EMC Unity Family, EMC UnityVSA, EMC Unity All Flash, EMC UnityHybrid Security Configuration Manual
Page 1

EMC Unity™ Family
EMC Unity™ All Flash, EMC Unity™ Hybrid,
EMC UnityVSA
™
Version 4.0
Security Configuration Guide
P/N 302-002-564 REV 03
Page 2

Copyright © 2016 EMC Corporation All rights reserved.
Published December 2016
Dell believes the information in this publication is accurate as of its publication date. The information is subject to change
without notice.
THE INFORMATION IN THIS PUBLICATION IS PROVIDED “AS-IS.“ DELL MAKES NO REPRESENTATIONS OR
WARRANTIES OF ANY KIND WITH RESPECT TO THE INFORMATION IN THIS PUBLICATION, AND SPECIFICALLY
DISCLAIMS IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. USE,
COPYING, AND DISTRIBUTION OF ANY DELL SOFTWARE DESCRIBED IN THIS PUBLICATION REQUIRES AN
APPLICABLE SOFTWARE LICENSE.
Dell, EMC, and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be the property of
their respective owners. Published in the USA.
EMC Corporation
Hopkinton, Massachusetts 01748-9103
1-508-435-1000 In North America 1-866-464-7381
www.EMC.com
2 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 3

5
Introduction 7
Overview...................................................................................................... 8
Related features and functionality information............................................. 8
Access Control 9
Alert settings.............................................................................................. 10
Storage system factory default management and service accounts............ 11
Storage system account management.........................................................11
Unisphere....................................................................................................12
Unisphere command line interface (CLI)..................................................... 14
Storage system service SSH interface........................................................15
Storage system SP Ethernet service port and IPMItool.............................. 16
SMI-S provider............................................................................................17
vSphere Storage API for Storage Awareness support................................. 17
Single sign-on with Unisphere Central........................................................ 19
Single sign-on process flows......................................................... 20
Logging in to a local storage system...............................................21
Single sign-on and NAT support.................................................... 22
Security on file system objects...................................................................22
File systems access in a multiprotocol environment....................................22
User mapping.................................................................................22
Access policies for NFS, SMB, and FTP........................................ 23
Credentials for file level security....................................................24
NFS secure.................................................................................................26
Dynamic Access Control............................................................................. 27
Logging 29
Logging...................................................................................................... 30
Remote logging options...............................................................................31
Communication Security 33
Port usage.................................................................................................. 34
Storage system network ports.......................................................34
Ports the storage system may contact.......................................... 39
Storage system certificate..........................................................................41
Storage system interfaces, services, and features that support Internet
Protocol version 6...................................................................................... 42
Storage system management interface access using IPv6......................... 43
Configuring the management interface using DHCP...................................44
Running the Connection Utility......................................................45
Protocol (SMB) encryption and signing......................................................46
IP packet reflect.........................................................................................48
IP multi-tenancy......................................................................................... 48
About VLANs................................................................................. 49
Preface
Chapter 1
Chapter 2
Chapter 3
Chapter 4
CONTENTS
EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide 3
Page 4

Management support for FIPS 140-2..........................................................49
Data Security Settings 51
About Data at Rest Encryption (physical deployments only)...................... 52
Encryption status.......................................................................... 52
Backup keystore file...................................................................... 53
Data at Rest Encryption audit logging........................................... 54
Hot spare operations..................................................................... 54
Adding a disk drive to a storage system with encryption activated....
55
Removing a disk drive from a storage system with encryption
enabled..........................................................................................55
Replacing a chassis and SPs from a storage system with encryption
enabled..........................................................................................55
Data security settings.................................................................................56
Security Maintenance 57
Secure maintenance...................................................................................58
License update.............................................................................. 58
Software upgrade..........................................................................58
EMC Secure Remote Services for your storage system............................. 59
Security Alert Settings 61
Alert settings..............................................................................................62
Configuring alert settings........................................................................... 63
Configure alert settings for email notifications ............................. 63
Configure alert settings for SNMP traps....................................... 63
Other Security Settings 65
Physical security controls (physical deployments only)..............................66
Antivirus protection....................................................................................66
TLS cipher suites 67
Supported TLS cipher suites...................................................................... 68
Chapter 5
Chapter 6
Chapter 7
Chapter 8
Appendix A
CONTENTS
4 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 5
Additional resources
As part of an effort to improve its product lines, EMC periodically releases revisions of
its software and hardware. Therefore, some functions described in this document
might not be supported by all versions of the software or hardware currently in use.
The product release notes provide the most up-to-date information on product
features. Contact your EMC technical support professional if a product does not
function properly or does not function as described in this document.
Where to get help
Support, product, and licensing information can be obtained as follows:
Product information
For product and feature documentation or release notes, go to Unity Technical
Documentation at: www.emc.com/en-us/documentation/unity-family.htm. You can
also access this page from the Unity product family page at: www.emc.com/en-us/
storage/unity.htm. In the Why EMC Unity Storage section, click Unity Product
Resources > Technical Documentation.
Troubleshooting
For information about EMC products, software updates, licensing, and service, go to
EMC Online Support (registration required) at: https://Support.EMC.com. After
logging in, locate the appropriate Support by Product page.
Technical support
For technical support and service requests, go to EMC Online Support at: https://
Support.EMC.com. After logging in, locate Create a service request. To open a
service request, you must have a valid support agreement. Contact your EMC Sales
Representative for details about obtaining a valid support agreement or to answer any
questions about your account.
Special notice conventions used in this document
EMC uses the following conventions for special notices:
DANGER
Indicates a hazardous situation which, if not avoided, will result in death or
serious injury.
WARNING
Indicates a hazardous situation which, if not avoided, could result in death or
serious injury.
CAUTION
Indicates a hazardous situation which, if not avoided, could result in minor or
moderate injury.
NOTICE
Addresses practices not related to personal injury.
EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide 5
Page 6

Note
Presents information that is important, but not hazard-related.
Additional resources
6 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 7

CHAPTER 1
Introduction
This chapter briefly describes a variety of security features implemented on the
storage system.
Topics include:
l
Overview..............................................................................................................8
l
Related features and functionality information.....................................................8
Introduction 7
Page 8
Overview
The storage system uses a variety of security features to control user and network
access, monitor system access and use, and support the transmission of storage data.
This document describes available security features.
This document is intended for administrators responsible for storage system
configuration and operation.
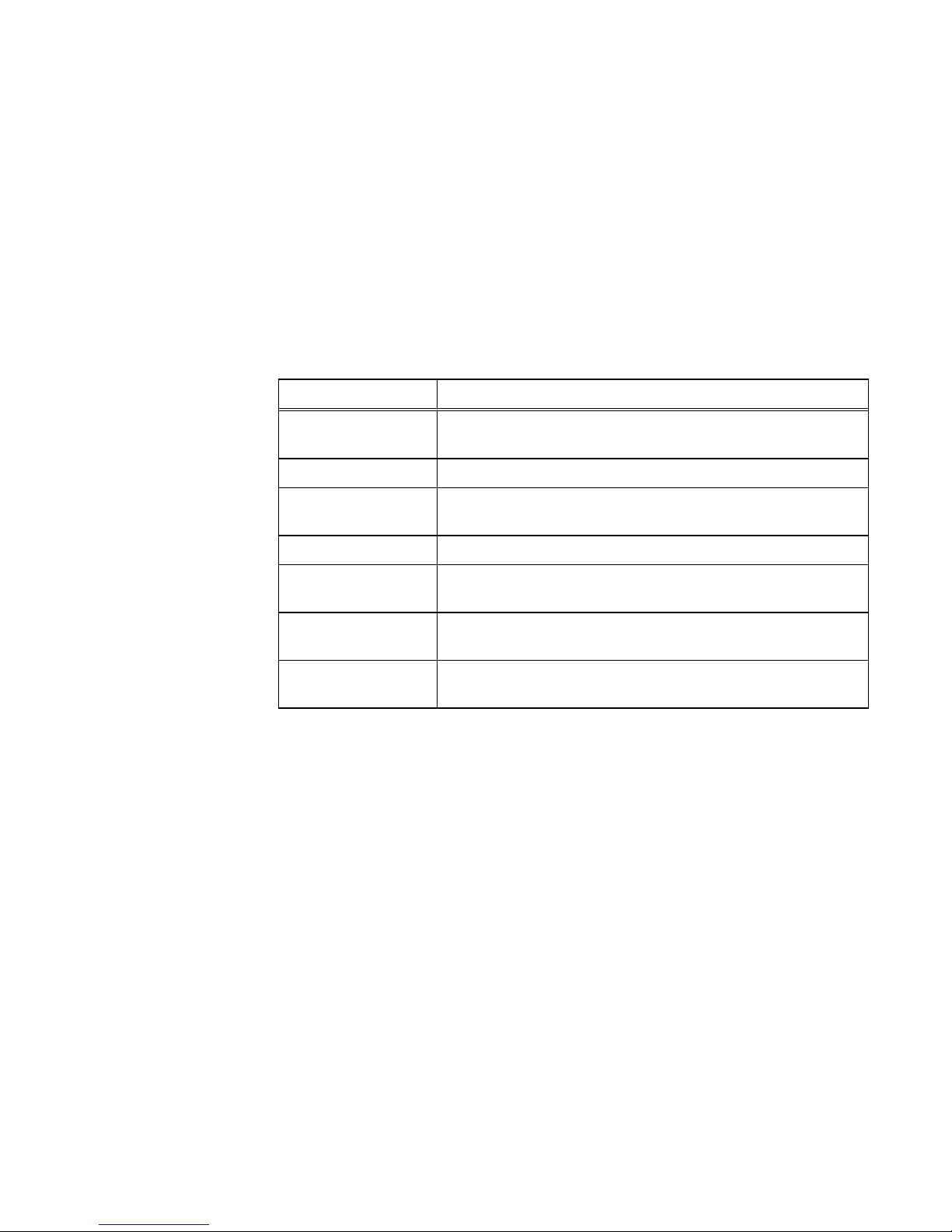
The guide approaches security settings within the categories shown in Table 1 on
page 8:
Table 1 Security settings categories
Security category Description
Access control Limiting access by end-user or by other entities to protect
hardware, software, or specific product features.
Logs Managing the logging of events.
Communication
security
Securing product network communications.
Data security Providing protection for product data.
Serviceability Maintaining control of product service operations performed by the
manufacturer or its service partners.
Alert system Managing the alerts and notifications generated for security-related
events.
Other security settings Security settings that do not fall in one of the previous sections,
such as physical security.
Related features and functionality information
Specific information related to the features and functionality described in this
document is included in the following for Unity:
l
Unisphere Command Line Interface User Guide
l
Unisphere Online Help
l
SMI-S Provider Programmer's Guide
l
Service Commands Technical Notes
l
Secure Remote Services Requirements and Configuration
The complete set of EMC customer publications is available on the EMC Online
Support website at http://Support.EMC.com. After logging in to the website, click
the Support by Product page, to locate information for the specific feature required.
Introduction
8 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 9

CHAPTER 2
Access Control
This chapter describes a variety of access control features implemented on the
storage system.
Topics include:
l
Alert settings......................................................................................................10
l
Storage system factory default management and service accounts....................11
l
Storage system account management................................................................ 11
l
Unisphere........................................................................................................... 12
l
Unisphere command line interface (CLI).............................................................14
l
Storage system service SSH interface............................................................... 15
l
Storage system SP Ethernet service port and IPMItool......................................16
l
SMI-S provider................................................................................................... 17
l
vSphere Storage API for Storage Awareness support.........................................17
l
Single sign-on with Unisphere Central................................................................ 19
l
Security on file system objects.......................................................................... 22
l
File systems access in a multiprotocol environment........................................... 22
l
NFS secure........................................................................................................ 26
l
Dynamic Access Control.....................................................................................27
Access Control
9
Page 10
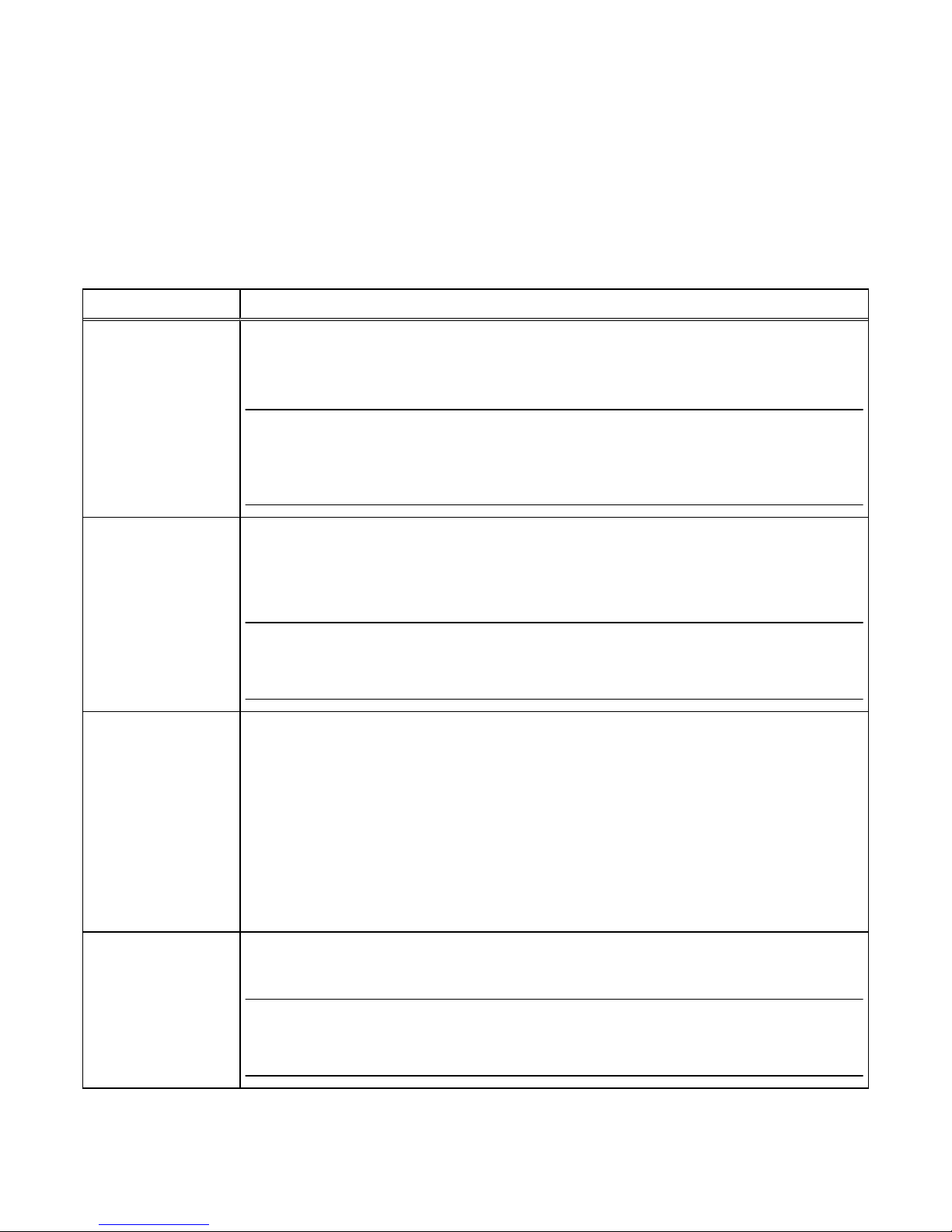
Alert settings
Storage system alerts inform administrators of actionable events that occur on the
storage system. Storage system events can be reported as shown in Table 2 on page
10.
Table 2 Alert settings
Alert type Description
Visual notification Displays informational pop-up messages when users log in to the interface and in real-time to
indicate when alert conditions occur. Pop-ups provide basic information about the alert condition.
You can obtain additional information from the Settings > Alerts > Specify Email Alerts and
SMTP Configuration.
Note
Storage system visual alert notifications are not configurable. Also, the storage system does not
have an option of authentication to an SMTP mail server. If your mail server requires all clients to
authenticate to relay an email, the storage system cannot send email alerts through that mail server.
Email notification Enables you to specify one or more email addresses to which to send alert messages. You can
configure the following settings:
l
Email addresses to which to send storage system alerts.
l
Severity level (critical, error, warning, notice, or information) required for email notification.
Note
For storage system alert email notification to work, you must configure a target SMTP server for the
storage system.
SNMP traps Transfer alert information to designated hosts (trap destinations) that act as repositories for
generated alert information by the storage network system. You can configure SNMP traps through
Unisphere. Settings include:
l
IP address of a network SNMP trap destination
l
Optional security settings for trap data transmission
n
Authentication protocol: Hashing algorithm used for SNMP traps (SHA or MD5)
n
Privacy protocol: Encryption algorithm used for SNMP traps (DES, AES, AES192, or
AES256)
The Unisphere Online Help provides more information.
EMC Secure Remote
Services (ESRS)
ESRS provides an IP-based connection that enables EMC Support to receive error files and alert
messages from your storage system, and to perform remote troubleshooting resulting in a fast and
efficient time to resolution.
Note
Available with operating environment (OE) version 4.0 or later. For ESRS to work, you must enable it
on the storage system.
Access Control
10 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 11

Storage system factory default management and service
accounts
The storage system comes with factory default user account settings to use when
initially accessing and configuring the storage system. See Table 3 on page 11.
Table 3 Factory default user account settings
Account type Username Password Privileges
Management
(Unisphere)
admin Password123# Administrator privileges for resetting
default passwords, configure system
settings, create user accounts, and
allocate storage.
Service service service Perform service operations.
Note
During the initial configuration process, you are required to change the default
password for the Management and Service accounts.
Storage system account management
Table 4 on page 11 illustrates the ways in which you can manage the storage system
accounts.
Table 4
Account management methods
Account roles Description
Management After the storage system initial system
configuration process is complete, you can
manage the storage system management
accounts from Unisphere or the Unisphere
CLI. You can create, modify, delete, or reset
password settings for the storage system
local accounts, and assign or change roles to
accounts that determine the privileges
provided to users who use them.
Service You cannot create or delete storage system
service accounts. You can reset the service
account password from Unisphere. Under
System, select Service > Service Tasks >
Change Service Password function.
Access Control
Storage system factory default management and service accounts 11
Page 12

Note
You can reset the storage system factory default account passwords by pressing the
password reset button on the storage system chassis. The
Unisphere Online Help
provides more information.
Unisphere
Authentication for access to Unisphere is performed based on the credentials of the
user (local or LDAP) account. User accounts are created and subsequently managed
through the Unisphere Manage Administration page. The authorizations that apply to
Unisphere depend on the role associated with the user account.
Before a user can download the Unisphere UI content to a management workstation,
the user must provide credentials for authentication and establish a session on the
storage system. When the user specifies the network address of the storage system
as the URL in a web browser, the user will be presented with a login page from which
the user can select to authenticate either as a local user or through an LDAP directory
server. The credentials that the user provides will be authenticated and, upon
successful authentication, a UI management session will be created on the storage
system. Subsequently, the Unisphere UI will be downloaded and instantiated on the
user's management workstation. The user then will be able to monitor and manage the
storage system within the capabilities of the role assigned to the user.
LDAP
The Lightweight Directory Access Protocol (LDAP) is an application protocol for
querying directory services running on TCP/IP networks. LDAP provides central
management of authentication and identity and group information used for
authorization on the storage system. Integrating the system into an existing LDAP
environment provides a way to control user and user group access to the system
through Unisphere CLI or Unisphere.
After you configure LDAP settings for the system, you can manage users and user
groups, within the context of an established LDAP directory structure. For instance,
you can assign access roles (Administrator, Storage Administrator, Operator, VM
administrator) to the LDAP user or groups. The role applied will determine the level of
authorization the user or group will have in administering the storage system. The
system uses the LDAP settings only for facilitating control of access to Unisphere CLI
and Unisphere, not for access to storage resources.
Session rules
Unisphere sessions have the following characteristics:
l
Expiration term of one hour
l
Session timeout is not configurable
l
Session IDs are generated during authentication and used for the duration of each
session
Password usage
Unisphere account usernames and passwords must meet these requirements, as
shown in Table 5 on page 13.
Access Control
12 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 13
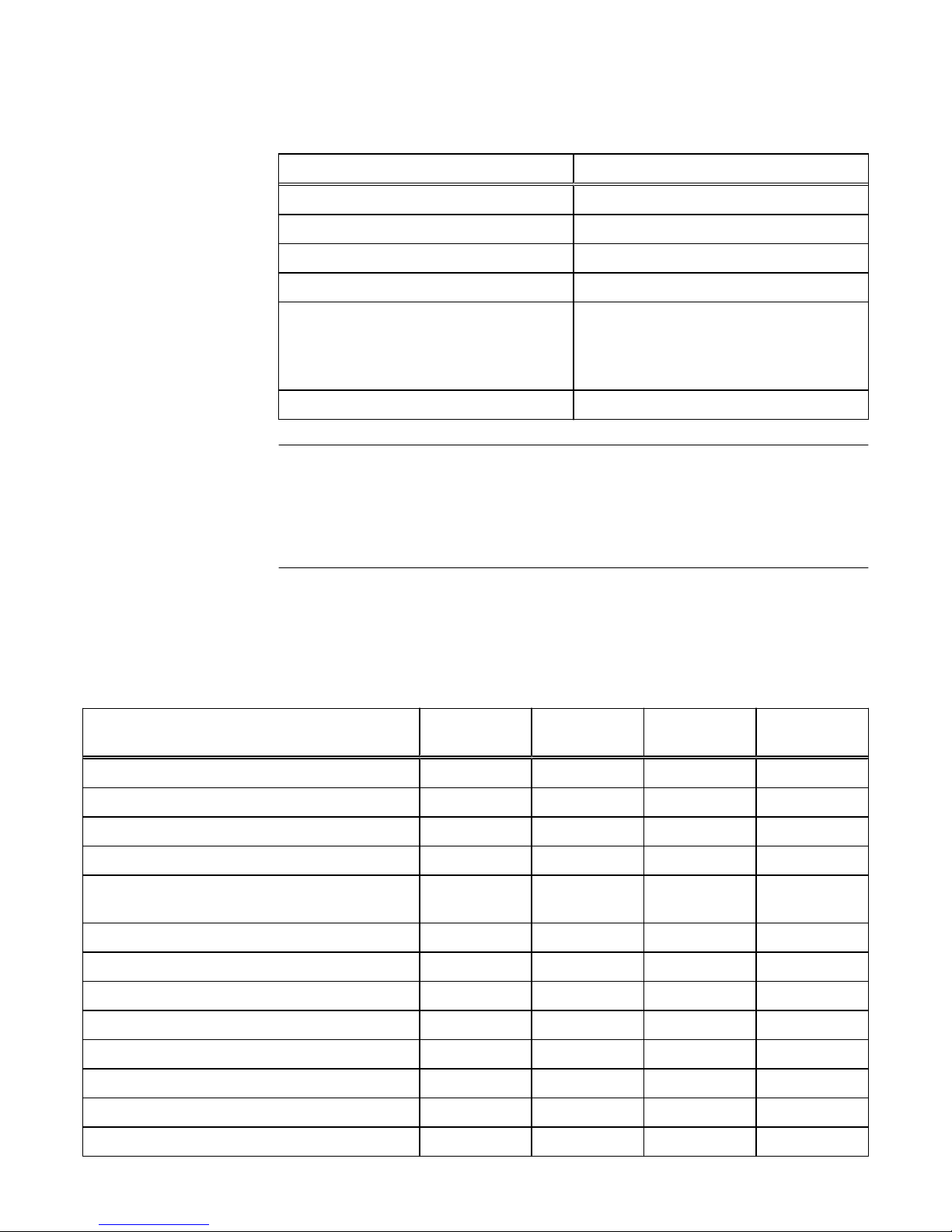
Table 5 Unisphere account requirements
Restriction Password requirement
Minimum number of characters 8
Minimum number of uppercase characters 1
Minimum number of lowercase characters 1
Minimum number of numeric characters 1
Minimum number of special characters
l
Supported special characters include:
n
!,@#$%^*_~?
1
Maximum number of characters 40
Note
You can change account passwords from Unisphere by selecting Settings and, under
Users and Groups, select User Management > More Actions > Reset Password.
When changing a password, you cannot reuse any of the last three passwords. The
Unisphere Online Help
provides more information.
Authorization
Table 6 on page 13 shows the roles you can assign to the storage system local users
and the privileges associated with these roles. In addition, you can assign these roles
to LDAP users and groups.
Table 6
Local user roles and privileges
Task Operator Storage
administrator
Administrator VM
administrator
Change own local login password x x x
Add, delete, or modify hosts x
Create storage x x
Delete storage x x
Add storage objects, such as LUNs, shares, and
storage groups to a storage resource
x x
View storage configuration and status x x x
View Unisphere user accounts x x
Add, delete or modify Unisphere user accounts x
View current software or license status x x x
Perform software or license upgrade x
Perform initial configuration x
Modify NAS server configuration x
Modify system settings x
Access Control
Unisphere 13
Page 14
Table 6 Local user roles and privileges (continued)
Task Operator Storage
administrator
Administrator VM
administrator
Modify network settings x
Change management interface language x x x
View log and alert information x x x
View encryption status x x x
Perform encryption keystore, auditlog, checksum
backup
x x
Establish VASA connections between vCenter and
the storage system
x x
In the case of the VM Administrator role, once connection is established between the
vCenter and the storage system, a vCenter user will be able to view the subset of the
storage configuration and status which is relevant to that vCenter and its ESXi
servers. The vCenter user can view only that information which is allowed through the
vCenter access control mechanisms.
Note
You can change account roles in Unisphere by selecting Settings and, under Users
and Groups, select User Management > More Actions > Change Role. The
Unisphere Online Help
provides more information.
NAT
NAT is not supported for local login through Unisphere to the storage system.
Unisphere command line interface (CLI)
The Unisphere CLI provides a command line interface for the same functionality
available through Unisphere.
Running the Unisphere CLI requires special storage system command line software.
You can download this software from the product page for your storage system on
EMC Online Support (https://support.emc.com).
Session rules
The Unisphere CLI client does not support sessions. You must use command line
syntax to specify the account username and password with each command that you
issue.
You can use the Unisphere CLI -saveuser command to save the access credentials
(username and password) for a specific account to a file in the secure lockbox that
resides locally on the host on which Unisphere CLI is installed. The stored data is only
available on the host where it was saved and to the user who saved it. After you save
the access credentials, the CLI automatically applies them to the specified storage
system destination and port each time you run a command.
Password usage
Authentication to the Unisphere CLI is performed in accordance with management
accounts created and managed through Unisphere. The same permissions that apply
Access Control
14 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 15

to Unisphere apply to specific commands depending on the role associated with the
current login account.
Saved settings
You can save the following settings on the host on which you run Unisphere CLI:
l
User access credentials, including your username and password, for each system
you access.
l
SSL certificates imported from the system.
l
Information about default system to access through Unisphere CLI, including the
system name or IP address and the system port number.
Unisphere CLI saves the settings to a secure lockbox that resides locally on the host
on which Unisphere CLI is installed. The stored data is only available on the host where
it was saved and to the user who saved it. The lockbox resides in the following
locations:
l
On Windows Server 2003 (XP): C:\Documents and Settings\
$<user_name>\Local Settings\ApplicationData\.emc\uemcli\cert
l
On Windows 7, Windows 8, and Windows 10: C:\Users\${user_name}
\AppData\Local\.emc\uemcli\cert
l
On UNIX/Linux: <home_directory>/.emc/uemcli/cert
Locate the files config.xml and config.key. If you uninstall Unisphere CLI, these
directories and files are not deleted, giving you the option of retaining them. If these
files are no longer needed, consider deleting them.
Storage system service SSH interface
The storage system SSH service interface when enabled provides a command line
interface for performing related and overlapping functionality to that which is available
from the Unisphere Service page (under System select Service > Service Tasks >
Enable SSH).
The service account enables users to perform the following functions:
l
Perform specialized storage system service commands for monitoring and
troubleshooting storage system settings and operations.
l
Operate standard Linux commands as a member of a non-privileged Linux user
account. This account does not have access to proprietary system files,
configuration files, or user/customer data.
To learn more about using service commands, see the technical notes document,
Service Commands
.
The storage system SSH service interface setting is persistent across system reboots,
failovers, and in both Service Mode and Normal Mode. Therefore, enabling the storage
system SSH service interface will keep the interface enabled until it is explicitly
disabled from the Unisphere Service page (under System select Service > Service
Tasks > Disable SSH).
For maximum system security, it is recommended to leave the storage system SSH
service interface disabled at all times unless it is specifically needed to perform service
operations on the storage system. After performing the necessary service operations,
disable the SSH interface to ensure that the system remains secure.
Access Control
Storage system service SSH interface 15
Page 16
Sessions
The storage system SSH service interface sessions are maintained according to the
settings established by the SSH client. Session characteristics are determined by the
SSH client configuration settings.
Password usage
The service account is an account that service personnel can use to perform basic
Linux commands.
The default password for the storage system service interface is service. When you
perform initial configuration for the storage system, you must change the default
service password. Password restrictions are the same as those that apply to
Unisphere management accounts (see Password usage on page 12). For information
on the storage system service command, svc_service_password, used to manage
the password settings for the storage system service account, see the technical notes
document,
Service Commands
.
Authorization
As shown in Table 7 on page 16, authorization for the service account is defined in
two ways.
Table 7 Service account authorization definitions
Authorization type Description
Linux file system
permissions
File system permissions define most of the tasks that the service
account can and cannot perform on the storage system. For example,
most Linux tools and utilities that modify system operation in any way
require superuser account privileges. Since the service account does
not have such access rights, the service account cannot use Linux
tools and utilities to which it does not have execute permissions and
cannot edit configuration files that require root access to read or
modify, or both.
Access control lists
(ACLs)
The ACL mechanism on the storage system uses a list of very specific
rules to explicitly grant or deny access to system resources by the
service account. These rules specify service account permissions to
other areas of the storage system that are not otherwise defined by
standard Linux file system permissions.
Storage system service commands
A set of problem diagnostic, system configuration, and system recovery commands
are installed on the storage system's operating environment (OE). These commands
provide an in-depth level of information and a lower level of system control than is
available through Unisphere. The technical notes document,
Service Commands
,
describes these commands and their common use cases.
Storage system SP Ethernet service port and IPMItool
Your storage system provides console access over an Ethernet service port that is on
each SP. This access requires the use of the IPMItool. The IPMItool is a network tool
similar to ssh or telnet that interfaces with each SP over an Ethernet connection by
using the IPMI protocol. The IPMItool is a Windows utility that negotiates a secure
communication channel to access the SP console of a storage system. This utility
requires login credentials and an IP address to activate the console. For more
information about the IPMItool, see the
IPMItool User Guide Technical Notes
.
Access Control
16 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 17

The SP Ethernet service port interface provides the same functions and features as
the service SSH interface and is also subject to the same restrictions. The difference
is that users access the interface through an Ethernet port connection rather than an
SSH client.
For a list of service commands refer to the
Service Commands Technical Notes
.
SMI-S provider
The SMI-S provider does not introduce any change with regards to security. An SMI-S
client connects to the storage system through HTTPS port 5989. The login
credentials are the same as those of Unisphere UI or CLI users. All security rules that
apply to UI and CLI users also apply to SMI-S connections. Unisphere UI and CLI users
can authenticate using the SMI-S interface. No separate users are defined for the
SMI-S interface. Once authenticated, the SMI-S client has the same privilege as
defined for those Unisphere UI and CLI users. The
SMI-S Provider Programmer's Guide
for your storage system product provides information about configuring this service.
vSphere Storage API for Storage Awareness support
vSphere Storage API for Storage Awareness (VASA) is a VMware-defined, vendorneutral API for storage awareness. A VASA Provider (VP) is a storage‐side software
component that acts as a storage awareness service for vSphere. ESXi hosts and
vCenter Server connect to the VP and obtain information about available storage
topology, capabilities, and status. Subsequently, vCenter Server provides this
information to vSphere clients. VASA is used by VMware clients rather than Unisphere
clients.
The VP runs on the active Storage Processor (SP) of the storage system. The
vSphere user must configure this VP instance as the provider of VASA information for
each storage system. In the event that an SP goes down, the related process will
restart on the peer SP, along with the VASA VP. The IP address fails over
automatically. Internally, the protocol will see a fault when obtaining configuration
change events from the newly active VP, but this will cause an automatic
resynchronization of the VASA objects without user intervention.
The storage system provides VASA 3.0 and VASA 2.0 interfaces for vSphere 6, and
VASA 1.0 interfaces for vSphere 5.x.
VASA 1.0 is used for monitoring only and is used by VMware clients rather than
Unisphere clients. VASA 1.0 is a reporting interface only and is used to request basic
information about the storage system and the storage devices it exposes to the virtual
environment in order to facilitate day-to-day provisioning, monitoring, and
troubleshooting through vSphere:
l
Storage visibilty: internally detects property changes, sending the updated
information to vCenter
l
Health and Capacity alarms: internally monitors for health status changes and for
capacity related thresholds being crossed, raising the appropriate alarms to
vCenter:
n
health status for the array, SPs, I/O ports, LUNs, and File Systems
n
class-level change indications for a change in health status for any of these
objects
n
space capacity alarms for LUNs and File Systems
l
VASA storage capabilities: internally monitor for storage capability changes,
reporting updated capabilities to vCenter
Access Control
SMI-S provider 17
Page 18
l
Storage DRS integration: vSphere will rely on information obtained internally from
the VP and feed it into its business logic for various Storage DRS work-flows.
VASA 3.0 and 2.0 support Virtual Volumes (VVols). VASA 3.0 and VASA 2.0 support
interfaces to query storage abstractions such as VVols and Storage Containers. This
information helps storage policy based management (SPBM) make decisions about
virtual disk placement and compliance. VASA 3.0 and VASA 2.0 also support interfaces
to provision and manage the lifecycle of Virtual Volumes used to back virtual disks.
These interfaces are directly invoked by ESXi hosts.
For more information related to VASA, vSphere, and VVols, refer to the VMware
documentation and the Unisphere online help.
Authentication related to VASA
In order to initiate a connection from vCenter to the Unisphere VP, you must use the
vSphere client to enter three key pieces of information:
l
the URL of the VP, using the following format:
n
For VASA 3.0 and VASA 2.0, https://<Management IP address>:8443/vasa/
version.xml
n
For VASA 1.0, https://<Management IP address>:8444/vasa/version.xml or
https://<Management IP address>:8444/vasa/services/vasaService
l
the username of a Unisphere user (the role must be either VM Administrator or
administrator):
Note
The VM Administrator role is strictly used as a means to register certificates.
n
for local users use the syntax: local/<username>
n
for LDAP users use the syntax: <domain>/<username>
l
the password associated with this user
The Unisphere credentials used here are only used during this initial step of the
connection. If the Unisphere credentials are valid for the target storage system, the
certificate of the vCenter Server is automatically registered with the storage system.
It is this certificate that is used to authenticate all subsequent requests from the
vCenter. No manual steps are required to install or upload this certificate to the VP. If
the certificate has expired, the vCenter must register a new certificate to support a
new session. If the certificate is revoked by the user, the session is invalidated and the
connection is severed.
vCenter session, secure connection and credentials
A vCenter session begins when a vSphere administrator uses the vSphere Client to
supply the vCenter Server with the VP URL and login credentials. The vCenter Server
uses the URL, credentials, and the SSL certificate of the VP to establish a secure
connection with the VP. A vCenter session ends when one of the following events
occurs:
l
An administrator uses the vSphere Client to remove the VP from the vCenter
configuration and the vCenter Server terminates the connection.
l
The vCenter Server fails or a vCenter Server service fails, terminating the
connection. When vCenter or the service starts again, it will attempt to reestablish
the SSL connection. If it cannot, it will start a new SSL connection.
l
The VASA Provider fails, terminating the connection. When the VASA Provider
starts up, it can respond to communication from the vCenter Server to reestablish
the SSL connection and VASA session.
Access Control
18 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 19
A vCenter session is based on secure HTTPS communication between a vCenter
Server and a VP. The VASA architecture uses SSL certificates and VASA session
identifiers to support secure connections. With VASA 1.0, the vCenter Server added
the VP certificate to its truststore as part of the VP installation, or when it created a
VASA session connection. The VP added the vCenter Server certificate to its
truststore when Storage Monitoring Service (SMS) called the
registerVASACertificate function. In VASA 3.0 and VASA 2.0, vCenter Server acts as
the VMware certificate authority (VMCA). The VP transmits a self‐signed certificate
on request, after authorizing the request. It adds the vCenter Server certificate to its
truststore, then issues a certificate signing request, and replaces its self‐signed
certificate with the VMCA signed certificate. Future connections will be authenticated
by the server (the VP) using the client (SMS) certificate validated against the
previously registered root signing certificate. A VP generates unique identifiers for
storage entity objects, and vCenter Server uses the identifier to request data for a
specific entity.
A VP uses SSL certificates and the VASA session identifier to validate VASA sessions.
After the session is established, a VP must validate both the SSL certificate and the
VASA session identifier associated with each function call from the vCenter Server.
The VP uses the vCenter Server certificate stored in its truststore to validate the
certificate associated with function calls from the vCenter SMS. A VASA session
persists across multiple SSL connections. If an SSL connection is dropped, the
vCenter Server will perform an SSL handshake with the VP to re‐establish the SSL
connection within the context of the same VASA session. If an SSL certificate expires,
the vSphere administrator must generate a new certificate. The vCenter Server will
establish a new SSL connection and register the new certificate with the VP.
Note
Unregistration of 3.0 and 2.0 VPs differs from unregistration of 1.0 VPs. SMS does not
call the unregisterVASACertificate function against a 3.0 or 2.0 VP, so even after
unregistration, the VP can continue to use its VMCA signed certificate obtained from
SMS and continues to have access to the VMCA root certificate.
Single sign-on with Unisphere Central
The single sign-on capability added to Unisphere Central provides authentication
services for multiple storage systems that are configured to use this feature. This
feature provides an easy way for a user to log in to each system without requiring the
user to re-authenticate to each system.
Unisphere Central is the centralized authentication server that facilitates single signon. This functionality allows a user to:
l
Log in to Unisphere Central, then select and launch Unisphere on a storage system
without supplying your login credentials again.
l
Log in to one storage system and then select other storage systems associated
with the same Unisphere Central to log in to without supplying your login
credentials again.
Unisphere Central will periodically execute a query to request status information from
the storage systems that it is managing. The identity associated with requests
executed in this context is the Unisphere Central SSL/X.509 certificate. This
certificate is signed by the Unisphere Central Certificate Authority, which is trusted by
each storage system instance that Unisphere Central is configured to manage.
Additionally, this feature provides a single sign-off capability; that is, when you log off
Unisphere Central, you log off all of the associated storage system sessions at once.
Access Control
Single sign-on with Unisphere Central 19
Page 20
Requirements
To use single sign-on:
l
Unity and UnityVSA storage systems must be running OE version 4.0 or later.
l
Unisphere Central version 4.0 or later must be used.
l
Both the Unisphere Central server and the storage systems must be configured to
authenticate against the same AD/LDAP directory.
l
The LDAP user must be directly mapped to a Unisphere role, or be a member of an
AD/LDAP group that maps to a Unisphere role on both the storage system and
Unisphere Central.
l
Each storage system must have single sign-on enabled.
l
The user must log in as an LDAP user.
Note
In cases where these requirements are not met, the user must log in to the individual
system as a local user and provide authentication credentials to access that system.
You must have Administrator privileges to enable single sign-on. Users with Storage
Administrator, Operator, or VM Administrator privileges cannot enable single sign-on.
Use the following uemcli command to enable single sign-on:
Uemcli -d <IP address> -u <username> -p <password> /sys/ur set ssoEnabled yes
Each storage system that is configured with this feature enabled can be a client of the
centralized authentication server and participate in the single sign-on environment.
For more information about this command, refer to the
Unisphere Command Line
Interface User Guide
.
Considerations and Restrictions
The following web browsers are supported:
l
Google Chrome version 33 or higher
l
Microsoft Internet Explorer version 10 or higher
l
Mozilla Firefox version 28 or higher
l
Apple Safari version 6 or higher
The user session timeout between the web client and centralized authentication
server is 45 minutes.
The application session timeout between the web client and the storage system is one
hour.
Single sign-on process flows
The following sequences represent the authentication process flows related to single
sign-on associated with Unisphere Central.
Access to a storage system through Unisphere Central
1. User launches a web browser on a management workstation and specifies the
network address of Unisphere Central as the URL.
2. The browser is redirected by the web server to a local Unisphere Central login URL
and the user is presented with a login screen.
3. The user types and submits LDAP login credentials. The username is in the form
<LDAP DOMAIN>/username.
Access Control
20 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 21

4. A session token is set and the browser is redirected by the system back to the
original URL that was specified.
5. The browser downloads the Unisphere content and Unisphere Central is
instantiated.
6. The user then navigates through Unisphere to a particular storage system to
monitor.
7. The user clicks on the network address for the storage system.
8. A new browser window is created with the URL of the storage system.
9. The browser is redirected to the Unisphere Central authentication server where
the user has already authenticated.
10. The browser is redirected back to the Unisphere download page and a session is
established with the storage system using the new service ticket.
11. Unisphere is downloaded and instantiated.
12. The user starts managing/monitoring the storage system.
Access to storage systems associated with Unisphere Central
1. User launches a web browser on a management workstation and specifies the
network address of a storage system as the URL.
2. The browser is redirected to the local Unisphere Central login service and the user
is presented with a login screen.
3. The user types and submits LDAP login credentials. The username is in the form
<LDAP DOMAIN>/username.
4. A session token is set as a cookie and the browser is redirected by the system
back to the original URL that was specified.
5. The browser downloads the Unisphere content and Unisphere is instantiated.
6. The user then opens another web browser window or tab and specifies the
network address of another storage system as the URL.
7. The browser is redirected to the Unisphere Central authentication server where
the user is already authenticated. A new service ticket is obtained.
8. The browser is redirected back to the Unisphere download page and establishes a
session with the second storage system using the new service ticket.
9. Unisphere for the second storage system is downloaded and instantiated.
10. The user starts managing/monitoring the second storage system.
Logging in to a local storage system
When you use a local account, or, if connectivity to the Unisphere Central
authentication server is not available, you can log in to a local storage system using
the authentication server resident on the system instead of logging in through
Unisphere Central. There are two ways to log into the storage system locally:
l
When the browser is redirected to the Unisphere Central authentication server, an
option is available that allows the user to redirect back to the system and log in
locally.
l
If Unisphere Central is inaccessible, the following url syntax can be used to browse
or access the system and log in locally: https://<storagesystemIP>?
casHome=LOCAL
where
storagesystemIP
is the IP address of the storage system.
Access Control
Logging in to a local storage system 21
Page 22

Single sign-on and NAT support
Single sign-on does not support a NAT configuration. Also, NAT is not supported for
local login through Unisphere to the storage system.
Security on file system objects
In a multiprotocol environment, the storage system uses its security policies to
determine how to reconcile the differences between NFS and SMB access control
semantics.
Unix security model
UNIX access rights are referred to as the mode bits of a file system object. They are
represented by a bit string in which each bit represents an access mode or privilege
granted to the user owning the file, the group associated with the file system object,
and all other users. UNIX mode bits are represented as three sets of concatenated rwx
(read, write, and execute) triplets for each category of users (user, or group, or
other).
Windows security model
The Windows security model is based primarily on per-object rights, which involve the
use of a security descriptor (SD) and its access control list (ACL).
Access to a file system object is based on whether permissions have been set to Allow
or Deny through the use of a security descriptor. The SD describes the owner of the
object and group SIDs for the object along with its ACLs. An ACL is part of the
security descriptor for each object. Each ACL contains access control entries (ACEs).
Each ACE in turn, contains a single SID that identifies a user, group, or computer and a
list of rights that are denied or allowed for that SID.
File systems access in a multiprotocol environment
File access is provided through NAS servers. A NAS server contains a set of file
systems where data is stored. The NAS server provides access to this data for NFS,
SMB, and FTP file protocols by exporting file systems through SMB shares and NFS
shares (also known as NFS exports). The NAS server mode for multiprotocol sharing
allows the sharing of the same data between SMB and NFS. Because the
multiprotocol sharing mode provides simultaneous SMB and NFS access to a file
system, the mapping of Windows users to Unix users and defining the security rules to
use (mode bits, ACL, and user credentials) must be considered and configured
properly for multiprotocol sharing.
Note
For information about configuring and managing NAS servers with regards to
multiprotocol sharing, user mapping, access policies, and user credentials, refer to the
Unisphere online help and the
Unisphere Command Line Interface User Guide
.
User mapping
In a multiprotocol context, a Windows user needs to be matched to a UNIX user and
conversely, so file system security can be enforced, even if it is not native to the
protocol. The following components are involved in user mapping:
l
UNIX Directory Services
Access Control
22 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 23

l
Windows resolvers
l
Secmap
l
NTXMAP
UNIX Directory Services
UNIX Directory Services (UDSs) are used to determine the following for user
mapping:
l
Given a user identidier (UID), return the corresponding UNIX account name.
l
Given a UNIX account name, return the corresponding UID and primary group
identifier (GID).
The supported services are:
l
LDAP
l
NIS
There is at most one UDS active at a time for each NAS server. One UDS must be
enabled when multiprotocol sharing is enabled. The UDS to use is determined by the
unix-directory-service property of the NAS server.
Windows resolvers
Windows resolvers are used to determine the following for user mapping:
l
Given a security identifier (SID) return the corresponding Windows account name
l
Given a Windows account name, return the corresponding SID
The Windows resolvers are:
l
The domain controller (DC) of the domain
l
The local group database (LGDB) of the SMB server
Secmap
The function of Secmap is to store all SID-to-UID/primary GID and UID-to-SID
mappings to ensure coherency across all file systems of the NAS server.
NTXMAP
NTXMAP is used to associate a Windows account to a UNIX account when the name
is different. For example, if there is a user who has an account called Gerald on
Windows but the account on UNIX is called Gerry, NTXMAP is used to make the
correlation between the two.
Access policies for NFS, SMB, and FTP
In a multiprotocol environment, the storage system uses file system access policies to
manage user access control of its file systems. There are two kinds of security, UNIX
and Windows.
For UNIX security authentication, the credential is built from the UNIX Directory
Services (UDS). User rights are determined from the mode bits. The user and group
identifiers (UID and GID, respectively) are used for identification. There are no
privileges associated with UNIX security.
For Windows security authentication, the credential is built from the Windows Domain
Controller (DC) and Local Group Database (LGDB) of the SMB server. User rights are
determined from the SMB ACLs. The security identifier (SID) is used for identification.
There are privileges associated with Windows security, such as TakeOwnership,
Backup, and Restore, that are granted by the LGDB of the SMB server.
There are three access policies that define what security is used by which protocols:
Access Control
Access policies for NFS, SMB, and FTP 23
Page 24

l
UNIX - UNIX security is used for both NFS and SMB.
l
Windows - Windows security is used for both NFS and SMB.
l
Native - Uses the security that is native to the protocol, UNIX for NFS or Windows
for SMB.
The UNIX access policy secures file level access using UNIX security, which uses a
UNIX credential for all protocols and enforces only mode bits for all protocols. Upon
processing file level protocol requests for SMB access, the UNIX credential built from
the enabled UDS is used to check mode bits. The access is then granted or denied
based on the mode bits. Windows ACLs are ignored, even for user access through
SMB.
The Windows access policy secures file level access using Windows security. This
policy uses a Windows credential for all protocols and enforces only the SMB ACL for
all protocols. Upon processing file level protocol requests for NFS access, the
Windows credential built from the DC and LGDB is used to check the SMB ACL. The
access is then granted or denied based on the SMB ACL. UNIX mode bits are ignored,
even for user access through NFS.
The Native access policy secures file level access using Native security that uses a
UNIX credential for the NFS protocol or a Windows credential for the SMB protocol
and enforces only mode bits for NFS or SMB ACL for SMB. Upon processing file level
NFS requests, the UNIX credential associated to the request is used to check mode
bits. The access is then granted or denied. Upon processing file level SMB requests,
the Windows credential associated to the request is used to check the SMB ACL. The
access is then granted or denied. There is no synchronization between mode bits and
the SMB discretionary access list (DACL). They are independent.
For FTP, authentication with windows or Unix depends on the user name format that
is used. If windows authentication is used, FTP access control is similar to that for
SMB; otherwise, authentication is similar to that for NFS. FTP and SFTP clients are
authenticated when they connect to the server of the storage processor (SP). It could
be a SMB authentication (when the format of the user name is domain\user or
user@domain) or a Unix authentication (for the other formats of user name). The
SMB authentication is ensured by the Windows DC of the domain defined in the VDM.
The Unix authentication is ensured by the DM according to the encrypted password
stored in either a remote LDAP server, a remote NIS server, or in the local password
file of the VDM.
Credentials for file level security
To enforce file-level security, the storage system must build a credential that is
associated with the SMB or NFS request being handled. There are two kinds of
credentials, Windows and UNIX. In most cases, Windows and UNIX credentials are
built by the NAS server. The only exceptions are:
l
Building a Windows credential for a SMB connection using Kerberos.
l
Building a UNIX credential for an NFS request if extended credential is disabled.
A persistent credential cache is used for the following:
l
Windows credentials built for access through NFS.
l
Unix credential for access through NFS if the extended credential option is
enabled.
There is one cache instance for each NAS server.
Granting access to unmapped users
Multiprotocol requires the following:
Access Control
24 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 25

l
A Windows user must be mapped to a UNIX user.
l
A UNIX user must be mapped to a Windows user in order to build the Windows
credential when the user is accessing a file system that has a Windows access
policy.
In storage system OE version 3.1, two new properties are associated to the NAS
server:
l
The default UNIX user.
l
The default Windows user.
When a Windows user is not mapped, the user identifier (UID) and primary group
identifier (GID) of the default UNIX user are used in the Windows credential. Similarly
when a UNIX user is not mapped, the Windows credential of the default Windows user
is used.
Note
If the default UNIX user is not set in the UNIX Directory Services (UDS), SMB access
is denied. If the default Windows user is not found in the Windows DC or the LGDB,
NFS access on a file system that has a Windows access policy is denied.
UNIX credential for NFS requests
The UNIX credential is always embedded in each request; however, the credential is
limited to 16 extra groups. The NAS server extended-unix-cred property provides the
ability to build a credential with more than 16 groups. If this property is set, the active
UDS is queried with the UID to get the primary GID and all the group GIDs to which it
belongs. If the UID is not found in the UDS, the UNIX credential embedded in the
request is used.
UNIX credential for SMB requests
In order to connect, a Windows credential must first be built for a SMB user at the
session setup time. The UID of the user is included in the Windows credential. When
accessing a file system with a UNIX access policy, the UID of the user is used to query
the UDS to build the UNIX credential, similar to building an extended credential for
NFS.
Windows credential for SMB requests
The Windows credential for SMB needs to be built only once at the session setup
request time when the user connects.
When using Kerberos authentication, the credential of the user is included in the
Kerberos ticket of the session setup request, unlike when using NTLM. Other
information is queried from the Windows DC or the LGDB. For Kerberos the list of
extra group SIDs is taken from the Kerberos ticket and the list of extra local group
SIDs and the list of privileges are taken from the LGDB. For NTLM the list of extra
group SIDs is taken from the Windows DC and the list of extra local group SIDs and
the list of privileges are taken from the LGDB.
Additionally, the corresponding UID is also retrieved from the user mapping
component. Since the primary group SID is not used for access checking, the UNIX
primary GID is used instead.
Windows credential for NFS requests
The Windows credential is only built/retrieved when a user is accessing a file system
that has a Windows access policy. The UID is extracted from the NFS request. There
is a global Windows credential cache to help avoid building the credential on each NFS
request with an associated retention time. If the Windows credential is found in this
cache, no other action is required. If the credential is not found, an attempt is made to
map the UID to an SID using the user mapping component. If a mapping is found the
Access Control
Credentials for file level security 25
Page 26

credential is retrieved from the Windows DC or LGDB. If the mapping is not found, the
Windows credential of the default Windows user is used instead or the access is
denied.
NFS secure
NFS secure is the use of Kerberos for authenticating users with NFSv3 and NFSv4.
Kerberos provides integrity (signing) and privacy (encryption). Integrity and privacy
are not required to be enabled, they are NFS export options.
Without Kerberos, the server relies entirely on the client to authenticate users: the
server trusts the client. With Kerberos this is not the case, the server trusts the Key
Distribution Center (KDC). It is the KDC which handles the authentication and
manages accounts (principals) and password. Moreover, no password in any forms is
sent on the wire.
Without Kerberos, the credential of the user is sent on the wire un-encrypted and thus
can easily be spoofed. With Kerberos, the identity (principal) of the user is included in
the encrypted Kerberos ticket, which can only be read by the target server and KDC.
They are the only ones to know the encryption key.
In conjunction with NFS secure, AES128 and AES256 encryption in Kerberos is
supported. Along with NFS secure, this also impacts SMB and LDAP. These
encryptions are now supported by default by Windows and Linux. These new
encryptions are much more secure; however, it is up to the client whether they are
used. From that user principal, the server builds the credential of that user by querying
the active UDS. Since NIS is not secured, it is not recommended to use it with NFS
secure. It is recommended to use Kerberos with LDAP or LDAPS.
NFS secure can be configured either through Unisphere or the UEM CLI.
File protocol relationships
With Kerberos the following is required:
l
DNS - You must use DNS name in place of IP addresses
l
NTP - All participants must be timely synchronized
l
UDS - To build credentials
l
Hostname - Kerberos works with names and not IP addresses
NFS secure uses one or two SPNs depending on the value of the hostname. If the
hostname is in FQDN format host.domain:
l
The short SPN: nfs/host@REALM
l
The long SPN: nfs/host.domainFQDN@REALM
If the hostname is not in FQDN format, only the short SPN will be used.
Similarly to SMB, where a SMB server can be joined to a domain, a NFS server can be
joined to a realm (the Kerberos equivalent term for domain). There are two options for
this:
l
Use the configured windows domain if any
l
Entirely configure a UNIX KDC based Kerberos realm
If the administrator selects to use the configured windows domain, there is nothing
else to do. Every SPN used by the NFS service is automatically added/removed into
the KDC when joining/unjoining the SMB server. Note that the SMB server cannot be
destroyed if NFS secure is configured to use the SMB configuration.
If the administrator selects to use a UNIX based Kerberos realm, more configuration is
needed:
Access Control
26 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 27

l
Realm name: The name of the Kerberos realm, which generally contains all uppercase letters.
l
Entirely configure a UNIX KDC based Kerberos realm.
To ensure that a client mounts an NFS export with a specific security, a security
parameter, sec, is provided that indicates which minimal security is allowed. There are
4 kinds of security:
l
AUTH_SYS: Standard legacy security which does not use Kerberos. The server
trust the credential provided by the client
l
KRB5: Authentication using Kerberos v5
l
KRB5i: Kerberos authentication plus integrity (signing)
l
KRB5p: Kerberos authentication plus integrity plus privacy (encryption)
If a NFS client tries to mount an export with a security that is lower than the
configured minimal security, the access will be denied. For example, if minimal access
is KRB5i, any mount using AUTH_SYS or KRB5 will be rejected.
Building a credential
When a user connects to the system, it presents only its principal, user@REALM,
which is extracted from the Kerberos ticket. Unlike AUTH_SYS security, the
credential is not included in the NFS request. From the principal, the user part (before
the @) is extracted and used to lookup the UDS for the corresponding uid. From that
uid, the credential is built by the system using the active UDS, similar to when the
Extended NFS credential is enabled (with the exception that, without Kerberos, the
uid is provided directly by the request).
If the principal is not mapped in the UDS, the configured default UNIX user credential
is used instead. If the default UNIX user is not set, the credential used will be nobody.
Replication
When a NAS server is the target of a replication, there is the possibility to access data
through NFS for backup or disaster recovery. NFS secure cannot be used in these
case since the usage of direct IP addresses is not compatible with Kerberos. Also,
FQDN cannot be used because it could resolve to either the production interfaces on
the source or the local interfaces on the destination.
Dynamic Access Control
Dynamic Access Control (DAC) enables administrators to apply access-control
permissions and restrictions on resources based on well-defined rules that can include
the sensitivity of the resources, the job or role of the user, and the configuration of
the device that is used to access these resources.
DAC Claims Based Access Control (CBAC) is a feature of Windows Server 2012 that
allows access control to be defined on the domain controller through a set of Central
Access Policies (CAPs). Each Central Access Policy (identified by its CAPID) has a
number of Central Access Rules (CARs) associated with it. CAPs can be assigned to
Group Policy Objects (GPOs). This is the mechanism used to distribute CAPs to
individual file servers. The CAP that applies to a particular resource (that is, a
directory or file) is determined by the CAPID. When a NAS Server is created with
Windows Shares (SMB), it will pick up the correct CAP and CAR when it joins the
domain.
Each CAR has the following attributes:
l
Resource Target Expression
Access Control
Dynamic Access Control 27
Page 28

l
Current Permissions ACL
l
Proposed Permissions ACL (optional)
The Resource Target Expression (applicability expression) is evaluated to determine
whether or not the CAR is applicable to a given resource or not (for example,
@Resource.Department != @User.Department). If this expression evaluates to TRUE,
the Current Permissions ACL is used during the access check; otherwise, the rule is
ignored. The Proposed Permissions ACL allows the administrator to see the effect of
proposed changes to the current permissions. When the evaluation of proposed
permissions is enabled, any differences between current and proposed permissions
during an access check are logged (in the server log).
A Windows client (Windows Server 2012 or Windows 8.x) can be used to associate a
CAP with resources (that is, directories or files), if required (it is optional). When this
is done, the specified CAP will be enforced by the NAS Server for the applicable
resources. A Windows client can also be used to perform manual classification of
resources (for example, setting the country or department).
DAC CBAC is enabled on the storage system by default; however, a service command,
svc_dac, allows you to do the following:
l
Enable or disable the DAC feature - when disabled the CAP associated with a
resource is ignored (that is, only the DACL determines access).
l
Enable or disable the evaluation of proposed permissions. Each CAR may have
proposed permissions and these are distributed to the file servers. Usually, only
these permissions are not evaluated. The svc_dac command can be used to
enable the evaluation of these permissions. Once enabled any differences between
the effective permissions and the proposed permissions will be sent to the server
log. The evaluation of proposed permissions allows you to safely test proposed
changes to CARs.
l
Query the CAPs or CARs associated with a NAS Server compname (all, by
distinguished name or by id).
l
Add or remove custom recovery rules (to replace the default recovery rule).
l
Control the verbosity of the logging produced by DAC for diagnostic purposes.
For detailed information about the svc_dac command, refer to the
EMC Unity Family
Service Commands Technical Notes
.
Access Control
28 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 29

CHAPTER 3
Logging
This chapter describes a variety of logging features implemented on the storage
system.
Topics include:
l
Logging..............................................................................................................30
l
Remote logging options...................................................................................... 31
Logging 29
Page 30

Logging
The storage system maintains the following types of logs for tracking events that
occur on the system. See Table 8 on page 30.
Table 8 Logs
Log type Description
System log Information displayed in Unisphere to notify users about storage system user-
actionable events. These records are localized according to the default language
setting specified for the system. Note that "user-actionable events" includes
audit events. However, not all logged events show up in the GUI. Those audit log
entries that don't don't meet a certain severity threshold are logged by the
system but don't appear in the GUI.
System
alert
Information used by the Service personnel to diagnose or monitor the storage
system status or behavior. These records are recorded in English only.
Viewing and managing logs
The following logging features are available for storage systems. See Table 9 on page
30.
Table 9
Logging features
Feature Description
Log roll-over When the storage system log system accumulates two million log
entries, it purges the oldest 500K entries (as determined by log
record time) to return to 1.5 million log entries. You can archive log
entries by enabling remote logging so that log entries are uploaded
to a remote network node where they can be archived or backed
up. The Logging on page 30 section provides more information.
Logging levels Logging levels are not configurable for the storage system. Log
levels can only be configured for exported log files as described in
the Logging on page 30 section.
Alert integration You can view storage system alert information in the following
ways:
l
View alerts only:
n
In Unisphere, go to Events > Alerts.
l
View log events:
n
Using the Unisphere CLI, type the command uemcli /
event/alert/hist show.
External log management You can archive log entries by enabling remote logging so that log
entries are uploaded to a remote network node where they can be
archived or backed up. There, you can use tools such as syslog to
filter and analyze log results. The Logging on page 30 section
provides more information.
Logging
30 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 31

Table 9 Logging features (continued)
Feature Description
Time synchronization Log time is recorded in GMT format and is maintained according to
the storage system time (which may be synchronized to the local
network time through an NTP server).
Remote logging options
The storage system supports logging user/audit messages to a remote host. By
default, the storage system transfers log information on port 514 using UDP. The
following remote logging settings are configurable through Unisphere. Log into
Unisphere and click Settings > Management > Remote Logging.
l
Enable logging to a remote host.
l
Network name or IP address where the storage system sends remote log
information.
l
Type of log messages to send. Use the Facility field to set the type of log
messages. It is recommended that you select the User-Level Messages options.
l
Port number and type (UDP or TCP) to use for log transmission.
Configuring a host to receive storage system log messages
Before configuring remote logging for a storage system, you must configure a remote
system running syslog to receive logging messages from the storage system. In many
scenarios, a root/administrator on the receiving computer can configure the remote
syslog server to receive log information by editing the syslog-ng.conf file on the
remote system.
Note
For more information on setting up and running a remote syslog server, refer to the
documentation for the operating system running on the remote system.
Logging
Remote logging options 31
Page 32

Logging
32 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 33

CHAPTER 4
Communication Security
This chapter describes a variety of communication security features implemented on
the storage system.
Topics include:
l
Port usage..........................................................................................................34
l
Storage system certificate................................................................................. 41
l
Storage system interfaces, services, and features that support Internet Protocol
version 6............................................................................................................ 42
l
Storage system management interface access using IPv6.................................43
l
Configuring the management interface using DHCP.......................................... 44
l
Protocol (SMB) encryption and signing............................................................. 46
l
IP packet reflect................................................................................................ 48
l
IP multi-tenancy.................................................................................................48
l
Management support for FIPS 140-2................................................................. 49
Communication Security
33
Page 34
Port usage
Communications with the Unisphere and CLI interfaces are conducted through HTTPS
on port 443. Attempts to access Unisphere on port 80 (through HTTP) are
automatically redirected to port 443.
Storage system network ports
Table 10 on page 34 outlines the collection of network services (and the
corresponding ports) that may be found on the storage system.
Table 10 Storage system network ports
Service Protocol Port Description
FTP TCP 21 Port 21 is the control port on which the
FTP service listens for incoming FTP
requests.
SFTP TCP 22 Allows alert notifications through SFTP
(FTP over SSH). SFTP is a client/server
protocol. Users can use SFTP to
perform file transfers on a storage
system on the local subnet. Also
provides outgoing FTP control
connection. If closed, FTP will not be
available.
SSH/SSHD, VSI TCP 22 Allows SSH access (if enabled). Also
used for VSI plugin. If closed,
management connections using SSH will
be unavailable and VSI plugin will not be
available.
Dynamic DNS update TCP/UDP 53 Used to transmit DNS queries to the
DNS server in conjunction with the
Dynamic Host Control Protocol (DHCP).
If closed, DNS name resolution will not
work.
DHCP client UDP 67 Allows the storage system to act as a
DHCP client during the initial
configuration process and is used to
transmit messages from the client
(storage system) to the DHCP server to
automatically obtain management
interface information. Also, used to
configure DHCP for the management
interface of a storage system which has
already been deployed. If closed,
dynamic IP addresses will not be
assigned using DHCP.
DHCP client UDP 68 Allows the storage system to act as a
DHCP client during the initial
configuration process and is used to
Communication Security
34 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 35
Table 10 Storage system network ports (continued)
Service Protocol Port Description
receive messages from DHCP server to
the client (storage system) to
automatically obtain its management
interface information. Also, used to
configure DHCP for the management
interface of a storage system which has
already been deployed. If closed,
dynamic IP addresses will not be
assigned using DHCP.
HTTP TCP 80 Redirect for HTTP traffic to Unisphere
and the Unisphere CLI. If closed,
management traffic to the default HTTP
port will be unavailable.
NAS, VAAI-NAS TCP 111 Provides NAS datastores for VMware
and is used for VAAI-NAS. If closed,
NAS datastores and VAAI-NAS will be
unavailable.
Portmapper, rpcbind (Network
infrastructure)
TCP/UDP 111 Opened by the standard portmapper or
rpcbind service and is an ancillary
storage system network service. It
cannot be stopped. By definition, if a
client system has network connectivity
to the port, it can query it. No
authentication is performed.
NTP UDP 123 NTP time synchronization. If closed,
time will not be synchronized among
arrays.
DCE Remote Procedure Call (DCERPC)
and NDMP
UDP 135 Multiple purposes for MicroSoft Client.
Also used for NDMP.
NETBIOS Name Service (SMB) TCP/UDP 137 The NETBIOS Name Service is
associated with the storage system SMB
file sharing services and is a core
component of that feature (Wins). If
disabled, this port disables all SMBrelated services.
NETBIOS Datagram Service (SMB) UDP 138 The NETBIOS Datagram Service is
associated with the storage system SMB
file sharing services and is a core
component of that feature. Only Browse
service is used. If disabled, this port
disables Browsing capability.
NETBIOS Session Service (SMB) TCP/UDP 139 The NETBIOS Session Service is
associated with storage system SMB file
sharing services and is a core
component of that functionality. If SMB
services are enabled, this port is open. It
is specifically required for earlier
Communication Security
Storage system network ports 35
Page 36
Table 10 Storage system network ports (continued)
Service Protocol Port Description
versions of the Windows OS (preWindows 2000). Clients with legitimate
access to the storage system SMB
services must have network connectivity
to the port for continued operation.
SNMP Unix Multiplexer TCP 199 SNMP communications. If closed,
storage system alert mechanisms which
rely on SNMP will not be sent.
Service Location Protocol (SLP) TCP/UDP 427 Allows hosts (or other resources) to
discover available services provided by a
storage system.
HTTPS TCP 443 Secure HTTP traffic to the Unisphere
and Unisphere CLI. If closed,
communication with the array will be
unavailable.
Note
For SMI-S, used for array management;
however, port 5989 is the default port
used for this purpose.
SMB TCP 445 SMB (on domain controller) and SMB
connectivity port for Windows 2000 and
later clients. Clients with legitimate
access to the storage system SMB
services must have network connectivity
to the port for continued operation.
Disabling this port disables all SMBrelated services. If port 139 is also
disabled, SMB file sharing is disabled.
DHCP (IPv6 only) UDP 546 DHCP(v6) Client. If closed, dynamic IP
addresses will not be assigned using
DHCP.
DHCP (IPv6 only) UDP 547 DHCP(v6) Server. If closed, dynamic IP
addresses will not be assigned using
DHCP.
FTP TCP 1024:65535 Used for passive FTP. Port 1024:65535
is related to data while port 1025:65535
is related to management.
mountd (NFS) TCP/UDP 1234 Used for the mount service, which is a
core component of the NFS service
(versions 2, 3, and 4) and is an important
component of the SP to NAS Server
interaction.
NAS, VAAI-NAS TCP 2049 Provides NAS datastores for VMware
and is used for VAAI-NAS. If closed,
Communication Security
36 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 37

Table 10 Storage system network ports (continued)
Service Protocol Port Description
NAS datastores and VAAI-NAS will be
unavailable.
NFS TCP/UDP 2049 Used to provide NFS services.
UDI SSH TCP 2222 Redirects traffic from port 22 for device
eth*.
iSCSI TCP 3260 Provides access to iSCSI services. If
closed, file-based iSCSI services will be
unavailable.
NFS TCP/UDP 4000 Used to provide NFS statd services.
statd is the NFS file-locking status
monitor and works in conjunction with
lockd to provide crash and recovery
functions for NFS. If closed, NAS statd
services will be unavailable.
NFS TCP/UDP 4001 Used to provide NFS lockd services.
lockd is the NFS file-locking daemon. It
processes lock requests from NFS
clients and works in conjunction with the
statd daemon. If closed, NAS lockd
services will be unavailable.
NFS TCP/UDP 4002 Used to provide NFS rquotad services.
The rquotad daemon provides quota
information to NFS clients that have
mounted a file system. If closed, NAS
rquotad services will be unavailable.
Portable Archive Interchange (PAX)
(Backup Services)
TCP 4658
l
PAX is a storage system archive
protocol that works with standard
UNIX tape formats.
l
This service must bind to multiple
internal network interfaces and as a
consequence, it binds to the
external interface as well. However,
incoming requests over the external
network are rejected.
l
Background information on PAX is
contained in the relevant EMC
documentation on backups. There
are several technical modules on this
topic to deal with a variety of
backup tools.
VSI TCP 5080 This port provides for VSI plugin. If
closed, VSI plugin will not be available.
Replication services TCP 5085 Associated with replication services
Communication Security
Storage system network ports 37
Page 38
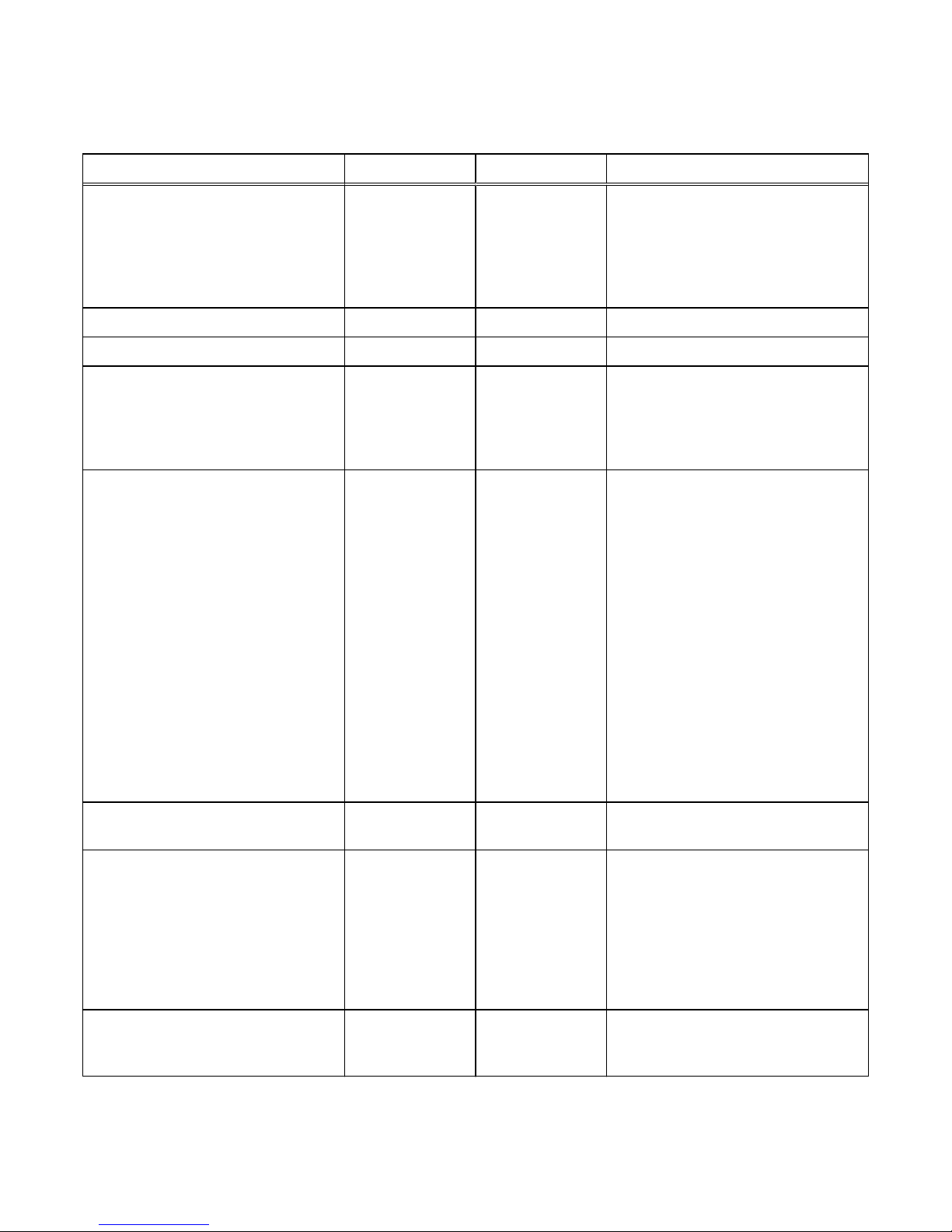
Table 10 Storage system network ports (continued)
Service Protocol Port Description
SMI-S TCP 5989 For SMI-S, used for array management.
SMI-S client connects to array using
SMI-S TCP 5989 HTTPS. The
SMI-S
Provider Programmer's Guide
provides
more information about configuring this
service.
VASA TCP 8443 VASA Vendor provider for VASA 2.0.
VASA TCP 8444 VASA Vendor provider for VASA 1.0.
RCP (Replication services) TCP 8888 Used by the replicator (on the secondary
side). It is left open by the replicator as
soon as some data has to be replicated.
After it is started, there is no way to
stop the service.
NDMP TCP 10000
l
Enables you to control the backup
and recovery of a Network Data
Management Protocol (NDMP)
server through a network backup
application, without installing thirdparty software on the server. In a
storage system, the NAS Server
functions as the NDMP server.
l
The NDMP service can be disabled if
NDMP tape backup is not used.
l
The NDMP service is authenticated
with a username/password pair. The
username is configurable. The
NDMP documentation describes
how to configure the password for a
variety of environments.
NDMP TCP 10500:10531 For three-way backup/restore sessions,
NAS Servers use ports 10500 to 10531.
usermapper, SMB TCP 12345 The usermapper service opens this port.
It is a core service associated with
storage system SMB services and should
not be stopped in specific environments.
This is the method by which Windows
credentials (which are SID-based) are
mapped to UNIX-based UID and GID
values.
IWD Internal 60260 IWD initial configuration daemon. If
closed, initialization of the array will be
unavailable through the network.
Communication Security
38 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 39
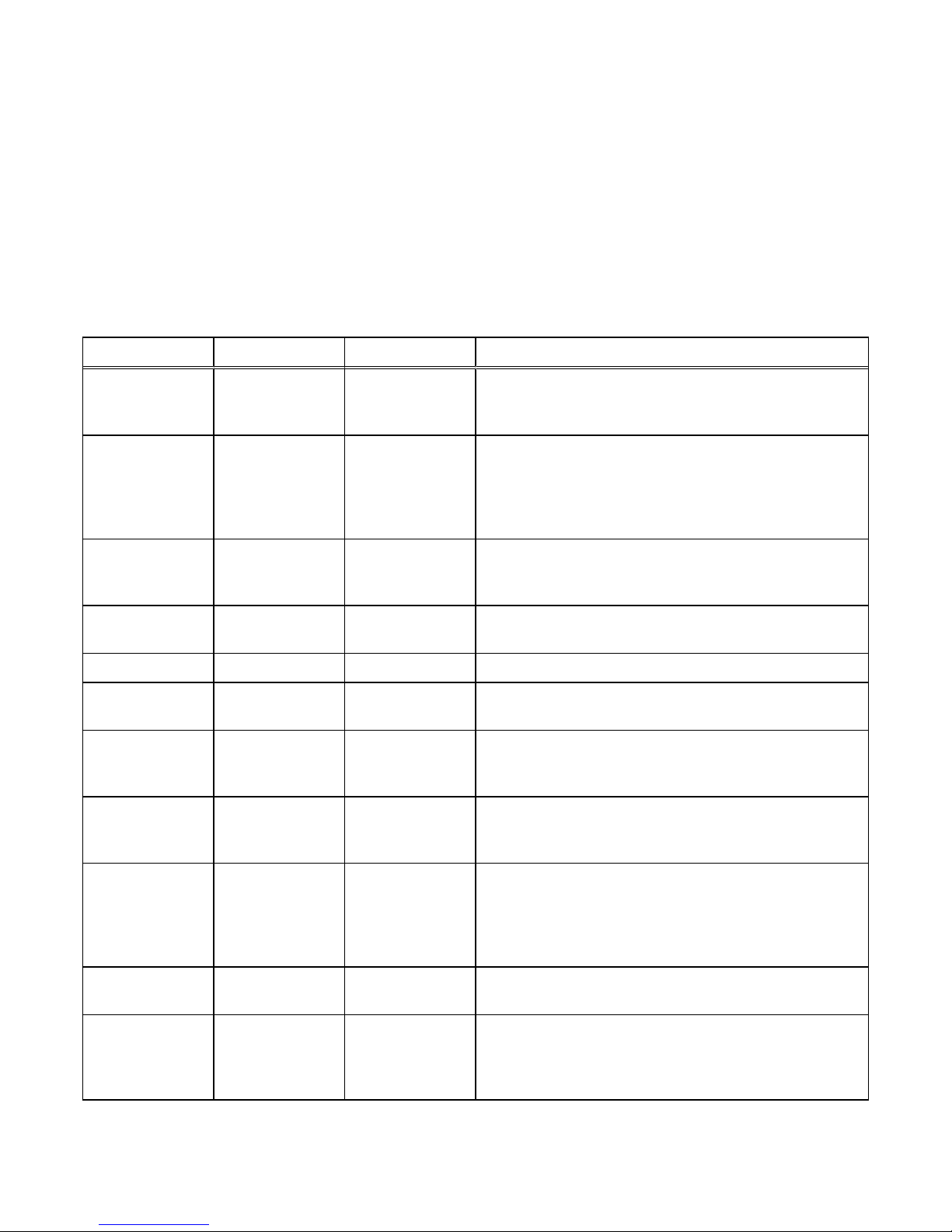
Ports the storage system may contact
The storage system functions as a network client in several circumstances, for
example, in communicating with an LDAP server. In these instances, the storage
system initiates communication and the network infrastructure will need to support
these connections. Table 11 on page 39 describes the ports that a storage system
must be allowed to access for the corresponding service to function properly. This
includes the Unisphere CLI.
Table 11 Network connections that may be initiated by the storage system
Service Protocol Port Description
FTP TCP 20 Port used for FTP data transfers. This port can be opened by
enabling FTP as described in the next row. Authentication is
performed on port 21 and defined by the FTP protocol.
SFTP TCP 22 Allows alert notifications through SFTP (FTP over SSH).
SFTP is a client/server protocol. Users can use SFTP to
perform file transfers on a storage system on the local subnet.
Also provides outgoing FTP control connection. If closed, FTP
will not be available.
SSH/SSHD, VSI TCP 22 Allows SSH access (if enabled). Also used for VSI plugin. If
closed, management connections using SSH and VSI plugin
will not be available.
SMTP TCP 25 Allows the system to send email. If closed, email notifications
will be unavailable.
DNS TCP/UDP 53 DNS queries. If closed, DNS name resolution will not work.
DHCP UDP 67-68 Allows the storage system to act as a DHCP client. If closed,
dynamic IP addresses will not be assigned using DHCP.
HTTP TCP 80 Redirect for HTTP traffic to Unisphere and the Unisphere CLI.
If closed, management traffic to the default HTTP port will be
unavailable.
Kerberos TCP/UDP 88 Provides outgoing Kerberos ticket. If closed, Kerberos
authentication and all protocols that use it; for example, SMB,
LDAP, GPO, secNFS, and such, will not be available.
Portmapper,
rpcbind (Network
infrastructure)
TCP/UDP 111 Opened by the standard portmapper or rpcbind service and is
an ancillary storage system network service. It cannot be
stopped. By definition, if a client system has network
connectivity to the port, it can query it. No authentication is
performed.
NTP UDP 123 NTP time synchronization. If closed, time will not be
synchronized among arrays.
NETBIOS Name
Service (SMB)
TCP/UDP 137 The NETBIOS Name Service is associated with the storage
system SMB file sharing services and is a core component of
that feature (Wins). If disabled, this port disables all SMBrelated services.
Communication Security
Ports the storage system may contact 39
Page 40
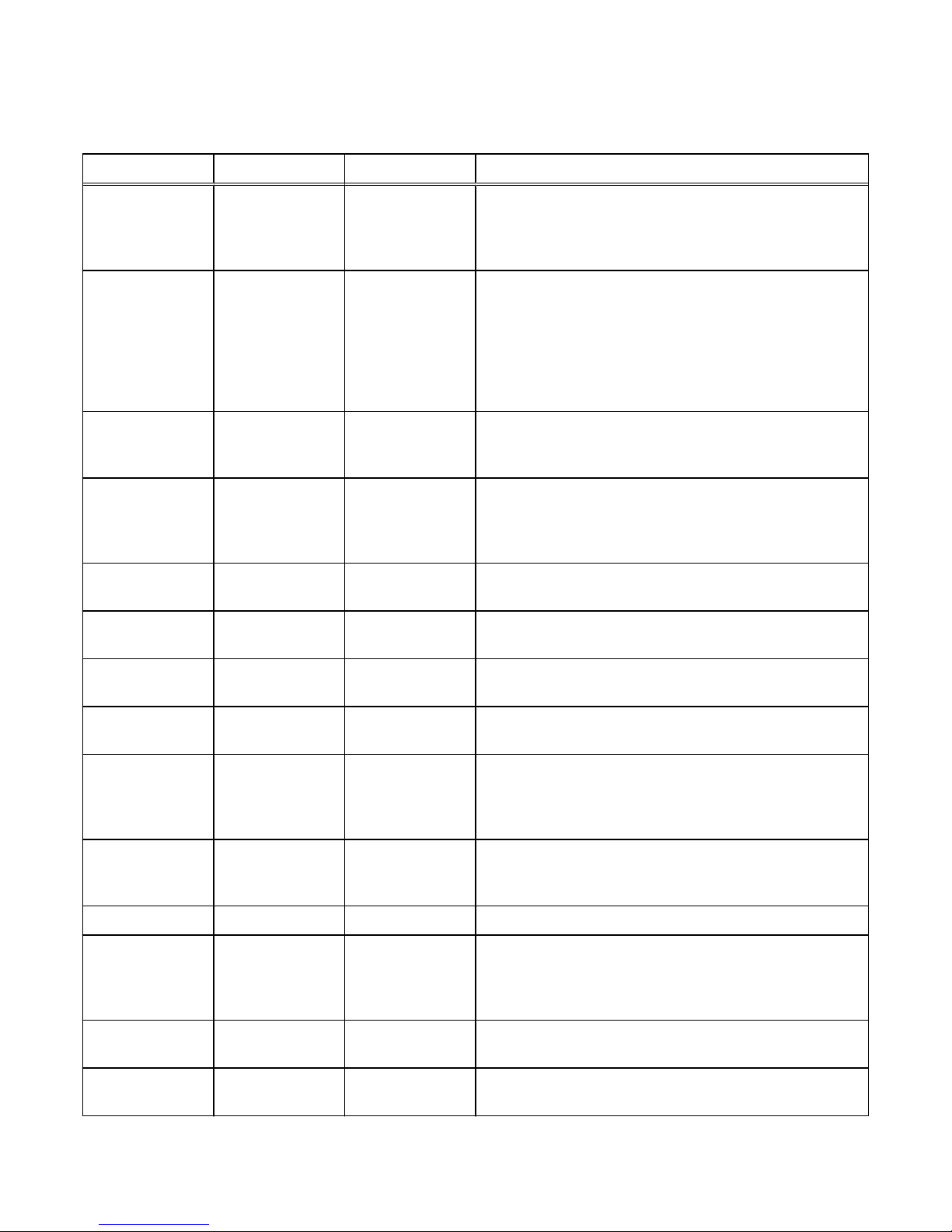
Table 11 Network connections that may be initiated by the storage system (continued)
Service Protocol Port Description
NETBIOS
Datagram Service
(SMB)
UDP 138 The NETBIOS Datagram Service is associated with the
storage system SMB file sharing services and is a core
component of that feature. Only Browse service is used. If
disabled, this port disables Browsing capability.
NETBIOS Session
Service (SMB)
TCP/UDP 139 The NETBIOS Session Service is associated with storage
system SMB file sharing services and is a core component of
that functionality. If SMB services are enabled, this port is
open. It is specifically required for earlier versions of the
Windows OS (pre-Windows 2000). Clients with legitimate
access to the storage system SMB services must have
network connectivity to the port for continued operation.
LDAP TCP/UDP 389
a
Unsecure LDAP queries. If closed, Unsecure LDAP
authentication queries will be unavailable. Secure LDAP is
configurable as an alternative.
HTTPS TCP 443 HTTPS traffic to the Unisphere and Unisphere CLI, and for
secure remote services when ESRS is enabled and Integrated
ESRS is configured on the storage system. If closed,
communication with the array will be unavailable.
Kerberos TCP/UDP 464 Provides Kerberos Password Change and Set. If closed,
impacts SMB.
Remote Syslog UDP 514
a
Syslog - Log system messages to a remote host. You can
configure the host port that the system uses.
LDAPS TCP/UDP 636
a
Secure LDAP queries. If closed, secure LDAP authentication
will be unavailable.
VMware TCP 843 VMawareness - Allows VMware SDK communication with
vSphere. If closed, VCenter/ESX discovery will be unavailable.
SOCKS TCP 1080 When ESRS is enabled and Integrated ESRS is configured on
the storage system, and a firewall is employed between the
storage system and a Proxy server. If closed, communication
with the array will be unavailable.
mountd (NFS) TCP/UDP 1234 Used for the mount service, which is a core component of the
NFS service (versions 2, 3, and 4) and is an important
component of the SP to NAS Server interaction.
NFS TCP/UDP 2049 Used to provide NFS services.
HTTP TCP 3128 When ESRS is enabled and Integrated ESRS is configured on
the storage system, and a firewall is employed between the
storage system and a Proxy server. If closed, communication
with the array will be unavailable.
iSNS TCP 3205 Used to send Internet storage naming service (iSNS)
registrations to the iSNS server.
iSCSI TCP 3260 Provides access to iSCSI services. If closed, file-based iSCSI
services will be unavailable.
Communication Security
40 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 41
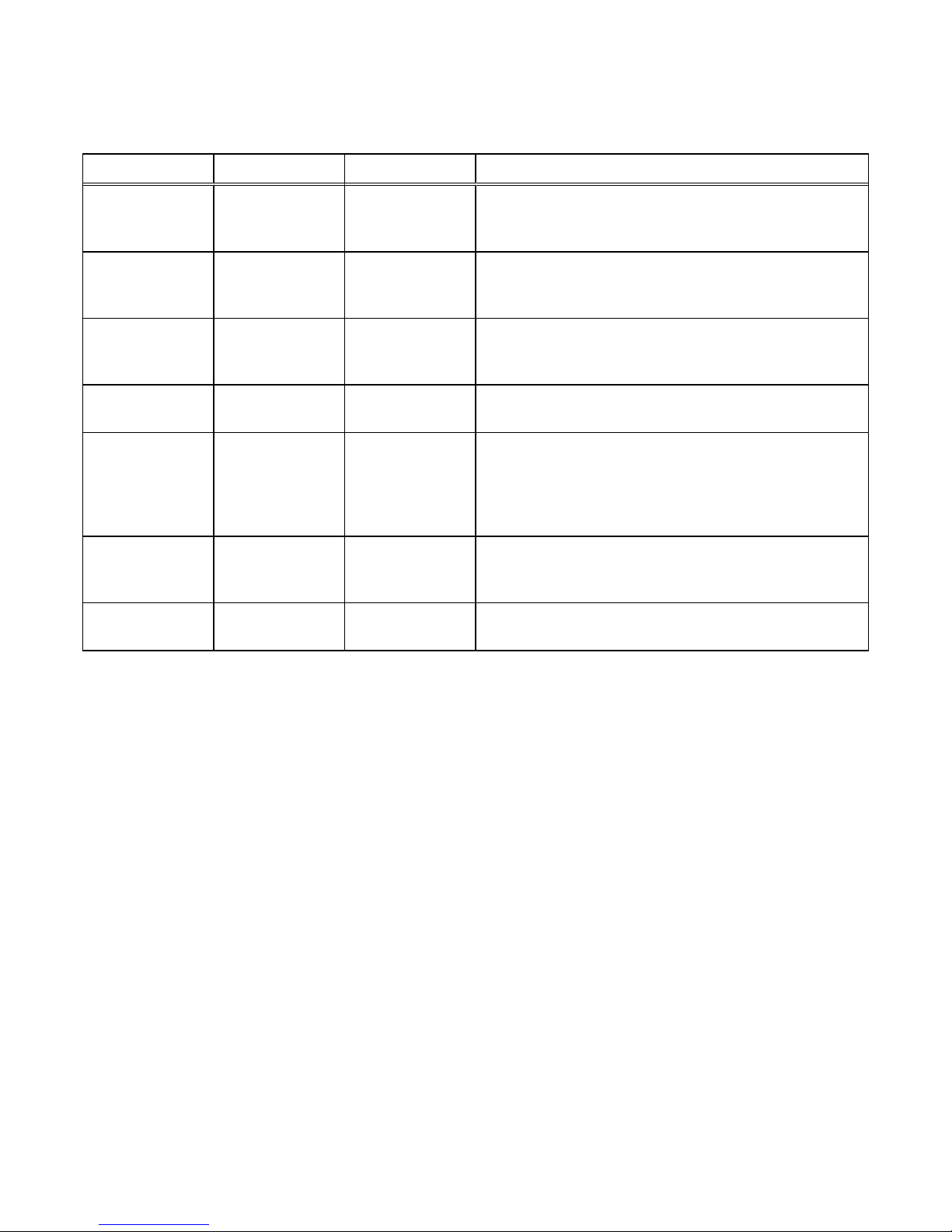
Table 11 Network connections that may be initiated by the storage system (continued)
Service Protocol Port Description
NFS TCP/UDP 4000 Used to provide NFS statd services. statd is the NFS file-
locking status monitor and works in conjunction with lockd to
provide crash and recovery functions for NFS.
NFS TCP/UDP 4001 Used to provide NFS lockd services.lockd is the NFS file-
locking daemon. It processes lock requests from NFS clients
and works in conjunction with the statd daemon.
NFS TCP/UDP 4002 Used to provide NFS rquotad services. The rquotad daemon
provides quota information to NFS clients that have mounted
a file system.
VSI TCP 5080 This port provides for VSI plugin. If closed, VSI plugin will not
be available.
HTTPS TCP 8443 HTTPS traffic for secure remote support when ESRS is
enabled and Integrated ESRS is configured on the storage
system. If closed, there will be a significant decrease in
remote support performance, which will directly impact the
time to resolve issues on the Unity storage system.
REST TCP 9443 Used to send service notifications to an ESRS gateway server
when ESRS is enabled and Centralized ESRS is configured on
the storage system.
IWD Internal 60260 IWD initial configuration daemon. If closed, initialization of the
array will be unavailable through the network.
a.
The LDAP and LDAPS port numbers can be overridden from inside Unisphere when configuring Directory Services. The default
port number is displayed in an entry box that can be overridden by the user. Also, the Remote Syslog port number can be
overridden from inside Unisphere.
Storage system certificate
The storage system automatically generates a self-signed certificate during its first
initialization. The certificate is preserved both in NVRAM and on the backend LUN.
Later, the storage system presents it to a client when the client attempts to connect
to the storage system through the management port.
The certificate is set to expire after 3 years; however, the storage system will
regenerate the certificate one month before its expiration date. Also, you can upload a
new certificate by using the svc_custom_cert service command. This command
installs a specified SSL certificate in PEM format for use with the Unisphere
management interface. For more information about this service command, see the
Service Commands Technical Notes
document. You cannot view the certificate through
Unisphere or the Unisphere CLI; however, you can view the certificate through a
browser client or a web tool that tries to connect to the management port.
Communication Security
Storage system certificate 41
Page 42

Note
When the array is in FIPS mode and a certificate is generated off-array, in addition to
the certificate being in PEM format, the private key needs to be in PKCS#1 format.
You can use an openssl command to do this conversion. Once the .cer and .pk files are
generated, this additional step is required when the certificate will be used on an array
in FIPS mode.
To increase security, some organizations use CA certificate chaining. Certificate
chaining links two or more CA certificates together. The primary CA certificate is the
root certificate at the end of the CA certificate chain. Since the system needs the
complete certificate chain to verify the authenticity of a certificate that is received,
ask the directory server administrator if certificate chaining is used. If so, you must
concatenate all the relevant certificates into a single file and upload that version. The
certificate must be in PEM/Base64 encoded format and use the suffix .cer.
Storage system interfaces, services, and features that
support Internet Protocol version 6
You can configure the interfaces on a system and use Internet Protocol version 6
(IPv6) addresses to configure different services and features. The following list
contains features where IPv6 protocol is supported:
l
Interfaces (SF, iSCSI) - to statically assign an IPv4 or IPv6 address to an interface
l
Hosts - to enter a network name, an IPv4 address or an IPv6 address of a host
l
Routes - to configure a route for IPv4 or IPv6 protocol
l
Diagnostics - to initiate a diagnostic ping CLI command using either an IPv4 or
IPv6 destination address. In Unisphere select Settings > Access > Routing >
Ping/Trace to access the Ping/Trace screen which supports the IPv6 destination
addresses as well.
All storage system components support IPv4, and most support IPv6. Table 12 on
page 42 shows the availability of IPv6 support by setting type and component:
Table 12
IPv6 support by setting type and component
Setting Type Component IPv6 Supported
Unisphere management
settings
Management port Yes
Domain Name Server (DNS) Yes
NTP (network time protocol)
server
Yes
Remote logging server Yes
LDAP server No
Unisphere host configuration
setting
Microsoft Exchange Yes
VMware datastore (NFS) Yes
VMware datastore (VMFS) Yes
Hyper-V datastore Yes
Communication Security
42 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 43

Table 12 IPv6 support by setting type and component (continued)
Setting Type Component IPv6 Supported
Unisphere alert setting SNMP trap destinations Yes
SMTP server Yes
EMC Secure Remote Support
(ESRS)
No
Storage server setting iSCSI server Yes
Shared Folder server Yes
Network Information Service
(NIS) server (for NFS NAS
Servers)
Yes
Active Directory server (for
SMB NAS Servers)
Yes
Internet Storage Service
(iSNS) server
Yes
Other PING destinations Yes
Remote log Yes
LDAP Yes
IPv6 address standard
Internet Protocol version 6 (IPv6) is an Internet Protocol address standard developed
by the Internet Engineering Task Force (IETF) to supplement and eventually replace
the IPv4 address standard that most Internet services use today.
IPv4 uses 32-bit IP addresses, which provides approximately 4.3 billion possible
addresses. With the explosive growth of Internet users and Internet-connected
devices, the available IPv4 address space is insufficient. IPv6 solves the address
shortage issue, because it uses 128-bit addresses, which provides approximately 340
trillion addresses. IPv6 also solves other IPv4 issues, including mobility,
autoconfiguration, and overall extensibility issues.
An IPv6 address is a hexadecimal value that contains eight, 16-bit, colon-separated
fields:
hhhh:hhhh:hhhh:hhhh:hhhh:hhhh:hhhh:hhhh
Each digit in an IPv6 address can be a number from 0-9 or a letter from A-F.
For more information about the IPv6 standard, see information about the IPv6
standard (RFC 2460) on the IETF website (http://www.ietf.org).
Storage system management interface access using IPv6
When you set up management connections in the storage system, you can configure
the system to accept the following types of IP addresses:
l
Static Internet Protocol version 6 (IPv6) addresses, IPv4 addresses obtained
through DHCP, and static IPv4 addresses
l
IPv4 addresses only
Communication Security
Storage system management interface access using IPv6 43
Page 44

You can statically assign the IPv6 addresses to the management interface. An IPv6
address on the management interface can be set to one of two modes, manual/static
or disabled. When you disable IPv6, the protocol does not unbind from the interface.
The disable command removes any unicast IPv6 addresses assigned to the
management interface and the storage system will no longer answer requests
addressed over IPv6. IPv6 is disabled by default.
After you finish installing, cabling, and powering up the system, an IP address must be
assigned to the storage system management interface. If you are not running the
storage system on a dynamic network, or if you would rather manually assign a static
IP address, you must download, install, and run the Connection Utility. For more
information about the Connection Utility, see Running the Connection Utility on page
45.
Inbound requests using IPv6 to the storage system through the management interface
are supported. You can configure the management interface on a storage system to
operate in an IPv4-only, IPv6-only, or a combined IPv4 and IPv6 environment and you
can manage the storage system using Unisphere UI and the command line interface
(CLI).
Outbound services such as Network Time Protocol (NTP) and Domain Naming System
(DNS) support IPv6 addressing either by using explicit IPv6 addresses or by using
DNS names. If a DNS name resolves to both IPv6 and IPv4, the storage system will
communicate with the server over IPv6.
The manage network interface set and show CLI commands that are used to manage
the management interfaces include attributes related to IPv6. For more information
about these manage network interface commands and attributes, refer to the
Unisphere Command Line Interface User Guide
.
Configuring the management interface using DHCP
After you finish installing, cabling, and powering up the system, an IP address must be
assigned to the storage system management interface. If you are running the storage
system on a dynamic network that includes a Dynamic Host Control Protocol (DHCP)
server and a Domain Name System (DNS) server, the management IP address can be
assigned automatically.
Note
If you are not running the storage system in a dynamic network environment, or you
would rather manually assign a static IP address, you must install and run the
Connection Utility. For more information concerning the Connection Utility, see
Running the Connection Utility on page 45.
The appropriate network configuration must include setting the range of available IP
addresses, the correct subnet masks, and gateway and name server addresses.
Consult your specific network's documentation for more information on setting up
DHCP and DNS servers.
DHCP is a protocol for assigning dynamic Internet Protocol (IP) addresses to devices
on a network. DHCP allows you to control Internet Protocol (IP) addresses from a
centralized server and automatically assign a new, unique IP address when a storage
system is plugged into your organization's network. This dynamic addressing simplifies
network administration because the software keeps track of IP addresses rather than
requiring an administrator to manage the task.
The DNS server is an IP-based server that translates domain names into IP addresses.
As opposed to numeric IP addresses, domain names are alphabetic and are usually
Communication Security
44 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 45

easier to remember. Since an IP network is based on IP addresses, every time you use
a domain name, the DNS server must translate the name into a corresponding IP
address. For example, the domain name www.Javanet.com translates to the IP
address 209.94.128.8.
No administrative information such as user names, passwords, and such are
exchanged during the DHCP/Dynamic DNS configuration. Configuration of the
management IP items (DHCP preference, DNS and NTP server configuration) fall
under the existing Unisphere framework related to security. DNS and DHCP events
including obtaining a new IP address on lease expiration are recorded in storage
system audit logs. If DHCP is not used for the storage system management IP
configuration, no additional network ports will be opened.
Dynamic IP addresses (DHCP) should not be used for any components of the EMC
Secure Remote Services Virtual Edition (ESRS VE) servers, Policy Manager servers,
or managed devices.
Note
If you use DHCP to assign IP addresses to any EMC Secure Remote Services (ESRS)
components (ESRS Virtual Edition servers, Policy Manager, or managed devices),
they must have static IP addresses. Leases for the IP addresses that EMC devices use
cannot be set to expire. EMC recommends that you assign static IP addresses to
those devices you plan to have managed by ESRS.
Running the Connection Utility
Note
If you are running the storage system in a dynamic network environment that includes
a DHCP server and a DNS server, you do not have to use the Connection Utility and
instead can automatically assign a dynamic IP address (IPv4 only) for the storage
system management interface. When a storage system uses a static IP address, it is
manually configured with the Connection Utility to use a specific IP address. One
problem with static assignment, which can result from a mistake or inattention to
detail, occurs when two storage systems are configured with the same management
IP address. This creates a conflict that could result in loss of network connectivity.
Using DHCP to dynamically assign IP addresses minimizes these types of conflicts.
Storage systems configured to use DHCP for IP assignment do not need to use
statically assigned IP addresses.
Connection Utility installation software is available from the EMC Online Support
website (https://support.emc.com), under the Downloads selection on the menu bar
of the product page for your storage system. After you download the software, install
the program on a Windows host. When you run the Connection Utility from a
computer on the same subnet as the storage system, the Connection Utility
automatically discovers any unconfigured storage systems. If you run the Connection
Utility on a different subnet, you can save the configuration to a USB drive and then
transfer it to the storage system. If the storage system is located on a different
subnet than the host running the Connection Utility, you can select to manually
configure and save IP network and Hostname information to a USB drive as a text file,
then insert the USB drive into either SP, which will then automatically set the IP
network and Hostname information.
Communication Security
Running the Connection Utility 45
Page 46

Note
You cannot change the management IP address when both of the Storage Processors
(SP) are in Service mode.
After you run the Connection Utility and transfer the configuration to your storage
system, you can connect to the storage system through a web browser using the IP
address that you assigned to the storage system management interface.
The first time you connect to the storage system, the storage system Initial
Configuration Wizard starts. The Initial Configuration Wizard lets you set up the initial
configuration of the storage system so that you can start to create storage resources.
Note
For more information concerning the Connection Utility, see the
Unity Series
Installation Guide
.
Protocol (SMB) encryption and signing
SMB 3.0 and Windows 2012 support on the storage system provides SMB encryption
for those hosts capable of using SMB. SMB Encryption provides secure access to data
on SMB file shares. This encryption provides security to data on untrusted networks,
that is, it provides end-to-end encryption of SMB data sent between the array and the
host. The data is protected from eavesdropping/snooping attacks on untrusted
networks.
SMB Encryption can be configured for each share. Once a share is defined as
encrypted, any SMB3 client must encrypt all its requests related to the share;
otherwise, access to the share will be denied.
To enable SMB Encryption, you either set the Protocol Encryption option in the
advanced SMB share properties in Unisphere or set it through the create and set
CLI commands for SMB shares. There is no setting required on the SMB client.
Note
For more information about setting SMB encryption, refer to the Unisphere online help
and the
Unisphere Command Line Interface User Guide
.
SMB also provides data integrity validation (signing). This mechanism ensures that
packets have not been intercepted, changed, or replayed. SMB signing adds a
signature to every packet and guarantees that a third party has not changed the
packets.
To use SMB signing, the client and the server in a transaction must have SMB signing
enabled. By default, Windows Server domain controllers require that the clients use
SMB signing. For Windows Server domains (Windows 2000 and later), SMB signing is
set by using a group policy object (GPO) policy. For Windows XP, GPO services for
SMB signing are not available; you must use the Windows Registry settings.
Note
Configuring SMB signing through GPOs affects all clients and servers within the
domain and overrides individual Registry settings. Refer to Microsoft's security
documentation for detailed information about enabling and configuring SMB signing.
Communication Security
46 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 47

In SMB1, enabling signing significantly decreases performance, especially when going
across a WAN. There is limited degradation in performance with SMB2 and SMB3
signing as compared to SMB1. The performance impact of signing will be greater when
using faster networks.
Configure SMB signing with GPOs
Table 13 on page 47 explains the GPOs available for SMB1 signing.
Note
For SMB2 and SMB3, each version has a GPO for each side (server-side and clientside) to enable the Digitally sign communications (always) option. Neither server-side
nor client-side has a GPO to enable the Digitally sign communications (if client agrees)
option.
Table 13 SMB1 signing GPOs
GPO name What it controls Default setting
Microsoft network server:
Digitally sign communications
(always)
Whether the server-side SMB
component requires signing
Disabled
Microsoft network server:
Digitally sign communications
(if client agrees)
Whether the server-side SMB
component has signing
enabled
Disabled
Microsoft network client:
Digitally sign communications
(always)
Whether the client-side SMB
component requires signing
Disabled
Microsoft network client:
Digitally sign communications
(if server agrees)
Whether the client-side SMB
component has signing
enabled
Enabled
You can also configure SMB signing through the Windows Registry. If a GPO service is
not available, such as in a Windows NT environment, the Registry settings are used.
Configure SMB signing with the Windows Registry
Registry settings affect only the individual server or client that you configure. Registry
settings are configured on individual Windows workstations and servers and affect
individual Windows workstations and servers.
Note
The following Registry settings pertain to Windows NT with SP 4 or later. These
Registry entries exist in Windows Server, but should be set through GPOs.
The server-side settings are located in: HKEY_LOCAL_MACHINE\System
\CurrentControlSet\Services\lanmanserver\parameters\
Note
For SMB2 and SMB3, each version has a Registry key for each side (server-side and
client-side) to enable the requiresecuritysignature option. Neither server-side nor
client-side has a Registry key to enable the enablesecuritysignature option.
Communication Security
Protocol (SMB) encryption and signing 47
Page 48
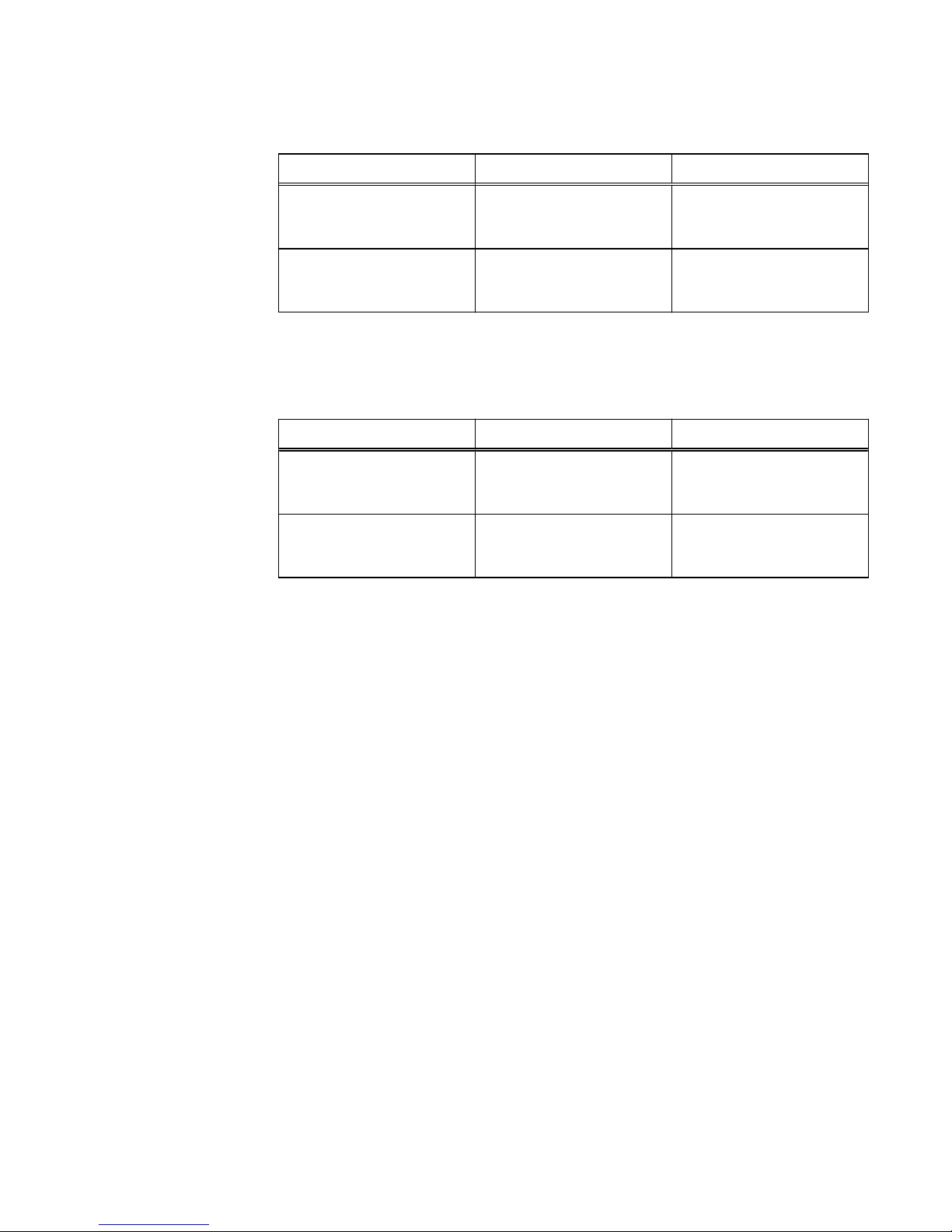
Table 14 Server-side SMB1 signing Registry entries
Registry entries Values Purpose
enablesecuritysignatur
e
l
0 disabled (default)
l
1 enabled
Determines if SMB signing is
enabled.
requiresecuritysignatu
re
l
0 disabled (default)
l
1 enabled
Determines if SMB signing is
required.
The client-side settings are located in: HKEY_LOCAL_MACHINE\System
\CurrentControlSet\Services\lanmanworkstation\parameters\
Table 15 Client-side SMB1 signing Registry entries
Registry entries Values Purpose
enablesecuritysignatur
e
l
0 disabled
l
1 enabled (default)
Determines if SMB signing is
enabled.
requiresecuritysignatu
re
l
0 disabled (default)
l
1 enabled
Determines if SMB signing is
required.
IP packet reflect
IP packet reflect provides your network with an additional security level. Because the
majority of network traffic on a NAS server (including all file system I/O) is client
initiated, the NAS server uses Packet Reflect to reply to client requests. With Packet
Reflect, there is no need to determine the route to send the reply packets. Because
reply packets always go out the same interface as the request packets, request
packets cannot be used to indirectly flood other LANs. In cases where two network
devices exist, one connected to the Internet and the other connected to the intranet,
replies to Internet requests do not appear on the intranet. Also, the internal networks
used by the storage system are not affected by any packet from external networks.
IP multi-tenancy
IP multi-tenancy provides the ability to assign isolated, file-based storage partitions to
the NAS servers on a storage processor. Tenants are used to enable the costeffective management of available resources, while at the same time ensuring that
tenant visibility and management is restricted to assigned resources only.
With IP multi-tenancy, each tenant can have its own:
l
IP addresses and port numbers.
l
VLAN domain.
l
Routing table.
l
IP firewall.
l
DNS server or other administrative servers to allow the tenant to have its own
authentication and security validation.
Communication Security
48 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 49

IP multi-tenancy is implemented by adding a tenant to the storage system, associating
a set of VLANs with the tenant, and then creating one NAS server for each of the
tenant's VLANs, as needed. It is recommended that you create a separate pool for the
tenant and that you associate that pool with all of the tenant's NAS servers.
Note the following about the IP multi-tenancy feature:
l
There is a one-to-many relationship between tenants and NAS servers. A tenant
can be associated with multiple NAS servers, but a NAS server can be associated
with only one tenant.
l
You can associate a NAS server with a tenant when you create the NAS server.
Once you create a NAS server that is associated with a tenant, you cannot change
any of its properties.
l
During replication, data for a tenant is transferred over the service provider's
network rather than the tenant's network.
l
Because multiple tenants can share the same storage system, a spike in traffic for
one tenant can negatively impact the response time for other tenants.
About VLANs
VLANs are logical networks that function independently of the physical network
configuration. For example, VLANs enable you to put all of a department's computers
on the same logical subnet, which can increase security and reduce network broadcast
traffic.
When a single NIC is assigned multiple logical interfaces, a different VLAN can be
assigned to each interface. When each interface has a different VLAN, a packet is
accepted only if its destination IP address is the same as the IP address of the
interface, and the packet's VLAN tag is the same as the interface's VLAN ID. If the
VLAN ID of an interface is set to zero, packets are sent without VLAN tags.
There are two ways to work with VLANs:
l
Configure a switch port with a VLAN identifier and connect a NAS server port or
iSCSI interface to that switch port. The Unity system is unaware that it is part of
the VLAN, and no special configuration of the NAS server or iSCSI interface is
needed. In this case, the VLAN ID is set to zero.
l
Implement IP multi-tenancy using VLANs. In this scenario, each tenant is
associated with a set of one or more VLANs, and the NAS server is responsible for
interpreting the VLAN tags and processing the packets appropriately. This enables
the NAS server to connect to multiple VLANs and their corresponding subnets
through a single physical connection. In this method, the switch ports for servers
are configured to include VLAN tags on packets sent to the server.
Management support for FIPS 140-2
Federal Information Processing Standard 140-2 (FIPS 140-2) is a standard that
describes US Federal government requirements that IT products should meet for
Sensitive, but Unclassified (SBU) use. The standard defines the security requirements
that must be satisfied by a cryptographic module used in a security system protecting
unclassified information within IT systems. To learn more about FIPS 140-2, refer to
FIPS 1402-2 publication.
The storage system supports FIPS 140-2 mode for the SSL modules that handle client
management traffic. Management communication into and out of the system is
encrypted using SSL. As a part of this process, the client and the storage
management software negotiate a cipher suite to use in the exchange. Enabling FIPS
140-2 mode restricts the negotiable set of cipher suites to only those that are listed in
Communication Security
About VLANs 49
Page 50

the FIPS 140-2 Approved Security Functions publication. If FIPS 140-2 mode is
enabled, you may find that some of your existing clients can no longer communicate
with the management ports of the system if they do not support FIPS 140-2 Approved
cipher suites. FIPS 140-2 mode cannot be enabled on a storage system when nonFIPS-compliant certificates exist in the certificate store. You must remove all nonFIPS compliant certificates from the storage system before you enable the FIPS 140-2
mode.
Managing FIPS 140-2 mode on the storage system
Only the Administrator has the privileges to manage the FIPS 140-2 mode setting. Use
the following CLI command to set the FIPS 140-2 mode setting on a storage system:
uemcli /sys/security set -fips140Enabled yes will set it to FIPS 140-2 mode.
uemcli /sys/security set -fips140Enabled no will set it to non-FIPS 140-2
mode.
Use the following CLI command to determine the current FIPS 140-2 mode for the
storage system:
uemcli /sys/security show
When you change the FIPS 140-2 mode setting on a storage system, you must reboot
both SPs in order to apply the new setting. To do this, after changing the FIPS mode
setting, reboot one of the SPs (in Unisphere, go to Service > Service Tasks and
select Reboot for the SP). Wait for that SP's Status and Mode to change to OK and
Normal, respectively, which indicates that the SP has completed rebooting. When the
first SP has completed rebooting, reboot the other SP. The system will only operate
fully in the configured FIPS 140-2 mode after both SPs have completed rebooting.
Communication Security
50 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 51

CHAPTER 5
Data Security Settings
This chapter describes the security features that are available on the storage system
for supported storage types.
Topics include:
l
About Data at Rest Encryption (physical deployments only)..............................52
l
Data security settings........................................................................................ 56
Data Security Settings 51
Page 52

About Data at Rest Encryption (physical deployments only)
Data at Rest Encryption (D@RE) is provided through controller-based encryption
(CBE) at a physical drive level. A unique data encryption key (DEK) is generated for
each drive and is used to encrypt data as it is sent to the drive. The goal of this feature
is to ensure that all customer data and identifying information will be encrypted with
strong encryption, primarily to ensure security in the event of loss of a drive.
Separate from CBE, system space on the Storage Processors (SPs) is encrypted
using an encryption capability (dm_crypt) that is native to the Linux distribution.
Specific partitions on the system drive are encrypted by default unless encryption is
not activated on the system at manufacture time. For those system partitions that are
not encrypted, some unencrypted data, such as diagnostic dumps, could be present. In
addition, there is potential for small amounts of unencrypted user data as a result of
writing diagnostic materials to the system partition. All the data written to the array by
using regular I/O protocols (iSCSI, FC) are encrypted. Anything that comes into the
array by using the control path will not be encrypted by this solution; however,
information that is sensitive (for example, passwords) are encrypted by a different
mechanism (as they are on non-encrypting arrays).
A component, referred to as the Key Manager, is responsible for generating, storing
and otherwise managing the encryption keys for the system. The keystore that is
generated to store the encryption keys resides on a managed LUN in private space on
the system. Keys are generated or deleted in response to notifications that a storage
pool has been added or removed. Key backups are performed automatically by the
system. In addition, changes to the configuration of the system that result in changes
to the keystore will generate information alerts that recommend key backups be
created. When an operation that results in a change to the keystore occurs, an alert
will appear and persist.
A separate auditing function is provided for general key operations that track all key
establishment, deletion, backup, and restore changes as well as SLIC addition.
For additional information about the Data at Rest Encryption feature, refer to the
EMC
Unity: Data at Rest Encryption
white paper.
Feature activation
D@RE is a licensed feature. The license must be installed during the initial
configuration of your system. Once activated, the encryption operation cannot be
reverted.
The encryption operation will cause data encryption keys to be created and all user
data will begin to be encrypted. The encryption keys are stored in a keystore file. The
keystore file that is generated resides on a managed LUN in private space on the
system.
It is strongly recommended that you backup the generated keystore file to another
location which is external to the system where the keystore can be kept safe and
secret. In the event that the keystore on the system becomes corrupted, the system
will be nonfunctional. The system will enter service mode; only the operating system
boots. In this state, attempts to access the system through Unisphere will return an
error indicating that the keystore is in an inaccessible state. In this case, the backup
keystore file and a service engagement are required for resolution.
Encryption status
The following D@RE feature status can be viewed either through Unisphere or a CLI
command:
Data Security Settings
52 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 53

l
Encryption Mode: type of encryption in use; for example, Controller-Based
Encryption.
l
Encryption Status: based on the actual encryption status:
n
Unsupported, encryption of the system space on the SPs is disabled.
n
Not licensed, the Data at Rest Encryption license has not been installed on the
system.
n
Encrypted, encryption is complete.
n
Not encrypting, CBE is disabled.
n
Scrubbing, the process of writing random data to unused space on drives or
zeroing unbound drives to erase residual data from previous use.
Note
For SAS Flash 2 drives, unmap is used to scrub the drives rather than zeroing.
For more information about Data at Rest Encryption and the scrubbing
process, refer to the
EMC Unity: Data at Rest Encryption
white paper located at
EMC Online Support (https://support.emc.com).
n
Encrypting, encryption is in progress.
To view the status of the D@RE feature in Unisphere, select Settings >
Management > Encryption. The status of the encryption appears under Manage
Encryption > Encryption.
Note
As an alternative, use the CLI command uemcli -u <username> -p
<password> /prot/encrypt show -detail to view the feature status. You can
also use this CLI command to view the status of the keystore and to determine
whether any user operations are required. See the
Unisphere Command Line Interface
User Guide
for detailed information about these CLI commands.
Backup keystore file
Changes to the configuration of the system that result in changes to the keystore
generate information alerts which persist and recommend key backups be created. A
new alert will be generated only after the keystore has been retrieved from the system
for backup.
Note
EMC strongly recommends that you backup the generated keystore file to another
location which is external to the system where the keystore can be kept safe and
secret. In the event that the keystore files on the system become corrupted and in an
inaccessible state, the system will enter service mode. In this case, the backup
keystore file and a service engagement are required for resolution.
A user role of administrator or storage administrator is required to backup the
keystore file. To backup the keystore file to a location that is external to the system
where the keystore can be kept safe and secret, select Settings > Management >
Encryption and, under Manage Encryption > Keystore, select Backup Keystore File.
The dialog box that appears directs you through the steps to backup the generated
keystore file.
Data Security Settings
Backup keystore file 53
Page 54

Note
As an alternative, use the CLI command uemcli -u<username> -p<password>
-download encryption -type backupKeys to backup the keystore file to a
location that is external to the system where the keystore can be kept safe and
secret. See the
Unisphere Command Line Interface User Guide
for detailed information
about this CLI command.
Data at Rest Encryption audit logging
The D@RE feature provides a separate auditing function that supports logging of the
following keystore operations:
l
Feature activation
l
Key creation
l
Key destroy
l
Keystore backup
l
Disk encryption completed
l
SLIC addition
The audit log for keystore operations is stored in the private space on the system. To
download either the entire audit log and checksum information or the information for a
specific year and month, select Settings > Management > Encryption and, under
Manage Encryption > Audit Log, select Download Audit Log & Chksum. To
download a newly generated checksum file for the audit log file that was retrieved at
an earlier time, select Settings > Management > Encryption and, under Manage
Encryption > Audit Log, select Download Chksum. The filename that you supply
must match exactly to the auditlog file that was retrieved previously.
Note
As an alternative, use the uemcli -u<username> -p<password> -download
encryption -type auditLog -entries <all or YYYY-MM> CLI command
to download the entire audit log and checksum information or a partial audit log,
respectively. See the
Unisphere Command Line Interface User Guide
for detailed
information about this CLI command.
Hot spare operations
When a system is already configured with DEKs for all the disk drives in the system
that are in provisioned pools, drives that are not currently in a provisioned pool are
considered unbound drives. Removal of unbound drives or unbound drives that
become faulted have no affect on the keystore and therefore do not require a backup
of the keystore file. Likewise, replacement of an unbound drive has no affect on the
keystore and therefore does not require a backup of the keystore file.
Note
Disk drives that are not bound will be overwritten with default data to remove preexisting data.
When a system is already configured with DEKs for all the drives in the system that
are in provisioned pools, those drives are considered bound drives. If a bound drive is
removed or the drive becomes faulted, and after a period of five minutes a permanent
hot spare replaces the removed or faulted drive, a DEK is generated for the hot spare,
Data Security Settings
54 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 55
and rebuild begins. The DEK from the removed drive will be removed immediately from
the keystore. A keystore modified status will be set by the Key Manager at this point
and will trigger an alert to back up the keystore because DEK modifications were made
to the keystore.
If the removed disk drive is reinserted anywhere in the system before the five minute
period has expired, a rebuild will not be required and modifications will not be made to
the keystore. The DEK will remain the same because the key is associated with the
disk drive, not the slot. Also, a keystore modified status alert will not be generated.
Note
If sanitizing or destruction of the removed drive is required, it should be done
independently.
Adding a disk drive to a storage system with encryption activated
Inserting one or more new disks into the system does not trigger generation of a new
DEK for each disk. This operation will not occur for a new disk until the disk is
provisioned into a pool. A keystore modified status will be set by the Key Manager at
this point and will trigger an alert to back up the keystore because DEK modifications
were made to the keystore.
When you add a new disk drive to a storage system, the drive is considered unbound.
Disk drives that are not bound are overwritten with default data to remove preexisting data. Only the addressable space of the drive is overwritten. Any residual
plaintext data that may be hidden in obscured locations within the drive will not be
overwritten.
NOTICE
If the potential access to data remnants from the previous use of a drive violates your
security policy, you must independently sanitize the drive before it is inserted in the
storage system with encryption activated.
Removing a disk drive from a storage system with encryption enabled
When a system is already configured with DEKs for all the drives in the system that
are in provisioned pools, those drives are considered bound drives. If a bound drive is
removed and after a period of five minutes is not replaced, the DEK for the drive will
not be removed from the keystore. The key will remain valid until the provisioned pool
is deleted, or until a new drive is swapped in. If the removed disk drive is reinserted
anywhere in the system before the five minute period has expired, a rebuild will not be
required, as in the case of a replacement drive, and modifications will not be made to
the keystore. The DEK will remain the same because the key is associated with the
disk drive, not the slot. Also, a keystore modified status alert will not be generated.
Note
If sanitizing or destruction of the removed drive is required, it should be done
independently.
Replacing a chassis and SPs from a storage system with encryption enabled
The generated keystore has a relationship to the hardware in the storage system. A
service engagement is required to replace a chassis and SPs from a storage system
with encryption enabled.
Data Security Settings
Adding a disk drive to a storage system with encryption activated 55
Page 56
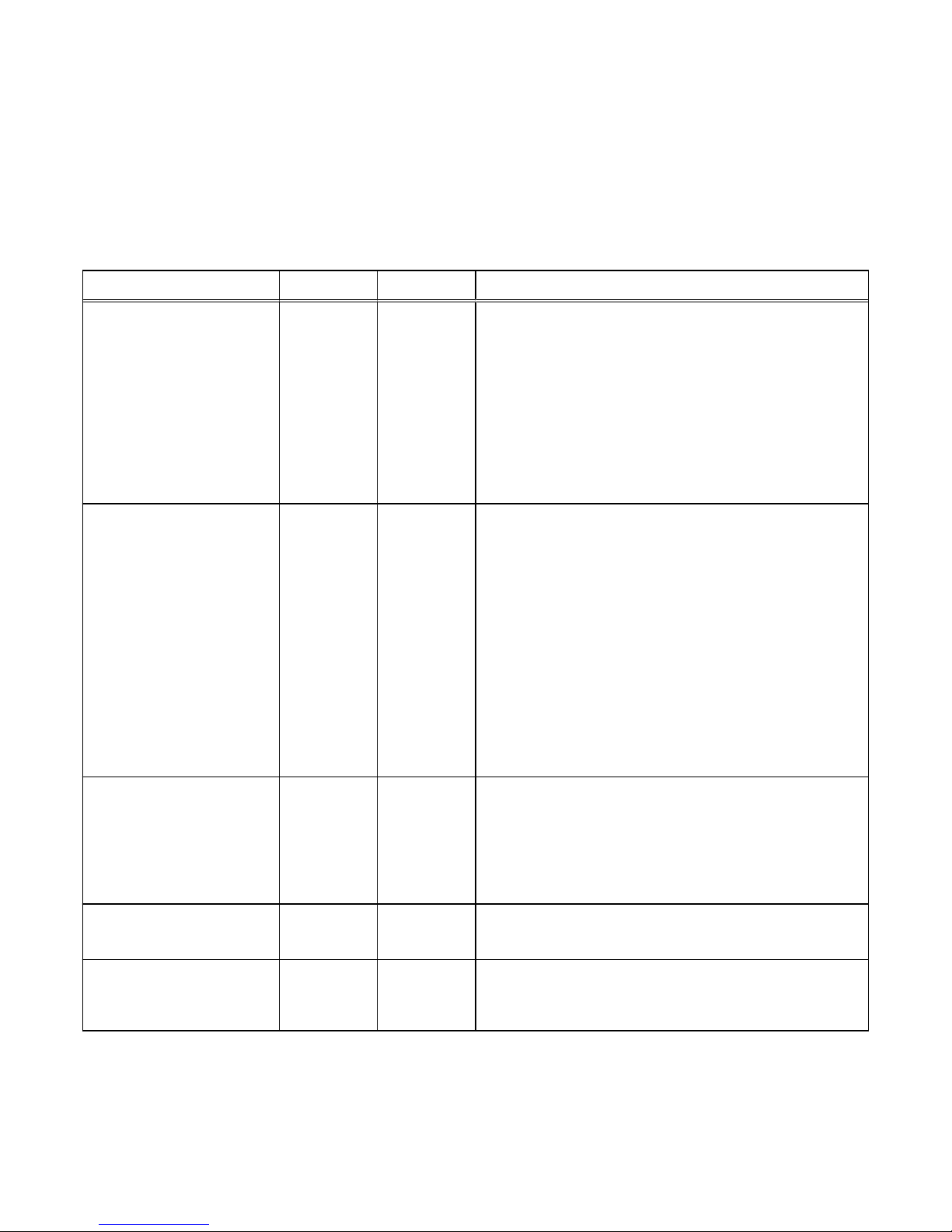
Data security settings
Table 16 on page 56 shows security features available for supported storage system
storage types.
Table 16 Security features
Storage type Port Protocol Security settings
iSCSI storage 3260 TCP
l
iSCSI host (initiator) level access control is available
through Unisphere (allowing clients to access primary
storage, snapshots, or both).
l
CHAP authentication is supported so that storage system
iSCSI Servers (targets) can authenticate iSCSI hosts
(initiators) that attempt to access iSCSI-based storage.
l
Mutual CHAP authentication is supported so that iSCSI
hosts (initiators) can authenticate storage system iSCSI
Servers.
SMB storage 445 TCP, UDP
l
Authentication for domain and administrative actions is
provided through Active Directory user and group
accounts.
l
File and share access controls are provided through
Windows directory services. SMB share access control
list (ACL) can also be configured through an SMI-S
interface.
l
Security signatures are supported through SMB signing.
l
SMB encryption is provided through SMB 3.0 and
Windows 2012 for those hosts capable of using SMB.
l
Supports optional file-level retention services through
add-on software.
NFS storage 2049 TCP
l
Share-based access control provided through Unisphere.
l
Support for NFS authentication and access control
methods identified in NFS versions 3 and 4.
l
Supports optional file-level retention services through
add-on software.
KDC 88
l
Key Distribution Center. Kerberos server that delivers
Kerberos tickets to connect to Kerberos services.
Backup and restore
l
NDMP security can be implemented based on NDMP
shared secrets.
Data Security Settings
56 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 57

CHAPTER 6
Security Maintenance
This chapter describes a variety of security maintenance features implemented on the
storage system.
Topics include:
l
Secure maintenance.......................................................................................... 58
l
EMC Secure Remote Services for your storage system.....................................59
Security Maintenance 57
Page 58

Secure maintenance
The storage system provides the following secure functions for performing remote
system maintenance and update tasks:
l
License activation
l
Software upgrade
l
Software Hotfixes
License update
The license update feature allows users to obtain and install licenses for specific
storage system functionality. Table 17 on page 58 shows security features that are
associated with the license update feature.
Table 17 License update security features
Process Security
Obtaining licenses from the EMC Online
Support website
License acquisition is performed from within
an authenticated session on the EMC Online
Support website.
Receiving license files Licenses are sent to an email address
specified within an authenticated EMC Online
Support website transaction.
Uploading and installing licenses through
Unisphere client to the storage system
l
License file uploads to the storage system
occur within Unisphere sessions
authenticated through HTTPS.
l
The storage system validates received
license files using digital signatures. Each
licensed feature is validated by a unique
signature within the license file.
Software upgrade
The storage system software update feature allows users to obtain and install
software for upgrading or updating the software running on the storage system. Table
18 on page 58 shows security features that are associated with the storage system
software upgrade feature.
Table 18
Software upgrade security features
Process Description
Downloading storage system software from
the EMC Online Support website
License acquisition is performed from within
an authenticated session on the EMC Online
Support website.
Security Maintenance
58 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 59

Table 18 Software upgrade security features (continued)
Process Description
Uploading storage system software Software upload to the storage system occurs
within an authenticated Unisphere session
through HTTPS.
EMC Secure Remote Services for your storage system
The EMC Secure Remote Services (ESRS) feature provides your authorized service
provider with remote access capabilities to your storage system using a secure and
encrypted tunnel. For outbound access, the storage system management IP network
must allow outbound and inbound HTTPS traffic. The secure tunnel that ESRS
establishes between the storage system device and authorized systems on the EMC
network can also be used to transfer files out to the storage system or transfer files
back to EMC’s network.
Two remote service options are available by which to send storage system information
to EMC for remote troubleshooting:
l
Centralized EMC Secure Remote Services Virtual Edition (ESRS VE)
l
Intregrated EMC Secure Remote Services (physical deployments only)
Centralized EMC Secure Remote Services
Centralized ESRS runs on a gateway server. When you select this option, your storage
system is added to other storage systems in an ESRS cluster. The cluster resides
behind a single common (centralized) secure connection between EMC servers and an
off-array ESRS Gateway. The ESRS Gateway is the single point of entry and exit for
all IP-based EMC remote support activities for the storage systems associated with
the gateway.
The ESRS Gateway is a remote support solution application that is installed on one or
more customer-supplied dedicated servers. The ESRS Gateway functions as a
communication broker between the associated storage systems, Policy Manager and
proxy servers (optional), and the EMC enterprise. Connections to the Policy Manager
and associated proxy servers are configured through the ESRS Gateway interface
along with add (register), modify, delete (unregister), and querying status capabilities
that ESRS clients can use to register with the ESRS Gateway.
For more information about ESRS Gateway and Policy Manager, go to the EMC
Secure Remote Services product page on EMC Online Support (https://
support.emc.com).
Intregrated EMC Secure Remote Services (physical deployments only)
Note
This feature may not be available in your implementation.
Integrated ESRS runs directly on your storage system. When you select this option,
your storage system sets up a secure connection between itself and EMC servers.
This option enables remote connectivity for dial in and dial out capabilities with this
storage system. The connection from this storage system to a Policy Manager and any
associated proxy servers (optional) must be configured through either Unisphere or
the CLI.
Security Maintenance
EMC Secure Remote Services for your storage system 59
Page 60

Security Maintenance
60 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 61

CHAPTER 7
Security Alert Settings
This chapter describes the different methods available to notify administrators of
alerts that occur on the storage system.
Topics include:
l
Alert settings..................................................................................................... 62
l
Configuring alert settings...................................................................................63
Security Alert Settings 61
Page 62

Alert settings
Storage system alerts inform administrators of actionable events that occur on the
storage system. Storage system events can be reported as shown in Table 19 on page
62.
Table 19 Alert settings
Alert type Description
Visual notification Displays informational pop-up messages when users log in to the interface and in real-time to
indicate when alert conditions occur. Pop-ups provide basic information about the alert condition.
You can obtain additional information from the Settings > Alerts > Specify Email Alerts and
SMTP Configuration.
Note
Storage system visual alert notifications are not configurable. Also, the storage system does not
have an option of authentication to an SMTP mail server. If your mail server requires all clients to
authenticate to relay an email, the storage system cannot send email alerts through that mail server.
Email notification Enables you to specify one or more email addresses to which to send alert messages. You can
configure the following settings:
l
Email addresses to which to send storage system alerts.
l
Severity level (critical, error, warning, notice, or information) required for email notification.
Note
For storage system alert email notification to work, you must configure a target SMTP server for the
storage system.
SNMP traps Transfer alert information to designated hosts (trap destinations) that act as repositories for
generated alert information by the storage network system. You can configure SNMP traps through
Unisphere. Settings include:
l
IP address of a network SNMP trap destination
l
Optional security settings for trap data transmission
n
Authentication protocol: Hashing algorithm used for SNMP traps (SHA or MD5)
n
Privacy protocol: Encryption algorithm used for SNMP traps (DES, AES, AES192, or
AES256)
The Unisphere Online Help provides more information.
EMC Secure Remote
Services (ESRS)
ESRS provides an IP-based connection that enables EMC Support to receive error files and alert
messages from your storage system, and to perform remote troubleshooting resulting in a fast and
efficient time to resolution.
Note
Available with operating environment (OE) version 4.0 or later. For ESRS to work, you must enable it
on the storage system.
Security Alert Settings
62 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 63

Configuring alert settings
You can configure storage system alert settings for email notifications and SNMP
traps from the storage system.
Configure alert settings for email notifications
Using Unisphere:
Procedure
1. Select Settings > Alerts > Email and SMTP.
2. In the Specify Email Alerts and SMTP Configuration section under Send
email Alerts to the following email list, configure the email addresses to
which to send alert notifications.
3. Under Severity level of alerts to send:, configure the severity level at which
alert email messages are generated to one of the following:
l
Critical
l
Error and Above
l
Warning and Above
l
Notice and Above
l
Information and Above
Note
For the storage system alert email mechanism to work, a target SMTP server
must be configured for the storage system.
4. Under Specify SMTP network settings:, configure the target SMTP server.
Configure alert settings for SNMP traps
Using Unisphere:
Procedure
1. Select Settings > Alerts > SNMP.
2. In the Manage SNMP Alerts section under Send alerts through SNMP traps
to these destinations:, configure the following information for the SNMP trap
destinations:
l
Network name or IP address
l
Authentication protocol to use
l
Privacy protocol to use
3. Under Severity level of alerts to send:, configure the severity level at which
SNMP traps are generated to one of the following:
l
Critical
l
Error and above
Security Alert Settings
Configuring alert settings 63
Page 64

l
Warning and above
l
Notice and above
l
Information and above
Security Alert Settings
64 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 65

CHAPTER 8
Other Security Settings
This chapter contains other information that is relevant for ensuring the secure
operation of the storage system.
Topics include:
l
Physical security controls (physical deployments only)..................................... 66
l
Antivirus protection........................................................................................... 66
Other Security Settings 65
Page 66

Physical security controls (physical deployments only)
The area where the storage system resides must be chosen and modified to provide
for the physical security of the storage system. These include basic measures such as
providing sufficient doors and locks, permitting only authorized and monitored
physical access to the system, providing reliable power source, and following standard
cabling best practices.
In addition, the following storage system components require particular care:
l
Password reset button: Temporarily resets the factory default passwords for both
the storage system default administrator account and service account - until an
administrator resets the password.
l
SP Ethernet service port connector: Allows authenticated access through an SP
Ethernet service port connection.
Antivirus protection
The storage system supports Common AntiVirus Agent (CAVA). CAVA, a component
of the Event Enabler (EE) 4.9.3.0, provides an antivirus solution to clients using a
storage system. It uses an industry-standard SMB protocol in a Microsoft Windows
Server environment. CAVA uses third-party antivirus software to identify and
eliminate known viruses before they infect files on the storage system. The EE
installer, which contains the CAVA installer, and the EE release notes are available at
the EMC Online Support website under Support By Product for Unity Family, Unity
VSA, Unity Hybrid, or Unity All Flash in Downloads > Full Release.
Other Security Settings
66 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 67

APPENDIX A
TLS cipher suites
This appendix lists the TLS cipher suites supported by the storage system.
Topics include:
l
Supported TLS cipher suites..............................................................................68
TLS cipher suites 67
Page 68
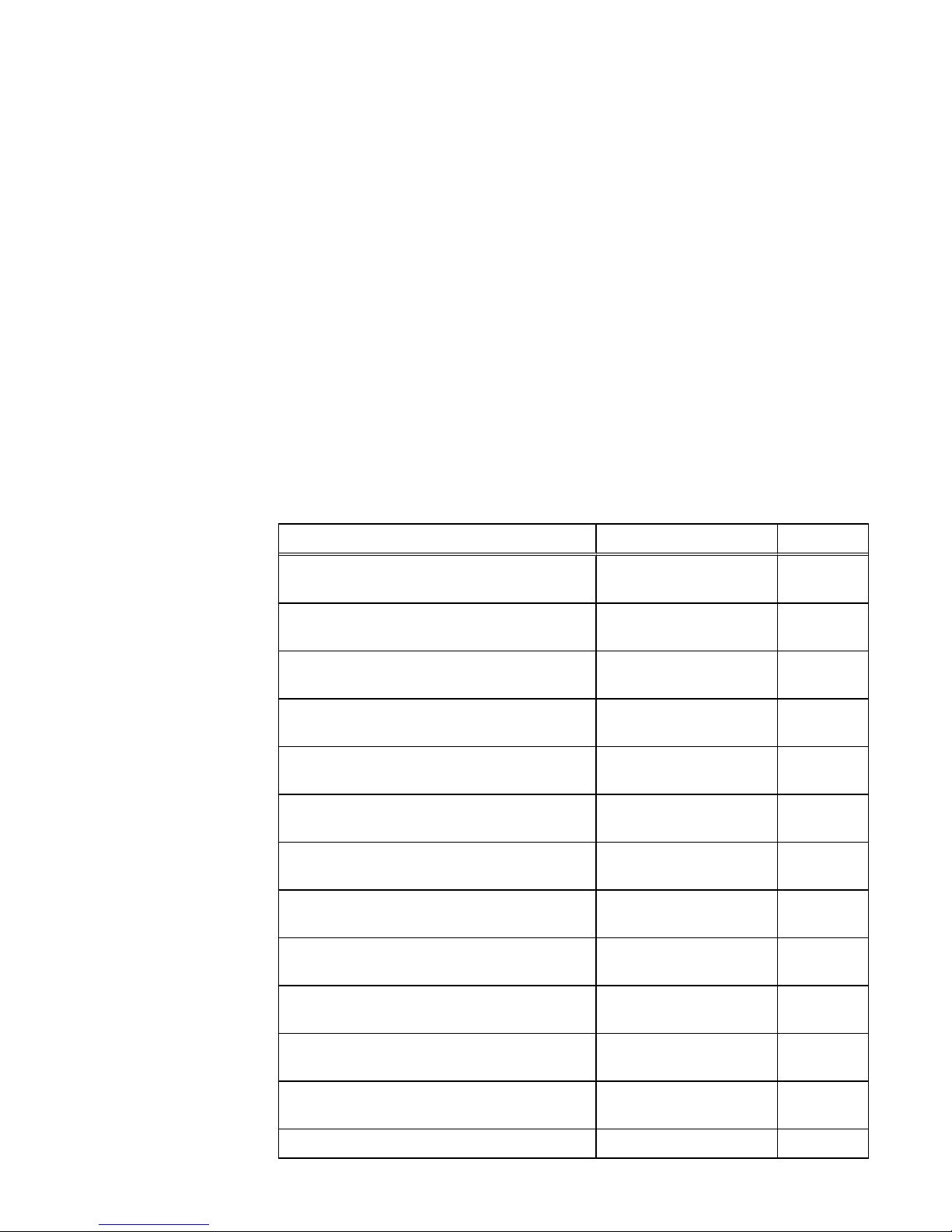
Supported TLS cipher suites
A cipher suite defines a set of technologies to secure your TLS communications:
l
Key exchange algorithm (how the secret key used to encrypt the data is
communicated from the client to the server). Examples: RSA key or Diffie-Hellman
(DH)
l
Authentication method (how hosts can authenticate the identity of remote hosts).
Examples: RSA certificate, DSS certificate, or no authentication
l
Encryption cipher (how to encrypt data). Examples: AES (256 or 128 bits) or
3DES (168 bits)
l
Hash algorithm (ensuring data by providing a way to determine if data has been
modified). Examples: SHA-2 or SHA-1
The supported cipher suites combine all these items.
The following list gives the OpenSSL names of the TLS cipher suites for the storage
system and the associated ports.
Table 20 Default/Supported TLS cipher suites supported on the storage system
Cipher Suites Protocols Ports
TLS_DHE_RSA_WITH_AES_128_CBC_SHA TLSv1, TLSv1.1, TLSv1.2 443, 8443,
8444
TLS_DHE_RSA_WITH_AES_256_CBC_SHA TLSv1, TLSv1.1, TLSv1.2 443, 8443,
8444
TLS_DHE_RSA_WITH_AES_128_CBC_SHA256 TLSv1.2 443, 8443,
8444
TLS_DHE_RSA_WITH_AES_256_CBC_SHA256 TLSv1.2 443, 8443,
8444
TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 TLSv1.2 443, 8443,
8444
TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 TLSv1.2 443, 8443,
8444
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA TLSv1, TLSv1.1, TLSv1.2 443, 8443,
8444
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA TLSv1, TLSv1.1, TLSv1.2 443, 8443,
8444
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256TLSv1.2 443, 8443,
8444
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384TLSv1.2 443, 8443,
8444
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256TLSv1.2 443, 8443,
8444
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384TLSv1.2 443, 8443,
8444
TLS_RSA_WITH_AES_128_CBC_SHA TLSv1, TLSv1.1, TLSv1.2 5989
TLS cipher suites
68 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
Page 69

Table 20 Default/Supported TLS cipher suites supported on the storage system (continued)
Cipher Suites Protocols Ports
TLS_RSA_WITH_AES_256_CBC_SHA TLSv1, TLSv1.1, TLSv1.2 5989
TLS_RSA_WITH_3DES-EDE-CBC-SHA TLSv1, TLSv1.1, TLSv1.2 5989
TLS cipher suites
Supported TLS cipher suites 69
Page 70

TLS cipher suites
70 EMC Unity All Flash, EMC Unity Hybrid, EMC UnityVSA 4.0 Security Configuration Guide
 Loading...
Loading...