Page 1

ActivIdentity® 4TRESS AAA Web Tokens
and F5
®
BIG-IP® Access Policy Manager
Integration Handbook
Document Version 1.1 | Released | July 11, 2012
Page 2

ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 2
External Use | July 12, 2012 | © 2012 ActivIdentity
Table of Contents
Table of Contents ....................................................................................................................................................... 2
1.0 Introduction ....................................................................................................................................................... 3
1.1 Scope of Document .................................................................................................................................... 3
1.2 Prerequisites .............................................................................................................................................. 3
2.0 BIG-IP APM Configuration ................................................................................................................................ 4
2.1 Procedure 1: Create New Radius Server Instance .................................................................................... 4
2.2 Procedure 2: Access Policy Manager Configuration .................................................................................. 6
2.3 Procedure 3: Customization ..................................................................................................................... 12
2.3.1 Adding Images and the Web Token Applet with the Image Browser .............................................. 12
2.3.2 Personalizing Page Appearance ..................................................................................................... 16
3.0 ActivIdentity 4TRESS AAA Configuration ....................................................................................................... 19
3.1 Procedure 1: Configure F5 Gate .............................................................................................................. 19
3.2 Procedure 2: Assigning Group(s) to the F5 Gate ..................................................................................... 21
4.0 Configure for Soft Token Activation ................................................................................................................ 22
4.1 Procedure 1: Enable Soft Token Activation ............................................................................................. 22
4.2 Procedure 2: Configure Soft Token Activation Portal .............................................................................. 23
5.0 Sample Authentication Using Web Soft Token Authentication ....................................................................... 26
5.1 Prerequisite: User Enrolls Web Token and Computer ............................................................................. 26
5.2 Authenticating with Web Soft Token Launched in the Sign-In Page ....................................................... 28
Page 3

ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 3
External Use | July 12, 2012 | © 2012 ActivIdentity
Note: Using F5 double authentication (an LDAP password plus a one-time password) is optional. You
1.0 Introduction
The F5® Networks BIG-IP
®
Access Policy Manager (APM) is a software component of the BIG-IP hardware
platform that provides users with secured connections to specific Web applications or the entire corporate
network. By leveraging standard Web browsers and security technology, the APM enables your corporation or
organization to provide users access to various internal resources easily and cost-effectively, with no special
software or configuration on user systems.
The ActivIdentity solutions that work with F5 incorporate SSL VPN solutions with versatile, strong authentication
that is flexible, scalable, and simple to manage. ActivIdentity offers two solutions:
• ActivIdentity® 4TRESS AAA Server for Remote Access—Addresses the security risks associated
with a mobile workforce remotely accessing systems and data.
• ActivIdentity 4TRESS Authentication Server (AS)—Offers support for multiple authentication methods
that are useful for diverse audiences across a variety of service channels (SAML, Radius, etc.),
including user name and password, mobile and PC soft tokens, one-time passwords, and transparent
Web soft tokens.
1.1 Scope of Document
This document explains how to set up ActivIdentity 4TRESS AAA Web token authentication with the F5 APM. Use
this handbook to enable authentication via a Web soft token for use with an SSL-protected F5 VPN.
1.2 Prerequisites
• The ActivIdentity 4TRESS AAA Server is up-to-date (v6.7) with LDAP users and groups already
configured.
• F5 BIG-IP APM version 11.1.x installed and configured.
• The Web soft token is configured to work with or without a PIN.
• Users have static LDAP passwords for access to the Self Help Desk to enroll Web tokens.
• The F5 login page has been customized (illustrated in this handbook).
can configure the sign-in page so that users use a static LDAP passwords instead of the Web soft
token PIN.
Page 4
ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 4
External Use | July 12, 2012 | © 2012 ActivIdentity
2.0 BIG-IP APM Configuration
This chapter describes how to manage F5 APM. When a user signs into an F5 APM appliance, The F5 appliance
forwards the user’s credentials to this authentication server to verify the user’s identity. You will create an
authentication server:
An ActivIdentity 4TRESS AAA RADIUS Server to validate the user’s one time password generated by a Web
token.
2.1 Procedure 1: Create New Radius Server Instance
When using an external RADIUS server to authenticate F5 users, you must configure the server to recognize the
F5 as a client and specify a shared secret for the RADIUS server to use to authenticate the client request. To
configure a connection to the RADIUS server on F5 APM appliance, perform the following steps.
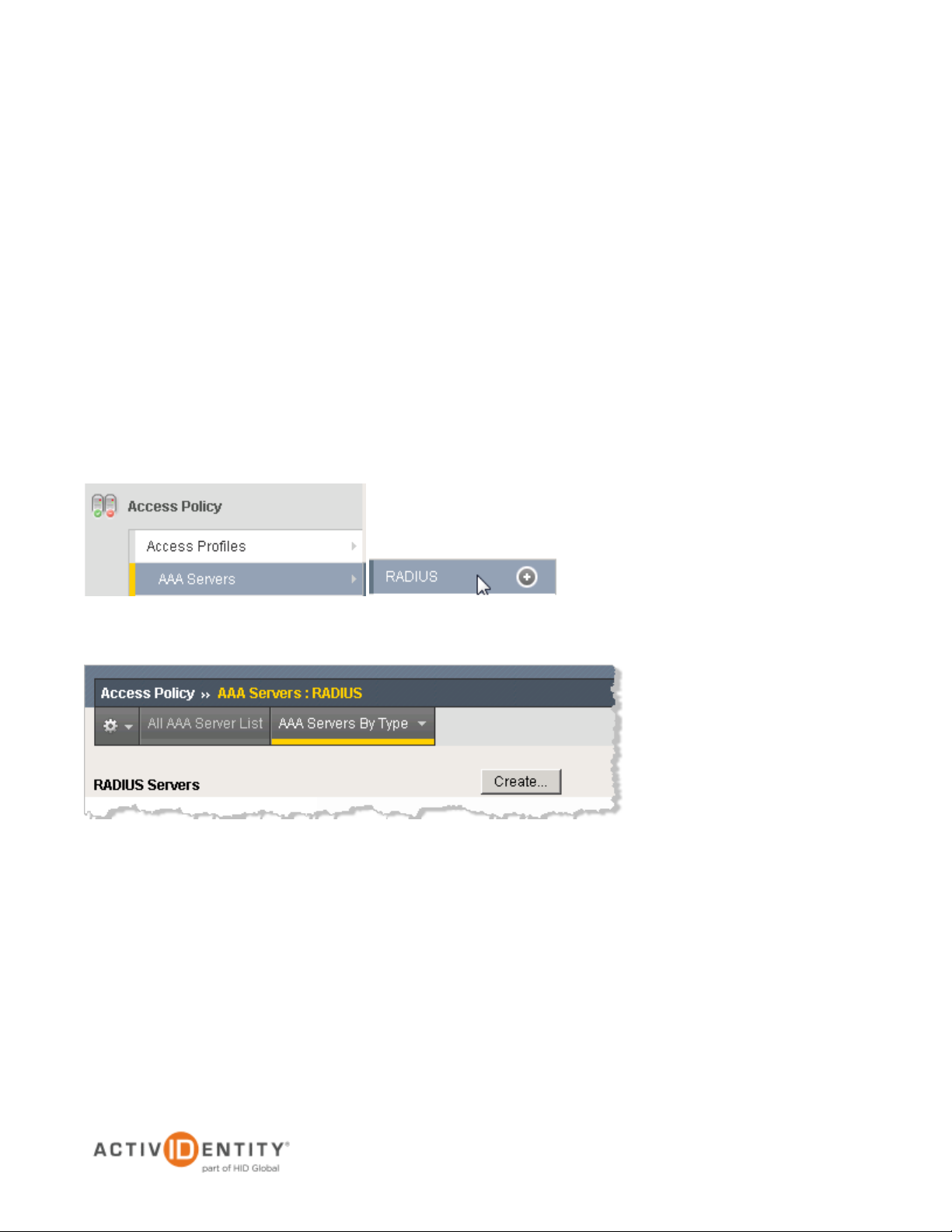
To define the RADIUS Server instance, perform the following steps.
1. On the main tab of the navigation pane, expand Access Policy, and then click AAA Servers.
2. Click the plus sign next to RADIUS.
3. Click Create.
Page 5
ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 5
External Use | July 12, 2012 | © 2012 ActivIdentity
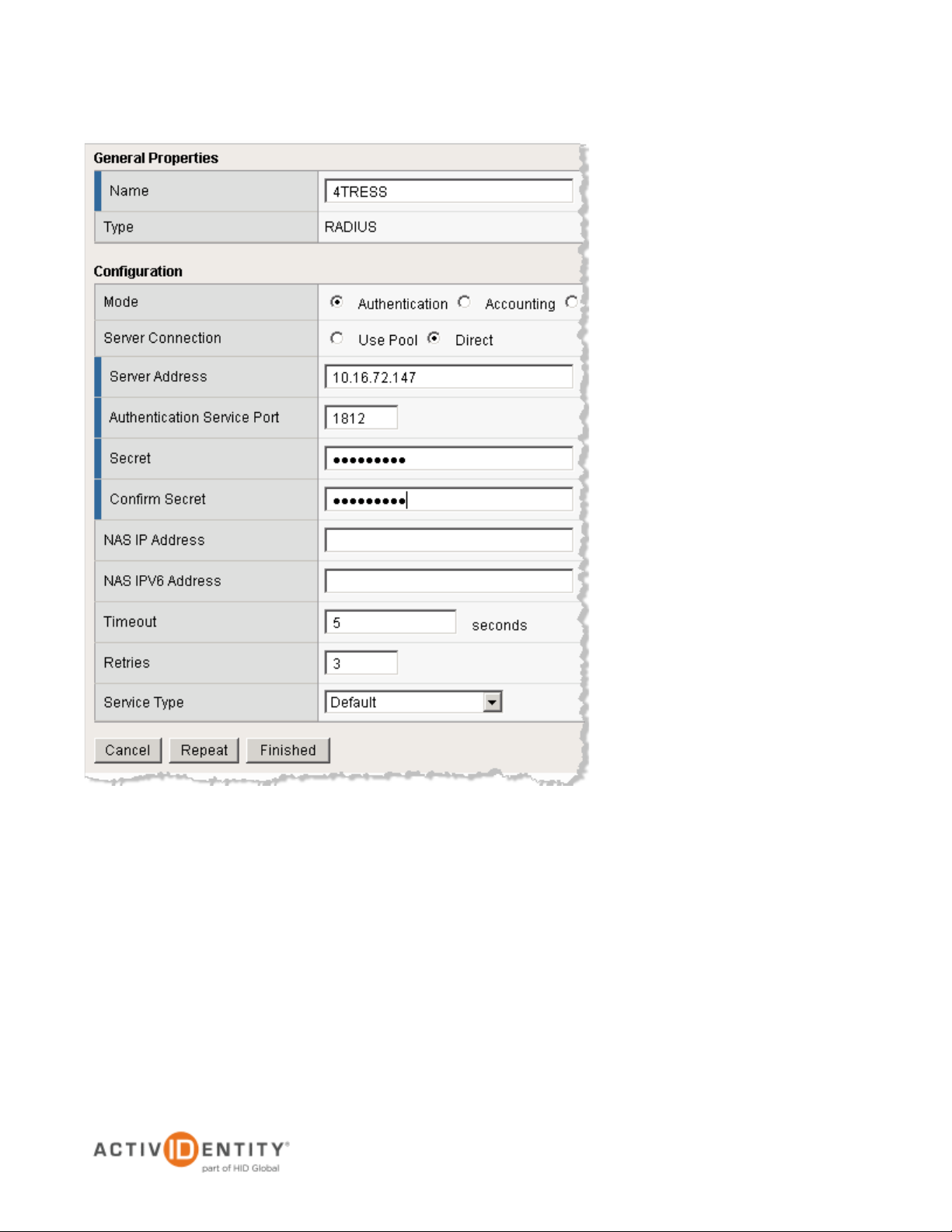
• Specify the Name of your RADIUS server.
• Select the Mode Authentication
• Specify the Server Address (IP of your RADIUS server).
• Specify the Authentication Service Port (the port for your RADIUS server).
• Enter and confirm the shared-secret for your RADIUS server.
• Accept all other default settings.
4. Click Finished.
Page 6
ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 6
External Use | July 12, 2012 | © 2012 ActivIdentity
2.2 Procedure 2: Access Policy Manager Configuration
With the APM wizards, you can quickly configure any of the three access types with a simple working
configuration. After you configure a connection with the wizard, you can go back and edit the configuration to
further customize the access policy.
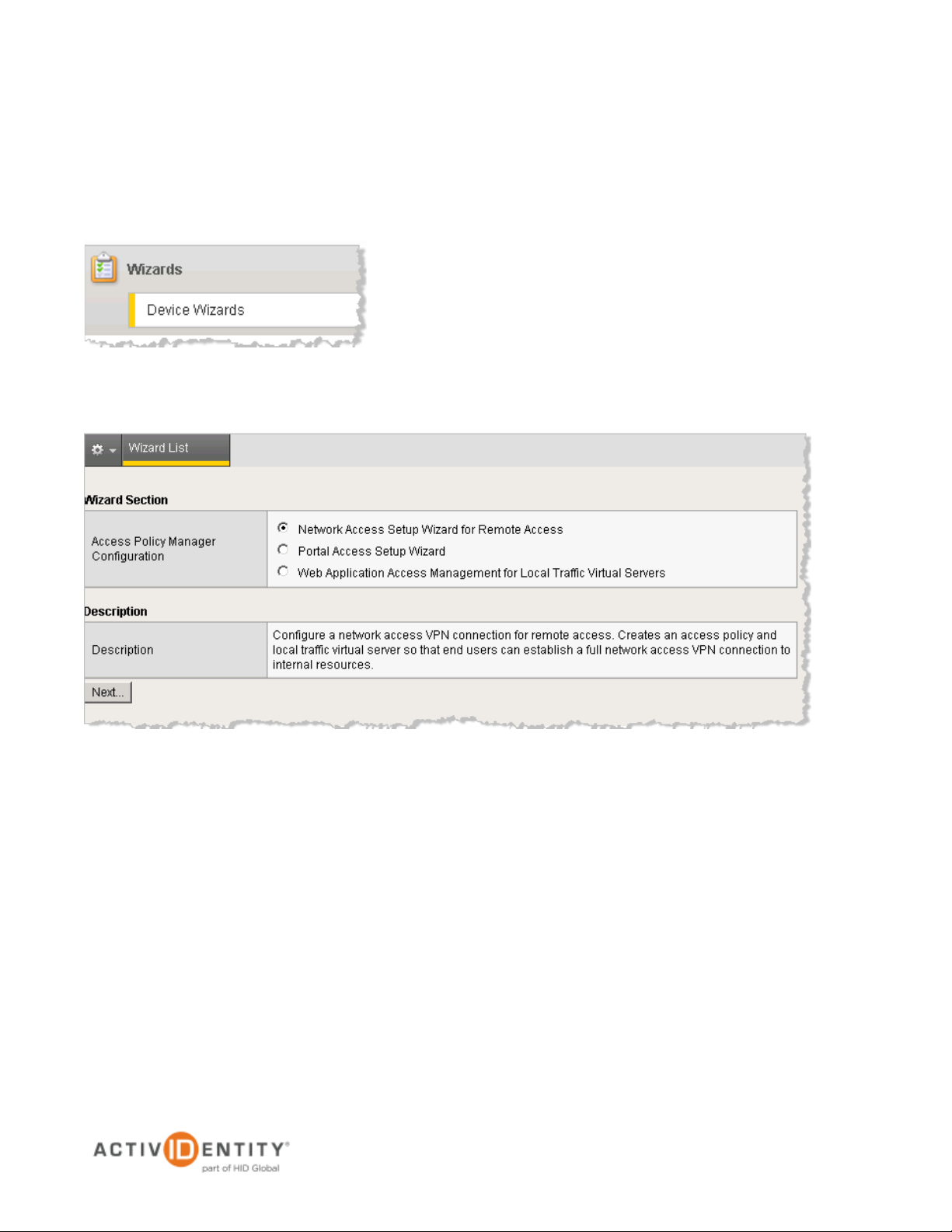
1. To access APM Wizards, in the navigation pane, expand Templates and Wizards, and then click Device
Wizards.
This wizard configures a working VPN connection. Typically, this allows users outside your network to
connect to specified networks and use their applications and network sites as if they are physically on the
network.
2. Select the Network Access Setup Wizard for Remote Access option, and then click Next.
Page 7
ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 7
External Use | July 12, 2012 | © 2012 ActivIdentity
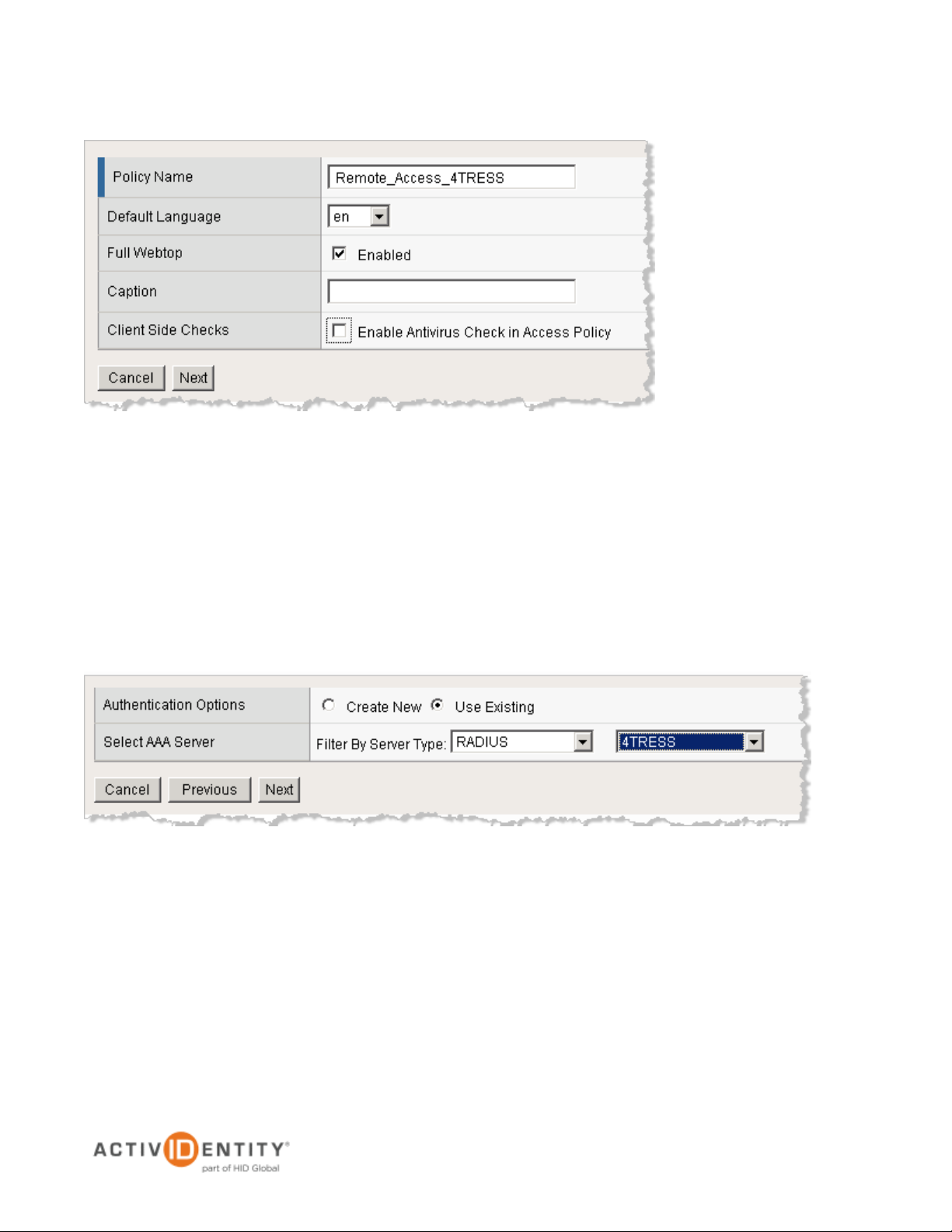
• Specify the Policy Name for the access policy to be created.
The Policy Name specifies the name of the access policy to be created, and is used as the naming
prefix for other objects configured with the access policy. Later, when you look for items created with
the wizard, they are named with this prefix.
• Accept the default language (English), or change it, if required.
• Select the Full Webtop ‘Enabled’ option.
• Deselect the Client Side Checks ‘Enable Antivirus Check in Access Policy option.(At a later
time, you can refine this client-side check to verify a specific antivirus product.)
3. Click Next.
4. For Authentication Options, select Use Existing.
5. For Select AAA Server, specify the 4TRESS server that you previously created.
6. Click Next.
Page 8
ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 8
External Use | July 12, 2012 | © 2012 ActivIdentity
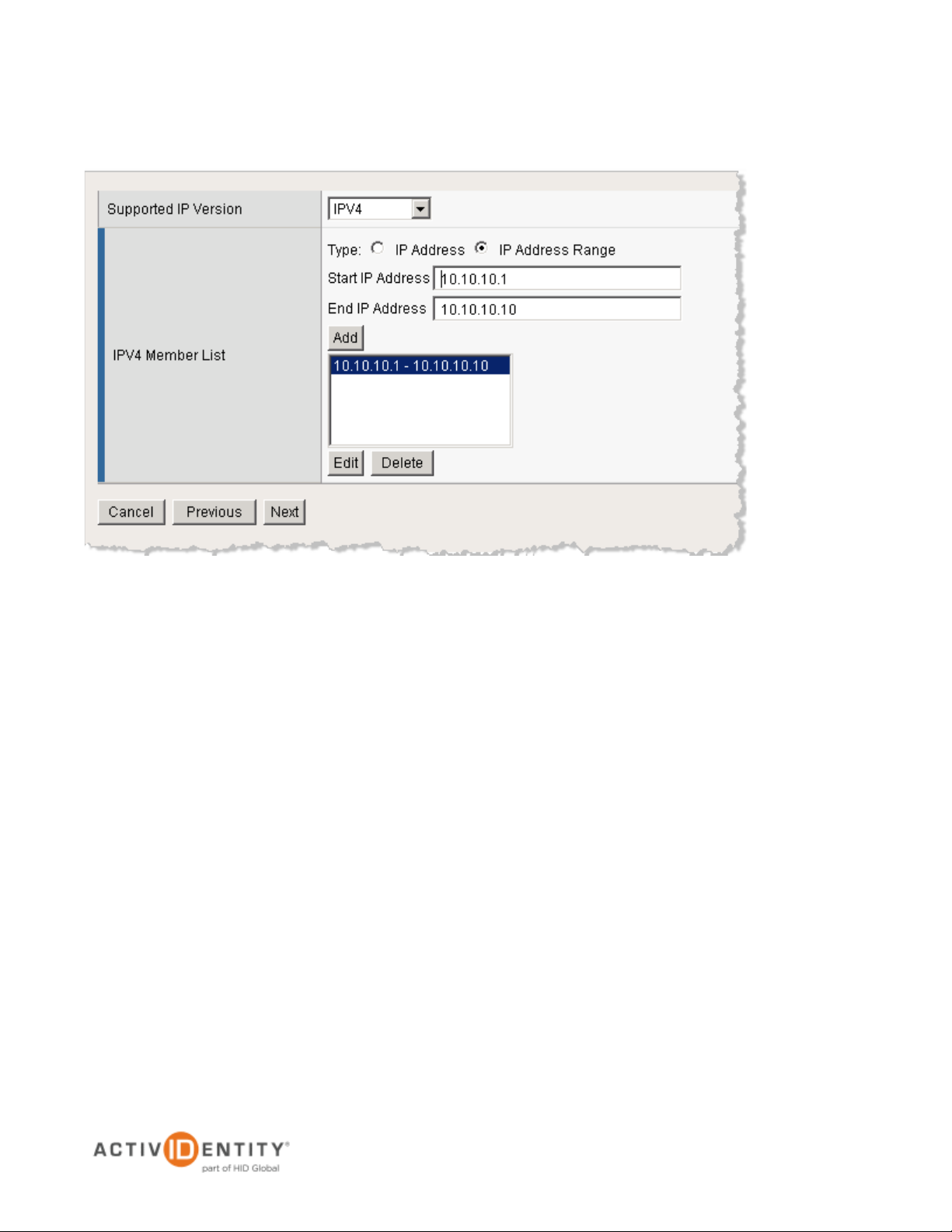
Lease pools are a configuration requirement for network access connections. Each connection is assigned an
IP address from the lease pool. You must configure a lease pool with as many IP addresses as required for
the number of connected users you expect to host.
• From the drop-down list, specify the Supported IP Version IPv4.
• Specify your Member List (either IP Address or IP Address Range).
• Click Add one time to specify an IP range, and click Add any time you specify a different IP
address.
7. Click Next.
Page 9
ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 9
External Use | July 12, 2012 | © 2012 ActivIdentity
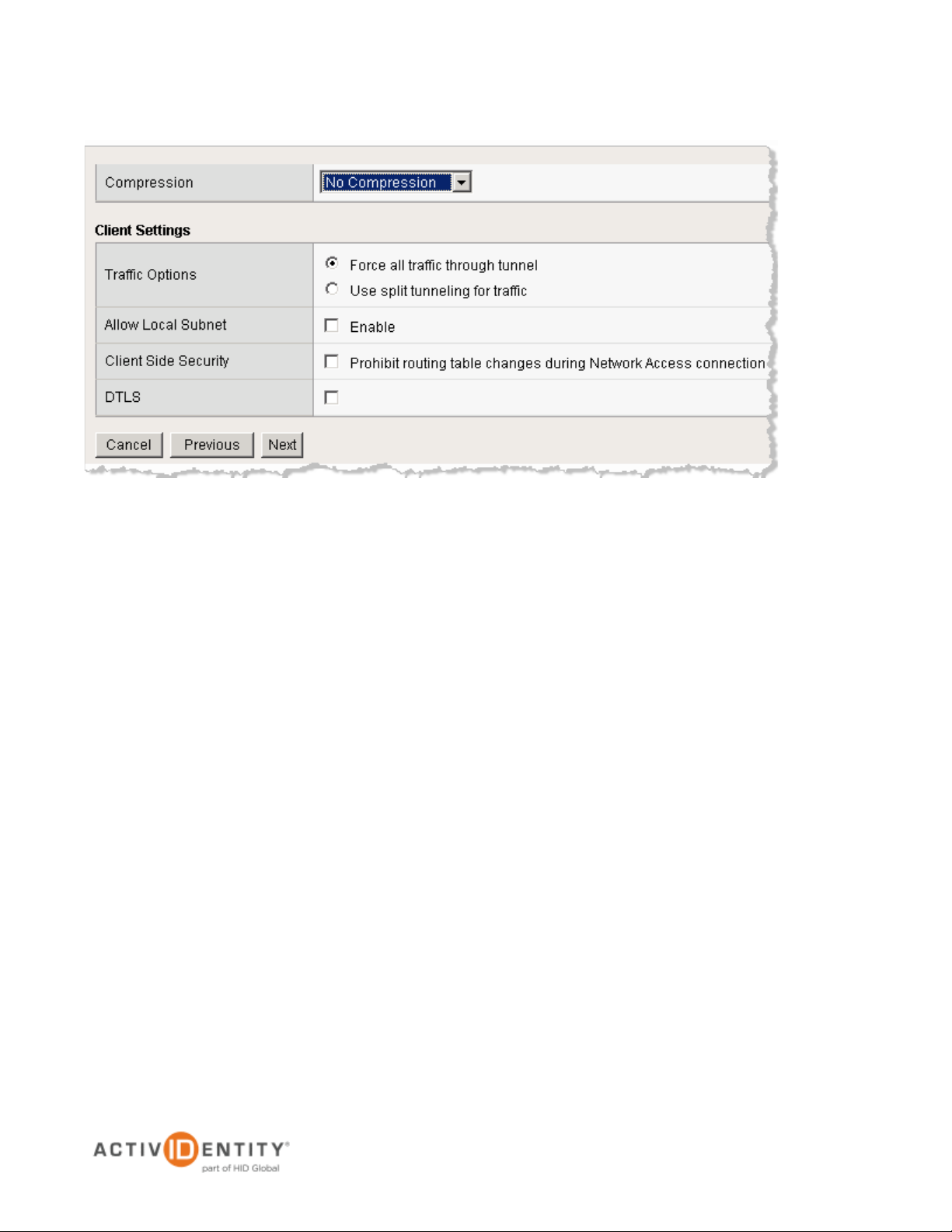
8. Specify the desired Traffic Options. (If you select the option to use split tunneling, then only network traffic
that you specify will go through the network access connection.
9. Click Next.
Page 10

ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 10
External Use | July 12, 2012 | © 2012 ActivIdentity
DNS hosts for network access are required for your users to have functioning name resolution and Windows®
networking on your internal network.
10. At a minimum, specify an IPV4 Primary Name Server. If you are using Microsoft® networking features on
your network, then specify a Primary WINS Server.
11. Click Next.
12. For Virtual Server IP Address, specify a host name.
In most cases, you should not specify a network when creating this virtual server. Enable the Redirect Server
to be created. This eliminates connection issues that users encounter when they do not type https before the
virtual server host name.
Page 11

ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 11
External Use | July 12, 2012 | © 2012 ActivIdentity
13. Click Next.
When you review the configuration, if you need to, then use the Previous and Next buttons to edit the
configuration before you click Finished. .
14. After reviewing and approving your settings, click Next.
When you are finished, you can still edit any setting associated with the access profile from the Access Profile
page (navigate to Access Policy > Access Profiles > name of access profile). Also, you can edit the
virtual server on the Virtual Server page (navigate to Local Traffic > Virtual Servers > name of virtual
server).
15. At the bottom of the page, click Finished.
The system creates and applies network access objects.
Page 12

ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 12
External Use | July 12, 2012 | © 2012 ActivIdentity
2.3 Procedure 3: Customization
The APM provides a Web-based Configuration utility. The Configuration utility includes tools for managing the
Access Policy Manager, configuring secure access, creating and assigning resources, certificate generation and
installation, and customization of the remote client user interface.
2.3.1 Adding Images and the Web Token Applet with the Image Browser
Reminder: You must have contacted your ActivIdentity representative to have appropriate images sent to you.
First, you will add images and the Web token applet to the APM using the image browser. Then you can select
and use these images using the Customization tool.
1. On the Main tab, navigate to Access Policy > Customization. The Customization tool appears, in the basic
customization view.
Page 13

ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 13
External Use | July 12, 2012 | © 2012 ActivIdentity
2. From the View drop-down list, click Advanced. The Customization tool switches to the Advanced (tree) view.
3. On the top pane of the Customization tool, click Image Browser. The image browser opens in a new window.
4. From the Filter Images drop-down list, select User Uploaded Images.
5. To add ActivIdentity images and the web token applet, click Add Image (located to the right of the page on
the same line as the Filter Images drop-down list.
6. Select the image, and then double-click to open it. On the standard Windows pop-up dialog, click Open to
load the image and save it.
Page 14

ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 14
External Use | July 12, 2012 | © 2012 ActivIdentity
7. From the View drop-down list, click Advanced, and then expand Customization Settings.
8. Expand Access Profiles, and then navigate to access_profile_name > Access Policy > Logon Pages >
Logon Page > Advanced Customization.
Page 15

ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 15
External Use | July 12, 2012 | © 2012 ActivIdentity
9. For image00 (the webtoken.jar file), click the icon to the right. The Replace button appears.
10. Click Replace. The following dialog is displayed.
11. Select the Webtoken.jar file, and then click Change.
12. For Image01 (the Web token.gif file), repeat steps 9, 10, and 11.
13. For Image02 (the ailogo.png file), repeat steps 9, 10, and 11.
Page 16

ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 16
External Use | July 12, 2012 | © 2012 ActivIdentity
When you have finished uploading the files, you will see them listed in the Value column, as illustrated above.
2.3.2 Personalizing Page Appearance
1. On the main tab, navigate to Access Policy > Customization. The Customization Tool appears.
2. From the View drop-down list, click Advanced, and then expand Customization Settings.
Page 17

ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 17
External Use | July 12, 2012 | © 2012 ActivIdentity
3. From the Form Factor drop-down list at the top of the page, click Full/Mobile Browser.
4. Select the Branding tab.
5. Expand Customization Settings and navigate to Access Profiles > access_profile_name > Access
Policy > Logon Pages > logon_page_name.
6. Customize the page with the sample obtained by your ActivIdentity technical representative.
Page 18

ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 18
External Use | July 12, 2012 | © 2012 ActivIdentity
7. After you customize settings, click the Save icon at the top of the Customization Tool. The access policy login
page will reflect your changes, as illustrated next.
8. When you are finished customizing your configuration, apply your access policy. Click Apply Access Policy
near the top of the page.
Page 19

ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 19
External Use | July 12, 2012 | © 2012 ActivIdentity
3.0 ActivIdentity 4TRESS AAA Configuration
This chapter describes how to configure the ActivIdentity 4TRESS AAA Authentication Server.
3.1 Procedure 1: Configure F5 Gate
A gate for the ActivIdentity 4TRESS AAA Server is a group of Network Access Servers (NAS) that is used to
simplify administration. For configuration details, refer to ActivIdentity 4TRESS AAA Server technical
documentation.
1. In the tree in the left pane of the Administration Console, expand the Servers line.
2. Right-click on the server to which you want to add a gate, and then click New Gate.
3. Enter a Gate name (can be any string).
4. Select the RADIUS option.
5. Use the Authorized IP addresses and host names section to specify filter(s) for the gate.
6. Click Add, and then click OK.
Page 20

ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 20
External Use | July 12, 2012 | © 2012 ActivIdentity
7. The ActivIdentity 4TRESS AAA Server uses the RADIUS shared secret to encrypt data between F5 and the
AAA authentication server. Click Shared Secret, and then modify the appropriate shared secret for your
system.
8. Click OK.
Page 21

ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 21
External Use | July 12, 2012 | © 2012 ActivIdentity
3.2 Procedure 2: Assigning Group(s) to the F5 Gate
Remember that you must have user groups created and the corresponding LDAP configured. For details, refer to
the ActivIdentity 4TRESS AAA Administration Guide.
1. To assign groups to the F5 Gate, in the tree in the left pane, select the group that you want to assign to the
gate.
2. Use the Group / Gate Assignments section of the page to specify gate(s) for the group’s users to utilize in
order to access a protected resource.
3. Click Add.
4. Select the Gate, the AZ profile. and the AC profile.
5. Click OK.
Page 22

ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 22
External Use | July 12, 2012 | © 2012 ActivIdentity
4.0 Configure for Soft Token Activation
4.1 Procedure 1: Enable Soft Token Activation
1. Launch the ActivIdentity 4TRESS AAA Server Administration Console and log in.
2. In the pane to the left, select Groups -> All Users.
3. Select the option, Allow Soft Token activation (for the corresponding group).
4. Click Save (not illustrated), and then export the changes to the AAA Server(s).
Page 23

ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 23
External Use | July 12, 2012 | © 2012 ActivIdentity
4.2 Procedure 2: Configure Soft Token Activation Portal
1. Launch the Web Help Desk Portal.
2. Select the Login type option, static.
3. Enter your Login and Password, and then click Login.
Page 24

ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 24
External Use | July 12, 2012 | © 2012 ActivIdentity
4. Select the Configuration tab.
• Initial PIN—Set the PIN.
• In the User Search method policy section, select By Groups or queries.
• In the Device Management section, set the following options and parameters.
• To activate the device assignment and unassignment functions of the Web Help Desk, select the
option, Enable device assignment functions.
• Select the option, Show initial PIN….
• To assign the same token to more than one user, select the option, Allow assign already
assigned tokens.
• To assign soft tokens, enter the Engine Soft Token init String for each type of soft token
required.
• Enter a string in the Engine Web Token init String field.
Note: For more information about the init strings, refer to the ActivIdentity 4TRESS
AAA Server Soft Token Solution Guide.
• For Max number of soft tokens per user, set the maximum number of soft tokens that each
user can be assigned.
Page 25

ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 25
External Use | July 12, 2012 | © 2012 ActivIdentity
For PIN options, apply the following:
PIN = 1 (Enforced). Soft Token application PIN enforcement policy.
PIN = 0 (No PIN)
Note: Depending on the activation code, a soft token forces the PIN.
It’s important to select an authentication policy (LDAP password at a minimum). By default, none are
selected.
5. In the Selfdesk portal self binding policy section, select the following options:
• To activate device self assignment functions, select Enable initial self binding.
• To activate additional device self assignment functions, select Enable self binding on
additional device. For this setting to work, you must make sure that the LDAP attribute mapped
to the device serial numbers is capable of storing multiple values.
Page 26

ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 26
External Use | July 12, 2012 | © 2012 ActivIdentity
5.0 Sample Authentication Using Web Soft Token Authentication
5.1 Prerequisite: User Enrolls Web Token and Computer
1. The user launches the Self Help Desk to enroll a Web token and computer.
2. When prompted, the user selects the LDAP password option, and then enters a username.
3. The user clicks Activate an additional device.
Page 27

ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 27
External Use | July 12, 2012 | © 2012 ActivIdentity
4. The user clicks Web Token.
5. The user enters and confirms a PIN and enters a Description (the use has to enter the PIN only if the system
is configured to ask for it.) A confirmation is displayed.
Now the user can use the Web token to access an F5 APM.
Page 28

ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 28
External Use | July 12, 2012 | © 2012 ActivIdentity
5.2 Authenticating with Web Soft Token Launched in the Sign-In Page
Important Notes:
• You must have customized the Sign-In Page to launch the Web token as an HTML page. To receive
a sample page, please contact your ActivIdentity technical representative.
• A user must have activated a Web soft token on his/her computer.
• You can configure to use a Web token with a PIN or without a PIN.
• You can use an LDAP password to replace the PIN or to complement it (depending on F5
configuration).
For details on how authenticating with a Web soft token works, please refer to 4TRESS AAA documentation.
Page 29

ActivIdentity 4TRESS AAA Web Tokens and F5 APM | Integration Handbook
P 29
External Use | July 12, 2012 | © 2012 ActivIdentity
Legal Disclaimer
Americas +1 510.574.0100
US Federal +1 571.522.1000
Europe +33 (0) 1.42.04.84.00
Asia Pacific +61 (0) 2.6208.4888
Email info@actividentity.com
Web www.actividentity.com
ActivIdentity, the ActivIdentity (logo), and/or other ActivIdentity products or marks referenced
herein are either registered trademarks or trademarks of HID Global Corporation in the United
States and/or other countries. The absence of a mark, product, service name or logo from this
list does not constitute a waiver of the trademark or other intellectual property rights concerning
that name or logo. F5 and the F5 logo are registered trademarks of F5, Inc. in the United States
and other countries.The names of other third-party companies, trademarks, trade names,
service marks, images and/or products that happened to be mentioned herein are trademarks
of their respective owners. Any rights not expressly granted herein are reserved.
 Loading...
Loading...