Cisco IPS-4255-K9 - Intrusion Protection Sys 4255, IPS 4255, IPS 4260, IPS 4270-20, AIP SSM-10 Installation Manual
...Page 1

Cisco Intrusion Prevention System
Appliance and Module Installation Guide
for IPS 7.0
Americas Headquarters
Cisco Systems, Inc.
170 West Tasman Drive
San Jose, CA 95134-1706
USA
http://www.cisco.com
Tel: 408 526-4000
800 553-NETS (6387)
Fax: 408 527-0883
Text Part Number: OL-18504-01
Page 2

THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL
STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT
WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS.
THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT
SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE
OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY.
The following information is for FCC compliance of Class A devices: This equipment has been tested and found to comply with the limits for a Class A digital device, pursuant
to part 15 of the FCC rules. These limits are designed to provide reasonable protection against harmful interference when the equipment is operated in a commercial
environment. This equipment generates, uses, and can radiate radio-frequency energy and, if not installed and used in accordance with the instruction manual, may cause
harmful interference to radio communications. Operation of this equipment in a residential area is likely to cause harmful interference, in which case users will be required
to correct the interference at their own expense.
The following information is for FCC compliance of Class B devices: This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant
to part 15 of the FCC rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates,
uses and can radiate radio frequency energy and, if not installed and used in accordance with the instructions, may cause harmful interference to radio communications.
However, there is no guarantee that interference will not occur in a particular installation. If the equipment causes interference to radio or television reception, which can be
determined by turning the equipment off and on, users are encouraged to try to correct the interference by using one or more of the following measures:
• Reorient or relocate the receiving antenna.
• Increase the separation between the equipment and receiver.
• Connect the equipment into an outlet on a circuit different from that to which the receiver is connected.
• Consult the dealer or an experienced radio/TV technician for help.
Modifications to this product not authorized by Cisco could void the FCC approval and negate your authority to operate the product.
The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public
domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California.
NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH
ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT
LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF
DEALING, USAGE, OR TRADE PRACTICE.
IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING,
WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO
OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this
URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership
relationship between Cisco and any other company. (1110R)
Any Internet Protocol (IP) addresses used in this document are not intended to be actual addresses. Any examples, command display output, and figures included in the
document are shown for illustrative purposes only. Any use of actual IP addresses in illustrative content is unintentional and coincidental.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
© 2010-2012 Cisco Systems, Inc. All rights reserved.
Page 3

CONTENTS
Preface xiii
Contents xiii
Audience xiii
Comply with Local and National Electrical Codes xiii
Organization xv
Conventions xv
Related Documentation xvi
Obtaining Documentation and Submitting a Service Request xvii
CHAPTER
1 Introducing the Sensor 1-1
How the Sensor Functions 1-1
Capturing Network Traffic 1-1
Your Network Topology 1-3
Correctly Deploying the Sensor 1-3
Tuning the IPS 1-3
Sensor Interfaces 1-4
Understanding Sensor Interfaces 1-4
Command and Control Interface 1-5
Sensing Interfaces 1-6
Interface Support 1-6
TCP Reset Interfaces 1-9
Interface Restrictions 1-10
Interface Modes 1-12
Promiscuous Mode 1-12
IPv6, Switches, and Lack of VACL Capture 1-13
Inline Interface Pair Mode 1-14
Inline VLAN Pair Mode 1-15
VLAN Group Mode 1-15
Deploying VLAN Groups 1-16
Supported Sensors 1-17
IPS Appliances 1-18
Introducing the IPS Appliance 1-18
Appliance Restrictions 1-19
Connecting an Appliance to a Terminal Server 1-19
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
iii
Page 4

Contents
IPS Modules 1-20
Introducing the AIM IPS 1-20
Introducing the AIP SSM 1-22
Introducing the IDSM2 1-24
Introducing the NME IPS 1-25
Time Sources and the Sensor 1-26
The Sensor and Time Sources 1-26
Synchronizing IPS Module System Clocks with the Parent Device System Clock 1-28
Verifying the Sensor is Synchronized with the NTP Server 1-28
Correcting the Time on the Sensor 1-29
Installation Preparation 1-29
Site and Safety Guidelines 1-30
Site Guidelines 1-30
Rack Configuration Guidelines 1-30
Electrical Safety Guidelines 1-31
Power Supply Guidelines 1-32
Working in an ESD Environment 1-32
CHAPTER
CHAPTER
Cable Pinouts 1-33
10/100BaseT and 10/100/1000BaseT Connectors 1-34
Console Port (RJ-45) 1-35
RJ-45 to DB-9 or DB-25 1-36
2 Installing the IPS 4240 and the IPS 4255 2-1
Introducing the IPS 4240 and the IPS 4255 2-1
Front and Back Panel Features 2-2
Specifications 2-4
Connecting the IPS 4240 to a Cisco 7200 Series Router 2-5
Accessories 2-5
Important Safety Instructions 2-5
Rack Mounting 2-6
Installing the IPS 4240 and the IPS 4255 2-7
Installing the IPS 4240-DC 2-10
3 Installing the IPS 4260 3-1
Introducing the IPS 4260 3-1
Supported Interface Cards 3-2
Hardware Bypass 3-4
4GE Bypass Interface Card 3-4
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
iv
OL-18504-01
Page 5

Hardware Bypass Configuration Restrictions 3-5
Hardware Bypass and Link Changes and Drops 3-6
Front and Back Panel Features 3-6
Specifications 3-9
Accessories 3-9
Important Safety Instructions 3-10
Rack Mounting 3-10
Installing the IPS 4260 in a 4-Post Rack 3-10
Installing the IPS 4260 in a 2-Post Rack 3-13
Installing the IPS 4260 3-15
Removing and Replacing the Chassis Cover 3-18
Installing and Removing Interface Cards 3-20
Installing and Removing the Power Supply 3-22
Contents
CHAPTER
4 Installing the IPS 4270-20 4-1
Introducing the IPS 4270-20 4-2
Supported Interface Cards 4-3
Hardware Bypass 4-5
4GE Bypass Interface Card 4-5
Hardware Bypass Configuration Restrictions 4-6
Hardware Bypass and Link Changes and Drops 4-7
Front and Back Panel Features 4-7
Diagnostic Panel 4-11
Internal Components 4-13
Specifications 4-14
Accessories 4-15
Installing the Rail System Kit 4-15
Understanding the Rail System Kit 4-15
Rail System Kit Contents 4-16
Space and Airflow Requirements 4-16
Installing the IPS 4270-20 in the Rack 4-17
Extending the IPS 4270-20 from the Rack 4-25
Installing the Cable Management Arm 4-28
Converting the Cable Management Arm 4-31
Installing the IPS 4270-20 4-35
Removing and Replacing the Chassis Cover 4-38
Accessing the Diagnostic Panel 4-41
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
v
Page 6

Contents
Installing and Removing Interface Cards 4-41
Installing and Removing the Power Supply 4-44
Installing and Removing Fans 4-49
Troubleshooting Loose Connections 4-51
CHAPTER
CHAPTER
5 Installing the AIM IPS 5-1
Specifications 5-1
Before Installing the AIM IPS 5-2
Software and Hardware Requirements 5-2
Interoperability With Other IPS Modules 5-3
Restrictions 5-3
Hardware Interfaces 5-4
Installation and Removal Instructions 5-5
Verifying Installation 5-6
6 Installing the AIP SSM 6-1
Specifications 6-1
Memory Specifications 6-2
Hardware and Software Requirements 6-2
Indicators 6-2
Installation and Removal Instructions 6-3
Installing the AIP SSM 6-3
Verifying the Status of the AIP SSM 6-4
Removing the AIP SSM 6-5
CHAPTER
7 Installing the IDSM2 7-1
Specifications 7-1
Software and Hardware Requirements 7-2
Minimum Supported the IDSM2 Configurations 7-2
Using the TCP Reset Interface 7-3
Front Panel Features 7-3
Installation and Removal Instructions 7-4
Required Tools 7-4
Slot Assignments 7-5
Installing the IDSM2 7-5
Verifying Installation 7-9
Removing the IDSM2 7-10
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
vi
OL-18504-01
Page 7

Enabling Full Memory Tests 7-12
Catalyst Software 7-12
Cisco IOS Software 7-13
Resetting the IDSM2 7-13
Catalyst Software 7-13
Cisco IOS Software 7-14
Powering the IDSM2 Up and Down 7-15
Catalyst Software 7-15
Cisco IOS Software 7-16
Contents
CHAPTER
CHAPTER
8 Installing the NME IPS 8-1
Specifications 8-1
Before Installing the NME IPS 8-2
Software and Hardware Requirements 8-2
Interoperability With Other IPS Modules 8-3
Restrictions 8-3
Hardware Interfaces 8-4
Installation and Removal Instructions 8-5
Verifying Installation 8-6
9 Logging In to the Sensor 9-1
Supported User Roles 9-1
Logging In to the Appliance 9-2
Connecting an Appliance to a Terminal Server 9-3
Logging In to the AIM IPS 9-4
The AIM IPS and the session Command 9-4
Sessioning In to the AIM IPS 9-5
Logging In to AIP SSM 9-6
Logging In to the IDSM2 9-8
Logging In to the NME IPS 9-9
The NME IPS and the session Command 9-9
Sessioning In to the NME IPS 9-10
Logging In to the Sensor 9-11
CHAPTER
10 Initializing the Sensor 10-1
Understanding Initialization 10-1
Simplified Setup Mode 10-1
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
vii
Page 8

Contents
System Configuration Dialog 10-2
Basic Sensor Setup 10-4
Advanced Setup 10-7
Advanced Setup for the Appliance 10-8
Advanced Setup for the AIM IPS 10-13
Advanced Setup for the AIP SSM 10-16
Advanced Setup for the IDSM2 10-20
Advanced Setup for the NME IPS 10-25
Verifying Initialization 10-28
CHAPTER
CHAPTER
11 Obtaining Software 11-1
Obtaining Cisco IPS Software 11-1
IPS Software Versioning 11-2
Software Release Examples 11-6
Upgrading Cisco IPS Software to 7.0 11-7
Accessing IPS Documentation 11-9
Cisco Security Intelligence Operations 11-9
Obtaining a License Key From Cisco.com 11-10
Understanding Licensing 11-10
Service Programs for IPS Products 11-11
Obtaining and Installing the License Key Using IDM or IME 11-11
Obtaining and Installing the License Key Using the CLI 11-13
12 Upgrading, Downgrading, and Installing System Images 12-1
Upgrades, Downgrades, and System Images 12-1
Supported FTP and HTTP/HTTPS Servers 12-2
Upgrading the Sensor 12-2
IPS 7.0 Upgrade Files 12-2
upgrade Command and Options 12-3
Using the upgrade Command 12-4
Upgrading the Recovery Partition 12-5
Configuring Automatic Upgrades 12-6
Automatic Upgrades 12-6
auto-upgrade Command and Options 12-7
Using the auto-upgrade Command 12-8
Automatic Upgrade Examples 12-10
Downgrading the Sensor 12-11
Recovering the Application Partition 12-12
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
viii
OL-18504-01
Page 9

Application Partition 12-12
Using the recover Command 12-12
Installing System Images 12-13
Understanding ROMMON 12-14
Supported TFTP Servers 12-14
Connecting an Appliance to a Terminal Server 12-14
Installing the IPS 4240 and IPS 4255 System Images 12-15
Installing the IPS 4260 System Image 12-18
Installing the IPS 4270-20 System Image 12-20
Installing the AIM IPS System Image 12-23
Installing the AIP SSM System Image 12-25
Reimaging the AIP SSM 12-26
Reimaging the AIP SSM Using the recover configure/boot Command 12-26
Installing the IDSM2 System Image 12-28
Understanding the IDSM2 System Image 12-28
Installing the IDSM2 System Image for Catalyst Software 12-28
Installing the IDSM2 System Image for Cisco IOS Software 12-29
Configuring the IDSM2 Maintenance Partition for Catalyst Software 12-31
Configuring the IDSM2 Maintenance Partition for Cisco IOS Software 12-35
Upgrading the IDSM2 Maintenance Partition for Catalyst Software 12-38
Upgrading the IDSM2 Maintenance Partition for Cisco IOS Software 12-39
Installing the NME IPS System Image 12-40
Contents
APPENDIX
OL-18504-01
A Troubleshooting A-1
Bug Toolkit A-1
Preventive Maintenance A-2
Understanding Preventive Maintenance A-2
Creating and Using a Backup Configuration File A-3
Backing Up and Restoring the Configuration File Using a Remote Server A-3
Creating the Service Account A-5
Disaster Recovery A-6
Recovering the Password A-7
Understanding Password Recovery A-8
Recovering the Appliance Password A-8
Using the GRUB Menu A-8
Using ROMMON A-9
Recovering the AIM IPS Password A-10
Recovering the AIP SSM Password A-10
Recovering the IDSM2 Password A-13
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
ix
Page 10

Contents
Recovering the NME IPS Password A-13
Disabling Password Recovery A-14
Verifying the State of Password Recovery A-15
Troubleshooting Password Recovery A-15
Time and the Sensor A-16
Time Sources and the Sensor A-16
Synchronizing IPS Module Clocks with Parent Device Clocks A-17
Verifying the Sensor is Synchronized with the NTP Server A-17
Correcting Time on the Sensor A-18
Advantages and Restrictions of Virtualization A-18
Supported MIBs A-19
When to Disable Anomaly Detection A-20
Troubleshooting Global Correlation A-20
Analysis Engine Not Responding A-21
Troubleshooting External Product Interfaces A-22
External Product Interfaces Issues A-22
External Product Interfaces Troubleshooting Tips A-23
Troubleshooting the Appliance A-23
Hardware Bypass and Link Changes and Drops A-24
Troubleshooting Loose Connections A-24
Analysis Engine is Busy A-25
Connecting the IPS 4240 to a Cisco 7200 Series Router A-25
Communication Problems A-26
Cannot Access the Sensor CLI Through Telnet or SSH A-26
Correcting a Misconfigured Access List A-28
Duplicate IP Address Shuts Interface Down A-29
SensorApp and Alerting A-30
SensorApp Not Running A-30
Physical Connectivity, SPAN, or VACL Port Issue A-32
Unable to See Alerts A-33
Sensor Not Seeing Packets A-35
Cleaning Up a Corrupted SensorApp Configuration A-37
Blocking A-37
Troubleshooting Blocking A-38
Verifying ARC is Running A-38
Verifying ARC Connections are Active A-39
Device Access Issues A-41
Verifying the Interfaces and Directions on the Network Device A-43
Enabling SSH Connections to the Network Device A-43
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
x
OL-18504-01
Page 11

Blocking Not Occurring for a Signature A-44
Verifying the Master Blocking Sensor Configuration A-45
Logging A-46
Understanding Debug Logging A-46
Enabling Debug Logging A-47
Zone Names A-50
Directing cidLog Messages to SysLog A-51
TCP Reset Not Occurring for a Signature A-52
Software Upgrades A-53
Upgrading and Analysis Engine A-54
Which Updates to Apply and Their Prerequisites A-54
Issues With Automatic Update A-55
Updating a Sensor with the Update Stored on the Sensor A-55
Troubleshooting IDM A-56
Cannot Launch IDM - Loading Java Applet Failed A-56
Cannot Launch IDM-Analysis Engine Busy A-57
IDM, Remote Manager, or Sensing Interfaces Cannot Access Sensor A-57
Signatures Not Producing Alerts A-58
Contents
Troubleshooting IME A-59
Time Synchronization on IME and the Sensor A-59
Not Supported Error Message A-59
Troubleshooting the IDSM2 A-59
Diagnosing IDSM2 Problems A-60
Minimum Supported IDSM2 Configurations A-61
Switch Commands for Troubleshooting A-61
Status LED Off A-62
Status LED On But the IDSM2 Does Not Come Online A-63
Cannot Communicate With the IDSM2 Command and Control Port A-64
Using the TCP Reset Interface A-66
Connecting a Serial Cable to the IDSM2 A-66
Troubleshooting the AIP SSM A-66
Health and Status Information A-67
The AIP SSM and the Data Plane A-69
AIM SSP and the Normalizer Engine A-69
Troubleshooting the AIM IPS and the NME IPS A-69
Interoperability With Other IPS Network Modules A-69
Gathering Information A-70
Health and Network Security Information A-70
Tech Support Information A-71
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
xi
Page 12

Contents
Understanding the show tech-support Command A-71
Displaying Tech Support Information A-71
Tech Support Command Output A-72
Version Information A-74
Understanding the show version Command A-74
Displaying Version Information A-74
Statistics Information A-76
Understanding the show statistics Command A-77
Displaying Statistics A-77
Interfaces Information A-87
Understanding the show interfaces Command A-87
Interfaces Command Output A-87
Events Information A-88
Sensor Events A-88
Understanding the show events Command A-89
Displaying Events A-89
Clearing Events A-92
cidDump Script A-92
Uploading and Accessing Files on the Cisco FTP Site A-93
G
LOSSARY
I
NDEX
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
xii
OL-18504-01
Page 13

Contents
Preface
Revised: April 4, 2012, OL-18504-01
This guide describes how to install appliances and modules that support Cisco IPS 7.0. It includes a
glossary that contains expanded acronyms and pertinent IPS terms. It is part of the documentation set
for Cisco Intrusion Prevention System 7.0. Use this guide in conjunction with the documents listed in
Related Documentation, page xvi. This preface contains the following sections:
• Audience, page xiii
• Comply with Local and National Electrical Codes, page xiii
• Organization, page xv
• Conventions, page xv
• Related Documentation, page xvi
• Obtaining Documentation and Submitting a Service Request, page xvii
Audience
This guide is for experienced network security administrators who install and maintain Cisco IPS
sensors, including the supported IPS appliances and modules.
Comply with Local and National Electrical Codes
Warning
Installation of the equipment must comply with local and national electrical codes.
Statement 1074
Waarschuwing
Varoitus
OL-18504-01
Bij installatie van de apparatuur moet worden voldaan aan de lokale en nationale
elektriciteitsvoorschriften.
Laitteisto tulee asentaa paikallisten ja kansallisten sähkömääräysten mukaisesti.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
xiii
Page 14

Contents
Preface
Attention
Warnung
Avvertenza
Advarsel
Aviso
¡Advertencia!
Varning!
L'équipement doit être installé conformément aux normes électriques nationales et locales.
Die Installation der Geräte muss den Sicherheitsstandards entsprechen.
L'installazione dell'impianto deve essere conforme ai codici elettrici locali e nazionali.
Installasjon av utstyret må samsvare med lokale og nasjonale elektrisitetsforskrifter.
A instalação do equipamento tem de estar em conformidade com os códigos eléctricos locais e
nacionais.
La instalación del equipo debe cumplir con las normativas de electricidad locales y nacionales.
Installation av utrustningen måste ske i enlighet med gällande elinstallationsföreskrifter.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
xiv
OL-18504-01
Page 15

Preface
Organization
This guide includes the following sections:
Section Title Description
1 “Introducing the Sensor” Describes IPS appliances and modules.
2 “Installing the IPS 4240 and the
3 “Installing the IPS 4260” Describes how to install the IPS 4260.
4 “Installing the IPS 4270-20” Describes how to install the IPS 4270-20.
5 “Installing the AIM IPS” Describes how to install the AIM IPS.
6 “Installing the AIP SSM” Describes how to install the AIP SSM.
7 “Installing the IDSM2” Describes how to install the IDSM2.
8 “Installing the NME IPS” Describes how to install the NME IPS
9 “Logging In to the Sensor” Describes how to log in to the various sensors.
10 “Initializing the Sensor” Describes how to use the setup command to
11 “Obtaining Software” Describes where to go to get the latest IPS
12 “Upgrading, Downgrading, and
A “Troubleshooting” Contains troubleshooting tips for IPS hardware
Describes how to install the IPS 4240 and the
IPS 4255”
Installing System Images”
“Glossary” Contains IPS acronyms and terms.
IPS 4255.
initialize sensors.
software and describes the naming conventions.
Describes how to upgrade sensors and reimage the
various sensors.
and software.
Contents
Conventions
This document uses the following conventions:
Convention Indication
bold font Commands and keywords and user-entered text appear in bold font.
italic font Document titles, new or emphasized terms, and arguments for which you supply
[ ] Elements in square brackets are optional.
OL-18504-01
values are in italic font.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
xv
Page 16

Contents
Preface
{x | y | z } Required alternative keywords are grouped in braces and separated by
vertical bars.
[ x | y | z ] Optional alternative keywords are grouped in brackets and separated by
vertical bars.
string A nonquoted set of characters. Do not use quotation marks around the string or
the string will include the quotation marks.
courier font Terminal sessions and information the system displays appear in courier font.
< > Nonprinting characters such as passwords are in angle brackets.
[ ] Default responses to system prompts are in square brackets.
!, # An exclamation point (!) or a pound sign (#) at the beginning of a line of code
indicates a comment line.
Note Means reader take note.
Tip Means the following information will help you solve a problem.
Caution Means reader be careful. In this situation, you might perform an action that could result in equipment
damage or loss of data.
Timesaver Means the described action saves time. You can save time by performing the action described in
the paragraph.
Warning
Means reader be warned. In this situation, you might perform an action that could result in
bodily injury.
Related Documentation
For more information on Cisco IPS, refer to the following documentation found at this URL:
http://www.cisco.com/en/US/products/hw/vpndevc/ps4077/tsd_products_support_series_home.html
• Documentation Roadmap for Cisco Intrusion Prevention System
• Release Notes for Cisco Intrusion Prevention System
• Installing and Using Cisco Intrusion Prevention System Device Manager
• Installing and Using Cisco Intrusion Prevention System Manager Express
• Cisco Intrusion Prevention System Command Reference
• Configuring the Cisco Intrusion Prevention System Sensor Using the Command Line Interface
• Installling and Removing Interface Cards in Cisco IPS-4260 and IPS 4270-20
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
xvi
OL-18504-01
Page 17

Preface
Contents
• Regulatory Compliance and Safety Information for the Cisco Intrusion Prevention System 4200
Series Appliance Sensor
Obtaining Documentation and Submitting a Service Request
For information on obtaining documentation, submitting a service request, and gathering additional
information, see the monthly What’s New in Cisco Product Documentation, which also lists all new and
revised Cisco technical documentation, at:
http://www.cisco.com/en/US/docs/general/whatsnew/whatsnew.html
Subscribe to the What’s New in Cisco Product Documentation as a Really Simple Syndication (RSS) feed
and set content to be delivered directly to your desktop using a reader application. The RSS feeds are a free
service and Cisco currently supports RSS Version 2.0.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
xvii
Page 18

Contents
Preface
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
xviii
OL-18504-01
Page 19

CHA P TER
1
Introducing the Sensor
This chapter introduces the sensor and provides information you should know before you install the
sensor. In this guide, the term sensor refers to all models unless noted otherwise. For a complete list of
supported sensors and their model numbers, see Supported Sensors, page 1-17. This chapter contains the
following sections:
• How the Sensor Functions, page 1-1
• Supported Sensors, page 1-17
• IPS Appliances, page 1-18
• IPS Modules, page 1-20
• Time Sources and the Sensor, page 1-26
• Installation Preparation, page 1-29
• Site and Safety Guidelines, page 1-30
• Cable Pinouts, page 1-33
How the Sensor Functions
This section describes how the sensor functions, and contains the following topics:
• Capturing Network Traffic, page 1-1
• Your Network Topology, page 1-3
• Correctly Deploying the Sensor, page 1-3
• Tuning the IPS, page 1-3
• Sensor Interfaces, page 1-4
• Interface Modes, page 1-12
Capturing Network Traffic
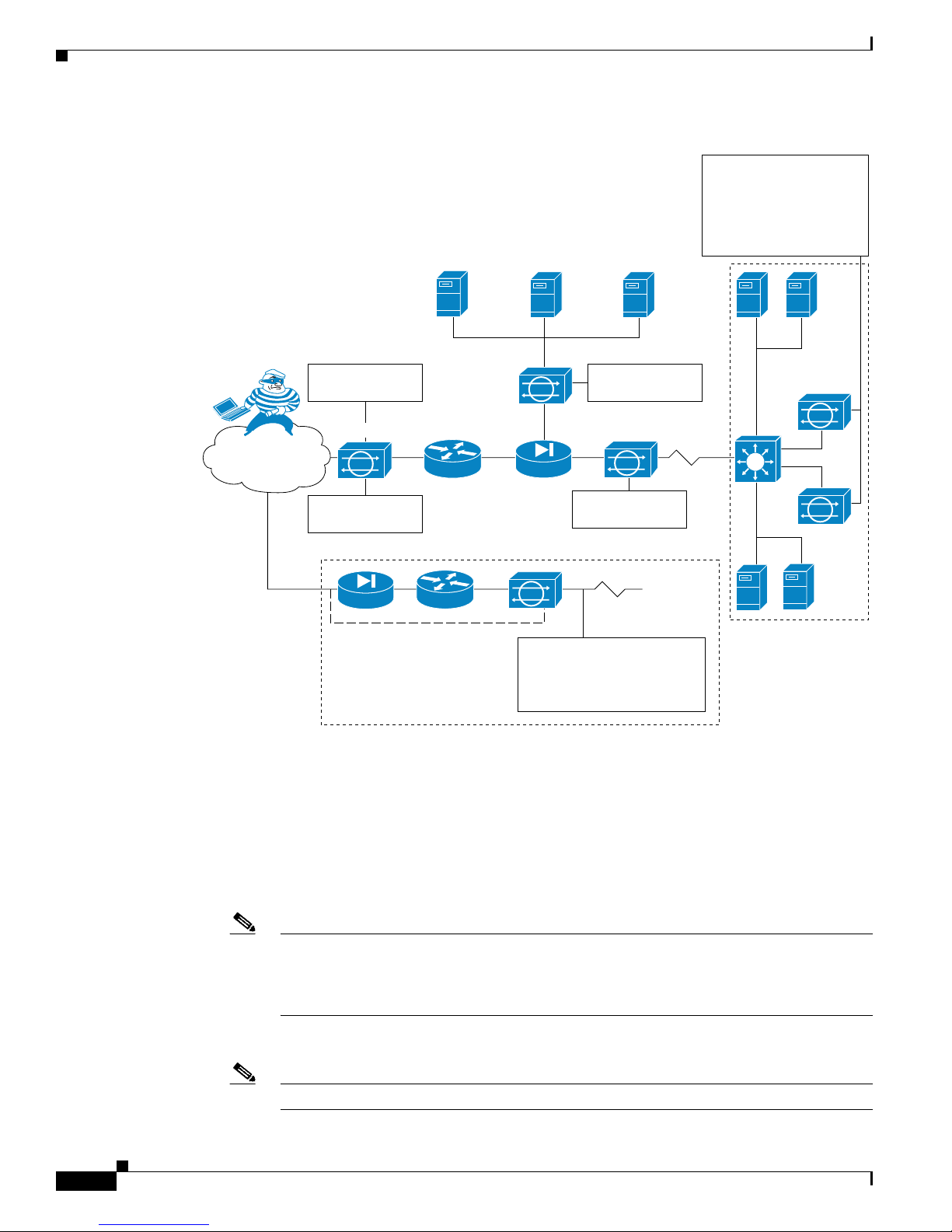
The sensor can operate in either promiscuous or inline mode. Figure 1-1 on page 1-2 shows how you can
deploy a combination of sensors operating in both inline (IPS) and promiscuous (IDS) modes to protect
your network.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
OL-18504-01
1-1
Page 20
How the Sensor Functions
Sensor deployed
in IDS mode
Public services segment
Campus core
Attacker
Internet
Sensor deployed
in IPS mode
Sensor deployed
in IPS mode
Sensor deployed
in IPS mode
Sensor deployed in hybrid
mode to deliver IDS services
outside router and IPS
services inside the firewall
Service provider,
partner, or branch
office network
Multiple IPS sensors
deliver a highly scalable,
load-balanced solution
via Cisco Etherchannel
technology on Cisco
Catalyst Switches
148416
Main campus
Figure 1-1 Comprehensive Deployment Solutions
Chapter 1 Introducing the Sensor
The command and control interface is always Ethernet. This interface has an assigned IP address, which
allows it to communicate with the manager workstation or network devices (Cisco switches, routers, and
firewalls). Because this interface is visible on the network, you should use encryption to maintain data
privacy. SSH is used to protect the CLI and TLS/SSL is used to protect the manager workstation. SSH
and TLS/SSL are enabled by default on the manager workstations.
When responding to attacks, the sensor can do the following:
• Insert TCP resets via the sensing interface.
Note You should select the TCP reset action only on signatures associated with a TCP-based
service. If selected as an action on non-TCP-based services, no action is taken. Additionally,
TCP resets are not guaranteed to tear down an offending session because of limitations in
the TCP protocol.
• Make ACL changes on switches, routers, and firewalls that the sensor manages.
Note ACLs may block only future traffic, not current traffic.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-2
OL-18504-01
Page 21

Chapter 1 Introducing the Sensor
• Generate IP session logs, session replay, and trigger packets display.
IP session logs are used to gather information about unauthorized use. IP log files are written when
events occur that you have configured the appliance to look for.
• Implement multiple packet drop actions to stop worms and viruses.
Your Network Topology
Before you deploy and configure your sensors, you should understand the following about your network:
• The size and complexity of your network.
• Connections between your network and other networks (and the Internet).
• The amount and type of network traffic on your network.
This knowledge will help you determine how many sensors are required, the hardware configuration for
each sensor (for example, the size and type of network interface cards), and how many managers are
needed.
How the Sensor Functions
Correctly Deploying the Sensor
You should always position the IPS sensor behind a perimeter-filtering device, such as a firewall or
adaptive security appliance. The perimeter device filters traffic to match your security policy thus
allowing acceptable traffic in to your network. Correct placement significantly reduces the number of
alerts, which increases the amount of actionable data you can use to investigate security violations. If
you position the IPS sensor on the edge of your network in front of a firewall, your sensor will produce
alerts on every single scan and attempted attack even if they have no significance to your network
implementation. You will receive hundreds, thousands, or even millions of alerts (in a large enterprise
environment) that are not really critical or actionable in your environment. Analyzing this type of data
is time consuming and costly.
Tuning the IPS
Tuning the IPS ensures that the alerts you see reflect true actionable information. Without tuning the IPS,
it is difficult to do security research or forensics on your network because you will have thousands of
benign events, also known as false positives. False positives are a by-product of all IPS devices, but they
occur much less frequently in Cisco IPS devices since Cisco IPS devices are stateful, normalized, and
use vulnerability signatures for attack evaluation. Cisco IPS devices also provide risk rating, which
identifies high risk events, and policy-based management, which lets you deploy rules to enforce IPS
signature actions based on risk rating.
Follow these tips when tuning your IPS sensors:
• Place your sensor on your network behind a perimeter-filtering device.
Proper sensor placement can reduce the number of alerts you need to examine by several thousands
a day.
• Deploy the sensor with the default signatures in place.
The default signature set provides you with a very high security protection posture. The Cisco
signature team has spent many hours on testing the defaults to give your sensor the highest
protection. If you think that you have lost these defaults, you can restore them.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-3
Page 22

How the Sensor Functions
Chapter 1 Introducing the Sensor
• Make sure that the event action override is set to drop packets with a risk rating greater than 90.
This is the default and ensures that high risk alerts are stopped immediately.
• Filter out known false positives caused by specialized software, such as vulnerability scanner and
load balancers by one of the following methods:
–
You can configure the sensor to ignore the alerts from the IP addresses of the scanner and load
balancer.
–
You can configure the sensor to allow these alerts and then use IME to filter out the false
positives.
• Filter the Informational alerts.
These low priority events notifications could indicate that another device is doing reconnaissance
on a device protected by the IPS. Research the source IP addresses from these Informational alerts
to determine what the source is.
• Analyze the remaining actionable alerts:
–
Research the alert.
–
Fix the attack source.
–
Fix the destination host.
For More Information
• For a detailed description of risk rating, refer to Calculating the Risk Rating.
• For information on Cisco signatures, for IDM and IME refer to Defining Signatures, and for the CLI
• For detailed information on event action overrides, for IDM and IME refer to Configuring Event
• For information on using Cisco IME, refer to Installing and Using Cisco Intrusion Prevention
Sensor Interfaces
This section describes the sensor interfaces, and contains the following topics:
• Understanding Sensor Interfaces, page 1-4
• Command and Control Interface, page 1-5
• Sensing Interfaces, page 1-6
• Interface Support, page 1-6
• TCP Reset Interfaces, page 1-9
• Interface Restrictions, page 1-10
–
Modify the IPS policy to provide more information.
refer to Defining Signatures.
Action Overrides, and for the CLI, refer to Configuring Event Action Overrides.
System Manager Express 7.0.
Understanding Sensor Interfaces
The sensor interfaces are named according to the maximum speed and physical location of the interface.
The physical location consists of a port number and a slot number. All interfaces that are built-in on the
sensor motherboard are in slot 0, and the PCI expansion slots are numbered beginning with slot 1 for the
bottom slot with the slot numbers increasing from bottom to top (except for the IPS 4270-20, where the
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-4
OL-18504-01
Page 23

Chapter 1 Introducing the Sensor
ports are numbered from top to bottom). Interfaces with a given slot are numbered beginning with port
0 for the right port with the port numbers increasing from right to left. For example, GigabitEthernet2/1
supports a maximum speed of 1 Gigabit and is the second-from-the-right interface in the
second-from-the bottom PCI expansion slot. The IPS 4240, IPS 4255, IPS 4260, and IPS 4270-20 are
exceptions to this rule. The command and control interface on these sensors is called Management0/0
rather than GigabitEthernet0/0. The IPS 4270-20 has an additional interface called Management0/1,
which is reserved for future use.
There are three interface roles:
• Command and control
• Sensing
• Alternate TCP reset
There are restrictions on which roles you can assign to specific interfaces and some interfaces have
multiple roles. You can configure any sensing interface to any other sensing interface as its TCP reset
interface. The TCP reset interface can also serve as an IDS (promiscuous) sensing interface at the same
time. The following restrictions apply:
• Because the AIM IPS, AIP SSM, and NME IPS only have one sensing interface, you cannot
configure a TCP reset interface.
• Because of hardware limitations on the Catalyst switch, both of the IDSM2 sensing interfaces are
permanently configured to use System0/1 as the TCP reset interface.
How the Sensor Functions
• The TCP reset interface that is assigned to a sensing interface has no effect in inline interface or
inline VLAN pair mode, because TCP resets are always sent on the sensing interfaces in those
modes.
Note Each physical interface can be divided into VLAN group subinterfaces, each of which
consists of a group of VLANs on that interface.
Command and Control Interface
The command and control interface has an IP address and is used for configuring the sensor. It receives
security and status events from the sensor and queries the sensor for statistics.
The command and control interface is permanently enabled. It is permanently mapped to a specific
physical interface, which depends on the specific model of sensor. You cannot use the command and
control interface as either a sensing or alternate TCP reset interface.
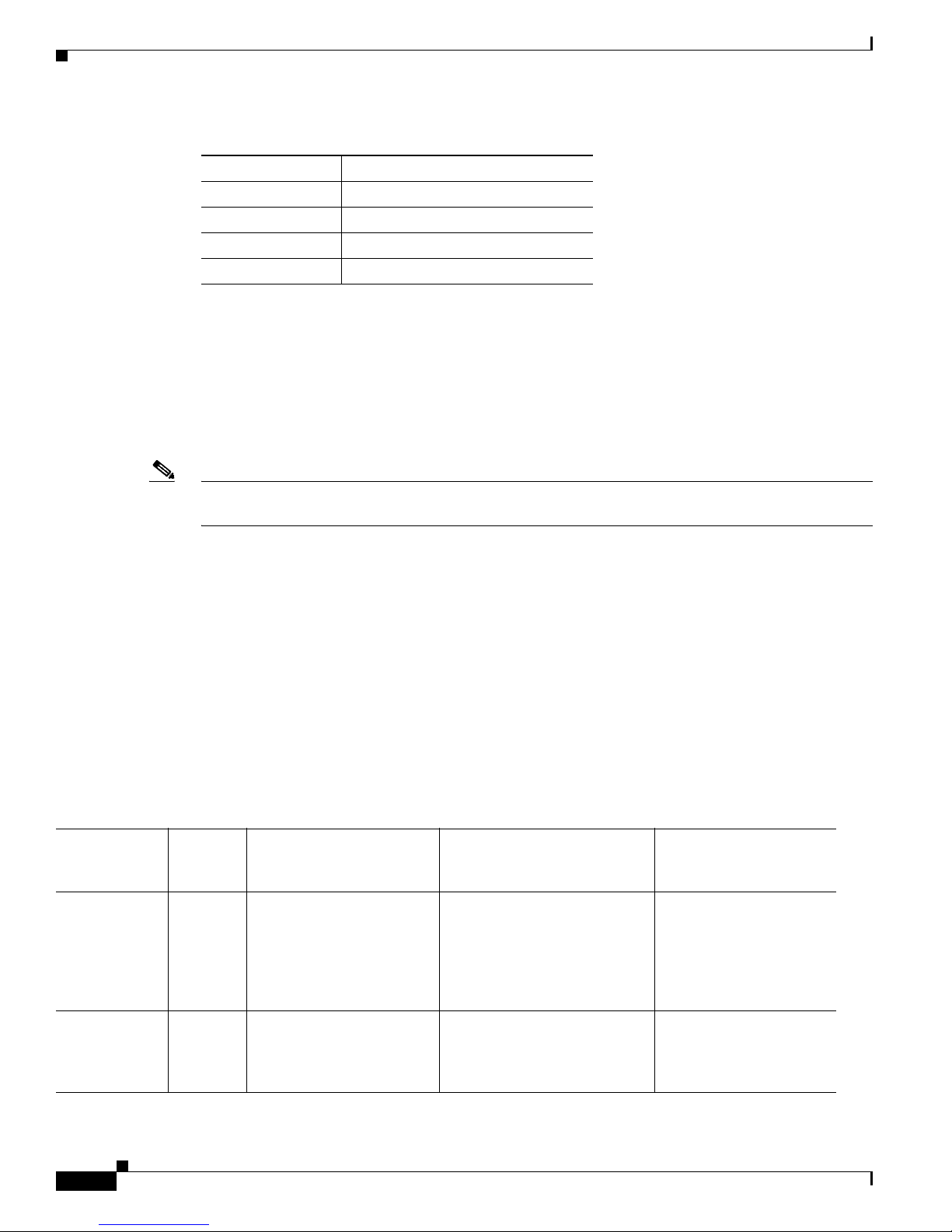
Table 1 -1 lists the command and control interfaces for each sensor.
Table 1-1 Command and Control Interfaces
Sensor Command and Control Interface
AIM IPS Management0/0
AIP SSM-10 GigabitEthernet0/0
AIP SSM-20 GigabitEthernet0/0
AIP SSM-40 GigabitEthernet0/0
IDSM2 GigabitEthernet0/2
IPS 4240 Management0/0
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-5
Page 24
How the Sensor Functions
Sensing Interfaces
Chapter 1 Introducing the Sensor
Table 1-1 Command and Control Interfaces (continued)
Sensor Command and Control Interface
IPS 4255 Management0/0
IPS 4260 Management0/0
IPS 4270-20 Management0/0
NME IPS Management0/01
Sensing interfaces are used by the sensor to analyze traffic for security violations. A sensor has one or
more sensing interfaces depending on the sensor. Sensing interfaces can operate individually in
promiscuous mode or you can pair them to create inline interfaces.
Note On appliances, all sensing interfaces are disabled by default. You must enable them to use them. On
modules, the sensing interfaces are permanently enabled.
Some appliances support optional interface cards that add sensing interfaces to the sensor. You must
insert or remove these optional cards while the sensor is powered off. The sensor detects the addition or
removal of a supported interface card. If you remove an optional interface card, some of the interface
configuration is deleted, such as the speed, duplex, description string, enabled/disabled state of the
interface, and any inline interface pairings. These settings are restored to their default settings when the
card is reinstalled. However, the assignment of promiscuous and inline interfaces to the Analysis Engine
is not deleted from the Analysis Engine configuration, but is ignored until those cards are reinserted and
you create the inline interface pairs again.
Interface Support
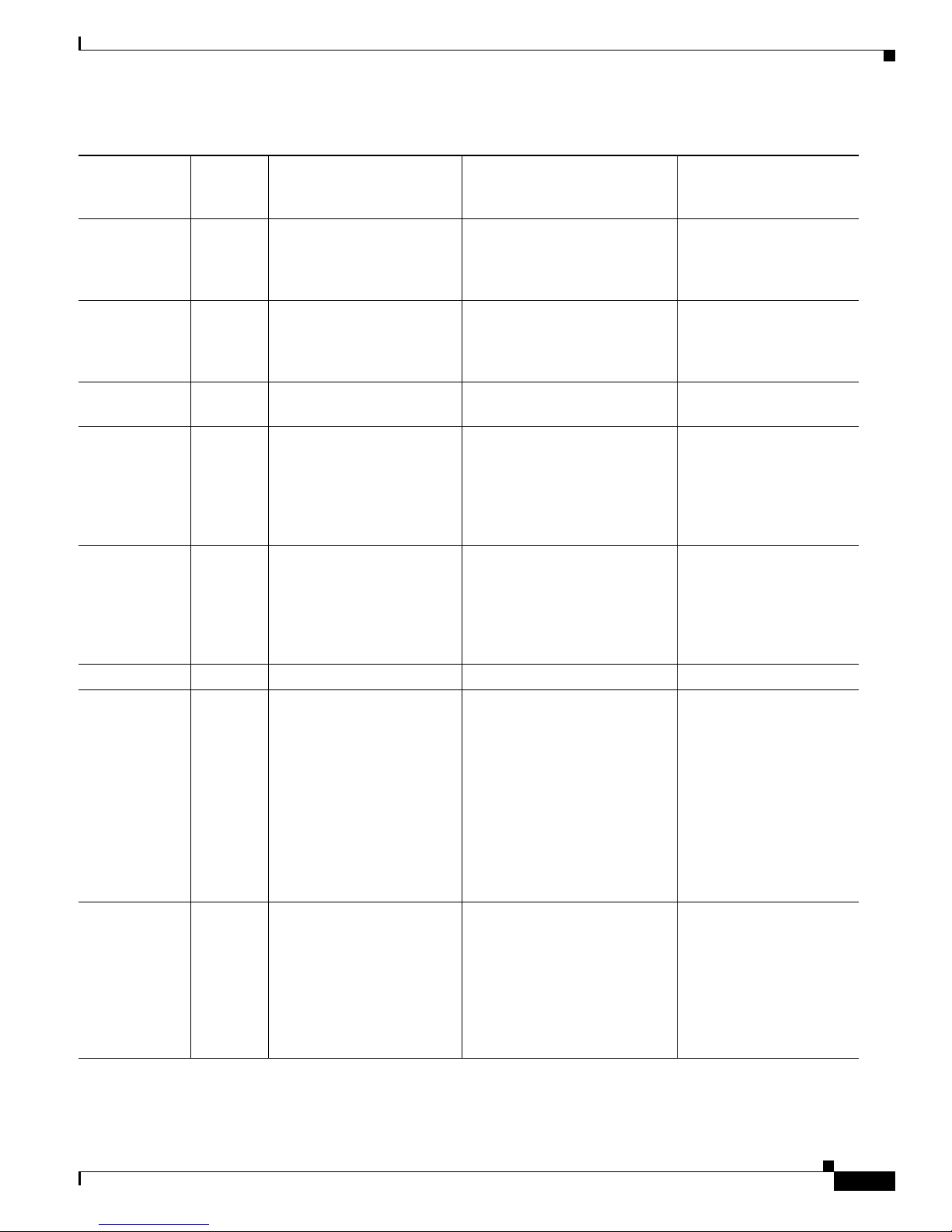
Table 1 -2 describes the interface support for appliances and modules running Cisco IPS.
Table 1-2 Interface Support
Added
Interface
Base Chassis
Cards
AIM IPS — GigabitEthernet0/1 by
AIP SSM-10 — GigabitEthernet0/1 by
Interfaces Supporting
Inline VLAN Pairs (Sensing
Ports)
ids-service-module
command in the router
configuration instead of
VLAN pair or inline
interface pair
security context instead of
VLAN pair or inline
interface pair
Combinations Supporting Inline
Interface Pairs
GigabitEthernet0/1 by
ids-service-module command
in the router configuration
instead of VLAN pair or inline
interface pair
GigabitEthernet0/1 by security
context instead of VLAN pair
or inline interface pair
Interfaces Not Supporting
Inline (Command and
Control Port)
Management0/0
GigabitEthernet0/0
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-6
OL-18504-01
Page 25
Chapter 1 Introducing the Sensor
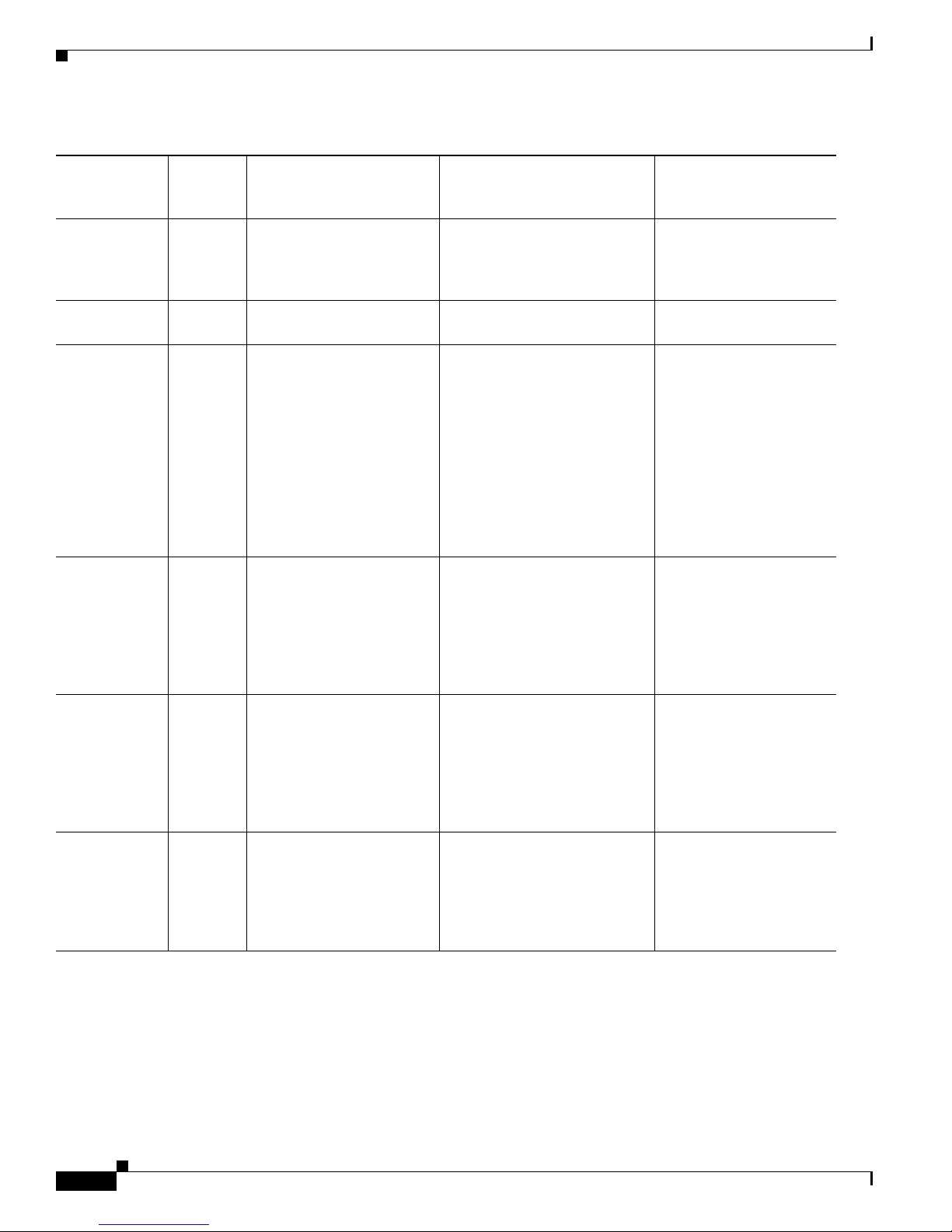
Table 1-2 Interface Support (continued)
How the Sensor Functions
Added
Interface
Base Chassis
Cards
AIP SSM-20 — GigabitEthernet0/1 by
Interfaces Supporting
Inline VLAN Pairs (Sensing
Ports)
security context instead of
VLAN pair or inline
Combinations Supporting Inline
Interface Pairs
GigabitEthernet0/1 by security
context instead of VLAN pair
or inline interface pair
Interfaces Not Supporting
Inline (Command and
Control Port)
GigabitEthernet0/0
interface pair
AIP SSM-40 — GigabitEthernet0/1 by
security context instead of
VLAN pair or inline
GigabitEthernet0/1 by security
context instead of VLAN pair
or inline interface pair
GigabitEthernet0/0
interface pair
IDSM2 — GigabitEthernet0/7
0/7<->0/8 GigabitEthernet0/2
GigabitEthernet0/8
IPS 4240 — GigabitEthernet0/0
GigabitEthernet0/1
GigabitEthernet0/2
GigabitEthernet0/3
0/0<->0/1
0/0<->0/2
0/0<->0/3
0/1<->0/2
Management0/0
0/1<->0/3
0/2<->0/3
IPS 4255 — GigabitEthernet0/0
GigabitEthernet0/1
GigabitEthernet0/2
GigabitEthernet0/3
0/0<->0/1
0/0<->0/2
0/0<->0/3
0/1<->0/2
Management0/0
0/1<->0/3
0/2<->0/3
IPS 4260 — GigabitEthernet0/1 N/A Management0/0
IPS 4260 4GE-BP
GigabitEthernet0/1
Management0/0
Slot 1
Slot 2
IPS 4260 2SX
Slot 1
Slot 2
OL-18504-01
GigabitEthernet2/0
GigabitEthernet2/1
GigabitEthernet2/2
GigabitEthernet2/3
GigabitEthernet3/0
GigabitEthernet3/1
GigabitEthernet3/2
GigabitEthernet3/3
GigabitEthernet0/1
GigabitEthernet2/0
GigabitEthernet2/1
GigabitEthernet3/0
GigabitEthernet3/1
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
2/0<->2/1
1
2/2<->2/3
3/0<->3/1
3/2<->3/3
All sensing ports can be paired
together
Management0/0
1-7
Page 26
How the Sensor Functions
Table 1-2 Interface Support (continued)
Chapter 1 Introducing the Sensor
Added
Interface
Base Chassis
Cards
IPS 4260 10GE
Slot 1
Interfaces Supporting
Inline VLAN Pairs (Sensing
Ports)
GigabitEthernet0/1
TenGigabitEthernet2/0
Combinations Supporting Inline
Interface Pairs
2/0<->2/1
2
Interfaces Not Supporting
Inline (Command and
Control Port)
Management0/0
TenGigabitEthernet2/1
IPS 4270-20 — — N/A Management0/0
Management0/1
IPS 4270-20 4GE-BP
Management0/0
Management0/1
Slot 1
GigabitEthernet3/0
GigabitEthernet3/1
3/0<->3/1
3/2<->3/3
4
GigabitEthernet3/2
GigabitEthernet3/3
Slot 2
GigabitEthernet4/0
GigabitEthernet4/1
4/0<->4/1
4/2<->4/3
GigabitEthernet4/2
GigabitEthernet4/3
IPS 4270-20 2SX
Slot 1
All sensing ports can be paired
together
GigabitEthernet3/0
Management0/0
Management0/1
GigabitEthernet3/1
3
5
6
Slot 2
GigabitEthernet4/0
GigabitEthernet4/1
IPS 4270-20 10GE
Slot 1
All sensing ports can be paired
together
TenGigabitEthernet5/0
Management0/0
Management0/1
TenGigabitEthernet5/1
Slot 2
TenGigabitEthernet7/0
TenGigabitEthernet7/1
NME IPS — GigabitEthernet0/1 by
ids-service-module
command in the router
configuration instead of
VLAN pair or inline
GigabitEthernet0/1 by
ids-service-module command
in the router configuration
instead of VLAN pair or inline
interface pair
Management0/1
interface pair
1. To disable hardware bypass, pair the interfaces in any other combination (2/0<->2/2 and 2/1<->2/3, for example).
2. To disable hardware bypass, pair the interfaces in any other combination (2/0<->2/2 and 2/1<->2/3, for example).
3. Reserved for future use.
4. To disable hardware bypass, pair the interfaces in any other combination (2/0<->2/2 and 2/1<->2/3, for example).
5. Reserved for future use.
6. Reserved for future use.
7. Reserved for future use.
7
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-8
OL-18504-01
Page 27
Chapter 1 Introducing the Sensor
Note The IPS 4260 supports a mixture of 4GE-BP, 2SX, and 10GE cards. The IPS 4270-20 also supports a
mixture of 4GE-BP, 2SX, and 10GE cards up to a total of either six cards, or sixteen total ports, which
ever is reached first, but is limited to only two 10GE card in the mix of cards.
TCP Reset Interfaces
This section explains the TCP reset interfaces and when to use them. It contains the following topics:
• Understanding Alternate TCP Reset Interfaces, page 1-9
• Designating the Alternate TCP Reset Interface, page 1-10
Understanding Alternate TCP Reset Interfaces
Note The alternate TCP reset interface setting is ignored in inline interface or inline VLAN pair mode,
because resets are sent inline in these modes.
How the Sensor Functions
You can configure sensors to send TCP reset packets to try to reset a network connection between an
attacker host and its intended target host. In some installations when the interface is operating in
promiscuous mode, the sensor may not be able to send the TCP reset packets over the same sensing
interface on which the attack was detected. In such cases, you can associate the sensing interface with
an alternate TCP reset interface and any TCP resets that would otherwise be sent on the sensing interface
when it is operating in promiscuous mode are instead sent out on the associated alternate TCP reset
interface.
If a sensing interface is associated with an alternate TCP reset interface, that association applies when
the sensor is configured for promiscuous mode but is ignored when the sensing interface is configured
for inline mode.
With the exception of the IDSM2, any sensing interface can serve as the alternate TCP reset interface
for another sensing interface. The alternate TCP reset interface on the IDSM2 is fixed because of
hardware limitation.
Note There is only one sensing interface on IPS modules (AIM IPS, AIP SSM, and NME IPS).
Table 1 -3 lists the alternate TCP reset interfaces.
Table 1-3 Alternate TCP Reset Interfaces
Sensor Alternate TCP Reset Interface
AIM IPS None
AIP SSM-10 None
AIP SSM-20 None
AIP SSM-40 None
IDSM2 System0/1
1
IPS 4240 Any sensing interface
IPS 4255 Any sensing interface
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-9
Page 28

How the Sensor Functions
Table 1-3 Alternate TCP Reset Interfaces (continued)
Sensor Alternate TCP Reset Interface
IPS 4260 Any sensing interface
IPS 4270-20 Any sensing interface
NME IPS None
1. This is an internal interface on the Catalyst backplane.
Designating the Alternate TCP Reset Interface
You need to designate an alternate TCP reset interface in the following situations:
• When a switch is being monitored with either SPAN or VACL capture and the switch does not accept
incoming packets on the SPAN or VACL capture port.
• When a switch is being monitored with either SPAN or VACL capture for multiple VLANs, and the
switch does not accept incoming packets with 802.1q headers.
Chapter 1 Introducing the Sensor
• When a network tap is used for monitoring a connection.
Interface Restrictions
The following restrictions apply to configuring interfaces on the sensor:
• Physical Interfaces
Note The TCP resets need 802.1q headers to tell which VLAN the resets should be sent on.
Note Taps do not permit incoming traffic from the sensor.
You can only assign a sensing interface as an alternate TCP reset interface. You cannot configure
the management interface as an alternate TCP reset interface.
–
On modules (AIM IPS, AIP SSM, IDSM2, and NME IPS), all backplane interfaces have fixed
speed, duplex, and state settings. These settings are protected in the default configuration on all
backplane interfaces.
–
For nonbackplane FastEthernet interfaces the valid speed settings are 10 Mbps, 100 Mbps, and
auto. Valid duplex settings are full, half, and auto.
–
For Gigabit copper interfaces (1000-TX on the IPS 4240, IPS 4255, IPS 4260, and
IPS 4270-20), valid speed settings are 10 Mbps, 100 Mbps, 1000 Mbps, and auto. Valid duplex
settings are full, half, and auto.
–
For Gigabit (copper or fiber) interfaces, if the speed is configured for 1000 Mbps, the only valid
duplex setting is auto.
–
The command and control interface cannot also serve as a sensing interface.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-10
OL-18504-01
Page 29

Chapter 1 Introducing the Sensor
• Inline Interface Pairs
• Inline VLAN Pairs
How the Sensor Functions
–
Inline interface pairs can contain any combination of sensing interfaces regardless of the
physical interface type (copper versus fiber), speed, or duplex settings of the interface.
However, pairing interfaces of different media type, speeds, and duplex settings may not be
fully tested or supported.
–
The command and control interface cannot be a member of an inline interface pair.
–
You cannot pair a physical interface with itself in an inline interface pair.
–
A physical interface can be a member of only one inline interface pair.
–
You can only configure bypass mode and create inline interface pairs on sensor platforms that
support inline mode.
–
A physical interface cannot be a member of an inline interface pair unless the subinterface mode
of the physical interface is none.
–
You cannot pair a VLAN with itself.
–
You cannot use the default VLAN as one of the paired VLANs in an inline VLAN pair.
–
For a given sensing interface, a VLAN can be a member of only one inline VLAN pair.
However, a given VLAN can be a member of an inline VLAN pair on more than one sensing
interface.
–
The order in which you specify the VLANs in an inline VLAN pair is not significant.
–
A sensing interface in inline VLAN pair mode can have from 1 to 255 inline VLAN pairs.
• Alternate TCP Reset Interface
–
You can only assign the alternate TCP reset interface to a sensing interface. You cannot
configure the command and control interface as an alternate TCP reset interface. The alternate
TCP reset interface option is set to none as the default and is protected for all interfaces except
the sensing interfaces.
–
You can assign the same physical interface as an alternate TCP reset interface for multiple
sensing interfaces.
–
A physical interface can serve as both a sensing interface and an alternate TCP reset interface.
–
The command and control interface cannot serve as the alternate TCP reset interface for a
sensing interface.
–
A sensing interface cannot serve as its own alternate TCP reset interface.
–
You can only configure interfaces that are capable of TCP resets as alternate TCP reset
interfaces.
Note The exception to this restriction is the IDSM2. The alternate TCP reset interface
assignments for both sensing interfaces is System0/1 (protected).
• VLAN Groups
–
You can configure any single interface for promiscuous, inline interface pair, or inline VLAN
pair mode, but no combination of these modes is allowed.
–
You cannot add a VLAN to more than one group on each interface.
–
You cannot add a VLAN group to multiple virtual sensors.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-11
Page 30

How the Sensor Functions
Interface Modes
Chapter 1 Introducing the Sensor
–
An interface can have no more than 255 user-defined VLAN groups.
–
When you pair a physical interface, you cannot subdivide it; you can subdivide the pair.
–
You can use a VLAN on multiple interfaces; however, you receive a warning for this
configuration.
–
You can assign a virtual sensor to any combination of one or more physical interfaces and inline
VLAN pairs, subdivided or not.
–
You can subdivide both physical and logical interfaces into VLAN groups.
–
CLI, IDM, and IME prompt you to remove any dangling references. You can leave the dangling
references and continue editing the configuration.
–
CLI, IDM, and IME do not allow configuration changes in Analysis Engine that conflict with
the interface configuration.
–
CLI allows configuration changes in the interface configuration that cause conflicts in the
Analysis Engine configuration. IDM and IME do not allow changes in the interface
configuration that cause conflicts in the Analysis Engine configuration.
The following section describes the interface modes, and contains the following topics:
Promiscuous Mode
In promiscuous mode, packets do not flow through the sensor. The sensor analyzes a copy of the
monitored traffic rather than the actual forwarded packet. The advantage of operating in promiscuous
mode is that the sensor does not affect the packet flow with the forwarded traffic. The disadvantage of
operating in promiscuous mode, however, is the sensor cannot stop malicious traffic from reaching its
intended target for certain types of attacks, such as atomic attacks (single-packet attacks). The response
actions implemented by promiscuous sensor devices are post-event responses and often require
assistance from other networking devices, for example, routers and firewalls, to respond to an attack.
While such response actions can prevent some classes of attacks, in atomic attacks the single packet has
the chance of reaching the target system before the promiscuous-based sensor can apply an ACL
modification on a managed device (such as a firewall, switch, or router).
By default, all sensing interfaces are in promiscuous mode. To change an interface from inline interface
mode to promiscuous mode, delete any inline interface that contains that interface and delete any inline
VLAN pair subinterfaces of that interface from the interface configuration.
• Promiscuous Mode, page 1-12
• IPv6, Switches, and Lack of VACL Capture, page 1-13
• Inline Interface Pair Mode, page 1-14
• Inline VLAN Pair Mode, page 1-15
• VLAN Group Mode, page 1-15
• Deploying VLAN Groups, page 1-16
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-12
OL-18504-01
Page 31

Chapter 1 Introducing the Sensor
Router
Host
Sensor
Switch
Span port sending
copies of VLAN A traffic
253443
VLAN A
Figure 1-2 illustrates promiscuous mode.
Figure 1-2 Promiscuous Mode
For More Information
For a list of restrictions pertaining to IPS sensor interfaces, see Interface Restrictions, page 1-10.
How the Sensor Functions
IPv6, Switches, and Lack of VACL Capture
VACLs on Catalyst switches do not have IPv6 support. The most common method for copying traffic to
a sensor configured in promiscuous mode is to use VACL capture. If you want to have IPv6 support, you
can use SPAN ports.
However, you can only configure up to two monitor sessions on a switch unless you use the following
configuration:
• Monitor session
• Multiple trunks to one or more sensors
• Restrict per trunk port which VLANs are allowed to perform monitoring of many VLANs to more
than two different sensors or virtual sensors within one IPS
The following configuration uses one SPAN session to send all of the traffic on any of the specified
VLANs to all of the specified ports. Each port configuration only allows a particular VLAN or VLANs
to pass. Thus you can send data from different VLANs to different sensors or virtual sensors all with one
SPAN configuration line:
clear trunk 4/1-4 1-4094
set trunk 4/1 on dot1q 930
set trunk 4/2 on dot1q 932
set trunk 4/3 on dot1q 960
set trunk 4/4 on dot1q 962
set span 930, 932, 960, 962 4/1-4 both
Note The SPAN/Monitor configuration is valuable when you want to assign different IPS policies per VLAN
or when you have more bandwidth to monitor than one interface can handle.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-13
Page 32

How the Sensor Functions
Host
Sensor
Switch
Traffic passes
through interface pair
253444
Router
VLAN A
For More Information
• For more information on configuring SPAN/monitor on switches, refer to the following sections in
Catalyst 6500 Series Software Configuration Guide, 8.7:
–
Configuring SPAN, RSPAN and the Mini Protocol Analyzer
–
Configuring SPAN on the Switch
–
Configuring Ethernet VLAN Trunks
–
Defining the Allowed VLANs on a Trunk
• For more information on promiscuous mode, see Promiscuous Mode, page 1-12.
Inline Interface Pair Mode
Operating in inline interface pair mode puts the IPS directly into the traffic flow and affects
packet-forwarding rates making them slower by adding latency. This allows the sensor to stop attacks by
dropping malicious traffic before it reaches the intended target, thus providing a protective service. Not
only is the inline device processing information on Layers 3 and 4, but it is also analyzing the contents
and payload of the packets for more sophisticated embedded attacks (Layers 3 to 7). This deeper analysis
lets the system identify and stop and/or block attacks that would normally pass through a traditional
firewall device.
In inline interface pair mode, a packet comes in through the first interface of the pair on the sensor and
out the second interface of the pair. The packet is sent to the second interface of the pair unless that
packet is being denied or modified by a signature.
Chapter 1 Introducing the Sensor
Note You can configure the AIM IPS, AIP SSM, and NME IPS to operate inline even though these modules
have only one sensing interface.
Note If the paired interfaces are connected to the same switch, you should configure them on the switch as
access ports with different access VLANs for the two ports. Otherwise, traffic does not flow through the
inline interface.
Figure 1-3 illustrates inline interface pair mode.
Figure 1-3 Inline Interface Pair Mode
For More Information
For a list of restrictions pertaining to IPS sensor interfaces, see Interface Restrictions, page 1-10.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-14
OL-18504-01
Page 33

Chapter 1 Introducing the Sensor
Inline VLAN Pair Mode
Note Inline VLAN pairs are not supported on the AIM IPS, AIP SSM, and NME IPS.
You can associate VLANs in pairs on a physical interface. This is known as inline VLAN pair mode.
Packets received on one of the paired VLANs are analyzed and then forwarded to the other VLAN in the
pair.
Inline VLAN pair mode is an active sensing mode where a sensing interface acts as an 802.1q trunk port,
and the sensor performs VLAN bridging between pairs of VLANs on the trunk. The sensor inspects the
traffic it receives on each VLAN in each pair, and can either forward the packets on the other VLAN in
the pair, or drop the packet if an intrusion attempt is detected. You can configure an IPS sensor to
simultaneously bridge up to 255 VLAN pairs on each sensing interface. The sensor replaces the
VLAN ID field in the 802.1q header of each received packet with the ID of the egress VLAN on which
the sensor forwards the packet. The sensor drops all packets received on any VLANs that are not
assigned to inline VLAN pairs.
Figure 1-4 illustrates inline VLAN pair mode.
How the Sensor Functions
VLAN Group Mode
Note You cannot divide physical interfaces that are in inline VLAN pairs into VLAN groups.
Figure 1-4 Inline VLAN Pair Mode
Switch
VLAN B
Router
For More Information
VLAN A
253445
Host
Trunk port carrying
VLAN A and B
Pairing VLAN A and B
Sensor
For a list of restrictions pertaining to IPS sensor interfaces, see Interface Restrictions, page 1-10
You can divide each physical interface or inline interface into VLAN group subinterfaces, each of which
consists of a group of VLANs on that interface. Analysis Engine supports multiple virtual sensors, each
of which can monitor one or more of these interfaces. This lets you apply multiple policies to the same
sensor. The advantage is that now you can use a sensor with only a few interfaces as if it had many
interfaces.
VLAN group subinterfaces associate a set of VLANs with a physical or inline interface. No VLAN can
be a member of more than one VLAN group subinterface. Each VLAN group subinterface is identified
by a number between 1 and 255.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-15
Page 34

How the Sensor Functions
Subinterface 0 is a reserved subinterface number used to represent the entire unvirtualized physical or
logical interface. You cannot create, delete, or modify subinterface 0 and no statistics are reported for it.
An unassigned VLAN group is maintained that contains all VLANs that are not specifically assigned to
another VLAN group. You cannot directly specify the VLANs that are in the unassigned group. When a
VLAN is added to or deleted from another VLAN group subinterface, the unassigned group is updated.
Packets in the native VLAN of an 802.1q trunk do not normally have 802.1q encapsulation headers to
identify the VLAN number to which the packets belong. A default VLAN variable is associated with
each physical interface and you should set this variable to the VLAN number of the native VLAN or to 0.
The value 0 indicates that the native VLAN is either unknown or you do not care if it is specified. If the
default VLAN setting is 0, the following occurs:
Note You can configure a port on a switch as either an access port or a trunk port. On an access port, all traffic
is in a single VLAN is called the access VLAN. On a trunk port, multiple VLANs can be carried over
the port, and each packet has a special header attached called the 802.1q header that contains the VLAN
ID. This header is commonly referred as the VLAN tag. However, a trunk port has a special VLAN called
the native VLAN. Packets in the native VLAN do not have the 802.1q headers attached. The IDSM2 can
read the 802.1q headers for all nonnative traffic to determine the VLAN ID for that packet. However, the
IDSM2 does not know which VLAN is configured as the native VLAN for the port in the switch
configuration, so it does not know what VLAN the native packets are in. Therefore, you must tell the
IDSM2 which VLAN is the native VLAN for that port. Then the IDSM2 treats any untagged packets as
if they were tagged with the native VLAN ID.
Chapter 1 Introducing the Sensor
• Any alerts triggered by packets without 802.1q encapsulation have a VLAN value of 0 reported in
the alert.
• Non-802.1q encapsulated traffic is associated with the unassigned VLAN group and it is not
possible to assign the native VLAN to any other VLAN group.
For More Information
For a list of restrictions pertaining to IPS sensor interfaces, see Interface Restrictions, page 1-10.
Deploying VLAN Groups
Because a VLAN group of an inline pair does not translate the VLAN ID, an inline paired interface must
exist between two switches to use VLAN groups on a logical interface. For an appliance, you can connect
the two pairs to the same switch, make them access ports, and then set the access VLANs for the two
ports differently. In this configuration, the sensor connects between two VLANs, because each of the
two ports is in access mode and carries only one VLAN. In this case the two ports must be in different
VLANs, and the sensor bridges the two VLANs, monitoring any traffic that flows between the two
VLANs. The IDSM2 also operates in this manner, because its two data ports are always connected to the
same switch.
You can also connect appliances between two switches. There are two variations. In the first variation,
the two ports are configured as access ports, so they carry a single VLAN. In this way, the sensor bridges
a single VLAN between the two switches.
In the second variation, the two ports are configured as trunk ports, so they can carry multiple VLANs.
In this configuration, the sensor bridges multiple VLANs between the two switches. Because multiple
VLANs are carried over the inline interface pair, the VLANs can be divided into groups and each group
can be assigned to a virtual sensor. The second variation does not apply to the IDSM2 because it cannot
be connected in this way.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-16
OL-18504-01
Page 35

Chapter 1 Introducing the Sensor
For More Information
For the procedures for configuring VLAN groups for the IDSM2, refer to Configuring the IDSM2.
Supported Sensors
Caution Installing the most recent software on unsupported sensors may yield unpredictable results. We do not
support software installed on unsupported platforms.
Table 1 -4 lists the sensors (IPS appliances and modules) that are supported by Cisco IPS 7.0.
Table 1-4 Supported Sensors
Model Name Part Number Optional Interfaces
Appliances
IPS 4240 IPS 4240-K9
IPS 4255 IPS 4255-K9 —
IPS 4260 IPS 4260-K9
IPS 4240-DC-K9
Supported Sensors
1
—
—
IPS-4GE-BP-INT=
IPS-2SX-INT=
IPS 4260-4GE-BP-K9
IPS 4260-2SX-K9
IPS 4270-20 IPS-4270-K9
—
—
IPS-4GE-BP-INT=
IPS-2SX-INT=
IPS-4270-4GE-BP-K9
IPS-4270-2SX-K9
—
—
Modules
AIM IPS AIM IPS-K9 —
AIP SSM-10 ASA-SSM-AIP-10-K9 —
AIP SSM-20 ASA-SSM-AIP-20-K9 —
AIP SSM-40 ASA-SSM-AIP-40-K9 —
IDSM2 WS-SVC-IDSM2-K9 —
NME IPS NM-IPS-K9 —
1. The IPS 4240-DC-K9 is a NEBS-compliant product.
The following NRS and IDS appliance models are legacy models and are not supported in this document:
• NRS-2E
• NRS-2E-DM
• NRS-2FE
• NRS-2FE-DM
• NRS-TR
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-17
Page 36

IPS Appliances
Chapter 1 Introducing the Sensor
• NRS-TR-DM
• NRS-SFDDI
• NRS-SFDDI-DM
• NRS-DFDDI
• NRS-DFDDI-DM
• IDS-4220-E
• IDS-4220-TR
• IDS-4230-FE
• IDS-4230-SFDDI
• IDS-4230-DFDDI
• IDS-4210
• IDS-4215
• IDS-4235
• IDS-4250
• NM-CIDS
Note The WS-X6381, the IDSM, is a legacy model and is not supported in this document.
For More Information
For instructions on how to obtain the most recent Cisco IPS software, see Obtaining Cisco IPS Software,
page 11-1.
IPS Appliances
This section describes the Cisco 4200 series appliance, and contains the following topics:
• Introducing the IPS Appliance, page 1-18
• Appliance Restrictions, page 1-19
• Connecting an Appliance to a Terminal Server, page 1-19
Introducing the IPS Appliance
The IPS appliance is a high-performance, plug-and-play device. The appliance is a component of the
IPS, a network-based, real-time intrusion prevention system. You can use the IPS CLI, IDM, IME,
ASDM, or CSM to configure the appliance.
You can configure the appliance to respond to recognized signatures as it captures and analyzes network
traffic. These responses include logging the event, forwarding the event to the manager, performing a
TCP reset, generating an IP log, capturing the alert trigger packet, and reconfiguring a router. The
appliance offer significant protection to your network by helping to detect, classify, and stop threats
including worms, spyware and adware, network viruses, and application abuse.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-18
OL-18504-01
Page 37

Chapter 1 Introducing the Sensor
After being installed at key points in the network, the appliance monitors and performs real-time analysis
of network traffic by looking for anomalies and misuse based on an extensive, embedded signature
library. When the system detects unauthorized activity, appliances can terminate the specific connection,
permanently block the attacking host, log the incident, and send an alert to the manager. Other legitimate
connections continue to operate independently without interruption.
Appliances are optimized for specific data rates and are packaged in Ethernet, Fast Ethernet, and Gigabit
Ethernet configurations. In switched environments, appliances must be connected to the SPAN port or
VACL capture port of the switch.
The Cisco IPS 4200 series appliances provide the following:
• Protection of multiple network subnets through the use of up to eight interfaces
• Simultaneous, dual operation in both promiscuous and inline modes
• A wide array of performance options—from 80 Mbps to multiple gigabits
• Embedded web-based management solutions packaged with the sensor
For More Information
• For a list of IPS documents and how to access them, refer to Documentation Roadmap for Cisco
Intrusion Prevention System 7.0.
IPS Appliances
• For a list of supported appliances, see Supported Sensors, page 1-17.
• For a description of each IPS appliance, see the following chapters in this document:
–
Chapter 2, “Installing the IPS 4240 and the IPS 4255”
–
Chapter 3, “Installing the IPS 4260”
–
Chapter 4, “Installing the IPS 4270-20”
Appliance Restrictions
The following restrictions apply to using and operating the appliance:
• The appliance is not a general purpose workstation.
• Cisco Systems prohibits using the appliance for anything other than operating Cisco IPS.
• Cisco Systems prohibits modifying or installing any hardware or software in the appliance that is
not part of the normal operation of the Cisco IPS.
Connecting an Appliance to a Terminal Server
A terminal server is a router with multiple, low speed, asynchronous ports that are connected to other
serial devices. You can use terminal servers to remotely manage network equipment, including
appliances.
To set up a Cisco terminal server with RJ-45 or hydra cable assembly connections, follow these steps:
Step 1 Connect to a terminal server using one of the following methods:
• For terminal servers with RJ-45 connections, connect a 180 rollover cable from the console port on
the appliance to a port on the terminal server.
• For hydra cable assemblies, connect a straight-through patch cable from the console port on the
appliance to a port on the terminal server.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-19
Page 38

IPS Modules
Caution Always exit your session and return to a login prompt before terminating the application used to establish
Chapter 1 Introducing the Sensor
Step 2 Configure the line and port on the terminal server. In enable mode, enter the following configuration,
where # is the line number of the port to be configured.
config t
line #
login
transport input all
stopbits 1
flowcontrol hardware
speed 9600
exit
exit
wr mem
Step 3 Be sure to properly close a terminal session to avoid unauthorized access to the appliance.
If a terminal session is not stopped properly, that is, if it does not receive an exit(0) signal from the
application that initiated the session, the terminal session can remain open. When terminal sessions are
not stopped properly, authentication is not performed on the next session that is opened on the serial port.
the connection.
Caution If a connection is dropped or terminated by accident, you should reestablish the connection and exit
normally to prevent unauthorized access to the appliance.
IPS Modules
This section describes the IPS modules, and contains the following topics:
• Introducing the AIM IPS, page 1-20
• Introducing the AIP SSM, page 1-22
• Introducing the IDSM2, page 1-24
• Introducing the NME IPS, page 1-25
Introducing the AIM IPS
Cisco Intrusion Prevention System Advanced Integration Module (AIM IPS) integrates and bring inline
Cisco IPS functionality to Cisco access routers. You can install the AIM IPS in Cisco 1841, 2800 series,
and 3800 series routers.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-20
OL-18504-01
Page 39

Chapter 1 Introducing the Sensor
Threat
Threat
Employees
192.168.1.x/24
Servers
192.168.14-16/24
IPSec tunnel
Internet
Corporate
office
Protect server
at branch
Cisco 3845 with
Cisco AIM-IPS
Threat
Wireless guests
192.168.2.x/24
Protect WAN Link
and upstream
corporate
resources
202382
Figure 1-5 demonstrates the integration of IPS and the branch office router.
Figure 1-5 AIM IPS and the Branch Router
IPS Modules
The AIM IPS has its own operating system, Cisco IPS software, startup, and run-time configurations.
You launch and configure the AIM IPS through the router by means of a configuration session on the
module. After the session, you return to the router CLI and clear the session.
The AIM IPS has a backplane interface, which means that all management traffic passes through the
router interface rather than a dedicated port on the module. The AIM IPS does not have an external
FastEthernet interface for handling management traffic. Management traffic includes all
communications between applications, such as IDM, IME, CSM, and CS-MARS, and the servers on the
module for exchange of IPS events, IP logs, configuration, and control messages.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-21
Page 40

IPS Modules
191866
Chapter 1 Introducing the Sensor
The AIM IPS plugs in to a connector on the motherboard of the router and requires no external interfaces
or connections. Figure 1-6 shows the AIM IPS.
Figure 1-6 AIM IPS
For More Information
• For a list of supported router and AIM IPS combinations, see Software and Hardware Requirements,
page 5-2.
• For information on installing the AIM IPS, see Installation and Removal Instructions, page 5-5.
• For more information about sessioning to the AIM IPS, see Logging In to the AIM IPS, page 9-4.
• For more information about configuring the AIM IPS, refer to Configuring the AIM IPS.
Introducing the AIP SSM
The Cisco ASA Advanced Inspection and Prevention Security Services Module (AIP SSM) is the IPS
plug-in module in the Cisco ASA 5500 series adaptive security appliance. The adaptive security
appliance software integrates firewall, VPN, and intrusion detection and prevention capabilities in a
single platform.
AIP SSM monitors and performs real-time analysis of network traffic by looking for anomalies and
misuse based on an extensive, embedded signature library. When AIP SSM detects unauthorized activity,
it can terminate the specific connection, permanently block the attacking host, log the incident, and send
an alert to the device manager.
There are three models of AIP SSM:
• ASA-SSM-AIP-10-K9
–
Supports 150 Mbps of IPS throughput when installed in ASA 5510
–
Supports 225 Mbps of IPS throughput when installed in ASA 5520
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-22
OL-18504-01
Page 41

Chapter 1 Introducing the Sensor
270535
LN
K
S
PD
0
CISCO ASA SSM- 40
ST
ATU
S
POW
ER
• ASA-SSM-AIP-20-K9
• ASA-SSM-AIP-40-K9
Figure 1-7 shows the AIP SSM-40.
Figure 1-7 AIP SSM-40
–
Supports 375 Mbps of IPS throughput when installed in ASA 5520
–
Supports 500 Mbps of IPS throughput when installed in ASA 5540
–
Supports 450 Mbps of IPS throughput on the ASA 5520
–
Supports 650 Mbps IPS throughput on ASA 5540
IPS Modules
OL-18504-01
The AIP SSM runs in either inline mode or promiscuous mode. The adaptive security appliance diverts
packets to the AIP SSM just before the packet exits the egress interface (or before VPN encryption
occurs, if configured) and after other firewall policies are applied. For example, packets that are blocked
by an access list are not forwarded to the AIP SSM.
In promiscuous mode, the IPS receives packets over the GigabitEthernet interface, examines them for
intrusive behavior, and generates alerts based on a positive result of the examination. In inline mode,
there is the additional step of sending all packets, which did not result in an intrusion, back out the
GigabitEthernet interface.
Figure 1-8 on page 1-24 shows the adaptive security appliance with the AIP SSM in a typical DMZ
configuration. A DMZ is a separate network located in the neutral zone between a private (inside)
network and a public (outside) network. The web server is on the DMZ interface, and HTTP clients from
both the inside and outside networks can access the web server securely.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-23
Page 42

IPS Modules
148403
Internet
HTTP client
10.10.10.10
Web server
10.30.30.30
DMZ
10.30.30.0
Inside
10.10.10.0
HTTP client
HTTP client
Outside
209.165.200.225
ASA security
appliance
Chapter 1 Introducing the Sensor
Figure 1-8 DMZ Configuration
In Figure 1-8 an HTTP client (10.10.10.10) on the inside network initiates HTTP communications with
the DMZ web server (30.30.30.30). HTTP access to the DMZ web server is provided for all clients on
the Internet; all other communications are denied. The network is configured to use an IP pool (a range
of IP addresses available to the DMZ interface) of addresses between 30.30.30.50 and 30.30.30.60.
For More Information
• For more information on setting up ASA, refer to the Getting Started Guides found at this URL:
http://www.cisco.com/en/US/products/ps6120/prod_installation_guides_list.html
• For more information on installing the AIP SSM, see Installing the AIP SSM, page 6-3.
• For more information on configuring the AIP SSM to receive IPS traffic, refer to Configuring the
AIP SSM.
Introducing the IDSM2
The Cisco Catalyst 6500 Series Intrusion Detection System Services Module (IDSM2) is a switching
module that performs intrusion prevention in the Catalyst 6500 series switch and 7600 series router. You
can use the CLI or IDSM to configure the IDSM2. You can configure the IDSM2 for promiscuous or
inline mode.
The IDSM2 performs network sensing—real-time monitoring of network packets through packet capture
and analysis. The IDSM2 captures network packets and then reassembles and compares the packet data
against attack signatures indicating typical intrusion activity. Network traffic is either copied to the
IDSM2 based on security VACLs in the switch or is copied to the IDSM2 through the SPAN port feature
of the switch. These methods route user-specified traffic to the IDSM2 based on switch ports, VLANs,
or traffic type to be inspected (Figure 1-9 on page 1-25).
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-24
OL-18504-01
Page 43

Chapter 1 Introducing the Sensor
Cisco 6500 switch
IDSM-2
Alarms and configuration through
IDSM-2 command and control port
IPS management console
Source traffic
Destination traffic
Source traffic
Destination traffic
Switch
backplane
Copied VACL traffic
or SPAN traffic to
IDSM-2 monitor port
Figure 1-9 IDSM2 Block Diagram
The IDSM2 searches for patterns of misuse by examining either the data portion and/or the header
portion of network packets. Content-based attacks contain potentially malicious data in the packet
payload, whereas, context-based attacks contain potentially malicious data in the packet headers.
IPS Modules
Introducing the NME IPS
You can configure the IDSM2 to generate an alert when it detects potential attacks. Additionally, you
can configure the IDSM2 to transmit TCP resets on the source VLAN, generate an IP log, and/or initiate
blocking countermeasures on a firewall or other managed device. Alerts are generated by the IDSM2
through the Catalyst 6500 series switch backplane to the IPS manager, where they are logged or
displayed on a graphical user interface.
For More Information
• For more information on installing the IDSM2, see Installing the IDSM2, page 7-5.
• For more information on configuring the IDSM2 to receive IPS traffic, refer to Configuring the
IDSM2.
Cisco Intrusion Prevention System Network Module (NME IPS) integrates and brings inline Cisco IPS
functionality to Cisco access routers. You can install the NME IPS in any one of the network module
slots in the 2800 and 3800 series router.
The NME IPS has its own operating system, Cisco IPS software, startup, and run-time configurations.
You launch and configure the modules through the router by means of a configuration session on the
modules. After the session, you return to the router CLI and clear the session.
For the NME IPS, all management traffic passes through the external FastEthernet interface on the
module. Management traffic includes all communications between applications, such as IDM, IME,
CSM, and CS-MARS, and the servers on the module for exchange of IPS events, IP logs, configuration,
and control messages.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-25
Page 44

Time Sources and the Sensor
191864
NM-CIPS
EN
LINK
DUPLEX
SYS
MODULE
The NME IPS installs in any slot in the 2800 and 3800 series access routers. Figure 1-10 shows the
NME IPS.
Figure 1-10 NME IPS
For More Information
• For a list of supported router and NME IPS combinations, see Software and Hardware
• For information on installing the NME IPS, see Installation and Removal Instructions, page 8-5.
Chapter 1 Introducing the Sensor
Requirements, page 8-2.
• For more information about sessioning to the NME IPS, see Logging In to the NME IPS, page 9-9.
• For more information on configuring the NME IPS, refer to Configuring the NME IPS.
Time Sources and the Sensor
This section explains the importance of having a reliable time source for the sensors and how to correct
the time if there is an error. It contains the following topics:
• The Sensor and Time Sources, page 1-26
• Synchronizing IPS Module System Clocks with the Parent Device System Clock, page 1-28
• Verifying the Sensor is Synchronized with the NTP Server, page 1-28
• Correcting the Time on the Sensor, page 1-29
The Sensor and Time Sources
The sensor requires a reliable time source. All events (alerts) must have the correct UTC and local time
stamp, otherwise, you cannot correctly analyze the logs after an attack. When you initialize the sensor,
you set up the time zones and summertime settings.
Note We recommend that you use an NTP server. You can use authenticated or unauthenticated NTP. For
authenticated NTP, you must obtain the NTP server IP address, NTP server key ID, and the key value
from the NTP server. You can set up NTP during initialization or you can configure NTP through the
CLI, IDM, IME, or ASDM.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-26
OL-18504-01
Page 45

Chapter 1 Introducing the Sensor
Here is a summary of ways to set the time on sensors:
• For appliances
• For the IDSM2
Time Sources and the Sensor
–
Use the clock set command to set the time. This is the default.
–
Use NTP—You can configure the appliance to get its time from an NTP time synchronization
source.
–
The IDSM2 can automatically synchronize its clock with the switch time. This is the default.
The UTC time is synchronized between the switch and the IDSM2. The time zone and
summertime settings are not synchronized between the switch and the IDSM2.
Note Be sure to set the time zone and summertime settings on both the switch and the IDSM2
to ensure that the UTC time settings are correct. The local time of the IDSM2 could be
incorrect if the time zone and/or summertime settings do not match between the IDSM2
and the switch.
–
Use NTP—You can configure the IDSM2 to get its time from an NTP time synchronization
source.
• For the AIM IPS and the NME IPS
–
The AIM IPS and the NME IPS can automatically synchronize their clock with the clock in the
router chassis in which they are installed (parent router). This is the default. The UTC time is
synchronized between the parent router and the AIM IPS and the NME IPS. The time zone and
summertime settings are not synchronized between the parent router and the AIM IPS and the
NME IPS.
Note Be sure to set the time zone and summertime settings on both the parent router and the
AIM IPS and the NME IPS to ensure that the UTC time settings are correct. The local
time of the AIM IPS and the NME IPS could be incorrect if the time zone and/or
summertime settings do not match between the AIM IPS and the NME IPS and the
router.
–
Use NTP—You can configure the AIM IPS and the NME IPS to get their time from an NTP time
synchronization source, such as a Cisco router, other than the parent router.
• For the AIP SSM
–
The AIP SSM can automatically synchronize its clock with the clock in the adaptive security
appliance in which it is installed. This is the default. The UTC time is synchronized between
the adaptive security appliance and the AIP SSM. The time zone and summertime settings are
not synchronized between the adaptive security appliance and the AIP SSM.
Note Be sure to set the time zone and summertime settings on both the adaptive security
–
Use NTP—You can configure the AIP SSM to get its time from an NTP time synchronization
source, such as a Cisco router other than the parent router.
OL-18504-01
appliance and the AIP SSM to ensure that the UTC time settings are correct. The local
time of the AIP SSM could be incorrect if the time zone and/or summertime settings do
not match between the AIP SSM and the adaptive security appliance.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-27
Page 46

Chapter 1 Introducing the Sensor
Time Sources and the Sensor
Synchronizing IPS Module System Clocks with the Parent Device System Clock
All IPS modules (AIM IPS, AIP SSM, IDSM2, and NME IPS) synchronize their system clocks to the
parent chassis clock (switch, router, or security appliance) each time the module boots up and any time
the parent chassis clock is set. The module clock and parent chassis clock tend to drift apart over time.
The difference can be as much as several seconds per day. To avoid this problem, make sure that both
the module clock and the parent clock are synchronized to an external NTP server. If only the module
clock or only the parent chassis clock is synchronized to an NTP server, the time drift occurs.
Verifying the Sensor is Synchronized with the NTP Server
In Cisco IPS, you cannot apply an incorrect NTP configuration, such as an invalid NTP key value or ID,
to the sensor. If you try to apply an incorrect configuration, you receive an error message. To verify the
NTP configuration, use the show statistics host command to gather sensor statistics. The NTP statistics
section provides NTP statistics including feedback on sensor synchronization with the NTP server.
To verify the NTP configuration, follow these steps:
Step 1 Log in to the sensor.
Step 2 Generate the host statistics:
sensor# show statistics host
...
NTP Statistics
remote refid st t when poll reach delay offset jitter
11.22.33.44 CHU_AUDIO(1) 8 u 36 64 1 0.536 0.069 0.001
LOCAL(0) 73.78.73.84 5 l 35 64 1 0.000 0.000 0.001
ind assID status conf reach auth condition last_event cnt
1 10372 f014 yes yes ok reject reachable 1
2 10373 9014 yes yes none reject reachable 1
status = Not Synchronized
...
Step 3 Generate the hosts statistics again after a few minutes:
sensor# show statistics host
...
NTP Statistics
remote refid st t when poll reach delay offset jitter
*11.22.33.44 CHU_AUDIO(1) 8 u 22 64 377 0.518 37.975 33.465
LOCAL(0) 73.78.73.84 5 l 22 64 377 0.000 0.000 0.001
ind assID status conf reach auth condition last_event cnt
1 10372 f624 yes yes ok sys.peer reachable 2
2 10373 9024 yes yes none reject reachable 2
status = Synchronized
Step 4 If the status continues to read Not Synchronized, check with the NTP server administrator to make sure
the NTP server is configured correctly.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-28
OL-18504-01
Page 47

Chapter 1 Introducing the Sensor
Correcting the Time on the Sensor
If you set the time incorrectly, your stored events will have the incorrect time because they are stamped
with the time the event was created.
The Event Store time stamp is always based on UTC time. If during the original sensor setup, you set
the time incorrectly by specifying 8:00 p.m. rather than 8:00 a.m., when you do correct the error, the
corrected time will be set backwards. New events might have times older than old events.
For example, if during the initial setup, you configure the sensor as central time with daylight saving
time enabled and the local time is 8:04 p.m., the time is displayed as 20:04:37 CDT and has an offset
from UTC of -5 hours (01:04:37 UTC, the next day). A week later at 9:00 a.m., you discover the error:
the clock shows 21:00:23 CDT. You then change the time to 9:00 a.m. and now the clock shows
09:01:33 CDT. Because the offset from UTC has not changed, it requires that the UTC time now be
14:01:33 UTC, which creates the time stamp problem.
To ensure the integrity of the time stamp on the event records, you must clear the event archive of the
older events by using the clear events command.
Note You cannot remove individual events.
Installation Preparation
For More Information
For the procedure for clearing events, refer to Clearing Events from Event Store.
Installation Preparation
To prepare for installing sensors, follow these steps:
Step 1 Review the safety precautions outlined in Regulatory Compliance and Safety Information for the Cisco
Intrusion Prevention System 4200 Series Appliance Sensor.
Step 2 To familiarize yourself with the IPS and related documentation and where to find it on Cisco.com, read
Documentation Roadmap for Cisco Intrusion Prevention System 7.0.
Step 3 Before proceeding with sensor installation, read the appropriate Release Notes.
Step 4 Unpack the sensor.
Step 5 Place the sensor in an ESD-controlled environment.
Step 6 Place the sensor on a stable work surface.
Step 7 In this book, Installing and Using Cisco Intrusion Prevention System Sensors and Modules 7.0, see the
chapter that pertains to your sensor model.
For More Information
• For ESD guidelines, see Electrical Safety Guidelines, page 1-31.
• For the procedure for working in an ESD environment, see Working in an ESD Environment, page
1-32.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-29
Page 48

Site and Safety Guidelines
Site and Safety Guidelines
This section describes site guidelines and safety precautions to take when working with electricity, with
power supplies, and in an ESD environment. It contains the following topics:
• Site Guidelines, page 1-30
• Rack Configuration Guidelines, page 1-30
• Electrical Safety Guidelines, page 1-31
• Power Supply Guidelines, page 1-32
• Working in an ESD Environment, page 1-32
Site Guidelines
Place the appliance on a desktop or mount it in a rack. The location of the appliance and the layout of
the equipment rack or wiring room are extremely important for proper system operation. Equipment
placed too close together, inadequate ventilation, and inaccessible panels can cause system malfunctions
and shutdowns, and can make appliance maintenance difficult.
Chapter 1 Introducing the Sensor
When planning the site layout and equipment locations, keep in mind the following precautions to help
avoid equipment failures and reduce the possibility of environmentally-caused shutdowns. If you are
experiencing shutdowns or unusually high errors with your existing equipment, these precautions may
help you isolate the cause of failures and prevent future problems.
• Electrical equipment generates heat. Ambient air temperature might not be adequate to cool
equipment to acceptable operating temperatures without adequate circulation. Make sure that the
room in which you operate your system has adequate air circulation.
• Always follow the ESD-prevention procedures to avoid damage to equipment. Damage from static
discharge can cause immediate or intermittent equipment failure.
• Make sure that the chassis top panel is secure. The chassis is designed to allow cooling air to flow
effectively within it. An open chassis allows air leaks, which can interrupt and redirect the flow of
cooling air from the internal components.
Rack Configuration Guidelines
Follow these guidelines to plan your equipment rack configuration:
• Enclosed racks must have adequate ventilation. Make sure the rack is not overly congested because
each chassis generates heat. An enclosed rack should have louvered sides and a fan to provide
cooling air.
• When mounting a chassis in an open rack, make sure the rack frame does not block the intake or
exhaust ports. If the chassis is installed on slides, check the position of the chassis when it is seated
all the way into the rack.
• In an enclosed rack with a ventilation fan in the top, excessive heat generated by equipment near the
bottom of the rack can be drawn upward and into the intake ports of the equipment above it in the
rack. Make sure you provide adequate ventilation for equipment at the bottom of the rack.
• Baffles can help to isolate exhaust air from intake air, which also helps to draw cooling air through
the chassis. The best placement of the baffles depends on the airflow patterns in the rack.
Experiment with different arrangements to position the baffles effectively.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-30
OL-18504-01
Page 49

Chapter 1 Introducing the Sensor
Electrical Safety Guidelines
Site and Safety Guidelines
Warning
Before working on a chassis or working near power supplies, unplug the power cord on AC units;
disconnect the power at the circuit breaker on DC units.
Follow these guidelines when working on equipment powered by electricity:
• Before beginning procedures that require access to the interior of the chassis, locate the emergency
power-off switch for the room in which you are working. Then, if an electrical accident occurs, you
can act quickly to turn off the power.
• Do not work alone if potentially hazardous conditions exist anywhere in your work space.
• Never assume that power is disconnected from a circuit; always check the circuit.
• Look carefully for possible hazards in your work area, such as moist floors, ungrounded power
extension cables, frayed power cords, and missing safety grounds.
• If an electrical accident occurs, proceed as follows:
–
Use caution; do not become a victim yourself.
–
Disconnect power from the system.
–
If possible, send another person to get medical aid. Otherwise, assess the condition of the victim
and then call for help.
–
Determine if the person needs rescue breathing or external cardiac compressions; then take
appropriate action.
• Use the chassis within its marked electrical ratings and product usage instructions.
• Install the sensor in compliance with local and national electrical codes as listed in Regulatory
Compliance and Safety Information for the Cisco Intrusion Prevention System 4200 Series
Appliance Sensor.
• The sensor models equipped with AC-input power supplies are shipped with a 3-wire electrical cord
with a grounding-type plug that fits only a grounding-type power outlet. This is a safety feature that
you should not circumvent. Equipment grounding should comply with local and national electrical
codes.
• The sensor models equipped with DC-input power supplies must be terminated with the DC input
wiring on a DC source capable of supplying at least 15 amps. A 15-amp circuit breaker is required
at the 48 VDC facility power source. An easily accessible disconnect device should be incorporated
into the facility wiring. Be sure to connect the grounding wire conduit to a solid earth ground. We
recommend that you use a Listed closed-loop ring to terminate the ground conductor at the ground
stud. The DC return connection to this system is to remain isolated from the system frame and
chassis.
Other DC power guidelines are listed in Regulatory Compliance and Safety Information for the
Cisco Intrusion Prevention System 4200 Series Appliance Sensor.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-31
Page 50

Site and Safety Guidelines
Power Supply Guidelines
Follow these guidelines for power supplies:
• Check the power at the site before installing the chassis to ensure that the power is free of spikes
and noise. Install a power conditioner if necessary, to ensure proper voltages and power levels in the
source voltage.
• Install proper grounding for the site to avoid damage from lightning and power surges.
• The following applies to a chassis equipped with an AC-input power supply:
–
The chassis does not have a user-selectable operating range. Refer to the label on the chassis for
the correct AC-input power requirement.
–
Several types of AC-input power supply cords are available; make sure you have the correct type
for your site.
–
Install a UPS for your site.
–
Install proper site-grounding facilities to guard against damage from lightning or power surges.
• The following applies to a chassis equipped with a DC-input power supply:
–
Each DC-input power supply requires dedicated 15-amp service.
Chapter 1 Introducing the Sensor
–
For DC power cables, we recommend a minimum of 14 AWG wire cable.
–
The DC return connection to this system is to remain isolated from the system frame and
chassis.
Working in an ESD Environment
Work on ESD-sensitive parts only at an approved static-safe station on a grounded static dissipative work
surface, for example, an ESD workbench or static dissipative mat.
To remove and replace components in a sensor, follow these steps:
Step 1 Remove all static-generating items from your work area.
Step 2 Use a static dissipative work surface and wrist strap.
Note Disposable wrist straps, typically those included with an upgrade part, are designed for one time
use.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-32
OL-18504-01
Page 51

Chapter 1 Introducing the Sensor
DO NOT INSTALL INTERFACE
CARDS WITH POWER APPLIED
CON
SOLE10/100 ETHERNET 0/0
L
ink
F
D
X
F
D
X
1
00
M
bp
s
L
ink
10
0
M
bp
s
F
AIL
O
V
E
R
10/100 ETHERNET 0/0
PIX-515
148409
Copper foil
Step 3 Attach the wrist strap to your wrist and to the terminal on the work surface. If you are using a disposable
wrist strap, connect the wrist strap directly to an unpainted metal surface of the chassis.
Cable Pinouts
Step 4 Connect the work surface to the chassis using a grounding cable and alligator clip.
Caution Always follow ESD-prevention procedures when removing, replacing, or repairing components.
Note If you are upgrading a component, do not remove the component from the ESD packaging until
Cable Pinouts
This section describes pinout information for 10/100/1000BaseT, console, and RJ 45 to DB 9 ports, and the
MGMT 10/100 Ethernet port. It contains the following topics:
• 10/100BaseT and 10/100/1000BaseT Connectors, page 1-34
• Console Port (RJ-45), page 1-35
• RJ-45 to DB-9 or DB-25, page 1-36
you are ready to install it.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-33
Page 52

Cable Pinouts
148407
231 45678Pin Label
1
2
3
4
5
6
7
8
TD+
TD-
RD+
NC
NC
RD-
NC
NC
231 45678Pin Label
1
2
3
4
5
6
7
8
TP0+
TP0-
TP1+
TP2+
TP2-
TP1-
TP3+
TP3-
10/100BaseT and 10/100/1000BaseT Connectors
Sensors support 10/100/1000BaseT ports. You must use at least a Category 5 cable for
100/1000Base-TX operations. You can use a Category 3 cable for 10Base-TX operations.
Note Some sensors support 10/100BaseT (IDS-4210, IDS-4215, and the optional 4FE card) while others
support 10/100/1000BaseT (IDS-4235, IDS-4250-TX, IPS 4240, and IPS 4255). This only applies to the
copper appliances. The fiber appliances support 1000Base-SX only.
The 10/100/1000BaseT ports use standard RJ-45 connectors and support MDI and MDI-X connectors.
Ethernet ports normally use MDI connectors and Ethernet ports on a hub normally use MDI-X connectors.
An Ethernet straight-through cable is used to connect an MDI to an MDI-X port. A cross-over cable is used
to connect an MDI to an MDI port, or an MDI-X to an MDI-X port.
Figure 1-11 shows the 10/100BaseT (RJ-45) port pinouts.
Figure 1-11 10/100 Port Pinouts
Chapter 1 Introducing the Sensor
Figure 1-12 shows the 10/100/1000BaseT (RJ-45) port pinouts.
Figure 1-12 10/100/1000 Port Pinouts
1-34
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
OL-18504-01
Page 53

Chapter 1 Introducing the Sensor
148418
8 7 6 5 4 3 2 1
RJ-45 connector
148419
Console Port (RJ-45)
Cisco products use the following types of RJ-45 cables:
• Straight-through
• Cross-over
• Rolled (console)
Note Cisco does not provide these cables; however, they are widely available from other sources.
Figure 1-13 shows the RJ 45 cable.
Figure 1-13 RJ-45 Cable
Cable Pinouts
To identify the RJ-45 cable type, hold the two ends of the cable next to each other so that you can see
the colored wires inside the ends, as shown in Figure 1-14.
Figure 1-14 RJ-45 Cable Identification
Examine the sequence of colored wires to determine the type of RJ-45 cable, as follows:
• Straight-through—The colored wires are in the same sequence at both ends of the cable.
• Cross-over—The first (far left) colored wire at one end of the cable is the third colored wire at the
other end of the cable.
• Rolled—The colored wires are in the opposite sequence at either end of the cable.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-35
Page 54

Cable Pinouts
RJ-45 to DB-9 or DB-25
Table 1 -5 lists the cable pinouts for RJ-45 to DB-9 or DB-25.
Table 1-5 Cable Pinouts for RJ-45 to DB-9 or DB-25
Signal RJ-45 Pin DB-9 /DB-25 Pin
RTS 8 8
DTR 7 6
TxD 6 2
GND 5 5
GND 4 5
RxD 3 3
DSR 2 4
CTS 1 7
Chapter 1 Introducing the Sensor
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
1-36
OL-18504-01
Page 55

Installing the IPS 4240 and the IPS 4255
Note All IPS platforms allow ten concurrent CLI sessions.
This chapter describes the IPS 4240 and the IPS 4255 and how to install them. It also describes the
accessories and how to install them. This chapter contains the following sections:
• Introducing the IPS 4240 and the IPS 4255, page 2-1
• Front and Back Panel Features, page 2-2
• Specifications, page 2-4
• Connecting the IPS 4240 to a Cisco 7200 Series Router, page 2-5
• Accessories, page 2-5
• Important Safety Instructions, page 2-5
• Rack Mounting, page 2-6
CHAP T ER
2
• Installing the IPS 4240 and the IPS 4255, page 2-7
• Installing the IPS 4240-DC, page 2-10
Introducing the IPS 4240 and the IPS 4255
The IPS 4240 and the IPS 4255 deliver high port density in a small form factor. They use a compact flash
device for storage rather than the hard-disk drives used in other sensor models. The IPS 4240 and the
IPS 4255 do not support redundant power supplies.
The IPS 4240 replaces the IDS-4235. There are four 10/100/1000 copper sensing interfaces. The
IPS 4240 is available with either AC or DC power. It monitors up to 250 Mbps of aggregate network
traffic on multiple sensing interfaces and is inline ready. The 250-Mbps performance for the IPS 4240 is
based on the following conditions:
• 2500 new TCP connections per second
• 2500 HTTP transactions per second
• Average packet size of 445 bytes
• Running Cisco IPS 5.1 or later
Note The 250-Mbps performance is traffic combined from all four sensing interfaces.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
2-1
Page 56

Front and Back Panel Features
114003
PWR STATUS FLASH
Cisco IPS 4240 series
Intrusion Prevention Sensor
Power
Flash
Status
The IPS 4255 replaces the IDS-4250-TX. There are four 10/100/1000 copper sensing interfaces. It
monitors up to 600 Mbps of aggregate network traffic on multiple sensing interfaces and is also inline
ready. The 600-Mbps performance for the IPS 4255 is based on the following conditions:
• 6000 new TCP connections per second
• 6000 HTTP transactions per second
• Average packet size of 445 bytes
• Running Cisco IPS 5.1 or later
Note The 600-Mbps performance is traffic combined from all four sensing interfaces.
Front and Back Panel Features
Note Although the illustrations show the IPS 4240, the IPS 4255 has the same front and back panel features
and indicators.
Chapter 2 Installing the IPS 4240 and the IPS 4255
This section describes the IPS 4240 and the IPS 4255 front and back panel features and indicators.
Figure 2-1 shows the front view of the IPS 4240 and the IPS 4255.
Figure 2-1 IPS 4240/IPS 4255 Front Panel Features
Table 2 -1 describes the front panel indicators on the IPS 4240 and the IPS 4255.
Table 2-1 Front Panel Indicators
Indicator Description
Power Off indicates no power. Green when the power supply is running.
Status Blinks green while the power-up diagnostics are running or the system is booting. Solid
green when the system has passed power-up diagnostics. Solid amber when the
power-up diagnostics have failed.
Flash Off when the compact flash device is not being accessed. Blinks green when the
compact flash device is being accessed.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
2-2
OL-18504-01
Page 57

Chapter 2 Installing the IPS 4240 and the IPS 4255
114002
LINK SPD2LINK SPD1LINK SPD
0
LINK SPD
3
MGMT
USB2
USB1
FLASH
CONSOLE
AUX
POWER
STATUS
FLASH
Powe r
connector
Powe r
switch
Indicator
light
Auxiliary
port
(not used)
Serial
console
port
External
compact
flash device
(not used)
Compact
flash device
indicator
Status
indicator
Powe r
indicator
GigabitEthernet0/0
USB ports
(not used)
Management0/0
114417
USB2
USB1
LNK SPD
3
LNK SPD2LNK SPD1LNK SPD
0
MGMT
Indicators
Figure 2-2 shows the back view of the IPS 4240 and the IPS 4255.
Figure 2-2 IPS 4240 and IPS 4255 Back Panel Features
Figure 2-3 shows the four built-in Ethernet ports, which have two indicators per port.
Front and Back Panel Features
Figure 2-3 Ethernet Port Indicators
Table 2 -2 lists the back panel indicators.
Table 2-2 Back Panel Indicators
Indicator Color Description
Left side Green solid
Right side Not lit
OL-18504-01
Physical link
Green blinking
Network activity
10 Mbps
Green
Amber
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
100 Mbps
1000 Mbps
2-3
Page 58

Specifications
Specifications
Table 2 -3 lists the specifications for the IPS 4240 and the IPS 4255.
Table 2-3 IPS 4240 and IPS 4255 Specifications
Dimensions and Weight
Height 1.75 in. (4.45 cm)
Width 17.5 in. (44.45 cm)
Depth 14.5 in. (36.83 cm)
Weight 20.0 lb (9.07 kg)
Form factor 1 RU, standard 19-inch rack-mountable
Expansion One chassis expansion slot (not used)
Power
Autoswitching 100V to 240V AC
Frequency 47 to 63 Hz, single phase
Operating current 3.0 A
Steady state 150 W
Maximum peak 190 W
Maximum heat dissipation 648 BTU/hr, full power usage (65 W)
Environment
Temperature Operating +32°F to +104°F (+0°C to +40°C)
Relative humidity Operating 5% to 95% (noncondensing)
Altitude Operating 0 to 9843 ft (3000 m)
Shock Operating 1.14 m/sec (45 in./sec) ½ sine input
Vibration 0.41 Grms2 (3 to 500 Hz) random input
Acoustic noise 60 dBa (maximum)
Chapter 2 Installing the IPS 4240 and the IPS 4255
Nonoperating -13°F to +158°F (-25°C to +70°C)
Nonoperating 5% to 95% (noncondensing)
Nonoperating 0 to 15,000 ft (4750 m)
Nonoperating 30 G
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
2-4
OL-18504-01
Page 59

Chapter 2 Installing the IPS 4240 and the IPS 4255
Connecting the IPS 4240 to a Cisco 7200 Series Router
Connecting the IPS 4240 to a Cisco 7200 Series Router
When an IPS 4240 is connected directly to a 7200 series router and both the IPS 4240 and the router
interfaces are hard-coded to speed 100 with duplex Full, the connection does not work. If you set the
IPS 4240 to speed Auto and duplex Auto, it connects to the router but only at speed 100 and duplex Half.
To connect correctly at speed 100 and duplex Full, set the interfaces of both the IPS 4240 and the router
to speed Auto and duplex Auto. Also, if either interface is hard-coded, you must make the connection
using a crossover cable.
Accessories
The IPS 4240 and the IPS 4255 accessories kit contains the following:
• DB25 connector
• DB9 connector
• Rack mounting kit—screws, washers, and metal bracket
• RJ45 console cable
• Two 6-ft Ethernet cables
Important Safety Instructions
Warning
Warning
IMPORTANT SAFETY INSTRUCTIONS
This warning symbol means danger. You are in a situation that could cause bodily injury. Before you
work on any equipment, be aware of the hazards involved with electrical circuitry and be familiar
with standard practices for preventing accidents. Use the statement number provided at the end of
each warning to locate its translation in the translated safety warnings that accompanied this device.
Statement 1071
SAVE THESE INSTRUCTIONS
Only trained and qualified personnel should be allowed to install, replace, or service this equipment.
Statement 1030
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
2-5
Page 60

Rack Mounting
114016
Cisco IPS 4240
series
Intrusion Prevention Sensor
Rack Mounting
To rack mount the IPS 4240 and the IPS 4255, follow these steps:
Step 1 Attach the bracket to the appliance using the supplied screws.
You can attach the brackets to the holes near the front of the appliance.
Chapter 2 Installing the IPS 4240 and the IPS 4255
Note The top hole on the left bracket is a banana jack you can use for ESD grounding purposes when
you are servicing the system. You can use the two threaded holes to mount a ground lug to
ground the chassis.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
2-6
OL-18504-01
Page 61

Chapter 2 Installing the IPS 4240 and the IPS 4255
114017
P
W
R
S
T
A
T
U
S
F
L
A
S
H
C
isco
A
S
A
4
24
0
In
tru
sion
D
e
tec
tio
n S
ens
o
r
Step 2 Use the supplied screws to attach the appliance to the equipment rack.
Installing the IPS 4240 and the IPS 4255
Step 3 To remove the appliance from the rack, remove the screws that attach the appliance to the rack, and then
remove the appliance.
Installing the IPS 4240 and the IPS 4255
Warning
Caution Follow proper safety procedures when performing these steps by reading the safety warnings in
Only trained and qualified personnel should be allowed to install, replace, or service this equipment.
Statement 1030
Regulatory Compliance and Safety Information for the Cisco Intrusion Prevention System 4200 Series
Appliance Sensor.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
2-7
Page 62

Installing the IPS 4240 and the IPS 4255
Cisco IPS 4240
series
Intrusion Prevention Sensor
To install the IPS 4240 and the IPS 4255 on the network, follow these steps:
Step 1 Position the appliance on the network.
Step 2 Attach the grounding lug to the side of the appliance.
Note Use 8-32 screws to connect a copper standard barrel grounding lug to the holes. The appliance requires
a lug where the distance between the center of each hole is 0.56 inches. The ground lug must be NRTL
listed or recognized. In addition, the copper conductor (wires) must be used and the copper conductor
must comply with the NEC code for ampacity. A lug is not supplied with the appliance.
Chapter 2 Installing the IPS 4240 and the IPS 4255
Step 3 Place the appliance in a rack, if you are rack mounting it.
Step 4 Attach the power cord to the appliance and plug it in to a power source (a UPS is recommended).
Step 5 Connect the cable as shown in Step 6 so that you have either a DB-9 or DB-25 connector on one end as
required by the serial port for your computer, and the other end is the RJ-45 connector.
Note Use the console port to connect to a computer to enter configuration commands. Locate the serial
cable from the accessory kit. The serial cable assembly consists of a 180/rollover cable with
RJ-45 connectors (DB-9 connector adapter PN 74-0495-01 and DB-25 connector adapter PN
29-0810-01).
Note You can use a 180/rollover or straight-through patch cable to connect the appliance to a port on
a terminal server with RJ-45 or hydra cable assembly connections. Connect the appropriate cable
from the console port on the appliance to a port on the terminal server.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
2-8
OL-18504-01
Page 63

Chapter 2 Installing the IPS 4240 and the IPS 4255
114418
RJ-45 to
DB-9 or DB-25
serial cable
(null-modem)
Computer serial port
DB-9 or DB-25
FLASH
CONSOLE
AUX
POWER
STATUS
FLASH
Console
port (RJ-45)
114417
USB2
USB1
LNK SPD
3
LNK SPD2LNK SPD1LNK SPD
0
MGMT
Indicators
Step 6 Connect the RJ-45 connector to the console port and connect the other end to the DB-9 or DB-25
connector on your computer.
Step 7 Attach the network cables to the following interfaces:
• GigabitEthernet0/0, GigabitEthernet0/1, GigabitEthernet0/2, and GigabitEthernet0/3 (from right to
left) are sensing ports.
• Management0/0 is the command and control port.
Installing the IPS 4240 and the IPS 4255
Caution Management and console ports are privileged administrative ports. Connecting them to an untrusted
network can create security concerns.
Step 8 Power on the appliance.
Step 9 Initialize the appliance.
Step 10 Upgrade the appliance with the most recent Cisco IPS software. You are now ready to configure intrusion
prevention on the appliance.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
2-9
Page 64

Installing the IPS 4240-DC
For More Information
Chapter 2 Installing the IPS 4240 and the IPS 4255
• DC power guidelines are listed in Regulatory Compliance and Safety Information for the Cisco
Intrusion Detection and Prevention System 4200 Series Appliance Sensor.
• For more information on working with electrical power and in an ESD environment, see Site and
Safety Guidelines, page 1-30.
• For the procedure for placing IPS 4250-DC in a rack, see Rack Mounting, page 2-6.
• For the instructions for setting up a terminal server, see Connecting an Appliance to a Terminal
Server, page 1-19.
• For the procedure for using the setup command to initialize IPS 4250-DC, see Basic Sensor Setup,
page 10-4.
• For the procedure for updating IPS-4250-DC with the most recent cisco IPS software, see Obtaining
Cisco IPS Software, page 11-1.
• If you have the IPS 4240-DC model, see Installing the IPS 4240-DC, page 2-10.
• For the procedure for using HTTPS to log in to IDM, refer to Logging In to IDM.
• For the procedures for configuring intrusion prevention on your sensor, refer to the following
documents:
–
Installing and Using Cisco Intrusion Prevention System Device Manager 7.0
–
Installing and Using Cisco Intrusion Prevention System Manager Express 7.0
–
Configuring the Cisco Intrusion Prevention System Sensor Using the Command Line Interface
7.0
Installing the IPS 4240-DC
The the IPS 4240-DC-K9 (NEBS-compliant) model equipped with DC-input power supply must be
terminated with the DC input wiring on a DC source capable of supplying at least 15 amps. A 15-amp
circuit breaker is required at the 48 VDC facility power source. An easily accessible disconnect device
should be incorporated into the facility wiring.
Warning
Note The DC return connection should remain isolated from the system frame and chassis (DC-I). This
Before performing any of the following procedures, ensure that power is removed from the DC circuit.
To ensure that all power is OFF, locate the circuit breaker on the panel board that services the DC
circuit, switch the circuit breaker to the OFF position, and tape the switch handle of the circuit
breaker in the OFF position.
equipment is suitable for connection to intra-building wiring only.
Warning
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
Only trained and qualified personnel should be allowed to install, replace, or service this equipment.
Statement 1030
2-10
OL-18504-01
Page 65

Chapter 2 Installing the IPS 4240 and the IPS 4255
Cisco IPS 4240
series
Intrusion Prevention Sensor
To install the IPS 4240-DC, follow these steps:
Step 1 Position the IPS 4240-DC on the network.
Step 2 Attach the grounding lug to the side of the appliance.
Note Use 8-32 screws to connect a copper standard barrel grounding lug to the holes. The appliance requires
a lug where the distance between the center of each hole is 0.56 inches. The ground lug must be NRTL
listed or recognized. In addition, the copper conductor (wires) must be used and the copper conductor
must comply with the NEC code for ampacity. A lug is not supplied with the appliance.
Installing the IPS 4240-DC
Step 3 Place the appliance in a rack, if you are rack mounting it.
Step 4 Terminate the DC input wiring on a DC source capable of supplying at least 15 amps. A 15-amp circuit
breaker is required at the 48-VDC facility power source. An easily accessible disconnect device should
be incorporated into the facility wiring.
Step 5 Locate the DC-input terminal box.
Step 6 Power off the IPS 4240-DC.
Make sure that power is removed from the DC circuit. To make sure all power is OFF, locate the circuit
breaker on the panel board that services the DC circuit, switch the circuit breaker to the OFF position,
and tape the switch handle of the circuit breaker in the OFF position.
Step 7 Remove the DC power supply plastic shield.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
2-11
Page 66

Installing the IPS 4240-DC
148401
4
+ –
1
3
2
+ –
+ –
148405
5
6
7
1
4
3
2
Step 8 Strip the ends of the wires for insertion into the power connect lugs on the IPS 4240-DC.
Chapter 2 Installing the IPS 4240 and the IPS 4255
Step 9 Insert the ground wire into the connector for the earth ground and tighten the screw on the connector.
Using the same method as for the ground wire, connect the negative wire and then the positive wire.
1 Negative 5 Negative
2 Positive 6 Positive
3 Ground 7 Ground
4 On/Off Switch
2-12
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
OL-18504-01
Page 67

Chapter 2 Installing the IPS 4240 and the IPS 4255
Note The DC return connection to this system is to remain isolated from the system frame and chassis.
Step 10 After wiring the DC power supply, remove the tape from the circuit breaker switch handle and reinstate
power by moving the handle of the circuit breaker to the ON position.
Step 11 Replace the DC power supply plastic shield.
Step 12 Power on the IPS 4240-DC from the switch at the back of the chassis.
Note If you need to power cycle the IPS 4240-DC, wait at least 5 seconds between powering it off and
powering it back on.
Step 13 Initialize the IPS 4240-DC.
Step 14 Upgrade the IPS 4240-DC with the most recent Cisco IPS software.
You are now ready to configure intrusion prevention on the appliance.
Installing the IPS 4240-DC
For More Information
• DC power guidelines are listed in Regulatory Compliance and Safety Information for the Cisco
Intrusion Prevention System 4200 Series Appliance Sensor.
• For more information on working with electrical power and in an ESD environment, see Site and
Safety Guidelines, page 1-30.
• For the procedure for placing IPS 4250-DC in a rack, see Rack Mounting, page 2-6.
• For the procedure for using the setup command to initialize IPS 4250-DC, see Basic Sensor Setup,
page 10-4.
• For the procedure for updating IPS 4250-DC with the most recent cisco IPS software, see Obtaining
Cisco IPS Software, page 11-1.
• For the procedure for using HTTPS to log in to IDM, refer to Logging In to IDM.
• For the procedures for configuring intrusion prevention on your sensor, refer to the following guides:
–
Installing and Using Cisco Intrusion Prevention System Device Manager 7.0
–
Installing and Using Cisco Intrusion Prevention System Manager Express 7.0
–
Configuring the Cisco Intrusion Prevention System Sensor Using the Command Line Interface
7.0
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
2-13
Page 68

Installing the IPS 4240-DC
Chapter 2 Installing the IPS 4240 and the IPS 4255
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
2-14
OL-18504-01
Page 69

Installing the IPS 4260
Note All IPS platforms allow ten concurrent CLI sessions.
This chapter describes the IPS 4260 and how to install it. It also describes the accessories and how to
install them. This chapter contains the following sections:
• Introducing the IPS 4260, page 3-1
• Supported Interface Cards, page 3-2
• Hardware Bypass, page 3-4
• Front and Back Panel Features, page 3-6
• Specifications, page 3-9
• Accessories, page 3-9
• Important Safety Instructions, page 3-10
CHA P TER
3
• Rack Mounting, page 3-10
• Installing the IPS 4260, page 3-15
• Removing and Replacing the Chassis Cover, page 3-18
• Installing and Removing Interface Cards, page 3-20
• Installing and Removing the Power Supply, page 3-22
Introducing the IPS 4260
Caution The BIOS on the IPS 4260 is specific to the IPS 4260 and must only be upgraded under instructions from
Cisco with BIOS files obtained from the Cisco website. Installing a non-Cisco or third-party BIOS on
the IPS 4260 voids the warranty.
The IPS 4260 delivers 1 Gigabit of intrusion prevention performance. You can use the IPS 4260 to
protect both Gigabit subnets and aggregated traffic traversing switches from multiple subnets. The
IPS 4260 is a purpose-built device that has support for both copper and fiber NIC environments thus
providing flexibility of deployment in any environment. It replaces IDS-4250-XL.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
3-1
Page 70

Supported Interface Cards
The IPS 4260 has two built-in Gigabit Ethernet network ports and six expansion slots. The network port
numbers increase from right to left and the expansion slot numbers increase from bottom to top and from
right to left as shown in Figure 3-5 on page 3-7. Slots 2 and 3 are PCI-Express connectors and the other
expansion slots are PCI-X slots. Slots 1 through 3 are full-height slots and slots 4 though 6 are
half-height slots. The built-in management port is called Management0/0 and the built-in sensing
interface is Gigabit-Ethernet0/1.
Note Only expansion slots 2 and 3 are supported at this time.
For improved reliability, the IPS 4260 uses a flash device for storage rather than a hard-disk drive. The
IPS 4260 supports two optional network interface cards, the 2SX Fiber card, and the 4GE bypass
interface card that contains the hardware-bypass feature. Initially the IPS 4260 supports only the built-in
interfaces and these two interface cards.
The IPS 4260 monitors greater than 1 Gbps of aggregate network traffic on multiple sensing interfaces
and is also inline ready. It supports both copper and fiber interfaces. The 1-Gbps performance is traffic
combined from all sensing interfaces. The 1-Gbps performance for the IPS 4260 is based on the
following conditions:
Chapter 3 Installing the IPS 4260
• 10,000 new TCP connections per second
• 100,000 HTTP transactions per second
• Average packet size of 450 bytes
• System running IPS 6.0 software
The IPS 4260 ships with one power supply, but it supports redundant power supplies. The IPS 4260
operates in load-sharing mode when the optional redundant power supply is installed.
For More Information
• For more information on how to obtain instructions and BIOS files from the Cisco website, see
Obtaining Cisco IPS Software, page 11-1.
• For more information on sensor interfaces, see Sensor Interfaces, page 1-4.
• For more information on the 4GE bypass interface card, see Hardware Bypass, page 3-4.
• For more information on installing and removing the power supply, see Installing and Removing the
Power Supply, page 3-22.
Supported Interface Cards
The IPS 4260 supports three interface cards: the 4GE bypass interface card, the 2SX interface card, and
the 10GE interface card.
4GE Bypass Interface Card
The 4GE bypass interface card (part numbers IPS-4GE-BP-INT and IPS-4GE-BP-INT=) provides four
10/100/1000BASE-T (4GE) monitoring interfaces. The IPS 4260 supports up to two 4GE bypass
interfaces cards for a total of eight GE bypass interfaces. The 4GE bypass interface card supports
hardware bypass.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
3-2
OL-18504-01
Page 71

Chapter 3 Installing the IPS 4260
153325
190474
Figure 3-1 shows the 4GE bypass interface card.
Figure 3-1 4GE Bypass Interface Card
Supported Interface Cards
2SX Interface Card
The 2SX interface card (part numbers IPS-2SX-INT and IPS-2SX-INT=) provides two 1000BASE-SX
(fiber) monitoring interfaces. The IPS 4260 supports up to two 2SX interface cards for a total of four SX
interfaces. The 2SX card ports require a multi-mode fiber cable with an LC connector to connect to the
SX interface of the sensor. The 2SX interface card does not support hardware bypass.
Figure 3-2 shows the 2SX interface card.
Figure 3-2 2SX Interface Card
10GE Interface Card
The 10GE interface card (part numbers IPS-2X10GE-SR-INT and IPS-2X10GE-SR-INT=) provides two
10000 Base-SX (fiber) interfaces. The IPS 4260 supports one 10GE interface card for a total of two
10GE fiber interfaces. The card ports require a multi-mode fiber cable with an LC connector to connect
to the SX interface of the IPS 4260. The 10GE interface card does not support hardware bypass.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
3-3
Page 72

Hardware Bypass
253975
Figure 3-3 shows the 10GE interface card.
Figure 3-3 10GE Interface Card
GigabitEthernetslot_number/port_number is the expansion card interface naming convention for the
IPS 4260. The slot number is shown to the right of the slot in the chassis and the port number is
numbered from right to left starting with 0.
Hardware Bypass
Chapter 3 Installing the IPS 4260
This section describes the 4GE bypass interface card and its configuration restrictions. It contains the
following topics:
• 4GE Bypass Interface Card, page 3-4
• Hardware Bypass Configuration Restrictions, page 3-5
• Hardware Bypass and Link Changes and Drops, page 3-6
4GE Bypass Interface Card
The IPS 4260 supports the 4-port GigabitEthernet card (part number IPS-4GE-BP-INT=) with hardware
bypass. This 4GE bypass interface card supports hardware bypass only between ports 0 and 1 and
between ports 2 and 3.
Note To disable hardware bypass, pair the interfaces in any other combination, for example 2/0<->2/2 and
2/1<->2/3.
Hardware bypass complements the existing software bypass feature in Cisco IPS. The following
conditions apply to hardware bypass and software bypass:
• When bypass is set to OFF, software bypass is not active.
For each inline interface for which hardware bypass is available, the component interfaces are set to
disable the fail-open capability. If SensorApp fails, the sensor is powered off, reset, or if the NIC
interface drivers fail or are unloaded, the paired interfaces enter the fail-closed state (no traffic flows
through inline interface or inline VLAN subinterfaces).
• When bypass is set to ON, software bypass is active.
Software bypass forwards packets between the paired physical interfaces in each inline interface and
between the paired VLANs in each inline VLAN subinterface. For each inline interface on which
hardware bypass is available, the component interfaces are set to standby mode. If the sensor is
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
3-4
OL-18504-01
Page 73

Chapter 3 Installing the IPS 4260
powered off, reset, or if the NIC interfaces fail or are unloaded, those paired interfaces enter
fail-open state in hardware (traffic flows unimpeded through inline interface). Any other inline
interfaces enter fail-closed state.
• When bypass is set to AUTO (traffic flows without inspection), software bypass is activated if
SensorApp fails.
For each inline interface on which hardware bypass is available, the component interfaces are set to
standby mode. If the sensor is powered off, reset, or if the NIC interfaces fail or are unloaded, those
paired interfaces enter fail-open state in hardware. Any other inline interfaces enter the fail-closed
state.
Note To test fail-over, set the bypass mode to ON or AUTO, create one or more inline interfaces and power
down the sensor and verify that traffic still flows through the inline path.
For More Information
For the procedure for installing and removing the 4GE bypass interface card, see Installing and
Removing Interface Cards, page 3-20.
Hardware Bypass
Hardware Bypass Configuration Restrictions
To use the hardware bypass feature on the 4GE bypass interface card, you must pair interfaces to support
the hardware design of the card. If you create an inline interface that pairs a hardware-bypass-capable
interface with an interface that violates one or more of the hardware-bypass configuration restrictions,
hardware bypass is deactivated on the inline interface and you receive a warning message similar to the
following:
Hardware bypass functionality is not available on Inline-interface pair0.
Physical-interface GigabitEthernet2/0 is capable of performing hardware bypass only when
paired with GigabitEthernet2/1, and both interfaces are enabled and configured with the
same speed and duplex settings.
The following configuration restrictions apply to hardware bypass:
• The 4-port bypass card is only supported on the IPS 4260.
• Fail-open hardware bypass only works on inline interfaces (interface pairs), not on inline VLAN
pairs.
• Fail-open hardware bypass is available on an inline interface if all of the following conditions are
met:
–
Both of the physical interfaces support hardware bypass.
–
Both of the physical interfaces are on the same interface card.
–
The two physical interfaces are associated in hardware as a bypass pair.
–
The speed and duplex settings are identical on the physical interfaces.
–
Both of the interfaces are administratively enabled.
• Autonegotiation must be set on MDI/X switch ports connected to the IPS 4260.
You must configure both the sensor ports and the switch ports for autonegotiation for hardware
bypass to work. The switch ports must support MDI/X, which automatically reverses the transmit
and receive lines if necessary to correct any cabling problems. The sensor is only guaranteed to
operate correctly with the switch if both of them are configured for identical speed and duplex,
which means that the sensor must be set for autonegotiation too.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
3-5
Page 74

Front and Back Panel Features
Cisco IPS 4260 series
Intrusion Prevention Sensor
POWER STATUSFLASH
ID NIC
Power
Flash
Status
ID
NIC
RESET
ID
153095
POWER
RESET
ID
Hardware Bypass and Link Changes and Drops
Properly configuring and deploying hardware bypass protects against complete link failure if the IPS
appliance experiences a power loss, critical hardware failure, or is rebooted; however, a link status
change still occurs when hardware bypass engages (and again when it disengages).
During engagement, the interface card disconnects both physical connections from itself and bridges
them together. The interfaces of the connected devices can then negotiate the link and traffic forwarding
can resume. Once the appliance is back online, hardware bypass disengages and the interface card
interrupts the bypass and reconnects the links back to itself. The interface card then negotiates both links
and traffic resumes.
There is no built-in way to completely avoid link status changes and drops. However, you can greatly
reduce the interruption time (in some cases to sub-second times) by doing the following:
• Make sure you use CAT 5e/6-certified cabling for all connections.
• Make sure the interfaces of the connected devices are configured to match the interfaces of the
appliance for speed/duplex negotiation (auto/auto).
• Enable portfast on connected switchports to reduce spanning-tree forwarding delays.
Chapter 3 Installing the IPS 4260
Front and Back Panel Features
This section describes the IPS 4260 front and back panel features and indicators.
Figure 3-4 shows the front view of the IPS 4260.
Figure 3-4 IPS 4260Front Panel Features
There are three switches on the front panel of the IPS 4260:
• Power—Toggles the system power.
• Reset—Resets the system.
• ID—Toggles the system ID indicator.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
3-6
OL-18504-01
Page 75

Chapter 3 Installing the IPS 4260
153094
USB ports
(not used)
Mouse
connector
(not supported)
Keyboard
connector
(not supported)
Sensing interface
expansion slots
Video
connector
(not supported)
3
2
1
6
5
4
Powe r
connector
Indicator
light
Powe r
supply 2
Powe r
supply 1
GE 0/1CONSOLE
MGMT
Console
port
Management
0/0
Gigabit
Ethernet 0/1
Table 3 -1 describes the front panel indicators on the IPS 4260.
Table 3-1 Front Panel Indicators
Indicator Description
ID (blue) Continuously lit when activated by the front panel ID switch.
NIC (green) Indicates activity on either the GigabitEthernetO/1 or MGMT interfaces.
Power (green) When continuously lit, indicates DC power. The indicator is off when power is
Flash (green/amber) Off when the compact flash device is not being accessed. Blinks green when the
Status (green/amber) Blinks green while the power-up diagnostics are running or the system is
Figure 3-5 shows the back view of the IPS 4260.
Front and Back Panel Features
turned off or the power source is disrupted.
compact flash device is being accessed. Solid amber when a device has failed.
booting. Solid green when the system has passed power-up diagnostics. Solid
amber when the power-up diagnostics have failed.
Figure 3-5 IPS 4260 Back Panel Features
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
3-7
Page 76

Front and Back Panel Features
153308
6
5
4
SPD indicator
Link/ACT indicator
GE 0/1CONSOLE
MGMT
SPD
LNK
SPD
LNK
SPD indicator
"SPD"
Link/ACT indicator
"LINK"
Diagnostic
indicators
(for TAC use)
System ID
indicator
Status
indicator
Figure 3-6 shows the two built-in Ethernet ports, which have two indicators per port.
Figure 3-6 Ethernet Port Indicators
Chapter 3 Installing the IPS 4260
Table 3 -2 lists the back panel indicators.
Table 3-2 Back Panel Indicators
Indicator Color Description
Left side Green solid
Green blinking
Right side Not lit
Green
Amber
Physical link
Network activity
10 Mbps
100 Mbps
1000 Mbps
Table 3 -3 lists the power supply indicator.
Table 3-3 Power Supply Indicators
Color Description
Off No AC power to all power supplies.
Green solid Output on and ok.
Green blinking AC present, only 5Vsb on (power supply off).
Amber No AC power to this power supply (for 1+1 configuration)
or
power supply critical event causing a shutdown: failure, fuse blown (1+1
only), OCP 12 V, OVP 12 V, or fan failed.
Amber blinking Power supply warning events where the power supply continues to operate:
high temperature, high power/high current, or slow fan.
3-8
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
OL-18504-01
Page 77

Chapter 3 Installing the IPS 4260
Specifications
Table 3 -4 lists the specifications for the IPS 4260.
Table 3-4 IPS 4260 Specifications
Dimensions and Weight
Height 3.45 in. (87.6 cm)
Width 17.14 in. (435.3 cm)
Depth 20 in. (508 cm)
Weight 20.0 lb (9.07 kg)
Form factor 2 RU, standard 19-inch rack-mountable
Power
Autoswitching 100V to 240V AC
Frequency 47 to 63 Hz, single phase
Operating current 8.9 A
Steady state 588 W max continuous
Maximum peak 657 W
Maximum heat dissipation 648 BTU/hr
Environment
Temperature Operating +32°F to +104°F (+0°C to +40°C)
Relative humidity Operating 10% to 85% (noncondensing)
Altitude Operating 0 to 9843 ft (3000 m)
Shock Operating Half-sine 2 G, 11 ms pulse, 100 pulses
Vibration 2.2 Grms, 10 minutes per axis on all three axes
Specifications
Nonoperating -104°F to +158°F (-40°C to +70°C)
Nonoperating 5% to 95% (noncondensing)
Nonoperating 0 to 15,000 ft (4750 m)
Nonoperating 25 G, 170 inches/sec delta V
Accessories
The IPS 4260 accessories kit contains the following:
• DB25 connector
• DB9 connector
• Rack mounting kit—screws, washers, and metal bracket
• RJ45 console cable
• Two 6-ft Ethernet cables
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
3-9
Page 78

Important Safety Instructions
153314
Cisco IPS 4260 series
In
tru
s
io
n
P
re
v
e
n
tio
n
S
e
n
s
o
r
PO
W
ER STATUS
FLASH
ID
NIC
RESET
ID
Important Safety Instructions
Chapter 3 Installing the IPS 4260
Warning
IMPORTANT SAFETY INSTRUCTIONS
This warning symbol means danger. You are in a situation that could cause bodily injury. Before you
work on any equipment, be aware of the hazards involved with electrical circuitry and be familiar
with standard practices for preventing accidents. Use the statement number provided at the end of
each warning to locate its translation in the translated safety warnings that accompanied this device.
Statement 1071
SAVE THESE INSTRUCTIONS
Warning
Only trained and qualified personnel should be allowed to install, replace, or service this equipment.
Statement 1030
Rack Mounting
You can rack mount the IPS 4260 in a 2- or 4-post rack. This section describes how to rack mount the
IPS 4260 and contains the following topics:
• Installing the IPS 4260 in a 4-Post Rack, page 3-10
• Installing the IPS 4260 in a 2-Post Rack, page 3-13
Installing the IPS 4260 in a 4-Post Rack
To rack mount the IPS 4260 in a 4-post rack, follow these steps:
Step 1 Attach each inner rail to each side of the chassis with three 8-32x1/4” SEMS screws.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
3-10
OL-18504-01
Page 79

Chapter 3 Installing the IPS 4260
153315
Cisco IPS 4260 series
In
tru
s
io
n
P
re
ve
n
tio
n
S
e
n
s
o
r
POW
ER STATU
S
FLASH
ID
NIC
RESET
ID
153316
Step 2 Attach the front-tab mounting bracket to the chassis with two 8-32x1/4’ SEMS screws. You can flip the
bracket to push the system forward in the rack.
Rack Mounting
Step 3 Using the four inner studs, install the mounting brackets to the outer rail with four 8-32 KEPS nuts. Insert
four thread covers over the four outer studs on each side.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
3-11
Page 80

Rack Mounting
153317
153318
C
isc
o
IP
S
4
2
6
0
se
rie
s
In
tru
sio
n
Preven
tion
S
en
so
r
P
O
W
E
R
S
T
A
T
U
S
F
L
A
S
H
ID
NIC
RESET
ID
Step 4 Install the two outer rail subassemblies in the rack using eight 10-32x1/2” SEMS screws. You can use
Chapter 3 Installing the IPS 4260
four bar nuts if necessary.
Note Adjust the mounting brackets based on rack depth.
Step 5 Slide the IPS 4260 into the rack making sure the inner rail is aligned with the outer rail.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
3-12
OL-18504-01
Page 81

Chapter 3 Installing the IPS 4260
C
isc
o
IPS 4
2
6
0
serie
s
In
trusion
P
reve
ntion
Sen
so
r
P
O
W
E
R
S
TA
T
U
S
F
L
A
S
H
ID
NIC
RESET
ID
153319
153320
Cisco IPS 4260 series
In
tru
s
io
n
P
r
e
v
e
n
tio
n
S
e
n
s
o
r
PO
WER STATUS
FLASH
ID
NIC
RESET
ID
153321
Step 6 Install two 10-32x1/2” SEMS screws to hold the front-tab mounting bracket to the rail.
Installing the IPS 4260 in a 2-Post Rack
Rack Mounting
To rack mount the IPS 4260 in a 2-post rack, follow these steps:
Step 1 Attach the inner rail to each side of the chassis with three 8-32x1/4” SEMS screws.
Step 2 Using the four inner studs, install the mounting brackets to the outer rail with four 8-32 KEPS nuts. Insert
four thread covers over the four outer studs on each side.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
3-13
Page 82

Rack Mounting
153322
153323
Cisco IPS 4260 series
In
t
ru
s
io
n
P
re
v
e
n
t
io
n
S
e
n
s
o
r
P
O
W
E
R
S
T
A
T
U
S
F
L
A
S
H
I
D
N
I
C
R
E
S
E
T
I
D
Step 3 Install the two outer rail subassemblies in the rack using twelve 10-32x1/2” SEMS screws or whatever
Chapter 3 Installing the IPS 4260
rack hardware is necessary.
Note Adjust the mounting brackets based on the rack-channel depth.
Step 4 Slide the IPS 4260 into the rack making sure the inner rail is aligned with the outer rail.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
3-14
OL-18504-01
Page 83

Chapter 3 Installing the IPS 4260
153324
Cisco IPS 4260 series
In
trusio
n P
re
ven
tio
n S
en
sor
P
O
W
E
R
S
T
A
T
U
S
F
L
A
S
H
ID NIC
RE
SE
T
ID
Step 5 Install four 8-32x7/16” SEMS screws through the clearance slots in the side of each outer rail assembly
into the inner rail.
Installing the IPS 4260
Installing the IPS 4260
Warning
Caution Follow proper safety procedures when performing these steps by reading the safety warnings in
Only trained and qualified personnel should be allowed to install, replace, or service this equipment.
Statement 1030
Regulatory Compliance and Safety Information for the Cisco Intrusion Prevention System 4200 Series
Appliance Sensor.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
3-15
Page 84

Installing the IPS 4260
153309
!
!
G
E
0
/1
C
O
N
S
O
L
E
M
G
M
T
SPD
LN
K
SPD
LNK
Step 1 Position the IPS 4260 on the network.
Step 2 Attach the grounding lugs to the back of the IPS 4260.
Chapter 3 Installing the IPS 4260
To install the IPS 4260 on the network, follow these steps:
Note Use 8-32 locknuts to connect a copper standard barrel grounding lug to the holes. The appliance requires
a lug where the distance between the center of each hole is 0.56 inches. The ground lug must be NRTL
listed or recognized. In addition, the copper conductor (wires) must be used and the copper conductor
must comply with the NEC code for ampacity. A lug is not supplied with the appliance.
Step 3 Place the IPS 4260 in a rack, if you are rack mounting it.
Step 4 Attach the power cord to the IPS 4260 and plug it in to a power source (a UPS is recommended).
Step 5 Connect the cable as shown in Step 6 so that you have either a DB-9 or DB-25 connector on one end as
required by the serial port for your computer, and the other end is the RJ-45 connector.
Note Use the console port to connect to a computer to enter configuration commands. Locate the serial
cable from the accessory kit. The serial cable assembly consists of a 180/rollover cable with
RJ-45 connectors (DB-9 connector adapter PN 74-0495-01 and DB-25 connector adapter PN
29-0810-01).
Note You can use a 180/rollover or straight-through patch cable to connect the appliance to a port on
a terminal server with RJ-45 or hydra cable assembly connections. Connect the appropriate cable
from the console port on the appliance to a port on the terminal server.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
3-16
OL-18504-01
Page 85

Chapter 3 Installing the IPS 4260
153309
RJ-45 to
DB-9 or DB-25
serial cable
(null-modem)
Computer serial port
DB-9 or DB-25
MGMTCONSOLE
Console
port (RJ-45)
153308
6
5
4
SPD indicator
Link/ACT indicator
GE 0/1CONSOLE
MGMT
SPD
LNK
SPD
LNK
SPD indicator
"SPD"
Link/ACT indicator
"LINK"
Diagnostic
indicators
(for TAC use)
System ID
indicator
Status
indicator
Step 6 Connect the RJ-45 connector to the console port and connect the other end to the DB-9 or DB-25
connector on your computer.
Installing the IPS 4260
Step 7 Attach the network cables to the following interfaces:
• GigabitEthernet0/1 (GE 0/1) is the sensing port.
• Management0/0 (MGMT) is the command and control port.
• GigabitEthernetslot_number/port_number through GigabitEthernetslot_number/port_number are
the additional expansion port slots.
Caution Management and console ports are privileged administrative ports. Connecting them to an untrusted
network can create security concerns.
Step 8 Power on the IPS 4260.
Step 9 Initialize the IPS 4260.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
3-17
Page 86

Removing and Replacing the Chassis Cover
Step 10 Upgrade the IPS 4260 with the most recent Cisco IPS software. You are now ready to configure intrusion
prevention on the IPS 4260.
For More Information
• For more information on working with electrical power and in an ESD environment, see Site and
Safety Guidelines, page 1-30.
• For the procedure for installing the IPS 4260 in a rack, see Rack Mounting, page 3-10.
• For the instructions for setting up a terminal server, see Connecting an Appliance to a Terminal
Server, page 1-19.
• For the procedure for using the setup command to initialize the IPS 4260, see Initializing the Sensor,
page 10-1.
• For the procedure for obtaining and installing the most recent IPS software, see Obtaining Cisco IPS
Software, page 11-1.
• For the procedure for using HTTPS to log in to IDM, refer to Logging In to IDM.
• For the procedures for configuring intrusion prevention, refer to the following documents:
–
Installing and Using Cisco Intrusion Prevention System Device Manager 7.0
–
Installing and Using Cisco Intrusion Prevention System Manager Express 7.0
Chapter 3 Installing the IPS 4260
–
Configuring the Cisco Intrusion Prevention System Sensor Using the Command Line Interface
7.0
Removing and Replacing the Chassis Cover
Warning
Warning
Warning
This product relies on the building’s installation for short-circuit (overcurrent) protection. Ensure that
the protective device is rated not greater than 120 VAC, 20 A U.S. (240 VAC, 16-20 A International).
Statement 1005
This equipment must be grounded. Never defeat the ground conductor or operate the equipment in the
absence of a suitably installed ground conductor. Contact the appropriate electrical inspection
authority or an electrician if you are uncertain that suitable grounding is available. Statement 1024
Blank faceplates and cover panels serve three important functions: they prevent exposure to
hazardous voltages and currents inside the chassis; they contain electromagnetic interference (EMI)
that might disrupt other equipment; and they direct the flow of cooling air through the chassis. Do not
operate the system unless all cards, faceplates, front covers, and rear covers are in place. Statement
1029
Warning
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
This unit might have more than one power supply connection. All connections must be removed to
de-energize the unit. Statement 1028
3-18
OL-18504-01
Page 87

Chapter 3 Installing the IPS 4260
153311
!
!
Caution Follow proper safety procedures when removing and replacing the chassis cover by reading the safety
warnings in Regulatory Compliance and Safety Information for the Cisco Intrusion Prevention System
4200 Series Appliance Sensor.
Note Removing the appliance chassis cover does not affect your Cisco warranty. Upgrading the IPS 4260 does
not require any special tools and does not create any radio frequency leaks.
To remove and replace the chassis cover, follow these steps:
Step 1 Log in to the CLI.
Step 2 Prepare the IPS 4260 to be powered off:
sensor# reset powerdown
Wait for the power down message before continuing with Step 3.
Removing and Replacing the Chassis Cover
Note You can also power down the IPS 4260 using IDM or IME.
Step 3 Power off the IPS 4260.
Step 4 Remove the power cord and other cables from the IPS 4260.
Step 5 If rack-mounted, remove the IPS 4260 from the rack.
Step 6 Make sure the IPS 4260 is in an ESD-controlled environment.
Step 7 Press the blue button on the top of the chassis cover and slide the chassis cover back.
Caution Do not operate the IPS 4260 without the chassis cover installed. The chassis cover protects the internal
components, prevents electrical shorts, and provides proper air flow for cooling the electronic
components.
Step 8 To replace the chassis cover, position it at the back of the chassis and slide it on until it snaps into place.
Step 9 Reattach the power cord and other cables to the IPS 4260.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
3-19
Page 88

Installing and Removing Interface Cards
Step 10 Reinstall the IPS 4260 on a rack, desktop, or table.
Step 11 Power on the IPS 4260.
For More Information
• For the IDM procedure for resetting the IPS 4260, refer to Rebooting the Sensor; for the IME
procedure for resetting the IPS 4260, refer to Rebooting the Sensor.
• For the procedure for removing the IPS 4260 from a rack, see Rack Mounting, page 3-10.
• For more information on ESD-controlled environments, see Working in an ESD Environment, page
1-32.
• If you are reinstalling the IPS 4260 in a rack, see Rack Mounting, page 3-10.
Installing and Removing Interface Cards
The IPS 4260 has 6 expansion card slots, three full-height and three half-height slots. You can install the
optional network interface cards in the two top full-height slots, slots 2 and 3. The IPS 4260 supports up
to two network interface cards.
Chapter 3 Installing the IPS 4260
Note The IPS 4260 supports only one 10GE fiber interface card, which you can install in either of the
supported slots (slots 2 and 3).
Note We recommend that you install the 4GE bypass interface card in slot 2 if you are installing only one 4GE
bypass card. This improves accessibility to the RJ45 cable connectors.
To install and remove interface cards, follow these steps:
Step 1 Log in to the CLI.
Step 2 Prepare the IPS 4260 to be powered off:
sensor# reset powerdown
Wait for the power down message before continuing with Step 3.
Note You can also power down the IPS 4260 using IDM or IME.
Step 3 Power off the IPS 4260.
Step 4 Remove the power cable and other cables from the IPS 4260.
Step 5 If rack-mounted, remove the IPS 4260 from the rack.
Step 6 Make sure the IPS 4260 is in an ESD-controlled environment.
Step 7 Remove the chassis cover.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
3-20
OL-18504-01
Page 89

Chapter 3 Installing the IPS 4260
153312
!
!
!
!
190471
Step 8 Remove the card carrier by pulling up on the two blue release tabs. Use equal pressure and lift the card
carrier out of the chassis.
Installing and Removing Interface Cards
Step 9 With a screw driver, remove the screw from the desired slot cover.
Step 10 Remove the slot cover by pressing on it from inside the chassis.
If the card is full length, use a screw driver to remove the blue thumb screw from the card support at the
back of the card carrier.
Step 11 Carefully align the interface card with the PCI-Express connector and alignment grooves for the
appropriate slot. Apply firm even pressure until the card is fully seated in the connector.
Step 12 Reinstall the slot cover screw to hold the card to the carrier. If necessary, reinstall the card support at the
back of the card carrier.
Step 13 Replace the card carrier in the chassis.
Step 14 Replace the chassis cover.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
3-21
Page 90

Installing and Removing the Power Supply
For More Information
• For the procedure for attaching power cords and cables to the IPS 4260, see Installing the IPS 4260,
page 3-15.
• For an illustration of the expansion card slots, see Figure 3-6 on page 3-8.
• For an illustration of the supported interface cards, see Supported Interface Cards, page 3-2.
• For the IDM procedure for resetting the IPS 4260, refer to Rebooting the Sensor; for the IME
procedure for resetting the IPS 4260, refer to Rebooting the Sensor.
• For the procedure for removing the IPS 4260 from a rack, see Rack Mounting, page 3-10.
• For more information on ESD-controlled environments, see Working in an ESD Environment, page
1-32.
• For the procedure for removing the chassis cover, see Removing and Replacing the Chassis Cover,
page 3-18.
Installing and Removing the Power Supply
Chapter 3 Installing the IPS 4260
The IPS 4260 ships with one power supply, but you can order it with two power supplies so that you have
a redundant power supply.
To install and remove power supplies, follow these steps:
Step 1 Log in to the CLI.
Step 2 Prepare the IPS 4260 to be powered off:
sensor# reset powerdown
Wait for the power down message before continuing with Step 3.
Note You can also power down the IPS 4260 using IDM or IME.
Step 3 Power off the IPS 4260.
Step 4 Remove the power cable and other cables from the IPS 4260.
Note Power supplies are hot-swappable. You can replace a power supply while the IPS 4260 is
running, if you are replacing a redundant power supply.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
3-22
OL-18504-01
Page 91

Chapter 3 Installing the IPS 4260
!
!
!
!
!
Step 5 Squeeze the tabs to remove the filler plate.
Step 6 Install the power supply.
Installing and Removing the Power Supply
Step 7 To remove the power supply, push down the green tab and pull out the power supply.
Step 8 After installing or removing the power supply, replace the power cord and other cables.
Step 9 Power on the IPS 4260.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
3-23
Page 92

Installing and Removing the Power Supply
For More Information
For the IDM procedure for resetting the IPS 4260, refer to Rebooting the Sensor; for the IME procedure
for resetting the IPS 4260, refer to Rebooting the Sensor.
Chapter 3 Installing the IPS 4260
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
3-24
OL-18504-01
Page 93

Installing the IPS 4270-20
Note All IPS platforms allow ten concurrent CLI sessions.
This chapter describes the IPS 4270-20 and how to install it. It also describes the accessories and how
to install them. This chapter contains the following sections:
• Introducing the IPS 4270-20, page 4-2
• Supported Interface Cards, page 4-3
• Hardware Bypass, page 4-5
• Front and Back Panel Features, page 4-7
• Diagnostic Panel, page 4-11
• Internal Components, page 4-13
• Specifications, page 4-14
CHAP T ER
4
• Accessories, page 4-15
• Installing the Rail System Kit, page 4-15
• Installing the IPS 4270-20, page 4-35
• Removing and Replacing the Chassis Cover, page 4-38
• Accessing the Diagnostic Panel, page 4-41
• Installing and Removing Interface Cards, page 4-41
• Installing and Removing the Power Supply, page 4-44
• Installing and Removing Fans, page 4-49
• Troubleshooting Loose Connections, page 4-51
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
4-1
Page 94

Introducing the IPS 4270-20
MEDIA-RICHTRANSACTIONAL
Commerce
Gaming
Streaming
Video
WWW
Instant
Messaging
Voice
Collaborative
Workspaces
Data
Replication
Web 2.0
Introducing the IPS 4270-20
Caution The BIOS on the IPS 4270-20 is specific to the IPS 4270-20 and must only be upgraded under
instructions from Cisco with BIOS files obtained from the Cisco website. Installing a non-Cisco or
third-party BIOS on the IPS 4270-20 voids the warranty.
The IPS 4270-20 delivers up to 4 Gbps of performance in media-rich environments and 2 Gbps in
transactional environments enabling you to protect fully saturated Gigabit networks and aggregate
network traffic on multiple sensing interfaces. The IPS 4270-20 is also inline ready and has support for
both copper and fiber NICs thus providing flexibility of deployment in any environment.
Media-rich environments are characterized by content, such as that seen on popular websites with video
and file transfer. Transactional environments are characterized by connections, such as E-commerce,
instant messaging, and voice. Figure 4-1 demonstrates the spectrum of media-rich and transactional
environments.
Figure 4-1 Media-rich and Transactional Environments
Chapter 4 Installing the IPS 4270-20
The IPS 4270-20 has two built-in GigabitEthernet network ports and nine expansion slots. The network
port numbers are numbered from top to bottom beginning with 0 and the expansion slot numbers increase
from right to left. The two built-in GigabitEthernet ports are used for management and are called
Management0/0 and Management0/1. Management0/1 is reserved for future use. Slots 1 and 2 are
reserved for future use. You can populate slots 3 through 8 with supported network interface cards. Slot
9 is populated by a RAID controller card and is not available for use by network interface cards. The
sensing interfaces are called GigabitEthernet.
Because of the multiple interfaces on the IPS 4270-20, it can cover multiple subnets, each of which have
bandwidth requirements in the multi-T3 range or Gigabit range, and the multiple interfaces can be
connected directly to the additional monitoring interfaces without needing to SPAN the traffic through
a switch.
For improved reliability, the IPS 4270-20 uses a compact flash device for storage rather than a hard-disk
drive. The IPS 4270-20 supports two optional network interface cards, the 2SX interface card with
fiber-optic ports, and the 4GE bypass interface card with copper ports that contains the hardware-bypass
feature. Initially the IPS 4270-20 supports only the built-in interfaces and these two interface cards.
The IPS 4270-20 supports a maximum of 16 sensing ports. Any additional configured ports will not be
monitored and will not appear in the IPS configuration or statistics and no inline traffic will be forwarded
on or between these ports. You receive the following error if you exceed the number of supported ports:
The number of installed network interfaces exceeds the limit of 16. The excess interfaces
are ignored.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
4-2
OL-18504-01
Page 95

Chapter 4 Installing the IPS 4270-20
Note If you add a new interface card that exceeds the limit, one or more of the previous sensing interfaces may
become disabled.
The IPS 4270-20 ships with two power supplies, thus supporting a redundant power supply
configuration. The IPS 4270-20 operates in load-sharing mode when the redundant power supply is
installed.
For More Information
• For more information on how to obtain instructions and BIOS files from the Cisco website, see
Obtaining Cisco IPS Software, page 11-1.
• For more information on sensor interfaces, see Sensor Interfaces, page 1-4.
• For more information on the supported interface cards, see Supported Interface Cards, page 4-3.
• For more information on the 4GE bypass interface card, see Hardware Bypass, page 4-5.
• For more information about the power supplies, see Installing and Removing the Power Supply,
page 4-44.
Supported Interface Cards
Supported Interface Cards
The IPS 4270-20 supports three interface cards: the 4GE bypass interface card, the 2SX interface card,
and the 10GE interface card.
4GE Bypass Interface Card
The 4GE bypass interface card (part numbers IPS-4GE-BP-INT and IPS-4GE-BP-INT=) provides four
10/100/1000BASE-T (4GE) monitoring interfaces. The IPS 4270-20 supports up to four 4GE bypass
interface cards for a total of sixteen GE bypass interfaces. The 4GE bypass interface card supports
hardware bypass.
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
4-3
Page 96

Supported Interface Cards
153325
190474
Figure 4-2 shows the 4GE bypass interface card.
Figure 4-2 4GE Bypass Interface Card
Chapter 4 Installing the IPS 4270-20
2SX Interface Card
The 2SX interface card (part numbers IPS-2SX-INT and IPS-2SX-INT=) provides two 1000BASE-SX
(fiber) monitoring interfaces. The IPS 4270-20 supports up to six 2SX interface cards for a total of
twelve SX interfaces. The 2SX card ports require a multi-mode fiber cable with an LC connector to
connect to the SX interface of the sensor. The 2SX interface card does not support hardware bypass.
Figure 4-3 shows the 2SX interface card.
Figure 4-3 2SX Interface Card
10GE Interface Card
The 10GE interface card (part numbers IPS-2X10GE-SR-INT and IPS-2X10GE-SR-INT=) provides two
10000 Base-SX (fiber) interfaces. The IPS 4270-20 supports up to two 10GE interface cards for a total
of four 10GE fiber interfaces. The card ports require a multi-mode fiber cable with an LC connector to
connect to the SX interface of the IPS 4270-20. The 10GE interface card does not support hardware
bypass.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
4-4
OL-18504-01
Page 97

Chapter 4 Installing the IPS 4270-20
253975
Figure 4-4 shows the 10GE interface card.
Figure 4-4 10GE Interface Card
GigabitEthernetslot_number/port_number is the expansion card interface naming convention for the
IPS 4270-20. The slot number is shown above the slot in the chassis and the port number is numbered
from top to bottom starting with 0.
Hardware Bypass
Hardware Bypass
This section describes the 4GE bypass interface card and its configuration restrictions. IT contains the
following topics:
• 4GE Bypass Interface Card, page 4-5
• Hardware Bypass Configuration Restrictions, page 4-6
• Hardware Bypass and Link Changes and Drops, page 4-7
4GE Bypass Interface Card
The IPS 4270-20 supports the 4-port GigabitEthernet card (part number IPS-4GE-BP-INT=) with
hardware bypass. This 4GE bypass interface card supports hardware bypass only between ports 0 and 1
and between ports 2 and 3.
Note To disable hardware bypass, pair the interfaces in any other combination, for example 2/0<->2/2 and
2/1<->2/3.
Hardware bypass complements the existing software bypass feature in Cisco IPS. The following
conditions apply to hardware bypass and software bypass:
• When bypass is set to OFF, software bypass is not active.
For each inline interface for which hardware bypass is available, the component interfaces are set to
disable the fail-open capability. If SensorApp fails, the sensor is powered off, reset, or if the NIC
interface drivers fail or are unloaded, the paired interfaces enter the fail-closed state (no traffic flows
through inline interface or inline VLAN subinterfaces).
• When bypass is set to ON, software bypass is active.
Software bypass forwards packets between the paired physical interfaces in each inline interface and
between the paired VLANs in each inline VLAN subinterface. For each inline interface on which
hardware bypass is available, the component interfaces are set to standby mode. If the sensor is
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
4-5
Page 98

Hardware Bypass
Note To test fail-over, set the bypass mode to ON or AUTO, create one or more inline interfaces and power
Chapter 4 Installing the IPS 4270-20
powered off, reset, or if the NIC interfaces fail or are unloaded, those paired interfaces enter
fail-open state in hardware (traffic flows unimpeded through inline interface). Any other inline
interfaces enter fail-closed state.
• When bypass is set to AUTO (traffic flows without inspection), software bypass is activated if
SensorApp fails.
For each inline interface on which hardware bypass is available, the component interfaces are set to
standby mode. If the sensor is powered off, reset, or if the NIC interfaces fail or are unloaded, those
paired interfaces enter fail-open state in hardware. Any other inline interfaces enter the fail-closed
state.
down the sensor and verify that traffic still flows through the inline path.
For More Information
For the procedure for installing and removing the 4GE bypass interface card, see Installing and
Removing Interface Cards, page 4-41.
Hardware Bypass Configuration Restrictions
To use the hardware bypass feature on the 4GE bypass interface card, you must pair interfaces to support
the hardware design of the card. If you create an inline interface that pairs a hardware-bypass-capable
interface with an interface that violates one or more of the hardware-bypass configuration restrictions,
hardware bypass is deactivated on the inline interface and you receive a warning message similar to the
following:
Hardware bypass functionality is not available on Inline-interface pair0.
Physical-interface GigabitEthernet2/0 is capable of performing hardware bypass only when
paired with GigabitEthernet2/1, and both interfaces are enabled and configured with the
same speed and duplex settings.
The following configuration restrictions apply to hardware bypass:
• The 4-port bypass card is only supported on the IPS 4270-20.
• Fail-open hardware bypass only works on inline interfaces (interface pairs), not on inline VLAN
pairs.
• Fail-open hardware bypass is available on an inline interface if all of the following conditions are
met:
–
Both of the physical interfaces support hardware bypass.
–
Both of the physical interfaces are on the same interface card.
–
The two physical interfaces are associated in hardware as a bypass pair.
–
The speed and duplex settings are identical on the physical interfaces.
–
Both of the interfaces are administratively enabled.
• Autonegotiation must be set on MDI/X switch ports connected to the IPS 4270-20.
You must configure both the sensor ports and the switch ports for autonegotiation for hardware
bypass to work. The switch ports must support MDI/X, which automatically reverses the transmit
and receive lines if necessary to correct any cabling problems. The sensor is only guaranteed to
operate correctly with the switch if both of them are configured for identical speed and duplex,
which means that the sensor must be set for autonegotiation too.
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
4-6
OL-18504-01
Page 99

Chapter 4 Installing the IPS 4270-20
Hardware Bypass and Link Changes and Drops
Properly configuring and deploying hardware bypass protects against complete link failure if the IPS
appliance experiences a power loss, critical hardware failure, or is rebooted; however, a link status
change still occurs when hardware bypass engages (and again when it disengages).
During engagement, the interface card disconnects both physical connections from itself and bridges
them together. The interfaces of the connected devices can then negotiate the link and traffic forwarding
can resume. Once the appliance is back online, hardware bypass disengages and the interface card
interrupts the bypass and reconnects the links back to itself. The interface card then negotiates both links
and traffic resumes.
There is no built-in way to completely avoid link status changes and drops. However, you can greatly
reduce the interruption time (in some cases to sub-second times) by doing the following:
• Make sure you use CAT 5e/6-certified cabling for all connections.
• Make sure the interfaces of the connected devices are configured to match the interfaces of the
appliance for speed/duplex negotiation (auto/auto).
• Enable portfast on connected switchports to reduce spanning-tree forwarding delays.
Front and Back Panel Features
Front and Back Panel Features
This section describes the IPS 4270-20 front and back panel features and indicators. Figure 4-5 shows
the front view of the IPS 4270-20.
Figure 4-5 IPS 4270-20 Front View
1
2345678
Switches/Indicators
Cisco IPS 4270 SERIES
Intrusion Prevention Sensor
GMT 0
UID
PWR STATUS
MGMT 1
SYSTEM
M
250082
OL-18504-01
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
4-7
Page 100

Front and Back Panel Features
Figure 4-6 shows the front panel switches and indicators.
Figure 4-6 IPS 4270-20 Front Panel Switches and Indicators
System
UID
Management0/0
Power
status
Cisco IPS 4270 SERIES
Intrusion Prevention Sensor
UID
PWR STA
SYSTEM
MGMT 0
Chapter 4 Installing the IPS 4270-20
Management0/1
(reserved for
future use)
Power
TUS
MGMT 1
250108
Table 4 -1 describes the front panel switches and indicators on the IPS 4270-20.
Table 4-1 Front Panel Switches and Indicators
Indicator Description
UID switch and
indicator
Internal system
health indicator
Power status
indicator
Toggles the system ID indicator, which assists with chassis location in a rack:
• Blue—Activated
• Off—Deactivated
Note The ID switch is activated by a switch on the front of the chassis.
Indicates internal system health:
• Green—System on
• Flashing amber—System health degraded
• Flashing red—System health critical
• Off—System off
Indicates the power supply status:
• Green—Power supply on
• Flashing amber—Power supply health degraded
• Flashing red—Power supply health critical
• Off—Power supply off
MGMT0/0 indicator Indicates the status of the management port:
• Green—Linked to network
• Flashing green—Linked with activity on the network
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0
4-8
• Off—No network connection
OL-18504-01
 Loading...
Loading...