Page 1

Americas Headquarters
Cisco Systems, Inc.
170 West Tasman Drive
San Jose, CA 95134-1706
USA
http://www.cisco.com
Tel: 408 526-4000
800 553-NETS (6387)
Fax: 408 527-0883
Text Part Number: OL-11157-01
Cisco 4700 Series Application Control
Engine Appliance Administration Guide
Software Version A1(7)
November 2007
Page 2

THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT
NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT
ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR
THEIR APPLICATION OF ANY PRODUCTS.
THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION
P
ACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO
LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY.
The Cisco implementation of TCP header compress
ion is an adaptation of a program developed by the University of California, Berkeley (UCB) as
part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California.
NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE
PR
OVIDED “AS IS” WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED
OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND
NO
NINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE.
IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR A
NY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL
DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR
INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH
DAMAGES.
CCDE, CCVP, Cisco Eos, Cisco StadiumVision, the Cisco logo, DCE, and Welcome to the Human Networ
k are trademarks; Changing the Way We
Work, Live, Play, and Learn is a service mark; and Access Registrar, Aironet, AsyncOS, Bringing the Meeting To You, Catalyst, CCDA, CCDP, CCIE,
CCIP, CCNA, CCNP, CCSP, Cisco, the Cisco Certified Internetwork Expert logo, Cisco IOS, Cisco Press, Cisco Systems, Cisco Systems Capital, the
Cis
co Systems logo, Cisco Unity, Collaboration Without Limitation, Enterprise/Solver, Eth
erChannel, EtherFast, EtherSwitch, Event Center, Fast
Step, Follow Me Browsing, FormShare, GigaDrive, HomeLink, Internet Quotient, IOS, iPhone, IP/TV, iQ Expertise, the iQ logo, iQ Net Readiness
Scorecard, iQuick Study, IronPort, the IronPort logo, LightStream, Linksys, MediaTone, MeetingPlace,
MGX, Networkers, Networking Academy,
Network Registrar, PCNow, PIX, PowerPanels, ProConnect, ScriptShare, SenderBase, SMARTnet, Spectrum Expert, StackWise, The Fastest Way to
Increase Your Internet Quotient, TransPath, WebEx, and the WebEx logo are registered trademarks of Cisco Systems, Inc. and/or its affiliates in the
Uni
ted States and certain other countries.
All other trademarks mentioned in this document or Website are the
property of their respective owners. The use of the word partner does not imply
a partnership relationship between Cisco and any other company. (0801R)
Any Internet Protocol (IP) addresses used in this document are not intended to be actual addresses. Any examples, command display ou
tput, and
figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses in illustrative content is unintentional and
coincidental.
Cisco 4700 Series Application Control Engine Appliance Administration Guide
Copyright © 2007 Cisco Systems, Inc. All rights reserved.
Page 3

iii
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
CONTENTS
Preface xv
Audience xvi
How to Use This Guide xvi
Related Documentation xviii
Symbols and Conventions xxi
Obtaining Documentation, Obtaining Support, and Security Guidelines xxiii
Open Source License Acknowledgements xxiii
OpenSSL/Open SSL Project xxiii
License Issues xxiii
CHAPTER
1 Setting Up the ACE 1-1
Establishing a Console Connection on the ACE 1-2
Using the Setup Script to Enable Connectivity to the Device Manager 1-3
Connecting and Logging into the ACE 1-7
Changing the Administrative Password 1-9
Resetting the Administrator CLI Account Password 1-10
Assigning a Name to the ACE 1-12
Configuring an ACE Inactivity Timeout 1-12
Configuring a Message-of-the-Day Banner 1-13
Configuring the Time, Date, and Time Zone 1-15
Setting the System Time and Date 1-15
Setting the Time Zone 1-16
Adjusting for Daylight Saving Time 1-19
Page 4

Contents
iv
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Viewing the System Clock Settings 1-21
Synchronizing the ACE with an NTP Server 1-21
Configuring NTP Server and Peer Associations 1-22
Viewing NTP Statistics and Information 1-23
.Clearing NTP Statistics 1-28
Configuring Terminal Settings 1-30
Configuring Terminal Display Attributes 1-30
Configuring Terminal Line Settings 1-32
Configuring Console Line Settings 1-32
Configuring Virtual Terminal Line Settings 1-34
Modifying the Boot Configuration 1-35
Setting the Boot Method from the Configuration Register 1-35
Setting the BOOT Environment Variable 1-37
Configuring the ACE to Bypass the Startup Configuration File During the Boot
Process
1-38
Displaying the ACE Boot Configuration 1-41
Restarting the ACE 1-41
Shutting Down the ACE 1-42
CHAPTER
2 Enabling Remote Access to the ACE 2-1
Remote Access Configuration Quick Start 2-2
Configuring Remote Network Management Traffic Services 2-4
Creating and Configuring a Remote Management Class Map 2-5
Defining a Class Map Description 2-6
Defining Remote Network Management Protocol Match Criteria 2-7
Creating a Layer 3 and Layer 4 Remote Access Policy Map 2-9
Creating a Layer 3 and Layer 4 Policy Map for Network Management
Traffic Received by the ACE
2-9
Defining a Layer 3 and Layer 4 Policy Map Description 2-10
Page 5

v
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Contents
Specifying a Layer 3 and Layer 4 Traffic Class With the Traffic
Policy
2-10
Defining Layer 3 and Layer 4 Management Traffic Policy Actions 2-12
Applying a Service Policy 2-13
Configuring Telnet Management Sessions 2-15
Configuring SSH Management Sessions 2-16
Configuring Maximum Number of SSH Sessions 2-16
Generating SSH Host Key Pairs 2-17
Terminating an Active User Session 2-19
Enabling ICMP Messages to the ACE 2-19
Directly Accessing a User Context Through SSH 2-21
Example of a Remote Access Configuration 2-23
Viewing Session Information 2-24
Showing Telnet Session Information 2-24
Showing SSH Session Information 2-26
Showing SSH Session Information 2-26
Showing SSH Key Details 2-27
CHAPTER
3 Managing ACE Software Licenses 3-1
Available ACE Licenses 3-2
Ordering an Upgrade License and Generating a Key 3-5
Copying a License File to the ACE 3-6
Installing a New or Upgrade License File 3-7
Replacing a Demo License with a Permanent License 3-8
Removing a License 3-9
Removing an Appliance Performance Throughput License 3-10
Removing an SSL TPS License 3-10
Removing a Virtualization Context License 3-10
Removing an HTTP Compression Performance License 3-13
Page 6

Contents
vi
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Removing the Application Acceleration Software Feature Pack License 3-14
Backing Up a License File 3-15
Displaying License Configurations and Statistics 3-16
CHAPTER
4 Configuring Class Maps and Policy Maps 4-1
Class Map and Policy Map Overview 4-2
Class Maps 4-5
Policy Maps 4-6
Service Policies 4-9
Class Map and Policy Map Configuration Quick Start 4-10
Configuring Layer 3 and Layer 4 Class Maps 4-24
Defining Layer 3 and Layer 4 Classifications for Network Traffic Passing
Through the ACE
4-24
Creating a Layer 3 and Layer 4 Network Traffic Class Map 4-25
Defining a Class Map Description 4-27
Defining Access-List Match Criteria 4-28
Defining Match Any Criteria 4-28
Defining Destination IP Address and Subnet Mask Match Criteria 4-29
Defining TCP/UDP Port Number or Port Range Match Criteria 4-30
Defining the Source IP Address and Subnet Mask Match Criteria 4-31
Defining the VIP Address Match Criteria 4-32
Defining Layer 3 and Layer 4 Classifications for Network Management Traffic
Received by the ACE
4-35
Creating a Layer 3 and Layer 4 Network Management Traffic Class
Map
4-35
Defining Network Management Access Match Criteria 4-37
Configuring Layer 7 Class Maps 4-38
Defining Layer 7 Classifications for HTTP Server Load Balancing 4-39
Defining Layer 7 Classifications for HTTP Deep Packet Inspection 4-41
Defining Layer 7 Classifications for FTP Command Inspection 4-42
Page 7

vii
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Contents
Configuring a Layer 3 and Layer 4 Policy Map 4-43
Creating a Layer 3 and Layer 4 Policy Map for Network Management Traffic
Received by the ACE
4-44
Creating a Layer 3 and Layer 4 Policy Map for Network Traffic Passing
Through the ACE
4-45
Defining a Layer 3 and Layer 4 Policy Map Description 4-45
Specifying a Layer 3 and Layer 4 Traffic Class With the Traffic Policy 4-46
Specifying Layer 3 and Layer 4 Policy Actions 4-47
Using Parameter Maps in a Layer 3 and Layer 4 Policy Map 4-49
Configuring a Layer 7 Policy Map 4-50
Creating a Layer 7 Policy Map 4-51
Adding a Layer 7 Policy Map Description 4-53
Including Inline Match Statements in a Layer 7 Policy Map 4-53
Specifying a Layer 7 Traffic Class with the Traffic Policy 4-54
Specifying Layer 7 Policy Actions 4-55
Associating the Layer 7 Policy Map with a Layer 3 and Layer 4 Policy
Map
4-57
Applying a Service Policy 4-58
Class Maps and Policy Map Examples 4-60
Firewall Example 4-60
Layer 7 Load-Balancing Example 4-63
Layer 3 and Layer 4 Load-Balancing Example 4-65
VIP With Connection Parameters Example 4-66
Example of a Traffic Policy Configuration 4-68
Viewing Class Maps, Policy Maps, and Service Policies 4-71
Displaying Class Map Configuration Information 4-71
Displaying Policy Map Configuration Information 4-71
Displaying Service Policy Configuration Information 4-72
Page 8

Contents
viii
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
CHAPTER
5 Managing the ACE Software 5-1
Saving Configuration Files 5-1
Saving the Configuration File in Flash Memory 5-3
Saving Configuration Files to a Remote Server 5-4
Copying the Configuration File to the disk0: File System 5-5
Merging the Startup-Configuration File with the Running-Configuration
File
5-6
Viewing Configuration Files 5-7
Viewing User Context Running-Config Files from the Admin Context 5-10
Clearing the Startup-Configuration File 5-10
Loading Configuration Files from a Remote Server 5-11
Using the File System on the ACE 5-12
Listing the Files in a Directory 5-13
Copying Files 5-15
Copying Files to Another Directory on the ACE 5-15
Copying Licenses 5-16
Copying a Packet Capture Buffer 5-16
Copying Files to a Remote Server 5-17
Copying Files from a Remote Server 5-19
Copying an ACE Software System Image to a Remote Server 5-20
Uncompressing Files in the disk0: File System 5-21
Untarring Files in the disk0: File System 5-22
Creating a New Directory 5-22
Deleting an Existing Directory 5-23
Moving Files 5-23
Deleting Files 5-24
Displaying File Contents 5-25
Saving show Command Output to a File 5-26
Viewing and Copying Core Dumps 5-27
Copying Core Dumps 5-28
Page 9

ix
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Contents
Clearing the Core Directory 5-29
Deleting a Core Dump File 5-29
Capturing and Copying Packet Information 5-30
Capturing Packet Information 5-30
Copying Capture Buffer Information 5-32
Viewing Packet Capture Information 5-33
Using the Configuration Checkpoint and Rollback Service 5-37
Overview 5-37
Creating a Configuration Checkpoint 5-38
Deleting a Configuration Checkpoint 5-38
Rolling Back a Running Configuration 5-39
Displaying Checkpoint Information 5-39
Reformatting Flash Memory 5-40
CHAPTER
6 Viewing ACE Hardware and Software Configuration Information 6-1
Displaying Software Version Information 6-2
Displaying Software Copyright Information 6-3
Displaying Hardware Information 6-3
Displaying the Hardware Inventory 6-4
Displaying ACE Environment Information 6-5
Displaying System Processes 6-6
Displaying Process Status Information and Memory Resource Limits 6-11
Displaying System Information 6-14
Displaying ICMP Statistics 6-16
Displaying Technical Support Information 6-17
CHAPTER
7 Configuring Redundant ACE Appliances 7-1
Overview of Redundancy 7-1
Page 10

Contents
x
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Redundancy Protocol 7-2
Stateful Failover 7-5
FT VLAN 7-6
Configuration Synchronization 7-7
Configuration Requirements and Restrictions 7-8
Redundancy Configuration Quick Start 7-8
Configuring Redundancy 7-12
Configuring an FT VLAN 7-12
Creating an FT VLAN 7-13
Configuring an FT VLAN IP Address 7-13
Configuring the Peer IP Address 7-14
Enabling the FT VLAN 7-15
Configuring an Alias IP Address 7-15
Configuring an FT Peer 7-16
Associating the FT VLAN with the Local Peer 7-16
Configuring the Heartbeat Interval and Count 7-17
Configuring a Query Interface 7-18
Configuring an FT Group 7-19
Associating a Context with an FT Group 7-19
Associating a Peer with an FT Group 7-20
Assigning a Priority to the Active FT Group Member 7-20
Assigning a Priority to the Standby FT Group Member 7-21
Configuring Preemption 7-22
Placing an FT Group in Service 7-23
Modifying an FT Group 7-23
Forcing a Failover 7-24
Synchronizing Redundant Configurations 7-25
Configuring Tracking and Failure Detection 7-28
Overview of Tracking and Failure Detection 7-28
Configuring Tracking and Failure Detection for a Host or Gateway 7-29
Page 11

xi
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Contents
Creating a Tracking and Failure Detection Process for a Host or
Gateway
7-30
Configuring the Gateway or Host IP Address Tracked by the Active
Member
7-30
Configuring a Probe on the Active Member for Host Tracking 7-31
Configuring a Priority on the Active Member for Multiple Probes 7-32
Configuring the Gateway or Host IP Address Tracked by the Standby
Member
7-32
Configuring a Probe on the Standby Member for Host Tracking 7-33
Configuring a Priority on the Standby Member for Multiple Probes 7-33
Example of a Tracking Configuration for a Gateway 7-34
Configuring Tracking and Failure Detection for an Interface 7-35
Creating a Tracking and Failure Detection Process for an Interface 7-35
Configuring the Interface Tracked by the Active Member 7-36
Configuring a Priority for a Tracked Interface on the Active Member 7-36
Configuring the Interface Tracked by the Standby Member 7-37
Configuring a Priority for a Tracked Interface on the Standby
Member
7-37
Example of a Tracking Configuration for an Interface 7-38
Example of a Redundancy Configuration 7-38
Displaying Redundancy Information 7-41
Displaying Redundancy Configurations 7-41
Displaying FT Group Information 7-41
Displaying the IDMAP Table 7-46
Displaying the Redundancy Internal Software History 7-47
Displaying Memory Statistics 7-47
Displaying Peer Information 7-47
Displaying FT Statistics 7-51
Displaying FT Tracking Information 7-54
Clearing Redundancy Statistics 7-58
Clearing FT Statistics 7-58
Page 12

Contents
xii
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Clearing the Redundancy History 7-58
CHAPTER
8 Configuring SNMP 8-1
SNMP Overview 8-2
Managers and Agents 8-3
SNMP Manager and Agent Communication 8-4
SNMP Traps and Informs 8-5
SNMPv3 CLI User Management and AAA Integration 8-6
CLI and SNMP User Synchronization 8-6
Supported MIBs and Notifications 8-7
SNMP Limitations 8-24
SNMP Configuration Quick Start 8-25
Configuring SNMP Users 8-27
Defining SNMP Communities 8-29
Configuring an SNMP Contact 8-31
Configuring an SNMP Location 8-31
Configuring SNMP Notifications 8-32
Configuring SNMP Notification Hosts 8-32
Enabling SNMP Notifications 8-34
Enabling the IETF Standard for SNMP linkUp and linkDown Traps 8-36
Assigning a Trap-Source Interface for SNMP Traps 8-37
Configuring SNMP Management Traffic Services 8-38
Creating and Configuring a Layer 3 and Layer 4 Class Map 8-39
Defining a Class Map Description 8-40
Defining SNMP Protocol Match Criteria 8-41
Creating a Layer 3 and Layer 4 Policy Map 8-42
Creating a Layer 3 and Layer 4 Policy Map for SNMP Network
Management Traffic Received by the ACE
8-42
Specifying a Layer 3 and Layer 4 Traffic Class with the Traffic Policy 8-43
Page 13

xiii
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Contents
Specifying Layer 3 and Layer 4 Policy Actions 8-44
Applying a Service Policy 8-45
Example of an SNMP Configuration 8-47
Displaying SNMP Statistics 8-50
CHAPTER
9 Configuring the XML Interface 9-1
XML Overview 9-2
XML Usage with the ACE 9-2
HTTP and HTTPS Support with the ACE 9-4
HTTP Return Codes 9-5
Document Type Definition 9-7
Sample XML Configuration 9-9
XML Configuration Quick Start 9-11
Configuring HTTP and HTTPS Management Traffic Services 9-13
Creating and Configuring a Class Map 9-14
Defining a Class Map Description 9-15
Defining HTTP and HTTPS Protocol Match Criteria 9-16
Creating a Layer 3 and Layer 4 Policy Map 9-17
Creating a Layer 3 and Layer 4 Policy Map for Network Management
Traffic Received by the ACE
9-17
Specifying a Layer 3 and Layer 4 Traffic Class with the Traffic Policy 9-18
Specifying Layer 3 and Layer 4 Policy Actions 9-20
Applying a Service Policy 9-20
Enabling the Display of Raw XML Request show Command Output in XML
Format
9-24
Accessing the ACE DTD File 9-27
APPENDIX
A Upgrading Your ACE Software A-1
Overview of Upgrading ACE Software A-2
Page 14

Contents
xiv
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Before You Begin A-2
Changing the Admin Password A-2
Changing the www User Password A-3
Checking Your Configuration for FT Priority and Preempt A-3
Creating a Checkpoint A-3
Software Upgrade Quick Start A-4
Copying the Software Upgrade Image to the ACE A-7
Configuring the ACE to Autoboot the Software Image A-8
Setting the Boot Variable A-8
Configuring the Configuration Register to Autoboot the Boot Variable A-9
Verifying the Boot Variable and Configuration Register A-10
Reloading the ACE A-10
Displaying Software Image Information A-11
I
NDEX
Page 15

xv
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Preface
This guide provides instructions for the administration of the Cisco 4700 Series
Application Control Engine (ACE) appliance. It describes how to perform
administration tasks on the ACE, including initial setup, establish remote access,
manage software licenses, configure class maps and policy maps, manage the
ACE software, configure SNMP, configure redundancy, configure the XML
interface, and upgrade your ACE software.
You can configure the ACE by using the following interfaces:
• The command-line interface (CLI), a line-oriented user interface that
provides commands for configuring, managing, and monitoring the ACE.
• Device Manager graphic user interface (GUI), a Web browser-based GUI
interface that provides a graphical user interface for configuring, managing,
and monitoring the ACE.
This preface contains the following major sections:
• Audience
• How to Use This Guide
• Related Documentation
• Symbols and Conventions
• Obtaining Documentation, Obtaining Support, and Security Guidelines
• Open Source License Acknowledgements
Page 16
Preface
xvi
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Audience
This guide is intended for the following trained and qualified service personnel
who are responsible for configuring the ACE:
• System administrator
• System operator
How to Use This Guide
This guide is organized as follows:
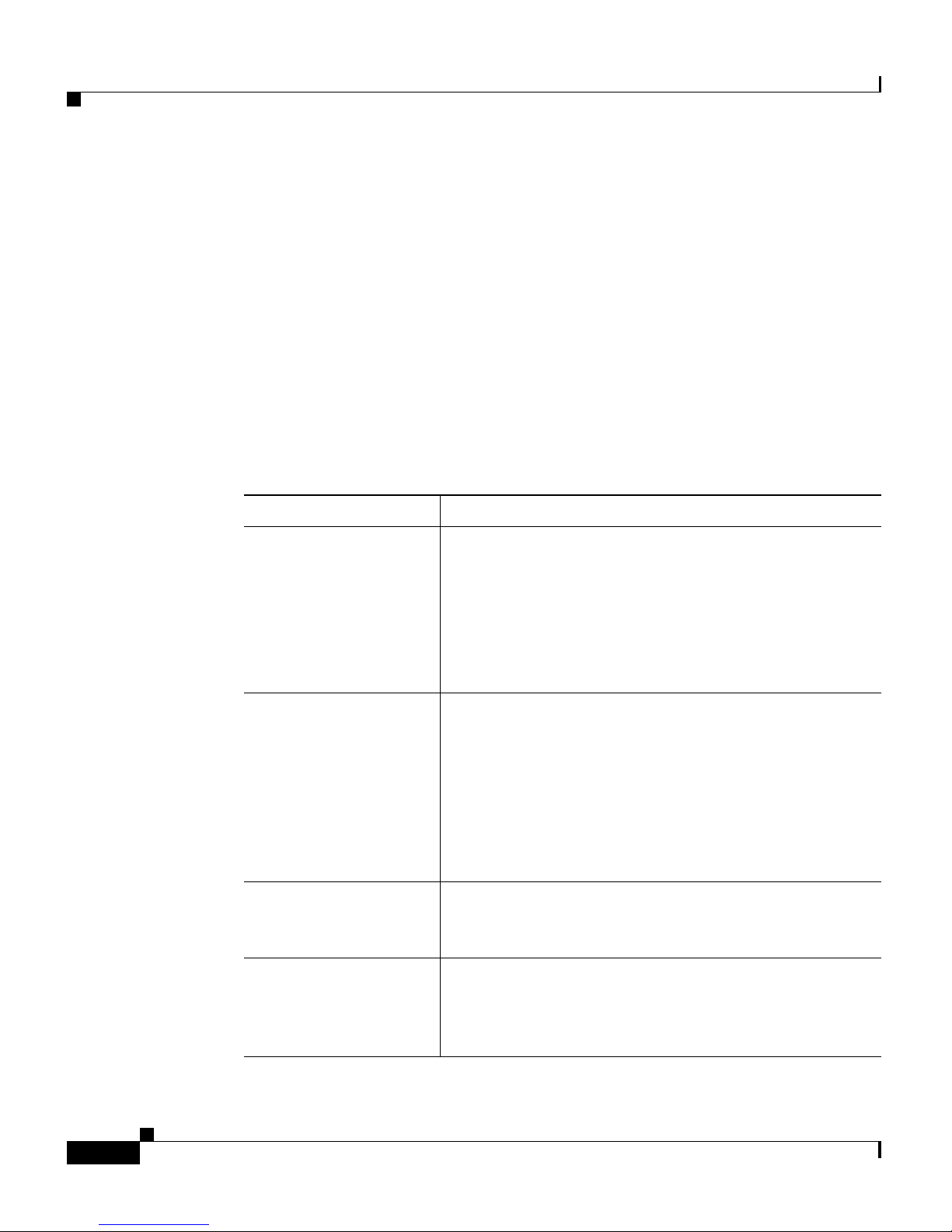
Chapter Description
Chapter 1, Setting Up
the ACE
Describes how to configure basic settings on the ACE,
incl
uding topics such as how to session and log in to
the ACE, change the administrative username and
password, assign a name to the ACE, configure a
message-of-the-day banner, configure date and time,
configure terminal settings, modify the boot
configuration, and restart the ACE.
Chapter 2, Enabling
Remote Access to the
ACE
Describes how to configure remote access to the Cisco
47
00 Series Application Control Engine (ACE)
appliance by establishing a remote connection using
the Secure Shell (SSH) or Telnet protocols. It also
describes how to configure the ACE to provide direct
access to a user context from SSH. This chapter also
covers how to configure the ACE to receive ICMP
messages from a host.
Chapter 3, Managing
ACE Software
Licenses
Describes how to manage the softw
are licenses for
your ACE.
Chapter 4, Configuring
Class Maps and Policy
Maps
Describes how to configure class maps and policy
maps to pro
vide a global level of classification for
filtering traffic received by or passing through the
ACE.
Page 17

xvii
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Preface
Chapter 5, Managing
the ACE Software
Describes how to save and download configuration
files, use the file system, view and copy core dumps,
capture and copy packet information, use the
configuration checkpoint and rollback service, display
configuration information, and display technical
support information.
Chapter 6, Viewing
ACE Hardware and
Software
Configuration
Information
Describes how to display ACE hardware and software
co
nfiguration information, and display technical
support information.
Chapter 7, Configuring
Redundant ACE
Appliances
Describes how to configure the ACE for redundancy,
wh
ich provides fault tolerance for the stateful failover
of flows.
Chapter 8, Configuring
SNMP
Describes how to configure Simple Network
Manag
ement Protocol (SNMP) to query the ACE for
Cisco Management Information Bases (MIBs) and to
send event notifications to a network management
system (NMS).
Chapter 9, Configuring
the XML Interface
Describes how to provide a mechanism using XML to
transfer
, configure, and monitor objects in the ACE.
This XML capability allows you to easily shape or
extend the CLI query and reply data in XML format to
meet different specific business needs.
Appendix A,
Upgrading Your ACE
Software
Describes how to upgrade the software on your ACE.
Chapter Description
Page 18

Preface
xviii
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Related Documentation
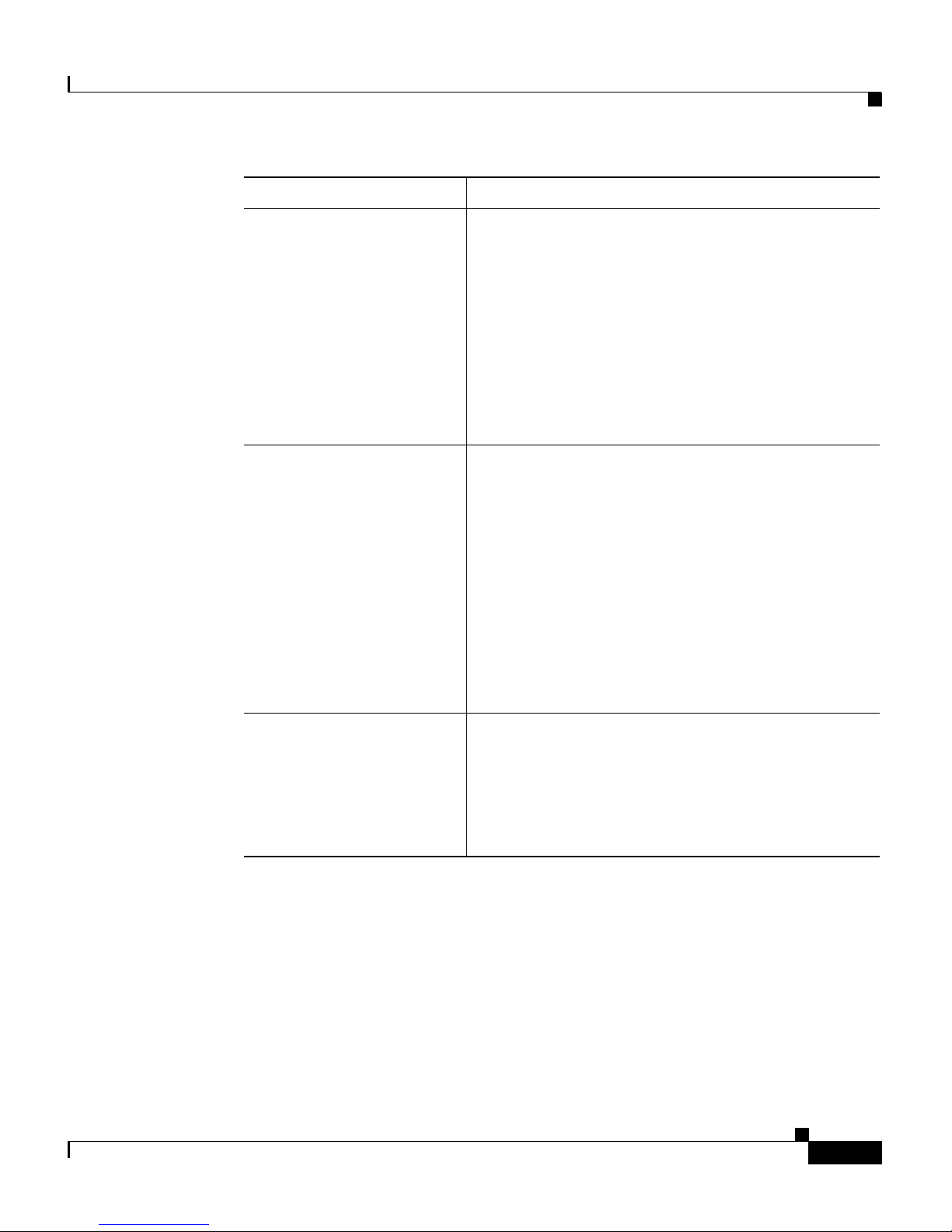
In addition to this document, the ACE documentation set includes the following:
Document Title Description
Release Note for the Cisco
47
00 Series Application
Control Engine Appliance
Provides information about operating
considerations, caveats, and command-line
interface (CLI) commands for the ACE.
Cisco Application Control
Engi
ne Appliance
Hardware Installation
Guide
Provides information for
installing the ACE
appliance.
Regulatory Compliance
an
d Safety Information for
the Cisco Application
Control Engine Appliance
Regulatory compliance and safety information for
the A
CE appliance.
Cisco ACE 4700 Series
Appl
ication Control
Engine Appliance CLI
Quick Configuration Note
Describes how to use the ACE CLI to perform the
i
nitial setup and VIP load-balancing configuration
tasks.
Cisco 4700 Series
Appl
ication Control
Engine Appliance Device
Manager GUI Quick
Configuration Note
Describes how to use the ACE Device Manager
GUI to
perform the initial setup and VIP
load-balancing configuration tasks.
Cisco 4700 Series
Appl
ication Control
Engine Appliance
Virtualization
Configuration Guide
Describes how to operate your ACE in a single
co
ntext or in multiple contexts.
Page 19
xix
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Preface
Cisco 4700 Series
Application Control
Engine Appliance Routing
and Bridging
Configuration Guide
Describes how to perform the following routing
a
nd bridging tasks on the ACE:
• Configuring Ethernet ports
• Configuring VLAN interfaces
• Configuring routing
• Configuring bridging
• Configuring Dynamic Host Configuration
Protocol (DHCP)
Cisco 4700 Series
Appl
ication Control
Engine Appliance Server
Load-Balancing
Configuration Guide
Describes how to configure the following server
load-balancing tasks on the A
CE:
• Real servers and server farms
• Class maps and policy maps to load-balance
traffic to real servers in server farms
• Server health monitoring (probes)
• Stickiness
• Firewall load balancing
• TCL scripts
Cisco 4700 Series
Appl
ication Control
Engine Appliance
Application Acceleration
and Optimization
Configuration Guide
Describes the configuration of the application
a
cceleration and optimization features of the ACE.
It also provides an overview and description of
those features.
Document Title Description
Page 20
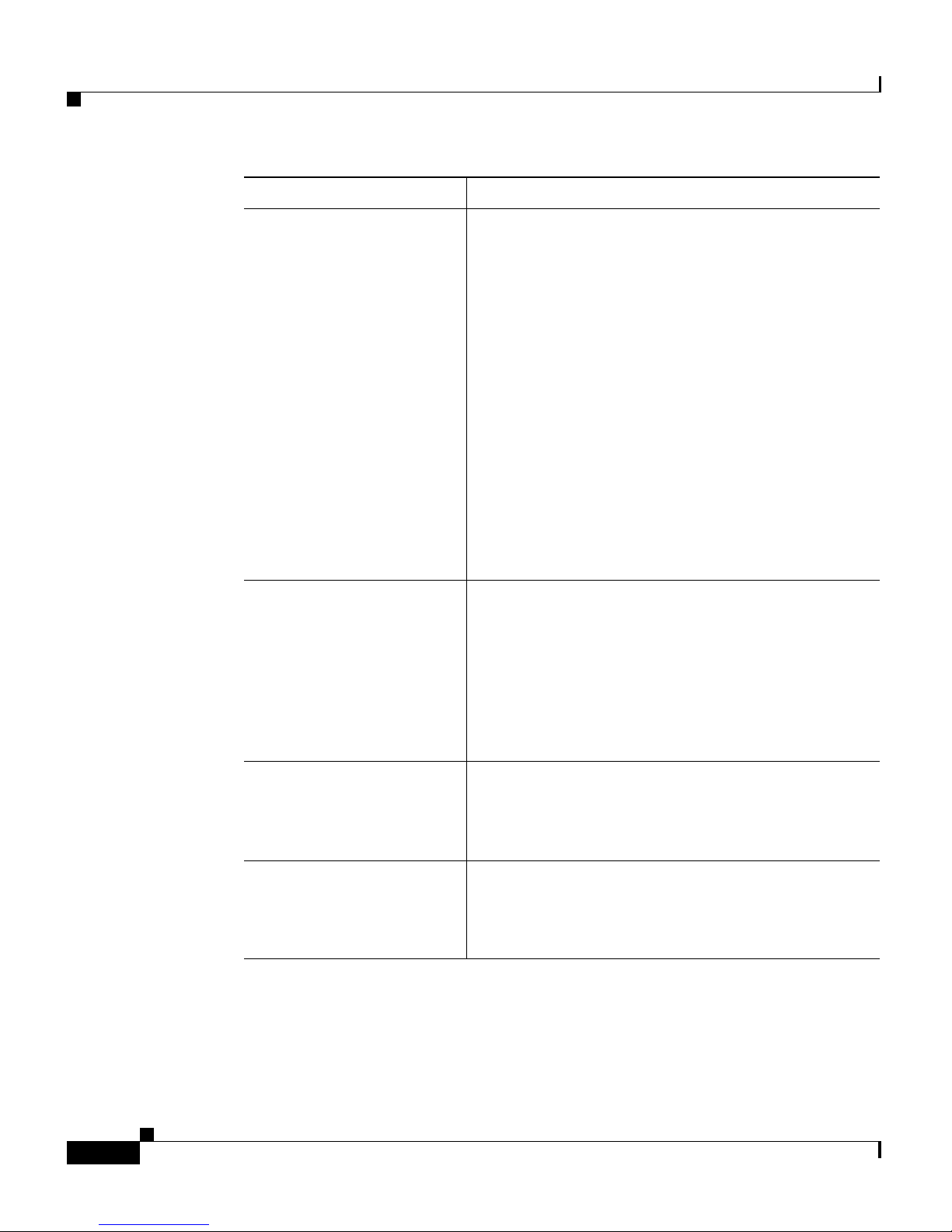
Preface
xx
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Cisco 4700 Series
Application Control
Engine Appliance Security
Configuration Guide
Describes how to perform fo
llowing ACE security
configuration tasks:
• Security access control lists (ACLs)
• User authentication and accounting using a
Terminal Access Controller Access Control
System Plus (TACACS+), Remote
Authentication Dial-In User Service
(RADIUS), or Lightweight Directory Access
Protocol (LDAP) server
• Application protocol and HTTP deep packet
inspection
• TCP/IP normalization and termination
parameters
• Network address translation (NAT)
Cisco 4700 Series
Appl
ication Control
Engine Appliance SSL
Configuration Guide
Describes how to configure the following Secure
Sock
ets Layer (SSL) tasks on the ACE:
• SSL certificates and keys
• SSL initiation
• SSL termination
• End-to-end SSL
Cisco 4700 Series
Appl
ication Control
Engine Appliance System
Message Guide
Describes how to configure system message
log
ging on the ACE. This guide also lists and
describes the system log (syslog) messages generated
by the ACE.
Cisco 4700 Series
Appl
ication Control
Engine Appliance
Command Reference
Provides an alphabetical list and descriptions of all
CLI com
mands by mode, including syntax,
options, and related commands.
Document Title Description
Page 21
xxi
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Preface
Symbols and Conventions
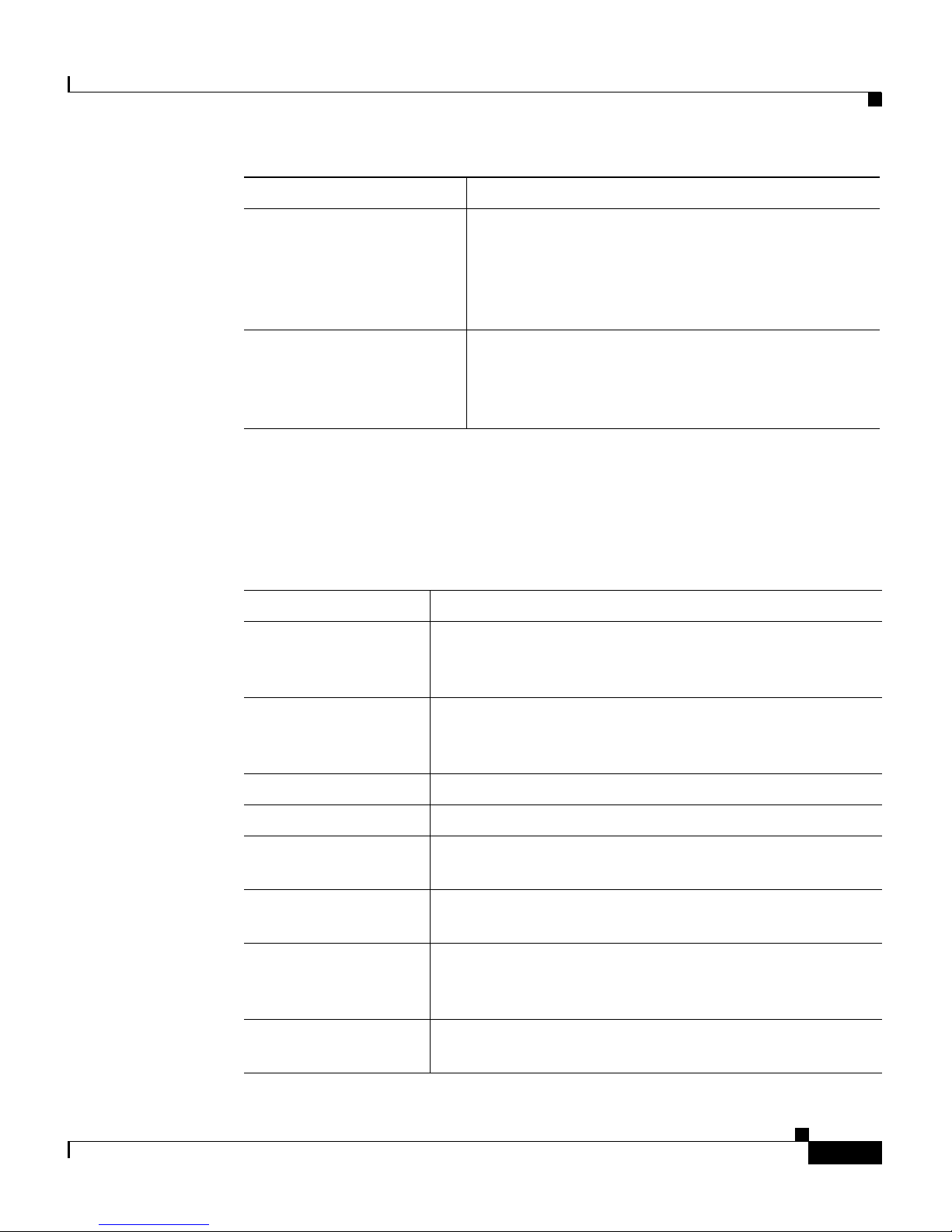
This publication uses the following conventions:
Cisco 4700 Series
Appl
ication Control
Engine Appliance Device
Manager Configuration
Guide
Describes how to use the Device Manager GUI,
wh
ich resides in flash memory on the ACE, to
provide a browser-based interface for configuring
and managing the appliance.
Cisco CSS-to-ACE
Co
nversion Tool User
Guide
Describes how to use the CSS-to-ACE conversion
tool to migrate Cisco Content Services Switches
(CSS) running-configuration or
startup-configuration files to the ACE.
Document Title Description
Convention Description
boldface font Commands, command options, and keywords are in
bol
dface. Bold text also indicates a command in a
paragraph.
italic f
ont Arguments for which you supply values are in italics.
Italic text also indicates the first occurrence of a new
term, book title, emphasized text.
{ } Encloses required arguments and keywords.
[ ] Encloses optional arguments and keywords.
{x | y | z} Required alternative keywords are grouped in braces and
se
parated by vertical bars.
[x | y | z] Optional alternative keywords are grouped in brackets
an
d separated by vertical bars.
string A nonquoted set of characters. Do not use quotation
marks arou
nd the string or the string will include the
quotation marks.
screen font Terminal sessions and information the system displays
are in
screen font.
Page 22
Preface
xxii
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Notes use the following conventions:
Note Means reader take note. Notes contain helpful suggestions or references to
material not covered in the publication.
Cautions use the following conventions:
Caution Means reader be careful. In this situation, you might do something that could
result in equipment damage or loss of data.
Warnings use the following conventions:
Warning
Means possible physical harm or equipment damage. A warning describes an
action that could cause you physical harm or damage the equipment.
For additional information about CLI syntax formatting, see the Cisco 4700
Series Application Control Engine Appliance Command Reference.
boldface screen
font
Information you must enter in a command line is in
boldface screen font.
italic screen font Arguments for which you supply values are in i
talic
screen font.
^ The symbol ^ represents the k
ey labeled Control—for
example, the key combination ^D in a screen display
means hold down the Control key while you press the D
key.
< > Nonprinting characters, such as passwords are in angle
brack
ets.
Convention Description
Page 23

xxiii
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Preface
Obtaining Documentation, Obtaining Support, and
Security Guidelines
For information on obtaining documentation, obtaining support, providing
documentation feedback, security guidelines, and also recommended aliases and
general Cisco documents, see the monthly What’
s New in Cisco Product
Documentation, which also lists all new and revised Cisco technical
d
ocumentation, at:
http://www.cisco.com/en/US/docs/general/whatsnew/whatsnew.html
Open Source License Acknowledgements
The following acknowledgements pertain to this software license.
OpenSSL/Open SSL Project
This product includes software developed by the OpenSSL Project for use in the
OpenSSL Toolkit (http://www.openssl.org/).
This product includes cryptographic software written by Eric Young
(eay@cryptsoft.com)
.
This product includes software written by Tim Hudson (tjh@cryptsoft.com).
License Issues
The OpenSSL toolkit stays under a dual license, i.e. both the conditions of the
OpenSSL License and the original SSLeay license apply to the toolkit. See below
for the actual license texts. Actually both licenses are BSD-style Open Source
licenses. In case of any license issues related to OpenSSL please contact
openssl-core@openssl.org.
OpenSSL License:
© 1998-1999 The OpenSSL Project. All rights reserved.
Page 24

Preface
xxiv
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Redistribution and use in source and binary forms, with or without modification,
are permitted provided that the following conditions are met:
1. Redistributions of source code must retain the copyright notice, this list of
conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice,
this list of conditions, and the following disclaimer in the documentation
and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software must
display the following acknowledgment: “This product includes software
developed by the OpenSSL Project for use in the OpenSSL Toolkit.
(http://www.openssl.org/)”
4. The names “OpenSSL Toolkit” and “OpenSSL Project” must not be used to
endorse or promote products derived from this software without prior written
permission. For written permission, please contact
openssl-core@openssl.org.
5. Products derived from this software may not be called “OpenSSL” nor may
“OpenSSL” appear in their names without prior written permission of the
OpenSSL Project.
6. Redistributions of any form whatsoever must retain the following
acknowledgment:
“This product includes software developed by the OpenSSL Project for use in
t
he OpenSSL Toolkit (http://www.openssl.org/)”
THIS SOFTWARE IS PROVIDED BY THE
OpenSSL PROJECT “AS IS”' AND
ANY EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO
EVENT SHALL THE OpenSSL PROJECT OR ITS CONTRIBUTORS BE
LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN
CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE
OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH
DAMAGE.
Page 25

xxv
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Preface
This product includes cryptographic software written by Eric Young
(eay@cryptsoft.com). This product includes software written by Tim Hudson
(tjh@cryptsoft.com).
Original SSLeay License:
© 1995-1998 Eric Young (eay@cryptsoft.com). All rights reserved.
This package is an SSL implementation written by Eric Young
(eay@cryptsoft.com)
.
The implementation was written so as to conform with Netscapes SSL.
This library is free for commercial and
non-commercial use as long as the
following conditions are adhered to. The following conditions apply to all code
found in this distribution, be it the RC4, RSA, lhash, DES, etc., code; not just the
SSL code. The SSL documentation included with this distribution is covered by
the same copyright terms except that the holder is Tim Hudson
(tjh@cryptsoft.com).
Copyright remains Eric Young’s, and as such any Copyright notices in the code
are
not to be removed. If this package is used in a product, Eric Young should be
given attribution as the author of the parts of the library used. This can be in the
form of a textual message at program startup or in documentation (online or
textual) provided with the package.
Redistribution and use in source and binary forms, with or without modification,
are permi
tted provided that the following conditions are met:
1. Redistributions of source code must retain the copyright notice, this list of
conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice,
this list of conditions and the following disclaimer in the documentation
and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software must
display the following acknowledgement:
“This product includes cryptographic software written by Eric Young
(eay@cryptsoft.com)
”.
The word ‘cryptographic’ can be left out if the routines from the library being
us
ed are not cryptography-related.
Page 26

Preface
xxvi
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
4. If you include any Windows specific code (or a derivative thereof) from the
apps directory (application code) you must include an acknowledgement:
“This product includes software written by Tim Hudson
(tjh@cryptsoft.com)”.
THIS SOFTWARE IS PROVIDED BY ERIC YOUNG “AS IS” AND ANY
EXPRESS OR IMPLIED W
ARRANTIES, INCLUDING, BUT NOT LIMITED
TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS
FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL
THE AUTHOR OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT,
INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS;
OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY,
OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY
WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.
The license and distribution terms for any publicly available version or derivative
of this c
ode cannot be changed. i.e. this code cannot simply be copied and put
under another distribution license [including the GNU Public License].
Page 27

1-1
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
CHAPTER
1
Setting Up the ACE
This chapter describes how to initially configure basic settings on the Cisco 4700
Series Application Control Engine (ACE) appliance. It includes the following
major sections:
• Establishing a Console Connection on the ACE
• Using the Setup Script to Enable Connectivity to the Device Manager
• Connecting and Logging into the ACE
• Changing the Administrative Password
• Assigning a Name to the ACE
• Configuring an ACE Inactivity Timeout
• Configuring a Message-of-the-Day Banner
• Configuring the Time, Date, and Time Zone
• Synchronizing the ACE with an NTP Server
• Configuring Terminal Settings
• Modifying the Boot Configuration
• Restarting the ACE
• Shutting Down the ACE
For details on assigning VLANs to the ACE, configuring VLAN interfaces on the
A
CE, and configuring a default or static route on the ACE, see the Cisco 4700
Series Application Control Engine Appliance Routing and Bridging
Configuration Guide.
Page 28

Chapter 1 Setting Up the ACE
Establishing a Console Connection on the ACE
1-2
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Establishing a Console Connection on the ACE
You establish a direct serial connection between your terminal or a PC and the
ACE by making a serial connection to the console port on the rear panel of the
ACE. The ACE has one standard RS-232 serial port found on the rear panel that
operates as the console port. The integrated serial port uses a 9-pin male D-shell
connector. Use a straight-through cable to connect the switch to a DTE device,
such as a terminal or a PC. For instructions on connecting a console cable to your
ACE appliance, see the Cisco Application Control Engine Appliance Hardware
Installation Guide.
Any device connected to this port must be capable of asynchronous transmission.
Conn
ection requires a terminal configured as 9600 baud, 8 data bits, hardware
flow control on, 1 stop bit, no parity.
Note Only the Admin context is accessible through the console port; all other contexts
can be reached through Telnet or SSH sessions.
Once connected, use any termi
nal communications application to access the ACE
CLI. The following procedure uses HyperTerminal for Windows.
To access the ACE by using a direct seria
l connection, perform the following
steps:
Step 1 Launch HyperTerminal. The Connection Description window appears.
Step 2 Enter a name for your session in the Name field.
Step 3 Click OK. The Connect To window appears.
Step 4 From the drop-down list, choose the COM port to which the device is connected.
Step 5 Click OK. The Port Properties window appears.
Step 6 Set the following port properties as follows:
• Baud Rate = 9600
• Data Bits = 8
• Hardware Flow Control = On
• Parity = none
• Stop Bits = 1
Step 7 Click OK to connect.
Page 29

1-3
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 1 Setting Up the ACE
Using the Setup Script to Enable Connectivity to the Device Manager
Step 8 Press Enter to access the CLI prompt.
switch login:
Once a session is created, choose Save As from the File menu to save the
connection description. Saving the connection description has the following two
advantages:
• The next time that you launch HyperTerminal, the session is listed as an
option under Start > Programs > A
ccessories > HyperTerminal >
Name_of_session. This option lets you reach the CLI prompt directly
without going through the configuration steps.
• You can connect your cable to a different device without configuring a new
HyperTerminal session. If you use this option, make sure that you connect to
the same port on the new device as was configured in the saved
HyperTerminal session. Otherwise, a blank screen appears without a prompt.
Using the Setup Script to Enable Connectivity to the
Device Manager
When you boot the ACE for the first time and the appliance does not detect a
startup-configuration file, a setup script appears to guide you through the process
of configuring a management VLAN on the ACE through one of its Gigabit
Ethernet ports. The primary intent of the setup script is to simplify connectivity
to the Device Manager GUI (as described in the Cisco 4700 Series Application
Control Engine Appliance Device Manager GUI Quick Configuration Guide)
.
After you specify a gigabit Ethernet port, port mode, and a management VLAN,
the setup script automatically applies the following default configuration:
• Management VLAN allocated to the specified Ethernet port.
• Extended IP access list that allows IP traffic originating from any other host
addresses.
• Traffic classification (class map and policy map) created for management
protocols HTTP, HTTPS, ICMP, SSH, Telnet, and XML-HTTPS. HTTPS is
dedicated for connectivity with the Device Manager GUI.
• VLAN interface configured on the ACE and a policy map assigned to the
VLAN interface.
Page 30

Chapter 1 Setting Up the ACE
Using the Setup Script to Enable Connectivity to the Device Manager
1-4
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
The ACE provides a default answer in brackets [ ] for each question in the setup
script. To accept a default configuration prompt, press Enter, and the ACE
accepts the setting. To skip the remaining configuration prompts, press Ctrl-C
any time during the configuration sequence.
Note The script configuration process described in this section is identical to the script
configuration process performed using the setup CLI command.
To configure the ACE from the setup script, perform the following steps:
Step 1 Ensure that you have established a direct serial connection between your terminal
or a PC and the ACE (see the “Establishing a Console Co
nnection on the ACE”
section).
Step 2 Press the power button on the front of the ACE and the boot process occurs. See
the Cisco Application Control Engine Appliance Hardware Installation Guide for
details.
Step 3 At the login prompt, log into the ACE by entering the login username and
password. By default, the username and password are admin. For example, enter:
switch login: admin
Password: admin
---- Basic System Configuration Dialog ----
This setup utility will guide you through the basic configuration of
the syste
m. Setup configures only enough connectivity to the
ACE appliance Device Manager GUI of the system.
*Note: setup is mainly used for configuring the system initially,
when no configuration is present. So setup always assumes system
defaults and not the current system configuration values.
Press Enter at anytime to skip a dialog. Use ctrl-c at anytime
to skip the remaining dialogs.
Would you like to enter the basic configuration dialog (yes/no):
Caution For software versions A1(8.0a) and higher, you must change the default Admin
password if you have not already done so. Otherwise, you will be able to log in to
the ACE only through the console port.
Page 31

1-5
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 1 Setting Up the ACE
Using the Setup Script to Enable Connectivity to the Device Manager
Step 4 At the prompt “Would you like to enter the basic configuration dialog? (yes/no):”,
type yes to continue the setup (or select no to or bypass its operation and directly
access the CLI).
Step 5 At the prompt “Which port is used to carry Management vlan (1 - 4)? [1]:”,
specify the Ethernet port that you want to use to access the Device Manager GUI.
Valid entries are 1 through 4. The default is Ethernet port 1. Press Enter.
Step 6 At the prompt “Configure GigabitEthernet port mode (Access/Trunk) [Trunk]:”,
identify whether the Ethernet port is to be configured as a VLAN access port or
as a VLAN trunk port. The default is Trunk. Press Enter.
Step 7 At the prompt “Which vlan is used as Management vlan (2 - 4095)? [10]:”, specify
the number you want to assign to the VLAN interface. Valid values are from 2 to
4094. The default is VLAN 10. Press Enter.
Step 8 At the prompt “What is the Management VLAN ip address [192.168.1.10]:”,
assign an IP address to the management VLAN interface. When you assign an IP
address to a VLAN interface, the ACE automatically makes it a routed mode
interface. Press Enter.
Step 9 At the prompt “What is the Management VLAN ip netmask [255.255.255.0]:”,
assign a subnet mask to the management VLAN interface. Press Enter.
Step 10 At the prompt “Configure the default gateway? (yes/no) [y]:”, choose whether to
assign an IP address of the gateway router (the next-hop address for this route). If
you specify yes, enter the IP address of default gateway. The gateway address must
be in the same network as specified in the IP address for a VLAN interface. Press
Enter.
Step 11 After you configure the Ethernet port, port mode, and management VLAN, the
setup script automatically applies the appropriate configuration:
The following configuration will be applied:
interface gigabitEthernet 1/1
switchport trunk allowed vlan 2
no shut
access-list ALL extended permit ip any any
class-map type management match-any remote_access
match protocol xml-https any
match protocol icmp any
match protocol telnet any
match protocol ssh any
match protocol http any
match protocol https any
Page 32

Chapter 1 Setting Up the ACE
Using the Setup Script to Enable Connectivity to the Device Manager
1-6
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
policy-map type management first-match first-match
remote_mgmt_allow_policy
class remote_access
permit
interface vlan 2
ip address 192.168.1.10 255.255.255.0
access-group input ALL
service-policy input remote_mgmt_allow_policy
no shutdown
ip route 0.0.0.0 0.0.0.0 172.16.2.1
Step 12 At the prompt “Would you like to edit the configuration? (yes/no) [n]:”, enter one
of the following replies:
• Type y to modify the configuration at the CLI.
• Type n to accept the configuration without any additional changes. This
setting is the default.
Step 13 At the prompt “Use this configuration? (yes/no) [y]”:, enter one of the following
replies:
• Type y to instruct the ACE to boot using the newly created
running-configuration file. This is the default.
• Type n to bypass using the newly created running-configuration file and boot
with an empty configuration.
Step 14 At the prompt “Would you like to save the running-config to startup-config?
(yes/no) [n]:, enter one of the following replies:
• Type y to save the running-configuration to the startup-configuration file.
• Type n to bypass saving the running-configuration to the
startup-configuration file.
Page 33

1-7
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 1 Setting Up the ACE
Connecting and Logging into the ACE
Connecting and Logging into the ACE
This section describes how to connect to the ACE as the default user from the ACE
console port. Once you connect to the ACE as the default user, you can then log
in and enter the configuration mode to configure the ACE. Only the Admin
context is accessible through the console port; all other contexts can be reached
through a Telnet or SSH remote access session.
The ACE creates the following default users at startup: admin, dm, and www.
• The admin user is the global administrator and cannot be deleted.
• The dm user is for accessing the Device Manager GUI and cannot be deleted.
The dm user is an internal user required by the Device Manager GUI; it is
hidden on the ACE CLI.
Note Do not modify the dm user password from the ACE CLI. If the password
is changed, the Device Manager GUI will become inoperative. If this
occurs, restart the Device Manager using the dm reload command (you
must be the global administrator to access the dm reload command). Note
that restarting the Device Manager does not impact ACE functionality;
however, it may take a few minutes for the Device Manager to reinitialize
as it reads the ACE CLI configuration. This command is available only in
software versions A1(8.0) and higher.
• The ACE uses the www user account for the XML interface and cannot be
deleted.
Later, when you configure interfaces and IP addresses on the ACE itself, you can
remotely ac
cess the ACE CLI through an ACE interface by using a Telnet or SSH
session. To configure remote access to the ACE CLI, see Chapter 2, Enabling
Remote Access to the ACE. For details on configuring inte
rfaces on the ACE, see
the Ci
sco 4700 Series Application Control Engine Appliance Routing and
Bridging Configuration Guide.
You can configure the ACE to provide a h
igher level of security for users
accessing the ACE. For information about configuring user authentication for
login access, see the Cisco 4700 Series Application Control Engine Appliance
Security Configuration Guide.
Page 34

Chapter 1 Setting Up the ACE
Connecting and Logging into the ACE
1-8
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
To connect to the ACE and access configuration mode to perform initial
configuration, perform the following steps:
Step 1 Access the ACE directly by its console port, attach a terminal to the asynchronous
RS-232 serial port on the rear panel of the ACE. The ACE has one standard
RS-232 serial port found on the rear panel that operates as the console port. Any
device connected to this port must be capable of asynchronous transmission.
Connection requires a terminal configured as 9600 baud, 8 data bits, hardware
flow control on, 1 stop bit, no parity.See the “Establishing a Console Connection
on the ACE” section.
Step 2 Log into the ACE by entering the login username and password at the following
prompt:
switch login: admin
Password: admin
By default, both the username and password are admin.
The prompt changes to the following:
switch/Admin#
To change the default login password, see the “Changing the Administrative
Password” section for details.
Note When you boot the ACE for the first time and the appliance does not
detect a startup-configuration file, a setup script appears to enable
connectivity to the ACE Device Manager GUI. The start-up script is not
intended for use with the CLI. Select no to skip the use of the setup script
and proceed directly to the CLI. See “Using the Setup Script to Enable
Connectivity to the Device Manager” section for details.
Caution For software versions A1(8.0a) and higher, you must change the default Admin
password if you have not already done so. Otherwise, you will be able to log in to
the ACE only through the console port.
Page 35

1-9
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 1 Setting Up the ACE
Changing the Administrative Password
Step 3 To access configuration mode, enter the following command:
switch/Admin# configure
Enter configuration commands, one per line. End with CNTL/Z
The prompt changes to the following:
switch/Admin(config)#
Changing the Administrative Password
During the initial login process to the ACE, you enter the default user name
admin and the default password admin in lowercase text. You cannot modify or
delete the default administrative username; however, for security reasons, you
must change the administrative password. If you do not change the administrative
password, security on your ACE can be compromised because the administrative
password is configured to be the same for every ACE shipped from Cisco
Systems.
Caution For software versions A1(8.0a) and higher, you must change the default Admin
password if you have not already done so. Otherwise, you will be able to log in to
the ACE only through the console port.
The administrative username and password are stored in Flash memory. Each time
t
hat you reboot the ACE, it reads the username and password from Flash memory.
Global administrative status is assigned to the administrative username by default.
Note For users that you create in the Admin context, the default scope of access is for
the entire ACE. If you do not assign a user role to a new user, the default user role
is Network-Monitor. For users that you create in other contexts, the default scope
of access is the entire context. To verify the account and permission for each user,
use the show user-account Exec command. For details on contexts, user roles,
and domains, see the Cisco 4700 Series Application Control Engine Appliance
Virtualization Configuration Guide.
Page 36

Chapter 1 Setting Up the ACE
Changing the Administrative Password
1-10
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
To change the default administrative password, use the username command in
configuration mode. The syntax of this command is as follows:
username admin [passw
ord [0 | 5] {password}]
The keywords, arguments, and options are:
• admin—Specifies the default administrative user name.
• password—(Optional) Keyword that indicates that a password follows.
• 0—(Optional) Specifies a clear text password.
• 5—(Optional) Specifies an MD5-hashed strong encryption password.
• password—The password in clear text, encrypted text, or MD5 strong
encryption, depending on the numbered option (0 or 5) that you enter. If you
do not enter a numbered option, the password is in clear text by default. Enter
a password as an unquoted text string with a maximum of 64 characters. The
ACE supports the following special characters in a password:
, . / = + - ^ @ ! % ~ # $ * ( )
Note that the ACE encrypts clear text passwords in the running-config.
For example, to create a user named user1 that uses the clear text password
my
secret_801, enter the following command:
switch/Admin(config)# username user1 password 0 mysecret_801
To remove the username from the configuration, enter the following command:
switch/Admin(config)# no username user1
Resetting the Administrator CLI Account Password
If you forget the password for the ACE administrator account and cannot access
the ACE, you can recover the admin password during the initial bootup sequence
of the ACE. You must have access to the ACE through the console port to be able
to reset the password for the Admin user back to the factory-default value of
admin.
Note Only the Admin context is accessible through the console port.
Page 37

1-11
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 1 Setting Up the ACE
Changing the Administrative Password
To reset the password that allows the Admin user access to the ACE, perform the
following steps:
Step 1 Connect to the console port on the ACE.
Step 2 Log in to the ACE. See the “Connecting and Logging into the ACE” section.
Step 3 Reboot the ACE. See the “Restarting the ACE” section.
Step 4 During the bootup process, output appears on the console terminal. Press ESC
when the “Starting services...” message appears on the terminal (see the example
below). The setup mode appears. If you miss the time window, wait for the ACE
to properly complete booting, reboot the ACE, and try again to access the setup
mode by pressing ESC.
Daughter Card Found. Continuing...
INIT: Entering runlevel: 3
Testing PCI path ....
This may take some time, Please wait ....
PCI test loop , count 0
PCI path is ready
Starting services... <<<<< Press
ESC when you see this message
Entering setup sequence...
Reset Admin password [y/n] (default: n): y
Resetting admin password to factory default...
.
Starting sysmgr processes.. Please wait...Done!!!
switch login:
Step 5 The setup mode prompts if you want to reset the admin password. Enter y. The
“Resetting admin password to factory default” message appears. The ACE deletes
the admin user password configuration from the startup-configuration and resets
the password back to the factory default value of admin.
The boot process continues as normal and you are able to enter the admi
n
password at the login prompt.
Page 38

Chapter 1 Setting Up the ACE
Assigning a Name to the ACE
1-12
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Assigning a Name to the ACE
The hostname is used for the command-line prompts and default configuration
filenames. If you establish sessions to multiple devices, the hostname helps you
track where you enter commands. By default, the hostname for the ACE is
“switch.” To specify a hostname for the ACE, use the host configuration mode
command.
The syntax of this command is as follows:
hostname nam
e
The na
me argument specifies a new hostname for the ACE. Enter a case-sensitive
text string that contains from 1 to 32 alphanumeric characters.
For example, to change the hostname of the ACE from switch to ACE_1, enter the
fo
llowing command:
switch/Admin(config)# hostname ACE_1
ACE_1/Admin(config)#
Configuring an ACE Inactivity Timeout
By default, the inactivity timeout value is 5 minutes. You can modify the length
of time that can occur before the ACE automatically logs off an inactive user by
using the login timeout command in configuration mode. This command
specifies the length of time that a user session can be idle before the ACE
terminates the console, Telnet, or SSH session.
Note The login timeout command setting overrides the terminal session-timeout
setting (see the “Configuring Terminal Display Attributes” section).
The syntax for the login ti
meout command is as follows:
login timeout min
utes
The min
utes argument specifies the length of time that a user can be idle before
the ACE terminates the session. Valid entries are from 0 to 60 minutes. A value
of 0 instructs the ACE never to timeout. The default is 5 minutes.
Page 39

1-13
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 1 Setting Up the ACE
Configuring a Message-of-the-Day Banner
For example, to specify a timeout period of 10 minutes, enter the following
command:
host1/Admin(config)# login timeout 10
To restore the default timeout value of 5 minutes, enter the following command.
host1/Admin(config)# no login timeout
To display the configured login time value, use the show login timeout command
in Exec mode. For example, enter the following command:
host1/Admin# show login timeout
Login Timeout 10 minutes.
Configuring a Message-of-the-Day Banner
You can configure a message in configuration mode to display as the
message-of-the-day banner when a user connects to the ACE. Once connected to
the ACE, the message-of-the-day banner appears, followed by the login banner
and Exec mode prompt.
The syntax of this command is as follows:
banner mot
d text
The te
xt argument is a line of message text to be displayed as the
message-of-the-day banner. The text string consists of all characters following the
first space until the end of the line (carriage return or line feed).
The # character functions as the delimiting charac
ter for each line. For the banner
text, spaces are allowed but tabs cannot be entered at the CLI. To instruct the ACE
to display multiple lines in a message-of -the-day banner, enter a new banner
motd command for each line that you wish to add.
The banner message is a maximum of 80 characters per line, up to a maximum of
3
000 characters (3000 bytes) total for a message-of-the-day banner. This
maximum value includes all line feeds and the last delimiting character in the
message.
To add multiple lines in a message-of -the-day banner, precede each line by using
th
e banner motd command. The ACE appends each line to the end of the existing
banner. If the text is empty, the ACE adds a carriage return (CR) to the banner.
Page 40

Chapter 1 Setting Up the ACE
Configuring a Message-of-the-Day Banner
1-14
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
You can include tokens in the form $(token) in the message text. Tokens will be
replaced with the corresponding configuration variable. For example:
• $(hostname)—Displays the hostname for the ACE during run time.
• $(line)—Displays the tty (teletypewriter) line or name (for example,
"/dev/console", "/dev/pts/0", or "1").
To use the $(hostname) in single line banner motd input, you must include double
q
uotes (") around the $(hostname) so that the $ is interpreted as a special character
at the beginning of a variable in the single line. For example:
switch/Admin(config)# banner motd #Welcome to "$(hostname)"...#
Do not use the double quote character (") or the percent sign character (%) as a
delimiting character in a single line message string.
For multi-line input, double quotes (") are not required for the token because the
i
nput mode is different from the single line mode. When you operate in multi-line
mode, the ACE interprets the double quote character (") literally. The following
example shows how to span multiple lines and uses tokens to configure the banner
message:
switch/Admin(config)# banner motd #
Enter TEXT message. End with the character '#'.
================================
Welcome to Admin Context
-------------------------------Hostname: $(hostname)
Tty Line: $(line)
=================================
#
To replace a banner or a line in a multi-line banner, use the no banner motd command
before adding the new lines.
To display the configured banner message, use the sho
w banner motd command
in Exec mode as follows:
host1/Admin# show banner motd
Page 41

1-15
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 1 Setting Up the ACE
Configuring the Time, Date, and Time Zone
Configuring the Time, Date, and Time Zone
To manually configure the date, time, and time zone settings for an ACE, use the
clock command.
You can automatically set the date and time of t
he ACE by synchronizing to a
Network Time Protocol (NTP) server. For details, see the “Synchronizing the
ACE with an NTP Server” section.
This section includes the following topics:
• Setting the System Time and Date
• Setting the Time Zone
• Adjusting for Daylight Saving Time
• Viewing the System Clock Settings
Setting the System Time and Date
To set the time and the date for an ACE, use the clock set command in Exec mode.
When you enter this command, the ACE displays the current configured date and
time.
The syntax of this command is as follows:
clock set hh
:mm:ss DD MONTH YYYY
The arguments are:
• hh:mm:ss—Current time to which the ACE clock is being reset. Specify two
digits for the hours, minutes, and seconds.
• DD MONTH YYYY—Current date to which the ACE clock is being reset.
Specify one or two digits for the day, the full name of the month, and four
digits for the year. The following month names are recognized: January,
February, March, April, May, June, July, August, September, October,
November, and December.
For example, to specify a time of 1:38:30 and a date of October 7, 2007, enter:
host1/Admin# clock set 01:38:30 7 October 2007
Tues Oct 7 01:38:30 PST 2007
Page 42

Chapter 1 Setting Up the ACE
Configuring the Time, Date, and Time Zone
1-16
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Follow these guidelines when you use NTP to automatically configure the ACE
system clock:
• If you wish to use the Network Time Protocol (NTP) to automatically
synchronize the ACE system clock to an authoritative time server (such as a
radio clock or an atomic clock), see the “Synchronizing the ACE with an NTP
Server” section. In this case, the NTP time server automatically sets the ACE
system clock.
• If you previously configured NTP on an ACE, the ACE prevents you from
using the clock set command and displays an error message. To manually set
the ACE system clock, remove the NTP peer and NTP server from the
configuration before setting the clock on an ACE. See the “Synchronizing the
ACE with an NTP Server” section for more information.
Setting the Time Zone
To set the time zone for the ACE, use the clock timezone command in
configuration mode. The ACE keeps time internally in Universal Time
Coordinated (UTC) offset.
The syntax of this command is as follows:
clock timezone {zo
ne_name{+ | –} hours minutes} | {standard timezone}
The keywords, arguments, and options are:
• zone_name—Eight-character name of the time zone (for example, PDT) to be
displayed when the time zone is in effect. Table 1-1 lists the common time
zone acronyms used for the zone argument.
• {+ | –} hours—Hours offset from UTC (plus or minus).
• minutes—Minutes offset from UTC. The range is from 0 to 59 minutes.
• standard timezone—Displays a list of well-known time zones that include an
applicable UTC hours offset. Available choices are as follows:
–
ACST—Australian Central Standard Time as UTC +9.5 hours
–
AKST—Alaska Standard Time as UTC –9 hours
–
AST—Atlantic Standard Time as UTC –4 hours
–
BST—British Summer Time as UTC +1 hour
Page 43

1-17
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 1 Setting Up the ACE
Configuring the Time, Date, and Time Zone
–
CEST—Central Europe Summer Time as UTC +2 hours
–
CET—Central Europe Time as UTC +1 hour
–
CST—Central Standard Time as UTC –6 hours
–
EEST—Eastern Europe Summer Time as UTC +3 hours
–
EET—Eastern Europe Time as UTC +2 hours
–
EST—Eastern Standard Time as UTC –5 hours
–
GMT—Greenwich Mean Time as UTC
–
HST—Hawaiian Standard Time as UTC –10 hours
–
IST—Irish Summer Time as UTC +1 hour
–
MSD—Moscow Summer Time as UTC +4 hours
–
MSK—Moscow Time as UTC +3 hours
–
MST—Mountain Standard Time as UTC –7 hours
–
PST—Pacific Standard Time as UTC –8 hours
–
WEST—Western Europe Summer Time as UTC +1 hour
–
WST—Western Standard Time as UTC +8 hours
Table 1-1 lists t
he common time zone acronyms that you can specify for the
zone_name ar
gument.
Ta b l e 1-1 Common Time Zone Acronyms
Acronym Time Zone Name and UTC Offset
Europe
BST British Summer Time, as UTC +1 hour
CET Central Europe Time, as UTC +1 hour
CEST Central Europe Summer Time, as UTC +2 hours
EET Eastern Europe Time, as UTC +2 hours
EEST Eastern Europe Summer Time, as UTC +3 hours
GMT Greenwich Mean Time, as UTC
IST Irish Summer Time, as UTC +1 hour
MSD Moscow Summer Time as UTC +4 hours
Page 44

Chapter 1 Setting Up the ACE
Configuring the Time, Date, and Time Zone
1-18
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
MSK Moscow Time, as UTC +3 hours
WET Western Europe Time as UTC
WEST Western Europe Summer Time as UTC +1 hour
United States and Canada
AST Atlantic Standard Time as UTC –4 hours
ADT Atlantic Daylight Time as UTC –3 hours
CT Central Time, either as CST or CD
T, depending on the place and
the time of year
CST Central Standard Time as UTC –6 hours
CDT Central Daylight Saving Time as UTC –5 hours
ET Eastern Time, either as EST or EDT
, depending on the place and
the time of year
EST Eastern Standard Time as UTC –5 hours
EDT Eastern Daylight Saving Time as UTC –4 hours
MT Mountain Time, either as MST or MDT, depending on the place
a
nd the time of year
MDT Mountain Daylight Saving Time as UTC –6 hours
MST Mountain Standard Time as UTC –7 hours
PT Pacific Time, either as PST or PDT, depending on place and time
of y
ear
PDT Pacific Daylight Saving Time as UTC –7 hours
PST Pacific Standard Time as UTC –8 hours
AKST Alaska Standard Time as UTC –9 hours
AKDT Alaska Standard Daylight Saving Time as UTC –8 hours
HST Hawaiian Standard Time as UTC –10 hours
Australia
CST Central Standard Time as UTC +9.5 hours
Table 1-1 Common Time Zone Acronyms (continued)
Acronym Time Zone Name and UTC Offset
Page 45

1-19
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 1 Setting Up the ACE
Configuring the Time, Date, and Time Zone
For example, to set the time zone to PDT and to set an UTC offset of –8 hours,
enter:
host1/Admin(config)# clock timezone PDT -8 0
To remove the clock timezone setting, use the no form of this command. For
example, enter:
host1/Admin(config)# no clock timezone
Adjusting for Daylight Saving Time
To configure the ACE to change the time automatically to summer time (daylight
savings time), use the clock summer-time command in configuration mode.
The first part of the command specifies when summer time begins, and the second
p
art of the command specifies when summer time ends. All times are relative to
the local time zone; the start time is relative to the standard time and the end time
is relative to the summer time. If the starting month is after the ending month, the
ACE assumes that you are found in the Southern Hemisphere.
The syntax of this command is as follows:
clock summer-time {da
ylight_timezone_name start_week start_day
start_month start_time end_week end_day end_month end_time
daylight_offset | standard timezone}
The keywords, arguments, and options are:
• daylight_timezone_name—Eight-character name of the time zone (for
example, PDT) to be displayed when summer time is in effect. See Tabl e 1-1
for the list the common time zone acronyms used for the
d
aylight_timezone_name argument.
• start_week end_week—The week, ranging from 1 through 5.
EST Eastern Standard/Summer Time as UTC +10 hours (+11 hours
du
ring summer time)
WST Western Standard Time as UTC +8 hours
Table 1-1 Common Time Zone Acronyms (continued)
Acronym Time Zone Name and UTC Offset
Page 46

Chapter 1 Setting Up the ACE
Configuring the Time, Date, and Time Zone
1-20
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
• start_day end_day—The day, ranging from Sunday through Saturday.
• start_month end_month—The month, ranging from January through
December.
• start_time end_time—Time, in military format, specified in hours and
minutes.
• daylight_offset—Number of minutes to add during the summer time. Valid
entries are from 1 to 1440.
• standard timezone—Displays a list of well known time zones that include an
applicable daylight time start and end range along with a daylight offset.
Available choices are:
–
ADT—Atlantic Daylight Time: 2 am on the first Sunday in April to 2 am
on the last Sunday in October, +60 min
–
AKDT—Alaska Standard Daylight Time: 2 am on the first Sunday in
April to 2 am on the last Sunday in October, +60 min
–
CDT—Central Daylight Time: 2 am on the first Sunday in April to 2 am
on the last Sunday in October, +60 min
–
EDT—Eastern Daylight Time: 2 am on the first Sunday in April to 2 am
on the last Sunday in October, +60 min
–
MDT—Mountain Daylight Time: 2 am on the first Sunday in April to 2
am on the last Sunday in October, +60 min
–
PDT—Pacific Daylight Time: 2 am on the first Sunday in April to 2 am
on the last Sunday in October, +60 min
For example, to specify that summer time begins on the first Sunday in April at
0
2:00 and ends on the last Sunday in October at 02:00, with a daylight offset of
60 minutes, enter:
host1/Admin(config)# clock summer-time Pacific 1 Sun Apr 02:00 5 Sun
Oct 02:00 60
To remove the clock summer-time setting, use the no form of this command. For
example, enter:
host1/Admin(config)# no clock summer-time
Page 47

1-21
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 1 Setting Up the ACE
Synchronizing the ACE with an NTP Server
Viewing the System Clock Settings
To display the system clock of the ACE, use the show clock command in Exec
mode. The syntax of this command is as follows:
show clock
For example, to view the current cloc
k settings, enter:
host1/Admin# show clock
Sun Oct 7 07:43:02 UTC 2007
Synchronizing the ACE with an NTP Server
The Network Time Protocol (NTP) enables you to synchronize the ACE system
clock to a time server. NTP is an Internet protocol designed to synchronize the
clocks of computers over a network. Typically, an NTP network receives its time
from an authoritative time source, such as a radio clock or an atomic clock
attached to a time server, and assures accurate local time-keeping. NTP distributes
this time across the network. The NTP protocol can synchronize distributed
clocks within milliseconds over long time periods.
NTP runs over User Datagram Protocol (UDP), which runs over IP. NTP is
d
ocumented in RFC 1305. All NTP communication uses Coordinated Universal
Time (UTC), which is the same as Greenwich Mean Time.
An NTP server must be accessible by the client ACE.
Note If you are configuring application acceleration and optimization functionality (as
described in the Cisco 4700 Series Application Control Engine Appliance
Application Acceleration and Optimization Configuration Guide), and you plan
to use an optional Cisco AVS 3180A Management Console with multiple ACE
nodes, we strongly recommend that you synchronize the system clock of each
ACE node with an NTP server. AppScope performance monitoring relies on very
accurate time measurement, in the millisecond range. If you instal multiple ACE
appliances, you must synchronize the clocks so that different parts of a single
transaction can be handled by different nodes.
Page 48

Chapter 1 Setting Up the ACE
Synchronizing the ACE with an NTP Server
1-22
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
This section contains the following topics:
• Configuring NTP Server and Peer Associations
• Viewing NTP Statistics and Information
• .Clearing NTP Statistics
Configuring NTP Server and Peer Associations
An NTP association can be a peer association, which means that the ACE is
willing to synchronize to the other system or to allow the other system to
synchronize to the ACE. An NTP association can also be a server association,
which means that only this system will synchronize to the other system, not the
other way around. You can identify multiple servers; the ACE uses the most
accurate server. To configure the ACE system clock to synchronize a peer (or to
be synchronized by a peer) or to be synchronized by a time server, use the ntp
command.
The syntax of this command is as follows:
ntp {peer i
p_address1 [prefer] | server ip_address2 [prefer]}
Note Only users authenticated in the Admin context can use the ntp peer and ntp
server commands.
The keywords, arguments, and options are:
• peer—Configure the ACE system clock to synchronize a peer or to be
synchronized by a peer. You can specify multiple associations.
• ip_address1—IP address of the peer providing or being provided by the clock
synchronization.
• prefer—(Optional) Makes this peer the preferred peer that provides
synchronization. Using the prefer keyword reduces switching back and forth
between peers.
• server—Configures the ACE system clock to be synchronized by a time
server. You can specify multiple associations.
• ip_address2—IP address of the time server that provides the clock
synchronization.
Page 49

1-23
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 1 Setting Up the ACE
Synchronizing the ACE with an NTP Server
• prefer—(Optional) Makes this server the preferred server that provides
synchronization. The prefer keyword sets this NTP server as the preferred
server if multiple servers have similar accuracy. NTP uses an algorithm to
determine which server is the most accurate and synchronizes to that one. If
servers have similar accuracy, then the prefer keyword specifies which server
to use.
For example, to specify multiple NTP serve
r IP addresses and identify a preferred
server, enter:
host1/Admin(config)# ntp server 192.168.10.10 prefer
host1/Admin(config)# ntp server 1
92.168.4.143
host1/Admin(config)# ntp server 1
92.168.5.10
For example, to form a peer association with a preferred peer, enter:
host1/Admin(config)# ntp peer 192.168.10.0 prefer
To remove an NTP peer or server from the configuration, use the no form of this
command. For example:
host1/Admin(config)# no ntp peer 192.168.10.0
Viewing NTP Statistics and Information
You can configure the ACE to display the following NTP statistics and
information:
• NTP peer statistics
• Input/output statistics
• Counters maintained by the local NTP
• Counters related to the memory code
• Listing of all associated peers
The syntax of this command is as follows:
show ntp {peer
-status | peers | statistics [io | local | memory | peer
ip_address]
Page 50

Chapter 1 Setting Up the ACE
Synchronizing the ACE with an NTP Server
1-24
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Note Only users who are authenticated in the Admin context can use the show ntp
command.
The keywords, arguments, and options are:
• peer-status—Displays the status for all configured NTP servers and peers.
• peers—Displays a listing of all NTP peers.
• statistics—Displays the NTP statistics.
• io—Displays the input/output statistics.
• local—Displays the counters maintained by the local NTP.
• memory—Displays the statistic counters related to the memory code.
• peer—Displays the per-peer statistics counter of a peer.
• ip_address—Displays the peer statistics for the specified IP address.
For example, to display the status for all N
TP servers and peers, enter:
switch/Admin# show ntp peer-status
Table 1-2 describes the fields in the show ntp peer-status command output.
Ta b l e 1-2 Field Descriptions for the show ntp peer-status Command
Field Description
Total Peers Number of associated peers
Remote IP addresses that correspond
to the remote server and
peer entries listed in the configuration file
Local IP addresses that correspond to the local server and peer
en
tries listed in the configuration file
St The stratum
Poll The poll interval (in seconds)
Reach The status of the reachability register (see RFC-1305)
in
octal
Delay The latest delay (in microseconds)
Page 51

1-25
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 1 Setting Up the ACE
Synchronizing the ACE with an NTP Server
For example, to display a summary of all peers, enter:
switch/Admin# show ntp peers
Table 1-3 describes the fields in the show ntp peers command output.
Ta b l e 1-3 Field Descriptions for the show ntp peers Command
Field Description
Peer IP Address The IP address of each associated peer
Serv/Peer Indicates whether the peer functions as an NTP server
or NTP peer
For example, to display the NTP input/output statistics, enter:
switch/Admin# show ntp statistics io
Table 1-4 describes the fields in the show ntp statistics io command output.
Peer IP Address IP address of each associated
peer
Serv/Peer Indication of whether the peer functions
as an NTP
server or NTP peer
Table 1-2 Field Descriptions for the show ntp peer-status Command
Field Description
Ta b l e 1-4 Field Descriptions for show ntp statistics io Command
Field Description
Time since reset Time since the last reset of the NTP software on the
pr
imary server
Receive buffers Total number of UDP client-receive buffers
Free receive buffers Current number of available client-receive buffers
Used receive buffers Current number of unavailable client-recei
ve buffers
Low water refills Total number of times buffers were added, which also
indicates
the number of times there have been low
memory resources during buffer creation
Page 52

Chapter 1 Setting Up the ACE
Synchronizing the ACE with an NTP Server
1-26
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
For example, to display the counters maintained by the local NTP, enter:
switch/Admin# show ntp statistics local
Table 1-5 describes the fields in the show ntp statistics local command output.
Ta b l e 1-5 Field Descriptions for show ntp statistics local Command
Field Description
System uptime Length of time that the ACE has been running.
Time since reset Time in hours since the ACE was last rebooted.
Old version packets Number of packets that m
atch the previous NTP
version. The version number is in every NTP packet.
New version packets Number of packets that match the current NTP v
ersion.
The version number is in every NTP packet.
Unknown version number Number of packets with an unknown NTP version.
Bad packet format Number of NTP packets that were received and
d
ropped by the ACE due to an invalid packet format.
Packets processed Number of NTP packets received and processed by the
AC
E.
Bad authentication Number of packets not v
erified as authentic.
Dropped packets Total number of NTP packets dropped by the ACE
Ignored packets Total number of NTP packets ignored by the ACE
Received packets Total number of NTP packets received by the ACE
Packets sent Total number of NTP packets transmitted by the ACE
Packets not sent Total number of NTP packets not sent by the ACE due
to an error
Interrupts handled Total number of NTP timer interrupts handled by the
AC
E
Received by int Total number of pulses recei
ved that triggered an
interrupt
Table 1-4 Field Descriptions for show ntp statistics io Command (continued)
Field Description
Page 53

1-27
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 1 Setting Up the ACE
Synchronizing the ACE with an NTP Server
For example, to display the statistic counters related to the memory code, enter:
switch/Admin# show ntp statistics memory
Table 1-6 describes the fields in the show ntp statistics memory command
output.
Ta b l e 1-6 Field Descriptions for show ntp statistics memory Command
Field Description
Time since reset Time in hours since the ACE was last rebooted.
Total peer memory Total peer memory available for the allocation of
memory to
peer structures.
Free peer memory Current available peer memory.
Calls to findpeer The number of calls to findpeer.
Note findpeer is an entry point to the allocation of
memory to peer structures that looks for
matching peer structures in the peer list.
New peer allocations Number of allocations from the free list.
Peer demobilizations Number of structures freed
to the free list.
Hash table counts The count of peers in each hash table.
For example, to display the per-peer statistics counter of a peer, enter:
switch/Admin# show ntp statistics peer 192.168.1.2
Table 1-7 describes the fields in the show ntp statistics peer command output.
Ta b l e 1-7 Field Descriptions for show ntp statistics peer Command
Field Description
Remote Host IP address of the specif
ied peer.
Local Interface IP address of specified local interface.
Time Last Received Time that the last NTP response was received.
Time Until Next Send Length of time until the next send attempt.
Reachability Change The reachability status for the peer.
Page 54

Chapter 1 Setting Up the ACE
Synchronizing the ACE with an NTP Server
1-28
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
.Clearing NTP Statistics
To clear NTP information, use the clear ntp statistics command in Exec mode.
The syntax of this command is as follows:
clear ntp statistics {all-peers
| io | local | memory}
The keywords are:
• all-peers—Clears I/O statistics for all peers
• io—Clears I/O statistics for I/O devices
• local—Clears I/O statistics for local devices
• memory—Clears I/O statistics for memory
For example, to clear the NTP statistics for all peers, enter:
host1/Admin# clear ntp statistics all-peers
Packets Sent
Number of packets sent to the NTP peer.
Packets Received Number of packets received from the NTP peer.
Bogus Origin Number of packets received from
the NTP peer of a
suspect origin.
Duplicate Number of duplicate packets
received from the NTP
peer.
Bad Dispersion Number of packets with an in
valid dispersion.
Note Dispersion measures the errors of the offset
values, based on the round-trip delay and the
precision of the system and the server.
Bad Reference Time Number of packets with an invalid reference time
source.
Candidate Order Order in which the ACE may consider this server when
it c
hooses the master.
Table 1-7 Field Descriptions for show ntp statistics peer Command
Field Description
Page 55

1-29
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 1 Setting Up the ACE
Synchronizing the ACE with an NTP Server
For example, to clear the NTP statistics for the I/O devices, enter:
host1/Admin# clear ntp statistics io
For example, to clear the NTP statistics for the local devices, enter:
host1/Admin# clear ntp statistics local
For example, to clear the NTP statistics for memory, enter:
host1/Admin# clear ntp statistics memory
Page 56

Chapter 1 Setting Up the ACE
Configuring Terminal Settings
1-30
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Configuring Terminal Settings
You can access the ACE CLI as follows:
• Make a direct connection using a dedicated terminal attached to the console
port on the front of the ACE.
• Establish a remote connection to the ACE by using the Secure Shell (SSH) or
Telnet protocols.
Note Only the Admin context is accessible through the console port; all other contexts
can be reached through Telnet or SSH.
This section contains the following topics:
• Configuring Terminal Display Attributes
• Configuring Terminal Line Settings
For details on configuring remote access to the ACE CLI using SSH or Telnet, see
Chapter 2, Enabling Remote Access to the ACE.
Configuring Terminal Display Attributes
You can specify the number of lines and the width for displaying information on
a terminal during a console session. The maximum number of displayed screen
lines is 511 columns. To configure the terminal display settings, use the terminal
command in Exec mode. The terminal command allows you to set the width for
displaying command output.
The syntax for the command is as follows:
terminal {length lin
es | monitor | session-timeout minutes | terminal-type
text | width characters}
The keywords, arguments, and options are as follows:
• length lines—Sets the number of lines displayed on the current terminal
screen. This command is specific to only the console port. Telnet and SSH
sessions set the length automatically. Valid entries are from 0 to 511. The
default is 24 lines. A selection of 0 instructs the ACE to scroll continuously
(no pausing).
Page 57

1-31
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 1 Setting Up the ACE
Configuring Terminal Settings
• monitor—Displays syslog output on the terminal for the current terminal and
session. To enable the various levels of syslog messages to the terminal, use
the logging monitor command (see the Cisco 4700 Series Application
Control Engine Appliance System Message Guide for details).
• session-timeout minutes—Specifies the inactivity timeout value in minutes
to configure the automatic logout time for the current terminal session on the
ACE. When inactivity exceeds the time limit configured by this command, the
ACE closes the session and exits. The range is from 0 to 525600. The default
is 5 minutes. You can set the terminal sessi
on-timeout value to 0 to disable
this feature so that the terminal remains active until you choose to exit the
ACE. The ACE does not save this change in the configuration file.
Note The login timeout command setting overrides the terminal
session-timeout setting (see the “Configuring an ACE Inactivity
Timeout” section).
• terminal-type text—Specifies the name and type of the terminal used to
access the ACE. If a Telnet or SSH session specifies an unknown terminal
type, the ACE uses the VT100 terminal by default. Specify a text string from
1 to 80 alphanumeric characters.
• width characters—Sets the number of characters displayed on the current
terminal screen. This command is specific to only the console port. Telnet and
SSH sessions set the width automatically. Valid entries are from 24 to 512
.
The default is 80 columns.
For example, to specify the VT200 terminal, set the number of screen lines to 35,
and se
t the number of characters to 250, enter:
host1/Admin# terminal terminal-type vt200
host1/Admin# terminal length 35
host1/Admin# terminal width 250
For example, to specify a terminal timeout of 600 minutes for the current session,
enter:
host1/Admin# terminal session-timeout 600
To reset a terminal setting to its default value, such as the screen line length, use
the no form of the command:
host1/Admin# terminal no width
Page 58

Chapter 1 Setting Up the ACE
Configuring Terminal Settings
1-32
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
For example, to start the current terminal monitoring session, enter:
host1/Admin# terminal monitor
host/Admin# %ACE-7-111009: User 'admin' executed cmd: terminal monitor
%ACE-7-111009: User 'admin' executed cmd: terminal monitor......
To stop the current terminal monitoring session, enter:
host1/Admin# terminal no monitor
To display the console terminal settings, use the show terminal Exec mode
command. For example, enter:
host1/Admin# show terminal
TTY: /dev/pts/0 Type: "vt100"
Length: 25 lines, Width: 80 columns
Session Timeout: 60 minutes
Configuring Terminal Line Settings
This section describes how to configure the terminal line settings for accessing the
ACE by a console or a virtual terminal. It includes the following procedures:
• Configuring Console Line Settings
• Configuring Virtual Terminal Line Settings
Configuring Console Line Settings
The console port is an asynchronous serial port on the ACE that allows you to
directly access the appliance to perform an initial configuration through a
standard RS-232 port with an RJ-45 connector. Any device connected to this port
must be capable of asynchronous transmission. Connection requires a terminal
configured as 9600 baud, 8 data bits, 1 stop bit, no parity.
Use the line console
configuration mode command to configure the console
interface settings. The CLI displays the console configuration mode.
To configure the line console settings from the console configuration mode,
specify
one or more of the following commands:
• databits number—Specifies the number of data bits per character. The range
is from 5 to 8. The default is 8 data bits.
Page 59

1-33
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 1 Setting Up the ACE
Configuring Terminal Settings
• parity—Sets the parity for the console connection. The supported choices
are: even (even parity), none (no parity), or odd (odd parity). The default is
none.
• speed speed—Sets the transmit and receive speeds for the serial console. The
range is between 110 and 115200 baud (110, 150, 300, 600, 1200, 2400,
4800, 9600,19200, 28800, 38400, 57600, or 115200). The default is 9600
baud.
• stopbits—Sets the stop bits for the console connection. Valid values are 1 or
2 stop bits. The default is 1 stop bit.
For example, to configure the console line settings for the ACE, enter:
host1/Admin# config
Enter configuration commands, one per line. End with CNTL/Z
host1/Admin(config)#
host1/Admin(config)# line console
host1/Admin(config-console)# data
bits 6
host1/Admin(config-console)# pari
ty even
host1/Admin(config-console)# spee
d 19200
host1/Admin(config-console)# stop
bits 1
To disable a setting for the configured console line, use the no form of the
command. For example:
host1/Admin(config-console)# no stopbits 1
Use the show line console Exec mode command to verify the configured console
settings for the ACE.
The syntax for this command is as follows:
show line console [co
nnected]
The optional conne
cted keyword displays the physical connection status.
For example, to display the configured console settings, enter:
host1/Admin# show line console
line Console:
Speed: 9600 bauds
Databits: 8 bits per byte
Stopbits: 1 bit(s)
Parity: none
Page 60

Chapter 1 Setting Up the ACE
Configuring Terminal Settings
1-34
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Configuring Virtual Terminal Line Settings
Virtual terminal lines allow remote access to the ACE. A virtual terminal line is
not associated with the console port; instead, it is a virtual port that allows you to
access the ACE.
Use the line vty c
onfiguration mode command to configure the virtual terminal line
settings. The CLI displays the line configuration mode. Use the session-limit
command to configure the maximum number of terminal sessions per line.
The syntax for this command is as follows:
session-limit num
ber
The numb
er argument configures the maximum number of terminal sessions per line.
The range is from 1 to 251.
For example, to configure a vir
tual terminal line, enter:
host1/Admin# config
Enter configuration commands, one per line. End with CNTL/Z
host1/Admin(config)#
host1/Admin(config)# line vty
host1/Admin(config-line)# session
-limit 23
To disable a setting for the configured virtual terminal line, use the no form of the
command. For example:
host1/Admin(config-line)# no session-limit 23
Use the clear line command in Exec mode to close a specified vty session. The
syntax for this command is as follows:
clear line vt
y_name
The vty_nam
e argument specifies the name of the VTY session. Enter a maximum
of 64 characters for the name of the virtual terminal.
For example, to close a spec
ified vty session, enter:
host1/Admin# clear line vty vty1
Page 61

1-35
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 1 Setting Up the ACE
Modifying the Boot Configuration
Modifying the Boot Configuration
You can control how the ACE performs its boot process. You can instruct the ACE
to automatically boot the system image identified in the BOOT environment
variable or you can manually identify the system boot image to use. In addition,
you can choose to have the ACE load the startup-configuration file or ignore the
startup-configuration file upon reboot.
This section describes how to modify the boot configuration of the ACE. It
contains the follo
wing procedures:
• Setting the Boot Method from the Configuration Register
• Setting the BOOT Environment Variable
• Configuring the ACE to Bypass the Startup Configuration File During the
Boot Process
• Displaying the ACE Boot Configuration
Setting the Boot Method from the Configuration Register
The configuration register can be used to modify how the ACE performs its boot
process, automatically or manually.
You can modify the boot method that the A
CE uses at the next startup by setting
the boot field in the software configuration register. The configuration register
identifies how the ACE should boot.
To specify the configuration register boot setting, use the conf
ig-register
configuration command. This command affects only the configuration register
bits that control the boot field and leaves the remaining bits unaltered.
The syntax for the command is as follows:
config-register value
The supported value e
ntries are as follows:
• 0x0—Upon reboot, the ACE boots to the GNU GRand Unified Bootloader
(GRUB). From the GRUB boot loader, you specify the system boot image to
use to boot the ACE. Upon startup, the ACE loads the startup-configuration
file stored in the Flash memory (nonvolatile memory) to the
running-configuration file stored in RAM (volatile memory).
Page 62

Chapter 1 Setting Up the ACE
Modifying the Boot Configuration
1-36
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
• 0x1—Upon reboot, the ACE boots the system image identified in the BOOT
environment variable (see the “Setting the BOOT Environment Variable”
section). The BOOT environment variable specifies a list of image files on
v
arious devices from which the ACE can boot at startup. If the ACE
encounters an error or if the image is not valid, it will try the second image
(if one is specified). Upon startup, the ACE loads the startup-configuration
file stored in the Flash memory (nonvolatile memory) to the
running-configuration file stored in RAM (volatile memory).
To set the boot field in the configuration register to automatically boot the system
im
age identified in the BOOT environment variable upon reboot and to load the
startup-configuration file stored in Flash memory, enter:
host1/Admin(config)# config-register 0x1
To reset the config-register setting, enter:
host1/Admin(config)# no config-register 0x1
Press Esc when the count down initiates on the GNU GRUB multiboot loader.
The following GRUB menu appears.
GNU GRUB version 0.95 (639K lower / 3144640K upper memory)
*********
*************************************************************
* image(c4710ace-mz.3.0.0_AB0_0.453.bin)
*
* image(c4710ace-mz.3.0.0_AB0_0.488.bin)
*
*
*
*
*
*********
*************************************************************
In the GRUB menu, use the arrow keys to select from the ACE images loaded in
the Flash memory. The ACE image entry is highlighted in the list.
Perform one of the following actions:
• Press enter to boot the selected software version.
• Type e to edit the commands before booting.
• Type c to access a command line.
Page 63

1-37
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 1 Setting Up the ACE
Modifying the Boot Configuration
If no ACE images are loaded in the Flash memory, the GNU GRUB multiboot
loader appears as follows:
grub>
Setting the BOOT Environment Variable
The BOOT environment variable specifies a list of image files on various devices
from which the ACE can boot at startup. You can add several images to the BOOT
environment variable to provide a fail-safe boot configuration. If the first file fails
to boot the ACE, subsequent images that are specified in the BOOT environment
variable are tried until the ACE boots or there are no additional images to attempt
to boot. If there is no valid image to boot, the ACE enters ROMMON mode where
you can manually specify an image to boot.
The ACE stores and executes images in the order in which you added them to the
BOO
T environment variable. If you want to change the order in which images are
tried at startup, you can either prepend and clear images from the BOOT
environment variable to attain the desired order or you can clear the entire BOOT
environment variable and then redefine the list in the desired order.
To set the BOOT environment variable, use the boot
system image: command.
The syntax for this command is as follows:
boot system image:i
mage_name
The i
mage_name argument specifies the name of the system image file. If the file
does not exist (for example, if you entered the wrong filename), then the filename
is appended to the bootstring, and this message displays, “Warning: File not found
but still added in the bootstring.” If the file does exist, but is not a valid image, the
file is not added to the bootstring, and the message “Warning: file found but it is
not a valid boot image” displays.
For example, to set the BOOT en
vironment variable, enter:
host1/Admin(config)# boot system image:c4710ace-mz.3.0.0_AB0_0.488.bin
Page 64

Chapter 1 Setting Up the ACE
Modifying the Boot Configuration
1-38
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Configuring the ACE to Bypass the Startup Configuration File
During the Boot Process
From the GRUB bootloader, the ACE includes an option that allows you to
instruct the ACE to bypass the startup-configuration file stored on the appliance
in the Flash memory (nonvolatile memory) during the boot process. You may
require the ACE to bypass the startup configuration file during bootup in the
following instances:
• Certain configurations cause problems that result in the ACE becoming
nonresponsive. You can bypass the startup configuration file to safely boot
the ACE and then resolve issues with the configuration.
• You forget the password for the ACE administrator CLI account and cannot
access the ACE. You can bypass the startup configuration file and log in with
the default password of admin.
Note For the procedure on resetting the administrator CLI account password,
see the “Resetting the Administrator CLI Account Password” section.
To instruct the ACE to bypass the startup-configuration file during the boot
proces
s from the GRUB bootloader, perform the following steps:
1. Enter the config-register command so that upon reboot the ACE boots to the
GRUB bootloader. See the “Setting the Boot Method from the Configuration
Register” section.
2. Reboot the ACE. See the “Restarting the ACE” section. Upon reboot, the
ACE boots to the GRUB bootloader.
Page 65

1-39
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 1 Setting Up the ACE
Modifying the Boot Configuration
3. Press Esc when the countdown initiates on the GNU GRUB multiboot loader.
The following GRUB menu appears.
GNU GRUB version 0.95 (639K lower / 3144640K upper memory)
******************************************************************
* image(c4710ace-mz.3.0.0_AB0_0.453.bin)
*
* image(c4710ace-mz.3.0.0_AB0_0.488.bin)
*
*
*
*
*
*********
*********************************************************
4. In the GRUB menu, use the arrow keys to select from the ACE images loaded
in Flash memory. The ACE image entry is highlighted in the list.
5. Type e to edit the kernel command line. From the GRUB menu, choose
ignorestartupcfg=1.
6. Press Esc to return to the GRUB menu.
7. Press enter to boot the selected software version. The ACE boot screen
appears as follows:
kernel=(hd0,0)/ACE_APPLIANCE_RECOVERY_IMAGE.bin ro root=LABEL=/
auto console=tt
yS0,9600n8 quiet bigphysarea=32768 ignorestartupcfg=1
[Linux-bzImage, setup=0x1400, size=0x43ff5d2]
IP-Config: Incomplete network configuration information.
INIT: version 2.85 booting
INIT: Entering runlevel: 3
Testing PCI path ....
This may take some time, Please wait ....
PCI test loop , count 0
PCI path is ready
Starting services...
.
Starting sysmgr processes.. Please wait...Done!!!
switch login: admin
Password: admin
Page 66

Chapter 1 Setting Up the ACE
Modifying the Boot Configuration
1-40
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
---- Basic System Configuration Dialog ----
This setup utility will guide you through the basic configuration
of
the system. Setup configures only enough connectivity to the
ACE appliance Device Manager GUI of the system.
*Note: setup is mainly used for configuring the system initially,
when no configuration is present. So setup always assumes system
defaults and not the current system configuration values.
Press Enter at anytime to skip a dialog. Use ctrl-c at anytime
to skip the remaining dialogs.
Would you like to enter the basic configuration dialog (yes/no):no
Cisco Application Control Software (ACSW)
TAC support: http://www.cisco.com/tac
Copyright (c) 1985-2007 by Cisco Systems, Inc. All rights
reserved.
The copyrights to certain works contained herein are owned by
other third parties and are used and distributed under license.
Some parts of this software are covered under the GNU Public
License. A copy of the license is available at
http://www.gnu.org/licenses/gpl.html.
Note When you boot the ACE for the first time and the appliance does not detect a
startup-configuration file, a setup script appears to enable connectivity to the ACE
Device Manager GUI. The start-up script is not intended for use with the CLI.
Choose no to skip the use of the setup script and proceed directly to the CLI. See
the “Using the Setup Script to Enable Connectivity to the Device Manager”
section for details.
You may now configure the ACE to define basic configuration settings for the
appliance.
Page 67

1-41
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 1 Setting Up the ACE
Restarting the ACE
Displaying the ACE Boot Configuration
To display the current BOOT environment variable and configuration register
setting, use the show bootvar command in Exec mode.
For example, to display the BOOT environment variable settings, enter:
host1/Admin# show bootvar
BOOT variable =
"image:/c
4710ace-mz.3.0.0_AB0_0.488.bin;image:/c4710ace-mz.3.0.0
_AB0_0.453.bin"
Configuration register is 0x1
Restarting the ACE
To reboot the ACE directly from its CLI and reload the configuration, use the reload
command in Exec mode. The reload command reboots the ACE and performs a
full power cycle of both the hardware and software. The reset process can take
several minutes. Any open connections with the ACE are dropped after you enter
the reload command.
Caution Configuration changes that are not written to the Flash partition are lost after a
reload. Before rebooting, enter the copy running-conf startup-config command
in Exec mode to store the current configuration in Flash memory. If you fail to save
your configuration changes, the ACE reverts to its previous settings upon restart.
When you specify re
load, the ACE prompts you for confirmation and performs a
cold restart of the ACE:
host1/Admin# reload
This command will reboot the system
Save configurations for all the contexts. Save? [yes/no]: yes
Generating configuration....
running config of context Admin saved
Perform system reload. [yes/no]: [yes] yes
Page 68

Chapter 1 Setting Up the ACE
Shutting Down the ACE
1-42
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Shutting Down the ACE
To remove power from the ACE, press the power button found on the front panel.
Caution Configuration changes that are not written to the Flash partition are lost after a
shutdown. Before you shut down the ACE, enter the copy running-conf
startup-config command in Exec mode to store the current configuration in Flash
memory. If you fail to save your configuration changes, the ACE reverts to its
previous settings upon restart.
Page 69

2-1
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
CHAPTER
2
Enabling Remote Access to the ACE
This chapter describes how to configure remote access to the Cisco 4700 Series
Application Control Engine (ACE) appliance by establishing a remote connection
by using the Secure Shell (SSH) or Telnet protocols. It also describes how to
configure the ACE to provide direct access to a user context from SSH. This
chapter also covers how to configure the ACE to receive ICMP messages from a
host.
This chapter includes the following major sections:
• Remote Access Configuration Quick Start
• Configuring Remote Network Management Traffic Services
• Configuring Telnet Management Sessions
• Configuring SSH Management Sessions
• Terminating an Active User Session
• Enabling ICMP Messages to the ACE
• Directly Accessing a User Context Through SSH
• Example of a Remote Access Configuration
• Viewing Session Information
Note For information about how to make a direct connection using a dedicated terminal
attached to the Console port on the front of the ACE, configure terminal display
attributes, and configure terminal line settings for accessing the ACE by console
or virtual terminal connection, see Chapter 1, Setting Up the ACE.
Page 70

Chapter 2 Enabling Remote Access to the ACE
Remote Access Configuration Quick Start
2-2
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Remote Access Configuration Quick Start
Table 2-1 provides a quick overview of the steps required to configure remote
network management access for the ACE.
Each step includes the CLI command
required to complete the task.
Ta b l e 2-1 Remote Network Management Configuration
Quick Start
Task and Command Example
1. If you are operating in multiple contexts, observe the CLI prompt to verify
that you are operating in the desired context. If necessary, log directly in to,
or change to, the correct context.
host1/Admin# changeto C1
host1/C1#
The rest of the examples in this table use the Admin context, unless
otherwise specified. For details on creating contexts, see the Cisco 4700
Series Application Control Engine Appliance Virtualization Configuration
Guide.
2. Enter configuration mode.
host1/Admin# config
Enter configuration commands, one per line. End with CNTL/Z
host1/Admin(config)#
3. Create a class map that permits network management traffic to be received
by the ACE based on the network management protocol (SSH or Telnet) and
client source IP address.
host1/Admin(config)# class-map type management match-all
SSH-ALLOW_CLASS
host1/Admin(config-cmap-mgmt)# match proto
col ssh source-address
172.16.10.0 255.255.255.254
host1/Admin(config-cmap-mgmt)# exit
host1/Admin(config)#
host1/Admin(config)# class-map type manage
ment match-all
TELNET-ALLOW_CLASS
host1/Admin(config-cmap-mgmt)# match proto
col telnet
source-address 172.16.10.0 255.255.255.254
host1/Admin(config-cmap-mgmt)# exit
host1/Admin(config)#
Page 71

2-3
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 2 Enabling Remote Access to the ACE
Remote Access Configuration Quick Start
4. Configure a policy map that activates the SSH and Telnet management
protocol classifications.
host1/Admin(config)# policy-map type management first-match
REMOTE_MGMT_ALLOW_POLICY
host1/Admin(config-pmap-mgmt)# class SSH-A
LLOW_CLASS
host1/Admin(config-pmap-mgmt-c)# permit
host1/Admin(config-pmap-mgmt-c)# exit
host1/Admin(config-pmap-mgmt)# class TELNE
T-ALLOW_CLASS
host1/Admin(config-pmap-mgmt-c)# permit
host1/Admin(config-pmap-mgmt-c)# exit
host1/Admin(config-pmap-mgmt)# exit
host1/Admin(config)#
5. Attach the traffic policy to a single VLAN interface or globally to all VLAN
interfaces in the same context. For example, to specify an interface VLAN
and apply the remote management policy map to the VLAN, enter:
host1/Admin(config)# interface vlan 50
host1/Admin(config-if)# ip address 172.16.
1.100 255.255.0.0
host1/Admin(config-if)# service-policy inp
ut
REMOTE_MGMT_ALLOW_POLICY
host1/Admin(config-if)# exit
6. (Optional) Configure the maximum number of Telnet sessions allowed for
each context.
host1/Admin(config)# telnet maxsessions 3
7. (Optional) Configure the maximum number of SSH sessions allowed for
each context.
host1/Admin(config)# ssh maxsessions 3
Table 2-1 Remote Network Management Configuration
Quick Start (continued)
Task and Command Example
Page 72

Chapter 2 Enabling Remote Access to the ACE
Configuring Remote Network Management Traffic Services
2-4
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Configuring Remote Network Management Traffic
Services
You configure rules for remote access to the ACE through the use of class maps,
policy maps, and service policies. The following items summarize the role of each
function in configuring remote network management access to the ACE:
• Class map—Provides the remote network traffic match criteria to permit
traffic based on:
–
Remote access network management protocols (SSH, Telnet, or ICMP)
–
Client source IP address
• Policy map—Enables remote network management access for a traffic
classification that matches the criteria listed in the class map.
• Service policy—Activates the policy map and attaches the traffic policy to an
interface or globally on all interfaces.
This section provides an overview on crea
ting a class map, policy map, and
service policy for remote network access. For detailed information on creating
class maps, policy maps, and service policies, see Chapter 4, Configuring Class
Maps and Policy Maps.
8. If you have global administrator privileges, use the ssh key command to
generate the SSH private key and the corresponding public key for use by
the SSH server. There is only one host-key pair. For example, to generate an
RSA1 key pair in the Admin context, enter:
host1/Admin(config)# ssh key rsa1 1024
generating rsa1 key
.....
generated rsa1 key
9. (Optional) Save your configuration changes to Flash memory.
host1/Admin(config)# exit
host1/Admin# copy
running-config startup-config
Table 2-1 Remote Network Management Configuration
Quick Start (continued)
Task and Command Example
Page 73

2-5
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 2 Enabling Remote Access to the ACE
Configuring Remote Network Management Traffic Services
Telnet and SSH remote access sessions are established to the ACE on a per context
basis. For details on creating users and contexts, see the Cisco 4700 Series
Application Control Engine Appliance Virtualization Configuration Guide.
This section includes the following topics:
• Creating and Configuring a Remote Management Class Map
• Creating a Layer 3 and Layer 4 Remote Access Policy Map
• Applying a Service Policy
Creating and Configuring a Remote Management Class Map
To create a Layer 3 and Layer 4 class map to classify the remote network
management traffic received by the ACE, use the class-map type management
configuration-mode command. This command permits network management
traffic to be received by the ACE by identifying the incoming IP protocols that the
ACE can receive as well as the client source IP address and subnet mask as the
matching criteria. The type management keywords define the allowed network
traffic to manage security for protocols such as SSH, Telnet, and ICMP.
A class map can have multiple mat
ch commands. You can configure class maps
to define multiple management protocol and source IP address match commands
in a group that you then associate with a traffic policy. The match-all and
match-any keywords determine how the ACE evaluates multiple match
statements operations when multiple match criteria exist in a class map.
The syntax of this command is:
class-map typ
e management [match-all | match-any] map_name
The keywords, arguments, and options are:
• match-all | match-any—(Optional) Determines how the ACE evaluates
Layer 3 and Layer 4 network management traffic when multiple match
crit
eria exist in a class map. The class map is considered a match if the match
commands meet one of the following conditions.
–
match-all —(Default) All of the match criteria listed in the class map are
satisfied to match the network traffic class in the class map, typically
match commands of the same type.
Page 74

Chapter 2 Enabling Remote Access to the ACE
Configuring Remote Network Management Traffic Services
2-6
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
–
match-any—Any one of the match criteria listed in the class map is
satisfied to match the network traffic class in the class map, typically
match commands of different types.
• map_name—Specifies the name assigned to the class map. Enter an unquoted
text string with no spaces and a maximum of 64 alphanumeric characters.
The CLI enters the class map management co
nfiguration mode. To classify the
remote network management traffic received by the ACE, include one or more of
the match protocol commands to configure the match criteria for the class map:
For example, to allow SSH and Telnet access to the ACE from IP address
17
2.16.10.0, enter:
host1/Admin(config)# class-map type management match-all
SSH-TELNET_ALLOW_CLASS
host1/Admin(config-cmap-mgmt)# ma
tch protocol ssh source-address
172.16.10.0 255.255.255.254
host1/Admin(config-cmap-mgmt)# ma
tch protocol telnet source-address
172.16.10.0 255.255.255.254
host1/Admin(config-cmap-mgmt)# ex
it
host1/Admin(config)#
To remove a Layer 3 and Layer 4 network management class map from the ACE,
enter:
host1/Admin(config)# no class-map type management match-all
SSH-TELNET_ALLOW_CLASS
Defining a Class Map Description
To provide a brief summary about the Layer 3 and Layer 4 remote management
class map, use the description command in class map configuration mode.
The syntax of this command is:
description te
xt
Use the te
xt argument to enter an unquoted text string with a maximum of 240
alphanumeric characters.
For example, to specify a description that the class map is to allow remote Telnet
acc
ess, enter:
host1/Admin(config)# class-map type management TELNET-ALLOW_CLASS
host1/Admin(config-cmap-mgmt)# de
scription Allow Telnet access to the
ACE
Page 75

2-7
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 2 Enabling Remote Access to the ACE
Configuring Remote Network Management Traffic Services
To remove the description from the class map, enter:
host1/Admin(config-cmap-mgmt)# no description
Defining Remote Network Management Protocol Match Criteria
To configure the class map to identify the remote network access management
protocols that can be received by the ACE, use the match protocol command in
class map configuration mode. You configure the associated policy map to permit
access to the ACE for the specified management protocols. As part of the network
management access traffic classification, you also specify either a client source
host IP address and subnet mask as the matching criteria or instruct the ACE to
allow any client source address for the management traffic classification.
The syntax of this command is:
[l
ine_number] match protocol {http | https | icmp | snmp | ssh | telnet |
xml-https} {any | source-address ip_address mask}
• line_number—(Optional) Assists you in editing or deleting individual match
commands. Enter an integer from 2 to 255 as the line number. You can enter
no line_number to delete long match commands instead of entering the entire
line. The line numbers do not dictate a priority or sequence for the match
statements.
• http—Specifies the Hypertext Transfer Protocol (HTTP). The use of the
HTTP management protocol for XML usage is described in Chapter 9,
Configuring the XML Interface.
• https—Specifies secure (SSL) Hypertext Transfer Protocol (HTTP) for
connectivity with the Device Manager GUI on the ACE.
• icmp—Specifies Internet Control Message Protocol messages to the ACE.
The configuration of the ICMP management protocol is described in the
“Enabling ICMP Messages to the ACE” section.
• snmp—Specifies the Simple Network Management Protocol (SNMP). The
use of the SNMP management protocol is described in Chapter 8,
Configuring SNMP.
• ssh—Specifies a Secure Shell (SSH) remote connection to the ACE. The ACE
supports the SSH remote shell functionality provided in SSH Version 1 and
supports DES and 3DES ciphers. The configuration of SSH sessions is
described in the “Configuring SSH Management Sessions” section.
Page 76

Chapter 2 Enabling Remote Access to the ACE
Configuring Remote Network Management Traffic Services
2-8
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Note SSH v1.x and v2 are entirely different protocols and are not
compatible. Make sure that you use an SSH v1.x client when
accessing the ACE.
• telnet—Specifies a Telnet remote connection to the ACE. The configuration
of Telnet sessions is described in the “Configuring Telnet Management
Sessions” section.
• xml-https—Specifies HTTPS as transfer protocol to send and receive XML
documents between the ACE and a Network Management System (NMS).
The use of the HTTPS management protocol for XML usage is described in
Chapter 9, Configuring the XML Interface.
• any—Specifies any client source address for the management traffic
classification.
• source-address—Specifies a client source host IP address and subnet mask
as the network traffic matching criteria. As part of the classification, the ACE
implicitly obtains the destination IP address from the interface on which you
apply the policy map.
• ip_address—Source IP address of the client. Enter the IP address in
dotted-decimal notation (for example, 192.168.11.1).
• mask—The subnet mask of the client in dotted-decimal notation (for example,
255.255.255.0).
For example, to specify that the clas
s map allows SSH access to the ACE, enter:
host1/Admin(config)# class-map type management SSH-ALLOW_CLASS
host1/Admin(config-cmap-mgmt)# ma
tch protocol ssh source-address
172.16.10.0 255.255.255.254
To deselect the specified network management protocol match criteria from the
class map, enter:
host1/Admin(config-cmap-mgmt)# no match protocol ssh source-address
172.16.10.0 255.255.255.254
Page 77

2-9
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 2 Enabling Remote Access to the ACE
Configuring Remote Network Management Traffic Services
Creating a Layer 3 and Layer 4 Remote Access Policy Map
For a Layer 3 and Layer 4 traffic classification, you create a Layer 3 and Layer 4
policy map with actions to configure the network management traffic received by
the ACE This section outlines the general steps to configure a Layer 3 and Layer
4 network traffic policy and contains the following topics:
• Creating a Layer 3 and Layer 4 Policy Map for Network Management Traffic
Received by the ACE
• Defining a Layer 3 and Layer 4 Policy Map Description
• Specifying a Layer 3 and Layer 4 Traffic Class With the Traffic Policy
• Defining Layer 3 and Layer 4 Management Traffic Policy Actions
Creating a Layer 3 and Layer 4 Policy Map for Network Management Traffic
Received by the ACE
To configure a Layer 3 and Layer 4 policy map that defines the different actions
that are applied to the IP management traffic received by the ACE, use the
policy-map type management first-match configuration command. The ACE
executes the specified action only for traffic that meets the first matching
classification with a policy map. The ACE does not execute any additional
actions.
The syntax of this command is as follows:
policy-map type management f
irst-match map_name
The ma
p_name argument specifies the name assigned to the Layer 3 and Layer 4
network management policy map. Enter an unquoted text string with no spaces
and a maximum of 64 alphanumeric characters.
When you use this command, you will access policy map management
con
figuration mode.
For example, to create a Layer 3 and Layer 4
network traffic management policy
map, enter:
host1/Admin(config)# policy-map type management first-match
REMOTE_MGMT_ALLOW_POLICY
host1/Admin(config-pmap-mgmt)#
Page 78

Chapter 2 Enabling Remote Access to the ACE
Configuring Remote Network Management Traffic Services
2-10
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
To remove a policy map from the ACE, enter:
host1/Admin(config)# no policy-map type management first-match
REMOTE_MGMT_ALLOW_POLICY
Defining a Layer 3 and Layer 4 Policy Map Description
To provide a brief summary about the Layer 3 and Layer 4 remote management
policy map, use the description command in policy map configuration mode.
The syntax of this command is as follows:
description te
xt
The te
xt argument specifies the description that you want to provide. Enter an
unquoted text string with a maximum of 240 alphanumeric characters.
For example, to specify a description that the policy map is to allow remote Telnet
acc
ess, enter:
host1/Admin(config-pmap-mgmt)# description Allow Telnet access to the
ACE
To remove a description from the policy map, enter:
host1/Admin(config-pmap-mgmt)# no description
Specifying a Layer 3 and Layer 4 Traffic Class With the Traffic Policy
To specify a Layer 3 and Layer 4 traffic class created with the class-map
command to associate network traffic with the traffic policy, use the class
command in policy map configuration mode. This command enters the policy map
management class configuration mode.
The syntax of this command is as follows:
class {na
me1 [insert-before name2] | class-default}
Page 79

2-11
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 2 Enabling Remote Access to the ACE
Configuring Remote Network Management Traffic Services
The arguments and keywords, and options are as follows:
• name1—The name of a previously defined Layer 3 and Layer 4 traffic class,
configured with the class-map command, to associate traffic to the traffic
policy. Enter an unquoted text string with no spaces and a maximum of 64
alphanumeric characters.
• insert-before name2—(Optional) Places the current class map ahead of an
existing class map or inline match condition specified by the name2 argument
in the policy map configuration. The ACE does not save the sequence
reordering as part of the configuration. Enter an unquoted text string with no
spaces and a maximum of 64 alphanumeric characters.
• class-default—Specifies the class-default class map for the Layer 3 and
Layer 4 traffic policy. This class map is a reserved class map created by the
ACE. You cannot delete or modify this class. All network traffic that fails to
meet the other matching criteria in the named class map belongs to the default
traffic class. If none of the specified classifications match, the ACE then
matches the action specified under the class class-default command. The
class-default class map has an implicit match any statement in it and is used
to match any traffic classification. The class-default class map has an
implicit match any statement that matches all traffic.
For example, to specify an e
xisting class map within the Layer 3 and Layer 4
remote access policy map, enter:
host1/Admin(config-pmap-mgmt)# class L4_REMOTE_ACCESS_CLASS
host1/Admin(config-pmap-mgmt-c)#
To use the insert-before command to define the sequential order of two class
maps in the policy map, enter:
host1/Admin(config-pmap-mgmt)# class L4_SSH_CLASS insert-before
L4_REMOTE_ACCESS_CLASS
To specify the class-default class map for the Layer 3 and Layer 4 traffic policy,
enter:
host1/Admin(config-pmap-mgmt)# class class-default
host1/Admin(config-pmap-mgmt-c)#
To remove a class map from a Layer 3 and Layer 4 policy map, enter:
host1/Admin(config-pmap-mgmt)# no class L4_REMOTE_ACCESS_CLASS
Page 80

Chapter 2 Enabling Remote Access to the ACE
Configuring Remote Network Management Traffic Services
2-12
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Defining Layer 3 and Layer 4 Management Traffic Policy Actions
To allow the network management traffic listed in the Layer 3 and Layer 4 class
map to be received or rejected by the ACE, specify either the permit or deny
command in policy map class configuration mode.
• Use the permit command in policy map class configuration mode to allow the
remote management protocols listed in the class map to be received by the
ACE.
• Use the deny command in policy map class configuration mode to refuse the
remote management protocols listed in the class map to be received by the
ACE.
For example, to create a Layer 3 and Layer 4 remot
e network traffic management
policy map that permits SSH, Telnet, and ICMP connections to be received by the
ACE, enter:
host1/Admin(config)# policy-map type management first-match
REMOTE_MGMT_ALLOW_POLICY
host1/Admin(config-pmap-mgmt)# cl
ass SSH-ALLOW_CLASS
host1/Admin(config-pmap-mgmt-c)# permit
host1/Admin(config-pmap-mgmt-c)# exit
host1/Admin(config-pmap-mgmt)# cl
ass TELNET-ALLOW_CLASS
host1/Admin(config-pmap-mgmt-c)# permit
host1/Admin(config-pmap-mgmt-c)# exit
host1/Admin(config-pmap-mgmt)# cl
ass ICMP-ALLOW_CLASS
host1/Admin(config-pmap-mgmt-c)# permit
host1/Admin(config-pmap-mgmt-c)# exit
For example, to create a policy map that restricts an ICMP connection by the ACE,
enter:
host1/Admin(config)# policy-map type management first-action
ICMP_RESTRICT_POLICY
host1/Admin(config-pmap-mgmt)# cl
ass ICMP-ALLOW_CLASS
host1/Admin(config-pmap-mgmt-c)# deny
Page 81

2-13
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 2 Enabling Remote Access to the ACE
Configuring Remote Network Management Traffic Services
Applying a Service Policy
Use the service-policy command to perform the following tasks:
• Apply a previously created policy map.
• Attach the traffic policy to a specific VLAN interface or globally to all VLAN
interfaces in the same context.
• Specify that the traffic policy is to be attached to the input direction of an
interface.
The ser
vice-policy command is available at both the interface configuration mode
and at the configuration mode. Specifying a policy map in the interface
configuration mode applies the policy map to a specific VLAN interface.
Specifying a policy map in the configuration mode applies the policy to all of the
VLAN interfaces associated with a context.
The syntax of this command is:
service-policy input po
licy_name
The keywords, arguments, and options are:
• input—Specifies that the traffic policy is to be attached to the input direction
of an interface. The traffic policy evaluates all traffic received by that
interface.
• policy_name—Specifies the name of a previously defined policy map,
configured with a previously created policy-map command. The name can be
a maximum of 40 alphanumeric characters.
For example, to specify a
n interface VLAN and apply the remote access policy
map to a VLAN, enter:
host1/Admin(config)# interface vlan 50
host1/Admin(config-if)# ip addres
s 172.16.1.100 255.255.0.0
host1/Admin(config-if)# service-p
olicy input REMOTE_MGMT_ALLOW_POLICY
For example, to globally apply the remote access policy map to all of the VLANs
associated with a context, enter:
host1/Admin(config)# service-policy input REMOTE_MGMT_ALLOW_POLICY
To detach the remote access traffic policy from an interface, enter:
host1/Admin(config-if)# no service-policy input
REMOTE_MGMT_ALLOW_POLICY
Page 82

Chapter 2 Enabling Remote Access to the ACE
Configuring Remote Network Management Traffic Services
2-14
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
To globally detach the remote access traffic policy from all VLANs associated
with a context, enter:
host1/Admin(config)# no service-policy input REMOTE_MGMT_ALLOW_POLICY
You can detach a traffic policy by either of the following methods:
• Individually from the last VLAN interface on which you applied the service
policy
• Globally from all VLAN interfaces in the same context
The ACE automatically resets the associated service policy statistics to provide a
n
ew starting point for the service policy statistics the next time that you attach a
traffic policy to a specific VLAN interface or globally to all VLAN interfaces in
the same context.
Note the following guidelines and restric
tions when creating a service policy:
• Policy maps, applied globally in a context, are internally applied on all
interfaces existing in the context.
• A policy activated on an interface overwrites any specified global policies for
overlapping classification and actions.
• The ACE allows only one policy of a specific feature type to be activated on
a given interface.
To display service policy statistics for a Lay
er 3 and Layer 4 remote network
traffic management policy map, use the show service-policy command in Exec
mode.
The syntax of this command is:
show service-policy po
licy_name [detail]
The keywords, options, and arguments are as follows:
• policy_name—The identifies an existing policy map that is currently in
service (applied to an interface) as an unquoted text string with a maximum
of 64 alphanumeric characters.
• detail—(Optional) Displays a more detailed listing of policy map statistics
and status information.
Page 83

2-15
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 2 Enabling Remote Access to the ACE
Configuring Telnet Management Sessions
Note The ACE updates the counters that the show service-policy command displays
after the applicable connections are closed.
For example, to display service policy statistics for the
REMO
TE_MGMT_ALLOW_POLICY policy map, enter:
host1/Admin# show service-policy REMOTE_MGMT_ALLOW_POLICY
Status : ACTIVE
Description: Allow mgmt protocols
----------------------------------------Context Global Policy:
service-policy: REMOTE_MGMT_ALLOW_POLICY
To clear the service policy statistics, use the clear service-policy command. The
syntax of this command is:
clear service-policy pol
icy_name
For the p
olicy_name argument, enter the identifier of an existing policy map that
is currently in service (applied to an interface).
For example, to clear the stati
stics for the policy map
REMOTE_MGMT_ALLOW_POLICY that is currently in service, enter:
host1/Admin# clear service-policy REMOTE_MGMT_ALLOW_POLICY
Configuring Telnet Management Sessions
The ACE supports a maximum 16 concurrent Telnet management sessions for the
Admin context and 4 concurrent Telnet management sessions for each user
context.
To control the maximum number of Telnet sessions allowed for each context, use
th
e telnet maxsessions command in configuration mode . The ACE supports a
total maximum of 256 concurrent Telnet sessions.
Telnet remote access sessions are established o
n the ACE per context. You can
create a context, assign an interface and IP address to it, and then log into the ACE
by using Telnet to connect to that IP address. This capability allows you to specify
a particular context when accessing the ACE. For details on creating users and
contexts, see the Cisco 4700 Series Application Control Engine Appliance
Virtualization Configuration Guide.
Page 84

Chapter 2 Enabling Remote Access to the ACE
Configuring SSH Management Sessions
2-16
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
The syntax of this command is:
telnet maxsessions max_se
ssions
The m
ax_sessions argument sets the maximum number of concurrent Telnet
sessions allowed for the associated context. The range is from 1 to 16 Telnet
sessions for the Admin context and from 1 to 4 Telnet sessions for each user
context. The defaults are 16 (Admin context) and 4 (user context).
For example, to configure the maximum number of concurrent Telnet sessions
to 3 in the Admin context, enter:
host1/Admin(config)# telnet maxsessions 3
To revert to the default of 16 Telnet sessions for the Admin context, enter:
host1/Admin(config)# no telnet maxsessions
Configuring SSH Management Sessions
This section includes the following topics:
• Configuring Maximum Number of SSH Sessions
• Generating SSH Host Key Pairs
SSH remote access sessions are established on the ACE per context. You can
crea
te a context, assign an interface and IP address to it, and then log into the ACE
by using SSH to connect to that IP address. This capability allows you to specify
a particular context when accessing the ACE. For details on creating users and
contexts, see the Cisco 4700 Series Application Control Engine Appliance
Virtualization Configuration Guide.
Configuring Maximum Number of SSH Sessions
The ACE supports a maximum of 16 concurrent SSH management sessions for the
Admin context and 4 concurrent SSH management sessions for each user context.
To control the maximum number of SSH sessions allowed for each context, use
th
e ssh maxsessions command in configuration mode. The ACE supports a total
maximum of 256 concurrent SSH sessions.
Page 85

2-17
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 2 Enabling Remote Access to the ACE
Configuring SSH Management Sessions
The syntax of this command is:
ssh maxsessions max_sessions
The m
ax_sessions argument sets the maximum number of concurrent SSH
sessions allowed for the associated context. The range is from 1 to 16 SSH
sessions for the Admin context and from 1 to 4 SSH sessions for each user
context. The defaults are 16 (Admin context) and 4 (user context).
For example, to configure the maximum number of concurrent SSH sessions in
t
he Admin context to 3, enter:
host1/Admin(config)# ssh maxsessions 3
To revert to the default of 16 Telnet sessions for the Admin context, enter:
host1/Admin(config)# no ssh maxsessions
Generating SSH Host Key Pairs
The ACE supports remote login over an SSH session that uses private and public
key pairs to perform authentication for the context. DSA and RSA keys are
generated in pairs—one public key and one private key. With this method of
remote connection, use a generated private and public key pair to participate in a
secure communication by encrypting and decrypting messages.
The global administrator performs the key generation in the Admin context. All
c
ontexts associated with the ACE share the common key. There is only a single
host-key pair.
Note If you are the administrator or another user authorized in the Admin context, use
the changeto command in Exec mode to move to the Admin context. An
administrator can perform all allowable functions within the Admin context.
Ensure that you have an SSH host key pair with the appropriate version before
enabling the
SSH service. The SSH service accepts three types of key pairs for
use by SSH versions 1 and 2. Generate the SSH host key pair according to the SSH
client version used. The number of bits specified for each key pair ranges from
768 to 4096.
To generate the SSH private key and the correspo
nding public key for use by the
SSH server, use the ssh key command in configuration mode.
Page 86

Chapter 2 Enabling Remote Access to the ACE
Configuring SSH Management Sessions
2-18
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
The syntax of this command is:
ssh key {ds
a | rsa | rsa1} [bits [force]]
The arguments, keywords, and options are:
• dsa—Generates the DSA key pair for the SSH version 2 protocol.
• rsa—Generates the RSA key pair for the SSH version 2 protocol.
• rsa1—Generates the RSA1 key pair for the SSH version 1 protocol.
• bits—(Optional) Specifies the number of bits for the key pair. For DSA, the
range is from 768 to 2048. For RSA and RSA1, the range is from 768 to 4096.
The greater the number of bits that you specify, the longer it takes to generate
the key. The default is 768.
• force—(Optional) Forces the generation of a DSA or RSA key even when
previous keys exist. If the SSH key pair option is already generated for the
required version, use the force option to overwrite the previously generated
key pair.
Before you generate the key, set the hostname and the domain name. These two
settings
are used in the key. See Chapter 1, Setting Up the ACE, for details on
setting a hostname and to the Ci
sco 4700 Series Application Control Engine
Appliance Virtualization Configuration Guide for details on configuring a
domain.
For example, to generate an RSA1 key pair in the Admin context, enter:
host1/Admin(config)# ssh key rsa1 1024
generating rsa1 key
.....
generated rsa1 key
To remove the SSH host key pair, enter:
host1/Admin(config)# no ssh key rsa1
To clear the public keys of all trusted hosts, use the clear ssh hosts Exec
command. These keys are either sent to an SSH client by an SSH server or are
entered manually. When a SSH connection is made from the ACE, the SSH client
receives the public key and stores it locally. To clear all these keys, use the clear
ssh hosts command in Exec mode.
Page 87

2-19
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 2 Enabling Remote Access to the ACE
Terminating an Active User Session
Terminating an Active User Session
To terminate an active SSH or Telnet session for the active context, use one of the
following commands in Exec mode:
• clear ssh {session_id | hosts}
• clear telnet {session_id}
The arguments, keywords, and options are:
• session_id—Specifies the identifier of the SSH or Telnet session to
disconnect. You can obtain the specific session_id value using either the show
ssh session-info command or the show telnet command in Exec mode. See
the “Directly Accessing a User Context Through SSH” section for details.
• hosts—Clears the list of trusted SSH hosts from the ACE configuration.
For example, to terminate an SSH session, enter:
host1/Admin # clear ssh 345
Enabling ICMP Messages to the ACE
By default, the ACE does not allow ICMP messages to be received by an ACE
interface or to pass through the ACE interface. ICMP is an important tool for
testing your network connectivity; however, network hackers can also use ICMP
to attack the ACE or your network. We recommend that you allow ICMP during
your initial testing, but then disallow it during normal operation.
To permit or deny address(es) to reach an ACE interface with ICMP messages,
eit
her from a host to the ACE, or from the ACE to a host which requires the ICMP
reply to be allowed back, configure a:
• Class map to provide the ICMP network traffic match criteria for the ACE.
• Policy map to enable ICMP network management access to and from the
ACE.
• Service policy to activate the policy map, attach the traffic policy to an
interface or globally on all interfaces, and specify the direction in which the
policy should be applied.
Page 88

Chapter 2 Enabling Remote Access to the ACE
Enabling ICMP Messages to the ACE
2-20
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
See the “Configuring Remote Network Management Traffic Services” section for
details on configuring a network management class map, policy map, and service
poli
cy for the ACE.
To allow ICMP messages to pass through th
e ACE, configure an ICMP ACL to
permit or deny network connections based on the ICMP type (for example, echo,
echo-reply, or unreachable). See the Cisco 4700 Series Application Control
Engine Appliance Security Configuration Guide for details.
Note If you want only to allow the ACE to ping a host (and allow the echo reply back
to the interface), but not allow hosts to ping the ACE, enable the ICMP application
protocol inspection function instead of defining a class map and policy map. See
the Cisco 4700 Series Application Control Engine Appliance Security
Configuration Guide for details.
For example, to allow the ACE to recei
ve ICMP pings, enter the following
commands:
host1/Admin(config)# class-map type management match-all
ICMP-ALLOW_CLASS
host1/Admin(config-cmap-mgmt)# de
scription Allow ICMP packets
host1/Admin(config-cmap-mgmt)# ma
tch protocol icmp source-address
172.16.10.0 255.255.255.254
host1/Admin(config-cmap-mgmt)# ex
it
host1/Admin(config)# policy-map t
ype management first-action
ICMP_ALLOW_POLICY
host1/Admin(config-pmap-mgmt)# cl
ass ICMP-ALLOW_CLASS
host1/Admin(config-pmap-mgmt-c)# permit
host1/Admin(config-pmap-mgmt-c)# exit
host1/Admin(config-pmap-mgmt)# ex
it
host1/Admin(config)# interface vl
an 50
host1/Admin(config-if)# ip addres
s 172.16.1.100 255.255.0.0
host1/Admin(config-if)# service-p
olicy input ICMP_ALLOW_POLICY
Page 89

2-21
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 2 Enabling Remote Access to the ACE
Directly Accessing a User Context Through SSH
Directly Accessing a User Context Through SSH
As the global administrator, from the Admin context, you can configure a user
context and enable direct login access to that user context from a remote SSH
session. To configure the ACE to provide direct access to a user context from SSH,
perform the following steps:
Step 1 Create a user context by entering the following command:
host1/Admin(config)# context C1
host1/Admin(config-context)#
See the Cisco 4700 Series Application Control Engine Appliance Virtualization
Configuration Guide.
Step 2 Associate an existing VLAN with the user context so that the context can receive
traffic classified for it by entering the following command:
host1/Admin(config-context)# allocate-interface vlan 100
See the Cisco 4700 Series Application Control Engine Appliance Routing and
Bridging Configuration Guide.
Step 3 Generate the SSH host key pair by entering the following command:
host1/Admin(config-context)# ssh key rsa1 1024
generating rsa1 key
.....
generated rsa1 key
See the “Generating SSH Host Key Pairs” section.
Step 4 Change to the C1 context that you created in Step 1 and enter configuration mode
in that context by entering the following commands:
host1/Admin(config-context)# do changeto C1
host1/C1(config-context)# exit
host1/C1(config)#
Only users authenticated in the Admin context can use the changeto command.
Page 90

Chapter 2 Enabling Remote Access to the ACE
Directly Accessing a User Context Through SSH
2-22
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Step 5 Configure the VLAN interface that you allocated to the user context in Step 2 by
entering the following commands:
host1/C1(config)# interface vlan 50
host1/C1(config-if)# ip address 1
92.168.1.1 255.255.255.0
host1/C1(config-if)# no shutdown
host1/C1(config-if)# exit
host1/C1(config)#
For example, assign an IP address to the interface and reenable the interface
within the context with the no shutdown command. See the Cisco 4700 Series
Application Control Engine Appliance Routing and Bridging Configuration
Guide.
Step 6 Create an SSH remote management policy and apply the associated service policy
to all VLAN interfaces or just to the VLAN interface allocated to the user context
by entering the following commands:
host1/C1(config)# class-map type management match-all SSH-ALLOW_CLASS
host1/C1(config-cmap-mgmt)# match
protocol ssh source-address
172.16.10.0 255.255.255.254
host1/C1(config-cmap-mgmt)# exit
host1/C1(config)#
host1/C1(config)# policy-map type
management first-match
REMOTE_MGMT_ALLOW_POLICY
host1/C1(config-pmap-mgmt)# class
SSH-ALLOW_CLASS
host1/C1(config-pmap-mgmt-c)# per
mit
host1/C1(config-pmap-mgmt-c)# exi
t
host1/C1(config)# interface vlan
50
host1/C1(config-if)# ip address 1
92.168.1.1 255.255.255.0
host1/C1(config-if)# service-poli
cy input REMOTE_MGMT_ALLOW_POLICY
host1/C1(config-if)# exit
host1/C1(config)#
See the “Configuring Remote Network Management Traffic Services” section.
Step 7 Create an IP route by entering the following command:
host1/C1(config)# ip route 0.0.0.0 255.255.255.0 192.168.4.8
See the Cisco 4700 Series Application Control Engine Appliance Security
Configuration Guide.
Page 91

2-23
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 2 Enabling Remote Access to the ACE
Example of a Remote Access Configuration
To directly access the user context from an SSH client, perform the following
steps:
Step 1 From the SSH client, establish a remote SSH session to the IP address of the user
context VLAN interface.
Step 2 Enter the password for the user context VLAN interface. The ACE CLI prompt
appears in Exec mode of the user context.
host1/C1#
Example of a Remote Access Configuration
The following example illustrates a running-configuration that defines rules for
remote access to the ACE through the use of class maps, policy maps, and service
policies. The remote access configuration appears in bold in the example
telnet maxsessions 3
ssh maxsessions 3
access-list ACL1 line 10 extended permit ip any any
class-map type management match-any L4_REMOTE-MGT_CLASS
description Allows Telnet, SSH, and ICMP protocols
2 match protocol telnet any
3 match protocol ssh any
4 match protocol icmp any
policy-map type management first-match L4_REMOTE-MGT_POLICY
class L4_REMOTE-MGT_CLASS
permit
interface vlan 50
ip address 192.168.1.1 255.255.255.0
access-group input ACL1
service-policy input L4_REMOTE-MGT_POLICY
no shutdown
ssh key rsa1 1024 force
Page 92

Chapter 2 Enabling Remote Access to the ACE
Viewing Session Information
2-24
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Viewing Session Information
This section includes the following procedures:
• Showing Telnet Session Information
• Showing SSH Session Information
Showing Telnet Session Information
To display information related to the Telnet session, use the show telnet command
in Exec mode. Only the context administrator can view Telnet information
associated with a particular context.
The syntax of this command is:
show telnet [cont
ext_name]
The optional cont
ext_name argument specifies the name of the context for which
you want to view specific Telnet session information. The context_name argument
is case sensitive.
For example, enter:
host1/Admin# show telnet
Page 93

2-25
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 2 Enabling Remote Access to the ACE
Viewing Session Information
Table 2-2 describes the fields in the show telnet command output.
Ta b l e 2-2 Field Descriptions for the show telnet Command
Field Description
SessionID Unique session identifier for the Telnet session.
Remote Host IP address and port of the remote Telnet client.
Active Time Time since the Telnet connec
tion request was
received by the ACE.
To display the maximum number of enabled Telnet sessions, use the sho
w telnet
maxsessions command in Exec mode. Only context administrators can view
Telnet session information associated with a particular context.
The syntax of this command is:
show telnet maxsessions [co
ntext_name]
The optional cont
ext_name argument specifies the name of the context for which
you want to view the maximum number of Telnet sessions. The context_name
argument is case sensitive.
For example, enter:
host1/Admin# show telnet maxsessions
Maximum Sessions Allowed is 4
Page 94

Chapter 2 Enabling Remote Access to the ACE
Viewing Session Information
2-26
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Showing SSH Session Information
This section contains the following procedures:
• Showing SSH Session Information
• Showing SSH Key Details
Showing SSH Session Information
To display information related to the SSH session, use the show ssh session-info
command in Exec mode. Only context administrators can view SSH session
information associated with a particular context.
The syntax of this command is:
show ssh session-info [cont
ext_name]
The optional cont
ext_name argument specifies the name of the context for which
you want to view specific SSH session information. The context_name argument
is case sensitive.
For example, enter:
host1/Admin# show ssh session-info
Table 2-3 describes the fields in the show ssh session-info command output.
Ta b l e 2-3 Field Descriptions for the show ssh session-info Command
Field Description
SessionID Unique session identifier for the SSH session.
Remote Host IP address and port of the remote SSH client.
Active Time Time since the SSH connection request was received
by
the ACE.
To display the maximum number of enabled SSH sessions, use the sho
w ssh
maxsessions command in Exec mode. Only context administrators can view SSH
session information associated with a particular context.
Page 95

2-27
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 2 Enabling Remote Access to the ACE
Viewing Session Information
The syntax of this command is:
show ssh maxsessions [co
ntext_name]
The optional cont
ext_name argument specifies the name of the context for which
the context administrator wants to view the maximum number of SSH sessions.
The context_name argument is case sensitive.
For example, enter:
host1/Admin# show ssh maxsessions
Maximum Sessions Allowed is 4(SSH Server is enabled)
Showing SSH Key Details
Use the show ssh key command in Exec mode to display the host key pair details
for the specified key or for all keys if you do not specify a key.
The syntax of this command is:
show ssh key [dsa | rsa | rsa1]
The arguments, keywords, and options are:
• dsa—Specifies the DSA key pair for the SSH version 2 protocol.
• rsa—Specifies the RSA key pair for the SSH version 2 protocol.
• rsa1—Specifies the RSA1 key pair for the SSH version 1 protocol.
For example, enter:
host1/Admin # show ssh key
**************************************
could not retrieve rsa1 key information
**************************************
rsa Keys generated:Tue May 8 19:37:17 2007
ssh-rsa
AAAAB3Nza
C1yc2EAAAABIwAAAIEA4v4DQ8aNl482qDTRju9G07hEIxCgTWanPm+WOCU1ki
hZ
QNd5ZwA50CBAJSfIIIB4iED6iQbhOkbXSneCvTb5mVoish2wvJrETpIDIeGxxh/jWVsU/M
eBbA/7o5t
v
gCeT6p7pGF5oUNYFP0OeZ9BiIWDc4jBmYEQLEqJHPrMhSFE=
bitcount:1024
fingerprint:
f5:55:00:18:bc:af:41:74:b6:bc:aa:8e:46:31:74:4f
**************************************
Page 96

Chapter 2 Enabling Remote Access to the ACE
Viewing Session Information
2-28
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
dsa Keys generated:Tue May 8 19:37:17 2007
ssh-dss
AAAAB3Nza
C1kc3MAAACBAPqDdEqU+0gNtKRXM+DQAXnvcB+H89nq8jA4WgJ7uQcuDCLaG7
Lq
jtKTltJjA6aZVywsQWQ6n4kTlkavZy3cj6PUbSyqvmCTsaYyYo4UQ6CKrK9V+NsfgzTSLW
TH8iDUvYj
L
c3nU51QEKjy7mPsQeX31y1M1rhp8qhkbMKxkc49XAAAAFQCPM0QJrq6+kkaghJpeNxeXhU
H9HwAAAIE
A
keZ1ZJM6sfKqJDYPLHkTro+lpbV9uR4VyYoZmSoehi/LmSaZDq+Mc8UN1LM+i5vkOgnKce
arD9lM4/h
K
zZGYx5hJOiYCKj/ny2a5p/8HK152cnsOAg6ebkiTTWAprcWrcHDS/1mcaI5GzLrZCdlXW5
gBFZtMTJG
s
tICmVWjibewAAACBAJQ66zdZQqYiCWtZfmakridEGDTLV6ixIDjBNgb84qlj+Y1XMzqLL0
D4oMSb7id
E
L3BmhQYQW7hkTK0oS4kVawI1VmW2kvrqoGQnLNQRMvisAXuJWKk1Ln6vWPGZZe8KoALv0G
XxsOv2gk/
z
TDk01oCaTVw//bXJtoVRgIlWXLIP
bitcount:1024
fingerprint:
8e:13:5c:3e:1a:9c:7a:ed:d0:84:eb:96:12:db:82:be
**************************************
Page 97

3-1
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
CHAPTER
3
Managing ACE Software Licenses
This chapter describes how to manage the software licenses for your Cisco 4700
Series Application Control Engine (ACE) appliance. It contains the following
major sections:
• Available ACE Licenses
• Ordering an Upgrade License and Generating a Key
• Copying a License File to the ACE
• Installing a New or Upgrade License File
• Replacing a Demo License with a Permanent License
• Removing a License
• Backing Up a License File
• Displaying License Configurations and Statistics
Note You can access the license and show license commands only in the Admin
context. You must have the Admin role in the Admin context to install, remove,
and update the license file.
Page 98

Chapter 3 Managing ACE Software Licenses
Available ACE Licenses
3-2
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Available ACE Licenses
By default, the ACE supports the following features and capabilities:
• Performance: 1 gigabit per second (Gbps) appliance throughput
• Virtualization: 1 admin context and 5 user contexts
• Secure Sockets Layer (SSL): 1000 transactions per second (TPS)
• Hypertext Transfer Protocol (HTTP) compression: 100 megabits per second
(Mbps)
You can increase the performance and
operating capabilities of your ACE product
by purchasing one of the licensing options.
There are two methods to order your ACE product:
• Ordering a license bundle. Each license bundles includes the ACE appliance
and a series of software licenses.
• Ordering separate license options.
Table 3-1
summarizes the contents of the available license bundles. Tab le 3-2
provides a list of the default and upgrade ACE appliance licensing options.
Page 99

Ta b l e 3-1 ACE Licensing Bundles
License Model Description
ACE-4710-2F-K9 This license bundle includes the following items:
• ACE 4710 appliance
• 2 Gbps throughput license
• 7500 SSL transactions per second (TPS) license
• 1 Gbps compression license
• 5 virtual contexts license (default)
• Application acceleration license
ACE-4710-1F-K9 This license bundle includes the following items:
• ACE 4710 appliance
• 1 Gbps throughput license
• 5000 SSL TPS license
• 500 Mbps compression license
• 5 virtual contexts license (default)
• Application acceleration license
3-3
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
Chapter 3 Managing ACE Software Licenses
Available ACE Licenses
Ta b l e 3-2 ACE Licensing Options
Feature License Model Description
Performance
Thro
ughput
ACE-AP-01-LIC
(default)
1 Gbps throughput.
ACE-AP-02-LIC 2 Gbps throughput.
Virtualization Default 1 admin/5 user contexts.
ACE-AP-VIRT-020 1 admin/20 user contexts.
SSL Default 1000 TPS.
ACE-AP-SSL-05K-K9 5000 TPS.
ACE-AP-SSL-07K-K9 7500 TPS.
ACE-AP-SSL-UP1-K9 Upgrade from 5000 TPS to 7500 TPS.
Page 100

Chapter 3 Managing ACE Software Licenses
Available ACE Licenses
3-4
Cisco 4700 Series Application Control Engine Appliance Administration Guide
OL-11157-01
ACE demo licenses are available through your Cisco account representative. A
demo license is valid for only 60 days. At the end of this period, you must update
the demo license with a permanent license to continue to use the ACE software.
To view the expiration of a demo license, use the show license usage command
in Exec mode.
Note If you need to replace the ACE, you can copy and install the license file for the
license onto the replacement appliance.
HTTP
C
ompression
Default 100 Mbps.
ACE-AP-C-500-LIC 500 Mbps
ACE-AP-C-1000-LIC 1 Gbps
ACE-AP-C-UP1 Upgrade from 500 Mbps to 1 Gbps.
Application
A
cceleration
Feature Pack
License
ACE-AP-OPT-LIC-K9 Application acceleration and
opt
imization. By default, the ACE
performs up to 50 concurrent
connections per second. With the
application acceleration and
optimization software feature pack
installed, the ACE can provide greater
than 50 concurrent connections. This
license increases the operating
capabilities of the following features:
• Delta optimization
• Adaptive dynamic caching
• Flashforward
• Etag
Table 3-2 ACE Licensing Options
Feature License Model Description
 Loading...
Loading...