Page 1

9304m
9308m
9315m
9408sl
ProCurve Routing Switches
Software versions 07.8.00a (9300 series)
and 01.0.02 (9408sl)
Security Guide
www.procurve.com
Page 2

Page 3

Security Guide
for
ProCurve 9300/9400 Series Routing
Switches
Software versions 07.8.00a (9300 series)
and 01.0.02 (9408sl)
Page 4

©
Copyright 2000, 2003, 2005 Hewlett-Packard
Development Company, L.P. The information
contained herein is subject to change without
notice.
Publication number
5990-6029
June 2005
Applicable Products
ProCurve 9304M (J4139A)
ProCurve 9308M (J4138A)
ProCurve 9315M (J4874A)
ProCurve 9408sl (J8680A)
Trademark Credits
®
Microsoft
, Windows®, and Windows NT® are US
registered trademarks of Microsoft Corporation.
Disclaimer
The information contained in this document is
subject to change without notice.
HEWLETT-PACKARD COMPANY MAKES NO
WARRANTY OF ANY KIND WITH REGARD TO
THIS MATERIAL, INCLUDING BUT NOT LIMITED
TO, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE. Hewlett-Packard shall
not be liable for errors contained herein or for
incidental or consequential damages in connection
with the furnishing, performance or use of this
material.
The only warranties for HP products and services
are set forth in the express warranty statements
accompanying such products and services. Nothing
herein should be construed as constituting an
additional warranty. HP shall not be liable for
technical or editorial errors or omissions contained
herein.
Hewlett-Packard assumes no responsibility for the
use or reliability of its software on equipment that is
not furnished by Hewlett-Packard.
A copy of the specific warranty terms applicable to
your HP product and replacement parts can be
obtained from your HP Sales and Service Office or
authorized dealer.
Warranty
See the Customer Support/Warranty booklet
included with the product.
A copy of the specific warranty terms applicable to
your Hewlett-Packard products and replacement
parts can be obtained from your HP Sales and
Service Office or authorized dealer.
Safety Considerations
Prior to the installation and use of this product,
review all safety markings and instructions.
Instruction Manual Symbol.
If the product is marked with the above symbol, refer
to the product manual to protect the product from
damage.
WARNING Denotes a hazard that can cause injury.
CAUTION Denotes a hazard that can damage
equipment or data.
Do not proceed beyond a WARNING or CAUTION
notice until you have understood the hazard and
have taken appropriate precautions.
Use of control, adjustments or performance
procedures other than those specified herein may
result in hazardous radiation exposure.
Grounding
This product provides a protective earthing terminal.
There must be an uninterrupted safety earth ground
from the main power source to the product’s input
wiring terminals, power cord or supplied power cord
set. Whenever it is likely that the protection has
been impaired, disconnect the power cord until the
ground has been restored.
If your LAN covers an area served by more than one
power distribution system, be sure their safety
grounds are securely interconnected.
LAN cables may occasionally be subject to
hazardous transient voltages (such as lightning or
disturbances in the electrical utilities power grid).
Handle exposed metal components of the network
with caution.
For more safety information, see the Installation and
Basic Configuration Guide for ProCurve 9300 Series
Routing Switches and the Quick Start Guide for your
HP 9300M Routing Switch product.
Servicing
There are no user-serviceable parts inside the userinstallable modules comprising the product. Any
servicing, adjustment, maintenance or repair must
be performed only by service-trained personnel.
June 2005 ii
Page 5

Contents
Organization of Product Documentation ............................................... ix
HAPTER
C
ETTING STARTED
G
I
NTRODUCTION
S
OFTWARE VERSIONS COVERED
A
UDIENCE
C
ONVENTIONS
T
ERMINOLOGY
S
UPPORT AND WARRANTY INFORMATION
R
ELATED PUBLICATIONS
C
HAPTER
ECURING ACCESS TO MANAGEMENT FUNCTIONS
S
S
ECURING ACCESS METHODS
R
ESTRICTING REMOTE ACCESS TO MANAGEMENT FUNCTIONS
U
SING
R
ESTRICTING REMOTE ACCESS TO THE DEVICE TO SPECIFIC
R
ESTRICTING TELNET AND
S
PECIFYING THE MAXIMUM NUMBER OF LOGIN ATTEMPTS FOR TELNET ACCESS
R
ESTRICTING REMOTE ACCESS TO THE DEVICE TO SPECIFIC
D
ISABLING SPECIFIC ACCESS METHODS
D
ISABLING AN INTERFACE’S ACCESS TO MANAGEMENT FUNCTIONS
S
ETTING PASSWORDS
S
ETTING A TELNET PASSWORD
S
ETTING PASSWORDS FOR MANAGEMENT PRIVILEGE LEVELS
R
ECOVERING FROM A LOST PASSWORD
D
ISPLAYING THE
D
ISABLING PASSWORD ENCRYPTION
1
...................................................................................... 1-1
...........................................................................................................................................1-1
.................................................................................................................1-1
..................................................................................................................................................1-1
............................................................................................................................................1-2
............................................................................................................................................1-2
.....................................................................................................1-2
.............................................................................................................................1-2
2
.....................................................................................................................2-1
.....................................................................2-3
ACL
S TO RESTRICT REMOTE ACCESS
SSH A
CCESS BASED ON A CLIENT’S
..............................................................................................................................2-13
.........................................................................................................2-13
SNMP C
OMMUNITY STRING
...................................................................................................2-16
.......................................................................................2-4
IP A
MAC A
VLAN IDS ...............................................2-9
.............................................................................................2-10
..............................................................2-14
..............................................................................................2-15
......................................................................................2-16
....................................... 2-1
DDRESSES
.....................................................2-12
.........................................2-7
DDRESS
....................................2-8
....................................2-8
June 2005 iii
Page 6

Security Guide for ProCurve 9300/9400 Series Routing Switches
S
PECIFYING A MINIMUM PASSWORD LENGTH
S
ETTING UP LOCAL USER ACCOUNTS
C
ONFIGURING A LOCAL USER ACCOUNT
C
ONFIGURING
E
NABLING THE
I
MPORTING DIGITAL CERTIFICATES AND
G
ENERATING AN
C
ONFIGURING
H
OW
TACACS/TACACS+ A
TACACS/TACACS+ C
I
DENTIFYING THE
S
PECIFYING DIFFERENT SERVERS FOR INDIVIDUAL
S
ETTING OPTIONAL
C
ONFIGURING AUTHENTICATION-METHOD LISTS FOR
C
ONFIGURING
C
ONFIGURING
C
ONFIGURING AN INTERFACE AS THE SOURCE FOR ALL
D
ISPLAYING
C
ONFIGURING
RADIUS A
RADIUS C
RADIUS C
C
ONFIGURING
I
DENTIFYING THE
S
PECIFYING DIFFERENT SERVERS FOR INDIVIDUAL
S
ETTING
C
ONFIGURING AUTHENTICATION-METHOD LISTS FOR
C
ONFIGURING
C
ONFIGURING
C
ONFIGURING AN INTERFACE AS THE SOURCE FOR ALL
D
ISPLAYING
C
ONFIGURING AUTHENTICATION-METHOD LISTS
NCONFIGURATION CONSIDERATIONS FOR AUTHENTICATION-METHOD LISTS
E
XAMPLES OF AUTHENTICATION-METHOD LISTS
SSL S
ECURITY FOR THE WEB MANAGEMENT INTERFACE
SSL S
ERVER ON THE
SSL C
ERTIFICATE
TACACS/TACACS+ S
TACACS+ D
IFFERS FROM
UTHENTICATION
ONFIGURATION CONSIDERATIONS
TACACS/TACACS+ S
TACACS/TACACS+ P
TACACS+ A
TACACS+ A
TACACS/TACACS+ S
RADIUS S
UTHENTICATION
ONFIGURATION CONSIDERATIONS
ONFIGURATION PROCEDURE
HP-S
ECURITY
PECIFIC ATTRIBUTES ON THE
RADIUS S
RADIUS P
RADIUS C
ARAMETERS
RADIUS A
RADIUS A
ONFIGURATION INFORMATION
UTHORIZATION
CCOUNTING
.......................................................................................................2-16
HP D
....................................................................................................2-20
ECURITY
TACACS .........................................................................................2-20
UTHORIZATION
CCOUNTING
TATISTICS AND CONFIGURATION INFORMATION
............................................................................................................2-38
, A
UTHORIZATION, AND ACCOUNTING
ERVER TO THE
........................................................................................................2-44
......................................................................................2-16
.............................................................................................2-17
EVICE
................................................................................2-19
RSA P
RIVATE KEY FILES
.........................................................................................2-20
, A
UTHORIZATION, AND ACCOUNTING
....................................................................2-24
ERVERS
...............................................................................2-25
AAA F
ARAMETERS
UNCTIONS
.....................................................................2-26
TACACS/TACACS+ .........................................2-27
.........................................................................................2-29
..............................................................................................2-32
TACACS/TACACS+ P
......................................................................................2-42
..............................................................................................2-42
HP D
RADIUS S
EVICE
AAA F
ERVER
......................................................................2-43
UNCTIONS
RADIUS ............................................................2-45
.............................................................................................2-47
.................................................................................................2-48
RADIUS P
..........................................................................2-50
........................................................................................2-54
..................................................................................2-56
.....................................................2-19
........................................................2-19
.......................................2-21
...................................................2-25
ACKETS
......................2-33
..............................2-33
..........................................................2-39
....................................................2-42
...................................................2-44
ACKETS
.........................................2-49
.........................................2-55
C
HAPTER
ONFIGURING SECURE SHELL
C
O
VERVIEW
SSH V
C
ONFIGURING
S
ETTING THE HOST NAME AND DOMAIN NAME
G
ENERATING A HOST
C
ONFIGURING
S
ETTING OPTIONAL PARAMETERS
3
..................................................................................................................................................3-1
ERSION
2 S
UPPORT
...................................................................................................................3-1
SSH ....................................................................................................................................3-2
RSA KEY P
RSA C
HALLENGE-RESPONSE AUTHENTICATION
..................................................................... 3-1
......................................................................................3-3
AIR
...................................................................................................3-3
..............................................................3-4
.........................................................................................................3-6
June 2005 iv
Page 7

D
ISPLAYING
S
AMPLE
U
SING SECURE COPY
C
HAPTER
ONFIGURING
C
O
VERVIEW
IETF RFC S
H
OW
D
C
C
M
A
802.1X P
C
ONFIGURING
C
S
E
S
C
R
S
S
S
S
S
S
I
A
D
C
D
ISPLAYING
D
D
C
D
D
D
S
AMPLE
P
H
SSH C
SSH C
ONNECTION INFORMATION
ONFIGURATION
.................................................................................................................3-11
.............................................................................................3-9
...............................................................................................................................3-11
4
802.1X P
..................................................................................................................................................4-1
UPPORT
802.1X P
EVICE ROLES IN AN
OMMUNICATION BETWEEN THE DEVICES
ONTROLLED AND UNCONTROLLED PORTS
ESSAGE EXCHANGE DURING AUTHENTICATION
UTHENTICATING MULTIPLE HOSTS CONNECTED TO THE SAME PORT
ORT SECURITY WORKS
ORT SECURITY AND SFLOW
802.1X P
ONFIGURING AN AUTHENTICATION METHOD LIST FOR
ETTING
RADIUS P
NABLING
ETTING THE PORT CONTROL
ONFIGURING PERIODIC RE-AUTHENTICATION
E-AUTHENTICATING A PORT MANUALLY
ETTING THE QUIET PERIOD
ETTING THE INTERVAL FOR RETRANSMISSION OF
PECIFYING THE SECURITY HOLD TIME
PECIFYING THE NUMBER OF
PECIFYING A TIMEOUT FOR RETRANSMISSION OF MESSAGES TO THE AUTHENTICATION SERVER
PECIFYING A TIMEOUT FOR RETRANSMISSION OF
NITIALIZING
LLOWING ACCESS TO MULTIPLE HOSTS
EFINING
ONFIGURING DYNAMIC
802.1X P
802.1X
MAC F
802.1X I
ISPLAYING
ISPLAYING
LEARING
ISPLAYING DYNAMICALLY ASSIGNED
ISPLAYING INFORMATION ABOUT DYNAMICALLY APPLIED
ISPLAYING
802.1X C
802.1X S
802.1X S
802.1X M
802.1X C
OINT-TO-POINT CONFIGURATION
UB CONFIGURATION
............................................................................................................................4-1
802.1X C
ORT SECURITY
ARAMETERS
ORT SECURITY
ON A PORT
ILTERS FOR
NFORMATION
ONFIGURATION INFORMATION
TATISTICS
TATISTICS
ULTIPLE-HOST AUTHENTICATION INFORMATION
ONFIGURATIONS
(R
ORT SECURITY
....................................................... 4-1
........................................................................................................4-1
ONFIGURATION
......................................................................................4-1
.............................................................................................4-2
...........................................................................................4-3
...................................................................................4-4
....................................................4-6
...................................................................................................4-9
.......................................................................................................4-9
802.1X ...........................................................4-10
........................................................................................................4-10
....................................................................................................4-10
............................................................................................................4-11
....................................................................................4-12
............................................................................................4-12
...............................................................................................................4-12
EAP-R
EQUEST/IDENTITY FRAMES
...............................................................................................4-13
EAP-R
EQUEST/IDENTITY FRAME RETRANSMISSIONS
EAP-R
EQUEST FRAMES TO THE CLIENT
..............................4-13
.........................................................................................................4-14
............................................................................................4-14
EAP F
VLAN A
RAMES
........................................................................................4-16
SSIGNMENT FOR
802.1X P
ORTS
........................................................4-16
............................................................................................................4-18
............................................................................4-18
.........................................................................................................4-21
...........................................................................................................4-22
VLAN I
NFORMATION
.................................................................4-22
MAC F
ILTERS AND
(R
ELEASE
IP ACLS .......................4-23
07.8.00
...........................................................................................................4-28
.......................................................................................................4-28
ELEASES PRIOR TO
07.8.00) .........................................................................4-29
Contents
...........................4-12
.........4-13
..................4-14
AND LATER
) ..4-24
C
HAPTER
SING THE
U
June 2005 v
5
MAC P
ORT SECURITY FEATURE
................................................ 5-1
Page 8

Security Guide for ProCurve 9300/9400 Series Routing Switches
O
VERVIEW
C
ONFIGURING THE
D
ISPLAYING PORT SECURITY INFORMATION
C
HAPTER
..................................................................................................................................................5-1
L
OCAL AND GLOBAL RESOURCES
MAC P
E
NABLING THE
S
ETTING THE MAXIMUM NUMBER OF SECURE
S
ETTING THE PORT SECURITY AGE TIMER
S
PECIFYING SECURE
A
UTOSAVING SECURE
S
PECIFYING THE ACTION TAKEN WHEN A SECURITY VIOLATION OCCURS
MAC P
ORT SECURITY FEATURE
ORT SECURITY FEATURE
MAC A
MAC A
.........................................................................................................5-1
....................................................................................5-2
....................................................................................5-2
MAC A
DDRESSES FOR AN INTERFACE
............................................................................................5-2
DDRESSES
DDRESSES TO THE STARTUP-CONFIG FILE
................................................................................................5-3
.................................................................................................5-4
D
ISPLAYING AUTOSAVED
D
ISPLAYING PORT SECURITY SETTINGS
D
ISPLAYING THE SECURE
D
ISPLAYING PORT SECURITY STATISTICS
MAC A
MAC A
DDRESSES
..........................................................................................5-4
................................................................................................5-4
DDRESSES ON THE DEVICE
..............................................................................................5-5
6
..............................5-2
...............................................5-3
...............................................5-3
.................................................................5-5
ONFIGURING MULTI-DEVICE PORT AUTHENTICATION
C
O
VERVIEWN
H
OW MULTI-DEVICE PORT AUTHENTICATION WORKS
RADIUS A
A
D
S
C
ONFIGURING MULTI-DEVICE PORT AUTHENTICATION
E
S
S
D
C
S
S
E
C
D
S
D
ISPLAYING MULTI-DEVICE PORT AUTHENTICATION INFORMATION
D
D
D
...............................................................................................................................................6-1
...................................................................................6-1
UTHENTICATION
UTHENTICATION-FAILURE ACTIONS
YNAMIC
UPPORT FOR AUTHENTICATING MULTIPLE
VLAN A
SSIGNMENT
...................................................................................................................6-1
.....................................................................................................6-2
..............................................................................................................6-2
MAC A
DDRESSES ON AN INTERFACE
..................................................................................6-2
NABLING MULTI-DEVICE PORT AUTHENTICATION
PECIFYING THE FORMAT OF THE
PECIFYING THE AUTHENTICATION-FAILURE ACTION
EFINING
ONFIGURING DYNAMIC
PECIFYING TO WHICH
AVING DYNAMIC
NABLING DENIAL OF SERVICE ATTACK PROTECTION
LEARING AUTHENTICATED
ISABLING AGING FOR AUTHENTICATED
PECIFYING THE AGING TIME FOR BLOCKED
E
XPIRES
MAC A
DDRESS FILTERS
VLAN A
VLAN A P
........................................................................................................................................6-5
VLAN A
MAC A
DDRESSES SENT TO THE
.......................................................................................................6-4
SSIGNMENT
ORT IS MOVED AFTER ITS
SSIGNMENTS TO THE STARTUP-CONFIG FILE
MAC A
DDRESSES
MAC A
.................................................................................6-3
RADIUS S
..............................................................................6-3
........................................................................................6-4
RADIUS-S
............................................................................6-6
......................................................................................6-7
DDRESSES
MAC A
....................................................................6-7
DDRESSES
.............................................................6-8
................................................................6-8
ISPLAYING AUTHENTICATED
ISPLAYING MULTI-DEVICE PORT AUTHENTICATION CONFIGURATION INFORMATION
ISPLAYING MULTI-DEVICE PORT AUTHENTICATION INFORMATION FOR A SPECIFIC
MAC A
DDRESS INFORMATION
..................................................................6-8
6-10
D
ISPLAYING MULTI-DEVICE PORT AUTHENTICATION SETTINGS AND AUTHENTICATED
D
ISPLAYING THE AUTHENTICATED
D
ISPLAYING THE NON-AUTHENTICATED
MAC A
MAC A
DDRESSES
DDRESSES
...........................................................................6-13
...................................................................6-13
.................................. 6-1
...................................6-2
ERVER
............................6-3
PECIFIED
.................................................6-6
VLAN A
SSIGNMENT
...............................6-9
MAC A
DDRESS OR PORT
MAC A
DDRESSES
6-11
June 2005 vi
Page 9

C
HAPTER
Contents
7
ROTECTING AGAINST DENIAL OF SERVICE ATTACKS
P
P
ROTECTING AGAINST SMURF ATTACKS
A
VOIDING BEING AN INTERMEDIARY IN A SMURF ATTACK
A
VOIDING BEING A VICTIM IN A SMURF ATTACK
P
ROTECTING AGAINST
TCP S
ECURITY ENHANCEMENT IN RELEASE
D
ISPLAYING STATISTICS ABOUT PACKETS DROPPED BECAUSE OF DO
C
HAPTER
ONFIGURING
C
O
VERVIEW
H
OW THE
C
ONDITIONS
A
CTIONS
C
ONFIGURING
E
NABLING
D
EFAULT
S
PECIFYING ACTIONS
D
ISPLAYING
D
ISPLAYING CONDITION INFORMATION
D
ISPLAYING ACTION INFORMATION
8
..................................................................................................................................................8-1
CPU P
..............................................................................................................................................8-2
CPU P
CPU P
CPU P
CPU P
TCP SYN A
CPU P
ROTECTION FEATURE WORKS
ROTECTION
.........................................................................................................................................8-1
ROTECTION
ROTECTION
ROTECTION CONDITIONS AND ACTIONS
...........................................................................................................................8-4
ROTECTION INFORMATION
......................................................................................................7-1
.......................................................................7-2
.....................................................................................7-2
TTACKS
.................................................................................................7-3
07.6.06 .............................................................................7-4
................................................................ 8-1
....................................................................................8-1
................................................................................................................8-2
...............................................................................................................8-2
........................................................................8-3
..............................................................................................8-4
..................................................................................................8-4
........................................................................................................8-5
.................................. 7-1
S A
TTACKS
.........................................7-5
C
HAPTER
ONFIGURING UNICAST
C
O
VERVIEW
C
ONFIGURING UNICAST
S
PECIFYING A PREFIX LIST FOR UNICAST
D
ISPLAYING UNICAST
C
LEARING UNICAST
C
HAPTER
ECURING
S
E
STABLISHING
E
NCRYPTION OF
A
DDING AN
D
ISPLAYING THE
U
SING THE USER-BASED SECURITY MODEL
C
ONFIGURING YOUR
C
ONFIGURING
D
EFINING THE ENGINE
D
EFINING AN
D
EFINING AN
D
ISPLAYING THE ENGINE
9
RPF....................................................................... 9-1
..................................................................................................................................................9-1
RPF ......................................................................................................................9-3
RPF I
NFORMATION
RPF CAM E
NTRIES
10
SNMP A
SNMP C
SNMP C
SNMP C
SNMP C
SNMP V
SNMP G
SNMP U
CCESS
OMMUNITY STRINGS
OMMUNITY STRINGS
OMMUNITY STRING
OMMUNITY STRINGS
NMS .................................................................................................................10-6
ERSION
ID ...................................................................................................................10-6
ROUP
SER ACCOUNT
3 ON HP D
..............................................................................................................10-7
ID ...............................................................................................................10-9
RPF ......................................................................................9-4
....................................................................................................9-4
...............................................................................................9-5
....................................................................... 10-1
.............................................................................................10-1
...................................................................................10-2
.............................................................................................10-2
....................................................................................10-5
..............................................................................................10-5
EVICES
..............................................................................10-6
.................................................................................................10-8
June 2005 vii
Page 10

Security Guide for ProCurve 9300/9400 Series Routing Switches
D
ISPLAYING
D
ISPLAYING USER INFORMATION
I
NTERPRETING VARBINDS IN REPORT PACKETS
D
EFINING
I
NDEX
..................................................................................................Index-1
SNMP G
SNMP V
ROUPS
..............................................................................................................10-9
......................................................................................................10-10
.................................................................................10-10
IEWS
.........................................................................................................................10-10
viii June 2005
Page 11
Organization of Product Documentation
NOTE: HP periodically updates the ProCurve 9300/9400 Series Routing Switch documentation. For the latest
version of any of these publications, visit the ProCurve website at:
http://www.procurve.com
Click on Technical Support, then Product manuals.
NOTE: All manuals listed below are available on the ProCurve website, and also on the Documentation CD
shipped with your HP product.
Installation and Basic Configuration Guide for ProCurve 9300 Series Routing Switches
This is an electronic (PDF) guide containing product safety and EMC regulatory statements as well as installation
and basic configuration information, and software and hardware specifications.
Topics Specific to the 9300 Series Routing Switches
• Product mounting instructions
• Module installation
• Basic access and connectivity configuration (passwords, IP addresses)
• Redundant management module commands and file systems
• Cooling system commands and information
• Basic software feature configuration (SNMP, clock, mirror/monitor ports)
• Configuring for these features:
• Uni-Directional Link Detection (UDLD)
• Metro Ring Protocol (MRP)
• Virtual Switch Redundancy Protocol (VSRP)
• GVRP (dynamic VLANs)
• Software update instructions
• Hardware specs
• Software specs (e.g. RFC support, IEEE compliance)
June 2005 ix
Page 12

Security Guide for ProCurve 9300/9400 Series Routing Switches
Information on Configuring Features for 9300 Series and 9408sl Routing Switches
• Port settings
• VLANS
• Trunks
• Spanning Tree Protocol
• Syslog
Quick Start Guide for ProCurve 9300 Series Routing Switches
This is a printed guide you can use as an easy reference to the installation and product safety information needed
for out-of-box setup, plus the general product safety and EMC regulatory statements of which you should be aware
when installing and using a Routing Switch.
Installation and Basic Configuration Guide for the ProCurve 9408sl Routing Switch
This is a printed guide that describes the ProCurve 9408sl and provides procedures for installing modules and AC
power supplies into the ProCurve 9408sl, cabling the 10-Gigabit Ethernet interface ports, and performing a basic
configuration of the software.
Topics Specific to the 9408sl Routing Switch
• Product overview and architecture
• Product mounting instructions
• Module installation
• Basic access and connectivity configuration (passwords, IP addresses)
• Management Module redundancy and file systems
• Interacting with the cooling system, switch fabric module, and interface modules
• Basic software feature configuration (SNMP, clock, mirror/monitor ports)
• Hardware maintenance instructions
• Software update instructions
• Hardware specs
• Safety and regulatory statements
• Software specs (e.g. RFC support, IEEE compliance)
Advanced Configuration and Management Guide for ProCurve 9300/9400 Series Routing Switches
This is an electronic (PDF) guide that contains advanced configuration information for routing protocols and
Quality of Service (QoS). In addition, appendixes in this guide contain reference information for network
monitoring, policies, and filters.
Information on Configuring Features
• Quality of Service (QoS)
• Access Control Lists (ACLs)
• Rate limiting
• IPv4 routing
• RIP
• IP Multicast
• OSPF
• BGP4
• Multi-protocol BGP (MBGP)
• Network Address Translation (NAT)
June 2005 x
Page 13

• VRRP and VRRPE (VRRP extended)
• IPX routing
• AppleTalk routing
• Route health injection
• RMON, NetFlow, and sFlow monitoring
IPv6 Configuration Guide for the ProCurve 9408sl Routing Switch
This is an electronic (PDF) guide that describes the IPv6 software and features. It provides conceptual information
about IPv6 addressing and explains how to configure basic IPv6 connectivity and the IPv6 routing protocols. The
software procedures explain how to perform tasks using the CLI.
Command Line Interface Reference for ProCurve 9300/9400 Series Routing Switches
This is an electronic (PDF) guide that provides a dictionary of CLI commands and syntax.
Security Guide for ProCurve 9300/9400 Series Routing Switches
This is an electronic (PDF) guide that provides procedures for securing management access to HP devices and for
protecting against Denial of Service (DoS) attacks.
Diagnostic Guide for ProCurve 9300/9400 Series Routing Switches
This is an electronic (PDF) guide that describes the diagnostic commands available on HP devices. The software
procedures show how to perform tasks using the Command Line Interface (CLI).
Removing and Installing XENPAK Optics
This is a printed instruction sheet describing the correct preparation and procedure for removing and installing
XENPAK optics on the 10-Gigabit Ethernet modules.
Read Me First
The "Read Me First" document, printed on bright yellow paper, is included with every chassis and module. It
contains an overview of software release information, a brief "Getting Started" section, an included parts list,
troubleshooting tips, operating notes, and other information that is not included elsewhere in the product
documentation. It also includes:
• software update instructions
• operating notes for this release
Release Notes
These documents describe features and other information that becomes available between revisions of the main
product guides. New releases of such documents will be available on HP's ProCurve website. To register to
receive email notice from HP when a new software release is available, visit:
http://www.procurve.com
In the "My Procurve" box on the right, click on "Register".
Product Documentation CD: A Tool for Finding Specific Information and/or Printing Selected Pages
This CD is shipped with your ProCurve Routing Switch product and provides the following:
• A README file describing the CD contents and use, including easy instructions on how to search the book
files for specific information
• A Contents file to give you easy access to the documentation on the CD
• Separate PDF files of the individual chapters and appendixes in the major guides, enabling you to easily print
individual chapters, appendixes, and selected pages
• Single PDF files for each of the major guides, enabling you to use the Adobe® Acrobat® Reader to easily
search for detailed information
• Additional files. These may include such items as additional Read Me files and release notes.
June 2005 xi
Page 14

Security Guide for ProCurve 9300/9400 Series Routing Switches
June 2005 xii
Page 15

Chapter 1
Getting Started
Introduction
This guide describes how to secure access to management functions on the following ProCurve Routing
Switches:
• ProCurve Routing Switch 9315M
• ProCurve Routing Switch 9308M
• ProCurve Routing Switch 9304M
• ProCurve Routing Switch 9408sl
In addition, this guide explains how to secure SNMP access to these ProCurve Routing Switches, as well as how
to protect them from Denial of Service (DoS) attacks.
Software Versions Covered
This edition describes software release 07.8.00a for the following ProCurve products:
• 9304M
• 9308M
• 9315M
This edition also describes software release 01.0.02 for the ProCurve 9408sl Routing Switch.
NOTE: The software release for the 9408sl is 02.1.00. See the Release Notes for the most current information,
which supercedes the information in this guide.
Audience
This manual is designed for system administrators with a working knowledge of Layer 2 and Layer 3 switching and
routing.
If you are using a ProCurve Routing Switch, you should be familiar with the following protocols if applicable to your
network—IP, RIP, OSPF, BGP4, IGMP, PIM, DVMRP, IPX, AppleTalk, and VRRP.
1 - 1
Page 16
Security Guide for ProCurve 9300/9400 Series Routing Switches
Conventions
This guide uses the following typographical conventions:
Italic highlights the title of another publication and occasionally emphasizes a word or phrase.
Bold highlights a CLI command.
Bold Italic highlights a term that is being defined.
Underline
Capitals highlights field names and buttons that appear in the Web management interface.
NOTE: A note emphasizes an important fact or calls your attention to a dependency.
WAR NING: A warning calls your attention to a possible hazard that can cause injury or death.
CAUTION: A caution calls your attention to either a possible hazard that can damage equipment or an action
that can produce an operating problem or other unwanted results.
highlights a link on the Web management interface.
Terminology
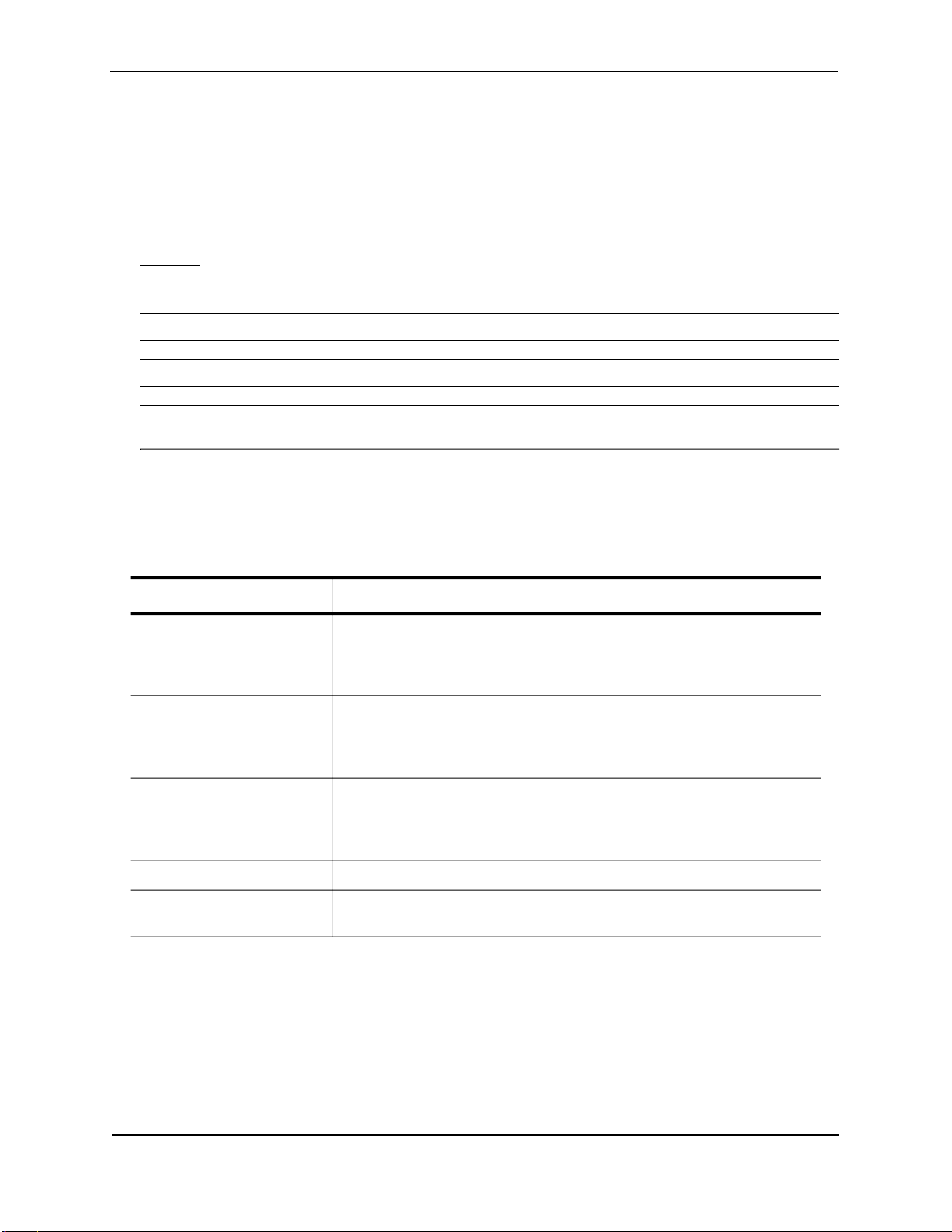
The following table defines basic product terms used in this guide.
Term
chassis
or
Chassis device
EP
and
Standard
Routing Switch
or
router
Switch
ProCurveRS#
Definition
A Routing Switch that accepts optional modules or power supplies. The
ProCurve 9304M, 9308M, 9315M, and 9408sl Routing Switches are Chassis
devices.
9300 Series Chassis devices can be EP or Standard devices, depending on
whether the management module is an EP or Standard module.
A Layer 2 and Layer 3 device that switches and routes network traffic. The
term router is sometimes used in this document in descriptions of a Routing
Switch’s Layer 3 routing protocol features.
A Layer 2 device that switches network traffic.
An example Command Line Interface (CLI) prompt. Actual prompts show
the product number for the device, such as HP9304#.
Support and Warranty Information
Refer to Support is as Close as the World Wide Web, which was shipped with your ProCurve Routing Switch.
Related Publications
Refer to the “Organization of Product Documentation” on page vii for a list of publications for your HP Routing
Switch.
1 - 2
Page 17
Chapter 2
Securing Access to Management Functions
This chapter explains how to secure access to management functions on an HP device.The ProCurve Routing
Switches provide the following methods for securing access to the device. You can use one or more of these
methods:
• “Securing Access Methods” on page 2-1 lists the management access methods available on an HP device
and the ways you can secure each one
• “Restricting Remote Access to Management Functions” on page 2-3 explains how to restrict access to
management functions from remote sources, including Telnet, the Web management interface, and SNMP
• “Setting Passwords” on page 2-13 explains how to set passwords for Telnet access and management
privilege levels
• “Setting Up Local User Accounts” on page 2-16 explains how to define user accounts to regulate who can
access management functions
• “Configuring TACACS/TACACS+ Security” on page 2-20 explains how to configure SNMP read-only and
read-write community strings on an HP device
• “Configuring TACACS/TACACS+ Security” on page 2-20 explains how to configure TACACS/TACACS+
authentication, authorization, and accounting
• “Configuring RADIUS Security” on page 2-38 explains how to configure RADIUS authentication,
authorization, and accounting
• “Configuring Authentication-Method Lists” on page 2-54 explains how to set the order that authentication
methods are consulted when more than one is used with an access method
Securing Access Methods
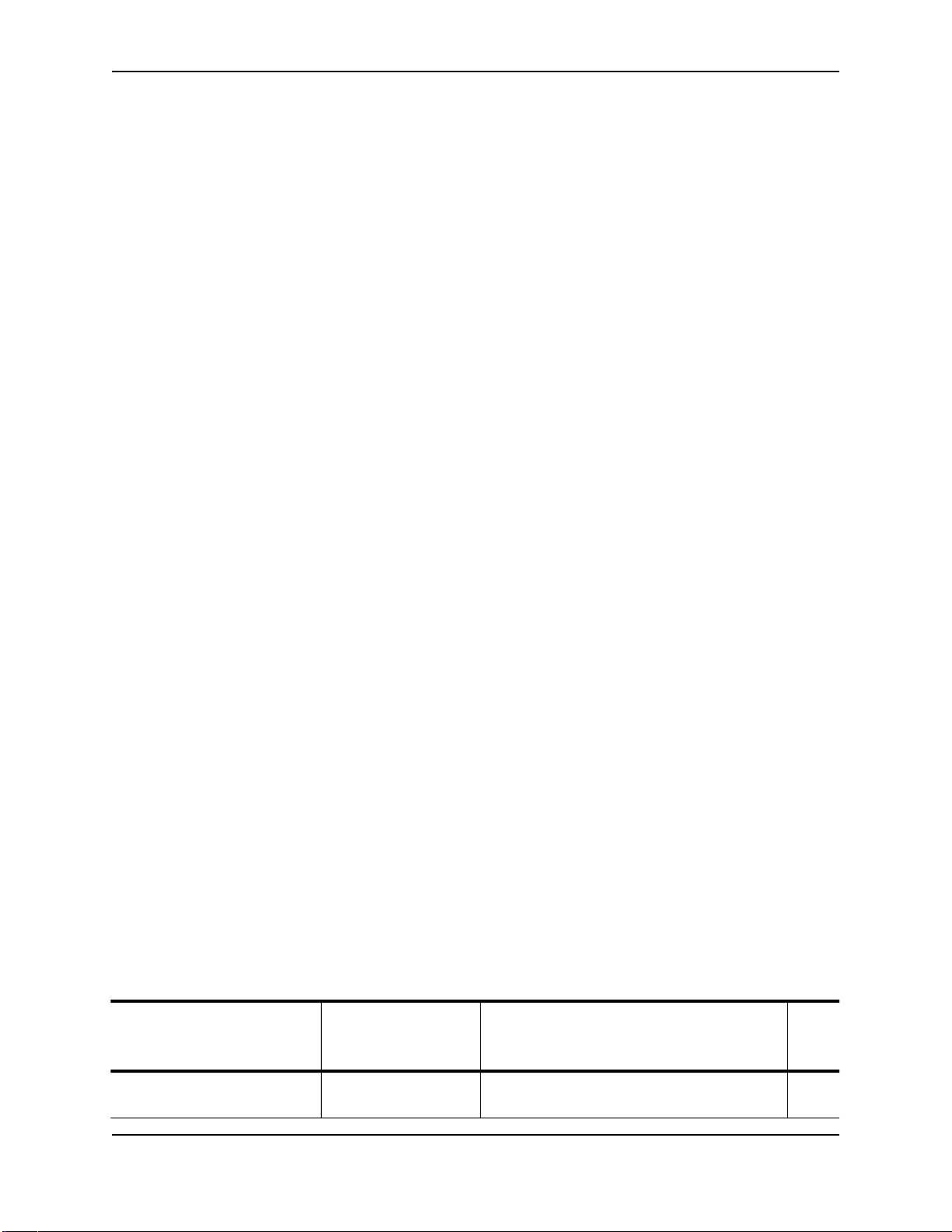
The following table lists the management access methods available on an HP device, how they are secured by
default, and the ways in which they can be secured.
Table 2.1: Ways to secure management access to HP devices
Access method How the access Ways to secure the access method See
method is secured page
by default
Serial access to the CLI Not secured Establish passwords for management privilege
levels
June 2005 2 - 1
2-14
Page 18
Security Guide for ProCurve 9300/9400 Series Routing Switches
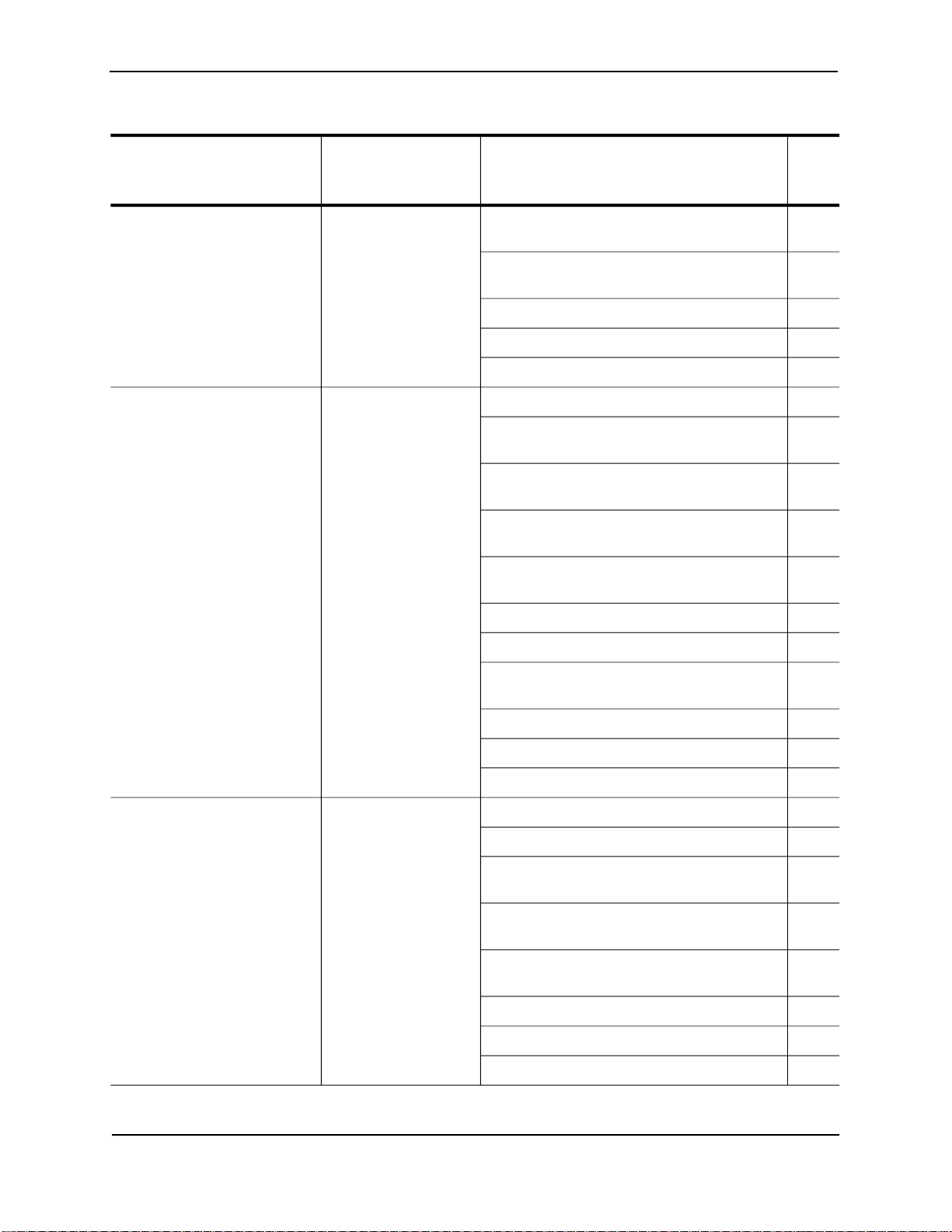
Table 2.1: Ways to secure management access to HP devices (Continued)
Access method How the access Ways to secure the access method See
method is secured page
by default
Access to the Privileged EXEC Not secured Establish a password for Telnet access to the 2-13
and CONFIG levels of the CLI CLI
Establish passwords for management privilege 2-14
levels
Set up local user accounts 2-16
Configure TACACS/TACACS+ security 2-20
Configure RADIUS security 2-38
Telnet access Not secured Regulate Telnet access using ACLs 2-4
Allow Telnet access only from specific IP 2-7
addresses
Restrict Telnet access based on a client’s MAC 2-8
address
Allow Telnet access only to clients connected 2-9
to a specific VLAN
Specify the maximum number of login 2-8
attempts for Telnet access
Disable Telnet access 2-10
Establish a password for Telnet access 2-13
Establish passwords for privilege levels of the
CLI
Set up local user accounts 2-16
Configure TACACS/TACACS+ security 2-20
Configure RADIUS security 2-38
Secure Shell (SSH) access Not configured Configure SSH 3-1
Regulate SSH access using ACLs 2-5
Allow SSH access only from specific IP 2-7
addresses
Restrict SSH access based on a client’s MAC 2-8
address
Establish passwords for privilege levels of the
CLI
2-14
2-14
Set up local user accounts 2-16
Configure TACACS/TACACS+ security 2-20
Configure RADIUS security 2-38
2 - 2 June 2005
Page 19
Securing Access to Management Functions
Table 2.1: Ways to secure management access to HP devices (Continued)
Access method How the access Ways to secure the access method See
method is secured page
by default
Web management access SNMP read or read- Regulate Web management access using 2-5
write community ACLs
strings
Allow Web management access only from 2-8
specific IP addresses
Allow Web management access only to clients 2-9
connected to a specific VLAN
Disable Web management access 2-10
Configure SSL security for the Web 2-19
management interface
Set up local user accounts 2-16
Establish SNMP read or read-write community 10-1
strings for SNMP versions 1 and 2
Establishing user groups for SNMP version 3 10-7
Configure TACACS/TACACS+ security 2-20
Configure RADIUS security 2-38
SNMP access SNMP read or read-
write community
strings and the
password to the Super
User privilege level
Note: SNMP read or
read-write community
strings are always
required for SNMP
access to the device.
TFTP access Not secured Allow TFTP access only to clients connected
Regulate SNMP access using ACLs 2-5
Allow SNMP access only from specific IP
addresses
Disable SNMP access 2-11
Allow SNMP access only to clients connected
to a specific VLAN
Establish passwords to management levels of
the CLI
Set up local user accounts 2-16
Establish SNMP read or read-write community 2-20
strings
to a specific VLAN
Restricting Remote Access to Management Functions
You can restrict access to management functions from remote sources, including Telnet, the Web management
interface, and SNMP. The following methods for restricting remote access are supported:
2-8
2-9
2-14
2-9
• Using ACLs to restrict Telnet, Web management interface, or SNMP access
• Allowing remote access only from specific IP addresses
• Allowing remote access only to clients connected to a specific VLAN
• Specifically disabling Telnet, Web management interface, or SNMP access to the device
June 2005 2 - 3
Page 20
Security Guide for ProCurve 9300/9400 Series Routing Switches
The following sections describe how to restrict remote access to an HP device using these methods.
Using ACLs to Restrict Remote Access
You can use standard ACLs to control the following access methods to management functions on an HP device:
• Telnet access
• SSH access
• Web management access
• SNMP access
To configure access control for these management access methods:
1. Configure an ACL with the IP addresses you want to allow to access the device
2. Configure a Telnet access group, SSH access group, web access group, and SNMP community strings. Each
of these configuration items accepts an ACL as a parameter. The ACL contains entries that identify the IP
addresses that can use the access method.
The following sections present examples of how to secure management access using ACLs. See the “IP Access
Control Lists (ACLs)” chapter in the Advanced Configuration and Management Guide for ProCurve 9300/9400
Series Routing Switches for more information on configuring ACLs.
NOTE: In releases prior to 07.7.00, ACL filtering for remote management access was done in software (that is,
by the CPU). Starting with release 07.7.00, you can configure EP devices to perform the filtering in hardware.
See
“Hardware Filtering for Remote Management Access ( EP Devices Running Release 07.7.00 and Higher)” on
page 2-6.
Using an ACL to Restrict Telnet Access
To configure an ACL that restricts Telnet access to the device, enter commands such as the following:
ProCurveRS(config)# access-list 10 deny host 209.157.22.32 log
ProCurveRS(config)# access-list 10 deny 209.157.23.0 0.0.0.255 log
ProCurveRS(config)# access-list 10 deny 209.157.24.0 0.0.0.255 log
ProCurveRS(config)# access-list 10 deny 209.157.25.0/24 log
ProCurveRS(config)# access-list 10 permit any
ProCurveRS(config)# telnet access-group 10
ProCurveRS(config)# write memory
Syntax: telnet access-group <num>
The <num> parameter specifies the number of a standard ACL and must be from 1 – 99.
The commands above configure ACL 10, then apply the ACL as the access list for Telnet access. The device
allows Telnet access to all IP addresses except those listed in ACL 10.
To configure a more restrictive ACL, create permit entries and omit the permit any entry at the end of the ACL.
For example:
ProCurveRS(config)# access-list 10 permit host 209.157.22.32
ProCurveRS(config)# access-list 10 permit 209.157.23.0 0.0.0.255
ProCurveRS(config)# access-list 10 permit 209.157.24.0 0.0.0.255
ProCurveRS(config)# access-list 10 permit 209.157.25.0/24
ProCurveRS(config)# telnet access-group 10
ProCurveRS(config)# write memory
The ACL in this example permits Telnet access only to the IP addresses in the permit entries and denies Telnet
access from all other IP addresses.
2 - 4 June 2005
Page 21

Securing Access to Management Functions
Using an ACL to Restrict SSH Access
To configure an ACL that restricts SSH access to the device, enter commands such as the following:
ProCurveRS(config)# access-list 12 deny host 209.157.22.98 log
ProCurveRS(config)# access-list 12 deny 209.157.23.0 0.0.0.255 log
ProCurveRS(config)# access-list 12 deny 209.157.24.0/24 log
ProCurveRS(config)# access-list 12 permit any
ProCurveRS(config)# ssh access-group 12
ProCurveRS(config)# write memory
Syntax: ssh access-group <num>
The <num> parameter specifies the number of a standard ACL and must be from 1 – 99.
These commands configure ACL 12, then apply the ACL as the access list for SSH access. The device denies
SSH access from the IP addresses listed in ACL 12 and permits SSH access from all other IP addresses. Without
the last ACL entry for permitting all packets, this ACL would deny SSH access from all IP addresses.
NOTE: In this example, the command ssh access-group 10 could have been used to apply the ACL configured
in the example for Telnet access. You can use the same ACL multiple times.
Using an ACL to Restrict Web Management Access
To configure an ACL that restricts Web management access to the device, enter commands such as the following:
ProCurveRS(config)# access-list 12 deny host 209.157.22.98 log
ProCurveRS(config)# access-list 12 deny 209.157.23.0 0.0.0.255 log
ProCurveRS(config)# access-list 12 deny 209.157.24.0/24 log
ProCurveRS(config)# access-list 12 permit any
ProCurveRS(config)# web access-group 12
ProCurveRS(config)# write memory
Syntax: web access-group <num>
The <num> parameter specifies the number of a standard ACL and must be from 1 – 99.
These commands configure ACL 12, then apply the ACL as the access list for Web management access. The
device denies Web management access from the IP addresses listed in ACL 12 and permits Web management
access from all other IP addresses. Without the last ACL entry for permitting all packets, this ACL would deny
Web management access from all IP addresses.
Using ACLs to Restrict SNMP Access
To restrict SNMP access to the device using ACLs, enter commands such as the following:
June 2005 2 - 5
Page 22

Security Guide for ProCurve 9300/9400 Series Routing Switches
NOTE: The syntax for using ACLs for SNMP access is different from the syntax for controlling Telnet, SSH, and
Web management access using ACLs.
ProCurveRS(config)# access-list 25 deny host 209.157.22.98 log
ProCurveRS(config)# access-list 25 deny 209.157.23.0 0.0.0.255 log
ProCurveRS(config)# access-list 25 deny 209.157.24.0 0.0.0.255 log
ProCurveRS(config)# access-list 25 permit any
ProCurveRS(config)# access-list 30 deny 209.157.25.0 0.0.0.255 log
ProCurveRS(config)# access-list 30 deny 209.157.26.0/24 log
ProCurveRS(config)# access-list 30 permit any
ProCurveRS(config)# snmp-server community public ro 25
ProCurveRS(config)# snmp-server community private rw 30
ProCurveRS(config)# write memory
Syntax: snmp-server community <string> ro | rw <num>
The <string> parameter specifies the SNMP community string the user must enter to gain SNMP access.
The ro parameter indicates that the community string is for read-only (“get”) access. The rw parameter indicates
the community string is for read-write (“set”) access.
The <num> parameter specifies the number of a standard ACL and must be from 1 – 99.
These commands configure ACLs 25 and 30, then apply the ACLs to community strings.
ACL 25 is used to control read-only access using the “public” community string. ACL 30 is used to control readwrite access using the “private” community string.
NOTE: When snmp-server community is configured, all incoming SNMP packets are validated first by their
community strings and then by their bound ACLs. Before software release 07.7.00, packets are denied if filters are
not configured for an ACL. Beginning with software release 07.7.00, packets are permitted if no filters are
configured for an ACL.
Hardware Filtering for Remote Management Access ( EP Devices Running Release 07.7.00 and Higher)
In releases prior to 07.7.00, ACL filtering for remote management access was done in software (that is, by the
CPU). Starting with release 07.7.00, you can configure EP devices to perform the filtering in hardware.
Configuring Hardware-Based Remote Access Filtering on Routing Switches
The following is an example of configuring an EP Routing Switch to perform hardware filtering for Telnet access.
ProCurveRS(config)# vlan 3 by port
ProCurveRS(config-vlan-3)# untagged ethe 3/1 to 3/5
ProCurveRS(config-vlan-3)# router-interface ve 3
ProCurveRS(config-vlan-3)# exit
ProCurveRS(config)# interface ve 3
ProCurveRS(config-ve-1)# ip address 10.10.11.1 255.255.255.0
ProCurveRS(config-ve-1)# exit
ProCurveRS(config)# access-list 10 permit host 10.10.11.254
ProCurveRS(config)# access-list 10 permit host 192.168.2.254
ProCurveRS(config)# access-list 10 permit host 192.168.12.254
ProCurveRS(config)# access-list 10 permit host 192.64.22.254
ProCurveRS(config)# access-list 10 deny any
ProCurveRS(config)# telnet access-group 10 vlan 3
ProCurveRS(config)# ssh access-group 10 vlan 3
2 - 6 June 2005
Page 23

Securing Access to Management Functions
ProCurveRS(config)# web access-group 10 vlan 3
ProCurveRS(config)# snmp-server community private rw 10 vlan 3
In this example, a Layer 3 VLAN is configured as a remote-access management VLAN and a router interface. The
IP address specified for the router interface becomes the management IP address of the VLAN.
When you make changes to the ACL configuration and/or make changes to the management VLAN, you must
enter the following command after making the configuration changes:
ProCurveRS(config)# remote-management rebind
Syntax: remote-management rebind
The show cam l4 command displays the following information about the hardware filtering in this configuration:
ProCurveRS# show cam l4 3/1
Sl Index Src IP_Addr SPort Dest IP_Addr DPort Prot Age Out Port
3 40960 192.64.22.254/32 Any 10.10.11.1/24 23 TCP dis Use L2/L3
3 40962 192.168.12.254/32 Any 10.10.11.1/24 23 TCP dis Use L2/L3
3 40964 192.168.2.254/32 Any 10.10.11.1/24 23 TCP dis Use L2/L3
3 40966 10.10.11.254/32 Any 10.10.11.1/24 23 TCP dis Use L2/L3
3 40968 Any Any 10.10.11.1/24 23 TCP dis Discard
The IP address in standard ACL 10 is the source IP address of the filter entry, and the IP address of the router
interface is the destination IP address of the filter entry.
Restricting Remote Access to the Device to Specific IP Addresses
By default, an HP device does not control remote management access based on the IP address of the managing
device. You can restrict remote management access to a single IP address for the following access methods:
• Telnet access
• Web management access
• SNMP access
In addition, if you want to restrict all three access methods to the same IP address, you can do so using a single
command.
The following examples show the CLI commands for restricting remote access. You can specify only one IP
address with each command. However, you can enter each command ten times to specify up to ten IP addresses.
NOTE: You cannot restrict remote management access using the Web management interface.
Restricting Telnet Access to a Specific IP Address
To allow Telnet access to the HP device only to the host with IP address 209.157.22.39, enter the following
command:
ProCurveRS(config)# telnet-client 209.157.22.39
Syntax: [no] telnet-client <ip-addr>
Restricting SSH Access to a Specific IP Address
To allow SSH access to the HP device only to the host with IP address 209.157.22.39, enter the following
command:
ProCurveRS(config)# ip ssh client 209.157.22.39
Syntax: [no] ip ssh client <ip-addr>
June 2005 2 - 7
Page 24

Security Guide for ProCurve 9300/9400 Series Routing Switches
Restricting Web Management Access to a Specific IP Address
To allow Web management access to the HP device only to the host with IP address 209.157.22.26, enter the
following command:
ProCurveRS(config)# web-client 209.157.22.26
Syntax: [no] web-client <ip-addr>
Restricting SNMP Access to a Specific IP Address
To allow SNMP access to the HP device only to the host with IP address 209.157.22.14, enter the following
command:
ProCurveRS(config)# snmp-client 209.157.22.14
Syntax: [no] snmp-client <ip-addr>
Restricting All Remote Management Access to a Specific IP Address
To allow Telnet, Web, and SNMP management access to the HP device only to the host with IP address
209.157.22.69, you can enter three separate commands (one for each access type) or you can enter the following
command:
ProCurveRS(config)# all-client 209.157.22.69
Syntax: [no] all-client <ip-addr>
Restricting Telnet and SSH Access Based on a Client’s MAC Address
Starting in release 07.8.00, you can restrict remote management access to the HP device based on the MAC
address of a connecting client. This feature applies to Telnet and SSH access to the device.
For example, the following command allows Telnet access to the HP device only to the host with IP address
209.157.22.39 and MAC address 0007.e90f.e9a0:
ProCurveRS(config)# telnet-client 209.157.22.39 0007.e90f.e9a0
Syntax: [no] telnet-client <ip-addr> <mac-addr>
The following command allows Telnet access to the HP device to a host with any IP address and MAC address
0007.e90f.e9a0:
ProCurveRS(config)# telnet-client any 0007.e90f.e9a0
Syntax: [no] telnet-client any <mac-addr>
To allow SSH access to the HP device only to the host with IP address 209.157.22.39 and MAC address
0007.e90f.e9a0, enter the following command:
ProCurveRS(config)# ip ssh client 209.157.22.39 0007.e90f.e9a0
Syntax: [no] ip ssh client <ip-addr> <mac-addr>
To allow SSH access to the HP device to a host with any IP address and MAC address 0007.e90f.e9a0, enter the
following command:
ProCurveRS(config)# ip ssh client any 0007.e90f.e9a0
Syntax: [no] ip ssh client any <mac-addr>
Specifying the Maximum Number of Login Attempts for Telnet Access
If you are connecting to the HP device using Telnet, the device prompts you for a username and password. By
default, you have up to 4 chances to enter a correct username and password. If you do not enter a correct
username or password after 4 attempts, the HP device disconnects the Telnet session.
In this release, you can specify the number of attempts a Telnet user has to enter a correct username and
password before the device disconnects the Telnet session. For example, to allow a Telnet user up to 5 chances
to enter a correct username and password, enter the following command:
2 - 8 June 2005
Page 25

Securing Access to Management Functions
ProCurveRS(config)# telnet login-retries 5
Syntax: [no] telnet login-retries <number>
You can specify from 0 – 5 attempts. The default is 4 attempts.
Restricting Remote Access to the Device to Specific VLAN IDs
You can restrict management access to an HP device to ports within a specific port-based VLAN. VLAN-based
access control applies to the following access methods:
• Telnet access
• Web management access
• SNMP access
• TFTP access
By default, access is allowed for all the methods listed above on all ports. Once you configure security for a given
access method based on VLAN ID, access to the device using that method is restricted to only the ports within the
specified VLAN.
VLAN-based access control works in conjunction with other access control methods. For example, suppose you
configure an ACL to permit Telnet access only to specific client IP addresses, and you also configure VLAN-based
access control for Telnet access. In this case, the only Telnet clients that can access the device are clients that
have one of the IP addresses permitted by the ACL and are connected to a port that is in a permitted VLAN.
Clients who have a permitted IP address but are connected to a port in a VLAN that is not permitted still cannot
access the device through Telnet.
Restricting Telnet Access to a Specific VLAN
To allow Telnet access only to clients in a specific VLAN, enter a command such as the following:
ProCurveRS(config)# telnet server enable vlan 10
The command in this example configures the device to allow Telnet management access only to clients connected
to ports within port-based VLAN 10. Clients connected to ports that are not in VLAN 10 are denied management
access.
Syntax: [no] telnet server enable vlan <vlan-id>
Restricting Web Management Access to a Specific VLAN
To allow Web management access only to clients in a specific VLAN, enter a command such as the following:
ProCurveRS(config)# web-management enable vlan 10
The command in this example configures the device to allow Web management access only to clients connected
to ports within port-based VLAN 10. Clients connected to ports that are not in VLAN 10 are denied management
access.
Syntax: [no] web-management enable vlan <vlan-id>
Restricting SNMP Access to a Specific VLAN
To allow SNMP access only to clients in a specific VLAN, enter a command such as the following:
ProCurveRS(config)# snmp-server enable vlan 40
The command in this example configures the device to allow SNMP access only to clients connected to ports
within port-based VLAN 40. Clients connected to ports that are not in VLAN 40 are denied access.
Syntax: [no] snmp-server enable vlan <vlan-id>
Restricting TFTP Access to a Specific VLAN
To allow TFTP access only to clients in a specific VLAN, enter a command such as the following:
ProCurveRS(config)# tftp client enable vlan 40
June 2005 2 - 9
Page 26
Security Guide for ProCurve 9300/9400 Series Routing Switches
The command in this example configures the device to allow TFTP access only to clients connected to ports within
port-based VLAN 40. Clients connected to ports that are not in VLAN 40 are denied access.
Syntax: [no] tftp client enable vlan <vlan-id>
Disabling Specific Access Methods
You can specifically disable the following access methods:
• Telnet access
• Web management access
• SNMP access
NOTE: If you disable Telnet access, you will not be able to access the CLI except through a serial connection to
the management module. If you disable SNMP access, you will not be able to use SNMP management
applications.
NOTE: In software releases 07.7.00 and later, you can disable access to the Management IP address through
the device’s Content Addressable Memory (CAM). See
Functions” on page 2-12.
Disabling Telnet Access
“Disabling an Interface’s Access to Management
Telnet access is enabled by default. You can use a Telnet client to access the CLI on the device over the network.
If you do not plan to use the CLI over the network and want to disable Telnet access to prevent others from
establishing CLI sessions with the device, enter the following command:
ProCurveRS(config)# no telnet-server
To re-enable Telnet operation, enter the following command:
ProCurveRS(config)# telnet-server
Syntax: [no] telnet-server
Disabling Web Management Access
If you want to prevent access to the device through the Web management interface, you can disable the Web
management interface.
NOTE: As soon as you make this change, the device stops responding to Web management sessions. If you
make this change using your Web browser, your browser can contact the device, but the device will not reply once
the change takes place.
USING THE CLI
To disable the Web management interface, enter the following command:
ProCurveRS(config)# no web-management
To re-enable the Web management interface, enter the following command:
ProCurveRS(config)# web-management
Syntax: [no] web-management
2 - 10 June 2005
Page 27
Securing Access to Management Functions
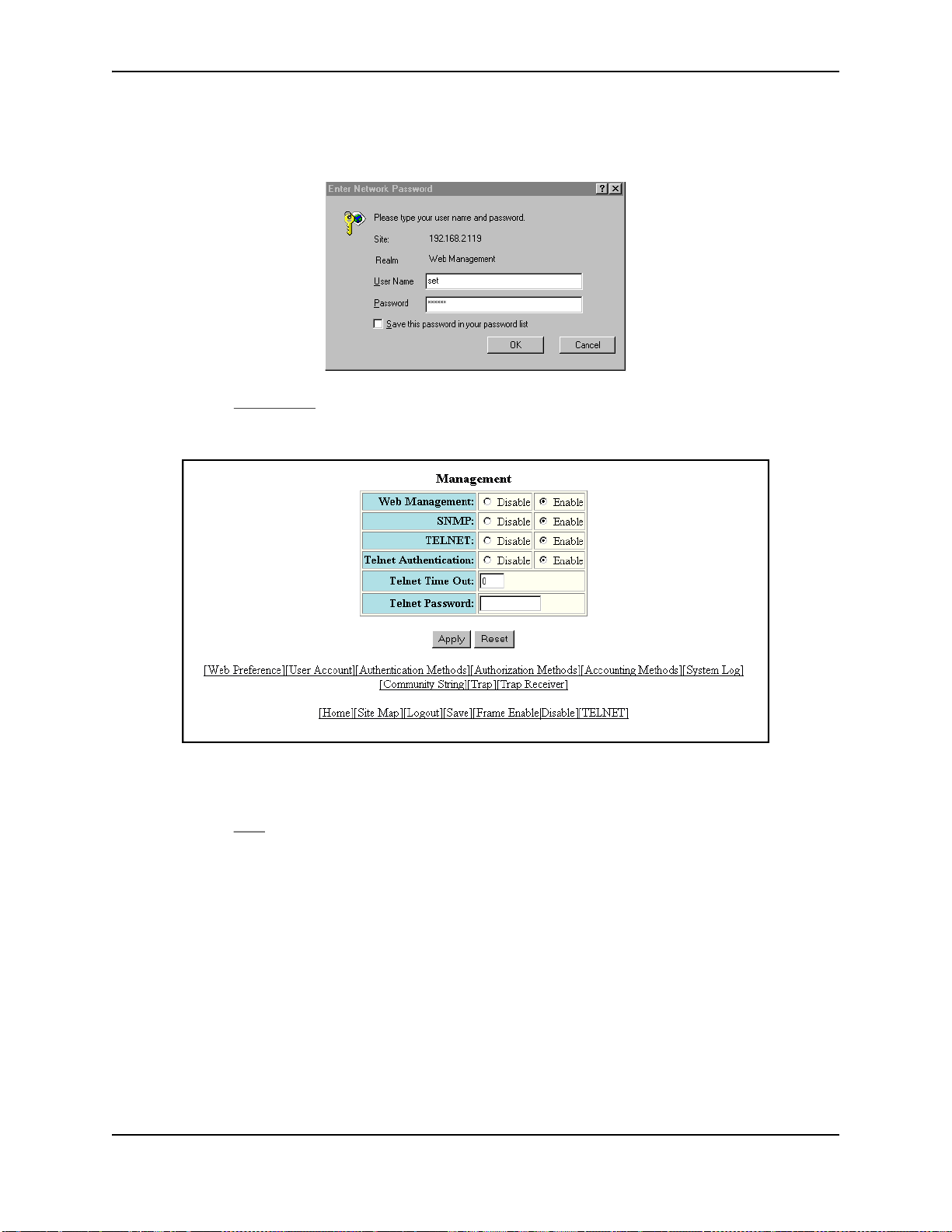
USING THE WEB MANAGEMENT INTERFACE
1. Log on to the device using a valid user name and password for read-write access.
2. Select the Management
panel.
3. Click Disable next to Web Management.
4. Click the Apply button to save the change to the device’s running-config file.
5. Select the Save
to the startup-config file on the device’s flash memory.
link at the bottom of the dialog. Select Yes when prompted to save the configuration change
link from the System configuration panel to display the Management configuration
Disabling SNMP Access
SNMP is enabled by default on all HP devices. To disable SNMP, use one of the following methods.
USING THE CLI
To disable SNMP management of the device:
ProCurveRS(config)# snmp disable
To later re-enable SNMP management of the device:
ProCurveRS(config)# no snmp disable
Syntax: [no] snmp disable
June 2005 2 - 11
Page 28

Security Guide for ProCurve 9300/9400 Series Routing Switches
USING THE WEB MANAGEMENT INTERFACE
1. Log on to the device using a valid user name and password for read-write access. The System configuration
dialog is displayed.
2. Select the Management
panel.
3. Click Disable next to SNMP.
4. Click the Apply button to save the change to the device’s running-config file.
link from the System configuration panel to display the Management configuration
5. Select the Save link at the bottom of the dialog. Select Ye
to the startup-config file on the device’s flash memory.
s when prompted to save the configuration change
Disabling an Interface’s Access to Management Functions
Beginning In software release 07.7.00, you can protect the CPU from remote access to management functions
such as:
• Telnet
• SSH
• Web Management Interface
• SNMP
• TFTP
• RADIUS
• TACACS
• TACACS+
To enable this feature, disable access to the Management IP address through the device’s Content Addressable
Memory (CAM). The following shows an example configuration.
NOTE: This feature does not affect Layer 3 routing functions.
ProCurveRS(config)# int e 3/10
ProCurveRS(config-if-e1000-3/10)# ip address 10.10.10.1 255.255.255.0
ProCurveRS(config-if-e1000-3/10)# exit
ProCurveRS(config)# int e 3/11
ProCurveRS(config-if-e1000-3/11)# ip address 11.11.11.1 255.255.255.0
ProCurveRS(config-if-e1000-3/11)# management-ip-disable
ProCurveRS(config-if-e1000-3/11)# exit
ProCurveRS(config)# int e 3/12
ProCurveRS(config-if-e1000-3/12)# ip address 12.12.12.1 255.255.255.0
ProCurveRS(config-if-e1000-3/12)# management-ip-disable
ProCurveRS(config-if-e1000-3/12)# exit
ProCurveRS(config)# int e 3/13
ProCurveRS(config-if-e1000-3/13)# ip address 13.13.13.1 255.255.255.0
ProCurveRS(config-if-e1000-3/13)# management-ip-disable
ProCurveRS(config-if-e1000-3/13)# exit
Syntax: [no] ip address <ip-addr> <ip-mask>
where <ip-addr> and <ip-mask> are the destination IP address and subnet mask.
Syntax: [no] management-ip-disable
Use the no form of the command to re-enable access to the Management IP address.
2 - 12 June 2005
Page 29

Securing Access to Management Functions
Viewing Information about Disabled Management IP Addresses
Use the show cam l4 command to display information about CAM entries for disabled management IP addresses.
Setting Passwords
Passwords can be used to secure the following access methods:
• Telnet access can be secured by setting a Telnet password. See “Setting a Telnet Password” on page 2-13.
• Access to the Privileged EXEC and CONFIG levels of the CLI can be secured by setting passwords for
management privilege levels. See “Setting Passwords for Management Privilege Levels” on page 2-14.
This section also provides procedures for enhancing management privilege levels, recovering from a lost
password, and disabling password encryption.
NOTE: You also can configure up to 16 user accounts consisting of a user name and password, and assign each
user account a management privilege level.
Setting a Telnet Password
By default, the device does not require a user name or password when you log in to the CLI using Telnet. You can
assign a password for Telnet access using one of the following methods.
USING THE CLI
To set the password “letmein” for Telnet access to the CLI, enter the following command at the global CONFIG
level:
ProCurveRS(config)# enable telnet password letmein
See “Setting Up Local User Accounts” on page 2-16.
Syntax: [no] enable telnet password <string>
USING THE WEB MANAGEMENT INTERFACE
1. Log on to the device using a valid user name and password for read-write access. The System configuration
panel is displayed.
2. Select the Management
panel.
3. Enter the password in the Telnet Password field.
4. Click the Apply button to save the change to the device’s running-config file.
5. Select the Save
to the startup-config file on the device’s flash memory.
link at the bottom of the dialog. Select Yes when prompted to save the configuration change
link from the System configuration panel to display the Management configuration
Suppressing Telnet Connection Rejection Messages
By default, if an HP device denies Telnet management access to the device, the software sends a message to the
denied Telnet client. You can optionally suppress the rejection message. When you enable the option, a denied
Telnet client does not receive a message from the HP device. Instead, the denied client simply does not gain
access.
To suppress the connection rejection message, use the following CLI method.
USING THE CLI
To suppress the connection rejection message sent by the device to a denied Telnet client, enter the following
command at the global CONFIG level of the CLI:
ProCurveRS(config)# telnet server suppress-reject-message
Syntax: [no] telnet server suppress-reject-message
June 2005 2 - 13
Page 30

Security Guide for ProCurve 9300/9400 Series Routing Switches
USING THE WEB MANAGEMENT INTERFACE
You cannot configure this option using the Web management interface.
Setting Passwords for Management Privilege Levels
You can set one password for each of the following management privilege levels:
• Super User level – Allows complete read-and-write access to the system. This is generally for system
administrators and is the only management privilege level that allows you to configure passwords.
• Port Configuration level – Allows read-and-write access for specific ports but not for global (system-wide)
parameters.
• Read Only level – Allows access to the Privileged EXEC mode and CONFIG mode of the CLI but only with
read access.
You can assign a password to each management privilege level. You also can configure up to 16 user accounts
consisting of a user name and password, and assign each user account to one of the three privilege levels. See
“Setting Up Local User Accounts” on page 2-16.
NOTE: You must use the CLI to assign a password for management privilege levels. You cannot assign a
password using the Web management interface.
If you configure user accounts in addition to privilege level passwords, the device will validate a user’s access
attempt using one or both methods (local user account or privilege level password), depending on the order you
specify in the authentication-method lists.
USING THE CLI
To set passwords for management privilege levels:
1. At the opening CLI prompt, enter the following command to change to the Pr
See “Configuring Authentication-Method Lists” on page 2-54.
ivileged level of the EXEC mode:
ProCurveRS> enable
ProCurveRS#
2. Access the CONFIG level of the CLI by entering the following command:
ProCurveRS# configure terminal
ProCurveRS(config)#
3. Enter the following command to set the Super User level password:
ProCurveRS(config)# enable super-user-password <text>
NOTE: You must set the Super User level password before you can set other types of passwords. The
Super User level password can be an alphanumeric string, but cannot begin with a number.
4. Enter the following commands to set the Port Configuration level and Read Only level passwords:
ProCurveRS(config)# enable port-config-password <text>
ProCurveRS(config)# enable read-only-password <text>
NOTE: If you forget your Super User level password, see “Recovering from a Lost Password” on page 2-15.
Augmenting Management Privilege Levels
Each management privilege level provides access to specific areas of the CLI by default:
• Super User level provides access to all commands and displays.
• Port Configuration level gives access to:
• The User EXEC and Privileged EXEC levels
• The port-specific parts of the CONFIG level
2 - 14 June 2005
Page 31

Securing Access to Management Functions
• All interface configuration levels
• Read Only level gives access to:
• The User EXEC and Privileged EXEC levels
You can grant additional access to a privilege level on an individual command basis. To grant the additional
access, you specify the privilege level you are enhancing, the CLI level that contains the command, and the
individual command.
NOTE: This feature applies only to management privilege levels on the CLI. You cannot augment management
access levels for the Web management interface.
To enhance the Port Configuration privilege level so users also can enter IP commands at the global CONFIG
level:
ProCurveRS(config)# privilege configure level 4 ip
In this command, configure specifies that the enhanced access is for a command at the global CONFIG level of
the CLI. The level 4 parameter indicates that the enhanced access is for management privilege level 4 (Port
Configuration). All users with Port Configuration privileges will have the enhanced access. The ip parameter
indicates that the enhanced access is for the IP commands. Users who log in with valid Port Configuration level
user names and passwords can enter commands that begin with “ip” at the global CONFIG level.
Syntax: [no] privilege <cli-level> level <privilege-level> <command-string>
The <cli-level> parameter specifies the CLI level and can be one of the following values:
• exec – EXEC level; for example, ProCurveRS> or ProCurveRS#
• configure – CONFIG level; for example, ProCurveRS(config)#
• interface – Interface level; for example, ProCurveRS(config-if-6)#
• virtual-interface – Virtual-interface level; for example, ProCurveRS(config-vif-6)#
• rip-router – RIP router level; for example, ProCurveRS(config-rip-router)#
• ospf-router – OSPF router level; for example, ProCurveRS(config-ospf-router)#
• dvmrp-router – DVMRP router level; for example, ProCurveRS(config-dvmrp-router)#
• pim-router – PIM router level; for example, ProCurveRS(config-pim-router)#
• bgp-router – BGP4 router level; for example, ProCurveRS(config-bgp-router)#
• port-vlan – Port-based VLAN level; for example, ProCurveRS(config-vlan)#
• protocol-vlan – Protocol-based VLAN level
The <privilege-level> indicates the number of the management privilege level you are augmenting. You can
specify one of the following:
• 0 – Super User level (full read-write access)
• 4 – Port Configuration level
• 5 – Read Only level
The <command-string> parameter specifies the command you are allowing users with the specified privilege level
to enter. To display a list of the commands at a CLI level, enter “?” at that level's command prompt.
Recovering from a Lost Password
Recovery from a lost password requires direct access to the serial port and a system reset.
NOTE: You can perform this procedure only from the CLI.
To recover from a lost password:
June 2005 2 - 15
Page 32

Security Guide for ProCurve 9300/9400 Series Routing Switches
1. Start a CLI session over the serial interface to the device.
2. Reboot the device.
3. At the initial boot prompt at system startup, enter b to enter the boot monitor mode.
4. Enter no password at the prompt. (You cannot abbreviate this command.) This command will cause the
device to bypass the system password check.
5. Enter boot system flash primary at the prompt.
6. After the console prompt reappears, assign a new password.
Displaying the SNMP Community String
If you want to display the SNMP community string, enter the following commands:
ProCurveRS(config)# enable password-display
ProCurveRS(config)# show snmp server
The enable password-display command enables display of the community string, but only in the output of the
show snmp server command. Display of the string is still encrypted in the startup-config file and running-config.
Enter the command at the global CONFIG level of the CLI.
Disabling Password Encryption
When you configure a password, then save the configuration to the HP device’s flash memory, the password is
also saved to flash as part of the configuration file. By default, the passwords are encrypted so that the passwords
cannot be observed by another user who displays the configuration file. Even if someone observes the file while it
is being transmitted over TFTP, the password is encrypted.
NOTE: You cannot disable password encryption using the Web management interface.
If you want to remove the password encryption, you can disable encryption by entering the following command:
ProCurveRS(config)# no service password-encryption
Syntax: [no] service password-encryption
Specifying a Minimum Password Length
By default, the HP device imposes no minimum length on the Line (Telnet), Enable, or Local passwords. You can
configure the device to require that Line, Enable, and Local passwords be at least a specified length.
For example, to specify that the Line, Enable, and Local passwords be at least 8 characters, enter the following
command:
ProCurveRS(config)# enable password-min-length 8
Syntax: enable password-min-length <number-of-characters>
The <number-of-characters> can be from 1 – 48.
Setting Up Local User Accounts
You can define up to 16 local user accounts on an HP device. User accounts regulate who can access the
management functions in the CLI using the following methods:
• Telnet access
• Web management access
• SNMP access
Local user accounts provide greater flexibility for controlling management access to HP devices than do
management privilege level passwords and SNMP community strings of SNMP versions 1 and 2. You can
2 - 16 June 2005
Page 33

Securing Access to Management Functions
continue to use the privilege level passwords and the SNMP community strings as additional means of access
authentication. Alternatively, you can choose not to use local user accounts and instead continue to use only the
privilege level passwords and SNMP community strings. Local user accounts are backward-compatible with
configuration files that contain privilege level passwords.
Levels” on page 2-14.
If you configure local user accounts, you also need to configure an authentication-method list for Telnet access,
Web management access, and SNMP access. See “Configuring Authentication-Method Lists” on page 2-54.
For each local user account, you specify a user name. You also can specify the following parameters:
• A password
• A management privilege level, which can be one of the following:
• Super User level – Allows complete read-and-write access to the system. This is generally for system
administrators and is the only privilege level that allows you to configure passwords. This is the default.
• Port Configuration level – Allows read-and-write access for specific ports but not for global (system-wide)
parameters.
• Read Only level – Allows access to the Privileged EXEC mode and CONFIG mode but only with read
access.
See “Setting Passwords for Management Privilege
Configuring a Local User Account
To configure a local user account, use one of the following methods.
USING THE CLI
To configure a local user account, enter a command such as the following at the global CONFIG level of the CLI.
ProCurveRS(config)# username wonka password willy
This command adds a local user account with the user name “wonka” and the password “willy”. This account has
the Super User privilege level; this user has full access to all configuration and display features.
NOTE: If you configure local user accounts, you must grant Super User level access to at least one account
before you add accounts with other privilege levels. You need the Super User account to make further
administrative changes.
ProCurveRS(config)# username waldo privilege 5 password whereis
This command adds a user account for user name “waldo”, password “whereis”, with the Read Only privilege
level. Waldo can look for information but cannot make configuration changes.
Syntax: [no] username <user-string> privilege <privilege-level> password | nopassword <password-string>
The privilege parameter specifies the privilege level for the account. You can specify one of the following:
• 0 – Super User level (full read-write access)
• 4 – Port Configuration level
• 5 – Read Only level
The default privilege level is 0. If you want to assign Super User level access to the account, you can enter the
command without privilege 0, as shown in the command example above.
The password | nopassword parameter indicates whether the user must enter a password. If you specify
password, enter the string for the user's password.
NOTE: You must be logged on with Super User access (privilege level 0) to add user accounts or configure other
access parameters.
To display user account information, enter the following command:
ProCurveRS(config)# show users
June 2005 2 - 17
Page 34

Security Guide for ProCurve 9300/9400 Series Routing Switches
Syntax: show users
Note About Changing Local User Passwords
Starting in release 07.8.00, the HP device stores not only the current password configured for a local user, but the
previous two passwords configured for the user as well. The local user's password cannot be changed to one of
the stored passwords.
Consequently, if you change the password for a local user, you must select a password that is different from the
current password, as well as different from the previous two passwords that had been configured for that user.
For example, say local user waldo originally had a password of "whereis", and the password was subsequently
changed to “whois”, then later changed to “whyis”. If you change waldo's password again, you cannot change it to
"whereis", "whois", or "whyis".
The current and previous passwords are stored in the device’s running-config file in encrypted form. For example:
ProCurveRS# show run
...
username waldo password 8 $1$Ro2..Ox0$udBu7pQT5XyuaXMUiUHy9. history
$1$eq...T62$IfpxIcxnDWX7CSVQKIodu. $1$QD3..2Q0$DYxgxCI64ZOSsYmSSaA28/
...
In the running-config file, the user’s previous two passwords are displayed in encrypted form following the history
parameter.
USING THE WEB MANAGEMENT INTERFACE
To configure a local user account using the Web management interface, use the following procedure.
NOTE: Before you can add a local user account using the Web management interface, you must enable this
capability by entering the password any command at the global CONFIG level of the CLI.
1. Log on to the device using a valid user name and password for read-write access.
2. Select the Management
panel.
3. Select the User Account
• If any user accounts are already configured on the device, the account information is listed in a table.
Select the Add User Account
encrypted. If you want the passwords to be displayed in clear text, you can use the CLI to disable
encryption of password displays. See
• If the device does not have any user accounts configured, the following panel is displayed.
link from the System configuration panel to display the Management configuration
link.
link to display the following panel. Notice that the password display is
“Disabling Password Encryption” on page 2-16.
4. Enter the user name in the User Name field. The name cannot contain blanks.
5. Enter the password in the Password field. The password cannot contain blanks.
6. Select the management privilege level from the Privilege pulldown menu. You can select one of the following:
2 - 18 June 2005
Page 35

Securing Access to Management Functions
• 0 (Read-Write) – equivalent to Super User level access. The user can display and configure everything.
• 4 (Port-Config) – allows the user to configure port parameters but not global parameters.
• 5 (Read-Only) – allows the user to display information but not to make configuration changes.
7. Click the Add button to save the change to the device’s running-config file.
8. Repeat steps 4 – 7 for each user account. You can add up to 16 accounts.
9. Select the Save
to the startup-config file on the device’s flash memory.
link at the bottom of the dialog. Select Yes when prompted to save the configuration change
Configuring SSL Security for the Web Management Interface
Starting with release 07.8.00, HP devices support Secure Sockets Layer (SSL) for configuring the device using the
Web Management interface. When enabled, the SSL protocol uses digital certificates and public-private key pairs
to establish a secure connection to the HP device. Digital certificates serve to prove the identity of a connecting
client, and public-private key pairs provide a means to encrypt data sent between the device and the client.
Configuring SSL for the Web management interface consists of the following tasks:
• Enabling the SSL server on the HP device
• Importing an RSA certificate and private key file from a client (optional)
• Generating a certificate
Enabling the SSL Server on the HP Device
To enable the SSL server on the HP device, enter the following command:
ProCurveRS(config)# web-management https
Syntax: [no] web-management http | https
You can enable either the HTTP or HTTPs servers with this command. You can disable both the HTTP and
HTTPs servers by entering the following command:
ProCurveRS(config)# no web-management
Syntax: no web-management
Specifying a Port for SSL Communication
By default, SSL protocol exchanges occur on TCP port 443. You can optionally change the port number used for
SSL communication.
For example, the following command causes the device to use TCP port 334 for SSL communication:
ProCurveRS(config)# ip ssl port 334
Syntax: [no] ip ssl port <port-number>
The default port for SSL communication is 443.
Importing Digital Certificates and RSA Private Key Files
To allow a client to communicate with the HP device using an SSL connection, you configure a set of digital
certificates and RSA public-private key pairs on the device. A digital certificate is used for identifying the
connecting client to the server. It contains information about the issuing Certificate Authority, as well as a public
key. You can either import digital certificates and private keys from a server, or you can allow the HP device to
create them.
If you want to allow the HP device to create the digital certificates, see the next section, “Generating an SSL
Certificate”. If you choose to import an RSA certificate and private key file from a client, you can use TFTP to
transfer the files.
For example, to import a digital certificate using TFTP, enter a command such as the following:
June 2005 2 - 19
Page 36

Security Guide for ProCurve 9300/9400 Series Routing Switches
ProCurveRS(config)# ip ssl certificate-data-file tftp 192.168.9.210 certfile
Syntax: [no] ip ssl certificate-data-file tftp <ip-addr> <certificate-filename>
NOTE: If you import a digital certificate from a client, it can be no larger than 2048 bytes.
To import an RSA private key from a client using TFTP, enter a command such as the following:
ProCurveRS(config)# ip ssl private-key-file tftp 192.168.9.210 keyfile
Syntax: [no] ip ssl private-key-file tftp <ip-addr> <key-filename>
The <ip-addr> is the IP address of a TFTP server that contains the digital certificate or private key.
Generating an SSL Certificate
After you have imported the digital certificate, generate the SSL certificate by entering the following command:
ProCurveRS(config)# crypto-ssl certificate generate
Syntax: [no] crypto-ssl certificate generate
If you did not already import a digital certificate from a client, the device can create a default certificate. To do this,
enter the following command:
ProCurveRS(config)# crypto-ssl certificate generate default
Syntax: [no] crypto-ssl certificate generate default
Deleting the SSL Certificate
To delete the SSL certificate, enter the following command:
ProCurveRS(config)# crypto-ssl certificate zeroize
Syntax: [no] crypto-ssl certificate zeroize
Configuring TACACS/TACACS+ Security
You can use the security protocol Terminal Access Controller Access Control System (TACACS) or TACACS+ to
authenticate the following kinds of access to the HP device
• Telnet access
• SSH access
• Web management access
• Access to the Privileged EXEC level and CONFIG levels of the CLI
The TACACS and TACACS+ protocols define how authentication, authorization, and accounting information is
sent between an HP device and an authentication database on a TACACS/TACACS+ server. TACACS/TACACS+
services are maintained in a database, typically on a UNIX workstation or PC with a TACACS/TACACS+ server
running.
How TACACS+ Differs from TACACS
TACACS is a simple UDP-based access control protocol originally developed by BBN for MILNET. TACACS+ is an
enhancement to TACACS and uses TCP to ensure reliable delivery.
TACACS+ is an enhancement to the TACACS security protocol. TACACS+ improves on TACACS by separating
the functions of authentication, authorization, and accounting (AAA) and by encrypting all traffic between the HP
device and the TACACS+ server. TACACS+ allows for arbitrary length and content authentication exchanges,
which allow any authentication mechanism to be utilized with the HP device. TACACS+ is extensible to provide for
site customization and future development features. The protocol allows the HP device to request very precise
access control and allows the TACACS+ server to respond to each component of that request.
2 - 20 June 2005
Page 37

Securing Access to Management Functions
NOTE: TACACS+ provides for authentication, authorization, and accounting, but an implementation or
configuration is not required to employ all three.
TACACS/TACACS+ Authentication, Authorization, and Accounting
When you configure an HP device to use a TACACS/TACACS+ server for authentication, the device prompts users
who are trying to access the CLI for a user name and password, then verifies the password with the TACACS/
TAC A C S + s e r ve r.
If you are using TACACS+, HP recommends that you also configure authorization, in which the HP device
consults a TACACS+ server to determine which management privilege level (and which associated set of
commands) an authenticated user is allowed to use. You can also optionally configure accounting, which causes
the HP device to log information on the TACACS+ server when specified events occur on the device.
NOTE: By default, a user logging into the device via Telnet or SSH would first enter the User EXEC level. The
user can enter the enable command to get to the Privileged EXEC level.
Starting with release 07.1.08, a user that is successfully authenticated can be automatically placed at the
Privileged EXEC level after login.
28.
TACACS Authentication
See “Entering Privileged EXEC Mode After a Telnet or SSH Login” on page 2-
When TACACS authentication takes place, the following events occur:
1. A user attempts to gain access to the HP device by doing one of the following:
• Logging into the device using Telnet, SSH, or the Web management interface
• Entering the Privileged EXEC level or CONFIG level of the CLI
2. The user is prompted for a username and password.
3. The user enters a username and password.
4. The HP device sends a request containing the username and password to the TACACS server.
5. The username and password are validated in the TACACS server’s database.
6. If the password is valid, the user is authenticated.
TACACS+ Authentication
When TACACS+ authentication takes place, the following events occur:
1. A user attempts to gain access to the HP device by doing one of the following:
• Logging into the device using Telnet, SSH, or the Web management interface
• Entering the Privileged EXEC level or CONFIG level of the CLI
2. The user is prompted for a username.
3. The user enters a username.
4. The HP device obtains a password prompt from a TACACS+ server.
5. The user is prompted for a password.
6. The user enters a password.
7. The HP device sends the password to the TACACS+ server.
8. The password is validated in the TACACS+ server’s database.
9. If the password is valid, the user is authenticated.
June 2005 2 - 21
Page 38

Security Guide for ProCurve 9300/9400 Series Routing Switches
TACACS+ Authorization
HP devices support two kinds of TACACS+ authorization:
• Exec authorization determines a user’s privilege level when they are authenticated
• Command authorization consults a TACACS+ server to get authorization for commands entered by the user
When TACACS+ exec authorization takes place, the following events occur:
1. A user logs into the HP device using Telnet, SSH, or the Web management interface
2. The user is authenticated.
3. The HP device consults the TACACS+ server to determine the privilege level of the user.
4. The TACACS+ server sends back a response containing an A-V (Attribute-Value) pair with the privilege level
of the user.
5. The user is granted the specified privilege level.
When TACACS+ command authorization takes place, the following events occur:
1. A Telnet, SSH, or Web management interface user previously authenticated by a TACACS+ server enters a
command on the HP device.
2. The HP device looks at its configuration to see if the command is at a privilege level that requires TACACS+
command authorization.
3. If the command belongs to a privilege level that requires authorization, the HP device consults the TACACS+
server to see if the user is authorized to use the command.
4. If the user is authorized to use the command, the command is executed.
TACACS+ Accounting
TACACS+ accounting works as follows:
1. One of the following events occur on the HP device:
• A user logs into the management interface using Telnet or SSH
• A user enters a command for which accounting has been configured
• A system event occurs, such as a reboot or reloading of the configuration file
2. The HP device checks its configuration to see if the event is one for which TACACS+ accounting is required.
3. If the event requires TACACS+ accounting, the HP device sends a TACACS+ Accounting Start packet to the
TACACS+ accounting server, containing information about the event.
4. The TACACS+ accounting server acknowledges the Accounting Start packet.
5. The TACACS+ accounting server records information about the event.
6. When the event is concluded, the HP device sends an Accounting Stop packet to the TACACS+ accounting
server.
7. The TACACS+ accounting server acknowledges the Accounting Stop packet.
2 - 22 June 2005
Page 39

Securing Access to Management Functions
AAA Operations for TACACS/TACACS+
The following table lists the sequence of authentication, authorization, and accounting operations that take place
when a user gains access to an HP device that has TACACS/TACACS+ security configured.
User Action
User attempts to gain access to the
Privileged EXEC and CONFIG levels of
the CLI
User logs in using Telnet/SSH
User logs into the Web management
interface
Applicable AAA Operations
Enable authentication:
aaa authentication enable default <method-list>
Exec authorization (TACACS+):
aaa authorization exec default tacacs+
System accounting start (TACACS+):
aaa accounting system default start-stop <method-list>
Login authentication:
aaa authentication login default <method-list>
Exec authorization (TACACS+):
aaa authorization exec default tacacs+
Exec accounting start (TACACS+):
aaa accounting exec default <method-list>
System accounting start (TACACS+):
aaa accounting system default start-stop <method-list>
Web authentication:
aaa authentication web-server default <method-list>
Exec authorization (TACACS+):
aaa authorization exec default tacacs+
User logs out of Telnet/SSH session
User enters system commands
(for example, reload, boot system)
June 2005 2 - 23
Command accounting (TACACS+):
aaa accounting commands <privilege-level> default start-stop
<method-list>
EXEC accounting stop (TACACS+):
aaa accounting exec default start-stop <method-list>
Command authorization (TACACS+):
aaa authorization commands <privilege-level> default <method-list>
Command accounting (TACACS+):
aaa accounting commands <privilege-level> default start-stop
<method-list>
System accounting stop (TACACS+):
aaa accounting system default start-stop <method-list>
Page 40

Security Guide for ProCurve 9300/9400 Series Routing Switches
User Action
User enters the command:
[no] aaa accounting system default
start-stop <method-list>
User enters other commands
Applicable AAA Operations
Command authorization (TACACS+):
aaa authorization commands <privilege-level> default <method-list>
Command accounting (TACACS+):
aaa accounting commands <privilege-level> default start-stop
<method-list>
System accounting start (TACACS+):
aaa accounting system default start-stop <method-list>
Command authorization (TACACS+):
aaa authorization commands <privilege-level> default <method-list>
Command accounting (TACACS+):
aaa accounting commands <privilege-level> default start-stop
<method-list>
AAA Security for Commands Pasted Into the Running-Config
If AAA security is enabled on the device, commands pasted into the running-config are subject to the same AAA
operations as if they were entered manually.
When you paste commands into the running-config, and AAA command authorization and/or accounting is
configured on the device, AAA operations are performed on the pasted commands. The AAA operations are
performed before the commands are actually added to the running-config. The server performing the AAA
operations should be reachable when you paste the commands into the running-config file. If the device
determines that a pasted command is invalid, AAA operations are halted on the remaining commands. The
remaining commands may not be executed if command authorization is configured.
TACACS/TACACS+ Configuration Considerations
• You must deploy at least one TACACS/TACACS+ server in your network.
• HP devices support authentication using up to eight TACACS/TACACS+ servers. The device tries to use the
servers in the order you add them to the device’s configuration.
• You can select only one primary authentication method for each type of access to a device (CLI through
Telnet, CLI Privileged EXEC and CONFIG levels). For example, you can select TACACS+ as the primary
authentication method for Telnet CLI access, but you cannot also select RADIUS authentication as a primary
method for the same type of access. However, you can configure backup authentication methods for each
access type.
• You can configure the HP device to authenticate using a TACACS or TACACS+ server, not both.
TACACS Configuration Procedure
For TACACS configurations, use the following procedure:
1. Identify TACACS servers. See “Identifying the TACACS/TACACS+ Servers” on page 2-25.
2. Set optional parameters. See “Setting Optional TACACS/TACACS+ Parameters” on page 2-26.
3. Configure authentication-method lists. See “Configuring Authentication-Method Lists for TACACS/TACACS+”
on page 2-27.
TACACS+ Configuration Procedure
For TACACS+ configurations, use the following procedure:
1. Identify TACACS+ servers. See “Identifying the TACACS/TACACS+ Servers” on page 2-25.
2 - 24 June 2005
Page 41

Securing Access to Management Functions
2. Set optional parameters. See “Setting Optional TACACS/TACACS+ Parameters” on page 2-26.
3. Configure authentication-method lists. See “Configuring Authentication-Method Lists for TACACS/TACACS+”
on page 2-27.
4. Optionally configure TACACS+ authorization. See “Configuring TACACS+ Authorization” on page 2-29.
5. Optionally configure TACACS+ accounting. See “Configuring TACACS+ Accounting” on page 2-32.
Identifying the TACACS/TACACS+ Servers
To use TACACS/TACACS+ servers to authenticate access to an HP device, you must identify the servers to the
HP device.
For example, to identify three TACACS/TACACS+ servers, enter commands such as the following:
ProCurveRS(config)# tacacs-server host 207.94.6.161
ProCurveRS(config)# tacacs-server host 207.94.6.191
ProCurveRS(config)# tacacs-server host 207.94.6.122
Syntax: tacacs-server <ip-addr>|<hostname> [auth-port <number>]
The <ip-addr>|<hostname> parameter specifies the IP address or host name of the server. You can enter up to
eight tacacs-server host commands to specify up to eight different servers.
NOTE: To specify the server's host name instead of its IP address, you must first identify a DNS server using the
ip dns server-address <ip-addr> command at the global CONFIG level.
If you add multiple TACACS/TACACS+ authentication servers to the HP device, the device tries to reach them in
the order you add them. For example, if you add three servers in the following order, the software tries the servers
in the same order:
1. 207.94.6.161
2. 207.94.6.191
3. 207.94.6.122
You can remove a TACACS/TACACS+ server by entering no followed by the tacacs-server command. For
example, to remove 207.94.6.161, enter the following command:
ProCurveRS(config)# no tacacs-server host 207.94.6.161
NOTE: If you erase a tacacs-server command (by entering “no” followed by the command), make sure you also
erase the aaa commands that specify TACACS/TACACS+ as an authentication method. (See “Configuring
Authentication-Method Lists for TACACS/TACACS+” on page 2-27.) Otherwise, when you exit from the CONFIG
mode or from a Telnet session, the system continues to believe it is TACACS/TACACS+ enabled and you will not
be able to access the system.
The auth-port parameter specifies the UDP (for TACACS) or TCP (for TACACS+) port number of the
authentication port on the server. The default port number is 49.
Specifying Different Servers for Individual AAA Functions
In a TACACS+ configuration, you can designate a server to handle a specific AAA task. For example, you can
designate one TACACS+ server to handle authorization and another TACACS+ server to handle accounting. You
can set the TACACS+ key for each server.
June 2005 2 - 25
Page 42

Security Guide for ProCurve 9300/9400 Series Routing Switches
To specify different TACACS+ servers for authentication, authorization, and accounting:
ProCurveRS(config)# tacacs-server host 1.2.3.4 auth-port 49 authentication-only
key abc
ProCurveRS(config)# tacacs-server host 1.2.3.5 auth-port 49 authorization-only
key def
ProCurveRS(config)# tacacs-server host 1.2.3.6 auth-port 49 accounting-only key
ghi
Syntax: tacacs-server host <ip-addr> | <server-name> [authentication-only | authorization-only |
accounting-only | default] [key <string>]
The default parameter causes the server to be used for all AAA functions.
After authentication takes place, the server that performed the authentication is used for authorization and/or
accounting. If the authenticating server cannot perform the requested function, then the next server in the
configured list of servers is tried; this process repeats until a server that can perform the requested function is
found, or every server in the configured list has been tried.
Setting Optional TACACS/TACACS+ Parameters
You can set the following optional parameters in a TACACS/TACACS+ configuration:
• TACACS+ key – This parameter specifies the value that the HP device sends to the TACACS+ server when
trying to authenticate user access.
• Retransmit interval – This parameter specifies how many times the HP device will resend an authentication
request when the TACACS/TACACS+ server does not respond. The retransmit value can be from 1 – 5 times.
The default is 3 times.
• Dead time – This parameter specifies how long the HP device waits for the primary authentication server to
reply before deciding the server is dead and trying to authenticate using the next server. The dead-time value
can be from 1 – 5 seconds. The default is 3 seconds.
• Timeout – This parameter specifies how many seconds the HP device waits for a response from a TACACS/
TACACS+ server before either retrying the authentication request, or determining that the TACACS/TACACS+
servers are unavailable and moving on to the next authentication method in the authentication-method list.
The timeout can be from 1 – 15 seconds. The default is 3 seconds.
Setting the TACACS+ Key
The key parameter in the tacacs-server command is used to encrypt TACACS+ packets before they are sent over
the network. The value for the key parameter on the HP device should match the one configured on the
TACACS+ server. The key can be from 1 – 32 characters in length and cannot include any space characters.
NOTE: The tacacs-server key command applies only to TACACS+ servers, not to TACACS servers. If you are
configuring TACACS, do not configure a key on the TACACS server and do not enter a key on the HP device.
To specify a TACACS+ server key:
ProCurveRS(config)# tacacs-server key rkwong
Syntax: tacacs-server key [0 | 1] <string>
When you display the configuration of the HP device, the TACACS+ keys are encrypted. For example:
ProCurveRS(config)# tacacs-server key 1 abc
ProCurveRS(config)# write terminal
...
tacacs-server host 1.2.3.5 auth-port 49
tacacs key 1 $!2d
2 - 26 June 2005
Page 43

Securing Access to Management Functions
NOTE: Encryption of the TACACS+ keys is done by default. The 0 parameter disables encryption. The 1
parameter is not required; it is provided for backwards compatibility.
Setting the Retransmission Limit
The retransmit parameter specifies how many times the HP device will resend an authentication request when
the TACACS/TACACS+ server does not respond. The retransmit limit can be from 1 – 5 times. The default is 3
times.
To set the TACACS/TACACS+ retransmit limit:
ProCurveRS(config)# tacacs-server retransmit 5
Syntax: tacacs-server retransmit <number>
Setting the Dead Time Parameter
The dead-time parameter specifies how long the HP device waits for the primary authentication server to reply
before deciding the server is dead and trying to authenticate using the next server. The dead-time value can be
from 1 – 5 seconds. The default is 3 seconds.
To set the TACACS/TACACS+ dead-time value:
ProCurveRS(config)# tacacs-server dead-time 5
Syntax: tacacs-server dead-time <number>
Setting the Timeout Parameter
The timeout parameter specifies how many seconds the HP device waits for a response from the TACACS/
TACACS+ server before either retrying the authentication request, or determining that the TACACS/TACACS+
server is unavailable and moving on to the next authentication method in the authentication-method list. The
timeout can be from 1 – 15 seconds. The default is 3 seconds.
ProCurveRS(config)# tacacs-server timeout 5
Syntax: tacacs-server timeout <number>
Configuring Authentication-Method Lists for TACACS/TACACS+
You can use TACACS/TACACS+ to authenticate Telnet/SSH access and access to Privileged EXEC level and
CONFIG levels of the CLI. When configuring TACACS/TACACS+ authentication, you create authenticationmethod lists specifically for these access methods, specifying TACACS/TACACS+ as the primary authentication
method.
Within the authentication-method list, TACACS/TACACS+ is specified as the primary authentication method and
up to six backup authentication methods are specified as alternates. If TACACS/TACACS+ authentication fails
due to an error, the device tries the backup authentication methods in the order they appear in the list.
When you configure authentication-method lists for TACACS/TACACS+ authentication, you must create a
separate authentication-method list for Telnet/SSH CLI access, and for access to the Privileged EXEC level and
CONFIG levels of the CLI.
To create an authentication-method list that specifies TACACS/TACACS+ as the primary authentication method for
securing Telnet/SSH access to the CLI:
ProCurveRS(config)# enable telnet authentication
ProCurveRS(config)# aaa authentication login default tacacs local
The commands above cause TACACS/TACACS+ to be the primary authentication method for securing Telnet/SSH
access to the CLI. If TACACS/TACACS+ authentication fails due to an error with the server, authentication is
performed using local user accounts instead.
To create an authentication-method list that specifies TACACS/TACACS+ as the primary authentication method for
securing access to Privileged EXEC level and CONFIG levels of the CLI:
ProCurveRS(config)# aaa authentication enable default tacacs local none
June 2005 2 - 27
Page 44

Security Guide for ProCurve 9300/9400 Series Routing Switches
The command above causes TACACS/TACACS+ to be the primary authentication method for securing access to
Privileged EXEC level and CONFIG levels of the CLI. If TACACS/TACACS+ authentication fails due to an error
with the server, local authentication is used instead. If local authentication fails, no authentication is used; the
device automatically permits access.
Syntax: [no] aaa authentication enable | login default <method1> [<method2>] [<method3>] [<method4>]
[<method5>] [<method6>] [<method7>]
The web-server | enable | login parameter specifies the type of access this authentication-method list controls.
You can configure one authentication-method list for each type of access.
NOTE: If you configure authentication for Web management access, authentication is performed each time a
page is requested from the server. When frames are enabled on the Web management interface, the browser
sends an HTTP request for each frame. The HP device authenticates each HTTP request from the browser. To
limit authentications to one per page, disable frames on the Web management interface.
The <method1> parameter specifies the primary authentication method. The remaining optional <method>
parameters specify additional methods to try if an error occurs with the primary method. A method can be one of
the values listed in the Method Parameter column in the following table.
Table 2.2: Authentication Method Values
Method Parameter
line
enable
local
tacacs
tacacs+
radius
none
Description
Authenticate using the password you configured for Telnet access. The
Telnet password is configured using the enable telnet password…
command.
Authenticate using the password you configured for the Super User
privilege level. This password is configured using the enable super-
user-password… command. See
Privilege Levels” on page 2-14.
Authenticate using a local user name and password you configured on
the device. Local user names and passwords are configured using the
username… command. See
page 2-17.
Authenticate using the database on a TACACS server. You also must
identify the server to the device using the tacacs-server command.
Authenticate using the database on a TACACS+ server. You also must
identify the server to the device using the tacacs-server command.
Authenticate using the database on a RADIUS server. You also must
identify the server to the device using the radius-server command.
Do not use any authentication method. The device automatically
permits access.
See “Setting a Telnet Password” on page 2-13.
“Setting Passwords for Management
“Configuring a Local User Account” on
NOTE: For examples of how to define authentication-method lists for types of authentication other than TACACS/
TACACS+, see “Configuring Authentication-Method Lists” on page 2-54.
Entering Privileged EXEC Mode After a Telnet or SSH Login
By default, a user enters User EXEC mode after a successful login through Telnet or SSH. Optionally, you can
configure the device so that a user enters Privileged EXEC mode after a Telnet or SSH login. To do this, use the
following command:
ProCurveRS(config)# aaa authentication login privilege-mode
2 - 28 June 2005
Page 45

Securing Access to Management Functions
Syntax: aaa authentication login privilege-mode
The user’s privilege level is based on the privilege level granted during login.
Configuring Enable Authentication to Prompt for Password Only
If Enable authentication is configured on the device, when a user attempts to gain Super User access to the
Privileged EXEC and CONFIG levels of the CLI, by default he or she is prompted for a username and password.
In this release, you can configure the HP device to prompt only for a password. The device uses the username
entered at login, if one is available. If no username was entered at login, the device prompts for both username
and password.
To configure the HP device to prompt only for a password when a user attempts to gain Super User access to the
Privileged EXEC and CONFIG levels of the CLI:
ProCurveRS(config)# aaa authentication enable implicit-user
Syntax: [no] aaa authentication enable implicit-user
Telnet/SSH Prompts When the TACACS+ Server is Unavailable
When TACACS+ is the first method in the authentication method list, the device displays the login prompt received
from the TACACS+ server. If a user attempts to login through Telnet or SSH, but none of the configured TACACS+
servers are available, the following takes place:
• If the next method in the authentication method list is "enable", the login prompt is skipped, and the user is
prompted for the Enable password (that is, the password configured with the enable super-user-password
command).
• If the next method in the authentication method list is "line", the login prompt is skipped, and the user is
prompted for the Line password (that is, the password configured with the enable telnet password
command).
Configuring TACACS+ Authorization
HP devices support TACACS+ authorization for controlling access to management functions in the CLI. Two
kinds of TACACS+ authorization are supported:
• Exec authorization determines a user’s privilege level when they are authenticated
• Command authorization consults a TACACS+ server to get authorization for commands entered by the user
Configuring Exec Authorization
When TACACS+ exec authorization is performed, the HP device consults a TACACS+ server to determine the
privilege level of the authenticated user. To configure TACACS+ exec authorization on the HP device, enter the
following command:
ProCurveRS(config)# aaa authorization exec default tacacs+
Syntax: aaa authorization exec default tacacs+ | none
If you specify none, or omit the aaa authorization exec command from the device’s configuration, no exec
authorization is performed.
A user’s privilege level is obtained from the TACACS+ server in the “hp-privlvl” A-V pair. If the aaa authorization
exec default tacacs command exists in the configuration, the device assigns the user the privilege level specified
by this A-V pair. If the command does not exist in the configuration, then the value in the “hp-privlvl” A-V pair is
ignored, and the user is granted Super User access.
NOTE: If the aaa authorization exec default tacacs+ command exists in the configuration, following successful
authentication the device assigns the user the privilege level specified by the “hp-privlvl” A-V pair received from
the TACACS+ server. If the aaa authorization exec default tacacs+ command does not exist in the
configuration, then the value in the “hp-privlvl” A-V pair is ignored, and the user is granted Super User access.
June 2005 2 - 29
Page 46

Security Guide for ProCurve 9300/9400 Series Routing Switches
Also note that in order for the aaa authorization exec default tacacs+ command to work, either the
aaa authentication enable default tacacs+ command, or the aaa authentication login privilege-mode
command must also exist in the configuration.
Configuring an Attribute-Value Pair on the TACACS+ Server
During TACACS+ exec authorization, the HP device expects the TACACS+ server to send a response containing
an A-V (Attribute-Value) pair that specifies the privilege level of the user. When the HP device receives the
response, it extracts an A-V pair configured for the Exec service and uses it to determine the user’s privilege level.
To set a user’s privilege level, you can configure the “hp-privlvl” A-V pair for the Exec service on the TACACS+
server. For example:
user=bob {
default service = permit
member admin
# Global password
global = cleartext "cat"
service = exec {
hp-privlvl = 0
}
}
In this example, the A-V pair hp-privlvl = 0 grants the user full read-write access. The value in the hp-privlvl
A-V pair is an integer that indicates the privilege level of the user. Possible values are 0 for super-user level, 4 for
port-config level, or 5 for read-only level. If a value other than 0, 4, or 5 is specified in the hp-privlvl A-V pair, the
default privilege level of 5 (read-only) is used. The hp-privlvl A-V pair can also be embedded in the group
configuration for the user. See your TACACS+ documentation for the configuration syntax relevant to your server.
If the hp-privlvl A-V pair is not present, the HP device extracts the last A-V pair configured for the Exec service that
has a numeric value. The HP device uses this A-V pair to determine the user’s privilege level. For example:
user=bob {
default service = permit
member admin
# Global password
global = cleartext "cat"
service = exec {
privlvl = 15
}
}
The attribute name in the A-V pair is not significant; the HP device uses the last one that has a numeric value.
However, the HP device interprets the value for a non-”hp-privlvl” A-V pair differently than it does for an “hp-privlvl”
A-V pair. The following table lists how the HP device associates a value from a non-”hp-privlvl” A-V pair with an
HP privilege level.
Table 2.3: HP Equivalents for non-“hp-privlvl” A-V Pair Values
Value for non-“hp-privlvl” A-V Pair
15
From 14 – 1
Any other number or 0
In the example above, the A-V pair configured for the Exec service is privlvl = 15. The HP device uses the
value in this A-V pair to set the user’s privilege level to 0 (super-user), granting the user full read-write access.
HP Privilege Level
0 (super-user)
4 (port-config)
5 (read-only)
2 - 30 June 2005
Page 47

Securing Access to Management Functions
In a configuration that has both an “hp-privlvl” A-V pair and a non-”hp-privlvl” A-V pair for the Exec service, the
non-”hp-privlvl” A-V pair is ignored. For example:
user=bob {
default service = permit
member admin
# Global password
global = cleartext "cat"
service = exec {
hp-privlvl = 4
privlvl = 15
}
}
In this example, the user would be granted a privilege level of 4 (port-config level). The privlvl = 15 A-V pair
is ignored by the HP device.
If the TACACS+ server has no A-V pair configured for the Exec service, the default privilege level of 5 (read-only)
is used.
Configuring Command Authorization
When TACACS+ command authorization is enabled, the HP device consults a TACACS+ server to get
authorization for commands entered by the user.
You enable TACACS+ command authorization by specifying a privilege level whose commands require
authorization. For example, to configure the HP device to perform authorization for the commands available at the
Super User privilege level (that is, all commands on the device), enter the following command:
ProCurveRS(config)# aaa authorization commands 0 default tacacs+
Syntax: aaa authorization commands <privilege-level> default tacacs+ | radius | none
The <privilege-level> parameter can be one of the following:
• 0 – Authorization is performed for commands available at the Super User level (all commands)
• 4 – Authorization is performed for commands available at the Port Configuration level (port-config and readonly commands)
• 5 – Authorization is performed for commands available at the Read Only level (read-only commands)
NOTE: TACACS+ command authorization can be performed only for commands entered from Telnet or SSH
sessions, or from the console. No authorization is performed for commands entered at the Web management
interface or SNMP management applications.
TACACS+ command authorization is not performed for the following commands:
• At all levels: exit, logout, end, and quit.
• At the Privileged EXEC level: enable or enable <text>, where <text> is the password configured for the Super
User privilege level.
If configured, command accounting is performed for these commands.
AAA Support for Console Commands
To enable AAA support for commands entered at the console, enter the following command:
ProCurveRS(config)# enable aaa console
Syntax: [no] enable aaa console
June 2005 2 - 31
Page 48

Security Guide for ProCurve 9300/9400 Series Routing Switches
NOTE: In releases prior to 07.8.00, the enable aaa console command only enabled command authorization
and command accounting for CLI commands entered at the console. Starting with release 07.8.00, AAA support
for commands entered at the console can include the following:
• Login prompt that uses AAA authentication, using authentication-method lists
• Exec Authorization
• Exec Accounting
• System Accounting
Configuring TACACS+ Accounting
HP devices support TACACS+ accounting for recording information about user activity and system events. When
you configure TACACS+ accounting on an HP device, information is sent to a TACACS+ accounting server when
specified events occur, such as when a user logs into the device or the system is rebooted.
Configuring TACACS+ Accounting for Telnet/SSH (Shell) Access
To send an Accounting Start packet to the TACACS+ accounting server when an authenticated user establishes a
Telnet or SSH session on the HP device, and an Accounting Stop packet when the user logs out:
ProCurveRS(config)# aaa accounting exec default start-stop tacacs+
Syntax: aaa accounting exec default start-stop radius | tacacs+ | none
Configuring TACACS+ Accounting for CLI Commands
You can configure TACACS+ accounting for CLI commands by specifying a privilege level whose commands
require accounting. For example, to configure the HP device to perform TACACS+ accounting for the commands
available at the Super User privilege level (that is; all commands on the device), enter the following command:
ProCurveRS(config)# aaa accounting commands 0 default start-stop tacacs+
An Accounting Start packet is sent to the TACACS+ accounting server when a user enters a command, and an
Accounting Stop packet is sent when the service provided by the command is completed.
NOTE: If authorization is enabled, and the command requires authorization, then authorization is performed
before accounting takes place. If authorization fails for the command, no accounting takes place.
Syntax: aaa accounting commands <privilege-level> default start-stop radius | tacacs+ | none
The <privilege-level> parameter can be one of the following:
• 0 – Records commands available at the Super User level (all commands)
• 4 – Records commands available at the Port Configuration level (port-config and read-only commands)
• 5 – Records commands available at the Read Only level (read-only commands)
Configuring TACACS+ Accounting for System Events
You can configure TACACS+ accounting to record when system events occur on the HP device. System events
include rebooting and when changes to the active configuration are made.
The following command causes an Accounting Start packet to be sent to the TACACS+ accounting server when a
system event occurs, and a Accounting Stop packet to be sent when the system event is completed:
ProCurveRS(config)# aaa accounting system default start-stop tacacs+
Syntax: aaa accounting system default start-stop radius | tacacs+ | none
2 - 32 June 2005
Page 49

Securing Access to Management Functions
Configuring an Interface as the Source for All TACACS/TACACS+ Packets
You can designate the lowest-numbered IP address configured an Ethernet port, loopback interface, or virtual
interface as the source IP address for all TACACS/TACACS+ packets from the Routing Switch. Identifying a single
source IP address for TACACS/TACACS+ packets provides the following benefits:
• If your TACACS/TACACS+ server is configured to accept packets only from specific links or IP addresses, you
can use this feature to simplify configuration of the TACACS/TACACS+ server by configuring the HP device to
always send the TACACS/TACACS+ packets from the same link or source address.
• If you specify a loopback interface as the single source for TACACS/TACACS+ packets, TACACS/TACACS+
servers can receive the packets regardless of the states of individual links. Thus, if a link to the TACACS/
TACACS+ server becomes unavailable but the client or server can be reached through another link, the client
or server still receives the packets, and the packets still have the source IP address of the loopback interface.
The software contains separate CLI commands for specifying the source interface for Telnet, TACACS/TACACS+,
and RADIUS packets. You can configure a source interface for one or more of these types of packets.
To specify an Ethernet port or a loopback or virtual interface as the source for all TACACS/TACACS+ packets from
the device, use the following CLI method. The software uses the lowest-numbered IP address configured on the
port or interface as the source IP address for TACACS/TACACS+ packets originated by the device.
To specify the lowest-numbered IP address configured on a virtual interface as the device’s source for all TACACS/
TACACS+ packets, enter commands such as the following:
ProCurveRS(config)# int ve 1
ProCurveRS(config-vif-1)# ip address 10.0.0.3/24
ProCurveRS(config-vif-1)# exit
ProCurveRS(config)# ip tacacs source-interface ve 1
The commands in this example configure virtual interface 1, assign IP address 10.0.0.3/24 to the interface, then
designate the interface as the source for all TACACS/TACACS+ packets from the Routing Switch.
Syntax: ip tacacs source-interface ethernet <portnum> | loopback <num> | ve <num>
The <num> parameter is a loopback interface or virtual interface number. If you specify an Ethernet port, the
<portnum> is the port’s number (including the slot number, if you are configuring a Routing Switch).
Displaying TACACS/TACACS+ Statistics and Configuration Information
The show aaa command displays information about all TACACS+ and RADIUS servers identified on the device.
For example:
ProCurveRS# show aaa
Tacacs+ key: hp
Tacacs+ retries: 1
Tacacs+ timeout: 15 seconds
Tacacs+ dead-time: 3 minutes
Tacacs+ Server: 207.95.6.90 Port:49:
opens=6 closes=3 timeouts=3 errors=0
packets in=4 packets out=4
no connection
Radius key: networks
Radius retries: 3
Radius timeout: 3 seconds
Radius dead-time: 3 minutes
Radius Server: 207.95.6.90 Auth Port=1645 Acct Port=1646:
opens=2 closes=1 timeouts=1 errors=0
packets in=1 packets out=4
no connection
June 2005 2 - 33
Page 50

Security Guide for ProCurve 9300/9400 Series Routing Switches
The following table describes the TACACS/TACACS+ information displayed by the show aaa command.
Table 2.4: Output of the show aaa command for TACACS/TACACS+
Field
Tacacs+ key
Tacacs+ retries
Tacacs+ timeout
Tacacs+ dead-time
Tacacs+ Server
connection
The show web command displays the privilege level of Web management interface users. For example:
Description
The setting configured with the tacacs-server key command. At the Super User
privilege level, the actual text of the key is displayed. At the other privilege levels, a
string of periods (....) is displayed instead of the text.
The setting configured with the tacacs-server retransmit command.
The setting configured with the tacacs-server timeout command.
The setting configured with the tacacs-server dead-time command.
For each TACACS/TACACS+ server, the IP address, port, and the following
statistics are displayed:
opens Number of times the port was opened for communication with the
server
closes Number of times the port was closed normally
timeouts Number of times port was closed due to a timeout
errors Number of times an error occurred while opening the port
packets in Number of packets received from the server
packets out Number of packets sent to the server
The current connection status. This can be “no connection” or “connection active”.
ProCurveRS(config)#show web
User Privilege IP address
set 0 192.168.1.234
Syntax: show web
USING THE WEB MANAGEMENT INTERFACE
To configure TACACS/TACACS+ using the Web management interface:
1. Log on to the device using a valid user name and password for read-write access. The System configuration
panel is displayed.
2. If you configuring TACACS/TACACS+ authentication for Telnet access to the CLI, go to step 3. Otherwise, go
to step 7.
3. Select the Management
4. Select Enable next to Telnet Authentication. You must enable Telnet authentication if you want to use
TACACS/TACACS+ or RADIUS to authenticate Telnet access to the device.
5. Click Apply to apply the change.
6. Select the Home
7. Select the TACACS
8. If needed, change the Authentication port and Accounting port. (The default values work in most networks.)
link to return to the System configuration panel.
link to display the Management configuration panel.
link from the System configuration panel to display the TACACS panel.
2 - 34 June 2005
Page 51

Securing Access to Management Functions
9. Enter the key if applicable.
NOTE: The key parameter applies only to TACACS+ servers, not to TACACS servers. If you are configuring
for TACACS authentication, do not configure a key on the TACACS server and do not enter a key on the HP
device.
10. Click Apply if you changed any TACACS/TACACS+ parameters.
11. Select the TACACS Server link.
• If any TACACS/TACACS+ servers are already configured on the device, the servers are listed in a table.
Select the Add TACACS Server link to display the TACACS configuration panel.
• If the device does not have any TACACS
servers configured, the following panel is displayed.
12. Enter the server’s IP address in the IP Address field.
13. If needed, change the Authentication port and Accounting port. (The default values work in most networks.)
14. Click Home
Select Yes when prompted to save the configuration change to the startup-config file on the device’s flash
memory.
15. Select the Management
to return to the System configuration panel, then select the Save link at the bottom of the dialog.
link to display the Management configuration panel.
June 2005 2 - 35
Page 52

Security Guide for ProCurve 9300/9400 Series Routing Switches
16. Select the Authentication Methods
following example.
17. Select the type of access for which you are defining the authentication method list from the Type field’s
pulldown menu. Each type of access must have a separate authentication-method list. For example, to
define the authentication-method list for logging into the CLI, select Login.
18. Select the primary authentication method by clicking on the radio button next to the method. For example, to
use a TACACS+ server as the primary means of authentication for logging on to the CLI, select TACACS+.
link to display the Login Authentication Sequence panel, as shown in the
19. Click the Add button to save the change to the device’s running-config file.
The access type and authentication method you selected are displayed in the table at the top of the dialog.
Each time you add an authentication method for a given access type, the software assigns a sequence
number to the entry. When the user tries to log in using the access type you selected, the software tries the
authentication sources in ascending sequence order until the access request is either approved or denied.
Each time you add an entry for a given access type, the software increments the sequence number. Thus, if
you want to use multiple authentication methods, make sure you enter the primary authentication method
first, the secondary authentication method second, and so on.
If you need to delete an entry, select the access type and authentication method for the entry, then click
Delete.
20. Click Home
Select Yes when prompted to save the configuration change to the startup-config file on the device’s flash
memory.
to return to the System configuration panel, then select the Save link at the bottom of the dialog.
2 - 36 June 2005
Page 53

Securing Access to Management Functions
21. To configure TACACS+ authorization, select the Management
panel and select the Authorization Methods
following example.
22. To configure TACACS+ exec authorization, select Exec from the Type field’s pulldown menu.
23. To configure TACACS+ command authorization, select Commands from the Type field’s pulldown menu and
select a privilege level by clicking on one of the following radio buttons:
• 0 – Authorization is performed for commands available at the Super User level (all commands)
• 4 – Authorization is performed for commands available at the Port Configuration level (port-config and
read-only commands)
• 5 – Authorization is performed for commands available at the Read Only level (read-only commands)
link to display the Authorization Method panel, as shown in the
link to display the Management configuration
NOTE: TACACS+ command authorization can be performed only for commands entered from Telnet or SSH
sessions, or from the console. No authorization is performed for commands entered at the Web management
interface or SNMP management applications.
24. Click on the radio button next to TACACS+.
25. Click the Add button to save the change to the device’s running-config file.
The authorization method you selected are displayed in the table at the top of the dialog. Each time you add
an authorization method for a given access type, the software assigns a sequence number to the entry.
When authorization is performed, the software tries the authorization sources in ascending sequence order
until the request is either approved or denied. Each time you add an entry for a given access type, the
software increments the sequence number. Thus, if you want to use multiple authentication methods, make
sure you enter the primary authentication method first, the secondary authentication method second, and so
on.
If you need to delete an entry, select the access type and authorization method for the entry, then click Delete.
June 2005 2 - 37
Page 54

Security Guide for ProCurve 9300/9400 Series Routing Switches
26. To configure TACACS+ accounting, select the Management
panel and select the Accounting Methods
following example.
27. To send an Accounting Start packet to the TACACS+ accounting server when an authenticated user
establishes a Telnet or SSH session on the HP device, and an Accounting Stop packet when the user logs
out, select Exec from the Type field’s pulldown menu.
28. To configure TACACS+ accounting for CLI commands, select Commands from the Type field’s pulldown menu
and select a privilege level by clicking on one of the following radio buttons:
• 0 – Records commands available at the Super User level (all commands)
• 4 – Records commands available at the Port Configuration level (port-config and read-only commands)
link to display the Accounting Method panel, as shown in the
link to display the Management configuration
• 5 – Records commands available at the Read Only level (read-only commands)
29. To configure TACACS+ accounting to record when system events occur on the HP device, select System from
the Type field’s pulldown menu.
30. Click on the radio button next to TACACS+.
31. Click the Add button to save the change to the device’s running-config file.
The accounting method you selected are displayed in the table at the top of the dialog. Each time you add an
accounting method for a given access type, the software assigns a sequence number to the entry. When
accounting is performed, the software tries the accounting sources in ascending sequence order until the
request is either approved or denied. Each time you add an entry for a given access type, the software
increments the sequence number. Thus, if you want to use multiple accounting methods, make sure you
enter the primary accounting method first, the secondary accounting method second, and so on.
If you need to delete an entry, select the access type and accounting method for the entry, then click Delete.
32. Select the Save
to the startup-config file on the device’s flash memory.
link at the bottom of the dialog. Select Yes when prompted to save the configuration change
Configuring RADIUS Security
You can use a Remote Authentication Dial In User Service (RADIUS) server to secure the following types of
access to the HP Routing Switch:
• Telnet access
• SSH access
• Web management access
2 - 38 June 2005
Page 55

Securing Access to Management Functions
• Access to the Privileged EXEC level and CONFIG levels of the CLI
NOTE: HP devices do not support RADIUS security for SNMP access.
RADIUS Authentication, Authorization, and Accounting
When RADIUS authentication is implemented, the HP device consults a RADIUS server to verify user names
and passwords. You can optionally configure RADIUS authorization, in which the HP device consults a list of
commands supplied by the RADIUS server to determine whether a user can execute a command he or she has
entered, as well as accounting, which causes the HP device to log information on a RADIUS accounting server
when specified events occur on the device.
NOTE: By default, a user logging into the device via Telnet or SSH first enters the User EXEC level. The user
can then enter the enable command to get to the Privileged EXEC level.
Starting with release 07.1.00, a user that is successfully authenticated can be automatically placed at the
Privileged EXEC level after login. See “Entering Privileged EXEC Mode After a Telnet or SSH Login” on page 2-
46.
RADIUS Authentication
When RADIUS authentication takes place, the following events occur:
1. A user attempts to gain access to the HP device by doing one of the following:
• Logging into the device using Telnet, SSH, or the Web management interface
• Entering the Privileged EXEC level or CONFIG level of the CLI
2. The user is prompted for a username and password.
3. The user enters a username and password.
4. The HP device sends a RADIUS Access-Request packet containing the username and password to the
RADIUS server.
5. The RADIUS server validates the HP device using a shared secret (the RADIUS key).
6. The RADIUS server looks up the username in its database.
7. If the username is found in the database, the RADIUS server validates the password.
8. If the password is valid, the RADIUS server sends an Access-Accept packet to the HP device, authenticating
the user. Within the Access-Accept packet are three HP vendor-specific attributes that indicate:
• The privilege level of the user
• A list of commands
• Whether the user is allowed or denied usage of the commands in the list
The last two attributes are used with RADIUS authorization, if configured.
9. The user is authenticated, and the information supplied in the Access-Accept packet for the user is stored on
the HP device. The user is granted the specified privilege level. If you configure RADIUS authorization, the
user is allowed or denied usage of the commands in the list.
RADIUS Authorization
When RADIUS authorization takes place, the following events occur:
1. A user previously authenticated by a RADIUS server enters a command on the HP device.
2. The HP device looks at its configuration to see if the command is at a privilege level that requires RADIUS
command authorization.
June 2005 2 - 39
Page 56

Security Guide for ProCurve 9300/9400 Series Routing Switches
3. If the command belongs to a privilege level that requires authorization, the HP device looks at the list of
commands delivered to it in the RADIUS Access-Accept packet when the user was authenticated. (Along
with the command list, an attribute was sent that specifies whether the user is permitted or denied usage of
the commands in the list.)
NOTE: After RADIUS authentication takes place, the command list resides on the HP device. The RADIUS
server is not consulted again once the user has been authenticated. This means that any changes made to
the user’s command list on the RADIUS server are not reflected until the next time the user is authenticated
by the RADIUS server, and the new command list is sent to the HP device.
4. If the command list indicates that the user is authorized to use the command, the command is executed.
RADIUS Accounting
RADIUS accounting works as follows:
1. One of the following events occur on the HP device:
• A user logs into the management interface using Telnet or SSH
• A user enters a command for which accounting has been configured
• A system event occurs, such as a reboot or reloading of the configuration file
2. The HP device checks its configuration to see if the event is one for which RADIUS accounting is required.
3. If the event requires RADIUS accounting, the HP device sends a RADIUS Accounting Start packet to the
RADIUS accounting server, containing information about the event.
4. The RADIUS accounting server acknowledges the Accounting Start packet.
5. The RADIUS accounting server records information about the event.
6. When the event is concluded, the HP device sends an Accounting Stop packet to the RADIUS accounting
server.
7. The RADIUS accounting server acknowledges the Accounting Stop packet.
AAA Operations for RADIUS
The following table lists the sequence of authentication, authorization, and accounting operations that take place
when a user gains access to an HP device that has RADIUS security configured.
User Action
User attempts to gain access to the
Privileged EXEC and CONFIG levels of
the CLI
User logs in using Telnet/SSH
Applicable AAA Operations
Enable authentication:
aaa authentication enable default <method-list>
System accounting start:
aaa accounting system default start-stop <method-list>
Login authentication:
aaa authentication login default <method-list>
EXEC accounting Start:
aaa accounting exec default start-stop <method-list>
System accounting Start:
aaa accounting system default start-stop <method-list>
2 - 40 June 2005
Page 57

Securing Access to Management Functions
User Action
User logs into the Web management
interface
User logs out of Telnet/SSH session
User enters system commands
(for example, reload, boot system)
Applicable AAA Operations
Web authentication:
aaa authentication web-server default <method-list>
Command authorization for logout command:
aaa authorization commands <privilege-level> default <method-list>
Command accounting:
aaa accounting commands <privilege-level> default start-stop
<method-list>
EXEC accounting stop:
aaa accounting exec default start-stop <method-list>
Command authorization:
aaa authorization commands <privilege-level> default <method-list>
Command accounting:
aaa accounting commands <privilege-level> default start-stop
<method-list>
System accounting stop:
aaa accounting system default start-stop <method-list>
User enters the command:
[no] aaa accounting system default
start-stop <method-list>
User enters other commands
Command authorization:
aaa authorization commands <privilege-level> default <method-list>
Command accounting:
aaa accounting commands <privilege-level> default start-stop
<method-list>
System accounting start:
aaa accounting system default start-stop <method-list>
Command authorization:
aaa authorization commands <privilege-level> default <method-list>
Command accounting:
aaa accounting commands <privilege-level> default start-stop
<method-list>
AAA Security for Commands Pasted Into the Running-Config
If AAA security is enabled on the device, commands pasted into the running-config are subject to the same AAA
operations as if they were entered manually.
When you paste commands into the running-config, and AAA command authorization and/or accounting is
configured on the device, AAA operations are performed on the pasted commands. The AAA operations are
performed before the commands are actually added to the running-config. The server performing the AAA
operations should be reachable when you paste the commands into the running-config file. If the device
determines that a pasted command is invalid, AAA operations are halted on the remaining commands. The
remaining commands may not be executed if command authorization is configured.
June 2005 2 - 41
Page 58

Security Guide for ProCurve 9300/9400 Series Routing Switches
NOTE: Since RADIUS command authorization relies on a list of commands received from the RADIUS server
when authentication is performed, it is important that you use RADIUS authentication when you also use RADIUS
command authorization.
RADIUS Configuration Considerations
• You must deploy at least one RADIUS server in your network.
• HP devices support authentication using up to eight RADIUS servers. The device tries to use the servers in
the order you add them to the device’s configuration. If one RADIUS server is not responding, the HP device
tries the next one in the list.
• You can select only one primary authentication method for each type of access to a device (CLI through
Telnet, CLI Privileged EXEC and CONFIG levels). For example, you can select RADIUS as the primary
authentication method for Telnet CLI access, but you cannot also select TACACS+ authentication as the
primary method for the same type of access. However, you can configure backup authentication methods for
each access type.
RADIUS Configuration Procedure
Use the following procedure to configure an HP device for RADIUS:
1. Configure HP vendor-specific attributes on the RADIUS server. See “Configuring HP-Specific Attributes on
the RADIUS Server” on page 2-42.
2. Identify the RADIUS server to the HP device. See “Identifying the RADIUS Server to the HP Device” on
page 2-43.
3. Set RADIUS parameters. See “Setting RADIUS Parameters” on page 2-44.
4. Configure authentication-method lists. See “Configuring Authentication-Method Lists for RADIUS” on page 2-
45.
5. Optionally configure RADIUS authorization. See “Configuring RADIUS Authorization” on page 2-47.
6. Optionally configure RADIUS accounting. “Configuring RADIUS Accounting” on page 2-48.
Configuring HP-Specific Attributes on the RADIUS Server
During the RADIUS authentication process, if a user supplies a valid username and password, the RADIUS server
sends an Access-Accept packet to the HP device, authenticating the user. Within the Access-Accept packet are
three HP vendor-specific attributes that indicate:
• The privilege level of the user
• A list of commands
• Whether the user is allowed or denied usage of the commands in the list
You must add these three HP vendor-specific attributes to your RADIUS server’s configuration, and configure the
attributes in the individual or group profiles of the users that will access the HP device.
2 - 42 June 2005
Page 59

Securing Access to Management Functions
HP’s Vendor-ID is 11, with Vendor-Type 1. The following table describes the HP vendor-specific attributes.
Table 2.5: HP vendor-specific attributes for RADIUS
Attribute Name Attribute ID Data Type Description
hp-privilege-level 1 integer Specifies the privilege level for the user.
This attribute can be set to one of the
following:
0 Super User level – Allows complete
read-and-write access to the system.
This is generally for system
administrators and is the only
management privilege level that
allows you to configure passwords.
4 Port Configuration level – Allows read-
and-write access for specific ports but
not for global (system-wide)
parameters.
5 Read Only level – Allows access to
the Privileged EXEC mode and
CONFIG mode of the CLI but only
with read access.
hp-command-string 2 string Specifies a list of CLI commands that are
permitted or denied to the user when
RADIUS authorization is configured.
The commands are delimited by semicolons (;). You can specify an asterisk (*)
as a wildcard at the end of a command
string.
For example, the following command list
specifies all show and debug ip
commands, as well as the write terminal
command:
show *; debug ip *; write term*
hp-command-exception-flag 3 integer Specifies whether the commands indicated
by the hp-command-string attribute are
permitted or denied to the user. This
attribute can be set to one of the following:
0 Permit execution of the commands
indicated by hp-command-string, deny
all other commands.
1 Deny execution of the commands
indicated by hp-command-string,
permit all other commands.
Identifying the RADIUS Server to the HP Device
To use a RADIUS server to authenticate access to an HP device, you must identify the server to the HP device.
For example:
ProCurveRS(config)# radius-server host 209.157.22.99
June 2005 2 - 43
Page 60

Security Guide for ProCurve 9300/9400 Series Routing Switches
Syntax: radius-server host <ip-addr> | <server-name> [auth-port <number> acct-port <number>]
The host <ip-addr> | <server-name> parameter is either an IP address or an ASCII text string.
The <auth-port> parameter is the Authentication port number; it is an optional parameter. The default is 1645.
The <acct-port> parameter is the Accounting port number; it is an optional parameter. The default is 1646.
Specifying Different Servers for Individual AAA Functions
In a RADIUS configuration, you can designate a server to handle a specific AAA task. For example, you can
designate one RADIUS server to handle authorization and another RADIUS server to handle accounting. You can
specify individual servers for authentication and accounting, but not for authorization. You can set the RADIUS key
for each server.
To specify different RADIUS servers for authentication, authorization, and accounting:
ProCurveRS(config)# radius-server host 1.2.3.4 authentication-only key abc
ProCurveRS(config)# radius-server host 1.2.3.5 authorization-only key def
ProCurveRS(config)# radius-server host 1.2.3.6 accounting-only key ghi
Syntax: radius-server host <ip-addr> | <server-name> [authentication-only | accounting-only | default] [key 0 | 1
<string>]
The default parameter causes the server to be used for all AAA functions.
After authentication takes place, the server that performed the authentication is used for authorization and/or
accounting. If the authenticating server cannot perform the requested function, then the next server in the
configured list of servers is tried; this process repeats until a server that can perform the requested function is
found, or every server in the configured list has been tried.
Setting RADIUS Parameters
You can set the following parameters in a RADIUS configuration:
• RADIUS key – This parameter specifies the value that the HP device sends to the RADIUS server when trying
to authenticate user access.
• Retransmit interval – This parameter specifies how many times the HP device will resend an authentication
request when the RADIUS server does not respond. The retransmit value can be from 1 – 5 times. The
default is 3 times.
• Timeout – This parameter specifies how many seconds the HP device waits for a response from a RADIUS
server before either retrying the authentication request, or determining that the RADIUS servers are
unavailable and moving on to the next authentication method in the authentication-method list. The timeout
can be from 1 – 15 seconds. The default is 3 seconds.
Setting the RADIUS Key
The key parameter in the radius-server command is used to encrypt RADIUS packets before they are sent over
the network. The value for the key parameter on the HP device should match the one configured on the RADIUS
server. The key can be from 1 – 32 characters in length and cannot include any space characters.
To specify a RADIUS server key:
ProCurveRS(config)# radius-server key mirabeau
Syntax: radius-server key [0 | 1] <string>
When you display the configuration of the HP device, the RADIUS key is encrypted. For example:
ProCurveRS(config)# radius-server key 1 abc
ProCurveRS(config)# write terminal
...
radius-server host 1.2.3.5
radius key 1 $!2d
2 - 44 June 2005
Page 61

Securing Access to Management Functions
NOTE: Encryption of the RADIUS keys is done by default. The 0 parameter disables encryption. The 1
parameter is not required; it is provided for backwards compatibility.
Setting the Retransmission Limit
The retransmit parameter specifies the maximum number of retransmission attempts. When an authentication
request times out, the HP software will retransmit the request up to the maximum number of retransmissions
configured. The default retransmit value is 3 retries. The range of retransmit values is from 1 – 5.
To set the RADIUS retransmit limit:
ProCurveRS(config)# radius-server retransmit 5
Syntax: radius-server retransmit <number>
Setting the Timeout Parameter
The timeout parameter specifies how many seconds the HP device waits for a response from the RADIUS server
before either retrying the authentication request, or determining that the RADIUS server is unavailable and moving
on to the next authentication method in the authentication-method list. The timeout can be from 1 – 15 seconds.
The default is 3 seconds.
ProCurveRS(config)# radius-server timeout 5
Syntax: radius-server timeout <number>
Configuring Authentication-Method Lists for RADIUS
You can use RADIUS to authenticate Telnet/SSH access and access to Privileged EXEC level and CONFIG levels
of the CLI. When configuring RADIUS authentication, you create authentication-method lists specifically for these
access methods, specifying RADIUS as the primary authentication method.
Within the authentication-method list, RADIUS is specified as the primary authentication method and up to six
backup authentication methods are specified as alternates. If RADIUS authentication fails due to an error, the
device tries the backup authentication methods in the order they appear in the list.
When you configure authentication-method lists for RADIUS, you must create a separate authentication-method
list for Telnet or SSH CLI access and for CLI access to the Privileged EXEC level and CONFIG levels of the CLI.
To create an authentication-method list that specifies RADIUS as the primary authentication method for securing
Telnet access to the CLI:
ProCurveRS(config)# enable telnet authentication
ProCurveRS(config)# aaa authentication login default radius local
The commands above cause RADIUS to be the primary authentication method for securing Telnet access to the
CLI. If RADIUS authentication fails due to an error with the server, local authentication is used instead.
To create an authentication-method list that specifies RADIUS as the primary authentication method for securing
access to Privileged EXEC level and CONFIG levels of the CLI:
ProCurveRS(config)# aaa authentication enable default radius local none
The command above causes RADIUS to be the primary authentication method for securing access to Privileged
EXEC level and CONFIG levels of the CLI. If RADIUS authentication fails due to an error with the server, local
authentication is used instead. If local authentication fails, no authentication is used; the device automatically
permits access.
Syntax: [no] aaa authentication enable | login default <method1> [<method2>] [<method3>] [<method4>]
[<method5>] [<method6>] [<method7>]
The web-server | enable | login parameter specifies the type of access this authentication-method list controls.
You can configure one authentication-method list for each type of access.
June 2005 2 - 45
Page 62

Security Guide for ProCurve 9300/9400 Series Routing Switches
NOTE: If you configure authentication for Web management access, authentication is performed each time a
page is requested from the server. When frames are enabled on the Web management interface, the browser
sends an HTTP request for each frame. The HP device authenticates each HTTP request from the browser. To
limit authentications to one per page, disable frames on the Web management interface.
The <method1> parameter specifies the primary authentication method. The remaining optional <method>
parameters specify additional methods to try if an error occurs with the primary method. A method can be one of
the values listed in the Method Parameter column in the following table.
Table 2.6: Authentication Method Values
Method Parameter
line
enable
local
tacacs
tacacs+
radius
none
Description
Authenticate using the password you configured for Telnet access. The
Telnet password is configured using the enable telnet password…
command.
Authenticate using the password you configured for the Super User
privilege level. This password is configured using the enable super-
user-password… command. See “Setting Passwords for Management
Privilege Levels” on page 2-14.
Authenticate using a local user name and password you configured on
the device. Local user names and passwords are configured using the
username… command. See
page 2-17.
Authenticate using the database on a TACACS server. You also must
identify the server to the device using the tacacs-server command.
Authenticate using the database on a TACACS+ server. You also must
identify the server to the device using the tacacs-server command.
Authenticate using the database on a RADIUS server. You also must
identify the server to the device using the radius-server command.
Do not use any authentication method. The device automatically
permits access.
See “Setting a Telnet Password” on page 2-13.
“Configuring a Local User Account” on
NOTE: For examples of how to define authentication-method lists for types of authentication other than RADIUS,
“Configuring Authentication-Method Lists” on page 2-54.
see
Entering Privileged EXEC Mode After a Telnet or SSH Login
By default, a user enters User EXEC mode after a successful login through Telnet or SSH. Optionally, you can
configure the device so that a user enters Privileged EXEC mode after a Telnet or SSH login. To do this, use the
following command:
ProCurveRS(config)# aaa authentication login privilege-mode
Syntax: aaa authentication login privilege-mode
The user’s privilege level is based on the privilege level granted during login.
Configuring Enable Authentication to Prompt for Password Only
If Enable authentication is configured on the device, when a user attempts to gain Super User access to the
Privileged EXEC and CONFIG levels of the CLI, by default he or she is prompted for a username and password.
In this release, you can configure the HP device to prompt only for a password. The device uses the username
2 - 46 June 2005
Page 63

Securing Access to Management Functions
entered at login, if one is available. If no username was entered at login, the device prompts for both username
and password.
To configure the HP device to prompt only for a password when a user attempts to gain Super User access to the
Privileged EXEC and CONFIG levels of the CLI:
ProCurveRS(config)# aaa authentication enable implicit-user
Syntax: [no] aaa authentication enable implicit-user
Configuring RADIUS Authorization
HP devices support RADIUS authorization for controlling access to management functions in the CLI. Two kinds
of RADIUS authorization are supported:
• Exec authorization determines a user’s privilege level when they are authenticated
• Command authorization consults a RADIUS server to get authorization for commands entered by the user
Configuring Exec Authorization
When RADIUS exec authorization is performed, the HP device consults a RADIUS server to determine the
privilege level of the authenticated user. To configure RADIUS exec authorization on the HP device, enter the
following command:
ProCurveRS(config)# aaa authorization exec default radius
Syntax: aaa authorization exec default radius | none
If you specify none, or omit the aaa authorization exec command from the device’s configuration, no exec
authorization is performed.
NOTE: If the aaa authorization exec default radius command exists in the configuration, following successful
authentication the device assigns the user the privilege level specified by the hp-privilege-level attribute received
from the RADIUS server. If the aaa authorization exec default radius command does not exist in the
configuration, then the value in the hp-privilege-level attribute is ignored, and the user is granted Super User
access.
Also note that in order for the aaa authorization exec default radius command to work, either the
aaa authentication enable default radius command, or the aaa authentication login privilege-mode
command must also exist in the configuration.
Configuring Command Authorization
When RADIUS command authorization is enabled, the HP device consults the list of commands supplied by the
RADIUS server during authentication to determine whether a user can execute a command he or she has
entered.
You enable RADIUS command authorization by specifying a privilege level whose commands require
authorization. For example, to configure the HP device to perform authorization for the commands available at the
Super User privilege level (that is; all commands on the device), enter the following command:
ProCurveRS(config)# aaa authorization commands 0 default radius
Syntax: aaa authorization commands <privilege-level> default radius | tacacs+ | none
The <privilege-level> parameter can be one of the following:
• 0 – Authorization is performed (that is, the HP device looks at the command list) for commands available at
the Super User level (all commands)
• 4 – Authorization is performed for commands available at the Port Configuration level (port-config and readonly commands)
• 5 – Authorization is performed for commands available at the Read Only level (read-only commands)
June 2005 2 - 47
Page 64

Security Guide for ProCurve 9300/9400 Series Routing Switches
NOTE: RADIUS command authorization can be performed only for commands entered from Telnet or SSH
sessions, or from the console. No authorization is performed for commands entered at the Web management
interface or SNMP management applications.
NOTE: Since RADIUS command authorization relies on the command list supplied by the RADIUS server during
authentication, you cannot perform RADIUS authorization without RADIUS authentication.
Command Authorization and Accounting for Console Commands
The HP device supports command authorization and command accounting for CLI commands entered at the
console. To configure the device to perform command authorization and command accounting for console
commands, enter the following:
ProCurveRS(config)# enable aaa console
Syntax: enable aaa console
CAUTION: If you have previously configured the device to perform command authorization using a RADIUS
server, entering the enable aaa console command may prevent the execution of any subsequent commands
entered on the console.
This happens because RADIUS command authorization requires a list of allowable commands from the RADIUS
server. This list is obtained during RADIUS authentication. For console sessions, RADIUS authentication is
performed only if you have configured Enable authentication and specified RADIUS as the authentication method
(for example, with the aaa authentication enable default radius command). If RADIUS authentication is never
performed, the list of allowable commands is never obtained from the RADIUS server. Consequently, there would
be no allowable commands on the console.
Configuring RADIUS Accounting
HP devices support RADIUS accounting for recording information about user activity and system events. When
you configure RADIUS accounting on an HP device, information is sent to a RADIUS accounting server when
specified events occur, such as when a user logs into the device or the system is rebooted.
Configuring RADIUS Accounting for Telnet/SSH (Shell) Access
To send an Accounting Start packet to the RADIUS accounting server when an authenticated user establishes a
Telnet or SSH session on the HP device, and an Accounting Stop packet when the user logs out:
ProCurveRS(config)# aaa accounting exec default start-stop radius
Syntax: aaa accounting exec default start-stop radius | tacacs+ | none
Configuring RADIUS Accounting for CLI Commands
You can configure RADIUS accounting for CLI commands by specifying a privilege level whose commands require
accounting. For example, to configure the HP device to perform RADIUS accounting for the commands available
at the Super User privilege level (that is; all commands on the device), enter the following command:
ProCurveRS(config)# aaa accounting commands 0 default start-stop radius
An Accounting Start packet is sent to the RADIUS accounting server when a user enters a command, and an
Accounting Stop packet is sent when the service provided by the command is completed.
NOTE: If authorization is enabled, and the command requires authorization, then authorization is performed
before accounting takes place. If authorization fails for the command, no accounting takes place.
Syntax: aaa accounting commands <privilege-level> default start-stop radius | tacacs | none
The <privilege-level> parameter can be one of the following:
• 0 – Records commands available at the Super User level (all commands)
2 - 48 June 2005
Page 65

Securing Access to Management Functions
• 4 – Records commands available at the Port Configuration level (port-config and read-only commands)
• 5 – Records commands available at the Read Only level (read-only commands)
Configuring RADIUS Accounting for System Events
You can configure RADIUS accounting to record when system events occur on the HP device. System events
include rebooting and when changes to the active configuration are made.
The following command causes an Accounting Start packet to be sent to the RADIUS accounting server when a
system event occurs, and a Accounting Stop packet to be sent when the system event is completed:
ProCurveRS(config)# aaa accounting system default start-stop radius
Syntax: aaa accounting system default start-stop radius | tacacs+ | none
Configuring an Interface as the Source for All RADIUS Packets
You can designate the lowest-numbered IP address configured an Ethernet port, loopback interface, or virtual
interface as the source IP address for all RADIUS packets from the Routing Switch. Identifying a single source IP
address for RADIUS packets provides the following benefits:
• If your RADIUS server is configured to accept packets only from specific links or IP addresses, you can use
this feature to simplify configuration of the RADIUS server by configuring the HP device to always send the
RADIUS packets from the same link or source address.
• If you specify a loopback interface as the single source for RADIUS packets, RADIUS servers can receive the
packets regardless of the states of individual links. Thus, if a link to the RADIUS server becomes unavailable
but the client or server can be reached through another link, the client or server still receives the packets, and
the packets still have the source IP address of the loopback interface.
The software contains separate CLI commands for specifying the source interface for Telnet, TACACS/TACACS+,
and RADIUS packets. You can configure a source interface for one or more of these types of packets.
To specify an Ethernet port or a loopback or virtual interface as the source for all RADIUS packets from the device,
use the following CLI method. The software uses the lowest-numbered IP address configured on the port or
interface as the source IP address for RADIUS packets originated by the device.
To specify the lowest-numbered IP address configured on a virtual interface as the device’s source for all RADIUS
packets, enter commands such as the following:
ProCurveRS(config)# int ve 1
ProCurveRS(config-vif-1)# ip address 10.0.0.3/24
ProCurveRS(config-vif-1)# exit
ProCurveRS(config)# ip radius source-interface ve 1
The commands in this example configure virtual interface 1, assign IP address 10.0.0.3/24 to the interface, then
designate the interface as the source for all RADIUS packets from the Routing Switch.
Syntax: ip radius source-interface ethernet <portnum> | loopback <num> | ve <num>
The <num> parameter is a loopback interface or virtual interface number. If you specify an Ethernet port, the
<portnum> is the port’s number (including the slot number, if you are configuring a Routing Switch).
June 2005 2 - 49
Page 66

Security Guide for ProCurve 9300/9400 Series Routing Switches
Displaying RADIUS Configuration Information
The show aaa command displays information about all TACACS/TACACS+ and RADIUS servers identified on the
device. For example:
ProCurveRS# show aaa
Tacacs+ key: hp
Tacacs+ retries: 1
Tacacs+ timeout: 15 seconds
Tacacs+ dead-time: 3 minutes
Tacacs+ Server: 207.95.6.90 Port:49:
opens=6 closes=3 timeouts=3 errors=0
packets in=4 packets out=4
no connection
Radius key: networks
Radius retries: 3
Radius timeout: 3 seconds
Radius dead-time: 3 minutes
Radius Server: 207.95.6.90 Auth Port=1645 Acct Port=1646:
opens=2 closes=1 timeouts=1 errors=0
packets in=1 packets out=4
no connection
The following table describes the RADIUS information displayed by the show aaa command.
Table 2.7: Output of the show aaa command for RADIUS
Field
Radius key
Radius retries
Radius timeout
Radius dead-time
Radius Server
Description
The setting configured with the radius-server key command. At the Super User
privilege level, the actual text of the key is displayed. At the other privilege levels, a
string of periods (....) is displayed instead of the text.
The setting configured with the radius-server retransmit command.
The setting configured with the radius-server timeout command.
The setting configured with the radius-server dead-time command.
For each RADIUS server, the IP address, and the following statistics are displayed:
Auth Port RADIUS authentication port number (default 1645)
Acct Port RADIUS accounting port number (default 1646)
opens Number of times the port was opened for communication with the
server
closes Number of times the port was closed normally
timeouts Number of times port was closed due to a timeout
errors Number of times an error occurred while opening the port
packets in Number of packets received from the server
packets out Number of packets sent to the server
connection
2 - 50 June 2005
The current connection status. This can be “no connection” or “connection active”.
Page 67

Securing Access to Management Functions
The show web command displays the privilege level of Web management interface users. For example:
ProCurveRS(config)# show web
User Privilege IP address
set 0 192.168.1.234
Syntax: show web
USING THE WEB MANAGEMENT INTERFACE
To configure RADIUS using the Web management interface:
1. Log on to the device using a valid user name and password for read-write access. The System configuration
panel is displayed.
2. If you configuring RADIUS authentication for Telnet access to the CLI, go to step 3. Otherwise, go to step 7.
3. Select the Management
4. Select Enable next to Telnet Authentication. You must enable Telnet authentication if you want to use
TACACS/TACACS+ or RADIUS to authenticate Telnet access to the device.
5. Click Apply to apply the change.
6. Select the Home
link to return to the System configuration panel.
link to display the Management configuration panel.
7. Select the RADIUS
8. Change the retransmit interval, time out, and dead time if needed.
9. Enter the authentication key if applicable.
10. Click Apply if you changed any RADIUS parameters.
11. Select the RADIUS Server
• If any RADIUS servers are already configured on the device, the servers are listed in a table. Select the
Add RADIUS Server
• If the device does not have any RADIUS servers configured, the following panel is displayed.
link from the System configuration panel to display the RADIUS panel.
link.
link to display the following panel.
12. Enter the server’s IP address in the IP Address field.
13. If needed, change the Authentication port and Accounting port. (The default values work in most networks.)
June 2005 2 - 51
Page 68

Security Guide for ProCurve 9300/9400 Series Routing Switches
14. Click Home
Select Yes when prompted to save the configuration change to the startup-config file on the device’s flash
memory.
15. Select the Management
16. Select the Authentication Methods
following example.
to return to the System configuration panel, then select the Save link at the bottom of the dialog.
link to display the Management configuration panel.
link to display the Login Authentication Sequence panel, as shown in the
17. Select the type of access for which you are defining the authentication method list from the Type field’s
pulldown menu. Each type of access must have a separate authentication-method list. For example, to
define the authentication-method list for logging into the CLI, select Login.
18. Select the primary authentication method by clicking on the radio button next to the method. For example, to
use a RADIUS server as the primary means of authentication for logging on to the CLI, select RADIUS.
19. Click the Add button to save the change to the device’s running-config file.
The access type and authentication method you selected are displayed in the table at the top of the dialog.
Each time you add an authentication method for a given access type, the software assigns a sequence
number to the entry. When the user tries to log in using the access type you selected, the software tries the
authentication sources in ascending sequence order until the access request is either approved or denied.
Each time you add an entry for a given access type, the software increments the sequence number. Thus, if
you want to use multiple authentication methods, make sure you enter the primary authentication method
first, the secondary authentication method second, and so on.
If you need to delete an entry, select the access type and authentication method for the entry, then click
Delete.
20. Click Home
Select Yes when prompted to save the configuration change to the startup-config file on the device’s flash
memory.
to return to the System configuration panel, then select the Save link at the bottom of the dialog.
2 - 52 June 2005
Page 69

Securing Access to Management Functions
21. To configure RADIUS command authorization, select the Management
configuration panel and select the Authorization Methods
shown in the following example.
22. Select Commands from the Type field’s pulldown menu.
23. Select a privilege level by clicking on one of the following radio buttons:
• 0 – Authorization is performed for commands available at the Super User level (all commands)
• 4 – Authorization is performed for commands available at the Port Configuration level (port-config and
read-only commands)
• 5 – Authorization is performed for commands available at the Read Only level (read-only commands)
link to display the Authorization Method panel, as
link to display the Management
NOTE: RADIUS authorization can be performed only for commands entered from Telnet or SSH sessions,
or from the console. No authorization is performed for commands entered at the Web management interface
or SNMP management applications.
NOTE: Since RADIUS authorization relies on the command list supplied by the RADIUS server during
authentication, you cannot perform RADIUS authorization without RADIUS authentication.
24. Click on the radio button next to Radius.
25. Click the Add button to save the change to the device’s running-config file.
The authorization method you selected are displayed in the table at the top of the dialog. Each time you add
an authorization method for a given access type, the software assigns a sequence number to the entry.
When authorization is performed, the software tries the authorization sources in ascending sequence order
until the request is either approved or denied. Each time you add an entry for a given access type, the
software increments the sequence number. Thus, if you want to use multiple authentication methods, make
sure you enter the primary authentication method first, the secondary authentication method second, and so
on.
If you need to delete an entry, select the access type and authorization method for the entry, then click Delete.
June 2005 2 - 53
Page 70

Security Guide for ProCurve 9300/9400 Series Routing Switches
26. To configure RADIUS accounting, select the Management
and select the Accounting Methods
example.
27. To send an Accounting Start packet to the RADIUS accounting server when an authenticated user
establishes a Telnet or SSH session on the HP device, and an Accounting Stop packet when the user logs
out, select Exec from the Type field’s pulldown menu.
28. To configure RADIUS accounting for CLI commands, select Commands from the Type field’s pulldown menu
and select a privilege level by clicking on one of the following radio buttons:
• 0 – Records commands available at the Super User level (all commands)
link to display the Accounting Method panel, as shown in the following
link to display the Management configuration panel
• 4 – Records commands available at the Port Configuration level (port-config and read-only commands)
• 5 – Records commands available at the Read Only level (read-only commands)
29. To configure RADIUS accounting to record when system events occur on the HP device, select System from
the Type field’s pulldown menu.
30. Click on the radio button next to Radius.
31. Click the Add button to save the change to the device’s running-config file.
The accounting method you selected are displayed in the table at the top of the dialog. Each time you add an
accounting method for a given access type, the software assigns a sequence number to the entry. When
accounting is performed, the software tries the accounting sources in ascending sequence order until the
request is either approved or denied. Each time you add an entry for a given access type, the software
increments the sequence number. Thus, if you want to use multiple accounting methods, make sure you
enter the primary accounting method first, the secondary accounting method second, and so on.
If you need to delete an entry, select the access type and accounting method for the entry, then click Delete.
32. Select the Save
to the startup-config file on the device’s flash memory.
link at the bottom of the dialog. Select Yes when prompted to save the configuration change
Configuring Authentication-Method Lists
To implement one or more authentication methods for securing access to the device, you configure authenticationmethod lists that set the order in which the authentication methods are consulted.
In an authentication-method list, you specify the access method (Telnet, Web, SNMP, and so on) and the order in
which the device tries one or more of the following authentication methods:
• Local Telnet login password
2 - 54 June 2005
Page 71

Securing Access to Management Functions
• Local password for the Super User privilege level
• Local user accounts configured on the device
• Database on a TACACS or TACACS+ server
• Database on a RADIUS server
• No authentication
NOTE: The TACACS/TACACS+, RADIUS, and Telnet login password authentication methods are not supported
for SNMP access.
NOTE: To authenticate Telnet access to the CLI, you also must enable the authentication by entering the
enable telnet authentication command at the global CONFIG level of the CLI. You cannot enable Telnet
authentication using the Web management interface.
NOTE: You do not need an authentication-method list to secure access based on ACLs or a list of IP addresses.
See “Using ACLs to Restrict Remote Access” on page 2-4 or “Restricting Remote Access to the Device to Specific
IP Addresses” on page 2-7.
In an authentication-method list for a particular access method, you can specify up to seven authentication
methods. If the first authentication method is successful, the software grants access and stops the authentication
process. If the access is rejected by the first authentication method, the software denies access and stops
checking.
However, if an error occurs with an authentication method, the software tries the next method on the list, and so
on. For example, if the first authentication method is the RADIUS server, but the link to the server is down, the
software will try the next authentication method in the list.
NOTE: If an authentication method is working properly and the password (and user name, if applicable) is not
known to that method, this is not an error. The authentication attempt stops, and the user is denied access.
The software will continue this process until either the authentication method is passed or the software reaches
the end of the method list. If the Super User level password is not rejected after all the access methods in the list
have been tried, access is granted.
n
Configuration Considerations for Authentication-Method Lists
• For CLI access, you must configure authentication-method lists if you want the device to authenticate access
using local user accounts or a RADIUS server. Otherwise, the device will authenticate using only the locally
based password for the Super User privilege level.
• When no authentication-method list is configured specifically for Web management access, the device
performs authentication using the SNMP community strings:
• For read-only access, you can use the user name “get” and the password “public”. The default read-only
community string is “public”.
• Beginning with software release 05.1.00, there is no default read-write community string. Thus, by
default, you cannot open a read-write management session using the Web management interface. You
first must configure a read-write community string using the CLI. Then you can log on using “set” as the
user name and the read-write community string you configure as the password.
TACACS/TACACS+ Security” on page 2-20.
See “Configuring
• If you configure an authentication-method list for Web management access and specify “local” as the primary
authentication method, users who attempt to access the device using the Web management interface must
supply a user name and password configured in one of the local user accounts on the device. The user
cannot access the device by entering “set” or “get” and the corresponding SNMP community string.
• For devices that can be managed using SNMP management applications, the default authentication method
(if no authentication-method list is configured for SNMP) is the CLI Super User level password. If no Super
June 2005 2 - 55
Page 72

Security Guide for ProCurve 9300/9400 Series Routing Switches
User level password is configured, then access through SNMP management applications is not
authenticated. To use local user accounts to authenticate access through SNMP management applications,
configure an authentication-method list for SNMP access and specify “local” as the primary authentication
method.
Examples of Authentication-Method Lists
Example 1: The following example shows how to configure authentication-method lists for the Web management
interface, SNMP management applications, and the Privileged EXEC and CONFIG levels of the CLI. In this
example, the primary authentication method for each is “local”. The device will authenticate access attempts
using the locally configured user names and passwords first.
To configure an authentication-method list for the Web management interface, enter a command such as the
following:
ProCurveRS(config)# aaa authentication web-server default local
This command configures the device to use the local user accounts to authenticate access to the device through
the Web management interface. If the device does not have a user account that matches the user name and
password entered by the user, the user is not granted access.
To configure an authentication-method list for SNMP management applications, enter a command such as the
following:
ProCurveRS(config)# aaa authentication snmp-server default local
This command configures the device to use the local user accounts to authenticate access attempts through any
network management software, such as SNMP management applications.
To configure an authentication-method list for the Privileged EXEC and CONFIG levels of the CLI, enter the
following command:
ProCurveRS(config)# aaa authentication enable default local
This command configures the device to use the local user accounts to authenticate attempts to access the
Privileged EXEC and CONFIG levels of the CLI.
Example 2: To configure the device to consult a RADIUS server first to authenticate attempts to access the
Privileged EXEC and CONFIG levels of the CLI, then consult the local user accounts if the RADIUS server is
unavailable, enter the following command:
ProCurveRS(config)# aaa authentication enable default radius local
Syntax: [no] aaa authentication snmp-server | web-server | enable | login default <method1> [<method2>]
[<method3>] [<method4>] [<method5>] [<method6>] [<method7>]
The snmp-server | web-server | enable | login parameter specifies the type of access this authenticationmethod list controls. You can configure one authentication-method list for each type of access.
NOTE: TACACS/TACACS+ and RADIUS are supported only with the enable and login parameters.
The <method1> parameter specifies the primary authentication method. The remaining optional <method>
parameters specify additional methods to try if an error occurs with the primary method. A method can be one of
the values listed in the Method Parameter column in the following table.
Table 2.8: Authentication Method Values
Method Parameter Description
line Authenticate using the password you configured for Telnet access. The
Telnet password is configured using the enable telnet password…
command. See “Setting a Telnet Password” on page 2-13.
2 - 56 June 2005
Page 73

Securing Access to Management Functions
Table 2.8: Authentication Method Values (Continued)
Method Parameter
enable
local
tacacs
tacacs+
radius
none
USING THE WEB MANAGEMENT INTERFACE
To configure an authentication-method list with the Web management interface, use the following procedure. This
example to causes the device to use a RADIUS server to authenticate attempts to log in through the CLI:
1. Log on to the device using a valid user name and password for read-write access. The System configuration
panel is displayed.
2. Select the Management
3. Select the Authentication Methods
following example.
link to display the Management configuration panel.
Description
Authenticate using the password you configured for the Super User
privilege level. This password is configured using the enable super-
user-password… command. See
Privilege Levels” on page 2-14.
Authenticate using a local user name and password you configured on
the device. Local user names and passwords are configured using the
username… command. See
page 2-17.
Authenticate using the database on a TACACS server. You also must
identify the server to the device using the tacacs-server command.
Authenticate using the database on a TACACS+ server. You also must
identify the server to the device using the tacacs-server command.
Authenticate using the database on a RADIUS server. You also must
identify the server to the device using the radius-server command.
See
“Configuring RADIUS Security” on page 2-38.
Do not use any authentication method. The device automatically
permits access.
link to display the Login Authentication Sequence panel, as shown in the
“Setting Passwords for Management
“Configuring a Local User Account” on
June 2005 2 - 57
Page 74

Security Guide for ProCurve 9300/9400 Series Routing Switches
4. Select the type of access for which you are defining the authentication method list from the Type field’s
pulldown menu. Each type of access must have a separate authentication-method list. For example, to
define the authentication-method list for logging into the CLI, select Login.
5. Select the primary authentication method by clicking the button next to the method. For example, to use a
RADIUS server as the primary means of authentication for logging on to the CLI, select RADIUS.
6. Click the Add button to save the change to the device’s running-config file. The access type and
authentication method you selected are displayed in the table at the top of the dialog. Each time you add an
authentication method for a given access type, the software assigns a sequence number to the entry. When
the user tries to log in using the access type you selected, the software tries the authentication sources in
ascending sequence order until the access request is either approved or denied. Each time you add an entry
for a given access type, the software increments the sequence number. Thus, if you want to use multiple
authentication methods, make sure you enter the primary authentication method first, the secondary
authentication method second, and so on.
If you need to delete an entry, select the access type and authentication method for the entry, then click
Delete.
7. Select the Save
to the startup-config file on the device’s flash memory.
link at the bottom of the dialog. Select Yes when prompted to save the configuration change
2 - 58 June 2005
Page 75

Chapter 3
Configuring Secure Shell
Overview
Secure Shell (SSH) is a mechanism for allowing secure remote access to management functions on an HP
device. SSH provides a function similar to Telnet. Users can log into and configure the device using a publicly or
commercially available SSH client program, just as they can with Telnet. However, unlike Telnet, which provides
no security, SSH provides a secure, encrypted connection to the device.
SSH supports Arcfour, IDEA, Blowfish, DES (56-bit) and Triple DES (168-bit) data encryption methods. Nine
levels of data compression are available. You can configure your SSH client to use any one of these data
compression levels when connecting to an HP device.
HP devices also support Secure Copy (SCP) for securely transferring files between an HP device and SCPenabled remote hosts. See “Using Secure Copy” on page 3-11 for more information.
NOTE: SSH is supported only on 9304M, 9308M, and 9315M Routing Switches with redundant management.
SSH Version 2 Support
In releases prior to 07.8.00, HP devices supported SSH version 1 (SSHv1). Starting with release 07.8.00, HP
devices support SSH version 2 (SSHv2).
SSHv2 is a substantial revision of Secure Shell, comprising the following hybrid protocols and definitions:
• SSH Transport Layer Protocol
• SSH Authentication Protocol
• SSH Connection Protocol
• GSSAPI Authentication and Key Exchange for the Secure Shell Protocol
• Generic Message Exchange Authentication For SSH
• SECSH Public Key File Format
• SSH Fingerprint Format
• SSH Protocol Assigned Numbers
• DNS to Securely Publish SSH Key Fingerprints
• SSH Transport Layer Encryption Modes
• Session Channel Break Extension
June 2005 3 - 1
Page 76

Security Guide for ProCurve 9300/9400 Series Routing Switches
• SCP/SFTP/SSH URI Format
NOTE: The CLI commands for setting up and configuring SSHv2 on an HP device are identical to those for
SSHv1.
If you are using redundant management modules, you can synchronize the RSA host key pair between the active
and standby modules by entering the sync-standby code command at the Privileged EXEC level of the CLI.
When you subsequently enter the write memory command, the RSA host key pair is synchronized to the standby
module.
HP’s SSHv2 implementation is compatible with all versions of the SSHv2 protocol (2.1, 2.2, and so on). At the
beginning of an SSH session, the HP device negotiates the version of SSHv2 to be used. The highest version of
SSHv2 supported by both the HP device and the client is the version that is used for the session. Once the
SSHv2 version is negotiated, the encryption algorithm with the highest security ranking is selected to be used for
the session.
Tested SSHv2 Clients
The following SSH clients have been tested with SSHv2:
• SSH Secure Shell 3.2.3
• Van Dyke SecureCRT 4.0
• F-Secure SSH Client 5.3
• Tera Term Pro 3.1.3
• PuTTY 0.54
• OpenSSH 3.5_p1
Supported Encryption Algorithms for SSHv2
The following encryption algorithms are supported with HP implementation of SSHv2:
• AES
• Twofish
• Blowfish
• 3DES
• Arcfour(RC4)
• CAST
• None selected
Supported MAC (Message Authentication Code) Algorithms
The following MAC algorithms are supported with HP implementation of SSHv2:
• MD5
• SHA
• None selected
Configuring SSH
HP’s implementation of SSH supports two kinds of user authentication:
• RSA challenge-response authentication, where a collection of public keys are stored on the device. Only
clients with a private key that corresponds to one of the stored public keys can gain access to the device using
SSH.
• Password authentication, where users attempting to gain access to the device using an SSH client are
3 - 2 June 2005
Page 77

Configuring Secure Shell
authenticated with passwords stored on the device or on a TACACS/TACACS+ or RADIUS server
Both kinds of user authentication are enabled by default. You can configure the device to use one or both of them.
Configuring Secure Shell on an HP device consists of the following steps:
1. Setting the HP device’s host name and domain name
2. Generating a host RSA public and private key pair for the device
3. Configuring RSA challenge-response authentication
4. Setting optional parameters
You can also view information about active SSH connections on the device as well as terminate them.
Setting the Host Name and Domain Name
If you have not already done so, establish a host name and domain name for the HP device. For example:
ProCurveRS(config)# hostname ProCurveRS
ProCurveRS(config)# ip dns domain-name hp.com
Syntax: hostname <name>
Syntax: ip dns domain-name <name>
Generating a Host RSA Key Pair
When SSH is configured, a public and private host RSA key pair is generated for the HP device. The SSH server
on the HP device uses this host RSA key pair, along with a dynamically generated server RSA key pair, to
negotiate a session key and encryption method with the client trying to connect to it.
The host RSA key pair is stored in the HP device’s system-config file. Only the public key is readable. The public
key should be added to a “known hosts” file (for example, $HOME/.ssh/known_hosts on UNIX systems) on the
clients who want to access the device. Some SSH client programs add the public key to the known hosts file
automatically; in other cases, you must manually create a known hosts file and place the HP device’s public key in
it. See
To generate a public and private RSA host key pair for the HP device:
ProCurveRS(config)# crypto key generate rsa
ProCurveRS(config)# write memory
The crypto key generate rsa command places an RSA host key pair in the running-config file and enables SSH
on the device. To disable SSH, you must delete the RSA host key pair. To do this, enter the following commands:
“Providing the Public Key to Clients” on page 3-4 for an example of what to place in the known hosts file.
ProCurveRS(config)# crypto key zeroize rsa
ProCurveRS(config)# write memory
The crypto key zeroize rsa command deletes the RSA host key pair in the running-config file and disables SSH
on the device.
Syntax: crypto key generate | zeroize rsa
You can optionally configure the HP device to hide the RSA host key pair in the running-config file. To do this,
enter the following command:
ProCurveRS# ssh no-show-host-keys
Syntax: ssh no-show-host-keys
After entering the ssh no-show-host-keys command, you can display the RSA host key pair in the running-config
file with the following command:
ProCurveRS# ssh show-host-keys
Syntax: ssh show-host-keys
June 2005 3 - 3
Page 78

Security Guide for ProCurve 9300/9400 Series Routing Switches
Notes:
• If an RSA host key pair is stored in internal memory on the HP device, it is used even if the startup-config file
contains a different RSA host key pair.
• If no RSA host key pair is stored in internal memory, but the startup-config file contains an RSA host key pair,
the key pair in the startup-config file is used. If you later generate an RSA host key pair with the crypto key
generate rsa command, the new key pair takes effect only after you store it in internal memory with the write
memory command and reboot the HP device.
• If no RSA host key pair is stored in internal memory, and the startup-config file contains an RSA host key pair,
the first time you enter the write memory command, it will save the RSA host key pair in the startup-config
file to internal memory and remove it from the startup-config file.
• If no RSA host key pair is stored in internal memory, the startup-config file contains an RSA host key pair, and
you generate an RSA host key pair with the crypto key generate rsa command, the new pair is stored in
internal memory the first time you enter the write memory command.
• The crypto key zeroize rsa command disables the currently active RSA host key pair. If you subsequently
enter the write memory command without generating another RSA host key pair, the RSA host key pair
stored in internal memory is removed.
• On devices managed by the T-Flow, if you erase the startup-config file, the RSA host key pair will still reside in
internal memory. To remove the RSA host key pair from internal memory, you must enter the crypto key
zeroize rsa command.
• If you enter the ssh no-show-host-keys command to hide the RSA host key pair in the running-config file,
then reload the software, the RSA host key pair is once again visible in the running-config file. The setting to
hide the RSA host key pair is not carried across software reloads.
• In a configuration using redundant management modules, if the active module has an RSA host key pair, but
the standby module does not, the RSA host key pair is not carried over when switchover occurs. You must
create an RSA host key pair on the standby module manually.
• The SSH key generation process causes UDLD-enabled interfaces to go down instantaneously. This in turn
requires the reconvergence of the route tables on the Routing Switches across the network. Non-UDLDenabled interfaces do not experience this issue.
Providing the Public Key to Clients
If you are using SSH to connect to an HP device from a UNIX system, you may need to add the HP device’s public
key to a “known hosts” file; for example, $HOME/.ssh/known_hosts. The following is an example of an entry in a
known hosts file:
10.10.20.10 1024 37 118771881862677030464851288737258046856031640635887679230111
84247022636175804896633384620574930068397650231698985431857279323745963240790218
03229084221453472515782437007702806627934784079949643404159653290224014833380339
09542147367974638560060162945329307563502804231039654388220432832662804242569361
58342816331
In this example, 10.10.20.10 is the IP address of an SSH-enabled HP Routing Switch. The second number, 1024,
is the size of the host key, and the third number, 37, is the encoded public exponent. The remaining text is the
encoded modulus.
Configuring RSA Challenge-Response Authentication
With RSA challenge-response authentication, a collection of clients’ public keys are stored on the HP device.
Clients are authenticated using these stored public keys. Only clients that have a private key that corresponds to
one of the stored public keys can gain access to the device using SSH.
When RSA challenge-response authentication is enabled, the following events occur when a client attempts to
gain access to the device using SSH:
3 - 4 June 2005
Page 79

Configuring Secure Shell
1. The client sends its public key to the HP device.
2. The HP device compares the client’s public key to those stored in memory.
3. If there is a match, the HP device uses the public key to encrypt a random sequence of bytes.
4. The HP device sends these encrypted bytes to the client.
5. The client uses its private key to decrypt the bytes.
6. The client sends the decrypted bytes back to the HP device.
7. The HP device compares the decrypted bytes to the original bytes it sent to the client. If the two sets of bytes
match, it means that the client’s private key corresponds to an authorized public key, and the client is
authenticated.
Setting up RSA challenge-response authentication consists of the following steps:
8. Importing authorized public keys into the HP device.
9. Enabling RSA challenge response authentication
Importing Authorized Public Keys into the HP Device
SSH clients that support RSA authentication normally provide a utility to generate an RSA key pair. The private
key is usually stored in a password-protected file on the local host; the public key is stored in another file and is not
protected. You should collect one public key from each client to be granted access to the HP device and place all
of these keys into one file. This public key file is imported into the HP device.
The following is an example of a public key file containing two public keys:
1024 65537 162566050678380006149460550286514061230306797782065166110686648548574
94957339232259963157379681924847634614532742178652767231995746941441604714682680
00644536790333304202912490569077182886541839656556769025432881477252978135927821
67540629478392662275128774861815448523997023618173312328476660721888873946758201
user@csp_client
1024 35 152676199889856769693556155614587291553826312328095300428421494164360924
76207475545234679268443233762295312979418833525975695775705101805212541008074877
26586119857422702897004112168852145074087969840642408451742714558592361693705908
74837875599405503479603024287131312793895007927438074972787423695977635251943 ro
ot@unix_machine
You can import the authorized public keys into the active configuration by loading them from a file on a TFTP
server. Once the authorized public keys are loaded, you can optionally save them to the startup-config file. If you
import a public key file from a TFTP server, the file is automatically loaded into the active configuration the next
time the device is booted.
HP devices support Secure Copy (SCP) for securely transferring files between hosts on a network. Note that
when you copy files using SCP, you enter the commands on the SCP-enabled client, rather than the console on
the HP device.
If password authentication is enabled for SSH, the user will be prompted for a password in order to copy the file.
See “Using Secure Copy” on page 3-11 for more information on SCP.
After the file is loaded onto the TFTP server, it can be imported into the active configuration each time the device
is booted.
To cause a public key file called pkeys.txt to be loaded from a TFTP server each time the HP device is booted,
enter a command such as the following:
ProCurveRS(config)# ip ssh pub-key-file tftp 192.168.1.234 pkeys.txt
Syntax: ip ssh pub-key-file tftp <tftp-server-ip-addr> <filename>
To display the currently loaded public keys, enter the following command:
June 2005 3 - 5
Page 80

Security Guide for ProCurve 9300/9400 Series Routing Switches
ProCurveRS# show ip client-pub-key
1024 65537 162566050678380006149460550286514061230306797782065166110686648548574
94957339232259963157379681924847634614532742178652767231995746941441604714682680
00644536790333304202912490569077182886541839656556769025432881477252978135927821
67540629478392662275128774861815448523997023618173312328476660721888873946758201
user@csp_client
1024 35 152676199889856769693556155614587291553826312328095300428421494164360924
76207475545234679268443233762295312979418833525975695775705101805212541008074877
26586119857422702897004112168852145074087969840642408451742714558592361693705908
74837875599405503479603024287131312793895007927438074972787423695977635251943 ro
ot@unix_machine
There are 2 authorized client public keys configured
Syntax: show ip client-pub-key
To clear the public keys from the active configuration, enter the following command:
ProCurveRS# clear public-key
Syntax: clear public-key
To reload the public keys from the file on the TFTP server, enter the following command:
ProCurveRS(config)# ip ssh pub-key-file reload
Syntax: ip ssh pub-key-file reload
Once the public keys are part of the active configuration, you can make them part of the startup-config file. The
startup-config file can contain a maximum of 10 public keys. If you want to store more than 10 public keys, keep
them in a file on a TFTP server, where they will be loaded into the active configuration when the device is booted.
To make the public keys in the active configuration part of the startup-config file, enter the following commands:
ProCurveRS(config)# ip ssh pub-key-file flash-memory
ProCurveRS(config)# write memory
Syntax: ip ssh pub-key-file flash-memory
To clear the public keys from the startup-config file (if they are located there), enter the following commands:
ProCurveRS# clear public-key
ProCurveRS# write memory
Enabling RSA Challenge-Response Authentication
RSA challenge-response authentication is enabled by default. You can disable or re-enable it manually.
To enable RSA challenge-response authentication:
ProCurveRS(config)# ip ssh rsa-authentication yes
To disable RSA challenge-response authentication:
ProCurveRS(config)# ip ssh rsa-authentication no
Syntax: ip ssh rsa-authentication yes | no
Setting Optional Parameters
You can adjust the following SSH settings on the HP device:
• The number of SSH authentication retries
• The server RSA key size
3 - 6 June 2005
Page 81

Configuring Secure Shell
• The user authentication method the HP device uses for SSH connections
• Whether the HP device allows users to log in without supplying a password
• The port number for SSH connections
• The SSH login timeout value
• A specific interface to be used as the source for all SSH traffic from the device
• The maximum idle time for SSH sessions
Setting the Number of SSH Authentication Retries
By default, the HP device attempts to negotiate a connection with the connecting host three times. The number of
authentication retries can be changed to between 1 – 5.
For example, the following command changes the number of authentication retries to 5:
ProCurveRS(config)# ip ssh authentication-retries 5
Syntax: ip ssh authentication-retries <number>
Setting the Server RSA Key Size
The default size of the dynamically generated server RSA key is 768 bits. The size of the server RSA key can be
between 512 – 896 bits.
For example, the following command changes the server RSA key size to 896 bits:
ProCurveRS(config)# ip ssh key-size 896
Syntax: ip ssh key-size <number>
NOTE: The size of the host RSA key that resides in the system-config file is always 1024 bits and cannot be
changed.
Deactivating User Authentication
After the SSH server on the HP device negotiates a session key and encryption method with the connecting client,
user authentication takes place. HP’s implementation of SSH supports RSA challenge-response authentication
and password authentication.
With RSA challenge-response authentication, a collection of clients’ public keys are stored on the HP device.
Clients are authenticated using these stored public keys. Only clients that have a private key that corresponds to
one of the stored public keys can gain access to the device using SSH.
With password authentication, users are prompted for a password when they attempt to log into the device
(provided empty password logins are not allowed; see “Enabling Empty Password Logins” on page 3-7). If there is
no user account that matches the user name and password supplied by the user, the user is not granted access.
You can deactivate one or both user authentication methods for SSH. Note that deactivating both authentication
methods essentially disables the SSH server entirely.
To disable RSA challenge-response authentication:
ProCurveRS(config)# ip ssh rsa-authentication no
Syntax: ip ssh rsa-authentication no | yes
To deactivate password authentication:
ProCurveRS(config)# ip ssh password-authentication no
Syntax: ip ssh password-authentication no | yes
Enabling Empty Password Logins
By default, empty password logins are not allowed. This means that users with an SSH client are always
prompted for a password when they log into the device. To gain access to the device, each user must have a user
June 2005 3 - 7
Page 82

Security Guide for ProCurve 9300/9400 Series Routing Switches
name and password. Without a user name and password, a user is not granted access. See “Setting Up Local
User Accounts” on page 2-16 for information on setting up user names and passwords on HP devices.
If you enable empty password logins, users are not prompted for a password when they log in. Any user with an
SSH client can log in without being prompted for a password.
To enable empty password logins:
ProCurveRS(config)# ip ssh permit-empty-passwd yes
Syntax: ip ssh permit-empty-passwd no | yes
Setting the SSH Port Number
By default, SSH traffic occurs on TCP port 22. You can change this port number. For example, the following
command changes the SSH port number to 2200:
ProCurveRS(config)# ip ssh port 2200
Note that if you change the default SSH port number, you must configure SSH clients to connect to the new port.
Also, you should be careful not to assign SSH to a port that is used by another service. If you change the SSH
port number, HP recommends that you change it to a port number greater than 1024.
Syntax: ip ssh port <number>
Setting the SSH Login Timeout Value
When the SSH server attempts to negotiate a session key and encryption method with a connecting client, it waits
a maximum of 120 seconds for a response from the client. If there is no response from the client after 120
seconds, the SSH server disconnects. You can change this timeout value to between 1 – 120 seconds. For
example, to change the timeout value to 60 seconds:
ProCurveRS(config)# ip ssh timeout 60
Syntax: ip ssh timeout <seconds>
Designating an Interface as the Source for All SSH Packets
You can designate a loopback interface, virtual interface, or Ethernet port as the source for all SSH packets from
the device. The software uses the IP address with the numerically lowest value configured on the port or interface
as the source IP address for SSH packets originated by the device.
NOTE: When you specify a single SSH source, you can use only that source address to establish SSH
management sessions with the HP device.
To specify the numerically lowest IP address configured on a loopback interface as the device’s source for all SSH
packets, enter commands such as a the following:
ProCurveRS(config)# int loopback 2
ProCurveRS(config-lbif-2)# ip address 10.0.0.2/24
ProCurveRS(config-lbif-2)# exit
ProCurveRS(config)# ip ssh source-interface loopback 2
The commands in this example configure loopback interface 2, assign IP address 10.0.0.2/24 to the interface, then
designate the interface as the source for all SSH packets from the Routing Switch.
Syntax: ip ssh source-interface ethernet <portnum> | loopback <num> | ve <num>
The <num> parameter is a loopback interface or virtual interface number. If you specify an Ethernet port, the
<portnum> is the port’s number. For example:
ProCurveRS(config)# interface ethernet 1/4
ProCurveRS(config-if-1/4)# ip address 209.157.22.110/24
ProCurveRS(config-if-1/4)# exit
ProCurveRS(config)# ip ssh source-interface ethernet 1/4
3 - 8 June 2005
Page 83

Configuring Secure Shell
Configuring Maximum Idle Time for SSH Sessions
By default, SSH sessions do not time out. Optionally, you can set the amount of time an SSH session can be
inactive before the HP device closes it. For example, to set the maximum idle time for SSH sessions to 30
minutes:
ProCurveRS(config)# ip ssh idle-time 30
Syntax: ip ssh idle-time <minutes>
If an established SSH session has no activity for the specified number of minutes, the HP device closes it. An idle
time of 0 minutes (the default value) means that SSH sessions never timeout. The maximum idle time for SSH
sessions is 240 minutes.
Displaying SSH Connection Information
Up to five SSH connections can be active on the HP device. To display information about SSH connections, enter
the following command:
ProCurveRS# show ip ssh
Connection 1 Version
1.5
2
3
4
5 1.5 none 0x00
Encryption
ARCFOUR
1.5
1.5
1.5
IDEA
3DES
none
State
Username
0x82
neville
0x82
lynval
0x82
terry
0x00
Syntax: show ip ssh
This display shows the following information about the active SSH connections:.
Table 3.1: SSH Connection Information
This Field...
Connection
Version
Encryption
Displays...
The SSH connection ID. This can be from 1 – 5.
The SSH version number. This should always be 1.5.
The encryption method used for the connection. This can be IDEA,
ARCFOUR, DES, 3DES, or BLOWFISH.
June 2005 3 - 9
Page 84

Security Guide for ProCurve 9300/9400 Series Routing Switches
Table 3.1: SSH Connection Information (Continued)
This Field... Displays...
State The connection state. This can be one of the following:
0x00 Server started to send version number to client.
0x01
Server sent version number to client.
0x02
Server received version number from client.
0x20
Server sent public key to client.
0x21
Server is waiting for client’s session key.
0x22
Server received session key from client.
0x23
Server is verifying client’s session key.
0x24
Client’s session key is verified.
0x25
Server received client’s name.
0x40
Server is authenticating client.
0x41
Server is continuing to authenticate client after one or more
failed attempts.
0x80
Server main loop started after successful authentication.
0x81
Server main loop sent a message to client.
0x82
Server main loop received a message from client.
Username The user name for the connection.
The show who command also displays information about SSH connections. For example:
ProCurveRS#show who
Console connections:
established, active
Telnet connections:
1 closed
2 closed
3 closed
4 closed
5 closed
SSH connections:
1 established, client ip address 209.157.22.8
16 seconds in idle
2 established, client ip address 209.157.22.21
42 seconds in idle
3 established, client ip address 209.157.22.68
49 seconds in idle
4 closed
5 closed
Syntax: show who
To terminate one of the active SSH connections, enter the following command:
ProCurveRS# kill ssh 1
Syntax: kill ssh <connection-id>
3 - 10 June 2005
Page 85

Configuring Secure Shell
Sample SSH Configuration
The following is a sample SSH configuration for an HP device.
hostname ProCurveRS
ip dns domain-name hp.com
!
aaa authentication login default local
username neville password .....
username lynval password .....
username terry password .....
!
ip ssh permit-empty-passwd no
!
ip ssh pub-key-file tftp 192.168.1.234 pkeys.txt
!
crypto key generate rsa public_key "1024 35 144460146631716543532035011163035196
41193195125205894452637462409522275505020845087302985209960346239172995676329357
24777530188666267898195648253181551624681394520681672610828188310413962242301296
26883937176769776184984093100984017075369387071006637966650877224677979486802651
458324218055083313313948534902409 ProCurveRS@hp.com"
!
crypto key generate rsa private_key "*************************"
!
ip ssh authentication-retries 5
This aaa authentication login default local command configures the device to use the local user accounts to
authenticate users attempting to log in.
Three user accounts are configured on the device. The ip ssh permit-empty-passwd no command causes
users always to be prompted for a password when they attempt to establish an SSH connection. Since the device
uses local user accounts for authentication, only these three users are allowed to connect to the device using
SSH.
The ip ssh pub-key-file tftp command causes a public key file called pkeys.txt to be loaded from a TFTP server
at 192.168.1.234. To gain access to the HP device using SSH, a user must have a private key that corresponds to
one of the public keys in this file.
The crypto key generate rsa public_key and crypto key generate rsa private_key statements are both
generated by the crypto key generate rsa command. By default, the RSA host key pair appears in the runningconfig file, but not in the startup-config file. You can optionally configure the HP device to hide the RSA host key
pair in the running-config file with the ssh no-show-host-keys command. The actual private key is never visible
in either the running-config file or the startup-config file.
You may need to copy the public key to a “known hosts” file (for example, $HOME/.ssh/known_hosts on UNIX
systems) on the clients who want to access the device. See
an example of what to place in the known hosts file.
The ip ssh authentication-retries 5 command sets the number of times the HP device attempts to negotiate a
connection with the connecting host to 5.
“Providing the Public Key to Clients” on page 3-4 for
Using Secure Copy
Secure Copy (SCP) uses security built into SSH to transfer files between hosts on a network, providing a more
secure file transfer method than Remote Copy (RCP) or FTP. SCP automatically uses the authentication
methods, encryption algorithm, and data compression level configured for SSH. For example, if password
authentication is enabled for SSH, the user is prompted for a user name and password before SCP allows a file to
be transferred. No additional configuration is required for SCP on top of SSH.
June 2005 3 - 11
Page 86

Security Guide for ProCurve 9300/9400 Series Routing Switches
You can use SCP to copy files on the HP device, including the startup-config and running-config files, to or from an
SCP-enabled remote host.
SCP is enabled by default and can be disabled. To disable SCP, enter the following command:
ProCurveRS(config)# ip ssh scp disable
Syntax: ip ssh scp disable | enable
NOTE: If you disable SSH, SCP is also disabled.
The following are examples of using SCP to transfer files from and to an HP device
NOTE: When using SCP, you enter the scp commands on the SCP-enabled client, rather than the console on
the HP device.
NOTE: Certain SCP client options, including -p and -r, are ignored by the SCP server on the HP device. If an
option is ignored, the client is notified.
To copy a configuration file (c:\cfg\hp.cfg) to the running-config file on an HP device at 192.168.1.50 and log in as
user terry, enter the following command on the SCP-enabled client:
C:\> scp c:\cfg\hp.cfg terry@192.168.1.50:runConfig
If password authentication is enabled for SSH, the user is prompted for user terry’s password before the file
transfer takes place.
To copy the configuration file to the startup-config file:
C:\> scp c:\cfg\hp.cfg terry@192.168.1.50:startConfig
To copy the running-config file on an HP device to a file called c:\cfg\hprun.cfg on the SCP-enabled client:
C:\> scp terry@192.168.1.50:runConfig c:\cfg\hprun.cfg
To copy the startup-config file on an HP device to a file called c:\cfg\hpstart.cfg on the SCP-enabled client:
C:\> scp terry@192.168.1.50:startConfig c:\cfg\hpstart.cfg
3 - 12 June 2005
Page 87

Chapter 4
Configuring 802.1X Port Security
Overview
HP devices support the IEEE 802.1X standard for authenticating devices attached to LAN ports. Using 802.1X
port security, you can configure an HP device to grant access to a port based on information supplied by a client to
an authentication server.
When a user logs on to a network that uses 802.1X port security, the HP device grants (or doesn’t grant) access to
network services after the user is authenticated by an authentication server. The user-based authentication in
802.1X port security provides an alternative to granting network access based on a user’s IP address, MAC
address, or subnetwork.
This chapter is divided into the following sections:
• “How 802.1X Port Security Works” on page 4-1 explains basic concepts about 802.1X port security.
• “Configuring 802.1X Port Security” on page 4-9 describes how to set up 802.1X port security on HP devices
using the Command Line Interface (CLI).
• “Displaying 802.1X Information” on page 4-18 describes the commands used to display information about an
802.1X port security configuration.
• “Sample 802.1X Configurations” on page 4-28 shows diagrams of two 802.1X port security configurations
and the CLI commands used for implementing them.
IETF RFC Support
HP’s implementation of 802.1X port security supports the following RFCs:
• RFC 2284 PPP Extensible Authentication Protocol (EAP)
• RFC 2865 Remote Authentication Dial In User Service (RADIUS)
• RFC 2869 RADIUS Extensions
How 802.1X Port Security Works
This section explains the basic concepts behind 802.1X port security, including device roles, how the devices
communicate, and the procedure used for authenticating clients.
Device Roles in an 802.1X Configuration
The 802.1X standard defines the roles of Client/Supplicant, Authenticator, and Authentication Server in a
network.
June 2005 4 - 1
Page 88

Security Guide for ProCurve 9300/9400 Series Routing Switches
The Client (known as a Supplicant in the 802.1X standard) provides username/password information to the
Authenticator. The Authenticator sends this information to the Authentication Server. Based on the Client's
information, the Authentication Server determines whether the Client can use services provided by the
Authenticator. The Authentication Server passes this information to the Authenticator, which then provides
services to the Client, based on the authentication result.
Figure 4.1 illustrates these roles.
Figure 4.1 Authenticator, Client/Supplicant, and Authentication Server in an 802.1X configuration
RADIUS Server
(Authentication Server)
HP Device
(Authenticator)
Client/Supplicant
Authenticator – The device that controls access to the network. In an 802.1X configuration, the HP device
serves as the Authenticator. The Authenticator passes messages between the Client and the Authentication
Server. Based on the identity information supplied by the Client, and the authentication information supplied by
the Authentication Server, the Authenticator either grants or does not grant network access to the Client.
Client/Supplicant – The device that seeks to gain access to the network. Clients must be running software that
supports the 802.1X standard (for example, the Windows XP operating system). Clients can either be directly
connected to a port on the Authenticator, or can be connected by way of a hub.
Authentication Server – The device that validates the Client and specifies whether or not the Client may access
services on the device. HP supports Authentication Servers running RADIUS.
Communication Between the Devices
For communication between the devices, 802.1X port security uses the Extensible Authentication Protocol
(EAP), defined in RFC 2284. The 802.1X standard specifies a method for encapsulating EAP messages so that
they can be carried over a LAN. This encapsulated form of EAP is known as EAP over LAN (EAPOL). The
standard also specifies a means of transferring the EAPOL information between the Client/Supplicant,
Authenticator, and Authentication Server.
4 - 2 June 2005
Page 89

Configuring 802.1X Port Security
EAPOL messages are passed between the Port Access Entity (PAE) on the Supplicant and the Authenticator.
Figure 4.2 shows the relationship between the Authenticator PAE and the Supplicant PAE.
Figure 4.2 Authenticator PAE and Supplicant PAE
Authentication
Server
HP Device
(Authenticator)
802.1X-Enabled
Supplicant
Authenticator PAE – The Authenticator PAE communicates with the Supplicant PAE, receiving identifying
information from the Supplicant. Acting as a RADIUS client, the Authenticator PAE passes the Supplicant’s
information to the Authentication Server, which decides whether the Supplicant can gain access to the port. If the
Supplicant passes authentication, the Authenticator PAE grants it access to the port.
Supplicant PAE – The Supplicant PAE supplies information about the Client to the Authenticator PAE and
responds to requests from the Authenticator PAE. The Supplicant PAE can also initiate the authentication
procedure with the Authenticator PAE, as well as send logoff messages.
Controlled and Uncontrolled Ports
A physical port on the device used with 802.1X port security has two virtual access points: a controlled port and
an uncontrolled port. The controlled port provides full access to the network. The uncontrolled port provides
access only for EAPOL traffic between the Client and the Authentication Server. When a Client is successfully
authenticated, the controlled port is opened to the Client.
Figure 4.3 illustrates this concept.
June 2005 4 - 3
Page 90

Security Guide for ProCurve 9300/9400 Series Routing Switches
Figure 4.3 Controlled and Uncontrolled Ports before and after Client authentication
HP Device
(Authenticator)
Authentication
Server
Authentication
Server
HP Device
(Authenticator)
802.1X-Enabled
Supplicant Supplicant
Before Authentication After Authentication
802.1X-Enabled
Before a Client is authenticated, only the uncontrolled port on the Authenticator is open. The uncontrolled port
allows only EAPOL frames to be exchanged between the Client and the Authentication Server. The controlled
port is in the unauthorized state and allows no traffic to pass through.
During authentication, EAPOL messages are exchanged between the Supplicant PAE and the Authenticator PAE,
and RADIUS messages are exchanged between the Authenticator PAE and the Authentication Server. See
“Message Exchange During Authentication” on page 4-4 for an example of this process. If the Client is
successfully authenticated, the controlled port becomes authorized, and traffic from the Client can flow through
the port normally.
By default, all controlled ports on the HP device are placed in the authorized state, allowing all traffic. When
authentication is activated on an 802.1X-enabled interface, the interface’s controlled port is placed initially in the
unauthorized state. When a Client connected to the port is successfully authenticated, the controlled port is then
placed in the authorized state until the Client logs off. See
“Enabling 802.1X Port Security” on page 4-10 for more
information.
Message Exchange During Authentication
Figure 4.4 illustrates a sample exchange of messages between an 802.1X-enabled Client, an HP device acting as
Authenticator, and a RADIUS server acting as an Authentication Server.
4 - 4 June 2005
Page 91

Configuring 802.1X Port Security
Figure 4.4 Message exchange between Client/Supplicant, Authenticator, and Authentication Server
Client/Supplicant
HP Device RADIUS Server
(Authenticator) (Authentication Server)
In this example, the Authenticator (the HP device) initiates communication with an 802.1X-enabled Client. When
the Client responds, it is prompted for a username (255 characters maximum) and password. The Authenticator
passes this information to the Authentication Server, which determines whether the Client can access services
provided by the Authenticator. When the Client is successfully authenticated by the RADIUS server, the port is
authorized. When the Client logs off, the port becomes unauthorized again.
Starting in release 07.6.04, HP’s 802.1X implementation supports dynamic VLAN assignment. If one of the
attributes in the Access-Accept message sent by the RADIUS server specifies a VLAN identifier, and this VLAN is
available on the HP device, the client’s port is moved from its default VLAN to the specified VLAN. When the client
disconnects from the network, the port is placed back in its default VLAN.
See “Configuring Dynamic VLAN
Assignment for 802.1X Ports” on page 4-16 for more information.
If a Client does not support 802.1X, authentication cannot take place. The HP device sends EAP-Request/Identity
frames to the Client, but the Client does not respond to them.
When a Client that supports 802.1X attempts to gain access through a non-802.1X-enabled port, it sends an EAP
start frame to the HP device. When the device does not respond, the Client considers the port to be authorized,
and starts sending normal traffic.
HP devices support Identity and MD5-challenge request types in EAP Request/Response messages. However,
devices running software release 07.8.00 has support for the following 802.1X authentication challenge types:
• EAP-TLS (RFC 2716) – EAP Transport Level Security (TLS) provides strong security by requiring both client
and authentication server to be identified and validated through the use of public key infrastructure (PKI)
digital certificates. EAP-TLS establishes a tunnel between the client and the authentication server to protect
messages from unauthorized users’ eavesdropping activities. Since EAP-TLS requires PKI digital certificates
June 2005 4 - 5
Page 92

Security Guide for ProCurve 9300/9400 Series Routing Switches
on both the clients and the authentication servers, the roll out, maintenance, and scalability of this
authentication method is much more complex than other methods. EAP-TLS is best for installations with
existing PKI certificate infrastructures.
• EAP-TTLS (Internet-Draft) – The EAP Tunneled Transport Level Security (TTLS) is an extension of EAP-TLS
Like TLS, EAP-TTLS provides strong authentication; however it requires only the authentication server to be
validated by the client through a certificate exchange between the server and the client. Clients are
authenticated by the authentication server using user names and passwords.
A TLS tunnel can be used to protect EAP messages and existing user credential services such as Active
Directory, RADIUS, and LDAP. Backward compatibility for other authentication protocols such as PAP, CHAP,
MS-CHAP, and MS-CHAP-V2 are also provided by EAP-TTLS. EAP-TTLS is not considered foolproof and
can be fooled into sending identity credentials if TLS tunnels are not used. EAP-TTLS is suited for
installations that require strong authentication without the use of mutual PKI digital certificates.
• PEAP (Internet-Draft) – Protected EAP Protocol (PEAP) is an Internet-Draft that is similar to EAP-TTLS.
PEAP client authenticates directly with the backend authentication server. The authenticator acts as a passthrough device, which does not need to understand the specific EAP authentication protocols.
Unlike EAP-TTLS, PEAP does not natively support user name and password to authenticate clients against
an existing user database such as LDAP. PEAP secures the transmission between the client and
authentication server with a TLS encrypted tunnel. PEAP also allows other EAP authentication protocols to
be used. It relies on the mature TLS keying method for its key creation and exchange. PEAP is best suited for
installations that require strong authentication without the use of mutual certificates.
NOTE: If the 802.1X Client will be sending a packet that is larger than 1500 bytes, then the following must be
configured on the HP device:
• On devices with EP modules, default-mtu 1700 must be configured.
• On devices with Standard modules, jumbo 1920 must be configured.
Configuration for these challenge types is the same as for the EAP-MD5 challenge type.
Authenticating Multiple Hosts Connected to the Same Port
HP devices support 802.1X authentication for ports with more than one host connected to them. Figure 4.5
illustrates a sample configuration where multiple hosts are connected to a single 802.1X port.
4 - 6 June 2005
Page 93

Figure 4.5 Multiple hosts connected to a single 802.1X-enabled port
RADIUS Server
(Authentication Server)
HP Device
(Authenticator)
Hub
Configuring 802.1X Port Security
Clients/Supplicants running 802.1X-compliant client software
The way the HP device authenticates Clients in a multiple-host configuration depends on the software release
running on the device:
• In releases prior to 07.8.00, services are provided on a port based on the authentication of a single Client.
When one Client is successfully authenticated, all hosts connected to the port are allowed access to the
network. The HP device forwards traffic from all of the connected hosts for as long as the authenticated Client
stays connected. When the authenticated Client disconnects from the network, authentication is removed for
the other connected hosts as well.
• Starting in release 07.8.00, if there are multiple hosts connected to a single 802.1X-enabled port, the HP
device authenticates each of them individually. Each host’s authentication status is independent of the
others, so that if one authenticated host disconnects from the network, it has no effect on the authentication
status of any of the other authenticated hosts.
By default, traffic from hosts that cannot be authenticated by the RADIUS server is dropped in hardware. You
can optionally configure the HP device to assign the port to a “restricted” VLAN if authentication of the Client
is unsuccessful.
How 802.1X Multiple-Host Authentication Works (Release 07.8.00 and Later)
In release 07.8.00 and later, when multiple hosts are connected to a single 802.1X-enabled port on an HP device
(as in
Figure 4.5), 802.1X authentication is performed in the following way:
1. One of the 802.1X-enabled Clients attempts to log into a network in which an HP device serves as an
Authenticator.
2. The HP device creates an internal session (called a dot1x-mac-session) for the Client. A dot1x-macsession serves to associate a Client’s MAC address and username with its authentication status.
June 2005 4 - 7
Page 94

Security Guide for ProCurve 9300/9400 Series Routing Switches
3. The HP device performs 802.1X authentication for the Client. Messages are exchanged between the HP
device and the Client, and between the device and the Authentication Server (RADIUS server). The result of
this process is that the Client is either successfully authenticated or not authenticated, based on the
username and password supplied by the client.
4. If the Client is successfully authenticated, the Client’s dot1x-mac-session is set to “access-is-allowed”. This
means that traffic from the Client can be forwarded normally.
5. If authentication for the Client is unsuccessful, an authentication-failure action is taken. The
authentication-failure action can be either to drop traffic from the Client in hardware (the default), or to place
the port in a “restricted” VLAN.
• If the authentication-failure action is to drop traffic from the Client, then the device waits for a specified
amount of time (defined with the timeout quiet-period command, by default 60 seconds), then attempts
to authenticate the Client again. After three unsuccessful authentication attempts, the Client’s dot1xmac-session is set to “access-denied”, causing traffic from the Client to be dropped in hardware.
You can optionally configure the number of authentication attempts the device makes before dropping
traffic from the Client. See
Dropping Packets” on page 4-15 for information on how to do this.
• If the authentication-failure action is to place the port in a “restricted” VLAN, If the Client’s dot1x-mac-
session is set to “access-restricted” then the port is moved to the specified restricted VLAN, and traffic
from the Client is forwarded normally.
6. When the Client disconnects from the network, the HP device deletes the Client’s dot1x-mac-session. This
does not affect the dot1x-mac-session or authentication status (if any) of the other hosts connected on the
port.
“Specifying the Number of Authentication Attempts the Device Makes Before
Notes
• The Client’s dot1x-mac-session establishes a relationship between the username and MAC address used for
authentication. If a user attempts to gain access from different Clients (with different MAC addresses), he or
she would need to be authenticated from each Client.
• If a Client has been denied access to the network (that is, the Client’s dot1x-mac-session is set to “accessdenied”), then you can cause the Client to be re-authenticated by manually disconnecting the Client from the
network, or by using the clear dot1x mac-session command.
Address” on page 4-16 for information on this command.
• When a Client has been denied access to the network, its dot1x-mac-session is aged out if no traffic is
received from the Client’s MAC address over a fixed hardware aging period (70 seconds), plus a configurable
software aging period. You can optionally change the software aging period for dot1x-mac-sessions or
disable aging altogether. After the denied Client’s dot1x-mac-session is aged out, traffic from that Client is no
longer blocked, and the Client can be re-authenticated.
In addition, you can configure disable aging for the dot1x-mac-session of Clients that have been granted
either full access to the network, or have been placed in a restricted VLAN. After a Client’s dot1x-macsession ages out, the Client must be re-authenticated. See “Disabling Aging for dot1x-mac-sessions” on
page 4-15 for more information.
• Dynamic IP ACL and MAC address filter assignment is not supported in an 802.1X multiple-host
configuration. If a RADIUS server returns an Access-Accept message that specifies an IP ACL or MAC
address filter for the Client, these attributes are ignored.
See “Clearing a dot1x-mac-session for a MAC
Dynamic VLAN Assignment in an 802.1X Multiple-Host Configuration (Release 07.8.00 and Later)
Dynamic VLAN assignment allows an 802.1X-enabled port to be assigned to a VLAN based on information
received from the RADIUS server. Attributes in the RADIUS Access-Accept message can specify a VLAN
identifier; if this VLAN is available on the HP device, the Client’s port can be moved from its default VLAN to the
specified VLAN.
4 - 8 June 2005
Page 95

Configuring 802.1X Port Security
Dynamic VLAN assignment is supported in 802.1X multiple-host configurations. The following considerations
apply when a Client in a 802.1X multiple-host configuration is successfully authenticated, and the RADIUS
Access-Accept message specifies a VLAN for the port:
• If the port is not already a member of a RADIUS-specified VLAN, and the RADIUS Access-Accept message
specifies the name or ID of a valid VLAN on the HP device, then the port is placed in that VLAN.
• If the port is already a member of a RADIUS-specified VLAN, and the RADIUS Access-Accept message
specifies the name or ID of a different VLAN, then it is considered an authentication failure. The port’s VLAN
membership is not changed.
• If the port is already a member of a RADIUS-specified VLAN, and the RADIUS Access-Accept message
specifies the name or ID of that same VLAN, then traffic from the Client is forwarded normally.
• If the RADIUS Access-Accept message specifies the name or ID of a VLAN that does not exist on the HP
device, then it is considered an authentication failure.
• If the port is a tagged or dual-mode port, and the RADIUS Access-Accept message specifies the name or ID
of a valid VLAN on the HP device, then the port is placed in that VLAN. If the port is already a member of the
RADIUS-specified VLAN, no further action is taken. Note that the Client’s dot1x-mac-session is set to
“access-is-allowed” for the RADIUS-specified VLAN only. If traffic from the Client’s MAC address is received
on any other VLAN, it is dropped.
• If the RADIUS Access-Accept message does not contain any VLAN information, the Client’s dot1x-macsession is set to “access-is-allowed”. If the port is already in a RADIUS-specified VLAN, it remains in that
VLAN.
802.1X Port Security and sFlow
sFlow is a system for observing traffic flow patterns and quantities within and among a set of Routing Switches.
sFlow works by taking periodic samples of network data and exporting this information to a collector.
When you enable sFlow forwarding on an 802.1X-enabled interface, the samples taken from the interface include
the user name string at the inbound and/or outbound port, if that information is available.
For more information on sFlow, see the “sFlow“ section in the “Remote Network Monitoring“ chapter of the
Advanced Configuration and Management Guide for ProCurve 9300/9400 Series Routing Switches.
Configuring 802.1X Port Security
Configuring 802.1X port security on an HP device consists of the following tasks:
1. Configuring the HP device’s interaction with the Authentication Server:
• “Configuring an Authentication Method List for 802.1X” on page 4-10
• “Setting RADIUS Parameters” on page 4-10
• “Configuring Dynamic VLAN Assignment for 802.1X Ports” on page 4-16 (optional)
2. Configuring the HP device’s role as the Authenticator:
• “Enabling 802.1X Port Security” on page 4-10
• “Initializing 802.1X on a Port” on page 4-14 (optional)
3. Configuring the HP device’s interaction with Clients:
• “Configuring Periodic Re-Authentication” on page 4-12 (optional)
• “Re-Authenticating a Port Manually” on page 4-12 (optional)
• “Setting the Quiet Period” on page 4-12 (optional)
• “Setting the Interval for Retransmission of EAP-Request/Identity Frames” on page 4-12 (optional)
• “Specifying the Number of EAP-Request/Identity Frame Retransmissions” on page 4-13 (optional)
June 2005 4 - 9
Page 96

Security Guide for ProCurve 9300/9400 Series Routing Switches
• “Specifying the Security Hold Time” on page 4-13 (optional)
• “Specifying a Timeout for Retransmission of EAP-Request Frames to the Client” on page 4-14 (optional)
• “Allowing Access to Multiple Hosts” on page 4-14 (optional)
• “Defining MAC Filters for EAP Frames” on page 4-16 (optional)
Configuring an Authentication Method List for 802.1X
To use 802.1X port security, you must specify an authentication method to be used to authenticate Clients. HP
supports RADIUS authentication with 802.1X port security. To use RADIUS authentication with 802.1X port
security, you create an authentication method list for 802.1X and specify RADIUS as an authentication method,
then configure communication between the HP device and RADIUS server.
For example:
ProCurveRS(config)# aaa authentication dot1x default radius
Syntax: [no] aaa authentication dot1x default <method-list>
For the <method-list>, enter at least one of the following authentication methods:
radius – Use the list of all RADIUS servers that support 802.1X for authentication.
none – Use no authentication. The Client is automatically authenticated without the device using information
supplied by the Client.
NOTE: If you specify both radius and none, make sure radius comes before none in the method list.
Setting RADIUS Parameters
To use a RADIUS server to authenticate access to an HP device, you must identify the server to the HP device.
For example:
ProCurveRS(config)# radius-server host 209.157.22.99 auth-port 1812 acct-port 1813
default key mirabeau dot1x
ProCurveRS(config)# radius-server host 209.157.22.99 auth-port 1812 acct-port 1813
default key mirabeau dot1x
Syntax: radius-server host <ip-addr> | <server-name> [authentication-only | accounting-only | default] [key 0 | 1
<string>] [dot1x]
The host <ip-addr> | <server-name> parameter is either an IP address or an ASCII text string.
The dot1x parameter indicates that this RADIUS server supports the 802.1X standard. A RADIUS server that
supports the 802.1X standard can also be used to authenticate non-802.1X authentication requests.
NOTE: To implement 802.1X port security, at least one of the RADIUS servers identified to the HP device must
support the 802.1X standard.
Enabling 802.1X Port Security
By default, 802.1X port security is disabled on HP devices. To enable the feature on the device and enter the
dot1x configuration level, enter the following command:
ProCurveRS(config)# dot1x-enable
ProCurveRS(config-dot1x)#
Syntax: [no] dot1x-enable
4 - 10 June 2005
Page 97

Configuring 802.1X Port Security
At the dot1x configuration level, you can enable 802.1X port security on all interfaces at once, on individual
interfaces, or on a range of interfaces.
For example, to enable 802.1X port security on all interfaces on the device, enter the following command:
ProCurveRS(config-dot1x)# enable all
Syntax: [no] enable all
To enable 802.1X port security on interface 3/11, enter the following command:
ProCurveRS(config-dot1x)# enable ethernet 3/11
Syntax: [no] enable <portnum>
To enable 802.1X port security on interfaces 3/11 through 3/16, enter the following command:
ProCurveRS(config-dot1x)# enable ethernet 3/11 to 3/16
Syntax: [no] enable <portnum> to <portnum>
Setting the Port Control
To activate authentication on an 802.1X-enabled interface, you specify the kind of port control to be used on the
interface. An interface used with 802.1X port security has two virtual access points: a controlled port and an
uncontrolled port.
• The controlled port can be either the authorized or unauthorized state. In the authorized state, it allows
normal traffic to pass between the Client and the Authenticator. In the unauthorized state, it allows no traffic
to pass through.
• The uncontrolled port allows only EAPOL traffic between the Client and the Authentication Server.
See Figure 4.3 on page 4-4 for an illustration of this concept.
By default, all controlled ports on the device are in the authorized state, allowing all traffic. When you activate
authentication on an 802.1X-enabled interface, its controlled port is placed in the unauthorized state. When a
Client connected to the interface is successfully authenticated, the controlled port is then placed in the authorized
state. The controlled port remains in the authorized state until the Client logs off.
To activate authentication on an 802.1X-enabled interface, you configure the interface to place its controlled port in
the authorized state when a Client is authenticated by an Authentication Server. To do this, enter commands such
as the following.
ProCurveRS(config)# interface e 3/1
ProCurveRS(config-if-3/1)# dot1x port-control auto
Syntax: [no] dot1x port-control [force-authorized | force-unauthorized | auto]
When an interface’s control type is set to auto, the its controlled port is initially set to unauthorized, but is changed
to authorized when the connecting Client is successfully authenticated by an Authentication Server.
The port control type can be one of the following:
force-authorized – The port’s controlled port is placed unconditionally in the authorized state, allowing all traffic.
This is the default state for ports on the HP device.
force-unauthorized – The controlled port is placed unconditionally in the unauthorized state.
auto – The controlled port is unauthorized until authentication takes place between the Client and Authentication
Server. Once the Client passes authentication, the port becomes authorized. This has the effect of activating
authentication on an 802.1X-enabled interface.
June 2005 4 - 11
Page 98

Security Guide for ProCurve 9300/9400 Series Routing Switches
NOTE: You cannot enable 802.1X port security on ports that have any of the following features enabled:
• Link aggregation
• Metro Ring Protocol (MRP)
• Tagged port
• Mirror port
• Trunk port
In releases prior to 07.6.04, 802.1X port security could not be enabled on a port where Layer 2 switching was
disabled (with the route-only command), and an 802.1X port could not be specified as a member of a virtual
interface (ve). Both of these restrictions were removed in release 07.6.04.
Configuring Periodic Re-Authentication
You can configure the device to periodically re-authenticate Clients connected to 802.1X-enabled interfaces.
When you enable periodic re-authentication, the device re-authenticates Clients every 3,600 seconds by default.
You can optionally specify a different re-authentication interval of between 1 – 4294967295 seconds.
To configure periodic re-authentication using the default interval of 3,600 seconds, enter the following command:
ProCurveRS(config-dot1x)# re-authentication
Syntax: [no] re-authentication
To configure periodic re-authentication with an interval of 2,000 seconds, enter the following commands:
ProCurveRS(config-dot1x)# re-authentication
ProCurveRS(config-dot1x)# timeout re-authperiod 2000
Syntax: [no] timeout re-authperiod <seconds>
The re-authentication interval is a global setting, applicable to all 802.1X-enabled interfaces. If you want to reauthenticate Clients connected to a specific port manually, use the dot1x re-authenticate command. See “ReAuthenticating a Port Manually”, below.
Re-Authenticating a Port Manually
When periodic re-authentication is enabled, by default the HP device re-authenticates Clients connected to an
802.1X-enabled interface every 3,600 seconds (or the time specified by the dot1x timeout re-authperiod
command). You can also manually re-authenticate Clients connected to a specific port.
For example, to re-authenticate Clients connected to interface 3/1, enter the following command:
ProCurveRS# dot1x re-authenticate e 3/1
Syntax: dot1x re-authenticate <portnum>
Setting the Quiet Period
If the HP device is unable to authenticate the Client, the HP device waits a specified amount of time before trying
again. The amount of time the HP device waits is specified with the quiet-period parameter. The quiet-period
parameter can be from 0 – 4294967295 seconds. The default is 60 seconds.
For example, to set the quiet period to 30 seconds, enter the following command:
ProCurveRS(config-dot1x)# timeout quiet-period 30
Syntax: [no] timeout quiet-period <seconds>
Setting the Interval for Retransmission of EAP-Request/Identity Frames
When the HP device sends a Client an EAP-request/identity frame, it expects to receive an EAP-response/identity
frame from the Client. If the Client does not send back an EAP-response/identity frame, the device waits a
4 - 12 June 2005
Page 99

Configuring 802.1X Port Security
specified amount of time and then retransmits the EAP-request/identity frame. You can specify the amount of time
the HP device waits before retransmitting the EAP-request/identity frame to the Client. This amount of time is
specified with the tx-period parameter. The tx-period parameter can be from 0 – 4294967295 seconds. The
default is 30 seconds.
For example, to cause the HP device to wait 60 seconds before retransmitting an EAP-request/identity frame to a
Client, enter the following command:
ProCurveRS(config-dot1x)# timeout tx-period 60
Syntax: [no] timeout tx-period <seconds>
If the Client does not send back an EAP-response/identity frame within 60 seconds, the device will transmit
another EAP-request/identity frame.
Specifying the Security Hold Time
The multiple-hosts command (see “Allowing Access to Multiple Hosts” on page 4-14) allows more than one
802.1X Client to connect on an interface. However, when the multiple-hosts command is not used in a interface’s
configuration, only one Client can connect on the interface. If the HP device detects multiple Clients trying to
connect on an interface when the multiple-hosts command is not present in the interface’s configuration, the
interface enters the unauthorized state for a specified amount of time. This amount of time is specified with the
security-hold-time parameter. The security-hold-time parameter can be from 1 – 4294967295 seconds. The
default is 60 seconds.
For example, the following command causes the device to place an interface in the unauthorized state for 120
seconds when it detects more than one 802.1X Client trying to connect on the interface:
ProCurveRS(config-dot1x)# timeout security-hold-time 120
Syntax: [no] timeout security-hold-time <seconds>
NOTE: When the port-control parameter on an 802.1X-enabled interface is set to force-authorized, the HP
device allows connections from multiple Clients, regardless of whether the multiple-hosts parameter is used in
the interface's configuration.
Specifying the Number of EAP-Request/Identity Frame Retransmissions
If the HP device does not receive a EAP-response/identity frame from a Client, the device waits 30 seconds (or the
amount of time specified with the timeout tx-period command), then retransmits the EAP-request/identity frame.
By default, the HP device retransmits the EAP-request/identity frame a maximum of two times. If no EAPresponse/identity frame is received from the Client after two EAP-request/identity frame retransmissions, the
device restarts the authentication process with the Client.
You can optionally specify between 1 – 10 frame retransmissions. For example, to configure the device to
retransmit an EAP-request/identity frame to a Client a maximum of three times, enter the following command:
ProCurveRS(config-dot1x)# maxreq 3
Syntax: maxreq <value>
Specifying a Timeout for Retransmission of Messages to the Authentication Server
When performing authentication, the HP device receives EAPOL frames from the Client and passes the
messages on to the RADIUS server. The device expects a response from the RADIUS server within 30 seconds.
If the RADIUS server does not send a response within 30 seconds, the HP device retransmits the message to the
RADIUS server. The time constraint for retransmission of messages to the Authentication Server can be between
0 – 4294967295 seconds.
For example, to configure the device to retransmit a message if the Authentication Server does not respond within
45 seconds, enter the following command:
ProCurveRS(config-dot1x)# servertimeout 45
June 2005 4 - 13
Page 100

Security Guide for ProCurve 9300/9400 Series Routing Switches
Syntax: servertimeout <seconds>
Specifying a Timeout for Retransmission of EAP-Request Frames to the Client
Acting as an intermediary between the RADIUS Authentication Server and the Client, the HP device receives
RADIUS messages from the RADIUS server, encapsulates them as EAPOL frames, and sends them to the Client.
When the HP device relays an EAP-Request frame from the RADIUS server to the Client, it expects to receive a
response from the Client within 30 seconds. If the Client does not respond within the allotted time, the device
retransmits the EAP-Request frame to the Client. The time constraint for retransmission of EAP-Request frames
to the Client can be between 0 – 4294967295 seconds.
For example, to configure the device to retransmit an EAP-Request frame if the Client does not respond within 45
seconds, enter the following command:
ProCurveRS(config-dot1x)# supptimeout 45
Syntax: supptimeout <seconds>
Initializing 802.1X on a Port
To initialize 802.1X port security on a port, enter a command such as the following:
ProCurveRS# dot1x initialize e 3/1
Syntax: dot1x initialize <portnum>
Allowing Access to Multiple Hosts
HP devices support 802.1X authentication for ports with more than one host connected to them. Multiple-host
authentication works differently according to the software release running on the HP device:
• In releases prior to 07.8.00, services are provided on a port based on the authentication of a single Client.
When one Client is successfully authenticated, all hosts connected to the port are allowed access to the
network.
• Starting in release 07.8.00, if there are multiple hosts connected to a single 802.1X-enabled port, the HP
device authenticates each of them individually. See “Configuring 802.1X Multiple-Host Authentication
(Release 07.8.00 and Later)”.
Configuring 802.1X Multiple-Host Authentication (Releases Prior to 07.8.00)
To enable 802.1X port security in a multiple-host configuration, an HP device running a release prior to 07.8.00
must be configured to allow multiple Clients on the same port. When one Client is successfully authenticated, all
Clients connected to the port are allowed access to the network. When the authenticated Client logs off the
network, the port becomes unauthorized again. Each time an authenticated Client logs off, the port becomes
unauthorized.
To allow multiple 802.1X Clients on the same port, enter the following command:
ProCurveRS(config-if-3/1)# dot1x multiple-hosts
Syntax: [no] dot1x multiple-hosts
By default multiple-host access is disabled. See Figure 4.7 on page 4-29 for a sample 802.1X configuration with
multiple hosts connected to one port.
NOTE: When the port-control parameter on an 802.1X-enabled interface is set to force-authorized, the HP
device allows connections from multiple Clients, regardless of whether the multiple-hosts parameter is used in
the interface's configuration.
See “Configuring 802.1X Multiple-Host Authentication (Releases Prior to 07.8.00)”.
Configuring 802.1X Multiple-Host Authentication (Release 07.8.00 and Later)
When multiple hosts are connected to the same 802.1X-enabled port, the functionality described in “How 802.1X
Multiple-Host Authentication Works (Release 07.8.00 and Later)” on page 4-7 is enabled by default. You can
optionally do the following:
4 - 14 June 2005
 Loading...
Loading...