Page 1

Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
First Published: 2018-06-14
Americas Headquarters
Cisco Systems, Inc.
170 West Tasman Drive
San Jose, CA 95134-1706
USA
http://www.cisco.com
Tel: 408 526-4000
800 553-NETS (6387)
Fax: 408 527-0883
Page 2

THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS,
INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS.
THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH
THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY,
CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY.
The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB's public domain version of
the UNIX operating system. All rights reserved. Copyright©1981, Regents of the University of California.
NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS" WITH ALL FAULTS.
CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE.
IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT
LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS
HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network
topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses or phone numbers in illustrative content is unintentional
and coincidental.
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL:
https://www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship
between Cisco and any other company. (1721R)
©
2018 Cisco Systems, Inc. All rights reserved.
Page 3

CONTENTS
PREFACE
CHAPTER 1
CHAPTER 2
CHAPTER 3
Preface xiii
Audience xiii
Document Conventions xiii
Obtaining Documentation and Submitting a Service Request xiv
Documentation Feedback xiv
Related Documentation for Cisco Nexus 3000 Series Switches xiv
New and Changed Information 1
New and Changed Information 1
Overview 3
System Management Features 3
Configuring PTP 7
Information About PTP 7
PTP Device Types 8
PTP Process 9
High Availability for PTP 9
Licensing Requirements for PTP 10
Guidelines and Limitations for PTP 10
Default Settings for PTP 10
Configuring PTP 11
Configuring PTP Globally 11
Configuring PTP on an Interface 13
Configuring Multiple PTP Domains 14
Configuring PTP Grandmaster Clock 17
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
iii
Page 4

Contents
Configuring PTP Cost Interface 18
Configuring clock Identity 19
Verifying the PTP Configuration 20
CHAPTER 4
Configuring NTP 21
Information About NTP 21
NTP as a Time Server 22
Distributing NTP Using CFS 22
Clock Manager 22
Virtualization Support 22
Licensing Requirements for NTP 23
Guidelines and Limitations for NTP 23
Default Settings 24
Configuring NTP 24
Configuring NTP Server and Peer 24
Configuring NTP Authentication 26
Configuring NTP Access Restrictions 27
Configuring the NTP Source IP Address 28
Configuring the NTP Source Interface 29
Configuring NTP Logging 29
CHAPTER 5
Enabling CFS Distribution for NTP 30
Commiting NTP Configuration Changes 31
Discarding NTP Configuration Changes 31
Releasing the CFS Session Lock 32
Verifying the NTP Configuration 32
Configuration Examples for NTP 33
Related Documents for NTP 34
Feature History for NTP 34
Configuring System Message Logging 35
Information About System Message Logging 35
Syslog Servers 36
Licensing Requirements for System Message Logging 36
Guidelines and Limitations for System Message Logging 36
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
iv
Page 5

Default Settings for System Message Logging 36
Configuring System Message Logging 37
Configuring System Message Logging to Terminal Sessions 37
Configuring System Message Logging to a File 39
Configuring Module and Facility Messages Logging 41
Configuring Logging Timestamps 42
Configuring Syslog Servers 43
Configuring syslog on a UNIX or Linux System 45
Configuring syslog Server Configuration Distribution 46
Displaying and Clearing Log Files 47
Configuring DOM Logging 48
Enabling DOM Logging 48
Disabling DOM Logging 48
Contents
CHAPTER 6
Verifying the DOM Logging Configuration 48
Verifying the System Message Logging Configuration 49
Configuring Smart Call Home 51
Information About Smart Call Home 51
Smart Call Home Overview 52
Smart Call Home Destination Profiles 52
Smart Call Home Alert Groups 53
Smart Call Home Message Levels 54
Call Home Message Formats 55
Guidelines and Limitations for Smart Call Home 59
Prerequisites for Smart Call Home 59
Default Call Home Settings 59
Configuring Smart Call Home 60
Registering for Smart Call Home 60
Configuring Contact Information 60
Creating a Destination Profile 62
Modifying a Destination Profile 63
Associating an Alert Group with a Destination Profile 65
Adding Show Commands to an Alert Group 65
Configuring E-Mail Server Details 66
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
v
Page 6
Contents
Configuring Periodic Inventory Notifications 67
Disabling Duplicate Message Throttling 68
Enabling or Disabling Smart Call Home 69
Testing the Smart Call Home Configuration 69
Verifying the Smart Call Home Configuration 70
Sample Syslog Alert Notification in Full-Text Format 70
Sample Syslog Alert Notification in XML Format 71
CHAPTER 7
CHAPTER 8
Configuring Session Manager 75
Information About Session Manager 75
Guidelines and Limitations for Session Manager 75
Configuring Session Manager 76
Creating a Session 76
Configuring ACLs in a Session 76
Verifying a Session 77
Committing a Session 77
Saving a Session 77
Discarding a Session 77
Configuration Example for Session Manager 77
Verifying the Session Manager Configuration 78
Configuring the Scheduler 79
Information About the Scheduler 79
Remote User Authentication 80
Scheduler Log Files 80
Licensing Requirements for the Scheduler 80
Guidelines and Limitations for the Scheduler 80
Default Settings for the Scheduler 81
Configuring the Scheduler 81
Enabling the Scheduler 81
Defining the Scheduler Log File Size 82
Configuring Remote User Authentication 82
Defining a Job 83
Deleting a Job 84
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
vi
Page 7

Defining a Timetable 84
Clearing the Scheduler Log File 86
Disabling the Scheduler 87
Verifying the Scheduler Configuration 87
Configuration Examples for the Scheduler 88
Creating a Scheduler Job 88
Scheduling a Scheduler Job 88
Displaying the Job Schedule 88
Displaying the Results of Running Scheduler Jobs 88
Standards for the Scheduler 89
Contents
CHAPTER 9
Configuring SNMP 91
Information About SNMP 91
SNMP Functional Overview 91
SNMP Notifications 92
SNMPv3 92
Security Models and Levels for SNMPv1, v2, and v3 92
User-Based Security Model 93
CLI and SNMP User Synchronization 94
Group-Based SNMP Access 95
Licensing Requirements for SNMP 95
Guidelines and Limitations for SNMP 95
Default SNMP Settings 95
Configuring SNMP 96
Configuring SNMP Users 96
Enforcing SNMP Message Encryption 97
Assigning SNMPv3 Users to Multiple Roles 97
Creating SNMP Communities 97
Filtering SNMP Requests 97
Configuring SNMP Notification Receivers 98
Configuring SNMP Notification Receivers with VRFs 99
Filtering SNMP Notifications Based on a VRF 100
Configuring SNMP for Inband Access 101
Enabling SNMP Notifications 102
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
vii
Page 8
Contents
Configuring Link Notifications 104
Disabling Link Notifications on an Interface 104
Enabling One-Time Authentication for SNMP over TCP 105
Assigning SNMP Switch Contact and Location Information 105
Configuring the Context to Network Entity Mapping 105
Disabling SNMP 106
Verifying the SNMP Configuration 106
CHAPTER 10
CHAPTER 11
Configuring RMON 109
Information About RMON 109
RMON Alarms 109
RMON Events 110
Configuration Guidelines and Limitations for RMON 110
Configuring RMON 110
Configuring RMON Alarms 110
Configuring RMON Events 112
Verifying the RMON Configuration 112
Default RMON Settings 112
Configuring Online Diagnostics 115
Information About Online Diagnostics 115
Bootup Diagnostics 115
Health Monitoring Diagnostics 116
Expansion Module Diagnostics 116
CHAPTER 12
viii
Configuring Online Diagnostics 117
Verifying the Online Diagnostics Configuration 118
Default Settings for Online Diagnostics 118
Configuring Embedded Event Manager 119
About Embedded Event Manager 119
Embedded Event Manager Policies 120
Event Statements 120
Action Statements 121
VSH Script Policies 122
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
Page 9

Licensing Requirements for Embedded Event Manager 122
Prerequisites for Embedded Event Manager 122
Default Settings for Embedded Event Manager 122
Defining an Environment Variable 122
Defining a User Policy Using the CLI 123
Configuring Event Statements 124
Configuring Action Statements 127
Defining a Policy Using a VSH Script 129
Registering and Activating a VSH Script Policy 129
Overriding a System Policy 130
Configuring Syslog as an EEM Publisher 131
Contents
CHAPTER 13
Configuring SPAN 133
Information About SPAN 133
Guidelines and Limitations for SPAN 133
SPAN Sources 134
Characteristics of Source Ports 134
SPAN Destinations 134
Characteristics of Destination Ports 135
SPAN and ERSPAN Filtering 135
Guidelines and Limitations for SPAN and ERSPAN Filtering 135
SPAN and ERSPAN Control-packet Filtering 136
SPAN and ERSPAN Sampling 136
Guidelines and Limitations for SPAN and ERSPAN Sampling 137
SPAN and ERSPAN Truncation 137
Guidelines and Limitations for SPAN and ERSPAN Truncation 137
Creating or Deleting a SPAN Session 137
Configuring an Ethernet Destination Port 138
Configuring Source Ports 139
Configuring Source Port Channels or VLANs 140
Configuring the Description of a SPAN Session 140
Activating a SPAN Session 141
Suspending a SPAN Session 141
Configuring a SPAN Filter 142
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
ix
Page 10

Contents
Configuring SPAN Sampling 143
Configuring SPAN Truncation 144
Displaying SPAN Information 145
CHAPTER 14
Configuring ERSPAN 147
Information About ERSPAN 147
ERSPAN Types 147
ERSPAN Sources 147
ERSPAN Destinations 148
ERSPAN Sessions 148
Multiple ERSPAN Sessions 149
ERSPAN Marker Packet 149
High Availability 149
Licensing Requirements for ERSPAN 149
Prerequisites for ERSPAN 150
Guidelines and Limitations for ERSPAN 150
Default Settings for ERSPAN 152
Configuring ERSPAN 152
Configuring an ERSPAN Source Session 152
Configuring an ERSPAN Destination Session 155
CHAPTER 15
Shutting Down or Activating an ERSPAN Session 157
Configuring ERSPAN Filtering 158
Configuring ERSPAN Sampling 160
Configuring ERSPAN Truncation 161
Configuring an ERSPAN Marker Packet 163
Verifying the ERSPAN Configuration 164
Configuration Examples for ERSPAN 164
Configuration Example for an ERSPAN Source Session 164
Configuration Example for an ERSPAN Destination Session 165
Additional References 165
Related Documents 165
Configuring Warp SPAN 167
Information About Warp SPAN 167
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
x
Page 11

Guidelines and Limitations for Warp Span 168
Configuring Warp SPAN 168
Verifying Warp SPAN Mode Configuration 169
Feature History for Warp SPAN 171
Contents
CHAPTER 16
CHAPTER 17
Configuring DNS 173
Information About DNS Client 173
Name Servers 173
DNS Operation 173
High Availability 174
Prerequisites for DNS Clients 174
Licensing Requirements for DNS Clients 174
Default Settings for DNS Clients 174
Configuring DNS Clients 174
Configuring Traffic Forwarding Modes 177
Information About Warp Mode 177
Guidelines and Limitations for Warp Mode 177
Enabling and Disabling Warp Mode 178
Verifying Warp Mode Status 178
Feature History for Warp Mode 179
CHAPTER 18
CHAPTER 19
Configuring Active Buffer Monitoring 181
Information About Active Buffer Monitoring 181
Active Buffer Monitoring Overview 181
Buffer Histogram Data Access and Collection 182
Configuring Active Buffer Monitoring 182
Displaying Buffer Histogram Data 183
Performing Software Maintenance Upgrades (SMUs) 189
About SMUs 189
Package Management 190
Prerequisites for SMUs 190
Guidelines and Limitations for SMUs 190
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
xi
Page 12

Contents
Performing a Software Maintenance Upgrade for Cisco NX-OS 191
Preparing for Package Installation 191
Copying the Package File to a Local Storage Device or Network Server 192
Adding and Activating Packages 193
Committing the Active Package Set 194
Deactivating and Removing Packages 194
Displaying Installation Log Information 195
CHAPTER 20
CHAPTER 21
Configuring Rollback 197
Information About Rollbacks 197
Guidelines and Limitations for Rollbacks 197
Creating a Checkpoint 198
Implementing a Rollback 199
Verifying the Rollback Configuration 199
Configuring User Accounts and RBAC 201
Information About User Accounts and RBAC 201
User Roles 201
Rules 202
User Role Policies 202
User Account Configuration Restrictions 203
User Password Requirements 203
Guidelines and Limitations for User Accounts 204
Configuring User Accounts 205
xii
Configuring RBAC 206
Creating User Roles and Rules 206
Creating Feature Groups 207
Changing User Role Interface Policies 208
Changing User Role VLAN Policies 208
Verifying the User Accounts and RBAC Configuration 209
Configuring User Accounts Default Settings for the User Accounts and RBAC 209
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
Page 13

Preface
The preface contains the following sections:
• Audience, on page xiii
• Document Conventions, on page xiii
• Obtaining Documentation and Submitting a Service Request, on page xiv
• Documentation Feedback, on page xiv
• Related Documentation for Cisco Nexus 3000 Series Switches, on page xiv
Audience
This publication is for network administrators who install, configure, and maintain Cisco Nexus switches.
Document Conventions
Command descriptions use the following conventions:
bold
DescriptionConvention
Bold text indicates the commands and keywords that you enter literally
as shown.
Italic
[x | y]
{x | y}
[x {y | z}]
Italic text indicates arguments for which the user supplies the values.
Square brackets enclose an optional element (keyword or argument).[x]
Square brackets enclosing keywords or arguments separated by a vertical
bar indicate an optional choice.
Braces enclosing keywords or arguments separated by a vertical bar
indicate a required choice.
Nested set of square brackets or braces indicate optional or required
choices within optional or required elements. Braces and a vertical bar
within square brackets indicate a required choice within an optional
element.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
xiii
Page 14

Obtaining Documentation and Submitting a Service Request
Preface
DescriptionConvention
variable
string
Examples use the following conventions:
italic screen font
!, #
Indicates a variable for which you supply values, in context where italics
cannot be used.
A nonquoted set of characters. Do not use quotation marks around the
string or the string will include the quotation marks.
DescriptionConvention
Terminal sessions and information the switch displays are in screen font.screen font
Information you must enter is in boldface screen font.boldface screen font
Arguments for which you supply values are in italic screen font.
Nonprinting characters, such as passwords, are in angle brackets.< >
Default responses to system prompts are in square brackets.[ ]
An exclamation point (!) or a pound sign (#) at the beginning of a line
of code indicates a comment line.
Obtaining Documentation and Submitting a Service Request
For information on obtaining documentation, using the Cisco Bug Search Tool (BST), submitting a service
request, and gathering additional information, see What's New in Cisco Product Documentation at:
http://www.cisco.com/c/en/us/td/docs/general/whatsnew/whatsnew.html.
Subscribe to What's New in Cisco Product Documentation, which lists all new and revised Cisco technical
documentation as an RSS feed and delivers content directly to your desktop using a reader application. The
RSS feeds are a free service.
Documentation Feedback
To provide technical feedback on this document, or to report an error or omission, please send your comments
to nexus3k-docfeedback@cisco.com. We appreciate your feedback.
Related Documentation for Cisco Nexus 3000 Series Switches
The entire Cisco Nexus 3000 Series switch documentation set is available at the following URL:
https://www.cisco.com/c/en/us/support/switches/nexus-3000-series-switches/
tsd-products-support-series-home.html
xiv
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
Page 15

New and Changed Information
This chapter contains the following sections:
• New and Changed Information, on page 1
New and Changed Information
The following table provides an overview of the significant changes to this guide for this current release. The
table does not provide an exhaustive list of all changes made to the configuration guides or of the new features
in this release.
Table 1: New and Changed Features
CHAPTER 1
Release 6.x
DescriptionFeature
Changed in
Release
Where DocumentedAdded or
Not applicableNot applicableFirst 7.x release.No updates since Cisco NX-OS
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
1
Page 16

New and Changed Information
New and Changed Information
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
2
Page 17

Overview
This chapter contains the following sections:
• System Management Features, on page 3
System Management Features
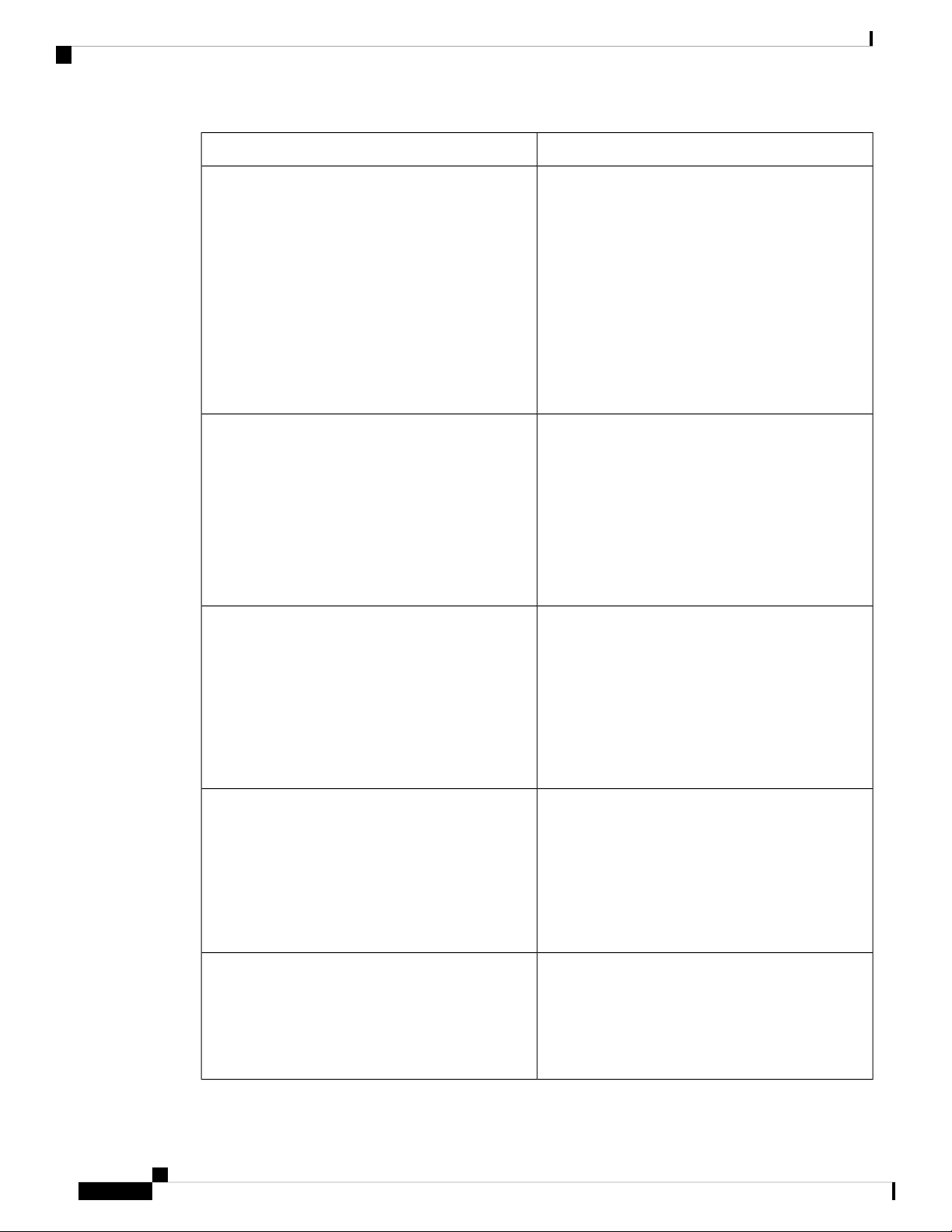
The system management features documented in this guide are described below:
CHAPTER 2
DescriptionFeature
Active Buffer Monitoring
Warp Mode
User Accounts and RBAC
Session Manager
The Active Buffer Monitoring feature provides
detailed buffer occupancy data to help you detect
network congestion, review past events to understand
when and how network congestion is affecting
network operations, understand historical trending,
and identify patterns of application traffic flow.
In warp mode, the access path is shortened by
consolidating the forwarding table into single table,
resulting in faster processing of frames and packets.
In warp mode, latency is reduced by up to 20 percent.
User accounts and role-based access control (RBAC)
allow you to define the rules for an assigned role.
Roles restrict the authorization that the user has to
access management operations. Each user role can
contain multiple rules and each user can have multiple
roles.
Session Manager allows you to create a configuration
and apply it in batch mode after the configuration is
reviewed and verified for accuracy and completeness.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
3
Page 18
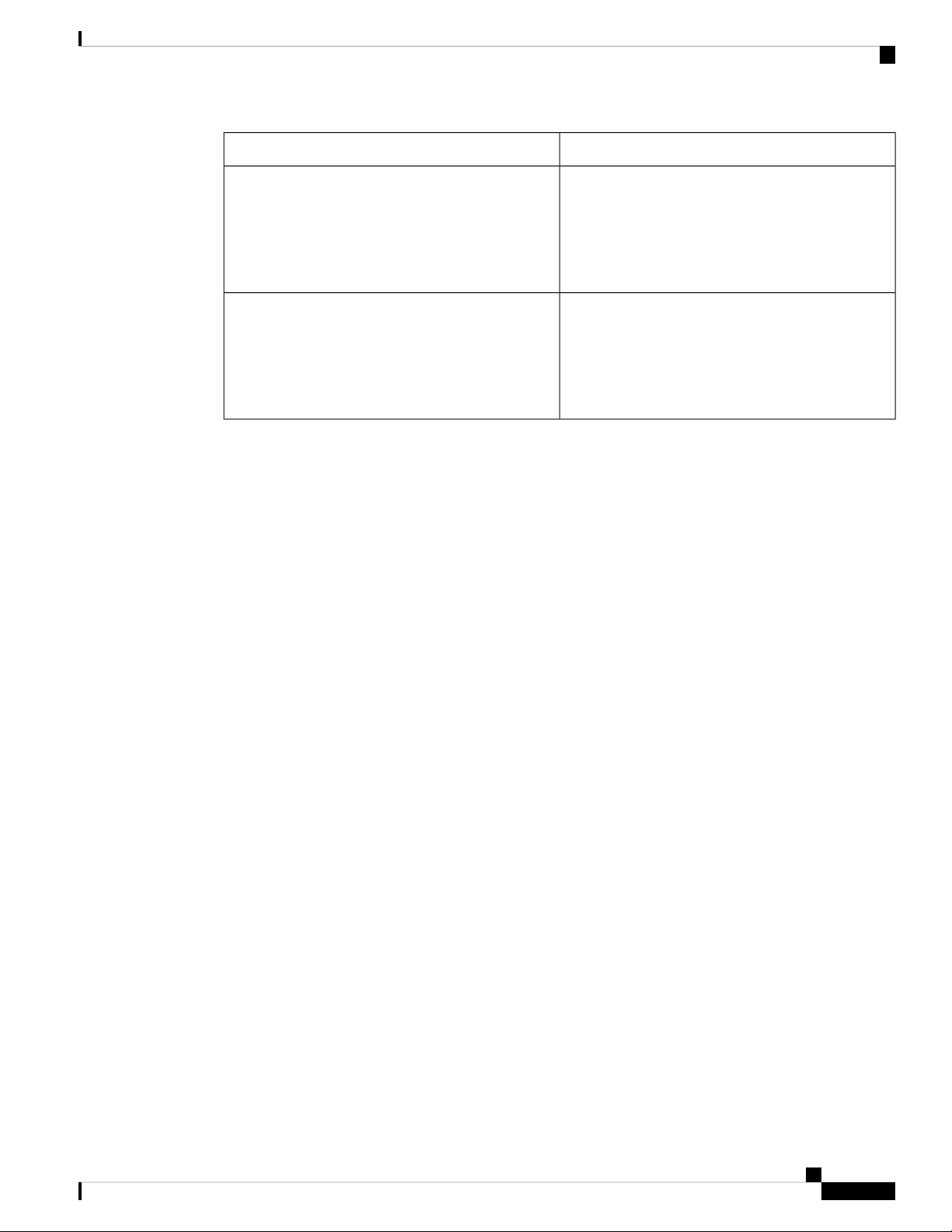
System Management Features
Overview
DescriptionFeature
Online Diagnostics
System Message Logging
Smart Call Home
Cisco Generic Online Diagnostics (GOLD) define a
common framework for diagnostic operations across
Cisco platforms. The online diagnostic framework
specifies the platform-independent fault-detection
architecture for centralized and distributed systems,
including the common diagnostics CLI and the
platform-independent fault-detection procedures for
boot-up and run-time diagnostics.
The platform-specific diagnostics provide
hardware-specific fault-detection tests and allow you
to take appropriate corrective action in response to
diagnostic test results.
You can use system message logging to control the
destination and to filter the severity level of messages
that system processes generate. You can configure
logging to a terminal session, a log file, and syslog
servers on remote systems.
System message logging is based on RFC 3164. For
more information about the system message format
and the messages that the device generates, see the
Cisco NX-OS System Messages Reference.
Call Home provides an e-mail-based notification of
critical system policies. Cisco NX-OS provides a
range of message formats for optimal compatibility
with pager services, standard e-mail, or XML-based
automated parsing applications. You can use this
feature to page a network support engineer, e-mail a
Network Operations Center, or use Cisco Smart Call
Home services to automatically generate a case with
the Technical Assistance Center.
Configuration Rollback
The configuration rollback feature allows users to
take a snapshot, or user checkpoint, of the Cisco
NX-OS configuration and then reapply that
configuration to a switch at any point without having
to reload the switch. A rollback allows any authorized
administrator to apply this checkpoint configuration
without requiring expert knowledge of the features
configured in the checkpoint.
SNMP
The Simple Network Management Protocol (SNMP)
is an application-layer protocol that provides a
message format for communication between SNMP
managers and agents. SNMP provides a standardized
framework and a common language used for the
monitoring and management of devices in a network.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
4
Page 19
Overview
System Management Features
DescriptionFeature
RMON
SPAN
RMON is an Internet Engineering Task Force (IETF)
standard monitoring specification that allows various
network agents and console systems to exchange
network monitoring data. Cisco NX-OS supports
RMON alarms, events, and logs to monitor Cisco
NX-OS devices.
The Switched Port Analyzer (SPAN) feature
(sometimes called port mirroring or port monitoring)
selects network traffic for analysis by a network
analyzer. The network analyzer can be a Cisco
SwitchProbe, a Fibre Channel Analyzer, or other
Remote Monitoring (RMON) probes.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
5
Page 20

System Management Features
Overview
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
6
Page 21

Configuring PTP
This chapter contains the following sections:
• Information About PTP, on page 7
• PTP Device Types, on page 8
• PTP Process, on page 9
• High Availability for PTP, on page 9
• Licensing Requirements for PTP, on page 10
• Guidelines and Limitations for PTP, on page 10
• Default Settings for PTP, on page 10
• Configuring PTP, on page 11
Information About PTP
PTP is a time synchronization protocol for nodes distributed across a network. Its hardware timestamp feature
provides greater accuracy than other time synchronization protocols such as the Network Time Protocol (NTP).
A PTP system can consist of a combination of PTP and non-PTP devices. PTP devices include ordinary clocks,
boundary clocks, and transparent clocks. Non-PTP devices include ordinary network switches, routers, and
other infrastructure devices.
CHAPTER 3
PTP is a distributed protocol that specifies how real-time PTP clocks in the system synchronize with each
other. These clocks are organized into a master-slave synchronization hierarchy with the grandmaster clock,
which is the clock at the top of the hierarchy, determining the reference time for the entire system.
Synchronization is achieved by exchanging PTP timing messages, with the members using the timing
information to adjust their clocks to the time of their master in the hierarchy. PTP operates within a logical
scope called a PTP domain.
Starting from Cisco NXOS Release 6.0(2)A8(3), PTP supports configuring multiple PTP clocking domains,
PTP grandmaster capability, PTP cost on interfaces for slave and passive election, and clock identity.
All the switches in a multi-domain environment, belong to one domain. The switches that are the part of
boundary clock, must have multi-domain feature enabled on them. Each domain has user configurable
parameters such as domain priority, clock class threshold and clock accuracy threshold. The clocks in each
domain remain synchronized with the master clock in that domain. If the GPS in a domain fails, the master
clock in the domain synchronizes time and data sets associated with the announce messages from the master
clock in the domain where the GPS is active. If the master clock from the highest priority domain does not
meet the clock quality attributes, a clock in the subsequent domain that match the criteria is selected. The Best
Master Clock Algorithm (BMCA) is used to select the master clock if none of the domains has the desired
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
7
Page 22

PTP Device Types
Configuring PTP
clock quality attributes. If all the domains have equal priority and the threshold values less than master clock
attributes or if the threshold values are greater than the master clock attributes, BMCA is used to select the
master clock.
Grandmaster capability feature controls the switch’s ability of propagating its clock to other devices that it is
connected to. When the switch receives announce messages on an interface, it checks the clock class threshold
and clock accuracy threshold values. If the values of these parameters are within the predefined limits, then
the switch acts as per PTP standards specified in IEEE 1588v2. If the switch does not receive announce
messages from external sources or if the parameters of the announce messages received are not within the
predefined limits, the port state will be changed to listening mode. On a switch with no slave ports, the state
of all the PTP enabled ports is rendered as listening and on a switch with one slave port, the BMCA is used
to determine states on all PTP enabled ports. Convergence time prevents timing loops at the PTP level when
grandmaster capability is disabled on a switch. If the slave port is not selected on the switch, all the ports on
the switch will be in listening state for a minimum interval specified in the convergence time. The convergence
time range is from 3 to 2600 seconds and the default value is 3 seconds.
The interface cost applies to each PTP enabled port if the switch has more than one path to grandmaster clock.
The port with the least cost value is elected as slave and the rest of the ports will remain as passive ports.
The clock identity is a unique 8-octet array presented in the form of a character array based on the switch
MAC address. The clock identity is determined from MAC according to the IEEE1588v2-2008 specifications.
The clock ID is a combination of bytes in a VLAN MAC address as defined in IEEE1588v2.
PTP Device Types
The following clocks are common PTP devices:
Ordinary clock
Communicates with the network based on a single physical port, similar to an end host. An ordinary
clock can function as a grandmaster clock.
Boundary clock
Typically has several physical ports, with each port behaving like a port of an ordinary clock. However,
each port shares the local clock, and the clock data sets are common to all ports. Each port decides its
individual state, either master (synchronizing other ports connected to it) or slave (synchronizing to a
downstream port), based on the best clock available to it through all of the other ports on the boundary
clock. Messages that are related to synchronization and establishing the master-slave hierarchy terminate
in the protocol engine of a boundary clock and are not forwarded.
Transparent clock
Forwards all PTP messages like an ordinary switch or router but measures the residence time of a packet
in the switch (the time that the packet takes to traverse the transparent clock) and in some cases the link
delay of the ingress port for the packet. The ports have no state because the transparent clock does not
need to synchronize to the grandmaster clock.
There are two kinds of transparent clocks:
End-to-end transparent clock
Measures the residence time of a PTP message and accumulates the times in the correction field of
the PTP message or an associated follow-up message.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
8
Page 23

Configuring PTP
Note
PTP operates only in boundary clock mode. We recommend that you deploy a Grand Master Clock (10 MHz)
upstream. The servers contain clocks that require synchronization and are connected to the switch.
End-to-end transparent clock and peer-to-peer transparent clock modes are not supported.
PTP Process
The PTP process consists of two phases: establishing the master-slave hierarchy and synchronizing the clocks.
Within a PTP domain, each port of an ordinary or boundary clock follows this process to determine its state:
PTP Process
Peer-to-peer transparent clock
Measures the residence time of a PTP message and computes the link delay between each port and
a similarly equipped port on another node that shares the link. For a packet, this incoming link delay
is added to the residence time in the correction field of the PTP message or an associated follow-up
message.
• Examines the contents of all received announce messages (issued by ports in the master state)
• Compares the data sets of the foreign master (in the announce message) and the local clock for priority,
clock class, accuracy, and so on
• Determines its own state as either master or slave
After the master-slave hierarchy has been established, the clocks are synchronized as follows:
• The master sends a synchronization message to the slave and notes the time it was sent.
• The slave receives the synchronization message and notes the time that it was received. For every
synchronization message, there is a follow-up message. The number of sync messages should be equal
to the number of follow-up messages.
• The slave sends a delay-request message to the master and notes the time it was sent.
• The master receives the delay-request message and notes the time it was received.
• The master sends a delay-response message to the slave. The number of delay request messages should
be equal to the number of delay response messages.
• The slave uses these timestamps to adjust its clock to the time of its master.
High Availability for PTP
Stateful restarts are not supported for PTP
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
9
Page 24

Licensing Requirements for PTP
Licensing Requirements for PTP
PTP requires no license. Any feature not included in a license package is bundled with the Cisco NX-OS
system images and is provided at no extra charge to you. For a complete explanation of the Cisco NX-OS
licensing scheme, see the Cisco NX-OS Licensing Guide.
Guidelines and Limitations for PTP
• In a Cisco Nexus 3500 only environment, PTP clock correction is expected to be in the 1- to 2-digit
range, from 1 to 99 nanoseconds. However, in a mixed environment, PTP clock correction is expected
to be up to 3 digits, from 100 to 999 nanoseconds.
• PTP operates only in boundary clock mode. End-to-end transparent clock and peer-to-peer transparent
clock modes are not supported.
• PTP operates when the clock protocol is set to PTP. Configuring PTP and NTP together is not supported.
Configuring PTP
• PTP supports transport over User Datagram Protocol (UDP). Transport over Ethernet is not supported.
• PTP supports only multicast communication. Negotiated unicast communication is not supported.
• PTP is limited to a single domain per network.
• PTP-capable ports do not identify PTP packets and do not time-stamp or redirect those packets to CPU
for processing unless you enable PTP on those ports. This means that if the PTP is disabled on a port,
then the device will be capable of routing any multicast PTP packets, regardless of their type, assuming
that there is a multicast state present for this. None of these multicast PTP packets from this port will be
redirected to CPU for processing, because the exception used to redirect them to the CPU is programmed
on a per-port basis, based on whether the PTP is enabled or not on the respective port.
• 1 packet per second (1 pps) input is not supported.
• PTP over IPv6 is not supported.
• Cisco Nexus 3500 Series switches support a maximum of 48 PTP sessions.
• Cisco Nexus switches should be synchronized from the neighboring master using a synchronization log
interval that ranges from –3 to 1.
• Beginning with Cisco NX-OS Release 6.0(2)A8(7), all unicast and multicast PTP management messages
will be forwarded as per the forwarding rules. All PTP management messages will be treated as regular
multicast packets and process these in the same way as the other non-PTP multicast packets are processed
by Cisco Nexus 3500 switches.
• Cisco Nexus 3500 Series switches do not support PTP on 40G interfaces.
• You must configure the incoming port as L3/SVI to enable forwarding of the PTP unicast packets.
Default Settings for PTP
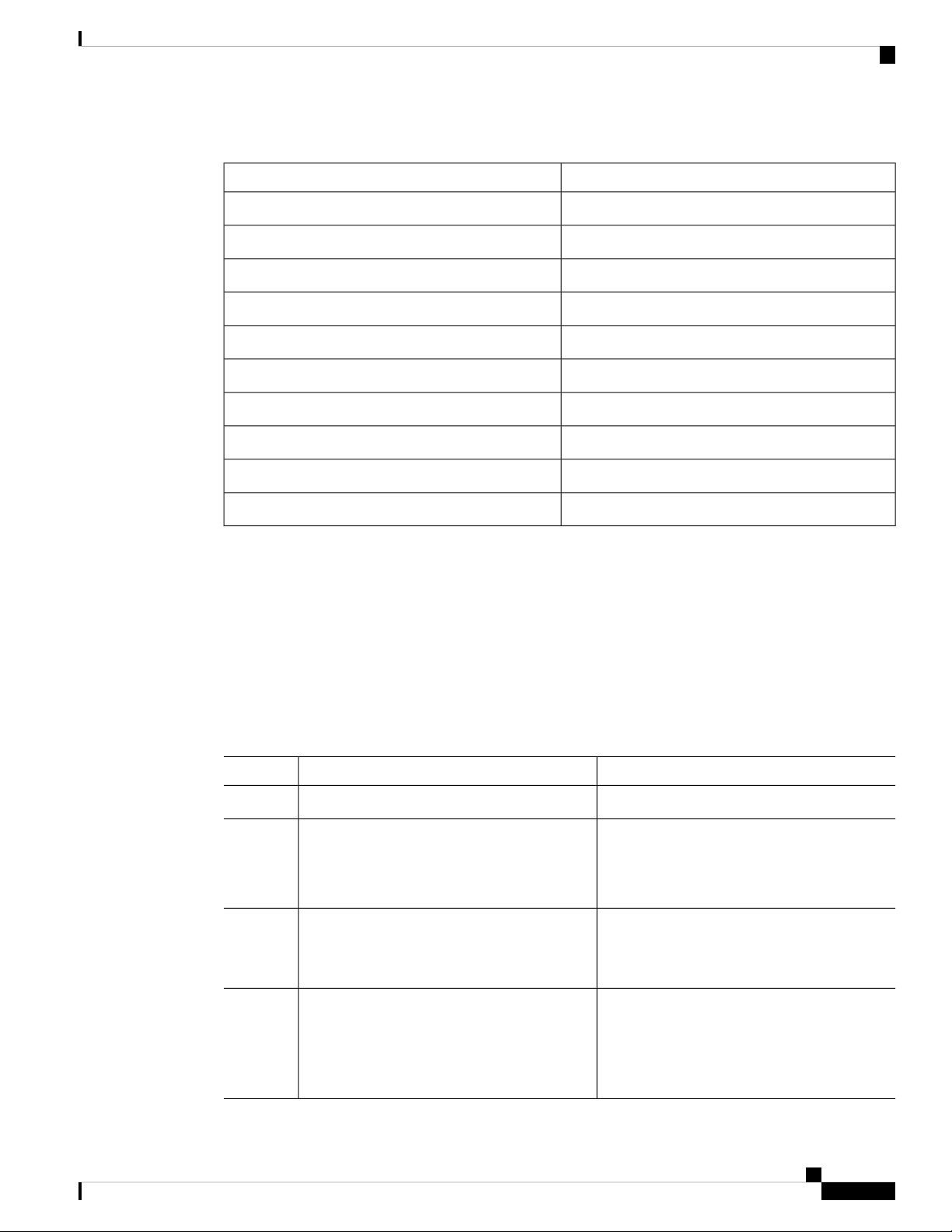
The following table lists the default settings for PTP parameters.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
10
Page 25
Configuring PTP
Configuring PTP
Table 2: Default PTP Parameters
DefaultParameters
DisabledPTP
2PTP version
0. PTP multi domain is disabled by default.PTP domain
255PTP priority 1 value when advertising the clock
255PTP priority 2 value when advertising the clock
1 log secondPTP announce interval
1 log secondPTP sync interval
3 announce intervalsPTP announce timeout
1 log secondPTP minimum delay request interval
Configuring PTP
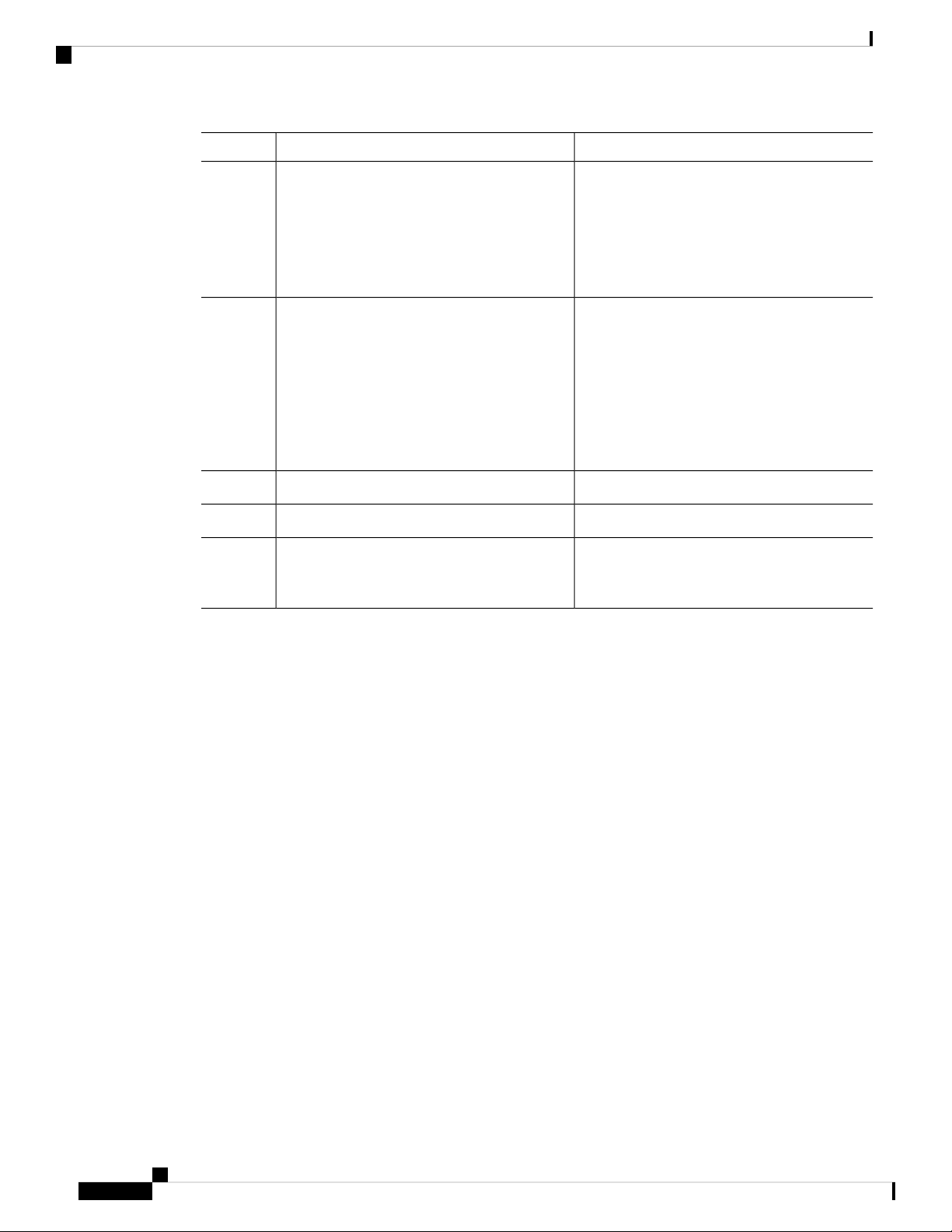
Configuring PTP Globally
You can enable or disable PTP globally on a device. You can also configure various PTP clock parameters
to help determine which clock in the network has the highest priority to be selected as the grandmaster.
Procedure
Step 1
Step 2
Step 3
switch(config) # [no] ptp source ip-address
[vrf vrf]
1PTP VLAN
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Enables or disables PTP on the device.switch(config) # [no] feature ptp
Note
Configures the source IP address for all PTP
packets.
Enabling PTP on the switch does not
enable PTP on each interface.
Step 4
(Optional) switch(config) # [no] ptp domain
number
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
The ip-address can be in IPv4 format.
Configures the domain number to use for this
clock. PTP domains allow you to use multiple
independent PTP clocking subdomains on a
single network.
The range for the number is from 0 to 128.
11
Page 26
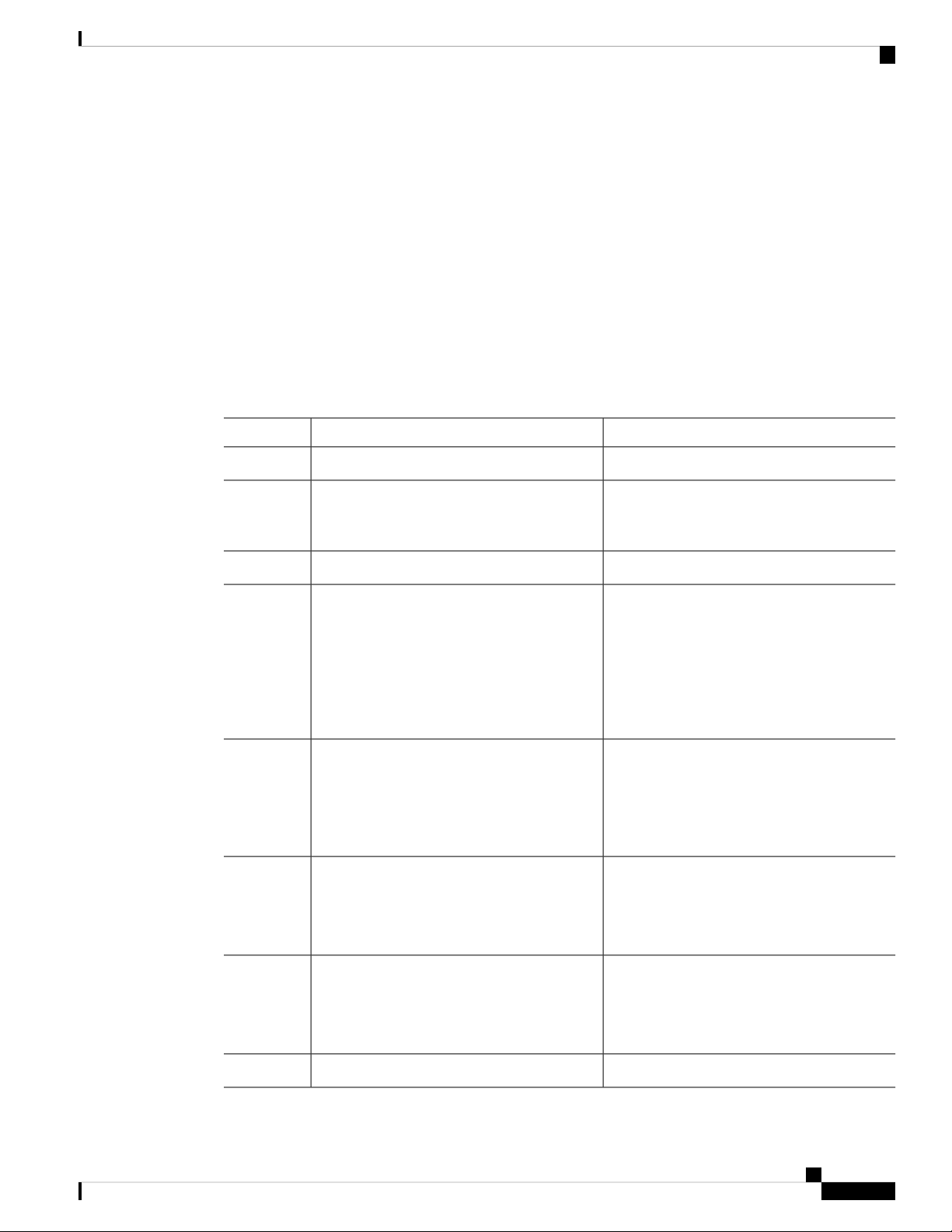
Configuring PTP Globally
Configuring PTP
PurposeCommand or Action
Step 5
Step 6
Step 7
Step 8
Step 9
(Optional) switch(config) # [no] ptp priority1
value
(Optional) switch(config) # [no] ptp priority2
value
(Optional) switch(config)# copy
running-config startup-config
Configures the priority1 value to use when
advertising this clock. This value overrides the
default criteria (clock quality, clock class, and
so on) for the best master clock selection. Lower
values take precedence.
The range for the value is from 0 to 255.
Configures the priority2 value to use when
advertising this clock. This value is used to
decide between two devices that are otherwise
equally matched in the default criteria. For
example, you can use the priority2 value to give
a specific switch priority over other identical
switches.
The range for the value is from 0 to 255.
Displays the PTP status.(Optional) switch(config) # show ptp brief
Displays the properties of the local clock.(Optional) switch(config) # show ptp clock
Saves the change persistently through reboots
and restarts by copying the running
configuration to the startup configuration.
Example
The following example shows how to configure PTP globally on the device, specify the source IP
address for PTP communications, and configure a preference level for the clock:
switch# configure terminal
switch(config)# feature ptp
switch(config)# ptp source 10.10.10.1
switch(config)# ptp priority1 1
switch(config)# ptp priority2 1
switch(config)# show ptp brief
PTP port status
----------------------Port State
------- -------------switch(config)# show ptp clock
PTP Device Type: Boundary clock
Clock Identity : 0:22:55:ff:ff:79:a4:c1
Clock Domain: 0
Number of PTP ports: 0
Priority1 : 1
Priority2 : 1
Clock Quality:
Class : 248
Accuracy : 254
Offset (log variance) : 65535
Offset From Master : 0
Mean Path Delay : 0
Steps removed : 0
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
12
Page 27
Configuring PTP
Local clock time:Sun Jul 3 14:13:24 2011
switch(config)#
Configuring PTP on an Interface
After you globally enable PTP, it is not enabled on all supported interfaces by default. You must enable PTP
interfaces individually.
Before you begin
Make sure that you have globally enabled PTP on the switch and configured the source IP address for PTP
communication.
Procedure
Configuring PTP on an Interface
PurposeCommand or Action
Step 1
Step 2
Step 3
Step 4
Step 5
Step 6
switch(config) # interface ethernet slot/port
(Optional) switch(config-if) # [no] ptp
announce {interval log seconds | timeout
count}
(Optional) switch(config-if) # [no] ptp delay
request minimum interval log seconds
(Optional) switch(config-if) # [no] ptp sync
interval log seconds
Enters global configuration mode.switch# configure terminal
Specifies the interface on which you are
enabling PTP and enters interface
configuration mode.
Enables or disables PTP on an interface.switch(config-if) # [no] feature ptp
Configures the interval between PTP announce
messages on an interface or the number of PTP
intervals before a timeout occurs on an
interface.
The range for the PTP announcement interval
is from 0 to 4 seconds, and the range for the
interval timeout is from 2 to 10.
Configures the minimum interval allowed
between PTP delay-request messages when
the port is in the master state.
The range is from log(-6) to log(1) seconds.
Where, log(-2) = 2 frames per second.
Configures the interval between PTP
synchronization messages on an interface.
Step 7
Step 8
The range for the PTP synchronization interval
is from -3 log second to 1 log second
(Optional) switch(config-if) # [no] ptp vlan
vlan-id
Specifies the VLAN for the interface where
PTP is being enabled. You can only enable
PTP on one VLAN on an interface.
The range is from 1 to 4094.
Displays the PTP status.(Optional) switch(config-if) # show ptp brief
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
13
Page 28
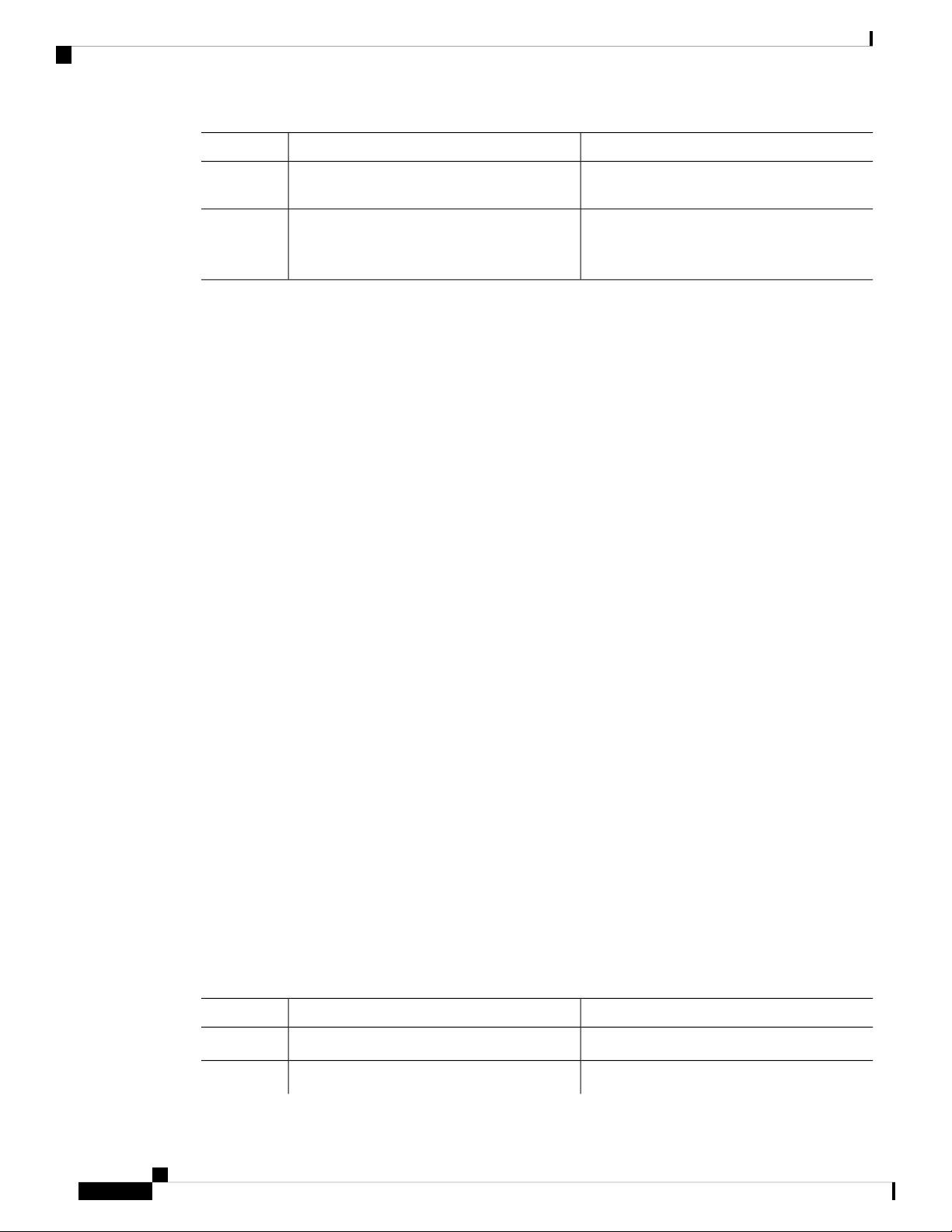
Configuring Multiple PTP Domains
Configuring PTP
PurposeCommand or Action
Step 9
Displays the status of the PTP port.(Optional) switch(config-if) # show ptp port
interface interface slot/port
Step 10
(Optional) switch(config-if)# copy
running-config startup-config
Saves the change persistently through reboots
and restarts by copying the running
configuration to the startup configuration.
Example
This example shows how to configure PTP on an interface and configure the intervals for the announce,
delay-request, and synchronization messages:
switch# configure terminal
switch(config)# interface ethernet 2/1
switch(config-if)# ptp
switch(config-if)# ptp announce interval 3
switch(config-if)# ptp announce timeout 2
switch(config-if)# ptp delay-request minimum interval 4
switch(config-if)# ptp sync interval -1
switch(config-if)# show ptp brief
PTP port status
----------------------Port State
------- -------------Eth2/1 Master
switch(config-if)# show ptp port interface ethernet 1/1
PTP Port Dataset: Eth1/1
Port identity: clock identity: f4:4e:05:ff:fe:84:7e:7c
Port identity: port number: 0
PTP version: 2
Port state: Slave
VLAN info: 1
Delay request interval(log mean): 0
Announce receipt time out: 3
Peer mean path delay: 0
Announce interval(log mean): 1
Sync interval(log mean): 1
Delay Mechanism: End to End
Cost: 255
Domain: 5
switch(config-if)#
Configuring Multiple PTP Domains
You can configure multiple PTP clocking domains on a single network. Each domain has a priority value
associated with it. The default value is 255.
Procedure
Step 1
Step 2
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
14
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Enables or disables PTP on the device.switch(config) # [no] feature ptp
Page 29
Configuring PTP
PurposeCommand or Action
Note
Configuring Multiple PTP Domains
Enabling PTP on the switch does
not enable PTP on each interface.
Step 3
Step 4
Step 5
Step 6
switch(config) # [no] ptp source ip-address
[vrf vrf]
switch(config) # [no] ptp multi-domain
switch(config) # [no] ptp domain value
priority value
switch(config) # [no] ptp domain value
clock-class-threshold value
Configures the source IP address for all PTP
packets.
The ip-address can be in IPv4 format.
Enables configuring multi domain feature on
the switch. It also allow you to set the
attributes such as priority, clock-class threshold
, clock-accuracy threshold, transition priorities
etc. on the switch.
Specify the values for the domain and priority.
The range for the domain value is from 0 to
127. The default value of the domain is 0
The range for the priority value is from 0 to
255. The default value of the priority is 255
Specify the values for domain and clock class
threshold. The default value is 248.
The range for the domain value is from 0 to
127.
The range for the clock-class-threshold value
is from 0 to 255.
Step 7
switch(config) # [no] ptp domain value
clock-accuracy-threshold value
Note
It is not necessary that a clock class
threshold value ensure election of
the slave clock on any ports. The
switch uses this value to determine
whether the source clock is
traceable. If the clock class value
from the peer is higher or equal than
the clock class threshold value in
a domain, the switch runs BMCA
to elect the slave port from a
domain. If none of the domains has
the clock class below the threshold
value, the switch runs BMCA on
all the PTP enabled ports to elect
the best clock.
Specify the values for domain and clock
accuracy threshold. The default value is 254.
The range for the domain value is from 0 to
127.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
15
Page 30
Configuring Multiple PTP Domains
Configuring PTP
PurposeCommand or Action
The range for the clock-accuracy-threshold
value is from 0 to 255.
Step 8
Step 9
switch(config) # [no] ptp multi-domain
transition-attributes priority1 value
switch(config) # [no] ptp multi-domain
transition-attributes priority2 value
Sets the domain transition-attributes priority1
value that is used when sending a packet out
from this domain to a peer domain. The value
of the priority1 in the announce message from
the remote port is replaced by the value of
domain transition-attributes priority1 when
the announce message has to be transmitted to
a peer in a domain, that is different from that
of the slave interface. The default value is 255.
The range for the transition-attributes priority1
value is from 0 to 255.
Sets the domain transition-attributes priority2
value that is used when sending a packet out
from this domain to a peer domain. The value
of the priority2 in the announce message from
the remote port is replaced by the value of
domain transition-attributes priority2 when
the announce message has to be transmitted to
a peer in a domain, that is different from that
of the slave interface. The default value is 255.
The range for the transition-attributes priority2
value is from 0 to 255.
Step 10
switch(config-if) # [no] ptp domain value
Associates a domain on a PTP enabled
interface. If you do not configure the domain
specifically on an interface, it takes the default
value (0).
The range for the domain value is from 0 to
127.
Example
The following example shows the PTP domains configured on a switch:
switch(config)# show ptp domain data
MULTI DOMAIN : ENABLED
GM CAPABILITY : ENABLED
PTP DEFAULT DOMAIN : 0
PTP TRANSITION PRIORITY1 : 20
PTP TRANSITION PRIORITY2 : 255
PTP DOMAIN PROPERTY
Domain-Number Domain-Priority Clock-Class Clock-Accuracy Ports
0 255 248 254 Eth1/1
1 1 1 254
switch(config)#
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
16
Page 31

Configuring PTP
The following example shows the domains associated with each PTP enabled interfaces:
switch(config)# show ptp interface domain
PTP port interface domain
-------------------------Port Domain
------- ----------------Eth1/1 0
1 1 254
switch(config)#
Configuring PTP Grandmaster Clock
You can configure convergence time to prevent timing loops at the PTP level when grandmaster capability
is disabled on a switch. Grandmaster capability is enabled on the device by default.
.
Procedure
Configuring PTP Grandmaster Clock
Step 1
Step 2
Step 3
Step 4
Step 5
switch(config) # [no] ptp source ip-address
[vrf vrf]
switch(config) # no ptp grandmaster-capable
[ convergence-time]
switch(config) # [no] ptp domain value
clock-class-threshold value
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Enables or disables PTP on the device.switch(config) # [no] feature ptp
Note
Enabling PTP on the switch does not
enable PTP on each interface.
Configures the source IP address for all PTP
packets.
The ip-address can be in IPv4 format.
Disables grandmaster capability on the switch.
Prevents the device from acting as a
grandmaster when there is no external
grandmaster available in any domains. The
default convergence time is 30 seconds.
Specify the values for domain and clock class
threshold. Clock class threshold defines the
threshold value of clock class that the device
uses to determine whether the source clock can
be considered as a grandmaster clock.
The range for the domain value is from 0 to
127.
The range for the clock-class-threshold value
is from 0 to 255.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
17
Page 32

Configuring PTP Cost Interface
PurposeCommand or Action
Note
Configuring PTP
The switch uses this value to
determine whether the source clock
is traceable. If the clock class value
from all the peers is higher than the
clock class threshold value, the
BMCA may change all the port state
to listening.
Step 6
switch(config) # [no] ptp domain value
clock-accuracy-threshold value
Step 7
Example
The following example displays the PTP clock information:
switch(config-if)# show ptp clock
PTP Device Type: Boundary clock
Clock Identity : f4:4e:05:ff:fe:84:7e:7c
Clock Domain: 5
Number of PTP ports: 2
Priority1 : 129
Priority2 : 255
Clock Quality:
Class : 248
Accuracy : 254
Offset (log variance) : 65535
Offset From Master : 0
Mean Path Delay : 391
Steps removed : 1
Local clock time:Wed Nov 9 10:31:21 2016
switch(config-if)#
Specify the values for domain and clock
accuracy threshold
The range for the domain value is from 0 to
127.
The range for the clock-accuracy-threshold
value is from 0 to 255.
Enables grandmaster capability on a switch.switch(config) # ptp grandmaster-capable
Configuring PTP Cost Interface
You can configure interface cost on each PTP enabled port on a Cisco Nexus 3500 switch. The cost applies
to each PTP enabled port if the switch has more than one path to grandmaster clock.
.
Procedure
Step 1
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
18
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Page 33

Configuring PTP
Configuring clock Identity
PurposeCommand or Action
Step 2
Enables or disables PTP on the device.switch(config) # [no] feature ptp
Note
Enabling PTP on the switch does not
enable PTP on each interface.
Step 3
switch(config) # [no] ptp source ip-address
[vrf vrf]
Configures the source IP address for all PTP
packets.
The ip-address can be in IPv4 format.
Step 4
Step 5
switch(config-if) # [no] ptp cost value
Enables or disables PTP on the interface.switch(config-if) # [no] feature ptp
Associate cost on a PTP enabled interface. The
interface having the least cost becomes the slave
interface.
The range for the cost is from 0 to 255. The
default value is 255.
Example
The following example shows cost that is associated with each PTP enabled interfaces:
switch(config)# show ptp cost
PTP port costs
----------------------Port Cost
------- -------------Eth1/1 255
switch(config)#
Configuring clock Identity
You can configure clock identity on a Cisco Nexus 3500 switch. The default clock identity is a unique 8-octet
array presented in the form of a character array based on the switch MAC address.
.
Procedure
Step 1
Step 2
Step 3
switch(config-if) # ptp clock-identity MAC
Address
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Enables or disables PTP on the device.switch(config) # [no] feature ptp
Note
Enabling PTP on the switch does not
enable PTP on each interface.
Assigns 6 byte MAC address for PTP
clock-identity. Default clock identity is based
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
19
Page 34

Verifying the PTP Configuration
Verifying the PTP Configuration
Use one of the following commands to verify the configuration:
Table 3: PTP Show Commands
Configuring PTP
PurposeCommand or Action
on the MAC address of the switch. The
clock-identity is defined as per IEEE standard
(MAC-48 Byte0 | MAC-48 Byte1 | MAC-48
Byte2 | FF | FE | MAC-48 Bytes3-5).
PurposeCommand
Displays the PTP status.show ptp brief
show ptp clock
show ptp clock foreign-masters-record
show ptp port interface ethernet slot/port
show ptp domain data
show ptp interface domain
Displays the properties of the local clock, including
the clock identity.
Displays the state of foreign masters known to the
PTP process. For each foreign master, the output
displays the clock identity, basic clock properties, and
whether the clock is being used as a grandmaster.
Displays the last few PTP corrections.show ptp corrections
Displays the properties of the PTP parent.show ptp parent
Displays the status of the PTP port on the switch.
Displays multiple domain data, domain priority, clock
threshold and information about grandmaster
capabilities.
Displays information about the interface to domain
association.
Displays PTP port to cost association.show ptp cost
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
20
Page 35

Configuring NTP
This chapter contains the following sections:
• Information About NTP, on page 21
• NTP as a Time Server, on page 22
• Distributing NTP Using CFS, on page 22
• Clock Manager, on page 22
• Virtualization Support, on page 22
• Licensing Requirements for NTP, on page 23
• Guidelines and Limitations for NTP, on page 23
• Default Settings, on page 24
• Configuring NTP, on page 24
• Related Documents for NTP, on page 34
• Feature History for NTP, on page 34
Information About NTP
CHAPTER 4
The Network Time Protocol (NTP) synchronizes the time of day among a set of distributed time servers and
clients so that you can correlate events when you receive system logs and other time-specific events from
multiple network devices. NTP uses the User Datagram Protocol (UDP) as its transport protocol. All NTP
communications use Coordinated Universal Time (UTC).
An NTP server usually receives its time from an authoritative time source, such as a radio clock or an atomic
clock attached to a time server, and then distributes this time across the network. NTP is extremely efficient;
no more than one packet per minute is necessary to synchronize two machines to within a millisecond of each
other.
NTP uses a stratum to describe the distance between a network device and an authoritative time source:
• A stratum 1 time server is directly attached to an authoritative time source (such as a radio or atomic
clock or a GPS time source).
• A stratum 2 NTP server receives its time through NTP from a stratum 1 time server.
Before synchronizing, NTP compares the time reported by several network devices and does not synchronize
with one that is significantly different, even if it is a stratum 1. Because Cisco NX-OS cannot connect to a
radio or atomic clock and act as a stratum 1 server, we recommend that you use the public NTP servers
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
21
Page 36

NTP as a Time Server
available on the Internet. If the network is isolated from the Internet, Cisco NX-OS allows you to configure
the time as though it were synchronized through NTP, even though it was not.
Note
You can create NTP peer relationships to designate the time-serving hosts that you want your network device
to consider synchronizing with and to keep accurate time if a server failure occurs.
The time kept on a device is a critical resource, so we strongly recommend that you use the security features
of NTP to avoid the accidental or malicious setting of incorrect time. Two mechanisms are available: an access
list-based restriction scheme and an encrypted authentication mechanism.
NTP as a Time Server
the Cisco NX-OS device can use NTP to distribute time. Other devices can configure it as a time server. You
can also configure the device to act as an authoritative NTP server, enabling it to distribute time even when
it is not synchronized to an outside time source.
Configuring NTP
Distributing NTP Using CFS
Cisco Fabric Services (CFS) distributes the local NTP configuration to all Cisco devices in the network. After
enabling CFS on your device, a network-wide lock is applied to NTP whenever an NTP configuration is
started. After making the NTP configuration changes, you can discard or commit them. In either case, the
CFS lock is then released from the NTP application.
Clock Manager
Clocks are resources that need to be shared across different processes. Multiple time synchronization protocols,
such as NTP and Precision Time Protocol (PTP), might be running in the system.
The clock manager allows you to specify the protocol to control the various clocks in the system. Once you
specify the protocol, the system clock starts updating.
Virtualization Support
NTP recognizes virtual routing and forwarding (VRF) instances. NTP uses the default VRF if you do not
configure a specific VRF for the NTP server and NTP peer.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
22
Page 37

Configuring NTP
Licensing Requirements for NTP
The following table shows the licensing requirements for this feature:
License RequirementProduct
Licensing Requirements for NTP
Cisco
NX-OS
NTP requires no license. Any feature not included in a license package is bundled with the
Cisco NX-OS system images and is provided at no extra charge to you.
Guidelines and Limitations for NTP
NTP has the following configuration guidelines and limitations:
• To configure NTP, you must have connectivity to at least one server that is running NTP.
• NTP operates when the clock protocol is set to NTP. Configuring PTP and NTP together is not supported.
• You should have a peer association with another device only when you are sure that your clock is reliable
(which means that you are a client of a reliable NTP server).
• A peer configured alone takes on the role of a server and should be used as a backup. If you have two
servers, you can configure several devices to point to one server and the remaining devices to point to
the other server. You can then configure a peer association between these two servers to create a more
reliable NTP configuration.
• If you have only one server, you should configure all the devices as clients to that server.
• You can configure up to 64 NTP entities (servers and peers).
• If CFS is disabled for NTP, then NTP does not distribute any configuration and does not accept a
distribution from other devices in the network.
• After CFS distribution is enabled for NTP, the entry of an NTP configuration command locks the network
for NTP configuration until a commit command is entered. During the lock, no changes can be made to
the NTP configuration by any other device in the network except the device that initiated the lock.
• If you use CFS to distribute NTP, all devices in the network should have the same VRFs configured as
you use for NTP.
• If you configure NTP in a VRF, ensure that the NTP server and peers can reach each other through the
configured VRFs.
• You must manually distribute NTP authentication keys on the NTP server and Cisco NX-OS devices
across the network.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
23
Page 38

Default Settings
Default Settings
Table 4: Default NTP Parameters
Configuring NTP
Configuring NTP
DefaultParameters
disabledNTP authentication
enabledNTP access
disabledNTP logging
Configuring NTP Server and Peer
You can configure an NTP server and peer.
Before you begin
Make sure you know the IP address or DNS names of your NTP server and its peers.
If you plan to use CFS to distribute your NTP configuration to other devices, then you should have already
completed the following:
• Enabled CFS distribution.
• Enabled CFS for NTP.
Procedure
Step 1
Step 2
switch(config)# [no] ntp server {ip-address |
ipv6-address | dns-name} [key key-id] [maxpoll
max-poll] [minpoll min-poll] [prefer] [use-vrf
vrf-name]
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Forms an association with a server.
Use the key keyword to configure a key to be
used while communicating with the NTP server.
The range for the key-id argument is from 1 to
65535.
Use the maxpoll and minpoll keywords to
configure the maximum and minimum intervals
in which to poll a peer. The range for the
max-poll and min-poll arguments is from 4 to
16 seconds, and the default values are 6 and 4,
respectively.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
24
Page 39

Configuring NTP
Configuring NTP Server and Peer
PurposeCommand or Action
Use the prefer keyword to make this the
preferred NTP server for the device.
Use the use-vrf keyword to configure the NTP
server to communicate over the specified VRF.
The vrf-name argument can be default,
management, or any case-sensitive
alphanumeric string up to 32 characters.
Step 3
switch(config)# [no] ntp peer {ip-address |
ipv6-address | dns-name} [key key-id] [maxpoll
max-poll] [minpoll min-poll] [prefer] [use-vrf
vrf-name]
Note
If you configure a key to be used
while communicating with the NTP
server, make sure that the key exists
as a trusted key on the device.
Forms an association with a peer. You can
specify multiple peer associations.
Use the key keyword to configure a key to be
used while communicating with the NTP peer.
The range for the key-id argument is from 1 to
65535.
Use the maxpoll and minpoll keywords to
configure the maximum and minimum intervals
in which to poll a peer. The range for the
max-poll and min-poll arguments is from 4 to
16 seconds, and the default values are 6 and 4,
respectively.
Use the prefer keyword to make this the
preferred NTP server for the device.
Use the use-vrf keyword to configure the NTP
server to communicate over the specified VRF.
The vrf-name argument can be default,
management, or any case-sensitive
alphanumeric string up to 32 characters.
Step 4
Step 5
(Optional) switch(config)# copy
running-config startup-config
Displays the configured server and peers.(Optional) switch(config)# show ntp peers
Note
Saves the change persistently through reboots
and restarts by copying the running
configuration to the startup configuration.
Example
This example shows how to configure an NTP server and peer:
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
A domain name is resolved only
when you have a DNS server
configured.
25
Page 40

Configuring NTP Authentication
switch# config t
Enter configuration commands, one per line. End with CNTL/Z.
switch(config)# ntp server 192.0.2.10 key 10 use-vrf Red
switch(config)# ntp peer 2001:0db8::4101 prefer use-vrf Red
switch(config)# show ntp peers
-------------------------------------------------Peer IP Address Serv/Peer
-------------------------------------------------2001:0db8::4101 Peer (configured)
192.0.2.10 Server (configured)
switch(config)# copy running-config startup-config
[########################################] 100%
switch(config)#
Configuring NTP Authentication
You can configure the device to authenticate the time sources to which the local clock is synchronized. When
you enable NTP authentication, the device synchronizes to a time source only if the source carries one of the
authentication keys specified by the ntp trusted-key command. The device drops any packets that fail the
authentication check and prevents them from updating the local clock. NTP authentication is disabled by
default.
Configuring NTP
Before you begin
Make sure that you configured the NTP server with the authentication keys that you plan to specify in this
procedure.
Procedure
PurposeCommand or Action
Step 1
Step 2
switch(config)# [no] ntp authentication-key
number md5 md5-string
Enters global configuration mode.switch# configure terminal
Defines the authentication keys. The device
does not synchronize to a time source unless
the source has one of these authentication keys
and the key number is specified by the ntp
trusted-key number command.
Step 3
Step 4
(Optional) switch(config)# show ntp
authentication-keys
switch(config)# [no]ntp trusted-key number
Displays the configured NTP authentication
keys.
Specifies one or more keys that a time source
must provide in its NTP packets in order for the
device to synchronize to it. The range for trusted
keys is from 1 to 65535.
This command provides protection against
accidentally synchronizing the device to a time
source that is not trusted.
Step 5
Displays the configured NTP trusted keys.(Optional) switch(config)# show ntp
trusted-keys
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
26
Page 41

Configuring NTP
Configuring NTP Access Restrictions
PurposeCommand or Action
Step 6
switch(config)# [no] ntp authenticate
Enables or disables the NTP authentication
feature. NTP authentication is disabled by
default.
Step 7
Displays the status of NTP authentication.(Optional) switch(config)# show ntp
authentication-status
Step 8
(Optional) switch(config)# copy
running-config startup-config
Saves the change persistently through reboots
and restarts by copying the running
configuration to the startup configuration.
Example
This example shows how to configure the device to synchronize only to time sources that provide
authentication key 42 in their NTP packets:
switch# config t
Enter configuration commands, one per line. End with CNTL/Z.
switch(config)# ntp authentication-key 42 md5 aNiceKey
switch(config)# ntp trusted-key 42
switch(config)# ntp authenticate
switch(config)# copy running-config startup-config
[########################################] 100%
switch(config)#
Configuring NTP Access Restrictions
You can control access to NTP services by using access groups. Specifically, you can specify the types of
requests that the device allows and the servers from which it accepts responses.
If you do not configure any access groups, NTP access is granted to all devices. If you configure any access
groups, NTP access is granted only to the remote device whose source IP address passes the access list criteria.
Procedure
Step 1
Step 2
switch(config)# [no] ntp access-group {peer
| serve | serve-only | query-only}
access-list-name
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Creates or removes an access group to control
NTP access and applies a basic IP access list.
The access group options are scanned in the
following order, from least restrictive to most
restrictive. However, if NTP matches a deny
ACL rule in a configured peer, ACL processing
stops and does not continue to the next access
group option.
• The peer keyword enables the device to
receive time requests and NTP control
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
27
Page 42

Configuring the NTP Source IP Address
Configuring NTP
PurposeCommand or Action
queries and to synchronize itself to the
servers specified in the access list.
• The serve keyword enables the device to
receive time requests and NTP control
queries from the servers specified in the
access list but not to synchronize itself to
the specified servers.
• The serve-only keyword enables the
device to receive only time requests from
servers specified in the access list.
• The query-only keyword enables the
device to receive only NTP control queries
from the servers specified in the access
list.
Step 3
access-groups
Step 4
(Optional) switch(config)# copy
running-config startup-config
Example
This example shows how to configure the device to allow it to synchronize to a peer from access
group “accesslist1”:
switch# config t
switch(config)# ntp access-group peer accesslist1
switch(config)# show ntp access-groups
Access List Type
----------------------------accesslist1 Peer
switch(config)# copy running-config startup-config
[########################################] 100%
switch(config)#
Configuring the NTP Source IP Address
NTP sets the source IP address for all NTP packets based on the address of the interface through which the
NTP packets are sent. You can configure NTP to use a specific source IP address.
Displays the NTP access group configuration.(Optional) switch(config)# show ntp
Saves the change persistently through reboots
and restarts by copying the running
configuration to the startup configuration.
To configure the NTP source IP address, use the following command in global configuration mode:
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
28
Page 43

Configuring NTP
Configuring the NTP Source Interface
Procedure
PurposeCommand or Action
Step 1
Example
This example shows how to configure NTP to a source IP address:
switch(config)# ntp source 192.0.2.1
switch(config)# [no] ntp source ip-address
Configuring the NTP Source Interface
You can configure NTP to use a specific interface.
To configure the NTP source interface, use the following command in global configuration mode:
Procedure
Step 1
switch(config)# [no] ntp source-interface
interface
Configures the source IP address for all NTP
packets. The ip-address can be in IPv4 or IPv6
format.
PurposeCommand or Action
Configures the source interface for all NTP
packets. Use the ? keyword to display a list of
supported interfaces.
Example
This example shows how to configure NTP to a specific interface:
switch(config)# ntp source-interface
ethernet 2/1
Configuring NTP Logging
You can configure NTP logging in order to generate system logs with significant NTP events. NTP logging
is disabled by default.
Procedure
Step 1
Step 2
switch(config)# [no] ntp logging
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Enables or disables system logs to be generated
with significant NTP events. NTP logging is
disabled by default.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
29
Page 44

Enabling CFS Distribution for NTP
Configuring NTP
PurposeCommand or Action
Step 3
logging-status
Step 4
(Optional) switch(config)# copy
running-config startup-config
Example
This example shows how to enable NTP logging in order to generate system logs with significant
NTP events:
switch# config t
switch(config)# ntp logging
switch(config)# copy running-config startup-config
[########################################] 100%
switch(config)#
Enabling CFS Distribution for NTP
You can enable CFS distribution for NTP in order to distribute the NTP configuration to other CFS-enabled
devices.
Before you begin
Displays the NTP logging configuration status.(Optional) switch(config)# show ntp
Saves the change persistently through reboots
and restarts by copying the running
configuration to the startup configuration.
Make sure that you have enabled CFS distribution for the device.
Procedure
PurposeCommand or Action
Step 1
Step 2
switch(config)# [no] ntp distribute
Enters global configuration mode.switch# configure terminal
Enables or disables the device to receive NTP
configuration updates that are distributed
through CFS.
Step 3
Step 4
(Optional) switch(config)# copy
running-config startup-config
Displays the NTP CFS distribution status.(Optional) switch(config)# show ntp status
Saves the change persistently through reboots
and restarts by copying the running
configuration to the startup configuration.
Example
This example shows how to enable CFS distribution for NTP:
switch# config t
Enter configuration commands, one per
line. End with CNTL/Z.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
30
Page 45

Configuring NTP
switch(config)# ntp distribute
switch(config)# copy running-config
startup-config
Commiting NTP Configuration Changes
When you commit the NTP configuration changes, the effective database is overwritten by the configuration
changes in the pending database and all the devices in the network receive the same configuration.
Procedure
Commiting NTP Configuration Changes
PurposeCommand or Action
Step 1
Step 2
switch(config)# ntp commit
Example
This example shows how to commit the NTP configuration changes:
switch(config)# ntp commit
Discarding NTP Configuration Changes
After making the configuration changes, you can choose to discard the changes instead of committing them.
If you discard the changes, Cisco NX-OS removes the pending database changes and releases the CFS lock.
To discard NTP configuration changes, use the following command in global configuration mode:
Procedure
Enters global configuration mode.switch# configure terminal
Distributes the NTP configuration changes to
all Cisco NX-OS devices in the network and
releases the CFS lock. This command
overwrites the effective database with the
changes made to the pending database.
PurposeCommand or Action
Step 1
switch(config)# ntp abort
Discards the NTP configuration changes in the
pending database and releases the CFS lock.
Use this command on the device where you
started the NTP configuration.
Example
This example shows how to discard the NTP configuration changes:
switch(config)# ntp abort
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
31
Page 46

Releasing the CFS Session Lock
Releasing the CFS Session Lock
If you have performed an NTP configuration and have forgotten to release the lock by either committing or
discarding the changes, you or another administrator can release the lock from any device in the network.
This action also discards pending database changes.
To release the session lock from any device and discard any pending database changes, use the following
command in global configuration mode:
Procedure
Configuring NTP
PurposeCommand or Action
Step 1
Example
This example shows how to release the CFS session lock:
switch(config)# clear ntp session
switch(config)# clear ntp session
Verifying the NTP Configuration
To display the NTP configuration, perform one of the following tasks:
Use the clear ntp session command to clear the NTP sessions.
Use the clear ntp statistics command to clear the NTP statistics.
Procedure
Step 1
Step 2
show ntp authentication-keys
Discards the NTP configuration changes in the
pending database and releases the CFS lock.
PurposeCommand or Action
Displays the NTP access group configuration.show ntp access-groups
Displays the configured NTP authentication
keys.
Step 3
Step 4
Step 5
Step 6
Step 7
Step 8
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
32
show ntp peer-status
show ntp pending-diff
Displays the status of NTP authentication.show ntp authentication-status
Displays the NTP logging status.show ntp logging-status
Displays the status for all NTP servers and
peers.
Displays all the NTP peers.show ntp peers
Displays the temporary CFS database for NTP.show ntp pending
Displays the difference between the pending
CFS database and the current NTP
configuration.
Page 47

Configuring NTP
Configuration Examples for NTP
PurposeCommand or Action
Step 9
Step 10
Step 11
show ntp session status
show ntp source
Step 12
Step 13
{ipaddr {ipv4-addr | ipv6-addr} | name
peer-name}}
Step 14
Step 15
Step 16
Configuration Examples for NTP
This example shows how to configure an NTP server and peer, enable NTP authentication, enable NTP
logging, and then save the configuration in startup so that it is saved across reboots and restarts:
switch# config terminal
Enter configuration commands, one per line. End with CNTL/Z.
switch(config)# ntp server 192.0.2.105 key 42
switch(config)# ntp peer 2001:0db8::4101
switch(config)# show ntp peers
-------------------------------------------------Peer IP Address Serv/Peer
-------------------------------------------------2001:db8::4101 Peer (configured)
192.0.2.105 Server (configured)
switch(config)# ntp authentication-key 42 md5 aNiceKey
switch(config)# show ntp authentication-keys
-----------------------------
Auth key MD5 String
----------------------------42 aNicekey
switch(config)# ntp trusted-key 42
switch(config)# show ntp trusted-keys
Trusted Keys:
42
switch(config)# ntp authenticate
switch(config)# show ntp authentication-status
Authentication enabled.
switch(config)# ntp logging
switch(config)# show ntp logging
NTP logging enabled.
switch(config)# copy running-config startup-config
[########################################] 100%
switch(config)#
Displays the RTS update status.show ntp rts-update
Displays the NTP CFS distribution session
information.
Displays the configured NTP source IP
address.
Displays the configured NTP source interface.show ntp source-interface
Displays the NTP statistics.show ntp statistics {io | local | memory | peer
Displays the NTP CFS distribution status.show ntp status
Displays the configured NTP trusted keys.show ntp trusted-keys
Displays NTP information.show running-config ntp
This example shows an NTP access group configuration with the following restrictions:
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
33
Page 48

Related Documents for NTP
switch# config terminal
switch(config)# ntp peer 10.1.1.1
switch(config)# ntp peer 10.2.2.2
switch(config)# ntp peer 10.3.3.3
switch(config)# ntp peer 10.4.4.4
switch(config)# ntp peer 10.5.5.5
switch(config)# ntp peer 10.6.6.6
switch(config)# ntp peer 10.7.7.7
switch(config)# ntp peer 10.8.8.8
switch(config)# ntp access-group peer peer-acl
switch(config)# ntp access-group serve serve-acl
switch(config)# ntp access-group serve-only serve-only-acl
switch(config)# ntp access-group query-only query-only-acl
Configuring NTP
• Peer restrictions are applied to IP addresses that pass the criteria of the access list named “peer-acl.”
• Serve restrictions are applied to IP addresses that pass the criteria of the access list named “serve-acl.”
• Serve-only restrictions are applied to IP addresses that pass the criteria of the access list named
“serve-only-acl.”
• Query-only restrictions are applied to IP addresses that pass the criteria of the access list named
“query-only-acl.”
switch(config)# ip access-list peer-acl
switch(config-acl)# 10 permit ip host 10.1.1.1 any
switch(config-acl)# 20 permit ip host 10.8.8.8 any
switch(config)# ip access-list serve-acl
switch(config-acl)# 10 permit ip host 10.4.4.4 any
switch(config-acl)# 20 permit ip host 10.5.5.5 any
switch(config)# ip access-list serve-only-acl
switch(config-acl)# 10 permit ip host 10.6.6.6 any
switch(config-acl)# 20 permit ip host 10.7.7.7 any
switch(config)# ip access-list query-only-acl
switch(config-acl)# 10 permit ip host 10.2.2.2 any
switch(config-acl)# 20 permit ip host 10.3.3.3 any
Related Documents for NTP
Document TitleRelated Topic
NTP CLI
commands
Cisco Nexus 3548 Switch NX-OS System Management Command Reference Guide
Feature History for NTP
This table includes only the updates for those releases that have resulted in additions or changes to the feature.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
34
Feature InformationReleasesFeature Name
This feature was introduced.5.0(3)A1(1)NTP
Page 49

CHAPTER 5
Configuring System Message Logging
This chapter contains the following sections:
• Information About System Message Logging, on page 35
• Licensing Requirements for System Message Logging, on page 36
• Guidelines and Limitations for System Message Logging, on page 36
• Default Settings for System Message Logging, on page 36
• Configuring System Message Logging, on page 37
• Configuring DOM Logging, on page 48
• Verifying the System Message Logging Configuration, on page 49
Information About System Message Logging
You can use system message logging to control the destination and to filter the severity level of messages that
system processes generate. You can configure logging to terminal sessions, a log file, and syslog servers on
remote systems.
System message logging is based on RFC 3164. For more information about the system message format and
the messages that the device generates, see the Cisco NX-OS System Messages Reference.
By default, the Cisco Nexus device outputs messages to terminal sessions.
By default, the switch logs system messages to a log file.
The following table describes the severity levels used in system messages. When you configure the severity
level, the system outputs messages at that level and lower.
Table 5: System Message Severity Levels
DescriptionLevel
System unusable0 – emergency
Immediate action needed1 – alert
Critical condition2 – critical
Error condition3 – error
Warning condition4 – warning
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
35
Page 50

Syslog Servers
The switch logs the most recent 100 messages of severity 0, 1, or 2 to the NVRAM log. You cannot configure
logging to the NVRAM.
You can configure which system messages should be logged based on the facility that generated the message
and its severity level.
Syslog Servers
Syslog servers run on remote systems that are configured to log system messages based on the syslog protocol.
You can configure the Cisco Nexus Series switch to sends logs to up to eight syslog servers.
Configuring System Message Logging
DescriptionLevel
Normal but significant condition5 – notification
Informational message only6 –
informational
Appears during debugging only7 – debugging
To support the same configuration of syslog servers on all switches in a fabric, you can use Cisco Fabric
Services (CFS) to distribute the syslog server configuration.
Note
When the switch first initializes, messages are sent to syslog servers only after the network is initialized.
Licensing Requirements for System Message Logging
License RequirementProduct
Cisco NX-OS
System message logging requires no license. Any
feature not included in a license package is bundled
with the Cisco NX-OS system images and is provided
at no extra charge to you. For a complete explanation
of the Cisco NX-OS licensing scheme, see the Cisco
NX-OS Licensing Guide.
Guidelines and Limitations for System Message Logging
System messages are logged to the console and the logfile by default.
Default Settings for System Message Logging
The following table lists the default settings for system message logging parameters.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
36
Page 51

Configuring System Message Logging
Table 6: Default System Message Logging Parameters
Configuring System Message Logging
DefaultParameters
Enabled at severity level 2Console logging
Enabled at severity level 2Monitor logging
Log file logging
Enabled to log messages at severity level
5
Enabled at severity level 5Module logging
EnabledFacility logging
SecondsTime-stamp units
DisabledSyslog server logging
DisabledSyslog server configuration distribution
Configuring System Message Logging
Configuring System Message Logging to Terminal Sessions
You can configure the switch to log messages by their severity level to console, Telnet, and Secure Shell
sessions.
By default, logging is enabled for terminal sessions.
Procedure
Step 1
Step 2
Step 3
switch# terminal monitor
switch(config)# logging console [severity-level]
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
PurposeCommand or Action
Copies syslog messages from the console to the
current terminal session.
Enters global configuration mode.switch# configure terminal
Enables the switch to log messages to the
console session based on a specified severity
level or higher (a lower number value indicates
a higher severity level). Severity levels range
from 0 to 7:
• 0 – emergency
• 1 – alert
• 2 – critical
• 3 – error
37
Page 52

Configuring System Message Logging to Terminal Sessions
Configuring System Message Logging
PurposeCommand or Action
• 4 – warning
• 5 – notification
• 6 – informational
• 7 – debugging
If the severity level is not specified, the default
of 2 is used.
Step 4
Step 5
[severity-level]
switch(config)# logging monitor
[severity-level]
Disables logging messages to the console.(Optional) switch(config)# no logging console
Enables the switch to log messages to the
monitor based on a specified severity level or
higher (a lower number value indicates a higher
severity level). Severity levels range from 0 to
7:
• 0 – emergency
• 1 – alert
• 2 – critical
• 3 – error
• 4 – warning
• 5 – notification
• 6 – informational
• 7 – debugging
If the severity level is not specified, the default
of 2 is used.
The configuration applies to Telnet and SSH
sessions.
Step 6
Step 7
Step 8
Step 9
(Optional) switch(config)# no logging monitor
[severity-level]
(Optional) switch# copy running-config
startup-config
Disables logging messages to Telnet and SSH
sessions.
Displays the console logging configuration.(Optional) switch# show logging console
Displays the monitor logging configuration.(Optional) switch# show logging monitor
Copies the running configuration to the startup
configuration.
Example
The following example shows how to configure a logging level of 3 for the console:
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
38
Page 53

Configuring System Message Logging
switch# configure terminal
switch(config)# logging console 3
The following example shows how to display the console logging configuration:
switch# show logging console
Logging console: enabled (Severity: error)
The following example shows how to disable logging for the console:
switch# configure terminal
switch(config)# no logging console
The following example shows how to configure a logging level of 4 for the terminal session:
switch# terminal monitor
switch# configure terminal
switch(config)# logging monitor 4
Configuring System Message Logging to a File
The following example shows how to display the terminal session logging configuration:
switch# show logging monitor
Logging monitor: enabled (Severity: warning)
The following example shows how to disable logging for the terminal session:
switch# configure terminal
switch(config)# no logging monitor
Configuring System Message Logging to a File
You can configure the switch to log system messages to a file. By default, system messages are logged to the
file log:messages.
Procedure
Step 1
Step 2
switch(config)# logging logfile logfile-name
severity-level [size bytes]
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Configures the name of the log file used to store
system messages and the minimum severity
level to log. You can optionally specify a
maximum file size. The default severity level
is 5 and the file size is 4194304.
Severity levels range from 0 to 7:
• 0 – emergency
• 1 – alert
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
39
Page 54

Configuring System Message Logging to a File
Configuring System Message Logging
PurposeCommand or Action
• 2 – critical
• 3 – error
• 4 – warning
• 5 – notification
• 6 – informational
• 7 – debugging
The file size is from 4096 to 10485760 bytes.
Step 3
(Optional) switch(config)# no logging logfile
[logfile-name severity-level [size bytes]]
Disables logging to the log file. You can
optionally specify a maximum file size. The
default severity level is 5 and the file size is
4194304.
Step 4
(Optional) switch# show logging info
Displays the logging configuration. You can
optionally specify a maximum file size. The
default severity level is 5 and the file size is
4194304.
Step 5
(Optional) switch# copy running-config
startup-config
Copies the running configuration to the startup
configuration.
Example
The following example shows how to configure a switch to log system messages to a file:
switch# configure terminal
switch(config)# logging logfile my_log 6 size 4194304
The following example shows how to display the logging configuration (some of the output has been
removed for brevity):
switch# show logging info
Logging console: enabled (Severity: debugging)
Logging monitor: enabled (Severity: debugging)
Logging timestamp: Seconds
Logging server: disabled
Logging logfile: enabled
Facility Default Severity Current Session Severity
-------- ---------------- -----------------------aaa 3 3
afm 3 3
altos 3 3
auth 0 0
authpriv 3 3
bootvar 5 5
callhome 2 2
capability 2 2
cdp 2 2
Name - my_log: Severity - informational Size - 4194304
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
40
Page 55

Configuring System Message Logging
Configuring Module and Facility Messages Logging
cert_enroll 2 2
...
Configuring Module and Facility Messages Logging
You can configure the severity level and time-stamp units of messages logged by modules and facilities.
Procedure
PurposeCommand or Action
Step 1
Step 2
Step 3
switch(config)# logging module [severity-level]
switch(config)# logging level facility
severity-level
Enters global configuration mode.switch# configure terminal
Enables module log messages that have the
specified severity level or higher. Severity levels
range from 0 to 7:
• 0 – emergency
• 1 – alert
• 2 – critical
• 3 – error
• 4 – warning
• 5 – notification
• 6 – informational
• 7 – debugging
If the severity level is not specified, the default
of 5 is used.
Enables logging messages from the specified
facility that have the specified severity level or
higher. Severity levels from 0 to 7:
• 0 – emergency
• 1 – alert
• 2 – critical
• 3 – error
• 4 – warning
• 5 – notification
• 6 – informational
• 7 – debugging
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
41
Page 56

Configuring Logging Timestamps
Configuring System Message Logging
PurposeCommand or Action
To apply the same severity level to all facilities,
use the all facility. For defaults, see the show
logging level command.
Step 4
Step 5
Step 6
Step 7
Step 8
[severity-level]
(Optional) switch(config)# no logging level
[facility severity-level]
(Optional) switch# show logging level [facility]
(Optional) switch# copy running-config
startup-config
Note
If the default severity and current
session severity of a component is
the same, then the logging level for
the component will not be displayed
in the running configuration.
Disables module log messages.(Optional) switch(config)# no logging module
Resets the logging severity level for the
specified facility to its default level. If you do
not specify a facility and severity level, the
switch resets all facilities to their default levels.
Displays the module logging configuration.(Optional) switch# show logging module
Displays the logging level configuration and
the system default level by facility. If you do
not specify a facility, the switch displays levels
for all facilities.
Copies the running configuration to the startup
configuration.
Example
The following example shows how to configure the severity level of module and specific facility
messages:
switch# configure terminal
switch(config)# logging module 3
switch(config)# logging level aaa 2
Configuring Logging Timestamps
You can configure the time-stamp units of messages logged by the Cisco Nexus Series switch.
Procedure
Step 1
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
42
Page 57

Configuring System Message Logging
Configuring Syslog Servers
PurposeCommand or Action
Step 2
switch(config)# logging timestamp
{microseconds | milliseconds | seconds}
Step 3
(Optional) switch(config)# no logging
timestamp {microseconds | milliseconds |
seconds}
Step 4
Step 5
(Optional) switch# show logging timestamp
(Optional) switch# copy running-config
startup-config
Example
The following example shows how to configure the time-stamp units of messages:
switch# configure terminal
switch(config)# logging timestamp milliseconds
switch(config)# exit
switch# show logging timestamp
Logging timestamp: Milliseconds
Configuring Syslog Servers
Sets the logging time-stamp units. By default,
the units are seconds.
Resets the logging time-stamp units to the
default of seconds.
Displays the logging time-stamp units
configured.
Copies the running configuration to the startup
configuration.
You can configure up to eight syslog servers that reference remote systems where you want to log system
messages.
Procedure
PurposeCommand or Action
Step 1
Enters global configuration mode.configure terminal
Example:
switch# configure terminal
switch(config)#
Step 2
logging server host [severity-level [use-vrf
vrf-name [facility facility]]]
Example:
switch(config)# logging server
172.28.254.254 5
use-vrf default facility local3
Configures a host to receive syslog messages.
• The host argument identifies the hostname
or the IPv4 or IPv6 address of the syslog
server host.
• The severity-level argument limits the
logging of messages to the syslog server
to a specified level. Severity levels range
from 0 to 7. See Table 5: System Message
Severity Levels , on page 35.
• The use vrf vrf-name keyword and
argument identify the default or
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
43
Page 58

Configuring Syslog Servers
Configuring System Message Logging
PurposeCommand or Action
management values for the virtual routing
and forwarding (VRF) name. If a specific
VRF is not identified, management is the
default. However, if management is
configured, it will not be listed in the
output of the show-running command
because it is the default. If a specific VRF
is configured, the show-running command
output will list the VRF for each server.
Step 3
(Optional) no logging server host
Example:
switch(config)# no logging server
172.28.254.254 5
Note
The current Cisco Fabric
Services (CFS) distribution
does not support VRF. If CFS
distribution is enabled, the
logging server configured with
the default VRF is distributed
as the management VRF.
• The facility argument names the syslog
facility type. The default outgoing facility
is local7.
The facilities are listed in the command
reference for the Cisco Nexus Series
software that you are using.
Note
Debugging is a CLI facility but the
debug syslogs are not sent to the
server.
Removes the logging server for the specified
host.
Step 4
Displays the syslog server configuration.(Optional) show logging server
Example:
switch# show logging server
Step 5
(Optional) copy running-config startup-config
Example:
switch(config)# copy running-config
startup-config
Saves the change persistently through reboots
and restarts by copying the running
configuration to the startup configuration.
Example
The following examples show how to configure a syslog server:
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
44
Page 59

Configuring System Message Logging
switch# configure terminal
switch(config)# logging server 172.28.254.254 5
use-vrf default facility local3
switch# configure terminal
switch(config)# logging server 172.28.254.254 5 use-vrf management facility local3
Configuring syslog on a UNIX or Linux System
You can configure a syslog server on a UNIX or Linux system by adding the following line to the
/etc/syslog.conf file:
facility.level <five tab characters> action
The following table describes the syslog fields that you can configure.
Table 7: syslog Fields in syslog.conf
DescriptionField
Configuring syslog on a UNIX or Linux System
Facility
Creator of the message, which can be auth, authpriv, cron, daemon, kern, lpr, mail, mark, news,
syslog, user, local0 through local7, or an asterisk (*) for all. These facility designators allow you to
control the destination of messages based on their origin.
Level
Note
Minimum severity level at which messages are logged, which can be debug, info, notice, warning,
Check your configuration before using a local facility.
err, crit, alert, emerg, or an asterisk (*) for all. You can use none to disable a facility.
Action
Destination for messages, which can be a filename, a hostname preceded by the at sign (@), or a
comma-separated list of users or an asterisk (*) for all logged-in users.
Procedure
Step 1 Log debug messages with the local7 facility in the file /var/log/myfile.log by adding the following line to the
/etc/syslog.conf file:
debug.local7 /var/log/myfile.log
Step 2 Create the log file by entering these commands at the shell prompt:
$ touch /var/log/myfile.log
$ chmod 666 /var/log/myfile.log
Step 3 Make sure that the system message logging daemon reads the new changes by checking myfile.log after
entering this command:
$ kill -HUP ~cat /etc/syslog.pid~
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
45
Page 60

Configuring syslog Server Configuration Distribution
Configuring syslog Server Configuration Distribution
You can distribute the syslog server configuration to other switches in the network by using the Cisco Fabric
Services (CFS) infrastructure.
After you enable syslog server configuration distribution, you can modify the syslog server configuration and
view the pending changes before committing the configuration for distribution. As long as distribution is
enabled, the switch maintains pending changes to the syslog server configuration.
Note
If the switch is restarted, the syslog server configuration changes that are kept in volatile memory might get
lost.
Before you begin
You must have configured one or more syslog servers.
Procedure
Configuring System Message Logging
Step 1
Step 2
Step 3
Step 4
Step 5
Step 6
switch(config)# logging distribute
switch(config)# logging commit
switch(config)# logging abort
(Optional) switch(config)# no logging
distribute
(Optional) switch# show logging pending
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Enables distribution of the syslog server
configuration to network switches using the
CFS infrastructure. By default, distribution is
disabled.
Commits the pending changes to the syslog
server configuration for distribution to the
switches in the fabric.
Cancels the pending changes to the syslog
server configuration.
Disables the distribution of the syslog server
configuration to network switches using the
CFS infrastructure. You cannot disable
distribution when configuration changes are
pending. See the logging commit and logging
abort commands. By default, distribution is
disabled.
Displays the pending changes to the syslog
server configuration.
Step 7
(Optional) switch# show logging pending-diff
Displays the differences from the current syslog
server configuration to the pending changes of
the syslog server configuration.
Step 8
(Optional) switch# copy running-config
startup-config
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
46
Copies the running configuration to the startup
configuration.
Page 61

Configuring System Message Logging
Displaying and Clearing Log Files
You can display or clear messages in the log file and the NVRAM.
Procedure
Displaying and Clearing Log Files
PurposeCommand or Action
Step 1
switch# show logging last number-lines
Displays the last number of lines in the logging
file. You can specify from 1 to 9999 for the last
number of lines.
Step 2
switch# show logging logfile [start-time yyyy
mmm dd hh:mm:ss] [end-time yyyy mmm dd
hh:mm:ss]
Displays the messages in the log file that have
a time stamp within the span entered. If you do
not enter an end time, the current time is used.
You enter three characters for the month time
field and digits for the year and day time fields.
Step 3
switch# show logging nvram [last
number-lines]
Displays the messages in the NVRAM. To limit
the number of lines displayed, you can enter the
last number of lines to display. You can specify
from 1 to 100 for the last number of lines.
Step 4
Step 5
Clears the contents of the log file.switch# clear logging logfile
Clears the logged messages in NVRAM.switch# clear logging nvram
Example
The following example shows how to display messages in a log file:
switch# show logging last 40
switch# show logging logfile start-time 2007 nov 1 15:10:0
switch# show logging nvram last 10
The following example shows how to clear messages in a log file:
switch# clear logging logfile
switch# clear logging nvram
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
47
Page 62

Configuring DOM Logging
Configuring DOM Logging
Enabling DOM Logging
Procedure
Configuring System Message Logging
PurposeCommand or Action
Step 1
Step 2
Example
The following example shows how to enable DOM logging.
switch# configure terminal
switch(config)# system ethernet dom polling
switch(config)# system ethernet dom polling
Disabling DOM Logging
Procedure
Step 1
Step 2
switch(config)# no system ethernet dom
polling
Enters global configuration mode.switch# configure terminal
Enables transceiver digital optical monitoring
periodic polling.
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Disables transceiver digital optical monitoring
periodic polling.
Example
The following example shows how to disable DOM logging.
switch# configure terminal
switch(config)# no system ethernet dom polling
Verifying the DOM Logging Configuration
show system ethernet dom polling status
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
48
PurposeCommand
Displays the transceiver digital optical monitoring
periodic polling status.
Page 63

Configuring System Message Logging
Verifying the System Message Logging Configuration
Verifying the System Message Logging Configuration
Use these commands to verify system message logging configuration information:
PurposeCommand
Displays the console logging configuration.show logging console
Displays the logging configuration.show logging info
Displays the IP access list cache.show logging ip access-list cache
Displays detailed information about the IP access list cache.show logging ip access-list cache detail
Displays the status of the IP access list cache.show logging ip access-list status
show logging last number-lines
show logging level [facility]
show logging logfile [start-time yyyy mmm dd
hh:mm:ss] [end-time yyyy mmm dd hh:mm:ss]
show logging nvram [last number-lines]
show logging pending
show logging pending-diff
Displays the last number of lines of the log file.
Displays the facility logging severity level configuration.
Displays the messages in the log file.
Displays the module logging configuration.show logging module
Displays the monitor logging configuration.show logging monitor
Displays the messages in the NVRAM log.
Displays the syslog server pending distribution
configuration.
Displays the syslog server pending distribution
configuration differences.
Displays the syslog server configuration.show logging server
Displays the logging session status.show logging session
Displays the logging status.show logging status
Displays the logging time-stamp units configuration.show logging timestamp
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
49
Page 64

Verifying the System Message Logging Configuration
Configuring System Message Logging
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
50
Page 65

Configuring Smart Call Home
This chapter contains the following sections:
• Information About Smart Call Home, on page 51
• Guidelines and Limitations for Smart Call Home, on page 59
• Prerequisites for Smart Call Home, on page 59
• Default Call Home Settings, on page 59
• Configuring Smart Call Home, on page 60
• Verifying the Smart Call Home Configuration, on page 70
• Sample Syslog Alert Notification in Full-Text Format, on page 70
• Sample Syslog Alert Notification in XML Format, on page 71
Information About Smart Call Home
Smart Call Home provides e-mail-based notification of critical system events. Cisco Nexus Series switches
provide a range of message formats for optimal compatibility with pager services, standard e-mail, or
XML-based automated parsing applications. You can use this feature to page a network support engineer,
e-mail a Network Operations Center, or use Cisco Smart Call Home services to automatically generate a case
with the Technical Assistance Center (TAC).
CHAPTER 6
If you have a service contract directly with Cisco, you can register your devices for the Smart Call Home
service. Smart Call Home provides fast resolution of system problems by analyzing Smart Call Home messages
sent from your devices and providing background information and recommendations. For issues that can be
identified as known, particularly GOLD diagnostics failures, Automatic Service Requests will be generated
by the Cisco TAC.
Smart Call Home offers the following features:
• Continuous device health monitoring and real-time diagnostic alerts.
• Analysis of Smart Call Home messages from your device and, where appropriate, Automatic Service
Request generation, routed to the appropriate TAC team, including detailed diagnostic information to
speed problem resolution.
• Secure message transport directly from your device or through a downloadable Transport Gateway (TG)
aggregation point. You can use a TG aggregation point in cases that require support for multiple devices
or in cases where security requirements mandate that your devices may not be connected directly to the
Internet.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
51
Page 66

Smart Call Home Overview
• Web-based access to Smart Call Home messages and recommendations, inventory and configuration
information for all Smart Call Home devices, and field notices, security advisories, and end-of-life
information.
Smart Call Home Overview
You can use Smart Call Home to notify an external entity when an important event occurs on your device.
Smart Call Home delivers alerts to multiple recipients that you configure in destination profiles.
Smart Call Home includes a fixed set of predefined alerts on your switch. These alerts are grouped into alert
groups and CLI commands that are assigned to execute when an alert in an alert group occurs. The switch
includes the command output in the transmitted Smart Call Home message.
The Smart Call Home feature offers the following:
• Automatic execution and attachment of relevant CLI command output.
• Multiple message format options such as the following:
• Short Text—Text that is suitable for pagers or printed reports.
Configuring Smart Call Home
• Full Text—Fully formatted message information that is suitable for human reading.
• XML—Matching readable format that uses the Extensible Markup Language (XML) and the
Adaptive Messaging Language (AML) XML schema definition (XSD). The XML format enables
communication with the Cisco TAC.
• Multiple concurrent message destinations. You can configure up to 50 e-mail destination addresses for
each destination profile.
Smart Call Home Destination Profiles
A Smart Call Home destination profile includes the following information:
• One or more alert groups—The group of alerts that trigger a specific Smart Call Home message if the
alert occurs.
• One or more e-mail destinations—The list of recipients for the Smart Call Home messages that are
generated by alert groups assigned to this destination profile.
• Message format—The format for the Smart Call Home message (short text, full text, or XML).
• Message severity level—The Smart Call Home severity level that the alert must meet before the switch
generates a Smart Call Home message to all e-mail addresses in the destination profile. The switch does
not generate an alert if the Smart Call Home severity level of the alert is lower than the message severity
level set for the destination profile.
You can also configure a destination profile to allow periodic inventory update messages by using the inventory
alert group that will send out periodic messages daily, weekly, or monthly.
Cisco Nexus switches support the following predefined destination profiles:
• CiscoTAC-1—Supports the Cisco-TAC alert group in XML message format.
• full-text-destination—Supports the full text message format.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
52
Page 67

Configuring Smart Call Home
• short-text-destination—Supports the short text message format.
Smart Call Home Alert Groups
An alert group is a predefined subset of Smart Call Home alerts that are supported in all Cisco Nexus devices.
Alert groups allow you to select the set of Smart Call Home alerts that you want to send to a predefined or
custom destination profile. The switch sends Smart Call Home alerts to e-mail destinations in a destination
profile only if that Smart Call Home alert belongs to one of the alert groups associated with that destination
profile and if the alert has a Smart Call Home message severity at or above the message severity set in the
destination profile.
The following table lists the supported alert groups and the default CLI command output included in Smart
Call Home messages generated for the alert group.
Table 8: Alert Groups and Executed Commands
Smart Call Home Alert Groups
Executed CommandsDescriptionAlert Group
Cisco-TAC
hardware
Linecard
hardware
System
All critical alerts from the other alert
groups destined for Smart Call Home.
Events generated by diagnostics.Diagnostic
Events related to supervisor modules.Supervisor
Events related to standard or intelligent
switching modules.
Periodic events related to configuration.Configuration
Events generated by a failure of a
software system that is critical to unit
operation.
Execute commands based on the alert group
that originates the alert.
show diagnostic result module all detail
show moduleshow version
show tech-support platform callhome
show diagnostic result module all detail
show moduleshow version
show tech-support platform callhome
show diagnostic result module all detail
show moduleshow version
show tech-support platform callhome
show version
show module
show running-config all
show startup-config
show system redundancy status
show tech-support
Environmental
Events related to power, fan, and
environment-sensing elements such as
temperature alarms.
show environment
show logging last 1000
show module show version
show tech-support platform callhome
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
53
Page 68

Smart Call Home Message Levels
Configuring Smart Call Home
Executed CommandsDescriptionAlert Group
Inventory
Inventory status that is provided
whenever a unit is cold booted, or when
FRUs are inserted or removed. This alert
is considered a noncritical event, and the
information is used for status and
entitlement.
Smart Call Home maps the syslog severity level to the corresponding Smart Call Home severity level for
syslog port group messages.
You can customize predefined alert groups to execute additional show commands when specific events occur
and send that show output with the Smart Call Home message.
You can add show commands only to full text and XML destination profiles. Short text destination profiles
do not support additional show commands because they only allow 128 bytes of text.
Smart Call Home Message Levels
Smart Call Home allows you to filter messages based on their level of urgency. You can associate each
destination profile (predefined and user defined) with a Smart Call Home message level threshold. The switch
does not generate any Smart Call Home messages with a value lower than this threshold for the destination
profile. The Smart Call Home message level ranges from 0 (lowest level of urgency) to 9 (highest level of
urgency), and the default is 0 (the switch sends all messages).
show module
show version
show license usage
show inventory
show sprom all
show system uptime
Smart Call Home messages that are sent for syslog alert groups have the syslog severity level mapped to the
Smart Call Home message level.
Note
Smart Call Home does not change the syslog message level in the message text.
The following table shows each Smart Call Home message level keyword and the corresponding syslog level
for the syslog port alert group.
Table 9: Severity and Syslog Level Mapping
DescriptionSyslog LevelKeywordSmart Call Home
Level
Network-wide catastrophic failure.N/ACatastrophic9
Significant network impact.N/ADisaster8
System is unusable.Emergency (0)Fatal7
Alert (1)Critical6
Critical conditions that indicate that immediate attention
is needed.
Major conditions.Critical (2)Major5
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
54
Page 69

Configuring Smart Call Home
Call Home Message Formats
DescriptionSyslog LevelKeywordSmart Call Home
Level
Minor conditions.Error (3)Minor4
Warning conditions.Warning (4)Warning3
Basic notification and informational messages.Notice (5)Notification2
Normal1
Call Home Message Formats
Call Home supports the following message formats:
• Short text message format
• Common fields for all full text and XML messages
• Inserted fields for a reactive or proactive event message
• Inserted fields for an inventory event message
• Inserted fields for a user-generated test message
The following table describes the short text formatting option for all message types.
Table 10: Short Text Message Format
Normal event signifying return to normal state.Information
(6)
Debugging messages.Debug (7)Debugging0
DescriptionData Item
Configured device nameDevice identification
Time stamp of the triggering eventDate/time stamp
Plain English description of triggering eventError isolation message
Error level such as that applied to a system messageAlarm urgency level
The following table describes the common event message format for full text or XML.
Table 11: Common Fields for All Full Text and XML Messages
XML Tag (XML Only)Description (Plain Text and XML)Data Item (Plain Text and XML)
Time stamp
/aml/header/timeDate and time stamp of event in
ISO time notation:
YYYY-MM-DD HH:MM:SS
GMT+HH:MM
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
55
Page 70

Call Home Message Formats
Configuring Smart Call Home
XML Tag (XML Only)Description (Plain Text and XML)Data Item (Plain Text and XML)
Message name
Message type
Message group
Device ID
/aml/header/nameName of message. Specific event
names are listed in the preceding
table.
/aml/header/typeName of message type, such as
reactive or proactive.
/aml/header/groupName of alert group, such as
syslog.
/aml/header/levelSeverity level of message.Severity level
/aml/header/sourceProduct type for routing.Source ID
/aml/ header/deviceIDUnique device identifier (UDI) for
the end device that generated the
message. This field should be
empty if the message is nonspecific
to a device. The format is
type@Sid@serial:
• type is the product model
number from backplane
IDPROM.
• @ is a separator character.
Customer ID
Contract ID
Site ID
• Sid is C, identifying the serial
ID as a chassis serial number.
• serial is the number identified
by the Sid field.
An example is
WS-C6509@C@12345678
/aml/ header/customerIDOptional user-configurable field
used for contract information or
other ID by any support service.
/aml/ header /contractIDOptional user-configurable field
used for contract information or
other ID by any support service.
/aml/ header/siteIDOptional user-configurable field
used for Cisco-supplied site ID or
other data meaningful to alternate
support service.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
56
Page 71

Configuring Smart Call Home
Call Home Message Formats
XML Tag (XML Only)Description (Plain Text and XML)Data Item (Plain Text and XML)
Server ID
Device name
Contact name
/aml/header/serverIDIf the message is generated from
the device, this is the unique device
identifier (UDI) of the device.
The format is type@Sid@serial:
• type is the product model
number from backplane
IDPROM.
• @ is a separator character.
• Sid is C, identifying the serial
ID as a chassis serial number.
• serial is the number identified
by the Sid field.
An example is
WS-C6509@C@12345678
/aml/body/msgDescShort text that describes the error.Message description
/aml/body/sysNameNode that experienced the event
(hostname of the device).
/aml/body/sysContactName of person to contact for
issues associated with the node that
experienced the event.
Contact e-mail
/aml/body/sysContactEmailE-mail address of person identified
as the contact for this unit.
Contact phone number
/aml/body/sysContactPhoneNumberPhone number of the person
identified as the contact for this
unit.
Street address
/aml/body/sysStreetAddressOptional field that contains the
street address for RMA part
shipments associated with this unit.
Model name
/aml/body/chassis/nameModel name of the device (the
specific model as part of a product
family name).
/aml/body/chassis/serialNoChassis serial number of the unit.Serial number
Chassis part number
/aml/body/chassis/partNoTop assembly number of the
chassis.
Fields specific to a particular alert group message are inserted here.
The following fields may be repeated if multiple CLI commands are executed for this alert group.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
57
Page 72

Call Home Message Formats
Configuring Smart Call Home
XML Tag (XML Only)Description (Plain Text and XML)Data Item (Plain Text and XML)
Command output name
/aml/attachments/attachment/nameExact name of the issued CLI
command.
/aml/attachments/attachment/typeSpecific command output.Attachment type
/aml/attachments/attachment/mimeEither plain text or encoding type.MIME type
Command output text
/aml/attachments/attachment/atdataOutput of command automatically
executed.
The following table describes the reactive event message format for full text or XML.
Table 12: Inserted Fields for a Reactive or Proactive Event Message
XML Tag (XML Only)Description (Plain Text and XML)Data Item (Plain Text and XML)
/aml/body/chassis/hwVersionHardware version of chassis.Chassis hardware version
/aml/body/chassis/swVersionTop-level software version.Supervisor module software
version
Affected FRU name
/aml/body/fru/nameName of the affected FRU that is
generating the event message.
/aml/body/fru/serialNoSerial number of the affected FRU.Affected FRU serial number
/aml/body/fru/partNoPart number of the affected FRU.Affected FRU part number
FRU slot
/aml/body/fru/slotSlot number of the FRU that is generating
the event message.
/aml/body/fru/hwVersionHardware version of the affected FRU.FRU hardware version
FRU software version
/aml/body/fru/swVersionSoftware version(s) that is running on the
affected FRU.
The following table describes the inventory event message format for full text or XML.
Table 13: Inserted Fields for an Inventory Event Message
XML Tag (XML Only)Description (Plain Text and XML)Data Item (Plain Text and XML)
/aml/body/chassis/hwVersionHardware version of the chassis.Chassis hardware version
/aml/body/chassis/swVersionTop-level software version.Supervisor module software
version
FRU name
/aml/body/fru/nameName of the affected FRU that is
generating the event message.
/aml/body/fru/serialNoSerial number of the FRU.FRU s/n
/aml/body/fru/partNoPart number of the FRU.FRU part number
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
58
Page 73

Configuring Smart Call Home
Guidelines and Limitations for Smart Call Home
XML Tag (XML Only)Description (Plain Text and XML)Data Item (Plain Text and XML)
/aml/body/fru/slotSlot number of the FRU.FRU slot
/aml/body/fru/hwVersionHardware version of the FRU.FRU hardware version
FRU software version
FRU.
The following table describes the user-generated test message format for full text or XML.
Table 14: Inserted Fields for a User-Generated Test Message
Process state
halted).
Guidelines and Limitations for Smart Call Home
• If there is no IP connectivity, or if the interface in the virtual routing and forwarding (VRF) instance to
the profile destination is down, the switch cannot send Smart Call Home messages.
• Operates with any SMTP e-mail server.
/aml/body/fru/swVersionSoftware version(s) that is running on the
XML Tag (XML Only)Description (Plain Text and XML)Data Item(Plain Text and XML)
/aml/body/process/idUnique process ID.Process ID
/aml/body/process/processStateState of process (for example, running or
/aml/body/process/exceptionException or reason code.Process exception
Prerequisites for Smart Call Home
• You must have e-mail server connectivity.
• You must have access to contact name (SNMP server contact), phone, and street address information.
• You must have IP connectivity between the switch and the e-mail server.
• You must have an active service contract for the device that you are configuring.
Default Call Home Settings
Table 15: Default Call Home Parameters
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
DefaultParameters
4000000Destination message size for a message sent in full text format
4000000Destination message size for a message sent in XML format
59
Page 74

Configuring Smart Call Home
format
Configuring Smart Call Home
DefaultParameters
4000Destination message size for a message sent in short text
25SMTP server port number if no port is specified
Alert group association with profile
Configuring Smart Call Home
Registering for Smart Call Home
Before you begin
• Know the sMARTnet contract number for your switch
• Know your e-mail address
• Know your Cisco.com ID
Procedure
All for full-text-destination and
short-text-destination profiles. The cisco-tac
alert group for the CiscoTAC-1 destination
profile.
XMLFormat type
0 (zero)Call Home message level
Step 1 In a browser, navigate to the Smart Call Home web page:
http://www.cisco.com/go/smartcall/
Step 2 Under Getting Started, follow the directions to register Smart Call Home.
What to do next
Configure contact information.
Configuring Contact Information
You must configure the e-mail, phone, and street address information for Smart Call Home. You can optionally
configure the contract ID, customer ID, site ID, and switch priority information.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
60
Page 75

Configuring Smart Call Home
Procedure
Configuring Contact Information
PurposeCommand or Action
Step 1
Step 2
Step 3
Step 4
Step 5
sys-contact
switch(config-callhome)# email-contact
email-address
switch(config-callhome)# phone-contact
international-phone-number
Enters global configuration mode.switch# configure terminal
Configures the SNMP sysContact.switch(config)# snmp-server contact
Enters Smart Call Home configuration mode.switch(config)# callhome
Configures the e-mail address for the primary
person responsible for the switch.
The email-address can be up to 255
alphanumeric characters in an e-mail address
format.
Note
You can use any valid e-mail
address. The address cannot contain
spaces.
Configures the phone number in international
phone number format for the primary person
responsible for the device. The
international-phone-number can be up to 17
alphanumeric characters and must be in
international phone number format.
Note
The phone number cannot contain
spaces. Use the plus (+) prefix
before the number.
Step 6
Step 7
Step 8
Step 9
switch(config-callhome)# streetaddress
address
(Optional) switch(config-callhome)#
contract-id contract-number
(Optional) switch(config-callhome)#
customer-id customer-number
site-number
Configures the street address for the primary
person responsible for the switch.
The address can be up to 255 alphanumeric
characters. Spaces are accepted.
Configures the contract number for this switch
from the service agreement.
The contract-number can be up to 255
alphanumeric characters.
Configures the customer number for this
switch from the service agreement.
The customer-number can be up to 255
alphanumeric characters.
Configures the site number for this switch.(Optional) switch(config-callhome)# site-id
The site-number can be up to 255
alphanumeric characters in free format.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
61
Page 76

Creating a Destination Profile
Configuring Smart Call Home
PurposeCommand or Action
Step 10
switch-priority number
Configures the switch priority for this switch.(Optional) switch(config-callhome)#
The range is from 0 to 7, with 0 being the
highest priority and 7 the lowest. The default
is 7.
Note
Switch priority is used by the
operations personnel or TAC
support personnel to decide which
Call Home message should be
responded to first. You can
prioritize Call Home alerts of the
same severity from each switch.
Step 11
(Optional) switch# show callhome
Displays a summary of the Smart Call Home
configuration.
Step 12
(Optional) switch(config)# copy
running-config startup-config
Saves the change persistently through reboots
and restarts by copying the running
configuration to the startup configuration.
Example
The following example shows how to configure the contact information for Call Home:
switch# configuration terminal
switch(config)# snmp-server contact personname@companyname.com
switch(config)# callhome
switch(config-callhome)# email-contact personname@companyname.com
switch(config-callhome)# phone-contact +1-800-123-4567
switch(config-callhome)# street-address 123 Anystreet St., Anycity, Anywhere
What to do next
Create a destination profile.
Creating a Destination Profile
You must create a user-defined destination profile and configure the message format for that new destination
profile.
Procedure
Step 1
Step 2
Step 3
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
62
switch(config-callhome)# destination-profile
{ciscoTAC-1 {alert-group group | email-addr
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Enters Smart Call Home configuration mode.switch(config)# callhome
Creates a new destination profile and sets the
message format for the profile. The
Page 77

Configuring Smart Call Home
address | http URL | transport-method {email
| http}} | profilename {alert-group group |
email-addr address | format {XML | full-txt
| short-txt} | http URL | message-level level |
message-size size | transport-method {email
| http}} | full-txt-destination {alert-group
group | email-addr address | http URL |
message-level level | message-size size |
transport-method {email | http}} |
short-txt-destination {alert-group group |
email-addr address | http URL | message-level
level | message-size size | transport-method
{email | http}}}
Modifying a Destination Profile
PurposeCommand or Action
profile-name can be any alphanumeric string
up to 31 characters.
For further details about this command, see the
command reference for your platform.
Step 4
(Optional) switch# show callhome
destination-profile [profile name]
Step 5
(Optional) switch(config)# copy
running-config startup-config
Example
The following example shows how to create a destination profile for Smart Call Home:
switch# configuration terminal
switch(config)# callhome
switch(config-callhome)# destination-profile Noc101 format full-text
Modifying a Destination Profile
You can modify the following attributes for a predefined or user-defined destination profile:
• Destination address—The actual address, pertinent to the transport mechanism, to which the alert should
be sent.
• Message formatting—The message format used for sending the alert (full text, short text, or XML).
• Message level—The Call Home message severity level for this destination profile.
Displays information about one or more
destination profiles.
Saves the change persistently through reboots
and restarts by copying the running
configuration to the startup configuration.
• Message size—The allowed length of a Call Home message sent to the e-mail addresses in this destination
profile.
Note
You cannot modify or delete the CiscoTAC-1 destination profile.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
63
Page 78

Modifying a Destination Profile
Procedure
Configuring Smart Call Home
PurposeCommand or Action
Step 1
Step 2
Step 3
Step 4
Step 5
Step 6
switch(config-callhome)# destination-profile
{name | full-txt-destination |
short-txt-destination} email-addr address
destination-profile {name | full-txt-destination
| short-txt-destination} message-level number
switch(config-callhome)# destination-profile
{name | full-txt-destination |
short-txt-destination} message-size number
(Optional) switch# show callhome
destination-profile [profile name]
Enters global configuration mode.switch# configure terminal
Enters Smart Call Home configuration mode.switch(config)# callhome
Configures an e-mail address for a user-defined
or predefined destination profile. You can
configure up to 50 e-mail addresses in a
destination profile.
Configures the Smart Call Home message
severity level for this destination profile. The
switch sends only alerts that have a matching
or higher Smart Call Home severity level to
destinations in this profile. The range for the
number is from 0 to 9, where 9 is the highest
severity level.
Configures the maximum message size for this
destination profile. The range is from 0 to
5000000 for full-txt-destination and the default
is 2500000. The range is from 0 to 100000 for
short-txt-destination and the default is 4000.
The value is 5000000 for CiscoTAC-1, which
is not changeable.
Displays information about one or more
destination profiles.
Step 7
(Optional) switch(config)# copy
running-config startup-config
Saves the change persistently through reboots
and restarts by copying the running
configuration to the startup configuration.
Example
The following example shows how to modify a destination profile for Smart Call Home:
switch# configuration terminal
switch(config)# callhome
switch(config-callhome)# destination-profile full-text-destination email-addr
person@example.com
switch(config-callhome)# destination-profile full-text-destination message-level 5
switch(config-callhome)# destination-profile full-text-destination message-size 10000
switch(config-callhome)#
What to do next
Associate an alert group with a destination profile.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
64
Page 79

Configuring Smart Call Home
Associating an Alert Group with a Destination Profile
Associating an Alert Group with a Destination Profile
Procedure
PurposeCommand or Action
Step 1
Step 2
Step 3
switch(config-callhome)# destination-profile
name alert-group {All | Cisco-TAC |
Configuration | Diagnostic | Environmental
Enters global configuration mode.switch# configure terminal
Enters Smart Call Home configuration mode.switch(config)# callhome
Associates an alert group with this destination
profile. Use the All keyword to associate all
alert groups with the destination profile.
| Inventory | License | Linecard-Hardware |
Supervisor-Hardware | Syslog-group-port |
System | Test}
Step 4
Step 5
(Optional) switch# show callhome
destination-profile [profile name]
(Optional) switch(config)# copy
running-config startup-config
Displays information about one or more
destination profiles.
Saves the change persistently through reboots
and restarts by copying the running
configuration to the startup configuration.
Example
The following example shows how to associate all alert groups with the destination profile Noc101:
switch# configuration terminal
switch(config)# callhome
switch(config-callhome)# destination-profile Noc101 alert-group All
switch(config-callhome)#
What to do next
Optionally, you can add show commands to an alert group and configure the SMTP e-mail server.
Adding Show Commands to an Alert Group
You can assign a maximum of five user-defined show commands to an alert group.
Procedure
Step 1
Step 2
Step 3
switch(config-callhome)# alert-group
{Configuration | Diagnostic | Environmental
| Inventory | License | Linecard-Hardware |
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Enters Smart Call Home configuration mode.switch(config)# callhome
Adds the show command output to any Call
Home messages sent for this alert group. Only
valid show commands are accepted.
65
Page 80

Configuring E-Mail Server Details
Supervisor-Hardware | Syslog-group-port |
System | Test} user-def-cmd show-cmd
PurposeCommand or Action
Note
Configuring Smart Call Home
You cannot add user-defined show
commands to the CiscoTAC-1
destination profile.
Step 4
(Optional) switch# show callhome
user-def-cmds
Step 5
(Optional) switch(config)# copy
running-config startup-config
Example
The following example shows how to add the show ip routing command to the Cisco-TAC alert
group:
switch# configuration terminal
switch(config)# callhome
switch(config-callhome)# alert-group Configuration user-def-cmd show ip routing
switch(config-callhome)#
What to do next
Configure Smart Call Home to connect to the SMTP e-mail server.
Configuring E-Mail Server Details
You must configure the SMTP server address for the Smart Call Home functionality to work. You can also
configure the from and reply-to e-mail addresses.
Displays information about all user-defined
show commands added to alert groups.
Saves the change persistently through reboots
and restarts by copying the running
configuration to the startup configuration.
Procedure
PurposeCommand or Action
Step 1
Step 2
Step 3
switch(config-callhome)# transport email
smtp-server ip-address [port number] [use-vrf
vrf-name]
Enters global configuration mode.switch# configure terminal
Enters Smart Call Home configuration mode.switch(config)# callhome
Configures the SMTP server as either the
domain name server (DNS) name, IPv4 address,
or IPv6 address.
The number range is from1 to 65535. The
default port number is 25.
Optionally, you can configure the VRF instance
to use when communicating with this SMTP
server.
Step 4
(Optional) switch(config-callhome)# transport
email from email-address
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
66
Configures the e-mail from field for Smart Call
Home messages.
Page 81

Configuring Smart Call Home
Configuring Periodic Inventory Notifications
PurposeCommand or Action
Step 5
Step 6
Step 7
(Optional) switch(config-callhome)# transport
email reply-to email-address
(Optional) switch# show callhome
transport-email
(Optional) switch(config)# copy
running-config startup-config
Configures the e-mail reply-to field for Smart
Call Home messages.
Displays information about the e-mail
configuration for Smart Call Home.
Saves the change persistently through reboots
and restarts by copying the running
configuration to the startup configuration.
Example
The following example shows how to configure the e-mail options for Smart Call Home messages:
switch# configuration terminal
switch(config)# callhome
switch(config-callhome)# transport email smtp-server 192.0.2.10 use-vrf Red
switch(config-callhome)# transport email from person@example.com
switch(config-callhome)# transport email reply-to person@example.com
switch(config-callhome)#
What to do next
Configure periodic inventory notifications.
Configuring Periodic Inventory Notifications
You can configure the switch to periodically send a message with an inventory of all software services currently
enabled and running on the device with hardware inventory information. The switch generates two Smart Call
Home notifications; periodic configuration messages and periodic inventory messages.
Procedure
Step 1
Step 2
Step 3
notification [interval days] [timeofday time]
Step 4
Step 5
(Optional) switch(config)# copy
running-config startup-config
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Enters Smart Call Home configuration mode.switch(config)# callhome
Configures periodic inventory messages.switch(config-callhome)# periodic-inventory
The interval days range is from 1 to 30 days.
The default is 7 days.
The timeofday time is in HH:MM format.
Displays information about Smart Call Home.(Optional) switch# show callhome
Saves the change persistently through reboots
and restarts by copying the running
configuration to the startup configuration.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
67
Page 82

Disabling Duplicate Message Throttling
Example
The following example shows how to configure the periodic inventory messages to generate every
20 days:
switch# configuration terminal
switch(config)# callhome
switch(config-callhome)# periodic-inventory notification interval 20
switch(config-callhome)#
What to do next
Disable duplicate message throttling.
Disabling Duplicate Message Throttling
You can limit the number of duplicate messages received for the same event. By default, the switch limits the
number of duplicate messages received for the same event. If the number of duplicate messages sent exceeds
30 messages within a 2-hour time frame, the switch discards further messages for that alert type.
Configuring Smart Call Home
Procedure
PurposeCommand or Action
Step 1
Step 2
Step 3
switch(config-callhome) # no
duplicate-message throttle
Enters global configuration mode.switch# configure terminal
Enters Smart Call Home configuration mode.switch(config)# callhome
Disables duplicate message throttling for Smart
Call Home.
Duplicate message throttling is enabled by
default.
Step 4
(Optional) switch(config)# copy
running-config startup-config
Saves the change persistently through reboots
and restarts by copying the running
configuration to the startup configuration.
Example
The following example shows how to disable duplicate message throttling:
switch# configuration terminal
switch(config)# callhome
switch(config-callhome)# no duplicate-message throttle
switch(config-callhome)#
What to do next
Enable Smart Call Home.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
68
Page 83

Configuring Smart Call Home
Enabling or Disabling Smart Call Home
Procedure
Enabling or Disabling Smart Call Home
PurposeCommand or Action
Step 1
Step 2
Step 3
Enters global configuration mode.switch# configure terminal
Enters Smart Call Home configuration mode.switch(config)# callhome
Enables or disables Smart Call Home.switch(config-callhome) # [no] enable
Smart Call Home is disabled by default.
Step 4
(Optional) switch(config)# copy
running-config startup-config
Saves the change persistently through reboots
and restarts by copying the running
configuration to the startup configuration.
Example
The following example shows how to enable Smart Call Home:
switch# configuration terminal
switch(config)# callhome
switch(config-callhome)# enable
switch(config-callhome)#
What to do next
Optionally, generate a test message.
Testing the Smart Call Home Configuration
Before you begin
Verify that the message level for the destination profile is set to 2 or lower.
Important
Smart Call Home testing fails when the message level for the destination profile is set to 3 or higher.
Procedure
Step 1
Step 2
Step 3
switch(config-callhome) # callhome send
diagnostic
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Enters Smart Call Home configuration mode.switch(config)# callhome
Sends the specified Smart Call Home message
to all configured destinations.
69
Page 84

Verifying the Smart Call Home Configuration
Configuring Smart Call Home
PurposeCommand or Action
Step 4
Step 5
Example
The following example shows how to enable Smart Call Home:
switch# configuration terminal
switch(config)# callhome
switch(config-callhome)# callhome send diagnostic
switch(config-callhome)# callhome test
switch(config-callhome)#
switch(config-callhome) # callhome test
(Optional) switch(config)# copy
running-config startup-config
Sends a test message to all configured
destinations.
Saves the change persistently through reboots
and restarts by copying the running
configuration to the startup configuration.
Verifying the Smart Call Home Configuration
Use one of the following commands to verify the configuration:
PurposeCommand
Displays the status for Smart Call Home.show callhome
show callhome destination-profile name
show callhome pending-diff
callhome-all]
Displays one or more Smart Call Home destination profiles.
Displays the differences between he pending and running
Smart Call Home configuration.
Displays the Smart Call Home status.show callhome status
Displays the e-mail configuration for Smart Call Home.show callhome transport-email
Displays CLI commands added to any alert groups.show callhome user-def-cmds
Displays the running configuration for Smart Call Home.show running-config [callhome |
Displays the startup configuration for Smart Call Home.show startup-config callhome
Displays the technical support output for Smart Call Home.show tech-support callhome
Sample Syslog Alert Notification in Full-Text Format
This sample shows the full-text format for a syslog port alert-group notification:
source:MDS9000
Switch Priority:7
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
70
Page 85

Configuring Smart Call Home
Device Id:WS-C6509@C@FG@07120011
Customer Id:Example.com
Contract Id:123
Site Id:San Jose
Server Id:WS-C6509@C@FG@07120011
Time of Event:2018-02-08T11:10:44
Message Name:SYSLOG_ALERT
Message Type:Syslog
Severity Level:2
System Name:10.76.100.177
Contact Name:User Name
Contact Email:person@example.com
Contact Phone:+1-408-555-1212
Street Address:#1234 Any Street, Any City, Any State, 12345
Event Description:2018 Feb 8 11:10:44 10.76.100.177 %PORT-5-IF_TRUNK_UP:
%$VLAN 1%$ Interface e2/5, vlan 1 is up
syslog_facility:PORT
start chassis information:
Affected Chassis:WS-C6509
Affected Chassis Serial Number:FG@07120011
Affected Chassis Hardware Version:0.104
Affected Chassis Software Version:3.1(1)
Affected Chassis Part No:73-8607-01
end chassis information:
Sample Syslog Alert Notification in XML Format
Sample Syslog Alert Notification in XML Format
This sample shows the XML format for a syslog port alert-group notification:
From: example
Sent: Wednesday, Feb 25, 2018 7:20 AM
To: User (user)
Subject: System Notification From Router - syslog - 2018-02-25 14:19:55
GMT+00:00
<?xml version="1.0" encoding="UTF-8"?>
<soap-env:Envelope xmlns:soap-env="http://www.w3.org/2003/05/soap-envelope">
<soap-env:Header>
<aml-session:Session xmlns:aml-session="http://www.example.com/2004/01/aml-session"
soap-env:mustUnderstand="true" soap-env:role=
"http://www.w3.org/2003/05/soap-envelope/role/next">
<aml-session:To>http://tools.example.com/services/DDCEService</aml-session:To>
<aml-session:Path>
<aml-session:Via>http://www.example.com/appliance/uri</aml-session:Via>
</aml-session:Path>
<aml-session:From>http://www.example.com/appliance/uri</aml-session:From>
<aml-session:MessageId>M2:69000101:C9D9E20B</aml-session:MessageId>
</aml-session:Session>
</soap-env:Header>
<soap-env:Body>
<aml-block:Block xmlns:aml-block="http://www.example.com/2004/01/aml-block">
<aml-block:Header>
<aml-block:Type>http://www.example.com/2005/05/callhome/syslog</aml-block:Type>
<aml-block:CreationDate>2018-02-25 14:19:55 GMT+00:00</aml-block:CreationDate>
<aml-block:Builder>
<aml-block:Name>Cat6500</aml-block:Name>
<aml-block:Version>2.0</aml-block:Version>
</aml-block:Builder>
<aml-block:BlockGroup>
<aml-block:GroupId>G3:69000101:C9F9E20C</aml-block:GroupId>
<aml-block:Number>0</aml-block:Number>
<aml-block:IsLast>true</aml-block:IsLast>
<aml-block:IsPrimary>true</aml-block:IsPrimary>
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
71
Page 86

Sample Syslog Alert Notification in XML Format
<aml-block:WaitForPrimary>false</aml-block:WaitForPrimary>
</aml-block:BlockGroup>
<aml-block:Severity>2</aml-block:Severity>
</aml-block:Header>
<aml-block:Content>
<ch:Call Home xmlns:ch="http://www.example.com/2005/05/callhome" version="1.0">
<ch:EventTime>2018-02-25 14:19:55 GMT+00:00</ch:EventTime>
<ch:MessageDescription>03:29:29: %CLEAR-5-COUNTERS: Clear counter on all
interfaces by console</ch:MessageDescription>
<ch:Event>
<ch:Type>syslog</ch:Type>
<ch:SubType>
</ch:SubType>
<ch:Brand>Cisco Systems</ch:Brand>
<ch:Series>Catalyst 6500 Series Switches</ch:Series>
</ch:Event>
<ch:CustomerData>
<ch:UserData>
<ch:Email>person@example.com</ch:Email>
</ch:UserData>
<ch:ContractData>
<ch:CustomerId>12345</ch:CustomerId>
<ch:SiteId>building 1</ch:SiteId>
<ch:ContractId>abcdefg12345</ch:ContractId>
<ch:DeviceId>WS-C6509@C@69000101</ch:DeviceId>
</ch:ContractData>
<ch:SystemInfo>
<ch:Name>Router</ch:Name>
<ch:Contact>
</ch:Contact>
<ch:ContactEmail>user@example.com</ch:ContactEmail>
<ch:ContactPhoneNumber>+1-408-555-1212</ch:ContactPhoneNumber>
<ch:StreetAddress>#1234 Any Street, Any City, Any State, 12345
</ch:StreetAddress>
</ch:SystemInfo>
</ch:CustomerData>
<ch:Device>
<rme:Chassis xmlns:rme="http://www.example.com/rme/4.0">
<rme:Model>WS-C6509</rme:Model>
<rme:HardwareVersion>1.0</rme:HardwareVersion>
<rme:SerialNumber>69000101</rme:SerialNumber>
<rme:AdditionalInformation>
<rme:AD name="PartNumber" value="73-3438-03 01" />
<rme:AD name="SoftwareVersion" value="4.0(20080421:012711)" />
</rme:AdditionalInformation>
</rme:Chassis>
</ch:Device>
</ch:Call Home>
</aml-block:Content>
<aml-block:Attachments>
<aml-block:Attachment type="inline">
<aml-block:Name>show logging</aml-block:Name>
<aml-block:Data encoding="plain">
<
Configuring Smart Call Home
00:01:05: %SYS-5-CONFIG_I: Configured from memory by console
00:01:09: %SYS-5-RESTART: System restarted --Cisco IOS Software,
s72033_rp Software (s72033_rp-ADVENTERPRISEK9_DBG-VM), Experimental
Version 12.2(20070421:012711) Copyright (c) 1986-2007 by Cisco Systems, Inc.
Compiled Thu 26-Feb-18 15:54 by xxx
Firmware compiled 11-Apr-07 03:34 by integ Build [100]00:01:01: %PFREDUN-6-ACTIVE:
System was paused for 00:00:00 to ensure console debugging output.00:03:00: SP: SP:
_ENABLED: The default factory setting for config register is 0x2102.It is advisable
Compiled Thu 26-Apr-07 18:00 by xxx
00:03:18: %SYS-SP-6-BOOTTIME: Time taken to reboot after reload = 339 seconds
00:03:18: %OIR-SP-6-INSPS: Power supply inserted in slot 1
00:03:18: %C6KPWR-SP-4-PSOK: power supply 1 turned on.
00:03:18: %OIR-SP-6-INSPS: Power supply inserted in slot00:01:09: %SSH-5-ENABLED:
00:03:18: %C6KPWR-SP-4-PSOK: power supply 2 turned on.
00:03:18: %C6KPWR-SP-4-PSREDUNDANTMISMATCH: power supplies rated outputs do not match.
00:03:18: %C6KPWR-SP-4-PSREDUNDANTBOTHSUPPLY: in power-redundancy mode, system is
00:01:10: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is OFF
00:01:10: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is OFF
00:03:20: %C6KENV-SP-4-FANHIOUTPUT: Version 2 high-output fan-tray is in effect
00:03:22: %C6KPWR-SP-4-PSNOREDUNDANCY: Power supplies are not in full redundancy,
00:03:26: %FABRIC-SP-5-FABRIC_MODULE_ACTIVE: The Switch Fabric Module in slot 6
00:03:28: %DIAG-SP-6-RUN_MINIMUM: Module 6: Running Minimal Diagnostics...
00:03:50: %DIAG-SP-6-DIAG_OK: Module 6: Passed Online Diagnostics
00:03:50: %OIR-SP-6-INSCARD: Card inserted in slot 6, interfaces are now online
00:03:51: %DIAG-SP-6-RUN_MINIMUM: Module 3: Running Minimal Diagnostics...
00:03:51: %DIAG-SP-6-RUN_MINIMUM: Module 7: Running Minimal Diagnostics...
00:03:51: %DIAG-SP-6-RUN_MINIMUM: Module 9: Running Minimal Diagnostics...
00:01:51: %MFIB_CONST_RP-6-REPLICATION_MODE_CHANGE: Replication Mode Change Detected.
00:04:01: %DIAG-SP-6-DIAG_OK: Module 3: Passed Online Diagnostics
00:04:01: %OIR-SP-6-DOWNGRADE: Fabric capable module 3 not at an appropriate hardware
00:04:02: %OIR-SP-6-INSCARD: Card inserted in slot 3, interfaces are now online
00:04:11: %DIAG-SP-6-DIAG_OK: Module 7: Passed Online Diagnostics
00:04:14: %OIR-SP-6-INSCARD: Card inserted in slot 7, interfaces are now online
00:04:35: %DIAG-SP-6-DIAG_OK: Module 9: Passed Online Diagnostics
00:04:37: %OIR-SP-6-INSCARD: Card inserted in slot 9, interfaces are now online
00:00:09: DaughterBoard (Distributed Forwarding Card 3)
Firmware compiled 11-Apr-07 03:34 by integ Build [100]
00:00:22: %SYS-DFC4-5-RESTART: System restarted -Cisco DCOS Software, c6lc2 Software (c6lc2-SPDBG-VM), Experimental Version 4.0
(20080421:012711)Copyright (c) 1986-2018 by Cisco Systems, Inc.
Compiled Thu 26-Feb-18 17:20 by xxx
00:00:23: DFC4: Currently running ROMMON from F2 region
00:00:25: %SYS-DFC2-5-RESTART: System restarted -Cisco IOS Software, c6slc Software (c6slc-SPDBG-VM), Experimental Version 12.2
(20070421:012711)Copyright (c) 1986-2007 by Cisco Systems, Inc.
Compiled Thu 26-Apr-08 16:40 by username1
00:00:26: DFC2: Currently running ROMMON from F2 region
00:04:56: %DIAG-SP-6-RUN_MINIMUM: Module 4: Running Minimal Diagnostics...
00:00:09: DaughterBoard (Distributed Forwarding Card 3)
Firmware compiled 11-Apr-08 03:34 by integ Build [100]
slot_id is 8
00:00:31: %FLASHFS_HES-DFC8-3-BADCARD: /bootflash:: The flash card seems to
Sample Syslog Alert Notification in XML Format
Initializing as ACTIVE processor for this switch00:01:01: %SYS-3-LOGGER_FLUSHED:
Currently running ROMMON from F1 region00:03:07: %C6K_PLATFORM-SP-4-CONFREG_BREAK
to retain 1 in 0x2102 as it prevents returning to ROMMON when break is issued.00:03:18:
%SYS-SP-5-RESTART: System restarted --Cisco IOS Software, s72033_sp Software
(s72033_sp-ADVENTERPRISEK9_DBG-VM), Experimental Version 12.2(20070421:012711)Copyright
(c) 1986-2007 by Cisco Systems, Inc.
SSH 1.99 has been enabled
operating on both power supplies.
power usage exceeds lower capacity supply
became active.
Current system replication mode is Ingress
revision level, and can only run in flowthrough mode
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
73
Page 88

Sample Syslog Alert Notification in XML Format
be corrupted
00:00:31: %SYS-DFC8-5-RESTART: System restarted -Cisco DCOS Software, c6lc2 Software (c6lc2-SPDBG-VM), Experimental Version 4.0
(20080421:012711)Copyright (c) 1986-2008 by Cisco Systems, Inc.
Compiled Thu 26-Feb-18 17:20 by username1
00:00:31: DFC8: Currently running ROMMON from S (Gold) region
00:04:59: %DIAG-SP-6-RUN_MINIMUM: Module 2: Running Minimal Diagnostics...
00:05:12: %DIAG-SP-6-RUN_MINIMUM: Module 8: Running Minimal Diagnostics...
00:05:13: %DIAG-SP-6-RUN_MINIMUM: Module 1: Running Minimal Diagnostics...
00:00:24: %SYS-DFC1-5-RESTART: System restarted -Cisco DCOS Software, c6slc Software (c6slc-SPDBG-VM), Experimental Version 4.0
(20080421:012711)Copyright (c) 1986-2008 by Cisco Systems, Inc.
Compiled Thu 26-Feb-18 16:40 by username1
00:00:25: DFC1: Currently running ROMMON from F2 region
00:05:30: %DIAG-SP-6-DIAG_OK: Module 4: Passed Online Diagnostics
00:05:31: %SPAN-SP-6-SPAN_EGRESS_REPLICATION_MODE_CHANGE: Span Egress HW
Replication Mode Change Detected. Current replication mode for unused asic
session 0 is Centralized
00:05:31: %SPAN-SP-6-SPAN_EGRESS_REPLICATION_MODE_CHANGE: Span Egress HW
Replication Mode Change Detected. Current replication mode for unused asic
session 1 is Centralized
00:05:31: %OIR-SP-6-INSCARD: Card inserted in slot 4, interfaces are now online
00:06:02: %DIAG-SP-6-DIAG_OK: Module 1: Passed Online Diagnostics
00:06:03: %OIR-SP-6-INSCARD: Card inserted in slot 1, interfaces are now online
00:06:31: %DIAG-SP-6-DIAG_OK: Module 2: Passed Online Diagnostics
00:06:33: %OIR-SP-6-INSCARD: Card inserted in slot 2, interfaces are now online
00:04:30: %XDR-6-XDRIPCNOTIFY: Message not sent to slot 4/0 (4) because of IPC
error timeout. Disabling linecard. (Expected during linecard OIR)
00:06:59: %DIAG-SP-6-DIAG_OK: Module 8: Passed Online Diagnostics
00:06:59: %OIR-SP-6-DOWNGRADE_EARL: Module 8 DFC installed is not identical to
system PFC and will perform at current system operating mode.
00:07:06: %OIR-SP-6-INSCARD: Card inserted in slot 8, interfaces are now online
Router#]]>
</aml-block:Data>
</aml-block:Attachment>
</aml-block:Attachments>
</aml-block:Block>
</soap-env:Body>
</soap-env:Envelope>
Configuring Smart Call Home
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
74
Page 89

Configuring Session Manager
This chapter contains the following sections:
• Information About Session Manager, on page 75
• Guidelines and Limitations for Session Manager, on page 75
• Configuring Session Manager, on page 76
• Verifying the Session Manager Configuration, on page 78
Information About Session Manager
Session Manager allows you to implement your configuration changes in batch mode. Session Manager works
in the following phases:
• Configuration session—Creates a list of commands that you want to implement in session manager mode.
• Validation—Provides a basic semantic check on your configuration. Cisco NX-OS returns an error if
the semantic check fails on any part of the configuration.
• Verification—Verifies the configuration as a whole, based on the existing hardware and software
configuration and resources. Cisco NX-OS returns an error if the configuration does not pass this
verification phase.
CHAPTER 7
• Commit— Cisco NX-OS verifies the complete configuration and implements the changes atomically to
the device. If a failure occurs, Cisco NX-OS reverts to the original configuration.
• Abort—Discards the configuration changes before implementation.
You can optionally end a configuration session without committing the changes. You can also save a
configuration session.
Guidelines and Limitations for Session Manager
Session Manager has the following configuration guidelines and limitations:
• Session Manager supports only the access control list (ACL) feature.
• You can create up to 32 configuration sessions.
• You can configure a maximum of 20,000 commands across all sessions.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
75
Page 90

Configuring Session Manager
Configuring Session Manager
Creating a Session
You can create up to 32 configuration sessions.
Procedure
Configuring Session Manager
PurposeCommand or Action
Step 1
Step 2
Step 3
switch# configure session name
configuration session [name]
(Optional) switch(config-s)# save location
Configuring ACLs in a Session
You can configure ACLs within a configuration session.
Procedure
Step 1
Step 2
switch# configure session name
switch(config-s)# ip access-list name
Creates a configuration session and enters
session configuration mode. The name can be
any alphanumeric string.
Displays the contents of the session.
Displays the contents of the session.(Optional) switch(config-s)# show
Saves the session to a file. The location can be
in bootflash or volatile.
PurposeCommand or Action
Creates a configuration session and enters
session configuration mode. The name can be
any alphanumeric string.
Creates an ACL.
Step 3
protocol source destination
Step 4
Step 5
Step 6
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
76
switch(config-s-acl)# interface interface-type
number
switch(config-s-if)# ip port access-group name
in
[name]
Adds a permit statement to the ACL.(Optional) switch(config-s-acl)# permit
Enters interface configuration mode.
Adds a port access group to the interface.
Displays the contents of the session.(Optional) switch# show configuration session
Page 91

Configuring Session Manager
Verifying a Session
To verify a session, use the following command in session mode:
Committing a Session
To commit a session, use the following command in session mode:
Saving a Session
Verifying a Session
PurposeCommand
Verifies the commands in the configuration session.switch(config-s)# verify [verbose]
PurposeCommand
Commits the commands in the configuration session.switch(config-s)# commit [verbose]
To save a session, use the following command in session mode:
PurposeCommand
switch(config-s)# save location
(Optional) Saves the session to a file. The location can be in bootflash or
volatile.
Discarding a Session
To discard a session, use the following command in session mode:
PurposeCommand
Discards the configuration session without applying the commands.switch(config-s)# abort
Configuration Example for Session Manager
The following example shows how to create a configuration session for ACLs:
switch# configure session name test2
switch(config-s)# ip access-list acl2
switch(config-s-acl)# permit tcp any any
switch(config-s-acl)# exit
switch(config-s)# interface Ethernet 1/4
switch(config-s-ip)# ip port access-group acl2 in
switch(config-s-ip)# exit
switch(config-s)# verify
switch(config-s)# exit
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
77
Page 92

Verifying the Session Manager Configuration
switch# show configuration session test2
Verifying the Session Manager Configuration
To verify Session Manager configuration information, perform one of the following tasks:
PurposeCommand
Configuring Session Manager
show configuration session [name]
show configuration session status [name]
Displays the contents of the configuration session.
Displays the status of the configuration session.
Displays a summary of all the configuration sessions.show configuration session summary
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
78
Page 93

Configuring the Scheduler
This chapter contains the following sections:
• Information About the Scheduler, on page 79
• Licensing Requirements for the Scheduler, on page 80
• Guidelines and Limitations for the Scheduler, on page 80
• Default Settings for the Scheduler, on page 81
• Configuring the Scheduler, on page 81
• Verifying the Scheduler Configuration, on page 87
• Configuration Examples for the Scheduler, on page 88
• Standards for the Scheduler, on page 89
Information About the Scheduler
The scheduler allows you to define and set a timetable for maintenance activities such as the following:
• Quality of service policy changes
CHAPTER 8
• Data backup
• Saving a configuration
Jobs consist of a single command or multiple commands that define routine activities. Jobs can be scheduled
one time or at periodic intervals.
The scheduler defines a job and its timetable as follows:
Job
A routine task or tasks defined as a command list and completed according to a specified schedule.
Schedule
The timetable for completing a job. You can assign multiple jobs to a schedule.
A schedule is defined as either periodic or one-time only:
• Periodic mode— A recurring interval that continues until you delete the job. You can configure the
following types of intervals:
• Daily— Job is completed once a day.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
79
Page 94

Remote User Authentication
• Weekly— Job is completed once a week.
• Monthly—Job is completed once a month.
• Delta—Job begins at the specified start time and then at specified intervals (days:hours:minutes).
• One-time mode—Job is completed only once at a specified time.
Remote User Authentication
Before starting a job, the scheduler authenticates the user who created the job. Because user credentials from
a remote authentication are not retained long enough to support a scheduled job, you must locally configure
the authentication passwords for users who create jobs. These passwords are part of the scheduler configuration
and are not considered a locally configured user.
Before starting the job, the scheduler validates the local password against the password from the remote
authentication server.
Configuring the Scheduler
Scheduler Log Files
The scheduler maintains a log file that contains the job output. If the size of the job output is greater than the
size of the log file, the output is truncated.
Licensing Requirements for the Scheduler
This feature does not require a license. Any feature not included in a license package is bundled with the Cisco
NX-OS system images and is provided at no extra charge to you. For a complete explanation of the Cisco
NX-OS licensing scheme, see the Cisco NX-OS Licensing Guide.
Guidelines and Limitations for the Scheduler
• The scheduler can fail if it encounters one of the following while performing a job:
• If a feature license is expired when a job for that feature is scheduled.
• If a feature is disabled at the time when a job for that feature is scheduled.
• Verify that you have configured the time. The scheduler does not apply a default timetable. If you create
a schedule, assign jobs, and do not configure the time, the job is not started.
• While defining a job, verify that no interactive or disruptive commands (for example, copy bootflash:
file ftp:URI, write erase, and other similar commands) are specified because the job is started and
conducted noninteractively.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
80
Page 95

Configuring the Scheduler
Default Settings for the Scheduler
Table 16: Default Command Scheduler Parameters
Configuring the Scheduler
Enabling the Scheduler
Default Settings for the Scheduler
DefaultParameters
DisabledScheduler state
16 KBLog file size
Procedure
Step 1
Step 2
Step 3
config
Step 4
Example
This example shows how to enable the scheduler:
switch# configure terminal
switch(config)# feature scheduler
switch(config)# show scheduler config
config terminal
feature scheduler
scheduler logfile size 16
end
switch(config)#
(Optional) switch(config)# copy
running-config startup-config
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Enables the scheduler.switch(config) # feature scheduler
Displays the scheduler configuration.(Optional) switch(config) # show scheduler
Saves the change persistently through reboots
and restarts by copying the running
configuration to the startup configuration.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
81
Page 96

Defining the Scheduler Log File Size
Defining the Scheduler Log File Size
Procedure
Configuring the Scheduler
PurposeCommand or Action
Step 1
Step 2
Step 3
switch(config) # scheduler logfile size value
(Optional) switch(config)# copy
running-config startup-config
Example
This example shows how to define the scheduler log file size:
switch# configure terminal
switch(config)# scheduler logfile size 1024
switch(config)#
Configuring Remote User Authentication
Enters global configuration mode.switch# configure terminal
Defines the scheduler log file size in kilobytes.
The range is from 16 to 1024. The default log
file size is 16.
Note
If the size of the job output is greater
than the size of the log file, the
output is truncated.
Saves the change persistently through reboots
and restarts by copying the running
configuration to the startup configuration.
Remote users must authenticate with their clear text password before creating and configuring jobs.
Remote user passwords are always shown in encrypted form in the output of the show running-config
command. The encrypted option (7) in the command supports the ASCII device configuration.
Procedure
PurposeCommand or Action
Step 1
Step 2
switch(config) # scheduler aaa-authentication
password [0 | 7] password
Enters global configuration mode.switch# configure terminal
Configures a password for the user who is
currently logged in.
To configure a clear text password, enter 0.
To configure an encrypted password, enter 7.
Step 3
switch(config) # scheduler aaa-authentication
username name password [0 | 7] password
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
82
Configures a clear text password for a remote
user.
Page 97

Configuring the Scheduler
Defining a Job
PurposeCommand or Action
Defining a Job
Step 4
Displays the scheduler password information.(Optional) switch(config) # show
running-config | include "scheduler
aaa-authentication"
Step 5
(Optional) switch(config)# copy
running-config startup-config
Saves the change persistently through reboots
and restarts by copying the running
configuration to the startup configuration.
Example
This example shows how to configure a clear text password for a remote user called NewUser:
switch# configure terminal
switch(config) # scheduler aaa-authentication
username NewUser password z98y76x54b
switch(config) # copy running-config startup-config
switch(config) #
Once a job is defined, you cannot modify or remove a command. To change the job, you must delete it and
create a new one.
Procedure
Step 1
Step 2
Step 3
Step 4
Step 5
switch(config) # scheduler job name name
switch(config-job) # command1 ; [command2
;command3 ; ...
job [name]
(Optional) switch(config-job) # copy
running-config startup-config
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Creates a job with the specified name and enters
job configuration mode.
The name is restricted to 31 characters.
Defines the sequence of commands for the
specified job. You must separate commands
with a space and a semicolon ( ;).
The filename is created using the current time
stamp and switch name.
Displays the job information.(Optional) switch(config-job) # show scheduler
The name is restricted to 31 characters.
Saves the change persistently through reboots
and restarts by copying the running
configuration to the startup configuration.
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
83
Page 98

Deleting a Job
Deleting a Job
Configuring the Scheduler
Example
This example shows how to create a scheduler job named backup-cfg, save the running configuration
to a file in bootflash, copy the file from bootflash to a TFTP server, and save the change to the startup
configuration:
switch# configure terminal
switch(config) # scheduler job name backup-cfg
switch(config-job) # cli var name timestamp
$(timestamp) ;copy running-config
bootflash:/$(SWITCHNAME)-cfg.$(timestamp) ;copy
bootflash:/$(SWITCHNAME)-cfg.$(timestamp)
tftp://1.2.3.4/ vrf management
switch(config-job) # copy running-config startup-config
Procedure
PurposeCommand or Action
Step 1
Step 2
switch(config) # no scheduler job name name
Enters global configuration mode.switch# configure terminal
Deletes the specified job and all commands
defined within it.
The name is restricted to 31 characters.
Step 3
Displays the job information.(Optional) switch(config-job) # show scheduler
job [name]
Step 4
(Optional) switch(config-job) # copy
running-config startup-config
Saves the change persistently through reboots
and restarts by copying the running
configuration to the startup configuration.
Example
This example shows how to delete a job called configsave:
switch# configure terminal
switch(config)# no scheduler job name configsave
switch(config-job)# copy running-config startup-config
switch(config-job)#
Defining a Timetable
You must configure a timetable. Otherwise, jobs will not be scheduled.
If you do not specify the time for the time commands, the scheduler assumes the current time. For example,
if the current time is March 24, 2008, 22:00 hours,jobs are started as follows:
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
84
Page 99

Configuring the Scheduler
Note
Defining a Timetable
• For the time start 23:00 repeat 4:00:00 command, the scheduler assumes a start time of March 24,
2008, 23:00 hours.
• For the time daily 55 command, the scheduler assumes a start time every day at 22:55 hours.
• For the time weekly 23:00 command, the scheduler assumes a start time every Friday at 23:00 hours.
• For the time monthly 23:00 command, the scheduler assumes a start time on the 24th of every month
at 23:00 hours.
The scheduler will not begin the next occurrence of a job before the last one completes. For example, you
have scheduled a job to be completed at one-minute intervals beginning at 22:00; but the job requires two
minutes to complete. The scheduler starts the first job at 22:00, completes it at 22:02, and then observes a
one-minute interval before starting the next job at 22:03.
Procedure
Step 1
Step 2
Step 3
Step 4
Step 5
Step 6
switch(config) # scheduler schedule name
name
switch(config-schedule) # job name name
switch(config-schedule) # time daily time
switch(config-schedule) # time weekly
[[day-of-week:] HH:] MM
switch(config-schedule) # time monthly
[[day-of-month:] HH:] MM
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Creates a new scheduler and enters schedule
configuration mode for that schedule.
The name is restricted to 31 characters.
Associates a job with this schedule. You can
add multiple jobs to a schedule.
The name is restricted to 31 characters.
Indicates the job starts every day at a designated
time, specified as HH:MM.
Indicates that the job starts on a specified day
of the week.
The day of the week is represented by an integer
(for example, 1 for Sunday, 2 for Monday) or
as an abbreviation (for example, sun, mon).
The maximum length for the entire argument
is 10 characters.
Indicates that the job starts on a specified day
each month.
Step 7
repeat repeat-interval | delta-time [repeat
repeat-interval]}
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
If you specify 29, 30, or 31, the job is started
on the last day of each month.
Indicates the job starts periodically.switch(config-schedule) # time start {now
The start-time format is
[[[[yyyy:]mmm:]dd:]HH]:MM.
85
Page 100

Clearing the Scheduler Log File
Configuring the Scheduler
PurposeCommand or Action
• delta-time— Specifies the amount of time
to wait after the schedule is configured
before starting a job.
• now— Specifies that the job starts two
minutes from now.
• repeat repeat-interval— Specifies the
frequency at which the job is repeated.
Step 8
scheduler config
Step 9
(Optional) switch(config-schedule) # copy
running-config startup-config
Example
This example shows how to define a timetable where jobs start on the 28th of each month at 23:00
hours:
switch# configure terminal
switch(config)# scheduler schedule name weekendbackupqos
switch(config-scheduler)# job name offpeakzoning
switch(config-scheduler)# time monthly 28:23:00
switch(config-scheduler)# copy running-config startup-config
switch(config-scheduler)#
Clearing the Scheduler Log File
Procedure
Displays the scheduler information.(Optional) switch(config-schedule) # show
Saves the change persistently through reboots
and restarts by copying the running
configuration to the startup configuration.
PurposeCommand or Action
Step 1
Step 2
Enters global configuration mode.switch# configure terminal
Clears the scheduler log file.switch(config) # clear scheduler logfile
Example
This example shows how to clear the scheduler log file:
switch# configure terminal
switch(config)# clear scheduler logfile
Cisco Nexus 3548 Switch NX-OS System Management Configuration Guide, Release 7.x
86
 Loading...
Loading...