Page 1

HP ProLiant Storage Server
user guide
Part number: 440584-005
First edition: June 2008
Page 2

Legal and notice information
© Copyright 1999, 2008 Hewlett-Packard Development Company, L.P.
Confidential computer software. Valid license from HP required for possession, use or copying. Consistent with FAR 12.211
and 12.212, Commercial Computer Software, Computer Software Documentation, and Technical Data for Commercial Items
are licensed to the U.S. Government under vendor's standard commercial license.
The information contained herein is subject to change without notice. The only warranties for HP products and services are set
forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as
constituting an additional warranty. HP shall not be liable for technical or editorial errors or omissions contained herein.
Intel, Itanium, Pentium, Intel Inside, and the Intel Inside logo are trademarks or registered trademarks of Intel Corporation or
its subsidiaries in the United States and other countries.
Microsoft, Windows, Windows XP, and Windows NT are U.S. registered trademarks of Microsoft Corporation.
Adobe and Acrobat are trademarks of Adobe Systems Incorporated.
Java is a US trademark of Sun Microsystems, Inc.
Oracle is a registered US trademark of Oracle Corporation, Redwood City, California.
UNIX is a registered trademark of The Open Group.
Page 3

Contents
About this guide ................................................................................. 13
Intended audience .................................................................................................................... 13
Related documentation .............................................................................................................. 13
Document conventions and symbols ............................................................................................. 13
Rack stability ............................................................................................................................ 14
HP technical support ................................................................................................................. 15
Customer self repair .................................................................................................................. 15
Product warranties .................................................................................................................... 15
Subscription service .................................................................................................................. 15
HP websites ............................................................................................................................. 16
Documentation feedback ........................................................................................................... 16
1 Installing and configuring the server ................................................... 17
Setup overview ......................................................................................................................... 17
Planning for installation .......................................................................................................17
Planning a network configuration ......................................................................................... 18
Configuration checklist ........................................................................................................ 19
Installing the server ................................................................................................................... 19
Locating and writing down the serial number ......................................................................... 19
Checking kit contents .......................................................................................................... 20
Powering on the server ........................................................................................................ 20
Factory image ...................................................................................................................20
Physical configuration ................................................................................................... 21
Default boot sequence .................................................................................................. 22
Accessing the HP Storage Server Management console ................................................................. 22
Using the direct attach method ............................................................................................. 23
Using the remote browser method ......................................................................................... 23
Using the Remote Desktop method ........................................................................................ 26
Logging off and disconnecting ............................................................................................. 27
Telnet Server ...................................................................................................................... 27
Enabling Telnet Server .................................................................................................. 27
Using remote management methods ..................................................................................... 28
Using the Lights-Out 100 method ................................................................................... 28
Using the Integrated Lights-Out 2 method ........................................................................ 29
Configuring the server on the network ......................................................................................... 30
Before you begin ................................................................................................................30
Running the Rapid Startup Wizard ........................................................................................ 32
Completing system configuration .................................................................................................32
2 Server components ........................................................................... 35
ML110 G5 hardware components .............................................................................................. 35
DL160 G5 hardware components ............................................................................................... 38
DL185 G5 hardware components ............................................................................................... 40
DL380 G5 hardware components ............................................................................................... 42
HP ProLiant Storage Server 3
Page 4

DL585 G2 hardware components ............................................................................................... 45
SAS and SATA hard drive LEDs ................................................................................................... 48
Systems Insight Display LEDs and internal health LED combinations ................................................. 50
3 Storage management overview .......................................................... 53
Storage management elements ................................................................................................... 53
Storage management example ............................................................................................. 53
Physical storage elements .................................................................................................... 54
Arrays ........................................................................................................................ 55
Fault tolerance ............................................................................................................. 56
Online spares ............................................................................................................. 56
Logical storage elements ..................................................................................................... 56
Logical drives (LUNs) .................................................................................................... 56
Partitions .................................................................................................................... 57
Volumes ..................................................................................................................... 57
File system elements ............................................................................................................58
File sharing elements .......................................................................................................... 58
Volume Shadow Copy Service overview ................................................................................ 58
Using storage elements ....................................................................................................... 59
Clustered server elements .................................................................................................... 59
Network adapter teaming .......................................................................................................... 59
Management tools .................................................................................................................... 59
HP Systems Insight Manager ................................................................................................ 59
Management Agents .......................................................................................................... 60
4 File server management .................................................................... 61
File services features in Windows Storage Server 2003 R2 ............................................................ 61
Storage Manager for SANs ................................................................................................. 61
Single Instance Storage ....................................................................................................... 61
File Server Resource Manager .............................................................................................. 61
Windows SharePoint Services .............................................................................................. 62
HP Storage Server Management Console .............................................................................. 62
File services management .......................................................................................................... 62
Configurable and pre-configured storage .............................................................................. 63
Storage management utilities ............................................................................................... 63
Array management utilities ............................................................................................ 63
Array Configuration Utility ............................................................................................ 64
Disk Management utility ............................................................................................... 65
Guidelines for managing disks and volumes .......................................................................... 65
Scheduling defragmentation ................................................................................................ 65
Disk quotas ....................................................................................................................... 66
Adding storage ..................................................................................................................67
Expanding storage ...................................................................................................... 67
Extending storage using Windows Storage Utilities .......................................................... 67
Expanding storage for EVA arrays using Command View EVA ........................................... 68
Expanding storage using the Array Configuration Utility ................................................... 68
Volume shadow copies .............................................................................................................. 69
Shadow copy planning ....................................................................................................... 69
Identifying the volume .................................................................................................. 69
Allocating disk space ................................................................................................... 70
Identifying the storage area .......................................................................................... 71
Determining creation frequency ..................................................................................... 71
Shadow copies and drive defragmentation ............................................................................ 71
Mounted drives ..................................................................................................................72
4
Page 5

Managing shadow copies ................................................................................................... 72
The shadow copy cache file .......................................................................................... 73
Enabling and creating shadow copies ............................................................................ 74
Viewing a list of shadow copies ..................................................................................... 75
Set schedules .............................................................................................................. 75
Viewing shadow copy properties ................................................................................... 75
Redirecting shadow copies to an alternate volume ........................................................... 76
Disabling shadow copies .............................................................................................. 76
Managing shadow copies from the storage server desktop ...................................................... 77
Shadow Copies for Shared Folders ....................................................................................... 77
SMB shadow copies .................................................................................................... 78
NFS shadow copies ..................................................................................................... 79
Recovery of files or folders ............................................................................................ 80
Recovering a deleted file or folder .................................................................................. 80
Recovering an overwritten or corrupted file ...................................................................... 81
Recovering a folder ...................................................................................................... 81
Backup and shadow copies .......................................................................................... 82
Shadow Copy Transport ...................................................................................................... 82
Folder and share management ................................................................................................... 83
Folder management ............................................................................................................ 83
Share management ............................................................................................................ 89
Share considerations .................................................................................................... 89
Defining Access Control Lists ......................................................................................... 90
Integrating local file system security into Windows domain environments ............................. 90
Comparing administrative (hidden) and standard shares ................................................... 90
Managing shares ........................................................................................................ 91
File Server Resource Manager ....................................................................................................91
Quota management ........................................................................................................... 91
File screening management ................................................................................................. 92
Storage reports .................................................................................................................. 92
Other Windows disk and data management tools ......................................................................... 92
Additional information and references for file services .................................................................... 92
Backup ............................................................................................................................. 92
HP StorageWorks Library and Tape Tools .............................................................................. 93
Antivirus ............................................................................................................................ 93
Security ............................................................................................................................ 93
More information ............................................................................................................... 93
5 Print services ................................................................................... 95
Microsoft Print Management Console .......................................................................................... 95
New or improved HP print server features .................................................................................... 95
HP Web Jetadmin .............................................................................................................. 95
HP Install Network Printer Wizard ........................................................................................ 95
HP Download Manager for Jetdirect Printer Devices ................................................................ 95
Microsoft Print Migrator utility .............................................................................................. 95
Network printer drivers ....................................................................................................... 96
Print services management ......................................................................................................... 96
Microsoft Print Management Console .................................................................................... 96
HP Web Jetadmin installation .............................................................................................. 96
Web-based printer management and Internet printing ............................................................. 96
Planning considerations for print services ............................................................................... 97
Print queue creation ............................................................................................................97
Sustaining print administration tasks ............................................................................................ 98
Driver updates ................................................................................................................... 98
HP ProLiant Storage Server 5
Page 6

Print drivers ................................................................................................................. 98
User-mode vs. kernel-mode drivers .................................................................................. 98
Kernel-mode driver installation blocked by default ............................................................ 98
HP Jetdirect firmware .................................................................................................... 98
Printer server scalability and sizing ....................................................................................... 99
Backup ............................................................................................................................. 99
Best practices ........................................................................................................................... 99
Troubleshooting ...................................................................................................................... 100
Additional references for print services ....................................................................................... 100
6 Microsoft Services for Network File System (MSNFS) ........................... 101
MSNFS Features ..................................................................................................................... 101
UNIX Identity Management ............................................................................................... 101
MSNFS use scenarios .............................................................................................................. 102
MSNFS components ......................................................................................................... 102
Administering MSNFS ................................................................................................ 103
Server for NFS .......................................................................................................... 103
User Name Mapping ................................................................................................. 108
Microsoft Services for NFS troubleshooting .................................................................... 110
Microsoft Services for NFS command-line tools .............................................................. 110
Optimizing Server for NFS performance ....................................................................... 110
Print services for UNIX ................................................................................................ 110
7 Other network file and print services ................................................. 113
File and Print Services for NetWare (FPNW) .............................................................................. 113
Installing Services for NetWare .......................................................................................... 113
Managing File and Print Services for NetWare .................................................................... 114
Creating and managing NetWare users .............................................................................. 115
Adding local NetWare users ....................................................................................... 116
Enabling local NetWare user accounts ......................................................................... 116
Managing NCP volumes (shares) ....................................................................................... 117
Creating a new NCP share ......................................................................................... 118
Modifying NCP share properties ................................................................................. 118
Print Services for NetWare ................................................................................................ 118
Point and Print from Novell to Windows Server 2003 ..................................................... 118
Additional resources .................................................................................................. 119
AppleTalk and file services for Macintosh ................................................................................... 119
Installing the AppleTalk protocol ......................................................................................... 119
Installing File Services for Macintosh ................................................................................... 119
Completing setup of AppleTalk protocol and shares .............................................................. 119
Print services for Macintosh ................................................................................................ 120
Installing Print Services for Macintosh .................................................................................. 120
Point and Print from Macintosh to Windows Server 2003 ...................................................... 120
8 Enterprise storage servers ................................................................ 121
Windows Server Remote Administration Applet .......................................................................... 121
Microsoft iSCSI Software Target ................................................................................................ 122
Virtual disk storage ........................................................................................................... 122
Snapshots ....................................................................................................................... 122
Wizards .......................................................................................................................... 123
Create iSCSI Target Wizard ........................................................................................ 123
Create Virtual Disk Wizard ......................................................................................... 124
Import Virtual Disk Wizard .......................................................................................... 125
6
Page 7

Extend Virtual Disk Wizard ......................................................................................... 125
Schedule Snapshot Wizard ......................................................................................... 125
Hardware provider ........................................................................................................... 126
Cluster support ................................................................................................................. 126
9 Cluster administration ..................................................................... 127
Cluster overview ..................................................................................................................... 127
Cluster terms and components .................................................................................................. 128
Nodes ............................................................................................................................ 128
Resources ........................................................................................................................ 128
Cluster groups ................................................................................................................. 129
Virtual servers .................................................................................................................. 129
Failover and failback ........................................................................................................ 129
Quorum disk ................................................................................................................... 129
Cluster concepts ..................................................................................................................... 130
Sequence of events for cluster resources .............................................................................. 130
Hierarchy of cluster resource components ............................................................................ 131
Cluster planning ..................................................................................................................... 131
Storage planning ............................................................................................................. 132
Network planning ............................................................................................................ 132
Protocol planning ............................................................................................................. 133
Preparing for cluster installation ................................................................................................ 134
Before beginning installation ............................................................................................. 134
Using multipath data paths for high availability .................................................................... 134
Enabling cluster aware Microsoft Services for NFS (optional) .................................................. 134
Checklists for cluster server installation ................................................................................ 135
Network requirements ................................................................................................ 135
Shared disk requirements ............................................................................................ 136
Cluster installation ................................................................................................................... 136
Setting up networks .......................................................................................................... 137
Configuring the private network adapter ....................................................................... 137
Configuring the public network adapter ........................................................................ 137
Renaming the local area connection icons .................................................................... 137
Verifying connectivity and name resolution .................................................................... 137
Verifying domain membership ..................................................................................... 138
Setting up a cluster account ........................................................................................ 138
About the Quorum disk .............................................................................................. 138
Configuring shared disks ............................................................................................ 138
Verifying disk access and functionality .......................................................................... 138
Configuring cluster service software ........................................................................................... 138
Using Cluster Administrator ............................................................................................... 139
Using Cluster Administrator remotely ............................................................................ 139
The HP Storage Server Management Console ................................................................ 139
Creating a cluster ............................................................................................................. 139
Adding nodes to a cluster .................................................................................................. 139
Geographically dispersed clusters ...................................................................................... 140
Cluster groups and resources, including file shares ...................................................................... 140
Cluster group overview ..................................................................................................... 140
Node-based cluster groups ......................................................................................... 140
Load balancing ......................................................................................................... 141
File share resource planning issues ..................................................................................... 141
Resource planning ..................................................................................................... 141
Permissions and access rights on share resources ........................................................... 141
NFS cluster-specific issues ........................................................................................... 142
HP ProLiant Storage Server 7
Page 8

Non cluster aware file sharing protocols .............................................................................. 142
Adding new storage to a cluster ......................................................................................... 142
Creating physical disk resources .................................................................................. 143
Creating file share resources ....................................................................................... 143
Creating NFS share resources ..................................................................................... 143
Shadow copies in a cluster ................................................................................................ 143
Extend a LUN in a cluster .................................................................................................. 144
MSNFS administration on a server cluster ............................................................................ 144
Best practices for running Server for NFS in a server cluster ............................................. 144
Print services in a cluster .......................................................................................................... 145
Creating a cluster printer spooler ........................................................................................ 145
Advanced cluster administration procedures ............................................................................... 146
Failing over and failing back ............................................................................................. 146
Restarting one cluster node ................................................................................................ 146
Shutting down one cluster node .......................................................................................... 146
Powering down the cluster ................................................................................................. 147
Powering up the cluster ..................................................................................................... 147
Additional information and references for cluster services ............................................................. 148
10 Troubleshooting, servicing, and maintenance ................................... 149
Troubleshooting the storage server ............................................................................................ 149
WEBES (Web Based Enterprise Services) ................................................................................... 150
Maintenance and service ......................................................................................................... 150
Maintenance and service documentation ............................................................................. 150
Maintenance updates ....................................................................................................... 150
System updates .......................................................................................................... 150
Firmware updates ............................................................................................................. 150
Certificate of Authenticity ......................................................................................................... 151
11 System recovery ........................................................................... 153
The System Recovery DVD ........................................................................................................ 153
To restore a factory image ....................................................................................................... 153
Systems with a DON'T ERASE partition ...................................................................................... 153
Managing disks after a restoration ............................................................................................ 153
A Configuring storage server for Web access (optional) ......................... 155
Setting up an Internet connection .............................................................................................. 155
B Regulatory compliance and safety .................................................... 157
Federal Communications Commission notice .............................................................................. 157
Class A equipment ........................................................................................................... 157
Class B equipment ............................................................................................................ 157
Declaration of conformity for products marked with the FCC logo, United States only ................ 158
Modifications .................................................................................................................. 158
Cables ............................................................................................................................ 158
Laser compliance .................................................................................................................... 158
International notices and statements .......................................................................................... 159
Canadian notice (Avis Canadien) ....................................................................................... 159
Class A equipment ..................................................................................................... 159
Class B equipment ..................................................................................................... 159
European Union notice ...................................................................................................... 159
BSMI notice ..................................................................................................................... 160
Japanese notice ............................................................................................................... 160
8
Page 9

Korean notice A&B ........................................................................................................... 160
Class A equipment ..................................................................................................... 160
Class B equipment ..................................................................................................... 160
Safety ................................................................................................................................... 161
Battery replacement notice ................................................................................................ 161
Taiwan battery recycling notice .......................................................................................... 161
Power cords ..................................................................................................................... 161
Japanese power cord notice .............................................................................................. 162
Electrostatic discharge ....................................................................................................... 162
Preventing electrostatic discharge ................................................................................. 162
Grounding methods ................................................................................................... 162
Waste Electrical and Electronic Equipment (WEEE) directive ......................................................... 162
Czechoslovakian notice ..................................................................................................... 162
Danish notice .................................................................................................................. 163
Dutch notice .................................................................................................................... 163
English notice .................................................................................................................. 163
Estonian notice ................................................................................................................ 164
Finnish notice ................................................................................................................... 164
French notice ................................................................................................................... 164
German notice ................................................................................................................. 164
Greek notice .................................................................................................................... 165
Hungarian notice ............................................................................................................. 165
Italian notice .................................................................................................................... 165
Latvian notice .................................................................................................................. 165
Lithuanian notice .............................................................................................................. 166
Polish notice .................................................................................................................... 166
Portuguese notice ............................................................................................................. 166
Slovakian notice ............................................................................................................... 167
Slovenian notice ............................................................................................................... 167
Spanish notice ................................................................................................................. 167
Swedish notice ................................................................................................................. 167
Index ............................................................................................... 169
HP ProLiant Storage Server 9
Page 10

Figures
Internet options screen ............................................................................................. 241
HP Storage Server Management console ................................................................... 262
ML110 G5 front panel (bezel on) ............................................................................. 353
ML110 G5 front panel (bezel off) ............................................................................. 364
ML110 G5 rear panel ............................................................................................. 375
DL160 G5 front panel ............................................................................................. 386
DL160 G5 rear panel ............................................................................................. 397
DL185 G5 front panel ............................................................................................. 408
DL185 G5 rear panel .............................................................................................. 419
DL380 G5 front panel ............................................................................................. 4210
DL380 G5 rear panel .............................................................................................. 4411
DL585 G2 front panel ............................................................................................. 4612
DL585 G2 rear panel .............................................................................................. 4713
SAS/SATA hard drive LEDs ....................................................................................... 4914
Storage management process example ...................................................................... 5415
Configuring arrays from physical drives ...................................................................... 5516
RAID 0 (data striping) (S1-S4) of data blocks (B1-B12) ................................................ 5517
Two arrays (A1, A2) and five logical drives (L1 through L5) spread over five physical
18
drives .................................................................................................................... 57
System administrator view of Shadow Copies for Shared Folders ................................... 7319
Shadow copies stored on a source volume ................................................................. 7320
Shadow copies stored on a separate volume .............................................................. 7421
Accessing shadow copies from My Computer ............................................................. 7722
Client GUI ............................................................................................................. 7923
Recovering a deleted file or folder ............................................................................. 8124
Properties dialog box, Security tab ............................................................................ 8425
Advanced Security settings dialog box, Permissions tab ............................................... 8526
User or group Permission Entry dialog box ................................................................. 8627
Advanced Security Settings dialog box, Auditing tab ................................................... 8728
Select User or Group dialog box ............................................................................... 8729
Auditing Entry dialog box for folder name NTFS Test ................................................... 8830
10
Advanced Security Settings dialog box, Owner tab ..................................................... 8931
Page 11

Accessing MSNFS from HP Storage Server Management console ................................ 10332
File and Print Services for NetWare dialog box ......................................................... 11533
New User dialog box ............................................................................................ 11634
NetWare Services tab ........................................................................................... 11735
iSCSI Initiators Identifiers page ............................................................................... 12336
Advanced Identifiers page ..................................................................................... 12437
Add/Edit Identifier page ........................................................................................ 12438
Storage server cluster diagram ................................................................................ 12839
Cluster concepts diagram ....................................................................................... 13040
Automatic configuration settings .............................................................................. 15541
Proxy server settings .............................................................................................. 15642
HP ProLiant Storage Server 11
Page 12

Tables
Document conventions ............................................................................................. 131
Network access methods ......................................................................................... 182
Installation and configuration checklist ....................................................................... 193
HP ProLiant RAID configurations ................................................................................ 214
Server configuration worksheet ................................................................................. 305
ML110 G5 front panel components (bezel on) ............................................................ 376
ML110 G5 front panel components (bezel off) ............................................................ 367
ML110 G5 rear panel components ........................................................................... 378
DL160 G5 front panel components ........................................................................... 389
DL160 G5 rear panel components ............................................................................ 3910
DL185 G5 front panel components ........................................................................... 4011
DL185 G5 rear panel components ............................................................................ 4112
DL380 G5 front panel components ........................................................................... 4213
DL380 G5 rear panel components ............................................................................ 4414
DL585 G2 front panel components ............................................................................ 4615
DL585 G2 rear panel components ............................................................................ 4716
SAS and SATA hard drive LED combinations ............................................................... 4917
Systems Insight Display LEDs and internal health LED combinations ................................ 5018
Summary of RAID methods ....................................................................................... 5619
Tasks and utilities needed for storage server configuration ............................................ 6320
Authentication table .............................................................................................. 10421
MSNFS command-line administration tools ............................................................... 11022
Sharing protocol cluster support .............................................................................. 13323
Power sequencing for cluster installation ................................................................... 13624
12
Page 13
About this guide
This guide provides information about installing, configuring, managing, and troubleshooting the
following HP ProLiant Storage Servers:
• HP ProLiant ML110 G5 Storage Server
• HP ProLiant DL160 G5 Storage Server
• HP ProLiant DL185 G5 Storage Server
• HP ProLiant DL380 G5 Storage Server
• HP ProLiant DL585 G2 Storage Server
Intended audience
This guide is intended for technical professionals with knowledge of:
• Microsoft® administrative procedures
• System and storage configurations
Related documentation
The following documents [and websites] provide related information:
• HP Integrated Lights-Out 2 User Guide
• HP ProLiant Lights-Out 100 Remote Management User Guide
You can find these documents from the Manuals page of the HP Business Support Center website:
http://www.hp.com/support/manuals
In the Storage section, click Disk Storage Systems and then select your product.
Document conventions and symbols
Table 1 Document conventions
ElementConvention
Cross-reference links and e-mail addressesBlue text: Table 1
ttp://www.hp.com
Bold text
Website addressesBlue, underlined text: h
• Keys that are pressed
• Text typed into a GUI element, such as a box
• GUI elements that are clicked or selected, such as menu
and list items, buttons, tabs, and check boxes
Text emphasisItalic text
HP ProLiant Storage Server 13
Page 14

Monospace text
ElementConvention
• File and directory names
• System output
• Code
• Commands, their arguments, and argument values
Monospace, italic text
Monospace, bold text
• Code variables
• Command variables
Emphasized monospace text
WARNING!
Indicates that failure to follow directions could result in bodily harm or death.
CAUTION:
Indicates that failure to follow directions could result in damage to equipment or data.
IMPORTANT:
Provides clarifying information or specific instructions.
NOTE:
Provides additional information.
TIP:
Provides helpful hints and shortcuts.
Rack stability
Rack stability protects personnel and equipment.
About this guide14
Page 15

WARNING!
To reduce the risk of personal injury or damage to equipment:
• Extend leveling jacks to the floor.
• Ensure that the full weight of the rack rests on the leveling jacks.
• Install stabilizing feet on the rack.
• In multiple-rack installations, fasten racks together securely.
• Extend only one rack component at a time. Racks can become unstable if more than one component
is extended.
HP technical support
For worldwide technical support information, see the HP support website:
http://www.hp.com/support
Before contacting HP, collect the following information:
• Product model names and numbers
• Technical support registration number (if applicable)
• Product serial numbers
• Error messages
• Operating system type and revision level
• Detailed questions
Customer self repair
HP customer self repair (CSR) programs allow you to repair your StorageWorks product. If a CSR
part needs replacing, HP ships the part directly to you so that you can install it at your convenience.
Some parts do not qualify for CSR. Your HP-authorized service provider will determine whether a
repair can be accomplished by CSR.
For more information about CSR, contact your local service provider. For North America, see the CSR
website:
http://www.hp.com/go/selfrepair
Product warranties
For information about HP StorageWorks product warranties, see the warranty information website:
http://www.hp.com/go/storagewarranty
Subscription service
HP recommends that you register your product at the Subscriber's Choice for Business website:
http://www.hp.com/go/e-updates
After registering, you will receive e-mail notification of product enhancements, new driver versions,
firmware updates, and other product resources.
HP ProLiant Storage Server 15
Page 16

HP websites
For additional information, see the following HP websites:
•http://www.hp.com
•http://www.hp.com/go/storage
•http://www.hp.com/service_locator
•http://www.hp.com/support/manuals
•http://www.hp.com/support/downloads
Documentation feedback
HP welcomes your feedback.
To make comments and suggestions about product documentation, please send a message to
storagedocsFeedback@hp.com. All submissions become the property of HP.
About this guide16
Page 17
1 Installing and configuring the server
Setup overview
Your HP ProLiant Storage Server comes preinstalled with either the Windows® Storage Server™ 2003
R2 operating system (32-bit or 64-bit version) or the Microsoft® Windows® Unified Data Storage
Server 2003, Enterprise x64 Edition operating system.
Microsoft Windows Storage Server 2003 R2 extends the Windows Storage Server 2003 operating
system, providing a more efficient way to manage and control access to local and remote resources.
In addition, Windows Storage Server 2003 R2 provides a scalable, security-enhanced Web platform
for simplified branch server management, improved identity and access management, and more
efficient storage management.
IMPORTANT:
The Microsoft® Windows® Storage Server 2003 x64 Edition operating system is designed to support
32–bit applications without modification; however, any 32–bit applications that are run on this operating
system should be thoroughly tested before releasing the storage server to a production environment.
Microsoft® Windows® Unified Data Storage Server 2003, Enterprise x64 Edition operating system
provides unified storage server management capabilities, simplified setup and management of storage
and shared folders, and support for Microsoft iSCSI Software Target.
IMPORTANT:
For more information about Microsoft® Windows® Unified Data Storage Server 2003 operating system,
see “Enterprise storage servers” on page 121.
Planning for installation
Before you install your HP ProLiant Storage Server, you need to make a few decisions.
Determining a network access method
Before beginning setup and startup procedures, decide upon an access method to connect to the
storage server. The type of network access you select is determined by whether or not the network
has a Dynamic Host Configuration Protocol (DHCP) server. If the network has a DHCP server, you
can access the storage server through the direct attachment, remote browser, Remote Desktop, or
remote management methods. If your network does not have a DHCP server, you must access the
storage server through the direct attachment method.
HP ProLiant Storage Server 17
Page 18
NOTE:
The direct attachment method requires a display, keyboard, and mouse.
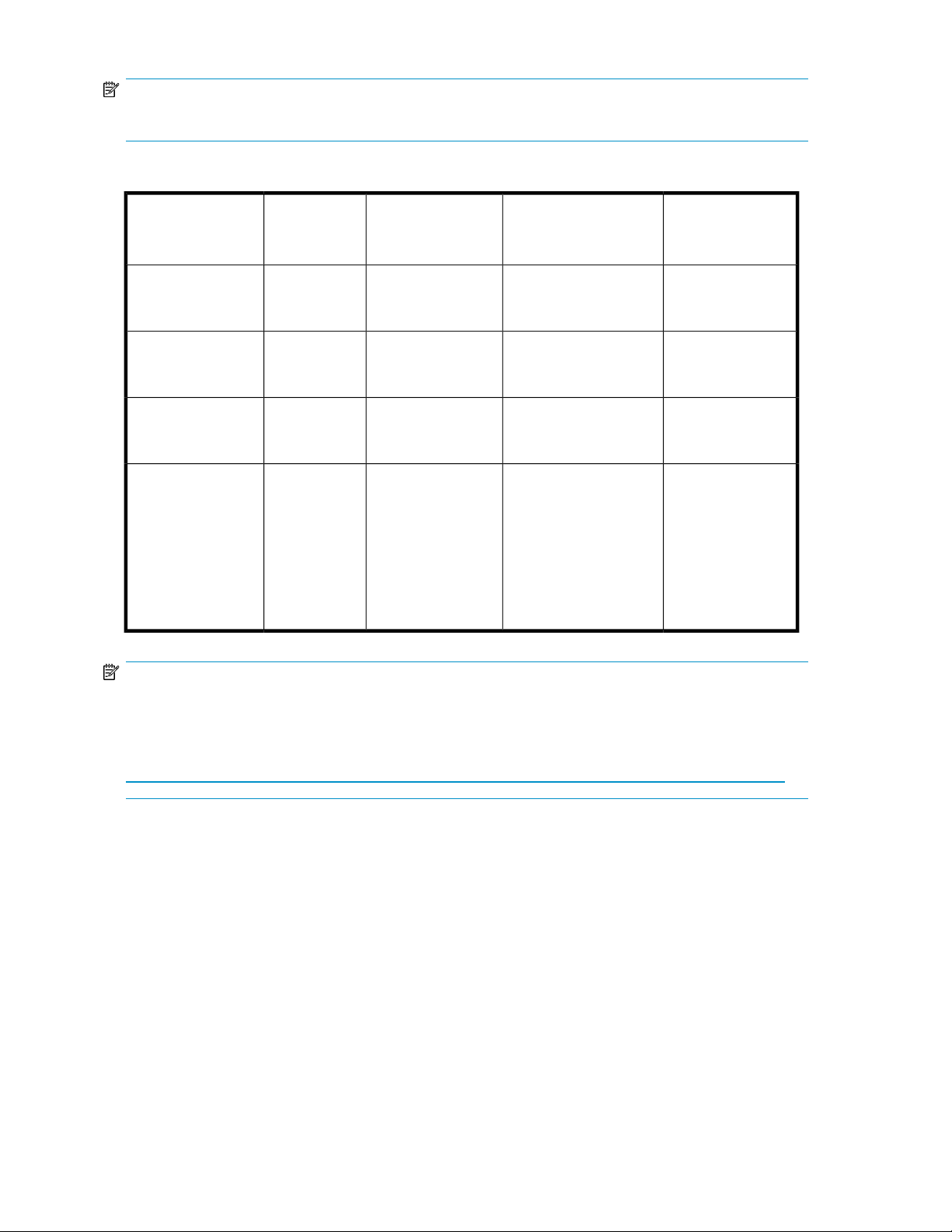
Table 2 Network access methods
Access method
Remote management
(Lights-Out 100 or
Integrated Lights-Out
2)
I.E. 5.5 or
later
required?
Storage server
desktop
accessible?
YesNoDirect attachment
NoYesRemote browser
YesNoRemote Desktop
YesYes
Startup Wizard access
Directly from the storage
server desktop.
Directly from the HP
ProLiant Storage Server
Management console.
Indirectly from the
storage server desktop.
Indirectly from the
storage server desktop.
NotesHP ProLiant Rapid
Requires a monitor,
mouse, and
keyboard.
Does not display the
storage server
desktop.
Windows Remote
Desktop capability
required on client.
See the HP ProLiant
Lights-Out 100
Remote
Management User
Guide or HP
Integrated
Lights-Out 2 User
Guide for server
access instructions.
NOTE:
The ML110 G5 Storage Server does not include embedded Lights-Out 100 remote management support.
This server requires the purchase and installation of the Lights-Out 100c Remote Management Card in
order to use Lights-Out 100 remote management features. For more information about the Lights-Out 100c
Remote Management Card, see
http://h18004.www1.hp.com/products/servers/management/remotemgmt/lightsout100/index.html.
Planning a network configuration
You use the Rapid Startup Wizard to configure your storage server. This wizard is displayed
automatically when you first start your system. Before you run the Rapid Startup Wizard, it is helpful
to gather the network configuration information you need, including:
• User name and administrator password (the system provides you with defaults you need to change)
• E-mail addresses to set up system alerts
• SNMP settings
• Local area network (LAN) configuration settings
To help you gather this information, see “Configuring the server on the network” on page 30.
Installing and configuring the server18
Page 19

Configuration checklist
Use the following checklist to make sure you have completed all configuration tasks for your HP
ProLiant Storage Server. The steps for each task are explained in more detail in subsequent chapters
of this guide.
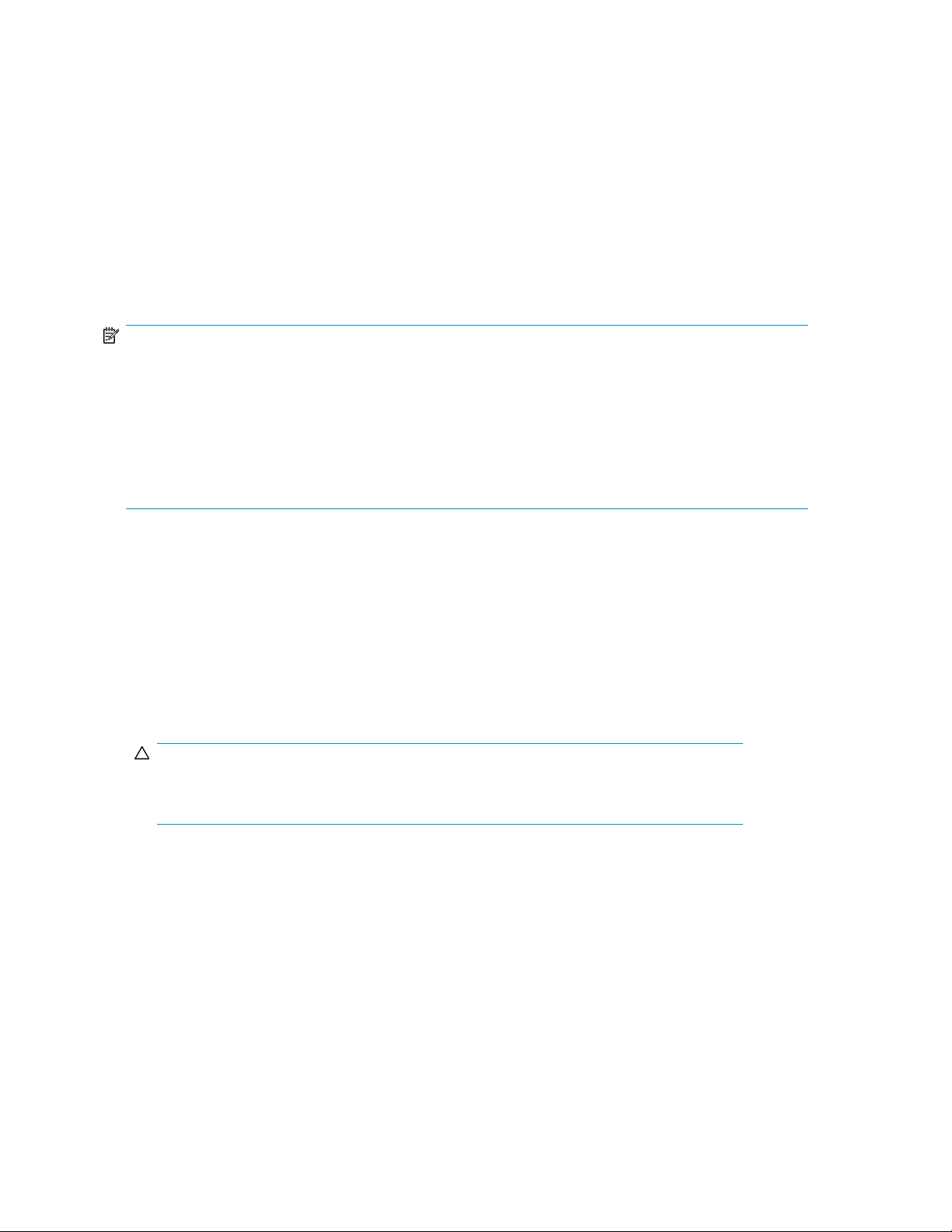
Table 3 Installation and configuration checklist
1. Unpack server, check kit contents, and
become familiar with front and back
panels of storage server. Locate and write
down serial number of storage server.
ReferenceSteps
See “Checking kit contents” on page 20.
2. If you plan to rack the server, complete
the rail installation instructions.
3. Connect cables; (optional) connect a
keyboard, mouse, and monitor; power
on server; and log on to the server.
4. Access the HP Storage Server
Management console.
5. Complete the storage server
configuration worksheet.
8. Configure storage server for Web
access, if necessary.
Installing the server
To install your HP ProLiant Storage Server, follow the instructions in the sections below:
• Locating and writing down the serial number
• Checking kit contents
• Powering on the server
See the HP ProLiant rail installation instructions and
tower-to-rack conversion instructions, if applicable.
See “Powering on the server” on page 20 and “Using the
direct attach method” on page 23.
See “Accessing the HP Storage Server Management
console” on page 22.
See “Server configuration worksheet” on page 30.
See “Running the Rapid Startup Wizard” on page 32.6. Run Rapid Startup Wizard.
See “Completing system configuration” on page 32.7. Complete system configuration.
See “Configuring storage server for Web access
(optional)” on page 155.
Locating and writing down the serial number
Before completing the installation portion of this guide, locate and write down the storage server's
serial number, which you may need to access the HP Storage Server Management console later on
during the set up process.
The HP ProLiant Storage Server's serial number is located in three places:
• Top of the storage server
• Back of the storage server
• Inside the storage server shipping box
HP ProLiant Storage Server 19
Page 20
Checking kit contents
Remove the contents, making sure you have all the components listed below. If components are missing,
contact HP technical support.
• HP ProLiant Storage Server (with operating system preloaded)
• Power cord(s)
• Product Documentation and Safety and Disposal Documentation CD
• HP ProLiant Storage Server Installation and System Recovery DVD
• End User License Agreement
• Certificate of Authenticity Card
NOTE:
Depending on your system, the following components might also be included:
• Bezel, bezel brackets, and screws
• Slide rail assembly
• Tower-to-rack conversion kit
•
HP ProLiant Essentials Integrated Lights-Out 2 Advanced Pack
•
HP ProLiant Essentials Lights-Out 100i Advanced Pack
Powering on the server
Power on the server after connecting the cables. For more information on your storage server model's
hardware components, see “Server components” on page 35.
1. Power on server by pushing the power button. The power LED illuminates green.
2. When the server powers on, an installation progress screen displays. The installation process
takes approximately 10 to 15 minutes to complete and the server will reboot twice. No user
interaction is required.
CAUTION:
Do not interrupt the installation process; when the installation sequence is complete, the
system prompt appears.
3. Go to “Accessing the HP Storage Server Management console” on page 22 to set up server
access.
Factory image
HP ProLiant Storage Servers are preconfigured with default storage settings and preinstalled with
either the Windows Storage Server 2003 R2 operating system or the Microsoft® Windows® Unified
Data Storage Server 2003 operating system. This section provides additional details about the
preconfigured storage.
Installing and configuring the server20
Page 21
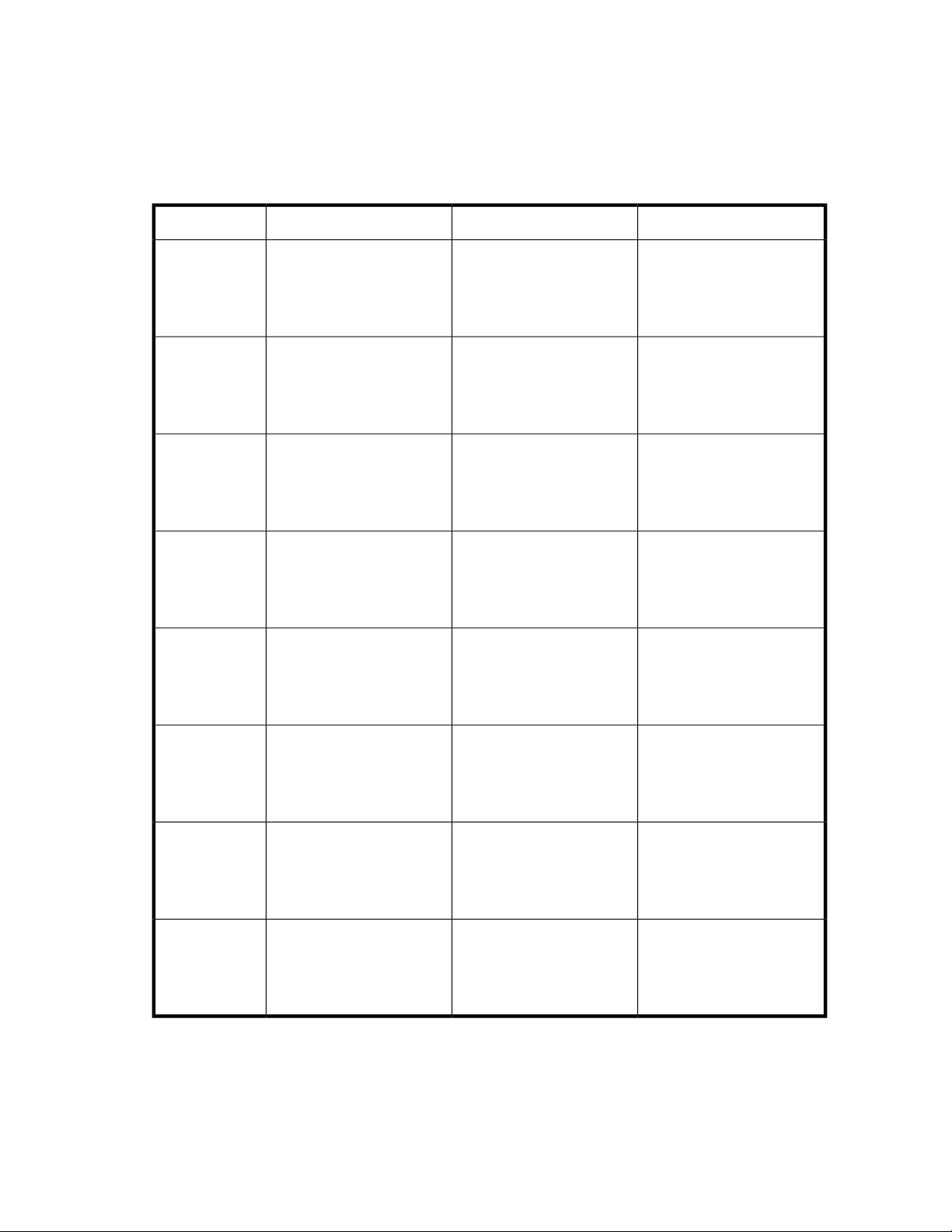
Physical configuration
The logical disks reside on physical drives as shown in “HP ProLiant RAID configurations” on page 21.
The DON'T ERASE volume contains an image that is deployed onto the OS partition during system
installation.
Table 4 HP ProLiant RAID configurations
Logical Disk 3 — nLogical Disk 2Logical Disk 1Server model
ML110 G5 (2
HDD 320 GB
SATA)
• ML110 G5
(4 HDD)
• DL160 G5
DL185 G5
(2HDD)
DL185 G5
(8HDD)
DL185 (12
HDD)
• Operating System
Volume
• RAID 1
• Physical Drives 1–2
• Operating System
Volume
• RAID 5
• Physical Drives 1–4
• Operating System
Volume
• RAID 1
• Physical Drives 1–2
• Operating System
Volume
• RAID 1
• Physical Drives 1–2
• Operating System
Volume
• RAID 1
• Physical Drives 1–2
• Data Volume
• RAID 1
• Physical Drives 1–2
• DON'T ERASE Volume
• RAID 5
• Physical Drives 1–4
• DON'T ERASE Volume
• RAID 1
• Physical Drives 1–2
• DON'T ERASE Volume
• RAID 1
• Physical Drives 1–2
• DON'T ERASE Volume
• RAID 1
• Physical Drives 1–2
N/A
• Data Volume
• RAID 5
• Physical Drives 1–4
N/A
• Data Volume
• RAID 5
• Physical Drives 3–8
• Data Volume
• RAID 5 (SAS models);
RAID 6 (SATA models)
• Physical Drives 3–12
DL380 G5
DL380 G5 1.16
TB SAS
DL585 G2
• Operating System
Volume
• RAID 1+0
• Physical Drives 1–2
• Operating System
Volume
• RAID 5
• Physical Drives 1–8
• Operating System
Volume
• RAID 1+0
• Physical Drives 1–2
DON'T ERASE Volume
•
• RAID 1+0
• Physical Drives 1–2
• DON'T ERASE Volume
• RAID 5
• Physical Drives 1–8
• DON'T ERASE Volume
• RAID 1+0
• Physical Drives 1–2
HP ProLiant Storage Server 21
N/A
• Data Volume
• RAID 5
• Physical Drives 1–8
N/A
Page 22

NOTE:
The HDDs included with the ML110 G5 2 HDD 320 GB SATA storage server are configured for software
RAID fault tolerance using the motherboard SATA controllers. In the event of a hard disk failure, user
intervention is required to rebuild the arrays. Microsoft Disk Manager is used to present the HDDs to the
system as dynamic disks. The primary OS logical drive resides on physical disk 1 and is mirrored on
physical disk 2. The data volume is the second logical drive mirroring the remaining space on disk 1 with
disk 2.
NOTE:
The hardware RAID configuration information listed for the DL380 G5 applies to all DL380 G5 models
except for the DL380 G5 1.16 TB SAS model.
NOTE:
In the HP Array Configuration Utility (ACU), logical disks are labeled 1 and 2. In Microsoft Disk Manager,
logical disks are displayed as 0 and 1. For HP Smart Array configuration information, see
http://h18004.www1.hp.com/products/servers/proliantstorage/arraycontrollers/.
The DON’T ERASE logical disk supports the recovery process only and does not host a secondary
operating system. If the operating system has a failure that might result from corrupt system files, a
corrupt registry, or the system hangs during boot, see “System recovery” on page 153.
If the data volume is not carved at the factory or during the installation process, it must be configured
manually by the end user. Be sure to back up your user data, and then use the System Recovery DVD
to restore the server to the factory default state as soon as conveniently possible.
Default boot sequence
The BIOS supports the following default boot sequence:
1. DVD-ROM
2. HDD
3. PXE (network boot)
Under normal circumstances, the storage servers boot up from the OS logical drive.
• If the system experiences a drive failure, the drive displays an amber disk failure LED.
• If a single drive failure occurs, it is transparent to the OS.
Accessing the HP Storage Server Management console
Before accessing the HP Storage Server Management console, verify that the storage server is
completely installed in the rack and that all cables and cords are connected.
To access the HP Storage Server Management console, you can use these access methods:
Direct attach To connect directly to the storage server without using the network.
Installing and configuring the server22
Page 23
Remote browser To establish a browser-based connection to the HP ProLiant Storage
Server Management console from a remote client running Internet
Explorer 5.5 (or later).
Remote Desktop To establish a connection from a remote client without using a browser.
This method requires the client to have Windows Remote Desktop
capability.
Remote management To establish a browser-based connection from a remote client using the
HP Lights-Out 100 (LO100) or HP Integrated Lights-Out 2 (iLO 2)
interface.
For more information, see “Planning for installation” on page 17.
IMPORTANT:
An IP address can be substituted for a storage server's serial number and hyphen when using either remote
browser or Remote Desktop methods to access the HP Storage Server Management console. For example:
192.0.0.1 can be substituted for TWT08466-.
Using the direct attach method
You can access the HP Storage Server Management console using a monitor, mouse, and keyboard
directly attached to the storage server.
To connect the storage server to a network using the direct attach method
1. Log on to the HP ProLiant Storage Server with the default user name administrator and the
password hpinvent.
The HP ProLiant Storage Server Management console and Rapid Startup Wizard will start
automatically.
NOTE:
You can change the administrator name and password when you configure the server using
the Rapid Startup Wizard.
2. To complete network configuration using the Rapid Startup Wizard, see
“Configuring the server on the network” on page 30.
Using the remote browser method
The storage server ships with DHCP enabled on the network port. If the server is placed on a
DHCP-enabled network and the serial number of the device is known, the server can be accessed
through a client running Internet Explorer 5.5 (or later) on that network, using the TCP/IP 3202 port.
HP ProLiant Storage Server 23
Page 24
IMPORTANT:
Before you begin this procedure, ensure that you have the following:
• Windows-based PC loaded with Internet Explorer 5.5 (or later) on the same local network as the storage
server
• DHCP-enabled network
• Serial number or IP address of the storage server
To connect the server to a network using the remote browser method, you must first ensure that the
client is configured to download signed ActiveX controls.
To enable ActiveX controls
1. On the remote client machine, open the Internet Explorer web browser and select Tools > Internet
Options > Security.
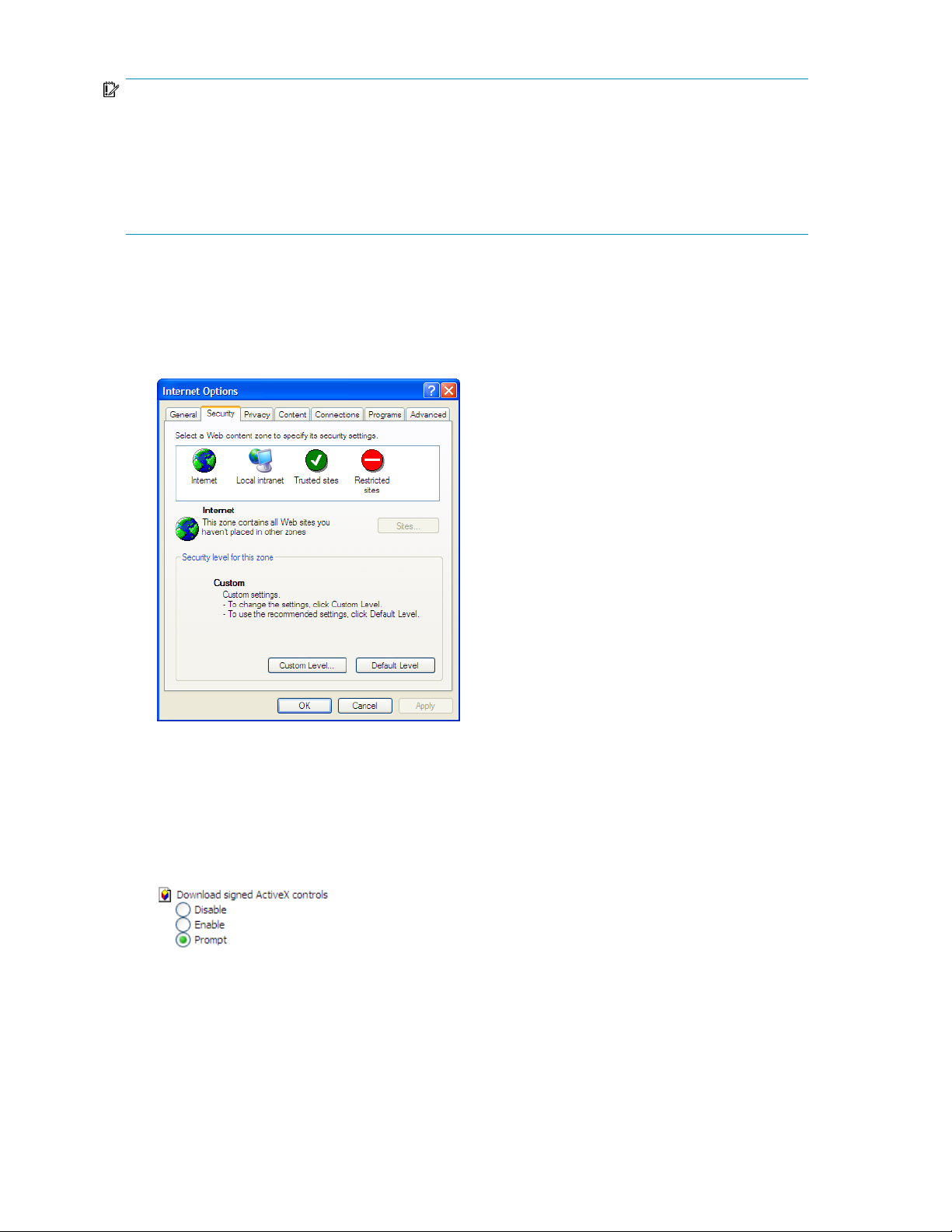
Figure 1 Internet options screen
2. On the Security screen, select Internet or Local intranet Web content zone, then click Custom
Level.
3. Scroll down to locate the ActiveX Controls and plug-ins settings.
4. At Download signed ActiveX controls settings, select Enable to enable ActiveX or Prompt to launch
a notice requiring approval before ActiveX is enabled.
5. Click OK to close the Security Settings dialog box.
6. If prompted Are you sure you want to change the security settings for this zone, click YES.
7. On the Internet Options dialog box, click OK to finish.
To connect the storage server to a network using the remote browser method
Installing and configuring the server24
Page 25

1. On the remote client machine open Internet Explorer and enter https:// and the serial number
of the storage server followed by a hyphen (-), and then:3202. For example,
https://D4059ABC3433-:3202. Press Enter.
NOTE:
If you are able to determine the IP address from your DHCP server, you can substitute the
IP address for the serial number and hyphen (-). For example: 192.100.0.1:3202.
2. Click OK on the Security Alert prompt.
3. Log on to the HP ProLiant Storage Server Management console with the default user name
administrator and the password hpinvent.
NOTE:
You can change the administrator name and password when you configure the server using
the Rapid Startup Wizard.
4. To complete network configuration using the Rapid Startup Wizard, see
“Configuring the server on the network” on page 30.
IMPORTANT:
If you are using the remote browser method to access the HP Storage Server Management console and
Rapid Startup Wizard, always close the remote session before closing your Internet browser. Closing the
Internet browser does not close the remote session. Failure to close your remote session impacts the limited
number of remote sessions allowed on the storage server at any given time.
Connecting to the storage server permits you to access the HP Storage Server Management console
(Figure 2). From the console, you can access snap-ins that allow complete server system management.
HP ProLiant Storage Server 25
Page 26
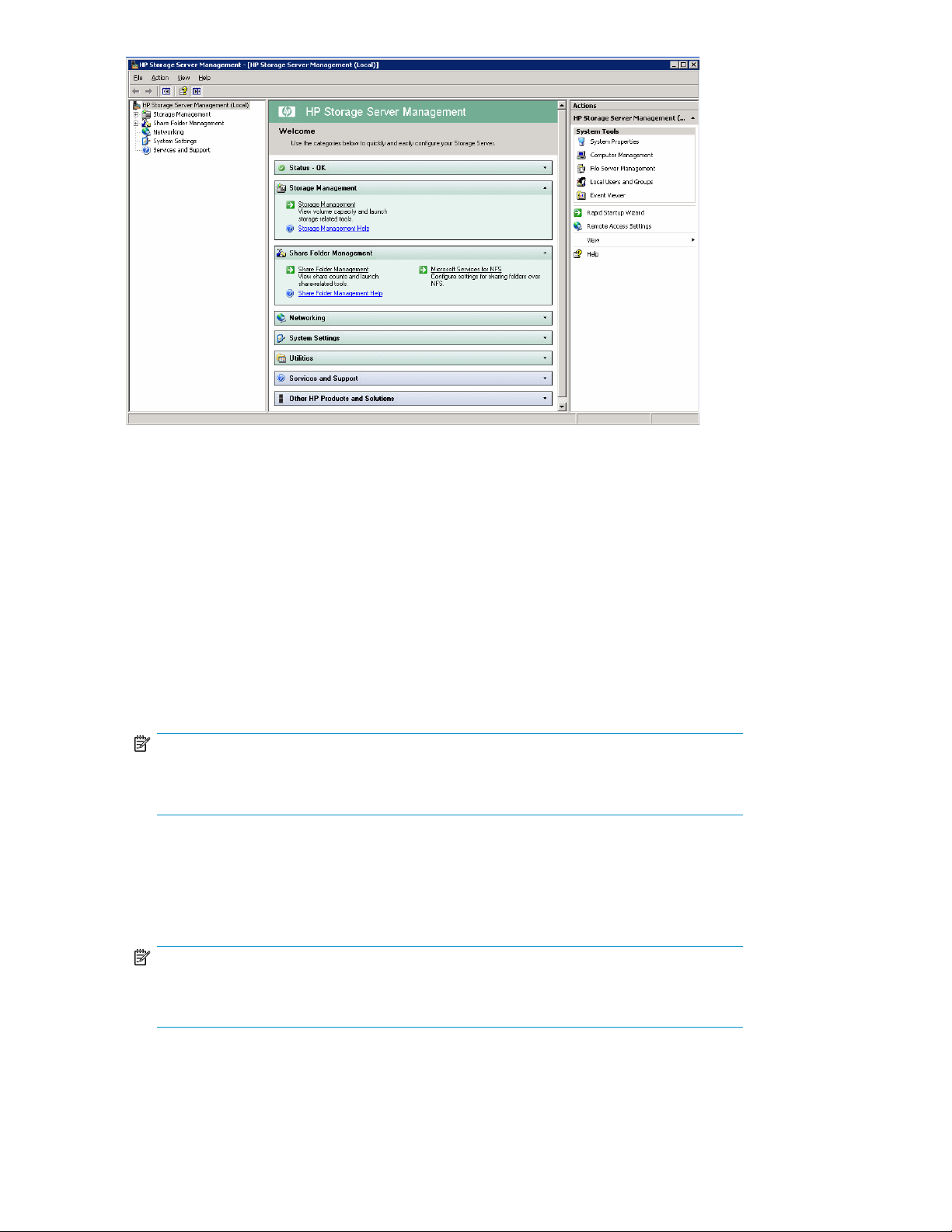
Figure 2 HP Storage Server Management console
Using the Remote Desktop method
Remote Desktop provides the ability for you to log onto and remotely administer your server, giving
you a method of managing it from any client. Installed for remote administration, Remote Desktop
allows only two concurrent sessions. Leaving a session running takes up one license and can affect
other users. If two sessions are running, additional users will be denied access.
To connect the storage server to a network using the Remote Desktop method
1. On the PC client, select Start > Run. At Open, type mstsc, then click OK.
2. Enter the serial number of the storage server followed by a hyphen (-) in the Computer box and
click Connect. For example: D4059ABC3433-.
NOTE:
If you are able to determine the IP address from your DHCP server, you can substitute the
IP address for the serial number and hyphen (-). For example: 192.100.0.1.
3. Log on to the HP ProLiant Storage Server with the default user name administrator and the
password hpinvent.
The HP ProLiant Data Protection Storage Server Management console and Rapid Startup Wizard
will start automatically.
NOTE:
You can change the administrator name and password when you configure the server using
the Rapid Startup Wizard.
4. To complete network configuration using the Rapid Startup Wizard, see
“Configuring the server on the network” on page 30.
Installing and configuring the server26
Page 27

Logging off and disconnecting
Remote Desktop provides two options when closing a client; you can either disconnect or log off the
system.
Disconnecting leaves the session running on the server. You can reconnect to the server and resume
the session. If you are performing a task on the server, you can start the task and disconnect from the
session. Later, you can log back on the server, re-enter the session, and either resume the task or
check results. This is especially helpful when operating over a remote connection on a long-distance
toll line.
Ending the session is known as logging off. Logging off ends the session running on the server. Any
applications running within the session are closed, and unsaved changes made to open files will be
lost. The next time you log onto the server, a new session is created.
Remote Desktop requires that all connecting users be authenticated, which is why users must log on
each time they start a session.
Telnet Server
Telnet Server is a utility that lets users connect to machines, log on, and obtain a command prompt
remotely. Telnet Server is preinstalled on the storage server but must be activated before use.
CAUTION:
For security reasons, the Telnet Server is disabled by default. The service needs to be modified to enable
access to the storage server with Telnet.
Enabling Telnet Server
The Telnet Server service needs to be enabled prior to its access. The service can be enabled by
opening the services MMC:
1. Select Start > Run, and then enter services.msc.
2. Locate and right-click the Telnet service and then select Properties.
3. Choose one of the following:
• For the Telnet service to start up automatically on every reboot, in the Startup Type drop-down
box click Automatic, and then click OK.
• For the Telnet service to be started manually on every reboot, in the Startup Type drop-down
box click Manual, and then click OK.
On the storage server, access the command line interface, either by Remote Desktop or a direct
connection, and then enter the following command:
net start tlntsvr
Sessions information
The sessions screen provides the ability to view or terminate active sessions.
HP ProLiant Storage Server 27
Page 28
Using remote management methods
HP ProLiant Storage Servers provide remote management functionality through HP ProLiant Lights-Out
technologies. The DL160 G5 and DL185 G5 Storage Servers include a Lights-Out 100 (LO100) port
with Advanced features. The DL380 G5, and DL585 G2 Storage Servers include an Integrated
Lights-Out 2 (iLO 2) port with Advanced features.
The ML110 G5 Storage Server does not include embedded Lights-Out 100 remote management
support. This server requires the purchase and installation of the Lights-Out 100c Remote Management
Card in order to use Lights-Out 100 remote management features. For more information about the
Lights-Out 100c Remote Management Card, see http://h18004.www1.hp.com/products/servers/
management/remotemgmt/lightsout100/index.html.
For more information about HP ProLiant Lights-Out technologies, see http://h18013.www1.hp.com/
products/servers/management/remotemgmt.html.
Using the Lights-Out 100 method
HP Lights-Out 100 allows you to remotely manage HP ProLiant Storage Servers remotely over an
Ethernet connection. It provides embedded KVM over IP for full remote graphical console capabilities.
This complements the virtual media and power control for complete entry level Lights-out remote
management. LO100 also enables anytime access to system management information such as hardware
health and event logs.
For more information on using HP LO100, see the HP ProLiant Lights-Out 100 Remote Management
User Guide.
To quickly set up LO100 using the default settings for LO100 Advanced features on DL160 G5, Dl185
G5, and ML110 G5 Storage Servers, follow these steps:
1. Ensure that a network cable is connected to the LO100 port located on the back of the storage
server.
NOTE:
This connection method is easiest when the connection is to a DHCP and DNS supported
network.
2. If you are using DHCP (IP addressing), you will need to input a static IP address by using the
direct attach method and the IPMI section of the BIOS to read the DHCP address. If you are not
using DHCP, use this procedure to set a static IP address.
3. Using the methods described in the HP ProLiant Lights-Out 100 Remote Management User Guide,
connect to the LO100 port.
IMPORTANT:
Log on using the default LO100 user name admin and password admin.
4. If desired, you can change the default user name and password on the administrator account to
your predefined selections.
5. Set up your user accounts, if using the local accounts feature.
6. Ensure that LO100 advanced features are activated. If they are not, activate these features by
entering a license key from the included HP ProLiant Essentials Lights-Out 100i Advanced Pack.
Installing and configuring the server28
Page 29

7. Access the HP ProLiant Storage Server using the LO100 Remote Console functionality. Log on to
the HP ProLiant Storage Server with the default user name administrator and the password
hpinvent. The HP ProLiant Storage Server Management console starts automatically.
NOTE:
When the Remote Console feature is enabled, you can get access to the storage server's
login screen.
The Lights-Out 100 port comes with factory default settings, which the administrator can change. See
the HP ProLiant Lights-Out 100 Remote Management User Guide for information about changing these
settings. To obtain this guide, go to http://www.hp.com/support/manuals, navigate to the servers
section, and select Server management. In the Server Management Software section, select HP
Lights-Out 100i (LO100i) Software.
Using the Integrated Lights-Out 2 method
Integrated Lights-Out 2 (iLO 2) is HP's fourth generation of Lights-Out management technology that
allows you to perform virtually any system administrator or maintenance task remotely as if you were
using its keyboard; mouse; monitor; power button; and floppy, CD or USB key, whether or not the
server is operating. It is available in two forms, iLO 2 Standard and iLO 2 Advanced. iLO 2 Standard
provides basic system board management functions, diagnostics and essential Lights-Out functionality
on supported ProLiant servers. iLO 2 Advanced provides advanced remote administration functionality
as a licensed option, which is included with the ProLiant Storage Server.
The Integrated Lights-Out port on the storage server can be configured through the Rapid Startup
Wizard or through the iLO 2 ROM-Based Setup Utility (RBSU). SNMP is enabled and the Insight
Management Agents are preinstalled.
The HP iLO 2 management processor provides multiple ways to configure, update, operate, and
manage servers remotely. The HP ProLiant Storage Server comes preconfigured with iLO 2 default
factory settings including a default user account and password. These settings can be found on the
iLO 2 Default Network Settings tag on the front of the server. If iLO 2 is connected to a network
running DNS and DHCP, you can use it immediately without changing any settings.
For more information on using HP iLO 2, see the HP Integrated Lights-Out 2 User Guide.
To quickly set up iLO 2 using the default settings for iLO 2 Standard and iLO 2 Advanced features on
DL380 G5, and DL585 G2 Storage Servers, follow these steps:
1. Ensure that a network cable is connected to the iLO 2 port located on the back of the storage
server.
NOTE:
This connection method is easiest when the connection is to a DHCP and DNS supported
network.
2. If you are not using dynamic DHCP (IP addressing), you will need to input a static IP address by
using the direct attach method and the iLO 2 RBSU.
HP ProLiant Storage Server 29
Page 30

3. Using the methods described in the HP Integrated Lights–Out 2 User Guide, connect to the iLO
2 port.
NOTE:
To find the default iLO 2 log on settings, see the iLO 2 Default Network Settings card attached
to your server. The default DNS, administrator name, and password needed to log on will
be on this card.
4. If desired, you can change the default user name and password on the administrator account to
your predefined selections.
5. Set up your user accounts, if using the local accounts feature.
6. Activate iLO 2 advanced features by entering a license key from the included HP ProLiant Essentials
Integrated Lights-Out 2 Advanced Pack.
7. Access the HP ProLiant Storage Server using the iLO 2 Remote Console functionality. Log on to
the HP ProLiant Storage Server with the default user name administrator and the password
hpinvent. The HP ProLiant Storage Server Management console starts automatically.
NOTE:
When the Remote Console feature is enabled, you can get access to the storage server's
login screen.
The Integrated Lights-Out 2 port comes with factory default settings, which the administrator can
change. Administrators may want to add users, change SNMP trap destinations, or change networking
settings. See the HP Integrated Lights-Out 2 User Guide for information about changing these settings.
To obtain this guide, go to http://www.hp.com/support/manuals, navigate to the servers section,
and select Server management. In the ProLiant Essentials Software section, select HP Integrated
Lights-Out 2 (iLO 2) Standard Firmware.
Configuring the server on the network
Before you begin
When first powering on the storage server you need to have some configuration data readily available
to complete the Running the Rapid Startup Wizard. Complete the Server configuration worksheet and
use the data collected to initialize the storage server.
NOTE:
Ensure you are logged into the HP ProLiant Storage Server as a local or domain administrator.
Table 5 Server configuration worksheet
Configuration Worksheet
Administrative Identity
Installing and configuring the server30
Page 31
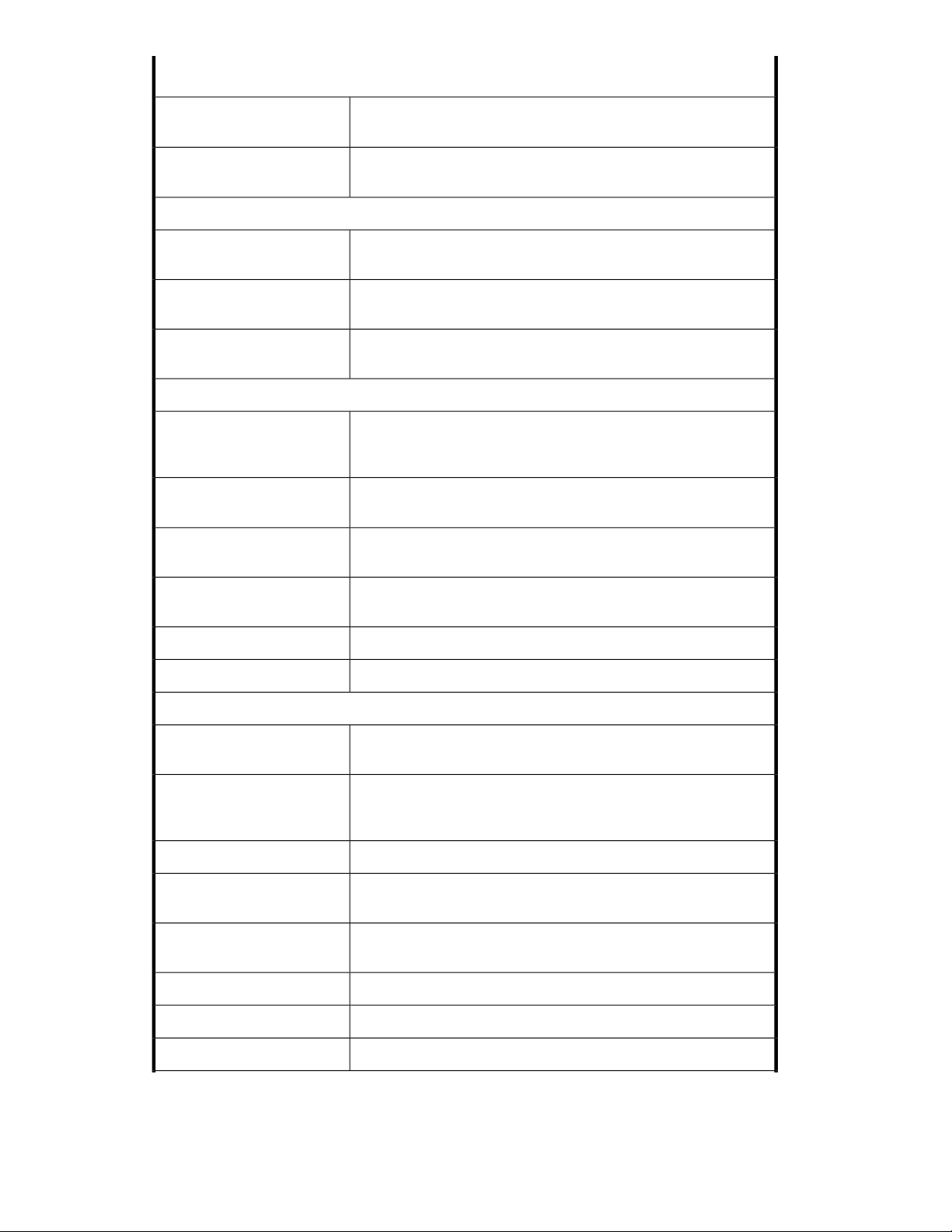
Configuration Worksheet
User name
User password
Alert E-mail Notification
E-mail address alert sent to
E-mail address alert sent from
SMTP server name or IP
address
SNMP Settings (to be completed only if needed)
Contact person
System location
Community name No. 1
Change system administrator's user name, which is set by default to
administrator.
Change system administrator's password, which is set by default to
hpinvent.
E-mail address for critical, warning, or informational messages about
server status.
Must be a valid, well-formed e-mail address that will appear as the
sender of server status e-mail alerts.
Must be an e-mail server on your network that supports the Simple
Mail Transfer Protocol (SMTP).
System administrator for the storage server. The contact and location
will be provided to any SNMP management computer that requests
them.
Any text string, such as a location or phone number. For example,
Floor #3, Financial Services Bldg.
The community name is used for network authentication when sending
outgoing SNMP messages.
Trap destination No. 1
Network Interfaces (to be completed for non-DHCP configurations)
Local area connection 1
IP address
Default gateway
Local area connection 2
The IP address of a management computer that will receive SNMP
messages from the storage server using the above community name.
Same as above.Community name No. 2
Same as above.Trap destination No. 2
A local area connection is automatically created for each network
adapter that is detected.
An Internet Protocol (IP) address is assigned to the server. If it is not
automatically assigned, enter the IP address that you want to assign
to this server.
A mask is used to determine what subnet an IP address belongs to.Subnet mask
The gateway in a network that the network adapter will use to access
all other networks.
Any additional local area connections can be renamed to prevent
confusion.
Same as above.IP address
Same as above.Subnet mask
Same as above.Default gateway
HP ProLiant Storage Server 31
Page 32

Configuration Worksheet
Change the host name, IP settings, and administrator settings.iLO 2 settings
DNS server
WINS server
Server Name
Server name
A Domain Name System (DNS) server name is required to provide
for domain name to IP address resolution.
A Windows Internet Naming Service (WINS) server name is required
to determine the IP address associated with a particular network
computer.
Assign a unique name to the storage server. This name identifies the
storage server on the network.
Running the Rapid Startup Wizard
The Rapid Startup Wizard is only displayed during the initial setup process. This wizard guides you
through configuring the following system settings:
• Date, time, and time zone
• Administrator identity (user name and password)
• Alert e-mail notification
• Lights-Out 100 (LO100) / Integrated Lights-Out 2 (iLO 2) settings
• Simple Network Management Protocol (SNMP) settings
• Network interfaces
• Server name
For more information about the configuration settings available in the Rapid Startup Wizard, click
Help to see the corresponding Rapid Startup Wizard online help topic.
Completing system configuration
After the storage server is physically set up and the basic configuration is established, you must
complete additional setup tasks. Depending on the deployment scenario of the storage server, these
steps can vary. These additional steps can include:
• Running Microsoft Windows Update—HP highly recommends that you run Microsoft Windows
updates to identify, review, and install the latest, applicable, critical security updates on the storage
server. For recommendations, instructions, and documentation to help manage the software update,
hotfix, and security patches process on the storage server, see Microsoft Software Updates on HP
ProLiant Storage Servers at http://h18006.www1.hp.com/storage/storageservers.html.
• Creating and managing users and groups—User and group information and permissions determine
whether a user can access files. If the storage server is deployed into a workgroup environment,
this user and group information is stored locally on the device. By contrast, if the storage server
is deployed into a domain environment, user and group information is stored on the domain.
• Joining workgroup and domains—These are the two system environments for users and groups.
Because users and groups in a domain environment are managed through standard Windows or
Active Directory domain administration methods, this document discusses only local users and
groups, which are stored and managed on the storage server. For information on managing users
and groups on a domain, see the domain documentation available on the Microsoft web site.
Installing and configuring the server32
Page 33

• Using Ethernet NIC teaming (optional)—Select models are equipped with an HP or Broadcom
NIC Teaming utility. The utility allows administrators to configure and monitor Ethernet network
interface controller (NIC) teams in a Windows-based operating system. These teams provide
options for increasing fault tolerance and throughput.
• Activating iLO 2 Advanced features using a license key—The Remote Console feature of iLO 2
requires a license key. The key is included with the storage server inside the Country Kit. See the
iLO 2 Advanced License Pack for activation instructions.
• Adjusting logging for system, application, and security events.
• Installing third-party software applications—For example, these might include an antivirus
application that you install.
• Registering the server — To register the server, refer to the HP Registration website (http://
register.hp.com).
HP ProLiant Storage Server 33
Page 34

Installing and configuring the server34
Page 35

2 Server components
This chapter provides illustrations of the storage server hardware components.
NOTE:
Connecting the storage server power cord illuminates the LEDs on the front of the unit, the Systems Insight
Display LED (if applicable), and the LEDs on the NIC connector (rear panel). The Lights-Out NIC LED (rear
panel) illuminates if the Lights-Out port is connected. Connecting the power cord also restores the storage
server to whatever previous powered state it was last in. This could result in the server powering up, the
fans operating, and the power indicator coming on.
NOTE:
The keyboard, mouse, and monitor are used only for the direct attached method of accessing the server.
They are not provided with your storage server.
ML110 G5 hardware components
The following figures show components, controls, and indicators located on the front and rear panels
of the ML110 G5 storage server.
Figure 3 ML110 G5 front panel (bezel on)
Table 6 ML110 G5 front panel components (bezel on)
StatusDescriptionItem
N/ADVD ROM drive1
HP ProLiant Storage Server 35
Page 36
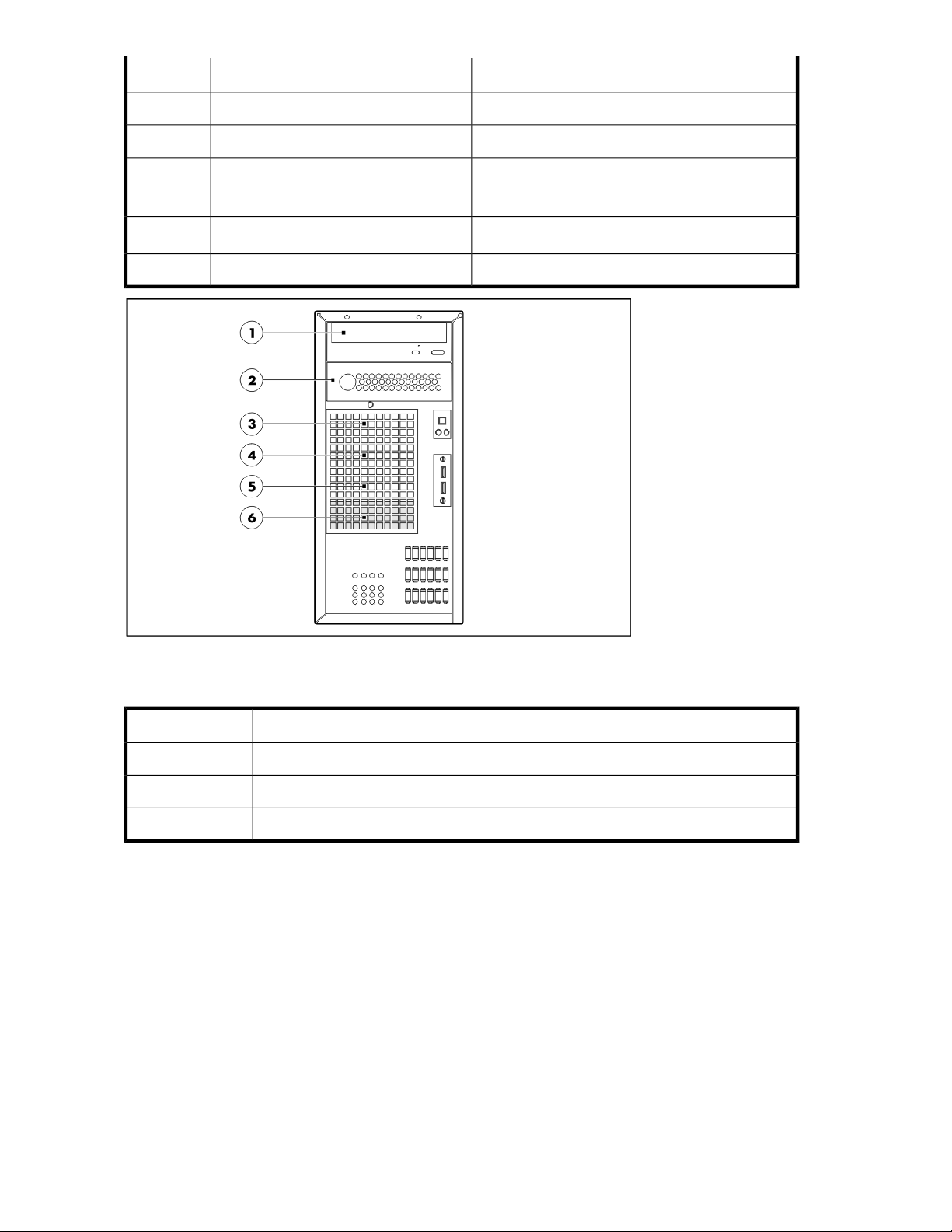
StatusDescriptionItem
N/A2nd removable media drive bay cover2
N/APower button3
System power4
HDD activity5
Green = Power on mode
Amber = Standby mode
Green = Ongoing HDD activity
N/AUSB 2.0 ports6
Figure 4 ML110 G5 front panel (bezel off)
Table 7 ML110 G5 front panel components (bezel off)
DescriptionItem
DVD ROM drive1
2nd removable media drive bay EMI shield2
Hard disk drives 1 – 4 behind EMI shield3 — 6
Server components36
Page 37

Figure 5 ML110 G5 rear panel
Table 8 ML110 G5 rear panel components
StatusDescriptionItem
N/AKensington lock notch1
N/AAccess panel thumbscrew2
N/ASystem fan3
N/ACable lock provision notch4
N/APCI slot cover retainer5
N/APCI slot cover retainer thumbscrew6
PCI slot covers7
8
Lights-Out remote management
port (optional)
Embedded NIC port (RJ-45)9
One slot populated with HP Smart Array E200 controller
(excluding the 2HDD 320 GB SATA model)
Management NIC activity and link
Blinking green = Ongoing network activity
Green = Existing network link
Embedded NIC link and activity
Orange = 10/100 Mbps connection
Green = GbE link connection
Blinking yellow = Ongoing network activity
N/AUSB 2.0 ports10
N/ASerial port11
N/AVideo port12
N/APS/2 keyboard port13
HP ProLiant Storage Server 37
Page 38
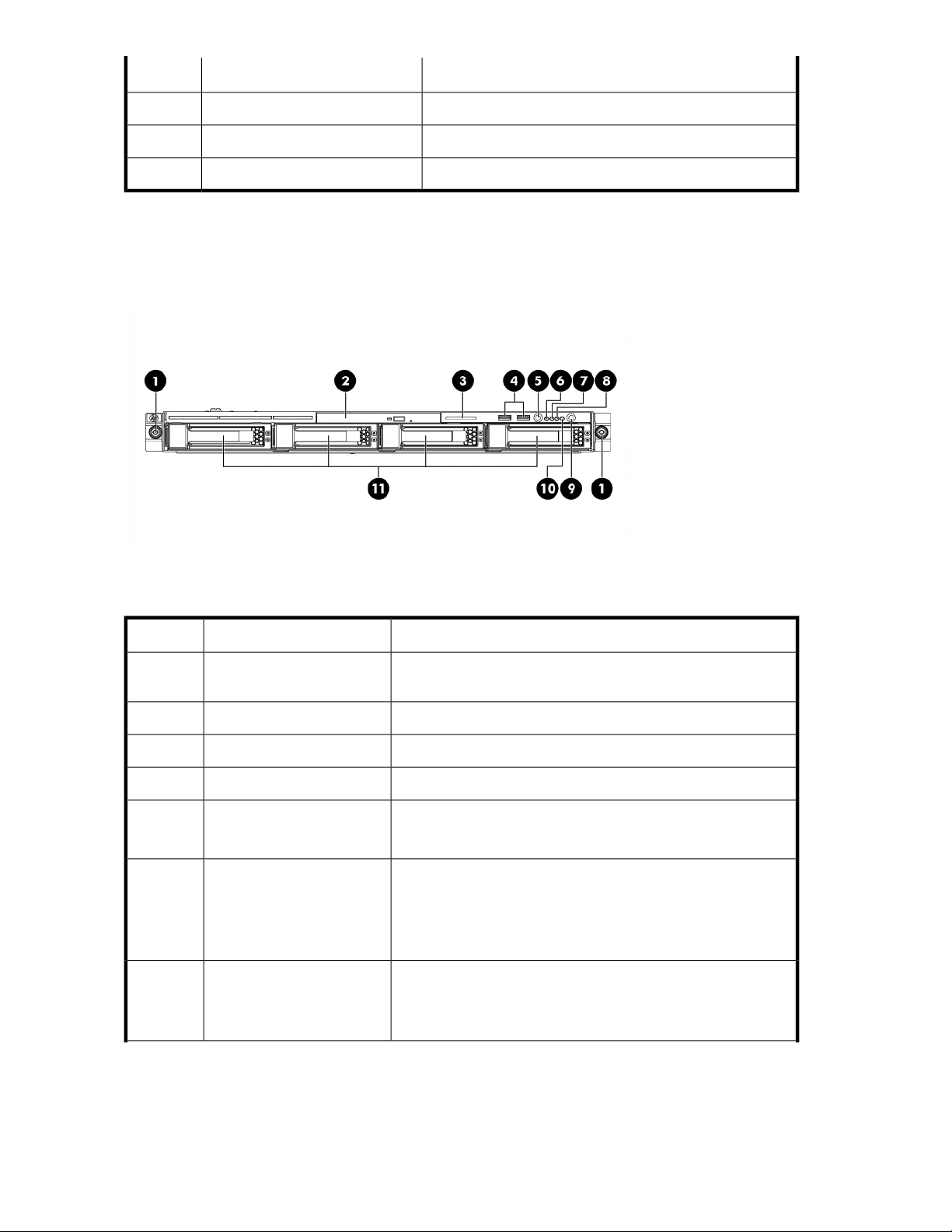
StatusDescriptionItem
N/APS/2 mouse port14
N/APower supply cable socket15
N/APSU fan16
DL160 G5 hardware components
The following figures show components, controls, and indicators located on the front and rear panels
of the DL160 G5 storage server.
Figure 6 DL160 G5 front panel
Table 9 DL160 G5 front panel components
1
5
Thumbscrews for rack
mounting
Unit identification (UID) LED
button
System health LED6
NIC1 LED7
StatusDescriptionItem
N/A
N/ADVD ROM drive2
N/ASerial number pull tab3
N/ATwo front USB 2.0 ports4
Blue = Activated
Off = Deactivated
Green = Normal (system on)
Flashing amber = System health degraded
Flashing red = System health critical
Off = Normal (system off)
Green = Network link
Flashing = Network link and activity
Off = No network connection
Server components38
Page 39

StatusDescriptionItem
Green = Network link
NIC2 LED8
Flashing = Network link and activity
Off = No network connection
Green = System on
Amber = System off
Green = HDD install ready
Flashing green = Data access
Off = No access
See “SAS and SATA hard drive LED combinations” on page 49
for HDD LED status descriptions.
11
Power button9
HDD LED10
Hard disk drive (HDD) bays
1– 4
Figure 7 DL160 G5 rear panel
Table 10 DL160 G5 rear panel components
StatusDescriptionItem
N/APower supply cable socket1
N/APS/2 mouse port (green)2
GbE LAN port for NIC23
Captive thumbscrew for top
4
cover
Low profile/Half length
6
expansion slot
Full height/Full length
7
expansion slot
Green = 10/100 Mbps connection
Orange = 1000 Mbps connection
N/A
N/ASerial port5
N/A
Populated with HP Smart Array E200 controller
N/AT10/T15 Wrench8
N/AThumbscrew for PCI cage9
HP ProLiant Storage Server 39
Page 40
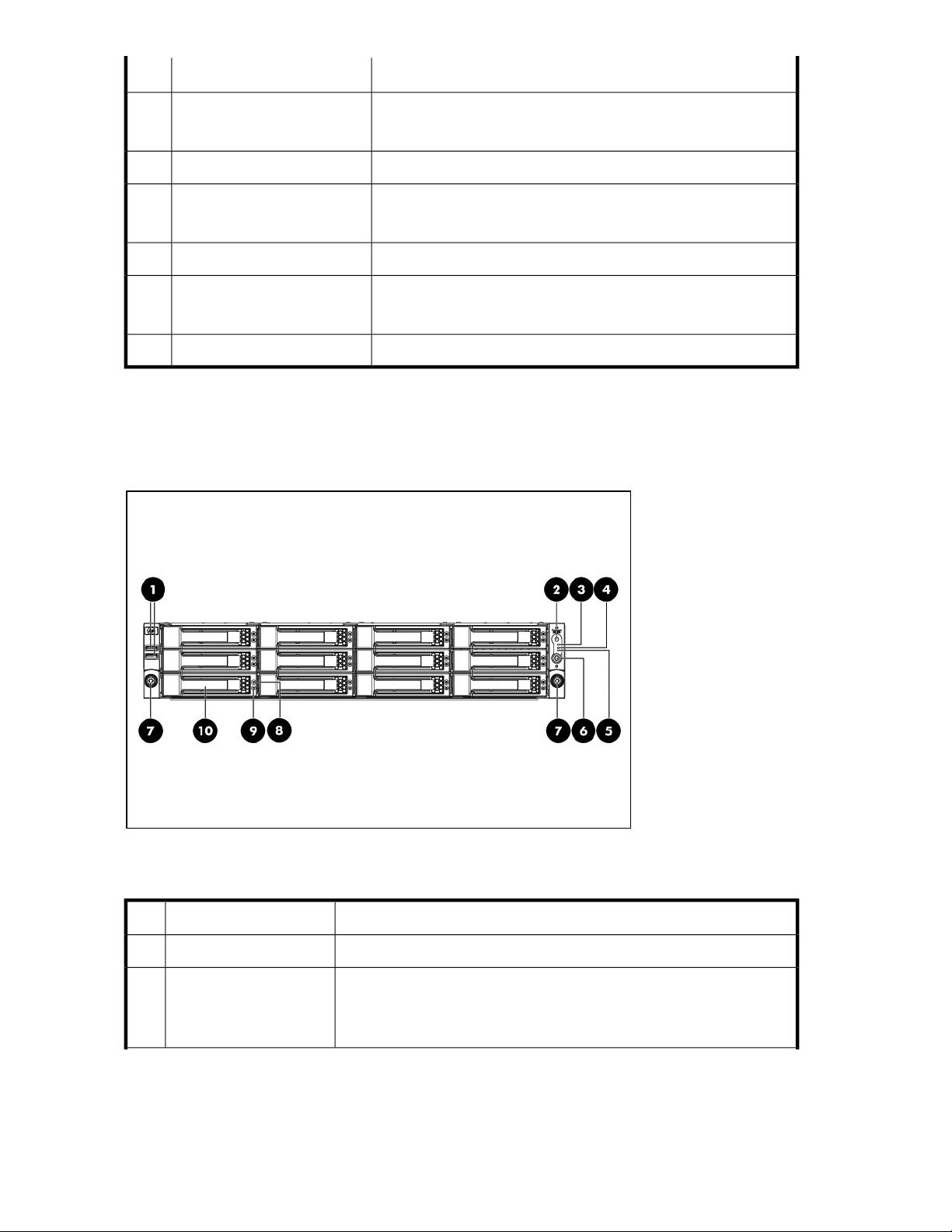
StatusDescriptionItem
UID LED button10
HP LO100i Management LAN
12
Port
GbE LAN port for
14
NIC1/Management
Blue = Activated
Off = Deactivated
N/AVGA port11
Flashing green = Ongoing network activity
Green = Existing network link
N/AUSB 2.0 ports13
Green = 10/100 Mbps connection
Orange = 1000 Mbps connection
N/APS/2 keyboard port (purple)15
DL185 G5 hardware components
The following figures show components, controls, and indicators located on the front and rear panels
of the DL185 G5.
Figure 8 DL185 G5 front panel
Table 11 DL185 G5 front panel components
StatusDescriptionItem
N/AUSB 2.0 ports1
Unit identification (UID)
2
button
Server components40
Blue = Activated
Flashing = System remotely managed
Off = Deactivated
Page 41

StatusDescriptionItem
Green = Normal (system on)
System Health LED3
NIC 1 activity LED4
NIC 2 activity LED5
Flashing amber = System health degraded
Flashing red = System health critical
Off = Normal (system off)
Green = Network link
Flashing = Network link and activity
Off= No network connection
Green = Network link
Flashing = Network link and activity
Off= No network connection
N/APower button6
Thumbscrews for rack
7
mounting
Fault/UID LED8
Online LED9
Hard disk drive (HDD)
10
bay
N/A
See “SAS and SATA hard drive LED combinations” on page 49 for HDD
LED status descriptions.
See “SAS and SATA hard drive LED combinations” on page 49 for HDD
LED status descriptions.
N/A
Figure 9 DL185 G5 rear panel
Table 12 DL185 G5 rear panel components
Status / DescriptionDescriptionItem
N/APower supply cable sockets1
HP ProLiant Storage Server 41
Page 42
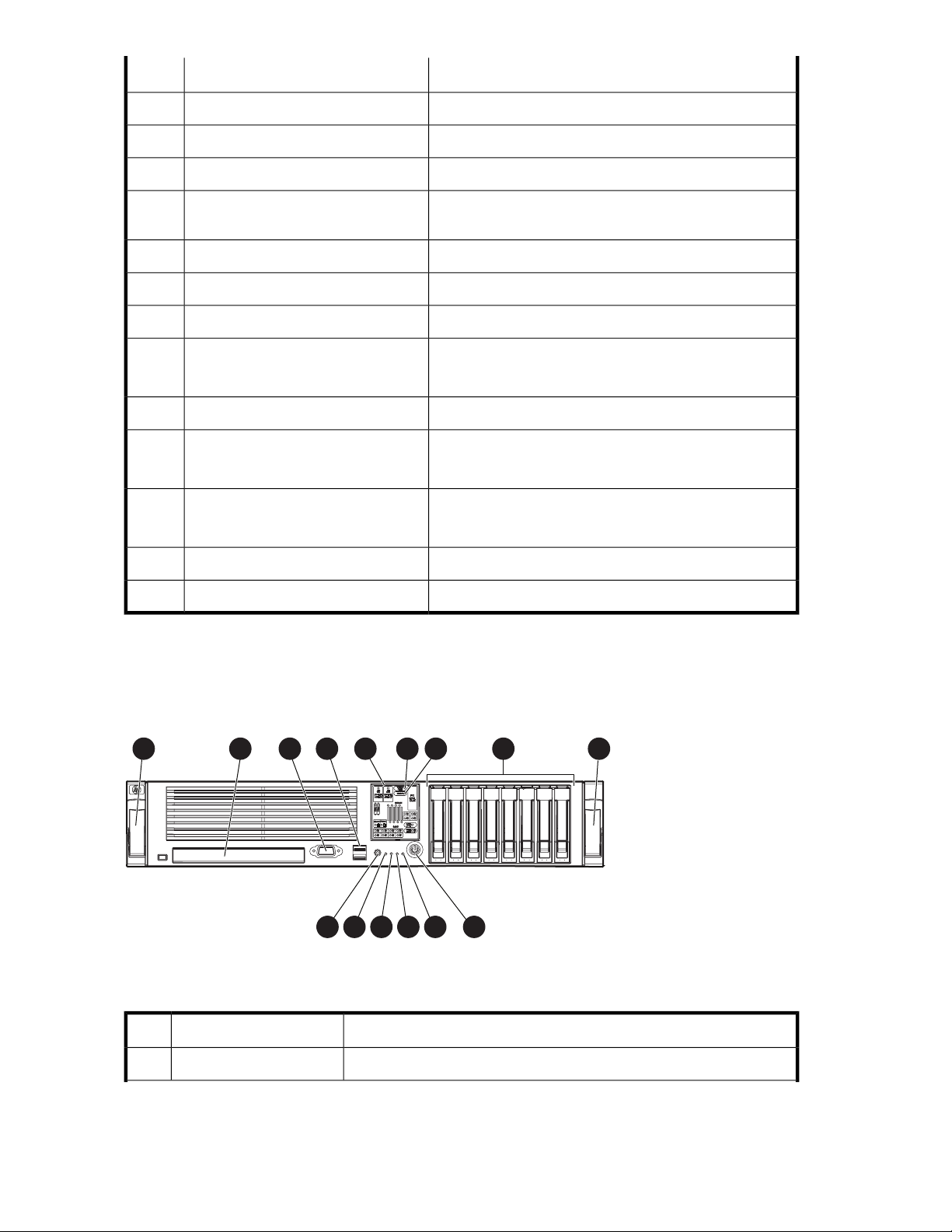
Status / DescriptionDescriptionItem
N/AT10/T15 Wrench2
N/ACaptive thumbscrew for top cover3
N/ADVD ROM drive4
5
PCI expansion card slot (top is slot 2,
bottom is slot 1)
HP LO100i Management LAN port9
GbE LAN port for NIC 211
GbE LAN port for NIC 1/Management12
Slot 2 populated with HP Smart Array P800 controller
N/AThumbscrew for PCI cage6
N/ASerial port7
N/AVGA port8
Blinking green = Ongoing network activity
Green = Existing network link
N/AUSB 2.0 ports10
Green = 10/100 Mbps connection
Orange = 1000 Mbps connection
Green = 10/100 Mbps connection
Orange = 1000 Mbps connection
N/APS/2 keyboard port (purple)13
N/APS/2 mouse port (green)14
DL380 G5 hardware components
The following figures show components, controls, and indicators located on the front and rear panels
of the DL380 G5 storage server.
1 2
Figure 10 DL380 G5 front panel
Table 13 DL380 G5 front panel components
3
4 5 6 7
StatusDescriptionItem
N/AQuick release lever1
8
151413121110
9
9
15681
Server components42
Page 43

StatusDescriptionItem
N/ADVD-RW drive2
N/AVideo connector3
N/AUSB connectors (2)4
LEDs off = Normal
LEDs amber = Failure
Systems Insight Display5
Online spare LED6
Mirror LED7
See “Systems Insight Display LEDs and internal health LED
combinations” on page 50 for LED status information.
See below for online spare and mirror LED status.
Off = No protection
Green = Protection enabled
Amber = Memory failure occurred
Flashing amber = Memory configuration error
Off = No protection
Green = Protection enabled
Amber = Memory failure occurred
Flashing amber = Memory configuration error
Hard disk drive (HDD)
8
bays
UID LED button10
Internal health LED11
External health LED (power
12
supply)
NIC 1 link/activity LED13
NIC 2 link/activity LED14
See “SAS and SATA hard drive LED combinations” on page 49 for HDD
LED status descriptions.
N/AQuick release lever9
Blue = Activated
Flashing = System being remotely managed
Off = Deactivated
Green = Normal
Amber = System degraded
Red = System critical
Green = Normal
Amber = Power redundancy failure
Red = Critical power supply failure
Green = Network link
Flashing = Network link and activity
Off = No link to network. If power is off, view the rear panel RJ-45 LEDs
for status.
Green = Network link
Flashing = Network link and activity
Off = No link to network. If power is off, view the rear panel RJ-45 LEDs
for status.
HP ProLiant Storage Server 43
Page 44
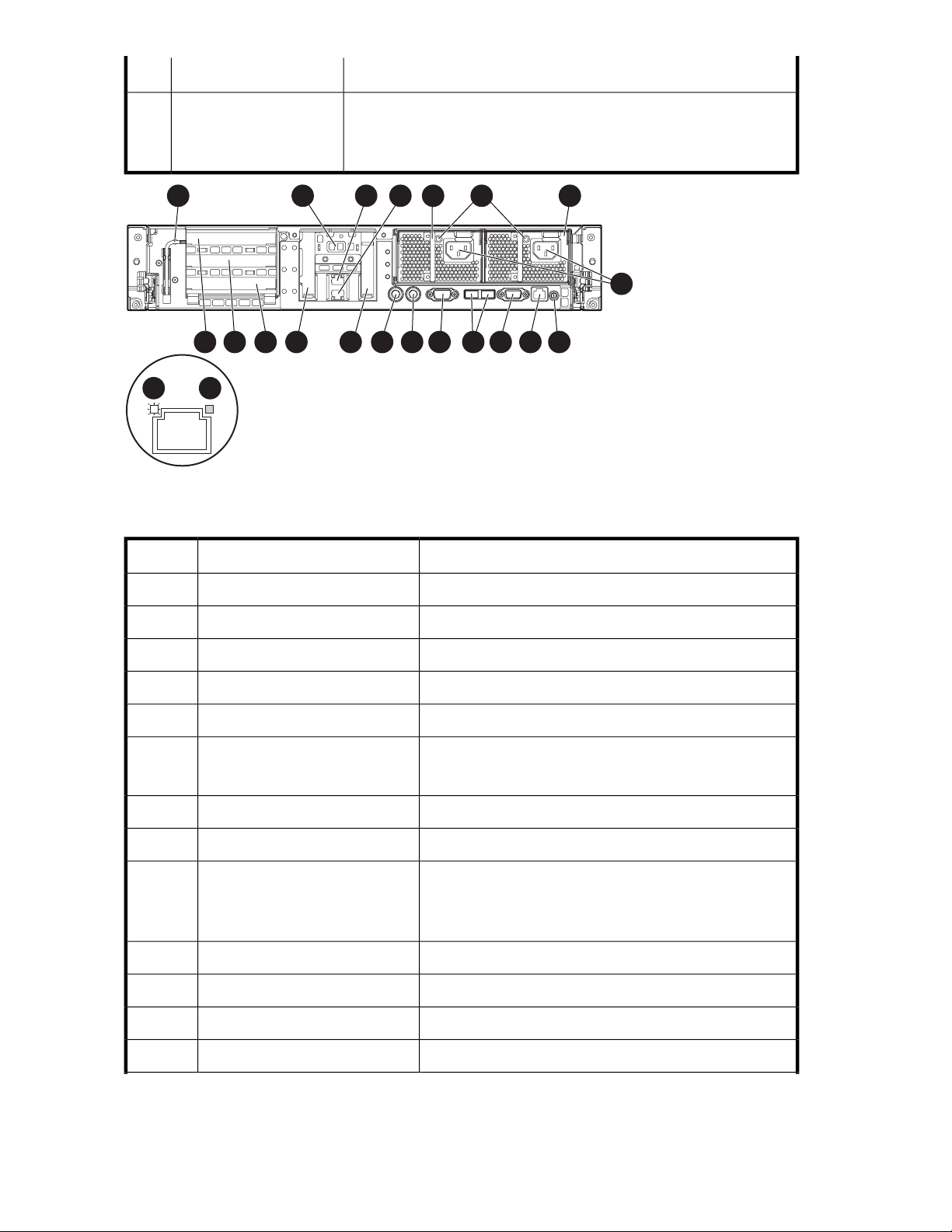
StatusDescriptionItem
Power On/Standby
15
button/system power LED
1 2 3 4 5 6 7
21 22
Green = System on
Amber = System shut down, but power still applied
Off = Power cord not attached or power supply failure
Figure 11 DL380 G5 rear panel
Table 14 DL380 G5 rear panel components
8
91011121314151617181920
15682
Status / DefinitionDescriptionItem
N/AT-10/T-15 Torx screwdriver1
N/AExternal option blank2
N/ANIC 2 connector3
N/ANIC 1 connector4
N/APower supply bay 25
Power supply LED6
UID LED button9
Green = Normal
Off = System is off or power supply has failed
N/APower supply bay 17
N/APower cord connectors (Black)8
Blue = Activated
Flashing = System being remotely managed
Off = Deactivated
N/AiLO 2 connector10
N/AVideo connector (Blue)11
N/AUSB connectors (2) (Black)12
N/ASerial connector13
Server components44
Page 45
16
17
18
19
20
Status / DefinitionDescriptionItem
N/AMouse connector (Green)14
N/AKeyboard connector (Purple)15
x4, bus 6 (populated with HP Smart Array P400 controller)Expansion slot 1 (32–bit models)
x4, bus 6Expansion slot 1 (64–bit models)
x4, bus 11Expansion slot 2 (32–bit models)
x4, bus 11Expansion slot 2 (64–bit models)
x8, bus 23Expansion slot 3 (32–bit models)
x4, bus 14Expansion slot 3 (64–bit models)
64–bit/133 MHz, bus 18Expansion slot 4 (32–bit models)
x8, bus 23Expansion slot 4 (64–bit models)
64–bit/133 MHz, bus 18Expansion slot 5 (32–bit models)
x8, bus 19 (populated with HP SmartArray P800 controller)Expansion slot 5 (64–bit models)
Green = Network activity
NIC/iLO 2 activity LED21
Flashing = Network activity
Off = No network activity
NIC/iLO 2 link LED22
Green = Network link
Off = No network activity
NOTE:
The following specifications apply to expansion slots.
x4 slots: x8 cards are supported, but will run at x4 speeds.
x8 slots: x16 cards are supported, but will run at x8 speeds.
All slots are non-hot-plug.
Expansion slots 1 and 2 support half-length low profile cards.
DL585 G2 hardware components
The following figures show components, controls, and indicators located on the front and rear panels
of the DL585 G2 storage server.
HP ProLiant Storage Server 45
Page 46

1 2 3 4 5 6 7 8199 10 11 12 13 14 15 16 17 18
Figure 12 DL585 G2 front panel
Table 15 DL585 G2 front panel components
StatusDescriptionItem
11
Hard disk drive (HDD) bays 1 – 81 – 8
Media drive blank or optional
media drive
UID switch and LED13
Internal system health LED14
External system health LED15
See “SAS and SATA hard drive LED combinations” on page
49 for HDD LED status descriptions.
N/AVideo connector9
N/AUSB connectors (two)10
N/A
N/ADVD drive12
Blue = Activated
Flashing blue = Server managed remotely
Off = Deactivated
Green = Normal (system on)
Flashing amber = System health degraded
Flashing red = System health critical
Off = Normal (system off)
Green = Normal (system on)
Flashing amber = System health degraded
Flashing red = System health critical
Off = Normal (system off)
Green = Linked to network
NIC 1 link/ activity LED16
Server components46
Flashing green = Linked with activity on the network
Off = No network connection
Page 47
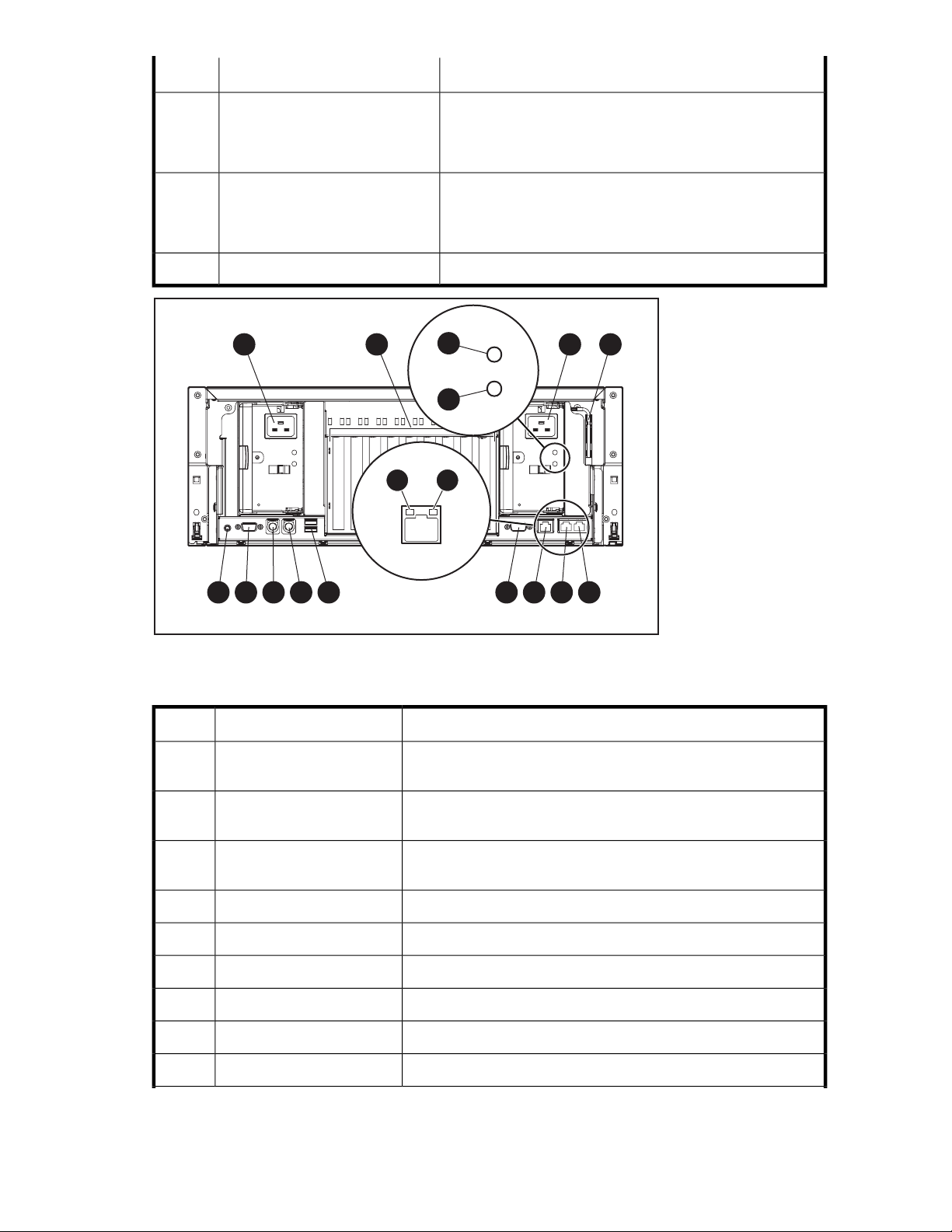
StatusDescriptionItem
Green = Linked to network
NIC 2 link/ activity LED17
Power on/Standby button and LED18
Flashing green = Linked with activity on the network
Off = No network connection
Amber = System has AC power and is in standby mode
Green = System has AC power and is turned on
Off = System has no AC power
N/AProcessor memory module19
1 2
13 12 11 10 9 8 7 6 5
Figure 13 DL585 G2 rear panel
Table 16 DL585 G2 rear panel components
StatusDescriptionItem
1
Redundant hot-plug power
supply (optional)
N/A
14
15
1716
3 4
2
3
PCI Express and PCI-X
non-hot-plug expansion slots
Hot-plug power supply
(primary)
N/A
N/A
N/AT-15 Torx screwdriver4
N/ANIC connector 25
N/ANIC connector 16
N/AiLO 2 connector7
N/ASerial connector8
N/AUSB connectors (two)9
HP ProLiant Storage Server 47
Page 48
StatusDescriptionItem
N/AMouse connector10
N/AKeyboard connector11
N/AVideo connector12
Blue = Activated
Rear UID button and LED13
Flashing blue = Server remotely managed
Off = Deactivated
Fail LED (amber)14
Power LED (green)15
Activity LED16
Link LED17
Both off = No AC power to any power supply
Fail LED flashing amber, Power LED off = Power supply failure (over
current)
Fail LED amber, Power LED off = No AC power to this power supply
Fail LED off, Power LED flashing green = AC power present, standby
mode
Fail LED = off, Power LED green = Normal
Green or flashing green = Network activity
Off = No network activity
Green = Linked to network
Off = Not linked to network
SAS and SATA hard drive LEDs
The following figure shows SAS/SATA hard drive LEDs. These LEDs are located on all HP ProLiant
hot plug hard drives.
Server components48
Page 49
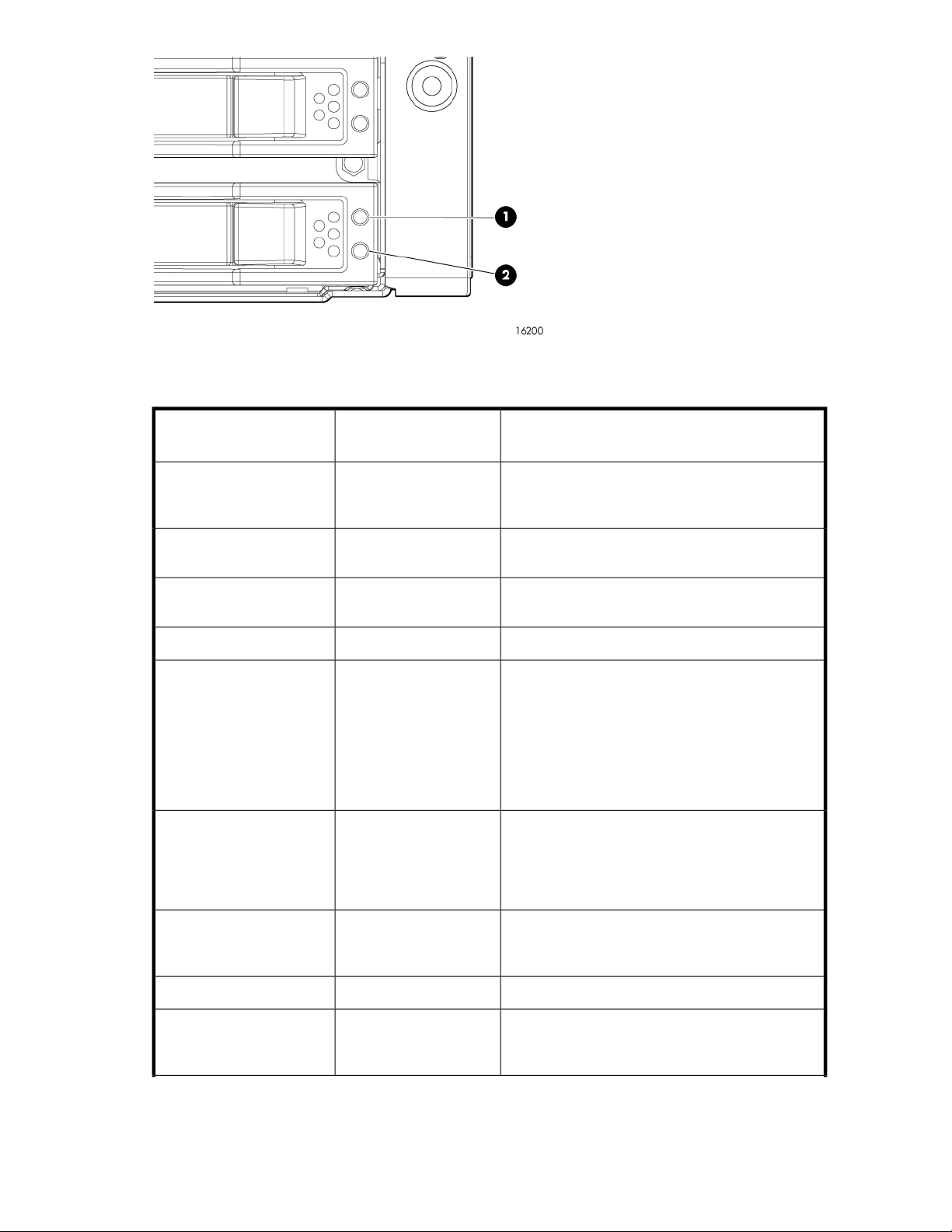
Figure 14 SAS/SATA hard drive LEDs
Table 17 SAS and SATA hard drive LED combinations
1. Fault/UID LED
(amber/blue)
Amber, flashing regularly (1
Hz)
Amber, flashing regularly (1
Hz)
(green)
On, off, or flashingAlternating amber and blue
On, off, or flashingSteadily blue
On
Flashing regularly (1 Hz)
Flashing regularly (1 Hz)Off
Status2. Online/activity LED
The drive has failed, or a predictive failure alert has
been received for this drive; it also has been selected
by a management application.
The drive is operating normally, and it has been
selected by a management application.
A predictive failure alert has been received for this
drive. Replace the drive as soon as possible.
The drive is online, but it is not active currently.OnOff
Do not remove the drive. Removing a drive may
terminate the current operation and cause data loss.
The drive is part of an array that is undergoing
capacity expansion or stripe migration, but a
predictive failure alert has been received for this
drive. To minimize the risk of data loss, do not
replace the drive until the expansion or migration is
complete.
Do not remove the drive. Removing a drive may
terminate the current operation and cause data loss.
The drive is rebuilding, or it is part of an array that
is undergoing capacity expansion or stripe
migration.
Amber, flashing regularly (1
Hz)
Flashing irregularly
OffSteadily amber
The drive is active, but a predictive failure alert has
been received for this drive. Replace the drive as
soon as possible.
The drive is active, and it is operating normally.Flashing irregularlyOff
A critical fault condition has been identified for this
drive, and the controller has placed it offline.
Replace the drive as soon as possible.
HP ProLiant Storage Server 49
Page 50
1. Fault/UID LED
(amber/blue)
Status2. Online/activity LED
(green)
Amber, flashing regularly (1
Hz)
Off
OffOff
A predictive failure alert has been received for this
drive. Replace the drive as soon as possible.
The drive is offline, a spare, or not configured as
part of an array.
Systems Insight Display LEDs and internal health LED combinations
When the internal health LED on the front panel illuminates either amber or red, the server is
experiencing a health event. Combinations of illuminated system LEDs and the internal health LED
indicate system status.
Table 18 Systems Insight Display LEDs and internal health LED combinations
Systems Insight
Display LED and
color
Processor failure,
socket X (amber)
color
Red
StatusInternal health LED
One or more of the following conditions may exist:
• Processor in socket X has failed.
• Processor X is not installed in the socket.
• Processor X is unsupported.
• ROM detects a failed processor during POST.
PPM failure, slot X
(amber)
FBDIMM failure, slot
X (amber)
FBDIMM failure, all
slots in one bank
(amber)
FBDIMM failure, all
slots in all banks
(amber)
Online spare
memory (amber)
Online spare
memory (flashing
amber)
Red
Red
Red
Processor in socket X is in a pre-failure condition.Amber
One or more of the following conditions may exist:
• PPM in slot X has failed.
• PPM is not installed in slot X, but the corresponding
processor is installed.
FBDIMM in slot X has failed.Red
FBDIMM in slot X is in a pre-failure condition.Amber
One or more FBDIMMs has failed. Test each bank of FBDIMMs
by removing all other FBDIMMs. Isolate the failed FBDIMM by
replacing each FBDIMM in a bank with a known working
FBDIMM.
One or more FBDIMMs has failed. Test each bank of FBDIMMs
by removing all other FBDIMMs. Isolate the failed FBDIMM by
replacing each FBDIMM in a bank with a known working
FBDIMM.
Bank X failed over to the online spare memory bank.Amber
Invalid online spare memory configuration.Red
Server components50
Page 51
Systems Insight
Display LED and
color
StatusInternal health LED
color
Online spare
memory (green)
Mirrored memory
(amber)
Mirrored memory
(flashing (amber)
Mirrored memory
(green)
Overtemperature
(amber)
Riser interlock
(amber)
Fan (amber)
Online spare memory enabled and not failed.Green
Bank(s) X failed over to the mirrored memory bank(s).Amber
Invalid mirrored memory configuration.Red
Mirrored memory enabled and not failed.Green
The Health Driver has detected a cautionary temperature level.Amber
The server has detected a hardware critical temperature level.Red
PCI riser cage is not seated.Red
One fan has failed or is removed.Amber
Two or more fans have failed or are removed.Red
HP ProLiant Storage Server 51
Page 52

Server components52
Page 53

3 Storage management overview
This chapter provides an overview of some of the components that make up the storage structure of
the HP ProLiant Storage Server.
Storage management elements
Storage is divided into four major divisions:
• Physical storage elements
• Logical storage elements
• File system elements
• File sharing elements
Each of these elements is composed of the previous level's elements.
Storage management example
Figure 15 depicts many of the storage elements that one would find on a storage device. The following
sections provide an overview of the storage elements.
HP ProLiant Storage Server 53
Page 54

Storage
g
Elements
Physical Disks
RAID Arrays
Logical Drives
Selective Storage
Presentaion
Visible Disks
Single Server Cluster Implementation
Logical
Storage
Elements
File
System
Elements
Shadow Copy
Elements
Cluster
Elements
Partitioning
NTFS Volumes
File Folders
Shadow Copies
(Snapshots)
Cluster Physical
Disk Resources
Cluster Virtual
Server Groups
(Network Name)
(IP Address)
(Cluster Admin)
Fault-tolerant
CIFS/SMB and
NFS File Shares
Q:
\Engineering
\Marketing
Q:
from 02/10/03 09:30 \snapshot.0
from 02/10/03 11:30 \snapshot.1
Q:
\Users
\Sales
\Marketing
\Engineering
\Snapshot.0
\Snapshot.1
\Users \Sales \Engineering
CIFS and NFS
File Shares
File
Sharing
Elements
S:
R:
\Marketing
R:
R:
\Users \Sales \Customers
from 02/10/03 09:30 \snapshot.0
from 02/10/03 11:30 \snapshot.1
R:T:S:
\\VirtualServerA
IP Addresss 172.1.1.1.
\Sales
\Marketing
\Engineering
\Snapshot.0
\Snapshot.1
U:
U:
T:
\\VirtualServerA
IP Addresss 172.1.1.2.
\Users
\Customers
l0044
Figure 15 Storage management process example
Physical storage elements
The lowest level of storage management occurs at the physical drive level. Minimally, choosing the
best disk carving strategy includes the following policies:
• Analyze current corporate and departmental structure.
• Analyze the current file server structure and environment.
• Plan properly to ensure the best configuration and use of storage.
• Determine the desired priority of fault tolerance, performance, and storage capacity.
• Use the determined priority of system characteristics to determine the optimal striping policy
and RAID level.
Storage management overview54
Page 55
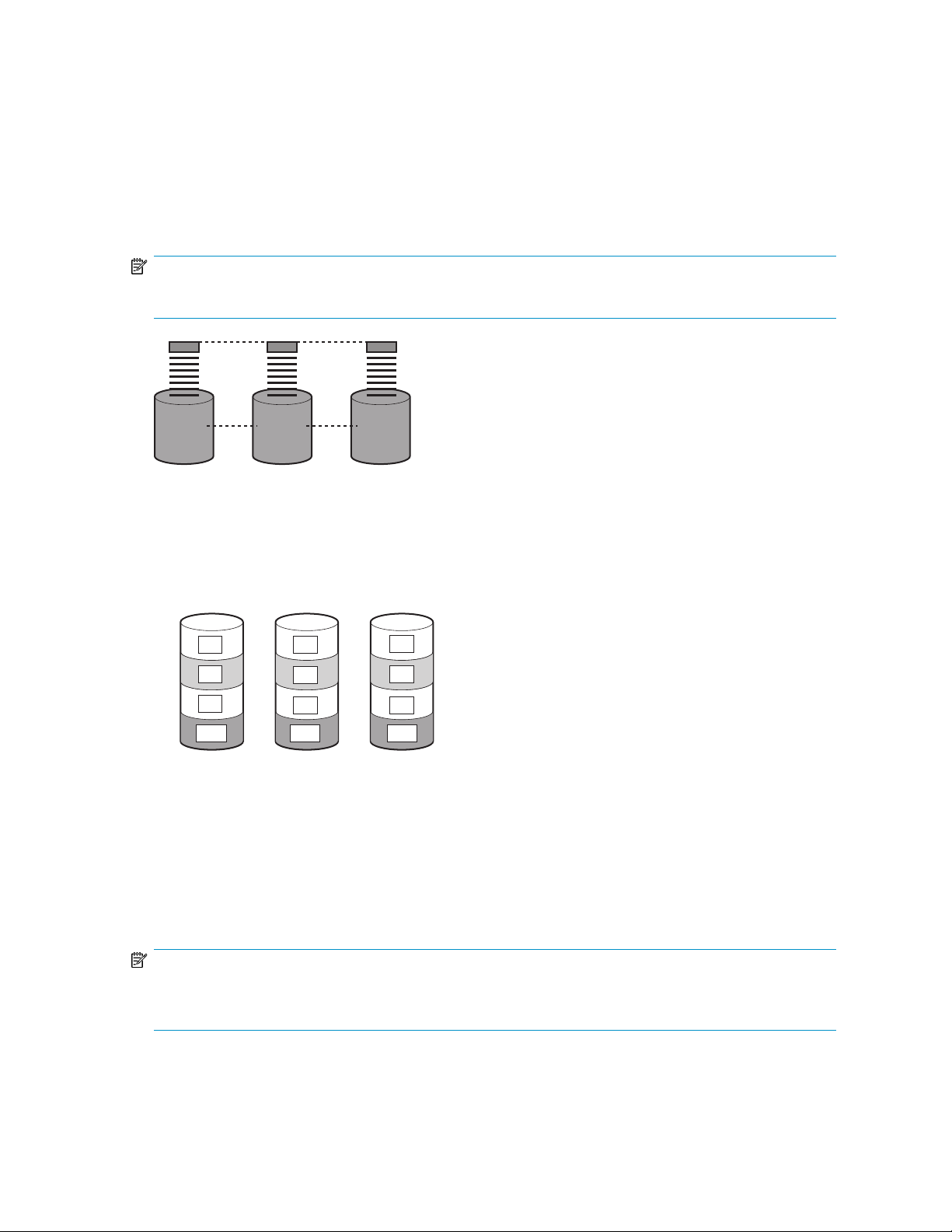
Arrays
S
S
S
S
g
• Include the appropriate number of physical drives in the arrays to create logical storage elements
of desired sizes.
See Figure 16. With an array controller installed in the system, the capacity of several physical drives
(P1–P3) can be logically combined into one or more logical units (L1) called arrays. When this is
done, the read/write heads of all the constituent physical drives are active simultaneously, dramatically
reducing the overall time required for data transfer.
NOTE:
Depending on the storage server model, array configuration may not be possible or necessary.
L1
P1 P3P2
gl0042
Figure 16 Configuring arrays from physical drives
Because the read/write heads are simultaneously active, the same amount of data is written to each
drive during any given time interval. Each unit of data is termed a block. The blocks form a set of
data stripes over all the hard drives in an array, as shown in Figure 17.
1
B1
2
B4
3
B7
4
B2
B5
B8
B11B10 B12
B3
B6
B9
l0043
Figure 17 RAID 0 (data striping) (S1-S4) of data blocks (B1-B12)
For data in the array to be readable, the data block sequence within each stripe must be the same.
This sequencing process is performed by the array controller, which sends the data blocks to the drive
write heads in the correct order.
A natural consequence of the striping process is that each hard drive in a given array contains the
same number of data blocks.
NOTE:
If one hard drive has a larger capacity than other hard drives in the same array, the extra capacity is
wasted because it cannot be used by the array.
HP ProLiant Storage Server 55
Page 56
Fault tolerance
Drive failure, although rare, is potentially catastrophic. For example, using simple striping as shown
in Figure 17, failure of any hard drive leads to failure of all logical drives in the same array, and
hence to data loss.
To protect against data loss from hard drive failure, storage servers should be configured with fault
tolerance. HP recommends adhering to RAID 5 configurations.
The table below summarizes the important features of the different kinds of RAID supported by the
Smart Array controllers. The decision chart in the following table can help determine which option is
best for different situations.
Table 19 Summary of RAID methods
Maximum number of hard
drives
Tolerant of single hard
drive failure?
Tolerant of multiple
simultaneous hard drive
failures?
Online spares
Further protection against data loss can be achieved by assigning an online spare (or hot spare) to
any configuration except RAID 0. This hard drive contains no data and is contained within the same
storage subsystem as the other drives in the array. When a hard drive in the array fails, the controller
can then automatically rebuild information that was originally on the failed drive onto the online spare.
This quickly restores the system to full RAID level fault tolerance protection. However, unless RAID
Advanced Data Guarding (ADG) is being used, which can support two drive failures in an array, in
the unlikely event that a third drive in the array should fail while data is being rewritten to the spare,
the logical drive still fails.
RAID 0
Striping (no
fault tolerance)
No
RAID 1+0
Mirroring
If the failed
drives are not
mirrored to
each other
RAID 5
Distributed
Data Guarding
RAID 6 (ADG)
Storage system dependent14N/AN/A
YesYesYesNo
Yes (two drives can fail)No
Logical storage elements
Logical storage elements consist of those components that translate the physical storage elements to
file system elements. The storage server uses the Window Disk Management utility to manage the
various types of disks presented to the file system. There are two types of LUN presentation: basic
disk and dynamic disk. Each of these types of disk has special features that enable different types of
management.
Logical drives (LUNs)
While an array is a physical grouping of hard drives, a logical drive consists of components that
translate physical storage elements into file system elements.
Storage management overview56
Page 57

It is important to note that a LUN may span all physical drives within a storage controller subsystem,
L
L
A2
but cannot span multiple storage controller subsystems.
A1
L3
1
2
L4
L5
gl0045
Figure 18 Two arrays (A1, A2) and five logical drives (L1 through L5) spread over five physical drives
NOTE:
This type of configuration may not apply to all storage servers and serves only as an example.
Through the use of basic disks, you can create primary partitions or extended partitions. Partitions
can only encompass one LUN. Through the use of dynamic disks, you can create volumes that span
multiple LUNs. You can use the Windows Disk Management utility to convert disks to dynamic and
back to basic and to manage the volumes residing on dynamic disks. Other options include the ability
to delete, extend, mirror, and repair these elements.
Partitions
Volumes
Partitions exist as either primary partitions or extended partitions and can be composed of only one
basic disk no larger than 2 TB. Basic disks can also only contain up to four primary partitions, or
three primary partitions and one extended partition. In addition, the partitions on them cannot be
extended beyond the limits of a single LUN. Extended partitions allow the user to create multiple
logical drives. These partitions or logical disks can be assigned drive letters or be used as mount
points on existing disks. If mount points are used, it should be noted that Services for UNIX (SFU) does
not support mount points at this time. The use of mount points in conjunction with NFS shares is not
supported.
When planning dynamic disks and volumes, there is a limit to the amount of growth a single volume
can undergo. Volumes are limited in size and can have no more than 32 separate LUNs, with each
LUN not exceeding 2 terabytes (TB), and volumes totaling no more than 64 TB of disk space.
The RAID level of the LUNs included in a volume must be considered. All of the units that make up a
volume should have the same high-availability characteristics. In other words, the units should all be
of the same RAID level. For example, it would not be a good practice to include both a RAID 1+0
and a RAID 5 array in the same volume set. By keeping all the units the same, the entire volume retains
the same performance and high-availability characteristics, making managing and maintaining the
volume much easier. If a dynamic disk goes offline, the entire volume dependent on the one or more
dynamic disks is unavailable. There could be a potential for data loss depending on the nature of the
failed LUN.
Volumes are created out of the dynamic disks, and can be expanded on the fly to extend over multiple
dynamic disks if they are spanned volumes. However, after a type of volume is selected, it cannot be
altered. For example, a spanning volume cannot be altered to a mirrored volume without deleting
and recreating the volume, unless it is a simple volume. Simple volumes can be mirrored or converted
to spanned volumes. Fault-tolerant disks cannot be extended. Therefore, selection of the volume type
HP ProLiant Storage Server 57
Page 58

is important. The same performance characteristics on numbers of reads and writes apply when using
fault-tolerant configurations, as is the case with controller-based RAID. These volumes can also be
assigned drive letters or be mounted as mount points off existing drive letters.
The administrator should carefully consider how the volumes will be carved up and what groups or
applications will be using them. For example, putting several storage-intensive applications or groups
into the same dynamic disk set would not be efficient. These applications or groups would be better
served by being divided up into separate dynamic disks, which could then grow as their space
requirements increased, within the allowable growth limits.
NOTE:
Dynamic disks cannot be used for clustering configurations because Microsoft Cluster only supports basic
disks.
File system elements
File system elements are composed of the folders and subfolders that are created under each logical
storage element (partitions, logical disks, and volumes). Folders are used to further subdivide the
available file system, providing another level of granularity for management of the information space.
Each of these folders can contain separate permissions and share names that can be used for network
access. Folders can be created for individual users, groups, projects, and so on.
File sharing elements
The storage server supports several file sharing protocols, including Distributed File System (DFS),
Network File System (NFS), File Transfer Protocol (FTP), Hypertext Transfer Protocol (HTTP), and
Microsoft Server Message Block (SMB). On each folder or logical storage element, different file sharing
protocols can be enabled using specific network names for access across a network to a variety of
clients. Permissions can then be granted to those shares based on users or groups of users in each of
the file sharing protocols.
Volume Shadow Copy Service overview
The Volume Shadow Copy Service (VSS) provides an infrastructure for creating point-in-time snapshots
(shadow copies) of volumes. VSS supports 64 shadow copies per volume.
Shadow Copies of Shared Folders resides within this infrastructure, and helps alleviate data loss by
creating shadow copies of files or folders that are stored on network file shares at pre-determined
time intervals. In essence, a shadow copy is a previous version of the file or folder at a specific point
in time.
By using shadow copies, a storage server can maintain a set of previous versions of all files on the
selected volumes. End users access the file or folder by using a separate client add-on program, which
enables them to view the file in Windows Explorer.
Shadow copies should not replace the current backup, archive, or business recovery system, but they
can help to simplify restore procedures. For example, shadow copies cannot protect against data loss
due to media failures; however, recovering data from shadow copies can reduce the number of times
needed to restore data from tape.
Storage management overview58
Page 59

Using storage elements
The last step in creating the element is determining its drive letter or mount point and formatting the
element. Each element created can exist as a drive letter, assuming one is available, and/or as mount
points on an existing folder or drive letter. Either method is supported. However, mount points cannot
be used for shares that will be shared using Microsoft Services for Unix. They can be set up with both
but the use of the mount point in conjunction with NFS shares causes instability with the NFS shares.
Formats consist of NTFS, FAT32, and FAT. All three types can be used on the storage server. However,
VSS can only use volumes that are NTFS formatted. Also, quota management is possible only on
NTFS.
Clustered server elements
Select storage servers support clustering. The HP ProLiant Storage Server supports several file sharing
protocols including DFS, NFS, FTP, HTTP, and Microsoft SMB. Only NFS, FTP, and Microsoft SMB
are cluster-aware protocols. HTTP can be installed on each node but the protocols cannot be set up
through cluster administrator, and they will not fail over during a node failure.
CAUTION:
AppleTalk shares should not be created on clustered resources as this is not supported by Microsoft
Clustering, and data loss may occur.
Network names and IP address resources for the clustered file share resource can also be established
for access across a network to a variety of clients. Permissions can then be granted to those shares
based on users or groups of users in each of the file sharing protocols.
Network adapter teaming
Network adapter teaming is software-based technology used to increase a server's network availability
and performance. Teaming enables the logical grouping of physical adapters in the same server
(regardless of whether they are embedded devices or Peripheral Component Interconnect (PCI)
adapters) into a virtual adapter. This virtual adapter is seen by the network and server-resident
network-aware applications as a single network connection.
Management tools
HP Systems Insight Manager
HP SIM is a web-based application that allows system administrators to accomplish normal
administrative tasks from any remote location, using a web browser. HP SIM provides device
management capabilities that consolidate and integrate management data from HP and third-party
devices.
IMPORTANT:
You must install and use HP SIM to benefit from the Pre-Failure Warranty for processors, SAS and SCSI
hard drives, and memory modules.
HP ProLiant Storage Server 59
Page 60

For additional information, refer to the Management CD in the HP ProLiant Essentials Foundation Pack
or the HP SIM website (http://www.hp.com/go/hpsim).
Management Agents
Management Agents provide the information to enable fault, performance, and configuration
management. The agents allow easy manageability of the server through HP SIM software, and
thirdparty SNMP management platforms. Management Agents are installed with every SmartStart
assisted installation or can be installed through the HP PSP. The Systems Management homepage
provides status and direct access to in-depth subsystem information by accessing data reported through
the Management Agents. For additional information, refer to the Management CD in the HP ProLiant
Essentials Foundation Pack or the HP website (http://www.hp.com/servers/manage).
Storage management overview60
Page 61

4 File server management
This chapter begins by identifying file services in Windows Storage Server 2003 R2. The remainder
of the chapter describes the many tasks and utilities that play a role in file server management.
File services features in Windows Storage Server 2003 R2
Storage Manager for SANs
The Storage Manager for SANs (also called Simple SAN) snap-in enables you to create and manage
the LUNs that are used to allocate space on storage arrays. Storage Manager for SANs can be used
on SANs that support Virtual Disk Server (VDS). It can be used in both Fibre Channel and iSCSI
environments.
For more information on Storage Manager for SANs, see the online help. A Microsoft document titled
Storage Management in Windows Storage Server 2003 R2: File Server Resource Manager and
Storage Manager for Storage Area Networks is available at h
download/7/4/7/7472bf9b-3023-48b7-87be-d2cedc38f15a/WS03R2_Storage_Management.doc.
NOTE:
Storage Manager for SANs is only available on Standard and Enterprise editions of Windows Storage
Server 2003 R2.
ttp://download.microsoft.com/
Single Instance Storage
Single Instance Storage (SIS) provides a copy-on-write link between multiple files. Disk space is
recovered by reducing the amount of redundant data stored on a server. If a user has two files sharing
disk storage by using SIS, and someone modifies one of the files, users of the other files do not see
the changes. The underlying shared disk storage that backs SIS links is maintained by the system and
is only deleted if all the SIS links pointing to it are deleted. SIS automatically determines that two or
more files have the same content and links them together.
NOTE:
Single Instance Storage is only available on Standard and Enterprise editions of Windows Storage Server
2003 R2.
File Server Resource Manager
File Server Resource Manager is a suite of tools that allows administrators to understand, control, and
manage the quantity and type of data stored on their servers. By using File Server Resource Manager,
HP ProLiant Storage Server 61
Page 62

administrators can place quotas on volumes, actively screen files and folders, and generate
comprehensive storage reports.
By using File Server Resource Manager, you can perform the following tasks:
• Create quotas to limit the space allowed for a volume or folder and to generate notifications when
the quota limits are approached and exceeded.
• Create file screens to screen the files that users can save on volumes and in folders and to send
notifications when users attempt to save blocked files.
• Schedule periodic storage reports that allow users to identify trends in disk usage and to monitor
attempts to save unauthorized files, or generate the reports on demand.
Windows SharePoint Services
Windows SharePoint Services is an integrated set of collaboration and communication services
designed to connect people, information, processes, and systems, within and beyond the organization
firewall.
NOTE:
Windows SharePoint Services is only available on Standard and Enterprise editions of Windows Storage
Server 2003 R2.
HP Storage Server Management Console
The HP Storage Server Management Console is a user interface in Windows Storage Server 2003
R2 and Windows Unified Data Storage Server 2003 that provides one place to manage files or print
serving components. The console is accessible using Remote Desktop or a web browser.
The Storage Management page provides a portal to:
• File Server Resource Manager
• DFS Management
• Disk and Volume Management
• Single Instance Storage
• Indexing Service
• MSNFS (under Share folder)
• Cluster Management (under “Utilities”)
The Share Folder Management page provides a portal to Shared Folders, consisting of:
• Shares
• Sessions
• Open files
File services management
Information about the storage server in a SAN environment is provided in the HP ProLiant Storage
Server SAN Connection and Management document located on the HP web site at http://
h20000.www2.hp.com/bc/docs/support/SupportManual/c00663737/c00663737.pdf.
File server management62
Page 63

Configurable and pre-configured storage
Certain storage servers ship with storage configured only for the operating system. The administrator
must configure data storage for the storage server. Other storage servers ship with pre-configured
storage for data. Depending on the type of storage server purchased, additional storage configuration
is required.
Configuring additional storage involves creating arrays, logical disks, and volumes. Table 20 shows
the general task areas to be performed as well as the utilities needed to configure storage for an HP
Smart Array-based storage server.
Table 20 Tasks and utilities needed for storage server configuration
• Create disk arrays—On storage servers with configurable storage, physical disks can be arranged
as RAID arrays for fault tolerance and enhanced performance, and then segmented into logical
disks of appropriate sizes for particular storage needs. These logical disks then become the volumes
that appear as drives on the storage server.
Storage management utilityTask
HP Array Configuration Utility or Storage ManagerCreate disk arrays
HP Array Configuration Utility or Storage ManagerCreate logical disks from the array space
Windows Disk ManagementVerify newly created logical disks
Windows Disk ManagementCreate a volume on the new logical disk
CAUTION:
The first two logical drives are configured for the storage server operating system and should not
be altered in any manner. If the first two logical drives are altered, the system recovery process
may not function properly when using the System Recovery DVD. Do not tamper with the “DON’T
ERASE” or local C: volume. These are reserved volumes and must be maintained as they exist.
The fault tolerance level depends on the amount of disks selected when the array was created. A
minimum of two disks is required for RAID 0+1 configuration, three disks for a RAID 5 configuration,
and four disks for a RAID 6 (ADG) configuration.
• Create logical disks from the array space—Select the desired fault tolerance, stripe size, and size
of the logical disk.
• Verify newly created logical disks—Verify that disks matching the newly created sizes are displayed.
• Create a volume on the new logical disk—Select a drive letter and enter a volume label, volume
size, allocation unit size, and mount point (if desired).
Storage management utilities
The storage management utilities preinstalled on the storage server include the HP Array Configuration
Utility (ACU).
Array management utilities
Storage devices for RAID arrays and LUNs are created and managed using the array management
utilities mentioned previously. For HP Smart Arrays use the ACU.
HP ProLiant Storage Server 63
Page 64

NOTE:
The ACU is used to configure and manage array-based storage. Software RAID-based storage servers use
Microsoft Disk Manager to manage storage. You need administrator or root privileges to run the ACU.
Array Configuration Utility
The HP ACU supports the Smart Array controllers and hard drives installed on the storage server.
To open the ACU from the storage server desktop:
NOTE:
If this is the first time that the ACU is being run, you will be prompted to select the Execution Mode for
ACU. Selecting Local Application Mode allows you to run the ACU from a Remote Desktop, remote console,
or storage server web access mode. Remote service mode allows you to access the ACU from a remote
browser.
1. Select Start > Programs > HP Management Tools > Array Configuration Utility.
2. If the Execution Mode for ACU is set to Remote Mode, log on to the HP System Management
Homepage. The default user name is administrator and the default password is hpinvent.
To open the ACU in browser mode:
NOTE:
Confirm that the ACU Execution Mode is set to remote service.
1. Open a browser and enter the server name or IP address of the destination server. For example,
http://servername:2301 or http://192.0.0.1:2301.
2. Log on to the HP System Management Homepage. The default user name is administrator and
the default password is hpinvent.
3. Click Array Configuration Utility on the left side of the window. The ACU opens and identifies
the controllers that are connected to the system.
Some ACU guidelines to consider:
• Do not modify the first two logical drives of the storage server; they are configured for the storage
server operating system.
• Spanning more than 14 disks with a RAID 5 volume is not recommended.
• Designate spares for RAID sets to provide greater protection against failures.
• RAID sets cannot span controllers.
• A single array can contain multiple logical drives of varying RAID settings.
• Extending and expanding arrays and logical drives is supported.
The HP Array Configuration Utility User Guide is available for download at http://www.hp.com/
support/manuals.
File server management64
Page 65

Disk Management utility
The Disk Management tool is a system utility for managing hard disks and the volumes, or partitions,
that they contain. Disk Management is used to initialize disks, create volumes, format volumes with
the FAT, FAT32, or NTFS file systems, and create fault-tolerant disk systems. Most disk-related tasks
can be performed in Disk Management without restarting the system or interrupting users. Most
configuration changes take effect immediately. A complete online help facility is provided with the
Disk Management utility for assistance in using the product.
NOTE:
• When the Disk Management utility is accessed through a Remote Desktop connection, this connection
can only be used to manage disks and volumes on the server. Using the Remote Desktop connection
for other operations during an open session closes the session.
• When closing Disk Management through a Remote Desktop connection, it may take a few moments
for the remote session to log off.
Guidelines for managing disks and volumes
• The first two logical drives are configured for the storage server operating system and should not
be altered in any manner. If the first two logical drives are altered, the system recovery process
may not function properly when using the System Recovery DVD. Do not tamper with the “DON’T
ERASE” or local C: volume. These are reserved volumes and must be maintained as they exist.
• HP does not recommend spanning array controllers with dynamic volumes. The use of software
RAID-based dynamic volumes is not recommended. Use the array controller instead; it is more
efficient.
• Use meaningful volume labels with the intended drive letter embedded in the volume label, if
possible. (For example, volume e: might be named “Disk E:.”) Volume labels often serve as the
only means of identification.
• Record all volume labels and drive letters in case the system needs to be restored.
• When managing basic disks, only the last partition on the disk can be extended unless the disk
is changed to dynamic.
• Basic disks can be converted to dynamic, but cannot be converted back to basic without deleting
all data on the disk.
• Basic disks can contain up to four primary partitions (or three primary partitions and one extended
partition).
• Format drives with a 16 K allocation size for best support of shadow copies, performance, and
defragmentation.
• NTFS formatted drives are recommended because they provide the greatest level of support for
shadow copies, encryption, and compression.
• Only basic disks can be formatted as FAT or FAT32.
• Read the online Disk Management help found in the utility.
Scheduling defragmentation
Defragmentation is the process of analyzing local volumes and consolidating fragmented files and
folders so that each occupies a single, contiguous space on the volume. This improves file system
performance. Because defragmentation consolidates files and folders, it also consolidates the free
space on a volume. This reduces the likelihood that new files will be fragmented.
HP ProLiant Storage Server 65
Page 66

Defragmentation for a volume can be scheduled to occur automatically at convenient times.
Defragmentation can also be done once, or on a recurring basis.
NOTE:
Scheduling defragmentation to run no later than a specific time prevents the defragmentation process from
running later than that time. If the defragmentation process is running when the time is reached, the process
is stopped. This setting is useful to ensure that the defragmentation process ends before the demand for
server access is likely to increase.
If defragmenting volumes on which shadow copies are enabled, use a cluster (or allocation unit) size
of 16 KB or larger during the format. Otherwise defragmentation registers as a change by the Shadow
Copy process. This increase in the number of changes forces Shadow Copy to delete snapshots as
the limit for the cache file is reached.
CAUTION:
Allocation unit size cannot be altered without reformatting the drive. Data on a reformatted drive cannot
be recovered.
For more information about disk defragmentation, read the online help.
Disk quotas
Disk quotas track and control disk space use in volumes.
NOTE:
To limit the size of a folder or share, see “Quota management” on page 91 .
Configure the volumes on the server to perform the following tasks:
• Prevent further disk space use and log an event when a user exceeds a specified disk space limit.
• Log an event when a user exceeds a specified disk space warning level.
When enabling disk quotas, it is possible to set both the disk quota limit and the disk quota warning
level. The disk quota limit specifies the amount of disk space a user is allowed to use. The warning
level specifies the point at which a user is nearing his or her quota limit. For example, a user's disk
quota limit can be set to 50 megabytes (MB), and the disk quota warning level to 45 MB. In this case,
the user can store no more than 50 MB on the volume. If the user stores more than 45 MB on the
volume, the disk quota system logs a system event.
In addition, it is possible to specify that users can exceed their quota limit. Enabling quotas and not
limiting disk space use is useful to still allow users access to a volume, but track disk space use on a
per-user basis. It is also possible to specify whether or not to log an event when users exceed either
their quota warning level or their quota limit.
When enabling disk quotas for a volume, volume usage is automatically tracked from that point
forward, but existing volume users have no disk quotas applied to them. Apply disk quotas to existing
volume users by adding new quota entries on the Quota Entries page.
File server management66
Page 67
NOTE:
When enabling disk quotas on a volume, any users with write access to the volume who have not exceeded
their quota limit can store data on the volume. The first time a user writes data to a quota-enabled volume,
default values for disk space limit and warning level are automatically assigned by the quota system.
For more information about disk quotas, read the online help.
Adding storage
Expansion is the process of adding physical disks to an array that has already been configured.
Extension is the process of adding new storage space to an existing logical drive on the same array,
usually after the array has been expanded.
Storage growth may occur in three forms:
• Extend unallocated space from the original logical disks or LUNs.
• Alter LUNs to contain additional storage.
• Add new LUNs to the system.
The additional space is then extended through a variety of means, depending on which type of disk
structure is in use.
NOTE:
This section addresses only single storage server node configurations. If your server has Windows Storage
Server 2003 R2 Enterprise Edition, see the Cluster Administration chapter for expanding and extending
storage in a cluster environment.
Expanding storage
Expansion is the process of adding physical disks to an array that has already been configured. The
logical drives (or volumes) that exist in the array before the expansion takes place are unchanged,
because only the amount of free space in the array changes. The expansion process is entirely
independent of the operating system.
NOTE:
See your storage array hardware user documentation for further details about expanding storage on the
array.
Extending storage using Windows Storage Utilities
Volume extension grows the storage space of a logical drive. During this process, the administrator
adds new storage space to an existing logical drive on the same array, usually after the array has
been expanded. An administrator may have gained this new storage space by either expansion or
by deleting another logical drive on the same array. Unlike drive expansion, the operating system
must be aware of changes to the logical drive size.
You extend a volume to:
HP ProLiant Storage Server 67
Page 68

• Increase raw data storage
• Improve performance by increasing the number of spindles in a logical drive volume
• Change fault-tolerance (RAID) configurations
For more information about RAID levels, see the Smart Array Controller User Guide, or the document
titled Assessing RAID ADG vs. RAID 5 vs. RAID 1+0. Both are available at the Smart Array controller
web page or at http://h18000.www1.hp.com/products/servers/proliantstorage/arraycontrollers/
documentation.html.
Extend volumes using Disk Management
The Disk Management snap-in provides management of hard disks, volumes or partitions. It can be
used to extend a dynamic volume only.
NOTE:
Disk Management cannot be used to extend basic disk partitions.
Guidelines for extending a dynamic volume:
• Use the Disk Management utility.
• You can extend a volume only if it does not have a file system or if it is formatted NTFS.
• You cannot extend volumes formatted using FAT or FAT32.
• You cannot extend striped volumes, mirrored volumes, or RAID 5 volumes.
For more information, see the Disk Management online help.
Expanding storage for EVA arrays using Command View EVA
Presenting a virtual disk offers its storage to a host. To make a virtual disk available to a host, you
must present it. You can present a virtual disk to a host during or after virtual disk creation. The virtual
disk must be completely created before the host presentation can occur. If you choose host presentation
during virtual disk creation, the management agent cannot complete any other task until that virtual
disk is created and presented. Therefore, HP recommends that you wait until a virtual disk is created
before presenting it to a host.
For more information, see the HP StorageWorks Command View EVA User Guide.
Expanding storage using the Array Configuration Utility
The Array Configuration Utility enables online capacity expansion of the array and logical drive for
specific MSA storage arrays, such as the MSA1000 and MSA1500. For more information, use the
ACU online help, or the procedures to “Expand Array” in the HP Array Configuration Utility User
Guide
Expand logical drive
This option in the ACU increases the storage capacity of a logical drive by adding unused space on
an array to the logical drive on the same array. The unused space is obtained either by expanding
an array or by deleting another logical drive on the same array. For more information, use the ACU
online help, or the “Extend logical drive” procedure in the HP Array Configuration Utility User Guide
File server management68
Page 69

Volume shadow copies
NOTE:
Select storage servers can be deployed in a clustered as well as a non-clustered configuration. This chapter
discusses using shadow copies in a non-clustered environment.
The Volume Shadow Copy Service provides an infrastructure for creating point-in-time snapshots
(shadow copies) of volumes. Shadow Copy supports 64 shadow copies per volume.
A shadow copy contains previous versions of the files or folders contained on a volume at a specific
point in time. While the shadow copy mechanism is managed at the server, previous versions of files
and folders are only available over the network from clients, and are seen on a per folder or file level,
and not as an entire volume.
The shadow copy feature uses data blocks. As changes are made to the file system, the Shadow Copy
Service copies the original blocks to a special cache file to maintain a consistent view of the file at a
particular point in time. Because the snapshot only contains a subset of the original blocks, the cache
file is typically smaller than the original volume. In the snapshot's original form, it takes up no space
because blocks are not moved until an update to the disk occurs.
By using shadow copies, a storage server can maintain a set of previous versions of all files on the
selected volumes. End users access the file or folder by using a separate client add-on program, which
enables them to view the file in Windows Explorer. Accessing previous versions of files, or shadow
copies, enables users to:
• Recover files that were accidentally deleted. Previous versions can be opened and copied to a
safe location.
• Recover from accidentally overwriting a file. A previous version of that file can be accessed.
• Compare several versions of a file while working. Use previous versions to compare changes
between two versions of a file.
Shadow copies cannot replace the current backup, archive, or business recovery system, but they
can help to simplify restore procedures. Because a snapshot only contains a portion of the original
data blocks, shadow copies cannot protect against data loss due to media failures. However, the
strength of snapshots is the ability to instantly recover data from shadow copies, reducing the number
of times needed to restore data from tape.
Shadow copy planning
Before setup is initiated on the server and the client interface is made available to end users, consider
the following:
• From what volume will shadow copies be taken?
• How much disk space should be allocated for shadow copies?
• Will separate disks be used to store shadow copies?
• How frequently will shadow copies be made?
Identifying the volume
Shadow copies are taken for a complete volume, but not for a specific directory. Shadow copies
work best when the server stores user files, such as documents, spreadsheets, presentations, graphics,
or database files.
HP ProLiant Storage Server 69
Page 70
NOTE:
Shadow copies should not be used to provide access to previous versions of application or e-mail databases.
Shadow copies are designed for volumes that store user data such as home directories and My
Documents folders that are redirected by using Group Policy or other shared folders in which users
store data.
Shadow copies work with compressed or encrypted files and retain whatever permissions were set
on the files when the shadow copies were taken. For example, if a user is denied permission to read
a file, that user would not be able to restore a previous version of the file, or be able to read the file
after it has been restored.
Although shadow copies are taken for an entire volume, users must use shared folders to access
shadow copies. Administrators on the local server must also specify the \\servername\sharename
path to access shadow copies. If administrators or end users want to access a previous version of a
file that does not reside in a shared folder, the administrator must first share the folder.
NOTE:
Shadow copies are available only on NTFS, not FAT or FAT32 volumes.
Files or folders that are recorded by using Shadow Copy appear static, even though the original data
is changing.
Allocating disk space
When determining the amount of space to allocate for storing shadow copies, consider both the
number and size of files that are being copied, as well as the frequency of changes between copies.
For example, 100 files that only change monthly require less storage space than 10 files that change
daily. If the frequency of changes to each file is greater than the amount of space allocated to storing
shadow copies, no shadow copy is created.
Administrators should also consider user expectations of how many versions they will want to have
available. End users might expect only a single shadow copy to be available, or they might expect
three days or three weeks worth of shadow copies. The more shadow copies users expect, the more
storage space administrators must allocate for storing them.
Setting the limit too low also affects backup programs that use shadow copy technology because
these programs are also limited to using the amount of disk space specified by administrators.
NOTE:
Regardless of the volume space that is allocated for shadow copies, there is a maximum of 64 shadow
copies for any volume. When the 65th shadow copy is taken, the oldest shadow copy is purged.
The minimum amount of storage space that can be specified is 350 megabytes (MB). The default
storage size is 10 percent of the source volume (the volume being copied). If the shadow copies are
stored on a separate volume, change the default to reflect the space available on the storage volume
instead of the source volume. Remember that when the storage limit is reached, older versions of the
shadow copies are deleted and cannot be restored.
File server management70
Page 71

CAUTION:
To change the storage volume, shadow copies must be deleted. The existing file change history that is kept
on the original storage volume is lost. To avoid this problem, verify that the storage volume that is initially
selected is large enough.
Identifying the storage area
To store the shadow copies of another volume on the same file server, a volume can be dedicated
on separate disks. For example, if user files are stored on H:\, another volume such as S:\can be
used to store the shadow copies. Using a separate volume on separate disks provides better
performance and is recommended for heavily used storage servers.
If a separate volume will be used for the storage area (where shadow copies are stored), the maximum
size should be changed to No Limit to reflect the space available on the storage area volume instead
of the source volume (where the user files are stored).
Disk space for shadow copies can be allocated on either the same volume as the source files or a
different volume. There is a trade-off between ease of use and maintenance versus performance and
reliability that the system administrator must consider.
By keeping the shadow copy on the same volume, there is a potential gain in ease of setup and
maintenance; however, there may be a reduction in performance and reliability.
CAUTION:
If shadow copies are stored on the same volume as the user files, note that a burst of disk input/output
(I/O) can cause all shadow copies to be deleted. If the sudden deletion of shadow copies is unacceptable
to administrators or end users, it is best to use a separate volume on separate disks to store shadow copies.
Determining creation frequency
The more frequently shadow copies are created, the more likely that end users will get the version
that they want. However, with a maximum of 64 shadow copies per volume, there is a trade-off
between the frequency of making shadow copies and the amount of time that the earlier files will be
available.
By default, the storage server creates shadow copies at 0700 and 1200, Monday through Friday.
However, these settings are easily modified by the administrator so that the shadow copy schedule
can better accommodate end user needs.
Shadow copies and drive defragmentation
When running Disk Defragmenter on a volume with shadow copies activated, all or some of the
shadow copies may be lost, starting with the oldest shadow copies.
If defragmenting volumes on which shadow copies are enabled, use a cluster (or allocation unit) size
of 16 KB or larger. Using this allocation unit size reduces the number of copy outs occurring on the
snapshot. Otherwise, the number of changes caused by the defragmentation process can cause
shadow copies to be deleted faster than expected. Note, however, that NTFS compression is supported
only if the cluster size is 4 KB or smaller.
HP ProLiant Storage Server 71
Page 72
NOTE:
To check the cluster size of a volume, use the fsutil fsinfo ntfsinfo command. To change the
cluster size on a volume that contains data, back up the data on the volume, reformat it using the new
cluster size, and then restore the data.
Mounted drives
A mounted drive is a local volume attached to an empty folder (called a mount point) on an NTFS
volume. When enabling shadow copies on a volume that contains mounted drives, the mounted drives
are not included when shadow copies are taken. In addition, if a mounted drive is shared and shadow
copies are enabled on it, users cannot access the shadow copies if they traverse from the host volume
(where the mount point is stored) to the mounted drive.
For example, assume there is a folder F:\data\users, and the Users folder is a mount point for
G:\. If shadow copies are enabled on both F:\ and G:\, F:\data is shared as \\server1\data,
and G:\data\users is shared as \\server1\users. In this example, users can access previous
versions of \\server1\data and \\server1\users but not \\server1\data\users.
Managing shadow copies
The vssadmin tool provides a command line capability to create, list, resize, and delete volume shadow
copies.
The system administrator can make shadow copies available to end users through a feature called
“Shadow Copies for Shared Folders.” The administrator uses the Properties menu (see Figure 19) to
turn on the Shadow Copies feature, select the volumes to be copied, and determine the frequency
with which shadow copies are made.
File server management72
Page 73

Figure 19 System administrator view of Shadow Copies for Shared Folders
The shadow copy cache file
The default shadow copy settings allocate 10 percent of the source volume being copied (with a
minimum of 350 MB), and store the shadow copies on the same volume as the original volume. (See
Figure 20). The cache file is located in a hidden protected directory titled “System Volume Information”
off of the root of each volume for which shadow copy is enabled.
F:
cache file
G:
cache file
H:
cache file
Figure 20 Shadow copies stored on a source volume
The cache file location can be altered to reside on a dedicated volume separate from the volumes
containing files shares. (See Figure 21).
HP ProLiant Storage Server 73
Page 74

F:
G: H:
L:
cache file
cache file
cache file
Figure 21 Shadow copies stored on a separate volume
The main advantage to storing shadow copies on a separate volume is ease of management and
performance. Shadow copies on a source volume must be continually monitored and can consume
space designated for file sharing. Setting the limit too high takes up valuable storage space. Setting
the limit too low can cause shadow copies to be purged too soon, or not created at all. By storing
shadow copies on a separate volume space, limits can generally be set higher, or set to No Limit.
See the online help for instructions on altering the cache file location.
CAUTION:
If the data on the separate volume L: is lost, the shadow copies cannot be recovered.
Enabling and creating shadow copies
Enabling shadow copies on a volume automatically results in several actions:
• Creates a shadow copy of the selected volume.
• Sets the maximum storage space for the shadow copies.
• Schedules shadow copies to be made at 7 a.m. and 12 noon on weekdays.
NOTE:
Creating a shadow copy only makes one copy of the volume; it does not create a schedule.
File server management74
Page 75

NOTE:
After the first shadow copy is created, it cannot be relocated. Relocate the cache file by altering the cache
file location under Properties prior to enabling shadow copy. See
“Viewing shadow copy properties” on page 75.
Viewing a list of shadow copies
To view a list of shadow copies on a volume:
1. Access Disk Management.
2. Select the volume or logical drive, then right-click on it.
3. Select Properties.
4. Select Shadow Copies tab.
All shadow copies are listed, sorted by the date and time they were created.
NOTE:
It is also possible to create new shadow copies or delete shadow copies from this page.
Set schedules
Shadow copy schedules control how frequently shadow copies of a volume are made. There are a
number of factors that can help determine the most effective shadow copy schedule for an organization.
These include the work habits and locations of the users. For example, if users do not all live in the
same time zone, or they work on different schedules, it is possible to adjust the daily shadow copy
schedule to allow for these differences.
Do not schedule shadow copies more frequently than once per hour.
NOTE:
When deleting a shadow copy schedule, that action has no effect on existing shadow copies.
Viewing shadow copy properties
The Shadow Copy Properties page lists the number of copies, the date and time the most recent
shadow copy was made, and the maximum size setting.
NOTE:
For volumes where shadow copies do not exist currently, it is possible to change the location of the cache
file. Managing the cache files on a separate disk is recommended.
HP ProLiant Storage Server 75
Page 76
CAUTION:
Use caution when reducing the size limit for all shadow copies. When the size is set to less than the total
size currently used for all shadow copies, enough shadow copies are deleted to reduce the total size to
the new limit. A shadow copy cannot be recovered after it has been deleted.
Redirecting shadow copies to an alternate volume
IMPORTANT:
Shadow copies must be initially disabled on the volume before redirecting to an alternate volume. If shadow
copies are enabled and you disable them, a message appears informing you that all existing shadow
copies on the volume will be permanently deleted.
To redirect shadow copies to an alternate volume:
1. Access Disk Management.
2. Select the volume or logical drive, then right-click on it.
3. Select Properties.
4. Select the Shadow Copies tab.
5. Select the volume that you want to redirect shadow copies from and ensure that shadow copies
are disabled on that volume; if enabled, click Disable.
6. Click Settings.
7. In the Located on this volume field, select an available alternate volume from the list.
NOTE:
To change the default shadow copy schedule settings, click Schedule.
8. Click OK.
9. On the Shadow Copies tab, ensure that the volume is selected, and then click Enable.
Shadow copies are now scheduled to be made on the alternate volume.
Disabling shadow copies
When shadow copies are disabled on a volume, all existing shadow copies on the volume are deleted
as well as the schedule for making new shadow copies.
CAUTION:
When the Shadow Copies Service is disabled, all shadow copies on the selected volumes are deleted.
Once deleted, shadow copies cannot be restored.
File server management76
Page 77

Managing shadow copies from the storage server desktop
To access shadow copies from the storage server desktop:
The storage server desktop can be accessed by using Remote Desktop to manage shadow copies.
1. On the storage server desktop, double-click My Computer.
2. Right-click the volume name, and select Properties.
3. Click the Shadow Copies tab. See Figure 22.
Figure 22 Accessing shadow copies from My Computer
Shadow Copies for Shared Folders
Shadow copies are accessed over the network by supported clients and protocols. There are two sets
of supported protocols, SMB and NFS. All other protocols are not supported; this includes HTTP, FTP,
AppleTalk, and NetWare Shares. For SMB support, a client-side application denoted as Shadow
Copies for Shared Folders is required. The client-side application is currently only available for
Windows XP and Windows 2000 SP3+.
No additional software is required to enable UNIX users to independently retrieve previous versions
of files stored on NFS shares.
NOTE:
Shadow Copies for Shared Folders supports retrieval only of shadow copies of network shares. It does not
support retrieval of shadow copies of local folders.
HP ProLiant Storage Server 77
Page 78

NOTE:
Shadow Copies for Shared Folders clients are not available for HTTP, FTP, AppleTalk, or NetWare shares.
Consequently, users of these protocols cannot use Shadow Copies for Shared Folders to independently
retrieve previous versions of their files. However, administrators can take advantage of Shadow Copies
for Shared Folders to restore files for these users.
SMB shadow copies
Windows users can independently access previous versions of files stored on SMB shares by using
the Shadow Copies for Shared Folders client. After the Shadow Copies for Shared Folders client is
installed on the user's computer, the user can access shadow copies for a share by right-clicking on
the share to open its Properties window, clicking the Previous Versions tab, and then selecting the
desired shadow copy. Users can view, copy, and restore all available shadow copies.
Shadow Copies for Shared Folders preserves the permissions set in the access control list (ACL) of
the original folders and files. Consequently, users can only access shadow copies for shares to which
they have access. In other words, if a user does not have access to a share, he also does not have
access to the share's shadow copies.
The Shadow Copies for Shared Folders client pack installs a Previous Versions tab in the Properties
window of files and folders on network shares.
Users access shadow copies with Windows Explorer by selecting View, Copy, or Restore from the
Previous Versions tab. (See Figure 23). Both individual files and folders can be restored.
File server management78
Page 79

Figure 23 Client GUI
When users view a network folder hosted on the storage server for which shadow copies are enabled,
old versions (prior to the snapshot) of a file or directory are available. Viewing the properties of the
file or folder presents users with the folder or file history—a list of read-only, point-in-time copies of
the file or folder contents that users can then open and explore like any other file or folder. Users can
view files in the folder history, copy files from the folder history, and so on.
NFS shadow copies
UNIX users can independently access previous versions of files stored on NFS shares via the NFS
client; no additional software is required. Server for NFS exposes each of a share's available shadow
copies as a pseudo-subdirectory of the share. Each of these pseudo-subdirectories is displayed in
exactly the same way as a regular subdirectory is displayed.
The name of each pseudo-subdirectory reflects the creation time of the shadow copy, using the format
.@GMT-YYYY.MM.DD-HH:MM:SS. To prevent common tools from needlessly enumerating the
pseudo-subdirectories, the name of each pseudo-subdirectory begins with the dot character, thus
rendering it hidden.
The following example shows an NFS share named “NFSShare” with three shadow copies, taken on
April 27, 28, and 29 of 2003 at 4 a.m.
NFSShare
.@GMT-2003.04.27-04:00:00
.@GMT-2003.04.28-04:00:00
.@GMT-2003.04.29-04:00:00
HP ProLiant Storage Server 79
Page 80

Access to NFS shadow copy pseudo-subdirectories is governed by normal access-control mechanisms
using the permissions stored in the file system. Users can access only those shadow copies to which
they have read access at the time the shadow copy is taken. To prevent users from modifying shadow
copies, all pseudo-subdirectories are marked read-only, regardless of the user's ownership or access
rights, or the permissions set on the original files.
Server for NFS periodically polls the system for the arrival or removal of shadow copies and updates
the root directory view accordingly. Clients then capture the updated view the next time they issue a
directory read on the root of the share.
Recovery of files or folders
There are three common situations that may require recovery of files or folders:
• Accidental file deletion, the most common situation
• Accidental file replacement, which may occur if a user selects Save instead of Save As
• File corruption
It is possible to recover from all of these scenarios by accessing shadow copies. There are separate
steps for accessing a file compared to accessing a folder.
Recovering a deleted file or folder
To recover a deleted file or folder within a folder:
1. Access to the folder where the deleted file was stored.
2. Position the cursor over a blank space in the folder. If the cursor hovers over a file, that file is
selected.
3. Right-click, select Properties from the bottom of the menu, and then click the Previous Versions
tab.
4. Select the version of the folder that contains the file before it was deleted, and then click View.
5. View the folder and select the file or folder to recover. The view may be navigated multiple folders
deep.
6. Click Restore to restore the file or folder to its original location. Click Copy... to allow the placement
of the file or folder to a new location.
File server management80
Page 81
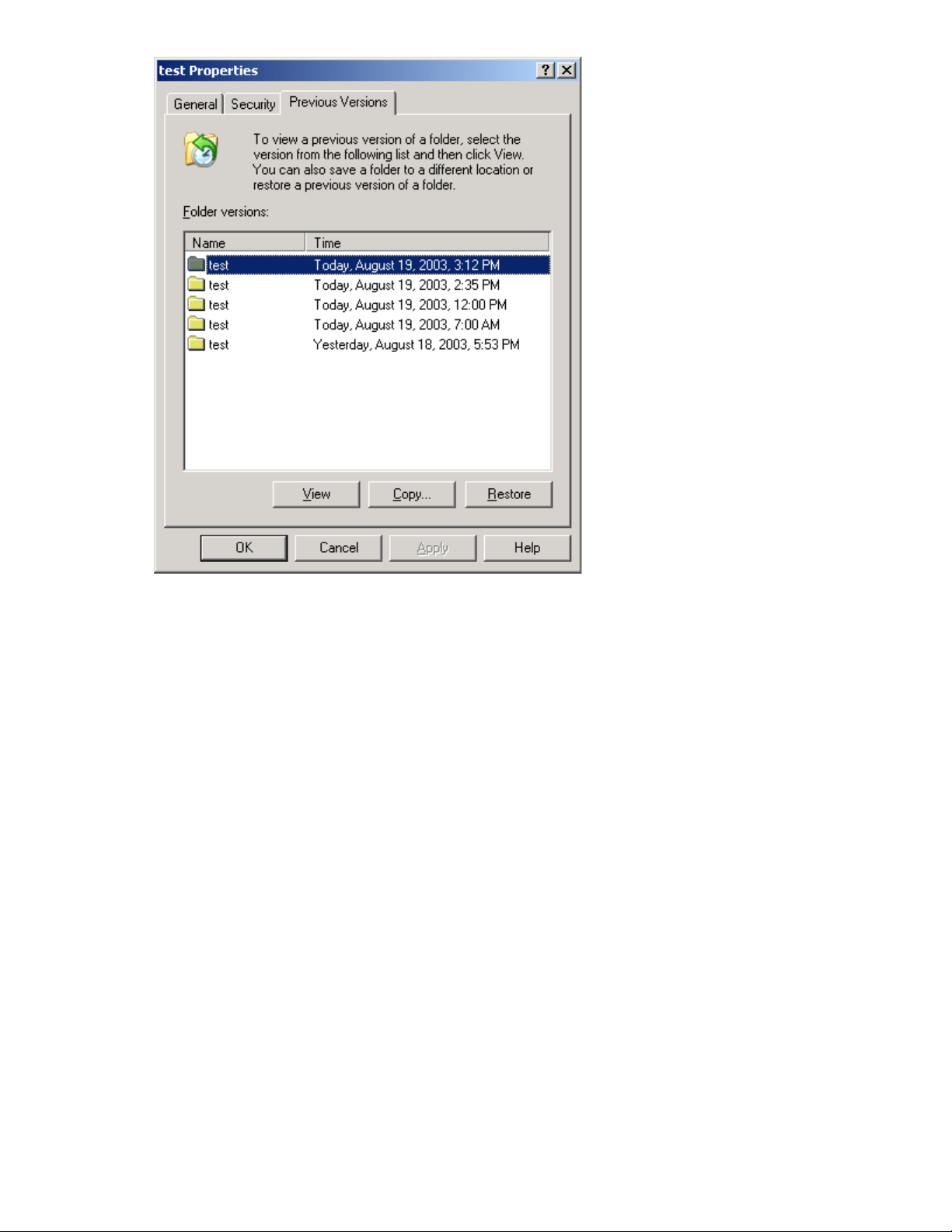
Figure 24 Recovering a deleted file or folder
Recovering an overwritten or corrupted file
Recovering an overwritten or corrupted file is easier than recovering a deleted file because the file
itself can be right-clicked instead of the folder. To recover an overwritten or corrupted file:
1. Right-click the overwritten or corrupted file, and then click Properties.
2. Click Previous Versions.
3. To view the old version, click View. To copy the old version to another location, click Copy... to
replace the current version with the older version, click Restore.
Recovering a folder
To recover a folder:
1. Position the cursor so that it is over a blank space in the folder to be recovered. If the cursor
hovers over a file, that file is selected.
2. Right-click, select Properties from the bottom of the menu, and then click the Previous Versions
tab.
3. Click either Copy... or Restore.
Clicking Restore enables the user to recover everything in that folder as well as all subfolders.
Clicking Restore does not delete any files.
HP ProLiant Storage Server 81
Page 82

Backup and shadow copies
Shadow copies are only available on the network via the client application, and only at a file or
folder level as opposed to the entire volume. Hence, the standard backup associated with a volume
backup will not work to back up the previous versions of the file system. To answer this particular
issue, shadow copies are available for backup in two situations. If the backup software in question
supports the use of shadow copies and can communicate with underlying block device, it is supported,
and the previous version of the file system will be listed in the backup application as a complete file
system snapshot. If the built-in backup application NTbackup is used, the backup software forces a
snapshot, and then uses the snapshot as the means for backup. The user is unaware of this activity
and it is not self-evident although it does address the issue of open files.
Shadow Copy Transport
Shadow Copy Transport provides the ability to transport data on a Storage Area Network (SAN).
With a storage array and a VSS-aware hardware provider, it is possible to create a shadow copy
on one server and import it on another server. This process, essentially “virtual” transport, is
accomplished in a matter of minutes, regardless of the size of the data.
NOTE:
Shadow copy transport is supported only on Windows Server 2003 Enterprise Edition, Windows Storage
Server 2003 Enterprise Edition, and Windows Server 2003 Datacenter Edition. It is an advanced solution
that works only if it has a hardware provider on the storage array.
A shadow copy transport can be used for a number of purposes, including:
• Tape backups
An alternative to traditional backup to tape processes is transport of shadow copies from the
production server onto a backup server, where they can then be backed up to tape. Like the other
two alternatives, this option removes backup traffic from the production server. While some backup
applications might be designed with the hardware provider software that enables transport, others
are not. The administrator should determine whether or not this functionality is included in the
backup application.
• Data mining
The data in use by a particular production server is often useful to different groups or departments
within an organization. Rather than add additional traffic to the production server, a shadow copy
of the data can be made available through transport to another server. The shadow copy can
then be processed for different purposes, without any performance impact on the original server.
The transport process is accomplished through a series of DISKRAID command steps:
1. Create a shadow copy of the source data on the source server (read-only).
2. Mask off (hide) the shadow copy from the source server.
3. Unmask the shadow copy to a target server.
4. Optionally, clear the read-only flags on the shadow copy.
The data is now ready to use.
File server management82
Page 83

Folder and share management
The HP ProLiant Storage Server supports several file-sharing protocols, including DFS, NFS, FTP, HTTP,
and Microsoft SMB. This section discusses overview information as well as procedures for the setup
and management of the file shares for the supported protocols. Security at the file level and at the
share level is also discussed.
NOTE:
Detailed information on setting up and managing NFS and NCP shares is discussed in
Microsoft Services for Network File System (MSNFS).
NOTE:
Select servers can be deployed in a clustered or non-clustered configuration. This section discusses share
setup for a non-clustered deployment.
Folder management
Volumes and folders on any system are used to organize data. Regardless of system size, systematic
structuring and naming conventions of volumes and folders eases the administrative burden. Moving
from volumes to folders to shares increases the level of granularity of the types of data stored in the
unit and the level of security access allowed.
Folders can be managed using the HP Storage Server Management Console. Tasks include:
• Accessing a specific volume or folder
• Creating a new folder
• Deleting a folder
• Modifying folder properties
• Creating a new share for a volume or folder
• Managing shares for a volume or folder
Managing file-level permissions
Security at the file level is managed using Windows Explorer.
File level security includes settings for permissions, ownership, and auditing for individual files.
To enter file permissions:
1. Using Windows Explorer, access the folder or file that needs to be changed, and then right-click
the folder.
HP ProLiant Storage Server 83
Page 84
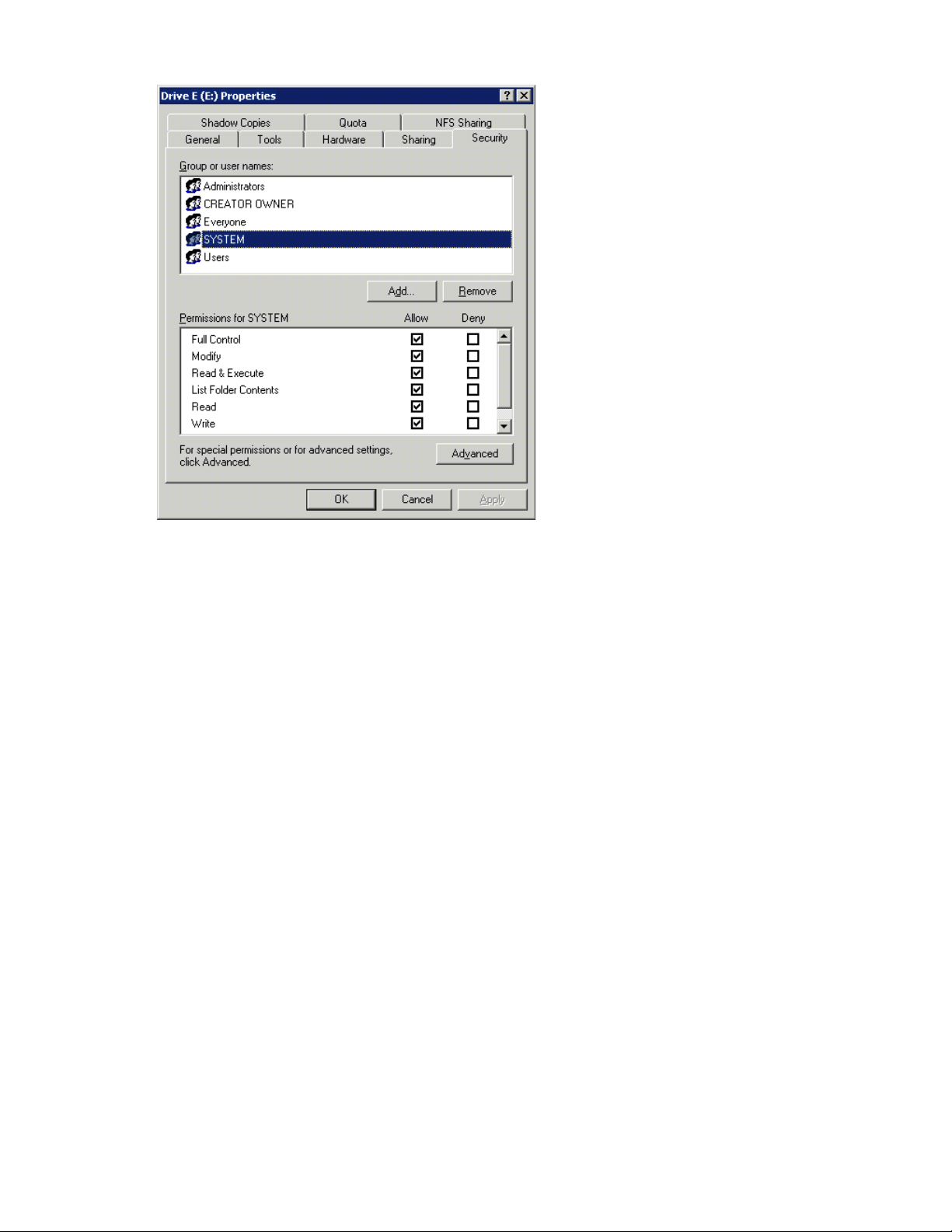
2. Click Properties, and then click the Security tab.
Figure 25 Properties dialog box, Security tab
Several options are available on the Security tab:
• To add users and groups to the permissions list, click Add. Follow the dialog box instructions.
• To remove users and groups from the permissions list, highlight the desired user or group,
and then click Remove.
• The center section of the Security tab lists permission levels. When new users or groups are
added to the permissions list, select the appropriate boxes to configure the common file-access
levels.
File server management84
Page 85

3. To modify ownership of files, or to modify individual file access level permissions, click Advanced.
Figure 26 illustrates the properties available on the Advanced Security Settings dialog box.
Figure 26 Advanced Security settings dialog box, Permissions tab
Other functionality available in the Advanced Security Settings dialog box is illustrated in Figure 26
and includes:
• Add a new user or group—Click Add, and then follow the dialog box instructions.
• Remove a user or group— Click Remove.
• Replace permission entries on all child objects with entries shown here that apply to child
objects—This allows all child folders and files to inherit the current folder permissions by
default.
• Modify specific permissions assigned to a particular user or group—Select the desired user
or group, and then click Edit.
HP ProLiant Storage Server 85
Page 86
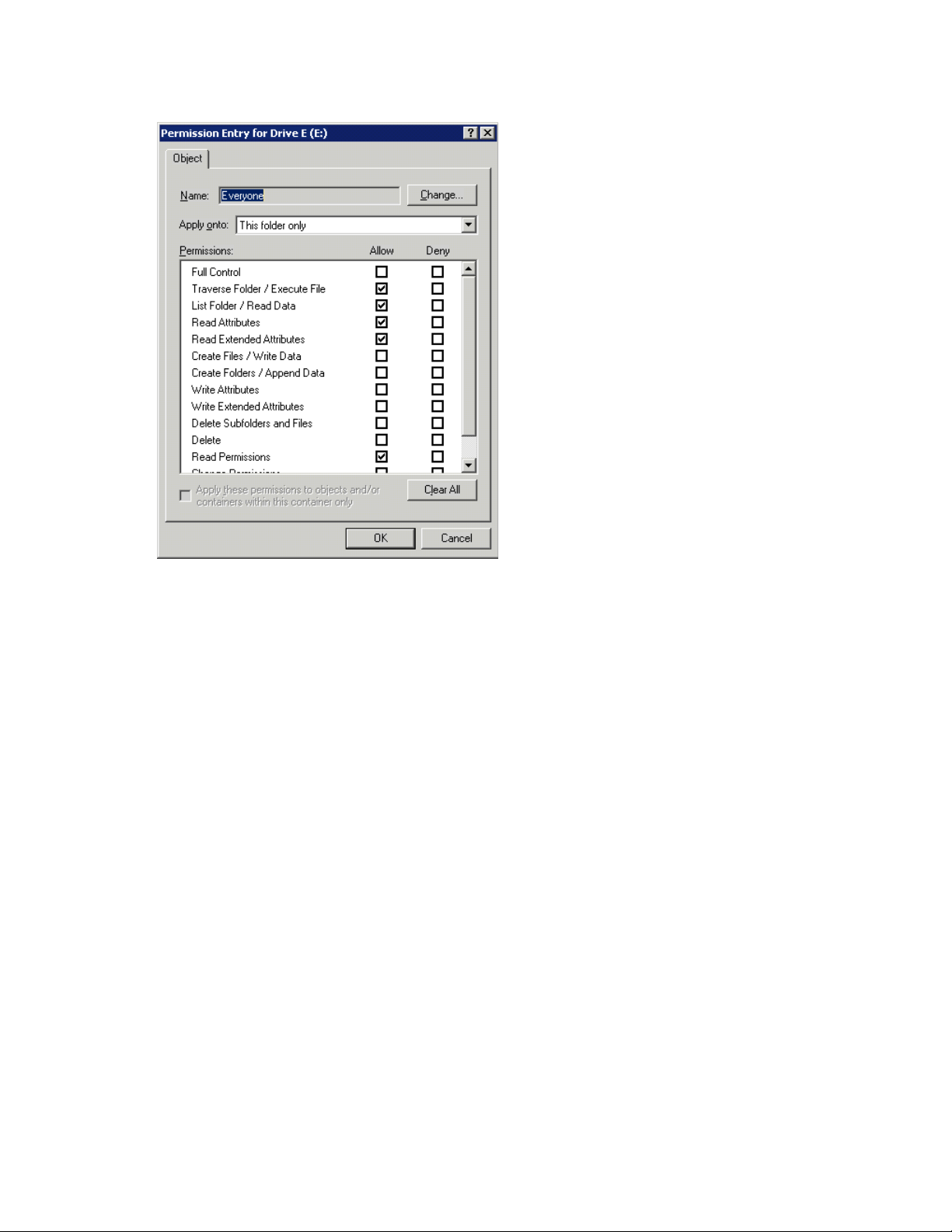
4. Enable or disable permissions by selecting the Allow box to enable permission or the Deny box
to disable permission. If neither box is selected, permission is automatically disabled. Figure 27
illustrates the Edit screen and some of the permissions.
Figure 27 User or group Permission Entry dialog box
Another area of the Advanced Security Settings is the Auditing tab. Auditing allows you to set
rules for the auditing of access, or attempted access, to files or folders. Users or groups can be
added, deleted, viewed, or modified through the Advanced Security Settings Auditing tab.
File server management86
Page 87
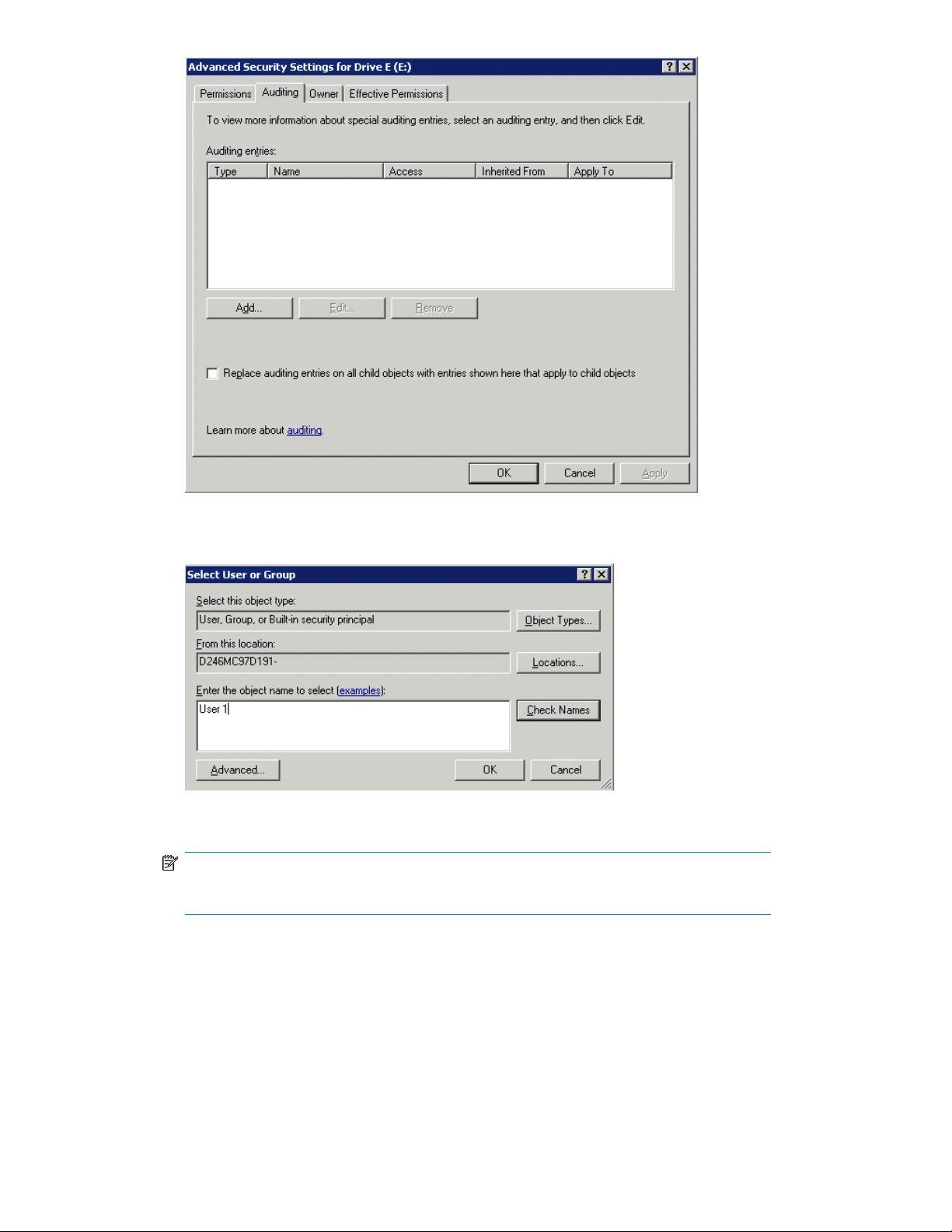
Figure 28 Advanced Security Settings dialog box, Auditing tab
5. Click Add to display the Select User or Group dialog box.
Figure 29 Select User or Group dialog box
NOTE:
Click Advanced to search for users or groups.
6. Select the user or group.
HP ProLiant Storage Server 87
Page 88
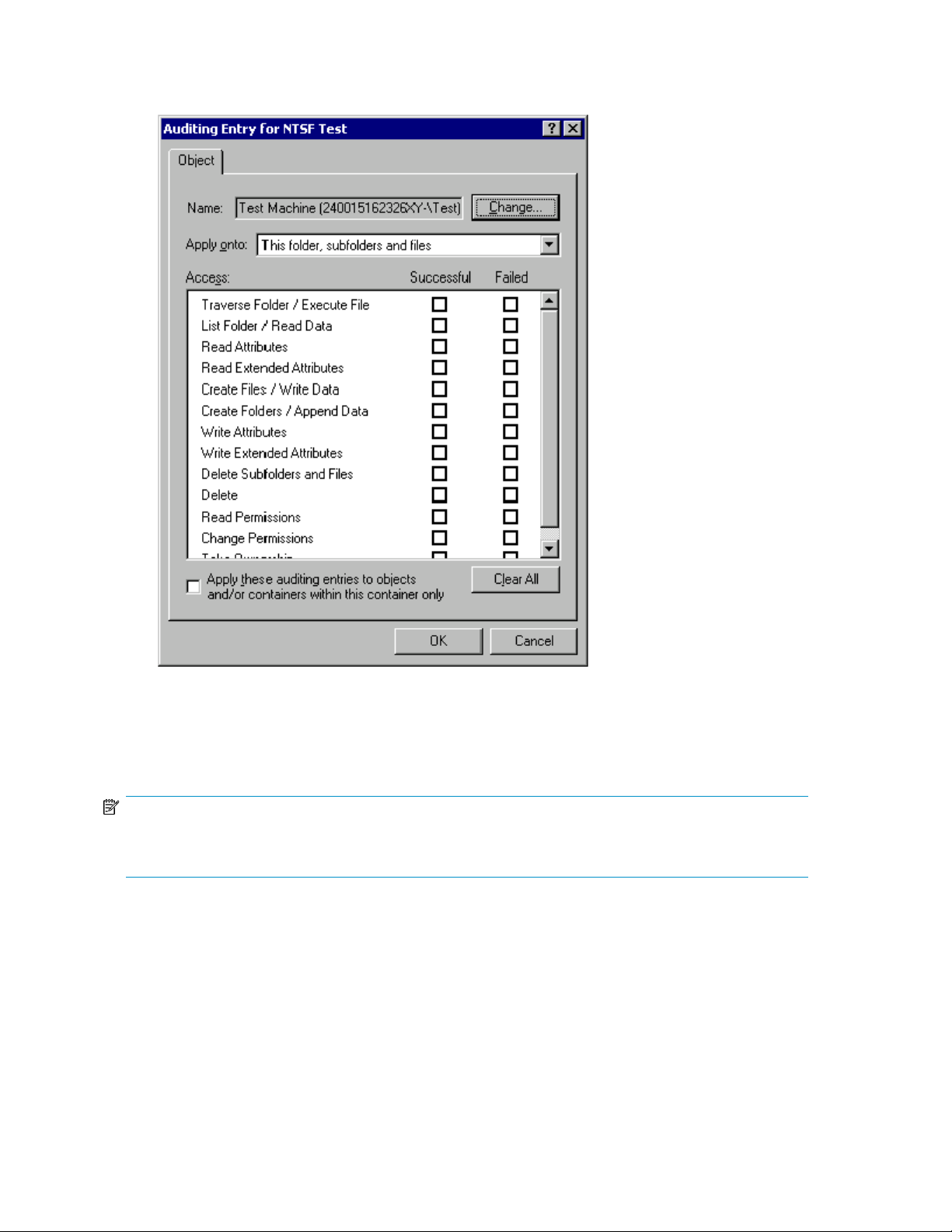
7. Click OK.
The Auditing Entry dialog box is displayed.
Figure 30 Auditing Entry dialog box for folder name NTFS Test
8. Select the desired Successful and Failed audits for the user or group.
9. Click OK.
NOTE:
Auditing must be enabled to configure this information. Use the local Computer Policy Editor to configure
the audit policy on the storage server.
The Owner tab allows taking ownership of files. Typically, administrators use this area to take ownership
of files when the file ACL is incomplete or corrupt. By taking ownership, you gain access to the files,
and then manually apply the appropriate security configurations.
File server management88
Page 89

Figure 31 Advanced Security Settings dialog box, Owner tab
The current owner of the file or folder is listed at the top of the screen. To take ownership:
1. Click the appropriate user or group in the Change owner to list.
2. If it is also necessary to take ownership of subfolders and files, enable the Replace owner on
subcontainers and objects box.
3. Click OK.
Share management
There are several ways to set up and manage shares. Methods include using Windows Explorer, a
command line interface, or the HP Storage Server Management Console.
NOTE:
Select servers can be deployed in a clustered as well as a non-clustered configuration. This chapter discusses
share setup for a non-clustered deployment.
As previously mentioned, the file-sharing security model of the storage server is based on the NTFS
file-level security model. Share security seamlessly integrates with file security. In addition to discussing
share management, this section discusses share security.
Share considerations
Planning the content, size, and distribution of shares on the storage server can improve performance,
manageability, and ease of use.
HP ProLiant Storage Server 89
Page 90

The content of shares should be carefully chosen to avoid two common pitfalls: either having too many
shares of a very specific nature, or of having very few shares of a generic nature. For example, shares
for general use are easier to set up in the beginning, but can cause problems later. Frequently, a
better approach is to create separate shares with a specific purpose or group of users in mind.
However, creating too many shares also has its drawbacks. For example, if it is sufficient to create
a single share for user home directories, create a “homes” share rather than creating separate shares
for each user.
By keeping the number of shares and other resources low, the performance of the storage server is
optimized. For example, instead of sharing out each individual user's home directory as its own share,
share out the top-level directory and let the users map personal drives to their own subdirectory.
Defining Access Control Lists
The Access Control List (ACL) contains the information that dictates which users and groups have
access to a share, as well as the type of access that is permitted. Each share on an NTFS file system
has one ACL with multiple associated user permissions. For example, an ACL can define that User1
has read and write access to a share, User2 has read only access, and User3 has no access to the
share. The ACL also includes group access information that applies to every user in a configured
group. ACLs are also referred to as permissions.
Integrating local file system security into Windows domain environments
ACLs include properties specific to users and groups from a particular workgroup server or domain
environment. In a multidomain environment, user and group permissions from several domains can
apply to files stored on the same device. Users and groups local to the storage server can be given
access permissions to shares managed by the device. The domain name of the storage server supplies
the context in which the user or group is understood. Permission configuration depends on the network
and domain infrastructure where the server resides.
File-sharing protocols (except NFS) supply a user and group context for all connections over the
network. (NFS supplies a machine-based context.) When new files are created by those users or
machines, the appropriate ACLs are applied.
Configuration tools provide the ability to share permissions out to clients. These shared permissions
are propagated into a file system ACL, and when new files are created over the network, the user
creating the file becomes the file owner. In cases where a specific subdirectory of a share has different
permissions from the share itself, the NTFS permissions on the subdirectory apply instead. This method
results in a hierarchical security model where the network protocol permissions and the file permissions
work together to provide appropriate security for shares on the device.
NOTE:
Share permissions and file-level permissions are implemented separately. It is possible for files on a file
system to have different permissions from those applied to a share. When this situation occurs, the file-level
permissions override the share permissions.
Comparing administrative (hidden) and standard shares
CIFS supports both administrative shares and standard shares.
• Administrative shares are shares with a last character of $. Administrative shares are not included
in the list of shares when a client browses for available shares on a CIFS server.
File server management90
Page 91

• Standard shares are shares that do not end in a $ character. Standard shares are listed whenever
a CIFS client browses for available shares on a CIFS server.
The storage server supports both administrative and standard CIFS shares. To create an administrative
share, end the share name with the $ character when setting up the share. Do not type a $ character
at the end of the share name when creating a standard share.
Managing shares
Shares can be managed using the HP Storage Server Management Console. Tasks include:
• Creating a new share
• Deleting a share
• Modifying share properties
• Publishing in DFS
NOTE:
These functions can operate in a cluster on select servers, but should only be used for non-cluster-aware
shares. Use Cluster Administrator to manage shares for a cluster. The page will display cluster share
resources.
CAUTION:
Before deleting a share, warn all users to exit that share and confirm that no one is using that share.
File Server Resource Manager
File Server Resource Manager (FSRM) is a suite of tools that allows administrators to understand,
control, and manage the quantity and type of data stored on their servers. Some of the tasks you can
perform are:
• Quota management
• File screening management
• Storage reports
The HP Storage Server Management Console provides access to FSRM tasks.
For procedures and methods beyond what are described below, see the online help. In addition, see
a Microsoft File Server Resource Manager white paper available at http://download.microsoft.com/
download/7/4/7/7472bf9b-3023-48b7-87be-d2cedc38f15a/WS03R2_Storage_Management.doc
.
Quota management
On the Quota Management node of the File Server Resource Manager snap-in, you can perform the
following tasks:
• Create quotas to limit the space allowed for a volume or folder and generate notifications when
the quota limits are approached or exceeded.
• Generate auto quotas that apply to all existing folders in a volume or folder, as well as to any
new subfolders created in the future.
HP ProLiant Storage Server 91
Page 92

• Define quota templates that can be easily applied to new volumes or folders and that can be used
across an organization.
File screening management
On the File Screening Management node of the File Server Resource Manager snap-in, you can
perform the following tasks:
• Create file screens to control the types of files that users can save and to send notifications when
users attempt to save blocked files.
• Define file screening templates that can be easily applied to new volumes or folders and that can
be used across an organization.
• Create file screening exceptions that extend the flexibility of the file screening rules.
Storage reports
On the Storage Reports node of the File Server Resource Manager snap-in, you can perform the
following tasks:
• Schedule periodic storage reports that allow you to identify trends in disk usage.
• Monitor attempts to save unauthorized files for all users or a selected group of users.
• Generate storage reports instantly.
Other Windows disk and data management tools
When you install certain tools, such as Windows Support Tools or Windows Resource Kit Tools,
information about these tools might appear in Help and Support Center. To see the tools that are
available to you, look in the Help and Support Center under Support Tasks, click Tools, and then click
Tools by Category.
NOTE:
The Windows Support Tools and Windows Resource Kit Tools, including documentation for these tools,
are available in English only. If you install them on a non-English language operating system or on an
operating system with a Multilingual User Interface Pack (MUI), you see English content mixed with
non-English content in Help and Support Center. To see the tools that are available to you, click Start, click
Help and Support Center, and then, under Support Tasks, click Tools.
Additional information and references for file services
Backup
HP recommends that you back up the print server configuration whenever a new printer is added to
the network and the print server configuration is modified. For details on implementing the backup
solution, see the Medium Business Guide for Backup and Recovery. The guide can be viewed or
downloaded from Microsoft at http://www.microsoft.com/technet/itsolutions/smbiz/mits/br/
mit_br.mspx.
File server management92
Page 93

HP StorageWorks Library and Tape Tools
HP StorageWorks Library and Tape Tools (L&TT) provides functionality for firmware downloads,
verification of device operation, maintenance procedures, failure analysis, corrective service actions,
and some utility functions. It also provides seamless integration with HP hardware support by generating
and e-mailing support tickets that deliver a snapshot of the storage system.
For more information, and to download the utility, see the StorageWorks L&TT web site at http://
h18006.www1.hp.com/products/storageworks/ltt.
Antivirus
The server should be secured by installing the appropriate antivirus software. For details on
implementing antivirus, see the Medium Business Guide for Antivirus. The guide can be viewed or
downloaded from Microsoft at http://www.microsoft.com/technet/itsolutions/smbiz/mits/av/
mit_av.mspx.
Security
For guidance on hardening file servers, see the Microsoft Windows Server 2003 Security Guide. The
guide can be viewed or downloaded at http://www.microsoft.com/technet/security/prodtech/
windowsserver2003/w2003hg/sgch00.mspx.
More information
The following web sites provide detailed information for using print services with Windows Server
2003, which also applies to Windows Storage Server 2003.
• Microsoft Storage
http://www.microsoft.com/windowsserversystem/storage/default.mspx
• Microsoft Windows Storage Server 2003
http://www.microsoft.com/windowsserversystem/wss2003/default.mspx
• Performance Tuning Guidelines for Windows Server 2003
http://www.microsoft.com/windowsserver2003/evaluation/performance/tuning.mspx
• Windows SharePoint Services
http://www.microsoft.com/windowsserver2003/technologies/sharepoint/default.mspx
HP ProLiant Storage Server 93
Page 94

File server management94
Page 95

5 Print services
Microsoft Print Management Console
Print Management in the Microsoft Windows Server 2003 R2 operating system is a Microsoft
Management Console (MMC) snap-on that system administrators can use to perform common print
management tasks in a large enterprise. It provides a single interface that administrators can use to
perform printer and print server management tasks efficiently with detailed control. You can use Print
Management from any computer running Windows Server 2003 R2, and you can manage all network
printers on print servers running Windows 2000 Server, Windows Server 2003, or Windows Server
2003 R2.
New or improved HP print server features
HP Web Jetadmin
HP Web Jetadmin (WJA )is a web-based tool for remotely installing, configuring, and managing a
wide variety of HP and non-HP network peripherals using only a web browser. It supports a modular
design whereby plug-ins can be installed to provide additional device, language, and application
functionality. WJA is not preinstalled on the storage server, but can be installed (see
“HP Web Jetadmin installation” on page 96).
HP Install Network Printer Wizard
The inclusion of the HP Install Network Printer Wizard (INPW) utility on the factory image is new.
INPW simplifies the process of installing network printers, including configuration settings on the print
server. INPW identifies HP Jetdirect network print devices and allows the user to select the printer to
install on the print server.
HP Download Manager for Jetdirect Printer Devices
The inclusion of the HP Download Manager (DLM) for Jetdirect Printer Devices on the factory image
is new. DLM is used to upgrade HP Jetdirect print server firmware on HP network printers. The utility
obtains the latest firmware catalog from either from the Internet or from a computer with the download
firmware images already in place. The DLM discovers all or user-selected Jetdirect devices and
upgrades those based on the firmware catalog.
Microsoft Print Migrator utility
The inclusion of the Microsoft Print Migrator utility on the factory image is new. The utility provides
complete printer configuration backup of the print server to a user-specified CAB file. Print Migrator
supports migration of print configuration data between different versions of Windows, and supports
conversion of line printer remote (LPR) ports to the Standard TCP/IP Port Monitor on Windows 2000,
Windows XP, and Windows Server 2003.
HP ProLiant Storage Server 95
Page 96

Network printer drivers
Updated print drivers for HP network printers are preinstalled on the storage server. If a Service
Release DVD has been run on the server, there are updated HP network print drivers in the
C:\hpnas\PRINTERS folder.
Print services management
Print services information to plan, set up, manage, administer, and troubleshoot print servers and print
devices are available online using the Help and Support Center feature. To access the Help and
Support Center, select Start > Help and Support, then Printers and Faxes under Help Contents.
Microsoft Print Management Console
The Print Management Console (PMC) can be started from the HP Storage Server Management
Console, or the PMC snap-in can be added to the Microsoft Management Console.
HP recommends that you use the Microsoft Print Management Step-by-Step Guide on the Documentation
CD for print concepts, use of the PMC, and management of network printers. The guide can also be
downloaded from http://www.microsoft.com/printserver.
When running the PMC on a server that has Windows Firewall enabled, no printers will be displayed
in the printers folder of the PMC. In order for printers to be displayed, you need to open the file and
print sharing ports (TCP 139 and 445, and UDP 137 and 138). If this does not fix the problem, or
if these ports are already open, you may need to turn off the Windows Firewall to display printers.
To open the file and print sharing ports:
1. Click Start, point to Control Panel, and click Windows Firewall.
2. On the Exceptions tab, ensure that the File and Printer Sharing check box is selected and click
OK.
To turn off Windows Firewall:
1. Click Start, point to Control Panel, and click Windows Firewall.
2. Select Off (not recommended) and click OK.
HP Web Jetadmin installation
HP Web Jetadmin is used to manage a fleet of HP and non-HP network printers and other peripherals
using a web browser. Although not preinstalled, the Web Jetadmin software is located in the
C:\hpnas\Components\WebJetadmin folder, and can be installed by running the setup program.
Follow the installation wizard and supply a password for the local “Admin” username account and
a system name.
For more information about Web Jetadmin and Web Jetadmin plug-ins, see http://www.hp.com/
go/webjetadmin. For an article on optimizing performance, go to http://h10010.www1.hp.com/
wwpc/pscmisc/vac/us/product_pdfs/weboptim.pdf.
Web-based printer management and Internet printing
Internet printing is enabled by default on the print server. Internet printing consists of two main
components:
Print services96
Page 97

• Web-based printer management with the ability to administer, connect to, and view printers
through a web browser.
• Internet printing enabling users to connect to a printer using the printer's URL.
A Microsoft white paper discussing the uses of both components can be obtained at http://
www.microsoft.com/windowsserver2003/techinfo/overview/internetprint.mspx.
Planning considerations for print services
Before configuring the print server, the following checklist of items should be followed:
1. Determine the operating system version of the clients that will send jobs to this printer. This
information is used to select the correct client printer drivers for the client and server computers
using the printer. Enabling this role on the print server allows the automatic distribution of these
drivers to the clients. Additionally, the set of client operating systems determines which of these
drivers need to be installed on the server during the print server role installation.
2. At the printer, print a configuration or test page that includes manufacturer, model, language,
and installed options. This information is needed to choose the correct printer driver. The
manufacturer and model are usually enough to uniquely identify the printer and its language.
However, some printers support multiple languages, and the configuration printout usually lists
them. Also, the configuration printout often lists installed options, such as extra memory, paper
trays, envelope feeders, and duplex units.
3. Choose a printer name. Users running Windows-based client computers choose a printer by using
the printer name. The wizard that you will use to configure your print server provides a default
name, consisting of the printer manufacturer and model. The printer name is usually fewer than
31 characters in length.
4. Choose a share name. A user can connect to a shared printer by entering this name, or by
selecting it from a list of share names. The share name is usually fewer than 8 characters for
compatibility with MS-DOS and Windows 3.x clients.
5. (Optional) Choose a location description and a comment. These can help identify the location of
the printer and provide additional information. For example, the location could be “Second floor,
copy room” and the comment could be “Additional toner cartridges are available in the supply
room on floor 1."
6. Enable management features for Active Directory and Workgroup Environments. If the print server
is part of an Active Directory domain rather than Workgroup, the print server enables the following
management features:
• Restrict access to printer-based domain user accounts.
• Publish shared printers to Active Directory to aid in search for the resource.
7. Deploy printers using group policy. Print management can be used with Group Policy to
automatically add printer connections to a server's Printers and Faxes folder. For more information,
see the Microsoft article at http://technet2.microsoft.com/WindowsServer/en/Library/
ab8d75f8-9b35-4e3e-a344-90d7799927231033.mspx.
8. Determine whether printer spooling be enabled. Two or more identical printers that are connected
to one print server can act as a single printer. As a means to load-balance print queues when
you print a document, the print job is sent to the first available printer in the pool. See “Setting
printer properties” in the Windows online help for additional information.
Print queue creation
In addition to Windows Printer and Faxes, Add Printer Wizard, the HP Install Network Printer Wizard
(INPW) utility discovers HP Jetdirect network printers on the local network and allows print queues to
HP ProLiant Storage Server 97
Page 98

be created on the print server. The utility is located on the storage server in the
C:\hpnas\Components\Install Network Printer Wizard folder.
Sustaining print administration tasks
Tasks that need to be performed regularly to support the print services include:
• Monitoring print server performance using the built-in performance monitoring tool in the Windows
Server operating system.
• Supporting printers that include adding, moving, and removing printers as requirements change.
• Installing new printer drivers.
• Recording information about the printer's name, share names, printer features, and the location
where the printers are physically installed. This information should be kept in an easily accessible
place.
For process suggestions for recurring tasks, see the Microsoft Print Service Product Operations Guide
at http://www.microsoft.com/technet/itsolutions/cits/mo/winsrvmg/pspog/pspog3/mspx.
Driver updates
Print drivers
The latest print drivers for many HP network printers are supplied on the Service Release DVD. If
selected as part of the service release installation process, updated print drivers are copied to the
print drivers folder C:\hpnas\PRINTERS on the storage server. Print drivers are also available for
download on the HP Support web site for individual network printers.
User-mode vs. kernel-mode drivers
Drivers can be written in either user mode (also called version 3 drivers) or kernel mode (also called
version 2 drivers). Native drivers on Windows 2000 and later run in user mode. Windows Server
2003 and Windows Storage Server 2003 can run kernel-mode drivers, although this is not
recommended for stability reasons.
Kernel-mode driver installation blocked by default
In Windows Server 2003 and Windows Storage Server 2003, installation of kernel-mode drivers is
blocked by default.
To allow kernal-mode drivers to be installed, perform the following steps:
1. Open Group Policy, click Start > Run, then type gpedit.msc, and press Enter.
2. Under Local Computer Policy, double-click Computer Configuration.
3. Right-click Disallow installation of printers using kernel-mode drivers, and then click Properties.
4. On the Setting tab, click either Not Configured or Disabled, and then click OK.
HP Jetdirect firmware
The HP Download Manager (DLM) utility for Jetdirect printers provides upgrades of HP Jetdirect print
server firmware on HP network printers. The utility is located on the storage server in the
C:\hpnas\Components\Download Manager for Jetdirect folder. A connection to the
Print services98
Page 99

Internet is required, or the utility can be pointed to a local location where the firmware images are
stored. For more information on upgrading HP Jetdirect print server firmware, see http://
h20000.www2.hp.com/bizsupport/TechSupport/Document.jsp?objectID=bpj06917.
Printer server scalability and sizing
A Microsoft technical paper overviews several key factors that influence the capacity of a given print
server configuration. While this paper cannot provide a predictive formula to determine the printing
throughput of a given configuration, it does describe several reference systems and their capacity.
This paper also presents the information necessary to help the system administrator or capacity planner
estimate, and later monitor, their server workload. The current version of this paper is maintained at
http://www.microsoft.com/printserver.
Backup
It is recommended that you back up the print server configuration whenever a new printer is added
to the network and the print server configuration is modified. For details on implementing the backup
solution, see the Medium Business Guide for Backup and Recovery. The guide can be viewed or
downloaded from Microsoft at http://www.microsoft.com/technet/itsolutions/smbiz/mits/br/
mit_br.mspx.
The Print Migrator utility is recommended as a print-specific alternative to backing up print configuration
settings on the print server. The Print Migrator utility is located in the
C:\hpnas\Components\PrintMigrator folder on the storage server.
For more information about the Print Migrator utility, see http://www.microsoft.com/
WindowsServer2003/techinfo/overview/printmigrator3.1.mspx.
Best practices
The following is practical advice for managing print devices:
• Printers and print servers should be published in Active Directory.
• Locate printers in common areas, such as near conference rooms.
• Protect print servers using antivirus software.
• Ensure the print server is included in the backup configuration.
• Use Microsoft Printer Migrator to back up a print server configuration and restore settings on a
new print server. This eliminates the need to manually re-create print queues and printer ports,
install drivers, and change the IP configuration.
• Use Microsoft Printer Migrator to backup new printers configured on the print server.
• Use Microsoft Printer Migrator when migrating to new print servers.
• Perform a full backup of the print server, including the state information, before releasing the
system to the users in the production environment.
• Whenever a new configuration is made or existing configuration is modified, a backup should
be performed.
• To optimize performance, move the print spooler to another disk, separate from the disk supporting
the operating system. To move the print spooler to another disk:
• Start Printer and Faxes.
• On the File menu, click Server Properties, and then click the Advanced tab.
• In the Spool folder window, enter the path and the name of the new default spool folder for
the print server and then click Apply or OK.
HP ProLiant Storage Server 99
Page 100

• Stop and restart the spooler service, or restart the print server.
Troubleshooting
The online help or Help and Support Center feature should be used to troubleshoot general and
common print-related problems. Printing help can be accessed by selecting Start > Help and Support,
then the Printers and Faxes selection under Help Contents.
The same print troubleshooting information can be accessed at http://www.microsoft.com/technet/
prodtechnol/windowsserver2003/library/ServerHelp/
2048a7ba-ec57-429c-95a3-226eea32d126.mspx
Specific print server related problems as well as other system related known issues and workarounds
are addressed in release notes. To view the latest version, visit http://www.hp.com/go/support.
Select See support and troubleshooting information and enter a product name/number. Under self-help
resources, select the manuals (guides, supplements, addendums, etc) link.
Additional references for print services
The following web sites provide detailed information for using print services with Windows Server
2003, which also applies to Windows Storage Server 2003.
• Windows Server 2003 print services home page at http://www.microsoft.com/
windowsserver2003/technologies/print/default.mspx
• Medium Business Solution for Print Services at http://www.microsoft.com/technet/itsolutions/
smbiz/mits/ps/mit_ps.mspx.
Print services100
 Loading...
Loading...