Page 1

HP 10Gb Ethernet BL-c Switch
Command Reference Guide
Part number BMD00022
January 2008
2350 Mission College Blvd.
Suite 600
Santa Clara, CA 95054
www.bladenetwork.net
Page 2

Legal notices
© 2007 Blade Network Technologies. Inc.
This document is protected by copyright and distributed under licenses restricting its use, copying, distribution, and decompilation. No part
of this document may be reproduced in any form by any means without prior written authorization of Blade Network Technologies, Inc.
Documentation is provided “as is” without warranty of any kind, either express or implied, including any kind of implied or express
warranty of non-infringement or the implied warranties of merchantability or fitness for a particular purpose.
U.S. Government End Users: This document is provided with a “commercial item” as defined by FAR 2.101 (Oct. 1995) and contains
“commercial technical data” and “commercial software documentation” as those terms are used in FAR 12.211-12.212 (Oct. 1995).
Government End Users are authorized to use this documentation only in accordance with those rights and restrictions set forth herein,
consistent with FAR 12.211- 12.212 (Oct. 1995), DFARS 227.7202 (JUN 1995) and DFARS 252.227-7015 (Nov. 1995).
Blade Network Technologies, Inc. reserves the right to change any products described herein at any time, and without notice. Blade
Network Technologies, Inc. assumes no responsibility or liability arising from the use of products described herein, except as expressly
agreed to in writing by Blade Network Technologies, Inc. The use and purchase of this product does not convey a license under any patent
rights, trademark rights, or any other intellectual property rights of Blade Network Technologies, Inc.
Microsoft®, Windows®, and Windows NT® are U.S. registered trademarks of Microsoft Corporation.
SunOS™ and Solaris™ are trademarks of Sun Microsystems, Inc. in the U.S. and other countries.
Cisco® is a registered trademark of Cisco Systems, Inc. and/or its affiliates in the U.S. and certain other countries.
Part number: BMD00022
January 2008
Page 3

Contents
Command line interface.......................................................................................................................... 8
Introduction............................................................................................................................................. 8
Additional references ............................................................................................................................... 8
Connecting to the switch........................................................................................................................... 8
Establishing a console connection ......................................................................................................... 9
Setting an IP address ........................................................................................................................... 9
Establishing a Telnet connection.......................................................................................................... 10
Establishing an SSH connection .......................................................................................................... 10
Accessing the switch .............................................................................................................................. 11
Idle timeout ........................................................................................................................................... 12
Typographical conventions...................................................................................................................... 13
Menu basics ........................................................................................................................................ 14
Introduction........................................................................................................................................... 14
Main Menu ........................................................................................................................................... 14
Menu summary...................................................................................................................................... 14
Global commands.................................................................................................................................. 15
Command line history and editing............................................................................................................ 17
Command line interface shortcuts............................................................................................................. 18
Command stacking ........................................................................................................................... 18
Command abbreviation ..................................................................................................................... 18
Tab completion................................................................................................................................. 18
First-time configuration .......................................................................................................................... 19
Introduction........................................................................................................................................... 19
Configuring Simple Network Management Protocol support ................................................................... 20
Setting passwords .................................................................................................................................. 20
Changing the default administrator password ....................................................................................... 20
Changing the default user password.................................................................................................... 22
Changing the default operator password ............................................................................................. 22
Information Menu................................................................................................................................. 24
Introduction........................................................................................................................................... 24
Menu overview...................................................................................................................................... 24
System Information Menu ........................................................................................................................ 25
SNMPv3 Information Menu ................................................................................................................ 26
SNMPv3 dump ................................................................................................................................. 32
System information............................................................................................................................ 33
Show last 100 syslog messages.......................................................................................................... 34
System user information ..................................................................................................................... 35
Layer 2 information ................................................................................................................................ 36
FDB information menu ....................................................................................................................... 37
Link Aggregation Control Protocol information ...................................................................................... 38
Hot Links Trigger information .............................................................................................................. 39
802.1X information........................................................................................................................... 40
Spanning Tree information ................................................................................................................. 42
Rapid Spanning Tree / Multiple Spanning Tree information.................................................................... 44
Common Internal Spanning Tree information ........................................................................................ 46
Trunk group information..................................................................................................................... 48
Contents 3
Page 4

VLAN information ............................................................................................................................. 48
Fast Uplink Convergence status........................................................................................................... 49
Layer 3 information ................................................................................................................................ 50
Route information.............................................................................................................................. 51
Show all IP Route information ............................................................................................................. 51
ARP information................................................................................................................................ 53
OSPF information.............................................................................................................................. 54
Routing Information Protocol information .............................................................................................. 58
IP information ................................................................................................................................... 59
IGMP multicast group information ....................................................................................................... 60
VRRP information .............................................................................................................................. 62
Server Mobility Port information .......................................................................................................... 63
QoS information .................................................................................................................................... 64
802.1p information........................................................................................................................... 64
ACL information..................................................................................................................................... 65
RMON Information Menu ....................................................................................................................... 66
RMON history information ................................................................................................................. 66
RMON alarm information .................................................................................................................. 67
RMON event information ................................................................................................................... 68
Link status information ............................................................................................................................ 69
Port information ..................................................................................................................................... 70
Transceiver status................................................................................................................................... 70
Uplink Failure Detection information ......................................................................................................... 71
Information dump................................................................................................................................... 71
Statistics Menu.....................................................................................................................................72
Introduction........................................................................................................................................... 72
Menu information .................................................................................................................................. 72
Port Statistics Menu ................................................................................................................................ 73
802.1X statistics ............................................................................................................................... 74
Bridging statistics .............................................................................................................................. 76
Ethernet statistics............................................................................................................................... 77
Interface statistics .............................................................................................................................. 79
Internet Protocol (IP) statistics .............................................................................................................. 81
Link statistics..................................................................................................................................... 81
Port RMON statistics.......................................................................................................................... 82
Layer 2 statistics..................................................................................................................................... 84
FDB statistics .................................................................................................................................... 84
LACP statistics................................................................................................................................... 84
Hot Links statistics.............................................................................................................................. 85
Layer 3 statistics..................................................................................................................................... 86
GEA Layer 3 statistics menu ............................................................................................................... 87
IP statistics........................................................................................................................................ 88
ARP statistics .................................................................................................................................... 89
DNS statistics ................................................................................................................................... 89
ICMP statistics .................................................................................................................................. 90
TCP statistics..................................................................................................................................... 91
UDP statistics .................................................................................................................................... 93
IGMP Multicast Group statistics........................................................................................................... 93
OSPF statistics menu.......................................................................................................................... 94
VRRP statistics................................................................................................................................... 98
RIP statistics...................................................................................................................................... 99
Management Processor statistics ............................................................................................................ 100
Packet statistics ............................................................................................................................... 100
Contents 4
Page 5

TCP statistics................................................................................................................................... 101
UDP statistics .................................................................................................................................. 101
CPU statistics.................................................................................................................................. 102
Access Control List (ACL) statistics menu.................................................................................................. 102
ACL statistics .................................................................................................................................. 102
SNMP statistics.................................................................................................................................... 103
NTP statistics ....................................................................................................................................... 105
Uplink Failure Detection statistics............................................................................................................ 106
Statistics dump..................................................................................................................................... 107
Configuration Menu ...........................................................................................................................108
Introduction......................................................................................................................................... 108
Menu information ................................................................................................................................ 108
Viewing, applying, reverting, and saving changes ................................................................................... 109
Viewing pending changes..................................................................................................................... 109
Applying pending changes ................................................................................................................... 109
Reverting changes................................................................................................................................ 109
Saving the configuration ....................................................................................................................... 110
Reminders........................................................................................................................................... 110
System configuration ............................................................................................................................ 111
System host log configuration ........................................................................................................... 112
Secure Shell Server configuration ...................................................................................................... 114
RADIUS server configuration............................................................................................................. 115
TACACS+ server configuration ......................................................................................................... 116
NTP server configuration.................................................................................................................. 118
System SNMP configuration ............................................................................................................. 119
SNMPv3 configuration .................................................................................................................... 120
System Access configuration............................................................................................................. 127
Port configuration................................................................................................................................. 131
Temporarily disabling a port ............................................................................................................ 132
Port link configuration...................................................................................................................... 132
Port ACL/QoS configuration............................................................................................................. 133
Port PVRST configuration .................................................................................................................. 134
Layer 2 configuration ........................................................................................................................... 135
802.1X configuration ...................................................................................................................... 136
Rapid Spanning Tree Protocol/ Multiple Spanning Tree Protocol configuration........................................ 140
Common Internal Spanning Tree configuration.................................................................................... 141
Spanning Tree configuration............................................................................................................. 144
Forwarding Database configuration .................................................................................................. 148
Static FDB configuration................................................................................................................... 148
Trunk configuration ......................................................................................................................... 149
IP Trunk Hash configuration.............................................................................................................. 150
Link Aggregation Control Protocol configuration.................................................................................. 151
VLAN configuration......................................................................................................................... 152
Protocol VLAN configuration............................................................................................................. 153
Private VLAN configuration .............................................................................................................. 154
Hot Links configuration .................................................................................................................... 155
Layer 3 configuration ........................................................................................................................... 158
IP interface configuration ................................................................................................................. 159
Default Gateway configuration ......................................................................................................... 160
IP Static Route configuration ............................................................................................................. 161
Address Resolution Protocol configuration .......................................................................................... 161
Static ARP configuration................................................................................................................... 162
IP Forwarding configuration ............................................................................................................. 162
Contents 5
Page 6

Network Filter configuration ............................................................................................................. 163
Route Map configuration.................................................................................................................. 163
IP Access List configuration............................................................................................................... 164
Routing Information Protocol configuration.......................................................................................... 165
Open Shortest Path First configuration ............................................................................................... 168
OSPF Interface configuration ............................................................................................................ 170
IGMP configuration ......................................................................................................................... 175
Domain Name System configuration.................................................................................................. 180
Bootstrap Protocol Relay configuration ............................................................................................... 180
Server Mobility configuration............................................................................................................ 181
Virtual Router Redundancy Protocol configuration................................................................................ 183
Quality of Service configuration............................................................................................................. 190
QoS 802.1p configuration............................................................................................................... 190
Access Control configuration ................................................................................................................. 191
Access Control List configuration ....................................................................................................... 191
ACL Ethernet Filter configuration ....................................................................................................... 192
ACL IP Version 4 Filter configuration.................................................................................................. 193
ACL TCP/UDP Filter configuration ..................................................................................................... 194
ACL Meter configuration .................................................................................................................. 195
ACL Re-mark configuration ............................................................................................................... 195
ACL Packet Format configuration....................................................................................................... 197
ACL Group configuration ................................................................................................................. 198
Remote Monitoring configuration ........................................................................................................... 199
RMON history configuration............................................................................................................. 199
RMON event configuration .............................................................................................................. 200
RMON alarm configuration.............................................................................................................. 201
Port mirroring ...................................................................................................................................... 202
Port-based port mirroring ................................................................................................................. 203
Uplink Failure Detection configuration..................................................................................................... 204
Failure Detection Pair configuration ................................................................................................... 204
Link to Monitor configuration ............................................................................................................ 205
Link to Disable configuration............................................................................................................. 206
Dump ................................................................................................................................................. 207
Saving the active switch configuration .................................................................................................... 207
Restoring the active switch configuration ................................................................................................. 207
Operations Menu ...............................................................................................................................208
Introduction......................................................................................................................................... 208
Menu information ................................................................................................................................ 208
Operations-level port options ............................................................................................................ 208
Operations-level port 802.1X options ................................................................................................ 209
Operations-level VRRP options .......................................................................................................... 210
Boot Options Menu ............................................................................................................................211
Introduction......................................................................................................................................... 211
Menu information ................................................................................................................................ 211
Updating the switch software image....................................................................................................... 211
Downloading new software to the switch ........................................................................................... 211
Selecting a software image to run .......................................................................................................... 213
Uploading a software image from the switch ........................................................................................... 213
Selecting a configuration block .............................................................................................................. 214
Resetting the switch .............................................................................................................................. 214
Accessing the ISCLI .............................................................................................................................. 215
Maintenance Menu ............................................................................................................................216
Contents 6
Page 7

Introduction......................................................................................................................................... 216
Menu information ................................................................................................................................ 216
System maintenance options............................................................................................................. 217
Forwarding Database options........................................................................................................... 218
Debugging options.......................................................................................................................... 218
ARP cache options .......................................................................................................................... 219
IP Route Manipulation options........................................................................................................... 220
IGMP Multicast Group options.......................................................................................................... 220
IGMP Snooping options................................................................................................................... 221
IGMP Mrouter options ..................................................................................................................... 221
Uuencode flash dump...................................................................................................................... 222
FTP/TFTP system dump put ............................................................................................................... 222
Clearing dump information............................................................................................................... 222
Panic command .............................................................................................................................. 223
Unscheduled system dumps ................................................................................................................... 223
Index ................................................................................................................................................ 224
Contents 7
Page 8

Command line interface
Introduction
The HP 10Gb Ethernet BL-c Switch is ready to perform basic switching functions right out of the box.
Some of the more advanced features, however, require some administrative configuration before they
can be used effectively. This guide provides a command reference for the HP 10Gb Ethernet BL-c
Switch.
The extensive switching software included in the switch provides a variety of options for accessing
and configuring the switch:
• Built-in, text-based command line interfaces (AOS CLI and ISCLI) for access via a local terminal
or remote Telnet/Secure Shell (SSH) session
• Simple Network Management Protocol (SNMP) support for access through network management
software such as HP Systems Insight Manager
• A browser-based management interface for interactive network access through the Web browser
The command line interface provides a direct method for collecting switch information and performing
switch configuration. Using a basic terminal, you can view information and statistics about the switch,
and perform any necessary configuration.
This chapter explains how to access the AOS CLI to the switch.
Additional references
Additional information about installing and configuring the switch is available in the following guides:
• HP 10Gb Ethernet BL-c Switch User Guide
• HP 10Gb Ethernet BL-c Switch BladeSystem ISCLI Reference
• HP 10Gb Ethernet BL-c Switch Application Guide
• HP 10Gb Ethernet BL-c Switch Browser-based Interface Reference
• HP 10Gb Ethernet BL-c Switch Quick Setup Instructions
Connecting to the switch
You can access the command line interface in one of the following ways:
• Using a console connection via the console port
• Using a Telnet connection over the network
• Using a Secure Shell (SSH) connection to securely log in over a network
Command line interface 8
Page 9

Establishing a console connection
To establish a console connection with the switch, you need:
• A null modem cable with a female DB-9 connector (See the HP 10Gb Ethernet BL-c Switch User
Guide for more information.)
• An ASCII terminal or a computer running terminal emulation software set to the parameters
shown in the table below
Table 1
Parameter Value
Baud Rate 9600
Data Bits 8
Parity None
Stop Bits 1
Flow Control None
To establish a console connection with the switch:
1. Connect the terminal to the console port using the null modem cable.
2. Power on the terminal.
3. Press the Enter key a few times on the terminal to establish the connection.
4. You will be required to enter a password for access to the switch. (For more information, see the
Console configuration parameters
“Setting passwords” section in the “First-time configuration” chapter.)
Setting an IP address
To access the switch via a Telnet or an SSH connection, you need to have an Internet Protocol (IP)
address set for the switch. The switch can get its IP address in one of the following ways:
• Management port access:
○ Using a Dynamic Host Control Protocol (DHCP) server—When the /cfg/sys/dhcp
command is enabled, the management interface (interface 250) requests its IP address from
a DHCP server. The default value for the /cfg/sys/dhcp command is enabled.
○ Configuring manually—If the network does not support DHCP, you must configure the
management interface (interface 250) with an IP address. If you want to access the switch
from a remote network, you also must configure the management gateway (gateway 254).
• Uplink port access:
○ Using a Bootstrap Protocol (BOOTP) server—By default, the management interface is set up
to request its IP address from a BOOTP server. If you have a BOOTP server on the network,
add the Media Access Control (MAC) address of the switch to the BOOTP configuration file
located on the BOOTP server. The MAC address can be found in the System Information
menu. (See the “System information” section in the “Information Menu” chapter.) If you are
using a DHCP server that also does BOOTP, you do not have to configure the MAC address.
○ Configuring manually—If the network does not support BOOTP, you must configure the
management port with an IP address.
Command line interface 9
Page 10

Establishing a Telnet connection
A Telnet connection offers the convenience of accessing the switch from any workstation connected to
the network. Telnet provides the same options for user, operator, and administrator access as those
available through the console port. By default, Telnet is enabled on the switch. The switch supports
four concurrent Telnet connections.
Once the IP parameters are configured, you can access the CLI using a Telnet connection. To
establish a Telnet connection with the switch, run the Telnet program on the workstation and enter the
telnet command, followed by the switch IP address:
telnet <10GbE switch IP address>
You will then be prompted to enter a password. The password entered determines the access level:
administrator, operator, or user. See the “Accessing the switch” section later in this chapter for
description of default passwords.
Establishing an SSH connection
Although a remote network administrator can manage the configuration of a switch via Telnet, this
method does not provide a secure connection. The Secure Shell (SSH) protocol enables you to
securely log into the switch over the network.
As a secure alternative to using Telnet to manage switch configuration, SSH ensures that all data sent
over the network is encrypted and secure. In order to use SSH, you must first configure it on the
switch. See the “Secure Shell Server configuration” section in the “Configuration Menu” chapter for
information on how to configure SSH.
The switch can perform only one session of key/cipher generation at a time. Therefore, an
SSH/Secure Copy (SCP) client will not be able to log in if the switch is performing key generation at
that time or if another client has just logged in before this client. Similarly, the system will fail to
perform the key generation if an SSH/SCP client is logging in at that time.
The supported SSH encryption and authentication methods are listed below.
• Server Host Authentication—Client RSA authenticates the switch in the beginning of every
connection
• Key Exchange—RSA
• Encryption:
○ AES256-CBC
○ AES192-CBC
○ AES128-CBC
○ 3DES-CBC
○ 3DES
○ ARCFOUR
• User Authentication—Local password authentication; Remote Authentication Dial-in User Service
(RADIUS)
Command line interface 10
Page 11

The following SSH clients are supported:
• SSH 3.0.1 for Linux (freeware)
• SecureCRT® 4.1.8 (VanDyke Technologies, Inc.)
• OpenSSH_3.9 for Linux (FC 3)
• FedoraCore 3 for SCP commands
• PuTTY Release 0.58 (Simon Tatham) for Windows
NOTE: The switch implementation of SSH is based on versions 1.5 and 2.0, and supports SSH
clients from version 1.0 through version 2.0. SSH clients of other versions are not supported. You
may configure the client software to use protocol SSH version 1 or version 2.
By default, SSH service is not enabled on the switch. Once the IP parameters are configured, you can
access the command line interface to enable SSH.
To establish an SSH connection with the switch, run the SSH program on the workstation by issuing
the ssh command, followed by the user account name and the switch IP address:
>> # ssh <user>@<10Gb switch IP address>
You will then be prompted to enter your password.
NOTE: The first time you run SSH from the workstation, a warning message might appear. At the
prompt, enter yes to continue.
Accessing the switch
To enable better switch management and user accountability, the switch provides different levels or
classes of user access. Levels of access to the CLI and Web management functions and screens
increase as needed to perform various switch management tasks. The three levels of access are:
• User—User interaction with the switch is completely passive; nothing can be changed on the
switch. Users may display information that has no security or privacy implications, such as switch
statistics and current operational state information.
• Operator—Operators can only effect temporary changes on the switch. These changes will be
lost when the switch is rebooted/reset. Operators have access to the switch management
features used for daily switch operations. Because any changes an operator makes are undone
by a reset of the switch, operators cannot severely impact switch operation, but do have access
to the Maintenance menu.
• Administrator—Only administrators can make permanent changes to the switch configuration,
changes that are persistent across a reboot/reset of the switch. Administrators can access switch
functions to configure and troubleshoot problems on the switch. Because administrators can also
make temporary (operator-level) changes as well, they must be aware of the interactions
between temporary and permanent changes.
Access to switch functions is controlled through the use of unique usernames and passwords. Once
you are connected to the switch via the local console, Telnet, or SSH, you are prompted to enter a
password. The password entered determines the access level. The default user names/password for
each access level is listed in the following table.
NOTE: It is recommended that you change default switch passwords after initial configuration and
as regularly as required under your network security policies. For more information, see the “Setting
passwords” section in the “First-time configuration” chapter.
Command line interface 11
Page 12

Table 2 User access levels
User account Description and tasks performed
User The user has no direct responsibility for switch management. He or she can view all switch
status information and statistics, but cannot make any configuration changes to the switch.
The user account is enabled by default, and the default password is user.
Oper The operator manages all functions of the switch. The operator can reset ports or the entire
switch. By default, the operator account is disabled and has no password.
Admin The super user administrator has complete access to all menus, information, and
configuration commands on the switch, including the ability to change both the user and
administrator passwords. The admin account is enabled by default, and the default
password is admin.
NOTE: With the exception of the admin user, setting the password to an empty value can disable
access to each user level.
Once you enter the administrator password and it is verified, you are given complete access to the
switch.
After logging in, the Main Menu of the CLI is displayed. See the “Menu basics” chapter for a
summary of the Main Menu options.
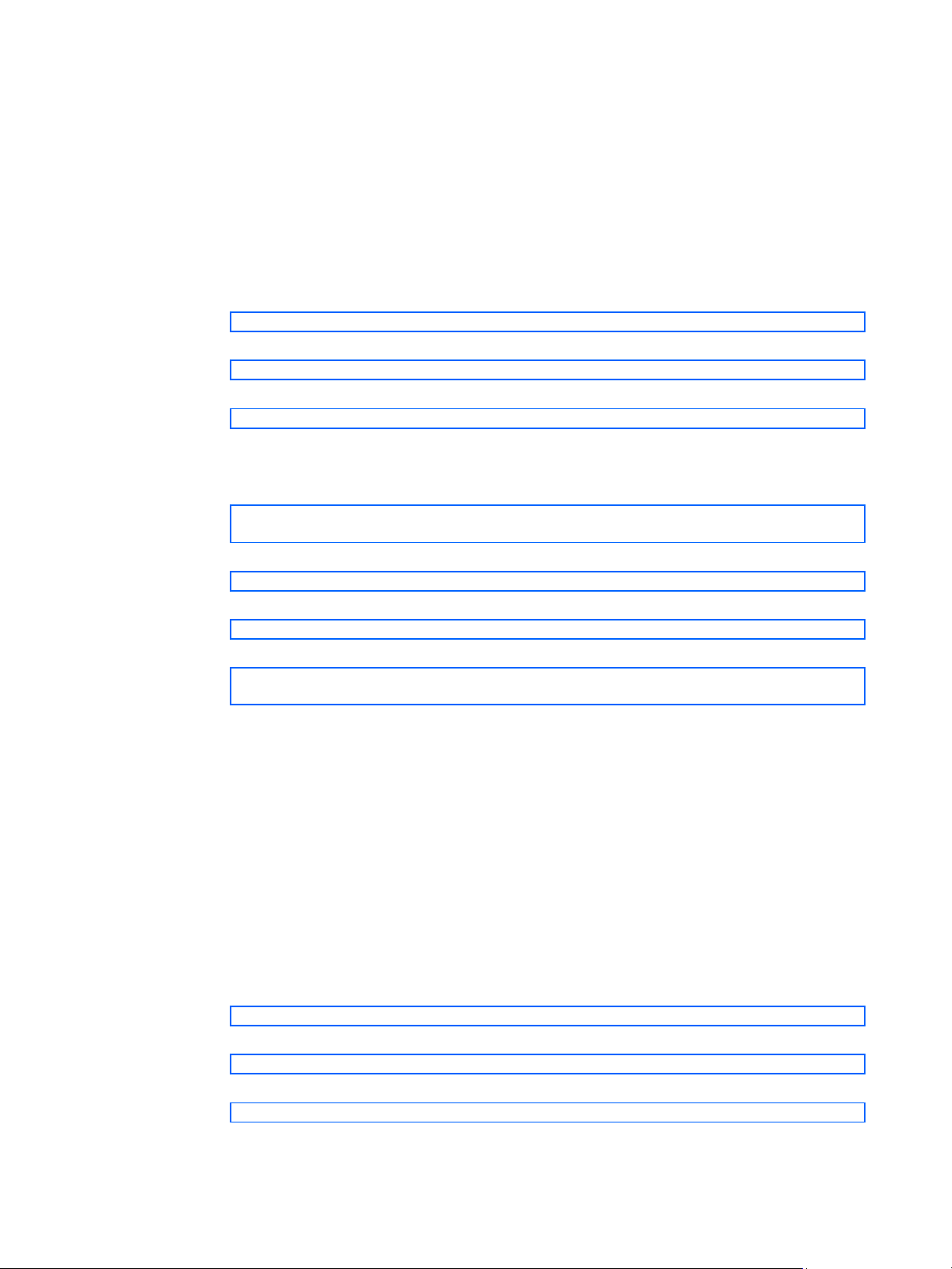
[Main Menu]
info - Information Menu
stats - Statistics Menu
cfg - Configuration Menu
oper - Operations Command Menu
boot - Boot Options Menu
maint - Maintenance Menu
diff - Show pending config changes [global command]
apply - Apply pending config changes [global command]
save - Save updated config to FLASH [global command]
revert - Revert pending or applied changes [global command]
exit - Exit [global command, always available]
>> Main#
Idle timeout
By default, the switch will disconnect the console, Telnet, or SSH session after five minutes of
inactivity. This function is controlled by the idle timeout parameter, which can be set from 1 to 60
minutes. For information on changing this parameter, see the “System configuration” section in the
“Configuration Menu” chapter.
Command line interface 12
Page 13
Typographical conventions
The following table describes the typographic styles used in this guide:
Table 3
Typographical conventions
Typeface or
symbol
AaBbCc123
AaBbCc123
<AaBbCc123>
[ ]
Meaning Example
This type depicts onscreen computer output and prompts.
This type displays in command examples and shows text
that must be typed in exactly as shown.
This italicized type displays in command examples as a
parameter placeholder. Replace the indicated text with the
appropriate real name or value when using the command.
Do not type the brackets.
This also shows guide titles, special terms, or words to be
emphasized.
Command items shown inside brackets are optional and
can be used or excluded as the situation demands. Do not
type the brackets.
Main#
Main# sys
To establish a Telnet session,
enter:
host# telnet <IP
address>
Read the user guide
thoroughly.
host# ls [-a]
Command line interface 13
Page 14
Menu basics
Introduction
The AOS CLI is used for viewing switch information and statistics. In addition, the administrator can
use the CLI for performing all levels of switch configuration.
To make the CLI easy to use, the various commands have been logically grouped into a series of
menus and submenus. Each menu displays a list of commands and/or submenus that are available,
along with a summary of what each command will do. Below each menu is a prompt where you can
enter any command appropriate to the current menu.
This chapter describes the Main Menu commands, and provides a list of commands and shortcuts that
commonly are available from all the menus within the CLI.
Main Menu
The Main Menu displays after a successful connection and login. The following table shows the Main
Menu for the administrator login. Some features are not available under the user login.
[Main Menu]
info - Information Menu
stats - Statistics Menu
cfg - Configuration Menu
oper - Operations Command Menu
boot - Boot Options Menu
maint - Maintenance Menu
diff - Show pending config changes [global command]
apply - Apply pending config changes [global command]
save - Save updated config to FLASH [global command]
revert - Revert pending or applied changes [global command]
exit - Exit [global command, always available]
Menu summary
The Main Menu displays the following submenus:
• Information Menu
The Information Menu provides submenus for displaying information about the current status of
the switch: from basic system settings to VLANs, and more.
• Statistics Menu
This menu provides submenus for displaying switch performance statistics. Included are port, IP,
ICMP, TCP, UDP, SNMP, routing, ARP, and DNS.
• Configuration Menu
This menu is available only from an administrator login. It includes submenus for configuring
every aspect of the switch. Changes to configuration are not active until explicitly applied.
Changes can be saved to non-volatile memory (NVRAM).
• Operations Command Menu
Menu basics 14
Page 15

Operations-level commands are used for making immediate and temporary changes to switch
configuration. This menu is used for bringing ports temporarily in and out of service. This menu is
available only from an administrator and operator login.
• Boot Options Menu
The Boot Options Menu is available only from an administrator login. This menu is used for
upgrading switch software, selecting configuration blocks, and for resetting the switch when
necessary. This menu is also used to set the switch back to factory settings.
• Maintenance Menu
This menu is used for debugging purposes, enabling you to generate a technical support dump
of the critical state information in the switch, and to clear entries in the Forwarding Database
and the Address Resolution Protocol (ARP) and routing tables. This menu is available only from
an administrator and operator login.
Global commands
Some basic commands are recognized throughout the menu hierarchy. These commands are useful
for obtaining online Help, navigating through menus, and for applying and saving configuration
changes.
For help on a specific command, enter help. The following screen displays:
Global Commands: [can be issued from any menu]
help up print pwd
lines verbose exit quit
diff apply save revert
ping traceroute telnet history
pushd popd who
The following are used to navigate the menu structure:
. Print current menu
.. Move up one menu level
/ Top menu if first, or command separator
! Execute command from history
The following table describes the global commands.
Table 4
Global commands
Command Action
? command or
help
. or print Displays the current menu.
.. or up Moves up one level in the menu structure.
/
Provides usage information about a specific command on the current menu. When used
without the command parameter, a summary of the global commands is displayed.
If placed at the beginning of a command, displays the Main Menu. Otherwise, this is
used to separate multiple commands placed on the same line.
lines
diff
apply
Sets the number of lines (n) that display on the screen at one time. The default is 24 lines.
When used without a value, the current setting is displayed.
Shows any pending configuration changes that have not been applied.
diff flash displays all pending configuration changes that have been applied but not
saved to flash memory (NVRAM), as well as those that have not been applied.
Applies pending configuration changes.
Menu basics 15
Page 16

Table 4 Global commands
Command Action
save
Saves the active configuration to backup, and saves the current configuration as active.
save n saves the current configuration as active, without saving the active configuration
to backup.
revert
Exit or quit Exits from the command line interface and logs out.
ping
Removes changes that have been made, but not applied.
revert apply removes all changes that have not been saved.
Verifies station-to-station connectivity across the network. The format is:
ping <host name>|<IP address> [attempts (1-32)> [msec delay]]
[-m|-mgt|-d|-data]
• IP address is the hostname or IP address of the device.
• number of tries (optional) is the number of attempts (1-32).
• msec delay (optional) is the number of milliseconds between attempts.
• By default, the -m or -mgt option for the management port is used. To use data
ports, specify the -d or –data option.
traceroute
Identifies the route used for station-to-station connectivity across the network. The format
is:
traceroute <host name>|<IP address> [<max-hops> [ msec delay ]]
• IP address is the hostname or IP address of the target station.
• max-hops (optional) is the maximum distance to trace (1-32 devices).
• msec delay (optional) is the number of milliseconds to wait for the response.
pwd
verbose n
Displays the command path used to reach the current menu.
Sets the level of information displayed on the screen:
• 0 = Quiet: Nothing displays except errors, not even prompts.
• 1 = Normal: Prompts and requested output are shown, but no menus.
• 2 = Verbose: Everything is shown. This is the default.
• When used without a value, the current setting is displayed.
telnet
history
pushd
popd
who
This command is used to Telnet out of the switch. The format is:
telnet <hostname> | <IP address> [port] [-m|-mgt|-d|-data]
By default, the -m or -mgt option for the management port is used. To use data ports,
specify the -d or –data option.
Displays the history of the last ten commands.
Remembers the current location in the directory of menu commands.
Returns to the last pushd location.
Displays users who are logged in.
Menu basics 16
Page 17

Command line history and editing
Using the command line interface, you can retrieve and modify previously entered commands with
just a few keystrokes. The following options are available globally at the command line:
Table 5
Command line history and editing options
Option Description
history
!!
!n
<Ctrl-p> or Up arrow key Recalls the previous command from the history list. This can be used multiple
<Ctrl-n> or Down arrow
key
<Ctrl-a>
<Ctrl-e>
<Ctrl-b> or Left arrow key Moves the cursor back one position to the left.
<Ctrl-f> or Right arrow
key
<Backspace> or Delete key Erases one character to the left of the cursor position.
Displays a numbered list of the last ten previously entered commands.
Repeats the last entered command.
Repeats the nth command shown on the history list.
times to work backward through the last ten commands. The recalled command
can be entered as is, or edited using the options below.
Recalls the next command from the history list. This can be used multiple times to
work forward through the last ten commands. The recalled command can be
entered as is, or edited using the options below.
Moves the cursor to the beginning of the command line.
Moves cursor to the end of the command line.
Moves the cursor forward one position to the right.
<Ctrl-d>
<Ctrl-k>
<Ctrl-l>
<Ctrl-u>
Other keys Inserts new characters at the cursor position.
.
..
Deletes one character at the cursor position.
Erases all characters from the cursor position to the end of the command line.
Redisplays the current line.
Clears the entire line.
Prints the current level menu list.
Moves to the previous directory level.
Menu basics 17
Page 18

Command line interface shortcuts
The following shortcuts allow you to enter commands quickly and easily.
Command stacking
As a shortcut, you can type multiple commands on a single line, separated by forward slashes (/).
You can connect as many commands as required to access the menu option that you want.
For example, the keyboard shortcut to access the Simple Network Management Protocol (SNMP)
Configuration Menu from the Main# prompt is:
Main# cfg/sys/ssnmp/name
Command abbreviation
Most commands can be abbreviated by entering the first characters that distinguish the command
from the others in the same menu or submenu.
For example, the command shown above could also be entered as:
Main# c/sys/ssn/n
Tab completion
By entering the first letter of a command at any menu prompt and pressing the Tab key, the CLI will
display all commands or options in that menu that begin with that letter. Entering additional letters will
further refine the list of commands or options displayed.
If only one command fits the input text when the Tab key is pressed, that command will be supplied
on the command line, waiting to be entered. If the Tab key is pressed without any input on the
command line, the currently active menu displays.
Menu basics 18
Page 19

First-time configuration
Introduction
This chapter describes how to perform first-time configuration and how to change system passwords.
To begin first-time configuration of the switch, perform the following steps.
1. Connect to the switch console. After connecting, the login prompt displays.
HP 10Gb Ethernet BL-c Switch
Copyright(C)2006 Hewlett-Packard Development Company, L.P.
Password:
2. Enter admin as the default administrator password.
The system displays the Main Menu with administrator privileges.
[Main Menu]
info - Information Menu
stats - Statistics Menu
cfg - Configuration Menu
oper - Operations Command Menu
boot - Boot Options Menu
maint - Maintenance Menu
diff - Show pending config changes [global command]
apply - Apply pending config changes [global command]
save - Save updated config to FLASH [global command]
revert - Revert pending or applied changes [global command]
exit - Exit [global command, always available]
>> Main#
3. From the Main Menu, enter the following command to access the Configuration Menu:
Main# /cfg
The Configuration Menu is displayed.
[Configuration Menu]
sys - System-wide Parameter Menu
port - Port Menu
l2 - Layer 2 Menu
l3 - Layer 3 Menu
qos - QOS Menu
acl - Access Control List Menu
rmon - RMON Menu
pmirr - Port Mirroring Menu
ufd - Uplink Failure Detection Menu
dump - Dump current configuration to script file
ptcfg - Backup current configuration to FTP/TFTP server
gtcfg - Restore current configuration from FTP/TFTP server
cur - Display current configuration
First-time configuration 19
Page 20

Configuring Simple Network Management Protocol support
NOTE: SNMP support is enabled by default.
1. Use the following command to enable SNMP:
>> # /cfg/sys/access/snmp disable|read only|read/write
2. Set SNMP read or write community string. By default, they are public and private respectively:
>> # /cfg/sys/ssnmp/rcomm|wcomm
3. When prompted, enter the proper community string.
4. Apply and save configuration if you are not configuring the switch with Telnet support.
Otherwise apply and save after the performing the “Optional Setup for Telnet Support” steps.
>> System# apply
>> System# save
Setting passwords
HP recommends that you change all passwords after initial configuration and as regularly as required
under the network security policies. See the “Accessing the switch” section in the “Command line
interface” chapter for a description of the user access levels.
To change the user, operator, or administrator password, you must log in using the administrator
password. Passwords cannot be modified from the user or operator command mode.
NOTE: If you forget your administrator password, call HP technical support for help using the
password fix-up mode.
Changing the default administrator password
The administrator has complete access to all menus, information, and configuration commands,
including the ability to change the user, operator, and administrator passwords.
The default password for the administrator account is admin. To change the default password:
1. Connect to the switch and log in using the admin password.
2. From the Main Menu, use the following command to access the Configuration Menu:
Main# /cfg
The Configuration Menu is displayed.
[Configuration Menu]
sys - System-wide Parameter Menu
port - Port Menu
l2 - Layer 2 Menu
l3 - Layer 3 Menu
qos - QOS Menu
acl - Access Control List Menu
rmon - RMON Menu
pmirr - Port Mirroring Menu
ufd - Uplink Failure Detection Menu
dump - Dump current configuration to script file
ptcfg - Backup current configuration to FTP/TFTP server
gtcfg - Restore current configuration from FTP/TFTP server
cur - Display current configuration
First-time configuration 20
Page 21

3.
From the Configuration Menu, use the following command to select the System Menu:
>> Configuration# sys
The System Menu is displayed.
[System Menu]
syslog - Syslog Menu
sshd - SSH Server Menu
radius - RADIUS Authentication Menu
tacacs+ - TACACS+ Authentication Menu
ntp - NTP Server Menu
ssnmp - System SNMP Menu
access - System Access Menu
date - Set system date
time - Set system time
timezone - Set system timezone (daylight savings)
olddst - Set system DST for US
dlight - Set system daylight savings
idle - Set timeout for idle CLI sessions
notice - Set login notice
bannr - Set login banner
hprompt - Enable/disable display hostname (sysName) in CLI prompt
bootp - Enable/disable use of BOOTP
dhcp - Enable/disable use of DHCP on Mgmt interface
reminders - Enable/disable Reminders
cur - Display current system-wide parameters
4. Enter the following command to set the administrator password:
System# access/user/admpw
5. Enter the current administrator password at the prompt:
Changing ADMINISTRATOR password; validation required...
NOTE: If you forget your administrator password, call your technical support representative for help
Enter current administrator password:
using the password fix-up mode.
6. Enter the new administrator password at the prompt:
Enter new administrator password:
7. Enter the new administrator password, again, at the prompt:
Re-enter new administrator password:
8. Apply and save the change by entering the following commands:
System# apply
System# save
First-time configuration 21
Page 22
Changing the default user password
The user login has limited control of the switch. Through a user account, you can view switch
information and statistics, but you cannot make configuration changes.
The default password for the user account is user. This password cannot be changed from the user
account. Only the administrator has the ability to change passwords, as shown in the following
procedure.
1. Connect to the switch and log in using the admin password.
2. From the Main Menu, use the following command to access the Configuration Menu:
Main# cfg
3. From the Configuration Menu, use the following command to select the System Menu:
>> Configuration# sys
4. Enter the following command to set the user password:
System# access/user/usrpw
5. Enter the current administrator password at the prompt.
Only the administrator can change the user password. Entering the administrator password
confirms your authority.
Changing USER password; validation required...
Enter current administrator password:
6. Enter the new user password at the prompt:
Enter new user password:
7. Enter the new user password, again, at the prompt:
Re-enter new user password:
8. Apply and save the changes:
System# apply
System# save
Changing the default operator password
The operator manages all functions of the switch. The operator can reset ports or the entire switch.
Operators can only effect temporary changes on the switch. These changes will be lost when the
switch is rebooted/reset. Operators have access to the switch management features used for daily
switch operations. Because any changes an operator makes are undone by a reset of the switch,
operators cannot severely impact switch operation.
By default, the operator account is disabled and has no password. This password cannot be changed
from the operator account. Only the administrator has the ability to change passwords, as shown in
the following procedure.
1. Connect to the switch and log in using the admin password.
2. From the Main Menu, use the following command to access the Configuration Menu:
Main# cfg
3. From the Configuration Menu, use the following command to select the System Menu:
>> Configuration# sys
4. Enter the following command to set the operator password:
System# access/user/opw
5. Enter the current administrator password at the prompt.
First-time configuration 22
Page 23

Only the administrator can change the user password. Entering the administrator password
confirms your authority.
Changing OPERATOR password; validation required...
Enter current administrator password:
6. Enter the new operator password at the prompt:
Enter new operator password:
7. Enter the new operator password, again, at the prompt:
Re-enter new operator password:
8. Apply and save the changes:
System# apply
System# save
First-time configuration 23
Page 24

Information Menu
Introduction
You can view configuration information for the switch in the user, operator, and administrator
command modes. This chapter discusses how to use the CLI to display switch information.
Menu overview
Command: /info
[Information Menu]
sys - System Information Menu
l2 - Layer 2 Information Menu
l3 - Layer 3 Information Menu
qos - QoS Menu
acl - Show ACL information
rmon - Show RMON information
link - Show link status
port - Show port information
transcvr - Show Port Transceiver status
ufd - Show Uplink Failure Detection information
sfd - Show Server Link Failure Detection information
dump - Dump all information
The following table describes the Information Menu options.
Table 6
Command Usage
sys
l2
l3
qos
acl
rmon
link
Information Menu options
Displays system information.
Displays the Layer 2 Information Menu.
Displays the Layer 3 Information Menu.
Displays the Quality of Service (QoS) Information Menu.
Displays the Access Control List Information Menu.
Displays the Remote Monitoring Information Menu.
Displays configuration information about each port, including:
• Port number
• Port speed
• Duplex mode (half, full, or any)
• Flow control for transmit and receive (no, yes, or any)
• Link status (up or down)
Information Menu 24
Page 25

Table 6 Information Menu options
Command Usage
port
Displays port status information, including:
• Port number
• Whether the port uses VLAN tagging or not
• Port VLAN ID (PVID)
• Port name
• VLAN membership
transcvr
ufd
sfd
dump
Displays the status of the Small Form Pluggable (SFP) module on each Fiber
External Port.
Displays Uplink Failure Detection information.
Displays Server Link Failure Detection information.
Dumps all switch information available from the Information Menu (10K or more,
depending on your configuration).
If you want to capture dump data to a file, set your communication software on
your workstation to capture session data prior to issuing the dump commands.
System Information Menu
Command: /info/sys
[System Menu]
snmpv3 - SNMPv3 Information Menu
general - Show general system information
log - Show last 100 syslog messages
user - Show current user status
dump - Dump all system information
The following table describes the System Information Menu options.
Table 7
System Information Menu options
Command Usage
snmpv3
general
Displays the SNMP v3 Menu.
Displays system information, including:
• System date and time
• Switch model name and number
• Switch name and location
• Time of last boot
• MAC address of the switch management processor
• IP address of IP interface #1
• Hardware version and part number
• Software image file and version number
• Configuration name
• Log-in banner, if one is configured
log
Displays 100 most recent syslog messages.
Information Menu 25
Page 26

Table 7 System Information Menu options
Command Usage
user
Displays the User Access Information Menu.
dump
Dumps all switch information available from the Information Menu (10K or more,
depending on your configuration).
SNMPv3 Information Menu
Command: /info/sys/snmpv3
[SNMPv3 Information Menu]
usm - Show usmUser table information
view - Show vacmViewTreeFamily table information
access - Show vacmAccess table information
group - Show vacmSecurityToGroup table information
comm - Show community table information
taddr - Show targetAddr table information
tparam - Show targetParams table information
notify - Show notify table information
dump - Show all SNMPv3 information
SNMP version 3 (SNMPv3) is an extensible SNMP Framework that supplements the SNMPv2
Framework by supporting the following:
• a new SNMP message format
• security for messages
• access control
• remote configuration of SNMP parameters
For more details on the SNMPv3 architecture, see RFC2271 to RFC2276.
The following table describes the SNMPv3 Information Menu options.
Table 8
SNMPv3 Information Menu options
Command Usage
usm
view
access
group
comm
taddr
tparam
notify
dump
Displays User Security Model (USM) table information.
Displays information about view name, subtrees, mask and type of view.
Displays View-based Access Control information.
Displays information about the group that includes the security model, user name, and
group name.
Displays information about the community table.
Displays the Target Address table.
Displays the Target parameters table.
Displays the Notify table.
Displays all the SNMPv3 information.
Information Menu 26
Page 27

SNMPv3 USM User Table information
Command: /info/sys/snmpv3/usm
usmUser Table:
User Name Protocol
-------------------------------- -------------------------------adminmd5 HMAC_MD5, DES PRIVACY
adminsha HMAC_SHA, DES PRIVACY
v1v2only NO AUTH, NO PRIVACY
The User-based Security Model (USM) in SNMPv3 provides security services such as authentication
and privacy of messages. This security model makes use of a defined set of user identities displayed
in the USM user table. The USM user table contains information like:
• the user name
• a security name in the form of a string whose format is independent of the Security Model
• an authentication protocol, which is an indication that the messages sent on behalf of the user
can be authenticated
• the privacy protocol.
The following table describes the SNMPv3 User Table information.
Table 9
User Table parameters
Field Description
User Name
Protocol
This is a string that represents the name of the user that you can use to access the switch.
This indicates whether messages sent on behalf of this user are protected from disclosure
using a privacy protocol. Switch software supports DES algorithm for privacy. The
software also supports two authentication algorithms: MD5 and HMAC-SHA.
SNMPv3 View Table information
Command: /info/sys/snmpv3/view
View Name Subtree Mask Type
----------------- ---------------------- ------------- --------
iso 1 included
v1v2only 1 included
v1v2only 1.3.6.1.6.3.15 excluded
v1v2only 1.3.6.1.6.3.16 excluded
v1v2only 1.3.6.1.6.3.18 excluded
The user can control and restrict the access allowed to a group to only a subset of the management
information in the management domain that the group can access within each context by specifying
the group’s rights in terms of a particular MIB view for security reasons.
Information Menu 27
Page 28

The following table describes the SNMPv3 View Table information.
Table 10
View Table parameters
Field Description
View Name
Subtree
Mask
Type
Displays the name of the view.
Displays the MIB subtree as an OID string. A view subtree is the set of all MIB object
instances which have a common Object Identifier prefix to their names.
Displays the bit mask.
Displays whether a family of view subtrees is included or excluded from the MIB view.
SNMPv3 Access Table information
Command: /info/sys/snmpv3/access
Group Name Model Level ReadV WriteV NotifyV
---------- ------- ------------ --------- -------- ------v1v2grp snmpv1 noAuthNoPriv iso iso v1v2only
admingrp usm authPriv iso iso iso
The access control sub system provides authorization services.
The vacmAccessTable maps a group name, security information, a context, and a message type,
which could be the read or write type of operation or notification into a MIB view.
The View-based Access Control Model defines a set of services that an application can use for
checking access rights of a group. This group’s access rights are determined by a read-view, a writeview, and a notify-view. The read-view represents the set of object instances authorized for the group
while reading the objects. The write-view represents the set of object instances authorized for the
group when writing objects. The notify-view represents the set of object instances authorized for the
group when sending a notification.
The following table describes the SNMPv3 Access Table information.
Table 11
Access Table parameters
Field Description
Group Name
Prefix
Model
Level
ReadV
WriteV
NotifyV
Displays the name of group.
Displays the prefix that is configured to match the values.
Displays the security model used, for example, SNMPv1, or SNMPv2 or USM.
Displays the minimum level of security required to gain rights of access. For
example, noAuthNoPriv, authNoPriv, or auth-Priv.
Displays the MIB view to which this entry authorizes the read access.
Displays the MIB view to which this entry authorizes the write access.
Displays the Notify view to which this entry authorizes the notify access.
Information Menu 28
Page 29

SNMPv3 Group Table information
Command: /info/sys/snmpv3/group
Sec Model User Name Group Name
--------- ----------------------------- -------------------snmpv1 v1v2only v1v2grp
usm adminmd5 admingrp
usm adminsha admingrp
A group is a combination of security model and security name that defines the access rights assigned
to all the security names belonging to that group. The group is identified by a group name.
The following table describes the SNMPv3 Group Table information.
Table 12
Group Table parameters
Field Description
Sec Model
User Name
Group Name
Displays the security model used, which is any one of: USM, SNMPv1, SNMPv2, and
SNMPv3.
Displays the name for the group.
Displays the access name of the group.
SNMPv3 Community Table information
Command: /info/sys/snmpv3/comm
Index Name User Name Tag
---------- ---------- -------------------- ---------trap1 public v1v2only v1v2trap
This command displays the community table information stored in the SNMP engine.
The following table describes the SNMPv3 Community Table information.
Table 13
Field Description
Community Table parameters
Index
Name
User Name
Tag
Displays the unique index value of a row in this table.
Displays the community string, which represents the configuration.
Displays the User Security Model (USM) user name.
Displays the community tag. This tag specifies a set of transport endpoints from which a
command responder application accepts management requests and to which a
command responder application sends an SNMP trap.
Information Menu 29
Page 30

SNMPv3 Target Address Table information
Command: /info/sys/snmpv3/taddr
Name Transport Addr Port Taglist Params
---------- --------------- ---- ---------- --------------trap1 47.81.25.66 162 v1v2trap v1v2param
This command displays the SNMPv3 target address table information, which is stored in the SNMP
engine.
The following table describes the SNMPv3 Target Address Table information.
Table 14
Target Address Table parameters
Field Description
Name
Transport Addr
Port
Taglist
Params
Displays the locally arbitrary, but unique identifier associated with this
snmpTargetAddrEntry.
Displays the transport addresses.
Displays the SNMP UDP port number.
This column contains a list of tag values which are used to select target addresses
for a particular SNMP message.
The value of this object identifies an entry in the snmpTargetParamsTable. The
identified entry contains SNMP parameters to be used when generating messages
to be sent to this transport address.
SNMPv3 Target Parameters Table information
Command: /info/sys/snmpv3/tparam
Name MP Model User Name Sec Model Sec Level
-------------- --------- ----------------- ---------- --------v1v2param snmpv2c v1v2only snmpv1 noAuthNoPriv
The following table describes the SNMPv3 Target Parameters Table information.
Table 15
Target Parameters Table
Field Description
Name
MP Model
User Name
Sec Model
Sec Level
Displays the locally arbitrary, but unique identifier associated with this snmpTargeParamsEntry.
Displays the Message Processing Model used when generating SNMP messages using this
entry.
Displays the securityName, which identifies the entry on whose behalf SNMP messages will be
generated using this entry.
Displays the security model used when generating SNMP messages using this entry. The
system may choose to return an inconsistentValue error if an attempt is made to set this
variable to a value for a security model which the system does not support.
Displays the level of security used when generating SNMP messages using this entry.
Information Menu 30
Page 31

SNMPv3 Notify Table information
Command: /info/sys/snmpv3/notify
Name Tag
-------------------- -------------------v1v2trap v1v2trap
The following table describes the SNMPv3 Notify Table information.
Table 16
SNMPv3 Notify Table
Field Description
Name
Tag
The locally arbitrary, but unique identifier associated with this snmpNotifyEntry.
This represents a single tag value which is used to select entries in the
snmpTargetAddrTable. Any entry in the snmpTargetAddrTable that contains a tag
value equal to the value of this entry is selected. If this entry contains a value of zero length,
no entries are selected.
Information Menu 31
Page 32

SNMPv3 dump
Command: /info/sys/snmpv3/dump
Engine ID = 80:00:07:50:03:00:0F:6A:F8:EF:00
usmUser Table:
User Name Protocol
-------------------------------- -------------------------------admin NO AUTH, NO PRIVACY
adminmd5 HMAC_MD5, DES PRIVACY
adminsha HMAC_SHA, DES PRIVACY
v1v2only NO AUTH, NO PRIVACY
vacmAccess Table:
Group Name Prefix Model Level Match ReadV WriteV NotifyV
---------- ------ ------- ------------ ------ ------- -------- -----admin usm noAuthNoPriv exact org org org
v1v2grp snmpv1 noAuthNoPriv exact org org v1v2only
admingrp usm authPriv exact org org org
vacmViewTreeFamily Table:
View Name Subtree Mask Type
-------------------- --------------- ------------ -------------org 1.3 included
v1v2only 1.3 included
v1v2only 1.3.6.1.6.3.15 excluded
v1v2only 1.3.6.1.6.3.16 excluded
v1v2only 1.3.6.1.6.3.18 excluded
vacmSecurityToGroup Table:
Sec Model User Name Group Name
---------- ------------------------------- ----------------------snmpv1 v1v2only v1v2grp
usm admin admin
usm adminsha admingrp
snmpCommunity Table:
Index Name User Name Tag
---------- ---------- -------------------- ----------
snmpNotify Table:
Name Tag
-------------------- --------------------
snmpTargetAddr Table:
Name Transport Addr Port Taglist Params
---------- --------------- ---- ---------- ---------------
snmpTargetParams Table:
Name MP Model User Name Sec Model Sec Level
-------------------- -------- ------------------ --------- -------
Information Menu 32
Page 33

System information
Command: /info/sys/gen
System Information at 6:56:22 Thu Jan 10, 2008
Time zone: America/US/Pacific
HP 10Gb Ethernet BL-c Switch
sysName:
sysLocation:
RackName: Default Rack Name
EnclosureName: Default Chassis Name
BayNumber: 1
Switch has been up for 3 days, 14 hours, 56 minutes and 22 seconds.
Last boot: 17:25:38 Mon Jan 8, 2007 (software reset)
MAC address: 00:10:00:01:00:01 IP (If 1) address: 10.14.4.16
Management Port MAC Address: 00:10:18:00:00:00
Management Port IP Address (if 250): 10.20.7.15
Revision: 0A
Switch Serial No: BLK7GEFR-3
Hardware Part No: 445680-B21 Spare Part No: 447126-001
Software Version 4.0.0 (FLASH image2), active configuration.
System information includes:
• System date and time
• Switch model name and number
• HP c-Class Rack name and location
• Time of last boot
• MAC address of the switch management processor
• IP address of the switch
• Software image file and version number
• Current configuration block (active, backup, or factory default)
• Login banner, if one is configured
Information Menu 33
Page 34

Show last 100 syslog messages
Command: /info/sys/log
Date Time Severity level Message
---- ---- ----------------- -----------Jul 8 17:25:41 NOTICE system: link up on port 1
Jul 8 17:25:41 NOTICE system: link up on port 8
Jul 8 17:25:41 NOTICE system: link up on port 7
Jul 8 17:25:41 NOTICE system: link up on port 12
Jul 8 17:25:41 NOTICE system: link up on port 11
Jul 8 17:25:41 NOTICE system: link up on port 14
Jul 8 17:25:41 NOTICE system: link up on port 13
Jul 8 17:25:41 NOTICE system: link up on port 16
Jul 8 17:25:41 NOTICE system: link up on port 15
Jul 8 17:25:41 NOTICE system: link up on port 17
Jul 8 17:25:41 NOTICE system: link up on port 20
Jul 8 17:25:41 NOTICE system: link up on port 18
Jul 8 17:25:41 NOTICE system: link up on port 19
Jul 8 17:25:41 NOTICE system: link up on port 21
Jul 8 17:25:42 NOTICE system: link up on port 4
Jul 8 17:25:42 NOTICE system: link up on port 3
Jul 8 17:25:42 NOTICE system: link up on port 6
Jul 8 17:25:42 NOTICE system: link up on port 5
Jul 8 17:25:42 NOTICE system: link up on port 10
Jul 8 17:25:42 NOTICE system: link up on port 9
Each message contains a date and time field and has a severity level associated with it. One of eight
different prefixes is used to indicate the condition:
• EMERG—indicates the system is unusable
• ALERT—indicates action should be taken immediately
• CRIT—indicates critical conditions
• ERR—indicates error conditions or eroded operations
• WARNING—indicates warning conditions
• NOTICE—indicates a normal but significant condition
• INFO—indicates an information message
• DEBUG—indicates a debug-level message
Information Menu 34
Page 35

System user information
Command: /info/sys/user
Usernames:
user - enabled
oper - disabled
admin - Always Enabled
Current User ID table:
1: name tech1 , ena, cos user , password valid, online
2: name tech2 , ena, cos user , password valid, offline
The following table describes the User Name information.
Table 17
User Name information menu
Field Usage
user
oper
admin
Current User ID Table
Displays the status of the user access level.
Displays the status of the oper (operator) access level.
Displays the status of the admin (administrator) access level.
Displays the status of configured user IDs. To configure new user IDs, use the
/cfg/sys/access/user/uid command.
Information Menu 35
Page 36

Layer 2 information
Command: /info/l2
[Layer 2 Menu]
fdb - Forwarding Database Information Menu
lacp - Link Aggregation Control Protocol Menu
hotlink - Show Hot Links information
8021x - Show 802.1X information
stp - Show STP information
cist - Show CIST information
trunk - Show Trunk Group information
vlan - Show VLAN information
uplink - Show uplink information
dump - Dump all layer 2 information
The following table describes the Layer 2 Information Menu options.
Table 18
Layer 2 Information Menu options
Command Usage
fdb
lacp
hotlink
8021x
stp
Displays the Forwarding Database Information Menu.
Displays the Link Aggregation Control Protocol Information Menu.
Displays the Hot Links Information Menu.
Displays the 802.1X Information Menu.
In addition to seeing if STP is enabled or disabled, you can view the following STP bridge
information:
• Priority
• Hello interval
• Maximum age value
• Forwarding delay
• Aging time
You can also refer to the following port-specific STP information:
• Port number and priority
• Cost
• State
cist
Displays Common internal Spanning Tree (CIST) bridge information, including the
following:
• Priority
• Hello interval
• Maximum age value
• Forwarding delay
You can also view port-specific CIST information, including the following:
• Port number and priority
• Cost
• State
trunk
When trunk groups are configured, you can view the state of each port in the various
trunk groups.
Information Menu 36
Page 37

Table 18 Layer 2 Information Menu options
Command Usage
vlan
Displays VLAN configuration information, including:
• VLAN Number
• VLAN Name
• Status
• Port membership of the VLAN
uplink
dump
Displays the status of Spanning Tree Uplink Fast.
Dumps all switch information available from the Layer 2 menu (10K or more, depending
on your configuration).
If you want to capture dump data to a file, set your communication software on your
workstation to capture session data prior to issuing the dump commands.
FDB information menu
Command: /info/l2/fdb
[Forwarding Database Menu]
find - Show a single FDB entry by MAC address
port - Show FDB entries on a single port
vlan - Show FDB entries on a single VLAN
state - Show FDB entries by state
dump - Show all FDB entries
The forwarding database (FDB) contains information that maps the media access control (MAC)
address of each known device to the switch port where the device address was learned. The FDB also
shows which other ports have seen frames destined for a particular MAC address.
NOTE: The master forwarding database supports up to 8K MAC address entries on the
management processor (MP) per switch.
Table 19 FDB information menu
Command Usage
find <MAC address> [<VLAN>]
port <port number>
vlan <1-4095>
state unknown|ignore|
forward|flood|trunk|ifmac
dump
Displays a single database entry by its MAC address. You are
prompted to enter the MAC address of the device.
Enter the MAC address using the format: xx:xx:xx:xx:xx:xx.
(For example: 08:00:20:12:34:56)
You can also enter the MAC address using the format:
xxxxxxxxxxxx. (For example: 080020123456)
Displays all FDB entries for a particular port.
Displays all FDB entries on a single VLAN. The range is 1-4095.
Displays all FDB entries that match a particular state.
Displays all entries in the Forwarding Database.
Information Menu 37
Page 38

Show all FDB information
Command: /info/l2/fdb/dump
MAC address VLAN Port Trnk State
----------------- ---- ---- ---- -----
00:02:01:00:00:00 300 1 TRK
00:02:01:00:00:01 300 20 FWD
00:02:01:00:00:02 300 20 FWD
00:02:01:00:00:03 300 20 FWD
00:02:01:00:00:04 300 20 FWD
00:02:01:00:00:05 300 20 FWD
00:02:01:00:00:06 300 20 FWD
00:02:01:00:00:07 300 20 FWD
00:02:01:00:00:08 300 20 FWD
00:02:01:00:00:09 300 20 FWD
00:02:01:00:00:0a 300 20 FWD
00:02:01:00:00:0b 300 20 FWD
00:02:01:00:00:0c 300 20 FWD
An address that is in the forwarding (FWD) state indicates that the switch has learned it. When in the
trunking (TRK) state, the Trnk field displays the trunk group number. If the state for the port is listed
as unknown (UNK), the MAC address has not yet been learned by the switch, but has only been seen
as a destination address. When an address is in the unknown state, no outbound port is indicated.
Clearing entries from the forwarding database
To delete a static MAC address from the forwarding database (FDB), see the “Static FDB
configuration” section in the “Configuration Menu” chapter. To clear the entire forwarding database
(FDB), see the “Forwarding Database options” section in the “Maintenance Menu” chapter.
Link Aggregation Control Protocol information
Command: /info/l2/lacp
[LACP Menu]
aggr - Show LACP aggregator information for the port
port - Show LACP port information
dump - Show all LACP ports information
The following table describes the Link Aggregation Control Protocol Menu options.
Table 20
Command Usage
aggr
port
dump
LACP information
Displays LACP aggregator information for the port.
Displays LACP information for the port.
Displays all LACP information parameters.
Information Menu 38
Page 39

LACP dump
Command: /info/l2/lacp/dump
>> LACP# dump
port lacp adminkey operkey selected prio attached trunk
aggr
----------------------------------------------------------------- 1 off 1 1 n 32768 -- - 2 off 2 2 n 32768 -- - 3 off 3 3 n 32768 -- - 4 off 4 4 n 32768 -- - 5 off 5 5 n 32768 -- - 6 off 6 6 n 32768 -- - 7 off 7 7 n 32768 -- - 8 off 8 8 n 32768 -- -…
LACP dump includes the following information for each port in the switch:
• lacp—Displays the port’s LACP mode (active, passive, or off)
• adminkey—Displays the value of the port’s adminkey.
• operkey—Shows the value of the port’s operational key.
• selected—Indicates whether the port has been selected to be part of a Link Aggregation
Group.
• prio—Shows the value of the port priority.
• attached aggr—Displays the aggregator associated with each port.
• trunk—This value represents the LACP trunk group number.
Hot Links Trigger information
Command: /info/l2/hotlink/trigger
Hot Links Info: Trigger
Current global Hot Links setting: ON
bpdu disabled
sndfdb disabled
Current Trigger 1 setting: enabled
name "Trigger 1", preempt enabled, fdelay 1 sec
Active state: None
Master settings:
port 20
Backup settings:
Hot Links trigger information includes the following:
• Hot Links status (on or off)
• Status of BPDU flood option
• Status of FDB send option
• Status and configuration of each Hot Links trigger
port 21
Information Menu 39
Page 40

802.1X information
Command: /info/l2/8021x
System capability : Authenticator
System status : disabled
Protocol version : 1
Authenticator Backend
Port Auth Mode Auth Status PAE State Auth State
---- ------------ ------------ -------------- --------- 1 force-auth unauthorized initialize initialize
2 force-auth unauthorized initialize initialize
3 force-auth unauthorized initialize initialize
4 force-auth unauthorized initialize initialize
5 force-auth unauthorized initialize initialize
6 force-auth unauthorized initialize initialize
7 force-auth unauthorized initialize initialize
8 force-auth unauthorized initialize initialize
9 force-auth unauthorized initialize initialize
10 force-auth unauthorized initialize initialize
11 force-auth unauthorized initialize initialize
12 force-auth unauthorized initialize initialize
13 force-auth unauthorized initialize initialize
14 force-auth unauthorized initialize initialize
15 force-auth unauthorized initialize initialize
16 force-auth unauthorized initialize initialize
*18 force-auth unauthorized initialize initialize
*19 force-auth unauthorized initialize initialize
*20 force-auth unauthorized initialize initialize
*21 force-auth unauthorized initialize initialize
-----------------------------------------------------------------* - Port down or disabled
The following table describes the IEEE 802.1X parameters.
Table 21
802.1X information
Field Description
Port
Auth Mode
Displays each port’s name.
Displays the Access Control authorization mode for the port. The
Authorization mode can be one of the following:
• force-unauth
• auto
• force-auth
Auth Status
Displays the current authorization status of the port, either authorized or
unauthorized.
Information Menu 40
Page 41

Table 21 802.1X information
Field Description
Authenticator PAE State
Displays the Authenticator Port Access Entity State. The PAE state can be one
of the following:
• initialize
• disconnected
• connecting
• authenticating
• authenticated
• aborting
• held
• forceAuth
Backend Auth State
Displays the Backend Authorization State. The Backend Authorization state
can be one of the following:
• request
• response
• success
• fail
• timeout
• idle
Information Menu 41
Page 42

Spanning Tree information
Command: /info/l2/stp
-----------------------------------------------------------------upfast disabled, update 40
BPDU Guard disabled
Pvst+ compatibility mode enabled
------------------------------------------------------------------
Spanning Tree Group 1: On (STP/PVST+)
VLANs: 1
Current Root: Path-Cost Port Hello MaxAge FwdDel
8000 00:02:a5:d1:0f:ed 8 20 2 20 15
Parameters: Priority Hello MaxAge FwdDel Aging
32768 2 20 15 300
Port Priority Cost FastFwd State Designated Bridge Des Port
---- -------- ---- -------- ----------- ----------------- ------ 1 0 0 n FORWARDING *
2 0 0 n FORWARDING *
3 0 0 n FORWARDING *
The switch software uses the IEEE 802.1D Spanning Tree Protocol (STP). If RSTP/MSTP is turned on,
see the “Rapid Spanning Tree information” section for Spanning Tree Group information. In addition
to seeing if STP is enabled or disabled, you can view the following STP bridge information:
• Status of Uplink Fast (upfast)
• Current root MAC address
• Path-Cost
• Port
• Hello interval
• Maximum age value
• Forwarding delay
• Aging time
Information Menu 42
Page 43

You can also refer to the following port-specific STP information:
• Port number and priority
• Cost
• State
• Port Fast Forwarding state
• Designated bridge
• Designated port
The following table describes the STP parameters.
Table 22
STP parameters
Parameters Description
Current Root
Path-Cost
Port
Priority (bridge)
Hello
MaxAge
FwdDel
Shows information about the root bridge for the Spanning Tree. Information
includes the priority (hex) and MAC address of the root.
Path-cost is the total path cost to the root bridge. It is the summation of the path
cost between bridges (up to the root bridge).
The current root port refers to the port on the switch that receives data from the
current root. Zero (0) indicates the root bridge of the STP.
The bridge priority parameter controls which bridge on the network will become
the STP root bridge.
The hello time parameter specifies, in seconds, how often the root bridge transmits
a configuration bridge protocol data unit (BPDU). Any bridge that is not the root
bridge uses the root bridge hello value.
The maximum age parameter specifies, in seconds, the maximum time the bridge
waits without receiving a configuration bridge protocol data unit before it
reconfigures the STP network. If the bridge is not the root bridge, it uses the
MaxAge value of the root bridge.
The forward delay parameter specifies, in seconds, the amount of time that a
bridge port has to wait before it changes from learning state to forwarding state. If
the bridge is not the root bridge, it uses the FwdDel value of the root bridge.
Aging
Priority (port)
Cost
State
Designated bridge
Designated port
The aging time parameter specifies, in seconds, the amount of time the bridge
waits without receiving a packet from a station before removing the station from
the Forwarding Database.
The port priority parameter helps determine which bridge port becomes the
designated port. In a network topology that has multiple bridge ports connected to
a single segment, the port with the lowest port priority becomes the designated
port for the segment.
The port path cost parameter is used to help determine the designated port for a
segment. Generally speaking, the faster the port, the lower the path cost.
The State field shows the current state of the port. The State field can be one of the
following: BLOCKING, LISTENING, LEARNING, FORWARDING, or DISABLED.
Shows information about the bridge connected to each port, if applicable.
Information includes the priority (hex) and MAC address of the Designated Bridge.
The port ID of the port on the Designated Bridge to which this port is connected.
This information includes the port priority (hex) and the port number (hex).
Information Menu 43
Page 44

Rapid Spanning Tree / Multiple Spanning Tree information
Command: /info/l2/stp
-----------------------------------------------------------------upfast disabled, update 40
BPDU Guard disabled
Pvst+ compatibility mode enabled
-----------------------------------------------------------------Spanning Tree Group 1: On (RSTP)
VLANs: 1-3
Current Root: Path-Cost Port Hello MaxAge FwdDel
8000 00:00:01:00:19:00 0 0 9 20 15
Parameters: Priority Hello MaxAge FwdDel Aging
32768 9 20 15 300
Port Prio Cost State Role Designated Bridge Des Port Type
---- ---- ---- ------ ---- ------------------- -------- --- 1 0 0 DSB
2 0 0 DSB
3 0 0 DSB
4 0 0 DSB
5 0 0 DSB
6 0 0 DSB
7 0 0 DSB
8 0 0 DSB
9 0 0 DSB
10 0 0 DISC
11 0 0 FWD DESG 8000-00:00:01:00:19:00 8017 P2P2,Edge
12 0 0 FWD DESG 8000-00:00:01:00:19:00 8018 P2P
The switch software can be set to use the IEEE 802.1w Rapid Spanning Tree Protocol (RSTP) or the
IEEE 802.1s Multiple Spanning Tree Protocol (MSTP). If RSTP/MSTP is turned on, you can view the
following RSTP bridge information for the Spanning Tree Group:
• Status of Uplink Fast (upfast)
• Current root MAC address
• Path-Cost
• Port
• Hello interval
• Maximum age value
• Forwarding delay
• Aging time
You can also refer to the following port-specific RSTP information:
• Port number and priority
• Cost
• State
• Role
• Designated bridge and port
• Link type
Information Menu 44
Page 45

The following table describes the STP parameters in RSTP or MSTP mode.
Table 23
Rapid Spanning Tree parameter descriptions
Parameter Description
Current Root
Path-Cost
Port
Priority (bridge)
Hello
MaxAge
FwdDel
Shows information about the root bridge for the Spanning Tree. Information
includes the priority (hex) and MAC address of the root.
Path-cost is the total path cost to the root bridge. It is the summation of the path cost
between bridges (up to the root bridge).
The current root port refers to the port on the switch that receives data from the
current root. Zero (0) indicates the root bridge of the STP.
The bridge priority parameter controls which bridge on the network will become the
STP root bridge.
The hello time parameter specifies, in seconds, how often the root bridge transmits
a configuration bridge protocol data unit (BPDU). Any bridge that is not the root
bridge uses the root bridge hello value.
The maximum age parameter specifies, in seconds, the maximum time the bridge
waits without receiving a configuration bridge protocol data unit before it
reconfigures the STP network. If the bridge is not the root bridge, it uses the
MaxAge value of the root bridge.
The forward delay parameter specifies, in seconds, the amount of time that a
bridge port has to wait before it changes from learning state to forwarding state. If
the bridge is not the root bridge, it uses the FwdDel value of the root bridge.
Aging
Priority (port)
Cost
State
Role
Designated bridge
Designated port
Type
The aging time parameter specifies, in seconds, the amount of time the bridge
waits without receiving a packet from a station before removing the station from the
Forwarding Database.
The port priority parameter helps determine which bridge port becomes the
designated port. In a network topology that has multiple bridge ports connected to
a single segment, the port with the lowest port priority becomes the designated port
for the segment.
The port path cost parameter is used to help determine the designated port for a
segment. Generally speaking, the faster the port, the lower the path cost. A setting
of zero (0) indicates that the cost will be set to the appropriate default after the link
speed has been auto-negotiated.
Shows the current state of the port. The State field in RSTP/MSTP mode can be one
of the following: Discarding (DISC), Learning (LRN), Forwarding (FWD), or
Disabled (DSB).
Shows the current role of this port in the Spanning Tree. The port role can be one of
the following: Designated (DESG), Root (ROOT), Alternate (ALTN), Backup (BKUP),
Master (MAST), or Unknown (UNK).
Shows information about the bridge connected to each port, if applicable.
Information includes the priority (hex) and MAC address of the Designated Bridge.
The port ID of the port on the Designated Bridge to which this port is connected.
Type of link connected to the port, and whether the port is an edge port. Link type
values are AUTO, P2P, or SHARED.
MSTP: The Type field appears in /info/cist.
Information Menu 45
Page 46

Common Internal Spanning Tree information
Command: /info/l2/cist
Mstp Digest: 0xac36177f50283cd4b83821d8ab26de62
Common Internal Spanning Tree:
VLANs MAPPED: 1-16 18-31 33-4094
VLANs: 1 25 26 4095
Current Root: Path-Cost Port MaxAge FwdDel
8000 00:03:42:fa:3b:80 0 1 20 15
CIST Regional Root: Path-Cost
8000 00:03:42:fa:3b:81 11
Parameters: Priority MaxAge FwdDel Hops
32768 20 15 20
Port Prio Cost State Role Designated Bridge Des Port Hello Type
---- ---- ---- ------ ---- --------------------- -------- ----- --- 1 128 2000 FWD DESG 8000-00:03:42:fa:3b:80 8001 4 P2P, Edge
2 128 2000 FWD DESG 8000-00:03:42:fa:3b:80 8002
3 128 2000 DSB
4 128 2000 DSB
5 128 2000 DSB
6 128 2000 DSB
7 128 2000 DSB
8 128 2000 DSB
9 128 2000 DSB
10 128 0 DSB
11 128 2000 FWD DESG 8000-00:03:42:fa:3b:80
12 128 2000 DSB
...
In addition to seeing if Common Internal Spanning Tree (CIST) is enabled or disabled, you can view
the following CIST bridge information:
• Status of Uplink Fast (upfast)
• CIST root
• CIST regional root
• Priority
• Maximum age value
• Forwarding delay
• Hops
You can also refer to the following port-specific CIST information:
• Port number and priority
• Cost
• State
• Role
• Designated bridge and port
• Hello interval
• Link type and port type
Information Menu 46
Page 47

The following table describes the CIST parameters.
Table 24
Common Internal Spanning Tree parameter description
Parameter Description
CIST Root
CIST Regional Root
Priority (bridge)
MaxAge
FwdDel
Hops
Priority (port)
Cost
Shows information about the root bridge for the Common Internal Spanning Tree
(CIST). Values on this row of information refer to the CIST root.
Shows information about the root bridge for this MSTP region. Values on this row
of information refer to the regional root.
The bridge priority parameter controls which bridge on the network will become the
STP root bridge.
The maximum age parameter specifies, in seconds, the maximum time the bridge
waits without receiving a configuration bridge protocol data unit before it
reconfigures the STP network.
The forward delay parameter specifies, in seconds, the amount of time that a
bridge port has to wait before it changes from learning state to forwarding state.
Shows the maximum number of bridge hops allowed before a packet is dropped.
The port priority parameter helps determine which bridge port becomes the
designated port. In a network topology that has multiple bridge ports connected to
a single segment, the port with the lowest port priority becomes the designated port
for the segment.
The port path cost parameter is used to help determine the designated port for a
segment. Generally speaking, the faster the port, the lower the path cost. A setting
of zero (0) indicates that the cost will be set to the appropriate default after the link
speed has been auto-negotiated.
State
Role
Designated Bridge
Designated Port
Hello
Type
Shows the current state of the port. The state field can be one of the following:
Discarding (DISC), Forwarding (FWD), or Disabled (DSB).
Shows the current role of this port in the Spanning Tree. The port role can be one of
the following: Designated (DESG), Root (ROOT), Alternate (ALTN), Backup (BKUP),
Master (MAST).
Shows information about the bridge connected to each port, if applicable.
Information includes the priority (hex) and MAC address of the Designated Bridge.
The port ID of the port on the Designated Bridge to which this port is connected.
Information includes the port priority (hex) and the port number (hex).
The hello time parameter specifies, in seconds, how often the root bridge transmits
a configuration bridge protocol data unit (BPDU). Any bridge that is not the root
bridge uses the root bridge hello value.
Type of link connected to the port, and whether the port is an edge port. Link type
values are AUTO, P2P, or SHARED.
Information Menu 47
Page 48

Trunk group information
Command: /info/l2/trunk
Trunk group 1, Enabled
port state:
20: STG 1 forwarding
21: STG 1 forwarding
When trunk groups are configured, you can view the state of each port in the various trunk groups.
NOTE: If Spanning Tree Protocol on any port in the trunk group is set to forwarding, the remaining
ports in the trunk group will also be set to forwarding.
VLAN information
Command: /info/l2/vlan
VLAN Name Status Ports
---- -------------------------------- ------ ---------------1 Default VLAN ena 4 5
2 pc03p ena 2
7 pc07f ena 7
11 pc04u ena 11
14 8600-14 ena 14
15 8600-15 ena 15
16 8600-16 ena 16
17 8600-17 ena 6
18 35k-1 ena 18
19 35k-2 ena 19
20 35k-3 ena 20
21 35k-4 ena 21
22 pc07z ena 21
24 redlan ena 21
300 ixiaTraffic ena 1 12 13 23
4000 bpsports ena 3-6 8-10
4095 Mgmt VLAN ena 17
PVLAN Protocol FrameType EtherType Priority Status Ports
----- -------- -------------------- -------- ------ ----------------1 1 Ether2 0080 0 ena 4
PVLAN PVLAN-Tagged Ports
----- --------------------------none none
Private-VLAN Type Mapped-To Status Ports
------------ --------- ---------- ---------- -----------------
20 primary empty ena empty
Information Menu 48
Page 49

This information display includes all configured VLANs and all member ports that have an active link
state.
VLAN information includes:
• VLAN Number
• VLAN Name
• Status
• Port membership of the VLAN
• Protocol VLAN information
• Private VLAN information
Fast Uplink Convergence status
Command: /info/l2/uplink
STP uplink fast mode : disabled
The following table describes the status of Fast Uplink Convergence.
Table 25
Field Description
STP uplink fast mode
L2 general information
Displays the status of STP Uplink Fast: enabled or disabled.
Information Menu 49
Page 50

Layer 3 information
Command: /info/l3
[Layer 3 Menu]
route - IP Routing Information Menu
arp - ARP Information Menu
ospf - OSPF Routing Information Menu
rip - RIP Routing Information Menu
ip - Show IP information
igmp - Show IGMP Snooping Multicast Group information
vrrp - Show Virtual Router Redundancy Protocol information
sm - Server Mobility Information Menu
dump - Dump all layer 3 information
The following table describes the Layer 3 Information Menu options.
Table 26
Layer 3 Information Menu options
Command Usage
route
Displays the IP Routing Menu. Using the options of this menu, the system displays the
following for each configured or learned route:
• Route destination IP address, subnet mask, and gateway address
• Type of route
• Tag indicating origin of route
• Metric for RIP tagged routes, specifying the number of hops to the destination (1-15
hops, or 16 for infinite hops)
• The IP interface that the route uses
arp
ospf
rip
ip
Displays the Address Resolution Protocol (ARP) Information Menu.
Displays OSPF routing Information Menu.
Displays Routing Information Protocol Menu.
Displays IP Information. IP information, includes:
• IP interface information: Interface number, IP address, subnet mask, VLAN number,
and operational status.
• Default gateway information: Metric for selecting which configured gateway to use,
gateway number, IP address, and health status
• IP forwarding information: Enable status, lnet and lmask
• Port status
igmp
vrrp
sm
dump
Displays IGMP Information Menu.
Displays the VRRP Information Menu.
Displays the Server Mobility Information Menu.
Dumps all switch information available from the Layer 3 Menu (10K or more, depending
on your configuration).
If you want to capture dump data to a file, set your communication software on your
workstation to capture session data prior to issuing the dump commands.
Information Menu 50
Page 51

Route information
Command: /info/l3/route
[IP Routing Menu]
find - Show a single route by destination IP address
gw - Show routes to a single gateway
type - Show routes of a single type
tag - Show routes of a single tag
if - Show routes on a single interface
dump - Show all routes
Using the commands listed below, you can display all or a portion of the IP routes currently held in
the switch.
Table 27
Route Information menu options
Command Usage
find <IP address>
gw <IP address>
type indirect|direct|local|
broadcast|martian|multicast
tag fixed|static|addr|rip|ospf|
broadcast|martian|multicast
if <1-250>
dump
Show all IP Route information
Command: /info/l3/route/dump
Status code: * - best
Destination Mask Gateway Type Tag Metr If
--------------- --------------- --------------- --------- --------- ---- -* 11.0.0.0 255.0.0.0 11.0.0.1 direct fixed 211
* 11.0.0.1 255.255.255.255 11.0.0.1 local addr 211
* 11.255.255.255 255.255.255.255 11.255.255.255 broadcast broadcast 211
* 12.0.0.0 255.0.0.0 12.0.0.1 direct fixed 12
* 12.0.0.1 255.255.255.255 12.0.0.1 local addr 12
* 12.255.255.255 255.255.255.255 12.255.255.255 broadcast broadcast 12
* 13.0.0.0 255.0.0.0 11.0.0.2 indirect ospf 2 211
* 47.0.0.0 255.0.0.0 47.133.88.1 indirect static 24
* 47.133.88.0 255.255.255.0 47.133.88.46 direct fixed 24
* 172.30.52.223 255.255.255.255 172.30.52.223 broadcast broadcast 2
* 224.0.0.0 224.0.0.0 0.0.0.0 martian martian
* 224.0.0.5 255.255.255.255 0.0.0.0 multicast addr
Displays a single route by IP address. For example,
100.10.1.1.
Displays routes to a single gateway. For example, 100.10.1.2.
Displays routes of a single type.
Displays routes of a single tag.
Displays routes on a single interface.
Displays all routes configured in the switch.
Information Menu 51
Page 52

The following table describes the Type parameter.
Table 28
IP Routing Type information
Field Description
indirect
direct
local
broadcast
martian
multicast
The next hop to the host or subnet destination will be forwarded through a router at the
Gateway address.
Packets will be delivered to a destination host or subnet attached to the switch.
Indicates a route to one of the switch’s IP interfaces.
Indicates a broadcast route.
The destination belongs to a host or subnet which is filtered out. Packets to this
destination are discarded.
Indicates a multicast route.
The following table describes the Tag parameter.
Table 29
IP Routing Tag information
Field Description
fixed
static
The address belongs to a host or subnet attached to the switch.
The address is a static route which has been configured on the switch.
addr
rip
ospf
broadcast
martian
The address belongs to one of the switch’s IP interfaces.
The address was learned by the Routing Information Protocol (RIP).
The address was learned by Open Shortest Path First (OSPF).
Indicates a broadcast address.
The address belongs to a filtered group.
Information Menu 52
Page 53

ARP information
Command: /info/arp
[Address Resolution Protocol Menu]
find - Show a single ARP entry by IP address
port - Show ARP entries on a single port
vlan - Show ARP entries on a single VLAN
addr - Show ARP entries for switch's interfaces
dump - Show all ARP entries
The Address Resolution Protocol (ARP) information includes IP address and MAC address of each
entry, address status flags, VLAN, and port for the address, and port referencing information.
The following table describes the Address Resolution Protocol Menu options.
Table 30
ARP information
Command Usage
find <IP address>
port <port number>
vlan <1-4095>
addr
dump
Displays a single ARP entry by IP address. For example, 192.4.17.101.
Displays the ARP entries on a single port.
Displays the ARP entries on a single VLAN.
Displays the ARP address list: IP address, IP mask, MAC address, and VLAN
flags.
Displays all ARP entries, including:
• IP address and MAC address of each entry
• Address status flag
• The VLAN and port to which the address belongs
• The ports which have referenced the address (empty if no port has routed
traffic to the IP address shown)
Show all ARP entry information
Command: /info/arp/dump
IP address Flags MAC address VLAN Port
--------------- ----- ----------------- ---- ----
192.168.2.4 00:50:8b:b2:32:cb 1 18
192.168.2.19 00:0e:7f:25:89:b5 1 17
192.168.2.61 P 00:0f:6a:ed:46:00 1
The Flag field provides additional information about an entry. If no flag displays, the entry is normal.
Table 31
ARP dump flag parameters
Flag Description
P
R
U
Permanent entry created for switch IP interface.
Indirect route entry.
Unresolved ARP entry. The MAC address has not been learned.
Information Menu 53
Page 54

ARP address list information
Command: /info/arp/addr
IP address IP mask MAC address VLAN Flags
--------------- --------------- ----------------- ---- -----
205.178.18.66 255.255.255.255 00:70:cf:03:20:04 P
205.178.50.1 255.255.255.255 00:70:cf:03:20:06 1
205.178.18.64 255.255.255.255 00:70:cf:03:20:05 1
This screen displays all entries in the ARP cache.
OSPF information
Command: /info/l3/ospf
[OSPF Information Menu]
general - Show general information
aindex - Show area(s) information
if - Show interface(s) information
virtual - Show details of virtual links
nbr - Show neighbor(s) information
dbase - Database Menu
sumaddr - Show summary address list
nsumadd - Show NSSA summary address list
routes - Show OSPF routes
dump - Show OSPF information
The following table describes the OSPF Menu options.
Table 32
OSPF information
Command Usage
general
aindex <0-2>
if <1-249>
virtual
nbr <nbr router-id (A.B.C.D)>
dbase
sumaddr <0-2>
nsumadd <0-2>
routes
dump
Displays general OSPF information.
Displays area information for a particular area index. If no
parameter is supplied, it displays area information for all the areas.
Displays interface information for a particular interface. If no
parameter is supplied, it displays information for all the interfaces.
Displays information about all the configured virtual links.
Displays the status of a neighbor with a particular router ID. If no
router ID is supplied, it displays the information about all the current
neighbors.
Displays OSPF database menu.
Displays the list of summary ranges belonging to non-NSSA areas.
Displays the list of summary ranges belonging to NSSA areas.
Displays OSPF routing table.
Displays all OSPF information.
Information Menu 54
Page 55

OSPF general information
Command: /info/l3/ospf/general
OSPF Version 2
Router ID: 10.10.10.1
Started at 1663 and the process uptime is 4626
Area Border Router: yes, AS Boundary Router: no
LS types supported are 6
External LSA count 0
External LSA checksum sum 0x0
Number of interfaces in this router is 2
Number of virtual links in this router is 1
16 new lsa received and 34 lsa originated from this router
Total number of entries in the LSDB 10
Database checksum sum 0x0
Total neighbors are 1, of which
2 are >=INIT state,
2 are >=EXCH state,
2 are =FULL state
Number of areas is 2, of which 3-transit 0-nssa 0-stub
Area Id : 0.0.0.0
Authentication : none
Import ASExtern : yes
Number of times SPF ran : 8
Area Border Router count : 2
AS Boundary Router count : 0
LSA count : 5
Summary : noSummary
OSPF interface information
Command: /info/l3/ospf/if
Ip Address 10.10.12.1, Area 0.0.0.1, Admin Status UP
Router ID 10.10.10.1, State DR, Priority 1
Designated Router (ID) 10.10.10.1, Ip Address 10.10.12.1
Backup Designated Router (ID) 10.10.14.1, Ip Address 10.10.12.2
Timer intervals, Hello 10, Dead 40, Wait 40, Retransmit 5,
Transit delay 1
Neighbor count is 1 If Events 4, Authentication type none
Information Menu 55
Page 56

OSPF Database information menu
Command: /info/l3/ospf/dbase
[OSPF Database Menu]
advrtr - LS Database info for an Advertising Router
asbrsum - ASBR Summary LS Database info
dbsumm - LS Database summary
ext - External LS Database info
nw - Network LS Database info
nssa - NSSA External LS Database info
rtr - Router LS Database info
self - Self Originated LS Database info
summ - Network-Summary LS Database info
all - All
The following table describes the OSPF Database information menu options.
Table 33
OSPF Database information
Command Usage
advrtr <router-id (A.B.C.D)>
asbrsum <adv-rtr (A.B.C.D)>|
<link_state_id (A.B.C.D)>|<self>
Takes advertising router as a parameter. Displays all the Link
State Advertisements (LSAs) in the LS database that have the
advertising router with the specified router ID, for example:
20.1.1.1.
Displays ASBR summary LSAs. The usage of this command is as
follows:
• asbrsum adv-rtr 20.1.1.1 displays ASBR summary
LSAs having the advertising router 20.1.1.1.
• asbrsum link_state_id 10.1.1.1 displays ASBR
summary LSAs having the link state ID 10.1.1.1.
• asbrsum self displays the self advertised ASBR summary
LSAs.
• asbrsum with no parameters displays all the ASBR summary
LSAs.
dbsumm
Displays the following information about the LS database in a
table format:
• The number of LSAs of each type in each area.
• The total number of LSAs for each area.
• The total number of LSAs for each LSA type for all areas
combined.
• The total number of LSAs for all LSA types for all areas
combined.
No parameters are required.
ext <adv-rtr (A.B.C.D)>|
<link_state_id (A.B.C.D)>|<self>
nw <adv-rtr (A.B.C.D)>|
<link_state_id (A.B.C.D)>|<self>
nssa <adv-rtr (A.B.C.D)>|
<link_state_id (A.B.C.D)>|<self>
Displays the AS-external (type 5) LSAs with detailed information
of each field of the LSAs. The usage of this command is the same
as the usage of the command asbrsum.
Displays the network (type 2) LSAs with detailed information of
each field of the LSA.network LS database. The usage of this
command is the same as the usage of the command asbrsum.
Displays the NSSA (type 7) LSAs with detailed information of
each field of the LSAs. The usage of this command is the same
as the usage of the command asbrsum.
Information Menu 56
Page 57

Table 33 OSPF Database information
Command Usage
rtr <adv-rtr (A.B.C.D)>|
<link_state_id (A.B.C.D)>|<self>
Displays the router (type 1) LSAs with detailed information of
each field of the LSAs. The usage of this command is the same
as the usage of the command asbrsum.
self
summ <adv-rtr (A.B.C.D)>|
<link_state_id (A.B.C.D)>|<self>
all
OSPF route codes information
Command: /info/l3/ospf/routes
Codes: IA - OSPF inter area,
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
* - best
IA 10.10.0.0/16 via 200.1.1.2
IA 40.1.1.0/28 via 20.1.1.2
IA 80.1.1.0/24 via 200.1.1.2
IA 100.1.1.0/24 via 20.1.1.2
IA 140.1.1.0/27 via 20.1.1.2
IA 150.1.1.0/28 via 200.1.1.2
E2 172.18.1.1/32 via 30.1.1.2
E2 172.18.1.2/32 via 30.1.1.2
E2 172.18.1.3/32 via 30.1.1.2
E2 172.18.1.4/32 via 30.1.1.2
E2 172.18.1.5/32 via 30.1.1.2
E2 172.18.1.6/32 via 30.1.1.2
E2 172.18.1.7/32 via 30.1.1.2
E2 172.18.1.8/32 via 30.1.1.2
Displays all the self-advertised LSAs. No parameters are
required.
Displays the network summary (type 3) LSAs with detailed
information of each field of the LSAs.
The usage of this command is the same as the usage of the
command asbrsum.
Displays all the LSAs.
Information Menu 57
Page 58

Routing Information Protocol information
Command: /info/l3/rip
[RIP Information Menu]
routes - Show RIP routes
dump - Show RIP user's configuration
The following table describes the Routing Information Protocol information menu options.
Table 34
RIP information
Command Usage
routes
dump <0-249>
RIP Routes information
Command: /info/l3/rip/routes
>> IP Routing# /info/l3/rip/routes
3.0.0.0/8 via 30.1.1.11 metric 4
4.0.0.0/16 via 30.1.1.11 metric 16
10.0.0.0/8 via 30.1.1.2 metric 3
20.0.0.0/8 via 30.1.1.2 metric 2
This table contains all dynamic routes learned through RIP, including the routes that are undergoing
garbage collection with metric = 16. This table does not contain directly connected routes and locally
configured static routes.
RIP user configuration
Displays information about RIP routes.
Displays RIP user’s configuration. Enter 0 (zero) for all interfaces.
Command: /info/l3/rip/dump <1-249>
RIP USER CONFIGURATION :
RIP on update 30
RIP Interface 2 : 102.1.1.1, enabled
version 2, listen enabled, supply enabled, default none
poison disabled, trigg enabled, mcast enabled, metric 1
auth none, key none
RIP Interface 3 : 103.1.1.1, enabled
version 2, listen enabled, supply enabled, default none
poison disabled, trigg enabled, mcast enabled, metric 1
Information Menu 58
Page 59

IP information
Command: /info/l3/ip
IP information:
Interface information:
1: 10.80.23.243 255.255.254.0 10.80.23.255, vlan 1, up
250: 10.20.7.144 255.255.0.0 10.20.255.255, vlan 4095, up
Default gateway information: metric strict
1: 10.80.22.1, vlan any, up active
254: 10.20.1.1, vlan 4095, up active
Current ServerMobility settings: OFF
ServerMobility ports: empty
DHCP request filtering enabled ports: empty
Relay on non-ServerMobility ports: Ena
Active-Backup ports:
Current IP forwarding settings: OFF, dirbr disabled
Current network filter settings:
none
Current route map settings:
The following interface and default gateway information is displayed:
• Interface number
• IP address
• IP mask
• IP broadcast address
• Operational status
• BootP relay settings
• Server Mobility settings
• IP forwarding settings
• Network filter settings
• Route map settings
Information Menu 59
Page 60

IGMP multicast group information
Command: /info/l3/igmp
[IGMP Multicast Group Menu]
mrouter - Show IGMP Snooping Multicast Router Port information
find - Show a single group by IP group address
vlan - Show groups on a single vlan
port - Show groups on a single port
trunk - Show groups on a single trunk
detail - Show detail of a single group by IP group address
dump - Show all groups
The following table describes the commands used to display information about IGMP groups learned
by the switch.
Table 35
IGMP Multicast Group menu options
Command Usage
mrouter
find <IP address>
vlan <1-4094>
port <port number>
trunk <1-40>
detail
dump
IGMP group information
Command: /info/l3/igmp/dump
Note: Local groups (224.0.0.x) are not snooped/relayed and will not appear.
Source Group VLAN Port Version Mode Expires Fwd
-------------- --------------- ------- ------ -------- ----- ------- ---
10.1.1.1 232.1.1.1 2 21 V3 INC 4:16 Yes
10.1.1.5 232.1.1.1 2 21 V3 INC 4:16 Yes
* 232.1.1.1 2 21 V3 INC - No
10.10.10.43 235.0.0.1 9 21 V3 INC 2:26 Yes
* 236.0.0.1 9 21 V3 EXC - Yes
Displays the Multicast Router Menu.
Displays a single IGMP multicast group by its IP address.
Displays all IGMP multicast groups on a single VLAN.
Displays all IGMP multicast groups on a single port.
Displays all IGMP multicast groups on a single trunk group.
Displays details about IGMP multicast groups, including source
and timer information.
Displays information for all multicast groups.
IGMP Group information includes:
• IGMP source address
• IGMP Group address
• VLAN and port
• IGMP version
• IGMPv3 filter mode
• Expiration timer value
• IGMP multicast forwarding state
Information Menu 60
Page 61

IGMP multicast router information
Command: /info/l3/igmp/mrouter
[IGMP Multicast Router Menu]
vlan - Show all multicast router ports on a single vlan
dump - Show all learned multicast router ports
The following table describes the commands used to display information about multicast routers
learned through IGMP Snooping.
Table 36
IGMP Multicast Router menu options
Command Usage
vlan <1-4094>
dump
Displays information for all multicast groups on a single VLAN.
Displays information for all multicast groups learned by the switch.
Information Menu 61
Page 62

VRRP information
Virtual Router Redundancy Protocol (VRRP) support on the HP 10GbE switch provides redundancy
between routers in a LAN. This is accomplished by configuring the same virtual router IP address and
ID number on each participating VRRP-capable routing device. One of the virtual routers is then
elected as the master, based on a number of priority criteria, and assumes control of the shared
virtual router IP address. If the master fails, one of the backup virtual routers will assume routing
authority and take control of the virtual router IP address.
Command: /info/l3/vrrp
VRRP information:
1: vrid 2, 205.178.18.210, if 1, renter, prio 100, master, server
2: vrid 1, 205.178.18.202, if 1, renter, prio 100, backup
3: vrid 3, 205.178.18.204, if 1, renter, prio 100, master, proxy
When virtual routers are configured, you can view the status of each virtual router using this
command. VRRP information includes:
• Virtual router number
• Virtual router ID and IP address
• Interface number
• Ownership status
○ owner identifies the preferred master virtual router. A virtual router is the owner when the IP
address of the virtual router and its IP interface are the same.
○ renter identifies virtual routers which are not owned by this device
• Priority value. During the election process, the virtual router with the highest priority becomes
master.
• Activity status
○ master identifies the elected master virtual router.
○ backup identifies that the virtual router is in backup mode.
○ init identifies that the virtual router is waiting for a startup event. Once it receives a startup
event, it transitions to master if its priority is 255, (the IP address owner), or transitions to
backup if it is not the IP address owner.
• Server status. The server state identifies virtual routers.
• Proxy status. The proxy state identifies virtual proxy routers, where the virtual router shares the
same IP address as a proxy IP address. The use of virtual proxy routers enables redundant
switches to share the same IP address, minimizing the number of unique IP addresses that must
be configured.
Information Menu 62
Page 63

Server Mobility Port information
Command: /info/l3/sm/port
-----------------------------------------------------Server Mobility Port 2 Information:
agent.circuit-id = 55:53:45:36:33:35:31:4d:34:36:00:00:00:00:00:00
agent.remote-id = 02:00:00:00:02
Server Mobility : enabled
Filtering : enabled
This display includes the following information for each port that has Server Mobility configured:
• Agent Circuit ID—hexadecimal value of the DHCP option 82 Agent Circuit ID
• Agent Remote ID—hexadecimal value of the DHCP option 82 Agent Remote ID
• Server Mobility status (enabled or disabled)
• Status of Server Mobility filtering
• Backup port
Port 2 has no backup port
Information Menu 63
Page 64
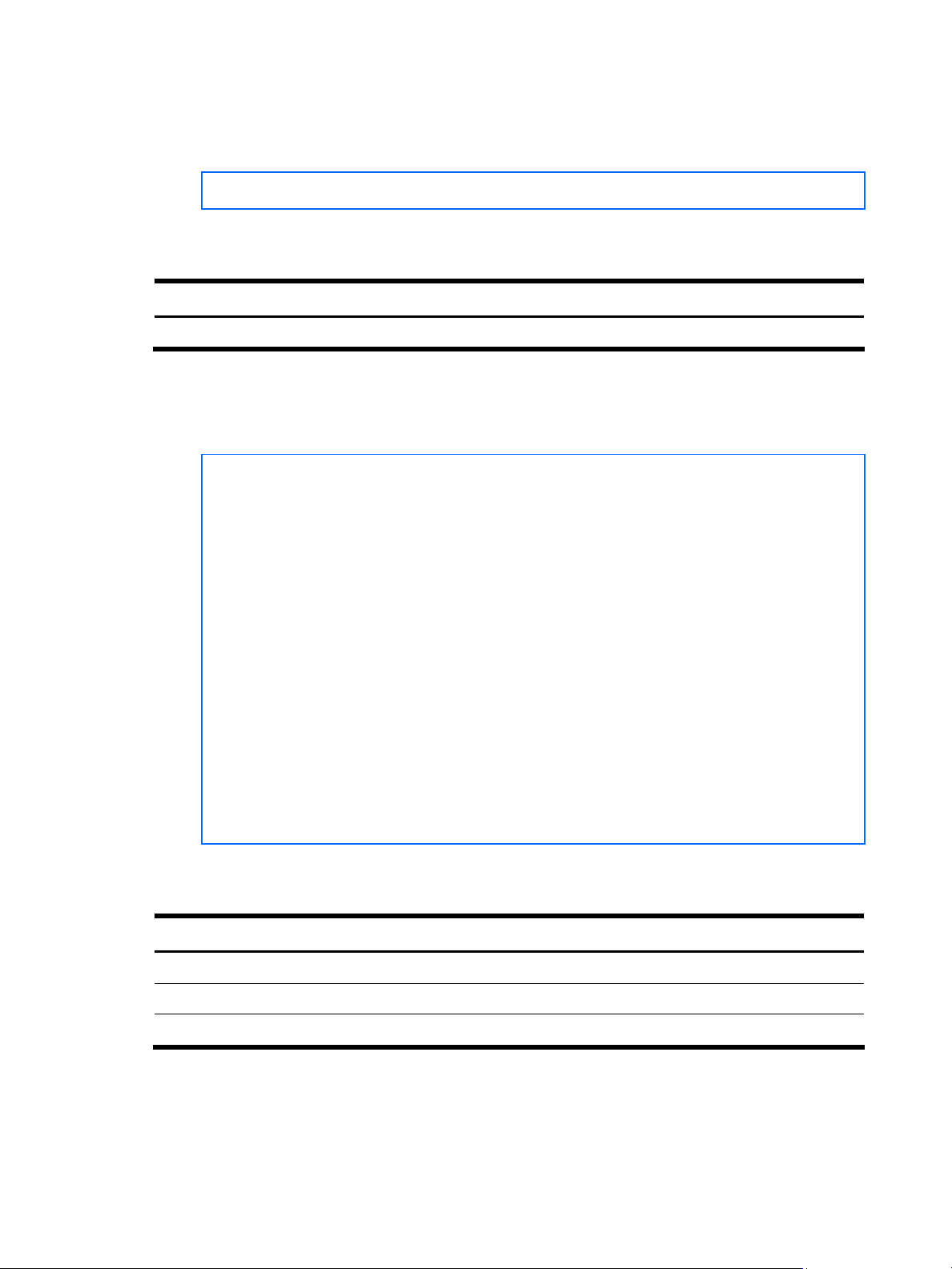
QoS information
Command: /info/qos
[QoS Menu]
8021p - Show QOS 802.1p information
The following table describes the commands used to display Quality of Service (QoS) information.
Table 37
QoS menu options
Command Usage
8021p
802.1p information
Command: /info/qos/8021p
Current priority to COS queue information:
Priority COSq Weight
-------- ---- ----- 0 0 1
1 0 1
2 0 1
3 0 1
4 1 2
5 1 2
6 1 2
7 1 2
Current port priority information:
Port Priority COSq Weight
----- -------- ---- ----- 1 0 0 1
2 0 0 1
3 0 0 1
4 0 0 1
…
20 0 0 1
21 0 0 1
Displays the QoS 802.1p Information Menu.
The following table describes the IEEE 802.1p priority to COS queue information.
Table 38
802.1p Priority to COS Queue information
Field Description
Priority
Cosq
Weight
Displays the 802.1p Priority level.
Displays the Class of Service queue.
Displays the scheduling weight of the COS queue.
Information Menu 64
Page 65

The following table describes the IEEE 802.1p port priority information.
Table 39
802.1p Port Priority information
Field Description
Port
Priority
Cosq
Weight
ACL information
Command: /info/acl
Current ACL information:
----------------------- Filter 1 profile:
Ethernet
- VID : 1/0xfff
Actions : Set COS to 0
Filter 2 profile:
Ethernet
- VID : 1/0xfff
Actions : Permit
No ACL groups configured.
Displays the port number.
Displays the 802.1p Priority level.
Displays the Class of Service queue.
Displays the scheduling weight.
Access Control List (ACL) information provides configuration parameters for each Access Control List.
It also shows which ACLs are included in each ACL Group.
Information Menu 65
Page 66

RMON Information Menu
Command: /info/rmon
[RMON Information Menu]
hist - Show RMON History group information
alarm - Show RMON Alarm group information
event - Show RMON Event group information
dump - Show all RMON information
The following table describes the RMON Information parameters.
Table 40
RMON History Information Menu
Command Usage
hist
alarm
event
dump
Displays the RMON History Information menu.
Displays the RMON Alarm Information menu.
Displays the RMON Event Information menu.
Displays all RMON Information parameters.
RMON history information
Command: /info/rmon/hist
RMON History group configuration:
Index IFOID Interval Rbnum Gbnum
----- ------------------------------ -------- ----- ---- 1 1.3.6.1.2.1.2.2.1.1.21 30 5 5
2 1.3.6.1.2.1.2.2.1.1.18 30 5 5
3 1.3.6.1.2.1.2.2.1.1.20 30 5 5
4 1.3.6.1.2.1.2.2.1.1.19 30 5 5
5 1.3.6.1.2.1.2.2.1.1.21 1800 5 5
The following table describes the RMON History Information parameters.
Table 41
RMON History Information Menu
Field Description
Index
IFOID
Interval
Rbnum
Gbnum
Displays the index number that identifies each history instance.
Displays the MIB Object Identifier.
Displays the time interval for each sampling bucket.
Displays the number of requested buckets, which is the number of data slots into
which data is to be saved.
Displays the number of granted buckets that may hold sampled data.
Information Menu 66
Page 67

RMON alarm information
Command: /info/rmon/alarm
RMON Alarm group configuration:
Index Interval Type rLimit fLimit rEvtIdx fEvtIdx last value
----- -------- ---- -------- -------- ------- ------- --------- 1 30 abs 10 0 1 0 0
2 900 abs 0 10 0 2 0
3 300 abs 10 20 0 0 0
4 1800 abs 10 0 1 0 0
5 1800 abs 10 0 1 0 0
8 1800 abs 10 0 1 0 56344540
10 1800 abs 10 0 1 0 0
11 1800 abs 10 0 1 0 0
15 1800 abs 10 0 1 0 0
18 1800 abs 10 0 1 0 0
100 1800 abs 10 0 1 0 0
Index OID
----- ----------------------------- 1 1.3.6.1.2.1.2.2.1.10.257
2 1.3.6.1.2.1.2.2.1.11.258
3 1.3.6.1.2.1.2.2.1.12.259
4 1.3.6.1.2.1.2.2.1.13.260
5 1.3.6.1.2.1.2.2.1.14.261
8 1.3.6.1.2.1.2.2.1.10.271
10 1.3.6.1.2.1.2.2.1.15.262
11 1.3.6.1.2.1.2.2.1.16.263
15 1.3.6.1.2.1.2.2.1.19.266
18 1.3.6.1.2.1.2.2.1.10.270
100 1.3.6.1.2.1.2.2.1.17.264
The following table describes the RMON Alarm Information parameters.
Table 42
RMON Alarm Information Menu
Field Description
Index
Interval
Type
Displays the index number that identifies each alarm instance.
Displays the time interval over which data is sampled and compared with the rising
and falling thresholds.
Displays the method of sampling the selected variable and calculating the value to be
compared against the thresholds, as follows:
• abs—absolute value, the value of the selected variable is compared directly with
the thresholds at the end of the sampling interval.
• delta—delta value, the value of the selected variable at the last sample is
subtracted from the current value, and the difference compared with the thresholds.
rLimit
fLimit
rEvtIdx
fEvtIdx
Displays the rising threshold for the sampled statistic.
Displays the falling threshold for the sampled statistic.
Displays the rising alarm event index that is triggered when a rising threshold is
crossed.
Displays the falling alarm event index that is triggered when a falling threshold is
crossed.
Information Menu 67
Page 68

Table 42 RMON Alarm Information Menu
Field Description
Last value
Displays the last sampled value.
OID
Displays the MIB Object Identifier for each alarm index.
RMON event information
Command: /info/rmon/event
RMON Event group configuration:
Index Type Last Sent Description
----- ---- ---------------- -------------------------------- 1 both 0D: 0H: 1M:20S Event_1
2 none 0D: 0H: 0M: 0S Event_2
3 log 0D: 0H: 0M: 0S Event_3
4 trap 0D: 0H: 0M: 0S Event_4
5 both 0D: 0H: 0M: 0S Log and trap event for Link Down
10 both 0D: 0H: 0M: 0S Log and trap event for Link Up
11 both 0D: 0H: 0M: 0S Send log and trap for icmpInMsg
15 both 0D: 0H: 0M: 0S Send log and trap for icmpInEchos
100 both 0D: 0H: 0M: 0S Event_100
The following table describes the RMON Event Information parameters.
Table 43
Field Description
RMON Event Information Menu
Index
Type
Last Sent
Description
Displays the index number that identifies each event instance.
Displays the type of notification provided for this event, as follows: none, log,
trap, both.
Displays the time that passed since the last switch reboot, when the most recent
event was triggered. This value is cleared when the switch reboots.
Displays a text description of the event.
Information Menu 68
Page 69

Link status information
Command: /info/link
-----------------------------------------------------------------Port Speed Duplex Flow Ctrl Link
---- ----- -------- --TX-----RX-- ----- 1 10000 full yes yes down
2 10000 full yes yes down
3 10000 full yes yes down
4 10000 full yes yes down
5 10000 full yes yes down
6 10000 full yes yes down
7 10000 full yes yes down
8 10000 full yes yes down
9 10000 full yes yes up
10 10000 full yes yes down
11 10000 full yes yes down
12 10000 full yes yes down
13 10000 full yes yes down
14 10000 full yes yes down
15 10000 full yes yes down
16 10000 full yes yes down
17 100 full yes yes up
18 10000 full yes yes down
19 10000 full yes yes down
20 10000 full yes yes down
21 10000 full yes yes down
Use this command to display link status information about each port on a switch, including:
• Port number
• Port speed (10000 Mb/s or 100 Mb/s)
• Duplex mode (half, full, or any)
• Flow control for transmit and receive (no, yes, or any)
• Link status (up, down, or disabled)
Information Menu 69
Page 70

Port information
Command: /info/port
Port Tag RMON PVID NAME VLAN(s)
---- --- ---- ---- -------------- ------------------------------ 1 n d 1 Downlink1 1
2 n d 1 Downlink2 1
3 n d 1 Downlink3 1
4 n d 1 Downlink4 1
5 n d 1 Downlink5 1
6 n d 1 Downlink6 1
7 n d 1 Downlink7 1
8 n d 1 Downlink8 1
9 n d 1 Downlink9 1
10 n d 1 Downlink10 1
11 n d 1 Downlink11 1
12 n d 1 Downlink12 1
13 n d 1 Downlink13 1
14 n d 1*Downlink14 1
15 n d 1*Downlink15 1
16 n d 1*Downlink16 1
17 n d 4095 Mgmt 4095
18 n d 1*Uplink1 1
19 n d 1*Uplink2 1
20 n d 1*Uplink3 1
21 n d 1*Uplink4 1
* = PVID is tagged.
Port information includes:
• Port number
• Whether the port uses VLAN tagging or not (y or n)
• Whether Remote Monitoring (RMON) is enabled or disabled (e or d)
• Port VLAN ID (PVID)
• Port name
• VLAN membership
Transceiver status
Command: /info/transcvr
-----------------------------------------Port Device TX-Enable RX-Signal TX-Fault
------ ------ --------- --------- ------- XFP1 SR-XFP enabled ok N/A
XFP2 SR-XFP enabled LOST N/A
XFP3 SR-XFP enabled ok N/A
XFP4 SR-XFP **** NOT Installed ****
This command displays the status of the Small Form Pluggable (SFP) module on each Fiber External
Port.
Information Menu 70
Page 71

Uplink Failure Detection information
Command: /info/ufd
Uplink Failure Detection: Enabled
LtM status: Down
Member STG STG State Link Status
--------- --- ------------ ---------- port 20 down
1 DISABLED
10 DISABLED *
15 DISABLED *
* = STP turned off for this port.
LtD status: Auto Disabled
Member Link Status
--------- ---------- port 1 disabled
port 2 disabled
port 3 disabled
port 4 disabled
Uplink Failure Detection (UFD) information includes:
• UFD status, either enabled or disabled
• LtM status and member ports
• Spanning Tree status for LtM ports
• LtD status and member ports
Information dump
Command: /info/dump
Use the dump command to dump all switch information available from the Information Menu (10K or
more, depending on your configuration). This data is useful for tuning and debugging switch
performance.
If you want to capture dump data to a file, set the communication software on your workstation to
capture session data prior to issuing the dump commands.
Information Menu 71
Page 72

Statistics Menu
Introduction
You can view switch performance statistics in the user, operator, and administrator command modes.
This chapter discusses how to use the CLI to display switch statistics.
Menu information
Command: /stats
[Statistics Menu]
port - Port Stats Menu
clrports - Clear stats for all ports
l2 - Layer 2 Stats Menu
l3 - Layer 3 Stats Menu
mp - MP-specific Stats Menu
acl - ACL Stats Menu
snmp - Show SNMP stats
ntp - Show NTP stats
ufd - Show Uplink Failure Detection stats
sfd - Show Server Link Failure Detection stats
clrmp - Clear all MP related stats
dump - Dump all stats
The following table describes the Statistics Menu options.
Table 44
Statistics Menu options
Command Usage
port <port number>
clrports
l2
l3
mp
acl
snmp
ntp <clear>
ufd <clear>
Displays the Port Statistics Menu for the specified port. Use this command to
display traffic statistics on a port-by-port basis. Traffic statistics are included in
SNMP Management Information Base (MIB) objects.
Clear statistics counters for all ports.
Displays the Layer 2 Statistics Menu.
Displays the Layer 3 Statistics Menu.
Displays the Management Processor Statistics Menu. Use this command to view
information on how switch management processes and resources are currently
being allocated.
Displays the Access Control List Statistics Menu.
Displays SNMP statistics.
Displays Network Time Protocol (NTP) Statistics.
You can execute the clear command option to delete all statistics.
Displays Uplink Failure Detection statistics.
Add the argument, clear, to clear UFD statistics.
Statistics Menu 72
Page 73

Table 44 Statistics Menu options
Command Usage
sfd <clear>
Displays Server Link Failure Detection (SFD) statistics.
Add the argument, clear, to clear SFD statistics.
clrmp
dump
Clears all Management Processor statistics.
Dumps all switch statistics. Use this command to gather data for tuning and
debugging switch performance. If you want to capture dump data to a file, set
your communication software on your workstation to capture session data prior to
issuing the dump command.
Port Statistics Menu
Command: /stats/port <port number>
[Port Statistics Menu]
8021x - Show 802.1x stats
brg - Show bridging ("dot1") stats
ether - Show Ethernet ("dot3") stats
if - Show interface ("if") stats
ip - Show Internet Protocol ("IP") stats
link - Show link stats
rmon - Show RMON stats
clear - Clear all port stats
This menu displays traffic statistics on a port-by-port basis.
The following table describes the Port Statistics Menu options:
Table 45
Port Statistics Menu options
Command Usage
8021x
brg
ether
if
ip
link
rmon
clear
Displays IEEE 802.1X statistics
Displays bridging (“dot1”) statistics for the port.
Displays Ethernet (“dot3”) statistics for the port.
Displays interface statistics for the port.
Displays Internet Protocol statistics for the port.
Displays link statistics for the port.
Displays Remote Monitoring (RMON) statistics for the port.
Clears all the statistics on the port.
Statistics Menu 73
Page 74

802.1X statistics
Command: /stats/port <port number>/8021x
Authenticator Statistics:
eapolFramesRx = 0
eapolFramesTx = 0
eapolStartFramesRx = 0
eapolLogoffFramesRx = 0
eapolRespIdFramesRx = 0
eapolRespFramesRx = 0
eapolReqIdFramesTx = 0
eapolReqFramesTx = 0
invalidEapolFramesRx = 0
eapLengthErrorFramesRx = 0
lastEapolFrameVersion = 0
lastEapolFrameSource = 00:00:00:00:00:00
Authenticator Diagnostics:
authEntersConnecting = 0
authEapLogoffsWhileConnecting = 0
authEntersAuthenticating = 0
authSuccessesWhileAuthenticating = 0
authTimeoutsWhileAuthenticating = 0
authFailWhileAuthenticating = 0
authReauthsWhileAuthenticating = 0
authEapStartsWhileAuthenticating = 0
authEapLogoffWhileAuthenticating = 0
authReauthsWhileAuthenticated = 0
authEapStartsWhileAuthenticated = 0
authEapLogoffWhileAuthenticated = 0
backendResponses = 0
backendAccessChallenges = 0
backendOtherRequestsToSupplicant = 0
backendNonNakResponsesFromSupplicant = 0
backendAuthSuccesses = 0
backendAuthFails = 0
The following table describes the 802.1X authenticator diagnostics for a selected port:
Table 46
802.1X statistics for port
Statistics Port
Authenticator Diagnostics
authEntersConnecting
authEapLogoffsWhileConnecting
authEntersAuthenticating
authSuccessesWhileAuthenticating
Total number of times that the state machine transitions to the
CONNECTING state from any other state.
Total number of times that the state machine transitions from
CONNECTING to DISCONNECTED as a result of receiving an
EAPOL-Logoff message.
Total number of times that the state machine transitions from
CONNECTING to AUTHENTICATING, as a result of an
EAPResponse/ Identity message being received from the
Supplicant.
Total number of times that the state machine transitions from
AUTHENTICATING to AUTHENTICATED, as a result of the
Backend Authentication state machine indicating successful
authentication of the Supplicant.
Statistics Menu 74
Page 75

Table 46 802.1X statistics for port
Statistics Port
authTimeoutsWhileAuthenticating
Total number of times that the state machine transitions from
AUTHENTICATING to ABORTING, as a result of the Backend
Authentication state machine indicating authentication timeout.
authFailWhileAuthenticating
authReauthsWhileAuthenticating
authEapStartsWhileAuthenticating
authEapLogoffWhileAuthenticating
authReauthsWhileAuthenticated
authEapStartsWhileAuthenticated
authEapLogoffWhileAuthenticated
Total number of times that the state machine transitions from
AUTHENTICATING to HELD, as a result of the Backend
Authentication state machine indicating authentication failure.
Total number of times that the state machine transitions from
AUTHENTICATING to ABORTING, as a result of a reauthentication request.
Total number of times that the state machine transitions from
AUTHENTICATING to ABORTING, as a result of an EAPOLStart message being received from the Supplicant.
Total number of times that the state machine transitions from
AUTHENTICATING to ABORTING, as a result of an EAPOLLogoff message being received from the Supplicant.
Total number of times that the state machine transitions from
AUTHENTICATED to CONNECTING, as a result of a reauthentication request.
Total number of times that the state machine transitions from
AUTHENTICATED to CONNECTING, as a result of an EAPOLStart message being received from the Supplicant.
Total number of times that the state machine transitions from
AUTHENTICATED to DISCONNECTED, as a result of an
EAPOLLogoff message being received from the Supplicant.
backendResponses
backendAccessChallenges
backendOtherRequestsToSupplicant
backendNonNakResponsesFromSupplic
ant
backendAuthSuccesses
Total number of times that the state machine sends an initial
Access-Request packet to the Authentication server. Indicates
that the Authenticator attempted communication with the
Authentication Server.
Total number of times that the state machine receives an initial
Access-Challenge packet from the Authentication server.
Indicates that the Authentication Server has communication with
the Authenticator.
Total number of times that the state machine sends an EAPRequest packet (other than an Identity, Notification, Failure, or
Success message) to the Supplicant. Indicates that the
Authenticator chose an EAP-method.
Total number of times that the state machine receives a
response from the Supplicant to an initial EAP-Request, and the
response is something other than EAP-NAK. Indicates that the
Supplicant can respond to the Authenticators chosen EAPmethod.
Total number of times that the state machine receives an Accept
message from the Authentication Server. Indicates that the
Supplicant has successfully authenticated to the Authentication
Server.
Statistics Menu 75
Page 76

Table 46 802.1X statistics for port
Statistics Port
backendAuthFails
Total number of times that the state machine receives a Reject
message from the Authentication Server. Indicates that the
Supplicant has not authenticated to the Authentication Server.
Bridging statistics
Command: /stats/port <port number>/brg
Bridging statistics for port 1:
dot1PortInFrames: 63242584
dot1PortOutFrames: 63277826
dot1PortInDiscards: 0
dot1TpLearnedEntryDiscards: 0
dot1StpPortForwardTransitions: 0
The following table describes the bridging statistics for a selected port:
Table 47
Bridging statistics for port
Statistics Description
dot1PortInFrames
dot1PortOutFrames
dot1PortInDiscards
dot1TpLearnedEntryDiscards
The number of frames that have been received by this port from its
segment.
A frame received on the interface corresponding to this port is
counted by this object, if and only if, it is for a protocol being
processed by the local bridging function, including bridge
management frames.
The number of frames that have been transmitted by this port to its
segment.
A frame transmitted on the interface corresponding to this port is
counted by this object, if and only if, it is for a protocol being
processed by the local bridging function, including bridge
management frames.
Count of valid frames received which were discarded (that is,
filtered) by the forwarding process.
The total number of Forwarding Database entries, which have been
or would have been learned, but have been discarded due to a lack
of space to store them in the Forwarding Database.
If this counter is increasing, it indicates that the Forwarding
Database is regularly becoming full (a condition which has adverse
performance effects on the sub network).
If this counter has a significant value but is not presently increasing,
it indicates that the problem has been occurring but is not persistent.
dot1StpPortForwardTransitions
The number of times this port has transitioned from the Learning state
to the Forwarding state.
Statistics Menu 76
Page 77

Ethernet statistics
Command: /stats/port <port number>/ether
Ethernet statistics for port 1:
dot3StatsAlignmentErrors: 0
dot3StatsFCSErrors: 0
dot3StatsSingleCollisionFrames: 0
dot3StatsMultipleCollisionFrames: 0
dot3StatsLateCollisions: 0
dot3StatsExcessiveCollisions: 0
dot3StatsInternalMacTransmitErrors: NA
dot3StatsFrameTooLongs: 0
dot3StatsInternalMacReceiveErrors: 0
The following table describes the Ethernet statistics for a selected port:
Table 48
Ethernet statistics for port
Statistics Description
dot3StatsAlignmentErrors
dot3StatsFCSErrors
A count of frames received on a particular interface that are
not an integral number of octets in length and do not pass the
Frame Check Sequence (FCS) check.
The count represented by an instance of this object is
incremented when the AlignmentError status is returned
by the MAC service to the Logical Link Control (LLC) (or other
MAC user).
Received frames for which multiple error conditions obtained
are, according to the conventions of IEEE 802.3 Layer
Management, counted exclusively according to the error
status presented to the LLC.
A count of frames received on a particular interface that are
an integral number of octets in length but do not pass the
Frame Check Sequence (FCS) check.
The count represented by an instance of this object is
incremented when the frameCheckError status is returned by
the MAC service to the LLC (or other MAC user).
Received frames for which multiple error conditions obtained
are, according to the conventions of IEEE 802.3 Layer
Management, counted exclusively according to the error
status presented to the LLC.
dot3StatsSingleCollisionFrames
A count of successfully transmitted frames on a particular
interface for which transmission is inhibited by exactly one
collision.
A frame that is counted by an instance of this object is also
counted by the corresponding instance of the
ifOutUcastPkts, ifOutMulticastPkts, or
ifOutBroadcastPkts, and is not counted by the
corresponding instance of the
dot3StatsMultipleCollisionFrame object.
Statistics Menu 77
Page 78

Table 48 Ethernet statistics for port
Statistics Description
dot3StatsMultipleCollisionFrames
A count of successfully transmitted frames on a particular
interface for which transmission is inhibited by more than one
collision.
A frame that is counted by an instance of this object is also
counted by the corresponding instance of either the
ifOutUcastPkts, ifOutMulticastPkts, or
ifOutBroadcastPkts, and is not counted by the
corresponding instance of the
dot3StatsSingleCollisionFrames object.
dot3StatsLateCollisions
dot3StatsExcessiveCollisions
dot3StatsInternalMacTransmitErrors
dot3StatsFrameTooLongs
The number of times that a collision is detected on a
particular interface later than 512 bit-times into the
transmission of a packet.
Five hundred and twelve bit-times corresponds to 51.2
microseconds on a 10 Mbps system. A (late) collision
included in a count represented by an instance of this object
is also considered as a (generic) collision for purposes of
other collision-related statistics.
A count of frames for which transmission on a particular
interface fails due to excessive collisions.
A count of frames for which transmission on a particular
interface fails due to an internal MAC sublayer transmit error.
A frame is only counted by an instance of this object if it is
not counted by the corresponding instance of either the
dot3StatsLateCollisions object, the
dot3StatsExcessiveCollisions object, or the
dot3StatsCarrierSenseErrors object.
The precise meaning of the count represented by an instance
of this object is implementation specific. In particular, an
instance of this object may represent a count of transmission
errors on a particular interface that are not otherwise
counted.
A count of frames received on a particular interface that
exceeds the maximum permitted frame size.
The count represented by an instance of this object is
incremented when the frameTooLong status is returned by the
MAC service to the LLC (or other MAC user).
Received frames for which multiple error conditions obtained
are, according to the conventions of IEEE 802.3 Layer
Management, counted exclusively according to the error
status presented to the LLC.
Statistics Menu 78
Page 79

Table 48 Ethernet statistics for port
Statistics Description
dot3StatsInternalMacReceiveErrors
A count of frames for which reception on a particular
interface fails due to an internal MAC sublayer receive error.
A frame is only counted by an instance of this object if it is
not counted by the corresponding instance of the
dot3StatsFrameTooLongs object, the
dot3StatsAlignmentErrors object, or the
dot3StatsFCSErrors object.
The precise meaning of the count represented by an instance
of this object is implementation specific. In particular, an
instance of this object may represent a count of received
errors on a particular interface that are not otherwise
counted.
Interface statistics
Command: /stats/port <port number>/if
Interface statistics for port 1:
ifHCIn Counters ifHCOut Counters
Octets: 51697080313 51721056808
UcastPkts: 65356399 65385714
BroadcastPkts: 0 6516
MulticastPkts: 0 0
Discards: 0 0
Errors: 0 21187
The following table describes the interface (IF) statistics for a selected port:
Table 49
Interface statistics for port
Statistics Description
Octets—IfHCIn
UcastPkts—IfHCIn
BroadcastPkts—IfHCIn
MulticastPkts—IfHCIn
Discards—IfHCIn
The total number of octets received on the interface, including framing
characters.
The number of packets, delivered by this sublayer to a higher sublayer, which
were not addressed to a multicast or broadcast address at this sublayer.
The number of packets, delivered by this sublayer to a higher sublayer, which
were addressed to a broadcast address at this sublayer.
The total number of packets, delivered by this sublayer. These are the packets
that higher-level protocols requested to be transmitted, and which were
addressed to a multicast address at this sublayer, including those that were
discarded or not sent.
For a MAC layer protocol, this includes both group and functional addresses.
The number of inbound packets which were chosen to be discarded even
though no errors were detected to prevent their being delivered to a higherlayer protocol. One possible reason for discarding such a packet could be to
free up buffer space.
Statistics Menu 79
Page 80

Table 49 Interface statistics for port
Statistics Description
Errors—IfHCIn
For packet-oriented interfaces, the number of inbound packets that contained
errors preventing them from being delivered to a higher-layer protocol.
For character-oriented or fixed-length interfaces, the number of inbound
transmission units that contained errors preventing them from being
deliverable to a higher-layer protocol.
Octets—IfHCOut
UcastPkts—IfHCOut
BroadcastPkts—IfHCOut
MulticastPkts—IfHCOut
Discards—IfHCOut
Errors—IfHCOut
The total number of octets transmitted out of the interface, including framing
characters.
The total number of packets that higher-level protocols requested to be
transmitted, and which were not addressed to a multicast or broadcast
address at this sublayer, including those that were discarded or not sent.
The total number of packets that higher-level protocols requested to be
transmitted, and which were addressed to a broadcast address at this
sublayer, including those that were discarded or not sent. This object is a 64bit version of ifOutBroadcastPkts.
The total number of packets that higher-level protocols requested to be
transmitted, and which were addressed to a multicast address at this
sublayer, including those that were discarded or not sent.
For a MAC layer protocol, this includes both group and functional addresses.
This object is a 64-bit version of ifOutMulticastPkts.
The number of outbound packets that were chosen to be discarded even
though no errors had been detected to prevent their being transmitted. One
possible reason for discarding such a packet could be to free up buffer
space.
For packet-oriented interfaces, the number of outbound packets that could not
be transmitted because of errors.
For character-oriented or fixed-length interfaces, the number of outbound
transmission units that could not be transmitted because of errors.
Statistics Menu 80
Page 81

Internet Protocol (IP) statistics
Command: /stats/port <port number>/ip
GEA IP statistics for port 1:
ipInReceives : 0
ipInHeaderError: 0
ipInDiscards : 0
The following table describes the Internet Protocol (IP) statistics for a selected port:
Table 50
IP statistics for port
Statistics Description
ipInReceives
ipInHeaderError
ipInDiscards
Link statistics
Command: /stats/port <port number>/link
Link statistics for port 1:
linkStateChange: 2
The following table describes the link statistics for a selected port:
Table 51
Link statistics for port
The total number of input datagrams received from interfaces, including those
received in error.
The number of input datagrams discarded because the IP address in their IP
header's destination field was not a valid address to be received at this entity (the
switch).
The number of input IP datagrams for which no problems were encountered to
prevent their continued processing, but which were discarded (for example, for lack
of buffer space). Note that this counter does not include any datagrams discarded
while awaiting re-assembly.
Statistics Description
linkStateChange
The total number of link state changes.
Statistics Menu 81
Page 82

Port RMON statistics
Command: /stats/port <port number>/rmon
RMON statistics for port 2:
etherStatsDropEvents: NA
etherStatsOctets: 0
etherStatsPkts: 0
etherStatsBroadcastPkts: 0
etherStatsMulticastPkts: 0
etherStatsCRCAlignErrors: 0
etherStatsUndersizePkts: 0
etherStatsOversizePkts: 0
etherStatsFragments: NA
etherStatsJabbers: 0
etherStatsCollisions: 0
etherStatsPkts64Octets: 0
etherStatsPkts65to127Octets: 0
etherStatsPkts128to255Octets: 0
etherStatsPkts256to511Octets: 0
etherStatsPkts64Octets: 0
etherStatsPkts1024to1518Octets: 0
The following table describes the Remote Monitoring (RMON) statistics of the selected port:
Table 52 RMON statistics
Statistics Description
etherStatsDropEvents
etherStatsOctets
etherStatsPkts
etherStatsBroadcastPkts
etherStatsMulticastPkts
etherStatsCRCAlignErrors
etherStatsUndersizePkts
The total number of packets received that were dropped because of
system resource constraints.
The total number of octets of data (including those in bad packets)
received on the network (excluding framing bits but including
FCS octets).
The total number of packets (including bad packets, broadcast
packets, and multicast packets) received.
The total number of good packets received that were directed to the
broadcast address.
The total number of good packets received that were directed to a
multicast address.
The total number of packets received that had a length (excluding
framing bits, but including FCS octets) of between 64 and 1518
octets, inclusive, but had either a bad Frame Check Sequence
(FCS) with an integral number of octets (FCS Error) or a bad FCS
with a non-integral number of octets (Alignment Error).
The total number of packets received that were less than 64 octets
long (excluding framing bits but including FCS octets) and were
otherwise well formed.
etherStatsOversizePkts
The total number of packets received that were longer than
1518 octets (excluding framing bits but including FCS octets) and
were otherwise well formed.
Statistics Menu 82
Page 83

Table 52 RMON statistics
Statistics Description
etherStatsFragments
The total number of packets received that were less than 64 octets
in length (excluding framing bits but including FCS octets) and had
either a bad Frame Check Sequence (FCS) with an integral number
of octets (FCS Error) or a bad FCS with a non-integral number of
octets (Alignment Error).
etherStatsJabbers
etherStatsCollisions
etherStatsPkts64Octets
etherStatsPkts65to127Octets
etherStatsPkts128to255Octets
etherStatsPkts256to511Octets
The total number of packets received that were longer than
1518 octets (excluding framing bits, but including FCS octets), and
had either a bad Frame Check Sequence (FCS) with an integral
number of octets (FCS Error) or a bad FCS with a non-integral
number of octets (Alignment Error). Jabber is defined as the
condition where any packet exceeds 20 ms. The allowed range to
detect jabber is between 20 ms and 150 ms.
The best estimate of the total number of collisions on this Ethernet
segment.
The total number of packets (including bad packets) received that
were less than or equal to 64 octets in length (excluding framing
bits but including FCS octets).
The total number of packets (including bad packets) received that
were greater than 64 octets in length (excluding framing bits but
including FCS octets).
The total number of packets (including bad packets) received that
were greater than 127 octets in length (excluding framing bits but
including FCS octets).
The total number of packets (including bad packets) received that
were greater than 255 octets in length (excluding framing bits but
including FCS octets).
etherStatsPkts512to1023Octets
etherStatsPkts1024to1518Octets
The total number of packets (including bad packets) received that
were greater than 511 octets in length (excluding framing bits but
including FCS octets).
The total number of packets (including bad packets) received that
were greater than 1023 octets in length (excluding framing bits but
including FCS octets).
Statistics Menu 83
Page 84

Layer 2 statistics
Command: /stats/l2
[Layer 2 Statistics Menu]
fdb - Show FDB stats
lacp - Show LACP stats
hotlink - Show Hot Links stats
The following table describes the Layer 2 Statistics Menu options.
Table 53
Layer 2 Statistics Menu options
Command Usage
fdb
lacp
hotlink
FDB statistics
Command: /stats/l2/fdb
FDB statistics:
current: 91 hiwat: 91
This menu option enables you to display statistics regarding the use of the forwarding database,
including the number of current entries and the maximum number of entries ever recorded.
The following table describes the Forwarding Database (FDB) statistics:
Table 54
Statistics Description
Forwarding Database statistics
Displays the Forwarding Database statistics menu.
Displays the Link Aggregation Control Protocol statistics menu.
Displays Hot Links statistics.
current
hiwat
LACP statistics
Command: /stats/l2/lacp <port number>
Valid LACPDUs received - 0
Valid Marker PDUs received - 0
Valid Marker Rsp PDUs received - 0
Unknown version/TLV type - 0
Illegal subtype received - 0
LACPDUs transmitted - 0
Marker PDUs transmitted - 0
Marker Rsp PDUs transmitted - 0
Current number of entries in the Forwarding Database.
Highest number of entries recorded at any given time in the Forwarding Database.
Statistics Menu 84
Page 85

Hot Links statistics
Command: /stats/l2/hotlink
Trigger 1 statistics:
Trigger Name: Trigger 1
Master active: 0
Backup active: 0
The following table describes the Hot Links statistics:
FDB update: 0 failed: 0
Table 55
Hot Links statistics
Statistic Description
Master active
Backup active
FDB update
failed
Total number of times the Master interface transitioned to the Active state.
Total number of times the Backup interface transitioned to the Active state.
Total number of FDB update requests sent.
Total number of FDB update requests that failed.
Statistics Menu 85
Page 86

Layer 3 statistics
Command: /stats/l3
[Layer 3 Statistics Menu]
geal3 - GEA Layer 3 Stats Menu
ip - Show IP stats
route - Show route stats
arp - Show ARP stats
dns - Show DNS stats
icmp - Show ICMP stats
tcp - Show TCP stats
udp - Show UDP stats
igmp - Show IGMP stats
ospf - OSPF stats
vrrp - Show VRRP stats
clrvrrp - Clear VRRP stats
rip - Show RIP stats
igmpgrps - Total number of IGMP groups
ipmcgrps - Total number of IPMC groups
clrigmp - Clear IGMP stats
ipclear - Clear IP stats
ripclear - Clear RIP stats
ospfclear - Clear all OSPF stats
dump - Dump layer 3 stats
The following table describes the Layer 3 Statistics Menu options.
Table 56
Layer 3 Statistics Menu options
Command Usage
geal3
ip
route
arp <clear>
dns
icmp
tcp
udp
igmp
ospf
Displays the GEA statistics menu.
Displays IP statistics.
Displays route statistics.
Displays Address Resolution Protocol (ARP) statistics. Add the
argument clear, to clear ARP statistics.
Displays Domain Name System (DNS) statistics.
Displays ICMP statistics.
Displays Transmission Control Protocol (TCP) statistics. Add the
argument, clear, to clear TCP statistics.
Displays User Datagram Protocol (UDP) statistics. Add the argument,
clear, to clear UDP statistics.
Displays IGMP statistics.
Displays OSPF statistics menu.
vrrp
clrvrrp
rip
igmpgrps
When virtual routers are configured, you can display statistics for the
virtual routers.
Clears VRRP statistics.
Displays Routing Information Protocol (RIP) statistics.
Displays the total number of Internet Group Management Protocol
(IGMP) groups registered the switch.
Statistics Menu 86
Page 87

Table 56 Layer 3 Statistics Menu options
Command Usage
ipmcgrps
Displays the total number of Internet Protocol Multicast (IPMC) groups
registered on the switch.
clrigmp <1-4094>|all
ipclear
ripclear
ospfclear
dump
Clears all IGMP statistics for the selected VLANs.
Clears IP statistics. Use this command with caution as it will delete all
the IP statistics.
Clears all Routing Information Protocol (RIP) statistics.
Clears all Open Shortest Path First (OSPF) statistics.
Displays all Layer 3 statistics.
GEA Layer 3 statistics menu
Command: /stats/l3/geal3
[GEA Layer 3 Statistics Menu]
l3bucket - Show GEA L3 bucket for an IP address
dump - Dump GEA layer 3 stats counter
The following table describes the Layer 3 GEA Statistics Menu options.
Table 57
Command Usage
l3bucket
Layer 3 GEA statistics menu options
Displays GEA statistics for a specific IP address.
Dump
GEA statistics
Command: /stats/l3/geal3/dump
Displays all GEA statistics.
GEA L3 statistics:
Max L3 table size : 4096
Number of L3 entries used : 3
Max LPM table size : 512
Number of LPM entries used : 4
Statistics Menu 87
Page 88

IP statistics
Command: /stats/l3/ip
IP statistics:
ipInReceives: 36475 ipInHdrErrors: 0
ipInAddrErrors: 905
ipInUnknownProtos: 0 ipInDiscards: 0
ipInDelivers: 4103 ipOutRequests: 30974
ipOutDiscards: 0
ipDefaultTTL: 255
The following table describes the IP statistics:
Table 58 IP statistics
Statistics Description
ipInReceives
ipInHdrErrors
ipInAddrErrors
ipInUnknownProtos
ipInDiscards
ipInDelivers
The total number of input datagrams received from interfaces, including those
received in error.
The number of input datagrams discarded due to errors in their IP headers,
including bad checksums, version number mismatch, other format errors, timeto-live exceeded, errors discovered in processing their IP options, and so on.
The number of input datagrams discarded because the IP address in their IP
header destination field was not a valid address to be received at this switch.
This count includes invalid addresses (for example, 0.0.0.0) and addresses of
unsupported classes (for example, Class E).
For entities which are not IP gateways and therefore do not forward
datagrams, this counter includes datagrams discarded because the destination
address was not a local address.
The number of locally addressed datagrams received successfully but discarded
because of an unknown or unsupported protocol.
The number of input IP datagrams for which no problems were encountered to
prevent their continued processing, but which were discarded (for example, for
lack of buffer space).
This counter does not include any datagrams discarded while awaiting reassembly.
The total number of input datagrams successfully delivered to IP user-protocols
(including ICMP).
ipOutRequests
ipOutDiscards
ipDefaultTTL
The total number of IP datagrams that local IP user-protocols (including ICMP)
supplied to IP in requests for transmission.
This counter does not include any datagrams counted in ipForwDatagrams.
The number of output IP datagrams for which no problem was encountered to
prevent their transmission to their destination, but which were discarded (for
example, for lack of buffer space).
This counter would include datagrams counted in ipForwDatagrams if any
such packets met this (discretionary) discard criterion.
The default value inserted into the Time-To-Live (TTL) field of the IP header of
datagrams originated at this switch, whenever a TTL value is not supplied by
the transport layer protocol.
Statistics Menu 88
Page 89

Route statistics
Command: /stats/l3/route
Route statistics:
ipRoutesCur: 8 ipRoutesHighWater: 8
ipRoutesMax: 4096
The following table describes the Route statistics:
Table 59
Route statistics
Statistics Description
ipRoutesCur
ipRoutesMax
ipRoutesHighWater
ARP statistics
Command: /stats/l3/arp
ARP statistics:
arpEntriesCur: 2 arpEntriesHighWater: 4
arpEntriesMax: 4095
The following table describes the Address Resolution Protocol (ARP) statistics:
Table 60
Statistics Description
arpEntriesCur
arpEntriesMax
ARP statistics
The total number of outstanding routes in the route table.
The maximum number of supported routes.
The highest number of routes ever recorded in the route table.
The total number of outstanding ARP entries in the ARP table.
The maximum number of ARP entries that are supported.
arpEntriesHighWater
DNS statistics
Command: /stats/l3/dns
DNS statistics:
dnsInRequests: 0 dnsOutRequests: 0
dnsBadRequests: 0
The following table describes the Domain Name System (DNS) statistics:
Table 61
Statistics Description
dnsInRequests
dnsOutRequests
dnsBadRequests
DNS statistics
The highest number of ARP entries ever recorded in the ARP table.
The total number of DNS request packets that have been received.
The total number of DNS response packets that have been transmitted.
The total number of DNS request packets received that were dropped.
Statistics Menu 89
Page 90

ICMP statistics
Command: /stats/l3/icmp
ICMP statistics:
icmpInMsgs: 245802 icmpInErrors: 1393
icmpInDestUnreachs: 41 icmpInTimeExcds: 0
icmpInParmProbs: 0 icmpInSrcQuenchs: 0
icmpInRedirects: 0 icmpInEchos: 18
icmpInEchoReps: 244350 icmpInTimestamps: 0
icmpInTimestampReps: 0 icmpInAddrMasks: 0
icmpInAddrMaskReps: 0 icmpOutMsgs: 253810
icmpOutErrors: 0 icmpOutDestUnreachs: 15
icmpOutTimeExcds: 0 icmpOutParmProbs: 0
icmpOutSrcQuenchs: 0 icmpOutRedirects: 0
icmpOutEchos: 253777 icmpOutEchoReps: 18
icmpOutTimestamps: 0 icmpOutTimestampReps: 0
icmpOutAddrMasks: 0 icmpOutAddrMaskReps: 0
The following table describes the Internet Control Messaging Protocol (ICMP) statistics:
Table 62
ICMP statistics
Statistics Description
icmpInMsgs
icmpInErrors
icmpInDestUnreachs
icmpInTimeExcds
icmpInParmProbs
icmpInSrcQuenchs
icmpInRedirects
icmpInEchos
icmpInEchoReps
icmpInTimestamps
icmpInTimestampReps
The total number of ICMP messages which the switch received. Note that this
counter includes all those counted by icmpInErrors.
The number of ICMP messages which the switch received but determined as
having ICMP specific errors (for example bad ICMP checksums and bad
length).
The number of ICMP Destination Unreachable messages received.
The number of ICMP Time Exceeded messages received.
The number of ICMP Parameter Problem messages received.
The number of ICMP Source Quench (buffer almost full, stop sending data)
messages received.
The number of ICMP Redirect messages received.
The number of ICMP Echo (request) messages received.
The number of ICMP Echo Reply messages received.
The number of ICMP Timestamp (request) messages received.
The number of ICMP Timestamp Reply messages received.
icmpInAddrMasks
icmpInAddrMaskReps
icmpOutMsgs
icmpOutErrors
The number of ICMP Address Mask Request messages received.
The number of ICMP Address Mask Reply messages received.
The total number of ICMP messages which this switch attempted to send. Note
that this counter includes all those counted by icmpOutErrors.
The number of ICMP messages that this switch did not send due to problems
discovered within ICMP such as a lack of buffer. This value should not include
errors discovered outside the ICMP layer such as the inability of IP to route the
resultant datagram. In some implementations there may be no types of errors
that contribute to this counter's value.
Statistics Menu 90
Page 91

Table 62 ICMP statistics
Statistics Description
icmpOutDestUnreachs
The number of ICMP Destination Unreachable messages sent.
icmpOutTimeExcds
icmpOutParmProbs
icmpOutSrcQuenchs
icmpOutRedirects
icmpOutEchos
icmpOutEchoReps
icmpOutTimestamps
icmpOutTimestampReps
icmpOutAddrMasks
icmpOutAddrMaskReps
TCP statistics
Command: /stats/l3/tcp
TCP statistics:
tcpRtoAlgorithm: 4 tcpRtoMin: 0
tcpRtoMax: 240000 tcpMaxConn: 512
tcpActiveOpens: 252214 tcpPassiveOpens: 7
tcpAttemptFails: 528 tcpEstabResets: 4
tcpInSegs: 756401 tcpOutSegs: 756655
tcpRetransSegs: 0 tcpInErrs: 0
tcpCurBuff: 0 tcpCurConn: 3
tcpOutRsts: 417
The number of ICMP Time Exceeded messages sent.
The number of ICMP Parameter Problem messages sent.
The number of ICMP Source Quench (buffer almost full, stop sending data)
messages sent.
The number of ICMP Redirect messages sent.
The number of ICMP Echo (request) messages sent.
The number of ICMP Echo Reply messages sent.
The number of ICMP Timestamp (request) messages sent.
The number of ICMP Timestamp Reply messages sent.
The number of ICMP Address Mask Request messages sent.
The number of ICMP Address Mask Reply messages sent.
The following table describes the Transmission Control Protocol (TCP) statistics:
Table 63
TCP statistics
Statistics Description
tcpRtoAlgorithm
tcpRtoMin
The algorithm used to determine the timeout value used for retransmitting
unacknowledged octets.
The minimum value permitted by a TCP implementation for the retransmission
timeout, measured in milliseconds. More refined semantics for objects of this type
depend upon the algorithm used to determine the retransmission timeout. In
particular, when the timeout algorithm is rsre(3), an object of this type has the
semantics of the LBOUND quantity described in Request For Comments (RFC)
793.
Statistics Menu 91
Page 92

Table 63 TCP statistics
Statistics Description
tcpRtoMax
The maximum value permitted by a TCP implementation for the retransmission
timeout, measured in milliseconds. More refined semantics for objects of this type
depend upon the algorithm used to determine the retransmission timeout. In
particular, when the timeout algorithm is rsre(3), an object of this type has the
semantics of the UBOUND quantity described in RFC 793.
tcpMaxConn
tcpActiveOpens
tcpPassiveOpens
tcpAttemptFails
tcpEstabResets
tcpInSegs
tcpOutSegs
tcpRetransSegs
tcpInErrs
The limit on the total number of TCP connections the switch can support. In
entities where the maximum number of connections is dynamic, this object should
contain the value -1.
The number of times TCP connections have made a direct transition to the SYNSENT state from the CLOSED state.
The number of times TCP connections have made a direct transition to the SYNRCVD state from the LISTEN state.
The number of times TCP connections have made a direct transition to the
CLOSED state from either the SYN-SENT state or the SYN-RCVD state, plus the
number of times TCP connections have made a direct transition to the LISTEN
state from the SYN-RCVD state.
The number of times TCP connections have made a direct transition to the
CLOSED state from either the ESTABLISHED state or the CLOSE- WAIT state.
The total number of segments received, including those received in error. This
count includes segments received on currently established connections.
The total number of segments sent, including those on current connections but
excluding those containing only retransmitted octets.
The total number of segments retransmitted, that is, the number of TCP segments
transmitted containing one or more previously transmitted octets.
The total number of segments received in error (for example, bad TCP
checksums).
tcpCurBuff
tcpCurConn
tcpOutRsts
The total number of outstanding memory allocations from heap by TCP protocol
stack.
The total number of outstanding TCP sessions that are currently opened.
The number of TCP segments sent containing the reset (RST) flag.
Statistics Menu 92
Page 93

UDP statistics
Command: /stats/l3/udp
UDP statistics:
udpInDatagrams: 54 udpOutDatagrams: 43
udpInErrors: 0 udpNoPorts: 1578077
The following table describes the User Datagram Protocol (UDP) statistics:
Table 64
UDP statistics
Statistics Description
udpInDatagrams
udpOutDatagrams
udpInErrors
udpNoPorts
The total number of UDP datagrams delivered to the switch.
The total number of UDP datagrams sent from this switch.
The number of received UDP datagrams that could not be delivered for
reasons other than the lack of an application at the destination port.
The total number of received UDP datagrams for which there was no
application at the destination port.
IGMP Multicast Group statistics
Command: /stats/l3/igmp <VLAN number>
-----------------------------------------------------------IGMP Snoop vlan 1 statistics:
------------------------------------------------------------
rxIgmpValidPkts: 0 rxIgmpInvalidPkts: 0
rxIgmpGenQueries: 0 rxIgmpGrpSpecificQueries: 0
rxIgmpGroupSrcSpecificQueries: 0
rxIgmpLeaves: 0 rxIgmpReports: 0
txIgmpReports: 0 txIgmpGrpSpecificQueries: 0
txIgmpLeaves: 0 rxIgmpV3CurrentStateRecords: 0
rxIgmpV3SourceListChangeRecords: 0 rxIgmpV3FilterChangeRecords: 0
This menu option enables you to display statistics regarding the use of the IGMP Multicast Groups.
The following table describes the IGMP statistics:
Table 65
IGMP statistics
Statistic Description
rxIgmpValidPkts
rxIgmpInvalidPkts
rxIgmpGenQueries
rxIgmpGrpSpecificQueries
rxIgmpGroupSrcSpecificQueries
rxIgmpLeaves
Total number of valid IGMP packets received
Total number of invalid packets received
Total number of General Membership Query packets received
Total number of Membership Query packets received from
specific groups
Total number of Group Source-Specific Queries (GSSQ) received
Total number of Leave requests received
Statistics Menu 93
Page 94

Table 65 IGMP statistics
Statistic Description
rxIgmpReports
Total number of Membership Reports received
txIgmpReports
txIgmpGrpSpecificQueries
txIgmpLeaves
rxIgmpV3CurrentStateRecords
rxIgmpV3SourceListChangeRecords
rxIgmpV3FilterChangeRecords
OSPF statistics menu
Command: /stats/l3/ospf
[OSPF stats Menu]
general - Show global stats
aindex - Show area(s) stats
if - Show interface(s) stats
The following table describes the OSPF statistics menu options.
Table 66
OSPF statistics menu options
Total number of Membership reports transmitted
Total number of Membership Query packets transmitted to specific
groups
Total number of Leave messages transmitted
Total number of Current State records received
Total number of Source List Change records received
Total number of Filter Change records received.
Command Usage
general
aindex <0-2>
if <1-249>
Displays OSPF global statistics.
Displays area index statistics.
Displays interface statistics.
Statistics Menu 94
Page 95

OSPF global statistics
Command: /stats/l3/ospf/general
OSPF stats
---------Rx/Tx Stats: Rx Tx
-------- -------Pkts 0 0
hello 23 518
database 4 12
ls requests 3 1
ls acks 7 7
ls updates 9 7
Nbr change stats: Intf change Stats:
hello 2 up 4
start 0 down 2
n2way 2 loop 0
adjoint ok 2 unloop 0
negotiation done 2 wait timer 2
exchange done 2 backup 0
bad requests 0 nbr change 5
bad sequence 0
loading done 2
n1way 0
rst_ad 0
down 1
Timers kickoff
hello 514
retransmit 1028
lsa lock 0
lsa ack 0
dbage 0
summary 0
ase export 0
The following table describes the OSPF global statistics:
Table 67
OSPF global statistics
Statistic Description
Rx Tx stats:
Rx Pkts
Tx Pkts
Rx Hello
Tx Hello
Rx Database
Tx Database
Rx ls Requests
Tx ls Requests
The sum total of all OSPF packets received on all OSPF areas and interfaces.
The sum total of all OSPF packets transmitted on all OSPF areas and interfaces.
The sum total of all Hello packets received on all OSPF areas and interfaces.
The sum total of all Hello packets transmitted on all OSPF areas and interfaces.
The sum total of all Database Description packets received on all OSPF areas
and interfaces.
The sum total of all Database Description packets transmitted on all OSPF areas
and interfaces.
The sum total of all Link State Request packets received on all OSPF
areas and interfaces.
The sum total of all Link State Request packets transmitted on all OSPF areas and
interfaces.
Statistics Menu 95
Page 96

Table 67 OSPF global statistics
Statistic Description
Rx ls Acks
The sum total of all Link State Acknowledgement packets received on all OSPF
areas and interfaces.
Tx ls Acks
Rx ls Updates
Tx ls Updates
Nbr change stats:
hello
Start
n2way
adjoint ok
negotiation done
The sum total of all Link State Acknowledgement packets transmitted on all OSPF
areas and interfaces.
The sum total of all Link State Update packets received on all OSPF areas and
interfaces.
The sum total of all Link State Update packets transmitted on all OSPF areas and
interfaces.
The sum total of all Hello packets received from neighbors on all OSPF areas and
interfaces.
The sum total number of neighbors in this state (that is, an indication that Hello
packets should now be sent to the neighbor at intervals of HelloInterval seconds)
across all OSPF areas and interfaces.
The sum total number of bidirectional communication establishment between this
router and other neighboring routers.
The sum total number of decisions to be made (again) as to whether an
adjacency should be established/maintained with the neighbor across all OSPF
areas and interfaces.
The sum total number of neighbors in this state wherein the Master/slave
relationship has been negotiated, and sequence numbers have been exchanged,
across all OSPF areas and interfaces.
exchange done
bad requests
bad sequence
loading done
n1way
rst_ad
The sum total number of neighbors in this state (that is, in an adjacency's final
state) having transmitted a full sequence of Database Description packets, across
all OSPF areas and interfaces.
The sum total number of Link State Requests which have been received for a link
state advertisement not contained in the database across all interfaces and OSPF
areas.
The sum total number of Database Description packets which have been received
that either:
• Has an unexpected DD sequence number
• Unexpectedly has the init bit set
• Has an options field differing from the last Options field received in a
Database Description packet.
Any of these conditions indicate that some error has occurred during adjacency
establishment for all OSPF areas and interfaces.
The sum total number of link state updates received for all out-of-date portions of
the database across all OSPF areas and interfaces.
The sum total number of Hello packets received from neighbors, in which this
router is not mentioned across all OSPF interfaces and areas.
The sum total number of times the Neighbor adjacency has been reset across all
OPSF areas and interfaces.
Statistics Menu 96
Page 97

Table 67 OSPF global statistics
Statistic Description
down
The total number of Neighboring routers down (that is, in the initial state of a
neighbor conversation) across all OSPF areas and interfaces.
Intf Change Stats:
up
down
loop
unloop
wait timer
backup
nbr change
Timers Kickoff:
hello
retransmit
The sum total number of interfaces up in all OSPF areas.
The sum total number of interfaces down in all OSPF areas.
The sum total of interfaces no longer connected to the attached network across all
OSPF areas and interfaces.
The sum total number of interfaces, connected to the attached network in all
OSPF areas.
The sum total number of times the Wait Timer has been fired, indicating the end
of the waiting period that is required before electing a (Backup) Designated
Router across all OSPF areas and interfaces.
The sum total number of Backup Designated Routers on the attached network for
all OSPF areas and interfaces.
The sum total number of changes in the set of bidirectional neighbors associated
with any interface across all OSPF areas.
The sum total number of times the Hello timer has been fired (which triggers the
send of a Hello packet) across all OPSF areas and interfaces.
The sum total number of times the Retransmit timer has been fired across all OPSF
areas and interfaces.
lsa lock
lsa ack
dbage
summary
ase export
The sum total number of times the Link State Advertisement (LSA) lock timer has
been fired across all OSPF areas and interfaces.
The sum total number of times the LSA Ack timer has been fired across all OSPF
areas and interfaces.
The total number of times the data base age (Dbage) has been fired.
The total number of times the Summary timer has been fired.
The total number of times the Autonomous System Export (ASE) timer has been
fired.
Statistics Menu 97
Page 98

VRRP statistics
Virtual Router Redundancy Protocol (VRRP) support on the HP 10GbE switch provides redundancy
between routers in a LAN. This is accomplished by configuring the same virtual router IP address and
ID number on each participating VRRP-capable routing device.
One of the virtual routers is then elected as the master, based on a number of priority criteria, and
assumes control of the shared virtual router IP address. If the master fails, one of the backup virtual
routers will assume routing authority and take control of the virtual router IP address.
When virtual routers are configured, you can display protocol statistics for VRRP.
Command: /stats/l3/vrrp
>> Layer 3 Statistics# vrrp
VRRP statistics:
vrrpInAdvers: 0 vrrpBadAdvers: 0
vrrpOutAdvers: 0
vrrpBadVersion: 0 vrrpBadVrid: 0
vrrpBadAddress: 0 vrrpBadData: 0
vrrpBadPassword: 0 vrrpBadInterval: 0
The following table describes the VRRP statistics.
Table 68
VRRP statistics
Field Description
vrrpInAdvers
vrrpOutAdvers
vrrpBadVersion
vrrpBadAddress
vrrpBadPassword
vrrpBadAdvers
vrrpBadVrid
vrrpBadData
vrrpBadInterval
The total number of VRRP advertisements that have been received.
The total number of VRRP advertisements that have been sent.
The total number of VRRP advertisements that had a bad version number.
The total number of VRRP advertisements that had a bad address.
The total number of VRRP advertisements that had a bad password.
The total number of VRRP advertisements received that were dropped.
The total number of VRRP advertisements that had a bad virtual router ID.
The total number of VRRP advertisements that had bad data.
The total number of VRRP advertisements that had a bad interval.
Statistics Menu 98
Page 99

RIP statistics
Command: /stats/l3/rip
RIP ALL STATS INFORMATION:
RIP packets received = 12
RIP packets sent = 75
RIP request received = 0
RIP response received = 12
RIP request sent = 3
RIP response sent = 72
RIP route timeout = 0
RIP bad size packet received = 0
RIP bad version received = 0
RIP bad zeros received = 0
RIP bad src port received = 0
RIP bad src IP received = 0
RIP packets from self received = 0
Statistics Menu 99
Page 100

Management Processor statistics
Command: /stats/mp
[MP-specific Statistics Menu]
pkt - Show Packet stats
tcb - Show All TCP control blocks in use
ucb - Show All UDP control blocks in use
cpu - Show CPU utilization
The following table describes the Statistics Menu options for the management processor (MP):
Table 69
MP-specific Statistics Menu options
Command Usage
pkt
tcb
ucb
cpu
Packet statistics
Command: /stats/mp/pkt
Packet counts:
allocs: 36692 frees: 36692
mediums: 0 mediums hi-watermark: 3
jumbos: 0 jumbos hi-watermark: 0
smalls: 0 smalls hi-watermark: 2
failures: 0
The following table describes the packet statistics.
Table 70
MP specific packet statistics
Displays packet statistics, to check for leads and load.
Displays all Transmission Control Protocol (TCP) control blocks (TCB) that are in use.
Displays all User Datagram Protocol (UDP) control blocks (UCB) that are in use.
Displays CPU utilization for periods of up to 1, 4, and 64 seconds.
Description Example statistic
allocs Total number of packet allocations from the packet buffer pool by the TCP/IP
protocol stack.
frees Total number of times the packet buffers are freed (released) to the packet buffer
pool by the TCP/IP protocol stack.
mediums Total number of packet allocations with size between 128 to 1536 bytes from the
packet buffer pool by the TCP/IP protocol stack.
mediums hi-watermark The highest number of packet allocation with size between 128 to 1536 bytes from
the packet buffer pool by the TCP/IP protocol stack.
jumbos Total number of packet allocations with more than 1536 bytes from the packet
buffer pool by the TCP/IP protocol stack.
jumbos hi-watermark The highest number of packet allocation with more than 1536 bytes from the
packet buffer pool by the TCP/IP protocol stack.
smalls Total number of packet allocations with size less than 128 bytes from the packet
buffer pool by the TCP/IP protocol stack.
Statistics Menu 100
 Loading...
Loading...