Page 1
Dell PowerConnect W-
AirWave 7.3
User Guide
Page 2

Copyright
© 2011 Aruba Networks, Inc. Aruba Networks trademarks include , Aruba Networks
®
registered Aruba the Mobile Edge Company logo, and Aruba Mobility Management System
. Dell™, the DELL™ logo, and PowerConnect™ are
®
, Aruba Wireless Networks®, the
trademarks of Dell Inc.
All rights reserved. Specifications in this manual are subject to change without notice.
Originated in the USA. All other trademarks are the property of their respective owners.
Open Source Code
Certain Aruba products include Open Source software code developed by third parties, including software code subject to the GNU General
Public License (GPL), GNU Lesser General Public License (LGPL), or other Open Source Licenses. The Open Source code used can be found at
this site:
http://www.arubanetworks.com/open_source
Legal Notice
The use of Aruba Networks, Inc. switching platforms and software, by all individuals or corporations, to terminate other vendors’ VPN client
devices constitutes complete acceptance of liability by that individual or corporation for this action and indemnifies, in full, Aruba Networks, Inc.
from any and all legal actions that might be taken against it with respect to infringement of copyright on behalf of those vendors.
Dell PowerConnect W-AirWave |User Guide 0510897-08 | August 2011
Page 3

Contents
Preface.....................................................................................................................................................................11
Document Organization................................................................................................................... 11
Note, Caution, and Warning Icons ................................................................................................12
Contacting Support ..........................................................................................................................12
Chapter 1 Introduction ........................................................................................................................13
AirWave—A Unified Wireless Network Command Center....................................................... 13
AirWave Management Platform ............................................................................................ 13
Dell PowerConnect W Configuration.................................................................................... 14
VisualRF......................................................................................................................................14
RAPIDS....................................................................................................................................... 14
Master Console and Failover.................................................................................................. 15
Integrating AirWave into the Network and Organizational Hierarchy ....................................15
Supported Browsers........................................................................................................................ 16
Chapter 2 Installing and Getting Started in AirWave.....................................................................17
AirWave Hardware Requirements and Installation Media ....................................................... 17
Installing Linux CentOS 5 (Phase 1)............................................................................................... 17
Installing AirWave Software (Phase 2)......................................................................................... 18
Getting Started.......................................................................................................................... 18
Step 1: Configuring Date and Time, Checking for Prior Installations .............................. 18
Date and Time...................................................................................................................18
Previous AirWave Installations .....................................................................................18
Step 2: Installing AirWave Software .....................................................................................19
Step 3: Checking the AirWave Installation .......................................................................... 19
Step 4: Assigning an IP Address to the AirWave System ................................................. 19
Step 5: Naming the AirWave Network Administration System ........................................20
Step 6: Assigning a Host Name to AirWave ........................................................................ 20
Step 7: Changing the Default Root Password...................................................................... 20
Completing the Installation .....................................................................................................20
Configuring and Mapping Port Usage for AMP........................................................................... 21
AirWave Navigation Basics............................................................................................................ 22
Status Section...........................................................................................................................22
Navigation Section................................................................................................................... 23
Activity Section......................................................................................................................... 25
Help Links in the UI................................................................................................................... 25
Common List Settings ..............................................................................................................25
Buttons and Icons ....................................................................................................................25
Getting Started with AirWave ........................................................................................................27
Chapter 3 Configuring AMP................................................................................................................29
Before You Begin.............................................................................................................................. 29
Formatting the Top Header .............................................................................................................29
Customizing Columns in Lists .........................................................................................................30
Resetting Pagination Records........................................................................................................ 31
Using the Pagination Widget.......................................................................................................... 31
Dell PowerConnect W-AirWave |User Guide | 3
Page 4

Using Export CSV for Lists and Reports........................................................................................ 31
Defining Interactive Graph Display Preferences ........................................................................ 32
Customizing the Dashboard............................................................................................................ 32
Customized Search ..........................................................................................................................34
Setting Severe Alert Warning Behavior .......................................................................................34
Defining General AMP Server Settings ........................................................................................35
Defining AMP Network Settings.................................................................................................... 42
Creating AMP Users ........................................................................................................................43
Creating AMP User Roles ...............................................................................................................45
Configuring Timeout, Login Message, TACACS+ and RADIUS Authentication ..................... 48
Setting Up Login Configuration Options ............................................................................... 48
Configuring TACACS+ Authentication ..................................................................................49
Configuring RADIUS Authentication and Authorization .................................................... 50
Integrating a RADIUS Accounting Server............................................................................ 51
Enabling AMP to Manage Your Devices ......................................................................................52
Configuring Communication Settings for Discovered Devices ........................................ 52
Loading Device Firmware Onto AMP (optional).................................................................. 54
Overview of the Device Setup > Upload Firmware & Files Page ............................. 54
Loading Firmware Files to AMP..................................................................................... 55
Using Web Auth Bundles in AMP.................................................................................. 56
Setting Up Device Types .................................................................................................................57
Configuring Cisco WLSE and WLSE Rogue Scanning................................................................ 58
Introduction to Cisco WLSE.................................................................................................... 58
Configuring WLSE Initially in AMP ........................................................................................58
Adding an ACS Server for WLSE ...................................................................................59
Enabling Rogue Alerts for Cisco WLSE ........................................................................59
Configuring WLSE to Communicate with APs .............................................................59
Discovering Devices........................................................................................................ 59
Managing Devices ........................................................................................................... 59
Inventory Reporting .........................................................................................................60
Defining Access ...............................................................................................................60
Grouping ............................................................................................................................60
Configuring IOS APs for WDS Participation ........................................................................60
WDS Participation............................................................................................................ 60
Primary or Secondary WDS ...........................................................................................60
Configuring ACS for WDS Authentication............................................................................ 61
Configuring Cisco WLSE Rogue Scanning ........................................................................... 61
Configuring ACS Servers................................................................................................................. 62
Integrating AMP with an Existing Network Management Solution (NMS) ............................63
Auditing PCI Compliance on the Network.................................................................................... 65
Introduction to PCI Requirements .........................................................................................65
PCI Auditing in the AMP Interface ........................................................................................65
Enabling or Disabling PCI Auditing........................................................................................ 66
Deploying WMS Offload.................................................................................................................. 67
Overview of WMS Offload in AMP........................................................................................ 67
General Configuration Tasks Supporting WMS Offload in AMP...................................... 68
Additional Information Supporting WMS Offload............................................................... 68
Chapter 4 Configuring and Using Device Groups in AMP.............................................................69
AMP Groups Overview ....................................................................................................................70
Viewing All Defined Device Groups ......................................................................................71
Configuring Basic Group Settings .................................................................................................72
Adding and Configuring Group AAA Servers............................................................................... 79
4 | Dell PowerConnect W-AirWave |Version 7.3
Page 5

Configuring Group Security Settings.............................................................................................80
Configuring Group SSIDs and VLANs ...........................................................................................82
Configuring Radio Settings for Device Groups............................................................................ 86
Cisco WLC Group Configuration ....................................................................................................89
Accessing Cisco WLC Configuration ....................................................................................89
Navigating Cisco WLC Configuration....................................................................................89
Configuring WLANs for Cisco WLC Devices ....................................................................... 90
Defining and Configuring LWAPP AP Groups for Cisco Devices..................................... 92
Viewing and Creating Cisco AP Groups ...............................................................................92
Configuring Cisco Controller Settings...................................................................................93
Configuring Wireless Parameters for Cisco Controllers ................................................... 93
Configuring Cisco WLC Security Parameters and Functions ........................................... 93
Configuring Management Settings for Cisco WLC ............................................................ 94
Configuring Group PTMP Settings.................................................................................................94
Configuring Proxim Mesh Radio Settings..................................................................................... 95
Configuring Group MAC Access Control Lists............................................................................. 96
Specifying Minimum Firmware Versions for APs in a Group.................................................... 97
Comparing Device Groups .............................................................................................................. 98
Deleting a Group............................................................................................................................... 98
Changing Multiple Group Configurations .....................................................................................99
Modifying Multiple Devices.......................................................................................................... 100
Using Global Groups for Group Configuration ........................................................................... 102
Chapter 5 Discovering, Adding, and Managing Devices.............................................................105
Device Discovery Overview.......................................................................................................... 105
Discovering and Adding Devices................................................................................................. 105
SNMP/HTTP Scanning ..........................................................................................................106
Adding Networks for SNMP/HTTP Scanning............................................................ 106
Adding Credentials for Scanning................................................................................. 106
Defining a Scan Set .......................................................................................................107
Running a Scan Set........................................................................................................ 108
Enabling Cisco Discovery Protocol (CDP).......................................................................... 109
Authorizing Devices to AMP from APs/Devices > New Page ........................................109
Manually Adding Individual Devices .................................................................................. 110
Adding Devices with the Device Setup > Add Page ................................................ 110
Adding Multiple Devices from a CSV File................................................................... 112
Adding Universal Devices............................................................................................. 113
Assigning Devices to the Ignored Page .............................................................................114
Monitoring Devices........................................................................................................................ 114
Viewing Device Monitoring Statistics ................................................................................ 115
Understanding the APs/Devices > Monitor Pages for All Device Types ......................116
Monitoring Data Specific to Wireless Devices ................................................................. 116
Evaluating Radio Statistics for an AP ................................................................................. 121
Overview of the Radio Statistics Page .......................................................................122
Viewing Real-Time ARM Statistics .............................................................................122
Issues Summary section............................................................................................... 122
802.11 Radio Counters Summary .................................................................................123
Radio Statistics Interactive Graphs ............................................................................123
Recent ARM Events Log................................................................................................ 124
Detected Interfering Devices Table............................................................................ 125
Active BSSIDs Table...................................................................................................... 126
Monitoring Data for Mesh Devices ..................................................................................... 126
Monitoring Data for Wired Devices (Routers and Switches) .........................................127
Understanding the APs/Devices > Interfaces Page......................................................... 129
Dell PowerConnect W-AirWave |User Guide | 5
Page 6

Auditing Device Configuration .............................................................................................130
Using Device Folders (Optional) .......................................................................................... 130
Configuring and Managing Devices............................................................................................ 131
Moving a Device from Monitor Only to Manage Read/Write Mode.............................. 132
Configuring AP Settings ........................................................................................................132
Configuring Device Interfaces for Switches ..................................................................... 138
Individual Device Support and Firmware Upgrades ........................................................ 140
Troubleshooting a Newly Discovered Down Device................................................................ 142
Setting up Dell Spectrum Analysis in AMP................................................................................ 143
Spectrum Configurations and Prerequisites ..................................................................... 144
Setting up a Permanent Spectrum Dell AP Group ............................................................144
Configuring an Individual AP to run in Spectrum Mode ..................................................145
Configuring a Controller to use the Spectrum Profile ......................................................146
Chapter 6 Creating and Using Templates ......................................................................................147
Group Templates ............................................................................................................................147
Supported Device Templates ............................................................................................... 147
Template Variables ................................................................................................................147
Viewing and Adding Templates ...................................................................................................148
Configuring General Template Files and Variables ..................................................................151
Configuring General Templates ...........................................................................................151
IOS Configuration File Template .................................................................................. 152
Device Configuration File on APs/Devices > Audit Configuration Page ...............152
Using Template Syntax..........................................................................................................152
Using Directives to Eliminate Reporting of Configuration Mismatches ........................ 153
Ignore_and_do_not_push Command ......................................................................... 153
Push_and_exclude Command .....................................................................................153
Using Conditional Variables in Templates ......................................................................... 154
Using Substitution Variables in Templates ........................................................................154
Using AP-Specific Variables ................................................................................................155
Configuring Cisco IOS Templates ................................................................................................ 156
Applying Startup-config Files............................................................................................... 156
WDS Settings in Templates.................................................................................................. 156
SCP Required Settings in Templates .................................................................................. 157
Supporting Multiple Radio Types via a Single IOS Template ......................................... 157
Configuring Single and Dual-Radio APs via a Single IOS Template ..............................157
Configuring Cisco Catalyst Switch Templates........................................................................... 158
Configuring Symbol Controller / HP WESM Templates............................................................ 158
Configuring a Global Template..................................................................................................... 160
Chapter 7 Using RAPIDS and Rogue Classification .....................................................................163
Introduction to RAPIDS .................................................................................................................163
Viewing Overall Network Health on RAPIDS > Overview........................................................ 164
Setting Up RAPIDS .........................................................................................................................165
Basic Configuration................................................................................................................ 165
Rogue Containment Options ................................................................................................. 167
Additional Settings................................................................................................................. 168
Defining RAPIDS Rules.................................................................................................................. 168
Controller Classification with WMS Offload...................................................................... 168
Device OUI Score ................................................................................................................... 169
Rogue Device Threat Level................................................................................................... 169
Viewing and Configuring RAPIDS Rules............................................................................. 170
Deleting or Editing a Rule.............................................................................................. 171
Recommended RAPIDS Rules.............................................................................................. 172
6 | Dell PowerConnect W-AirWave |Version 7.3
Page 7

Using RAPIDS Rules with Additional AMP Functions...................................................... 172
Viewing Rogues on the RAPIDS > List Page.............................................................................. 172
Overview of the RAPIDS > Detail Page....................................................................................... 175
Viewing Ignored Rogue Devices ......................................................................................... 176
Using RAPIDS Workflow to Process Rogue Devices....................................................... 176
Score Override................................................................................................................................ 176
Using the Audit Log ........................................................................................................................177
Additional Resources..................................................................................................................... 178
Chapter 8 Performing Daily Administration in AirWave ..............................................................179
Monitoring and Supporting AMP with the System Pages....................................................... 179
Using the System > Status Page..........................................................................................180
Viewing Device Events in System > Syslog & Traps ........................................................ 181
Using the System > Event Log Page....................................................................................182
Viewing, Delivering and Responding to Triggers and Alerts ..........................................183
Viewing Triggers..................................................................................................................... 183
Creating New Triggers ..........................................................................................................183
Setting Triggers for Devices......................................................................................... 186
Setting Triggers for Interfaces and Radios................................................................ 187
Setting Triggers for Discovery ..................................................................................... 187
Setting Triggers for Users............................................................................................. 188
Setting Triggers for RADIUS Authentication Issues ................................................188
Setting Triggers for IDS Events.................................................................................... 189
Setting Triggers for AMP Health .................................................................................189
Delivering Triggered Alerts................................................................................................... 189
Viewing Alerts.........................................................................................................................190
Responding to Alerts.............................................................................................................. 191
Monitoring and Supporting WLAN Users................................................................................... 191
Overview of the Users Pages............................................................................................... 192
Monitoring WLAN Users with the Users > Connected and Users > All Pages............ 192
Supporting Guest WLAN Users With the Users > Guest Users Page ...........................195
Supporting RFID Tags With the Users > Tags Page .........................................................197
Evaluating and Diagnosing User Status and Issues................................................................. 198
Evaluating User Status with the Users > User Detail Page............................................. 198
Mobile Device Access Control in Users > User Detail and Users > Connected . 199
Classifying Dell PowerConnect W Devices in User Detail...................................... 200
Quick Links for Users on Dell Devices........................................................................ 201
Using the Deauthenticate User Feature..................................................................... 201
Viewing a User’s Association History......................................................................... 201
Evaluating User Status with the Users > Diagnostics Page ........................................... 202
Managing Mobile Devices with SOTI MobiControl and AirWave.......................................... 204
Overview of SOTI MobiControl ............................................................................................ 204
Prerequisites for Using MobiControl with AirWave ......................................................... 204
Adding a Mobile Device Management Server for MobiControl..................................... 205
Accessing MobiControl from the Users > User Detail Page........................................... 205
Monitoring and Supporting AMP with the Home Pages.......................................................... 206
Monitoring AMP with the Home > Overview Page........................................................... 206
Viewing and Updating License Information....................................................................... 208
Searching AMP with the Home > Search Page ................................................................ 210
Accessing AirWave Documentation...................................................................................211
Configuring Your Own User Information with the Home > User Info Page .................. 211
Using the System > Configuration Change Jobs Page .................................................... 212
Using the System > Firmware Upgrade Jobs Page .......................................................... 213
Using the System > Performance Page.............................................................................. 214
Supporting AMP Servers with the Master Console .................................................................218
Dell PowerConnect W-AirWave |User Guide | 7
Page 8

Using the Public Portal on Master Console....................................................................... 218
Adding a Managed AMP with the Master Console.......................................................... 219
Using Global Groups with Master Console ........................................................................ 220
Upgrading AirWave........................................................................................................................ 220
Upgrade Instructions............................................................................................................. 220
Backing Up AirWave...................................................................................................................... 221
Viewing and Downloading Backups ...................................................................................221
Running Backup on Demand ................................................................................................ 221
Restoring from a Backup....................................................................................................... 221
Using AirWave Failover for Backup ............................................................................................222
Navigation Section of AMP Failover ...................................................................................222
Adding Watched AMP Stations........................................................................................... 222
Logging out of AirWave................................................................................................................. 223
Chapter 9 Creating, Running, and Emailing Reports ....................................................................225
Overview of AMP Reports............................................................................................................. 225
Reports > Definitions Page Overview .................................................................................225
Reports > Generated Page Overview ................................................................................. 227
Using Daily Reports........................................................................................................................ 228
Viewing Generated Reports ................................................................................................. 228
Using Custom Reports ...........................................................................................................229
Using the Dell License Report.............................................................................................. 230
Using the Capacity Planning Report ................................................................................... 230
Using the Configuration Audit Report .................................................................................232
Using the Device Summary Report ..................................................................................... 233
Using the Device Uptime Report..........................................................................................235
Using the IDS Events Report ................................................................................................ 236
Using the Inventory Report................................................................................................... 237
Using the Memory and CPU Utilization Report.................................................................. 239
Using the Network Usage Report........................................................................................ 239
Using the New Rogue Devices Report ............................................................................... 240
Using the New Users Report................................................................................................ 243
Using the PCI Compliance Report ....................................................................................... 243
Using the Port Usage Report................................................................................................ 244
Using the RADIUS Authentication Issues Report .............................................................244
Using the RF Health Report................................................................................................... 245
Using the Rogue Containment Audit Report ......................................................................247
Using the User Session Report ............................................................................................247
Defining Reports ............................................................................................................................. 249
Emailing and Exporting Reports ................................................................................................... 252
Emailing Reports in General Email Applications ............................................................... 252
Emailing Reports to Smarthost............................................................................................. 252
Exporting Reports to XML or CSV........................................................................................ 252
Transferring Reports Using FTP........................................................................................... 252
Chapter 10 Using the AMP Helpdesk................................................................................................253
Helpdesk Overview ........................................................................................................................253
Enabling Helpdesk.......................................................................................................................... 253
Monitoring Incidents with Helpdesk ........................................................................................... 253
Creating a New Incident with Helpdesk..................................................................................... 255
Creating New Snapshots or Incident Relationships................................................................. 256
Using the Helpdesk Tab with an Existing Remedy Server....................................................... 256
Chapter 11 Using VisualRF..................................................................................................................259
8 | Dell PowerConnect W-AirWave |Version 7.3
Page 9

Features ...........................................................................................................................................260
Useful Terms ...................................................................................................................................260
Starting VisualRF ............................................................................................................................261
Basic QuickView Navigation ........................................................................................................ 261
Network View Navigation..................................................................................................... 262
Overlays ........................................................................................................................... 262
Display Menu .................................................................................................................. 263
Edit Menu......................................................................................................................... 263
Using the Settings in the VisualRF > Setup Page...................................................................... 265
VisualRF Resource Utilization ..............................................................................................267
Configuring QuickView Personal Preferences.......................................................................... 268
Increasing Location Accuracy..................................................................................................... 269
Adding Exterior Walls............................................................................................................ 270
Location Training for Stationary Devices........................................................................... 270
Adding Client Surveys............................................................................................................ 271
Adding Location Probability Regions .................................................................................. 272
Adding an IDF.......................................................................................................................... 273
Viewing Port Status on Deployed Switches ......................................................................274
Fine-Tuning Location Service in VisualRF > Setup ........................................................... 274
Configuring Infrastructure ............................................................................................275
Deploying APs for Client Location Accuracy ............................................................275
Using QuickView to Assess RF Environments ........................................................................... 276
Viewing a Wireless User's RF Environment....................................................................... 276
Tracking Location History............................................................................................. 277
Checking Signal Strength to Client Location ............................................................. 278
Viewing an AP’s Wireless RF Environment........................................................................ 278
Viewing a Floor Plan’s RF Environment ..............................................................................279
Viewing a Network, Campus, Building’s RF Environment ............................................... 280
Viewing Campuses, Buildings, or Floors from a Tree View ............................................ 280
Planning and Provisioning ............................................................................................................280
Creating a New Campus ....................................................................................................... 281
Building Creation.................................................................................................................... 282
Importing a Floor Plan............................................................................................................ 283
Editing a Floor Plan Image ....................................................................................................283
Cropping the Floor Plan Image..................................................................................... 284
Sizing a Non-CAD Floor Plan........................................................................................ 284
Removing Color from a Floor Plan Image................................................................... 285
Assigning Campus, Building and Floor Numbers...................................................... 285
Assigning Optional Planner, Owner, or Installer Information for the Floor Plan .285
Controlling the Layers in the Uploaded Floor Plan (CAD only) ...............................285
Error Checking of CAD Images ....................................................................................285
Last Steps in Editing an Uploaded Image................................................................... 286
Provisioning Existing Access Points onto the Floor Plan ................................................286
Automatically Provisioning APs onto a Floor Plan ........................................................... 287
Tweaking a Planning Region ................................................................................................288
Printing a Bill of Materials Report .......................................................................................289
Importing and Exporting in VisualRF ...........................................................................................290
Exporting a campus................................................................................................................ 290
Importing from CAD................................................................................................................ 290
Batch Importing CAD Files.................................................................................................... 290
Requirements.................................................................................................................. 290
Pre Processing Steps .................................................................................................... 291
Upload Processing Steps.............................................................................................. 291
Post Processing Steps ..................................................................................................291
Sample Upload Instruction XML File........................................................................... 291
Common Importation Problems ...................................................................................292
Dell PowerConnect W-AirWave |User Guide | 9
Page 10

Importing from a Dell PowerConnect W-Series Controller............................................. 292
Pre-Conversion Checklist .............................................................................................292
Process on Controller.................................................................................................... 292
Process on AMP............................................................................................................. 292
VisualRF Location APIs.................................................................................................................. 292
Sample Device Location Response..................................................................................... 293
Sample Site Inventory Response.........................................................................................293
Appendix A Setting Up Dell PowerConnect W-Instant in AirWave..............................................295
Overview of Dell PowerConnect W-Instant............................................................................... 295
Using Dell PowerConnect W-Instant with AMP .......................................................................295
Workflow of the Dell PowerConnect W-Instant and AMP Integration Process .................296
Setting up Dell PowerConnect W-Instant Hardware .......................................................296
Required Personnel................................................................................................................ 296
Creating your Organization String .......................................................................................296
The Shared Secret Key ......................................................................................................... 297
Entering the Organization String and AirWave Information into the IAP ..................... 297
Receiving the Virtual Controller as a New Device in AMP .............................................298
Verifying the Shared Secret and Adding the Device ....................................................... 298
Remaining Manual Admin Tasks in AMP........................................................................... 299
AMP Pages with Instant-Specific Features............................................................................... 299
Other Available Features............................................................................................................... 300
Firmware Image Management............................................................................................. 300
Intrusion Detection System ..................................................................................................300
Appendix B Installing AirWave on VMware ESX 4.1.......................................................................301
Creating a New Virtual Machine to Run AirWave .................................................................... 301
Installing AirWave on the Virtual Machine................................................................................ 301
AirWave Post-Installation Issues on VMware .......................................................................... 302
Index .......................................................................................................................................................................303
10 | Dell PowerConnect W-AirWave |Version 7.3
Page 11
Preface
This preface provides an overview of this user guide and contact information for Dell in the following sections:
“Document Organization” on page11
“Note, Caution, and Warning Icons” on page12
“Contacting Support” on page12
Document Organization
This user guide includes instructions and examples of the graphical user interface (UI) for installation,
configuration, and daily operation of the Dell PowerConnect W-AirWave. This includes wide deployment of
wireless access points (APs), device administration, rogue detection and classification, wireless controller devices,
security, reports, and additional features of AirWave.
Table 1 Document Organization and Purposes
Chapter Description
Chapter 1, “Introduction” Introduces and presents AirWave, its components, and general network functions.
Chapter 2, “Installing and Getting
Started in AirWave”
Chapter 3, “Configuring AMP” Describes the primary and required configurations for startup and launch of AirWave,
Chapter 4, “Configuring and Using
Device Groups in AMP”
Chapter 5, “Discovering, Adding,
and Managing Devices”
Chapter 6, “Creating and Using
Templates”
Chapter 7, “Using RAPIDS and
Rogue Classification”
Chapter 8, “Performing Daily
Administration in AirWave”
Chapter 9, “Creating, Running, and
Emailing Reports”
Chapter 10, “Using the AMP
Helpdesk”
Describes system and network requirements, Linux OS installation, and AirWave
installation.
with frequently used optional configurations.
Describes configuration and deployment for group device profiles.
Describes how to discover and manage devices on the network.
Describes and illustrates the use of templates in group and global device configuration.
Describes RAPIDS module of AirWave, and enhanced rogue classification supported in
AirWave.
Describes common daily operations and tools in AirWave, to include general user
administration, the use of triggers and alerts, network monitoring, and backups.
Describes AirWave reports, scheduling and generation options, and distribution of
reports from AirWave.
Describes how to use the AirWave Helpdesk UI and related functions.
Chapter 11, “Using VisualRF” Describes how to use VisualRF.
Appendix A, “Setting Up Dell
PowerConnect W-Instant in
AirWave” on page295
Appendix B, “Installing AirWave on
VMware ESX 4.1” on page301
Index Provides extensive citation of and links to document topics, with emphasis on the
Dell PowerConnect W-AirWave |User Guide Preface | 11
Ddescribes the Dell PowerConnect W-Instant access point and Virtual Controller system,
and how to integrate this system with AMP.
Provides instructions for an alternative installation option on VMware ESX for
AirWave UI and tasks relating to AirWave installation and operation.
Page 12

Note, Caution, and Warning Icons
This document uses the following note, caution, and warning icons to emphasize advisories for certain actions,
configurations, or concepts:
NOTE: Indicates helpful suggestions, pertinent information, and important things to remember.
CAUTION: Indicates a risk of damage to your hardware or loss of data.
WARNING: Indicates a risk of personal injury or death.
Contacting Support
Table 2 Web Support
Web Support
Main Website dell.com
Support Website support.dell.com
Documentation Website support.dell.com/manuals
12 | Preface Dell PowerConnect W-AirWave |Version 7.3
Page 13
Chapter 1
Introduction
Thank you for choosing Dell PowerConnect W-AirWave. AirWave makes it easy and efficient to manage your
wireless network by combining industry-leading functionality with an intuitive user interface, enabling network
administrators and helpdesk staff to support and control even the largest wireless networks in the world.
This User Guide provides instructions for the installation, configuration, and operation of AirWave. This chapter
includes the following topics:
“AirWave—A Unified Wireless Network Command Center” on page13
“Integrating AirWave into the Network and Organizational Hierarchy” on page15
“Supported Browsers” on page16
If you have any questions or comments, please contact Dell support at support.dell.com.
AirWave—A Unified Wireless Network Command Center
Dell PowerConnect W-AirWave is the only network management software that offers you a single intelligent
console from which to monitor, analyze, and configure wireless networks in automatic fashion. Whether your
wireless network is simple or a large, complex, multi-vendor installation, AirWave manages it all.
AirWave supports hardware from leading wireless vendors including Dell PowerConnect W-Series, Avaya, Cisco
(Aironet and WLC), Enterasys, Juniper Networks, LANCOM Systems, Meru, Nortel, ProCurve by HP, Proxim,
Symbol, Trapeze, Tropos, and many others.
The components of the AirWave are listed here, and detailed below:
The AirWave Management Platform (AMP) wireless network management software, including the ArubaOS
Configuration feature that supports global and group configuration of Dell PowerConnect W-Series devices,
as well as the VisualRF location and RF mapping software module and the RAPIDS rogue access point
detection software module
Master Console and Failover tabs
NOTE: Dell PowerConnect W-Series AirWave Wireless Management Suite (AWMS), AirWave, and AirWave Management
Platform (AMP) refer to the same product set and are used interchangeably.
AirWave Management Platform
The AirWave Management Platform (AMP) is the centerpiece of AirWave, offering the following functions and
benefits:
Core network management functionality:
Network discovery
Configuration of APs & controllers
Automated compliance audits
Firmware distribution
Monitoring of every device and user connected to the network
Real-time and historical trend reports
Granular administrative access
Dell PowerConnect W-AirWave |User Guide Introduction | 13
Page 14

Role-based (for example, Administrator contrasted with Help Desk)
Network segment (for example, "Retail Store" network contrasted with "Corporate HQ" network)
Flexible device support
Thin, thick, mesh network architecture
Multi-vendor support
Current and legacy hardware support
Dell PowerConnect W Configuration
Dell PowerConnect W-AirWave supports global and group-level configuration of ArubaOS (AOS), the operating
system, software suite, and application engine that operates Dell PowerConnect W mobility and centralizes
control over the entire mobile environment. For a complete description of AOS, refer to the Dell PowerConnect
W-Series ArubaOS User Guide at support.dell.com/manuals.
AirWave consolidates ArubaOS configuration and pushes global Dell PowerConnect W configurations from
within AirWave.
Two pages in AirWave support Dell PowerConnect W Configuration:
Device Setup > Dell PowerConnect W Configuration for global Dell PowerConnect W Configuration
Groups > Dell PowerConnect W Config for group-level Dell PowerConnect W Configuration
For additional information that includes a comprehensive inventory of all pages and settings that support Dell
PowerConnect W Configuration, refer to the Dell PowerConnect W-AirWave Configuration Guide at
support.dell.com/manuals.
VisualRF
VisualRF is a powerful tool for monitoring and managing radio frequency (RF) dynamics within your wireless
network, to include the following functions and benefits:
Accurate location information for all wireless users and devices
Up-to-date heat maps and channel maps for RF diagnostics
Adjusts for building materials.
Supports multiple antenna types.
Floor plan, building, and campus views
Visual display of errors and alerts
Easy import of existing floor plans and building maps
Planning of new floor plans and AP placement recommendations
RAPIDS
RAPIDS is a powerful and easy-to-use tool for monitoring and managing security on your wireless network, to
include the following features and benefits:
Automatic detection of unauthorized wireless devices
Rogue device classification that supports multiple methods of rogue detection
Wireless detection:
Uses authorized wireless APs to report other devices within range.
Calculates and displays rogue location on VisualRF map.
Wired network detection:
Discovers rogue APs located beyond the range of authorized APs/sensors.
14 |Introduction Dell PowerConnect W-AirWave |Version 7.3
Page 15
Queries routers and switches.
Ranks devices according to the likelihood they are rogues.
Multiple tests to eliminate false positive results.
Provides rogue discovery that identifies the switch and port to which a rogue device is connected.
Master Console and Failover
The Dell PowerConnect W-AirWave Master Console and Failover tools enable network-wide information in
easy-to-understand presentation, to entail operational information and high-availability for failover scenarios.
The benefits of these tools include the following:
Provides network-wide visibility, even when the WLAN grows to 50,000+ devices
Executive Portal allows executives to view high-level usage and performance data
Aggregated alerts
Failover
Many-to-one failover
One-to-one failover
The Master Console and Failover servers can be configured with a Device Down trigger that generates an alert if
communication is lost. In addition to generating an alert, the Master Console or Failover server can also send
email or NMS notifications about the event.
Integrating AirWave into the Network and Organizational Hierarchy
Dell PowerConnect W-AirWave generally resides in the NOC and communicates with various components of
your WLAN infrastructure. In basic deployments, AirWave communicates solely with indoor wireless access
points (and WLAN controllers over the wired network. In more complex deployments, AirWave seamlessly
integrates and communicates with authentication servers, accounting servers, TACACS+ servers, routers,
switches, network management servers, wireless IDS solutions, helpdesk systems, indoor wireless access points,
mesh devices. AirWave has the flexibility to manage devices on local networks, remote networks, and networks
using Network Address Translation (NAT). AirWave communicates over-the-air or over-the-wire using a variety
of protocols.
The power, performance, and usability of the AirWave solution become more apparent when considering the
diverse components within a WLAN. Table 3 itemizes such network components, as an example.
Table 3 Components of a WLAN
Component Description
Autonomous AP Standalone device which performs radio and authentication functions
Thin AP Radio-only device coupled with WLAN controller to perform authentication
WLAN controller Used in conjunction with thin APs to coordinate authentication and roaming
NMS Network Management Systems and Event Correlation (OpenView, Tivoli, and so forth)
RADIUS Authentication RADIUS authentication servers (Funk, FreeRADIUS, ACS, or IAS)
RADIUS Accounting AirWave itself serves as a RADIUS accounting client
Wireless Gateways Provide HTML redirect and/or wireless VPNs
TACACS+ Used to authenticate AirWave administrative users
Routers/Switches Provide AirWave with data for user information and AP and Rogue discovery
Help Desk Systems Remedy EPICOR
Rogue APs Unauthorized APs not registered in the AirWave database of managed APs
Dell PowerConnect W-AirWave |User Guide Introduction | 15
Page 16

The flexibility of AirWave enables it to integrate seamlessly into your business hierarchy as well as your network
topology. AirWave facilitates various administrative roles to match each individual user's role and responsibility:
A Help Desk user may be given read-only access to monitoring data without being permitted to make
configuration changes.
A U.S.-based network engineer may be given read-write access to manage device configurations in North
America, but not to control devices in the rest of the world.
A security auditor may be given read-write access to configure security policies across the entire WLAN.
NOC personnel may be given read-only access to monitoring all devices from the Master Console.
Supported Browsers
Windows (XP, Vista, Windows 7)
Internet Explorer 7/8/9
Firefox 3.x
Google Chrome 9.x (stable)
Mac (OS X, 10.5, 10.6)
Safari 4.x and higher,
Firefox 3.x
Google Chrome 9.x
16 |Introduction Dell PowerConnect W-AirWave |Version 7.3
Page 17

Chapter 2
Installing and Getting Started in AirWave
This chapter contains information and procedures for installing and launching AirWave, and includes the
following topics:
“AirWave Hardware Requirements and Installation Media” on page17
“Installing Linux CentOS 5 (Phase 1)” on page17
“Installing AirWave Software (Phase 2)” on page18
“Configuring and Mapping Port Usage for AMP” on page21
“AirWave Navigation Basics” on page22
“Getting Started with AirWave” on page27
NOTE: AirWave does not support downgrading to older versions of AMP. Significant data could be lost or compromised in such a
downgrade. In unusual circumstances requiring that you return to an earlier version of AMP, we recommend you perform a fresh
installation of the earlier AMP version, and then restore data from a pre-upgrade backup.
AirWave Hardware Requirements and Installation Media
The AirWave installation disk image includes all software (including the Linux OS) required to complete the
installation of AirWave. AirWave supports any hardware that is Red Hat Enterprise Linux 5 certified. By default,
all installs are based on a 64-bit operating system.
AirWave hardware requirements vary by version and managed devices. As additional features and devices are
added to AirWave, increased hardware resources become necessary. For the most recent hardware requirements,
refer to the Dell PowerConnect W-AirWave Server Sizing Guide at support.dell.com/manuals.
AirWave is intended to operate as a soft appliance. Other applications should not run on the same installation.
Additionally, local shell users can access data on AirWave, so it is important to restrict access to the shell only to
authorized users.
You can create sudo users in place of root for companies that don't allow root logins.
Installing Linux CentOS 5 (Phase 1)
Perform the following steps to install the Linux CentOS 5 operating system. The Linux installation is a
prerequisite to installing AirWave on the network management system.
CAUTION: This procedure erases the hard drive(s) on the server.
1. Insert the AirWave installation CD-ROM into the drive and boot the server.
2. If this is a new installation of the AirWave software, type install and press Enter.
To configure the partitions manually, type expert and press Enter.
The following message appears on the screen:
Welcome to AMP Installer Phase I
- To install a new AMP, type install <ENTER>.
WARNING: This will ERASE all data on your hard drive.
Dell PowerConnect W-AirWave | User Guide Installing and Getting Started in AirWave | 17
Page 18

- To install AMP and manually configure hard drive settings, type expert <ENTER>.
boot:
3. Allow the installation process to continue. Installing the CentOS software (Phase I) takes 10 to 20 minutes to
complete. This process formats the hard drive and launches Anaconda to install all necessary packages.
Anaconda gauges the progress of the installation.
Upon completion, the system will prompt you to eject the installation CD and reboot the system.
4. Remove the CD from the drive and store in a safe location.
Installing AirWave Software (Phase 2)
Getting Started
After the reboot, the GRUB screen appears.
1. Press Enter or wait six seconds, and the system automatically loads the kernel.
2. When the kernel is loaded, log into the server using the following credentials:
login = root
password = admin
3. Start the AirWave software installation script by executing the ./amp-install command.
./amp-install at the command prompt and press Enter to execute the script.
Type
Step 1: Configuring Date and Time, Checking for Prior Installations
Date and Time
The following message appears, and this step ensures the proper date and time are set on the server.
------------------------ Date and Time Configuration -----------------Current Time: Fri Nov 21 09:18:12 PST 2008
1) Change Date and Time
2) Change Time Zone
0) Finish
Ensure that you enter the accurate date and time during this process. Errors will arise later in the installation if
the specified date varies significantly from the actual date, especially if the specified date is in the future and it is
fixed later. It is recommended to configure ntpd to gradually adjust your clock to the correct time.
1. Select 1 to set the date and select 2 to set the time zone. Press Enter after each configuration to return to the
message menu above.
CAUTION: Changing these settings after the installation can cause data loss, especially for time-series data such as bandwidth
and user count graphs. Avoid delayed configuration.
2. Press 0 to complete the configuration of date and time information, and to continue to the next step.
Previous AirWave Installations
The following message appears after date and time are set:
Welcome to AMP Installer Phase 2
STEP 1: Checking for previous AMP installations
18 | Installing and Getting Started in AirWave Dell PowerConnect W-AirWave |Version 7.3
Page 19

If a previous version of AirWave software is not discovered, the installation program automatically proceeds to
“Step 2: Installing AirWave Software” on page19. If a previous version of the software is discovered, the
following message appears on the screen:
The installation program discovered a previous version of the software. Would you like to
reinstall AMP? This will erase AMP's database. Reinstall (y/n)?
Type y and press Enter to proceed.
CAUTION: This action erases the current database, including all historical information. To ensure that the AMP database is
backed up prior to reinstallation, answer `n` at the prompt above and contact your Value Added Reseller or directly contact Dell
support at support.dell.com.
Step 2: Installing AirWave Software
The following message appears while AirWave software is transferred and compiled.
STEP 2: Installing AMP software
This will take a few minutes.
Press Alt-F9 to see detailed messages.
Press Alt-F1 return to this screen.
This step requires no user input, but you can follow the instructions to monitor its progress and switch back to
the installation screen.
Step 3: Checking the AirWave Installation
After the AirWave software installation is complete, the following message appears:
STEP 3: Checking AMP installation
Database is up.
AMP is running version: (version number)
This step requires no user input. Proceed to the next step as prompted to do so.
Step 4: Assigning an IP Address to the AirWave System
While the AirWave primary network interface accepts a DHCP address initially during installation, AirWave does
not function when launched unless a static IP is assigned. Complete these tasks to assign the static IP address. The
following message appears:
STEP 4: Assigning AMP's address
AMP must be configured with a static IP.
--------------- Primary Network Interface Configuration -------------
1) IP Address : xxx.xxx.xxx.xxx
2) Netmask : xxx.xxx.xxx.xxx
3) Gateway : xxx.xxx.xxx.xxx
4) Primary DNS : xxx.xxx.xxx.xxx
5) Secondary DNS: xxx.xxx.xxx.xxx
9) Commit Changes
0) Exit (discard changes)
If you want to configure a second network interface, please
use AMP's web interface, AMP Setup --> Network Tab
1. Enter the network information.
NOTE: The Secondary DNS setting is an optional field.
2. Commit the changes by typing 9 and pressing Enter.
To discard the changes, type 0 and press Enter.
Dell PowerConnect W-AirWave | User Guide Installing and Getting Started in AirWave | 19
Page 20

Step 5: Naming the AirWave Network Administration System
Upon completion of the previous step, the following message appears.
STEP 5: Naming AMP
AMP name is currently set to: New AMP
Please enter a name for your AMP:
At the prompt, enter a name for your AirWave server and press Enter.
Step 6: Assigning a Host Name to AirWave
Upon completion of the previous step, the following message appears on the screen.
STEP 6: Assigning AMP's hostname
Does AMP have a valid DNS name on your network (y/n)?
1. If AirWave does not have a valid host name on the network, enter n at the prompt. The following appears:
Generating SSL certificate for < IP Address >
2. If AirWave does have a valid host name on the network, enter y at the prompt. The following appears:
Enter AMP's DNS name:
3. Type the AirWave DNS name and press Enter. The following message appears:
Generating SSL certificate for < IP Address >
Proceed to the next step as the system prompts you.
Step 7: Changing the Default Root Password
Upon completion of the prior step, the following message appears.
STEP 7: Changing default root password.
You will now change the password for the 'root' shell user.
Changing password for user root.
New Password:
Enter the new root password and press Enter. The Linux root password is similar to a Windows administrator
password. The root user is a super user who has full access to all commands and directories on the computer.
This password should be kept as secure as possible because it allows full access to the machine. This password is
not often needed on a day-to-day basis, but is required to perform AirWave upgrades and advanced
troubleshooting. If you lose this password, contact Dell support at support.dell.com for resetting instructions.
Completing the Installation
Upon completion of all previous steps, the following message appears.
CONGRATULATIONS! AMP is configured properly.
To access AMP web console, browse to https://<IP Address>
Login with the following credentials:
Username: admin
Password: admin
To view the Phase 1 installation log file, type cat /root/install.log.
To view the Phase 2 installation log file, type cat /tmp/amp-install.log.
To access the AirWave UI, enter the AirWave IP address in the address bar of any browser. The AirWave UI
then prompts for your license key. If you are entering a dedicated Master Console or AirWave Failover
license, refer to “Supporting AMP Servers with the Master Console” on page218 for additional information.
20 | Installing and Getting Started in AirWave Dell PowerConnect W-AirWave |Version 7.3
Page 21

Configuring and Mapping Port Usage for AMP
The following diagram itemizes the communication protocols and ports necessary for AirWave to communicate
with wireless LAN infrastructure devices, including access points (APs), controllers, routers, switches, and
RADIUS servers. Assign or adjust port usage on the network administration system as required to support these
components.
Table 4 AirWave Protocol and Port Chart
Port Ty pe Protocol Description Direction Device Type
21 TCP FTP Firmware distribution > APs or controllers
22 TCP SSH Configure devices > APs or controllers
22 TCP SSH Configure AMP from CLI < Laptop or workstation
22 TCP VTUN Support connection (optional) > Support home office
22 TCP SCP Transfer configuration files or FW < APs or controllers
23 TCP Telnet Configure devices > APs or controllers
23 TCP VTUN Support connection (Optional) > Support home office
25 TCP SMTP Support email (optional) > Support email server
49 UDP TACACS AMP Administrative Authentication > Cisco TACACS+
53 UDP DNS DNS lookup from AMP > DNS Server
69 UDP TFTP Transfer configuration files or firmware < APs or controllers
80 TCP HTTP Configure devices > Legacy APs
80 TCP VTUN Support connection (optional) > Support home office
161 UDP SNMP Get and Set operations > APs or controllers
162 UDP SNMP Traps from devices < APs or controllers
162 UDP SNMP Traps from AMP > NMS
443 TCP HTTPS Web management < Laptop or workstation
443 TCP HTTPS WLSE polling > WLSE
443 TCP VTUN Support connection (optional) > Support home office
1701 TCP HTTPS AP and rogue discovery > WLSE
1741 TCP HTTP WLSE polling > WLSE
1813 UDP RADIUS Retrieve client authentication info < Accounting Server
1813 UDP RADIUS Retrieve client authentication info < APs or controllers
1813 UDP RADIUS Outbound from AMP to a RADIUS server
for AMP admin authentication
> RADIUS server
2002 TCP HTTPS Retrieve client authentication info > ACS
5050 UDP RTLS Real Time Location Feed < Dell PowerConnect W thin APs
8211 UDP PAPI Real Time Feed < > WLAN switches
ICMP Ping Probe > APs or controllers
Dell PowerConnect W-AirWave | User Guide Installing and Getting Started in AirWave | 21
Page 22
AirWave Navigation Basics
Every AirWave page contains three basic sections of the page:
Status Section
Navigation Section
Activity Section
AirWave pages also contain Help links with UI-specific help information and certain standard buttons.
Status Section
The Status section is a snapshot view of overall WLAN performance and provides direct links for immediate
access to key system components. AirWave includes the ability to customize the contents of the Status section
from the Home > User Info page, to include support for both wireless and wired network components. Refer to
“Configuring Your Own User Information with the Home > User Info Page” on page211.
The table below describes these elements in further detail.
Table 5 Status Section Components of the AMP UI
Field Description
New Devices The number of wireless APs or wireless LAN controllers that have been discovered by AMP but not yet
Up The number of managed authorized devices that are currently responding to AMP requests. When selected,
Down The number of managed, authorized devices that are not currently responding to AMP SNMP requests.
Mismatched The total number of Mismatched devices. A device is considered mismatched when the desired
Rogue The number of devices that have been classified by the RAPIDS rules engine above the threshold defined on
Users The number of wireless users currently associated to the wireless network via all the APs managed by AMP.
Alerts Displays the number of non-acknowledged AMP alerts generated by user-configured triggers. When
Severe Alerts
(conditional)
Device Types to
Include in Header
Stats
managed by network administrators. When selected, AMP directs you to a page that displays a detailed list
of devices awaiting authorization.
AMP shows a detailed list of all Up devices.
When selected, AMP shows a detailed list of all Down devices.
configuration in AMP does not match the actual device configuration read from the device.
the Home > User Info page.
When selected, AMP shows a list of users that are associated.
selected, AMP shows a detailed list of active alerts.
When triggers are given a severity of Critical, they generate Severe Alerts. When a Severe Alert exists, a
new component appears at the right of the Status field in bold red font. Only users configured on the Home >
User Info page to be enabled to view critical alerts can see Severe Alerts. The functionality of Severe Alerts
is the same as that described above for Alerts. Unlike Alerts, the Severe Alerts section is hidden if there are
no Severe Alerts.
You can support statistics for any combination of the following device types:
Autonomous APs
Controllers
Routers/Switches
Thin APs
Universal Devices
Refer to “Configuring Your Own User Information with the Home > User Info Page” on page211.
Search Search performs partial string searches on a large number of fields including the notes, version, secondary
version, radio serial number, device serial number, LAN MAC, radio MAC and apparent IP of all the APs as
well as the client MAC, VPN user, LAN IP, VPN IP fields.
22 | Installing and Getting Started in AirWave Dell PowerConnect W-AirWave |Version 7.3
Page 23
Navigation Section
The Navigation Section displays tabs for all main UI pages within AirWave. The top bar is a static navigation bar
containing tabs for the main components of AirWave, while the lower bar is context-sensitive and displays the
subtabs for the highlighted tab.
Table 6 Components and Subtabs of AirWave Navigation
Main Tab Description Subtabs
Home The Home tab provides basic AirWave information including system
name, host name, IP address, current time, running time, and software
version.
The Home page also provides a central point for network status
information and monitoring tools, giving graphical display of network
activity, and links to many of the most frequent tools in AirWave. For
additional information, refer to “Monitoring and Supporting AMP with the
Home Pages” on page206.
Helpdesk The Helpdesk pages provide an interface for support and diagnostic tools.
For additional information refer to Chapter 10, “Using the AMP Helpdesk”
on page253.
Groups The Groups pages provide information on the logical "groups" of devices
that have been established for efficient monitoring and configuration. For
additional information, see Chapter 4, “Configuring and Using Device
Groups in AMP” on page69.
NOTE: Some of the focused subtabs will not appear for all groups.
Focused subtabs are visible based on the device type field on the Groups
> Basic page. This subtab is the first page to appear when adding or
editing groups.
NOTE: When individual device configurations are specified, device-level
settings override the Group-level settings to which a device belongs.
Overview
Search
Documentation
License
User Info
Incidents
Setup
List
Focused Subtabs
Monitor
Basic
Templates
Security
SSIDs
AAA Servers
Radio
Dell PowerConnect W
Config
Cisco WLC Config
PTMP
Proxim Mesh
MAC ACL
Firmware
Compare
APs/Devices The APs/Devices pages provide detailed information about all authorized
APs and wireless LAN switches or controllers on the network, including
all configuration and current monitoring data.
These pages interact with several additional pages in AirWave. Refer to
Chapter 5, “Discovering, Adding, and Managing Devices” on page105.
NOTE: When specified, device-level settings override the default Grouplevel settings.
Users The Users pages provide detailed information about all client devices and
users currently associated to the WLAN. For additional information, refer
to “Monitoring and Supporting WLAN Users” on page191.
Dell PowerConnect W-AirWave | User Guide Installing and Getting Started in AirWave | 23
List
New
Up
Down
Mismatched
Ignored
Focused Subtabs
Monitor
Manage
Interfaces
Audit
Compliance
Containment Status
Connected
All
Guest Users
User Detail
Diagnostics
Tags
Page 24
Table 6 Components and Subtabs of AirWave Navigation (Continued)
Main Tab Description Subtabs
Reports The Reports pages list all the standard and custom reports generated by
AMP. For additional information, refer to Chapter 9, “Creating, Running,
and Emailing Reports” on page225.
System The System page provides information about AirWave operation and
administration, including overall system status, the job scheduler, trigger/
alert administration, and so forth.
For additional information, refer to “Monitoring and Supporting AMP with
the System Pages” on page179.
Device Setup The Device Setup pages provide the ability to add, configure, and monitor
devices, to include setting AP discovery parameters, performing firmware
management, defining VLANs, and so forth. For additional information,
refer to “Enabling AMP to Manage Your Devices” on page52.
AMP Setup The AMP Setup pages provide all information relating to the configuration
of AirWave itself and its connection to your network. This page entails
several processes, configurations, or tools in AMP. For additional
information, start with Chapter 3, “Configuring AMP” on page29.
NOTE: The AMP Setup pages may not be visible, depending on the role of
the logged-in user set in AMP.
Generated
Definition
Detail
Status
Syslog & Traps
Event Log
Triggers
Alerts
Backups
Configuration Change Jobs
Firmware Upgrade Jobs
Performance
Discover
Add
Communication
Dell PowerConnect W
Configuration (if global Dell
PowerConnect W
Configuration is enabled)
Upload Firmware & Files
General
Network
Users
Roles
Guest Users
Authentication
MDM Server
Device Type Setup
WLSE
ACS
NMS
RADIUS Accounting
PCI Compliance
RAPIDS The RAPIDS pages provide all information relating to rogue access
points, including methods of discovery and lists of discovered and
possible rogues. For additional information, refer to Chapter 7, “Using
RAPIDS and Rogue Classification” on page163.
NOTE: The RAPIDS pages may not be visible to the logged-in user,
depending on their role set in AMP.
VisualRF VisualRF pages provide graphical access to floor plans, client location,
and RF visualization for floors, buildings, and campuses that host your
network. Refer to Chapter 11, “Using VisualRF” on page259.
Overview
List
IDS Events
Setup
Rules
Score Override
Audit Log
Floor Plans
Setup
Import
Audit Log
NOTE: The AMP Setup tab varies with user role. The RAPIDS and VisualRF tabs appear based on the license entered on the Home
> License page, and might not be visible on your AMP view.
24 | Installing and Getting Started in AirWave Dell PowerConnect W-AirWave |Version 7.3
Page 25
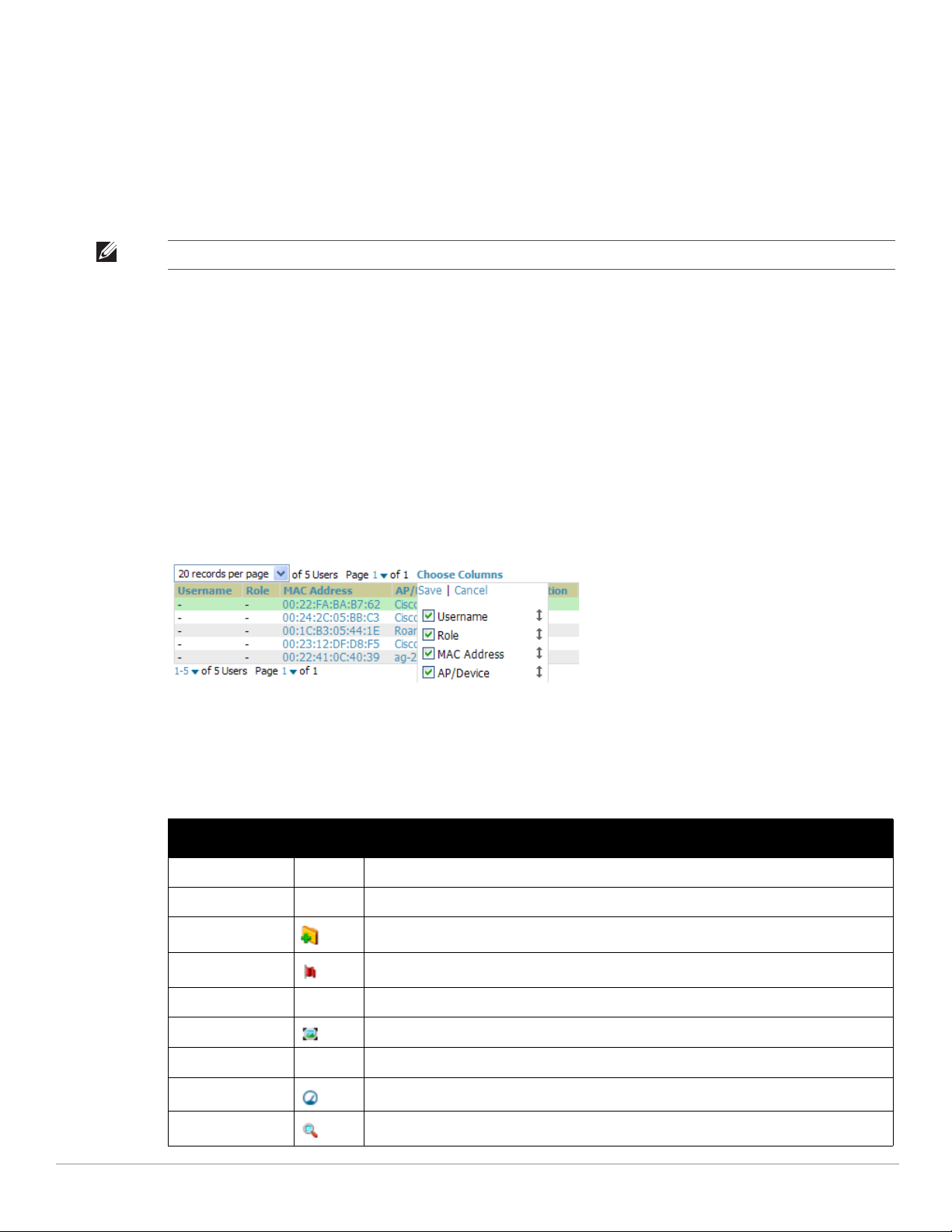
Activity Section
The Activity section displays all detailed configuration and monitoring information, and is where you implement
changes.
Help Links in the UI
The Help link is available on every page within AirWave. When selected, this launches the Dell PowerConnect W
AirWave User Guide PDF with information describing the AirWave page that is currently displayed.
NOTE: Adobe Reader must be installed to view the settings and default values in the PDF help file.
Common List Settings
All of the lists in AirWave have some common options. All lists are paginated with a configurable number of
items per page. Selecting the Records Per Page dropdown menu (which usually looks like a range such as 1-20 on
the upper left hand side of a list table) enables you select or enter the number of rows that appear at a time in the
list. The next down arrow displays a dropdown menu that allows you to select the exact page you would like to
view, as shown in Figure 1.
The Choose Columns option, illustrated on Figure 1, allows you to configure the columns that are presented in
the list and the order in which they are presented. To disable a column, clear its checkbox. To reorder the
columns, drag a row to the appropriate new position. When you are satisfied with the enabled columns and their
order, select Save at the top of the columns list.
Figure 1 Common List Settings Choose Columns Illustration
These settings are user specific. To reset them, select Reset List Preferences on Home > User Info.
Buttons and Icons
Standard buttons and icons are used throughout AirWave as follows:
Table 7 Standard Buttons and Icons of the AMP User Page
Function ImageaDescription
Acknowledge Acknowledges and clears an AMP alert.
Add Adds the object to both AMP's database and the onscreen display list.
Add Folder Adds a new folder to hierarchically organize APs.
Alert Indicates an alert.
Apply Applies all "saved" configuration changes to devices on the WLAN.
Attach Attaches a snapshot of an AMP screen to a Helpdesk incident.
Audit Reads device configuration, compare to desired, and update status.
Bandwidth Displays current bandwidth for group.
Choose Chooses a new Helpdesk incident to be the Current Incident.
Dell PowerConnect W-AirWave | User Guide Installing and Getting Started in AirWave | 25
Page 26
Table 7 Standard Buttons and Icons of the AMP User Page (Continued)
Function ImageaDescription
Create Creates a new Helpdesk incident.
Customize Ignores selected settings when calculating the configuration status.
Delete Deletes an object from AMP's database.
Down Indicates down devices and radios.
Drag and Drop Dragging and dropping objects with this icon changes the sequence of items in relation to
each other. Refer to “Using RAPIDS and Rogue Classification” on page163 as one example
of drag-and-drop.
Duplicate Duplicates or makes a copy of the configuration of an AMP object.
Edit Edits the object properties.
Email Links to email reports.
Filter (Funnel icon) Filters list by values of the selected column. To reset all filters in all columns, click Reset
filters link at the bottom of the table.
Google Earth Views device's location in Google Earth (requires plug-in).
Manage Manages the object properties.
Mismatched Indicates mismatched device configuration, in which the most recent configuration in AMP
and the current configuration on a device are mismatched.
Monitor Indicates an access point is in “monitor only" mode.
Ignore Ignores specific device(s) - devices selected with check boxes.
Import Updates a Group's desired settings to match current settings.
New Devices Indicates new access points and devices.
Poll Now Polls device (or controller) immediately, override group polling settings.
Preview Displays a preview of changes applicable to multiple groups.
Print Prints the report.
Reboot Reboots devices or AMP.
Refresh Refreshes the display of interactive graphs when settings have changed.
Relate Relates an AP, Group or Client to a Helpdesk incident.
Replace Hardware Confers configuration and history of one AP to a replacement device.
Revert Returns all configurable data on the screen to its original status.
Rogue Indicates a rogue access point and links to RAPIDS.
Run Runs a new user-defined report.
Save Saves the information on the page in the AMP database.
Save & Apply Saves changes to AMP's database and apply all changes to devices.
Scan Scans for devices and rogues using selected networks.
Schedule Schedules a window for reports, device changes, or maintenance.
26 | Installing and Getting Started in AirWave Dell PowerConnect W-AirWave |Version 7.3
Page 27
Table 7 Standard Buttons and Icons of the AMP User Page (Continued)
Function ImageaDescription
Search Searches AMP for the specified name, MAC or IP address.
Set Time Range Sets the time range for interactive graphs to the range specified.
Up Indicates access points which are in the up status.
Update Firmware Applies a new firmware image to an AP/device.
User Indicates a user.
View Historical
Graph in New
Window
VisualRF Links to VisualRF - real time visualization.
XML Links to export XHTML versions of reports.
a. Not all AMP UI components are itemized in graphic format in this table.
Displays all data series for the selected graph over the last two hours, last day, last week,
last month, and last year in one page.
Getting Started with AirWave
This topic describes how to perform an initial launch of the AirWave network management solution on the
session-based authentication scheme introduced in AirWave 7.3.
When an AirWave URL is accessed either interactively using a browser or programatically using an API, a sent
cookie may match a session stored in the database, granting authentication (but not necessarily access, depending
on how the user's role matches the required role for the URL). If the cookie is not present or the session in the
database has expired, the request is denied.
For browser requests, this results in a login form being displayed. When you submit the login form, the supplied
credentials are checked against the AMP's user database, an external RADIUS server, or external TACACS+
server per the AMP's configuration. If the credentials are valid, the user's browser is sent a session cookie to use in
subsequent requests.
Use your browser to navigate to the static IP address assigned to the internal page of the AMP, as shown in Figure
2. Enter the User Name and Password as admin/admin for your initial login, and then select Log In.
Figure 2 AirWave Login Form
Dell PowerConnect W-AirWave | User Guide Installing and Getting Started in AirWave | 27
Page 28
After successful authentication, your browser launches the AirWave Home > Overview page.
NOTE: AirWave pages are protected via SSL. Some browsers will display a confirmation dialog for your self-signed certificate.
Signing your certificate will prevent this dialog from displaying. Changing the default login and password on the AMP Setup >
Users page is recommended. Refer to the procedure “Creating AMP User Roles” on page45 for additional information.
28 | Installing and Getting Started in AirWave Dell PowerConnect W-AirWave |Version 7.3
Page 29

Chapter 3
Configuring AMP
This chapter contains the following procedures to deploy initial AMP configuration:
“Formatting the Top Header” on page29
“Customizing Columns in Lists” on page30
“Resetting Pagination Records” on page31
“Using the Pagination Widget” on page31
“Using Export CSV for Lists and Reports” on page31
“Defining Interactive Graph Display Preferences” on page32
“Customizing the Dashboard” on page32
“Setting Severe Alert Warning Behavior” on page34
“Defining General AMP Server Settings” on page35
“Defining AMP Network Settings” on page42
“Creating AMP Users” on page43
“Creating AMP User Roles” on page45
“Configuring Timeout, Login Message, TACACS+ and RADIUS Authentication” on page48
“Enabling AMP to Manage Your Devices” on page52
“Setting Up Device Types” on page57
“Configuring Cisco WLSE and WLSE Rogue Scanning” on page58
“Configuring ACS Servers” on page62
“Integrating AMP with an Existing Network Management Solution (NMS)” on page63
“Auditing PCI Compliance on the Network” on page65
“Deploying WMS Offload” on page67
NOTE: Additional configurations of multiple types are available after basic configuration is complete.
Before You Begin
Remember to complete the required configurations in this chapter before proceeding.
Formatting the Top Header
The AMP interface centers around a horizontal row of tabs with nested subtabs.
A row of statistics hyperlinks called Top Header Stats above the tabs represents many commonly used subtabs.
These hyperlinks provide the ability to view certain key statistics by mousing over, such as number and type of
Down devices, and serve as shortcuts to frequently viewed subtabs. Figure 3 illustrates the navigation bar. For
more details on hyperlinks, tabs and subtabs, see “AirWave Navigation Basics” on page22.
Figure 3 Navigation Bar Displaying Home Subtabs and Down Device Statistics
Dell PowerConnect W-AirWave |User Guide Configuring AMP | 29
Page 30
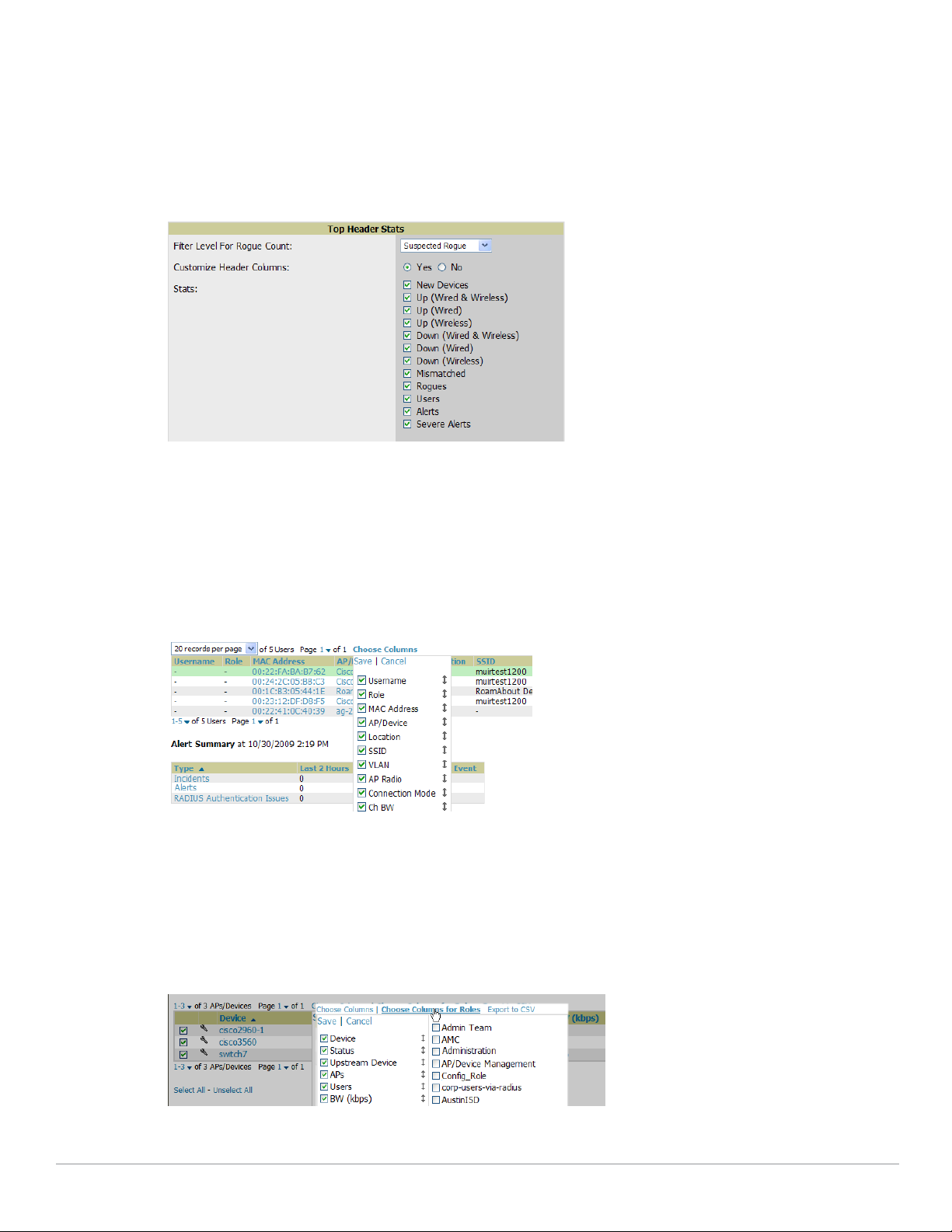
You can control which Top Header Stats links appear from the AMP Setup > General page, as described in
“Defining General AMP Server Settings” on page35. Top Header Stats can also be customized for individual
user on the Home > User Info page. There you can select the statistics to display for certain device types, and
override the AMP Setup page.
All possible display options for users are shown in Figure 4, and these fields are described in detail in “Configuring
Your Own User Information with the Home > User Info Page” on page211.
Figure 4 Home > User Info Top Header Stats Display Options
You can also set the severity level of critical alerts displayed for a user role. For details including a description of
what constitutes a severe alert, see “Setting Severe Alert Warning Behavior” on page34.
Customizing Columns in Lists
Customize the columns for any list table selecting Choose Columns as shown in Figure 5. Use the up/down
arrows to change the order in which the column heads appear.
Figure 5 Choose Columns Dropdown List
For more information on the universal list elements, see “Common List Settings” on page25.
You can also control which column heads appear for each user role by selecting Yes in the Customize Header
Columns field in Home > User Info, as also appears in Figure 4. This exposes the Choose Columns for Roles
dropdown menu in all tables shown in Figure 6.
The first column shows the user roles that were customized, if any. The second column allows you to establish left
to right columns and order them using the arrows.
Figure 6 Table With Choose Columns for Roles Menu Selected
30 | Configuring AMP Dell PowerConnect W-AirWave |Version 7.3
Page 31

Resetting Pagination Records
To control the number of records in any individual list, select the link with Records Per Page mouseover text at
the top left of the table, as shown in Figure 7. AMP remembers each list table’s pagination preferences.
Figure 7 Records Per Page Drop Down Menu
To reset all Records Per Page preferences, select Reset in the Display Preferences section of the Home > User
Info page, as shown in Figure 8.
Figure 8 Home > User Info Display Preferences section
Using the Pagination Widget
The pagination widget is located at the top and bottom of every list table, as shown in Figure 9.
Figure 9 Pagination Widget
Use the down arrow next to Page 1 to see all the page numbers for that table in a dropdown menu. From here,
you can jump to any portion of the table. Select the > symbol to jump to the next page, and >| to jump to the
last page.
Using Export CSV for Lists and Reports
Some tables have a Export CSV setting you can use export the data as a spreadsheet. See Figure 10 for an
example of a list with the Export CSV option selected.
Figure 10 List with CSV Export Selected
AMP also enables CSV exporting of all report types. For more information, see “Exporting Reports to XML or
CSV” on page252.
Dell PowerConnect W-AirWave |User Guide Configuring AMP | 31
Page 32

Defining Interactive Graph Display Preferences
Many of the graphs in AMP are Flash-based which allows you adjust the graph settings attributes, as shown in
Figure 11.
Figure 11 Interactive Graphs on the Home > Overview Page
This Flash-enabled UI allows for custom settings and adjustments, as follows:
Drag the slider at the bottom of the screen to move the scope of the graph between one year ago and the
current time.
Drag the slider between graphs to change the relative sizes of each.
Deselect checkboxes to change the data displayed on each graph. The button with green arrows refreshes data
on the graph.
The Show All link displays all of the available checkboxes supporting the Flash graphs.
Once a change to the slider bars or to the display boxes has been made, the same change can be applied to all
other Flash graphs with an apply button (appears on mouse-over only).
For non-Flash graphs, select the graph to open a popup window that shows historical data.
A non-Flash version of the AMP user page is available if desired; instead of Flash it uses the RRD graphs that were
used in earlier versions of AirWave. Contact Dell support at support.dell.com for more information on activating
this feature in the AMP database.
Customizing the Dashboard
You can rearrange or remove widgets appearing on the Home > Overview dashboard by selecting the Customize
link to the right of this window, as shown in Figure 12.
Figure 12 Customize Button on the Home > Overview Page
The Customize workspace that appears is shown in Figure 13.
32 | Configuring AMP Dell PowerConnect W-AirWave |Version 7.3
Page 33

Figure 13 Customize Overview Page
The Available Widgets section on the left with no gridlines holds all possible (available) graphical elements
(widgets). Select any blue widget tile with a verbal description enclosed, and it immediately turns into a graphical
element with a description.
Drag the widgets you want to appear on the Overview dashboard across to the gridlines and arrange them in the
right section, within the gridlines. A widget snaps back to the nearest available gridline if you drop it across two or
more lines, and turns red if you attempt to place it over gridlines already occupied by widgets.
Green widgets are properly placed and set to appear when you select Save. Widgets that remain in the left section
will not appear (although they can be reinstated by selecting Restore Defaults).
Dell PowerConnect W-AirWave |User Guide Configuring AMP | 33
Page 34

Customized Search
You can customize search results to display only desired categories of matches on the Home > User Info page.
Go to the Search Preferences section and select Yes in the Customize Search field, then select or unselect
categories of results and save your changes. Customized search is turned off by default, and all boxes are selected.
Figure 14 Home > User Info Customized Search Preferences
Setting Severe Alert Warning Behavior
You can control the alert levels you can see on the Alerts top header stats link from the Home > User Info page.
When a trigger is assigned a severity of Critical, it generates a severe alert. When a severe alert exists, a new
component named Severe Alerts appears at the right of the Status field in bold red font.
Only users who are enabled for viewing critical alerts on the Home > User Info page can see severe alerts. The
Severe Alert Threshold dropdown menu, located in the Top Header Stats section of the Home > User Info page
is shown in Figure 15.
Figure 15 Home > User Info > Severe Alert Threshold Dropdown Menu
34 | Configuring AMP Dell PowerConnect W-AirWave |Version 7.3
Page 35

Defining General AMP Server Settings
This section describes all pages accessed from the AMP Setup tab and describes two pages in the Device Setup
tab—the Communication and Upload Files pages. Once required and optional configurations in this chapter are
complete, continue to later chapters in this document to create and deploy device groups and device
configuration and discovery on the network.
The first step in configuring AMP is to specify the general settings for the AMP server. Figure 16 illustrates the
AMP Setup > General page:
Figure 16 AMP Setup > General Page Illustration
Dell PowerConnect W-AirWave |User Guide Configuring AMP | 35
Page 36

Perform the following steps to configure AMP server settings globally across the product (for all users).
1. Browse to the AMP Setup > General page, locate the General area, and enter the information described in
Table 8:
Table 8 AMP Setup > General > General Section Fields and Default Values
Setting Default Description
System Name Defines your name for the AMP server, with a maximum limit of 20 alphanumeric
characters.
Automatically
No Launches a drop-down menu that specifies the behavior AMP should follow when
monitor/manage new
devices
Default Group Access
Points
Device Configuration
Daily If enabled, this setting defines the interval of queries which compares actual
Audit Interval
it discovers a new device. Devices are placed in the default group which is defined
in the next field. Choose one of these options:
Monitor Only: AMP compares the current configuration with the policy, and
displays any discrepancies on the APs/Devices > Audit page, but does not
change the configuration of the device.
Manage Read/Write: AMP compares the device's current configuration
settings with the Group configuration settings and automatically updates the
device's configuration to match the Group policy. Automatically placing
devices in Managed Read/Write mode will overwrite the configuration with the
desired configuration in AMP, and should only be used when you are certain
AMP has the correct configuration. This can be risky, and generally, devices
should be placed in Monitor Only mode as the default.
Thin APs Only: Only thin APs will be automatically authorized in Monitor Only
mode. This setting is ideal for mixed environments of thin and autonomous APs,
or for very large subnets in which you don’t want to auto-monitor all switches.
Sets the device group that this AMP server uses as the default for device-level
configuration. Select a device group from the drop-down menu. A group must first
be defined on the Groups > List page to appear in this drop-down menu. For
additional information, refer to Chapter 4, “Configuring and Using Device Groups in
AMP” on page69.
device settings to the Group configuration policies stored in the AMP database. If
the settings do not match, the AP is flagged as mismatched and AMP sends an alert
via email, log, or SNMP.
Enable this feature with a frequency of Daily or more frequently to ensure that your
AP configurations comply with your established policies.
Automatically Repair
Misconfigured
Devices
Send Debugging
Messages
Nightly Maintenance
Time (00:00 - 23:59)
Disabled If enabled, this setting automatically reconfigures the settings on the device when
the device is in Manage mode and AMP detects a variance between actual device
settings and the Group configuration policy in the AMP database.
Enabled If enabled, AMP automatically emails any system errors to AirWave Support to
assist in debugging.
04:15 Specifies the local time of day AMP should perform daily maintenance. During
maintenance, AMP cleans the database, performs backups, and completes a few
other housekeeping tasks. Such processes should not be performed during peak
hours of demand.
Check for Software
Updates
Yes Enables AMP to check automatically for multiple update types. Check daily for AMP
updates, to include enhancements, device template files, important security
updates, and other important news. This setting requires a direct internet
connection via AMP.
2. Select the Top Header Stats to be displayed at the top of the interface. For more detailed information about
each option, refer to Table 5 on page 22.
36 | Configuring AMP Dell PowerConnect W-AirWave |Version 7.3
Page 37

3. On the AMP Setup > General page, locate the Home Overview Preferences section. Table 10 describes the
settings and default values in this section.
Table 9 AMP Setup > General > Home Overview Preferences Fields and Default Values
Setting Default Description
Configure Channel
Busy Threshold
Channel Busy
Yes Whether you want to configure the threshold at which a channel is considered to be
busy at the Top Folders By Radio Channel Usage Overview widget.
10 The threshold percent at which the radio channel is considered busier than normal.
Threshold (%)
4. On the AMP Setup > General page, locate the Display section and select the Group tabs and options to
appear by default in new device groups.
NOTE: Changes to this section apply across all of AMP. These changes affect all users and all new device groups.
Table 10 describes the settings and default values in this section.
Table 10 AMP Setup > General > Display Fields and Default Values
Setting Default Description
Use fully qualified
domain names
Show vendor-specific
device settings for
No Sets AMP to use fully qualified domain names for APs instead of the AP name. For
example, "testap.yourdomain.com" would be used instead of "testap."
This option is supported only for Dell PowerConnect W, Aruba Networks, Cisco IOS,
and Alcatel-Lucent devices.
All Devices Displays a drop-down menu that determines which Group tabs and options are
viewable by default in new groups, and selects the device types that use fully qualified
domain names. This field has three options, as follows:
All devices—When selected, AMP displays all Group tabs and setting options.
Only devices on this AMP—When selected, AMP hides all options and tabs that
do not apply to the APs and devices currently on AMP.
Selected device type—When selected, a new field appears listing many device
types. This option allows you to specify the device types for which AMP displays
group settings. You can override this setting.
Look up wireless user
hostnames
DNS Hostname
Lifetime
Device
Troubleshooting Hint
Yes Enables AMP to look up the DNS for new user hostnames. This setting can be turned
off to troubleshoot performance issues.
24 hours Defines the length of time, in hours, for which a DNS server hostname remains valid on
AMP, after which AMP refreshes DNS lookup:
1 hour
2 hours
4 hours
12 hours
24 hours
N/A The message included in this field is displayed along with the Down if a device’s
upstream device is up. This applies to all APs and controllers but not to routers and
switches.
Dell PowerConnect W-AirWave |User Guide Configuring AMP | 37
Page 38

5. Locate the Device Configuration section and adjust the settings. Table 11 describes the settings and default
values of this section.
Table 11 AMP Setup > General > Device Configuration Section Fields and Default Values
Setting Default Description
Guest User
Configuration
Allow WMS offload
configuration in
monitor-only mode
Allow disconnecting
users while in monitoronly mode
Allow non-UTF8
characters
Use Global Dell
PowerConnect W
Configuration
Disabled Enables or prevents guest users to/from pushing configurations to devices. Options are
Disabled (default), Enabled for Devices in Manage (Read/Write), Enabled for all
Devices.
No When Yes is selected, you can enable the ArubaOS WMS offload feature on the
Groups > Basic page for WLAN switches in Monitor Only mode. Enabling WMS offload
does not cause a controller to reboot. This option is supported only for Aruba Networks
and Dell PowerConnect W-Series devices.
No Sets whether you can deauthenticate a user for a device in monitor-only mode. If set to
No, the Deauthenticate User button for in a Users > User Detail page is enabled only for
Managed devices.
No Whether AMP can use character sets other than UTF-8 for configuration settings.
Yes Enables Dell PowerConnect W configuration profile settings to be globally configured
and then assigned to device groups. If disabled, settings can be defined entirely within
Groups > Aruba Config instead of globally.
NOTE: Changing this setting may require importing configuration on your devices.
When an existing Aruba configuration setup is to be converted from global to group,
follow these steps:
1. Set all the devices to Monitor Only mode before setting the flag.
2. Each device Group will need to have an import performed from the Audit page of a
controller in the AMP group.
3. All of the thin APs need to have their settings imported after the device group
settings have finished importing.
4. If the devices were set to Monitor Only mode, set them back to Managed mode.
5. Locate the AMP Features section and adjust settings to enable or disable VisualRF and RAPIDS. Table 12
describes these settings and default values
Table 12 AMP Setup > General > AMP Features Fields and Default Values
.
Setting Default Description
Display VisualRF No Enable or disable the VisualRF navigation tab.
Display RAPIDS No Enable or disable the RAPIDS navigation tab.
Display Helpdesk No Enable or disable the Helpdesk navigation tab and Helpdesk links
6. Locate the External Logging section and adjust settings to send audit and system events to an external syslog
server. Table 13 describes these settings and default values. You can send a test message using the Send Test
Message button once any of the logging options are enabled.
Table 13 AMP Setup > General > External Logging Section Fields and Default Values
Setting Default Description
Include event log
messages
Syslog Server N/A Enter the IP address of the syslog server.
Syslog Port 514 Enter the port of the syslog server.
No Select Ye s to send event log messages to an external syslog server.
38 | Configuring AMP Dell PowerConnect W-AirWave |Version 7.3
Page 39

Table 13 AMP Setup > General > External Logging Section Fields and Default Values (Continued)
Setting Default Description
Event log facility local1 Select the facility for the event log from the drop-down menu.
Include audit log
messages
Audit log facility local1 Select the facility for the audit log from the drop-down menu.
No Select Ye s to send audit log messages to an external syslog server.
7. Locate the Historical Data Retention section and specify the number of days you wish to keep client session
records and rogue discovery events. Table 14 describes the settings and default values of this section. Many
settings can be set to have no expiration date.
Table 14 AMP Setup > General > Historical Data Retention Fields and Default Values
Setting Default Description
Inactive User Data
(2-1500 days)
User Association
History (2-550 days)
Tag History
(2-550 days)
Rogue AP Discovery
Events
(2-550 days)
Reports
(2-550 days)
60 Defines the number of days AMP stores basic information about inactive users. A shorter
setting of 60 days is recommended for customers with high user turnover such as hotels.
The longer you store inactive user data, the more hard disk space you require.
14 Defines the number of days AMP stores client session records. The longer you store
client session records, the more hard disk space you require.
14 Sets the number of days AMP retains location history for Wi-Fi tags.
14 Defines the number of days AMP stores Rogue Discovery Events. The longer you store
discovery event records, the more hard disk space you require.
60 Defines the number of days AMP stores Reports. Large numbers of reports, over 1000, can
cause the Reports > Generated page to be slow to respond.
Automatically
Acknowledged Alerts
(0-550 days, zero
disables)
Acknowledged Alerts
(2-550 days)
Radius/ARM/IDS
Events
(0-550 days, zero
disables)
Archived Device
Configurations
(1-100)
Guest Users
(0-550 days, zero
disables)
Closed Helpdesk
Incidents
(0-550 days, zero
disables)
Inactive SSIDs
(0-550 days, zero
disables)
14 Defines automatically acknowledged alerts as the number of days AMP retains alerts that
have been automatically acknowledged. Setting this value to 0 disables this function, and
alerts will never expire or be deleted from the database.
60 Defines the number of days AMP retains information about acknowledged alerts. Large
numbers of Alerts, over 2000, can cause the System > Alerts page to be slow to respond.
14 Defines the number of days AMP retains information about RADIUS, ARM, and IDS
events. Setting this value to 0 disables this function, and the information will never expire
or be deleted from the database.
10 Sets the number of archived configurations to retain for each device.
30 Sets the number of days that AMP is to support any guest user. A value of 0 disables this
function, and guest users will never expire or be deleted from the AMP database.
30 Sets the number of days that AMP is to retain records of closed Helpdesk incidents once
closed. Setting this value to 0 disables this function, and Helpdesk information will never
expire or be deleted from the database. This field only appears if you have enabled
Helpdesk in the AMP Features section.
425 Sets the number of days AMP retains historical information after AMP last saw a client on
a specific SSID. Setting this value to 0 disables this function, and inactive SSIDs will never
expire or be deleted from the database.
Inactive Interfaces (0550 days, zero
disables)
Dell PowerConnect W-AirWave |User Guide Configuring AMP | 39
425 Sets the number of days AMP retains inactive interface information after the interface has
been removed or deleted from the device. Se
and inactive interface information will never expire or be deleted from the database.
tting this value to 0 disables this function,
Page 40

Table 14 AMP Setup > General > Historical Data Retention Fields and Default Values (Continued)
Setting Default Description
Interface Status
History
(0-550 days, zero
disables)
Interfering Devices (0550 days, zero
disables)
Device Events (Syslog,
Traps)
425 Sets the number of days AMP retains historical information on interface status. Setting
this value to 0 disables this function.
14 Sets the number of days AMP retains historical information on interfering devices. Setting
this value to 0 disables this function.
2 Sets the number of days AirWave retains historical information on device events such as
syslog entries and SNMP traps. Setting this value to 0 disables this function. Refer to
“Viewing Device Events in System > Syslog & Traps” on page181.
8. Locate the Firmware Upgrade Defaults section and adjust settings as required. This section allows you to
configure the default firmware upgrade behavior for AMP. Table 15 describes the settings and default values
of this section.
Table 15 AMP Setup > General > Firmware Upgrade Defaults Fields and Default Values
Setting Default Description
Allow firmware
upgrades in monitoronly mode
Simultaneous Jobs (1-
20)
No If Yes is selected, AMP upgrades the firmware for APs in Monitor Only mode. When AMP
upgrades the firmware in this mode, the desired configuration are not be pushed to AMP.
Only the firmware is applied. The firmware upgrade may result in configuration changes.
AMP does not correct those changes when the AP is in Monitor Only mode.
20 Defines the number of jobs AMP runs at the same time. A job can include multiple APs.
Simultaneous Devices
Per Job
(1-1000)
Failures before
stopping (0-20)
20 Defines the number of devices that can be in the process of upgrading at the same time.
AMP only runs one TFTP transfer at a time. As soon as the transfer to a device has
completed, the next transfer begins, even if the first device is still in the process of
rebooting or verifying configuration.
1 Sets the default number of upgrade failures before AMP pauses the upgrade process.
User intervention is required to resume the upgrade process. Setting this value to 0
disables this function.
9. Locate the Additional AMP Services section, and adjust settings as required. Table 16 describes the settings
and default values of this section.
Table 16 AMP Setup > General > Additional AMP Services Fields and Default Values
Setting Default Description
Enable FTP Server No Enables or disables the FTP server on AMP. The FTP server is only used to manage Cisco
Aironet 4800 APs. Disabling the FTP server if you do not have any Cisco Aironet 4800 APs in
the network.
Enable RTLS Collector No Enables or disables the RTLS Collector, which is used to allow ArubaOS controllers to send
signed and encrypted RTLS (real time locating system) packets to VisualRF-- in other
words, AMP becomes the acting RTLS server. The RTLS server IP address must be
configured on each controller. This function is used for VisualRF to improve location
accuracy and to locate chirping asset tags. This function is supported only for Dell
PowerConnect W, Alcatel-Lucent and Aruba Networks devices.
With selection of Yes , the following additional fields appear, which you should populate to
match the settings configured on the controller:
RTLS Port—Specify the port for the AMP RTLS server.
RTLS Username—Enter the user name used by the controller to decode RTLS
messages.
RTLS Password—Enter the RTLS server password that matches the controllers’ value.
40 | Configuring AMP Dell PowerConnect W-AirWave |Version 7.3
Page 41

Table 16 AMP Setup > General > Additional AMP Services Fields and Default Values (Continued)
Setting Default Description
Use embedded mail
server
Process user roaming
traps from Cisco WLC
Enable AMON data
collection
Yes Enables or disables the embedded mail server that is included with AMP.This field
supports a Send Test Email button for testing server functionality. This button prompts you
with a To and From field in which you must enter valid email addresses, and a button to
send a test email.
Yes Whether AMP should parse client association and authentication traps from Cisco WLC
controllers to give real time information on users connected to the wireless network.
Yes All ow s
AMP to collect enhanced data from Dell PowerConnect W-Series devices on
certain firmware versions; see the Dell PowerConnect W-AirWave Best Practices Guide
for more details.
10. Locate the Performance section. Performance tuning is unlikely to be necessary for many AMP
implementations, and likely provides the most improvements for customers with extremely large Pro or
Enterprise installations. Please contact Dell support at support.dell.com if you think you might need to
change any of these settings. Table 17 describes the settings and default values of this section.
Table 17 AMP Setup > General > Performance Fields and Default Values
Setting Default Description
Monitoring
Processes
Maximum number of
configuration
processes
Based on the
number of
cores for your
server
5 Increases the number of processes that are pushing configurations to your
Optional setting configures the throughput of monitoring data. Increasing this
setting allows AMP to process more data per second, but it can take resources
away from other AMP processes. Please contact Dell support at at
support.dell.com if you think you might need to increase this setting for your
network.
devices, as an option. The optimal setting for your network depends on the
resources available, especially RAM. Please contact Dell support at
support.dell.com if you think you might need to increase this setting for your
network.
Maximum number of
audit processes
Verbose Logging of
SNMP Configuration
SNMP Rate Limiting
for Monitored
Devices
RAPIDS Processing
Priority
3 Increases the number of processes that audit configurations for your devices,
as an option. The optimal setting for your network depends on the resources
available, especially RAM. Contact Dell support at support.dell.com if you are
considering increasing this setting for your network.
No Enables or disables logging detailed records of SNMP configuration
information.
No When enabled, AMP fetches SNMP data more slowly, potentially reducing
device CPU load. Enable this global setting when monitoring Dell PowerConnect
W controllers only if your network contains a majority of legacy controllers (800,
2400, 5000, controllers that use Supervisor Module II).
NOTE: If your network mainly uses newer processors (3000 series, 600 series,
the M3 module in the 6000 series), disabling this setting is strongly
recommended.
Low Defines the processing and system resource priority for RAPIDS in relation to
AMP as a whole.
When AMP is processing data at or near its maximum capacity, reducing the
priority of RAPIDS can ensure that processing of other data (such as client
connections and bandwidth) is not adversely impacted.
The default priority is Low. You can also tune your system performance by
changing group poll periods.
11. Select Save when the General Server settings are complete and whenever making subsequent changes.
Dell PowerConnect W-AirWave |User Guide Configuring AMP | 41
Page 42

What Next?
Go to additional tabs in the AMP Setup section to continue additional setup configurations.
Complete the required configurations in this chapter before proceeding.
Defining AMP Network Settings
The next step in configuring AMP is to confirm the AMP network settings. Define these settings by navigating to
the AMP Setup > Network page. Figure 17 illustrates the contents of this page.
Figure 17 AMP Setup > Network Page Illustration
Perform the following steps to define the AMP network settings:
1. Locate the Primary and Secondary Network Interface sections. The information in these sections should
match what you defined during initial network configuration and should not require changes. Table 18
describes the settings and default values.
Table 18 Primary and Secondary Network Interface Fields and Default Values
Setting
IP Address None Sets the IP address of the AMP network interface.
Hostname None Sets the DNS name assigned to the AMP server.
Subnet Mask None Sets the subnet mask for the primary network interface.
Gateway None Sets the default gateway for the network interface.
Primary DNS IP None Sets the primary DNS IP address for the network interface.
Secondary DNS IP None Sets the secondary DNS IP address for the network interface.
Secondary Network
Interface
Default Description
This address must be a static IP address.
No Select Yes to enable a secondary network interface. You must also define the IP
address and subnet mask.
2. On the AMP Setup > Network page, locate the Network Time Protocol (NTP) section. The Network Time
Protocol is used to synchronize the time between AMP and your network reference NTP server. NTP servers
synchronize with external reference time sources, such as satellites, radios, or modems.
NOTE: Specifying NTP servers is optional. NTP servers synchronize the time on the AMP server, not on individual access points.
To disable NTP services, clear both the Primary and Secondary NTP server fields. Any problem related to
communication between AMP and the NTP servers creates an entry in the event log. Table 19 describes the
42 | Configuring AMP Dell PowerConnect W-AirWave |Version 7.3
Page 43

settings and default values in more detail. For more information on ensuring that AMP servers have the
correct time, please see http://support.ntp.org/bin/view/Servers/NTPPoolServers.
Table 19 AMP Setup > Network > Secondary Network Fields and Default Values
Setting Default Description
Primary ntp1.yourdomain.com Sets the IP address or DNS name for the primary NTP server.
Secondary ntp2.yourdomain.com Sets the IP address or DNS name for the secondary NTP server.
3. On the AMP Setup > Network page, locate the Static Routes area. This section displays network, subnet
mask, and gateway settings that you have defined elsewhere from a command-line interface.
NOTE: This section does not enable you to configure new routes or remove existing routes.
4. Select Save when you have completed all changes on the AMP Setup > Network page, or select Revert to
return to the last settings. Save restarts any affected services and may temporarily disrupt your network
connection.
What Next?
Go to additional tabs in the AMP Setup section to continue additional setup configurations.
Complete the required configurations in this chapter before proceeding.
Creating AMP Users
AMP installs with only one AMP user—the admin, who is authorized to:
define additional users with varying levels of privilege, be it manage read/write or monitoring.
limit the viewable devices as well as the level of access a user has to the devices.
Each general user that you add needs a Username, a Password, and a Role. Use unique and meaningful user
names as they are recorded in the log files when you or other users make changes in AMP.
NOTE: Username and password are not required if you configure AMP to use RADIUS or TACACS authentication. You do not need
to add individual users to the AMP server if you use RADIUS or TACACS authentication.
The user role defines the user type, access level, and the top folder for that user. User roles are defined on the
AMP Setup > Roles page. Refer to the next procedure in this chapter for additional information, “Creating AMP
User Roles” on page45.
The admin user can provide optional additional information about the user including the user's real name, email
address, phone number, and so forth.
Perform the following steps to display, add, edit, or delete AMP users of any privilege level. You must be an
admin user to complete these steps.
Dell PowerConnect W-AirWave |User Guide Configuring AMP | 43
Page 44

1. Go to the AMP Setup > Users page. This page displays all users currently configured in AMP. Figure 18
illustrates the contents and layout of this page.
Figure 18 AMP Setup > Users Page Illustration
2. Select Add to create a new user, select the pencil icon to edit an existing user, or select a user and select
Delete to remove that user from AMP. When you select Add or the edit icon, the Add User page appears,
illustrated in Figure 19.
Figure 19 AMP Setup > Users > Add/Edit User Page Illustration
3. Enter or edit the settings on this page. Table 20 describes these settings in additional detail.
Table 20 AMP Setup > User > Add/Edit User Fields and Default Values
Setting Default Description
Username None Sets the username as an alphanumeric string. The Username is used when logging in to AMP and
appears in AMP log files.
Role None Specifies the User Role that defines the Top viewable folder, type and access level of the user
specified in the previous field.
The admin user defines user roles on the AMP Setup > Roles page, and each user in the system is
assigned to a role.
Password None Sets the password for the user being created or edited. Enter an alphanumeric string without
spaces, and enter the password again in the Confirm Password field.
NOTE: Because the default user's password is identical to the name, it is strongly recommended
that you change this password.
Name None Allows you to define an optional and alphanumeric text field that takes note of the user's actual
name.
Email Address None Allows you to specify a specific email address that will propagate throughout many additional
Phone None Allows you to enter an optional phone number for the user.
Notes None Enables you to cite any additional notes about the user, including the reason they were granted
pages in AMP for that user, including reports, triggers, and alerts.
access, the user's department, or job title.
44 | Configuring AMP Dell PowerConnect W-AirWave |Version 7.3
Page 45

4. Select Add to create the new user, Save to retain changes to an existing user, or Cancel to cancel out of this
screen. The user information you have configured appears on the AMP Setup > Users page and the user
propagates to all other AMP pages and relevant functions.
NOTE: AMP enables user roles to be created with access to folders within multiple branches of the overall hierarchy. This feature
assists non-administrator users who support a subset of accounts or sites within a single AMP deployment, such as help desk or
IT staff.
What Next?
Go to additional tabs in the AMP Setup section to continue additional setup configurations.
Complete the required configurations in this chapter before proceeding.
Creating AMP User Roles
The AMP Setup > Roles page defines the viewable devices, the operations that can be performed on devices, and
general AMP access. VisualRF uses the same user roles as defined for AMP—users can see floor plans that contain
an AP to which they have access in AMP, although only visible APs appear on the floor plan.
Users can also see any building that contains a visible floor plan, and any campus that contains a visible building.
NOTE: In VisualRF > Setup > Server Settings, a new flag added in AMP 7.2 allows you to restrict the visibility of empty floor plans to
the role of the user who created them. In previous versions, a floor plan without APs could be visible to all users. By default, this
setting is set to No.
When a new role is added to AMP, VisualRF must be restarted for the new user to be enabled. Refer to Chapter
11, “Using VisualRF” on page259 for additional information.
User roles can be created that have access to folders within multiple branches of the overall hierarchy. This
feature assists non-administrative users, such as help desk or IT staff, who support a subset of accounts or sites
within a single AMP deployment. You can restrict user roles to multiple folders within the overall hierarchy even
if they do not share the same top-level folder. Non-admin users are only able to see data and users for devices
within their assigned subset of folders.
Perform the following steps to view, add, edit, or delete user roles:
1. Go to the AMP Setup > Roles page. This page displays all roles currently configured in AMP. Figure 20
illustrates the contents and layout of this page.
Figure 20 AMP Setup > Roles Page Illustration
Dell PowerConnect W-AirWave |User Guide Configuring AMP | 45
Page 46

2. Select Add to create a new role, select the pencil icon to edit an existing role, or select a checkbox and select
Delete to remove that role from AMP. When you select Add or the edit icon, the Add/Edit Role page appears,
illustrated in Figure 21.
Figure 21 AMP Setup > Roles > Add/Edit Role Page Illustration
3. Enter or edit the settings on this page. Table 21 describes these settings in additional detail.
As explained earlier in this section, Roles define the type of user-level access, the user-level privileges, and the
view available to the user for device groups and devices in AMP. Table 21 describes the settings and default
values of this section.
Table 21 AMP Setup > Roles > Add/Edit Roles Fields and Default Values
Setting Default Description
Name None Sets the administrator-definable string that names the role. The role name should ideally indicate
the devices and groups that are viewable, as well as the privileges granted to that role.
Enabled Yes Disables or enables the role. Disabling a role prevents all users of that role from logging in to
Type AP/Device
Manager
AMP.
Defines the type of role. AMP supports the following role types:
AMP Administrator—The AMP Administrator has full access to AMP and all of the devices.
Only the AMP Administrator can create new users or access the AMP Setup page, the
VisualRF > Setup page, VisualRF > Audit Log page, System > AMP Events, and System >
Performance.
AP/Device Manager—AP/Device Managers have access to a limited number of devices and
groups based on the Top folder and varying levels of control based on the Access Level.
AirWave Management Client—The AirWave Management Client (AMC) software allows
WiFi-enabled devices to serve as additional sensors to gather data for RAPIDS. Use this role
type to set up a client to be treated as a user with the AMC role. The user information defined
in AMC must match the user with the Dell PowerConnect W Management Client type.
Guest Access Sponsor—Limited-functionality role to allow helpdesk or reception desk staff
to grant wireless access to temporary personnel. This role only has access to the defined
top folder of APs.
46 | Configuring AMP Dell PowerConnect W-AirWave |Version 7.3
Page 47

Table 21 AMP Setup > Roles > Add/Edit Roles Fields and Default Values (Continued)
Setting Default Description
AP/Device
Access Level
None Defines the privileges the role has over the viewable APs. AMP supports three privilege levels,
as follows:
Manage (Read/Write)—Manage users can view and modify devices and Groups. Selecting
this option causes a new field, Allow authorization of APs/Devices, to appear on the page,
and is enabled by default.
Audit (Read Only)—Audit users have read only access to the viewable devices and Groups.
Audit users have access to the APs/Devices > Audit page, which may contain sensitive
information including AP passwords.
Monitor (Read Only)—Monitor users have read-only access to devices and groups and
VisualRF. Monitor users cannot view the APs/Devices > Audit page which may contain
sensitive information, including passwords.
Top Folder None Defines the Top viewable folder for the role. The role is able to view all devices and groups
contained by the Top folder. The top folder and its subfolders must contain all of the devices in
any of the groups it can view.
NOTE: AMP enables user roles to be created with access to folders within multiple branches of
the overall hierarchy. This feature assists non-administrator users who support a subset of
accounts or sites within a single AMP deployment, such as help desk or IT staff.
User roles can be restricted to multiple folders within the overall hierarchy, even if they do not
share the same top-level folder. Non-administrator users are only able to see data and users for
devices within their assigned subset of folders.
RAPIDS None Sets the RAPIDS privileges, which are set separately from the APs/Devices. This field specifies
the RAPIDS privileges for the role, and options are as follows:
None— Cannot view the RAPIDS tab or any Rogue APs.
Read Only—The user can view the RAPIDS pages but cannot make any changes to rogue
APs or perform OS scans.
Read/Write—The user may edit individual rogues, classification, threat levels and notes,
and perform OS scans.
Administrator—Has the same privileges as the Read/Write user, but can also set up RAPIDS
rules, override scores, and is the only user who can access the RAPIDS > Setup page.
VisualRF None Sets the VisualRF privileges, which are set separately from the APs/Devices, for this role.
Options are as follows:
Read Only—The user can view the VisualRF pages but cannot make any changes to floor
plans.
Read/Write—The user may edit individual floor plans, buildings, and campuses.
Helpdesk No Sets the role to support helpdesk users, with parameters that are specific to the needs of
helpdesk personnel supporting users on a wireless network.
Enable Adobe
Flash
Yes Enables the Adobe Flash application for all users who are assigned this role. Adobe Flash
supports interactive graphics on the Home > Overview page, VisualRF, Quickview functions, the
Radio Statistics page for thin AP radios, and additional AMP pages.
NOTE: This field is only visible if a specific flag is set in the AMP database. By default this option
is hidden and Flash is enabled for all users.
Allow creation
of Guest Users
Yes If this option is enabled, users with an assigned role of Monitoring or Audit can be given access
to guest user account creation along with the option to allow a sponsor to change its username.
A custom message can also be included. The Guest User Preferences section does not apear if
Guest User Configuration is disabled in AMP Setup > General.
What Next?
Go to additional tabs in the AMP Setup section to continue additional setup configurations.
Complete the required configurations in this chapter before proceeding.
Dell PowerConnect W-AirWave |User Guide Configuring AMP | 47
Page 48

Configuring Timeout, Login Message, TACACS+ and RADIUS Authentication
As of 7.3, AMP uses session-based authentication with a configurable login message and idle timeout. As an
option, you can set AMP to use an external user database to simplify password management for AMP
administrators and users. This section contains the following procedures to be followed in AMP Setup >
Authentication:
Setting Up Login Configuration Options
Setting Up Login Configuration Options
Configuring RADIUS Authentication and Authorization
Integrating a RADIUS Accounting Server
Setting Up Login Configuration Options
Administrators can optionally configure AMP’s user idle timeout or a message-of-the-day that appears across the
top of Home > Overview when a user first logs in, as shown in Figure 22:
Figure 22 Login configuration field and results in AMP Login page
1. Go to AMP Setup > Authentication.
2. Complete the fields described on Table 22:
Table 22 Login Configuration section of AMP Setup > Authentication
Field Default Description
AMP User Idle
Timeout
Login message A persistent message that will appear for all of this AMP’s users after they log in.
3. Select Save if you are finished, or you can follow the next procedure to configure TACACS+ and RADIUS
Authentication options.
60 Number of minutes of idle time until AMP automatically ends the user session. Affects all
users of this AMP. The range is 10-240 minutes.
48 | Configuring AMP Dell PowerConnect W-AirWave |Version 7.3
Page 49

Configuring TACACS+ Authentication
For TACACS+ capability, you must configure the IP/Hostname of the TACACS+ server, the TCP port, and the
server shared secret. This TACACS+ configuration is for AMP users, and does not affect APs or users logging into
APs.
1. Go to the AMP Setup > Authentication page. This page displays current status of TACACS+. Figure 23
illustrates this page when neither TACACS+ nor RADIUS authentication is enabled in AMP.
Figure 23 TACACS+ section AMP Setup > Authentication
2. Select No to disable or Yes to enable TACACS+ authentication. If you select Yes, several new fields appear.
Complete the fields described in Table 23.
Table 23 AMP Setup > Authentication Fields and Default Values
Field Default Description
Primary Server Hostname/IP
Address
Primary Server Port 49 Enter the port for the primary TACACS+ server.
Primary Server Secret N/A Specify and confirm the primary shared secret for the primary TACACS+
Secondary Server Hostname/IP
Address
Secondary Server Port 49 Enter the port for the secondary TACACS+ server.
Secondary Server Secret N/A Enter the shared secret for the secondary TACACS+ server.
3. Select Save and continue with additional steps.
4. To configure Cisco ACS to work with AMP, you must define a new service named AMP that uses https on the
ACS server.
The AMP https service is added to the TACACS+ (Cisco) interface under the Interface Configuration
tab.
Select a checkbox for a new service.
Enter AMP in the service column and https in the protocol column.
Select Save.
N/A Enter the IP address or the hostname of the primary TACACS+ server.
server.
N/A Enter the IP address or hostname of the secondary TACACS+ server.
5. Edit the existing groups or users in TACACS to use the “AMP service” and define a role for the group or user.
The role defined on the Group Setup page in ACS must match the exact name of the role defined on the
AMP Setup > Roles page.
The defined role should use the following format: role=<name_of_AMP_role>. One example is as
follows:
role=DormMonitoring
Dell PowerConnect W-AirWave |User Guide Configuring AMP | 49
Page 50

As with routers and switches, AMP does not need to know usernames.
6. AMP also needs to be configured as an AAA client.
On the Network Configuration page, select Add Entry.
Enter the IP address of AMP as the AAA Client IP Address.
The secret should be the same value that was entered on the AMP Setup > TACACS+ page.
7. Select TACACS+ (Cisco IOS) in the Authenticate Using drop down menu and select submit + restart.
NOTE: AMP checks the local username and password store before checking with the TACACS+ server. If the user is found locally,
the local password and local role apply. When using TACAS+, it is not necessary or recommended to define users on the AMP
server. The only recommended user is the backup administrator, in the event that the TACAS+ server goes down.
What Next?
Go to additional tabs in the AMP Setup section to continue additional setup configurations.
Complete the required configurations in this chapter before proceeding.
Configuring RADIUS Authentication and Authorization
For RADIUS capability, you must configure the IP/Hostname of the RADIUS server, the TCP port, and the
server shared secret. Perform these steps to configuration RADIUS authentication:
1. Go to the AMP Setup > Authentication page. This page displays current status of RADIUS. Figure 24
illustrates this page.
Figure 24 AMP Setup > Authentication Page Illustration
2. Select No to disable or Yes to enable TACACS+ or RADIUS authentication. If you select Yes, several new
fields appear. Complete the fields described in Table 24.
Table 24 AMP Setup > Authentication Fields and Default Values
Field Default Description
Primary Server
Hostname/IP Address
Primary Server Port 1812 Enter the TCP port for the primary RADIUS server.
Primary Server Secret N/A Specify and confirm the primary shared secret for the primary RADIUS server.
N/A Enter the IP address or the hostname of the primary RADIUS server.
Secondary Server
Hostname/IP Address
Secondary Server Port 1812 Enter the TCP port for the secondary RADIUS server.
Secondary Server
Secret
50 | Configuring AMP Dell PowerConnect W-AirWave |Version 7.3
N/A Enter the IP address or the hostname of the secondary RADIUS server.
N/A Enter the shared secret for the secondary RADIUS server.
Page 51

Integrating a RADIUS Accounting Server
NOTE: AMP checks the local username and password before checking with the RADIUS server. If the user is found locally, the
local password and role apply. When using RADIUS, it’s not necessary or recommended to define users on the AMP server. The
only recommended user is the backup admin, in case the RADIUS server goes down.
Optionally, you can configure RADIUS server accounting on AMP Setup > RADIUS Accounting. This
capability is not required for basic AMP operation, but can increase the user-friendliness of AMP administration
in large networks. Figure 25 illustrates the settings of this optional configuration interface.
Perform the following steps and configurations to enable AMP to receive accounting records from a separate
RADIUS server. Figure 25 illustrates the display of RADIUS accounting clients already configured, and Figure 26
illustrates the Add RADIUS Accounting Client page.
Figure 25 AMP Setup > RADIUS Accounting Page Illustration
Figure 26 AMP Setup > RADIUS > Add RADIUS Accounting Client Page Illustration
1. To specify the RADIUS authentication server or network, browse to the AMP Setup > RADIUS Accounting
page and select Add, illustrated in Figure 26, and provide the information in Table 25.
2. Select Add, then complete the following fields:
Table 25 AMP Setup > Radius Accounting Fields and Default Values
Setting Default Description
Nickname None Sets a user-defined name for the authentication server.
IP/Network None Cites the IP address or DNS Hostname for the authentication server if you only want to accept
packets from one device. To accept packets from an entire network enter the IP/Netmask of the
network (for example, 10.51.0.0/24).
Shared Secret
(Confirm)
None Sets the Shared Secret that is used to establish communication between AMP and the RADIUS
authentication server.
What Next?
Go to additional subtabs in AMP Setup to continue additional setup configurations.
Complete the required configurations in this chapter before proceeding.
Dell PowerConnect W-AirWave |User Guide Configuring AMP | 51
Page 52

Enabling AMP to Manage Your Devices
Once AMP is installed and active on the network, the next task is to define the basic settings that allow AMP to
communicate with and manage your devices. Device-specific firmware files are often required or are highly
desirable. Furthermore, the use of Web Auth bundles is advantageous for deployment of Cisco WLC wireless
LAN controllers when they are present on the network.
This section contains the following procedures:
Configuring Communication Settings for Discovered Devices
Loading Device Firmware Onto AMP (optional)
Overview of the Device Setup > Upload Firmware & Files Page
Loading Firmware Files to AMP
Configuring Communication Settings for Discovered Devices
To configure AMP to communicate with your devices, to define the default shared secrets, and to set SNMP
polling information, navigate to the Device Setup > Communication page, illustrated in Figure 27.
Figure 27 Device Setup > Communication Page Illustration
Perform the following steps to define the default credentials and SNMP settings for the wireless network.
1. On the Device Setup > Communication page, locate the Default Credentials area. Enter the credentials for
each device model on your network. The default credentials are assigned to all newly discovered APs.
52 | Configuring AMP Dell PowerConnect W-AirWave |Version 7.3
Page 53

The Edit button edits the default credentials for newly discovered devices. To modify the credentials for
existing devices, use the APs/Devices > Manage page or the Modify Devices link on the APs/Devices > List
page.
NOTE: Community strings and shared secrets must have read-write access for AMP to configure the devices. Without read-write
access, AMP may be able to monitor the devices but cannot apply any configuration changes.
2. Browse to the Device Setup > Communication page, locate the SNMP Settings section, and enter or revise
the following information. Table 26 lists the settings and default values.
Table 26 Device Setup > Communication > SNMP Settings Fields and Default Values
Setting Default Description
SNMP Timeout 3 Sets the time, in seconds, that AMP waits for a response from a device after sending an
SNMP request.
SNMP Retries 3 Sets the number of times AMP tries to poll a device when it does not receive a response
within the SNMP Timeout Period or the Group's Missed SNMP Poll Threshold setting (1-100).
If AMP does not receive an SNMP response from the device after the specified number of
retries, AMP classifies that device as Down.
3. Locate the SNMP v3 Informs section. Select Add New SNMP v3 User to reveal its configuration section.
AMP users will need to configure all v3 users that are configured on the controller; the SNMP Inform receiver
in the AMP will be restarted when users are changed or added to the controller.
Username - Username of the SNMP v3 user as configured on the controller.
Auth Protocol - Can be MD5 or SHA. The default setting is SHA.
Auth and Priv Passphrases - Enter the auth and priv passphrases for the user as configured on the
controller.
Priv Protocol - Can be DES or AES. The default setting is DES.
4. Locate the Telnet/SSH Settings section, and complete or adjust the default value for the field. Table 27
shows the setting and default value.
Table 27 Device Setup > Communication > Telnet/SSH Settings Fields and Default Values
Setting Default Description
Telnet/SSH Timeout
(3-120 sec)
10 Sets the timeout period in seconds used when performing Telnet and SSH commands.
5. Locate the HTTP Discovery Settings section and adjust the default value. Table 28 shows the setting and
default value.
Table 28 Device Setup > Communication > HTTP Discovery Settings Fields and Default Values
Setting Default Description
HTTP Timeout
(3-120 sec)
Dell PowerConnect W-AirWave |User Guide Configuring AMP | 53
5 Sets the timeout period in seconds used when running an HTTP discovery scan.
Page 54

6. Locate the ICMP Settings section and adjust the default value as required. Table 29 shows the setting and
default value.
Table 29 Device Setup > Communication > ICMP Settings Fields and Default Values
Setting Default Description
Attempt to ping
devices that
were
unreachable
via SNMP
Yes When Yes is selected, AMP attempts to ping the AP device.
Select No if performance is affected in negative fashion by this function. If a large number
of APs are unreachable by ICMP, likely to occur where there is in excess of 100 APs, the
timeouts start to impede network performance.
NOTE: If ICMP is disabled on the network, select No to avoid the performance penalty caused
by numerous ping requests.
7. Locate the Symbol 4131 and Cisco Aironet IOS SNMP Initialization area. Select one of the options listed.
Table 30 describes the settings and default values:
Table 30 Device Setup > Communication > Symbol 4131 and Cisco Aironet IOS SNMP Initialization Fields and Default Values
Setting Default Description
Do Not Modify
SNMP Settings
Enable read-write
SNMP
Yes When selected, specifies that AMP not modify any SNMP settings. If SNMP is not already
initialized on the Symbol, Nomadix, and Cisco IOS APs, AMP is not able to manage them.
No When selected, and when on networks where the Symbol, Nomadix, and Cisco IOS APs do
not have SNMP initialized, this setting enables SNMP so the devices can be managed by
AMP.
Loading Device Firmware Onto AMP (optional)
Overview of the Device Setup > Upload Firmware & Files Page
AMP enables automated firmware distribution to the devices on your network. Once you have downloaded the
firmware files from the vendor, you can upload this firmware to AMP for distribution to devices via the Device
Setup > Upload Firmware & Files page.
This page lists all firmware files on AMP with file information. This page also enables you to add new firmware
files, to delete firmware files, and to add New Web Auth Bundle files.
The following additional pages support firmware file information:
Firmware files uploaded to AMP appear as options in the drop-down menus on the Group > Firmware page
and on individual APs/Devices > Manage pages.
Use the AMP Setup page to configure AMP-wide default firmware options.
Table 31 below itemizes the contents, settings, and default values for the Upload Firmware & Files page.
Table 31 Device Setup > Upload Firmware & Files Fields and Default Values
Setting Default Description
Type Aruba
Controller
(any model)
Owner Role None Displays the user role that uploaded the firmware file. This is the role that has access to
Description None Displays a user-configurable text description of the firmware file.
Server Protocol None Displays the file transfer protocol by which the firmware file was obtained from the server.
Displays a drop-down list of the primary AP makes and models that AMP supports with
automated firmware distribution.
the file when an upgrade is attempted.
54 | Configuring AMP Dell PowerConnect W-AirWave |Version 7.3
Page 55

Table 31 Device Setup > Upload Firmware & Files Fields and Default Values (Continued)
Setting Default Description
Use Group File
Server
Firmware Filename None Displays the name of the file that was uploaded to AMP and to be transferred to an AP
Firmware Version None Displays the firmware version number. This is a user-configurable field.
Firmware MD5
Checksum
Firmware File Size None Displays the size of the firmware file in bytes.
HTML Filename None Supporting HTML, displays the name of the file that was uploaded to AMP and to be
HTML Version None Supporting HTML, displays the version of HTML used for file transfer.
HTML MD5
Checksum
HTML File Size None Supporting HTML, displays the size of the file in bytes.
Desired Firmware
File for Specified
Groups
None Displays the name of the file server supporting the group.
when the file is used in an upgrade.
None Displays the MD5 checksum of the file after it was uploaded to AMP. The MD5 checksum
is used to verify that the file was uploaded to AMP without issue. The checksum should
match the checksum of the file before it was uploaded.
transferred to an AP when the file is used in an upgrade.
None Supporting HTML, displays the MD5 checksum of the file after it was uploaded to AMP.
The MD5 checksum is used to verify that the file was uploaded to AMP without issue. The
checksum should match the checksum of the file before it was uploaded.
None The firmware file is set as the desired firmware version on the Groups > Firmware Files
page of the specified groups. You cannot delete a firmware file that is set as the desired
firmware version for a group.
Loading Firmware Files to AMP
Perform the following steps to load a device firmware file onto AMP:
1. Go to the Device Setup > Upload Firmware & Files page.
2. Select Add. The Add Firmware File page appears. Figure 28 illustrates this page.
Figure 28 Device Setup > Upload Firmware and Files > Add Page Illustration
3. Select Supported Firmware Versions and Features to view supported firmware versions.
NOTE: Unsupported and untested firmware may cause device mismatches and other problems. Please contact Dell support
before installing non-certified firmware.
4. Enter the appropriate information and select Add. The file uploads to AMP and once complete, this file
appears on the Device Setup > Upload Firmware & Files page. This file also appears on additional pages that
display firmware files (such as the Group > Firmware page and on individual APs/Devices > Manage pages).
Dell PowerConnect W-AirWave |User Guide Configuring AMP | 55
Page 56

5. You can also import a CSV list of groups and their external TFTP firmware servers. Table 32 itemizes the
settings of this page.
Table 32 Supported Firmware Versions and Features Fields and Default Values
Setting Default Description
Type Aruba
Firmware Version None Provides a user-configurable field to specify the firmware version number. Appears if you
Description None Provides a user-configurable text description of the firmware file.
Upload firmware
files (and use built-in
firmware)
Use an external
firmware file server
Use Group File
Server
Firmware File Server
IP Address
Controller
Built-in Selects the TFTP server that access points use to download their firmware. The built-in
N/A You can also choose to assign the external TFTP server on a per-group basis. If you select
Disabled If you opt to use an external firmware file server, this additional option appears. This
None Provides the IP address of the External TFTP Server (like SolarWinds) used for the
Indicates the firmware file is used with the specified type. If you select an IOS device from
the Typ e drop-down menu, you have the option of choosing a server protocol of TFTP or
FTP. If you choose FTP, you may later notice that the firmware files are pushed to the
device more quickly.
With selection of some types, particularly Cisco controllers, you can specify the boot
software version.
did not select the default Dell PowerConnect Controller type.
TFTP server is recommended.
If you choose to use an external TFTP server, enter the File Server IP Address and the
Firmware Filename.
this option, you must enter the IP address on the Groups > Firmware page. Complete the
Firmware File Server IP Address field.
NOTE: With selection of some Types, you are prompted with the Server Protocol field that
lets you select which protocol to use, and this varies from device to device. If you select
FTP, AMP uses an anonymous user for file upload.
setting instructs AMP to use the server that is associated with the group instead of
defining a server.
firmware upgrade. This option displays when the user selects the Use an external
firmware file option.
Firmware Filename None Enter the name of the firmware file that needs to be uploaded. Ensure that the firmware
NOTE: Additional fields may appear for multiple device types. AMP prompts you for additional firmware information as required.
For example, Intel and Symbol distribute their firmware in two separate files: an image file and an HTML file. Both files must be
uploaded to AMP for the firmware to be distributed successfully via AMP.
file is in the TFTP root directory. If you are using a non-external server, you select Choose
File to find your local copy of the file.
6. Select Add to import the firmware file.
To delete a firmware file that has already been uploaded to AMP, return to the Device Setup > Upload Firmware
& Files page, select the checkbox for the firmware file and select Delete.
NOTE: A firmware file may not be deleted if it is the desired version for a group. Use the Group > Firmware page to investigate this
potential setting and status.
Using Web Auth Bundles in AMP
Web authentication bundles are configuration files that support Cisco WLC wireless LAN controllers. This
procedure requires that you have local or network access to a Web Auth configuration file for Cisco WLC
devices.
56 | Configuring AMP Dell PowerConnect W-AirWave |Version 7.3
Page 57

Perform these steps to add or edit Web Auth bundles in AMP.
1. Go to the Device Setup > Upload Firmware & Files page. This page displays any existing Web Auth bundles
that are currently configured in AMP, and allows you to add or delete Web Auth bundles.
2. Scroll to the bottom of the page. Select Add New Web Auth Bundle to create a new Web Auth bundle (see
Figure 29), or select the pencil icon next to an existing bundle to edit. You may also delete Web Auth bundles
by selecting that bundle with the checkbox, and selecting Delete.
Figure 29 Add Web Auth Bundle Page Illustration
3. Enter a descriptive label in the description field. This is the label used to identify and track Web Auth bundles
on the page.
4. Enter the path and filename of the Web Auth configuration file in the Web Auth Bundle field or select
Choose File to locate the file.
5. Select Add to complete the Web Auth bundle creation, or Save if replacing a previous Web Auth
configuration file, or Cancel to abort the Web Auth integration.
For additional information and a case study that illustrates the use of Web Auth bundles with Cisco WLC
controllers, refer to the following document on Cisco.com:
Wireless LAN controller Web Authentication Configuration Example, Document ID: 69340
http://www.cisco.com/en/US/tech/tk722/tk809/technologies_configuration_example09186a008067489f.shtml
Setting Up Device Types
On AMP Setup > Device Type Setup, you can define how the Device Type displayed for users on your network
is calculated from available data. The first matching property is used. These rules cannot be edited or deleted, but
only reordered or enabled.
You can change the priority order of rules by dragging and dropping rows, as shown in Figure 30.
Check or uncheck the checkbox under the Enabled column to turn device setup rules on or off.
Refer to “Monitoring and Supporting WLAN Users” on page191 for more information on the Device Type
column that appears in Users list tables.
Figure 30 AMP Setup > Device Type Setup Page Illustration
Dell PowerConnect W-AirWave |User Guide Configuring AMP | 57
Page 58

Configuring Cisco WLSE and WLSE Rogue Scanning
The Cisco Wireless LAN Solution Engine (WLSE) includes rogue scanning functions that AMP supports. This
section contains the following topics and procedures, and several of these sections have additional subprocedures:
Introduction to Cisco WLSE
Configuring WLSE Initially in AMP
Configuring IOS APs for WDS Participation
Configuring ACS for WDS Authentication
Configuring Cisco WLSE Rogue Scanning
You must enter one or more CiscoWorks WLSE hosts to be polled for discovery of Cisco devices and rogue AP
information.
Introduction to Cisco WLSE
Cisco WLSE functions as an integral part of the Cisco Structured Wireless-Aware Network (SWAN)
architecture, which includes IOS Access Points, a Wireless Domain Service, an Access Control Server, and a
WLSE. In order for AMP to obtain Rogue AP information from the WLSE, all SWAN components must be
properly configured. Table 33 describes these components.
Table 33 Cisco SWAN Architecture Components
SWAN Component Requirements
WDS (Wireless Domain
Services)
WLSE (Wireless LAN
Solution Engine)
ACS (Access Control
Server)
APs
WDS Name
Primary and backup IP address for WDS devices (IOS AP or WLSM)
WDS Credentials APs within WDS Group
NOTE: WDS can be either a WLSM or an IOS AP. WLSM (WDS) can control up to 250 access
points. AP (WDS) can control up to 30 access points.
IP Address
Login
IP Address
Login
APs within WDS Group
Configuring WLSE Initially in AMP
Use the following general procedures to configure and deploy a WLSE device in AMP:
Adding an ACS Server for WLSE
Enabling Rogue Alerts for Cisco WLSE
Configuring WLSE to Communicate with APs
Discovering Devices
Managing Devices
Inventory Reporting
Defining Access
Grouping
WDS Participation
Primary or Secondary WDS
58 | Configuring AMP Dell PowerConnect W-AirWave |Version 7.3
Page 59

Adding an ACS Server for WLSE
1. Go to the Devices > Discover > AAA Server page.
2. Select New from the drop-down list.
3. Enter the Server Name, Server Port (default 2002), Username, Password, and Secret.
4. Select Save.
Enabling Rogue Alerts for Cisco WLSE
1. Go to the Faults > Network Wide Settings > Rogue AP Detection page.
2. Select the Enable.
3. Select Apply.
Additional information about rogue device detection is available in “Configuring Cisco WLSE Rogue Scanning”
on page 61.
Configuring WLSE to Communicate with APs
1. Go to the Device Setup > Discover page.
2. Configure SNMP Information.
3. Configure HTTP Information.
4. Configure Telnet/SSH Credentials.
5. Configure HTTP ports for IOS access points.
6. Configure WLCCP credentials.
7. Configure AAA information.
Discovering Devices
There are three methods to discover access points within WLSE, as follows:
Using Cisco Discovery Protocol (CDP)
Importing from a file
Importing from CiscoWorks
Perform these steps to discover access points.
1. Go to the Device > Managed Devices > Discovery Wizard page.
2. Import devices from a file.
3. Import devices from Cisco Works.
4. Import using CDP.
Managing Devices
Prior to enabling radio resource management on IOS access points, the access points must be under WLSE
management.
NOTE: AMP becomes the primary management/monitoring vehicle for IOS access points, but for AMP to gather Rogue
information, the WLSE must be an NMS manager to the APs.
Use these pages to make such configurations:
1. Go to Device > Discover > Advanced Options.
2. Select the method to bring APs into management Auto, or specify via filter.
Dell PowerConnect W-AirWave |User Guide Configuring AMP | 59
Page 60

Inventory Reporting
When new devices are managed, the WLSE generates an inventory report detailing the new APs. AMP accesses
the inventory report via the SOAP API to auto-discover access points. This is an optional step to enable another
form of AP discovery in addition to AMP's CDP, SNMP scanning, and HTTP scanning discovery for Cisco IOS
access points. Perform these steps for inventory reporting.
1. Go to Devices > Inventory > Run Inventory.
2. Run Inventory executes immediately between WLSE polling cycles.
Defining Access
AMP requires System Admin access to WLSE. Use these pages to make these configurations.
1. Go to Administration > User Admin.
2. Configure Role and User.
Grouping
It’s much easier to generate reports or faults if APs are grouped in WLSE. Use these pages to make such
configurations.
1. Go to Devices > Group Management.
2. Configure Role and User.
Configuring IOS APs for WDS Participation
IOS APs (1100, 1200) can function in three roles within SWAN:
Primary WDS
Backup WDS
WDS Member
AMP monitors AP WDS role and displays this information on AP Monitoring page.
NOTE: APs functioning as WDS Master or Primary WDS will no longer show up as Down is the radios are enabled.
WDS Participation
Perform these steps to configure WDS participation.
1. Log in to the AP.
2. Go to the Wireless Services > AP page.
3. Select Enable participation in SWAN Infrastructure.
4. Select Specified Discovery and enter the IP address of the Primary WDS device (AP or WLSM).
5. Enter the Username and Password for the WLSE server.
Primary or Secondary WDS
Perform these steps to configure primary or secondary functions for WDS.
1. Go to the Wireless Services > WDS > General Setup page.
2. If the AP is the Primary or Backup WDS, select Use the AP as Wireless Domain Services.
Select Priority (set 200 for Primary, 100 for Secondary).
Configure the Wireless Network Manager (configure the IP address of WLSE).
3. If the AP is Member Only, leave all options unchecked.
60 | Configuring AMP Dell PowerConnect W-AirWave |Version 7.3
Page 61

4. Go to the Security > Server Manager page.
5. Enter the IP address and Shared Secret for the ACS server and select Apply.
6. Go to the Wireless Services > WDS > Server Group page.
7. Enter the WDS Group of AP.
8. Select the ACS server in the Priority 1 drop-down menu and select Apply.
Configuring ACS for WDS Authentication
ACS authenticates all components of the WDS and must be configured first. Perform these steps to make this
configuration.
1. Login to the ACS.
2. Go to the System Configuration > ACS Certificate Setup page.
3. Install a New Certificate by selecting the Install New Certificate button, or skip to the next step if the
certificate was previously installed.
4. Select User Setup in the left frame.
5. Enter the Username that will be used to authenticate into the WDS and select Add/Edit.
6. Enter the Password that will be used to authenticate into the WDS and select Submit.
7. Go to the Network Configuration > Add AAA Client page.
8. Add AP Hostname, AP IP Address, and Community String (for the key).
9. Enter the Password that will be used to authenticate into the WDS and select Submit.
For additional and more general information about ACS, refer to “Configuring ACS Servers” on page62.
Configuring Cisco WLSE Rogue Scanning
The AMP Setup > WLSE page allows AMP to integrate with the Cisco Wireless LAN Solution Engine (WLSE).
AMP can discover APs and gather rogue scanning data from the Cisco WLSE.
Figure 31 illustrates and itemizes the AMP settings for communication that is enabled between AMP and WLSE.
Figure 31 AMP Setup > WLSE > Add WLSE Page Illustration
Perform the following steps for optional configuration of AMP for support of Cisco WLSE rogue scanning.
1. To add a Cisco WLSE server to AMP, navigate to the AMP Setup > WLSE page and select Add. Complete
the fields in this page. Table 34 describes the settings and default values.
Table 34 AMP Setup > WLSE Fields and Default Values
Setting Default Description
Hostname/IP Address None Designates the IP address or DNS Hostname for the WLSE server, which must
already be configured on the Cisco WLSE server.
Protocol HTTP Specifies the protocol to be used when polling the WLSE.
Dell PowerConnect W-AirWave |User Guide Configuring AMP | 61
Page 62

Table 34 AMP Setup > WLSE Fields and Default Values (Continued)
Setting Default Description
Port 1741 Defines the port AMP uses to communicate with the WLSE server.
Username None Defines the username AMP uses to communicate with the WLSE server. The
username and password must be configured the same way on the WLSE server
and on AMP.
The user needs permission to display faults to discover rogues and inventory
API (XML API) to discover manageable APs. As derived from a Cisco limitation,
only credentials with alphanumeric characters (that have only letters and
numbers, not other symbols) allow AMP to pull the necessary XML APIs.
Password None Defines the password AMP uses to communicate with the WLSE server. The
username and password must be configured the same way on the WLSE server
and on AMP.
As derived from a Cisco limitation, only credentials with alphanumeric
characters (that have only letters and numbers, not other symbols) allow AMP
to pull the necessary XML APIs.
Poll for AP Discovery; Poll for
Rogue Discovery
Last Contacted None Displays the last time AMP was able to contact the WLSE server.
Polling Period 10 minutes Determines how frequently AMP polls WLSE to gather rogue scanning data.
Yes Sets the method by which AMP uses WLSE to poll for discovery of new APs
and/or new rogue devices on the network.
2. After you have completed all fields, select Save. AMP is now configured to gather rogue information from
WLSE rogue scans. As a result of this configuration, any rogues found by WLSE appear on the RAPIDS >
List page.
What Next?
Go to additional tabs in the AMP Setup section to continue additional setup configurations.
Complete the required configurations in this chapter before proceeding.
Configuring ACS Servers
This is an optional configuration. The AMP Setup > ACS page allows AMP to poll one or more Cisco ACS
servers for wireless username information. When you specify an ACS server, AMP gathers information about your
wireless users. Refer to “Configuring ACS for WDS Authentication” on page61 if you want to use your ACS
server to manage your AMP users.
Perform these steps to configure ACS servers:
1. Go to the AMP Setup > ACS page. This page displays current ACS setup, as illustrated in Figure 32.
Figure 32 AMP Setup > ACS Page Illustration
62 | Configuring AMP Dell PowerConnect W-AirWave |Version 7.3
Page 63

2. Select Add to create a new ACS server, or select a pencil icon to edit an existing server. To delete an ACS
server, select that server and select Delete. When selecting Add or edit, the Details page appears, as
illustrated in Figure 33.
Figure 33 AMP Setup > ACS > Add/Edit Details Page Illustration
3. Complete the settings on AMP Setup > ACS > Add/Edit Details. Table 35 describes these fields:
Table 35 AMP Setup > ACS > Add/Edit Details Fields and Default Values
Field Default Description
IP/Hostname None Sets the DNS name or the IP address of the ACS Server.
Protocol HTTP Launches a drop-down menu specifying the protocol AMP uses when it polls the ACS server.
Port 2002 Sets the port through which AMP communicates with the ACS.
AMP generally communicates via SNMP traps on port 162.
Username None Sets the Username of the account AMP uses to poll the ACS server.
Password None Sets the password of the account AMP uses to poll the ACS server.
Polling Period 10 min Launches a drop-down menu that specifies how frequently AMP polls the ACS server for
username information.
4. Select Add to finish creating the new ACS server, or Save to finish editing an existing ACS server.
5. The ACS server must have logging enabled for passed authentications. Enable the Log to CSV Passed
Authentications report option, as follows:
Log in to the ACS server, select System Configuration, then in the Select frame, select Logging.
Under Enable Logging, select CSV Passed Authentications. The default logging options function and
support AMP. These include the two columns AMP requires: User-Name and Caller-ID.
What Next?
Go to additional tabs in the AMP Setup section to continue additional setup configurations.
Complete the required configurations in this chapter before proceeding.
Integrating AMP with an Existing Network Management Solution (NMS)
This is an optional configuration. The AMP Setup > NMS configuration page allows AMP to integrate with
other Network Management Solution (NMS) consoles. This configuration enables advanced and interoperable
functionality as follows:
AMP can forward WLAN-related SNMP traps to the NMS, or AMP can send SNMPv1 or SNMPv2 traps to
the NMS.
AMP can be used in conjunction with Hewlett-Packard’s ProCurve Manager.
Dell PowerConnect W-AirWave |User Guide Configuring AMP | 63
Page 64

The necessary files for either type of NMS interoperability are downloaded from the AMP Setup > NMS page
as follows. For additional information, contact support.
Perform these steps to configure NMS support in AMP:
1. Go to AMP Setup > NMS, illustrated in Figure 34.
Figure 34 AMP Setup > NMS Page Illustration
2. Select Add to integrate a new NMS server, or select the pencil icon to edit an existing server. Provide the
information described in Table 36:
Table 36 AMP Setup > NMS Integration Add/Edit Fields and Default Values
Setting Default Description
Hostname None Cites the DNS name or the IP address of the NMS.
Port 162 Sets the port AMP uses to communicate with the NMS.
NOTE: AMP generally communicates via SNMP traps on port 162.
Community String None Sets the community string used to communicate with the NMS.
SNMP Version v2C Sets the SNMP version of the traps sent to the Host.
Enabled Yes Enables or disables trap logging to the specified NMS.
Send Configuration Traps Yes Enables NMS servers to transmit SNMP configuration traps.
3. The NMS Integration Add/Edit page includes the Netcool/OMNIbus Integration link to information and
instructions. The IBM Tivoli Netcool/OMNIbus operations management software enables automated event
correlation and additional features resulting in optimized network uptime.
4. The NMS Integration Add/Edit page includes the HP ProCurve Manager Integration link. Select this link
for additional information, zip file download, and brief instructions for installation with AMP. Select Add to
finish creating the NMS server, or Save to configure an existing NMS server.
What Next?
Go to additional tabs in the AMP Setup section to continue additional setup configurations.
Complete the required configurations in this chapter before proceeding.
64 | Configuring AMP Dell PowerConnect W-AirWave |Version 7.3
Page 65

Auditing PCI Compliance on the Network
This section describes PCI requirements and auditing functions in AMP in the following topics:
Introduction to PCI Requirements
PCI Auditing in the AMP Interface
Enabling or Disabling PCI Auditing
Introduction to PCI Requirements
AMP supports wide security standards and functions in the wireless network. One component of network security
is the optional deployment of Payment Card Industry (PCI) Auditing.
The Payment Card Industry (PCI) Data Security Standard (DSS) establishes multiple levels in which payment
cardholder data is protected in a wireless network. AMP supports PCI requirements according to the standards
and specifications set forth by the following authority:
Payment Card Industry (PCI) Data Security Standard (DSS)
PCI Security Standards Council Website
https://www.pcisecuritystandards.org
PCI Quick Reference Guide, Version 1.2 (October 2008)
https://www.pcisecuritystandards.org/pdfs/pci_ssc_quick_guide.pdf
PCI Auditing in the AMP Interface
PCI Auditing in AMP allows you to monitor, audit, and demonstrate PCI compliance on the network. There are
five primary pages in which you establish, monitor, and access PCI auditing, as follows:
The AMP Setup > PCI Compliance page enables or disables PCI Compliance monitoring on the network,
and displays the current compliance status on the network. See “Enabling or Disabling PCI Auditing” on
page66.
The Reports > Definitions page allows you to create custom-configured and custom-scheduled PCI
Compliance reports. See “Reports > Definitions Page Overview” on page225.
The Reports > Generated page lists PCI Compliance reports currently available, and allows you to generate
the latest daily version of the PCI Compliance Report with a single select. Refer to “Reports > Generated
Page Overview” on page227.
The APs/Devices > PCI Compliance page enables you to analyze PCI Compliance for any specific device on
the network. This page is accessible when you select a specific device from the APs/Devices > Monitor page.
First, you must enable this function through AMP Setup. See “Enabling or Disabling PCI Auditing” on
page66.
The PCI Compliance Report offers additional information. Refer to “Using the PCI Compliance Report” on
page243. This report not only contains Pass or Fail status for each PCI requirement, but cites the action
required to resolve a Fail status when sufficient information is available.
NOTE: When any PCI requirement is enabled on AMP, then AMP grades the network as pass or fail for the respective PCI
requirement. Whenever a PCI requirement is not enabled in AMP, then AMP does not monitor the network’s status in relation to
that requirement, and cannot designate Pass or Fail network status. AirWave users without RAPIDS visibility enabled will not see
the 11.1 PCI requirements in the PCI Compliance Report.
Dell PowerConnect W-AirWave |User Guide Configuring AMP | 65
Page 66

Table 37 PCI Requirements and Support in AMP
Requirement Description
1.1 Monitoring configuration standards for network firewall devices
When Enabled: PCI Requirement 1.1 establishes firewall and router configuration standards.
A device fails Requirement 1.1 if there are mismatches between the desired configuration and the
configuration on the device.
When Disabled: firewall router and device configurations are not checked for PCI compliance, and
Pass or Fail status is not reported or monitored.
1.2.3 Monitoring firewall installation between any wireless networks and the cardholder data environment
When Enabled: A device passes requirement 1.2.3 if it can function as a stateful firewall.
When Disabled: firewall router and device installation are not checked for PCI compliance.
2.1 Monitoring the presence of vendor-supplied default security settings
When Enabled: PCI Requirement 2 establishes the standard in which all vendor-supplied default
passwords are changed prior to a device’s presence and operation in the network.
A device fails requirement 2.1 if the username, passwords or SNMP credentials being used by AMP to
communicate with the device are on a list of forbidden default credentials. The list includes common
vendor default passwords, for example.
When Disabled: device passwords and other vendor default settings are not checked for PCI
compliance.
2.1.1 Changing vendor-supplied defaults for wireless environments
When Enabled: A device fails requirement 2.1.1 if the passphrases, SSIDs, or other security-related
settings are on a list of forbidden values that AMP establishes and tracks. The list includes common
vendor default passwords. The user can input new values to achieve compliance.
When Disabled: network devices are not checked for forbidden information and PCI Compliance is not
established.
4.1.1 Using strong encryption in wireless networks
When Enabled: PCI Requirement 4 establishes the standard by which payment cardholder data is
encrypted prior to transmission across open public networks. PCI disallows WEP encryption as an
approved encryption method after June 20, 2010. A device fails requirement 4.1.1 if the desired or actual
configuration reflect that WEP is enabled on the network, or if associated users can connect with WEP.
When Disabled: AMP cannot establish a pass or fail status with regard to PCI encryption requirements
on the network.
11.4 Using intrusion-detection or intrusion-prevention systems to monitor all traffic
When Enabled: AMP reports pass or fail status when monitoring devices capable of reporting IDS
events. Recent IDS events are summarized in the PCI Compliance report or the IDS Report.
When Disabled: AMP does not monitor the presence of PCI-compliant intrusion detection or prevention
systems, nor can it report Pass or Fail status with regard to IDS events.
Enabling or Disabling PCI Auditing
Perform these steps to verify status and to enable or disable AMP support for PCI 1.2 requirements. enabling one
or all PCI standards on AMP enables real-time information and generated reports that advise on Pass or Fail
status. The PCI auditing supported in AMP is reported in Table 37.
1. To determine what PCI Compliance standards are enabled or disabled on AMP, navigate to the AMP Setup
> PCI Compliance page, illustrated in Figure 35.
66 | Configuring AMP Dell PowerConnect W-AirWave |Version 7.3
Page 67

Figure 35 AMP Setup > PCI Compliance Page Illustration
2. To enable, disable, or edit any category of PCI Compliance monitoring in AMP, select the pencil icon next to
the category. The Default Credential Compliance page displays for the respective PCI standard.
3. Create changes as required. Specific credentials can be cited in the Forbidden Credentials section of any Edit
page to enforce PCI requirements in AMP. Figure 36 shows one example.
Figure 36 Default Credential Compliance for PCI Requirements
4. Select Save.
5. To view and monitor PCI auditing on the network, use generated or daily reports. See Chapter 9, “Creating,
Running, and Emailing Reports” . In addition, you can view the real-time PCI auditing of any given device
online. Perform these steps:
a. Go to the APs/Devices > List page, select a specific device, and the Monitor page for that device displays.
The Monitor page displays a PCI Compliance subtab in the menu bar.
b. Select PCI Compliance to view complete PCI compliance auditing for that specific device.
What Next?
Go to other tabs in the AMP Setup section to continue additional setup configurations.
Complete the required configurations in this chapter before proceeding.
Deploying WMS Offload
Overview of WMS Offload in AMP
This section describes the Dell PowerConnect W Wireless LAN Management Server (WMS) offload
infrastructure. WMS Offload is supported with the following two requirements:
Dell PowerConnect W-AirWave |User Guide Configuring AMP | 67
Page 68

Dell PowerConnect W-Series ArubaOS Version 5.0 or later
Dell PowerConnect W-AirWave Version 6.0 or later
The Dell PowerConnect W WMS feature is an enterprise-level hardware device and server architecture with
managing software for security and network policy. There are three primary components of the WMS
deployment:
Air Monitor AP devices establish and monitor RF activity on the network.
The WMS server manages devices and network activity, to include rogue AP detection and enforcement of
network policy.
The AMP graphical user interface (UI) allows users to access and use the WMS functionality.
WMS Offload is the ability to place the burden of the WMS server data and UI functions on AMP. WMS master
controllers provide this data so that AMP can support rigorous network monitoring capabilities.
General Configuration Tasks Supporting WMS Offload in AMP
WMS Offload must be enabled with a six-fold process and related configuration tasks, as follows:
1. Configure WLAN switches for optimal AMP monitoring.
Disable debugging.
Ensure AMP server is a trap receiver host.
Ensure proper traps are enabled.
2. Configure AMP to optimally monitor the AirWave infrastructure.
Enable WMS offload.
Configure SNMP communication.
Create a proper policy for monitoring AirWave infrastructure.
Discover the infrastructure.
3. Configure device classification.
Set up rogue classification.
Set up rogue classification override.
Establish user classification override devices.
4. Deploy ArubaOS-specific monitoring features.
Enable remote AP and wired network monitoring.
View controller license information.
5. Convert existing floor plans to VisualRF, to include the following elements:
Dell PowerConnect W-Series ArubaOS
RF Plan
6. Use RTLS for increasing location accuracy (optional).
Enable RTLS service on the AMP server.
Enable RTLS on ArubaOS Infrastructure.
Additional Information Supporting WMS Offload
For additional information, including detailed concepts, configuration procedures, restrictions, ArubaOS
infrastructure, and AMP version differences in support of WMS Offload, refer to the Dell PowerConnect W-
AirWave Best Practices Guide at support.dell.com/manuals.
68 | Configuring AMP Dell PowerConnect W-AirWave |Version 7.3
Page 69

Chapter 4
Configuring and Using Device Groups in AMP
This chapter describes the deployment of device groups within AMP. The section below describes the pages or
focused subtabs available on the Groups tab. Note that the available subtabs can vary significantly from one
device group to another—one or more subtabs may not appear, depending on the Default Group display option
selected on the AMP Setup > General page and the types of devices you add to AMP.
Figure 37 Subtabs under the Group tab
List—This page is the default page in the Groups section of AMP. It lists all groups currently configured in
AMP and provides the foundation for all group-level configurations. See “Viewing All Defined Device
Groups” on page71.
Monitor—This page displays user and bandwidth information, lists devices in a given group, provides an Alert
Summary table for monitoring alerts for the group, and provides a detailed Audit Log for group-level activity.
NOTE: The Incidents portion of the Alert Summary table only increments the counter for incidents that are open and associated to
an AP in that group, associated with the group itself. It does not include incidents associated with any folder. To view all incidents
including those not associated to an AP, go to the Helpdesk > Incidents page.
Basic—This page appears when you create a new group on the Groups > List page. Once you define a group
name, AMP displays the Basic page from which you configure many group-level settings. This page remains
available for any device group configured in AMP. Refer to “Configuring Basic Group Settings” on page72.
Templates—This page manages templates for any device group. Templates allow you to manage the
configuration of Dell PowerConnect W-Series, 3Com, Alcatel-Lucent, Aruba Networks, Cisco Aironet IOS,
Cisco Catalyst switches, Enterasys, HP, Nortel, Symbol and Trapeze devices in a given group using a
configuration file. Variables in such templates configure device-specific properties, such as name, IP address
and channel. Variables also define group-level properties. For additional information about using the
Templates page, refer to Chapter 6, “Creating and Using Templates” on page147.
Security—This page defines general security settings for device groups, to include RADIUS, encryption, and
additional security settings on devices. Refer to “Configuring Group Security Settings” on page80.
SSIDs—This page sets SSIDs, VLANs, and related parameters in device groups. Refer to “Configuring Group
SSIDs and VLANs” on page82.
AAA Servers—This page configures authentication, authorization, and accounting settings in support of
RADIUS servers for device groups. Refer to “Adding and Configuring Group AAA Servers” on page79.
Radio—This page defines general 802.11 radio settings for device groups. Refer to “Configuring Radio
Settings for Device Groups” on page86.
Dell Config—This page manages ArubaOS Device Groups, AP Overrides, and other profiles specific to Dell
PowerConnect W-Series devices on the network. Use this page as an alternative to the Device Setup > Dell
PowerConnect W Configuration page. The apperance of this page varies depending on whether AMP is
configured for global configuration or group configuration. For additional information, refer to theDell
PowerConnect W-AirWave Configuration Guide at support.dell.com/manuals.
Cisco WLC Config—This page consolidates controller-level settings from the Group Radio, Security, SSIDs,
Cisco WLC Radio and AAA Server pages into one navigation tree that is easier to navigate, and has familiar
layout and terminology. Bulk configuration for per-thin AP settings, previously configured on the Group
Dell PowerConnect W-AirWave | User Guide Configuring and Using Device Groups in AMP | 69
Page 70

LWAPP APs tab, can now be performed from Modify Devices on the APs/Devices > List page. Refer to
“Cisco WLC Group Configuration” on page89.
PTMP—This page defines settings specific to Proxim MP devices when present. Refer to “Configuring Group
PTMP Settings” on page94.
Proxim Mesh—This page defines mesh AP settings specific to Proxim devices when present. Refer to
“Configuring Proxim Mesh Radio Settings” on page95.
MAC ACL—This page defines MAC-specific settings that apply to Proxim, Symbol, and ProCurve 520
devices when present. Refer to “Configuring Group MAC Access Control Lists” on page96.
Firmware—This page manages firmware files for many devices. “Specifying Minimum Firmware Versions for
APs in a Group” on page97.
Compare—This page allows you to compare line item-settings between two device groups. On the Groups >
List page, select Compare Two Groups, select the two groups from the drop-down menus, then select
Compare. “Comparing Device Groups” on page98.
This chapter also provides the following additional procedures for group-level configurations:
“Deleting a Group” on page98
“Changing Multiple Group Configurations” on page99
“Modifying Multiple Devices” on page100
“Using Global Groups for Group Configuration” on page102
AMP Groups Overview
Enterprise APs, controllers, routers, and switches have hundreds of variable settings that must be configured
precisely to achieve optimal performance and network security. Configuring all settings on each device
individually is time consuming and error prone. AMP addresses this challenge by automating the processes of
device configuration and compliance auditing. At the core of this approach is the concept of Device Groups, with
the following functions and benefits:
AMP allows certain settings to be managed efficiently at Group-level while others are managed at an
individual device level.
AMP defines a Group as a subset of the devices on the wireless LAN, ranging in size from one device to
hundreds of devices that share certain common configuration settings.
Groups may be defined based on geography (such as “5th Floor APs”), usage or security policies (such as
“Guest Access APs”), function (such as “Manufacturing APs”), or any other appropriate variable.
Devices within a group may be from different vendors or hardware models. All devices within a Group share
certain basic configuration settings.
Typical group configuration variables include basic settings (SSID, SNMP polling interval, and so forth), security
settings (VLANs, WEP, 802.1x, ACLs, and so forth), and some radio settings (data rates, fragmentation
threshold, RTS threshold, DTIM, preamble, and so forth). When configuration changes are applied at a group
level, they are assigned automatically to every device within that group. Such changes must be applied with every
device in Managed mode. Monitor mode is the more common mode.
CAUTION: Always review the Audit page before pushing configuration to a device or group.
Individual device settings—such as device name, RF channel selection, RF transmission power, antenna settings,
and so forth—typically should not be managed at a group level and must be individually configured for optimal
performance. Individual AP settings are configured on the APs/Devices > Manage page.
70 | Configuring and Using Device Groups in AMP Dell PowerConnect W-AirWave |Version 7.3
Page 71

You can create as many different groups as required. Administrators usually establish groups that range in size
from five to 100 wireless devices.
Group configuration can be enhanced with the AMP Global Groups feature, which lets you create Global Groups
with configurations that are pushed to individual Subscriber Groups.
Viewing All Defined Device Groups
To display a list of all defined groups, browse to the Groups > List page, illustrated in Figure 38.
Figure 38 Groups > List Page Illustration
Table 38 describes the columns in the Groups > List page.
Table 38 Groups > List Columns
Column Description
Add New Group Launches a page that enables you to add a new group by name and to define group parameters for devices
in that group. For additional information, refer to “Configuring Basic Group Settings” on page72.
Manage
(wrench icon)
Name Uniquely identifies the group by location, vendor, department or any other identifier (such as "Accounting
Up/Down Status
Polling Period
Is Global Group If a group is designated as global, it may not contain APs but it may be used as a template for other groups.
Global Group Specifies which group this Subscriber Group is using as its template.
SSID The SSID assigned to supported device types within the group.
Total Devices Total number of devices contained in the group including APs, controllers, routers, or switches.
Down The number of access points within the group that are not reachable via SNMP or are no longer associated
Mismatched The number of devices within the group that are in a mismatched state.
Ignored The number of ignored devices in that group.
Users The number of mobile users associated with all access points within the group. To avoid double counting of
Goes to the Groups > Basic configuration page for that group. Hover your mouse over the icon to see a list of
shortcuts to group-specific subtabs that would appear across the navigation section if this group is
selected.
APs," "Floor 1 APs," "Cisco devices," "802.1x APs," and so forth).
The time between Up/Down SNMP polling periods for each device in the group. Detailed SNMP polling
period information is available on the Groups > Basic configuration page. Note that by default, most polling
intervals do not match the up/down period.
This column may also indicate Yes if this group has been pushed to the AMP from a Master Console.
to a controller. Note that thin APs are not directly polled with SNMP, but are polled through the controller.
That controller may report that the thin AP is down or is no longer on the controller. At this point, AMP
classifies the device as down.
users, users are only listed in the group of the AP with which they are associated. Note that device groups
with only controllers in them report no users.
BW Bandwidth: A running average of the sum of bytes in and bytes out for the managed radio page.
Duplicate Creates a new group with the name Copy of <Group Name> with configuration settings. (Dell PowerConnect
W configuration settings will have to be manually added back.)
Changes Whether the group has unapplied changes.
Dell PowerConnect W-AirWave | User Guide Configuring and Using Device Groups in AMP | 71
Page 72

NOTE: When you first configure AMP, there is only one default group labeled Access Points. If you have no other groups
configured, refer to “Configuring Basic Group Settings” on page72.
Configuring Basic Group Settings
The first default device group that AMP sets up is the Access Points group, but you can use this procedure to add
and configure any device group. Perform these steps to configure basic group settings, then continue to additional
procedures to define additional settings as required.
1. Go to the Groups > List page. Existing device groups appear on this page.
2. To create a new group, select Add. Enter a group name and select Add. The Groups > Basic page appears.
To edit an existing device group, select the manage (wrench) icon next to the group. The Groups > Basic
page appears. If you mouse over an existing group’s wrench, a popup menu allows you to select Basic,
Templates, Security, SSIDs, AAA Servers, Radio, Dell PowerConnect W Config or Cisco WLC Config to
edit those pages as desired, as illustrated in Figure 39.
Figure 39 Pop-up When Hovering over Wrench Icon in Groups > List
72 | Configuring and Using Device Groups in AMP Dell PowerConnect W-AirWave |Version 7.3
Page 73

Figure 40 illustrates an example Groups > Basic page.
Figure 40 Groups > Basic Page Illustration
3. Define the settings in the Basic and Global Group sections. Table 39 describes several typical settings and
default values of this Basic section.
Dell PowerConnect W-AirWave | User Guide Configuring and Using Device Groups in AMP | 73
Page 74

Table 39 Basic and Global Groups Fields and Default Values
Setting Default Description
Name Defined when
first adding the
group
Missed SNMP
Poll Threshold
Regulatory
Domain
Timezone AMP System
Allow One-toOne NAT
Audit
Configuration on
Devices
Use Global
Group
1 Sets the number of Up/Down SNMP polls that must be missed before AMP considers a
United States Sets the regulatory domain in AMP, limiting the selectable channels for APs in the group.
Tim e
No Allows AMP to talk to the devices on a different IP address than the one configured on the
Yes Auditing and pushing of configuration to devices can be disabled on all the devices in the
No When enabled, this field allows you to define the device group to be a Global Group. Refer
Displays or changes the group name. As desired, use this field to set the name to uniquely
identify the group by location, vendor, department, or any other identifier (such as
“Accounting APs,” “Cisco devices,” “802.1x APs,” and so forth).
device to be down. The number of SNMP retries and the SNMP timeout of a poll can be set
on the Device Setup > Communication page.
Allows group configuration changes to be scheduled relative to the time zone in which the
devices are located. This setting is used for scheduling group-level configuration changes.
device.
NOTE: If enabled, the LAN IP Address listed on the AP/Devices > Manage configuration
page under the Settings area is different than the IP Address under the Device
Communication area.
group. Once disabled, all the devices in the groups will not be counted towards
mismatched devices.
to “Using Global Groups for Group Configuration” on page102.
4. Complete the SNMP Polling Periods section. The information in this section overrides default settings.
Table 40 describes the SNMP polling settings.
Table 40 SNMP Polling Periods Fields and Default Values
Setting Default Description
Up/Down Status Polling
Period
Override Polling Period for
Other Services
AP Interface Polling Period 5 minutes Sets the interval at which AMP polls for radio monitoring and bandwidth being
User Data Polling Period 5 minutes Sets time between SNMP polls for User Data for devices in the group.
Thin AP Discovery Polling
Period
Device-to-Device link Polling
Period
802.11 Counters Polling Period 5 minutes Sets time between SNMP polls for 802.11 Counter information.
Rogue AP and Device
Location Data Polling Period
5 minutes Sets time between Up/Down SNMP polling for each device in the group.
The Group SNMP Polling Interval overrides the global parameter configured on
the Device Setup > Communication page. An initial polling interval of 5 minutes is
best for most networks.
No Enables or disables overriding the base SNMP Polling Period. If you select Ye s,
the other settings in the SNMP Polling Periods section are activated, and you
can override default values.
used by a device.
5 minutes Sets time between SNMP polls for Thin AP Device Discovery. Controllers are the
only devices affected by this polling interval.
5 minutes Sets time between SNMP polls for Device-to-Device link polling. Mesh APs are
the only devices affected by this polling interval.
5 minutes Sets time between SNMP polls for Rogue AP and Device Location Data polling.
CDP Neighbor Data Polling
Period
74 | Configuring and Using Device Groups in AMP Dell PowerConnect W-AirWave |Version 7.3
30 minutes Sets the frequency in which this group polls the network for Cisco Discovery
Protocol (CDP) neighbors.
Page 75

5. Record additional information and comments about the group in the Notes section.
6. To configure which options and tabs are visible for the group, complete the settings in the Group Display
Options section. Table 41 describes the settings and default values.
Table 41 Group Display Options Fields and Default Values
Setting Default Description
Show device
settings for:
Selected Device
Types
Only
devices on
this AMP
N/A This option appears if you chose to display selected device types, allowing you to select the
Drop-down menu determines which Group tabs and options are to be viewable by default in
new groups. Settings include the following:
All Devices—AMP displays all Group tabs and setting options.
Only devices in this group—AMP hides all options and tabs that do not apply to the devices
in the group. If you use this setting, then to get the group list to display the correct SSIDs
for the group, you must Save and Apply on the group.
Only devices on this AMP— hides all options and tabs that do not apply to the APs and
devices currently on AMP.
Use system defaults—Use the default settings on AMP Setup > General.
Selected device types—Allows you to specify the device types for which AMP displays
Group settings.
device types to display group settings. Use Select devices in this group to display only devices
in the group being configured.
7. To assign dynamically a range of static IP addresses to new devices as they are added into the group, locate the
Automatic Static IP Assignment section on the Groups > Basic configuration page. If you select Yes in this
section, additional fields appear. Complete these fields as required. Table 42 describes the settings and
default values This section is only relevant for a small number of device types, and will appear when they are
present.
Table 42 Automatic Static IP Assignment Fields and Default Values
Setting Default Description
Assign Static IP
Addresses to
Devices
Start IP Address Blank Sets the first address AMP assigns to the devices in the Group.
Number of
Addresses
Subnet Mask Blank Sets the subnet mask to be assigned to the devices in the Group.
Subnet Gateway Blank Sets the gateway to be assigned to the devices in the Group.
Next IP Address Blank Defines the next IP address queued for assignment. This field is disabled for the initial Access
No Enables AMP to statically assign IP addresses from a specified range to all devices in the
Group.
Blank Sets the number of addresses in the pool from which AMP can assign IP addresses.
Points group.
Dell PowerConnect W-AirWave | User Guide Configuring and Using Device Groups in AMP | 75
Page 76

8. To configure Spanning Tree Protocol on WLC devices and Proxim APs, locate the Spanning Tree Protocol
section on the Groups > Basic configuration page. Adjust these settings as required. Table 43 describes the
settings and default values.
Table 43 Spanning Tree Protocol Fields and Default Values
Setting Default Description
Spanning Tree
Protocol
Bridge Priority 32768 Sets the priority for the AP. Values range from 0 to 65535. Lower values have higher priority.
Bridge Maximum
Age
Bridge Hello Time 2 Sets the time, in seconds, between Hello message broadcasts.
Bridge Forward
Delay
No Enables or disables Spanning Tree Protocol on Proxim APs.
The lowest value is the root of the spanning tree. If all devices are at default the device with
the lowest MAC address will become the root.
20 Sets the maximum time, in seconds, that the device stores protocol information. The
supported range is from 6 to 40.
15 Sets the time, in seconds, that the port spends in listening and learning mode if the spanning
tree has changed.
9. To configure NTP settings locate the NTP section and adjust these settings as required. Table 44 describes
the settings and default values.
Table 44 NTP Fields and Default Values
Setting Default Description
NTP Server #1,2,3 None Sets the IP address of the NTP server to be configured on the AP.
UTC Time Zone 0 Sets the hour offset from UTC time to local time for the AP. Times displayed in AMP graphs and
logs use the time set on the AMP server.
Daylight Saving
Time
No Enables or disables the advanced daylight saving time settings in the Proxim section of the
Groups > Basic configuration page.
10. To configure settings specific to Cisco IOS/Catalyst, locate the Cisco IOS/Catalyst section and adjust these
settings as required. Table 45 describes the settings and default values.
Table 45 Cisco IOS/Catalyst Fields and Default Values
Setting Default Description
SNMP Version 2c The version of SNMP used by AMP to communicate to the AP.
Cisco IOS CLI
Communication
Cisco IOS Config File
Communication
Telnet The protocol AMP uses to communicate with Cisco IOS devices. Selecting SSH uses
the secure shell for command line page (CLI) communication. Selecting Telnet sends
the data in clear text via Telnet.
TFTP The protocol AMP uses to communicate with Cisco IOS devices. Selecting SCP uses
the secure copy protocol for file transfers and displays the SCP Version option.
Selecting TFTP will use the insecure trivial file transfer protocol. The SCP login and
password should be entered in the Telnet username and password fields.
76 | Configuring and Using Device Groups in AMP Dell PowerConnect W-AirWave |Version 7.3
Page 77

11. To configure settings specific to Cisco WLC, locate the Cisco WLC section and adjust these settings as
required. Table 46 describes the settings and default values.
Table 46 Cisco WLC Fields and Default Values
Setting Default Description
SNMP Version 2c Sets the version of SNMP used by AMP to communicate to WLC controllers.
CLI Communication Telnet Sets the protocol AMP uses to communicate with Cisco IOS devices. Selecting SSH
uses the secure shell for command line page (CLI) communication. Selecting Telnet
sends the data in clear text via Telnet.
NOTE: When configuring Cisco WLC controllers, refer to “Configuring Wireless Parameters for Cisco Controllers” on page93.
12. To configure Proxim/Avaya specific settings locate the Proxim/Avaya section and adjust these settings as
required. Table 47 describes the settings and default values.
Table 47 Proxim/Avaya Fields and Default Values
Setting Default Description
SNMP Version 1 Sets the version of SNMP used by AMP to communicate to the AP.
Enable DNS
Client
Primary DNS
server
Secondary DNS
server
Default DNS
domains
HTTP Server Port 80 Sets this port as the HTTP server port on all Proxim APs in the group.
Country Code United
No Enables the DNS client on the AP. Enabling the DNS client allows you to set some values on the
AP by hostname instead of IP address. If you select Ye s for this setting, additional DNS fields
display.
Blank Sets the IP address of the Primary DNS server.
Blank Sets the IP address of the Secondary DNS server.
Blank Sets the default DNS domain used by the AP.
States
Configures AMP to derive its time settings based on the country of location, as specified in this
field.
13. To configure HP ProCurve specific settings, locate the HP ProCurve section and adjust these settings as
required. Table 48 describes the settings and default values.
Table 48 HP ProCurve Fields and Default Values
Setting Default Description
SNMP Version 2c Sets the version of SNMP used by AMP to communicate to the AP.
ProCurve XL/ZWeSM CLI
Communication
Telnet Sets the protocol AMP uses to communicate with ProCurve XLWeSM devices. Selecting
SSH will use the secure shell for command line (CLI) communication. Selecting Telnet
will send the data in clear text via telnet.
Controller SNMP Version 2c Specifies the version of SNMP used by AMP to communicate to the controller.
NOTE: DST Start Month, Start Day, End Month, End Day, and DST Offset are only visible if Daylight Saving Time is enabled in the
NTP section of the Groups > Basic configuration page.
Dell PowerConnect W-AirWave | User Guide Configuring and Using Device Groups in AMP | 77
Page 78

14. To configure Symbol settings, locate the Symbol section and adjust these settings as required. Table 49
describes the settings and default values of this section.
Table 49 Symbol Fields and Default Values
Setting Default Description
SNMP Version 2c Specifies the version of SNMP used by AMP to communicate to the device.
Client Inactivity
Timeout (3-600 min)
Symbol Controller
CLI Communication
Web Config
Interface
3 Sets the minutes of inactivity after which a client associated to a Symbol AP will be
considered "inactive." A lower value typically provides a more accurate representation of
current WLAN usage.
NOTE: For other APs, AMP has more precise methods to determine when inactive clients are
no longer associated to an AP.
Telnet The connection type to support the command-line interface (CLI) connection. The options are
Telnet and secure shell (SSH). This is supported for WS5100, RFS4000, RFS6000 and RFS7000
devices only.
Yes Enables or disables the http/https configuration page for the Symbol 4131 devices.
15. To configure settings specific to Dell PowerConnect W-Series, locate the Dell PowerConnect W section and
adjust these settings as required. Table 50 describes the settings and default values of this section.
Table 50 Dell PowerConnect W Fields and Default Values
Setting Default Description
SNMP Version 2c The version of SNMP used by AMP to communicate to the AP.
Offload WMS
Database
No Configures commands previously documented in the Dell PowerConnect W-AirWave Best
Practices Guide at support.dell.com/manuals. When enabled, this feature allows AMP to
display historical information for WLAN switches.
Changing the setting to Yes pushes commands via SSH to all WLAN switches in Monitor Only
mode without rebooting the controller. The command can be pushed to controllers in manage
mode (also without rebooting the controller) if the Allow WMS Offload setting on AMP Setup >
General is changed to Yes.
Dell PowerConnect
W UI Config
Yes This setting selects whether you'd like to configure your Dell PowerConnect W-Series devices
using the Groups > Dell PowerConnect W Config method (either global or group) or using
Templates.
16. To configure settings for 3Com, Enterasys, Nortel, or Trapeze devices, locate the 3Com/Enterasys/Nortel/
Trapeze section and define the version of SNMP to be supported.
17. To configure support for routers and switches in the group, locate the Routers and Switches section and
adjust these settings as required. This section defines the frequency in which all devices in the group polled.
These settings can be disabled entirely as desired. Table 51 describes the settings and default values of this
section.
Table 51 Routers and Switches Fields and Default Values
Setting Default Description
Read ARP Table 4 hours Sets the frequency in which devices poll routers and switches for Address Resolution
Protocol (ARP) table information. This setting can be disabled, or set to poll for ARP
information in a range from every 15 seconds to 12 hours.
Read CDP Table for
Device Discovery
4 hours For Cisco devices, sets the frequency in which devices poll routers and switches for Cisco
Discovery Protocol (CDP) information. This setting can be disabled, or set to poll for CDP
neighbor information in a range from every 15 seconds to 12 hours.
78 | Configuring and Using Device Groups in AMP Dell PowerConnect W-AirWave |Version 7.3
Page 79

Table 51 Routers and Switches Fields and Default Values (Continued)
Setting Default Description
Read Bridge
Forwarding Table
Interface Up/Down
Polling Period
Interface
Bandwidth Polling
Period
Interface Error
Counter Polling
Period
Poll 802.3 error
counters
Poll Cisco interface
error counters
4 hours Sets the frequency in which devices poll the network for bridge forwarding information. This
setting can be disabled, or set to poll bridge forwarding tables from switches in a range from
every 15 seconds to 12 hours.
5 minutes Sets the frequency in which network interfaces are polled for up/down status. This setting
can be disabled, or set to poll from switches in a range from every 15 seconds to 30 minutes.
15
minutes
30
minutes
No Sets whether 802.3 error counters should be polled.
No Sets whether the interface error counters for Cisco devices should be polled.
Sets the frequency in which network interfaces are polled for bandwidth usage. This setting
can be disabled, or set to poll from switches in a range from every 5 minutes to 30 minutes.
Sets the frequency in which network interfaces are polled for up/down status. This setting
can be disabled, or set to poll bridge forwarding tables from switches in a range from every 5
minutes to 30 minutes.
18. To configure settings for universal devices on the network, including routers and switches that support both
wired and wireless networks, locate the Universal Devices, Routers and Switches section of the Groups >
Basic page and define the version of SNMP to be supported.
19. Select Save when the configurations of the Groups > Basic configuration page are complete to retain these
settings, but without pushing these settings to all devices in the group. Save is a good option if you intend to
make additional device changes in the group, and wish to wait until all configurations are complete before you
push all configurations at one time.
Select Save and Apply to make the changes permanent, or select Revert to discard all unapplied changes.
What Next?
Continue to additional sections in this chapter to create new groups or to edit existing groups.
Once general group-level configurations are complete, continue to later chapters in this document to add or edit
additional device-level configurations and to use several additional AMP functions.
Adding and Configuring Group AAA Servers
Configure RADIUS servers on the Groups > AAA Servers page.
Once defined on this page, RADIUS servers are selectable in the drop-down menus on the Groups > Security
and Groups > SSIDs configuration pages. Perform these steps to create RADIUS servers.
NOTE: TACACS+ servers are configurable only for Cisco WLC devices. Refer to “Configuring Cisco WLC Security Parameters and
Functions” on page93.
1. Go to the Groups > List page and select the group for which to define AAA servers by selecting the group
name. The Monitor page appears.
2. Select the AAA Servers page. The AAA Servers page appears, enabling you to add a RADIUS server. Figure 41
illustrate this page for AAA RADIUS Servers:
Dell PowerConnect W-AirWave | User Guide Configuring and Using Device Groups in AMP | 79
Page 80

Figure 41 Groups > AAA Servers Page Illustration
3. To add a RADIUS server or edit an existing server, select Add New RADIUS Server or the corresponding
pencil icon to edit an existing server. Table 52 describes the settings and default values of the Add/Edit page.
Table 52 Adding a RADIUS Server Fields and Default Values
Setting Default Description
Hostname/IP Address None Sets the IP Address or DNS name for RADIUS Server.
NOTE: IP Address is required for Proxim/ORiNOCO and Cisco Aironet IOS APs.
Secret and Confirm
Secret
Authentication No Sets the RADIUS server to perform authentication when this setting is enabled with Yes .
Authorization Port 1812 Appears when Authentication is enabled. Sets the port used for communication between
Accounting No Sets the RADIUS server to perform accounting functions when enabled with Yes.
Accounting Port No Appears when Accounting is enabled.Sets the port used for communication between the
Timeout (0-86400) None Sets the time (in seconds) that the access point waits for a response from the RADIUS
Max Retries
(0-20)
None Sets the shared secret that is used to establish communication between AMP and the
RADIUS server.
NOTE: The shared secret entered in AMP must match the shared secret on the server.
the AP and the RADIUS server.
AP and the RADIUS server.
server.
None Sets the number of times a RADIUS request is resent to a RADIUS server before failing.
NOTE: If a RADIUS server is not responding or appears to be responding slowly, consider
increasing the number of retries.
4. Select Add to complete the creation of the RADIUS server, or select Save if editing an existing RADIUS
server. The Groups > AAA Servers page displays this new or edited server. You can now reference this server
on the Groups > Security page.
AMP supports reports for subsequent RADIUS Authentication. These are viewable by selecting Reports >
Generated, scrolling to the bottom of the page, and selecting Latest RADIUS Authentication Issues Report.
5. To make additional RADIUS configurations for device groups, use the Groups > Security page and continue
to the next topic.
Configuring Group Security Settings
The Groups > Security page allows you to set security policies for APs in a device group:
1. Select the device group for which to define security settings from the Groups > List page.
2. Go to Groups > Security. Some controls on this page interact with additional AMP pages. Figure 42
illustrates this page and Table 53 explains the fields and default values.
80 | Configuring and Using Device Groups in AMP Dell PowerConnect W-AirWave |Version 7.3
Page 81

Figure 42 Groups > Security Page Illustration
Table 53 Groups > Security Page Fields and Default Values
Setting Default Description
VLANs Section
VLAN Tagging and Multiple
SSIDs
Management VLAN ID Untagged This setting sets the ID for the management VLAN when VLANs are enabled in
General Section
Create Closed Network No If enabled, the APs in the Group do not broadcast their SSIDs.
Block All Inter-client
Communication
EAP Options Section
WEP Key Rotation Interval 300 Sets the frequency at which the Wired Equivalent Privacy (WEP) keys are rotated in
Enabled This field enables support for VLANs and multiple SSIDs on the wireless network. If
this setting is enabled, define additional VLANs and SSIDs on the Groups > SSIDs
page. Refer to “Configuring Group SSIDs and VLANs” on page82.
AMP. This setting is supported only for the following devices:
Proxim AP-600, AP-700, AP-2000, AP-4000
Avaya AP-3, Avaya AP-7, AP-4/5/6, AP-8
ProCurve520WL
NOTE: Creating a closed network will make it more difficult for intruders to detect
your wireless network.
No If enabled, this setting blocks client devices associated with an AP from
communicating with other client devices on the wireless network.
NOTE: This option may also be identified as PSPF (Publicly Secure Packet
Forwarding), which can be useful for enhanced security on public wireless
networks.
the device group being configured. The supported range is from 0 to 10,000,000
seconds.
RADIUS Authentication Servers Section
RADIUS Authentication
Server #1 - #4
Not selected Defines one or more RADIUS Authentication servers to be supported in this device
group. Select up to four RADIUS authentication servers from the four drop-down
menus.
Dell PowerConnect W-AirWave | User Guide Configuring and Using Device Groups in AMP | 81
Page 82

Table 53 Groups > Security Page Fields and Default Values (Continued)
Setting Default Description
Authentication Profile
Name
Authentication Profile
Index
RADIUS Accounting Servers Section
RADIUS Accounting Server
#1 - #4
Authentication Profile
Name
Authentication Profile
Index
MAC Address Authentication Section
MAC Address
Authentication
MAC Address Format Single Dash Allows selection of the format for MAC addresses used in RADIUS authentication
AMPDefined
Server #1
1 For Proxim devices only, this field sets the name of the authentication profile index
Not selected Defines one or more RADIUS Accounting servers to be supported in this device
3 For Proxim devices only, this field sets the name of the accounting profile index to
No If enabled, only MAC addresses known to the RADIUS server are permitted to
For Proxim devices only, this field sets the name of the authentication profile to be
supported in this device group.
to be supported in this device group.
group. Select up to four RADIUS accounting servers from the four drop-down
menus.
For Proxim devices only, this field sets the name of the accounting profile to be
supported in this device group.
be supported in this device group.
associate to APs in the Group.
and accounting requests:
Dash Delimited: xx-xx-xx-xx-xx-xx (default)
Colon Delimited: xx:xx:xx:xx:xx:xx
Single-Dash: xxxxxx-xxxxxx
No Delimiter: xxxxxxxxxxxx
This option is supported only for Proxim AP-600, AP-700, AP-2000, AP-4000, Avaya
AP3/4/5/6/7/8, HP ProCurve 520WL
Authorization Lifetime 1800 Sets the amount of time a user can be connected before reauthorization is required.
The supported range is from 900 to 43,200 seconds.
Primary RADIUS Server
Reattempt Period
0 Specifies the time (in minutes) that the AP awaits responses from the primary
RADIUS server before communicating with the secondary RADIUS server, and so
forth
3. Select Save to retain these security configurations for the group, select Save and Apply to make the changes
permanent, or select Revert to discard all unapplied changes.
4. Continue with additional security-related procedures in this document for additional RADIUS and SSID
settings for device groups, as required.
Configuring Group SSIDs and VLANs
The Groups > SSIDs configuration page allows you to create and edit SSIDs and VLANs that apply to a device
group. Perform these steps to create or edit VLANs and to set SSIDs.
NOTE: WLANs that are supported from one or more Cisco WLC controllers can be configured on the Groups > Cisco WLC Config
page.
82 | Configuring and Using Device Groups in AMP Dell PowerConnect W-AirWave |Version 7.3
Page 83

Figure 43 illustrates an example of the Groups > SSIDs page.
Figure 43 Groups > SSIDs Page Illustration
NOTE: AMP reports users by radio and by SSID. Graphs on the AP and controller monitoring pages display bandwidth in and out
based on SSID. AMP reports can also be run and filtered by SSID. An option on the AMP Setup > General page can age out SSIDs
and their associated graphical data; by default, this is set to 365 days.
1. Go to Groups > List and select the group name for which to define SSIDs/VLANs.
2. Select the Groups > SSIDs configuration page. Table 54 describes the information that appears for SSIDs
and VLANs that are currently configured for the device group.
Table 54 Groups > SSIDs Fields and Descriptions
Field Description
SSID Displays the SSID associated with the VLAN.
VLAN ID Identifies the number of the primary VLAN SSID on which encrypted or unencrypted packets can
pass between the AP and the switch.
Name Displays the name of the VLAN.
Encryption Mode Displays the encryption on the VLAN.
First or Second Radio
Enabled
First or Second Radio
Primary
Native VLAN Sets this VLAN to be the native VLAN. Native VLANs are untagged and typically used for
3. Select Add to create a new SSID or VLAN, or select the pencil icon next to an existing SSID/VLAN to edit
that existing SSID or VLAN. The Add SSID/VLAN configuration page appears as illustrated in Figure 44 and
explained in Table 55.
Enables the VLAN, SSID and Encryption Mode on the radio control.
Specifies which VLAN to be used as the primary VLAN. A primary VLAN is required.
NOTE: If you create an open network (see the Create Closed Network setting below) in which the
APs broadcast an SSID, the primary SSID is broadcast.
management traffic only. AMP requires a Native VLAN to be set. For AP types do not require a
native VLAN, create a dummy VLAN, disable it on both radio controls, and ensure that it has the
highest VLAN ID.
Dell PowerConnect W-AirWave | User Guide Configuring and Using Device Groups in AMP | 83
Page 84

Figure 44 Groups > SSIDs > Add SSID/VLAN Page Illustration
4. Locate the SSID/VLAN section on the Groups > SSIDs configuration page and adjust these settings as
required. This section encompasses the basic VLAN configuration. Table 55 describes the settings and default
values. Note that the displayed settings can vary.
Table 55 Groups > SSIDs > SSID/VLAN Section Fields and Default Values
Setting Default Description
Specify Interface Name Yes Enables or disables an interface name for the VLAN interface. Selecting No for this
option displays the Enable VLAN Tagging and VLAN ID options.
Interface None Sets the interface to support the SSID/VLAN combination.
SSID None Sets the Service Set Identifier (SSID), which is a 32-character user-defined identifier
attached to the header of packets sent over a WLAN. It acts as a password when a
mobile device tries to connect to the network through the AP, and a device is not
permitted to join the network unless it can provide the unique SSID.
Name None Sets a user-definable name associated with SSID/VLAN combination.
VLAN ID (1-4094) None Indicates the number of the VLAN designated as the Native VLAN, typically for
management purposes
Maximum Allowed
Associations (0-2007)
Broadcast SSID (Cisco
WLC, Proxim and Symbol
4131 only)
Partial Closed System
(Proxim only)
Unique Beacon
(Proxim only)
255 Indicates the maximum number of mobile users which can associate with the
specified VLAN/SSID.
NOTE: 0 means unlimited for Cisco.
No For specific devices as cited, this setting enables the AP to broadcast the SSID for
the specified VLAN/SSID. This setting works in conjunction with the Create Closed
Network setting on the Groups > Security configuration page. Proxim devices support
a maximum of four SSIDs.
NOTE: This option should be enabled to ensure support of legacy users.
No For Proxim only, this setting enables to AP to send its SSID in every beacon, but it
does not respond to any probe requests.
No For Proxim only, if more than one SSID is enabled, this option enables them to be sent
in separate beacons.
Block All Inter-Client
Communication
84 | Configuring and Using Device Groups in AMP Dell PowerConnect W-AirWave |Version 7.3
Yes This setting blocks communication between client devices based on SSID.
Page 85

5. Locate the Encryption area on the Groups > SSIDs page and adjust these settings as required. Table 56
describes the settings and default values.
Table 56 Groups > SSIDs > Encryption Section Fields and Default Values
Setting Default Description
Encryption Mode No Encryption Drop-down menu determines the level of encryption required for devices to associate
to the APs. The drop-down menu options are as follows. Each option displays
additional encryption settings that must be defined. Complete the associated settings
for any encryption type chosen:
No Encryption
Optional WEP—Wired Equivalent Privacy, not PCI compliant as of 2010
Require WEP—Wired Equivalent Privacy, not PCI compliant as of 2010
Require 802.1x—Based on the WEP algorithm
Require Leap—Lightweight Extensible Authentication Protocol
802.1x+WEP—Combines the two encryption types shown
802.1x+LEAP—Combines the two encryption types shown
LEAP+WEP—Combines the two encryption types shown
Static CKIP—Cisco Key Integrity Protocol
WPA—Wi-Fi Protected Access protocol
WPA/PSK—Combines WPA with Pre-Shared Key encryption
WPA2—Wi-Fi Protected Access 2 encryption
WPA2/PSK—Combines the two encryption methods shown
xSec—FIPS-compliant encryption including Layer 2 header info
6. Locate the EAP Options area on the Groups > SSIDs page, and complete the settings. Table 57 describes the
settings and default values.
Table 57 Groups > SSIDs > EAP Options Section Fields and Default Values
Setting Default Description
WEP Key Rotation
120 Time (in seconds) between WEP key rotation on the AP.
Interval
7. Locate the RADIUS Authentication Servers area on the Groups > SSIDs configuration page and define the
settings. Table 58 describes the settings and default values.
Table 58 Groups > SSIDs > RADIUS Authentication Servers Fields and Default Values
Setting Default Description
RADIUS Authentication Server
1-3
(Cisco WLC, Proxim only)
Authentication Profile Name
(Cisco WLC, Proxim Only)
Authentication Profile Index
(Cisco WLC, Proxim Only)
8. Select Save when the security settings and configurations in this procedure are complete.
NOTE: You may need to return to the Groups > Security configuration page to configure or reconfigure RADIUS servers.
None Drop-down menu to select RADIUS Authentication servers previously entered on
the Groups > RADIUS configuration page. These RADIUS servers dictate how
wireless clients authenticate onto the network.
None Sets the Authentication Profile Name for Proxim AP-600, AP-700, AP-2000, AP-4000.
None Sets the Authentication Profile Index for Proxim AP-600, AP-700, AP-2000, AP-4000.
Dell PowerConnect W-AirWave | User Guide Configuring and Using Device Groups in AMP | 85
Page 86

9. Locate the RADIUS Accounting Servers area on the Groups > SSIDs configuration page and define the
settings. Table 59 describes the settings and default values.
Table 59 Groups > SSIDs > Radius Accounting Servers Fields and Default Values
Setting Default Description
RADIUS Accounting Server
1-3 (Cisco WLC, Proxim
Only)
Accounting Profile Name
(Cisco WLC, Proxim Only)
Accounting Profile Index
(Cisco WLC, Proxim Only)
None Pull-down menu selects RADIUS Accounting servers previously entered on the Groups
> RADIUS
RADIUS Accounting packets for this SSID/VLAN.
None Sets the Accounting Profile Name for Proxim AP-600, AP-700, AP-2000, AP-4000.
None Sets the Accounting Profile Index for Proxim AP-600, AP-700, AP-2000, AP-4000.
configuration page. These RADIUS servers dictate where the AP sends
10. Select Save to retain these Security configurations for the group, select Save and Apply to make the changes
permanent, or select Revert to discard all unapplied changes.
11. Continue with additional security-related procedures in this document for additional RADIUS, and SSID
settings for device groups, as required.
Configuring Radio Settings for Device Groups
The Groups > Radio configuration page allows you to specify detailed RF-related settings for devices in a
particular group.
NOTE: If you have existing deployed devices, you may want to use the current RF settings on those devices as a guide for
configuring the settings in your default Group.
Perform the following steps to define RF-related radio settings for groups.
1. Go to the Groups > List page and select the group for which to define radio settings by selecting the group
name. Alternatively, select Add from the Groups > List page to create a new group, define a group name. In
either case, the Monitor page appears.
2. Go to the Groups > Radio page. Figure 45 illustrates this page.
Figure 45 Groups > Radio Page Illustration
86 | Configuring and Using Device Groups in AMP Dell PowerConnect W-AirWave |Version 7.3
Page 87

3. Locate the Radio Settings area and adjust these settings as required. Table 60 describes the settings and
default values.
Table 60 Groups > Radio > Radio Settings Fields and Default Values
Setting Default Description
Allow Automatic Channel
Selection (2.4, 5, and
4.9GHz Public Safety)
No If enabled, whenever the AP is rebooted it uses its radio to scan the airspace and
select its optimal RF channel based on observed signal strength from other radios.
NOTE: If you enable this feature, AMP automatically reboots the APs in the group
when the change is implemented.
802.11b Data Rates
(Mbps)
Required:
1.0
2.0
Optional:
5.5
11.0
Displays pull-down menus for various data rates for transmitting data.
NOTE: This setting does not apply to Cisco LWAPP devices.
The three values in each of the pull-down menus are as follows:
Required—The AP transmits only unicast packets at the specified data rate;
multicast packets are sent at a higher data rate set to optional. (Corresponds to a
setting of yes on Cisco devices.)
Optional—The AP transmits both unicast and multicast at the specified data
rate. (Corresponds to a setting of basic on Cisco devices.)
Not Used—The AP does not transmit data at the specified data rate.
(Corresponds to a setting of no on Cisco devices.)
Frag Threshold Enabled No If enabled, this setting enables packets to be sent as several pieces instead of as one
block. In most cases, leave this option disabled.
Threshold Value 2337 If Fragmentation Threshold is enabled, this specifies the size (in bytes) at which
packets are fragmented. A lower Fragmentation Threshold
setting might be required
if there is a great deal of radio interference.
RTS/CTS Threshold
Enabled
No If enabled, this setting configures the AP to issue a RTS (Request to Send) before
sending a packet. In most cases, leave this option disabled.
RTS/CTS Threshold Value 2338 If RTS/CTS is enabled, this specifies the size of the packet (in bytes) at which the AP
sends the RTS before sending the packet.
RTS/CTS Maximum
Retries
32 If RTS/CTS is enabled, this specifies the maximum number of times the AP issues an
RTS before stopping the attempt to send the packet through the radio.
Acceptable values range from 1
to 128.
Maximum Data Retries 32 The maximum number of attempts the AP makes to send a packet before giving up
and dropping the packet. Acceptable values range from 1 to 255.
Beacon Period (19-5000
100 Time between beacons (in microseconds).
msec)
DTIM Period (1-255) 2 DTIM alerts power-save devices that a packet is waiting for them. This setting
configures DTIM packet frequency as a multiple of the number of beacon packets.
The DTIM Interval indicates how many beacons equal one cycle.
Ethernet Encapsulation RFC1042 This setting selects either the RFC1042 or 802.1h Ethernet encapsulation standard for
use by the group.
Radio Preamble Long This setting determines whether the APs uses a short or long preamble. The
preamble is generated by the AP and attached to the packet prior to transmission.
The short preamble is 50 percent shorter than the long preamble and thus may
improve wireless network performance.
NOTE: Because older WLAN hardware may not support the "short" preamble, the
"long" preamble is recommended as a default setting in most environments.
4. Certain wireless access points offer proprietary settings or advanced functionality that differ from prevailing
industry standards. If you use these APs in the device group, you may wish to take advantage of this
proprietary functionality.
Dell PowerConnect W-AirWave | User Guide Configuring and Using Device Groups in AMP | 87
Page 88

To configure these settings, locate the proprietary settings areas on the Groups > Radio page and continue
with the additional steps in this procedure.
NOTE: Proprietary settings are only applied to devices in the group from the specific vendor and are not configured on devices
from vendors that do not support the functionality.
5. To configure settings specific to the Proxim AP-600, AP-700, AP-2000, AP-4000; Avaya AP-3/4/5/6//7/8, and
ProCurve 520WL, locate the appropriate section of Groups > Radio page and define the required fields.
Table 61 describes the settings and default values.
Table 61 Groups > Radio > Proxim AP-600, AP-700, AP-2000, AP-4000; Avaya AP-3, Avaya AP-7, AP-4/5/6, AP-8; ProCurve520WL
Fields and Default Values
Setting Default Description
Load Balancing No If enabled, this setting allows client devices associating to an AP with two radio cards
Interference Robustness No If enabled, this option will fragment packets greater than 500 bytes in size to reduce
Distance Between APs Large This setting adjusts the receiver sensitivity. Reducing receiver sensitivity from its
802.11g Operational
Mode
802.11abg Operational
Mode
802.11b Transmit Rate Auto
802.11g Transmit Rate Auto
802.11a Transmit Rate Auto
Rogue Scanning Yes If enabled, any ORiNOCO or Avaya APs in the group (with the appropriate firmware)
802.11b
+802.11g
802.11b
+802.11g
Fallback
Fallback
Fallback
to determine which card to associate with, based on the load (# of clients) on each
card.
NOTE: This feature is only available when two 802.11b wireless cards are used in an
AP-2000.
the impact of radio frequency interference on wireless data throughput.
maximum may help reduce the amount of crosstalk between wireless stations to
better support roaming users. Reducing the receiver sensitivity, user stations will be
more likely to connect with the nearest access point.
This setting sets the operational mode of all g radios in the group to either b only, g
only or b + g.
This setting sets the operational mode of all a/b/g radios in the group to either a only, b
only, g only or b + g.
This setting specifies the minimum transmit rate required for the AP to permit a user
device to associate.
This setting specifies the minimum transmit rate required for the AP to permit a user
device to associate.
This setting specifies the minimum transmit rate required for the AP to permit a user
device to associate.
will passively scan for rogue access points at the specified interval. This rogue scan
will not break users' association to the network.
NOTE: This feature can affect the data performance of the access point.
Rogue Scanning Interval 15 minutes If rogue scanning is enabled, this setting controls the frequency with which scans are
conducted (in minutes). Frequent scans provide the greatest security, but AP
performance and throughput available to user devices may be impacted modestly
during a rogue scan.
6. To configure settings specific to Proxim 4900M, locate the Proxim 4900M section and define the required
fields. Table 62 describes the settings and default values.
Table 62 Groups > Radio > Proxim 4900M Fields and Default Values
Setting Default Description
4.9GHz Public Safety
Channel Bandwidth
88 | Configuring and Using Device Groups in AMP Dell PowerConnect W-AirWave |Version 7.3
20 This setting specifies the channel bandwidth for the 4.9 GHz radio. It is only applicable
if you are running the 802.11a/4.9GHz radio in 4.9GHz mode.
Page 89

Table 62 Groups > Radio > Proxim 4900M Fields and Default Values (Continued)
Setting Default Description
802.11a/4.9GHz Public
Safety Operational Mode
802.11a This setting specifies if the AP will run the 802.11a/4.9GHz radio in 802.11a mode or in
4.9 GHz mode. Please note that 4.9 GHz is a licensed frequency used for public safety.
7. To configure Symbol-only settings, locate the Symbol section and define the required fields. Table 63
describes the settings and default values.
Table 63 Groups > Radio > Symbol Fields and Default Values
Setting Default Description
Rogue Scanning Yes If enabled, Symbol access points with 3.9.2 or later firmware in the group will passively scan
for rogue access points at the specified interval. This rogue scan will not break a user’s
association to the network.
Rogue Scanning
Interval (5-480 min)
240 If rogue scanning is enabled, this setting controls the frequency with which scans are
conducted (in minutes). Frequent scans provide the greatest security, but AP performance
and throughput available to user devices may be impacted modestly during a rogue scan.
8. Select Save when radio configurations as described above are complete, select Save and Apply to make the
changes permanent, or select Revert to discard all unapplied changes.
Cisco WLC Group Configuration
The Groups > Cisco WLC Config page consolidates the settings for Cisco WLC devices from all group pages.
The Groups > SSIDs subtab applies to all device types except for Cisco WLC, which have WLANs configured
on the Cisco WLC Config page. It is not recommended to have Symbol 4131 and Proxim APs in the same group
as Cisco devices. Also, it is recommended that users set device preferences to Only devices in this group. This
topic describes how to access and navigate the Groups > Cisco WLC Config page.
Accessing Cisco WLC Configuration
Go to the Cisco WLC Config page in one of these two ways:
1. In Groups > List, select a group that has been defined to support Cisco devices and the Cisco WLC Config
option appears in the subtabs.
2. In Groups > List, create a new group to support Cisco devices with these steps:
Select Add from the Groups > List page to create a new group, enter a group name, and select Add.
Once AMP prompts you with the Groups > Basic page, ensure that you enable device-specific settings for
Cisco WLC.
Once you select Save or Save and Apply, then the Groups > Cisco WLC Config subtab appears in the
navigation pane at the top in association with that group.
Navigating Cisco WLC Configuration
The navigation pane on the left side of the Groups > Cisco WLC Config page is expandable, and displays the
Cisco configurations supported and deployed. Figure 46 and Figure 47 illustrate this navigation pane.
You can pre-populate the group WLC settings from a controller in the same group by performing an import on
the controller’s Audit page.
Dell PowerConnect W-AirWave | User Guide Configuring and Using Device Groups in AMP | 89
Page 90

Figure 46 Groups > Cisco WLC Config Page Illustration, collapsed view
Figure 47 Groups > Cisco WLC Config Page Illustration, expanded view
Configuring WLANs for Cisco WLC Devices
In Cisco WLC Config, WLANs are based on SSIDs or VLANs that are dedicated to Cisco WLC controllers.
Perform the following steps to define and configure WLANs for Cisco WLC controllers.
1. Go to the Groups > Cisco WLC Config page, and select WLANs in the navigation pane at left. This page
displays the SSIDs or VLANs that are available for use with Cisco WLC devices, and enables you to define
new SSIDs or VLANs. Figure 48 illustrates this page.
2. To change the ID/position of a WLAN on the controller by dragging and dropping, set the toggle to yes. Note
that the by setting this flag to yes, AMP will display a mismatch if the WLANs in the desired and device
config differ only on the order.
Figure 48 Groups > Cisco WLC Config > WLANS page illustration
3. To add or edit SSIDs or VLANs that are dedicated to Cisco WLC devices, either select the Add New SSID/
VLAN button, or select the pencil icon for an existing SSID/VLAN. A new page appears comprised of four
tabs, as follows:
General—Defines general administrative parameters for the Cisco WLC WLAN.
Security—Defines encryption and RADIUS servers.
QoS—Defines quality of service (QoS) parameters for the Cisco WLC WLAN.
90 | Configuring and Using Device Groups in AMP Dell PowerConnect W-AirWave |Version 7.3
Page 91

Advanced—Defines advanced settings that are available only with Cisco WLC devices, for example, AAA
override, coverage, DHCP and DTIM period.
NOTE: Refer to Cisco documentation for additional information about Cisco WLC devices and related features.
Figure 49 Groups > Cisco WLC Config > WLANs > Add New SSID/VLAN > General Tab Illustration
Figure 50 Groups > Cisco WLC Config > WLANs > Add New SSID/VLAN > Security Tab Illustration
Figure 51 Groups > Cisco WLC Config > WLANs > Add New SSID/VLAN > QoS Tab Illustration
Dell PowerConnect W-AirWave | User Guide Configuring and Using Device Groups in AMP | 91
Page 92

Figure 52 Groups > Cisco WLC Config > WLANs > Add New SSID/VLAN > Advanced Tab Illustration
Defining and Configuring LWAPP AP Groups for Cisco Devices
The Groups > Cisco WLC Config > WLANs > Advanced > AP Groups page allows you to add/edit/delete AP
Groups on the Cisco WLC. LWAPP AP Groups are used to limit the WLANs available on each AP. Cisco thin
APs are assigned to LWAPP AP Groups.
Viewing and Creating Cisco AP Groups
1. Go to the Groups > Cisco WLC Config page, and select WLANs > Advanced > AP Groups in the
navigation pane at left. This page displays the configured LWAPP APs. Figure 53 illustrates this page.
Figure 53 Groups > Cisco WLC Config > WLANS > Advanced > AP Groups Page Illustration
92 | Configuring and Using Device Groups in AMP Dell PowerConnect W-AirWave |Version 7.3
Page 93

2. To add a new LWAPP AP group, select Yes in the AP Groups section. Additional controls appear.
3. Select Add to create a new LWAPP AP group. To edit an existing LWAPP AP group, select the pencil icon
next to that group. Add one or more SSIDs and the interface/VLAN ID mapping on the Add/Edit page of the
LWAPP AP Group.
4. Select Save and Apply to make these changes permanent, or select Save to retain these changes to be pushed
to controllers at a later time.
Configuring Cisco Controller Settings
The Groups > Cisco WLC Config > Controller page defines general Cisco WLC settings, Multicast settings,
Cisco mobility groups to be supported on Cisco controllers, Network Transfer Protocol (NTP), and Spanning
Tree Protocol settings.
Go to the Groups > Cisco WLC Config > Controller page. This navigation is illustrated in Figure 54.
Figure 54 Groups > Cisco WLC Config > Controller Navigation
Configuring Wireless Parameters for Cisco Controllers
This section illustrates the configuration of Wireless settings in support of Cisco WLC controllers. The navigation
for Wireless settings is illustrated in Figure 55.
Figure 55 Groups > Cisco WLC Config > Wireless Navigation Illustration
Configuring Cisco WLC Security Parameters and Functions
AMP enables you to configure many security settings that are specific to Cisco WLC controllers. This section
supports four overriding types of configuration, as follows:
AAA, to cover both RADIUS and TACACS+ server configuration
Priority Order
Wireless Protection Policies
Web Auth
Dell PowerConnect W-AirWave | User Guide Configuring and Using Device Groups in AMP | 93
Page 94

Figure 56 illustrates these components and this navigation:
Figure 56 Groups > Cisco WLC Config > Security Navigation Illustration
Configuring Management Settings for Cisco WLC
AMP allows you to configure of SNMP and Syslog Server settings for Cisco WLC controllers. Users should be
able to configure up to four trap receivers on the Cisco WLC including the AMP IP that can be used in Global
Groups. To define SNMP and server settings, go to the Groups > Cisco WLC Config > Management page,
illustrated in Figure 57.
Figure 57 Groups > Cisco WLC Config > Management Navigation Illustration
Configuring Group PTMP Settings
The Groups > PTMP configuration page configures Point-to-Multipoint (PTMP) for all subscriber and base
stations in the device group. Subscriber stations must be in the same group as all base stations with which they
might connect.
Perform the following steps to configure these functions.
1. Go to the Groups > List page and select the group for which to define PTMP settings by selecting the group
name. Alternatively, select Add from the Groups > List page to create a new group, define a group name. In
either case, the Monitor page appears.
2. Select the PTMP tab in the AMP navigation menu. Figure 58 illustrates this page.
Figure 58 Groups > PTMP Page Illustration
94 | Configuring and Using Device Groups in AMP Dell PowerConnect W-AirWave |Version 7.3
Page 95

3. Define the settings on this page. Table 64 describes the settings and default values.
Table 64 Groups > PTMP Fields and Default Values
Setting Default Description
802.11a Radio Channel 58 Selects the channel used for 802.11a radios by the devices in this group.
802.11g Radio Channel 10 Selects the channel used for 802.11g radios by the devices in this group.
Channel Bandwidth 20 Defines the channel bandwidth used by the devices in this group.
Network Name Wireless Network Sets the Network name, with a range of length supported from two to 32
alphanumeric characters.
Network Secret None Sets a shared password to authenticate clients to the network.
4. Select Save and Apply when configurations are complete to make them permanent, or select Save to retain
these settings prior to pushing to controllers at a later time.
Configuring Proxim Mesh Radio Settings
1. Go to the Groups > Proxim Mesh configuration page to configure Mesh-specific radio settings.
2. Define the settings as required for your network. Figure 59 illustrates this page. Table 65 and Table 66
describe the settings and default values.
Figure 59 Groups > Proxim Mesh Page Illustration
The General section contains settings for mesh radio, number of mesh links, RSSI smoothing, roaming
threshold and de-auth client.
Table 65 Groups > Proxim Mesh > General Fields and Default Values
Setting Default Description
Mesh Radio 4.9/5Ghz Drop-down selects the radio that acts as the backhaul to the network.
Max Number of Mesh
Links
Neighbor RSSI
Smoothing
6 Sets the maximum number of mesh links allowed on an AP. This number includes
the uplink to the portal as well as downlinks to other mesh APs.
16 Specifies the number of beacons to wait before switching to a new link.
Roaming Threshold 80 Specifies the difference in cost between two paths that must be exceeded before
the AP roams. To switch to a new path it must have a cost that is less by at least the
roaming threshold. A high threshold results in fewer mesh roams.
Deauth Client when
Uplink is Down
Dell PowerConnect W-AirWave | User Guide Configuring and Using Device Groups in AMP | 95
Yes W it h Ye s selected, clients have authentication removed (are deauthenticated) if the
uplink is lost.
Page 96

The Security section contains settings for SSID and enabling AES encryption.
Table 66 Groups > Proxim Mesh > Security Fields and Default Values
Setting Default Description
SSID None Sets the SSID used by the Mesh Radio to connect to the mesh network.
Enable AES No Enable or disable AES encryption.
3. The Mesh Cost Matrix configuration section contains settings for hop factor and maximum hops to portal,
RSSI factor and cut-off, medium occupancy factor and current medium occupancy weight. Adjust these
settings as required for your network. Table 67 describes these settings and default values.
Table 67 Groups > Proxim Mesh > Mesh Cost Matrix Fields and Default Values
Setting Default Description
Hop Factor 5 Sets the factor associated with each hop when calculating the best path to the portal AP.
Higher factors will have more impact when deciding the best uplink.
Maximum Hops
to Portal
RSSI Factor 5 Sets the factor associated with the RSSI values used when calculating the best path to the
RSSI Cutoff 10 Specifies the minimum RSSI needed to become a mesh neighbor.
Medium
Occupancy
Factor
Current Medium
Occupancy
Weight
4 Set the maximum number of hops for the AP to reach the Portal AP.
portal AP. Higher factors will have more impact when deciding the best uplink.
5 Sets the factor associated with Medium Occupancy when calculating the best path to the
portal AP. Higher factors will have more impact when deciding the best uplink.
7 Specifies the importance given to the most recently observed Medium Occupancy against all
of the previously viewed medium occupancies. Lower values place more importance on
previously observed Medium Occupancies.
4. Select Save when configurations are complete to retain these settings. Select Save and Apply to make the
changes permanent, or select Revert to discard all unapplied changes.
Configuring Group MAC Access Control Lists
This configuration is optional. If you use Symbol, Proxim, or ProCurve 520WL wireless access points, AMP
enables you to specify the MAC addresses of devices that are permitted to associate with APs in the Group. Other
devices are not able to associate to APs in the Group, even if the users of those devices are authorized users on the
network.
Perform the following steps to use the MAC ACL function.
1. Browse to the Groups > MAC ACL configuration page. Figure 60 illustrates this page.
Figure 60 Groups > MAC ACL Page Illustration
96 | Configuring and Using Device Groups in AMP Dell PowerConnect W-AirWave |Version 7.3
Page 97

2. Select Yes on the Use MAC ACL drop-down menu. Enter all authorized MAC addresses, separated by white
spaces.
3. Select Save when configurations are complete to retain these settings. Select Save and Apply to make the
changes permanent, or select Revert to discard all unapplied changes.
Specifying Minimum Firmware Versions for APs in a Group
This configuration is optional. AMP allows you the option of defining the minimum firmware version for each AP
type in a group on the Groups > Firmware configuration page. At the time that you define the minimum version,
AMP automatically upgrades all eligible APs.
When you add APs into the group in the future, you will be able to upgrade APs manually. The firmware for an
AP is not upgraded automatically when it is added to a group. Perform the following steps to make this firmware
configuration.
1. Browse to the Groups > Firmware configuration page. Figure 61 illustrates this page.
Figure 61 Groups > Firmware Page Illustration
2. For each device type in the group, specify the minimum acceptable firmware version. If no firmware versions
are listed, go to the Device Setup > Firmware configuration page to upload the firmware files to AMP.
3. Select Upgrade to apply firmware preferences to devices in the group. Refer to the firmware upgrade help
under APs/Devices > Manage configuration page for detailed help on Firmware job options.
4. Select Save to save the firmware file as the desired version for the group.
5. If you have opted to assign an external TFTP server on a per-group basis on the Device Setup > Firmware
configuration page, you can enter the IP address in the Firmware Upgrade Options field on the top of this
configuration page.
6. Once you have defined your first group, you can configure that group to be the default group on your network.
When AMP discovers new devices that need to be assigned to a management group, the default group appears
at the top of all drop-down menus and lists. Newly discovered devices are place automatically in the default
group if AMP is set to Automatically Monitor/Manage New Devices on the AMP configuration page.
7. Browse to the Groups > List configuration page.
8. From the list of groups, check the Default radio button next to the desired default group to make it the
default.
Dell PowerConnect W-AirWave | User Guide Configuring and Using Device Groups in AMP | 97
Page 98

Comparing Device Groups
You can compare two existing device groups with a detailed line-item comparison. Group comparison allows
several levels of analysis to include the following:
compare performance, bandwidth consumption, or troubleshooting metrics between two groups
debug one device group against the settings of a similar and better performing device group
use one group as a model by which to fine-tune configurations for additional device groups
This topic presumes that at least two device groups are at least partly configured in AMP, each with saved
configurations. Perform the following steps to compare two existing device groups:
1. From the Groups > List page, select Compare two groups. Two drop-down menus appear.
2. Select the two groups to compare to each other in the drop-down menus, and select Compare. The Compare
page appears, displaying some or many configuration categories. Figure 62 illustrates this page.
Figure 62 Comparing Two Devices Groups on the Groups > List > Compare Page (Partial View)
3. Note the following factors when using the Compare page:
The Compare page can be very long or very abbreviated, depending on how many configurations the
device groups share or do not share.
When a configuration differs between two groups, the setting is flagged in red text for the group on the
right.
The default setting of the Compare page is to highlight settings that differ between two groups.
To display settings that are similar or identical between two device groups, select Show Similar Fields
at the top left of the page. The result may be a high volume of information.
Select Hide Similar Fields to return to the default display, emphasizing configuration settings that
differ between two groups.
You can change the configuration for either or both groups by selecting Edit in the corresponding column
heading. The appropriate configuration page appears.
If you make and save changes to either or both groups, go back to the Groups > List page and select
Compare two groups. Select the same two groups again for updated information.
Additional topics in this document describe the many fields that can appear on the Groups > List >
Compare page.
Deleting a Group
Perform the following steps to delete an existing Group from the AMP database:
1. Browse to the Groups > List configuration page.
2. Ensure that the Group you wish to delete is not marked as the default group. AMP does not permit you to
delete the current default Group.
3. Ensure that there are no devices in the Group you wish to delete. AMP does not permit you to delete a Group
that still contains managed devices. You must move all devices to other Groups before deleting a Group.
98 | Configuring and Using Device Groups in AMP Dell PowerConnect W-AirWave |Version 7.3
Page 99

4. Ensure that the Group is not a Global Group which has Subscriber Groups, and is not a Group that was
pushed from a Master Console. AMP will not delete a Group in which either of those is true.
5. Select the checkbox and select Delete.
Changing Multiple Group Configurations
Perform the following steps to make any changes to an existing group's configuration:
1. Browse to the Groups > List configuration page.
2. Select the Manage link (the pencil icon) for the group you wish to edit. The Groups > Basic configuration
page appears.
3. Select the fields to be edited on the Basic configuration page or go to Radio, Security, VLANs, or MAC ACL
configuration page and edit the fields. Use the Save button to store the changes prior to applying them.
4. When all changes for the group are complete select the Save and Apply button to make the changes
permanent. Figure 63 illustrates the confirmation message that appears.
Figure 63 Groups > Basic Configuration Change Confirmation Page Illustration
5. AMP displays a Configuration Change screen confirming the changes that will be applied to the group's
settings.
6. There are several action possibilities from within this confirmation configuration page.
Apply Changes Now — Applies the changes immediately to access points within the group. If you wish to
edit multiple groups, you must use the Preview button.
NOTE: You cannot apply Dell PowerConnect W Config changes to other groups. If the only changes on the configuration page are
to Dell PowerConnect W-Series devices, the list of groups and the preview button will not appear.
Schedule — Schedules the changes to be applied to this group in the future. Enter the desired change date
in the Start Date/Time field. AMP takes the time zone into account for the group if a time zone other
than AMP System Time has been configured on the Groups > Basic configuration page.
Dell PowerConnect W-AirWave | User Guide Configuring and Using Device Groups in AMP | 99
Page 100

Cancel — Cancels the application of changes (immediately or scheduled).
NOTE: To completely nullify the change request, select Revert on one of the group configuration pages after you have selected
Cancel.
7. Apply changes to multiple groups by selecting the appropriate group or groups and selecting Preview.
Modifying Multiple Devices
AMP provides a very powerful utility that modifies all APs or a subset of access points unrelated to the typical
AMP group construct. This utility provides the ability to delete simultaneously multiple devices, migrate multiple
devices to another group and/or folder, update credentials and optimize channels. Perform these steps to modify
multiple devices.
1. To modify multiple devices, go to one of the following pages with a device list:
APs/Devices > List
APs/Devices > Up
APs/Devices > Down
APs/Devices > Mismatched
Groups > Monitor configuration pages
Each of these pages displays a list of devices. Controller monitoring pages also have lists of their thin APs
which can be modified using Modify Devices.
2. Select Modify Devices to make the checkboxes at the left of all devices appear. In addition, a new section
appears in this page location to display various settings that can be configured for multiple devices at one time
(some operations cannot be performed on the selected devices). Figure 64 illustrates this page.
100 | Configuring and Using Device Groups in AMP Dell PowerConnect W-AirWave |Version 7.3
 Loading...
Loading...