Grandstream Networks UCM Series, UCM6510, UCM6102, UCM6202, UCM6204 Security Manual
...
Grandstream Networks, Inc.
UCM series IP PBX
Security Manual

P a g e | 1
UCM Security Manual
Table of Contents
OVERVIEW ..................................................................................................................... 4
WEB UI ACCESS ........................................................................................................... 5
UCM HTTP Server Access .................................................................................................................... 5
Protocol Type ......................................................................................................................................... 5
User Login .............................................................................................................................................. 6
Login Settings ........................................................................................................................................ 8
User Management Levels ...................................................................................................................... 9
EXTENSION SECURITY .............................................................................................. 11
SIP/IAX Password ................................................................................................................................ 11
Strategy of IP Access Control .............................................................................................................. 11
Example: Local Subnet Only ........................................................................................................ 11
SRTP .................................................................................................................................................... 14
TRUNK SECURITY ....................................................................................................... 15
Outbound Rule Permissions ................................................................................................................ 15
Privilege Level .............................................................................................................................. 15
Source Caller ID Filter .................................................................................................................. 16
Password protection ..................................................................................................................... 16
PIN Groups ................................................................................................................................... 17
IVR Dial Trunk ...................................................................................................................................... 19
Allow Guest Calls ................................................................................................................................. 20
TLS ............................................................................................................................... 21
FIREWALL .................................................................................................................... 23
Static Defense ...................................................................................................................................... 23
Static Defense Example: Blocking TCP Connection from a Specific Host ................................... 24
Static Defense Example: Blocking SSH Connection to UCM ...................................................... 25
Dynamic Defense ................................................................................................................................. 28

P a g e | 2
UCM Security Manual
Fail2ban ............................................................................................................................................... 28
AMI ................................................................................................................................ 31

P a g e | 3
UCM Security Manual
Table of Figures
Figure 1: UCM6202 Web UI Login ................................................................................................................ 6
Figure 2: Default Random Password ............................................................................................................ 7
Figure 3: Login Settings ................................................................................................................................ 8
Figure 4: Creating Custom Privilege Levels ................................................................................................ 10
Figure 5: Strategy – Local Subnet Only ...................................................................................................... 12
Figure 6: Registration Failed from Subnet Not Allowed for Registration .................................................... 13
Figure 7: Registration Successful from Allowed Subnet ............................................................................. 13
Figure 8: Enabling SRTP ............................................................................................................................ 14
Figure 9: Outbound Rule Permissions ........................................................................................................ 15
Figure 10: Source Caller ID Filter ............................................................................................................... 16
Figure 11: Password Protection .................................................................................................................. 17
Figure 12: Adding PIN Groups .................................................................................................................... 17
Figure 13: Outbound route with PIN group ................................................................................................. 18
Figure 15: IVR Dial Trunk ............................................................................................................................ 19
Figure 16: PBX SettingsSIP SettingsTCP/TLS .................................................................................... 21
Figure 17: Firewall Rule Custom Configuration .......................................................................................... 24
Figure 18: Static Defense Blocking Host 192.168.40.142 Using TCP Connection .................................... 24
Figure 19: Host blocked by UCM ................................................................................................................ 25
Figure 20: UCM SSH Access ...................................................................................................................... 26
Figure 21: Block SSH Connection .............................................................................................................. 27
Figure 22: Putty Setup for SSH Connection ............................................................................................... 27
Figure 23: SSH Connection Blocked by UCM ............................................................................................ 28
Figure 24: Fail2Ban Default Configuration .................................................................................................. 29
Figure 25: Asterisk Service Fail2Ban setting .............................................................................................. 30

P a g e | 4
UCM Security Manual
OVERVIEW
This document presents a summary of security concerns on UCM. It covers the security risks and related
configurations that users need to consider when deploying the UCM.
The following sections are covered in this document:
• Web UI access
Web UI is secured by user login and login timeout mechanism. Two-level user management is
configurable. Admin with limited access can be created by the default super administrator.
• Extension security
This includes SIP/IAX password for authentication, IP access control and SRTP.
• Trunk security
Trunk security is achieved mainly by setting the privilege level, configuring source caller ID filter to filter
out outbound call requests from unwanted source
• TLS
This is to secure the SIP signaling.
• Firewall mechanism
Three types of firewall mechanism can be configured to protect UCM against malicious attacks: Static
Defense, Dynamic Defense (UCM6510 and UCM6102/UCM6202/UCM6204/UCM6208 only) and
Fail2ban.
• AMI
Using AMI feature comes with security concerns for UCM administrators to consider.
This document is subject to change without notice. The latest electronic version of this document is available
for download here:
http://www.grandstream.com/support
Reproduction or transmittal of the entire or any part, in any form or by any means, electronic or print, for
any purpose without the express written permission of Grandstream Networks, Inc. is not permitted.
P a g e | 5
UCM Security Manual
WEB UI ACCESS
UCM HTTP Server Access
The UCM embedded web server responds to HTTP/HTTPS GET/POST requests. Embedded HTML pages
allow users to configure the device through a web browser such as Microsoft IE, Mozilla Firefox, Google
Chrome and etc. This is the most important tool to configure all the settings on the UCM. It’s also the
immediate interface for the administrator to access configurations, user status and all the system
information. Therefore, it’s crucial to understand that directly placing the UCM on public network could
expose the domain name / IP address of the UCM and pose serious security concerns.
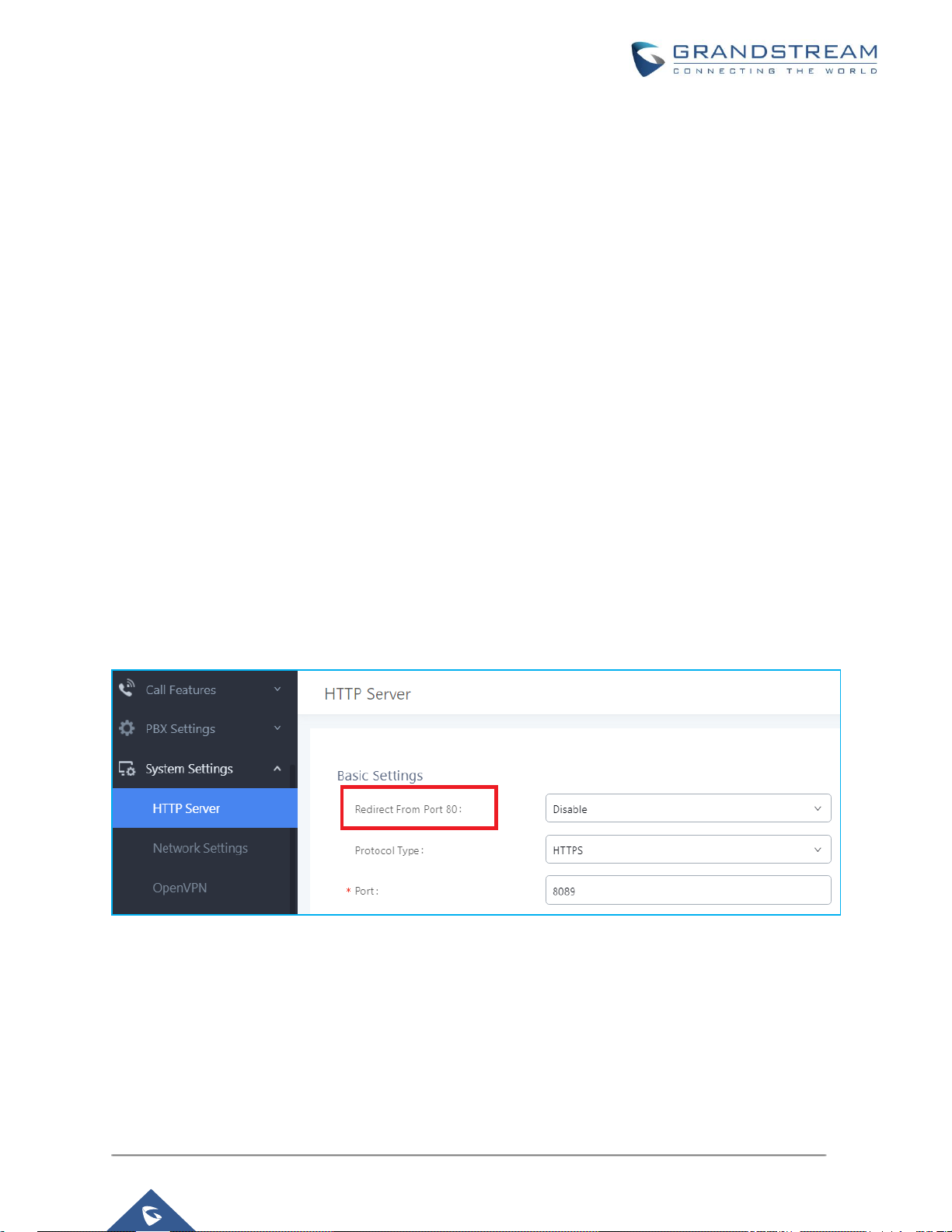
Protocol Type
HTTP and HTTPS web access are supported to access the UCM web UI. It can be configured under web
UISettingsHTTP Server. The protocol type is also the protocol used for zero config when the endpoint
device downloads the config file from the UCM. Therefore, it’s recommended to use HTTPS instead of
HTTP to secure the transactions and prevent unauthorized access.
Note also that by default we are using HTTP/HTTPS ports that are different from the well know ports 80
and 443.
It is recommended to disable the option “Redirect From Port 80”.
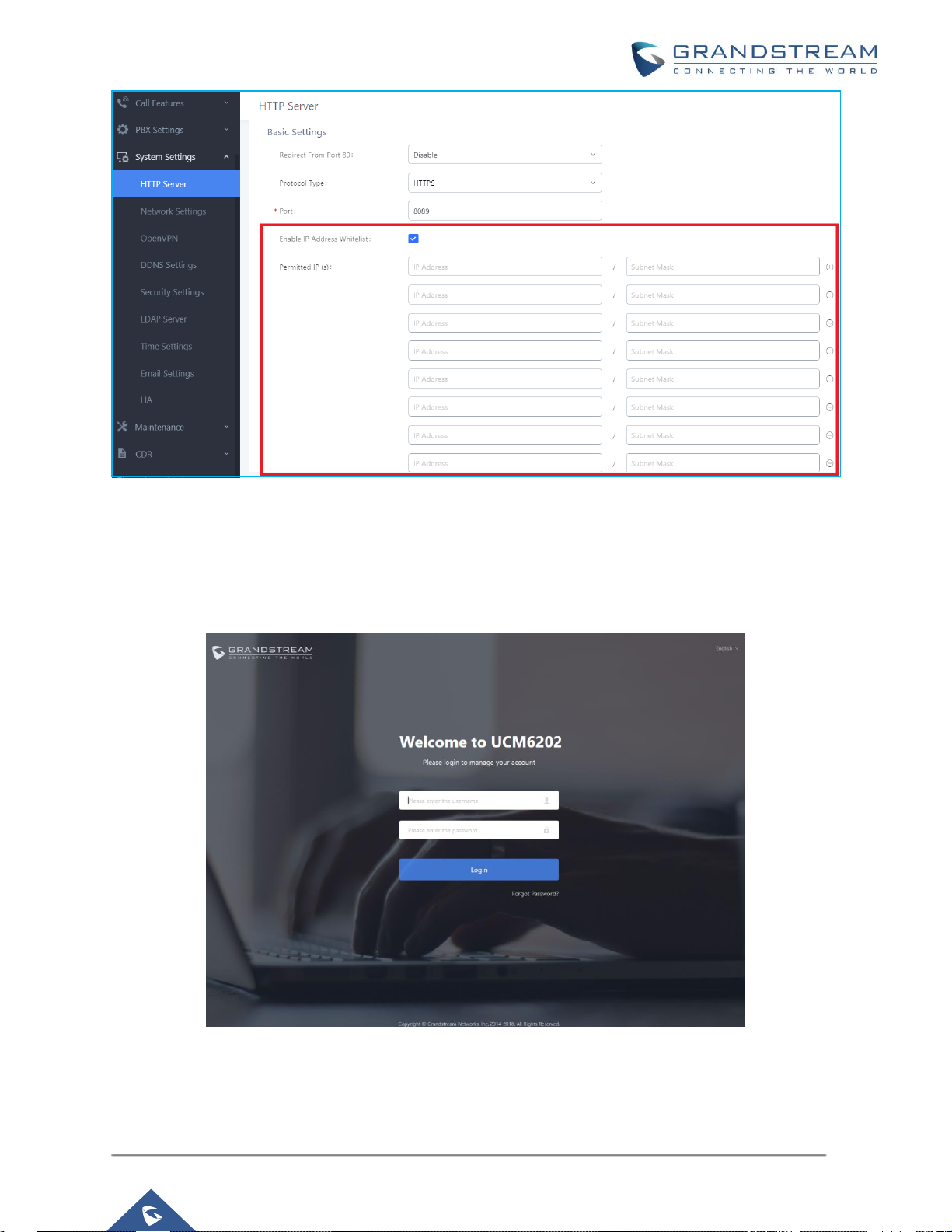
Finally, users have the option to specify a list of UP to 10 IP addresses which will be allowed to access the
UCM web GUI, otherwise the connection will be refused for any IP address not figuring in the white list.
To add IPs to the whitelist, go under menu web UISettingsHTTP Server:
• Enable the option “Enable IP Address Whitelist”
• Enter the permitted IP(s) by specifying both the address and the Subnet mask.
P a g e | 6
UCM Security Manual
User Login
UCM web UI access is restricted by user login. Username and password are required when logging in to
web UI.
Figure 1: UCM6202 Web UI Login
The factory default value of “Username” is “admin” while the default random password can be found on the
sticker at the back of the unit.

P a g e | 7
UCM Security Manual
Note: Units manufactured starting January 2017 have a unique random password printed on the sticker.
Older units and UCM6100 series have default password “admin”.
Figure 2: Default Random Password
It is highly recommended to change the default password after login for the first time.
To change the password for the default user “admin”, go to web GUISettingsChange Password page.
The new password has to be at least 4 characters. The maximum length of the password is 30 characters.
The minimum requirement for the login password is as below if “Enable Strong Password” (on web GUI
PBXInternal OptionsGeneral) is turned on:
• Must contain numeric digit.
• Must contain at least one lowercase alphabet, uppercase alphabet or special character.
Strong password with a combination of numbers, lowercase alphabet characters, uppercase characters
and special characters is always recommended to protect your login.

P a g e | 8
UCM Security Manual
Login Settings
An authenticated user of the UCM web UI may log in the system and then leave the active session on a
terminal unattended without intentionally logging-off from the system. An adversary with access to the
terminal could then have access to the UCM, meaning all the configuration and status information could be
exposed and changed intentionally or unintentionally.
UCM provides protection from such vulnerability using login timeout. After the user logs in the UCM web UI,
the user will be automatically logged out after certain timeout. This timeout value can be specified under
UCM web GUIMaintenanceChange InformationLogin Settings page. In the case that the user doesn’t
make any operation on web GUI within the timeout period, the user will be logged out automatically and the
web UI will be redirected to the login page, requiring password to access the web pages.
If the login timeout period is set to a short enough time, the chances of an adversary gaining access to an
unattended terminal are significantly reduced. However, the timeout period cannot be too short that an
authenticated user becomes annoyed by frequent automatic logouts during normal use. Therefore, users
shall set it to a value according to actual usage and situation. The default value of login timeout is 10
minutes.
Along with the login timeout feature, the UCM supports also user banning upon unsuccessful login attempts
with the possibility to configure the maximum number of allowed failed login attempts as well as settings
the ban period as shown on the below figure.
Figure 3: Login Settings

P a g e | 9
UCM Security Manual
User Management Levels
On UCM, Four privilege levels for web UI users are supported:
• Super Admin: high priority.
• Admin: low priority.
• Custom level: custom priority.
• Consumer: Low Priority
Super administrator can access all pages on UCM web UI, change configuration for all options and execute
all the operations, while normal administrator created by super administrator has limited access. Normal
administrator can access all pages on UCM web UI except the following:
• MaintenanceUpgrade
• MaintenanceBackup
• MaintenanceCleaner
• MaintenanceReset/Reboot
• SettingsUser ManagementOperation Log
A “Super Admin” user with username “admin” is innately configured in the UCM at the factory setting. It is
the only allowed “Super Admin” account and cannot be deleted and changed. This super administrator
could create, edit and delete new user accounts with lower privileges “Admin”, “Custom” and “Consumer”.
Super Admin also has the authority to view operations done by all the users in web
GUIMaintenanceOperation Log where normal users with lower privilege level “Admin” don’t have
access.
If there are more than one PBX administrator required to manage the UCM in your enterprise, it’s highly
recommended for the super administrator to create lower privilege administrators in order to manage the
UCM together, instead of handing out super administrator password to all the other users who may need
access the UCM web UI. The super administrator can also monitor the operation log to keep a record as
well as ensure no abnormal operations done on the PBX.
While In case the super admin wants to assign some users specific privileges, the custom privilege user
level can be helpful by giving him access to one or more of the following items:
▪ View Status Information
▪ Manage Conferences
▪ System Events
▪ CDR Reports
▪ CDR API
▪ Wakeup Service
 Loading...
Loading...