Page 1

Title Page
Bridge/Router Interface (BRIM)
User’s Guide
Page 2

Page 3

Notice
Cabletron Systems reserves the right to make changes in speciÞcations and other information
contained in this document without prior notice. The reader should in all cases consult Cabletron
Systems to determine whether any such changes have been made.
The hardware, Þrmware, or software described in this manual is subject to change without notice.
IN NO EVENT SHALL CABLETRON SYSTEMS BE LIABLE FOR ANY INCIDENTAL, INDIRECT,
SPECIAL, OR CONSEQUENTIAL DAMAGES WHATSOEVER (INCLUDING BUT NOT LIMITED
TO LOST PROFITS) ARISING OUT OF OR RELATED TO THIS MANUAL OR THE INFORMATION
CONTAINED IN IT, EVEN IF CABLETRON SYSTEMS HAS BEEN ADVISED OF, KNOWN, OR
SHOULD HAVE KNOWN, THE POSSIBILITY OF SUCH DAMAGES.
Virus Disclaimer
Cabletron has tested its software with current virus checking technologies. However, because no antivirus system is 100% reliable, we strongly caution you to write protect and then verify that the
Licensed Software, prior to installing it, is virus-free with an anti-virus system in which you have
conÞdence.
Cabletron Systems makes no representations or warranties to the effect that the Licensed Software is
virus-free.
Copyright © 1999 by Cabletron Systems, Inc. All rights reserved.
Printed in the United States of America.
Order Number: 9031617-04 April 1999
Cabletron Systems, Inc.
P.O. Box 5005
Rochester, NH 03866-5005
SPECTRUM , MiniMMAC , FNB , Multi Media Access Center , and DNI are registered trademarks,
and Portable Management Application , IRM , IRM2 , IRM3 , IRBM , ESXMIM , ETSMIM , EMME ,
EMM-E6 , ETWMIM , FDMMIM , FDCMIM , MicroMMAC , MRXI , MRXI-24 , NB20E , NB25E , NB30 ,
NB35E , NBR , SEHI , STHI , TRBMIM , TRMM , TRMM-2 , TRMM-4 , TRMMIM , TRXI , Media
Interface Module , MIM , and Flexible Network Bus are trademarks of Cabletron Systems, Inc.
UNIX and OPENLOOK are trademarks of Unix System Laboratories, Inc. OSF/Motif and Motif are
trademarks of the Open Software Foundation, Inc. X Window System is a trademark of X Consortium,
Inc. Ethernet and XNS are trademarks of Xerox Corporation. Apple and AppleTalk are registered
trademarks of Apple Computer, Inc. Banyan is a registered trademark of Banyan Systems, Inc.
DECnet is a registered trademark of Digital Equipment Corporation. Novell is a registered trademark
of Novell, Inc. CompuServe is a registered trademark of CompuServe. Sun Microsystems is a
registered trademark, and Sun , SunNet , and OpenWindows are trademarks of Sun Microsystems,
Inc.
i
Page 4

Restricted Rights Notice
(Applicable to licenses to the United States Government only.)
1. Use, duplication, or disclosure by the Government is subject to restrictions as set forth in
subparagraph (c) (1) (ii) of the Rights in Technical Data and Computer Software clause at DFARS
252.227-7013.
Cabletron Systems, Inc., 35 Industrial Way, Rochester, New Hampshire 03867-0505.
2. (a) This computer software is submitted with restricted rights. It may not be used, reproduced, or
disclosed by the Government except as provided in paragraph (b) of this Notice or as otherwise
expressly stated in the contract.
(b) This computer software may be:
(1) Used or copied for use in or with the computer or computers for which it was acquired,
including use at any Government installation to which such computer or computers may
be transferred;
(2) Used or copied for use in a backup computer if any computer for which it was acquired
is inoperative;
(3) Reproduced for safekeeping (archives) or backup purposes;
(4) Modified, adapted, or combined with other computer software, provided that the
modified, combined, or adapted portions of the derivative software incorporating
restricted computer software are made subject to the same restricted rights;
(5) Disclosed to and reproduced for use by support service contractors in accordance with
subparagraphs (b) (1) through (4) of this clause, provided the Government makes such
disclosure or reproduction subject to these restricted rights; and
(6) Used or copied for use in or transferred to a replacement computer.
(c) Notwithstanding the foregoing, if this computer software is published copyrighted computer
software, it is licensed to the Government, without disclosure prohibitions, with the minimum
rights set forth in paragraph (b) of this clause.
(d) Any other rights or limitations regarding the use, duplication, or disclosure of this computer
software are to be expressly stated in, or incorporated in, the contract.
(e) This Notice shall be marked on any reproduction of this computer software, in whole or in part.
ii
Page 5

Chapter 1 Introduction
Using the BRIM UserÕs Guide..................................................................................... 1-2
Related Manuals............................................................................................................ 1-3
BRIM Management Applications ...............................................................................1-3
Software Conventions .................................................................................................. 1-4
Using the Mouse ....................................................................................................1-4
Common Device Window Fields......................................................................... 1-6
Using Window Buttons......................................................................................... 1-7
Getting Help .................................................................................................................. 1-8
Using On-line Help................................................................................................ 1-8
Accessing On-line Documentation...................................................................... 1-8
Getting Help from the Cabletron Systems Global Call Center .......................1-9
Contents
Chapter 2 Bridging
Bridging Basics .............................................................................................................. 2-1
About Transparent Bridging ................................................................................ 2-1
About Source Route Bridging .............................................................................. 2-2
About Source Route-Transparent Bridges.......................................................... 2-3
About Source Route-Translational Bridges ........................................................ 2-4
Viewing and Managing Bridging Interfaces............................................................. 2-5
The Bridge Status Window.......................................................................................... 2-7
Accessing Bridge Status Window Options......................................................... 2-9
Enabling and Disabling Bridging .............................................................................2-14
Enabling and Disabling Individual Interfaces................................................. 2-14
Enabling and Disabling All Installed Interfaces.............................................. 2-14
Bridge Statistics ........................................................................................................... 2-15
Performance Graphs............................................................................................ 2-15
ConÞguring Performance Graphs.............................................................. 2-17
Bridge Detail Breakdown ............................................................................2-18
Bridge Port Detail Breakdown.................................................................... 2-19
Interface Statistics ................................................................................................2-20
CSMACD Statistics .............................................................................................. 2-23
PPP Link Statistics ............................................................................................... 2-25
Dot5 Errors............................................................................................................ 2-28
Source Route Statistics ........................................................................................2-31
Spanning Tree ..............................................................................................................2-34
Bridge Level.......................................................................................................... 2-35
Bridge Port Level .................................................................................................2-37
ConÞguring Spanning Tree ................................................................................ 2-39
iii
Page 6

Contents
Changing Bridge Priority ............................................................................2-39
Changing the Spanning Tree Algorithm Protocol Type ..........................2-39
Changing Hello Time ................................................................................... 2-40
Changing Max Age Time .............................................................................2-40
Changing Forwarding Delay Time............................................................. 2-40
Changing Port Priority.................................................................................2-41
Changing Path Cost......................................................................................2-41
Filtering Database .......................................................................................................2-41
ConÞguring the Filtering Database................................................................... 2-45
Special Filter Databases.............................................................................................. 2-47
Ethernet and Token Ring Special Filter Database Windows .........................2-48
Special Filter Database Window........................................................................ 2-49
DeÞning and Editing Filters in the Special Database .....................................2-51
Changing the Receive Ports................................................................................ 2-52
Changing the Port Filtering Action ...................................................................2-52
Setting the Port Filtering Action................................................................. 2-52
Clearing the Port Filtering Action ..............................................................2-53
Enabling and Disabling a Filter .........................................................................2-53
Saving a Set of Filters to a File............................................................................ 2-53
Interface ConÞguration ..............................................................................................2-54
Bridge Methods ....................................................................................................2-55
Setting the Bridge Method.................................................................................. 2-56
Protocol Transmission Methods.........................................................................2-56
Source Route ConÞguration ......................................................................................2-57
Source Routing Information............................................................................... 2-58
Source Route ConÞguration ...............................................................................2-59
Making and Setting Changes .............................................................................2-62
Using the Find Source Address Feature................................................................... 2-63
Using the Port Source Addresses Window..............................................................2-64
Setting the Aging Time ........................................................................................2-65
Using the Token Ring Bridge and Port ConÞguration Windows......................... 2-65
Duplex Modes.............................................................................................................. 2-70
Setting the Duplex Mode ............................................................................. 2-72
Ethernet Port ConÞguration............................................................................... 2-72
Fast Ethernet Port ConÞguration....................................................................... 2-73
Setting the Operational Mode for the FE-100TX ......................................2-76
Setting the Operational Mode for the FE-100FX ......................................2-77
SONET Port ConÞguration........................................................................................2-77
SONET/SDH ConÞguration ..............................................................................2-77
SONET/SDH Statistics........................................................................................ 2-79
ConÞguring SmartTrunking ......................................................................................2-85
ConÞguring Broadcast Suppression......................................................................... 2-88
Token Ring Bridge Mode ........................................................................................... 2-89
Setting Token Ring Bridge Mode .......................................................................2-90
Setting Bridge Translation.......................................................................................... 2-91
Enabling and Disabling Auto and Dual Translate Modes .............................2-92
ConÞguring Token Ring Packet Translation ....................................................2-93
ConÞguring Novell Token Ring Packet Translation................................ 2-93
The IBM Translation Table.................................................................................. 2-94
The SNAP Translation Table...............................................................................2-96
iv
Page 7

ConÞguring SNAP Translation................................................................... 2-96
Using the Novell Translation Window ....................................................................2-97
Using the Physical View Windows for the ETWMIM ...........................................2-99
Ethernet Port Physical View............................................................................... 2-99
Token Ring Port Physical View........................................................................ 2-101
Chapter 3 FDDI Applications
Accessing the FDDI Menu ........................................................................................... 3-2
The ConÞguration Window......................................................................................... 3-2
Connection Policy Window......................................................................................... 3-5
Station List Window ..................................................................................................... 3-8
FDDI Performance Window...................................................................................... 3-10
Setting the Time Interval..................................................................................... 3-11
Contents
Chapter 4 WAN Applications
Accessing the WAN Status Windows ........................................................................ 4-1
Viewing WAN Interface Status ...................................................................................4-2
ConÞguring the Synchronous Connection......................................................... 4-3
ConÞguring T-1 Ports............................................................................................ 4-5
Using the T1 FracTable ConÞguration Window ........................................ 4-7
ConÞguring the Fractional Table........................................................... 4-8
Restoring a Fractional Table................................................................... 4-9
Changing the Interface Line Coding .................................................... 4-9
Displaying the WAN Logical View .......................................................................... 4-10
Changing WAN Logical Settings ....................................................................... 4-11
Viewing the WAN Port Admin/Status.................................................................... 4-12
Synchronous Admin/Status............................................................................... 4-12
T1 Admin/Status .................................................................................................4-13
Enabling and Disabling WAN T1 Interfaces............................................. 4-14
Displaying Synchronous Port Statistics................................................................... 4-14
Chapter 5 ATM Configuration
Accessing the ATM Connections Window................................................................ 5-1
ConÞguring Connections............................................................................................. 5-3
Adding a New Connection................................................................................... 5-4
Deleting a Connection........................................................................................... 5-5
Index
v
Page 8

Contents
vi
Page 9

Chapter 1
Introduction
Using this guide; related manuals; management applications available for BRIMs; software
conventions; getting help; contacting Cabletron Systems Global Call Center
Welcome to the Cabletron SystemsÕ SPECTRUM
Bridge/Router Interface (BRIM) UserÕs Guide . We have designed this guide
to serve as a reference for using SPECTRUM Element Manager for all types
of BRIMs.
Cabletron SystemsÕ Bridge/Router Interface Modules (BRIMs) provide ßexible,
integrated bridging functionality (including trafÞc Þltering by destination, source,
type Þeld, and 64-byte data offset, and support for the Spanning Tree Algorithm)
or routing functionality to the network hub. By accommodating several media
types and topologies, these network interfaces connect to any standard Local Area
Network (LAN) or Wide Area Network (WAN).
Since BRIMs plug into CabletronÕs Intel i960-based products (e.g., EMM-E6,
ESXMIM, MicroMMAC, and MicroMMAC-T), SPECTRUM Element Manager
views the hub and bridge/router as a single entity. The following BRIMs are
supported by SPECTRUM Element Manager:
BRIM-A6
BRIM-A6DP
The ATM Bridge/Router Interface Modules feature high
speed ATM connectivity (at rates up to 155 Mbps). They
are fully compatible with the 9A000 ATM Switch Module
for the SmartSwitch
They support the IETF AToM MIB, Multi-Protocol
Encapsulation over AAL5, and many other protocols,
and meet ATM Forum UNI speciÞcations. The BRIM-A6
supports a single ATM interface, and the BRIM-A6DP
supports two redundant ATM interfaces.
¨
Element Manager
¨
9000, and Fore SystemsÕ ASX-200.
BRIM-E6
The Ethernet BRIM has a user-conÞgurable Ethernet Port
Interface Module (EPIM) port that provides media
ßexibility for AUI, UTP, STP, Þber or coax cable.
1-1
Page 10

Introduction
NOTE
BRIM-E100
BRIM-F6
BRIM-W6
Cabletron Systems has discontinued manufacturing several BRIMs, including the
BRIM-WT1, the Cisco BRIM-W/E, the BRIM-A100, the BRIM-T6, the BRIM-FO, the
BRIM-FD1, the BRIM-FD2, and the BRIM-F5.
The Fast Ethernet BRIM has a user-conÞgurable Fast
Ethernet Port Interface Module (FEPIM) port that
provides either 100BASE-TX connectivity (via an RJ-45
interface) or 100BASE-FX connectivity (via an MMF
interface with an SC connector).
The FDDI Bridge/Router Interface Module is a
translational FDDI to Ethernet bridge, via media
conÞgurable Fiber Port Interface Module (FPIM)
connectors using MMF or SMF Þber, or UTP or STP
copper. The BRIM-F6 supports the IETF FDDI MIB and
dual homing. Its DAS attachment is ANSI-compliant.
The WAN Bridge/Router Interface Module supports
Synchronous, T1 and E1 connections. It carries PPP,
Frame Relay and X.25 protocols through its WAN Port
Interface Modules.
Using the BRIM User’s Guide
Each chapter in this guide describes one major functionality or a collection of
several smaller functionalities that the BRIM adds to the device. This guide
contains information about software functions which are accessed directly from
the device icon; for information about management functions which are accessed
via the SPECTRUM Element Manager platform, consult the SPECTRUM Element
Manager UserÕs Guide , and SPECTRUM Element Manager Tools Guide , and the
Remote Administration Tools UserÕs Guide .
Chapter 1, Introduction , provides a list of related documentation, describes
certain software conventions, and shows you how to contact Cabletron SystemsÕ
Global Call Center.
Chapter 2, Bridging , provides a comprehensive look at all management options
associated with the bridge portion of the device, including Bridge Performance
Graphs, Spanning Tree, and the Filtering and Special Filtering Databases.
Chapter 3, FDDI Applications , describes the FDDI management windows,
including ConÞguration, Connection Policy, Station List, and Performance.
Chapter 4, WAN Applications , describes the windows available for WAN Port
conÞguration, and the Synchronous Port Statistics window.
Chapter 5, ATM ConÞguration , describes how to conÞgure Permanent Virtual
Circuits (PVCs) for the ATM interface(s) available on the ATM BRIM.
1-2 Using the BRIM User’s Guide
Page 11

We assume that you have a general working knowledge of Ethernet IEEE 802.3,
FDDI, WAN, and ATM type data communications networks and their physical
layer components, and that you are familiar with general bridging concepts.
Related Manuals
The BRIM UserÕs Guide is only part of a complete document set designed to
provide comprehensive information about the features available to you through
SPECTRUM Element Manager. Other guides which include important
information related to managing the BRIM include:
Cabletron SystemsÕ SPECTRUM Element Manager UserÕs Guide
Cabletron SystemsÕ SPECTRUM Element Manager Tools Guide
Cabletron SystemsÕ SPECTRUM Element Manager Remote Administration Tools
UserÕs Guide
Introduction
Cabletron SystemsÕ SPECTRUM Element Manager Remote Monitoring (RMON)
UserÕs Guide
Cabletron SystemsÕ SPECTRUM Element Manager Alarm and Event Handling
UserÕs Guide
Cabletron SystemsÕ Network Troubleshooting Guide
Microsoft CorporationÕs Microsoft Windows UserÕs Guide
For more information about the capabilities of the BRIM and the host device in
which it is installed, consult the appropriate hardware documentation.
For more information about the capabilities of SPECTRUM Element Manager for
the host device, consult its UserÕs Guide.
BRIM Management Applications
When a device (e.g., MicroMMAC, NBR-620, EMM-E6, or ESXMIM) has a BRIM
installed and enabled, additional applications will be available from the Chassis
View window. These applications will depend on the type of BRIM installed in
your device.
¥ Bridge Status will be available from the Device menu for all devices with
BRIMs installed. The Bridging options that are available from the Bridge Status
window will vary depending on the device and the type of BRIM you have
installed; see Chapter 2, Bridging, for details on the bridge applications.
¥ Router Utilities ( Basic Router ConÞguration and Advanced Router
ConÞguration ) will be available from the Tools menu when a BRIM is
installed and enabled on your device. For more information, see the Routing
Services ConÞguration Guide.
Related Manuals 1-3
Page 12

Introduction
¥ FDDI menu will be available on devices that have an FDDI BRIM installed and
enabled; see Chapter 3, FDDI Applications, for details.
¥ WAN Status will be available from the Device menu for devices that have a
WAN BRIM installed and enabled; see Chapter 4, WAN Applications, for
details.
¥ ATM Connections will be available from the Device menu for devices that
have an ATM BRIM installed and enabled; see Chapter 5, ATM ConÞguration,
for details.
If you cannot determine if you have a BRIM installed in your device or are unsure of the
TIP
type of installed BRIM, the I/F Summary window can help you Þnd the answer. To access
this window, select DeviceÐ>I/F Summary from your deviceÕs Chassis View window.
This windowÕs Description Þeld lists the interface descriptions for the device, including
the type of BRIM installed in the device (e.g., Ctron FDDI BRIM port). The BRIM port(s)
will always be listed at the end of the interface list, after all the non-BRIM interfaces.
Software Conventions
SPECTRUM Element ManagerÕs device user interface contains a number of
elements which are common to most windows and which operate the same
regardless of which window they appear in. A brief description of some of the
most common elements appears below; note that the information provided here is
not repeated in the descriptions of speciÞc windows and/or functions.
In accordance with Year 2000 compliance requirements, SPECTRUM Element Manager
NOTE
displays and allows you to set all dates with four-digit year values.
Using the Mouse
This document assumes you are using a Windows-compatible mouse with two
buttons; if you are using a three button mouse, you should ignore the operation of
the middle button when following procedures in this document. Procedures
within the SPECTRUM Element Manager document set refer to these buttons as
follows:
1-4 Software Conventions
Page 13

Introduction
Left Mouse Button
Right Mouse Button
Figure 1-1. Mouse Buttons
For many mouse operations, this document assumes that the left (primary) mouse
button is to be used, and references to activating a menu or button will not
include instructions about which mouse button to use.
However, in instances in which right (secondary) mouse button functionality is
available, instructions will explicitly refer to right mouse button usage. Also, in
situations where you may be switching between mouse buttons in the same area
or window, instructions may also explicitly refer to both left and right mouse
buttons.
Instructions to perform a mouse operation include the following terms:
¥ Pointing means to position the mouse cursor over an area without pressing
either mouse button.
¥ Clicking means to position the mouse pointer over the indicated target, then
press and release the appropriate mouse button. This is most commonly used
to select or activate objects, such as menus or buttons.
¥ Double-clicking means to position the mouse pointer over the indicated
target, then press and release the mouse button two times in rapid succession.
This is commonly used to activate an objectÕs default operation, such as
opening a window from an icon. Note that there is a distinction made between
Òclick twiceÓ and Òdouble-click,Ó since Òclick twiceÓ implies a slower motion.
¥ Pressing means to position the mouse pointer over the indicated target, then
press and hold the mouse button until the described action is completed. It is
often a pre-cursor to Drag operations.
¥ Dragging means to move the mouse pointer across the screen while holding
the mouse button down. It is often used for drag-and-drop operations to copy
information from one window of the screen into another, and to highlight
editable text.
Software Conventions 1-5
Page 14
Introduction
Common Device Window Fields
Similar descriptive information is displayed in boxes at the top of most
device-speciÞc windows in SPECTRUM Element Manager, as shown in
Figure 1-2.
IP Address
Figure 1-2. Sample Window Showing Group Boxes
Device
Name
Location
MAC
Address
Device Name
Displays the user-deÞned name of the device. The device name can be changed
via the System Group window; see the Generic SNMP UserÕs Guide for details.
IP Address
Displays the deviceÕs IP (Internet Protocol) address; this will be the IP address
used to deÞne the device icon. IP addresses are assigned via Local Management
for the device; they cannot be changed via SPECTRUM Element Manager.
Location
Displays the user-deÞned location of the device. The location is entered through
the System Group window; see the Generic SNMP UserÕs Guide for details.
1-6 Software Conventions
Page 15

Introduction
MAC Address
The physical layer address assigned to the interface associated with the IP address
used to deÞne the device icon when it was added to SPECTRUM Element
Manager. MAC addresses are hard-coded in the device, and are not conÞgurable.
Informational Þelds describing the boards and/or ports being modeled are also
displayed in most windows:
Board Number
Displays the number indicating the position of the monitored board in the chassis.
Port Number
Displays the number of the monitored port.
Active Users
Indicates the number of users processing information through the deviceÕs
repeater channel, board, or port, as determined by MAC addresses.
Uptime
Displays the amount of time, in a days hh:mm:ss format, that the device has been
running since the last start-up.
Using Window Buttons
The Cancel button that appears at the bottom of most windows allows you to exit
a window and terminate any unsaved changes you have made. You may also
have to use this button to close a window after you have made any necessary
changes and set them by clicking on the OK, Set, or Apply button.
An OK, Set, or Apply button appears in windows that have conÞgurable values;
it allows you to conÞrm and SET changes you have made to those values. In some
windows, you may have to use this button to conÞrm each individual set; in other
windows, you can set several values at once and conÞrm the sets with one click
on the button.
The Help button brings up a Help text box with information speciÞc to the
current window. For more information on the Help button, see Using On-line
Help, page 1-8.
The command buttons, for example Bridge, call up a menu listing the windows,
screens, or commands available for that topic.
Any menu topic followed by ... (three dots) Ñ for example Statistics... Ñ calls up
a window or screen associated with that topic.
Software Conventions 1-7
Page 16

Introduction
Getting Help
This section describes different methods of getting help for questions or concerns
you may have while using SPECTRUM Element Manager.
Using On-line Help
You can use the BRIM window Help buttons to obtain information speciÞc to the
device. When you click on a Help button, a window will appear which contains
context-sensitive on-screen documentation that will assist you in the use of the
window and its associated command and menu options. Note that if a Help
button is grayed out, on-line help has not yet been implemented for the associated
window.
From the Help menu accessed from the host deviceÕs Chassis View window menu
bar, you can access on-line Help speciÞc to the Chassis View window, as well as
bring up the Chassis Manager window for reference. Refer to the deviceÕs userÕs
guide for information on the Chassis View and Chassis Manager windows.
All of the online help windows use the standard Microsoft Windows help facility. If you
NOTE
are unfamiliar with this feature of Windows, you can select Help from the Windows
Start menu, or Help Ñ>How to Use Help from the primary SPECTRUM Element
Manager window, or consult your Microsoft Windows product UserÕs Guide.
Accessing On-line Documentation
The complete suite of documents available for SPECTRUM Element Manager
can be accessed via a menu option from the primary window menu bar:
Help Ñ> Online Documents. If you chose to install the documentation when you
installed SPECTRUM Element Manager, selecting this option will launch AdobeÕs
Acrobat Reader and a menu Þle which provides links to all other available
documents.
If you have not yet installed the documentation, the Online Documents option will not
TIP
be able to access the menu Þle. In order to activate this option, you must run the
setup.exe again to install the documentation component. See your Installation Guide
for details.
1-8 Getting Help
Page 17

Getting Help from the Cabletron Systems Global Call Center
If you need technical support related to SPECTRUM Element Manager, or if you
have any questions, comments, or suggestions related to this manual or any of
our products, please feel free to contact the Cabletron Systems Global Call Center
via one of the following methods:
By phone: (603) 332-9400
24 hours a day, 365 days a year
By mail: Cabletron Systems, Inc.
PO Box 5005
Rochester, NH 03866-5005
By Internet mail: support@ctron.com
FTP: ftp.ctron.com (134.141.197.25)
Login anonymous
Password your email address
By BBS: (603) 335-3358
Introduction
Modem Setting 8N1: 8 data bits, 1 stop bit, No parity
For additional information about Cabletron Systems products, visit our
World Wide Web site: http://www.cabletron.com/. For technical support,
select Service and Support.
Getting Help 1-9
Page 18

Introduction
1-10 Getting Help
Page 19

Chapter 2
Bridging
About bridging methods; viewing and managing bridging interfaces; using the Bridge Status window;
viewing bridge statistics; using Spanning Tree; using the Filtering Database; configuring duplex
modes; using the Interface Configuration window; and setting Bridge Translation
Bridging Basics
Bridges are used in local area networks to connect two or more network segments
and to control the ßow of packets between the segments. Ideally, bridges forward
packets to another network segment only when necessary.
Bridges are also used to increase the fault tolerance in a local area network by
creating redundant bridge paths between network segments. In the event of a
bridge or bridge segment failure, an alternate bridge path will be available to
network trafÞc, without signiÞcant interruption to its ßow.
The method a bridge uses to forward packets, choose a bridge path, and ensure
that a sending stationÕs messages take only one bridge path depends on the
bridgeÕs type: Transparent (generally used in Ethernet or FDDI environments) or
Source Routing (generally used in Token Ring environments), source
routing-transparent, or source route-transparentÑthe two latter being
combinations that are found in a mixed network environment.
About T ransparent Bridging
Transparent bridges are most common in Ethernet networks. Individual
Transparent bridges monitor packet trafÞc on attached network segments to learn
where end stations reside in relation to each segment by mapping the Source
Address of each received frame to the port (and segment) it was detected on. This
information gets stored in the bridgeÕs Filtering Database.
When in the Forwarding state, the bridge compares a packetÕs destination address
to the information in the Filtering Database to determine if the packet should be
forwarded to another network segment or Þltered (i.e., not forwarded). A bridge
2-1
Page 20

Bridging
Þlters a packet if it determines that the packetÕs destination address exists on the
same side of the bridge as the source address.
If two or more bridges are connected to the same Ethernet LAN segmentÑplaced
in parallelÑonly a single bridge must be allowed to forward data frames onto
that segment. If two or more bridges were forwarding data frames onto the same
Ethernet segment, the network would soon be ßooded.
With a data loop in the topology, bridges would erroneously associate a single
source address with multiple bridge ports, and keep proliferating data by
forwarding packets in response to the ever-changing (but incorrect) information
stored in their Filtering Database.
To avoid such data storms, Transparent bridges communicate with one another
on the network by exchanging Bridge Protocol Data Units (BPDUs) to determine
the network topology and collectively implement a Spanning Tree Algorithm
(STA) that selects a controlling bridge for each LAN segment. This ensures that
only a single data route exists between any two end stations and that topology
information remains current.
About Source Route Bridging
Source Routing is typically used to connect two or more Token Ring network
segments. Source Route bridges differ from Transparent bridges in that they do
not build and then use a physical address database to make forwarding decisions.
Instead, the source end station transmits packets with a header that contains
routing information (added by bridges in the network topology during a route
discovery process between end stations); once a route has been determined, a
Source Route bridge simply reads the header of a source routed packet to
determine whether it is a participant in routing the packet.
In Source Routing, sending and receiving devices employ broadcast
packetsÑknown as explorer packetsÑto determine the most efÞcient route for a
message to travel. Generally, before a station sends a message, it will Þrst send a
test packet to all stations on the same ring; if the sending station receives a
response to this packet, it assumes that the destination station is on the same ring
and therefore it will not include routing information in frames sent to that station
in the future. Any further packets issued between stations will appear to be
transparent-style frames without embedded routing information.
If the sending station does not receive a response to the test packet, it will send
explorer packets to the destination; the explorer packets will be propagated by the
networkÕs bridges as either All Paths Explorer (APE) packets or as Spanning Tree
Explorer (STE) packets. The task of both packet types is to get the destination
station to return speciÞc route information to the sending station. They achieve
this by including an identiÞer for each ring the explorer packet traversed and for
each bridge between any rings).
Since the data ßow on a Source Routed network is determined by end stations
(unlike a Transparently bridged network), a looped bridge topology is not an
issue for data ßow. APE packets are sent from the source station over every
2-2 Bridging Basics
Page 21

Bridging
possible bridge path to the end station. The original APE frame contains no
routing information (e.g., bridge numbers and ring numbers). As the frame is
propagated along all available paths to the destination station, each bridge along
the way adds its own bridge and ring numbers to the packetÕs RIF before
forwarding it, thereby providing route information.
In response to each received APE packet, the destination station directs a reply to
the sending station. On receiving the replies, the sending station ideally assumes
that the Þrst returned reply contains the most efÞcient route. The sending station
then stores the route information and uses it to send subsequent transmissions to
the same station.
Because APE frames do increase network trafÞc, some sites may use STE explorer
frames as an alternate method of route discovery. With STE exploration, a
Spanning Tree Algorithm (either conÞgured automatically via BPDUs or
manually via management) is maintained for the sole purpose of determining
how to direct an explorer frame during route discovery.
During the discovery process, a source station will send out STE explorer frames
into a bridged topology. If a bridge is in a forwarding state according to Spanning
Tree, it will forward an explorer frame onto its attached LAN segment (appending
the Bridge and LAN Segment IdentiÞers in the appropriate area of the RIF); if the
bridge is Þltering, it will discard the explorer frames. In this fashion, only a single
explorer frame will reach each individual LAN segment.
Ultimately, the destination station will receive only a single STE packet, and will
respond with APE packets (that return to the sending station on all possible
bridge paths) or an STE packet (that returns to the sending station via in the
reverse route of the STE explorer packet).
Although the Spanning Tree Algorithm determines the bridge path an STE takes
to the destination station, during future communication between the stations,
bridges along the route will use Source Routing to forward the packet (i.e., the
bridges will read the Routing Information Field in the header of speciÞcally
routed frames to decide whether to forward them).
About Source Route-Transparent Bridges
Because network topologies have developed in which bridges must be able to
handle network trafÞc from end stations which support source routing and others
which do not, a hybrid type of bridgeÑSource Route-Transparent (SRT) Ñ
combines elements of both bridging methods.
An end stationÕs network drivers can be conÞgured in software to use a bit setting
in the source address portion of a data frame to indicate whether the station is to
operate in a Source Route or Transparently bridged network environment. The
Routing Information Indicator (RII) bit of the source address is set to 1 if the
station is to use Source Routing; if the station is to operate in a Transparently
bridged environment, the RII bit is left unchanged (i.e., at 0).
Bridging Basics 2-3
Page 22

Bridging
Not all end stations in a Token Ring environment have network drivers which
support Source RoutingÑwhether the drivers are improperly conÞgured via
management or they simply are not source-route capable.
In a network with a mix of Source Route and Transparent end stations, data
frames from both station types must be bridged correctly. An SRT bridge inspects
the RII bit setting of incoming frames to determine whether they should be
Transparently bridged (if the RII bit was at 0) or Source Routed (if the RII bit was
set to 1) to their destination and will use the appropriate bridge method to
forward the frame.
Cabletron has extended the functionality of Ethernet ports on translational bridges, so the
NOTE
ports can be set to Source Route mode. When an Ethernet port is in Source Route mode
and receives an SR packet from a Token Ring port, it will save the Source Routing
information and send out the packet transparently. When the response comes back, the
source routing information will be restored and then sent to the Token Ring port.
About Source Route-Translational Bridges
Because SmartSwitch 2000, 6000, and 9000 modules have the ability to combine
mixed network topologies, yet another hybrid bridge methodÑcalled a Source
Route Translational bridge (SR-TB)Ñis used by a number of these SmartSwitch
modules.
An SR-TB bridge supports both Source Routing and Transparent bridging
capabilities, with the added requirement of maintaining Source Route
information across an FDDI interfaceÑeither the SmartSwitch 9000 FNB
backplane, or an installed FDDI High Speed Interface Module (HSIM).
An SR-TB bridge does this by ÒtranslatingÓ the Token Ring physical frame format
(by stripping out routing information, if necessary) so that the frameÕs source
address can be recognized on an FDDI, Ethernet, or ATM segment; then, when
data is returned to the source, the bridge restores the necessary route information
to forward it along a bridged Token Ring environment.
For data that is restricted to the Token Ring networks available from the SR-TB
bridgeÕs front panel, the bridging method is user-conÞgurable via local
management to be Source Route-only (bridged packets must include RIF
information and will be source routed; no transparent bridging is enabled),
Source Route-Transparent (bridging method will be determined by whether the
RII bit is set), or Transparent only (no source routed packets will be bridged).
Remote management of these interfaces is based upon their current mode (as set
through local management).
For data that will ultimately be sent across an FDDI interface to an ATM, Ethernet,
FDDI, or another Token Ring segment, the Routing Information Field will be
stripped from the packet so the packet can be transparently bridged onto Ethernet
or FDDI media; however, the RIF information as well as the source address of the
packet is stored in a RIF cache of the SR-TB bridge. When data is returned to that
source address, the SR-TB bridge can look up the address information in its RIF
2-4 Bridging Basics
Page 23

Bridging
cache, append the proper Routing Information onto the packet, and then forward
the data to the Token Ring segment.
The RIF cache is a software table that can store up to 8192 entries. An SR-TB
bridge updates its RIF cache much like a Transparent bridge dynamically updates
its Filtering Database: it learns new address information by listening to incoming
packets on each port, saves that information to an Address Database, andÑif the
address was learned to be Source-Route capableÑupdates routing information
for that source address in the RIF cache. Every time a packet arrives from an FDDI
interface for a MAC address that is communicating through the SR-TB bridgeÕs
front panel, the RIF cache table is searched for an address/RIF match.
There are conÞguration issues when a Token Ring module receives a packet from
an FDDI interface for a destination address that is unknown, and not in its
Address Database or RIF cache. You must conÞgure your SR-TB bridge to treat
incoming packets with an unknown destination address as either a Source Route
or Transparently bridged packet (since Token Ring end stations attached to the
module may or may not support Source Routing).
If the bridge is conÞgured to treat an incoming packet with unknown addresses as
a Source Routed frame, it will forward it using either STE or ARE frames. If the
bridge is conÞgured to treat an incoming packet with an unknown destination as
a Transparently bridged frame, it simply forwards the frame.
After a packet with a previously unknown destination has been bridged
successfully, and communication begins between the two end nodes, the RIF
cache will be updated and packets will be translated as described previously.
Viewing and Managing Bridging Interfaces
With SPECTRUM Element Manager, you can view and manage each bridging
interface supported by your device, including any installed interface modules,
such as BRIMs (Bridge/Router Interface Modules) and HSIMs (High Speed
Interface Modules).
You can manage your bridge by using the following windows:
¥ The Bridge Status window provides you with basic information about the
current status of the deviceÕs bridging interfaces, and allow you to enable or
disable bridging at each of those interfaces. The Bridge Status window also lets
you access further windows to conÞgure bridging at the device. See The
Bridge Status Window, page 2-7, for details.
¥ Bridge statisticsÑincluding the Performance Graph, Interface Statistics,
CSMACD Statistics, PPP Link Statistics, Dot5 Error Statistics, and Source
Route Statistics windowsÑgraphically display the trafÞc passing between
your bridged networks, and let you compare and contrast trafÞc and errors
processed by each interface. See Bridge Statistics, page 2-15 for details.
Viewing and Managing Bridging Interfaces 2-5
Page 24

Bridging
¥ The Spanning Tree window shows bridge port information and protocol
parameters relating to the Spanning Tree AlgorithmÑthe method of
determining the controlling bridge when a series of bridges are placed in
parallel; see Spanning Tree, page 2-34, for details.
¥ With the Filtering Database window, you can see the contents of the Static and
Learned databasesÑthe two address databases which construct the IEEE 802.1
Source Address Table. The bridge uses the contents of these databases to make
its packet Þltering and forwarding decisions. You can conÞgure entries in these
databases to increase bridging efÞciency across your network. See Filtering
Database, page 2-41, for details.
¥ The Ethernet Special Filter Database and Token Ring Special Filter Database
windows let you conÞgure special Þltering schemes. With these schemes, you
can enter Þlter parameters for a frame based on the contents of its source or
destination address Þeld, type Þeld, or data Þeld (with offset)Ñthen specify
the bridging action to take place at each port when a frame matching your
speciÞcations is encountered (see Special Filter Databases, page 2-47).
¥ The I/F ConÞguration port-level menu option invokes the Interface
ConÞguration window, which allows you to select a bridging method for a
Token Ring bridging interface. This window also allows you to select one of
three transmission methods that should be used when unknown addresses are
received from end stations attached to the selected bridge port. See Using the
Novell Translation Window, page 2-97, for details.
¥ The Source Route ConÞguration option enables you to conÞgure source
routed trafÞc passing between bridge ports; see Source Route ConÞguration,
page 2-57, for details.
¥ The Bridge ConÞguration option allows you to set address and routing
information for all interfaces on a Token Ring bridging device, including the
Bridge Number and the Virtual Ring Number. It also allows you to set source
route bridging parameters at the device level. See Using the Token Ring
Bridge and Port ConÞguration Windows, page 2-65, for details.
¥ The Port ConÞguration option allows you to view the address and routing
information for an individual Token Ring bridging interface. This window
displays information that is set at the device level via the Bridge ConÞguration
window, such as the Bridge Number and the Virtual Ring Number. It also
allows you to set source route bridging parameters for that port. See Using the
Token Ring Bridge and Port ConÞguration Windows, page 2-65, for details.
¥ The Duplex Modes window lists each interface on your device and whether
or not it is operating in Full Duplex mode. The window allows you to switch
full duplex mode on and off for each interface on the device. Full Duplex
Switched Ethernet (FDSE) mode allows the interface to transmit and receive
information simultaneously, effectively doubling the available bandwidth. See
Using the Token Ring Bridge and Port ConÞguration Windows, page 2-65,
for details.
2-6 Viewing and Managing Bridging Interfaces
Page 25

Bridging
¥ The SmartTrunk option invokes the SmartTrunk ConÞguration and Status
window, which enables you to group interfaces logically to achieve greater
bandwidth between devices that support this feature. There is no limit to the
number of ports that can be included in a single trunk, nor is there a limit to
the number of trunked instances that can be supported. See ConÞguring
SmartTrunking, page 2-85, for details.
¥ The Broadcast Suppression window enables you to monitor the number of
broadcast packets received by each interface of a selected device, and
conÞgure the maximum number of broadcast packets that will be forwarded
to other interfaces; see ConÞguring SmartTrunking, page 2-85, for details.
¥ The Token Ring Bridge Mode window lets you select which type of bridging
will be used by the Token Ring bridging deviceÑTransparent, Source Routing,
or Source Route Transparent; see Token Ring Bridge Mode, page 2-89, for
details.
¥ The Bridge Translation window allows you to control the necessary
translation of frames that must occur for Token Ring frames to be bridged to
Ethernet. This window offers Auto and Dual modes for translation and
includes the IBM and SNAP Translation tables. See Setting Bridge
Translation, page 2-91, for details.
¥ The Novell Translation window enables you to conÞgure each module port
for translation of Novell packets that are received and transmitted across a
Token Ring bridge; see Using the Novell Translation Window, page 2-97, for
details.
The menu options that are available will vary depending on the type of device you are
NOTE
monitoring, and on the type of bridge interfaces supported by the device.
The following sections detail how to use each of the bridge management
windows.
The Bridge Status Window
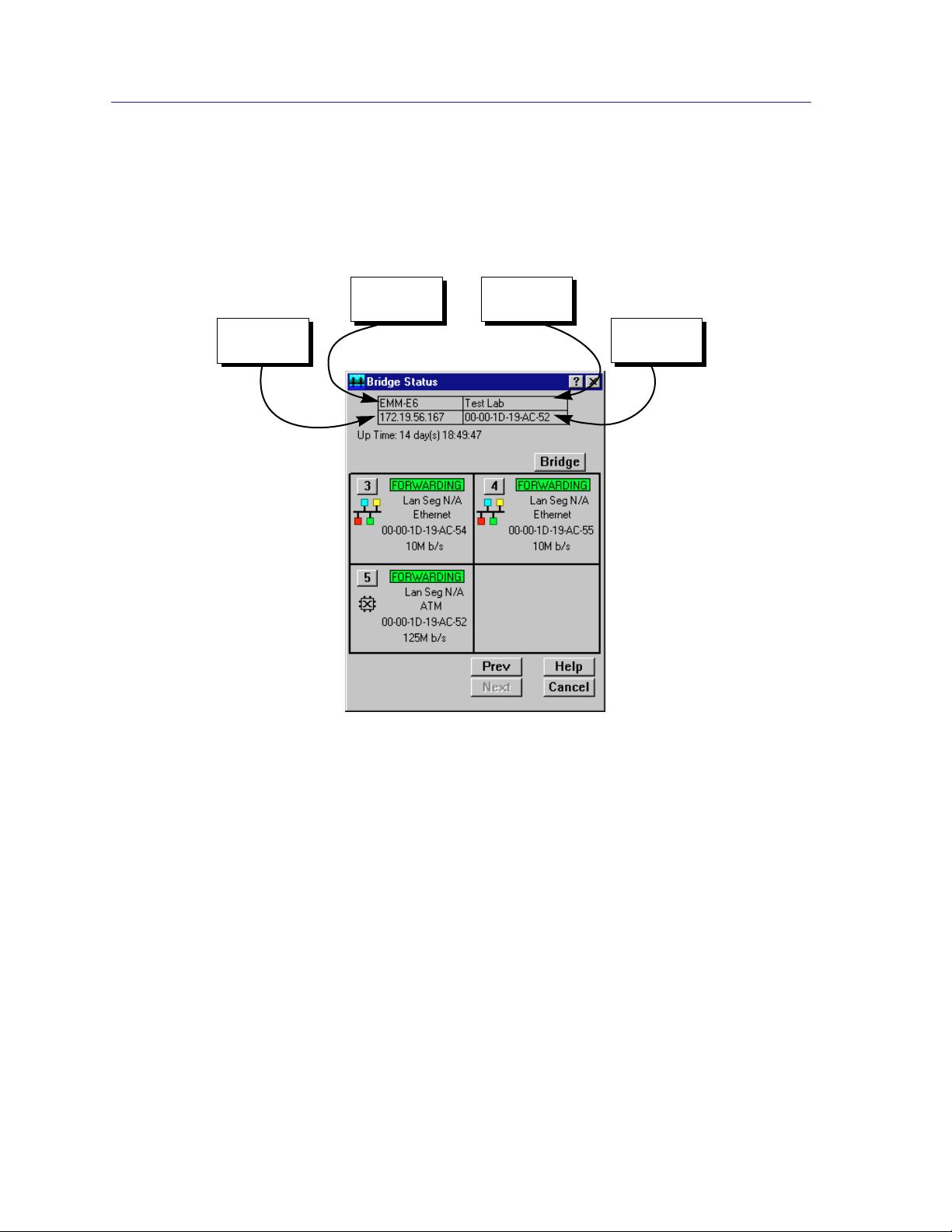
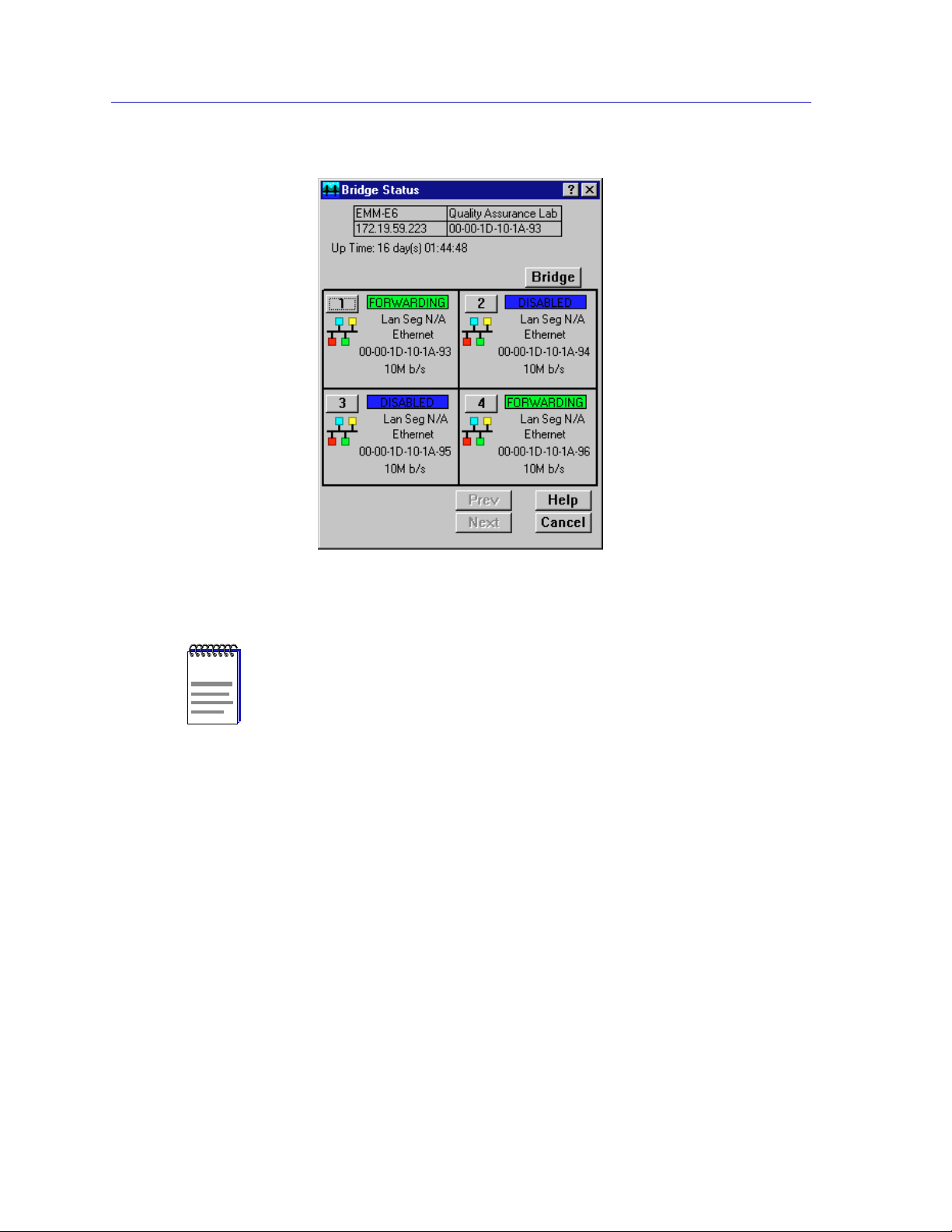
The Bridge Status window provides you with basic information about the current
status of bridging across your device. Color-coding of each port display allows
you to quickly ascertain the status of each interface. The Bridge Status window
also lets you access further windows to control bridging at your device.
To access the Bridge Status window from the Chassis View window:
1. Click on the Device selection in the menu bar. A menu will appear.
2. Click on Bridge Status. The Bridge Status window, Figure 2-1, will appear.
The Bridge Status Window 2-7
Page 26
Bridging
NOTE
Figure 2-1. The Bridge Status Window
When you Þrst open the Bridge Status window the Prev and Next buttons will be grayed
out, and a message will appear stating that the application is initializing and processing
each interface. You will not be able to scroll the display until after all the bridging
interfaces have been processed. The Prev and Next buttons are activated when a device
supports over four bridge interfaces, so that you can scroll the display to show all
interfaces.
The following information is provided by the Bridge Status window for the
monitored device as a whole and for each individual bridging interface.
Up Time
At the top of the Bridge Status window, you can see the time period (in a days,
hours, minutes, seconds format) that has elapsed since the device was last reset or
initialized.
2-8 The Bridge Status Window
Page 27

Bridging
Bridge State on Interface
Indicates the state of bridging over the port interface. Possible bridge states and
their corresponding colors are:
¥ Forwarding (green)ÑThe port is on-line and forwarding packets across the
bridge from one network segment to another.
¥ Disabled (blue)ÑBridging at the port has been disabled by management; no
trafÞc can be received or forwarded on this port, including conÞguration
information for the bridged topology.
¥ Listening (magenta)ÑThe port is not adding information to the Þltering
database. It is monitoring Bridge Protocol Data Unit (BPDU) trafÞc while
preparing to move to the forwarding state.
¥ Learning (magenta)ÑThe Forwarding database is being created, or the
Spanning Tree Algorithm is being executed because of a network topology
change. The port is monitoring network trafÞc, and learning network
addresses.
¥ Blocking (orange)ÑThe port is on-line, but Þltering trafÞc from going across
the bridge from one network segment to another. Bridge topology information
will be forwarded by the port.
Interface Type
Indicates the interface type which applies to each device bridging port interface
(e.g., ethernet). The interface type (ifType) is a mandatory object type from the
SNMP MIB II Interface (if) Group.
Bridge Address
Indicates the physical address of the bridge interface.
Speed
Indicates the speed of the interface in Mbps or Gbps.
Accessing Bridge Status Window Options
At the top of the Bridge Status window, you can click Bridge to access a menu
that provides other bridge management options. Depending on which device you
are monitoring via SPECTRUM Element Manager, the following bridge
management options will be available:
¥ The Module Type window displays a description of the device that is
currently being monitored.
¥ The Find Source Address window allows you to discover the bridge interface
through which a particular MAC address is communicating; see Using the
Find Source Address Feature, page 2-62, for details.
¥ The Performance Graph window displays statistics for trafÞc across the entire
bridge; see Performance Graphs, page 2-15, for details.
The Bridge Status Window 2-9
Page 28

Bridging
¥ The Spanning Tree window allows you to set the Spanning Tree Algorithm
parameters for bridging on your device; see Spanning Tree, page 2-34, for
details.
¥ The SmartTrunk option invokes the SmartTrunk ConÞguration and Status
window, which enables you to group interfaces logically to achieve greater
bandwidth between devices, if both devices support the SmartTrunk feature.
There is no limit to the number of ports that can be included in a single
Òtrunk,Ó nor is there a limit to the number of trunked ÒinstancesÓ that can be
supported. See ConÞguring SmartTrunking, page 2-85, for details.
¥ The Filtering Database window lets you see the contents of the Static and
Learned databasesÑthe two address databases which construct the IEEE 802.1
Source Address Table. The bridge uses the contents of these databases to make
its packet Þltering and forwarding decisions. You can conÞgure the bridgeÕs
acquired and permanent Þltering databases to Þlter or forward trafÞc across
the device. See Filtering Database, page 2-41, for details.
¥ The Ethernet Special Filter Database window lets you conÞgure a special
Þltering scheme at your bridge. With this scheme, you can enter Þlter
parameters for a frame based on the contents of its source or destination
address Þeld, type Þeld, or data Þeld (with offset); you can then specify the
bridging action to take place at each port when a frame matching your
speciÞcations is encountered. See Special Filter Databases, page 2-47, for
details.
¥ The Token Ring Special Filter Database window enables you to deÞne
complex Þlters for transparently-bridged Token Ring frames based upon
receive port, source or destination MAC address, Token Ring data type, or data
Þeld information (up to 64 bytes); see Special Filter Databases, page 2-47, for
details.
¥ The Token Ring Bridge Mode window lets you select which type of bridging
will be used by the Token Ring bridging deviceÑTransparent, Source Routing,
or Source Route Transparent; see Token Ring Bridge Mode, page 2-89, for
details.
¥ The Bridge Translation window allows you to control the necessary
translation of frames that must occur for Token Ring frames to be bridged to
Ethernet. This window offers Auto and Dual modes for translation and
includes the IBM and SNAP Translation tables. See Setting Bridge
Translation, page 2-91, for details.
¥ The Novell Translation window enables you to conÞgure each module port
for translation of Novell packets that are received and transmitted across a
Token Ring bridge; see Using the Novell Translation Window, page 2-97, for
details.
¥ The Duplex Modes window allows you to conÞgure duplex mode (on or off)
for supporting interfaces on the device; see Using the Token Ring Bridge and
Port ConÞguration Windows, page 2-65, for details.
2-10 The Bridge Status Window
Page 29

Bridging
¥ Enable Bridge and Disable Bridge options allow you to administratively
activate or deactivate bridging at the device level; see (Enabling and
Disabling Bridging, page 2-14, for details.
¥ The Bridge ConÞguration option opens a window that allows you to set
address and routing information for all interfaces on a Token Ring bridging
device, including the Bridge Number and the Virtual Ring Number. It also
allows you to set source route bridging parameters at the device level. See
Using the Token Ring Bridge and Port ConÞguration Windows, page 2-65,
for details.
The individual bridge port index ( ) menu that you can access from the Bridge
Status window will provide the following options, depending on which device
you are monitoring through SPECTRUM Element Manager:
¥ The Connection Type window displays a text description of the connection
type of the selected bridge interface.
¥ The Description option displays a text description of a bridge interface from
the ifDescr value of the ifIndex related to the selected port.
¥ The Performance Graph window graphically displays the trafÞc passing
between your bridged networks, and lets you compare and contrast trafÞc
processed by each interface; see Performance Graphs, page 2-15, for details.
¥ The Source Addressing window displays the contents of the deviceÕs Filtering
Database with respect to a selected port. This will display the source MAC
addresses that have been detected by the port as it forwards data across the
network. The window also lets you set the aging timer that controls how long
an inactive MAC address will continue to be stored in the Source Address
Database before being aged out. See Source Route ConÞguration, page 2-62,
for details.
¥ The PPP Link Status option invokes the PPP Link Statistics Window, which
enables you to view color-coded statistics related to the PPP (Point-to-Point
Protocol) link at the selected interface; see PPP Link Statistics, page 2-25, for
details.
¥ The Source Route Statistics option opens a window that allows you to view
statistics for source routed trafÞc passing between bridging ports. The window
enables you to view the frames that were received, transmitted, and discarded
by the bridge. See Source Route Statistics, page 2-31, for details.
¥ The I/F ConÞguration port-level menu option invokes the Interface
ConÞguration window, which allows you to select a bridging method for a
Token Ring bridging interface. This window also allows you to select one of
three transmission methods that should be used when unknown addresses are
received from end stations attached to the selected bridge port. See Using the
Novell Translation Window, page 2-97, for details.
¥ The Source Route ConÞguration option opens a window that enables you to
conÞgure source routed trafÞc passing between bridging ports; see Source
Route ConÞguration, page 2-57, for details.
The Bridge Status Window 2-11
Page 30

Bridging
¥ The Port ConÞguration option opens a window that allows you to view the
address and routing information for an individual Token Ring bridging
interface. This window displays information that is set at the device level via
the Bridge ConÞguration window, such as the Bridge Number and the Virtual
Ring Number. It also allows you to set source route bridging parameters for
that port. See Using the Token Ring Bridge and Port ConÞguration
Windows, page 2-65, for details.
¥ The Dot5 Errors invokes a window that allows you to view 802.5 statistics for
the selected bridging interface on a Token Ring bridging device; see Dot5
Errors, page 2-28, for details.
¥ The RMON MAC Layer option opens the Token Ring Statistics window for
Token Ring devices that support RMON, which enables you to view a
statistical breakdown of trafÞc on the monitored Token Ring interface
(network segment). Note that if the RMON Default MIB component is
disabled, the RMON MAC Layer menu option will launch the Interface
Statistics window. Refer to the RMON UserÕs Guide for more information on
how to enable and disable RMON MIB components. For more information
about this menu option, refer to the Statistics chapter in the Remote
Monitoring (RMON) UserÕs Guide, and/or the appropriate device-speciÞc
UserÕs Guide.
¥ The RMON Promiscuous Stats option opens the Token Ring Promiscuous
Statistics window, which allows you to view statistical information about
those packets that carry the normal data ßow across a bridging interface
(network segment). Note that if the RMON Default MIB component is
disabled, the RMON Promiscuous Stats menu option will launch the Interface
Statistics window. Refer to the Remote Monitoring (RMON) UserÕs Guide for
more information on how to enable and disable RMON MIB components. For
more information about this menu option, refer to the Statistics chapter in the
RMON UserÕs Guide, and/or the appropriate device-speciÞc UserÕs Guide.
¥ The I/F Statistics option activates the Interface Statistics Port window, which
allows you to view color-coded statistical information about each individual
bridge port on the currently monitored device; see Interface Statistics,
page 2-20, for details.
¥ The ConÞguration option opens a window that enables you to conÞgure the
selected bridge interface for either full duplex or standard mode; see Ethernet
Port ConÞguration, page 2-72, for details.
¥ The Alarm ConÞguration option appears as a menu choice for Ethernet
devices which support RMON, and invokes the RMON Basic Alarm
ConÞguration window that enables you to create alarms or actions at a speciÞc
bridge interface based on rising and falling thresholds for Broadcast/Multicast
packets, Kilobits, or Total Errors. Note that if the RMON Default MIB
component is disabled, the Alarm ConÞguration menu option will still appear
and the window will still display; however, you will not have the ability to set
anything. Refer to the Remote Monitoring (RMON) UserÕs Guide for more
information on how to enable and disable RMON MIB components. For more
2-12 The Bridge Status Window
Page 31

Bridging
information about this window, refer to the RMON Alarms and Events
chapter in the RMON UserÕs Guide, and/or the appropriate device-speciÞc
UserÕs Guide.
¥ The Statistics option appears as a menu choice for Ethernet devices which
support RMON, and it opens the Ethernet Statistics window, which enables
you to view a statistical breakdown of trafÞc at the monitored Ethernet
network segment. Note that if the RMON Default MIB component is disabled,
the Statistics menu option will launch the Interface Statistics window. Refer to
the Remote Monitoring (RMON) UserÕs Guide for more information on how
to enable and disable RMON MIB components. For more information about
this menu option, refer to the Statistics chapter in the RMON UserÕs Guide,
and/or the appropriate device-speciÞc UserÕs Guide.
¥ The Sonet/SDH ConÞguration window enables you to determine whether
any installed FE-100Sx Fast Ethernet Port Interface Modules or APIM-2x ATM
Port Interface Modules, both of which provide direct access to SONET
(Synchronous Optical Network) networks, will operate according to SONET
or SDH (Synchronous Digital Hierarchy) standards; see SONET/SDH
ConÞguration, page 2-77, for details.
¥ The Sonet Statistics option opens a window that will let you view some of the
statistical information related to any installed FE100-Sx Fast Ethernet Port
Interface Modules or APIM-2x ATM Port Interface Modules; see SONET/SDH
Statistics, page 2-79, for details.
¥ The Physical View option allows you to view the physical state of the Ethernet
bridge port through the ETW EtherPhysStatus window and the Token Ring
bridge port through the Token Ring Phys Status window when you are
monitoring an ETWMIM via SPECTRUM Element Manager; see Using the
Physical View Windows for the ETWMIM, page 2-99, for details.
¥ The CSMACD Stats option opens a window that enables you to view
color-coded statistical information for some Ethernet bridging interfaces,
including receive errors, transmission errors, and collision errors. See
CSMACD Statistics, page 2-23, for details.
¥ Enable and Disable options allow you to administratively enable or disable
bridging at the selected interface; see Enabling and Disabling Bridging,
page 2-14, for details.
The Bridge Status Window 2-13
Page 32

Bridging
Enabling and Disabling Bridging
When you disable a bridge port, you disconnect that portÕs network from the
bridge entirely. The port does not forward any packets, nor does it participate in
Spanning Tree operations. Nodes connected to the network can still communicate
with each other, but they canÕt communicate with the bridge and other networks
connected to the bridge. When you enable a port, the port moves from the
Disabled state through the Learning and Listening states to the Forwarding or
Blocking state (as determined by Spanning Tree).
Enabling and Disabling Individual Interfaces
To disable an individual port interface from the Bridge Status window:
1. Click on the desired Port button ( ) to display the port menu.
2. Click on Enable to restart bridging on the selected interface, or Disable to
halt bridging across the selected interface.
To disable an individual port interface from the Chassis View window:
1. Click on the appropriate port index to access the Port menu.
2. Click on Enable to restart bridging on the selected interface, or Disable to
halt bridging across the selected interface.
Enabling and Disabling All Installed Interfaces
To disable bridging across all interfaces installed in a device from the Bridge
Status window:
1. Click on Bridge to display the Bridge menu.
2. Click on Enable Bridge to enable bridging across all installed interf aces, or to
Disable Bridge to disable bridging across all installed interfaces.
To disable bridging across all interfaces installed in a device from the Chassis
View window:
1. Click on the Board Index of the device of interest; the Board menu will
appear.
2. Click on Enable Bridge to enable bridging across all installed interfaces , or to
Disable Bridge to disable bridging across all installed interfaces.
2-14 Enabling and Disabling Bridging
Page 33

Bridge Statistics
The following sections describe Statistics windows that are available for the
bridge that is being monitored via SPECTRUM Element Manager, both at the
device and port levels.
Performance Graphs
You use Bridge Performance Graphs to view a color-coded strip chart that shows
you the trafÞc being bridged through all networks or an individual network
supported by your device. You can conÞgure the display to show frames Þltered,
forwarded, or transmitted across the device or its individual bridging interfaces,
as well as the number of errors experienced at both levels. The graph has an X axis
that indicates the 60-second interval over which charting occurs continuously,
while its Y axis measures the number of packets or errors that are processed by
the device or its bridging interfaces.
You can select the type of errors you wish to monitor by using the available menu
buttons. When you click on the error type you wish to view, the name of that error
will appear in the button, and the Performance Graph will refresh. The graph will
now generate a strip chart based on the newly deÞned parameters.
Bridging
At the device level, a Detail button on the window allows you to compare the
packets forwarded, Þltered, or transmitted on all networks supported by the
device, as well as errors on all networks.
For a selected bridged network, the Detail button allows you to view the number
of packets forwarded to, or received from, each other network supported by the
device.
To access the device-level Bridge Performance Graph window from the Bridge
Status window:
1. Click on Bridge to display the Bridge menu.
2. Click on Performance Graph. The Bridge Performance Graph window,
Figure 2-2, will appear. (The individual port Bridge Performance Graph
windows are similar, except that they display a graph applicable to the
selected interface.)
To access the device-level Bridge Performance Graph window from the Chassis
View window:
1. Click on the Board Index of the device of interest; the Board menu will
appear.
2. Click on Performance Graph. The Bridge Performance Graph window,
Figure 2-2, will appear.
Bridge Statistics 2-15
Page 34

Bridging
NOTE
To access the port-level Bridge Performance Graph window from the Bridge
Status window:
1. Click on the desired Port button ( ) to display the Port menu.
2. Click on Performance Graph. The Bridge Performance Graph window will
appear.
To access the port-level Bridge Performance Graph window from the Chassis
View window:
1. Click on the appropriate port index to access the Port menu.
2. Click on Performance Graph. The Bridge Performance Graph window will
appear.
The graphic displayed in Figure 2-2 is a device-level window; the window that is
displayed at the port level is virtually identical to the one at the device level.
Figure 2-2. Bridge Performance Graph
You can select the following statistics to display in the Bridge Performance Graph
or Bridge Port Performance Graph. Statistics are provided numerically (as an
average or peak value) and graphically. The device is polled for the graphed
information every 2 seconds, and numeric values are updated based on this poll.
The graph updates at the Þxed two-second interval. For the Þrst 60 seconds of
graphing, you will note the graph lines extending as each intervalÕs data is added
to the graph. Once the Þrst 60 seconds has passed, the newest data is added at the
right edge of the graph, and the oldest data is scrolled off to the left.
2-16 Bridge Statistics
Page 35

Bridging
Peak statistics are based on the peak level of activity returned from a single poll
since the Performance Graph window was invoked. A date and time is provided
for peak levels.
The Average statistics are updated every two seconds as averaged over the
previous four poll intervals (i.e., averaged over a sliding eight-second time
window).
Frames Forwarded (Green)
Forwarded The number of frames forwarded by an individual port
or the device as a whole.
Nothing The Frames Forwarded function is currently not
measuring any statistics.
Filtered (Magenta)
Filtered The total number of frames Þltered by an individual port
or the device as a whole.
Nothing The Filtered scale is not currently measuring the number
of packets Þltered by the bridge at the device or port
level.
Errors (Red)
Total Errors The total number of errors detected at a single port or on
Nothing The Errors scale is currently not measuring any type of
Xmitted (Blue)
Xmitted The total number of frames transmitted by the selected
Nothing The Xmitted scale is not currently measuring the number
Configuring Performance Graphs
To conÞgure the Bridge Performance Graph:
1. Using the mouse, click on Forwarded (with green statistics to the right). The
Forwarded menu will appear. Click on the desired mode.
2. Click on Filtered (with magenta statistics to the right). The Filtered menu will
appear. Click on the desired mode.
the device as a whole.
error packets coming through the device or port.
bridge interface, or all bridge interfaces.
of packets Þltered by the bridge or the individual
interface.
3. Click on Total Errors (with red statistics to the right). The Errors menu will
appear. Click on the desired mode.
Bridge Statistics 2-17
Page 36

Bridging
4. Click on Xmitted (with blue statistics to the right). The Xmitted menu will
appear. Click on the desired mode.
Once you have selected a new mode, it will appear in its respective button, and
after the next poll the Performance Graph will refresh and begin to measure using
the new mode.
Bridge Detail Breakdown
The Bridge Detail Breakdown window allows you to compare the number of
frames forwarded, Þltered, and transmitted on the network segments connected
to each interface of your device bridge, as well as the number of errors
experienced on each interface.
The Bridge Detail Breakdown window will not be available if your device has more than
NOTE
13 bridge ports.
To access this window from the Bridge performance graph, click on Detail. The
Bridge Detail Breakdown window, Figure 2-3, will appear.
Figure 2-3. The Bridge Detail Breakdown Window
The following information is available for the network segments connected to
each of the bridge ports on the device, and any installed BRIM or HSIM port.
The information is expressed both numerically and in pie charts. Each portÕs
2-18 Bridge Statistics
Page 37

Bridging
network segment has a corresponding color for its statistics or pie chart segments.
Depending on your particular bridge and its conÞguration, the segments are
color-coded as follows:
¥ LAN 1 = light red
¥ LAN 2 = light green
¥ LAN 3 = yellow
¥ LAN 4 = light gray
¥ LAN 5 = light cyan
¥ LAN 6 = light blue
¥ LAN 7 = green
¥ LAN 8 = red
¥ LAN 9 = hot pink =
¥ LAN 10 = light magenta
¥ LAN 11 = blue
¥ LAN 12 = cyan
¥ LAN 13 = black
The values given in these Þelds are cumulative totals.
Frames Forwarded
The total number of frames forwarded on each portÕs network segment, as read
from the device after each poll interval.
Filtered
The total number of frames Þltered on each portÕs network segment, as read from
the device after each poll interval.
Errors
The total number of frames (either inbound or outbound) containing errors which
prevented them from being processed by each bridge interface, as reported from
the device during the last poll interval.
Xmitted
The total number of frames transmitted over each portÕs network segment, as
read from the device after each poll interval.
Bridge Port Detail Breakdown
For the selected bridge interface, the Bridge Port Detail Breakdown window
allows you to view the number of packets forwarded to or received from each of
the other interfaces on your device.
To access the Bridge Port Detail Breakdown window from the port Bridge
performance graph, click Detail. The Bridge Port Detail Breakdown window,
Figure 2-4, will appear.
Bridge Statistics 2-19
Page 38

Bridging
Figure 2-4. The Bridge Port Detail Breakdown Window
The following information is available for each bridge interface on the device. The
information is expressed both numerically and in pie charts. The colors
corresponding to the forwarding interfaces will vary, depending on which
interface is selected.
Forwarded to
The number of frames forwarded by the selected bridge interface to each other
interface on the bridge, as read from the device after each poll interval.
Forwarded from
The total number of frames received by the selected bridge interface from each of
the other bridge interfaces, as read from the device after each poll interval.
Interface Statistics
You can use the interface Statistics window to view color-coded statistical
information for each individual bridge port on your device. Statistics are
provided for both transmit and receive packets at each port, as well as error and
buffering information.
Color-coded pie charts in the middle of the window lets you graphically view
statistics for Unicast, Non-Unicast, Discarded and Error packets.
To access the Statistics window from the Bridge Status window:
1. Click on the desired Port button ( ) to display the Port menu.
2. Click on I/F Statistics. The port I/F Statistics window will appear.
2-20 Bridge Statistics
Page 39

To access the Statistics window from the Chassis View window:
1. Click on the appropriate port index to access the Port menu.
2. Click on I/F Statistics. The port I/F Statistics window will appear.
Bridging
NOTE
Figure 2-5. I/F Statistics Window
The following three informational Þelds appear in the upper portion of the
window:
Description
Displays the interface description for the currently selected port.
Address
Displays the MAC (physical) address of the selected port.
Type
Displays the interface type of the selected port.
The polling interval is set using the Device Management page of the options window
accessed via the ToolsÑ>Options selection from the SPECTRUM Element Manager
primary window menu bar. Refer to the UserÕs Guide for information on setting device
polling intervals.
Bridge Statistics 2-21
Page 40

Bridging
The following transmit and receive statistics Þelds are displayed in the lower
portion of the window. The Þrst four statistics are also graphically displayed in a
pie chart. The statistics are read directly from the device, and are updated with
each poll from SPECTRUM Element Manager to the device.
Unicast
Displays the number of packets transmitted to, or received from, this interface
that had a single, unique source or destination address. These statistics are
displayed in the pie chart (color-coded green).
Non-Unicast
Displays the number of packets transmitted to, or received from, this interface
that had a source or destination address that is recognized by more than one
device on the network segment. The non-unicast Þeld includes a count of
broadcast packetsÑthose that are recognized by all devices on a segment. These
statistics are displayed in the pie chart (color-coded dark blue).
Discarded
Displays the number of packets which were discarded even though no errors
were detected to prevent transmission. One possible reason for discarding such a
packet could be to free up buffer space.
The discarding of good packets indicates a very busy network. If a device
routinely discards packets, it usually means that network trafÞc is overwhelming
the device. A change in network conÞguration (such as the addition of a bridge or
switch) may help reduce network congestion.
These statistics are displayed in the pie chart (color-coded hot pink).
Error
Displays the number of packets received or transmitted that contained errors.
These statistics are displayed in the pie chart (color-coded red).
Unknown Protocol
Displays the number of packets received which were discarded because of an
unknown or unsupported protocol. The device bridge interface will discard the
packet and increment this counter if it canÕt recognize the packet.
Packets Received
Displays the number of packets received by this interface.
Transmit Queue Size
The number of packets currently queued by the device for transmission from this
interface. The amount of device memory devoted to buffer space, and the trafÞc
level on the target network, determine how large the output packet queue can
grow before the device begins to discard packets.
Packets T ransmitted
Displays the number of packets transmitted by this interface.
2-22 Bridge Statistics
Page 41

CSMACD Statistics
The CSCMACD Statistics menu option is available for some Ethernet bridging
interfaces. Receive errors, transmission errors, and collision errors are the
statistics displayed in this window. Three color-coded pie charts allow you to
graphically view the breakdowns of each statistics group.
To access the CSMACD Statistics window from the Bridge Status window:
1. Click on the desired Port button ( ) to display the Port menu.
2. Click on CSMACD Stats. The device CSMACD Statistics window, Figure 2-6,
will appear.
To access the CSMACD Statistics window from the Chassis View window:
1. Click on the appropriate port index to access the Port menu.
2. Click on CSMACD Stats. The device CSMACD Statistics window, Figure 2-6,
will appear.
Bridging
Figure 2-6. CSMACD Statistics Window
Each of the receive, transmission, and collision errors are described in detail
below.
Receive Errors
Indicates the errors detected while the selected interface was receiving a
transmission. Possible receive errors are:
Bridge Statistics 2-23
Page 42

Bridging
¥ AlignmentÑThe number of frames received on a particular interface that
contain a nonintegral number of bytes (color-coded green). Misaligned
packets can result from a MAC layer packet formation problem, or from a
cabling problem that is corrupting or losing data.
¥ FCSÑThe number of frames received on a particular interface that are an
integral number of bytes in length, but do not pass the FCS (Frame Check
Sequence) check.
FCS, or Frame Check Sequence, errors occur when packets are somehow
damaged in transit. When each packet is transmitted, the transmitting
interface computes a frame check sequence (FCS) value based on the contents
of the packet, and appends that value to the packet. The receiving interface
performs the same computation; if the FCS values differ, the packet is assumed
to have been corrupted and is counted as an FCS error.
¥ SQE TestÑDisplays the number of times that the SQE Test Error message is
generated by the PLS sublayer on the selected interface.
The SQE (Signal Quality Error) Test tests the collision detect circuitry after each
transmission. If the SQE Test fails, a SQE Test Error is sent to the interface to
indicate that the collision detect circuitry is malfunctioning.
¥ Carrier SenseÑDisplays the number of times that the carrier sense condition
was lost or never asserted when attempting to transmit a frame on a particular
interface.
Carrier sense describes the action an interface desiring to transmit will take to
listen to the communication channel to see if any other interface is
transmitting. If a Òcarrier is sensed,Ó the sensing interface will wait a random
length of time, and then attempt to transmit.
¥ Frame Too LongÑDisplays the number of frames received on this interface
that exceed the maximum permitted frame size.
¥ Internal MACÑThe number of frames that could not be received by the
interface due to an internal MAC sublayer receive error. These errors are only
counted if a Frame Too Long, Alignment, or FCS Error did not occur along
with the internal MAC error.
¥ Receive ErrorsÑDisplays the total number of receive errors of all types that
were detected by the selected interface while it was receiving a transmission.
Transmission Errors
Indicates the errors that occurred while the selected interface was attempting to
transmit frames. Possible transmission errors are:
¥ DeferredÑ Displays the number of frames for which the Þrst transmission
attempt on this interface is delayed because the medium is busy.
2-24 Bridge Statistics
Page 43

Bridging
¥ Internal MACÑThe number of frames for which transmission fails due to an
internal MAC sublayer transmit error. This error is only counted in this
window if there have not been corresponding Late Collisions, Excessive
Collisions, or Carrier Sense Errors.
¥ Transmit ErrorsÑThe total number of transmission errors of all types that
occurred while the selected interface was attempting to transmit frames.
Collision Errors
Indicates the collision errors that occurred during transmission from this
interface. Possible collision errors are:
¥ SingleÑDisplays the number of transmitted frames on the selected interface
for which transmission was prevented by one collision.
¥ MultipleÑDisplays the number of transmitted frames on the selected
interface for which transmission was prevented by more than one collision.
¥ LateÑDisplays the number of times that a collision has been detected on this
interface later than 51.2 microseconds into the transmission of the packet on a
10 Mbit/s system or later than 5.12 microseconds on a 100 Mbit/s system.
¥ ExcessiveÑDisplays the number of transmitted frames on the selected
interface for which transmission was prevented by excessive collisions.
¥ Collision ErrorsÑDisplays the total number of collision errors of all types that
occurred during transmission from this interface.
PPP Link Statistics
The PPP Link Status option opens the PPP Link Statistics window, which enables
you to view color-coded statistics related to the PPP (Point-to-Point Protocol) link
at the selected interface.
The Point-to-Point Protocol is a standard method of transporting multiprotocol
datagrams over point-to-point links. A PPP Link provides full-duplex
communication between the endpoints, allowing a simultaneous bidirectional
operation that should maintain the order in which data packets are transmitted.
To access the PPP Link Statistics window from the Bridge Status window:
1. Click on the desired Port button ( ) to display the port menu.
2. Click on PPP Link Status. The PPP Link Statistics window, Figure 2-7, will
appear.
To access the PPP Link Statistics window from the Chassis View window:
1. Click on the appropriate port index to access the Port menu.
2. Click on PPP Link Status. The PPP Link Statistics window, Figure 2-7, will
appear.
Bridge Statistics 2-25
Page 44

Bridging
Figure 2-7. PPP Link Statistics Window
Each of the errors and statistics related to the PPP Link at the selected bridging
interface is described in detail below.
Errors
Indicates the errors that occurred which relate to the PPP Link at the selected
bridging interface. Possible error types are:
¥ Bad AddressesÑThe Bad Addresses Þeld displays the number of packets
received with an incorrect Address Þeld.
¥ Bad ControlsÑThe Bad Controls Þeld displays the number of packets
received on the selected interface that have an incorrect Control Þeld.
¥ Packets Too LongÑThe Packets Too Long Þeld displays the number of
received packets that were discarded because their length exceeded the MRU
(Maximum Receive Unit). Note that packets that are longer than the MRU and
that are successfully received and processed are not included in the count.
¥ Bad FCSsÑThe Bad FCSs Þeld displays the number of received packets that
were discarded due to having an incorrect FCS (Frame Check Sequence) value.
2-26 Bridge Statistics
Page 45

Bridging
¥ Total ErrorsÑThe Total Errors Þeld displays the total number of errors of all
types: Bad Addresses, Bad Controls, Packets Too Long, and Bad FCSs.
Statistics
Lists statistics Þelds which are related to the PPP Link at the selected bridging
interface. Possible statistics Þelds are:
¥ Local MRUÑThe Local MRU Þeld displays the current value of the MRU
(Maximum Receive Unit) for the local PPP entity. This value is the MRU that
the remote entity uses when sending packets to the local PPP entity. The MRU
is the maximum length of data information (included ÒpaddedÓ data octets,
but excluding the Protocol Þeld which identiÞes the datagramÕs protocol type)
that can be received by this interface. The default MRU size is 1500 octets. The
auto-negotiation process may establish another value for MRU if consent is
given at both ends of the PPP link (if either the local or remote PPP entity
informs the other that larger packets can be sent, or requests that smaller
packets be sent).
¥ Remote MRUÑThe Remote MRU Þeld displays the current value of the MRU
(Maximum Receive Unit) established for the remote interface at the other end
of the PPP Link. This value is the MRU that the local entity uses when sending
packets to the remote PPP entity.
¥ Local to Peer ACC MapÑThe Local to Peer ACC Map Þeld displays the
current value of the Asynchronous Control Character (ACC) Map used for
sending packets from the local PPP entity to the remote PPP entity. In effect,
this is the ACC Map that is required to ensure that all characters can be
successfully transmitted through the local modem. The actual ACC Map used
on the transmit side of the link will be a combination of the local nodeÕs
pppLinkConÞgTransmitACCMap and the remote nodeÕs
pppLinkConÞgReceiveACCMap.
¥ Peer to Local ACC MapÑThe Peer to Local ACC Map Þeld displays the
Asynchronous Control Character (ACC) Map used by the remote PPP entity
when transmitting packets to the local PPP entity. In effect, this is the ACC
Map that is required to ensure that the local modem will successfully receive
all characters. The actual ACC Map used on the receive side of the link will be
a combination of the local nodeÕs pppLinkConÞgReceiveACCMap and the remote
nodeÕs pppLinkConÞgTransmitACCMap.
¥ Local to Remote Protocol CompressionÑThe Local to Remote Protocol
Compression Þeld determines whether or not the local PPP entity uses
Protocol Compression when transmitting packets to the remote PPP entity.
¥ Remote to Local Protocol CompressionÑThe Remote to Local Protocol
Compression Þeld determines whether or not the remote PPP entity uses
Protocol Compression when transmitting packets to the local PPP entity.
¥ Local to Remote AC CompressionÑThe Local to Remote AC Compression
Þeld determines whether or not the local PPP entity uses Address and Control
(AC) Compression when transmitting packets to the remote PPP entity.
Bridge Statistics 2-27
Page 46

Bridging
Dot5 Errors
¥ Remote to Local AC CompressionÑThe Remote to Local AC Compression
Þeld determines whether or not the remote PPP entity uses Address and
Control (AC) Compression when transmitting packets to the local PPP entity.
¥ Transmit FCS SizeÑThe Transmit FCS Size Þeld displays the size of the Frame
Check Sequence (FCS), in bits, that the local node generates when sending
packets to the remote node.
¥ Receive FCS SizeÑThe Receive FCS Size Þeld displays the size of the Frame
Check Sequence (FCS), in bits, that the remote node generates when sending
packets to the local node.
The Dot5 Errors menu option invokes the Station Statistics window, which
enables you to view IEEE 802.5 error statistics reported for a Token Ring bridge
interface.
To access the Station Statistics window from the Bridge Status window:
1. Click on the desired Port button ( ) to display the port menu.
2. Click on Dot5 Errors. The Station Statistics window, Figure 2-8, will appear.
To access the Station Statistics window from the Chassis View window:
1. Click on the appropriate port index to access the Port menu.
2. Click on Dot5 Errors. The Station Statistics window, Figure 2-8, will appear.
2-28 Bridge Statistics
Page 47

Bridging
Figure 2-8. Dot5 Errors Statistics Window
Each type of IEEE 802.5 error detected by the selected station port is described in
detail below.
Line Errors
The Line Errors Þeld displays the number of the line errors detected by the
selected port. This error indicates the presence of a non-data bit between the
starting and ending delimiters of data or a frame check sequence (FCS) error.
Burst Errors
The Burst Errors Þeld displays the number of burst errors detected by the selected
port. This error indicates a bit information encoding error when there are no
transitions between 0 and 1 over Þve half-bit times.
A. C. Errors
The A. C. Errors Þeld displays the number of A. C. errors detected by the selected
port. These errors count protocol data units (PDUs) that contain errors in the A or
C bits.
Bridge Statistics 2-29
Page 48

Bridging
Abort Sequences
The Abort Sequences Þeld displays the number of abort sequences transmitted by
the selected port. These occur when an adapter has frames to transmit and
receives a token, but does not detect an ending delimiter on the token after its
access control Þeld. This indicates that the token is corrupted. The station
transmits abort delimiters to halt frame transmission before its expected
end-frame sequence, re-queues the frame(s) for transmission, but does not release
the corrupt token.
Internal Errors
The Internal Errors Þeld displays the number of recoverable internal errors
detected by the selected port. These are recorded when a station recognizes a
recoverable internal error in its adapter, and removes itself from the ring. This is
considered a solid hard error, since the ring automatically reconÞgures.
Lost Frames
The Lost Frames Þeld displays the number of non-returned frames detected by
the selected port. These occur when a transmitting stationÕs TRR (Timer, Return to
Repeat) timer expires (after 4.1 milliseconds) before the end of its frame returns.
This timer ensures that the station returns to the data repeat state (i.e., retrieves
the token, strips it of data, and issues a new token to the ring). Lost frames are
usually caused by a station entering or leaving the ring as the frame is circulating.
Congestion Errors
The Congestion Errors Þeld displays the number of times the selected port has not
been able to copy a protocol data unit (PDU) addressed to it because of a lack of
internal buffering.
F. C. Errors
The F. C. Errors Þeld displays the number of protocol data units (PDUs)
addressed to the selected station with the A bits already set to 1. This error
indicates that a possible electrical line disturbance or a duplicate address has
occurred on the ring.
Token Errors
The Token Errors Þeld displays the number of times that the selected station,
acting as the active monitor, detected an error condition that needed a token
transmitted.
Soft Errors
The Soft Errors Þeld displays the number of soft errors detected by the selected
port. Although soft errors do not cause ring failure, they degrade the performance
of the ring network.
Hard Errors
The Hard Errors Þeld displays the number of immediately recoverable fatal errors
detected by the selected port. These are errors which halt normal operation of the
ring, and are usually caused by faults in the ring hardware, equipment, or wiring.
2-30 Bridge Statistics
Page 49

Bridging
Signal Loss
The Signal Loss Þeld displays the number of times that the selected port has
detected the loss of a signal condition from the ring.
Transmit Beacons
The Transmit Beacons Þeld displays the number of beacon frames transmitted by
the selected station.
Recoveries
The Recoveries Þeld displays the number of claim token frames the monitored
station has received or transmitted after a ring purge frame.
Lobe Wires
The Lobe Wires Þeld displays the number of open or short circuits detected in the
lobe data path.
Removes
The Removes Þeld displays the number of Remove Ring Station MAC frame
requests detected by the selected port.
Singles
The Singles Þeld displays the number of times the selected station has detected
that it is the only station on the ring. This error may indicate that the station is the
Þrst on the ring or that there is a hardware problem.
Frequency Errors
The Frequency Errors Þeld displays the number of times that the selected station
detected a larger-than-allowed difference between the incoming frequency and
the expected frequency.
Source Route Statistics
The Source Route Statistics menu option invokes the Bridge Source Routing
window, which allows you to compare the statistics on frames received,
transmitted, and discarded at the Token Ring interfaces of devices that are
bridging from a source routing network to a transparent network.
To access the Bridge Source Routing window from the Bridge Status window:
1. Click on the desired Port button ( ) to display the port menu.
2. Click on Source Route Statistics. The Bridge Source Routing window,
Figure 2-9, will appear.
Bridge Statistics 2-31
Page 50

Bridging
To access the Bridge Source Routing window from the Chassis View window:
1. Click on the appropriate port index to access the Port menu.
2. Click on Source Route Statistics. The Bridge Source Routing window,
Figure 2-9, will appear.
Figure 2-9. The Bridge Source Routing Window
The Bridge Source Routing window provides basic statistics for source routed
trafÞc passing between the bridging ports. Pie charts graphically break down the
statistical information. All statistics are calculated since the device was last reset
or powered up. The following window Þelds are listed in the Bridge Source
Routing window:
Received Frames
Frame types received by the bridge ports
¥ Specif. RoutedÑDisplays the total number of SpeciÞcally Routed Explorer
frames received by the indicated port from its attached segment.
These frames have data and routing information and are following a known
route from source to destination.
¥ All Paths Expl.ÑDisplays the total number of All Path Explorer frames
received by the indicated port from its attached segment.
When a sending station needs to determine the best route to an intended
destination, it transmits an All Paths Explorer (APE) frame. The APE frame
contains no routing information; it is propagated along all available paths to
2-32 Bridge Statistics
Page 51

Bridging
the destination station, which then directs a reply back to the source. The Þrst
reply received by the original sending station is considered the most efÞcient
route and is used in subsequent transmissions.
¥ Span. Tree Expl.ÑDisplays the total number of Spanning Tree Explorer (STE)
frames received by the indicated port from its attached segment. STE frames,
also known as Single Route Broadcast frames, follow the topology established
by the Spanning Tree Algorithm.
Transmitted Frames
List of Frame types transmitted by the bridge ports
¥ Specif. RoutedÑDisplays the total number of SpeciÞcally Routed Frames
transmitted by the indicated port onto its attached segment.
¥ All Paths Expl.ÑDisplays the total number of All Path Explorer frames
transmitted by the indicated port onto its attached segment.
¥ Span Tree Expl.ÑDisplays the total number of Spanning Tree Explorer (STE)
frames transmitted by the indicated port onto its attached segment.
Discards
List of Frames discarded by the bridge ports.
¥ Segment MismatchÑDisplays the number of explorer frames discarded
because their routing descriptor Þeld contained an invalid value for a segment
attached to the port.
The routing information Þeld of a SpeciÞcally Routed frame contains LAN
Segment In (Ring In)ÐBridge NumberÐLAN Segment Out (Ring Out)
information. If the bridgeÕs LAN Segment Out value does not match the LAN
Segment Out speciÞed in the frameÕs Routing Information Field, the bridge
logs a Segment Mismatch and discards the frame.
¥ Duplicate SegmentÑDisplays the number of frames discarded because the
frameÕs Routing Information Field identiÞes a particular segment more than
once.
¥ Hop Cnt. ExceededÑDisplays the number of All Paths Explorer frames
discarded at the speciÞed port because they exceeded the number of routing
descriptors (bridge hops) speciÞed by the Hop Count Limit.
Bridge Statistics 2-33
Page 52

Bridging
Spanning T ree
The Bridge Spanning Tree window allows you to display and modify the deviceÕs
bridge port information and protocol parameters relating to the Spanning Tree
Algorithm.
In a network design with multiple bridges placed in parallel (i.e, attached to the
same LAN), data loops must be prevented. The Spanning Tree Algorithm (STA) is
the method that bridges use to communicate with each other to ensure that only a
single data route exists between any two end stations.
On a LAN interconnected by multiple bridges, Spanning Tree selects a controlling
Root Bridge and Port for the entire bridged LAN, and a Designated Bridge and
Port for each individual LAN segment. A Designated Port/Bridge for a LAN
segment forwards frames from that LAN towards the Root Bridge, or from the
Root Bridge onto the LAN. All other bridge ports attached to that LAN are
conÞgured to Þlter (block) frames.
When data passes from one end station to another across a bridged LAN, it is
forwarded through the Designated Bridge/Port for each LAN segment towards
the Root Bridge, which in turn forwards frames towards Designated
Bridges/Ports on its opposite side.
During the Root Bridge Selection process, all bridges on the network
communicate STA information via Bridge Protocol Data Units (BPDUs). With
BPDUs, all network bridges collectively determine the current network topology
and communicate with each other to ensure that the topology information is kept
current.
To access the Bridge Spanning Tree window from the Bridge Status window:
1. Click on Bridge to display the Bridge menu.
2. Click on Spanning T ree. The Bridge Spanning Tree window, Figure 2-10, will
appear.
To access the Bridge Spanning Tree window from the Chassis View window:
1. Click on the Board Index of the device of interest; the Board menu will
appear.
2. Click on Spanning T ree. The Bridge Spanning Tree window, Figure 2-10, will
appear.
2-34 Spanning Tree
Page 53

Bridging
Bridge Level
Figure 2-10. Bridge Spanning Tree Window
The Bridge Spanning Tree window displays STA parameters and allows you to
alter parameters for the device bridge as a whole, and for each individual
bridging interface.
The values displayed apply to the currently-selected bridging interface,
highlighted in the lower right quadrant of the window. To view or alter the
parameters of another interface, click on the appropriate Port X name listed in the
quadrant.
Bridge Priority
This Þeld displays the ÒpriorityÓ component of the deviceÕs unique bridge
identiÞer. The Spanning Tree Algorithm assigns each bridge a unique identiÞer,
which is derived from the bridgeÕs MAC address and the Priority. The bridge with
the lowest value of bridge identiÞer is selected as the Root. A lower priority
number indicates a higher priority; a higher priority enhances a bridgeÕs chance
of being selected as the Root.
You can edit this text box to change network topology, if needed. The default
value is 8000; the range is 0ÑFFFF hexadecimal.
Spanning Tree 2-35
Page 54

Bridging
TIP
Part of a bridgeÕs IdentiÞer is based on its MAC address. In most network installations,
performance differences between bridges may be negligible. You may, however, Þnd your
data bottle-necked in installations where both a low-performance bridge and a
high-performance bridge are attached to the same LAN segment and the two (or more)
bridges have the same Priority component set (e.g., at the default 8000 Hex). In such a
scenario you may want to alter the Priority component of the higher performance bridge to
ensure that it becomes root for the segment (or overall root). Remember, if Priority
components are equal, the bridge on the segment with the lowest MAC address would
have a better chance of being selected as the root bridgeÑas it would have a lower Bridge
IdentiÞer. If your bridges come from multiple vendors, they will have different MAC
address values (e.g., Cabletron devices have a lower MAC address than 3Com devices); if
they come from the same vendor, the bridge with the earlier manufacture date will have the
lower MAC address value.
Root Bridge
Displays the MAC address of the bridge that is currently functioning as the Root
Bridge.
Root Cost
Indicates the cost of the data path from this bridge to the Root Bridge. Each port
on each bridge adds a ÒcostÓ to a particular path that a frame must travel. For
example, if each port in a particular path has a Path Cost of 1, the Root Cost
would be a count of the number of bridges along the path. (You can edit the Path
Cost of bridge ports as described later.) The Root BridgeÕs Root Cost is 0.
Root Port
This Þeld displays the identiÞer (the physical index number) of the device bridge
port that has the lowest cost path to the Root Bridge on the network. If the device
is currently the Root Bridge, this Þeld will read 0.
Protocol
Displays the Spanning Tree Algorithm Protocol type the device is currently using.
The choices are:
¥ 802.1
¥ DEC (DEC Lanbridge 100)
¥ None
The following four Þelds display values used for various Spanning Tree timers
that are set at the Root Bridge and this bridge. In Spanning Tree operations, the
value used for the tree is the one set at the Root Bridge (with the exception of
Hold Time, which is a Þxed value), but you can change the value for each bridge
on your network in the event that it becomes Root.
2-36 Spanning Tree
Page 55

Bridging
Hello Time
This parameter indicates, in seconds, the length of time the Root Bridge (or bridge
attempting to become the Root) waits before resending ConÞguration BPDUs.
The range for this Þeld is 1 to 10 seconds, with a default value of 2 seconds. The
Root Bridge sets the Hello Time.
Max Age
This parameter displays the bridgeÕs BPDU aging timer. This controls the
maximum time a BPDU can be retained by the bridge before it is discarded.
During normal operation, each bridge in the network receives a new
ConÞguration BPDU before the timer expires. If the timer expires before a
ConÞguration BPDU is received, it indicates that the former Root is no longer
active. The remaining bridges begin Spanning Tree operation to select a new Root.
The current Root Bridge on the network sets the Max Age time. The range for this
Þeld is 6 to 40 seconds, with a default value of 20 seconds.
Forwarding Delay
This parameter displays the time period which elapses between states while the
bridge is moving to the Forwarding state. For example, while moving from a
Blocking to a Forwarding state, the port Þrst moves from Blocking to Listening to
BPDU activity on the network, remains there for the Forward Delay period, then
moves to the Learning State (and remains in it for the Forward Delay period), and
Þnally moves into a Forwarding state. This timer is set by the Root Bridge. During
a topology change, the Forward Delay is also used as the Filtering Database
Aging Time, which ensures that the Filtering Database maintains current
topology information.
Hold Time
This parameter displays, in seconds, the minimum time that can elapse between
the transmission of ConÞguration BPDUs through a bridge port. The Hold Time
ensures that ConÞguration BPDUs are not transmitted too frequently through any
bridge port. Receiving a BPDU starts the Hold Timer. After the Hold Timer
expires, the port transmits its ConÞguration BPDU to send conÞguration
information to the Root. The Hold Time is a Þxed value, as speciÞed by the IEEE
802.1d speciÞcation.
Bridge Port Level
The following Þelds are applicable to each bridge port on the device.
Priority
If two or more ports on the same bridge are connected to the same LAN segment,
they will receive the same Root ID/Root Cost/Bridge ID information in
ConÞguration BPDUs received at each port. In this case, the BPDUÕs Port ID
informationÑthe transmitting portÕs identiÞer and its manageable Priority
componentÑis used to determine which is the Designated Port for that segment.
Spanning Tree 2-37
Page 56

Bridging
A lower assigned value gives the port a higher Priority when BPDUs are
compared. The allowable range is 0ÑFF hexadecimal (0Ñ255 decimal); the
default is 80 hexadecimal.
Path Cost
Displays the cost that this port will contribute to the calculation of the overall
Root path cost in a ConÞguration BPDU transmitted by this bridge port. You can
lower a portÕs Path Cost to make the port more competitive in the selection of the
Designated PortÑfor example, you may want to assign a lower path cost to a port
on a higher performance bridge. The allowable range is 1 to 65,535.
Designated Cost
Displays the cost of the path to the Root Bridge of the Designated Port on the
LAN to which this port is attached. This cost is added to the Path Cost to test the
value of the Root Path Cost parameter received in ConÞguration BPDUs.
Designated Root
Displays the unique bridge identiÞer of the bridge that is assumed to be the Root
Bridge.
Designated Bridge
Displays the network address portion of the Bridge ID (MAC address/priority
component) for the bridge that is believed to be the Designated Bridge for the
LAN associated with this port.
The Designated Bridge ID, along with the Designated Port and Port IdentiÞer
parameters for the port, is used to determine whether this port should be the
Designated Port for the LAN to which it is attached. The Designated Bridge ID is
also used to test the value of the Bridge IdentiÞer parameter in received BPDUs.
Designated Port
Displays the network address portion of the Port ID (which includes a
manageable priority component) of the port believed to be the Designated Port
for the LAN associated with this port.
The Designated Port ID, along with the Designated Bridge and Port IdentiÞer
parameters for the port, is used to determine whether this port should be the
Designated Port for the LAN to which it is attached. Management also uses it to
determine the Bridged LAN topology.
Topology
This indicates how many times the bridgeÕs Topology Change ßag has been
changed since the device was last powered up or initialized. It also indicates the
time elapsed since the topology last changed. The Topology Change ßag
increments each time a bridge enters or leaves the network, or when the Root
Bridge ID changes.
2-38 Spanning Tree
Page 57

Configuring Spanning Tree
The Bridge Spanning Tree window allows you to update the following
parameters for your device bridge. When you have Þnished making changes to
the following individual parameters, you must click on Set at the bottom of the
Spanning Tree window to write the changes to the device.
Any values you set at the bridge will cause a Topology Change ßag to be issued in the next
NOTE
Changing Bridge Priority
ConÞguration BPDUs it transmits. This will cause the bridged network to immediately
recalculate Spanning Tree and change topology accordingly.
To change the part of the bridge address that contains the identiÞer used in the
Spanning Tree Algorithm for priority comparisons:
1. Highlight the Bridge Priority field.
Bridging
2. Enter the new identifier, in hexadecimal format; the allowed range is 0-FFFF
hexadecimal.
3. Click on Set.
The selected Bridge Priority will be applied to the bridge (a lower number
indicates a higher priority in the root selection process).
Changing the Spanning Tree Algorithm Protocol Type
To change the type of protocol used in Spanning Tree:
1. Click the mouse on the appropriate option button: 802.1, DEC, or None.
2. Click on Set.
The selected Spanning Tree Algorithm protocol type will be applied to the bridge.
If you selected None, the Spanning Tree Algorithm will be disabled (if it already
was enabled). If STA Protocol Type was changed from None to IEEE 802.1 or DEC,
you must restart the bridge for the newly selected STA protocol to be applied.
All bridges in a network must use the same Spanning Tree version. Mixing Spanning Tree
!
CAUTION
Algorithm protocols will cause an unstable network.
Spanning Tree 2-39
Page 58

Bridging
Changing Hello Time
If the bridge is the Root Bridge, or is attempting to become the Root, and you
want to change the length of time the bridge waits between sending conÞguration
BPDUs:
1. Highlight the Hello Time field, and type in a new value.
2. Click on Set.
The IEEE 802.1d speciÞcation recommends that Hello Time = 2 seconds, with an
allowable range of 1 to 10 seconds.
Changing Max Age Time
If the device is the Root Bridge or attempting to become the Root, and you want to
change the maximum time that bridge protocol information will be kept before it
is discarded:
1. Highlight the Max Age field, and type in a new value.
2. Click on Set.
The IEEE 802.1d speciÞcation recommends that Max Age = 20 seconds, with an
allowable range of 6 to 40 seconds.
Changing Forwarding Delay Time
If the device is the Root Bridge or attempting to become the Root, and you want to
change the time period the bridge will spend in the Listening state (e.g. either
listening to BPDU activity on the network while moving from the Blocking to the
Learning state or in the Learning state while the bridge is moving from the
Listening to the Forwarding state):
1. Highlight the Forwarding Delay field, and type in a new value.
2. Click on Set.
The IEEE 802.1d speciÞcation recommends that Forward Delay = 15 seconds, with
an allowable range of 4 to 30 seconds.
To ensure proper operation of the Spanning Tree Algorithm, the IEEE 802.1d speciÞcation
NOTE
recommends that you always observe the following relationship between Forwarding
Delay, Max Age, and Hello Time:
2 x (Forwarding Delay - 1.0) > Max Age > 2 x (Hello Time +1.0)
2-40 Spanning Tree
Page 59

Changing Port Priority
To change the part of the Port Priority used in priority comparisons:
1. If necessary , select the desired port by clicking the mouse to highlight the port
2. Highlight the port Priority field, and enter the new priority identifier. Only valid
3. Click on Set. The new port priority will be saved.
Changing Path Cost
To change the Path Cost:
1. If necessary , select the desired port by clicking the mouse to highlight the port
Bridging
in the lower right quadrant of the window. The lower left quadrant of the
window will now allow you to edit parameters for the selected port.
hexadecimal numbers (0 to FF) are allowed in this field. The default is 80
hexadecimal.
in the lower right quadrant of the window. The lower left quadrant of the
window will now allow you to edit parameters for the selected port.
2. Highlight the Path Cost field, and type in a new v alue from 1 to 65535 decimal
(default is 100 decimal).
3. Click on Set.
The new path cost will be applied to the port.
Filtering Database
The Filtering Database, which makes up the IEEE 802.1 Source Address Table, is
used to determine which frames will be forwarded or Þltered across the deviceÕs
bridging ports.
During initialization, the bridge copies the contents of its Permanent Database to
the Filtering Database. Next, the bridge learns network addresses by entering the
source address and port association of each received packet into the Filtering
Database. When in the Forwarding state, the bridge examines each received
packet, checks it against the Special Database (refer to Special Filter Databases,
page 2-47), and then (if no special Þltering applies) compares the destination
address to the contents of the Filtering Database.
If the destination address is located on the network from which the packet was
received, the bridge Þlters (does not forward) the packet. If the destination
address is located on a different network, the bridge forwards the packet to the
appropriate network. If the destination address is not found in the Filtering
Database, the bridge forwards the packet to all networks. To keep Filtering
Database entries current, older entries are purged after a period of time, which is
called the Dynamic Aging Time.
Filtering Database 2-41
Page 60

Bridging
The Filtering Database consists of two separate databases: the Static and the
Learned Databases.
The Static Database contains addresses that are entered by a network
administrator. You add these addresses directly to the database while the bridge is
powered up, or to the deviceÕs battery-backed RAM so that they are stored on
shutdown until the next power-up.
The Learned Database consists of addresses that accumulate as part of the
bridgeÕs learning process as it is up and running. These do not remain in the
Source Address Table when the system is shut down. The Learned Database also
contains the addresses that are in the Static Database upon start-up of the bridge.
Entries to the Source Address Table are one of four types: Permanent, Static,
Dynamic, or Learned.
¥ Permanent entries are addresses that you add to the Static Database (via the
Filtering Database window) that are stored in the deviceÕs battery-backed
RAM. Since they remain in the device on shutdown or restart, they are
considered ÒPermanent.Ó
¥ Static entries are addresses that you add to the Static Database (via the
Filtering Database window). These entries remain in the device until it is shut
down.
NOTE
¥ Dynamic entries are addresses that you add to the Static Database (via the
Filtering Database window). With the Aging Time feature, you set the time
period that these addresses are saved in the Source Address Table. Addresses
that have not transmitted a packet during one complete cycle of the aging
timer are deleted from the database.
¥ Learned entries are addresses that are added to the Learned Database through
the bridgeÕs learning process. With the Aging Time feature, you set the time
period that these addresses are saved in the Source Address Table. Addresses
which are inactive within a cycle of the aging timer are dropped from the
database.
Learned address entries are divided into two types, Learned and Self. Address
entries classiÞed as Learned have transmitted frames destined for a device
attached to a device portÕs connected segment. Address entries classiÞed as
Self are those that have sent a frame with a destination address of one of the
deviceÕs bridging ports.
At the Filtering Database window (Figure 2-11, page 2-43), you can view the
number of entries of each type: Permanent, Static, Dynamic, or Learned.
Even though new entries into the Filtering Database are added as Static entries by
default, note that some devices do not support Static entries. For these devices, once you
add an entry into the Filtering Database, it must be changed to a Permanent type before
clicking on OK to apply the change. If the entry is not changed to a Permanent type before
clicking on OK, you will receive a Set Failed message.
2-42 Filtering Database
Page 61

Bridging
A scrollable Address Entry panel allows you to:
¥ View the address entries in the Filtering Database.
¥ Alter an entryÕs type (e.g., from Learned to Permanent, Dynamic, or Static).
¥ View and conÞgure the bridging action taking place on the packets entering
each of the bridging ports.
In addition, you can use buttons to add individual addresses to, or delete them
from, these databases, or clear all Permanent, Static, or Dynamic entries in the
database.
To access the Filtering Database window from the Bridge Status window:
1. Click on Bridge to display the Bridge menu.
2. Click on Filtering Database. The Filtering Database window, Figure 2-11, will
appear.
To access the Filtering Database window from the Chassis View window:
1. Click on the Board Index of the device of interest; the Board menu will
appear.
2. Click on Filtering Database. The Filtering Database window, Figure 2-11, will
appear.
Figure 2-11. The Filtering Database Window
Filtering Database 2-43
Page 62

Bridging
The following Þelds are listed in the top portion of the Filtering Database
window.
List
The List checkboxes indicate whether the associated entry type (Permanent,
Static, Dynamic, or Learned) will be displayed in the scrollable table of address
entries. A check next to the entry type indicates that it will be displayed.
Type
Indicates the type of entry in the database.
Number
Displays the current number of Permanent, Static, Dynamic, and Learned
Address entries.
Capacity
Indicates the total capacity of each entry type in the Static and Learned databases.
Aging Time
Indicates the length of time, in seconds, that Dynamic and Learned Addresses in
the Source Address Table are allowed to remain inactive before they are dropped
from the database. The allowable time range for these entries is 10 to 1,000,000
seconds. Aging time is not applicable to Static or Permanent entries. You can
conÞgure this Þeld, as described in the next section.
The following Þelds are applicable to the scrollable Address Entry panel of
Filtering Database entries.
Address
Lists the addresses for which the bridgeÕs Filtering Database has forwarding
and/or Þltering information.
Type
Indicates the type of an entry in the database. The possible types are Static,
Dynamic, Learned, Self, or Permanent. You can alter the entry type, as described
in the next section.
Source Port
Indicates the port number on which the address entry was Þrst detected. A
question mark (?) indicates that the address entry was not a learned entry, but
Port Filtering information applies to it (i.e., the entry is a created Permanent,
Dynamic, or Static entry and has corresponding Þltering information).
Receive Port
Indicates the number of the port on which a frame must be received in order for
the entryÕs Port Filtering information to apply. An asterisk (*) indicates that the
receive port is promiscuous, and applies to all ports of the bridge (assuming no
conßicting entry applies). You can change the receive port, as described in the
following section.
2-44 Filtering Database
Page 63

Port Filtering
Indicates the action that will take place at each bridge port when it receives
frames from the selected address entry. A green arrow indicates that the frames
received from the address will be forwarded to the portÕs associated segment
( ). A red circle indicates that frames will be Þltered (blocked) from the portÕs
associated segment ( ). You can change the Port Filtering action, as described
in the next section. (Note that port Þltering is scrollable among all the potential
ports; however, only two consecutive ports can be viewed simultaneously.)
Configuring the Filtering Database
You can conÞgure the Filtering Database by:
¥ Altering the Aging Time for Dynamic and Learned entries.
¥ Changing the type of entry with the Type buttons.
¥ Changing the Receive port for the Þlter.
¥ Changing the Port Filtering action at each bridge port.
Bridging
NOTE
¥ Adding or deleting individual Filtering Database entries.
¥ Clearing all Permanent, Static, or Dynamic entries from the Filtering Database.
Note that although conÞguration changes will appear in the window, no action
actually takes place in the bridgeÕs Filtering Database until you click on the OK
button in the bottom right of the window. This saves the new conÞguration.
When you reconÞgure the Filtering Database and click OK, the screen will clear
temporarily and a message will appear to indicate that the information is being updated.
When the changes have been successfully set and the Filtering Database has updated, the
screen information will be refreshed.
If you change the window without clicking on OK, then attempt to exit the
window by clicking on Cancel, a text box will appear stating ÒChanges have been
made. Cancel them?Ó. Click on Yes to exit the window without changing the
Filtering Database, or select No to return to the window.
Altering the Aging Time
To alter the Aging Time for Dynamic and Learned entries:
1. Highlight the Aging Time field with the cursor.
2. Type in the new Aging Time (allowable range is 10 to 1,000,000 seconds).
Filtering Database 2-45
Page 64

Bridging
NOTE
Note that the Filtering Database Aging Time is the same as the Aging Time displayed
(and conÞgured) via the Source Addresses window. Setting the Aging Time in the
Filtering Database window also changes the time in the Source Addresses window, and
vice versa.
Changing the Type of Entry
You can change any entry type from its current type (Learned, Self, Permanent,
Static, or Dynamic) to either a Permanent, Static, or Dynamic entry. To do so:
1. Click on the shadowed Type button. A menu will appear with the three types
to which the entry can be changed.
2. Highlight the desired type.
Changing the Receive Port
You can change the Receive port of an address entry in the scrollable panel, so
that a frame must be received at the speciÞed port for the Þltering action to apply.
To do so, click on the Receive port in the panel. With each click, the Receive port
will cycle to the next port (e.g., from * (promiscuous), to 1, to 2, to 3, to 4, to 5, etc.).
Changing the Port Filtering Action
You can change the Port Filtering action at each bridge port from its current action
to the opposing action.
1. Maneuver the scroll bar until the desired port is in the Port Filtering panel.
2. Click on the port to alter its filtering action from forwarding frames from the
associated address (), to filtering frames ( ) (or vice versa).
Adding or Deleting Individual Entries
You can add or delete entries individually from the Filtering Database.
To add an address:
1. Click on the New button. A window (Figure 2-12) will appear.
Figure 2-12. Filter DatabaseÑNew Filter Window
2. In the Filter Address field, type in the address (Hex format) for which you
desire bridging. Be sure to add “-” as a separator between each byte in the
address.
2-46 Filtering Database
Page 65

Bridging
3. In the Receive Port field, type in the port at which the address must be
detected for bridging to take place. If you enter a value of 0 in this field, the
Receive Port is considered promiscuous (i.e., any port), and will be
designated by an “*” in the Address Entry panel.
4. Click on OK.
5. Specify the Port Filtering action on the address entry as described in the
previous section.
To delete an address:
1. Click to highlight the address entry in the Address Entry panel that you wish to
delete from the filtering database.
2. Click on Delete.
Clearing All Permanent, Static, or Dynamic Entries
To erase all Permanent, Static, or Dynamic entries from the Filtering Database,
click on the associated Clear button in the upper portion of the window.
Special Filter Databases
While the Filtering Database deÞnes Þlters for all packets from a particular source
address, the Ethernet Special Filter Database and the Token Ring Special Filtering
Databases allow you to Þlter packets through an Ethernet or a Token Ring bridge,
respectively, using a special Þltering scheme.
When a packet is received at an Ethernet bridging interface, it is Þrst checked
against the Ethernet Special Filter Database to see if any Þltering action applies to
it. Because of this, an entry in the Ethernet Special Filter Database takes
precedence over a Þlter entry in the Filtering Database that would otherwise
apply to the packet.
The Ethernet Special Filter Database allows you to:
¥ DeÞne and save a Þlter based on a combination of Source Address, Destination
Address, Ethernet Data Type, and Data (including the offset).
¥ Specify the receive ports at which the Þlter will take effect.
¥ Specify the forwarding/Þltering action at each bridging port of the device.
When checking for Transparent Þltering information, the bridge Þrst checks the
Token Ring Special Filter Database to see if any Þltering action applies to it.
Because of this, a Þlter entry in the Token Ring Special Filter Database takes
precedence over a Þlter entry in the Filtering Database that would otherwise
apply to the packet.
Special Filter Databases 2-47
Page 66

Bridging
Looking at each enabled Þlter, starting with the lowest numbered Þlter, the bridge
compares the following Þelds to the corresponding Þelds in the received packet:
¥ Destination address
¥ Source address
¥ Ethernet or Token Ring data type
¥ Up to 16 hex integers (64 bytes) of the data Þeld
In addition, a Þlter can also specify at which port or ports the packet must be
received for the Þlter to be applicable. If a received packet matches all the contents
of an enabled Þlter, the bridge forwards the packet to the deÞned set of ports.
Filters provide broad conÞguration ßexibility. For example, you can deÞne
multiple scenarios for a single Þlter by specifying different combinations of
receive port/destination port. You can use wildcard characters in Þlter Þelds to
force a match with particular bits of the received packetÕs destination address,
source address, type, or data. You can specify an offset for the data Þeld, to specify
the starting point in the data where the bridge looks for the match. For entries that
donÕt match any of the enabled Þlters, you can conÞgure the bridge to Þlter or
forward the entry or pass the Þlter/forward decision to the Filtering Database.
Ethernet and Token Ring Special Filter Database Windows
At the Ethernet and Token ring Special Filter Database windows, Figure 2-13, you
can view a list of the special Þlters for the selected bridge. There are 19 available
Þlters in the Special Filter Database. You can not add any additional Þlters. You
can view Þve of these Þlters at a time in the Special Filter Database window. Use
the scroll bars to view the other fourteen Þlters.
When you Þrst open the window, all Þlters will be undeÞned. For each Þeld,
bytes will be initialized with Òmatch-anyÓ characters (xx) for each digit. Any
hexadecimal byte will be accepted as valid for the corresponding wildcard (xx)
characters. For example, a Source Address Þlter deÞned as Òxx-xx-xx-xx-bf-coÓ
will pass the Þrst four bytes of a frameÕs source address unconditionally, but the
last two bytes must match the Òbf-coÓ Þlter.
To access the Ethernet or Token Ring Special Filter Database window from the
Bridge Status window:
1. Click on Bridge to display the Bridge menu.
2. Click on Ethernet or Token Ring Special Filter Database. The selected
Special Filter Database window, Figure 2-13, will appear.
To access the Ethernet or Token Ring Special Filter Database window from the
Chassis View window:
1. Click on the Board Index of the device of interest; the Board menu will
appear.
2. Click on Ethernet or Token Ring Special Filter Database. The selected
Special Filter Database window, Figure 2-13, will appear.
2-48 Special Filter Databases
Page 67

Bridging
Figure 2-13. Ethernet and Token Ring Special Filter Database Windows
Special Filter Database Window
The following Þelds are available in the Special Filter Database window:
File
An X in this checkbox indicates that the Þlter is associated with the Þle name
shown in the title bar of the window. If a Þle has not yet been saved, the title bar
will display the Þlter name Òuntitled. ßtÓ. A saved Þle name is only displayed in
the title bar after you have opened a saved Þlter Þle or saved your current Þlters.
Enable
A Þlled-in circle indicates the Þlter is enabled.
Special Filter Databases 2-49
Page 68

Bridging
Destination Address
Displays a six-byte hexadecimal Þeld for the Þlter which can be used to Þlter on
Destination Addresses, in whole or in part.
Source Address
Displays a six-byte hexadecimal Þeld for the Þlter which can be used to Þlter on
Source Addresses, in whole or in part.
Data Type
Displays the hexadecimal two-byte Þeld for the Þlter which can be used to mask
out a speciÞed protocol type Þeld. Examples of protocol type are:
¥ 0800 = IP
¥ 8137 = Novell
¥ 0bad = Banyan
¥ 80f3 = AppletalkARP
Data Offset
Indicates the offset (in bytes, from the beginning of the data in the packet) where
the Data Mask will be applied. The default for this Þeld is 0000 (no data offset).
An example of a valid offset to enter into this Þeld is 0016 (16 bytes).
Data Mask
Displays the 64-byte overlay used to Þlter on packets. The Data Mask is applied to
the packet after the Þxed part of the packet, data includes Source Address,
Destination Address, and Type Þelds. The Þlter applies the mask directly at the
start of the data portion of the packet unless there is a Data Offset. If a Data Offset
has been deÞned, the mask will apply to the data that comes after the speciÞed
offset in the packet.
Receive Port(s)
Indicates the ports at which the packet must be received for Þltering information
to be applied. Note that you can only immediately see one receive port per Þlter,
even though you can set more than one receive port for the Þltering action to
apply. The receive port Þeld can display each individual device bridge port, or
Ò*.Ó The Ò*Ó indicates that a packet can be received at any port for the Þlter to
apply (i.e., the port is promiscuous).
Port Filtering
forwarding Indicates the forwarding/blocking information for the
Þlter at each port on the device. Note that you can only
view two ports at a time.
blocking Use the scroll bar at the top of the column to view the
hidden ports.
Selected Filter
This Þeld, visible at the bottom of the window, displays the number of the Þlter
that is currently highlighted. The possible range is from 01-19.
2-50 Special Filter Databases
Page 69

Defining and Editing Filters in the Special Database
You can edit an existing Þlter or deÞne a new Þlter using the following steps:
1. Click to select the filter you wish to edit. The filter is selected when it is
highlighted. When the bridge uses the Special Database, it starts with the
lowest numbered enabled filter.
2. Click Edit. The Special Database Filter window, Figure 2-14, will appear with
the following fields:
Destination Address (six-byte hexadecimal field)
Source Address (six-byte hexadecimal field)
Type (two-byte hexadecimal field)
Data Offset (decimal field)
Data Mask (64-byte hexadecimal data mask)
Bridging
Figure 2-14. The Special Database Filter Window
3. If you are editing an existing filter, the fields will reflect the current
configuration. A filter that has not yet been defined will have wildcards (xx) in
every field.
If you want to completely reconfigure an existing filter, click on Clear. This will
revert all the fields to all xx’s.
4. Highlight the field which you want to define, and enter the appropriate
information.
5. When you have finished defining the filter, click on OK. This will save the filter
you created and return you to the Special Filter Database window, where the
configured filter will be displayed.
Special Filter Databases 2-51
Page 70

Bridging
If you do not wish to save what you have entered in the Special Database Filter Window,
NOTE
click on the Cancel button. This will cancel what you have entered into this window and
return you to the Special Filter Database window.
6. Click on OK to save the changes you have made and exit the Special
Database Filter window.
Changing the Receive Ports
You can set the receive ports in the Special Filter Database window either before
or after you deÞne a Þlter. These are the ports at which the frame must be received
for the Þltering parameters to apply. The default selection is Port 1.
To designate a receive port, click on the receive port icon ( ) for the Þlter. As you
click on the icon, it will cycle though the ports (e.g., 1, 2, 3, 4, etc. until the end of
the interface table, and Ò*Ó). When you have selected a port, you can set the port
Þltering action that will apply when the packet is received at that particular port
(refer to the following section for further information).
In this fashion, you can specify all receive ports at which the packet must be
received and the designated Þltering action which will apply when the packet is
received at each port. Selecting Ò*Ó (promiscuous or any port) will apply the Þlter
and its speciÞed Þltering action to all ports on the device.
Remember that you can only view a single receive port and its Þltering action. To
check all receive ports for a single Þlter, you must click on the receive port icon to
cycle through the series of ports.
Changing the Port Filtering Action
Use the port icons under the Port Filtering section of the Special Filter Database
window to determine the port Þltering action associated with the Þlter when it is
received at a speciÞed receive port. You can select the port Þltering action either
before or after deÞning the Þlter. By default, the Þltering action is initially not set
at any port. You must click on a port to invoke the Þltering action symbols. After
the Þrst port is set (either to Þltering or blocking), the remaining ports in the Þlter
are set to blocking until you specify otherwise.
Setting the Port Filtering Action
When you set the port Þltering action for a Þlter, you determine whether the port
will block or forward packets which match the ÞlterÕs speciÞcations. To set port
Þltering action, click on the desired port icon (e.g., 1, 2, 3, 4, 5, 6, up to 32) to toggle
from blocking ( ) to forwarding ( ) or vice versa.
2-52 Special Filter Databases
Page 71

You can set the port Þltering action for the bridging port on each port of the
device, as well any BRIM ports.
Clearing the Port Filtering Action
When you clear the port Þltering action of a Þlter, all ports that were conÞgured to
forwarding or blocking will be reset to no action. Note that when you clear port
Þltering for a Þlter, the Þltering or blocking action will be simultaneously cleared
at all of its receive ports.
In order to clear the port Þltering action, use the following steps.
1. Click to select the filter whose port filtering action you would like to disable.
2. Click on Clear Port Filtering. This will clear the port filtering action for the
selected filter at all of its receive ports. The port filtering symbols will appear in
cleared mode.
Enabling and Disabling a Filter
Bridging
To determine if a Þlter is enabled, check the Enable option button.
To enable a Þlter:
1. Click on the empty Enable button. When the button is filled ( ), the filter is
enabled.
To disable a Þlter:
1. Click on the filled Enable button. When the button is empty ( ), the filter is
disabled.
Saving a Set of Filters to a File
When you have deÞned a set of Þlters, you can save that set to a Þle. This allows
you to conveniently recall a series of Þlters when the need arises.
To save a set of Þlters:
1. Make sure that all filters that you want contained in the set have the File
checkbox checked.
2. Click on Filters. A menu will appear.
3. Click on Save As. A standard Microsoft Windows Save File window will
appear.
4. In the File name field, specify the file name and file path in which you want to
save the filter series.
5. Click on OK. The file will be saved as indicated.
Special Filter Databases 2-53
Page 72

Bridging
To update the file while it is still open, click on the Save selection from the
Filters pull-down menu.
To open an existing Þle containing a Þlter set:
1. Click on Filters. A menu will appear.
2. Click on Open. A standard Microsoft Windows Open File window will appear.
3. To specify the file:
In the File name field, specify the file to open by path and name
or
Use the Look in drop-down list box and associated file list to select the
desired file, and click to highlight it.
4. Click on Open.
The Þlters will appear in the Special Filter Database window, with all parameters
(File, Enable, Source and Destination Address, Data Type and Offset, Data Mask,
Receive Port, and Port Filtering Action) displayed as they were conÞgured at the
last Þle save.
Interface Configuration
The I/F ConÞguration port-level menu option invokes the Interface
ConÞguration window, which allows you to select a bridging method for a Token
Ring bridging interface. You can also make this selection via the Token Ring
Bridge Mode window; see Token Ring Bridge Mode, page 2-89, for details.
This window also allows you to select one of three transmission methods that
should be used when unknown addresses are received from end stations attached
to the selected bridge port.
To access the Interface ConÞguration window from the Bridge Status window:
1. Click on the desired Port button ( ) to display the Port menu.
2. Click on I/F Configuration. The Interface Configuration window, Figure 2-15,
will appear.
To access the Interface ConÞguration window from the Chassis View window:
1. Click on the appropriate bridge port index to access the Port menu.
2. Click on I/F Configuration. The Interface Configuration window, Figure 2-15,
will appear.
2-54 Interface Configuration
Page 73

Bridging
Bridge Methods
The options available in the Bridge Method Þeld are as follows:
Transparent
When the bridge is set to Transparent mode, the bridge will only transmit
transparent frames from the Token Ring connection. If a source route frame is
received by the bridge, the Source Route information in the frame will be dropped
from the packet. (A transparent frame is the same as a source route frame without
a RIFÑRouting Information Field.)
Source Routing
When the bridge is set to Source Routing mode, the bridge will only transmit
source route frames from the Token Ring connection.You should set the bridging
mode to Source Route when you are bridging from Ethernet to Token Ring. The
source route information (as conÞgured via the Ethernet portÕs Source Route
ConÞguration window, page 2-57) will be appended to the RIF for frames
transmitted on the Token Ring.
Figure 2-15. Interface ConÞguration Window
Interface Configuration 2-55
Page 74

Bridging
Source Route Transparent
When the bridge is set to Source Route Transparent, the bridge will transmit both
transparent and source route frames. The frames received which have source
route information will be transmitted as source route, while frames received that
are transparent will be transmitted as transparent.
Setting the Bridge Method
1. Click on the option button ne xt to the bridging mode you would lik e y our Token
Ring bridge port to use: Transparent Bridge, Source Routing, or Source
Route T ransparent.
2. Click on Set to apply the desired mode.
Protocol T ransmission Methods
The options in the Protocol Transmission for Unknown Address Þeld are as
follows:
TCP/IP
Determines whether IP frames received at the interface should be forwarded as
transparent frames, source route frames, or both.
IPX
Determines whether IPX frames received at the interface should be forwarded as
transparent frames, source route frames, or both.
NetBIOS
Determines whether NetBIOS frames received at the interface should be
forwarded as transparent frames, source route frames, or both.
SNA
Determines whether SNA frames received at the interface should be forwarded as
transparent frames, source route frames, or both.
Other
Determines whether frames of all other protocols not mentioned above (IP, IPX,
NetBIOS, and SNA) that are received at the interface should be forwarded as
transparent frames, source route frames, or both.
If Transparent is selected, the frame is forwarded out of the bridge interface as a
transparent frame. If Source Route is selected, the frame is forwarded out of the
bridge interface as a source route frame. If Auto is selected, the frame is
forwarded out of the bridge interface as both a transparent frame and as a source
route frame.
2-56 Interface Configuration
Page 75

To select the transmission method for TCP/IP, IPX, SNA, NetBIOS or Other
protocols:
1. Click on the option button ne xt to the transmission method y ou would lik e your
Token Ring bridge port to use: Transparent, Source Route, or Auto.
2. Click on Set to apply the desired mode.
Source Route Configuration
With the Source Route ConÞguration window, you can view address and routing
information, and set source route bridging parameters for bridging interfaces.
To access the Source Route ConÞguration window from the Bridge Status
window:
1. Click on the desired Port button ( ) to display the port menu.
2. Click on Source Route Configuration. The Source Route Configuration
window, Figure 2-16, will appear.
Bridging
To access the Source Route ConÞguration window from the Chassis View window:
1. Click on the appropriate bridge port index to access the Port menu.
2. Click on Source Route Configuration. The Source Route Configuration
window, Figure 2-16, will appear.
Figure 2-16. Source Route ConÞguration Window
Source Route Configuration 2-57
Page 76

Bridging
Source Routing Information
Source Routing is a bridging technique developed by IBM and the 802.5 standards
committee in which a bridge routes frames based on the contents of their media
access control frame header, rather than by maintaining a Þltering database to
determine whether a packet should be forwarded or Þltered. Source Routing
functions as follows:
¥ An end point station transmits discovery (explorer) frames to a particular
destination address in order to seek the best route through a bridged topology
to that node. These frames are broadcast over the entire network.
In a network topology with parallel bridges, multiple paths may be available
to the same destination. In this case, the explorer frame may be further deÞned
as:
- All Routes Explorer, so that all possible routes to the destination are
recorded, and multiple explorer frames can reach the same segment.
- Spanning Tree Explorer (also known as Single Route Broadcast), so that
only one path is possible to a segment (i.e., through a designated bridge in
a Spanning Tree topology), and only one explorer frame will be forwarded
onto each segment. The Spanning Tree can be conÞgured either
automatically (i.e., by algorithm) or manually.
¥ When a source routing bridge processes the explorer frame, it adds a unique
identiÞer to the frame in a reserved portion of the frame. This identiÞes the
segment the frame was received from, followed by the speciÞc bridge, and
Þnally the segment it was forwarded onto.
¥ When the discovery frame (or frames if more than one route is possible)
reaches its destination, it contains a complete record of bridge hops on its
route.
¥ The destination address then returns All Routes Explorer (using speciÞcally
routed frames) and Single Route (Spanning Tree) Explorer frames (using All
Routes Broadcast frames), to the source address.
¥ The source station selects one path from the returned explorer frames, and
includes that path speciÞcation (with bridge and segment identiÞers) in
subsequent transmissions to that particular destination.
All bridges in the topology then examine the routing information Þeld of a
speciÞcally source routed frame and either forward it if there is a match in the
routing informationÑor if it is an All Routes explorer frameÑor discard it.
Source Route Configuration
The Source Route ConÞguration window allows you to view IP address and
routing information, and to view and set source route bridging parameters for
any bridging device which supports this menu option.
2-58 Source Route Configuration
Page 77

NOTE
Bridging
It is recommended that the device be restarted when changes are made that affect source
route bridging in order to clear the buffers, but you do not need to restart for the changes
to take effect.
The following Þelds are available in the Source Route ConÞguration Window:
IP Address
This Þeld displays the Internet Protocol (IP) address, which acts as a logical
identiÞer on the network, currently assigned to each port on the device. This is
needed for SNMP network management capability. The IP address is expressed in
dotted decimal notation (four decimal values between 0 and 255, separated by a
period, e.g., 255.255.255.255).
This Þeld can only be edited (with the correct security access) via Local
Management for the device. Refer to the appropriate device-speciÞc UserÕs Guide
for more information.
Subnet Mask
A subnet mask is used by a device to determine whether a destination address
exists within its own subnetwork (logical division of the network by router or
gateway) and can be reached directly, or whether it is unknown and therefore
must be delivered to a router (as speciÞed by the deviceÕs IP routing table or
default gateway address).
A subnet mask should be set at the device if it will issue SNMP traps in a routed
environment, so that the trap messages it generates will be routed correctly.
A subnet mask acts as a Þlter for destination IP addresses. It is a 32-bit quantity in
which all bits that correspond to the network portion (both site and subnet
identifying bits) of the deviceÕs IP address are set to 1, and all bits that correspond
to the host portion are set to 0.
The device will logically AND a destination trap IP address with the subnet mask
to determine which portion of the address identiÞes the network/ subnetwork.
The device then compares the result on a bit-to-bit basis with the
network-identifying bits in its own IP address. If the network portions match, the
bridging device transmits the trap onto its subnetwork. If they do not match, the
device transmits the trap through a router or gateway.
This Þeld can only be edited (with the correct security access) via Local
Management for the device (or the MIBTree utility). Refer to the appropriate
device-speciÞc UserÕs Guide for more information.
MAC Address
This Þeld displays the Media Access Control (MAC) layer address which
identiÞes the ports/interfaces of the bridging device on a network. This six-byte
address is set at the factory and is unique to each interface. Each byte is identiÞed
in bit order starting with the most signiÞcant bit. You cannot conÞgure this Þeld.
Source Route Configuration 2-59
Page 78

Bridging
The following Þelds apply to the Source Route ConÞguration window:
Local Segment
This Þeld displays the unique segment number that identiÞes the segment
attached to the selected interface (either of the Token Ring or FDDI interfaces).
The bridge adds the Local Segment number to the routing information Þeld of
source route discovery frames. Valid values range from 0 to 4095.
Target Segment
This Þeld displays the unique segment number of the target segment that the
source routed frame will be forwarded to. Valid values range from 0 to 4095.
Hop Count Limit
The maximum number of routing descriptors (i.e., bridge hops) allowed for an All
Routes Explorer or a Spanning Tree Explorer frame received by the device. This
will reduce the unnecessary propagation of explorer frames through the network.
You can use the Set button at the bottom of the window to change the Hop
Count for the port, as explained in Making and Setting Changes, page 2-62.
The allowable range of values for this Þeld is 0 to 28.
Spanning T ree Expl.
This read-only Þeld displays the action currently being applied to Spanning Tree
Explorer frames received by the indicated port. This Þeld will appear in one of
two ways:
¥ If the Spanning Tree Mode for the bridge is set to Auto (as explained in the
following section), this Þeld will display the Spanning Tree Port State for the
indicated port.
If set to Auto, the device is subject to the Spanning Tree Algorithm. Each port
will treat incoming frames according to its current Spanning Tree bridging
state (i.e., Forwarding, Disabled, Listening, Learning, Blocking, or Broken).
¥ If the Spanning Tree Mode is set to Manual (as explained in the following
section) this Þeld will display either Enabled or Disabled as the Spanning Tree
Port Enable State for the indicated port.
2-60 Source Route Configuration
Page 79

Bridging
Bridge Number
The Bridge Number uniquely identiÞes a bridge port when more than one bridge
is used to span the same two segments. The Bridge Number should be in the
range of 0 to 15.
You can use the Set button at the bottom of the window to change the bridge
number of the port, as explained in Making and Setting Changes, page 2-62.
Current source routing protocols allow a range of 0 to 15 (0ÐF hexadecimal) for
the bridge number identiÞer. If no bridge number is assigned to the device, a
default value of 1 will appear in this Þeld.
Spanning T ree Mode
Indicates how a port on the device will behave with an incoming single-route
broadcast (Spanning Tree ExplorerÑSTE) frame. You can conÞgure this Þeld with
the option buttons and checkboxes, or via the MIBTools utility or local
management.
This Þeld allows you to conÞgure a Spanning Tree for your network. You can set
the Spanning Tree Mode to Auto or Manual using the option buttons. We
recommend that all bridges in your network topology have the same setting for
Spanning Tree Mode (i.e., all set to Auto or all set to Manual).
Auto If the Spanning Tree Mode is set to Auto, a port that implements
the Spanning Tree Algorithm (STA) and is enabled and in the
forwarding state will accept and relay STE frames onto its
attached segment.
Using STA, a bridge port will only forward frames if it is the
designated port for its attached segment. A port is ÒdesignatedÓ
for its segment if it has the lowest Root Path Cost of all bridge
ports attached to that segment. The Root Path Cost is the lowest
total path cost calculated by adding the costs of each port along
the path of a frame that traverses the bridge topology from the
root to that port (including its own path cost).
If two ports on a segment have equal Root Path Costs, the port on
the bridge with the highest priority bridge identiÞer (for
convenience sake, that have the lowest numerical value) will be
chosen as the root port.
You can affect Spanning Tree topology by changing the deviceÕs
bridge priority (Bridge Label) and path cost for its port pair (path
cost increment) via the Spanning Tree window, page 2-34.
Manual If the Spanning Tree Mode is set to Manual, you can manually
conÞgure the bridge to forward STE frames (i.e., manually
establish a Spanning Tree for STE frames by determining which
bridge in a parallel series of bridges will forward these frames).
If you set the Spanning Tree Mode to Manual, you can use the Enable or Disable
checkboxes to set a portÕs Spanning Tree Enable State to:
¥ Enabled (participating in frame relay).
Source Route Configuration 2-61
Page 80

Bridging
¥ Disabled (not participating in the bridging process or in operation of the
Spanning Tree Algorithm and protocol). If the Spanning Tree Mode is set to
Disabled, the bridge port will not send or accept any STE frames. Any STE
frame received will be discarded. The Spanning Tree Expl Þeld at the
ConÞguration window, and the STE Frames Þeld at the Status window will
both read ÒDisabled.Ó
Making and Setting Changes
The Source Route ConÞguration window allows you to affect changes for the
following Source Route Bridging parameters: Bridge Number, Local Segment,
Target Segment, Hop Count Limit, and the deviceÕs Spanning Tree Mode.
To make a change to Bridge Number, Local Segment, Target Segment, or Hop
Count Limit, use the mouse to highlight the existing value in the desired Þeld,
and type in a new value.
To set the Spanning Tree Mode to Auto or Manual, click on the option button next
to the appropriate selection. If set to Auto, a Spanning Tree Algorithm will
calculate the deviceÕs priority in a series of parallel bridges to determine a root
bridge on the network. If set to Manual, you conÞgure a Spanning Tree by
administratively enabling or disabling each bridging port on the network.
When the deviceÕs Spanning Tree Mode is set to Manual, you can change how a
bridge port will treat a Spanning Tree Explorer frame. Use the Enable checkbox to
allow STE frame forwarding at the port, or use the Disabled checkbox to prevent
STE frame forwarding at the port. Click on the Enabled or Disabled checkbox to
make your selection.
When you make changes in the Source Route ConÞguration window, they are not
implemented at the device until you click on the Set button. This will cause the
device to reboot. Since rebooting the device will bring it down for several
minutes, a ÒReset with new parameters?Ó pop-up dialog box will appear to
ensure that you are ready. Click on OK to set the changes, or Cancel to return to
the Source Route ConÞguration window.
Using the Find Source Address Feature
You can select the Find Source Address option to discover which bridging
interface a speciÞed source MAC address is communicating through. When you
select the Find Source Address option, a search is made of the 802.1d Bridge
Filtering Database to discover the bridge interface associated with the address
that you specify. If the search is successful, the corresponding interface will ßash
in the Chassis View window. See Filtering Database, page 2-41, for details.
Use the Find Source Address feature as follows:
1. Click to display the Device menu.
2. Click again on Find Source Address. The following window will appear.
2-62 Using the Find Source Address Feature
Page 81

Bridging
Figure 2-17. Find Source Address Window
3. In the text field in the middle of the window, enter a valid MAC address in
hexadecimal format and then click OK.
If the address is found in the 802.1d Bridge Filtering Database, the port through
which the address is communicating will ßash in the front panel Chassis View
display.
If the address is not found in the Filtering Database, a separate window will
appear with a ÒCanÕt Find Source AddressÓ message.
Using the Port Source Addresses Window
You can use the port-level Source Addresses window to view all the MAC
addresses that are communicating through a selected bridge interface.
To open the Source Addresses window from the Bridge Status window:
1. Click on the desired Port button ( ) to display the Port menu.
2. Click on Source Addressing. The Port Source Addresses window,
Figure 2-18, will appear.
To open the Source Addresses window from the Chassis View window:
1. Click on the appropriate port index to access the Port menu.
2. Click on Source Addressing. The Port Source Addresses window,
Figure 2-18, will appear.
Using the Port Source Addresses Window 2-63
Page 82

Bridging
Figure 2-18. Port Source Addresses Window
The Port Source Addresses window displays the MAC addresses of all devices
that have transmitted packets that have been forwarded through the selected
bridging interface during the last cycle of the Filtering DatabaseÕs deÞned aging
timer (learned addresses that have not transmitted a packet during one complete
cycle of the aging timer are purged from the Source Address Table). For more
information, see Filtering Database, page 2-41.
The aging time displayed in the Port Source Addresses window is the same as the aging
NOTE
time displayed in the Filtering Database window. The aging time can be set from either
window, and any changes to its value will be reßected in both locations.
Setting the Aging Time
The Filtering Database Aging Time is user-conÞgurable through the Device Aging
Time window.
To alter the Aging Time for Dynamic and Learned entries:
1. Click the I-bar cursor ( ) next to the Device Aging Time field. The Device
Aging Time window, Figure 2-19, will appear.
2-64 Using the Port Source Addresses Window
Page 83
Bridging
Figure 2-19. Device Aging Time Window
2. Type in the new Aging Time, in seconds, then click on OK. The allowable
range is 10 to 1000000 seconds; the default is 300 seconds.
Using the Token Ring Bridge and Port Configuration
Windows
The Bridge ConÞguration and the Port ConÞguration windows available for
Token Ring devices look similar and are used for similar purposes, with the only
exception being that the former window contains values that apply to the device
as a whole, while the latter contains values that apply to the selected port.
The Bridge ConÞguration window provides a global capability to conÞgure all of
the Token Ring bridging interfaces on a device simultaneously as well as set the
bridge number and virtual ring number (target ring).
The Port ConÞguration window provides the capability to conÞgure individual
Token Ring bridging interfaces on a device. This window displays the
information that is set at the device level via the Bridge ConÞguration window,
such as the Bridge Number and the Virtual Ring NumberÑboth of which are
read-only Þelds in the Port ConÞguration window.
The Ring Number Þeld is the only Þeld that is not common to both windows,
because this value cannot be set globally on a device. It appears in the Port
ConÞguration window only, since the value assigned to this Þeld must be unique
to each interface.
To access the Bridge ConÞguration window from the Bridge Status window:
1. Click on Bridge to display the Bridge menu.
2. Click on Bridge Configuration. The Bridge Configuration window,
Figure 2-20, will appear.
Using the Token Ring Bridge and Port Configuration Windows 2-65
Page 84

Bridging
To access the Bridge ConÞguration window from the Chassis View window:
1. Click on the Board Index of the device of interest; the Board menu will
appear.
2. Click on Bridge Configuration. The Bridge Configuration window,
Figure 2-20, will appear.
Figure 2-20. Bridge ConÞguration Window
To access the Port ConÞguration window from the Bridge Status window:
1. Click on the desired Port button ( ) to display the port menu.
2. Click on Port Configuration. The Port Configuration window , Figure 2-21, will
appear.
To access the Port ConÞguration window from the Chassis View window:
1. Click on the appropriate port index to access the Port menu.
2. Click on Port Configuration. The Port Configuration window , Figure 2-21, will
appear.
2-66 Using the Token Ring Bridge and Port Configuration Windows
Page 85

Bridging
Figure 2-21. Port ConÞguration Window
The Bridge ConÞguration and Port ConÞguration window Þelds are deÞned as
follows:
Bridge Number
Displays and allows you to set the number assigned to Token Ring bridge. This
value is limited to the hexadecimal range of 0 through F. This Þeld is settable in
the Bridge ConÞguration window and read-only in the Port ConÞguration
window.
Virtual Ring Number
Displays and allows you to set the number of the target segment connected to the
selected bridge. This value is limited to the hexadecimal range of 001 through FFF.
This Þeld is settable in the Bridge ConÞguration window and read-only in the
Port ConÞguration window.
Ring Number
Displays and allows you to set the segment number that uniquely identiÞes the
segment to which this port is connected. This value is limited to the hexadecimal
range of 001 through FFF. This Þeld appears in the Port ConÞguration window
only.
Using the Token Ring Bridge and Port Configuration Windows 2-67
Page 86

Bridging
Port Mode
Displays the three port mode options that are deÞned as follows:
¥ LobeÑallows direct-attach station connections (acting as a concentrator port).
¥ StationÑprovides station emulation.
¥ TPIM RI/ROÑallows attachment to Þber TPIMs on standard workgroup
hubs or direct-attachment to devices, such as servers, via Þber adapter cards.
If the device does not support this mode of operation, this option will be
grayed out.
Novell T ranslation
Displays the three bit-order options that are available for translationÑEnable
LLC (Logical Link Control Translation), Enable DLC (Data Link Layer
Translation), and Disable (No translation will take place). See Using the Novell
Translation Window, page 2-97, for more information.
Ring Speed
Displays the selected ring speed, 4 Mbps or 16 Mbps.
Bridge Mode/Explorer Type
Displays the available bridging mode and explorer frame type combinations:
Source Route Indicates the bridge forwards packets
Transparent/Transparent so they know the route and the devices they
pass through to reach their destination.
Explorer frames have no embedded routing
information
Source Route Indicates that the bridge forwards packets
Transparent/Are so they know the route and the devices they
pass through to reach their destination.
ARE (All Routes Explorer) packets are sent
to the destination station if the sending
station does not receive a response to a test
packet.
Source Route Indicates that the bridge forwards packets so
Transparent/STE they know the route and the devices they
pass through to reach their destination.
STE (Spanning Tree Explorer) packets are
sent to the destination station if the sending
station does not receive a response to a test
packet.
Source Route/ARE Indicates that the bridge forwards packets
so they do not know the route or the
devices they pass through to reach their
destination. ARE (All Routes Explorer)
2-68 Using the Token Ring Bridge and Port Configuration Windows
Page 87

WARNING
Bridging
packets are sent to the destination station if
the sending station does not receive a
response to a test packet.
Source Route/STE Indicates that the bridge forwards packets so
they do not know the route or the devices
they pass through to reach their destination.
STE (Spanning Tree Explorer) packets are
sent to the destination station if the sending
station does not receive a response to a test
packet.
Transparent/Transparent Indicates that the two network segments are
connected so that a single data route exists
between any two end stations. Explorer
frames have no embedded routing
information
If the ports on the selected bridge have different conÞgurations, none of these options are
selected. Do not select any of these options unless you want to set all ports on the selected
bridge to a single mode.
To set the Bridge number or the Virtual Ring Number in the Bridge ConÞguration
window:
1. Click in the Bridge Number or the Virtual Ring Number field in the upper
portion of the Bridge Configuration window. Enter a hexadecimal value
between 0 and F in the Bridge Number field, or a hexadecimal value between
001 and FFF in the Virtual Ring Number field.
2. Click on Set to apply the change, or click on Cancel to e xit the window without
applying the change.
To set the Ring Number in the Port ConÞguration window:
1. Click in the Ring Number field in the upper portion of the Port Configuration
window. Enter a hexadecimal value between 001 and FFF.
2. Click on Set to apply the change, or click on Cancel to e xit the window without
applying the change.
To set the Port Mode, Novell Translation, or Ring Speed globally for all bridge
interfaces on a device in the Bridge ConÞguration window or for an individual
interface in the Port ConÞguration window:
1. Click on the empty option button adjacent to one of the choices in the selected
field. When the option button is filled ( ), the selected choice will be enabled.
2. Click on Set to apply the change, or click on Cancel to e xit the window without
applying the change.
Using the Token Ring Bridge and Port Configuration Windows 2-69
Page 88

Bridging
To select the Bridge Mode/Explorer Type globally for all bridge interfaces on a
device in the Bridge ConÞguration window or for an individual interface in the
Port ConÞguration window:
1. Click in the Bridge Mode/Explorer Type pull-down list box. Select one of the
available choices: Source Route Transparent/Transparent, Source Route
Transparent/ARE, Source Route Transparent/STE, Source Route/ARE,
Source Route/STE, and Transparent/Transparent. The default selection is
Transparent/Transparent.
2. Click on Set to apply the change, or click on Cancel to e xit the window without
applying the change.
Duplex Modes
Some of the bridge interfaces on a device will support Full Duplex Switched
Ethernet (FDSE) mode. Enabling full duplex mode on an interface allows the
interface to receive and transmit packets at the same time, effectively doubling the
available bandwidth.
WARNING
On an Ethernet connection that is not using full duplex mode, the interface can
either transmit or receive packets. The interface has to wait for one activity to be
completed before switching to the next activity (receive or transmit).
Using the full duplex mode allows for faster transmission of packets over
Ethernet connections because the bridging interface can transmit and receive
packets; the interface does not have to wait for one activity to be completed before
switching to the next one.
Full Duplex should only be enabled on an interface that has a connection to a single
destination address at the other end of the connection (i.e., it is not a segment with an
attached repeater cascading the connection to multiple destination addresses).
Full Duplex mode disables the collision detection circuitry at the interface, so that both
Transmit and Receive wires can be used simultaneously. With a single destination address
at the other end of the connection (for example, if the connection was to a full duplex
interface on another switching module, or if a single Þle server was connected to the full
duplex switch port), this essentially doubles the available bandwidth from 10 Mbit/sec to
20 Mbit/sec. Note that the interface at the other end of the connection must also have Full
Duplex enabled at the attached interface.
Full Duplex mode must be disabled if the interface is communicating with multiple
destinations simultaneously (i.e., if a repeater is cascaded from the interface), since
Ethernet relies on Collision Sense for proper operation.
2-70 Duplex Modes
Page 89

Bridging
The Duplex Modes Window
The bridge-level Duplex Modes window allows you to enable and disable full
duplex mode capability for each bridging interface on your device. The window
lists each interface on the device and whether full duplex is ÒONÓ or ÒOFFÓ for
each interface.
To access the Duplex Modes window from the Bridge Status window:
1. Click on Bridge to display the Bridge menu.
2. Click on Duplex Modes. The Duplex Modes window, Figure 2-22, will appear.
To access the Duplex Modes window from the Chassis View window:
1. Click on the Board Index of the device of interest; the Board menu will
appear.
2. Click on Duplex Modes. The Duplex Modes window, Figure 2-22, will appear.
Figure 2-22. Duplex Modes Window
The following information is displayed in the Duplex Modes window:
Interface
Lists the bridging interfaces available on the device (Interface 1, Interface 2, and
so on).
Full Duplex
Displays the current state of full duplex on each interface. Possible values for this
Þeld are as follows:
Connect A Indicates that the interface is connected to MMAC
Channel A and does not support full duplex mode
(Interface 1 only). You will not be able to change the
value of this Þeld from this window.
Duplex Modes 2-71
Page 90

Bridging
ON Indicates that full duplex mode is being used on this
OFF Indicates that full duplex mode is not being used on this
N/A Indicates that full duplex mode is not available on this
Setting the Duplex Mode
You set an interface to use or not use Full Duplex Switched Ethernet by turning
the full duplex capability ON or OFF from this window.
To turn the full duplex mode ON or OFF:
1. In the Duplex Modes window, highlight the interface you want to change.
2. Double-click on the highlighted interface. The interface list will be briefly
grayed-out as the set is being made to the device.
If the set is successful, the interface list will reactivate and the Full Duplex:
indicator will switch from ON to OFF or OFF to ON.
interface.
interface.
interface.
If you attempt to set an interface to full duple x mode that does not support this
feature, you will receive a “Set Failed” error message.
3. Click on Cancel to close the window.
Because full duplex conÞguration takes place as you set each change individually, any
NOTE
changes that have been completed up to the point of clicking on Cancel will have been set
at the device. Make sure that you have undone any unwanted changes before exiting the
window.
Ethernet Port Configuration
You can also conÞgure duplex modes from the Port ConÞguration window.
To access the Port ConÞguration window from the Bridge Status window:
1. Click on the desired Port button ( ) to display the Port menu.
2. Click on Configuration. The Port Configuration window for the selected
Ethernet interface, Figure 2-23, will appear.
To access the Port ConÞguration window from the Chassis View window:
1. Click on the appropriate port index to access the Port menu.
2. Click on Configuration. The Port Configuration window for the selected
Ethernet interface, Figure 2-23, will appear.
2-72 Duplex Modes
Page 91

Bridging
Figure 2-23. Port ConÞguration Window
This window will indicate which mode is being used on the interface, standard
mode or full duplex mode.
Standard Mode
Standard mode is being used on this interface. In standard mode, the interface can
transmit or receive packets. The interface has to wait for one activity to be
completed before switching to the next activity (receive or transmit).
Full Duplex
Full duplex mode is being used on this interface. In full duplex mode, the
interface receives and transmits packets at the same time.
You set an interface to use standard or full duplex by selecting the appropriate
mode from this window. When you open the Port ConÞguration window the
currently used mode appears selected.
To change the mode from standard to full duplex mode or from full duplex to
standard mode, click in the option button of the appropriate option and then click
on Apply. To cancel the action without applying any changes, click on Cancel.
Fast Ethernet Port Configuration
You can use the port-level Fast Ethernet ConÞguration window to manually
conÞgure 100Base-TX Fast Ethernet ports and FE100-TX Fast Ethernet Interface
Modules (FEPIMs) for 10Base-T and 100Base-TX full or half duplex operation.
You can also conÞgure them to auto-negotiate with the device at the other end of
the connection, based upon each deviceÕs Advertised and Remote Capabilities.
If you are monitoring a device with 100Base-FX Fast Ethernet ports, you can use
the Fast Ethernet ConÞguration window to manually conÞgure them to full or
half duplex operation. No auto-negotiation is available for the 100Base-FX ports,
and by extension, no Advertised or Remote capabilities.
Duplex Modes 2-73
Page 92

Bridging
From this window you can manually set the operational mode of the port,
determining the speed of the port (10 Mbps or 100 Mbps), and whether it uses full
duplex or standard mode bridging.
You can also set a 100Base-TX port to auto-negotiation so that the appropriate
operational mode can be determined automatically (using the Advertised
Abilities of the local interface that you determine, and the Remote Capabilities of
the Remote Link). The mode you set will determine the speed of the port and
whether it uses full duplex or standard mode bridging.
To access the Fast Ethernet ConÞguration window from the Bridge Status
window:
1. Click on the desired Port button ( ) to display the Port menu.
2. Click on Configuration. The Fast Ethernet Configuration Port X window
(where X represents the port number of the selected interface), Figure 2-24,
will appear.
To access the Fast Ethernet ConÞguration window from the Chassis View window:
1. Click on the appropriate port index to access the Port menu.
2. Click on Configuration. The Fast Ethernet Configuration Port X window
(where X represents the port number of the selected interface), Figure 2-24,
will appear.
Figure 2-24. Fast Ethernet ConÞguration Port X Window
From this window you can manually set the operational mode of the port, orÑfor
100Base-TX interfacesÑset the port to auto-negotiation so that the appropriate
operational mode can be determined automatically. The mode you set will
2-74 Duplex Modes
Page 93

Bridging
determine the speed of the port and whether it uses full duplex or standard mode
bridging.
The following information about the selected Fast Ethernet port is displayed:
Port T ype
Displays the type of Fast Ethernet port for example, FE-100TX or FE-100FX.
Link State
Displays the connection status of the selected port: Link or No Link.
Current Operational Mode
Displays the mode that the port is operating in at the present time. Possible
operational modes include 10Base-T, 10Base-T Full Duplex, 100Base-TX,
100Base-TX Full Duplex, 100Base-FX or 100Base-FX Full Duplex.
If no current operational mode is returned, it indicates the port is operating under
auto-negotiation.
Desired Operational Mode
Displays the operational mode that you want to conÞgure for this port. The
following operational modes are available for each port:
FE-100TX Auto-Negotiation, 10Base-T, 10Base-T Full Duplex,
100Base-TX, and 100Base-TX Full Duplex.
FE-100FX 100Base-FX and 100Base-FX Full Duplex
See Setting the Operational Mode for the FE-100TX, page 2-76, and Setting the
Operational Mode for the FE-100FX, page 2-77, for details.
Advertised Abilities
This Þeld works in conjunction with auto-negotiation on FE-100TX ports. During
auto-negotiation, the local hardware will advertise all selected modes in
descending bandwidth order: 100Base-TX Full Duplex, 100Base-TX, 10Base-T Full
Duplex, and 10Base-T.
Of the selected abilities, the highest mode available on the port on the other side
of the connection will automatically be used. The Advertised Abilities will only be
used when auto-negotiation is enabled.
Remote Capabilities
This Þeld displays the advertised abilities of the remote hardware at the other end
of the link from the FE-100TX port. Again, possible advertised abilities by the
remote partner include 10Base-T, 10Base-T Full Duplex, 100Base-TX, or
100Base-TX Full Duplex.
If auto-negotiation is not enabled or supported at either the local or remote
interface, or if there is no active link, all entries in this Þeld will be grayed out.
Duplex Modes 2-75
Page 94

Bridging
Auto-negotiation is not available on the FE-100FX; therefore, the Advertised Abilities
NOTE
!
CAUTION
Setting the Operational Mode for the FE-100TX
and Remote Capabilities section of the Fast Ethernet ConÞguration window will be
grayed out when you are viewing the port conÞguration of an FE-100FX.
If you choose to select a speciÞc mode of operation (rather than auto-negotiation), you
should be sure that the link partner supports the same mode. Otherwise, no link will be
achieved.
If you select a full duplex mode and the link partner supports the same wire speed but not
full duplex, a link will be achieved, but it will be unstable and will behave erratically.
If you select auto-negotiation, the local node will try to match the mode of the link partner,
even if the link partner is not set to auto-negotiate, and even if the local node must use a
mode which it is not currently advertising.
You can manually set the FE-100TX to use any one of four operational modes. You
can also set the port to auto-negotiation, which allows the port to determine for
itself the best operational mode using the Advertised Abilities and Remote
Capabilities of the local and remote interface, respectively.
If you want to manually conÞgure the mode:
1. Click on the Desired Operational Mode list-box, and select one of the
following modes:
10Base-T—10 Mbps connection, Standard Mode
10Base-T Full Duplex—10 Mbps connection, Duplex Mode
100Base-TX—100 Mbps connection, Standard Mode
100Base-TX Full Duplex—100 Mbps connection, Duplex Mode
2. Click on Apply. The mode that you have chosen will be set at the port.
If you want the port to use auto-negotiation:
1. Click on the Desired Operational Mode list-box and select Auto
Negotiation.
2. Click in the Advertised Abilities check boxes to select either 10Base-T,
10Base-T Full Duplex, 100Base-TX, or 100Base-TX Full Duplex.
3. Click on Apply.
2-76 Duplex Modes
Page 95

When an active link is established, the operational mode will be dynamically
set based on the modes selected in the Advertised Abilities field and the
speeds and modes supported by the attached device; see the definition for
Advertised Abilities on page 2-75.
Setting the Operational Mode for the FE-100FX
You can manually set the FE-100FX to use either of two operational modes:
1. Click on the Desired Operational Mode list-box, and select one of the
following modes:
• 100Base-FX—100 Mbps connection, Standard Mode
• 100Base-FX Full Duplex—100 Mbps connection, Duplex Mode
2. Click on Apply. The mode that you have chosen will be set at the port.
SONET Port Configuration
Bridging
The FE100-Sx series of Fast Ethernet Port Interface Modules, and the APIM-2x
series of ATM Port Interface Modules provide SONET (Synchronous Optical
Network) access for some of CabletronÕs devices. SONET interfaces link
high-speed local or metropolitan area networks by using an OC-3 connection
(leased from your local telco or Internet service provider) to a SONET ring.
If your device is equipped with an FE100-Sx or an APIM-2x port interface
module, you can use the SONET/SDH ConÞguration window to set its operating
parameters, and the SONET/SDH Statistics window to view performance
information for the interface (which can tell you if your telco/service provider is
meeting any guarantees regarding network reliability).
SONET/SDH Configuration
The SONET/SDH ConÞguration window lets you determine whether your
FE-100Sx or APIM-2x port interface module will operate according to SONET or
SDH (Synchronous Digital Hierarchy) standards.
SONET is the ANSI (American National Standards Institute) standard for the
optical transport of data according to the transmission standards in effect in
North America (United States/Canada), Korea, Taiwan, and Hong Kong.
ANSI sets industry standards in the U.S. for the telecommunications industry,
among other industries.
The basic SONET building block signal (transmitted at 51.84 Mbps) is referred to
as STS-1 (Synchronous Transport Signal Level 1). SONET can multiplex (or
combine) STS-1 signals into STS-N signals, where N is some integer multiple of
STS-1 signals.
SONET Port Configuration 2-77
Page 96

Bridging
The ITU, or International Telecommunications Union (formerly known as the
CCITTÑthe Consultative Committee on International Telegraph and Telephone)
incorporated the SONET standard into its Synchronous Digital Hierarchy (SDH)
recommendations, which address differences between the European and North
American transmission standards. The ITU sets standards for international
communications (except for nations adhering to ANSI standards). SDH is a world
standard, and as such, the SONET standard is considered a subset within it.
The SDH transmission hierarchy uses the STM-1 (Synchronous Transfer Module
Level 1) as its basic building block signal (transmitted at 155.52 Mbps). Again,
there are STM-N signals, which are STM-1 signals that have been multiplexed into
a higher signaling rate.
Table 2-1. SONET/SDH Transmission Hierarchies
SONET Bit Rate SDH
STS-1/OC-1 51.84 Mbps Ñ
STS-3/OC-3 (supports
FE-100Sx and APIM-2x
in SONET operational
mode)
STS-12/OC-12 622.08 Mbps STM-4
STS-24/OC-24 1244.16 Mbps Ñ
STS-48/OC-48 2588.32 Mbps STM-16
STS-192/OC-192 9953.28 Mbps STM-64
You should be sure that the operational mode for both the local and remote ends
of the SONET connection is set appropriately for your region. Setting the wrong
operational mode may cause errors to be generated during transmission, since
there are slight differences in framing SONET and SDH signals.
To access the SONET/SDH ConÞguration window from the Bridge Status
window:
1. Click on the desired Port button ( ) to display the Port menu.
2. Click on SONET/SDH Configuration. The SONET/SDH Configuration: P ort X
window , Figure 2-25, will appear.
To access the SONET/SDH ConÞguration window from the Chassis View
window:
155.52 Mbps STM-1 (supports
FE-100Sx and APIM-2x
in SDH operational
mode)
1. Click on the appropriate port index to access the Port menu.
2. Click on SONET/SDH Configuration. The SONET/SDH Configuration: P ort X
window , Figure 2-25, will appear.
2-78 SONET Port Configuration
Page 97

Bridging
Figure 2-25. SONET/SDH ConÞguration Window
To set the operational mode of the SONET port via the SONET/SDH
ConÞguration window:
1. Click on the option button adjacent to the appropriate selection, SONET or
SDH, to choose the data transmission standard to be used by the interface.
2. Click on Apply to set your change at the interface, or Cancel to exit the
SONET/SDH Configuration window without applying any changes.
SONET/SDH Statistics
SONET/SDH statistics are available for each FE100-Sx, APIM-2x, or other SONET
port interface modules installed in your device. The same statistics apply whether
you have conÞgured the interface to operate according to SONET or SDH
transmission standards.
The FE100-Sx and the APIM-2x port interface modules are SONET
path-terminating equipment (PTE). They act as an endpoint of an end-to-end
connection between themselves and another similar port interface module. As
endpoints, they are capable of generating and receiving the Path Overhead
information contained within the SPE (Synchronous Payload Envelope) of the
base-level SONET or SDH signals. Simply put, overhead is the extra bits in the
digital stream that relay information besides trafÞc signals.
The Path Overhead provides for end-to-end performance monitoring of the link,
the signal label (the content of the SPE, including status of mapped payloads), the
pathÕs current status, and path trace capabilities.
The SONET/SDH Statistics window enables you to view some of the error
information contained within the Path Overhead that your FE100-Sx or APIM-2x
is receiving from the remote endpoint.
The window will inform you whether there have been speciÞc defects
experienced on the SONET link, and if the network has experienced any
signiÞcant unavailability time as a result.
SONET Port Configuration 2-79
Page 98

Bridging
With a SONET link, there are three levels of error conditionsÑanomalies, defects,
and failures.
¥ Anomalies are small discrepancies between a desired and actual characteristic
of an item, which when occurring singly will not interrupt the ability of the
SONET network elements to perform their required functions.
¥ Defects indicate that anomalies have reached a level where the ability of the
SONET network elements to perform their required functions has been
interrupted. Defects are used in performance monitoring and in determining
the faultÕs cause, and have impact on consequent actions on the network.
¥ Failures indicate that a network element has been unable to perform its
required functions beyond a maximum time allocated to a given error
condition.
These errors can occur in any of the four optical layers of a SONET network,
which are (in order from lowest to highest layer in the hierarchy) the physical
Medium, Section, Line, and Path layers.
¥ The Medium layer is the Photonic layer that physically converts electrical
signals to optical signals.
¥ The Section layer deals with the transport of frames across the optical
medium, including framing and scrambling data for transmission, the error
monitoring and maintenance between section-layer elements (such as signal
regenerators/repeaters), and orderwire (provisioning channels).
¥ The Line layer is responsible for reliably transporting the higher-level Path
layer payload and overhead across the physical medium. It is responsible for
synchronizing (clocking) the data transmission, multiplexing signals into a
single channel, error monitoring and maintenance between line-layer
elements (such as Add/Drop Multiplexers), and switching to secondary data
paths should the primary path experience failure.
¥ The Path layer transports services between path-terminating equipment.
It maps signals into a format required by the line layer, and reads, interprets,
and modiÞes path overhead for performance monitoring and automatic
protection switching.
Error reporting occurs at the Section, Line, and Path layers, and is carried within
the corresponding SONET overhead. In terms of the SONET protocol stack, the
three layers with overhead are mapped to the SONET link as shown in the
following diagram.
2-80 SONET Port Configuration
Page 99

Bridging
The statistics and errors indicators provided in the SONET/SDH statistics
window are taken from both the end-to-end Path layer, and from the Section layer
between the FE100-Sx or APIM-2x and the Add/Drop Multiplexer to which it is
connected. They reßect errors that may be occurring on your customer premises
equipment, as well as errors that may be occurring at the Line or Section layers
within the SONET MAN/WAN ring itself.
Path-
Terminating
Equipment—
(FE100-Sx
or APIM-2x)
OC-3c
link
Line-
Terminating
Equipment—
T elco/SP ADM
(Add/Drop
Multiplexer)
Regenerators
Section
Line-
T erminating
Equipment—
T elco/SP ADM
(Add/Drop
Multiplexer)
OC-3c
link
T erminating
Equipment—
(FE100-Sx
or APIM-2x)
Line
Path
To access the SONET/SDH Statistics window from the Bridge Status window:
1. Click on the desired Port button ( ) to display the Port menu.
2. Click on SONET/SDH Statistics. The SONET/SDH Statistics window for that
interface, Figure 2-26, will appear.
To access the SONET/SDH Statistics window from the Chassis View window:
1. Click on the appropriate port index to access the Port menu.
2. Click on SONET/SDH Statistics. The SONET/SDH Statistics window for that
interface, Figure 2-26, will appear.
Path-
Figure 2-26. The SONET/SDH Statistics Window
SONET Port Configuration 2-81
Page 100

Bridging
Errors
The Errors indicators at the bottom of the SONET/SDH Statistics window show
the status of the SONET link as reported by the monitored interface, by indicating
whether the link has experienced Loss of Pointer, Loss of Signal, or Loss of
Frame defects or failures during the current 15-minute interval.
Note that Loss of Pointer is detected at the Path level on the SONET link, meaning
that the error occurred anywhere on the end-to-end link between the connected
FE100-Sx or APIM-2x devices that are customer premises equipment (CPE); Loss
of Signal and Loss of Frame are detected at the Section level, meaning that the
error occurred on the SONET section between the monitored CPE device and the
ADM node (line-terminating equipmentÑLTE) to which it is connected.
Note also that these indicators simply show which error conditions have been
detected during the last 15-minute interval; they do not alter the display of the
statistics above.
¥ Loss of PointerÑSONET uses ÒpointersÓ to compensate for frequency and
phase variations as data is being transmitted across the optical network, so that
data is not delayed or lost on the network. Basically, a pointer is a data offset
value that indicates where in the frame that the ÒpayloadÓ (user data and path
overhead) begins, so that it can be differentiated from the Òtransport
overheadÓ (the information in the frame used for transporting it across the
SONET network).
A Loss of Pointer (LOP) defect occurs when either a valid pointer is not
detected in eight consecutive SONET STS-N frames, or when eight
consecutive frames are detected with the New Data Flag (NDF) set without
being validly combined into an STS-N(c)Ña concatenated STS-N signalÑto
carry a larger payload.
An LOP defect is cleared when three consecutive frames are detected with
either a valid pointer and a normal NDF, or a valid concatenation indicator.
Note that incoming Alarm Indicator Signals (which are alarm messages
generated by the line and section layers that are propagated along the path to
indicate a loss of signal condition on upstream network elements) cannot
contribute to an LOP defect.
A Loss of Pointer failure is declared when a defect condition persists for a
period of 2 to 3 seconds; the LOP failure is cleared when there is no defect
condition detected for 9.5 to 10.5 seconds
¥ Loss of SignalÑIncoming SONET signals are monitored for Loss of Signal
(LOS) errors, which indicate a loss of physical signal failure (either optical or
electrical) at the source (e.g., a laser failure) or in the transmission facility (e.g.,
a Þber cut). Loss of signal is detected in the data (before scrambling) by an Òall
zerosÓ pattern, which indicates that there are no light pulses for OC-N optical
interfaces (on the line-terminating equipment or a regenerator), or no voltage
transitions for STS-1 or STS-3 electrical interfaces (on path-terminating
equipment, such as the FE100-Sx or APIM-2x).
A state of no transitions that lasts 2.3 µs (microseconds) or less is insigniÞcant.
2-82 SONET Port Configuration
 Loading...
Loading...