
15370 Barranca Parkway
Irvine, CA 92618
ADMINISTRATION GUIDE
Product Version C1150
November 2013
HID GLOBAL CONFIDENTIAL AND PROPRIETARY INFORMATION. Use and disclosure of this information is
strictly restricted by the terms of a non-disclosure agreement with HID Global Corporation. If you have received this
information and are not an intended recipient or are not subject to or do not agree to be bound by the terms of the
non-disclosure agreement, please immediately return this document to HID Global Corporation, 15370 Barranca
Pkwy, Irvine, CA 92618-3106. © 2013 HID Global Corporation. All rights reserved.

HID Global Crescendo C1150 – Administration Guide
Page 2 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
Contents
About this Guide ............................................................................................................................ 6
1.1 Purpose ................................................................................................................. 6
1.2 Audience ................................................................................................................ 7
1.3 Scope of Document ............................................................................................... 7
1.4 Typographic Conventions ...................................................................................... 7
2.0 Introduction ....................................................................................................................... 8
2.1 Product Overview .................................................................................................. 8
2.2 Installation and Upgrades ...................................................................................... 9
2.3 Supported Deployment Modes .............................................................................. 9
2.3.1 Standalone Mode with Mini Driver ............................................................ 10
2.3.2 Standalone Mode with Advanced Middleware ......................................... 10
2.3.3 Managed Mode with Microsoft Forefront Identity Manager (FIM) ............ 11
2.3.4 Managed Mode with HID Global naviGO ................................................. 11
2.3.5 Managed Mode with HID Global 4TRESS AAA Server ........................... 11
2.3.6 Managed Mode with HID Global ActivID CMS and ActivID CMS Appliance
.................................................................................................................. 12
2.4 Choosing Smart Card Middleware ........................................................................ 12
2.4.1 Services Available with Both Mini Driver and ActivClient ......................... 12
2.4.2 Additional Services Available with ActivClient .......................................... 13
3.0 Installing the Mini Driver .................................................................................................. 15
3.1 Mini Driver System Requirements ......................................................................... 15
3.2 Automatic Download .............................................................................................. 15
3.3 Manually Download and Install the Mini Driver ..................................................... 15
3.4 Uninstall the Mini Driver ......................................................................................... 19
4.0 Managing a Smart Card with the Mini Driver ................................................................. 20
4.1 Prerequisites .......................................................................................................... 20
4.2 Issuing a Smart Card using Microsoft Certificate Authority ................................... 21
4.2.1 Enroll a Smart Card for a User with Internet Explorer .............................. 21
4.2.2 Enroll a Smart Card for a User with MMC ................................................ 22
4.3 Importing Certificates Using Microsoft Windows ................................................... 30
4.3.1 Download a PKI Certificate with Internet Explorer ................................... 30
4.3.2 Download a PKI Certificate with MMC ..................................................... 31
4.4 Changing the PIN Code Using Microsoft Windows ............................................... 40
4.4.1 Change the PIN Code on Microsoft Windows Vista, Windows 7 or Windows 8
.................................................................................................................. 40
4.4.2 Change the PIN Code on Microsoft Windows XP .................................... 41
4.5 Unlocking the PIN Code Using Microsoft Windows .............................................. 44
4.5.1 Unlock the PIN Code on Microsoft Windows Vista, Windows 7 or Windows 8
.................................................................................................................. 44
4.5.2 Unlock the PIN Code on Microsoft Windows XP ...................................... 47

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 3 of 115
© 2013 HID Global Corporation. All rights reserved.
5.0 Managing a Smart Card using Microsoft Forefront Identify Manager (FIM) ............... 50
5.1 Prerequisites .......................................................................................................... 50
5.2 Initialize a Permanent Card ................................................................................... 51
5.3 Change the PIN Code Using FIM .......................................................................... 53
5.4 Unlocking the Smart Card Using FIM - Online ...................................................... 55
5.4.1 Unlock the Smart Card as an Administrator ............................................. 55
5.4.2 Unlock the Smart Card as an End User ................................................... 59
5.4.3 Using the Unblock Wizard ........................................................................ 60
5.5 Unlocking the Smart Card Using FIM - Offline ...................................................... 61
5.5.1 Verify that the Offline Unlock Policy is Enabled ....................................... 61
5.5.2 Launch Offline Unlock Request ................................................................ 64
5.6 Reset the Smart Card Using FIM .......................................................................... 71
6.0 Managing a Smart Card with ActivClient ....................................................................... 73
6.1 Issue a Smart Card with ActivClient ...................................................................... 73
6.2 Change the PIN Code with ActivClient .................................................................. 76
6.3 Unlock the Smart Card Using ActivClient .............................................................. 78
6.4 Reset the Smart Card Using ActivClient ............................................................... 80
6.5 Importing Certificates Using ActivClient ................................................................ 83
6.5.1 Request a Certificate ................................................................................ 83
6.5.2 Import the Certificate ................................................................................ 84
7.0 Managing a Smart Card with naviGO ............................................................................. 85
7.1 Prerequisites .......................................................................................................... 85
7.2 Initialize a Smart Card ........................................................................................... 85
8.0 Managing a Smart Card with 4TRESS AAA Server ....................................................... 97
8.1 Issue a Smart Card Using 4TRESS AAA Server .................................................. 98
8.2 Change the PIN Code ........................................................................................... 102
8.3 Unlock the Smart Card with 4TRESS AAA Server ................................................ 102
8.3.1 Unlock the Smart Card with the Administration Console ......................... 102
8.3.2 Unlock the Smart Card with the Web Help Desk ..................................... 103
8.3.3 Unlock the Smart Card with the Web Self Help Desk .............................. 103
8.4 Importing Certificates ............................................................................................. 105
9.0 Using the Smart Card ....................................................................................................... 106
9.1 Logging On to Microsoft Windows ......................................................................... 106
9.2 Authenticating to Secure Websites ....................................................................... 106
9.3 Sending and Reading Secure Emails .................................................................... 107
9.3.1 Send Signed/Encrypted Emails ................................................................ 107
9.3.2 Read Signed/Encrypted Emails ................................................................ 107
9.4 Encrypting and Decrypting Files ............................................................................ 107
9.4.1 Encrypt a File or Folder ............................................................................ 107
9.4.2 Decrypt a File or Folder ............................................................................ 108

HID Global Crescendo C1150 – Administration Guide
Page 4 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
10.0 Troubleshooting ............................................................................................................... 109
10.1 ActiveX Error During Certificate Requests ............................................................ 109
10.2 Smart Card Enrollment Errors ............................................................................... 109
10.2.1 Wrong CSP ............................................................................................... 109
10.2.2 Key Length Setting ................................................................................... 109
10.2.3 Enrollment Rights ..................................................................................... 110
11.0 Security Guidelines .......................................................................................................... 111
11.1 SHA-2 Compliance ................................................................................................ 111
11.1.1 Card Content Signed with SHA-2 ............................................................. 111
11.1.2 Using SHA-2 for Digital Signature Operations ......................................... 112
11.2 PIN Policies ........................................................................................................... 113
11.3 Log Handling ......................................................................................................... 113
11.4 Additional Recommendations ................................................................................ 113

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 5 of 115
© 2013 HID Global Corporation. All rights reserved.
Date
Author
Description
Document Version
JAN13
SIS
Added managed with 4TRESS AAA Server
procedures.
A.1
NOV13
SIS
Updated with default PIN details and HID Unblock
tool.
A.2
North America
15370 Barranca Parkway
Irvine, CA 92618
USA
Phone: 800 237 7769
Fax: 949 732 2120
Copyright
© 2013 HID Global Corporation. All rights reserved.
Trademarks
HID GLOBAL, HID, the HID logo, Crescendo, OMNIKEY, ActivID ActivClient, 4TRESS and
ActivID CMS are trademarks or registered trademarks of HID Global Corporation, or its
licensors, in the U.S. and other countries.
Revision History
Contacts
support.hidglobal.com

HID Global Crescendo C1150 – Administration Guide
Page 6 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
NOTE
The instructions provided for third party products are meant as guidance
only. HID Global cannot be held liable for any malfunctioning from
configuring these products; refer to the vendor documentation for complete
information.
About this Guide
The information contained in this document is provided “AS IS” without any warranty.
HID GLOBAL HEREBY DISCLAIMS ALL WARRANTIES AND CONDITIONS WITH REGARD TO
THE INFORMATION CONTAINED HEREIN, INCLUDING ALL IMPLIED WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, TITLE AND NONINFRINGEMENT.
IN NO EVENT SHALL HID GLOBAL BE LIABLE, WHETHER IN CONTRACT, TORT OR
OTHERWISE FOR ANY INDIRECT, SPECIAL OR CONSEQUENTIAL DAMAGES ARISING FROM
USE OF INFORMATION CONTAINED IN THIS DOCUMENT.
Windows is a registered trademark of Microsoft Corporation in the United States and other
countries.
1.1 Purpose
This document describes different options how you can manage and use your HID®
Crescendo™ smart card with a variety of software options.
The Crescendo C1150 smart card is versatile and can be deployed in standalone mode (that
is, without any central card management system) or in an enterprise-managed environment
(that is, with a central card management system).
The Crescendo C1150 smart card can be used on a variety of environments, providing a wide
range of strong authentication, digital signature and encryption services – such as secure
Windows logon, secure authentication to web sites, secure authentication to remote sessions,
email digital signature, email and file encryption.
This document presents the services available via the Crescendo C1150 Mini Driver, a free
middleware from HID Global designed specifically for this card. The Mini Driver is compatible
with a number of card management systems (such as Microsoft® Forefront Identity Manager
or HID Global naviGO™) and end-user applications (such as Microsoft Windows®, Internet
Explorer®, Microsoft Office® or Adobe® Acrobat).
The document also presents additional services available via the HID Global ActivID
ActivClient™ middleware, bringing support for additional applications (such as Mozilla®
Firefox® or remote access / VPN products).

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 7 of 115
© 2013 HID Global Corporation. All rights reserved.
Typography
Description
Arial bold
Action steps: paths, buttons, options (checkboxes). Field and dropdown list labels. Notes, important notes, and warnings. Emphasis
and captions.
Italic black
File names, document titles, and file extensions.
ARIAL BOLD SMALL CAPS
CUSTOM BLUE
“Callouts” used to flag important tips or technical information.
Arial blue
Cross-references within the document (no underlines).
1.2 Audience
This manual is specifically designed for IT administrators, who want to use their HID
Crescendo C1150 card to obtain strong authentication in their Microsoft environment.
1.3 Scope of Document
This document assumes that the system administrator has already installed and configured
other necessary components (such as Microsoft Windows, a certificate server) and that you
have a Crescendo C1150 card.
1.4 Typographic Conventions

HID Global Crescendo C1150 – Administration Guide
Page 8 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
2.0 Introduction
2.1 Product Overview
This release of the Mini Driver is designed to support the Crescendo C1150 and is a key
component of the HID logical and physical access convergence solution.
Crescendo smart cards include a PKI chip that provides extended cryptographic capabilities,
expanding the number of supported services:
Authenticate to Microsoft Windows (online or offline).
Authenticate to secure web sites.
Authenticate to remote networks via a VPN.
Authenticate to remote sessions authentication using Citrix® or Microsoft terminal
server technologies.
Sign emails, forms and documents.
Encrypt emails, documents and disks.
The Mini Driver also enables users to personalize their smart cards by:
Defining a PIN code.
Downloading certificates.
If the same smart card is used on a workstation with ActivID ActivClient instead of the Mini
Driver, you have access to additional services, such as:
PKI services with a PKCS#11 library (compatibility with Mozilla Firefox, Thunderbird®).
Automated configuration for PKI applications (such as Microsoft Outlook).
One-Time Password services enabling support for a wider range of remote access and
VPN services.
User-based card management services (card content viewer, diagnostics tool,
notifications, standalone management services, etc.).

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 9 of 115
© 2013 HID Global Corporation. All rights reserved.
NOTE
If a supported middleware is already installed on the machine, the Windows
Update download is not triggered.
NOTE
If the Crescendo C1150 card is used with its Mini Driver (installed either from
Windows Update or by the MSI package), you can upgrade to ActivClient 6.2
(version 6.2.0.162 or later) to gain access to additional services. When
ActivClient is installed, it takes precedence over the Mini Driver.
2.2 Installation and Upgrades
The Mini Driver is a free component and can be automatically downloaded from Microsoft
Windows Update (applicable to Windows 7, Windows Server 2008 R2 and later versions).
It is also available for download as a Microsoft Windows installer package (.msi) from the HID
web site http://www.hidglobal.com/main/crescendo/
This is useful for:
Older Windows versions where the automatic download is not available.
Workstations not connected to the internet, or with Windows Update disabled.
For further information about the installation process, see chapter 3.0 Installing the Mini Driver
on page 15.
In addition, the installer package detects potential middleware existing on the machine and
acts accordingly. For example, if the ActivClient middleware is detected, the Mini Driver
installation is not possible as you cannot have two middleware for the same card on the same
Windows workstation, and as ActivClient provides enhanced services compared to the Mini
Driver.
2.3 Supported Deployment Modes
This section describes several Crescendo C1150 deployment modes, either in standalone
mode (that is without any central card management system), or in an enterprise managed
environment (that is, with a central card management system).
Some of these deployment modes require the Crescendo C1150 Mini Driver, which is free
middleware from HID Global. Some deployment modes require additional software products,
such as ActivID ActivClient, Microsoft Forefront Identity Manager, and HID Global naviGO.
Contact the product vendor for licensing information.

HID Global Crescendo C1150 – Administration Guide
Page 10 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
2.3.1 Standalone Mode with Mini Driver
This is the simplest (and also least secure) mode in which the Mini Driver can be installed and
used with the Crescendo C1150 card to provide the following services:
The card comes with a default PIN code (00000000) that you can change at any time:
On Microsoft Windows Vista and 7 - using the native Ctrl+Alt+Del Change
Password feature.
On Microsoft Windows XP - using the Microsoft PIN Tool (pintool.exe) included
with the Base Smart Card CSP package.
While there is no “simple” PIN unlock feature, if you know the ADMIN Key (set to a
default binary value 000000000000000000000000000000000000000000000000) and
have a tool to generate a response based on the challenge (3DES algorithm), you can
unlock the card.
The user can then use the Microsoft Windows 7 or Windows 8 PIN Unlock user
interface. It is recommended that you use card management software to manage these
keys.
You can download a certificate onto the card from the Microsoft Certificate Authority (or
other CA), by selecting the Microsoft Base Smart Card CSP.
You can use certificates for standard PKI services based on the Mini Driver, such as
Windows logon, authentication to web sites (with Internet Explorer) and PKI-compatible
VPNs, email signature and encryption (with Microsoft Outlook).
For further information, see chapter 4.0 Managing a Smart Card with the Mini Driver on page
20.
2.3.2 Standalone Mode with Advanced Middleware
Using advanced middleware such as ActivID ActivClient, you have access to additional card
management services, and you can use your card with more applications.
You can initialize a Crescendo C1150 card with the ActivClient PIN Initialization Tool,
resetting the PIN from the default value and obtaining a static unlock code.
You can change the PIN using the ActivClient PIN Change Tool (on any Windows
version).
If the card PIN is locked, you can unlock it with the static unlock code displayed at
initialization.
You can reset the card with the ActivClient PIN Initialization Tool.
You can download a certificate onto the card from the Microsoft CA (or other CA) by
selecting the ActivClient CSP.
You can use certificates for standard PKI services based on the CSP or PKCS#11
technologies, which provides more options than in the previous mode – such as
Windows logon, authentication to web sites (with Internet Explorer or Mozilla Firefox)
and PKI-compatible VPNs, email signature and encryption (with Microsoft Outlook or
Lotus Notes).
The user can use other ActivClient services for improved usability (card management
utility, card activity notification, application auto-configuration, etc.).

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 11 of 115
© 2013 HID Global Corporation. All rights reserved.
For further information, see chapter 6.0 Managing a Smart Card with ActivClient on page 73.
2.3.3 Managed Mode with Microsoft Forefront Identity Manager (FIM)
In this mode, the card is managed with Microsoft Forefront Identity Manager (FIM), and end
users can use the card on their workstation with either the Mini Driver or with advanced
middleware.
The card is managed by Microsoft FIM 2010 via the Mini Driver.
The card comes with a default PIN (00000000) and default ADMIN Key (binary value
000000000000000000000000000000000000000000000000).
The Administrator imports this data into FIM.
With FIM, the administrator can load certificates on the card (and update them later),
and unlock the card PIN if it is locked.
If the end user has the Crescendo C1150 Mini Driver on his workstation, he can use
certificates for standard PKI services based on the Mini Driver.
If the end user has ActivClient on his workstation, he can use certificates for standard
PKI services based on the CSP or PKCS#11 technologies. He can also use other
ActivClient services for improved usability.
For further information, see chapter 5.0 Managing a Smart Card using Microsoft Forefront
Identify Manager (FIM) on page 50.
2.3.4 Managed Mode with HID Global naviGO
In this mode, the card is managed with naviGO; end users use the card on their workstation
with the Crescendo Mini Driver.
The card is managed by naviGO via the Mini Driver.
With naviGO, the administrator can load certificates on the card (and update them
later), and unlock the card PIN if it is locked.
The default PIN code (00000000) is used during the issuance process.
The default ADMIN Key is 000000000000000000000000000000000000000000000000
(binary value).
The end user has the Crescendo C1150 Mini Driver on his workstation; he can use
certificates for standard PKI services based on the Mini Driver.
naviGO also provides emergency access authentication in case the card is lost or
forgotten.
For further information, see chapter 7.0 Managing a Smart Card with naviGO on page 85.
2.3.5 Managed Mode with HID Global 4TRESS AAA Server
In this mode, the card is managed with 4TRESS AAA Server 6.7 (version 6.7.2.15 or later),
and end users can use the card on their workstation with the ActivClient middleware (version
6.2.0.162 or later).

HID Global Crescendo C1150 – Administration Guide
Page 12 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
4TRESS AAA Server adds one-time password services to Crescendo C1150 cards, enabling
support for legacy applications that are not PKI-enabled, such as many remote access and
VPN applications.
The card is managed by 4TRESS AAA Server via the ActivClient middleware.
The administrator initializes the Crescendo C1150 cards with 4TRESS AAA Server,
adding one-time password (OTP) capabilities to the cards.
Administrators or end users can download a certificate onto the card from the Microsoft
CA (or other CA), by selecting the ActivClient CSP.
If the card PIN is locked, you can unlock it with the challenge/response unlock code
managed by 4TRESS AAA Server.
The end user has ActivClient on his workstation; he can use certificates for standard
PKI services based on the CSP or PKCS#11 technologies.
He can also use the Crescendo C1150 for remote access/VPN services using one-time
passwords.
He can also use other ActivClient services for improved usability.
For further information, see section 8.0 Managing a Smart Card with 4TRESS AAA Server on
page 97.
2.3.6 Managed Mode with HID Global ActivID CMS and ActivID CMS Appliance
To deploy Crescendo cards with ActivID Card Management System (CMS), use the
Crescendo C1100 instead of the Crescendo C1150.
To deploy Crescendo cards with ActivID CMS Appliance, use the Crescendo C800 instead of
the Crescendo C1150.
2.4 C hoosi ng S mart Car d Mid dlew are
You have a choice of Crescendo C1150 smart card middleware for end user workstations:
You can choose to deploy the Crescendo C1150 Mini Driver, which is available free of
charge.
You can choose to deploy the ActivClient software that provides enhanced capabilities.
This section presents the similarities and differences between the two options.
2.4.1 Services Available with Both Mini Driver and ActivClient
Both middleware options support the same applications for PKI services:
Windows Logon
Web authentication with Internet Explorer and Google Chrome
VPN authentication with Windows, Cisco, Juniper, etc.
Authentication to Citrix or Terminal Server sessions
Email signature and encryption with Microsoft Outlook and Exchange

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 13 of 115
© 2013 HID Global Corporation. All rights reserved.
Document signature with Microsoft Office and Adobe Acrobat
File encryption with Windows EFS
Disk encryption with Windows BitLocker To Go
Compatibility with more applications based on Microsoft CAPI / CNG
Both middleware options support some basic card management services:
PIN change
PIN unlock (with Mini Driver, not applicable to all deployment modes – requires a card
management system or utility to support the challenge / response unlock model)
2.4.2 Additional Services Available with ActivClient
The following services are available only with the ActivClient middleware:
ActivClient is compatible with a wider range of PKI-enabled applications thanks to a
PKCS#11 compliant library:
Web authentication with Firefox.
Email signature and encryption with Lotus Notes and Thunderbird.
Compatibility with more applications based on PKCS#11.
ActivClient provides usability enhancements with Microsoft Outlook, enabling users to
sign and encrypt emails without the need to learn how to configure and use it.
Outlook is automatically configured on card insertion with the user’s signature and
encryption certificates. This guarantees that users are using up-to-date credentials,
and no longer use software certificates. This also automatically configures the hash
and encryption algorithms for consistency within an organization.
Certificates are automatically published to the Exchange Global Address List (GAL)
on card insertion. This guarantees that all email encryption is performed with up-todate certificates.
Contacts’ certificates are automatically added to the user’s Outlook Contacts upon
reception of an email.
Option to automatically decrypt and save encrypted emails. This guarantees that
older encrypted emails can be read even if old encryption key is not on the card.
ActivClient provides usability enhancements with Firefox and Thunderbird, making it
easier to use PKI services with Mozilla products: ActivClient PKCS#11 library is
automatically registered into these apps, to automatically enable new users with smart
card services, negating the need for additional configuration and training.

HID Global Crescendo C1150 – Administration Guide
Page 14 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
ActivClient enables using smart cards with additional credentials than PKI keys and
certificates. ActivClient supports one-time passwords (OTP) on the Crescendo C1150
card, enabling organizations to use smart cards for remote access (authentication to
VPNs) even if these systems are not PKI-capable. Organizations that have deployed
an OTP Strong Authentication Server (such as 4TRESS AAA Server) and OTP
hardware tokens or soft tokens can now deploy smart cards to additional users and
enable a mixed OTP token / Crescendo smart card deployment. This enables a smooth
transition to PKI environments.
ActivClient includes a User Console to view and edit the card content (certificates and
other credentials). This console helps identify certificates on the card vs. all the
certificates loaded on the PC, as Windows does. The console also enables importing
keys and certificates into the card, and exporting certificates from the card. Users can
also select a “default certificate” in the case several Windows Logon certificates are
present on the card.
ActivClient includes utilities to manage the Crescendo smart cards in standalone mode:
initialization, unlock, reset cards. This provides organizations with a simple and efficient
model to deploy and manage smart cards in small deployments when a card
management system may be considered too complex.
ActivClient includes a smart Card indicator icon in Windows notification area, which,
helps identify when the card is in use.
ActivClient provides notifications to end users, helping them use and manage their
smart card. For example:
Certificate expiration notification, informing users that their certificates need to be
updated before they expire, preventing users to log on.
Unattended card notification, reminding users to take their card when they leave
their workstation.
No smart card reader notification, informing users when no reader is detected.
ActivClient has close to 100 policies, enabling organizations to configure the
middleware to match their specific security and usability requirements. For example:
Option to unregister certificates on card removal or logoff: this is a security feature
for shared workstations.
PIN cache for increased usability: the ActivClient PIN Cache provides a sort of
SSO for the PIN: users enter the PIN once, use it for multiple services (Windows
Logon, secure email, secure web, etc.), and securely! PIN Cache policies provide
the right mix of security and usability; for example PIN Cache timeout (by default
15 min – configurable), or “Per-process” PIN cache (one PIN entry per application).
ActivClient supports additional smart cards in addition to the Crescendo C1150, and is
certified by NIST and GSA to support the FIPS 201 PIV standard smart cards.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 15 of 115
© 2013 HID Global Corporation. All rights reserved.
NOTES
Microsoft Windows XP and Server 2003 require a Windows update
available at http://support.microsoft.com/kb/909520 to install the Microsoft
Smart Card Base CSP.
The Crescendo C1150 Mini Driver is supported with PC/SC smart card
readers.
3.0 Installing the Mini Driver
3.1 Mini Driver System Requirements
One of the following Microsoft operating systems is required:
Windows XP SP3 (32 and 64-bit)
Windows Vista SP1 (32 and 64-bit)
Windows 7 and Windows 7 SP1 (32 and 64-bit)
Windows 8 (32 and 64-bit)
Windows Server 2003 (32 and 64-bit)
Windows Server 2008 and 2008 SP2 (32 and 64-bit)
Windows Server 2008 R2 (64-bit)
Windows Server 2012 (64-bit)
3.2 Automatic Download
Crescendo C1150 Mini Driver can be downloaded automatically using the Microsoft Windows
Update feature.
When you insert the Crescendo C1150 card into a reader connected to Microsoft Windows 7
or Windows 8 (32 and 64-bit) workstation, or Windows Server 2008 R2 or Windows Server
2012 (64-bit) server, the driver is automatically downloaded and installed.
3.3 Manually Download and Install the Mini Driver
If the automatic download is not available, the Mini Driver can also be downloaded as a
Windows Installer (MSI) package from HID’s web site:
http://www.hidglobal.com/main/crescendo/.
Crescendo C1150 Mini Driver x64 2.0.msi
Crescendo C1150 Mini Driver x86 2.0.msi
HID Global Crescendo C1150 – Administration Guide
Page 16 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
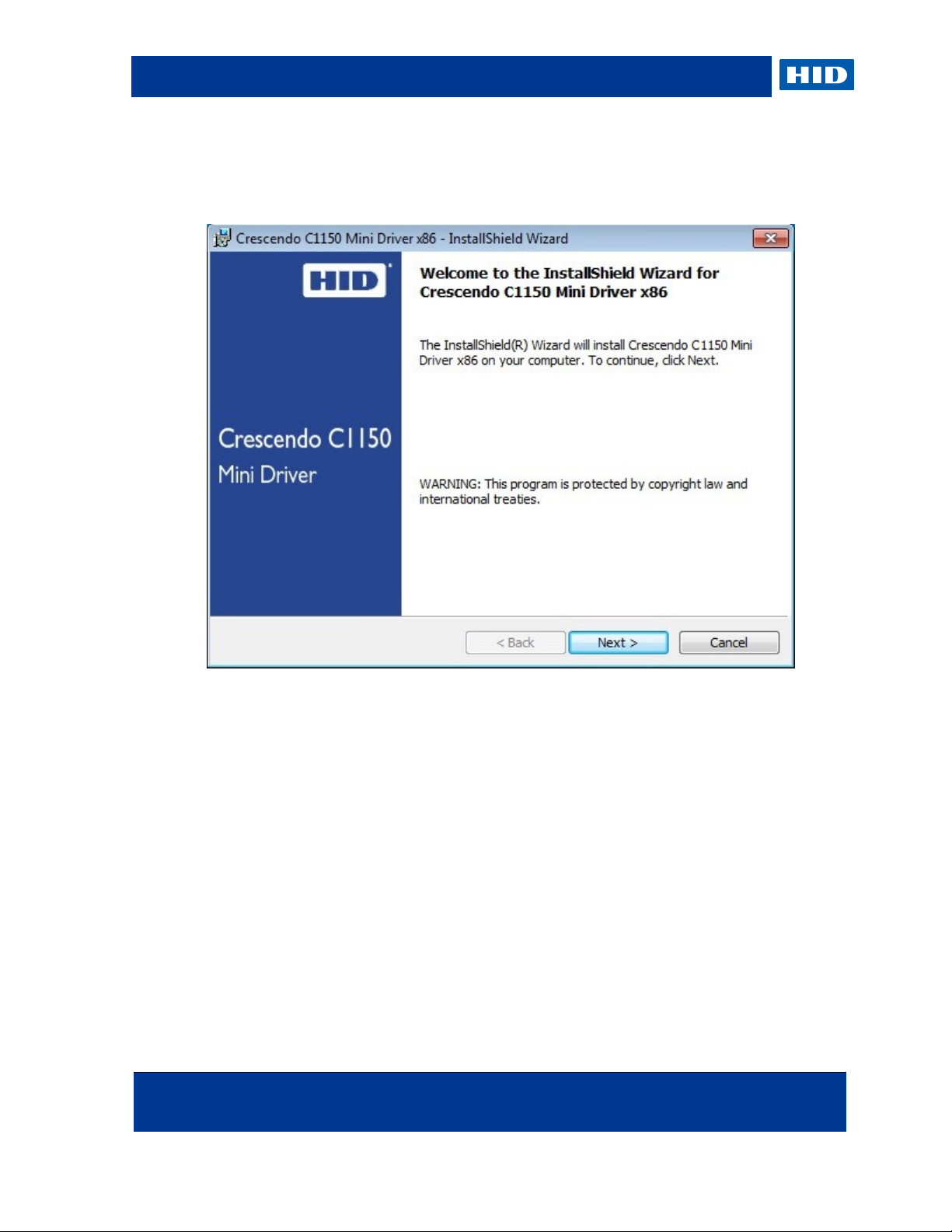
1. Launch the Mini Driver setup using the .msi file that corresponds to your operating
system.
2. Click Next.
HID Global Crescendo C1150 – Administration Guide
November 2013 Page 17 of 115
© 2013 HID Global Corporation. All rights reserved.
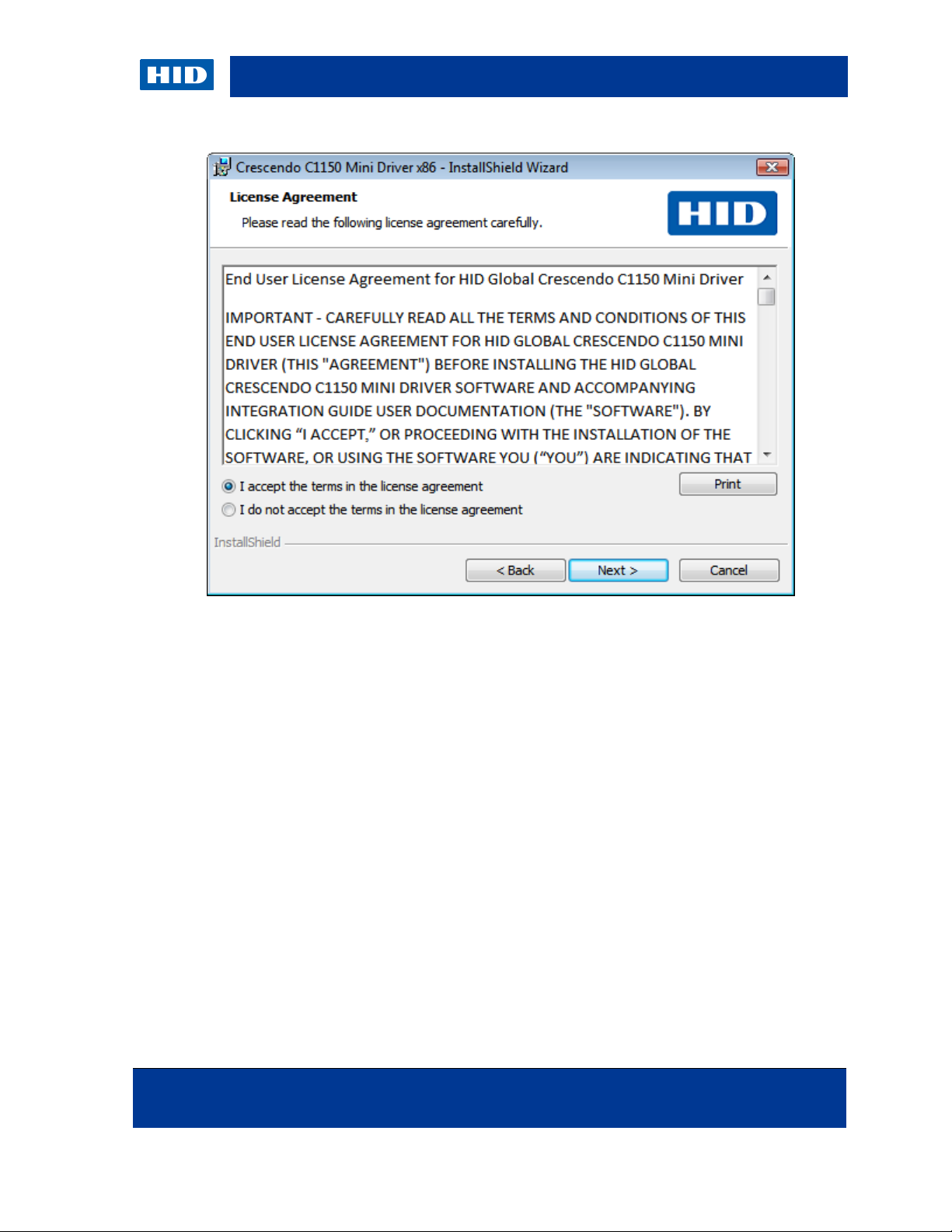
3. Select I accept… and click Next.
HID Global Crescendo C1150 – Administration Guide
Page 18 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
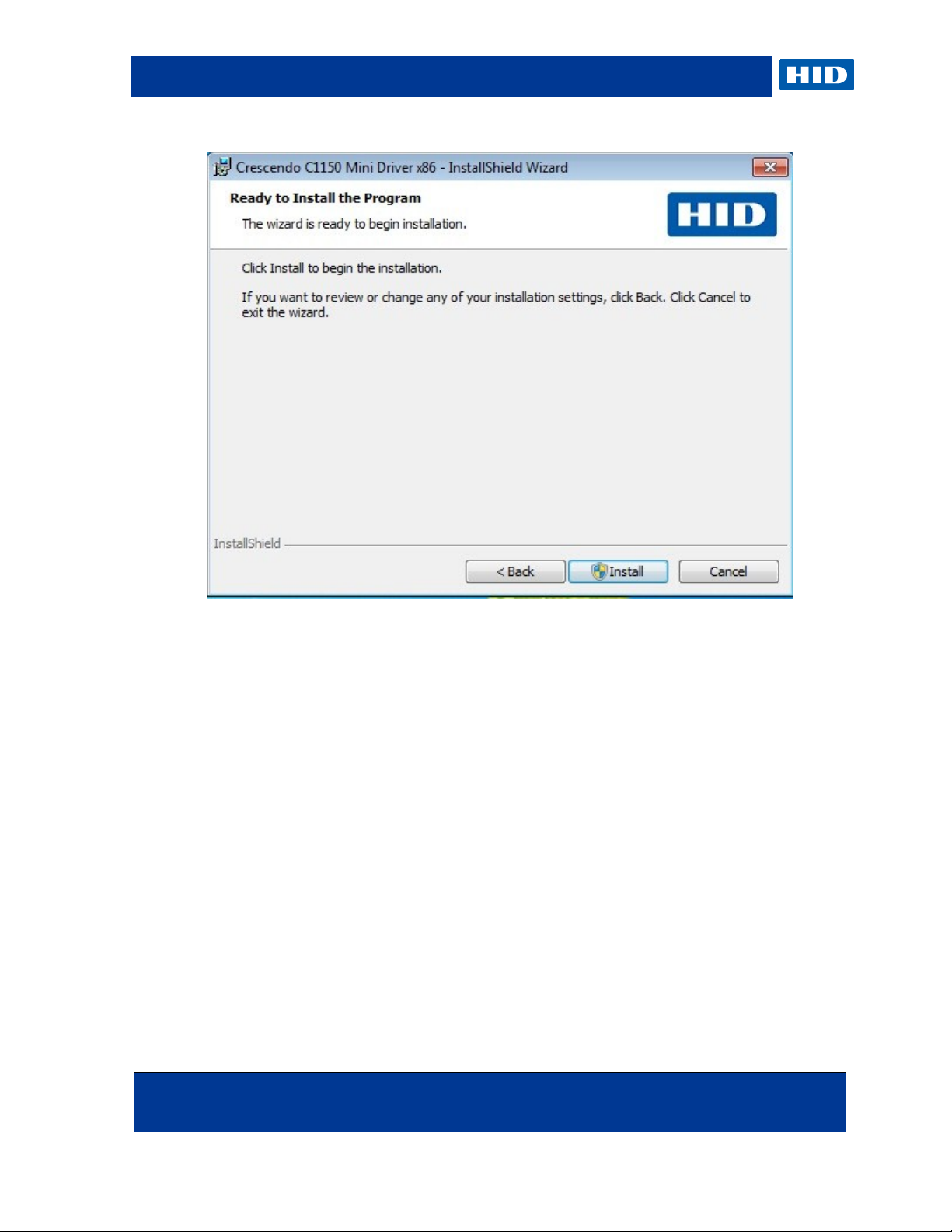
4. Click Install.
HID Global Crescendo C1150 – Administration Guide
November 2013 Page 19 of 115
© 2013 HID Global Corporation. All rights reserved.
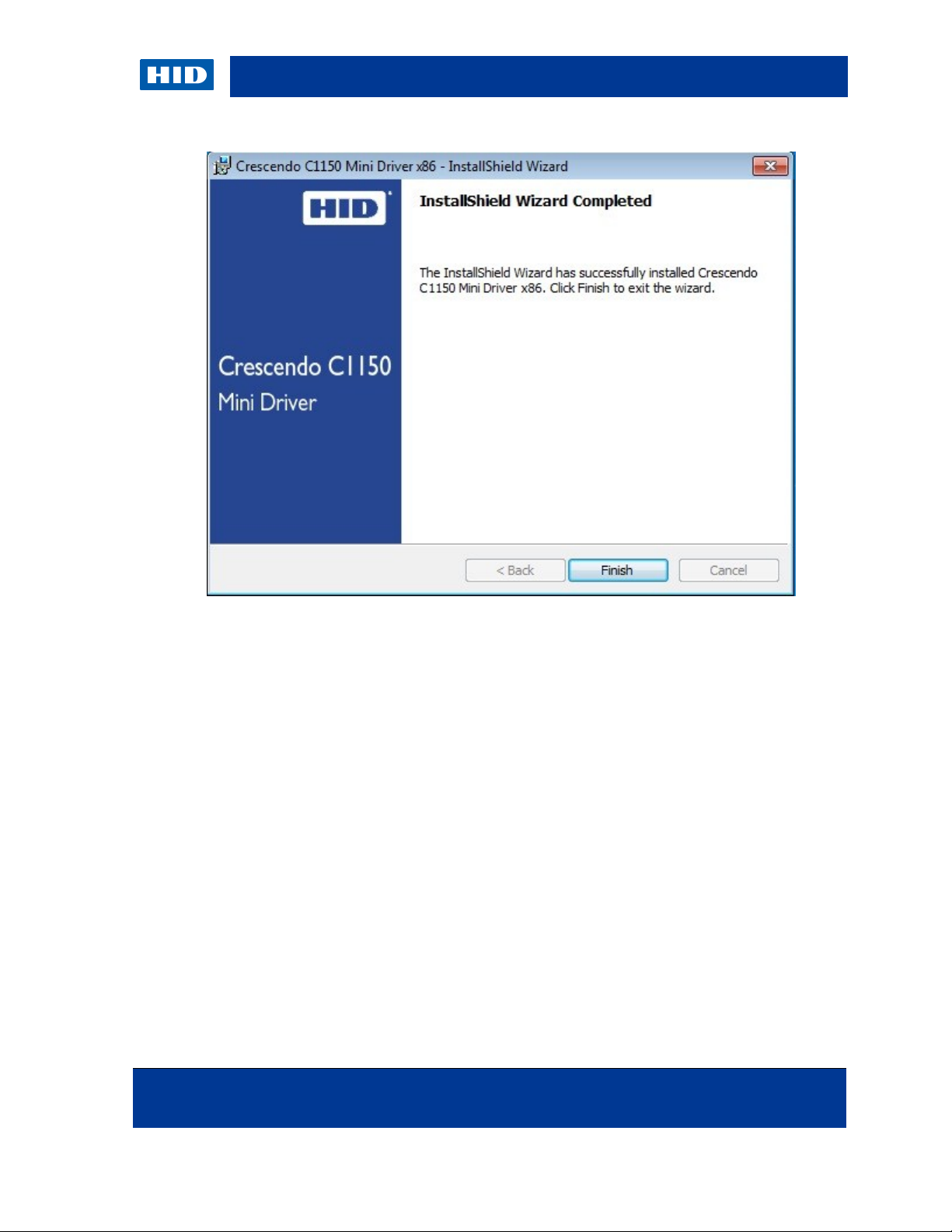
5. Click Finish.
The Mini Driver is installed in the following directory:
[ProgramFiles]\HID Global\Crescendo C1150 Mini Driver
3.4 Uninstall the Mini Driver
You can remove the Crescendo C1150 Mini Driver using the standard Add/Remove Programs
(Microsoft Windows XP) or Programs and Features (Microsoft Windows 7 and Windows 8)
tools.

HID Global Crescendo C1150 – Administration Guide
Page 20 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
NOTE
Enrollment for a smart card certificate must be a controlled procedure, in the
same manner that employee badges are controlled for purposes of
identification and physical access.
The recommended method for enrolling users for smart card-based
certificates and keys is through the Smart Card Enrollment station that is
integrated with Certificate Services in Microsoft Windows Server 2008.
Therefore, section 4.2 describes the process of how to enroll for a smart card
user or smart card logon certificate through the Smart Card Enrollment
Station. This process is likely completed by your system administrator.
As a user, request your own certificate through the Microsoft Certificate
Services interface on your local workstation. In this case, a domain user
cannot enroll for a Smart Card Logon certificate (which provides
authentication) or a Smart Card User certificate (which provides
authentication plus the capability to secure e-mail) unless a system
administrator has granted the user access rights to the certificate template
stored in Active Directory. This is described in section 4.3.
4.0 Managing a Smart Card with the Mini Driver
This section explains how to issue a smart card for other users as well as for you.
4.1 Prerequisites
Microsoft Windows 2008 Server is installed and configured as a Primary Domain
Controller.
Active Directory is configured to manage users and computers.
DNS Server is configured with your domain name.
Internet Information Services (IIS) is installed (to be able to request a certificate through
the Smart Card Enrollment Station.
Microsoft Windows Certificate Services is installed and configured.
Microsoft CA is configured with an issuance Certificate Template for smart card logon
onto the domain. It must include the following certificates:
Enrollment Agent - a certificate intended for the entity that should be able to enroll
certificates for other entities than itself. For example, when an administrator wants
Microsoft CA Registration Authority (RA) station is created with:
to deploy smart card logon certificates for the employees in an organization, he
would require an “Enrollment Agent” certificate.
Smartcard Logon - intended for smart card logon onto the domain.
Smartcard User - an all-round certificate, intended both for smart card logon and,
for example, signing and encrypting e-mail messages and web authentication.
All the drivers required for your HID Crescendo C1150 card and smart card reader.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 21 of 115
© 2013 HID Global Corporation. All rights reserved.
NOTE
If you encounter an “ActiveX” error upon connecting to this page, see section
10.1 ActiveX Error During Certificate Requests on page 109.
An Enrollment Agent Certificate configured with Microsoft Enhanced
Cryptographic Provider 1.0 or similar as the CSP.
4.2 Issuing a Smart Card using Microsoft Certificate Authority
4.2.1 Enroll a Smart Card for a User with Internet Explorer
1. From the enrollment station, connect to the “Smart card Certificate Enrollment Station”
web page of the CA.
This smart card enrollment web page can be found at http://<machine-name>/certsrv/
where the <machine-name> is the machine where you have installed the CA.
2. Select Request a certificate.
3. Select advanced certificate request.
4. Select Request a certificate for a smart card on behalf of another user by using the smart
card certificate enrollment station.
The Smart Card Certificate Enrollment Station window opens.
5. Under Enrollment Options:
6. From the Certificate Template drop-down list, choose Smartcard User.
7. From the Cryptographic Service Provider drop-down list, select Microsoft Base Smart
Card Crypto Provider.
8. Ensure the correct Enrollment Agent certificate is selected in the Administrator Signing
Certificate box.
9. Select a User to Enroll by clicking Select User.
10. Enter the user name in which you are enrolling a certificate in the Enter the object name
to select field.
11. Click Check Names to verify the entry, and then click OK.
12. Verify the user’s smart card is inserted into the smart card reader.
13. Click Enroll to enroll a smartcard user certificate for the user.
14. Enter the PIN, and then click OK to continue.
After the certificate request has been made, the CA will sign the request and return a
certificate. This certificate is automatically placed on the smart card. You might be
prompted to confirm the issuance of a certificate.
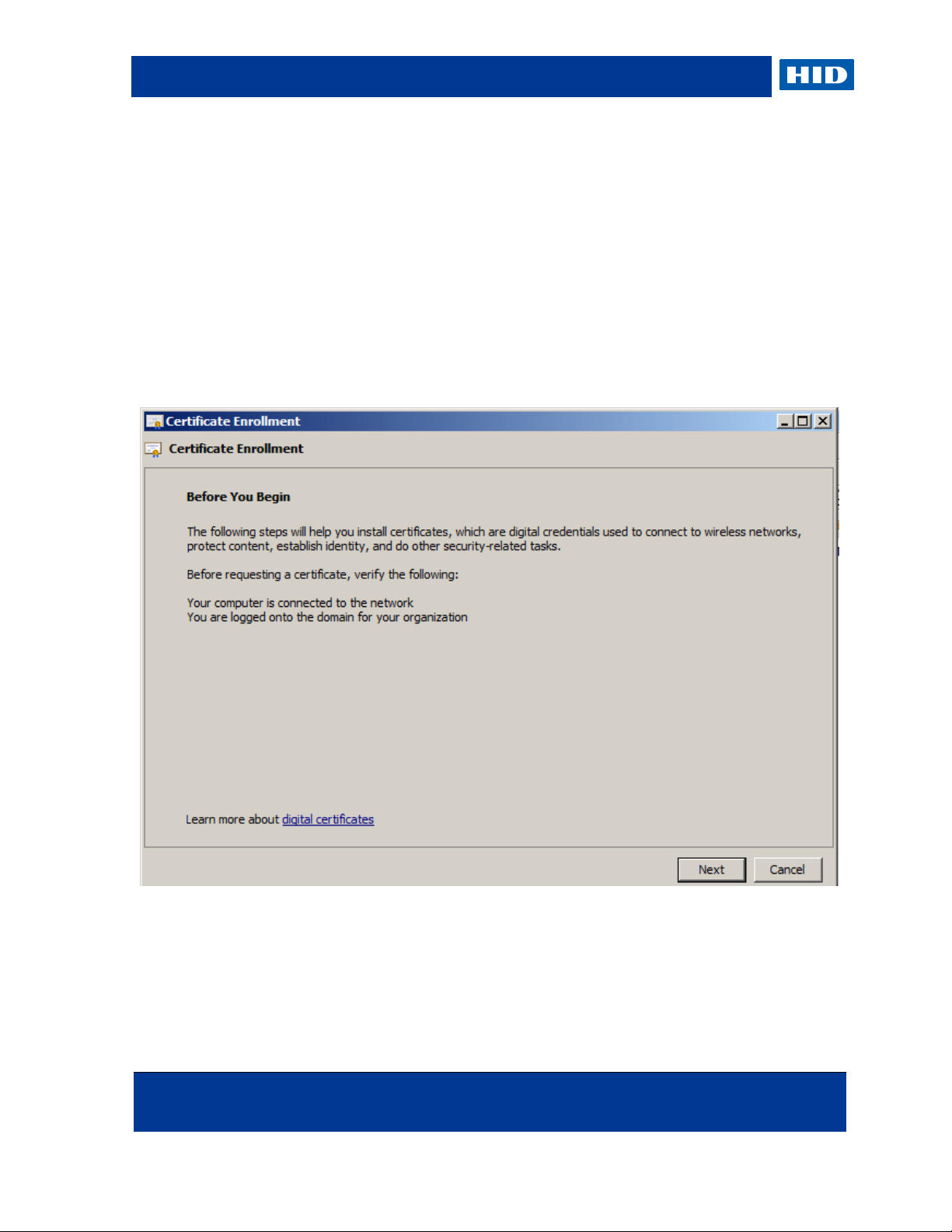
At the end of the smart card enrollment process, you are informed that the smart card is
ready for use.
HID Global Crescendo C1150 – Administration Guide
Page 22 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
15. You can verify if the certificate contains the correct personal information about the user by
clicking View Certificate. You also have the opportunity to enroll a new user by clicking
New User.
4.2.2 Enroll a Smart Card for a User with MMC
1. Open the management console by typing mmc in the Start > Run menu.
2. Add the Certificates snap-in from the File > Add/Remove Snap-in menu.
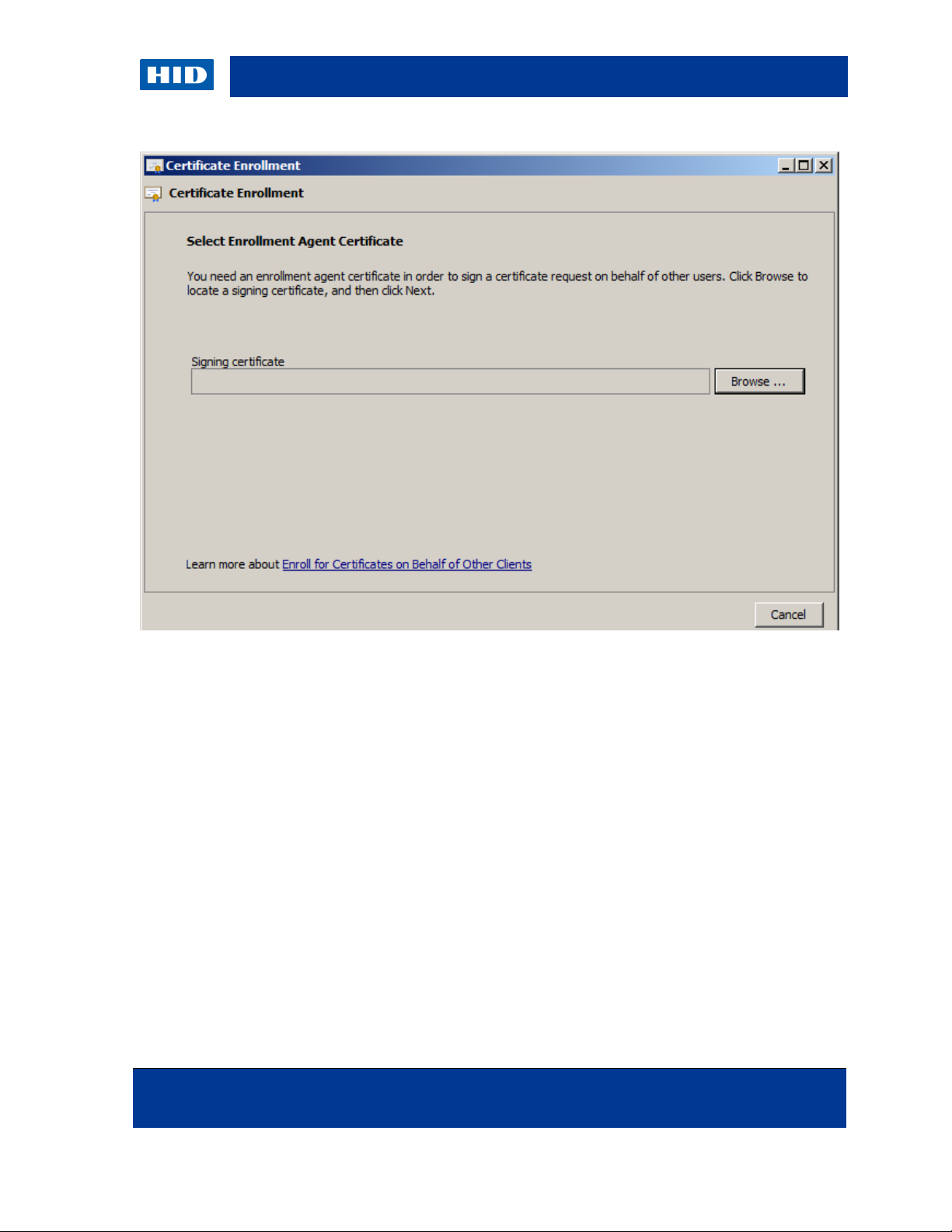
3. Right-click on the Certificates node.
4. Go to All Tasks, then Advanced Operations, and then click Enroll on behalf of.
5. Click Next.
HID Global Crescendo C1150 – Administration Guide
November 2013 Page 23 of 115
© 2013 HID Global Corporation. All rights reserved.
6. Browse to the Enrollment Agent Certificate that you created on the enrollment station.
HID Global Crescendo C1150 – Administration Guide
Page 24 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
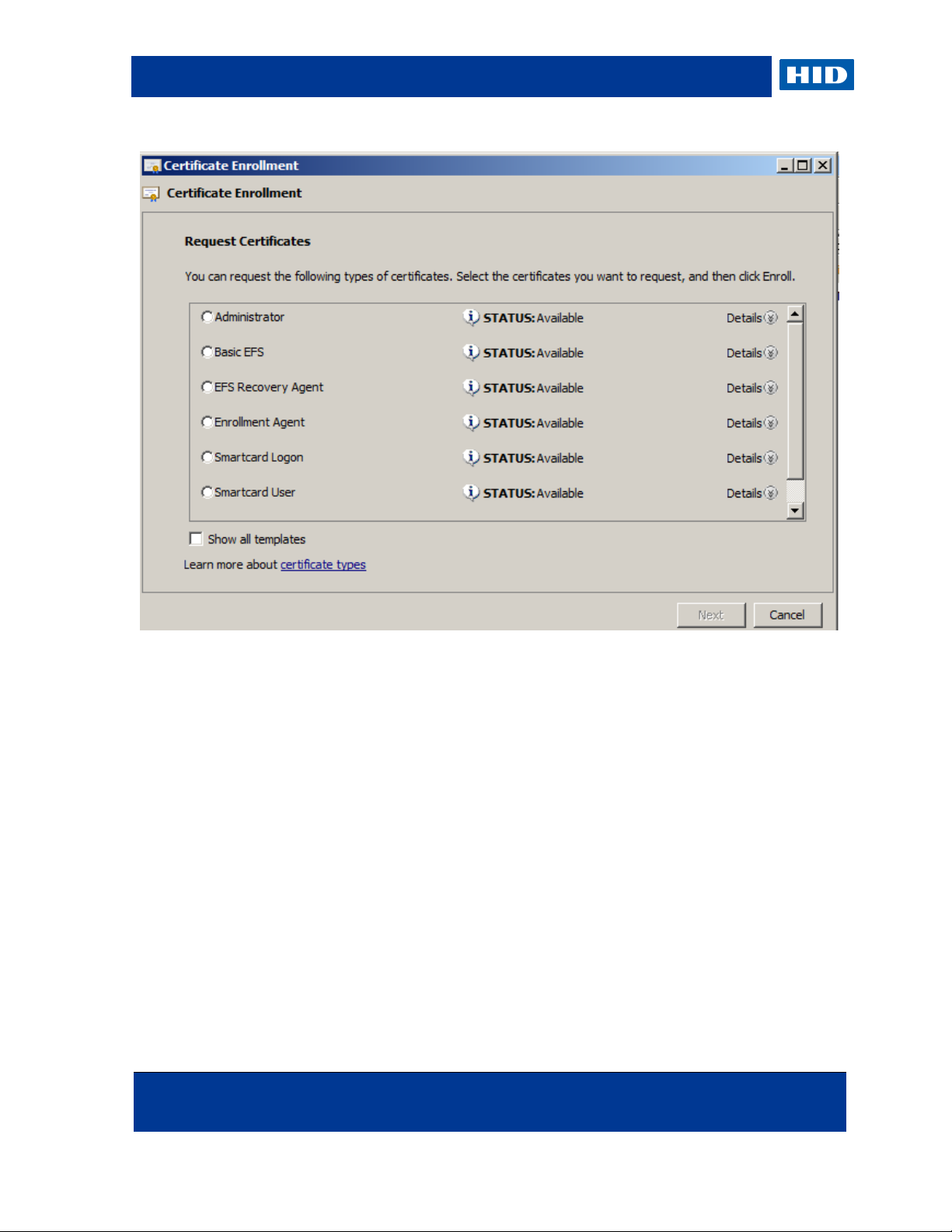
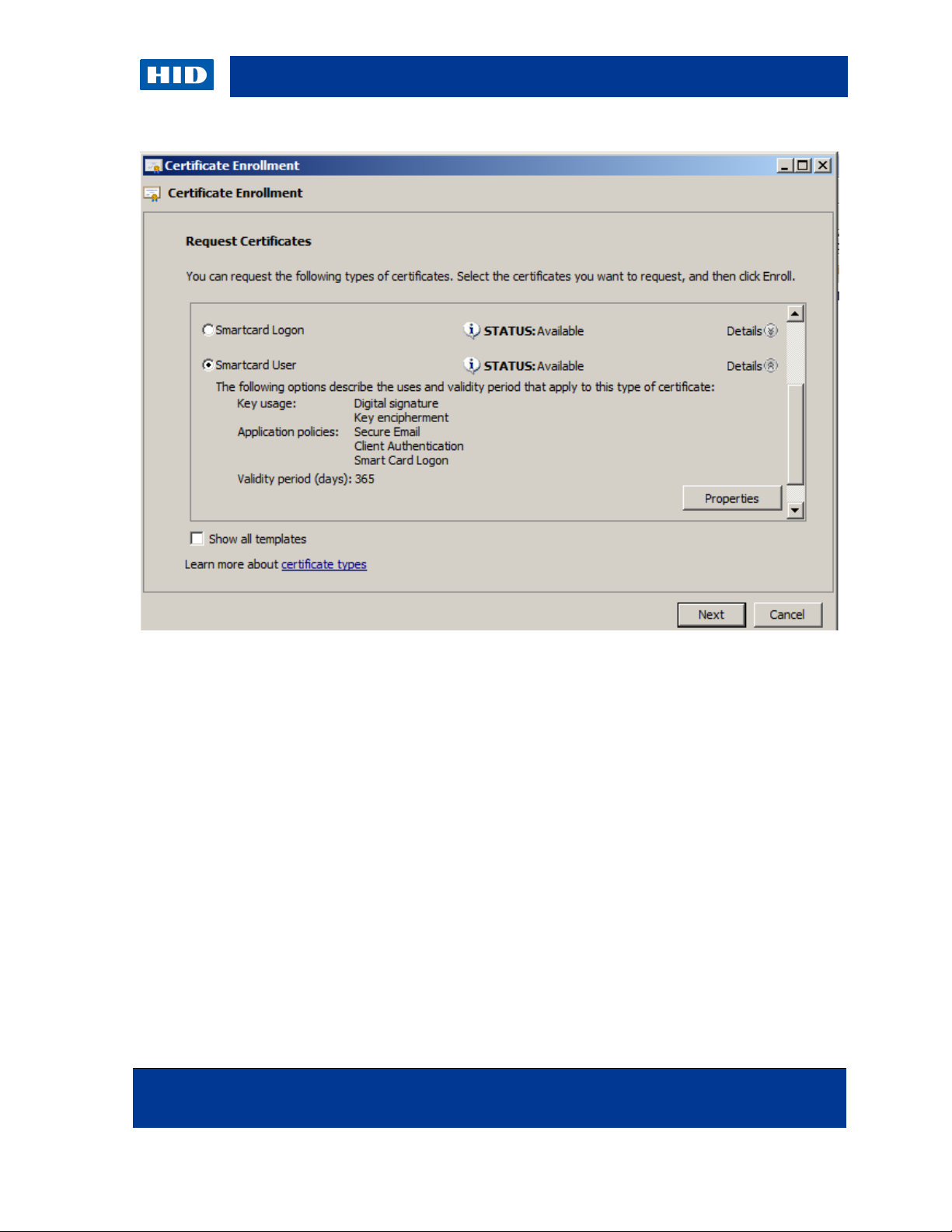
7. Select Smartcard User, and expand the Details view.
HID Global Crescendo C1150 – Administration Guide
November 2013 Page 25 of 115
© 2013 HID Global Corporation. All rights reserved.
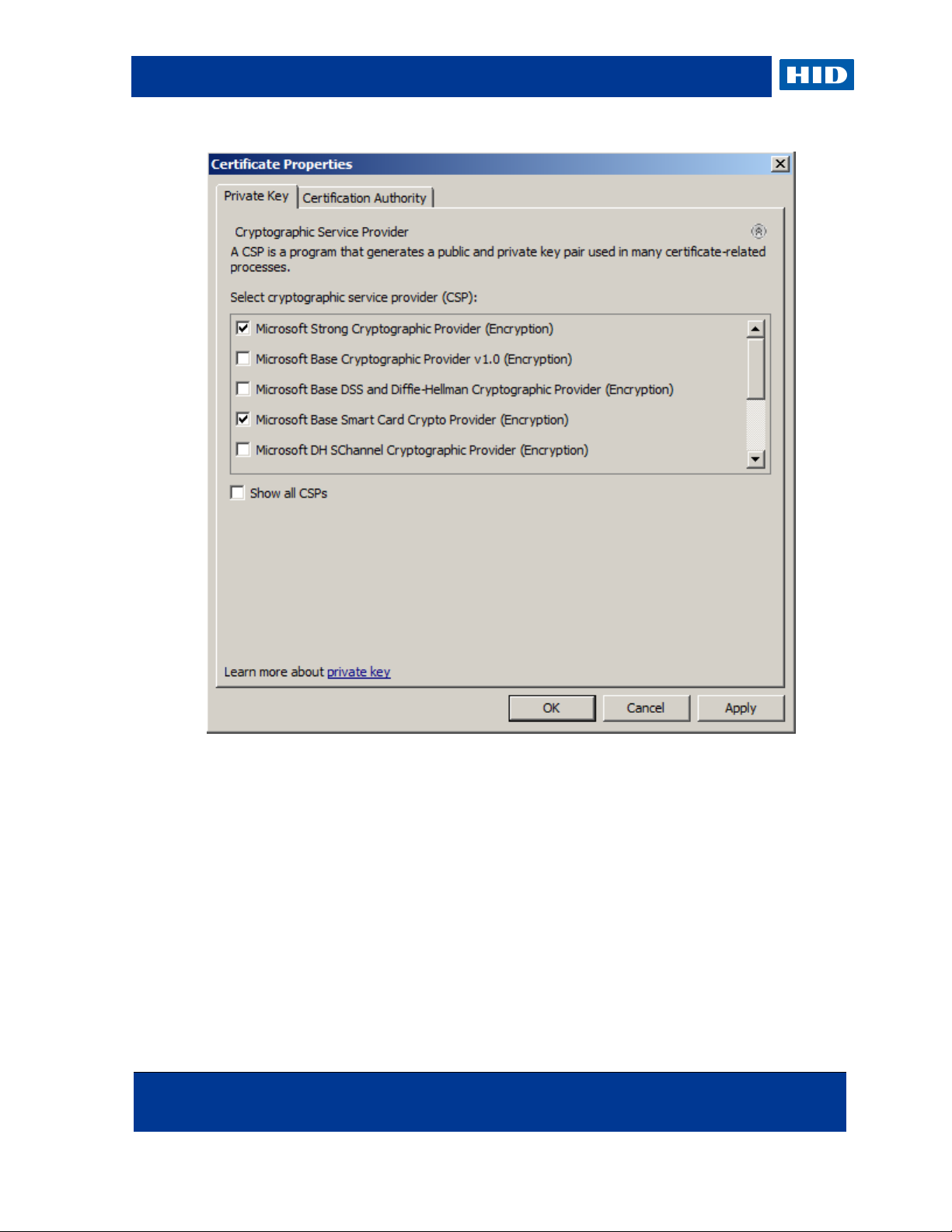
8. Click Properties.
HID Global Crescendo C1150 – Administration Guide
Page 26 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
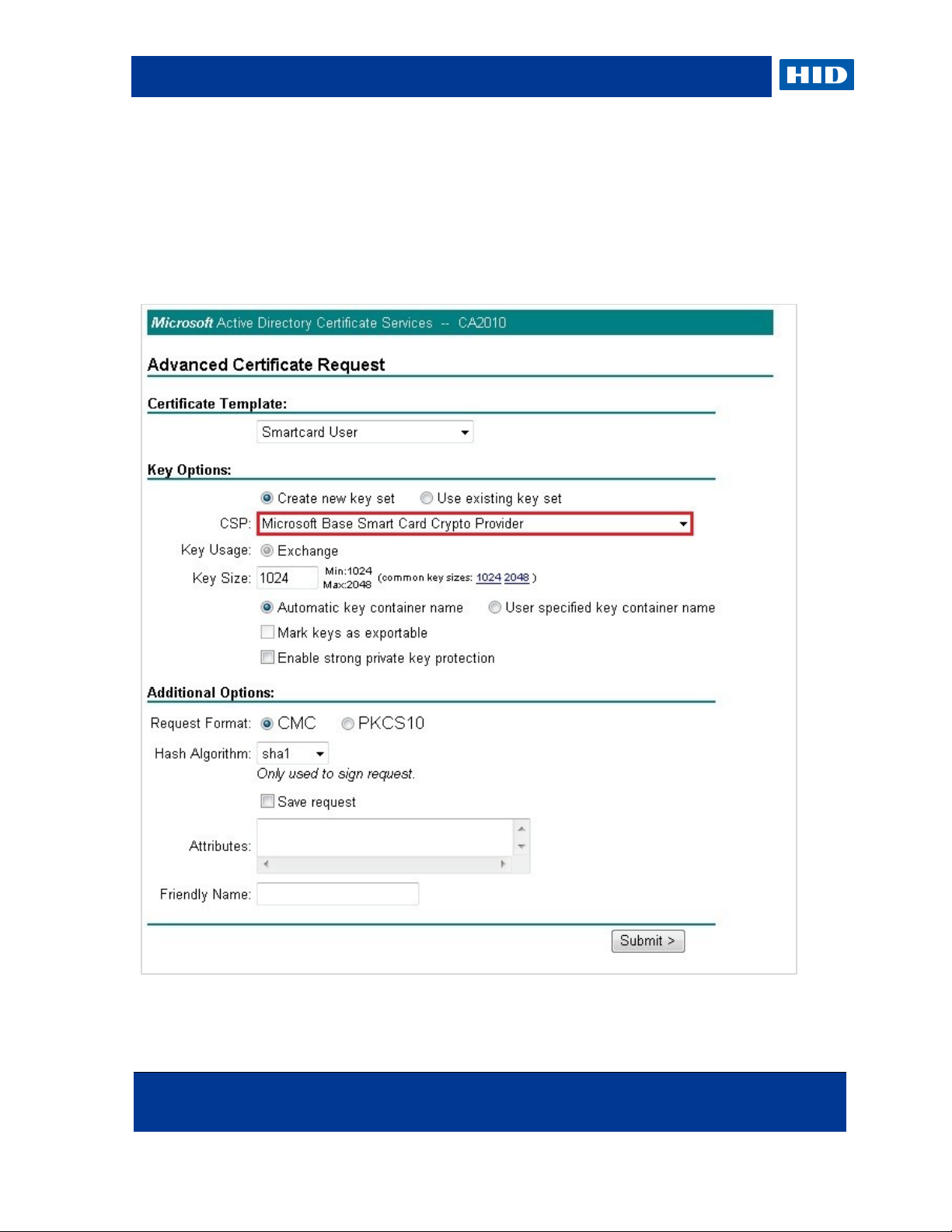
9. Make sure that Microsoft Base Smart Card Crypto Provider is selected as the CSP,
and click OK.
HID Global Crescendo C1150 – Administration Guide
November 2013 Page 27 of 115
© 2013 HID Global Corporation. All rights reserved.
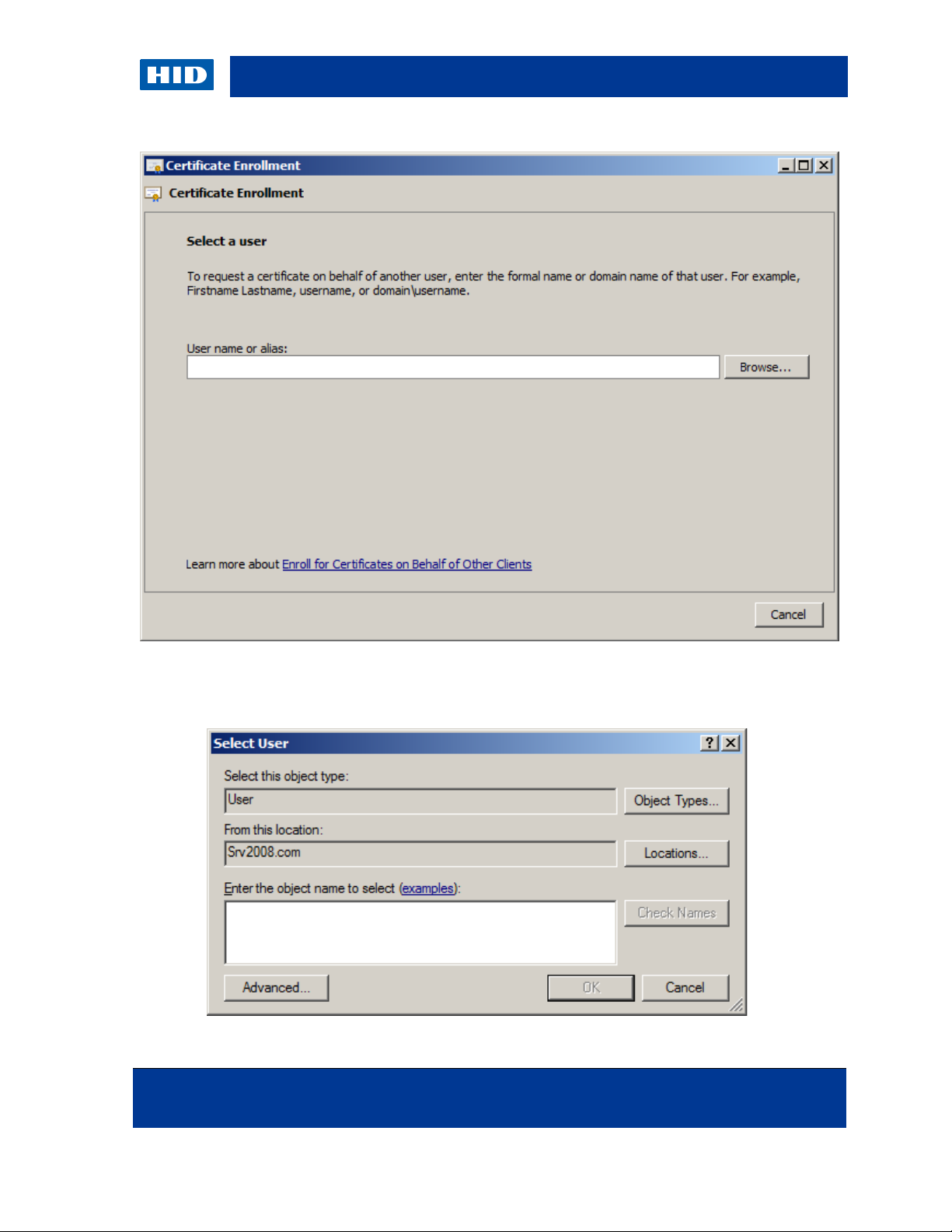
10. Click Browse to select the user for whom you want to enroll the smart card.
HID Global Crescendo C1150 – Administration Guide
Page 28 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
11. Enter the user name, and click OK. If necessary, click Check Names to make sure you
have selected the correct user.
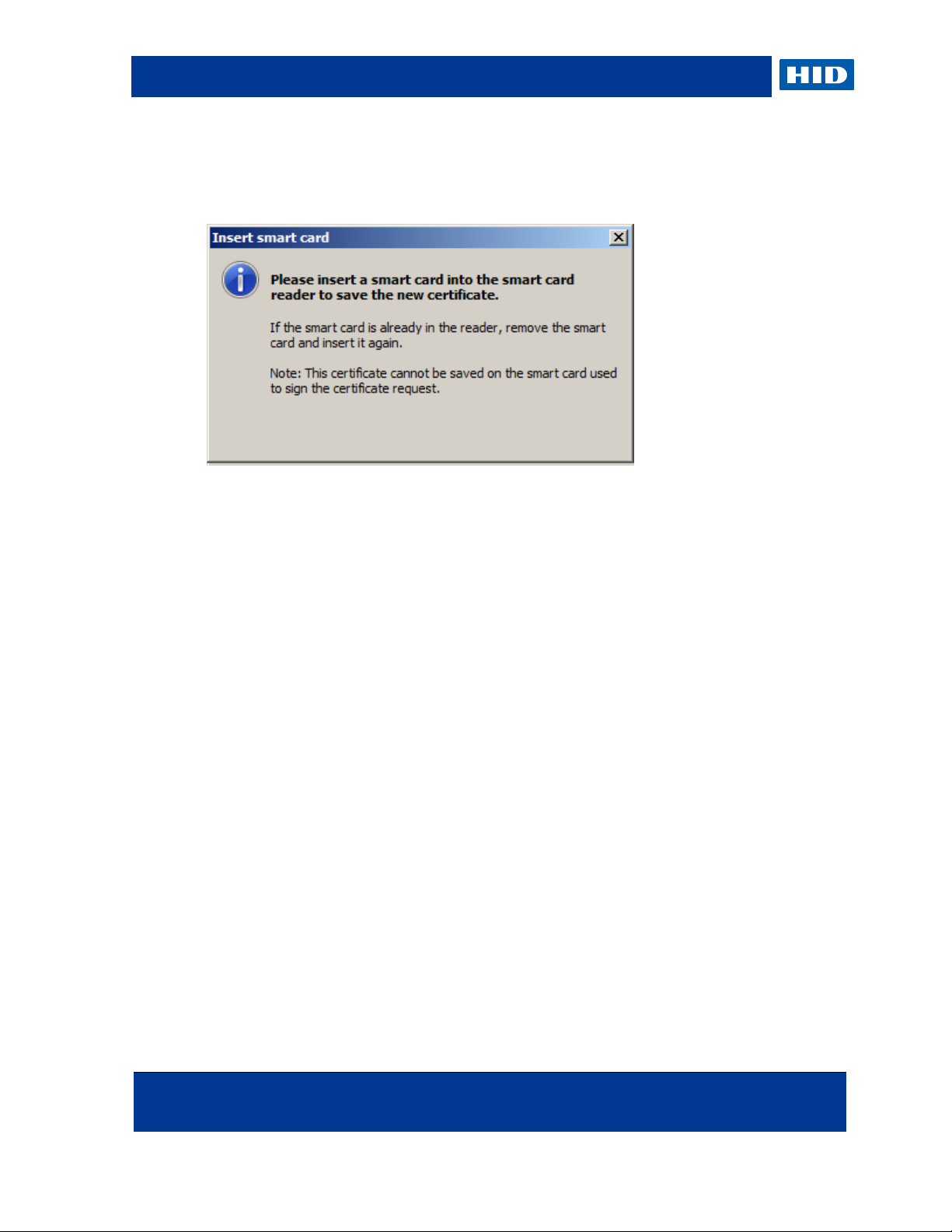
12. When prompted, insert the smart card into the reader.
13. If you are prompted to enter the PIN, do so and then click OK to continue.
After the certificate request has been made, the CA will sign the request and return a
certificate. This certificate is automatically placed on the smart card.
HID Global Crescendo C1150 – Administration Guide
November 2013 Page 29 of 115
© 2013 HID Global Corporation. All rights reserved.
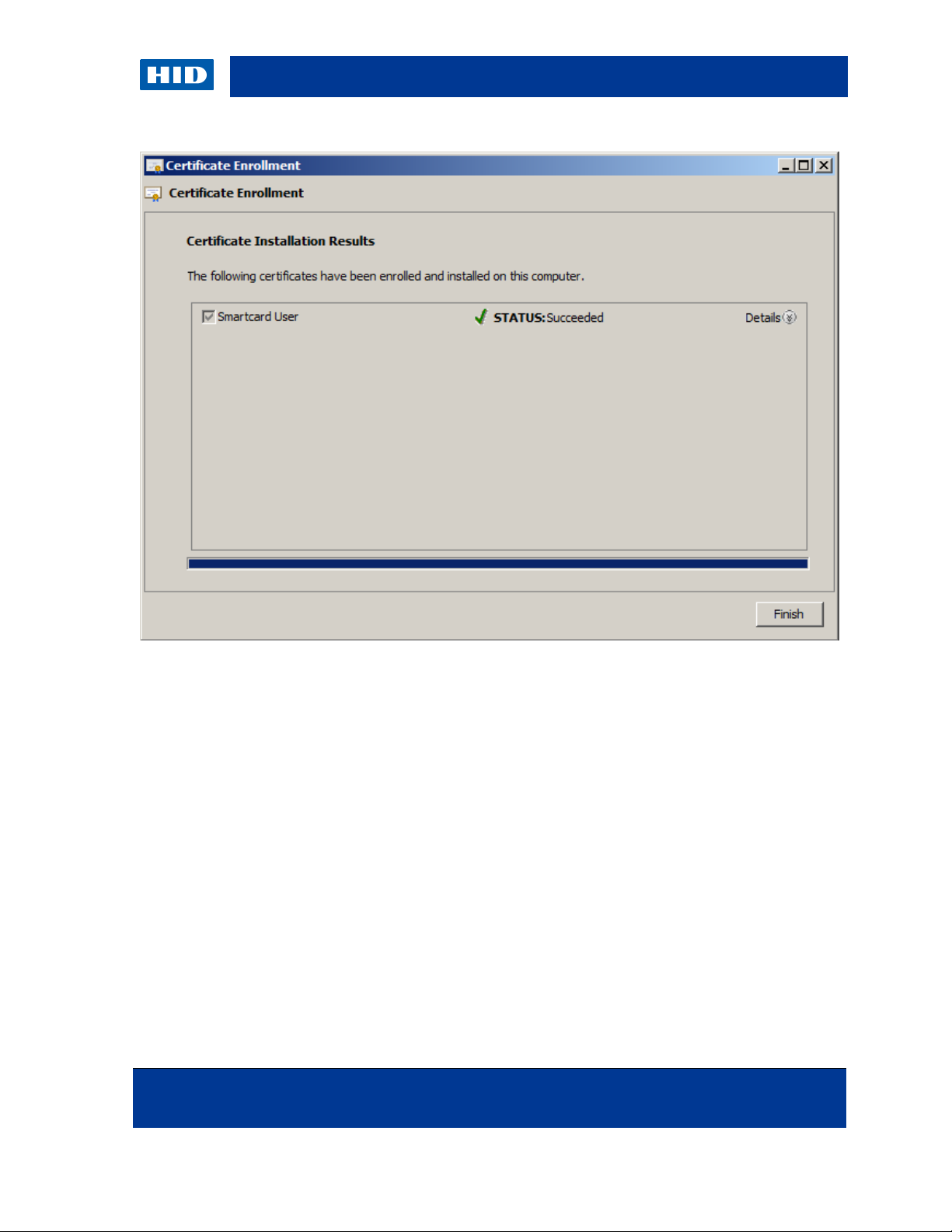
14. Click Finish.
HID Global Crescendo C1150 – Administration Guide
Page 30 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
4.3 Importing Certificates Using Microsoft Windows
You can download PKI certificates from the CA onto the smart card using Internet Explorer or
Microsoft Management Console (MMC).
4.3.1 Download a PKI Certificate with Internet Explorer
When creating the certificate request, make sure that the Microsoft Base Smart Card
Crypto Provider is selected as the CSP.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 31 of 115
© 2013 HID Global Corporation. All rights reserved.
You will then be prompted for your PIN code to sign the certificate request, and asked to
install the certificate on your smart card.
4.3.2 Download a PKI Certificate with MMC
1. Open the management console by typing mmc in the Start > Run menu.
2. Add the Certificates snap-in from the File > Add/Remove Snap-in menu.
3. Right-click on the Certificates node.
4. Go to All Tasks, and then click Request New Certificate.

HID Global Crescendo C1150 – Administration Guide
Page 32 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
5. Click Next.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 33 of 115
© 2013 HID Global Corporation. All rights reserved.
6. Verify that the correct Enrollment Policy is configured and click Next.

HID Global Crescendo C1150 – Administration Guide
Page 34 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
7. Expand the Details view to display the template settings.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 35 of 115
© 2013 HID Global Corporation. All rights reserved.
8. If you need to edit the template settings, click Properties, and then select the Private
Key tab.

HID Global Crescendo C1150 – Administration Guide
Page 36 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
9. Make sure that the Microsoft Base Smart Card Crypto Provider is selected as the CSP
and that the Key size is set to 1024 or 2048.
10. Click Apply and then OK.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 37 of 115
© 2013 HID Global Corporation. All rights reserved.
11. Click Enroll.
You might be prompted to enter your PIN code.

HID Global Crescendo C1150 – Administration Guide
Page 38 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
12. Enter the PIN code and click OK.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 39 of 115
© 2013 HID Global Corporation. All rights reserved.
The new certificate and the corresponding key are stored on your smart card.

HID Global Crescendo C1150 – Administration Guide
Page 40 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
NOTE
The default PIN code is 00000000.
4.4 Changing the PIN Code Using Microsoft Windows
You can change the PIN code using tools specific to your operating system.
4.4.1 Change the PIN Code on Microsoft Windows Vista, Windows 7 or Windows 8
You can change the PIN code using the Change Password option from the
CTRL+ALT+DELETE feature.
1. Enter the current PIN code in the PIN field (the default PIN code is 00000000).
2. Enter and confirm the new PIN code, and then click the arrow (or press Enter).
The new PIN code must meet the PIN policy:
PIN is 4 to 14 characters long.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 41 of 115
© 2013 HID Global Corporation. All rights reserved.
Weak PIN values are not allowed (a PIN is considered weak if the difference
between consecutive characters is fixed – for example, 1234, ABCD, 86420,
acegik are considered weak PINs).
3. Click OK to return to your Windows session.
4.4.2 Change the PIN Code on Microsoft Windows XP
You can change your PIN code using the Microsoft PIN Tool (pintool.exe) included with the
Base Smart Card CSP Package (for further information, see
http://support.microsoft.com/kb/909520).
The PINTool.exe is located in the %WINDOWS%\system32 directory.
1. Insert a valid smart card into the reader.

HID Global Crescendo C1150 – Administration Guide
Page 42 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
2. Click OK.
3. Enter your current PIN code in the Old PIN field (the default PIN code is 00000000).
4. Enter and confirm the new PIN code, and then click Change Pin.
The new PIN code must meet the PIN policy:
PIN is 4 to 14 characters long.
Weak PIN values are not allowed (a PIN is considered weak if the difference
between consecutive characters is fixed – for example, 1234, ABCD, 86420,

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 43 of 115
© 2013 HID Global Corporation. All rights reserved.
acegik are considered weak PINs).
5. Click OK.

HID Global Crescendo C1150 – Administration Guide
Page 44 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
NOTE
In order to get access to the Microsoft SmartCard Credential Provider
Unblock Feature, the following policy must be enabled by launching Microsoft
Management Console (mmc), and then by adding the “Group Policy Object”
Snap-In:
Local Computer Policy\Computer Configuration\Administrative
Templates\Windows Components\Smart Card\Allow Integrated Unblock
screen to be displayed at the time of logon
NOTE
The Microsoft Windows refers to the smart card being “blocked”; this is similar
to the smart card PIN being “locked”.
4.5 Unlocking the PIN Code Using Microsoft Windows
The Crescendo C1150 PIN will lock if the user presents six consecutive incorrect PINs. When
the PIN is locked, you cannot use the card until you unlock the PIN.
In this deployment mode, an additional tool is needed to generate the cryptogram based on
the input challenge and the default ADMIN key (binary value
000000000000000000000000000000000000000000000000).
Other deployment modes with a central card management system are recommended for a
simplified unlock process.
4.5.1 Unlock the PIN Code on Microsoft Windows Vista, Windows 7 or Windows 8
If you try to log on with a blocked smart card, or if you exceed the number of incorrect PIN
entries, you are prompted to unlock the smart card.
1. Click OK to start the procedure.
Alternatively, you can use the Change Password option from the CTRL+ALT+DEL menu.
In coordination with your administrator, you obtain an unlock code based on the
generated challenge.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 45 of 115
© 2013 HID Global Corporation. All rights reserved.
2. Select Unblock smart card.

HID Global Crescendo C1150 – Administration Guide
Page 46 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
NOTE
If your administrator does not manage your Crescendo card, you can generate
the unlock code using the HID Global Crescendo C1150 Unblock utility available
at http://www.hidglobal.com/drivers.
3. Provide the Challenge to your administrator, who will generate the unlock code.
4. Enter the unlock code in the Response field.
5. Enter and confirm a new PIN code.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 47 of 115
© 2013 HID Global Corporation. All rights reserved.
6. Click OK to return to your Windows session.
4.5.2 Unlock the PIN Code on Microsoft Windows XP
You can unlock your PIN code using the Microsoft PIN Tool (pintool.exe) included with the
Base Smart Card CSP Package (for further information, see
http://support.microsoft.com/kb/909520).
The PINTool.exe is located in the %WINDOWS%\system32 directory.
1. Select the Unblock tab in the Smart Card PIN Tool.

HID Global Crescendo C1150 – Administration Guide
Page 48 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
NOTE
The Microsoft Windows refers to the smart card being “blocked”; this is
similar to the smart card PIN being “locked”.
2. Click Unblock to generate the unlock challenge.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 49 of 115
© 2013 HID Global Corporation. All rights reserved.
NOTE
If your administrator does not manage your Crescendo card, you can generate
the unlock code using the HID Global Crescendo C1150 Unblock utility available
at http://www.hidglobal.com/drivers.
3. Provide the Challenge to your administrator, who will generate the unlock code.
4. Enter the unlock code in the Response field.
5. Then, enter and confirm a new PIN code, and then click OK.
6. Click OK to return to your Windows session.

HID Global Crescendo C1150 – Administration Guide
Page 50 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
5.0 Managing a Smart Card using Microsoft Forefront Identify Manager (FIM)
Forefront Identity Manager (FIM) 2010 delivers solutions to manage user accounts and
access, password- and certificate-based credentials such as smart cards, and identity-based
policies across Windows and heterogeneous environments.
5.1 Prerequisites
Install the Crescendo C1150 Mini Driver (either from the Microsoft Windows Update or
from the HID web site http://www.hidglobal.com/main/crescendo/).
Install and configure Microsoft Forefront Identity Manager (FIM) 2010 server as
described in the Microsoft technical guide – http://technet.microsoft.com/en-
us/library/fim-cm-getting-started-test-lab-guide(WS.10).aspx
Make sure that the profile template is configured so that the ADMIN key is diversified
during the initialization.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 51 of 115
© 2013 HID Global Corporation. All rights reserved.
NOTE
The default PIN code is 00000000.
The card is also personalized with a default ADMIN Key set to the binary
value 000000000000000000000000000000000000000000000000.
5.2 Initialize a Permanent Card
1. Log on to Forefront Identity Manager Certificate Management console.
2. In the Manage my info view, select Request a permanent smart card.

HID Global Crescendo C1150 – Administration Guide
Page 52 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
3. Select the profile template and then click Next.
The certificates are generated and the card is initialized.
4. When prompted, enter and confirm a PIN code for the card, and then click OK.
Important: The PIN must respect the specified PIN Rules.
PIN is 4 to 14 characters long;
Weak PIN values are not allowed (a PIN is considered weak if the difference
between consecutive characters is fixed – for example, 1234, ABCD, 86420,
acegik are considered weak PINs).

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 53 of 115
© 2013 HID Global Corporation. All rights reserved.
The card is now ready to use.
5.3 Change the PIN Code Using FIM
1. In the Manage my info view, select Change my smart card PIN.

HID Global Crescendo C1150 – Administration Guide
Page 54 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
NOTE
Your PIN code is checked to make sure that it meets the length
requirements, and that it is not weak (a PIN is considered weak when the
difference between consecutive characters is fixed – for example, 1234,
ABCD, 86420, acegik).
2. Enter your current PIN code.
3. Enter and confirm your new PIN code, and click OK.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 55 of 115
© 2013 HID Global Corporation. All rights reserved.
5.4 Unlocking the Smart Card Using FIM - Online
The Crescendo C1150 PIN will lock if the user presents six consecutive incorrect PINs. When
the PIN is locked, you cannot use the card until you unlock the PIN.
5.4.1 Unlock the Smart Card as an Administrator
1. Log on to Forefront Identity Manager Certificate Management console and select the
Manager operations view.
2. Under Manage User Smart Cards, select Unblock a user’s smart card.

HID Global Crescendo C1150 – Administration Guide
Page 56 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
3. Search for the required user using the Look Up function.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 57 of 115
© 2013 HID Global Corporation. All rights reserved.

HID Global Crescendo C1150 – Administration Guide
Page 58 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
4. In the returned results, select the smart card to unlock.
5. Verify the smart card details and then select Unblock this smart card.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 59 of 115
© 2013 HID Global Corporation. All rights reserved.
6. Follow the Unblock Wizard instructions (see section 5.4.3 Using the Unblock Wizard on
page 60).
5.4.2 Unlock the Smart Card as an End User
1. In the Manage my info view, select Show details of my smart card.
2. Verify the smart card details and then select Unblock this smart card.

HID Global Crescendo C1150 – Administration Guide
Page 60 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
3. Follow the Unblock Wizard instructions (see section 5.4.3 Using the Unblock Wizard on
page 60).
5.4.3 Using the Unblock Wizard
As part of the smart card unlock process, the Unblock Wizard launches.
If configured, the wizard prompts for additional data.
1. Enter the data and click Next.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 61 of 115
© 2013 HID Global Corporation. All rights reserved.
NOTE
Your PIN code is checked to make sure that it meets the length
requirements, and that it is not weak (a PIN is considered weak when the
difference between consecutive characters is fixed – for example, 1234,
ABCD, 86420, acegik).
2. Enter and confirm a New PIN code, and then click OK.
The new PIN code must respect the specified PIN rules.
5.5 Unlocking the Smart Card Using FIM - Offline
The Crescendo C1150 PIN will lock if the user presents six consecutive incorrect PINs. When
the PIN is locked, you cannot use the card until you unlock the PIN.
5.5.1 Verify that the Offline Unlock Policy is Enabled
To be able to perform the Offline Unlock operation, the profile template must have the Offline
Unblock Policy enabled.
1. Log on to Forefront Identity Manager Certificate Management console, and select the
Manager operations view.

HID Global Crescendo C1150 – Administration Guide
Page 62 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
2. Under Administration, click Manage profile templates.
3. Select your profile template.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 63 of 115
© 2013 HID Global Corporation. All rights reserved.
4. In the left menu pane, select Offline Unlock Policy.

HID Global Crescendo C1150 – Administration Guide
Page 64 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
5. Under the Workflow: General section, verify that the policy is enabled.
If it is not, click Change general settings to enable the policy.
5.5.2 Launch Offline Unlock Request
1. To launch an Offline unlock request, return to the Manager operations view.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 65 of 115
© 2013 HID Global Corporation. All rights reserved.
2. Under Manage User Smart Cards, click Unblock a user’s smart card.

HID Global Crescendo C1150 – Administration Guide
Page 66 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
3. Search for the required user using the Look Up function.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 67 of 115
© 2013 HID Global Corporation. All rights reserved.

HID Global Crescendo C1150 – Administration Guide
Page 68 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
4. Select the smart card to be unlocked.
5. Click Offline unblock this smart card.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 69 of 115
© 2013 HID Global Corporation. All rights reserved.
6. Enter any additional information and click OK.
7. Click Execute.

HID Global Crescendo C1150 – Administration Guide
Page 70 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
8. Ask the smart card user to provide the challenge displayed when they attempt to unlock
the smart card using the native Windows tools (see section 4.5 Unlocking the PIN Code
Using Microsoft Windows on page 44).
9. Enter the Challenge and click Compute Response.
10. Provide the computed Response to the smart card user and instruct him to enter it into
the corresponding field in the Windows unlock dialog.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 71 of 115
© 2013 HID Global Corporation. All rights reserved.
5.6 Reset the Smart Card Using FIM
1. In the Manage my info view, select Show details of my smart card.
2. Click Retire this smart card.

HID Global Crescendo C1150 – Administration Guide
Page 72 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
3. Verify the actions that will be performed when the card is retired and click Next.
The smart card ADMIN key is set back to the initial value, all the PKI containers are reset, but
the PIN code is unchanged.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 73 of 115
© 2013 HID Global Corporation. All rights reserved.
6.0 Managing a Smart Card with ActivClient
ActivClient enables the use of PKI certificates and keys, one-time passwords and static
password credentials on a smart card or USB token to secure:
Desktop applications
Network logon
Remote access
Web logon
E-mail messages
Electronic transactions
In addition to smart card middleware (Cryptographic Service Provider and PKCS#11 libraries),
ActivClient includes additional utilities that enable you to manage your smart card, including:
User Console
PIN Initialization Tool
PIN Change Tool
The next sections present common card management operations with ActivClient. See the
ActivClient documentation for complete instructions on installation, management and usage
services.
6.1 Issue a Smart Card with ActivClient
When you receive a blank smart card, you must initialize it using the ActivClient PIN
Initialization Tool.
1. Use one of the following options to launch the ActivClient PIN Initialization Tool:
From the ActivClient notification area icon:
Right-click on the icon and select PIN Initialization Tool in the menu:

HID Global Crescendo C1150 – Administration Guide
Page 74 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
From the ActivClient User Console:
From the Tools menu, select New Card.
From the Start Menu:
Select PIN Initialization Tool in the menu.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 75 of 115
© 2013 HID Global Corporation. All rights reserved.
2. Enter and confirm a PIN code and click Next.
The PIN code must meet the specified conditions.

HID Global Crescendo C1150 – Administration Guide
Page 76 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
3. Make a note of your unlock code and store it in a safe place.
If you do not select the Never display the Unlock Code again option, the unlock code
will display each time you enter your smart card PIN code.
4. Click Finish.
6.2 Change the PIN Code with ActivClient
1. Use one of the following options to launch the ActivClient PIN Change Tool:
From the ActivClient notification area icon:
Right-click on the icon and select PIN Change Tool in the menu:

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 77 of 115
© 2013 HID Global Corporation. All rights reserved.
From the ActivClient User Console:
From the Tools menu, select Change PIN.
From the Start Menu:
Select PIN Change Tool in the menu.

HID Global Crescendo C1150 – Administration Guide
Page 78 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
2. Enter your current PIN code.
3. Enter and confirm a PIN code and click Next.
The PIN code must meet the specified conditions.
6.3 Unlock the Smart Card Using ActivClient
If the Unlock Smart Card tool does not display automatically when ActivClient detects that the
card is locked, from the ActivClient User Console Tools menu, select Unlock Card.
If the smart card was initialized with ActivClient, you can unlock it with the static unlock
code displayed during initialization.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 79 of 115
© 2013 HID Global Corporation. All rights reserved.
a. Retrieve the unlock code that you saved when you initialized your smart card.
You might be able to retrieve the code from the ActivClient User Console Tools
menu, using the View Unlock Code option.
b. In the Unlock Code field, type the unlock code that you retrieved.
c. In the New PIN field, type the new PIN.
d. In the Verify field, re-type the new PIN, and click OK.
If the smart card was initialized by your administrator with a card management product
(such as the 4TRESS AAA Server, or Microsoft FIM), you can unlock it using a
challenge/response unlock process.

HID Global Crescendo C1150 – Administration Guide
Page 80 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
a. Provide the Challenge Code to your help desk.
b. In the Unlock Code field, type the unlock code that the help desk operator gives
you.
c. In the New PIN field, type the new PIN.
d. In the Verify field, re-type the new PIN, and click OK.
6.4 Reset the Smart Card Using ActivClient
If you want to reset a smart card that is already initialized (either using ActivClient or the Mini
Driver), you can use the ActivClient Reset Card function.
1. Open the ActivClient User Console.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 81 of 115
© 2013 HID Global Corporation. All rights reserved.
2. From the Tools menu, select Reset Card.
If the smart card was initialized with ActivClient, you can reset it with the PIN code or
the static unlock code displayed during initialization.
a. Select one of the options and enter the corresponding code.
b. Click OK.
If the smart card was initialized with ActivClient in a 4TRESS AAA Server deployment
or with the Mini Driver, you can reset it with the PIN code or a dynamic unlock code.

HID Global Crescendo C1150 – Administration Guide
Page 82 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
a. Select the PIN option and enter your PIN code.
b. Alternatively, select the Unlock Code option and provide the Challenge Code to
your Help Desk.
Then enter the Unlock Code given to you by your Help Desk.
c. Click OK.
3. Click OK when the reset process is complete.
The smart card is now blank and can be initialized for new use.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 83 of 115
© 2013 HID Global Corporation. All rights reserved.
6.5 Importing Certificates Using ActivClient
You can download PKI certificates from the CA onto the smart card using Internet Explorer or
Microsoft Management Console (MMC).
6.5.1 Request a Certificate

HID Global Crescendo C1150 – Administration Guide
Page 84 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
When creating the certificate request, make sure that the ActivClient Cryptographic Service
Provider is selected as the CSP.
If the ActivClient detects that the card is not initialized, then the PIN Initialization Tool
launches (see section 6.1 Issue a Smart Card with ActivClient on page 73).
The certificate request process resumes, and you are asked to install the certificate on your
smart card.
6.5.2 Import the Certificate
1. Insert your smart card into the reader.
2. Open the ActivClient User Console.
3. Select Import from the File menu. Alternatively, in the Tasks view, under My
Certificates Tasks, select Import a certificate.
4. Browse to the certificate file. If the certificate is password-protected, enter the password
and click OK.
5. Click OK.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 85 of 115
© 2013 HID Global Corporation. All rights reserved.
NOTE
The default PIN is 00000000.
The card is also personalized with a default ADMIN Key set to
000000000000000000000000000000000000000000000000 (binary value).
7.0 Managing a Smart Card with naviGO
naviGO Server provides the capability for administrators and end-users to enroll Crescendo
contact cards with PKI credentials. naviGO also enables the use of emergency credentials
(knowledge-based authentication) for cases where users have lost or forgotten their card.
The next sections present common card management operations with naviGO. See the
naviGO documentation for complete instructions on installation, management and usage
services.
7.1 Prerequisites
The Crescendo C1150 Mini Driver is installed (either from Microsoft Windows Update
or from the HID web site http://www.hidglobal.com/main/crescendo/).
naviGO Server 3.0 is installed.
The administrator must be assigned the role of navigo_sys_admin or Security Officer,
or the function of Enroll on Behalf must be manually assigned to the Role for which the
administrator is logged into naviGO.
7.2 Initialize a Smart Card
This section presents how administrators can issue a smart card for their end users.
naviGO also enables users to self-enroll using the naviGO self-service portal. The steps
below starting at step 8 show this self-enrollment process. See the naviGO Server User Guide
for additional information.

HID Global Crescendo C1150 – Administration Guide
Page 86 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
1. Log on to the naviGO Administrator Portal.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 87 of 115
© 2013 HID Global Corporation. All rights reserved.
2. Enter your Administrator Username and Password and click Validate.
3. Click Manage Users to select the user to whom you want to issue the smart card.

HID Global Crescendo C1150 – Administration Guide
Page 88 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
4. Search for the user and then click the Username to view the User Information.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 89 of 115
© 2013 HID Global Corporation. All rights reserved.
5. Click Edit User.

HID Global Crescendo C1150 – Administration Guide
Page 90 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
6. From the Current User State drop-down list, select New Credential, and then click
Save.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 91 of 115
© 2013 HID Global Corporation. All rights reserved.
7. Click Enroll On Behalf.

HID Global Crescendo C1150 – Administration Guide
Page 92 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
You are re-directed to the naviGO User Portal.
8. Insert the user’s smart card into the reader and click OK.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 93 of 115
© 2013 HID Global Corporation. All rights reserved.
9. Ask the user to set the PIN code for the smart card and click OK.
The PIN code must meet the specified conditions.

HID Global Crescendo C1150 – Administration Guide
Page 94 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
10. Ask the user to enter their PIN code and click OK.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 95 of 115
© 2013 HID Global Corporation. All rights reserved.
When the enrollment process is complete, the user is now in Steady State and can
authenticate with his smart card.

HID Global Crescendo C1150 – Administration Guide
Page 96 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 97 of 115
© 2013 HID Global Corporation. All rights reserved.
8.0 Managing a Smart Card with 4TRESS AAA Server
The 4TRESS AAA Server for Remote Access (the AAA Server) is a strong RADIUS,
TACACS+ and IEEE 802.1x authentication server that maps to your LDAP directory to
provide strong user authentication services for a wide range of access points.
AAA stands for:
Authentication - accepts or rejects user authentication requests based on stored
credentials and/or one-time passwords.
Authorization - controls user access based on the appropriate attributes transmitted to
the network remote access point (VPN, firewall, router etc.,)
Accounting - stores information concerning user activity while connected remotely
(connection times, data transfers etc.,)
Users authenticate through the AAA Server with smart cards, hardware and software tokens,
USB keys, mobile devices, PDAs, (and optionally, with static or static LDAP passwords).
A secure remote access solution, the AAA Server enables you to protect the following
network access methods:
Web access
Remote access via dial-up
Remote access via VPN
Remote desktop environments (Microsoft Windows and Citrix®)
SSL VPN
Wireless LAN access
The Crescendo C1150 card is initialized with 4TRESS AAA Server Administration Console to
add the one-time password (OTP) capabilities.
When the card is initialized, it can be issued (assigned) by the:
Administrator using the AAA Server Administration Console or the Web Help Desk.
End user using the self-assignment feature of the AAA Server Web Self Help Desk.
The cards can then be managed by the:
Administrator (or help desk operator) using the AAA Server Administration Console or
the Web Help Desk
End user using the AAA Server Web Self Help Desk, which provides services such as
Unlock PIN and Synchronize Device.
Users can also use and manage the card on their workstation with the ActivClient middleware
(to generate OTPs, change the PIN code and import certificates).

HID Global Crescendo C1150 – Administration Guide
Page 98 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
The next sections present the initialization and issuance operations with 4TRESS AAA
Server, as well as common card management tasks. See the 4TRESS AAA Server
documentation for complete instructions on installation, management and usage services.
8.1 Issue a Smart Card Using 4TRESS AAA Server
Before the card can be issued, it must be initialized with 4TRESS AAA Server to add one-time
password (OTP) capabilities to the cards.
Once the card is initialized, you can assign it to the required user.
Prerequisites:
ActivClient 6.2.0.162 or later is installed on the AAA Server Administration Console
machine.
The adimCard.spl file (usually located in \Program Files\ActivIdentity\AAA\spl\card)
must be updated to set the DESKeyType to des3.
A PC/SC compatible smart card reader is connected to the machine.
On Microsoft Windows 64-bit platforms, you must also install the AAA Server hot fix
FIXS1207015.
1. Log on to the AAA Server Administration Console as a Device Manager.
2. In the tree in the left pane, right-click on Devices, then select Initialize Device from the
menu. Or select Devices, and then click Initialize.

HID Global Crescendo C1150 – Administration Guide
November 2013 Page 99 of 115
© 2013 HID Global Corporation. All rights reserved.
NOTE
You MUST select this option if using ActivClient middleware.
3. From the Device Type drop-down list, select the type of device to initialize (in this case,
smart card).
4. From the Device Reader drop-down list, select the reader that you want to use with the
device that you have selected.
5. Select Assign user after Initialization to immediately assign the device to a user after
you initialize it.
6. In the PIN Parameters section of the window, select the required options:
PIN MAX number of tries - enter the maximum number of consecutive wrong PIN
codes that a user can enter on a device before the device automatically locks.
When set to zero (0), the user can enter an unlimited number of consecutive wrong
PIN codes. The default number for the selected device profile is displayed in this
field.
Initial PIN Code - initializes all the devices with the same initial PIN code value
specified in the field. It is recommended that users change the initial PIN code
during the first connection. You cannot enter a “weak” PIN code. Examples of weak
PIN codes are 1357, 1234, and 1111 (ones with a constant amount between each
of the digits).
Generate Random PIN Code - select this option to have the AAA Server

HID Global Crescendo C1150 – Administration Guide
Page 100 of 115 November 2013
© 2013 HID Global Corporation. All rights reserved.
NOTE
The default PIN code is 1254.
randomly generate a different initial PIN code for each device during initialization. If
you select this option, then in the Length field, enter a length for the random PIN
code. This length must be within the minimum and maximum PIN length values for
the selected device profile.
7. The Store Initialized Device in Repository field displays the default repository where
the AAA Server will store the initialized card’s information.
If you are logged into the Administration Console as a user who has Device Manager
rights, you can select a different repository:
a. Click to select the repository where you want to store the initialized device.
b. Select the repository in which to store the device that you are initializing.
The name of the folder is displayed in the field at the top of the window.
(Repositories with arrows indicate there are devices stored in those folders.)
c. Click OK.
The repository name automatically appears in the Repository field in the Device
Initialization window.
8. Insert the Crescendo C1150 smart card into your smart card reader, and then click
Initialize.
Once the AAA Server has finished initializing the card, a message is displayed stating
that the initialization was successful. It also displays the initial PIN code value of the
device.
9. Click OK.
 Loading...
Loading...