Page 1
Non-Volatile or
PCH Internal CMOS
Up to 8
Varies (not factory
CPU
Volatile
CPU1 / CPU2
iDRAC DDR
Volatile
U_IDRAC_MEM1
256MByte
iDRAC
Volatile
U_IDRAC1
U_LOM1_ROM
Power Supplies
Up to 2MB. Varies by part
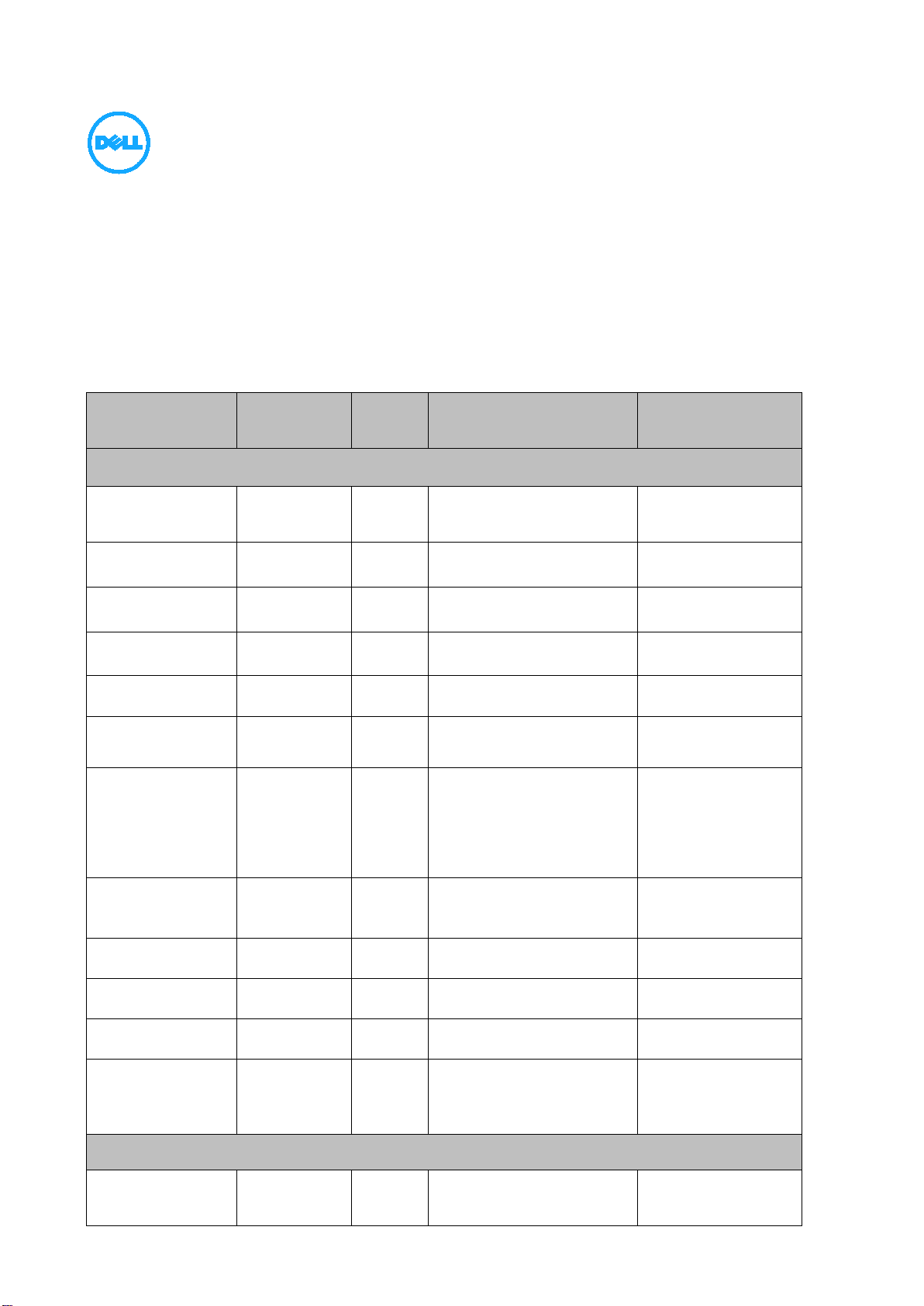
Statement of Volatility – Dell PowerEdge R430
Dell PowerEdge R430 contains both volatile and non-volatile (NV) components. Volatile components lose their data
immediately upon removal of power from the component. Non-volatile components continue to retain their data even
after the power has been removed from the component. Components chosen as user-definable configuration options
(those not soldered to the motherboard) are not included in the Statement of Volatility. Configuration option information
(pertinent to options such as microprocessors, remote access controllers, and storage controllers) is available by
component separately. The following NV components are present in the PowerEdge R430 server.
Item
Planer
RAM
BIOS Password Non-Volatile 1
BIOS SPI Flash Non-Volatile 1
iDRAC SPI Flash Non-Volatile 1
BMC EMMC Non-Volatile 1
System CPLD RAM Volatile 1 U_CPLD1 1 KB
System Memory Volatile
Volatile
Non-Volatile 1
Quantity Reference Designator Size
256 Bytes
16 bytes
16 MB
4 MB
4 GB
Up to 32GB per DIMM
(RDIMM)
for CPU1
Up to 4
for CPU2
U_PCH1
U_PCH1
U_SPI_BIOS1
U_IDRAC_SPI-1
U_EMMC1
CPU1: DIMM1~DIMM8,
CPU2: DIMM9~DIMM12
Internal USB Key Non-Volatile Up to 1 N/A
LOM EEPROM Non-Volatile
PSU FW Non-Volatile 1 per PSU Varies by part number
Dell - Internal Use - Confidential
02 - 2013
1 or 2
1
1
2
installed)
Various
64 kbyte + registers
U_LOM2_ROM 8Mb
number
Page 2
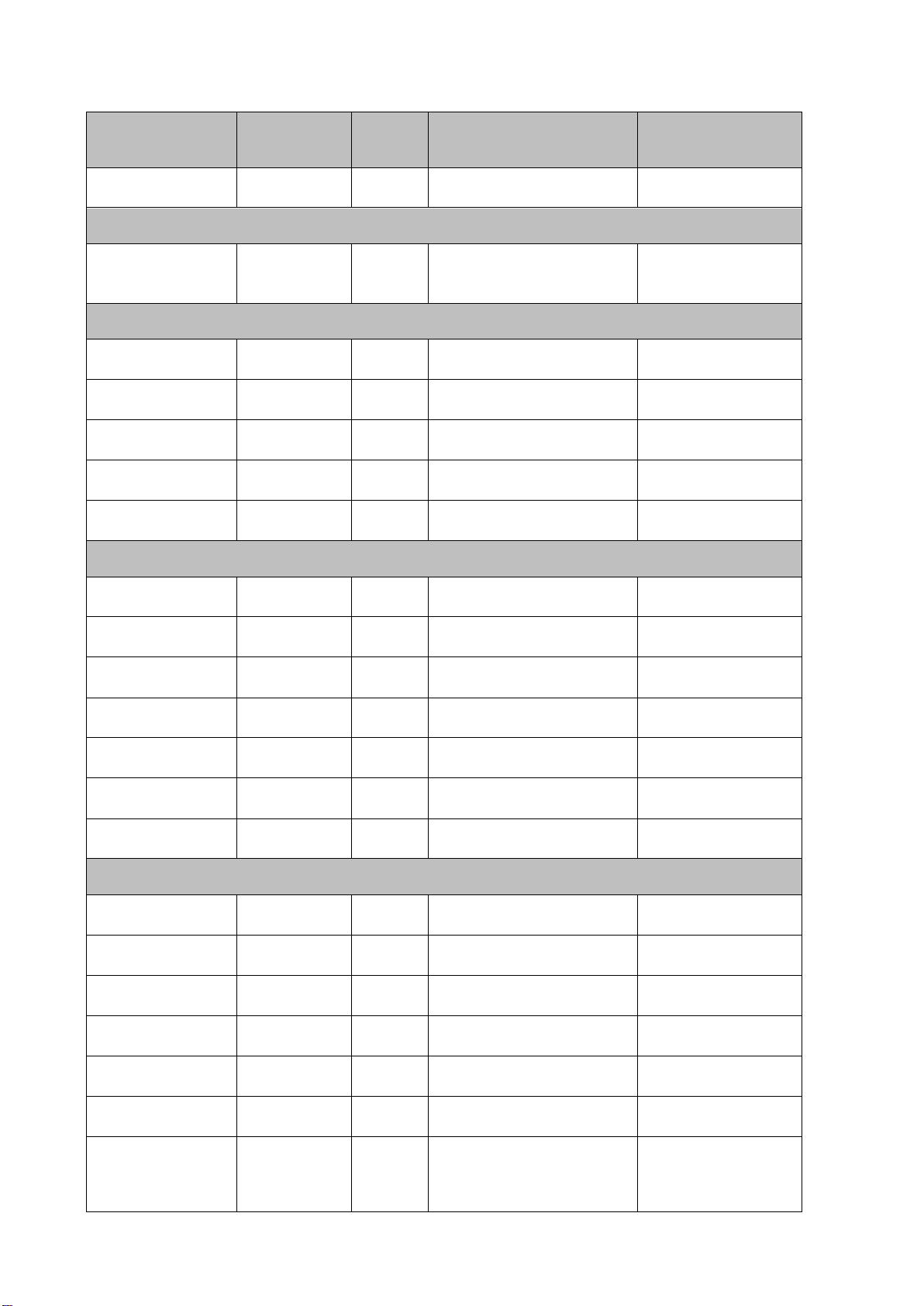
Item
Non-Volatile or
1U 4x3.5”, 1U 10x2.5” and 1U 8x2.5”Backplanes
Flash:32KB+4KB
SAS12G HBA Card
NVSRAM
Non-volatile
1
U1033
128KB
FRU
Non-volatile
1
U1019
256B
1-Wire EEPROM
Non-volatile
1
U1004
128B
SBR
Non-volatile
1
U1020
8KB
Flash
Non-volatile
1
U3
16MB
H830 PERC
NVSRAM
Non-volatile
1
U1033
128KB
FRU
Non-volatile
1
U1019
256B
1-Wire EEPROM
Non-volatile
1
U1004
128B
SPD
Non-volatile
1
U22
256B
SBR
Non-volatile
1
U1020
8KB
Flash
Non-volatile
1
U1031
16MB
ONFI Backup Flash
Non-volatile
1
U1059
4GB
H730, Mini PERC
NVSRAM
Non-volatile
1
U1033
128KB
FRU
Non-volatile
1
U1019
256B
1-Wire EEPROM
Non-volatile
1
U1004
128B
SPD
Non-volatile
1
U22
256B
SBR
Non-volatile
1
U1020
8KB
Flash
Non-volatile
1
U1049
16MB
ONFI Backup Flash
Non-volatile
1
U1059
4GB
Volatile
Quantity Reference Designator Size
SEP internal flash Non-Volatile 1
U_SEP1
EEPROM: 2KB
Dell - Internal Use - Confidential
Page 3
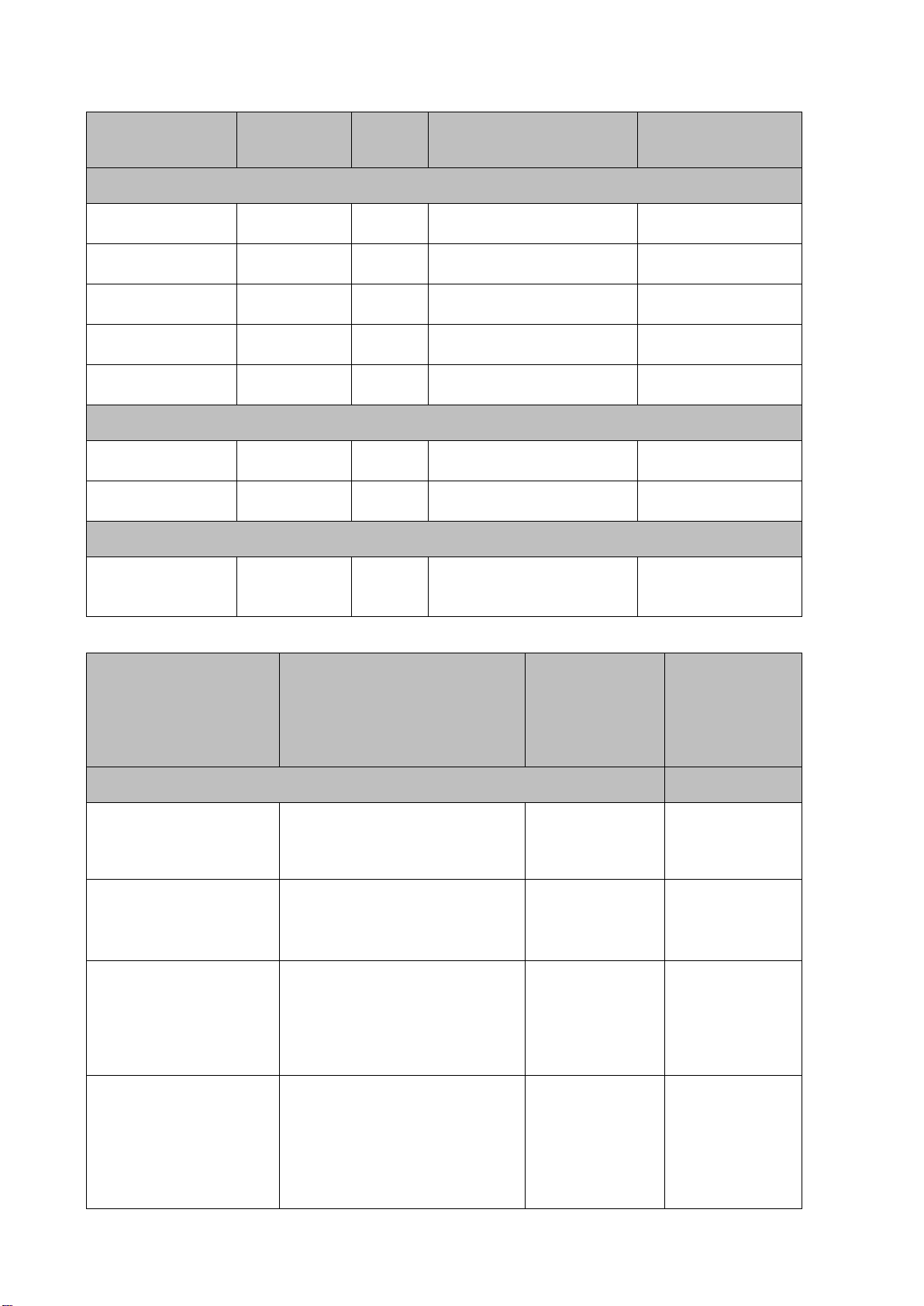
Item
Non-Volatile or
H330, Mini PERC
NVSRAM
Non-volatile
1
U1033
128KB
FRU
Non-volatile
1
U1019
256B
1-Wire EEPROM
Non-volatile
1
U1004
128B
SBR
Non-volatile
1
U1020
8KB
Flash
Non-volatile
1
U3
16MB
IDSDM
SPI Flash
Non-Volatile
1
U2
8Mb
MCU
Non-Volatile
1
U6
512KB
TPM
Trusted Platform
Item
Type (e.g. Flash PROM, EEPROM)
Can user programs
Purpose? (e.g.
Planer
PCH Internal CMOS RAM
Battery-backed CMOS RAM
No
Real-time clock
settings
BIOS Password
Battery-backed CMOS RAM
Yes
Password to
BIOS SPI Flash
SPI Flash
No
Boot code, system
ME
iDRAC SPI Flash
SPI Flash
No
iDRAC Uboot
boot variables),
Volatile
Quantity Reference Designator Size
Module (TPM)
Non-Volatile 1 U_TPM 128 Bytes
or operating system
write data to it
during normal
operation?
boot code)
and BIOS
configuration
change BIOS
settings
configuration
information, UEFI
environment,
Flash Disceptor,
Dell - Internal Use - Confidential
(bootloader),
server managent
persistent store
(i.e. IDRAC MAC
Address, iDRAC
Page 4

Item
Type (e.g. Flash PROM, EEPROM)
Can user programs
or operating system
Purpose? (e.g.
lifecycle log cache,
System Event Log,
BMC EMMC
eMMC NAND Flash
No
Operational iDRAC
firmware
System CPLD RAM
RAM
No
Not utilized
System Memory
DRAM
Yes
System OS RAM
Internal USB Key
Flash
Yes
General purpose
CPU
Cache + registers
Yes
Processor cache +
iDRAC DDR
DRAM
No
iDRAC local
iDRAC
Cache + registers
No
Processor cache +
LOM EEPROM
EEPROM
No
Onboard LOM FW
Power Supplies
PSU FW
Embedded microcontroller flash
No
Power Supply
behaviors
1U 4x3.5”, 1U 10x2.5” and 1U 8x2.5”Backplanes
SEP internal flash
Integrated Flash+EEPROM
No
Firmware + FRU
SAS12G HBA Card
NVSRAM
NVSRAM
No
Configuration data
FRU
FRU
No
Card
write data to it
during normal
operation?
boot code)
virtual planar FRU
and EPPID, rac log,
FW, Lifecycle
Controller (LC) USC
partition, LC
service diags, LC
OS drivers, USC
USB key drive
registers
memory
registers
operation, power
management data
and fault
Dell - Internal Use - Confidential
manufacturing
information
Page 5

Item
Type (e.g. Flash PROM, EEPROM)
Can user programs
or operating system
Purpose? (e.g.
1-Wire EEPROM
1-Wire EEPROM
No
Holds default
SBR
SBR
No
Bootloader
Flash
Flash
No
Card firmware
H730 Mini, H830 PERCs
NVSRAM
NVSRAM
No
Configuration data
FRU
FRU
No
Card
1-Wire EEPROM
1-Wire EEPROM
No
Holds default
SPD
SPD
No
Memory
SBR
SBR
No
Bootloader
Flash
Flash
No
Card firmware
ONFI Backup Flash
ONFI Backup Flash
No
Holds cache data
SDRAM
SDRAM
No
Cache for HDD I/O
H330, Mini PERC
NVSRAM
NVSRAM
No
Configuration data
FRU
FRU
No
Card
1-Wire EEPROM
1-Wire EEPROM
No
Holds default
SBR
SBR
No
Bootloader
Flash
Flash
No
Card firmware
write data to it
during normal
operation?
boot code)
controller
properties/settings
manufacturing
information
controller
properties/settings
configuration data
during power loss
manufacturing
information
controller
properties/settings
Dell - Internal Use - Confidential
Page 6

Item
Type (e.g. Flash PROM, EEPROM)
Can user programs
or operating system
Purpose? (e.g.
IDSDM
SPI Flash
SPI Flash
No
Exclusively used by
MCU
Embedded Flash
Yes
Firmware
TPM
Trusted Platform Module
EEPROM
Yes
Storage of
Item
How is data input to this
How is this memory
How is the memory cleared?
Planar
PCH Internal
BIOS
N/A – BIOS only
1) Set NVRAM_CLR jumper to clear BIOS
BIOS Password
Keyboard
N/A
Place shunt on J_PSWD_NVRAM jumper
BIOS SPI Flash
SPI interface via iDRAC
Software write
Not possible with any utilities or
iDRAC SPI Flash
SPI interface via iDRAC
Embedded iDRAC
Not completely user clearable; however,
BMC EMMC
NAND Flash interface via
Embedded FW write
Not completely user clearable; however,
write data to it
during normal
operation?
boot code)
the controller
(TPM)
CMOS RAM
memory?
write protected?
control
protected
encryption keys
configuration settings at boot and
reboot system; 2) AC power off system,
remove coin cell battery for 30 seconds,
replace battery and power back on; 3)
restore default configuration in F2
system setup menu.
pins 2 and 4.
applications and system is not functional
if corrupted/removed.
iDRAC
Dell - Internal Use - Confidential
subsystem firmware
actively controls sub
area based write
protection as needed.
protected
user data, lifecycle log and archive, SEL,
fw image repository can be cleared via
Delete Configuration and Retire System,
accessible in Lifecycle Controller
interface
user data, lifecycle log and archive, SEL,
fw image repository can be cleared via
Delete Configuration and Retire System,
accessible in Lifecycle Controller
interface
Page 7

System CPLD
RAM
Not utilized
Not accessible
Not accessible
System Memory
System OS
OS Control
Reboot or power down system
Internal USB Key
USB interface via PCH.
No write protect
Can be cleared in system OS
CPU
Various
Various
Power off
iDRAC DDR
iDRAC Firmware
NA
Power off
iDRAC
iDRAC Firmware
NA
Power off
LOM EEPROM
SPI interface via i350
NA
Not user clearable
LOM Flash
SPI interface via i350
NA
Not user clearable
Expander FRU
I2C interface via expander
Hardware strapping
Not user clearable
BP FRU image
I2C interface via iDRAC
Hardware strapping
Not user clearable
Power Supplies
PSU FW
Different vendors have
NA
Protected by the embedded
1U 4x3.5”, 1U 10x2.5” and 1U 8x2.5”Backplanes
SEP internal
I2C interface via iDRAC
Program write protect
Not user clearable
SAS12G HBA Card
NVSRAM
ROC writes configuration
Not WP. Not visible to
Cannot be cleared with existing tools
FRU
Programmed at ICT during
Not WP
Cannot be cleared with existing tools
1-Wire EEPROM
ROC writes data to this
Not WP. Not visible to
Cannot be cleared with existing tools
SBR
Pre-programmed before
Not WP. Not visible to
Cannot be cleared with existing tools
Flash
Pre-programmed before
Not WP. Not visible to
Cannot be cleared with existing tools
image
Accessed via system OS
flash
different utilities and
tools to load the data to
memory. It can also be
loaded by Dell Update
Package from LC or OS
(Windows and Linux)
data to NVSRAM
production
memory
bit
Host Processor
Host Processor
microcontroller. Special keys are used by
special vendor provided utilities to
unlock the ROM with various CRC checks
during load.
available to the customer
available to the customer
available to the customer
assembly
assembly. Can be updated
Dell - Internal Use - Confidential
Host Processor
Host Processor
available to the customer
available to the customer
Page 8

using Dell/LSI tools
H730 mini, H830 PERCs
NVSRAM
ROC writes configuration
data to NVSRAM
Not WP. Not visible to
Cannot be cleared with existing tools
FRU
Programmed at ICT during
Not WP
Cannot be cleared with existing tools
1-Wire EEPROM
ROC writes data to this
Not WP. Not visible to
Cannot be cleared with existing tools
SPD
Pre-programmed before
Not WP. Not visible to
Cannot be cleared with existing tools
SBR
Pre-programmed before
Not WP. Not visible to
Cannot be cleared with existing tools
Flash
Pre-programmed before
Not WP. Not visible to
Cannot be cleared with existing tools
ONFI Backup
FPGA backs up DDR data
Not WP. Not visible to
Flash can be cleared by powering up the
SDRAM
ROC writes to this
Not WP. Not visible to
Cache can be cleared by powering off
H330, Mini PERC
NVSRAM
ROC writes configuration
Not WP. Not visible to
Cannot be cleared with existing tools
FRU
Programmed at ICT during
Not WP
Cannot be cleared with existing tools
1-Wire EEPROM
ROC writes data to this
Not WP. Not visible to
Cannot be cleared with existing tools
SBR
Pre-programmed before
Not WP. Not visible to
Cannot be cleared with existing tools
Flash
Pre-programmed before
Not WP. Not visible to
Cannot be cleared with existing tools
Host Processor
available to the customer
Flash
production.
memory
assembly
assembly
assembly. Can be updated
using Dell/LSI tools
to this device in case of a
power failure
Host Processor
Host Processor
Host Processor
Host Processor
Host Processor
available to the customer
available to the customer
available to the customer
available to the customer
available to the customer
card and allowing the controller to flush
the contents to VDs. If the VDs are no
longer available, cache can be cleared by
going into controller bios and selecting
Discard Preserved Cache.
memory - using it as
cache for data IO to HDDs
data to NVSRAM
production
memory
assembly
assembly. Can be updated
using Dell/LSI tools
Host Processor
Host Processor
Host Processor
Host Processor
Host Processor
the card
available to the customer
available to the customer
available to the customer
available to the customer
available to the customer
Dell - Internal Use - Confidential
Page 9

IDSDM
SPI Flash
SPI interface via iDRAC
Hardware strapping
Not user clearable
MCU
USB3.0 interface via PCH,
FW can be updated via
N/A
Not user clearable
TPM
Trusted Platform
Using TPM Enabled
SW write protected
F2 Setup option
iDRAC which runs on
Linux
Module (TPM)
operating systems
To obtain optional component information, please refer to the Dell Statement of Volatility for the individual
components. Please direct any questions to your Dell Marketing contact.
Sincerely,
Dell Enterprise Server Marketing
NOTE:
For any information that you may need, direct your questions to your Dell Marketing contact.
______________
© 2014 Dell Inc.
Trademarks used in this text: Dell™, the DELL logo, and PowerEdge™ are trademarks of Dell Inc.
Dell - Internal Use - Confidential
 Loading...
Loading...