Page 1

Dell™ PowerConnect™
28xx Systems
User Guide
www.dell.com | support.dell.com
Page 2

Notes, Notices, and Cautions
NOTE: A NOTE indicates important information that helps you make better use of your computer.
NOTICE: A NOTICE indicates either potential damage to hardware or loss of data and tells you how to avoid the problem.
CAUTION: A CAUTION indicates a potential for property damage, personal injury, or death.
____________________
Information in this document is subject to change without notice.
© 2008 Dell Inc. All rights reserved.
Reproduction in any manner whatsoever without the written permission of Dell Inc. is strictly forbidden.
Trademarks used in this text: Dell, Dell OpenManage, the DELL logo, Inspiron, Dell Precision, Dimension, OptiPlex, PowerConnect,
PowerApp, PowerVault, Axim, DellNet, and Latitude are trademarks of Dell Inc. Microsoft and Windows are either trademarks or registered
trademarks of Microsoft Corporation in the United States and/or other countries.
Other trademarks and trade names may be used in this document to refer to either the entities claiming the marks and names or their products.
Dell Inc. disclaims any proprietary interest in trademarks and trade names other than its own.
December 2008 Rev. A00
Page 3

Contents
1 Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
System Description. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
PowerConnect 2808
PowerConnect 2816
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
PowerConnect 2824. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
PowerConnect 2848
Summary of PowerConnect Models
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
. . . . . . . . . . . . . . . . . . . . 11
Features
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
General Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
MAC Address Supported Features . . . . . . . . . . . . . . . . . . . . . 13
Layer 2 Features
VLAN Supported Features
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
. . . . . . . . . . . . . . . . . . . . . . . . . 14
Spanning Tree Protocol Features. . . . . . . . . . . . . . . . . . . . . . 15
Class of Service (CoS) Features
Ethernet Switch Management Features
. . . . . . . . . . . . . . . . . . . . . . 16
. . . . . . . . . . . . . . . . . . 16
2 Hardware Description . . . . . . . . . . . . . . . . . . . . . . . . . . 17
Switch Port Configurations . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
PowerConnect 28xx Front and Back Panel Port Description. . . . . . . . 17
Physical Dimensions
LED Definitions
Power LED
Managed Mode LED
Fan LED (2824/2848 only)
Port LEDs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
Managed Mode Button
Switch Ventilation Fan
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
. . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
. . . . . . . . . . . . . . . . . . . . . . . . . . 22
. . . . . . . . . . . . . . . . . . . . . . . . . . . 23
. . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Cables, Port Connections, and Pinout Information
. . . . . . . . . . . . . . . 24
1000BASE-T Cable Requirements . . . . . . . . . . . . . . . . . . . . . 24
RJ-45 Connections for 10/100/1000BASE-T Ports . . . . . . . . . . . . . 24
SFP Ports
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
Contents 3
Page 4

Power Connectors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
Internal Power Supply Connector
. . . . . . . . . . . . . . . . . . . . . 26
3 Installing the PowerConnect Device . . . . . . . . . . . . . . . . 27
Installation Precautions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Site Requirements
Unpacking
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
Package Contents. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
Unpacking the Device . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
Mounting the Device
Overview
Device Rack Installation
Installing on a Flat Surface
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
. . . . . . . . . . . . . . . . . . . . . . . . . . 29
. . . . . . . . . . . . . . . . . . . . . . . . . 30
Installing on a Wall . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Connecting the Device
Connecting the Device to the Network
Connecting the Terminal to the Device
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
. . . . . . . . . . . . . . . . . . . . . 32
. . . . . . . . . . . . . . . . . . . . . 33
Connecting a Device to a Power Supply . . . . . . . . . . . . . . . . . . 34
Port Connections, Cables, and Pinout Information
. . . . . . . . . . . . . . . 35
RJ-45 Connections for 10/100/1000BaseT Ports . . . . . . . . . . . . . . 35
Port Default Settings
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
Auto-Negotiation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
MDI/MDIX. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
Flow Control
Back Pressure
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
Switching Port Default Settings . . . . . . . . . . . . . . . . . . . . . . 37
4 Starting and Configuring the Device . . . . . . . . . . . . . . . . 39
4 Contents
Booting the Device - Managed Mode . . . . . . . . . . . . . . . . . . . . . . 40
Initial Configuration - Managed Mode
Advanced Configuration
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
Retrieving an IP Address From a DHCP Server
. . . . . . . . . . . . . . . . . . . . . 41
. . . . . . . . . . . . . . . . . 45
Page 5

Startup Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
Startup Menu Procedures
Software Download
Erase FLASH File
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
. . . . . . . . . . . . . . . . . . . . . . . . . 45
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
Erasing the Device Configuration. . . . . . . . . . . . . . . . . . . . . . 47
Password Recovery
Software Download Through TFTP Server
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
. . . . . . . . . . . . . . . . . 47
Management Modes
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
Default Values. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
Transitioning Between Modes . . . . . . . . . . . . . . . . . . . . . . . 50
Returning to Managed Mode
. . . . . . . . . . . . . . . . . . . . . . . . 51
5 Using Dell OpenManage Switch Administrator . . . . . . . . . 53
Understanding the Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
Device Representation
Using the Switch Administrator Buttons
Information Buttons
Device Management Buttons
Starting the Application
. . . . . . . . . . . . . . . . . . . . . . . . . . . 54
. . . . . . . . . . . . . . . . . . . . 55
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
. . . . . . . . . . . . . . . . . . . . . . . . 56
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56
Access Levels. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56
6 Configuring System Information . . . . . . . . . . . . . . . . . . . 59
Defining General Device Information . . . . . . . . . . . . . . . . . . . . . . 59
Viewing Device Information . . . . . . . . . . . . . . . . . . . . . . . . 59
Viewing the Versions Page . . . . . . . . . . . . . . . . . . . . . . . . . 61
Resetting the Device
Entering Secure Mode
. . . . . . . . . . . . . . . . . . . . . . . . . . . . 62
. . . . . . . . . . . . . . . . . . . . . . . . . . . 63
Defining Device IP Addresses
. . . . . . . . . . . . . . . . . . . . . . . . . . 64
Defining IP Interface Parameters . . . . . . . . . . . . . . . . . . . . . 64
Running Cable Diagnostics
. . . . . . . . . . . . . . . . . . . . . . . . . . . 65
Viewing Copper Cable Diagnostics . . . . . . . . . . . . . . . . . . . . . 65
Viewing Optical Transceiver Diagnostics . . . . . . . . . . . . . . . . . 67
Managing Device Security
. . . . . . . . . . . . . . . . . . . . . . . . . . . 69
Defining the Local User Databases. . . . . . . . . . . . . . . . . . . . . 69
Contents 5
Page 6

Configuring RADIUS Global Parameters . . . . . . . . . . . . . . . . . . 71
Defining SNMP Parameters
Defining SNMP Global Parameters
Defining Communities
. . . . . . . . . . . . . . . . . . . . . . . . . . . 74
. . . . . . . . . . . . . . . . . . . . . 75
. . . . . . . . . . . . . . . . . . . . . . . . . . . . 76
Defining SNMP Notification Recipients . . . . . . . . . . . . . . . . . . 78
Managing Files
Downloading Files
Uploading Files
Restoring Default Settings
Defining DHCP Server Settings
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 82
. . . . . . . . . . . . . . . . . . . . . . . . . 83
. . . . . . . . . . . . . . . . . . . . . . . . . 83
Configuring DHCP Properties . . . . . . . . . . . . . . . . . . . . . . . . 84
Defining Network Pool . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
Excluding Addresses
Manually Allocating IP Addresses (Static Hosts)
. . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
. . . . . . . . . . . . . 89
Configuring Address Binding . . . . . . . . . . . . . . . . . . . . . . . . 92
Defining Advanced Settings
Configuring General Device Parameters
. . . . . . . . . . . . . . . . . . . . . . . . . . . 93
. . . . . . . . . . . . . . . . . . 93
7 Configuring Device Switching. . . . . . . . . . . . . . . . . . . . . 95
Configuring Network Security. . . . . . . . . . . . . . . . . . . . . . . . . . 95
Configuring Port Based Authentication
Configuring Advanced Port Based Authentication
Authenticating Users
. . . . . . . . . . . . . . . . . . . . . . . . . . . 102
. . . . . . . . . . . . . . . . . . 96
. . . . . . . . . . . . 100
6 Contents
Configuring Ports
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
Defining Port Parameters . . . . . . . . . . . . . . . . . . . . . . . . 103
Aggregating Ports. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 105
Configuring Green Ethernet
Enabling Storm Control
. . . . . . . . . . . . . . . . . . . . . . . . 108
. . . . . . . . . . . . . . . . . . . . . . . . . . 110
Defining Port Mirroring Sessions. . . . . . . . . . . . . . . . . . . . . 112
Configuring Address Tables
Viewing Dynamic Addresses
Configuring the Spanning Tree Protocol
Defining STP Global Settings
Defining STP Port Settings
Defining STP LAG Settings
. . . . . . . . . . . . . . . . . . . . . . . . . . 114
. . . . . . . . . . . . . . . . . . . . . . . 114
. . . . . . . . . . . . . . . . . . . 116
. . . . . . . . . . . . . . . . . . . . . . . 116
. . . . . . . . . . . . . . . . . . . . . . . . 119
. . . . . . . . . . . . . . . . . . . . . . . . 122
Page 7

Configuring Rapid Spanning Tree. . . . . . . . . . . . . . . . . . . . . 124
Configuring VLANs
Defining VLAN Members
VLAN Port Membership Table
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 126
. . . . . . . . . . . . . . . . . . . . . . . . . 126
. . . . . . . . . . . . . . . . . . . . . . 128
Defining VLAN Ports Settings. . . . . . . . . . . . . . . . . . . . . . . 130
Defining VLAN LAG Settings
Aggregating Ports
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 133
Defining LAG Membership
Multicast Forwarding Support
Defining Multicast Global Parameters
Adding Bridge Multicast Address Members
. . . . . . . . . . . . . . . . . . . . . . . 131
. . . . . . . . . . . . . . . . . . . . . . . . 134
. . . . . . . . . . . . . . . . . . . . . . . . . 134
. . . . . . . . . . . . . . . . . . 135
. . . . . . . . . . . . . . . 136
Assigning Multicast Forward All Parameters . . . . . . . . . . . . . . 138
IGMP Snooping
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 141
8 Viewing Statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143
Viewing RMON Statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . 144
Viewing RMON Statistics Group
Viewing Charts
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 145
Viewing the CPU Utilization
. . . . . . . . . . . . . . . . . . . . . 144
. . . . . . . . . . . . . . . . . . . . . . . . 146
9 Configuring Quality of Service. . . . . . . . . . . . . . . . . . . . 147
Defining CoS Global Parameters . . . . . . . . . . . . . . . . . . . . . . . 149
Defining QoS Interface Settings
Defining Queue Settings
Mapping CoS Values to Queues
Mapping DSCP Values to Queues
. . . . . . . . . . . . . . . . . . . . . . . . 150
. . . . . . . . . . . . . . . . . . . . . . . . . . . . 151
. . . . . . . . . . . . . . . . . . . . . . . . 153
. . . . . . . . . . . . . . . . . . . . . . . 154
A Managing the Device Using the CLI. . . . . . . . . . . . . . . . 157
Accessing the Device Through the CLI . . . . . . . . . . . . . . . . . . . . 157
Console Connection
Telnet Connection
. . . . . . . . . . . . . . . . . . . . . . . . . . . . 157
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 157
Contents 7
Page 8

Using the CLI . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 158
Command Mode Overview
User EXEC Mode
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 158
Privileged EXEC Mode
. . . . . . . . . . . . . . . . . . . . . . . . 158
. . . . . . . . . . . . . . . . . . . . . . . . . . 159
Global Configuration Mode . . . . . . . . . . . . . . . . . . . . . . . . 159
Interface Configuration Mode
. . . . . . . . . . . . . . . . . . . . . . 160
CLI Commands
Command: asset-tag
Command: copy
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 161
. . . . . . . . . . . . . . . . . . . . . . . . . . . 161
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 161
Command: debug-mode . . . . . . . . . . . . . . . . . . . . . . . . . 162
Command: do
Command: end
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 163
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 163
Command: exit (configuration) . . . . . . . . . . . . . . . . . . . . . . 163
Command: exit (EXEC)
Command: help
. . . . . . . . . . . . . . . . . . . . . . . . . . 164
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 164
Command: interface ethernet. . . . . . . . . . . . . . . . . . . . . . . 165
Command: interface port-channel
Command: interface vlan
. . . . . . . . . . . . . . . . . . . . 165
. . . . . . . . . . . . . . . . . . . . . . . . . 166
Command: ip address . . . . . . . . . . . . . . . . . . . . . . . . . . . 166
Command: ip default-gateway
Command: login
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
. . . . . . . . . . . . . . . . . . . . . . 167
Command: ping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
Commad: reload
Command: show tech-support command
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 169
. . . . . . . . . . . . . . . . 169
Command: snmp-server community . . . . . . . . . . . . . . . . . . . 171
Command: username
. . . . . . . . . . . . . . . . . . . . . . . . . . . 172
Glossary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173
Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 183
8 Contents
Page 9

Introduction
This User’s Guide contains the information needed for installing, configuring and maintaining the
PowerConnect 2808, PowerConnect 2816, PowerConnect 2824, and PowerConnect 2848 Webmanaged Gigabit Ethernet switches.
The PowerConnect 28xx switches can be used to connect workstations and other network devices,
such as:
•Servers
•Hubs
•Routers
The PowerConnect devices are primarily designated for the Small Office/Home Office (SOHO) that
require high performance edge connectivity. These PowerConnect devices are ideal for the small to
medium business that requires high performance network connectivity along with advanced web
management features. The PowerConnect management features are designed to minimize
administrative management effort, while enhancing and improving network traffic control.
System Description
This section describes the hardware configurations of the PowerConnect 28xx. The switches are
managed by Dell’s OpenManage Switch Administrator.
1
1
PowerConnect 2808
The following figure illustrates the PowerConnect 2808 front panel.
Figure 1-1. PowerConnect 2808 Front Panel
The PowerConnect 2808 supports the following ports:
• 8 Gigabit Ethernet copper ports
PowerConnect 2816
The following figure illustrates the PowerConnect 2816 front panel.
Dell PowerConnect 28xx Systems User Guide 9
Page 10

Figure 1-2. PowerConnect 2816 Front Panel
The PowerConnect 2816 supports the following ports:
• 16 Gigabit Ethernet copper ports
PowerConnect 2824
The following figure illustrates the PowerConnect 2824 front panel.
Figure 1-3. PowerConnect 2824 Front Panel
The PowerConnect 2824 supports the following ports:
• 24 Gigabit Ethernet copper ports
• 2 SFP combo ports (1000BASE-SX or 1000BASE-LX)
PowerConnect 2848
The following figure illustrates the PowerConnect 2848 front panel.
Figure 1-4. PowerConnect 2848 Front Panel
The PowerConnect 2848 supports the following ports:
• 48 Gigabit Ethernet copper ports
• 4 SFP combo ports (1000BASE-SX or 1000BASE-LX)
10 Dell PowerConnect 28xx Systems User Guide
Page 11

Summary of PowerConnect Models
The following table summarizes the PowerConnect models.
Table 1-1. PowerConnect Models
Model Copper Ports/
RJ-45 Connectors
PowerConnect 2808 8 built-in 10/100/1000 Base-T ports none Internal console port none
PowerConnect 2816 16 built-in 10/100/1000 Base-T ports none External console port none
PowerConnect 2824 24 built-in 10/100/1000 Base-T ports 2 SFP (combo) External console port 1
PowerConnect 2848 48 built-in 10/100/1000 Base-T ports 4 SFP (combo) External console port 2
Optical Ports/
GbE
RS232 serial port baud rate is 9600 bps
Fans
Features
General Features
Management Modes
The device supports the following modes:
•
Managed Mode
•
Unmanaged Mode
configuration cannot be changed.
•
Secure Mode
configuration changes by removing the IP address of the device so that it becomes inaccessible for
configuration.
For more information about the management modes, see "Management Modes" on page 49.
— Provides switch management through the web interface.
— In this mode, the device operates as a hub with default configuration, and
— This mode keeps the existing configuration active, but it prevents users from making
Head of Line Blocking Prevention
Head of Line (HOL) blocking results in traffic delays and frame loss caused by traffic competing for the
same egress port resources. HOL blocking queues packets, and the packets at the head of the queue are
forwarded before packets at the end of the queue. By default, the device is configured so that the HOL
blocking prevention mechanism is active at all times, except when QoS (Quality of Service), Flow
Control or Back Pressure is active on a port where the HOL blocking prevention mechanism is disabled
on the whole system.
Back Pressure Support
On half-duplex links, the receiving port prevents buffer overflows by occupying the link so that it is
unavailable for additional incoming traffic. The user may enable or disable this feature on a
per-port basis. The default status on all ports is set to OFF.
Dell PowerConnect 28xx Systems User Guide 11
Page 12

Auto Negotiation
Auto negotiation allows an Ethernet switch to advertise modes of operation. The auto negotiation
function provides the means to exchange information between two Ethernet switches that share a pointto-point link segment, and to automatically configure both Ethernet switches to take maximum
advantage of their transmission capabilities. Port advertisement allows the system administrator to
configure the port speeds advertised.
Jumbo Frames Support
Jumbo frames are frames with an MTU (Maximum Transmission Unit) size of up to 10K bytes. The
Jumbo Frames Support feature, utilizes the network optimally by transporting the same data using less
frames.
The main benefits of this facility are reduced transmission overhead and reduced host processing
overhead. Jumbo frames are used for server-to-server transfers.
AutoMDI/MDIX Support
The switch automatically detects whether the cable connected to an RJ-45 port is crossed or straight
through.
Standard wiring for end stations is Media-Dependent Interface (MDI) and the
s
tandard wiring for hubs
and switches is known as Media-Dependent Interface with Crossover (MDIX).
Auto MDI/MDIX works on 10/100/1000BASE-T Ethernet ports. This feature is automatically enabled for
the entire system and cannot be turned off by the user.
Flow Control Support (IEEE802.3X)
On Full Duplex links (FDX), the flow control mechanism allows the receiving side to signal to the
sending side that transmission must be halted temporarily, in order to prevent buffer overflows. Flow
control is enabled by default.
Virtual Cable Testing (VCT)
VCT technology provides the mechanism to detect and report potential cabling issues, such as cable
opens and cable shorts on copper links.
Cable analysis is available on Copper Cables (10BASE-T/100BASE-T/1000BASE-T), and is only done
when the link is down. When the system initiates a cable-testing operation, upon explicit user action, the
following parameters are detected:
• Cable Type and Status
•Cable Length
• Fault-Distance
12 Dell PowerConnect 28xx Systems User Guide
Page 13

MAC Address Supported Features
MAC Address Capacity Support
The PowerConnect 2808, 2816, 2824 switches support a total of 8K MAC addresses, and the
PowerConnect 2848 supports a total of 16K MAC addresses.
Auto-Learning MAC Addresses
The switch enables MAC address auto-learning from incoming packets. The MAC addresses are stored in
the Bridging Table.
Automatic Aging for MAC Addresses
MAC addresses from which no traffic is received for a given period of time are aged out. This prevents
the Bridging Table from overflowing.
VLAN-aware MAC-based Switching in Managed and Secure Modes
In Managed or Secure mode, the switch system always performs VLAN-aware bridging. Classic bridging
(IEEE802.1D) is not performed (where frames are forwarded based only on their destination MAC
address). However, a similar functionality may be configured for untagged frames. Addresses are
associated with ports by learning them from the incoming frames source address.
802.1D Bridging in Unmanaged Mode
In Unmanaged Mode, the switch performs classic bridging. Frames are forwarded based on their
destination MAC address only, regardless of the VLAN tag.
MAC Multicast Support
Multicast service is a limited broadcast service, which allows one-to-many and many-to-many
connections for information distribution. Layer 2 Multicast service is where a single frame is addressed to
a specific Multicast address, from where copies of the frame are transmitted to the relevant ports. IGMP
Snooping is supported, including IGMP Querier which simulates the behavior of a multicast router,
allowing snooping of the layer 2 multicast domain even though there is no multicast router. When
Multicast groups are statically enabled, you can set the destination port of registered groups, as well as
define the behavior of unregistered multicast frames.
Layer 2 Features
Green Ethernet
Green Ethernet, also known as Energy Efficient Ethernet, is an effort to make networking equipment
environmentally friendly, specifically by reducing power usage of Ethernet connections. The following
methods are supported by the device:
•
Energy-Detect
— Auto-detection of inactivity on a port, and subsequent reducing of transmit power.
Dell PowerConnect 28xx Systems User Guide 13
Page 14

•
Short-Reach
IGMP Snooping
— Reduction of power over Ethernet cables shorter than 40m.
Internet Group Membership Protocol (IGMP) Snooping examines IGMP frame contents, when they are
forwarded by the device from work stations to an upstream Multicast router. From the frame, the device
identifies work stations configured for Multicast sessions, and which Multicast routers are sending
Multicast frames.
Port Mirroring
The port mirroring mechanism monitors and mirrors network traffic by forwarding copies of incoming
and outgoing packets from a monitored port to a monitoring port. Users can specify which target port
receives copies of all traffic passing through one or more source ports.
Storm Control
Storm Control enables limiting the amount of Multicast, Broadcast and Unknown Unicast frames
accepted and forwarded by the switch. When Layer 2 frames are forwarded, Broadcast and Multicast
frames are flooded to all ports on the relevant VLAN. All nodes connected to these ports accept and
attempt to process these frames, thus placing load on both the network links and the host operating
system.
Dynamic VLAN Assignment (DVA)
Dynamic VLAN Assignment allows automatic assignment of users to VLANs during the RADIUS server
authentication. When a user is authenticated by the RADIUS server, the user is automatically joined to
the VLAN configured on the RADIUS server.
VLAN Supported Features
VLAN Support
VLANs are collections of switching ports that comprise a single broadcast domain. Packets are classified
as belonging to a VLAN based on either the VLAN tag or based on a combination of the ingress port and
package contents. Packets sharing common attributes can be grouped in the same VLAN.
Port Based Virtual LANs (VLANs)
Port-based VLANs classify incoming packets to VLANs based on their ingress port.
Link Aggregation
The PowerConnect 28xx switches support up to six aggregated links. Each of the six aggregated links may
be defined with up to four member ports to form a single Link Aggregated Group (LAG).
The benefits of this facility are:
• Fault tolerance protection from physical link disruption
14 Dell PowerConnect 28xx Systems User Guide
Page 15

• Higher bandwidth connections
• Improved bandwidth granularity
• High bandwidth server connectivity
A LAG is composed of ports with the same speed set to full-duplex operation.
DHCP Server
Dynamic Host Configuration Protocol is a method of managing network parameter assignment from a
single DHCP server. The Dynamic Host Configuration Protocol (DHCP) automates the assignment of
IP addresses, subnet masks, default gateway, and other IP parameters.
BootP and DHCP Clients
DHCP (Dynamic Host Configuration Protocol) enables additional setup parameters to be received from
a network server upon system startup. DHCP service is an on-going process. DHCP is an extension to
BootP.
The BootP client is operational if there is a corrupted or invalid software image. The BootP client then
continuously attempts to find a BootP server, by sending BootP requests to all ports on the default
VLAN, until a BootP server replies. The information replied is then used to provide the switch system
with a TFTP server IP address and a download file name. The switch can then configure these values to
the TFTP client and try to download a valid runtime image.
Spanning Tree Protocol Features
Spanning Tree Protocol (STP)
802.1d Spanning tree is a standard Layer 2 switch requirement that allows bridges to automatically
prevent and resolve L2 forwarding loops. Switches exchange configuration messages using specifically
formatted frames and selectively enable and disable forwarding on ports.
Fast Link
STP can take up to 30-60 seconds to converge. During this time, STP detects possible loops, allowing
time for status changes to propagate and for relevant devices to respond. 30-60 seconds is considered too
long of a response time for many applications. The Fast Link option bypasses this delay, and can be used
in network topologies where forwarding loops do not occur.
IEEE 802.1w Rapid Spanning Tree
Spanning Tree can take 30-60 seconds for each host to decide whether its ports are actively forwarding
traffic. Rapid Spanning Tree (RSTP) detects uses of network topologies to enable faster convergence,
without creating forwarding loops.
STP Root Guard
Root guard restricts the interface from functioning as the root port for the switch
Dell PowerConnect 28xx Systems User Guide 15
Page 16

Class of Service (CoS) Features
The PowerConnect 28xx system enables users to define various services for traffic classes of service. The
underlying mechanism for supporting bandwidth management and control is based on the use of
multiple priority queues for classifying traffic. The switches support four queues per port.
A CoS is defined by the user, whereby packets are related to the same Class of Service. After a packet has
been classified, it is assigned to one of the queues. The PowerConnect 28xx system can classify according
to IPv4 information (DSCP).
Class of Service 802.1p Support
The IEEE 802.1p signaling technique is an OSI Layer 2 standard for marking and prioritizing network
traffic at the data link/MAC sub-layer. 802.1p traffic is classified and sent to the destination. No
bandwidth reservations or limits are established or enforced. 802.1p is a spin-off of the 802.1Q (VLANs)
standard.
Ethernet Switch Management Features
Web-Based Management
With a Web-based management interface, the Ethernet Switches’ system can be managed from any
Web browser. The system contains an Embedded Web Server (EWS), which serves HTML pages,
through which the system can be monitored and configured.
TFTP Trivial File Transfer Protocol
The PowerConnect 28xx switches support software boot image and software download through TFTP.
Remote Monitoring
Remote Monitoring (RMON) is an extension to the Simple Network Management Protocol (SNMP),
which provides network traffic statistics. RMON defines current and historical MAC-layer statistics and
control objects, allowing real-time information to be captured across the entire network. The switches
support one RMON group for Ethernet statistics. The system provides a means to collect the statistics
defined in RMON and to view the results, using the Web management interface in the system.
16 Dell PowerConnect 28xx Systems User Guide
Page 17

Hardware Description
Switch Port Configurations
PowerConnect 28xx Front and Back Panel Port Description
The Dell™ PowerConnect™ 28xx switches use 10/100/1000BASE-T ports on the front panel for
connecting to a network.
The Gigabit Ethernet ports can operate at 10, 100 or 1000 Mbps. These ports support autonegotiation, duplex mode (Half or Full duplex), and flow control. The combo 1000 Mbps optical
ports can only operate at 1000 Mbps, full-duplex mode.
The following figures illustrate the front panels and back panels of the PowerConnect 28xx switches.
Figure 2-1. PowerConnect 2808 Front Panel
2
On the front panel there are eight ports which are numbered 1 to 8, top down and left to right. On
each port there are LEDs (Light Emitting Diode) to indicate the port status.
On the left side of the front panel is the Managed Mode LED which indicates the Ethernet switch
operational status and the management mode. The Power LED on the front panel indicates whether
the device is powered on or not. A Mode push-button, located on the right side on the front panel is
used to transition between management modes and to reset the device. For more information about
management modes and transitioning between them, see "Management Modes" on page 49.
Dell PowerConnect 28xx Systems User Guide 17
Page 18
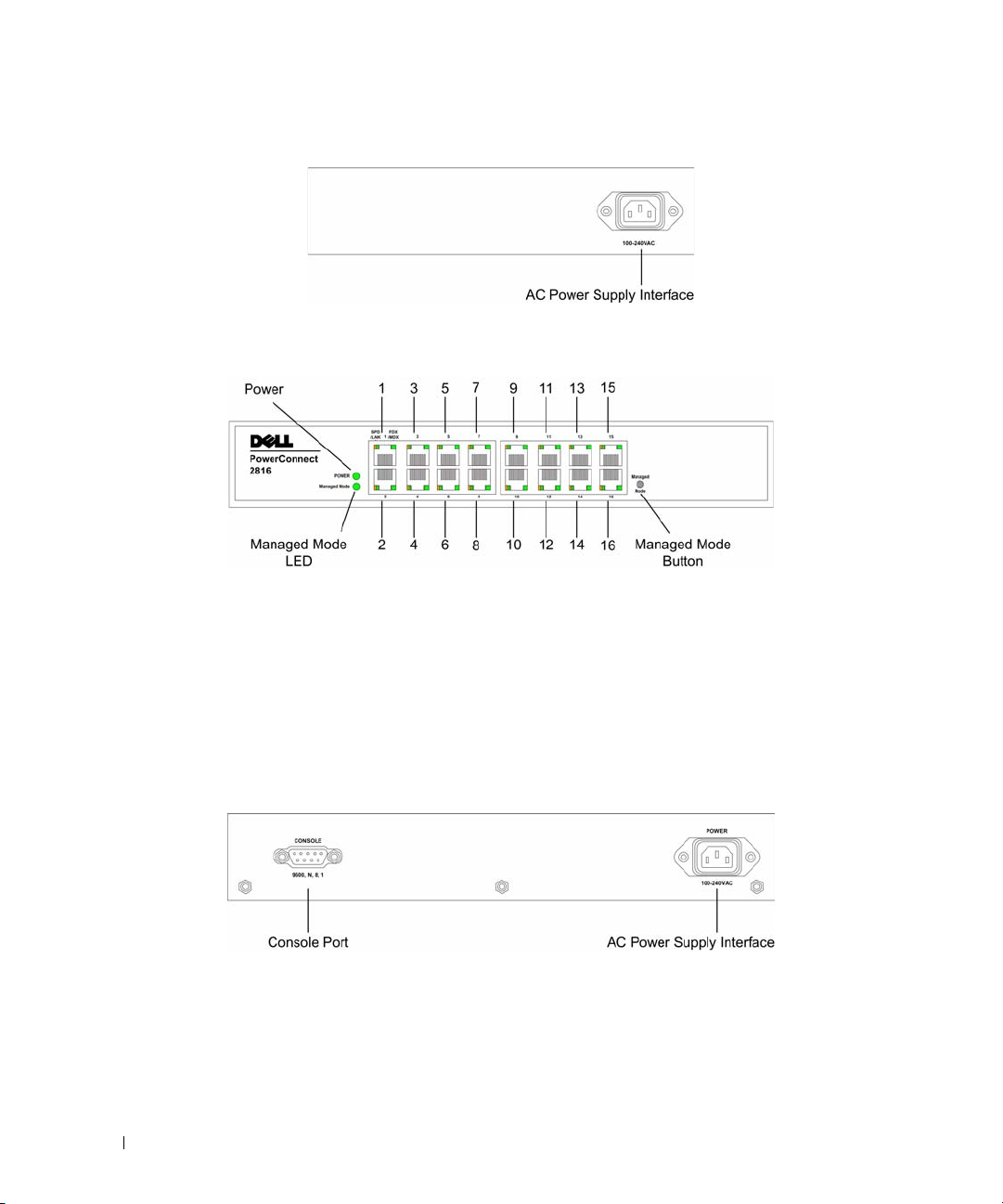
Figure 2-2. PowerConnect 2808 Back Panel
Figure 2-3. PowerConnect 2816 Front Panel
On the front panel there are 16 ports which are numbered 1 to 16, top down and left to right. On each
port there are LEDs to indicate the port status.
On the left side of the front panel is the Managed Mode LED which indicates the Ethernet switch
operational status and the management mode. The Power LED on the front panel indicates whether the
device is powered on or not. A Mode push-button, located on the right side on the front panel, is used to
transition between management modes and to reset the device. For more information about
management modes and transitioning between them, see "Management Modes" on page 49.
Figure 2-4. PowerConnect 2816 Back Panel
18 Dell PowerConnect 28xx Systems User Guide
Page 19

Figure 2-5. PowerConnect 2824 Front Panel
On the front panel there are 24 ports which are numbered 1 to 24, top down and left to right. On each
port there are LEDs to indicate the port status. There are two SFP (Small Form-Factor Plugable) ports,
designated as ports 23 and 24, for fiber connection. The two combo ports are logical ports with two
physical connections:
• An RJ-45 connection for Twisted Pair (TP) copper cabling
• An SFP port for swappable optical transceiver, which offers high-speed 1000BASE-SX or 1000BASELX connection.
NOTE: Only one of the two physical connections of a combo port can be used at any one time. Port features and
port controls are determined by the physical connection used. The system automatically detects the media used on
a combo port, and utilizes the information in all the control interfaces.
NOTE: The system can switch from the RJ-45 to the SFP (or vice versa) without resetting the device. If both RJ-45
and SFP ports are present, the SFP port will be the active port, whereas the RJ-45 port will be disabled.
On the front panel is the Managed Mode LED which indicates the Ethernet switch operational status
and the management mode. The Fan LED indicates the device fan operations status, and the Power
LED on the front panel indicates whether the device is powered on or not. A Mode push-button, located
on the right side on the front panel is used to transition between management modes and to reset the
device. For more information about management modes and transitioning between them, see
"Management Modes" on page 49.
Dell PowerConnect 28xx Systems User Guide 19
Page 20
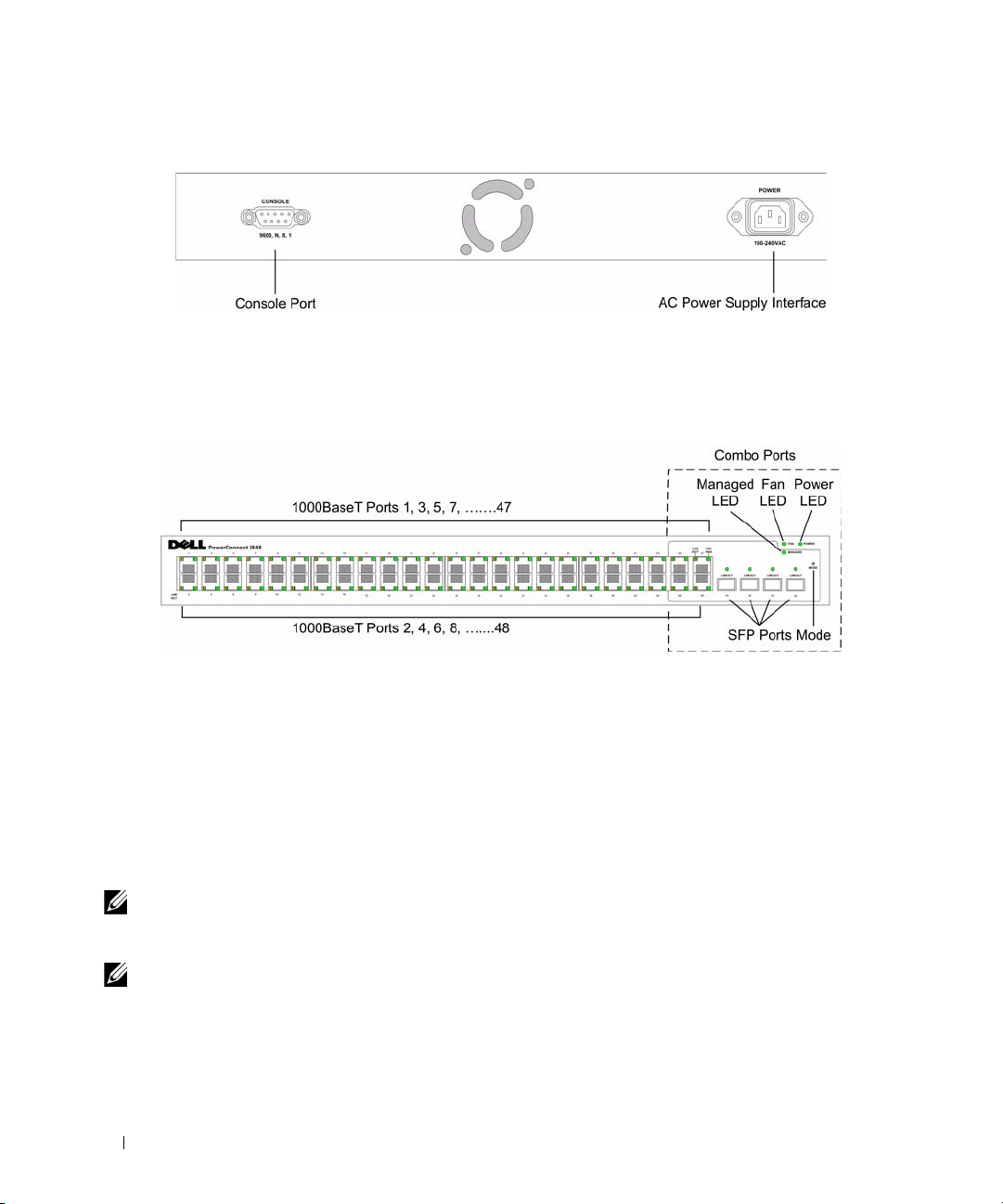
Figure 2-6. PowerConnect 2824 Back Panel
Figure 2-7. PowerConnect 2848 Front Panel
On the front panel there are 48 ports, which are numbered 1 to 48, top down and left to right. On each
port, there are LEDs to indicate the port status. There are four SFP (Small Form-Factor Plugable) ports,
designated as ports 45, 46, 47 and 48, for fiber connection. The four combo ports are logical ports with
two physical connections:
• An RJ-45 connection for Twisted Pair (TP) copper cabling.
• An SFP port for swappable optical transceiver, which offers high-speed 1000BASE-SX or
1000BASE-LX connection.
NOTE: Only one of the two physical connections of a combo port can be used at any one time. Port features and
port controls are determined by the physical connection used. The system automatically detects the media used on
a combo port, and utilizes the information in all the control interfaces.
NOTE: The system can switch from the RJ-45 to the SFP (or vice versa) without resetting the device. If both RJ-45
and SFP ports are present, the SFP port will be the active port, whereas the RJ-45 port will be disabled.
On the top right side of the front panel is the Managed Mode LED which indicates the Ethernet switch
operational status and the management mode. The Fan LED indicates the device fan operations status,
and the Power LED on the front panel indicates whether the device is powered on or not. A Mode push-
20 Dell PowerConnect 28xx Systems User Guide
Page 21
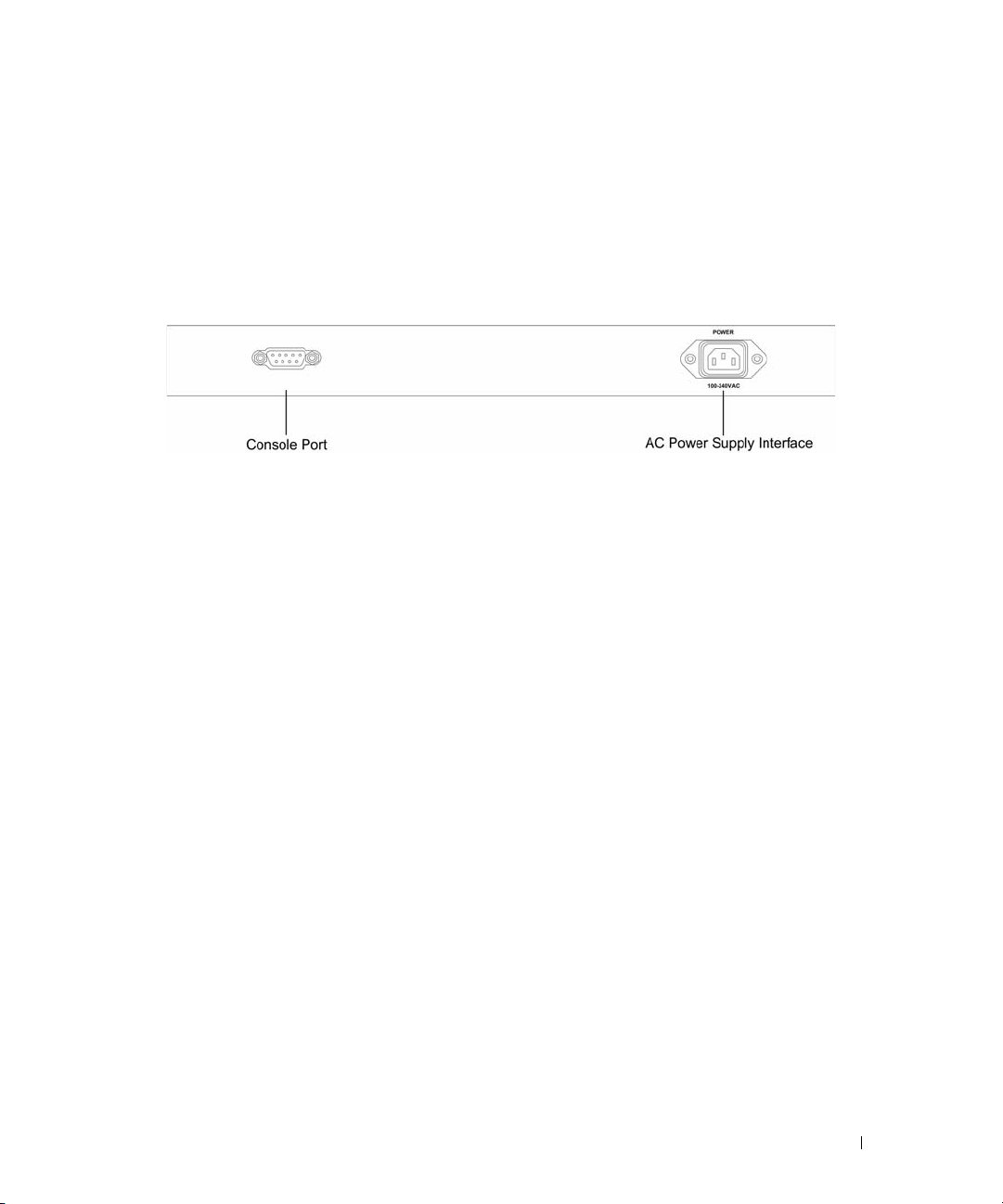
button, located on the right side on the front panel is used to transition between management modes
and to reset the device. For more information about management modes and transitioning between
them, see "Management Modes" on page 49.
Fans are provided on the side panel. The back panel contains an AC Power Supply Interface.
The following figure illustrates the back panel of the PowerConnect 2848 device.
Figure 2-8. PowerConnect 2848 Back Panel
Physical Dimensions
The PowerConnect 2808 switch has the following physical dimensions:
• Height — 43.2 mm (1.7008 in.)
• Width — 256 mm (10.079 in.)
• Depth — 161.7 mm (6.366 in.)
The PowerConnect 2816 and PowerConnect 2824 switches have the following physical dimensions:
• Height — 43.2 mm (1.7008 in.)
• Width — 330 mm (12.992 in.)
• Depth — 230.50 mm (9.075 in.)
The PowerConnect 2848 switch has the following physical dimensions:
• Height — 43.2 mm (1.70 in.)
• Width — 440 mm (17.32 in)
• Depth — 255 mm (10.04 in.)
LED Definitions
The front panel contains LEDs that indicate the status of links, power supply, fan status, and Managed
Mode status.
Dell PowerConnect 28xx Systems User Guide 21
Page 22

Power LED
On the PowerConnect 28xx front panel there is a Power LED. The following table describes the Power
Supply status LED indications.
Table 2-1. Power LED Indications
LED Color Description
Green Solid The switch is turned on.
Off The switch is not turned on.
Managed Mode LED
On the PowerConnect 28xx front panel there is a Managed Mode LED monitoring the switch node as
well as indicating diagnostic test results. The following table describes the Managed Mode LED
indications. For more information about management modes and transitioning between them, see
"Management Modes" on page 49.
Table 2-2. Managed Mode LED Indications
LED Color Description
Green Flashing Indicates diagnostics in progress, firmware loading, or Management Mode transition.
Green Solid Indicates the switch is in Managed Mode.
Amber Solid Diagnostics has failed.
Amber Flashing No valid image.
Off Indicates Unmanaged mode or Secure mode.
Fan LED (2824/2848 only)
On the PowerConnect 2824 and PowerConnect 2848 front panel there is a fan LED. The following table
describes the fan status LED indications.
Table 2-3. Fan LED Indications
LED Color Description
Green Solid All fans are operating correctly.
Red Solid One or more fans have failed.
Port LEDs
10/100/1000BASE-T Port LEDs
Each 10/100/1000BASE-T port has two LEDs. Speed/Link/Activity is indicated on the left LED and the
duplex mode is indicated on the right LED.
The following figure illustrates the RJ-45 10/100/1000BASE-T LEDs.
22 Dell PowerConnect 28xx Systems User Guide
Page 23
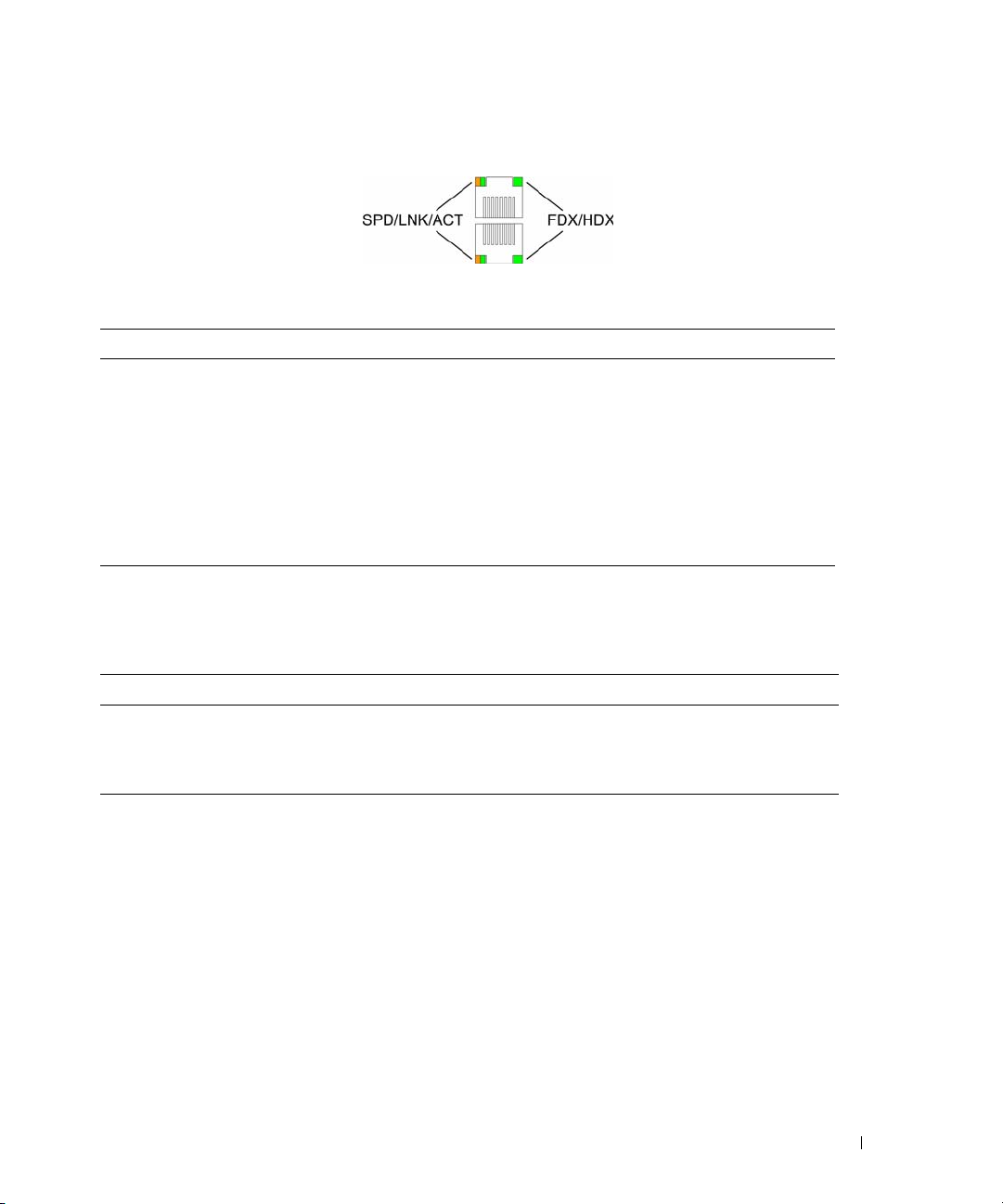
Figure 2-9. RJ-45 Copper-based 10/100/1000BASE-T LEDs
The RJ-45 LED indications are described in the following table:
Table 2-4. RJ-45 Copper based 10/100/ 1000BASE-T LED Indications
LED Color Description
Left LED Green Solid The port is linked at 1000 Mbps.
Green Flashing The port is transmitting or receiving data at 1000 Mbps.
Amber Solid The port is linked at either 10 or 100 Mbps.
Amber Flashing The port is transmitting or receiving data at 10 or 100 Mbps.
Off No link is established.
Right LED Green Solid The port is currently transmitting in Full Duplex mode.
Off The port is operating in Half Duplex mode.
SFP Port LED
The following table describes the SFP LED indications.
Table 2-5. SFP LED Indications
LED Color Description
Green Solid Link is established.
Green Flashing Activity is occurring.
Off No link is established.
Managed Mode Button
The PowerConnect 28xx has a Mode push button on the front panel. The Mode button is for changing
between Managed Mode and Unmanaged (or Secure) Mode and for resetting the device. To transition
between modes, press the button normally. To reset the device, press and hold the button for at least 7 seconds. For more information about management modes and transitioning between them, see "Management
Modes" on page 49.
Switch Ventilation Fan
The PowerConnect 2848 switch has three fans and the PowerConnect 2824 switch has one fan for system
ventilation. The PowerConnect 2808 and PowerConnect 2816 devices have no internal fans.
Dell PowerConnect 28xx Systems User Guide 23
Page 24
Cables, Port Connections, and Pinout Information
This section explains the switch physical interfaces, and provides information about cables and port
connections. Copper cable diagnostics are supported. High-speed workstations, hubs, routers, or other
switches are connected through standard RJ-45 connectors to the switch physical interface ports, located
on the front panel. For each device, the supported mode is set to Half Duplex, Full Duplex, and Auto.
1000BASE-T Cable Requirements
All Category 5 UTP cables that are used for 100BASE-TX connections also operate with 1000BASE-T,
provided if all four wire pairs are connected. However, it is recommended that enhanced Category 5
(Category 5e)cable is used for all critical connections or any new cable installations. The Category 5e
specification includes test parameters that are only recommendations for Category 5, and comply with
the IEEE 802.3ab standards.
RJ-45 Connections for 10/100/1000BASE-T Ports
The 10/100/1000BASE-T ports are copper Twisted-Pair ports.
Table 2-6. Port Default Settings
Connector Port/Interface Cable
RJ-45 10/100/1000BASE-T Port Cat.5
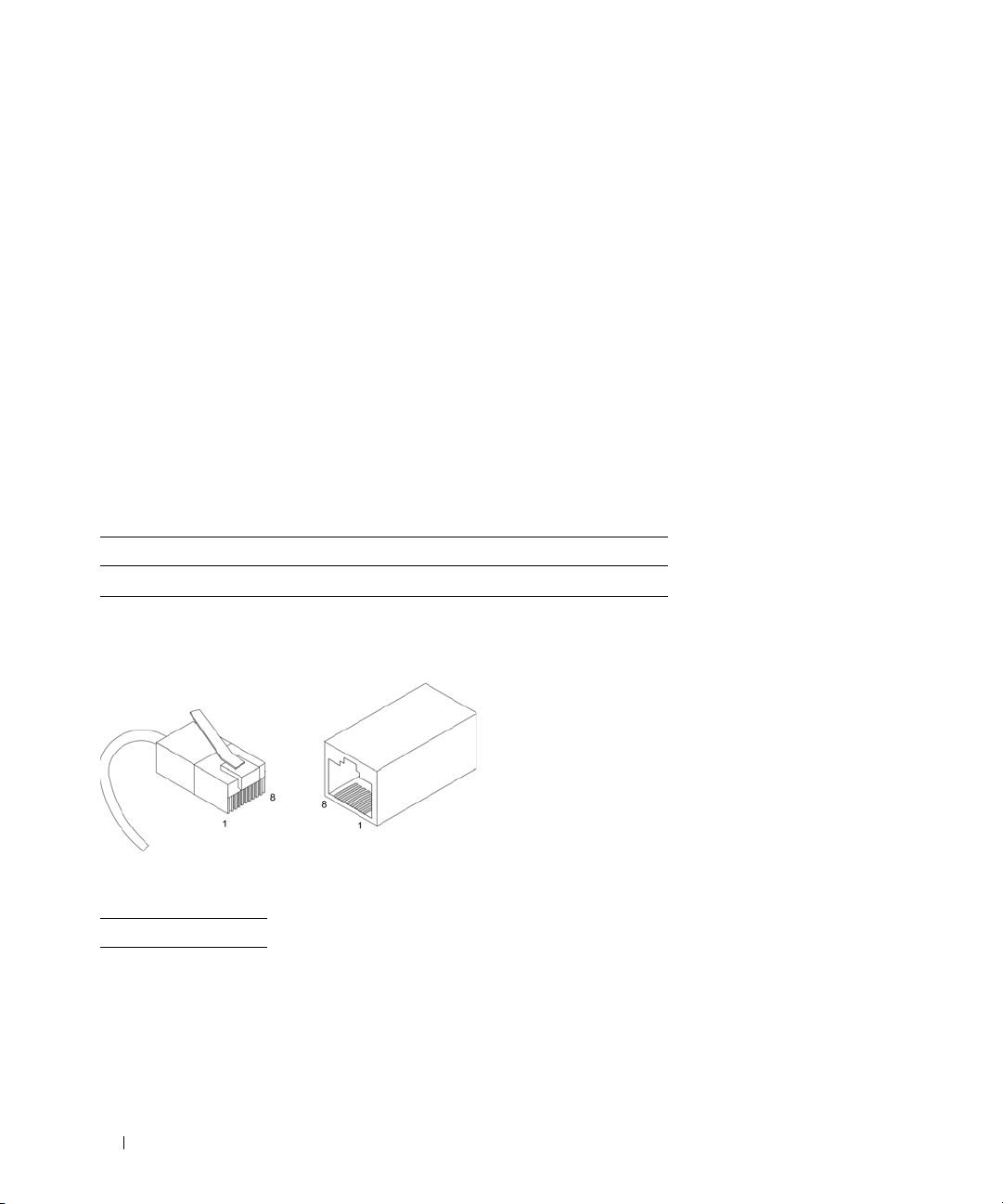
The following figure illustrates the RJ-45 pin connector pin numbers.
Figure 2-10. RJ-45 Pin Numbers
The RJ-45 pin number allocation for the 10/100/1000BASE-T ports is listed in the following table.
Table 2-7. RJ-45 Pin Number Allocation for 10/100/ 1000BASE-T Ethernet Port
Pin No Function
1 TxRx 1+
2 TxRx 1-
3 TxRx 2+
4 TxRx 2-
5 TxRx 3+
24 Dell PowerConnect 28xx Systems User Guide
Page 25

Table 2-7. RJ-45 Pin Number Allocation for 10/100/ 1000BASE-T Ethernet Port
Pin No Function
6 TxRx 3-
7 TxRx 4+
8 TxRx 4-
SFP Ports
The PowerConnect 2824 switch supports two SFP transceivers combo ports, and the PowerConnect 2848
switch supports four SFP transceivers combo ports for various fiber-based modules (1000BASE-SX or
1000BASE-LX). Only one of the two physical connections of a combo port can be used at any time. The
system can switch from the RJ-45 to the SFP (or vice versa) without a system reset. The system
automatically detects the media used on a combo port, and utilizes this information in the control
interfaces.
PowerConnect 2824 switch supports SFP diagnostics. The optical transceiver provides access to a set of
parameters that can be monitored and displayed to the system administrator.
NOTE: If both RJ-45 and SFP ports are present, the SFP port will be the active port, whereas the RJ-45 port will be
disabled and ignored.
The pin number allocation for the SFP ports is listed in the following table.
Table 2-8. SFP Pin Connections
Pin No Use
1 Transmitter ground (common with receiver ground)
2 Transmitter fault
3 Transmitter disable; laser output disabled on high or open.
4 Module definition 2; data line for serial ID.
5 Module definition 1; clock line for serial ID.
6 Module definition 0; grounded within the module.
7 Rate select; no connection required.
8 Loss of signal indication; logic 0 indicates normal operation.
9 Receiver ground (common with transmitter ground)
10 Receiver ground (common with transmitter ground)
11 Receiver ground (common with transmitter ground)
12 Receiver inverted data out; AC coupled.
13 Receiver non-inverted data out; AC coupled.
14 Receiver ground (common with transmitter ground)
Dell PowerConnect 28xx Systems User Guide 25
Page 26

Table 2-8. SFP Pin Connections
Pin No Use
15 Receiver power supply
16 Transmitter power supply
17 Transmitter ground (common with receiver ground)
18 Transmitter non-inverted data in
19 Transmitter inverted data in
20 Transmitter ground (common with receiver ground)
Power Connectors
The PowerConnect 28xx is powered by using the AC internal power supply.
Internal Power Supply Connector
The PowerConnect 28xx supports a single internal power supply to provide power for switching
operations. The internal power supply supports input voltages between 100 and 240 VAC. The AC power
connector is located on the back panel of the switch.
26 Dell PowerConnect 28xx Systems User Guide
Page 27

Installing the PowerConnect Device
This section contains information about device unpacking, location, installation, and cable
connections.
Installation Precautions
CAUTION Before performing any of the following procedures, read and follow the safety instructions located
in the
System Information Guide
CAUTION Observe the following points before performing the procedures in this section:
• Ensure that the rack or cabinet housing the device is adequately secured to prevent it from
becoming unstable and/or falling over.
• Ensure that the power source circuits are properly grounded.
• Observe and follow the service markings. Do not service any device except as explained in the
system documentation. Opening or removing covers marked with a triangular symbol with a
lighting bolt may cause electrical shock. These components are to be serviced by trained service
technicians only.
• Ensure that the power cable, extension cable, and/or plug is not damaged.
• Ensure that the device is not exposed to water.
• Ensure that the device is not exposed to radiators and/or heat sources.
• Ensure that the cooling vents are not blocked.
• Do not push foreign objects into the device, as it may cause a fire or electric shock.
• Use the device only with approved equipment.
• Allow the device to cool before removing covers or touching internal equipment.
• Ensure that the device does not overload the power circuits, wiring, and over-current protection.
To determine the possibility of overloading the supply circuits, add together the ampere ratings of
all switches installed on the same circuit as the device. Compare this total with the rating limit for
the circuit.
• Do not install the device in an environment where the operating ambient temperature might
exceed 45ºC (113ºF).
• Ensure that the airflow around the front, sides, and back of the device is not restricted.
included in the Dell Documentation.
3
Dell PowerConnect 28xx Systems User Guide 27
Page 28

Site Requirements
The PowerConnect 28xx can be mounted in a standard equipment rack, placed on a tabletop, or
mounted on the wall.
Before installing the device, verify that the site selected for the device meets the following site
requirements:
•
Power
— The device is installed within 1.5 m (5 feet) of a grounded, easily accessible outlet 220/110
VAC, 50/60 Hz. If the device has two power supplies, the site should have two power outlets with
different power feeders.
•
General
•
Clearance
power connections, and ventilation.
•
Cabling
amplifiers, power lines, and fluorescent lighting fixtures.
•
Ambient Requirements
113 °F) at a relative humidity of up to 95%, non-condensing. Verify that water or moisture cannot enter
the device case.
— Ensure that the power supply is correctly installed.
— There is adequate frontal clearance for operator access. Allow clearance for cabling,
— Cabling is routed to avoid sources of electrical noise such as radio transmitters, broadcast
— The ambient device operating temperature range is 0 to 45 °C (32 to
Unpacking
Package Contents
While unpacking the device, ensure that the following items are included:
•The device
• AC power cable
• Self-adhesive rubber pads (for on-shelf installation)
• Rack-mount kit for installation
• Documentation CD
• Product Information Guide
Unpacking the Device
To unpack the PowerConnect device:
NOTE: Before unpacking the device, inspect the packaging and report any evidence of damage.
1
Place the box on a clean flat surface.
2
Open the box or remove the box top.
3
Carefully remove the device from the package and place it on a secure, stable and clean surface.
4
Remove all packing material.
28 Dell PowerConnect 28xx Systems User Guide
Page 29

5
Inspect the product for damage. Report any damage immediately.
Mounting the Device
Overview
There are three device mounting options:
• Installing in a Rack
• Installing on a Flat Surface
• Installing on a Wall
Device Rack Installation
CAUTION Read the safety information in the Product Information Guide as well as the safety information for other
devices that connect to or support the switch.
CAUTION Disconnect all cables from the device before mounting the device in a rack or cabinet.
CAUTION When mounting multiple devices into a rack, mount the devices from the bottom up.
Install the device in a rack as follows:
1
Place the supplied rack-mounting bracket on one side of the device ensuring the mounting holes on
the device line up to the mounting holes on the rack mounting bracket. The following figure illustrates
where to mount the brackets.
Dell PowerConnect 28xx Systems User Guide 29
Page 30
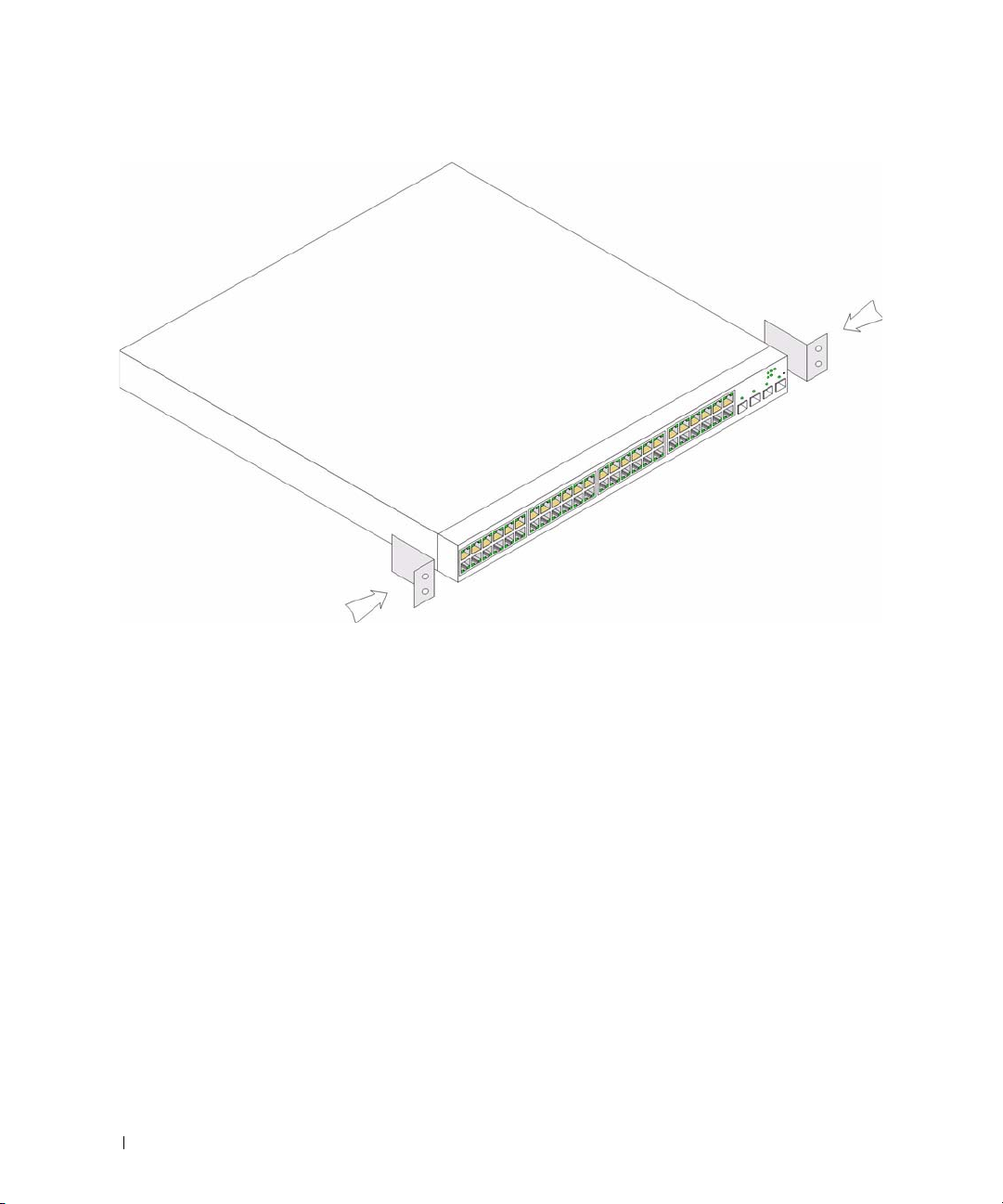
Figure 3-1. Bracket Installation for Rack Mounting
2
Insert the supplied screws into the rack mounting holes and tighten with a screwdriver.
3
Repeat the process for the rack-mounting bracket on the other side of the device.
4
Insert the device into the rack, ensuring the rack-mounting holes on the device line up to the
mounting hole on the rack.
5
Secure the device to the rack with the rack screws (not provided). Fasten the lower pair of screws before
the upper pair of screws. Ensure that the ventilation holes are not obstructed.
Installing on a Flat Surface
The device must be installed on a flat surface if it is not installed on a rack. The surface must be able to
support the weight of the device and the device cables.
1
Attach the self-adhesive rubber pads (provided with the device) on each marked location on the
bottom of the chassis.
2
Set the device on a flat surface, while leaving 2 inches (5.08 cm) on each side and 5 inches (12.7 cm) at
the back.
3
Ensure that the device has proper ventilation.
30 Dell PowerConnect 28xx Systems User Guide
Page 31

Installing on a Wall
To mount the device on a wall:
1
Ensure that the mounting location meets the following requirements:
• The surface of the wall must be capable of supporting the device.
• Allow at least 2 inches (5.1 cm) space on the sides for proper ventilation and 5 inches (12.7 cm) at
the back for power cable clearance.
• The location must not be exposed to direct sunlight.
• The location must be at least 2 feet (61 cm) away from any heating vents, and no area-heating
vent should point towards the device.
• The location must be ventilated to prevent heat buildup.
• Do not locate the device near any data or electrical cabling.
• The power cable must be able to reach an outlet.
2
Place the supplied wall-mounting bracket on one side of the device, ensuring that the mounting holes
on the device line up to the mounting holes on the rack-mounting bracket. The following figure
illustrates where to mount the brackets.
Figure 3-2. Bracket Installation for Wall Mounting
3
Insert the supplied screws into the rack-mounting holes and tighten with a screwdriver.
4
Repeat the process for the wall-mounting bracket on the other side of the device.
5
Place the device on the wall in the location where the device is being installed.
Dell PowerConnect 28xx Systems User Guide 31
Page 32

6
On the wall mark the locations where the screws to hold the device must be prepared.
7
On the marked locations, drill the holes and place all plugs (not provided) in the holes.
8
Secure the device to the wall with screws (not provided). Ensure that the ventilation holes are not
obstructed.
Figure 3-3. Mounting Device on a Wall
Connecting the Device
To configure the device, the device must be connected to a terminal.
Connecting the Device to the Network
To connect to an uplink port, use Category 5 Unshielded Twisted-Pair (UTP) cables with RJ-45
connectors at both ends. The RJ-45 ports on the Ethernet device support automatic Media-Dependent
Interface/Media-Dependent Interface with internal crossover wiring (MDI/MDIX) operation under
Auto-Negotiation mode. Standard straight-through twisted-pair cables can be used to connect to any
other Ethernet network (systems, servers, switches or routers) that supports auto-negotiation.
32 Dell PowerConnect 28xx Systems User Guide
Page 33

NOTE: Do not plug a phone jack connector into an RJ-45 port. This will damage the Ethernet device. Use only
twisted-pair cables with RJ-45 connectors that conform to FCC standards.
NOTE: If auto negotiation is turned off on the ports, a straight through cable must be used.
To connect the device to the network:
1
Attach one end of a Twisted-Pair cable to the device’s RJ-45 connector and the other end to a switch or
server.
2
Make sure each twisted pair cable does not exceed 328 feet (100 meters) in length.
As each connection is made, the link LED corresponding to each port on the device is illuminated (green
or amber) indicating that the connection is valid.
Connecting the Terminal to the Device
The device provides an external console port in models 28016/24/48. The console port enables a
connection to a terminal desktop system running terminal emulation software for monitoring and
configuring the device.
The Console port connector is a male DB-9 connector, implemented as a data terminal equipment
(DTE) connector..
To use the Console port, the following is required:
• VT100 compatible terminal or a desktop or portable system with a serial port and running VT100
terminal emulation software.
• An RS-232 crossover cable with a female DB-9 connector for the Console port and the appropriate
connector for the terminal.
To connect a terminal to the device Console port, perform the following:
1
Connect the supplied RS-232 crossover cable to the terminal running VT100 terminal emulation
software.
2
Ensure that the terminal emulation software is set as follows:
a
Select the appropriate serial port (serial port 1 or serial port 2) to connect to the console.
b
Set the data rate to 9600 baud.
c
Set the data format to 8 data bits, 1 stop bit, and no parity.
d
Set flow control to none.
e
Under Properties, select VT100 for Emulation mode.
f
Select Terminal keys for Function, Arrow, and Ctrl keys. Ensure that the setting is for Terminal
keys (not Windows keys).
NOTE: When using HyperTerminal with Microsoft® Windows 2000, Windows XP, or Windows Vista, ensure that
you have the latest service packs installed. With Windows 2000 Service Pack 2, the arrow keys function properly in
HyperTerminal’s VT100 emulation. Go to
Windows Vista service packs.
www.microsoft.com
for information on Windows 2000, Windows XP, and
Dell PowerConnect 28xx Systems User Guide 33
Page 34

3
Connect the female connector of the RS-232 crossover cable directly to the device Console port on the
device, and tighten the captive retaining screws. The Console port is located on the back panel.
Connecting to Console Port
Connecting a Device to a Power Supply
1
Connect the supplied standard AC power cable to the AC connector on the back panel.
2
Do not connect the power cable to a grounded AC outlet at this time. Connect the device to a power
source in the steps detailed in Starting and Configuring the Device.
Figure 3-4. Connecting to Power Supply
3
After connecting the device to a power source, confirm that the device is connected and operating
correctly by examining the LEDs on the front panel.
34 Dell PowerConnect 28xx Systems User Guide
Page 35

Port Connections, Cables, and Pinout Information
This section explains the device’s physical interfaces, and provides information about port connections.
Connector types, ports and cables are summarized in Ports, Connectors, and Cables. Copper Cable and
Optical Transceiver Diagnostics are supported.
RJ-45 Connections for 10/100/1000BaseT Ports
The 10/100/1000BaseT ports are copper twisted-pair ports.
To establish a link for the twisted-pair ports, Tx pair on one cable end must be connected to the Rx pair
on the other cable end, and vice versa. If the cabling is done such that Tx on one end is wired to Tx on
the other end, and Rx is wired to Rx, a link is not established.
When selecting cables to connect the device ports to their networking peers, straight through cables must
be used to connect the device to a station, and crossover cables must be used to connect one transmission
device (switch or hub) to another. Both the straight through and crossover cables are category 5.
After a port is connected, its LINK indication LED is lit.
Table 3-1. Ports, Connectors and Cables
Connector Port/Interface Cable
RJ-45 10/100/1000BaseT Port Cat.5
The RJ-45pin number allocation for the 10/100/1000BaseT ports is listed in the table following.
Table 3-2. RJ-45 Pin Number Allocation for 10/100/1000BaseT Ethernet Port
Pin No Functi on
1 TxRx 1+
2 TxRx 1-
3 TxRx 2+
4 TxRx 2-
5 TxRx 3+
6 TxRx 3-
7 TxRx 4+
8 TxRx 4-
Dell PowerConnect 28xx Systems User Guide 35
Page 36

Port Default Settings
The general information for configuring the device ports includes the short description of the autonegotiation mechanism and the default settings for switching ports.
Auto-Negotiation
Auto-negotiation enables automatic detection of speed, duplex mode and flow control on switching
10/100/1000BaseT ports. Auto-negotiation is enabled per port by default.
Auto-negotiation is a mechanism established between two link partners to enable a port to advertise its
transmission rate, duplex mode and flow control (the flow control by default is enabled) abilities to its
partner. The ports then both operate at the highest common denominator between them.
If connecting a NIC that does not support auto-negotiation or is not set to auto-negotiation, both the
device switching port and the NIC must be manually set to the same speed and duplex mode.
If the station on the other side of the link attempts to auto-negotiate with a device 10/100/1000BaseT
port that is configured to full duplex, the auto-negotiation results in the station attempting to operate in
half duplex.
MDI/MDIX
The device supports auto-detection of straight through and crossed cables on all switching
10/100/1000BaseT ports. The feature is part of the Auto-negotiation and is enabled when Auto-negotiation
is enabled.
When the MDI/MDIX (Media Dependent Interface with Crossover) is enabled, the automatic
correction of errors in cable selection is possible, making the distinction between a straight through cable
and a crossover cable irrelevant. (The standard wiring for end stations is known as MDI (Media
Dependent Interface), and the standard wiring for hubs and switches is known as MDIX.)
Flow Control
The device supports 802.3x Flow Control for ports configured with the Full Duplex mode. By default,
this feature is enabled. It can be enabled per port. The flow control mechanism allows the receiving side
to signal to the transmitting side that transmission must temporarily be halted to prevent buffer
overflow.
Back Pressure
The device supports back pressure for ports configured to half duplex mode. By default, this feature is
disabled. It can be enabled per port. The back pressure mechanism prevents the transmitting side from
transmitting additional traffic temporarily. The receiving side may occupy a link so it becomes
unavailable for additional traffic.
36 Dell PowerConnect 28xx Systems User Guide
Page 37

Switching Port Default Settings
The following table gives the port default settings.
Table 3-3. Port Default Settings
Function Default Setting
Port speed and mode 10/100/1000BaseT copper: auto-negotiation full duplex
Port forwarding state Enabled
Port tagging No tagging
Flow Control On
Back Pressure Off (disabled on ingress)
MDIX (not user-configurable) On (relevant to coppers ports only)
Dell PowerConnect 28xx Systems User Guide 37
Page 38

38 Dell PowerConnect 28xx Systems User Guide
Page 39

Starting and Configuring the Device
After completing all external connections, procede as follows:
• If the device is to be used as an unmanaged switch, there is no need for a terminal connection.
• A terminal connection is required if the device is to be used in a managed mode.
NOTE: The PowerConnect 2808 has an internal serial port.
NOTE: Before proceeding, read the release notes for this product. The release notes can be downloaded
from http://support.dell.com.
NOTE: It is recommended that you obtain the most recent revision of the user documentation from the Dell
support website at http://support.dell.com.
After completing all external connections, connect a terminal to the device to configure the device
and for other procedures. For initial configuration, the standard device configuration is performed.
4
Dell PowerConnect 28xx Systems User Guide 39
Page 40

Figure 4-1. Installation and Configuration Flow
Connect Device and
Console
Power On
Suspend
Bootup
Yes
Press Esc
Startup Menu (Special
Functions)
Reboot
No
Loading Program from
flash to RAM
Enter Wizard
Yes
No
Initial Configuration:
IP Address, Subnet
mask, Users Basic
Security Configuration
Wizard Configuration
Process
Advanced Configuration:
IP Address from DHCP
Standard
Device
Installation
Advanced
Device
Installation
Hardware
Setup
Booting the Device - Managed Mode
The procedure described in this section refers to the device when set to operate as a managed switch.
The PowerConnect 2808/16/24/48 models include a built-in dual purpose Mode Button. To change between
managed and unmanaged modes, press the Mode Button for less than seven seconds.
Once the device is set to operate as a managed switch the boot procedure can be monitored on the
connected terminal as follows:
1
Ensure that the device console port is connected to a VT100 terminal device or VT100 terminal
emulator via the RS-232 crossover cable.
2
Locate an AC power receptacle.
40 Dell PowerConnect 28xx Systems User Guide
Page 41

3
Deactivate the AC power receptacle.
4
Connect the device to the AC receptacle.
5
Activate the AC power receptacle.
When the power is turned on with the local terminal already connected, the device goes through Power
On Self Test (POST). POST runs every time the device is initialized and checks hardware components to
determine if the device is fully operational before completely booting. If a critical problem is detected,
the program flow stops. If POST passes successfully, a valid executable image is loaded into RAM. POST
messages are displayed on the terminal and indicate test success or failure.
The boot process runs less than 45 seconds when in unmanaged mode (and approximately 90 seconds
when in other modes.
Initial Configuration - Managed Mode
The information and procedures described in this section apply to the dewvice when set as a Managed
Mode switch.
NOTE: The switch is factory-set in Unmanaged Mode.
NOTE: The initial simple configuration uses the following assumptions:
• The PowerConnect device was never configured before, and is in the same state as when you received it.
• The PowerConnect device booted successfully.
• The console connection is established and the console prompt is displayed on the screen of a VT100 terminal
device. (Press the <Enter> key several times to verify that the prompt displays correctly.)
The initial device configuration is through the Serial port. After the initial configuration, the device can
then be managed either from the already connected Serial port or remotely through an interface defined
during the initial configuration.
The system prompts you to use the Set-up wizard when the device boots up for the first time or if the
configuration file is empty because the device is not configured. The Setup Wizard provides guidance
through the initial device configuration, and gets the device up and running as quickly as possible.
NOTE: Obtain the following information from your network administrator before configuring the device:
• SNMP Community String and SNMP Management System IP address (optional).
• Username and Password.
• The IP address to be assigned to the VLAN 1 interface through which the device is to be managed (by default,
every external and internal port is a member of the VLAN 1)
• The IP subnet mask for the network
• The default gateway (next hop router) IP address for configuring the default route.
The Setup Wizard guides you through the initial device configuration, and gets the system up and running
as quickly as possible. You can skip using the setup wizard and configure the device manually through the
device CLI mode (see "Managing the Device Using the CLI" on page 157.
The Setup Wizard configures the following fields.
Dell PowerConnect 28xx Systems User Guide 41
Page 42

• SNMP Community String and SNMP Management System IP address (optional)
• Username and Password
• Device IP address
• IP subnet mask
• Default Gateway IP address
The Setup Wizard displays the following information:
Welcome to Dell Easy Setup Wizard.
The Setup Wizard guides you through the initial switch configuration,
and gets you up and running as quickly as possible. You can skip the
setup wizard, and enter CLI mode to manually configure the switch.
The system will prompt you with a default answer; by pressing enter,
you accept the default. You must respond to the next question to run
the setup wizard within 60 seconds, otherwise the system will
continue with normal operation using the default system
configuration.
Would you like to enter the setup wizard (you must answer this
question within 60 seconds)? (Y/N)[Y] Y
If you select not to use the Setup Wizard, you can access the Web inteface by using the default IP
NOTE:
address/mask (192.168.2.1/255.255.255.0).
NOTE: You can exit the Setup Wizard at any time by entering [Ctrl+Z].
Wizard Step 1
The following information displays:
The system is not setup for SNMP management by default.
To manage the switch using SNMP (required for Dell Network Manager)
you can:
*Setup the initial SNMP Version 2 account now
*Return later and setup additional SNMP v1/v2 accounts
For more information on setting up SNMP accounts, please see the user
documentation.
Would you like to setup the SNMP management interface now? (Y/N)[Y] Y
Enter [N] to skip to Step 2.
Enter [Y] to continue the Set-up wizard. The following information displays:
42 Dell PowerConnect 28xx Systems User Guide
Page 43

To setup the SNMP management account you must specify the management
system IP address and the "community string" or password that the
particular management system uses to access the switch. The wizard
automatically assigns the highest access level [Privilege Level 15]
to this account.
You can use Dell Network Manager or CLI to change this setting, and
to add additional management systems. For more information on adding
management systems, see the user documentation.
To add a management station:
Please enter the SNMP community string to be used:
[Dell_Network_Manager]
Please enter the IP address of the Management System (A.B.C.D) or wildcard(0.0.0.0) to manage from
any Management Station:[0.0.0.0]
Wizard Step 2
The following information displays:
Now we need to setup your initial privilege (Level 15) user account.
This account is used to login to the CLI, Telnet and Web interface.
You may setup other accounts and change privilege levels later.
For more information on setting up user accounts and changing
privilege levels,see the user documentation.
To setup a user account:
Enter the user name<1-20>:[admin]
Please enter the user password:*****
Please reenter the user password:*****
Wizard Step 3
The following information displays:
Next, an IP address is setup.
The IP address is defined on the default VLAN ,(VLAN #2) . This is
the IP address you use to access the Telnet, Web interface, or SNMP
interface for the switch. To setup an IP address:
Please enter the IP address of the device (A.B.C.D):10.6.22.100
Please enter the IP subnet mask (A.B.C.D or nn):[255.255.255.224]
Dell PowerConnect 28xx Systems User Guide 43
Page 44

Wizard Step 4
The following information displays:
Finally, setup the default gateway.
Please enter the IP address of the gateway from which this network is
reachable(e.g. 192.168.1.1).Default gateway (A.B.C.D):[10.6.22.97]
Enter the default gateway.
Press Enter. The following is displayed (as per the example parameters described):
This is the configuration information that has been collected:
==============================================================
SNMP Interface = Dell_Network_Manager@0.0.0.0
User Account setup = admin
Password = **********
Management IP address = 10.6.22.100 255.255.255.224
Default Gateway is 10.6.22.97
==============================================================
Wizard Step 5
The following information displays:
If the information is correct, please select (Y) to save the
configuration, and copy to the start-up configuration file. If the
information is incorrect,select (N) to discard configuration and
restart the wizard: (Y/N)[Y] Y
Configuring SNMP management interface.
Configuring user account.......
Configuring IP and subnet......
Thank you for using Dell Easy Setup Wizard.
Advanced Configuration
This section provides information about dynamic allocation of IP addresses.
When configuring/receiving IP addresses through DHCP, the configuration received from the server
includes the IP address, and may include subnet mask and default gateway.
44 Dell PowerConnect 28xx Systems User Guide
Page 45

Retrieving an IP Address From a DHCP Server
When using the DHCP protocol to retrieve an IP address, the device acts as a DHCP client. When the
device is reset, the DHCP command is saved in the configuration file, but not the IP address. To
configure the device so it will retrieve an IP address from a DHCP server, use the web interface (see
"Defining DHCP Server Settings" on page 83).
NOTE: It is not necessary to delete the device configuration to retrieve an IP address from the DHCP server.
Startup Procedures
Startup Menu Procedures
The procedures called from the Startup menu cover software download, flash handling and password
only
recovery. The diagnostics procedures are for use by technical support personnel
in the document.
The Startup menu can be entered when booting the device – a user input must be entered immediately
after the POST test.
To enter the Startup menu:
1
Turn the power on and watch for the auto-boot message.
**************************************************
***************** SYSTEM RESET *****************
**************************************************
and are not disclosed
------ Performing the Power-On Self Test (POST) ------
UART Channel Loopback Test........................PASS
Testing the System SDRAM..........................PASS
Boot1 Checksum Test...............................PASS
Boot2 Checksum Test...............................PASS
Flash Image Validation Test.......................PASS
BOOT Software Version 1.0.0.20 Built 22-Jan-xxxx 15:09:28
Dell PowerConnect 28xx Systems User Guide 45
Page 46

Processor: FireFox 88E6218 ARM946E-S , 64 MByte SDRAM.
I-Cache 8 KB. D-Cache 8 KB. Cache Enabled.
Autoboot in 2 seconds - press RETURN or Esc. to abort and enter prom.
Preparing to decompress...
2
When the auto-boot message appears, press <Enter> to get the Startup menu. The Startup menu
procedures can be done using the ASCII terminal or Windows HyperTerminal.
[1] Download Software
[2] Erase Flash File
[3] Password Recovery Procedure
[4] Enter Diagnostic Mode
[5] Set Terminal Baud-Rate
[6] Back
Enter your choice or press 'ESC' to exit
The following sections describe the available Startup menu options.
NOTE: When selecting an option form the Startup menu, time out must be taken into account: if no selection is
made within 35 seconds (default), the device times out. This default value can be changed through CLI.
Software Download
The software download procedure is performed when a new version must be downloaded to replace the
corrupted files, update or upgrade the system software. To download software from the Startup menu:
1
From the Startup menu,
press [1]
. The following prompt appears:
Downloading code using XMODEM
2
When using the HyperTerminal, click
3
In the
Filename
4
Ensure that the
5
Press
Send
NOTE: After software download, the device reboots automatically.
NOTE: The length of time taken by the download varies according to the tool used.
field, enter the file path for the file to be downloaded.
Xmodem
protocol is selected in the
. The software is downloaded.
Tr an sf e r
on the HyperTerminal Menu Bar.
Protocol
field.
Erase FLASH File
In some cases, the device configuration must be erased. If the configuration is erased, all parameters
configured via CLI, EWS or SNMP must be reconfigured.
46 Dell PowerConnect 28xx Systems User Guide
Page 47

Erasing the Device Configuration
1
From the Startup menu,
displayed:
Warning! About to erase a Flash file.
Are you sure (Y/N)? y
2
Press Y. The following message is displayed.
Write Flash file name (Up to 8 characters, Enter for none.):config
File config (if present) will be erased after system initialization
======== Press Enter To Continue ========
3
Enter
config
4
Repeat the device initial configuration.
as the name of the flash file. The configuration is erased and the device reboots.
press [2]
within two seconds to erase flash file. The following message is
Password Recovery
If a password is lost, the Password Recovery procedure can be called from the Startup menu. The
procedure enables entry to the device once without password.
To recover a lost password for the local terminal only:
1
From the Startup menu, type 3
The password is deleted.
NOTE: To ensure device security, reconfigure passwords for applicable management methods.
and press <Enter>.
Software Download Through TFTP Server
This section contains instructions for downloading device software (system and boot images) through a
TFTP server. The TFTP server must be configured before beginning to download the software.
System Image Download
The device boots and runs when decompressing the system image from the flash memory area where a
copy of the system image is stored. When a new image is downloaded, it is saved in the other area
allocated for the other system image copy.
On the next boot, the device will decompress and run the currently active system image unless chosen
otherwise.
To download a system image through the TFTP server:
1
Ensure that an IP address is configured on one of the device ports and pings can be sent to a TFTP
server.
2
Make sure that the file to be downloaded is saved on the TFTP server (the
Dell PowerConnect 28xx Systems User Guide 47
ros
file).
Page 48

3
Enter
copy tftp://{tftp address}/{file name} i mage
to copy a new system image to the
device. When the new image is downloaded, it is saved in the area allocated for the other copy of system
image. The following is an example of the information that appears:
console# copy tftp://176.215.31.3/file1.ros image
Accessing file ‘file1’ on 176.215.31.3Ö
Loading file1 from 176.215.31.3:
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Copy took 00:01:11 [hh:mm:ss]
Exclamation symbols indicate that a copying process is in progress. Each symbol (!) corresponds to
512 bytes transferred successfully. A period indicates that the copying process is timed out. Many
periods in a row indicate that the copying process failed.
4
Enter the
console# reload
This command will reset the whole system and disconnect your current
session. Do you want to continue (y/n) [n]?
5
Enter y. The device reboots.
Boot Image Download
reload
command. The following message is displayed:
Loading a new boot image from the TFTP server and programming it into the flash updates the boot
no
image. The boot image is loaded when the device is powered on. A user has
control over the boot
image copies. To download a boot image through the TFTP server:
1
Ensure that an IP address is configured on one of the device ports and pings can be sent to a
TFTP server.
2
Ensure that the file to be downloaded is saved on the TFTP server (the
3
Enter
copy tftp://{tftp address}/{file name} boot
rfb
file).
to copy the boot image to the
device. The following is an example of the information that appears:
console# copy tftp://176.215.31.3/332448-10018.rfb boot
Erasing file..done.
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Copy: 2739187 bytes copied in 00:01:13 [hh:mm:ss]
4
Enter the
reload
command. The following message is displayed:
console# reload
This command will reset the whole system and disconnect your current
48 Dell PowerConnect 28xx Systems User Guide
Page 49

session. Do you want to continue (y/n) [n]?
5
Enter y.
The device reboots.
Management Modes
The device supports the following modes:
•
Managed Mode
you can move to Unmanaged mode by pressing the Mode button on the device, or you can move to
Secure mode using the web interface (see "Entering Secure Mode" on page 63). Before leaving
Managed mode it is highly recommended to save the configuration (see "Uploading Files" on page 82).
Unmanaged Mode
•
web management interface, the CLI works in debug mode only; and there is no configuration in the
CDB—default configuration is used. From this mode, you can return to Managed mode by pressing
the Mode button on the device.
Secure Mode
•
configuration changes by removing the IP address of the device so that it becomes inaccessible for
configuration. In this mode, no web management interface is available, and CLI works in debug mode
only. From this mode, you can return to Managed mode by pressing the Mode button on the device.
All modes are maintained through power cycles. The Managed Mode LED provides an indication of the
current mode (see "On the PowerConnect 28xx front panel there is a Managed Mode LED monitoring
the switch node as well as indicating diagnostic test results. The following table describes the Managed
Mode LED indications. For more information about management modes and transitioning between
them, see "Management Modes" on page 50." on page 22).
— Provides switch management through the web interface. From Managed mode,
— In this mode, the device does not have an IP address; STP is disabled; there is no
— This mode keeps the existing configuration active, but it prevents users from making
Default Values
The factory default values, used when the device is in Unmanaged mode, include:
• IP Address — 192.168.2.1
• Netmask — 255.255.255.0
•Username — admin
• Permission — R/W privilege
•DHCP Client — Off
• Flow Control — On
•STP — Off
Dell PowerConnect 28xx Systems User Guide 49
Page 50

Transitioning Between Modes
The following diagram summarizes movement between modes:
Figure 4-2. Transitioning Between Management Modes
50 Dell PowerConnect 28xx Systems User Guide
Page 51

Returning to Managed Mode
When returning to Managed mode from either Unmanaged or Secure mode, the Restore Saved
Configuration page appears. This page can be used to retrieve a saved configuration. You can also change
the device IP address using this page.
Figure 4-3. Restore Saved Configuration
•
Local Configuration
•
Server IP Address/File Name
•
Use Saved IP/User Name/Password —
— No saved configuration is loaded.
— Loads a previously saved configuration.
When restoring local configuration, this option uses the IP
address, user name and password that were automatically saved when you exited Managed mode.
When restoring a saved configuration, this option uses the IP address, user name and password inside
the saved configuration.
Use Current IP/User Name/Password —
•
When restoring local configuration, this option uses the
system default IP address, user name and password.
•
Apply Changes
— The selected configuration is restored and the device reboots.
Dell PowerConnect 28xx Systems User Guide 51
Page 52

52 Dell PowerConnect 28xx Systems User Guide
Page 53

Using Dell OpenManage Switch Administrator
This section provides an introduction to the user interface.
Understanding the Interface
The home page contains the following views:
•
Tree View
of the features and their components.
•
Device View
device, an information or table area, and configuration instructions.
Figure 5-1. Switch Administrator Components
— Located on the left side of the home page, the tree view provides an expandable view
— Located on the right side of the home page, the device view provides a view of the
5
Table 5-1 lists the interface components with their corresponding numbers.
Dell PowerConnect 28xx Systems User Guide 53
Page 54

Table 5-1. Interface Components
Component Name
1 The tree view contains a list of the different
device features. The branches in the tree view
can be expanded to view all the components
under a specific feature, or retracted to hide the
feature's components. By dragging the vertical
bar to the right, the tree area can be expanded to
display the full name of a component.
2 The device view provides information about
device ports, current configuration and status,
table information, and feature components.
Depending on the option selected, the area at
the bottom of the device view displays other
device information and/or dialogs for configuring
parameters.
3 The components list contains a list of the feature
components. Components can also be viewed by
expanding a feature in the tree view.
4 The information buttons provide access to
information about the device and access to Dell
Support. For more information, see "Information
Buttons."
Device Representation
The PowerConnect home page contains a graphical device representation of the front panel.
Figure 5-2. Port LED Indicators
54 Dell PowerConnect 28xx Systems User Guide
Page 55

The port coloring indicates if a specific port is currently active. Ports can be the following colors:
Table 5-2. Led Indicators
Component Name
Port Indicators
Green The port is currently enabled.
Red An error has occurred on the port.
Blue The port is currently disabled.
NOTE: The Port LEDs are not reflected in PowerConnect front panel in the PowerConnect OpenManage Switch
Administrator. LED status can only be determined by viewing the actual device. For more information about LEDs,
see "LED Definitions" on page 21.
Using the Switch Administrator Buttons
This section describes the buttons found on the OpenManage Switch Administrator interface.
Information Buttons
Information buttons provide access to on-line support and online help, as well as information about the
OpenManage Switch Administrator interfaces.
Table 5-3. Information Buttons
Button Description
Support Opens the Dell Support page at
support.dell.com.
Help Online help containing information to assist in
configuring and managing the
online help pages are linked directly to the page
currently open. For example, if the IP
Addressing page is open, the help topic for that
page opens when Help is clicked.
About Contains the version and build number and Dell
copyright information.
Log Out Logs out of the application and closes the
browser window.
device
. The
Dell PowerConnect 28xx Systems User Guide 55
Page 56

Device Management Buttons
Device Management buttons provide an easy method of configuring device information, and includes
the following:
Table 5-4. Device Management Buttons
Button Description
Apply Changes Applies changes to the device.
Add Adds information to tables or dialogs.
Te ln e t Starts a Telnet session.
Query Queries tables.
Show All Displays the
Left arrow/Right arrow Moves information between lists.
Refresh Refreshes device information.
Reset All Counters Clears statistic counters.
Print Prints the Network Management System page and/or
table information.
Draw Creates statistics charts on-the-fly.
device tables.
Starting the Application
1
Open a web browser.
2
Enter the device’s IP address (as defined in the CLI) in the address bar and press <Enter>.
For information about assigning an IP address to a device, see "Static IP Address and Subnet Mask."
3
When the
management modes, see "Management Modes" on page 49.
4
Click OK.
The
Enter Network Password
NOTE: The device is not configured with a default password, and can be configured without entering a
password. For information about recovering a lost password, see “Password Recovery.
NOTE: Passwords are both case sensitive and alpha-numeric.
NOTE: The device can be managed via web interface only in Managed mode. For more information about
Dell PowerConnect OpenManage™ Switch Administrator
window opens, enter a user name and password.
home page opens.
Access Levels
When you login to the device, you are automatically assigned one of the following modes, based upon
the access level assigned to you:
56 Dell PowerConnect 28xx Systems User Guide
Page 57

•
Management
•
Monitor
— This is a read-write mode where you can see and edit all pages of the interface.
— This is a read-only mode where you can see a subset of the interface pages, but you cannot
edit them.
For more information about setting the access level, see ("Defining the Local User Databases" on
page 69).
Dell PowerConnect 28xx Systems User Guide 57
Page 58

58 Dell PowerConnect 28xx Systems User Guide
Page 59

Configuring System Information
This section provides information for defining system parameters including security features,
downloading device software, and resetting the device. To open the System page, click System in the
tree view.
Figure 6-1. System
6
Defining General Device Information
The General page contains links to pages for configuring device parameters.
Viewing Device Information
The Asset page contains parameters for configuring general device information, including the
system name, location, and contact, the system MAC Address, System Object ID, date, time, and
System Up Time. To open the Asset page, click System
→ General → Asset in the tree view.
Update with your book title 59
Page 60

Figure 6-2. Asset
•
System Name (0-159 Characters)
•
System Contact (0-159 Characters)
•
System Location (0-159 Characters)
•
MAC Address
•
Sys Object ID
— Specifies the device MAC address.
— Specifies the vendor's authoritative identification of the network management
— Defines the user-defined device name.
— Specifies the name of the contact person.
— Specifies the location where the system is currently running.
subsystem contained in the entity.
•
Service Tag
•
Asset Tag (0-16 Characters)
•
Serial No.
•
Date (DD/MMM/YY
— Specifies the service reference number used when servicing the device.
— Specifies the user-defined device reference.
— Specifies the device serial number.
) — Specifies the current date. The format is day, month, year, for example,
10/NOV/02 is November 10, 2002.
•
Time (HH:MM:SS)
— Specifies the time. The format is hour, minute, second, for example, 20:12:03
is eight twelve and three seconds in the evening.
•
System Up Time
— Specifies the amount of time since the last device reset. The system time is
displayed in the following format: Days, Hours, Minutes and Seconds. For example, 41 days, 2 hours,
22 minutes and 15 seconds.
60 Update with your book title
Page 61

Defining System Information:
1
Open the
2
Define the relevant fields.
3
Click
Asset
page.
Apply Changes
.
The system parameters are defined, and the device is updated.
Initiating a Telnet Session:
1
Open the
2
Click
Asset
Te ln et
page.
.
A Telnet session is initiated.
Viewing the Versions Page
The Ver si on s page contains information about the hardware and software versions currently running. To
open the Ve rs io ns
Figure 6-3. Versions
page, click System→ General→ Vers ion s in the tree view.
•
Software Version
•
Boot Version
•
Hardware Version
— The current software version running on the device.
— The current Boot version running on the device.
— The current hardware version.
Update with your book title 61
Page 62

Resetting the Device
The Reset page enables the device to be reset from a remote location. For more information about saved
Configuration files, see "Managing Files" on page 80
. To op en th e Reset
Reset in the tree view.
Figure 6-4. Reset
Resetting the Device
1
Open the
2
Click
Reset page
reset
.
A confirmation message displays.
3
Click OK.
The device is reset. After the device is reset, a prompt for a user name and password displays.
page, click System → General →
4
Enter a user name and password to reconnect to the Web Interface.
62 Update with your book title
Page 63

Entering Secure Mode
The Secure Mode page allows you to put the device in the
prevents users from making any further configuration changes to the switch. This is done by removing
the IP address of the switch so that it becomes inaccessible. In Secure Mode the switch retains
configuration through power cycles just like in Managed Mode.
To use Secure Mode, configure the device in Managed Mode, and then switch to Secure Mode via the
web interface. To exit Secure Mode, press the Managed Mode button on the device to enter the
Managed Mode default configuration with the default IP address of 192.168.2.1. For information about
management modes, see "Management Modes" on page 49. For information about saving Configuration
files, see "Managing Files" on page 80
.
To open the Secure Mode page, click System → General → Secure Mode in the tree view.
Figure 6-5. Secure Mode
Secure
management mode. Once enabled, it
Entering Secure Mode
1
Open the
2
Click
Secure Mode page.
Secure
.
A confirmation message displays.
3
Click OK.
The device enters Secure mode.
Update with your book title 63
Page 64

Defining Device IP Addresses
The IP Addressing page contains links for assigning interface and default gateway IP addresses, and
enabling or disabling DHCP.
To open the IP Addressing page, click System
Defining IP Interface Parameters
The IP Interface Parameters page is used to select whether the device IP address, mask and/or gateway is
assigned statically, or dynamically using DHCP. The page is also used to make static assignments, and to
approve dynamic assignments received from the DHCP server before they go into affect (until approval,
the old address is used).
To op en th e
the tree view.
Figure 6-6. IP Interface Parameters
IP Interface Parameters page, click System→ IP Addressing → IP Interface Parameters in
→ IP Addressing in the tree view.
•
DHCP
— The DHCP client can be enabled to acquire the network configuration dynamically. The
DHCP default value is Disable. This field enables the DHCP client.
•
IP Address
•
Subnet Mask
•
Default Gateway
•
DHCP IP Address
•
DHCP Subnet Mask
64 Update with your book title
— Specifies the static IP Address currently assigned to the device.
— Specifies the subnet mask of the static IP Address, currently assigned to the device.
— Specifies the static Default Gateway Address, currently assigned to the device.
— Specifies the IP Address received from the DHCP server.
— Specifies the Subnet Mask received from the DHCP server.
Page 65

•
DHCP Default Gateway
•
Apply DHCP Address
Address, received from the DHCP server.
Enabling DHCP:
1
Open the
2
Set
3
Click the
4
Click
DHCP is enabled and the device is updated.
Setting static IP Interface parameters:
1
Open the
2
Set
3
Set the
4
Click
The static interface parameters are set and the device is updated.
IP Interface Parameters
DHCP
to
Enable
Apply DHCP Address
Apply Changes
IP Interface Parameters
DHCP
to
Disable
IP Address, Subnet Mask
Apply Changes
— Defines the Default Gateway Address received from the DHCP server.
— Activates the IP Address, Subnet Mask Address, and Default Gateway
page
.
.
checkbox.
.
page
.
.
and
Default Gateway
.
.
Running Cable Diagnostics
The Diagnostics page contains links to pages for performing virtual cable tests on copper and fiber optics
cables.To open the Diagnostics page, click System → Diagnostics in the tree view.
Viewing Copper Cable Diagnostics
The Integrated Cable Test for Copper Cables page contains fields for performing tests on copper cables.
Cable testing provides information about where errors occurred in the cable, the last time a cable test
was performed, and the type of cable error which occurred. The tests use Time Domain Reflectometry
(TDR) technology to test the quality and characteristics of a copper cable attached to a port. Cables up
to 120 meters long can be tested. Cables are tested when the ports are in the down state, with the
exception of the Approximated Cable Length test. The cable length returned is an approximation in the
ranges of up to 50 meters, 50m-80m, 80m-110m, 110m-120m, or more than 120m. The deviation may be
up to 20 meters.
To open the Integrated Cable Test for Copper Cables page, click System→ Diagnostics→ Integrated
Cable Test in the tree view.
Update with your book title 65
Page 66

Figure 6-7. Integrated Cable Test for Copper Cables
•
Port
— The port to which the cable is connected.
•
Test Result
–
No Cable
–
Open Cable
–
Short Cable
–
OK
–
Fiber Cable
•
Cable Fault Distance
•
Last Update
•
Approximate Cable Length
— The cable test results. Possible values are:
— There is no cable connected to the port.
— The cable is connected on only one side.
— The cable is 2 meters long.
— The cable passed the test.
— A fiber cable is connected to the port.
— The distance from the port where the cable error occurred.
— The last time the port was tested.
— The approximate cable length. This test can only be performed when
the port is up and operating at 1 Gbps.
Performing a Cable Test
1
Ensure that both ends of the copper cable are connected to a device.
2
Open the
3
Click
Integrated Cable Test for Copper Cables
Test No w
.
The copper cable test is performed, and the results are displayed on the
Copper Cables
page.
66 Update with your book title
page.
Integrated Cable Test for
Page 67

Displaying Virtual Cable Test Results Table
1
Open the
2
Click
The
Viewing Optical Transceiver Diagnostics
Integrated Cable Test for Copper Cables
Show All
Virtual Cable Test Results Table
.
opens.
page.
The Optical Transceiver Diagnostics page contains fields for performing tests on Fiber Optic cables.
Optical transceiver diagnostics can be performed only when the link is present. To open the Optical
Transceiver Diagnostics page, click System→ Diagnostics→ Optical Transceiver Diagnostics in the tree
view.
Figure 6-8. Optical Transceiver Diagnostics
•
Port
— The port to which the fiber cable is connected.
•
Te mp e ra t ur e
•
Vo lt ag e
•
Current
•
Output Power
•
Input Power
•
Transmitter Fault
— The voltage at which the cable is operating.
— The current at which the cable is operating.
— The temperature (in Celsius) at which the cable is operating.
— The rate at which the output power is transmitted.
— The rate at which the input power is transmitted.
— Indicates if a fault occurred during transmission.
Update with your book title 67
Page 68

•
Loss of Signal
•
Data Ready
Displaying Optical Transceiver Diagnostics Test Results Table
1
Open the
2
Click
Show All
— Indicates if a signal loss occurred in the cable.
— The transceiver has achieved power up and data is ready.
Optical Transceiver Diagnostics
page.
.
The test is run and the Virtual Cable Test Results Table opens with the following columns:
•
Te mp
— Internally measured transceiver temperature.
•
Vo lt ag e
•
Current
•
Output Power
•
Input Power
•
TX Fault
— Internally measured supply voltage.
— Measured TX bias current.
— Measured TX output power in milliwatts.
— Measured RX received power in milliwatts.
— Transmitter fault.
Finisair transceivers do not support the transmitter fault diagnostic testing.
•
LOS
— Loss of signal.
•
Data Ready
•
N/A
— Not Available, N/S - Not Supported, W - Warning, E - Error.
— The transceiver has archived power up and data is ready.
Fiber Optic analysis feature works only on SFPs that support the digital diagnostic standard SFF-4872.
68 Update with your book title
Page 69

Managing Device Security
The Management Security page provides access to security pages that contain fields for setting security
parameters for user database, password and RADIUS security. To open the Management Security page
click System→Management Security in the tree view.
Defining the Local User Databases
The Local User Database page contains fields for defining users, passwords and access levels. To open the
Local User Database
Figure 6-9. Local User Database
page, click System→ Management Security→ Local User Database in the tree view.
,
•
User Name
•
Access Level
level. Users with access level 15 are Privileged Users, and only they can access and edit all pages of the
OpenManage Switch Administrator.
•
Password (0-64 Characters)
•
Confirm Password
•
Remove
Assigning Access Rights to a User:
1
Open the
2
Select a user in the
3
Define the fields.
— List of users.
— User access level. The lowest user access level is 1 and 15 is the highest user access
— User-defined password.
— Confirms the user-defined password.
— Removes users from the
Local User Database page.
User Name
field.
User Name
list, when selected.
Update with your book title 69
Page 70

4
Click
Apply Changes
.
The user access rights and passwords are defined, and the device is updated.
Defining a New User:
1
Open the
2
Click
The
Figure 6-10. Add a User
3
Define the fields.
4
Click
Local User Database page.
Add
.
Add User page opens:
Apply Changes
.
The new user is defined, and the device is updated.
Displaying the Local User Table:
1
Open the
2
Click
The
Figure 6-11. Local User Table
Deleting Users:
1
Open the
Local User Database page.
Show All.
Local User Table
opens:
Local User Database page.
70 Update with your book title
Page 71

2
Click
Show All.
The
3
Select a
4
Select the
5
Click
Local User Table
User Name.
Remove
Apply Changes
opens.
check box.
.
The selected user is deleted and the device is updated.
Configuring RADIUS Global Parameters
Remote Authorization Dial-In User Service
RADIUS servers provide a centralized authentication method for:
•Telnet Access
•Web Access
• Console to Device Access
To open the RADIUS Settings page, click System → Management Security → RADIUS in the tree view.
Figure 6-12. RADIUS Settings
(RADIUS) servers provide additional security for networks.
•
IP Address
— The list of Authentication Server IP addresses.
Update with your book title 71
Page 72

•
Priority (0-65535)
— Specifies the server priority. The possible values are 0-65535, where 0 is the
highest value. This is used to configure the order in which servers are queried.
•
Authentication Port
— Identifies the authentication port. The authentication port is used to verify
the RADIUS server authentication.
•
Number of Retries (1-10)
— Specifies the number of transmitted requests sent to RADIUS server
before a failure occurs. The possible field values are 1 - 10. Three is the default value.
•
Timeout for Reply (1-30
) — Specifies the amount of the time in seconds the device waits for an
answer from the RADIUS server before retrying the query, or switching to the next server. The possible
field values are 1 - 30. The default is 3.
•
Dead Time (0-2000)
— Specifies the amount of time (in seconds) that a RADIUS server is bypassed
for service requests. The range is 0-2000.
•
Key String (0-128 Characters)
— Specifies the Key string used for authenticating and encrypting all
RADIUS communications between the device and the RADIUS server. This key is encrypted.
•
Source IP Address
— Specifies the source IP address that is used for communication with RADIUS
servers.
If host-specific Timeouts, Retries, or Dead time values are not specified, the Global values (Defaults) are
applied to each host. The following fields set the RADIUS default values:
•
Default Retries (1-10)
— Specifies the default number of transmitted requests sent to RADIUS server
before a failure occurs.
•
Default Timeout for Reply (1-30)
— Specifies the default amount of the time (in seconds) the device
waits for an answer from the RADIUS server before timing out.
•
Default Dead time (0-2000)
— Specifies the default amount of time (in seconds) that a RADIUS
server is bypassed for service requests. The range is 0-2000.
•
Default Key String (0-128 Characters)
— Specifies the Default Key string used for authenticating and
encrypting all RADIUS communications between the device and the RADIUS server. This key is
encrypted.
•
Source Address
— Specifies the source IP address that is used for communication with RADIUS
servers.
Defining RADIUS Parameters:
1
Open the
2
Define the fields.
3
Click
RADIUS Settings
Apply Changes
.
The RADIUS setting are updated to the device.
Adding a RADIUS Server:
1
Open the
RADIUS Settings
72 Update with your book title
page.
page.
Page 73

2
Click
Add
.
The
Add RADIUS Server
Figure 6-13. Add RADIUS Server Page
3
Define the fields.
4
Click
Apply Changes
page opens:
.
The new RADIUS server is added, and the device is updated.
Displaying the RADIUS Server List:
1
Open the
2
Click
The
RADIUS Settings
Show All
.
page.
Show all RADIUS Servers page opens:
Figure 6-14. Show all RADIUS Servers
Modifying the RADIUS Server Settings:
1
Open the
RADIUS Settings
page.
Update with your book title 73
Page 74

2
Click
Show All
The
RADIUS Servers List
3
Modify the relevant fields.
4
Click
Apply Changes
The RADIUS Server settings are modified, and the device is updated.
Deleting a RADIUS Server for the RADIUS Servers List:
1
Open the
2
Click
Show All
The
RADIUS Servers List
3
Select a RADIUS Server in the
4
Select the
5
Click
Apply Changes
The RADIUS server is removed from the
.
page opens.
.
RADIUS Settings
.
page opens.
Remove check box.
.
page.
RADIUS Servers List
RADIUS Servers List
.
.
Defining SNMP Parameters
Simple Network Management Protocol (SNMP) provides a method for managing network devices.
Devices supporting SNMP run a local software (agent).
The SNMP agents maintain a list of variables, which are used to manage the device. The variables are
defined in the Management Information Base (MIB). The MIB contains the variables controlled by the
agent. The SNMP protocol defines the MIB specification format, as well as the format used to access the
information over the network.
Access rights to the SNMP agents are controlled by access strings. To communicate with the device, the
Embedded Web Server submits a valid community string for authentication. To open the SNMP page,
click System → SNMP in the tree view.
This section contains information for managing the SNMP configuration.
74 Update with your book title
Page 75

Defining SNMP Global Parameters
The SNMP Global Parameters page permits enabling both SNMP and Authentication notifications.To
open the SNMP Global Parameters page, click System → SNMP → Global Parameters in the tree view.
Figure 6-15. Global Parameters
•
SNMP Notifications
•
Authentication Notifications
authentication fails.
Enabling SNMP Notifications
1
Open the
2
Select
3
Click
SNMP Global Parameters
Enable
Apply Changes
SNMP notifications are enabled, and the device is updated.
— Enables or disables the device sending SNMP notifications.
— Enables or disables the device sending SNMP traps when
page.
in the
SNMP Notifications
field.
.
Enabling Authentication Notifications
1
Open the
2
Select Enable in the
3
Click
SNMP Global Parameters
Authentication Notifications
Apply Changes
.
page.
field.
Update with your book title 75
Page 76

Defining Communities
Access rights are managed by defining communities in the Community Table. When the community
names are changed, access rights are also changed.To open the SNMP Community page, click System →
SNMP → Community in the tree view.
Figure 6-16. SNMP Community
•
SNMP Management Station
•
Community String
— Functions as a password and used to authenticate the selected management
station to the device.
•
Access Mode
–
Read Only
— Defines the access rights of the community. The possible field values are:
— The management access is restricted to read-only, for all MIBs except the
community table, for which there is no access.
–
Read Write
— The management access is read-write, for all MIBs except the community table, for
which there is no access.
–
SNMP Admin
— The management access is read-write for all MIBs, including the community
table.
•
Remove
Defining a New Community
1
Open the
2
Click
The
— Removes a community, when selected.
SNMP Community
Add
.
Add SNMP Community
76 Update with your book title
— A list of management station IP addresses.
page.
page opens:
Page 77

Figure 6-17. Add SNMP Community
3
Select one of the following:
–
SNMP Management Station
–
All
— Defines an SNMP community for all management stations.
4
Define the remaining fields.
5
Click
Apply Changes
.
— Defines an SNMP community for a specific management station.
The new community is saved, and the device is updated.
Displaying all Communities
1
Open the
2
Click
The
Figure 6-18. Community Table
SNMP Community
Show All.
Community Table
page.
opens:
Deleting Communities
1
Open the
2
Click
The
3
Select a community from the
Community Table
Show All.
Community Table
page.
opens.
Community Table.
Update with your book title 77
Page 78

4
Select the
5
Click
The selected community entry is deleted, and the device is updated.
Remove
Apply Changes
check box.
.
Defining SNMP Notification Recipients
The Notification Recipients page contains information for defining filters that determine whether traps
are sent to specific users, and the trap type sent. SNMP notification filters provide the following services:
• Identifying Management Trap Targets
•Trap Filtering
• Selecting Trap Generation Parameters
• Providing Access Control Checks
To open the Notification Recipients page, click System → SNMP → Notification Recipient in the
tree view.
Figure 6-19. Notification Recipients
•
Recipient IP
•
Community String
station to the device.
•
Notification Version
–
SNMPv1
78 Update with your book title
— Indicates the IP address to whom the traps are sent.
— Functions as a password and used to authenticate the selected management
— Determines the trap type. The possible field values are:
— SNMP Version 1 traps are sent.
Page 79

–
SNMPv2
•
Remove Notification Recipient
Adding a new Trap Recipients
1
Open
2
Click
Add
— SNMP Version 2 traps are sent.
Notification Recipients
page.
.
— When checked, removes selected notification recipients.
The Add Notification Recipients page opens:
3
Define the relevant fields.
4
Click
Apply Changes
.
The notification recipient is added, and the device is updated.
Displaying Notification Recipients Tables
1
Open
2
Notification Recipients
Click
Show All
.
page.
The Notification Recipients Tables page opens:
Figure 6-20. Notification Recipients Tables
Deleting Notification Recipients
1
Open
Notification Recipients
page.
Update with your book title 79
Page 80

2
Click
Show All
The Notification Recipients Tables page opens.
3
Select a notification recipient.
4
Check the
5
Click
Apply Changes
.
Remove
checkbox.
. The recipient is deleted, and the device is updated.
Managing Files
The File Management page contains fields for managing device software, the Image Files, and the
Configuration Files. Files can be downloaded from a TFTP server.
The configuration file structure consists of the following configuration files:
•
Startup Configuration File
settings as when the device is powered down or rebooted.
•
Running Configuration File
during the current session. After the device is powered down or rebooted, all commands stored in the
Running Configuration file are lost. During the startup process, all commands in the Startup file are
copied to the Running Configuration File and applied to the device. During the session, all new
commands entered are added to the commands existing in the Running Configuration file.
Commands are not overwritten.
Image File
•
from the image.
To op en th e File Management page, click System → File Management in the tree view.
— System file images are saved in a Flash File called an image. The device boots and runs
— Contains the commands required to reconfigure the device to the same
— Contains all Startup file commands, as well as all commands entered
Downloading Files
The File Download From Server page contains fields for downloading system image and Configuration
files from the TFTP server or HTTP client to the device. To open the File Download From Server page,
click System → File Management → File Download in the tree view.
80 Update with your book title
Page 81

Figure 6-21. File Download From Server
•
Firmware Download —
Configuration Download
•
Configuration Download —
selected, the
•
Download via TFTP
•
Download via HTTP
Firmware Download
The Firmware file is downloaded. If
fields are grayed out.
The Configuration file is downloaded. If
— Enables initiating an image download via the TFTP server.
— Enables initiating an image download via the HTTP server.
fields are grayed out.
Firmware Download
Configuration Download
is selected, the
is
Firmware Download
•
Server IP Address —
•
Source File Name —
•
Destination File Name
possible field values are:
–
Software Image
–
Boot Code
Configuration Download
•
Server IP Address
The Server IP Address from which the firmware files are downloaded.
Indicates the file to be downloaded.
— The destination file to which the configuration file is downloaded. The
— Downloads the software image file.
— Downloads the boot file.
— The Server IP Address from which the configuration files are downloaded.
Update with your book title 81
Page 82

•
Source File Name (1-64 Characters)
— Indicates the configuration files to be downloaded.
During the image file download, a dialog box opens which displays the download progress.
Downloading Files
1
Open the
2
Define the fields.
3
Click
File Download From Server
Apply Changes
.
page.
The software is downloaded to the device.
Uploading Files
The File Upload to Server page contains fields for uploading the Configuration file from the device to
the TFTP server. To open the File Upload to Server page, click System → File Management → File
Upload in the tree view.
Figure 6-22. File Upload to Server
The File Upload to Server page contains the following fields:
•
Upload via TFTP
•
Upload via HTTP
•
TFTP Server IP Address
•
Destination File Name (1-64 Characters) —
— Enables initiating a configuration file upload via the TFTP server.
— Enables initiating a configuration file upload via the FTP server.
— The Server IP Address to which the file is uploaded.
Indicates the file path to which the file is uploaded.
82 Update with your book title
Page 83

Uploading Files
1
Open the
2
Define the fields.
3
Click
The software is uploaded to the device.
File Upload to Server
Apply Changes
page.
.
Restoring Default Settings
The Restore Defaults page allows you to restore the device settings to their factory default values. To
open the Restore Defaults page, click System → File Management → Restore Defaults in the tree view.
Figure 6-23. Restore Defaults
The Restore Defaults page contains the following field:
•
Restore Configuration Factory Defaults
Restoring Default Settings
1
Open the
2
Check the
3
Click
The settings are restored.
Restore Defaults
Restore Configuration Factory Defaults
Apply Changes
page.
.
— Sets the device settings to their factory default values.
checkbox.
Defining DHCP Server Settings
The DHCP server is used mainly for centralized control over assignment of IP addresses to attached
hosts.
A switch can operate as either a DHCP client (obtaining its own IP from a DHCP server) and as a DHCP
server.
Update with your book title 83
Page 84

The DHCP server uses a defined pool of IP addresses (user-defined) from which it allocates IP addresses
to DHCP clients.
The DHCP server can allocate IP addresses in three configuration modes:
•
Static allocation
— The network administrator maps the hardware address of a host to an IP address
on the DHCP server.
•
Permanent allocation
— An IP address received through a standard request-reply mechanism is owned
by a client permanently (unless changes in the network environment/connections take place, for any
reason).
•
Dynamic allocation
— A network device obtains a leased IP address for a specified period of time. The
IP address is revoked at the end of this period and the switch must request another IP address.
This section contains information for configuring a DHCP server on a DHCP-server-enabled switch.
To open the DHCP Server page, click System
→ DHCP Server in the tree view.
Configuring DHCP Properties
The DHCP Server Properties page contains fields for enabling the DHCP server and configuring pinging
capability. The DHCP Server pings a pool address before assigning this address to a requesting client. If
the ping is unanswered, the DHCP Server assumes (with a high probaility) that the address is not in use
and assigns the address to the requesting client. To open the DHCP Server Properties page, click System
→ DHCP Server → DHCP Server Properties in the tree view.
Figure 6-24. DHCP Server Properties
•
DHCP Server Status
–
Enable
— Enables the DHCP server.
–
Disable
— Disables the DHCP server. This is the default value.
— Indicates if the DHCP server is enabled. The possible field values are:
84 Update with your book title
Page 85

•
DHCP Ping
— Indicates if the DHCP server is set to ping the offered IP address before responding to
a client request, to ensure that the address is not in use. The possible field values are:
–
Enable
— Enables ping on the DHCP server.
–
Disable
•
DHCP Ping Retries
— Disables ping on the DHCP server. This is the default value.
— Optionally specifies the number of pings that are sent before an IP address can
be assigned to a requesting client. The range is 1 to 10 and the default value is two.
–
Use Default
•
DHCP Ping Timeout
— Reverts to the default Ping Retries setting (2 retries).
— Optionally specifies the amount of time (in milliseconds) the DHCP server
waits for a ping reply before it stops attempting to reach a pool address, prior to assigning this address
to a requesting client. Default timeout is 500 milliseconds.
–
Use Default
Enabling the DHCP Server
1
Open the
2
Select
Enable
3
Optionally, select
4
Define the number of ping retries in the
— Reverts to the default Ping Timeout (500 milliseconds).
DHCP Server Properties
in the
DHCP Server Status
Enable
in the
page.
field.
DHCP Ping
field to enable ping globally.
DHCP Ping Retries
field, or click
Use Default
to select the
default number of two retries.
5
Define the amount of time (in milliseconds) the DHCP server waits for a ping reply in the
Ping Timeout
6
Click
field, or click
Apply Changes
.
Use Default
to select the default timeout of 500 milliseconds.
The server is enabled.
DHCP
Defining Network Pool
The Network Pool page displays the DHCP Server's created pool name. The pool name, which is
typically assigned to a network segment, consists of an IP address range from which the DHCP Server
allocates IP addresses to DHCP clients. You can define the lease duration of the network pool.
To open the Network Pool page, click System
→ DHCP Server → Network Pool in the tree view.
Update with your book title 85
Page 86

Figure 6-25. Network Pool
•
Subnet IP Address
•
Network Mask
•
Prefix Length
•
Address Pool Start —
•
Address Pool End —
•
Lease Duration
— Specifies the IP address of the subnet in which the network pool resides.
— Specifies the pool’s network mask.
— Specifies the number of bits that comprise the address prefix.
Specifies the first IP address in the range of the network pool.
Specifies the last IP address in the range of the network pool.
— Specifies the amount of time a DHCP client can use an IP address from this pool.
The total lease duration is 4294967295 seconds, i.e. 49710.2696 days. Thus a lease of 49710 days, 0
hours, 0 minutes and 0 seconds is a legal value, while a lease of 49710 days, 23 hours, 59 minutes and
59 seconds results in an Out of Range alert.
Days
–
–
— Specifies the duration of the lease in number of days. The range is 0 to 49710 days.
Hours
— Specifies the number of hours in the lease. A days value must be supplied before an
hours value can be added. The range is 0 to 23 hours.
–
Minutes
— Specifies the number of minutes in the lease. A days value and an hours value must be
added before a minutes value can be added. The range is 0 to 59 minutes.
–
Infinite
•
Used Pool’s Addresses —
•
Default Router —
•
Domain Name Server —
— Specifies that the duration of the lease is unlimited.
Specifies the number of the pool’s addresses that are currently used.
Specifies the default router for the DHCP client.
Specifies the DNS server available to the DHCP client.
86 Update with your book title
Page 87

•
Domain Name —
Specifies the domain name for a DHCP client. The domain name may contain up
to 32 characters.
•
NetBIOS WINS Server —
•
NetBIOS Node Type —
Specifies the NetBIOS WINS name server available to a DHCP client.
A parameter that informs the workstation how to resolve the NetBIOS name.
Valid node types are:
–
Blank —
–
Broadcast —
The workstation is not informed as to what type of NetBIOS node the client is.
IP broadcast messages are used to register and resolve NetBIOS names to IP
addresses.
–
Peer-to-Peer —
Point-to-point communications with a NetBIOS name server are used to register
and resolve computer names to IP addresses.
–
Mixed —
A combination (mix) of b-node and p-node communications is used to register and
resolve NetBIOS names. M-node first uses b-node; then, if necessary, p-node. M-node is typically
not the best choice for larger networks because its preference for b-node broadcasts increases
network traffic.
Hybrid —
–
A hybrid combination of b-node and p-node is used. When configured to use h-node, a
computer always tries p-node first and uses b-node only if p-node fails. This is the default.
•
SNTP Server —
•
Next Server —
Specifies the time server for the DHCP client.
Specifies the IP address of the next server in the boot process of a DHCP client. If the
next server in the boot process is not configured, the DHCP Server uses inbound interface helper
addresses as boot servers.
•
Next Server Name —
Specifies the name of the next server in the boot process. The server name may
contain up to 64 characters.
•
Image File Name —
Specifies the name of the file that is used as a boot image. The file name may
contain up to 128 characters.
Excluding Addresses
By default, the DHCP Server assumes that all pool addresses may be assigned to DHCP clients. The user
can specify IP addresses that must not be used. These addresses are referred to as excluded addresses. A
single IP address or a range of IP addresses can be excluded.
The Excluded Addresses page lists the excluded addresses. To open the Excluded Addresses page, click
System
→ DHCP Server → Excluded Addresses in the tree view.
Update with your book title 87
Page 88

Figure 6-26. Excluded Addresses
•
Start IP Address —
•
End IP Address —
Adding an Excluded Address
1
Open the
2
Click
Excluded Addresses
Add
.
Displays the first IP address in the range of excluded IP addresses.
Displays the last IP address in the range of excluded IP addresses.
The Add Excluded page opens:
Figure 6-27. Add Excluded
page.
3
Define the relevant fields.
4
Click
Apply Changes
.
The address is excluded, and the device is updated.
Deleting Excluded Addresses
1
Open the
2
Check the
3
Click
Excluded Addresses
Remove
checkbox next to an address.
Apply Changes
page.
. The address is deleted, and the device is updated.
88 Update with your book title
Page 89

Manually Allocating IP Addresses (Static Hosts)
The Static Hosts page is used to manually allocate IP addresses to network hosts. To open the Static
Hosts page, click System
Figure 6-28. Static Hosts
→ DHCP Server → Static Hosts in the tree view.
•
Host Name —
Indicates the host pool name, which can be a string of symbols and an integer (for
example, piy4). The range is up to 32 characters.
•
IP Address —
•
Network Mask —
•
Prefix Length —
•
Client Identifier —
Specifies the IP address that was statically assigned to the host.
Specifies the pool’s network mask.
Specifies the number of bits that comprise the address prefix.
A unique identification of the client specified in dotted hexadecimal notation,
e.g., 01b6.0819.6811.72.
•
MAC Address —
•
Client Name —
Specifies the MAC Address of DHCP static host.
Specifies the name of the client, using a standard set of ASCII characters. The client
name must not include the domain name. The range is up to 32 characters.
•
Default Router —
•
Domain Name Server —
•
Domain Name —
Specifies the default router for the DHCP static host.
Specifies the DNS server available to the DHCP client.
Specifies the domain name for a DHCP static host. The domain name may contain
up to 32 characters.
Update with your book title 89
Page 90

•
NetBIOS WINS Server —
Specifies the NetBIOS WINS name server available to a Microsoft DHCP
static host.
•
NetBIOS Node Type —
Informs the workstation how to resolve the NetBIOS name. Valid node types
are:
–
Blank —
–
Broadcast —
The workstation is not informed as to which type of NetBIOS node the client is.
IP broadcast messages are used to register and resolve NetBIOS names to IP
addresses.
–
Peer-to-Peer —
Point-to-point communications with a NetBIOS name server are used to register
and resolve computer names to IP addresses.
–
Mixed —
A combination (mix) of b-node and p-node communications is used to register and
resolve NetBIOS names. M-node first uses b-node; then, if necessary, p-node. M-node is typically
not the best choice for larger networks because its preference for b-node broadcasts increases
network traffic.
Hybrid —
–
A hybrid combination of b-node and p-node is used. When configured to use h-node, a
computer always tries p-node first and uses b-node only if p-node fails. This is the default.
•
SNTP Server —
•
Next Server —
Specifies the time server for the DHCP static host.
Specifies the IP address of the next server in the boot process of a DHCP client. If the
next server in the boot process is not configured, the DHCP Server uses inbound interface helper
addresses as boot servers.
•
Next Server Name —
Specifies the name of the next server in the boot process. The server name may
contain up to 64 characters.
•
Image File Name —
Specifies the name of the file that is used as a boot image. The file name may
contain up to 128 characters.
Adding a new Static Host
1
Open the
2
Click
Static Hosts
Add
.
The Add Static Host page opens:
90 Update with your book title
page.
Page 91

Figure 6-29. Add Static Host
3
Define the relevant fields.
4
Click
Apply Changes
.
The static host is added, and the device is updated.
Displaying Static Hosts Tables
1
Open the
2
Click
Static Hosts
Show All
page.
.
The Static Hosts Table page opens:
Figure 6-30. Static Hosts Table
Update with your book title 91
Page 92

Deleting Static Hosts
1
Open the
2
Click
Static Hosts
Show All
page.
.
The Static Hosts Table page opens.
3
Check the
4
Click
Remove
checkbox next to a static host.
Apply Changes
. The host is deleted, and the device is updated.
Configuring Address Binding
The Address Binding page displays a list of the DHCP server’s allocated IP addresses and each IP
address’s client identifier, lease expiration time, and allocation type. Open the Address Binding page,
click System
Figure 6-31. Address Binding
→ DHCP Server → Address Binding in the tree view.
•
IP Address
•
Client Identifier
— Displays the IP addresses of the clients whose bindings are displayed.
— A unique identification of the client specified in dotted hexadecimal notation,
e.g., 01b6.0819.6811.72.
•
Lease Expiration
•
Ty p e
— Displays the manner in which the IP address was assigned to the host:
–
Static allocation
— Displays the lease expiration date and time of the host’s IP address.
— The network administrator maps the hardware address of a host to an IP
address on the DHCP server.
–
Permanent allocation
owned by a client permanently (unless changes in the network environment/connections take
place, for any reason).
–
Dynamic allocation
The IP address is revoked at the end of this period and the switch must request another IP address.
92 Update with your book title
— An IP address received through a standard request-reply mechanism is
— A network device obtains a leased IP address for a specified period of time.
Page 93

Defining Advanced Settings
The Advanced Settings page contains information for configuring general settings. Use Advanced
Settings to set miscellaneous global attributes for the device. The changes to these attributes are applied
only after the device is reset. To open the Advanced Settings page, click System
the tree view.
Configuring General Device Parameters
The General Settings page provides information for defining general device parameters.To open the
General Settings page, click System
Figure 6-32. General Settings
→ Advanced Settings → General in the tree view.
→ Advanced Settings in
•
Attribute
•
Current
•
After Reset
•
Jumbo Frames
transportation of identical data in fewer frames. This ensures less overhead, lower processing time, and
fewer interrupts.
— The general setting attribute.
— The currently configured value.
— The future (after reset) value.
— Enables or disables the Jumbo Frames feature. Jumbo Frames enable the
Update with your book title 93
Page 94

94 Update with your book title
Page 95

Configuring Device Switching
This section provides all system operation and general information for configuring network security,
ports, Address tables, GARP, VLANs, Spanning Tree, Port Aggregation, and Multicast Support.
Configuring Network Security
The device enables network security through both Access Control Lists and Locked Ports.
Port Based Authentication (802.1x)
Port based authentication enables authenticating system users on a per-port basis via a external
server. Only authenticated and approved system users can transmit and receive data. Ports are
authenticated via the RADIUS server using the Extensible Authentication Protocol (EAP). Port
Authentication includes:
•
Authenticators
•
Supplicants
services.
•
Authentication Server
performs the authentication on behalf of the authenticator, and indicates whether the user is
authorized to access system services.
Port based authentication creates two access states:
•
Controlled Access
authorized.
•
Uncontrolled Access
The device currently supports Port Based Authentication via RADIUS servers.
— Specifies the port that is authenticated before permitting system access.
— Specifies host connected to the authenticated port requesting to access the system
— Specifies the external server, for example, the RADIUS server that
— Permits communication between the user and the system, if the user is
— Permits uncontrolled communication regardless of the port state.
7
Advanced Port Based Authentication
Advanced Port Based Authentication enables multiple hosts to be attached to a single port.
Advanced Port Based Authentication requires only one host to be authorized for all hosts to have
system access. If the port is unauthorized all attached hosts are denied access to the network.
Advanced Port Based Authentication also enables user based authentication. Specific VLANs in the
device are always available, even if specific ports attached to the VLAN are unauthorized. For
example, Voice over IP does not require authentication, while data traffic requires authentication.
VLANs for which authorization is not required can be defined. Unauthenticated VLANs are
available to users, even if the ports attached to the VLAN are defined as authorized.
Update with your book title 95
Page 96

Advanced Port Based Authentication is implemented in the following modes:
•
Single Host Mode
•
Multiple Host Mode
access. Only one host must be authorized for all hosts to access the network. If the host authentication
fails or an EAPOL-logoff message is received, all attached clients are denied network access.
•
Multiple Session Mode
•
Guest VLANs
access via port-based authorization, but the Guest VLAN is enabled, the port receives limited network
access. For example, a network administrator can use Guest VLANs to deny network access via portbased authentication, but grant Internet access to unauthorized users.
To open the Network Security page select Switch → Network Security.
— Enables only the authorized host for single-session access to the port.
— Enables multiple hosts to be attached to a single port, for single-session
— Enables only the authorized host for multiple-session access to the port.
— Provides limited network access to unauthorized ports. If a port is denied network
Configuring Port Based Authentication
The Port Based Authentication page contains fields for configuring port based authentication and for
enabling Guest VLANs. To open the Port Based Authentication page, click Switch → Network Security
→ Port Based Authentication.
Figure 7-1. Port Based Authentication
•
Port Based Authentication State
field values are:
–
Enable
— Enables port based authentication on the device.
–
Disable
•
Authentication Method
96 Update with your book title
— Disables port based authentication on the device.
— Permits port based authentication on the device. The possible
— The Authentication method used. The possible field values are:
Page 97

–
None
— No authentication method is used to authenticate the port.
–
RADIUS
–
RADIUS, None
— Port authentication is performed using the RADIUS server.
— Port authentication is performed first using the RADIUS server. If the port is
not authenticated, then no authentication method is used, and the session is permitted.
•
Guest VLAN
— Specifies whether the Guest VLAN is enabled on the device. The possible field values
are:
–
Enable
— Enables using a Guest VLAN for unauthorized ports. If a Guest VLAN is enabled, the
unauthorized port automatically joins the VLAN selected in the VLAN List field.
–
Disable
•
VLAN List
•
Interface
•
User Name
•
Admin Interface Control
–
Auto
— Disables using a Guest VLAN for unauthorized ports. This is the default.
— When Guest VLAN is enabled, this field specifies which VLAN the guest will belong to.
— Contains an interface list.
— The user name as configured in the RADIUS server.
— Defines the port authorization state. The possible field values are:
— Enables port-based authentication on the device. The interface moves between an
authorized or unauthorized state based on the authentication exchange between the device and
the client.
–
ForceAuthorized
— Indicates the interface is in an authorized state without being authenticated.
The interface re-sends and receives normal traffic without client port-based authentication.
–
ForceUnauthorized
— Denies the selected interface system access by moving the interface into
unauthorized state. The device cannot provide authentication services to the client through the
interface.
•
Current Interface Control
• Authentication Type
–
802.1x Only
–
MAC Only
–
802.1x & MAC
— Sets the authentication type to 802.1x based authentication only.
— Sets the authentication type to MAC based authentication only.
— The currently configured port authorization state.
— Specifies the type of authentication on the port. The possible field values are:
— Sets the authentication type to 802.1x based authentication and MAC based
authentication.
•
Dynamic VLAN Assignment
— Indicates whether dynamic VLAN assignment is enabled for this port.
This feature allows network administrators to automatically assign users to VLANs during the RADIUS
server authentication. When a user is authenticated by the RADIUS server, the user is automatically
joined to the VLAN configured on the RADIUS server.
– Port Lock and Port Monitor should be disabled when DVA is enabled.
– Dynamic VLAN Assignment (DVA) can occur only if a RADIUS server is configured, and port
authentication is enabled and set to 802.1x multi-session mode.
– If the Radius Accept Message doesn’t contain the supplicant’s VLAN, the supplicant is rejected.
– Authenticated ports are added to the supplicant VLAN as untagged.
Update with your book title 97
Page 98

– Authenticated ports remain unauthenticated VLAN and Guest VLAN members. Static VLAN
configuration is not applied to the port.
– The following list of VLANs cannot participate in DVA: an Unauthenticated VLAN, a Dynamic
VLAN that was created by GVRP, a Voice VLAN, a Default VLAN and a Guest VLAN.
– Network administrators can delete the supplicant VLAN while the supplicant is logged in. The
supplicant is authorized during the next re-authentication if this supplicant VLAN is re-created or
a new VLAN is configured on the RADIUS server.
•
Guest VLAN
•
Periodic Reauthentication
reauthentication period is defined in the
•
Reauthentication Period (300-4294967295)
— Specifies whether the Guest VLAN is enabled on the interface.
— Reauthenticates the selected port periodically, when enabled. The
Reauthentication Period (300-4294967295) field.
— Indicate the time span in which the selected port is
reauthenticated. The field value is in seconds. The field default is 3600 seconds.
•
Reauthenticate Now
•
Authentication Server Timeout (1-65535)
— Permits immediate port reauthentication, when selected.
— Defines the amount of time that lapses before the
device resends a request to the authentication server. The field value is in seconds. The field default is
30 seconds.
•
Resending EAP Identity Request (30-65535)
— Defines the amount of time that lapses before EAP
request are resent. The field default is 30 seconds.
•
Quiet Period (0-65535)
— The number of seconds that the device remains in the quiet state following
a failed authentication exchange. The possible field range is 0-65535. The field default is 60 seconds.
•
Supplicant Timeout (1-65535)
— The amount of time that lapses before EAP requests are resent to
the user. The field value is in seconds. The field default is 30 seconds.
•
Max EAP Requests (1-10)
— The total amount of EAP requests sent. If a response is not received after
the defined period, the authentication process is restarted. The field default is 2 retries.
Displaying the Port Based Authentication Table
1
Display the
2
Click
The
Port Based Authentication
Show All
.
Port Based Authentication Table
98 Update with your book title
page.
opens:
Page 99

Figure 7-2. Port Based Authentication Table
Termination Cause — The reason for which the port authentication was terminated.
Copy To Checkbox — Copies port parameters from one port to the selected ports.
Select All — Selects all ports in the Port Based Authentication Table.
Copying Parameters in the Port Based Authentication Table
1
Open the
2
Click
The
3
Select the interface in the
4
Select an interface in the
5
Select the
Port Based Authentication page.
Show All
Port Based Authentication Table
.
opens.
Copy Parameters from
Port Based Authentication Table
field.
.
Copy to check box to define the interfaces to which the Port based authentication
parameters are copied.
6
Click
Apply Changes
The parameters are copied to the selected port in the
.
Port Based Authentication Table
is updated.
, and the device
Update with your book title 99
Page 100

Configuring Advanced Port Based Authentication
The Multiple Hosts page provides information for defining advanced port based authentication settings
for specific ports. To open the Multiple Hosts, click Switch →Network Security → Multiple Hosts.
Figure 7-3. Multiple Hosts
•
Port
— The port number for which Advanced Port Based Authentication is enabled.
• Host Authentication
–Single
–
–
•
Action on Single Host Violation
mode, from a host whose MAC address is not the client (supplicant) MAC address. The
Single Host Violation
possible field values are:
–
–
–
•
Tr ap s
— Enables a single authorized host for single-session access to the system.
Multiple Host
system.
Multiple Session
Forward
learned.
Discard
Shutdown
locked until they are activated, or the device is reset.
— Enables or disables sending traps to the host if a violation occurs.
— Forwards the packets from an unknown source, however, the MAC address is not
— Discards the packets from any unlearned source. This is the default value.
— Defines the host authentication type. The possible fields are:
— Enables a single host to authorize multiple hosts for single-session access to the
— Enables a single authorized host for multiple-session access to the system.
— Defines the action to be applied to packets arriving in single-host
Action on
field can be defined only if the
— Discards the packet from any unlearned source and locks the port. Ports remain
Multiple Hosts
field is defined as
Disable
. The
100 Update with your book title
 Loading...
Loading...