Page 1

hp traffic director
server appliances
user guide for the hp e-commerce
traffic director server appliance
sa8200/sa8220 and the hp traffic
director server appliance sa7200/
sa7220
Page 2

© Copyright 2001 Hewlett-Packard Company. All rights
reserved.
Hewlett-Packard Company
3000 Hanover Street
Palo Alto, CA 94304-1185
Publication Number
5971-0900
February 2001
Disclaimer
The information contained in this document is subject to change
without notice.
HEWLETT-PACKARD COMPANY MAKES NO WARRANTY
OF ANY KIND WITH REGARD TO THIS MATERIAL,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE. Hewlett-Packard shall not be liable for
errors contained he rein or f or incidental or conseque ntial dama ges in
connection with the furnishing, performance, or use of this material.
Hewlett-Packard assumes no responsibility for the use or reliability
of its software on equipment that is not furnished by HewlettPackard.
Warranty
A copy of the specific warranty te rm s a pplicable to your Hewle ttPackard products and replacement parts can be obtained from
http://www.hp.com/serverappliances/support.
*Other brands and names are th e property of their resp ectiv e owners.
Page 3
Contents
Chapter 1: Introduction 1
Introduction to the Traffic Director Server Appliances . . . . . . . . . . . . . . . . . . . . . . . . 2
Assumptions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
Benefits. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
Specifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6
Typographic Conventions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
Chapter 2: Theory of Operations 11
General Operating Principles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
Layer 4 (HOT) Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
Layer 7 (RICH) Services (all models except the SA7200). . . . . . . . . . . . . . . . 13
Out-of-Path Return (OPR) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
FTP Limitations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
Page 4

C O N T E N T S HP Traffic Director Server Appliances User Guide
Sticky Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
Sticky Persistence . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
Sticky-timeout. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
Server-timeout (SA8200/SA8220 only) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
SSL and Sticky (SA8200/SA8220 only). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
Grouping Services. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
SSL Acceleration (SA8200/SA8220 only) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
SSL Fundamentals (SA8200/SA8220 only) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18
Application Message Traffic Management. . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
HTTPS Redirect . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
Client Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
HTTP Header Option Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
Load Balancing Across Multiple Servers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Balancing Algorithms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Response-Time Metrics. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Primary and Backup Servers. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
Server Configuration Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
Source Address Preservation. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
Multi-hop Source Address Preservation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
RICH Expressions (not available on the SA7200) . . . . . . . . . . . . . . . . . . . . . . 25
Order of Expressions (not available on the SA7200) . . . . . . . . . . . . . . . . . . . . 26
Routing with Dual Interfaces. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Prioritization and Policy Groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
Routing Method for VIP Addresses. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
Error Detection. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Server Status Detection. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
HTTP Error Detection. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Serial Cable Failover . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
Serial Cable Failover Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
Replicating the Configuration. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
Status Information. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
ii
Page 5

Contents
Chapter 3: Boot Monitor 41
Using the Boot Monitor CLI. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
System Requirements. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
Accessing the Boot Monitor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
Interrupting the Bootup Sequence. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
Using the Run Time CLI. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
Boot Monitor Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
Chapter 4: Graphical User Interface 59
Before You Begin. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 60
Logon Screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 61
Logging on to the GUI. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 61
Topology Screen. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 63
Using the Topology Screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 63
Purposes of the Topology Screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 63
Topology Screen Toolbar . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 64
Online Help. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 64
Topology Screen Elements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 65
Window Controls . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 66
Policy Manager Screen. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
Policy Manager Controls and Displays . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 68
Policy Manager Toolbar. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 68
Policy Manager’s Pop-up Menu. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
Policy Groups. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
Creating Policy Groups. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 70
Throttling. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 71
Deleting Policy Groups. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 71
Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 72
Creating Services. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 72
Additional Service Tab Controls and Displays. . . . . . . . . . . . . . . . . . . . . . . . . 73
Balance Strategy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 75
Deleting Services. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 76
Servers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 76
RICH Controls (all models except the SA7200). . . . . . . . . . . . . . . . . . . . . . . . 79
Order of Expressions (all models except the SA7200) . . . . . . . . . . . . . . . . . . . 81
Deleting Servers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 81
iii
Page 6

C O N T E N T S HP Traffic Director Server Appliances User Guide
Administration Screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 82
Settings Tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 82
Software Tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83
System Software . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 84
Agent Software . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
Users Tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89
Routing Tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 92
System Role. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93
Active Routing Protocol . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93
RIP Protocol . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93
OSPF Protocol. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 94
Security Tab. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 95
Source IP Filtering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96
Access Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96
GUI Tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 97
CLI Tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 99
SNMP Tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 101
SNMP Agent. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 101
Multi-Site Tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
Logging Tab. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 104
Specifying System Log Parameters. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 104
Viewing the Log File. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 105
Configuration Screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 107
Saving Configuration Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
Restoring Configuration Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
Deleting Configuration Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
Copying Configuration Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
Viewing Configuration Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 110
Resetting the Factory Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 112
Sending and Retrieving Configuration Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114
Tools Screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
ARP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116
Ether. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
Ping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 118
Netstat . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
iv
Page 7

Contents
Nslookup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 121
Reboot . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 122
Trace. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
Traceroute . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 127
Statistics Screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 128
Statistics Screen Controls. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 128
Statistics Box. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 129
Graph Options. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 130
Selection List. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 131
Window Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 131
Graphing Statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 132
Chapter 5: Command Line Interface 133
CLI Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 134
Secure Shell Support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 134
Online Help . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 134
Pipes. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 135
Syntax. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 136
Categorical List of CLI Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137
Global System Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137
Admin Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137
File Management Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
CLI Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
IRV Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
GUI Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
Routing Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139
Policy Group Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139
Service Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139
Server Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 140
System Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 140
Security Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 141
SNMP Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 142
SSL Commands (SA8200/SA8220 only) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 142
Logging Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143
Show Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143
v
Page 8

C O N T E N T S HP Traffic Director Server Appliances User Guide
Run-Time CLI Command Reference . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 145
Global System Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 145
Admin Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 152
File Management Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 152
CLI Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 155
IRV Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 158
GUI Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 158
Routing Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 160
Policy Group Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 163
System Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 175
Security Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
SNMP Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 182
SSL Commands (SA8200/SA8220 only) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 185
Logging Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 199
Show Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 201
Chapter 6: Scenarios 207
e-Commerce Appliance Scenarios . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 208
Scenario 1: Load Balancing a Web Site with Two Servers and the SA8220 in Inline
Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 208
Prerequisites for Scenario 1. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 209
Procedure for Scenario 1. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 209
Scenario 2: Load Balancing Servers with Source Address Preservation . . . . . . 214
Prerequisites for Scenario 2. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 215
Procedure for Scenario 2. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 215
Scenario 3: Routing Outbound Data Away from the SA8220 for OPR . . . . . . . 217
Prerequisites for Scenario 3. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 218
Procedure for Scenario 3. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 218
Scenario 4: Content Routing (SA7220 and SA8200/SA8220 only). . . . . . . . . . 220
Prerequisites for Scenario 4. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 221
Procedure for Scenario 4. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 221
Scenario 5: Using SSL Acceleration (SA8200/SA8220 only) . . . . . . . . . . . . . . 226
Procedure for Scenario 5. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 227
Scenario 6: Using CRLs (SA8200/SA8220 only). . . . . . . . . . . . . . . . . . . . . . . . 228
vi
Page 9

Contents
Chapter 7: SNMP Support 233
Using SNMP. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 234
Standards Compliance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 234
HP MIB Tree . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 235
Supported MIBs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 236
Where to find MIB Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 236
Trap Summary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 242
Standard SNMP Traps. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 242
Displaying SNMP Parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 243
Configuring Community Authentication and Security Parameters . . . . . . . . . . . 243
Configuring Trap Parameters. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 245
Other Configurable SNMP Parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 245
Chapter 8: Software Updates 247
Updating Your System Software . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 248
Multiple Software Images . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 248
Software Image Media. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 248
Saving Your Current Configuration. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 248
Downloading and Installing the Software . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 249
Rebooting with the New Image and Verifying Installation. . . . . . . . . . . . . . . . . 250
Upgrading Under Serial Cable Failover Configuration. . . . . . . . . . . . . . . . . . . . 251
Appendix A: Security Configuration 253
Recommended Security Configuration. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 253
Appendix B: SSL Configuration 255
Obtaining Keys and Certificates. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 255
Copying and Pasting Keys and Certificates. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 256
Obtaining a Certificate from Verisign or another CA . . . . . . . . . . . . . . . . . . . . . 257
Procedure. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 257
Importing Keys into the SA8220. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 258
Importing Certificates into the SA8220. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 259
Creating a new Key/Certificate on the SA8220. . . . . . . . . . . . . . . . . . . . . . . . . . 260
Procedure. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 260
vii
Page 10

C O N T E N T S HP Traffic Director Server Appliances User Guide
Using Global Site Certificates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 261
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 261
Using the CLI . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 261
Generating a Client CA. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 263
Generating a CRL. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 264
Revoking a Certificate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 265
Using Ciphers with the SA8220 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 265
HTTP Header Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 267
Appendix C: Failover Method Dependencies 269
Failover Modes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 269
Appendix D: Configuring Out-of-Path Return 273
Configure OPR for Windows* 2000* . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 273
Set the Loopback . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 273
Configure OPR for Windows* NT*. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 288
Set the Loopback . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 288
Run a Web Service on the Loopback Interface Using IIS 3.0 . . . . . . . . . . . . 295
Run a Web Service on the Loopback Interface Using IIS 4.0 . . . . . . . . . . . . 296
Configuring OPR for Apache Web Server on a UNIX* machine . . . . . . . . . . . . . . 297
Appendix E: Diagnostics and Troubleshooting 299
Running Diagnostics. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 299
Diagnostic LEDs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 300
Power Indication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 300
Boot-time LED Diagnostics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 301
Run time LED Diagnostics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 301
Run time Errors. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 302
Troubleshooting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 303
Appendix F: Cleaning the Dust Filter 307
Background. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 307
Dust Filter Cleaning Procedure. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 308
viii
Page 11

Contents
Regulatory Information 309
Taiwan Class A EMI Statement . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 309
VCCI Class A (Japan). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 309
VCCI Statement . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 310
Australia . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 310
FCC Part 15 Compliance Statement. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 311
Canada Compliance Statement (Industry Canada). . . . . . . . . . . . . . . . . . . . . . . . . . 312
CE Compliance Statement . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 312
CISPR 22 Statement . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 312
WARNING. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 313
AVERTISSEMENT . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 314
WARNUNG . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 315
AVVERTENZA . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 316
ADVERTENCIAS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 317
Wichtige Sicherheitshinweise. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 318
Software License Agreements 321
Support Services 325
Support for your SA8220 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 325
U.S. and Canada. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 325
Europe . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 326
Asia . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 327
Latin America . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 328
Other Countries . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 328
Glossary 329
ix
Page 12
C O N T E N T S HP Traffic Director Server Appliances User Guide
Notes
x
Page 13
Introduction
This chapter covers the following topics:
NOTE: For ease of
reading, all models are
referred to as the SA 8220
throughout this
document. Unless noted
otherwise, all SA8220
references refer to all
models.
• Introduction to the Traffic Director Server Appliances
• Assumptions
• Benefits
• Specifications
• Typographic Conventions
Page 14

C H A P T E R 1 HP Traffic Director Server Appliances User Guide
Introduction to the Traffic Director Server
Appliances
The HP e-Commerce Traffic Director Server Appliance SA8200/
SA8220s and the HP Traffic Director Server Appliance SA7200/
SA7220s provide reli able load balancing, failover , and pol icy -based
management to Web sites, Intranets, and e-Commerce sites. These
models also include intelligen t c ont ent routi ng, a nd are t he best lo ad
balancing solution available for the reasons shown below.
Feature Description
Reliability
Fault Resistance
Policy-based
Management
Intelligent Content
Routing (SA8200/
SA8220 only)
Error Recovery
Secure Sockets Layer
Acceleration (SA8200/
SA8220 only)
The SA8220 provides 7 x 24 uptime through failover systems and
the inherent robustness of leading network protocols.
The SA8220-managed configurations offer many features and
capabilities that improve the ava ilability and re liability of ser verbased services.
The SA8220 allows system administrators to implement classes of
service, assign priority le vels, and set target response times.
The SA8220 takes application-aware routing to a new level with
the ability to segment Internet content according to the requested
URL.
Application intelligence allows the SA8220 to understand and
correct application errors transparently to the end user.
The SA8220 can of fload en crypted web traf fic (HTTPS) providi ng
a significant performance improvement over web server based
Secure Sockets Layer (SSL) processing.
2
Page 15
C H A P T E R 1 Assumptions
Assumptions
This User Guide assumes that you are a network administrator and
that you have at least a basic understanding of the following:
• Networking concepts and terminology
• Network topologies
• Networks and IP routing
Benefits
SA8220 benefits are listed below.
Benefit Description
Substantial performance
boost and reliability for
e-Commerce
(SA8200/SA8220 only)
Up to 150 times SSL
acceleration
(SA8200/SA8220 only)
The SA8220 can increase the speed, scalability, and reliability of
multi-server e-Commerce sites. It regains the speed lost by servers
processing secure transactions by delivering faster SSL
processing. It integrates SSL processing with third generation
traffic management technology, eliminating errors and improving
Quality of Service (QoS). This unique capability ensures that
customers working with sensitive information or buying online
receive timely responses, do not see error messages, and are
confident that delivery of their information is kept private.
E-Commerce sites suffer dramatic performance degradation as
secure transactions increase. Using patent-pending technology to
perform cryptographic processing offloaded from the server, the
SA8220 (only) can support up to 1200 SSL connections per
second.
The SA8220 enables e-Commerce sites to transact secure busine ss
and deliver sen s itive information quickly, and confidentially. It
performs all key management and encryption. The result is a
tremendous performance boost for heavil y traf fi cked e-Commerce
sites.
3
Page 16

C H A P T E R 1 HP Traffic Director Server Appliances User Guide
Benefit Description
Substantial economic
benefits
(SA8200/SA8220 only)
SSL acceleration and
intelligent traffic
management benefits
(SA8200/SA8220 only)
The SA8220 improves customer satisfaction by improving the
response time for secure transactions. E-Commerce sites can now
enjoy the benefits provided by having secure transactions
participate in layer 7 intelligent traffic management. This creates
substantial economic savings for e-Commerce sites through
improve d customer satisfact ion, lower cost of ownership, and
reduced server provisioning requirements.
Performance degrades dramatically as more customers access a
site in secure S SL mode, frustrating to the very customers who ar e
trying to make a purchase. The SA8220 is essential to providing
high performance and superior levels of service when building
reliable, scalable, and secure e-Commerce sites.
Off-loading SSL handling from e-Commerce servers improves
overall site performance and customer response time
Accelerated SSL processing eliminates over-provisioning capacity
Lower processing demands on the server creates greater capacity
for your e-Commerce site
Drop-in installation avoids impacting your mission critical e-
Commerce servers
Response-time based prioritized service for secure transactions
Improved responsiveness, reliability, and QoS for secure
transactions means delivering the highest levels of support for
paying customers
Ensures that e-Commerce merchants are always open for business
by preventing “Server Too Busy” and “File Not Found” errors,
even for secure transactions
4
Page 17

C H A P T E R 1Benefits
Benefit Description
Intelligent content
routing for SSL
transactions
(SA8200/SA8220 only)
Intelligent session
recovery for
transactions
(all models except the
SA7200)
Response-time base
prioritized service for
secure transactions
The SA8220 incor porates intel ligent traf fic manag ement for secur e
transactions, dramatically improving an e-Commerce site’s
responsiveness, reliability, and QoS. While typica l traffic
management devices make decisio ns based o nly on i nfor mat io n at
Layer 4 in the network stack, the SA8220 combines Layer 4
through 7 (application/content) awareness to speed up response
times and eliminate error messages for secure transactions. It
keeps e-Commerce sites open for business, even during back-end
transaction problems or content glitches.
The SA8220 provid es Int ellige nt Session R ecover y tech nology for
transactions. By monitoring co ntent within the response sent back
by the server, Intelligent Session Re covery detects HTTP 400,
500, or 600 series errors, transparently rolls back the session, and
redirects the transaction to another server until the request is
fulfilled.
The SA8220 enables system administrators to implement varying
classes of service, assign priority levels, and set target response
times for secure transactions. The SA8220 continually measures
the response times of each class of service group and assigns
incoming reque s ts to the server that can fu lfill those requests
within the predefined response time. If the response time exceeds
the predefined threshold, requests designated as high priority
receive preference over those of lower priority. The SA8220
allows you to offer predictable performance for high-priority
secure requests.
5
Page 18
C H A P T E R 1 HP Traffic Director Server Appliances User Guide
Specifications
SA8220 specifications are listed below.
Specification Description
Servers
supported
Any Web server (Apache, Microsoft,
Netscape, etc.)
Any operating system (UNIX*, Solaris*,
Windows NT*, BSD*/BSDI*, AIX*,
etc.)
Any server hardware (SUN, HP, IBM,
Compaq, SGI, Intel-based platforms,
etc.)
No practical limit on number of servers XXX
System
Administration
Command line interface XXX
Web-based GUI XXX
SNMP monitoring (MIB II and Private
MIB)
SA7200 SA7220 SA8200/
SA8220
XXX
XXX
XXX
XXX
Dynamic configuration through
XXX
password-protected serial console,
telnet, SSH v1, and SSH v2
6
Page 19
C H A P T E R 1 Specifications
Specification Description
Performance
SA8220 is rated up to 1200 HTTPS
connections/sec, 2500 RICH HTTP
connections/sec, 3500 HOT connect ions/
sec, 95 Mb/sec.
SA8200 is rated up to 600 HTTPS
connections/sec, 1300 RICH HTTP
connections/sec, 2800 HOT connect ions/
sec. Both the SA8200 and the SA8220
are rated up to 6600 Max HTTP/
HTTPS/sec.
Layer 7 traffic management XX
Patent-pending technol ogy offloads all
cryptographic processing from server
Dimensions
Mounting: Standard 19-inch rack mount XXX
Height: 3.5 inches (8.9 cm) XXX
SA7200 SA7220 SA8200/
SA8220
XXX
XXX
Weight
Interface
Connections
Transparent
Operation
Priority Classes
Width: 17 inches (43.2 cm) XXX
Depth: 20.16 inches (51.21 cm) for the
XXX
SA7200, SA7220, and SA8220
Depth: 23.75 inches (60.3 cm) for the
SA8200
24 pounds (10.89 kg) XXX
Dual 10/100 Ethernet XXX
TTY Serial - console XXX
Failover port XXX
Supports single or multiple Virtual IP
XXX
(VIP) addresses per domain
Application/protocol types supported:
XXX
Any TCP Port, e.g., HTTP, HTTPS, FTP
7
Page 20
C H A P T E R 1 HP Traffic Director Server Appliances User Guide
Specification Description
Intelligent
Content Routing
Content: URL, file types such as *.GIF,
file paths such as \ads\, file names such
as Index.html
Transactions: Transaction types such as
*.CGI
Intelligent
Session
Recovery
(HTTPS is
available on the
SA8200/SA8220
only)
Response-time
based Priority
for secure and
non-secure
transactions)
Automatically resubmits requests XX
Traps 400, 500, and 600 series errors for
HTTP and HTTPS
Sets and enacts target response times XX
Real-time performance monitoring XX
SA7200 SA7220 SA8200/
SA8220
XX
XX
XX
System Fault
Tolerance
Automatic server weighting and tuning XX
Server-state aware (“sticky”) based on:
- Source IP XXX
- SSL session ID X
- HTTP cookie XX
Single site, single or multiple
XXX
connections
Automatic detection of status change
XXX
and health of servers
Intelligent Resource Verification (IRV) XXX
8
Page 21

C H A P T E R 1 Typographic Conventions
Specification Description
Security
Features
Supported
SSL v2 and v3 for transaction security XX
SSH for secure Command Line Interface XX
IP filtering XX
Serial port logon XX
Typographic Co nventions
The following typographic conventions are used throughout this
manual.
ONE MODEL NUMBER (SA8220): For ea se of reading , all models
are referred to as the SA8220 throughout this document. Unless
noted otherwise, all SA8220 references refer to all models.
NOTE: This is an
example of a note.
NOTES clarify a point, emphasize vital information, or describe
options, alternatives, or shortcuts.
SA7200 SA7220 SA8200/
SA8220
CAUTION: This is an
example of a caution.
CAUTIONS are designed to prevent possible mistakes that could
result in injury or equip m ent damage.
WARNINGS alert you to potential haza rds to life or limb. E xcept for
tables, warnings are always found in the left margin.
NUMBERED LISTS indicate step-by-st ep procedures th at you must
follow in numeric order, as shown below:
1. This is the first step.
2. This is the second step.
3. This is the third step, etc.
BULLETED LISTS indicate options or features available to you, as
shown below:
• The first feature or option
• The second feature or option
• The third feature or option, etc.
ITALICS are used for emphasis or to indicate onscreen controls, as
shown in this example:
9
Page 22

C H A P T E R 1 HP Traffic Director Server Appliances User Guide
4. To edit the configuration settings, press the Configure tab.
COMMANDS are shown in the following ways:
• Any command or command response text that appears on the
terminal is presen ted in the
courier font.
• Any text that you need to type at the command line appears in
bold courier, for example:
HP SA8220/config/policygroup#create gold
• Angled brackets (< >) designate where you enter variable
parameters
• Straight brackets ([ ]) show parameter choices, separated by
vertical bars
• Braces ({ }) show optional commands and parameters
• VERTICAL BARS ( | ) separate the choice s of input parameter s
within straight brackets. You can choose only one of the set of
choices separated by vertical bars. Do not include the vertical
bar in the command.
10
Page 23
Theory of
Operations
This chapter covers the following topics:
NOTE: For ease of
reading, all models are
referred to as the SA 8220
throughout this
document. Unless noted
otherwise, all SA8220
references refer to all
models. Also, all
references to “RICH”
functionality or
“Expressions” in this
chapter do not apply to
the SA7200.
• Services
• FTP Limitations
• Sticky Options
• SSL Acceleration (SA8200/SA8220 only)
• Load Balancing Across Mul tiple Servers
• Server Configuration Options
• Routing with Dual Interfaces
• Prioritization and Policy Groups
• Error Detection
• Serial Cable Failover
Page 24

C H A P T E R 2 HP Traffic Director Server Appliances User Guide
General Operating Principles
This chapter discusses the general operating principles for the HP eCommerce Traffic Director Ser ver Appliance SA8200/SA8220s, and
the Traffic Direct or Server App liance SA7 200/SA7220s. F or detail s
about the SA8220 command set, please see “Command Line
Interface” in Chapter 5. For information about completing specific
tasks, please see “Scenarios” in Chapter 6.
Services
NOTE: The sample
commands used in this
chapter are meant as
examples only.
Services are the virtual resources that the SA8220 provides to
network clients. Services are defined by their Virtual Internet
Protocol (VIP) address and virtual port number. The SA8220 load
balances network client requests for a service by receiving requests
from the user and directing them for fulfillment to the m ost
appropriate resource in the provider's server farm. Services are
defined and created within Policy Groups (please see “Prioritization
and Policy Groups in Chapter 2) and are manage d using the followin g
commands:
config policygroup <policy-name> service create
<service-name>
vip <ipaddr> port <n umber> {type [T CP | UDP |
RICH_HTTP]} {sticky [disable| src-ip |
cookie]} {sticky-timeout <seconds>} {backups
[enable | disable]} {response <milli-sec>}
{priority <level>} {balancing [load | robin]}
{server-timeout <seconds>}
config policygroup <name> service delete [<name>
| -all]
config policygroup <name> service <name>
{enable}{disable} {balancing [robin | load]}
{sticky [disable | src-ip | cookie]}
{sticky-timeout <seconds>} {backups [enable |
disable]} {resp onse <milli-s ec> } {dup-syn
<micro-sec>} {p riority <leve l>}
{server-timeout <seconds>}
12
Page 25

C H A P T E R 2 Services
Layer 4 (HOT) Services
HOT services provide very fast brokering performance. HOT
services are defined in full by their VIP and port number.
In HOT or “Brokered” mode, the SA8220 performs Network Address
Translation (NAT) on all incoming packets passing through the
connection. NAT changes the destination IP address and port of
incoming packets to those of the selected fulfillment server. The
source IP address is modified to be that of the SA8220.
Fulfillment servers can be addressable by IP address, and thus can be
on either local or wide area networks.
By default in HOT mode, the fulfillment server sees all requests as
coming from the SA8220 rather than from the actual client. In some
environments, it may be desirable to have the fu lfillment server see
the requests as if they were coming directly from the client. The
Source Address Preservati on (SAP) mode of the SA8220 allows t his
to happen ( see “Source Address Preservation” for more detailed
information).
Layer 7 (RICH) Services (all models except the
SA7200)
The SA8220 allows more flexible service fulfillment for RICH (Realtime Intelligent Co ntent Handling) services. The service type
“RICH_HTTP” is available on the SA8220 and enables it to make
fulfillment decisions based on the content of the URL of each client
HTTP request. R ICH servi ces also incl ude ad vanced e rror de tecti on,
and automatic resubmission of HTTP requests under most error
conditions.
As with HOT services above, fulfillment servers can be addressable
by IP address, and thus can be on either local or wide area networks.
13
Page 26

C H A P T E R 2 HP Traffic Director Server Appliances User Guide
Out-of-Path Return (OPR)
Ordinarily, the SA8220 processes all traffic in both directions
between clients and the server farm. Viewing the server return traffic
helps the SA8220 accurately determine server response times and
handle HTTP errors. Often, the volume of data sent from the server
to the client is much larger than the traffic from client to server, and
checking for HTTP errors i s not required . In such situatio ns, you can
use OPR mode to increase performance . OPR is enabled by typing the
following command:
config policygroup <name> service <name> server
<name> port <port> mode [opr]
NOTE: OPR is not
applicable to Layer 7
services.
FTP
Limitations
Each server for which OPR is e nabled must have its loopback
interface configured to identify itself as the VIP of the brokered
service. This allows the server to respond directly to the client. The
server’s loopback interface, or an equivalent interface that will not
respond to ARP requests, must be configured before setting up the
SA8220 for OPR. For more information, please see “Configuring
Out-of-Path Return in Appendix D.
The table below l ists those limitati ons of FTP on the SA8200.
Mode Active FTP Passive FTP
HOT
HOT with SAP
OPR
HOT with SAP does not change the server 's IP address during Passive
FTP because the server is making the co nnection directly to the client,
using its real IP address. If the server’s IP address is not a "real" IP
address, this mode will not work.
No Yes
Yes Yes (see below )
No No
14
Page 27
C H A P T E R 2 Sticky Options
Sticky Options
Some services operate best if all requ ests from a specific client during
a single session are directed to the same fulfillment server. For
example, if the server maintains a local database of client act i vity or
context (shopping ca rt, registration info, navigation history, etc. ), it is
important that subsequent client requests go to the server with these
database records. The SA8220's “sticky” options allow this to occur.
Sticky is available in the two modes shown below.
Mode Description
Source IP
address
(“src-ip”)
Cookie
Requests from a given IP address are directed to a
single server.
The requesting browser is given a cookie, which
subsequently identifies it as a unique requestor to
be directed to a single server . This method uni quely
identifies the client even if the request passes
through a proxy server. RICH service is required.
Sticky source IP for SSL uses the SSL session ID for stickiness
instead of the source IP of the client.
Both HTTP and HTTPS services can be RICH. However, i nco ming
RICH SSL connections will always be decrypted and sent on to the
fulfillment servers in clear text. Sticky cookie must be used when the
clients need to remain stuck to the same server bet we en HTTPS and
HTTP.
There is no sticky cookie requirement for HTTPS traffic.
Each brokered service can be configured with sticky cookie, sticky
IP, or no sticky option enabled. When a sticky option is configured,
all client requests (identified according to the enabled sticky mode)
during a session are routed to the same fulfillment server. When the
sticky option is disabled, the SA8220 determines the best fulfillment
server for each client request and directs them accordingly.
15
Page 28

C H A P T E R 2 HP Traffic Director Server Appliances User Guide
Sticky Per sis te nce
For source-ip based sticky, the relationship between the client IP
address and the fulfillment server remains in effect for the entire time
the SA8220 is on li ne or un ti l t he st i cky ti meou t value expires. In the
event of failover, the sticky r elationship is lost. Cookie sticky re mains
in effect while the browser is running or until the sticky timeout value
expires. Since the browser maintains the cookie, cookie sticky is
maintained in the event of failover. The system clocks on both
SA8220s must be synchr onized for failover handli ng to work. You do
this by enabling NTP (Network Time Protocol) using the Boot
Monitor. The administrator can control th e length of time a server is
forced to handle serial requests from a single client using the sticky
timeout value.
NOTE: SA7200 sticky
support allows for source
IP ONLY. All cookie
sticky RICH services will
be stuck to the same
server for the duration of
the sticky timeout value.
Sticky-timeout
The current software version for the SA8220 treats the timeo ut
differently for cookie versus source-ip sticky. With source-ip sticky,
the timeout is reset with every connection from the client (so that the
timeout is effectivel y an "idle time"). With cookie st icky, the timeout
starts with the first connection from the client to the server, and never
gets reset. When the cookie expires, even if actively being used, the
next connection will be load balanced to a new server.
We recommend that you set the cookie sti cky timeout value to at least
1.5 times the maximum amou nt of time a user will expect to be stu ck
to a server. If you are uncertain of the exact setting, we recommend
using 43200 seconds (12 hours).
Server-timeout (SA8200/SA8220 only)
A server timeout, which causes a change in servers, can appear as a
cookie sticky state change. The recommended value for server
timeout is at least 1.5 times the maximum server response time.
We recommend that you set the value to 120 seconds.
16
Page 29

C H A P T E R 2 SSL Acceleration (SA8200/SA8220 only)
SSL and Sticky (SA8200/SA8220 only)
SSL (Secure Sockets Layer, o r HTTPS)-enabled servic es can also be
made sticky by specifying “sticky cookie” or “sticky src-ip” on the
CLI. For SSL services, sticky cookie behaves exactly as it does for
ordinary HTTP services. Source IP sticky uses the SSL session ID to
maintain server conte xt. The server relation s hip will not survive
failover. As with sticky cookie, use of the session ID uniquely
identifies the cli ent even i f the req uest passes throug h a prox y server.
Grouping Services
NOTE: RICH is required
for sticky service
grouping.
SSL
Acceleration
(SA8200/
SA8220 only)
The SA8220's sticky capabilities can ensure that all service requests
from the same user are routed to the same server. Enabling sticky
cookie on multiple services ensures t hat requests from the same client
will be routed to the same fulfillment server for the duration of the
sticky relationship. Of course the server must be able to fulfill all
service requests to have a true one-to-one client-server relationship.
The SA8220 is a powerful addition to any web site desiring high
security levels. It was specifically created to manage secure traffic
going to and fr om critical appli cations. It handl es SSL traffic i nto and
out of the customer's environment, as well as providing load
balancing, fault management, and error recovery.
The SA8220 includes cryptograph ic software f eatures an d hardwarebased acceleration . It provid es up to 1200 S SL (HTTPS) connections
per second (SA8220 only), far e xceeding the performance of even the
most powerful web servers on the market today.
The SA8220 allows users t o of floa d S SL pr ocessi ng fr om t heir bac k
end servers, and at the same time achieve full-featured traffic
management. In a SA8220 environment, all encrypted traffic—
required by e-commerce applications—is handled at the SA8220.
The interaction between the SA8220 and the servers is done in the
clear, allowing load balancing and session management.
SSL processing is enabled by assigning an RSA pri vate key (a public
encryption key alg orit hm invented in 1977) and an X.509 certificate
to a Layer 7 service. The SA8220 Command Line Interface (CLI)
allows you to crea te or impo rt keys a nd certific ate when you define a
service. Once the key and certificate are in place, secure HTTP
(HTTPS) requests are decrypted and passed on to the web server. The
17
Page 30
C H A P T E R 2 HP Traffic Director Server Appliances User Guide
SA8220’s dual NIC and packet filtering capabilities can be used to
isolate the web servers from the Internet, further preventing
unauthorized access.
SSL
Fundamentals
(SA8200/
SA8220 only)
SSL involves an interchange of keys used both to authenticate the
parties and to provide information to securely encrypt confidential
data. The keys distributed in this medium are “one way,” or
asymmetric. That is, they can only be used to encrypt confidential
data, and only t he “owner” of the public key can decrypt the data on ce
it is encrypted using the publ ic key information. SSL assures the three
things shown below.
Benefit Description
Authenticity Verifies the identities of the two parties
Privacy None other than the transacting partie s can access
the information being exchanged.
Integrity The message cannot be altered in t ra nsit bet ween
the two parties by a third party without the
alteration being detected.
To establish a secure session with a server, the client sends a “hello”
message to which the server responds with its certificate and an
encryption methodol ogy. The client then responds wit h an encrypted
random challenge, which is used to establish the session keys. This
method allows two parties to quickly establish each others’ identities
and establish a secure connection.
Several encryption methods are employed. Common ones are DES,
3DES, RC2, and RC4. Key size can be varied to determine the level
of security desired. A longer key is more secure.
The SA8220 supports all common keys and ciphers, as well as the
following encryption methods: DES, DES3, and RC2 & RC4. The
SA8220 includes a licensed version of t he RSA code embedded in the
security module as well. The device's session management software
has been certified by prominent security agencies and meets all
standards for SSL traffic.
The SA8220 handles all the handshaking, key establishment, and
bulk encryption for SSL transactions. Essentially, the SA8220 is a
full-featured, SSL-enabled web server. Traditionally, these functions
18
Page 31

C H A P T E R 2 SSL Fundamentals (SA8200/SA8220 only)
are performed either at the server level, by web servers generally
providing SSL functionality by way of standalone software
components, or by embedded encryption software.
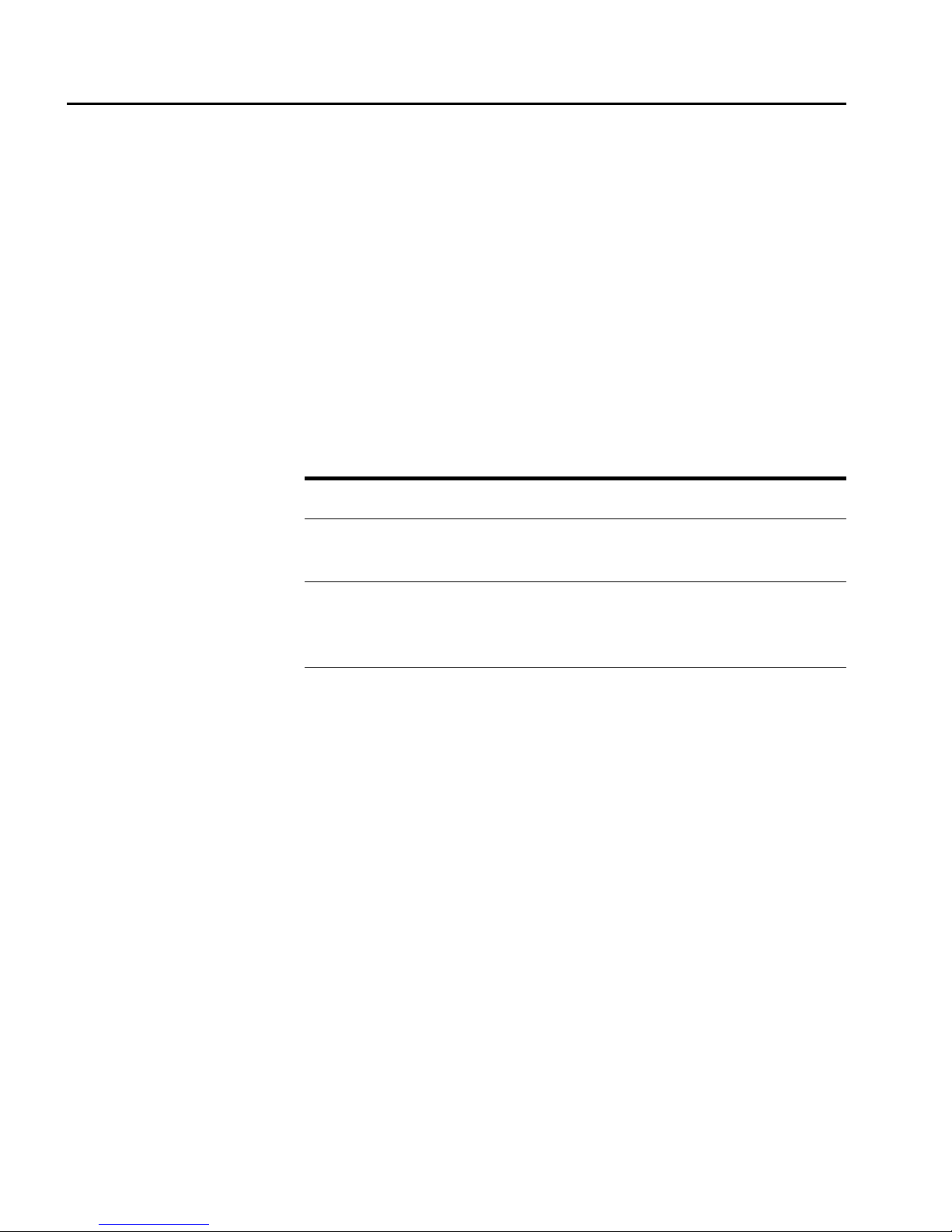
The HP methodology places encryption processing on the network
side, thus eliminating the need for processing on the servers (see the
figure on the next page). The servers never see any of the SSL
connection dialo gue or the encrypted data. T his removes a substantial
processing load from the servers allowing improved response times
and greater availability of system resources.
Server Server Server
c
i
f
f
a
r
T
d
e
t
p
y
r
c
n
E
1. Client connects to s erver
2. Server responds w ith certificate
3. Client encrypts rand om key
4. Server generates working key
5. Session established
Client
SA8220
Client
Server Server Server
1. Client connects to SA8220 with ClientHello
(includes ciphers supported)
2. SA8220 responds w ith SSL S erverHello
(includes selected cipher & ses sion ID)
3. SA8220 sends cer tificate for s er ver
4. Client sends C lientKey E xchange messa ge;
includes PK (session key)
5. S A8 220 and client send ChangeC ipherS pec
message to indicate readiness
6. SA8220 and client send "finished" messa ges ;
includes hash of whole conversat ion
7. Encr ypted data sent to SA 8 220, d ec ry pted and
forwarded to least bu s y s erv er
8. Clear respons e sent to SA 8220, encr ypted and
sent to client.
Basic SSL Operations
19
Page 32

C H A P T E R 2 HP Traffic Director Server Appliances User Guide
Application Message Traffic Management
The SA8220 was developed to perform load balancing in SSL
environments. The SA8220 allows users to load balance based on
application content (Layer 7, or RICH mode), as well as server
address and port (Layer 4, or HOT mode). SSL management is
handled independently of RICH mode processing. That is, once a
session is establishe d and the message i s decrypted, i t is passed to th e
SA8220’s RICH processing component. This allows even SSL traffic
to take full advantage of the features of the device, including error
recovery and session rollback.
The SA8220 allows non-encrypted traffic to be processed
independently of S SL tr af fic . The advant age of this is that it permi ts
load balancing (i n either HOT or RICH mode ) configuratio n on a per
virtual IP addre ss, thus allowi ng you to is olate t he im pact of the SSL
processing. Many users t une their sites fo r maximum performance by
assigning HOT load balancing to all traffic except SSL.
One of other advantages of the SA8220 is its ability to reco gnize SSL
session IDs. This permits “sticky” (or persistent) sessions to be
established on a given server.
HTTPS Redirect
If desired, you can specify a page to return to the client if a successful
session cannot be negotiated because the client does not support the
required cipher suite. The SA8220 accomplishes this by sending an
HTTP 302 “redirect” message back to the client in the case of a cipher
negotiation failure. For example: The server supports 128-bit
encryption, but the client’s software is only capable of 40-bit
encryption.
The CLI p arameter
page the client is redirected to.
where <URL> is the fully qualified location of the page. For
example:
error.html.
redirectpage=http://www.companyname.com/
The default configuration file setting is: redirectpage=none.
redirectpage=<URL> allows you to set which
20
Page 33

C H A P T E R 2 SSL Fundamentals (SA8200/SA8220 only)
Fulfillment of each virtual service is load balanced across a number
of real servers depending on the load balancing algorithm chosen.
Servers capable of fulfilling requests for a service are identified and
managed with the following commands:
config policygroup <name> service <name> server
delete <name> port <port>
config policygroup <name> service <name> server
create <name> port <port>
Client Authentication
By default, the SA8200/SA8220 does not authenticate client
identities; however you can configure services to request client
certificates for the purp ose of verifyi ng ident ities. When you enable
this feature, the SA8200/SA8220 verifies that client certificates are
signed by a known CA.
Issued client certificates are expected to be in use for their entire
validity period. The CA periodically issues a signed data structure,
called a Certificate Revocation List (CRL), containing the serial
numbers of all expired certificates. You can configure the SA8200/
SA8220 to obtain and use a CRL using LDAP, HTTP or FTP
protocols. The SA8200/SA8220 first verifies a client certificate
against the installed CA certificate, and then looks up its serial
number in the installed CRL. If the serial number exists in the CRL,
then the client connection is terminated. Before the connection is
closed, the SA8200/SA8 220 returns a message to the client indicating
that the client’s certificate was revoked.
21
Page 34

C H A P T E R 2 HP Traffic Director Server Appliances User Guide
HTTP Header Option Fields
Both the SA7220 and the SA8200/SA8220 can make the IP address
of a requesting client available to a fulfillment server by constructing
a custom HTTP header option, with the client’s IP as the value:
HP_SOURCE_IP:<client-IP>
SSL-related HTT P header option fields a re only used by the S A8200/
SA8220 with any SSL service. The HP_CIPHER_USED header
option is used whenever HP_SOURCE_IP is used, to provide the
name of the SSL-cip her negotiated betwee n the SA8200/SA8220 and
the client:
HP_CIPHER_USED:<ssl-cipher>
These two header fields are used only by the SA8200/SA8220 whe n
client authentica tion is in use:
HP_CLIENT_CERTIFICATE:<client-certificate>
HP_SESSION_ ID: <SSL-sess io n-ID>
Because a client certificate co ntains information useful for client/user
authorization, the SA8200/SA8220 inserts the client certificate in the
request header before sending the request to the server. The server
can then extract the certificate from the request header and use it for
authorization or other purposes.
The client certificate is inserted in the request header only once per
session. Requests followi ng the initial request will be sent to the
server with only the SSL-session-id in the header. The SSL- sessi onid is unique for each session and allows the server to work with
multiple sessions. The client certificate is inserted in the request
header with a new SSL-session-id o nly when the client certificate h as
been re-negotiated between theSA8200/SA8220 and the client:
• New Session/Initial Request:SA8200/SA8220 sends both the
HP_CLIENT_CERTIFICATE and HP_SESSION_ID header
options.
• Existing Session/Subsequent Requests: SA8200/SA8220 sends
only the HP_SESSION_ID header option.
The use of header option fields is an efficient way of supplying
information to the server about the client. To ease the use of this
important feature, SA7220/SA8200/SA8220 all ows customization of
all the above header option field names. For more information, see
Chapter 5.
22
Page 35

C H A P T E R 2 Load Balancing Across Multiple Servers
Load
Balancing
Across
Multiple
Servers
Balancing Algorithms
The SA8220 provides a choice of loa d balancing algorithms. Services
can be separately configu red to load balance using a round-robin or a
response time algorithm. In most networks, the best performance
results from use of the response time algorithm. Under this algorithm,
the SA8220 measures the response time of each request to each server
in the server farm. It then balances requests to the service among the
servers, sending more requests to the fastest servers an d fewer to the
slower ones, thus optimizing the average response time.
In cases where Out-of-Path Return (please see “Out-of-Path Return
(OPR) in Chapter 2) is used in unpredictable WAN environments,
response time metrics may be obscured by WAN latency varianc e. In
these situations, round-robin load balancing can provide equal
distribution of clien t re quests to each fulfillment server.
The balancing algorithm is specified with the command:
config policygroup <name> service <name>
balancing [robin | load]
Response-Time Metrics
For both balancing algorithms, servers can be assigned target
response times. These values indicate the desired average response
time for requests for specified services to be fulfilled, and instructs
the SA8220 to use alternate resources for fulfillment if the average
response time exceeds ta rget response time. Target response time is
controlled with the following command:
config policygroup <name> service <name>
response <mil-s econds>
If the servers do not meet the specified response time threshold,
backup servers, if available and enabled, are activated. In addition,
the servers providing lower priority services are throttled if the
response time is still not being met (if
policygroup). Both mechanisms are available for both of the loadbalancing algorithms.
throttle is enabled in the
23
Page 36

C H A P T E R 2 HP Traffic Director Server Appliances User Guide
Primary and Backup Servers
Each server is identified as either a Primary or Backup for a given
service. Primary servers are always considered first for request
fulfillment. By default, Backup servers are considered for use only if
a primary server goes down, though they can optionally be
configured for use to maintain target response times. A server’s type
is established with the following comm and:
config policygroup <name> service <name> server
<name> port <port> type [primary | ba ck up]
Backup servers are enab led to maintain target response times with the
following command:
config policygroup <name> service <name> backups
[enable | disable]
Server
Configuration
Options
NOTE: For the SA8220
to operate in SAP mode,
the default gateway for
each SAP-enabled server
must be set to the
SA8220’s physical IP
address, not the VIP.
Source Address Preservation
By default, brokered service requests arriving at a fulfillment server
appear to the server as requests originating from the SA8220.
Consequently, server log files record the SA8220 as the source of
these requests. When Source Address Preservat i on (SAP) i s enab le d
however, the SA8220 preserves the original source addresses of
requests delivered to the server farm. If you use the log files from
your server farm to gather information based on client source
addresses, use Source Address Preservation. SAP is controlled with
the following command:
config policygroup <name> service <name> server
<name> port <port> mode [sap]
SAP cannot be used in WAN or multiple router LAN envir onmen ts.
To use SAP, each server must be configured so that its default
gateway is set to t he physical IP address of the SA8220, thus there can
be no routers between the SA8220 and the fulfillment servers.
Limitations of SAP mode operation are listed below:
• The client machine cannot be on the same subnet as the SA8220.
• The SA8220 and server must be on the same subnet.
When SAP is enabled, serial cable failover is the only failover
option—routing failover is not available.
24
Page 37

C H A P T E R 2 Server Configuration Options
Multi-hop Source Address Preservation
It is possible in sophisticated network topologies to require requests
to pass through two SA8220s. In such configurations, the SA8220
topologically closest to the clients must be configured with the Multihop Source Address Preservation (MSAP) feature enabled.
MSAP allows requests to pass through two cascaded SA8220s in
different geographical areas. Enabling MSAP ensures that the actual
IP addresses of requesting clients, rather than the virtual IP address of
the SA8220 that deliv ered the request, are recorded in the server logs.
This is similar to SAP (described in the prece din g secti on), ho wever
this feature allows SA8220s to be geographically-dispersed, as
shown in below.
BostonSan Diego
BostonSan Diego
NOTE: In most
configurations, the
default setting (MSAP
disabled) is required.
SA8220 #1
SA8220 #1
SA8220 #1
wi th M S AP
wi th M S AP
Client Server 1
ClientClient Server 1Server 1
wi th M S AP
Enabled
Enabled
Enabled
SA8220 #2
SA8220 #2
SA8220 #2
wi th M S AP
wi th M S AP
wi th M S AP
Disabled
Disabled
Disabled
MSAP on a Geographically-Dispersed Network
In the figure above, a client in San Diego sends a request to a
fulfillment server in Boston. MSAP is en abled on SA8 220 Broker 1,
and Server 1’s default route is set to SA8220 Broker 2. The SA8220
Broker 2 doesn’t need SAP enabled for this service, since SAP is
automatically use d on MSAP requests from SA8220 Broker 1. Un der
this configuration, the San Diego client's IP address will be preserved
in the Boston fulfillment servers' logs. MSAP is enab led at the CLI
with the following command:
config policygroup <policy-name> service
<service-name > server <serve r-n ame>
port < > msap [enable]
RICH Expressions (not available on the SA7200)
Layer 7 RICH_HTTP service configurations use rich expressions to
assign particular classes of URLs to particular servers for fulfillment.
RICH expressions are used, for example, to distinguish content
requested by clients performing online transactions, from content
typically requested by casual br owsers. In this way, users performing
online transactions are given higher priority access to server
resources (and better response times) than other users.
25
Page 38

C H A P T E R 2 HP Traffic Director Server Appliances User Guide
Each server listed for fulfillment of a RICH_HTTP service can be
configured to serve any number of specific rich expressions.
Applicable expressions are listed below:
• File type expressions, such as *.gif, or */index.html
• Path expressions, such as /home/*, or /home/images/*, or /home/
images/a*.
• Unique file expressions, such as /index.html
• Wildcard expression, such as *.
• Negation expressions, such as !*.gif or !*/index.html
RICH expressions are managed with the following commands:
config policygroup <name> service <name> server
<name> port <port> expression create
<expression>, and
NOTE: The “*” and “!”
are allowed in
expressions, but they can
only exist at the
beginning or end of the
expression. Also, a
positive expression is
required after a not (!)
expression, otherwise the
(!) expression has no
effect.
config policygroup <name> service <name> server
<name> port <port> expression delete
<expression>
Order of Expressions (not available on the
SA7200)
When using expressions in L ayer 7 (RICH) operations, the order of
expressions is significant only when the "not" (!) operator is used.
Expressions are described below.
Expression Yields
!*.gif;*
*;!*.gif
!*.html;/home/*
All non-GIF files
All files, because after specifying “all” (*), the
!*.gif expression is never reached
Matches all requests of the form “/home/*”
except HTML files
/home/*;!*.html
!/home/*
!/home/*;*
26
Matches all files of the fo rm “/home/*.” The
!*.html has no effect.
No matches
All matches except ones starting with "/home"
Page 39

C H A P T E R 2 Routing with Dual Interfaces
Routing with
Dual Interfaces
NOTE: The SA8220
cannot route multiple
subnets on one interface.
Because the SA8220 has two network interfaces, it can act as a router
in some contexts. This means that it can route between two subnets.
To do this, you must designat e the SA8220 as the default gate way for
your fulfillment servers. Routes to the inside subnet are n ot
advertised to the outside router, but host routes are advertised to the
VIPs. Packets destined for defined VIPs are always routed through
the SA8220 to the server-side subnet. Other packets are forwarded
through the SA8220 only when the security mode is set to OPEN or
when set to CUSTOM and IP For warding is turned on . The SA8220’s
routing capabilities vary depending on which routing and failover
methods are used. For more details about these variations and their
relationships to routing and failover configurations, please see
“Failover Method Dependencies” in Appendix C.
Terms pertinent to SA8220 routing a re listed below.
Term Description
Network-side
subnet
The SA8220 interface attached to the side of the
physic al network on whic h client r equests arrive.
Server-side
subnet
The SA8220 interface attached to the side of the
physical network that includes the fulfillment
servers.
“Outside”
device
“Inside”
device
The router or switch on e hop from the S A8220 on
the brokered subnet
The router or switch on e hop from the S A8220 on
the server-side subnet
The figure below shows an example of t he SA8220 routi ng topology.
Brokered
Brokered
Subnet
Subnet
Router
RouterRouter
“Outs i de”
“Outs i de”
Router
Router
SA8220
SA8220SA8220
Server-side
Server-side
Subnet
Subnet
Hub or
Hub or
Hub or
Switch
Switch
Switch
“I ns i de” Hub
“I ns i de” Hub
or S witch
or S witch
Server
ServerServer
Server
ServerServer
Server
ServerServer
SA8220 Routing Topology
27
Page 40

C H A P T E R 2 HP Traffic Director Server Appliances User Guide
Prioritization
and Policy
Groups
Policy groups are containers used to organize services. Service
prioritization u ses poli cy group i nformat ion to mak e decisi ons about
which services should get more or less server resources. Although the
assignment of services to po licy groups can be a rbitrarily det ermined
by the operator, effective use requi res that ea ch pol icy group co ntain
services related by their shared u se o f server resources. Serv ice s and
servers are assigned to Policy Groups at their time of creation.
Policy group management commands are listed below:
config policygroup create <name>
config policygroup delete <name>
config policygroup <name> throttle [enable |
disable]
The policy group framework allows th e prioritization of categorie s of
client requests. Each service defined in a policy group is assigned a
priority within that group and a target response time. When the
average response time of a service exceeds its target response time,
that service is allocated, on the basis of its priority, a greater share of
common server resources to attempt to bring response time back
within the target range (this assumes that the throttling option is
enabled for the policy group).
28
Server 1:
HTTP
SA8220
Server 2:
HTTPS
Server 3:
HTTP/HTTPS
VIP: 10.2.2.4
HTTPS : 10 ms
HTTP: 10 ms
Target Response Time Satisfied
Page 41

C H A P T E R 2 Prioritization and Policy Groups
For example, the services HTTP and HTTPS are both assigned to a
single policy group. HTTPS is desig nated the highest pri ority service,
and HTTP the second priority. The SA8220 monitors th e response
time of each service, and if necessary re-prioritizes server resources
of subordinate services to keep the response time for the highest
priority service within the specified range. The figu re above shows a
policy group with services sharing a defined VIP, two services, and
their associated target response times. When the average response
time of HTTPS is less than or equal to 10ms, Server 1 fulfills HTTP
requests, Server 2 fulfills HT TPS request s, and Server 3 fulfil ls both
HTTP and HTTPS request s. T he n ext figure illustrates server
utilization after HTTPS response time exc eeds 10 ms.
Server 1:
HTTP
Server 2:
HTTPS
Server 3:
HTTP
V IP : 10 .2.2 .4
HTTPS: 12 m s
HTTP: 10 ms
SA8220
Target Response Time Exceeded
Upon noticing a break in the target response time threshold, the
SA8220 scans the policy group’s active service and server pools for
shared resources. In this example, both the HTTP and HTTPS
services use Server 3. To provide the greatest server resources for the
highest priority service, shared resources are eliminated from
subordinate service pools (although each service will always have at
least one point of fulfillment .) For e xample, in the figure above, new
HTTP connections are no longer sent to Server 3 in an effort to
guarantee the target response time for HTTPS. Server 3 will again
serve HTTP when target response times are met.
29
Page 42

C H A P T E R 2 HP Traffic Director Server Appliances User Guide
Routing
Method for VIP
Addresses
After setting up th e service, y ou must con figure th e SA8220 t o route
the VIP address to the Internet. There are two possibilities:
• In single SA8220 instal lations, “Standalone” mode is preferred
as it allows the VIP to be ARP-accessible from the router.
• If there are multiple address spaces (such as a SA8220 on the
10.x.x.x network and a VIP on the 209.x.x.x), then a routing
protocol might be the best method to advertise the VIP. When
configuring routing on the SA8220, always match the router's
configuration. The SA8220 can be programmed to use RIP v1,
RIP v2, or OSPF.
For example (standalone mode):
HP SA8220#config route
HP SA8220/config/route#info
Route configu ration:
---------------------------Broker role: standalone
RIP Info:
Active:no
Version:2
OSPF Info:
Active: no
Area: backbone
Hello interval: 10 (seconds)
Router dead interval : 40 (seconds)
30
Page 43

C H A P T E R 2 Error Detection
Error
Detection
The SA8220 is capable of recognizing and reacting to server error
conditions, detecting non-responsive (comatose) servers, and
directing traffic to alternate resources until the server is back in
operation. The SA8220 can also capture many HTTP errors before
they reach the client, and redirect the request to an alternate server.
Server Status Detection
The SA8220 uses multiple means to monitor the status of the
fulfillment servers. The “In telligent Resour ce Ve rification” (IRV)
module periodically pings the servers to verify they are alive. The
SA8220 also monitors a “dup-syn” interval to calculate packet loss
rate.
Intelligent Resource Verification
When the IRV module pings a server and receives no response, it tries
to connect to each port on which the suspect server is configured to
listen. If the SA8220 itself does not receive a response from a given
port, then that server/port combination is declared d ead. If the server
maintains network connectivity and responds positively to IRV
pings, but ports stop responding, t hen t he dup -sy n in terval threshold
(described below) is used to decide if the server is declared dead.
Dup-syn Interval
The SA8220 dynamically calcul at es th e t hr eshol d for t he acceptable
number of dropped packets within a given interval. If at any time in
this interval the number of dropped packets exceeds this threshold,
the server is considered dead. After the specified time value has
expired the lost packet (or dup-syn) count is divided by two and the
time interval starts again. In this way, some history information is
kept between time inter vals.
The dup-syn inte rval for this threshold is established with the
syn
CLI command, and ranges in value f rom 1000 to 2 ,147,483,6 47
microseconds. The default time interval value is 500,000
microseconds (one half second), which is appropriate for most
environments. By lowering or raising this value, you render the
SA8220 respectively less or more sensitive to dropped packets, and
less or more likely to declare a server dead. The volume of network
traffic must be taken into ac count when set ti ng the dup -sy n in ter v al.
Higher volumes of traffic require a shorter dup-syn interval to avoid
mistakenly declaring a server dead due to network congestion.
dup-
31
Page 44

C H A P T E R 2 HP Traffic Director Server Appliances User Guide
The dup-syn command uses the following syntax:
config policygroup <name> service <name>
dup-syn <micro-seconds>
HTTP Error Detection
NOTE: This section
applies to all models
except the SA7200.
The SA8220 offers HTTP error detection for RICH services. When
HTTP error detection is enabled, the SA8220 scans the headers of
server responses for errors. If an HTTP error is found, the original
request is rerouted to another server for fulfillment, transparently to
the client. This process continues until a server responds without an
error, or all applicable servers have been tried. Conversely, if HTTP
error detection is disabled, the error is returned directly to the client.
HTTP error detection for errors 401-405 and 500-503 (as defined in
the HTTP specification) is configured with the command:
config policygroup <name> service <name> server
<name> port <port> http [enable | disable]
The SA8220 extends standard HTTP error handling by allowing the
server to return a special 606 error code. Detection and handling of
606 errors is separately configurable. In this way, standard errors may
be passed to the client while 606 errors are hand led transparently by
the HP system. If 606 error han dling is enabled, the SA8220 scans t he
returned HTTP header for an HTTP 606 response code. If the 606
response code is found and another server is available to handle the
request, it is sent automatically. This process continues until a server
responds without an error, or until all applicable servers have been
tried.
The HTTP header for 606 handling is of the form: “HTTP/1.0 606
Error.” Users can generate this response through a variety of methods
including CGI and nph scripts. Consult your web server
documentation for information about generating custom error
messages.
32
config policygroup <name> service <name> server
<name> port <port> 606 [enable | disable]
Page 45

C H A P T E R 2 Serial Cable Failover
Serial Cable
Failover
NOTE: DHCP is not
available when serial
cable failover is en abl ed.
NOTE: You can log on to
the Backup SA8220, but
the full command set is
not available.
The SA8220 offers two failover methods:
• Router Failover (including OSPF, RIPv1 and RIPv2), and
• Serial Cable Failover
When serial cable failover is configured, the Primary and Backup
SA8220s communicate heartbeat, configuration, and status
information using the incl uded null modem ser ial cable. The Backup
SA8220 assumes control from th e Primary when any of the followi ng
occur:
• The Backup SA8220 does not detect the Primary SA8220's
heartbeat within the timeout period (the default is 3 seconds).
• The Primary SA8220's Ethernet interface beco mes inactive. For
example, if the Ethernet cable is disconnected.
• The Primary SA8220 experiences an internal software error.
Both the Primary and Backup SA8220s need to know their own
identity and the “Online Identity” by address and name to satisfy
internal communication parameters. The SA8220s' own names and
the shared online iden tity are automatically entered into their host
files during failover configuration. If Dual NIC is enabled, the
identities for both the Outside (network-side) and Inside (server-side)
NICs are shared.
NOTE: Before
configuring serial cable
failover, both the primary
and backup SA8220s
must be configured with
the
setup command.
For more information,
please see “Setup” in
Chapter 3.
For information on failover method dependencies, see Appendix C.
Serial Cable Failover Configuration
The following procedures are used to configure the Primary and
Secondary SA8220s for serial cable failover operation.
Configure the Primary SA8220
1. Connect the two SA8220s using their failover ports using the
provided null modem serial cable.
2. Reboot the SA8220 that will be the Primary and press a key at
the prompt to enter the Boot Monitor.
3. At the prompt, type the following command:
monitor>failover
33
Page 46

C H A P T E R 2 HP Traffic Director Server Appliances User Guide
NOTE: The Online IP
Address is the address
used by the SA8220 that is
currently accepting
remote administration
connections — this can be
either the Primary or the
Backup SA8220 (though
it is typically the
Primary). The Online IP
Address is the address by
which you can access the
Online SA8220 using
telnet for administrati on.
4. Follow the prompts as illustrated below (for single NIC
operation):
Specify failo ver method (dis ab led, serial,
route) :[disabl ed]--->serial
Checking for fa ilover unit.. .
Failover unit not detected or may not be
configured.
Is this machine Primary or Backup? [Primary]--->
Enter the Netwo rk’s ONline IP Add re ss
--->10.6.3.200
Enter the Netwo rk’s Online hos tna me
--->netonline
Serial failover successfully configured
If Dual NIC operation is enabled, failover configuration looks
like the example shown below:
monitor>failover
Specify failo ver method (dis ab led, serial,
route) [disable d] --->serial
Checking for fa ilover unit.. .
Failover unit not detected or may not be
configured.
Is this machine Primary or Backup? [Primary]
--->primary
Enter the Net work side Online IP Ad dr ess
[10.6.3.200]--->
Enter the Ser ver side Online IP Add ress
[10.6.4.200] -- ->
Enter the Net work side Online hos tn ame
[netonline] --->
Enter the Ser ver side Online hostn ame --->
servonline
34
Serial failover successfully configured
Page 47

C H A P T E R 2 Serial Cable Failover
5. Save the Primary configuration.
monitor>save
List of currently saved configuration files(s).
You may save over an existing configuration file
or enter a new name.
File name
---------active.cfg
backup.cfg
cris.cfg
‘active.cfg’ is the last booted configuration.
Enter configu ration file nam e (- to cancel):
[active.cfg] -- ->
Configuration has been saved.
6. Boot the SA8220.
monitor>boot
Do you really want to continue boot? [y]
---> <Enter>
Boot which conf iguration? [a ct ive.cfg]
---> <Enter>
Please stand by , the system is bein g bo oted.
.... Done
Login>
Configure the Backup SA8220
1. Reboot the SA8220 th at wi l l b e the Secondary and press a key at
the prompt to enter the Boot Monitor.
2. At the prompt, type the following command:
monitor>failover
3. Follow the prompts as listed below:
Specify failo ver method (dis ab led, serial,
route) [ ] --->s
Checking for fa ilover unit.. .
Failover unit detected
-------------------------Version : 2.3
Type : PRIMARY
State : ONLINE
Name : online13
35
Page 48

C H A P T E R 2 HP Traffic Director Server Appliances User Guide
IP : 13.1.1.20
Mac : 0:1:c9:ed:a6:fb
NOTE: Use the same
Online IP Address and
name for the Backup
SA8220 as the Primary
(these appear by default).
Is this machine Primary or Backup? [Backup]
---> <Enter>
Enter Online IP Address [13.1. 1.2 0] ---> <Enter>
Enter Online Name [online13] ---> <Enter>
Serial failover successfully configured
monitor>
4. Save the Backup configuration.
monitor>save
List of currently saved configuration file(s).
You may save over an existing confi gu ration file
or enter a new name.
File name
---------active.cfg
backup.cfg
cris.cfg
‘active.cfg’ is the last booted configuration.
Enter configu ration file nam e (- to cancel):
[active.cfg] -- ->
Configuration has been saved.
5. Boot the SA8220.
monitor>boot
... current configuration ...
... list of saved configuration files ...
Boot configuration file name? [active.cfg]
---> <Enter>
Do you really want to boot ‘active.cfg’? [y]
---> <Enter>
Please stand by , the system is bein g bo oted.
36
Page 49

C H A P T E R 2 Serial Cable Failover
Replicating the Configuration
The active configuration is replicated upon changes to the Backup
SA8220 from the Primary. For most configurations, faults are
detected within 3 se conds, and the Backup is fully online within 25
seconds. The latter interval increases as the number of services
increases.
Status Information
You can display inf ormatio n about the SA8220s’ function and
failover status either via the Command Line Interface or the GUI.
Below are the commands to display status information followed by a
list of status messages and their explanations.
1. Log in to the SA8220.
2. At the CLI prompt, type the following command:
HP SA8220>info
The status appears on the last line of the info command’s output.
A description of the status message can be found below.
Failover Status Message Description
The broker is ONLINE, and
serial failover is NONE
(disabled).
The broker is PRIMARY and
ONLINE, the remote's serial
failover is NONE (disabled ).
The broker is PRIMARY and
One of the SA8220s is configured
for either “none” or “route”
failover.
One of the SA8220s is configured
for either “none” or “route”
failover.
Normal Serial Failover Operation
ONLINE, the remote's state is
READY.
The broker is BACKUP and
READY, and the remote's
state is ONLINE.
37
Page 50

C H A P T E R 2 HP Traffic Director Server Appliances User Guide
Failover Status Message Description
The broker is PRIMARY and
NIC_FAILED, and the
remote’s state is ONLINE .
The broker is BACKUP and
ONLINE, and the remote’s
state is NIC_F AILED.
The broker is PRIMARY and
ONLINE, the connection to
the remote has TIMED OUT.
The broker is BACKUP and
IP_IN_USE_ERROR, the
connection to the remote has
TIMED OUT.
Ethernet cable disconnected, or
cable, NIC, or HUB port failure
The serial cable connecting the
SA8220s is disconnected
38
Page 51

C H A P T E R 2 Serial Cable Failover
NOTE: The notation,
PRIMARY/BACKUP
indicates that ei ther
“PRIMARY” or
“BACKUP” will be
displayed.
The Failover Status messages in this table are not specific to the
Primary or Backup SA8220s.
Failover Status Message Description
The broker is PRIMARY/
BACKUP and
WAITING_FOR_SYNC
One of the SA8220s has been
restarted. This status persists
while the configuration files are
loaded from the online SA8220.
The time this state persists
depends on the number of VIPs
and services configured.
The broker is PRIMARY/
BACKUP and
CONFIGURATION_
ERROR
The broker is PRIMARY/
BACKUP and DNS_FAILED
Both SA8220s are configured as
Primary or as Backup. Neither
SA8220 will come online until
this condition is corrected
The online IP address is missing
form both the local host file and
the DNS server.
The broker is PRIMARY/
BACKUP and
CORE_APP_FAILED.
The broker is PRIMARY/
BACKUP and
RICH_APP_FAILED.
Indeterminate error . Use an earlier
working configuration. If the
condition persists, contact
Customer Support for assistance.
39
Page 52

C H A P T E R 2 HP Traffic Director Server Appliances User Guide
Notes
40
Page 53

Boot Monitor
This chapter covers the following topics:
NOTE: For ease of
reading, all models are
referred to as the SA 8220
throughout this
document. Unless noted
otherwise, all SA8220
references refer to all
models.
• System Requirements
• Accessing the Boot Monitor
• Boot Monitor Commands
Page 54

C H A P T E R 3 HP Traffic Director Server Appliances User Guide
Using the Boot Monitor CLI
CAUTION: After
configuring the SA8220
with the Boot Monitor,
you must enable Aut oboot
with the
command or the SA8220
will not operate.
autoboot
System
Requirements
The HP e-Commerce Traffic Director Server Appliance SA8200/
SA8220s’ and the HP Traffic Director Server Appliance SA7200/
SA7220s’ Boot Monitor Command Line Interface (CLI) allow you to
configure boot options and manage boot configuration files.
Typically, you will us e the Boot Monitor only during the initial
configuration or after major reconfigurations, if the latter becomes
necessary. Day-to-day operations are managed using the Graphical
User Interface (please see “Graphical User Interface”, Chapter 4) or
the Run Time CLI (please see “Command Line Interface, Chapter 5).
General categories of tasks performed by the Boot Monitor include:
• Configure and display boot options, including the configuration
file
• Manage the boot configuration file system
• Configure and change IP parameters
You can use any terminal or workstat ion with a t erminal emul ator as
the CLI command station, provided the terminal has the following
features:
• 9600 bits per second, 8 data bits, 1 stop bit no parity, no flow
control (9600-8-N-1)
• A terminal emulation program, such as HyperTermi nal*
• Cable and connector to match the male DTE connector (DB-9)
42
Page 55

C H A P T E R 3 Using the Boot Monitor CLI
Accessing the
Boot Monitor
You can access the Boot Monitor Command Line Interface in either
of the two ways described in this section.
Interrupting the Bootup Sequence
1. Interrupt the SA8220’s bootup sequence by pressing a key at the
following prompt:
Press any key to sto p autoboot.
In a few seconds the monitor> prompt displays, confirming
that the Boot Monitor is running:
Using the Run Time CLI
1. Type this command at the prompt:
config sys auto boot disable
2. Then, at the HP SA8220# prompt, t ype this command:
reboot
The monitor> prompt displays, confirming that the Boot
Monitor is running.
43
Page 56

C H A P T E R 3 HP Traffic Director Server Appliances User Guide
Boot Monitor
Commands
autoboot Enables or disables the Autoboot function. When Autoboot is
Boot Monitor CLI commands (listed below) are described in this
chapter.
• autoboot • info
• boot • interface
• delete • ip
• dhcp • load
• dir • netmask
• dns • rich_bias
• dual • save
• factory_reset • settime
• failover • setup
• gateway • static_routes
• help • version
• host
enabled, the SA8220 prompts you to press a key during restart to
enter the Boot Monitor command line interface. If you ignore the
prompt, restart finishes with the SA8220 in normal operating mode.
If Autoboot is disabled, the restart sequence ends by displaying the
Boot Monitor interface.
44
Example:
monitor>autoboot
Enable Autobo ot? (yes,no) [y es ] --->
boot Boots the device with a specific configuration. Variations on use of
the reboot command are desc ribed below.
Reboot with No Configur ation Changes
1. Type the boot command.
The Boot Monitor displays the current configuration pr ompts
you for confirmation, as shown in the example below:
Page 57

C H A P T E R 3 Using the Boot Monitor CLI
Current active configuration
---------------------------Product: HP
Version: 2.7
Patch Level: 0.0
Build: 12
Current time: Tue Sep 12 17:02:05 2000
Hostname: CSLab7k
------------Network side NIC:
IP Address: 10.6.3.21
Netmask: 255.255.255.0
MAC address: 0:a0:c9:ed:6c:c c
------------Service side NIC:
IP Address 10.6.5.21
Netmask: 255.255.255.0
MAC address: 0:d0:b7:6:c1:85
------------Default Gateway: 10.6.3.1
Domain: None
Primary name server: None
DHCP: Disabled
Failover mode : Disabled
Network NIC setup: Auto
Server NIC setup: Auto
NTP: Disabled
Autoboot: Disabled
Static Routes: None
RICH_Biased: Enabled
Do you really want to boot active.cfg? [y] --->
SA8220
2. To boot to the normal operational prompt, type y.
3. To return to the
monitor> prompt, type n.
Reboot with Configuration Changes
When you use the boot command after changing the SA8220’s
configuration, you are presented with a number of options. These
allow you to use the changed configuration, revert to the last saved
45
Page 58

C H A P T E R 3 HP Traffic Director Server Appliances User Guide
configuration, or choose among a list of previously saved
configurations. Procedures for choosing among these options are
organized within three groups, described below.
1. Type the
boot command.
2. The Boot Monitor displays the changed configuration
information and prompts you to save the new configuration, as
shown in the example below:
Current active configuration
---------------------------Product: HP
Version: 2.7
Patch Level: 0.0
Build: 12
Current time: Tue Sep 12 17:02:05 2000
Hostname: CSLab7k
------------Network side NIC:
IP Address: 10.6.3.21
Netmask: 255.255.255.0
MAC address: 0:a0:c9:ed:6c:c c
------------Service side NIC:
IP Address 10.6.5.21
Netmask: 255.255.255.0
MAC address: 0:d0:b7:6:c1:85
------------Default Gateway: 10.6.3.1
Domain: None
Primary name server: None
DHCP: Disabled
Failover mode : Disabled
Network NIC setup: Auto
Server NIC setup: Auto
NTP: Disabled
Autoboot: Disabled
Static Routes: None
RICH_Biased: Enabled
The configuration has changed, save it? [y] --->
SA8220
46
Page 59

C H A P T E R 3 Using the Boot Monitor CLI
First Options:
NOTE: This list includes
backup.cfg, a backup
of the most recently
booted configuration.
This file is automatically
created when you c hange
the configuration and
save.
1. If you select the defa ult,
figuration as either
Configuration file name? [active.cfg] --->
2. You can either accept the default,
y, the system allows you to save the con-
active.cfg or the last loaded filename.
active.cfg, or type a new
filename. The system then saves the file and presen ts a list of all
saved files.
Select a boot con figuration fr om th e following
files.
active.cfg
backup.cfg
Boot configuration file name? [active.cfg] --->
3. You can accept the defaul t, active.cfg, or select another
previously saved c onf igur at io n. R eg ar dle ss of t he f ile you select,
the configuratio n fi le you a re abou t to b oot i s displa yed to e nsure
that the last file displayed is the conf iguration that is bo oted.
4. If you select the default,
operational prompt, if you type
y, the system boots to the normal
n, it returns to the monitor>
prompt.
Second Options:
1. If you choose not to save the modifi ed fi le, the system displays a
warning that it is reverting to th e previously booted configuration, as shown below:
Warning: The cu rrent configu ra tion has NOT been
saved and will no t be booted. Rever ti ng to last
saved active. cfg.
2. If there are no additional saved configurations then the system
prompts you to confirm that want to boot the last saved
configuration, which will always be
Do you really want to boot active.cfg? [y] --->
active.cfg.
3. If you select the default, y, the system boots to the normal
operational prompt. If you type
n, it returns to the monitor>
prompt.
47
Page 60

C H A P T E R 3 HP Traffic Director Server Appliances User Guide
Third Options:
1. If there are any previously saved configurations on the system,
you are offered a choice of configuration files to boot from.
Select a boot con figuration fr om th e following
files.
active.cfg
backup.cfg
Boot configuration file name? [active.cfg] --->
2. You can accept the offered default, active.cfg, or select
another previously saved configuration. If you select
active.cfg, the configuration is not redisplayed. If you select
a file other than
active.cfg, the file’s contents are displayed to
ensure that the last file displayed is the configuration that is
booted.
3. If you select the default,
operational prompt, if you type
y, the system boots to the normal
n, it returns to the monitor>
prompt.
delete Deletes the specified configuration file.
Example:
monitor>delete
Select a config uration to dele te fr om the
following files.
Note: You canno t delete the activ e
configuration file active.cfg.
File name
-------------active.cfg
backup.cfg
cris.cfg
‘active.cfg’ is the last booted configuration.
Enter the confi guration file na me to delete:
--->broker1.cfg
broker1.cfg successfully deleted.
48
Page 61

C H A P T E R 3 Using the Boot Monitor CLI
dhcp Enables or disables the SA8220’s use of DHCP. When DHCP is
enabled, the SA8220 receives its configuration parameters from the
DHCP server at startup. When DHCP i s disabled, the SA8220 ignores
the DHCP server, and so it must be manually configured at restart.
Respond to the prompt with
y to enable, or n to disable. DHCP is
disabled by default.
Example:
monitor> dhcp
Enable DHCP (yes, no)? [no] --->
dir Displays the list of saved boot configuration files.
dns Specifies the domain and (optionally) nameserver(s). The system
prompts you for the required information.
Example:
Would you like to configure DNS (yes, no)?
[no] --->
monitor>dns
Would you like to configure DNS (yes, no)?
[no] --->yes
Enter Domain na me (‘-’ to cancel)
--->mydomain.com
Enter the IP Addr ess of the Primary nam e server
(‘-’ to cancel) --->10.6.3.5
Specify additional name server
( <return> to end ) ---> 10.6.3.10
Specify additional name server
( <return> to end ) --->
dual Selects single or dual NIC operation.
Example:
monitor>dual
Enable dual NIC operation (yes, no) [no] --->
49
Page 62

C H A P T E R 3 HP Traffic Director Server Appliances User Guide
factory_reset Resets the system to factory defaults, listed belo w.
NOTE: The first boot
after a
command or a new
installation will prompt
factory_reset
Parameter Setting
All added user accounts Deleted
you for the root
password. Also, the
factory_reset
command does not delete
Policy groups, services, and servers Deleted
Route parameters Deleted
saved configuration files.
CLI parameters Deleted
IP address Deleted
Default route Deleted
Hostname Deleted
Domain Deleted
Name servers Deleted
DHCP Disabled
Dual NIC Disabled
Failover mode Disabled
Autoboot Disabled
Autoboot timeout 5 seconds
Added hosts in the host file Deleted
New root password on next boot Forced
Rich bias Enabled
Static routes Deleted
50
Page 63

C H A P T E R 3 Using the Boot Monitor CLI
failover Specifies the SA8220’s failover method. Three failover options are
available:
• disabled : no failover method will be used
• serial: serial cable failover will be used
• route: router failover will be used
Example:
monitor>failover
Specify failo ver method (dis ab led, serial,
route): [disabled] --->serial
Checking for fa ilover unit.. .
Failover unit not detected or may not be
configured.
Is this machine Primary or Backup?
[Primary] --->
Enter the Network side Online IP Address
--->
Enter the Serve r side Online Addr es s
--->10.6.5.200
Enter the Network side Online hostname
--->net-onlinehost
Enter the Serve r side Online host na me
--->serv-onlinehost
Serial failover successfully configured
10.6.3.200
gateway Specifies the default gateway.
Example:
monitor>gateway
Enter default gateway: --->10.6.3.1
help Lists all Boot Monitor commands or optionally displ ays syntax for a
specified command.
Example:
gateway Set default gateway
interface Configure network interface card
51
Page 64

C H A P T E R 3 HP Traffic Director Server Appliances User Guide
host Sets the S A8220’s host name.
Example:
monitor>host
Enter the hostname you would like to assign to
the Network NIC: --->CSLab7k
info Displays the current boot configuration.
interface Configures Ethernet port parameters. Compatibility with some older
switches, hubs, or router s, may require t hat you manual ly specify the
Ethernet speed and duplex mode of the SA8220's network interface
card.
Single NIC configuration example:
Auto configure the network NIC speed and duplex
(yes,no)? [yes] --->no
1 - 100BaseTx
2 - 10BaseTx
Select Media Type (1 or 2): [1] --->
Use Full Duplex ? [n] --->n
2
Dual NIC configuration example:
Auto configure the Network side NIC speed and
duplex (yes,no)? [yes] --->
Auto configur e the Server side NIC sp eed and
duplex (yes,no)? [yes] --->
ip Specifies the SA8220's IP address.
Example:
monitor>ip
Enter the IP address for the Network side NIC
[10.6.3.21] --->
Enter the IP address for the Server side NIC
[10.6.5.21] --->
52
Page 65

C H A P T E R 3 Using the Boot Monitor CLI
load Loads a previously saved configuration file into memory.
Example:
monitor>load
Select a configuration file to load from the
following files.
File name
-------------active.cfg
backup.cfg
cris.cfg
‘active.cfg’ is the last booted configuration.
Enter the confi guration file na me to load
(- to cancel): [active.cfg] --->
Configuration loaded: active.cfg
netmask Specifies the netmask.
rich-bias
(not available on the
SA7200)
Example:
monitor>netmask
Enter Netmask for Network side NIC
[255.255.255.0] --->
Enter Netmask for Service side NIC
[255.255.255.0] --->
Optimizes RICH_HTTP ser v ice performance. If your RICH_HTTP
service responses consist mostly of fi les greater tha n 8K, the enab led
(default) setting of
rich_bias will optimize performance. If your
site is experiencing performance problems and the RICH_HTTP
service responses are less than 8K, you may want to disable
rich_bias.
This command has no effect on SSL terminated connections.
Example:
monitor>rich_bias
Unit is currently ‘RICH_Biased’, change it
(yes, no) [no] --->
RICH_Biased (enable, disable) [enable]
--->
disable
yes
53
Page 66

C H A P T E R 3 HP Traffic Director Server Appliances User Guide
save Saves the current configuration. Changes made during the current
Boot Monitor session are lost unless you use the
save command.
Example:
monitor>save
List of currently saved configuration file(s).
You may save over an existing confi gu ration file
or enter a new name.
File name
------------active.cfg
bckup.cfg
cris.cfg
‘active.cfg’ is the last booted configuration.
Enter configu ration file nam e (- to cancel):
[active.cfg] -- ->-monitor>
settime Selects a method for setting the SA8220’s system time and date. If
NOTE: Example 1 is for
setting the tim e using
Greenwich Mean Time
(GMT). For example, the
GMT-14 timezone is
GMT minus 14 hours.
you select NTP, you will be prompted for the IP address of the NTP
server(s) you want to use. If you set the date manually, you will be
prompted first for the timezone, then for the date in 24-hour format.
Example, with NTP:
monitor>settime
Use NTP? [enable] --->
Enter IP addres s of NTP server or <re tu rn> to
end: --->
Enter IP addres s of NTP server or <re tu rn> to
end: --->
Enter IP addres s of NTP server or <re tu rn> to
end: --->
209.218.240.1
209.218.240.238
Example 1, without NTP (manual setting):
monitor>settime
Use NTP? [disab le] --->
Select TIMEZO NEs to list (GMT, US, Other or q to
quit: [GMT] --->GMT
54
Page 67

C H A P T E R 3 Using the Boot Monitor CLI
Select a TIMEZONE from the ‘GMT’ li st .
1) GMT-14 2) GMT-13 3) GMT-12
4) GMT-11 5) GMT-10 6) GMT-9
7) GMT-8 8) GMT-7 9) GMT-6
10)GMT-5 11)GMT-4 12)GMT-3
13)GMT-2 14)GMT-1 15)GMT
16)GMT+1 17)GMT+2 18)GMT+3
19)GMT+4 20)GMT+5 21)GMT+6
22)GMT+7 23)GMT+8 24)GMT+9
25)GMT+10 26)GMT+11 27)GMT+12
Select a number between 1 and 27
(q to quit)--->2
Selected TIMEZONE ‘GMT-13’
The current tim e is now: Fri Sep 29 05: 38 :38
GMT-13 2000
Enter the year (YYYY): [2000] --->
Enter the month (MM): [09] --->
Enter the day (DD): [29] --->
Enter the hour (HH): [05] --->
Enter the minute (MM): [38] --->
Enter the seconds (SS): [38] --->
Fri Sep 29 05:38: 38 GMT-13 2000
NOTE: Example 2 is for
setting the tim e using
United States time (US).
Example 2, without NTP (manual setting):
monitor>settime
Use NTP? [disabl e] --->
Select TIMEZO NEs to list (GMT, US, Other or q to
quit: [GMT] --->US
Select a TIMEZONE from the ‘US’ list.
1) Alaska 2) Aleutian 3) Arizona
4) Central 5) Eastern 6) Hawaii
7) Indiana-East 8) Indiana-Starke 9) Michigan
10)Mountain 11)Pacific 12)Somoa
Select a number between 1 and 12
(q to quit): [11}--->5
55
Page 68

C H A P T E R 3 HP Traffic Director Server Appliances User Guide
Selected TIME ZONE ‘Eastern’
The current tim e is now: Sat Oct 28 23: 59 :42
2000
Enter the year (Y YYY): [2000]- -->
Enter the month(MM): [10]--->
Enter the day (DD): [28]--->29
Enter the hour (H H): [23]--->01
Enter the minut e (MM): [59]--> 57
Enter the seconds (SS): [39]--->
Sun Oct 29 01:57: 39 EDT 2000
Example 3, without NTP (manual setting):
NOTE: Example 3 is for
setting the time using any
timezone OTHER THAN
GMT or US.
monitor>settime
Use NTP? [disabl e] --->
Select TIMEZO NEs to list (GMT, US, Other or q to
quit: [GMT] --->O
Select a TIMEZONE from the ‘Other’ list.
1) Bangkok 2) Belfast 3) Belgrade
4) Berlin 5) Brussels 6) Copenhagen
7) Hongkong 8) Israel 9) Japan
10)London 11)Madrid 12)Manila
13)Paris 14)Poland 15)Portugal
16)Prague 17)Rome 18)Singapore
19)Stockholm 20)Turkey 21)Warsaw
22)Zulu 23)Zurich
Select a number between 1 and 23 (q to qu it) :
[10]--->22
Selected TIME ZONE ‘Zulu’
The current tim e is now: Sat Oct 28 23: 59 :42
2000
Enter the year (Y YYY): [2000]- -->
Enter the month(MM): [10]--->
Enter the day (DD): [28]--->29
Enter the hour (H H): [23]--->01
Enter the minut e (MM): [59]--> 57
Enter the seconds (SS): [39]--->
Sun Oct 29 01:57: 39 EDT 2000
56
Page 69

C H A P T E R 3 Using the Boot Monitor CLI
setup Initiates the SA8220’s setup procedure. The system displays p rompts
for all inputs necessary to initialize it.
Example:
monitor>setup
Enable dual NIC operation(yes,no)? [no] ---> yes
Autoconfigure the Network side NIC speed and
duplex? (yes,no )? [yes] --->
Autoconfigure the Server side NIC speed and
duplex? (yes,no )? [yes] --->
DHCP is disabled for dual NIC operation.
Enter the hostname you would like to assign to
the Network NIC: --->
Enter the IP address for the Network side NIC
--->10.6.3.21
Enter the IP address for the Server side NIC
--->10.6.5.21
Enter the Netma sk for the Network sid e NIC
--->255.255.255.0
Enter the Netma sk for the Server si de NIC
--->[255.255. 255.0] --->255.255.255.0
Enter default gateway: --->10.6.3.1
Would you like to configure DNS (yes, no)? [no]
--->DNS not configured.
Specify failo ver method (dis ab led, serial,
route): [disabled] --->
Set Autoboot? (yes,no) [no] --->
CSLab7k
57
Page 70

C H A P T E R 3 HP Traffic Director Server Appliances User Guide
static_routes Deletes and adds any number of static IP routes. Shows the current
static IP routes (if any) when the function is entered. You are
prompted for the destination and gateway IP addresses. The
info
command will show any static IP routes that are known to the Boot
Monitor, and
factory_reset will remove all static IP routes as
part of its cleanup.
Example:
monitor>static_routes
Static Route information.
Enter Static ro ute (1) dest IP(- to del , q to
quit): --->10.7.16.5
Enter Static ro ute (1) gate IP(- to del , q to
quit): --->10.8.15.40
Enter Static ro ute (2) dest IP(- to del , q to
quit): --->10.7.18.50
Enter Static ro ute (2) gate IP(- to del , q to
quit): --->10.8.15.40
Enter Static ro ute (3) dest IP(- to del , q to
quit): --->q
{2} Static Rout e(s).
version Displays software version information.
Example:
monitor>version
Product: HP SA7220
Version: 2.4
Patch Level: 0.1
Build: 40
58
Page 71

Graphical User
Interface
This chapter covers the following topics:
NOTE: For ease of
reading, all models are
referred to as the SA 8220
throughout this
document. Unless noted
otherwise, all SA8220
references refer to all
models.
• Before You Begin
• Logon Screen
• Topology Screen
• Policy Manager Screen
• Administration Screen
• Configuration Screen
• Tools Screen
• Statistics Screen
Page 72

C H A P T E R 4 HP Traffic Director Server Appliances User Guide
Before You Begin
NOTE: Some functions
and features are not
available in the GUI.
The HP e-Commerce Traffic Director Server Appliance SA8200/
SA8220s and HP Traffic Director Server Appliance SA7200/
SA7220s have features and functions that are controlled through
either the browser-based Graphical User Interface (GUI), as
discussed in this chapter, or the Command L ine Interface (CLI), as
discussed in Chapter 5.
In order to use th e inside IP or i nside online IP for administrati on, the
client must be on the same subnet as the inside interface , or must have
an alternate path back through the outside interface.
60
Page 73

C H A P T E R 4 Logon Screen
Logon Screen
To access the various GUI services available to you on the SA8220,
you must first log on to the system as described in this section.
Logging on to
the GUI
NOTE: If Internet
Explorer* 5.01 (or later)
is your browser, you must
add a trailing slash (/) to
the URL, as shown in step
(2). Also, the default GUI
port (1095) can be
changed. For details,
please see “GUI Tab” in
this chapter.
1. Launch your browser.
2. In your browser’s Address or Location field, type the SA822 0’s
address and specify port 1095. For example:
http://system_name:1095/
where system_name is the actual name or IP address of your
SA8220.
3. Press Enter.
The Logon screen displays, as shown below.
Logon Screen
61
Page 74

C H A P T E R 4 HP Traffic Director Server Appliances User Guide
NOTE: The factory
default for both th e user
name and password is
admin (lowercase
required). To change
them, please see “Users
Tab” in this chapter.
4. In the space provided, type your User name.
5. In the space provided, type your Password.
6. Click Logon.
The Topology screen displays, as shown on the next page. The
number of server icons varies, depending upon your network
configuration.
62
Page 75

C H A P T E R 4 Topology Screen
Topology Screen
Using the
Topology
Screen
Topology Screen
Purposes of the Topology Screen
• Displays a graphical representation of the current topological
relationships between the SA8220 and network servers. The
SA8220’s status and Serial Cable failover, i f configured, are also
reflected here.
• Serves as a gateway to the Administration and Policy Manager
screens, and the Configuration and Tools screens.
63
Page 76

C H A P T E R 4 HP Traffic Director Server Appliances User Guide
Topology Screen Toolbar
Policy
Back
Administration
Manager
Log File
Configuration
Tools
Statistics
Topology Screen Toolbar
Located at the top left of the window, the toolbar is shown above.
The toolbar’s buttons, from left to right, are described below:
• Back returns you to the previous screen. From the Topology
screen, this will log you off the system and return you to the
logon screen.
• Configuration displays the Configuration Screen
• Administration displays the Administration Screen
• Tools displays the Tools Screen
• Policy Manager displays the Policy Manager Screen
• Statistics displays the Statistics Screen
• Log File displays the SA8220's log file.
Online Help
Located at the top right of the window, the Help button is shown
iabove. Click Help to display the online help file .
64
Online Help Button
Page 77

C H A P T E R 4 Topology Screen
Topolo gy Screen Elements
SA8220 Icon
The SA8220 is represent ed onscreen by a horizontal "rack unit" icon,
as shown above.
• Right-clicking on the SA8220 icon displays a popup menu that
can take you to other screens.
• Double-clicking the SA8220 icon takes you to the Policy
Management screen by defaul t, but this can be changed in the
Administration screen (please see “Administration Screen” in
this chapter).
Server Icon
Servers are represented onscreen by vertical "tower case" icons, as
shown above.
• Right-clicking on a server icon displays a popup menu that can
take you to other screens.
• Double-clicking the server icon takes you to the Statistics screen
by default, but this can be changed in the Administration screen
(please see “Administration Screen” in this chapter).
65
Page 78

C H A P T E R 4 HP Traffic Director Server Appliances User Guide
Window Controls
Slider Control
To resize the Topology screen elements, click and drag the slider
control located in the upper right hand corner of the screen, as shown
above.
• Move the slider control to the far right, as shown above, for the
largest display.
• Move the slider control to the far left for the smallest display.
Background Zoom and Refresh Control
The Topology screen elements can also be resized by right-clicking
on the background of the screen. The popup menu shown above
displays onscreen.
• Zoom In enlarges the displ ay and is the equivalent of moving the
slider control to the right.
• Zoom Out reduces the display and is t he equivalent of movi ng the
slider control to the left.
• Refresh Display updates the Topology screen.
66
Page 79

C H A P T E R 4 Policy Manager Screen
Policy Manager Screen
When you double-click a SA8220 icon in the Topology screen (or
right-click and select Policy Management), the Policy Manager
screen displays, as shown below.
Policy Manager Screen
The Policy Manager consists of a series of screens with multiple tabs
that includes the controls used in the implement ation of Policies. The
discrete items created, altered, and deleted in the course of Policy
management are listed below:
• Policy Groups
• Services
• Servers
67
Page 80

C H A P T E R 4 HP Traffic Director Server Appliances User Guide
Policy
Manager
Controls and
Displays
The Policy Manager screen contains two main regions, as described
below:
• The Policies display, on the left side o f the Policy Manag er
screen
• The Details display, on the right side of the Policy Manager
screen
The relative sizes of the Policies and Details displays are adjustable
by clicking and dragging th e vertical line between the panels. The
Policies display includes existing Policy Groups, Services, and
Servers, reflecting the previously mentioned hierarchy. The Details
display includes controls and status displays relating to the item
selected in the Policies display, and changes according to the type
(Policy Group, Service, or Server) of t he item selected. If a Service or
Server is selected, then the Details screen contains two tabs, each
containing related controls.
The three types of items form a hierarchy: policy groups contain
Services. Services in turn contain Servers. A lower hierarchy item
cannot be created unless its immedi ately super ior type exi sts, that is,
a policy group must exist before you can create a Service, and a
Service must exist before you can create a Server.
Policy
Manager
Toolbar
New
Policy
Group
New
Server
New
Service
Policy Manager Toolbar
Delete
Selected
Item
68
Page 81

C H A P T E R 4 Policy Manager Screen
The Policy Manager toolbar contai ns three buttons for creating Policy
Groups, Services and Servers, and on e button to delete the currently
selected item, regardless of its type. The toolbar’s buttons are enabled
or disabled (dimmed) according to th e type of item selected in the
Policies display.
Policy
Manager’s
Pop-up Menu
You can display the Poli cy Manager ’s pop-up menu, shown below,
by right-clicking in the Policies display.
Display
Commands
Sort
Commands
Create/
Delete
Commands
Policy Manager’s Pop-up Menu
Policy Groups
Services are virtual resources provided to a client . However, Services
can exist only in the context of Policy Groups. Policy Groups are
regarded as containers used to organize Services. Therefore, before
Services can be defined, Policy Groups must be created to contain
them.
The Policy Manager's Policy Group Details screen provides two
functions:
• Naming of newly created Policy Groups
• Enabling or disabling of the selected Policy Group's throttling
function
69
Page 82

C H A P T E R 4 HP Traffic Director Server Appliances User Guide
Creating Policy Groups
You can create Policy Groups in either of two ways:
1. Click New Policy Group, in the left of the Policy Man ager
toolbar, or
2. Right-click to display the menu, then select the New Policy
Group command.
A new Policy Group icon and the Detail screen displays in the
Policies display, as shown below.
NOTE: The names of
existing Policy Groups
cannot be changed.
Adding a New Policy Group
3. T ype a name for the new Poli cy Group in the Pol icy Gr oup Name
field. Policy Group names must adhere to the following
conventions:
• From 1 to 25 characters in length
• Any alphanumeric character
• Other eligible characters include hyphens ("-"), periods ("." ), and
underscores ("_")
• Spaces must not be used.
Within these restrictions, the naming of Policy Groups is at your
discretion, though convenient naming schemes might include
serial names ("Group1," "Group2," etc.), or names that reflect a
Policy Group’s content, such as "e-CommerceGrp" or
"HTTP_Group."
70
Page 83

C H A P T E R 4 Policy Manager Screen
Naming the New Policy Group
4. To accept the speci fied name, click Apply. The new Policy
Group’s new name displays in the Policies display.
When the new Policy Group name displays, Create Service (see
above), becomes available. This reflects the fact that Services
cannot be created unless at least one Policy Group already exists.
Throttling
When throttling is enabled, requests to eligible servers in lowerpriority services are stopped until response times of higher priority
services are met, or all eligible servers have been throttled. An
eligible server is one that is shared by both higher and lower priority
services. Throttling affects all services within a Policy Group.
To enable or disable throttling for the selected Policy Group, follow
the steps below:
1. Select the Enable Server T hrottling check box (see figure above).
2. Click Apply.
Deleting Policy Groups
To delete a Policy Group, follow the steps belo w:
1. In the Policies display, click to select the name of the Policy
Group to be deleted.
2. In the Policy Manager toolbar, click Delete (X), or right-click to
display the menu and click the Delete Selected Item command.
71
Page 84

C H A P T E R 4 HP Traffic Director Server Appliances User Guide
Services
Once a Policy Group exists, you can create Services.
Creating Services
Follow these steps to create a Service:
1. In the Policies displa y, click to select a Policy Gr oup.
2. In the Policy Manager toolbar, click New Service, or right-click
in the Policies display and select New Service from the pop-up
menu.
The Service Details tab displays in the De ta ils screen, as shown
below.
NOTE: All fields
mentioned in steps (3)
through (6) become readonly after the service is
created.
72
3. In the Service Name field, Type a name for the service.
4. From the Service Type pull-down menu, click the desired Service
Service Details Tab
type. The choices are HOT TCP (the default), or RICH_HTTP.
Page 85

C H A P T E R 4 Policy Manager Screen
5. From the Virtual IP pull-down menu, click the desi red Virtual IP
(VIP) address. If there are no VIPs in the menu, or if the desired
one is absent, type it in.
NOTE: The VIP/port
combination must be
unique.
6. Type a port in the Port field. The port is th e listening port for
incoming connections, and you can select port numbers between
1 and 65535.
7. When you have finishe d filli ng in th e fields i n the Service Details
tab, click Apply.
The Policies display now reflects the name of the new Service
below the name of the Policy Group from which it was created.
Additional Service Tab Controls and Displays
The items listed below can be changed aft er the Service has been
created.
Control or Display Description
Enabled
Priority
Select this check box to activate the selected Service. Clear the check
box to disable the Service.
Services within a singl e Polic y Group can be prioriti zed. T he SA8220
assures more server resources to Services with high priority numbers
than to those with lower numbers. The Pri ority setting is an inte ger
from 1 (highest prior ity) to 5 (lowest priority), and the default is 1.
Duplicate SYN
Timeout
This value is the time interval (in microseconds) after which the
fulfillment server is declared dead if the dynamically calculated
number of duplicate SYNs (lost packets) to that server is detected. You
can specify a value from 1000 to 2,147,483,647, and the default is
500,000.
Server Timeout
(RICH only on all
models except the
SA7200)
Enable Backup
Servers
This value is the time interval (in seconds) during whi ch a server must
respond before it is declared dead. If the server fails to respond before
the end of timeout interval, the outstanding request is passed to another
server. This value is only available for RICH_HTTP services.
This check box allows you to enable or disable servers designated as
type "Backup" to come on line if necessary to assure target response
times. For more details about servers, please see “Servers” in this
chapter.
73
Page 86

C H A P T E R 4 HP Traffic Director Server Appliances User Guide
Control or Display Description
Insert Source IP in
HTTP Header
(RICH only on all
models except the
SA7200)
Sticky Mode
NOTE: If using SSL
services on the
SA8200/SA8220, the
SSL session ID
maintains a sticky
relationship when
Source IP sticky is
selected
This check box specifies whether or not the Source IP address is
embedded within the HTTP header information.
The SA8220 is configure d to maintain a session’s state so that serial
requests from a single client are allocated to the same server. This is
called a "sticky" port. This setting may be disabled, based on Source
IP, or based on a Cookie as described below:
Source IP: Source IP sticky mode uses the client’s source IP address
to identify a series of requests to be directed to a single server.
Cookie: In cases where requests come through a proxy server, all
requests display to originate from that server’s IP address, thus IP
address is of n o use i n identi fyi ng in divid ual requ estor s. Coo kie stic ky
mode provides an active method of identifying requ estors in such
situations. When Cookie sticky mode is enabled, a cookie is given to
requesting browsers. Subsequent requests from clients who have
received cookies contain ident ifying informat io n all owi ng the SA8220
to direct them to a single server. Cookie mode is available only for
RICH_HTTP, so it is no t available on the SA7200.
Sticky Timeout
Protocol
Status
74
The current software version for the SA8220 treats the timeout
differently for cookie versus Source IP sticky. With Source IP sticky,
the timeout is reset with every connection from the clien t (so that the
timeout is effectively an "idle time"). Wi th cookie sticky, the timeout
starts with the first connection from the client to the server, and never
gets reset. When the cookie expires, even if actively being used, the
next connection will be load balanced to a new server.
Work around: We recommend that you set the cookie sticky timeout
value to at least 1.5 times the maximum amount of time a user will
expect to be stuck to a server. The default is 90 seconds
This read-only field displays the protocol of the Service (TCP).
This read-only field displays the status of the selected Service
("Active" or "Inactive").
Page 87

C H A P T E R 4 Policy Manager Screen
Balance Strategy
HOT Services are assigned server resources according to either of
two Balance Algorithms. Click the Balance Strategy tab of the
Service Details screen to display the Balanc e Algorithm controls, as
shown below.
Service Balance Strategy Screen
Two Balance Algorithms are available:
• Response Time: Requests for a Service using the Response
Time algorithm are forwarded to the serv er that can fulfill them
within the shortest time.
• Round Robin: Requests for a Service using the Round Robin
algorithm are distributed evenly among the available servers.
1. From the pull-down menu, click to select the desired Balance
Algorithm for the Service selected in the Policies display. If you
select Response Time, type a value (in milliseconds) in the Max
response ti me (ms) field. For more details, please see “Response-
Time Metrics” in Chapter 2.
75
Page 88

C H A P T E R 4 HP Traffic Director Server Appliances User Guide
Deleting Services
To delete a Service:
1. In the Tree, click select the name of the Service to be deleted.
2. In the Policy Manager toolbar, click Delete, or right-click to
display the menu and click the Delete Selected Item command.
Servers
After you create Servi ces, you must desi gnate, or "cr eate" Servers t o
fulfill client requests for Services. As Services mu st exist within
Policy Groups, a Server (for example, a fulfillment host) must be
mapped to a Service.
To create Servers, follow the steps below:
1. In the tree, click an existing Service.
2. In the Policy Manager toolbar, Click Create Server , or right-click
in the Policies display and click New Server from the pop-up
menu.
The Server Details tab displays in the Deta ils screen, as shown
below.
76
Page 89

C H A P T E R 4 Policy Manager Screen
The Policy Manager’s Server Detail Screen
3. In the Server Name field, type an IP address or server name
known to the SA8220 via DNS or static host table. This value
cannot be changed after the server is created.
4. If appropriate, edit the Port field. The default value is th e port
number of the Service under which this Server displays in the
Tree. This value cannot be changed after the server is created.
77
Page 90

C H A P T E R 4 HP Traffic Director Server Appliances User Guide
5. From the drop down menu, click to select the desired Server
Type. Availa ble types are liste d below:
• Primary: Primary servers are immediately available to
accept client requests forwarded from the SA8220.
• Backup: Backup servers are sent requests under only two
circumstances: First, when the primary servers are unable to
meet the configured targ et response times a backup server
may be used if and only if "backups" is enabled for this
service. Second, backup servers are given requests when a
primary server is unavailable. As primary servers become
inactive, backup servers are brought into service to handle
requests.
• Disabled: Renders the server unavailable to accept client
requests.
6. From the drop down menu, click to select the desired Server
Mode. This command enables or disables Source Address
Preservation (SAP) on the named server. When Out-of-Path
Return (OPR) is enabled, the user-designated server port is
ignored and the configured service server port is used. By
default, SAP is enable d (and cannot be disa bl ed) when OPR is in
effect.
• For more details about SAP, please see Source Address
Preservation” in Chap ter 2.
• For more details about OPR, please see “Out-of-Path Return
(OPR)” in Chapter 2.
78
Page 91

C H A P T E R 4 Policy Manager Screen
RICH Controls (all models except the SA7200)
NOTE: OPR cannot be
used in conjunction with
Services of type
RICH_HTTP.
If the type of the Service under which you create a Server is
RICH_HTTP, the Server Details tab displays some additional
controls, as shown below.
Server Details Screen with RICH Controls Displayed
The RICH controls are listed below:
• Multi-hop Source Address Preservation: It is possible in
sophisticated network topologies to require that requests pass
through two cascaded SA8220s. In such configurations, the
SA8220 topologically closest to the clients must be configured
with the MSAP feature enabled. In most configurations, the
default setting (MSAP disabled) must be used.
• 606 Error Detection: "60 6" is a user -defined error code, that is,
you can specify an application level error as a "606 er ror " so it i s
detectable by the SA8220. When 606 Error Detection is enabled,
requests that generate a 606 error are rerouted, transparently to
the client, to the next avail able server. When disabled, the error is
sent back to the requesting client.
79
Page 92

C H A P T E R 4 HP Traffic Director Server Appliances User Guide
• HTTP Error Detection: When HTTP Error Detection is
enabled, requests that generate HTTP errors 401-405 and 500503 are rerouted, transparently to the client, to the next available
server. When disabled, these errors are sent back to the
requesting client.
• RICH Expression List: Expressions allow the SA8220 to parse
requests at the levels of path name, file type, and filename and
direct them to the appropriate server. E x pressions can include
wildcards. To define an expression list, type a series of
expressions separated by the semicolon character into the RICH
Expression List: field according to the following usage:
Valid expressions inclu de the following:
NOTE: The “*” and “!”
are allowed in
expressions, but they can
only exist at the
beginning or end of the
expression. Also, a
positive expression is
required after a not (!)
expression, otherwise the
(!) expression has no
effect.
• File type expressions, such as *.gif, or */index.html
• Path expressions, such as /home/*, or /home/images/*, or /home/
images/a*
• Unique file expressions, such as /index.html
• Wildcard expression, such as *
• The negation operator (!), e.g., !*.gif, or !*/index.html
Invalid expressions include the following:
• Text on either side of the asterisk, e.g., /index*.gif
• Expressions containing more than one asterisk, e.g., /index*.*
• Expressions containing one or more spaces or the dollar sign ($)
character
80
Page 93

C H A P T E R 4 Policy Manager Screen
Order of Expressions (all models except the
SA7200)
When using expressions in L ayer 7 (RICH) operations, the order of
expressions is significant only when the "not" (!) operator is used.
Expressions are described below.
Expression Yields
!*.gif;*
*;!*.gif
All non-GIF files
All files, because after specifying “all” (*),
the !*.gif expression is never reached
!*.html;/home/*
Matches all entries of the form “/home/*”
except HTML files
/home/*;!*.html
Matches all files of the form “/home/*.” The
!*.html has no effect.
!/home/*
!/home/*;*
No matches
all matches except ones starting with "/
home."
Deleting Servers
To delete a Server:
1. In the Tree, click the name of the Server to be deleted.
2. In the Policy Manager toolbar, click Delete, or right click to
display the menu and click the Delete Selected Item command.
81
Page 94

C H A P T E R 4 HP Traffic Director Server Appliances User Guide
Administration Screen
The Administration Screen is a set of ten tabs containing the
functions used to manag e the SA8220. Each tab include s controls and
displays related to a specific category of administration tasks.
Settings Tab
82
The Settings tab includes controls used to set the following:
• System ID: Edit this field to set the un it ident ifier. The SA8220s
Administration Screen — Settings Tab
are shipped with the unit serial number in this field. You can use
this control to chan ge the identifier if your site requires alternate
asset tracking information. The new ID can be an alphanumeric
value from 1 to 64 characters. To change this value, type the
desired identifier, and then click Apply.
Page 95

C H A P T E R 4 Administration Screen
• Server Verification Interval: Edit this field to change the
interval in seconds at which servers are "pi nged" to verify they
are available and able to handle traf fic requests. (See "IRV" in the
Command Line Interface chapter). The valid range for this field
is 0 to 99999. A value of 0 disables IRV.
In addition to the above controls, the Settings tab also contains
the following read-only displays:
• System Name: Displays the name given the SA8220 in its initi al
configuration.
• MAC Address: Displays the SA8220's Media Access Control
address.
• Status: The Status field displays information about the
SA8220's function and failover status. For more details about
status messages, please see “Status Information” in Chapter 2.
Software Tab
The Software tab contains controls and displays allowing you to
perform the following tasks:
• Specify image category as either System software or Agent
Software (Agent software lists software components other than
the SA8220 system image that may be installed on the un it, such
as the HP Multi-Site Traffic Director Server Appliance SA9200
agent).
• View the list of currently installed system software im ages (the
SA8220 can have up to five system images installed).
• View the list of currently installed agent software im ages (the
SA8220 can have up to four agents installed in addition to those
accompanying each system software image).
• Specify which of the installed software ima ges is to be active.
• Install or update software images.
• Delete software images.
• Enable or disable Passive FTP.
• FTP or TFTP new Multi-Site Agents to the SA8220.
83
Page 96

C H A P T E R 4 HP Traffic Director Server Appliances User Guide
System Software
The SA8220 provides sufficient local storage for five software
images (though at any time , only o ne imag e is active a nd execu ting.)
The "System Softwa re" area of the Software ta b displays the list of
currently installed syst em images, including the following det ails for
each:
• Image index number
• "Active" status (yes/no)
• Product name
84
Administration Screen — Software Tab (System Software View)
Page 97

C H A P T E R 4 Administration Screen
• Product version number
• Patch number
• Build number
Agent Software
The SA8220 can interface with other HP units by using Agent
Software images. The SA8220 provides sufficient local storage for
at least five Agent software images (though at any time, only one
image is enabled). To display the "Agent Software" area of the
Software tab, click Agent Software, which displays the list of
currently installed Multi-Site Director Agent images, as shown
below.
Software Tab in Agent Software View
Details displayed for each Agent include:
• Image index number
• "Active" status (yes/no)
85
Page 98

C H A P T E R 4 HP Traffic Director Server Appliances User Guide
• Product version number
• Patch number
• Build number
• Compatible Mu lti-Site Traffic Director version number
Specifying the Active System Software Image
To change the active system image:
1. Click System Software.
2. In the System Software box, click the image you want to activate.
3. Click Boot. The SA8220 displays a message prompting you to
proceed but warning you that the SA8220 will reboot as shown
below.
NOTE: You can also
perform a soft reboot of
the SA8220 by selecting
the currently active
software image and
clicking Boot.
86
Boot Warning Window
4. Click Yes.
As the SA8220 reboots, the screen shown below displays.
Reboot Screen
You must close all browser windows to ensure your browser uses
the newly activated Administration Application.
5. Wait three to five minutes for the SA8220 to finish rebooting,
and then run the administration application.
6. Go to the Software tab of the Administration screen and veri fy
that the "Active" column of the selected image displays yes.
Page 99

C H A P T E R 4 Administration Screen
Installing Software Images
You can download and install new system and ag ent software images
for the SA8220 using the controls in the Update Software box at the
bottom of the Software tab.
NOTE: A key is not
required to obtain Agent
Software.
Downloading a System Software Update
1. To download the new image, contact HP Customer Support or
your System Administrator to obtain the URL, Key, User, and
Password information.
For more details about software installation and updates, please
see Software Updates and Upgrades” in Chapter 8.
Deleting Software Ima ges
To delete a software image fro m the list of installed im ages:
1. In the Software View box, click the software type to be deleted.
2. In the Installed Software box, click the image to be deleted.
3. Click Delete. The SA8220 prompt s you to co nfirm that you want
to delete the selected image, as shown be low.
Delete Image Confirmation (System View )
87
Page 100

C H A P T E R 4 HP Traffic Director Server Appliances User Guide
4. Click Yes.
If you selected Agent Software, the prompt shown below
displays.
Delete Image Confirmation (Agent View)
5. Click Yes.
88
 Loading...
Loading...