINT
of
letters are specified
of
letters between m
The
and
n argument
n.
to
DEFUSRn
The
DEFUSRn
assembly-language, PL/M-SO,
USR function. The argument n may be an integer from 0 to 24; if
given, 0 is assumed.
statement
Two
examples
is
used to specify the starting address
or
Fortran-SO subroutine so they may be called by the
of
DEFUSRn
statements are given below:
of
no
an
SOSO/SOS5
argument
is
DEFUSR =
DEFUSR7 =
Because
value for
decimal values in a
The program below shows how DEFUSR defines a subroutine. Refer
for further details
of
an
10
INPUT
20
IF
30
DEFUSR11 = A
10
REM This
20
REM Integers,
30
REM Returns
40
DEFINT A-Z
50
DEFUSR 1 =
60
PRINT
70
INPUT A,
80
P R IN T
90
RESULT =
100
PRINT
110
END
OFOOOH
1%
the way BASIC-SO represents numbers internally, 32767
integer expression. The following code can be used to specify higher
A>
DEFUSRn
"ENTER
32767
THEN A =
of
using DEFUSR.
program
"Enter
B,
"A
=
";
USRo/01
"A+
B+C+
statement.
ENTRY ADDRESS
A-65536
asks
for
passes
the
OEOOOH
three
C
A;
them
result.
numbers:"
"B
=
";
(A, B, C)
="
B;
"C
RESULT
IN
three
to
USR1, and
= " ; C
DECIMAL";
A
is
the largest
to
Appendix E
6-4
Page 45

BASIC-SO
Commands and Statements
DELETE'
The DELETE command removes specified instruction lines from program
or
block
of
single line
lines may be deleted,
as
shown in the syntactic format and
tex,t.
A
example below. Instruction lines prior to and including the specified line may be
deleted by adding a dash
line numbers specified as end points must exist.
DELETE
10 PRINT CHR$(12)
20
30
40
50
60
70
DELETE-40
OK
LIST
50
60
70
OK
DELETE
OK
LIST
50
60
Ok
line
PRINT:PRINT:PRINT
REM THIS PROGRAM FINDS THE AVERAGE
REM
OFTHREE
INPUT
PRINT
END
INPUT
PRINT (A + B +
END
INPUT
PRINT
A,B,C
(A+
A,B,C
70
A,B,C
(A+
(-)
before a line number. When deleting a range
numberlline
NUMBERS
B+C)/3
C)l3
B+
C)/3
number-line
If
not, an error results.
numberl-line
number
of
lines, the
DIM
The DIM statement defines the number
is
variable
as
the maximum possible subscript range for each dimension in the reference.
not dimensioned before it
given, DIM statements must allocate space before you refer to the arrays they
dimension, since once
If
an
OPTION
an
array
is
BASE n statement
for arrays, it should precede the first DIM statement, or array reference.
DIM variable
In the example below, A
of
value
from 0 to 20. I
(integer
[,integer]
is
a single precision array with
is
an integer array with
three dimensional string array with
22
double precision array with
10
DEFINT I-N
20
DIM A (20), 1(12,13),
elements.
S$
of
elements in an array variable.
is
referenced, a default value
of
10
If
an
is
assumed
array
If
dimensioned, these dimensions cannot be changed.
is
used in the program to specify starting points
... ) [,variable
125
elements. DD#
(4,4,4), DD#
(21)
13
(integer
times
[,integer]
21
elements, indexed with a
14
(=
182)
is
a singly dimensioned
... ) ... ]
elements.
S$
is
a
6-5
Page 46

Commands
and
Statements
DIR
The
DIR
command
the
files saved
drive
O.
DIR
DIR
EDIT
The
EDIT
a selection
changing. These
and
Editing BASIC-80.
The
EDIT
execution.
be
entered by typing
BASIC-80.
displays
on
the
specified disk.
may
be used as a
[drive number]
command
of
editing
mode
It
can
is
used
subcommands
subcommands
is entered automatically when a syntax
also
be
EDIT
the
names,
command
to
modify
and
entered when.entering text by typing
line
number.
number
If
no
or
single
that
facilitate character insertion, deletion
their uses
Refer
of
blocks,
drive
number
as a statement.
program
are
to
lines.
explained in
Chapter
and
is specified, the
error
3: Entering
length (in bytes)
default
In
this mode, you have
Chapter
Control
3: Entering
prevents
A,
and
program
or
it
Editing
BASIC-SO
of
is
and
may
The
error.
EDIT line
period
numbeq
(.) is used
END
The
END
statement halts
level. Files are closed,
logical conclusion
"BREAK
optional
as
IN
the
END
The
program
10 INPUT A,B,C
20
D=(A + B + C)/3
30
PRINT
40
END
point
line
number"
last line
below contains
"THE
.
to
represent the last line changed, listed
program
but
variables
within
message,
of a program.
an
AVERAGE
execution
can
program
and
END
statement in line 40.
and
be examined.
text.
STOP
does
not
returns
acts like
close files.
OF";A;" + ";8;" + ";C;"EQUALS";D;"."
to
END
or
that
BASIC-80
may
be
END,
but
An
END
contained
command
used
at
also prints a
command
an
any
is
6-6
ERROR
The
ERROR
The
user-supplied integer expression will generate
its value, as shown in
be greater
that
does
will
print.
formation,
statement simulates the occurrence.
the
example listed below.
than 0 and
not
correspond
All errors
refer
to
Chapter
less
can
than
to
a BASIC
be
trapped
4:
Error
or
equal
to
error
by
Handling.
255.
the
of
an
The
If
ERROR
message,
ON
ERROR
an
error
in
program
error
message
integer expression supplied
is
executed with a
"UNPRINTABLE
statement.
execution.
appropriate
number
ERROR"
For
further in-
to
must
Page 47

BASIC-SO
ERROR expression
10
INPUT
12
IF
B=O
14
PRINT
20
END
RUN
? 40,0,17
DIVISION BY ZERO
Ok
EXIT
A,B,C
THEN ERROR
AlB
IN
12
11
Commands
and
Statements
The EXIT command terminates operation
control to ISIS-II.
If
grams.
you EXIT without saving the current program, it will be lost.
EXIT
EXIT
closes all open files, but does not automatically save pro-
of
the BASIC-80 interpreter and returns
FIELD
The FIELD statement
random file buffers. When a random
the specified random file buffer to
associates the data with its position in the
specified variable will access the proper string characters or numbers within the
record stored in the random file buffer. The example below shows how FIELD
used. For further information, refer to the BASIC-80 Disk
FIELD # file number,
number of characters
[,number of characters
The program below opens random file
strings to insert into
10
OPEN
20
FIELD #1,30 AS A$
30
FOR 1=1 to 5
40
INPUT
50
LSET
A$ = Z$
60
PUT#1,1
70
NEXT I
80
CLOSE#1
90
END
"R"
Z$
is
used to allocate space within one
110 transaction occurs, data move to or from
or
from disk sectors. The FIELD statement
110
buffer
AS string variable
AS string variable] ...
:F1
:FILE.1 and asks for five 30-character
:Fl
:FILE.1.
,#1,
":F1
:FILE.1"
of
six
128-byte BASIC-80
so
that future references to the
Input/Output
section.
is
FOR-NEXT-STEP
The FOR-NEXT statement allows the execution
number
value A
STEP
taining the
Program control returns to the
A, and the routine
of
times. As shown in the example below,
is
incremented by the value given in the STEP instruction.
is
specified, the increment
FOR
instruction are executed until the NEXT instruction
is
1.
The instruction lines following the line con-
FOR instruction line, STEP
is
reentered. When variable A exceeds the TO expression, control
passes to the instruction line following the NEXT instruction line.
of
a given group
on
each iteration
is
added to the value of
of
lines a given
of
the routine,
If
no value for
is
encountered.
6-7
Page 48

Commands
and
Statements
If
the
TO
expression
is
larger than the starting expression and the step expression
negative then the loop will not execute. Similarly, if the TO expression is less than
the starting expression and the
execute. After the conclusion
ed
in the loop.
STEP expression
of
the loop, variable A contains the first value not us-
is
positive, then the loop will not
BASIC-SO
is
Control cannot be passed to a statement within a
GO SUB
etc, but a GO
TO
can be used to jump out
FOR ... NEXT loops may be nested so long as each inner loop
loop~,
contained in all outer
If
possible, integer index variables should be used to speed execution. Double preci-
and they employ different index variables.
FOR ... NEXT loop with GO TO,
of
a FOR ... NEXT loop.
is
completely
sion index variables are not allowed.
FOR variable=expression TO expression [STEP expression]
10
FOR A = 1 TO 5
20
PRINT A * A,
30
NEXT A
40
END
RUN
1 4 9
16
25
GET
The GET statement reads the specified sector from the specified file into
If
random buffer. The file must be open for random access.
specIfied, the sector number
is
sector
read. A GET without a sector number immediately after a file
the previous GET
or
of
return the first sector. The largest possible sector number
mand
is
issued for a sector that has not yet been written, buffer contents are
is
undefined, and there
been
PUT
or
GET, the file will be extended.
no error message. However, if no greater record has ever
the sector number
PUT
is
incremented and this
is
2046.
If
128-
is
opened will
the GET com-
byte
is
not
GET
[I]
file number [,record number]
10
OPEN
20GET#3,1
30
FIELD
40
PRINT N$,SS$
"R"
#3,
,#3, "F1
20
:PERSON"
AS N$, 9 AS
SS$
RUN
JONES, JOHN J.
Ok
517317010
GOSUB
The GOSUB statement transfers program control to the line number specified as an
is
argument. This line number
typically the first line number
used several times during a program. The RETURN statement transfers control
back to the first instruction that follows the last
GOSUB
10
20
30
100
110
line number
lNPUT
IF
GOTO
PRINT SQR(AO);SIN(A);TAN(A)
RETURN
A
A>O
THEN GOSUB
10
100
ELSE PRINT
GOSUB statement executed.
"A
of
a subroutine that
MUST BE
is
>0"
6-8
Page 49

BASIC-SO
Commands and Statements
GOTO
The GOTO (line number) statement transfers execution
to
current line
the line number specified. There
of
instruction lines from the
is
no provision for a return to the
branching point.
GOTO
line
numberl
GO
TO
line number
The GO TO in line 270 causes a jump to line 100.
250
IF
260
270
300
310
EOF(6) THEN
PRINT
GOTO
PRINT
END
"FILE
100
"FILE
300
STILL CONTAINS
";F$;"IS
OUTOF
DATA"
DATA."
IF-THEN-ELSE
The IF-THEN-ELSE statement evaluates the given logical expression and executes
the THEN instruction if true, the
is
tion
optional; if it
is
left out, and the logical expression
executed. Line numbers can be used in place
as
GO TOs.
An
IF statement must always be on one line. IF statements may also be
nested, as shown in the example below. In this example, an
last unmatched
IF
expression THEN instruction [ELSE instruction]
THEN.
ELSE instruction if it
of
instructions and have the same effect
is
false. The ELSE instruc-
is
false, the next line
ELSE clause matches the
is
IF
S$
="
5
10
IF
S$ = "+"
20
GOT040
30
PRINT"lnvalid
40
END
"THEN
40
THEN A = A+B ELSE
S$"
IF
S$
=
"-"
THEN
A=A-B
ELSE
30
INPUT
The INPUT statement returns a prompt (question mark) and waits for the user
enter data. String literals
or
numeric values may be expected, according to the type
of variable specified as an argument.
INPUT
If
a string expression follows INPUT and
the question mark as the prompt.
do not agree with the number
[quoted
string;] variable [,variable] ...
is
followed
If
the number
or
type
of
or
type of data items in the response
variables requested, BASIC-80 returns a
by a ";"
it
is
used in place
prompt to re-enter the line. Strings which are input need not be surrounded by
not
quotes as long as they do
contain commas (,). Leading and trailing blanks are
ignored in this mode.
10
INPUT A,B,C
20
PRINT(A+B+C)/5
30
END
RUN
?
40,2,18
12
Ok
to
of
6-9
Page 50

Commands and Statements
KILL
BASIC-SO
The KILL command deletes files from disk storage,
the deleted file from the directory.
KILL filename
Once a file has been killed, it cannot be reopened.
and
removes all references to
LET
The LET statement
left
of
an
equal sign not preceded by the word LET,
is
statement
implied. When assigning a literal value to a string variable, the value
must be enclosed in quotation marks.
[LET] variable = expression
10
LET
20
PRINT A
RUN
5
Ok
A=5
is
used to give a value to a variable.
If
a variable appears to the
BASIC-SO
assumes that a LET
LINE INPUT
The LINE INPUT statement reads
the specified string variable. LINE INPUT does this in two ways: first, data may be
read from the terminal and assigned; second, data may be read from a disk file and
assigned.
an
entire line
of
data and assigns it as the value
of
When entering data from a terminal, the syntactic format is:
LINE
INPUT
This statement
string
is
entered and a carriage return has been entered. Entering a Control-C
abort LINE INPUT and return
mand may then be used to re-enter the LINE
When entering data from a disk file, the syntactic format used
LINE
INPUT
This statement reads data from the specified disk file until a carriage return
countered. The data
[string expression;] string variable
will
print the string expression as a prompt and will haIt until the
BASIC-SO
to the Command Mode. A CONT com-
INPUT statement.
is:
.file
number,string variable
is
assigned as a value for the specified string variable, and LINE
is
will
en-
INPUT skips over the encountered carriage return-line feed to point to the beginning
of
the next
file
I10~
the next string.
255
characters
If
no carriage return
of
data.
See
Chapter 5 for further information about disk
is
encountered, the statement returns
LIST
The LIST command prints the current program's text
lines are listed in sequential order. As shown below, the
to display the entire program, all instruction lines up to or after a given line, or a
of
block
instruction lines within the program. The period may be used as
abbreviation for the last line which was changed, contained an error, or was listed.
to
the console. Instruction
LIST command may be used
an
6-10
LIST [line numberl-line numbeq line number-I line number-line number}
Page 51

BASIC-SO
Commands
and
Statements
In the example below, LIST
including
40,
30; list 30- prints all lines after 30, including
and 50; LIST prints the entire program text.
10
PRINT CHR$(12)
20
INPUT
30
PRINT (A + B + C)/3
40
PRINT
50
END
LIST
30
PRINT(A+B+C)/3
LlST-30
10
PRINT CHR$(12)
20
INPUT
30
PRINT(A+B+C)/3
LIST 3030
PRINT
40
PRINT
50
END
LIST
30
PRINT (A + B + C)/3
40
PRINT
50
END
LIST
10
PRINT CHR$(12)
20
INPUT
30
PRINT
40
PRINT
50
END
30
30-50
A,B,C
A,B,C
(A+
A,B,C
(A
+ B + C)/3
30
B+C)/3
prints line
30
only; LIST -30 prints all lines up
30;
LIST 30-50 prints lines 30,
to
and
To
obtain a listing
mand, which
of
a file on a line printer
is
described on page 6-22.
or
other device, use the SAVE com-
LOAD
The LOAD command reads a file from disk and stores it
current file. The string expression must be an
LOAD
LOAD"
OK
RUN
THIS PROGRAM PLOTS
FUNCTION ON
LSET,
filename
:F1:
PLOT"
RSET
AN X-Y
ANY
USER-DEFINED
GRAPH.
ISIS-II filename.
in
memory, making it the
The LSET and RSET statements store the specified string expression into string
space
that
has been allocated in a random file buffer by a FIELD statement. When
string variables are assigned to a random file buffer with the FIELD statement, they
6-11
Page 52

Commands
and
Statements
BASIC-80
cannot later be assigned values with the LET statement. This
new
assigned
storage locations when given new values and this destroys the effect
is
because strings are
of
the FIELD statement. Accordingly, the LSET and RSET statements must be used to
assign new values. These commands may also be used with normal string statements.
If
the assigned string value
in the FIELD statement,
as needed. RSf:T right justifies the string in the same way.
the space reserved, the extra characters are ignored.
with string variables that have not been fielded.
the length of the receiving string
LSET
string
RSET string variable = string
10
A$
= "1
23456"
20
RSET
A$
=
30
40
50
RUN
CO
Ok
PRINT
LSET
PRINT
ABX
X
A$;
A$
A$;
=
is
shorter than the space reserved for the string variable
LSET left justifies the string, adding blanks (ASCII 20H)
If
the string
is
longer than
LSET and RSET may be used
Unlike normal string assignment,
is
not changed by an LSET or RSET assignment.
variable = string
"A
B"
expression
expression
"X"
"C
0"
"X"
MERGE
The MERGE command reads a program from disk and combines it with the current
If
program without changing line numbers of either program.
the new program and
the current program have instruction lines with the same line numbers, the new in-
new
struction lines replace the current ones. The
ASCII format. MERGE sets all variables and arrays to zero.
gram, the program will end. A given string expression must resolve to an
program must have been saved in
If
used within a pro-
ISIS-II
filename.
MERGE
MERGE ":F4:
Ok
string
expression
EVAL.BAS"
NEW
The NEW command deletes the current program and clears all variables and arrays.
If
a program has not been saved and the NEW command
lost.
NEW
In the sample program below, the program has been deleted by the NEW command.
LIST command will not list it, or any program, until another
The
peripheral device or entered line-by-line.
240
250
260
270
NEW
Ok
LIST
Ok
PRINT
PRINT
PRINT
END
"end
of
program"
is
given, the program
is
read from a
is
6-12
Page 53

BASIC-80
NEXT
Commands
and
Statements
The NEXT statement
is
used with a previous FOR statement
to
end
an
iteration of a
FOR-NEXT loop; when BASIC-SO encounters a NEXT statement, control passes
back to the statement line containing the last
FOR statement.
If
no index variable
specified, BASIC-SO increments the variable specified in the last FOR statement.
Each NEXT can end more than one loop if the index variables used in each loop are
given separated by commas.
The syntax
of
NEXT
NEXT [Variable] [, Variable] ...
10
FOR
20
PRINT A * A;
30
NEXT A
40
END
RUN
1 4 9 16
Ok
A=1
25
is:
TO 5
NULL
The NULL command specifies the number
printed line, following the carriage return. This feature
minals that require a certain number
timing.
of
null characters printed
is
used with hard copy ter-
of
null characters that set carriage return
at
the end of a
is
NULL
ON
number
ERROR
of
null
GOTO
characters
to
be
transmitted
The ON ERROR OOTO statement transfers program control to the specified line
or
number when error conditions occur
within a program. The
is
function
set to the applicable line number.
The instruction line
ERROR OOTO,
ERROR OOTO 0
before a
RESUME) the proper error message prints and execution halts
ERR
function
ON ERROR OOTO 0 removes the effect
so
that
errors cause messages to print and halt execution.
is
executed within
an ERROR instruction simulates an error
is
set to the applicable error code and the ERL
of
any previous ON
If
an
error-handling routine (after an error but
ON
immediately.
If
an error occurs in
before a
RESUME, the ON ERROR OOTO has no effect. This means that if an ON
ERROR OOTO
an intervening
an
error routine, after an ON ERROR OOTO branch and
is
in effect, and two errors (or ERROR commands) occur without
RESUME, the second error prints an error message and halt
execution.
ON ERROR GOTO
10
ON ERROR GOTO
20
ERROR
11
line
200
number
200
PRINT
210
RESUME NEXT
"ERROR"
ERR
"AT
LINE"
ERL
6-13
Page 54

Commands
and
Statements
ON ... GOSUB
The
ON
... GOSUB statement transfers
subroutines.The line numbers
tially, separated by commas.
third line
number
ON
expression
10
INPUT A
20
ON
following GOSUB.
GOSUB line
A GOSUB 200,300
program
of
the first lines
If
the expression evaluates
number
of
[,Iine number] ...
control to one
these subroutines follow sequen-
to
or
one
of
a set
3, control transfers to the
BASIC-SO
of
ON ...
The ON ...
numbers.
number following the line containing the
evaluates
GOTO
GOTO
The
expression X
to
3, control transfers
expression
ON
10
INPUT A
20
ON
A GOTO
statement transfers program control to one
is
evaluated
to
the third line number following GOSUB.
GOTO line
500,510,520
number
OPEN
The
OPEN
associates a file number from 1
Random
and
an I,
tactic
format
and less
the file in
statement makes
110
files are specified by
sequential
below.
than
or
110
transactions.
output
The
equal to 6,
an
ISIS-II file available
to
6 with
an
files are specified by
file number
is
preceded by a
or
one
of
a set
of
line
and
control
ON
...
[,Iine number] ...
the
R, sequential input files are specified by
is
an
is
transferred to the
GOTO
instruction.
file. File type can be I,
an
0,
integer expression greater
"#"
sign, and
If
the expression
to
BASIC.
as shown in the syn-
is
used
to
"nth"
It
0,
or
than
reference
line
also
R.
0
6-14
Only six files may be open
and
MERGE
they are executed.
BASIC-SO buffers files, so if :CI:
the first line
OPEN type, [I] file number, filename
where type
the file SYSLIB
OPEN
all require a file, so a maximum
of
console input.
is
a string expression equal to
is
opened as a
"R"
,#4,
"SYSLlB"
at
one time.
random
Note
that
SAVE, LOAD, DSKF; DIR
of
five files may be open before
is
opened for input, BASIC-SO will wait for
"0",
"I"
or
"R".
In the example below,
I/O
file, with number 4.
Page 55

BASIC-SO Commands and Statements
The example below shows a typical use of OPEN in an 110 program.See Chapter 5
for further details
10
OPEN
20
GET
30
FIELD #3,20 AS N$, 9 AS
40
PRINT N$,SS$
RUN
Ok
of
"R"
#3,1
JONES,
disk random 110.
,#3, "F1
JOHN
:PERSON"
SS$
J.
517317010
OPTION BASE
The OPTION BASE command
specifying
an
argument
of
OPTION BASE should precede all DIM statements and array references.
1
is
TION BASE
OPTION BASE
not specified, 0
011
is
used to begin indexing
0 or
1,
you can begin all arrays
is
the default value.
of
arrays
at 0 or
at
1.
1 or
If
present,
If
O.
By
OP-
OUT
The OUT statement writes the specified value
an integer expression in the range 0 to 255.
OUT
port
number,
This example rings the bell
OUTOF6H, 7
expression
on
Intellec development systems using the RS-232 port.
to
the specified 110 port. The value
is
POKE
The POKE statement places the specified value into the memory location specified.
is
The specified value
POKE
can also accept hexadecimal and octal arguments, even though octal and hex
constants over 32767 (decimal) are interpreted by
does this by adding 65536
an expression that must round to an integer in the range 0-255.
to
such arguments.
BASIC-80
as
negative numbers.
It
POKE
POKE OFFFFH, 0
POKE
POKE 1777770,0
POKE
location,
65535,0
-1,0
expression
The instructions above set the top byte of memory to 0 in
system having 64K
command to reserve free memory. A
BASIC
or
other software to fail.
of
memory. Before using POKE, you should use the CLEAR
POKE into BASIC
an
Intellec development
or
system code may cause
6-15
Page 56

Commands and Statements
PRINT
The
PRINT
console, or to any
(");
variables and expressions need no quotation marks.
You can print data
inserted following
of
ning
starts
ment, the next printing starts
prints one blank line. A
the next 14-column zone.
at
the next column.
PRINT
10
INPUT
20
PRINT
30
END
RUN
? A
string
YOUR STRING
Ok
statement returns the value
of
expressions
or
the text
of
ISIS-II file. Literal strings must be enclosed in quotation marks
to
any ISIS-II file by specifying a file number.
an
expression to be printed, the next printing starts
"?"
[II
filenumber,][[
"A
string";
"YOUR
IS
If
a semicolon (;)
If
no punctuation
at
the beginning
is
used at the end
is
inserted, the next printing
of
the next line. PRINT by itself
entered after a line number means PRINT.
expression],
X$
STRING
A string
IS
";X$
I;] ...
If
a comma (,)
of
the PRINT state-
strings to the
is
at
the begin-
BASIC-SO
PRINT USING
The PRINT USING statement specifies particular formats to print strings
numbers. The format string may include more
any literal character
format
of
PRINT
PRINT
[#
that
is
not a
PRINT
USING
file number,] USING format string; expression
is:
than
one field, and may also include
USING formatting character. The syntactic
[,
expression] ...
in which the format string specifies spacing and additional characters (such as
asterisks and dollar signs) when used with numeric fields, and which specify portions
of
the given string when used with string fields. Each expression
same format. The optional file number specifies the number
Chapter 5 for details
of
sequential disk file 110.
is
printed with the
of
an
open file. See
String Fields
There are two formatting choices when using
"!"
specifies that the first character
"\
n spaces
\"
specifies
that
of
the first 2+N characters are printed.
are used without spaces, two characters are printed.
If
the string field has more characters than the format string, the balance are
ignored; if there are fewer characters than specified, spaces are printed to fill out the
field. Here are examples
of
the string field formats:
PRINT
USING with string fields:
each specified string
is
printed.
If
the backslashes
or
6-16
10
X$="ONE"
20
Y$="TWO"
30
PRINT USING
40
PRINT
RUN
OT
ONE TWO
Ok
"!";
X$;
USING" \ \";
Y$
X$;
Y$
Page 57

BASIC-80
Commands
and
Statements
As can be seen,
each string.
characters from X$
Y$="SEVEN",
ONE SEVE
and if
X$="SEVEN"
SEVEEIGH
PRINT
PRINT
USING
"!"
USING \ 2 spaces \ prints a string consisting
(3
plus a space) and four from
the result printed when line
and
Y$="EIGHT",
prints a string consisting of the first letters
Y$
(also 3 plus a space).
40
is
executed would be:
the results of line 40 would be:
Numeric fields
The
PRINT
signs, plus or minus signs, exponentiation, asterisk fills, or insertion
of
Each
I The number
USING formatting characters specify right justification, leading dollar
the BASIC-80 format characters
or
be printed
sharp sign
is
too small to fill all
(H)
is
explained in the following section.
indicates the position of digits.
of
the digit positions specified
If
the decimal point, leading spaces print to fill the entire field. An integer can
print as up to five digits, single precision floating-point up
to
and double precision floating-point up to fifteen digits.
of
of
four
If
of
commas.
the number to
to
the left
of
seven digits,
• The decimal point can be inserted in any position in the field.
specifies
whether it
+ The plus sign
that
a digit follows the decimal point, the digit always prints,
is
a 0 or another number. Numbers are rounded as necessary.
PRINT USING
41.29
PRINT USING
0.71
(+)
"IH.II";
"IH.HI";
is
used
41.287
71/100
at
the beginning or end of the field
characters. Insertion of this character prints a plus or minus sign, depending
on the sign
of
the number,
at
the beginning or end of the number,
respectively.
The minus sign
printing
space
number
of
is
printed.
is
PRINT
+4.89
PRINT USING
5.8-
(-)
is
used
at
the right
of
the format character field to force
a trailing minus sign if the number
If
neither
printed with a leading
USING"
-2.67
"IH.H-";
96.2
(+)
+H.IH";
or
(-)
is
included in the format, a negative
(-).
4.89; -2.6689
-5.8;
96.2
is
negative.
If
If
the format
of
format
it is positive, a
**
The double asterisk (**) fills any leading blank spaces in the number format
with asterisks. This symbol also specifies positions for two more digits.
PRINT USING "**HH.H"; 4.8;
***4.8 *243.3
243.3
6-17
Page 58

Commands
and
Statements
BASIC-80
$$ The double dollar sign ($$) adds a single dollar sign to the immediate left
of
the number being formatted.
PRINT USING "$$###.##"; -48.28; 364.90
-$48.28 $364.90
($$)
specifies space for two additional characters, but the $ added takes up one posi-
tion. The exponential format cannot be used with
The double asterisk-dollar sign (**$) returns the results
**$
($$) format characters. Exponential format cannot be used;
three additional digit positions, one
is
The comma (,)
of
left
every third digit on the left
placed to the left of a decimal point to print a comma to the
specifies another digit position. A comma to the right
($$).
of
both the (**) and
"**$"
allows for
of
which
is
the dollar sign.
of
the decimal point. The comma also
of
the decimal point
prints in that position. The comma cannot be used with exponentiation.
PRINT USING
92,114.84
tttt Four carat signs (or vertical arrows) specifying exponentation. The carats
"11###11,.##";
92114.84
or
or arrdws are placed after the numeric format characters. Any decimal point
AM
format may be used. The significant digits are left justified, and the exponent
is
adjusted. The comma and floating ($) cannot be used when exponentiation
is
specified.
070
The percent
format has been encountered.
by a
(070)
field, the rounded number
(070)
character indicates that a number larger than the given
BASIC-80 returns the number itself preceded
sign; or, if rounding the number causes it
is
printed, preceded by a
to
exceed the specified
(070)
sign.
of specified digits exceeds 24, an ILLEGAL FUNCTION CALL error
results.
PRINT USING
40.48%
766784.00%
"11#.1111";
40.48;
99997.00
766784;
99997
PRUN
The
PRUN
address
command starts execution
of
the program
is
an integer argument. The program must be saved in
of
a program stored in PROM. The
ASCII, and followed by a (Control-Z).
PRUN
address
PUT
The
PUT
statement transfers
to the specified disk 'sector. The
when the random file was opened and the sector the data goes to.
is
number
written to.
specified, and no
If
data have been written to the disk, the number
written increments, and the next sector
exceed 2048.
data
from the previously formatted random file buffer
PUT
statement requires the file number assigned
data
have been written to the disk, the first disk sector
of
is
written to. The sector number may not
If
the number
If
no sector
is
the last sector
6-18
Page 59

BASIC-SO Commands and Statements
PUT
file
number,
[sector
number]
10 OPEN
20
FIELD 10 AS A$
30
INPUT
40
PUT 1,1
50
CLOSE
60
STOP
RUN
"A
?
Ok
"R",
A$
1
STRING"
1,
":F1:FILE.1"
RANDOMIZE
The RANDOMIZE statement prompts the user for a
If
the random number function RND.
the RANDOMIZE command
within a program, the same sequence of random numbers will repeat each time any
is
program
If
the optional expression is included, its value becomes the
is
issued.
run.
RANDOMIZE
10
RANDOMIZE
20
A=
RND
30
IF A < .5
40
IF A
>=
.5
RUN
Random
TAILS
Ok
number
[(expression)]
THEN
THEN
seed
PRINT
PRINT
"HEADS"
"TAILS"
(0-65529)?
123
new
random number seed for
is
new
seed and no prompt
not
given
READ
The READ statement sequentially assigns values found in the accompanying DATA
If
statements to the variables specified.
available,
DATA
error message will be printed.
an
OUT
OF
available to be read, the next READ statement will assign the next datum to the
specified variable. The READ pointer may be reset to the first item
statement with the
as the type
of
READ
10
DATA
20
READ A, B,C,
30
PRINT A;
40
READ
50
PRINT
RUN
246
81012
Ok
RESTORE command. Any type
the DATA
variable
2,4,6,8,10,12,14,16,18,20
D,E,F
D;E;F
is
[,variable]
B;C
appropriate for the type
...
more DATA fields are read than are
If
there
is
still data
of
any DATA
of
variable may be read as long
of
variable.
6-19
Page 60

Commands
and
Statements
REM
BASIC-SO
The REM statement
instruction line that begins with REM following its line number
program control passes to the next line. Within a remark, : (colon)
is
used to insert commentary remarks into program text. Any
is
passed over, and
is
simply another
character, not a statement separator.
REM
10 REM THIS PROGRAM FINDS
20
REM OF
30
INPUT
40
PRINT
50
END
THREE
A,B,C
(A+
B+C)/3
NUMBERS
THE
AVERAGE
RENAME
The RENAME command changes the name
Only the directory reference (accessed with the DIR command)
grams reference the old filename, a FILE
RENAME
"old
filename"
TO
of
the specified file to the new filename.
is
altered; if pro-
NOT FOUND error message will result.
"new
filename"
RENUM
The RENUM command resequences line numbers in a program, whether they ap-
at
pear
the beginning
specify up to three optional arguments: the first
be renumbered, the second
the third
number
is
the increment between lines.
of
the first line to be renumbered
renumbered, and the increment
of
a line or as the object
is
the old number
is
assumed to be
of
a OOTO statement. You can
is
the new number
of
the first line to be renumbered, and
If
you specify no arguments, the new
is
assumed to be
of
the first line to
10,
all lines are
10.
REN UM
20
40
15 RANDOMIZE
5 PRINT CHR$(12)
52
58
RENUM
LIST
10
20
30
40
50
60A2=
[new
number][,[old
INPUT
PRINT
A1 = A*RND
A2 = INT(A1)
PRINT CHR$(12)
RANDOMIZE
INPUT
PRINT
A1 = A*RND
A
"NEW:";
A
"NEW:";
INT(A1)
number][,increment]]
A
A
RESTORE
The RESTORE statement resets the READ pointer to the first DATA statement
within program text. The DATA statements can then be reread. A line number can
be specified following
next.
RESTORE; if included, data on the specified line will be read
6-20
Page 61

BASIC-SO Commands
and
Statements
RESTORE
10
DATA 48,49,51,53,58
20
DATA 104,108,116,132,164,5000,5000
30
READA,B
560
IF
570
RESTORE
580
READA,B
[line
number]
B<5000 THEN
30
RESUME
The RESUME statement restarts program execution after
and handled. Program execution begins
specified, execution resumes
ment
RESUME NEXT causes execution
at
the statement where the error occurred. The state-
statement.
RESUME
[line
numberlNEXT]
at
the line specified;
at
the statement following the erroneous
an
error has been detected
or
if no line number
is
140
ON ERROR GOTO
200
PRINT
210
PRINT
220
RESUME NEXT
"ERROR";ERR;"AT
200
LlNE";ERL;"."
RETURN
The RETURN statement
control back to the instruction line immediately following the last
GOSUB statement executed.
RETURN
50
GOSUB
60
PRINT
200
210
220
230
240
IF
IF
A=11
PRINT
PRINT
200
"TYPE
A>100 THEN PRINT
A<=O THEN PRINT
(B* B1)
"YOUR
is
placed
NEXT
NEW FIGURE
at
NUMBER"
"OUT
"A
the end
MUST BE
OF
IS
of
";A;
a subroutine, and transfers program
RANGE"
>0"
GOSUB
or
ON
...
6-21
Page 62

Commands
and
Statements
RUN
BASIC-SO
The RUN command starts the execution
enter
RUN
alone, it executes the current program starting
If
you enter RUN followed by a line number, it executes the current program start-
ing
at
the specified line number.
representing a file name, it looks for a file with
into memory,
latter form, an
Files can be left open only if the
command erases all variables before executing the program.
RUN
The RUN
together.
line number RUN
This feature
can fit into memory as one large program.
variables to zero, however, so if you want to pass some variables to the next program,
print
details) during execution
subsequent programs.
In the example below, the (tC) character halts program execution.
and
executes the program starting
"F"
may be added
program
[line
numberlstring
command
The
form
of
may
the
RUN
expression [,F]]
also be used as a program statement to chain programs
command
"filename"
is
especially useful for the execution
them
out
to a buffer
of
file (see the section
the first program. Then read them, when needed, into
of
a program or a set
If
you enter RUN followed by a string variable
that
name
at
the lowest line number. With the
to
leave files open. Otherwise, they are closed.
was saved in non-ASCII format.
that performs this function is:
of
programs
The
RUN command initializes all
on
of
programs.
at
the lowest line number.
on
disk, loads its contents
The
that
are larger
"Random
Disk
110"
If
you
RUN
than
for
LIST
10
INPUT A,B,C
20
PRINT (A+B+C+)/3
30
PRINT"NEXT SERIES"
40
PRINT: PRINT: PRINT
50
GOTO 10
60
END
RUN
?41,12,6
19.6
NEXT SERIES
6-22
?
tC
(This control character interrupts execution)
BREAK
IN
10
OK
RUN
30
NEXT SERIES
?
SAVE
The SAVE command stores the current program
The addition
with the specified name exists, it will be replaced by the new file. Any valid
file name may be used. You can use a string expression that resolves
filename.
printer. Refer to the
filenames.
of a comma
For
example, SAVE
and
an
A saves
":LP:",
the
A will list the current program
ISIS-II User's Guide for more information
on
disk with the specified filename.
file in ASCII format. Note
on
ISIS- II device
that
to
an ISIS-II
on
if a file
ISIS-II
the line
Page 63

BASIC-80
Commands
and
Statements
SAVE string
10
INPUT
20
PRINT (A + B +
30
END
SAVE
OK
RUN
"AVER"
expression
A,B,C
"AVER"
[,A]
C)/3
? 5,8,2
5
Ok
STOP
The STOP statement halts program execution and prints a BREAK IN (line number)
message. Following this,
STOP, program variables may be changed or printed, and, if the program
changed, execution may be resumed with the
also halts execution,
closes any open file.
STOP
BASIC-80
but
does not print a BREAK
is
in the command mode. After execution
of
is
not
CONT command. The END statement
IN
(line number) message, and
a
320
PRINT
330
STOP
RUN
END OF PROGRAM
BREAK
Ok
IN
"END
330
OF PROGRAM"
SWAP
The SWAP statement exchanges the values assigned to any two variables or string
that
variables, provided
SWAP variable1, variable2
110
IF
X>Y THEN SWAP X,Y
120
PRINT
TRON,
"NEW
TROFF
they are
VALUE
of
the same type.
OF X IS";X;""AND Y IS
NOW";Y
The two program tracing commands, TRON
and
TROFF, respectively enable and
disable the trace function in program execution. When enabled, the number of each
is
line
printed as it
is
executed, enclosed in square brackets. These commands can
also be used within programs to selectively enable and disable tracing.
6-23
Page 64

Commands
and
Statements
WAIT
TRON
TROFF
10
INPUT
20
PRINT(A+B+C)/3
30
END
TRON
OK
RUN
[10]42,
[20]45
[30]
OK
TROFF
OK
RUN
30,
18,12
20
Ok
48,
A,B,C
45
BASIC-80
The WAIT statement instructs BASIC-80 to monitor incoming bytes from a
is
specified port. These bytes are tested with a mask byte, which
sion in the range
bits
of
the comparison byte, also
I comparison byte
halted until the two sets
is
status
exclusive ORed with the comparison byte and the result
mask byte. Execution halts until a non-zero value
WAIT
0 to 255. The resulting bits are compared with the corresponding
an
integer expression in the range or 0 to 255.
is
port
not specified, the default value
of
bits differ. When the WAIT command
number,
mask
byte,[comparison
is
O.
Execution
is
obtained.
byte]
an integer expres-
of
program text
is
given, the port
is
ANDed with the
WIDTH
The WIDTH command adjusts the width
specified value, which
is
WIDTH
72.
WIDTH
10
CALIFORNIA"
20
30
40
50
60
RUN
ACTION, OHIO; WEAVERTON, VERMONT; HOLLOWAY, CALIFORNIA
ACTION, OHIO;
AVERTON, VERMON
T;
LlFORNIA
Ok
expression
A$
=
PRINT
WIDTH
PRINT
WIDTH
END
HOLLOWAY,CA
is
"ACTION,
A$
15
A$
72
WE
an expression in the range
OHIO; WEAVERTON, VERMONT; HOLLOWAY,
of
the lines printed
15
to 255. The default value for
at
the console to the
If
the
is
6-24
Page 65

ABS
CHAPTER 7
FUNCTIONS
The ABS function returns the absolute value
absolute value
ABS(expression)
10
20
30
40
RUN
?5
10
Ok
RUN
?
-5
10
Ok
of
an
expression
INPUT A
A = ABS(A *2)
PRINT A
END
is
its numeric value with a positive sign.
Ase
The ASC function returns the ASCII code
string.
of
of
the specified expression. The
the first character
of
the specified
ASC(string
PRINT ASC
48
expression)
("0"),
ASC("AB")
65
ATN
The ATN function returns the arctangent value
result, given in radians,
single precision,
ATN(expression)
10
INPUT A
20
B = ATN(A)
30
PRINT B
40
END
RUN
?5
1.373401
Ok
but
is
between
the argument may be any numeric type.
-PI/2
and
PI/2.
of
the specified expression. The
The calculation
is
performed in
7-1
Page 66

Functions
BASIC-80
COBl
The CDBL(X) function changes the type
floating-point representation. In this format, calculations are accurate to
places, compared to an accuracy
of
of
expression (X) into double precision
16
decimal
7 decimal places in single precision floating-
point representation.
Many fractions (such as
1/3
and .1) cannot be precisely represented with either
single or double precision floating point, due to BASIC-80's internal numeric
representation.
CDBL(expression)
10
A#=1/3
208#=CDBL(1)/3
30
PRINT A#,B#
40
END
RUN
.333333343267441
Ok
.333333333333333
CHR$
The CHR$ function evaluates the expression to an integer and returns the equivalent
ASCII character. The expression must evaluate to an integer between 0 and 255.
CHR$
(expression)
In the program below, the CHR$(12) command generates a form feed in line 110.
110
PRINT CHR$(12)
120
PRINT
130
140
150
PRINT
PRINT
PRINT
"TABLE
A;8;C;D;E
2-5:
COMMONLY
USED
CONSTANTS"
CINT
The CINT(X) function rounds the expression into an integer value and returns that
value.
If
the expression
result.
NOTE: The FIX and INT functions also convert to integer Formats. FIX
truncates; INT truncates to
CINT(expression)
This program averages three numeric values and returns an integer result:
10
INPUT
20
PRINT
30
END
RUN
?
45,
24,77
49
is
less than -32768
A,B,C
(CINT((A+
an
integer argument.
8+C)/3))
or
greater than + 32767 then overflow will
7-2
Page 67

BASIC-80
Functions
cos
The COS function returns the cosine value
given in radians.
COS(expression)
10
INPUT
20
B = COS (A)
30
PRINT B
40
END
RUN
The
calculation
A
is
performed
of
the specified expression. The input
in
single precision.
?5
.2836621
Ok
CSNG
The CSNG(X) function changes the type
point representation. In this format, calculations are accurate
places, compared
floating-point representation.
Performing calculations in single precision
not
be as accurate.
CSNG(expression)
to
an
accuracy
of
expression into single-precision floating-
of
sixteen decimal places in double precision
is
faster than
in
double precision
to
seven decimal
but
is
may
10 A# =
20
RUN
.1666667
1.00/3.00
PRINT
CSNG
(A#)
12,
A#/2
.1666666666666667
CVI
CVS
eve
The CVI, CVS,
two character string into
ternal integer representation.
sion, and
fashion.
These functions are used to retrieve numeric values from a random file buffer field,
and are the reverse
CVx(string
AO/o
B!=2
C#=3
0$ = MKI$(AO/o)
A
% = CVI
B! = CVS (MIO$(O$, 3))
C# = CVO (MIO$(O$, 7))
PRINT A,
and
CVD functions convert strings into numbers. CVI converts a
CVD converts
of
MKI$, MKS$, and MKD$.
expression)
= 1
+ MKS$(B!) + MKD$(C#)
(0$)
B!,
C#
1 2 3
an
integer by simply moving the two characters into the in-
CVS converts a four character string
an
eight character string into double precision in a similar
to
single preci-
7-3
Page 68

Functions
BASIC-SO
DSKF
The DSKF function returns the number
specified disk. The examples below signify
free space on disk
DSKF
PRINT DSKF (1)
50
OK
1.
(drive
number)
EOF
The
EOF
function detects when the end
tial
data
file.
If
there are no more
At
TRUE.
any other time,
open, an error results.
EOF
(file
number)
10
OPEN
20
IF EOF(1) THEN
30
LINE INPUT
40
PRINT
50
GOT020
60
END
"1",1,
A$
"[F1:
#1,
EOF
PROGRAM]
60
A$
of
data
will return 0, indicating FALSE.
of
128-byte sectors
that
there are
the file
in
is
reached when reading a sequen-
the file, EOF returns a -1, indicating
50*
that
128,
are free
or
6.4 kilobytes
If
the file
on
is
the
of
not
ERL
The
ERL
function returns the number
It
is
normally used after an ON ERROR GOTO ... error trapping routine.
ERL
of
the line in which the last error took place.
The program below uses the error-trapping instruction in line
description in line
code number
error code
11:
10
ON ERROR GOTO
20
A =
30
END
40
PRINT
50
RESUME NEXT
RUN
PROGRAM ENDS IN LINE
Ok
40. This line also contains the function ERR, which displays the
of
the error. In this example the error
40
is
division by 0, which has the
1/0
"PROGRAM
ENDS IN
20
WITH ERROR
LlNE"ERL"WITH
11
ERROR"ERR
ERR
The
ERR
function returns the code number
gram execution.
of
the last error encountered during pro-
10
to print the error
7-4
ERR
Page 69

BASIC-SO
Functions
The following program asks for a divisor
trapping routine in lines
stopping the execution:
10
ON ERROR GOTO
20
INPUT
30
Z =
40
PRINT
50
GOTO
60
IF ERR
70
PRINT
80
RESUME
90
ON ERROR GOTO 0
100
RUN
WHAT
?045,9
QUOTIENT
WHAT
"WHAT
X/Y
"QUOTIENT
20
<>
"YOU
END
ARE THE NUMBERS TO DIVIDE?
ARE THE NUMBERS TO DIVIDE? 11,0
60-90 to prevent division by zero (which has code 11) from
60
ARE THE NUMBERS TO DIVIDE";X,Y
IS";Z
11
20
IS
OR ERL
CAN'T
5
<>
30
THEN
HAVE A DIVISOR OF ZERO!"
? 11,0
YOU
CAN'T
WHAT
HAVE A DIVISOR OF ZERO!
ARE THE NUMBERS TO DIVIDE?
?
EXP
The function
The specified value must be less than 88.7,
performed in single precision.
EXP(expression)
10
20
30
40
RUN
?5
148.4131
OK
?
EXP
returns the result
INPUT A
B = EXP(A)
PRINT B
END
of
raising e (2.71828) to the specified power.
and
a dividend, and uses the error-
90
or
overflow occurs. The calculation
is
FIX
The FIX function truncates numbers with decimal fractions to their integer value.
FIX
(number)
PRINT FIX (41.99999)
41
Ok·
FRE
The
FRE
function returns the number
argument (X)
returns the number
FRE (X)I(X$)
PRINT
22490
is
given.
FRE(X)
Ok
If
you give a string variable as a dummy argument (X$),
of
free bytes in string storage space.
of
bytes
of
memory left when the dummy
FRE
7-5
Page 70

Functions
HEXS
The
HEX$(X) function returns a string
hexadecimal value
to
32767,
handle arguments in
but
HEX$
(expression)
of
the integer argument. In BASIC-SO, integers are from -3276S
SOSO/SOS5
both
memory
ranges correctly.
of
hexadecimal digits which represents the
addresses go from 0 to 65535 decimal.
HEX$
BASIC-80
will
PRINT HEX$
Returns:
FFFF FFFF
HEX$
10
PRINT
20
PRINT "NEEDED FOR YOUR PROGRAM,
30
PRINT
40
INPUT A
50
A$
60
PRINT
INP
The
INP
function returns the value
expression.
INP
50
IF
60
IF
(-1),
HEX$
(65535)
(expression)
"TYPE
THE NUMBER
= H EX$(A)
"YOU'LL
The
expression must be
(expression)
INP(A) =
INP(A) = 7 THEN PRINT
NEED
12
THEN PRINT
OF
BYTES OF
";
A$;
"BYTES"
of
a byte from the
an
integer expression in the range 0-255.
"FORM
"BELL"
FEED"
SPACE"
IN
DECIMAL:"
input
port
specified by the
7-6
INPUTS
The
INPUT$
quential file. In the example below you
the console into sequential file #2.
the first
INPUT$ treats Carriage
INPUT$ (characters,
10
20
30
40
RUN
1234567890
1234567890
function reads
10
characters
OPEN
PRINT
CLOSE#2
END
"1",
IN
to
of
file #2, and CLOSE concludes the reading
Return
filenumber)
#2,
":CI:"
PUT$ (10,2)
(CR)
a specified number
The
like any other character.
of
characters from a specified se-
can
type in any ten
:CI: specifies console input. Line 20 prints
or
more characters from
of
the
data.
Page 71

BASIC-80
Functions
INSTR
The INSTR function searches for the first occurrence
and
within the first given string,
returns the first position of the second string as an
ordinal number. The optional argument, an expression I greater than
at
255, starts the search
conditions: if I
not
be found in the first string,
INSTR ([I,]
10
20
30
40
50
RUN
1
13
Ok
is
greater than the length of the first string, if the second string can-
string
A$ = "RANDOM
B$ = "R"
PRINT INSTR(A$, B$)
PRINT INSTR(3,A$, B$)
END
I characters. The INSTR function returns a 0 under three
or
if the first string contains no characters.
expression,
NUMBER
string
expression)
SUBROUTINE"
of
the second given string
0
and
less than
INT
The INT function returns the largest integer value less than or equal to the specified
expression. The sign
expression.
of
the returned value
is
the same as the sign
of
the specified
INT(expression)
10 INPUT A
20
B = INT(A)
30
PRINT A
40
END
RUN
? 18.0427
18
OK
RUN
? -234.98
-235
LEFT$
The string function .LEFT$(X$,I) evaluates the string
characters. I
LEFT$
10
20
30
40
RUN
WHITE, SMITH, JONES, BLACK, GREEN
WHITE, SMITH
Ok
is
an integer in the range 0-255.
(string
X$ = "WHITE,
Y$
= LEFT$(X$,11)
PRINTX$
PRINTY$
expression,
SMITH, JONES, BLACK,
expression)
X$
and returns the leftmost I
GREEN"
7-7
Page 72

Functions
BASIC-80
LEN
The string function LEN(X$) returns the length, in number
X$. All characters are counted, including non-printing characters
LEN (string
10
X$ = "JOHN
20
PRINT LEN(X$)
30
END
RUN
13
Ok
expression)
J.
JONES"
of
characters,
and
of
blanks.
string
LOC
The LOC function has two uses. When used with a random file, LOC returns the
current sector number. The current sector is defined as the last sector
or
written.
with a sequential file,
last
OPEN
If
no sectors have been read
LOC returns the number
statement was executed
LOC (file number)
10
OPEN
20
GET #3,44
30
PRINT LOC
40
END
RUN
44
Ok
"R",
#3,
(3)
:F1
:RANDOM
on
or
written, LOC returns to
of
sectors read or written to since the
that
file.
that
was read
O.
When used
LOF
The
LOF
function returns the number
with a sequential file, it returns the number
of
sectors in a random file. When LOF
of
the file.
LOF (file
PRINT LOF(4)
33
number)
LOG
The LOG function returns the natural logarithm
performed in single precision.
LOG(expression)
10
INPUT A
20
B =
LOG
(A)
30
PRINT A
40
END
RUN
?
2488
7.81924
Ok
data sectors
of
the argument. The calculation
(128
bytes per sector) in
is
used
is
7-8
Page 73

BASIC-SO
Functions
MID$
The MID$(X$,1. [,J]) function examines string
characters starting
is
specified, J characters are returned, starting
LEN(X$), the MID$ function returns the null string.
the number
of
rest
The MID$ (X$,
statement. Employed in this context, it will replace the characters
ning
X$
are replaced.
displayed. The length
of
the
string.
MID$(string expression, expression [,expression])
10
X$ = "JOHN
20
PRINT MID$(X$,10,3)
30
PRINT MID$(X$,9)
40
END
RUN
ONE
JONES
Ok
at
position I with the string given
10
A$ = "ABCDEF"
20
B$ = "XXYYZZ"
30
MID$(A$,2,4) =
40
PRINT
50
END
RUN
AXXYYF
Ok
at
pointer
characters in X$ to the right
1.
[,J]) function may also appear on the left side
If
I
of
A$
1. I and
J.
JONES"
is
greater then LEN(X$) , an illegal function call error
X$
is
never changed.
B$
J are integers in the range 1-255.
of
on
the right.
X$
and
returns the rightmost
at
position
I or
is
not specified, MID$ returns the
If
J is specified, J characters
1.
If
argument J
If
argument J
If
I
is
greater
is
greater
of
an assignment
of
string X$ begin-
than
than
of
is
MKI$
MKS$
MKD$
The three functions MKI$, MKS$, and MKD$ convert
numerical values into two-, four-,
convert
value; and MKD$
These functions are used to place numeric values into fields
See Chapter 5 for discussion
an
integer value; MKS$
is
used
to
MKI$ (integer)
MKS$ (single-precision value)
MKD$ (double-precision value)
or
eight-byte strings, respectively. MKI$
is
used
to
convert a single-precision floating-poinf
convert a double-precision floating-point value.
of
MKI$, MKD$, and MKS$
OCT$
The
aCTS
integer argument.
function returns a string
The
expression
OCT$
(expression)
10
PRINT "TYPE DECIMAL INTEGER
20
INPUT A
30
A$
= OCT$(A)
40
PRINT
A,"EQUALS,"A$,"
of
is
rounded to an integer before conversion.
octal digits which represent the value
TO
BE
CONVERTED."
IN
OCTAL."
data
represented as
is
used
of
random file buffers.
of
to
the
7-9
Page 74

Functions
BASIC-80
PEEK
The PEEK function reads a single byte from memory
corresponding
PEEK (expression)
PRINT PEEK(OFABH)
200
POKE statement writes a byte into a specified memory location.
P~S
The POS function returns the position
is
The argument I
POS (integer)
10
INPUT
20
PRINT A$;
30
IF POS(1) >
40
PRINT
RUN
?AAAAA
AAAAA
OK
RUN
?AAAAAAAAAAA
AAAAAAAAAAA
HAS
Ok
a dummy argument. The leftmost position
A$
10
HAS
JUST
"HAS
JUST
BEEN
THEN
JUST
INPUT
PRINT
BEEN
BEEN
of
INPUT"
INPUT
the cursor after the last PRINT statement.
at
the location specified. The
is
1.
7-10
RIGHTS
The RIGHT$ function returns the rightmost I characters
exceeds the length
RIGHT$ (string,integer)
10
A$ = "JOHN
20
X$
30
PRINT
RUN
JONES
J.
Ok
of
X$, the entire string
J.
JONES"
= RIGHT$(A$,8)
X$
is
the result.
If
of
string X$.
I
is
0,
a null string results.
If
I equals
RND
The RND function returns a single precision random number between 0 and
sequence produced
(such as in games) use
RND
is
identical every time a program
is
run.
RANDOMIZE to prompt the user for a seed.
If
this
is
undesirable
1.
or
The
Page 75

BASIC-SO
Functions
SGN
The SON function returns the sign
greater than 0, SON returns
sion
is
less
than
0, SON returns -1.
SGN(expression)
10
INPUT A
20
LET B = 3.14159*SGN(A)
30
PRINT B
40
END
RUN
?
44
3.14159
OK
RUN
?
-12
-3.14159
OK
RUN
1.
of
the specified expression.
If
the expression
?O
o
Ok
SIN
The SIN function returns the sine value
radians. The calculation
SIN (expression)
is
performed in single precision.
If
is
0, SON returns a 0.
of
the argument. The input
the expression
If
the expres-
is
given
is
in
10
INPUT A
20
PRINT SIN(A)
30
END
RUN
?8
.989358
Ok
SPACES
The SP ACE$ function returns a string
expression.
NOTE
SPACE$ returns an actual string.
SPACE$
10 A
20
30
40
50
RUN
QUESTION 1 THEORY
(integer
=1
PRINT "QUESTION";A;SPACE$(10);"THEORY"
PRINT
PRINT SPACE$(21);"TEXT"
END
expression)
of
spaces equal to the value
of
the integer
TEXT
7-11
Page 76

Functions
SPC
The
SPC
function returns a string
PRINT
not
PRINT
statement, as in the example below.
return
an
actual string, only a series
statement.
SPC (integer)
10
PRINT
20
PRINT SPC
30
PRINT SPC (15);"How many states are there in binary
logic?":PRINT
40
INPUT A$:PRINT:PRINT
50
IF
A$ = "2"
saR
The
SQR function returns
sion must evaluate
returned.
SQR
is
calculated in single precision.
SQR(expression)
(10);
"Question
THEN PRINT
the
square
to
be greater
of
spaces n characters long when used with a
SPC,
of
unlike the
spaces.
It
SP
ACE$ function, does
may
only be used with a
1 ":PRINT:PRINT
"Correct"
root
than
or
ELSE GOTO
of
the specified expression.
equal
to
zero,
or
750
an
error
The
message
BASIC·SO
expres-
is
The
program
then displays it:
10
20
30
below finds the square
INPUT A
PRINT SQR(A)
END
root
of
input A, which
RUN
?
45
6.70821
RUN
?
-1
ILLEGAL FUNCTION CALL
IN
20
STRINGS
The
STRING$ function returns a string
number
numeric code
plied, the first character
of
times.
If
an
integer argument
is
returned the specified
of
the string
STRING$ (expression, expressionlstring expression)
10
A$
= STRING$(10,97)
20
PRINT
A$
RUN
aaaaaaaaaa
OK
of
the same character repeated the specified
is
used, the ASCII character having
number
is
returned the specified number
of
times.
is
entered by the user,
If
a string argument
of
times.
is
that
sup-
7-12
10
A$=STRING$(10,"A")
20
PRINT
A$
RUN
AAAAAAAAAA
Ok
Page 77

BASIC-SO
Functions
STR$
The STR$ function returns a string
integer expression.
STR$ (expression)
10 FOR
20
30
40
RUN
0123456789
Ok
1=0
TO 9
A$
= A$ + MID$ (STR$ (I),
NEXT 1
PRINT A$
TAB
The TAB function spaces to
most column
tion
is
before spacing
PRINT
the expression rounds
TAB
10 FOR
20
30
is 1 and
beyond the specified column, TAB will force a carriage return, line feed
to
the specified column. This function may only be used with the
statement.
If
the expression rounds
(expression)
1=
1TO 4
PRINT T
NEXT
AS
(I); I
I
RUN
1
2
Ok
the
specified column position
the rightmost is the
to
over
WIDTH
3
4
of
decimal digits that represent the value
2)
at
the terminal.
WIDTH
to
value, TAB (expression
value.
a value less
If
the current
than
1,
MOD
TAB(1) results.
width) results.
The
print
of
the
left-
posi-
If
TAN
The
TAN
function returns the tangent value
is
radians. The calculation
T
AN
(expression)
10
20
30
INPUT
PRINT
END
A
TAN
performed in single precision.
(A)
RUN
?
41
.160656
Ok
USRn
The USRn function is used
or
Fortran-80 subroutine. The DEFUSRn statement specifies the starting address
for the corresponding
to
24;
if
no
argument is given, 0
the result.
Hand
L.
If
none
is
to
reference a user-defined assembly-language, PL/M-80
USRn subroutine.
is
assumed.
indicated, the result must be returned as
of
the argument. The input
The
argument n may
The
type character indicates the type
is
given in
be
any integer from 0
an
integer in registers
of
7-13
Page 78

Functions
BASIC-80
Only integers can be used as arguments; other variables must
This
is
done with the V
ARPTR
function, which returns the address
be
passed by reference.
variable.
Here
USR[$I#l%
is
an
example of how the USRn statement
10
CLEAR 1000, ODFFFH
20
DEFUSR4 =
30
A$ = "A
40
A =
50
A# = 14D-3
60
AO/o
70
B = USR ! 4 (VARPTR(A!),VARPTR(K1),VARPTR(R#),VARPTR(LA%»
1E4
=
12
I!][n]
[(parameter
OEOOOH
STRING"
... )]
is
used:
Arguments are returned in a similar fashion, unless the type character
which case registers
Appendix E gives details
Hand
L are used.
of
loading and running ASM-80,
PL/M-80,
FORTRAN-80 subroutines that may be called with USRn.
VAL
The VAL function returns the numerical value
represent a valid number,
V AL(X$) equals
O.
of
string X$.
If
the string does not
of
the specified
is
omitted, in
and
VAL
(string
10
INPUT A$
20
IF VAL(A$) = 0 THEN
30
A1
40
PRINT A1,
50
END
60
PRINT
70
GOT010
RUN
expression)
= VAL(A$) *
A$
"ENTER
60
52
NUMERIC
DATA
ONLY."
?4
208
4
VARPTR
The V
ARPTR
put/
output buffer associated with a file number.
assigned a value, an ILLEGAL
V
ARPTR
Arrays are passed
BASE 1
is
simple variables should be assigned values in a program before calling
any array; otherwise, allocation
all arrays to change. See Appendix E for further information about using V ARPTR.
VARPTR
function returns the address in memory of a variable
If
the variable has not yet been
or
the in-
FUNCTION CALL error results. The main use
is
to pass variable or array addresses to assembly-language subroutines.
by
in effect)
(variablel#file
specifying V
so
that
the lowest addressed element
ARPTR
of
a new simple variable
number)
(A
(0»
(or V ARPTR
of
the array
will
cause the addresses
(A(l»
is
returned. All
V
if
OPTION
ARPTR
of
for
of
7-14
Page 79

APPENDIX A
Table
Error
NEXT without
SYNTAX
RETURN without
Outof
Illegal function call
Overflow
Out
of
Undefined line number
Subscript
Duplicate Definition
Division by zero
Illegal
Type mismatch
Out
of
String too long
String formula too complex
Can't continue
Undefined user function
No
RESUME
RESUME
Unprintable error
FOR
ERROR
GOSUB_
DATA
memory
out
of
range
direct
string space
without error
BASIC-SO
A-I.
BASIC-80
Program contains no corresponding
NEXT
Illegal usage
No
GOSUB statement found to RETURN to.
All DATA statements
read,
tle data was included in the program.
Parameter passed to a function was out
Possible reasons:
1. A negative array subscript
2.
An
3.
LOG
4.
SQR
5.
AtB with A negative and B not
6.
A call to
DEFUSR
7.
Calls to MID$, LEFT$,
WAIT,
SPACES$, INSTR,
proper arguments
Variable with magnitude greater than
(single-precision
(double-precision floating-point)
Program too large, contains too many loops,
subroutines, variables, or complicated expres-
sions.
A referenced line does not exist.
You referenced
dimensions of the array, or referenced the wrong
number
You redimensioned
dimensioned.
A 'division by zero' operation was attempted.
An
instruction was used illegally in the Command
Mode.
A function which expects a string or variable was
given the wrong data type; any improper mix of
data types.
String variables are larger than the allocated
space. You can
String exceeds
String was too long or complex; break into two.
An
attempt was made to continue a program
where an error occurred, or after modifications, or
with no program.
Reference to a non-defined
An error trapping routine has no RESUME.
RESUME
routine.
No error message exists for the given error.
Check
of
or
BASIC-80 tried to read too much,
array
subscript>
with a zero
with a negative argument
PEEK,
of
dimensions.
statement
ERROR
Error
Codes
Description
delimiters, characters, etc.
in
the program have been
32767
or
negative argument
USR
before a corresponding
POKE,
floating-point)
an
an
increas~
255
characters.
statements for undefined errors.
RIGHT$,
TAB,
or
ON
array variable outside the
array previously
space with CLEAR.
USR
without
ERROR CODES
FOR
for
or
too lit-
of
range.
an
integer
INP, OUT,
SPC,
...
STRING$,
GOTO
with im-
or
1.7D308
function.
error-trapping
3.4E38
Number
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
A-I
Page 80

BASIC.80
Error
Codes
Table
A-I.
BASIC-SO
Error
Codes
BASIC-80
(Cont'd.)
Error
Missing operand
line
buffer overflow
FOR
without NEXT
FIELD overflow
Internal
Bad
File not found
Bad
File already open
Disk
File already exists
Disk
Input
Bad
Bad
Direct statement
Too many files
error
file number
file mode
1/0
error
full
past end
record number
file name
Description Number
An operator was given without
A program
for
the line buffer. Divide into two
A
FOR
corresponding NEXT
More than
FIELD statement.
An error occurred in
If this
Intel representative.
An unopened
A LOAD, KILL,
file not found on the specified disk.
One
1.
2.
3.
4.
An attempt to open
made.
A
disk
means a sector read check failed
File already exists.
All disk space is full. Delete old files
disk.
An
INPUT statement has been given after the
end-of-file; check INPUT operations with the
function.
The record number in a PUT or
An invalid ISIS-II filename was given.
in
file
A
direct
program into BASIC-80. The LOAD is terminated.
An attempt to open a new
opened.
or
data line has too many characters
statement
128
characters were allocated in a
error
cannot be accounted for, contact your
file was referenced.
of
the following conditions apply:
The file mode is other than
PUT
or
GET
Opening a random file for sequential output,
or
vice versa.
Performing a PRINT to a random file.
1/0
error has occurred on disk (x); this
statement was found while loading a
BASIC-80 internal execution.
or
OPEN
to
a sequential file.
an
an
operand.
or
more parts.
was
found
statement referenced a
already opened file was
GET
file after 6 files were
I,
0,
18
without
or
R.
times.
or
is >
2048
try new
EOF
or
<
O.
22
23
a
24
50
51
52
53
54
55
57
58
61
62
63
64
66
67
A-2
Page 81

APPENDIX B
BASIC-SO
The following list shows 126 words that cannot be used
attempt to
one or more alphanumeric characters, the first
than
ABS
AND
ASC
ATN
ATTRIB
AUTO
BASE
CDBL
CHR$
CINT
CLEAR
CLOSE
CO
NT
COS
CSNG
CVD
CVI
CVS
DATA
DEF
DEFDBL
DEFFN
DEFINT
DEFSNG
DEFSTR
DEFUSR
DELETE
DIM
DIR
DSKF
EDIT
ELSE
END
EOF
EQV
ERASE
ERL
ERR
ERROR
EXIT
EXP
FIELD
FIX
do
so, errors,
two characters are given, the rest are ignored.
error
messages, or both will result. A valid variable name
of
FN
FOR
FRE
GET
GOSUB
GOTO
HEX$
IF
IMP
INP
INPUT
INPUT$
INSTR
INT
KILL
LEFT
LEN
LET
LINE
LIST
LOAD
LOC
LOF
LOG
LSET
MERGE
MID$
MKD$
MKI$
MKS$
MOD
NEW
NEXT
NOT
NULL
OCT$
ON
OPEN
OPTION
OR
OUT
PEEK
POKE
which must be a letter.
RESERVED WORDS
as
names
of
variables.
POS
PRINT
PRUN
PUT
RANDOMIZE
READ
REM
RENAME
RENUM
RESUME
RESTORE
RETURN
RIGHT$
RND
RSET
RUN
SAVE
SON
SIN
SPACES$
SPC
SQR
STEP
STOP
STR$
STRINOS$
SWAP
TAB
TAN
THEN
TO
TROFF
TRON
USING
USR
VAL
VARPTR
WAIT
WIDTH
XOR
If
If
you
more
is
B-1
Page 82

Page 83

APPENDIX C
BASIC-80
BASIC-80 has certain single control characters (characters produced by pressing the
letter and the
immediately. These characters are listed below.
To
edit the last line entered:
To
halt program execution and return
level:
To
tab across the line:
To
resume program execution after it
Control-S:
To
halt program execution until Control-Q
entered:
To
erase the current line:
To
retype the current line:
CONTROL key simultaneously) that cause something to happen
COMMAND
CONTROL-A
to
command
CONTROL-C
CONTROL-I
is
stopped by
CONTROL-Q
is
CONTROL-S
CONTROL-X
CONTROL-R
CHARACTERS
To
disable display to the terminal (until
CONTROL-O
completion):
is
given again or the program runs to
CONTROL-O
C-l
Page 84

Page 85

APPENDIX D
Table
D-l.
ASCII Code List
Decimal Octal Hexadecimal Character Decimal
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
0
1
2
3
4
5
6
7
8
9
000
001
002
003
004
005
006
007
010
011
012
013
014
015
016
017
020
021
022
023
024
025
026
027
030
031
032
033
034
035
036
037
040
041
042
043
044
045
046
047
050
051
052
053
054
055
056
057
060
061
062
063
064
065
066
067
070
071
072
073
074
075
076
077
00
01
02
03
04
05
06
07
08
09
OA
08
OC
00
OE
OF
10
11
12
13
14
15
16
17
18
19
1A
18
1C
10
1E
1F
20
21
22
23
24
25
26
27
28
29
2A
28
2C
20
2E
2F
30
31
32
33
34
35
36
37
38
39
3A
3B
3C
3D
3E
3F
NUL
SOH
STX
ETX
EOT
ENQ
ACK
BEL
BS
HT
IF
VT
FF
CR
SO
SI
OLE
DC1
OC2
OC3
DC4
NAK
SYN
ETB
CAN
EM
SUB
ESC
FS
GS
RS
US
SP
!
"
*
$
%
&
,
(
)
*
+
,
-
I
0
1
2
3
4
5
6
7
8
9
,
<
=
>
?
64
65
66
67
68
69
70
71
72
73
74
75
76
n
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
Octal
100
101
102
103
104
105
106
107
110
111
112
113
114
115
116
117
120
121
122
123
124
125
126
127
130
131
132
133
134
135
136
137
140
141
142
143
144
145
146
147
150
151
152
153
154
155
156
157
160
161
162
163
164
165
166
167
170
171
172
173
174
175
176
177
ASCII
Hexadecimal
40
41
42
43
44
45
46
47
48
49
4A
48 K
4C
40 M
4E
4F
50
51
52
53
54
55
56
57
58
59
5A
58 [
5C
50
5E
5F
60
61
62
63
64
65
66
67
68
69
6A
68 k
6C
60
6E
6F
70
71
72
73
74
75
76
77
78
79
7A
7B
7C
70
7E
7F
CODES
Character
@
A
8
C
D
E
F
G
H
I
J
L
N
0
P
Q
R
S
T
U
V
W
X
Y
Z
)
A
-
,
a
b
c
d
e
f
9
h
i
j
I
m
n
0
P
q
r
s
t
u
v
w
x
Y
z
{
I
}
-
DEL
D-l
Page 86

ASCII
Codes
BASIC-SO
Table D-2. ASCII
Abbreviation Meaning
NUL
SOH Start
STX Start
ETX End
EaT
ENQ Enquiry
ACK Acknowledge
BEL Bell 7
BS
HT Horizontal Tabulation
LF
VT
FF
CR
SO
SI
OLE
DC1
DC2
DC3
DC4
NAK
SYN Synchronous Idle
ETB End
CAN Cancel
EM
SUB
ESC Escape
FS
GS
RS
US
SP
DEL
NULL Character
End
Backspace
Line Feed
Vertical Tabulation
Form Feed
Carriage Return
Shift Out
Shift
Data Link Escape
Device Control 1
Device Control 2
Device Control 3
Device Control 4
Negative Acknowledge
End
Substitute
File Separator
Group Separator
Record Separator
Unit Separator
Space
Delete
Code
Definition
of Heading
of
Text
of
Text
of
Transmission
In
of
Transmission Block
of
Medium
Decimal
Code
0
1
2
3
4
5
6
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
127
D-2
Page 87

APPENDIXE
CALLING NON-BAStC-SO
SUBROUTINES
You can write a subroutine in FORTRAN-SO, PL/M':SO,
language, convert it into relocatable code, load
directly from BASIC-SO. Any number
PL/M
You will need the ISIS-II User's Guide and the publication relevant to the language
you use for the subroutine. The preface lists the Programming and
manuals for FORTRAN-SO, PL/M-SO, and
conventions for passing parameters
of
it
into free memory, and access
variables can be referenced, following
to
subroutines.
SOSO/SOS5
or
SOSO/SOS5
assembly language.
assembly
it
Operator's
Preparing Subroutines
Once you have written the desired subroutine, follow the instructions in the
appropriate compiler or Assembler
your source language.
or
The compiler
starting address
starting address you can use, as well as the total free memory space.
4SK
A
a highest usable address
taken by the monitor
Intellec system has the highest usable address
assembler
in
Intellec system memory.
output
of
OF6BFH. Higher-addressed memory in both systems
and/or
Operator's Manual
is
a relocatable object code. This code
monitor RAM.
To
to
generate object code from
is
given a
do this, you must know the highest
of
OBEBFH. A
64K
system has
is
When you invoke
The size
Suppose you have a 64K
usable memory address
it must start
OEECOH,
option when you invoke BASIC-SO. MEMTOP specifies the highest
BASIC-SO
OEECOH,
If
looks like this:
If
the most economical use
and strings.
of
your main program
and you
leaving the space fromOEECOH-OF6COH for your subroutine.
-:F1
:BASIC MEMTOP
ISIS-II BASIC-80
22620
you invoke BASIC-SO
-:F1:
ISIS-II BASIC-80
24668
you locate your program as high as possible in free memory,
BASIC-SO, it immediately returns the free memory space in bytes.
and
subroutine(s) must
system,and a 2K
is
OF6BFH.
at
OEECOH. You must
~ust
forbid
may use. In the example below, MEMTOP specifies a boundary
BYTES FREE
on
a 64K Intellec System without specifying MEMTOP, it
BASIC
BYTES FREE
of
its remaining workspaces for string constants, variables,
If
you place your program next to the monitor,
besure
BASIC-SO
(OEECOH)
byte
that there
to use this space with the MEMTOP
be
less than the free space.
(SOOH)
subroutine. The highest
is
2K
of
space available
BASIC-SO
RAlVI
can make
at
address
at
E-I
Page 88

Calling Non-BASIC-80 Subroutines
When you have determined the optimum starting address for your subroutine, you
can
LOCATE
it
there with this command. LOCATE converts the relocatable object
code to absolute object code, according to the starting address given. An example
giving the starting address for your subroutine code
is
shown below.
BASIC-80
of
LOCATE
This example converts the relocatable object code in
object code in the
subroutine relative
:F1
:PLMSUB.OBJ
output
to
OEECOH. Refer to the ISIS-II User's Guide for further details
file
TO
:F1
:PLMSUB.LD
:Fl
:PLMSUB.LD, and makes all addresses in the
CODE
:Fl
:PLMSUB.OBJ to absolute
(OEECOH)
of using LOCATE.
LOCATE has converted your relocatable code to absolute object code, you
After
can load it into memory with the
DEBUG followed
enter
by
the filename
ISIS-II Monitor DEBUG command. When you
of
the load module, the subroutine
is
loaded
into memory at the address specified in the load module. The starting address
displays
subroutine loaded
on
your terminal. You then enter GS, which returns you to ISIS-II with the
at
the specified address. From here.you can invoke
BASIC-SO
and
call the subroutine.
NOTE
You must give the MEMTOP option to reserve memory each time
BASIC-SO
is
invoked.
Calling Subroutines
After a subroutine
invoke
BASIC-SO as you normally do, and give the MEMTOP option as previously
specified.
is
loaded into memory, you can call it from BASIC-80. First,
is
The first step in calling a subroutine
tion. Up to
0-24. The starting address
25
subroutines can be addressed in this way, with an integer in the range
DEFUSR5=OEECOH
of
the subroutine
Once BASIC-SO knows where USR5
must supply any needed variables.
PL/M
addresses.
the
pass the addresses
BASIC-SO
where
conventions, you can only directly pass 2-byte integer variables or 2-byte
If
you specify a floating-point variable
V
ARPTR
120
function to pass the address
of
two floating-point numbers (Kl and
A = USR5 (VARPTR(K1), (VARPTR(K2»
goes to the address where
K2
is
stored (VARPTR(K2». Once it has found these two values, it passes
defining its address with the DEFUSR func-
is
given in hexadecimal:
is
located, you can call it. When you call it, you
Since the protocol for passing parameters follows
or
a string variable you must use
of
the desired variable.
For
example, to
K2):
Kl
is
stored (VARPTR(Kl) and the address
them to the subroutine.
If
BASIC-SO
locations
encounters new variables after executing line
of
Kl
and
K2
can change, causing errors.
120
above, the memory
Be
sure that all variables are
defined before using the VARPTR instruction.
In the example shown, once the parameters are passed, the subroutine executes.
of
Because
PL/M-80
a two-byte integer in the
calling conventions BASIC-80 expects the returned result to be
HL
register-pair, and assigns this 16-bit value to A.
E-2
Page 89

BASIC-80
Calling Non-BASIC-80 Subroutines
To return a single-precision floating-point, double-precision floating-point,
or
string result, you must use the appropriate data type character (see table
2-5
for a list
function.
of
these characters) before the subroutine number in the USR
For
example, to tell
BASIC-SO
that a user-written subroutine
returns a double-precision floating- point value:
240
A# = USR
#15
(VARPTR(L#), A1)
In this example, the sharp sign (#) following USR tells
S-
byte space for the double-precision result
of
USR #15. A#
BASIC-SO
is
to reserve an
also defined as
double- precision, but the parameters passed may be of any numeric type.
Your subroutine must interpret the
of
address
A#, and it must also place the result
References to string parameters are handled in a similar manner.
string
is
the address
of
the string descriptor,
subroutine returns a string then the user should code
255-character string and pass the address
first
parameter passed to it as the storage
of
USR
#15
there.
V
ARPTR
not
the string data. Thus if a user
USR$[n]. BASIC allocates a
of
the string descriptor to the subroutine.
of
Your routine may change the string length in the string descriptor to return a shorter
string,
but
may not change the string's address. Neither parameter strings nor
parameter string descriptors should be changed.
Array variables are passed as parameters by referencing the first element
BASIC-SO follows row-major order.
array.
To code in
8080/S0S5 assembly language, you must know the Intel format for
of
the
representing integer, single-precision floating-point, and double-precision floating
E-l
point numbers. Figure
~~D~ESS
ILS_f_I~~I
________________
shows these representations.
1_5_B_IT_S_O_F_DA_T_A
________________
LOW
ADDRESS
~
a
INTEGER
REPRESENTATION: 2 BYTES,
8
EXPONENT
11
EXPONENT
8
LENGTH
STRING DESCRIPTOR REPRESENTATION: 8
16
BITS, STRING ADDRESS.
DATA DATA
BITS
SINGLE-PRECISION FLOATING·POINT
4
BYTES,
32
BITS,
LOW
BITS
DOUBLE-PRECISION FLOATING-POINT
BYTES,
84
BITS,
LOW
STRING
DATA REPRESENTATION: 8
ORDER
ORDER
16
BYTE
BYTE
Figure B-1. Internal Representation
BITS,
LOW
ORDER
BYTE
23
MANTISSA
REPRESENTATION:
FIRST
52
MANTISSA
REPRESENTATION:
FIRST
BITS,
DATA
of
BITS
BITS
ADDRESS
STRING
LENGTH:
DATA
BIT
BYTES.
Numbers and Strings
FIRST
E-3
Page 90

Calling Non-BASIC-SO Subroutines
Some Real Examples
The three sample programs provided in Figures E-2, E-3, and E-4 show how the
subroutine-
same
PL/M-SO,
and
three parameters.
adding three integer
SOSO/SOS5
arguments-can
assembly language. Notice
be coded in FORTRAN-SO,
that
each program requires
BASIC-80
Once you have processed your subroutine through the PL/M-SO
compilers,
object code and place it in memory with the
filename
subroutine code. In the example below ,
whose first byte
-LOCATE
or
through the
SOSO/SOS5
assembler, you can convert it to absolute
LOCATE command. You must give the
of
your relocatable code file and the proper starting address for the
LOCATE returns absolute object code
is
at
address
:F1
:PLMSUB.OBJ
OEOOOH:
CODE
(OEOOOH)
or
FORTRAN-SO
This command returns the absolute object file :Fl:PLMSUB. You can now load this
located code into Intellec memory
at
its proper address with the monitor DEBUG
command. When you enter the DEBUG command with your filename, you invoke
the Monitor, as shown in the example below. The Monitor responds with a period
(.), expecting further commands:
-DEBUG:F1
#0000
:PLMSUB
You can now return to ISIS-II and test your subroutine. Leave the Monitor and
return to
ISIS-II by entering
.G8 (CR)
ISIS-II Vm.n
Invoke BASIC-SO, and specify the highest memory address
MEMTOP option:
the
GS
and a carriage return after the period:
BASIC-SO
can use with
-:F1
:BASIC MEMTOP(ODFFFH)
This prevents BASIC-SO from writing over your subroutine.
and tell you how much free memory you have left:
ISIS-II BASIC-80 V1.0
18157
BYTES FREE
Once in
BASIC-SO program defines your subroutine as
BASIC-SO
you can write programs that use your subroutine. The following
USRl,
asks for three integers, passes
these three integer values to the subroutine, defines the result
the variable
10
20
30
40
50
60
70
80
90
100
110
RESULT,
REM THIS PROGRAM ASKS
REM INTEGERS, PASSES THEM TO USR1, AND
REM RETURNS THE RESULT.
DEFINT A-Z
DEFUSR
PRINT"ENTER THREE
INPUT
PRINT"
RESULT=USR%1(VARPTR(A), VARPTR(B), VARPTR(C»)
PRINT"A+B+C=";
END
and
1=OEOOOH
A,B,C
A="
,A,
finally prints RESULT:
FOR
THREE
NUMBERS:"
"B="
,B,
"C="
,C
RESULT
BASIC-SO
of
will appear
the subroutine as
E-4
Page 91

BASIC-SO
Calling Non-BASIC-SO
Subroutines
ASN8B.OY3
ISIS-II
Lce
BBIS
BBBI
BSB4
BSB?
BIBA
IBBB
BBBC
BBBF
BBl8
B813
BB14
BUS
B81'
BB17
BU8
BBlB
BIIC
BII0
BIlE
BI
B82B
8121
B822
B823
BBBB
:Fl:USRASH.ASH
8181/8185
09J
El
229BBB
21BBBB
COICBB
5B
59
COICBI
01
CDICBB
EB
El
73
23
72
2AIBBB
E9
E5
EB
5E
IF
23
5'
El
19
C9
88BB
BBBB
PUBLIC
SYMBOLS
USRASH C BBBB
"ACRO
D
C
C
C
o
C
SEQ
1
2
3
4
S
6
7
8
9
IB
11
12
13
14
15
16
17
18
19
2B
21
22
23
24
25
26
27
28
29
38
31
32
33
34
3S
36
37
38
39
ASSEHBLER.
ASSE"BLER
Y2.1
SOURCE
STATE"ENT
ROUTINE
RESULT=ARGA+ARCB+ARCC
IGNORE
OVERFLOW
NAHE
PUBLIC
CSEC
USRAS
..
:
POP
SHLO H RETADR
LX
CALL
"CY
"Cy
CALL
PCP
CALL
H.8
I
AODDE
D.B
E.C
ADDDE
o
AODOE
XCHG
ADD
ROODE:
PCP
"CY
INX
"CY
LHLD
PCHL
2
BVTES
CHANCES
PUSH
H
PI.
H
H,D
RE"TADR
;
RETURN
ADDRESSED
A.D,E.H,L
H ;SAVE
XCHG
"o.Y
IN
HOV
PCP
DAD
E.H
X
H
0,"
H
o
RET
DATA
AREA
OSEG
RETAOR:
OW
END
B
USRASH
E
USRAS"
TO
TEST
;RETURN
;5ET
;
iAOD
i"OVE
iAOD
; ADDRESS
iADD
;TOTAL
JADDR
;LOW
;HI
; RETURN
;AODR
;LOW
;HI
;OLO
;
;SAVED
SET
BY
ADD
BASIC
ASIDE
TCTAL
ARCC
AOOR
ARCB
AReA
IN
o.F
BYTE
BYTE
DE
TO
TOTAL
IN
BYTE
BVTE
TOTAL
TO
RETURN
PACE
USR
AOOR
TO
8
TO.
TOTAL
o.F
ARCB
TO.
To.TAL
OF
ARG.A
TO.
To.TAL
DE
RESULT
OF
RESULT
OF
RESULT
ADDRESS
HL
L
TO
BE
TO.
BE
TOTAL
ADDRESS
TO
ADDED
ADDED
DE
EXTERNAL
USER
SY"BCLS
S'/HBOLS
AODDE C BBIC
ASSE"BLY
CO
..
RETAOR 0 BIBB
PLETE.
NO
ERRORS
USRAS" C BBBS
Figure E-2. 8080/8085 Assembly Language Program
E-5
Page 92

Calling
Non-BASIC-SO
Subroutines
BASIC-SO
ISIS-II
OBJECT
COMPILER
2
3
4
5
6
CODE
VARIABLE
~AXI"U"
11 LINES
a
PL/H-8B
",oDULE
INVOKED
1
2
2
2
2
1
AREA
STACK
PROGRAM
Vl.l
PLACED
COMPILATION
IN
BY:
PLH8B
:Fl:USRPLM.OBJ
:Fl:USRPLH.PLH
PLM:$HODULE:
DO;
USRPLH:
DECLARE
DECLARE
ARCA
ARCS
ARCC
PROCEDURE(PRESULT,PARGA;PARGB,PARGC);
(PRESULT,PARGA,PARGB,PARGC)
(RESULT
BASED
BASED
BAseD
RESULT=ARGA+ARG8+ARGC;
END
END
SIZE
AREA
USRPL";
PLIUHOOULE;
BB32H
SIZE
SIZE
BlUSH
BBB4H
READ
ERROR(S)
Figure E-3.
PL/M-80
OF
MODULE
BASED
PARCA.
PARCB.
PARCe)
SBD
SO
40
PLHHODULE
ADDRESS;
PRESULT~
ADDRESS;
Program
E-6
FORTRAN
1
2
3
4
CODE
VARIABLE
HAXI"UH
4
B
B
END
COMPILER
AREA
STACK
LI
NES READ
PROGRAM
TOTAL
OF
FORTRAN
PROGRAM
FUNCTION
IRTN(IARCA,IARGB,IARCC)
IRTH=IARGA+IARG8+IARGC
RETURN
END
SIZE
AREA
SIZE
SIZE
ERROR(S)
BB20H
OBB8H
BBB4H
IN
PROGRAM
450
UNIT
ERROR(S)
COMPILATION
Figure E-4. FORTRAN-80
SO
40
IRTN
Program
Page 93

APPENDIX F
RMX/SO
This appendix describes the differences between the
and the ISIS-II version,
generating disk-based or ROM-based versions
mended that you refer to the
for supplementary information.
Guide
What
The
Multi-Tasking Executive. With
computational
System, and apply them to solving a wide range
The
BASIC-SO modules, coded to run as tasks under RMX/SO, are supplied on both
single- and double-density diskettes. You can edit these modules with the
Text Editor or CREDIT, and combine them with
tasks. You use the Intellec Development
BASIC-SO
is
RMX/80
RMX/SO
iSBC
BASIC-SO Interpreter (iSBC
and
S02
software package gives you
tailor-made for your iSBC-based microcomputer system.
and
tells you the requirements and procedures for
RMX/SO
User's Guide and RMX/SO Installation
BASIC·80?
S02)
RMX/SO
input!
output capabilities of the iSBC/SO Microcomputer
BASIC-SO, you can easily use the powerful
RMX/SO
System to create a version
RMX/SO
of
RMX/SO
runs under the
of
application problems.
BASIC-SO
RMX/SO
version
BASIC-SO.
RMX/SO
in two forms. First,
and user application
BASIC-SO
of
BASIC-SO
It
is
recom-
Real-Time
ISIS-II
of
RMX/SO
This first
RMX/SO
describe how to configure your own
frequent references to the following publications:
("configure your
software and be familiar with its use. The portions of this appendix that
own")
option requires you to have a copy
RMX/SO
BASIC-SO
system will therefore make
of
the
RMX/SO User's Guide, manual order no. 9S00522
RMX/SO Installation Guide, manual order no.
Second, if you want
tional software routines, you can use the predefined
tion. This configuration includes three parts:
• The executable object module RMXSYS, supplied on both the single and double
density diskettes.
• Two boot strap PROMs that load RMXSYS into the iSBC memory.
• A cable that connects the iSBC 204 disk controller to the bulkhead connector
any Intellec disk drive chassis.
With this predefined version, you have a version
RESTART on your iSBC hardware configuration. You need only make the
necessary hardware connections, and
You should be aware
and ISIS-II based BASIC-SO. These are:
• Configuring the
available to the
figuration provides
• You must also specify the number
configure the
at
files
once.
an
"instant-on" BASIC-SO system, and have no need for addi-
BASIC-SO
of
the major differences between
RMX/SO
BASIC-SO interpreter and the program source. The sample con-
S.4K bytes
RMX/SO
modules determines how much memory will be
of
memory space.
of
modules. The sample configuration supports 6 open
9S030S7-01
RMX/SO
of
is
ready to run.
files available to BASIC-SO when you
BASIC-SO
RMX/SO
RMX/SO
configura-
on
that
appears on
based BASIC-SO
F-l
Page 94

RMX/SO
BASIC-SO
• With RMX/SO BASIC-SO, you can create BASIC programs and program them
PROMs for permanent reference.
into
• You can configure RMX/SO to execute a PROM-resident
immediately
•
If
you wish to interrupt program execution when
the console, you must enter
on
restart.
BASIC-SO
CONTROL-C followed by a carriage return.
wish to interrupt a program that has been stopped by a
BASIC-SO
expects input from
CONTROL-S, type
CONTROL-C followed by CONTROL-Q.
• RMX/SO BASIC-SO
does not have the EDIT Mode features supported by
ISIS-II BASIC-80.
• RMX/SO
BASIC-SO
supports only the console and disk files.
program
If
you
BASIC-SO
You should also be aware
of
two similarities between RMX/SO
BASIC-SO
ISIS-II BASIC-SO:
The
data
•
formats
(DFS) are identical. You can create
on
them
•
If
that
the other.
you use a random file
disk and insert another, you may destroy files on the new disk. You can
and
protocols
of
the ISIS-II
data
or
open a file for output
and
RMX·/SO
disk file systems
or program files on one system and use
on
one disk, and then remove
open files for input without problems.
Initializing
RMX/SO allows many different configurations
PROMs that you can use to load BASIC-SO from disk and to execute it.
the
Predefined RMX/SO BASIC-SO Configuration
of
its modules. Intel supplies two
If
the required hardware, as listed below, you can quickly run the predefined
BAS I
C-SO
configuration.
•
An
iSBC 80/30 Single Board Computer
• An additional32K bytes
•
An
iSBC
204
Disk Controller.
•
An
MDS-2DS Disk Drive attached through the cable supplied with the
of
RAM
on
two iSBC 016s, or one iSBC 032 board.
BASIC-SO package.
•
An
RS-232C compatible terminal.
• An iSBC chassis
and
power supply
and
you have
RMX/SO
F-2
If
you have the required hardware, it must be configured as shown below. Refer to
RMX/SO Installation Guide if you must alter your present configuration. Table
the
F-l
shows the jumper configurations described in the following paragraphs.
1.
The iSBC SO/30
board
must be wired to conform to the RMX/SO terminal
handler interrupt structure. This requires the wiring changes listed in Table
Check your iSBC SO/30 board to verify that these changes have been made. For
further information, refer to the
2. The iSBC on-board PROMs must be addressed at locations
RMX/SO User's Guide.
OOOO-OFFF.
This
the factory-wired default configuration. These default jumper settings are
shown in Table
Board Computer Hardware Reference Manual,
3.
The iSBC SO/30 on-board RAM must be addressed at locations 4000H-7FFFH.
This
is
the factory-wired default configuration. These default jumper settings
are shown in Table
that disables off-board access
to the
iSBC 80/30 Single Board Computer Hardware Reference Manual,
F-l.
F-l.
For
further information, refer to the iSBC
chapter 2.
Jumper IS0-171
of
on-board RAM.
is
a factory-wired default configuration
For
further information, refer
SO/30
Single
chapter 2.
F-l.
is
Page 95

BASIC-SO
Table
F-l.
Sample Configuration Jumper Wiring
RMX/SO
BASIC-SO
Board
iSBC 80/30
Handling
iSBC 80/30 PROM
Addressing
OOOOH-OFFFH
iSBC 80/30 RAM
Addressing
4000H-7FFFH
iSBC016 RAM
Addressing
8000H-OFFFFH
iSBC
AddreSSing
204
Interrupt
Base
Connect
131-152
141-132 (EVENT
47-51
(ClK
143-127 (RXR INTR-IR
142-126
145-140
145-139
112-113
157-158
100-101
104-103
155-156
86-85
98-92
180-171
W1
at
Board 1
Board 2
Settings·
S2
7
ON
OFF
6
OFF
5
4 OFF
Jumper
(INTERRUPT
(TXR INTR-IR
(Ground INTR 5.5)
(Ground
position
ClK-IR1)
0-A12-11)
INTR 6.5)
A-B
-7-6
-7-5
Remove
2)
123-138 (COUNT OUT-INTR 7.5)
46-47
(ClK
7)
6)
47-52
(ClK
1-ClK
O-ClK
Jumpers
0)
2)
*These
the
4.
5.
numbers
switch
If
you are using two iSBC 016 Random Access Memory boards, you must
jumper one to supply RAM memory from locations
other to supply RAM from locations
jumpers.
at
locations 8000H-OBFFFH. On the other board jumper
nected, enabling memory
16K
RAM
The iSBC
interrupt level 2. The base address
S2 are shown in Table
refer
to
the
silk-screened
bank.
numbers
on
the
PC
board,
not
to
the
numbers
8000H -OBFFFH and the
OCOOOH
to OFFFFH. Table
F-llists
On one board, jumper 7-6 must be connected, which enables memory
7-5
must be con-
at
addresses
OCOOOH-OFFFFH.
Refer to the
iSBC
Board Hardware Reference Manual for further information.
204
Disk Controller must be set to base address 80H and set
is
F-l.
Interrupt level 2
set by switch
S2.
The four switch settings
is
the factory-wired default configuration. To verify interrupt level 2 operation, check for a wire jumper connecting terminal posts
information, refer to the
Reference Manual,
6.
The iSBC 204 Disk Controller must be the highest priority bus master. You can
place the
iSBC 204 in the top chassis slot with the iSBC
or you can rewire the chassis backplane appropriately (see the
ware
Reference Manual for details). The supplied cable attaches from
204 controller to the plug
iSBC
63
and 67. Table F-l lists these connections. For further
iSBC
204 Flexible Diskette Controller Hardware
chapter 2.
80/30
directly under it,
iSBC
on
the rear
of
the MDS-2DS disk drive.
80/30 Hard-
11
these
016
of
the
on
at
of
F-3
Page 96

RMX/SO BASIC-SO
BASIC-SO
When you have configured your system, follow these steps
1.
Insert the supplied
80/30.
2.
Turn
on
power to the disk drives and iSBC system.
3. Insert your single density
4. Type
an
upper case U
RMX/80 BASIC-80 Vm.n
PROMl
at
in socket 0 and PROM2 in socket 1
BASIC-80 disk into drive
the terminal keyboard until the sign-on notice prints:
to
initiate BASIC-80:
O.
of
the iSBC
Generating Boot-Loaded and PROM-Based Versions of
RMX/SO
Intel supplies two diskettes with the following modules. One diskette
sity; the other double density. You can modify and configure these modules to suit
many possible combinations
BASIC-SO
of
hardware and software.
is
single den-
BASIC-80 Source Files
BOOPS.ASM This module contains options used by other assembler modules.
of
Figure F-I shows a sample listing
BOOTCM.ASM This module configures the BASIC Boot Loader.
BOBMEM.ASM This module allocates memory for the BASIC Boot Loader.
BASCM.ASM This module configures BASIC.
BOMEM.ASM This module allocates memory for BASIC.
this module.
BASIC-80 Object Files
BASIC.LlB This library contains all modules used by BASIC except for the
following, which are generated by assembling the corresponding
.ASM modules:
BOOTCM.OBJ
BOBMEM.OBJ
BASCM.OBJ
BOMEM.OBJ
CLOCK.OBJ
This module
is
a dummy clock module used with the iSBC 80/10.
BASIC-80 Executable Files
BOBOOT This module
PROM.
RMXSYS
This module
by the Boot Loader.
Software Requirements
You must have the following software tools and modules available in the appropriate drives to generate versions
Drive
0:
In drive 0, you must have a disk with these modules:
ISIS-II
All
Link, Locate, and the
is
the Boot Loaded system, which
is
the version
for
Generating
of
V3.4 (or later version)
of
the modules described above.
of
RMX/SO BASIC-80 which
RMX/80
BASIC-80.
ASMSO
is
also provided
BASIC-80
Macro Assembler
is
loaded
on
F-4
Page 97

BASIC-80
RMX/80
Drive 1: In drive I, you must have a disk with these modules:
RMX/SO nucleus, factory-configured for an iSBC
The
SO/IO,
SO/20,orSO/30.
The RMX/SO extension files, including the Disk File System,
and the RMX/SO Boot Loader files for the appropriate
CPU
board.
Once these two disks are present in the proper drives, you can begin configuring
your
RMX/SO BASIC-SO version. We'll look
kinds
of
BASIC-SOs-a
boot-loaded version and a PROM-based version.
at
procedures and examples
of
two
BASIC-80
Generating a Boot-Loaded
The software requirements
RMX/80
for
generating a boot loader and a compatible version
BASIC-80
of
BASIC-SO are listed above. You must have the two disks in their proper drives with
on
the given modules
The hardware requirements for the
each disk.
boot
loader and its accompanying version
of
BASIC-SO are:
An
iSBC 201, iSBC 202, iSBC 204, or iSBC
206
Disk Controller, with its
necessary cables, and the disk drives it controls.
An
iSBC SO/IO, iSBC SO/IOA, iSBC SO/20, iSBC
At
least
4SK
bytes
of
RAM if DFS
If
you use
total.
An
RS-232C compatible terminal, and accompanying cables.
an
iSBC SO/30, the
You can use any combination
There are three steps to generating a
1.
You must examine and,
2.
You must also examine the BOOTCM
if
necessary, modify the BQOPS.ASM module.
is
used, or
16K
bytes
of
of
iSBC RAM boards.
boot
loader
and
32K
SO/20-4,
bytes
or
of
RAM if
iSBC SO/30.
it
is
not
used.
RAM on-board count toward the
for
RMX/SO BASIC-SO:
BQBMEM modules and modify
them as needed.
3.
After you have verified that the various assembly modules accurately reflect
your hardware and software configurations, you
SUBMIT the GBOOT.CSD
module, shown in figure F-2, which assembles BOOTCM.ASM and
and
BQBMEM.ASM
LINKs
and
LOCATEs the boot loader.
Modifying
the
BQOPS.ASM
Module.
The BQOPS.ASM module contains
data
used by the BOOTCM.ASM, BQBMEM.ASM, BASCM.ASM, and BQMEM.
ASM modules. In most cases, this will be the only module you will modify before
assembling modules for a new configuration. The boot loader configuration requirements are dependent upon the
number
change from configuration
of
disk drives available, and the highest memory location; if these do not
to
CPU
model, the disk controller model, the
configuration, then the
boot
loader need not be
regenerated.
With the
ISIS-II Text Editor
listed in figure F-I
Guide for
an
explanation
to
support your exact configuration. Refer
of
or
CREDIT, you can edit the BQOPS.ASM module
to
the ISIS-II User's
the
Editor's
features and capabilities.
F-5
Page 98

·
RMX/SO
BASIC-SO
CPU
BOOTED
TERMH SET
RATE
CONTR
DFS
UIO SET
NFILES SET
HIRAM
BOTMEM
SET
SET
SET
SET
SET
SET OFFFFH
SET
;
MODEL
30
1 ; 1 IF BOOT VERSION, ELSE 0
1 ; 1 FOR
;
BAUD
0
; CONTROLLER NUMBER
204
;
NUMBER
6
; 1 IF USER
0
;
TOTAL
6
; HIGHEST RAM LOCATION
OFD40H
;
BOnOM
OF CPU
FULL
TH,O
RATE FACTOR
OF DFS FILES USED
110
FILES
OF BOOT
FOR MINI
DRIVERS ELSE 0
L9ADER
RAM
BASIC-SO
Figure
F-l.
Sample
Configuration
Each of the options in the sample configuration
is
explained
CPU
in
the following paragraphs.
This option specifies the type
or 80/10A, 20 for iSBC 80/20 or 80/20-4, or
80/30.
It
is
only referenced by the BQMEM.ASM module to
initiate interrupt polling for
boot
loaded.
to
allocate memory.
BOOTED
TERMH
that are not
This option is used
is
loader
used, or 0 if a PROM-based BASIC-80
With this option, a 1 specifies the Full Terminal Handler, and
a 0 specifies the Mini Terminal Handler. The Mini Terminal
Handler requires less RAM and
RATE
This option generates an RQRATE to specify a baud rate if
is
any non-zero value
given. For further information about
setting baud rates, refer to the
CONTR
This option specifies the type
indicates an iSBC 201;
DFS
dicates an
iSBC 204;
This option specifies the number of DFS files you wish to
at
have open
the same time. Specifying 0 means that DFS
206
not used.
BQOPS.ASM Module
BQOPS.ASM module listed above
of
CPU used:
10
for iSBC 80/10
30
for
iSBC
iSBC 80/10 based DFS systems
It
is
1 if the boot
is
generated.
PROM space.
RMX/SO User's Guide.
of
disk controller used.
202
indicates an iSBC 202;
indicates an
iSBC
206.
204
201
in-
is
F-6
UIO
NFILES
HIRAM
BOTMEM
This option enables your user-written
specify
1. See "Adding User-Written
I/O
drivers if you
I/O
Drivers" in this
Appendix for further details.
This option specifies the combined number
that
files
than
may be open
or
equal to the number specified in the DFS option.
at
once. The number must be greater
of
DFS and user
This option specifies the highest RAM location available in
the hardware configuration.
This option places
location. This address should be 2BFH
boot
loader RAM
at
the highest possible
less
than the address
given in HIRAM.
Page 99

BASIC-SO
RMX/SO BASIC-SO
After you modify BQOPS.ASM and verify the contents
of
the BOOTCM.ASM and
BQBMEM.ASM modules, you are ready to generate your boot loader. To do this,
you must assemble
the resultant object code. The GBOOT.CSD module
command. Figure F-2
BQOPS.ASM module in figure
The DATA location and the BOTMEM address must
configuration uses an
changed to
burned into
BOOTCM.ASM and BQBMEM.ASM, and LINK and LOCATE
will
do this with the SUBMIT
is
a listing
of
the GBOOT .CSD module used with the
F-l.
be
S20
or
iSBC
SO/20
or iSBC S0/10, each occurrence
SID.
After you have generated the boot
the same.
If
of
loader,
your hardware
S30
it should be
PROM and inserted into your CPU board. (See the Universal
should be
PROM
Programming Manual for details)
iSBC
SO/10
The
does not have an onboard clock.
clock, add the appropriate routines when linking
G of the
RMX/80
User's Guide for further information.)
in your configuration, include the dummy clockroutine
ASM80
ASM80
LINK
LOCATE
:FO:BOOTCM.ASM MACROFILE(:FO:) NOSYMBOLS
:FO:BQBMEM.ASM MACROFILE(:FO:) NOSYMBOLS
:F1
: BOT830.LlB(VECRST)
:F1
:RMX830.LlB(START)
:FO:BOOTCM.OBJ,
:FO:BQBMEM.OBJ, &
:F1 : BOT830.
:F1
:DI0830.LlB, &
:F1
:DFSUNR.LlB, &
:F1
:RMX830.LlB, &
:F1
:BOTUNR.LlB, &
:FO:PLM80.LlB
:F1
:BQ800T.LNK
CODE(40H)
LIB, &
&
TO
:F1:BQBOOT.LNK MAP PRINT(:F1:LNK.LST)
TO
DATA(OFD40H)
:FO:BQBOOT MAP PUBLICS PRINT(:F1 :LOC.LST)&
ST
ACKSIZE(O)
If
your configuration includes a
GBOOT.CSD. (Refer to Appendix
If
you
don't
have a clock
CLOCK.OBJ.
Figure F-2. Sample
Configuration
OBOOT
.CSD
Module
Generating a Boot-Loadable BASIC-80. Once you have determined how to
generate the boot loader that fits your particular
of your work
over. Generating
BASIC-SO
is
There are four steps to generating a boot loadable
BASCM.ASM and BQMEM.ASM modules, and linking and locating the
the
resulting
BASIC-SO
into RMXSYS. The GBASIC.CSD module
that performs these steps. Figure F-3 shows a listing of the
If
used with the sample configuration.
based system, you need
"S20"
with the ISIS-II Text Editor.
Editor, refer to the
to
modify the
ISIS-II User's Guide.
you are using an iSBC
"S30"
For
The CODE and START addresses should reflect the addresses
RMX/SO implementation, the bulk
is
relatively simple.
RMX/80
BASIC-80: assembling
is
a SUBMIT file
GBASIC.CSD module
80/10
or
iSBC
SO/20
references in the module to
"SI0"
or
further information about using the Text
at
the start of system
RAM. The following list shows typical starting addresses:
iSBC80/10or80/10-A
iSBC 80/20
iSBC 80/20-4
iSBC 80/30
3COOH
3800H
3000H
4000H
F-7
Page 100

RMX/80
BASIC-80
The
ed for the system clock) as EXTERNAL. This
tasks must define the exchanges as needed. Any
not used in a system, and therefore not declared in user code,
an unresolved external reference by the linker, the locater, ICE-80, and
ICE-85. Messages issued by these products
changes can be considered as warnings and ignored. The messages issued by
the various products are:
RMX/80
NOTE
Nucleus declares all interrupt exchanges except
is
because user interrupt
of
these interrupt exchanges
that
refer to unused interrupt ex-
RQLIEX
is
treated as
BASIC-80
(us-
Linker:
Locater:
ICE-80 ERR=069
ICE-85 *WARNING UNSATISFIED EXTERNALS
UNRESOLVED EXTERNAL NAMES
xxxxx
xxxxx
etc.
UNRESOLVED EXTERNAL REFERENCE AT xxxxH
(two messages
for
each exchange)
You should check the messages to be certain that none of them refers to
anything other
RMX/80
Reference Manual shows one way to
an unused interrupt exchange. Appendix J
"tie
off"
references to unus-
of
the
than
ed interrupt exchanges in a configuration module.
ASM80 :FO:BASCM.ASM MACROFILE(:FO:) NOSYMBOLS
ASM80 :FO:BOMEM.ASM MACROFILE(:FO:) NOSYMBOLS
LINK &
:F1
:LOD830.LlB(LODINI),&
:FO:BASCM.OBJ,&
:FO:RMXBAS.LlB,&
PUBLlCS(:FO:BOBOOT),&
:F1
:LOD830.LlB,&
:F1
:DFSDIR.LlB(SEEK,DIRECTORY ,ATTRIB,DELETE,RENAM E),&
:F1
:DI0830.LlB,&
:F1
:DFSUNR.LlB,&
:F1
:THI830.LlB,&
:F1
:TH0830.LlB,&
:F1
:RMX830.LlB,&
:F1
:UNRSLV.LlB,&
:F1
:PLM80.LlB,&
:FO:BOMEM.OBJ TO :F1:BOBAS.LNK MAP PRINT (:F1:LNK.LST)
LOCATE :F1:BOBAS.LNK TO :FO:RMXSYS MAP PUBLICS PRINT(:F1:LOC.LST)&
CODE(4000H) STACKSIZE(O) START(4000H) PURGE
F-8
Figure
Generating a PROM-Based
You can also configure
bytes
of
PROM, 2.8K bytes of RAM, and 400 bytes
F-3.
Sample
RMX/80
Configuration
RMX/80
GBASIC.CSD
BASIC-80
Module
BASIC-80 to reside in PROM. This requires
of
RAM for each DFS file
33K
BASIC-80 will use. You should also set aside as much RAM as possible as
workspace for
BASIC-80.
 Loading...
Loading...