Page 1
Dell Lifecycle Controller Web Services
Interface Guide for Linux
A Dell Technical White Paper about the Best Practices to
be followed for using the WS-Man based remote
services provided by iDRAC and Lifecycle Controller
Dell Engineering
December 2013
A Dell Best Practices
Page 2

Date
Description
December 2013
1.0 Release: Initial release
Revisions
Dell, the DELL logo, and the DELL badge are trademarks of Dell Inc. Symantec, NetBackup, and Backup Exec are
trademarks of Symantec Corporation in the U.S. and other countries. Microsoft, Windows, and Windows Server are
registered trademarks of Microsoft Corporation in the United States and/or other countries. Other trademarks and
trade names may be used in this document to refer to either the entities claiming the marks and names or their
products. Dell disclaims any proprietary interest in the marks and names of others.
Dell™, the Dell logo, Dell Boomi™, Dell Precision™ ,OptiPlex™, Latitude™, PowerEdge™, PowerVault™,
PowerConnect™, OpenManage™, EqualLogic™, Compellent™, KACE™, FlexAddress™, Force10™ and Vostro™ are
trademarks of Dell Inc. Other Dell trademarks may be used in this document. Cisco Nexus®, Cisco MDS®, Cisco NX0S®, and other Cisco Catalyst® are registered trademarks of Cisco System Inc. EMC VNX®, and EMC Unisphere® are
registered trademarks of EMC Corporation. Intel®, Pentium®, Xeon®, Core® and Celeron® are registered trademarks of
Intel Corporation in the U.S. and other countries. AMD® is a registered trademark and AMD Opteron™, AMD
Phenom™ and AMD Sempron™ are trademarks of Advanced Micro Devices, Inc. Microsoft®, Windows®, Windows
Server®, Internet Explorer®, MS-DOS®, Windows Vista® and Active Directory® are either trademarks or registered
trademarks of Microsoft Corporation in the United States and/or other countries. Red Hat® and Red Hat® Enterprise
Linux® are registered trademarks of Red Hat, Inc. in the United States and/or other countries. Novell® and SUSE® are
registered trademarks of Novell Inc. in the United States and other countries. Oracle® is a registered trademark of
Oracle Corporation and/or its affiliates. Citrix®, Xen®, XenServer® and XenMotion® are either registered trademarks or
trademarks of Citrix Systems, Inc. in the United States and/or other countries. VMware®, Virtual SMP®, vMotion®,
vCenter® and vSphere® are registered trademarks or trademarks of VMware, Inc. in the United States or other
countries. IBM® is a registered trademark of International Business Machines Corporation. Broadcom® and
NetXtreme® are registered trademarks of Broadcom Corporation. Qlogic is a registered trademark of QLogic
Corporation. Other trademarks and trade names may be used in this document to refer to either the entities claiming
2 Lifecycle Controller Integration – Web Services Interface Guide for Windows | Revision 1.0.
Page 3

the marks and/or names or their products and are the property of their respective owners. Dell disclaims proprietary
interest in the marks and names of others.
3 Lifecycle Controller Integration – Web Services Interface Guide for Windows | Revision 1.0.
Page 4

Contents
Revisions ............................................................................................................................................................................................ 2
Executive Summary ....................................................................................................................................................................... 14
1 Introduction .............................................................................................................................................................................. 15
2 References ................................................................................................................................................................................ 16
3 Overview.................................................................................................................................................................................... 17
3.1 Format for WS-Man CLI Examples in Document .................................................................................................... 17
3.2 WS-Man Security and Time Parameters ................................................................................................................... 18
3.2.1 Encryption Certificate Security ................................................................................................................................... 18
3.2.2 Handling Invalid Responses from WS-Man Commands ........................................................................................ 18
3.2.3 Improving WS-Man Enumeration Performance ...................................................................................................... 18
3.2.4 Specifying
3.2.5 Return Values ................................................................................................................................................................. 19
3.2.6 Glossary .......................................................................................................................................................................... 19
4 Discovery ................................................................................................................................................................................... 20
4.1 Discovering Web Service Capability .......................................................................................................................... 20
4.2 Discovering what Profiles are implemented ............................................................................................................ 20
4.3 Discovering Implementation Namespace ................................................................................................................ 21
5 Managing iDRAC Local User Accounts ................................................................................................................................ 23
5.1 Description of iDRAC Attributes Versus Standard DMTF Model ........................................................................... 23
5.2 Account Inventory (using iDRAC Attributes) ............................................................................................................ 23
5.2.1 Account and Capabilities (using iDRAC Attributes) ................................................................................................. 23
5.2.2 Privilege and Capabilities (using iDRAC Attributes) ................................................................................................. 24
5.3 Manage Account Settings (using iDRAC Attributes) ............................................................................................... 25
5.3.1 Modify User Name (using iDRAC Attributes) ............................................................................................................ 25
5.3.2 Modify Password (using iDRAC Attributes) ............................................................................................................... 26
5.3.3 Modify Account State (using iDRAC Attributes) ....................................................................................................... 26
StartTime, Until
Time, and
TIME_NOW
Parameters ............................................................................ 18
5.3.4 Modify User Privilege (using iDRAC Attributes) ........................................................................................................ 28
5.4 Account Inventory (using DMTF Model) ................................................................................................................... 28
5.4.1 Account and Capabilities (using DMTF Model) ........................................................................................................ 29
5.4.2 Privilege and Capabilities (using DMTF Model) ........................................................................................................ 32
5.5 Manage Account Settings (using DMTF Model) ...................................................................................................... 35
4 Lifecycle Controller Integration – Web Services Interface Guide for Windows | Revision 1.0.
Page 5

5.5.1 Modify User Name (using DMTF Model) ................................................................................................................... 35
5.5.2 Modify Password (using DMTF Model) ...................................................................................................................... 38
5.5.3 Modify Account State (using DMTF Model) .............................................................................................................. 38
5.5.4 Modify User Privilege (using DMTF Model) ............................................................................................................... 39
6 Firmware Inventory ................................................................................................................................................................. 41
6.1 Software Inventory Profile Specification ................................................................................................................... 41
6.2 Remote Inventory Method Invocation — Get Software Inventory ...................................................................... 41
7 Firmware Update ..................................................................................................................................................................... 43
7.1 Software Update Profile Specification....................................................................................................................... 43
7.2 ”Rollback” Firmware ...................................................................................................................................................... 43
7.2.1 Request “Rollback” Image ............................................................................................................................................ 43
7.2.2 Create Reboot Job ....................................................................................................................................................... 43
7.2.3 Schedule Update Jobs ................................................................................................................................................. 43
7.2.4 Monitor Update Jobs .................................................................................................................................................... 43
7.3 BIOS Firmware “Rollback” ............................................................................................................................................ 44
7.4 NIC Firmware “Rollback” .............................................................................................................................................. 45
7.5 Update from Network Source .................................................................................................................................... 46
7.5.1 Request Update Download ......................................................................................................................................... 47
7.5.2 Monitor Download Status ............................................................................................................................................ 47
7.5.3 Reboot to Perform Update .......................................................................................................................................... 47
7.5.4 Wait for Job Completion ............................................................................................................................................. 47
7.5.5 Delete Job ...................................................................................................................................................................... 47
7.6 Update NICs from HTTP, CIFS Share, NFS share, TFTP, or FTP ............................................................................ 47
7.7 Update BIOS from HTTP, CIFS Share, NFS share, TFTP, or FTP ........................................................................... 49
7.8 CreateRebootJob() ....................................................................................................................................................... 51
7.9 Automatic Updates ....................................................................................................................................................... 52
7.9.1 Enable automatic update ............................................................................................................................................. 52
7.9.2 Create a Config Job ..................................................................................................................................................... 52
7.9.3 Set Update Schedule .................................................................................................................................................... 53
7.9.4 Get the Update Schedule ............................................................................................................................................ 54
7.9.5 Clear the Update Schedule ......................................................................................................................................... 55
7.10 Device Update from Repository ................................................................................................................................. 55
5 Lifecycle Controller Integration – Web Services Interface Guide for Windows | Revision 1.0.
Page 6

7.10.1 Install From Repository ................................................................................................................................................ 55
7.10.2 Get Repo-Based Update List ....................................................................................................................................... 56
8 Power State Management ...................................................................................................................................................... 59
8.1 Description of Base Server versus Power State Management Methods ............................................................. 59
8.2 Get Power State ............................................................................................................................................................ 59
8.2.1 Base Server Method ...................................................................................................................................................... 59
8.2.2 Power State Management Method ........................................................................................................................... 60
8.3 Get Power Control Capabilites .................................................................................................................................. 60
8.3.1 Base Server Method ..................................................................................................................................................... 60
8.3.2 Power State Management Method ............................................................................................................................ 62
8.4 Power Control ............................................................................................................................................................... 63
8.4.1 Base Server Method ...................................................................................................................................................... 63
8.4.2 Power State Management Method ............................................................................................................................ 63
9 Hardware Inventory ................................................................................................................................................................. 65
9.1 Power Supply Inventory ............................................................................................................................................... 65
9.2 Fan Inventory ................................................................................................................................................................. 66
9.3 Memory Inventory ......................................................................................................................................................... 67
9.4 CPU Inventory................................................................................................................................................................ 67
9.5 iDRAC Card Inventory .................................................................................................................................................. 69
9.6 PCI Device Inventory .................................................................................................................................................... 69
9.7 Video Inventory ............................................................................................................................................................. 70
9.8 VFlash SD Card Inventory ............................................................................................................................................ 71
9.9 NIC Inventory and Configuration ............................................................................................................................... 71
9.10 RAID Inventory and Configuration ............................................................................................................................. 73
9.11 BIOS Inventory and Configuration ............................................................................................................................. 74
9.12 System Inventory (including CSIOR attribute) ......................................................................................................... 74
10 Job Control Management ...................................................................................................................................................... 77
10.1 Description of Job Management ............................................................................................................................... 77
10.2 Remote Job Control Examples .................................................................................................................................. 77
10.2.1 Setup Job Queue .......................................................................................................................................................... 77
10.2.2 Delete Job Queue .................................................................................................................................................... 78
10.2.3 List Jobs in Job Store .............................................................................................................................................. 79
6 Lifecycle Controller Integration – Web Services Interface Guide for Windows | Revision 1.0.
Page 7

11 Operating System Deployment ............................................................................................................................................. 81
11.1 OS Deployment Profile Implementation Conformance ........................................................................................ 81
11.2 Checking OS Deployment Service Availability ......................................................................................................... 81
11.3 OS Deployment Method Invocation Examples ....................................................................................................... 82
11.3.1 Get Driver Pack Information ....................................................................................................................................... 82
11.3.2 Unpack Selected Drivers and Attach to Host OS as USB Device ......................................................................... 83
11.3.3 Detach Emulated USB Device Containing Drivers .................................................................................................. 84
11.3.4 Unpack Selected Drivers and Copy to Network Share .......................................................................................... 85
11.3.5 Check Job Status .......................................................................................................................................................... 86
11.3.6 Boot to Network ISO .................................................................................................................................................... 87
11.3.7 Detach Network ISO USB Device ............................................................................................................................... 89
11.3.8 Boot To PXE ................................................................................................................................................................... 89
11.3.9 Get Host MAC Address Information ......................................................................................................................... 90
11.3.10 Download ISO to VFlash .................................................................................................................................... 90
11.3.11 Boot to ISO from VFlash ..................................................................................................................................... 92
11.3.12 Delete ISO from VFlash ....................................................................................................................................... 92
11.3.13 Detach ISO from VFlash ..................................................................................................................................... 93
11.3.14 Connect Network ISO Image ............................................................................................................................ 93
11.3.15 Disconnect Network ISO Image ....................................................................................................................... 94
11.3.16 Skip ISO Image Boot ............................................................................................................................................ 95
11.3.17 Get Network ISO Image Connection Information ......................................................................................... 95
11.3.18 Connect RFS ISO Image ..................................................................................................................................... 96
11.3.19 Disconnect RFS ISO Image ................................................................................................................................ 97
11.3.20 Get RFS ISO Image Connection Information ................................................................................................. 98
11.3.21 Boot To Hard Drive (HD) .................................................................................................................................... 98
11.3.22 Configurable Boot to Network ISO .................................................................................................................. 99
12 Lifecycle Controller Management Profile ......................................................................................................................... 101
12.1 Collect System Inventory on Restart (CSIOR) ........................................................................................................ 101
12.2 Part Replacement Configuration and Management ............................................................................................. 102
12.2.1 Create Config Job ...................................................................................................................................................... 102
12.2.2 Get LC Config Job Status .......................................................................................................................................... 103
12.2.3 List All LC Jobs ............................................................................................................................................................. 103
7 Lifecycle Controller Integration – Web Services Interface Guide for Windows | Revision 1.0.
Page 8

12.2.4 Get CSIOR Component Configuration Recovery (CCR) Attribute ..................................................................... 104
12.2.5 Get Part Firmware Update Attribute ........................................................................................................................ 105
12.3 Re-Initiate Auto-Discovery Client ............................................................................................................................ 105
12.4 Clear or Set Provisioning Server ............................................................................................................................... 106
12.5 Check VFlash License Enablement .......................................................................................................................... 107
12.6 Download Server Public Key ..................................................................................................................................... 108
12.7 Download Client Certificates .................................................................................................................................... 109
12.8 Delete Auto-Discovery Client Certificates ............................................................................................................. 110
12.9 Set Public Certificates ................................................................................................................................................ 110
12.10 Set iDRAC Certificate and Private Key ...................................................................................................................... 111
12.11 Delete Auto-Discovery Server Public Key .............................................................................................................. 112
12.12 Insert Comment in Lifecycle Controller Log ......................................................................................................... 113
12.13 Export Lifecycle Controller Log ................................................................................................................................ 113
12.14 ExportCompleteLCLog() ............................................................................................................................................ 114
12.15 Export Hardware Inventory from Lifecycle Controller ......................................................................................... 115
12.16 Export Factory Configuration ................................................................................................................................... 116
12.17 System Decommission .............................................................................................................................................. 118
12.18 Get Remote Services API Status ............................................................................................................................... 118
12.19 Export System Configuration .................................................................................................................................... 119
12.20 Import System Configuration ................................................................................................................................... 120
12.21 XML Template Preview ............................................................................................................................................... 121
12.22 Remote Diagnostics ................................................................................................................................................... 122
12.22.1 Run Diagnostics ................................................................................................................................................. 122
12.22.2 Export Diagnostics Results ............................................................................................................................... 123
12.22.3 Verify the Diagnostics Job Status ................................................................................................................... 123
13 VFlash SD Card Management .............................................................................................................................................. 125
13.1 Listing the SD Card Partitions ................................................................................................................................... 125
13.2 Initialize the Virtual Flash Media ............................................................................................................................... 126
13.2.1 Get VFlash SD Card Inventory .................................................................................................................................. 126
13.2.2 Initialize or Format Media .......................................................................................................................................... 126
13.2.3 Verify Initialization or Formatting ............................................................................................................................. 127
13.3 Enable or Disable VFlash using VFlash State Change ........................................................................................... 128
8 Lifecycle Controller Integration – Web Services Interface Guide for Windows | Revision 1.0.
Page 9

13.4 Create Partition ........................................................................................................................................................... 128
13.5 Create Partition using Image .................................................................................................................................... 130
13.6 Delete Partition ............................................................................................................................................................ 131
13.7 Format Partition ........................................................................................................................................................... 132
13.8 Modify Partition ........................................................................................................................................................... 133
13.9 Attach Partition ............................................................................................................................................................ 134
13.10 Detach Partition........................................................................................................................................................... 135
13.11 Export Data from Partition ........................................................................................................................................ 136
14 Boot Control Configuration Management ........................................................................................................................ 139
14.1 Listing the Boot Inventory-ConfigSetting Class .................................................................................................... 139
14.2 Getting a Boot ConfigSetting Instance ................................................................................................................... 140
14.3 Listing the Boot Inventory-SourceSetting Class ................................................................................................... 140
14.4 Changing the Boot Order by InstanceID-ChangeBootOrderByInstanceID() .................................................. 141
14.5 Enable or Disable the Boot Source-ChangeBootSourceState() ......................................................................... 142
15 NIC or CNA Card Management .......................................................................................................................................... 144
15.1 Listing the NIC or CNA Inventory-Enumeration Class ......................................................................................... 144
15.2 Listing the NIC or CNA Inventory-String Class ...................................................................................................... 145
15.3 Listing the CNA Inventory-Integer Class ................................................................................................................ 146
15.4 Listing the CNA Inventory-NICView Class ............................................................................................................. 147
15.5 Listing the CNA Inventory-NICCapabilities Class.................................................................................................. 148
15.6 Listing the CNA Inventory- NICStatistics Class ..................................................................................................... 149
15.7 Applying the Pending Values for CNA-CreateTargetedConfigJob() ................................................................. 150
15.8 Deleting the Pending Values for CNA-DeletePendingConfiguration() ............................................................. 151
15.9 Getting the CNA Enumeration Instance ................................................................................................................. 152
15.10 Setting the
IscsiOffloadMode
Attribute ................................................................................................................... 153
15.11 Setting the MaxBandwidth Attribute ........................................................................................................................ 154
15.12 Setting the VirtMacAddr Attribute ............................................................................................................................ 155
15.13 Setting the LegacyBootProto Attribute ................................................................................................................... 155
15.14 Setting CNA LAN Modes ............................................................................................................................................ 156
15.15 Setting the iSCSI Boot Target.................................................................................................................................... 157
15.16 Setting the FCoE Boot Target ................................................................................................................................... 158
16 RAID Storage Management .................................................................................................................................................. 160
9 Lifecycle Controller Integration – Web Services Interface Guide for Windows | Revision 1.0.
Page 10

16.1 Listing the RAID Inventory-Enumeration Class ..................................................................................................... 160
16.2 Getting a RAID Enumeration Instance .................................................................................................................... 161
16.3 Listing the RAID Inventory-Integer Class ................................................................................................................ 162
16.4 Getting a RAID Integer Instance ............................................................................................................................... 163
16.5 Listing the RAID Inventory-String Class .................................................................................................................. 164
16.6 Getting a RAID String Instance ................................................................................................................................. 165
16.7 Listing the RAID Inventory-ControllerView Class ................................................................................................. 165
16.8 Getting a RAID ControllerView Instance................................................................................................................. 166
16.9 Listing the RAID Inventory-PhysicalDiskView Class .............................................................................................. 167
16.10 Listing the RAID VirtualDiskView Inventory ............................................................................................................ 168
16.11 Listing the RAID EnclosureView Inventory ............................................................................................................. 169
16.12 Reset Configuration-ResetConfig() ......................................................................................................................... 170
16.13 Clearing the Foreign Configuration-ClearForeignConfig() .................................................................................. 171
16.14 Applying the Pending Values for RAID-CreateTargetedConfigJob() .................................................................. 171
16.15 Deleting the Pending Values for RAID-DeletePendingConfiguration() ............................................................. 173
16.16 Managing Hot-Spare .................................................................................................................................................. 173
16.16.1 Determining Potential Disks-GetDHSDisks() ................................................................................................ 173
16.16.2 Assigning the Hot-Spare-AssignSpare() ......................................................................................................... 174
16.16.3 Unassigning the Hot Spare-UnassignSpare() ................................................................................................ 175
16.17 Managing Keys for Self Encrypting Drives .............................................................................................................. 175
16.17.1 Setting the Key-SetControllerKey() ................................................................................................................. 176
16.17.2 Locking the Virtual Disk-LockVirtualDisk() .................................................................................................... 176
16.17.3 Locking the Controller with a Key-EnableControllerEncryption() ............................................................ 177
16.17.4 Rekeying the Controller-ReKey() .................................................................................................................... 178
16.17.5 Removing the Key-RemoveControllerKey() .................................................................................................. 179
16.18 Managing Virtual Disk ................................................................................................................................................. 180
16.18.1 Getting the Available RAID levels-GetRAIDLevels() ..................................................................................... 180
16.18.2 Getting the Available Disks-GetAvailableDisks() ........................................................................................... 181
16.18.3 Checking the Create VD Parameters Validity-CheckVDValues() .............................................................. 182
16.18.4 Creating a Single Virtual Disk-CreateVirtualDisk() ....................................................................................... 183
16.18.5 Creating a Sliced Virtual Disk-CreateVirtualDisk() ........................................................................................ 186
16.18.6 Creating a Cachecade Virtual Disk-CreateVirtualDisk() .............................................................................. 189
10 Lifecycle Controller Integration – Web Services Interface Guide for Windows | Revision 1.0.
Page 11

16.18.7 Deleting a Virtual Disk-DeleteVirtualDisk() .................................................................................................... 190
16.19 Setting Controller Attributes ..................................................................................................................................... 191
16.19.1 Changing the Value of a RAID Controller Enumeration Attribute ............................................................ 191
16.19.2 Changing Multiple Values of RAID Controller Enumeration Attributes.................................................... 191
16.19.3 Changing the Value of a RAID Controller Integer Attribute ....................................................................... 192
16.19.4 Changing Multiple Values of RAID Controller Integer Attributes .............................................................. 193
16.20 Convert Physical Disk Drives to RAID-ConvertToRAID() ..................................................................................... 194
16.21 Convert Physical Disk Drives to Non RAID-ConvertToNonRAID()..................................................................... 195
17 Managing BIOS Configuration............................................................................................................................................. 196
17.1 Listing the BIOS Inventory-Enumeration Class ..................................................................................................... 196
17.2 Getting a BIOS Enumeration Instance .................................................................................................................... 197
17.3 Changing the BIOS BootMode-SetAttribute()........................................................................................................ 198
17.4 Setting Multiple BIOS BootMode Parameters ........................................................................................................ 198
17.5 Listing the BIOS Inventory-Integer Class ................................................................................................................ 199
17.6 Listing the BIOS Inventory-String Class .................................................................................................................. 199
17.7 Applying the Pending Values for BIOS & Boot-CreateTargetedConfigJob() .................................................. 200
17.8 Deleting the Pending Values for BIOS and Boot-DeletePendingConfiguration() ........................................... 201
17.9 Managing BIOS Passwords ....................................................................................................................................... 202
17.9.1 Setting the BIOS Password ....................................................................................................................................... 202
17.9.2 Create Target Configuration Job ............................................................................................................................ 203
17.9.3 Monitor Set BIOS Password Status ......................................................................................................................... 203
17.10 Listing the BIOS Inventory-Password Class .......................................................................................................... 204
18 Exporting and Importing Server Profile ............................................................................................................................ 206
18.1 Exporting Server Profile ............................................................................................................................................ 206
18.1.1 Exporting Server Profile to iDRAC vFlash Card-BackupImage() ........................................................................ 206
18.1.2 Exporting Server Profile to NFS Share-BackupImage() ........................................................................................207
18.1.3 Exporting Server Profile to CIFS Share-BackupImage() .......................................................................................207
18.1.4 Monitoring Export status .......................................................................................................................................... 208
18.2 Automatic Backup ...................................................................................................................................................... 208
18.2.1 Enable the Automatic Backup ................................................................................................................................. 209
18.2.2 Set Backup Schedule .................................................................................................................................................. 210
18.2.3 Get the Backup Schedule .......................................................................................................................................... 210
11 Lifecycle Controller Integration – Web Services Interface Guide for Windows | Revision 1.0.
Page 12

18.2.4 Clear the Backup Schedule .................................................................................................................................. 210
18.3 Importing Server Profile ............................................................................................................................................. 211
18.3.1 Importing Server Profile from iDRAC vFlash Card-RestoreImage() ................................................................... 211
18.3.2 Importing Server Profile from NFS share-RestoreImage() ................................................................................... 211
18.3.3 Importing Server Profile from CIFS share-RestoreImage() .................................................................................. 212
18.3.4 Monitoring Import Status ...................................................................................................................................... 213
19 iDRAC Configuration ............................................................................................................................................................. 214
19.1 Listing the iDRAC Card Inventory-Enumeration Class ......................................................................................... 214
19.2 Getting an iDRAC Card Enumeration Instance ...................................................................................................... 215
19.3 Listing the iDRAC Card Inventory-Enumeration Class using
groupID
.............................................................. 216
19.4 Applying the Attributes and Polling Job Completion ........................................................................................... 217
19.4.1 Changing iDRAC Values-ApplyAttributes() (Immediate) ...................................................................................... 217
19.4.2 Polling Job Completion ........................................................................................................................................ 219
19.4.3 Set Attribute Verification ....................................................................................................................................... 219
19.5 Listing the iDRAC Card Inventory-Integer Class .................................................................................................. 220
19.6 Listing the iDRAC Card Inventory-Integer Class using
groupID
......................................................................... 221
19.7 Listing the iDRAC Card Inventory-String Class ...................................................................................................... 222
19.8 Listing the iDRAC Card Inventory-String Class using
groupID
.......................................................................... 224
19.9 Changing the iDRAC IP Change Notification......................................................................................................... 225
19.9.1 Getting the Current iDRAC IPChange State ........................................................................................................... 225
19.9.2 Setting the iDRAC IPChange Notification-SetAttribute() ............................................................................... 226
20 Remote Service Status .......................................................................................................................................................... 227
20.1 Getting Remote Service Status ................................................................................................................................. 227
20.2 Restarting Remote Service Status ........................................................................................................................... 228
21 System Information .............................................................................................................................................................. 230
21.1 Listing the System Inventory-SystemView Class .................................................................................................. 230
22 Sensor Information ................................................................................................................................................................ 232
22.1 Listing the Sensors Inventory-PSNumericSensor Class ....................................................................................... 232
23 Managing Fiber Channel (FC) Configuration .................................................................................................................... 233
23.1 Listing the FC Inventory-Attribute Class ................................................................................................................. 233
23.2 Listing the FC Inventory-Statistics Class ................................................................................................................ 234
23.3 Listing the FC Inventory-String Class ..................................................................................................................... 234
12 Lifecycle Controller Integration – Web Services Interface Guide for Windows | Revision 1.0.
Page 13

23.4 Listing the FC Inventory-Integer Class .................................................................................................................... 235
23.5 Listing the FC Inventory-Enumeration Class ........................................................................................................ 236
23.6 Changing the FC Attributes-SetAttribute() ............................................................................................................ 236
23.7 Applying the Pending Values for FC-CreateTargetedConfigJob() ..................................................................... 237
23.8 Deleting the Pending Values for FC-DeletePendingConfiguration() ................................................................ 238
23.9 Listing the FC Views ....................................................................................................................................................239
13 Lifecycle Controller Integration – Web Services Interface Guide for Windows | Revision 1.0.
Page 14

Executive Summary
Dell PowerEdge servers are equipped with the integrated Dell Remote
Access Controller and the Lifecycle Controller solution for remote
management – iDRAC6 on 11th Generation servers and iDRAC7 on 12th
Generation servers. These servers can be remotely managed by using the
WS-Man services for configuration, update, deployment, and
maintenance. This whitepaper provides information about the various WSMan interfaces with examples on how to use the interfaces in a Linux
environment.
Page 15

1 Introduction
This document serves as a guideline for utilizing the functionality available from embedded Lifecycle
Controller Remote Enablement Web Services. The purpose of this document is to provide
information and examples for utilizing the Web services for Management (WS-Man) protocol using
Windows WinRM and open source WSMANCLI command line utilities. Examples and invocation
information is provided for the following functionality:
Inventory for BIOS, component firmware and embedded software
Update of BIOS, component firmware and embedded software
Job Control of update tasks
Enhancement of Operating System Deployment using VFlash SD Card
Enhancement of Discovery and Handshake from LifeCycle Controller 1.x
Raid configuration management
iDRAC Inventory and configuration features
NIC configuration management
Boot configuration management
BIOS configuration management
The target audience for this document are script writers and the application that utilizes the remote
management capabilities using WS-Man protocol available from Dell Lifecycle Controller.
Page 16
2 References
Dell 12th Generation PowerEdge Server Resources:
http://www.delltechcenter.com/12thGen
Dell CIM Profiles:
http://www.delltechcenter.com/page/DCIM.Library.Profile
Managed Object Format (MOF) files:
http://www.delltechcenter.com/page/DCIM.Library.MOF
WinRM Scripting API, MSDN:
http://msdn.microsoft.com/en-us/library/aa384469(VS.85).aspx
Openwsman CLI:
http://www.openwsman.org/project/wsmancli
DMTF Common Information Model (CIM) Infrastructure Specification
(DSP0004):
http://www.dmtf.org/standards/published_documents/DSP0004_2.5.0.pdf
List of PCI IDs:
http://pciids.sourceforge.net/pci.ids
Page 17

3 Overview
The remote interface guidelines provided in this document are illustrated by command line examples of
the WS-Man protocol Web services APIs that expose the remote management capabilities of the Dell
Lifecycle Controller. The command line examples are from the Microsoft® Windows® and Linux
environments using WinRM 4 and WSMANCLI 5 respectively. The Lifecycle Controller remote
management capabilities are organized by management domain and documented in Dell CIM Profile
specifications 2. The remote enablement feature for Lifecycle Controller 2.0 provides the following
capabilities:
Remotely retrieve information about inventory of the BIOS, component firmware, and
embedded software including version information of both the installed as well as available
cached versions
Remote update of BIOS, component firmware, Diagnostic content, DRAC content, driver
pack, power supplies from remotely located Dell Update Packages or cached images
located in the Lifecycle Controller
Remotely schedule and track the status of update tasks (jobs)
Remotely manage the Part Replacement feature by allowing retrieving and setting auto
update and auto system inventory sync
Enable re-initiation of Lifecycle Controller Auto-Discovery feature
Enhancement of Operation System Deployment capabilities by supporting the downloading
of an ISO image to a Dell VFlash SD Card and booting to the ISO image on the VFlash SD
Card
NIC configuration enables the ability to get and set NIC attributes that are configurable
using NIC Option ROM or NIC UEFI HII.
Remote RAID configuration allows you to remotely query and configure the Hardware Raid
of the system
Multiple HW Inventory views allows you to remote query the inventory of Hardware
3.1 Format for WS-Man CLI Examples in Document
The examples of WinRM and WSMANCLI command line invocations in this document are formatted
for readability and often span multiple lines in the document. In actual use, scripted or hand-typed
invocations are incorporated in one line. The examples also use substitute values for the target iDRAC
IP address, username (with ExecuteServerCommand privilege), password and other site specific
information. Actual use of these examples would require using valid values for IP address, username,
password, and so on. These values are represented in the examples as follows:
Target iDRAC IP address = [IPADDRESS]
iDRAC Username = [USER]
iDRAC Password = [PASSWORD]
Additional substitute values are used in some of the examples and are described in the
specific example. The following example represents the format used in this document:
EXAMPLE:
Page 18

wsman enumerate http://schemas.dmtf.org/wbem/wscim/1/cimschema/2/root/dcim/DCIM_OSDeploymentService-h $IPADDRESS -V -v -c
dummy.cert -P 443 -u $USERNAME -p $PASSWORD -j utf-8 -y basic
3.2 WS-Man Security and Time Parameters
3.2.1 Encryption Certificate Security
For the WS-Man examples provided in this document, the strict checks of certificates such as
matching of CNs (Common Names) and verification with the actual CA (Certificate Authority) of the
certificate of the WS-Management protocol HTTPS encryption certificate is assumed to be already
configured and enabled. To disable the strict certificate checking, run the following command line
options to all WS-Man examples: –v and –V.
For more information about directions on setting up encryption certificates and executing WS-Man
invocations using full security capabilities for WS-Man, see the WS-Man documentation4 and related
documents. For more information about directions on configuring different encryption certificates for
the iDRAC Web server, see the Lifecycle Controller User Guide1. Dell recommends that the full
security and encryption capabilities of the WS- Management protocol is used for production level
utilization of the Lifecycle Controller Web services interfaces.
3.2.2 Handling Invalid Responses from WS-Man Commands
Check the network connection to make sure that the system is connected
Check the WS-Man syntax to ensure there are no typos in the command line
Check if there are other WS-Man commands sent from other systems
Wait for a few seconds and re-try running the WS-Man command
3.2.3 Improving WS-Man Enumeration Performance
Enumeration configuration only available for winRM.
3.2.4 Specifying
The several methods that attach a virtual USB device to the target system accept a StartTime and Until
parameter. The parameter data type is CIM date-time. If the StartTime parameter is null the action
will not be started. If the Until parameter is null, the default value will be 17 hours. The date-time data
type is defined in the CIM Infrastructure Specification4 as:
ddddddddhhmmss.mmmmmm
Where:
StartTime, Until
Time, and
TIME_NOW
Parameters
dddddddd is the number of days
hh is the remaining number of hours
mm is the remaining number of minutes
Page 19
Term
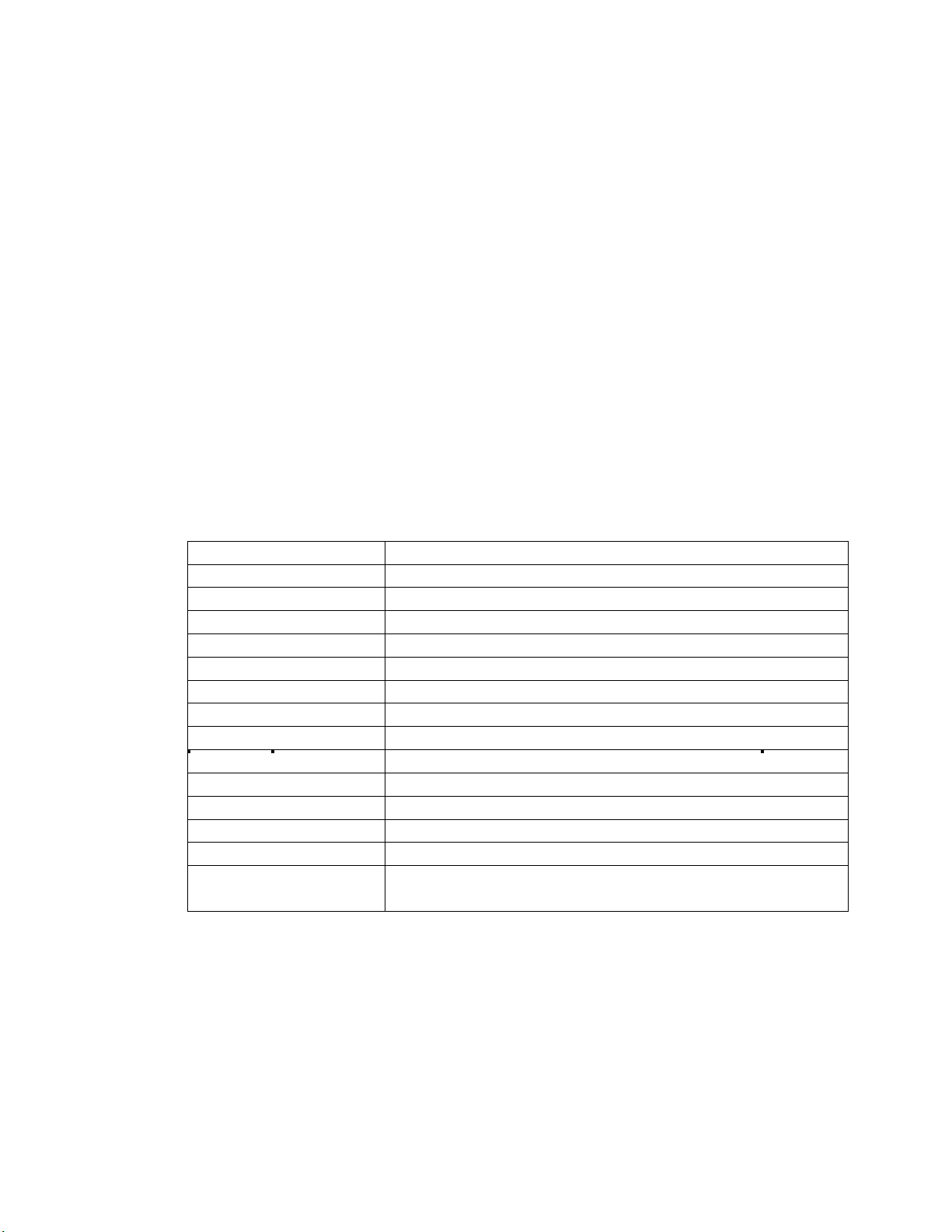
Meaning
BIOS
Basic Input / Output System
HW
Hardware
iDRAC
Integrated DELL Remote Access Controller
IPL
Initial Program Load
DUP
Dell Update Package
MOF
Managed Object File
CIM
Common Information Model
NIC
Network Interface Controller
RAID
Redundant Array of Independent Disks
FQDD
Fully Qualified Device Description
UEFI
Unified Extensible Firmware Interface
AMEA
Advanced Management Enablement Adapter
HII
Human Interface Infrastructure
WS-MAN
WS-Management is a specification of a SOAP-based protocol
for the management of servers, devices, applications and more
ss is the remaining number of seconds
mmmmmm is the remaining number of microseconds
The Lifecycle controller 2.0 firmware update, and set attribute related methods that require a date
time parameter, use the form YYYYMMDDhhmmss (Eg. 20090930112030). You are expected to enter
the date and time in this format for all Lifecycle Controller 2.0 updates and set attribute tasks.
TIME_NOW
3.2.5 Return Values
Many of the methods in this document have the following possible return values. They are
summarized here for convenience.
is a special value that represents “running the tasks immediately”.
0 = Success
1 = Not Supported
2 = Failed
4096 = Job Created
3.2.6 Glossary
Page 20

4 Discovery
4.1 Discovering Web Service Capability
Determine if the target system supports the Ws-Man interface using the ‘identify’ command.
Profiles: http://www.dmtf.org/sites/default/files/standards/documents/DSP0217_2.0.0.pdf
EXAMPLE:
wsman identify
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
-u:[USER] -p:[PASSWORD]
OUTPUT:
<wsmid:IdentifyResponse>
<wsmid:ProtocolVersion>http://schemas.dmtf.org/wbem/wsman/1/wsman
.xsd</wsmid:ProtocolVersion>
<wsmid:ProductVendor>Openwsman Project</wsmid:ProductVendor>
<wsmid:ProductVersion>2.2.4</wsmid:ProductVersion>
</wsmid:IdentifyResponse>
4.2 Discovering what Profiles are implemented
Implemented profiles are advertised using the class CIM_RegisteredProfile. Enumerate this class in the
“root/interop” CIM namespace.
Profiles:
http://www.dmtf.org/sites/default/files/standards/documents/DSP1033_1.0.0.pdf
EXAMPLE:
wsman enumerate http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/CIM_RegisteredProfile?__cimnamespace=root/interop
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT:
<n1:DCIM_LCRegisteredProfile>
<n1:AdvertiseTypeDescriptions>WS-Identify
</n1:AdvertiseTypeDescriptions>
<n1:AdvertiseTypeDescriptions>Interop Namespace
</n1:AdvertiseTypeDescriptions>
<n1:AdvertiseTypes>1</n1:AdvertiseTypes>
<n1:AdvertiseTypes>1</n1:AdvertiseTypes>
<n1:InstanceID>DCIM:Memory:1.0.0</n1:InstanceID>
Page 21

<n1:OtherRegisteredOrganization>DCIM</n1:OtherRegisteredOrganization>
<n1:RegisteredName>Memory</n1:RegisteredName>
<n1:RegisteredOrganization>1</n1:RegisteredOrganization>
<n1:RegisteredVersion>1.0.0</n1:RegisteredVersion>
</n1:DCIM_LCRegisteredProfile>
...
<n1:DCIM_RegisteredProfile>
<n1:AdvertiseTypeDescriptions>WS-Identify
</n1:AdvertiseTypeDescriptions>
<n1:AdvertiseTypes>1</n1:AdvertiseTypes>
<n1:Caption xsi:nil="true"/>
<n1:Description xsi:nil="true"/>
<n1:ElementName xsi:nil="true"/>
<n1:InstanceID>DCIM:CSRegisteredProfile:1</n1:InstanceID>
<n1:OtherRegisteredOrganization xsi:nil="true"/>
<n1:RegisteredName>Base Server</n1:RegisteredName>
<n1:RegisteredOrganization>2</n1:RegisteredOrganization>
<n1:RegisteredVersion>1.0.0</n1:RegisteredVersion>
</n1:DCIM_RegisteredProfile>DCIM_RegisteredProfile
.
.
.
The example above shows that the DMTF Base Server profile version 1.0.0 is implemented.
4.3 Discovering Implementation Namespace
The implementation CIM namespace may be discovered from the interop (root/interop) CIM
namespace using the class CIM_ElementConformsToProfile that associates an instance of
CIM_RegisteredProfile class with an instance of CIM_ComputerSystem class.
Profiles: n/a
EXAMPLE:
OUTPUT:
wsman associators http://schemas.dmtf.org/wbem/wscim/1/*
--filter "http://schemas.dell.com/wbem/wscim/1/cimschema/2/CIM_RegisteredProfile?InstanceID=DCIM:CSRegisteredProfile:1
"
--dialect
“http://schemas.dmtf.org/wbem/wsman/1/cimbinding/associationFilter”
-h $IPADDRESS -P 443 -u $USERNAME -p $PASSWORD -V -v -c dummy.cert
-j utf-8 -y basic -N root/interop
<n1:DCIM_ElementConformsToProfile>
<n1:ConformantStandard>
<wsa:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anon
ymous</wsa:Address>
<wsa:ReferenceParameters>
<wsman:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_RegisteredProfile</wsman:ResourceURI>
<wsman:SelectorSet>
<wsman:Selector
Name="InstanceID">DCIM:CSRegisteredProfile:1</wsman:Selector>
<wsman:Selector Name="__cimnamespace">root/interop</wsman:Selector>
</wsman:SelectorSet>
</wsa:ReferenceParameters>
</n1:ConformantStandard>
Page 22

<n1:ManagedElement>
<wsa:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anon
ymous</wsa:Address>
<wsa:ReferenceParameters>
<wsman:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_ComputerSystem</wsman:ResourceURI>
<wsman:SelectorSet>
<wsman:Selector Name="Name">srv:system</wsman:Selector>
<wsman:Selector
Name="CreationClassName">DCIM_ComputerSystem</wsman:Selector>
<wsman:Selector Name="__cimnamespace">root/dcim</wsman:Selector>
</wsman:SelectorSet>
</wsa:ReferenceParameters>
</n1:ManagedElement>
</n1:DCIM_ElementConformsToProfile>
The example shows that implementation namespace is “root/dcim”.
Page 23
Account Disabled as displayed
in
CurrentValue
attribute for
Users.1
5 Managing iDRAC Local User Accounts
5.1 Description of iDRAC Attributes Versus Standard DMTF
Model
The iDRAC user account management data model is represented by both DMTF and Dell Profiles.
Both models are currently offered. The DMTF Profiles for Simple Identity Management and Role Based
Authorization represent iDRAC user accounts and privileges. The DMTF data model is complex and
typically requires multiple transactions to accomplish simple operations such as specifying a
username and password or giving a user account admin privileges. For this reason, LC also offers a
Dell data model for managing iDRAC user accounts that is based on an attribute model. The DCIM
iDRAC Card Profile specifies the attributes for each user account name, password, and privilege.
iDRAC has 15 local user accounts that can be managed.
5.2 Account Inventory (using iDRAC Attributes)
The list of user accounts may be retrieved by enumerating the
class provides the user account name and enabled state properties.
Profile and Associated MOFs:
http://www.delltechcenter.com/page/DCIM.Library.Profile
5.2.1 Account and Capabilities (using iDRAC Attributes)
Enumerating the
attribute AttributeDisplayName = User Admin Enable, will display all of the 16 possible user
accounts and their respective status.
EXAMPLE:
wsman enumerate "http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_iDRACCardEnumeration"
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT:
<n1:DCIM_iDRACCardEnumeration>
</n1:DCIM_iDRACCardEnumeration>
DCIM_iDRACCard
classes. The
DCIM_iDRACCardEnumeration
class, Section 19.1, and parsing the output for the
<n1:AttributeDisplayName>User Admin Enable</n1:AttributeDisplayName>
<n1:AttributeName>Enable</n1:AttributeName>
<n1:CurrentValue>Disabled</n1:CurrentValue>
<n1:DefaultValue>Disabled</n1:DefaultValue>
<n1:Dependency xsi:nil="true"/>
<n1:DisplayOrder>0</n1:DisplayOrder>
<n1:FQDD>iDRAC.Embedded.1</n1:FQDD>
<n1:GroupDisplayName>Users</n1:GroupDisplayName>
<n1:GroupID>Users.1</n1:GroupID>
<n1:InstanceID>iDRAC.Embedded.1#Users.1#Enable</n1:InstanceID>
<n1:IsReadOnly>true</n1:IsReadOnly>
<n1:PossibleValues>Disabled</n1:PossibleValues>
<n1:PossibleValues>Enabled</n1:PossibleValues>
Page 24
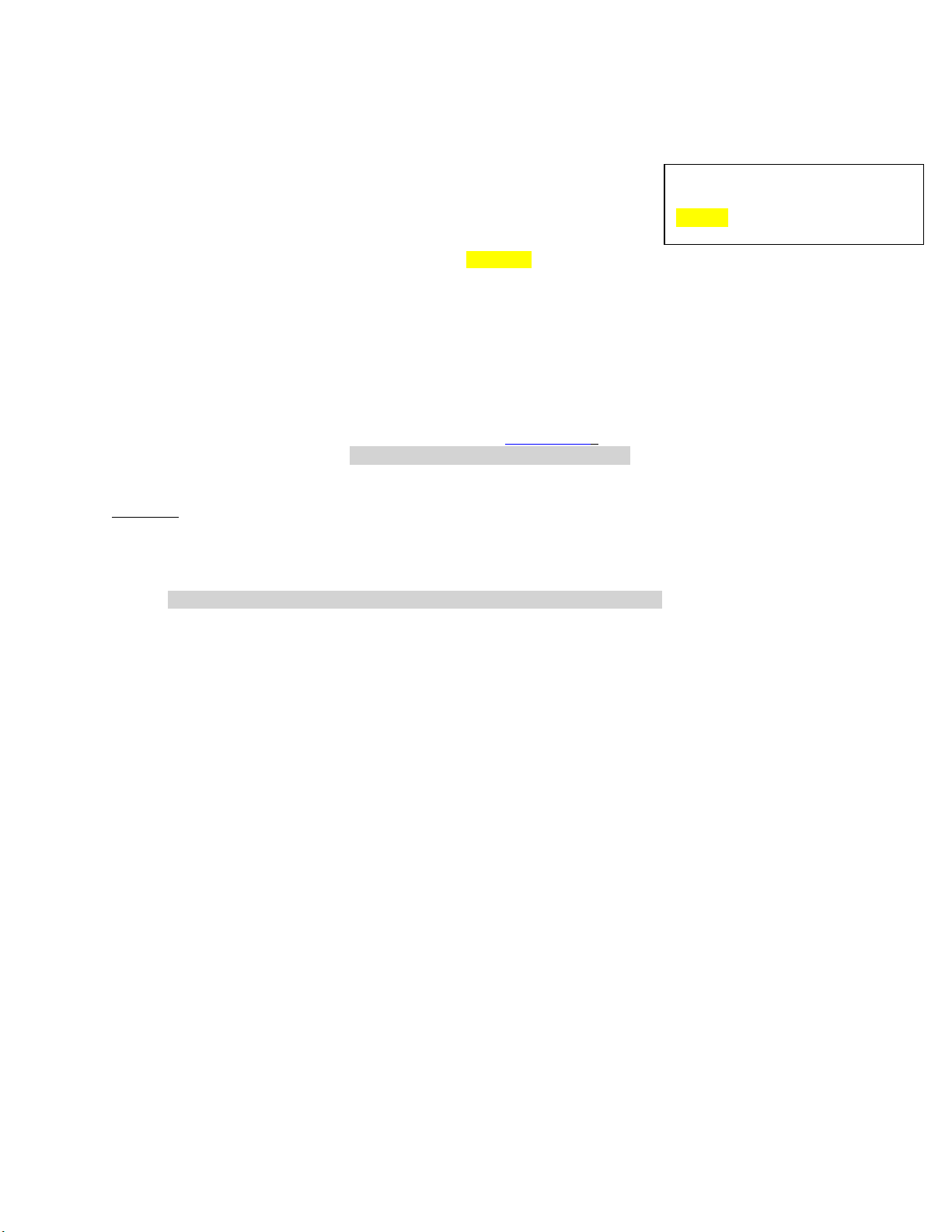
Account Enabled as displayed
in
CurrentValue
attribute for
Users.2
<n1:DCIM_iDRACCardEnumeration>
<n1:AttributeDisplayName>User Admin Enable</n1:AttributeDisplayName>
<n1:AttributeName>Enable</n1:AttributeName>
<n1:CurrentValue>Enabled</n1:CurrentValue>
<n1:DefaultValue>Enabled</n1:DefaultValue>
<n1:Dependency xsi:nil="true"/>
<n1:DisplayOrder>0</n1:DisplayOrder>
<n1:FQDD>iDRAC.Embedded.1</n1:FQDD>
<n1:GroupDisplayName>Users</n1:GroupDisplayName>
<n1:GroupID>Users.2</n1:GroupID>
<n1:InstanceID>iDRAC.Embedded.1#Users.2#Enable</n1:InstanceID>
<n1:IsReadOnly>false</n1:IsReadOnly>
<n1:PossibleValues>Disabled</n1:PossibleValues>
<n1:PossibleValues>Enabled</n1:PossibleValues>
</n1:DCIM_iDRACCardEnumeration>
.
.
5.2.2 Privilege and Capabilities (using iDRAC Attributes)
Enumerating the
attribute AttributeDisplayName = User Admin IPMI LAN(or Serial) Privilege, will display all of the 16
possible user accounts and their respective status.
EXAMPLE:
<n1:DCIM_iDRACCardEnumeration>
<n1:AttributeDisplayName>User Admin IPMI LAN Privilege
</n1:AttributeDisplayName>
<n1:AttributeName>IpmiLanPrivilege</n1:AttributeName>
<n1:CurrentValue>NoAccess</n1:CurrentValue>
<n1:DefaultValue>NoAccess</n1:DefaultValue>
<n1:Dependency xsi:nil="true"/>
<n1:DisplayOrder>0</n1:DisplayOrder>
<n1:FQDD>iDRAC.Embedded.1</n1:FQDD>
<n1:GroupDisplayName>Users</n1:GroupDisplayName>
<n1:GroupID>Users.1</n1:GroupID>
<n1:InstanceID>iDRAC.Embedded.1#Users.1#IpmiLanPrivilege
</n1:InstanceID>
<n1:IsReadOnly>true</n1:IsReadOnly>
<n1:PossibleValues>User</n1:PossibleValues>
<n1:PossibleValues>Operator</n1:PossibleValues>
<n1:PossibleValues>Administrator</n1:PossibleValues>
<n1:PossibleValues>NoAccess</n1:PossibleValues>
</n1:DCIM_iDRACCardEnumeration>
<n1:DCIM_iDRACCardEnumeration>
<n1:AttributeDisplayName>User Admin IPMI Serial
Privilege</n1:AttributeDisplayName>
<n1:AttributeName>IpmiSerialPrivilege</n1:AttributeName>
<n1:CurrentValue>NoAccess</n1:CurrentValue>
<n1:DefaultValue>NoAccess</n1:DefaultValue>
<n1:Dependency xsi:nil="true"/>
<n1:DisplayOrder>0</n1:DisplayOrder>
<n1:FQDD>iDRAC.Embedded.1</n1:FQDD>
<n1:GroupDisplayName>Users</n1:GroupDisplayName>
<n1:GroupID>Users.1</n1:GroupID>
<n1:InstanceID>iDRAC.Embedded.1#Users.1#IpmiSerialPrivilege
</n1:InstanceID>
<n1:IsReadOnly>true</n1:IsReadOnly>
<n1:PossibleValues>User</n1:PossibleValues>
<n1:PossibleValues>Operator</n1:PossibleValues>
DCIM_iDRACCardEnumeration
class, Section 19.1, and parsing the output for the
Page 25

<n1:PossibleValues>Administrator</n1:PossibleValues>
<n1:PossibleValues>NoAccess</n1:PossibleValues>
</n1:DCIM_iDRACCardEnumeration>
5.3 Manage Account Settings (using iDRAC Attributes)
When the account setting capability allows, the username of an account may be modified by
invoking the ApplyAttributes() method on the
username or password verification can be obtained by enumerating the
class( Section 19.6).
5.3.1 Modify User Name (using iDRAC Attributes)
EXAMPLE:
wsman invoke -a ApplyAttributes
http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_
iDRACCardService
?SystemCreationClassName=DCIM_ComputerSystem,
CreationClassName=DCIM_iDRACCardService,SystemName=DCIM:ComputerSystem,Name=D
CIM:iDRACC
ardService
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD -j utf-8 -y basic -J DracCard_UserName.xml
The input file, DracCard_UserName.xml, is shown below:
<p:ApplyAttributes_INPUT
xmlns:p="http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_iDRACCardService">
<p:Target>iDRAC.Embedded.1</p:Target>
<p:AttributeName>Users.4#UserName</p:AttributeName>
<p:AttributeValue>HELLO</p:AttributeValue>
</p:ApplyAttributes_INPUT>
OUTPUT:
When this method is executed, a
<n1:ApplyAttributes_OUTPUT>
<wsa:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anonymous<
/wsa:Address>
UserName
property. Confirmation of successful
DCIM_iDRACCardString
jobid
or a message is displayed indicating an error.
<n1:Job>
<wsa:ReferenceParameters>
<wsman:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_LifecycleJob</wsman:ResourceURI>
<wsman:SelectorSet>
<wsman:Selector Name="InstanceID">JID_001299682234</wsman:Selector>
<wsman:Selector Name="__cimnamespace">root/dcim</wsman:Selector>
</wsman:SelectorSet>
</wsa:ReferenceParameters>
</n1:Job>
<n1:ReturnValue>4096</n1:ReturnValue>
Page 26

</n1:ApplyAttributes_OUTPUT>
5.3.2 Modify Password (using iDRAC Attributes)
EXAMPLE:
wsman invoke -a ApplyAttributes
"http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_
iDRACCardService
?SystemCreationClassName=DCIM_ComputerSystem,
CreationClassName=DCIM_iDRACCardService,SystemName=DCIM:ComputerSystem,Name=D
CIM:iDRACC
ardService"
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD -j utf-8 -y basic -J DracCard_Password.xml
The input file, DracCard_Password.xml, is shown here:
<p:ApplyAttributes_INPUT
xmlns:p="http://schemas.dmtf.org/wbem/wscim/1/cim-
schema/2/root/dcim/DCIM_iDRACCardService">
<p:Target>iDRAC.Embedded.1</p:Target>
<p:AttributeName>Users.4#Enable</p:AttributeName>
<p:AttributeValue>Enabled</p:AttributeValue>
<p:AttributeName>Users.4#Password</p:AttributeName>
<p:AttributeValue>PWORDHERE</p:AttributeValue>
</p:ApplyAttributes_INPUT>
OUTPUT:
When this method is executed, a
jobid
or a message is displayed indicating an error.
<n1:ApplyAttributes_OUTPUT>
<n1:Job>
<wsa:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anon
ymous</wsa:Address>
<wsa:ReferenceParameters>
<wsman:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_LifecycleJob</wsman:ResourceURI>
<wsman:SelectorSet>
<wsman:Selector Name="InstanceID">JID_001299683297</wsman:Selector>
<wsman:Selector Name="__cimnamespace">root/dcim</wsman:Selector>
</wsman:SelectorSet>
</wsa:ReferenceParameters>
</n1:Job>
<n1:ReturnValue>4096</n1:ReturnValue>
</n1:ApplyAttributes_OUTPUT>
5.3.3 Modify Account State (using iDRAC Attributes)
When the account setting capability allows, the user account may be enabled or disabled by
invoking the method ApplyAttributes() method on the
can be obtained by enumerating the
Enable
DCIM_iDRACCardString
property. Confirmation of the change
class( Section 19.6).
EXAMPLE:
Page 27

wsman invoke -a ApplyAttributes
"http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_
iDRACCardService
?SystemCreationClassName=DCIM_ComputerSystem,
CreationClassName=DCIM_iDRACCardService,SystemName=DCIM:ComputerSystem,Name=D
CIM:iDRACC
ardService"
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD -j utf-8 -y basic -J DracCard_AccountChange.xml
The input file, DracCard_ AccountChange.xml, is shown below:
<p:ApplyAttributes_INPUT
xmlns:p="http://schemas.dmtf.org/wbem/wscim/1/cim-
schema/2/root/dcim/DCIM_iDRACCardService">
</p:ApplyAttributes_INPUT>
<p:Target>iDRAC.Embedded.1</p:Target>
<p:AttributeName>Users.4#Enable</p:AttributeName>
<p:AttributeValue>Enabled</p:AttributeValue>
<p:AttributeName>Users.4#Password</p:AttributeName>
<p:AttributeValue>PASSWORDHERE</p:AttributeValue>
OUTPUT:
When this method is executed, a
jobid
or a message is displayed indicating an error.
ApplyAttributes_OUTPUT
<n1:ApplyAttributes_OUTPUT>
<n1:Job>
<wsa:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anon
ymous</wsa:Address>
<wsa:ReferenceParameters>
<wsman:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_LifecycleJob</wsman:ResourceURI>
<wsman:SelectorSet>
<wsman:Selector Name="InstanceID">JID_001299683957</wsman:Selector>
<wsman:Selector
Name="__cimnamespace">root/dcim</wsman:Selector>
</wsman:SelectorSet>
</wsa:ReferenceParameters>
</n1:Job>
<n1:ReturnValue>4096</n1:ReturnValue>
</n1:ApplyAttributes_OUTPUT>
The following error may result if the password has not initially been set to a value. The password may
be set an initail value at the same time as the account is enabled by adding the
attribute name and corresponding attribute value, as shown above.
<n1:ApplyAttributes_OUTPUT>
<n1:Message>The User Password is not configured so cannot Enable the
User or set values for
User Password IPMILan IPMISerial or User Admin Privilege</n1:Message>
<n1:MessageArguments>NULL</n1:MessageArguments>
<n1:MessageID>RAC023</n1:MessageID>
<n1:ReturnValue>2</n1:ReturnValue>
</n1:ApplyAttributes_OUTPUT>
Users.4#Password
Page 28

5.3.4 Modify User Privilege (using iDRAC Attributes)
When the account setting capability allows, the user privileges may be enabled or disabled by
invoking the method ApplyAttributes() method on the
can be obtained by enumerating the
Enable
DCIM_iDRACCardString
property. Confirmation of the change
class( Section 19.6).
EXAMPLE:
wsman invoke -a ApplyAttributes
"http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_
iDRACCardService
?SystemCreationClassName=DCIM_ComputerSystem,
CreationClassName=DCIM_iDRACCardService,SystemName=DCIM:ComputerSystem,Name=D
CIM:iDRACC
ardService"
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD -j utf-8 -y basic
-J DracCard_PrivilegeChange.xml
The input file, DracCard_ PrivilegeChange.xml, is shown below:
<p:ApplyAttributes_INPUT
xmlns:p="http://schemas.dmtf.org/wbem/wscim/1/cim-
schema/2/root/dcim/DCIM_iDRACCardService">
<p:Target>iDRAC.Embedded.1</p:Target>
<p:AttributeName>Users.4#IpmiLanPrivilege</p:AttributeName>
<p:AttributeValue>Operator</p:AttributeValue>
</p:ApplyAttributes_INPUT>
OUTPUT:
When this method is executed, a
<n1:ApplyAttributes_OUTPUT>
<n1:Job>
<wsa:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anon
ymous</wsa:Address>
<wsa:ReferenceParameters>
<wsman:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_LifecycleJob</wsman:ResourceURI>
<wsman:SelectorSet>
<wsman:Selector Name="InstanceID">JID_001299684480</wsman:Selector>
<wsman:Selector Name="__cimnamespace">root/dcim</wsman:Selector>
</wsman:SelectorSet>
</wsa:ReferenceParameters>
</n1:Job>
<n1:ReturnValue>4096</n1:ReturnValue>
</n1:ApplyAttributes_OUTPUT>
jobid
or a message is displayed indicating an error.
5.4 Account Inventory (using DMTF Model)
The list of user accounts may be retrieved by enumerating the
provides the user account name and
included but it is a write-only property.
EnabledState
properties. The user account password is also
Profiles:
http://www.dmtf.org/sites/default/files/standards/documents/DSP1034_1.0.1.pdf
http://www.dmtf.org/sites/default/files/standards/documents/DSP1039_1.0.0.pdf
CIM_Account
class. The class
Page 29

5.4.1 Account and Capabilities (using DMTF Model)
Example-A demonstrates standard ouput. Example-B demonstrates EPR mode
output.
EXAMPLE-A:
wsman enumerate "http://schemas.dmtf.org/wbem/wscim/1/cimschema/2/CIM_Account"
-h $IPADDRESS -V –v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT-A:
<n1:DCIM_MFAAccount>
<n1:AuthenticateMethod xsi:nil="true"/>
<n1:AvailableRequestedStates xsi:nil="true"/>
<n1:Caption xsi:nil="true"/>
<n1:CommunicationStatus xsi:nil="true"/>
<n1:ComplexPasswordRulesEnforced xsi:nil="true"/>
<n1:CreationClassName>DCIM_MFAAccount</n1:CreationClassName>
<n1:Description xsi:nil="true"/>
<n1:Descriptions xsi:nil="true"/>
<n1:DetailedStatus xsi:nil="true"/>
<n1:ElementName>MFA Account 13</n1:ElementName>
<n1:EnabledDefault>2</n1:EnabledDefault>
<n1:EnabledState>3</n1:EnabledState>
<n1:HealthState xsi:nil="true"/>
<n1:Host xsi:nil="true"/>
<n1:InactivityTimeout xsi:nil="true"/>
<n1:InstallDate xsi:nil="true"/>
<n1:LastLogin xsi:nil="true"/>
<n1:LocalityName xsi:nil="true"/>
<n1:MaximumSuccessiveLoginFailures xsi:nil="true"/>
<n1:Name>DCIM User 13</n1:Name>
<n1:OU xsi:nil="true"/>
<n1:ObjectClass xsi:nil="true"/>
<n1:OperatingStatus xsi:nil="true"/>
<n1:OperationalStatus xsi:nil="true"/>
<n1:OrganizationName>DCIM</n1:OrganizationName>
<n1:OtherEnabledState xsi:nil="true"/>
<n1:PasswordExpiration xsi:nil="true"/>
<n1:PasswordHistoryDepth xsi:nil="true"/>
<n1:PrimaryStatus xsi:nil="true"/>
<n1:RequestedState>0</n1:RequestedState>
<n1:SeeAlso xsi:nil="true"/>
<n1:Status xsi:nil="true"/>
<n1:StatusDescriptions xsi:nil="true"/>
<n1:SystemCreationClassName>DCIM_SPComputerSystem
</n1:SystemCreationClassName>
<n1:SystemName>systemmc</n1:SystemName>
<n1:TimeOfLastStateChange xsi:nil="true"/>
<n1:TransitioningToState>12</n1:TransitioningToState>
<n1:UserCertificate xsi:nil="true"/>
<n1:UserID/>
<n1:UserPassword xsi:nil="true"/>
</n1:DCIM_MFAAccount>
Page 30

<n1:DCIM_MFAAccount>
<n1:AuthenticateMethod xsi:nil="true"/>
<n1:AvailableRequestedStates xsi:nil="true"/>
<n1:Caption xsi:nil="true"/>
<n1:CommunicationStatus xsi:nil="true"/>
<n1:ComplexPasswordRulesEnforced xsi:nil="true"/>
<n1:CreationClassName>DCIM_MFAAccount</n1:CreationClassName>
<n1:Description xsi:nil="true"/>
<n1:Descriptions xsi:nil="true"/>
<n1:DetailedStatus xsi:nil="true"/>
<n1:ElementName>MFA Account 2</n1:ElementName>
<n1:EnabledDefault>2</n1:EnabledDefault>
<n1:EnabledState>2</n1:EnabledState>
<n1:HealthState xsi:nil="true"/>
<n1:Host xsi:nil="true"/>
EXAMPLE-B:
wsman enumerate "http://schemas.dmtf.org/wbem/wscim/1/cim-schema/2/CIM_Account"
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
OUTPUT-B:
<wsa:EndpointReference>
<wsa:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anonymous<
/wsa:Address>
<wsa:ReferenceParameters>
<wsman:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_MFAAccount</wsman:ResourceURI>
<wsman:SelectorSet>
<wsman:Selector
Name="SystemCreationClassName">DCIM_SPComputerSystem</wsman:Selector>
<wsman:Selector Name="SystemName">systemmc</wsman:Selector>
<wsman:Selector Name="CreationClassName">DCIM_MFAAccount</wsman:Selector>
<wsman:Selector Name="Name">DCIM User 1</wsman:Selector>
</wsman:SelectorSet>
</wsa:ReferenceParameters>
</wsa:EndpointReference>
<wsa:EndpointReference>
<wsa:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anonymous<
/wsa:Address>
<wsa:ReferenceParameters>
<wsman:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_MFAAccount</wsman:ResourceURI>
<wsman:SelectorSet>
<wsman:Selector
Name="SystemCreationClassName">DCIM_SPComputerSystem</wsman:Selector>
<wsman:Selector Name="SystemName">systemmc</wsman:Selector>
<wsman:Selector Name="CreationClassName">DCIM_MFAAccount</wsman:Selector>
<wsman:Selector Name="Name">DCIM User 2</wsman:Selector>
</wsman:SelectorSet>
</wsa:ReferenceParameters>
</wsa:EndpointReference>
.
.
.
Page 31

Account setting capability is defined in the class
with the
capability class
CIM_Account
CIM_EnabledLogicalElementCapabilities
class instance. The ability to enable and disable an account is defined in the
CIM_AccountManagementCapabilities
associated with the
CIM_Account
associated
To determine account setting capabilities:
1. Get the CIM_Account class instance of interest using EnumerateEPR mode.
2. Enumerate the associators of the CIM_Account instance and search for
CIM_AccountManagementService class instance using EnumerateEPR mode.
3. Enumerate the associators of the CIM_AccountManagementService instance and search
for CIM_AccountManagementCapabilities class instance.
4. One exception is account index 0. The first account is static and cannot be set.
OUTPUT-C:
<n1:DCIM_MFAManagementCapabilities>
<n1:Caption xsi:nil="true"/>
<n1:Description xsi:nil="true"/>
<n1:ElementName>MFAManagementCapabilities</n1:ElementName>
<n1:ElementNameEditSupported>false
</n1:ElementNameEditSupported>
<n1:ElementNameMask xsi:nil="true"/>
<n1:InstanceID>DCIM:MFAManagementCapabilities:1
</n1:InstanceID>
<n1:MaxElementNameLen>0</n1:MaxElementNameLen>
<n1:OperationsSupported>3</n1:OperationsSupported>
<n1:RequestedStatesSupported xsi:nil="true"/>
<n1:StateAwareness xsi:nil="true"/>
<n1:SupportedAuthenticationMethod>0
</n1:SupportedAuthenticationMethod>
<n1:SupportedAuthenticationMethod>1
</n1:SupportedAuthenticationMethod>
<n1:SupportedAuthenticationMethod>2
</n1:SupportedAuthenticationMethod>
</n1:DCIM_MFAManagementCapabilities>
<n1:DCIM_IPMICLPAccountManagementCapabilities>
</n1:DCIM_IPMICLPAccountManagementCapabilities>
<n1:Caption xsi:nil="true"/>
<n1:Description xsi:nil="true"/>
<n1:ElementName>IPMICLPAccountManagementCapabilities
</n1:ElementName>
<n1:ElementNameEditSupported>false
</n1:ElementNameEditSupported>
<n1:ElementNameMask xsi:nil="true"/>
<n1:InstanceID>DCIM:IPMICLPAccountManagementCapabilities:1
</n1:InstanceID>
<n1:MaxElementNameLen>0</n1:MaxElementNameLen>
<n1:OperationsSupported>3</n1:OperationsSupported>
<n1:RequestedStatesSupported xsi:nil="true"/>
<n1:StateAwareness xsi:nil="true"/>
To determine account state setting capabilities:
1. Get the CIM_Account class instance of interest using EnumerateEPR mode.
2. Enumerate the associators of the CIM_Account instance and search
for CIM_EnabledLogicalElementCapabilities class instance.
class.
Page 32

3. The presence of “RequestedStatesSupported” determines which states could be set.
4. One exception is account index 0. The first account is static and cannot be set.
OUTPUT-D:
<n1:DCIM_MFAEnabledLogicalElementCapabilities>
</n1:DCIM_MFAEnabledLogicalElementCapabilities>
<n1:Caption xsi:nil="true"/>
<n1:Description xsi:nil="true"/>
<n1:ElementName>Account Capabilities</n1:ElementName>
<n1:ElementNameEditSupported>false
</n1:ElementNameEditSupported>
<n1:ElementNameMask xsi:nil="true"/>
<n1:InstanceID>DCIM:Account:Capabilities:1</n1:InstanceID>
<n1:MaxElementNameLen>0</n1:MaxElementNameLen>
<n1:RequestedStatesSupported>2</n1:RequestedStatesSupported>
<n1:RequestedStatesSupported>3</n1:RequestedStatesSupported>
<n1:StateAwareness xsi:nil="true"/>
.
.
.
5.4.2 Privilege and Capabilities (using DMTF Model)
The account privilege assigned to you is defined in the class
CIM_Account
CIM_Privilege
class. The class contains a list of privileges granted to the user account.
associated with the
Profiles:
http://www.dmtf.org/sites/default/files/standards/documents/DSP1034_1.0.1.pdf
http://www.dmtf.org/sites/default/files/standards/documents/DSP1039_1.0.0.pdf
To get the instance of
CIM_Privilege
for an account:
1. Get the CIM_Account class instance of interest using EnumerateEPR mode.
2. Enumerate the associators of the CIM_Account instance and search for CIM_Identity
class instance using EnumerateEPR mode.
3. Enumerate the associators of the CIM_Identity instance and search for CIM_Role class
instance using EnumerateEPR mode.
4. Enumerate the associators of the CIM_Role instance and search for CIM_Privilege class
instance.
An alternative to the above method, you can retrieve the specific
enumerating the class directly with filter. This method is similar to the example used to retrieve
CIM_Account
.
CIM_Privilege
instance by
EXAMPLE:
wsman enumerate http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_LocalRolePrivilege
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD -j utf-8 -y basic
OUTPUT:
<n1:DCIM_LocalRolePrivilege>
<n1:Activities xsi:nil="true"/>
<n1:ActivityQualifiers xsi:nil="true"/>
Page 33

<n1:Caption xsi:nil="true"/>
<n1:Description xsi:nil="true"/>
<n1:ElementName xsi:nil="true"/>
<n1:InstanceID>DCIM:Privilege:1</n1:InstanceID>
<n1:PrivilegeGranted>true</n1:PrivilegeGranted>
<n1:QualifierFormats xsi:nil="true"/>
<n1:RepresentsAuthorizationRights>false
</n1:RepresentsAuthorizationRights>
</n1:DCIM_LocalRolePrivilege>
<n1:DCIM_LocalRolePrivilege>
<n1:Activities>7</n1:Activities>
<n1:Activities>7</n1:Activities>
<n1:Activities>7</n1:Activities>
<n1:Activities>7</n1:Activities>
<n1:Activities>7</n1:Activities>
<n1:Activities>7</n1:Activities>
<n1:Activities>7</n1:Activities>
<n1:Activities>7</n1:Activities>
<n1:Activities>7</n1:Activities>
<n1:ActivityQualifiers>Login to DRAC</n1:ActivityQualifiers>
<n1:ActivityQualifiers>Configure DRAC</n1:ActivityQualifiers>
<n1:ActivityQualifiers>Configure Users
</n1:ActivityQualifiers>
<n1:ActivityQualifiers>Clear Logs</n1:ActivityQualifiers>
<n1:ActivityQualifiers>Execute Server Control Commands
</n1:ActivityQualifiers>
<n1:ActivityQualifiers>Access Console Redirection
</n1:ActivityQualifiers>
<n1:ActivityQualifiers>Access Virtual Media
</n1:ActivityQualifiers>
<n1:ActivityQualifiers>Test Alerts</n1:ActivityQualifiers>
<n1:ActivityQualifiers>Execute Diagnostic Commands
</n1:ActivityQualifiers>
<n1:Caption xsi:nil="true"/>
<n1:Description xsi:nil="true"/>
<n1:ElementName xsi:nil="true"/>
<n1:InstanceID>DCIM:Privilege:2</n1:InstanceID>
<n1:PrivilegeGranted>true</n1:PrivilegeGranted>
<n1:QualifierFormats>9</n1:QualifierFormats>
<n1:QualifierFormats>9</n1:QualifierFormats>
<n1:QualifierFormats>9</n1:QualifierFormats>
<n1:QualifierFormats>9</n1:QualifierFormats>
<n1:QualifierFormats>9</n1:QualifierFormats>
<n1:QualifierFormats>9</n1:QualifierFormats>
<n1:QualifierFormats>9</n1:QualifierFormats>
<n1:QualifierFormats>9</n1:QualifierFormats>
<n1:QualifierFormats>9</n1:QualifierFormats>
<n1:RepresentsAuthorizationRights>true
</n1:RepresentsAuthorizationRights>
</n1:DCIM_LocalRolePrivilege>
<n1:DCIM_LocalRolePrivilege>
<n1:Activities xsi:nil="true"/>
<n1:ActivityQualifiers xsi:nil="true"/>
<n1:Caption xsi:nil="true"/>
<n1:Description xsi:nil="true"/>
<n1:ElementName xsi:nil="true"/>
<n1:InstanceID>DCIM:Privilege:3</n1:InstanceID>
<n1:PrivilegeGranted>true</n1:PrivilegeGranted>
<n1:QualifierFormats xsi:nil="true"/>
<n1:RepresentsAuthorizationRights>false
</n1:RepresentsAuthorizationRights>
Page 34

</n1:DCIM_LocalRolePrivilege>
.
.
.
Privilege setting capability is defined in the class
associated with the
to assign privileges. Look for the property
CIM_Privilege
class instance. This class contains the list of possible values used
CIM_RoleBasedManagementCapabilities
ActivityQualifiersSupported
.
To determine privilege setting capabilities:
1. Acquire the class instance of CIM_Privilege of interest.
2. Enumerate the associators of the CIM_Privilege instance and search for
CIM_RoleBasedAuthorizationService class instance using EnumerateEPR mode.
3. Enumerate the associators of the CIM_RoleBasedAuthorizationService instance and search
for CIM_RoleBasedManagementCapabilities class instance using EnumerateEPR mode.
OUTPUT:
DCIM_LocalRoleBasedManagementCapabilities
ActivitiesSupported = 7, 7, 7, 7, 7, 7, 7, 7, 7
ActivityQualifiersSupported = Login to DRAC, Configure DRAC, Configure
Users, Clear Logs, Execute
Server Control Commands, Access Console Redirection, Access Virtual
Media, Test Alerts, Execute Di
agnostic Commands
Caption = null
Description = null
ElementName = Local Role Based Management Capabilities
InstanceID = DCIM:LocalRoleBasedManagementCapabilities
QualifierFormatsSupported = 9, 9, 9, 9, 9, 9, 9, 9, 9
SharedPrivilegeSupported = false
SupportedMethods = 8
DCIM_CLPRoleBasedManagementCapabilities
ActivitiesSupported = null
ActivityQualifiersSupported = null
Caption = null
Description = null
ElementName = CLP Role Based Management Capabilities
InstanceID = DCIM:CLPRoleBasedManagementCapabilities
QualifierFormatsSupported = null
SharedPrivilegeSupported = false
SupportedMethods = 6
DCIM_IPMIRoleBasedManagementCapabilities
ActivitiesSupported = null
ActivityQualifiersSupported = null
Caption = null
Description = null
ElementName = IPMI Role Based Management Capabilities
InstanceID = DCIM:IPMIRoleBasedManagementCapabilities
QualifierFormatsSupported = null
SharedPrivilegeSupported = false
SupportedMethods = 6
Page 35

5.5 Manage Account Settings (using DMTF Model)
5.5.1 Modify User Name (using DMTF Model)
When the account setting capability allows, the user name of an account may be modified by
running a set operation on the
requires an instance reference. The instance reference may be retrieved by adding
mode to enumerate or get of the class.
UserID
property of the
CIM_Account
class instance. The set operation
EnumerateEPR
Profiles:
http://www.dmtf.org/sites/default/files/standards/documents/DSP1034_1.0.1.pdf
http://www.dmtf.org/sites/default/files/standards/documents/DSP1039_1.0.0.pdf
To set the user name and password for local accounts:
A) Enumerate CIM_Account with EPR to identify all possible instance information to be used in
a subsequent put or set operations.
EXAMPLE-A:
wsman enumerate "http://schemas.dmtf.org/wbem/wscim/1/cimschema/2/CIM_Account
?__cimnamespace=root/dcim"
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
When this command is executed, a list of objects will be returned. Below is a snippet of the output.
OUTPUT-A:
<wsa:EndpointReference>
<wsa:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anonymous<
/wsa:Address>
<wsa:ReferenceParameters>
<wsman:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_MFAAccount</wsman:ResourceURI>
<wsman:SelectorSet>
<wsman:Selector Name="SystemCreationClassName">
DCIM_SPComputerSystem
</wsman:Selector>
<wsman:Selector Name="SystemName">systemmc
</wsman:Selector>
<wsman:Selector Name="CreationClassName">
DCIM_MFAAccount</wsman:Selector>
<wsman:Selector Name="Name">DCIM User 1</wsman:Selector>
</wsman:SelectorSet>
</wsa:ReferenceParameters>
</wsa:EndpointReference>
<wsa:ReferenceParameters>
<wsman:ResourceURI>http://schemas.dell.com/wbem/wscim/1/
cim-schema/2/DCIM_MFAAccount</wsman:ResourceURI>
<wsman:SelectorSet>
<wsman:Selector Name="SystemCreationClassName">
DCIM_SPComputerSystem</wsman:Selector>
<wsman:Selector Name="SystemName">systemmc
</wsman:Selector>
Page 36

<wsman:Selector Name="CreationClassName">
DCIM_MFAAccount</wsman:Selector>
<wsman:Selector Name="Name">DCIM User 2</wsman:Selector>
</wsman:SelectorSet>
</wsa:ReferenceParameters>
</wsa:EndpointReference>
.
.
.
B) Perform a ‘get’ on any instance from A) to ensure correctness of the URI.
EXAMPLE-B:
wsman get "http://schemas.dmtf.org/wbem/wscim/1/cim-schema/2/DCIM_MFAAccount
?__cimnamespace=root/dcim,SystemCreationClassName=DCIM_SPComputerSystem,Creat
ionClassNam
e=DCIM_MFAAccount,SystemName=systemmc,
Name=DCIM User 1"
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basiс
When this method is executed, the particular object will be returned. Below is the output.
OUTPUT-B:
<n1:DCIM_MFAAccount>
<n1:AuthenticateMethod xsi:nil="true"/>
<n1:AvailableRequestedStates xsi:nil="true"/>
<n1:Caption xsi:nil="true"/>
<n1:CommunicationStatus xsi:nil="true"/>
<n1:ComplexPasswordRulesEnforced xsi:nil="true"/>
<n1:CreationClassName>DCIM_MFAAccount</n1:CreationClassName>
<n1:Description xsi:nil="true"/>
<n1:Descriptions xsi:nil="true"/>
<n1:DetailedStatus xsi:nil="true"/>
<n1:ElementName>MFA Account 1</n1:ElementName>
<n1:EnabledDefault>2</n1:EnabledDefault>
<n1:EnabledState>3</n1:EnabledState>
<n1:HealthState xsi:nil="true"/>
<n1:Host xsi:nil="true"/>
<n1:InactivityTimeout xsi:nil="true"/>
<n1:InstallDate xsi:nil="true"/>
<n1:LastLogin xsi:nil="true"/>
<n1:LocalityName xsi:nil="true"/>
<n1:MaximumSuccessiveLoginFailures xsi:nil="true"/>
<n1:Name>DCIM User 1</n1:Name>
<n1:OU xsi:nil="true"/>
<n1:ObjectClass xsi:nil="true"/>
<n1:OperatingStatus xsi:nil="true"/>
<n1:OperationalStatus xsi:nil="true"/>
<n1:OrganizationName>DCIM</n1:OrganizationName>
<n1:OtherEnabledState xsi:nil="true"/>
<n1:PasswordExpiration xsi:nil="true"/>
<n1:PasswordHistoryDepth xsi:nil="true"/>
<n1:PrimaryStatus xsi:nil="true"/>
<n1:RequestedState>0</n1:RequestedState>
<n1:SeeAlso xsi:nil="true"/>
<n1:Status xsi:nil="true"/>
<n1:StatusDescriptions xsi:nil="true"/>
<n1:SystemCreationClassName>DCIM_SPComputerSystem
Page 37

</n1:SystemCreationClassName>
<n1:SystemName>systemmc</n1:SystemName>
<n1:TimeOfLastStateChange xsi:nil="true"/>
<n1:TransitioningToState>12</n1:TransitioningToState>
<n1:UserCertificate xsi:nil="true"/>
<n1:UserID/>
<n1:UserPassword xsi:nil="true"/>
</n1:DCIM_MFAAccount>
C) If B) is successful, set the new values for the specified instance.
EXAMPLE-C:
wsman put "http://schemas.dmtf.org/wbem/wscim/1/cimschema/2/DCIM_MFAAccount
?__cimnamespace=root/dcim,SystemCreationClassName=DCIM_SPComputerSyste,Creati
onClassName=
DCIM_MFAAccount,SystemName=systemmc,Name=DCIM User 16"
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-k UserID=testuser4 -k UserPassword=testuserpss4
-j utf-8 -y basic
When this command is executed, the
be displayed as null when the account is disabled. After the account is enabled, it will be displayed as
blank. The value of
UserPassword
UserID
will never be displayed.
will be displayed in the output. The
UserPassword
will
OUTPUT-C:
<n1:DCIM_MFAAccount>
<n1:AuthenticateMethod xsi:nil="true"/>
<n1:AvailableRequestedStates xsi:nil="true"/>
<n1:Caption xsi:nil="true"/>
<n1:CommunicationStatus xsi:nil="true"/>
<n1:ComplexPasswordRulesEnforced xsi:nil="true"/>
<n1:CreationClassName>DCIM_MFAAccount</n1:CreationClassName>
<n1:Description xsi:nil="true"/>
<n1:Descriptions xsi:nil="true"/>
<n1:DetailedStatus xsi:nil="true"/>
<n1:ElementName>MFA Account 16</n1:ElementName>
<n1:EnabledDefault>2</n1:EnabledDefault>
<n1:EnabledState>2</n1:EnabledState>
<n1:HealthState xsi:nil="true"/>
<n1:Host xsi:nil="true"/>
<n1:InactivityTimeout xsi:nil="true"/>
<n1:InstallDate xsi:nil="true"/>
<n1:LastLogin xsi:nil="true"/>
<n1:LocalityName xsi:nil="true"/>
<n1:MaximumSuccessiveLoginFailures xsi:nil="true"/>
<n1:Name>DCIM User 16</n1:Name>
<n1:OU xsi:nil="true"/>
<n1:ObjectClass xsi:nil="true"/>
<n1:OperatingStatus xsi:nil="true"/>
<n1:OperationalStatus xsi:nil="true"/>
<n1:OrganizationName>DCIM</n1:OrganizationName>
<n1:OtherEnabledState xsi:nil="true"/>
<n1:PasswordExpiration xsi:nil="true"/>
<n1:PasswordHistoryDepth xsi:nil="true"/>
<n1:PrimaryStatus xsi:nil="true"/>
<n1:RequestedState>0</n1:RequestedState>
<n1:SeeAlso xsi:nil="true"/>
Page 38

<n1:Status xsi:nil="true"/>
<n1:StatusDescriptions xsi:nil="true"/>
<n1:SystemCreationClassName>DCIM_SPComputerSystem
</n1:SystemCreationClassName>
<n1:SystemName>systemmc</n1:SystemName>
<n1:TimeOfLastStateChange xsi:nil="true"/>
<n1:TransitioningToState>12</n1:TransitioningToState>
<n1:UserCertificate xsi:nil="true"/>
<n1:UserID>testuser4</n1:UserID>
<n1:UserPassword>testuserpss4</n1:UserPassword>
</n1:DCIM_MFAAccount>
D) If the account specified is new or not yet enabled, it will not be accessible. Login as root in the UI
and verify the user name is set correctly and enable it.
E) Logout of the UI. Login with new user name and password.
Possible responses:
1. A fault is returned which suggests a possible error in the request payload.
2. An empty response which suggests an error occurred while processing the request.
3. An instance of the class is returned where the property value is unchanged.
4. An instance of the class is returned where the property value is modified. The set is successful.
5. The property value may be blank as intended by the implementation for security. To
determine success, try logging in with the new password. Ensure the account is enabled.
5.5.2 Modify Password (using DMTF Model)
When the account setting capability allows, the user password of an account may be modified
by running a set operation on the
The set operation requires an instance reference. The instance reference may be retrieved by
adding
EnumerateEPR
UserPassword
mode to enumerate or get of the class.
property of the
CIM_Account
class instance.
NOTE: The profile defines this property as a string array of type octet string. In this implementation,
the password is a string of type clear text. The security concern is resolved by transmission of this
information only through secure HTTPS communication.
Profiles:
http://www.dmtf.org/sites/default/files/standards/documents/DSP1034_1.0.1.pdf
http://www.dmtf.org/sites/default/files/standards/documents/DSP1039_1.0.0.pdf
See Section 5.5.1 for an implementation example.
5.5.3 Modify Account State (using DMTF Model)
When the account setting capability allows, the user account may be enabled or disabled by invoking the
RequestStateChange() method of the
an instance reference. The instance reference may be retrieved by adding
to enumerate or get of the class.
CIM_Account
class instance. The invoke operation requires
EnumerateEPR
mode
Profiles:
http://www.dmtf.org/sites/default/files/standards/documents/DSP1034_1.0.1.pdf
Page 39

http://www.dmtf.org/sites/default/files/standards/documents/DSP1039_1.0.0.pdf
Replace “DCIM User 16” with the applicable user name and “2” with the desired request state.
Invoke RequestStateChange() with the following parameters and syntax:
EXAMPLE:
wsman invoke -a RequestStateChange
"http://schemas.dmtf.org/wbem/wscim/1/cimschema/2/DCIM_MFAAccount
?__cimnamespace=root/dcim,SystemCreationClassName=DCIM_SPComputerSyste,Creati
onClassName=
DCIM_MFAAccount,SystemName=systemmc,
Name=DCIM User 16"
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-k RequestedState=2
-j utf-8 -y basic
OUTPUT:
<n1:RequestStateChange_OUTPUT>
<n1:Job xsi:nil="true"/>
<n1:ReturnValue>0</n1:ReturnValue>
</n1:RequestStateChange_OUTPUT>
Response status other than zero indicates an error has occurred and a message may be displayed.
5.5.4 Modify User Privilege (using DMTF Model)
When the account setting capability allows, the user account privileges may be modified by running
a set() operation on the
with the
instance reference may be retrieved by adding
class.
CIM_Account
ActivityQualifiers
class instance. The set() operation requires an instance reference. The
property of the
EnumerateEPR
CIM_Privilege
mode to enumerate or get of the
class instance associated
The profile defines this property as string array containing all the privileges to be allowed for the
account. Setting the list of privileges is a complete over-write of the earlier setting. This restriction is a
limitation where the protocol does not define how to set a particular index in the list. The new list will
replace the earlier list in its entirety.
Profiles:
http://www.dmtf.org/sites/default/files/standards/documents/DSP1034_1.0.1.pdf
http://www.dmtf.org/sites/default/files/standards/documents/DSP1039_1.0.0.pf
Here is an example list of available privileges from an instance of the class
CIM_RoleBasedManagementCapabilities:
DCIM_LocalRoleBasedManagementCapabilities
ActivitiesSupported = 7, 7, 7, 7, 7, 7, 7, 7, 7
ActivityQualifiersSupported = Login to DRAC, Configure DRAC, Configure
Users, Clear Logs, Execute Server Control Commands, Access Console
Redirection, Access Virtual Media, Test Alerts, Execute Di agnostic
Commands
ElementName = Local Role Based Management Capabilities
InstanceID = DCIM:LocalRoleBasedManagementCapabilities
Page 40

QualifierFormatsSupported = 9, 9, 9, 9, 9, 9, 9, 9, 9
SharedPrivilegeSupported = false
SupportedMethods = 8
The privilege property
need to provide the same key name more than once. The tool does not allow duplicate keys to be
entered through the command line. Instead, you need to perform two operations.
ActivityQualifiers
is an array of type string. To set more than one privilege, you
Get an instance of the CIM_Privilege class of interest.
Using the class instance, replace the property ActivityQualifiers with the new values.
Use the new instance XML as input to the set operation.
To determine if the new password has been successfully set, try logging in with the new
password. Make sure the account is enabled.
Page 41

6 Firmware Inventory
6.1 Software Inventory Profile Specification
The Dell Common Information Model (CIM) class extensions for supporting remote firmware
inventory are defined in the Dell OS Software Update 2 and related MOFs 3. The diagrams
representing the classes that are implemented by the Lifecycle Controller firmware can be found in
Dell Software Inventory Profile.
6.2 Remote Inventory Method Invocation — Get Software
Inventory
The
SoftwareIdentity
the target system as well as available firmware images cached in the Lifecycle Controller. The
enumeration of the
such as firmware type and version.
Profile and Associated MOFs:
http://www.delltechcenter.com/page/DCIM.Library.Profile
EXAMPLE:
wsman enumerate
http://schemas.dmtf.org/wbem/wscim/1/cimschema/2/root/dcim/DCIM_SoftwareIdent
ity
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
When this method is run, a list of software identity objects will be returned, including installed and
available firmware. Below is a snippet of the output.
OUTPUT:
<n1:DCIM_SoftwareIdentity>
class contains information for the BIOS and component firmware installed on
SoftwareIdentity
class returns a list of
SoftwareIdentity
objects with properties
<n1:BuildNumber>4846</n1:BuildNumber>
<n1:Classifications>10</n1:Classifications>
<n1:ComponentID>28897</n1:ComponentID>
<n1:ComponentType>APAC</n1:ComponentType>
<n1:DeviceID xsi:nil="true"/>
<n1:ElementName>Dell Lifecycle Controller 2, 1.0.0.4846, X79
</n1:ElementName>
<n1:FQDD>USC.Embedded.1:LC.Embedded.1</n1:FQDD>
<n1:IdentityInfoType>OrgID:ComponentType:ComponentID
</n1:IdentityInfoType>
<n1:IdentityInfoValue>DCIM:firmware:28897
</n1:IdentityInfoValue>
<n1:InstallationDate>2012-01-15T22:22:32Z
</n1:InstallationDate>
<n1:InstanceID>DCIM:INSTALLED#802__USC.Embedded.1:LC.Embedded.1
</n1:InstanceID>
<n1:IsEntity>true</n1:IsEntity>
<n1:MajorVersion>1</n1:MajorVersion>
<n1:MinorVersion>0</n1:MinorVersion>
Page 42

<n1:RevisionNumber>0</n1:RevisionNumber>
<n1:RevisionString xsi:nil="true"/>
<n1:Status>Installed</n1:Status>
<n1:SubDeviceID xsi:nil="true"/>
<n1:SubVendorID xsi:nil="true"/>
<n1:Updateable>true</n1:Updateable>
<n1:VendorID xsi:nil="true"/>
<n1:VersionString>1.0.0.4846</n1:VersionString>
<n1:impactsTPMmeasurements>false</n1:impactsTPMmeasurements>
</n1:DCIM_SoftwareIdentity>
The key properties in the above output include the following:
InstanceID: Normally identifies the firmware on a particular type of device. The substring right
after DCIM: is the status of a payload or firmware on the system. This can be installed or available.
ComponentID: Uniquely identifies a unique type of device such as BIOS, NIC, Storage and
Lifecycle controller firmware.
InstallationDate: The date when the payload was installed to the system. If the system time was
not set when the firmware installation took place the install date will be 1970-01-01. Factory
installed firmware will have the 1970-01-01 date.
VersionString: Displays the version of the firmware represented.
Page 43

7 Firmware Update
7.1 Software Update Profile Specification
The Dell Common Information Model (CIM) class extensions for supporting BIOS, component
firmware, and embedded software update are defined in the Dell Software Update Profile 2 and
related MOF files 3. The diagrams representing the classes that are implemented by the Lifecycle
Controller firmware can be found in Dell Software Update Profile as well.
Profile and Associated MOFs:
http://www.delltechcenter.com/page/DCIM.Library.Profile
7.2 ”Rollback” Firmware
The InstallFromSoftwareIdentity() method is used for installation of a earlier version of a component
firmware that is available on the Lifecycle Controller (that is “rollback” of component firmware). The
general “Rollback” firmware steps are performed in several stages as described in the next sections.
The tasks are demonstrated in examples in Section 7.3 and Section 7.4.
7.2.1 Request “Rollback” Image
The first stage is a request to initiate and download the rollback image from the Lifecycle
Controller by invoking the InstallFromSoftwareIdentity() method.
7.2.2 Create Reboot Job
The second stage is to create a reboot job as shown in Section 7.8.
7.2.3 Schedule Update Jobs
The third stage is to invoke the SetupJobQueue() method as shown in Section 10.2.1. Use the
jobID
may take several minutes as the UEFI performs the desired operation.
(JID) from InstallFromSoftwareIdentity() and
rebootID(RID)
from the reboot job. The reboot
7.2.4 Monitor Update Jobs
The output of getting the job status during various steps, Section 10.2.3, is shown below.
Initial job status after invoking
InstallFromSoftwareIdentity
<n1:DCIM_LifecycleJob>
<n1:InstanceID>JID_001299159345</n1:InstanceID>
<n1:JobStartTime/>
<n1:JobStatus>Downloaded</n1:JobStatus>
<n1:JobUntilTime/>
<n1:Message>Package successfully downloaded</n1:Message>
<n1:MessageArguments xsi:nil="true"/>
<n1:MessageID>RED002</n1:MessageID>
<n1:Name>Rollback:DCIM:AVAILABLE:NONPCI:159:2.1.4</n1:Name>
</n1:DCIM_LifecycleJob>
Job status after invoking
<n1:DCIM_LifecycleJob>
<n1:InstanceID>JID_001299159345</n1:InstanceID>
SetupJobQueue
Page 44

<n1:JobStartTime>00000101000000</n1:JobStartTime>
<n1:JobStatus>Scheduled</n1:JobStatus>
<n1:JobUntilTime>20100730121500</n1:JobUntilTime>
<n1:Message>Task successfully scheduled</n1:Message>
<n1:MessageArguments xsi:nil="true"/>
<n1:MessageID>JCP001</n1:MessageID>
<n1:Name>Rollback:DCIM:AVAILABLE:NONPCI:159:2.1.4</n1:Name>
</n1:DCIM_LifecycleJob>
Job status following reboot / install of operation
<n1:DCIM_LifecycleJob>
<n1:InstanceID>JID_001299159345</n1:InstanceID>
<n1:JobStartTime>00000101000000</n1:JobStartTime>
<n1:JobStatus>Completed</n1:JobStatus>
<n1:JobUntilTime>20100730121500</n1:JobUntilTime>
<n1:Message>Job finished successfully</n1:Message>
<n1:MessageArguments xsi:nil="true"/>
<n1:MessageID>USC1</n1:MessageID>
</n1:DCIM_LifecycleJob>
<n1:Name>Rollback:DCIM:AVAILABLE:NONPCI:159:2.1.4</n1:Name>
7.3 BIOS Firmware “Rollback”
The InstallFromSoftwareIdentity() method is used for installation of a earlier version of a component
firmware that is available on the Lifecycle Controller (that is “rollback” of component firmware).
All steps to complete a rollback successfully are listed below.
Invoke InstallFromSoftwareIdentity() with the following parameters and syntax:
[InstanceID]: This is the instanceID of the SoftwareIdentify that is to be used to rollback the
firmware to a earlier version. The InstanceID can have the following values:
EXAMPLE:
wsman invoke -a InstallFromSoftwareIdentity
http://schemas.dmtf.org/wbem/wscim/1/cimschema/2/root/dcim/DCIM_SoftwareInsta
llationService
?CreationClassName=DCIM_SoftwareInstallationService,
SystemCreationClassName=DCIM_ComputerSystem,
SystemName=IDRAC:ID,Name=SoftwareUpdate
-h $IPADDRESS -V –v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-J RollInputBIOS.xml -j utf-8 -y basic
The rollback input file, RollInputBIOS.xml, is shown below:
<p:InstallFromSoftwareIdentity_INPUT
xmlns:p="http://schemas.dmtf.org/wbem/wscim/1/cim-
schema/2/root/dcim/DCIM_SoftwareInstallationService">
DCIM:AVAILABLE:NONPCI:159:2.1.4
It is available firmware on a NONPCI device.
This refers BIOS version 2.1.4
<p:Target
xmlns:a="http://schemas.xmlsoap.org/ws/2004/08/addressing"
xmlns:w="http://schemas.dmtf.org/wbem/wsman/1/wsman.xsd">
<a:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/ro
Page 45

le/anonymous</a:Address>
<a:ReferenceParameters>
<w:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cim-
schema/2/DCIM_SoftwareIdentity</w:ResourceURI>
<w:SelectorSet>
<w:Selector Name="InstanceID">[InstanceID]</w:Selector>
</w:SelectorSet>
</a:ReferenceParameters>
</p:Target>
</p:InstallFromSoftwareIdentity_INPUT>
OUTPUT:
When this method is executed, a
jobid
or a message is displayed indicating an error.
<n1:InstallFromSoftwareIdentity_OUTPUT>
<n1:Job>
<wsa:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anon
ymous</wsa:Address>
<wsa:ReferenceParameters>
<wsman:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cimschema
/
2/DCIM_SoftUpdateConcreteJob</wsman:ResourceURI>
<wsman:SelectorSet>
<wsman:Selector
Name="InstanceID">JID_001299753229</wsman:Selector>
<wsman:Selector Name="__cimnamespace">root/dcim</wsman:Selector>
</wsman:SelectorSet>
</wsa:ReferenceParameters>
</n1:Job>
<n1:ReturnValue>4096</n1:ReturnValue>
</n1:InstallFromSoftwareIdentity_OUTPUT>
7.4 NIC Firmware “Rollback”
The InstallFromSoftwareIdentity() method is used for installation of a earlier version of a component
firmware that is available on the Lifecycle Controller (that is “rollback” of component firmware).
Invoke
EXAMPLE:
wsman invoke -a InstallFromSoftwareIdentity
http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_SoftwareInstallationService
InstallFromSoftwareIdentity
with the following parameters and syntax:
[InstanceID]: This is the instanceID of the SoftwareIdentify that is to be used to rollback the
firmware to a earlier version. The InstanceID can have the following value:
DCIM:PREVIOUS:PCI:14E4:1639:0237:1028
• It refers to a earlier firmware on a PCI device.
• ID (Vendor ID)= 14E4
• DID (Device ID) = 1639
• SSID (Subsystem ID) = 0237
• SVID (Subvendor ID) = 1028
• This refers to a Broadcom NetXtreme II BCM5709 network adaptor 7.
Page 46

?CreationClassName=DCIM_SoftwareInstallationService,
SystemCreationClassName=DCIM_ComputerSystem,SystemName=IDRAC:ID,
Name=SoftwareUpdate
-h $IPADDRESS -V –v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-J RollInputNIC.xml -j utf-8 -y basic
The rollback input file, RollInputNIC.xml, is shown below:
<p:InstallFromSoftwareIdentity_INPUT
xmlns:p="http://schemas.dmtf.org/wbem/wscim/1/cim-
schema/2/root/dcim/DCIM_SoftwareInstallationService">
<p:Target xmlns:a="http://schemas.xmlsoap.org/ws/2004/08/addressing"
xmlns:w="http://schemas.dmtf.org/wbem/wsman/1/wsman.xsd">
<a:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anonymous</a:A
ddress>
<a:ReferenceParameters>
<w:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cim-
schema/2/DCIM_SoftwareIdentity
</w:ResourceURI>
<w:SelectorSet>
<w:Selector Name="InstanceID">[InstanceID]</w:Selector> </w:SelectorSet>
</a:ReferenceParameters> </p:Target> </p:InstallFromSoftwareIdentity_INPUT>
OUTPUT:
When this method is executed, a
jobid
or a message is displayed indicating an error.
<n1:InstallFromSoftwareIdentity_OUTPUT>
<n1:Job>
<wsa:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anon
ymous</wsa:Address>
<wsa:ReferenceParameters>
<wsman:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_SoftUpdateConcreteJob</wsman:ResourceURI>
<wsman:SelectorSet>
<wsman:Selector Name="InstanceID">JID_001299753238</wsman:Selector>
<wsman:Selector Name="__cimnamespace">root/dcim</wsman:Selector>
</wsman:SelectorSet>
</wsa:ReferenceParameters>
</n1:Job>
<n1:ReturnValue>4096</n1:ReturnValue>
</n1:InstallFromSoftwareIdentity_OUTPUT>
Entering an invalid
instanceID
may yield the following error message:
<n1:InstallFromSoftwareIdentity_OUTPUT>
<n1:Message>Invalid InstanceID </n1:Message>
<n1:MessageID>SUP024</n1:MessageID>
<n1:ReturnValue>2</n1:ReturnValue>
</n1:InstallFromSoftwareIdentity_OUTPUT>
7.5 Update from Network Source
A firmware update can be performed by invoking the InstallFromURI() method in the class
DCIM_SoftwareInstallationService
the next sections. The tasks are demonstrated in examples in Section 7.6 and Section 7.7.
. Firmware update is performed in several stages as described in
Page 47

Note: When running a WS-Man command to initiate update jobs, make sure to wait for two seconds
before submitting a second job in order to avoid racing conditions.
7.5.1 Request Update Download
The first stage is a request to initiate and download the update image from a source defined by
the user by invoking the InstallFromURI() method.
7.5.2 Monitor Download Status
Downloading the update package may take several minutes. The second stage is to monitor
the download. The download status may be monitored by enumerating or getting the instance
of the corresponding job.
7.5.3 Reboot to Perform Update
Once downloaded, the request needs to be scheduled. The third stage is to schedule the update. To
schedule the update, use the SetupJobQueue() method of the class
7.5.4 Wait for Job Completion
The fourth stage is to wait for the job to be completed, which may take several minutes. The job
status can be monitored as shown in Section 10.2.3.
7.5.5 Delete Job
The fifth and final stage is to delete the completed job from the job store. Deleting the job queue is
shown in Section 10.2.2.
DCIM_JobService
in Section 10.2.1.
7.6 Update NICs from HTTP, CIFS Share, NFS share, TFTP, or
FTP
The InstallFromURI() method takes the following input and downloads the Dell Update Package to
the Lifecycle Controller in the target system. The method returns a
DCIM_SoftwareUpdateJob
following is the example of the method for updating a NIC firmware.
that can be scheduled to run or queried for status at a later time. The
Invoke InstallFromURI() with the following parameters and syntax:
[URI-IP-ADDRESS]: This is the IP address of the location for Dell Update Package. The Dell Update
Package will need to be the Windows type update package. The file share can be HTTP, CIFS, NFS,
TFTP, or FTP type as shown below:
HTTP Format:
http://[IP ADDRESS]/[PATH TO FILE.exe]
CIFS Format:
cifs://WORKGROUP_NAME\[USERNAME]:[PASSWORD]@[URI-IPADDRESS]/ [FILE.exe];mountpoint=[DIRECTORYNAME]
TFTP or FTP Format:
jobid
for an instance of
Page 48

tftp://[IP ADDRESS]/[PATH TO FILE.exe]
ftp://[IP ADDRESS]/[PATH TO FILE.exe]
[InstanceID]: The instanceID is the SoftwareIdentify instanceID that represents the firmware that
is to be updated. This instanceID can be retrieved as described in Section 6.2. For example, the
instanceID can be:
DCIM:INSTALLED:PCI:14E4:1639:0237:1028
It is installed firmware on a PCI device.
VID (Vendor ID)= 14E4
DID (Device ID) = 1636
SSID (Subsystem ID) = 0237
SVID (Subvendor ID) = 1028
This refers to a Broadcom NetXtreme II BCM5709 network adaptor
7
.
EXAMPLE:
wsman invoke -a InstallFromURI
http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_SoftwareInstallationService
?CreationClassName=DCIM_SoftwareInstallationService,
SystemCreationClassName=DCIM_ComputerSystem,SystemName=IDRAC:ID,
Name=SoftwareUpdate
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-J UpdateInputNIC.xml -j utf-8 -y basic
The above command takes in an input file named UpdateInputNic.xml to supply input
parameters required for the InstallFromURI() method.
The syntax for UpdateInputNIC.xml is:
<p:InstallFromURI_INPUT
xmlns:p="http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_SoftwareInstallationService">
<p:URI>http://[URI-IP-ADDRESS]/[PATH-TO-EXE]/[FILE.exe]</p:URI>
<p:Target xmlns:a="http://schemas.xmlsoap.org/ws/2004/08/addressing"
xmlns:w="http://schemas.dmtf.org/wbem/wsman/1/wsman.xsd">
<a:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anonymous</a
:Address>
<a:ReferenceParameters>
<w:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_SoftwareIdentity</w:ResourceURI>
<w:SelectorSet>
<w:Selector Name="InstanceID">[INSTANCEID]</w:Selector>
</w:SelectorSet>
</a:ReferenceParameters>
</p:Target>
</p:InstallFromURI_INPUT>
In the above sample, the [URI-IP-ADDRESS] must be replaced with the actual value of the IP address
of the server that stores update content, [PATH-TO-EXE] must be replaced with the applicable path to
the executable, [FILE.exe] must be replaced with the executable name, and [INSTANCEID] should be
Page 49

replaced with the actual
InstanceID
of the device to be updated.
OUTPUT:
When this method is run, a
used for subsequent processing with job control provider in Section 10.
jobid
or a message is displayed indicating an error. This
InstallFromURI_OUTPUT
Job
Address = http://schemas.xmlsoap.org/ws
ReferenceParameters
ResourceURI =
http://schemas.dell.com/wbem/wscim/1/cim-schema
/2/DCIM_SoftUpdateConcreteJob
SelectorSet
Selector: InstanceID = JID_001265810325,
__cimnamespace = root/dcim
ReturnValue = null
Missing XML parameters may yield the following error message:
<n1:InstallFromURI_OUTPUT>
<n1:Message>Insufficient Method Parameters </n1:Message>
<n1:MessageID>SUP001</n1:MessageID>
<n1:ReturnValue>2</n1:ReturnValue>
</n1:InstallFromURI_OUTPUT>
jobid
can then be
7.7 Update BIOS from HTTP, CIFS Share, NFS share, TFTP, or
FTP
The InstallFromURI() method takes the following input and downloads the Dell Update Package to
the Lifecycle Controller in the target system. The method returns a
DCIM_SoftwareUpdateJob
following is the example of the method for updating a BIOS firmware.
that can be scheduled to run or queried for status at a later time. The
Invoke InstallFromURI() with the following parameters and syntax:
[URI-IP-ADDRESS]: This is the IP address of the location for Dell Update Package. The Dell Update
Package will need to be the Windows type update package. The file share can be HTTP, CIFS, NFS,
TFTP, or FTP type as shown below:
HTTP Format:
http://[IP ADDRESS]/[PATH TO FILE.exe]
CIFS Format:
cifs://[USERNAME]:[PASSWORD]@[URI-IP-ADDRESS]/
[FILE.exe];mountpoint=/[DIRECTORYNAME]
TFTP or FTP Format:
tftp://[IP ADDRESS]/[PATH TO FILE.exe]
ftp://[IP ADDRESS]/[PATH TO FILE.exe]
jobid
for an instance of
Page 50

[InstanceID]: The
is to be updated. This
instanceID can be:
DCIM:AVAILABLE:NONPCI:159:2.1.4
It is available firmware on a NONPCI device.
This refers BIOS version 2.1.4
instanceID
instanceID
is the
SoftwareIdentify instanceID
can be retrieved as described in Section 6.2. For example, the
that represents the firmware that
EXAMPLE:
wsman invoke -a InstallFromURI
http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_SoftwareInstallationService
?CreationClassName=DCIM_SoftwareInstallationService,
SystemCreationClassName=DCIM_ComputerSystem,SystemName=IDRAC:ID,
Name=SoftwareUpdate
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-J UpdateInputBIOS.xml -j utf-8 -y basic
The above command takes in an input file named UpdateInputBIOS.xml to supply input
parameters required for the InstallFromURI() method.
The syntax for UpdateInputBIOS.xml is:
<p:InstallFromURI_INPUT
xmlns:p="http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_SoftwareInstallationService">
<p:URI>http://[URI-IP-ADDRESS]/[PATH-TO-EXE]/[FILE.exe]</p:URI>
<p:Target xmlns:a="http://schemas.xmlsoap.org/ws/2004/08/addressing"
xmlns:w="http://schemas.dmtf.org/wbem/wsman/1/wsman.xsd">
<a:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anonymous
</a:Address>
<a:ReferenceParameters>
<w:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_SoftwareIdentity</w:ResourceURI>
<w:SelectorSet>
<w:Selector Name="InstanceID">[INSTANCEID]</w:Selector>
</w:SelectorSet>
</a:ReferenceParameters>
</p:Target>
</p:InstallFromURI_INPUT>
In the above sample, the [URI-IP-ADDRESS] must be replaced with the actual value of the IP address
of the server that stores update content, [PATH-TO-EXE] must be replaced with the applicable path to
the executable, [FILE.exe] must be replaced with the executable name, and [INSTANCEID] should be
replaced with the actual
InstanceID
of the device to be updated.
OUTPUT:
When this method is run, a
used for subsequent processing with job control provider in section 10.
jobid
or a message is displayed indicating an error. This
jobid
can then be
InstallFromURI_OUTPUT
Page 51

Job
Address = http://schemas.xmlsoap.org/ws
ReferenceParameters
ResourceURI =
http://schemas.dell.com/wbem/wscim/1/cim-schema
/2/DCIM_SoftUpdateConcreteJob
SelectorSet
Selector: InstanceID = JID_001276741475,
__cimnamespace = root/dcim
ReturnValue = null
7.8 CreateRebootJob()
The CreateRebootJob() method creates a reboot job that can be scheduled to reboot immediately
or at a later time. When the reboot job is scheduled and then ran, using SetupJobQueue() (Section
10.2.1), the reboot will take several minutes depending on the system setup, including whether or
not collecting system inventory (CSIOR) is enabled.
Invoke
RebootJobType: There are three options for rebooting the system.
EXAMPLE:
wsman invoke -a CreateRebootJob
http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_SoftwareInstallationService
?CreationClassName=DCIM_SoftwareInstallationService,
SystemCreationClassName=DCIM_ComputerSystem,SystemName=IDRAC:ID,
Name=SoftwareUpdate
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-J reboot.xml -j utf-8 -y basic
-SkipCNCheck -auth:basic -encoding:utf-8
The syntax for reboot.xml is:
<p:CreateRebootJob_INPUT
xmlns:p="http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_SoftwareInstallationService">
</p:CreateRebootJob_INPUT>
OUTPUT:
This method will return a reboot
time.
<n1:CreateRebootJob_OUTPUT>
CreateRebootJob
with the following parameters and syntax:
1 = PowerCycle
2 = Graceful Reboot without forced shutdown
3 = Graceful reboot with forced shutdown
<p:RebootJobType>2</p:RebootJobType>
jobid
that can be set to reboot the system immediately or at a later
<n1:RebootJobID>
<wsa:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anon
ymous</wsa:Address>
<wsa:ReferenceParameters>
Page 52

<wsman:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_SoftUpdateConcreteJob</wsman:ResourceURI>
<wsman:SelectorSet>
<wsman:Selector Name="InstanceID">RID_001299756950</wsman:Selector>
<wsman:Selector Name="__cimnamespace">root/dcim</wsman:Selector>
</wsman:SelectorSet>
</wsa:ReferenceParameters>
</n1:RebootJobID>
<n1:ReturnValue>4096</n1:ReturnValue>
</n1:CreateRebootJob_OUTPUT>
The jobid in the above output is the instanceID:
Jobid = InstanceID = RID_001265648530
7.9 Automatic Updates
Automatic Updates feature allows for periodic firmware updates at regular intervals as configured by
the user.
7.9.1 Enable automatic update
This method enables or disables the “Automatic Update Feature ” attribute.
Example:
wsman invoke -a SetAttribute http://schemas.dmtf.org/wbem/wscim/1/cim-
schema/2/root/dcim/DCIM_LCService
?SystemCreationClassName=DCIM_ComputerSystem,CreationClassName=DCIM_LCService,SystemName
=DCIM:ComputerSystem,Name=DCIM:LCService -h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD -J SetAttribute_LC.xml -j utf-8 -y basic
The SetAttribute_LC.xml file is as follows:
<p:AttributeName>Automatic Update Feature</p:AttributeName>
<p:AttributeValue>Enabled</p:AttributeValue>
OUTPUT:
<p:SetAttribute_INPUT xmlns:p="http://schemas.dmtf.org/wbem/wscim/1/cim-
schema/2/root/dcim/DCIM_LCService">
</p:SetAttribute_INPUT>
<n1:SetAttribute_OUTPUT>
<n1:RebootRequired>No</n1:RebootRequired>
<n1:ReturnValue>0</n1:ReturnValue>
<n1:SetResult>Set PendingValue</n1:SetResult>
</n1:SetAttribute_OUTPUT>
7.9.2 Create a Config Job
CreateConfigJob sets the pending value set by SetAttribute() method.
Example:
wsman invoke -a CreateConfigJob http://schemas.dmtf.org/wbem/wscim/1/cim-
schema/2/root/dcim/DCIM_LCService
Page 53

?SystemCreationClassName=DCIM_ComputerSystem,
CreationClassName=DCIM_LCService,SystemName=DCIM:ComputerSystem,
Name=DCIM:LCService -h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD -j utf-8 -y basic
OUTPUT:
<n1:CreateConfigJob_OUTPUT>
<n1:Job>
<wsa:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anonymous</wsa:Address>
<wsa:ReferenceParameters>
schema/2/DCIM_LifecycleJob</wsman:ResourceURI>
</wsa:ReferenceParameters>
</n1:Job>
<n1:ReturnValue>4096</n1:ReturnValue>
</n1:CreateConfigJob_OUTPUT>
<wsman:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cim-
<wsman:SelectorSet>
<wsman:Selector Name="InstanceID">JID_001300726718</wsman:Selector>
<wsman:Selector Name="__cimnamespace">root/dcim</wsman:Selector>
</wsman:SelectorSet>
Verify the value of “Automatic Update Feature” attribute from DCIM_iDRACCardEnumeration. It has to
be “Enabled” to set Automatic update schedule.
7.9.3 Set Update Schedule
SetUpdateSchedule() method sets the schedule for the automatic updates and the source repository
from where the updates are to be applied from.
Example:
wsman invoke -a SetUpdateSchedule http://schemas.dmtf.org/wbem/wscim/1/cimschema/2/root/dcim/DCIM_SoftwareInstallationService?SystemCreationClassName=DCIM_SoftwareInstal
lationService,SystemName=IDRAC:ID,CreationClassName=DCIM_SoftwareInstallationService,Name=Softw
areUpdate -h $IPADDRESS -V -v -c dummy.cert -P 443 -u $USERNAME -p $PASSWORD -J SetSchedule.xml
-j utf-8 -y basic
The input file SetSchedule.xml is shown below:
<p:SetUpdateSchedule_INPUT xmlns:p="http://schemas.dmtf.org/wbem/wscim/1/cim-
schema/2/root/dcim/DCIM_SoftwareInstallationService">
<p:IPAddress>IPADDR</p:IPAddress>
<p:ShareName>Sharename/Repository</p:SharePath>
<p:ShareType>0</p:ShareType>
<p:Username>USER</p:Username>
<p:Password>PASS</p:Password>
Page 54

<p:Time>15:00</p:Time>
<p:DayofWeek>mon,Tue,wed</p:DayofWeek>
<p:WeekofMonth>2</p:WeekofMonth>
<p:Repeat>5</p:Repeat>
</p:SetUpdateSchedule_INPUT>
7.9.4 Get the Update Schedule
GetUpdateSchedule() lists the parameter set by SetUpdateSchedule()
Example:
wsman invoke -a GetUpdateSchedule http://schemas.dmtf.org/wbem/wscim/1/cimschema/2/root/dcim/DCIM_SoftwareInstallationService?SystemCreationClassName=DCI
M_SoftwareInstallationService,SystemName=IDRAC:ID,CreationClassName=DCIM_Softwa
reInstallationService,Name=SoftwareUpdate -h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p c$PASSWORD -j utf-8 -y basic
OUTPUT:
<?xml version="1.0" encoding="UTF-8"?>
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope"
xmlns:wsa="http://schemas.xmlsoap.org/ws/2004/08/addressing"
xmlns:n1="http://schemas.dmtf.org/wbem/wscim/1/cimschema/2/root/dcim/DCIM_SoftwareInstallationService">
<s:Header>
<wsa:To>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anonymous</wsa:To>
<wsa:Action>http://schemas.dmtf.org/wbem/wscim/1/cimschema/2/root/dcim/DCIM_SoftwareInstallationService/GetUpdateScheduleResponse</w
sa:Action>
<wsa:RelatesTo>uuid:4ecf5ed2-ecb2-1cb2-8002-5498f6b92600</wsa:RelatesTo>
<wsa:MessageID>uuid:dc17b9a2-ecb8-1cb8-801e-2b831e1cb190</wsa:MessageID>
</s:Header>
<s:Body>
<n1:GetUpdateSchedule_OUTPUT>
<n1:ApplyReboot>0</n1:ApplyReboot>
<n1:CatalogName>Sample.xml</n1:CatalogName>
<n1:DayofMonth>*</n1:DayofMonth>
<n1:IPAddress>10.94.192.100</n1:IPAddress>
<n1:Repeat>5</n1:Repeat>
<n1:ReturnValue>4096</n1:ReturnValue>
<n1:ShareName>Somepath</n1:ShareName>
<n1:ShareType>nfs</n1:ShareType>
<n1:Time>16:00</n1:Time>
</n1:GetUpdateSchedule_OUTPUT>
</s:Body>
</s:Envelope>
Page 55

ApplyUpdate
ReboootNeeded
Actions
0 X Only comparison report is
generated.
1
TRUE
All updates are applied
immediately.
Note: If the update requires a
restart, the system is
automatically
restarted immediately.
1
FALSE
Currently, only updates that
do not require a system
restart will
be applied. For example,
Driver Pack DUPs. For those
that
require a restart, a separate
reboot job will have to be
created by
the user with
CreateRebootJob. These
updates will go to a
scheduled state and are run
after a restart.
7.9.5 Clear the Update Schedule
Clears the schedule for the automatic updates, that has been set by the SetUpdateSchedule() method.
Example:
wsman invoke -a ClearUpdateSchedule http://schemas.dmtf.org/wbem/wscim/1/cimschema/2/root/dcim/DCIM_SoftwareInstallationService?SystemCreationClassName=DCI
M_SoftwareInstallationService,SystemName=IDRAC:ID,CreationClassName=DCIM_Softwa
reInstallationService,Name=SoftwareUpdate -h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD -j utf-8 -y basic
7.10 Device Update from Repository
This feature allows multiple firmware updates by specifying a network repository which contains a
catalog of available updates. All applicable updates contained in the repository are applied to the
system.
Following two methods introduced as a part of DCIM_SoftwareUpdate profile:
1. InstallFromRepository: Initiate a job for device updates and creates a comparison report.
2. GetRepoBasedUpdateList: Get the comparison report generated with InstallFromRepository
7.10.1 Install From Repository
The InstallFromRepository method applies the updates.
Options available for user to update devices from repositories using WS-Man
Example:
wsman invoke -a InstallFromRepository
http://schemas.dmtf.org/wbem/wscim/1/cim-
schema/2/root/dcim/DCIM_SoftwareInstallationService?SystemCreationCl
Page 56

assName=DCIM_SoftwareInstallationService,SystemName=IDRAC:ID,Creatio
nClassName=DCIM_SoftwareInstallationService,Name=SoftwareUpdate -h
$IPADDRESS -V -v -c dummy.cert -P 443 -u $USERNAME -p $PASSWORD -J
InstallFromRepository.xml -j utf-8 -y basic
Syntax for InstallFromRepository.xml
<p:InstallFromRepository_INPUT
xmlns:p="http://schemas.dmtf.org/wbem/wscim/1/cim-
schema/2/root/dcim/DCIM_SoftwareInstallationService">
<p:ipAddress></p:ipAddress>
<p:ShareName></p:ShareName>
<p:ShareType></p:ShareType>
<p:UserName>E</p:UserName>
<p:Password></p:Password>
<p:RebootNeeded></p:RebootNeeded>
<p:CatalogFile></p:CatalogFile>
<p:ApplyUpdate></p:ApplyUpdate>
</p:InstallFromRepository_INPUT>
OUTPUT:
InstallFromRepository_OUTPUT
Job
EndpointReference
Address =
http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anonymous
ReferenceParameters
ResourceURI = http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_LifecycleJob
SelectorSet
Selector: InstanceID = JID_776094296053, __cimnamespace =
root/dcim
ReturnValue = 4096
7.10.2 Get Repo-Based Update List
A comparison XML between the inventory available on the system and the updates available on the
repository can be obtained using the GetRepoBasedUpdateList() method.
Example:
wsman invoke -a GetRepoBasedUpdateList
http://schemas.dmtf.org/wbem/wscim/1/cimschema/2/root/dcim/DCIM_SoftwareInstallationService?SystemCreationCl
assName=DCIM_SoftwareInstallationService,SystemName=IDRAC:ID,Creatio
nClassName=DCIM_SoftwareInstallationService,Name=SoftwareUpdate -h
$IPADDRESS -V -v -c dummy.cert -P 443 -u $USERNAME -p $PASSWORD -j
utf-8 -y basic
OUTPUT:
Page 57

GetRepoBasedUpdateList_OUTPUT
PackageList = <?xml version="1.0"?>
<CIM xmlns:fo="http://www.w3.org/1999/XSL/Format" CIMVERSION="2.0"
DTDVERSION="2.0">
<MESSAGE ID="4711" PROTOCOLVERSION="1.0">
<SIMPLEREQ>
<VALUE.NAMEDINSTANCE>
<INSTANCENAME CLASSNAME="DCIM_RepoUpdateSWID">
<PROPERTY NAME="Criticality" TYPE="string">
<VALUE>1</VALUE>
</PROPERTY>
<PROPERTY NAME="DisplayName" TYPE="string">
<VALUE>Intel(R) Ethernet 10G 4P X540/I350 rNDC BC:30:5B:ED:50:38</VALUE>
</PROPERTY>
<PROPERTY NAME="BaseLocation" TYPE="string">
<VALUE/>
</PROPERTY>
<PROPERTY NAME="PackagePath" TYPE="string">
<VALUE>Network_Firmware_KTT4W_WN64_14.5.5_X03.EXE</VALUE>
</PROPERTY>
<PROPERTY NAME="PackageName" TYPE="string">
<VALUE>Network_Firmware_KTT4W_WN64_14.5.5_X03.EXE</VALUE>
</PROPERTY>
<PROPERTY NAME="PackageVersion" TYPE="string">
<VALUE>14.5.5</VALUE>
</PROPERTY>
<PROPERTY NAME="RebootType" TYPE="string">
<VALUE>HOST</VALUE>
</PROPERTY>
<PROPERTY NAME="JobID" TYPE="string">
<VALUE/>
</PROPERTY>
<PROPERTY NAME="Target" TYPE="string">
<VALUE>DCIM:INSTALLED#701__NIC.Integrated.1-1-1</VALUE>
</PROPERTY>
<PROPERTY NAME="ComponentID" TYPE="string">
<VALUE/>
</PROPERTY>
<PROPERTY NAME="ComponentType" TYPE="string">
<VALUE>FRMW</VALUE>
</PROPERTY>
<PROPERTY.ARRAY NAME="ComponentInfoValue" TYPE="string">
<VALUE.ARRAY>
<VALUE>8086:1528:1028:1F61</VALUE>
<VALUE>8086:1521:1028:1F62</VALUE>
</VALUE.ARRAY>
</PROPERTY.ARRAY>
<PROPERTY.ARRAY NAME="ComponentInfoName" TYPE="string">
<VALUE.ARRAY>
<VALUE>VendorID:DeviceID:SubVendorID:SubDeviceID</VALUE>
<VALUE>VendorID:DeviceID:SubVendorID:SubDeviceID</VALUE>
</VALUE.ARRAY>
</PROPERTY.ARRAY>
<PROPERTY.ARRAY NAME="ComponentInfoTarget" TYPE="string">
<VALUE.ARRAY>
<VALUE>DCIM:INSTALLED#701__NIC.Integrated.1-1-1</VALUE>
<VALUE>DCIM:INSTALLED#701__NIC.Integrated.1-3-1</VALUE>
Page 58

</VALUE.ARRAY>
</PROPERTY.ARRAY>
<PROPERTY.ARRAY NAME="ComponentInstalledVersion" TYPE="string">
<VALUE.ARRAY>
<VALUE>13.1.10</VALUE>
<VALUE>13.1.10</VALUE>
</VALUE.ARRAY>
</PROPERTY.ARRAY>
</INSTANCENAME>
</VALUE.NAMEDINSTANCE>
</SIMPLEREQ>
</MESSAGE>
</CIM>
ReturnValue = 0
Page 59

8 Power State Management
8.1 Description of Base Server versus Power State
Management Methods
The remote control of a server power state (On, Off) and methodology for cycling power is available
through data models specified in both the DMTF Base Server Profile and the DMTF Power State
Management Profile. The Base Server Profile offers the RequestStateChange() method on the
instance of the CIM_ComputerSystem class representing the server platform. The Power State
Management Profile offers the RequestPowerStateChange() method available on the instance of the
PowerStateManagmentService associated with the instance of CIM_ComputerSystem representing
the server platform.
Base Server Profile:
http://www.dmtf.org/sites/default/files/standards/documents/DSP1004_1.0.1.pdf
Power State Management Profile:
http://www.dmtf.org/sites/default/files/standards/documents/DSP1027_2.0.0.pdf
8.2 Get Power State
8.2.1 Base Server Method
The power state of the system is reported by the
DCIM_ComputerSystem
EXAMPLE:
wsman enumerate http://schemas.dmtf.org/wbem/wscim/1/cimschema/2/DCIM_ComputerSystem
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT:
<n1:DCIM_ComputerSystem>
EnabledState
class.
property of the
<n1:CreationClassName>DCIM_ComputerSystem
</n1:CreationClassName>
<n1:Dedicated>0</n1:Dedicated>
<n1:ElementName/>
<n1:EnabledState>2</n1:EnabledState>
<n1:HealthState>25</n1:HealthState>
<n1:IdentifyingDescriptions>CIM:GUID
</n1:IdentifyingDescriptions>
<n1:IdentifyingDescriptions>CIM:Tag
</n1:IdentifyingDescriptions>
<n1:IdentifyingDescriptions>DCIM:ServiceTag
</n1:IdentifyingDescriptions>
<n1:Name>srv:system</n1:Name>
<n1:OperationalStatus>6</n1:OperationalStatus>
<n1:OtherIdentifyingInfo>4c4c4544-0036-3510-8034-b7c04f333231
</n1:OtherIdentifyingInfo>
Page 60

<n1:OtherIdentifyingInfo>mainsystemchassis
</n1:OtherIdentifyingInfo>
<n1:OtherIdentifyingInfo>7654321</n1:OtherIdentifyingInfo>
<n1:PrimaryStatus>3</n1:PrimaryStatus>
<n1:RequestedState>0</n1:RequestedState>
</n1:DCIM_ComputerSystem>
8.2.2 Power State Management Method
The power state of the system is also reported by the
DCIM_CSAssociatedPowerManagementService
Power State Management Profile:
http://www.dmtf.org/sites/default/files/standards/documents/DSP1027_2.0.0.pdf
EXAMPLE:
wsman enumerate http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/DCIM_CSAssociatedPowerManagementService
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT:
PowerState:
2 (On): System is fully on
13 (Off): System is powered off
<n1:DCIM_CSAssociatedPowerManagementService>
class.
PowerState
property of the
8.3 Get Power Control Capabilites
8.3.1 Base Server Method
The power control capabilities are reported by the
CIM_EnabledLogicalElementCapabilities
CIM_ComputerSystem
class associated with the main system
class.
Base Server Profile:
http://www.dmtf.org/sites/default/files/standards/documents/DSP1004_1.0.1.pdf
In “Part A” enumerate the
DCIM_CSElementCapabilities
the
RequestedStatesSupported
CIM_ElementCapabilities
reference. Use the resulting
property.
EXAMPLE (Part A):
wsman enumerate
http://schemas.dmtf.org/wbem/wscim/1/cimschema/2/CIM_ElementCapabilities
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT (Part A):
RequestedStatesSupported
class and search for the
InstanceID
in “Part B” to obtain
property of the
Page 61

<n1:DCIM_CSElementCapabilities>
<n1:Capabilities>
<wsa:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anon
ymous</wsa:Address>
<wsa:ReferenceParameters>
<wsman:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_CSEnabledLogicalElementCapabilities</wsman:ResourceURI>
<wsman:SelectorSet>
<wsman:Selector Name="InstanceID">DCIM:ComputerCap:1</wsman:Selector>
<wsman:Selector Name="__cimnamespace">root/dcim</wsman:Selector>
</wsman:SelectorSet>
</wsa:ReferenceParameters>
</n1:Capabilities>
<n1:Characteristics xsi:nil="true"/>
<n1:ManagedElement>
<wsa:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anon
ymous</wsa:Address>
<wsa:ReferenceParameters>
<wsman:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_ComputerSystem</wsman:ResourceURI>
<wsman:SelectorSet>
<wsman:Selector Name="Name">srv:system</wsman:Selector>
<wsman:Selector
Name="CreationClassName">DCIM_ComputerSystem</wsman:Selector>
<wsman:Selector Name="__cimnamespace">root/dcim</wsman:Selector>
</wsman:SelectorSet>
</wsa:ReferenceParameters>
</n1:ManagedElement>
</n1:DCIM_CSElementCapabilities>
.
.
EXAMPLE (Part B):
wsman get
http://schemas.dell.com/wbem/wscim/1/cimschema/2/DCIM_CSEnabledLogicalElement
Capabilities
?__cimnamespace=root/dcim,InstanceID= DCIM:ComputerCap:1
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT (Part B):
RequestedStatesSupported:
A Enabled
B Disabled
11: Reset
<n1:DCIM_CSEnabledLogicalElementCapabilities>
<n1:Caption xsi:nil="true"/>
<n1:Description xsi:nil="true"/>
<n1:ElementName>Computer System Capabilities</n1:ElementName>
<n1:ElementNameEditSupported>false</n1:ElementNameEditSupported>
<n1:ElementNameMask xsi:nil="true"/>
<n1:InstanceID>DCIM:ComputerCap:1</n1:InstanceID>
<n1:MaxElementNameLen xsi:nil="true"/>
<n1:RequestedStatesSupported>2</n1:RequestedStatesSupported>
Page 62

PowerStatesSupported Value
PowerChangeCapabilites Value
2 (Power On)
3 (Sleep - Light)
4 (Sleep - Deep)
3
(Power State Settable)
5 (Power Cycle (Off Soft))
4
(Power Cycling Supported)
6 (Power Off - Hard)
7 (Hibernate)
8 (Power Off - Soft)
9 (Power Cycle (Off Hard))
6
(Off Hard Power Cycling Supported)
1
0 (Master Bus Reset)
7
(HW Reset Supported)
11 (Diagnostic Interrupt (NMI))
7
(HW Reset Supported)
12 (Power Off - Soft Graceful)
8
(Graceful Shutdown Supported)
13 (Power Off - Hard Graceful)
8
(Graceful Shutdown Supported)
14 (Master Bus Reset Graceful)
7
(HW Reset Supported) and
8
(Graceful Shutdown Supported)
15 (Power Cycle (Off - Soft Graceful))
4
(Power Cycling Supported) and
8
(Graceful Shutdown Supported)
16 (Power Cycle (Off - Hard Graceful))
6
(Off Hard Power Cycling Supported) and
<n1:RequestedStatesSupported>3</n1:RequestedStatesSupported>
<n1:RequestedStatesSupported>11</n1:RequestedStatesSupported>
<n1:StateAwareness xsi:nil="true"/>
</n1:DCIM_CSEnabledLogicalElementCapabilities>
8.3.2 Power State Management Method
The power control capabilities are also reported by the
CIM_PowerManagementCapabilities
(PMC) class associated with the
(PMS) class. Getting the instance of PMC is a two step process. First, enumerate the instance of PMS
with EPR. Second, enumerate the associated PMC class. When there is only one instance of PMC class
as in the case of iDRAC, the first step may be skipped and the PMC class may be enumerated directly.
Power State Management Profile:
http://www.dmtf.org/sites/default/files/standards/documents/DSP1027_2.0.0.pdf
EXAMPLE (iDRAC case):
wsman enumerate http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/CIM_PowerManagementCapabilities
?__cimnamespace=root/dcim
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT:
When the
Value” column, the
“PowerChangeCapabilities Value” column.
PowerStatesSupported
PowerChangeCapabilities
property contains the value in the “PowerStatesSupported
property shall contain the value specified in the
PowerStatesSupported
CIM_PowerManagementService
property of the
Page 63

8
(Graceful Shutdown Supported)
<n1:DCIM_CSPowerManagementCapabilities>
<n1:Caption xsi:nil="true"/>
<n1:Description xsi:nil="true"/>
<n1:ElementName>Power ManagementCapabilities</n1:ElementName>
<n1:InstanceID>DCIM:pwrmgtcap1</n1:InstanceID>
<n1:OtherPowerCapabilitiesDescriptions xsi:nil="true"/>
<n1:OtherPowerChangeCapabilities xsi:nil="true"/>
<n1:PowerCapabilities xsi:nil="true"/>
<n1:PowerChangeCapabilities>3</n1:PowerChangeCapabilities>
<n1:PowerChangeCapabilities>4</n1:PowerChangeCapabilities>
<n1:PowerChangeCapabilities>8</n1:PowerChangeCapabilities>
<n1:PowerStatesSupported>2</n1:PowerStatesSupported>
<n1:PowerStatesSupported>5</n1:PowerStatesSupported>
<n1:PowerStatesSupported>8</n1:PowerStatesSupported>
<n1:PowerStatesSupported>11</n1:PowerStatesSupported>
<n1:PowerStatesSupported>12</n1:PowerStatesSupported>
</n1:DCIM_CSPowerManagementCapabilities>
8.4 Power Control
8.4.1 Base Server Method
Changing the power state, such as cycling the power, is performed by invoking the
RequestStateChange() method of the
one instance for the main system and another for iDRAC. Use the main system instance. The
method requires you to specify the
possible values for this argument.
CIM_ComputerSystem
RequestedState
argument. Refer to Section 8.3 to get the
class instance. For iDRAC, there is
Base Server Profile:
http://www.dmtf.org/sites/default/files/standards/documents/DSP1004_1.0.1.pdf
EXAMPLE:
wsman invoke -a RequestStateChange
http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_ComputerSystem
?CreationClassName=DCIM_ComputerSystem,Name=srv:system
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic -k RequestedState="2"
OUTPUT:
<n1:RequestStateChange_OUTPUT>
<n1:ReturnValue>0</n1:ReturnValue>
</n1:RequestStateChange_OUTPUT>
If the value returned is zero then it implies that the command is successfully run. Else, other values
indicate failure and may display a message indicating an error.
8.4.2 Power State Management Method
Changing the power state is performed by invoking the RequestPowerStateChange() method of
the
DCIM_PowerManagementService
1) Enumerate the
(PMS) class instance. It is a three task process shown below:
DCIM_PowerManagementService
with EPR
Page 64

2) Enumerate the D
3) Use the EPR on steps 1) and 2) to invoke RequestPowerStateChange()
CIM_ComputerSystem
class and search for the Host instance
Power State Management Profile:
http://www.dmtf.org/sites/default/files/standards/documents/DSP1027_2.0.0.pd
f
EXAMPLE:
wsman invoke -a RequestPowerStateChange
"http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_CSPowerManagementService?CreationClassName=DCIM_CSPowerManagementServi
ce,
SystemCreationClassName=DCIM_SPComputerSystem,SystemName=systemmc,Name=pwrmgt
svc:1"
-k PowerState="2"
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD -j utf-8 -y basic
Page 65

9 Hardware Inventory
The Dell Common Information Model (CIM) class extensions for supporting remote hardware
inventories are defined in the various Dell profiles and related MOFs 3. The Hardware Inventory allows
you to remote query the inventory of hardware.
Each of the hardware inventory classes return the attribute
the last time ‘collect system inventory on restart’ or CSIOR was run. For more information about
CSIOR, see Section 12.1. It is an important attribute as it shows how recently the inventory was
updated.
9.1 Power Supply Inventory
This section describes the implementation for the
Supply Profile describes power supply information of each platform. Each platform power supply is
represented by an instance of
Profile and Associated MOFs:
http://www.delltechcenter.com/page/DCIM.Library.Profile
Enumerate
EXAMPLE:
wsman enumerate http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_PowerSupplyView
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT:
<n1:DCIM_PowerSupplyView>
</n1:DCIM_PowerSupplyView>
<n1:DCIM_PowerSupplyView>
LastSystemInventoryTime
DCIM_PowerSupplyView
DCIM_PowerSupplyView
class.
class. The Dell Power
DCIM_PowerSupplyView
with the following parameters and syntax:
<n1:DetailedState>Presence Detected</n1:DetailedState>
<n1:FQDD>PSU.Slot.1</n1:FQDD>
<n1:FirmwareVersion>04.09.00</n1:FirmwareVersion>
<n1:InputVoltage>122</n1:InputVoltage>
<n1:InstanceID>PSU.Slot.1</n1:InstanceID>
<n1:LastSystemInventoryTime>20110307121906.000000+000
</n1:LastSystemInventoryTime>
<n1:LastUpdateTime>20110119144251.000000+000
</n1:LastUpdateTime>
<n1:Manufacturer>Dell</n1:Manufacturer>
<n1:Model>PWR SPLY,502W,RDNT </n1:Model>
<n1:PartNumber>0KY091A02</n1:PartNumber>
<n1:PrimaryStatus>1</n1:PrimaryStatus>
<n1:RedundancyStatus>0</n1:RedundancyStatus>
<n1:SerialNumber>PH1629894U001C</n1:SerialNumber>
<n1:TotalOutputPower>502</n1:TotalOutputPower>
<n1:Type>0</n1:Type>
<n1:DetailedState>Absent</n1:DetailedState>
<n1:FQDD>PSU.Slot.2</n1:FQDD>
<n1:FirmwareVersion/>
<n1:InputVoltage>0</n1:InputVoltage>
<n1:InstanceID>PSU.Slot.2</n1:InstanceID>
<n1:LastSystemInventoryTime>20110307121906.000000+000
, which is when
Page 66

</n1:LastSystemInventoryTime>
<n1:LastUpdateTime>20110119144252.000000+000
</n1:LastUpdateTime>
<n1:Manufacturer/>
<n1:Model/>
<n1:PartNumber/>
<n1:PrimaryStatus>3</n1:PrimaryStatus>
<n1:RedundancyStatus>0</n1:RedundancyStatus>
<n1:SerialNumber/>
<n1:TotalOutputPower>0</n1:TotalOutputPower>
<n1:Type>0</n1:Type>
</n1:DCIM_PowerSupplyView>
9.2 Fan Inventory
This section describes the requirements and guidelines for implementing Dell Fan Profile. The Dell Fan
Profile describes the fans of each platform including the fan speed sensor information. Each platform
fan is represented by an instance of
Profile and Associated MOFs:
http://www.delltechcenter.com/page/DCIM.Library.Profile
Enumerate
EXAMPLE:
wsman enumerate http://schemas.dmtf.org/wbem/wscim/1/cimschema/2/root/dcim/DCIM_FanView
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT:
<n1:DCIM_FanView>
</n1:DCIM_FanView>
<n1:DCIM_FanView>
DCIM_FanView
class.
DCIM_FanView
with the following parameters and syntax:
<n1:ActiveCooling>true</n1:ActiveCooling>
<n1:BaseUnits>19</n1:BaseUnits>
<n1:CurrentReading>4920</n1:CurrentReading>
<n1:FQDD>Fan.Embedded.1A</n1:FQDD>
<n1:InstanceID>Fan.Embedded.1A</n1:InstanceID>
<n1:LastSystemInventoryTime>20110307121906.000000+000
</n1:LastSystemInventoryTime>
<n1:LastUpdateTime>20110316091932.000000+000
</n1:LastUpdateTime>
<n1:PrimaryStatus>1</n1:PrimaryStatus>
<n1:RateUnits>0</n1:RateUnits>
<n1:RedundancyStatus>2</n1:RedundancyStatus>
<n1:UnitModifier>0</n1:UnitModifier>
<n1:VariableSpeed>true</n1:VariableSpeed>
<n1:ActiveCooling>true</n1:ActiveCooling>
<n1:BaseUnits>19</n1:BaseUnits>
<n1:CurrentReading>5160</n1:CurrentReading>
<n1:FQDD>Fan.Embedded.2A</n1:FQDD>
<n1:InstanceID>Fan.Embedded.2A</n1:InstanceID>
<n1:LastSystemInventoryTime>20110307121906.000000+000
</n1:LastSystemInventoryTime>
Page 67

<n1:LastUpdateTime>20110316091932.000000+000
</n1:LastUpdateTime>
<n1:PrimaryStatus>1</n1:PrimaryStatus>
<n1:RateUnits>0</n1:RateUnits>
<n1:RedundancyStatus>2</n1:RedundancyStatus>
<n1:UnitModifier>0</n1:UnitModifier>
<n1:VariableSpeed>true</n1:VariableSpeed>
</n1:DCIM_FanView>
.
.
9.3 Memory Inventory
This section describes the implementation for the
Profile describes physical memory of each platform. Each DIMM’s information is represented by an
instance of
Profile and Associated MOFs:
DCIM_MemoryView
DCIM_MemoryView
class.
class. The Dell Memory
http://www.delltechcenter.com/page/DCIM.Library.Profile
Enumerate
DCIM_MemoryView
with the following parameters and syntax:
EXAMPLE:
wsman enumerate http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_MemoryView
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT:
<n1:DCIM_MemoryView>
<n1:BankLabel>A</n1:BankLabel>
<n1:CurrentOperatingSpeed>1333</n1:CurrentOperatingSpeed>
<n1:FQDD>DIMM.Socket.A1</n1:FQDD>
<n1:InstanceID>DIMM.Socket.A1</n1:InstanceID>
<n1:LastSystemInventoryTime>20120106113848.000000+000
</n1:LastSystemInventoryTime>
<n1:LastUpdateTime>20111214060202.000000+000
</n1:LastUpdateTime>
<n1:ManufactureDate>N/A</n1:ManufactureDate>
<n1:Manufacturer>Hynix Semiconductor</n1:Manufacturer>
<n1:MemoryType>24</n1:MemoryType>
<n1:Model>DDR3 DIMM</n1:Model>
<n1:PartNumber>HMT325R7BFR8A-H9</n1:PartNumber>
<n1:PrimaryStatus>1</n1:PrimaryStatus>
<n1:Rank>1</n1:Rank>
<n1:SerialNumber>1DC1FA2E</n1:SerialNumber>
<n1:Size>2048</n1:Size>
<n1:Speed>1333</n1:Speed>
</n1:DCIM_MemoryView>
.
.
.
9.4 CPU Inventory
Page 68

This section describes the implementation for the
describes CPUs of each platform. Each CPU’s information is represented by an instance of
DCIM_CPUView
class.
DCIM_CPUView
class. The Dell CPU Profile
Profile and Associated MOFs:
http://www.delltechcenter.com/page/DCIM.Library.Profile
Enumerate
DCIM_CPUView
with the following parameters and syntax:
EXAMPLE:
wsman enumerate http://schemas.dmtf.org/wbem/wscim/1/cimschema/2/root/dcim/DCIM_CPUView
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT:
<n1:DCIM_CPUView>
<n1:CPUFamily>B3</n1:CPUFamily>
<n1:CPUStatus>1</n1:CPUStatus>
<n1:Cache1Associativity>7</n1:Cache1Associativity>
<n1:Cache1ErrorMethodology>5</n1:Cache1ErrorMethodology>
<n1:Cache1Level>0</n1:Cache1Level>
<n1:Cache1PrimaryStatus>1</n1:Cache1PrimaryStatus>
<n1:Cache1SRAMType>2</n1:Cache1SRAMType>
<n1:Cache1Size>256</n1:Cache1Size>
<n1:Cache1Type>4</n1:Cache1Type>
<n1:Cache1WritePolicy>0</n1:Cache1WritePolicy>
<n1:Cache2Associativity>7</n1:Cache2Associativity>
<n1:Cache2ErrorMethodology>5</n1:Cache2ErrorMethodology>
<n1:Cache2Level>1</n1:Cache2Level>
<n1:Cache2PrimaryStatus>1</n1:Cache2PrimaryStatus>
<n1:Cache2SRAMType>2</n1:Cache2SRAMType>
<n1:Cache2Size>2048</n1:Cache2Size>
<n1:Cache2Type>5</n1:Cache2Type>
<n1:Cache2WritePolicy>0</n1:Cache2WritePolicy>
<n1:Cache3Associativity>14</n1:Cache3Associativity>
<n1:Cache3ErrorMethodology>5</n1:Cache3ErrorMethodology>
<n1:Cache3Level>2</n1:Cache3Level>
<n1:Cache3PrimaryStatus>1</n1:Cache3PrimaryStatus>
<n1:Cache3SRAMType>2</n1:Cache3SRAMType>
<n1:Cache3Size>20480</n1:Cache3Size>
<n1:Cache3Type>5</n1:Cache3Type>
<n1:Cache3WritePolicy>1</n1:Cache3WritePolicy>
<n1:Characteristics>4</n1:Characteristics>
<n1:CurrentClockSpeed>2900</n1:CurrentClockSpeed>
<n1:ExternalBusClockSpeed>6400</n1:ExternalBusClockSpeed>
<n1:FQDD>CPU.Socket.1</n1:FQDD>
<n1:InstanceID>CPU.Socket.1</n1:InstanceID>
<n1:LastSystemInventoryTime>20120106113848.000000+000
</n1:LastSystemInventoryTime>
<n1:LastUpdateTime>20111214060202.000000+000
</n1:LastUpdateTime>
<n1:Manufacturer>Intel</n1:Manufacturer>
<n1:MaxClockSpeed>3600</n1:MaxClockSpeed>
<n1:Model>Genuine Intel(R) CPU @ 2.90GHz</n1:Model>
<n1:NumberOfEnabledCores>8</n1:NumberOfEnabledCores>
<n1:NumberOfEnabledThreads>16</n1:NumberOfEnabledThreads>
<n1:NumberOfProcessorCores>8</n1:NumberOfProcessorCores>
Page 69

<n1:PrimaryStatus>1</n1:PrimaryStatus>
<n1:Voltage>1.2</n1:Voltage>
</n1:DCIM_CPUView>
9.5 iDRAC Card Inventory
This section describes the implementation for the
Profile describes the iDrac remote access card of each platform. Each remote access card’s
information is represented by an instance of
Profile and Associated MOFs:
http://www.delltechcenter.com/page/DCIM.Library.Profile
Enumerate
DCIM_iDRACCardView
with the following parameters and syntax:
EXAMPLE:
wsman enumerate http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_iDRACCardView
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT:
<n1:DCIM_iDRACCardView>
<n1:FQDD>iDRAC.Embedded.1-1</n1:FQDD>
<n1:FirmwareVersion>1.00.00</n1:FirmwareVersion>
<n1:GUID>3132334f-c0b7-3480-3510-00364c4c454</n1:GUID>
<n1:IPMIVersion>2.0</n1:IPMIVersion>
<n1:InstanceID>iDRAC.Embedded.1-1#IDRACinfo</n1:InstanceID>
<n1:LANEnabledState>1</n1:LANEnabledState>
<n1:LastSystemInventoryTime>20120106113848.000000+000
</n1:LastSystemInventoryTime>
<n1:LastUpdateTime>20120110193815.000000+000
</n1:LastUpdateTime>
<n1:Model>Enterprise</n1:Model>
<n1:PermanentMACAddress>78:2b:cb:54:54:11
</n1:PermanentMACAddress>
<n1:ProductDescription>This system component provides a complete set of
remote
management functions for Dell PowerEdge servers</n1:ProductDescription>
<n1:SOLEnabledState>1</n1:SOLEnabledState>
<n1:URLString>https://10.36.1.223:443</n1:URLString>
</n1:DCIM_iDRACCardView>
DCIM_iDRACCardView
DCIM_iDRACCARDView
class. The Dell iDrac
class.
9.6 PCI Device Inventory
This section describes the implementation for the
Profile describes PCI devices of each platform. Each PCI device’s information is represented by
an instance of
Profile and Associated MOFs:
http://www.delltechcenter.com/page/DCIM.Library.Profile
Enumerate
EXAMPLE:
DCIM_PCIDeviceView
DCIM_PCIDeviceView
DCIM_PCIDeviceView
class.
with the following parameters and syntax:
class. The Dell PCI
Page 70

wsman enumerate http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_PCIDeviceView
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT:
<n1:DCIM_PCIDeviceView>
<n1:BusNumber>1</n1:BusNumber>
<n1:DataBusWidth>0002</n1:DataBusWidth>
<n1:Description>PERC H310 Adapter</n1:Description>
<n1:DeviceNumber>0</n1:DeviceNumber>
<n1:FQDD>RAID.Slot.1-1</n1:FQDD>
<n1:FunctionNumber>0</n1:FunctionNumber>
<n1:InstanceID>RAID.Slot.1-1</n1:InstanceID>
<n1:LastSystemInventoryTime>20120106113848.000000+000
</n1:LastSystemInventoryTime>
<n1:LastUpdateTime>20120106113829.000000+000
</n1:LastUpdateTime>
<n1:Manufacturer>LSI Logic / Symbios Logic</n1:Manufacturer>
<n1:PCIDeviceID>0073</n1:PCIDeviceID>
<n1:PCISubDeviceID>1F4E</n1:PCISubDeviceID>
<n1:PCISubVendorID>1028</n1:PCISubVendorID>
<n1:PCIVendorID>1000</n1:PCIVendorID>
<n1:SlotLength>0002</n1:SlotLength>
<n1:SlotType>0002</n1:SlotType>
</n1:DCIM_PCIDeviceView>
9.7 Video Inventory
This section describes the implementation for the
describes videos of each platform. Each video controller’s information is represented by an
instance of
Profile and Associated MOFs:
http://www.delltechcenter.com/page/DCIM.Library.Profile
Enumerate
EXAMPLE:
wsman enumerate http://schemas.dmtf.org/wbem/wscim/1/cimschema/2/root/dcim/DCIM_VideoView
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT:
<n1:DCIM_VideoView>
DCIM_VideoView
DCIM_VideoView
class.
class. The Dell Video Profile
DCIM_VideoView
with the following parameters and syntax:
<n1:BusNumber>10</n1:BusNumber>
<n1:DataBusWidth>0002</n1:DataBusWidth>
<n1:Description> G200eR2</n1:Description>
<n1:DeviceNumber>0</n1:DeviceNumber>
<n1:FQDD>Video.Embedded.1-1</n1:FQDD>
<n1:FunctionNumber>0</n1:FunctionNumber>
<n1:InstanceID>Video.Embedded.1-1</n1:InstanceID>
<n1:LastSystemInventoryTime>20120106113848.000000+000
Page 71

</n1:LastSystemInventoryTime>
<n1:LastUpdateTime>20111214060202.000000+000
</n1:LastUpdateTime>
<n1:Manufacturer>Matrox Graphics, Inc.</n1:Manufacturer>
<n1:PCIDeviceID>0534</n1:PCIDeviceID>
<n1:PCISubDeviceID>04CF</n1:PCISubDeviceID>
<n1:PCISubVendorID>1028</n1:PCISubVendorID>
<n1:PCIVendorID>102B</n1:PCIVendorID>
<n1:SlotLength>0002</n1:SlotLength>
<n1:SlotType>0002</n1:SlotType>
</n1:DCIM_VideoView>
9.8 VFlash SD Card Inventory
Each SD card partition is represented by an instance of
physical attributes of the virtual flash media, such as total size, available size, category, on which the
partitions will reside. For more information, see Section 13.
Profile and Associated MOFs:
http://www.delltechcenter.com/page/DCIM.Library.Profile
Enumerate the
DCIM_VFlashView
with the following parameters and syntax:
EXAMPLE:
wsman enumerate http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_VFlashView
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT:
<n1:DCIM_VFlashView>
<n1:AvailableSize>1874</n1:AvailableSize>
<n1:Capacity>1882</n1:Capacity>
<n1:ComponentName>vFlash SD Card</n1:ComponentName>
<n1:FQDD>Disk.vFlashCard.1</n1:FQDD>
<n1:HealthStatus>OK</n1:HealthStatus>
<n1:InitializedState>Initialized</n1:InitializedState>
<n1:InstanceID>Disk.vFlashCard.1</n1:InstanceID>
<n1:LastSystemInventoryTime>20120110194751.000000+000
</n1:LastSystemInventoryTime>
<n1:LastUpdateTime>20120110194751.000000+000
</n1:LastUpdateTime>
<n1:Licensed>true</n1:Licensed>
<n1:VFlashEnabledState>true</n1:VFlashEnabledState>
<n1:WriteProtected>false</n1:WriteProtected>
</n1:DCIM_VFlashView>
DCIM_VFlashView
that is used to represent the
9.9 NIC Inventory and Configuration
The NIC Profile describes representation and configuration of NIC controller. The profile also
describes the relationship of the NIC classes to the DMTF or Dell profile version information. For
more information, see Section 15, including inventories for
NICEnumeration
.
Profile and Associated MOFs:
http://www.delltechcenter.com/page/DCIM.Library.Profile
NICString, NICInteger
, and
Page 72

Enumerate
NICView
with the following parameters and syntax:
EXAMPLE:
wsman enumerate http://schemas.dmtf.org/wbem/wscim/1/cimschema/2/root/dcim/DCIM_NICView
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT:
<n1:DCIM_NICView>
<n1:AutoNegotiation>2</n1:AutoNegotiation>
<n1:BusNumber>6</n1:BusNumber>
<n1:ControllerBIOSVersion xsi:nil="true"/>
<n1:CurrentMACAddress>78:2B:CB:54:54:13
</n1:CurrentMACAddress>
<n1:DataBusWidth>0002</n1:DataBusWidth>
<n1:DeviceNumber>0</n1:DeviceNumber>
<n1:EFIVersion xsi:nil="true"/>
<n1:FCoEOffloadMode>3</n1:FCoEOffloadMode>
<n1:FCoEWWNN xsi:nil="true"/>
<n1:FQDD>NIC.Embedded.1-1-1</n1:FQDD>
<n1:FamilyVersion>13.1.4</n1:FamilyVersion>
<n1:FunctionNumber>0</n1:FunctionNumber>
<n1:InstanceID>NIC.Embedded.1-1-1</n1:InstanceID>
<n1:LastSystemInventoryTime>20120106113848.000000+000
</n1:LastSystemInventoryTime>
<n1:LastUpdateTime>20111215170314.000000+000
</n1:LastUpdateTime>
<n1:LinkDuplex>0</n1:LinkDuplex>
<n1:LinkSpeed>0</n1:LinkSpeed>
<n1:MaxBandwidth>0</n1:MaxBandwidth>
<n1:MediaType>1</n1:MediaType>
<n1:MinBandwidth>0</n1:MinBandwidth>
<n1:NicMode>3</n1:NicMode>
<n1:PCIDeviceID>1521</n1:PCIDeviceID>
<n1:PCISubDeviceID>04cf</n1:PCISubDeviceID>
<n1:PCISubVendorID>1028</n1:PCISubVendorID>
<n1:PCIVendorID>8086</n1:PCIVendorID>
<n1:PermanentFCOEMACAddress/>
<n1:PermanentMACAddress>78:2B:CB:54:54:13
</n1:PermanentMACAddress>
<n1:PermanentiSCSIMACAddress/>
<n1:ProductName>Intel(R) Gigabit 2P I350-t LOM - 78:2B:CB:54:54:13
</n1:ProductName>
<n1:ReceiveFlowControl>3</n1:ReceiveFlowControl>
<n1:SlotLength>0002</n1:SlotLength>
<n1:SlotType>0002</n1:SlotType>
<n1:TransmitFlowControl>3</n1:TransmitFlowControl>
<n1:VendorName>Intel Corp</n1:VendorName>
<n1:WWPN xsi:nil="true"/>
<n1:iScsiOffloadMode>3</n1:iScsiOffloadMode>
</n1:DCIM_NICView>
Page 73

9.10 RAID Inventory and Configuration
The RAID profile extends the management capabilities of referencing profiles by adding the capability
to represent the configuration of RAID storage. The RAID storage is modeled as collections of
attributes where there are collections for the storage adaptors, physical disk drives, logical disks, end
enclosures and parent-child relationships between the collections. Additionally, there is a
configuration service that contains all the methods used to configure the RAID storage. For more
information, see Section 16, including inventories for
EnclosureView
.
Profile and Associated MOFs:
http://www.delltechcenter.com/page/DCIM.Library.Profile
Enumerate
ControllerView
with the following parameters and syntax:
EXAMPLE:
wsman enumerate http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_ControllerView
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT:
<n1:DCIM_ControllerView>
<n1:Bus>1</n1:Bus>
<n1:CacheSizeInMB>0</n1:CacheSizeInMB>
<n1:CachecadeCapability>0</n1:CachecadeCapability>
<n1:ControllerFirmwareVersion>20.10.1-0066
</n1:ControllerFirmwareVersion>
<n1:Device>0</n1:Device>
<n1:DeviceCardDataBusWidth>1</n1:DeviceCardDataBusWidth>
<n1:DeviceCardManufacturer>DELL</n1:DeviceCardManufacturer>
<n1:DeviceCardSlotLength>4</n1:DeviceCardSlotLength>
<n1:DeviceCardSlotType>PCI Express x8</n1:DeviceCardSlotType>
<n1:DriverVersion xsi:nil="true"/>
<n1:EncryptionCapability>0</n1:EncryptionCapability>
<n1:EncryptionMode>0</n1:EncryptionMode>
<n1:FQDD>RAID.Slot.1-1</n1:FQDD>
<n1:Function>0</n1:Function>
<n1:InstanceID>RAID.Slot.1-1</n1:InstanceID>
<n1:KeyID xsi:nil="true"/>
<n1:LastSystemInventoryTime>20120108174237.000000+000
</n1:LastSystemInventoryTime>
<n1:LastUpdateTime>20120108174237.000000+000
</n1:LastUpdateTime>
<n1:PCIDeviceID>73</n1:PCIDeviceID>
<n1:PCISlot>1</n1:PCISlot>
<n1:PCISubDeviceID>1F4E</n1:PCISubDeviceID>
<n1:PCISubVendorID>1028</n1:PCISubVendorID>
<n1:PCIVendorID>1000</n1:PCIVendorID>
<n1:PatrolReadState>1</n1:PatrolReadState>
<n1:PrimaryStatus>1</n1:PrimaryStatus>
<n1:ProductName>PERC H310 Adapter</n1:ProductName>
<n1:RollupStatus>1</n1:RollupStatus>
<n1:SASAddress>5782BCB00C577600</n1:SASAddress>
<n1:SecurityStatus>0</n1:SecurityStatus>
<n1:SlicedVDCapability>1</n1:SlicedVDCapability>
PhysicalDiskView, VirtualDiskView
, and
Page 74

</n1:DCIM_ControllerView>
9.11 BIOS Inventory and Configuration
The
BIOS Management Profile
adding the capability to represent and configure BIOS attributes, such as a Network Controller or
IDE Controller. The relationship between an individual BIOS attribute and a respective device is also
described. Additionally, the registration of a profile for the schema implementation version
information is described. For more information, see Section 17, including inventories for
BIOSString
, and
BIOSInteger
Profile and Associated MOFs:
http://www.delltechcenter.com/page/DCIM.Library.Profile
Enumerate
BIOSEnumeration
EXAMPLE:
wsman enumerate http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_BIOSEnumeration
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT:
<n1:DCIM_BIOSEnumeration>
<n1:AttributeDisplayName>System Memory Testing
</n1:AttributeDisplayName>
<n1:AttributeName>MemTest</n1:AttributeName>
<n1:CurrentValue>Disabled</n1:CurrentValue>
<n1:Dependency xsi:nil="true"/>
<n1:DisplayOrder>306</n1:DisplayOrder>
<n1:FQDD>BIOS.Setup.1-1</n1:FQDD>
<n1:GroupDisplayName>Memory Settings</n1:GroupDisplayName>
<n1:GroupID>MemSettings</n1:GroupID>
<n1:InstanceID>BIOS.Setup.1-1:MemTest</n1:InstanceID>
<n1:IsReadOnly>false</n1:IsReadOnly>
<n1:PendingValue xsi:nil="true"/>
<n1:PossibleValues>Enabled</n1:PossibleValues>
<n1:PossibleValues>Disabled</n1:PossibleValues>
<n1:PossibleValuesDescription>Enabled
</n1:PossibleValuesDescription>
<n1:PossibleValuesDescription>Disabled
</n1:PossibleValuesDescription>
</n1:DCIM_BIOSEnumeration>
.
.
extends the management capabilities of referencing profiles by
.
with the following parameters and syntax:
9.12 System Inventory (including CSIOR attribute)
This section describes the implementation for the
represent the higher level attributes of the system, such as asset tag, model, server manufacturer.
Profile and Associated MOFs:
http://www.delltechcenter.com/page/DCIM.Library.Profile
Enumerate
SystemView
DCIM_SystemView
with the following parameters and syntax:
class which is used to
Page 75

EXAMPLE:
wsman enumerate http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_SystemView
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT:
<n1:DCIM_SystemView>
<n1:AssetTag/>
<n1:BIOSReleaseDate>12/05/2011</n1:BIOSReleaseDate>
<n1:BIOSVersionString>0.3.33</n1:BIOSVersionString>
<n1:BaseBoardChassisSlot>NA</n1:BaseBoardChassisSlot>
<n1:BatteryRollupStatus>1</n1:BatteryRollupStatus>
<n1:BladeGeometry>4</n1:BladeGeometry>
<n1:BoardPartNumber>0MX4YFX04</n1:BoardPartNumber>
<n1:BoardSerialNumber>CN13740184000Q</n1:BoardSerialNumber>
<n1:CMCIP xsi:nil="true"/>
<n1:CPLDVersion>0.5.0</n1:CPLDVersion>
<n1:CPURollupStatus>1</n1:CPURollupStatus>
<n1:ChassisName>Main System Chassis</n1:ChassisName>
<n1:ChassisServiceTag>7654321</n1:ChassisServiceTag>
<n1:ChassisSystemHeight>5</n1:ChassisSystemHeight>
<n1:ExpressServiceCode>15608862073</n1:ExpressServiceCode>
<n1:FQDD>System.Embedded.1</n1:FQDD>
<n1:FanRollupStatus>3</n1:FanRollupStatus>
<n1:HostName/>
<n1:InstanceID>System.Embedded.1</n1:InstanceID>
<n1:LastSystemInventoryTime>20120106113848.000000+000
</n1:LastSystemInventoryTime>
<n1:LastUpdateTime>20111214060202.000000+000
</n1:LastUpdateTime>
<n1:LicensingRollupStatus>1
</n1:LicensingRollupStatus>
<n1:LifecycleControllerVersion>2.0.0
</n1:LifecycleControllerVersion>
<n1:Manufacturer>Dell Inc.</n1:Manufacturer>
<n1:MaxCPUSockets>2</n1:MaxCPUSockets>
<n1:MaxDIMMSlots>24</n1:MaxDIMMSlots>
<n1:MaxPCIeSlots>7</n1:MaxPCIeSlots>
<n1:MemoryOperationMode>OptimizerMode
</n1:MemoryOperationMode>
<n1:Model>PowerEdge T620</n1:Model>
<n1:PSRollupStatus>1</n1:PSRollupStatus>
<n1:PlatformGUID>3132334f-c0b7-3480-3510-00364c4c4544
</n1:PlatformGUID>
<n1:PopulatedCPUSockets>1</n1:PopulatedCPUSockets>
<n1:PopulatedDIMMSlots>1</n1:PopulatedDIMMSlots>
<n1:PopulatedPCIeSlots>1</n1:PopulatedPCIeSlots>
<n1:PowerCap>336</n1:PowerCap>
<n1:PowerCapEnabledState>3</n1:PowerCapEnabledState>
<n1:PowerState>2</n1:PowerState>
<n1:PrimaryStatus>3</n1:PrimaryStatus>
<n1:RollupStatus>3</n1:RollupStatus>
<n1:ServerAllocation xsi:nil="true"/>
<n1:ServiceTag>7654321</n1:ServiceTag>
<n1:StorageRollupStatus>1</n1:StorageRollupStatus>
<n1:SysMemErrorMethodology>6</n1:SysMemErrorMethodology>
Page 76

<n1:SysMemFailOverState>NotInUse</n1:SysMemFailOverState>
<n1:SysMemLocation>3</n1:SysMemLocation>
<n1:SysMemPrimaryStatus>1</n1:SysMemPrimaryStatus>
<n1:SysMemTotalSize>2048</n1:SysMemTotalSize>
<n1:SystemGeneration>12G Monolithic</n1:SystemGeneration>
<n1:SystemID>1231</n1:SystemID>
<n1:SystemRevision>0</n1:SystemRevision>
<n1:TempRollupStatus>1</n1:TempRollupStatus>
<n1:UUID>4c4c4544-0036-3510-8034-b7c04f333231</n1:UUID>
<n1:VoltRollupStatus>1</n1:VoltRollupStatus>
<n1:smbiosGUID>44454c4c-3600-1035-8034-b7c04f333231
</n1:smbiosGUID>
</n1:DCIM_SystemView>
Page 77

10 Job Control Management
10.1 Description of Job Management
The Dell Common Information Model (CIM) class extensions for supporting update and attribute
configuration job control are defined in the Dell Job Control Profile 2 and related MOF files 3. The
diagrams representing the classes that are implemented by the Lifecycle Controller firmware can
also be found in Dell Job Control Profile.
Profile and Associated MOFs:
http://www.delltechcenter.com/page/DCIM.Library.Profile
10.2 Remote Job Control Examples
10.2.1 Setup Job Queue
The SetupJobQueue() method takes in an array of
at a later time. The
Section 10.2.3. When there is a
reboot the UEFI (Unified Extensible Firmware Interface) at the scheduled time.
jobids
and schedules them to run immediately or
jobids
are acquired using enumerating
Reboot Job,
in a job array that contains multiple jobs, the system will
DCIM_LifecycleJob
as described in
Invoke SetupJobQueue() with the following parameters and syntax:
JobArray: The
execution sequence. If a system is to reboot at the scheduled start time, a reboot job will need to be
added to the list. This reboot job has a prefix of
jobids
are listed in the
JobArray
element. Multiple jobs are listed in the order of job
RID_
for its
jobid
.
Note: Scheduling a job that is already scheduled will display a message indicating an error.
If there is no reboot job in the job array, the system will schedule the jobs for execution at the
specified start time. The jobs will not be executed until the system is rebooted by something other
than Lifecycle Controller. At the specified
with an error indicating that the job was not executed in the specified maintenance window. For some
component updates such as Diagnostics, USC, and iDRAC firmware, a system reboot is not needed.
UntilTime
, any jobs that have not been executed are failed
EXAMPLE:
wsman invoke -a SetupJobQueue
http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_JobService
?SystemCreationClassName=DCIM_ComputerSystem,
CreationClassName=DCIM_JobService,SystemName=Idrac,Name=JobService
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD -J SetupJobQueue.xml
-j utf-8 -y basic
The syntax for SetupJobQueue.xml is:
<p:SetupJobQueue_INPUT
xmlns:p="http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_JobService">
<p:JobArray>JID_001249463339</p:JobArray>
<p:JobArray>RID_001265817718</p:JobArray>
<p:StartTimeInterval>TIME_NOW</p:StartTimeInterval>
<p:UntilTime>20100730121500</p:UntilTime>
Page 78

</p:SetupJobQueue_INPUT>
Here the
special value that represents “running the tasks immediately”. The
“maintenance windows”. Once a task is not run after passing
JobArray
element shows a list of
Jobids
that are to be scheduled to run.
UntilTime
UntilTime
TIME_NOW
value specifies the
, it should not be run again.
is a
Upon successfully invocation of the SetupJobQueue() method, the aforementioned times will be
listed when enumerated in Section 10.2.3.
OUTPUT:
Returns 0 for success or non-zero for error with
messageID
and message description.
<n1:SetupJobQueue_OUTPUT>
<n1:ReturnValue>0</n1:ReturnValue>
</n1:SetupJobQueue_OUTPUT>
Entering an invalid
<n1:SetupJobQueue_OUTPUT>
</n1:SetupJobQueue_OUTPUT>
<n1:SetupJobQueue_OUTPUT>
</n1:SetupJobQueue_OUTPUT>
jobid
or XML syntax error can yield one of the following error messages:
<n1:Message> Job Cannot be Scheduled </n1:Message>
<n1:MessageID>SUP016</n1:MessageID>
<n1:ReturnValue>2</n1:ReturnValue>
<n1:Message>Invalid Job Id </n1:Message>
<n1:MessageID>SUP011</n1:MessageID>
<n1:ReturnValue>2</n1:ReturnValue>
10.2.2 Delete Job Queue
The DeleteJobQueue() method takes in a
Note: When clearing all jobs and pending data using the keyword
example 2, the remote services instrumention is restarted to clear the cache [LC 1.x ONLY]. Users
should allow two minutes for this process to complete.
Invoke DeleteJobQueue() with the following parameters and syntax:
[JobID]: The jobID of a particular job instance to be deleted from a jobqueue
EXAMPLE 1:
wsman invoke -a DeleteJobQueue
http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_JobService
?SystemCreationClassName=DCIM_ComputerSystem,
CreationClassName=DCIM_JobService,SystemName=Idrac,Name=JobService
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD -k JobID="JobID"
-j utf-8 -y basic
The example below uses JID_CLEARALL for the
“deleting all jobs in the jobstore”.
jobID
and then deletes it from the job store.
JID_CLEARALL
jobID
, which is a predefined value that represents
, as shown in
Page 79

EXAMPLE 2:
wsman invoke -a DeleteJobQueue
http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_JobService
?SystemCreationClassName=DCIM_ComputerSystem,
CreationClassName=DCIM_JobService,SystemName=Idrac,Name=JobService
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD -k JobID="JID_CLEARALL"
-j utf-8 -y basic
OUTPUT:
Return 0 for success or non-zero for error with
messageID
and message description.
<n1:DeleteJobQueue_OUTPUT>
<n1:Message>The specified job was deleted</n1:Message>
<n1:MessageID>SUP020</n1:MessageID>
<n1:ReturnValue>0</n1:ReturnValue>
</n1:DeleteJobQueue_OUTPUT>
An XML syntax error could display the following message:
Syntax Error: input must be of the form
{KEY="VALUE"[;KEY="VALUE"]}
10.2.3 List Jobs in Job Store
The instances of this class will enumerate jobs in the job store along with status information.
Invoke
enumerate job status
with the following parameters and syntax:
[JobID]: The JobID of a particular job instance to be queried
To get the status of one particular job, use the following:
EXAMPLE 1:
wsman get http://schemas.dmtf.org/wbem/wscim/1/cimschema/2/root/dcim/DCIM_LifecycleJob
?InstanceID=JobID -h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD -j utf-8 -y basic
To get the status of all jobs, use the following:
EXAMPLE 2:
wsman enumerate http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_LifecycleJob
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT 1 & 2:
The method either returns a list of Concrete job objects or a message indicating an error. After job
instanceID
Several examples of job objects are shown below.
is returned through these status queries, they can be used for job scheduling and setup.
Page 80

<n1:DCIM_LifecycleJob>
<n1:InstanceID>JID_001299159055</n1:InstanceID>
<n1:JobStartTime/>
<n1:JobStatus>Completed</n1:JobStatus>
<n1:JobUntilTime/>
<n1:Message>Initialize media successful</n1:Message>
<n1:MessageArguments xsi:nil="true"/>
<n1:MessageID>VF048</n1:MessageID>
<n1:Name>VFlashInitialize:Media</n1:Name>
</n1:DCIM_LifecycleJob>
<n1:DCIM_LifecycleJob>
<n1:InstanceID>RID_001299247671</n1:InstanceID>
<n1:JobStartTime>00000101000000</n1:JobStartTime>
<n1:JobStatus>Reboot Completed</n1:JobStatus>
<n1:JobUntilTime>20111111111111</n1:JobUntilTime>
<n1:Message/>
<n1:MessageArguments xsi:nil="true"/>
<n1:MessageID/>
<n1:Name>Reboot1</n1:Name>
</n1:DCIM_LifecycleJob>
<n1:DCIM_LifecycleJob>
<n1:InstanceID>JID_001299499853</n1:InstanceID>
<n1:JobStartTime>00000101000000</n1:JobStartTime>
<n1:JobStatus>Completed</n1:JobStatus>
<n1:JobUntilTime>20111111111111</n1:JobUntilTime>
<n1:Message>Job completed successfully</n1:Message>
<n1:MessageArguments xsi:nil="true"/>
<n1:MessageID>PR19</n1:MessageID>
<n1:Name>ConfigBIOS:BIOS.Setup.1-1</n1:Name>
</n1:DCIM_LifecycleJob>
A message indicating an error similar to the following can occur if an invalid
<s:Fault>
<s:Code>
<s:Value>s:Sender</s:Value>
<s:Subcode>
<s:Value>wsa:DestinationUnreachable</s:Value>
</s:Subcode>
</s:Code>
<s:Reason>
<s:Text xml:lang="en">No route can be determined to reach the destination
role defined by the
WS-Addressing To.</s:Text>
</s:Reason>
<s:Detail>
<wsman:FaultDetail>
http://schemas.dmtf.org/wbem/wsman/1/wsman/faultDetail/InvalidResourceURI
</wsman:FaultDetail>
</s:Detail>
</s:Fault>
JobID
is entered:
Page 81

11 Operating System Deployment
The Dell Common Information Model (CIM) class extensions for supporting remote operating system
(OS) deployment are defined in the Dell OS Deployment Profile 2 and the
DCIM_OSDeploymentService
by the Lifecycle Controller firmware can be found in Dell OS Deployment Profile as well.
Profile and Associated MOFs:
http://www.delltechcenter.com/page/DCIM.Library.Profile
11.1 OS Deployment Profile Implementation Conformance
Use the following algorithm to test the instrumentation for OS Deployment Profile version
conformance and to discover the implementation namespace:
MOF file 3. The diagrams representing the classes that are implemented
1. Enumerate (namespace=’root/interop’, classname=”CIM_RegisteredProfile”).
2. Filter the returned enumeration using property filter (RegisteredName=”OS Deployment”).
3. Result shall contain one instance of
RegisteredVersion=”1.1.0”.
4. Associators (objectpath= “instance returned from step 3”, AssociationClass =
”CIM_ElementConformsToProfile”).
5. Result shall contain one instance of
CIM_RegisteredProfile
DCIM_OSDeploymentService
containing property
.
11.2 Checking OS Deployment Service Availability
Invoke
EXAMPLE:
wsman enumerate http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_OSDeploymentService
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT:
<n1:DCIM_OSDeploymentService>
enumerate
with the following syntax:
<n1:AvailableRequestedStates xsi:nil="true"/>
<n1:Caption xsi:nil="true"/>
<n1:CommunicationStatus xsi:nil="true"/>
<n1:CreationClassName>
DCIM_OSDeploymentService</n1:CreationClassName>
<n1:Description xsi:nil="true"/>
<n1:DetailedStatus xsi:nil="true"/>
<n1:ElementName>
Operating System Deployment Service</n1:ElementName>
<n1:EnabledDefault>2</n1:EnabledDefault>
<n1:EnabledState>5</n1:EnabledState>
<n1:HealthState xsi:nil="true"/>
<n1:InstallDate xsi:nil="true"/>
<n1:Name>DCIM:OSDeploymentService</n1:Name>
<n1:OperatingStatus xsi:nil="true"/>
Page 82

<n1:OperationalStatus xsi:nil="true"/>
<n1:OtherEnabledState xsi:nil="true"/>
<n1:PrimaryOwnerContact xsi:nil="true"/>
<n1:PrimaryOwnerName xsi:nil="true"/>
<n1:PrimaryStatus xsi:nil="true"/>
<n1:RequestedState>12</n1:RequestedState>
<n1:StartMode xsi:nil="true"/>
<n1:Started xsi:nil="true"/>
<n1:Status xsi:nil="true"/>
<n1:StatusDescriptions xsi:nil="true"/>
<n1:SystemCreationClassName>
DCIM_ComputerSystem</n1:SystemCreationClassName>
<n1:SystemName>DCIM:ComputerSystem</n1:SystemName>
<n1:TimeOfLastStateChange xsi:nil="true"/>
<n1:TransitioningToState>12</n1:TransitioningToState>
</n1:DCIM_OSDeploymentService>
11.3 OS Deployment Method Invocation Examples
11.3.1 Get Driver Pack Information
The GetDriverPackInfo() method returns the embedded driver pack version and list of supported OSs
for OS deployment that can be installed on the server using the embedded device drivers present in
the Lifecycle Controller.
1. Follow the tasks listed in Section 11.1 to test for profile conformance.
2. Invoke extrinsic method using the following parameters:
3. Invoke method returns the following output parameters:
4. If the Job output parameter from Step 2 contains a non-null value, then both Version and
EXAMPLE:
wsman invoke -a GetDriverPackInfo
http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_OSDeploymentService
?CreationClassName=DCIM_OSDeploymentService,
Name=DCIM:OSDeploymentService,
SystemCreationClassName=DCIM_ComputerSystem,
SystemName=DCIM:ComputerSystem
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT:
a. object path = object path returned from Section 11.1 (profile conformance)
b. Method name = “GetDriverPackInfo”
a. Version = String version
b. SupportedOperatingSystems = String array of OS names
OSList contain null values. The next call to GetDriverPackInfo() after the Job is completed will
Version
following syntax:
return non-null values for output parameters
and
OSList
. Invoke GetDriverPackInfo() with the
Page 83

<n1:GetDriverPackInfo_OUTPUT>
<n1:OSList>Windows Server(R) 2003 R2 with SP2
</n1:OSList>
<n1:OSList>Windows(R) Small Business Server 2003 R2 with SP2
</n1:OSList>
<n1:OSList>Windows Server(R) 2003, x64
</n1:OSList>
<n1:OSList>Windows Server(R) 2008
</n1:OSList>
<n1:OSList>Windows Server(R) 2008, x64
</n1:OSList>
<n1:OSList>Windows(R) Small Business Server 2008
</n1:OSList>
<n1:OSList>Windows(R) Essential Business Server 2008
</n1:OSList>
<n1:OSList>Windows Server(R) 2008, x64 R2
</n1:OSList>
<n1:OSList>Red Hat Enterprise Linux 4.7 32-bit
</n1:OSList>
<n1:OSList>Red Hat Linux Enterprise 4.7 64-bit
</n1:OSList>
<n1:OSList>Red Hat Enterprise Linux 5.3 32-bit
</n1:OSList>
<n1:OSList>Red Hat Enterprise Linux 5.3 64-bit
</n1:OSList>
<n1:OSList>SUSE Linux Enterprise Server 10 SP2 64-bit
</n1:OSList>
<n1:OSList>SUSE Linux Enterprise Server 11 64-bit
</n1:OSList>
<n1:OSList>ESX 3.5 U4
</n1:OSList>
<n1:OSList>ESX 4.0
</n1:OSList>
<n1:ReturnValue>0</n1:ReturnValue>
<n1:Version>6.1.0.7</n1:Version>
</n1:GetDriverPackInfo_OUTPUT>
11.3.2 Unpack Selected Drivers and Attach to Host OS as USB Device
This method is used to unpack the drivers for the selected OS to a virtual storage partition, and to
then attach this partition to the host OS as an emulated USB storage device.
1. Invoke extrinsic method using the following parameters section:
2. Invoke method shall return the following output parameters:
a. object path = object path returned from Section 11.1 (profile conformance)
b. Method name = “UnpackAndAttach”
c. OSName = “” (Has to be a valid value from the list returned by GetDriverPackInfo)
d. ExposureStartTime = “” (for this release the value is NULL)
e. ExposureDuration = “” (a string formatted as an interval in CIM_DateTime format)
This parameter denotes the interval of time after which the partition containing
OS drivers with label OEMDRV is to be detached from the Host OS
Page 84

a. Job = object path to CIM_ConcreteJob (reports the status of unpack and attach)
b. Enumerating this instance of CIM_ConcreteJob will display the status of the
current operation.
Invoke UnpackAndAttach() with the following syntax:
EXAMPLE:
wsman invoke -a UnpackAndAttach
http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_OSDeploymentService
?CreationClassName=DCIM_OSDeploymentService,
Name=DCIM:OSDeploymentService,
SystemCreationClassName=DCIM_ComputerSystem,
SystemName=DCIM:ComputerSystem
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-k OSName="OSName" -k ExposeDuration="00000000002200.000000:000"
-j utf-8 -y basic
Above example uses
Microsoft Windows Server 2008 with SP2
for OSName.
OUTPUT:
<n1:UnpackAndAttach_OUTPUT>
<n1:Job>
<wsa:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anon
ymous</wsa:Address>
<wsa:ReferenceParameters>
<wsman:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_OSDConcreteJob</wsman:ResourceURI>
<wsman:SelectorSet>
<wsman:Selector
Name="InstanceID">DCIM_OSDConcreteJob:1</wsman:Selector>
<wsman:Selector Name="__cimnamespace">root/dcim</wsman:Selector>
</wsman:SelectorSet>
</wsa:ReferenceParameters>
</n1:Job>
<n1:ReturnValue>4096</n1:ReturnValue>
</n1:UnpackAndAttach_OUTPUT>
11.3.3 Detach Emulated USB Device Containing Drivers
This method is used to detach the USB device attached to the system by a prior invocation of the
UnpackAndAttach() method.
Invoke DetachDrivers() with the following syntax:
EXAMPLE:
wsman invoke -a DetachDrivers http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_OSDeploymentService
?CreationClassName=DCIM_OSDeploymentService,Name=DCIM:OSDeploymentService,Sys
temCreationC
lassName=DCIM_ComputerSystem,
SystemName=DCIM:ComputerSystem
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
Page 85

-j utf-8 -y basic
OUTPUT:
Returns 0 for success or an integer for error or job in execution. A message indicating an error,
contains a
complete an earlier invoked method:
<n1:DetachDrivers_OUTPUT>
</n1:DetachDrivers_OUTPUT>
MessageID
<n1:Message>Unable to retrieve Lifecycle Controller handle
</n1:Message>
<n1:ReturnValue>2</n1:ReturnValue>
and
Message
<n1:MessageID>OSD7</n1:MessageID>
similar to the following is displayed if the system is waiting to
11.3.4 Unpack Selected Drivers and Copy to Network Share
The UnpackAndShare() method is used to unpack the drivers for the selected OS and copy them to
a specified network share; CIFS and NFS network share technologies are supported.
Note: The values for the CIFSUSER and CIFSPASSWORD must be alphanumeric characters, and must
not contain special characters.
Invoke UnpackAndShare() with the following syntax:
[CIFS_IPADDRESS]: This is the IP address of the file server.
[DRIVESHARE]: This is the directory path to the drivers.
[CIFS_USERNAME]: This is the username to the file share.
[CIFS_PASSWORD]: This is the password to the file share.
[OSName]: This example uses Windows Server® 2003 SP2.
[NFS_Password]: This is the corresponding password to the username containing the ISO.
EXAMPLE:
wsman invoke -a UnpackAndShare
http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_OSDeploymentService
?CreationClassName=DCIM_OSDeploymentService,
Name=DCIM:OSDeploymentService,
SystemCreationClassName=DCIM_ComputerSystem,
SystemName=DCIM:ComputerSystem
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-k IPAddress="[CIFS_IPADDRESS]" -k ShareName="/[DRIVERSHARE]" -k
ShareType="2" -k Username="
[CIFS_USERNAME]" –k Password="[CIFS_PASSWORD]" -k OSName="Windows Server(R)
2003 sp2"
-j utf-8 -y basic
OUTPUT:
Returns 0 for success or 1 if an error occurred in starting the processing of input parameters. The
MessageID
an error occurred.
and
Message
output parameters will further contain method invocation information if
Page 86

<n1:UnpackAndShare_OUTPUT>
<n1:Job>
<wsa:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anon
ymous</wsa:Address>
<wsa:ReferenceParameters>
<wsman:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_OSDConcreteJob</wsman:ResourceURI>
<wsman:SelectorSet>
<wsman:Selector
Name="InstanceID">DCIM_OSDConcreteJob:1</wsman:Selector>
<wsman:Selector Name="__cimnamespace">root/dcim</wsman:Selector>
</wsman:SelectorSet>
</wsa:ReferenceParameters>
</n1:Job>
<n1:ReturnValue>4096</n1:ReturnValue>
</n1:UnpackAndShare_OUTPUT>
A missing command line character, such as a “{“, could result in the following syntax error:
Connection failed. response code = 0
Couldn't connect to server
11.3.5 Check Job Status
The following methodology is used to determine the status of the jobs generated by the invocation
of the UnpackAndAttach() and UnpackAndShare() methods. The methodology involves
enumerating the
When the jobs are complete, the
successfully or “Failed” if an error occurred while executing the request. If the job failed, the
property on the returned
information on the cause of the failure.
DCIM_OSDConcreteJob instances
JobStatus
DCIM_OSDConcreteJob
, and checking the
property value will be “Successful” if the job completed
JobStatus
property value.
Message
instance will contain more detailed error
For the Lifecycle Controller version of the OS Deployment Profile there is only one instance of a job
generated by various method invocations, and it will persist until the next method that generates a job
is invoked. The job must complete before another method that generates a job can be called
successfully. This is unchanged from the Lifecycle Controller 1.2 for OS Deployment.
Invoke
enumerate DCIM_OSDConcreteJob instance
with the following syntax:
EXAMPLE:
wsman enumerate http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_OSDConcreteJob
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT:
The enumeration will return the instances of
OSDConcreteJob
as shown:
<n1:DCIM_OSDConcreteJob>
<n1:Caption xsi:nil="true"/>
<n1:CommunicationStatus xsi:nil="true"/>
<n1:DeleteOnCompletion>false</n1:DeleteOnCompletion>
<n1:Description xsi:nil="true"/>
Page 87

<n1:DetailedStatus xsi:nil="true"/>
<n1:ElapsedTime xsi:nil="true"/>
<n1:ElementName xsi:nil="true"/>
<n1:ErrorCode xsi:nil="true"/>
<n1:ErrorDescription xsi:nil="true"/>
<n1:HealthState xsi:nil="true"/>
<n1:InstallDate xsi:nil="true"/>
<n1:InstanceID>DCIM_OSDConcreteJob:1</n1:InstanceID>
<n1:JobName>UnpackAndShare</n1:JobName>
<n1:JobRunTimes>1</n1:JobRunTimes>
<n1:JobState xsi:nil="true"/>
<n1:JobStatus>Failed</n1:JobStatus>
<n1:LocalOrUtcTime xsi:nil="true"/>
<n1:Message>Installation not supported for the selected
operating system</n1:Message>
<n1:MessageArguments xsi:nil="true"/>
<n1:MessageID>OSD10</n1:MessageID>
<n1:Name xsi:nil="true"/>
<n1:Notify xsi:nil="true"/>
<n1:OperatingStatus xsi:nil="true"/>
<n1:OperationalStatus xsi:nil="true"/>
<n1:OtherRecoveryAction xsi:nil="true"/>
<n1:Owner xsi:nil="true"/>
<n1:PercentComplete xsi:nil="true"/>
<n1:PrimaryStatus xsi:nil="true"/>
<n1:Priority xsi:nil="true"/>
<n1:RecoveryAction xsi:nil="true"/>
<n1:RunDay xsi:nil="true"/>
<n1:RunDayOfWeek xsi:nil="true"/>
<n1:RunMonth xsi:nil="true"/>
<n1:RunStartInterval xsi:nil="true"/>
<n1:ScheduledStartTime xsi:nil="true"/>
<n1:StartTime xsi:nil="true"/>
<n1:Status xsi:nil="true"/>
<n1:StatusDescriptions xsi:nil="true"/>
<n1:TimeBeforeRemoval>00000000000500.000000:000
</n1:TimeBeforeRemoval>
<n1:TimeOfLastStateChange xsi:nil="true"/>
<n1:TimeSubmitted xsi:nil="true"/>
<n1:UntilTime xsi:nil="true"/>
</n1:DCIM_OSDConcreteJob>
11.3.6 Boot to Network ISO
The BootToNetworkISO() method can be used to boot the target system to a bootable ISO image
located on a CIFS or NFS share. The ISO image is attached to the host system as an emulated USB
CD-ROM storage device. By default the ISO will be attached for around 18 hours after which it will be
detached automatically. An optional parameter
than 18 hours if the ISO needs to be detached sooner.
ExposeDuration
can be used to specify a time less
Invoke BootToNetworkISO() using NFS share with the following syntax:
[NFS_IPADDRESS]: This is the IP address of the location of the ISO image.
[/NFS/OSISO]: This is the directory path to the ISO image.
[NFS_Username]: This is the username to the IP address of the ISO image.
[NFS_Password]: This is the corresponding password to the username containing the ISO image.
Page 88

[OS.ISO]: This is to be replaced by the actual name of the ISO image.
EXAMPLE:
wsman invoke -a BootToNetworkISO
http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_OSDeploymentService
?CreationClassName=DCIM_OSDeploymentService,
Name=DCIM:OSDeploymentService,
SystemCreationClassName=DCIM_ComputerSystem,
SystemName=DCIM:ComputerSystem
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD -k IPAddress="[NFS_IPADDRESS]" -k
ShareName="[/NFS/OSISO]" -k
ShareType="0" -k Username="[NFS_USERNAME]" -k Password="[NFS_PASSWORD]" -k
Workgroup="WORKGROUP"
-k ImageName="[OS.ISO]"
-j utf-8 -y basic
OUTPUT:
Returns 0 for success or 1 if an error occurred in starting the processing of input parameters. The
MessageID
an error occurred.
and
Message
output parameters will further contain method invocation information if
<n1:BootToNetworkISO_OUTPUT>
<n1:Job>
<wsa:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anon
ymous</wsa:Address>
<wsa:ReferenceParameters>
<wsman:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_OSDConcreteJob</wsman:ResourceURI>
<wsman:SelectorSet>
<wsman:Selector
Name="InstanceID">DCIM_OSDConcreteJob:1</wsman:Selector>
<wsman:Selector
Name="__cimnamespace">root/dcim</wsman:Selector>
</wsman:SelectorSet>
</wsa:ReferenceParameters>
</n1:Job>
<n1:ReturnValue>4096</n1:ReturnValue>
</n1:BootToNetworkISO_OUTPUT>
The following error message is caused by a typo in the wsman input. Careful attention must be paid
to the input capitalization of the attributes.
<s:Fault>
<s:Code>
<s:Value>s:Sender</s:Value>
<s:Subcode>
<s:Value>wsman:InvalidParameter</s:Value>
</s:Subcode>
</s:Code>
<s:Reason>
<s:Text xml:lang="en">An operation parameter is not valid.</s:Text>
</s:Reason>
<s:Detail>
<wsman:FaultDetail>http://schemas.dmtf.org/wbem/wsman/1/wsman/faultDetail/MissingValues</wsm
an:FaultDetail>
Page 89

</s:Detail>
</s:Fault>
11.3.7 Detach Network ISO USB Device
This method is used to detach the emulated USB device that had been attached by calling the
earlier BootToNetworkISO() method.
Invoke DetachISOImage() with the following syntax:
EXAMPLE:
wsman invoke -a DetachDrivers http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_OSDeploymentService
?CreationClassName=DCIM_OSDeploymentService,
Name=DCIM:OSDeploymentService,
SystemCreationClassName=DCIM_ComputerSystem,
SystemName=DCIM:ComputerSystem
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD -j utf-8 -y basic
OUTPUT:
Returns 0 for success or an integer for error or job in execution. An error such as the following can
occur if an ISO image is not attached.
<n1:DetachDrivers_OUTPUT>
<n1:Message>Unable to retrieve Lifecycle Controller handle
</n1:Message>
<n1:MessageID>OSD7</n1:MessageID>
<n1:ReturnValue>2</n1:ReturnValue>
</n1:DetachDrivers_OUTPUT>
11.3.8 Boot To PXE
The BootToPXE() method is used to boot to server using the PXE mechanism, which is to reboot
the host server and boot to PXE.
Invoke to boot target system to PXE with the following syntax:
EXAMPLE:
wsman invoke -a BootToPXE http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_OSDeploymentService
?CreationClassName=DCIM_OSDeploymentService,
Name=DCIM:OSDeploymentService,
SystemCreationClassName=DCIM_ComputerSystem,
SystemName=DCIM:ComputerSystem
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD -j utf-8 -y basic
Returns 0 for success or 1 if an error occurred in starting the processing of input parameters. The
MessageID
an error occurred.
OUTPUT:
<n1:BootToPXE_OUTPUT>
<n1:ReturnValue>0</n1:ReturnValue>
and
Message
output parameters will further contain method invocation information if
Page 90

</n1:BootToPXE_OUTPUT>
11.3.9 Get Host MAC Address Information
Invoke GethostMACInfo() with the following syntax:
EXAMPLE:
wsman invoke -a GetHostMACInfo
http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_OSDeploymentService
?CreationClassName=DCIM_OSDeploymentService,
Name=DCIM:OSDeploymentService,
SystemCreationClassName=DCIM_ComputerSystem,
SystemName=DCIM:ComputerSystem
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT:
Returns 0 for success and a list of MAC addresses or an integer for error or job in execution. The
MessageID
error occurred.
<n1:GetHostMACInfo_OUTPUT>
<n1:MACList>00221959b21f</n1:MACList>
<n1:MACList>00221959b221</n1:MACList>
<n1:MACList>00221959b223</n1:MACList>
<n1:MACList>00221959b225</n1:MACList>
<n1:ReturnValue>0</n1:ReturnValue>
</n1:GetHostMACInfo_OUTPUT>
and
Message
output parameters will further contain method invocation information if an
11.3.10 Download ISO to VFlash
The DownloadISOToVFlash() method allows using remote command to download an ISO
image to VFlash. The image needs to be an ISO image. After you download this image to VFlash,
it can be booted by running another WS-Man command.
Invoke DownloadISOToVFlash() with the following parameters and syntax:
[IPADDRESS-ISO]: The IP address of the server that stores ISO images.
[DRIVESHARE]: This is the directory path to the ISO image.
[SHARETYPE]: The type of the remote storage. 0: NFS, 1: TFTP, 2: CIFS
[SHAREUSER]: User account for the ISO share location
[SHAREPASSWORD]: Password of the share account
[WORKGROUP]: Applicable workgroup
[IMAGENAME]: Image name of the iso image, such as boot.iso.
[Port]: Port number for connecting to the share, such as 2049.
EXAMPLE:
Page 91

wsman invoke -a DownloadISOToVFlash
http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_OSDeploymentService
?CreationClassName=DCIM_OSDeploymentService,
Name=DCIM:OSDeploymentService,
SystemCreationClassName=DCIM_ComputerSystem,
SystemName=DCIM:ComputerSystem
-h $IPADDRESS -V -v –c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-k IPAddress="[IPADDRESS-ISO]"
-k ShareName="/[DIVESHARE]" -k ShareType="[SHARETYPE]" -k
Username="[SHAREUSER]" -k
Password="[SHAREPASSWORD]" -k ImageName="[IMAGENAME]" –k PORT=”[PORT]” -j
utf-8 -y basic
OUTPUT:
Returns 0 for success or 1 if an error occurred in starting the processing of input parameters. The
MessageID
an error occurred.
and
Message
output parameters will further contain method invocation information if
<n1:DownloadISOToVFlash_OUTPUT>
<n1:Job>
<wsa:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anon
ymous</wsa:Address>
<wsa:ReferenceParameters>
<wsman:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_OSDConcreteJob</wsman:ResourceURI>
<wsman:SelectorSet>
<wsman:Selector
Name="InstanceID">DCIM_OSDConcreteJob:1</wsman:Selector>
<wsman:Selector Name="__cimnamespace">root/dcim</wsman:Selector>
</wsman:SelectorSet>
</wsa:ReferenceParameters>
</n1:Job>
<n1:ReturnValue>4096</n1:ReturnValue>
</n1:DownloadISOToVFlash_OUTPUT>
The following error message is a direct result of a typo in the wsman input. Careful consideration must
be applied to capitalization.
<s:Fault>
<s:Code>
<s:Value>s:Sender</s:Value>
<s:Subcode>
<s:Value>wsman:InvalidParameter</s:Value>
</s:Subcode>
</s:Code>
<s:Reason>
<s:Text xml:lang="en">An operation parameter is not valid.</s:Text>
</s:Reason>
<s:Detail>
<wsman:FaultDetail>http://schemas.dmtf.org/wbem/wsman/1/wsman/faultDetail/MissingValues</wsm
an:FaultDetail>
</s:Detail>
</s:Fault>
Page 92

11.3.11 Boot to ISO from VFlash
This method will display the ISO Image available on
and boots to it.
Invoke BootToISOFromVFlash() with the following syntax:
EXAMPLE:
wsman invoke -a BootToISOFromVFlash
http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_OSDeploymentService
?CreationClassName=DCIM_OSDeploymentService,Name=DCIM:OSDeploymentService,Sys
temCreationC
lassName=DCIM_ComputerSystem,
SystemName=DCIM:ComputerSystem
-h $IPADDRESS -V -v –c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
VFlash
as a CD-ROM device to the host server
OUTPUT:
After running this command, a status or a message will be displayed indicating an error.
<n1:BootToISOFromVFlash_OUTPUT>
<n1:Job>
<wsa:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anon
ymous</wsa:Address>
<wsa:ReferenceParameters>
<wsman:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_OSDConcreteJob</wsman:ResourceURI>
<wsman:SelectorSet>
<wsman:Selector
Name="InstanceID">DCIM_OSDConcreteJob:1</wsman:Selector>
<wsman:Selector Name="__cimnamespace">root/dcim</wsman:Selector>
</wsman:SelectorSet>
</wsa:ReferenceParameters>
</n1:Job>
<n1:ReturnValue>4096</n1:ReturnValue>
</n1:BootToISOFromVFlash_OUTPUT>
11.3.12 Delete ISO from VFlash
The DeleteISOFromVFlash() method will delete the ISO image that was downloaded to the
Invoke DeleteISOFromVFlash() with the following syntax:
EXAMPLE:
wsman invoke -a DeleteISOFromVFlash
http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_OSDeploymentService
?CreationClassName=DCIM_OSDeploymentService,Name=DCIM:OSDeploymentService,Sys
temCreationC
lassName=DCIM_ComputerSystem,
SystemName=DCIM:ComputerSystem
-h $IPADDRESS -V -v –c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
VFlash
.
Page 93

OUTPUT:
After running this command, a status or a message will be displayed indicating an error. If an image is
not found the following message will be displayed:
<n1:DeleteISOFromVFlash_OUTPUT>
<n1:Message>ISO Image not found on VFlash</n1:Message>
<n1:MessageID>OSD41</n1:MessageID>
<n1:ReturnValue>2</n1:ReturnValue>
</n1:DeleteISOFromVFlash_OUTPUT>
11.3.13 Detach ISO from VFlash
The DetachISOFromVFlash() method will detach the ISO image in the
Invoke DetachISOFromVFlash() with the following syntax:
EXAMPLE:
wsman invoke -a DetachISOFromVFlash
http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_OSDeploymentService
?CreationClassName=DCIM_OSDeploymentService,Name=DCIM:OSDeploymentService,Sys
temCreationC
lassName=DCIM_ComputerSystem,
SystemName=DCIM:ComputerSystem
-h $IPADDRESS -V -v –c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT:
After running this command, a status or a message will be displayed indicating an error. If an image is
not found the following message will be displayed:
VFlash
from the system.
<n1:DetachISOFromVFlash_OUTPUT>
<n1:Message>ISO Image not found on VFlash</n1:Message>
<n1:MessageID>OSD41</n1:MessageID>
<n1:ReturnValue>2</n1:ReturnValue>
</n1:DetachISOFromVFlash_OUTPUT>
11.3.14 Connect Network ISO Image
This method can be used to connect to a bootable ISO image located on a CIFS or an NFS share.
The ISO image is attached to the host system as an emulated USB CD-ROM storage device.
Whenever the host system reboots it will boot to this ISO Image every single time until
DisconnectNetworkISOImage
Invoke ConnectNetworkISOImage() using a CIFS or an NFS share with the following syntax:
[CIFS_or_NFS_IPADDRESS]: This is the IP address of the location of the ISO image.
[/CIFS_or_NFS/OSISO]: This is the sharename directory path to the ISO image.
[2_or_0]: 2=CIFS, 0=NFS
[CIFS_or_NFS_Username]: This is the username to the IP address of the ISO image.
is called. The ISO will be reattached after iDRAC reset.
Page 94

[CIFS_or_NFS_Password]: This is the corresponding password to the username containing the
ISO image.
[OS.ISO]: This is to be replaced by the actual name of the ISO image.
EXAMPLE:
wsman invoke -a ConnectNetworkISOImage
http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_OSDeploymentService
?CreationClassName=DCIM_OSDeploymentService,Name=DCIM:OSDeploymentService,Sys
temCreationClassName=DCIM_ComputerSystem,
SystemName=DCIM:ComputerSystem
-h $IPADDRESS -V –v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-k IPAddress="[CIFS_or_NFS_IPaddress]" -k ShareName="/[CIFS_or_NFS]"
-k ShareType="[2_or_0]" -k Username="[CIFS_or_NFS_Username]"
-k Password="[CIFS_or_NFS_Password]" -k Workgroup="WORKGROUP"
–k ImageName="[OS.ISO]" -j utf-8 -y basic
OUTPUT:
Returns 0 for success or 1 if an error occurred in starting the processing of input parameters. The
MessageID
an error occurred.
<n1:ConnectNetworkISOImage_OUTPUT>
</n1:ConnectNetworkISOImage_OUTPUT>
and
Message
<n1:Job>
<wsa:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anon
ymous</wsa:Address>
<wsa:ReferenceParameters>
<wsman:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_OSDConcreteJob</wsman:ResourceURI>
<wsman:SelectorSet>
<wsman:Selector
Name="InstanceID">DCIM_OSDConcreteJob:1</wsman:Selector>
<wsman:Selector Name="__cimnamespace">root/dcim</wsman:Selector>
</wsman:SelectorSet>
</wsa:ReferenceParameters>
</n1:Job>
<n1:ReturnValue>4096</n1:ReturnValue>
output parameters will further contain method invocation information if
11.3.15 Disconnect Network ISO Image
This method can be used to disconnect the target system from a bootable ISO image located on a
CIFS or an NFS share.
Invoke DisconnectNetworkISOImage() with the following syntax:
EXAMPLE:
wsman invoke -a DisconnectNetworkISOImage
http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_OSDeploymentService
?CreationClassName=DCIM_OSDeploymentService,
Name=DCIM:OSDeploymentService,
Page 95

SystemCreationClassName=DCIM_ComputerSystem,
SystemName=DCIM:ComputerSystem
-h $IPADDRESS –V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-j utf-8 -y basic
OUTPUT:
Returns 0 for success or 1 if an error occurred in starting the processing of input parameters. The
MessageID
an error occurred.
<n1:DisconnectNetworkISOImage_OUTPUT>
<n1:ReturnValue>0</n1:ReturnValue>
</n1:DisconnectNetworkISOImage_OUTPUT>
and
Message
output parameters will further contain method invocation information if
11.3.16 Skip ISO Image Boot
This method can be used to skip the target system from booting to a bootable ISO image
(connected using
reboot. After that host server will continue to boot to the ISO image.
Invoke SkipISOImageBoot() using an NFS share with the following syntax:
EXAMPLE:
wsman invoke -a SkipISOImageBoot
http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_OSDeploymentService
?CreationClassName=DCIM_OSDeploymentService,
Name=DCIM:OSDeploymentService,
SystemCreationClassName=DCIM_ComputerSystem,
SystemName=DCIM:ComputerSystem
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD -j utf-8 -y basic
OUTPUT:
The return messages displayed here indicates the failure and success, 2 and 0, respectively. The
MessageID
error occurred.
and
Failure:
<n1:SkipISOImageBoot_OUTPUT>
<n1:Message>ISO image is not attached</n1:Message>
<n1:MessageID>OSD32</n1:MessageID>
<n1:ReturnValue>2</n1:ReturnValue>
</n1:SkipISOImageBoot_OUTPUT>
Success:
<n1:SkipISOImageBoot_OUTPUT>
<n1:ReturnValue>0</n1:ReturnValue>
</n1:SkipISOImageBoot_OUTPUT>
ConnectNetworkISOImage
Message
output parameters will further contain method invocation information if an
method) one time only for next immediate host
11.3.17 Get Network ISO Image Connection Information
This method outputs the ISO connection status of the image that has been made available to the host.
Page 96

Invoke GetNetworkISOImageConnectionInfo() with the following syntax:
EXAMPLE:
wsman invoke -a GetNetworkISOImageConnectionInfo
http://schemas.dmtf.org/wbem/wscim/1/cimschema/2/root/dcim/DCIM_OSDeploymentS
ervice
?CreationClassName=DCIM_OSDeploymentService,
Name=DCIM:OSDeploymentService,
SystemCreationClassName=DCIM_ComputerSystem,
SystemName=DCIM:ComputerSystem
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD -j utf-8 -y basic
OUTPUT:
<n1:GetNetworkISOImageConnectionInfo_OUTPUT>
<n1:Message>ISO image is not attached</n1:Message>
<n1:MessageID>OSD32</n1:MessageID>
<n1:ReturnValue>2</n1:ReturnValue>
</n1:GetNetworkISOImageConnectionInfo_OUTPUT>
11.3.18 Connect RFS ISO Image
The ConnectRFSISOImage() method is used to connect the ISO image that is mounted through
Remote File Share (RFS) and is made available to the host system as a USB-based CD-ROM device.
The successful execution of this method shall connect to the ISO located on NFS/CIFS share to the
host server and expose it as a virtual CD-ROM device using RFS USB endpoint. The successful
execution of the method shall not change the boot order of that device. In order to boot to the CDROM, the CD-ROM shall be configured in the boot order in a separate step (using BIOS and Boot
Management Profile), and the host server shall boot to the CD-ROM. Unlike the
ConnectNetworkISOImage() method, the Lifecycle Controller is not locked and may perform other
management tasks.
Invoke ConnectRFSISOImage() with the following syntax:
[IPADDRESS-ISO]: The IP address of the server that stores ISO images.
[DRIVESHARE]: This is the directory path to the ISO image.
[SHARETYPE]: The type of the remote storage. 0: NFS, 2: CIFS
[SHAREUSER]: User account for the ISO share location
[SHAREPASSWORD]: Password of the share account
[WORKGROUP]: Applicable workgroup
[IMAGENAME]: Image name of the iso image, such as boot.iso.
EXAMPLE:
wsman invoke -a ConnectRFSISOImage
http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_OSDeploymentService
?CreationClassName=DCIM_OSDeploymentService,
Name=DCIM:OSDeploymentService,
SystemCreationClassName=DCIM_ComputerSystem,
Page 97

SystemName=DCIM:ComputerSystem
-h $IPADDRESS -V -v –c dummy.cert -P 443
-u $USERNAME -p $PASSWORD
-k IPAddress="[IPADDRESS-ISO]"
-k ShareName="/[DIVESHARE]" -k ShareType="[SHARETYPE]" -k
Username="[SHAREUSER]" -k
Password="[SHAREPASSWORD]" -k ImageName="[IMAGENAME]" –k PORT=”[PORT]” -j
utf-8 -y basic
OUTPUT:
<n1: ConnectRFSISOImage_OUTPUT>
<n1:Job>
<wsa:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anonymous<
/wsa:Address>
<wsa:ReferenceParameters>
<wsman:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_OSDConcreteJob</wsman:ResourceURI>
<wsman:SelectorSet>
<wsman:Selector Name="InstanceID">DCIM_OSDConcreteJob:1</wsman:Selector>
<wsman:Selector Name="__cimnamespace">root/dcim</wsman:Selector>
</wsman:SelectorSet>
</wsa:ReferenceParameters>
</n1:Job>
<n1:ReturnValue>4096</n1:ReturnValue>
</n1: ConnectRFSISOImage_OUTPUT>
Concrete jobs return 4096 upon successful invocation. Poll for the concrete job “JobStatus
= Success”.
11.3.19 Disconnect RFS ISO Image
The DisconnectRFSISOImage() method is used to disconnect and detach the ISO Image that is mounted
through Remote File Share (RFS) and is made available to the host system as a USB-based CD-ROM
device.
Invoke DisconnectRFSISOImage() with the following syntax:
EXAMPLE:
wsman invoke -a DisconnectRFSISOImage
http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_OSDeploymentService
?CreationClassName=DCIM_OSDeploymentService,
Name=DCIM:OSDeploymentService,
SystemCreationClassName=DCIM_ComputerSystem,
SystemName=DCIM:ComputerSystem
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD -j utf-8 -y basic
OUTPUT:
<n1:DisconnectRFSISOImage_OUTPUT>
<n1:Message>Unable to connect to ISO using RFS.</n1:Message>
<n1:MessageID>OSD60</n1:MessageID>
<n1:ReturnValue>2</n1:ReturnValue>
</n1:DisconnectRFSISOImage_OUTPUT>
Page 98

11.3.20 Get RFS ISO Image Connection Information
The GetRFSISOImageConnectionInfo() method is used to provide the status of the ISO Image
connection that has been made available to the host system.
Invoke GetRFSISOImageConnectionInfo() with the following syntax:
EXAMPLE:
wsman invoke -a GetRFSISOImageConnectionInfo
http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_OSDeploymentService
?CreationClassName=DCIM_OSDeploymentService,
Name=DCIM:OSDeploymentService,
SystemCreationClassName=DCIM_ComputerSystem,
SystemName=DCIM:ComputerSystem
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD -j utf-8 -y basic
OUTPUT:
<n1:GetRFSISOImageConnectionInfo_OUTPUT>
<n1:Message>Unable to connect to ISO using RFS.</n1:Message>
<n1:MessageID>OSD60</n1:MessageID>
<n1:ReturnValue>2</n1:ReturnValue>
</n1:GetRFSISOImageConnectionInfo_OUTPUT>
A return value 0 indicates success, the above output indicates an image was not present to
retrieve the connection information from.
11.3.21 Boot To Hard Drive (HD)
The BootToHD() method is used for one time boot to hard disk drive of the host server. After this
method is ran, the host is rebooted immediately and will boot to the first configured hard disk drive
irrespective of its boot order.
Invoke BootToHD() with the following syntax:
EXAMPLE:
wsman invoke -a BootToHD http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_OSDeploymentService
?CreationClassName=DCIM_OSDeploymentService,
Name=DCIM:OSDeploymentService,
SystemCreationClassName=DCIM_ComputerSystem,
SystemName=DCIM:ComputerSystem
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD -j utf-8 -y basic
OUTPUT:
<n1:BootToPXE_OUTPUT>
<n1:ReturnValue>0</n1:ReturnValue>
</n1:BootToPXE_OUTPUT>
Page 99

11.3.22 Configurable Boot to Network ISO
This method was added during the LC2 Version 1.1 release.
The ConfigurableBootToNetworkISO() works similar to BootToNetworkISO() except that the
immediate boot to the ISO is not automatic and controlled by an input parameter called ResetType
which will enable you to do a warm reset or cold reset or no immediate reset.
Invoke ConfigurableBootToNetworkISO () through an NFS share with the following syntax:
[NFS_IPADDRESS]: This is the IP address of the location of the ISO image.
[/NFS/OSISO]: This is the directory path to the ISO image.
[NFS_Username]: This is the username to the IP address of the ISO image.
[NFS_Password]: This is the corresponding password to the username containing the ISO image.
[OS.ISO]: This is to be replaced by the actual name of the ISO image.
[RESET_TYPE]: 0=No reset, 1=warm reset 2=cold reset
EXAMPLE:
wsman invoke -a BootToNetworkISO
http://schemas.dmtf.org/wbem/wscim/1/cimschema/
2/root/dcim/DCIM_OSDeploymentService
?CreationClassName=DCIM_OSDeploymentService,
Name=DCIM:OSDeploymentService,
SystemCreationClassName=DCIM_ComputerSystem,
SystemName=DCIM:ComputerSystem
-h $IPADDRESS -V -v -c dummy.cert -P 443
-u $USERNAME -p $PASSWORD -k IPAddress="[NFS_IPADDRESS]" -k
ShareName="[/NFS/OSISO]" -k
ShareType="0" -k Username="[NFS_USERNAME]" -k Password="[NFS_PASSWORD]" -k
Workgroup="WORKGROUP" -k ResetType="[RESET_TYPE]"
-k ImageName="[OS.ISO]"
-j utf-8 -y basic
OUTPUT:
Returns 0 for success or 1 if an error occurred in starting the processing of input parameters. The
MessageID
an error occurred.
and
Message
output parameters will further contain method invocation information if
<n1:ConfigurableBootToNetworkISO_OUTPUT>
<n1:Job>
<wsa:Address>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anon
ymous</wsa:Address>
<wsa:ReferenceParameters>
<wsman:ResourceURI>http://schemas.dell.com/wbem/wscim/1/cimschema/
2/DCIM_OSDConcreteJob</wsman:ResourceURI>
<wsman:SelectorSet>
<wsman:Selector
Name="InstanceID">DCIM_OSDConcreteJob:1</wsman:Selector>
<wsman:Selector Name="__cimnamespace">root/dcim</wsman:Selector>
</wsman:SelectorSet>
</wsa:ReferenceParameters>
</n1:Job>
<n1:ReturnValue>4096</n1:ReturnValue>
Page 100

</n1:ConfigurableBootToNetworkISO_OUTPUT>
 Loading...
Loading...