Page 1

FortiRecorder™ 2.4.2
Administration Guide
Page 2

FortiRecorder 2.4.2 Administration Guide
November 4, 2016
1st Edition
Copyright © 2016 Fortinet, Inc. All rights reserved. Fortinet®, FortiGate®, FortiCare® and
FortiGuard®, and certain other marks are registered trademarks of Fortinet, Inc., and other
Fortinet names herein may also be registered and/or common law trademarks of Fortinet. All
other product or company names may be trademarks of their respective owners. Performance
and other metrics contained herein were attained in internal lab tests under ideal conditions,
and actual performance and other results may vary. Network variables, different network
environments and other conditions may affect performance results. Nothing herein represents
any binding commitment by Fortinet, and Fortinet disclaims all warranties, whether express or
implied, except to the extent Fortinet enters a binding written contract, signed by Fortinet’s
General Counsel, with a purchaser that expressly warrants that the identified product will
perform according to certain expressly-identified performance metrics and, in such event, only
the specific performance metrics expressly identified in such binding written contract shall be
binding on Fortinet. For absolute clarity, any such warranty will be limited to performance in the
same ideal conditions as in Fortinet’s internal lab tests. Fortinet disclaims in full any covenants,
representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves
the right to change, modify, transfer, or otherwise revise this publication without notice, and the
most current version of the publication shall be applicable.
Technical Documentation http://help.fortinet.com
Knowledge Base http://kb.fortinet.com
Forums https://support.fortinet.com/forum
Customer Service & Support https://support.fortinet.com
Training Services http://training.fortinet.com
FortiGuard Threat Research & Response http://www.fortiguard.com
Document Feedback Email: techdocs@fortinet.com
Page 3

Table of contents
Key concepts .................................................................................................... 7
FortiRecorder NVR................................................................................................... 7
Camera support ....................................................................................................... 7
Deployment scenarios and camera discovery......................................................... 8
Local camera deployments................................................................................ 8
Same network deployments ........................................................................ 8
Routed network deployments...................................................................... 8
Private network vs office network................................................................ 8
Remote camera deployments............................................................................ 9
Video clips ............................................................................................................... 9
Performance guidelines ........................................................................................... 9
NVR performance .............................................................................................. 9
Number of supported cameras.................................................................... 9
General performance factors ..................................................................... 10
Variable versus constant bit rate................................................................ 10
Bandwidth per camera or live view............................................................ 10
Storage capacity ........................................................................................ 11
Client Performance .......................................................................................... 12
GUI and CLI ........................................................................................................... 13
NVR configuration .......................................................................................... 14
Connecting to FortiRecorder web UI..................................................................... 14
Connecting to FortiRecorder CLI........................................................................... 15
Basic NVR configuration........................................................................................ 17
Setting the “admin” account password ........................................................... 17
Configuring the network settings..................................................................... 18
Configuring the DHCP server .......................................................................... 23
Setting the system time ................................................................................... 26
Configuring schedules ........................................................................................... 28
Setting the sunrise and sunset time................................................................. 29
Advanced/optional NVR configuration .................................................................. 29
Configuring system timeout, ports, and public access ................................... 29
About FortiRecorder logical interfaces ............................................................ 30
VLAN subinterfaces.................................................................................... 30
Redundant interfaces................................................................................. 31
Aggregate interfaces.................................................................................. 31
Loopback interfaces .................................................................................. 31
Configuring FortiRecorder system appearance............................................... 31
Configuring logging ......................................................................................... 31
Alert email ........................................................................................................ 34
Page 3
Page 4

Camera settings ............................................................................................. 36
Camera configuration workflow............................................................................. 36
Configuring video profiles...................................................................................... 36
Configuring camera profiles................................................................................... 37
Camera groups ...................................................................................................... 39
Camera connection........................................................................................ 40
Camera discovery and DHCP service ................................................................... 40
Connecting FortiRecorder to the cameras ............................................................ 41
Configuring cameras.............................................................................................. 44
User management .......................................................................................... 53
User types.............................................................................................................. 53
User configuration workflow .................................................................................. 53
Configuring access profiles ................................................................................... 54
Configuring user profiles........................................................................................ 54
Configuring user accounts..................................................................................... 54
Configuring LDAP authentication .......................................................................... 60
Configuring RADIUS authentication ...................................................................... 66
Notifications.................................................................................................... 68
Notification configuration workflow ....................................................................... 68
Configuring FortiRecorder to send notification email ............................................ 68
Configuring FortiRecorder to send SMS messages .............................................. 70
Configuring cameras to send notifications ............................................................ 71
Video monitoring ............................................................................................ 73
Watching live video feeds ...................................................................................... 73
Video and image sharing ....................................................................................... 74
Watching recorded video clips .............................................................................. 77
Reviewing motion detection notifications.............................................................. 79
Video management ........................................................................................ 81
Local storage ......................................................................................................... 81
Configuring RAID levels ................................................................................... 81
Recommended HDD models and capacities................................................... 81
Adding a RAID disk .......................................................................................... 82
Replacing a RAID disk ..................................................................................... 82
Replacing all RAID disks .................................................................................. 83
External storage..................................................................................................... 84
System monitoring ......................................................................................... 86
The dashboard....................................................................................................... 86
SNMP traps & queries ........................................................................................... 86
Configuring an SNMP community ................................................................... 88
Configuring SNMP v3 users............................................................................. 90
MIB support ..................................................................................................... 91
Table of contents Page 4 FortiRecorder 2.4.2 Administration Guide
Page 5

Logging ................................................................................................................. 92
About logs........................................................................................................ 92
Log types ................................................................................................... 92
Log severity levels...................................................................................... 93
Viewing log messages ..................................................................................... 93
Displaying & sorting log columns & rows......................................................... 95
Downloading log messages............................................................................. 96
Deleting log files............................................................................................... 96
Searching logs ................................................................................................. 97
Event Monitor......................................................................................................... 98
Secure connections and certificates............................................................ 99
Supported cipher suites & protocol versions................................................... 99
Replacing the default certificate for the web UI............................................. 100
Generating a certificate signing request .................................................. 103
Uploading & selecting to use a certificate ............................................... 105
Uploading trusted CAs’ certificates ............................................................... 107
Example: Downloading the CA’s certificate from
Microsoft Windows 2003 Server............................................................ 108
Revoking certificates...................................................................................... 109
Revoking certificates by OCSP query...................................................... 109
Updating the firmware ................................................................................. 111
Installing NVR firmware........................................................................................ 111
Installing alternate firmware ........................................................................... 114
Booting from the alternate partition ............................................................... 115
Upgrading/downgrading the camera firmware.................................................... 116
Fine-tuning & best practices ....................................................................... 118
Hardening security............................................................................................... 118
Topology ........................................................................................................ 118
Administrator access ..................................................................................... 119
Operator access............................................................................................. 120
Patches .......................................................................................................... 120
Improving performance........................................................................................ 121
Video performance......................................................................................... 121
System performance...................................................................................... 121
Logging & alert performance ......................................................................... 122
Packet capture performance ......................................................................... 122
Regular backups.................................................................................................. 122
Restoring a previous configuration ................................................................ 124
Troubleshooting ........................................................................................... 125
Solutions by issue type........................................................................................ 125
Video viewing issues...................................................................................... 125
Live feed delay ......................................................................................... 126
Video not being sent to the NVR.............................................................. 126
Snapshot notification issues .......................................................................... 126
Table of contents Page 5 FortiRecorder 2.4.2 Administration Guide
Page 6

Login issues ................................................................................................... 127
When an administrator account cannot log in from a specific IP ............ 127
Remote authentication query failures ...................................................... 127
Resetting passwords ............................................................................... 127
Connectivity issues ........................................................................................ 127
Checking hardware connections ............................................................. 128
Bringing up network interfaces ................................................................ 128
Examining the ARP table ......................................................................... 129
Checking routing...................................................................................... 129
Facilitating discovery ............................................................................... 133
DHCP issues ............................................................................................ 133
Unauthorized DHCP clients or DHCP pool exhaustion...................... 134
Establishing IP sessions........................................................................... 134
Resolving IP address conflicts................................................................. 136
Packet capture......................................................................................... 137
Resource issues............................................................................................. 142
Data storage issues ....................................................................................... 143
Resetting the configuration.................................................................................. 143
Restoring firmware (“clean install”)...................................................................... 144
Questions and answers ............................................................................... 147
How to connect cameras to FortiRecorder for the first time ............................... 147
Scenario 1: Direct connection........................................................................ 147
Scenario 2: Connection with a third party DHCP server................................ 150
How to use recorded video clips ......................................................................... 151
How to use DIDO terminal connectors on FortiCam MB13 cameras.................. 154
Appendix A: Port numbers........................................................................... 157
Appendix B: Maximum values ..................................................................... 159
Index .............................................................................................................. 161
Table of contents Page 6 FortiRecorder 2.4.2 Administration Guide
Page 7
Key concepts
This chapter defines basic FortiRecorder concepts and terms.
If you are new to FortiRecorder, or new to digital video surveillance systems, this chapter can
help you to quickly understand how to use your FortiRecorder system.
• FortiRecorder NVR
• Camera support
• Deployment scenarios and camera discovery
• Video clips
• Performance guidelines
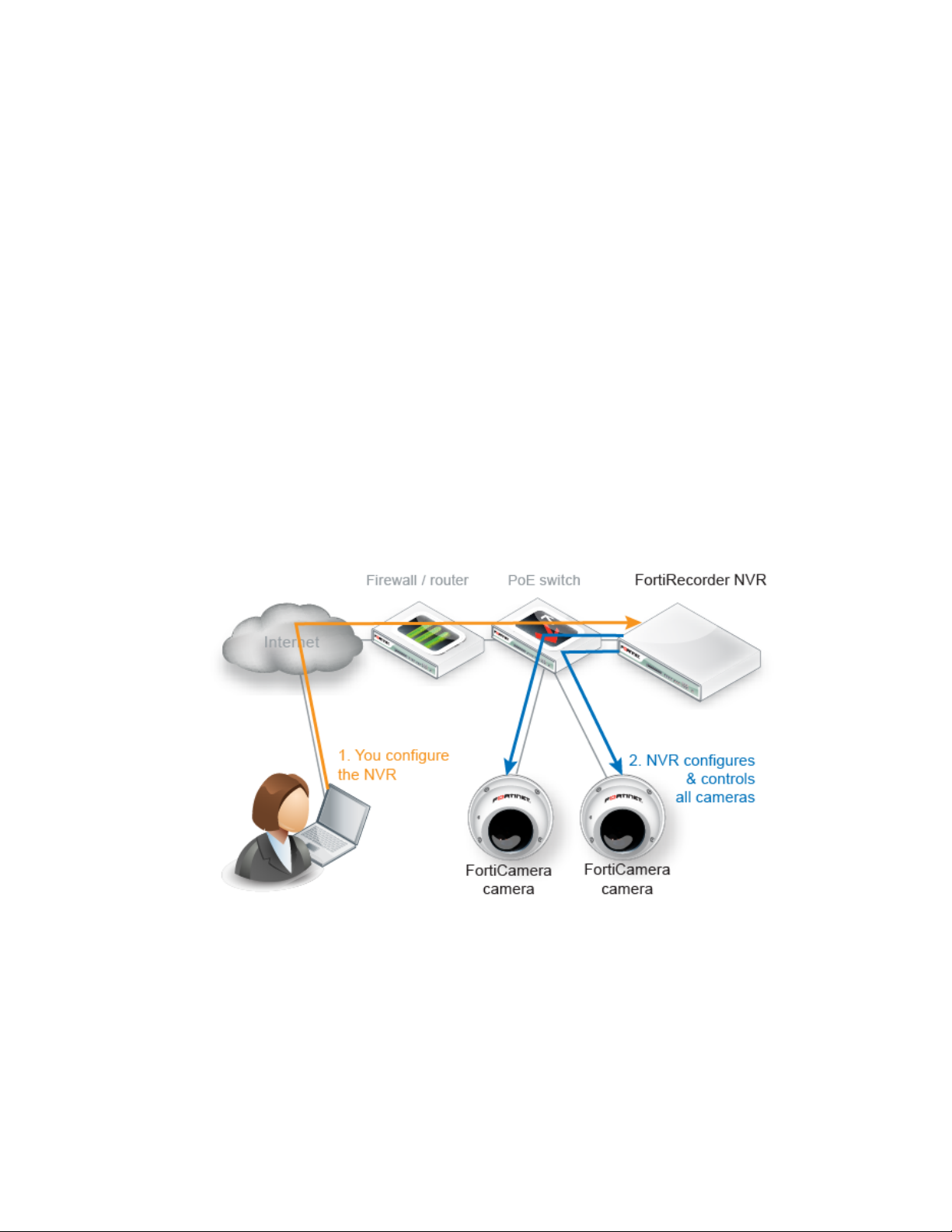
FortiRecorder NVR
The FortiRecorder network video recorder (NVR) provides central management for:
• configuring your cameras
• recording your video feeds
• viewing recordings and live video feeds
Camera support
The FortiRecorder NVR supports FortiCam series cameras from Fortinet and third-party
ONVIF-compliant cameras, although some of the third-party camera features may not be fully
supported. Therefore, you may want to configure those features through its built-in camera web
interface.
By default, every FortiRecorder or FortiRecorder-VM appliance supports one third-party
camera. If you want to connect more than one, you must purchase licenses from Fortinet. For
more information, please contact Fortinet or the resellers.
Page 7
Page 8
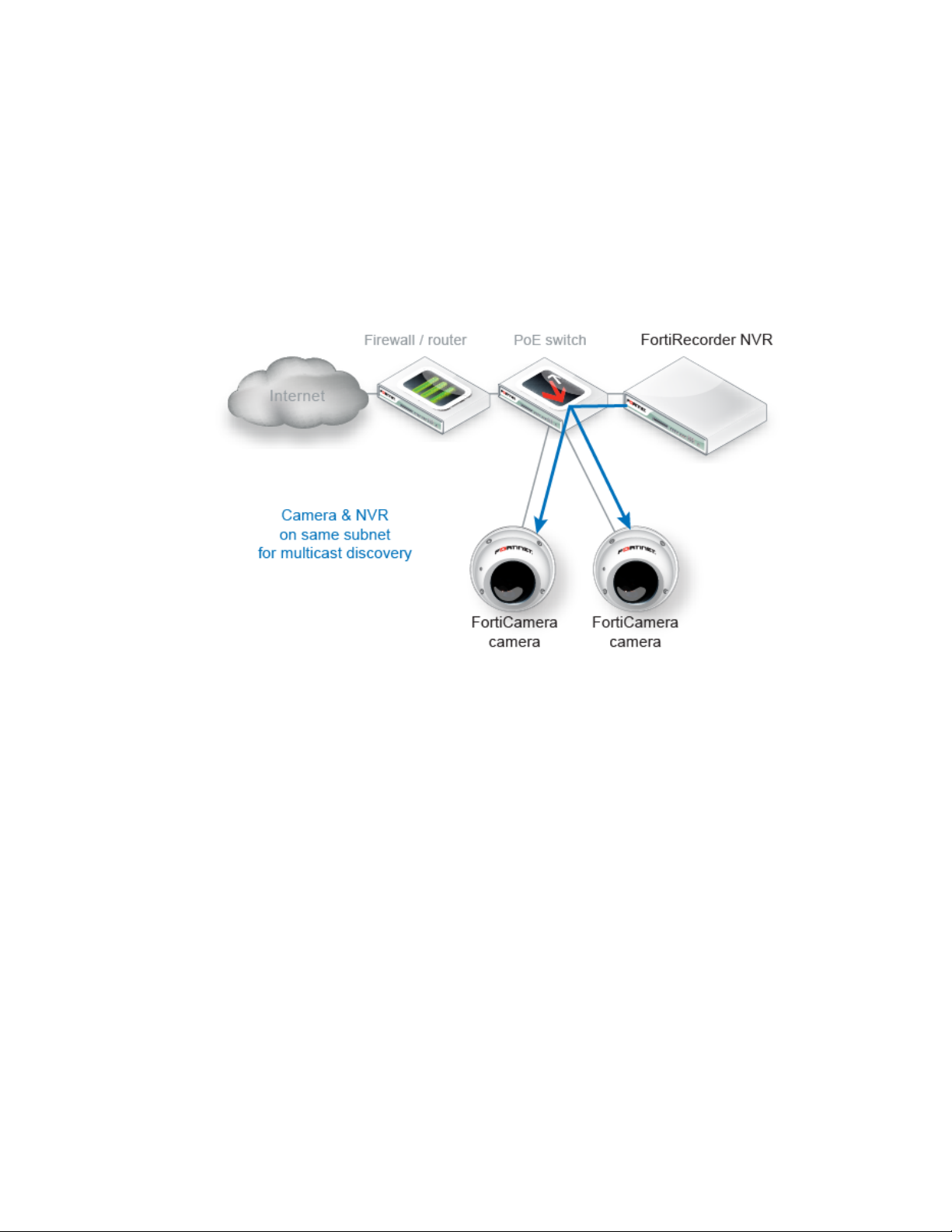
Deployment scenarios and camera discovery
Cameras are deployed in two basic scenarios: local to the NVR and remote to the NVR.
FortiCamera deployments can combine both scenarios.
Local camera deployments
Local cameras deployments have two specific scenarios:
• Cameras are installed on the same network as the NVR.
• Cameras are installed on a local network, but there are one or more routers between the
NVR and the cameras.
Same network deployments
Installing the cameras on the same subnet as the NVR is the easiest deployment scenario since
the NVR can automatically discover the cameras.
Routed network deployments
If there are routers between the cameras and the NVR, the routers must be configured to allow
mDNS multicast packets between the camera network and the NVR network in order for the
NVR to automatically discover the cameras. Once the cameras are discovered, you can leave
the address mode as DHCP or change it to static.
If the routers are not configured to pass the mDNS packets, the cameras can be configured
manually by selecting the static address mode on the camera configuration page.
Private network vs office network
You can install the NVR and cameras on your existing network, which saves your efforts and
costs. You can also install the system on a dedicated private network only reachable by the
Key concepts Page 8 FortiRecorder 2.4.2 Administration Guide
Page 9

Remote camera deployments
Video clips
NVR. Although this involves installing a new network and thus increasing the costs, there are
some advantages of using a private network:
• the video streams are protected.
• the cameras are protected because they cannot be reached from outside the network.
• easier to determine bandwidth requirements.
• better quality of service since bandwidth is known.
See also
• Facilitating discovery
Remote camera deployments refer to scenarios where there is a firewall between the NVR and
the cameras – i.e. camera discovery will not work and the cameras will likely have virtual IP
addresses on the firewall. The cameras are configured by selecting the VIP address mode on
the camera configuration page.
You can use FortiRecorder to:
• Manually record activities
• Continuously record activities by schedules
• Record sudden activities only (motion detection)
• Record audio activities (if the camera supports audio detection)
• Record on triggers from digital input (if the camera support DIDO)
• View live video
Motion detection will record a video clip up to about 40 seconds long each time the camera’s
sensor detects movement. In contrast, continuous video records for the entire duration of the
schedule, regardless of movement.
Performance guidelines
There are two components to consider when looking at FortiRecorder performance – the NVR
(FortiRecorder) and the Client computer with FortiRecorder Central or a browser. Overall
FortiRecorder performance is a combination of the video input (video compression, image
quality level, complexity of the scene, video resolution, frame rate per second, number of
cameras) and the video output (to the clients for live views and playback). The performance
bottleneck in a FortiCamera deployment will likely be the network bandwidth to and from
FortiRecorder and the CPU performance of the computer running the FortiRecorder Central or
browser client, which must decode and render the video streams from the NVR. Displaying
multiple video streams on the client is very CPU intensive.
NVR performance
Number of supported cameras
The FortiRecorder-100D can support 16 cameras, 200D and 400D can support up to 64
cameras depending on the camera configuration. VM version of FortiRecorder depends on the
hardware performance.
Key concepts Page 9 FortiRecorder 2.4.2 Administration Guide
Page 10

General performance factors
The following factors affect the input side of performance:
• Total number of video streams from the cameras (i.e. not just the number of cameras)
• The video recording types (motion only or continuous) per camera
• The video stream parameters per camera – i.e. video compression (constant or variable bit
rate mode), image quality level, complexity of the scene, video resolution and frame rate per
second.
The following factors affect the output side of performance:
• Number of administrator/operator/viewer sessions
• Peak number of simultaneous administrator/operator/viewer live views
• The video stream parameters per camera live view – i.e. video compression (constant or
variable bit rate mode), image quality level, complexity of the scene, video resolution and
frame rate per second.
Variable versus constant bit rate
The variable bit rate mode means the bandwidth used by the camera will vary according to what
the camera is seeing and the video profile settings. The video profile settings for the variable bit
rate mode are resolution, frame rate and image quality. High resolution creates more data than
medium or low resolution (see following sections for more detail). The degree of motion present
in a video stream also affects the amount of data created.
The constant bit rate mode means the bandwidth used by the camera will stay relatively
constant regardless of what the camera is seeing. The constant bit rate mode is therefore more
predictable in deployments where bandwidth and/or storage capacities are important
considerations. The video profile settings for the constant bit rate mode are resolution, frame
rate and bit rate. The bandwidth used by the stream is dictated by the bit rate setting.
In general, using the variable bit rate mode results in relatively consistent video quality but
fluctuating bandwidth and using the constant bit rate mode results in varying video quality but
predictable bandwidth. Choosing a high bandwidth constant bit rate mode avoids the video
quality drop e.g. during high motion, but may use some unnecessary bandwidth during times of
no activity.
However, in most cases the difference in video quality between the variable and constant bit
modes is negligible (assuming the same resolution and frame rates) and the constant bit rate
mode produces more reliable output from the cameras.
Bandwidth per camera or live view
Variable bit rate
Depending on resolution, frame rate and video quality a camera using H.264 compression may
generate the following bit rates:
• 352 x 240 @ 30 FPS, high quality = 0.4 Mbps
• 720 x 576 @ 30 FPS, high quality = 1 Mbps
• 1280 x 720 @ 30 FPS, high quality = 2 Mbps
• 1920 x 1080 @ 30 FPS, high quality = 4 Mbps
• 1920 x 1080 @ 30 FPS, medium quality = 2.8 Mbps
• 1920 x 1080 @ 30 FPS, low quality = 2 Mbps
• 1920 x 1080 @ 10 FPS, high quality = 2.4 Mbps
• 1920 x 1080 @ 10 FPS, low quality = 1.2 Mbps
Key concepts Page 10 FortiRecorder 2.4.2 Administration Guide
Page 11
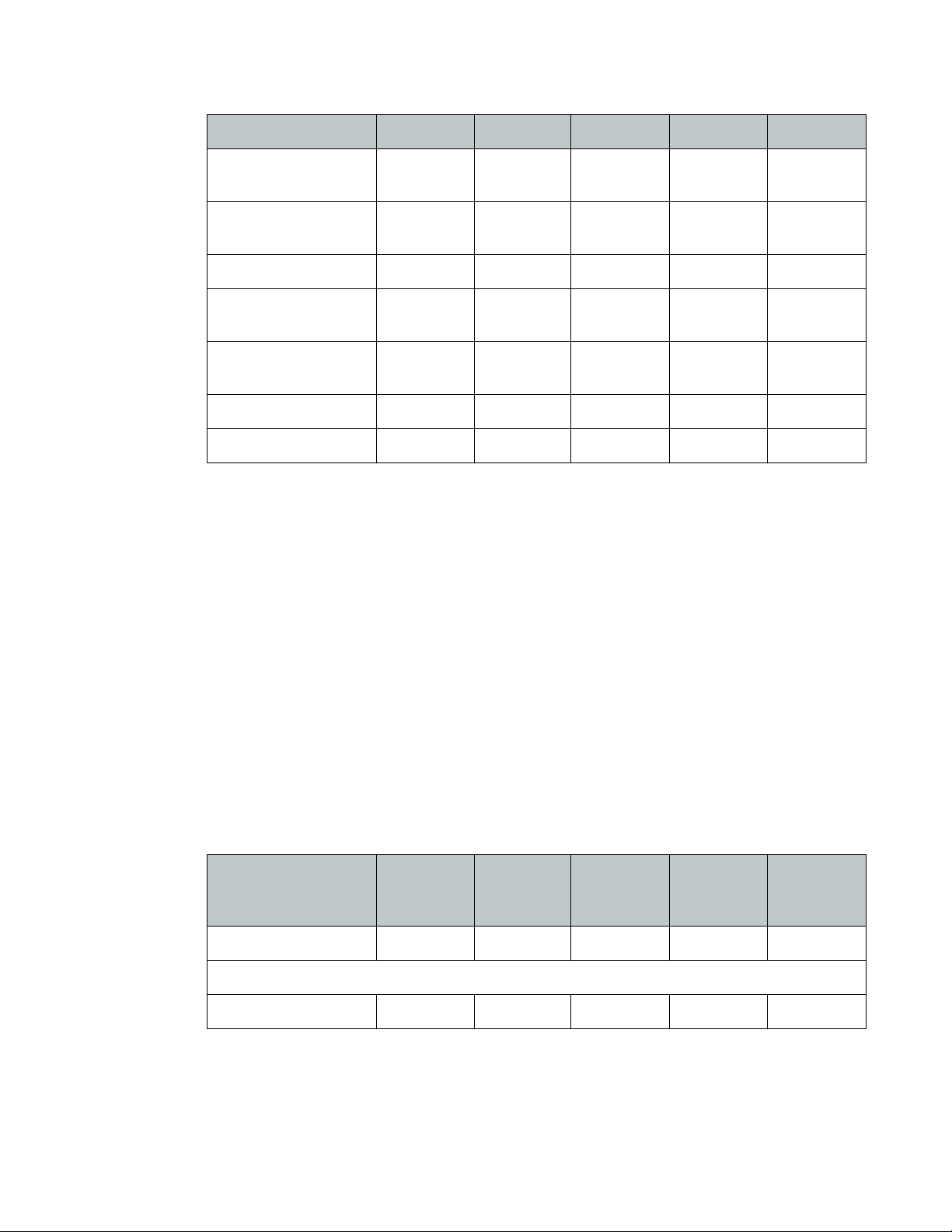
Table 1: Bitrate table (H.264 estimate) in Mbps with high quality image (x0.7 = standard quality)
Frames/s 1 6 10 15 30
CIF
0.16 0.2 0.24 0.3 0.4
(352x240)
D1 0.4M
0.4 0.5 0.6 0.75 1
(720x576)
720p 1M 0.8 1 1.2 1.5 2
SXGA 1.3M
1 1.25 1.5 1.9 2.5
(1280x1024)
HD 2M
1.6 2 2.4 3 4
(1920x1080)
3M 2 2.5 3 3.75 5
5M 3.2 4 4.8 6 8
Please note that these are estimates providing a high quality image under most conditions. If
the scene is less complex (indoors with little detail and not much motion) or the camera has very
little noise (daylight, good DNR) the bit rate can be lowered further. Generally do not use less
than half of the indicated values.
If video compression is set to lower quality or capped at a defined max bandwidth, the bit rate
can be significantly lower at the cost of lower image quality. DNR can further reduce bandwidth,
especially for grainy night images, but shows less detail during motion.
Storage capacity
We will use FortiRecorder 100D, 200D and 400D configuration with different camera parameters
to demonstrate the video retention period.
FortiRecorder 100D has a built in 1 TB hard drive and it can connect up to 16 cameras. We
configure 16 cameras with 1280 x 720 resolution using 30 FPS with high quality image in
continuous recording. Each camera will generate an estimated bandwidth of 2 Mbps. Referring
to the FortiRecorder Capacity calculator spreadsheet below, 100D can store approximately 3.2
days of video footage.
Table 2: Capacity Calculator
Bit rate
(Mbps)
Input 2 1 16 100 30
Resolve each for all other inputs as specified
Result 0.2 9.4 1.7 11 3.2
FortiRecorder 200D has 3 TB HD capacity. With the same configuration it can record 16
cameras for 10 days.
HD
Capacity
(TB)
Cameras
(#)
Usage
(%)
Time
(days)
FortiRecorder 400D has 6 TB HD capacity. With the same configuration it can record 16
cameras for 19 days.
Key concepts Page 11 FortiRecorder 2.4.2 Administration Guide
Page 12
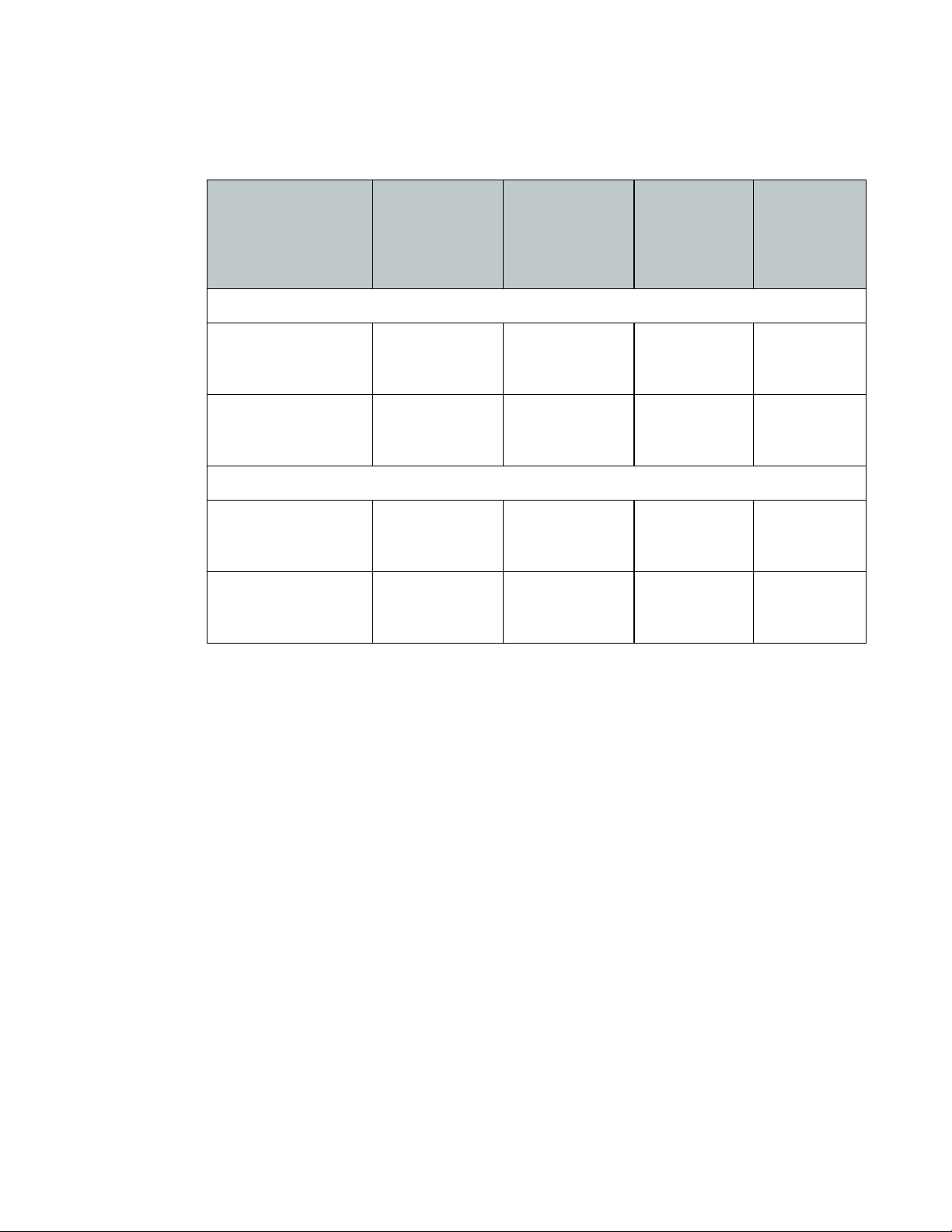
The above examples use the same configuration for 16 cameras with different hard drive
capacity per FortiRecorder model. The table below shows the number of days that one camera
can be stored in different configurations.
Table 3: Video retention period in days for one camera
The same resolution and frame rate with different video quality
1920x1080@15 FPS
high quality video = 3
Mbps
1920x1080@15 FPS
medium quality video
= 2.1 Mbps
The same resolution and video quality with different frame rate
2048x1536@10 FPS
high quality video = 3
Mbps
2048x1536@30 FPS
high quality video = 5
Mbps
FortiRecorder
100D with 1 TB
HD
34 102 645 204
49 145 921 291
34 102 645 204
20 61 387 122
FortiRecorder
200D with 3 TB
HD
FortiRecorder
200D with 3 TB
HD plus 16 TB
remote
storage
FortiRicorder
400D with 6
TB HD
Use the following guideline for a quick bandwidth consumption calculation:
• 1 TB HD can store 1 camera configured to consume 1Mbps for approximately 100 days.
Therefore:
• 1 TB HD can store 1 camera configured to consume 2 Mbps for approximately 50 days.
• 6 TB HD can store 10 cameras configured to consume 2 Mbps each for approximately 30
days.
For more information about bandwidth consumption calculation, see the FortiCamera
Bandwidth Calculator User Guide on
http://docs.fortinet.com/d/fortirecorder-forticamera-bandwidth-calculator-user-guide.
In practice Fortinet suggests to use the numbers provided in the bandwidth calculator as a
starting point and then adjust them after installation to achieve the desired balance between
quality and bandwidth.
Client Performance
If you need to display 8 or more camera live views, you may need to configure the second
camera stream so that viewing is done at a lower frame rate or resolution, depending on how
powerful the client PC is. RAM is less important than CPU for rendering video.
Video playback is very CPU intensive. If you are experiencing choppy video playback and
cameras “freezing” during playback, you likely have a client performance problem. Use the
diagnostic tools available on your client OS and look at the CPU usage when you are
experiencing video problems. If possible, keep the CPU usage below 50%.
Key concepts Page 12 FortiRecorder 2.4.2 Administration Guide
Page 13

GUI and CLI
To optimize client performance, use the video and camera profiles to define and assign a
second video stream for each camera. To increase the number of live views the client computer
can display, or to reduce the CPU requirement for a given number of live views, reduce the
resolution, quality and/or frames per second of the second video streams.
Ten FPS is a good general setting for live views, which provides a reasonable frame rate for the
live views, but significantly reduces the load on the client (compared to 30 FPS which is more
ideal for higher traffic area surveillance).
This document only describes how to use the web UI. If you are familiar with the command line
interface (CLI), go to Monitor > System Status > Console to use the CLI commands.
Key concepts Page 13 FortiRecorder 2.4.2 Administration Guide
Page 14
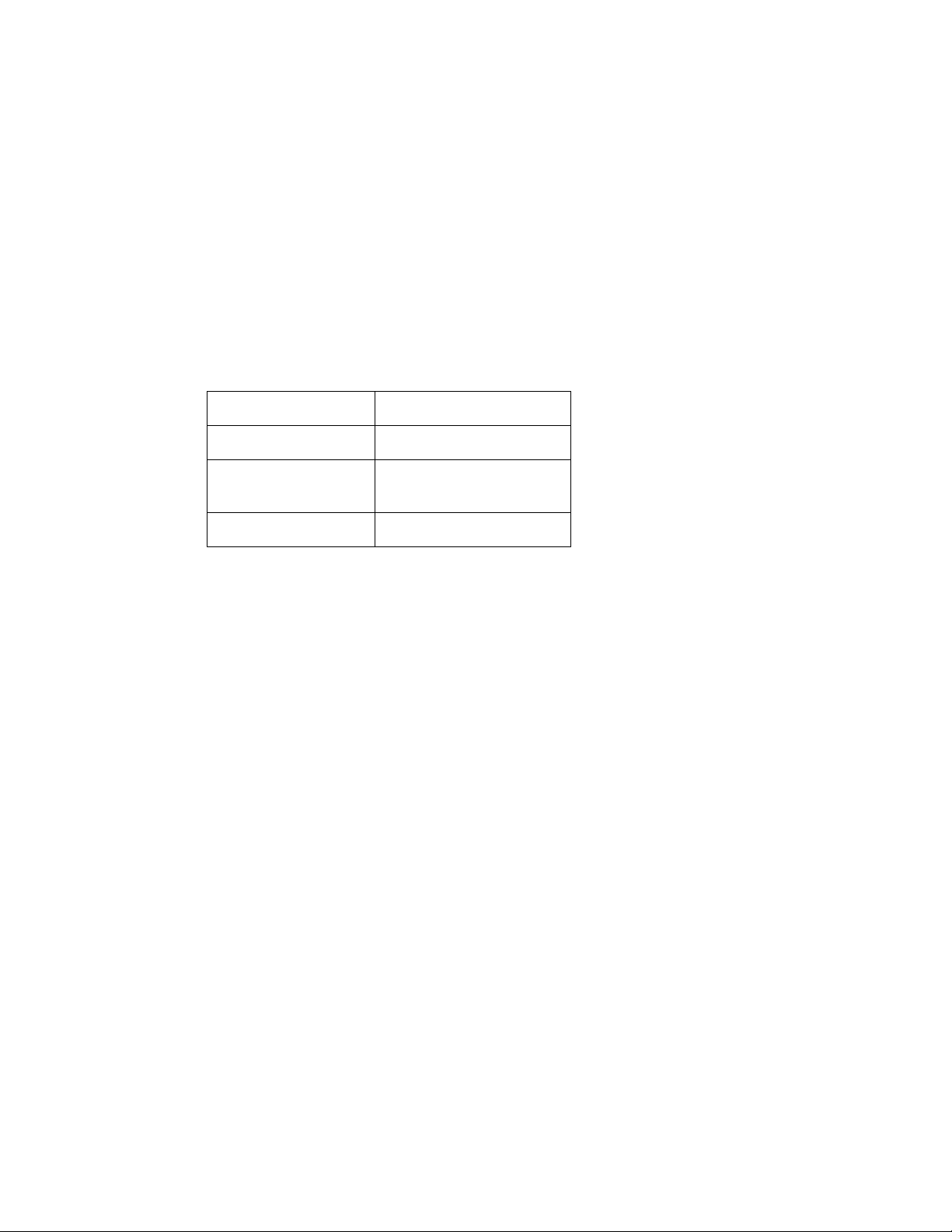
NVR configuration
To be able to configure the FortiRecorder NVR appliance, you must connect to its management
web UI or CLI console. This document mainly describes the web UI usage.
Connecting to FortiRecorder web UI
You can connect to the web UI using its default settings. (By default, HTTPS access to the
web UI is enabled.)
Table 4: Default settings for connecting to the web UI
Network Interface port1
URL https://192.168.1.99/
Administrator
Account
Password
Requirements
• a computer with an RJ-45 Ethernet network port
• a crossover Ethernet cable
• a web browser. For supported web browsers, see the release notes.
• If you are running FortiRecorder version 2.3 and older firmware, Apple QuickTime 7.1 or
greater plug-in is required for video display. Note that starting from QuickTime 7.7.9,
QuickTime typical install does not install the web plugin by default. You have to use
custom install and select the web plugin.
Starting from FortiRecorder version 2.4, HTML5 is supported. On most platforms, QuickTime
plugin is not required anymore. For details, see the FortiRecorder version 2.4 release notes.
To connect to the web UI
1. On your management computer, configure the Ethernet port with the static IP address
192.168.1.2 with a netmask of 255.255.255.0.
2. Using the Ethernet cable, connect your computer’s Ethernet port to the FortiRecorder
appliance’s port1.
3. Start your browser and enter the URL:
https://192.168.1.99/
(Remember to include the “s” in https://.)
Your browser connects the appliance.
admin
Page 14
Page 15
4. In the Name field of the login page, type admin, then click Login. (In its default state, there is
no password for this account.)
Login credentials entered are encrypted before they are sent to the FortiRecorder appliance.
If your login is successful, the web UI appears.
See also
• Connectivity issues
• Login issues
Connecting to FortiRecorder CLI
For initial configuration, you can access the CLI from your management computer using either
of these two ways:
• a local serial console connection
• an SSH connection, either local or through the network
To connect to the CLI using a local serial console connection, you must have:
• a computer with a serial communications (COM) port
• the RJ-45-to-DB-9 serial or null modem cable included in your FortiRecorder package
• terminal emulation software, such as HyperTerminal for Microsoft Windows
To connect to the CLI using an SSH connection, you must have:
• a computer with an Ethernet port
• a crossover Ethernet cable
• an SSH client, such as PuTTY
Table 5: Default settings for connecting to the CLI by SSH
Network Interface port1
IP Address 192.168.1.99
SSH Port Number 22
Administrator
Account
Password (none)
NVR configuration Page 15 FortiRecorder 2.4.2 Administration Guide
admin
Page 16
To connect to the CLI using a local serial console connection
The following procedure uses Microsoft HyperTerminal. Steps may vary with other terminal
emulators.
1. Using the RJ-45-to-DB-9 or null modem cable, connect your computer’s serial
communications (COM) port to the FortiRecorder unit’s console port.
2. Verify that the FortiRecorder unit is powered on.
3. On your management computer, start HyperTerminal.
4. On Connection Description, enter a Name for the connection, and select OK.
5. On Connect To, from Connect using, select the communications (COM) port where you
connected the FortiRecorder unit.
6. Select OK.
7. Select the following Port settings and select OK.
Bits per second 9600
Data bits 8
Parity None
Stop bits 1
Flow control None
8. Press Enter.
The terminal emulator connects to the CLI, and the CLI displays a login prompt.
9. Type admin and press Enter twice. (In its default state, there is no password for this
account.)
To connect to the CLI using an SSH connection
The following procedure uses PuTTY. Steps may vary with other SSH clients.
1. On your management computer, configure the Ethernet port with the static IP address
192.168.1.2 with a netmask of 255.255.255.0.
2. Using the Ethernet cable, connect your computer’s Ethernet port to the FortiRecorder unit’s
port1.
3. Verify that the FortiRecorder unit is powered on.
4. On your management computer, start your SSH client.
5. In Host Name (or IP Address), type 192.168.1.99.
6. In Port, type 22.
7. From Connection type, select SSH.
8. Select Open.
The SSH client connects to the FortiRecorder unit.
The SSH client may display a warning if this is the first time you are connecting to the
FortiRecorder unit and its SSH key is not yet recognized by your SSH client, or if you have
NVR configuration Page 16 FortiRecorder 2.4.2 Administration Guide
Page 17

previously connected to the FortiRecorder unit but it used a different IP address or SSH key.
If your management computer is directly connected to the FortiRecorder unit with no
network hosts between them, this is normal.
9. Click Yes to verify the fingerprint and accept the FortiRecorder unit’s SSH key. You will not
be able to log in until you have accepted the key.
The CLI displays a login prompt.
10.Type admin and press Enter. (In its default state, there is no password for this account.)
Basic NVR configuration
Either to integrate the FortiRecorder NVR into your existing network or to set it up in its
dedicated, private network, you must configure the following settings to have the appliance up
and running:
• Setting the “admin” account password
• Configuring the network settings
• Configuring the DHCP server
• Setting the system time
Setting the “admin” account password
The default administrator account, named admin, initially has no password.
Unlike other administrator accounts, the admin administrator account exists by default and
cannot be deleted. This administrator account always has full permission to view and change all
FortiRecorder configuration options, including viewing and changing all other administrator
accounts. Its name and permissions cannot be changed.
For security reasons, you must set a password for the admin account after you log on to
FortiRecorder. Set a strong password for the admin administrator account, and change the
password regularly.
To change the admin administrator password
1. Log in to the admin administrator account.
2. Go to System > Administrator > Administrator.
3. Change the password and log out.
The new password takes effect the next time that administrator account logs in.
See also
• Login issues
NVR configuration Page 17 FortiRecorder 2.4.2 Administration Guide
Page 18
Configuring the network settings
When shipped, each of the FortiRecorder appliance’s physical network adapter ports has a
default IP address and netmask. If these IP addresses and netmasks are not compatible with
the design of your unique network, you must configure them.
Table 6: Default IP addresses and netmasks
Network Interface* IP Address Netmask
port1 192.168.1.99 255.255.255.0
port2 192.168.2.99 255.255.255.0
port3 192.168.3.99 255.255.255.0
port4 192.168.4.99 255.255.255.0
* The number of network interfaces may vary by model.
To connect to the CLI and web UI, you should configure the following FortiRecorder network
settings:
• Interface: you Two configure at least one network interface on your FortiRecorder
appliance (usually port1) with an IP address and netmask so that it can receive your
connections.
• Static route: Depending on your network, you also usually must configure a static route so
that the FortiRecorder can connect to the Internet, your computer, and FortiCam cameras.
• DNS server: FortiRecorder appliances require connectivity to DNS servers for DNS lookups.
The appliance will query the DNS servers whenever it needs to resolve a domain name into
an IP address, such as for NTP servers defined by their domain names.
To configure a network interface’s IP address
1. Log in to the admin administrator account.
2. Go to System > Network > Interface.
3. Double-click the row to select the physical network interface that you want to modify.
4. If you want to manually assign an IP address and subnet mask to this network interface,
select Manual and then provide the IP address and netmask in IP/Netmask. IPv4 and IPv6
subnet masks should be provided in CIDR format, e.g. /24 instead of 255.255.255.0. The
IP address must be on the same subnet as the network to which the interface connects. Two
network interfaces cannot have IP addresses on the same subnet.
Otherwise, select DHCP and enable Connect to server to retrieve a DHCP lease when you
save this configuration. If you want the FortiRecorder appliance to also retrieve DNS and
default route (“gateway”) settings, also enable Retrieve default gateway and DNS from
server.
If you use DHCP on an interface and there are cameras connected to the interface, you must
make sure the IP address will ne change on that interface because the cameras need to
communicate with the NVR and thus need to be aware of the IP address of the NVR.
NVR configuration Page 18 FortiRecorder 2.4.2 Administration Guide
Page 19

Retrieve default gateway and DNS from server will overwrite the existing DNS and default route,
if any.
5. Configure these settings:
Setting name Description
Discover cameras
on this port
Enable to send multicast camera discovery traffic from this network
interface. For more information, see “Connecting FortiRecorder to the
cameras” on page 41.
Access Enable the types of administrative access that you want to permit to
this interface.
Caution: Enable administrative access only on network interfaces
connected to trusted private networks or directly to your management
computer. If possible, enable only secure administrative access
protocols such as HTTPS or SSH. Failure to restrict administrative
access could compromise the security of your FortiRecorder
appliance.
HTTPS Enable to allow secure HTTPS connections to the web UI through this
network interface. To configure the listening port number, see
“Configuring system timeout, ports, and public access”. To upload a
certificate, see “Replacing the default certificate for the web UI”.
PING Enable to allow:
• ICMP type 8 (ECHO_REQUEST)
• UDP ports 33434 to 33534
for ping and traceroute to be received on this network interface.
When it receives an ECHO_REQUEST, FortiRecorder will reply with
ICMP type 0 (ECHO_RESPONSE).
Note: Disabling PING only prevents FortiRecorder from receiving
ICMP type 8 (ECHO_REQUEST) and traceroute-related UDP.
It does not disable FortiRecorder CLI commands such as execute
ping or execute traceroute that send such traffic.
HTTP Enable to allow HTTP connections to the web UI through this network
interface. To configure the listening port number, see “Configuring
system timeout, ports, and public access”.
Caution: HTTP connections are not secure, and can be intercepted by
a third party. If possible, enable this option only for network interfaces
connected to a trusted private network, or directly to your
management computer. Failure to restrict administrative access
through this protocol could compromise the security of your
FortiRecorder appliance.
SSH Enable to allow SSH connections to the CLI through this network
interface.
NVR configuration Page 19 FortiRecorder 2.4.2 Administration Guide
Page 20
Setting name Description
SNMP Enable to allow SNMP queries to this network interface, if queries have
been configured and the sender is a configured SNMP manager. To
configure the listening port number and configure queries and traps,
see “SNMP traps & queries”.
TELNET Enable to allow Telnet connections to the CLI through this network
interface.
Caution: Telnet connections are not secure, and can be intercepted
by a third party. If possible, enable this option only for network
interfaces connected to a trusted private network, or directly to your
management computer. Failure to restrict administrative access
through this protocol could compromise the security of your
FortiRecorder appliance.
FRC-
Enable to allow access from FortiRecorder Central.
Central
MTU Enable to change the maximum transmission unit (MTU) value, then
enter the maximum packet or Ethernet frame size in bytes.
If network devices between the FortiRecorder unit and its traffic
destinations require smaller or larger units of traffic, packets may
require additional processing at each node in the network to fragment
or defragment the units, resulting in reduced network performance.
Adjusting the MTU to match your network can improve network
performance.
The default value is 1500 bytes. The MTU size must be between 576
and 1500 bytes. Change this if you need a lower value. For example,
RFC 2516 prescribes a value of 1492 for PPPoE.
Administrative
status
Select either:
• Up — Enable (that is, bring up) the network interface so that it can
send and receive traffic.
• Down — Disable (that is, bring down) the network interface so that
it cannot send or receive traffic.
6. Click OK.
If you were connected to the web UI through this network interface, you are now
disconnected from it.
7. To access the web UI again, in your web browser, modify the URL to match the new IP
address of the network interface. For example, if you configured the network interface with
the IP address 10.10.10.5, you would browse to: https://10.10.10.5
If the new IP address is on a different subnet than the previous IP address, and your
computer is directly connected to the FortiRecorder appliance, you may also need to modify
the IP address and subnet of your computer to match the FortiRecorder appliance’s new IP
address.
NVR configuration Page 20 FortiRecorder 2.4.2 Administration Guide
Page 21
To add a static route
If you used DHCP and Retrieve default gateway and DNS from server when configuring your
network interfaces, skip this step — the default route was configured automatically.
1. Log in to the admin administrator account.
Other accounts may not have permissions necessary to change this setting.
2. Go to System > Network > Routing.
3. Click New.
4. Configure these settings:
Setting name Description
Destination
IP/netmask
Type the destination IP address and network mask of packets that will
be subject to this static route, separated by a slash ( / ).
The value 0.0.0.0/0 results in a default route, which matches all
packets.
Gateway Type the IP address of the next-hop router where the FortiRecorder
appliance will forward packets subject to this static route. This router
must know how to route packets to the destination IP addresses that
you have specified in Destination IP/netmask, or forward packets to
another router with this information.
For a direct Internet connection, this will be the router that forwards
traffic towards the Internet, and could belong to your ISP.
Note: The gateway IP address must be in the same subnet as a
network interface’s IP address.
5. Click OK.
The FortiRecorder appliance should now be reachable to connections with networks
indicated by the mask. When you add a static route through the web UI, the FortiRecorder
appliance evaluates the route to determine if it represents a different route compared to any
other route already present in the list of static routes. If no route having the same destination
exists in the list of static routes, the FortiRecorder appliance adds the static route, using the
next unassigned route index number.
For small networks with only a few devices, often you will only need to configure one route: a
default route that forwards packets to your router that is the gateway to the Internet.
If you have redundant gateway routers (e.g. dual Internet/ISP links), or a larger network with
multiple routers (e.g. each of which should receive packets destined for a different subset of IP
addresses), you may need to configure multiple static routes.
NVR configuration Page 21 FortiRecorder 2.4.2 Administration Guide
Page 22
6. To verify connectivity, from a computer on the route’s network destination, attempt to ping
one of FortiRecorder’s network interfaces that should be reachable from that location.
If the connectivity test fails, you can use the CLI commands:
execute ping <destination_ipv4>
to determine if a complete route exists from the FortiRecorder to the host, and
execute traceroute <destination_ipv4>
to determine the point of connectivity failure.
Also enable PING on the FortiRecorder’s network interface, then use the equivalent
tracert or traceroute command on the computer (depending on its operating system)
to test routability for traffic traveling in the opposite direction: from the host to the
FortiRecorder.
• If these tests fail, or if you do not want to enable PING, first examine the static route
configuration on both the host and FortiRecorder.
To display the cached routing table, enter the CLI command:
diagnose netlink rtcache list
You may also need to verify that the physical cabling is reliable and not loose or broken,
that there are no IP address or MAC address conflicts or blacklisting, and otherwise rule
out problems at the physical, network, and transport layer.
• If these tests succeed, a route exists, but you cannot connect using HTTP or HTTPS, an
application-layer problem is preventing connectivity.
Verify that you have enabled HTTPS and/or HTTP on the network interface. Also examine
routers and firewalls between the host and the FortiRecorder appliance to verify that they
permit HTTP and/or HTTPS connectivity between them. Finally, you can also use the CLI
command:
diagnose system top 5 30
to verify that the daemons for the web UI and CLI, such as sshd, newcli, and httpd are
running and not overburdened.
To configure DNS settings
If you will use the settings DHCP and Retrieve default gateway and DNS from server when you
configure your network interfaces, skip this — DNS is configured automatically.
1. Log in to the admin administrator account.
Other accounts may not have permissions necessary to change this setting.
2. Go to System > Network > DNS and enter the IP addresses of a primary and secondary DNS
server. Your Internet service provider (ISP) may supply IP addresses of DNS servers, or you
may want to use the IP addresses of your own DNS servers.
Incorrect DNS settings or unreliable DNS connectivity can cause issues with other features,
including the NTP system time. For improved performance, use DNS servers on your local
network.
3. Click Apply.
NVR configuration Page 22 FortiRecorder 2.4.2 Administration Guide
Page 23
4. To verify your DNS settings, in the CLI, enter the following commands:
execute traceroute www.fortinet.com
DNS tests may not succeed if you have not yet completed “To add a static route”.
If the DNS query for the domain name succeeds, you should see results that indicate that
the host name resolved into an IP address, and the route from FortiRecorder to that IP
address:
traceroute to www.fortinet.com (192.0.43.10), 30 hops max, 60 byte
packets
1 172.20.130.2 (172.20.130.2) 0.426 ms 0.238 ms 0.374 ms
2 static-209-87-254-221.storm.ca (209.87.254.221) 2.223 ms 2.491
ms 2.552 ms
3 core-g0-0-1105.storm.ca (209.87.239.161) 3.079 ms 3.334 ms
3.357 ms
...
16 43-10.any.icann.org (192.0.43.10) 57.243 ms 57.146 ms 57.001
ms
If the DNS query fails, you will see an error message such as:
www.fortinet.com: Temporary failure in name resolution
Cannot handle "host" cmdline arg `www.fortinet.com' on position 1
(argc 3)
Verify your DNS server IPs, routing, and that your firewalls or routers do not block or proxy
UDP port 53.
See also
• Connectivity issues
Configuring the DHCP server
If you need the FortiRecorder DHCP service to connect cameras to the NVR, you can configure
the DHCP server on the interface that the cameras connect to. For information about DHCP
service and camera connection, see “Camera connection” on page 40.
To configure FortiRecorder's DHCP server via the web UI
1. Go to System > Network > DHCP.
2. Click New.
3. Mark the check box for Enable DHCP server.
NVR configuration Page 23 FortiRecorder 2.4.2 Administration Guide
Page 24
4. Configure these settings:
Setting name Description
Interface Select the name of the network interface where this DHCP server will
listen for requests from DHCP clients.
Gateway Type the IP address that DHCP clients will use as their next-hop
router.
On smaller networks, this is usually the same router that
FortiRecorder uses. It could be your office’s router, or cable/DSL
modem.
DNS options Select either:
• Default — Leave DHCP clients’ DNS settings at their default
values.
• Specify — Configure DHCP clients with the DNS servers that you
specify in DNS server 1 and DNS server 2.
DNS server 1 Type the IP address of a DNS server that DHCP clients can use to
resolve domain names. For performance reasons, if you have one, it
is preferable to use a DNS server on your local network.
This setting is available only if DNS options is set to Specify.
DNS server 2 Type the IP address of an alternative DNS server that DHCP clients
can use to resolve domain names. For performance reasons, if you
have one, it is preferable to use a DNS server on your local network.
This setting is available only if DNS options is set to Specify.
Domain Optional. Type the domain name, if any, that DHCP clients will use
when resolving host names on the local domain.
Netmask Type the subnet mask that DHCP clients will use in conjunction with
the IP address that is assigned by FortiRecorder’s DHCP server.
NVR configuration Page 24 FortiRecorder 2.4.2 Administration Guide
Page 25
5. If you want to fine-tune the behavior, configure these settings:
Setting name Description
Conflicted IP
timeout (Seconds)
Lease time
(Seconds)
Type the maximum amount of time that the DHCP server will wait for
an ICMP ECHO (ping) response from an IP before it determines that it
is not used, and therefore safe to allocate to a DHCP client that is
requesting an IP address. The default is 1,800 seconds (3 minutes).
To ensure that the DHCP server does not cause IP address conflicts
with misconfigured computers that are accidentally using the pool of
IP addresses used for DHCP, when a client request a new DHCP
lease, the built-in DHCP server will ping an unused IP address in the
pool first. If the ping test is successful, then a misconfigured
computer is currently using that IP, and allocating it also to the DHCP
client would cause an IP address conflict. To prevent this, the DHCP
server will temporarily abandon that IP (mark it as used by a static
host) and look for an other, available IP to give to the DHCP client. (It
will not try abandoned IPs again until the pool is exhausted.)
However, before the DHCP server can determine if the ping test is
successful, the it must first wait to see if there is any reply. This slows
down the search for an available IP address, and in rare cases, could
cause a significant delay before the DHCP client receives its
assigned IP address and other network settings. If your network is
smaller or typically has low latency to ping replies, you can safely
decrease this setting’s value to improve DHCP speed and
performance. In most cases, 3 seconds is enough.
Type the maximum amount of time that the DHCP client can use the
IP address assigned to it by the server. When the lease expires, the
DHCP client must either request a new IP address from the DHCP
server or renew its existing lease. Otherwise, the DHCP server may
attempt to assign it to the next DHCP client that requests an IP. The
default is 604,800 seconds (7 days).
If you have more or almost as many DHCP clients (cameras) as the
number of IP addresses available to give to DHCP clients, you can
decrease the lease. This will free up IP addresses from inactive
clients so that IPs are available to give to clients that are currently in
need of IP addresses. Keep in mind, however, that if the DHCP
server is attached to your overall network rather than directly to
cameras, this will slightly increase traffic volume and slightly
decrease performance.
DHCP IP Range To configure the DHCP lease pool — the range of IP addresses that
the DHCP server can assign to its clients — click New and configure
the first and last IP address in the range. To avoid DHCP pool
exhaustion that can occur in some cases, the pool should be slightly
larger than the total number of clients.
If you need to exclude some IP addresses from this range (e.g.
printers permanently occupy static IPs in the middle of the range),
also configure DHCP Excluded Range.
Tip: The built-in DHCP server can provide IP addresses to the
computers on your network too, not just to cameras.
NVR configuration Page 25 FortiRecorder 2.4.2 Administration Guide
Page 26
Setting name Description
DHCP Excluded
Range
Reserved IP
Address
6. Click Create.
As cameras join the network, they should appear in the list of DHCP clients on Monitor >
DHCP Status > DHCP.
See also
• DHCP issues
To configure IPs that should be omitted from the DHCP pool and
never given to DHCP clients (such if there are printers with manually
assigned static IP addresses in the middle of your DHCP range),
click New.
To bind specific MAC addresses to a specific DHCP lease,
guaranteeing that the DHCP server will never assign it to another
DHCP client, click New.
Caution: Reserved leases cannot prevent misconfigured computers
from taking the IP address, causing an IP address conflict, and
breaking the FortiRecorder NVR’s connection with the camera. See
“Resolving IP address conflicts”.
Tip: To mimic a static IP address for your cameras, yet still provide
the benefit that IP addresses are still centrally managed and
configured on your DHCP server, configure reserved IP addresses.
Setting the system time
For many features to work, including camera synchronization, scheduling, logging, and
SSL/TLS-dependent features, the FortiRecorder system time must be accurate.
You can either manually set the FortiRecorder system time or configure the FortiRecorder
appliance to automatically keep its system time correct by synchronizing with a Network Time
Protocol (NTP) server.
NTP is recommended to achieve better time accuracy. NTP requires that your FortiRecorder be
able to connect to the Internet on UDP port 123. Adjust your firewall, if any, to allow these
connections.
Later, when cameras are added to your surveillance system, your FortiRecorder NVR will
synchronize the camera clocks with its own to keep them in agreement.
To configure the system time
1. Go to System > Configuration > Time.
2. Either manually set the date and time or select to synchronize with NTP server.
3. Click Apply.
If you manually configured the time, or if you enabled NTP and the NTP query for the current
time succeeds, the new clock time should appear in System time. (If the query reply is slow,
NVR configuration Page 26 FortiRecorder 2.4.2 Administration Guide
Page 27
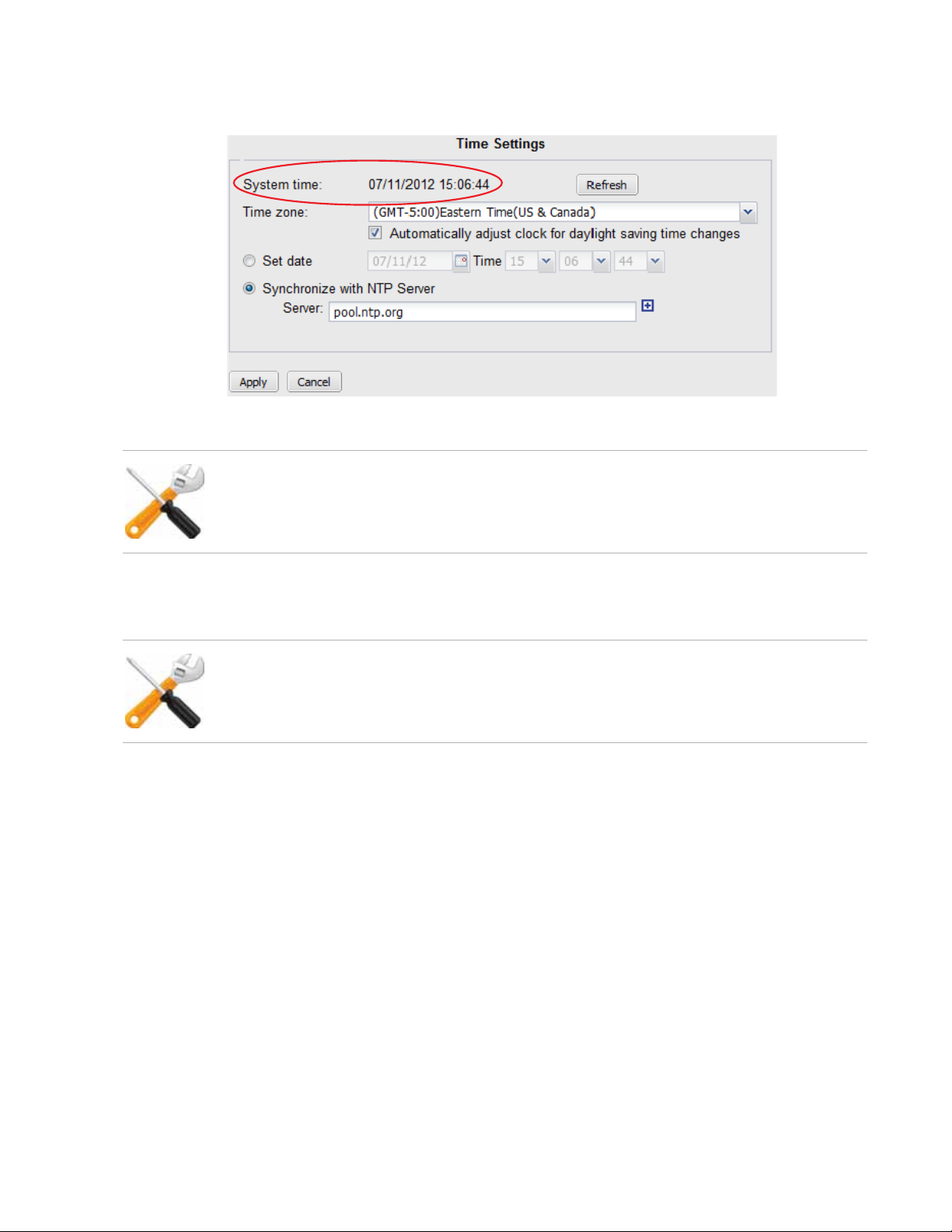
you may need to wait a couple of seconds, then click Refresh to update the display in
System time.)
If the NTP query fails, the system clock will continue without adjustment.
NTP on FortiRecorder complies with RFC 5905. If the current system time differs greatly from
the actual time, NTP will adjust the clock slowly to avoid incongruous jumps in log message
timestamps and other time-dependent features. If you want the time to be corrected
immediately, set the time zone and time manually first, then switch to NTP.
If FortiRecorder’s time was 3 hours late, for example, and NTP fails, the time will still be
exactly 3 hours late. Verify your DNS server IPs, your NTP server IP or name, routing, and
that your firewalls or routers do not block or proxy UDP port 123.
NTP queries may fail until you have configured gateway and DNS settings. See “Configuring the
network settings”.
See also
• Connectivity issues
NVR configuration Page 27 FortiRecorder 2.4.2 Administration Guide
Page 28
Configuring schedules
Schedules are used in several places:
• When configuring a user under System > Administrator > User Profile, schedules are used to
specify when the users can access the camera. For details, see “Configuring user accounts”
on page 54.
Note: For user access, schedule gaps are allowed. If not scheduled, then access is denied.
Scheduce overlaps are allowed. And one-time schedules take precedence over recurring
schedules.
• When configuring camera video settings under Camera > Configuration > Camera Profile,
schedules are used to specify when to use low or high quality video. For details, see
“Configuring camera profiles” on page 37.
Note: For video quality schedules, gaps and overlaps are not allowed. And one-time
schedules take precedence over recurring schedules.
• When configuring camera recording settings under Camera > Configuration > Camera
Profile, schedules are used to specify when to trigger the different types of recording. For
details, see “Configuring camera profiles” on page 37.
Note: For cameral recording schedules, gaps and overlaps are allowed. And one-time
schedules take precedence over recurring schedules.
• When configuring camera settings under Camera > Configuration > Camera, schedules are
used to specify when to use different camera settings, such as DNR level, brightness,
contrast, saturation, and sharpness. For details, see “Configuring cameras” on page 44.
Note: For cameral setting schedules, gaps are allowed. But overlaps are not allowed. And
one-time schedules take precedence over recurring schedules.
• When configuring camera notifications under Camera > Notification > Camera Notification,
schedules are used to control when to send out notifications. For details, see “Configuring
cameras to send notifications” on page 71.
Note: For camera notification schedules, overlaps are not allowed but gaps are allowed. And
one-time schedules take precedence over recurring schedules.
The default schedule is used when no schedules are selected or the selected schedules conflict
with each other.
You cannot create a recurring recording schedule where the hours vary by the day of the week,
but you can achieve the same effect if you create multiple schedules.
To configure schedules
1. Go to Schedule > Schedule.
2. Select New and configure the following settings.
Setting name Description
Name Enter a name for the schedule.
Description Optionally enter a description.
Type Select a schedule type:
• Recurring: the schedule happens at specified times on selected
days.
• One-time: the schedule happens only on a specific date and time.
NVR configuration Page 28 FortiRecorder 2.4.2 Administration Guide
Page 29
Setting name Description
Days and Time Select the days you want the camera to begin recording if you have
selected the Recurring schedule type.
All day Select this option if you want to record all day long.
Start time/End
time
Select the start and end time for the recurring recording or the start
and end date for the one-time recording.
You can use the sunrise and sunset time for the start and end time.
The sunrise and sunset time is calculated by the FortiRecorder’s
latitude and longitude location. For details, see “Setting the sunrise
and sunset time” on page 29.
When using sunrise and sunset time, you can a plus or minus two
hour offset to compensate for lighting conditions specific locations.
Setting the sunrise and sunset time
When specifying schedules, you can use specific day and time, or the sunrise and sunset time.
To get the sunrise and sunset time
1. Go to Schedule > Schedule > Settings.
2. Enter the latitude and longitude values of the FortiRecorder and camera location.
3. Click Calculate to retrieve the sunrise and sunset time. A few days’ sunrise and sunset time
will be displayed.
When using a combination of sunrise/sunset and the specific time, if the time cross the
boundary of sunrise/sunset, the schedule has no effect. For example, if the sunrise is at 8:00AM
and you set the schedule from sunrise to 7:00AM, the schedule has no effect.
Advanced/optional NVR configuration
After you have a basic working setup, depending on your specific requirements, you may want
to configure some advanced or optional settings.
• Configuring system timeout, ports, and public access
• Configuring FortiRecorder system appearance
• Configuring logging
• Alert email
Configuring system timeout, ports, and public access
Go to System > Configuration > Options to configure the system idle timeout, the HTTP, HTTPS,
SSH, Telnet, and FortiRecorder Central access ports, and the host name for public/remote
access.
If you want remote access — connecting from a home or a branch office through the Internet to
your FortiRecorder NVR— for either using the web UI or snapshot notification video clips while
you are out of the office, you must configure both your network and the NVR.
NVR configuration Page 29 FortiRecorder 2.4.2 Administration Guide
Page 30

First, on your office’s firewall or Internet router, configure port forwarding and/or a virtual IP (VIP)
to forward remote access connections from the Internet to your FortiRecorder NVR’s private
network IP. (See “Appendix A: Port numbers”.)
Remote access opens ports and can weaken the strength of your network security. To prevent
attackers on the Internet from gaining access to your surveillance system, configure your
firewall or router to require authentication, restrict which IP addresses can use your port
forward/virtual IP, and scan requests for viruses and hacking attempts.
If you are not sure what your network’s Internet address is, while connected to your office
network, you can use an online utility such as:
http://ping.eu/
Next, go to System > Configuration > Options and configure these settings:
Setting name Description
Public Access
Host name Type either your network’s IP on the Internet, or its domain
name, such as www.example.com.
This is either your Internet router’s WAN IP, or a virtual IP (VIP)
on your firewall whose NAT table will forward incoming
connections from this public network IP to your FortiRecorder
NVR’s private network IP.
HTTP/ HTTPS
Port number
FortiRecorder supports live streaming (HLS) for mobile devices. You can use the FortiRecorder
Mobile drop-down menu to enable live streaming over HTTP or HTTPS.
Type the port number, such as 8080, on your public IP that your
Internet router or firewall will redirect to your FortiRecorder
NVR’s listening port.
About FortiRecorder logical interfaces
In addition to the physical interfaces, you can create the following types of logical interfaces on
FortiRecorder:
• VLAN subinterfaces
• Redundant interfaces
• Aggregate interfaces
• Loopback interfaces
VLAN subinterfaces
A Virtual LAN (VLAN) subinterface, also called a VLAN, is a virtual interface on a physical
interface. The subinterface allows routing of VLAN tagged packets using that physical interface,
but it is separate from any other traffic on the physical interface.
Virtual LANs (VLANs) use ID tags to logically separate devices on a network into smaller
broadcast domains. These smaller domains forward packets only to devices that are part of that
VLAN domain. This reduces traffic and increases network security.
NVR configuration Page 30 FortiRecorder 2.4.2 Administration Guide
Page 31

One example of an application of VLANs is a company’s accounting department. Accounting
computers may be located at both main and branch offices. However, accounting computers
need to communicate with each other frequently and require increased security. VLANs allow
the accounting network traffic to be sent only to accounting computers and to connect
accounting computers in different locations as if they were on the same physical subnet.
Redundant interfaces
On the FortiRecorder unit, you can combine two or more physical interfaces to provide link
redundancy. This feature allows you to connect to two or more switches to ensure connectivity
in the event one physical interface or the equipment on that interface fails.
In a redundant interface, traffic is only going over one interface at any time. This differs from an
aggregated interface where traffic is going over all interfaces for increased bandwidth. This
difference means redundant interfaces can have more robust configurations with fewer possible
points of failure. This is important in a fully-meshed HA configuration.
A physical interface is available to be in a redundant interface if:
• it is a physical interface, not a VLAN interface
• it is not already part of a redundant interface
• it has no defined IP address and is not configured for DHCP
• it does not have any VLAN subinterfaces
• it is not monitored by HA
When a physical interface is included in a redundant interface, it is not listed on the System >
Network > Interface page. You cannot configure the interface anymore.
Aggregate interfaces
An aggregate interface is a logical interface which uses the Link Aggregation Control Protocol
(LACP) (802.3ad) and combines several interfaces to increase throughput. It also provides
redundancy in case one interface in the aggregation is down.
Loopback interfaces
A loopback interface is a logical interface that is always up (no physical link dependency) and
the attached subnet is always present in the routing table.
The loopback IP address does not depend on one specific external port, and is therefore
possible to access it through several physical or VLAN interfaces. In the current release, you
can only add one loopback interface on the FortiRecorder unit.
The loopback interface is useful when you use a layer 2 load balancer in front of several
FortiRecorder units. In this case, you can set the FortiRecorder loopback interface’s IP address
the same as the load balancer’s IP address and thus the FortiRecorder unit can pick up the
traffic forwarded to it from the load balancer.
Configuring FortiRecorder system appearance
To customize the logo and product name appearing on the FortiRecorder web UI, go to System
> Customization > Appearance.
Configuring logging
To diagnose problems or to track actions that the FortiRecorder appliance does as it receives
and processes video, configure the FortiRecorder appliance to record log messages. Log
messages can record camera and/or FortiRecorder appliance events.
NVR configuration Page 31 FortiRecorder 2.4.2 Administration Guide
Page 32

To view log messages, go to Monitor > Log Viewer > Event for the NVR log messages or go to
Monitor > Log Viewer > Event for the camera log messages.
To configure logging
1. Go to either Logs and Alerts > Log Setting > Local Log Settings or Log > Log Setting >
Remote Log Settings (depending on whether you want logs to be stored on FortiRecorder’s
hard drive, or remotely, on a Syslog server or FortiAnalyzer).
2. If configuring local log storage, configure the following settings:
Setting name Description
Log file size Type the file size limit of the current log file in megabytes (MB). The
log file size limit must be between 1 MB and 1000 MB.
Note: Large log files may decrease display and search
performance.
Log time Type the time (in days) of the file age limit. If the log is older than
this limit, even if has not exceeded the maximum file size, a new
current log file will be started.
Valid range is between 1 and 366 days.
At hour Select the hour of the day (24-hour format) when the file rotation
should start.
When a log file reaches either the age or size limit, the
FortiRecorder appliance rotates the current log file: that is, it
renames the current log file (elog.log) with a file name indicating its
sequential relationship to other log files of that type (elog2.log, and
so on), then creates a new current log file. For example, if you set
the log time to 10 days at hour 23, the log file will be rotated at 23
o’clock of the 10th day.
Log level Select the severity level that a log message must equal or exceed
in order to be recorded to this storage location.
For information about severity levels, see “Log severity levels”.
Caution: Avoid recording log messages using low severity
thresholds such as Information or Notification to the local hard disk
for an extended period of time. A low log severity threshold is one
possible cause of frequent logging. Excessive logging frequency
can cause undue wear on the hard disk and may cause premature
failure.
Log options when disk
is full
Select what the FortiRecorder will do when the local disk is full
and a new log message is caused, either:
• Do not log — Discard all new log messages.
• Overwrite — Delete the oldest log file in order to free disk
space, and store the new log message.
Logging Policy
Configuration
Select what type of NVR events and camera events you want to
log.
3. If configuring remote log storage, click New, then configure the following settings:
NVR configuration Page 32 FortiRecorder 2.4.2 Administration Guide
Page 33
Setting name Description
IP Type the IP address of a Syslog server or FortiAnalyzer.
Port Type the UDP port number on which the Syslog server listens for
log messages.
The default is 514.
Level Select the severity level that a log message must equal or exceed
in order to be recorded to this storage location.
For information about severity levels, see “Log severity levels”.
Caution: Avoid recording log messages using low severity
thresholds such as Information or Notification to the local hard disk
for an extended period of time. A low log severity threshold is one
possible cause of frequent logging. Excessive logging frequency
can cause undue wear on the hard disk and may cause premature
failure.
Facility Select the facility identifier the FortiRecorder will use to identify
itself to the Syslog server if it receives logs from multiple devices.
To easily identify log messages from the FortiRecorder when they
are stored on a remote logging server, enter a unique facility
identifier, and verify that no other network devices use the same
facility identifier.
CSV format Enable if your Syslog server requires comma-separated values
(CSV).
Note: Do not enable this option if the remote host is a
FortiAnalyzer. FortiAnalyzer does not support CSV-formatted log
messages.
Logging Policy
Configuration
Select what type of NVR events and camera events you want to
log.
4. To verify logging connectivity, from FortiRecorder, trigger a log message that matches the
type and severity levels that you have chosen to store on the remote Syslog server or
FortiAnalyzer. Then, on the remote host, confirm that it has received that log message.
If you will be sending logs to a FortiAnalyzer appliance, you must add the FortiRecorder NVR to
the FortiAnalyzer’s device list, and allocate enough disk space. Otherwise, depending on its
configuration for unknown devices, FortiAnalyzer may ignore the logs. When the allocated disk
space is full, it may drop subsequent logs.
If the remote host does not receive the log messages, verify the FortiRecorder’s static routes
(see “NVR configuration”) and the policies on any intermediary firewalls or routers (they must
allow Syslog traffic from the FortiRecorder network interface that is connected to the
gateway between it and the Syslog server). To determine the point of connectivity failure
along the network path, if the FortiAnalyzer or Syslog server is configured to respond to
NVR configuration Page 33 FortiRecorder 2.4.2 Administration Guide
Page 34
See also
• Connectivity issues
• Data storage issues
Alert email
As the FortiRecorder system administrator, you can receive alert email whenever an important
system event occurs, such as the hard disk being full and so on. Before you configure alert
email, you must configure the mail server settings so that FortiRecorder can send out email. For
details see “Configuring FortiRecorder to send notification email”.
You can configure up to 10 alert email addresses.
To configure alert email settings
1. Go to Logs and Alerts > Alert Email > Configuration.
2. Click New.
3. Type your email address, such as admin@example.com.
4. Click Create.
5. Go to Logs and Alerts > Alert Email > Categories. Mark the check boxes of all appliance
ICMP ECHO_REQUEST (ping), go to Monitor > System Status > Console and enter the
command:
execute traceroute <syslog_ipv4>
where <syslog_ipv4> is the IPv4 address of your FortiAnalyzer or Syslog server.
This setting is the recipient only for appliance-related notifications, such as the hard disk
being full. It does not configure the recipient of camera-related notifications, such as motion
detection. For this kind of video-related notifications, see “Notifications”.
events that you want to trigger an alert email to be sent, such as:
Setting name Description
Critical events Enable to notify when serious system events occur such as
daemon crashes. See also “Resource issues”.
Disk is full Enable to notify when the disk partition that stores log data is full.
See also “Data storage issues”.
Camera device Enable to notify when a defined camera configuration has been
enabled or disabled, or if there are problems with the camera. (The
FortiRecorder NVR will not control or record video from a camera
that is not enabled in its list of known, configured devices. See
“Camera settings”.)
Camera
communications
Camera recording Enable to notify when an issue prevents a camera from recording.
Camera disk Enable to notify when the disk partition that stores video data is
6. Click Apply.
Enable to notify when there has been a network error during
communications between the NVR and camera. See also
“Connectivity issues”.
See also “Video viewing issues” and “Connectivity issues”.
full. See also “Data storage issues”.
NVR configuration Page 34 FortiRecorder 2.4.2 Administration Guide
Page 35

NVR configuration Page 35 FortiRecorder 2.4.2 Administration Guide
Page 36

Camera settings
Before connecting to your cameras, you must configure the settings that will be used by them.
To reduce overhead, you don’t need to create settings for each camera. Instead, configure
items such as schedules and video quality once, then re-use those same settings for all
cameras that should be similarly configured.
Camera configuration workflow
Camera configuration involves the following steps:
1. Video profiles define video quality. Video profiles are used in camera profiles. To configure
video profiles, go to Camera > Configuration > Video Profile. For details, see “Configuring
video profiles”.
2. Camera profiles define video storage options and recording schedules (either continuous or
motion detection). Camera profiles will be used when you configure the discovered cameras.
To configure camera profiles, go to Camera > Configuration > Camera Profile. For details,
see “Configuring camera profiles”.
3. Connect the camera to the NVR. FortiRecorder NVR can discover the connected cameras
automatically and display them under Camera > Configuration > Camera with Status as Not
Configured. See “Connecting FortiRecorder to the cameras”.
4. After you configure the above settings, go to Camera > Configuration > Camera to configure
all other camera settings, such as IP address, motion detection windows, and so on. See
“Configuring cameras”.
5. Go to Camera > Configuration > Camera Group to add individual camera to different groups
to facilitate camera management. For details, see “Camera groups”. Camera groups are
used in user profiles. For details, see “User configuration workflow”.
Configuring video profiles
Video profiles define the video quality that you want the camera to capture and stream to the
NVR. Note that the higher the video quality, the more bandwidth it consumes.
The video profiles will be used in the camera profiles. For details, see “Configuring camera
profiles”.
To configure a video profile
1. Go to Camera > Configuration > Video Profile.
2. Click New.
Page 36
Page 37

3. Configure the following, then click Create.
Setting name Description
Name Type a name (such as live-stream1) that can be referenced
by other parts of the configuration. Do not use spaces or
special characters. The maximum length is 35 characters.
Resolution Select the amount of detail (the number of pixels) in the image.
from the dropdown menu.
Lower resolutions features less detail but are faster to
transmit. Higher resolutions produce a clearer image but
require more bandwidth. A higher resolution is preferable if the
camera is recording a large space, such as a parking lot,
where small details like faces and license plates could be
important.
Note: Resolution greatly impacts performance, bandwidth,
and the rate at which disk space is consumed. See “Video
performance”.
Frames per second Type the number of frames per second (FPS).
Conventional video is 24 frames per second. More frames per
second may be useful if you need to record very fast motion,
but increasing FPS will also increase disk usage and CPU
usage.
Bit rate mode Select the bit rate.
Bit rate Type the bit rate that will be used.
Quality Select the degree of compression.
Configuring camera profiles
A camera profile defines the video profiles to use, video storage options, and recording
schedules.
• Variable — Automatically adjust the stream to the
minimum bit rate required by the current video frames
while maintaining video quality.
• Fixed — Manually specify a constant bit rate in Bit rate.
Specifying a bit rate that is too low may result in poor
quality. Specifying a bit rate that is too high may needlessly
consume extra bandwidth.
This setting appears and is applicable only if Bit rate mode is
Fixed.
Greater compression reduces required network bandwidth but
causes greater CPU usage.
To configure camera profiles
1. Go to Camera > Configuration > Camera Profile.
2. Click New.
Camera settings Page 37 FortiRecorder 2.4.2 Administration Guide
Page 38

3. Configure the following, then click Create.
Setting name Description
Name Type a name (such as camera-settings1) that can be
referenced by other parts of the configuration. Do not use
spaces or special characters. The maximum length is 35
characters.
Video Select the Recording stream profile used to determine the
video quality of the recorded video.
Select the Viewing stream profile used to determine the video
quality of the streamed video when viewing.
Click Add schedule to specify when to use low or high quality
video. For example, you could improve the camera’s night
performance without sacrificing the quality of video during the
day.
Note: The higher the quality, the more bandwidth the stream
will use.
Recording Select the Recording type that will instruct the camera when
to begin filming.
• Continuous: records video for the entire duration of the
schedule, regardless of movement or any other triggers.
• Motion detection: records a video clip up to about 40
seconds long each time the camera’s sensor detects
movement.
• Digital input: records a video clip up to about 40 seconds
long each time the camera receives a trigger from the
digital input. For details about how to use digital input and
output (DIDO), see “Configuring cameras” on page 44.
This option only takes effect if the camera supports DIDO.
• Audio detection: records a video clip up to about 40
seconds long each time the camera detects audio
activities. You can define the audio sensitivity when
configuring camera settings. For details, see “Configuring
cameras” on page 44.
• PIR detection: PIR based motion detection senses the
movement of people, animals, and other objects that
produce heat energy.
Note: Some recording types may not be available for your
camera.
If you want to use different recording types at different times,
click Add schedule to specify them. For example, you could
instruct the camera to start recording for motion detection
during the day and PIR detection at night.
Camera settings Page 38 FortiRecorder 2.4.2 Administration Guide
Page 39

Setting name Description
Storage Options You can select the storage options of both continuous
recordings and detection recordings.
• Keep — Retain video until all available disk space is
consumed
• Delete — Remove video when it exceeds a maximum age.
• Move — Relocate video to external storage when it
exceeds a maximum age. This option appears if you have
configured network storage (see “External storage”).
If you choose to delete old video, also configure the maximum
amount of time to keep video recording files from this camera.
Files whose start time is older than this age will be deleted in
order to free disk space for new video recordings.
Continuous recordings will be stored on the hard disk as
multiple video files. In that case, the oldest part of the
recording will be deleted first.
Compression Options Select whether or not FortiRecorder compresses continuous
recordings.
If compression is enabled, also configure the maximum
amount of time to keep the files uncompressed. Files whose
start time is older than the specified time will be compressed.
Camera groups
After you have configured the cameras, you can group them to facilitate the camera
management. When you add administrators/operators/viewers later on, you can specify the
camera group they can access, instead of single cameras. For details, see “User management”.
To configure camera groups, go to Camera > Configuration > Camera Group.
Note: Selecting Compress will save storage space at the cost
of video quality.
Camera settings Page 39 FortiRecorder 2.4.2 Administration Guide
Page 40

Camera connection
After you have configured the NVR and camera settings, you can install and connect cameras to
the FortiRecorder NVR. For information about how to physically install a camera, see the
camera’s QuickStart Guide.
Camera discovery and DHCP service
In order for the FortiRecorder NVR to be able to discover cameras and receive video, cameras
Two first get their IP addresses and other network settings from either the FortiRecorder
built-in DHCP server or any other third-party DHCP server on your network.
• FortiRecorder DHCP server — If you do not have a DHCP server in your network, or you
are installing the FortiRecorder and the cameras in their dedicated network, you must
configure the built-in DHCP server on the FortiRecorder. For example, if you configured the
built-in DHCP server to provide DHCP service through port2, and port2 is connected to a
PoE switch, you would connect the cameras to the PoE switch. The switch would supply
power to the cameras, and through it, the cameras would be able to access the DHCP
server. For information about FortiRecorder DHCP server configuration, see “Configuring the
DHCP server” on page 23.
• Other DHCP server — If you already have a DHCP server in your network and the
FortiRecorder and cameras will be installed in the existing network, the cameras will get their
IP addresses from the DHCP server after you connect and power up the cameras.
If you connect a camera to FortiRecorder before any DHCP server is configured, the camera will
assign itself a default IP address, which might not be working in your subnet. In this case, you
must reboot the camera after you have configured a DHCP server, so that the camera can get
network settings from the DHCP server.
Since you can configure the camera to use a static IP address, you only need the DHCP server
for the initial camera discovery.
Later, after each camera has network settings from DHCP, you can either:
• Continue using DHCP— Leave the cameras plugged into their current network location.
Configure the DHCP server to reserve a specific IP lease for each camera. This will mimic
Page 40
Page 41

configuring the cameras with a static IP address, yet will provide the advantage that IP
addresses remain centrally managed.
If you continue to let your cameras use DHCP, you should configure Reserved IP Address (or,
on a third-party DHCP server, the equivalent setting). Failure to do this may appear to work
initially, but eventually could periodically, temporarily interrupt connectivity with the NVR,
resulting in lost video.
This can happen if either the DHCP pool is too small for the number of cameras, or if a
misconfigured computer accidentally takes a camera’s DHCP lease: the DHCP server will
ultimately be forced to assign the camera’s IP address to a different client. If this happens,
when the camera next requests a lease, it will receive a new, different IP address, and the NVR
will not be notified.
Connectivity interruptions are usually self-correcting: within a few minutes, the
FortiRecorder NVR should detect the camera’s IP address change. To restore connectivity
manually, either manually update the camera’s definition on the NVR to reflect the new IP, or
discover the camera again.
• Switch the camera to a static IP — Use the FortiRecorder NVR to configure the camera
with a static IP address. This removes the requirement of your cameras to remain within
reach of the DHCP server, which provides 2 advantages:
• You can disable DHCP if not otherwise required (recommended for better security).
• You can move the cameras to a remote location on your network that would not ordinarily
be reachable by your DHCP server.
Connecting FortiRecorder to the cameras
After you configure the DHCP server (you do not have to if you already have one), you can
connect and configure the cameras.
Once you connect the cameras to the NVR, the NVR can automatically discover the cameras.
Then you can configure the discovered cameras.
Requirements
• On your computer, the Apple QuickTime 7.1 or greater plug-in installed for your web
browsers
• At the camera’s location on the network, power over Ethernet (PoE)
This could be provided by a FortiSwitch-80-PoE or perhaps your ISP’s cable modem.
Camera connection Page 41 FortiRecorder 2.4.2 Administration Guide
Page 42

To connect FortiRecorder to your cameras
1. If this is the first time you connect to FortiRecorder, change your PC’s IP address to be on
the same subnet as the FortiRecorder port1’s default IP address 192.168.1.99. For example,
set your PC’s IP to 192.168.1.98.
2. Connect your PC and FortiRecorder’s port1to a PoE switch. Do ne connect the camera to
the switch at this stage.
3. On your PC, open a web browser and connect to https://192.168.1.99. Log in to the admin
administrator account with Name: admin and Password: (none).
4. If you want to use the FortiRecorder DHCP service, configure the DHCP server as described
in the next step. If you already have a DHCP server to use on your network, skip the next
step.
5. On the FortiRecorder web UI, go to System > Network > DHCP, and click New to create a
new DHCP server on port1.
Make sure to enable
DHCP server
Make sure to select
port1
Camera connection Page 42 FortiRecorder 2.4.2 Administration Guide
Page 43
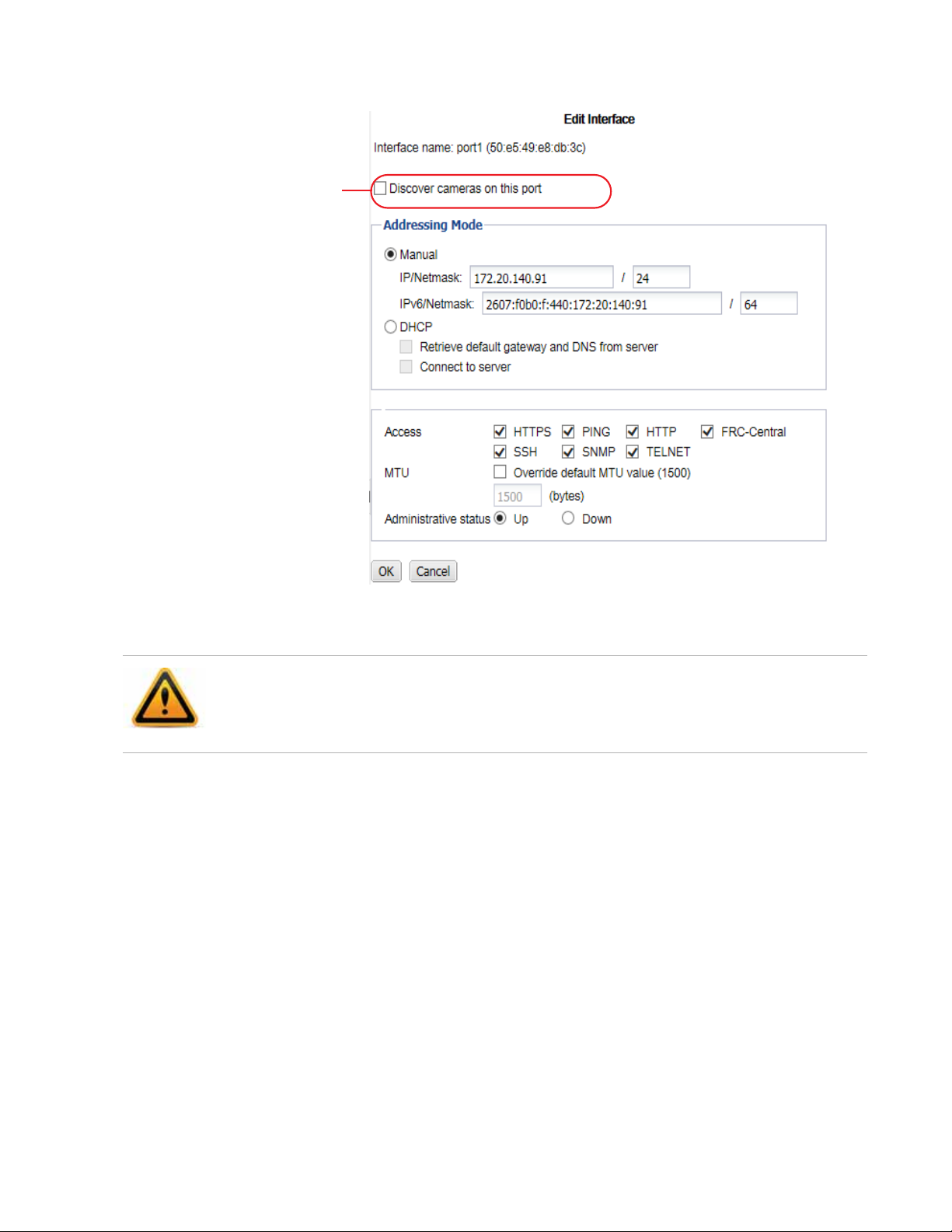
6. Go to System > Network > Interface. Select port1 and click Edit.
Make sure to
enable it
7. Make sure Discover cameras on this port is enabled.
8. Connect the camera to the PoE switch now.
If you connect the camera to the switch before you have configured and enabled the DHCP
server on FortiRecorder, the camera will use its default IP address, which might not be working
on your network. Therefore, you must reboot the camera to get an IP address from the
FortiRecorder DHCP server by unplugging the camera from the switch and plugging it back.
Camera connection Page 43 FortiRecorder 2.4.2 Administration Guide
Page 44

9. Go to Camera > Configuration > Camera, and click Discover. After several seconds, a list of
discovered cameras should appear. Newly discovered cameras will be highlighted in yellow,
and their Status column will contain Not Configured.
Discover button
Yellow: discovered but not configured cameras
10.Double click on the discovered camera to configure the camera settings. For details, see
“Configuring cameras” on page 44.
11.Go to Monitor > Video Monitor to view the live feed from the camera.
Configuring cameras
After you have connected the cameras to FortiRecorder, you can start to configure the
discovered cameras. Because most of the camera information has been retrieved from the
camera, you do not have to change the settings. But if you are adding a remote camera or
adding a new camera before connecting it to FortiRecorder, you must specify all the camera
settings.
1. Go to Camera > Configuration > Camera. For each discovered camera, click its row to select
it, click Configure, then configure these settings:
Setting name Description
Enable Mark this check box to enable the FortiRecorder NVR to
Configured cameras
communicate with this IP address. Communications are
required to trigger scheduled recordings and other camera
commands.
Name Type a name (such as front-door1) that can be referenced
by other parts of the configuration. Do not use spaces or
special characters. The maximum length is 35 characters.
Location Optional. Type a description of the camera’s physical location
that can be used if the camera is hidden, in case it is forgotten
or lost.
Camera connection Page 44 FortiRecorder 2.4.2 Administration Guide
Page 45
Setting name Description
Vendor/Camera FortiRecorder supports Fortinet cameras (FortiCam series)
and third-party, ONVIF-compliant cameras.
If you are configuring a discovered camera, most of the
camera information has been retrieved and displayed. You can
also click the Camera detail button to refresh the camera
information.
If you are adding a remote camera, or adding a new camera
before it is connected, you must specify all the settings. For
the Fortinet FortiCam cameras, you must specify the models;
for the non-Fortinet cameras, you must specify the camera’s
login credentials (user name and password) for FortiRecorder
to access it.
Model Select the name of the camera model, such as FCM-20A for a
FortiCam 20A.
Address mode Select either:
• Wired — Select this option if you want to keep the camera
connected with the Ethernet cable on the same subnet.
• Wireless — Select this option if you want to change the
camera connection from wired to wireless. Also configure
the WiFi settings on the WiFi tab.
• VIP — Allow the camera to continue using DHCP to
determine its IP address, but the camera will be on a
remote network, and therefore the FortiRecorder NVR will
not connect to the camera’s DHCP address. Instead, the
NVR will connect through the static external, usually public
network IP address and port numbers (called a virtual IP or
VIP on FortiGate firewalls) specified in Address, (HTTPS)
Port, and (RTSP) Port. The router or firewall will translate
and forward connections to the camera’s private network
address.
Likewise, communications in the other direction — from
the camera to the FortiRecorder NVR — are also affected:
the camera will use the public IP setting as its destination
(see “Configuring system timeout, ports, and public
access”), not the private network address of port1, for
example, which it would use if you select DHCP or Static.
Tip: Use this option if the camera is not located on the
same private network as the FortiRecorder NVR due to
NAT/ port forwarding, especially if the camera and NVR
are separated by the Internet.
Address If you want to deploy the camera to a different subnet, you can
specify its new IP address or the VIP that it will be using.
(HTTPS) Port Type the port number of configuration communications from
the FortiRecorder that the firewall or router will forward to the
camera. If using only a WAN/virtual IP without port
forwarding/translation, leave this setting at its default value,
443.
This setting is available only when Address mode is set to VIP.
Camera connection Page 45 FortiRecorder 2.4.2 Administration Guide
Page 46

Setting name Description
(RTSP) Port Type the port number of video streaming commands (RTSP)
from the FortiRecorder that the firewall or router will forward to
the camera, such as when beginning a continuous recording
schedule. If using only a WAN/virtual IP without port
forwarding/translation, leave this setting at its default value,
554.
This setting is available only when Address mode is set to VIP.
Transport Type Normally RTSP is used for video streaming, which is UDP. If
you want to use TCP, you can use HTTP tunnelling. If you want
the communication to be secure/encrypted, you can use
HTTPS tunnelling.
The tunnel is between the camera and the NVR.
Profile Select the camera profile that indicates the recording
schedule, video quality, and other settings that will be used by
this camera (see “Connecting FortiRecorder to the cameras”).
Or click New to create a new camera profile.
If a camera is disabled while you change its settings, or while it would normally be scheduled to
begin continuous or motion detection recording, the FortiRecorder NVR will not connect to the
camera.
This can break communications between them: if you reconfigure the IP while the camera is
disabled, your FortiRecorder NVR may later attempt to communicate with the camera at the
new address/gateway, but the camera will still be using the old address/gateway. It can also
cause cameras to become out-of-sync, because they will not receive time setting changes
while disabled. To fix this, disable the camera definition, revert the settings, enable the camera
definition again, then apply your changes while the camera definition is enabled.
2. Click the Preview button to retrieve a single still image from the camera. Then click Use As
Icon to use the captured image as the icon for the camera in the camera list. When you
select the camera from the list, the icon will pop up.
3. Depending on the camera model you are configuring, different tabs appear.
Camera connection Page 46 FortiRecorder 2.4.2 Administration Guide
Page 47

4. If the address mode is wired or wireless, under the network tab, configure the following:
Setting name Description
Wired settings Select DHCP if you want the camera to continue using DHCP to
dynamically determine its IP address. The FortiRecorder NVR will
attempt to keep track of any DHCP-related IP address changes
automatically using periodic mDNS probes. This requires that the
camera remain on the same subnet as the NVR.
Select Static to re-configure the camera with a static private network IP
address that you specify in Address. It will no longer use DHCP. This
option requires that the camera and NVR not be separated by NAT.
Caution: It is strongly recommended to either:
• configure your cameras with a static IP, or
• configure your DHCP server with lease reservations (see
“Configuring the DHCP server”).
Without reservations, the IP address provided by the DHCP server may
appear to work initially, but later, in some cases, the DHCP server could
change the IP address lease. If this happens, the DHCP server will not
update the list of known cameras with the camera’s new dynamic IP.
Until the appliance discovers that the IP address has changed,
FortiRecorder will still be trying to control the camera’s old address,
which no longer works. Connections with that camera will be broken
and all video from that camera will be lost during that interruption.
Wireless settings This area displays the wireless DHCP settings for the camera. You can
change the camera to use a static IP address. For more information
about wireless connection, see the following WiFi section.
5. If the camera has wireless function and you want it to connect to FortiRecorder through a
wireless router, you can specify the WiFi settings on the WiFi tab. After you configure the
WiFi settings, you can disconnect the discovered camera and connect it to the router.
Setting name Description
Enable Select to Enable the WiFi function of the camera.
SSID Specify the wireless router’s SSID that the camera will connect to.
Security Specify the security settings.
6. If the camera supports infra red recording or LED lighting, configure the settings on the Light
or Infrared tab.
Setting name Description
Mode Either off or auto. Auto means to turn on infra red mode at the
threshold.
LED Either off or auto. Auto means to turn on the LED lights when the infra
red mode is turned on.
Enable threshold Enter the light level when infra red mode should turn on.
Camera connection Page 47 FortiRecorder 2.4.2 Administration Guide
Page 48

Setting name Description
Disable threshold Enter the light level when infra red mode should turn off.
Threshold time Enter the time interval (in seconds) when the camera should wait to turn
on or off the infra red mode after the threshold is reached.
Current light level Display the current light level that the camera detects.
Refresh Click to get instant light level reading.
7. Configure the video and audio settings on the Video/Audio tab. Available setting vary on
different camera models. If the setting is greyed out, the setting is not supported on the
selected model.
Setting name Description
Horizontal flip Enable if the camera is positioned looking at a mirror or on a ceiling,
and the preview image appears to be reversed left to right.
Vertical flip Enable if the camera is positioned on a ceiling, and the preview image
appears to be upside down.
WDR If the camera supports WDR (wide dynamic range), enable it if there is
intense backlight in the camera view.
Environment Select if the camera is installed indoor or outdoor.
View angle Select the view angle if the camera support it.
Get feed/Stop
Click to view or stop the live video feed.
feed
(Other settings) Configure the brightness, contrast, saturation, sharpness, zoom level,
and audio input level as required.
8. In some cases, you may want to mask an area and do not want to show a certain portion of
the image. For example, for privacy reason, you may want to mask the area where an
employee sits. To do this, on the Privacy Mask tab, click the plus sign beside Mask Window
and tweak the window size. To add another mask window, click the plus sign again.
9. All FortiCam cameras are capable of detecting motion. Some camera models also supports
audio surveillance and digital input and output (DIDO).
By default, while using motion detection, cameras will be triggered to record if any motion
occurs within their entire field of vision. If some parts of the view, such as a fan, traffic, or
strobe light, would inadvertently trigger motion detection, in the Motion detection windows
area on the Detection tab, click the plus sign. A rectangle with a thick, white border will
appear over the preview image, indicating the area that will be monitored for movement. To
resize it to your intended area, click and drag the edges of the rectangle. To move it, hold
Camera connection Page 48 FortiRecorder 2.4.2 Administration Guide
Page 49

down the Shift key while you click and drag it. To add another motion detection area, click
the plus sign again.
For audio detection and DIDO, configure the following settings:
Setting name Description
Audio Sensitivity If the camera supports audio surveillance, specify the sensitivity level
that the camera recording will be triggered. You may need to tweak the
sensitivity level, for example, when there are some background noises.
Camera connection Page 49 FortiRecorder 2.4.2 Administration Guide
Page 50

Setting name Description
PIR Sensitivity
Digital
input/output
Some cameras come with DIDO terminals and support digital input and
output. For example, on the FortiCam MB13 camera, according to your
configuration, power signal from the digital input can trigger the
camera to record a video clip. You can also optionally connect other
devices to the digital output, such as a relay to turn on/off another
device.
DIDO connection diagram on FortiCam MB13
4. Power output +5V
3. Digital output
2. Digital input
1. Ground
The digital input (DI) can be configured to trigger when the signal is:
• LOW (ground)
• HIGH (+5V)
• Rising (transitioning from LOW to HIGH)
• or Falling (transitioning from HIGH to LOW)
If not connected, the camera will see the digital input as HIGH.
The digital output (DO) can be configured to either be grounded or
open when in the triggered state. When not triggered it will be in the
opposite state.
For example, if opening a door causes a sensor switch to open, then
the switch could be wired between DI and ground. DI will be grounded
(LOW) while the door is closed and will go HIGH when the door opens.
DI could then be configured to trigger on the rising edge. When the
door opens, DO would be set to its triggered state and a video clip will
also be recorded.
Triggering on the rising or falling edge can be useful if the DI might be
held in the triggered state for a long period. In the example above, if DI
were set to trigger on HIGH and the door is left open for a long period
then the camera would trigger repeatedly.
Camera connection Page 50 FortiRecorder 2.4.2 Administration Guide
Page 51

10.On the Miscellaneous tab, configure the following settings:
Setting name Description
Privacy button FortiCam MB13 has a privacy button on it. If enabled, you can press
the privacy button on the camera to stop and resume video and audio
monitoring.
To enable the functionality of the privacy button on the camera, select
the Privacy button checkbox.
To disable the functionality of the privacy button on the camera, clear
the Privacy button checkbox.
Status LEDs Most cameras come with LED indicators (for details, see the LED
description section in the camera’s QuickStart Guides). You can enable
or disable the LEDs by selecting or deselecting the Status LEDS
checkbox.
11.Click OK.
If you kept the Enabled check box marked, at this time, FortiRecorder connects to the
camera’s discovered IP address. FortiRecorder configures the camera with:
• the camera’s new Address and other network settings (if Address mode is set to Static)
• NTP settings (if you configured them for FortiRecorder during “Setting the system time”)
Afterwards, in order to control the camera according to your selected schedules,
FortiRecorder will periodically connect to the camera’s configured IP address. It will also
keep video recordings sent by that camera from its new IP address.
12.To confirm that FortiRecorder can receive video from the camera at its new IP address, go to
Monitor > Video Monitor.
If no video is available from that camera, verify that:
• Other video software such as Windows Media Player or VLC has not stolen the RTSP file
type association from QuickTime (Installing other video software after QuickTime is a
common cause of changes to media file type associations.)
• A route exists to the camera’s new IP address and, if applicable, its virtual IP/port forward
To confirm, go to Monitor > System Status > Console and enter the command:
execute ping <camera_ipv4>
where <camera_ipv4> is the camera’s IP address or virtual IP/port forward. If you
receive messages such as Timeout..., to locate the point of failure on the network,
enter the command:
execute traceroute <camera_ipv4>
• Firewalls and routers, if any, allow both RTSP and RTCP components of the RTP
streaming video protocol between FortiRecorder and the camera and between your
computer and FortiRecorder (see “Appendix A: Port numbers”)
• Web proxies or firewalls, if any, support streaming video
If you did not discover the camera but instead manually configured FortiRecorder with the
camera’s IP address, confirm that the camera is actually located at that address.
To receive notifications if the camera’s connection with the FortiRecorder NVR is interrupted,
see “Alert email”.
Camera connection Page 51 FortiRecorder 2.4.2 Administration Guide
Page 52

13.If desired, you can specify different camera settings, such as brightness and contrast, for the
camera to use as different times. For details, see “Configuring schedules” on page 28.
See also
• Watching live video feeds
• Connectivity issues
Camera connection Page 52 FortiRecorder 2.4.2 Administration Guide
Page 53

User management
In its factory default configuration, FortiRecorder has one administrator account named admin.
This administrator has permissions that grant full access to FortiRecorder’s settings and
features.
To prevent accidental changes to the configuration, it’s best if only network administrators —
and if possible, only a single person — use the admin account. You can use the admin
administrator account to configure more accounts for other people.
User types
To serve different purposes, you can configure the following three user types:
• Administrator — Suited to network technicians or administrators. Depending on the access
privileges, the administrator account can have full or partial access to configure all
FortiRecorder NVR network and camera settings, create accounts, receive all notifications
via email, and view live video feeds and previous recordings from all cameras.
• Operator — Suited to an office manager or perhaps security guard. The account can view
assigned live camera feeds and associated previous recordings, including camera-based
notifications via email (“snapshot notifications”). It can change its own password, but
otherwise trnne change the FortiRecorder NVR or camera configuration, reducing risk of
accidental misconfiguration.
• Viewer — Suited to a security guard. Only assigned live camera feeds. It cannot view
previous recordings, and therefore cannot receive snapshot notifications. It can change its
own password, but otherwise cannot change the FortiRecorder NVR or camera
configuration.
Multiple administrators should not be logged in simultaneously. If configuring the same item at
the same time, the administrators could inadvertently overwrite each others’ changes.
For user authentication, FortiRecorder supports local user authentication, LDAP authentication
and RADIUS authentication. Fort details, see “Configuring LDAP authentication” and
“Configuring RADIUS authentication”.
User configuration workflow
Administrators user type can access all the cameras all the time. For operator and viewer user
types, you can specify when and which cameras the users can access. To achieve this, you
must configure access schedules and user profiles first.
1. Go to System > Administrator > Access Profile to configure the access privileges for the
administrator accounts. The access profile will be used in the administrator settings. For
details, see “Configuring access profiles” on page 54.
2. Go to System > Administrator > User Profile to configure which camera group the user is
allowed to access. For details, see “Configuring user profiles” on page 54.
Page 53
Page 54

3. Go to System > Administrator > Administrator to configure all other user settings. For details,
see “Configuring user accounts” on page 54.
Configuring access profiles
Access profiles control which FortiRecorder funtions the users are allowed to access. Before
you configure user accounts, you must configure the access profiles, which will be used in the
user account settings.
To configure an access profile
1. Go to System > Administrator > Access Profile.
2. Click New.
3. Enter a profile name.
4. Specify the access privileges.
5. Click Create.
Configuring user profiles
User profiles controls which camera groups users are allowed to access and when users are
allowed to access the cameras. The user profiles will be used in the user settings you need to
configure in the next step. For details about configuring camera groups, see “Camera groups”.
If no camera group is specified, then the user can access all cameras.
If no access schedule is specified, then the user is allowed to access the video all the time.
To configure a user profile
1. Go to System > Administrator > User Profile.
2. Click New.
3. Enter a profile name.
4. Specify a camera group the user is allowed to access.
5. Add an access schedule.
6. Click Create.
Configuring user accounts
After you configure access profiles and user profiles, you can start to add user accounts.
To configure an account
1. Go to System > Administrator > Administrator.
To access this part of the web UI, your account’s Type must be Administrator.
2. Click New.
A dialog appears.
User management Page 54 FortiRecorder 2.4.2 Administration Guide
Page 55

3. Configure these settings:
Setting name Description
Username Type the name of the account, such as IT, that can be referenced in
other parts of the configuration.
Do not use spaces or special characters. The maximum length is 35
characters.
Note: This is the entire user name that the person must provide when
logging in to the CLI or web UI. Depending on Authentication, your
external authentication server may require that you enter both the user
name and the domain part, such as guard@example.com.
Display name Type a name for the recipient, such as FortiRecorder admin, as
you want it to appear in snapshot notifications, if any, sent by
FortiRecorder.
Email address Type the person’s email address or an email alias, such as
all-admins@example.com, that will receive snapshot notifications,
if any, sent by FortiRecorder (see “Configuring FortiRecorder to send
notification email”).
If you do not know the email address and cannot provide it, don’t
worry. The person still will be able to view camera-related notifications
whenever he or she logs in to the FortiRecorder NVR. Additionally, the
person can configure his or her own email address later, when he or
she logs in.
Note: This is not used by accounts whose Type is Viewer; they cannot
receive snapshot notifications.
Message method Select either Email or SMS to send notification messages to this user.
For detailed about notifications, see “Notifications”.
Password Type a password for the account.
This field is available only when Authentication is Local or RADIUS +
Local.
Tip: For improved security, the password should be at least eight
characters long, be sufficiently complex, and be changed regularly. To
check the strength of your password, you can use a utility such as
Microsoft’s password strength meter.
Confirm Password Re-enter the password to confirm its spelling.
This field is available only when Authentication is Local or RADIUS +
Local.
User management Page 55 FortiRecorder 2.4.2 Administration Guide
Page 56

Setting name Description
Trusted hosts Type the IP address and netmask from which the account is allowed to
log in to the FortiRecorder appliance. You can specify up to 10 trusted
network areas. Each area can be a single computer, a whole subnet, or
a mixture.
To allow login attempts from any IP address, enter 0.0.0.0/0.
To allow logins only from a single computer, enter its IP address and a
32-bit netmask, such as:
172.168.1.50/32
Caution: If you configure trusted hosts, do so for all accounts. Failure
to do so means that all accounts are still exposed to the risk of brute
force login attacks. This is because if you leave even one account
unrestricted (i.e. 0.0.0.0/0), the FortiRecorder appliance must allow
login attempts on all network interfaces where remote administrative
protocols are enabled, and wait until after a login attempt has been
received in order to check that user name’s trusted hosts list.
Tip: If you allow login from the Internet, set a longer and more complex
Password, and enable only secure administrative access protocols
(HTTPS and SSH) to minimize the security risk. For information on
administrative access protocols, see “NVR configuration”.
Tip: For improved security, restrict all trusted host addresses to single
IP addresses of computer(s) from which only this administrator will log
in.
Type Select either:
• Administrator — Suited to network technicians or administrators.
The account has full access to configure all FortiRecorder NVR
network and camera settings, create accounts, receive all
notifications via email, and view live video feeds and previous
recordings from all cameras.
• Operator — Suited to an office manager or perhaps security
guard. The account can view assigned live camera feeds and
associated previous recordings, including camera-based
notifications via email (“snapshot notifications”). It can change its
own password, but otherwise cannot change the FortiRecorder
NVR or camera configuration, reducing risk of accidental
misconfiguration.
• Viewer — Suited to a security guard. Only assigned live camera
feeds. It cannot view previous recordings, and therefore cannot
receive snapshot notifications. It can change its own password, but
otherwise cannot change the FortiRecorder NVR or camera
configuration.
This option does not appear for the admin administrator account,
which by definition is always an administrator.
User management Page 56 FortiRecorder 2.4.2 Administration Guide
Page 57

Setting name Description
User profile With a user profile, you can specify which group of camera video feeds
and recordings the account will be able to access. You can also use
schedules to control when the user is allowed to access the video. For
details, see “Configuring schedules” on page 28.
To configure a user profile, click New or go to System > Administrator
> User Profile.
kifnefwoacfsceihvafhofosathihaIPf danf dafwoacftrnfrttaoofrvvfeif daf
trTacrofrvvf daf hTa .
Access profile If you are creating an administrator account, you can specify an
access profile to grant the account certain access privileges.
To configure an access profile, go to System > Administrator > Access
Profile.
The administrator account can have read-only, read-write, or no
access rights to the following administrative categories:
• System Access — Controls settings critical to network
accessibility of FortiRecorder
• System Status page
• GUI console
• Network
• Administrator
• Authentication and certificates
• System — Controls other system settings
• Time
• Remote storage
• Log settings
• Alert email
• Camera Config — Controls camera installation and configuration
• Camera View — Monitor page with video, timeline and camera
control
• Other — Everything else
User management Page 57 FortiRecorder 2.4.2 Administration Guide
Page 58

Setting name Description
Authentication Select one of:
• Local — Authenticate using an account whose name, password,
and other settings are stored locally, in the FortiRecorder NVR’s
configuration.
• RADIUS — Authenticate by querying the remote RADIUS server
that stores the account’s name and password. Also configure
RADIUS profile and Check permission attribute on RADIUS server.
• RADIUS+Local — Authenticate either by querying the remote
RADIUS server that stores the account’s name and password, or
by querying the accounts stored locally, in the FortiRecorder
appliance’s configuration. Also configure RADIUS profile and
Check permission attribute on RADIUS server.
• LDAP — Authenticate by querying a remote LDAP server that
stores the account’s name and password. Also configure LDAP
profile.
RADIUS profile Select a RADIUS authentication profile that defines the RADIUS
connection settings. See “To configure a RADIUS query”.
This field appears only when Authentication is RADIUS or
RADIUS+Local.
Caution: Secure your authentication server and, if possible, all query
traffic to it. Compromise of the authentication server could allow
attackers to gain administrative access to your FortiRecorder
appliance.
User management Page 58 FortiRecorder 2.4.2 Administration Guide
Page 59

Setting name Description
Check permission
attribute on
RADIUS server
Enable to let the RADIUS server override Type when it replies to
authentication queries, so that the RADIUS server can specify the
account’s permissions. Also configure Vendor ID and Subtype ID.
This option requires that:
• Your RADIUS server must support vendor-specific attributes (VSAs)
similar to RFC 2548. (If your server does not support them, it may
reply with an “attribute not supported” error.)
• Your RADIUS server’s dictionary must have:
• a vendor ID for Fortinet/FortiRecorder
• an attribute ID for user types (“access profile” names)
• Each FortiRecorder account on your RADIUS server must have a
user type attribute with a value that specifies which Type to apply.
e.g.
Fortinet-Access-Profile = Administrator
or
Fortinet-Access-Profile = Operator
Some RADIUS servers already include the Fortinet vendor ID and
subtype ID in their default dictionaries. In this case, no server-side
configuration is necessary. Otherwise, you must configure your server.
Methods varies by vendor — FreeRADIUS and Internet Authentication
Services for Microsoft Windows 2008 Server, for example, are
configured differently. For instructions, consult its documentation. For
an example VSA dictionary, see the article FortiGate RADIUS VSA
Dictionary.
This field appears only when Authentication is RADIUS or
RADIUS+Local.
Vendor ID Type the vendor ID for Fortinet, as it is defined on your RADIUS server,
in decimal. On many RADIUS servers, Fortinet’s default vendor ID is
12356.
The vendor ID is an ID for the Fortinet client types. It should be present
in Access-Request packets from FortiRecorder, telling your RADIUS
server which settings are supported by accounts on FortiRecorder. It
should also be present when the RADIUS server replies with an
Access-Accept packet.
The default value is 0.
User management Page 59 FortiRecorder 2.4.2 Administration Guide
Page 60

Setting name Description
Subtype IDType the subtype ID for account permissions as it is defined on your
RADIUS server. On many RADIUS servers, Fortinet’s default subtype
ID for access profiles is 6.
The subtype ID is an ID for the user type (permissions) attribute. It
should be, but is not required to be, present in Access-Accept reply
packets from your RADIUS server to FortiRecorder.
Packets from your RADIUS server should use this attribute’s value to
refer to the name of a Type (e.g. Administrator) on FortiRecorder. If the
packet does not have this attribute-value pair, FortiRecorder will use
whichever permissions you defined locally for the account in Type. If
the packet does not contain the attribute-value pair and you have not
configured Type, when the person attempts to authenticate, even if
successfully authenticated, authorization will be null, and he or she will
receive a “permission denied” error message:
you do not have rights to view this page
The default value is 0.
LDAP profile Select an LDAP authentication profile that defines the connection
settings. See “To configure an LDAP query”.
Caution: Secure your authentication server and, if possible, all query
traffic to it. Compromise of the authentication server could allow
attackers to gain administrative access to your FortiRecorder
appliance.
Theme Select this administrator account’s preference for the initial web UI
color scheme or click Use Current to choose the theme currently in
effect for your own web UI session.
The administrator may switch the theme at any time after he or she
logs in by clicking Next Theme in the top right corner.
4. Click Create.
The account should now be able to log in.
Configuring LDAP authentication
FortiRecorder supports LDAP user authentication. You will use the LDAP authentication profiles
when you add user accounts.
To configure an LDAP query
1. Go to System > Authentication > LDAP.
2. Click New.
A dialog appears.
User management Page 60 FortiRecorder 2.4.2 Administration Guide
Page 61

3. Configure these settings:
Setting name Description
Profile name Type a name (such as LDAP-query) that can be referenced by other
parts of the configuration. Do not use spaces or special characters.
The maximum length is 35 characters.
Server name/IP Type the fully qualified domain name (FQDN) or IP address of the
LDAP or Active Directory server that will be queried when an account
referencing this profile attempts to authenticate.
Fallback server
name/IP
Type the fully qualified domain name (FQDN) or IP address of a
secondary LDAP or Active Directory server, if any, that can be queried
if the primary server fails to respond according to the threshold
configured in “Timeout” on page 64.
Port Type the port number on which the authentication server listens for
queries.
The IANA standard port number for LDAP is 389. LDAPS
(SSL/TLS-secured LDAP) is 636.
Use secure
connection
If your directory server uses SSL to encrypt query connections, select
SSL then upload the certificate of the CA that signed the LDAP
server’s certificate (see “Uploading trusted CAs’ certificates”).
Allow
unauthenticated
bind
Enable to perform the query without authenticating.
Disable to authenticate when querying. Also configure Bind DN, Bind
password, and User Authentication Options.
Many LDAP servers require LDAP queries to be authenticated
(“bound”) by supplying a bind DN and password to determine the
scope of permissions for the directory search. However, if your LDAP
server does not require binding, you can enable this option to improve
performance.
4. If your directory does not use OpenLDAP’s default schema, or if you need to configure a
query string, query cache, LDAP protocol version, or how the query will be authenticated
User management Page 61 FortiRecorder 2.4.2 Administration Guide
Page 62

(the bind DN), click the arrows to expand User Query Options, User Authentication Options,
and Advanced Options, then configure:
Setting name Description
Schema If your LDAP directory’s user objects uses one of these common
schema style:
• InetOrgPerson
• InetLocalMailRecipient
• Active Directory
• Lotus Domino
select the schema style. This automatically configures the query string
to match that schema style.
Otherwise, select User Defined, then manually configure the query
string in LDAP user query.
Base DN Enter the distinguished name (DN) of the part of the LDAP directory
tree within which FortiRecorder will search for user objects, such as
ou=People,dc=example,dc=com.
User objects should be child nodes of this location.
Bind DN Enter the bind DN, such as
cn=FortiRecorderA,dc=example,dc=com, of an LDAP user
account with permissions to query the Base DN.
Leave this field blank if you have enabled Allow unauthenticated bind.
Bind password Enter the password of the Bind DN.
Click Browse to locate the LDAP directory from the location that you
specified in Base DN, or, if you have not yet entered a Base DN,
beginning from the root of the LDAP directory tree.
Browsing the LDAP tree can be useful if you need to locate your Base
DN, or need to look up attribute names. For example, if the Base DN is
unknown, browsing can help you to locate it.
Before using, first configure Server name/IP, Use secure connection,
Bind DN, Bind password, and , then click Create or OK. These fields
provide minimum information required to establish the directory
browsing connection.
User management Page 62 FortiRecorder 2.4.2 Administration Guide
Page 63

Setting name Description
LDAP user query Enter an LDAP query filter that selects a set of user objects from the
LDAP directory.
The query string filters the result set, and should be based upon any
attributes that are common to all user objects but also exclude
non-user objects.
For example, if user objects in your directory have two distinguishing
characteristics, their objectClass and mail attributes, the query
filter might be:
(& (objectClass=inetOrgPerson) (mail=$m))
where $m is the FortiRecorder variable for a user's email address.
This option is preconfigured and read-only if you have selected from
Schema any schema style other than User Defined.
For details on query syntax, refer to any standard LDAP query filter
reference manual.
Scope Select which level of depth to query, starting from Base DN.
• One level — Query only the one level directly below the Base DN in
the LDAP directory tree.
• Subtree — Query recursively all levels below the Base DN in the
LDAP directory tree.
Derefer Select when, if ever, to dereference attributes whose values are
references.
• Never — Do not dereference.
• Always — Always dereference.
• Search — Dereference only when searching.
• Find — Dereference only when finding the base search object.
User
Authentication
Options
Select how, if the query requires authentication, the FortiRecorder
appliance will form the bind DN. The default setting is the third option:
Search user and try bind DN.
• Try UPN or email address as bind DN — Select to form the user’s
bind DN by prepending the user name portion of the email address
($u) to the User Principle Name (UPN, such as example.com).
By default, the FortiRecorder appliance will use the mail domain as
the UPN. If you want to use a UPN other than the mail domain,
enter that UPN in the field named Alternative UPN suffix. This can
be useful if users authenticate with a domain other than the mail
server’s principal domain name.
• Try common name with base DN as bind DN — Select to form
the user’s bind DN by prepending a common name to the base DN.
Also enter the name of the user objects’ common name attribute,
such as cn or uid into the field.
• Search user and try bind DN — Select to form the user’s bind DN
by using the DN retrieved for that user by User Query Options.
User management Page 63 FortiRecorder 2.4.2 Administration Guide
Page 64

Setting name Description
User Type
Attribute
User Profile
Attribute
Access Profile
Attribute
Notification
Options
Select this option to define the user’s type.
Valid entries for this field are: admin, operator, and viewer.
Select this option to define the user’s profile.
The entry for this field must match the profile name configured in
FortiRecorder.
The access profile attribute can only be set if the user is an
administrator.
Selecting this option will set the administrator user’s access profile.
The entry for this field must match the name of an access profile
configured in FortiRecorder.
Select the “Allow notification attributes” option to enable notifications.
FortiRecorder supports the following notifications:
• Email attribute: This attribute specifies the user’s email address
for notifications.
• SMS profile attribute: This attribute specifies which SMS profile
the user will use. The SMS profile attribute must match the name of
the profile configured in FortiRecorder.
• SMS number attribute: This attribute specifies the user SMS
number for notifaction.The number format must be the same as the
number in the user entry settings.
• Method attribute: This attribute specifies the method used to
notify a user. The two valid entries are “email” and “sms”.
• Embedded email images attribute: This attribute specifies
whether images are included in email messages to the user. The
two valid entries are “yes” and “no”.
Timeout Type the number of seconds that the FortiRecorder appliance will wait
for a reply to the query before assuming that the primary LDAP server
has failed, and will therefore query the secondary LDAP server.
The default value is 20.
Select the LDAP protocol version (either 2 or 3) used by the LDAP server.
Protocol version
User management Page 64 FortiRecorder 2.4.2 Administration Guide
Page 65

Setting name Description
Enable to cache LDAP query results.
Enable cache
Caching LDAP queries can introduce a delay between when you
update LDAP directory information and when the FortiRecorder
appliance begins using that new information, but also has the benefit
of reducing the amount of LDAP network traffic associated with
frequent queries for information that does not change frequently.
If this option is enabled but queries are not being cached, inspect the
value of TTL. Entering a TTL value of 0 effectively disables caching.
TTL Enter the amount of time, in minutes, that the FortiRecorder unit will
cache query results. After the TTL has elapsed, cached results expire,
and any subsequent request for that information causes the
FortiRecorder appliance to query the LDAP server, refreshing the
cache.
The default TTL value is 1440 minutes (one day). The maximum value
is 10080 minutes (one week). Entering a value of 0 effectively disables
caching.
This option is applicable only if is enabled.
5. Click Create.
6. To test the query, configure an account where this profile is used (“To configure an account”),
then attempt to authenticate using that account’s credentials.
Alternatively, click the row to select the query, click Edit, then click Test LDAP Query. From
the Select query type drop-down list, choose Authentication, then complete the Password
and Mail address fields that appear. Click Test. After a few seconds, a dialog should appear
to let you know that either the query succeeded, or the reason for its failure, such as a
connectivity error.
User management Page 65 FortiRecorder 2.4.2 Administration Guide
Page 66

Configuring RADIUS authentication
Except for local users, FortiRecorder also support RADIUS user authentication. You will use the
RADIUS authentication profiles when you add user accounts.
To configure a RADIUS query
1. Go to System > Authentication > RADIUS.
2. Click New.
A dialog appears.
3. Configure these settings:
Setting name Description
Profile name Type a name (such as RADIUS-query) that can be referenced by
other parts of the configuration. Do not use spaces or special
characters. The maximum length is 35 characters.
Server name/IP Type the fully qualified domain name (FQDN) or IP address of the
RADIUS server that will be queried when an account referencing this
profile attempts to authenticate.
Server port Type the port number on which the authentication server listens for
queries.
The IANA standard port number for RADIUS is 1812.
Protocol Select which authentication method is used by the RADIUS server:
• Password Authentication
• Challenge Handshake Authentication (CHAP)
• Microsoft Challenge Handshake Authentication (CHAP)
• Microsoft Challenge Handshake Authentication V2 (CHAP
version 2)
• Default Authentication Scheme
NAS IP/Called
station ID
Server secret Type the secret required by the RADIUS server. It must be the same as
Server requires
domain
Type the NAS IP address or Called Station ID (for more information
about RADIUS Attribute 31, see RFC 2548 Microsoft Vendor-specific
RADIUS Attributes). If you do not enter an IP address, the IP address
of the FortiRecorder network interface used to communicate with the
RADIUS server will be applied.
the secret that is configured on the RADIUS server.
Enable if the authentication server requires that users authenticate
using their full email address (such as user1@example.com) and not
just the user name (such as user1).
4. Click OK.
To test the query, select this profile when configuring an account (“To configure an account”),
then attempt to authenticate using that account’s credentials.
User management Page 66 FortiRecorder 2.4.2 Administration Guide
Page 67

See also
• NVR configuration
• Connectivity issues
• Login issues
User management Page 67 FortiRecorder 2.4.2 Administration Guide
Page 68

Notifications
When a significant event happens, such as motion-triggered video recording or the hard disk
being full, your FortiRecorder NVR can notify you, either by email or SMS messages.
Notification configuration workflow
To configure the notifications, follow these steps:
1. Configure the SMTP mail server settings so that FortiRecorder can send out notification
email. See “Configuring FortiRecorder to send notification email”.
2. Configure the SMS server settings so that FortiRecorder can send out SMS messages. See
“Configuring FortiRecorder to send SMS messages”.
3. Configure the camera settings about what, when and to whom the notifications should be
sent. See “Configuring cameras to send notifications”.
4. Monitor the record of notification events by going to Monitor > Camera Notifications >
Notification Events.
Configuring FortiRecorder to send notification email
For FortiRecorder to send email, you must specify an SMTP server to use.
1. Go to System > Configuration > Mail Server Settings.
Page 68
Page 69

2. Configure these settings:
Setting name Description
Host name Type the host name for the appliance. By default, it uses its serial
number.
The host name can be up to 35 characters in length. It can include
US-ASCII letters, numbers, hyphens, and underscores, but ne
spaces and special characters.
The host name of the FortiRecorder appliance is used in multiple
places.
• It is used in the command prompt of the CLI.
• It is used as the SNMP system name. For information about
SNMP, see “SNMP traps & queries”.
The get system status CLI command displays the full host
name. If the host name is longer than 16 characters, the name
may be truncated elsewhere and end with a tilde ( ~ ) to indicate
that additional characters exist, but are not displayed.
For example, if the host name is FortiRecorder1234567890, the
CLI prompt would be:
FortiRecorder123~#
Mail server name Type the fully-qualified domain name (FQDN) of your SMTP server,
such as mail.example.com.
If you do not have your own email server, this is often the name of
your ISP’s SMTP relay, or a 3rd-party email server such as Yahoo!
or Gmail.
Ensure that the DNS settings are configured. See “Configuring the
network settings”.
Mail server port Type the port number on which your email server or SMTP relay
listens for connections from clients.
The default varies by whether you enable Use SMTPS: disabled, it
is port 25; enabled, it is port 465.
Use SMTPS Enable to initiate SSL- and TLS-secured connections to the email
server if it supports SSL/TLS.
When disabled, SMTP connections from the FortiRecorder
appliance’s built-in email client to the SMTP server will occur as
clear text, unencrypted.
This option must be enabled to initiate SMTPS-secured
connections.
Notifications Page 69 FortiRecorder 2.4.2 Administration Guide
Page 70

3. If the email server requires SMTP authentication (i.e. it uses the SMTP AUTH command), also
enable Authentication Required, then configure these settings:
Setting name Description
User name Type the name of the account, such as jdoe or
fortirecorder@example.com, that FortiRecorder will use to
log in to the SMTP server.
Password Type the password for the account on the SMTP server.
Authentication type Select one of the following authentication methods:
• AUTO — Automatically detect and use the most secure SMTP
authentication type supported by the email server.
• PLAIN — Provides an unencrypted, scrambled password.
• LOGIN — Provides an unencrypted, scrambled password.
• DIGEST-MD5 — Provides an encrypted MD5 hash of the
password.
• CRAM-MD5 — Provides an encrypted MD5 hash of the
password, with hash replay prevention, combined with a
challenge and response mechanism.
4. If you want to customize the FortiRecorder’s sender email address so that, for example,
replies are sent to the network administrators rather than the appliance, then configure these
settings:
Setting name Description
Sender display name Type the display name, such as Surveillance System, that will
be displayed in the From field or column by email clients such as
Outlook and Thunderbird. Leaving this setting empty will cause
FortiRecorder to use the default value, postmaster.
Sender address Type the sender email address (From:), such as
donotreply@example.com, that will appear in the SMTP
header. Leaving this setting empty will cause FortiRecorder to use
the default value, postmaster@example.com.
Unlike the display name, depending on the client and its settings,
this may not be visible.
Configuring FortiRecorder to send SMS messages
For FortiRecorder to send SMS messages, you must specify the SMS service providers.
1. Go to System > Configuration > SMS.
2. Configure the following:
Setting name Description
Service provider Enter the SMS service provider name.
Notifications Page 70 FortiRecorder 2.4.2 Administration Guide
Page 71

Setting name Description
Description Enter a short description of the provider.
Type Select an SMS type: either SMTP or HTTP.
For SMTP, enter the Email to, Email subject, and Email body
information.
You can use the following tags when filing the fields:
• {{:country_code}} represents the country code portion of the
SMS number field in the user's configuration.
• {{:mobile_number}} represents the phone number portion of
the SMS number field in the user's configuration.
• {{:message}} represents the text of the message.
For HTTP, enter the following information:
• HTTP URL: the HTTP or HTTPS URL to contact to send SMS
messages, for example, https://myprovider.com/sendsms).
• HTTP method: either Get or Post.
• HTTP/S Parameters: configure all the parameters and values
required by the provider to send the SMS message. You can
use the same tags that were available above for SMTP. If you
select the Encrypt check-box in a parameter then the value will
not be displayed in clear-text when viewing the configuration.
The value will be sent as entered to the remote server which is
why using HTTPS is recommended.
For example, if your provider indicates that to send a message
the syntax should look like the following:
https://smsserver.com:8080/sendsms?api_id=1234&user=user
&to=<phone_number>&text=<message>&password=<passwd
>
Then the settings might be:
HTTP URL: https://smsserver.com:8080/sendsms
HTTP Method: Get
Parameters:
api_id id
user user
to {{:country_code}}{{:mobile_number}}
text {{:message}}
password password (the encrypt checkbox should be
selected so this will not show in clear-text when viewing the
configuration)
Configuring cameras to send notifications
After you have set up the SMTP server and SMS service provider, you can configure the
detailed notification settings, such as when and how the notifications should be sent.
1. Go to Camera > Notification > Camera Notification.
Notifications Page 71 FortiRecorder 2.4.2 Administration Guide
Page 72

2. Click New.
3. Configure the following setting and then click Create.
Setting name Description
Name Enter a name for the notification entry.
Description Optionally enter a descriptive comment.
Enable Select to enable this notification entry.
Trigger number Specify how many times the motion event should happen before
the notification is sent out.
Trigger period Specify the period in which these motion events occur.
Message method Select how the notification should be sent out: either Email or
SMS. At least one method should be selected.
Notification Period Specify when notifications should be sent out. For details, see
“Configuring schedules” on page 28.
Select Camera Specify which camera’s motion events should be notified.
Select User Specify which user should be notified.
4. To verify email connectivity, from FortiRecorder, trigger an alert event that matches the type
and severity levels that you have chosen. Then, check your email.
If you do not receive an alert email within a few minutes, verify that you have configured an
email address for the account. Next, verify the FortiRecorder NVR’s static routes (see
“Configuring the network settings”) and the policies on any firewalls or routers between the
appliance and the SMTP relay. (They must allow SMTP traffic from the FortiRecorder
network interface that is connected to the gateway between it and the email server.) To
determine the point of connectivity failure along the network path, if the SMTP server is
configured to respond to ICMP ECHO_REQUEST (ping), go to Monitor > System Status >
Console and enter the CLI command:
execute traceroute <syslog_ipv4>
where <syslog_ipv4> is the IPv4 address of your email server.
If that connectivity succeeds, verify that your alert email has not been classified as spam by
checking your junk mail folder.
To prevent classification as spam, it usually helps to add the FortiRecorder NVR’s email address
to your address book.
See also
• Connectivity issues
Notifications Page 72 FortiRecorder 2.4.2 Administration Guide
Page 73

Video monitoring
To get the most value out of your FortiRecorder system, use it to monitor your property — not
just to analyze after-the-fact. Your FortiRecorder NVR has a variety of monitoring tools for the
appliance itself, but administrators can also view the live video feeds from cameras.
You can use the tools in this section to monitor your FortiRecorder NVR and surveillance
cameras.
Watching live video feeds
Once the cameras are connected and configured, administrators can use the web UI to view
live video feeds from the cameras.
Administrators will use the surveillance system slightly differently than other users (“operators”
or “viewers”) such as security guards. Operators and viewers can only watch the live video and
do not have the privilege to configure the system settings.
Quality of live video feeds may be different for administrators than it is for operator or viewer
accounts, which use the camera’s settings in “Configuring video profiles” on page 36.
Page 73
Page 74

To view live video from your cameras as an administrator
1. Go to Monitor > Video Monitor
Buffering (a blue “Q” appears, with an oscillating dotted line underneath) may take a few
seconds, depending on the network, the Resolution of the camera, and your computer.
When buffering is done, the current live video feed should appear.
Live video feed Panel expansion arrows
2. There are very thin arrows at the bottom and (for administrators) right of the video viewer
frame. If you are an administrator, click the arrow on the right to expand the image
adjustment control panels.
3. If you logged in as an administrator, on the right pane, in the Selection area, choose which
cameras you want to view.
4. If you logged in using a non-administrator account, your cameras have already been
selected for you. If they are not correct, ask an administrator to reconfigure your account.
See also
• Watching recorded video clips
Video and image sharing
FortiRecorder supports video and image sharing on the web sites. Using FortirRecorder,
administrators can configure FortiRecorder and a third-party web site to allow users to access a
live feed of an established camera or an image from a camera without directly accessing
FortiRecorder.
Video monitoring Page 74 FortiRecorder 2.4.2 Administration Guide
Page 75

To allow users to access video sharing, you must first insert the video in your web page.
For example, if your FortiRecorder runs v2.3 and older firmware, you can insert the following
code in your web page:
<iframe frameborder="10" scrolling="no" width="640" height="480"
src="https://172.20.110.94/api?request=FRC_LiveView&id=FD20&width=
640&height=480&view_mode=3&hostName=172.20.110.94&username=videoSe
rvice&password=1234">
<p>iframes are not supported by your browser.</p> </iframe><br/>
Starting from v2.4, if your web browser supports HTML5, you can use the following code:
<iframe frameborder="10" scrolling="no" width="640" height="480"
src="https://172.20.110.94/api?request=FRC_LiveView&id=FD20&width=
640&height=480&view_mode=3&hostName=172.20.110.94&username=videoSe
rvice&password=1234">
<p>iframes are not supported by your browser.</p> </iframe><br/>
<script>
setInterval(function() {
var req = new XMLHttpRequest();
req.open('GET',
"https://172.20.110.94/api?request=FRC_LiveView&id=20A-b5fc&userna
me=videoService&password=1234&heartbeat=1", true);
req.send();
}, 10000);
</script>
The IP address at the beginning of the code is the IP of the FortiRecorder. The attribute ID is the
name of the camera as defined on the FRC. The attribute dimensions should match the size of
the iframe. The username and password values should match the configuration you specify
below.
Once you have entered the code into your web page, configure the FortiRecorder unit to allow
your web page to access the camera group via HTTPS.
If you want to share the video stream via RTSP, the user can use a RTSP client to access the
video at:
rtsp://<username>:<password>@<fortirecorder_ip>/camera=<id>
For example:
rtsp://videoService:1234@172.20.110.94/camera=FD20
To configure video sharing on FortiRecorder
1. Go to Service > Video > Stream.
2. Select the Status checkbox.
3. Enter your username and password.
4. Add the camera group you wish the user to view by selecting the group from the Camera
Group List and then selecting the right arrow button.
5. Select the HTTPS or RTSP protocol.
6. Select OK.
You can configure your FortiRecorder unit to upload images from a camera group. Using the
image service your cameras will capture a snapshot image at specified intervals. and upload the
image to a FTP site.
Similar to the shared video, you will need to upload the image to your web site. Once you have
finished that, configure image sharing in FortiRecorder.
Video monitoring Page 75 FortiRecorder 2.4.2 Administration Guide
Page 76

To configure image sharing on FortiRecorder
1. Go to Service > Video > Image.
2. Select the Status checkbox.
3. Enter the number of seconds in the Interval section that will dictate how often the cameras
capture a picture.
4. Enter the necessary FTP information.
5. Add the camera group you wish the user to view by selecting the group from the Camera
Group List and then selecting the right arrow button.
6. Select OK.
Watching recorded video clips
In addition to live video feeds, you can also watch the recorded video clips, which include the
scheduled recording, motion detection recording, and manual recording.
Color-coded video clips
Video monitoring Page 76 FortiRecorder 2.4.2 Administration Guide
Time line panel
Camera selection
and image control panel
Page 77

Time periods in the time line panel are color-coded:
• Yellow — A system event such as a software update, system reboot, or camera reboot.
Recordings cannot be stored while FortiRecorder is unavailable.
• Light blue — The lightest blue denotes previously recorded clips, the darker blue
denotes temporary recording (see descriptions below), the darkest blue denotes
manually initiated recording. If a camera is not currently recording a continuous or motion
detection-triggered video, operators can manually trigger the camera to record video
using the Control pane. Bright blue — A bright blue tag over a video clip represents
recording with an attached annotation/marker. While a camera is recording, you can
insert markers with notes about what is currently being seen. If the camera is not
recording, after you enter the marker and click Insert Marker, the camera will start to
record.
• Red — A motion detection-based recording that was not initiated by schedule.
• A white/blank space means there is no recording at that period of time.
About temporary recording
If the camera is not scheduled to record, but you are watching live feed from the camera, the
video feed from the camera will be temporarily recorded in memory but not saved on the hard
drive. When you stop watching the live feed from that camera, the temporary recording will be
deleted. However, if you initiate manual recording while watching the live feed from the camera,
the temporary recording will be saved on the hard drive.
To watch the recorded video
1. Go to Monitor > Video Monitor. The recorded video clips are in the Event Monitor area and
the video clips for each camera appears as a time line.
2. Be default, the time frame is minimized. To easily select a video clip, use the scroll wheel on
your mouse to zoom in a time frame. Ensure that the mouse cursor is centered in the area
that you want to zoom in. See the following pictures:
Video monitoring Page 77 FortiRecorder 2.4.2 Administration Guide
Page 78
Figure 1: Time line zoomed out
Figure 2: Time line zoomed in
Preview frames
After zooming in, double-click the enlarged segment to view the clip
3. After you select the segment (if it is a motion-detection clip, a few key frames will appear for
preview purpose), you can do the following:
• Click the Show button to view clip.
• Click the Download button to download the clip for archival or viewing on another
computer. If your cameras have recorded a crime or other incident, you may need to
provide the video clip to the police or other authorities. Your FortiRecorder NVR uses the
.mp4 file format with the H.264 video codec, which can be viewed on Windows, Mac OS
X, Linux, and other platforms using QuickTime, VLC or other compatible players. All
video files are signed with an RSA 2048-bit signature to provide tamper protection. This
applies to files stored locally, remotely, and downloaded. Quality of previously recorded
video depends on the camera’s settings in “Configuring video profiles” on page 36.
• Click the Lock button to lock the clip so that the operators and viewers will not be able to
view it.
4. To scroll through the time line, use your mouse to click and drag.
5. To set the time span of the time line, from Start date, select the beginning date of the
recording.
6. To manually control the camera to pause or start recording, in the pane on the right side,
click the Control bar to expand it, then click the buttons to pause or record.
You can’t stop a scheduled continuous or motion detection-based recording schedule. You can
only start/stop manual recording.
7. To adjust the image quality, in the pane on the right side, click the Control bar to expand it,
then click the + or - buttons to adjust Brightness, Contrast, Saturation, and Sharpness. Only
Video monitoring Page 78 FortiRecorder 2.4.2 Administration Guide
Page 79

administrators can use these controls, to prevent operators from accidentally or maliciously
blacking-out the view.
Set these settings with care. After video is recorded, it won’t be possible to adjust the image
quality again unless you download the file and use video editing software. Video editing
software may not be able to successfully correct for excessively bad image quality
8. To add a note to the video (e.g. “Suspicious light”), in the pane on the right side, click the
Control bar to expand it, type your note in the text area, then click the Insert Marker button.
A bright blue marker will appear on the clip and the added note will appear as mouse over
text. Note that you must zoom in to see the marker. Otherwise it is very small on the time
line. See the following picture.
Figure 3: Inserted marker
See also
• Watching live video feeds
Reviewing motion detection notifications
If you have configured camera-based notifications (see “Notifications”), accounts configured to
be notified can log in to the web UI in order to review the video clips. If you have configured
email settings, these accounts will also receive an email when a camera-based event occurs.
Notifications contain snapshot images from the video clip of the detected motion or, depending
on your configuration, a link directly to the video clip. In this way, recipients can quickly assess
whether or not the event is serious, or just a false alarm.
Occasionally, as an administrator, you may sometimes be required to review these notifications
if, for example, the usual recipient is on vacation. You can do this from the web UI, without
logging in to a separate operator account. Alternatively, you can add yourself to the list of
people that will receive a notification via email (see “Notifications”).
To review camera-based notifications
1. Go to Monitor > Camera Notifications > Notification Events.
2. From Select recipient, select either All (any recipient) or the name of an account that should
have received the notification.
The list of notifications will be filtered by the recipient criteria. Only matching notifications will
appear.
3. In the Message column, click the link to view the corresponding notification.
A pop-up window displays the notification that was included in the email body, if any. The
notification includes some images that are key frames from the motion detection video clip.
Inserted text marker in bright blue
Video monitoring Page 79 FortiRecorder 2.4.2 Administration Guide
Page 80

4. To view a video clip from the notification, click its key frame image.
The notification window will be replaced with a video clip player.
Video monitoring Page 80 FortiRecorder 2.4.2 Administration Guide
Page 81

Video management
If you need to store video for longer periods of time, you can extended your FortiRecorder
appliance’s built-in storage.
Local storage
Initially, your FortiRecorder appliance will store video data on its internal hard disk drive. By
default, it will continue to do so, regardless of the video clip’s age, until all available space is
consumed. By storing files locally first, your FortiRecorder appliance’s system resources are not
continuously consumed by transferring video that may not be needed, nor by transferring them
while it is recording (which is itself bandwidth-intensive). But on a per-camera basis, you can
configure your FortiRecorder appliance to either delete old videos, or to move older videos to an
external location.
Configuring RAID levels
FortiRecorder 400D model comes with two pre-installed hard drives in its four HDD bays and
supports software RAID. This means that you can add two more hard drives if required.
Table 7: FortiRecorder 400D supported RAID levels
Number of Installed Hard Disk
Drives
100
2 0, 1 1
3 0, 1 + hot spare, 5 5
4 5 + hot spare, 10 10
To configure RAID levels
Back up data on the HDD before beginning this procedure. Changing the device’s RAID level
temporarily suspends all data processing and erases all data on the HDD.
1. Connect to the CLI console.
2. Enter the following command:
execute raidlevel <level>
The FortiRecorder unit changes the RAID level and reboots.
Available RAID Levels Default RAID Level
Recommended HDD models and capacities
Use surveillance grade rated models, such as Western Digital WD40PURX and Seagate
ST4000VX000, with storage capacity between 2 to 4 TB.
Page 81
Page 82

If you are using old disks from another system (RAID or LVM), make sure to erase all the
metadata on the drives.
Adding a RAID disk
If desired, you can add one or two more hard disk drives to the FortiRecorder 400D unit.
Figure 4: Hard disk bays on FortiRecorder 400D unit
To add a disk to the RAID array
1. Remove the hard disk bay from the unit.
2. Install the hard disk in the bay.
3. Insert the bay into the unit.
4. Go to System > Storage > Local Storage.
5. Click Refresh.
6. The newly added disk will appear under Drives.
7. Add the disk to an array.
8. Click Refresh again. The new array will appear under RAID Arrays.
9. Select the new array, and adjust the portions you want to allocate to log and video storage.
10.Click Add To Logical Disks.
Replacing a RAID disk
When replacing a disk in the RAID array, the new disk must have the same or greater storage
capacity than the existing disks in the array. If the new disk has a larger capacity than the other
disks in the array, only the amount equal to the smallest hard disk will be used. For example, if
Video management Page 82 FortiRecorder 2.4.2 Administration Guide
Page 83

the RAID has 400 GB disks, and you replace one with a 500 GB disk, to be consistent with the
other disks, only 400 GB of the new disk will be used.
FortiRecorder units support hot swap; shutting down the unit during hard disk replacement is
not required.
To replace a disk in the array
1. Go to System > Storage > Local Storage.
2. In the row corresponding to the hard disk that you want to replace (for example, p4), select
the hard disk and click Delete.
The RAID controller removes the hard disk from the list.
3. Protect the FortiRecorder unit from static electricity by using measures such as applying an
antistatic wrist strap.
4. Physically remove the hard disk that corresponds to the one you removed in the web UI from
its drive bay.
5. Replace the hard disk with a new hard disk, inserting it into its drive bay.
6. Click Refresh.
The RAID controller will scan for available hard disks and should locate the new hard disk.
Depending on the RAID level, the FortiRecorder unit may either automatically add the new
hard disk to the RAID unit or allocate it as a spare that will be automatically added to the
array if one of the hard disks in the array fails.
The FortiRecorder unit rebuilds the RAID array with the new hard disk. Time required varies
by the size of the array.
Replacing all RAID disks
If you want to replace both of the pre-installed hard drives with your own on FortiRecorder 400B
and build the RAID array from scratch, follow these instructions.
Because the HTTPs certificates are stored on the hard drive, if you still need them, you must
back up the configuration first. The certificates will be backed up in the configuration file. After
you install the new hard drives, restore the configuration. But if you're not using the factory
certificates and you're planning to import your own certificate later on, you don't have to back
up the configuration/certificates.
To replace all disks in the array
1. Shut down the FortiRecorder unit.
2. Remove the hard disks.
3. Install the new hard disks.
4. Boot up the system.
5. Enter the following CLI command to rebuild the disks.
execute factoryreset disk
This command will use the default RAID level based on the number of drives used. You can
also use the following command to rebuild the disks with the specified RAID level. For the
supported RAID levels, see “Configuring RAID levels” on page 81.
execute raidlevel <level>
6. The system will reboot.
Video management Page 83 FortiRecorder 2.4.2 Administration Guide
Page 84
External storage
To extend your local storage, you can use an external USB storage device if your FortiRecorder
model has USB ports.
To safeguard your surveillance video in the event that your FortiRecorder appliance is destroyed
by fire, flood, intrusion, or other event that it is recording, configure your FortiRecorder
appliance to store its video at a remote location such as a branch office or cloud storage
provider.
It is recommended to connect the remote storage devices on a different interface than the
cameras.
To configure external storage
1. Go to System > Storage > External Storage.
2. Select the Enable check box.
3. Configure these settings:
Setting name Description
Protocol Select one of the following types of storage media:
• External USB — External USB device.
• iSCSI Server — An iSCSI (Internet Small Computer
System Interface), server.
• NFS — A network file system (NFS) server.
Note: Support for NFS varies. Many Linux-based NAS
solutions have been tested and are supported. Windows
2003 R2 and Windows 2008 Service for NFS are not
supported.
Maximum size Specify the maximum video file size that is allowed to be
stored on the external storage device.
You can view the remote storage usage information on the
Status page under Monitor > System Status.
Username Type the user name of the FortiRecorder’s account on the
server.
Alternatively, if using iSCSI, select Initiator name as username
to authenticate using a name that follows RFC 3721.
Password Type the password corresponding to the user name.
Hostname/IP Address Type either the IP address or fully-qualified domain name
(such as nas.example.com) of the server.
Port Type the port number on which the server listens for
connections.
The default is 2049 for NFS and 3260 for iSCSI.
Video management Page 84 FortiRecorder 2.4.2 Administration Guide
Page 85

Setting name Description
Directory Enter the path of the folder on the server, relative to the mount
point or user’s login directory, where the FortiRecorder
appliance will store the data.
This setting appears only if Protocol is NFS.
Note: Do not use special characters such as a tilde ( ~ ). This
will cause the storage to fail.
Encryption Key Enter the private key that will be used to encrypt data stored
on this location. Valid key lengths are between 6 and 64
single-byte characters.
This setting appears only if Protocol is ISCSI Server
iSCSI ID Enter the iSCSI identifier in the format expected by the iSCSI
server, such as an iSCSI Qualified Name (IQN), Extended
Unique Identifier (EUI), or T11 Network Address Authority
(NAA).
This setting appears only if Protocol is ISCSI Server.
4. Click Apply.
If the remote iSCSI device has not been formatted, before you can use it, you must format it
with the following CLI command: execute storage format
5. Go to Camera > Configuration > Camera, then click to select a camera’s row, then click Edit.
6. For Profile, click New or Edit.
7. From Storage Options, select Move. In the After n options that appear, select the age
threshold that will cause FortiRecorder to move the video clips to external storage. Note that
the Move option only appears after you have configured and enabled external storage.
8. Click Create.
See also
• Camera settings
Video management Page 85 FortiRecorder 2.4.2 Administration Guide
Page 86

System monitoring
FortiRecorder provides several methods, such as SNMP traps, system logs, and realtime
dashboard, for you to monitor the system status and diagnose system problems.
The dashboard
Monitor > System Status > Status appears when you log in to the web UI. It contains a
dashboard with widgets that each indicates performance level or other system statuses.
The Sessions tab displays the active TCP/UDP sessions to and from FortiRecorder.
The Console tab allows you to use the CLI commands.
To access the dashboard, you must have an administrator account. Operator accounts do not
have permission. For details, see “User types”.
SNMP traps & queries
You can configure the FortiRecorder appliance’s simple network management protocol (SNMP)
agent to allow queries for system information and to send traps (alarms or event messages) to
the computer that you designate as its SNMP manager. In this way you can use an SNMP
manager to monitor the FortiRecorder appliance.
Before you can use SNMP, you must activate the FortiRecorder appliance’s SNMP agent and
add it as a member of at least one community. You must also enable SNMP access on the
network interface through which the SNMP manager connects. (See “SNMP”.)
On the SNMP manager, you must also verify that the SNMP manager is a member of the
community to which the FortiRecorder appliance belongs, and compile the necessary
Fortinet-proprietary management information blocks (MIBs) and Fortinet-supported standard
MIBs. For information on MIBs, see “MIB support”.
Failure to configure the SNMP manager as a host in a community to which the FortiRecorder
appliance belongs, or to supply it with required MIBs, will make the SNMP monitor unable to
query or receive traps from the FortiRecorder appliance.
To configure the SNMP agent via the web UI
1. Add the MIBs to your SNMP manager so that you will be able to receive traps and perform
queries. For instructions, see the documentation for your SNMP manager.
2. Go to System > Configuration > SNMP.
Page 86
Page 87

3. Configure the following:
Setting name Description
SNMP agent enable Enable to activate the SNMP agent, so that the FortiRecorder
appliance can send traps for the communities in which you enabled
queries and traps. To receive queries, also SNMP on a network
interface.
For more information on communities, see “Configuring an SNMP
community”.
Description Type a comment about the FortiRecorder appliance, such as
dont-reboot. The description can be up to 35 characters long,
and can contain only letters (a-z, A-Z), numbers, hyphens ( - ) and
underscores ( _ ).
Location Type the physical location of the FortiRecorder appliance, such as
floor2. The location can be up to 35 characters long, and can
contain only letters (a-z, A-Z), numbers, hyphens ( - ) and
underscores ( _ ).
Contact Type the contact information for the administrator or other person
responsible for this FortiRecorder appliance, such as a phone
number (555-5555) or name (jdoe). The contact information can be
up to 35 characters long, and can contain only letters (a-z, A-Z),
numbers, hyphens ( - ) and underscores ( _ ).
4. If you want to use non-default thresholds to trigger SNMP traps such as high CPU usage,
memory (RAM) usage, or disk/partition usage, click the disclosure arrow next to SNMP
Threshold to expand the area, then configure these settings for each trap type:
Setting name Description
Trigger Click to edit, then type the percentage that when met or exceeded
will be considered an event.
Threshold Click to edit, then type the number of events that must be exceeded
during the sample period in order to cause the SNMP trap.
Sample Period (s) Click to edit, then type the amount of time in seconds during which
the appliance will count the number of trigger-exceeding events. If
the count exceeds the threshold number, the SNMP trap will be
sent.
Note: This must be equal to or greater than Sample Freq (s), so that
one or more samples are taken per time period.
Sample Freq (s) Click to edit, then type the interval in seconds between
measurements of the trap condition. If the trigger value is exceeded,
this counts as an event. You will not receive traps faster than this
rate, depending on the selected sample period.
Note: This must be equal to or less than Sample Period (s), so that
one or more samples are taken per time period.
5. Click Apply.
System monitoring Page 87 FortiRecorder 2.4.2 Administration Guide
Page 88

6. Create at least one SNMP community to define which hosts are allowed to query, and which
hosts will receive traps. See “Configuring an SNMP community”.
7. If using SNMPv3, see “Configuring SNMP v3 users”.
See also
• Configuring an SNMP community
• Configuring SNMP v3 users
Configuring an SNMP community
An SNMP community is a grouping of equipment for network administration purposes. You
must configure your FortiRecorder appliance to belong to at least one SNMP community so that
community’s SNMP managers can query the FortiRecorder appliance’s system information and
receive SNMP traps from the FortiRecorder appliance.
On FortiRecorder, SNMP communities are also where you enable the traps that will be sent to
that group of hosts.
You can add up to three SNMP communities. Each community can have a different
configuration for queries and traps, and the set of events that trigger a trap. You can also add
the IP addresses of up to 8 SNMP managers to each community to designate the destination of
traps and which IP addresses are permitted to query the FortiRecorder appliance.
To add an SNMP community via the web UI
1. Go to System > Configuration > SNMP.
2. If you have not already configured the agent, do so before continuing. See “To configure the
SNMP agent via the web UI”.
3. Under Community, click New.
A dialog appears.
4. Configure these settings:
Setting name Description
Name Type the name of the SNMP community to which the FortiRecorder
appliance and at least one SNMP manager belongs, such as public.
The FortiRecorder appliance will not respond to SNMP managers whose
query packets do not contain a matching community name. Similarly,
trap packets from the FortiRecorder appliance will include community
name, and an SNMP manager may not accept the trap if its community
name does not match.
Caution: Fortinet strongly recommends that you do ne add
FortiRecorder to the community named public. This popular default
name is well-known, and attackers that gain access to your network will
often try this name first.
Enable Enable this community entry.
System monitoring Page 88 FortiRecorder 2.4.2 Administration Guide
Page 89

Setting name Description
Community
Hosts
IP Address Type the IP address of the SNMP manager that, if traps or queries are
enabled in this community:
• will receive traps from the FortiRecorder appliance
• will be permitted to query the FortiRecorder appliance
SNMP managers have read-only access. You can add up to 8.
To allow any IP address using this SNMP community name to query the
FortiRecorder appliance, enter 0.0.0.0. For security best practice
reasons, however, this is not recommended.
Caution: FortiRecorder sends security-sensitive traps, which should be
sent only over a trusted network, and only to administrative equipment.
Note: If there are no other host IP entries, entering only 0.0.0.0
effectively disables traps because there is no specific destination for trap
packets. If you do not want to disable traps, you must add at least
one other entry that specifies the IP address of an SNMP manager.
Queries
Type each port number (161 by default) on which the FortiRecorder
appliance listens for SNMP queries from the SNMP managers in this
community, then enable it. Port numbers vary by SNMP v1 and SNMP
v2c.
Traps Type each port number (162 by default) that will be the source (Local)
port number and destination (Remote) port number for trap packets sent
to SNMP managers in this community, then enable it. Port numbers vary
by SNMP v1 and SNMP v2c.
SNMP Event
Enable the types of SNMP traps that you want the FortiRecorder
appliance to send to the SNMP managers in this community.
• System events (system reboot, system reload, system upgrade,
log disk formatting, and video disk formatting)
• Remote storage event
• Interface IP change
• Camera events (enabling, disabling, communication failure,
recording failure, IP change, and camera reboot)
While most trap events are described by their names, the following
events occur when a threshold has been exceeded:
• CPU Overusage
• Memory Low
• Log Disk Usage Threshold
• Video Disk Usage Threshold
To configure their thresholds, see “To configure the SNMP agent via the
web UI”. For more information on supported traps and queries, see “MIB
support”.
5. Click OK.
System monitoring Page 89 FortiRecorder 2.4.2 Administration Guide
Page 90

6. To verify your SNMP configuration and network connectivity between your SNMP manager
and your FortiRecorder appliance, be sure to test both traps and queries (assuming you
have enabled both). Traps and queries typically occur on different port numbers, and
therefore verifying one does not necessarily verify that the other is also functional. To test
queries, from your SNMP manager, query the FortiRecorder appliance. To test traps, cause
one of the events that should trigger a trap.
See also
• Configuring SNMP v3 users
• SNMP traps & queries
Configuring SNMP v3 users
If your SNMP manager supports SNMP v3, you can specify which of its user accounts is
permitted to access information about your FortiRecorder appliance. This provides greater
granularity of control over who can access potentially sensitive system information.
To specify access for an SNMP user via the web UI
1. Go to System > Configuration > SNMP.
2. If you have not already configured the agent, do so before continuing. See “To configure the
SNMP agent via the web UI”.
3. Under User, click New.
A dialog appears.
4. Configure these settings:
Setting name Description
User name Type the name of the SNMP user. This must match the name of the
account as it is configured on your SNMP manager.
You can add up to 16 users.
Enable Enable this user entry.
Security level Choose one of the three security levels:
• No authentication, no privacy — Causes SNMP v3 to behave
similar to SNMP v1 and v2, which provides neither secrecy nor
guarantees authenticity, and therefore is not secure. This option
should only be used on private management networks.
• Authentication, no privacy — Enables authentication only,
guaranteeing the authenticity of the message, but not safeguarding it
from eavesdropping. Also configure Authentication protocol.
• Authentication, privacy — Enables both authentication and
encryption, guaranteeing authenticity as well as secrecy. Also
configure Privacy protocol.
Authentication
protocol
Select either SHA-1 or MD5 hashes for authentication. Also configure a
salt in Password. Both the protocols and passwords on the SNMP
manager and FortiRecorder must match.
Privacy protocol
System monitoring Page 90 FortiRecorder 2.4.2 Administration Guide
Select either AES or DES encryption algorithms. Also configure a salt in
Password. Both the protocols and passwords on the SNMP manager
and FortiRecorder must match.
Page 91

5. Similar to configuring the SNMP community, configure the other settings to specify the trap
recipient IP, allowed query source IPs, and trap events (see “Configuring an SNMP
community”).
6. Click OK.
7. To verify your SNMP configuration and network connectivity between your SNMP manager
and your FortiRecorder appliance, be sure to test both traps and queries (assuming you
have enabled both). Traps and queries typically occur on different port numbers, and
therefore verifying one does not necessarily verify that the other is also functional. To test
queries, from your SNMP manager, query the FortiRecorder appliance. To test traps, cause
one of the events that should trigger a trap.
See also
• Configuring an SNMP community
• SNMP traps & queries
MIB support
The FortiRecorder SNMP agent supports the following management information blocks (MIBs):
Table 8: Supported MIBs
MIB or RFC Description
Fortinet Core MIB This Fortinet-proprietary MIB enables your SNMP manager to query for
FortiRecorder MIB This Fortinet-proprietary MIB enables your SNMP manager to query for
RFC-1213 (MIB II) The FortiRecorder SNMP agent supports MIB II groups, except:
system information and to receive traps that are common to multiple
Fortinet devices.
FortiRecorder-specific information and to receive
FortiRecorder-specific traps.
• There is no support for the EGP group from MIB II (RFC 1213,
section 3.11 and 6.10).
• Protocol statistics returned for MIB II groups (IP, ICMP, TCP, UDP,
and so on.) do not accurately capture all FortiRecorder traffic
activity. More accurate information can be obtained from the
information reported by the FortiRecorder MIB.
RFC-2665
(Ethernet-like MIB)
You can obtain these MIB files from the Fortinet Technical Support web site,
https://support.fortinet.com/.
To communicate with your FortiRecorder appliance’s SNMP agent, you must first compile these
MIBs into your SNMP manager. If the standard MIBs used by the SNMP agent are already
compiled into your SNMP manager, you do not have to compile them again.
To view a trap or query’s name, object identifier (OID), and description, open its MIB file in a
plain text editor.
All traps sent include the message, the FortiRecorder appliance’s serial number, and host name.
For instructions on how to configure traps and queries, see “SNMP traps & queries”.
See also
• SNMP traps & queries
The FortiRecorder SNMP agent supports Ethernet-like MIB information,
except the dot3Tests and dot3Errors groups.
System monitoring Page 91 FortiRecorder 2.4.2 Administration Guide
Page 92

Logging
About logs
Log messages, if you configured them (see “Configuring logging”), record important events on
your FortiRecorder system.
FortiRecorder appliances can log many different activities including:
• camera recording events
• administrator-triggered events including logouts and configuration changes
• system-triggered events including system failures
For more information about log types, see “Log types”.
You can select a priority level that log messages must meet in order to be recorded. For more
information, see “Log severity levels”.
The FortiRecorder appliance can save log messages to its memory, or to a remote location such
as a Syslog server or FortiAnalyzer appliance. For more information, see “Configuring logging”.
See also
• Log types
• Log severity levels
Log types
Each log message contains a Type (type) field that indicates its category, and in which log file it
is stored.
FortiRecorder appliances can record the following categories of log messages:
Table 9: Log types
Log type Description
Event Displays administrative events, such as downloading a backup copy of the
configuration, and hardware failures.
Camera Displays start/stop recording events, factory reset, and other camera events.
Avoid recording highly frequent log types such as traffic logs to the local hard disk for an
extended period of time. Excessive logging frequency can cause undue wear on the hard disk
and may cause premature failure.
System monitoring Page 92 FortiRecorder 2.4.2 Administration Guide
Page 93

Log severity levels
Each log message contains a Severity (pri) field that indicates the severity of the event that
caused the log message, such as pri=warning.
Table 10:Log severity levels
Level
(0 is greatest)
0 Emergency The system has become unusable.
1 Alert Immediate action is required.
2 Critical Functionality is affected.
3 Error An error condition exists and functionality could be
4 Warning Functionality could be affected.
5 Notification Information about normal events.
6 Information General information about system operations.
For each location where the FortiRecorder appliance can store log files (disk, Syslog or
FortiAnalyzer), you can define a severity threshold. The FortiRecorder appliance will store all log
messages equal to or exceeding the log severity level you select.
For example, if you select Error, the FortiRecorder appliance will store log messages whose log
severity level is Error, Critical, Alert, and Emergency.
Name Description
affected.
Avoid recording log messages using low log severity thresholds such as information or
notification to the local hard disk for an extended period of time. A low log severity threshold is
one possible cause of frequent logging. Excessive logging frequency can cause undue wear on
the hard disk and may cause premature failure.
Viewing log messages
You can use the web UI to view and download locally stored log messages. (You cannot use the
web UI to view log messages that are stored remotely on Syslog or FortiAnalyzer devices.) Log
messages are in human-readable format, where each log field’s name, such as Message (msg
field when viewing a raw, downloaded log file), indicates its contents.
To view log messages
1. Go to either Monitor > Log Viewer > Event (to view event logs about the appliance itself) or
Monitor > Log Viewer > Camera (to view logs about connected cameras).
Columns and appearance varies slightly by the log type.
Initially, the page displays a list of log files of that type.
2. Double-click the row of a log file to view the log messages that it contains.
System monitoring Page 93 FortiRecorder 2.4.2 Administration Guide
Page 94

Table 11: Monitor > Video Monitor > Event (viewing the contents of a log file)
Setting name Description
Level Select a severity level to hide log messages that are below this
threshold (see “Log severity levels”).
Subtype Select a subcategory (corresponding to the Subtype column) to hide
log messages whose subtype field does not match.
Go to line Type the index number of the log message (corresponding to the #
column) that you want to jump to in the display.
Search Click to find log messages matching specific criteria (see “Searching
logs”).
Back Click to return to the list of log files stored on FortiRecorder’s hard
drive.
Save View Click to keep your current log view settings for subsequent views and
sessions (see “Displaying & sorting log columns & rows”).
# The index number of the log message within the log file, not the order
of rows in the web UI.
By default, the rows are sorted by timestamp in descending order, the
same as they are within the log file, so the rows are in sequential
order, starting with the most recent log message, number 1, in the top
row. If you change the row sorting criteria (see “Displaying & sorting
log columns & rows”), these index numbers won’t be in the same
order as the rows.
For example, when sorting by the Message column’s contents, the
index numbers of the first 3 rows could be 14, 15, 9.
Note: In the current log file, each log’s index number changes as
new log messages are added, pushing older logs further down the
stack. To find the same log message later, remember its timestamp
and Message, not its #.
Date The date on which the log message was recorded.
When in raw format, this is the log’s date field.
Time The time at which the log message was recorded.
When in raw format, this is the log’s time field.
System monitoring Page 94 FortiRecorder 2.4.2 Administration Guide
Page 95

Setting name Description
Subtype The category of the log message, such as admin for events such as
authentication or configuration changes, or system for events such
as disk consumption or connection failures.
When in raw format, this is the log’s subtype field.
Log ID A dynamic log identifier within the system, not predictable, indicative
of the cause nor necessarily a unique identifier.
When in raw format, this is the log’s log_id field.
Message The log message that describes the specific occurrence of a
recordable event.
For example, all logout events follow a format similar to User admin
logout from GUI(172.16.1.5). but the exact message varies if
the account name, connection method, and IP address are different.
When in raw format, this is the log’s msg field.
3. To return to the list of log files, click the Back button.
See also
• Displaying & sorting log columns & rows
• Searching logs
Displaying & sorting log columns & rows
You can display, hide and re-order most columns — each column corresponds to a field in the
log messages — to display only relevant categories of information, in your preferred order.
If you need to sort and filter the log messages based on more complex criteria, you can
download the log file as a raw or CSV-formatted file for loading into external log or spreadsheet
software (see “Downloading log messages”).
To display or hide columns
1. Go to one of the log types, such as Monitor > Log Viewer > Event.
2. Double-click the row of a log file to view the log messages that it contains.
3. Hover your mouse cursor over one of the column headings. An arrow will appear on the right
side of the heading. Click the arrow to display a drop-down menu, then hover your mouse
cursor over the Columns item in the menu to display a list of check boxes — one for each
column.
4. Select which columns to hide or display:
System monitoring Page 95 FortiRecorder 2.4.2 Administration Guide
Page 96

5. To display a column such as Time, mark the check box next to its name. To disable the
display of a column, clear its check box.
The page refreshes immediately, displaying the columns that you selected.
6. Column settings will not usually persist when changing pages, nor from session to session.
If you want to keep the settings, you must click Save View. The log view settings will not
apply to other accounts. Each administrator must configure their own settings.
To arrange the columns & rows
1. Hover your mouse cursor over the column heading.
2. Click and drag the column into the position where you want it to be.
3. Hover your mouse cursor over one of the column headings. An arrow will appear on the right
side of the heading. Click the arrow to display a drop-down menu, then click either Sort
Ascending or Sort Descending to cause the rows to be sorted from either first to last, or last
to first, based upon the contents of that column.
4. Column settings will not usually persist when changing pages, nor from session to session.
If you want to keep the settings, you must click Save View.
See also
• Logging
• Searching logs
• About logs
Downloading log messages
You can download logs that are stored locally (i.e., on the FortiRecorder appliance’s hard drive)
to your computer.
To download a log file
1. Go to one of the log types, such as Monitor > Log Viewer > Event.
2. In the list of log files, mark the check box of the log message that you want to download.
(You can only download one log file at a time.)
3. Click Download.
A drop-down menu appears.
4. Select either:
• Normal Format — A plain text .log file.
• CSV Format — A comma-separated values (CSV) file that can be opened in spreadsheet
software such as Microsoft Excel or OpenOffice Calc.
• Compressed Format — A plain text .log file in a .gz compressed archive.
5. If a file download dialog appears, choose the directory where you want to save the file.
Your browser downloads the log file. Time required varies by the size of the file and the
speed of the network connection.
See also
• Deleting log files
Deleting log files
If you have downloaded log files to an external backup, or if you no longer require them, you
can delete one or more locally stored log files to free disk space.
System monitoring Page 96 FortiRecorder 2.4.2 Administration Guide
Page 97

To delete a log file
1. Go to one of the log types, such as Monitor > Log Viewer > Event.
2. Either:
• To delete all log files, mark the check box in the column heading. All rows’ check boxes
will become marked.
• To delete some log files, mark the check box next to each file that you want to delete.
3. Click Delete.
See also
• Downloading log messages
Searching logs
When viewing attack logs, you can locate a specific log using the event log search function.
To search an attack log
1. Go to one of the log types, such as Monitor > Log Viewer > Event.
2. Click Search.
A dialog appears.
3. Configure these settings:
Setting name Description
Keyword Type all or part of the exact word or phrase you want to search for.
The word may appear in any of the fields of the log message (e.g.
Action and/or Message), in any part of that field’s value. If entering
multiple words, they must occur uninterrupted in that exact order.
For example, entering admin as a keyword will include results such
as User admin2 logout from GUI(172.16.1.15) where part
of the word appears in the middle of the log message. However,
entering User logout would not yield any results, because in the
log messages, those two words are always interrupted by the name of
the account, and therefore do not exactly match your search key
phrase.
Depending on your setting of Match condition, you may be able to
use asterisks as wild cards to match multiple words.
This setting is optional.
Message Type all or part of the exact value of the Message (msg) field of the log
messages that you want to find.
This setting is optional.
Log ID Type all or part of the ID number of the log messages that you want to
find.
This setting is optional.
System monitoring Page 97 FortiRecorder 2.4.2 Administration Guide
Page 98

4. Click Apply to initiate the search.
Event Monitor
Although in the Video Monitor, you can view both the live video and motion detection events on
the timeline, the event monitor allows you to view the motion detection events only without
loading the live video stream. This will save bandwidth when the bandwidth is a concern.
To view the motion detection events
1. Go to Monitor > Event Monitor.
2. On the right side, select the cameras you want to view.
3. Be default, the time frame is minimized. To easily select a video clip, use the scroll wheel on
4. After you select the segment (if it is a motion-detection clip, a few key frames will appear for
5. To scroll through the time line, use your mouse to click and drag.
6. To set the time span of the time line, from Start date, select the beginning date of the
Setting name Description
Time Select the date and time range that contains the attack log that you
are searching for.
This setting is optional.
Note: The date fields default to the current date. Ensure the date
fields are set to the actual date range that you want to search.
Match condition Select whether your match criteria are specified exactly (Contain) or
you have indicated multiple possible matches using an asterisk in
Keyword (Wildcard).
The web UI displays log messages that match your search on a new tab.
your mouse to zoom in a time frame. Ensure that the mouse cursor is centered in the area
that you want to zoom in. See the following pictures:
preview purpose), you can do the following:
• Click the Show button to view clip.
• Click the Download button to download the clip for archival or viewing on another
computer. If your cameras have recorded a crime or other incident, you may need to
provide the video clip to the police or other authorities. Your FortiRecorder NVR uses the
.mp4 file format with the H.264 video codec, which can be viewed on Windows, Mac OS
X, Linux, and other platforms using QuickTime, VLC or other compatible players. All
video files are signed with an RSA 2048-bit signature to provide tamper protection. This
applies to files stored locally, remotely, and downloaded. Quality of previously recorded
video depends on the camera’s settings in “Configuring video profiles” on page 36.
• Click the Lock button to lock the clip so that the operators and viewers will not be able to
view it.
recording.
System monitoring Page 98 FortiRecorder 2.4.2 Administration Guide
Page 99

Secure connections and certificates
When a FortiRecorder appliance initiates or receives an SSL or TLS connection, it will use
certificates. Certificates can be used in secure connections for:
• encryption
• authentication of servers
FortiRecorder may require you to upload certificates and CRLs even if you do not use HTTPS.
For example, when sending alert email via SMTPS, or querying an authentication server via
LDAPS, FortiRecorder will validate the server’s certificate by comparing the server certificate’s
CA signature with the certificates of CAs that are known and trusted by the FortiRecorder
appliance. See “Uploading trusted CAs’ certificates” and “Revoking certificates”.
Supported cipher suites & protocol versions
How secure is an HTTPS connection?
A secure connection’s protocol version and cipher suite, including encryption bit strength and
encryption algorithms, is negotiated between the client and the SSL terminator during the
handshake. (When you connect to the web UI via HTTPS, your FortiRecorder appliance is the
SSL terminator.) matrwoafoatwch ufoa hnbofTwo frbcaaPf dafcaowv fIasanIof.e dfenf daf
rssvhrntafrnIfuewcfga.f.cegoac lf
Page 99
Page 100

FortiRecorder supports:
• SSL 2.0
• RC4-MD5 — 40-bit & 128-bit
• SSL 3.0
• AES-SHA — 256-bit & 128-bit
• CAMELLIA-SHA — 128-bit & 256-bit
• DES-CBC3-SHA — 168-bit
• DES-CBC-SHA — 40-bit & 56-bit
• DHE-RSA-AES-SHA — 256-bit & 128-bit
• DHE-RSA-CAMELLIA-SHA — 256-bit & 128-bit
• DHE-RSA-SEED-SHA — 128-bit
• EDH-RSA-DES-CBC3-SHA — 168-bit
• EDH-RSA-DES-CBC-SHA — 40-bit & 56-bit
• RC4-SHA — 128-bit
• RC4-MD5 — 40-bit & 128-bit
• SEED-SHA — 128-bit
• TLS 1.0
• AES-SHA — 256-bit & 128-bit
• CAMELLIA-SHA — 128-bit & 256-bit
• DES-CBC3-SHA — 168-bit
• DES-CBC-SHA — 40-bit & 56-bit
• DHE-RSA-AES-SHA — 256-bit & 128-bit
• DHE-RSA-CAMELLIA-SHA — 256-bit & 128-bit
• DHE-RSA-SEED-SHA — 128-bit
• EDH-RSA-DES-CBC3-SHA — 168-bit
• EDH-RSA-DES-CBC-SHA — 40-bit & 56-bit
• RC4-SHA — 128-bit
• RC4-MD5 — 40-bit & 128-bit
• SEED-SHA — 128-bit
AES-256 and SHA-1 are preferable. Generally speaking, for security reasons, avoid using:
• SSL 2.0
• TLS 1.0
• Older hash algorithms, such as MD5. (On modern computers, these can be cracked quickly.)
• Ciphers with known vulnerabilities, such as some implementations of RC4, AES and DES
(e.g. To protect clients with incorrect CBC implementations for AES and DES, prioritize RC4.)
• Encryption bit strengths less than 128
• Older styles of re-negotiation (These are vulnerable to man-in-the-middle (MITM) attacks.)
Replacing the default certificate for the web UI
For HTTPS connections with the web UI, FortiRecorder has its own X.509 server certificate.
By default, the FortiRecorder appliance presents the “Factory” certificate, which can be used to
encrypt the connection, but whose authenticity cannot be guaranteed and therefore may not be
Secure connections and certificates Page 100 FortiRecorder 2.4.2 Administration Guide
 Loading...
Loading...