dormakaba USA UVC4041 User Manual

B.A.S.I.S.® Offline
Setup Guide
•
•
•
•
•
•

Copyright ©
2004 Stanley Security Solutions, Inc.
and Stanley Logistics, Inc.
All rights reserved.
Printed in the United States of America.
Information in this document is subject to change without notice and does
not represent a commitment on the part of Stanley Security Solutions, Inc.
The software described in this document are furnished under a license
agreement or nondisclosure agreement.
This publication is intended to be an accurate description and set of
instructions pertaining to its subject matter. However, as with any publication of this complexity, errors or omissions are possible. Please call your
Stanley Security Solutions, Inc distributor or Best Access Systems at (317)
849-2250 if you see any errors or have any questions. No part of this manual and/or databases may be reproduced or transmitted in any form or by
any means, electronic or mechanical, including photocopying, recording,
or information storage and retrieval systems, for any purpose, without the
express written permission of Stanley Security Solutions, Inc.
This document is distributed as is, without warranty of any kind, either
express or implied, respecting the contents of this book, including but not
limited to implied warranties for the publication’s quality, performance,
merchantability, or fitness for any particular purpose. Neither Stanley
Security Solutions, Inc, nor its dealers or distributors shall be liable to the
user or any other person or entity with respect to any liability, loss, or
damage caused or alleged to be caused directly or indirectly by this publication.
The Best Access Systems logo and B.A.S.I.S. are registered trademarks of
Stanley Security Solutions, Inc.
Microsoft, Windows, CE, and ActiveSync are registered trademarks of
Microsoft Corporation.
T80946/Rev B ER-7991-40 April 2004

FCC Compliance Statement
Note: This equipment has been tested and found to comply with the limits for a Class B
digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide
reasonable protection against harmful interference in a residential installation. This
equipment generates, uses and can radiate radio frequency energy and, if not installed
and used in accordance with the instructions, may cause harmful interference to radio
communications. However, there is no guarantee that interference will not occur in a
particular installation. If this equipment does cause harmful interference to radio or
television reception, which can be determined by turning the equipment off and on, the
user is encouraged to try to correct the interference by one or more of the following
measures:
—Reorient or relocate the receiving antenna.
—Increase the separation between the equipment and receiver.
—Connect the equipment into an outlet on a circuit different from that to which the receiver
is connected.
—Consult the dealer or an experienced radio/TV technician for help.
Changes or modifications not expressly approved by the party responsible for compliance
could void the user's authority to operate the equipment.

Contents
1 Introduction
Related documents 1–1
Getting technical support 1–2
How to use this guide 1–2
2 Architectural overview
B.A.S.I.S. online and offline diagram 2–3
How B.A.S.I.S. G ‘Guest’ locks work 2–4
Components and connections 2–6
Feature comparison of B.A.S.I.S. G and B.A.S.I.S. V 2–7
Setup overview 2–10
3 First-time B.A.S.I.S.®
Offline System Configuration
Installing the system 3–2
Defining the system 3–7
i

4 Setting up and
Maintaining B.A.S.I.S.® Offline Locks
Introducing B.A.S.I.S. Transport 4–1
Programming locks 4–2
Retrieving history records 4–11
Using diagnostics features 4–14
5 Managing
B.A.S.I.S.® G Cardholders
Editing cardholders 5–2
Searching for cardholders 5–10
Encoding existing cardholders 5–12
A Glossary of Terms
Terms A–2
ii

C h a p t e r
Introduction
1
Thank you for choosing B.A.S.I.S.® G and V, the
world’s leading combination online and offline
access control system.
Use this guide to make sure that you set up your
system in the most efficient way and to get the
most out of it. The initial setup of the B.A.S.I.S. G
& V system is not trivial, but if done thoroughly it
will pay many dividends.
Related documents
The following documents are available to help
you install, maintain, or operate other related
systems. See your BEST Representative for more
information.
■ B.A.S.I.S. V Service Manual
■ B.A.S.I.S. G Service Manual
■ Alarm Monitoring User Guide
■ BadgeDesigner™ User Guide
■ FormsDesigner™ User Guide
1 – 1
Chapter 1: Introduction
Notes ■ ID CredentialCenter User Guide
■ Basic Import Utility User Guide
■ Installation & Setup User Guide
■ MapDesigner™ User Guide
■ System Administration User Guide
■ Universal Interface Server User Guide
■ Replicator User Guide
■ View/Edit Only Workstation User Guide
■ Alternative Wiring Configurations Guide
■ Legato® Co-StandbyServer™ User Guide
■ Hardware Installation Guide
■ Visitor Management User Guide
■ Area Access Manager User Guide
■ Digital Video User Guide
■ Video Archive Server User Guide
■ Replication Administration User Guide
■ Digital Video Hardware User Guide
■ B.A.S.I.S. Interface User Guide
Getting technical support
Best Access Systems Representatives provide telephone
technical support for all B.A.S.I.S. V products. You may locate
the representative nearest you by calling 317-849-2250 Monday through Friday, between 7:00 am and 4:00 pm, eastern
standard time, or visit us on the web at www.bestaccess.com.
How to use this guide
This manual is intended for use as a training guide and a reference in the setup of a B.A.S.I.S. offline system.
Chapter 2, Architectural Overview – This chapter provides an
overview of the B.A.S.I.S. online and offline worlds. If you are
already familiar with B.A.S.I.S. online and offline systems,
you can safely skip this chapter.
Chapter 3, First-time system configuration – This chapter provides complete step-by-step instructions in the proper setup
of a new offline system.
1 – 2
Chapter 4, Setting up and maintaining offline locks – This
chapter provides complete step-by-step instructions on the
proper setup of offline locks.
Chapter 5, Managing B.A.S.I.S. G Cardholders – This chapter
provides complete step-by-step instructions on adding, modifying, deleting and searching cardholders.
Chapter 1: Introduction
that are specifically used in the B.A.S.I.S. software. Terms that
appear in the glossary are set in italics when they are first
used.
NotesAppendix A, Glossary – This appendix provides a list of terms
1 – 3

Chapter 1: Introduction
1 – 4

C h a p t e r
Architectural overview
2
This chapter describes the ‘big picture’ of the
online B.A.S.I.S.® access control system world
and how the offline B.A.S.I.S. G and V product
fits into that world.
The B.A.S.I.S. product line is composed of two
general architectural models used to address the
security needs of most customer requirements
and applications. These two models can be generally categorized as
In an online application most access control decisions are performed by a component called an
Intelligent System Controller (ISC) or Access
Panel. The ISC is a circuit board with on-board
memory, and this on-board memory must be
configured by users who understand access control functions and features.
online and offline.
2 – 1
Chapter 2: Architectural overview
Notes This configuration is accomplished through an operator
entering data on or through a computer called a server. In the
world of B.A.S.I.S. this server is a computer where the access
control system database resides. An operator can enter configurations in the server database through a B.A.S.I.S. application that resides on the server or through one of many
possible B.A.S.I.S. workstations that exist on the access control network.
2 – 2
Chapter 2: Architectural overview
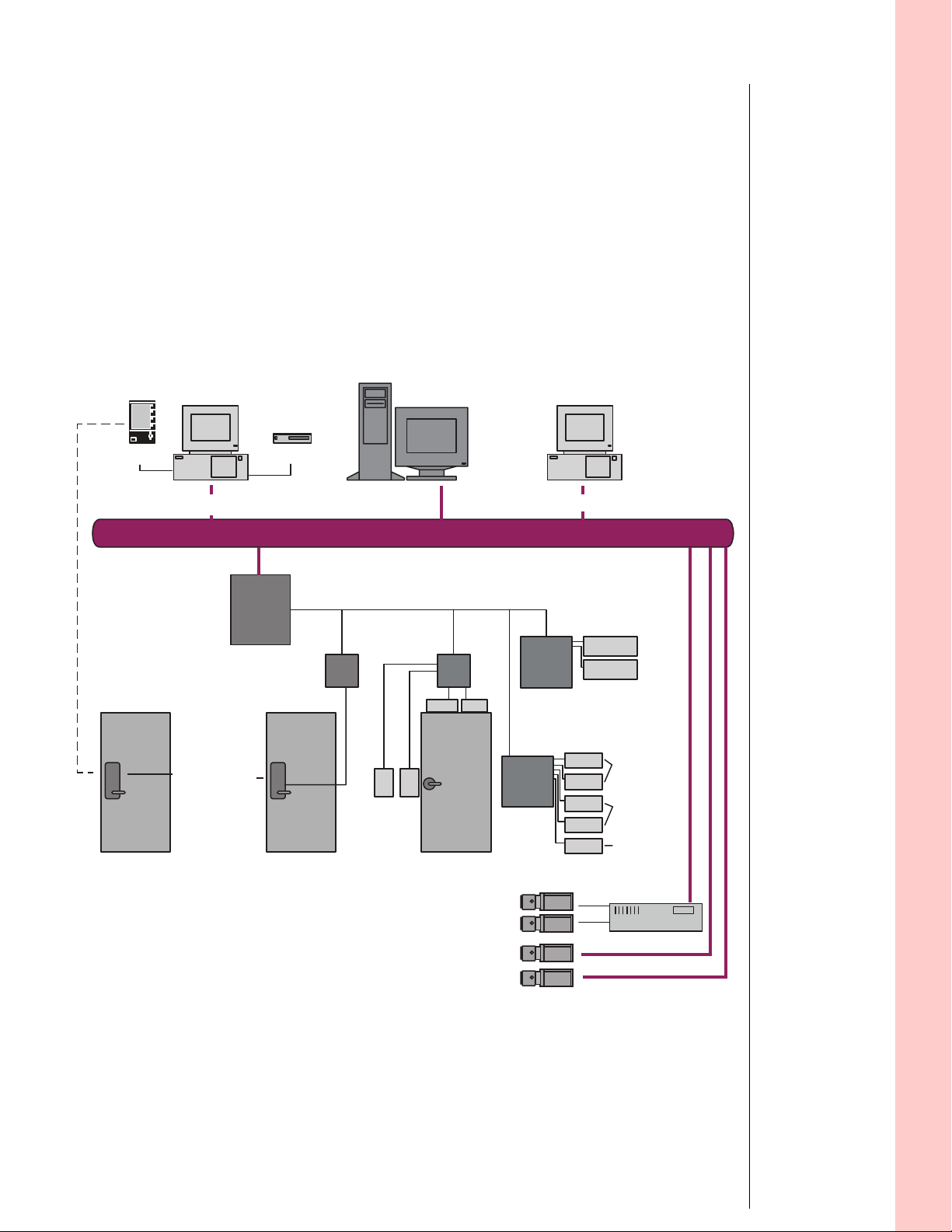
B.A.S.I.S. online and offline diagram
The B.A.S.I.S. system is capable of being configured as both
an online and an offline access control system. This means
that with B.A.S.I.S. you can manage readers, locks, controllers, in fact, any access control hardware, whether or not they
are wired directly to a panel or not.
This diagram describes a typical combined online and offline
B.A.S.I.S. system.
Figure 2.1 B.A.S.I.S. online and offline diagram overview
PDA
B.A.S.I.S. G/V Workstation
Encoder
Server
LAN/WAN
Notes
Workstation
ISC
RIM
B.A.S.I.S.
Offline
Lock
B.A.S.I.S. Best Access Systems Integrated Solutions
CR Card Reader
DC Door Contact
IDH Max Integrated Door Hardware Lock
ISC Intelligent System Controller
LAN Local Area Network
LK Lock
PDA Personal Digital Assistant
RIM Reader Interface Module
RQE Request-to-exit switch
WAN Wide Area Network
IDH
Max
Lock
CR
RIM
LK
Analog Camera
Analog Camera
DCRQE
IP Camera
IP Camera
Alarm
Output
Board
Alarm
Input
Board
Siren
Strobe
Motion
detectors
Glass brk
sensors
Tamper
sensor
Video Server
2 – 3
Chapter 2: Architectural overview
Notes
How B.A.S.I.S. G ‘Guest’ locks work
B.A.S.I.S. G offline locks are designed primarily for the college and university dormitory. But they can be effectively
used in any application where a room has continuous occupancy change over a period of time, or where the lock location is remote or isolated enough that going out to reprogram
the lock becomes undesirable.
Guest functionality then is the lock feature that enables you to
add and delete users to and from the lock without having to
go out and visit the lock to reprogram it.
Operation
B.A.S.I.S. G allows that a range of badge numbers be pre-programmed into the lock unit securing a dormitory room. These
badge numbers are available for issue and reuse as students
are assigned to their dormitory accommodations. The badge
number is automatically issued to a student when the lock for
the room is chosen in the cardholder setup screen. The card
number from the assigned range can then be encoded and
presented to the student for use in his or her assigned room.
New students may be assigned access to a particular room by
using badge IDs from the same range without ever needing to
re-program the lock. By taking advantage of the issue code
look ahead feature, a badge ID issued with an incrementally
higher issue code will deactivate any other like badge ID for
the lock.
The following diagram describes the design and process that
B.A.S.I.S. G locks use to achieve the guest functionality.
2 – 4
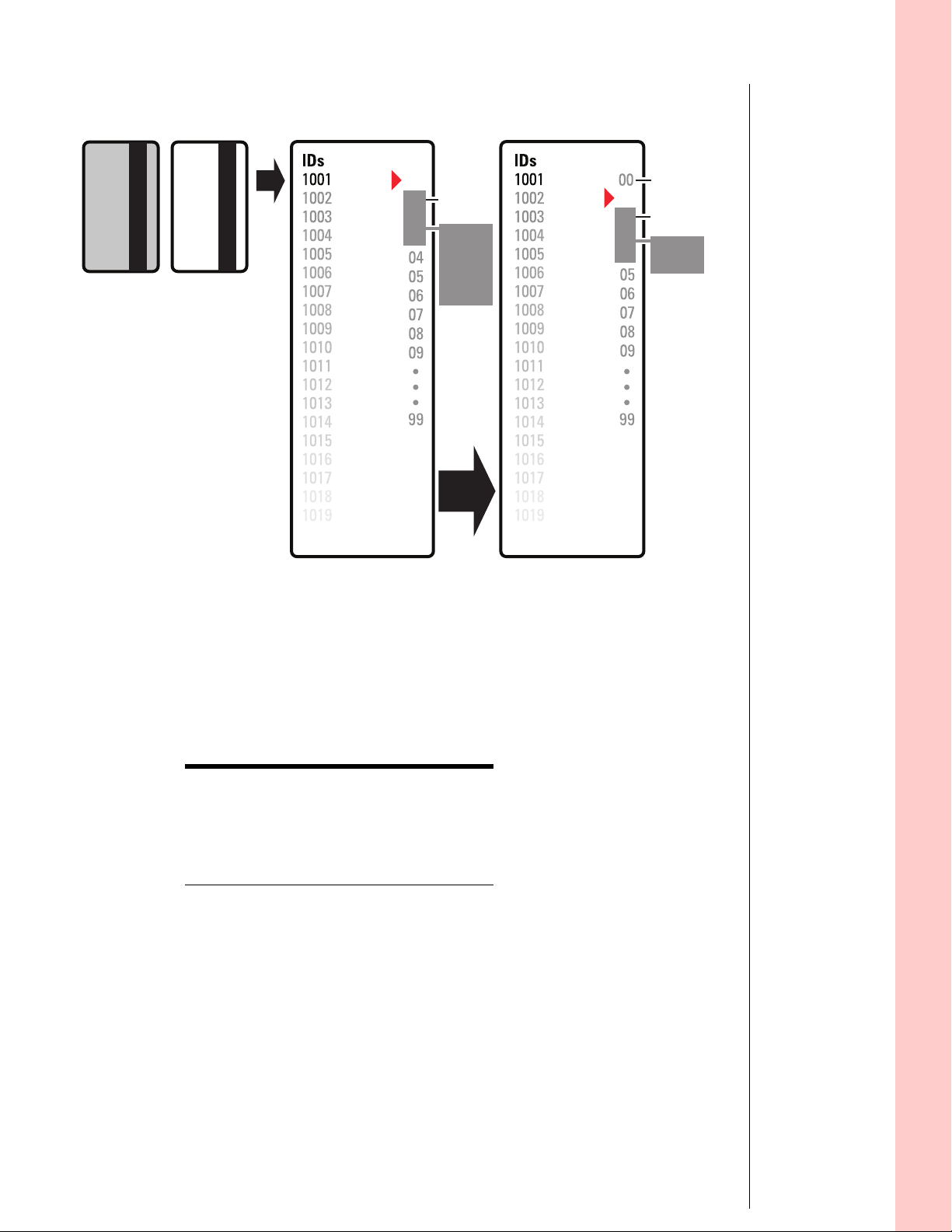
Figure 2.2 Guest functionality diagrammed
Chapter 2: Architectural overview
Notes
1001 issue code: 00
Lost card Newly
encoded
card
1001 issue code: 01
B.A.S.I.S. G Lock Same B.A.S.I.S. G Lock
Issue codes
00
01
02
03
offset
of 1
range
of 3
valid
issue
codes
Auto
update
Issue codes
01
02
03
04
after use of the 1001
issue code 01 card
lost card
does not work
new offset
new
range
The diagram uses the following issue code look ahead values:
Look ahead
Value
function
Offset 1
Range 3
Number of issue
2
code digits
Also instructive is to see what happens when the issue code
has reached its limit. Let’s look at another diagram to see
what happens in this case. The issue code look ahead values
remain the same.
2 – 5
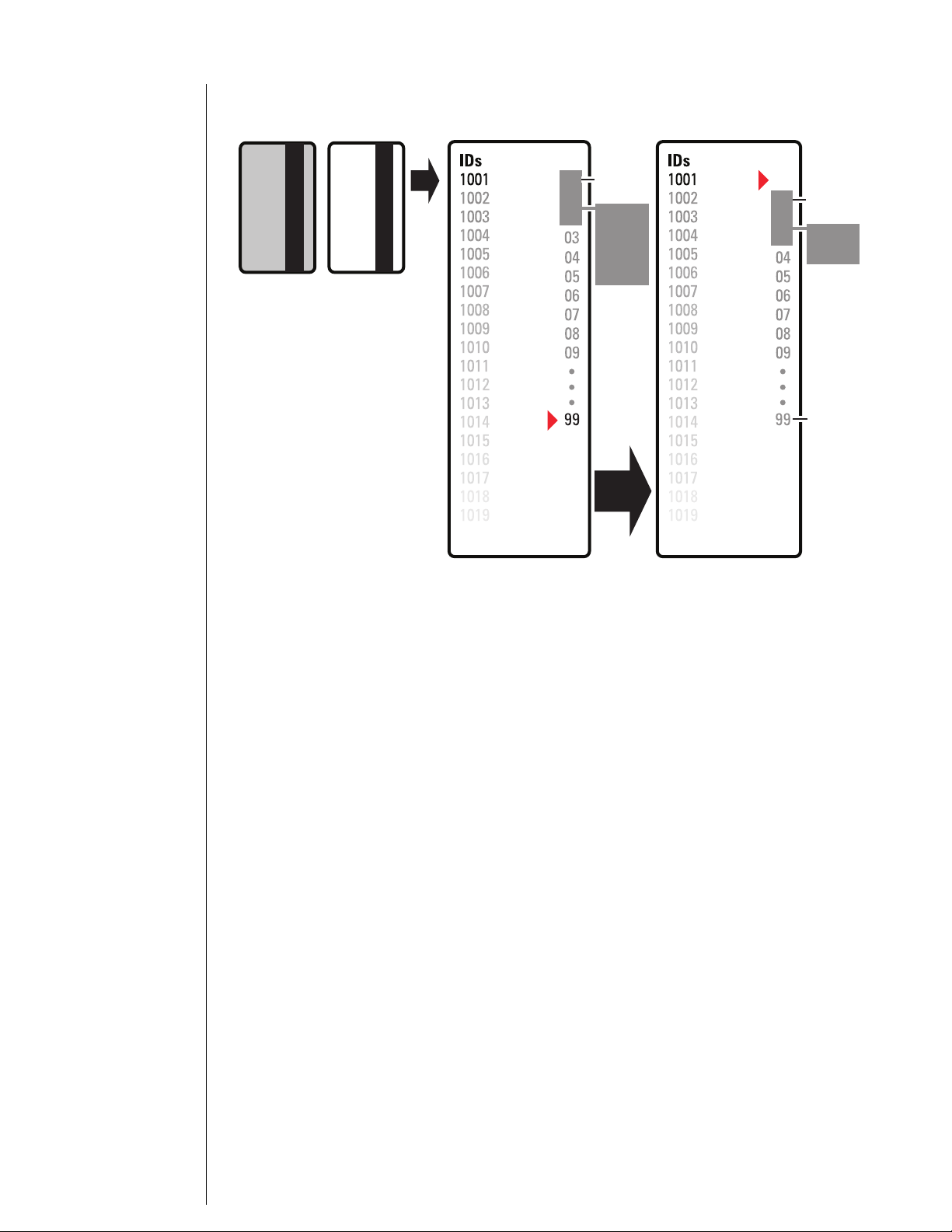
Chapter 2: Architectural overview
Notes
Figure 2.3 Guest functionality in rollover diagrammed
1001 issue code: 99
Lost card Newly
encoded
card
1001 issue code: 00
B.A.S.I.S. G Lock Same B.A.S.I.S. G Lock
Issue codes
00
01
02
offset
of 1
range
of 3
valid
issue
codes
Auto
update
Issue codes
00
01
02
03
after use of the 1001
issue code 00 card
new
offset
new
range
lost card
does not work
Components and connections
The following diagram describes the system ‘family’ – all the
types of hardware and software that it takes to create an
offline B.A.S.I.S. system.
Components include:
■ B.A.S.I.S. software, version 5.8, build 41b or higher
■ Dedicated computer, see your BEST representative for
complete details
■ B.A.S.I.S. G or V lock, includes cylindrical, mortise or exit
hardware trim models
■ Personal digital assistant (PDA). See www.bestaccess.com
for supported models.
■ Encoder
■ magnetic stripe
■ smart card (contact the factory for proper application)
■ Cables
■ computer to PDA
■ PDA to lock (requires PDA proprietary cable and BEST
part number BASD-CAB).
2 – 6

Chapter 2: Architectural overview
Feature comparison of B.A.S.I.S. G and B.A.S.I.S. V
The differences between B.A.S.I.S. G and B.A.S.I.S. V can be
confusing since they share many of the same features. The
following table compares the two systems side by side.
B.A.S.I.S.
Feature Description G V
Guest (dormitory feature
Look ahead Issue code look ahead feature through off-
Encoding Provides the ability to encode both mag-
Passage
mode
Deadbolt
override
Key override
event
activa-
Use
tion date
Use deactivation date
Two card control
Enforce use
limit
Provides the ability to issue pre-created
badge ID's to students. This supports the
assignment of one reader directly to the
badge. Other readers may be assigned to
the badge through normal access level
assignment.
set and range fields.
stripe and smart cards from the cardholder/badge tab. Smart cards are
encoded using magstripe or Wiegand
simulated formats.
Allows the cardholder to place the reader
into an unlocked mode. This status is
cleared only by another passage mode
attempt or reader mode change occurrence.
Allows the cardholder to retract the deadbolt.
An event logged into history whenever
the key override feature is used in a mortise lock. Not supported in Cylindrical.
Determines if the lockset will use the activation date field stored in the cardholder
record when validating. This option has
no impact on Dormitory functionality.
Determines if the lockset will use the
deactivation date field stored in the cardholder record when validating. This
option has no impact on Dormitory functionality.
Requires that two valid users must
present their cards in order to unlock the
door.
Allows for the temporary use of cards.
After a certain number of uses the card is
disabled. The number of uses is configured through the badge tab.
■ ■
■ ■
■ ■
■ ■
■ ■
■ ■
Notes
■
■
■
■
2 – 7

Chapter 2: Architectural overview
Notes
B.A.S.I.S.
Feature Description G V
Denied
attempts
Logging
(grant, denies,
status)
Daylight saving time
128K RAM 5000 Users/History
Card formats
(8)
Magnetic 5 bit ABA data only track 3 tracks
Wiegand Any valid Wiegand format
Online mode Automatic (time zone control of reader
Includes attempts count and time out
duration. Sometimes referred to as ‘Three
strikes your out.’
Provides the ability to filter the displaying/
logging of history events. This feature is
implemented at the Management System
level.
Support for all OS world time zones.
Support for up to eight card data formats
per reader. Facility codes are assigned
through card formats.
mode), Facility Code, Card Only,
Unlocked, Locked, Card and Pin, and Card
or Pin.
■
always
logged
■ ■
■ ■
■ ■
■ ■
■
■
configurable
1 & 2
■
Reader
modes (automatic unlock/
relock)
This feature provides the ability to change
operational modes at specified periods
through time zone control. The current
modes would be Facility Code, Card Only,
Unlocked, Locked, Card and Pin, Card or
Pin, and First Card Unlock.
Unlock duration
Extended
unlock
The amount of time that the lockset will
remain unlocked for a valid access grant.
This feature provides the ability to extend
the unlock duration for certain cardholders.
Chassis type Cylindrical & Mortise with support for a
user defined type ‘Custom’.
Holidays Special days of the year can be catego-
rized as one of eight types.
Time zones Time Zones are necessary for the use of
Access Levels. A time zone can be comprised of up to six intervals.
Access levels Access Level assignment to readers.
Battery warn/
alarm
Panel password
Diagnostics
(PDA)
Reported through the activation of LED’s
and the lock internal sounder.
Communication password is configured
at the Access Panel level.
The PDA will support the capability of performing diagnostics on the lockset.
2 32
■ ■
■ ■
■ ■
8 32
4 32
■ ■
■ ■
■ ■
■ ■
2 – 8

Chapter 2: Architectural overview
B.A.S.I.S.
Feature Description G V
Cycle count/
reset
DIagnostics
code
Backup bat-
tery level
Electronics
level
Unlock once This feature allows for the unlocking of
Reader mode This feature allows for the setting of the
Reader support
The lockset will maintain a current count
of access grants. The count can be reset
by the user.
This code provides some feedback of the
lockset's status.
Displays the current level of the backup
battery.
Displays the current level of the main
electronics battery.
the door for the unlock duration.
current operating mode directly to the
reader through the PDA. This action
would override the online mode set at the
management system level. All online
reader modes are supported.
Dual Validation
■ ■
■ ■
■ ■
■ ■
■ ■
■ ■
■ ■
Notes
Magstripe track 3 tracks
Smart Card
HID Proximity
Motorola Proximity
Batch update This feature allows for the bulk updating
of Activation/Deactivation Dates.
1 & 2
■ ■
■
■
■ ■
2 – 9
Chapter 2: Architectural overview
Notes
Setup overview
In the next chapter you will find complete step-by-step
instructions on the first-time configuration of a B.A.S.I.S.®
offline system. But listed here are the major steps of that process and cross-references where you can find each corresponding task.
Task 1 Install the system components. This task begins on page 3-2.
■ B.A.S.I.S. Software, see page 3-2.
■ Encoder, see page 3-3.
■ PDA, see page 3-5.
■ B.A.S.I.S. Transport, see page 3-6.
Task 2 Define the system. This task begins on page 3-7.
■ Card formats, see page 3-7.
■ Badge types, see page 3-9.
■ ‘Virtual’ offline access panels, see page 3-13.
■ Guest readers, see page 3-15.
Task 3 For B.A.S.I.S. V configuration only, set up time zones, holi-
days, access levels, and cardholders.
2 – 10

C h a p t e r
3
First-time B.A.S.I.S.®
Offline System Configuration
You are now ready to start setting up your
B.A.S.I.S.® offline system. The following tasks do
not include the installation of the locks themselves. The installation of the B.A.S.I.S. G or
B.A.S.I.S. V locks are fully described in the following installation instruction documents. Contact your BEST Representative for a copy of these
documents:
Title
Installation Instructions for Electronic
Stand-alone Cylindrical Locks
Installation Instructions for Electronic
Stand-alone Mortise Locks
Installation Instructions for Electronic
Stand-alone Exit Hardware Trim
Doc
number
T61835
T61836
T61828
3 – 1
Chapter 3: First-time B.A.S.I.S.® Offline System Configuration
Notes Make sure that the B.A.S.I.S. G or V locks are at least on site
and ready to be programmed. Locks may be programmed
before installation.
Installing the system
Make sure that you have the following components before
you start installing the B.A.S.I.S. Offline system:
■ B.A.S.I.S. software, version 5.8, build 41b or higher
■ Dedicated computer, see your BEST representative for
complete details.
■ Personal digital assistant (PDA). See www.bestaccess.com
for supported models.
■ Encoder,
■ magnetic stripe
■ smart card (contact the factory for proper application)
■ Cables
■ computer to PDA
■ PDA to lock (requires PDA proprietary cable and BEST
part number BASD-CAB).
Installing the B.A.S.I.S. software
Before installing the B.A.S.I.S. software, also make sure that
you have completed the following checklist.
Determine whether your database will use Microsoft SQL
Server, Oracle, or MSDE.
Make sure you have an Information Technology person
who can configure the computer’s TCP/IP protocol.
Make sure you have an Information Technology person
who can set up a server with the appropriate server software.
Get the hardware key or ‘dongle.’
For complete B.A.S.I.S. online software installation and configuration, see the
Guide. Contact your BEST Representative for a copy.
B.A.S.I.S. Installation and Setup User
3 – 2
Chapter 3: First-time B.A.S.I.S.® Offline System Configuration
Installing the encoder
Two types of encoders are available for the B.A.S.I.S. Offline
system:
■ Magnetic stripe encoder
Unitech model MSR206
part number MSR206-33
■ Smart card encoder
GemPlus model GEMPC410
part number GCR410-P
BEST part number 1825235
For proper setup of the smart card encoder, contact
your BEST Representative.
The card encoder or some type of encoding device (that is, an
encoder or a printer with a built-in encoder) is required for
B.A.S.I.S. G locks. So the following instructions are required
for B.A.S.I.S. G functionality, but optional for B.A.S.I.S. V. For
a comparison of B.A.S.I.S. G and V, See “Feature comparison
of B.A.S.I.S. G and B.A.S.I.S. V” on page 2-7.
Notes
These instructions assume a stand-alone encoder.
To set up the encoder
1 Click Start > Programs > B.A.S.I.S. ET > System
Administration.
2 At the login window type your user name and password
and then click OK.
If you do not know your user name or password, see your
System Administrator.
3 Click Administration > Workstations.
4 From the Workstation tab, confirm that the name of your
computer is in the list. If your computer is not in the list,
add your workstation by using the browse button and
select your workstation.
5 Click Add.
6 Type the name of your computer or click the browse
button and browse the network for your computer.
7 Click OK.
8 Click the Encoder tab.
9 Confirm that the encoder is physically connected to a COM
port on the computer, preferably COM1, and is powered
on.
3 – 3
Chapter 3: First-time B.A.S.I.S.® Offline System Configuration
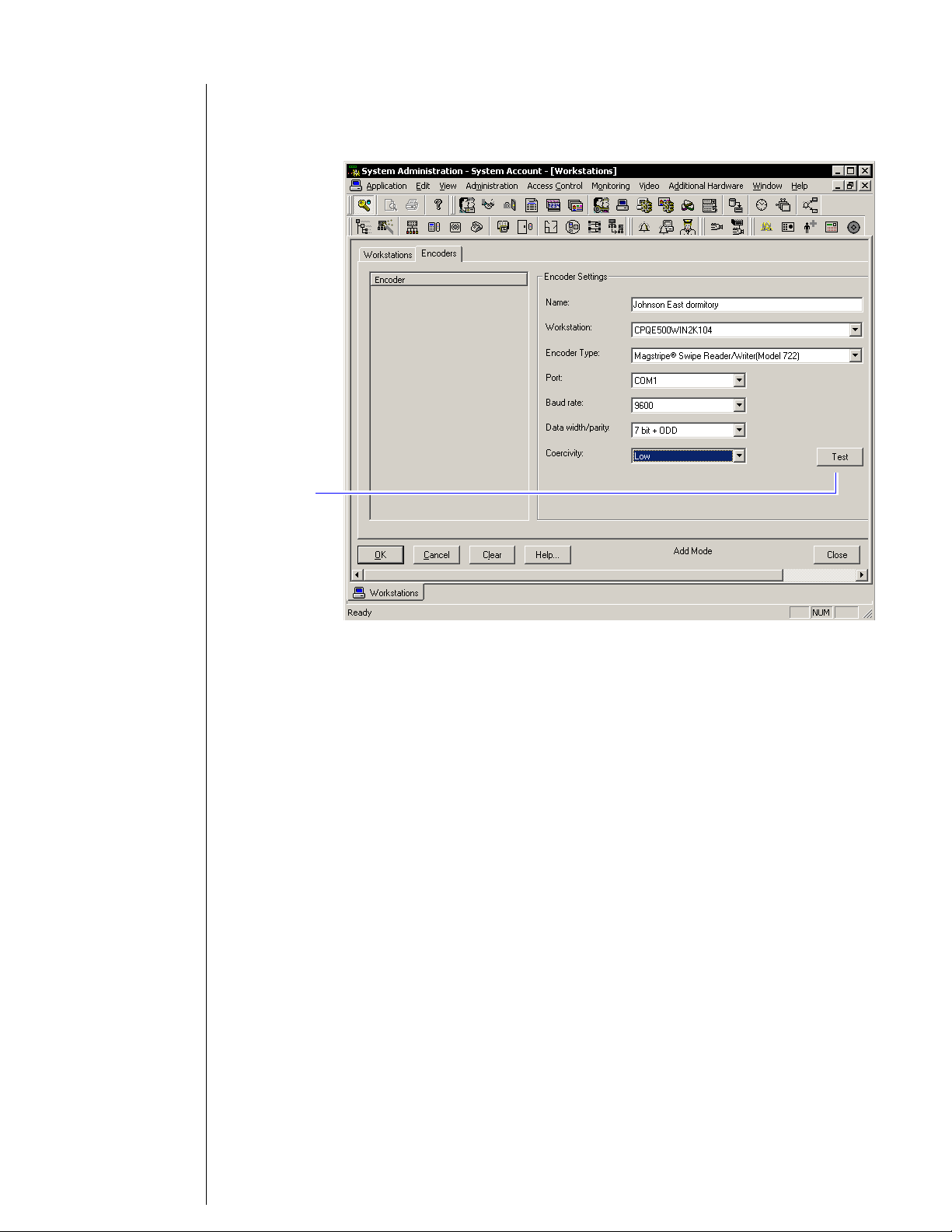
Notes 10 Click Add.
Figure 3.1 Configuring the encoder
Click to test
whether the
encoder is
online
11 Under Encoder Settings, in the name field, type a name for
the encoder.
12 In the Encoder Type field, select:
Magstripe Swipe Reader/Writer (Model 712 or 722)
13 Click Test.
Note The encoder can be tested at any time by returning to the
Encoder tab. You do not need to put the encoder in modify
mode to test the encoder.
14 Click OK.
15 Close System Administration.
3 – 4
Chapter 3: First-time B.A.S.I.S.® Offline System Configuration
Installing the PDA
The Personal Digital Assistant (PDA) is your link from the
B.A.S.I.S. workstation to the B.A.S.I.S. G and V lock.
With the help of your computer network administrator, if necessary, perform the following steps to set up the connection
between the PDA and the B.A.S.I.S. workstation.
To install Microsoft ActiveSync
1 Connect the PDA to the B.A.S.I.S. workstation.
2 Install Microsoft ActiveSync.
3 When prompted, set up a partnership with this computer
and remove all check marks associated with programs.
4 Restart the computer after ActiveSync completely installs.
5 Test the encoder and confirm ActiveSync connectivity
before proceeding. To test the encoder, see page 3-4.
Note When ActiveSync is running, the ActiveSync icon, shown in
the taskbar on the PC’s desktop, is green. When ActiveSync is
not running, the icon is gray.
Notes
3 – 5
 Loading...
Loading...