Eaton Network-M2 Service Manual

UPS Network Management Card
Network-M2
User's Guide
English
11/18/2019
1.7.4


Eaton is a registered trademark of Eaton Corporation or its subsidiaries and affiliates.
Phillips and Pozidriv are a registered trademarks of Phillips Screw Company.
National Electrical Code and NEC are registered trademarks of National Fire Protection Association, Inc.
Microsoft®, Windows®, and Windows Server® are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries.
UNIX® is a registered trademark of The Open Group.
Linux® is the registered trademark of Linus Torvalds in the U.S. and other countries.
VMware is a registered trademark or trademark of VMware, Inc. in the United States and/or other jurisdictions.
Google™ is a trademark of Google Inc.
All other trademarks are properties of their respective companies.
©Copyright 2019 Eaton Corporation. All rights reserved.
No part of this document may be reproduced in any way without the express written approval of Eaton Corporation.

1 Table of Contents
1 TABLE OF CONTENTS..................................................................................................................................... 4
2 CONTEXTUAL HELP ...................................................................................................................................... 13
2.1 Login page......................................................................................................................................................................... 13
2.1.1 Logging in for the first time ......................................................................................................................................... 13
2.1.2 Troubleshooting login issues ....................................................................................................................................... 13
2.2 Home................................................................................................................................................................................. 13
2.2.1 Menu structure............................................................................................................................................................ 14
2.2.2 Energy flow diagram.................................................................................................................................................... 16
2.2.2.1 Line interactive ........................................................................................................................................................ 16
2.2.2.2 Online ...................................................................................................................................................................... 18
2.2.3 Top bar......................................................................................................................................................................... 20
2.2.4 Details.......................................................................................................................................................................... 21
2.2.5 Show measures........................................................................................................................................................... 21
2.2.5.1 Example #1.............................................................................................................................................................. 21
2.2.5.2 Example #2.............................................................................................................................................................. 21
2.2.6 Outlet status................................................................................................................................................................ 21
2.2.7 Active Alarms .............................................................................................................................................................. 22
2.3 Alarms ............................................................................................................................................................................... 22
2.3.1 Alarm sorting ............................................................................................................................................................... 22
2.3.2 Alarm details................................................................................................................................................................ 22
2.3.3 Alarm paging................................................................................................................................................................ 22
2.3.4 Alarm export ................................................................................................................................................................ 23
2.3.5 Clear alarm logs ........................................................................................................................................................... 23
2.3.6 Alarm list with codes ................................................................................................................................................... 23
2.4 Settings ............................................................................................................................................................................. 23
2.4.1 General ........................................................................................................................................................................ 23
2.4.1.1 Location................................................................................................................................................................... 23
2.4.1.2 Contact .................................................................................................................................................................... 24
2.4.1.3 System name .......................................................................................................................................................... 24
2.4.1.4 Default settings parameters and limitations............................................................................................................ 24
2.4.2 Date & Time ................................................................................................................................................................ 24
2.4.2.1 Manual:Manually entering the date and time......................................................................................................... 24
2.4.2.2 Dynamic (NTP):Synchronizing the date and time with an NTP server.................................................................... 24
2.4.2.3 Default settings parameters and limitations............................................................................................................ 25
2.4.3 Users ........................................................................................................................................................................... 25
2.4.3.1 Password strength rules.......................................................................................................................................... 25
2.4.3.2 Account expiration................................................................................................................................................... 25
2.4.3.3 Session expiration ................................................................................................................................................... 26
2.4.3.4 Local users table...................................................................................................................................................... 26
2.4.3.5 LDAP ....................................................................................................................................................................... 29
2.4.3.6 RADIUS ................................................................................................................................................................... 32
2.4.3.7 Default settings parameters and limitations............................................................................................................ 35
2.4.4 Network....................................................................................................................................................................... 35
2.4.4.1 LAN.......................................................................................................................................................................... 35
2.4.4.2 IPv4.......................................................................................................................................................................... 35
2.4.4.3 Domain .................................................................................................................................................................... 37
2.4.4.4 IPv6.......................................................................................................................................................................... 38
2.4.4.5 Default settings parameters and limitations............................................................................................................ 40

2.4.5 Protocols...................................................................................................................................................................... 40
2.4.5.1 HTTPS...................................................................................................................................................................... 40
2.4.5.2 Syslog...................................................................................................................................................................... 40
2.4.5.3 Default settings parameters and limitations............................................................................................................ 41
2.4.6 SNMP .......................................................................................................................................................................... 41
2.4.6.1 SNMP tables............................................................................................................................................................ 42
2.4.6.2 Trap receivers......................................................................................................................................................... 44
2.4.6.3 Actions.................................................................................................................................................................... 45
2.4.6.4 Default settings parameters and limitations............................................................................................................ 46
2.4.7 Certificates .................................................................................................................................................................. 46
2.4.7.1 Local certificates...................................................................................................................................................... 46
2.4.7.2 Certificate authorities (CA)....................................................................................................................................... 48
2.4.7.3 Pairing with clients .................................................................................................................................................. 49
2.4.7.4 Trusted remote certificates ..................................................................................................................................... 50
2.4.7.5 Default settings parameters and limitations............................................................................................................ 50
2.4.8 Email............................................................................................................................................................................ 50
2.4.8.1 Email sending configuration .................................................................................................................................... 50
2.4.8.2 Default settings parameters and limitations............................................................................................................ 53
2.4.9 My preferences ........................................................................................................................................................... 53
2.4.9.1 Profile ...................................................................................................................................................................... 54
2.4.9.2 Temperature............................................................................................................................................................ 54
2.4.9.3 Date format ............................................................................................................................................................. 55
2.4.9.4 Time format............................................................................................................................................................. 55
2.4.9.5 Language................................................................................................................................................................ 56
2.4.9.6 Default settings parameters and limitations............................................................................................................ 56
2.5 Meters............................................................................................................................................................................... 56
2.5.1 Power .......................................................................................................................................................................... 56
2.5.1.1 Input ........................................................................................................................................................................ 56
2.5.1.2 Output ..................................................................................................................................................................... 57
2.5.2 Battery ......................................................................................................................................................................... 57
2.5.2.1 Overview ................................................................................................................................................................. 57
2.5.2.2 Details...................................................................................................................................................................... 57
2.5.2.3 Test.......................................................................................................................................................................... 57
2.5.3 Measure logs............................................................................................................................................................... 58
2.5.3.1 Configuration ........................................................................................................................................................... 58
2.5.3.2 Measure logs........................................................................................................................................................... 58
2.5.3.3 Default settings parameters and limitations............................................................................................................ 59
2.6 Controls ............................................................................................................................................................................. 59
2.6.1 UPS.............................................................................................................................................................................. 59
2.6.1.1 Entire UPS ............................................................................................................................................................... 59
2.6.2 Outlets......................................................................................................................................................................... 60
2.6.2.1 Group 1/ Group 2..................................................................................................................................................... 60
2.7 Protection .......................................................................................................................................................................... 61
2.7.1 Scheduled shutdowns ................................................................................................................................................. 61
2.7.1.1 Scheduled shutdowns table .................................................................................................................................... 61
2.7.1.2 Actions..................................................................................................................................................................... 61
2.7.2 Agent list ..................................................................................................................................................................... 62
2.7.2.1 Pairing with shutdown agents................................................................................................................................. 62
2.7.2.2 Agent list table......................................................................................................................................................... 62
2.7.2.3 Actions..................................................................................................................................................................... 63
2.7.3 Agent settings ............................................................................................................................................................. 63
2.7.3.1 Agent shutdown sequence timing .......................................................................................................................... 63
2.7.3.2 Actions..................................................................................................................................................................... 64
2.7.3.3 Examples................................................................................................................................................................. 64

2.7.4 Power outage policy .................................................................................................................................................... 64
2.7.4.1 On power outage..................................................................................................................................................... 65
2.7.4.2 On low battery warning........................................................................................................................................... 69
2.7.4.3 When utility comes back ......................................................................................................................................... 70
2.8 Card ................................................................................................................................................................................... 70
2.8.1 System information ..................................................................................................................................................... 70
2.8.1.1 Identification............................................................................................................................................................ 70
2.8.1.2 Firmware information .............................................................................................................................................. 71
2.8.2 Resources.................................................................................................................................................................... 71
2.8.2.1 Processor................................................................................................................................................................. 71
2.8.2.2 Memory................................................................................................................................................................... 71
2.8.2.3 Storage .................................................................................................................................................................... 72
2.8.3 System logs................................................................................................................................................................. 72
2.8.4 Administration ............................................................................................................................................................. 73
2.8.4.1 Network module firmware ...................................................................................................................................... 73
2.8.4.2 Sanitization .............................................................................................................................................................. 74
2.8.4.3 Reboot..................................................................................................................................................................... 75
2.8.4.4 Maintenance............................................................................................................................................................ 75
2.8.4.5 Settings ................................................................................................................................................................... 76
2.8.5 Commissioning (sensors) ............................................................................................................................................ 78
2.8.5.1 Sensors commissioning table.................................................................................................................................. 78
2.8.5.2 Actions..................................................................................................................................................................... 78
2.8.5.3 Note:........................................................................................................................................................................ 81
2.9 Sensors.............................................................................................................................................................................. 81
2.9.1 Status (sensors)........................................................................................................................................................... 81
2.9.1.1 Temperature table ................................................................................................................................................... 81
2.9.1.2 Humidity table ......................................................................................................................................................... 81
2.9.1.3 Dry contacts table.................................................................................................................................................... 82
2.9.2 Alarm configuration (sensors)...................................................................................................................................... 82
2.9.2.1 Temperature............................................................................................................................................................ 82
2.9.2.2 Humidity .................................................................................................................................................................. 83
2.9.2.3 Dry contacts ............................................................................................................................................................ 84
2.9.2.4 Default settings parameters and limitations............................................................................................................ 84
2.9.3 Information (sensors)................................................................................................................................................... 84
2.10 Legal information (footer) .................................................................................................................................................. 85
2.10.1 Component list ............................................................................................................................................................ 85
2.10.2 Notice for our proprietary (i.e. non-Open source) elements........................................................................................ 85
2.10.3 Availability of source code........................................................................................................................................... 86
2.11 Contextual help and full documentation............................................................................................................................ 86
2.11.1 Access to contextual help ........................................................................................................................................... 86
2.11.2 Access to full documentation...................................................................................................................................... 86
3 SERVICING THE NETWORK MANAGEMENT MODULE ............................................................................... 88
3.1 Unpacking the Network module........................................................................................................................................ 88
3.2 Installing the Network Module .......................................................................................................................................... 88
3.2.1 Mounting the Network Module ................................................................................................................................... 88
3.3 Accessing the Network Module........................................................................................................................................ 88
3.3.1 Accessing the web interface through Network ........................................................................................................... 88
3.3.1.1 Connecting the network cable................................................................................................................................. 88
3.3.1.2 Accessing the web interface................................................................................................................................... 89
3.3.2 Finding and setting the IP address .............................................................................................................................. 89
3.3.2.1 Your network is equipped with a BOOTP/DHCP server (default)............................................................................ 89
3.3.2.2 Your network is not equipped with a BOOTP/DHCP server.................................................................................... 89
3.3.3 Accessing the web interface through RNDIS .............................................................................................................. 90

3.3.3.1 Connecting the configuration cable......................................................................................................................... 90
3.3.3.2 Web interface access through RNDIS..................................................................................................................... 90
3.3.4 Accessing the card through serial terminal emulation................................................................................................. 92
3.3.4.1 Connecting the configuration cable......................................................................................................................... 92
3.3.4.2 Manual configuration of the serial connection......................................................................................................... 93
3.3.4.3 Accessing the card through Serial........................................................................................................................... 94
3.3.5 Modifying the Proxy exception list .............................................................................................................................. 94
3.4 Configuring the Network Module settings ........................................................................................................................ 96
3.5 Configuring/Commissioning/Testing LDAP ....................................................................................................................... 97
3.5.1 Commissioning............................................................................................................................................................ 97
3.5.1.1 Configuring connection to LDAP database.............................................................................................................. 97
3.5.1.2 Testing connection to LDAP database .................................................................................................................... 97
3.5.1.3 Map remote users to profile.................................................................................................................................... 98
3.5.1.4 Testing profile mapping.......................................................................................................................................... 98
3.5.1.5 Define LDAP user's preferences............................................................................................................................. 98
3.5.2 Testing LDAP authentication ....................................................................................................................................... 98
3.5.3 Limitations ................................................................................................................................................................... 98
3.6 Pairing agent to the Network Module ............................................................................................................................... 98
3.6.1 Pairing with credentials on the agent .......................................................................................................................... 99
3.6.2 Pairing with automatic acceptance (recommended if done in a secure and trusted network).................................... 99
3.6.3 Pairing with manual acceptance ................................................................................................................................. 99
3.7 Powering down/up applications (examples) .................................................................................................................... 100
3.7.1 Powering down IT system in a specific order ........................................................................................................... 100
3.7.1.1 Target .................................................................................................................................................................... 100
3.7.1.2 Step 1: Installation setup....................................................................................................................................... 100
3.7.1.3 Step 2: Agent settings........................................................................................................................................... 101
3.7.1.4 Step 3: Power outage policy settings.................................................................................................................... 101
3.7.2 Powering down non-priority equipment first ............................................................................................................. 102
3.7.2.1 Target .................................................................................................................................................................... 102
3.7.2.2 Step 1: Installation setup....................................................................................................................................... 103
3.7.2.3 Step 2: Agent settings........................................................................................................................................... 103
3.7.2.4 Step 3: Power outage policy settings.................................................................................................................... 104
3.7.3 Restart sequentially the IT equipment on utility recovery ......................................................................................... 105
3.7.3.1 Target .................................................................................................................................................................... 105
3.7.3.2 Step 1: Installation setup....................................................................................................................................... 106
3.7.3.3 Step 2: Power outage policy settings.................................................................................................................... 106
3.8 Checking the current firmware version of the Network Module..................................................................................... 107
3.9 Accessing to the latest Network Module firmware/driver/script..................................................................................... 107
3.10 Upgrading the card firmware (Web interface / shell script) ............................................................................................. 107
3.10.1 Web interface............................................................................................................................................................ 107
3.10.2 Shell script................................................................................................................................................................. 107
3.10.2.1 Prerequisite ........................................................................................................................................................... 107
3.10.2.2 Procedure .............................................................................................................................................................. 107
3.10.3 Example:.................................................................................................................................................................... 108
3.11 Changing the RTC battery cell......................................................................................................................................... 108
3.12 Updating the time of the Network Module precisely and permanently (ntp server) ....................................................... 110
3.13 Synchronizing the time of the Network Module and the UPS......................................................................................... 110
3.13.1 Automatic time synchronization ................................................................................................................................ 110
3.13.1.1 Every day at 5 a.m................................................................................................................................................. 110
3.13.1.2 If the Network Module time is lost........................................................................................................................ 110
3.13.2 Manual time synchronization..................................................................................................................................... 110
3.13.2.1 From the Network Module.................................................................................................................................... 110
3.13.2.2 From the UPS........................................................................................................................................................ 110
3.14 Changing the language of the web pages....................................................................................................................... 110

3.15 Resetting username and password................................................................................................................................. 111
3.15.1 As an admin for other users ...................................................................................................................................... 111
3.15.2 Resetting its own password...................................................................................................................................... 111
3.16 Recovering main administrator password ....................................................................................................................... 111
3.17 Switching to static IP (Manual) / Changing IP address of the Network Module.............................................................. 112
3.18 Reading product (UPS) information in a simple way ....................................................................................................... 112
3.18.1 Web page .................................................................................................................................................................. 112
3.19 Subscribing to a set of alarms for email notification........................................................................................................ 113
3.19.1 Example #1: subscribing only to one alarm (load unprotected)................................................................................. 113
3.19.2 Example #2: subscribing to all Critical alarms and some specific Warnings ............................................................. 115
3.20 Saving/Restoring/Duplicating Network module configuration settings ........................................................................... 117
3.20.1 Modifying the JSON configuration settings file......................................................................................................... 117
3.20.1.1 JSON file structure................................................................................................................................................ 117
3.20.1.2 Sensitive data (like passwords) ............................................................................................................................. 118
3.20.1.3 Modifying JSON file examples.............................................................................................................................. 119
3.20.1.4 Non-intuitive data values in the JSON file ............................................................................................................. 121
3.20.2 Saving/Restoring/Duplicating settings through the CLI............................................................................................. 124
3.20.3 Saving/Restoring/Duplicating settings through the Web interface............................................................................ 124
4 SECURING THE NETWORK MANAGEMENT MODULE.............................................................................. 125
4.1 Cybersecurity considerations for electrical distribution systems .................................................................................... 125
4.1.1 Purpose ..................................................................................................................................................................... 125
4.1.2 Introduction ............................................................................................................................................................... 125
4.1.3 Connectivity—why do we need to address cybersecurity for industrial control systems (ICS)? .............................. 125
4.1.4 Cybersecurity threat vectors ..................................................................................................................................... 125
4.1.4.1 Paths to the control network................................................................................................................................. 126
4.1.5 Defense in depth ....................................................................................................................................................... 126
4.1.6 Designing for the threat vectors................................................................................................................................ 127
4.1.6.1 Firewalls ................................................................................................................................................................ 127
4.1.6.2 Demilitarized zones (DMZ) .................................................................................................................................... 127
4.1.6.3 Intrusion detection and prevention systems (IDPS) .............................................................................................. 129
4.1.7 Policies, procedures, standards, and guidelines........................................................................................................ 129
4.1.7.1 Understanding an ICS network.............................................................................................................................. 129
4.1.7.2 Log and event management.................................................................................................................................. 129
4.1.7.3 Security policy and procedures.............................................................................................................................. 130
4.1.7.4 ICS hardening ........................................................................................................................................................ 130
4.1.7.5 Continuous assessment and security training....................................................................................................... 130
4.1.7.6 Patch management planning and procedures ....................................................................................................... 131
4.1.8 Conclusion ................................................................................................................................................................. 131
4.1.9 Terms and definitions ................................................................................................................................................ 131
4.1.10 Acronyms .................................................................................................................................................................. 131
4.1.11 References ................................................................................................................................................................ 132
4.2 Cybersecurity recommended secure hardening guidelines ............................................................................................ 133
4.2.1 Introduction ............................................................................................................................................................... 133
4.2.2 Secure configuration guidelines ................................................................................................................................ 133
4.2.2.1 Asset identification and Inventory ......................................................................................................................... 133
4.2.2.2 Physical Protection ................................................................................................................................................ 134
4.2.2.3 Authorization and Access Control.......................................................................................................................... 134
4.2.2.4 Deactivate unused features................................................................................................................................... 135
4.2.2.5 Logging and Event Management .......................................................................................................................... 136
4.2.2.6 Secure Maintenance.............................................................................................................................................. 136
4.2.3 References ................................................................................................................................................................ 136
4.3 Configuring user permissions through profiles................................................................................................................ 137
4.4 Decommissioning the Network Management module ................................................................................................... 137

5 SERVICING THE EMP .................................................................................................................................. 138
5.1 Description and features ................................................................................................................................................. 138
5.2 Unpacking the EMP......................................................................................................................................................... 138
5.3 Installing the EMP ........................................................................................................................................................... 139
5.3.1 Defining EMPs address and termination ................................................................................................................... 139
5.3.1.1 Manual addressing ................................................................................................................................................ 139
5.3.2 Mounting the EMP .................................................................................................................................................... 139
5.3.2.1 Rack mounting with keyhole example................................................................................................................... 140
5.3.2.2 Rack mounting with tie wraps example ................................................................................................................ 140
5.3.2.3 Wall mounting with screws example .................................................................................................................... 141
5.3.2.4 Wall mounting with nylon fastener example......................................................................................................... 141
5.3.3 Cabling the first EMP to the device........................................................................................................................... 142
5.3.3.1 Available Devices................................................................................................................................................... 142
5.3.3.2 Connecting the EMP to the device........................................................................................................................ 142
5.3.4 Daisy chaining EMPs ................................................................................................................................................. 143
5.3.4.1 Material needed:.................................................................................................................................................... 143
5.3.4.2 Steps ..................................................................................................................................................................... 144
5.3.5 Connecting an external contact device...................................................................................................................... 144
5.4 Commissioning the EMP................................................................................................................................................. 144
5.4.1 On the Network-M2 device ....................................................................................................................................... 144
5.5 Using the EMP for temperature compensated battery charging..................................................................................... 145
5.5.1 Addressing the EMP.................................................................................................................................................. 145
5.5.2 Commissioning the EMP........................................................................................................................................... 146
5.5.3 Enabling temperature compensated battery charging in the UPS............................................................................. 146
6 INFORMATION............................................................................................................................................. 147
6.1 Front panel connectors and LED indicators..................................................................................................................... 147
6.2 Default settings and possible parameters....................................................................................................................... 148
6.2.1 Settings ..................................................................................................................................................................... 148
6.2.1.1 General .................................................................................................................................................................. 148
6.2.1.2 Date & Time .......................................................................................................................................................... 148
6.2.1.3 Users ..................................................................................................................................................................... 148
6.2.1.4 Network................................................................................................................................................................. 151
6.2.1.5 Protocols................................................................................................................................................................ 151
6.2.1.6 SNMP .................................................................................................................................................................... 152
6.2.1.7 Certificate .............................................................................................................................................................. 153
6.2.1.8 Email...................................................................................................................................................................... 154
6.2.1.9 My preferences ..................................................................................................................................................... 154
6.2.2 Meters ....................................................................................................................................................................... 155
6.2.3 Sensors alarm configuration ...................................................................................................................................... 155
6.3 Specifications/Technical characteristics .......................................................................................................................... 156
6.4 List of event codes.......................................................................................................................................................... 156
6.5 Alarm log codes............................................................................................................................................................... 156
6.5.1 Critical........................................................................................................................................................................ 157
6.5.2 Warning ..................................................................................................................................................................... 158
6.5.3 Info ............................................................................................................................................................................ 160
6.5.4 With settable severity................................................................................................................................................ 161
6.6 System log codes............................................................................................................................................................ 162
6.6.1 Critical........................................................................................................................................................................ 162
6.6.2 Warning ..................................................................................................................................................................... 162
6.6.3 Info ............................................................................................................................................................................ 163
6.7 SNMP traps ..................................................................................................................................................................... 165
6.7.1 Sensor Mib traps ....................................................................................................................................................... 165

6.7.2 Xups Mib traps .......................................................................................................................................................... 165
6.7.3 IETF Mib-2 Ups traps................................................................................................................................................. 166
6.8 CLI ................................................................................................................................................................................... 166
6.8.1 Commands available.................................................................................................................................................. 167
6.8.2 Contextual help.......................................................................................................................................................... 167
6.8.3 get release info.......................................................................................................................................................... 168
6.8.3.1 Description ............................................................................................................................................................ 168
6.8.3.2 Access................................................................................................................................................................... 168
6.8.3.3 Help ....................................................................................................................................................................... 168
6.8.4 history........................................................................................................................................................................ 168
6.8.4.1 Description ............................................................................................................................................................ 168
6.8.4.2 Access................................................................................................................................................................... 168
6.8.4.3 Help ....................................................................................................................................................................... 168
6.8.5 ldap-test..................................................................................................................................................................... 168
6.8.5.1 Description ............................................................................................................................................................ 168
6.8.5.2 Access................................................................................................................................................................... 169
6.8.5.3 Help ....................................................................................................................................................................... 169
6.8.6 logout......................................................................................................................................................................... 169
6.8.6.1 Description ............................................................................................................................................................ 169
6.8.6.2 Access................................................................................................................................................................... 170
6.8.6.3 Help ....................................................................................................................................................................... 170
6.8.7 maintenance .............................................................................................................................................................. 170
6.8.7.1 Description ............................................................................................................................................................ 170
6.8.7.2 Access................................................................................................................................................................... 170
6.8.7.3 Help ....................................................................................................................................................................... 170
6.8.8 netconf ...................................................................................................................................................................... 170
6.8.8.1 Description ............................................................................................................................................................ 170
6.8.8.2 Access................................................................................................................................................................... 170
6.8.8.3 Help ....................................................................................................................................................................... 170
6.8.8.4 Examples of usage ................................................................................................................................................ 173
6.8.9 ping and ping6 ........................................................................................................................................................... 173
6.8.9.1 Description ............................................................................................................................................................ 173
6.8.9.2 Access................................................................................................................................................................... 173
6.8.9.3 Help ....................................................................................................................................................................... 173
6.8.10 reboot ........................................................................................................................................................................ 173
6.8.10.1 Description ............................................................................................................................................................ 173
6.8.10.2 Access................................................................................................................................................................... 174
6.8.10.3 Help ....................................................................................................................................................................... 174
6.8.11 save_configuration | restore_configuration................................................................................................................ 174
6.8.11.1 Description ............................................................................................................................................................ 174
6.8.11.2 Access................................................................................................................................................................... 174
6.8.11.3 Help ....................................................................................................................................................................... 174
6.8.11.4 Examples of usage ................................................................................................................................................ 174
6.8.12 sanitize....................................................................................................................................................................... 175
6.8.12.1 Description ............................................................................................................................................................ 175
6.8.12.2 Access................................................................................................................................................................... 175
6.8.12.3 Help ....................................................................................................................................................................... 175
6.8.13 ssh-keygen ................................................................................................................................................................ 175
6.8.13.1 Description ............................................................................................................................................................ 175
6.8.13.2 Access................................................................................................................................................................... 175
6.8.13.3 Help ....................................................................................................................................................................... 175
6.8.14 time ........................................................................................................................................................................... 175
6.8.14.1 Description ............................................................................................................................................................ 175
6.8.14.2 Access................................................................................................................................................................... 175

6.8.14.3 Help ....................................................................................................................................................................... 175
6.8.14.4 Examples of usage ................................................................................................................................................ 176
6.8.15 traceroute and traceroute6........................................................................................................................................ 176
6.8.15.1 Description ............................................................................................................................................................ 176
6.8.15.2 Access................................................................................................................................................................... 176
6.8.15.3 Help ....................................................................................................................................................................... 176
6.8.16 whoami...................................................................................................................................................................... 177
6.8.16.1 Description ............................................................................................................................................................ 177
6.8.16.2 Access................................................................................................................................................................... 177
6.8.17 email-test................................................................................................................................................................... 177
6.8.17.1 Description ............................................................................................................................................................ 177
6.8.17.2 Access................................................................................................................................................................... 177
6.8.17.3 Help ....................................................................................................................................................................... 177
6.8.18 systeminfo_statistics................................................................................................................................................. 177
6.8.18.1 Description ............................................................................................................................................................ 177
6.8.18.2 Access................................................................................................................................................................... 178
6.8.18.3 Help ....................................................................................................................................................................... 178
6.8.19 certificates................................................................................................................................................................. 178
6.8.19.1 Description ............................................................................................................................................................ 178
6.8.19.2 Access................................................................................................................................................................... 178
6.8.19.3 Help ....................................................................................................................................................................... 178
6.8.19.4 Examples of usage ................................................................................................................................................ 179
6.9 Legal information............................................................................................................................................................. 179
6.9.1 Availability of Source Code ........................................................................................................................................ 179
6.9.2 Notice for Open Source Elements............................................................................................................................. 179
6.9.3 Notice for our proprietary (i.e. non-Open source) elements ...................................................................................... 180
6.10 Acronyms and abbreviations ........................................................................................................................................... 181
7 TROUBLESHOOTING................................................................................................................................... 184
7.1 Action not allowed in Control/Schedule/Power outage policy......................................................................................... 184
7.1.1 Symptom ................................................................................................................................................................... 184
7.1.2 Possible Cause .......................................................................................................................................................... 184
7.1.3 Action ........................................................................................................................................................................ 184
7.2 Client server is not restarting .......................................................................................................................................... 184
7.2.1 Symptom ................................................................................................................................................................... 184
7.2.2 Possible Cause .......................................................................................................................................................... 184
7.2.3 Action ........................................................................................................................................................................ 184
7.3 EMP detection fails at discovery stage ........................................................................................................................... 184
7.3.1 Symptom #1 .............................................................................................................................................................. 184
7.3.1.1 Possible causes..................................................................................................................................................... 184
7.3.1.2 Action #1-1 ............................................................................................................................................................ 185
7.3.1.3 Action #1-2 ............................................................................................................................................................ 185
7.3.1.4 Action #1-3 ............................................................................................................................................................ 185
7.3.2 Symptom #2 .............................................................................................................................................................. 185
7.3.2.1 Possible causes..................................................................................................................................................... 185
7.3.2.2 Action #2-1 ............................................................................................................................................................ 185
7.3.2.3 Action #2-2 ............................................................................................................................................................ 185
7.4 How do I log in if I forgot my password? ........................................................................................................................ 185
7.4.1 Action ........................................................................................................................................................................ 185
7.5 Card wrong timestamp leads to "Full acquisition has failed" error message on IPM/IPP ................................................ 186
7.5.1 Symptoms: ................................................................................................................................................................ 186
7.5.2 Possible cause:.......................................................................................................................................................... 186
7.5.3 Action: ....................................................................................................................................................................... 186
7.6 IPP/IPM is not able to communicate with the Network module ..................................................................................... 186

7.6.1 Symptoms ................................................................................................................................................................. 186
7.6.2 Possible cause........................................................................................................................................................... 186
7.6.3 Setup ......................................................................................................................................................................... 186
7.6.4 Action #1 ................................................................................................................................................................... 186
7.6.5 Action #2 ................................................................................................................................................................... 187
7.7 LDAP configuration/commissioning is not working......................................................................................................... 187
7.8 Password change in My preferences is not working ...................................................................................................... 187
7.8.1 Symptoms ................................................................................................................................................................. 187
7.8.2 Possible cause........................................................................................................................................................... 187
7.8.3 Action ........................................................................................................................................................................ 187
7.9 SNMPv3 password management issue with Save and Restore ..................................................................................... 188
7.9.1 Affected FW versions................................................................................................................................................ 188
7.9.2 Symptom ................................................................................................................................................................... 188
7.9.3 Cause......................................................................................................................................................................... 188
7.9.4 Action ........................................................................................................................................................................ 188
7.10 The Network Module fails to boot after upgrading the firmware .................................................................................... 188
7.10.1 Possible Cause .......................................................................................................................................................... 188
7.10.2 Action ........................................................................................................................................................................ 188
7.11 Web user interface is not up to date after a FW upgrade ............................................................................................... 188
7.11.1 Symptom................................................................................................................................................................... 188
7.11.1.1 Possible causes..................................................................................................................................................... 188
7.11.1.2 Action .................................................................................................................................................................... 188
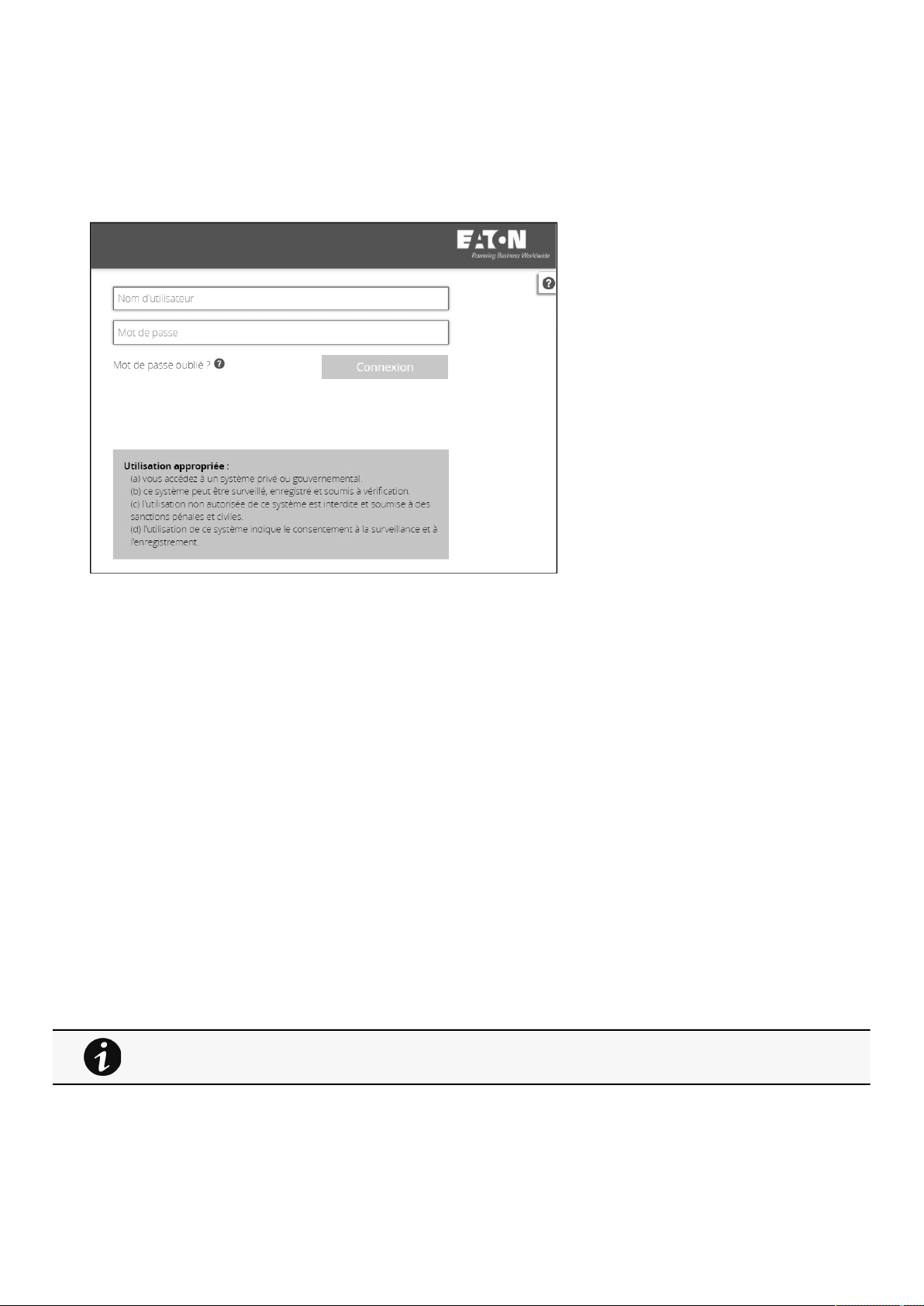
Login page
Contextual Help – 13
2 Contextual Help
2.1 Login page
The page language is set toEnglishby default but can be switched tobrowser language when it is managed.
After navigating to theassigned IP address, accept the untrusted certificate on the browser.
2.1.1 Logging in for the first time
1.Enter default password
As you are logging into the Network Module for the first time you must enter the factory set default username and password.
•
Username = admin
•
Password = admin
2. Change default password
Changing the default password is mandatory and requested in a dedicated window.
Enter your current password first, and then enter the new password twice.
Follow the password format recommendations on the tooltip in order to define a secure password.
3. Accept license agreement
On the next step, License Agreement is displayed.
Read and accept the agreement to continue.
2.1.2 Troubleshooting login issues
For details on troubleshooting, see the
Troubleshooting
section.
2.2 Home
The Home screen providesstatus informationfor the deviceincluding synoptic diagrams, key measures andactive alarms.
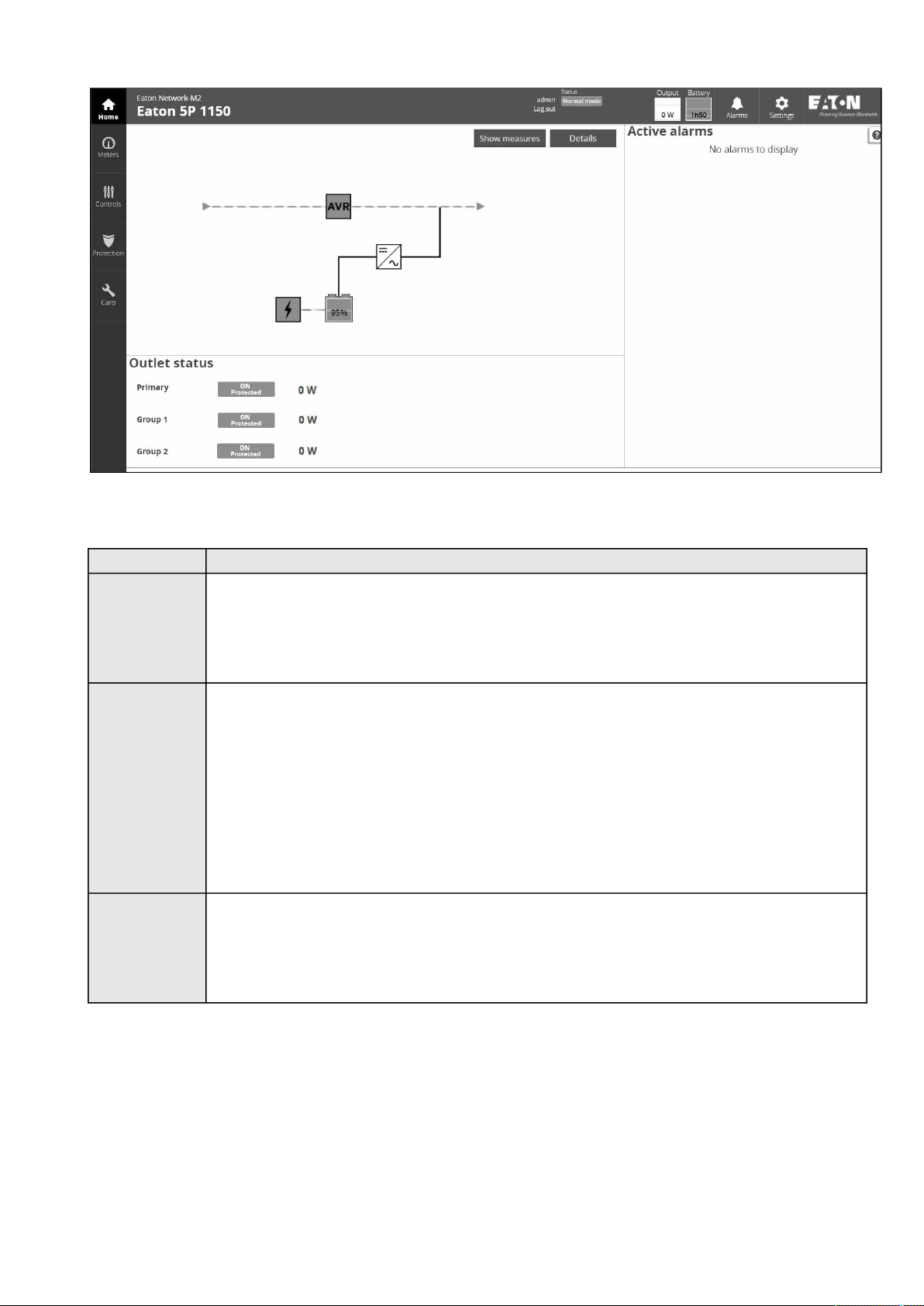
Home
Contextual Help – 14
2.2.1 Menu structure
Button Description
Home
Overview and status ofUPS Module:
•
Synoptic
•
Active alarms
•
Outlet status
Settings
Alarms
Module settings:
•
General
•
Date & Time
•
Users
•
Network
•
Protocols
•
SNMP
•
Certificates
•
Email
•
My preferences
List of alarms with date and time:
•
Details
•
Clear
•
Export
Home
Contextual Help – 15
Meters
Power:
•
Frequency
•
Voltage
•
Current
•
Power
Battery:
•
Overview
•
Details
•
Test
Measure logs:
•
Configuration
•
Measure logs
Controls
Protection
Sensors*
Card
Control of:
•
•
•
•
•
•
•
•
•
•
•
•
•
Entire UPS
Outlets
Scheduled shutdown
Agent list
Agent settings
Power outage policy
Status
Alarm configuration
Information
System information
System logs
Administration
Commissioning (Sensors)
*Displayed when sensors are commissioned in Card menu.
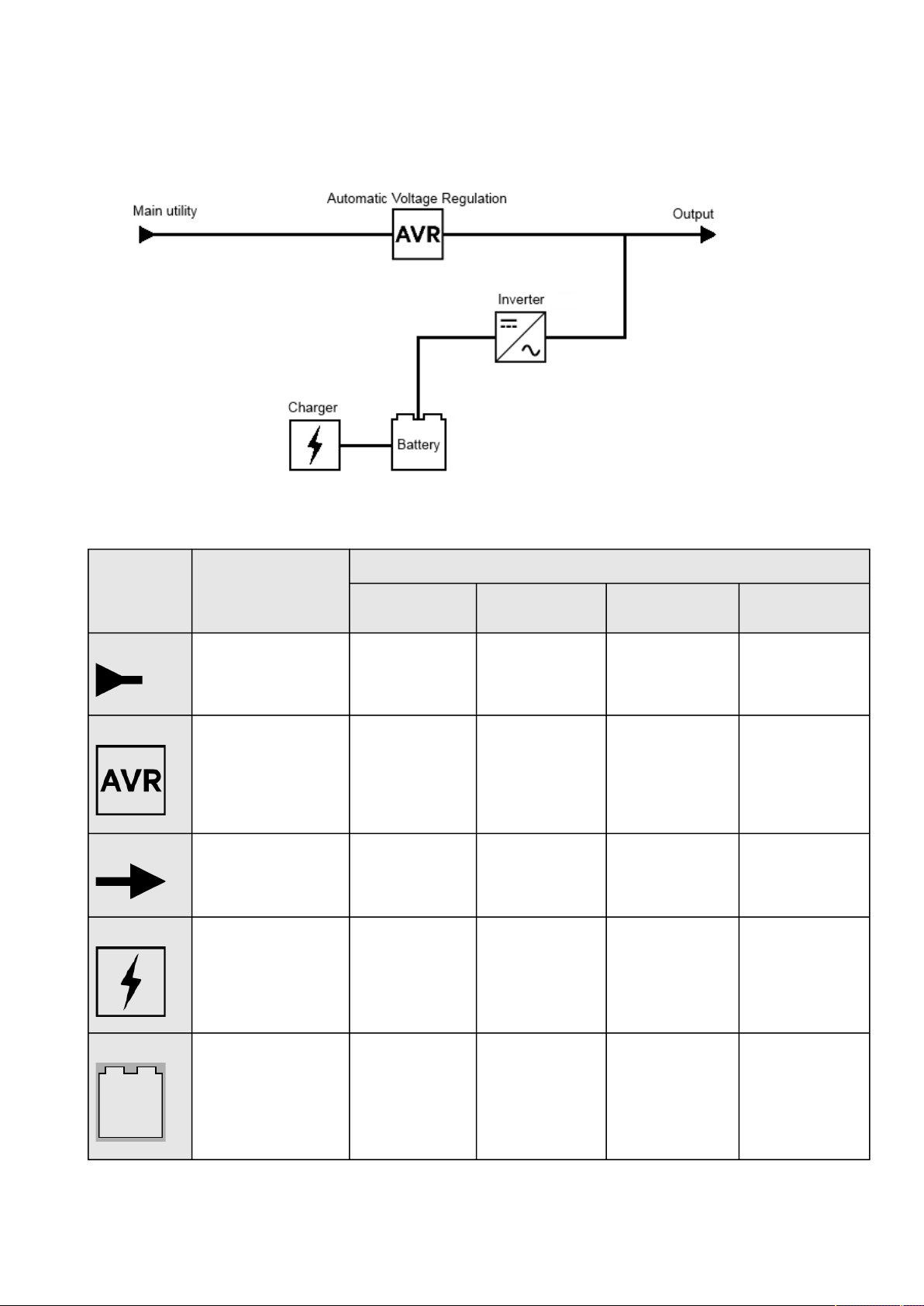
Home
Contextual Help – 16
2.2.2 Energy flow diagram
2.2.2.1 Line interactive
2.2.2.1.1 Diagram elements description
Description and
symbols
Input Main utility input. Powered Out of nominal range Not present
AVR device. The equipment is
Output Output of the UPS. Protected In overload
Charger Internal battery charger. Charging
Description Possible states
Green Yellow Red Black / White /
protected and powered
through an AVR device.
Normal mode
Buck mode
Boost mode
Floating
Greyed
Unknown
In overload Not powered
Unknown
In short circuit Not powered
Not protected
In fault Resting
Unknown
Not powered
Unknown
Battery status Battery status information. Powering the load End of life In fault
Not present
Not used to power
the load
Unknown
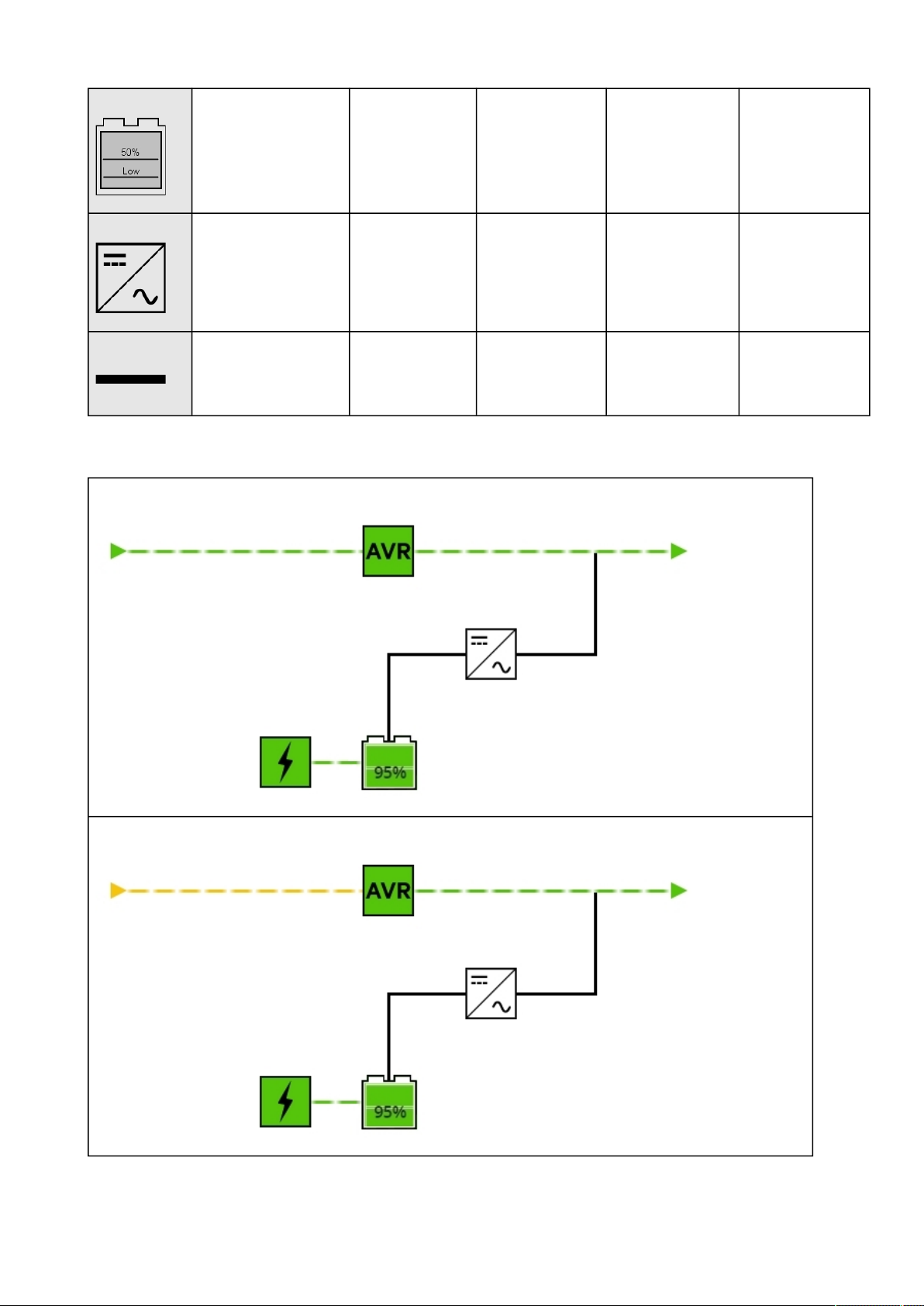
Home
Contextual Help – 17
Battery level Battery level for the
backup power.
> 50%
and
> low battery
threshold (Settable
on the UPS)
< 50%
and
> low battery
threshold (Settable
on the UPS)
< Below low battery
threshold (Settable on
the UPS)
Inverter Inverter: convert DC
power to AC power.
Wiring Electrical connection
between blocks.
Powered In overload In short circuit
Energy flow In overload
2.2.2.1.2 Line interactive diagram examples
Normal mode
Out of nominal range
In fault
Not powered
Unknown
No energy
Unknown
Buck/Boost mode
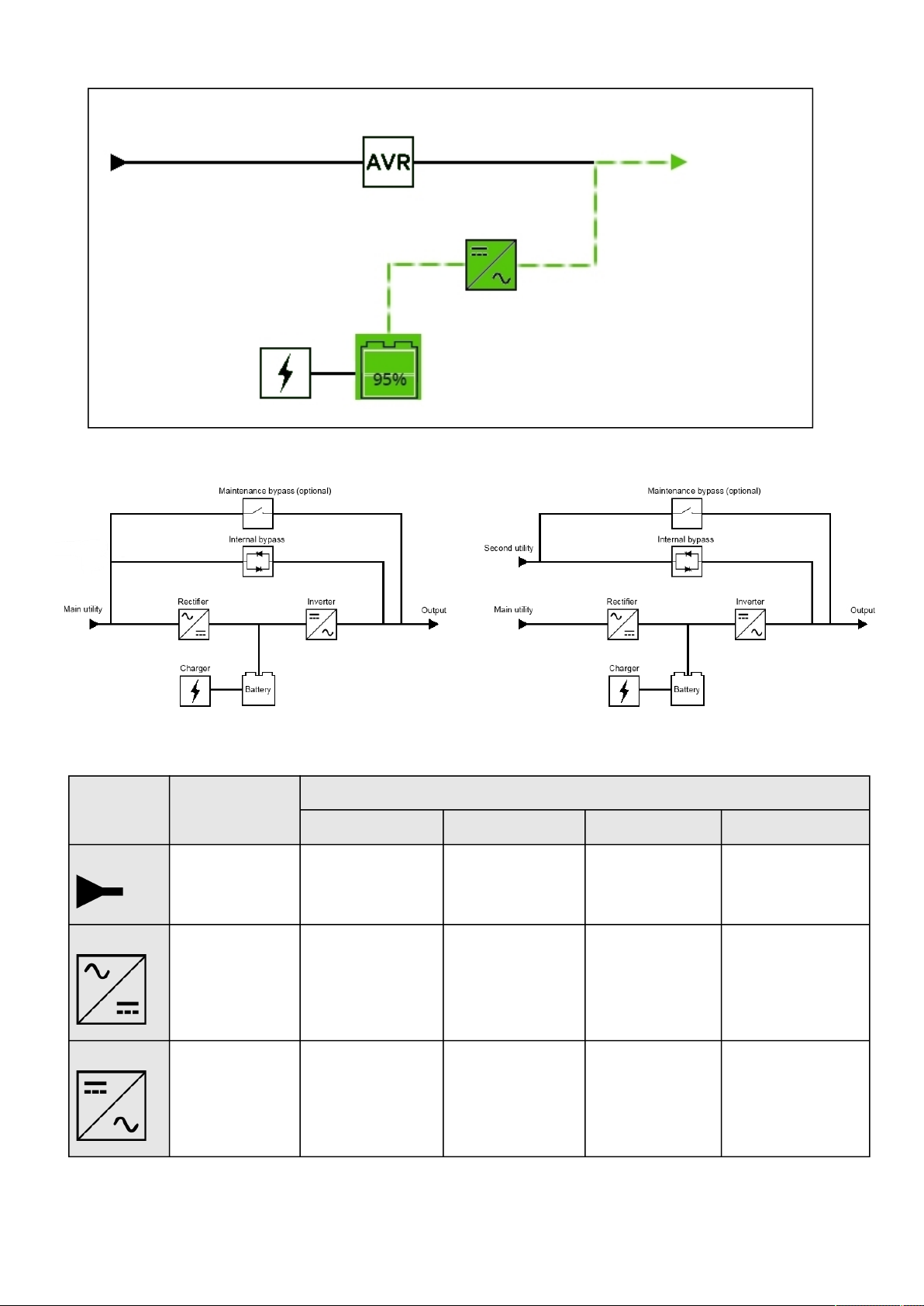
Home
Contextual Help – 18
Battery mode
2.2.2.2 Online
2.2.2.2.1 Diagram elements description
Description and
symbols
Input Main utility or second
Rectifier Rectifier: convert AC
Inverter Inverter: convert DC
Description Possible states
Green Yellow Red Black or white
utility.
power to DC power.
power to AC power.
Powered Out of nominal range Not present
Powered
HE mode (ready) / ESS
mode (ready)
Powered
HE mode (ready) / ESS
mode (ready)
In overload In short circuit
In fault
In overload In short circuit
In fault
Unknown
Not powered
Unknown
Not powered
Unknown
Home
Contextual Help – 19
Output Output of the UPS. Protected In overload
Not protected
In short circuit Not powered
Unknown
Charger Internal battery
Battery status Battery status
Battery level Battery level for the
Automatic
bypass
charger.
information.
backup power.
Automatic bypass. Powered (standby, auto
Charging
Floating
Powering the load End of life In fault
> 50% and > low
battery threshold
(Settable on the UPS)
bypass, forced bypass,
HE mode, ESS mode)
< 50% and > low
battery threshold
(Settable on the UPS)
In overload In fault Not powered
In fault Resting
Not present
< Below low battery
threshold (Settable on
the UPS)
Not powered
Unknown
Not used to power the
load
Unknown
Unknown
Maintenance
bypass
(optional)
Wiring Electrical connection
Maintenance bypass
closed.
Maintenance bypass
opened.
between blocks.
Powered (maintenance
bypass)
Energy flow In overload
2.2.2.2.2 Online diagram examples
Not powered
Unknown
No energy
Out of nominal range
Single input source
Dual input sources
Unknown
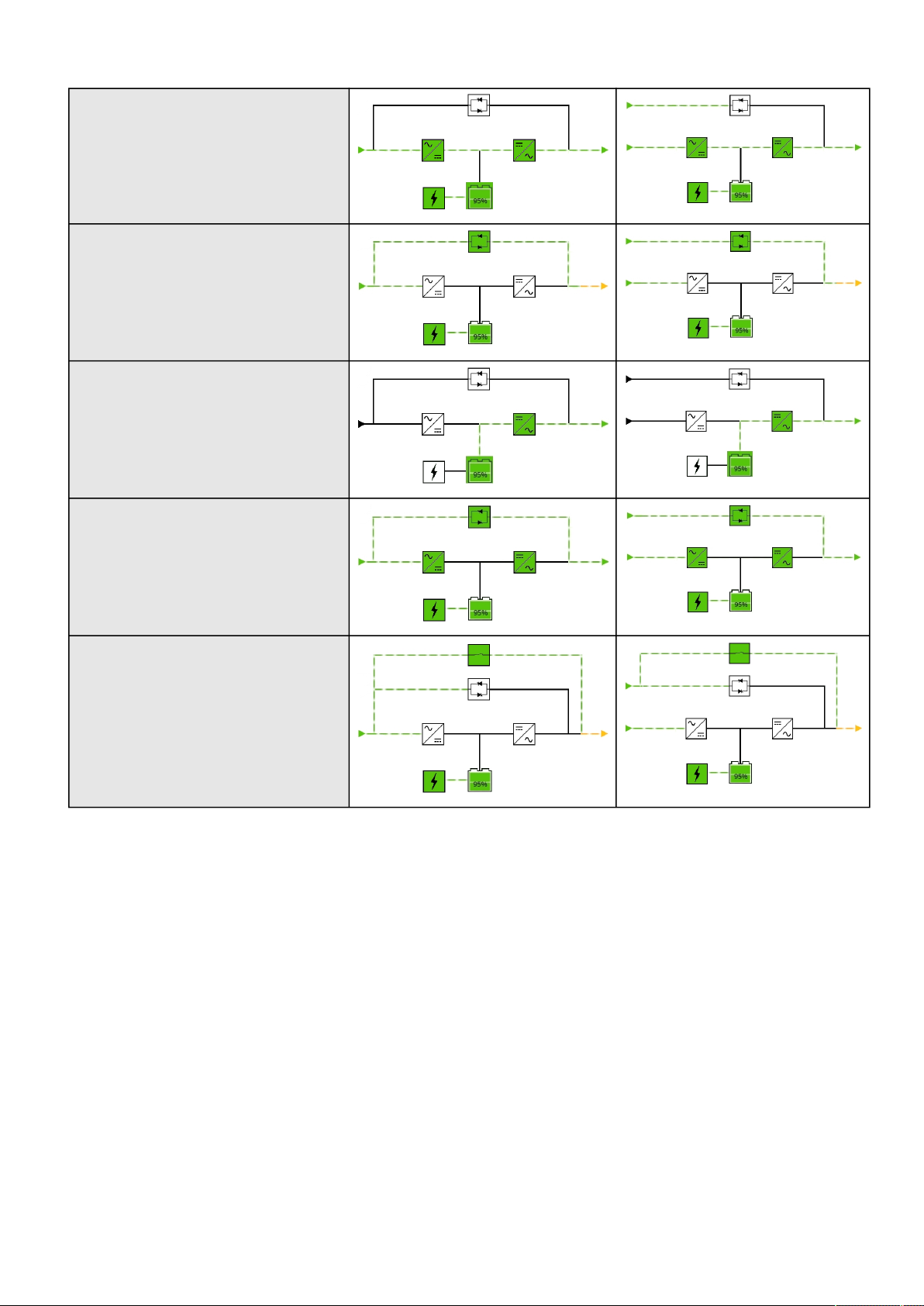
Home
Contextual Help – 20
Online mode
Bypass mode
Battery mode
HE mode / ESS mode
Maintenance bypass mode
2.2.3 Top bar
Card name– Displays the card name
UPS name – Displays by default the UPS model or the system name if filled in the section Card>>>System
information>>>System name
Current user– Displays current user name
Logout–Logs the current user out by destroying the current user session
Status–Provides device (example UPS) status information
Output power– Provides output power status information
Battery status– Provides battery status information
Alarms button– Open alarm page
Settings button– Open settings page
Home
Contextual Help – 21
2.2.4 Details
Thisview provides a summary of device identification information and nominal values:
•
Name
•
Model
•
P/N
•
S/N
•
Location
•
Firmware version
•
Input Voltage
•
Input Frequency
•
Output Voltage
•
Output Frequency
The COPY TO CLIPBOARD button will copy the information toyour clipboard so that it can be past.
For example, you can copy and paste information into an email.
2.2.5 Show measures
Provides input and output measures on the synoptic.
2.2.5.1 Example #1
Single input source with 1 phase in and 1 phase out:
Input measures Output measures
Voltage (V)
Current (A)
Frequency (Hz)
Voltage (V)
Current (A)
Frequency (Hz)
2.2.5.2 Example #2
Dual input sources with 3 phases in and 3 phases out
Input measures (main and secondary) Output measures
Phase #1
Voltage (V)
Current (A)
Frequency (Hz) Frequency (Hz)
Phase #2
Voltage (V)
Current (A)
Phase #3
Voltage (V)
Current (A)
Phase #1
Voltage (V)
Current (A)
2.2.6 Outlet status
Providesthe status of the UPS outlets (ON/OFF) by load segmentation:
Phase #2
Voltage (V)
Current (A)
Phase #3
Voltage (V)
Current (A)
Load (W)
Load (%)
•
Status (ON/OFF— Protected/Not protected/Not powered)
•
Load level (W)– availability depending on the UPS model
•
Shutdown countdown
•
Startup countdown
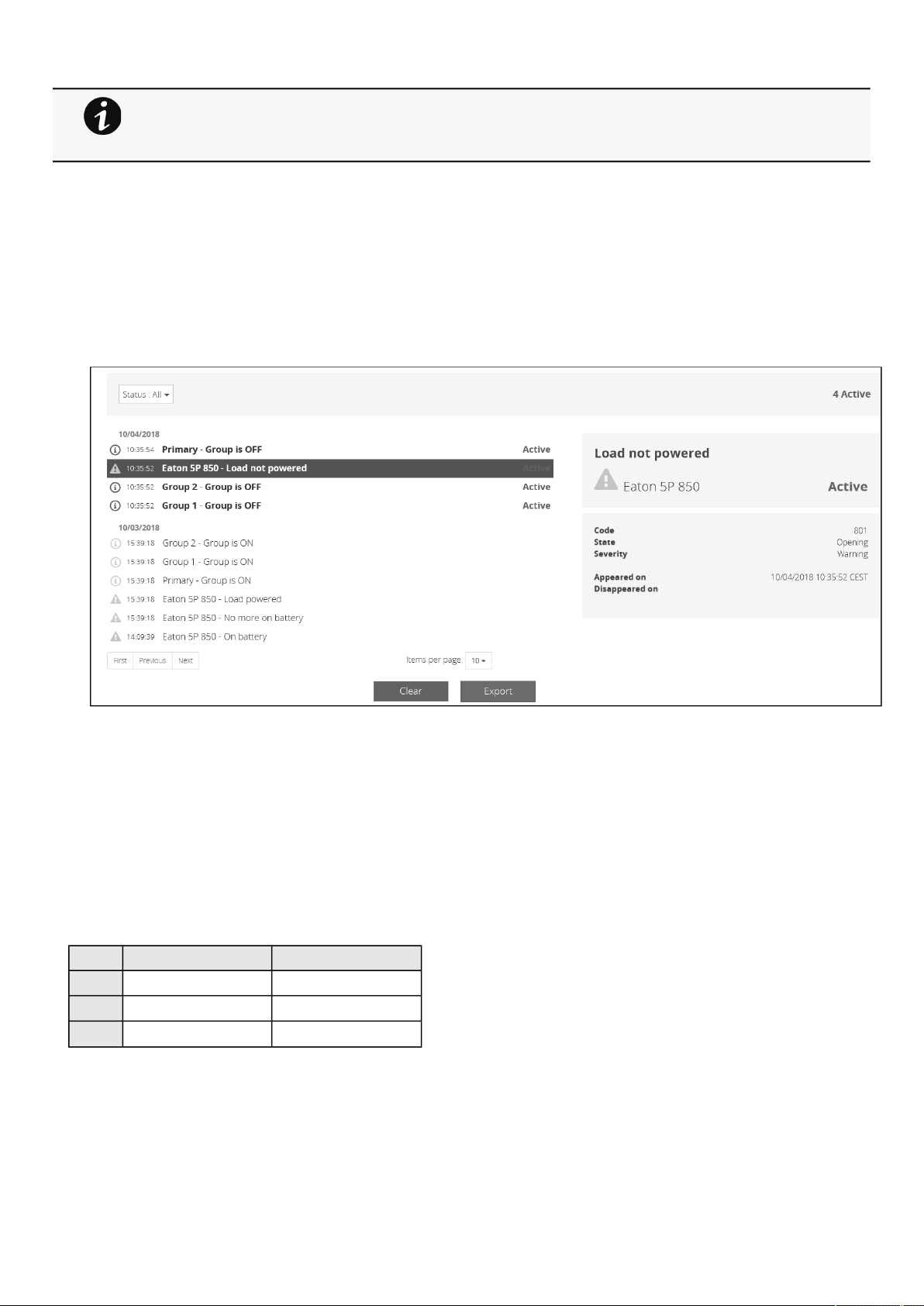
Alarms
Contextual Help – 22
Note: Load segmentations allow non-priority equipment to automatically power down during an
extended power outage to keep battery runtime on essential equipment.
This feature is also used toremote reboot and sequential startservers to restrict inrush currents.
2.2.7 Active Alarms
Only active alarms are displayed, the Alarmsicon will alsodisplay the number of active alarms.
Alarms are sorted by date,alert level, time, anddescription.
Note:To seethe alarm history,press the Alarms button.
2.3 Alarms
2.3.1 Alarm sorting
Alarms can be sorted by selecting:
•
All
•
Active only
2.3.2 Alarm details
Allalarms are displayed andsorted by date, with alert level, time, description, and status.
Info/Warning/Critical logo Alarm description text
Active In color In bold with "Active" label
Opened In color
Closed Greyed
2.3.3 Alarm paging
The number of alarms per page can be changed (10-15-25-50-100).
When the number of alarms is above the number of alarms per page,the buttons First, Previous andNextappears to allow
navigation in the Alarm list.
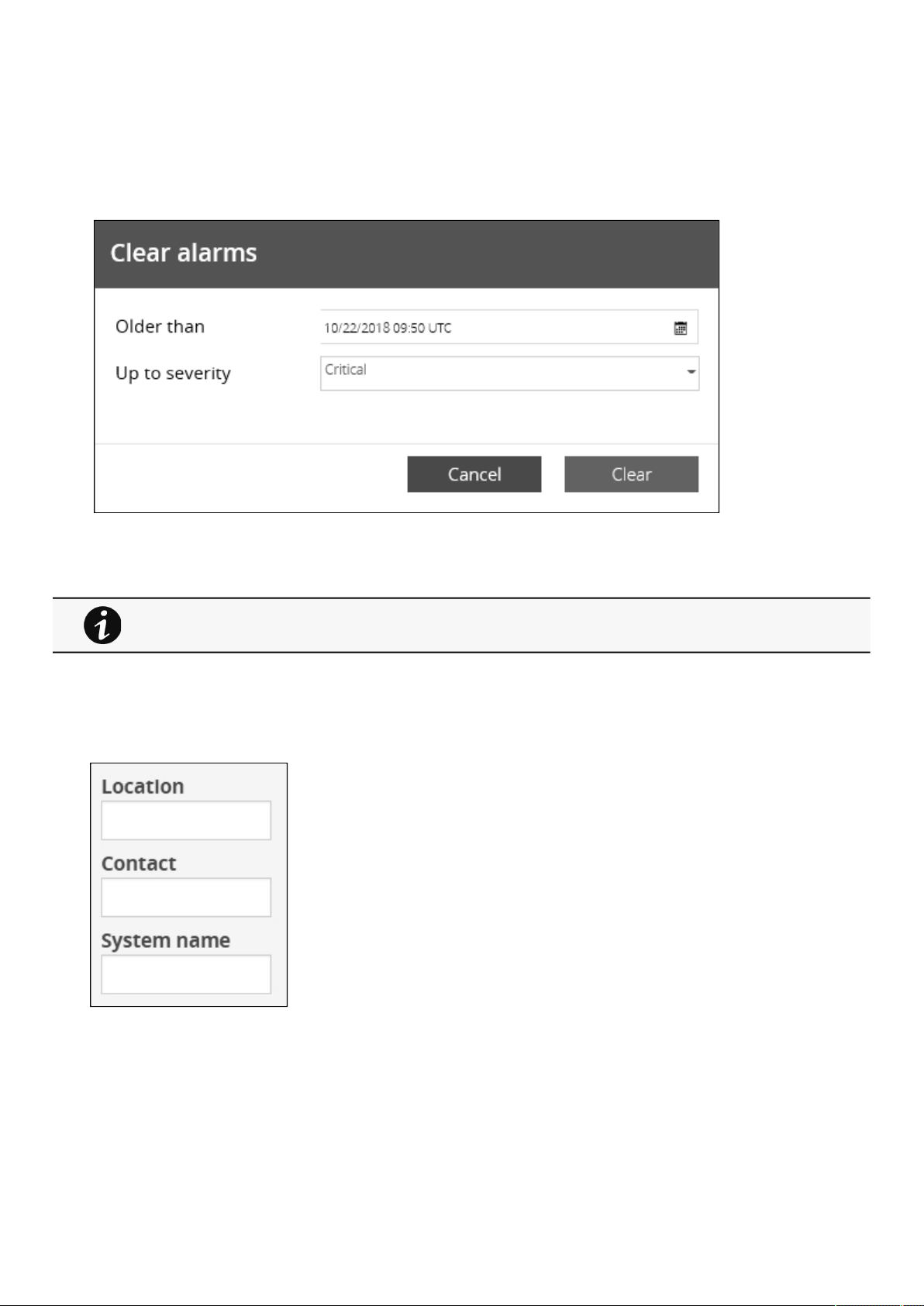
Settings
Contextual Help – 23
2.3.4 Alarm export
Press theExportbutton to download the file.
2.3.5 Clear alarm logs
Press theClearbutton to clear alarms that are older than a specified date and up to a defined severity.
2.3.6 Alarm list with codes
For details on alarm codes, see the
2.4 Settings
2.4.1 General
Information>>>Alarm log codes
section.
2.4.1.1 Location
Text field that is used to provide the card location information.
Card system information is updated to show the defined location.
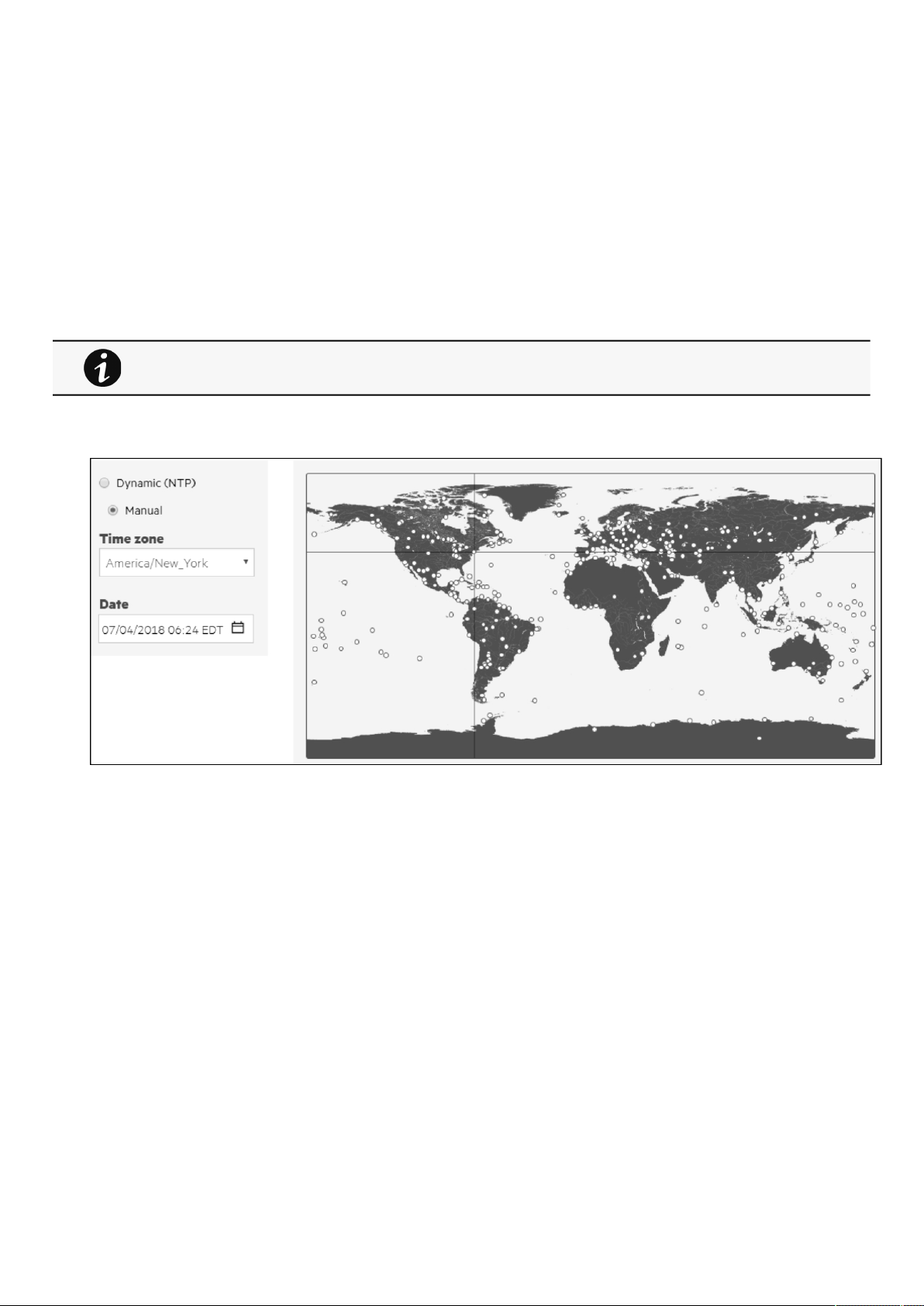
Settings
Contextual Help – 24
2.4.1.2 Contact
Text field that is used to provide the contact name information.
Card system information is updated to show the contact name.
2.4.1.3 System name
Text field that is used to provide the system name information.
Card system information is updated to show the system name.
2.4.1.4 Default settings parameters and limitations
For details on default parameters and limitations, see the
parameters
section.
2.4.2 Date & Time
The current date and time appearsin the footer at the bottom of the screen.
You can set the time either manually or automatically.
Information>>>Default settings
2.4.2.1 Manual:Manually entering the date and time
1.
2.
3.
2.4.2.2 Dynamic (NTP):Synchronizing the date and time with an NTP server
1.
2.
3.
Note:DST is managed based on the time zone.
Select the time zone for your geographic area from the time zone pull-down menu orwiththe map.
Select the date and time.
Save the changes.
Enter the IP address or host name of the NTP server in theNTP server field.
Select the time zone for your geographic area from the time zone pull-down menu orwiththe map.
Save the changes.
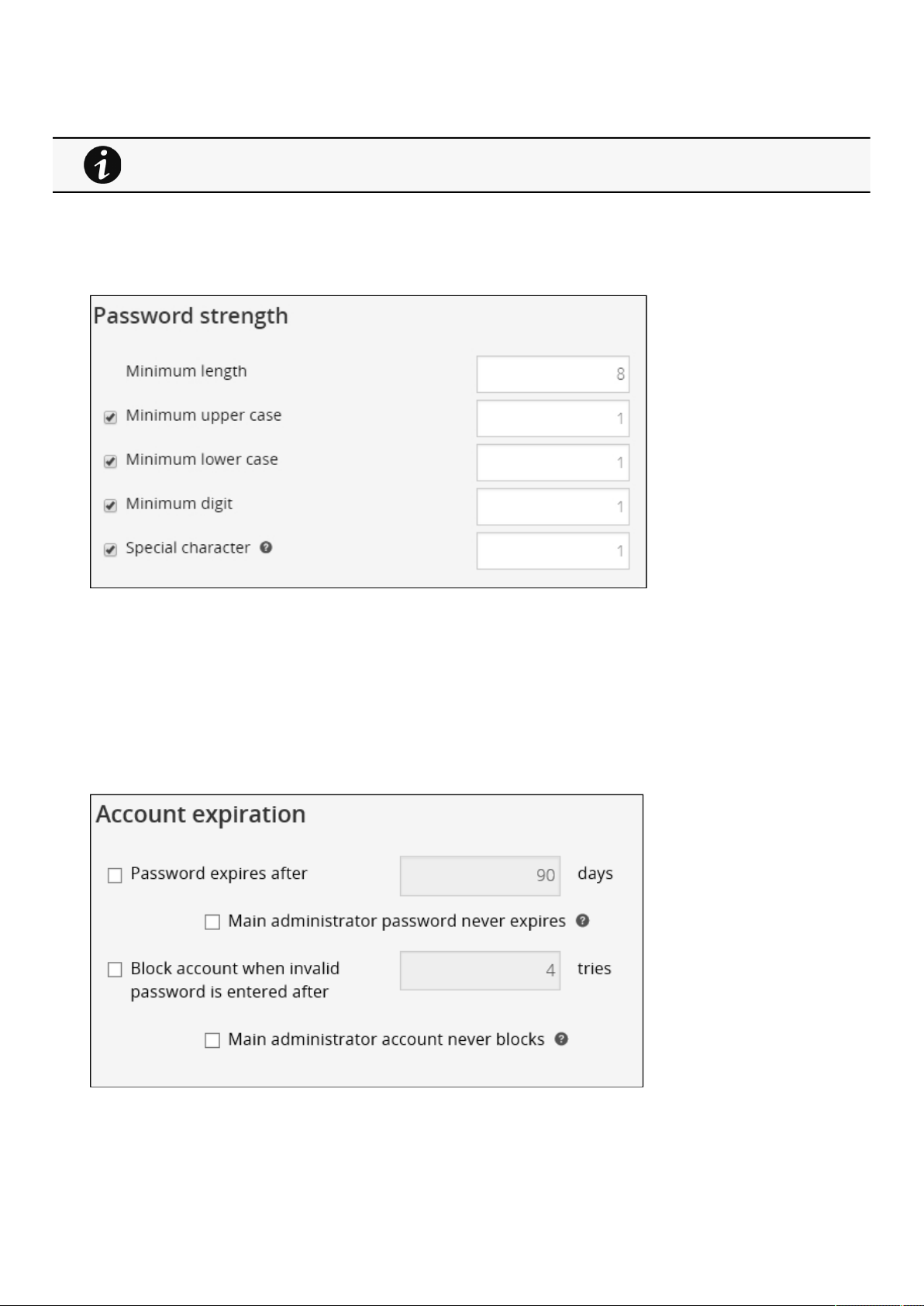
Settings
Contextual Help – 25
2.4.2.3 Default settings parameters and limitations
For details on default parameters and limitations, see the
parameters
section.
2.4.3 Users
2.4.3.1 Password strength rules
To set the password strength rules, apply the following restrictions:
•
Minimum length
•
Minimum upper case
•
Minimum lower case
•
Minimum digit
•
Special character
Information>>>Default settings
PressSaveafter modifications.
2.4.3.2 Account expiration
To set the account expiration rules, apply the following restrictions:
•
Password expires after (in days).
The main administrator password never expires.
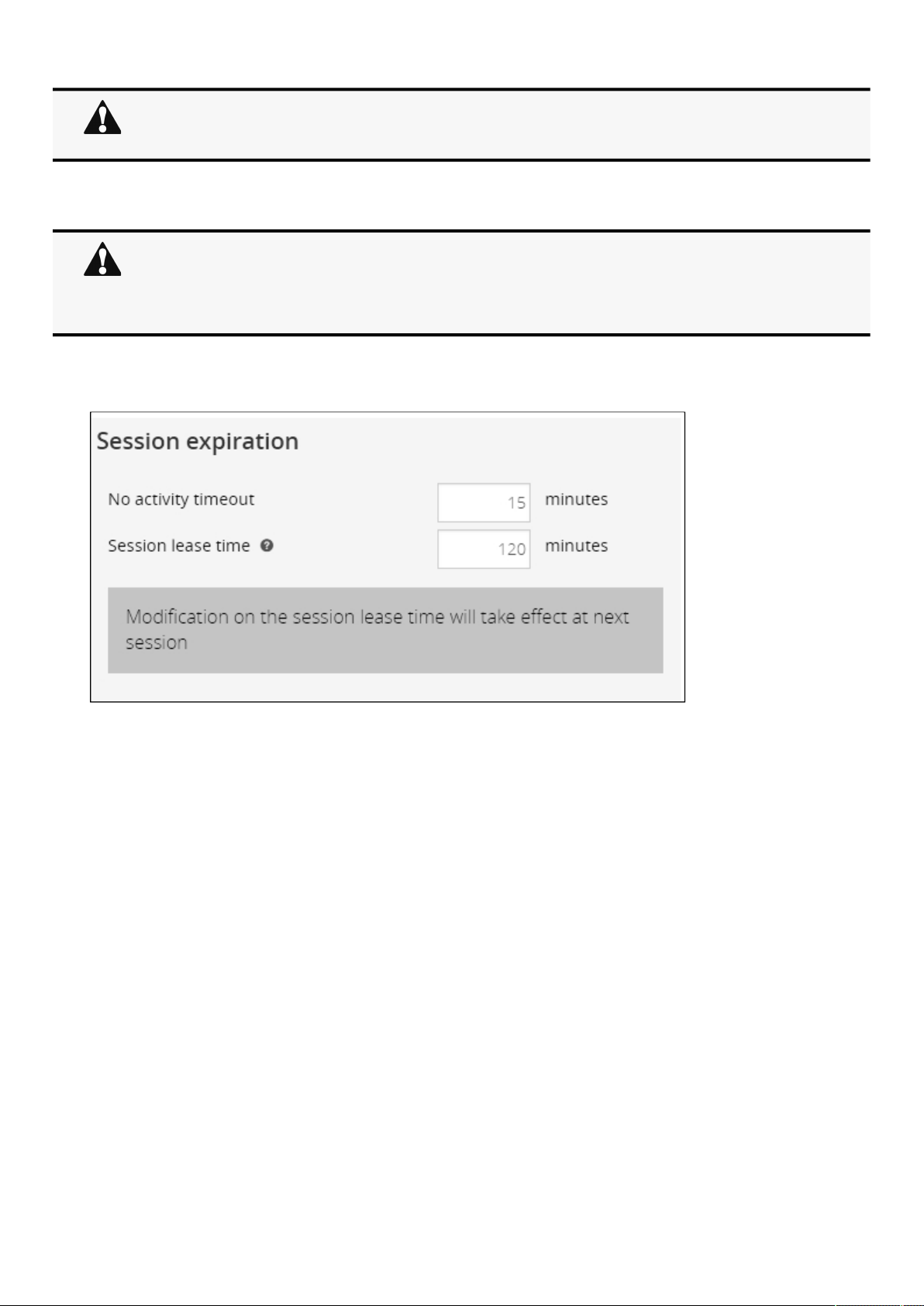
Settings
Contextual Help – 26
1.2.If this feature is disabled, the administrator account can be locked after the password expiration.
If Enabled, the administrator password never expires, make sure it is changed regularly.
•
Block account when invalid password is entered after (in number of attempts).
The main administrator account will never block.
1.2.If this feature is disabled, the administrator account can be locked after the number of failed connections
defined.
If Enabled, the security level of the administrator account is reduced because unlimited password entry
attempts are allowed.
PressSaveafter modifications.
2.4.3.3 Session expiration
To set the session expiration rules,apply the following restrictions:
•
No activity timeout (in minutes).
If there is no activity, session expires after the specified amount of time.
•
Session lease time (in minutes).
If there is activity, session still expires afterthe specified amount of time.
PressSaveafter modifications.
2.4.3.4 Local users table
Settings
Contextual Help – 27
The table shows all the supported local user accounts and includes the following details:
▪
Username
▪
Email
▪
Profile
Administrator Operator Viewer
Home
Alarms Alarm list
Export
Clear
Settings General
Date & Time
Users
Network
Protocols
SNMP
Certificates
Email
My preferences
Meters Power
Battery
Measure logs
Configuration
Controls
Protection
Sensors Status
Alarm configuration
Settings
Contextual Help – 28
Information
Card System information
Resources
System logs
Administration
Commissioning (Sensors)
Legal information (footer)
Contextual and Full documentation
Command Line
Interface
get release info
history
ldap-test
logout
maintenance
netconf (read-only)
(read-only) (read-only)
ping and ping6
reboot
save_configuration |
restore_configuration
sanitize
ssh-keygen
time
(read-only) (read-only)
traceroute and traceroute6
whoami
email-test
systeminfo_statistics
certificates
•
Status –Status could take following values– Inactive/Locked/Password expired/Active
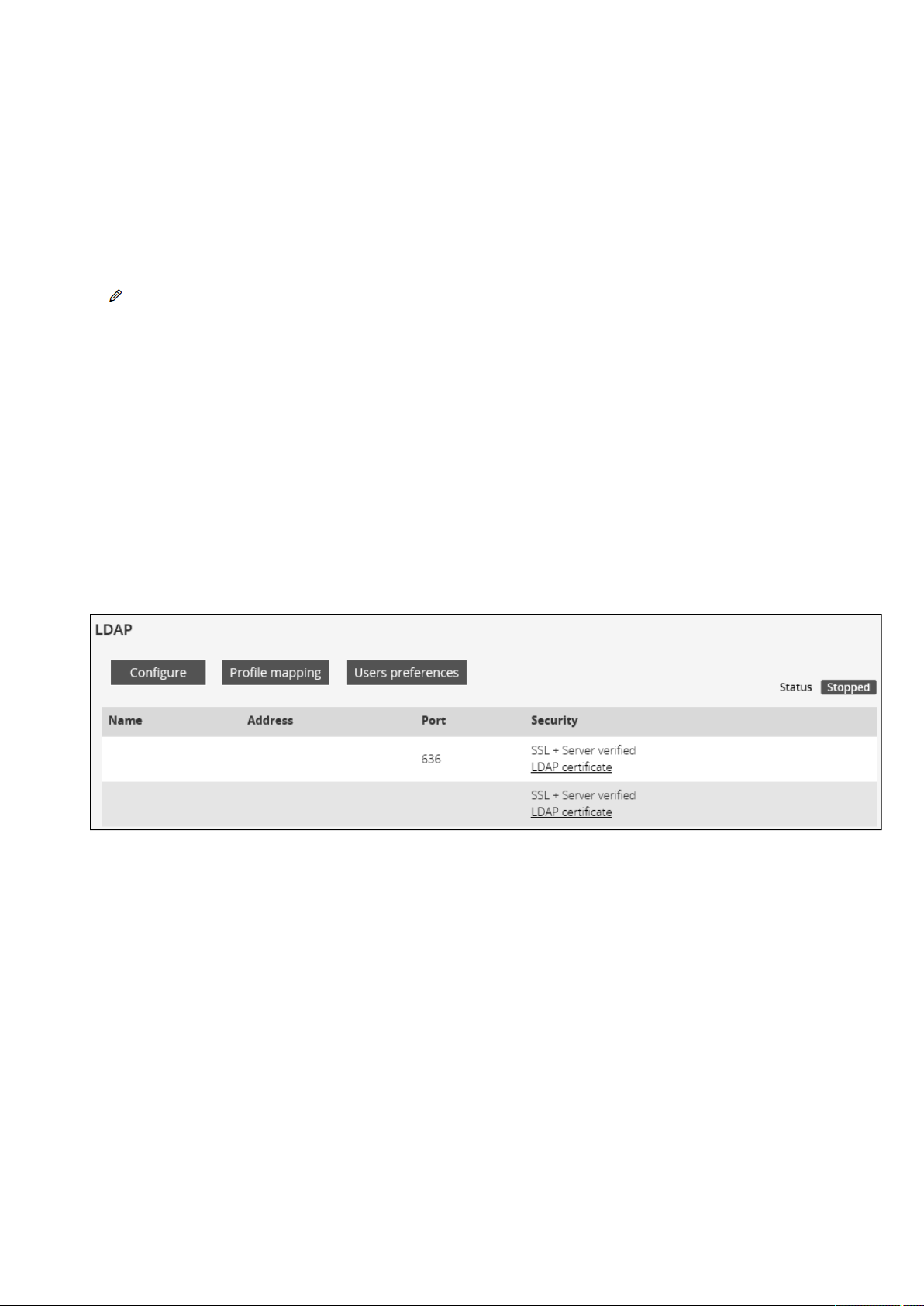
Settings
Contextual Help – 29
2.4.3.4.1 Actions
a Add
Press the New button to create up to ten new users.
b Remove
Select a user and press the Delete button to remove it.
c Edit
Press the pen logo to edit user information and access to the following settings:
•
Active
•
Profile
•
Username
•
Full name
•
Email
•
Phone
•
Organization– Notify by email about account modification/Password
•
Reset password
•
Generate randomly
•
Enter manually
•
Force password to be changed on next login
2.4.3.5 LDAP
The table shows all the supported severs and includes the following details:
•
Name
•
Address
•
Port
•
Security
•
Status–Status could take following values– Unreachable/Active
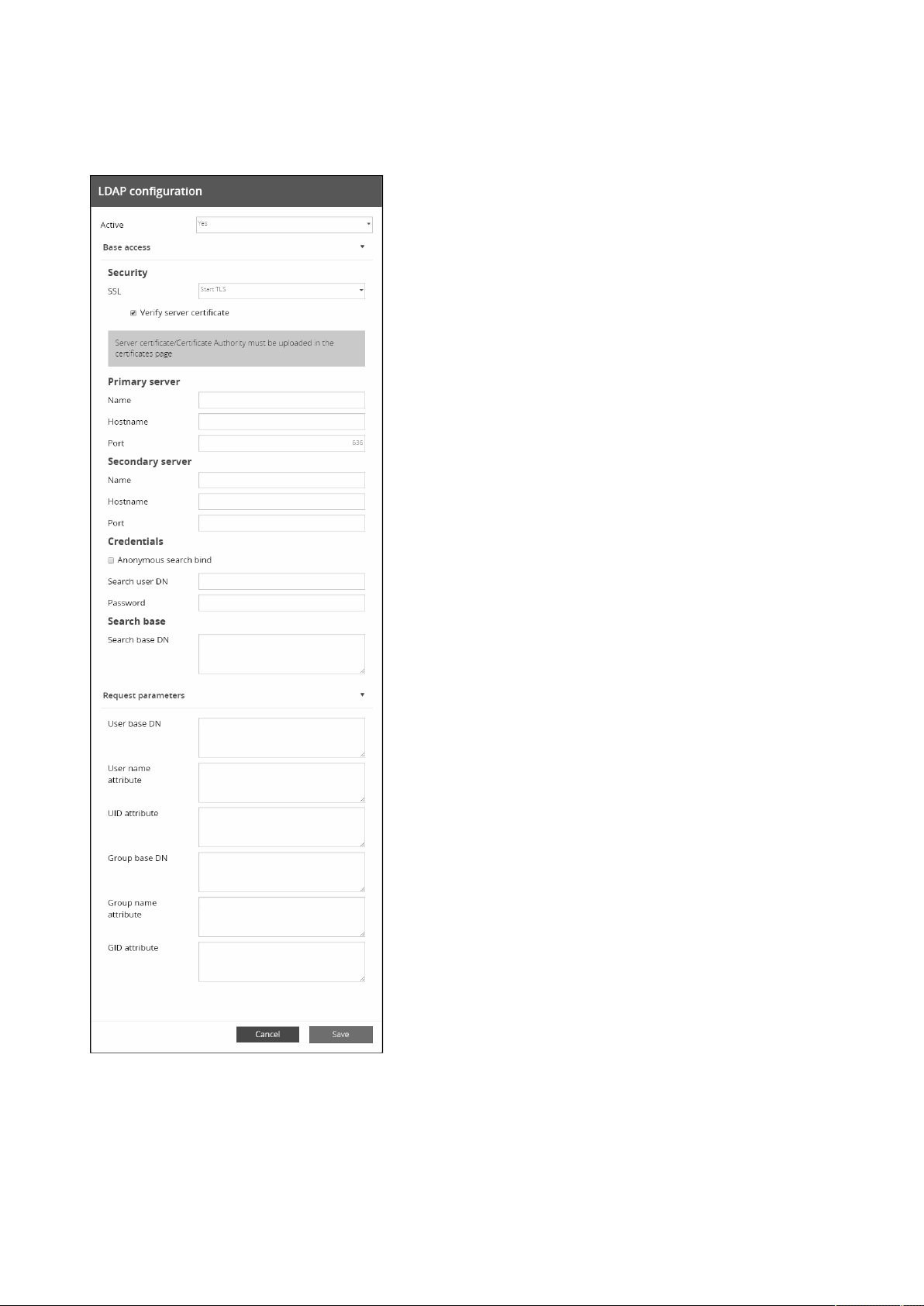
Settings
Contextual Help – 30
2.4.3.5.1 Actions
a Configure
1. Press Configureto access the following LDAP settings:
•
Active
•
Base access
 Loading...
Loading...