
NI-3101-SIG Operation/Reference Guide
Operation/Reference Guide
NI-3101-SIG
Signature Series NetLinx
Integrated Controller
Central Controllers
Last Revised: 9/13/2011

AMX Limited Warranty and Disclaimer
This Limited Warranty and Disclaimer extends only to products purchased directly from AMX or an AMX Authorized Partner which
include AMX Dealers, Distributors, VIP’s or other AMX authorized entity.
AMX warrants its products to be free of defects in material and workmanship under normal use for three (3) years from the date of
purchase, with the following exceptions:
• Electroluminescent and LCD Control Panels are warranted for three (3) years, except for the display and touch overlay components are warranted for a period of one (1) year.
• Disk drive mechanisms, pan/tilt heads, power supplies, and MX Series products are warranted for a period of one (1) year.
• AMX lighting products are guaranteed to switch on and off any load that is properly connected to our lighting products, as long
as the AMX lighting products are under warranty. AMX also guarantees the control of dimmable loads that are properly connected to our lighting products. The dimming performance or quality there of is not guaranteed, impart due to the random combinations of dimmers, lamps and ballasts or transformers.
• AMX software is warranted for a period of ninety (90) days.
• Batteries and incandescent lamps are not covered under the warranty.
• AMX AutoPatch Epica, Modula, Modula Series4, Modula CatPro Series and 8Y-3000 product models will be free of defects in
materials and manufacture at the time of sale and will remain in good working order for a period of three (3) years following the
date of the original sales invoice from AMX. The three-year warranty period will be extended to the life of the product (Limited
Lifetime Warranty) if the warranty card is filled out by the dealer and/or end user and returned to AMX so that AMX receives it
within thirty (30) days of the installation of equipment but no later than six (6) months from original AMX sales invoice date. The
life of the product extends until five (5) years after AMX ceases manufacturing the product model. The Limited Lifetime Warranty
applies to products in their original installation only. If a product is moved to a different installation, the Limited Lifetime Warranty
will no longer apply, and the product warranty will instead be the three (3) year Limited Warranty.
All products returned to AMX require a Return Material Authorization (RMA) number. The RMA number is obtained from the AMX
RMA Department. The RMA number must be clearly marked on the outside of each box. The RMA is valid for a 30-day period. After
the 30-day period the RMA will be cancelled. Any shipments received not consistent with the RMA, or after the RMA is cancelled, will
be refused. AMX is not responsible for products returned without a valid RMA number.
AMX is not liable for any damages caused by its products or for the failure of its products to perform. This includes any lost profits, lost
savings, incidental damages, or consequential damages. AMX is not liable for any claim made by a third party or by an AMX Authorized Partner for a third party.
This Limited Warranty does not apply to (a) any AMX product that has been modified, altered or repaired by an unauthorized agent or
improperly transported, stored, installed, used, or maintained; (b) damage caused by acts of nature, including flood, erosion, or earthquake; (c) damage caused by a sustained low or high voltage situation or by a low or high voltage disturbance, including brownouts,
sags, spikes, or power outages; or (d) damage caused by war, vandalism, theft, depletion, or obsolescence.
This limitation of liability applies whether damages are sought, or a claim is made, under this warranty or as a tort claim (including
negligence and strict product liability), a contract claim, or any other claim. This limitation of liability cannot be waived or amended by
any person. This limitation of liability will be effective even if AMX or an authorized representative of AMX has been advised of the
possibility of any such damages. This limitation of liability, however, will not apply to claims for personal injury.
Some states do not allow a limitation of how long an implied warranty last. Some states do not allow the limitation or exclusion of incidental or consequential damages for consumer products. In such states, the limitation or exclusion of the Limited Warranty may not
apply. This Limited Warranty gives the owner specific legal rights. The owner may also have other rights that vary from state to state.
The owner is advised to consult applicable state laws for full determination of rights.
EXCEPT AS EXPRESSLY SET FORTH IN THIS WARRANTY, AMX MAKES NO OTHER WARRANTIES, EXPRESSED OR
IMPLIED, INCLUDING ANY IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. AMX
EXPRESSLY DISCLAIMS ALL WARRANTIES NOT STATED IN THIS LIMITED WARRANTY. ANY IMPLIED WARRANTIES THAT
MAY BE IMPOSED BY LAW ARE LIMITED TO THE TERMS OF THIS LIMITED WARRANTY. EXCEPT AS OTHERWISE LIMITED
BY APPLICABLE LAW, AMX RESERVES THE RIGHT TO MODIFY OR DISCONTINUE DESIGNS, SPECIFICATIONS, WARRANTIES, PRICES, AND POLICIES WITHOUT NOTICE.

AMX Software License and Warranty Agreement
• LICENSE GRANT. AMX grants to Licensee the non-exclusive right to use the AMX Software in the manner described in this
License. The AMX Software is licensed, not sold. This license does not grant Licensee the right to create derivative works of the
AMX Software. The AMX Software consists of generally available programming and development software, product documentation, sample applications, tools and utilities, and miscellaneous technical information. Please refer to the README.TXT file on
the compact disc or download for further information regarding the components of the AMX Software. The AMX Software is subject to restrictions on distribution described in this License Agreement. AMX Dealer, Distributor, VIP or other AMX authorized
entity shall not, and shall not permit any other person to, disclose, display, loan, publish, transfer (whether by sale, assignment,
exchange, gift, operation of law or otherwise), license, sublicense, copy, or otherwise disseminate the AMX Software. Licensee
may not reverse engineer, decompile, or disassemble the AMX Software.
• ACKNOWLEDGEMENT. You hereby acknowledge that you are an authorized AMX dealer, distributor, VIP or other AMX authorized entity in good standing and have the right to enter into and be bound by the terms of this Agreement.
• INTELLECTUAL PROPERTY. The AMX Software is owned by AMX and is protected by United States copyright laws, patent
laws, international treaty provisions, and/or state of Texas trade secret laws. Licensee may make copies of the AMX Software
solely for backup or archival purposes. Licensee may not copy the written materials accompanying the AMX Software.
• TERMINATION. AMX RESERVES THE RIGHT, IN ITS SOLE DISCRETION, TO TERMINATE THIS LICENSE FOR ANY REASON UPON WRITTEN NOTICE TO LICENSEE. In the event that AMX terminates this License, the Licensee shall return or
destroy all originals and copies of the AMX Software to AMX and certify in writing that all originals and copies have been
returned or destroyed.
• PRE-RELEASE CODE. Portions of the AMX Software may, from time to time, as identified in the AMX Software, include PRERELEASE CODE and such code may not be at the level of performance, compatibility and functionality of the GA code. The
PRE-RELEASE CODE may not operate correctly and may be substantially modified prior to final release or certain features may
not be generally released. AMX is not obligated to make or support any PRE-RELEASE CODE. ALL PRE-RELEASE CODE IS
PROVIDED "AS IS" WITH NO WARRANTIES.
• LIMITED WARRANTY. AMX warrants that the AMX Software (other than pre-release code) will perform substantially in accordance with the accompanying written materials for a period of ninety (90) days from the date of receipt. AMX DISCLAIMS ALL
OTHER WARRANTIES, EITHER EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE, WITH REGARD TO THE AMX SOFTWARE. THIS LIMITED WARRANTY GIVES LICENSEE SPECIFIC LEGAL RIGHTS. Any supplements or updates to the AMX SOFTWARE,
including without limitation, any (if any) service packs or hot fixes provided to Licensee after the expiration of the ninety (90) day
Limited Warranty period are not covered by any warranty or condition, express, implied or statutory.
• LICENSEE REMEDIES. AMX's entire liability and Licensee's exclusive remedy shall be repair or replacement of the AMX Software that does not meet AMX's Limited Warranty and which is returned to AMX in accordance with AMX's current return policy.
This Limited Warranty is void if failure of the AMX Software has resulted from accident, abuse, or misapplication. Any replacement AMX Software will be warranted for the remainder of the original warranty period or thirty (30) days, whichever is longer.
Outside the United States, these remedies may not available. NO LIABILITY FOR CONSEQUENTIAL DAMAGES. IN NO
EVENT SHALL AMX BE LIABLE FOR ANY DAMAGES WHATSOEVER (INCLUDING, WITHOUT LIMITATION, DAMAGES
FOR LOSS OF BUSINESS PROFITS, BUSINESS INTERRUPTION, LOSS OF BUSINESS INFORMATION, OR ANY OTHER
PECUNIARY LOSS) ARISING OUT OF THE USE OF OR INABILITY TO USE THIS AMX SOFTWARE, EVEN IF AMX HAS
BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. BECAUSE SOME STATES/COUNTRIES DO NOT ALLOW
THE EXCLUSION OR LIMITATION OF LIABILITY FOR CONSEQUENTIAL OR INCIDENTAL DAMAGES, THE ABOVE LIMITATION MAY NOT APPLY TO LICENSEE.
• U.S. GOVERNMENT RESTRICTED RIGHTS. The AMX Software is provided with RESTRICTED RIGHTS. Use, duplication, or
disclosure by the Government is subject to restrictions as set forth in subparagraph ©(1)(ii) of The Rights in Technical Data and
Computer Software clause at DFARS 252.227-7013 or subparagraphs ©(1) and (2) of the Commercial Computer Software
Restricted Rights at 48 CFR 52.227-19, as applicable.
• SOFTWARE AND OTHER MATERIALS FROM AMX.COM MAY BE SUBJECT TO EXPORT CONTROL. The United States
Export Control laws prohibit the export of certain technical data and software to certain territories. No software from this Site may
be downloaded or exported (i) into (or to a national or resident of) Cuba, Iraq, Libya, North Korea, Iran, Syria, or any other country to which the United States has embargoed goods; or (ii) anyone on the United States Treasury Department's list of Specially
Designated Nationals or the U.S. Commerce Department's Table of Deny Orders. AMX does not authorize the downloading or
exporting of any software or technical data from this site to any jurisdiction prohibited by the United States Export Laws.
This Agreement replaces and supersedes all previous AMX Software License Agreements and is governed by the laws of
the State of Texas, and all disputes will be resolved in the courts in Collin County, Texas, USA. For any questions concerning this Agreement, or to contact AMX for any reason, please write: AMX License and Warranty Department, 3000 Research
Drive, Richardson, TX 75082.


Table of Contents
i
NI-3101-SIG Signature Series NetLinx Integrated Controller
Table of Contents
Introduction ........................................................................................................1
NI-3101-SIG Specifications........................................................................................ 2
Installation and Upgrading .................................................................................5
Device:Port:System (D:P:S) ....................................................................................... 5
Installation into an Equipment Rack.......................................................................... 5
Connections and Wiring .....................................................................................7
Setting the Configuration DIP Switch for the Configuration Port ............................. 7
Program Run Disable (PRD) mode................................................................................... 7
Working with the Configuration DIP switch .................................................................... 7
Configuration Port Connections and Wiring ............................................................. 7
Modes and Front Panel LED Blink Patterns .............................................................. 8
Port Assignments and Functionality.......................................................................... 8
AXlink Port and LED ................................................................................................. 8
Wiring Guidelines ..................................................................................................... 9
Wiring length guidelines ................................................................................................. 9
Preparing captive wires................................................................................................... 9
Wiring a power connection ............................................................................................. 9
Using the 4-pin mini-Phoenix connector for data and power ........................................ 10
Using the 4-pin mini-Phoenix connector for data with external power ......................... 10
DB9 Device Port: Connections and Wiring ............................................................. 11
Relay Port: Connections and Wiring ....................................................................... 11
Relay connections.......................................................................................................... 11
Input/Output (I/O) Port: Connections and Wiring ................................................... 12
IR/Serial Port: Connections and Wiring................................................................... 12
LAN (Ethernet/RJ-45 Port): Connections and Wiring .............................................. 13
LAN LEDs ..................................................................................................................... 14
LAN ports used by the Integrated Controllers .............................................................. 14
Replacing the Timekeeper Battery ......................................................................... 14
Configuration and Firmware Update ................................................................17
Overview ................................................................................................................ 17
Communicating with the Master via the Program Port........................................... 17
Setting the System Value........................................................................................ 18
Using Multiple NetLinx Masters .................................................................................... 20
Changing the Device Address of a NetLinx Device ................................................ 20
Recommended NetLinx Device Numbers...................................................................... 21
Using the ID Button to Change the Controller’s Device Value ............................... 21

ii
NI-3101-SIG Signature Series NetLinx Integrated Controller
Table of Contents
Resetting the Factory Default System and Device Values....................................... 22
Obtaining the Master’s IP Address (using DHCP) ................................................... 23
Assigning a Static IP to the NetLinx Master............................................................ 24
Communicating with the NI Device via an IP .......................................................... 26
Verifying the current version of NetLinx Master Firmware ..................................... 28
Upgrading the On-board Master Firmware via an IP .............................................. 29
Upgrading the NI Controller Firmware via IP.......................................................... 31
NetLinx Security within the Web Server ...........................................................33
NetLinx Security Terms ........................................................................................... 34
Accessing an Unsecured Master via an HTTP Address ............................................ 34
Browser Application Frames ................................................................................... 35
Default Security Configuration ............................................................................... 35
Master Firmware Security Access Parameters ........................................................ 37
Web Control ........................................................................................................... 37
Managing WebControl Connections.............................................................................. 37
Security Features .................................................................................................... 38
Security - System Level Security page ........................................................................... 39
Setting the system security options for a NetLinx Master............................................. 42
ICSP Authentication ...................................................................................................... 43
Security - Group Level Security page ............................................................................ 44
Adding a new Group ..................................................................................................... 46
Modifying the properties of an existing Group............................................................. 46
Deleting an existing Group ........................................................................................... 46
Security - User Level Security page ............................................................................... 47
Adding a new User ........................................................................................................ 49
Modifying the properties of an existing User................................................................ 50
Deleting an existing User .............................................................................................. 50
System Settings ...................................................................................................... 51
System Settings - Manage System page........................................................................ 51
Manage System - System Menu Buttons................................................................. 54
System Menu - Modifying the Date/Time ...................................................................... 54
System Menu - Changing the System Number .............................................................. 54
System Menu - Rebooting the Master ........................................................................... 55
System Menu - Controlling/Emulating Devices on the Master ...................................... 55
Manage System - Diagnostics........................................................................................ 57
Setting up and removing a Diagnostic Filter ................................................................. 58
Setting the Master’s Port Configurations ............................................................... 61
Manage System - Server................................................................................................ 61
Modifying the Server Port Settings ............................................................................... 62

Table of Contents
iii
NI-3101-SIG Signature Series NetLinx Integrated Controller
SSL Server Certificate Creation Procedures............................................................ 64
Server - Display SSL Server Certificate Information ...................................................... 66
Server - Creating a self-generated SSL Certificate ........................................................ 66
Server - Regenerating an SSL Server Certificate Request ............................................. 67
Server - Creating a Request for an SSL Certificate........................................................ 67
Common Steps for Requesting a Certificate from a CA.......................................... 68
Communicating with the CA ......................................................................................... 68
Server - Exporting an SSL Certificate Request .............................................................. 68
Server - Importing a CA created SSL Certificate ........................................................... 69
Manage System - Device Menu Buttons ................................................................. 71
Device Menu - Configuring the LAN Settings ............................................................... 71
Device Menu - Developing a URL List ........................................................................... 72
Device Menu - Changing the Device Number ............................................................... 73
Device Menu - Controlling or Emulating a device ......................................................... 74
Device Menu - Viewing the Log .................................................................................... 74
Device Menu - Running a Diagnostic Filter.................................................................... 74
System Settings - Manage License.......................................................................... 74
Adding a new license .................................................................................................... 75
Removing a license........................................................................................................ 76
System Settings - Manage NetLinx Devices............................................................ 76
Manage NetLinx Devices - Displaying NDP-capable devices......................................... 78
Manage NetLinx Devices - Binding/Unbinding - Explained ........................................... 78
Manage NetLinx Devices - Obtaining NetLinx Device information ............................... 79
System Settings - Manage Other Devices - Dynamic Device Discovery Pages........ 80
What is Dynamic Device Discovery? .............................................................................. 83
What is the difference between Program and Run-time defined binding? ................... 84
Manage Other Devices - Manage Device Bindings ................................................. 85
Configuring application-defined devices ....................................................................... 85
What are Application Devices and their association status? ......................................... 87
Manage Other Devices Menu - Viewing Discovered Devices ........................................ 88
Manage Other Devices Menu - Creating a new User-Defined Device ........................... 89
How do I write a program that uses Dynamic Device Discovery ................................... 90
How do I configure a Run-time installation ................................................................... 91
Accessing an SSL-Enabled Master via an IP Address .............................................. 92
Using your NetLinx Master to control the G4 panel...................................................... 95
What to do when a Certificate Expires ................................................................... 97
NetLinx Security with a Terminal Connection ...................................................99
Overview ................................................................................................................ 99
NetLinx Security Features....................................................................................... 99

iv
NI-3101-SIG Signature Series NetLinx Integrated Controller
Table of Contents
Initial Setup via a Terminal Connection................................................................... 99
Establishing a Terminal connection via the RS-232/USB Configuration Port ............... 100
Accessing the Security configuration options ....................................................... 100
Option 1 - Set system security options for NetLinx Master (Security Options Menu) . 101
Option 2 - Display system security options for NetLinx Master .................................. 102
Option 3 - Add user .................................................................................................... 103
Option 4 - Edit User .................................................................................................... 103
Edit User Menu............................................................................................................ 103
Access Rights Menu..................................................................................................... 104
Option 5 - Delete user................................................................................................. 105
Option 6 - Show the list of authorized users ............................................................... 105
Option 7 - Add Group ................................................................................................. 105
Edit Group Menu......................................................................................................... 105
Edit Group menu: Delete directory association........................................................... 106
Edit Group menu: List directory associations .............................................................. 107
Edit Group menu: Change Access Rights .................................................................... 107
Edit Group menu: Display Access Rights ..................................................................... 107
Option 8 - Edit Group ................................................................................................. 107
Option 9 - Delete Group ............................................................................................. 108
Option 10 - Show List of Authorized Groups .............................................................. 108
Option 11 - Set Telnet Timeout in seconds ................................................................. 108
Option 12 - Display Telnet Timeout in seconds ........................................................... 108
Option 13 - Make changes permanent by saving to flash ........................................... 108
Main Security Menu .............................................................................................. 109
Default Security Configuration ............................................................................. 110
Help menu ................................................................................................................... 111
Logging Into a Session.......................................................................................... 113
Logout .................................................................................................................. 113
Help Security ............................................................................................................... 113
Setup Security ............................................................................................................. 114
Programming ..................................................................................................115
Converting Axcess Code to NetLinx Code............................................................ 115
Master Send_Commands ...................................................................................... 115
Master IP Local Port Send_Commands ................................................................. 117
Using the ID Button .............................................................................................. 117
Device:Port:System (D:P:S).......................................................................................... 118
Configuration Port Commands ............................................................................. 118
ESC Pass Codes .................................................................................................... 131
Notes on Specific Telnet/Terminal Clients ............................................................ 131

Table of Contents
v
NI-3101-SIG Signature Series NetLinx Integrated Controller
WindowsTM client programs....................................................................................... 131
Linux Telnet client ....................................................................................................... 131
LED Disable/Enable Send_Commands .................................................................. 132
RS232/422/485 Ports Channels ............................................................................ 132
RS-232/422/485 Send_Commands ....................................................................... 132
RS-232/422/485 Send_String Escape Sequences.................................................. 135
IR / Serial Ports Channels ..................................................................................... 136
IR/Serial Send_Commands .................................................................................... 136
Input/Output Send_Commands ............................................................................ 142
Troubleshooting .............................................................................................143

vi
NI-3101-SIG Signature Series NetLinx Integrated Controller
Table of Contents

1
NI-3101-SIG Signature Series NetLinx Integrated Controller
Introduction
The NI-3101-SIG Signature Series NetLinx Integrated Controller satisfies the control and automation features
common in a larger area or multiple rooms, which may include the integration of a larger number of devices
including VCR and DVD players, projectors, lighting, thermostats and other electronic equipment. In
technology-driven environments, this solution allows for the future addition of more devices and control
capabilities.
The NI-3101-SIG features an easy-to-install form factor that mounts into 1 unit of rack space and provides
extended rack depth to simplify rear connections. Its sleek, gloss black faceplate complements the Tango
Distributed Audio line and Metreau Keypads. For smaller business and home applications, the NI-3101-SIG
includes just the right mix of ports and features.
NetLinx Integrated Master Controller Features
NI-3101-SIG
(FG2105-08)
The NI-3101-SIG is Duet-compatible and can be upgraded via firmware. Duet is a dual-interpreter firmware
platform from AMX which combines the proven reliability and power of NetLinx with the extensive
capabilities of the Java
includes third party devices by standardizing device and function definitions, defaulting touch panel button
assignments, and controlling feedback methods. Dynamic Device Discovery makes integration even easier by
automatically identifying and communicating with devices which support this new beaconing technology.
Refer to the System Settings - Manage Other Devices - Dynamic Device Discovery Pages section on page 80
for more detailed information on the use of Dynamic Device Discovery (DDD).
The NI-3101-SIG uses a combination lithium battery and clock crystal package called a Timekeeper. Only one
Tim ekeepe r unit is installed within a given NI-3101. The battery can be expected to have up to 3 years of
usable life under very adverse conditions. Actual life is appreciably longer under normal operating conditions.
This calculation is based on storing the unit without power in 50° C (120° F) temperature until battery levels
are no longer acceptable. The part number for a replacement battery is 57-0032.
RISK OF EXPLOSION IF BATTERY IS REPLACED WITH AN INCORRECT TYPE.
DISPOSE OF USED BATTERIES ACCORDING TO MANUFACTURER’S
INSTRUCTIONS.
Introduction
• 1 low-speed USB connection for configuration
• 6 RS-232/RS-422/RS-485 ports
• 8 IR/Serial Output ports
• 8 Digital Input/Output ports
•8 Relays
®
2 MicroEdition (J2ME) platform. Duet simplifies the programming of a system that

Introduction
2
NI-3101-SIG Signature Series NetLinx Integrated Controller
Link/Active-Status-I/O
RS-232/422/485
TX/RX LEDs
Relay LEDs
I/O LEDs
IR/Serial LEDs
Power
Front
RS-232/422/485
Ports (1-6)
Relays
(Port 8)
I/O
(Port 17)
IR/Serial
(Ports 9-16)
Configuration
switches
Programming
Port
ID
switch
LAN
10/100
Port
AXLink
Power
12 VDC
LED
AXLink
Port
Rear
NI-3101-SIG Specifications
The NI-3101-SIG (FIG. 1) provides support for 6 configurable RS-232/RS-422/RS-485 Ports, 8 IR/Serial
Output ports, 8 Digital Input/Output ports, and 8 Relays.
FIG. 1 NI-3101 NetLinx Integrated Controller (front view)
FIG. 2 NI-3101 front and rear panel connectors and components
NI-3101-SIG Specifications (Cont.)
Dimensions (HWD): • 2" (with feet) x 17" x 10" (5.1 cm x 43.2 cm x 26.35 cm)
• 1 RU (rack unit) high
Power Requirement: 900 mA @ 12 VDC
Memory: • 64 MB SDRAM
• 256 MB Flash
• 1 MB Non-volatile (NV) SRAM
Compact Flash: 128 MB Card (upgradeable) (refer to the Other AMX Equipment section for
Weight: 6.95 lbs (3.15 kg)
Enclosure: Metal with black matte finish and translucent polycarbonate faceplate
Certifications: • FCC Part 15 Class B
Front Panel Components:
POWER Blue LED bar lights when powered up
LINK/ACTIVE Blue LED blinks when the LAN cable is connected and an active link is
Status Blue LED blinks to indicate that the system is programmed and
more information)
•CE
• IEC 60950
established. This LED also blinks when receiving LAN data packets.
communicating properly.

Introduction
3
NI-3101-SIG Signature Series NetLinx Integrated Controller
NI-3101-SIG Specifications (Cont.)
Input/Output LEDs White Output LED blinks when the Controller transmits data, sets channels
RS-232/422/485 LEDs Six sets of blue and white LEDs light to indicate the rear serial Ports 1 - 6 are
Relay LEDs Eight blue LEDs light to indicate the rear relay channels 1 - 8 are active
IR/Serial LEDs Eight blue LEDs light to indicate the rear IR/Serial channels 1 - 8 are
I/O LEDs Eight white LEDs light when the rear I/O channels 1-8 are active
Rear Panel Connectors:
RS-232/422/485 (Ports 1 - 6) Six RS-232/422/485 control ports using DB9 (male) connectors with XON/
Relay (Port 8) Eight-channel single-pole single-throw relay ports.
Digital I/O (Port 17) Eight-channel binary I/O port for contact closure.
On/Off, sends data strings, etc. White Input LED blinks when it receives data
from button pushes, strings, commands, channel levels, etc.
transmitting or receiving RS-232, 422, or 485 data:
• TX LEDs (blue) light when transmitting data
• RX LEDs (white) light when receiving data
• LED activity reflects transmission and reception activity
(closed).
• These LEDs reflect the state of the relay on Port 8
• If the relay is engaged = LED On and if the relay is Off = LED Off
transmitting control data on Ports 9 - 16.
• LED indicator for each IR port remains lit for the length of time that IR/Serial
data is being generated.
• LED indicator for each I/O port reflects the state of that particular port.
XOFF (transmit on/transmit off), CTS/RTS (clear to send/ready to send), and
300-115,200 baud.
• Channel range = 1-255
• Channels 1-254 provide feedback
• Channel 255 (CTS Push channel): Reflects the state of the CTS Input if a
'CTSPSH' command was sent to the port
• Output data format for each port is selected via software
• Six DB9 connectors provide RS-232/422/485 termination
• Each relay is independently controlled.
• Supports up to 8 independent external relay devices
• Channel range = 1-8
• Each relay can switch up to 24 VDC or 28 VAC @ 1 A
• Two 8-pin 3.5 mm mini-Phoenix (female) connectors provide relay
termination
• Each input is capable of voltage sensing. Input format is software
selectable.
• Interactive power sensing for IR ports
• Channel range = 1-8
• All inputs are assigned to respective IR/Serial ports for "automatic" power
control through the use of software commands. Power control is provided
via commands such as: ’PON’, ’POF’, ’POD’, ’DELAY’, I/O Link etc.).
• Contact closure between GND and an I/O port is detected as a PUSH
• When used as voltage input - I/O port detects a low signal (0- 1.5 VDC) as a
PUSH and a high signal (3.5 - 5 VDC) as a RELEASE
• When used as an output - each I/O port acts as a switch to GND and is
rated at 200 mA @ 12 VDC
• 10-pin 3.5 mm mini-Phoenix (female) connector provides I/O port
termination
Note: This IO port uses 5V logic, but can handle up to 12V on the input
without harm. Higher voltages run a higher risk of surge damage.

Introduction
4
NI-3101-SIG Signature Series NetLinx Integrated Controller
NI-3101-SIG Specifications (Cont.)
IR/Serial (Ports 9 - 16) Eight IR/Serial control ports support high-frequency carriers up to
1.142 MHz.
• Each output is capable of three electrical formats: IR, Serial, and Data
• Eight IR/Serial data signals can be generated simultaneously.
• Channel range = 1-32,767
• Channels 1-128 (output): IR commands
• Channels 129-253: used as reference channels
• Channel 254 (feedback): Power Fail (used with 'PON' and 'POF'
commands)
• Channel 255 (feedback): Power status (when IO Link is set)
• IR ports support data mode (at limited baud rates and wiring distances).
• Two 8-pin 3.5 mm mini-Phoenix (female) connectors provide IR/Serial port
termination
Configuration Port USB connector (male) can be connected to a USB port on a computer. This
low-speed USB connection is used to configure system settings.
Not recommended for firmware updates or large file transfers.
Configuration DIP switch 4 configuration DIP switches used solely for enabling or disabling NetLinx
functionality.
ID pushbutton Provides the NetLinx ID (Device only) assignment for the device. Refer to
the Changing the Device Address of a NetLinx Device section on page 20.
• The D notation is used to represent a device number.
LAN port RJ-45 port for 10/100 Mbps communication.
This port automatically negotiates the connection speed (10 Mbps or 100
Mbps) and whether to use half duplex or full duplex mode.
LAN Link/Activity LED LEDs show communication activity, connection status, speeds, and mode
information:
• SPD (speed) - Yellow LED lights On when the connection speed is 100
Mbps and turns Off when the speed is 10 Mbps.
• L/A (link/activity) - Green LED lights On when the LAN cables are
connected/terminated correctly, and blinks when receiving LAN data
packets.
AXlink LED • Green LED indicates the state of the AXlink connector port.
• Normal AXlink activity = 1 blink/second
• Abnormal AXlink activity = cycle of 3 consecutive blinks and then Off
AXlink port 4-pin 3.5 mm mini-Phoenix (male) connector provides data and power to
external control devices.
Power port 2-pin 3.5 mm mini-Phoenix (male) connector
Included Accessories: • 2-pin 3.5 mm mini-Phoenix (female) PWR connector (41-5025)
• 4-pin 3.5 mm mini-Phoenix (female) AXlink connector (41-5047)
• 10-pin 3.5 mm mini-Phoenix (female) I/O connector (41-5107)
• Installation Kit (KA2105-02):
Two rack mount ears
Four #8-32 Phillips flat head screws
• NI-3101-SIG Quick Start Guide (93-2105-08)
• Two 8-pin 3.5 mm mini-Phoenix (female) Relay connectors (41-5083)
• Two CC-NIRC IR Emitters
Other AMX Equipment: • 2-pin 3.5 mm mini-Phoenix male connector (41-5026)
• CC-NIRC IR cables (FG10-000-11)
• CC-NSER IR/Serial cables (FG10-007-10)
• CSB Cable Support Bracket (FG517)
• NCK, NetLinx Connector Kit (FG2902)
• USB A to B cable (FG10-2105)

5
NI-3101-SIG Signature Series NetLinx Integrated Controller
Installation and Upgrading
Device:Port:System (D:P:S)
A device is any hardware component that can be connected to an AXlink bus. Each device must be assigned a
unique number to locate that device on the bus. Only the Device value can be set through the DIP switch
settings mentioned above.
NetLinx requires a Device:Port:System (D:P:S) specification. This D:P:S triplet can be expressed as a series of
constants, variables separated by colons, or a DEV structure. For example:
STRUCTURE DEV
{
INTEGER Number // Device number
INTEGER Port // Port on device
INTEGER System // System the device belongs to
}
The D:P:S notation is used to explicitly represent a device number, port and system. For example, 128:1:0
represents the first port on device 128 on this system.
If a device is declared in a NetLinx program with just the Device number (System and Port are omitted), the
NetLinx Compiler assumes it has a Port number of 1 and a System number of 0. However, all existing
device declarations should be converted using the D:P:S (Device:Port:System) notation. This enables certain
NetLinx specific debugging features and can help pinpoint other potentially obscure errors.
The syntax is as follows:
NUMBER:PORT:SYSTEM
where:
Installation and Upgrading
NUMBER: 16-bit integer represents the device number
PORT: 16-bit integer represents the port number (in the range 1 through the number of
ports on the Controller or device)
SYSTEM: 16-bit integer represents the system number (0 = this system)
Installation into an Equipment Rack
Use the rack-mounting ears supplied with the NI-3101-SIG controller for equipment rack installations. The
device comes installed with four rubber feet for flat surface installations.
The maximum operating ambient temperature is 40°C.
Connect the unit only to a properly-rated supply circuit.
Never restrict the airflow through the devices’ fan or vents.
When installing equipment into a rack, distribute the units evenly. Otherwise,
hazardous conditions may be created by an uneven weight distribution.
Reliable earthing (grounding) of rack-mounted equipment should be maintained.
Before completing the install process, completing any firmware upgrade of the
NetLinx Control Cards is highly recommended. This upgrade involves physically
cycling power to the unit and can become cumbersome if the unit is already installed
into a rack.
1. Discharge the static electricity from your body by touching a grounded object.
2. Position and install the mounting ears, using the screws supplied with the unit. The mounting ears may be
rotated to accommodate your mounting needs.

Installation and Upgrading
6
NI-3101-SIG Signature Series NetLinx Integrated Controller
3. Thread the cables through the opening in the equipment rack. Allow for enough slack in the cables to
4. Reconnect all cables to their appropriate source/terminal locations. Refer to theConnections and
To prevent repetition of the installation, test the incoming wiring by connecting the
Controller’s connectors to their terminal locations and applying power. Verify that the
unit is receiving power and functioning properly. Disconnect the terminal end of the
power cable from the connected 12 VDC-compliant power supply.
5. Slide the device into the rack until the attachment holes, along both sides, align to their corresponding
6. Secure the device to the rack by using the four flat-head Phillips screws supplied in the kit.
7. Apply power to the unit to complete the installation.
CAUTION: RACK MOUNT SAFETY INSTRUCTIONS
1. If installed in a closed or multi-unit rack assembly, the operating ambient temperature of the rack
2. Installation of the equipment in a rack should be such that the amount of air flow required for safe
3. Mounting of the equipment in the rack should be such that a hazardous condition is not achieved due to
4. Consideration should be given to the connection of the equipment to the supply circuit and the effect that
5. Reliable earthing of rack-mounted equipment should be maintained. Particular attention should be given
accommodate for movement during the installation process.
Wir ing section on page 7 for more detailed wiring and connection information.
Verify that the terminal end of the power cable is not connected to the a power supply before
plugging in the 2-pin power connector.
locations on the mounting ears.
environment may be greater than room ambient. Therefore, consideration should be given to installing
the equipment in an environment compatible with the maximum ambient temperature 50°C.
operation of the equipment is not compromised.
uneven mechanical loading.
overloading of the circuits might have on over current protection and supply wiring. Appropriate
consideration of equipment nameplate ratings should be used when addressing this concern.
to supply connections other than direct connections to the branch circuit (e.g. use of power strips).

7
NI-3101-SIG Signature Series NetLinx Integrated Controller
Connections and Wiring
Setting the Configuration DIP Switch for the Configuration Port
Prior to installing the Controller, use the Configuration DIP switch to set the information used by the
Configuration Port for communication. The DIP switchsets the starting address (the device number in the
D:P:S specification) for the Control Cards installed in the controller with a range of 1-1536. The four-pin
Configuration DIP switch is located on the rear of the device.
Program Run Disable (PRD) mode
The Configuration DIP switch is used to set the on-board Master to Program Run Disable (PRD) mode,
according to the settings listed in the table below.
PRD Mode Settings
PRD Mode Position 1
Normal mode (default) OFF
PRD Mode ON
Connections and Wiring
The PRD mode prevents the NetLinx program stored in the on-board Master from running during the device’s
power-up. This mode should only be used if the resident NetLinx program is causing inadvertent
communication and/or control problems. If necessary, place the on-board Master in PRD mode and use the
NetLinx Studio v 2.x program to resolve the communication and/or control problems with the resident
NetLinx program. After doing so, download the corrected program, reset the configuration DIP switch to
normal mode, recycle power, and try again.
Think of the PRD Mode (On) equating to a PC’s SAFE Mode setting. This mode
allows a user to continue powering a unit, update the firmware, and download a new
program while circumventing any problems with a currently downloaded program.
Power must be cycled to the unit after activating/deactivating this mode on the
Configuration Port DIP switch #1.
Working with the Configuration DIP switch
Disconnect the power supply from the 2-pin PWR (green) connector on the rear of the NetLinx Integrated
1.
Controller.
2. Set DIP switch positions according to the information listed in thePRD Mode Settings table.
3. Reconnect the 12 VDC power supply to the 2-pin 3.5 mm mini-Phoenix PWR connector.
Configuration Port Connections and Wiring
The NI-3101 is equipped with a low-speed USB connection located on the rear of the unit. Use a standard
USB cable to establish a connection between the device and your PC's USB port. This connection provides
communication with the NetLinx Integrated Controller. From there, configure the on-board Master as needed
for your application.

Connections and Wiring
8
NI-3101-SIG Signature Series NetLinx Integrated Controller
GND
AXM
AXP
PWR
AXLink
Modes and Front Panel LED Blink Patterns
The following table lists the modes and blink patterns for the front panel LEDs associated with each mode.
These patterns are not evident until after the unit is powered.
Modes and LED Blink Patterns
Mode Description
OS Start Starting the operating system (OS). On On On
Boot On-board Master is booting. On Off On
Contacting DHCP
server
Unknown DHCP
server
Downloading Boot
firmware
No program running Either no program is loaded, or the
Normal On-board Master is functioning normally. 1 blink per
On-board Master is contacting a DHCP
server for IP configuration information.
On-board Master could not find the DHCP
server.
Downloading Boot firmware to the Master’s
on-board flash memory.
Do not cycle power during this process!
program is disabled.
LEDs and Blink Patterns
STATUS
(blue)
On Off Fast Blink
Fast Blink Off Off
Fast Blink Fast Blink Fast Blink
On Normal Normal
second
OUTPUT
(white)
Indicates
activity
INPUT
(white)
Indicates
activity
Port Assignments and Functionality
The rear Port Assignments are as follows:
NI-3101 Port Assignments
Port ICSP Port # Port ICSP Port #
Serial Port #1 1 IR Serial Port #1 9
Serial Port #2 2 IR Serial Port #2 10
Serial Port #3 3 IR Serial Port #3 11
Serial Port #4 4 IR Serial Port #4 12
Serial Port #5 5 IR Serial Port #5 13
Serial Port #6 6 IR Serial Port #6 14
Relays Ports (1-8) 8 IR Serial Port #7 15
IR Serial Port #8 16
I/O Port 17
AXlink Port and LED
All NI units have an AXlink port and adjacent status LED (FIG. 3). This port allows the NI to support AMX
legacy AXlink devices such as G3 touch panels (ex: CP4/A) and PosiTrack Pilot devices. A green LED shows
AXlink data activity. When the AXlink port is operating normally, blink patterns include:
Off - No power, or the controller is not functioning properly.
1 blink per second - Normal operation.
3 blinks per second - AXlink bus error. Check all AXlink bus connections.
AXlink connector and LED
FIG. 3

Connections and Wiring
9
NI-3101-SIG Signature Series NetLinx Integrated Controller
The AXlink port can be used to supply power to downstream AXlink-compatible devices, so long as both the
power required is LESS THAN 2 Amps total and the external power supply feeding the device has the
necessary power capability.
Wiring Guidelines
The Integrated Controllers use a 12 VDC-compliant power supply to provide power through the rear
2-pin 3.5 mm mini-Phoenix PWR connector, or through the 4-pin 3.5 mm mini-Phoenix (female) captive-wire
connector used for data communication and power transfer. Use the power requirements referenced in the
product’s Specifications table to determine the power draw.
The incoming PWR and GND cable from the power supply must be connected to the corresponding locations
within the PWR connector.
Use only one power source for the device at a time. Using both the 2-pin miniPhoenix PWR connector and the 4-pin mini-Phoenix AXLink connector at the same
time may cause permanent damage to the device.
Apply power to the device only after installation is complete.
Wiring length guidelines
Refer to the following table for the wiring length information used with the NI-3101:
Wiring Guidelines - NI-3101 @ 900 mA
Wire size Maximum wiring length
18 AWG 120.41 feet (39.70 meters)
20 AWG 76.45 feet (23.30 meters)
22 AWG 49.36 feet (15.04meters)
24 AWG 30.08 feet (9.17 meters)
Preparing captive wires
You will need a wire stripper and flat-blade screwdriver to prepare and connect the captive wires.
Never pre-tin wires for compression-type connections.
1. Strip 0.25 inch (6.35 mm) of insulation off all wires.
2. Insert each wire into the appropriate opening on the connector (according to the wiring diagrams and
connector types described in this section).
3. Tighten the screws to secure the wire in the connector. Do not tighten the screws excessively. Doing so
may strip the threads and damage the connector.
Wiring a power connection
To use the 2-pin 3.5 mm mini-Phoenix connector with a 12 VDC-compliant power supply, the incoming PWR
and GND cables from the external source must be connected to their corresponding locations on the connector
(FIG. 4).
1. Insert the PWR and GND wires on the terminal end of the 2-pin 3.5 mm mini-Phoenix cable. Match the
wiring locations of the +/- on both the power supply and the terminal connector.
2. Tighten the clamp to secure the two wires. Do not tighten the screws excessively; doing so may strip the
threads and damage the connector.
3. Verify the connection of the 2-pin 3.5 mm mini-Phoenix to the external 12 VDC-compliant power supply.

Connections and Wiring
10
NI-3101-SIG Signature Series NetLinx Integrated Controller
PWR +
GND -
Integrated Controller
Power Supply
To the Integrated Controller’s
To the external AXlink device
AXlink/PWR connector
PWR +
AXP/TX
AXM/RX
GND -
Top view
Top view
PWR +
AXP/TX
AXM/RX
GND -
PWR (+)
GND (-)
Local +12 VDC
(coming from
To the Integrated Controller’s
To the external AXlink device
AXlink/PWR connector
power supply
an external
power supply)
Top view
Top view
AXP/TX
AXM/RX
GND -
AXP/TX
AXM/RX
GND -
FIG. 4 2-pin mini-Phoenix connector wiring diagram (direct power)
Using the 4-pin mini-Phoenix connector for data and power
Connect the 4-pin 3.5 mm mini-Phoenix (female) captive-wire connector to an external NetLinx device as
shown in FIG. 5.
FIG. 5 Mini-Phoenix connector wiring diagram (direct data and power)
Using the 4-pin mini-Phoenix connector for data with external power
To use the 4-pin 3.5 mm mini-Phoenix (female) captive-wire connector for data communication and power
transfer, the incoming PWR and GND cable from the 12 VDC-compliant power supply must be connected to
the AXlink cable connector going to the device (FIG. 6). Always use a local power supply to power the device.
FIG. 6 4-pin mini-Phoenix connector wiring diagram (using external power source)
When you connect an external power supply, do not connect the wire from the PWR
terminal (coming from the external device) to the PWR terminal on the Phoenix
connector attached to the Controller unit. Make sure to connect only the AXM, AXP,
and GND wires to the Controller’s Phoenix connector when using an external power
supply.
Make sure to connect only the GND wire on the AXlink/PWR connector when using a separate
12 VDC power supply. Do not connect the PWR wire to the AXlink connector’s PWR (+) opening.

Connections and Wiring
11
NI-3101-SIG Signature Series NetLinx Integrated Controller
5
4
3
2
1
9
8
7
6
Male
DB9 Serial Port pinouts (male connector)
Pin 2: RX signal
Pin 3: TX signal
Pin 5: GND
Pin 7: RTS
Pin 8: CTS
RS-232
Pin 1: RX Pin 4: TX +
Pin 5: GND
Pin 6: RX +
Pin 9: TX -
RS-422
Pin 1: A (strap to 9)
Pin 4: B (strap to 6)
Pin 5: GND
Pin 6: B (strap to 4)
Pin 9: A (strap to 1)
RS-485
DB9 Device Port: Connections and Wiring
FIG. 7 shows the connector pinouts for the rear RS-232/RS-422/RS-485 (DB9) Device Ports. These ports
support most standard RS-232 communication protocols for data transmission. This figure gives a visual
representation of the wiring specifications for the RS-232/422/485 Device connectors.
FIG. 7 RS-232/422/485 DB9 (male) connector pinouts for the rear Device Ports
The table below provides information about the connector pins, signal types, and signal functions. This table’s
wiring specifications are applicable to the rear RS-232/422/485 Device Port connectors on the NI-3101-SIG
(Ports 1-6).
RS-232/422/485 Device Port Wiring Specifications
Pin Signal Function RS-232 RS-422 RS-485
1 RX- Receive data X X (strap to pin 9)
2 RXD Receive data X
3 TXD Transmit data X
4 TX+ Transmit data X X (strap to pin 6)
5 GND Signal ground X X
6 RX+ Receive data X X (strap to pin 4)
7 RTS Request to send X
8 CTS Clear to send X
9 TX- Transmit data X X (strap to pin 1)
When wiring the 422/485 connections, do NOT use pre-made 9-wire cable or connect
the wire in the cable to any connection that will not be used by the DB9 serial port.
Only use wiring that connects the needed pins.
Relay Port: Connections and Wiring
Up to 8 independent external relay devices may be connected to the Relay connectors on the device.
Connectors labeled A are for common; B are for output.
Each relay is isolated and normally open.
A metal commoning strip is supplied with each device to connect multiple relays.
Relay connections
Use A for common and B for output (FIG. 8). Each relay is isolated and normally open. A metal connector
strip is also provided to common multiple relays.

Connections and Wiring
12
NI-3101-SIG Signature Series NetLinx Integrated Controller
24AB3
BAB
1
AA B
RELAYS (Port 4)
RELAYS (Port 8)
B
6
A8B BB7A
5
BAA4BA A
3A2B1
AB
NI-3101-SIG relay connector
configuration (Port 8)
I / O (Port 17)
4
+12V
78 6
5
GND
2
3
1
I / O (Port 9)
4
+12V
231
GND
NI-3101-SIG I/O connector
configuration (Port 17)
IR / SERIAL (Ports 5-8)
IR / SERIAL (Ports 9-16)
8 76 45 321
4 23 1
NI-3101-SIG IR/Serial connector
configuration (Port 9-16)
FIG. 8 RELAY connector (male) NI-3101-SIG
Input/Output (I/O) Port: Connections and Wiring
The I/O port responds to either switch closures or voltage level (high/low) changes, or it can be used for logiclevel outputs.
FIG. 9 INPUT/OUTPUT connector (male)
Up to eight devices may be connected to the I/O connectors on the NI-3101-SIG (FIG. 9). A contact closure
between the GND and an I/O port is detected as a Push.
I/O Port Wiring Specifications - NI-3101-SIG
When used for voltage inputs, the I/O port detects a low signal (0 - 1.5 VDC) as a Push, and a high
signal (3.5 - 5 VDC) as a Release (this IO port uses 5V logic but can handle up to 12V without
harm).
When used for outputs, the I/O port acts as a switch to GND and is rated for
200 mA @ 12 VDC. This device can use up to 8 I/O ports.
The PWR pin provides +12 VDC @ 200 mA and is designed as a power output for the PCS Power
Current Sensors, VSS2 Video Sync Sensors (or equivalent).
The GND connector is a common ground and is shared by all I/O ports. A common ground is
shared with I/O ports 1 - 8.
Pin Signal Function Pin Signal Function
1 GND Signal GND 6 I/O 5 Input/Output
2 I/O 1 Input/Output 7 I/O 6 Input/Output
3 I/O 2 Input/Output 8 I/O 7 Input/Output
4 I/O 3 Input/Output 9 I/O 8 Input/Output
5 I/O 4 Input/Output 10 12 VDC PWR
IR/Serial Port: Connections and Wiring
Up to eight IR- or Serial-controllable devices may be connected to the IR/Serial connectors on the rear of the
NI-3101 (FIG. 10). These connectors accept an IR Emitter (CC-NIRC) that mounts onto the device's IR
window, or a mini-plug (CC-NSER) that connects to the device's control jack. A data 0 - 5 VDC device may
also be connected. These units come with two CC-NIRC IR Emitters (FG10-000-11).
FIG. 10
IR/SERIAL (male)

13
NI-3101-SIG Signature Series NetLinx Integrated Controller
The IR/Serial connector wiring specifications are listed in the following table:
IR/Serial Connector Wiring Specifications (per Port)
Number of
IR connections NI-3101-SIG Port # Function
1 9 GND (-)
Signal 1 (+)
2 10 GND (-)
Signal 2 (+)
3 11 GND (-)
Signal 3 (+)
4 12 GND (-)
Signal 4 (+)
5 13 GND (-)
Signal 5 (+)
6 14 GND (-)
Signal 6 (+)
7 15 GND (-)
Signal 7 (+)
8 16 GND (-)
Signal 8 (+)
Connections and Wiring
LAN (Ethernet/RJ-45 Port): Connections and Wiring
The following table lists the pinouts, signals, and pairing for the LAN connector.
LAN RJ-45 Pinouts and Signals
Pin Signals Connections Pairing Color
1 TX + 1 --------- 1 1 --------- 2 Orange-White
2 TX - 2 --------- 2 Orange
3 RX + 3 --------- 3 3 --------- 6 Green-White
4 no connection 4 --------- 4 Blue
5 no connection 5 --------- 5 Blue-White
6 RX - 6 --------- 6 Green
7 no connection 7 --------- 7 Brown-White
8 no connection 8 --------- 8 Brown
FIG. 11 diagrams the RJ-45 pinouts and signals for the LAN RJ-45 connector and cable.
FIG. 11
RJ-45 wiring diagram

Connections and Wiring
14
NI-3101-SIG Signature Series NetLinx Integrated Controller
10/100
ETHERNET
SPD - Speed LED
connection speed is 100 Mbps
and turns Off when speed is
lights (yellow) when the
L/A - Link/Activity LED
lights (green) when the
LAN cables are
connected and terminated
10 Mbps.
correctly.
LAN LEDs
FIG. 12 LAN LEDs
LAN ports used by the Integrated Controllers
LAN Ports Used by the NetLinx Integrated Controllers
Port type Description Standard Port #
FTP The on-board Master has a built-in FTP server. 21/20 (TCP)
SSH The SSH port functions using the same interface as Telnet but over a
Telnet The NetLinx Telnet server provides a mechanism to configure and
HTTP The Master has a built-in web server that complies with the HTTP 1.0
HTTPS/SSL This port is used by a web browser for secure communication between
ICSP Peer-to-peer protocol used for both Master-to-Master and Master-to-
integration!
Solutions
secure shell where it uses SSL as a mechanism to configure and diagnose a NetLinx system. This port value is used for secure Telnet
communication.
Note: only SSH version 2 is supported.
diagnose a NetLinx system.
For maximum flexibility, the Master can be configured to utilize a different
port than 23, or disable Telnet completely from either Telnet or the
Program port located on the rear of the Master itself. Once disabled, the
only way to enable Telnet again is from the Master’s Program port.
specification and supports all of the required features of HTTP v1.1.
This port is used for unsecure HTTP Internet communication between
the web browser’s UI and the target Master.
the web server UI and the target Master. This port is also used for
simultaneous encryption of this data, using the SSL certificate information on the Master as a key.
device communications.
For maximum flexibility, the Master can be configured to utilize a different
port than 1319, or disable ICSP over LAN completely from either
Telnet or the Program Port located on the rear of the Master itself.
This type of communication is used by the various AMX products for
communication amongst themselves.
This feature on the Master uses, by default, port 10500 for the XML
based communication protocol. This port is connected to by the client
web browser’s JVM when integration! Solutions control pages are
retrieved from the on-board Master’s web server.
For maximum flexibility, the on-board Master can be configured to utilize
a different port than 10500 or to disable integration! Solutions completely.
22 (TCP)
23 (TCP)
80 (TCP)
443 (TCP)
1319 (UDP/TCP)
10500 (TCP)
Replacing the Timekeeper Battery
The NI-3101-SIG uses a combination lithium battery and clock crystal package called a Timekeeper. Only one
Tim ekeepe r unit is installed within a given NI-3101-SIG. The battery can be expected to have up to 3 years of
usable life under very adverse conditions. Actual life is appreciably longer under normal operating conditions.
This calculation is based on storing the unit without power in 50° C (120° F) temperature until battery levels
are no longer acceptable. The part number for a replacement battery is 57-0032.
To replace the Timekeeper battery:
1. Discharge the static electricity from your body by touching a grounded metal object.
2. Unplug all the connectors from the device.

Connections and Wiring
15
NI-3101-SIG Signature Series NetLinx Integrated Controller
3. Remove the rear panel from the device, and then disconnect the NXI control cable and remove the Master
card.
4. Locate the battery behind the Configuration Port on the circuit board.
5. Carefully slide the battery out of its socket and insert the new battery.
6. Plug the 2-pin 3.5 mm mini-Phoenix PWR (green) connector to reapply power. Wait approximately 1
minute, then remove the PWR connector again.
7. Carefully slide the other battery out of its socket and insert the new battery
8. Re-connect the NXI control cable to the Master card.
9. Replace and secure the rear faceplate using the mounting screws and reconnect all communication
connectors.
10. Reconnect the 12 VDC power supply to the respective PWR connector and apply power.
CAUTION: RISK OF EXPLOSION IF BATTERY IS REPLACED BY AN INCORRECT
TYPE. DISPOSE OF USED BATTERIES ACCORDING TO THE INSTRUCTIONS

Connections and Wiring
16
NI-3101-SIG Signature Series NetLinx Integrated Controller

Configuration and Firmware Update
17
NI-3101-SIG Signature Series NetLinx Integrated Controller
Configuration and Firmware Update
Overview
This section refers to steps necessary to both communicate with and upgrade the NI-3101-SIG.
Before continuing, verify that you are using the latest version of NetLinx Studio and
the latest firmware Kit file (this file contains both the NI Integrated Controller and onboard Master firmware).
The NI-3101-SIG Kit file begins with 2105_04_X100.
Before beginning:
1. Set up and configure the NI-3101-SIG. Refer to the previous Installation and Upgrading section.
2. Verify that the latest version of NetLinx Studio has been installed on the PC. If an update is necessary,
download the latest NetLinx Studio software from www.amx.com.
3. If the LAN port will be used for programming, verify that an LAN cable connects the Controller to the
PC being used for programming or to a LAN on the same subnet as the PC.
4. The low-speed USB connection is not recommended for firmware updates.
5. Verify that the NetLinx Master is receiving power and is turned ON. Refer to the previous Connections
and Wiring section on page 7 for more information.
If if communication has already been set up with the Controller via an IP Address,
continue with the firmware update procedures outlined in the Communicating with the
NI Device via an IP section on page 26.
Communicating with the Master via the Program Port
1. From your computer, launch NetLinx Studio 2.x.
2. Select Settings > Master Communication Settings, from the Main menu, to open the Master
Communication Settings dialog (FIG. 13).
FIG. 13 Master Communication Settings dialog
3. Click the Communications Settings button to open the Communications Settings dialog (FIG. 14).
4. Click the NetLinx Master radio button (from the Platform Selection section) to choose a NetLinx Master
such as the NI-3101-SIG.
5. Click the Serial radio button (from the Transport Connection Option section) to select communication to
the on-board Master via a (Serial) COM port.
6. Click the Edit Settings button to open the Serial Settings dialog (FIG. 15).

Configuration and Firmware Update
18
NI-3101-SIG Signature Series NetLinx Integrated Controller
FIG. 14 Communication Settings dialog box
FIG. 15 Serial Settings dialog box
No authentication username or password information is required when selecting a
direct connection such as USB or Serial.
7. Set the COM port parameters for the selected COM port used for communication to the NetLinx Master.
Default parameters are:
COM1
115200
8 Data Bits
No Parity
1 Stop Bit
No Flow Control
If communication fails on a known COM port, change the baud rate to 115200 and try again.
8. Click OK three times to close the open dialogs and save the chosen settings.
If the connection fails to establish, select a different COM port, press the Retry button
to reconnect using the same communication parameters, or press the Change button
to alter your communication parameters and repeat steps 2 thru 8.
Setting the System Value
1. Access/open the Device Addressing dialog (FIG. 16) by either one of these two methods:
Right-click on any System item listed (such as the NI Master entry) in the OnLine Tree tab of the
Workspace and select Device Addressing (from the popup list).
Select Diagnostics > Device Addressing from the Main menu.
This process should be done while communicating to the Master via a Serial
connection.

Configuration and Firmware Update
19
NI-3101-SIG Signature Series NetLinx Integrated Controller
System Address
(default for initial
system is 1)
Check-Off to
verify change
FIG. 16 Device Addressing tab (changing the system value)
This tab represents the only way to change the System Number associated to the
active on-board NI Master. The Master must have its power cycled to incorporate
the new System number, as often a simple reboot via Studio will not be enough
to incorporate this new number).
2. Select the Change System selection box from the System to Change section.
3. Enter both the current and new system address values.
4. Click the Change Device/System Number button. This configures the Master to accept the new value
and incorporate the information. The system information in the OnLine Tree tab of the Workspace window
refreshes and then displays the new information.
5. Click Done to close the Device Addressing dialog and return to the main program.
6. Click Reboot (from the Tools > Reboot the Master Controller dialog) and wait for the System Master
to reboot. The STATUS and OUTPUT LEDs should begin to alternately blink during the incorporation.
Wait until the STATUS LED is the only LED to blink.
7. Press Done once until the Master Reboot Status field reads *Reboot of System Complete*.
8. Click the OnLine Tree tab in the Workspace window to view the devices on the System. The default
System value is 1.
9. Right-click the associated System number (or anywhere within the tab itself) and select Refresh System.
This establishes a new connection to the specified System and populates the list with devices on that
system.
10. Use Ctrl+S to save your existing NetLinx Project with the new changes.
If the NetLinx device does not appear within the OnLine Tree tab, make sure that the
Integrated Controller’s on-board Master System Number (from within the Device
Addressing tab) is correctly assigned.
If there is a problem, use a system value of zero (0) on the NetLinx device.
The Master is set by default to DEVICE 0. Connected NetLinx device addresses
can only be changed through the Protected Setup page. The new address is
reflected within the OnLine Tree tab of the Workspace window only after the devices
are rebooted and the system is refreshed.
The system value on a Modero touch panel cannot be changed from the Device
Addressing dialog box and MUST be altered through the panel Protected Setup
page.

Configuration and Firmware Update
20
NI-3101-SIG Signature Series NetLinx Integrated Controller
Device Address
(original device
value)
Check-Off to
verify change
Enter new
device value
Using Multiple NetLinx Masters
When using more than one Master, each unit must be assigned to a separate System value.
A Master’s System value can be changed but its device Address must always be set to zero (00000). The
Device Addressing dialog will not allow you to alter the NetLinx Master address value.
Example: Using NetLinx Studio v 2.x to work with an NXC-ME260/64 and NI-3101-SIG:
The NXC-ME260/64 could be assigned to System 1 (with a value of 00000).
The NI-3101-SIG could be assigned to System 2 (with a value of 00000).
Changing the Device Address of a NetLinx Device
1. Access the Device Addressing dialog (FIG. 17) by either one of these two methods:
Right-click on any system device (such as a Modero panel) listed in the OnLine Tree tab of the
Workspace and select Device Addressing (from the popup list).
Select Diagnostics > Device Addressing from the Main menu.
FIG. 17 Device Addressing dialog (changing the device value)
This dialog represents the only way to change the device value of a selected NetLinx
device. Modero panels are one of the only devices that can have their Device values
changed within both this dialog and through the on-board firmware page.
2. Select the Change Device checkbox from the Device to Change section.
3. Verify the Current value and enter the New Device value for the target NetLinx device.
4. Click the Change Device/System Number button. This configures the specified Master to accept the
new value for the NetLinx device and incorporate the information (the system information in the
Workspace window refreshes and then displays the new information).
5. Click Done to close the Device Addressing dialog.
6. Click Reboot (from the Tools > Reboot the Master Controller dialog) and wait for the System Master to
reboot. The STATUS and OUTPUT LEDs should begin to alternately blink during the incorporation. Wait
until the STATUS LED is the only LED to blink.
7. Press Done once until the Master Reboot Status field reads *Reboot of System Complete*.
8. Click the OnLine Tree tab in the Workspace window to view the devices on the System.
The default System value is one (1).
9. Right-click the associated System number (or anywhere within the tab itself) and select Refresh System.
This establishes a new connection to the specified System and populates the list with devices on that
system.
10. Use Ctrl+S to save your existing NetLinx Project with the new changes.
If the Master does not appear in the Workspace window, make sure that the Master’s
System Number (from within the Device Addressing tab) is correctly assigned. If this
issue persists, use a system value of zero (0) on the Master.

Configuration and Firmware Update
21
NI-3101-SIG Signature Series NetLinx Integrated Controller
Recommended NetLinx Device Numbers
• 1 - 255 • Axcess Devices use Axcess standards
• 301 - 3072 • NetLinx CardFrames start at frame number 25 - (frame# * 12) + Card #
• 5001 - 5999 • ICSNet NetLinx devices: NXI, NXM-COM2, NXM-IRS4, etc.
• 6001 - 6999 • ICSNet Landmark devices: PLH-VS8, PLH-AS16, PLB-AS16
• 7001 - 7999 • InConcert Devices
• 8001 - 8999 • PCLink Device: PCLink devices are PC programs
• 10000 - 31999 • ICSNet Panels: DMS, IMS, and future panels
• 33001 - 36863 • Virtual devices: these start at 33001
• 32001 - 32767 • Dynamic devices: the actual range used by Master
• 32768 - 36863 • Virtual devices: the actual range used by Master
Using the ID Button to Change the Controller’s Device Value
Use the ID Button on the rear panel (in conjunction with ID Mode function in NetLinx Studio) to establish a
NetLinx Device ID for the device.
The steps described and the dialogs shown in this section are in the NetLinx Studio application.
NetLinx Studio is available to download from www.amx.com.
Refer to the NetLinx Studio on-line help for information on using NetLinx Studio.
1. Access the Device Addressing dialog (FIG. 18) by selecting Diagnostics > Device Addressing.
FIG. 18
Device Addressing dialog
2. Enter the system number in the Destination System field.
3. Enter the desired device number in the Change to Device box (Device field), and again enter the system
number (in the System field).
4. Click the Start Identify Mode button. This action activates Identify Mode on the named System.
"Identify Mode" means that the system is put on hold while it waits for an event from
any NetLinx device in the named system (for example, pushing the ID button on a
NetLinx device). The device that generates the first event is the device that gets
identified.
The Device Addressing dialog displays the "Waiting...Press Cancel to Quit..." message, indicating that
Identify Mode is currently active (NetLinx Studio is waiting to detect a device - FIG. 19).

Configuration and Firmware Update
22
NI-3101-SIG Signature Series NetLinx Integrated Controller
Identify Mode is
currently active
Device identified
ID Mode no longer active
FIG. 19 Device Addressing dialog - Identify Mode active
5. Press the NI Controller’s ID button to assign the new Device / System values entered in step 3 to the
Controller. At this point, the "Successful Identification Made " message is displayed (FIG. 20):
FIG. 20 Device Addressing dialog - Successful Identification Made
The previous Device and System numbers of the NI Controller are displayed below the red field.
Example: Previous D:S=5001:1,
where "5001" represents the previous device value of the
NI Controller (D) and "1" represents the
NI Controller’s System value (S).
Resetting the Factory Default System and Device Values
1. Access the Device Addressing dialog (FIG. 17 on page 20) by either one of these two methods:
Right-click on any system device listed in the Workspace and select Device Addressing.
Select Diagnostics > Device Addressing from the Main menu.
2. Click the Set Device/System to Factory Default button. This resets both the system value and device
addresses (for definable devices) to their factory default settings. The system information (in the OnLine
Tre e tab of the Workspace window) refreshes and then displays the new information.

Configuration and Firmware Update
23
NI-3101-SIG Signature Series NetLinx Integrated Controller
System Address
reflects the value
set in the Device
Addressing tab
Used to obtain a
Dynamic
IP Address
By setting the system to its default value (#1), Modero panels that were set to
connect to the Master on another System value will not appear in the OnLine Tree
tab of the Workspace window.
For example: A Modero touch panel was previously set to System #2. The system is
then reset to its default setting of System #1 and then refreshed from within the
Workspace window. The panel will not reappear until the system is changed (from
within the System Connection page on the Modero) to match the new value and both
the Master and panel are rebooted.
3. Click Done to close the Device Addressing dialog.
4. Click Reboot (from the Tools > Reboot the Master Controller dialog) and wait for the System Master to
reboot. The STATUS and OUTPUT LEDs should begin to alternately blink during the incorporation. Wait
until the STATUS LED is the only LED to blink.
5. Press Done once until the Master Reboot Status field reads *Reboot of System Complete*.
6. Click the OnLine Tree tab in the Workspace window to view the devices on the System. The default
System value is one (1).
7. Right-click the associated System number (or anywhere within the tab itself) and select Refresh System.
This establishes a new connection to the specified System and populates the list with devices on that
system.
8. Use Ctrl+S to save the existing NetLinx Project with the new changes.
Obtaining the Master’s IP Address (using DHCP)
Verify there is an active LAN connection on the LAN port of the NI-Series Controller
before beginning these procedures.
1. Select Diagnostics > Network Addresses from the Main menu to access the Network Addresses dialog
(FIG. 21).
FIG. 21 Network Addresses dialog (for a DHCP IP Address)
2. Verify that both the System number corresponds to the System value previously assigned within the
Device Addressing tab and that zero (0) is entered into the Device field.
The system value must correspond to the Device Address entered in the Device
Addressing dialog. Refer to the Setting the System Value section on page 18 for
more detailed instructions on setting a system value.
3. Click the Get IP Information button to configure the on-board Master for DHCP usage and then read the
IP Address obtained from the DHCP Server.

Configuration and Firmware Update
24
NI-3101-SIG Signature Series NetLinx Integrated Controller
System Address
reflects the value
set in the Device
Addressing tab
Used to retain an
IP Address
DO NOT enter ANY IP information at this time; this step only gets the System Master
to recognize that it should begin using an obtained DHCP Address.
4. Note the obtained IP Address (greyed-out and read-only). This information is later entered into the
Master Communication Settings dialog and used by NetLinx Studio v 2.x to communicate to the
Master via an IP. This address is reserved by the DHCP server and then given to the Master.
If the IP Address field is empty, give the Master a few minutes to negotiate a DHCP
Address with the DHCP Server, and try again. The DHCP Server can take anywhere
from a few seconds to a few minutes to provide the Master with an IP Address.
5. Verify that NetLinx appears in the Host Name field (if not, then enter it in at this time).
6. Click the Use DHCP radio button from the IP Address section (if not greyed-out).
7. Click the Set IP Information button to retain the IP Address from the DHCP server and assign it to the
on-board Master. A popup window then appears to notify you that Setting the IP information was
successful and it is recommended that the Master be rebooted.
8. Click OK to accept the change to the new IP/DNS information.
9. Click the Reboot Master button and select Ye s to close the Network Addresses dialog.
10. Click Reboot from the Tools > Reboot the Master Controller dialog, and wait for the System Master to
reboot and retain the newly obtained DHCP Address. The STATUS and OUTPUT LEDs should begin to
blink alternately during the incorporation. Wait until the STATUS LED is the only LED blinking.
11. Press Done once until the Master Reboot Status field reads *Reboot of System Complete*.
Verify that these IP values are also entered into the related fields within either the
IP Settings section of the System Connection page (on the touch panel) or within the
Address field on the web browser.
12. Complete the communication process by continuing on to the Communicating with the NI Device via an
IP section on page 26.
Assigning a Static IP to the NetLinx Master
Verify that the Controller has an active LAN connection before beginning these
procedures.
1. Select Diagnostics > Network Addresses from the Main menu to access the Network Addresses dialog
(FIG. 22).
FIG. 22 Network Addresses dialog (for a pre-obtained Static IP Address)

Configuration and Firmware Update
25
NI-3101-SIG Signature Series NetLinx Integrated Controller
2. Verify that both the System number corresponds to the System value previously assigned within the
Device Addressing tab and that zero (0) is entered into the Device field.
The system value must correspond to the Device Address previously entered in the
Device Addressing tab. Refer to the Setting the System Value section on page 18 for
more detailed instructions on setting a system value.
3. Click the Get IP Information button to temporarily configure the on-board Master for DHCP usage and
then read the IP Address obtained from the DHCP Server.
4. Click the Specify IP Address radio button from the IP Address section. With this action, all IP fields
become editable.
5. Verify that NetLinx appears in the Host Name field. If not, then enter it in at this time.
6. Enter the IP Address, Subnet Mask, and Gateway information into their respective fields.
7. Click the Set IP Information button to cause the on-board Master to retain the new IP Address
pre-obtained from the System Administrator.
8. Click OK to accept the change to the new IP/DNS information.
9. Click the Reboot Master button and select Yes to close the Network Addresses dialog.
10. Click Reboot from the Tools > Reboot the Master Controller dialog, and wait for the System Master to
reboot and retain the newly obtained DHCP Address. The STATUS and OUTPUT LEDs should begin to
blink alternately during the incorporation. Wait until the STATUS LED is the only LED blinking.
11. Press Done once until the Master Reboot Status field reads *Reboot of System Complete*.
Verify that these IP values are also entered into the related fields within either the IP
Settings section of the System Connection page (on the touch panel) or within the
Address field on the web browser.
12. Complete the communication process by continuing on to the Communicating with the NI Device via an
IP section on page 26.

Configuration and Firmware Update
26
NI-3101-SIG Signature Series NetLinx Integrated Controller
Communicating with the NI Device via an IP
Whether the on-board Master’s IP Address was Static Set (Set IP Info) or Dynamically obtained (Get IP Info),
use the IP Address information from the Network Addresses dialog to establish communication via the LANconnected Integrated Controller.
1. From your PC, launch NetLinx Studio 2.
2. Obtain the IP Address of the Master from the System Administrator. If you still do not have an IP
Address, follow the steps outlined in either the Obtaining the Master’s IP Address (using DHCP) section
on page 23 or Assigning a Static IP to the NetLinx Master section on page 24.
3. Select Settings > Master Communication Settings from the Main menu to open the Master
Communication Settings dialog (FIG. 23).
FIG. 23 Master Communication Settings dialog
4. Click the Communications Settings button to open the Communications Settings dialog (FIG. 24).
FIG. 24 Communications Settings dialog
5. Click on the NetLinx Master radio button to indicate you are working with a NetLinx Master, and click
on the TCP/IP radio button to indicate a connection to the Master via an IP Address.
6. Click the Edit Settings button (on the Communications Settings dialog) to open the TCP/IP Settings
dialog (FIG. 25). This dialog contains a series of previously entered IP Address/URLs and their
associated names, all of which are stored within NetLinx Studio and are user-editable.

Configuration and Firmware Update
27
NI-3101-SIG Signature Series NetLinx Integrated Controller
FIG. 25 TCP/IP Settings dialog
7. Click the New button to open the New TCP/IP Setting dialog box (FIG. 26), where you may enter both a
previously obtained DHCP or Static IP Address and an associated description for the connection into
their respective fields.
FIG. 26 New TCP/IP Setting dialog
8. Place a checkmark within the Automatically Ping the Master Controller to ensure availability radio box
to make sure the Master is initially responding online before establishing full communication.
9. Click OK to close the current New TCP/IP Settings dialog box and return to the previous TCP/IP Settings
dialog box. Locate the new entry within the List of Addresses section.
10. Click the Select button to make the new entry the currently used IP Address communication parameter.
11. Click OK to return to the Communications Settings dialog and place a checkmark within the
Authentication Required radio box if the Master has been previously secured with a username/password.
12. Press the User Name and Password button to open the Master Controller User Name and Password
dialog box (FIG. 27). Within this dialog, enter a previously configured username and password (with
sufficient rights) before attempting to connect to the Master.
FIG. 27 Master Controller User Name and Password dialog box

Configuration and Firmware Update
28
NI-3101-SIG Signature Series NetLinx Integrated Controller
13. Click OK to save the newly entered information and return to the previous Communication Settings
dialog box. Click OK again to begin the communication process to the Master.
If currently connected to the assigned Master, a popup asks about temporarily
stopping communication to the Master and applying the new settings.
14. Click Ye s to interrupt the current communication from the Master and apply the new settings.
15. Click Reboot from the Tools > Reboot the Master Controller dialog and wait for the System Master to
reboot. The STATUS and OUTPUT LEDs should begin to alternately blink during the incorporation.
Wait until the STATUS LED is the only LED to blink.
16. Press Done once until the Master Reboot Status field reads *Reboot of System Complete*.
17. Click the OnLine Tree tab in the Workspace window to view the devices on the System. The default
System value is one (1).
18. Right-click the associated System number and select Refresh System. This establishes a new connection
to the specified System and populates the list with devices on that system. The communication method is
then highlighted in green on the bottom of the NetLinx Studio window.
If the connection fails to establish, a Connection Failed dialog appears. Try selecting
a different IP Address if communication fails. Press the Retry button to reconnect
using the same communication parameters. Press the Change button to alter the
communication parameters and repeat steps 4 thru 18.
Verifying the current version of NetLinx Master Firmware
All NI Controllers contain both an on-board NI Master and an Integrated Controller.
The on-board Master shows up within the Online Tree as 00000 NI Master
The Integrated Controller of the NI device shows up as 0XXXX NI-XXXX
(ex: 050001 NI-700)
Each of these components has its own corresponding firmware shown in parenthesis ().
1. After Studio has establish a connection to the target Master, click on the OnLine Tree tab in the
Workspace window to view the devices on the System. The default System value is one (1).
2. Right-click the associated System number and select Refresh System. This establishes a new connection
to the specified System and populates the list with devices on that system. The communication method is
highlighted in green on the bottom of the NetLinx Studio window.
The current installed firmware version of the on-board NI Master is displayed to the
right of the device within the Online Tree tab as 00000 NI Master.
3. After the Communication Verification dialog window indicates active communication between the PC
and the Master, verify the NetLinx Master (00000 NI Master) appears within the OnLine Tree tab of the
Workspace window (FIG. 28). The default NI Master value is zero (00000) and cannot be changed.
4. If either the on-board NI Master or Integrated Controller is not the latest firmware version, follow the
procedures outlined in the following sections to obtain these Kit files from www.amx.com and then
transfer the new firmware Kit files to the device.

Configuration and Firmware Update
29
NI-3101-SIG Signature Series NetLinx Integrated Controller
On-board NI Master
Control cards
NetLinx Integrated Controller
NetLinx Studio app. version
Unbound Dynamic Device
FIG. 28 Sample NetLinx Workspace window (showing OnLine Tree tab)
Upgrading the On-board Master Firmware via an IP
The on-board Master firmware Kit file is not the same as the Integrated Controller Kit file. Below is a table
outlining the current sets of on-board Master and Integrated Controller Kit files used by the NI-Series of
products:
Firmware Kit File usage for NI Controllers
NI-3101 (FG2105-05/15) On-board Master Kit file: 2105_04_NI-X100_Master
Integrated Controller Kit file: 2105_04_NI-X100
Only Master firmware Kit files use the word _Master in the Kit file name.
1. Follow the procedures outlined within the Communicating with the NI Device via an IP section on
page 26 to connect to the target NI device via the web.
2. After Studio has established a connection to the target Master, click the OnLine Tree tab of the
Workspace window to view the devices on the System. The default System value is one (1).
3. Right-click the associated System number and select Refresh System. This establishes a new connection
to the specified System and populates the list with devices on that system. The communication method is
highlighted in green on the bottom of the NetLinx Studio window.
4. After the Communication Verification dialog window verifies active communication between the PC and
the Master, verify the NetLinx Master (00000 NI Master) appears in the OnLine Tree tab of the
Workspace window. The default NI Master value is zero (00000).
First upgrade of the on-board Master using the Master’s Kit file.
The Integrated Controller can later be upgraded using the Controller’s Kit file.
BOTH Kits should be used when upgrading any firmware associated with the
Integrated Controllers.
5. If the on-board Master firmware being used is not current, download the latest Kit file by first logging in
to www.amx.com and then navigating to Tech Center > Firmware Files to locate the desired file from
within the NetLinx section of the web page.
6. Click on the desired Kit file link, accept the Licensing Agreement, and verify download of the correct NI
Master firmware (Kit) file to a known location.
7. From within Studio, select Tools > Firmware Transfers > Send to NetLinx Device from the Main menu
to open the Send to NetLinx Device dialog (FIG. 29). Verify the target’s System number matches the

Configuration and Firmware Update
30
NI-3101-SIG Signature Series NetLinx Integrated Controller
Selected on-board Master firmware file
Description field for selected Kit file
Device and System Number
must match the Device and System values
listed in the Workspace window
Firmware download
status
value listed within the active System folder in the OnLine Tree tab of the Workspace. The Device
number is always 0 for the NI Master.
FIG. 29 Send to NetLinx Device dialog (showing on-board NI_Master firmware update via IP)
8. Select the NI Master’s Kit file from the Files section (FIG. 29).
The Kit file for the NI-2100/3100/3101-SIG/4100 Series of NI Masters begins with
2105_04_NI-X100_Master.
DO NOT use any Master Kit file other than the one specified, since each Master
Kit file is specifically configured to function on a specific NI unit.
9. Enter the System number associated with the target Master (listed in the OnLine Tree tab of the
Workspace window) and verify the Device number value. The Port field is greyed-out.
The Device number is always 0 for the NI Master.
10. Click the Reboot Device checkbox to reboot the NI unit after the firmware update process is complete.
11. Click Send to begin the transfer. The file transfer progress is indicated on the bottom right of the dialog
box (FIG. 29).
Only upon the initial installation of a new Kit file to an on-board Master will there
be a error message displayed indicating a failure of the last component to
successfully download. This is part of the NI Master update procedure and requires
that the firmware be reloaded after a reboot of the unit. This consecutive process
installs the final component of the new Kit file.
12. After the last component fails to install, click Done.
13. Click Reboot (from the Tools > Reboot the Master Controller dialog) and wait for the System Master to
reboot. The STATUS and OUTPUT LEDs should begin to alternately blink during the incorporation. Wait
until the STATUS LED is the only LED to blink.
14. Press Done once until the Master Reboot Status field reads *Reboot of System Complete*.
15. Repeat steps 5 - 9 again (the last component will now successfully be installed).
16. Click Close once the download process is complete.
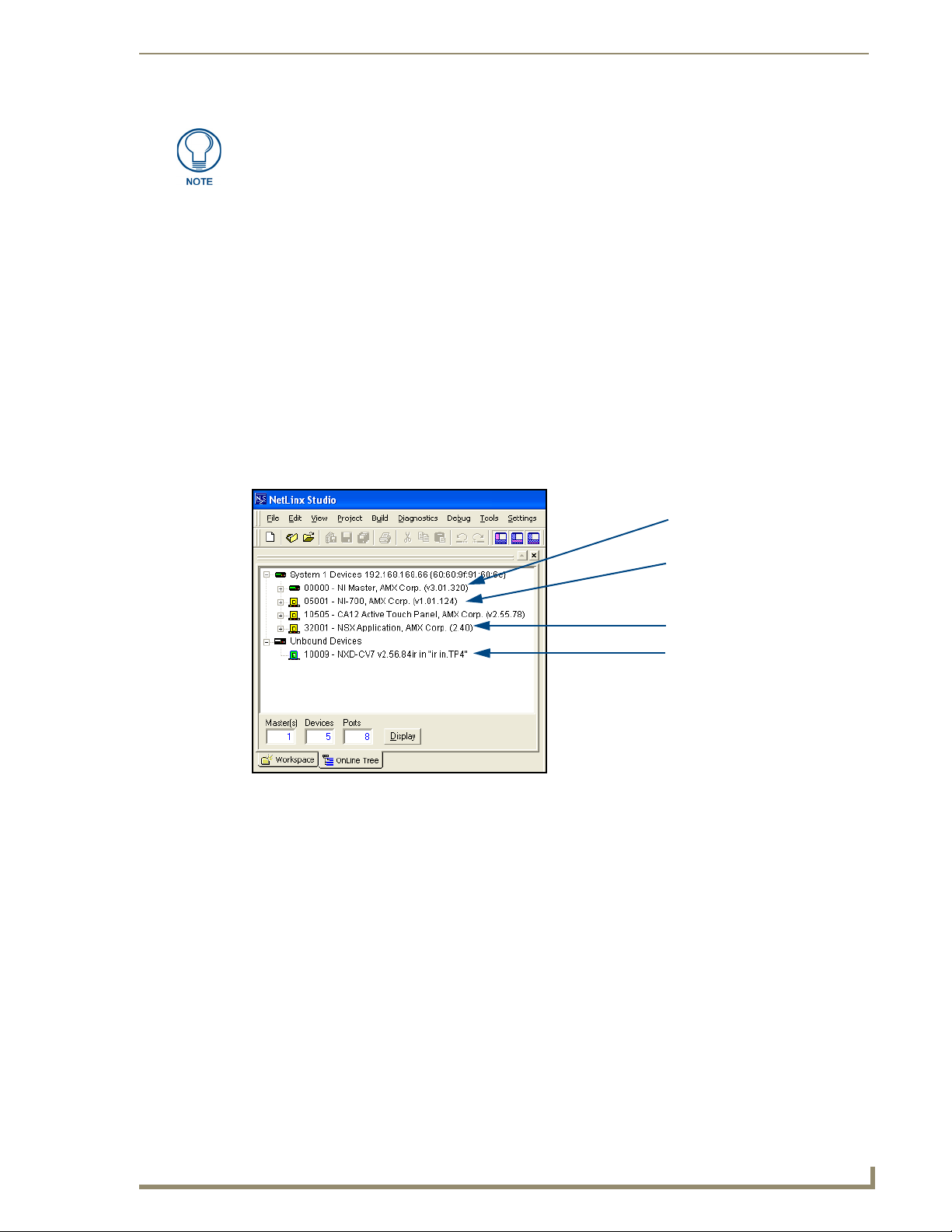
Configuration and Firmware Update
31
NI-3101-SIG Signature Series NetLinx Integrated Controller
On-board Integrated Controller
Unbound Dynamic Device
NetLinx Studio app. version
On-board NI Master
(NI-X000_Master) - Device 0
(NI-X000)
The OUTPUT and INPUT LEDs alternately blink to indicate the on-board Master is
incorporating the new firmware. Allow the Master 20 - 30 seconds to reboot and fully
restart.
17. Right-click the System number and select Refresh System. This establishes a new connection to the
System and populates the list with the current devices (and their firmware versions) on your system.
Upgrading the NI Controller Firmware via IP
1. Follow the procedures outlined within the Communicating with the NI Device via an IP section on
page 26 to connect to the target NI device via the Web.
2. After NetLinx Studio has established a connection to the target Master, click the OnLine Tree tab of the
Workspace window to view the devices on the System. The default System value is one (1).
3. Right-click the associated System number and select Refresh System. This establishes a new connection
to the specified System and populates the list with devices on that system. The communication method is
highlighted in green on the bottom of the NetLinx Studio window.
4. After the Communication Verification dialog window verifies active communication between the PC and
the NI unit, verify that the device appears in the OnLine Tree tab (FIG. 30) of the Workspace window
(ex: NI-3101). This entry is different than that of the NI Master, which uses a device value of 00000 (see
below):
FIG. 30 Sample NetLinx Workspace window (showing SEPERATE NI-Master and Controller)
5. If the NI Controller firmware being used is not current, download the latest Kit file by first logging in to
www.amx.com and then navigating to Tech Center > Firmware Files, locating the desired file from
within the NI Series Device (Integrated Controller) section of the web page.
6. Click on the desired Kit file link, accept the Licensing Agreement, and verify that the Integrated
Controller firmware (Kit) file has been downloaded to a known location.
7. From within NetLinx Studio, select Tools > Firmware Transfers > Send to NetLinx Device from the
Main menu to open the Send to NetLinx Device dialog (FIG. 31). Verify that the target’s System number
matches the value listed within the active System folder in the OnLine Tree tab of the Workspace. The
Device must match the entry for the on-board Integrated Controller (NI-X000/NI-X000) device.

Configuration and Firmware Update
32
NI-3101-SIG Signature Series NetLinx Integrated Controller
Selected on-board Integrated Controller firmware file
Description field for selected Kit file
Device and System Number
must match the Device and System
values listed in the Workspace window
Firmware download
status
FIG. 31 Send to NetLinx Device dialog (showing on-board Integrated Controller firmware update via IP)
The Kit file for the Integrated Controller on the NI-2100/3100/3101-SIG/4100 Series
begins with 2105_04_NI_X100.
DO NOT use any Kit file other than the one specified, since each Kit file is
specifically configured to function on a specific NI unit.
8. Select the Integrated Controller’s (_X00) from the Files section (FIG. 31).
9. Enter the System and Device numbers associated with the target Master (listed in the Workspace
window). The Port field is greyed-out.
10. Click the Reboot Device checkbox to reboot the NI device after the firmware update process is complete.
11. Click Send to begin the transfer. The file transfer progress is indicated on the bottom-right of the dialog
(FIG. 31).
12. Click Close once the download process is complete.
The OUTPUT and INPUT LEDs alternately blink to indicate the unit is incorporating
the new firmware. Allow the unit 20 - 30 seconds to reboot and fully restart.
13. Right-click the System number and select Refresh System. This establishes a new connection to the
System and populates the list with the devices and their firmware versions currently on the system.
If the connection fails to establish, a Connection Failed dialog appears.
Try selecting a different IP Address if communication fails.
Press the Retry button to reconnect using the same communication parameters.
Press the Change button to alter the communication parameters and repeat
steps 2 thru 11.

NetLinx Security within the Web Server
33
NI-3101-SIG Signature Series NetLinx Integrated Controller
NetLinx Security within the Web Server
NetLinx Masters incorporate built-in security for HTTPS and Terminal sessions (enhanced with SSL and SSH
respectively), ICSP data verification/encryption, and Server Port configuration. By using both SSL certificate
verification and encryption over a secured HTTP (HTTPS) connection, this version of NetLinx firmware
provides users with a more convenient web-based method of securing both the Master and its data
communications. Additional features in this release are the use of both authentication protocols and the ability
to perform online NetLinx Diagnostics via the web server.
Terminal setup and security configuration are still valid and supported in this build of the NetLinx Master
firmware.
This NetLinx Web Server is used to power Master security, data encryption, and SSL certificate/encryption
features on current AMX Masters such as the ME260/64 and NI-Series of Controllers. This web server not
only provides username and password security for the target Master, but also a new level of secure encryption
for ICSP data communication among the various AMX software and hardware components. New security
features for the Masters include:
Enhanced Username and Password requirements
HTTPS and SSL certificate interaction
Use of a pre-installed AMX SSL certificate
ICSP communication and encryption
The first layer of security for the Master involves prompting a user to enter a valid username and password
before gaining access to a secured feature on the target Master. This data is pre-configured by the administrator
within the Group and User Level pages of the Security section. If an option is enabled within the System
Security page, a user is prompted to enter a valid username and password before gaining access to the
corresponding feature. This access is only granted if their information matches a previously created profile
assigned sufficient rights for that action. An already logged in user can enter a new profile by using the Login
field to enter a new profile’s
username and profile.
This username and password information is also used by both G4 touch panels (within the System
Connection firmware page) and AMX software applications such as NetLinx Studio v 2.4 (via the
Master Communications dialog) to communicate securely with a Master using encrypted
communication.
The second layer of security uses a combination of secure HTTP (HTTPS) communication and SSL
encryption to secure data being transferred from the web server application and the target Master.
To ensure this higher degree of security on the Master, an administrator can disable the HTTP Port access,
enable HTTPS Port access (both from within the same Manage System > Server page), and then alter the
level of encryption on the current SSL Certificate to meet their security needs.
SSL (Secure Sockets Layer) is a protocol that works by encrypting data being transferred over an
HTTPS connection. URLs that require a secure connection begin with https: instead of http: (in
the browser’s Address field). These security capabilities are configured to function via a web
session within your browser. The encryption level (64 or 128-bit) achieved over the HTTPS Port is
done via the SSL Certificate currently in use on the target Master. Whereas SSL creates a secure
connection between a client and a server, over which any amount of data can be sent securely,
HTTPS is designed to transmit individual messages securely. Therefore both HTTPS and SSL can
be seen as complementary and are configured to communicate over the same port on the Master.
The third layer of protection is an SSL Certificate (specifically identifying the target Master and using a
unique key to encrypt data). SSL works by using a private key to encrypt data that's transferred over the SSL
connection. By default, current Masters are shipped with a default AMX SSL certificate called
sslexample.amx.com. This pre-configured certificate can be used as a road map to create a unique certificate.
The Master’s SSL certificate can be either requested (from an external CA) or self-generated, and then
installed/imported onto the target Master. This action adds the certificate to the trusted site certificate listing
within the computer’s Internet browser.
A fourth layer of security enables the encryption of data communication amongst the various AMX hardware
and software components (such as between NetLinx Studio and the Master, or TPDesign4 and the touch panel
(communicating through the Master)). Refer to theSecurity Features section on page 38 for more information.

NetLinx Security within the Web Server
34
NI-3101-SIG Signature Series NetLinx Integrated Controller
NetLinx Security Terms
The following table lists some commonly used NetLinx Security terms:
NetLinx Security Terms
User A user is a single potential client of the NetLinx Master.
Administrator An administrator has privileges to modify existing NetLinx Master access
Group A group is a logical collection of users. Note that any properties possessed by
Username A username is a valid character string (4 - 20 alpha-numeric characters)
Group name A group name is a valid character string (4 - 20 alpha-numeric characters)
Password A password is a valid character string (4 - 20 alpha-numeric characters) to
Access Rights Each of the NetLinx Master’s features has pre-defined security procedures.
groups, users, and their rights. The administrator can also assign NetLinx
communication access rights for different users or groups (ex: Telnet and
HTTP access) and configure the Master’s SSL server certificate.
a group (ex: access rights, directory associations, etc.) are inherited by all
members of that group.
defining the user. This string is case sensitive and each username must be
unique.
defining the group. This string is case sensitive and each group name must
be unique.
supplement the username in defining the potential client. This string is also
case sensitive.
The access right for a particular feature determines if a user or group has
access to that feature by entering a valid username and password.
The maximum length of a username or password is 20 characters. The minimum
length of a username or password is four characters. Characters such as # (pound)
& (ampersand) and ’ " (single and double quotes) are invalid and should not be
used in usernames, group names, or passwords.
Accessing an Unsecured Master via an HTTP Address
Refer to theUpgrading the On-board Master Firmware via an IP section on page 29 for more detailed
information on how to download the latest firmware from www.amx.com. This firmware build enables SSL
certificate identification and encryption, HTTPS communication, ICSP data encryption, and disables the
ability to alter the Master security properties via a TELNET session.
Although Telnet security configuration access can no longer be used on a Master with this
firmware, a Terminal connection (using HyperTerminal) can still be established using the Master’s
USB low-speed connection (if the Telnet Port is enabled via the Manage System > Server page).
Once the Master’s IP Address has been set through NetLinx Studio version 2.4 or higher:
1. Launch your web browser.
2. Enter the IP Address of the target Master (ex: http://198.198.99.99) into the web browser’s Address field.
3. Press the Enter key on your keyboard to begin the communication process between the target Master and
your computer.
Initially, the Master Security option is disabled (from within the System Security page) and no
username and password is required for access or configuration.
Both HTTP and HTTPS Ports are enabled by default (via the Manage System > Server page).
4. The first active page displayed within your open browser page is Manage WebControl Connections.
Once HTTP Access is enabled for a Master; certificate verification and username and
password verification must occur. Refer to theAccessing an SSL-Enabled Master via
an IP Address section on page 92 for more information.

NetLinx Security within the Web Server
35
NI-3101-SIG Signature Series NetLinx Integrated Controller
Active
frame
Navigation
frame
Browser Application Frames
A web page (FIG. 32) can be divided into separate sections or frames, each of which can be independent of
one another and display their own information.
Located on the left side of the populated Browser window is the Navigation frame which allows a user to
navigate throughout the application. Located on the right side of the Browser window is the Active frame
which displays the pages corresponding to the currently selected option from within the Navigation frame.
FIG. 32 Browser Application frames
The first Active frame displayed within the Browser is the Manage WebControl Connections page.
Default Security Configuration
Security for web pages is separated into two access groups: HTTP and Configuration:
HTTP Access allows an authorized user to view these web pages by first requiring the entry of a
username and password at the beginning of every connection session with the target Master. If
Master Security is not enabled, the username and password fields are not displayed and the
Master is openly accessible. The Master Security configuration prevents users from altering any
security or operational parameters. Unless this option is enabled, all subordinate options are
inaccessible and greyed-out.
Configuration access is initially greyed-out until the Master Security option is enabled. This
feature requires an authorized user provide a valid username and password before being granted
access to change configuration and communication parameters on the target Master. Only with this
type of access can a user begin to alter security or operational parameters such as access rights,
Port assignments, System values, and SSL certificate usage.
If a user is not currently logged-into the Master (via the initial Login screen) and they attempt to access a
feature wherein authentication is required, they are prompted with a message to log into the Master (via the
Log In button) (FIG. 33). After the user’s information and rights are confirmed, the login process is
successfully completed and the button changes state and displays Log Out. A user must be logged into the
system before their associated rights can be activated for the current session.

NetLinx Security within the Web Server
36
NI-3101-SIG Signature Series NetLinx Integrated Controller
Log In/Log Out
Username
Password
field
field
button
FIG. 33 Log In/Log Out fields
Authentication is based upon matching the user’s data to pre-configured username
and password information, and then assigning the rights assigned to that user.
The maximum length of a username or password is 20 characters. The minimum
length of a username or password is four characters. Characters such as # (pound) &
(ampersand) and ’ " (single and double quotes) are invalid and should not be used in
usernames, group names, or passwords.
There is no limit to the number of concurrent logins allowed for a single user. This feature facilitates the
creation of a single user (which is really an ICSP device such as a touch panel) that is provided to a number of
ICSP devices using the same login to obtain access to the Master.
As an example, if you had 50 devices connected to a Master, you would not have to create 50
individual user accounts-one for each device. Instead, you only need to create one to which all 50
devices use for access.
By default, the NetLinx Master creates the following accounts, access rights, directory associations, and
security options:
Default Security Configuration (case-sensitive)
Account 1 Account 2 Group 1
Username: administrator Username: NetLinx Group: administrator
Password: password Password: password Rights: All
Group: administrator Group: none Directory Association: /*
Rights: All Rights: FTP Access
Directory Association: /* Directory Association: none
Security Options: FTP Security - Enabled
Admin Change Password Security - Enabled
All other options - Disabled
By default, Master Security (and all subordinate options) are disabled. If the user/group is given
FTP access rights by the administrator, all directories can become accessible (read/write/modify).
The administrator user account cannot be deleted or modified with the exception of its password.
Only a user with both Configuration access and administrator rights can alter the administrator’s
password.
The NetLinx user account was created to be compatible with previous NetLinx Master firmware
versions. This account is initially created by default and can later be deleted or modified.
The administrator group account cannot be deleted or modified.

NetLinx Security within the Web Server
37
NI-3101-SIG Signature Series NetLinx Integrated Controller
Compatible
devices field
G4 panels
Compression
Options
(showing G4
WebControl links)
Master Firmware Security Access Parameters
Master Security Configuration
Terminal (RS232/USB Configuration port) security
HTTP (Web Server) Security (allows for access via a secure HTTP connection (if enabled) by
requiring a username and password)
Telnet Security
Configuration (allows the alteration of current communication, system, and security settings by
requiring a username and password)
ICSP Connectivity (for AMX product communication)
Encryption Requirement (only used if ICSP Connectivity is enabled - encrypts the data being
transferred among the different AMX products)
Installation of SSL functionality onto your Master causes security setup via Telnet to
be disabled. Although Telnet security configuration access can no longer be used on
the Master, a Terminal connection (using HyperTerminal) can still be established
using the Master’s RS232 Program port.
Web Control
This section of the Navigation frame contains the Mange Connections feature which allows control of
compatible devices communicating with the target Master.
Managing WebControl Connections
This page (FIG. 34) is accessed by clicking on the Manage connections link. Once activated, this page
displays links to G4 panels running the latest G4 Web Control feature.
FIG. 34 Manage WebControl Connections page (populated with compatible panels)
If the Master Security and HTTP Access options have not been previously enabled on the target Master, a
user does not need to Log into the Master to gain access to the Manage WebControl Connections page. This
page allows a user to view all G4 enabled touch panels running G4 WebControl.
To establish a secure connection between the touch panel and the target Master, the panel must be
using a valid username and password (that can be matched to a previously configured user on the
target Master) and the ICSP Connectivity option must be enabled within the System Level page.
If at some later point, that user profile is removed from the Master, reboot both the panel and
Master. After reboot, the connection status of the panel (from with the firmware Setup page) shows
"No Encryption".

NetLinx Security within the Web Server
38
NI-3101-SIG Signature Series NetLinx Integrated Controller
Security features
Clicking on a G4 WebControl link opens a separate browser window which is configured to display the current
information from the panel using the native resolution of the target panel. An example is a CA15 panel link
opening a new window using an 800 x 600 resolution.
The following table lists the features available to an administrator or other authorized user from the Manage
WebControl Connections page:
Manage WebControl Connection Page Features
Feature Description
Compatible Devices Field: This area displays G4 icons (with associated links) if a G4 panel
Communication Compression Options: Allows you to choose from among two compression options:
Security Features
This section of the Navigation frame (FIG. 35) contains the NetLinx system security parameter links which
allow an authorized user to define access rights at the system level and those for the various groups or users.
running Web Control is communicating with the target Master.
• These compression settings are most useful when working
either over a bandwidth-restricted LAN or over the Internet.
• Use Compression allows the user to specify that the
transmitted data packets be compressed. This speeds up the
visual responses from the panel by minimizing the size of the
information relayed through the web and onto the screen.
• Use Low Color allows the user to specify the number of colors
used to display the image from the panel be reduced. By
reducing the numbers of colors, both the size of the
information is reduced and the response delay is decreased.
FIG. 35
System Level Security - Enable/Disable System Security page
Security settings on related pages (such as the System Level, Group Level, and User
Level) require that an authorized user be logged into the Master and have
Configuration Access rights either directly assigned with that user or associated
with the related Group.

NetLinx Security within the Web Server
39
NI-3101-SIG Signature Series NetLinx Integrated Controller
The following table lists the NetLinx System Security options that can be granted or denied by an
administrator or other authorized user:
Security Features
Feature Description
System Level: Provides an authorized user with the ability to alter the current
security options of the system assigned to the target Master.
Group Level: Provides an authorized user with the ability to assign and alter
group properties such as creating, modifying, or deleting a
group’s rights, and also allows for the definition of the files/
directories accessible by a particular group.
• Any properties possessed by a group (access rights/directory
associations, etc.) are inherited by all members of that group.
User Level: Provides an authorized user with the ability to assign and alter
user properties such as creating, modifying, or deleting a users’
communication rights, and defining the files/directories
accessible by a particular user.
Enabling the Master Security option after the groups, users, and passwords have
been set up is highly recommended. If not, when the user accesses the Master from
within another session, the default administrator username and password must be
used for access.
Security - System Level Security page
To access this page, click the Security Level link from within the Security section of the Navigation frame.
This page is strictly used to guarantee that a valid username and password is entered prior to gaining access to
the listed features and options.
If the Master Security option is not selected, the Master is completely open and can
be modified by anyone accessing the target Master via the web server’s UI.
The options on the NetLinx Master Security page (FIG. 36) are only accessible and configurable if the Master
Security checkbox is selected. The Master Security checkbox selection toggles the appearance of the
NetLinx Master security options and makes them accessible. Enabling an option on this page requires that a
user enter a valid username and password before they are granted access to the specific feature. Some
examples are:
Requiring verification before accessing the Master - HTTP Access must be enabled.
Requiring verification before altering a current Master security setting - Master Security and
Configuration must be enabled.
Requiring verification from a communicating AMX software (such as NetLinx Studio
v 2.4 or TPD4 v 2.5) before accepting communication for file/firmware transfers, the
Configuration, ICSP Connectivity and Require Encryption options must be enabled.

NetLinx Security within the Web Server
40
NI-3101-SIG Signature Series NetLinx Integrated Controller
NetLinx Master
security features
Require Encryption
option (enable/disable)
Security Level features
FIG. 36 System Level Security - Enable/Disable System Security page
System Level Security Page
Feature Description
Master Security: This option allows an authorized user to require that a valid
Terminal (RS232/USB) Access: This selection determines if a username and password is
HTTP Access: This selection determines if a username and password is
username and password be required for access to a feature
listed on this page.
• These are global options that enable or disable the login
requirement for both users and groups.
• If the Master Security checkbox is not enabled, all subordinate
options are greyed-out and not selectable, meaning that the
Master is completely unsecured and can be altered by any
user (regardless of their rights).
required for Terminal communication (through the USB
connector).
• If Terminal Security is enabled, a user must have sufficient
access rights to login to a Terminal session and communicate
with the Master.
required for communication over HTTP or HTTPS Ports (see
FIG. 37).
• If enabled, a user must have sufficient access rights to browse
to the NetLinx Master via a Web Browser.
• Enabling this field requires the user (within a new session)
submit a valid username and password before being able to
view the web server pages.
• If disabled, the Master is open for viewing and does not ask for
this information during any consecutive sessions (until the
user attempts to access a feature which is enabled within this
page).
• This requirement of a valid username and password affects
both HTTP and HTTPS communication with the target Master
using the web server.

NetLinx Security within the Web Server
41
NI-3101-SIG Signature Series NetLinx Integrated Controller
System Level Security Page (Cont.)
Feature Description
Telnet Access: This selection determines if a username and password is
required for Telnet Access (see FIG. 37).
• If Telnet access is enabled, a username and password is
required before allowing communication over either the Telnet
and/or SSH Ports. SSH version 2 is only supported.
• This authorized user must have sufficient access rights to login
through a Telnet session to the Master.
• To establish a secure Telnet connection, an administrator can
decide to disable the Telnet Port and then enable the SSH
Port. Refer to theSetting the Master’s Port
Configurations section on page 61.
Configuration (security): This selection determines if a username and password is
required before allowing a group/user to alter the current
Master’s security configuration and communication settings (see
FIG. 37).
• Configuration access provides the user with the ability to
perform configuration functions on the NetLinx system through
NetLinx Studio. This includes such things as: IP
configuration/Reset, URL list settings, Master
communication settings, and security parameters.
• If security Configuration is enabled, a user/group must have
sufficient access rights to access the Main Security Menu.
• Any time a configuration operation is performed, the Master
verifies the current access rights for that feature and then
requires a valid username and password
(if not already logged in).
- An example would be if you are trying to add a New User or
modify the rights of an existing Group.
ICSP Connectivity: This selection determines if a username and password is
required prior to communication with a target NetLinx Master via
an ICSP connection using any transport method (TCP/IP, UDP/
IP, and RS-232) (see FIG. 37).
• If this access is enabled and the user is not logged-in, when
the user attempts to connect, the authentication fails and
displays an “Access not allowed” message.
• This feature allows communication amongst various AMX
hardware and software components. This feature works in
tandem with the Require Encryption option to require that any
application or hardware communicating with the Master must
provide a valid username and password.
• Refer to theICSP Authentication section below for more
detailed information.
Require Encryption: Requires that any data being transmitted or received via an
ICSP connection (among the various AMX products) be
encrypted and that any application or hardware communicating
with the Master over ICSP must provide a valid username and
password.
The following graphic illustrates the Ports which can be enabled for the validation of rights by
using a valid username and password. When one of the above options is enabled, the Master then
requires the entry of a valid username and password to validate rights for that action and then grant
or deny access.

NetLinx Security within the Web Server
42
NI-3101-SIG Signature Series NetLinx Integrated Controller
Telnet Port
ICSP Port
HTTP Port
HTTP/SSL Port
SSH Port
FTP Port
Master
HTTP Access option
Telnet Access option
ICSP Connectivity
and Encryption option
Username and
Password are
required when enabled
SS
SS
SS
SS
FTP Access option
SS
FIG. 37 Port Communication Settings
Setting the system security options for a NetLinx Master
This page simply toggles the requirement of a user to enter a valid username and password before gaining
access to a particular feature. For every action, the Master validates whether a username and password are
required and whether the user has sufficient rights. Refer to theSecurity - Group Level Security page section on
page 44 for more information on the assignment of the Group/User rights. For example, if the user were
attempting to modify the configuration parameters of the Master, their username and password must be
associated with a profile which was previously granted Configuration Access privileges within the web server.
If they their profile didn’t have enough rights to accomplish their action an "Insufficient Rights..." message
appears on top of the active page.
1. Enter the URL/IP Address of the target Master into the Address/URL field within the web browser.
Initially the connection is unsecured and communication can be made via an HTTP connection. Refer to
theAccessing an Unsecured Master via an HTTP Address section on page 34 for more detailed
instructions.
2. Click the Security Level link (from within the Security section of the Navigation frame) to open the
System Security page. The Master Security checkbox selection (FIG. 38) toggles the appearance of the
NetLinx Master security options.
3. Click on the Master Security checkbox to access to the security parameters on the target Master and
allow an authorized user (with configuration access rights such as an Administrator) the ability to alter
the subordinate security parameters. Refer to theSecurity - System Level Security page section on page 39
for more detailed field descriptions.
Each selection simply toggles the security setting from enabled to disabled.
By default, the Master Security option is disabled (unchecked), including the
subordinate Master Security components (even though they might show a
checkmark, they are greyed out). An open Master does not require a user to enter a
valid username and password.
4. Click on the desired access parameters and configuration checkboxes necessary to require user validation
prior to usage.
Enabling the Terminal, HTTP, and Telnet Access options require that a valid username and
password be entered prior to gaining access to the desired action. If the HTTP Access option is
enabled, upon the initial connection to the Master (via the web browser) the Login page
appears and requires a valid username and password be entered before allowing access to the
web server pages.
Enabling the Configuration option requires that the user be logged in and their rights validated
before allowing any modification to the current Master security configuration and communication

NetLinx Security within the Web Server
43
NI-3101-SIG Signature Series NetLinx Integrated Controller
NetLinx Master
security features
Require Encryption
option (enable/disable)
Security Level features
FIG. 38 System Level Security - Enable/Disable System Security page with selections
parameters. If the Configuration option is enabled and the user wants to modify the Master’s
IP Address; they would either be prompted to log in (via the Login button) or if already
logged in, notified whether their rights are sufficient to allow them to change the current
parameter.
The ICSP Connectivity option is required to allow authenticated and/or secure communication
between the Master and other AMX hardware/software. To establish an authenticated ICSP
connection (where the external AMX hardware/software would have to provide a valid username
and password). This option must be enabled (checked).
5. Click on the checkbox next to Require Encryption to enable the requirement of data encryption over the
ICSP connection. Note that this is optional and if enabled, requires more processor cycles to maintain.
6. Click the Update button to accept and save any changes on this page back to the Master. Updating these
changes is instantaneous and does not require a reboot. Successful incorporation of the changes to the
Master’s security configurations results in an on-screen message stating: "Security is enabled when it is
checked".
A Group represents a logical collection of individual users. Any properties possessed
by a group (ex: access rights, directory associations, etc.) are inherited by all
members of that group.
The "administrator" group account cannot be deleted or modified.
ICSP Authentication
In a Master-to-Master system, the Master which accepts the IP connection initiates the authentication process.
This configuration provides compatibility with existing implementations and provides more flexibility for the
implementation of other devices.

NetLinx Security within the Web Server
44
NI-3101-SIG Signature Series NetLinx Integrated Controller
Manage Groups page
Configure Group Properties
page (adding a new group)
Security - Group Level Security page
To access this page, click the Group Level link (from within the Security section of the Navigation frame).
This page (FIG. 39) allows an authorized user to both select and modify an existing group, delete an existing
group, or add a new group. Unless you are logged in with administrator privileges, you will not be allowed to
modify the default administrator profile.
FIG. 39 Group Level Security - Manage Groups Security page
Manage Group Page
Feature Description
Manage Groups page: This page allows a user to either modify the rights for a group
available from the displayed list or use the New button to access
a secondary window where a user can modify the rights for
either the new or existing group.
New • Clicking this button allows a user to add a new group and
Select • Clicking this button takes you to the selection’s corresponding
configure its settings through the Configure Group Properties
page.
Configure Group Properties page.
• This button is greyed-out if the current user doesn’t have the
right to modify the rights for that group.
Note: The “administrator” group can’t be modified unless you are
logged in as a user with Configuration Access rights.

NetLinx Security within the Web Server
45
NI-3101-SIG Signature Series NetLinx Integrated Controller
Configure Group Properties Page
Feature Description
Configure Group Properties: This page allows an authorized user to configure the options for
either a pre-existing or new group. Configuration on this page
consists of both the options and directories to which the group is
granted access.
Update • This button submits the modified page (form) information back
to the server.
• If the group was successfully added after pressing the Update
button; a status message of “Group XYZ was successfully
added” is displayed.
Back • This button returns the user to the Manage Groups page.
Delete • This button is only available when modifying/deleting an
existing group.
Group Security Details: • This section provides the user with several rights which can
either be enabled or disabled.
Group Name • A valid character string defining the name of the group
(4 - 20 alpha-numeric characters).
• The string is case sensitive and must be unique.
Admin Change Password Access • This selection enables or disables the group’s right to change
the administrator’s user passwords.
Note: Once the Administrator’s password has been changed,
the default password can no longer be used to gain access.
Terminal (RS232/USB) Access • This selection enables or disables Terminal Security Access
for the target group (through the USB connector).
FTP Access • This selection enables or disables FTP Access for the target
group.
HTTP Access • This selection enables or disables Web Server access for the
target group.
Telnet Access • This selection enables or disables Telnet Security access for
the target group.
Configuration Access • This selection enables or disables the ability of a group to alter
the security Configuration settings such as:
- IP configuration/Reset, URL list settings, Master
communication settings, and file transfers.
ICSP Access • This selection grants the members of this Group ICSP access.
• ICSP communication allows a user to connect to the target
NetLinx Master via ICSP connection using any transport
method (TCP/IP, UDP/IP, and RS-232/USB).
Encrypt ICSP Connection • This selection enables encryption of the ICSP communication.
• This checkbox is greyed-out until ICSP Access is enabled.
Group/Directory Associations: • Provides an authorized user with a view of current directories
on the target Master that are available to the selected group.
• A Directory Association defines the directory paths and files a
particular user or group can access via the Web Server on the
NetLinx Master.
• The displayed folders are the directory pathnames present on
the target Master. These folder/files can be placed on the
target Master via an FTP connection to the target Master.
A User represents a single potential client of the NetLinx Master, while a Group represents a
logical collection of users. Any properties possessed by groups (example: access rights, directory
associations, etc.) are inherited by all the members of the group.

NetLinx Security within the Web Server
46
NI-3101-SIG Signature Series NetLinx Integrated Controller
Adding a new Group
1.
Click the Group Level link (from within the Security section of the Navigation frame) to open the
Manage Groups page.
2. Click the New button to be transferred to the Configure Group Properties page (FIG. 39).
3. From within the Group Security Details section, enter a unique name for the new group. The name must
be a valid character string consisting of 4 - 20 alpha-numeric characters. The word administrator cannot
be used for a new group name since it already exists by default.
4. Enable the security access rights you want to provide to the group. By default, all of these options are
disabled.
5. From within the Group Directory Associations section, place a checkmark next to the directories
(available on the target Master) to provide an authorized group with access rights to the selected
directories. If you select a group directory note that all lower groups in that tree will be selected.
6. Click the Update button to save your changes to the target Master. If there are no errors within any of the
page parameters, a “Group added successfully” is displayed at the top of the page.
7. Click the Back button to return to the Manage Groups page.
Any security changes made to the Master from within the web browser are instantly
reflected within a Terminal session without the need to reboot.
Security changes made to the Master from within a Terminal window are not reflected
within the web browser until the Master is rebooted and the web browser connection
is refreshed.
Modifying the properties of an existing Group
Click the Group Level link (from within the Security section of the Navigation frame) to open the
1.
Manage Groups page.
The fields displayed when modifying groups are the same as those available when
adding a new group, except for the Group Name field which is pre-populated.
The Administrator’s rights are not editable and its Select button is greyed-out.
2. Click the Select button (next to the selected Group name) to open the Configure Group Properties page
for the particular group.
3. From within the Group Security Details section, modify the previously configured access rights by either
enabling or disabling any of the available checkboxes shown within the Configure Group Properties
page.
4. From within the Group Directory Associations section, place or remove any checkmarks next to the
available directories to modify an authorized group’s directory access rights.
5. Click the Update button to save the changes to the target Master. If the modification of any of this page’s
parameters has no errors, a “Group updated successfully” notice is displayed at the top of the page.
6. Click the Back button to return to the Manage Groups page.
Deleting an existing Group
1.
Click the Group Level link (from within the Security section of the Navigation frame) to open the
Manage Groups page.
2. Press the Select button (next to the selected Group name) to open the Configure Group Properties page
(FIG. 39) for the particular group.
3. Click the Delete button to remove the selected group and return to the Manage Groups page.
If you are not logged into the Master, you receive a reminder message: "You must login before
Security Settings can be changed".
Log into the Master and repeat the previous steps.
If the group is associated with several users, trying to delete the group might give an error notice. If
this happens, change the group association of those specific users utilizing the old group and either

NetLinx Security within the Web Server
47
NI-3101-SIG Signature Series NetLinx Integrated Controller
Manage Users page
Configure User Properties
page (adding a new user)
give them a new group or assign them (none) as a group. When returning to delete the desired
group, the "Group deleted successfully" notice is displayed.
Security - User Level Security page
To access the User Level Security page (FIG. 40), click on the User Level link (from within the Security
section of the Navigation frame). This page allows an authorized user to add a user account (FIG. 30) and then
assign that user’s current access rights.
FIG. 40 User Level Security - Manage Users Security page
Manage Users Page
Feature Description
Manage Users page: This page allows a user to either modify the rights for an existing
New • Clicking this button allows an authorized user to add a new
Select • Clicking this button opens the selection’s corresponding
user (available from the displayed list) or use the New button to
access a secondary window to create a new user.
user and configure their settings through the Configure User
Properties page.
Configure User Properties page.
• This button is greyed-out if the current authorized user doesn’t
have the right to modify the rights for that user.

NetLinx Security within the Web Server
48
NI-3101-SIG Signature Series NetLinx Integrated Controller
Configure User Properties Page
Feature Description
Configure User Properties: This page allows an authorized user to configure the options for
Update • This button submits the modified page (form) information back
Back • This button returns the user to the Manage Users page.
Delete • This button is only available when modifying/deleting an
User Security Details: • This section provides the user with several rights which can
User Name • A valid character string defining the name of the user (4 - 20
Group • This drop-down list allows the user to associate a pre-defined
Terminal (RS232USB) Access • This selection enables or disables Terminal Security Access
Admin Change Password Access • This selection enables or disables the user’s right to change
FTP Access • This selection enables or disables FTP Access for the target
HTTP Access • This selection enables or disables Web Server access for the
Telnet Access • This selection enables or disables Telnet Security access for
Configuration Access • This selection enables or disables the ability of a user to alter
either a pre-existing or new user. Configuration on this page
consists of both the options and directories to which the user is
granted access.
to the server.
• If the user was successfully added after pressing the Update
button; a status message of “User XYZ was successfully
added” is displayed.
• Always press the Update button after making any changes to
this page.
existing user.
either be enabled or disabled.
alpha-numeric characters).
• If a user is selected from the Manage Users page, this row is
populated with the name of the selected user.
• The string is case sensitive and must be unique.
series of Group rights to the current user profile.
• Once the Update button is clicked, the group rights then are
transferred to the user by placing a checkmark next to those
rights which are available to the associated group.
• Any properties possessed by groups (ex: access rights,
directory associations, etc.) are inherited by users assigned to
a particular group.
• Unchecking a security option (which is available within the
associated group) does not remove that right from the user.
The only way to remove a group’s available security right from
a target user is to either NOT associate a group to a user or to
alter the security rights of the group being associated.
for the target user (through the USB connector).
the administrator’s user passwords.
Note: Once the Administrator’s password has been changed,
the default password can no longer be used to gain access.
user.
target user.
the target group.
the global Configuration settings. Example: IP, Reset URL,
etc.

NetLinx Security within the Web Server
49
NI-3101-SIG Signature Series NetLinx Integrated Controller
ICSP Access • This selection grants this user ICSP access.
• ICSP communication allows a user to connect to the target
NetLinx Master via ICSP connection using any transport
method (TCP/IP, UDP/IP, and RS-232/USB).
Configure Users Properties Page (Cont.)
Feature Description
User Security Details (Cont.):
Encrypt ICSP Connection • This selection enables encryption of the ICSP communication.
• This checkbox is greyed-out until ICSP Access is enabled.
Password/Password Confirm Enter a password for the new user.
• A user password is a valid character string (4 - 20
alpha-numeric characters) that is used to supplement the
username/ID in defining the potential client. The string is
case sensitive and must be unique.
• If this field is left blank (during a user modification) the current
password is left unchanged.
• If a new alpha-numeric string is entered during modification of
the user, it becomes incorporated as the new password after
pressing the OK button.
User/Directory Associations: • Provides an authorized user with a view of current directories
on the target Master that are available to the selected group.
• A Directory Association is a path that defines the directories
and files a particular user or group can access via the Web
Server on the NetLinx Master.
• The displayed folders are the directory pathnames present on
the target Master.
Adding a new User
The information entered within this page can be used by Modero touch panels to verify and establish a secure
connection by encrypting the data being transmitted between the Master and the panel. This information must
be entered into the System Connection page of the panel’s firmware.
1. Click the User Level link (from within the Security section of the Navigation frame) to open the Manage
Users page.
2. Click the New button to be transferred to the Configure User Properties page (FIG. 40).
3. From within the User Security Details section, enter a unique name for the new group. The name must be
a valid character string consisting of 4 - 20 alpha-numeric characters. The usernames administrator and
NetLinx cannot be used since they already exist.
4. From within the Group drop-down list, choose from a list of pre-configured Groups and associate these
rights to the new user.
Any properties possessed by groups (ex: access rights, update rights, directory
associations, etc.) are inherited by users assigned to that particular group.
Unchecking a security option (which is available within the associated group) does
not remove that right from the user. The only way to remove a group’s available
security right from a target user is to either NOT associate a group to a user or to alter
the security rights of the group being associated.
5. Enable any additional security access rights you want to provide to the user. By default, all of these
options are disabled.
6. Enter a user password within both the Pas sw or d and Password Confirm fields. This password is a valid
character string (4 - 20 alpha-numeric characters) that is used to supplement the username/ID in defining
the potential client. The string is case sensitive.
7. From within the User Directory Associations section, place a checkmark next to the directories (on the
target Master) to provide an authorized user with access rights to them.

NetLinx Security within the Web Server
50
NI-3101-SIG Signature Series NetLinx Integrated Controller
Group Rights are
read-only and display the
previously configured
rights assigned to the
associated group
8. Click the Update button to save the changes to the target Master. A “User added successfully” notice is
displayed at the top of the page if the page parameters have no errors.
9. Click the Back button to return to the Manage User page.
Modifying the properties of an existing User
1.
Click the User Level link (from within the Security section of the Navigation frame) to open the Manage
Users page.
The fields displayed when modifying users are the same as those available when
adding a new user, except for the pre-populated User Name field.
2. Click the Select button next to the selected User’s name to open the Configure User Properties page for
the particular user (FIG. 41).
3. From within the User Security Details section, modify any previously configured access rights by either
placing or removing a checkmark from within any of the available checkboxes (FIG. 41).
FIG. 41 User Level Security - Modifying a User’s Security rights
4. From within the User Directory Associations section, place or remove any checkmarks next to the
available directories to modify an authorized user’s directory access rights. Removing a checkmark from
any folder prohibits that user from accessing any files contained therein via the Web Server.
5. Enter the same password for the user into both the Password and Password Confirm fields, if you want to
change the password. Leaving this field blank retains the current or previous password.
A user password is a valid character string (4 - 20 alpha-numeric characters) that is used to
supplement the Username/ID in defining the potential client. The string is case sensitive.
6. Click the Update button to save your changes to the target Master. If there are no errors with the
modification of any of this page’s parameters, a “User updated successfully” is displayed at the top of the
page.
7. Click the Back button to return to the Manage Users page.
Deleting an existing User
1.
Click on the User Level link (from within the Security section of the Navigation frame) to open the
Manage Users page.
2. Press the Select button next to the selected Username to open the Configure User Properties page
(FIG. 40) for the particular user.

NetLinx Security within the Web Server
51
NI-3101-SIG Signature Series NetLinx Integrated Controller
System and Licensing
management features
Online Tree
menu
Online Tree
Selection Item
Properties
Management menu options
(System, Device, and Port)
Control/Emulate & Diagnostics buttons
are available from within all menu options
3. Click the Delete button to remove the selected user and return to the Manage Users page.
The NetLinx account can be deleted from the Manage User page.The administrator
account cannot be deleted, nor can it have its directory associations modified.
System Settings
This section of the Navigation frame (FIG. 42) provides the ability to both manage existing and pending
license keys, manage the active NetLinx system communication parameters, and configure/modify the SSL
certificates on the target Master.
FIG. 42 System Settings - System an Licensing Management
System Settings - Manage System page
To view all of the available options within the right frame, it is recommended that you maximize the browser
window.
To access this page (FIG. 43), click on the Manage System link (from within the System Settings section of the
Navigation frame).
FIG. 43 System Settings - Manage System page

NetLinx Security within the Web Server
52
NI-3101-SIG Signature Series NetLinx Integrated Controller
System Number (purple)
Devices (violet)
Ports (blue)
Commands (orange)
Strings (red)
Channels (green)
Levels (yellow)
Manage System Page Components
Feature Description
Online Tree menu: The Online Tree menu contains button options relating to the
Online Tree: This frame displays a snapshot list of devices detected as
Selection Item Properties: This frame displays the properties of the last selected (clicked)
entries within the Online Tree.
• Expand - Expands the selected level to expose any
subfolders.
• Refresh - Refreshes the contents of the Online Tree frame.
• Collapse - Collapses the selected level to hide any subfolders.
currently online by the Master (and the firmware version for
each).
• By default, the Tree view begins fully collapsed.
• The online devices are organized according to the System
they belong to.
• Double-click any System icon (FIG. 44) to display a list of
devices that are currently online, within that System.
• Double-clicking on any of the colored blocks causes that
section of the Tree to expand.
Note: Sub-devices are hardware components contained within a
parent device, which may require their own firmware.
Refreshing/Rebooting the Master updates this Online Tree.
item from the Online Tree.
• Commands and Strings are not displayed, but a user is
directed to the Control/Emulate window.
• Channel properties show a list of all channels within the range
available to the port. Clicking a channel takes the user to the
Control/Emulate window where information such as the
channel, System, Device, and Port are already pre-populated.
FIG. 44
System - Online Tree frame

NetLinx Security within the Web Server
53
NI-3101-SIG Signature Series NetLinx Integrated Controller
Manage System Page Components (Cont.)
Feature Description
Management menu options: These management buttons change depending on the source
chosen from the Online Tree.
• There are three menu groupings available:
- System Menu (to configure Master properties).
- Device Menu (to configure device specific properties).
- Port Menu (to configure specific Port settings).
System menu buttons: The selected system number is displayed below these menu
buttons.
Modify Date/Time • Allows a user to set the date and time on the target Master.
System Number • Allows a user to change the current system number (value).
Reboot • Allows a user to reboot the target Master.
Control/Emulate • Allows a user to both control and emulate devices on a target
Master.
• This is done by allowing the user to control a device’s
channels, levels, and send both send commands and strings
to the target device.
• This button is available from within all Management menus.
Diagnostics • Allows a user to watch the system activity to/from a selected
device.
• This button is available from within all Management menus.
Server • Allows a user to both change the port numbers (used for
Device menu buttons: The selected system number: device number are displayed
Network Settings • Allows a user to configure the LAN IP/DNS settings.
URL List • Allows a user to setup the URL List for the specified device.
Device Number • Allows a user to change the device number of a selected
Control/Emulate • Allows a user to both control and emulate devices on a target
Log • Allows a user to view the log for the selected device.
Diagnostics • Allows a user to watch the system activity to/from a selected
Port menu buttons: The selected system number:device & number:port number are
Control/Emulate • Allows a user to both control and emulate devices on a target
Diagnostics • Allows a user to watch the system activity to/from a selected
various Web services) and configure the SSL settings used on
the Master.
below these menu buttons.
• Not all devices allow this functionality.
device.
Master.
• This is done by allowing the user to control a device’s
channels, levels, and send both send commands and strings
to the target device.
• This button is available from within all Management menus.
• Not all devices allow this functionality.
device.
• This button is available from within all Management menus.
displayed below these menu buttons.
Master.
• This button is available from within all Management menus.
device.
• This button is available from within all Management menus.

NetLinx Security within the Web Server
54
NI-3101-SIG Signature Series NetLinx Integrated Controller
Manage System - System Menu Buttons
These buttons appear (on the right) when a user clicks on the purple System icon from within the Online Tree.
The selected system number is displayed below these System menu buttons.
System Menu - Modifying the Date/Time
Click the Manage System link (from within the System Settings section of the Navigation frame).
1.
2. Click on the purple System icon from within the Online Tree to open the System menu buttons within the
right frame.
3. Click the Modify Date/Time button to open the Modify System Date/Time dialog (FIG. 45). This dialog
shows the current Date and Time settings for the target Master.
FIG. 45 Modify System/Date dialog
4. Alter any of these values by selecting the appropriate field and entering a new numeric value.
Highlighting any of the Date fields displays a small popup calendar window which assists with
selecting a new date.
Navigate through the calendar and click on a new date, which is then reflected back within the
Modify System Date/Time dialog.
Any of the Time fields can be modified by either manually entering the new values or highlighting
a field and using the arrow keys.
5. Click the Update button to save these settings to the target Master. The message "Time/date set
successfully" is displayed if the update process had no problems.
System Menu - Changing the System Number
Click the Manage System link (from within the System Settings section of the Navigation frame).
1.
2. Click on the purple System icon from within the Online Tree to open the System menu buttons within the
right frame.
3. Click the System Number button to open the Change System Number dialog (FIG. 46). This dialog
shows the current system number (read-only) on the target Master.
The current system number is also shown just below the System menu buttons.

NetLinx Security within the Web Server
55
NI-3101-SIG Signature Series NetLinx Integrated Controller
Current
System
Number
FIG. 46 Change System Number dialog
4. Enter a new numeric value into the New System Number field.
5. Click the Update button to save this new value to the system on the target Master. The following
message, "System number changed to X. Master must be rebooted for the change to take effect", reminds
the user the Master must first be rebooted before the new settings take effect. Once the Master is
rebooted, the IP Address must be re-entered and an authorized user must re-establish communication
with the target Master.
System Menu - Rebooting the Master
1.
Click the Manage System link (from within the System Settings section of the Navigation frame).
2. Click on the purple System icon from within the Online Tree to open the System menu buttons within the
right frame.
3. Click the Reboot button to remotely reboot the target Master. No dialog appears while using this button.
The Online Tree then reads "Rebooting....". After a few seconds, the Online Tree refreshes with the
current system information (showing the newly updated system number).
If the Online Tree contents do not refresh within a few minutes, press the browser’s Refresh button
and reconnect to the Master.
System Menu - Controlling/Emulating Devices on the Master
This button allows a user to either Control a device or Emulate a device. This is done by controlling a device’s
channels, levels, and sending both send commands and strings to the target device.
The Control/Emulate and Diagnostics buttons are common to all menus. These fields
are populated depending upon the items selected from the Online Tree (left frame).
For example, when navigating down to a specific channel on a device, the
Control/Emulate page then populates the D:P:S and Channel Code fields.
1. Click the Manage System link (from within the System Settings section of the Navigation frame).
2. Clicking on any of the Online Tree items opens menu items with the Control/Emulate button option
available.
3. Click the Control/Emulate button to open the Control/Emulate dialog (FIG. 47).
4. Click the Update Status button to query the Master for the status of the currently entered level and
channel.
The System Number, Device Number, and Port Number value fields are read-only
(disabled) if this window was opened by from a selection of an Online Tree item. By
default, these fields are otherwise editable.

NetLinx Security within the Web Server
56
NI-3101-SIG Signature Series NetLinx Integrated Controller
5. Select either the Control or Emulate option.
FIG. 47 Control/Emulate dialog
To Control a device means that the program generates messages which appear to a specified device
to have come from the Master. The options in this frame specify the <D:P:S> combination for the
device to be controlled.
To Emulate a device means that the program generates messages which appear to the Master to
have come from a specified <D:P:S> combination (real or fictitious). The options in this frame
specify the <D:P:S> combination for the device to be emulated.
Selecting this option adds a Push button with the Channel Code section of this page.
6. Enter a System Number, Device Number, and Port Number into the appropriate fields. These values
correspond to the device to be controlled, whether real or fictitious.
The Device, Port, and System value ranges are 1 - 65535.
7. Within the Channel Code section, enter a valid Channel number to emulate Channel messages (i.e., Push/
Release, CHON, and CHOFF) for the specified <D:P:S>.
The Channel number range is 1 - 65535.
8. Select the On or Off buttons to Emulate Channel ON (CHON) and Channel OFF (CHOFF) messages for
the specified <D:P:S>.
9. Select the Push button to Emulate a push/release on the channel specified. You can click and hold down
the Push button to see how the device/Master responds to the push message.
10. Within the Level Code section, enter a valid Level number and Level data value for the specified
<D:P:S> and press the Send button to transmit this data.
The Level number range is 1 - 65535.
The list below contains the valid Level data types and their ranges:

NetLinx Security within the Web Server
57
NI-3101-SIG Signature Series NetLinx Integrated Controller
Valid Level Data Types and Ranges
Minimum Value Maximum Value
CHAR 0 255
INTEGER 0 65535
SINTEGER -32768 32767
LONG 0 429497295
SLONG -2147483648 2147483647
FLOAT -3.402823466e+38 3.402823466e+38
11. Within the Command and String fields, you can enter any number of messages that can be sent as either a
String or Command.
12. To Emulate sending a String or Command, type a String or Command within the corresponding field and
press the Send button to transmit this data.
When entering a send command (in the context of this dialog) do not include the "send c" or
"send_command" in the statement - only type what would normally occur within the quotes, but
don't include the quotes either. For example to send the "CALIBRATE" send command, simply
type CALIBRATE (no quotes) rather than SEND_COMMAND <dev> "CALIBRATE".
String Expressions start and end with double quotes (" "). Double quotes are not escaped; instead,
they are embedded within single quotes. String expressions may contain string literals, decimal
numbers, ASCII characters and hexadecimal numbers (prepended with a $), and are
comma-delimited.
String Literals start and end with single quotes ( ' ). To escape a single quote, use ''' (three single
quotes).
Manage System - Diagnostics
This page allows an authorized user to setup and monitor diagnostic messages coming from and going to
devices available on the Online Tree. This dialog also allows the user to watch the ICSP commands being sent
to/from a device. There are several different types of asynchronous notifications that can be selected for a
device:port:system (D:P:S) combination. Each notification type is represented by a column in the table. All
messages are displayed in the Notifications tab of the Output Display window within NetLinx Studio v 2.4.
1. Click the Manage System link (from within the System Settings section of the Navigation frame).
2. Clicking on any of the Online Tree items opens menu items with the Diagnostics button option available.
3. Click the Diagnostics button to open the Diagnostics dialog (FIG. 48).
4. Use the Refresh Interval drop-down to select from the following values: 2 seconds, 5 seconds, or 10
seconds. This refresh interval allows you to select how often the messages are updated.

NetLinx Security within the Web Server
58
NI-3101-SIG Signature Series NetLinx Integrated Controller
Device Configuration
dialog
NetLinx
Notification
types
Selected device
FIG. 48 Diagnostics dialog (showing modify popup)
Setting up and removing a Diagnostic Filter
Setup a diagnostic filter by scrolling down the page and clicking the Modify button below the first empty
1.
column. This action opens the Device Configuration dialog as a secondary popup window.
Up to 8 concurrent diagnostic filter slots can be simultaneously active using any
eight of the 10 available user-configurable Presets available through the Device
Configuration dialog.
2. Configure a diagnostic filter using the parameters available within the Diagnostic Configuration dialog.
The Diagnostic Configuration dialog allows you to select both the notifications you wish to
receive and the target devices (within the Online Tree) for these notifications. Several different
types of asynchronous notifications can be selected for a device:port:system (D:P:S) combination.
Each notification type is represented by a column in the table. All messages are displayed in the
Notifications tab of the Output Display window within NetLinx Studio v 2.4.
3. A user can choose to either store these selections to a profile or recall a previously stored profile
configuration by either:
Select an open Preset number entry from within Presets drop-down list. Make all desired
notification selection and press the Store button. Pressing this button opens a popup field labeled
Explorer User Prompt - Preset Name?, intended for entering the name associated with this new
Preset.
Press OK to return to the previous Device Configuration popup dialog.
Click Cancel to exit this popup and return to the previous dialog box without making any
changes.

NetLinx Security within the Web Server
59
NI-3101-SIG Signature Series NetLinx Integrated Controller
Press the down arrow (adjacent to the Preset drop-down list) to display a listing of all currently
available Presets. Select a previously configured Preset and press the Recall button to populate all
available fields and radio buttons with the selections associated with this chosen Preset.
This preset mechanism is done via cookies so it does not persist across multiple browsers/
computers.
4. Once all modifications/selections within this dialog have been made, press the Update button to save the
changes and return to the Diagnostics dialog.
Diagnostic Configuration Dialog
Feature Description
Update: Click this button once you have completed setting up your filter. The popup
Remove: Click this button to remove a selected Preset from being available within the
Presets: This list of up to 10 presets comes defaulted with Preset 0: All Devices, All
System/Device/Port: Device, Port, System: Use these fields to enter a device:port:system (D:P:S)
then closes and returns you to the Diagnostics window.
• Watch the bottom Incoming Message pane for messages to begin coming in
from the target device(s).
Presets drop-down list.
Notifications
• Store: Save the current notification selections to a Preset profile. Pressing
this button opens a popup field labeled Explorer User Prompt - Preset
Name? where you enter the name associated with this new Preset.
- Click OK to save both the Preset parameters and name, and then return
to the Diagnostic Configuration Dialog.
- Click Cancel to exit this popup and return to the previous dialog without
making any changes.
• Recall: Allows a user to recall a previously existing Preset. This action then
populates every field and radio button with the selections associated with the
chosen Preset.
- This preset mechanism is done via cookies so that it does not persist
across multiple browsers/computers.
Note: A Preset MUST be Recalled before clicking the Update button.
If you do not press this button, none of the fields or checkboxes are
modified or selected. In essence, all options become disabled.
Note: The All Devices entry cannot be removed.
Note: The only way to modify the information within a Diagnostic filter is to
remove the assigned Preset, change the information, and assign a new Preset. Refer to step 5 of this section for more information.
combination for the device that you want to enable notifications for.
• The specified device then appear in the Device field within the Diagnostic
Configuration Dialog.
• A value of 0 for any option gives you all of the systems, devices, or ports.
This dialog also allows you to store/recall presets.

NetLinx Security within the Web Server
60
NI-3101-SIG Signature Series NetLinx Integrated Controller
Diagnostic Configuration Dialog (Cont.)
Feature Description
NetLinx Notification Types: All Notifications: Enables (selects) every notification field.
• Online/Offline Messages: Generates a message with a change in the target
device’s online/offline status.
• Configuration Messages: Generates a message with a change in the target
device’s configuration.
• Input Channel Changes: Generates a message with an input channel
change (i.e. Push/Release) in the target device.
• Output Channel Changes: Generates a message with an output channel
change (i.e. CHON/CHOFF) in the target device.
• Feedback Channel Changes: Generates a message with a feedback
channel change in the target device.
• Level Changes From Device: Generates a message with a level channel
change from the target device.
• Level Changes To Device: Generates a message with a level channel
change to the target device.
• String From Device: Generates a message with a string from the target
device.
• String To Device: Generates a message with a string sent to the target
device.
• Command From Device: Generates a message with a command from the
target device.
• Command To Device: Generates a message with a command to the target
device.
• Status Messages: Generates a message with a change in the target
device’s status.
• Custom Events From Device: Generates a message with a custom event
occurring from the target device.
5. Remove a diagnostic filter by clicking the Modify button below it (from the Diagnostics dialog), then
pressing the Remove button to delete this filter from the Diagnostics dialog.
Once a Preset is assigned to a specific Diagnostic filter "slot" (up to 8), its System:Device:Por t
fields are greyed-out, and can’t be modified unless the Preset in that slot is removed and replicated
with new information within these fields.
To modify a Diagnostic filter’s information (such as System/Device/Port):
Navigate to an empty Diagnostic filter slot and click the Modify button below the filter.
Select a previously unused Preset and store it with a new name.
Click the Remove button to remove this duplicate Preset from the specific filter slot.
Re-open the empty slot by clicking the Modify button, select the duplicated Preset and click
Recall.
Change the necessary information (such as the System/Device/Port), then save it as the original
Preset name, and click the Update button.
6. Use the Incoming Message field to view all the internal system diagnostic messages that are generated by
a NetLinx Master controller. This message field is a text box, where the text within it may be selected and
then copied or pasted for storage.

NetLinx Security within the Web Server
61
NI-3101-SIG Signature Series NetLinx Integrated Controller
Disabling the HTTP Port
requires that an
authorized user access
the Master ONLY via a
secure HTTPS connection.
SSH version 2 is only
supported.
Setting the Master’s Port Configurations
Manage System - Server
This page allows a user to both change the port numbers (used for various Web services) and configure the
SSL settings used on the Master by bringing up a submenu of options such as:
Server Submenu Options
Feature Description
Port Settings: Allows a user to modify the server settings; specifically those port
assignments associated with individual services.
• All items can be either enabled/disabled via the adjacent checkbox.
• The port number values can also be modified (except the FTP port).
• The default port for each service is listed to the right.
Create SSL Certificate: Takes the authorized user to the Server Certificate page to create a self-
generated SSL certificate.
• This dialog provides the ability to display an installed certificate, create
a certificate request, self-generate, and regenerate SSL Server
Certificates.
Export SSL Certificate Request: Takes the user to the Server Certificate page to view a previously created
Import SSL Certificate: Takes the user to the Import Certificate page where they can import and
certificate.
• An authorized user can also copy the raw text from a generated
Certificate request into their clipboard and then send it to the CA.
paste the raw text from a CA issued Certificate.
1. Click on the Manage System link (from within the System Settings section of the Navigation frame).
2. Click on the purple System icon from within the Online Tree to open the System menu buttons within the
right frame.
3. Click the Server button to open the Server dialog and its associated submenu options (FIG. 49).
FIG. 49
Server dialog and associated submenu options
The following graphic illustrates the Ports which can be enabled for validation using a valid
username and password, as well as what method of communication is used with each.

NetLinx Security within the Web Server
62
NI-3101-SIG Signature Series NetLinx Integrated Controller
Telnet Port
ICSP Port
HTTP Port
HTTP/SSL Port
SSH Port
FTP Port
NetLinx Master
HTTP Access option
Telnet Access option
ICSP Connectivity
and Encryption option
Username and
Password are
required when enabled
23
80
443
1319
22
21
Tel net
Web
Browser
Browser
or SSL
AMX
Software
&
Hardware
SSH
Client
Secure
Secure
Secure
SS
SS
SS
SS
SS
Secure
FTP
FIG. 50 Port Communication Settings
Modifying the Server Port Settings
1.
2. Uncheck any services (and corresponding ports) to disable their functionality.
3. Modify any preset service port value by first enabling that service with a checkmark within the Enabled
Server Port Settings
Feature Description
Telnet Port: The port value used for Telnet communication to the target Master.
ICSP Port: The port value used for ICSP data communication among the different AMX
From within the Server submenu, press the Port Settings button to open the Server Port Settings dialog
seen above in FIG. 49.
checkbox and then entering a value within the Por t N u m b e r field.
• The default port value is 23.
• Enabling this feature allows future communication with the Master via a
separate Telnet application (such as HyperTerminal).
• Refer to the NetLinx Security with a Terminal Connection section for more
information on the related procedures.
software and hardware products.
• The default port value is 1319.
• This type of communication is used by the various AMX product for
communication amongst themselves. Some examples would be: NetLinx
Studio communicating with a Master (for firmware or file information updates)
and TPDesign4 communicating with a touch panel (for panel page and
firmware updates).
Note: To further ensure a secure connection within this type of
communication, a user can enable the Require Encryption option which
requires additional processor cycles. Enabling of the encryption feature is
determined by the user.

NetLinx Security within the Web Server
63
NI-3101-SIG Signature Series NetLinx Integrated Controller
Server Port Settings (Cont.)
Feature Description
HTTP Port: The port value used for unsecure HTTP Internet communication between the
web browser’s UI and the target Master.
• The default port value is 80.
• By default, the Master does not have security enabled and must use http:// in
the Address field for communication.
• One method of adding security to HTTP communication would be to change
the port value.
- If the port value is changed, any consecutive session to the target Master
has to add the port value at the end of the address (within the Address field).
For example, if the port were changed to 99, the new address information
would be: http://192.192.192.192:99.
• By disabling this port, the administrator (or other authorized user) can require
that any consecutive sessions between the UI and the target Master are
done over a more secure HTTPS connection.
HTTPS/SSL Port: The port value used by web browser to securely communicate between the
web server UI and the target Master. This port is also used to simultaneously
encrypt this data using the SSL certificate information on the Master as a key.
• The default port value is 443.
• This port is used not only used to communicate securely between the
browser (using the web server UI) and the Master using HTTPS but also
provide a port for use by the SSL encryption key (embedded into the
certificate).
• Whereas SSL creates a secure connection between a client and a server,
over which any amount of data can be sent securely, HTTPS is designed to
transmit individual messages securely. Therefore both HTTPS and SSL can
be seen as complementary and are configured to communicate over the
same port on the Master.
• These two methods of security and encryption are occurring simultaneously
over this port as data is being transferred.
• Another method of adding security to HTTPS communication would be to
change the port value.
- If the port value is changed, any consecutive session to the target Master
has to add the port value at the end of the address (within the Address field).
For example, if the port were changed to 99, the new address information
would be: http://192.192.192.192:99.
SSH Port: The port value used for secure Telnet communication.
Note: SSH version 2 is only supported.
• The default port value is 22.
• A separate secure SSH Client would handle communication over this port.
• When using a secure SSH login, the entire login session (including the
transmission of passwords) is encrypted; therefore it is secure method of
preventing an external user from collecting passwords.
Note: If this port’s value is changed, make sure to use it within the Address field
of the SSH Client application.
FTP Port: The port value used for FTP communication. This port can be disabled/
enabled but the value can not be changed.
• The default port value is 21.
• When an application such as TPDesign uploads information to the target
Master via an FTP connection; it is this port which is used by default.
4. Once an authorized user has modified any of the server port settings, press the Update button to save
these changes to the Master. Once these changes are saved, the following message appears: "Unit must be
rebooted for the change to take effect".
5. Click the Reboot button (from the top of the page) to remotely reboot the target Master. No dialog
appears while using this button. The Online Tree then reads "Rebooting....". After a few seconds, the

NetLinx Security within the Web Server
64
NI-3101-SIG Signature Series NetLinx Integrated Controller
Server Certificate - available actions
Online Tree refreshes with the current system information and showing the newly updated system
number.
If the Online Tree contents do not refresh within a few minutes, press the browser’s Refresh button
and reconnect to the Master.
SSL Server Certificate Creation Procedures
Initially, a NetLinx Master is not equipped with any installed certificates. In order to prepare a Master for
later use with CA (officially issued) server certificates, it is necessary to:
First create a self-generated certificate which is automatically installed onto the Master.
Secondly, enable the SSL feature from the Enable Security page. Enabling SSL security after the
certificate has been self-generated insures that the target Master is utilizing a secure connection
during the process of importing a CA server certificate over the web.
A self-generated certificate has lower security than an external CA generated
certificate.
A certificate consists of two different Keys:
Master Key is generated by the Master and is incorporated into the text string sent to the CA
during a certificate request. It is unique to a particular request made on a specific Master.
Public Key is part of the text string that is returned from the CA as part of an approved SSL Server
Certificate. This public key is based off the submitted Master key from the original request.
Regenerating a previously requested and installed certificate invalidates that certificate because the
Master Key has been changed.
1. Navigate to the Server Certificate page by clicking System Settings > Manage System > Server >
Create SSL Certificate to open the Server Certificate page (FIG. 51).
FIG. 51 Create an SSL Certificate dialog
This page allows an authorized user to display an installed certificate, create a certificate request, selfgenerate, and regenerate SSL Server Certificates.

NetLinx Security within the Web Server
65
NI-3101-SIG Signature Series NetLinx Integrated Controller
Server Certificate Entries
Feature Description
Server Certificate Field
Information:
Update Updates the target Master with the information entered on this
page.
• This process can take a few minutes.
Bit Length Provides a drop-down selection with three available public key
lengths: 512, 1024, and 2048.
• Longer key lengths result in increased certificate processing
times.
• A longer key length results in more secure certificates.
Common Name The Common Name of the certificate MUST be the URL Domain
Organization Name Name of your business or organization. This is an alpha-numeric
Organizational Unit Name of the department using the certificate. This is an
City/Location Name of the city where the certificate is used. This is an
State/Province Name of the state or province where the certificate is used. This
Country Name Provides a drop-down selection with a listing of currently
Action Provides a drop-down selection with a listing of available
Name used.
• Example: If the address used is www.amxuser.com, that must
be the Common name and format used.
• The Common Name can not be an IP Address.
• If the server is internal, the Netbios name must be used.
• For every website using SSL that has a distinct DNS name,
there must be a certificate installed. Each website (external or
Internet) for SSL MUST also have a distinct IP Address.
string (1 - 50 characters in length).
alpha-numeric string (1 - 50 characters in length).
alpha-numeric string (1 - 50 characters in length).
is an alpha-numeric string (1 - 50 characters in length).
selectable countries.
certificate options:
• Display Certificate - Populates the Server Certificate fields with
the information from the certificate currently installed on the
Master. This action is used only to display the information
contained in the certificate on the target Master.
• Create Request - Takes the information entered into the
previous fields and formats the certificate so it can be
exported to the external Certificate Authority (CA) for later
receipt of an SSL Certificate. This action is used to request
a certificate from an external source.
• Self Generate Certificate - Takes the information entered into
the previous fields and generates its own SSL Certificate.
This action is used when no previous certificate has been
installed on the target Master, or a self-signed certificate
is desired.
• Regenerate Certificate - Takes the information entered into the
previous fields and regenerates an SSL Certificate. This
action changes the Master Key.
This method of certificate generation is used to modify or
recreate a previously existing certificate already on the
Master.

NetLinx Security within the Web Server
66
NI-3101-SIG Signature Series NetLinx Integrated Controller
Server - Display SSL Server Certificate Information
1.
Navigate to the Server Certificate page by clicking System Settings > Manage System > Server >
Create SSL Certificate to open the Server Certificate page.
By default, the Display Certificate Action is selected and these fields are populated
with information from an installed certificate. If the Master does not have a previously
installed certificate, these fields are blank.
2. Click the down arrow from the Action field to open a drop-down listing of available certificate generation
options.
3. Choose Display Certificate from the drop-down list.
4. Click Update to accept the action and populate the fields with the certificate information presently on the
Master.
Server - Creating a self-generated SSL Certificate
Navigate to the Server Certificate page by clicking System Settings > Manage System > Server >
1.
Create SSL Certificate to open the Server Certificate page.
2. Click the down arrow from the Bit length field to open a drop-down listing of available public key
lengths.
The three available public key lengths are: 512, 1024, and 2048. Higher selected key lengths result
in increased certificate processing times. A longer key length results in more secure certificates.
3. Enter the used Domain Name into the Common Name field.
Example: If the address being used is www.amxuser.com, that must be the Common name and
format used in the Common Name field. This string provides a unique name for the desired user.
This domain name must be associated to a resolvable URL Address when creating a request for a
purchased certificate. The address does not need to be resolvable when obtaining a free certificate.
4. Enter the name of the business or organization into the Organization Name field. This is an alpha-
numeric string, 1 - 50 characters in length.
5. Enter the name of the department using the certificate into the Organizational Unit field. This is an alpha-
numeric string, 1 - 50 characters in length.
6. Enter the name of the city where the certificate resides into the City/Location field. This is an alpha-
numeric string, 1 - 50 characters in length.
7. Enter the name of the state or province where the certificate resides into the State/Province field. This is
an alpha-numeric string, 1 - 50 characters in length. The state/province name must be fully spelled out.
8. Click the down arrow from the Country Name field to open a drop-down listing of listing of currently
selectable countries.
9. Click the down arrow from the Action field to open a drop-down listing of available certificate generation
options.
10. Choose Self Generate Certificate from the drop-down list. When this request is submitted, the
certificate is generated and installed into the Master in one step.
11. Click Update to save the new encrypted certificate information to the Master.
ONLY use the Regenerate certificate option when you have Self Generated your own
certificate. DO NOT regenerate an external CA-generated certificate.

NetLinx Security within the Web Server
67
NI-3101-SIG Signature Series NetLinx Integrated Controller
Server - Regenerating an SSL Server Certificate Request
1.
Navigate to the Server Certificate page by clicking System Settings > Manage System > Server >
Create SSL Certificate to open the Server Certificate page.
This method of certificate generation is used to modify or recreate a previously
existing certificate already on the Master.
By default, if a certificate is already present on the target Master, the Display
Certificate Action is selected and these fields are populated with information.
Example: if the company has moved from Dallas to Houston, all of the information is
reentered exactly except for the City.
2. Enter any new or changed information into its respective field.
3. Click the down arrow from the Action field to open a drop-down listing of available certificate generation
options.
4. Choose Regenerate Certificate from the drop-down list.
When this request is submitted, the certificate is generated and installed into the
Master in one step.
5. Click OK to save the newly modified certificate information to the Master or click Cancel to void any
changes made within this page and exit without making changes to the target Master.
6. Before exiting the Master and beginning another session:
Verify that all users have been assigned the correct rights, and are using the correct passwords.
In the Enable Security window of the Security tab, verify that the Master Security and HTTP
Access are enabled. Enabling HTTP Access prompts users to enter pre-configured usernames and
passwords.
Server - Creating a Request for an SSL Certificate
1.
Navigate to the Server Certificate page by clicking System Settings > Manage System > Server >
Create SSL Certificate to open the Server Certificate page.
2. Click the down arrow from the Bit length field to open a drop-down listing of available public key
lengths.
The three available public key lengths are 512, 1024, and 2048. Higher selected key lengths result
in increased certificate processing times. A longer key length results in more secure certificates.
3. Enter the used Domain Name into the Common Name field.
Example: If the address being used is www.amxuser.com, that must be the Common name and
format used in the Common Name field. This string provides a unique name for the desired user.
This domain name must be associated to a resolvable URL Address when creating a request for a
purchased certificate. The address does not need to be resolvable when obtaining a free certificate.
4. Enter the name of the business or organization into the Organization Name field. This is an alpha-
numeric string, 1 - 50 characters in length.
5. Enter the name of the department using the certificate into the Organizational Unit field. This is an alpha-
numeric string, 1 - 50 characters in length.
6. Enter the name of the city where the certificate resides into the City/Location field. This is an alpha-
numeric string, 1 - 50 characters in length.
7. Enter the name of the state or province where the certificate resides into the State/Province field. This is
an alpha-numeric string, 1 - 50 characters in length.
The state/province name must be fully spelled out.
8. Click the down arrow from the Country Name field to open a drop-down listing of listing of currently
selectable countries.
9. Click the down arrow from the Action field to open a drop-down listing of available certificate generation
options.

NetLinx Security within the Web Server
68
NI-3101-SIG Signature Series NetLinx Integrated Controller
10. Choose Create Request from the drop-down list.
11. Click the Update button to accept the information entered into the above fields and generate a certificate
file. Refer to theServer - Exporting an SSL Certificate Request section on page 68.
This refreshed the Server Certificate page and if the certificate request was successful, displays a
"Certified request generated" message.
12. Follow the exporting and importing an SSL certificate procedures outlined within the following section.
Common Steps for Requesting a Certificate from a CA
Once the request has begun, a user has the choice to either remain using their self-generated SSL certificate or
obtain a CA created certificate by exporting their request for the certificate and then, once received, import the
returned certificate information onto the Master.
Communicating with the CA
A certificate is a cryptographically signed object that associates a public key and an identity. Certificates also
include other information in extensions such as permissions and comments. A "CA" is short for Certification
Authority and is an internal entity or trusted third party that issues, signs, revokes, and manages these digital
certificates.
1. Navigate to the Web Server Certificate HTML page on your CA’s web site.
A Web Server certificate allows you to authenticate through a Web browser via SSL In order to
successfully verify other certificates it is also necessary to import the CA key into the Web Server.
Refer to theServer - Creating a Request for an SSL Certificate section on page 67.
This is done as part of the process of receiving your Web Server certificate.
Only a user with administrator privileges can request a server certificate.
2. Enter in the company information, such as: name, e-mail, address, state, and country.
3. Agree to any licensing agreements and continue to the next part of the registration process.
4. Enter the name of the server being used (this is the Master).
The server name is the name as it shows up in the URL of the Master you are securing with this
server certificate. For example, if the URL of the Master is
https://www.myNetLinxMaster.com/, then enter the server name as
www.myNetLinx Master.com.
5. Send the CA the text created by your certificate request through the Master by exporting this information
within the Server Certificate page. Refer to theServer - Creating a Request for an SSL Certificate section
on page 67 for the procedures necessary to generate the certificate text file.
6. Follow the procedures outlined in the following section to export the data to the CA.
Server - Exporting an SSL Certificate Request
1.
First follow the procedures outlined in theServer - Creating a Request for an SSL Certificate section on
page 67 to begin the process of requesting an SSL by creating a session-specific Master certificate.
2. Click the Export Certificate Request button to display the certificate text file within the Server
Certificate page (FIG. 52).

NetLinx Security within the Web Server
69
NI-3101-SIG Signature Series NetLinx Integrated Controller
Certificate text field
FIG. 52 Export SSL Certificate dialog
3. Place your cursor within the certificate text field.
4. Press the Ctrl + A keys simultaneously on your keyboard (this selects all the text within the field).
YOU MUST COPY ALL OF THE TEXT within this field, including the -----BEGIN
CERTIFICATE REQUEST----- and the -----END CERTIFICATE REQUEST-----. This
text in the CA submission must be included to receive a CA-approved certificate.
5. Press the Ctrl + C keys simultaneously on your keyboard (this takes the blue selected text within the field
and copies it to your temporary memory/clipboard).
6. Paste this text into the Submit Request field on the CA’s Retrieve Certificate web page.
7. Choose to view the certificate response in raw DER format.
8. Note the Authorization Code and Reference Number (for use in the e-mail submission of the request).
9. Submit the request.
10. Paste this certificate text field (copied from steps 4 & 5 above) into your e-mail document and then send
that information to a CA with its accompanying certificate application.
When a certificate request is generated, you are creating a private key on the Master.
YOU CANNOT REQUEST ANOTHER CERTIFICATE UNTIL THE PREVIOUS
REQUEST HAS BEEN FULFILLED. Doing so voids any information received from
the previously requested certificate and it becomes nonfunctional if attempted to be
used.
11. Once the returned CA certificate has been received, follow the procedures outlined in the following
section to import the returned certificate (over a secure connection) to the target Master.
Server - Importing a CA created SSL Certificate
Before importing a CA server certificate:
First, have a self-generated certificate installed onto the target Master.
Secondly, enable the SSL security feature from the Enable Security page, to establish a secure
connection to the Master prior to importing the encrypted CA certificate. Refer to theSecurity System Level Security page section on page 39 for more information about enabling SSL security.
1. Take the returned certificate (signed by the CA and encrypted with new information which makes it
different from the text string that was previously sent) and copy it into the clipboard.

NetLinx Security within the Web Server
70
NI-3101-SIG Signature Series NetLinx Integrated Controller
Certificate text field
2. Navigate to the Server Certificate page by clicking System Settings > Manage System > Server >
Import SSL Certificate to open the Import Certificate page (FIG. 53).
FIG. 53 Import SSL Certificate dialog
3. Place the cursor within the empty window and paste the raw text data (in its entirety) into the field.
4. Click the Update button to enter the new encrypted certificate information and save it to the Master.
Once a certificate has been purchased from an external CA and then installed onto a
specific Master, DO NOT regenerate the certificate or alter its properties
(example: bit length, city, etc.). If the purchased certificate is regenerated, it becomes
invalid.
A certificate consists of two different Keys:
Master Key is generated by the Master and is incorporated into the text string sent to the CA
during a certificate request. It is specific to a particular request made on a specific Master.
Public Key is part of the text string that is returned from the CA as part of an approved SSL Server
Certificate. This public key is based off the submitted Master key from the original request.
Regenerating a previously requested and installed certificate invalidates the previously purchased
certificate because the Master Key has been changed.
5. Use the Server > Create SSL Certificate > Display Certificate option to confirm that the new
certificate was imported properly to the target Master.
A CA server certificate can only be imported to a target Master only after both a
self-generated certificate has been created and the SSL Enable feature has been
selected on the Master. These actions configure the Master to the secure
communication necessary during the importing of the CA certificate.

NetLinx Security within the Web Server
71
NI-3101-SIG Signature Series NetLinx Integrated Controller
Manage System - Device Menu Buttons
The Device Menu buttons appear when a user clicks on any violet Device icon from within the Online Tree.
The selected system number: device number are displayed below these menu buttons.
Device Menu - Configuring the LAN Settings
1.
Click the System Settings > Manage System link from within the System Settings section of the
Navigation frame.
2. Click on a violet Device icon from within the Online Tree to open the Device menu buttons within the
right frame.
3. Click the Network Settings button to open the Network Settings dialog (FIG. 54). This dialog allows a
user to set up the LAN settings for the specified device. The fields are populated with the current settings
when initially loaded.
FIG. 54 Network Settings dialog
Network Settings Dialog
Feature Description
IP Address:
Host Name Use this field to view/edit the target Master's current Host Name.
DHCP/Specify IP Address Use these radio buttons to specify an address for the target Master:
• DHCP - obtained from a DHCP Server.
• Specify an IP Address - typically obtained from a System Administrator.
IP Address Use this field to view/edit the target Master's current IP Address.
Subnet Mask Use this field to view/edit the target Master's current Subnet Mask assignment.
Gateway Use this field to view/edit the target Master's current Gateway assignment.
DNS Address:
Domain Suffix Use this field to view/edit the target Master's current Domain Suffix.
DNS IP #1, #2, #3 Use these fields to view/edit the target Master's current DNS IP addresses.
4. Enter a new or updated name within the Host Name field. This entry can be 1 - 50 alphanumeric
characters in length.
5. Select either the DHCP or Specify and IP Address checkbox to choose the source of the IP Address
information being used within the remaining fields.
6. Enter or change any IP Address or DNS Address information within the remaining fields.
7. Click Update to save any changes. If the changes are successfully updated to the Master, the following
message appears: "Network Settings updated. Device must be rebooted for the setting to take effect".

NetLinx Security within the Web Server
72
NI-3101-SIG Signature Series NetLinx Integrated Controller
URL List dialog
Add New URL dialog
8. Return to the System menu by clicking on the purple System icon from within the Online Tree, click the
Reboot button, and then allow the Master a short time to reboot itself.
9. Click on the Refresh macro from the browser’s menu bar. If no security is currently enabled on the target
Master, the browser is directed back to the Manage WebControl Connections page. If security is enabled,
the browser is directed to the initial Username/Password page to enter personal access information.
Device Menu - Developing a URL List
Click the System Settings > Manage System link from within the System Settings section of the
1.
Navigation frame.
2. Click on a violet Device icon from within the Online Tree to open the Device menu buttons within the
right frame.
3. Click the URL List button to open the URL List dialog (FIG. 55). This dialog allows the user to view,
add, and remove URLs from the specified devices URL list.
FIG. 55 URL List dialog
4. Add a new URL to the list by pressing the New button, which opens the Add New URL dialog.
5. Enter either an IP Address or a resolvable name (ex: www.amx.com) into the URL field.
6. Enter the Port number used to connect to the other device within the Por t field. The default port provided
in 1319, which is used for ICSP communication. Refer to theManage System - Server section on page 61
for more information on the default Ports used for communication.
7. If a Username and/or Password is required for successful communication with the target URL, place a
checkmark in the Secure Connection checkbox and enter the necessary information within the
Username, Password, and Confirm (password) fields.
If this box is unchecked, the fields are greyed-out and the user is prevented from entering any text
into any of the remaining fields.
These fields are not greyed-out within Internet Explorer, even though they become
read-only.
8. Click the Update button to accept and save your changes. If you are able to enter your information, a
"URL added successfully" message is displayed at the top of the Add New URL dialog.
9. Click the Back button to return to the main URL List dialog.

NetLinx Security within the Web Server
73
NI-3101-SIG Signature Series NetLinx Integrated Controller
Successful connection
Connection could
Attempting to connect
established
not be made
Current
Device
Number
10. Confirm that the newly added URLs appear within the URL List dialog (FIG. 56).
FIG. 56 URL List dialog (with entries)
If the newly added URL doesn’t appear on this page, click the Refresh button.
11. URL entries can be removed either individually or as a whole:
Remove an individual URL entry by pressing the Remove button on that URLs row listing within
the URL List dialog (FIG. 56).
Remove all previously entered URLs by pressing the Remove All button. To confirm the removal
of all items, press the Refresh button.
Device Menu - Changing the Device Number
Click the System Settings > Manage System link from within the System Settings section of the
1.
Navigation frame.
2. Click on a violet Device icon from within the Online Tree to open the Device menu buttons within the
right frame.
3. Click the Device Number button to open the Device Number (FIG. 57). This dialog allows the user to
change the device number for the selected device.
FIG. 57 Device Number dialog
The current device number is also shown just below the System menu buttons.
4. Enter a new numeric value into the New Device Number field.
5. Click the Update button to save this new value to the device. The following message; "Device number
changed to XXX. Device must be rebooted for the change to take effect.", reminds the user that the Master
must first be rebooted before the new settings take effect.

NetLinx Security within the Web Server
74
NI-3101-SIG Signature Series NetLinx Integrated Controller
Device Menu - Controlling or Emulating a device
Refer to the procedures outlined within theSystem Menu - Controlling/Emulating Devices on the
Master section on page 55 for more information.
Device Menu - Viewing the Log
1.
Click on the System Settings > Manage System link from within the System Settings section of the
Navigation frame.
2. Click on a violet Device icon from within the Online Tree to open the Device menu buttons within the
right frame.
3. Click the Log button (FIG. 58). This dialog allows the user to view the log for the selected device
(currently only the Master supports this feature).
FIG. 58 Log dialog
4. Click the Refresh button to update the information on-screen.
Device Menu - Running a Diagnostic Filter
Refer to the procedures outlined within theManage System - Diagnostics section on page 57 for more
information.
System Settings - Manage License
This page (FIG. 59) displays both the currently used license keys and the pending keys.
The New button allows for the addition of new license keys associated with currently used
modules/products.
Adding new License Keys requires the use of both a Product ID and a Serial Key.
An example of this type of product is i!-Voting. The Master confirms this registration information
before running the module.

NetLinx Security within the Web Server
75
NI-3101-SIG Signature Series NetLinx Integrated Controller
New button allows for the
addition of new license keys
Shows exiting license keys
FIG. 59 System Settings - Manage License page
Adding a new license
1.
Click on the System Settings > Manage License link from within the System Settings section of the
Navigation frame.
2. Click the New button to be transferred to the Add new License Key page (FIG. 60).
FIG. 60 System Settings - Add New License Key page
3. Enter the Product ID (certificate number) provided with the product into the Product ID fields.
4. Contact the AMX Sales department with both the product serial number (or certificate number) and the
serial number of target Master to register your product and in turn receive the necessary Key information
(typically 32 to 36 digits in length) which is then entered into the Key fields on this page.
The Key is Master specific and is typically provided by AMX upon registration.
Example: AMX Meeting Manger and i!-Voting applications are examples of products that would
require both a Product serial number and a Master-specific key prior to usage.
5. Press the Update button to save the information. A “Key successfully added for Product ID XXXX” notice
is displayed at the top of the page if the information on this page has no errors.
6. Press the Back button to return to the previously active Manage License page.

NetLinx Security within the Web Server
76
NI-3101-SIG Signature Series NetLinx Integrated Controller
Removing a license
1.
Click on the System Settings > Manage License link from within the System Settings section of the
Navigation frame.
2. Click the Remove button.
3. Click OK from the "Are you sure you want to remove this?" popup.
System Settings - Manage NetLinx Devices
To access this page, click on the Manage NetLinx Devices link (from within the System Settings section of the
Navigation frame). These pages (FIG. 61) have some additions that have been incorporated as part of build
323 (or higher). These features include the display the device status as well as some background color
changes which indicate system groupings. These enhancements are visual changes which allow for easier
recognition of the information on a visual basis. IP connections are then able to utilize a LAN’s higher layers
of multicast to broadcast their existence.
FIG. 61 System Settings - Manage NetLinx Devices page
Manage NetLinx Devices Page
Feature Description
Clear List: Clicking this button causes the entries to be temporarily deleted
Refresh List: • Clicking this button allows the target Master to regenerate the
from the page until either the user chooses to refresh the entries
(using the Refresh List button) or the Master begins to detect
any multi-cast transmissions as devices send out their
announcements.
listing by looking for broadcasting devices.
• The button causes the Master to send out a message asking
devices to resend their NDP device announcements. The list
is then updated as those devices send back their
announcements to the “listening” Master.
• Due to system delays, message collisions, and multicast
routing, not all devices may respond immediately.
• The information displayed can not only include Masters and
devices on this system but Masters and devices on other
systems as well. By default, the target Master always appears
in the list.

NetLinx Security within the Web Server
77
NI-3101-SIG Signature Series NetLinx Integrated Controller
A large number of NDP-capable devices on the LAN can result in a large amount of
LAN traffic occurring at the same time.
Manage NetLinx Devices Page (Cont.)
Feature Description
Device Listings: • This page (in addition to the target Master which is typically the
first entry) lists those NetLinx Masters which have sent out
NetLinx Discovery Master Announce packets (NDPs).
• Each entry contains the data necessary to describe the
devices detected by the system.
• If a Master has a ‘+’ icon next to it, this indicates that this
Master is reading the presence of a NDP-capable devices
currently connected to it. This state can be toggled closed to
show a ‘-’ icon.
System Displays the System value being used by the listed NetLinx
Device • Displays the assigned device value of the listed unit. This
Device Type • Displays a description of the target Master or connected
File Name Displays the program name and/or file resident on the device.
Status Displays the Master or device state. Those states include:
Master.
Device entry applies to both the Master and those
NDP-capable devices currently connected to that Master.
device, and its current firmware version. An example is: NI
Master v3.01.323.
• This Master: Indicates its the target Master currently being
used and being browsed to. Its this Master’s web pages which
are currently being viewed.
• Orphan: Indicates that the device is currently not yet “bound”
or assigned to communicate with a particular Master.
- This state shows an adjacent Bind button which is used to
bind the device to the Master whose web pages are
currently being viewed.
• Searching: Indicates that the device is trying to establish
communication with it's associated Master.
• Bound: Indicates that the device has established
communication with it's associated Master.
- This state shows an adjacent Unbind button which is used to
release/disassociate the device from communicating with its
current Master.
• Lost: Indicates that the device has tried to establish
communication with it's associated or “bound” Master, but was
after a period of time, unable to establish communication.

NetLinx Security within the Web Server
78
NI-3101-SIG Signature Series NetLinx Integrated Controller
Expanded listing of
a Master containing
NDP-capable devices
This +/- icon toggles the
listing state of the Master
entry
Manage NetLinx Devices - Displaying NDP-capable devices
Note that in the previous example (FIG. 61), the first NetLinx Master has a "+" icon next to it, which shows
that this Master is indicating the presence of NDP-capable devices currently connected to it.
1. Click the "+" icon to expand the particular Master’s listing and reveal those NDP-capable devices
connected to it, as shown below in FIG. 62.
FIG. 62 Manage NetLinx Devices page - showing an expanded view
Note that in this example, the currently active Master’s Status description reads - This Master and
that the sub-devices are Bound to communicate with that Master. Even though they are currently
bound, clicking the adjacent Unbind button will release them from communication with a
particular Master.
2. Click the "-" icon to collapse the particular Master’s listing.
Manage NetLinx Devices - Binding/Unbinding - Explained
From below the Status column (which displays the Master or device state) you can determine whether a
device is Bound or Orphaned. For more information, refer to the section on page 82.
A Bound device is one which has established communication with it's associated Master. This
device was previously bound to communicate with a specific Master.
- This state shows an adjacent Unbind button which is used to release/disassociate the device from
its current Master.
- Once this button is pressed, the device then shows up as Orphaned (within the Status column).
An Orphan is an NDP-capable device which has not yet been assigned to communicate (bound)
with a specific Master.
- This state shows an adjacent Bind button which is used to then bind the device to the Master
whose pages are currently being viewed (displayed as This Master
within the Status column).
- Once this button is pressed, the device then shows up as Bound (within the Status column).

NetLinx Security within the Web Server
79
NI-3101-SIG Signature Series NetLinx Integrated Controller
NetLinx Master’s associated
property information
(displayed via a mouse-over
popup dialog)
This field illustrates the MAC Address
of the Master.
NDP device’s associated
property information
(displayed via a mouse-over
popup dialog)
This field illustrates the MAC Address
of the Master bound to this device
Manage NetLinx Devices - Obtaining NetLinx Device information
To obtain more description than is provided by the listing:
1. Hover the cursor over a particular device within the listing to display a mouse-over popup dialog
(FIG. 63).
FIG. 63 Manage NetLinx Devices page - showing a sample mouse-over popup dialog
The previous popup dialog shows the Master’s IP settings including the IP Address, ICSP Port, and
a MAC Address.
If the device is one that is bound to a Master, the popup also displays an additional Master MAC
Address field, which should match the MAC Address information for the bound target Master
(FIG. 64). Notice that the Master MAC Address in FIG. 64 should match the MAC Address of
the Master in FIG. 63.
FIG. 64 Manage NetLinx Devices page - showing a sample mouse-over popup dialog
In the above example, the moused-over device is bound to an NI Master on System 1 running
firmware v3.01.320. The device’s popup shows the MAC Address of the Master with which it is
bound (00:90:9f:90.....).
If this device is ever unbound from this Master (using the Unbind button), its Master MAC Address
would be left blank.

NetLinx Security within the Web Server
80
NI-3101-SIG Signature Series NetLinx Integrated Controller
Links to additional
Shows loaded Duet Modules
DDD pages
DDD configuration settings
Registered configuration
links (optional)
System Settings - Manage Other Devices - Dynamic Device Discovery Pages
Before beginning to manage any other devices, the target Master must be loaded
with the program which defines the new devices and modules. In addition to this
code, all IP/Serial devices must be pre-configured and connected to the system.
To access this page, click on the Manage Other Devices link (from within the System Settings section of the
Navigation frame). This page (FIG. 65) (within build 323 or higher) is used as the entry point for the
management of all 3rd party Dynamically Discovered Devices.
FIG. 65 System Settings - Manage Other Devices page
Manage Other Devices Page
Feature Description
Dynamic Device Discovery links: These links direct the user to additional Dynamic Device
Discovery (DDD) configuration pages which include:
• Manage Device Bindings page is used for configuring
application-defined Duet virtual devices by using discovered
physical devices.
- If your current NetLinx program (running on the target
Master)
has been written, and you have notified the Master of a set of
Dynamic Devices on your system, you will then want to start
by managing those devices through this page.
• Create User Defined Device page provides a Web interface
used in creating and managing the values necessary to add a
dynamic physical device to the system. The devices added on
this page do not support the DDD beaconing technology.
- If after confirming the presence of your programmed
Dynamic Devices (provided to the Master via the NetLinx
code), and have allowed the Master to confirm the presence of
any other Dynamic Devices, manually enter those remaining
devices on the system via the UserDefined Device page.
Note: IR-controlled devices (such as a VCR or Receiver) must
always be User-Defined devices.

NetLinx Security within the Web Server
81
NI-3101-SIG Signature Series NetLinx Integrated Controller
Manage Other Devices Page (Cont.)
Feature Description
Dynamic Device Discovery links (Cont.): • View Discovered Devices page displays a listing of all the
dynamic devices that have been discovered within the system.
- After confirming the presence of those previously coded
Dynamic Devices within the Manage Device Bindings page,
navigate to the View Discovered Devices page to continue the
process of detecting Dynamic Devices which have been
detected by the system, and then assign Module/drivers to
those devices via the View Discovered Devices page.
Configure Binding Options: This section contains configuration settings regarding the DDD
process.
Enable Auto Bind • This selection allows an end-user to toggle the state of the
automatic binding for DDD (On/Off).
• When auto-binding is enabled, the Master automatically
attempts to connect any newly discovered device with an
associated application device (defined in the running NetLinx
application).
• Auto-binding can only be accomplished if the Master's
firmware determines a one-to-one correlation between the
newly discovered device and a single entry within the list of
defined application devices (accessed by pressing the
Manage Device Bindings button at the top of the page).
• For example, if the application only has one VCR defined and
a VCR is detected in the system, auto-binding can then be
accomplished.
- If there were two VCRs defined within the application,
auto-binding could not be completed due to the lack of
a clearly defined one-to-one correspondence.
• When the Enable Auto Bind option is not selected, no
auto-binding activity takes place and all binding of the newly
discovered devices must be accomplished manually via the
Web control interfaceManage Other Devices - Manage Device
Bindings section on page 85.
Enable Subnet Match This selection allows an end-user to toggle whether or not
IP devices should only be detected/discovered if they are on the
same IP Subnet as the Master.
Purge Bound Modules on Reset • This selection indicates that all modules should be deleted
Save Settings Clicking this button causes the current selected checkbox values
from the /bound directory upon the next reboot.
• During the binding process, the associated Duet modules for a
device are copied from the /unbound directory into a
protected /bound area.
• Due to the dynamic nature of Java class loading, it is not safe
to delete a running .JAR file. Therefore, this selection provides
the administrator the capability of removing existing modules
upon reboot by forcing a re-acquisition of the module at bind
time.
• This selection is a one-time occurrence. Upon the next reboot,
the selection is cleared.
to be saved into the system.

NetLinx Security within the Web Server
82
NI-3101-SIG Signature Series NetLinx Integrated Controller
Manage Other Devices Page (Cont.)
Feature Description
Enable/Disable Module Search via
Internet
Device Configuration Pages: This section is optional and is only present when either
Manage Device Modules: This section displays a list of all currently loaded Duet Modules/
Select File to Delete • This field provides the listing of loaded Modules/.JAR files.
Delete Selected • Clicking this button deletes a selected module from the
Archive Selected • Clicking this button copies the selected JAR file to the PC
Select File to Upload • This section allows a user to browse for a target Module/.JAR
• Clicking this button toggles the capability of searching the
Internet (either AMX's site or a device specified site) for a
device’s compatible Duet modules. This capability is
automatically disabled if the Master does not have Internet
connectivity.
• Upon enabling Internet connectivity, the AMX License
Agreement is displayed for acceptance (FIG. 66). The AMX
License Agreement must be accepted (by pressing the
Accept button on the upper-right of the page) for the Internet
Module search to be enabled.
• When the Internet search for modules feature is enabled (the
button then reads Disable Module Search via Internet), the
Master queries either AMX's Online database of device
Modules and/or pulls Modules from a separate site specified
by the manufacturer's device.
• This feature may be disabled later by toggling the button.
configuration links have been previously registered by a running
Duet Module, or if a discovered device supplies configuration
link information.
• If present, this section displays each link along with a
mouse-over tool-tip.
• For Duet Modules this tool-tip describes the module
configuration link.
• For discovered devices this tool-tip indicates the physical
device the configuration link is associated with.
.JAR files on the Master (resident within the /unbound direc-
tory); as well as providing those interfaces necessary to delete,
add, and retrieve these modules.
• These entries can be selected for deletion or archiving.
/unbound directory. Any corresponding module within the
/bound directory will NOT be deleted. Bound modules must
be deleted via the Purge Bound Modules on Reset selection
described within the previous Configure Device Bindings
section.
which the user is browsing from.
• This option allows an administrator to archive those Duet
Modules resident on a target Master back to a PC.
file and then upload it to a target Master.
• Browse: Allows the user to browse for Duet Modules on the
PC/LAN.
• Upload File: Copies the specified Duet Module to the target
Master's /unbound directory.
- If a file of the same specified name already exists within the
/unbound directory; a prompt is displayed to confirm the
over-write of the existing .JAR file. Only JAR file types are
allowed for Upload to the target Master.

NetLinx Security within the Web Server
83
NI-3101-SIG Signature Series NetLinx Integrated Controller
Accept button
FIG. 66 System Settings - AMX License Agreement page
What is Dynamic Device Discovery?
The Dynamic Device Detector (DDD) monitors the system for newly connected devices. New devices can be
detected via either an external discovery protocol manager (built into firmware
build 320 or higher), Multicast reception of a Dynamic Device Beacon, or via the receipt of a beacon response
on an application specified list of serial devices. This DDD process begins by detecting new devices within a
NetLinx/Duet system, binding those devices to application instances, and then starting a Duet module to
control those new devices.
Dynamic Device Discovery was created to take advantage of Java's Dynamic Class Loading and the Duet
Standard NetLinx API (SNAPI). Java loads classes as they are needed. Therefore it is feasible to load a Duet
control/protocol module on the fly as each new device is discovered. SNAPI provides a fixed interface for
communicating with a certain type of device. The "glue code" refers to the developer defined NetLinx
program that runs on a Master and controls a system.
Take for example a VCR. The majority of control features are common to all VCRs (play, stop, pause, etc.).
SNAPI provides the "glue code" developer the ability to write common code that will control any type of VCR
having an associated Duet module. The underlying Duet module could be swapped in and out based on the
actual physical device with no changes needed to the higher level "glue code".
Dynamic Device Discovery Concepts
Feature Description
Application Device: • A Duet Device (41000-42000) that is used as a control interface to a physical device.
This is also referred to as the Duet virtual device.
• All control requests are made to the application device rather than to the physical
device.
Binding: • In concrete programming, the application device is forever associated with the NetLinx
Device Discovery: • In DDD, physical devices are detected in the system at run-time.
SDK Class: • Each application device in the DDD world is associated with a particular device type as
physical device. In DDD, this association is dynamic.
• The act of associating an application device with a physical device is called “binding".
• There are two different methods of detection: via Dynamic Device Discovery Protocol
(DDDP) or via user definition within the Master’s Web interface (page 89).
defined by SNAPI.
• When using a VCR or a Receiver as an example, each of these device types would
correspond with a Java Interface within the Duet Device Software Development Kit
(SDK).
• When writing programs for DDD, the developer specifies the device type of a particular
application device by using one of these SDK Class names.

NetLinx Security within the Web Server
84
NI-3101-SIG Signature Series NetLinx Integrated Controller
Polling: • Dynamic physical devices can be detected by DDDP through both Serial and IP
interfaces.
• While IP connections are then able to utilize the LAN’s higher layers of multicast to
broadcast their existence, Serial devices speak a fixed protocol that is incompatible with
DDDP.
• Serial devices are passive and will only broadcast their existence if polled to do so. The
program developer must specify which NetLinx interfaces/ports (i.e. serial ports) should
be polled for devices.
What is the difference between Program and Run-time defined binding?
In DDD, the device discovery activity is always dynamic because the devices will always be detected at runtime. Note that DDD splits the binding activity into two different categories:
Program defined binding (also known as static)
Run-time defined binding (also known as dynamic).
With program defined/static binding, the developer specifies a permanent binding between an application
device and a physical port, such as a particular serial or IR port. At run-time, any device detected on that port
is automatically associated with the designated application device. This binding type would be used when the
developer wants to hard code what port is used for a device, but does not know what manufacturer's device
will actually be connected. Static binding is not available for IP connected devices, since the IP Address value
of a device is subject to change due to IP LAN topology.
An example of its use would be if DHCP is enabled for the peripheral device. A
hard-coded IP Address within the NetLinx "glue-code" would be inadequate due to the nature of
the dynamically acquired DHCP IP Addresses. Only actual NetLinx D:P:S values are allowed for
static binding of physical ports.
With run-time defined/dynamic binding, the application device and the physical port are completely
disassociated (in a program sense). The developer defines the application devices and their associated SDK
class but does not specify what physical port they are bound to. At run-time, as those devices are discovered,
the new physical devices are then bound to an application device either automatically or via the Master's Web
access. Dynamic binding is the only binding option available for IP-connected peripheral devices due to the
dynamic nature of IP Addresses as discussed earlier.

NetLinx Security within the Web Server
85
NI-3101-SIG Signature Series NetLinx Integrated Controller
Manage Other Devices - Manage Device Bindings
To access this page, click on the Manage Device Bindings button (from within the Manage Other Device
page). This page is used to configure application-defined Duet virtual devices with discovered physical
devices. The on-screen table (FIG. 68) displays a list of all application-defined devices (including the defined
"friendly name"), the Duet virtual D:P:S, and the associated Duet Device SDK class (indicating the type of the
device). This information would have been pre-coded into the NetLinx file currently on the target Master
(FIG. 67).
Configuring application-defined devices
Elements such as DUET_DEV_TYPE_DISC_DEVICE and DUET_DEV_POLLED are defined within the
NetLinx axi. The latest version of the NetLinx.axi file contains both the new API definitions, as well as the
pre-defined constants that are used as some of the API arguments (ex: DUET_DEV_TYPE_DISC_DEVICE).
Sample code can be found within the DEFINE_START section seen in FIG. 67:
Physical device names are typically prefixed with "dv" and Virtual device names are
typically prefixed with "vdv". It is recommended that anyone working with these
modules should become familiar with this naming convention.
PROGRAM_NAME='DDD'
DEFINE_DEVICE
COM1 = 5001:1:0
COM2 = 5001:2:0
dvRECEIVER1 = 41000:1:0
dvDiscDevice = 41001:1:0
DEFINE_CONSTANT
DEFINE_TYPE
DEFINE_VARIABLE
DEFINE_START
STATIC_PORT_BINDING(dvDiscDevice, COM1, DUET_DEV_TYPE_DISC_DEVICE,
'My DVD', DUET_DEV_POLLED)
DYNAMIC_POLLED_PORT(COM2)
DYNAMIC_APPLICATION_DEVICE(dvRECEIVER1, DUET_DEV_TYPE_RECEIVER,
'My Receiver')
(***********************************************************)
(* THE EVENTS GO BELOW *)
(***********************************************************)
DEFINE_EVENT
DATA_EVENT [dvRECEIVER1]
{
// Duet Virtual device data events go here
}

NetLinx Security within the Web Server
86
NI-3101-SIG Signature Series NetLinx Integrated Controller
Device’s associated
property information
(displayed via a mouse-over
popup dialog)
Static bound application
devices (blank/Release)
Dynamic application devices
(Bind/Unbind)
FIG. 67 Manage Device Bindings page - showing the NetLinx code relation
This code would have given the Master a previous “heads-up” notification to look for those devices meeting
the criteria outlined within the code.
FIG. 68 Manage Device Bindings page

NetLinx Security within the Web Server
87
NI-3101-SIG Signature Series NetLinx Integrated Controller
List of available
unbound physical
devices
Discovered
physical device
properties
(displayed via a
mouse-over
popup dialog)
What are Application Devices and their association status?
There are two types of application devices: Static Bound application devices and Dynamic application devices.
Static Bound application devices specify both a Duet virtual device and its associated Device
SDK class type, as well as a NetLinx physical device port to which the application device is
ALWAYS associated (i.e. statically bound).
Dynamic application devices specify both the Duet virtual device and its associated Device SDK
with no association to a physical port. Binding of an application device to a physical device/port
occurs at run-time either via auto-binding or manual binding.
Application devices that have a "bound" physical device display their physical device ID within the Physical
Device column. If an associated Duet module has been started to communicate with the device, its associated
property information is then displayed in a mouse-over popup dialog when the cursor hovers over the physical
device ID.
Each entry in the table has one of four values appear within the far right of the Manage Device Bindings page
(FIG. 68).
Static bound application devices will either be blank or display a Release button.
- Static application devices that have not yet detected a physical device attached to
their associated port are left blank. Once a physical device is detected and
its associated Duet module has been started, a Release button is then displayed.
- By selecting Release, the administrator is forcing the associated Duet module to
be destroyed and the firmware then returns to detecting any physical devices
attached to the port.
Dynamic application devices either display a Bind or Unbind button.
- Dynamic application devices that have been bound display an Unbind button. When
the user selects Unbind, any associated Duet module is then destroyed and the
"link" between the application device and the physical device is then broken.
- Dynamic application devices that have not been bound to a physical device display
a Bind button. When this button is selected, a secondary display appears with a
listing of all available unbound physical devices that match the application device's
Device SDK class type (FIG. 69).
- If a currently bound device needs to be replaced or a Duet Module needs to be swapped
out, the device should be unbound and the new module/driver should then be bound.
FIG. 69 Manage Device Bindings - showing a listing of all unbound devices
The administrator/user can then select one of the available physical devices to bind with the
associated application device. When the Save button is selected, the binding is created and a
process begins within the target Master to find the appropriate Duet Module driver. Once a driver is
found, the Duet Module is then started and associated with the specified application device (Duet

NetLinx Security within the Web Server
88
NI-3101-SIG Signature Series NetLinx Integrated Controller
Properties of the
discovered physical
device
(displayed via a
mouse-over
popup dialog)
Listing of the discovered
Dynamic Devices
virtual device). If the Cancel button is selected, the binding activity is then aborted.
- A mouse-over popup dialog is provided to display the properties associated with
each discovered physical device that is listed (FIG. 69).
If the manufacturer device does not support Dynamic Device Discovery (DDD)
beaconing, you must use the Add New Device page to both create and manage
those values necessary to add a dynamic physical device. This process is described
in detail within the following section.
Manage Other Devices Menu - Viewing Discovered Devices
This page (FIG. 70) provides a listing with all of the dynamic devices that have been discovered in the system.
FIG. 70 View Discovered Devices page
Mousing-over a listed entry presents a popup which displays all of the properties associated with the physical
device. If the physical device is bound to an application device, the associated application device's “friendly
name” will be displayed in the Binding column. The Module Available column indicates if a Duet module is
currently available on the system for the target physical device (the results are: yes, no, or unknown).
For each physical device, a Search button is provided which initiates a search for compatible modules.
If the Module Search via the Internet option has been previously enabled (via the corresponding
button within the Configure Binding Options section of the Manage Other Devices page), the
search includes a query of the AMX online database for a compatible module based on the device's
properties.
If the device specified a URL in its DDD beacon, the file is retrieved from the URL either over the
Internet or from the physical device itself, provided the device has an inboard HTTP or FTP server.
If Module Search via Internet is NOT enabled, the search does NOT query the AMX online
database nor will it pull any manufacturer specified URLs that do not match the IP Address of the
physical device itself.
Modules that are retrieved from either the Internet or from the manufacturer's device are then placed into the /
unbound directory and automatically overwrite any existing module of the same name.
Once a list of all compatible modules is compiled, the Select Device Module page (FIG. 71) is then displayed
with a listing of each module along with its calculated “match” value. The greater the “match” value, the better
the match between the Duet Module's properties and the physical device's properties.

NetLinx Security within the Web Server
89
NI-3101-SIG Signature Series NetLinx Integrated Controller
Module Properties
(displayed via a
mouse-over
popup dialog)
List of discovered
physical devices
(manually entered info)
FIG. 71 Select Device Module page
Mousing-over a listed module entry presents a popup which displays the properties associated with the
selected module.
By selecting the module and clicking the Save button, the administrator can assign a Duet module to be
associated with the physical device.
This action will NOT affect any currently running Duet module associated with the
physical device. The module is associated with the device upon reboot.
Clicking the Cancel button aborts the association of a Duet module with the physical device BUT it does not
undo the process of pulling new modules from the Internet/device into the /unbound directory on the target
Master. These modules will remain resident in the /unbound directory until they are manually deleted via the
Manage Other Devices main web page. Refer to theSystem Settings - Manage Other Devices - Dynamic
Device Discovery Pages section on page 80.
Manage Other Devices Menu - Creating a new User-Defined Device
This page provides the ability to both add and remove any user-defined devices. Existing user-defined devices
are listed at the bottom of the display along with a corresponding Remove button alongside each new entry.
Although FIG. 72 shows a populated page, by default, all fields are blank and no devices are pre-populated.
FIG. 72 Add New Device page

NetLinx Security within the Web Server
90
NI-3101-SIG Signature Series NetLinx Integrated Controller
1. Click on the Create User Defined Device button (from within the Manage Other Device page).
2. Begin by entering the address of the physical device within the Address field. This information can be
either the NetLinx Master port value (D:P:S) or an IP Address (#.#.#.#).
3. From within the Device Category field, use the drop-down list to select the control method associated
with the physical target device (IR, IP, Serial, Relay, Other).
4. From within the SDK Class field, use the drop-down list to select the closest Device SDK class type
match for the physical target device. The following table provides a listing of the available choices.
SDK-Class Types
Amplifier DocumentCamera SlideProjector
AudioConferencer HVAC Switcher
AudioMixer Keypad Text Keypad
AudioProcessor Light TV
AudioTape Monitor Utility
AudioTunerDevice Motor VCR
Camera MultiWindow VideoConferencer
Digital Media Decoder PoolSpa VideoProcessor
Digital Media Encoder PreAmpSurroundSoundProcessor VideoProjector
Digital Media Server Receiver VideoWall
Digital Satellite System Security System VolumeController
Digital Video Recorder Sensor Device Weather
Disc Device SettopBox
5. Use the GUID field to enter the manufacturer-specified device’s Global Unique Identification
information. Either the GUID or Make/Model must be specified within this field.
6. Enter the name of the manufacturer for the device being used (up to 55 alpha-numeric characters) (ex:
Sony, ONKYO, etc.) into the Make field. Either the GUID or Make/Model must be specified within this
field. Note that spaces in the name will be converted to underscores.
7. Enter the model number of the device being used (up to 255 alpha-numeric characters)
(ex: Mega-Tuner 1000) into the Model field. Either the GUID or Make/Model must be specified within
this field.
8. Enter the firmware version used by the target device into the Revision field. Text is required within this
field.
The version must be in the format: major.minor.micro (where major, minor, and micro are
numbers). An example is: 1.0.0 (revision 1.0.0 of the device firmware).
9. Once you are done creating the profile for the new device, click the New button to assign additional
Name and Valu e property information for association with the new User Defined Device.
When the Add button is selected, the user-defined device is then inserted into the list of discovered
physical devices which appears within the lower section of the display (FIG. 72).
When the Cancel button is selected, the addition of the user defined device is aborted,
no amendment to the existing list is made, and the user is returned back to the Manage Device
Bindings page.
10. Once you have finished entering your devices, click the Back button (from within the Manage Device
Bindings page) and then navigate to the View Discovered Devices page to view the listing of all Dynamic
Devices discovered in the system.
How do I write a program that uses Dynamic Device Discovery
These procedures assume the NetLinx developer does not have the Manufacturer device information necessary
at the time of the initial setup. For more detailed UI information, refer to the Manage Other Devices - Manage
Device Bindings section on page 85. For information on the referenced NetLinx calls, refer to the NetLinx
Keywords Help file (found within NetLinx Studio).
 Loading...
Loading...