Page 1

Cisco Wireless ISR and HWIC Access Point
Configuration Guide
December 2006
Corporate Headquarters
Cisco Systems, Inc.
170 West Tasman Drive
San Jose, CA 95134-1706
USA
http://www.cisco.com
Tel: 408 526-4000
800 553-NETS (6387)
Fax: 408 526-4100
Text Part Number: 0L-6415-04
Page 2

THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL
STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT
WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS.
THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT
SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE
OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY.
The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public
domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California.
NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH
ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR
LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF
DEALING, USAGE, OR TRADE PRACTICE.
IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING,
WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO
OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
CCVP, the Cisco Logo, and the Cisco Square Bridge logo are trademarks of Cisco Systems, Inc.; Changing the Way We Work, Live, Play, and Learn is a service mark of
Cisco Systems, Inc.; and Access Registrar, Aironet, BPX, Catalyst, CCDA, CCDP, CCIE, CCIP, CCNA, CCNP, CCSP, Cisco, the Cisco Certified Internetwork Expert logo,
Cisco IOS, Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Cisco Unity, Enterprise/Solver, EtherChannel, EtherFast, EtherSwitch, Fast Step,
Follow Me Browsing, FormShare, GigaDrive, GigaStack, HomeLink, Internet Quotient, IOS, iPhone, IP/TV, iQ Expertise, the iQ logo, iQ Net Readiness Scorecard, iQuick
Study, LightStream, Linksys, MeetingPlace, MGX, Networking Academy, Network Registrar, Packet, PIX, ProConnect, RateMUX, ScriptShare, SlideCast, SMARTnet,
StackWise, The Fastest Way to Increase Your Internet Quotient, and TransPath are registered trademarks of Cisco Systems, Inc. and/or its affiliates in the United States and
certain other countries.
All other trademarks mentioned in this document or Website are the property of their respective owners. The use of the word partner does not imply a partnership relationship
between Cisco and any other company. (0612R)
IMPLIED, INCLUDING, WITHOUT
Cisco Wireless ISR and HWIC Access Point Configuration Guide
Copyright © 2006 Cisco Systems, Inc.
All rights reserved.
Page 3

Preface 9
Audience 9
Purpose 9
Organization 10
Conventions 10
Related Publications 12
Obtaining Documentation 13
Cisco.com 13
Product Documentation DVD 14
Ordering Documentation 14
Documentation Feedback 14
Cisco Product Security Overview 15
Reporting Security Problems in Cisco Products 15
Obtaining Technical Assistance 16
Cisco Technical Support & Documentation Website 16
Submitting a Service Request 16
Definitions of Service Request Severity 17
CONTENTS
CHAPTER
CHAPTER
OL-6415-04
Obtaining Additional Publications and Information 17
1 Overview 1
Wireless Device Management 1
Network Configuration Example 2
Root Unit on a Wired LAN 2
Features 3
5
2 Configuring Radio Settings 1
Enabling the Radio Interface 2
Roles in Radio Network 2
Configuring Network or Fallback Role 3
Bridge Features Not Supported 4
Sample Bridging Configuration 4
Universal Client Mode 7
Cisco Wireless Router and HWIC Configuration Guide
3
Page 4

Contents
Configuring Universal Client Mode 7
Configuring Radio Data Rates 10
Configuring Radio Transmit Power 12
Limiting the Power Level for Associated Client Devices 13
Configuring Radio Channel Settings 14
DFS Automatically Enabled on Some 5-GHz Radio Channels 19
Enabling and Disabling World Mode 20
Enabling and Disabling Short Radio Preambles 21
Configuring Transmit and Receive Antennas 22
Disabling and Enabling Access Point Extensions 23
Configuring the Ethernet Encapsulation Transformation Method 23
Enabling and Disabling Reliable Multicast to Workgroup Bridges 24
Enabling and Disabling Public Secure Packet Forwarding 25
Configuring Protected Ports 26
CHAPTER
Configuring Beacon Period and DTIM 26
Configuring RTS Threshold and Retries 27
Configuring Maximum Data Retries 27
Configuring Fragmentation Threshold 28
Enabling Short Slot Time for 802.11g Radios 28
Performing a Carrier Busy Test 29
3 Configuring Multiple SSIDs 1
Understanding Multiple SSIDs 2
SSID Configuration Methods Supported by Cisco IOS Releases 2
Configuring Multiple SSIDs 3
Creating an SSID Globally 3
Using a RADIUS Server to Restrict SSIDs 5
Configuring Multiple Basic SSIDs 6
Requirements for Configuring Multiple BSSIDs 6
Guidelines for Using Multiple BSSIDs 6
Enabling MBSSID and SSIDL at the same time 7
Sample Configuration for Enabling MBSSID and SSIDL 8
CHAPTER
4 Configuring an Access Point as a Local Authenticator 1
Understand Local Authentication 2
Configure a Local Authenticator 2
Guidelines for Local Authenticators 3
Cisco Wireless Router and HWIC Configuration Guide
4
OL-6415-04
Page 5

12
Contents
Configuration Overview 3
Configuring the Local Authenticator Access Point 3
Configuring Other Access Points to Use the Local Authenticator 8
Configuring EAP-FAST Settings 9
Limiting the Local Authenticator to One Authentication Type 11
Unblocking Locked Usernames 11
Viewing Local Authenticator Statistics 11
Using Debug Messages 12
CHAPTER
CHAPTER
5 Configuring Encryption Types 1
Understand Encryption Types 2
Configure Encryption Types 3
Creating WEP Keys 3
Creating Cipher Suites 5
Enabling and Disabling Broadcast Key Rotation 7
Security Type in Universal Client Mode 8
6 Configuring Authentication Types 1
Understand Authentication Types 2
Open Authentication to Access Point 2
Shared Key Authentication to Access Point 3
EAP Authentication to Network 4
MAC Address Authentication to the Network 5
Combining MAC-Based, EAP, and Open Authentication 6
Using WPA Key Management 6
Software and Firmware Requirements for WPA and WPA-TKIP 8
Configure Authentication Types 9
Assigning Authentication Types to an SSID 9
Configuring Authentication Holdoffs, Timeouts, and Intervals 15
Matching Access Point and Client Device Authentication Types 16
CHAPTER
7 Configuring RADIUS Servers 1
Configuring and Enabling RADIUS 2
Understanding RADIUS 2
RADIUS Operation 3
Configuring RADIUS 4
Displaying the RADIUS Configuration 17
OL-6415-04
Cisco Wireless Router and HWIC Configuration Guide
5
Page 6

Contents
RADIUS Attributes Sent by the Access Point 18
CHAPTER
CHAPTER
8 Configuring VLANs 1
Understanding VLANs 2
Related Documents 3
Incorporating Wireless Devices into VLANs 4
Configuring VLANs 4
Configuring a VLAN 5
Assigning Names to VLANs 7
Using a RADIUS Server to Assign Users to VLANs 7
Viewing VLANs Configured on the Access Point 8
VLAN Configuration Example 9
9 Configuring QoS 1
Understanding QoS for Wireless LANs 2
QoS for Wireless LANs Versus QoS on Wired LANs 2
Impact of QoS on a Wireless LAN 2
Precedence of QoS Settings 3
Using Wi-Fi Multimedia Mode 4
Configuring QoS 4
Configuration Guidelines 5
Adjusting Radio Access Categories 5
Disabling IGMP Snooping Helper 6
Sample Configuration Using the CLI 6
APPENDIX
A Channel Settings 1
IEEE 802.11b (2.4-GHz Band) 1
IEEE 802.11g (2.4-GHz Band) 2
IEEE 802.11a (5-GHz Band) 2
APPENDIX
APPENDIX
B Protocol Filters 1
C Supported MIBs 1
MIB List 1
Using FTP to Access the MIB Files 2
APPENDIX
D Error and Event Messages 1
How to Read System Messages 1
Cisco Wireless Router and HWIC Configuration Guide
6
OL-6415-04
Page 7

G
LOSSARY
I
NDEX
Contents
Message Traceback Reports 2
Association Management Messages 2
802.11 Subsystem Messages 3
Local Authenticator Messages 12
OL-6415-04
Cisco Wireless Router and HWIC Configuration Guide
7
Page 8

Contents
Cisco Wireless Router and HWIC Configuration Guide
8
OL-6415-04
Page 9

Audience
Preface
The Preface provides information on the following topics:
• Audience
• Purpose
• Organization
• Related Publications
• Obtaining Documentation
This guide is for the networking professional who installs and manages Cisco stationary routers with
wireless capabilities. You should have experience working with the Cisco IOS software and be familiar
with the concepts and terminology of wireless LANs.
This document provides information for the following interfaces:
• Access Point High-speed WAN Interface Card (AP HWIC)
• Cisco 800 series routers with wireless capabilities
• Cisco 1800 series routers with wireless capabilities.
Purpose
This guide provides the information you need to install and configure your Cisco wireless device, for
example, AP HWIC, Cisco
using the Cisco IOS software commands that have been created or changed for use with the wireless
device. It does not provide detailed information about these commands. For information about the
standard Cisco IOS software commands, see the Cisco IOS software documentation set available from
the Cisco.com home page at Service and Support > Technical Documents. On the Cisco Product
Documentation home page, select Release 12.4 from the Cisco IOS Software drop-down list.
OL-6415-04
800 series and Cisco 1800 series routers. This guide provides procedures for
Cisco Wireless ISR and HWIC Access Point Configuration Guide
9
Page 10

Organization
Organization
This guide consists of the following chapters:
Chapter 1, “Overview,” lists the software and hardware features of the wireless device and describes the
role of the wireless device in your network.
Chapter 2, “Configuring Radio Settings,” describes how to configure settings for the wireless device
radio such as the role in the radio network, data rates, transmit power, channel settings, and others.
Chapter 3, “Configuring Multiple SSIDs,” describes how to configure and manage multiple service set
identifiers (SSIDs) and multiple basic SSIDs (BSSIDs) on your wireless device. You can configure up
to 16 SSIDs and 16 BSSIDs on your wireless device and assign different configuration settings to each.
Chapter 4, “Configuring an Access Point as a Local Authenticator,” describes how to configure the
wireless device to act as a local RADIUS server for your wireless LAN. If the WAN connection to your
main RADIUS server fails, the wireless device acts as a backup server to authenticate wireless devices.
Chapter 5, “Configuring Encryption Types,” describes how to configure the cipher suites required to use
authenticated key management, Wired Equivalent Privacy (WEP), and WEP features.
Chapter 6, “Configuring Authentication Types,” describes how to configure authentication types on the
wireless device. Client devices use these authentication methods to join your network.
Chapter 7, “Configuring RADIUS Servers,” describes how to enable and configure the RADIUS, which
provides detailed accounting information and flexible administrative control over authentication and
authorization processes.
Chapter 8, “Configuring VLANs,” describes how to configure your wireless device to interoperate with
the VLANs set up on your wired LAN.
Preface
Chapter 9, “Configuring QoS,” describes how to configure quality of service (QoS) on your wireless
device. With this feature, you can provide preferential treatment to certain traffic at the expense of
others.
Appendix A, “Channel Settings,” lists the wireless device radio channels and the maximum power levels
supported by the world’s regulatory domains.
Appendix B, “Protocol Filters,” lists some of the protocols that you can filter on the wireless device.
Appendix C, “Supported MIBs,” lists the Simple Network Management Protocol (SNMP) Management
Information Bases (MIBs) that the wireless device supports for this software release.
Appendix D, “Error and Event Messages,” lists the CLI error and event messages and provides an
explanation and recommended action for each message.
Conventions
This publication uses these conventions to convey instructions and information:
Command descriptions use these conventions:
• Commands and keywords are in boldface text.
• Arguments for which you supply values are in italic.
• Square brackets ([ ]) mean optional elements.
• Braces ({ }) group required choices, and vertical bars ( | ) separate the alternative elements.
• Braces and vertical bars within square brackets ([{ | }]) mean a required choice within an optional
element.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
10
OL-6415-04
Page 11
Preface
Conventions
Interactive examples use these conventions:
• Terminal sessions and system displays are in screen font.
• Information you enter is in boldface screen font.
• Nonprinting characters, such as passwords or tabs, are in angle brackets (< >).
Notes, cautions, and timesavers use these conventions and symbols:
Tip Means the following will help you solve a problem. The tips information might not be troubleshooting
or even an action, but could be useful information.
Note Means reader take note. Notes contain helpful suggestions or references to materials not contained in
this manual.
Caution Means reader be careful. In this situation, you might do something that could result equipment damage
or loss of data.
Warning
Waarschuwing
Varoitus
Attention
This warning symbol means danger. You are in a situation that could cause bodily injury. Before you
work on any equipment, be aware of the hazards involved with electrical circuitry and be familiar
with standard practices for preventing accidents. (To see translations of the warnings that appear
in this publication, refer to the appendix “Translated Safety Warnings.”)
Dit waarschuwingssymbool betekent gevaar. U verkeert in een situatie die lichamelijk letsel kan
veroorzaken. Voordat u aan enige apparatuur gaat werken, dient u zich bewust te zijn van de bij
elektrische schakelingen betrokken risico’s en dient u op de hoogte te zijn van standaard
maatregelen om ongelukken te voorkomen. (Voor vertalingen van de waarschuwingen die in deze
publicatie verschijnen, kunt u het aanhangsel “Translated Safety Warnings” (Vertalingen van
veiligheidsvoorschriften) raadplegen.)
Tämä varoitusmerkki merkitsee vaaraa. Olet tilanteessa, joka voi johtaa ruumiinvammaan. Ennen
kuin työskentelet minkään laitteiston parissa, ota selvää sähkökytkentöihin liittyvistä vaaroista ja
tavanomaisista onnettomuuksien ehkäisykeinoista. (Tässä julkaisussa esiintyvien varoitusten
käännökset löydät liitteestä "Translated Safety Warnings" (käännetyt turvallisuutta koskevat
varoitukset).)
Ce symbole d’avertissement indique un danger. Vous vous trouvez dans une situation pouvant
entraîner des blessures. Avant d’accéder à cet équipement, soyez conscient des dangers posés par
les circuits électriques et familiarisez-vous avec les procédures courantes de prévention des
accidents. Pour obtenir les traductions des mises en garde figurant dans cette publication, veuillez
consulter l’annexe intitulée «
Translated Safety Warnings » (Traduction des avis de sécurité).
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
11
Page 12
Related Publications
Preface
Warnung
Avvertenza
Advarsel
Aviso
Dieses Warnsymbol bedeutet Gefahr. Sie befinden sich in einer Situation, die zu einer
Körperverletzung führen könnte. Bevor Sie mit der Arbeit an irgendeinem Gerät beginnen, seien Sie
sich der mit elektrischen Stromkreisen verbundenen Gefahren und der Standardpraktiken zur
Vermeidung von Unfällen bewußt. (Übersetzungen der in dieser Veröffentlichung enthaltenen
Warnhinweise finden Sie im Anhang mit dem Titel “Translated Safety Warnings” (Übersetzung der
Warnhinweise).)
Questo simbolo di avvertenza indica un pericolo. Si è in una situazione che può causare infortuni.
Prima di lavorare su qualsiasi apparecchiatura, occorre conoscere i pericoli relativi ai circuiti
elettrici ed essere al corrente delle pratiche standard per la prevenzione di incidenti. La traduzione
delle avvertenze riportate in questa pubblicazione si trova nell’appendice, “Translated Safety
Warnings” (Traduzione delle avvertenze di sicurezza).
Dette varselsymbolet betyr fare. Du befinner deg i en situasjon som kan føre til personskade. Før du
utfører arbeid på utstyr, må du være oppmerksom på de faremomentene som elektriske kretser
innebærer, samt gjøre deg kjent med vanlig praksis når det gjelder å unngå ulykker. (Hvis du vil se
oversettelser av de advarslene som finnes i denne publikasjonen, kan du se i vedlegget "Translated
Safety Warnings" [Oversatte sikkerhetsadvarsler].)
Este símbolo de aviso indica perigo. Encontra-se numa situação que lhe poderá causar danos
fisicos. Antes de começar a trabalhar com qualquer equipamento, familiarize-se com os perigos
relacionados com circuitos eléctricos, e com quaisquer práticas comuns que possam prevenir
possíveis acidentes. (Para ver as traduções dos avisos que constam desta publicação, consulte o
apêndice “Translated Safety Warnings” - “Traduções dos Avisos de Segurança”).
¡Advertencia!
Varning!
Este símbolo de aviso significa peligro. Existe riesgo para su integridad física. Antes de manipular
cualquier equipo, considerar los riesgos que entraña la corriente eléctrica y familiarizarse con los
procedimientos estándar de prevención de accidentes. (Para ver traducciones de las advertencias
que aparecen en esta publicación, consultar el apéndice titulado “Translated Safety Warnings.”)
Denna varningssymbol signalerar fara. Du befinner dig i en situation som kan leda till personskada.
Innan du utför arbete på någon utrustning måste du vara medveten om farorna med elkretsar och
känna till vanligt förfarande för att förebygga skador. (Se förklaringar av de varningar som
förekommer i denna publikation i appendix "Translated Safety Warnings" [Översatta
säkerhetsvarningar].)
Related Publications
Related Cisco technical documentation include the following:
Ta b l e 1 Related and Referenced Documents
Cisco Product Document Title
Cisco Access Point
High-Speed WAN Interface
Card
Cisco Interface Cards Installation Guide
Quick Start Guide: Interface Cards for Cisco Access Routers
Installing, Replacing, and Upgrading Components in Cisco Modular
Access Routers and Integrated Services Routers
Cisco Wireless ISR and HWIC Access Point Configuration Guide
12
OL-6415-04
Page 13
Preface
Obtaining Documentation
Table 1 Related and Referenced Documents (continued)
Cisco Product Document Title
Cisco 800 series routers Cisco 850 Series and Cisco 870 Series Routers Hardware Installation
Guide
Cisco 850 Series and Cisco 870 Series Access Routers Cabling and Setup
Quick Start Guide
Cisco 850 Series and Cisco 870 Series Access Routers Software
Configuration Guide
Regulatory Compliance and Safety Information for Cisco 800 Series and
SOHO Series Routers
Upgrading Memory in Cisco 800 Routers
Cisco 1800 series routers Cisco 1800 Series Integrated Services Routers (Modular) Quick Start
Guide
Cisco 1800 Series Routers Hardware Installation Documents
Cisco 1800 Series Software Configuration Guide
Cisco 1800 Series Cards and Modules
Regulatory Compliance and Safety Information for Cisco 1840 Routers
Cisco Modular Access Router Cable Specifications
Cisco IOS software Cisco IOS software documentation, all releases.
Additional Documentation Cisco AP HWIC and Access Router Wireless Configuration Guide
Obtaining Documentation
Cisco documentation and additional literature are available on Cisco.com. Cisco also provides several
ways to obtain technical assistance and other technical resources. These sections explain how to obtain
technical information from Cisco Systems.
Cisco.com
Refer to the documentation for the Cisco IOS software release installed
on your router.
Cisco Aironet 2.4-GHz Articulated Dipole Antenna (AIR-ANT4941
Cisco Aironet High Gain Omnidirectional Ceiling Mount Antenna
(AIR-ANT1728)
Cisco Aironet 2 dBi Diversity Omnidirectional Ceiling Mount Antenna
(AIR-ANT5959)
Antenna Cabling
Declarations of Conformity and Regulatory Information for Cisco Access
Products with 802.11a/b/g and 802.11b/g Radios
You can access the most current Cisco documentation at this URL:
http://www.cisco.com/techsupport
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
13
Page 14

Documentation Feedback
You can access the Cisco website at this URL:
http://www.cisco.com
You can access international Cisco websites at this URL:
http://www.cisco.com/public/countries_languages.shtml
Product Documentation DVD
Cisco documentation and additional literature are available in the Product Documentation DVD package,
which may have shipped with your product. The Product Documentation DVD is updated regularly and
may be more current than printed documentation.
The Product Documentation DVD is a comprehensive library of technical product documentation on
portable media. The DVD enables you to access multiple versions of hardware and software installation,
configuration, and command guides for Cisco products and to view technical documentation in HTML.
With the DVD, you have access to the same documentation that is found on the Cisco website without
being connected to the Internet. Certain products also have .pdf versions of the documentation available.
The Product Documentation DVD is available as a single unit or as a subscription. Registered Cisco.com
users (Cisco direct customers) can order a Product Documentation DVD (product number
DOC-DOCDVD=) from the Ordering tool or Cisco Marketplace.
Cisco Ordering tool:
http://www.cisco.com/en/US/partner/ordering/
Preface
Cisco Marketplace:
http://www.cisco.com/go/marketplace/
Ordering Documentation
Beginning June 30, 2005, registered Cisco.com users may order Cisco documentation at the Product
Documentation Store in the Cisco Marketplace at this
http://www.cisco.com/go/marketplace/
Cisco will continue to support documentation orders using the Ordering tool:
• Registered Cisco.com users (Cisco direct customers) can order documentation from the
Ordering
http://www.cisco.com/en/US/partner/ordering/
• Instructions for ordering documentation using the Ordering tool are at this URL:
http://www.cisco.com/univercd/cc/td/doc/es_inpck/pdi.htm
• Nonregistered Cisco.com users can order documentation through a local account representative by
calling Cisco Systems Corporate Headquarters (California, USA) at 408
North America, by calling 1 800
tool:
URL:
526-7208 or, elsewhere in
553-NETS (6387).
Documentation Feedback
You can rate and provide feedback about Cisco technical documents by completing the online feedback
form that appears with the technical documents on Cisco.com.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
14
OL-6415-04
Page 15
Preface
You can send comments about Cisco documentation to bug-doc@cisco.com.
You can submit comments by using the response card (if present) behind the front cover of your
document or by writing to the following address:
Cisco Systems
Attn: Customer Document Ordering
170 West Tasman Drive
San Jose, CA 95134-9883
We appreciate your comments.
Cisco Product Security Overview
Cisco provides a free online Security Vulnerability Policy portal at this URL:
http://www.cisco.com/en/US/products/products_security_vulnerability_policy.html
From this site, you can perform these tasks:
• Report security vulnerabilities in Cisco products.
Cisco Product Security Overview
• Obtain assistance with security incidents that involve Cisco products.
• Register to receive security information from Cisco.
A current list of security advisories and notices for Cisco products is available at this URL:
http://www.cisco.com/go/psirt
If you prefer to see advisories and notices as they are updated in real time, you can access a Product
Security Incident Response Team Really Simple Syndication (PSIRT RSS) feed from this
http://www.cisco.com/en/US/products/products_psirt_rss_feed.html
Reporting Security Problems in Cisco Products
Cisco is committed to delivering secure products. We test our products internally before we release them,
and we strive to correct all vulnerabilities quickly. If you think that you might have identified a
vulnerability in a Cisco product, contact PSIRT:
• Emergencies — security-alert@cisco.com
An emergency is either a condition in which a system is under active attack or a condition for which
a severe and urgent security vulnerability should be reported. All other conditions are considered
non emergencies.
• Non emergencies — psirt@cisco.com
In an emergency, you can also reach PSIRT by telephone:
• 1 877 228-7302
URL:
• 1 408 525-6532
Tip We encourage you to use Pretty Good Privacy (PGP) or a compatible product to encrypt any sensitive
information that you send to Cisco. PSIRT can work from encrypted information that is compatible with
PGP versions
OL-6415-04
2.x through 8.x.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
15
Page 16
Obtaining Technical Assistance
Never use a revoked or an expired encryption key. The correct public key to use in your correspondence
with PSIRT is the one linked in the Contact Summary section of the Security Vulnerability Policy page
at this
URL:
http://www.cisco.com/en/US/products/products_security_vulnerability_policy.htm
The link on this page has the current PGP key ID in use.
Obtaining Technical Assistance
Cisco Technical Support provides 24-hour-a-day award-winning technical assistance. The Cisco
Technical Support & Documentation website on Cisco.com features extensive online support resources.
In addition, if you have a valid Cisco service contract, Cisco Technical Assistance Center (TAC)
engineers provide telephone support. If you do not have a valid Cisco service contract, contact your
reseller.
Cisco Technical Support & Documentation Website
Preface
The Cisco Technical Support & Documentation website provides online documents and tools for
troubleshooting and resolving technical issues with Cisco products and technologies. The website is
available 24 hours a day, at this
http://www.cisco.com/techsupport
Access to all tools on the Cisco Technical Support & Documentation website requires a Cisco.com user
ID and password. If you have a valid service contract but do not have a user ID or password, you can
register at this
http://tools.cisco.com/RPF/register/register.do
Note Use the Cisco Product Identification (CPI) tool to locate your product serial number before submitting
a web or phone request for service. You can access the CPI tool from the Cisco Technical Support &
Documentation website by clicking the Tools & Resources link under Documentation & Tools. Choose
Cisco Product Identification Tool from the Alphabetical Index drop-down list, or click the Cisco
Product Identification Tool link under Alerts & RMAs. The CPI tool offers three search options: by
product ID or model name; by tree view; or for certain products, by copying and pasting show command
output. Search results show an illustration of your product with the serial number label location
highlighted. Locate the serial number label on your product and record the information before placing a
service call.
URL:
Submitting a Service Request
URL:
Using the online TAC Service Request Tool is the fastest way to open S3 and S4 service requests. (S3
and S4 service requests are those in which your network is minimally impaired or for which you require
product information.) After you describe your situation, the TAC Service Request Tool provides
recommended solutions. If your issue is not resolved using the recommended resources, your service
request is assigned to a Cisco engineer. The TAC Service Request Tool is located at this URL:
http://www.cisco.com/techsupport/servicerequest
Cisco Wireless ISR and HWIC Access Point Configuration Guide
16
OL-6415-04
Page 17

Preface
For S1 or S2 service requests or if you do not have Internet access, contact the Cisco TAC by telephone.
(S1 or S2 service requests are those in which your production network is down or severely degraded.)
Cisco engineers are assigned immediately to S1 and S2 service requests to help keep your business
operations running smoothly.
To open a service request by telephone, use one of the following numbers:
Asia-Pacific: +61 2 8446 7411 (Australia: 1 800 805 227)
EMEA: +32 2 704 55 55
USA: 1 800 553-2447
For a complete list of Cisco TAC contacts, go to this URL:
http://www.cisco.com/techsupport/contacts
Definitions of Service Request Severity
To ensure that all service requests are reported in a standard format, Cisco has established severity
definitions.
Severity 1 (S1)—Your network is “down,” or there is a critical impact to your business operations. You
and Cisco will commit all necessary resources around the clock to resolve the situation.
Severity 2 (S2)—Operation of an existing network is severely degraded, or significant aspects of your
business operation are negatively affected by inadequate performance of Cisco products. You and Cisco
will commit full-time resources during normal business hours to resolve the situation.
Severity 3 (S3)—Operational performance of your network is impaired, but most business operations
remain functional. You and Cisco will commit resources during normal business hours to restore service
to satisfactory levels.
Obtaining Additional Publications and Information
Severity 4 (S4)—You require information or assistance with Cisco product capabilities, installation, or
configuration. There is little or no effect on your business operations.
Obtaining Additional Publications and Information
Information about Cisco products, technologies, and network solutions is available from various online
and printed sources.
• Cisco Marketplace provides a variety of Cisco books, reference guides, documentation, and logo
merchandise. Visit Cisco Marketplace, the company store, at this
http://www.cisco.com/go/marketplace/
• Cisco Press publishes a wide range of general networking, training and certification titles. Both new
and experienced users will benefit from these publications. For current Cisco Press titles and other
information, go to Cisco Press at this
http://www.ciscopress.com
• Pack et magazine is the Cisco Systems technical user magazine for maximizing Internet and
networking investments. Each quarter, Packet delivers coverage of the latest industry trends,
technology breakthroughs, and Cisco products and solutions, as well as network deployment and
troubleshooting tips, configuration examples, customer case studies, certification and training
information, and links to scores of in-depth online resources. You can access Packet magazine at
this
URL:
http://www.cisco.com/packet
URL:
URL:
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
17
Page 18

Obtaining Additional Publications and Information
• iQ Magazine is the quarterly publication from Cisco Systems designed to help growing companies
learn how they can use technology to increase revenue, streamline their business, and expand
services. The publication identifies the challenges facing these companies and the technologies to
help solve them, using real-world case studies and business strategies to help readers make sound
technology investment decisions. You can access iQ Magazine at this URL:
http://www.cisco.com/go/iqmagazine
or view the digital edition at this URL:
http://ciscoiq.texterity.com/ciscoiq/sample/
• Internet Protocol Journal is a quarterly journal published by Cisco Systems for engineering
professionals involved in designing, developing, and operating public and private internets and
intranets. You can access the Internet Protocol Journal at this
http://www.cisco.com/ipj
• Networking products offered by Cisco Systems, as well as customer support services, can be
obtained at this
http://www.cisco.com/en/US/products/index.html
• Networking Professionals Connection is an interactive website for networking professionals to share
questions, suggestions, and information about networking products and technologies with Cisco
experts and other networking professionals. Join a discussion at this
http://www.cisco.com/discuss/networking
• World-class networking training is available from Cisco. You can view current offerings at
this
URL:
Preface
URL:
URL:
URL:
http://www.cisco.com/en/US/learning/index.html
Cisco Wireless ISR and HWIC Access Point Configuration Guide
18
OL-6415-04
Page 19

CHA P TER
1
Overview
Cisco wireless devices provide a secure, affordable, and easy-to-use wireless LAN solution that
combines mobility and flexibility with the enterprise-class features required by networking
professionals. With a management system based on Cisco IOS software, Cisco wireless devices are
Wi-Fi certified, 802.11b-compliant, 802.11g-compliant, or 802.11a-compliant wireless LAN
transceivers.
This document provides information for the following devices:
• Access Point High-speed WAN Interface Card (AP HWIC)
• Cisco 800 Series routers with wireless capabilities
• Cisco 1800 Series routers with wireless capabilities
This chapter provides information on the following topics:
• Wireless Device Management
• Network Configuration Example
• Features
Wireless Device Management
You can use the wireless device management system through the following interfaces:
• The Cisco IOS command-line interface (CLI), that can be used through a console port or a Telnet
session. Use the interface dot11radio configuration command in global mode to place the wireless
device into radio configuration mode.
• Simple Network Management Protocol (SNMP).
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
1-1
Page 20
Network Configuration Example
Access Point
(Root Unit)
Access Point
(Root Unit)
153370
Wired LAN
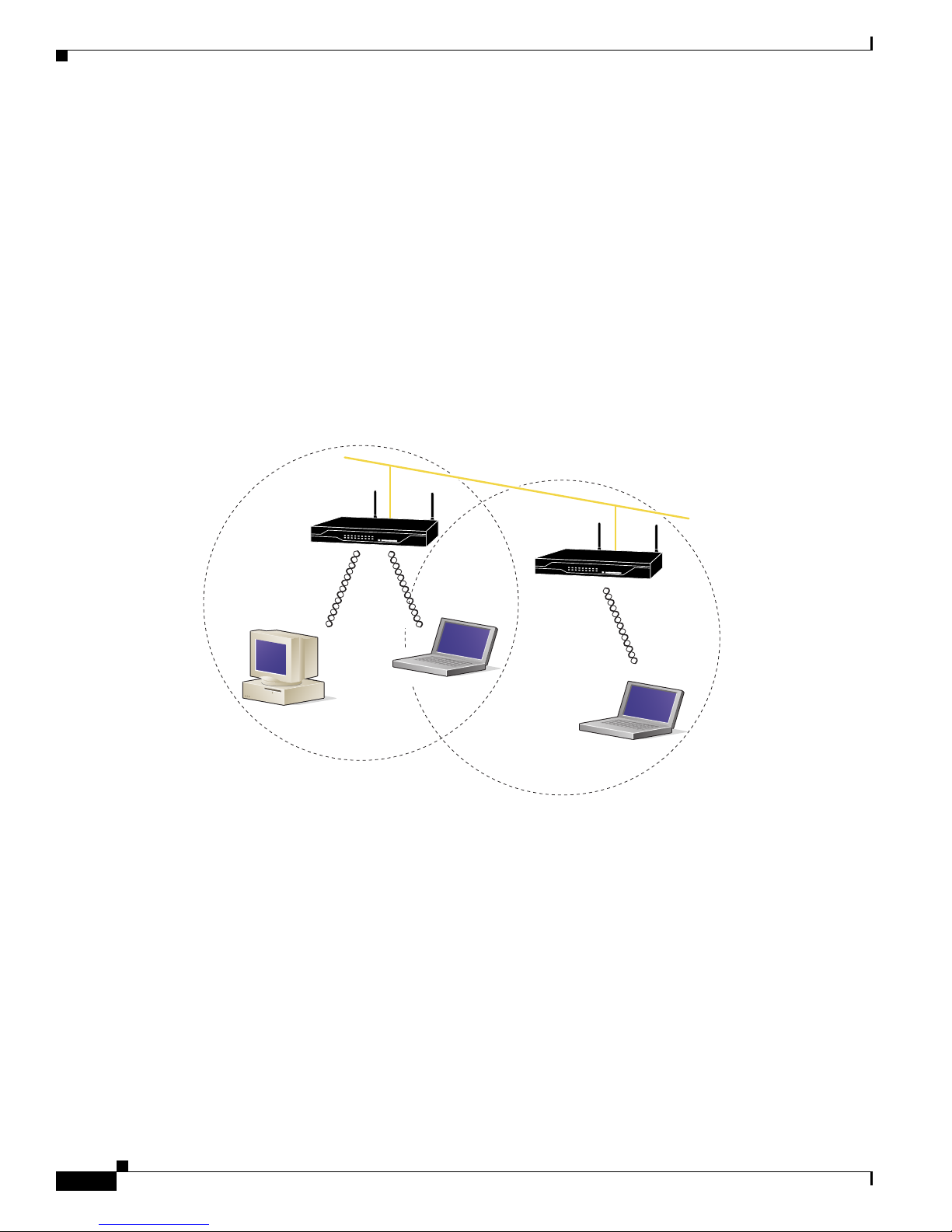
Network Configuration Example
This section describes the wireless device role in common wireless network configurations. The access
point default configuration is as a root unit connected to a wired LAN or as the central unit in an
all-wireless network.
Root Unit on a Wired LAN
An access point connected directly to a wired LAN provides a connection point for wireless users.
Figure 1-1 shows access points acting as root units on a wired LAN.
Figure 1-1 Access Points as Root Units on a Wired LAN
Chapter 1 Overview
Cisco Wireless Router and HWIC Configuration Guide
1-2
OL-6415-04
Page 21
Chapter 1 Overview
Features
Features
This section lists features supported on access points running Cisco IOS software.
• Access Point Link Role Flexibility—This feature allows the user to configure root and non-root
bridging mode functionality, universal client mode, and support of a WGB client device, in addition
to a root access point on the radio interface.
Note Root/Non-Root bridging mode is supported only on modular ISR platforms, such as Cisco
3800
series , Cisco 2800 and Cisco 1841 series. Fixed ISR platforms, such as the Cisco 800
and Cisco 1800 do not support this feature.
• QoS Basic Service Set (QBSS) support—This feature aligns Cisco QBSS implementation with the
evolving 802.11e standard. The QBSS element of the access point’s beacon advertises channel load
instead of traffic load. A new configuration command, dot11 phone dot11e has been added in
Release 12.4 that allows the standard QBSS Load element to be sent in the beacon. This command
should be used when compatible phones are employed in the network.
• Secure Shell version 2 (SSHv2) support—SSH v2 is a standards-based protocol to provide secure
Telnet capability for router configuration and administration.
• Support for Multiple BSSIDs—This feature permits a single access point to appear to the WLAN as
multiple virtual access points. It does this by assigning an access point with multiple Basic Service
Set IDs (MBSSIDs) or MAC addresses.
To determine whether a radio supports multiple basic SSIDs, enter the show controllers command
for the radio interface. The radio supports multiple basic SSIDs if the results include this line:
Number of supported simultaneous BSSID on radio_interface: 8
• Support for Wi-Fi 802.11h and Dynamic Frequency Selection (DFS)—This feature allows access
points configured at the factory for use in Europe to detect radar signals such as military and weather
sources and switch channels on the access points.
• SNMPv3—This feature enables SNMPv3 support on Cisco wireless devices to provide an additional
level of security.
• World mode—Use this feature to communicate the access point’s regulatory setting information,
including maximum transmit power and available channels, to world mode-enabled clients. Clients
using world mode can be used in countries with different regulatory settings and automatically
conform to local regulations. World mode is supported only on the 2.4-GHz radio.
• Multiple SSIDs—Create up to 16 SSIDs on the wireless device and assign any combination of these
settings to each SSID:
–
Broadcast SSID mode for guests on your network
–
Client authentication methods
–
Maximum number of client associations
–
VLAN identifier
–
RADIUS accounting list identifier
–
A separate SSID for infrastructure devices such as repeaters and workgroup bridges
Note Only 10 SSIDs are supported on the Cisco 800 series platforms.
OL-6415-04
Cisco Wireless Router and HWIC Configuration Guide
1-3
Page 22

Features
Chapter 1 Overview
• VLANs—Assign VLANs to the SSIDs on the wireless device (one VLAN per SSID) to differentiate
policies and services among users.
• QoS—Use this feature to support quality of service for prioritizing traffic from the Ethernet to the
access point. The access point also supports the voice-prioritization schemes used by 802.11b
wireless phones such as the Cisco
• RADIUS Accounting—Enable accounting on the access point to send accounting data about
wireless client devices to a RADIUS server on your network.
• Enhanced security—Enable three advanced security features to protect against sophisticated attacks
on your wireless network's WEP keys: Message Integrity Check (MIC), WEP key hashing, and
broadcast WEP key rotation.
• Enhanced authentication services—Set up repeater access points to authenticate to your network
like other wireless client devices. After you provide a network username and password for the
repeater, it authenticates to your network using Light Extensible Authentication Protocol (LEAP),
Cisco's wireless authentication method, and receives and uses dynamic WEP keys.
• Wi-Fi Protected Access (WPA)—Wi-Fi Protected Access is a standards-based, interoperable
security enhancement that strongly increases the level of data protection and access control for
existing and future wireless LAN systems. It is derived from and will be forward-compatible with
the upcoming IEEE 802.11i standard. WPA leverages Temporal Key Integrity Protocol (TKIP) for
data protection and 802.1X for authenticated key management.
• Access point as backup or stand-alone authentication server—You can configure an access point to
act as a local authentication server to provide authentication service for small wireless LANs
without a RADIUS server or to provide backup authentication service in case of a WAN link or a
server failure. The number of clients supported varies based on platform, with up to 1000 user
accounts supported on the higher end platforms.
• Support for 802.11g radios—Cisco IOS Releases 12.4(2)T or later support the standard 802.11g,
2.4-GHz radio.
7920 and Spectralink's Netlink™.
• Support for Cisco 802.11a Radios—The 802.11a radios support all access point features introduced
in Cisco IOS Release 12.4 and later.
• AES-CCMP—This feature supports Advanced Encryption Standard-Counter Mode with Cipher
Block Chaining Message Authentication Code Protocol (AES-CCMP). AES-CCMP is required for
Wi-Fi Protected Access 2 (WPA2) and IEEE 802.11i wireless LAN security.
• IEEE 802.1X Local Authentication Service for EAP-FAST—This feature expands wireless domain
services (WDS) IEEE 802.1X local authentication to include support for Extensible Authentication
Protocol-Flexible Authentication via Secure Tunneling (EAP-FAST).
• Wi-Fi Multimedia (WMM) Required Elements—This feature supports the required elements of
WMM. WMM is designed to improve the user experience for audio, video, and voice applications
over a Wi-Fi wireless connection. WMM is a subset of the IEEE 802.11e Quality of Service (QoS)
draft standard. WMM supports QoS prioritized media access via the Enhanced Distributed Channel
Access (EDCA) method. Optional elements of the WMM specification including call admission
control using traffic specifications (TSPEC) are not supported in this release.
• VLAN Assignment By Name—This feature allows the RADIUS server to assign a client to a virtual
LAN (VLAN) identified by its VLAN name. In releases before Cisco IOS Release 12.4(5)T, the
RADIUS server identified the VLAN by ID. This feature is important for deployments where VLAN
IDs are not used consistently throughout the network.
Cisco Wireless Router and HWIC Configuration Guide
1-4
OL-6415-04
Page 23

Chapter 1 Overview
• Microsoft WPS IE SSIDL—This feature allows the access point to broadcast a list of configured
SSIDs (the SSIDL) in the Microsoft Wireless Provisioning Services Information Element (WPS IE).
A client with the ability to read the SSIDL can alert the user to the availability of the SSIDs. This
feature provides a bandwidth-efficient, software-upgradeable alternative to multiple broadcast
SSIDs (MB/SSIDs).
• HTTP Web Server v1.1—This feature provides a consistent interface for users and applications by
implementing the HTTP 1.1 standard (see RFC 2616). In previous releases, Cisco software
supported only a partial implementation of HTTP 1.0. The integrated HTTP Server API supports
server application interfaces. When combined with the HTTPS and HTTP 1.1 Client features,
provides a complete, secure solution for HTTP services to and from Cisco devices.
OL-6415-04
Cisco Wireless Router and HWIC Configuration Guide
1-5
Page 24

Chapter 1 Overview
Cisco Wireless Router and HWIC Configuration Guide
1-6
OL-6415-04
Page 25

CHA P TER
2
Configuring Radio Settings
This chapter describes how to configure radio settings for the wireless device. This chapter includes
these sections:
• Enabling the Radio Interface, page 2-2
• Roles in Radio Network, page 2-2
• Configuring Network or Fallback Role, page 2-3
• Sample Bridging Configuration, page 2-4
• Universal Client Mode, page 2-7
• Configuring Universal Client Mode, page 2-7
• Configuring Radio Data Rates, page 2-10
• Configuring Radio Transmit Power, page 2-12
• Configuring Radio Channel Settings, page 2-14
• Enabling and Disabling World Mode, page 2-20
• Enabling and Disabling Short Radio Preambles, page 2-21
OL-6415-04
• Configuring Transmit and Receive Antennas, page 2-22
• Disabling and Enabling Access Point Extensions, page 2-23
• Configuring the Ethernet Encapsulation Transformation Method, page 2-23
• Enabling and Disabling Reliable Multicast to Workgroup Bridges, page 2-24
• Enabling and Disabling Public Secure Packet Forwarding, page 2-25
• Configuring Beacon Period and DTIM, page 2-26
• Configuring RTS Threshold and Retries, page 2-27
• Configuring Maximum Data Retries, page 2-27
• Configuring Fragmentation Threshold, page 2-28
• Enabling Short Slot Time for 802.11g Radios, page 2-28
• Performing a Carrier Busy Test, page 2-29
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-1
Page 26
Enabling the Radio Interface
Enabling the Radio Interface
The wireless device radios are disabled by default.
Note In Cisco IOS Release 12.4 there is no default SSID. You must create a Radio Service Set Identifier
(SSID) before you can enable the radio interface.
Beginning in privileged EXEC mode, follow these steps to enable the wireless device radio:
Command Purpose
Step 1
Step 2
Step 3
Step 4
Step 5
Step 6
configure terminal Enter global configuration mode.
interface dot11radio { 0 | 1 } Enter interface configuration mode for the radio interface. The
ssid Enter the SSID. The SSID can consist of up to 32 alphanumeric
no shutdown Enable the radio port.
end Return to privileged EXEC mode.
copy running-config startup-config (Optional) Save your entries in the configuration file.
Chapter 2 Configuring Radio Settings
2.4-GHz radio is radio 0, and the 5-GHz radio is radio 1.
characters. SSIDs are case sensitive.
Use the shutdown command to disable the radio port.
Roles in Radio Network
You can configure the following roles in a radio network:
• Network or Fallback Role
• Universal Client Mode
Table 2-1 shows the role in the radio network for each device.
Ta b l e 2-1 Device Role in Radio Network Configuration
Role in Radio Network
Root access point X X X X X
Root bridge with or without clients – – X X X
Non-root bridge without clients – – X X X
Universal client mode X X X X X
Support of Workgroup bridge
clients
Cisco 800 s
eries
ISRs
X X X X X
Cisco 1800
series ISRs
Cisco 1841
series
Cisco 2800
series ISRs
Cisco 3800
series ISRs
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-2
OL-6415-04
Page 27
Chapter 2 Configuring Radio Settings
Configuring Network or Fallback Role
You can also configure a fallback role for root access points. The wireless device automatically assumes
the fallback role when its Ethernet port is disabled or disconnected from the wired LAN. Thefallback
role is Shutdown—the wireless device shuts down its radio and disassociates all client devices.
Beginning in privileged EXEC mode, follow these steps to set the wireless device’s radio network role
and fallback role:
Command Purpose
Step 1
Step 2
Step 3
configure terminal Enter global configuration mode.
interface dot11radio { 0 | 1 } Enter interface configuration mode for the radio interface. The
2.4-GHz radio is radio 0, and the 5-GHz radio is radio 1.
station-role
non-root {bridge | return}
root {fallback | repeater | wireless
clients | shutdown]}
Sets the wireless device role to universal client mode.
• Set the role to non-root bridge with or without wireless
clients, repeater access point, root access point or bridge,
scanner, or workgroup bridge.
• The bridge mode radio supports point-to-point
configuration only.
• The Ethernet port is shut down when any one of the radios
is configured as a repeater. Only one radio per access point
may be configured as a workgroup bridge or repeater.
• The dot11radio 0|1 antenna-alignment command is
available when the access point is configured as a repeater.
Configuring Network or Fallback Role
Step 4
Step 5
• Spanning Tree Protocol (STP) is configurable on Cisco
ISR series access points in bridge modes.
• (Optional) Select the root access point’s fallback role. If
the wireless device’s Ethernet port is disabled or
disconnected from the wired LAN, the wireless device can
either shut down its radio port or become a repeater access
point associated to any nearby root access point.
end Return to privileged EXEC mode.
copy running-config startup-config (Optional) Save your entries in the configuration file.
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-3
Page 28

Configuring Network or Fallback Role
Bridge Features Not Supported
The following features are not supported when a Cisco ISR series access point is configured as a bridge:
• Clear Channel Assessment (CCA)
• Interoperability with 1400 series bridge
• Concatenation
• Install mode
• EtherChannel and PageP configuration on switch
For root and non-root bridging mode operations, only bridge-group mode using BVI interface is
supported. Routing mode is not supported for root and non-root bridging operations.
Sample Bridging Configuration
The following is a sample of a Root Bridge Configuration:
!
aaa new-model
!
!
aaa group server radius rad_eap
server 20.0.0.1 auth-port 1812 acct-port 1813
!
aaa authentication login eap_methods group rad_eap
!
aaa session-id common
!
resource policy
!
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
!
dot11 ssid airlink2-bridge
vlan 1
authentication open
authentication key-management wpa
wpa-psk ascii 0 12345678
!
dot11 priority-map avvid
ip cef
!
!
no ip domain lookup
!
!
bridge irb
!
!
interface FastEthernet0/0
no ip address
shutdown
duplex auto
speed auto
!
interface FastEthernet0/1
Chapter 2 Configuring Radio Settings
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-4
OL-6415-04
Page 29

Chapter 2 Configuring Radio Settings
ip address 30.0.0.1 255.0.0.0
duplex auto
speed auto
!
interface Dot11Radio0/0/0
no ip address
!
encryption vlan 1 mode ciphers tkip
!
ssid airlink2-bridge
!
speed basic-1.0 basic-2.0 basic-5.5 6.0 9.0 basic-11.0 12.0 18.0 24.0 36.0 48.0 54.0
station-role root bridge
!
interface Dot11Radio0/0/0.1
encapsulation dot1Q 1 native
no snmp trap link-status
bridge-group 1
bridge-group 1 spanning-disabled
!
interface Dot11Radio0/0/1
no ip address
speed basic-6.0 9.0 basic-12.0 18.0 basic-24.0 36.0 48.0 54.0
station-role root
!
interface BVI1
ip address 20.0.0.1 255.0.0.0
!
ip route 0.0.0.0 0.0.0.0 20.0.0.5
!
!
ip http server
no ip http secure-server
!
!
radius-server local
nas 20.0.0.1 key 0 wireless
user non-root nthash 0 3741A4EE66E1AA56CD8B3A9038580DC9
!
radius-server host 20.0.0.1 auth-port 1812 acct-port 1813 key wireless
!
control-plane
!
bridge 1 route ip
!
!
line con 0
exec-timeout 0 0
line aux 0
line vty 0 4
!
!
webvpn context Default_context
ssl authenticate verify all
!
no inservice
!
end
Configuring Network or Fallback Role
The following is a sample of Non-Root Bridge Configuration:
no aaa new-model
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-5
Page 30

Configuring Network or Fallback Role
!
resource policy
!
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
!
dot11 ssid airlink2-bridge
vlan 1
authentication open
authentication key-management wpa
wpa-psk ascii 0 12345678
!
dot11 priority-map avvid
ip cef
!
!
bridge irb
!
!
interface FastEthernet0/0
no ip address
duplex auto
speed auto
!
interface FastEthernet0/1
no ip address
duplex auto
speed auto
bridge-group 1
bridge-group 1 spanning-disabled
!
interface Dot11Radio0/1/0
no ip address
!
encryption vlan 1 mode ciphers tkip
!
ssid airlink2-bridge
!
speed basic-1.0 basic-2.0 basic-5.5 6.0 9.0 basic-11.0 12.0 18.0 24.0 36.0 48.0 54.0
station-role non-root bridge
!
interface Dot11Radio0/1/0.1
encapsulation dot1Q 1 native
no snmp trap link-status
bridge-group 1
bridge-group 1 spanning-disabled
!
interface BVI1
ip address 20.0.0.5 255.0.0.0
!
ip route 0.0.0.0 0.0.0.0 20.0.0.1
!
!
ip http server
no ip http secure-server
!
!
control-plane
!
bridge 1 route ip
!
!
Chapter 2 Configuring Radio Settings
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-6
OL-6415-04
Page 31

Chapter 2 Configuring Radio Settings
line con 0
exec-timeout 0 0
line aux 0
line vty 0 4
login
!
!
webvpn context Default_context
ssl authenticate verify all
!
no inservice
!
end
Universal Client Mode
Universal client mode is a wireless radio station role that allows the radio to act as a wireless client to
another access point or repeater. This feature is exclusive to the integrated radio running in the
Cisco
870, 1800, 2800, and 3800 Integrated Services Routers. It operates differently from the workgroup
bridge and non-root bridge modes that are supported on other Cisco wireless devices such as the
Cisco
AP 1200.
Universal client mode has the following features and limitations:
Universal Client Mode
• You can configure universal client mode on the main dot11radio interface only, sub-interfaces are
not supported.
• Universal client can associate to access points with radio VLANs.
• Layer-3 routing is supported over the radio interface. However, there is no support for L2-bridging.
The user cannot configure a dot11radio interface with a bridge-group when in universal client mode.
• SSIDs are required to be configured on the dot11 interface operating as a universal client;
association to an access point running in guest-mode is not supported.
• The universal client can associate to Cisco access points, 3rd party access points, and repeaters. It
cannot associate to Cisco root bridges or Cisco workgroup bridges.
Configuring Universal Client Mode
You can configure universal client mode in Cisco ISR series by setting the radio interface station-role to
non-root. This is different from configuring the dot11radio interface to operate in non-root bridge mode,
which requires specifying the word bridge at the end of the command, ex: "station-role non-root
bridge".
Note In other Cisco wireless products such as the Cisco AP1232, station-role non-root operates the same as
station-role non-root bridge. On the ISRs, the two commands are different: station-role non-root is
considered the universal client mode and station-role non-root bridge is considered the non-root bridge
mode.
Example using Cisco 2801 series router:
c2801#conf t
Enter configuration commands, one per line. End with CNTL/Z.
c2801(config)#interface Dot11Radio0/1/0
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-7
Page 32

Configuring Universal Client Mode
c2801(config-if)#station-role ?
non-root Non-root (bridge)
root Root access point or bridge
c2801(config-if)#station-role non-root ?
bridge Bridge non-rootThis CLI enables non-root bridge mode.
<cr> This CLI enables universal client mode
DHCP
IP DHCP addressing is supported in the Dot11Radio interface configured in universal client mode. The
following is an example of Dot11Radio configured with "ip address dhcp":
dot11 ssid test10
authentication open
!
interface Dot11Radio0/1/0
ip address dhcp
!
ssid test10
!
speed basic-1.0 basic-2.0 basic-5.5 6.0 9.0 basic-11.0 12.0 18.0 24.0 36.0 48.0 54.0
station-role non-root
Chapter 2 Configuring Radio Settings
Issuing a "show ip interface brief" will show the Virtual-Dot11Radio interface getting the IP address
from the DHCP server.
c2801_uc#sh ip int brief
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 unassigned YES NVRAM administratively down down
FastEthernet0/1 unassigned YES NVRAM administratively down down
Dot11Radio0/1/0 unassigned YES DHCP up up
Dot11Radio0/1/1 unassigned YES NVRAM administratively down down
Virtual-Dot11Radio0 200.1.1.2 YES DHCP up up
c2801_uc#
NAT (Network Address Translation):
NAT translation takes place if you overload the interface which has an ip address. In the case of universal
client, the virtual-interface has the ip address obtained from the DHCP. Hence we require to overload the
virtual interface to aid NAT translation.
Note NAT fails to translate with a DHCP address on the dot11 interface running in universal client mode.
The following configuration is supported on NAT:
ip nat inside source list 1 interface Virtual-Dot11Radio0 overload
The following is an example of a NAT configuration on a Cisco 1803 ISR:
C1803W_UC#
C1803W_UC#sh run
Building configuration...
Current configuration : 2189 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-8
OL-6415-04
Page 33

Chapter 2 Configuring Radio Settings
no service password-encryption
!
hostname C1803W_UC
!
boot-start-marker
boot-end-marker
!
logging buffered 4096 debugging
no logging console
!
no aaa new-model
!
resource policy
!
!
dot11 ssid hurricane
authentication open
authentication key-management wpa
wpa-psk ascii 0 allyouneedislove
!
dot11 ssid tsunami
authentication open
guest-mode
!
dot11 priority-map avvid
!
!
ip cef
no ip dhcp use vrf connected
ip dhcp excluded-address 100.1.1.1
!
ip dhcp pool jimmy
network 100.1.1.0 255.255.255.0
default-router 100.1.1.1
!
!
!
!
!
!
controller DSL 0
line-term cpe
!
!
bridge irb
!
interface Dot11Radio0
ip address 100.1.1.1 255.255.255.0
ip nat inside
ip virtual-reassembly
no ip route-cache cef
no ip route-cache
!
ssid tsunami
!
speed basic-1.0 basic-2.0 basic-5.5 6.0 9.0 basic-11.0 12.0 18.0 24.0 36.0 48.0 54.0
station-role root
rts threshold 2312
no cdp enable
!
interface Dot11Radio1
ip address dhcp
ip nat outside
ip virtual-reassembly
Configuring Universal Client Mode
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-9
Page 34

Configuring Radio Data Rates
!
encryption mode ciphers tkip
!
ssid hurricane
!
speed basic-6.0 9.0 basic-12.0 18.0 basic-24.0 36.0 48.0 54.0
station-role non-root
!
End
Configuring Radio Data Rates
You use the data rate settings to choose the data rates the wireless device uses for data transmission. The
rates are expressed in megabits per second. The wireless device always attempts to transmit at the highest
data rate set to Basic, also called Require on the browser-based interface. If there are obstacles or
interference, the wireless device steps down to the highest rate that allows data transmission. You can
set each data rate to one of three states:
• Basic (the GUI labels Basic rates as Required)—Allows transmission at this rate for all packets, both
unicast and multicast. At least one of the wireless device's data rates must be set to Basic.
• Enabled—The wireless device transmits only unicast packets at this rate; multicast packets are sent
at one of the data rates set to Basic.
• Disabled—The wireless device does not transmit data at this rate.
Chapter 2 Configuring Radio Settings
Note At least one data rate must be set to basic.
You can use the Data Rate settings to set an access point to serve client devices operating at specific data
rates. For example, to set the 2.4-GHz radio for 11 megabits per second (Mbps) service only, set the
11-Mbps rate to Basic and set the other data rates to Disabled. To set the wireless device to serve only
client devices operating at 1 and 2 Mbps, set 1 and 2 to Basic and set the rest of the data rates to
Disabled. To set the 2.4-GHz, 802.11g radio to serve only 802.11g client devices, set any Orthogonal
Frequency Division Multiplexing (OFDM) data rate (6, 9, 12, 18, 24, 36, 48, 54) to Basic. To set the
5-GHz radio for 54 Mbps service only, set the 54-Mbps rate to Basic and set the other data rates to
Disabled.
You can configure the wireless device to set the data rates automatically to optimize either the range or
the throughput. When you enter range for the data rate setting, the wireless device sets the 1 Mbps rate
to basic and the other rates to enabled. When you enter throughput for the data rate setting, the wireless
device sets all four data rates to basic.
Beginning in privileged EXEC mode, follow these steps to configure the radio data rates:
Command Purpose
Step 1
Step 2
configure terminal Enter global configuration mode.
interface dot11radio { 0 | 1 } Enter interface configuration mode for the radio interface. The
2.4-GHz radio is radio 0, and the 5-GHz radio is radio 1.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-10
OL-6415-04
Page 35

Chapter 2 Configuring Radio Settings
Command Purpose
Step 3
speed
These options are available for the
802.11b, 2.4-GHz radio:
{[1.0] [11.0] [2.0] [5.5] [basic-1.0]
[basic-11.0] [basic-2.0] [basic-5.5] |
range | throughput}
These options are available for the
802.11g, 2.4-GHz radio:
{[1.0] [2.0] [5.5] [6.0] [9.0] [11.0]
[12.0] [18.0] [24.0] [36.0] [48.0]
[54.0] [basic-1.0] [basic-2.0]
[basic-5.5] [basic-6.0] [basic-9.0]
[basic-11.0] [basic-12.0]
[basic-18.0] [basic-24.0]
[basic-36.0] [basic-48.0]
[basic-54.0] | range |
throughput [ofdm] | default }
These options are available for the
5-GHz radio:
{[6.0] [9.0] [12.0] [18.0] [24.0]
[36.0] [48.0] [54.0] [basic-6.0]
[basic-9.0] [basic-12.0] [basic-18.0]
[basic-24.0] [basic-36.0]
[basic-48.0] [basic-54.0] |
range | throughput |default }
Configuring Radio Data Rates
Set each data rate to basic or enabled, or enter range to
optimize range or throughput to optimize throughput.
• (Optional) Enter 1.0, 2.0, 5.5, and 11.0 to set these data
rates to enabled on the 802.11b, 2.4-GHz radio.
Enter 1.0, 2.0, 5.5, 6.0, 9.0, 11.0, 12.0, 18.0, 24.0, 36.0,
48.0, and 54.0 to set these data rates to enabled on the
802.11g, 2.4-GHz radio.
Enter 6.0, 9.0, 12.0, 18.0, 24.0, 36.0, 48.0, and 54.0 to set
these data rates to enabled on the 5-GHz radio.
• (Optional) Enter basic-1.0, basic-2.0, basic-5.5, and
basic-11.0 to set these data rates to basic on the 802.11b,
2.4-GHz radio.
Enter basic-1.0, basic-2.0, basic-5.5, basic-6.0, basic-9.0,
basic-11.0, basic-12.0, basic-18.0, basic-24.0, basic-36.0,
basic-48.0, and basic-54.0 to set these data rates to basic
on the 802.11g, 2.4-GHz radio.
Note The client must support the basic rate that you select or
it cannot associate to the wireless device. If you select
12 Mbps or higher for the basic data rate on the 802.11g
radio, 802.11b client devices cannot associate to the
wireless device’s 802.11g radio.
Enter basic-6.0, basic-9.0, basic-12.0, basic-18.0,
basic-24.0, basic-36.0, basic-48.0, and basic-54.0 to set
these data rates to basic on the 5-GHz radio.
• (Optional) Enter range or throughput to automatically
optimize radio range or throughput. When you enter
range, the wireless device sets the lowest data rate to basic
and the other rates to enabled. When you enter
throughput, the wireless device sets all data rates to basic.
(Optional) On the 802.11g radio, enter speed throughput
ofdm to set all OFDM rates (6, 9, 12, 18, 24, 36, and 48)
to basic (required) and set all the CCK rates (1, 2, 5.5, and
11) to disabled. This setting disables 802.11b protection
mechanisms and provides maximum throughput for
802.11g clients. However, it prevents 802.11b clients from
associating to the access point.
OL-6415-04
• (Optional) Enter default to set the data rates to factory
default settings (not supported on 802.11b radios).
On the 802.11g radio, the default option sets rates 1, 2, 5.5,
and 11 to basic, and rates 6, 9, 12, 18, 24, 36, 48, and 54 to
enabled. These rate settings allow both 802.11b and
802.11g client devices to associate to the wireless device’s
802.11g radio.
On the 5-GHz radio, the default option sets rates 6.0, 12.0,
and 24.0 to basic, and rates 9.0, 18.0, 36.0, 48.0, and 54.0
to enabled.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-11
Page 36

Configuring Radio Transmit Power
Command Purpose
Step 4
Step 5
end Return to privileged EXEC mode.
copy running-config startup-config (Optional) Save your entries in the configuration file.
Use the no form of the speed command to remove one or more data rates from the configuration. This
example shows how to remove data rates basic-2.0 and basic-5.5 from the configuration:
router# configure terminal
router(config)# interface dot11radio 0
router(config-if)# no speed basic-2.0 basic-5.5
router(config-if)# end
Configuring Radio Transmit Power
Radio transmit power is based on the type of radio or radios installed in your access point and the
regulatory domain in which it operates. To determine what transmit power is available for your access
point and which regulatory domain it operates in, refer to the hardware installation guide for that device.
hardware installation guides are available at cisco.com. Follow these steps to view and download them:
Chapter 2 Configuring Radio Settings
Step 1 Browse to http://www.cisco.com.
Step 2 Click Technical Support & Documentation. A small window appears containing a list of technical
support links.
Step 3 Click Technical Support & Documentation. The Technical Support and Documentation page appears.
Step 4 In the Documentation & Tools section, choose Wireless. The Wireless Support Resources page appears.
Step 5 In the Wireless LAN Access section, choose the device you are working with. An introduction page for
the device appears.
Step 6 In the Install and Upgrade section, choose Install and Upgrade Guides. The Install and Upgrade Guides
page for the device appears.
Step 7 Choose the hardware installation guide for the device. The home page for the guide appears.
Step 8 In the left frame, click Channels and Antenna Settings.
Table 2-2 shows the relationship between mW and dBm.
Ta b l e 2-2 Translation between mW and dBm
dBm -1 2 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24
mW 1 2 3 4 5 6 8 10 12 15 20 25 30 40 50 60 80 100 125 150 200 250
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-12
OL-6415-04
Page 37

Chapter 2 Configuring Radio Settings
Beginning in privileged EXEC mode, follow these steps to set the transmit power on access point radios:
Command Purpose
Step 1
Step 2
Step 3
configure terminal Enter global configuration mode.
interface dot11radio { 0 | 1 } Enter interface configuration mode for the radio interface. The
power local
power settings should be:
{3 | 4 | 5 | 6 | 7 | 10 | 13 | 15 | 17 | 18 |
20 | maximum}
Configuring Radio Transmit Power
2.4-GHz radio is radio 0, and the 5-GHz radio is radio 1.
Set the transmit power for the 802.11g, 2.4-GHz radio to one of
the power levels allowed in your regulatory domain. All
settings are in mW.
On the 2.4-GHz, 802.11g radio, you can set Orthogonal
Frequency Division Multiplexing (OFDM) power levels and
Complementary Code Keying (CCK) power levels. CCK
modulation is supported by 802.11b and 802.11g devices.
OFDM modulation is supported by 802.11g and 802.11a
devices.
Note See the hardware installation guide for your access
point to determine the power settings for your
regulatory domain.
Note The 802.11g radio transmits at up to 100 mW for the 1,
2, 5.5, and 11Mbps data rates. However, for the 6, 9, 12,
18, 24, 36, 48, and 54Mbps data rates, the maximum
transmit power for the 802.11g radio is 30 mW.
Step 4
Step 5
end Return to privileged EXEC mode.
copy running-config startup-config (Optional) Save your entries in the configuration file.
Use the no form of the power command to return the power setting to maximum, the default setting.
Limiting the Power Level for Associated Client Devices
You can also limit the power level on client devices that associate to the wireless device. When a client
device associates to the wireless device, the wireless device sends the maximum power level setting to
the client.
Note Cisco AVVID documentation uses the term Dynamic Power Control (DTPC) to refer to limiting the
power level on associated client devices.
Beginning in privileged EXEC mode, follow these steps to specify a maximum allowed power setting on
all client devices that associate to the wireless device:
Command Purpose
Step 1
Step 2
OL-6415-04
configure terminal Enter global configuration mode.
interface dot11radio { 0 | 1 } Enter interface configuration mode for the radio interface. The
2.4-GHz radio is radio 0, and the 5-GHz radio is radio 1.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-13
Page 38

Configuring Radio Channel Settings
Command Purpose
Step 3
power client
These options are available for
802.11b, 2.4-GHz clients (in mW):
{ 1 | 5 | 20 | 30 | 50 | 100 | maximum}
These options are available for
802.11g, 2.4-GHz clients (in mW):
{ 1 | 5 | 10 | 20 | 30 | 50 | 100 |
maximum}
These options are available for 5-GHz
clients (in mW):
{ 5 | 10 | 20 | 40 | maximum }
Step 4
Step 5
end Return to privileged EXEC mode.
copy running-config startup-config (Optional) Save your entries in the configuration file.
Chapter 2 Configuring Radio Settings
Set the maximum power level allowed on client devices that
associate to the wireless device.
Note The settings allowed in your regulatory domain might
differ from the settings listed here.
Use the no form of the client power command to disable the maximum power level for associated clients.
Note Access Point extensions must be enabled to limit the power level on associated client devices. Access
Point extensions are enabled by default.
Configuring Radio Channel Settings
The default channel setting for the wireless device radios is least congested; at startup, the wireless
device scans for and selects the least-congested channel. For the most consistent performance after a site
survey, however, we recommend that you assign a static channel setting for each access point. The
channel settings on the wireless device correspond to the frequencies available in your regulatory
domain. See the access point’s hardware installation guide for the frequencies allowed in your domain.
Each 2.4-GHz channel covers 22 MHz. The bandwidth for channels 1, 6, and 11 does not overlap, so you
can set up multiple access points in the same vicinity without causing interference. Both 802.11b and
802.11g 2.4-GHz radios use the same channels and frequencies.
The 5-GHz radio operates on eight channels from 5180 to 5320 MHz. Each channel covers 20 MHz, and
the bandwidth for the channels overlaps slightly. For best performance, use channels that are not adjacent
(44 and 46, for example) for radios that are close to each other.
Note Too many access points in the same vicinity creates radio congestion that can reduce throughput. A
careful site survey can determine the best placement of access points for maximum radio coverage and
throughput.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-14
OL-6415-04
Page 39

Chapter 2 Configuring Radio Settings
Beginning in privileged EXEC mode, follow these steps to set the wireless device’s radio channel:
Command Purpose
Step 1
Step 2
Step 3
configure terminal Enter global configuration mode.
interface dot11radio {0 | 1 } Enter interface configuration mode for the radio interface. The
channel
frequency | least-congested
Step 4
Step 5
end Return to privileged EXEC mode.
copy running-config
startup-config
Configuring Radio Channel Settings
2.4-GHz radio is radio 0, and the 5-GHz radio is radio 1.
Set the default channel for the wireless device radio. Table 2-3
through Table 2-6 show the available channels and frequencies for
all radios. To search for the least-congested channel on startup,
enter least-congested.
Note The channel command is disabled for 5-GHz radios that
comply with European Union regulations on dynamic
frequency selection (DFS). See the
Enabled on Some 5-GHz Radio Channels” section on
page 2-19 for more information.
(Optional) Save your entries in the configuration file.
“DFS Automatically
Table 2-3 shows the available channels and frequencies for the IEEE 802.11b 2.4-GHz radio.
Ta b l e 2-3 Channels and Frequencies for 802.11b 2.4 GHz Radio
Regulatory Domains
Channel
Identifier
Center
Frequency (MHz)
Americas
(–A)
China
(–C)
EMEA
(–E)
Japan
(–J)
1 2412 X X X X
2 2417 X X X X
3 2422 X X X X
4 2427 X X X X
5 2432 X X X X
6 2437 X X X X
7 2442 X X X X
8 2447 X X X X
9 2452 X X X X
10 2457 X X X X
11 2462 X X X X
12 2467 – – X X
13 2472 – – X X
14 2484 – – – –
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-15
Page 40

Configuring Radio Channel Settings
Table 2-4 shows the available frequencies for the 802.11g 2.4 GHz radio.
Ta b l e 2-4 Channels and Available Frequencies for 802.11g 2.4 GHz Radio
Chapter 2 Configuring Radio Settings
Regulatory Domains
Channel
Identifier
Center
Frequency
(MHz)
Americas (–A) EMEA (–E) Japan (–J)
CCK OFDM CCK OFDM CCK OFDM
1 2412 X X X X X X
2 2417 X X X X X X
3 2422 X X X X X X
4 2427 X X X X X X
5 2432 X X X X X X
6 2437 X X X X X X
7 2442 X X X X X X
8 2447 X X X X X X
9 2452 X X X X X X
10 2457 X X X X X X
11 2462 X X X X X X
12 2467 – – X X X X
13 2472 – – X X X X
14 2484 – – – – X –
Table 2-5 shows the available channels and frequencies for the RM20A IEEE 802.11a radio
Ta b l e 2-5 Channels and Available Frequencies for the 802.11a Radio
Regulatory Domains
Channel
Identifier
Center
Frequency
(MHz)
Americas (–A) EMEA (–N) Japan (–P)
CCK OFDM CCK OFDM CCK OFDM
1 2412 X X X X X X
2 2417 X X X X X X
3 2422 X X X X X X
4 2427 X X X X X X
5 2432 X X X X X X
6 2437 X X X X X X
7 2442 X X X X X X
8 2447 X X X X X X
9 2452 X X X X X X
10 2457 X X X X X X
11 2462 X X X X X X
12 2467 – – X X X X
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-16
OL-6415-04
Page 41

Chapter 2 Configuring Radio Settings
Configuring Radio Channel Settings
Regulatory Domains
Channel
Identifier
Center
Frequency
(MHz)
Americas (–A) EMEA (–N) Japan (–P)
CCK OFDM CCK OFDM CCK OFDM
13 2472 – – X X X X
14 2484 – – – – X –
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-17
Page 42

Configuring Radio Channel Settings
Table 2-6 shows the available frequencies for the RM21A and RM22A IEEE 802.11a 5-GHz radios.
Ta b l e 2-6 Channels and Available Frequencies for the 802.11a 5-GHz Radios
Chapter 2 Configuring Radio Settings
Channel IDCenter
Freq
(MHz)
Americas
(–B)
China
(–C)
EMEA
(–E)
New
Zealand,
Australia
(–N)
Japan
(–P)
34 5170 – – – – – –
36 5180 x – x x x –
38 5190 – – – – – –
40 5200 x – x x x –
42 5210 – – – – – –
44 5220 x – x x x –
46 5230 – – – – – –
48 5240 x – x x x –
52 5260 – – x x x –
56 5280 – – x x x –
60 5300 – – x x x –
64 5320 – – x x x –
100 5500 – – x – – –
104 5520 – – x – – –
108 5540 – – x – – –
112 5560 – – x – – –
116 5580 – – x – – –
120 5600 – – x – – –
124 5620 – – x – – –
128 5640 – – x – – –
132 5660 – – x – – –
136 5680 – – x – – –
140 5700 – – x – – –
149 5745 x x – x – –
153 5765 x x – x – –
157 5785 x x – x – –
161 5805 x x – x – –
165 5825 – – x – – –
–
Note The frequencies allowed in your regulatory domain might differ from the frequencies listed here.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-18
OL-6415-04
Page 43

Chapter 2 Configuring Radio Settings
DFS Automatically Enabled on Some 5-GHz Radio Channels
Access points with 5-GHz radios configured at the factory for use in Europe now comply with
regulations that require radio devices to use Dynamic Frequency Selection (DFS) to detect radar signals
and avoid interfering with them. Radios configured for use in other regulatory domains do not use DFS.
When a DFS-enabled 5-GHz radio operates on one of the 15 channels listed in Table 2-7, the access point
automatically uses DFS to set the operating frequency.
Note You cannot manually select a channel for DFS-enabled 5-GHz radios.
Ta b l e 2-7 DFS Automatically Enabled on these 5-GHz Channels
5-GHz Channels on Which DFS is Automatically Enabled
52 (5260 MHz) 104 (5520 MHz) 124 (5620 MHz)
56 (5280 MHz) 108 (5540 MHz) 128 (5640 MHz)
60 (5300 MHz) 112 (5560 MHz) 132 (5660 MHz)
64 (5320 MHz) 116 (5580 MHz) 136 (5680 MHz)
100 (5500 MHz) 120 (5600 MHz) 140 (5700 MHz)
Configuring Radio Channel Settings
When DFS is enabled, the access point monitors its operating frequency for radar signals. If it detects
radar signals on the channel, the access point takes these steps:
• Blocks new transmissions on the channel.
• Flushes the power-save client queues.
• Broadcasts an 802.11h channel-switch announcement.
• Disassociates remaining client devices.
• Randomly selects a different 5-GHz channel.
• If the channel selected is one of the channels in Table 2-7, scans the new channel for radar signals
for 60 seconds.
• If there are no radar signals on the new channel, enables beacons and accepts client associations.
Note The maximum legal transmit power is greater for some 5-GHz channels than for others. When it
randomly selects a 5-GHz channel on which power is restricted, the access point automatically reduces
transmit power to comply with power limits for that channel.
Note We recommend that you use the world-mode dot11d country-code configuration interface command to
configure a country code on DFS-enabled radios. The IEEE 802.11h protocol requires access points to
include the country information element (IE) in beacons and probe responses. By default, however, the
country code in the IE is blank. You use the world-mode command to populate the country code IE.
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-19
Page 44

Enabling and Disabling World Mode
Confirming that DFS is Enabled
Use the show controller dot11radio1 command to confirm that DFS is enabled. This example shows a
line from the output for the show controller command for a channel on which DFS is enabled:
Current Frequency: 5300 MHz Channel 60 (DFS enabled)
Blocking Channels from DFS Selection
If your regulatory domain limits the channels that you can use in specific locations--for example, indoors
or outdoors--you can block groups of channels to prevent the access point from selecting them when DFS
is enabled. Use this configuration interface command to block groups of channels from DFS selection:
[no] dfs band [1] [2] [3] [4] block
The 1, 2, 3, and 4 options designate blocks of channels:
• 1—Specifies frequencies 5.150 to 5.250 GHz. This group of frequencies is also known as the UNII-1
band.
• 2—Specifies frequencies 5.250 to 5.350 GHz. This group of frequencies is also known as the UNII-2
band.
• 3—Specifies frequencies 5.470 to 5.725 GHz.
• 4—Specifies frequencies 5.725 to 5.825 GHz. This group of frequencies is also known as the UNII-3
band.
Chapter 2 Configuring Radio Settings
This example shows how to prevent the access point from selecting frequencies 5.150 to 5.350 GHz
during DFS:
router(config-if)# dfs band 1 2 block
This example shows how to unblock frequencies 5.150 to 5.350 for DFS:
router(config-if)# no dfs band 1 2 block
This example shows how to unblock all frequencies for DFS:
router(config-if)# no dfs band block
Enabling and Disabling World Mode
You can configure the wireless device to support 802.11d world mode or Cisco legacy world mode.
When you enable world mode, the wireless device adds channel carrier set information to its beacon.
Client devices with world mode enabled receive the carrier set information and adjust their settings
automatically. For example, a client device used primarily in Japan could rely on world mode to adjust
its channel and power settings automatically when it travels to Italy and joins a network there. Cisco
client devices running firmware version 5.30.17 or later detect whether the wireless device is using
802.11d or Cisco legacy world mode and automatically use world mode that matches the mode used by
the wireless device. World mode is disabled by default.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-20
OL-6415-04
Page 45

Chapter 2 Configuring Radio Settings
Beginning in privileged EXEC mode, follow these steps to enable world mode:
Command Purpose
Step 1
Step 2
Step 3
configure terminal Enter global configuration mode.
interface dot11radio { 0 | 1} Enter interface configuration mode for the radio interface.
world-mode
dot11d country_code code
{ both | indoor | outdoor }
| legacy
Enabling and Disabling Short Radio Preambles
Enable world mode.
• Enter the dot11d option to enable 802.11d world mode.
–
When you enter the dot11d option, you must enter a
two-character ISO country code (for example, the ISO
country code for the United States is US). You can find
a list of ISO country codes at the ISO website.
–
After the country code, you must enter indoor,
outdoor, or both to indicate the placement of the
wireless device.
• Enter the legacy option to enable Cisco legacy world
mode.
Note Access Point extensions must be enabled for legacy
world mode operation, but Access Point extensions are
not required for 802.11d world mode. Access Point
extensions are enabled by default.
Step 4
Step 5
end Return to privileged EXEC mode.
copy running-config startup-config (Optional) Save your entries in the configuration file.
Use the no form of the command to disable world mode.
Enabling and Disabling Short Radio Preambles
The radio preamble (sometimes called a header) is a section of data at the head of a packet that contains
information that the wireless device and client devices need when sending and receiving packets. You
can set the radio preamble to long or short:
• Short—A short preamble improves throughput performance. Cisco Access Point Wireless LAN
Client Adapters support short preambles.
• Long—A long preamble ensures compatibility between the wireless device and all early models of
Cisco Access Point Wireless LAN Adapters (PC4800 and PC4800A). If these client devices do not
associate to the wireless devices, you should use short preambles.
You cannot configure short or long radio preambles on the 5-GHz radio.
Beginning in privileged EXEC mode, follow these steps to disable short radio preambles:
Command Purpose
Step 1
Step 2
OL-6415-04
configure terminal Enter global configuration mode.
interface dot11radio { 0 } Enter interface configuration mode for the 2.4-GHz radio
interface.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-21
Page 46

Configuring Transmit and Receive Antennas
Command Purpose
Step 3
Step 4
Step 5
no preamble-short Disable short preambles and enable long preambles.
end Return to privileged EXEC mode.
copy running-config startup-config (Optional) Save your entries in the configuration file.
Short preambles are enabled by default. Use the preamble-short command to enable short preambles if
they are disabled.
Configuring Transmit and Receive Antennas
You can select the antenna the wireless device uses to receive and transmit data. There are three options
for both the receive and the transmit antenna:
• Diversity—This default setting tells the wireless device to use the antenna that receives the best
signal. If the wireless device has two fixed (non-removable) antennas, you should use this setting
for both receive and transmit.
Chapter 2 Configuring Radio Settings
Step 1
Step 2
Step 3
Step 4
Step 5
Step 6
• Right—If the wireless device has removable antennas and you install a high-gain antenna on the
wireless device's right connector, you should use this setting for both receive and transmit. When
you look at the wireless device's back panel, the right antenna is on the right.
• Left—If the wireless device has removable antennas and you install a high-gain antenna on the
wireless device's left connector, you should use this setting for both receive and transmit. When you
look at the wireless device's back panel, the left antenna is on the left.
Beginning in privileged EXEC mode, follow these steps to select the antennas the wireless device uses
to receive and transmit data:
Command Purpose
configure terminal Enter global configuration mode.
interface dot11radio { 0 | 1 } Enter interface configuration mode for the radio interface. The
2.4-GHz radio is radio 0, and the 5-GHz radio is radio 1.
antenna receive
{diversity | left | right}
Set the receive antenna to diversity, left, or right.
Note For best performance, leave the receive antenna setting
at the default setting, diversity.
Note The Cisco 850 series routers do not support diversity.
antenna transmit
{diversity | left | right}
Set the transmit antenna to diversity, left, or right.
Note For best performance, leave the transmit antenna
setting at the default setting, diversity.
end Return to privileged EXEC mode.
copy running-config startup-config (Optional) Save your entries in the configuration file.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-22
OL-6415-04
Page 47

Chapter 2 Configuring Radio Settings
Disabling and Enabling Access Point Extensions
Disabling and Enabling Access Point Extensions
By default, the wireless device uses Cisco Access Point extensions to detect the capabilities of
Cisco
Access Point client devices and to support features that require specific interaction between the
wireless device and associated client devices. Cisco
these features:
• Load balancing—The wireless device uses Access Point extensions to direct client devices to an
access point that provides the best connection to the network based on factors such as number of
users, bit error rates, and signal strength.
• Message Integrity Check (MIC)—MIC is an additional WEP security feature that prevents attacks
on encrypted packets called bit-flip attacks. The MIC, implemented on both the wireless device and
all associated client devices, adds a few bytes to each packet to make the packets tamper-proof.
• World mode (legacy only)—Client devices with legacy world mode enabled receive carrier set
information from the wireless device and adjust their settings automatically. Access Point
extensions are not required for 802.11d world mode operation.
• Limiting the power level on associated client devices—When a client device associates to the
wireless device, the wireless device sends the maximum allowed power level setting to the client.
Disabling Access Point extensions disables the features listed above, but it sometimes improves the
ability of other companies devices to associate to the wireless device.
Access Point extensions must be enabled to support
Access Point extensions are enabled by default. Beginning in privileged EXEC mode, follow these steps
to disable Access Point extensions:
Command Purpose
Step 1
Step 2
Step 3
Step 4
Step 5
configure terminal Enter global configuration mode.
interface dot11radio { 0 | 1 } Enter interface configuration mode for the radio interface. The
2.4-GHz radio is radio 0, and the 5-GHz radio is radio 1.
no dot11 extension aironet Disable Access Point extensions.
end Return to privileged EXEC mode.
copy running-config startup-config (Optional) Save your entries in the configuration file.
Use the dot11 extension aironet command to enable Access Point extensions if they are disabled.
Configuring the Ethernet Encapsulation Transformation Method
When the wireless device receives data packets that are not 802.3 packets, the wireless device must
format the packets to 802.3 using an encapsulation transformation method. These are the two
transformation methods:
• 802.1H—This method provides optimum performance for Cisco Access Point wireless products.
This is the default setting.
• snap—Use this setting to ensure interoperability with non-Cisco Access Point wireless equipment.
RFC1042 does not provide the interoperability advantages of 802.1H but is used by other
manufacturers of wireless equipment. This is the default setting.
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-23
Page 48

Chapter 2 Configuring Radio Settings
Enabling and Disabling Reliable Multicast to Workgroup Bridges
Beginning in privileged EXEC mode, follow these steps to configure the encapsulation transformation
method:
Command Purpose
Step 1
Step 2
Step 3
Step 4
Step 5
configure terminal Enter global configuration mode.
interface dot11radio { 0 | 1 } Enter interface configuration mode for the radio interface. The
2.4-GHz radio is radio 0, and the 5-GHz radio is radio 1.
payload-encapsulation
snap | dot1h
end Return to privileged EXEC mode.
copy running-config startup-config (Optional) Save your entries in the configuration file.
Set the encapsulation transformation method to RFC1042
(snap) or 802.1h (dot1h, the default setting).
Enabling and Disabling Reliable Multicast to Workgroup
Bridges
The Reliable multicast messages from the access point to workgroup bridges setting limits reliable
delivery of multicast messages to approximately 20 Cisco Access Point Workgroup Bridges that are
associated to the wireless device. The default setting, disabled, reduces the reliability of multicast
delivery to allow more workgroup bridges to associate to the wireless device.
Access points and bridges normally treat workgroup bridges not as client devices but as infrastructure
devices, like access points or bridges. Treating a workgroup bridge as an infrastructure device means that
the wireless device reliably delivers multicast packets, including Address Resolution Protocol (ARP)
packets, to the workgroup bridge.
The performance cost of reliable multicast delivery—duplication of each multicast packet sent to each
workgroup bridge—limits the number of infrastructure devices, including workgroup bridges, that can
associate to the wireless device. To increase beyond 20 the number of workgroup bridges that can
maintain a radio link to the wireless device, the wireless device must reduce the delivery reliability of
multicast packets to workgroup bridges. With reduced reliability, the wireless device cannot confirm
whether multicast packets reach the intended workgroup bridge, so workgroup bridges at the edge of the
wireless device's coverage area might lose IP connectivity. When you treat workgroup bridges as client
devices, you increase performance but reduce reliability.
Note This feature is best suited for use with stationary workgroup bridges. Mobile workgroup bridges might
encounter spots in the wireless device's coverage area where they do not receive multicast packets and
lose communication with the wireless device even though they are still associated to it.
A Cisco Access Point Workgroup Bridge provides a wireless LAN connection for up to eight
Ethernet-enabled devices.
This feature is not supported on the 5-GHz radio.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-24
OL-6415-04
Page 49

Chapter 2 Configuring Radio Settings
Enabling and Disabling Public Secure Packet Forwarding
Beginning in privileged EXEC mode, follow these steps to configure the encapsulation transformation
method:
Command Purpose
Step 1
Step 2
configure terminal Enter global configuration mode.
interface dot11radio { 0 } Enter interface configuration mode for the 2.4-GHz radio
interface.
Step 3
Step 4
Step 5
infrastructure-client Enable reliable multicast messages to workgroup bridges.
end Return to privileged EXEC mode.
copy running-config startup-config (Optional) Save your entries in the configuration file.
Use the no form of the command to disable reliable multicast messages to workgroup bridges.
Enabling and Disabling Public Secure Packet Forwarding
Public Secure Packet Forwarding (PSPF) prevents client devices associated to an access point from
inadvertently sharing files or communicating with other client devices associated to the access point. It
provides Internet access to client devices without providing other capabilities of a LAN. This feature is
useful for public wireless networks like those installed in airports or on college campuses.
Note To prevent communication between clients associated to different access points, you must set up
protected ports on the switch to which the wireless devices are connected. See the
“Configuring
Protected Ports” section on page 2-26 for instructions on setting up protected ports.
To enable and disable PSPF using CLI commands on the wireless device, you use bridge groups. You
can find a detailed explanation of bridge groups and instructions for implementing them in this
document:
• Cisco IOS Bridging and IBM Networking Configuration Guide, Release 12.2. Click this link to
browse to the Configuring Transparent Bridging chapter:
http://www.cisco.com/univercd/cc/td/doc/product/software/ios122/122cgcr/fibm_c/bcfpart1/bcftb.
htm
You can also enable and disable PSPF using the web-browser interface. The PSPF setting is on the Radio
Settings pages.
PSPF is disabled by default. Beginning in privileged EXEC mode, follow these steps to enable PSPF:
Command Purpose
Step 1
Step 2
configure terminal Enter global configuration mode.
interface dot11radio { 0 | 1 } Enter interface configuration mode for the radio interface. The
2.4-GHz radio is radio 0, and the 5-GHz radio is radio 1.
Step 3
Step 4
Step 5
bridge-group group port-protected Enable PSPF.
end Return to privileged EXEC mode.
copy running-config startup-config (Optional) Save your entries in the configuration file.
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-25
Page 50

Configuring Beacon Period and DTIM
Use the no form of the command to disable PSPF.
Configuring Protected Ports
To prevent communication between client devices associated to different access points on your wireless
LAN, you must set up protected ports on the switch to which the wireless devices are connected.
Beginning in privileged EXEC mode, follow these steps to define a port on your switch as a protected
port:
Command Purpose
Step 1
Step 2
Step 3
Step 4
Step 5
Step 6
configure terminal Enter global configuration mode.
interface interface-id Enter interface configuration mode, and enter the type and
switchport protected Configure the interface to be a protected port.
end Return to privileged EXEC mode.
show interfaces interface-id
switchport
copy running-config startup-config (Optional) Save your entries in the configuration file.
Chapter 2 Configuring Radio Settings
number of the switchport interface to configure, such as
gigabitethernet0/1.
Verify your entries.
To disable protected port, use the no switchport protected interface configuration command.
For detailed information on protected ports and port blocking, see the “Configuring Port-Based Traffic
Control” chapter in the Catalyst 3550 Multilayer Switch Software Configuration Guide, 12.1(12c)EA1
at:
http://www.cisco.com/en/US/products/hw/switches/ps646/products_configuration_guide_book09186a
008011591c.html
Configuring Beacon Period and DTIM
The beacon period is the amount of time between access point beacons in kilo-microseconds. One
kilo-microseconds equals 1,024 microseconds. The Data Beacon Rate, always a multiple of the beacon
period, determines how often the beacon contains a delivery traffic indication message (DTIM). The
DTIM tells power-save client devices that a packet is waiting for them.
For example, if the beacon period is set at 100, its default setting, and the data beacon rate is set at 2, its
default setting, then the wireless device sends a beacon containing a DTIM every 200 kilo-microseconds.
One kilo-microsecond equals 1,024 microseconds.
The default beacon period is 100, and the default DTIM is 2. Beginning in privileged EXEC mode,
follow these steps to configure the beacon period and the DTIM:
Command Purpose
Step 1
Step 2
configure terminal Enter global configuration mode.
interface dot11radio { 0 | 1 } Enter interface configuration mode for the radio interface. The
2.4-GHz radio is radio 0, and the 5-GHz radio is radio 1.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-26
OL-6415-04
Page 51

Chapter 2 Configuring Radio Settings
Command Purpose
Step 3
Step 4
Step 5
Step 6
beacon period value Set the beacon period. Enter a value in Kilomicroseconds.
beacon dtim-period value Set the DTIM. Enter a value in Kilomicroseconds.
end Return to privileged EXEC mode.
copy running-config startup-config (Optional) Save your entries in the configuration file.
Configuring RTS Threshold and Retries
The RTS threshold determines the packet size at which the wireless device issues a request to send (RTS)
before sending the packet. A low RTS Threshold setting can be useful in areas where many client devices
are associating with the wireless device, or in areas where the clients are far apart and can detect only
the wireless device and not each other. You can enter a setting ranging from 0 to 2347 bytes.
Maximum RTS retries is the maximum number of times the wireless device issues an RTS before
stopping the attempt to send the packet over the radio. Enter a value from 1 to 128.
The default RTS threshold is 2312, and the default maximum RTS retries setting is 32. Beginning in
privileged EXEC mode, follow these steps to configure the RTS threshold and maximum RTS retries:
Configuring RTS Threshold and Retries
Command Purpose
Step 1
Step 2
Step 3
Step 4
Step 5
Step 6
configure terminal Enter global configuration mode.
interface dot11radio { 0 | 1 } Enter interface configuration mode for the radio interface. The
2.4-GHz radio is radio 0, and the 5-GHz radio is radio 1.
rts threshold value Set the RTS threshold. Enter an RTS threshold from 0 to 2347.
rts retries value Set the maximum RTS retries. Enter a setting from 1 to 128.
end Return to privileged EXEC mode.
copy running-config startup-config (Optional) Save your entries in the configuration file.
Use the no form of the command to reset the RTS settings to defaults.
Configuring Maximum Data Retries
The maximum data retries setting determines the number of attempts the wireless device makes to send
a packet before giving up and dropping the packet.
The default setting is 32. Beginning in privileged EXEC mode, follow these steps to configure the
maximum data retries:
Command Purpose
Step 1
Step 2
Step 3
configure terminal Enter global configuration mode.
interface dot11radio { 0 | 1 } Enter interface configuration mode for the radio interface. The
2.4-GHz radio is radio 0, and the 5-GHz radio is radio 1.
packet retries value Set the maximum data retries. Enter a setting from 1 to 128.
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-27
Page 52

Configuring Fragmentation Threshold
Command Purpose
Step 4
Step 5
end Return to privileged EXEC mode.
copy running-config startup-config (Optional) Save your entries in the configuration file.
Use the no form of the command to reset the setting to defaults.
Configuring Fragmentation Threshold
The fragmentation threshold determines the size at which packets are fragmented (sent as several pieces
instead of as one block). Use a low setting in areas where communication is poor or where there is a great
deal of radio interference.
The default setting is 2338 bytes. Beginning in privileged EXEC mode, follow these steps to configure
the fragmentation threshold:
Command Purpose
Step 1
Step 2
Step 3
Step 4
Step 5
configure terminal Enter global configuration mode.
interface dot11radio { 0 | 1 } Enter interface configuration mode for the radio interface. The
2.4-GHz radio is radio 0, and the 5-GHz radio is radio 1.
fragment-threshold value Set the fragmentation threshold. Enter a setting from 256 to
2346 bytes for the 2.4-GHz radio. Enter a setting from 256 to
2346 bytes for the 5-GHz radio.
end Return to privileged EXEC mode.
copy running-config startup-config (Optional) Save your entries in the configuration file.
Chapter 2 Configuring Radio Settings
Use the no form of the command to reset the setting to defaults.
Enabling Short Slot Time for 802.11g Radios
You can increase throughput on the 802.11g, 2.4-GHz radio by enabling short slot time. Reducing the
slot time from the standard 20 microseconds to the 9-microsecond short slot time decreases the overall
backoff, which increases throughput. Backoff, which is a multiple of the slot time, is the random length
of time that a station waits before sending a packet on the LAN.
Many 802.11g radios support short slot time, but some do not. When you enable short slot time, the
wireless device uses the short slot time only when all clients associated to the 802.11g, 2.4-GHz radio
support short slot time.
Short slot time is supported only on the 802.11g, 2.4-GHz radio. Short slot time is disabled by default.
Command Purpose
Step 1
Step 2
router(config-if)# slot-time-short In radio interface mode, enter this command to enable short slot
time.
no slot-time-short (optional) Enter no slot-time-short to disable short slot time.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-28
OL-6415-04
Page 53

Chapter 2 Configuring Radio Settings
Performing a Carrier Busy Test
You can perform a carrier busy test to check the radio activity on wireless channels. During the carrier
busy test, the wireless device drops all associations with wireless networking devices for 4 seconds while
it conducts the carrier test and then displays the test results.
In privileged EXEC mode, enter this command to perform a carrier busy test:
dot11 interface-number carrier busy
For interface-number, enter dot11radio 0 to run the test on the 2.4-GHz radio, or enter dot11radio 1 to
run the test on the 5-GHz radio.
Use the show dot11 carrier busy command to re-display the carrier busy test results.
Performing a Carrier Busy Test
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-29
Page 54

Performing a Carrier Busy Test
Chapter 2 Configuring Radio Settings
Cisco Wireless ISR and HWIC Access Point Configuration Guide
2-30
OL-6415-04
Page 55

CHA P TER
3
Configuring Multiple SSIDs
This chapter describes how to configure and manage multiple service set identifiers (SSIDs) on the
access point. This chapter contains the following sections:
• Understanding Multiple SSIDs, page 3-2
• Configuring Multiple SSIDs, page 3-3
• Configuring Multiple Basic SSIDs, page 3-6
• Enabling MBSSID and SSIDL at the same time, page 3-7
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
3-1
Page 56

Understanding Multiple SSIDs
Understanding Multiple SSIDs
The SSID is a unique identifier that wireless networking devices use to establish and maintain wireless
connectivity. Multiple access points on a network or subnetwork can use the same SSIDs. SSIDs are case
sensitive and can contain up to 32 alphanumeric characters. Do not include spaces in your SSIDs.
You can configure up to 16 SSIDs on your HWIC-APs and assign different configuration settings to each
SSID. All the SSIDs are active at the same time; that is, client devices can associate to the access point
using any of the SSIDs. These are the settings you can assign to each SSID:
• VLAN
• Client authentication method
Note For detailed information on client authentication types, see Chapter 6, “Configuring
Authentication Types.”
• Maximum number of client associations using the SSID
• RADIUS accounting for traffic using the SSID
• Guest mode
• Repeater mode, including authentication username and password
Chapter 3 Configuring Multiple SSIDs
• Redirection of packets received from client devices
If you want the access point to allow associations from client devices that do not specify an SSID in their
configurations, you can set up a guest SSID. The access point includes the guest SSID in its beacon.
If your access point will be a repeater or will be a root access point that acts as a parent for a repeater,
you can set up an SSID for use in repeater mode. You can assign an authentication username and
password to the repeater-mode SSID to allow the repeater to authenticate to your network like a client
device.
If your network uses VLANs, you can assign one SSID to a VLAN, and client devices using the SSID
are grouped in that VLAN.
SSID Configuration Methods Supported by Cisco IOS Releases
Cisco introduced global-mode SSID configuration in a prior Cisco IOS Release to simplify configuration
of SSID parameters under multiple interfaces. Configuration of SSID parameters at the interface level
was supported in some Cisco IOS releases for backward compatibility, but configuration of SSID
parameters at the interface level will be totally disabled in releases after Cisco IOS Release 12.4(15)T.
Cisco IOS Release 12.4(15)T supports configuration of SSID parameters at the interface level on the
CLI, but the SSIDs are stored in global mode. Storing all SSIDs in global mode ensures that the SSID
configuration remains correct when you upgrade to release later than Cisco IOS Release 12.4(15)T.
If you need to upgrade to a release later than 12.4(15)T, you should first upgrade to Cisco IOS Release
12.4(15)T, save the configuration file, upgrade to the target release, and load the saved configuration file.
This process ensures that your interface-level SSID configuration correctly translates to global mode.
If you upgrade directly from 12.4(15)T release or earlier to a 12.4(15)T or later release, your
interface-level SSID configuration is deleted.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
3-2
OL-6415-04
Page 57

Chapter 3 Configuring Multiple SSIDs
Configuring Multiple SSIDs
This section contains configuration information for multiple SSIDs:
• Creating an SSID Globally, page 3-3
• Using a RADIUS Server to Restrict SSIDs, page 3-5
Note In Cisco IOS Release 12.4(15)T and later, you configure SSIDs globally and then apply them to a
specific radio interface. Follow the instructions in the
to configure SSIDs globally.
Creating an SSID Globally
In Cisco IOS Releases 12.4 and later, you can configure SSIDs globally or for a specific radio interface.
When you use the dot11 ssid global configuration command to create an SSID, you can use the ssid
configuration interface command to assign the SSID to a specific interface.
Configuring Multiple SSIDs
“Creating an SSID Globally” section on page 3-3
When an SSID has been created in global configuration mode, the ssid configuration interface command
attaches the SSID to the interface but does not enter ssid configuration mode. However, if the SSID has
not been created in global configuration mode, the ssid command puts the CLI into SSID configuration
mode for the new SSID.
Note SSIDs created in Cisco IOS Releases 12.3(7)JA and later become invalid if you downgrade the software
version to an earlier release.
Beginning in privileged EXEC mode, follow these steps to create an SSID globally. After you create an
SSID, you can assign it to specific radio interfaces.
Command Purpose
Step 1
Step 2
Step 3
Step 4
configure terminal Enter global configuration mode.
dot11 ssid ssid-string Create an SSID and enter SSID configuration mode for the new
SSID. The SSID can consist of up to 32 alphanumeric
characters. SSIDs are case sensitive.
Note +, ., ], ?, $, TAB, and trailing spaces are invalid
characters for SSIDs.
authentication client
username username
password password
accounting list-name (Optional) Enable RADIUS accounting for this SSID. For
(Optional) Set an authentication username and password that
the access point uses to authenticate to the network when in
repeater mode. Set the username and password on the SSID that
the repeater access point uses to associate to a root access point,
or with another repeater.
list-name, specify the accounting method list. Click this link
for more information on method lists:
http://www.cisco.com/univercd/cc/td/doc/product/software/ios
122/122cgcr/fsecur_c/fsaaa/scfacct.htm#xtocid2
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
3-3
Page 58

Configuring Multiple SSIDs
Command Purpose
Step 5
Step 6
Step 7
Step 8
Step 9
Step 10
Step 11
vlan vlan-id (Optional) Assign the SSID to a VLAN on your network. Client
guest-mode (Optional) Designate the SSID as your access point’s
infrastructure-ssid [optional] (Optional) Designate the SSID as the SSID that other access
interface dot11radio { 0 | 1 } Enter interface configuration mode for the radio interface to
ssid ssid-string Assign the global SSID that you created in Step 2 to the radio
end Return to privileged EXEC mode.
copy running-config startup-config (Optional) Save your entries in the configuration file.
Chapter 3 Configuring Multiple SSIDs
devices that associate using the SSID are grouped into this
VLAN. You can assign only one SSID to a VLAN.
guest-mode SSID. The access point includes the SSID in its
beacon and allows associations from client devices that do not
specify an SSID.
points and workgroup bridges use to associate to this access
point. If you do not designate an SSID as the infrastructure
SSID, infrastructure devices can associate to the access point
using any SSID. If you designate an SSID as the infrastructure
SSID, infrastructure devices must associate to the access point
using that SSID unless you also enter the optional keyword.
which you want to assign the SSID. The 2.4-GHz radio is radio
0, and the 5-GHz radio is radio 1.
interface.
Note You use the ssid command’s authentication options to configure an authentication type for each SSID.
See
Chapter 6, “Configuring Authentication Types,” for instructions on configuring authentication
types.
Use the no form of the command to disable the SSID or to disable SSID features.
This example shows how to:
• Name an SSID
• Configure the SSID for RADIUS accounting
• Set the maximum number of client devices that can associate using this SSID to 15
• Assign the SSID to a VLAN
• Assign the SSID to a radio interface
router# configure terminal
router(config)# dot11 ssid batman
router(config-ssid)# accounting accounting-method-list
router(config-ssid)# max-associations 15
router(config-ssid)# vlan 3762
router(config-ssid)# exit
router(config)# interface dot11radio 0
router(config-if)# ssid batman
Cisco Wireless ISR and HWIC Access Point Configuration Guide
3-4
OL-6415-04
Page 59

Chapter 3 Configuring Multiple SSIDs
Viewing SSIDs Configured Globally
Use this command to view configuration details for SSIDs that are configured globally:
router# show running-config ssid ssid-string
Using Spaces in SSIDs
In Cisco IOS Release 12.4(15)T, you can include spaces in an SSID, but trailing spaces (spaces at the
end of an SSID) are invalid. However, any SSIDs created in previous versions having trailing spaces are
recognized. Trailing spaces make it appear that you have identical SSIDs configured on the same access
point. If you think identical SSIDs are on the access point, use the show dot11 associations privileged
EXEC command to check any SSIDs created in a previous release for trailing spaces.
For example, this sample output from a show configuration privileged EXEC command does not show
spaces in SSIDs:
ssid buffalo
vlan 77
authentication open
Configuring Multiple SSIDs
ssid buffalo
vlan 17
authentication open
ssid buffalo
vlan 7
authentication open
However, this sample output from a show dot11 associations privileged EXEC command shows the
spaces in the SSIDs:
SSID [buffalo] :
SSID [buffalo ] :
SSID [buffalo ] :
Using a RADIUS Server to Restrict SSIDs
To prevent client devices from associating to the access point using an unauthorized SSID, you can
create a list of authorized SSIDs that clients must use on your RADIUS authentication server.
The SSID authorization process consists of these steps:
1. A client device associates to the access point using any SSID configured on the access point.
2. The client begins RADIUS authentication.
3. The RADIUS server returns a list of SSIDs that the client is allowed to use. The access point checks
the list for a match of the SSID used by the client. There are three possible outcomes:
a. If the SSID that the client used to associate to the access point matches an entry in the allowed
list returned by the RADIUS server, the client is allowed network access after completing all
authentication requirements.
b. If the access point does not find a match for the client in the allowed list of SSIDs, the access
point disassociates the client.
c. If the RADIUS server does not return any SSIDs (no list) for the client, then the administrator
has not configured the list, and the client is allowed to associate and attempt to authenticate.
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
3-5
Page 60

Configuring Multiple Basic SSIDs
The allowed list of SSIDs from the RADIUS server are in the form of Cisco VSAs. The Internet
Engineering Task Force (IETF) draft standard specifies a method for communicating vendor-specific
information between the access point and the RADIUS server by using the vendor-specific attribute
(attribute 26). Vendor-specific attributes (VSAs) allow vendors to support their own extended attributes
not suitable for general use. The Cisco RADIUS implementation supports one vendor-specific option by
using the format recommended in the specification. Cisco’s vendor-ID is 9, and the supported option has
vendor-type 1, which is named cisco-avpair. The Radius server is allowed to have zero or more SSID
VSAs per client.
In this example, the following AV pair adds the SSID batman to the list of allowed SSIDs for a user:
cisco-avpair= ”ssid=batman”
For instructions on configuring the access point to recognize and use VSAs, see the “Configuring the
Access Point to Use Vendor-Specific RADIUS Attributes” section on page 7-14.
Configuring Multiple Basic SSIDs
Access point 802.11a and 802.11g radios now support up to 8 basic SSIDs (BSSIDs), which are similar
to MAC addresses. You use multiple BSSIDs to assign a unique DTIM setting for each SSID and to
broadcast more than one SSID in beacons. A large DTIM value increases battery life for power-save
client devices that use an SSID, and broadcasting multiple SSIDs makes your wireless LAN more
accessible to guests.
Chapter 3 Configuring Multiple SSIDs
Note Devices on your wireless LAN that are configured to associate to a specific access point based on the
access point MAC address (for example, client devices, repeaters, hot standby units, or workgroup
bridges) might lose their association when you add or delete a multiple BSSID. When you add or delete
a multiple BSSID, check the association status of devices configured to associate to a specific access
point. If necessary, reconfigure the disassociated device to use the BSSID’s new MAC address.
Requirements for Configuring Multiple BSSIDs
To configure multiple BSSIDs, your access points must meet these minimum requirements:
• VLANs must be configured
• Access points must run Cisco IOS Release 12.4(15)T or later
• Access points must contain an 802.11a or 802.11g radio that supports multiple BSSIDs. To
determine whether a radio supports multiple basic SSIDs, enter the show controllers
radio_interface command. The radio supports multiple basic SSIDs if the results include this line:
Number of supported simultaneous BSSID on radio_interface: 8
Guidelines for Using Multiple BSSIDs
Keep these guidelines in mind when configuring multiple BSSIDs:
• RADIUS-assigned VLANs are not supported when you enable multiple BSSIDs.
• When you enable BSSIDs, the access point automatically maps a BSSID to each SSID. You cannot
manually map a BSSID to a specific SSID.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
3-6
OL-6415-04
Page 61

Chapter 3 Configuring Multiple SSIDs
• When multiple BSSIDs are enabled on the access point, the SSIDL IE does not contain a list of
SSIDs; it contains only extended capabilities.
• Any Wi-Fi certified client device can associate to an access point using multiple BSSIDs.
• You can enable multiple BSSIDs on access points that participate in WDS.
CLI Configuration Example
This example shows the CLI commands that you use to enable multiple BSSIDs on a radio interface,
create an SSID called visitor, designate the SSID as a BSSID, specify that the BSSID is included in
beacons, set a DTIM period for the BSSID, and assign the SSID visitor to the radio interface:
router(config)# interface dot11 0
router(config-if)# mbssid
router(config-if)# exit
router(config)# dot11 ssid visitor
router(config-ssid)# mbssid guest-mode
router(config-ssid)# exit
router(config)# interface dot11 0
router(config-if)# ssid visitor
Enabling MBSSID and SSIDL at the same time
You can also use the dot11 mbssid global configuration command to simultaneously enable multiple
BSSIDs on all radio interfaces that support multiple BSSIDs.
Displaying Configured BSSIDs
Use the show dot11 bssid privileged EXEC command to display the relationship between SSIDs and
BSSIDs or MAC addresses. This example shows the command output:
router1230#show dot11 bssid
Interface BSSID Guest SSID
Dot11Radio1 0011.2161.b7c0 Yes atlantic
Dot11Radio0 0005.9a3e.7c0f Yes WPA2-TLS-g
Enabling MBSSID and SSIDL at the same time
When multiple BSSIDs are enabled on the access point, the SSIDL IE does not contain a list of SSIDs;
it contains only extended capabilities.
Beginning in privileged EXEC mode, follow these steps to include an SSID in an SSIDL IE:
Command Purpose
Step 1
Step 2
Step 3
Step 4
configure terminal Enter global configuration mode.
interface dot11radio { 0 | 1 } Enter interface configuration mode for the radio interface.
ssid ssid-string Enter configuration mode for a specific SSID.
information-element ssidl
[advertisement] [wps]
Include an SSIDL IE in the access point beacon that advertises
the access point’s extended capabilities, such as 802.1x and
support for Microsoft Wireless Provisioning Services (WPS).
OL-6415-04
Use the advertisement option to include the SSID name and
capabilities in the SSIDL IE. Use the wps option to set the WPS
capability flag in the SSIDL IE.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
3-7
Page 62

Enabling MBSSID and SSIDL at the same time
Use the no form of the command to disable SSIDL IEs.
Sample Configuration for Enabling MBSSID and SSIDL
Below is a sample configuration for enabling MBSSID:
dot11 ssid 181x_gvlan01
vlan 1
authentication open
mbssid guest-mode
!
dot11 ssid 181x_gvlan02
vlan 2
authentication open
wpa-psk ascii 0 12345678
mbssid guest-mode
!
dot11 ssid 181x_gvlan03
vlan 3
authentication open
authentication key-management wpa
wpa-psk ascii 0 12345678
!
dot11 ssid 181x_gvlan04
vlan 4
authentication open
authentication key-management wpa
wpa-psk ascii 0 12345678
!
interface Dot11Radio0
no ip address
!
encryption vlan 1 key 1 size 40bit 0 1234567890 transmit-key
encryption vlan 1 mode ciphers wep40
!
encryption vlan 2 mode ciphers tkip
!
encryption vlan 3 mode ciphers tkip
!
encryption vlan 4 mode ciphers tkip
!
ssid 181x_gvlan01
!
ssid 181x_gvlan02
!
ssid 181x_gvlan03
!
ssid 181x_gvlan04
!
speed basic-1.0 basic-2.0 basic-5.5 6.0 9.0 basic-11.0 12.0 18.0 24.0 36.0 48.0 54.0
mbssid
station-role root
!
Chapter 3 Configuring Multiple SSIDs
Below is a sample configuration for enabling SSIDL:
dot11 ssid 1841-wep128
vlan 1
authentication open
information-element ssidl advertisement
Cisco Wireless ISR and HWIC Access Point Configuration Guide
3-8
OL-6415-04
Page 63

Chapter 3 Configuring Multiple SSIDs
!
dot11 ssid 1841-tkip-psk
vlan 2
authentication open
authentication key-management wpa
wpa-psk ascii 0 12345678
information-element ssidl advertisement
!
dot11 ssid 1841-aes-psk
vlan 3
authentication open
authentication key-management wpa
wpa-psk ascii 0 12345678
information-element ssidl advertisement wps
!
interface Dot11Radio0/0/0
no ip address
no snmp trap link-status
!
encryption vlan 1 key 1 size 128bit 0 12345678901234567890123456 transmit-key
encryption vlan 1 key 2 size 128bit 0 12345678901234567890123456
encryption vlan 1 mode ciphers wep128
!
encryption vlan 2 mode ciphers tkip
!
encryption vlan 3 mode ciphers aes-ccm
!
ssid 1841-wep128
!
ssid 1841-tkip-psk
!
ssid 1841-aes-psk
!
speed basic-1.0 basic-2.0 basic-5.5 6.0 9.0 basic-11.0 12.0 18.0 24.0 36.0 48.0 54.0
station-role root
Enabling MBSSID and SSIDL at the same time
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
3-9
Page 64

Enabling MBSSID and SSIDL at the same time
Chapter 3 Configuring Multiple SSIDs
Cisco Wireless ISR and HWIC Access Point Configuration Guide
3-10
OL-6415-04
Page 65

CHA P TER
4
Configuring an Access Point as a Local
Authenticator
This chapter describes how to configure the access point as a local authenticator to serve as a stand-alone
authenticator for a small wireless LAN or to provide backup authentication service. As a local
authenticator, the access point performs LEAP, EAP-FAST, and MAC-based authentication for up to
1000 client devices. This chapter contains these sections:
• Understand Local Authentication, page 4-2
• Configure a Local Authenticator, page 4-2
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
4-1
Page 66

Understand Local Authentication
Understand Local Authentication
Many small wireless LANs that could be made more secure with 802.1x authentication do not have
access to a RADIUS server. On many wireless LANs that use 802.1x authentication, access points rely
on RADIUS servers housed in a distant location to authenticate client devices, and the authentication
traffic must cross a WAN link. If the WAN link fails, or if the access points cannot access the RADIUS
servers for any reason, client devices cannot access the wireless network even if the work they wish to
do is entirely local.
To provide local authentication service or backup authentication service in case of a WAN link or a
server failure, you can configure an access point to act as a local authentication server. The access point
can authenticate up to 50 wireless client devices using LEAP, EAP-FAST, or MAC-based authentication.
The access point performs up to 5 authentications per second.
You configure the local authenticator access point manually with client usernames and passwords
because it does not synchronize its database with the main RADIUS servers. You can also specify a
VLAN and a list of SSIDs that a client is allowed to use.
Note If your wireless LAN contains only one access point, you can configure the access point as both
the 802.1x authenticator and the local authenticator. However, users associated to the local
authenticator access point might notice a drop in performance when the access point
authenticates client devices.
Chapter 4 Configuring an Access Point as a Local Authenticator
You can configure your access points to use the local authenticator when they cannot reach the main
servers, or you can configure your access points to use the local authenticator or as the main
authenticator if you do not have a RADIUS server. When you configure the local authenticator as a
backup to your main servers, the access points periodically check the link to the main servers and stop
using the local authenticator automatically when the link to the main servers is restored.
Caution The access point you use as an authenticator contains detailed authentication information for your
wireless LAN, so you should secure it physically to protect its configuration.
Configure a Local Authenticator
This section provides instructions for setting up an access point as a local authenticator and includes
these sections:
• Guidelines for Local Authenticators, page 4-3
• Configuration Overview, page 4-3
• Configuring the Local Authenticator Access Point, page 4-3
• Configuring Other Access Points to Use the Local Authenticator, page 4-8
• Configuring EAP-FAST Settings, page 4-9
• Unblocking Locked Usernames, page 4-11
• Viewing Local Authenticator Statistics, page 4-11
• Using Debug Messages, page 4-12
Cisco Wireless ISR and HWIC Access Point Configuration Guide
4-2
OL-6415-04
Page 67

Chapter 4 Configuring an Access Point as a Local Authenticator
Guidelines for Local Authenticators
Follow these guidelines when configuring an access point as a local authenticator:
• Use an access point that does not serve a large number of client devices. When the access point acts
as an authenticator, performance might degrade for associated client devices.
• Secure the access point physically to protect its configuration.
Configuration Overview
You complete four major steps when you set up a local authenticator:
1. On the local authenticator, create a list of access points authorized to use the authenticator to
authenticate client devices. Each access point that uses the local authenticator is a network access
server (NAS).
Note If your local authenticator access point also serves client devices, you must enter the local
authenticator access point as a NAS. When a client associates to the local authenticator
access point, the access point uses itself to authenticate the client.
Configure a Local Authenticator
2. On the local authenticator, create user groups and configure parameters to be applied to each group
(optional).
3. On the local authenticator, create a list of up to 50 LEAP users, EAP-FAST users, or MAC addresses
that the local authenticator is authorized to authenticate.
Note You do not have to specify which type of authentication that you want the local authenticator
to perform. It automatically performs LEAP, EAP-FAST, or MAC-address authentication for
the users in its user database.
4. On the access points that use the local authenticator, enter the local authenticator as a RADIUS
server.
Note If your local authenticator access point also serves client devices, you must enter the local
authenticator as a RADIUS server in the local authenticator’s configuration. When a client
associates to the local authenticator access point, the access point uses itself to authenticate
the client.
Configuring the Local Authenticator Access Point
Beginning in Privileged Exec mode, follow these steps to configure the access point as a local
authenticator:
Command Purpose
Step 1
Step 2
OL-6415-04
configure terminal Enter global configuration mode.
aaa new-model Enable AAA.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
4-3
Page 68

Configure a Local Authenticator
Command Purpose
Step 3
Step 4
Step 5
Step 6
Step 7
Step 8
Step 9
radius-server local Enable the access point as a local authenticator and enter
nas ip-address key shared-key Add an access point to the list of units that use the local
group group-name (Optional) Enter user group configuration mode and configure a
vlan vlan (Optional) Specify a VLAN to be used by members of the user
ssid ssid (Optional) Enter up to 20 SSIDs to limit members of the user
reauthentication time seconds (Optional) Enter the number of seconds after which access points
block count count
time { seconds | infinite }
Chapter 4 Configuring an Access Point as a Local Authenticator
configuration mode for the authenticator.
authenticator. Enter the access point’s IP address and the shared
key used to authenticate communication between the local
authenticator and other access points. You must enter this shared
key on the access points that use the local authenticator. If your
local authenticator also serves client devices, you must enter the
local authenticator access point as a NAS.
Note Leading spaces in the key string are ignored, but spaces
within and at the end of the key are used. If you use spaces
in your key, do not enclose the key in quotation marks
unless the quotation marks are part of the key.
Repeat this step to add each access point that uses the local
authenticator.
user group to which you can assign shared settings.
group. The access point moves group members into that VLAN,
overriding other VLAN assignments. You can assign only one
VLAN to the group.
group to those SSIDs. The access point checks that the SSID that
the client used to associate matches one of the SSIDs in the list.
If the SSID does not match, the client is disassociated.
should reauthenticate members of the group. The
reauthentication provides users with a new encryption key. The
default setting is 0, which means that group members are never
required to reauthenticate.
(Optional) To help protect against password guessing attacks, you
can lock out members of a user group for a length of time after a
set number of incorrect passwords.
• count—The number of failed passwords that triggers a
lockout of the username.
Step 10
Cisco Wireless ISR and HWIC Access Point Configuration Guide
exit Exit group configuration mode and return to authenticator
4-4
• time—The number of seconds the lockout should last. If you
enter infinite, an administrator must manually unblock the
locked username. See the
“Unblocking Locked Usernames”
section on page 4-11 for instructions on unblocking client
devices.
configuration mode.
OL-6415-04
Page 69

Chapter 4 Configuring an Access Point as a Local Authenticator
Command Purpose
Step 11
user username
{ password | nthash } password
[ group group-name ]
[mac-auth-only]
Step 12
Step 13
end Return to privileged EXEC mode.
copy running-config
startup-config
Configure a Local Authenticator
Enter the LEAP and EAP-FAST users allowed to authenticate
using the local authenticator. You must enter a username and
password for each user. If you only know the NT value of the
password, which you can often find in the authentication server
database, you can enter the NT hash as a string of hexadecimal
digits.
To add a client device for MAC-based authentication, enter the
client’s MAC address as both the username and password. Enter
12 hexadecimal digits without a dot or dash between the numbers
as the username and the password. For example, for the MAC
address 0009.5125.d02b, enter 00095125d02b as both the
username and the password.
To limit the user to MAC authentication only, enter
mac-auth-only.
To add the user to a user group, enter the group name. If you do
not specify a group, the user is not assigned to a specific VLAN
and is never forced to reauthenticate.
(Optional) Save your entries in the configuration file.
This example shows how to set up a local authenticator used by three access points with three user groups
and several users:
router# configure terminal
router(config)# radius-server local
router(config-radsrv)# nas 10.91.6.159 key 110337
router(config-radsrv)# nas 10.91.6.162 key 110337
router(config-radsrv)# nas 10.91.6.181 key 110337
router(config-radsrv)# group clerks
router(config-radsrv-group)# vlan 87
router(config-radsrv-group)# ssid batman
router(config-radsrv-group)# ssid robin
router(config-radsrv-group)# reauthentication time 1800
router(config-radsrv-group)# block count 2 time 600
router(config-radsrv-group)# group cashiers
router(config-radsrv-group)# vlan 97
router(config-radsrv-group)# ssid deer
router(config-radsrv-group)# ssid antelope
router(config-radsrv-group)# ssid elk
router(config-radsrv-group)# reauthentication time 1800
router(config-radsrv-group)# block count 2 time 600
router(config-radsrv-group)# group managers
router(config-radsrv-group)# vlan 77
router(config-radsrv-group)# ssid mouse
router(config-radsrv-group)# ssid chipmunk
router(config-radsrv-group)# reauthentication time 1800
router(config-radsrv-group)# block count 2 time 600
router(config-radsrv-group)# exit
router(config-radsrv)# user jsmith password twain74 group clerks
router(config-radsrv)# user stpatrick password snake100 group clerks
router(config-radsrv)# user nick password uptown group clerks
router(config-radsrv)# user 00095125d02b password 00095125d02b group clerks mac-auth-only
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
4-5
Page 70

Configure a Local Authenticator
router(config-radsrv)# user 00095125d02b password 00095125d02b group cashiers
router(config-radsrv)# user 00079431f04a password 00079431f04a group cashiers
router(config-radsrv)# user carl password 272165 group managers
router(config-radsrv)# user vic password lid178 group managers
router(config-radsrv)# end
This example shows how to set up EAP-FAST authentication:
Router#show run
Building configuration...
Current configuration : 2119 bytes
!
version 12.3
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname Router
!
enable secret 5 $1$dkOn$EcccqZvFdjoEi3geC66da0
!
ip subnet-zero
!
!
aaa new-model
!
!
aaa group server radius rad_eap
server 192.168.1.66 auth-port 1812 acct-port 1813
!
aaa authentication login eap_methods group rad_eap
aaa session-id common
!
dot11 ssid test-ssid
authentication open eap eap_methods
authentication network-eap eap_methods
authentication key-management wpa
!
!
!
username Cisco password 7 00271A150754
!
bridge irb
!
!
interface Dot11Radio0
no ip address
no ip route-cache
!
encryption mode ciphers aes-ccm tkip
!
ssid test-ssid
!
speed basic-1.0 basic-2.0 basic-5.5 6.0 9.0 basic-11.0 12.0 18.0 24.0 36.0 48.0
54.0
station-role root
bridge-group 1
bridge-group 1 subscriber-loop-control
bridge-group 1 block-unknown-source
no bridge-group 1 source-learning
no bridge-group 1 unicast-flooding
bridge-group 1 spanning-disabled
Chapter 4 Configuring an Access Point as a Local Authenticator
Cisco Wireless ISR and HWIC Access Point Configuration Guide
4-6
OL-6415-04
Page 71

Chapter 4 Configuring an Access Point as a Local Authenticator
!
interface FastEthernet0
no ip address
no ip route-cache
duplex auto
speed auto
bridge-group 1
no bridge-group 1 source-learning
bridge-group 1 spanning-disabled
!
interface BVI1
ip address 192.168.1.66 255.255.255.0
no ip route-cache
!
ip http server
no ip http secure-server
ip http help-path http://www.cisco.com/warp/public/779/smbiz/prodconfig/help/eag
ip radius source-interface BVI1
!
radius-server local
eapfast authority id 12345678901234567890123456789012
eapfast authority info sample_eap-fast
eapfast server-key primary 7 41754A0073F16A0E093EA2089A3FDECD32
nas 192.168.1.66 key 7 110A1016141D
group EAP_FAST-usr
eapfast pac expiry 30 grace 120
!
user cisco nthash 7 06532C791C1E2F4856364128295C7C0E007A6661723723422656050A09
760D2F51
!
radius-server host 192.168.1.66 auth-port 1812 acct-port 1813 key 7 060506324F41
!
control-plane
!
bridge 1 route ip
!
!
!
line con 0
transport preferred all
transport output all
line vty 0 4
transport preferred all
transport input all
transport output all
line vty 5 15
transport preferred all
transport input all
transport output all
!
end
Configure a Local Authenticator
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
4-7
Page 72

Chapter 4 Configuring an Access Point as a Local Authenticator
Configure a Local Authenticator
Configuring Other Access Points to Use the Local Authenticator
You add the local authenticator to the list of servers on the access point the same way that you add other
servers. For detailed instructions on setting up RADIUS servers on your access points, see
“Configuring RADIUS Servers.”
Note If your local authenticator access point also serves client devices, you must configure the local
authenticator to use itself to authenticate client devices.
On the access points that use the local authenticator, use the radius-server host command to enter the
local authenticator as a RADIUS server. The order in which the access point attempts to use the servers
matches the order in which you enter the servers in the access point configuration. If you are configuring
the access point to use RADIUS for the first time, enter the main RADIUS servers first, and enter the
local authenticator last.
Note Yo u mu s t en te r 1812 as the authentication port and 1813 as the accounting port. The local
authenticator listens on UDP port 1813 for RADIUS accounting packets. It discards the
accounting packets but sends acknowledge packets back to RADIUS clients to prevent clients
from assuming that the server is down.
Chapter 7,
Use the radius-server deadtime command to set an interval during which the access point does not
attempt to use servers that do not respond, thus avoiding the wait for a request to time out before trying
the next configured server. A server marked as dead is skipped by additional requests for the duration of
minutes that you specify, up to 1440 (24 hours).
This example shows how to set up two main servers and a local authenticator with a server deadtime of
10 minutes:
router(config)# aaa new-model
router(config)# radius-server host 172.20.0.1 auth-port 1000 acct-port 1001 key 77654
router(config)# radius-server host 172.10.0.1 auth-port 1645 acct-port 1646 key 77654
router(config)# radius-server host 10.91.6.151 auth-port 1812 acct-port 1813 key 110337
router(config)# radius-server deadtime 10
In this example, if the WAN link to the main servers fails, the access point completes these steps when
a LEAP-enabled client device associates:
1. It tries the first server, times out multiple times, and marks the first server as dead.
2. It tries the second server, times out multiple times, and marks the second server as dead.
3. It tries and succeeds using the local authenticator.
If another client device needs to authenticate during the 10-minute dead-time interval, the access point
skips the first two servers and tries the local authenticator first. After the dead-time interval, the access
point tries to use the main servers for authentication. When setting a dead time, you must balance the
need to skip dead servers with the need to check the WAN link and begin using the main servers again
as soon as possible.
Each time the access point tries to use the main servers while they are down, the client device trying to
authenticate might report an authentication timeout. The client device retries and succeeds when the
main servers time out and the access point tries the local authenticator. You can extend the timeout value
on Cisco client devices to accommodate expected server timeouts.
To remove the local authenticator from the access point configuration, use the no radius-server host
hostname | ip-address global configuration command.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
4-8
OL-6415-04
Page 73

Chapter 4 Configuring an Access Point as a Local Authenticator
Configuring EAP-FAST Settings
The default settings for EAP-FAST authentication are suitable for most wireless LANs. However, you
can customize the credential timeout values, authority ID, and server keys to match your network
requirements.
Configuring PAC Settings
This section describes how to configure Protected Access Credential (PAC) settings. The first time that
an EAP-FAST client device attempts to authenticate to the local authenticator, the local authenticator
generates a PAC for the client. You can also generate PACs manually and use the Aironet Client Utility
to import the PAC file.
PAC Expiration Times
You can limit the number of days for which PACs are valid, and a grace period during which PACs are
valid after they have expired. By default, PACs are valid for infinite days, with a grace period of infinite
days. You apply the expiration time and the grace period settings to a group of users.
Configure a Local Authenticator
Use this command to configure the expiration time and grace period for PACs:
router(config-radsrv-group)# [no] eapfast pac expiry days [grace days]
Enter a number of days from 2 to 4095. Enter the no form of the command to reset the expiration time
or grace period to infinite days.
In this example, PACs for the user group expire in 100 days with a grace period of two days:
router(config-radsrv-group)# eapfast pac expiry 100 grace 2
Generating PACs Manually
The local authenticator automatically generates PACs for EAP-FAST clients that request them. However,
you might need to generate a PAC manually for some client devices. When you enter the command, the
local authenticator generates a PAC file and writes it to the network location that you specify. The user
imports the PAC file into the client profile.
Use this command to generate a PAC manually:
router# radius local-server pac-generate filename username [password password] [expiry days]
When you enter the PAC filename, enter the full path to which the local authenticator writes the PAC file
(such as tftp://172.1.1.1/test/user.pac). The password is optional and, if not specified, a default password
understood by the CCX client is used. Expiry is also optional and, if not specified, the default period is
1 day.
In this example, the local authenticator generates a PAC for the username joe, password-protects the file
with the password bingo, sets the PAC to expire in 10 days, and writes the PAC file to the TFTP server
at 10.0.0.5:
router# radius local-server pac-generate tftp://10.0.0.5 joe password bingo expiry 10
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
4-9
Page 74

Configure a Local Authenticator
Configuring an Authority ID
All EAP-FAST authenticators are identified by an authority identity (AID). The local authenticator sends
its AID to an authenticating client, and the client checks its database for a matching AID. If the client
does not recognize the AID, it requests a new PAC.
Use these commands to assign an AID to the local authenticator:
router(config-radserv)# [no] eapfast authority id identifier
router(config-radserv)# [no] eapfast authority info identifier
The eapfast authority id command assigns an AID that the client device uses during authentication.
Configuring Server Keys
The local authenticator uses server keys to encrypt PACs that it generates and to decrypt PACs when
authenticating clients. The server maintains two keys, a primary key and a secondary key, and uses the
primary key to encrypt PACs. By default, the server uses a default value as the primary key but does not
use a secondary key unless you configure one.
When the local authenticator receives a client PAC, it attempts to decrypt the PAC with the primary key.
If decryption fails with the primary, the authenticator attempts to decrypt the PAC with the secondary
key if one is configured. If decryption fails, the authenticator rejects the PAC as invalid.
Chapter 4 Configuring an Access Point as a Local Authenticator
Use these commands to configure server keys:
router(config-radsrv)# [no] eapfast server-key primary {[auto-generate] | [ [0 | 7] key]}
router(config-radsrv)# [no] eapfast server-key secondary [0 | 7] key
Keys can contain up to 32 hexadecimal digits. Enter 0 before the key to enter an unencrypted key. Enter
7 before the key to enter an encrypted key. Use the no form of the commands to reset the local
authenticator to the default setting, which is to use a default value as a primary key.
Possible PAC Failures Caused by Access Point Clock
The local authenticator uses the access point clock to both generate PACs and to determine whether PACs
are valid. However, relying on the access point clock can lead to PAC failures.
If your local authenticator access point receives its time setting from an NTP server, there is an interval
between boot up and synchronization with the NTP server during which the access point uses its default
time setting. If the local authenticator generates a PAC during that interval, the PAC might be expired
when the access point receives a new time setting from the NTP server. If an EAP-FAST client attempts
to authenticate during the interval between boot and NTP-synch, the local authenticator might reject the
client’s PAC as invalid.
If your local authenticator does not receive its time setting from an NTP server and it reboots frequently,
PACs generated by the local authenticator might not expire when they should. The access point clock is
reset when the access point reboots, so the elapsed time on the clock would not reach the PAC expiration
time.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
4-10
OL-6415-04
Page 75

Chapter 4 Configuring an Access Point as a Local Authenticator
Limiting the Local Authenticator to One Authentication Type
By default, a local authenticator access point performs LEAP, EAP-FAST, and MAC-based
authentication for client devices. However, you can limit the local authenticator to perform only one or
two authentication types. Use the no form of the authentication command to restrict the authenticator to
an authentication type:
router(config-radsrv)# [no] authentication [eapfast] [leap] [mac]
Because all authentication types are enabled by default, you enter the no form of the command to disable
authentication types. For example, if you want the authenticator to perform only LEAP authentication,
you enter these commands:
router(config-radsrv)# no authentication eapfast
router(config-radsrv)# no authentication mac
Unblocking Locked Usernames
You can unblock usernames before the lockout time expires, or when the lockout time is set to infinite.
In Privileged Exec mode on the local authenticator, enter this command to unblock a locked username:
router# clear radius local-server user username
Configure a Local Authenticator
Viewing Local Authenticator Statistics
In privileged exec mode, enter this command to view statistics collected by the local authenticator:
router# show radius local-server statistics
This example shows local authenticator statistics:
Successes : 0 Unknown usernames : 0
Client blocks : 0 Invalid passwords : 0
Unknown NAS : 0 Invalid packet from NAS: 0
NAS : 10.91.6.158
Successes : 0 Unknown usernames : 0
Client blocks : 0 Invalid passwords : 0
Corrupted packet : 0 Unknown RADIUS message : 0
No username attribute : 0 Missing auth attribute : 0
Shared key mismatch : 0 Invalid state attribute: 0
Unknown EAP message : 0 Unknown EAP auth type : 0
Auto provision success : 0 Auto provision failure : 0
PAC refresh : 0 Invalid PAC received : 0
Username Successes Failures Blocks
nicky 0 0 0
jones 0 0 0
jsmith 0 0 0
Router#sh radius local-server statistics
Successes : 1 Unknown usernames : 0
Client blocks : 0 Invalid passwords : 0
Unknown NAS : 0 Invalid packet from NAS: 0
The first section of statistics lists cumulative statistics from the local authenticator.
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
4-11
Page 76

Configure a Local Authenticator
The second section lists stats for each access point (NAS) authorized to use the local authenticator. The
EAP-FAST statistics in this section include these stats:
• Auto provision success—the number of PACs generated automatically
• Auto provision failure—the number of PACs not generated because of an invalid handshake packet
or invalid username or password
• PAC refresh—the number of PACs renewed by clients
• Invalid PAC received—the number of PACs received that were expired, that the authenticator could
not decrypt, or that were assigned to a client username not in the authenticator’s database
The third section lists stats for individual users. If a user is blocked and the lockout time is set to infinite,
blocked appears at the end of the stat line for that user. If the lockout time is not infinite, Unblocked in
x seconds appears at the end of the stat line for that user.
Use this privileged exec mode command to reset local authenticator statistics to zero:
router# clear radius local-server statistics
Using Debug Messages
Chapter 4
In privileged exec mode, enter this command to control the display of debug messages for the local
authenticator:
router# debug radius local-server { client | eapfast | error | packets}
Use the command options to display this debug information:
• Use the client option to display error messages related to failed client authentications.
• Use the eapfast option to display error messages related to EAP-FAST authentication. Use the
sub-options to select specific debugging information:
–
encryption —displays information on the encryption and decryption of received and
transmitted packets
–
events—displays information on all EAP-FAST events
–
pac—displays information on events related to PACs, such as PAC generation and verification
–
pkts—displays packets sent to and received from EAP-FAST clients
• Use the error option to display error messages related to the local authenticator.
• Use the packets option to turn on display of the content of RADIUS packets sent and received.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
4-12
OL-6415-04
Page 77

CHA P TER
5
Configuring Encryption Types
This chapter describes how to configure the encryption types required to use WPA authenticated key
management, Wired Equivalent Privacy (WEP), AES-CCM, Temporal Key Integrity Protocol (TKIP),
and broadcast key rotation. This chapter contains these sections:
• Understand Encryption Types, page 5-2
• Configure Encryption Types, page 5-3
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
5-1
Page 78

Understand Encryption Types
Understand Encryption Types
This section describes how encryption types protect traffic on your wireless LAN.
Just as anyone within range of a radio station can tune to the station's frequency and listen to the signal,
any wireless networking device within range of an access point can receive the access point's radio
transmissions. Because encryption is the first line of defense against intruders, Cisco recommends that
you use full encryption on your wireless network.
One type ofwireless encryption is Wired Equivalent Privacy (WEP). WEP encryption scrambles the
communication between the access point and client devices to keep the communication private. Both the
access point and client devices use the same WEP key to encrypt and unencrypt radio signals. WEP keys
encrypt both unicast and multicast messages. Unicast messages are addressed to just one device on the
network. Multicast messages are addressed to multiple devices on the network.
Extensible Authentication Protocol (EAP) authentication, also called 802.1x authentication, provides
dynamic WEP keys to wireless users. Dynamic WEP keys are more secure than static, or unchanging,
WEP keys. If an intruder passively receives enough packets encrypted by the same WEP key, the intruder
can perform a calculation to learn the key and use it to join your network. Because they change
frequently, dynamic WEP keys prevent intruders from performing the calculation and learning the key.
See
Chapter 6, “Configuring Authentication Types,” for detailed information on EAP and other
authentication types.
Cipher suites are sets of encryption and integrity algorithms designed to protect radio communication
on your wireless LAN. You must use a cipher suite to enable Wi-Fi Protected Access (WPA). Because
cipher suites provide the protection of WEP while also allowing use of authenticated key management,
Cisco recommends that you enable encryption by using the encryption mode cipher command in the
CLI or by using the cipher drop-down menu in the web-browser interface. Cipher suites that contain
AES-CCM provide the best security for your wireless LAN, and cipher suites that contain only WEP are
the least secure.
These security features protect the data traffic on your wireless LAN:
Chapter 5 Configuring Encryption Types
• AES-CCMP—Based on the Advanced Encryption Standard (AES) defined in the National Institute
of Standards and Technology’s FIPS Publication 197, AES-CCMP is a symmetric block cipher that
can encrypt and decrypt data using keys of 128, 192, and 256 bits. AES-CCMP is superior to WEP
encryption and is defined in the IEEE 802.11i standard.
• WEP—WEP is an 802.11 standard encryption algorithm originally designed to provide your
wireless LAN with the same level of privacy available on a wired LAN. However, the basic WEP
construction is flawed, and an attacker can compromise the privacy with reasonable effort.
• TKIP (Temporal Key Integrity Protocol)—TKIP is a suite of algorithms surrounding WEP that is
designed to achieve the best possible security on legacy hardware built to run WEP. TKIP adds four
enhancements to WEP:
–
A per-packet key mixing function to defeat weak-key attacks
–
A new IV sequencing discipline to detect replay attacks
–
A cryptographic message integrity check (MIC), called Michael, to detect forgeries such as bit
flipping and altering packet source and destination
–
An extension of IV space, to virtually eliminate the need for re-keying
• Broadcast key rotation (also known as Group Key Update)—Broadcast key rotation allows the
access point to generate the best possible random group key and update all key-management capable
clients periodically. Wi-Fi Protected Access (WPA) also provides additional options for group key
updates. See the
“Using WPA Key Management” section on page 6-6 for details on WPA.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
5-2
OL-6415-04
Page 79

Chapter 5 Configuring Encryption Types
Note Client devices using static WEP cannot use the access point when you enable broadcast key
rotation. When you enable broadcast key rotation, only wireless client devices using 802.1x
authentication (such as LEAP, EAP-TLS, or PEAP) can use the access point.
Configure Encryption Types
These sections describe how to configure encryption, such as WEP, AES-CCM, and and broadcast key
rotation:
• Creating WEP Keys, page 5-3
• Creating Cipher Suites, page 5-5
• Enabling and Disabling Broadcast Key Rotation, page 5-7
Note All encryption types are disabled by default.
Configure Encryption Types
Creating WEP Keys
Note You need to configure static WEP keys only if your access point needs to support client devices that use
static WEP. If all the client devices that associate to the access point use key management (WPA or
802.1x authentication) you do not need to configure static WEP keys.
Beginning in privileged EXEC mode, follow these steps to create a WEP key and set the key properties:
Command Purpose
Step 1
Step 2
configure terminal Enter global configuration mode.
interface dot11radio { 0 | 1 } Enter interface configuration mode for the radio interface. The
2.4-GHz radio is radio 0, and the 5-GHz radio is radio 1.
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
5-3
Page 80

Configure Encryption Types
Command Purpose
Step 3
encryption
[vlan vlan-id]
key 1-4
size { 40 | 128 } encryption-key
[ 0 | 7 ]
[transmit-key]
Step 4
Step 5
end Return to privileged EXEC mode.
copy running-config startup-config (Optional) Save your entries in the configuration file.
Chapter 5 Configuring Encryption Types
Create a WEP key and set up its properties.
• (Optional) Select the VLAN for which you want to create
a key.
• Name the key slot in which this WEP key resides. You can
assign up to 4 WEP keys for each VLAN.
• Enter the key and set the size of the key, either 40-bit or
128-bit. 40-bit keys contain 10 hexadecimal digits; 128-bit
keys contain 26 hexadecimal digits.
• (Optional) Specify whether the key is encrypted (7) or
unencrypted (0).
• (Optional) Set this key as the transmit key. The key in slot
1 is the transmit key by default.
Note Using security features such as authenticated key
management can limit WEP key configurations. See the
“WEP Key Restrictions” section on page 5-4 for a list
of features that impact WEP keys.
This example shows how to create a 128-bit WEP key in slot 3 for VLAN 22 and sets the key as the
transmit key:
router# configure terminal
router(config)# interface dot11radio 0
router(config-if)# encryption vlan 22 key 3 size 128 12345678901234567890123456
transmit-key
router(config-ssid)# end
WEP Key Restrictions
Table 5-1 lists WEP key restrictions based on your security configuration.
Ta b l e 5-1 WEP Key Restrictions
Security Configuration WEP Key Restriction
WPA authenticated key management Cannot configure a WEP key in key slot 1
LEAP or EAP authentication Cannot configure a WEP key in key slot 4
Cipher suite with 40-bit WEP Cannot configure a 128-bit key
Cipher suite with 128-bit WEP Cannot configure a 40-bit key
Cipher suite with TKIP Cannot configure any WEP keys
Cisco Wireless ISR and HWIC Access Point Configuration Guide
5-4
OL-6415-04
Page 81

Chapter 5 Configuring Encryption Types
Table 5-1 WEP Key Restrictions (continued)
Security Configuration WEP Key Restriction
Cipher suite with TKIP and 40-bit WEP or
128-bit WEP
Broadcast key rotation Keys in slots 2 and 3 are overwritten by rotating
Example WEP Key Setup
Table 5-2 shows an example WEP key setup that would work for the access point and an associated
device:
Configure Encryption Types
Cannot configure a WEP key in key slot 1 and 4
broadcast keys
Note Client devices using static WEP cannot use the
access point when you enable broadcast key
rotation. When you enable broadcast key
rotation, only wireless client devices using
802.1x authentication (such as LEAP, EAP-TLS,
or PEAP) can use the access point.
Ta b l e 5-2 WEP Key Setup Example
Key
Slot
Because the access point’s WEP key 1 is selected as the transmit key, WEP key 1 on the other device
must have the same contents. WEP key 4 on the other device is set, but because it is not selected as the
transmit key, WEP key 4 on the access point does not need to be set at all.
Access Point Associated Device
Transmit? Key Contents Tra ns mit? Key Contents
1 x 12345678901234567890abcdef
2
3
4
Creating Cipher Suites
Beginning in privileged EXEC mode, follow these steps to create a cipher suite:
Command Purpose
Step 1
Step 2
configure terminal Enter global configuration mode.
interface dot11radio { 0 | 1 } Enter interface configuration mode for the radio interface. The
–
–
–
–
09876543210987654321fedcba x 09876543210987654321fedcba
not set
not set
2.4-GHz radio is radio 0, and the 5-GHz radio is radio 1.
–
–
12345678901234567890abcdef
not set
FEDCBA09876543211234567890
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
5-5
Page 82

Configure Encryption Types
Command Purpose
Step 3
encryption
[vlan vlan-id]
mode ciphers
{[aes-ccm | tkip]} {[wep128 |
wep40]}
Step 4
Step 5
end Return to privileged EXEC mode.
copy running-config startup-config (Optional) Save your entries in the configuration file.
Chapter 5 Configuring Encryption Types
Enable a cipher suite containing the encryption you need.
Table 5-3 lists guidelines for selecting a cipher suite that
matches the type of authenticated key management you
configure.
• (Optional) Select the VLAN for which you want to enable
WEP and WEP features.
• Set the cipher options and WEP level. You can combine
TKIP with 128-bit or 40-bit WEP.
Note You can also use the encryption mode wep command
to set up static WEP. However, you should use
encryption mode wep only if no clients that associate
to the access point are capable of key management. See
the Cisco IOS Command Reference for Cisco Access
Points and Bridges for a detailed description of the
encryption mode wep command.
Note When you configure the cipher TKIP and AES-CCM
(not TKIP + WEP 128 or TKIP + WEP 40) for an
SSID, the SSID must use WPA key management. Client
authentication fails on an SSID that uses the cipher
TKIP without enabling WPA key management.
Use the no form of the encryption command to disable a cipher suite.
This example sets up a cipher suite for VLAN 22 that enables AES-CCM, and 128-bit WEP.
router# configure terminal
router(config)# interface dot11radio 0
router(config-if)# encryption vlan 22 mode ciphers aes-ccm wep128
router(config-if)# exit
Cipher Suites Compatible with WPA
If you configure your access point to use WPA authenticated key management, you must select a cipher
suite compatible with the authenticated key management type.
compatible with WPA.
Table 5-3 lists the cipher suites that are
Cisco Wireless ISR and HWIC Access Point Configuration Guide
5-6
OL-6415-04
Page 83

Chapter 5 Configuring Encryption Types
Ta b l e 5-3 Cipher Suites Compatible with WPA
Authenticated Key Management Types Compatible Cipher Suites
WPA • encryption mode ciphers aes-ccm
Configure Encryption Types
• encryption mode ciphers aes-ccm wep128
• encryption mode ciphers aes-ccm wep40
• encryption mode ciphers aes-ccm tkip
• encryption mode ciphers aes-ccm tkip
wep128
• encryption mode ciphers aes-ccm tkip
wep128 wep40
• encryption mode ciphers tkip wep128 wep40
•
Note When you configure AES-CCM-only, TKIP-only, or AES-CCM + TKIP cipher TKIP encryption (not
including any WEP 40 or WEP 128) on a radio interface or VLAN, every SSID on that radio or
VLANmust be set to use the WPA key management. If you configure AES-CCM or TKIP on a radio or
VLAN but do not configure key management on the SSIDs, client authentication fails on the SSIDs.
For a complete description of WPA and instructions for configuring authenticated key management, see
the
“Using WPA Key Management” section on page 6-6.
Enabling and Disabling Broadcast Key Rotation
Broadcast key rotation is disabled by default.
Note Client devices using static WEP cannot use the access point when you enable broadcast key rotation.
When you enable broadcast key rotation, only wireless client devices using 802.1x authentication (such
as LEAP, EAP-TLS, or PEAP) can use the access point.
Beginning in privileged EXEC mode, follow these steps to enable broadcast key rotation:
Command Purpose
Step 1
Step 2
configure terminal Enter global configuration mode.
interface dot11radio { 0 | 1 } Enter interface configuration mode for the radio interface. The
2.4-GHz radio is radio 0, and the 5-GHz radio is radio 1.
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
5-7
Page 84

Configure Encryption Types
Command Purpose
Step 3
broadcast-key
change seconds
[ vlan vlan-id ]
[ membership-termination ]
[ capability-change ]
Chapter 5 Configuring Encryption Types
Enable broadcast key rotation.
• Enter the number of seconds between each rotation of the
broadcast key.
• (Optional) Enter a VLAN for which you want to enable
broadcast key rotation.
• (Optional) If you enable WPA authenticated key
management, you can enable additional circumstances
under which the access point changes and distributes the
WPA group key.
–
Membership termination—the access point generates
and distributes a new group key when any
authenticated client device disassociates from the
access point. This feature protects the privacy of the
group key for associated clients. However, it might
generate some overhead if clients on your network
roam frequently.
–
Capability change—the access point generates and
distributes a dynamic group key when the last non-key
management (static WEP) client disassociates, and it
distributes the statically configured WEP key when the
first non-key management (static WEP) client
authenticates. In WPA migration mode, this feature
significantly improves the security of
key-management capable clients when there are no
static-WEP clients associated to the access point.
Step 4
Step 5
end Return to privileged EXEC mode.
copy running-config startup-config (Optional) Save your entries in the configuration file.
Use the no form of the encryption command to disable broadcast key rotation.
This example enables broadcast key rotation on VLAN 22 and sets the rotation interval to 300 seconds:
router# configure terminal
router(config)# interface dot11radio 0
routerrouter(config-if)# broadcast-key vlan 22 change 300
router(config-ssid)# end
Security Type in Universal Client Mode
Security
In universal client mode, the security type must be configured exactly as that of the access point it is
associating to. For example, if the access point is configured with AES and TKIP encryption, the
universal client must also have AES+TKIP in order for the devices to associate properly.
See Chapter 6, “Configuring Authentication Types,” for
detailed instructions on enabling authenticated key
management.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
5-8
OL-6415-04
Page 85

Chapter 5 Configuring Encryption Types
• TKIP
• AES
• TKIP+AES
• WEP 40-bit
• WEP 128-bit
Universal client configuration
!
dot11 ssid test10
authentication open
authentication key-management wpa
wpa-psk ascii 7 11584B5643475D5B5C737B
!
!
interface Dot11Radio0/1/0
ip address dhcp
!
encryption mode ciphers aes-ccm
!
ssid test10
!
speed basic-1.0 basic-2.0 basic-5.5 6.0 9.0 basic-11.0 12.0 18.0 24.0 36.0 48.0 54.0
station-role non-root
!
End
Configure Encryption Types
The access point is configured with AES+TKIP WPA-PSK encryption. The universal client will display
the following system message when there is a mismatch in the encryption types during association
between the AP and the universal client:
%DOT11-4-CANT_ASSOC: Interface Dot11Radio0/1/0, cannot associate: WPAIE invalid multicast
suite exp=0x0050F204 act=0x0050F202
In this example, the universal client would have the multicast suite of 0x0050F204 (for TKIP) but instead
received the multicast suite of 0x0050F202 (for AES+ TKIP). Here are the different scenarios:
• If the universal client is configured for AES WPAv2 (encryption mode ciphers aes-ccm), the access
point must be configured for AES WPAv2. The universal client will associate with AES encryption.
• If the universal client is configured for TKIP (encryption mode ciphers tkip) The access point must
be configured for either 1. TKIP WPA or 2. TKIP+AES. The universal client will associate with
TKIP encryption.
• If the universal client is configured for AES+TKIP (encryption mode ciphers tkip aes) The access
point must be configured for TKIP+AES. The universal client will associate with AES encryption.
• If the access point is configured for AES WPAv2 WPAv2 (encryption mode ciphers aes-ccm), and
the universal client is configured with TKIP+AES (encryption mode ciphers aes-ccm tkip), you will
get a system message stating the multicast suite was not found.
%DOT11-4-CANT_ASSOC: Interface Dot11Radio0/1/0, cannot associate: WPAIE not found and
required
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
5-9
Page 86

Configure Encryption Types
Debugging
To determine if the universal client has associated to the access point, the user can issue the 'show dot11
association all' command for a detailed output of which access point it was associating to and how it has
associated to the access point.
The "show dot11 association" command will have the following output:
c2801_uc#
c2801_uc#sh dot11 ass all
Address : 0015.2b06.17d0 Name : ap
IP Address : 200.1.1.1 Interface : Dot11Radio0/1/0
Device : ap1200-Parent Software Version : 12.3
CCX Version : NONE
State : Assoc Parent : Our Parent
SSID : test10 VLAN : 0
Hops to Infra : 0 Association Id : 1
Tunnel Address : 0.0.0.0
Key Mgmt type : NONE Encryption : Off
Current Rate : 54.0 Capability : WMM ShortHdr ShortSlot
Supported Rates : 1.0 2.0 5.5 6.0 9.0 11.0 12.0 18.0 24.0 36.0 48.0 54.0
Signal Strength : -14 dBm Connected for : 236 seconds
Signal Quality : N/A Activity Timeout : 15 seconds
Power-save : Off Last Activity : 0 seconds ago
Chapter 5 Configuring Encryption Types
Packets Input : 2449 Packets Output : 15
Bytes Input : 451711 Bytes Output : 4664
Duplicates Rcvd : 3 Data Retries : 1
Decrypt Failed : 0 RTS Retries : 0
MIC Failed : 0 MIC Missing : 0
Packets Redirected: 0 Redirect Filtered: 0
c2801_uc#
Caveats
When the Cisco dot11radio is in the universal client mode and associates to a 3rd party access point,
there are some additional caveats. The first is on the "show dot11 association" output. The "Device" area
shows a result of "unknown" when associated to a 3rd party access point (non-Cisco). In the example
below, a Cisco 876W universal client is associated to a Symbol 4131 Access Point. The "Software
Version" and "Name" fields also result in "NONE". This is because the Cisco Aironet messages between
Cisco devices carry this information and not between 3rd party and Cisco devices.
Example:
c876#sh dot11 assoc
802.11 Client Stations on Dot11Radio0:
SSID [symbol] :
MAC Address IP address Device Name Parent State
00a0.f8dc.133a 192.168.1.4 unknown - - Assoc
c876#sh dot11 ass all
Address : 00a0.f8dc.133a Name : NONE
IP Address : 192.168.1.4 Interface : Dot11Radio0
Device : unknown Software Version : NONE
CCX Version : NONE
State : Assoc Parent : Our Parent
Cisco Wireless ISR and HWIC Access Point Configuration Guide
5-10
OL-6415-04
Page 87

Chapter 5 Configuring Encryption Types
SSID : symbol VLAN : 0
Hops to Infra : -1 Association Id : 2
Tunnel Address : 0.0.0.0
Key Mgmt type : NONE Encryption : WEP
Current Rate : 11.0 Capability :
Supported Rates : 1.0 2.0 5.5 11.0
Signal Strength : -55 dBm Connected for : 39 seconds
Signal Quality : N/A Activity Timeout : 15 seconds
Power-save : Off Last Activity : 13 seconds ago
Packets Input : 408 Packets Output : 16
Bytes Input : 46619 Bytes Output : 3495
Duplicates Rcvd : 2 Data Retries : 8
Decrypt Failed : 0 RTS Retries : 0
MIC Failed : 0 MIC Missing : 0
Packets Redirected: 0 Redirect Filtered: 0
c876#
Configure Encryption Types
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
5-11
Page 88

Configure Encryption Types
Chapter 5 Configuring Encryption Types
Cisco Wireless ISR and HWIC Access Point Configuration Guide
5-12
OL-6415-04
Page 89

CHA P TER
6
Configuring Authentication Types
This chapter describes how to configure authentication types on the access point. This chapter contains
these sections:
• Understand Authentication Types, page 6-2
• Configure Authentication Types, page 6-9
• Matching Access Point and Client Device Authentication Types, page 6-16
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
6-1
Page 90

Understand Authentication Types
Understand Authentication Types
This section describes the authentication types that you can configure on the access point. The
authentication types are tied to the SSIDs that you configure for the access point. If you want to serve
different types of client devices with the same access point, you can configure multiple SSIDs. See
Chapter 3, “Configuring Multiple SSIDs,” for complete instructions on configuring multiple SSIDs.
Before a wireless client device can communicate on your network through the access point, it must
authenticate to the access point using open or shared-key authentication. For maximum security, client
devices should also authenticate to your network using MAC-address or EAP authentication,
authentication types that rely on an authentication server on your network.
Note By default, the access point sends reauthentication requests to the authentication server with the
service-type attribute set to authenticate-only. However, some Microsoft IAS servers do not support the
authenticate-only service-type attribute. Changing the service-type attribute to login-only ensures that
Microsoft IAS servers recognize reauthentication requests from the access point. Use the dot11 aaa
authentication attributes service-type login-only global configuration command to set the
service-type attribute in reauthentication requests to login-only.
Chapter 6 Configuring Authentication Types
The access point uses several authentication mechanisms or types and can use more than one at the same
time. These sections explain each authentication type:
• Open Authentication to Access Point, page 6-2
• Shared Key Authentication to Access Point, page 6-3
• EAP Authentication to Network, page 6-4
• MAC Address Authentication to the Network, page 6-5
• Combining MAC-Based, EAP, and Open Authentication, page 6-6
• Using WPA Key Management, page 6-6
• Using WPA Key Management, page 6-6
Open Authentication to Access Point
Open authentication allows any device to authenticate and then attempt to communicate with the access
point. Using open authentication, any wireless device can authenticate with the access point, but the
device can communicate only if its WEP keys match the access point’s. Devices not using WEP do not
attempt to authenticate with an access point that is using WEP. Open authentication does not rely on a
RADIUS server on your network.
Figure 6-1 shows the authentication sequence between a device trying to authenticate and an access point
using open authentication. In this example, the device’s WEP key does not match the access point’s key,
so it can authenticate but not pass data.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
6-2
OL-6415-04
Page 91

Chapter 6 Configuring Authentication Types
Access point
or bridge
Wired LAN
Client
device
Server
1. Authentication request
2. Authentication success
3. Association request
4. Association response
(block traffic from client)
5. Authentication request
6. Success
7. Access point or bridge unblocks
traffic from client
65584
Figure 6-1 Sequence for Open Authentication
Client device
with WEP key = 321
1. Authentication request
2. Authentication response
3. Association request
4. Association response
5. WEP data frame to wired network
6. Key mismatch, frame discarded
Shared Key Authentication to Access Point
Cisco provides shared key authentication to comply with the IEEE 802.11b standard. However, because
of shared key’s security flaws, Cisco recommends that you avoid using it.
During shared key authentication, the access point sends an unencrypted challenge text string to any
device attempting to communicate with the access point. The device requesting authentication encrypts
the challenge text and sends it back to the access point. If the challenge text is encrypted correctly, the
access point allows the requesting device to authenticate. Both the unencrypted challenge and the
encrypted challenge can be monitored, however, which leaves the access point open to attack from an
intruder who calculates the WEP key by comparing the unencrypted and encrypted text strings. Because
of this weakness, shared key authentication can be less secure than open authentication. Like open
authentication, shared key authentication does not rely on a RADIUS server on your network.
Figure 6-2 shows the authentication sequence between a device trying to authenticate and an access point
using shared key authentication. In this example the device’s WEP key matches the access point’s key,
so it can authenticate and communicate.
Understand Authentication Types
Access point
or bridge
with WEP key = 123
54583
Figure 6-2 Sequence for Shared Key Authentication
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
6-3
Page 92

Understand Authentication Types
Access point
or bridge
Wired LAN
Client
device
RADIUS Server
1. Authentication request
2. Identity request
3. Username
(relay to client)
(relay to server)
4. Authentication challenge
5. Authentication response
(relay to client)
(relay to server)
6. Authentication success
7. Authentication challenge
(relay to client)
(relay to server)
8. Authentication response
9. Successful authentication
(relay to server)
65583
EAP Authentication to Network
This authentication type provides the highest level of security for your wireless network. By using the
Extensible Authentication Protocol (EAP) to interact with an EAP-compatible RADIUS server, the
access point helps a wireless client device and the RADIUS server to perform mutual authentication and
derive a dynamic unicast WEP key. The RADIUS server sends the WEP key to the access point, which
uses it for all unicast data signals that it sends to or receives from the client. The access point also
encrypts its broadcast WEP key (entered in the access point’s WEP key slot 1) with the client’s unicast
key and sends it to the client.
When you enable EAP on your access points and client devices, authentication to the network occurs in
the sequence shown in
Figure 6-3 Sequence for EAP Authentication
Figure 6-3:
Chapter 6 Configuring Authentication Types
In Steps 1 through 9 in Figure 6-3, a wireless client device and a RADIUS server on the wired LAN use
802.1x and EAP to perform a mutual authentication through the access point. The RADIUS server sends
an authentication challenge to the client. The client uses a one-way encryption of the user-supplied
password to generate a response to the challenge and sends that response to the RADIUS server. Using
information from its user database, the RADIUS server creates its own response and compares that to
the response from the client. When the RADIUS server authenticates the client, the process repeats in
reverse, and the client authenticates the RADIUS server.
When mutual authentication is complete, the RADIUS server and the client determine a WEP key that
is unique to the client and provides the client with the appropriate level of network access, thereby
approximating the level of security in a wired switched segment to an individual desktop. The client
loads this key and prepares to use it for the logon session.
During the logon session, the RADIUS server encrypts and sends the WEP key, called a session key, over
the wired LAN to the access point. The access point encrypts its broadcast key with the session key and
sends the encrypted broadcast key to the client, which uses the session key to decrypt it. The client and
access point activate WEP and use the session and broadcast WEP keys for all communications during
the remainder of the session.
6-4
Cisco Wireless ISR and HWIC Access Point Configuration Guide
OL-6415-04
Page 93

Chapter 6 Configuring Authentication Types
There is more than one type of EAP authentication, but the access point behaves the same way for each
type: it relays authentication messages from the wireless client device to the RADIUS server and from
the RADIUS server to the wireless client device. See the
section on page 6-9 for instructions on setting up EAP on the access point.
Note If you use EAP authentication, you can select open or shared key authentication, but you don’t have to.
EAP authentication controls authentication both to your access point and to your network.
MAC Address Authentication to the Network
The access point relays the MAC address of the wireless client device to a RADIUS server on your
network, and the server checks the address against a list of allowed MAC addresses. Intruders can create
counterfeit MAC addresses, so MAC-based authentication is less secure than EAP authentication.
However, MAC-based authentication provides an alternate authentication method for client devices that
do not have EAP capability. See the
for instructions on enabling MAC-based authentication.
“Assigning Authentication Types to an SSID” section on page 6-9
Understand Authentication Types
“Assigning Authentication Types to an SSID”
Tip If you don’t have a RADIUS server on your network, you can create a list of allowed MAC addresses on
the access point’s Advanced Security: MAC Address Authentication page. Devices with MAC addresses
not on the list are not allowed to authenticate.
Tip If MAC-authenticated clients on your wireless LAN roam frequently, you can enable a MAC
authentication cache on your access points. MAC authentication caching reduces overhead because the
access point authenticates devices in its MAC-address cache without sending the request to your
authentication server. See the
“Configuring MAC Authentication Caching” section on page 6-14 for
instructions on enabling this feature.
Figure 6-4 shows the authentication sequence for MAC-based authentication.
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
6-5
Page 94

Understand Authentication Types
Access point
or bridge
Wired LAN
Client
device
Server
1. Authentication request
2. Authentication success
3. Association request
4. Association response
(block traffic from client)
5. Authentication request
6. Success
7. Access point or bridge unblocks
traffic from client
65584
Figure 6-4 Sequence for MAC-Based Authentication
Chapter 6 Configuring Authentication Types
Combining MAC-Based, EAP, and Open Authentication
You can set up the access point to authenticate client devices using a combination of MAC-based and
EAP authentication. When you enable this feature, client devices that associate to the access point using
802.11 open authentication first attempt MAC authentication; if MAC authentication succeeds, the client
device joins the network. If MAC authentication fails, the access point waits for the client device to
attempt EAP authentication. See the
“Assigning Authentication Types to an SSID” section on page 6-9
for instructions on setting up this combination of authentications.
Using WPA Key Management
Wi-Fi Protected Access is a standards-based, interoperable security enhancement that strongly increases
the level of data protection and access control for existing and future wireless LAN systems. It is derived
from and will be forward-compatible with the upcoming IEEE 802.11i standard. WPA leverages
AES-CCM and TKIP (Temporal Key Integrity Protocol) for data protection and 802.1X for authenticated
key management.
WPA key management supports two mutually exclusive management types: WPA and WPA-Pre-shared
key (WPA-PSK). Using WPA key management, clients and the authentication server authenticate to each
other using an EAP authentication method, and the client and server generate a pairwise master key
(PMK). Using WPA, the server generates the PMK dynamically and passes it to the access point. Using
WPA-PSK, however, you configure a pre-shared key on both the client and the access point, and that
pre-shared key is used as the PMK.
6-6
Note In Cisco IOS releases 12.3(4)JA and later, you cannot enable both MAC-address authentication and
WPA-PSK.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
OL-6415-04
Page 95

Chapter 6 Configuring Authentication Types
Client and server authenticate to each other, generating an EAP master key
Client device
Access point
Authentication
server
Wired LAN
Server uses the EAP master key to
generate a pairwise master key (PMK)
to protect communication between the
client and the access point. (However,
if the client is using 802.1x authentication
and both the access point and the client
are configured with the same pre-shared key,
the pre-shared key is used as the PMK and
the server does not generate a PMK.)
Client and access point complete
a four-way handshake to:
Client and access point complete
a two-way handshake to securely
deliver the group transient key from
the access point to the client.
Confirm that a PMK exists and that
knowledge of the PMK is current.
Derive a pairwise transient key from
the PMK.
Install encryption and integrity keys into
the encryption/integrity engine, if necessary.
Confirm installation of all keys.
Note Unicast and multicast cipher suites advertised in WPA information element (and negotiated during
802.11 association) may potentially mismatch with the cipher suite supported in an explicitly assigned
VLAN. If the RADIUS server assigns a new vlan ID which uses a different cipher suite from the
previously negotiated cipher suite, there is no way for the access point and client to switch back to the
new cipher suite. Currently, the WPA protocol does not allow the cipher suite to be changed after the
initial 802.11 cipher negotiation phase. In this scenario, the client device is disassociated from the
wireless LAN.
See the “Assigning Authentication Types to an SSID” section on page 6-9 for instructions on configuring
WPA key management on your access point.
Figure 6-5 shows the WPA key management process.
Figure 6-5 WPA Key Management Process
Understand Authentication Types
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
6-7
Page 96

Chapter 6 Configuring Authentication Types
Understand Authentication Types
Software and Firmware Requirements for WPA and WPA-TKIP
Table 6-1 lists the firmware and software requirements required on access points and Cisco client
devices to support WPA key management and WPA-TKIP encryption protocols.
To support the security combinations in Tab le 6-1, your access points and client devices must run the
following software and firmware versions:
• Cisco IOS Release 12.4(2)T or later on access points
• Install Wizard version 1.2 for 340, 350, and CB20A client devices, which includes these
components:
–
PC, LM, and PCI card driver version 8.4
–
Mini PCI and PC-cardbus card driver version 3.7
–
Aironet Client Utility (ACU) version 6.2
–
Client firmware version 5.30.13
Ta b l e 6-1 Software and Firmware Requirements for WPA and WPA-TKIP
Key Management and Encryption
Protocol
Third Party Host Supplicant1
Required?
Supported Platform Operating
Systems
LEAP with WPA-TKIP No Windows XP and 2000
LEAP with WPA No Windows XP and 2000
Host-based EAP (such as PEAP,
No
2
Windows XP
EAP-SIM, and EAP-TLS) with
WPA
Host-based EAP (such as PEAP,
Yes Windows 2000
EAP-SIM, and EAP-TLS) with
WPA
WPA-PSK Mode No
2
Windows XP
WPA-PSK Mode Yes Windows 2000
1. Such as Funk Odyssey Client supplicant version 2.2 or Meetinghouse Data Communications Aegis Client version 2.1.
2. Windows XP does not require a third-party supplicant, but you must install Windows XP Service Pack 1 and Microsoft support
patch 815485.
Note When you configure AES-CCM and TKIP-only cipher encryption (not TKIP + WEP 128 or TKIP +
WEP 40) on any radio interface or VLAN, every SSID on that radio or VLAN must be set to use WPA
key management. If you configure TKIP on a radio or VLAN but you do not configure key management
on the SSIDs, client authentication fails on the SSIDs.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
6-8
OL-6415-04
Page 97

Chapter 6 Configuring Authentication Types
Configure Authentication Types
This section describes how to configure authentication types. You attach configuration types to the
access point’s SSIDs. See
SSIDs. This section contains these topics:
• Assigning Authentication Types to an SSID, page 6-9
• Configuring Authentication Holdoffs, Timeouts, and Intervals, page 6-15
Assigning Authentication Types to an SSID
Beginning in privileged EXEC mode, follow these steps to configure authentication types for SSIDs:
Command Purpose
Step 1
Step 2
configure terminal Enter global configuration mode.
dot11 ssid ssid-string Create an SSID and enter SSID configuration mode for the new
Chapter 3, “Configuring Multiple SSIDs,” for details on setting up multiple
SSID. The SSID can consist of up to 32 alphanumeric
characters. SSIDs are case sensitive.
Configure Authentication Types
OL-6415-04
Cisco Wireless ISR and HWIC Access Point Configuration Guide
6-9
Page 98

Configure Authentication Types
Command Purpose
Step 3
authentication open
[mac-address list-name [alternate]]
[[optional] eap list-name]
Chapter 6 Configuring Authentication Types
(Optional) Set the authentication type to open for this SSID.
Open authentication allows any device to authenticate and then
attempt to communicate with the access point.
Note The following EAP methods are supported: EAP-MD5,
EAP_SIM, EAP-TTLS, EAP-LEAP, EAP-PEAP (v0
and v1), EAP-TLS, AND EAP-FAST.
• (Optional) Set the SSID authentication type to open with
MAC address authentication. The access point forces all
client devices to perform MAC-address authentication
before they are allowed to join the network. For list-name,
specify the authentication method list. Click this link for
more information on method lists:
http://www.cisco.com/univercd/cc/td/doc/product/softwar
e/ios122/122cgcr/fsecur_c/fsaaa/scfathen.htm#xtocid2
Use the alternate keyword to allow client devices to join
the network using either MAC or EAP authentication;
clients that successfully complete either authentication are
allowed to join the network.
• (Optional) Set the SSID authentication type to open with
EAP authentication. The access point forces all client
devices to perform EAP authentication before they are
allowed to join the network. For list-name, specify the
authentication method list.
Use the optional keyword to allow client devices using
either open or EAP authentication to associate and become
authenticated. This setting is used mainly by service
providers that require special client accessibility.
Note An access point configured for EAP authentication
forces all client devices that associate to perform EAP
authentication. Client devices that do not use EAP
cannot use the access point.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
6-10
OL-6415-04
Page 99

Chapter 6 Configuring Authentication Types
Command Purpose
Step 4
authentication shared
[mac-address list-name]
[eap list-name]
Step 5
authentication network-eap
list-name
[mac-address list-name]
Step 6
authentication key-management
{
[wpa]} [ optional ]
Configure Authentication Types
(Optional) Set the authentication type for the SSID to shared
key.
Note Because of shared key's security flaws, Cisco
recommends that you avoid using it.
Note You can assign shared key authentication to only one
SSID.
• (Optional) Set the SSID’s authentication type to shared key
with MAC address authentication. For list-name, specify
the authentication method list.
• (Optional) Set the SSID’s authentication type to shared key
with EAP authentication. For list-name, specify the
authentication method list.
(Optional) Set the authentication type for the SSID to
Network-EAP. Using the Extensible Authentication Protocol
(EAP) to interact with an EAP-compatible RADIUS server, the
access point helps a wireless client device and the RADIUS
server to perform mutual authentication and derive a dynamic
unicast WEP key. However, the access point does not force all
client devices to perform EAP authentication.
• (Optional) Set the SSID’s authentication type to
Network-EAP with MAC address authentication. All client
devices that associate to the access point are required to
perform MAC-address authentication. For list-name,
specify the authentication method list.
(Optional) Set the authentication type for the SSID to WPA. If
you use the optional keyword, client devices other than WPA
clients can use this SSID. If you do not use the optional
keyword, only WPA client devices are allowed to use the SSID.
OL-6415-04
When Network EAP is enabled for an SSID, client devices
using LEAP, EAP-FAST, PEAP/GTC, MSPEAP, and EAP-TLS
can authenticate using the SSID.
To enable WPA for an SSID, you must also enable Open
authentication or Network-EAP or both.
Note Before you can enable WPA, you must set the
encryption mode for the SSID’s VLAN to one of the
cipher suite options. See the
“Configure Encryption
Types” section on page 5-3 for instructions on
configuring the VLAN encryption mode.
Note If you enable WPA for an SSID without a pre-shared
key, the key management type is WPA. If you enable
WPA with a pre-shared key, the key management type
is WPA-PSK. See the
“Configuring Additional WPA
Settings” section on page 6-13 for instructions on
configuring a pre-shared key.
Cisco Wireless ISR and HWIC Access Point Configuration Guide
6-11
Page 100

Configure Authentication Types
Command Purpose
Step 7
Step 8
end Return to privileged EXEC mode.
copy running-config startup-config (Optional) Save your entries in the configuration file.
Use the no form of the SSID commands to disable the SSID or to disable SSID features.
This example sets the authentication type for the SSID batman to Network-EAP authenticated key
management. Client devices using the batman SSID authenticate using the adam server list.
router# configure terminal
router(config)# interface dot11radio 0
router(config-if)# ssid batman
router(config-ssid)# authentication network-eap adam
router(config-ssid)# authentication key-management optional
router(config-ssid)# end
Configuring WPA Migration Mode
WPA migration mode allows these client device types to associate to the access point using the same
SSID:
• WPA clients capable of AES-CCM, TKIP and authenticated key management
• 802.1X-2001 clients (such as legacy LEAP clients and clients using TLS) capable of authenticated
key management but not TKIP
Chapter 6 Configuring Authentication Types
• Static-WEP clients not capable of TKIP or authenticated key management
If all three client types associate using the same SSID, the multicast cipher suite for the SSID must be
WEP. If only the first two types of clients use the same SSID the multicast key can be dynamic, but if
the static-WEP clients use the SSID, the key must be static. The access point can switch automatically
between a static and a dynamic group key to accommodate associated client devices. To support all three
types of clients on the same SSID, you must configure the static key in key slots 2 or 3.
To set up an SSID for WPA migration mode, configure these settings:
• WPA optional
• A cipher suite containing TKIP and 40-bit or 128-bit WEP
• A static WEP key in key slot 2 or 3
This example sets the SSID migrate for WPA migration mode:
router# configure terminal
router(config)# interface dot11radio 0
router(config-if)# encryption mode cipher tkip wep128
router(config-if)# encryption key 3 size 128 12345678901234567890123456 transmit-key
router(config-if)# ssid migrate
router(config-ssid)# authentication open
router(config-ssid)# authentication network-eap adam
router(config-ssid)# authentication key-management wpa optional
router(config-ssid)# wpa-psk ascii batmobile65
router(config-ssid)# exit
Cisco Wireless ISR and HWIC Access Point Configuration Guide
6-12
OL-6415-04
 Loading...
Loading...