Page 1

hp e-commerce
server accelerator
sa7100/sa7120
user guide
Page 2

© Copyright 2001 Hewlett-Packard Company. All rights reserved.
Hewlett-Packard Company
3000 Hanover Street
Palo Alto, CA 94304-1185
Publication Number
5971-0894
February 2001
Disclaimer
The information contained in this document is subject to change without notice.
HEWLETT-PACKARD COMPANY MAKES NO WARRANTY OF ANY
KIND WITH REGARD TO THIS MATERIAL, INCLUDING, BUT NOT
LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY
AND FITNESS FOR A PARTICULAR PURPOSE. Hewlett-Packard shall not
be liable for errors contained herein or f or incidental or conse quential damages
in connection with the furnishing, performance, or use of this material.
Hewlett-Packard assumes no responsibility for the use or reliability of its
software on equipment that is not furnished by Hewlett-Packard.
Warranty
A copy of the specific warranty terms applicable to your Hewlett-Packard
products and replacement parts can be obtained from
http://www.hp.com/serverappliances/support.
*Other brands and names are the prop erty of their respective owners.
Page 3

Table of Contents
Chapter 1: Introduction
About this User Guide . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1
Who Should Use this Book. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2
Before You Begin. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2
How to Use this Book. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2
Chapter 2: Installation and Initial Configuration
Before You Begin. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5
Installing the SA7100/SA7120 Free-Standing or in a Rack. . . . . . . . . . . . . . . . . . . . . 6
Rack Installation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6
Free-Standing Installation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
Network Connections. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
Status Check. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
Network and Server LEDs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
Page 4

C O N T E N T S HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Inline LED. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
Admin Terminal Connection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
HyperTerminal* Paste Operations. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
Troubleshooting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
Server and Network LEDs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
Continuing Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
Chapter 3: Theory of Operation
Security. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
Single Server Acceleration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
Multiple Servers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
Working with Internet Traffic Management (ITM) Devices . . . . . . . . . . . . . . . . . . . 13
Positioning SA7100/SA7120 between ITM Device and Client Network . . . . . . . 13
Positioning SA7100/SA7120 between ITM Device and Server . . . . . . . . . . . . . . 14
Multiple SA7100/SA7120s and Cascading Processing . . . . . . . . . . . . . . . . . . . . . . . 14
Scalability and Cascading . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
Spilling and Throttling. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
Availability. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
Keys and Certificates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
Cutting and Pasting with HyperTerminal* . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
Obtaining a Certificate from VeriSign* or Other Certificate Authority . . . . . . . . 17
Procedure. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
Exporting a Key/Certificate from a Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
Apache* Interface to Open SSL* (mod_ssl). . . . . . . . . . . . . . . . . . . . . . . . . . . 20
Apache SSL*. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
Stronghold*. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
Importing into the SA7100/SA7120 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
Creating a new Key/Certificate on the SA7100/SA7120. . . . . . . . . . . . . . . . . . . . 22
Procedure. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
Global Site Certificates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Global Site Certificate Paste Procedure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
Redirection: Clients and Unsupported Ciphers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
Client Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Creating a Client CA Certificate using OpenSSL* . . . . . . . . . . . . . . . . . . . . . . . . 28
SSL Processing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
Server Assignment (“Mapping”) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
iv
Page 5

Table of Contents
Automapping. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
Automapping with user-specified key and certificate. . . . . . . . . . . . . . . . . . . . 30
Automapping with multiple port combinations . . . . . . . . . . . . . . . . . . . . . . . . 30
Deleting automapping entries . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
Manual mapping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Combining automapping and manual mapping . . . . . . . . . . . . . . . . . . . . . . . . 31
Blocking. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Specific IP, Specific Port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Subnet, Specific Port. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
All IPs, Specific Port. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Delete a Block. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
Failure Conditions, Fail-safe, and Fail-through . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
Chapter 4: Scenarios
Scenario 1—Single Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
Procedure for Scenario 1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
Automapping. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
Manual Configuration. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
Scenario 2—Multiple Servers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38
Procedure for Scenario 2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38
Scenario 3—Multiple SA7100/SA7120s, Cascaded . . . . . . . . . . . . . . . . . . . . . . . . . 40
Initial Configuration. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Procedure for Scenario 3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
Scenario 4—Different Ingress and Egress Routers . . . . . . . . . . . . . . . . . . . . . . . . . . 43
Procedure for Scenario 4 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
Scenario 5—Configuring a Firewall. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
Server Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
SA7120 Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
Chapter 5: Command Reference
Online Help . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
Command Line Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48
User Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48
Command Line Prompt . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48
Syntax. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48
Abbreviation to Uniqueness. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
Moving the Insertion Point . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
v
Page 6

C O N T E N T S HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Command History . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
Cutting Text . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51
Command Summary. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
Command Reference. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
Help Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
Status Command . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
SSL Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58
Port Mapping Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
Operational Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 70
Remote Management Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 73
Alarms and Monitoring Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 79
Configuration Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 82
Administration Commands
Logging Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
Chapter 6: Remote Management
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93
Limitations. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 94
Remote Management CLI Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 94
Remote Telnet Sessions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96
Local Serial Console . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96
Remote Console, Telnet. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 97
Changing the Telnet Port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 97
Disabling Telnet. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 98
Remote SSH Sessions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 98
Local Serial Console . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 98
Remote Console, SSH . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 99
Changing the SSH Port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100
Disabling SSH . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100
SNMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100
Standards Compliance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 101
HP MIB Tree . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 101
Supported MIBs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 102
Where to find MIB Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 102
Enterprise Private MIB Summary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 102
Trap Summary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 106
Standard SNMP Traps. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 106
vi
Page 7

Table of Contents
Private Traps in the HP private MIB
(hpssl-appliance-mib.my) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 106
Enabling SNMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 107
Specifying SNMP Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
Community String. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
Trap Community String . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
Chapter 7: Alarms and Monitoring
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 111
Alarm Types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 113
ESC: Encryption Status Change Alarm . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 113
Alarm Modifiers and Messages: . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 113
RSC: Refused SSL Connections . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 113
Alarm Modifiers and Messages. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114
Extended Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114
RSC Alarm CLI Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114
UTL: Utilization Threshold Alarm . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
Alarm Modifiers and Messages. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
Extended Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
UTL Alarm CLI commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116
OVL: Overload Alarm . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116
Alarm Modifiers and Messages. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
Extended Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
OVL Alarm CLI Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
NLS: Network Link Status Alarm . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
Alarm Modifiers and Messages. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
Extended Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 118
Alarm Logging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 118
Example: list logs command: . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 118
Example: status command. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
Example: status alarms command. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 121
Monitoring . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 121
Monitoring Reports . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 121
Report Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 121
Monitoring Reports CLI Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 122
vii
Page 8

C O N T E N T S HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Chapter 8: Software Updates
Before Upgrading. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 126
Monitoring output data can interfere with import/export operations.. . . . . . . 126
IP blocks may not persist across software upgrade. . . . . . . . . . . . . . . . . . . . . 126
Using Windows* HyperTerminal*. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 127
Chapter 9: Troubleshooting
Appendix A: Front Panel
Buttons and Switches . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 134
Front Panel LEDs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 134
Connectors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 136
Appendix B: Failure/Bypass Modes
Bypass Button. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
Fail-through Switch (Security Level) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
Appendix C: Supported Ciphers
Cipher Strength. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 141
SSL Version Level . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 142
Appendix D: Regulatory Information
Taiwan Class A EMI Statement . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 145
VCCI Statement . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 146
FCC Part 15 Compliance Statement. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 146
Canada Compliance Statement (Industry Canada). . . . . . . . . . . . . . . . . . . . . . . . . . 147
CE Compliance Statement . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 147
CISPR 22 Statement . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 148
VCCI Class A (Japan). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 148
Australia . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 148
WARNING . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 148
AVERTISSEMENT . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 149
WARNUNG . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 150
AVVERTENZA . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 150
viii
Page 9

Table of Contents
ADVERTENCIAS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 151
Wichtige Sicherheitshinweise. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 152
Appendix E: Software License Agreement
Mozilla* and expat* License Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 158
MOZILLA PUBLIC LICENSE, Version 1.1 . . . . . . . . . . . . . . . . . . . . . . . . . . . 158
Support Services
Support for your SA7100/SA7120 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
U.S. and Canada. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
Europe . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172
Asia . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173
Latin America . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 174
Other Countries . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 174
Glossary
Index
ix
Page 10

C O N T E N T S HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Notes
x
Page 11

Introduction
Congratulations on your choice of the HP e-Commerce Server
Accelerator SA7100/SA7120. The processing of secure tr ansact ions
through Secure Socket Layer (SSL) can use up to 90% of even the
largest servers’ CPU power and can degrade response time
significantly. The SA7100/SA7120 provides a completely
transparent way to increase the performance of Web sites for SSL
transactions. The SA7100/SA7120 i s positioned in front of t he server
farm, where it intercepts SSL transactions, processes them, and relays
them to the servers. The SA7100/SA7120 performs all encryption
and decryption management i n thi s environment with a minimum of
administrator interaction.
About this User Guide
This User Guide supports the HP e-Commerce Server Accelerator
SA7100 and the HP e-Commerce Server Accelerator SA7120. By
default this text refers to the product as “SA7100/SA7120.” Where
appropriate, the text refers to “SA7100” or “SA7120.” Additionally,
notes in the le ft-hand mar gin may be used to distingu ish the two products. Illustrations of the command prompt use:
“HP SA7120>”.
Page 12

C H A P T E R 1 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Who Should Use this Book
This User Guide is intended for ad m inistrators with the following
background:
• Familiarity with networking concepts and terminology.
• Basic knowledge of network topologies.
• Basic knowledge of networks and IP routing.
• Some knowledge of SSL, keys, and certificates.
• Knowledge of Web servers.
Before You Begin
SA7100/SA7120 setup can be divided into three basic procedures:
• Physically install single or multiple SA7100/SA7120s with sin-
gle or multiple servers.
• Configure your SA7100/SA7120 in the Command Line Inter-
face.
• Identify existing certificates or obtain new ones you want to use
in SSL operations.
How to Use this Book
The information in this book is organized as follows:
• Chapter 1: Introdu cti on provides an introduction and overview
of the SA7100/SA7120, and a summary of new features.
• Chapter 2: Installation and Initial Configuration contains
installation and initial configuration procedures. (This material is
also discussed in the separate Quick Start Guide.)
• Chapter 3: Theory of Operation explains the general principles
behind SA7100/SA7120 operation.
• Chapter 4: Scenarios provides examples of SA7100/SA7120
configurations, together with specific procedures for their
implementation.
• Chapter 5: Command Reference explains the Command Line
Interface (CLI), and lists the commands and their functions.
2
Page 13

C H A P T E R 1 How to Use this Book
• Chapter 6: Remote Management detail s how you can use Te lne t,
Secure Shell (SSH), and SNMP to manage the SA7100/SA7120
from remote locations.
• Chapter 7: Alarms and Monitoring explains the ways in which
you can configure the device to report information to you, either
routinely or as a result of abnormal events or conditions.
• Chapter 8: Software Updates provides procedures for obtaining
SA7100/SA7120 system software updates.
• Chapter 9: T roubleshooting is a table containing symptoms of
problems you may encounter with corresponding likely causes
and remedies.
• Appendix A: Front Panel diagrams and explains the SA7100/
SA7120’s front panel LEDs, buttons, and connections.
• Appendix B: Failure/Bypass Mode s explains how the SA7100/
SA7120 deals with failure conditions and details the bypass
function.
• Appendix C: Supported Ciphers lists the supported encryption
ciphers.
• Appendix D: Regulatory Information provides information
regarding the SA7100/SA7120’s compliance with applicable
regulations.
• Appendix E: Software License Agreement contains the software
license and terms and conditions of user of this product.
• Support Services contains customer support telephone numbers
for various locales.
• Glossary defines terms appearing in this User Guide.
3
Page 14
C H A P T E R 1 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Notes
4
Page 15

Installation and Initial Configuration
Before You Begin
WARNING: Do not
remove the device’s
cover. There are no userservicable parts inside.
Before you begin installation, you need the following:
• IP address for SA7100/SA7120 (only if you intend to use the
Remote Management).
• IP addresses and IP port numbers of servers.
• Keys/certificates. See Chapter 3 for information on obtaining
keys and certificates.
• Network cables, such as straight-through and/or crossover
cables. (The table in the section “Ne twork Con nect ions ” in this
chapter identifies the types of cables you must use.)
• Phillips screwdriver (rack-mounting only).
• Rack-mounting screws (rack-mounting only).
Page 16

C H A P T E R 2 HP e-Commerce Server Accelerator SA7100/7120 User Guide
Installing the SA7100/SA7120 Free-Standing or in a Rack
The HP e-Commerce Server Accelerator SA7100/SA7120 is
physically installed in either of two ways:
• In a standard 19” rack, cantilevered from the provided mounting
brackets.
• Free-standing on a flat surface with sufficient space for air-flow.
Rack Installation
Rack mounting requires the use of the mount ing brackets, and all four
of the included Phillip s screws.
1. Locate the two mounting brackets and the four screws. (Two
screws for each bracket.)
2. Attach a mounting bracket to each side of the SA7100/SA7120,
using two of the provided screws for each bracket. Use the holes
near the front of the SA7100/SA7120’s sides. The brackets have
both round and oval holes; the flange with round holes attaches
to the SA7100/SA7120, the flange with oval holes to the rack.
Mounting Bracket Orientation
3. Position the SA7100/SA7120 in the desired space of your 19”
rack and attach the front flange of each mounting bracket to the
rack with two screws each. (Rack-mounting screws are not
provided.)
6
Page 17

C H A P T E R 2 Installing the SA7100/SA7120 Free-Standing or in a Rack
Free-Standing Installation
Network Connections
NOTE: Use caution
when connecting both of
the SA7100/SA7120’s
network ports to the same
switch, hub, or router.
Doing so creates a
feedback loop that
adversely effects network
bandwidth.
1. Attach the provided self-adhesive rubber feet to the SA7100/
SA7120’s bottom.
2. Place the SA7100/SA7120 on a flat surface and make sure that
there is adequate airflow surrounding the unit (allow at le ast one
inch of air space on all sides).
Use the table below to select and install the approp r ia te cables. (All
cables must be Category 5 UTP or better.)
SA7100/SA7120’s
network
connector
Workstation or Server Crossover cable Straight-through cable
Switch or Hub Straight-through cable Crossover cable
Router Crossover cable Not recommended
SA7100/SA7120
network
connector*
SA7100/SA7120
server
connector*
* Applicable only to multiple, cascaded units.
N/A Straight-through cable
Straight-through cable N/A
SA7100/SA7120’s
server
connector
3. Connect the provided power cable to the bac k of the unit . (Ther e
is no power switch.) Under normal circumstances, the SA7100/
SA7120 requires approximately 30 seconds to boot. When the
boot is complete, the unit’s Power LED is steadily illuminated.
(If the Power LED is not steadily illuminated, see Chapter 9,
“Troubleshooting,” to rectify before proceeding to Step 3.)
4. The Inline LED should be either steadily illuminated or blinking
(to indicate Inline mode). If it is not, press the Bypass switch on
the device’s front panel to enable Inline mode.
7
Page 18
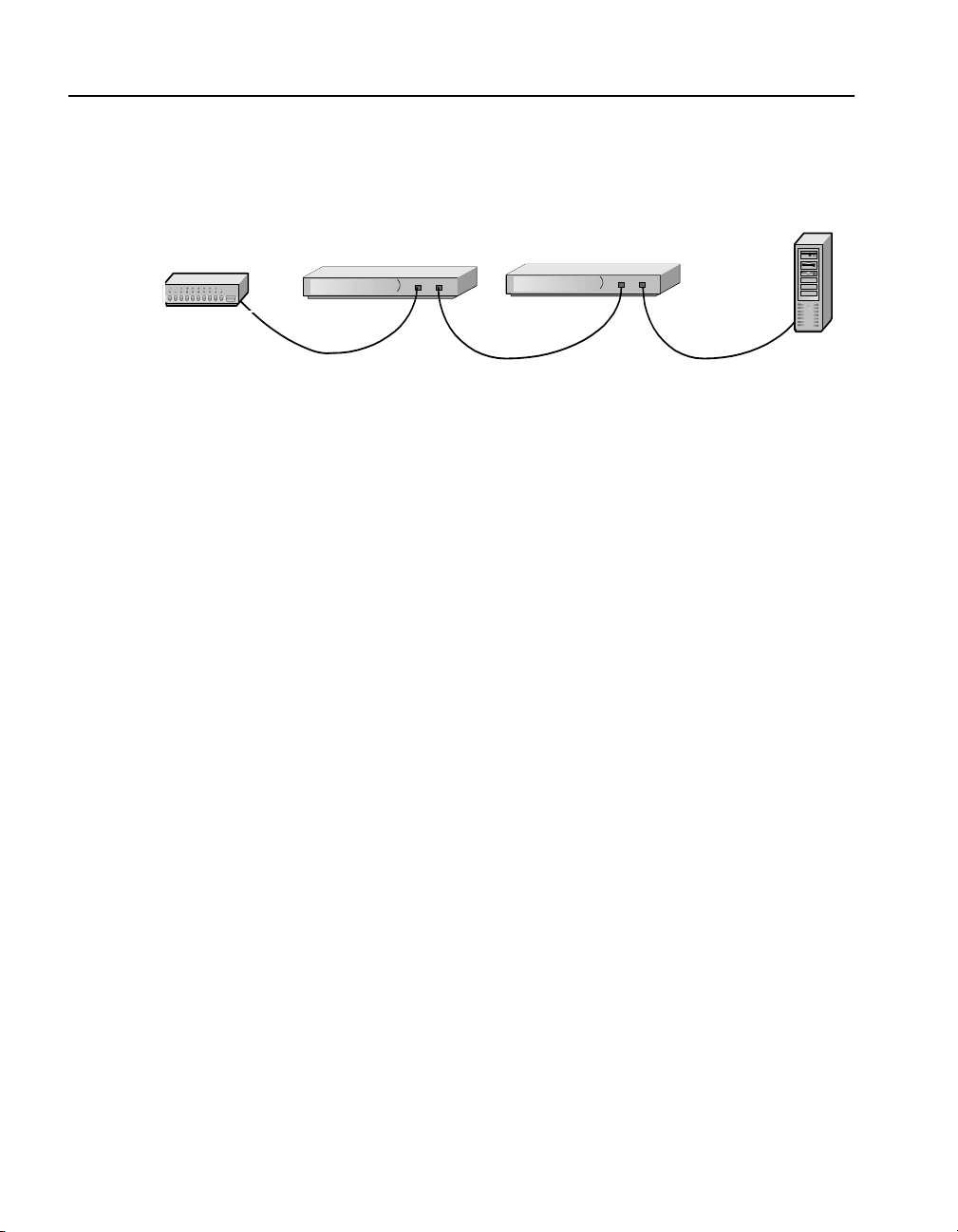
C H A P T E R 2 HP e-Commerce Server Accelerator SA7100/7120 User Guide
5. At this point both the Network and Server LEDs should be
steadily illuminated. If not, please see Chapter 9,
“Troubleshooting.”
HP e-Commerce Server Accelerators
Hub/Router/Switch
Status Check
Server
Network Connections
Before proceeding to the Admin Terminal Connect ion section, take a
moment to verify that the SA7100/SA7120 is correctly connected.
Network and Server LEDs
Verify that the Network and Server LEDs are both illuminated. If one
or both are not, re fer to the Troubleshooting sec tion at the end of t his
chapter.
Inline LED
A blinking Inline LED indicates that the syst em is online in F ail-safe
mode. Refer to the Troubleshooting secti on at the end o f this c hapter
or Appendix B, “Failure/Bypass Modes.”
8
Page 19

C H A P T E R 2 Installing the SA7100/SA7120 Free-Standing or in a Rack
Admin Terminal Connection
Power Error Overload Activity
(green) (red) (amber) (green)
Console
Run HyperTerminal* or a similar term inal emulator on your PC . The
steps below are illustrative of HyperTerminal*. Other terminals will
require different procedures.
1. Use the serial cable provided with the SA7100/SA7120 to connect the device’s serial port (the left-hand serial port labeled
“Console”) to the serial port of any termi nal. (A PC running Windows* HyperTerminal* is used here as an example.)
Aux Console
Network Link
(green)
Network Link
(RJ45)
Inline
(green)
Server Link
(green)
Server Link
(RJ45)
Front Panel Connectors and LEDs
2. Type an appropriate name in the Name field of the Connection
Description window (e.g., “Configuration”), and then click the
OK button. The Phone Number panel appears.
HyperTerminal* Paste Operations
3. In the Connect Using… field specify “COM1” (or the serial port
through which the PC is connected to the SA7100/SA7120 if
different from COM1).
4. Click the OK button. The COM1 Properties panel appears. Set
the values displayed here to 9600, 8, none, 1, and none.
5. Click the OK button.
If you’re using HyperTerminal* you must make the following
configuration change:
1. In the File menu, click Properties.
2. Click the Settings tab.
3. Click the ASCII Setup button.
4. Change the values of Line and Character delay from 0 to at least
1 millisecond.
9
Page 20

C H A P T E R 2 HP e-Commerce Server Accelerator SA7100/7120 User Guide
5. Click OK to exit ASCII Setup.
6. Click OK to exit Connection Properties.
Troubleshooting
Server and Network LEDs
If either the Network or Serv er LED fails to illuminate us ing either
straight-through or crossover network cables, the problem may be
elsewhere in the network. Verify by wiring around the SA7100/
SA7120.
Inline LED
The Fail-through switch allows you to control what happens in the
event of a failure. It is located in a recess between the Network and
Server connectors. Use a small screwdriver or paper clip to
manipulate the swit ch. The two options are:
• Allow traffic to flow through the SA7100/SA7120 unprocessed.
(Fail-through mode, indicated by a steadily illuminated Inline
LED.)
Continuing Configuration
10
• Block traffic flow through the SA7100/SA7120 entirely. (Fail-
safe mode, indicated by a blinking Inline LED.)
Please see Appendix B for a table describing all permutatio ns of LED
operation.
This concludes basic configuration of the SA7100/SA7120. To
configure the unit for production please continue with Chapter 3,
Theory of Operations, or Chapter 4, Scenarios.
Page 21

Security
Theory of Operation
The HP e-Commerce Server Accelerator SA7100/SA7120 offers
Remote Management capability. This feature require s that the
SA7100/SA7120’s network interface be assign ed an IP address, thus
security becomes a matter for your a ttention. If you i ntend to manage
your SA7100/SA7120 from a remote location, be sure to read the
section, “Access Control” in Chapter 6.
Single Server Accele r ati on
Typically, SA7100/SA7120 supports the SSL processing needs of a
single server. This is the simplest and most common configuration.
The SA7100/SA7120 is connected to the network between the ro uter
and the server.
Page 22

C H A P T E R 3 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Ideally, the SA7100/ SA7120 is installed in the network in su ch a way
as to minimize network latency.
HP e-Commerce Server Accelerator
SA7100/7120
Router
Single Server
SA7100/SA7120 in Single Server Configuration
Multiple Servers
Given the SSL processing power of the SA7100/SA7120, multiple
servers can be support ed. I n t hi s c onf i gurat i on, the SA7100/SA7120
sits between the router and the switch. SSL traffic intended for these
servers is intercepted and other traffic is passed through.
12
Server 1
Server 2
hub/switchRouter
Server 3
HP e-Commerce Server Accelerator
SA7100/7120
SA7100/SA7120 in Multiple Server Configuration
Page 23

C H A P T E R 3 Working with Internet Traffic Management (ITM) Devices
Working with Internet Traffic Management (ITM) Devices
The SA7100/SA7120 is compatible with Internet Traffic
Management (ITM) devices. In su ch environm ents, the SA7100/
SA7120 lies between the router and the ITM device, or between the
ITM device and the server. ITM devices distribute workload across
multiple servers and redirect traffic based on content.
Positioning SA7100/ SA7120 between ITM Device and Client Network
Router
Internet
Client
If the ITM device supports layer 7 traffic management, URLs must
be readable (that is, unencrypted). Therfore, in environments
performing layer 7 load balancing, it is recommended that the
SA7100/SA7120 be placed between the ITM device and the client
network.
HP e-Commerce Server Accelerator SA7100/7120
ITM Device
SA7100/SA7120 Between Router and ITM Device
Server 1
Server 2
Server 3
13
Page 24
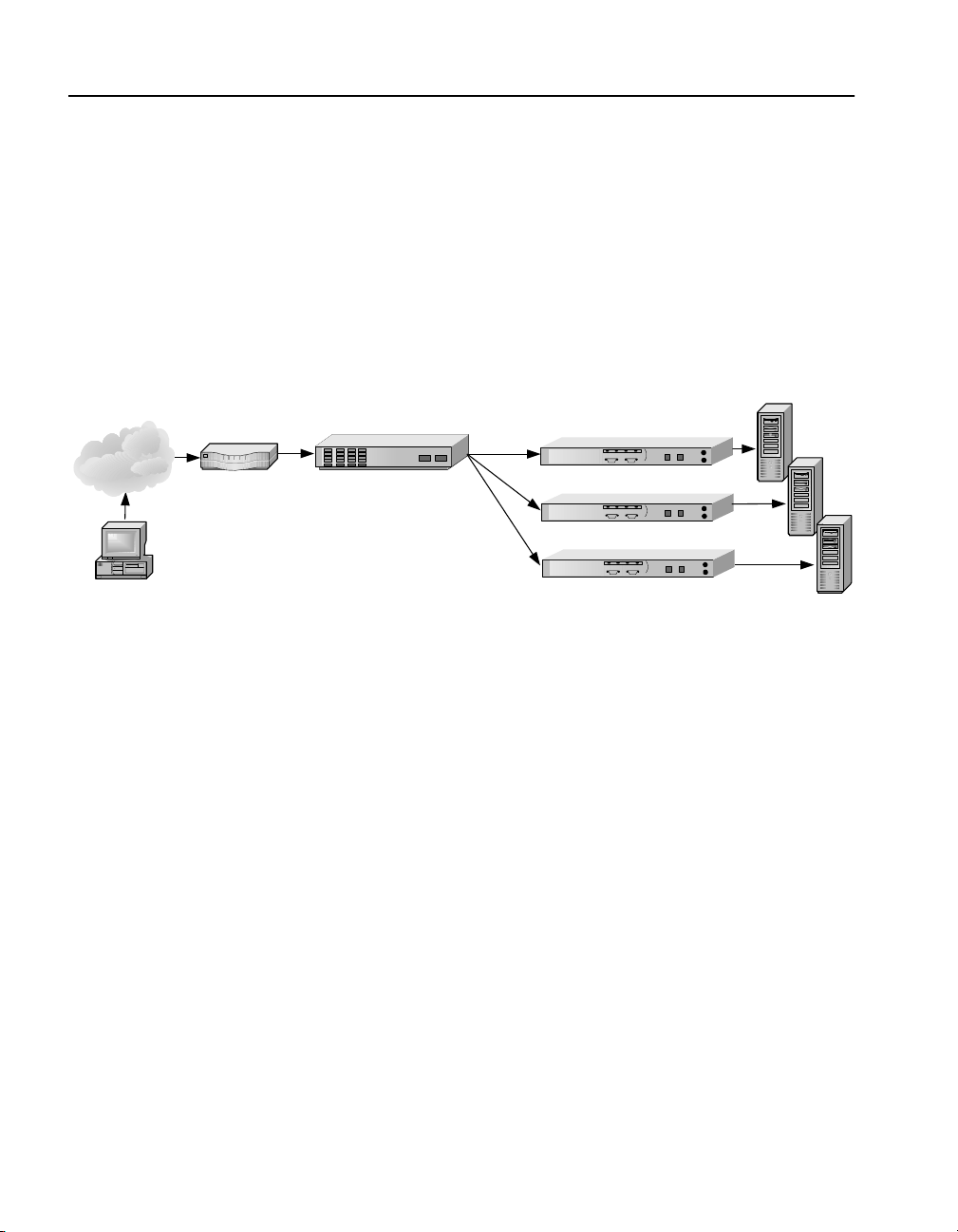
C H A P T E R 3 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Positioning SA7100/ SA7120 between ITM Device and Server
Router
Internet
Client
NOTE: The illustrated
configuration precludes
layer 7 load balancing
because secure traffic
through the ITM device is
encrypted.
If security considerations require limited network access to clear text,
the SA7100/SA7120 should be placed between the ITM device and
the server.
ITM Device
HP e-Commerce Server Accelerator
SA7100/SA7120s Between ITM Device and Servers
SA7100/7120s
Servers
Multiple SA7100/SA7120s and Cascading Processing
Scalability and Cascading
14
The SA7100/SA7120’s capabilities are scalable by chaining, or
“cascading,” multiple SA7100/SA7120s together. In such
configurations, each unit’s server side connector is wired to the
network side connector of the next SA7100/ SA7120 i n line . The last
SA7100/SA7120 in line is connected to the server, switch, or ITM
device.
Page 25

C H A P T E R 3 Multiple SA7100/SA7120s and Cascading Processing
Spilling and Throttling
Hub/Router/Switch
Availability
When the SA7100/SA7120’s “spill” option is enabled, if a given
SA7100/SA7120 cannot p rocess a request with in a specified interval,
the request is passed on, sti ll encrypt ed, t o the next SA7100/ SA7120
in line. The last SA7100/SA7120 on the server side can also be
enabled to spill to the server. Spilling is performed dynamically on a
connection-by-connection basis. (See spill command, Chapter 5,
“Command Reference.”) If spill is disabled, the SA7100/SA7120
“throttles,” that is, will not accept incoming requests when it becomes
overloaded.
HP e-Commerce Server Accelerator SA7100/7120s
Server
Cascaded SA7100/SA7120s
When a SA7100/SA7120 fails or is set to Bypass mode while Failthrough is enabled, the SA7100/SA7120’s network side and server
side network adapters are directly connected, allowing t raffic to pass
through to the next device until the failed unit is brought back into
service. This feature eliminates a single poi nt o f failure and provid es
a high level of availability, should there be a failure. In installations
with multiple SA7100/SA7120s, t he next unit in the casca de picks up
the encryption/decrypti on workload, while in single SA7100/SA7120
configurations, the server assumes the load. See “Failure/Bypass
Modes” in Appendix B for more information.
15
Page 26

C H A P T E R 3 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Keys and Certificates
WARNING: The
SA7100/SA7120 comes
with default keys and
certific ates for test
purposes. Certificates for
production use should be
obtained from a
recognized certificate
authority.
A necessa ry part of the SA7100/ SA7120 configurat ion is the use of
keys and certificates. A key is a set of numbers used to encrypt or
decrypt data. A certificate is a “form” that identifies a server or user.
The certificate contains information about your company as well as
information from a third party that verifies your identity.
There are three ways to obtain keys and certificates:
• Obtaining a certificate from VeriSign* or other Certificate
Authority (or “CA”)
• Using an existing key/certificate
• Creating a new key/certificate on the SA7100/SA7120
Cutting and Pasting with HyperTerminal*
Cutting and pasting is an in tegral part of the next several pr ocedures.
Below are procedures for cutting and pasting in HyperTerminal*. If
you use some other terminal program, consult that product’s
documentation for appropriate procedures.
To copy an item (key, certificate signing request, etc.) from
HyperTerminal*:
1. Open the HyperTerminal* window.
2. Click and drag to select the item.
16
3. After the item is selected, open the Edit menu and click Copy (or
type <ctrl-c>).
4. Open the window where you will paste the data, and position t he
cursor at the appropriate point.
5. In the Edit menu, click Paste (or type <ctrl-v>).
To paste an item (key, certificate signing request, etc.) into
HyperTerminal*:
1. Display the item in the appropriate appl ication window, then
click and drag to select the item.
2. Once the item is selected, click the Edit menu and select Copy
(or type <ctrl-c>).
Page 27

C H A P T E R 3 Keys and Certificates
3. Move to the HyperTerminal* window, and position the cursor at
the appropriate point.
4. Pull down the Edit menu, and select Paste to Host (or type
<ctrl-v>).
Obtaining a Certificate from VeriSign* or Other Certificate Authority
Use the create key command to create your key and the create si gn
command to create a signing request t o be sen t to VeriSign* o r ot her
CA for authentication. The CA will return it in approximately one to
five days. After you have recei ved the certificate, use t he import cert
command to import it into the SA7100/SA7120.
The fields input to create a signing request are called collectively a
Distinguished Name (DN). For optimal security, one or more fields
must be modified to make the DN unique.
Procedure
Create a key:
1. Type the create key command at the prompt:
HP SA7120> create key
Key strength (512 /1024) [512]:
New keyID [001]: mywebserver
Keypair was created for keyID: mywebserver
2. Create a Certificate Signing Request:
HP SA7120> create sign mywebserver
You are about to be asked to enter information
that will be incorporated into your
certificate request. The "common name" must be
unique. For other fields, you could use
default values.
Certifying authoriti es have specific guideli nes on how to answer each
of the questions. These guidelines may vary by certifying authority.
Please refer to th e guid eline s of th e cert ifyin g auth ority to who m you
submit your Certificate Signing Request (CSR). Please keep the
following in mind when entering the information that will be
incorporated into your certificate request:
• Country code: This is the two-letter ISO abbreviation for your
country (for example, US for the United States).
• State or Province: This is the name of the state or province
where your organizati on’s head office is located. Please enter the
full name of the state or province. Do not abbreviate.
17
Page 28

C H A P T E R 3 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
• Locality: This is usually the name of the city where your
organization’s head office is located.
• Organization: This should be the organization that owns the
domain name. The organization name (corporation, limited
partnership, university, or government agency) must be
registered with some authority at the n ational, state, or city level.
Use the legal name under which your organization is registered.
Please do not abbrevia te your or gani zation’s name and do not use
any of the following characters: < > ~ ! @ # $ % ^ * / \ ( ) ?.
• Organizat i onal unit: This is n ormally the name of the
department or group that will use the certificate.
• Common name: The common name is the “fully qualified
domain name,” (or FQDN) used for DNS lookups of your server
(for example, www.mysite.com). Browsers use this information
to identify your Web site. Some browsers will refuse to establish
a secure connection with your site if the server name does not
match the common name in the certificate. Please do not include
the protocol specifier “http://” or any port numbers or pat h names
in the common name. Do not u se wildcard characters su ch as * or
?, and do not use an IP address.
18
• E-mail address: This should be the e-mail address of the
administrator responsible for the certificate.
3. Export the Certificate Signing Request (CSR).
In this example, xmod em i s used t o send the CSR to a PC c onnected
to the console port.
HP SA7120> export sign mywebserver
Export protocol : (xmodem, ascii) [ascii]:x
<Enter>
Use Ctrl-x to kill transmission
Beginning export...
Export successful!
HP SA7120>
To submit the CSR to a certifying authority, paste it into the field
provided in the authority’s online request form. Remember to include
the “-----BEGIN CERTIFICATE REQUEST-----” and “-----END
CERTIFICATE REQUES T-----” lines.
Typically, the CSR will look something like this:
-----BEGIN CERT IFICATE REQUEST----MIIBnDCCAQUACQAwXjELMAkGA1UEBhMCQ0ExEDOABgNVBAgT
B09udGFayW8xEDAOBgNVBAcTB01vbnRyYWwxDDAKBgNVBAoT
Page 29

C H A P T E R 3 Keys and Certificates
A0tGQzEdMBsGA1UEAxMUd3d3Lmlsb3ZlY2hpY2tlbi5jb20w
gZ0wDQYJKoZIhvcNAQEBBQADgYsAMIGHAoGBALmJA2FLSGJ9
iCF8uwfPW2AKkyyKoe9aHnnwLLw8WWjhl[ww9pLietwX3bp6
Do87mwV3jrgQ1OIwarj9iKMLT6cSdeZ0OTNn7vvJaNv1iCBW
GNypQv3kVMMzzjEtOl2uGl8VOyeE7jImYj4HlMa+R168AmXT
82ubDR2ivqQwl7AgEDoAAwDQYJKoZIhvcNAQEEBQADgYEAn8
BTcPg4OwohGIMU2m39FVvh0M86ZBkANQCEHxMzzrnydXnvRM
KPSE208x3Bgh5cGBC47YghGZzdvxYJAT1vbkfCSBVR9GBxef
6ytkuJ9YnK84Q8x+pS2bEBDnw0D2MwdOSF1sBb1bcFfkmbpj
N2N+hqrrvA0mcNpAgk8nU=
-----END CERTIF ICATE REQUEST-----
4. When the CA returns th e certificate, import it into the SA7100/
SA7120. Use the impor t cert command, with the KeyID. As
with the import key, choose an import protocol for importing the
key . Use p for paste. After the paste is finished, add three periods
to display the command line.
HP SA7120> import cert mywebserver
keyid is mywebser ver;
Import protocol: (paste, xmodem) [paste]:
<Enter>
Type or paste in date, end with ... alone on line
-----BEGIN CERT IFICATE----MIIDKDCCAtKgAwIBAgIBADANBgkqhkiG9w0BAQQFADCBnDEL
MAkGA1UEBhMCVVMxCzAJBgNVBAgTAkNBMQ4wDAYDVQQHEwVQ
b3dheTEaMBgGA1UEChMRQ29tbWVyY2Ug
.
.
.
-----END CERTIF ICATE----- <Enter>
... <Enter>
Import successful!
HP SA7120>
5. Create mapping for Server 1. Use the create map command to
specify the server IP address, ports, and keyID.
HP SA7120> create map
Server IP (0.0.0.0): 10.1.1.30
SSL (network) port [443]: <Enter>
Cleartext (server) port [80]: <Enter>
KeyID to use for mappi ng: mywebserver
6. Save the configuration when the server has been mapped.
HP SA7120> config save
Saving configuration to flash...
Configuration saved to flash
HP SA7120>
19
Page 30

C H A P T E R 3 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Using an Existing Key/Certificate
Exporting a Key/Certificate from a Server
NOTE: Currently there
is no published method
for extracting private
keys from Microsoft* IIS
or Netscape* servers.
This method is used when it is important that the existing keys and
certificates are used.
Consult your server software documentat ion for detailed inst ructions
on how to export keys and certificates. Once you have exported the
keys and certificates, use the import key and import cert commands
to paste the keys and certificates into your SA7100/SA7120. Some
general instructions are provided bel ow for the Apache* Web Server.
Apache* Interface to Open SSL* (mod_ssl)
For key:
1. Look in $APACHEROOT/conf/httpd.conf for location of *.key
file.
2. Copy and paste the key file.
For certificate:
1. Look in $APACHEROOT/conf/httpd.conf for location of *.crt
file (certificate).
2. Copy and paste the certificate file.
20
Apache SSL*
For key:
1. Look in $APACHESSLROOT/conf/httpd.conf for location of
*.key file.
2. Copy and paste the key file.
For certificate:
1. Look in $APACHESSLROOT/conf/httpd.conf for location of
*.cert file.
2. Copy and paste the certificate file.
Page 31

C H A P T E R 3 Keys and Certificates
Stronghold*
For key:
1. Look in $STRONGHOLDROOT/conf/httpd.conf for location of
*.key file.
2. Copy and paste the key file.
For certificate:
1. Look in $STRONGHOLDROOT/conf/httpd.conf for location of
*.cert file.
2. Copy and paste the certificate file.
Importing into the SA7100/SA7120
1. Use the import key command with the keyID, and choose an
import protocol fo r importi ng the k ey. In this case, use the default
to “paste.” When the paste is finished, add a line break followed
by three periods to display the command line.
HP SA7120> import key mywebserver
Import protocol: (paste, xmodem) [paste]:
<Enter>
Type or paste in date, end with ... alone on line
-----BEGIN RSA PR IVATE KEY----MIIBOgIBAAJBALGOlBH14vIdtfuA+UnyRIoKya13ey8mj3GD
QakdwoDJALu+jtcC
.
.
.
S9dPdwp6zctsZeztn/ewPeNamz3q8QoEhY8CawEA
-----END RSA PRIV ATE KEY-----<Enter>
... <Enter>
Import successful!
HP SA7120>
2. Use the import cert command with the keyID. As with import
key, choose an import protocol for importing the key. Use the
default to “paste.” When the paste is finished, add a line break
followed by three periods to display the command line.
HP SA7120> import cert mywebserver
keyid is mywebser ver;
Import protocol: (paste, xmodem) [paste]:
<Enter>
Type or paste in date, end with ... alone on line
21
Page 32

C H A P T E R 3 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
-----BEGIN CERT IFICATE----MIIDKDCCAtKgAwIBAgIBADANBgkqhkiG9w0BAQQFADCBnDEL
MAkGA1UEBhMCVVMxCzAJBgNVBAgTAkNBMQ4wDAYDVQQHEwVQ
b3dheTEaMBgGA1UEChMRQ29tbWVyY2Ug
.
.
.
-----END CERTIF ICATE----- <Enter>
... <Enter>
Import successful!
HP SA7120>
3. Create a server mapping. Use the create map command to
specify the server IP address, ports, and keyID.
HP SA7120> create map
Server IP (0.0.0.0): 10.1.1.30
SSL (network) port [443]: <Enter>
Cleartext (server) port [80]: <Enter>
KeyID to use for mappi ng: mywebserver
4. Save the configuration when the server has been mapped.
HP SA7120> config save
Saving configuration to flash...
Configuration saved to flash
HP SA7120>
Creating a new Key/Certificate on the SA7100/ SA7120
22
Use the create key and create cert commands to create new keys and
certificates for SA7100/SA7120 operation. This procedure can be
used when there are no existing keys and certificates on the server.
The advantage is that this method is very fast, but a CA has not signed
the certificates.
The fields input to create a certificate are called a Distinguished
Name (DN). For optimal security, one or more fields must be
modified to make the DN unique.
Procedure
1. Create a key as follows:
HP SA7120> create key
Enter the key strength [512,1024]: 512
New keyID [001]: mywebserver
Keypair was created for keyID: mywebserver
2. Enter the create cert command with the keyID
HP SA7120> create cert mywebserver
You are about to be aske d to enter information…
Page 33

C H A P T E R 3 Keys and Certificates
Enter the information for the certificate, as prompted:
• Country
• State
• Locality
• Organization
• Organization unit
• Common name (for example, www.myserver.com)
• E-mail address
3. Create a server mapping. Use the create map command to
specify the server IP address, ports, and keyID.
HP SA7120> create map
Server IP (0.0.0.0): 10.1.1.30
SSL (network) port [443]: <Enter>
Cleartext (server) port [80]: <Enter>
KeyID to use for mappi ng: mywebserver
4. Save the configuration when the server has been mapped.
HP SA7120> config save
Saving configuration to flash...
Configuration saved to flash
HP SA7120>
Global Site Certificates
NOTE: The SA7100/
SA7120 supports only one
root CA certificate per
mapping. However,
multiple in terme dia te CA
certificates per single
mapping are supported.
Overview
Four types of certificates are involved in the following discussion:
• Root Certificate. The certificate of a trusted CA such as
VeriSign.*
• Server Certificate. Loaded on the server. Can be either self-
generated or received from a CA such as VeriSign*. Interacts
with requesting browser’s root certificate to establish encryption
level.
• Global Site Certificate. An extended server certificate. Allows
128-bit encryption for export-r est rict ed browser s.
• Intermediate certificate authority (CA) Certificate. A certificate
“signed,” that is, authenticated, by a recognized CA such as
VeriSign*, and used to validate a global si te ce rtificate. Cal led an
“intermediate CA certificate” in the following discussion.
23
Page 34

C H A P T E R 3 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Export versions of Inte rnet Exp lore r* and Netscap e* Communi cator
use 40-bit encryptio n to initiate connection s to SSL servers. Upon
receiving a client request, the server responds by sending a digital
certificate. If this certificate is a conventional server certificate (that
is, not a global site certificate), browser and serve r complete the SSL
handshake and use a 40-bit key to encrypt application data. If the
server responds to a requesting browser with a global site cer tificate ,
the client automatically renegotiates the connection to use 128-bit
encryption.
A global site certificate is validate d by an accompanying intermediate
CA certificate. (Such pairs are called “chained certificates.”)
Examples of intermediate CA certificates include Microsoft SGC
Root* and VeriSign Class 3*. When a requesting browser recei ves a
global site certificate along with an intermediate CA certificate, the
browser’s root certificate is used to validate the intermediate CA
certificate, which in turn is used to validate the global site certificate,
thus letting the browser know that it can renegotiate the connection to
use 128-bit encryption.
Global Site Certificate Paste Procedure
NOTE: There must be no
white space before,
between, or after
certificates, and the
“Begin...” headers and
“End...” trailers must all
be retained.
24
If you wish to use a global site certificate, you must import both the
global site certificate and its accompanying intermediate CA
certificate. Both certificates must be chained together in a single file.
Use the
import cert command to import either single or chained
certificates. In the latter case, paste the server ’s global site certificate
first, followed by the intermediate CA certificate. Follow the
intermediate CA certificate by typing three periods on a new line.
Example:
HP SA7120> import cert <keyID>
Import protocol: (paste, xmodem) [paste]:
Type or paste in data, end with ... alone on line
-----BEGIN CERT IFICATE----MIIFZTCCBM6gAwIBAgIQCTN2wvQH2CK+rgZKcTrNBzANBgkq
hkiG9w0BAQQFADCBujEfMB0GA1UEChMWVmVyaVNpZ24gVHJ1
c3QgTmV0d29yazEXMBUGA1UECxMOVmVyaVNpZ24sIEluYy4x
MzAxBgNVBAsTKlZlcmlTaWduIEludGVybmF0aW9uYWwgU2Vy
:
dmVyIENBIC0gQ2xhc3MgMzFJMEcGA1UECxNAd3d3LnZlcmlz
aWduLmNvbS9DUFMg
SW5jb3JwLmJ5IFJlZi4gTElBQklMSVRZIExURC4oYyk5NyBW
ZXJpU2lnbjAeFw05
OTExMTEwMDAwMDBaFw0wMDExMTAyMzU5NTlaMIHHMQswCQYD
Page 35

C H A P T E R 3 Keys and Certificates
VQQGEwJVUzETMBEG
-----END CERTIF ICATE-----
-----BEGIN CERT IFICATE----MIIEMTCCA5qgAwIBAgIQI2yXHivGDQv5dGDe8QjDwzANBgkq
hkiG9w0BAQIFADBfMQswCQYDVQQGEwJVUzEXMBUGA1UEChMO
VmVyaVNpZ24sIEluYy4xNzA1BgNVBAsTLkNsYXNzIDMgUHVi
bGljIFByaW1hcnkgQ2VydGlmaWNhdGlvbiBBdXRob3JpdHkw
HhcNOTcwNDE3MDAwMDAwWhcN
:
OTk3IFZlcmlTaWduMA0GCSqGSIb3DQEBAgUAA4GBALiMmMMr
SPVyzWgNGrN0Y7uxWLaYRSLsEY3HTjOLYlohJGyawEK0Rak6
+2fwkb4YH9VIGZNrjcs3S4bmfZv9jHiZ/4PC/
NlVBp4xZkZ9G3hg9FXUbFXIaWJwfE22iQYFm8hDjswMKNXRj
M1GUOMxlmaSESQeSltLZl5lVR5fN5qu
-----END CERTIF ICATE-----<Enter>
...<Enter>
Import successful!
HP SA7120>
25
Page 36

C H A P T E R 3 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Redirection: Clients and Unsupported Ciphers
NOTE: The user must
provide the redirect URL
and ensure that it is
available, as well as
define the content of the
redirect page.
WARNING: If the
redirect URL causes a
client to access the same
SA7100/SA7120 mappin g
that invoked the
redirection an infinite
loop condition will occur.
When a client that does not support t he selected ciph er suite att empts
to connect to the SA7100/S A7120, the default behavior is to reject the
connection, resulting in the client system repo r ting a fatal error.
However, the SA7100/SA7120 allows you to specify a “redirect
address” where you can provide clients with additional information.
The set redirect command allows you to specify a redirect Web
address for any Map ID. The show redirect command displays any
redirect addresses currently configured.
HP SA7120> list map
Map Net Ser Cipher Re- Client
ID KeyID Server IP Port Port Suites direct Auth
== ===== ========= ==== ==== ====== ===== ====
1 default Any 443 80 all(v2+v3) n n
2 sample 10.1.2.5 443 80 med(v2+v3) n n
HP SA7120> se t redirect 2
Enter a redirect URL at following prompt
e.g. http://www.e-comm_site.com/somebrowser.html
Enter redirect UR L []:http://www.e-
comm_site.com/cipher_info.html
HP SA7120> list map
Map Net Ser Cipher Re- Client
ID KeyID Server IP Port Port Suites direct Auth
== ===== ========= ==== ==== ====== ===== ====
1 default Any 443 80 all(v2+v3) n n
2 sample 10.1.2.5 443 80 med(v2+v3) y n
HP SA7120> show redirect 2
Redirect URL for map 2 is set: http://www.ecomm_site.com/cipher_info.html
26
To disable a redirect URL for a mapping:
HP SA7120> se t redirect 2 none
HP SA7120> show redirect 2
Redirect URL for map 2 is not set
Page 37

C H A P T E R 3 Client Authentication
Client Authentication
By default, the SA7100/SA7120 does not authenticate client
identities, however specific map IDs can be configured to request
client certificates for the purpose of verifying identities. When this
feature is enabled, the SA7100/SA7120 verifies that client
certificates are signed by a known CA. This feature is controlled by
the import client_ca command.
Example:
First, use the list map command to display the current map IDs and
their configurations including, in the last column, Client
Authentication, enabled (y) or disabled (n).
HP SA7120> list map
Map Net Ser Cipher Re- Client
ID KeyID Server IP Port Port Suites direct Auth
== ===== ========= ==== ==== ====== ===== ====
1 default Any 443 80 all(v2+v3) n n
2 sample 10.1.2.57 443 80 med(v2+v3) n n
Next, import the client CA certificate for Map ID 2.
HP SA7120> import client_ca 2
Import protocol: (paste, xmodem) [paste]:
<Enter>
Type or paste in data, end with ... alone on line
-----BEGIN CERT IFICATE----MIIDxzCCAzCgAwIBAgIBADANBgkqhkiG9w0BAQQFADCBpDEL
MAkGA1UEBhMCVVMxEzARBgNVBAgTCkNhbGlmb3JuaWExEjAQ
BgNVBAcTCVNhbiBEaWVnbzEUMBIGA1UE
.
.
.
XcCabZcfBRuYcZeUoNrGUl8tD80jp2YNG1vidgLEaD1YCli5
I9/mNrcB25mSfdAR
/08ROTMxm4VKOSA=
-----END CERTIF ICATE-----<Enter>
...<Enter>
27
Page 38

C H A P T E R 3 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Verify the import by using t he list map command aga in. Note that the
Client Auth column now shows client authentication for Map ID 2
enabled.
HP SA7120> list map
Map Net Ser Cipher Re- Client
ID KeyID Server IP Port Port Suites direct Auth
== ===== ========= ==== ==== ====== ===== ====
1 default Any 443 80 all(v2+v3) n n
2 sample 10.1.2.57 443 80 med(v2+v3) n y
Clients connecting to “map 2” are required to present a client
certificate signed by the CA whose certificate was imported above. If
they do not present a properly signed certificate, their connection
attempt is refused.
Creating a Client CA Certificate using OpenSSL*
NOTE: Generate the
client CA certificate:
NOTE: In this example,
ca_cert.pem is your
trusted CA and signing
certificate.
There are software packages available that handle the details of cl ient
certificate generation, however, you can implement them manually.
The following example illustrates the appropriate steps using
OpenSSL*:
1. Generate the key pair for the client CA:
openssl genrsa -o ut ca_key.pem 1024
To acquire a copy of OpenSSL* for your environment, access the
OpenSSL* Web site at www.openssl.org.
openssl req -new -x509 -config hp.cnf -key
ca_key.pem -day s 365 -out ca_cert.pem
2. Using the import client_ca command, import ca_cert.pem
For each client:
1. Generate a key pair:
openssl genrsa -o ut key.pem 1024
2. Generate a certificate signing request:
openssl req -new -config hp.cnf -days 365
-key key.pem -out csr.pem
28
Page 39

C H A P T E R 3 SSL Processing
3. Sign the client certificate signing request with the client CA
certificate:
openssl x509 -req -CAcreateserial -CAkey
ca_key.pem -CA ca_cert.pem -days 365 -in csr.pem
-out cert.pem
4. Combine the key.pem and cert.pem keys into one file by
typing this command:
cat key.pem cert.pem > all.pem
5. Convert to p12 format by typing this command:
openssl pkcs12 -export -in all.pem -out
<file>.p12 - name “MY NAME”
The output file <file>.p12 will be imported into the browser as a
personal certificate.
SSL Processing
The SA7100/SA7120 handles several SSL protocols, for example,
HTTPS (which is the default). For security purposes, you can block
access to specified IPs or ports (see “Blocking” section). Traffic that
is not mapped or blocked flows through transparently. Supported
protocols are listed below. (Ports listed are “well-known” port
assignments. Any available port may be used.)
Server Assignment (“Mapping”)
• HTTPS 443 (default)
• IMAPS 993
• POP3S 995
• SMTPS 465
• NNTPS 563
• LDAPS 636
Keypairs and their associated certificates are referenced b y a keyID.
A server is identified by a unique combination of server IP and
network port. Mapping is the process of associating a keyID with a
server (using server IP, network port, and server port). The SA7100/
SA7120 supports two types of mapping:
• Automapping
• Manual mapping
29
Page 40

C H A P T E R 3 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Automapping
NOTE: Remember to
save the configuration
(with the config save
command) after making
mapping changes.
Automapped entries are identified by a server IP address of zero
(0.0.0.0). When a server IP address of zero is specified, the SA7100/
SA7120 intercepts packe ts to any server IP address wit h the matching
network ports. As with any map ping entry, the combi nation of server
IP address and network port must be unique.
The initial configuration for the SA7100/SA7120 provides an
automapping entry for network port 443 and server port 80. This is
associated with the internally generated default keypair and
certificate with the keyID of “default.” Under this initial
configuration, automapping occurs on any server with this network
port (443) when traffic is routed through the SA7100/SA7120.
Automapping with user-specified key and certificate
When a user-specified key and certificate are to be automapped, the
user can replace t he initial automapping entry with the create map
command. By specifying the same unique identifier (server IP of
0.0.0.0, and network port of 443) with a user-generated keyID, the
user can overwrite the initial automapping entry. (The key and
certificate may be obtained through any of the methods described
previously in this chapter.)
Automapping with multiple port combinations
30
The user can specify multiple automap ping entries when the net work
port is unique. For example, a user might specify, in addition to the
initial network (443) and server (80) port combination, a combinat ion
of network (8010) and server (80) port.
Deleting automapping entries
Any automapping entry can be del eted, but if t he initial auto mapping
is deleted and no other mapping entry is specified, the SA7100/
SA7120 automatically r ecreates th e initial aut omapping entry. Either
replace the initial automapping entry or create another mapping/
automapping entry and then delete the initial automapping entry
using the delete map command.
Page 41

C H A P T E R 3 SSL Processing
Manual mapping
The user can create (with the create map command) one or more
mapping entries for indi vidual servers. This is th e only way to specify
unique keyIDs for each server. Normally, when manual mapping is
performed, the initial automapping entry is deleted, but this is not a
requirement.
Combining automapping and manual mapping
NOTE: If both manual
mappings and applicabl e
automappings are
available, the SA7100/
SA7120 always uses the
manual mapping.
Blocking
NOTE: Blocking
operations apply to both
TCP and UDP traffic.
Any combination of automappin g and manual mapping en tries, up to
a total of 1000, can be used provided the server IP address and
network port combinations are unique. Several of the scenarios in
Chapter 4 include step-by-step mapping procedures.
For security purposes, the SA7100/SA7120 allows the blocking of
particular IP addresses and ports. IP/port combinations can be
blocked on the basis of:
• Specific IP, specific port
• Subnet, specific port
• All IPs, specific port
Specific IP, Specific Port
To block a specific server IP and specific port combination:
1. Type the create block command.
2. Type the IP address.
3. Press Enter to accept the default IP mask.
4. Type the specific port.
5. Press Enter to accept the default port mask.
Example:
HP SA7120> create block
Client IP to block [0.0.0.0]: 10.1.2.1
Client IP mask [0.0.0.0]: 255.255.255.255
Server IP to block [0.0.0.0]: 20.1.2.1
Server IP mask [0.0.0.0]: 25 5.255.255.255
Server Port to block: 80
Server Port mask [0xffff]:<Enter>
31
Page 42

C H A P T E R 3 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Use the show block command to verify:
HP SA7120> show block
------- blocks :
--------(1) block 10.1.2.1 255.255.255.255 20.1.2.1
255.255.255.255 80 0xffff
Subnet, Specific Port
To block a subnet, and specific port combination:
1. Specify a subnet, using 0 as the address’s final octet. (In the
example below, all IPs from “10.1.2.x” to “20.1.2.x” are blocked
on port 80.)
2. Type the subnet mask, with 0 indicating the portion of the IP
address to be ignored.
3. Type the specific port.
4. Press Enter to accept the default port mask.
Example:
HP SA7120> create block
Client IP to block [0.0.0.0]: 10.1.2.0
Client IP mask [0.0.0.0]: 255.255.255.0
Server IP to block [0.0.0.0]: 20.1.2.0
Server IP mask [0.0.0.0]: 255.255.255.0
Server Port to block: 80
Server Port mask [0xffff]:<Enter>
32
Use show block to verify:
HP SA7120> show block
-----------
blocks :
----------(1) block 10.1.2.0 255.255.255.0 20.1.2.0
255.255.255.0 80 0xffff
-----------
All IPs, Specific Port
To block a specific port on all IP addresses:
1. Type all zeroes as the IP address to be blocked.
2. Type all zeroes as the IP wildcard mask to be blocked.
3. Type the specific port.
Page 43

C H A P T E R 3 SSL Processing
4. Press Enter to accept the default port mask.
Example:
HP SA7120> create block
Client IP to block [0.0.0.0]: <Enter>
Client IP mask [0.0.0.0]: <Enter>
Server IP to block [0.0.0.0]:<Enter>
Server IP mask [0.0.0.0]:<Enter>
Server Port to block: 80
Server Port mask [0xffff]:<Enter>
5. Use the show block command to confirm the block:
HP SA7120> show block
-----------
blocks :
----------(1) block
0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 80 0xffff
-----------
Delete a Block
The example below illus trates how to delete a subnet b lock. Type the
delete bloc k command with the block ID (block ID is 1 in the
example):
1. Use the show block command to ident if y th e bl ock t o b e del et ed.
HP SA7120> show block
-----------
blocks :
----------(1) block 10.1.2.1 255.255.255.255 20.1.2.1
255.255.255.255 80 0xffff
-----------
2. Use the delete block command followed by the block ID to
delete the block.
HP SA7120> delete block 1
33
Page 44

C H A P T E R 3 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Failure Conditions, Fail-safe, and Fail-through
During any failure condition of the SA7100/SA7120, unprocessed
data packets can either pass through or not, depending on whether
Fail-safe or Fail -through mode is enabled. The F ail-throug h switch is
by default in Fail-safe mode, meaning that during a failure no data
packets will pass from one side of the SA7100/SA7120 to the other.
For details, see “Failure/Bypass Modes” in Appendix B.
34
Page 45

Scenarios
This section contains scenarios illustrating examples of HP eCommerce Server Accelerator SA7100/SA7120 configurations:
• Scenario 1: Single server
• Scenario 2: Multiple serv ers
• Scenario 3: Multiple SA7100/SA7120s, cascaded
• Scenario 4: Different ingress and egress routers
• Scenario 5: Configuring a Firewall
Page 46

C H A P T E R 4 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Scenario 1—Single Server
This scenario describes a typ ical confi guration of a SA7100/SA712 0
with one server, using either automapping or manual configuration/
mapping. This scenario describes the fastest way to get up and
running with a SA7100/SA7120.
HP e-Commerce Server Accelerator
Router
Single Server
Single SA7100/SA7120, Single Server Installation
Procedure for Scenario 1
36
Automapping
1. Physically connect the SA7100/SA7120 to the router and to one
server.
2. Initiate HTTPS traffic to the server. The SA7100/SA7120
monitors traffic and uses the initial mapping (with associated
default key and certificate) to decrypt HTTPS traffic and pass
clear text HTTP traffic to the server.
Manual Configuration
1. Perform the installation as described in Chapter 2. Access the
SA7100/SA7120 command prompt.
2. Acquire the appropriate keys and certificates following the
procedure in the “Keys and Certificates” section in Chapter 3.
3. Create a mapping for the server. Use the create map command
to specify the server IP address, ports, and keyID.
HP SA7120> create map
Server IP (0.0.0.0): 10.1.1.30
SSL (network) port [443]: <Enter>
Cleartext (server) port [80]: <Enter>
KeyID to use for mappi ng: myserver
Page 47

C H A P T E R 4 Scenario 1—Single Server
4. You can delete the default mapping. After the user has manually
created the mapping, the default mappi ng can be del et ed. In this
case, delete MapID number 1. MapID number 2 becomes
MapID number 1 when the default is deleted.
HP SA7120> delete map 1
HP SA7120> li st maps
Map Net Ser Cipher Re- Client
ID KeyID Server IP Port Port Suites direct Auth
== ===== ========= ==== ==== ====== =====
====
1 myserver 10.1.1.30 443 80 med(v2+v3) n n
HP SA7120>
5. Save the configuration when the server has been mapped.
HP SA7120> config save
Saving configuration to flash...
Configuration saved to flash
HP SA7120>
37
Page 48

C H A P T E R 4 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Scenario 2—Multiple Servers
This scenario shows how to configure two or more servers.
Server 1
HP e-Commerce Se rver Ac ce lerator
Router
Hub/switch
Single SA7100/SA7120, Multiple Server Installation
10.1.1.30
Server 2
10.1.1.31
Procedure for Scenario 2
1. Perform the installation as described in Chapter 2. Access the
SA7120 command prompt.
2. Acquire the appropriate keys and certificates following the
procedure in the Keys and Certificates section in Chapter 3.
3. Create a mapping for Server 1. Use the create map command to
specify the server IP address, ports, and keyID.
HP SA7120> create map
Server IP: 10.1.1.30
SSL (network) port [443]: <Enter>
Cleartext (server) port [80]: <Enter>
KeyID to use for mappi ng: myserver
4. Create a mapping for Server 2. As in the previous step, use the
create map command to specify the server IP address, ports for
the second server, and the keyID.
HP SA7120> create map
Server IP: 10.1.1.31
SSL (network) port [443]: <Enter>
Cleartext (server) port [80]: <Enter>
KeyID to use for mappi ng: myserver2
5. Use the list map command to view the mapping. (Multiple keys
and certificates can also be imported and each mapped to
individual servers. If you do this, at least one field in the
certificate information—usually the common name—must be
unique.)
HP SA7120> list map
38
Page 49

C H A P T E R 4 Scenario 2—Multiple Servers
Map Net Ser Cipher Re- Client
ID KeyID Server IP Port Port Suites direct Auth
== ===== ========= ==== ==== ============ ====== ====
1 default Any 443 80 all(v2+v3) n n
2 myserver 10.1.1.30 443 80 med(v2+v3) n n
3 myserver2 10.1.1.31 443 80 med(v2+v3) n n
HP SA7120>
6. After you have manually created a mapping, the default
mapping can be deleted. In this case, delete MapID number 1.
MapID number 2 becomes Map ID number 1 when the default is
deleted.
HP SA7120> delete map 1
HP SA7120> li st map
Map Net Ser Cipher Re- Client
ID KeyID Server IP Port Port Suites direct
Auth
== ===== ========= ==== ==== ====== =====
====
1 myserver 10.1.1.30 443 80 med(v2+v3) n n
2 myserver2 10.1.1.31 443 80 med(v2+v3) n n
HP SA7120>
7. To configure a third or fourth web server to operate with the
SA7100/SA7120, repeat the steps above, specifying a different
IP address for each server.
8. Save the configuration when mapping is completed for the
server(s).
HP SA7120> config save
Saving configuration to flash...
Configuration saved to flash
HP SA7120>
39
Page 50

C H A P T E R 4 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Scenario 3—Multiple SA7100/SA7120s, Cascaded
This scenario shows how to casca de SA7100/SA7120s for additional
performance and availability. The same procedures apply that were
performed in Scenario 3. In addition, the complete configuration of
the first SA7100/SA7120 is expo rted to the second SA7100 /SA7120
in line.
Initial Configuration
Hub/Router/Switch
• Two or more SA7100/SA7120s must be physically installed on
the same network. To cascade multiple SA7100/SA7120s,
connect from the server port of the first SA7100/SA7120 to the
network port of the next SA7100/SA7120 in line, and then again
connect from the server port to the network port of the next
SA7100/SA7120 in line , or to th e server. (See Chapter 2 for more
information.)
• On the first SA7100/SA7120, the set spill enable command is
used to enable spilling so that the next SA7100/SA7120 in line
can handle the overflow. Spill is then enabled for each
subsequent SA7100/SA7120, except the last one. Do not
configure the last SA7100/SA7120 to spill to the server.
• The first SA7100/SA7120 should be fully configured; any
necessary keys, certificates or maps must exist. The complete
configuration is exported from the first, then imported to the next
SA7100/SA7120 in line. This procedure is repeated for any
additional SA7100/SA7120s in line.
HP e-Commerce Server Accelerators
Server
Multiple (Cascaded) SA7100/SA7120s
40
Page 51

C H A P T E R 4Scenario 3—Multiple SA7100/SA7120s, Cascaded
Procedure for Scenario 3
1. Configure the SA7100/SA7120 farthest from the server as
described in any of the preceding scenari os. Remain connecte d to
that specific SA7100/SA7120 for the export configuration
procedure.
2. At the co mmand prompt, type the set spi ll enable command.
This allows overflow traffic to be transferred to the second
SA7100/SA7120 for processing.
3. Save configuration.
HP SA7120> config save
Saving configuration to flash...
Configuration saved to flash
HP SA7120>
4. Export the configuration. Use the export config command.
Choose xmodem mode to export.
HP SA7120> export config
Export protocol: (xmodem, ascii) [ascii]: xmodem
<Enter>
Beginning export...
5. Select Receive from the HyperTerminal* Transfer menu.
6. Type or use the Browse button to specify the directory in which
you want to place the received file.
7. Select xmodem as the receiving protocol.
8. Click the Receive button.
9. Specify a filename for the received file and click OK. The
operation concludes and the normal prompt reappears.
Use Ctrl-X to kill transmission
Export successful!
HP SA7120>
10. Connect to the second SA7100/SA7120 (“Device 2”), either
through the console connection or another window (if both are
connected to the same PC).
11. Press the Bypass button on Device 2’s front panel to put the
machine in bypass mode.
12. Import the configuration. Use the import config command to
begin the process. Select xmodem and press Enter to begin the
import process.
HP SA7120> import config
Import protocol: (paste, xmodem) [paste]: xmodem
41
Page 52

C H A P T E R 4 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
<Enter>
Use Ctl-X to cancel up load
13. Select Send from the HyperTerminal* Transfer menu.
14. Type or use the Browse button to specify the file to send.
15. Select xmodem as the sending protocol.
16. Click the Send button. The transfer completes and then you are
prompted to verify that you want to install this configuration.
Do you want to install this config ? [y]:
17. After verification (y) or refusal (n), the prompt reappears.
HP SA7120>
18. Change Device 2’s IP address using the set ip command.
HP SA7120> set ip
Enter IP Address (’none’ to delete) [10.1.2.65]:
1.1.1.1
Enter Netmask (’n one’ to delete)
[255.255.255. 0]: 2.2.2.2
19. Save the configuration.
HP SA7120> config save
Saving configuration to flash...
Configuration saved to flash
HP SA7120>
42
20. Press the Bypass button on Device 2’s front panel to put the
machine in inline m ode.
21. Repeat steps 11 - 20 for any ad di ti ona l SA7100/SA7120s. On the
last SA7100/SA7120 in the chain, disable spilling with the set
spill disable command.
Page 53

C H A P T E R 4 Scenario 4—Different Ingress and Egress Routers
Scenario 4—Different Ingress and Egress Routers
This scenario describes the configurati on of a SA7100/SA712 0 when
the ingress and egress traffic paths are different. This scenario
includes:
• One or more servers
• One or more cascaded SA7100/SA7120s
• One or more ingress routers
• One egress router
HP e-Commerce Server
Accelerator
Server
Client
Ingress Router
Egress Router
Switch
Procedure for Scenario 4
NOTE: Execute an “arp
–a” (or equivalent
command for your OS) on
the server to display the
MAC address of the
default gateway. This is
the address you should
use.
Installation with Ingress and Egress Routers
1. Configure your SA7100/SA7120 (as described in any of the
previous scenarios).
2. Determine the MAC address of the egress router through which
you want to route outbound traffic.
3. At the CLI prompt, enter the default egress router.
HP SA7120> set egress_mac 00:11:22:33:4 4:55
Egress MAC set to 00:1 1:22:33:44:55
HP SA7120> config save
Saving configuration to flash...
Configuration saved to flash
HP SA7120>
4. To reverse this process:
HP SA7120> set egress_mac none
43
Page 54

C H A P T E R 4 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Scenario 5—Configuring a Firewall
This scenario describes the recommended network configuration to
allow a SA7100/SA7120 to provide SSL services for a single server
that also serves plain-text HTTP documents. Actual procedures for
adjusting the firewall and server configurations vary widely
depending upon the products used, so the steps outlined here are
necessarily approximations and must be adjusted as required by the
particulars of your environment. Please consult your server and
firewall documentation for additional information.
HP e-Commerce Server Appliance SA7100/SA7120
Firewall
Server
Single SA7100/SA7120 configured with single server and firewall
Server Configuration
44
Servers providing both HTTP and HTTPS services typically have
two instances of the Web Server process configured:
• One listening on the standard HTTP port of 80, providing
unencrypted access to non-sensitive information, and
• Another listening on port 443 provid ing access to SSL encr ypted
sensitive information.
Port Number Connection Type Content Served
80 HTTP Non-sensitive
443 HTTPS Sensitive
For the SA7120 to provide SSL services, the web server process
providing port 443 services requires two modifications.
Page 55

C H A P T E R 4Scenario 5—Configuring a Firewall
• First, because the SA7120 performs all of the SSL processing,
the web server process must be configured to expect only
standard HTTP (unencry pted) connections, even for sensitive
content.
• Second, the web server process must be configured to listen for
these HTTP connections on a port other than the standard
HTTPS port (443). In this scenario we configure the port 443
service to listen on port 81.
Port Number Connection Type Content Served
80 HTTP Non-sensitive
81 HTTP Sensitive
SA7120 Configuration
The SA7120 must be configured to intercep t HTTPS connect ions o n
port 443 and forward them to the server. In t he precedin g section, we
configured the server to provide access t o sensitive dat a through po rt
81, so that should be the clear text port when creating a server
assignment (or “map”) on the SA7120. Perform the following steps
to create the server assignment:
1. Perform the installation as described in Chapter 2 and access the
command line prompt.
2. Acquire the appropriate keys and certificates following the
procedure in the “Keys and Certificates” section in Chapter 3.
3. Create a mapping for the server. Use the create map command
to specify the server IP address, ports, and keyID.
HP SA7120> create map
Server IP (0.0.0.0): 10.1.1.30
SSL (network) port [443]: <Enter>
Cleartext (server) port [80]: 81
KeyID to use for mappi ng: serv1
45
Page 56

C H A P T E R 4 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
NOTE: The device
automatically adjust s the
list of MapIDs as they
are created and deleted,
thus MapID 2 becomes
MapID 1 when the default
(the original MapID 1) is
deleted.
4. Once a user-created server assignment exists, the default
mapping ca n be deleted. I n this example, delete MapID number
1.
HP SA7120> > delete map 1
HP SA7120> list maps
Map Net Ser Cipher Re- Client
ID KeyID Server IP Port Port Suites direct Auth
== ===== ========= ==== ==== ========== ===== ====
1 serv1 10.1.1.30 443 80 med(v2+v3) n n
HP SA7120>
5. Save the configuration.
HP SA7120> config save
Saving configuration to flash...
Configuration saved to flash
HP SA7120>
Firewall Configuration
Absent a firewall, outside clients woul d be able to connect to services
on the web server and possibly gain access to sensitive da ta—on port
80 using HTTP to access non-sensitive data, on port 443 using
HTTPS to access sensitive data, and on port 81 using HTTP to access
that same sensitive data. Obviously, allowing access to sensitive data
over an unencrypted connection on port 81 is not desirable.
Consequently a firewall should be configured to prevent such access.
NOTE: In this
configuration, the
firewall may occasionally
report the blocking of
outbound packets from
the Server on port 81.
This is normal—a sideeffect of the varying
latencies characteristic of
Internet traffic—and does
not indicate a problem
with the configura tio n
46
Port Access
80 Allowed
443 Allowed
All Others Denied
Page 57

Online Help
Command Reference
The HP e-Commerce Server Accelerator SA7100/SA7120 is fully
configurable through the Command Line Interface (CLI). The CLI is
accessible through both the console and aux console RS232 ports or
remotely via Telnet a nd SSH.
The SA7100/SA7120 provides online help with the following
options:
• Type help to display a summary of commands.
• Type help <command> (or ? <c om ma nd>) for a
description of a specific command or, if relevant, a list of
subcommands you can enter from within <command>.
• Type help usage (or ? <usage>)to display all commands
and their usage.
Page 58

C H A P T E R 5 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
• Type tty_char to display a list of special terminal editing
characters.
Command Line Interface
The CLI handles all user interactions on the console and auxiliary
console RS232 ports. One instance per port runs at all times.
User Authentication
Command Line
To gain access to the CLI, the user must first be authenticated by
providing a password at the logon ban ner prompt . The logon banner
provides build versio n information and the seri al number.
The standard command line prompt for the SA7120 is:
HP SA7120>
Prompt
The prompt for the SA7100 is:
HP SA7100>
The prompt can be changed with the set prompt command.
Syntax
Symbol Significance
Angled Brackets (<>)
Straight Brackets ([ ])
Braces ({})
Boldface
The CLI uses the following syntax:
Angled brackets designate where you type variable parameters.
Choices of parameters appear between straight bracket s, separated
by vertical bars.
Optional commands or parameters appear between braces.
Commands shown as they are typed after the CLI prompt appear
in boldface type. (The prompt appears in normal typeface to
distinguish it from the command text.)
Vertical Bar ( | )
48
Separates choices of input parameters within straight brackets.
You can choose only one of a set of choices separated by the
vertical bar. (Do not include the vertical bar in the command.)
Page 59

C H A P T E R 5 Command Line Interface
Abbreviation to Uniqueness
It is not always necessary to type t he entire command. CLI commands
can be abbreviated to uniqueness. For example, “del” as show bel ow
is sufficient to represent the delete command:
HP SA7120> del
Usage: delete item [arg]
block blockID
cert keyID
client_ca mapID
key keyID
logs logID|all
map mapID
patch
permit permitID
sign keyID
snmp_community
trap_community
However, “sh” as shown b elow, is not a n a bbreviat ion to u niquene ss
in that it does not distinguish between show and showsnmp.
HP SA7120> sh
The solitary letter “e” in the context of the next example, (i.e.,
preceded by “ssh”), uniquely indicates ssh enable.
HP SA7120> se t ssh e
SSH Service start ed.
49
Page 60

C H A P T E R 5 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Input Editing Commands
Moving the Insertion Point
Command Description
ctrl-b
ctrl-f
ctrl-a
ctrl-e
ctrl-l
Command
Move back one character.
Move forward one character.
Move to the start of the current line.
Move to the end of the line.
Clear the screen and redraw the current line, leaving the current
line at the top of the screen.
A history of recently executed commands is stored in a buffer and can
be accessed with the following commands:
History
Command Description
ctrl-p
ctrl-n
ctrl-r
ctrl-s
Move “up” through the history list
Move “down” through the history list
(Reverse-search-history) Search backward starting at the current
line and moving up incrementally through the command history.
(Forward-search-history) Search forward starting at the current
line and moving down incrementally through the command
history.
50
Page 61

C H A P T E R 5 Command Line Interface
Cutting Text
Command Description
ctrl-d
ctrl-k
ctrl-u
ctrl-w
ctrl-y
backspace/del
Delete the character underneath the cursor.
Delete the text from the current cursor position to the end of the
line.
Delete backward from the cursor to the beginning of the current
line.
Delete the word behind the cursor, using white space as a word
boundary.
Paste text that has been cut using any of the four above deletion
commands.
Delete the character to the left of the cursor.
51
Page 62

C H A P T E R 5 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Command Summary
This section contains a high-level view of the SA7100/SA7120’s
command structure. Details appear in the Command Reference.
Command Command Options
bypass
config
create
delete
exit
default
compare
reset
save
block
cert <keyID>
key <keyID>
map
permit
sign <keyID>
block <blockID>
cert <keyID>
client_ca <mapID>
key <keyID>
logs<logID | all>
map <mapID>
patch
permit <permitID>
sign <keyID>
snmp_community
trap_community
export
factory_default
help
52
key <keyID>
cert <keyID>
sign <keyID>
log <logID>
config
help
help <command>
help usage
Page 63

C H A P T E R 5 Command Summary
Command Command Options
import
inline
list
nic
password
reboot
cert <keyID>
client_ca <mapID>
config
key <keyID>
patch
upgrade
blocks
filters (shows blocks and permits)
keys
logs
maps
permit
monitoring
procs
snmp_community
system
trap_community
53
Page 64

C H A P T E R 5 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Command Command Options
set
alarms <all none esc rsc utl ovl nls>
cache <enable | disable>
ciphers <mapID>
ciphers <mapID> default
client_tmo <seconds>
date
defcert
egress_mac x:x:x:x:x:x
egress_mac none
ether
idleto <timeout>
ip <ip> <netmask>
kstrength
max_remote_sessions<0-5>
monitoring <enable | disable>
monitoring_interval <seconds>
monitoring_fields <seconds>
more
ovl_window <seconds>
prompt
redirect <mapID>
redirect <mapID> none
route x.x.x.x
rsc_window <seconds>
serial
server_tmo <seconds>
ssh <enabl e | disable>
ssh_port <port>
spill <enable | disable>
system
telnet <enable | disable>
telnet_port <port>
utl_highwater <percentage>
utl_lowwater <percentage>
utl_window <seconds>
54
Page 65

C H A P T E R 5 Command Summary
Command Command Options
show
alarms
blocks
cache
ciphers <mapID>
cert <keyID>
client_ca <mapID>
client_tmo
config
config default
config saved
date
defcert
egress_mac
ether
filters
idleto
info
ip
key <keyID>
kstrength
logs
map
max_remote_sessions
monitoring
monitoring_interval
monitoring_fields
more
ovl_window
permits
rsc_window
redirect <mapID>
route
serial
server_tmo
ssh
ssh_port
sign <keyID>
spill
status <arg>
telnet
55
Page 66

C H A P T E R 5 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Command Command Options
show
setsnmp
showsnmp
telnet_port
utl_highwater
utl_lowwater
utl_window
snmp <enable | disable>
snmp_community
snmp_port <port>
snmp_info
sys_contact
sys_location
sys_name
trap_authen <enable | disable>
trap_community
trap_port <port>
snmp
snmp_community
snmp_info
snmp_port
sys_contact
sys_location
sys_name
trap_authen
trap_community
trap_port
status
tty_char
56
line
realtime
alarms
<log>
Page 67

C H A P T E R 5 Command Reference
Command Reference
Help Commands
Command Description
help
help <command>
help usage
tty_char
Display the list of available commands.
Display usage for a single command.
Display all commands and their usage.
View the available list of keyboard shortcut commands.
Status Command
Command Description
status
Display device statistics. Severa l modes are available, as describe d
below. (Default: realtime.)
Syntax:
HP SA7120> status <arg>
where:
<line> specifies a line-oriented display of statistics.
<realtime> specifies that statistics be displayed in realtime.
<alarms> shows current alarm events.
<log> shows statistics and alarm events in log file.
57
Page 68

C H A P T E R 5 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
SSL Commands
Command Description
create key
delete key
import key
Create a new keypair and associate it with a Key ID.
Example:
HP SA7120> create key
Key strength (51 2/ 1024) [512]: 1024
New keyID [001]: <Enter>
Keypair was crea te d for keyID: 001.
HP SA7120>
Delete a specified keypair for a given Key ID.
Syntax:
HP SA7120> delete key <keyID>
<keyID> is the Key ID whose associated keypair you
where
want to delete.
Import a keypair for the specified Key ID.
Syntax:
HP SA7120> import key <keyID>
where <keyID> is the ID of the keypair you want to import.
58
Page 69

C H A P T E R 5 Command Reference
Command Description
export key
show key
Export a keypair for a specified Key ID (ASCII or xmodem).
Syntax:
HP SA7120> export key <keyID>
Export protocol: (xmodem, ascii) [ascii]:
<Enter>
Press any key to sta rt , then again when
done...<Enter>
-----BEGIN RSA PRIVATE KEY----MIIBOgIBAAJBALqeajCDgfa8fY8FROLi0B8fVp3m4EI
2MpOzKvEKKe6Kk5pDBkH83tUBkssGBtbnDYHkiAyGzA
.
.
.
UFFSNgBRvbkiNvaNiVqKeutwDEhgCL0PDueo
-----END RSA PRIVATE KEY-----<Enter>
HP SA7120>
where <keyID> is the identifier of the keypair you want to
export.
Display the expanded keypair (including PEM format) for a
specified Key ID. If no Key ID is specified, displays all keys.
Syntax:
HP SA7120> show key <keyID>
list keys
where
<keyID> is the Key ID whose associated keypair you
want to view.
List available Key IDs.
Example:
HP SA7120> list keys
001
default
HP SA7120>
59
Page 70

C H A P T E R 5 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Command Description
create cert
delete cert
import cert
export cert
Create a new certificate for a specified Key ID.
Syntax:
HP SA7120> create cert <keyID>
<keyID> is the Key IDfor which you want to create a
where
certificate.
Delete the certificate associated with a specified Key ID.
Syntax:
HP SA7120> delete cert <keyID>
<keyID> is the Key ID whose associated certificate you
where
want to delete.
Import a certificate to associate with a specified Key ID.
Syntax:
HP SA7120> import cert <keyID>
<keyID> is the Key ID whose associated certificate you
where
want to import.
Export the certificate for a specified Key ID.
60
Syntax:
HP SA7120> export cert <keyID>
where
<keyID> is the Key ID whose associated certificate you
want to export.
Page 71

C H A P T E R 5 Command Reference
Command Description
show cert
set ciphers
Display the expanded certificate (including PEM format)
associated with a specified Key ID. If no Key ID is specified,
displays all certificates.
Syntax:
HP SA7120> show cert <keyID>
where
<keyID> is the Key ID whose associated certificate you
want to view.
Establish the list of ciphers and cipher strengths that will be
recognized by the specified Map ID.
Syntax:
HP SA7120> se t ci ph ers <mapID>
1 - all
2 - high
3 - medium
4 - low
5 - export only
6 - Customized Cip he rs
Select cipher strength [1]: 1
1 - SSLv2
2 - SSLv3
3 - SSLv2 and SSLv3
Select ciphers fro m SSL version [3]: 2
HP SA7120>
where mapID is the identifier of the mapping whose ciphers you
want to set.
61
Page 72

C H A P T E R 5 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Command Description
set redirect
show redirect
Set an alternative address to which a client is directed in the event
it doesn’t support the specified Map ID’s selected cipher suites.
Syntax:
HP SA7120> set redirect <mapID> [none]
Enter redirect URL []: <URL>
where <mapID> is the Map ID for which you want to define a
redirect URL, and <URL> is the Web address to which you want
to redirect clients that don’t support the selected cipher suites.
Enter the optional pa rameter [none] to disable an existing
redirect URL for the specified Map ID.
Displays the alternative addr e ss, if one is configured for the
specified Map ID, to which a client is directed in the event it
doesn’t support the selected cipher suite.
Syntax:
HP SA7120> show redirect <mapID>
where <mapID> is the Map ID whose redirect URL you want to
display. If no redirect a ddress is defined, a co mmand line message
informs you of the fact:
HP SA7120> show redirect 1
Redirect URL for map 1 is not set.
HP SA7120>
show client_ca
62
Displays the expanded client certificate (including PEM format)
associated with the specified Map ID. If no client certificate has
been imported this command displays a message to that effect. If
no Map ID is specified, all client certificates are displayed.
Syntax:
HP SA7120> show client_ca <mapID>
where <mapID> is the mapID number of th e key whose import ed
client certificate you want to display.
Page 73

C H A P T E R 5 Command Reference
Command Description
import client_ca
delete client_ca
If you want to authenticate a client, use this command to im port
the trusted CA’s certificate. When enabled, clients without
certificates or with invalid certificates are refused connection.
Syntax:
HP SA7120> import client_ca <mapID>
Import protocol: (paste, xmodem) [paste]:
<Enter>
Type or paste in data, end with .. . alone on
line
(certificate pasted here...)
...
where <mapID> is the mapID number with which the client
certificate will be associated.
Deletes the client certificate associated with the specified Map
ID.
Syntax:
HP SA7120> delete client_ca <mapID>
where <mapID> is the mapID number whose associated client
certificate you wish to delete.
create si gn
Create the signing request for a specified Key ID.
Syntax:
HP SA7120> create sign <keyID>
where <keyID> is the Key ID number of the Key for which you
want to create a signing request.
63
Page 74

C H A P T E R 5 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Command Description
delete sign
export sign
show sign <keyID>
Delete the signing request for a specified Key ID.
Syntax:
HP SA7120> delete sign <keyID>
where <keyID> is the Key ID number of the Key whose signing
request you want to delete.
Export signing request (PEM format) for specified Key ID.
Syntax:
HP SA7120> export sign <keyID>
where <keyID> is the Key ID number of the Key whose signing
request you want to export.
Display expanded signing request (PEM format) for specified
Key ID. If no Key ID is specified, all signing requests are
displayed.
Syntax:
HP SA7120> show sign <keyID>
where <keyID> is the Key ID number of the key whose signing
request you want to display.
64
Page 75

C H A P T E R 5 Command Reference
Command Description
set defcert
show defcert
Set the default certificate creation information. For example,
country, state, city, organization, organization unit, issuer name,
and issuer e-mail address. You can change all, some or none of
the fields. Press Enter to accept a default and move to the next
field.
Example:
HP SA7120> se t de fc ert
Country name [US ]:
State [Califor ni a]:
City [Palo Alto]:
Organization [Hewlett-Packard Company]:
Organization uni t [Server Appliances
Division]:
Issuer name [www.hp.com]:
Issuer email address [support@hp.com]:
Make changes [y]:
Changes applie d
HP SA7120>
Display the default certificate creation information.
Example:
HP SA7120> show defcert
Country : US
State : California
City : Palo Alto
Organization : Hewlett-Packard Company
Unit : Server Appliances Division
Name : www.hp.com
Email : support@hp.com
HP SA7120>
65
Page 76

C H A P T E R 5 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Command Description
set kstrength
show kstrength
set client_tmo
show client_tmo
Set the default key strength. Usable values are 512 or 1024. The
default value is 512.
Syntax:
HP SA7120> se t ks tr ength <512 | 1024>
where <512> allows you to specify low key strength and
<1024> allows you to specify high key strength.
Display the default key strength value.
Example:
HP SA7120> show kstrength
Default key stre ng th: 512
Interval that the connection between the client and server can
remain idle (i.e., no data crosses the c onnection in either
direction) following a client request.
Syntax:
HP SA7120> se t cl ie nt_tmo <n>
where <n> is a value in seconds between 5 and 36000.
Displays the currently specified client timeout value.
66
Example:
HP SA7120> show client_tmo
Client timeout is 5 seconds
HP SA7120>
Page 77

C H A P T E R 5 Command Reference
Command Description
set server_tmo
show server_tmo
Port Mapping Commands
Limits the period of time to establish a connection wit h the server .
If the connection is not established within the specified time, the
client request is rejected.
NOTE: Typical causes for server timeout include: server
powered off, server not acce ssible, appl icatio n is not avai lable on
the specified port.
Syntax:
HP SA7120> set server_tmo <n>
where <n> is a value in seconds between 5 and 36000.
Displays the currently specified server timeout value.
Example:
HP SA7120> show server_tmo
Server timeout [secs]: 5
HP SA7120>
These commands are used to execute the operations described in
Chapter 3’s Mapping and Blocking sections.
Command Definition
create block
Create a block to preclude access to specified IP addresses or
through specified ports. A single IP, a single port, or all ports can
be blocked. If fewer than all ports are to be blocked, you must
repeat the create bloc k command for each one.
Example:
HP SA7120> create block
Client IP to block [0.0.0.0]: 10.1.2.1
Client IP mask [0.0.0.0]: 255.255.0.0
Server IP to block [0.0.0.0]: 20.1.2.1
Server IP mask [0.0.0.0]: 255.255.0.0
Server Port to block: 80
Server Port mask [0 xffff]:<Enter>
HP SA7120>
67
Page 78

C H A P T E R 5 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Command Definition
delete block
show block
create permit
Delete a block specified by index number. Use show block (see
below) to correlate existing blocks with their numbers.
Example:
HP SA7120> delete block 1
HP SA7120>
Display all existing blocks.
Example:
HP SA7120> show block
-------blocks :
--------(1) block 10.1.2. 1 255.255.0.0 20.1.2.1
255.255.0.0 80 0xffff
----------
Create a configuration allowing a specified user access to specified
servers and ports, and/or denying the specified user access to
specified servers and ports.
Example:
HP SA7120> create permit
Client IP to permit [0.0.0.0]:10.1.2.1
Client IP mask [0.0.0.0]:255.255.0.0
Server IP to permit [0.0.0.0]:20.1.2.1
Server IP mask [0.0.0.0]:255.255.0.0
Server Port to permit: 443
Server Port mask [0 xffff]:<Enter>
HP SA7120>
delete permit
68
Delete a permit specified by index number. Use show permit (see
below) to correlate existing permits with their numbers.
Example:
HP SA7120> delete permit 1
HP SA7120>
Page 79

C H A P T E R 5 Command Reference
Command Definition
show permit
create map
Display permits currently in force.
Example:
HP SA7120> show permit
-------permits :
--------(1) permit 10.1.2.1 255.255.0.0 20.1.2.1
255.255.0.0 44 3 0xffff
---------HP SA7120>
Create a mapping that associates server IP, SSL port, clear text
port, and Key ID.
Example:
HP SA7120> create map
Server IP (0.0.0.0): 1.1.1.1
SSL (network) port [443]: 443
Cleartext (server) port [80]: 8080
KeyID to use for ma ppi ng: 4
HP SA7120>
NOTE: The Key ID used with a new mapping must exist prior to
executing create map. Use create key to create a new Key ID. Also,
a certificate must be asso ci ated with the key ID prior to u s ing the
mapping. (See Chapter 3 for details.)
delete map <mapID>
show map
Delete a mapping.
NOTE: All MapIDs of a higher number than the one specified for
deletion are decremented by one when this command is executed.
Syntax:
HP SA7120> delete map <n>
where <n> is the Map ID of the mapping you want to delete.
Display all mappings. (Same as list maps.)
69
Page 80

C H A P T E R 5 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Command Definition
list maps
List all mappings. (Same as show map.)
Example:
HP SA7120> list maps
Map Net Ser Cipher Re- Client
ID KeyID Server IP Port Port Suites direct Auth
== ===== ========= ==== ==== ====== ===== ====
1 default Any 443 80 all(v2+v3) n n
2 sample 1.1.2.5 443 80 med(v2+v3) n n
HP SA7120>
Operational Commands
Command Description
bypass
WARNING: Do not issue
the bypass command f rom a
remote management session
(Telnet or SSH). Doing so
will result in an immediate
disconnect from the
SA7100/SA7120.
Enables bypass mode, in which traffic flows through SA7100/
SA7120 without being processed. See Failur e /B ypass Modes in
Appendix B for detail s. See the inline command below for
reversing bypass.
Example:
HP SA7120> bypass
The LED labeled “inline” on the SA7120’s front panel tu rns off
when bypass is enabled.
70
NOTE: The SA7100/SA7120 can be placed in bypass mode
simultaneously with the bypass switch and the CLI’s bypass
command. When this occurs, you must use both the bypass switch
and the CLI’s insert command to return the unit to inline mode.
Page 81

C H A P T E R 5 Command Reference
Command Description
inline
set route
show route
Enables inline mode, in which the SA7100/SA7120 processes
traffic normally. (As opposed to bypass mode, in whic h traf fic may
flow through the device unprocessed.)
Example:
HP SA7120> inline
The LED labeled “inline” on the SA7100/SA7120’s front panel is
illuminated when inline mode is enabled.
NOTE: Other factors may preclude the use of inline mode. See
Failure/Bypass Modes in Appendix B.
Specify the address of the router or gateway through which th e
SA7100/SA7120 communicates with the Internet.
Syntax:
HP SA7120> set route
Enter Defaul t Rou te (’n one’ to dele te) [non e]:
255.255.255.001
HP SA7120>
Display the currently specified address of the router or gateway
through which the SA7100/SA7120 communicates with the
Internet.
Syntax:
HP SA7120> show route
Default Route: 25 5.255.255.001
HP SA7120>
71
Page 82

C H A P T E R 5 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Command Description
set spill
show spill
reboot
Allows you to enable or disable spill mode. “Spill” is used to
offload processing of a request, when the SA7100/SA7120 has
reached a specified queue threshold, to a secondary SA7100/
SA7120 or to the server.
Example:
HP SA7120> set spill enable
Verify spill setting with the show spill command:
HP SA7120> show spill
Spill on overload : enabled
HP SA7120>
Display spill setting (enabled or disabled).
Example:
HP SA7120> show spill
Spill on overload : disabled
Reboots the SA7100/SA7120.
WARNING: Any configuration changes made during the current
CLI session will be lost upon rebooting. Refer to the config save
command for details regarding saving configuration changes.
72
Example:
HP SA7120> reboot
Are you sure you want to reboot [n]: y
System rebooting...done
(System reboots, eventually prompting you for your password.)
Page 83

C H A P T E R 5 Command Reference
Remote Management Commands
Command Description
list procs
set ip
set
max_remote_sessions
List all processes associated with the CLI and re mote management
commands (inetd, telnetd, sshd2, and snmpd).
Example:
HP SA7120> list procs
PID: 40 PROG: cli
PID: 41 PROG: cli
HP SA7120>
Assign an IP address and netmask to the SA7100/SA7120’s
network interface for Telnet and SSH sessions.
CAUTION: The assignment of an IP address introduces security
issues. Please refer to the “Access Control” section of Chapter 6.
NOTE: To disable a currently configured IP, use set ip followed
by none.
Example:
HP SA7120> set ip
Enter IP Address (’ none’ to delete)
[10.1.2.124]:
Enter Netmask [25 5.255.0.0]:
Set the maximum allowed number of concurrently running Telnet
and SSH sessions.
Syntax:
HP SA7120> set max_remote_sessions <0-5>
where <0-5> is the maximum number of remote sessions you
want to allow. Default: 5.
73
Page 84

C H A P T E R 5 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Command Description
set telnet
show telnet
set telnet_port
Enables or disables Telnet sessions. When this command is set to
“enable” and an IP address is assigned to the SA7100/SA7120’s
network interface, you can access the device’s CLI via remote
Telnet session. When disabled, the device refuses Telnet
connections. The console prompts for any missing parameters.
Default : disable.
Syntax:
HP SA7120> set telnet enable
Need an IP address to start Telnet service.
Enter IP Address [2 09.218.240.67]: 10.1.2.124
Need a netmask to start Telnet service.
Enter Netmask [25 5.255.255.0]:
Optional Default Route to start Telnet service.
Enter Default Rou te (’none’ to delete) [none]:
Telnet Services started.
HP SA7120>
Displays current Telnet status: enabled or disabled.
Example:
HP SA7120> show telnet
Telnet: enabled
Set the port on which Telnet connections are accepted. (Default
port: 23.)
show telnet_port
74
Syntax:
HP SA7120> set telnet_port <port>
where <port> is the numbe r of the port to which Telnet sessions
will connect.
Display the port on which Telnet sessions are currently accepted.
Example:
HP SA7120> show telnet_port
Telnet Port Number: 23
Page 85

C H A P T E R 5 Command Reference
Command Description
set ssh
show ssh
set ssh_port
show ssh_port
Enable or disable Secure Shell (SSH) sessions. When this
command is set to “enable” and an IP address is assigned to the
SA7100/SA7120’s network interface, you can access the device’s
CLI via remote SSH session. When disabled, the device refuses
SSH connections. Default: disable.
Syntax:
HP SA7120> set ssh <enable|disable>
Display current SSH status: enabled or disabled.
Example:
HP SA7120> show ssh
SSH: disabled
Set the port on which SSH connections are accepted. (Default port:
22.)
Syntax:
HP SA7120> set ssh_port <port>
where <port> is the numbe r of the port to which SSH session s
will connect.
Display port on which SSH sessions are currently accepted.
Example:
HP SA7120> show ssh_port
SSH Port Number: 22
setsnmp
showsnmp snmp
Enable or disable the SNMP agent. When enabled, you can set
configure SNMP information and parameters (s ee setsnmp
snmp_info, below) for the SA7100/SA7120. De fault: disable.
Syntax:
HP SA7120> setsnm p <enable|disable>
Displays the current status of the SNMP agent: enabled or
disabled.
Example:
HP SA7120> showsnmp snmp
SNMP: Enabled
75
Page 86

C H A P T E R 5 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Command Description
setsnmp snmp_info
showsnmp snmp_info
Set the following SNMP information and parameters:
• SNMP port (Default: 161)
• SNMP trap port (Default: 162)
• Contact person
• System name
• System location
Example:
HP SA7120> setsnm p snmp_info
SNMP Port [161]: 161
SNMP Trap Port [162]: 162
Contact Person []: support
System Location []:Palo Alto
System Name []: SA7120
Display the currently effective SNMP information and parameters.
Example:
HP SA7120> showsnmp snmp_info
SNMP Port Number : 161
SNMP Trap Port Number: 162
SNMP System Conta ct : support
SNMP System Name : SA7120
SNMP System Locat ion : Palo Alto
System IP Address : 10.1.2.124
System Netmask : 255.255.255.0
Default Route : None
setsnmp
snmp_community
76
Set SNMP community strings.
Example:
HP SA7120> setsnm p snmp_community
IP []:xxx.xxx.xxx.xxx
Community Stri ng []:<string>
Page 87

C H A P T E R 5 Command Reference
Command Description
list snmp_community
delete snmp_community
setsnmp trap_authen
shownmp trap_authen
Display currently configured SNMP community strings.
Example:
HP SA7120> list snmp_community
<2> Current SNMP Co mmunity String(s):
1.) IP: 0.0.0.0 => String: public
2.) IP: 0.0.0.0 => String: private
Delete SNMP community strings.
Example:
HP SA7120> delete snmp_commmunity
SNMP Community String(s) Deletion.
<2> Current Available SNMP Community String(s):
1.) IP: 0.0.0.0 => String: public
2.) IP: 0.0.0.0 => String: private
Enter number (1 to 2) to del ete (q to quit) [1]: 2
Enter number (1 to 2) to del ete (q to quit) [1]: q
When enabled, the SNMP manager receives traps upon failed
authentication attem pts.
Example:
HP SA7120> setsnmp trap_authen <enable|disable>
Displays current status of trap authentication trap.
setsnmp
trap_community
Example:
HP SA7120> showsnmp trap_authen
Trap Authentication: enabled
Sets SNMP trap comm unity strings.
Example:
HP SA7120> setsnmp trap_community
SNMP Trap Community String(s) Setting.
Enter a SNMP Trap Community IP (q to quit): 0.0.0.0
Enter a SNMP Trap Community String (q to quit):
private
Enter a SNMP Trap Community IP (q to quit): 0.0.0.0
Enter a SNMP Trap Community String (q to quit):
public
Enter a SNMP Trap Community IP (q to quit): q
77
Page 88

C H A P T E R 5 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Command Description
list trap_ communit y
delete trap_community
Display SNMP trap community strings.
Example:
HP SA7120> list trap_community
SNMP Trap Community String(s) information.
<2> Current SNMP Tr ap Community String(s):
1.) IP: 0.0.0.0 => String: public
2.) IP: 0.0.0.0 => String: private
Delete SNMP trap commun ity strings.
Example:
HP SA7120> delete trap_community
SNMP Trap Community String(s) Deletion.
<2> Current Available SNMP Trap Community
String(s):
1.) IP: 0.0.0.0 => String: public
2.) IP: 0.0.0.0 => String: private
Enter number (1 to 2) to del ete (q to quit) [1]: 2
Enter number (1 to 2) to del ete (q to quit) [1]: q
78
Page 89

C H A P T E R 5 Command Reference
Alarms and Monitoring Commands
Command Description
set alarms
show alarms
Enable all or a selection of the SA7120’s alarms.
Syntax:
HP SA7120> set alarms
<all none esc rsc utl ovl nls>
where
all enables all five of the SA7120’s alarms.
esc enables the Encryption Status Change Alarm.
rsc enables the Refused SSL Connection Alarm
utl enables the Utilization Threshold Alarm
ovl enables the Overload Alarm
nls enables the Network Link Status Alarm
To disable all alarms, use none:
Example:
HP SA7120> set alarms all
HP SA7120> show alarms
Alarms set: esc rsc utl ovl nls
Display the list of currently enabled alarms.
Example:
HP SA7120> set alarms none
HP SA7120> show alarms
Alarms set:
set rsc_window
NOTE: When no alarms are set (i.e., when none i s specified in set
alarms), the display shows an empty field.
Set interval (window) at which the device checks for refused SSL
connections and, if any are detected, issues an RSC Alarm.
(Range: 5-65000 seconds, default: 15)
Syntax:
HP SA7120> set rsc_window <sec>
where <sec> is the number of seconds of the desired interval.
79
Page 90

C H A P T E R 5 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Command Description
show rsc_window
set utl_window
Display current Refused SSL Connections Alarm interval.
Syntax:
HP SA7120> show rsc_window
Check for refused SSL connections [secs]:
Set interval (window) at which the device checks for exceeded
utilization thresh olds (CPU load , Connectio ns per Se cond, or Total
Open Connections) and, if any are detected, issues a Utilization
Threshold Alarm. (Range: 5-65000 seconds, default: 15)
NOTE: The data collected for utilization threshold metrics tends
to be bursty, so a smoothing algorithm is used to prevent
continuous alarms. The utilization window is a user-specified
sliding interval during which data is collected and averaged.
Consequently, shorter intervals are likely to result in some
extraneous alarms.
NOTE: See also set utl_highwater and set utl_lowwater.
Syntax:
HP SA7120> set utl_window <sec>
where <sec> is the number of seconds of the desired interval.
set utl_highwater
80
Set the Utilization Threshold Alarm high-water value. Expressed
as a percentage, the high-water value represents the highest CPU
utilization, Connections per Second, or Total Open Connections
required to trigger a UTL Alarm. (Range: 2-100%, default: 90)
NOTE: See also set utl_window and s et utl_lowwater.
Syntax:
HP SA7120> set utl_highwater <%>
where <%> is the percentage defining the upper threshold of CPU
utilization, Connections per Second, or Total Open Connections
required to trigger a Utilization Threshold Alarm.
Page 91

C H A P T E R 5 Command Reference
Command Description
set utl_lowwater
show utl_window
show utl_highwater
Set the Utilization Threshold Alarm low-water value. Expressed as
a percentage, the low-water value represents the lowest CPU
utilization, Connections per Second, or Total Open Connections
required to trigger a UTL Alarm . (Range: 1-99%, default: 60)
NOTE: See also set utl_window and s et ut l_highwater.
Syntax:
HP SA7120> set utl_lowwater <%>
where <%> is the percentage defining the lower threshold of CPU
utilization, Connections per Second, or Total Open Connections
required to trigger a Utilization Threshold Alarm.
Display the current Utilization Threshold Alarm window.
Example:
HP SA7120> show utl_window
Utilization wi ndow set [secs]: 10.
Display the Utilization Threshold Alarm’s current upper threshold.
Example:
HP SA7120> show utl_highwater
Utilization Hi gh water mark [%]: 80
show utl_lowwater
set ovl_window
Display the Utilization Threshold Alarm’s current lower threshold.
Example:
HP SA7120> show utl_lowwater
Utilization Low water mark [%]: 60
Set interval (window) at which the device checks for overloads
resulting in the device executing a spill or throttle and, if any are
detected, issues an Overload Alarm. (Range: 5-65000, default: 15)
Syntax:
HP SA7120> set ovl_window 10
81
Page 92

C H A P T E R 5 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Command Description
show ovl_window
Display the current Overload Alarm window.
Example:
HP SA7120> show ovl_window
Check for overloa d conditions [sec]: 10
Configuration Commands
Command Description
show config
show config saved
Display current volatile configuration settings.
Example:
HP SA7120> show config
# default config file created on Tues July 25
06:56:46 2000
(Configuraton parameters are displayed here...)
HP SA7120>
Display saved non-volatile configuration settings.
82
Example:
HP SA7120> show config saved
Saved configur ation
===================
(Configuraton parameters are displayed here...)
HP SA7120>
Page 93

C H A P T E R 5 Command Reference
Command Description
show config default
Display default configuration settings. These are values used when
factory default commands are executed.
Example:
HP SA7120> show config default
Default config uration
=====================
conlog 0xffffffef
ilog 0xffffffff
trace 0xfffff3 dd
media auto
logport tty01
cache 3
server_tmo 5
client_tmo 30
serverif exp1
netif exp0
map 0.0.0.0 443 80 default
kpanic reboot
monitoring_interval 15
monitoring_fields 0x1F
alarm_mask 0x00000000
ovl_window 15
rsc_window 15
utl_window 15
utl_highwate r 90
utl_lowwater 60
idle 300
kstrength 512
con_speed 9600
con_bits 8
con_stop 1
con_parity n
max_remote_sessions 5
trap_authen 1
defcert_cnam e US
defcert_stat e California
defcert_city San Diego
defcert_orgname Company Name
defcert_orgunit Company Division
defcert_name www.company.com
defcert_emai l support@company.com
prompt HP SA7120>
HP SA7120>
83
Page 94

C H A P T E R 5 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Command Description
config compare
config reset
config default
Display differences between saved and current configuration. For
optimal flexibility in configuration and testing, the SA7100/
SA7120 supports both “current” (volatile) and “saved” (nonvolatile) configurations. The config compare command displays
the differences, if any, between the two configurations.
Example:
HP SA7120> config compare
Only in /keys: 4
HP SA7120>
Restore saved configuration.
WARNING: Executing this command causes the system to reboot.
Example:
HP SA7120> config reset
Reverting to saved configuration
Reset (y/n) [n]: y
Reset to saved co nfi guration
System reboot in g...
Clears current and saved configurations and restores factory
defaults.
config save
84
WARNING: Executing this command causes the system to reboot.
Example:
HP SA7120> config default
Reset to factory default config uration [n]: y
Reset to factor y def aults
System reboot in g...
Save the current configuration to the flash (non-volatile) memory.
Example:
HP SA7120> config save
Saving config ur ation to flash...
Configuration saved to flash
HP SA7120>
Page 95

C H A P T E R 5 Command Reference
Command Description
export config
WARNING: Do not edit an
exported configuratio n file.
import config
Export all configuration, key, sign and certificate information
(ASCII, xmodem).
Example:
HP SA7120> export config
Export protoc ol : (xmodem, ascii) [ascii]:
Press any key to start, then again when
done...
# default config file created on Fri Jul 28
06:56:46 2000
(...configuration specifics are displayed...)
HP SA7120>
Import a configuration file (paste, xmodem).
Example:
HP SA7120> import config
Import protocol: (paste, xmodem) [paste]:
Type or past e in data , end with ... alo ne o n
line
.
.
.
Do you want to inst all this config ? [y]: n
HP SA7120>
85
Page 96

C H A P T E R 5 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Command Description
import upgrade
import patch
Import a complete software release. (See Chapter 8 for details
regarding software updates.)
Example:
HP SA7120> import upgrade
Import protoc ol : (xmodem) [xmodem]:
Start xmodem upload now
Use Ctl-x to cancel upload
Verifying upgrade image...
upgrade image valid
version x.x, build xxx
Continue with the upgrade? [n]:y
NOTE: All saved logs will be deleted and the system will reboot
upon sucessful completion of the upgrade.
Import a partial software upgrade
Example:
HP SA7120> import patch
Enter patch name [80.patch] <patch name>
Import protoc ol : (xmodem)
[xmodem]:
Start xmodem upload now
Use Ctl-x to cancel upload
list system
86
Patch: Import ed .
Displays the device’s CPU, memory and crypto card information.
HP SA7120> list system
=================================================
SYSTEM INFO
=================================================
* CPU : Pentium II (498 MHz)
* Real MEM : 536870912 (512.00 MB)
* Crypto : 3
Page 97

C H A P T E R 5 Command Reference
Command Description
factory_default
Administration
Commands
Returns to factory configuration settings.
Example:
HP SA7120> factory_default
Reset to defaul t co nfiguration [n]: y
Reset to factor y de faults
System reboot in g...done
T944 V2.31 DXC.
..
868242+361188O/S running
Generating 51 2 bi t default key
Generating de fa ult certificate
Saving defaul t ke y/cert to flash
Restricted Rights Legend
(...copyright and version information displayed here...)
Serial 0:a0:a 5: 11:4:9d
password:
Command Description
password
Set the password.
Example:
HP SA7120> password
Old password:<xxxxx>
Enter new admin pas sword (5 chars min.):<yyyyy>
Retype new password:<yyyyy>
admin Password changed...
HP SA7120>
87
Page 98

C H A P T E R 5 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Command Description
show info
set date
Display software version information.
Example:
HP SA7120> show info
============================================
=== hp e-commerce server accelerator sa7120
=== Copyright (c ) 200 1 Hewlett-Packard
Company
===
=== Version 2.3. 2, Bu ild xx
============================================
Set the date and time.
WARNING: Execution of this command reboots the SA7100/
SA7120.
Example:
HP SA7120> set date
Year [2000]:
Month [2]:
Day [16]:
Hour (24 hour clo ck) [15]:
Minute [10]:
The system must reboot for changes to take
affect. Reboot [y]: n
HP SA7120>
show date
set egress_mac
88
Displays current date and time.
Allows the configuration of a SA7100/SA7120 when the ingress
and egress traffic paths are different. (See Chapter 4, Scenario 4.)
Page 99

C H A P T E R 5 Command Reference
Command Description
set ether
show ether
set idleto
Specify ethernet settings.
Example:
HP SA7120> set ether
1 - auto
2 - 10baseT, half duplex
3 - 10baseT, full duplex
4 - 100baseTX, half duplex
5 - 100baseTX, full duplex
Select media ty pe [1]:
Media set to auto
HP SA7120>
Display ethernet settings.
Example:
HP SA7120> show ether
Ethernet medi a se t to auto
HP SA7120>
Set the console idle interv al. After <n > minutes absence of
keyboard activity, the user is automatically logged off.
Syntax:
HP SA7120> set idleto <n>
show idleto
set more
where <n> is a value in minutes from 0 to 525600. A value of “0”
specifies that the console never goes idle.
Display console timeout.
Example:
HP SA7120> sho w id le to
Idle timeout is 5 minu tes
HP SA7120>
Set the page length of the console display. Default is 300.
Syntax:
HP SA7120> set more <n>
where <n> is the desired number of lines. Valid inputs are 0 (to
disable), or 23 or greater.
89
Page 100

C H A P T E R 5 HP e-Commerce Server Accelerator SA7100/SA7120 User Guide
Command Description
show more
nic
set prompt
set serial
Display the current setting for the console display’s page length.
Default is 300.
Example:
HP SA7120> show more
Set 23 lines per pag e
Allows you to set the network interface card configuration.
Example:
HP SA7120> nic
1 - auto
2 - 10baseT, half duplex
3 - 10baseT, full duplex
4 - 100baseTX, half duplex
5 - 100baseTX, full duplex
Select media ty pe [1]:
Change the prompt from “HP SA7120>” to the desired prompt.
Example:
HP SA7120> set prompt
Prompt [
HP SA7120>
HP SA7120> ]: <Enter>
Allows user to set the console port to monitor the CLI or the output
logging, and set the speed, data bits, stop bits, and parity bits. The
aux console port is fixed a t 115200, 8, 1, N. This command returns
the user to the “password” prompt after setting the console port.
90
Example:
HP SA7120> set serial
Baud rate (9600 /1 15200) [9600]: <Enter>
Data bits (7/8) [8]: <Enter>
Stop bits (1/2) [1]: <Enter>
Parity (n/e/o ) [n ]: <Enter>
Set serial para me ters [y]: <Enter>
HP SA7120>
 Loading...
Loading...