Page 1

◆
User’s Guide
Management Software
AT-S20
For use with the AT-3726XL, AT-3716XL, AT-3714FXL,
AT-3726 and AT-3714F Switches
Version 3.1
PN 613-10773-00 Rev. C
Page 2

Copyright 1998, 1999 Allied Telesyn International, Corp.
960 Stewart Drive Suite B, Sunnyvale CA 94086
All rights reserved. No part of this publication may be reproduced without prior written permission from Allied Telesyn
International, Corp.
CentreCom is a regist ered trademark of Allied Telesyn International, Corp.
Netscape Navigator is a registered trademark of Netscape Communications Corporation. Ethernet is a registered trademark of
Xerox Corporation. All other product names, company names, logos or other designations mentioned herein are trademarks or
registered trademarks of their respective owners.
Allied Telesyn International, Corp. reserves the right to make changes in specifications and other information contained in this
document without prior written notice. The information provided herein is subject to change without notice. In no event shall
Allied Telesyn International, Corp. be liable for any incidental, special, indirect, or consequential damages whatsoever, including
but not limited to lost profits, arising out of or related to this manual or the information contained herein, even if Allied Telesyn
International, Corp. has been advised of, known, or should have known, the possibility of such damages.
Page 3

7DEOH#RI#&RQWHQWV
Preface ...............................................................................................................................................................Preface-i
Purpose of This Guide .................................. ............................. ......................................................................Preface-i
How This Guide is Organized .....................................................................................................................Preface-ii
Document Conventions ..............................................................................................................................Preface-iii
Related Guides ...................................... ............................. .............................................................................Preface-vi
Chapter 1
Features, Menu Tree, and Defaults ......................................................................... .......................................1-1
Software Features ...................................................... ............................. .......................................................... ..........1-1
Switch Naming and Security Features.............................................................. ............................. ............... 1-3
Switch Default Settings .............................................................................................................................................1-4
Setting Switch Defaults ............................................................... ....................................................................... .......1-5
Menu Tree ..... ............................. ............................. ............................. ................................................ ..........................1-6
Chapter 2
Getting Started with Local and Remote Omega ......................................................................................2-1
Getting Started with Local Omega .......................................................................................................................2-1
Configuring Your Terminal Emulator Program......................................................................................... 2-1
Starting an Omega Session............................................................... ................................................................ 2-2
Entering an IP Address.............................................................................................................. ......................... 2-3
Quitting a Session................................... ............................................................................................................. 2-3
Remote Management Requirements .................. ............................. ....................................................................2-4
Managing Your Switch in a TCP/IP-based Network .......................... ............................. .................................2-4
TCP/IP with BootP or DHCP........................................................................................ ...................................... 2-4
TCP/IP without BootP......... ................................................................................................................................ 2-5
Non-TCP/IP Networks............................................................................................................. ............................ 2-5
Configuration Options.......... .......................................................................................................... ................... 2-5
iii
Page 4

Table of Contents
Chapter 3
Getting Started With Browser Ma nagement .............................................................................................3-1
Browser Requirements ..............................................................................................................................................3-1
Starting a Browser Sessio n ................................ ............................. ............................. ...................................... .......3-2
Navigating Around the Switch ..................... ............................. ............................. ................................................3-3
Chapter 4
Configuration an d Administration ................................................................................................................4-1
Connecting to a Remote System ........................... ............................. ...................................................................4-3
Pinging a Remote System ............................................................................................................................ ............4-4
Enabling or Disabling a Port ............................. ............................. ....................................................... ...................4-5
Configuring IP Parameters ................... ....................................................................................................................4-6
Naming the Switch ............................................................................... ...................................................... ................4-8
Change/Delete the Switch Name...................... ......................................................................................... 4-10
Naming the Port ... ............................. ............................. ............................. .............................................................4-11
Changing or Deleting a Port Name................................................................................ ............................ 4-13
Assigning a Password to the Switch ................................. ............................. ............................. ......................4-14
Forgetting Your Password................................. ............................. ............................. ................... ............... 4-14
Enabling Store-and-forward or Cut-through (Fragment-Free) ......................................................... ...... 4-15
Enabling Auto-Negotiate/Half -Duplex/Full-Duplex ....................................................................................4-17
Enabling Transmit Pacing ........................................................................... ..........................................................4-18
Setting Up a VT100 ..................................................................................... .............................................................4-19
Setting Up a Generic (Dumb) Terminal..................................................................................................... 4-19
Setting Full-Duplex/ Half-Duplex Mode............................. ...................................................................... 4-19
Setting Baud Rates........................ ........................................................................................................... ........ 4-20
Setting Time Out Protection ................................... .............................................................................................4-21
Deleting a Previously Configured Time out Valu e................................................................................. 4-21
Enabling/Disabling Omega Access ................................................................................. ...................................4-22
Local Omega....................................................................................................................................................... 4-22
Remote Omega............................................................................ ...................................................................... 4-22
Web-based Omega....................................... ................................................................................. .................. 4-22
Enabling/Disabling Backpressure ............................................ ..........................................................................4-23
Performing Software Upgrades Via TFTP ........................................................................................................4-24
Conditions for Network Downloads via TFTP.......................................................................... ............... 4-24
Using TFTP........................................................................................................................................................... 4-24
Downloading from One Switch to Another................................................................... ......................... 4-25
Broadcast Updated Software to All Systems.......................................................................................... 4-26
Using XModem to Download.................................................................................. ..................................... 4-27
Configuring for Bridging ................................... ............................. ............................. ..........................................4-28
Configuring Spanning Tree Parameters................................................................................................... 4-29
Designating the Root Port............. ............................. ............................. ............................. ......................... 4-31
Selecting Global Configuration ........................... ............................. ...................................................................4-33
Enabling/Disabling Port Trunking ........................................................................ .............................................4-34
iv
Page 5

AT-S20 User’s Guide
Chapter 5
Virtual LAN Configuration ..................................................................................................................................5-1
Configuration Information................................................................................................................................ 5-5
Port Information................................................................................................................................................... 5-5
Adding a New VLAN............................................................................................................................................ 5-7
Port to VLAN Configuration.............................................................................................................................. 5-9
Deleting a Port from a VLAN or Changing Port’s VLAN Assignm ent.............................................. 5-10
Chapter 6
Monitoring .......................................................................... .......................................................................................6-1
Activity Monitor ...........................................................................................................................................................6-2
MAC Address Table ..................................................................................................................................... ................6-3
Show All MAC Addresses................................................................................................................................ ... 6-4
Show By Port MAC Addresses........................................................................................................... ............... 6-4
Get Port from MAC Address............................................................. ............................. ................................... 6-5
Static MAC Addresses ................................................................................................................................................6-6
Show All Static MAC Addresses.... ............................. ...................................................................................... 6-6
Show Per Port Static MAC Addresses............................................................................................................ 6-7
Delete/Add Static MAC Address..................................................................................................................... 6 -8
Add/Delete Static MAC Addresses and Selecting Ports for Multicasts............................................. 6-9
Clearing Static MAC Table.............................................. ................................................................................ 6-11
Locating Your Switch’s MAC Address........................................................................................................ 6-11
Security/Source Address Table ........................................ ............................. .......................................................6-12
Source Address Learning Mo de................................................................................................................... 6-13
Security Threshold............................................................................... ............................. .......................... ...... 6-15
Intruder Protection.................................................... ............................. ................................................. ......... 6-17
Setting Security/Source Address Table Options ...........................................................................................6-19
Setting Source Address Learning Mode................................................................................................... 6-19
Setting Security Threshold................................................................... ............................. ............................. 6-20
Setting Number of MAC Address................................................................................................................ 6-20
Setting Intruder Protection..................................................................... ............................. ......................... 6-21
Mirror Port ...................................................................................................................................................................6-23
Port Status ...................................................................................................................................................................6-25
Port Numbering ............................. ....................................................................................................... ....................6-26
Statistics: Received and Transmitted Ethernet Frames ...............................................................................6-28
Viewing Switch Statistics.......................................................................................................... ...................... 6-28
Viewing Port Statistics........................................................... ............................. ............................................. 6-33
Interpreting the Graphs.................................................................................................................................. 6-34
Using the Graphs as a Monitoring and Diagnostics Tool................................................................... 6-35
v
Page 6

Table of Contents
Chapter 7
Diagnostics ................................................................................................................................................................7-1
Resetting the Switch ..................................................................................................................................................7-2
To Reset the Switch.................................................................................... ......................................................... 7-2
Running Diagnostics ............................................................................... ...................................................................7-3
Getting Help ................. ................................................................................................................. ................................7-4
Resetting Statistics Counters ..................................................................................................................................7-5
To Reset Switch (System) Counters............................................................................................................... 7-5
AppendixA
Spanning Tree Protocol ......................................................................................................................................A-1
Concepts ....................................................................................................................................................................... A-1
Features.............................................................................................................................. .................................... A-2
Parameters............................................................................................................................................................ A-2
Operations..................................................... ............................. ........................................................................... A-3
Index ....................................................................................................................................................................Index-1
vi
Page 7

3UHIDFH
3XUSRVH#RI#7KLV#*XLGH
The purpose of this guide is to instruct network administrators on
how to manage their switch by using the Omega management
software to configure and monitor the device. By using the Omega
software, a network administrator can manage the switch in several
ways:
❑
Remotely
❑
Locally
❑
Web-based
Network administrators should be familiar with Ethernet switches,
bridging, and the spanning tree protoc ol.
Preface-i
Page 8

How This Guide is Organized
+RZ#7KLV#*XLGH#LV#2UJDQL]HG
This guide is composed of the following sections:
Chapter1, Features, Menu Tree, and Defaults, which presents the
major switch features, a menu tree that displays the primary and
secondary menus, and a list of switch defaults in tabular form.
Chapter2, Getting Started with Local and Remote Omega, provides
instructions on how to set up the switch for remotely or locally
managing the switch.
Chapter3, Getting Started With Browser Management, provides
instructions on how to use a browser to manage the switch.
Chapter4, Configuration and Administration, describes the
management tasks according to switch, configuration, port
configuration and administration.
Chapter5, Virtual LAN Configuration, provides a brief discussion of
Allied T elesyn’s implementation of VLANs.
Chapter6, Monitoring, describes the tasks related to monitoring the
switch.
Chapter7, Diagnostics, describes the testing procedures using the
Omega menus.
AppendixA, Spanning Tree Protocol, provides a brief explanation of
Spanning Tree Algorithm and its use with the switch
At the end of this guide is an Index according to subject matter.
Preface-ii
Page 9
'RFXPHQW#&RQYHQWLRQV
The conventions used in this guide are as follows:
To select an option Highlight the option by pressing the Up
AT-S20 User’s Guide
❑
For DEC VT100 or ANSI (the default) terminal configuration:
When directed You must
(↑) or Down (↓) arrow key; then press
RETURN
or
Type the first character of the option you
want at the prompt and then press
RETURN.
If two or more options have matching
initial characters, type the first characters
enough times until the option you want
is highlighted; then press RETURN.
To enter information, for
example, IP address
To return to the previous
Type the correct IP address and press
RETURN
Select the option
screen (Omega only)
or
Press ESC
To return to the previous
Select the Back button
screen (Browser)
To return to Main Menu
(Omega)
To return to Main Menu
Highlight Return to Main menu... and
then press RETURN
Select the Main Menu icon.
(Browser)
All procedures in this guide are based on the default terminal
configuration.
Preface-iii
Page 10

Document Conventions
❑
For generic (dumb terminal) terminal configuration:
When directed You must
To select an option Type the first character of the option you
want and then press RETURN.
If two or more options hav e mat ching initial
characters, type enough characters for
Omega to distinguish your choice from the
other options; then press RETURN. To guide
you, the characters you must type are in
uppercase.
For example:
Mirroring configu ration
MAC Address Table
If options on a list are preceded by numbers
(1:, 2:, 3:, etc.), type the number
corresponding to your choic e a t the pr o mpt;
then press RETURN.
To enter information,
for example, IP
address
To return to the
previous screen
❑
Selecting a configuration:
Omega denotes a def ault configur ation by preced ing it with a
>. For example, DEC VT100 configuration is shown to be the
terminal type in the following screen:
> VT100-compatible / ANSI
Generic dumb terminal
Type the correct IP address at the prompt
and press RETURN.
Press RETURN after making an entry.
Preface-iv
Page 11
AT-S20 User’s Guide
Warning
Caution
VT100-compatible / ANSI
> Generic dumb terminal
The default selection in a DEC VT100 terminal configuration
also appears darker. If you change the option, Omega changes
the user interface by moving the > to the new selection. For
example:
❑
Selecting menu options:
Menus and submenus are in courier type. Menu hierarchies
are separated by a >.
Menu:
Menu:
❑
Entering variables:
Administration
Administration>IP parameters
Variables are information you must supply, as in IP addresses,
MAC addresses, or port numbers. Variables are enclosed in
angle brackets (<>).
For example, to configure a specific port:
Select
Port status and
configuration><PortNumber>
where
<PortNumber>
can be Port 1, or 2, and so on.
Note
A note provides additional information.
A warning informs you that performing or omitting a specific action
may result to bodily injury.
A caution informs you that performing or omitting a specific action
may result to equipment damage or loss of data.
Preface-v
Page 12

Related Guides
5HODWHG#*XLGHV
Allied Telesyn wants our customers to be well informed b y pr ov iding
the most up- t o- date and easily ac c ess ib le g uid e s an d othe r te c hn ical
information.
Visit our website at: www.alliedtelesyn.com and download the
following guide:
AT-3726XL, AT-3716XL, AT-3714FXL Installation Guide,
613-10766-00
AT-3726, AT-3714F Installation Guide,
613-10708-00
The following guides are shipped with the product:
AT-3726XL and AT-3716XL Quick Install Guide,
613-10769-00
AT-3726XL and AT-371 6XL T rans lated Sa fety I nformati on
Booklet, 613-10768-00
AT-3714FXL Quick Install Guide,
613-10767-00
AT-3714FXL Translated Safety Informatio n B ooklet,
613-10770-00
AT-A10, AT-A11 Quick Install Guide,
613-10742-00
AT-3726 Quick Install Guide,
613-10668-00
AT-3726 Translated Safety Information Booklet,
PN 613-10673-00
AT-3714F Quick Install Guide,
613-10707-00
AT-3714F Translated Safety Information Booklet,
PN 613-10717-00
Preface-vi
AT-3701, AT-3701F/SC Quick Install Guide,
613-10669-00
Page 13

&KDSWHU 4
) HDWXUHV/#0HQX#7UHH/#DQG#'HIDXOWV
6RIWZDUH#)HDWXUHV
The switches have the following major software management
features:
❑
Supports industry-standard 802.1Q VLAN tagging and
supports a maximum of 32 port-based and tag-based VLANs
(XL versions only)
❑
Security (XL versions only)
❑
Backpressure (XL versions only) and transmit pacing provide
one-way flow control to relieve congested networks
❑
Port mirroring
❑
Firmware is factory-installed and ready to use
❑
User configuration for store-and-forward and cut-through
packet switching for non-XL versions; store and forward only
for XL versions
❑
Auto-negotiation on 10 Mbps and 10/100 Mbps UTP ports in
compliance with IEEE 802.3u
❑
Mulitcast address support which allows users to specify the
recipient port for multicast packets
❑
All UTP and fiber ports are software configurable for full- and
half-duplex
❑
Port B (optional uplink) can be configured as either a 10/100
Mbps UTP or a 100 Mbps fiber uplink
1-1
Page 14

Software Features
❑
Port Trunking allows configuring of Ports A and B to function
as a single uplink port which effectively increases the
throughput of the connection.
❑
Spanning Tree Protocol (STP) support
❑
System configuration, management, and diagnostics using
Allied Telesyn’s
Omega interface
, accessible locally via an
RS232 asynchronous terminal port, remotely via Telnet, or a
web browser.
❑
Software upgrades using Xmodem via the RS232 port or TFTP
to download software to switches on the network
❑
Broadcast software from a switch to one or all switches on the
network
❑
Web-based management
❑
SNMP agent that allows the switch management from the
user’s network management station
❑
Support for BootP and Dynamic Host Configuration Protocol
(DHCP) for IP parameters
❑
Support for DEC VT100/ANSI (the default), or generic (dumb)
terminal configuration
❑
Internet Control Message Protocol (ICMP) Echo PING support
❑
Domain name service support (DNS)
1-2
Page 15

AT-S20 User’s Guide
6ZLWFK#1DPLQJ
DQG#6HFXULW\
)HDWXUHV
The switch provides configurable options for customizing for
example,
❑
Naming the switch and its ports
Names are more descriptive and easier to remember than
addresses.
Port names can be associated with the user assigned to the
port or an office location. The need to use symbolic names
becomes more apparent as you add more switches and
therefore multiply the number of ports you must manage.
❑
Enabling security features
Although passwords are not required to access the
management menus, with the Omega Options menu, you can
prevent (disable) either Local Omega, Remote Omega, or webbased Omega, create password protection, and enable
timeout.
A timeout value automatically terminates a management
session after a given period when someone leaves a current
session unattended.
1-3
Page 16

Switch Default Settings
6ZLWFK#'HIDXOW#6HWWLQJV
Table 1-1 lists the switch default settings.
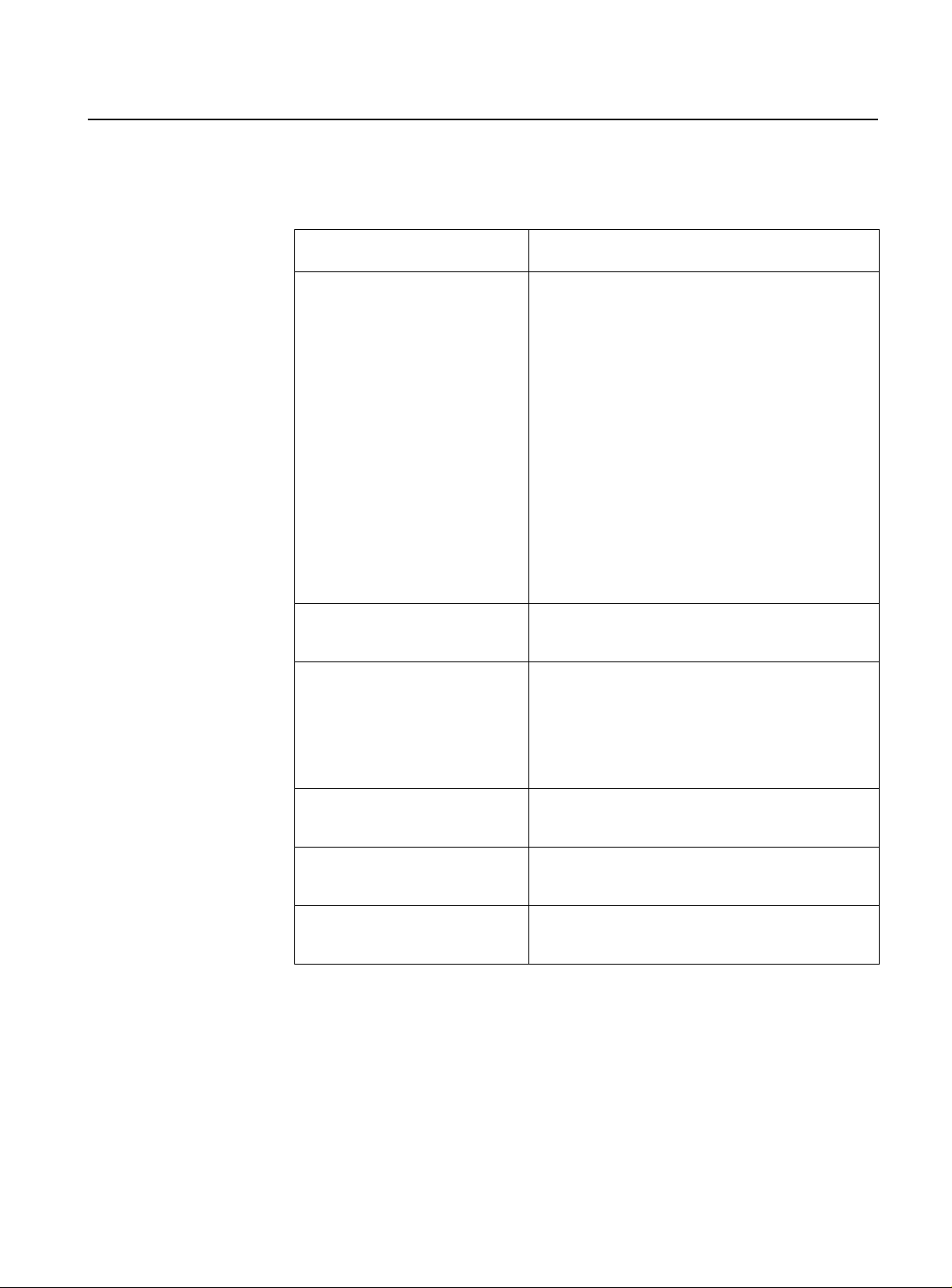
Table 1-1
Switch Default Settings
Settings Default
IP Address 0.0.0.0
Subnet Mask 0.0.0.0
Gateway Address 0.0.0.0
Get community string public
Set community string private
Trap community string public
Port mirroring st ate Disabled
Spanning Tree Protocol Disabled
Omega Access Enabled
System Name None
Password (Omega) No password assig n ed
Download Password ATS20
Port Priority 128
Port Path Cost 100 (AT-3726)
Auto-negotiate, Full-duplex or Half-duplex (per port) Auto-negotiate (AT-3726XL,AT-3726,
AT-3716XL)
Half-duplex (AT-3714FXL, AT-3714F)
Spanning Tree Priority 32768
Maximum Aging Time 20 seconds
Forwarding Delay 15
Hello Time 2 seconds
Transmit Pacing/Backpressure Disabled
Bridge Identifier (STP) 32768 (bridge priority)
Port Priority (STP) 128
Port Cost (STP) 100 for 10 Mbps ports
10 for 100 Mbps ports
Domain Name None
Timeout Value 5 minutes
Default VLAN Name Default VLAN
1-4
Page 17

6HWWLQJ#6ZLWFK#'HIDXOWV
Warning
To set your switch to the factory defaults, do the following:
This operation deletes existing switch configurations.
1. Attach a terminal or PC to the RS232 port located on the front
2. Press RESET located on the right side of the switch’s front panel.
AT-S20 User’s Guide
panel of the switch and start the terminal emulation program.
3. Immediately press any key when you see
diagnostics or to reload system software
Hit any key to run
.
A menu
then displays.
4. Select D from the menu. The following warning message displays:
WARNING: This will erase all current
configuration data!
Continue? Y/N
5. Select Y. The system displays:
been reset to factory default values
All configuration data has
.
6. Press B to boot the switch software.
1-5
Page 18

Menu Tree
0HQX#7UHH
The following illustration shows the Omega Menu tree.
Port status and
configuration
Enable this port
Disable (partition) this port
Auto negotiate
Full duplex
Half duplex
Store-and-forward
Cut-through
Transmit pacing enable
No transmit pacing
Global config
Port name
(fragment-free)1
Ethernet statistics
Receive Good Frames
Filtered Frames
Broadcasts
Multicasts
CRC Errors
Alignment Errors
Undersized Frames
Fragments
Long Frames
Transmit Statistics
Individual port overview
Administration
Update software in
another sytem
Broadcast updated
software to all systems
XModem software update
to this system
Connect to a remote
system
Ping a remote system
Activity monitor
Diagnostics
Reset and restart the
system
System
Configuration
System name
Default VLAN Aging Time
Omega Options
IP Parameters
Security/Source
Address T able
Terminal configuration
Back pressure
Port T runking
2
2
1. For non-XL versions only
2. For XL versions only
RMON Statistics
Port RMON Statistics
Zero all statistics counters
on the entire system
Figure1-1
Omega Menu Tree (1 of 2)
1-6
Page 19

AT-S20 User’s Guide
Traffic/Port
Mirroring
Enabled
Disabled
3. For XL versions only
Virtual LAN
Virtual LAN definitions
Port to VLAN
configuration
3
Bridge
Figure1-2
Spanning tree parameters
Port spanning tree
configuration
Omega Menu Tree (2 of 2)
MAC Address
Show all MAC addresses
By port MAC addresses
Get Port From MAC
Address
All static MAC addresses
Per port static MAC
addresses
Multicast addresses
Clear static MAC table
1-7
Page 20

Page 21
&KDSWHU 5
*HWWLQJ#6WDUWHG#ZLWK#/RFDO#DQG#5HPRWH#2PHJD
*HWWLQJ#6WDUWHG#ZLWK#/RFDO#2PHJD
To locally managing your switch, simply connect a terminal or PC
directly to the switch’s RS232 port to access the Omega menus. See
the following sections.
&RQILJXULQJ#<RXU
7HU PL QDO
(PXODWRU
3URJUDP
To set the terminal emulator program, do the following:
1. Access the terminal emulator program on your PC (VT100) and set the following:
❑
Data bits to 8
❑
Stop bits to 1
❑
Parity to None
❑
Full-duplex (using straight-through cable)
❑
Autobaud
Note
The diagnostics that run during the system boot output only at 9600
bps. Therefore, Allied Telesyn recommends this speed setting.
2. Press <Return> several times to ensure baud autoconfiguration.
2-1
Page 22
Getting Started with Local Omega
6WDUWLQJ#DQ
2PHJD#6HVVLRQ
Once you have established a connection to the switch, the Omega
Main Menu displays.
The banner reflects the name of your switch. This example shows
that the AT-3714FXL switch is operating and the switch name is
Accounting.
S
w
i
t
c
A
T
-
3
7
1
4
F
X
L
E
t
h
e
n
r
A
l
l
i
e
d
T
e
l
e
s
n
y
A
c
c
o
u
n
t
n
i
g
M
e
n
M
c
o
n
f
i
g
u
r
a
t
i
o
P
o
r
t
s
t
a
t
u
s
a
n
d
h
e
r
n
e
t
s
t
a
t
i
s
t
i
c
E
t
a
A
d
m
S
y
s
T
r
a
V
i
r
r
B
i
M
A
C
Q
u
i
t
i
i
n
s
t
r
t
e
m
o
c
n
f
f
f
i
c
/
P
o
r
A
N
t
u
a
l
L
d
g
i
n
g
A
d
d
r
e
s
s
t
s
i
o
n
t
i
o
i
t
s
n
g
u
r
a
M
i
r
r
o
r
i
n
T
a
b
l
e
n
g
u
a
i
n
e
h
t
Omega Main Menu (AT-3714FXL)
from the main menu, the
By selecting
Figure 2-1
System Configuration
following screen displays. The default settings are always in bold
print on the screen.
r
n
e
t
S
w
i
t
c
e
s
y
n
A
T
-
3
7
1
4
F
L
X
E
t
h
A
l
l
i
e
d
T
e
l
u
l
l
(
n
o
t
c
o
n
P
a
s
s
w
o
r
:
d
N
T
i
m
e
o
u
t
:
5
O
m
e
g
a
E
n
b
L
o
c
a
l
D
i
s
a
b
l
e
R
e
m
t
o
e
R
e
m
o
t
e
W
e
b
-
b
a
s
E
x
c
l
u
d
e
R
e
t
u
r
n
a
d
L
o
c
a
l
O
O
m
e
g
a
E
n
a
D
i
O
e
t
s
m
e
g
a
d
O
m
e
g
a
b
a
s
e
W
e
-
b
o
s
y
s
e
t
m
f
l
e
d
g
a
e
m
e
d
b
l
a
b
l
e
d
a
b
l
e
d
E
n
d
o
m
e
g
a
n
f
i
g
u
C
o
Figure2-2
c
A
c
o
u
n
t
M
a
i
n
M
i
u
g
r
e
d
)
r
a
t
i
o
n
e
M
n
u
.
System Conf iguration Menu
e
n
g
i
e
n
u
.
.
h
2-2
Page 23

AT-S20 User’s Guide
(QWHULQJ#DQ#,3
$GGUHVV
If you have a T CP/IP network but do not ha v e a BootP server, or DHCP
server, you must enter an IP address and subnet mask for the switch
through Omega.
1. Select
System administration IP Parameters
from the
Main Menu.
2. Select
3. Select
4. Select
IP address
Subnet mask
and enter a unique IP address for the switch.
and enter the switch’s subnet mask.
Gateway address
and enter the address if you are
sending packets to another IP network. The gateway address is
the router that can forward packets to the other IP networks.
Once the switch has an IP address, you may initiate Omega sessions
to it via Telnet. Note that you can only have one Telnet session
operating at any one time. The session can be either inbound or
outbound. If you have an inbound session to Omega, you do not
have the option of starting a new session (outbound connection).
Therefore, if you are already using Telnet, the Omega option
Connect to a remote system
will not be available (described
in detail in Chapter 4, Connecting to a Remote System on page 4-
3). In addition, a local RS232 connection blocks a Telnet session and
vice versa.
4XLWWLQJ#D
6HVVLRQ
Note
For non-IP environments, you can use MAC addresses to connect to
remote Allied Telesyn switches only if there are no routers between
the two switches. If you have assigned unique names, you may use
these also.
Select
accessed the switch through the network, selecting
Quit
from the Main Menu to terminate the session. If you
Quit
also cuts
the connection.
It is important to select
Quit
when you are done with Omega;
otherwise, you may block other remote sessions, local sessions, or
software downloads. To avoid possible lockouts, see Setting Time
Out Protect i o n on page 4-21.
Note
After you have configured your switch using the Omega
management software, you must quit the session and disconnect the
RS232 cable.
2-3
Page 24

Remote Management Requirements
5HPRWH#0DQDJHPHQW#5HTXLUHPHQWV
Y ou can remotely manage your switch, but first you must have one of
the following:
❑
The switch’s pre-configured MAC address (located below the
RS232 Terminal Port label on the switch’s front panel
❑
A unique IP address if you use TCP/IP (by either assigning one
to the remote switch or by having your BootP/DHCP server
provide the needed parameters
❑
A unique name for the switch that you assign via Omega (see
Naming the Switch on page 4-8.
0DQDJLQJ#<RXU#6ZLWFK#LQ#D#7&32,30EDVHG#1HWZRUN
To manage the switch in a TCP/IP based network, you must first:
7&32,3#ZLWK
%RRW3#RU#'+&3
❑
Configure the switch’s IP parameters, or
❑
Automatically get an IP address via BootP or DHCP
Note
You do have the option to manage the switch using either SNMP or
Omega Remote, via Telnet or web browser.
The function of the BootP utility within an IP server is to enter an IP
address into the switch. Whenever you reset or power on/off the
switch, the switch transmits a request packet to the server every
three seconds to obtain the required IP parameters. (The BootP
utility and the DHCP both make three attempts each.)
If the requesting switch does not receive a BootP or DHCP response
after the third request, it will operate with a computed pseudo IP
address based on the switch’s MAC address for Allied Telesyn switchto-switch communication, i.e., downloads.
If the switch receives a BootP or DHCP response, it extracts the IP
address, Subnet Mask, and Gateway/Router address from the
response packet and uses these parameters to configure itself until
the next power-on or reset. Additionally, if the BootP response
packet specifies a filename and a TFTP host address, then the switch
sends a TFTP “get” request to the specified host using the specified
filename. This initiates a TFTP download of operating software and
allows you to maintain the downloaded server software.
2-4
Page 25

AT-S20 User’s Guide
7&32,3#ZLWKRXW
%RRW3
1RQ07&32,3
1HWZRUNV
&RQILJXUDWLRQ
2SWLRQV
To manage the switch using SNMP, Telnet or web browser, you must
at least enter the IP address and subnet mask using the Omega
menus.
T o manage your switch on a non-TCP/IP network, you need to locally connect to one switch in the segment (see Configuration Options on page 2-5). You can then connect to other segments on the same segment using the techniques described in Chapter 4, Connecting to a Remote System.
Note
You cannot manage the switch using a web browser without configuring TCP /IP information.
Network administrators can use the configurable options for their
individualized switch performance. For example:
❑
Name the switch and its ports
Names are more descriptive and easier to remember than
addresses.
Port names can be associated with the user assigned to the
port or an office location. The need to use symbolic names
becomes more apparent as you add more switches and
therefore multiply the number of ports you must manage.
❑
Enable security features
Although passwords are not required to access the
management menus, with the Omega Options Menu, you can
prevent (disable) either Local Omega, Remote Omega, or webbased Omega, create password protection, and enable
timeout.
A timeout value automatically terminates a management
session after a given period when someone leaves a current
session unattended.
Proceed to Chapter4, Configura t io n an d Admi n is tr at i o n and
Chapter 6, Monitoring.
2-5
Page 26

Page 27
&KDSWHU 6
*HWWLQJ#6WDUWHG#:LWK#%URZVHU#
0DQDJHPHQW
%URZVHU#5HTXLUHPHQWV
To use AT-S20 software via a browser, you need the following:
❑
A computer connected to any network port
❑
A Web browser, such as Netscape Navigator®, installed on the
computer
❑
The IP address of the switch (see Chapter2, Confi guration
Options)
Note
While only one local or remote Omega session can be opened, there
can be multiple web-based sessions opened at any time.
3-1
Page 28

Starting a Browser Session
6WDUWLQJ#D#%URZVHU#6HVVLRQ
To access the switch using your browser, do the following:
1. If your network is using a proxy server, you will need to make
exceptions for the switches that you want to manage. Refer to the
documentation provided with your web browser.
At minimum, you must have Netscape version 3.0 or any other
industry-standard browser to manage the switch via a browser.
2. At the Universal Resource Locator (URL) prompt, enter the
switch’s IP address. The following screen is displayed.
Note
3-2
Note
For easy access, you may want to bookmark the URL for the switches you access frequently.
Page 29

1DYLJDWLQJ#$URXQG#WKH#6ZLWFK
The switch’s front panel is active. You can click anywhere on the
switch and a menu or table displays. For example, if you click Port 15,
that port’s settings appear, as shown in Figure3-1.
AT-S20 User’s Guide
Figure3-1
Port 15 Sett ings
3-3
Page 30

Navigating Around the Switch
If you click any other area other than a specified port on the switch’s
front panel, the following table displays.
Figure3-2
Port Link, Status, and Mode States
You also can click on the Omega Main Menu.
You are now ready to configure your switch. See Chapter 4,
Configuration and Administ ratio n .
3-4
Page 31

&KDSWHU 7
&RQILJXUDWLRQ#DQG#$GPLQLVWUDWLRQ
This chapter describes the management tasks according to switch,
configuration, port configuration and administration.
Switch configuration covers the following topics:
❑
Naming the Switch on page 4-8
❑
Assigning a Password to the Switch on page 4-14
❑
Setting Up a VT100 on page 4-19
❑
Setting Time Ou t P ro t e ction on page 4-21
❑
Enabling/Disabling Omega Access on page 4-22
❑
Enabling/Disabling Backpressure on page 4-23
❑
Enabling/Disabling Port Trunking on page 4-34
Port configuration covers the following topics:
❑
Enabling or Disabling a Port on page 4-5
❑
Naming the Port on page 4-11
❑
Enabling Auto-Negotiate/Half-Duplex/Full-Duplex on
page 4-17
❑
Enabling Transmit Pacing on page 4-18
❑
Selecting Global Config uration on page 4-33
4-1
Page 32

Administration covers the following topics:
❑
Pinging a Remote System on page 4-4
❑
Configuring IP Parameters on page 4-6
❑
Performing Software Upgrades Via TFTP on page 4-24
❑
Using XModem to Do wnload on page 4-27
❑
Configuring for Bridging on page 4-28
4-2
Page 33

&RQQHFWLQJ#WR#D#5HPRWH#6\VWHP
Please specify the system to connect to:
The system may be identified by name (‘name’),
by IP address (128.2.3.4), or by Ethernet
address (0000F4 123456)
->_
AT-S20 User’s Guide
0HQX1#
Administration> Connect to a remote system
This option allows you to use a AT-3726XL, AT-3726, AT-3716XL or
AT-3714FXL, AT-3714F switch to connect to and manage another
Allied Telesyn device. You can also use Telnet.
Select
3. Enter one of the following:
Administration> Connect to a remote system.
IP address
MAC address
, or
system name
.
DNS name
or
if any,
Once the information is validated and the connection to the
remote switch is open, you immediately get the Omega
menus. You may then use the Omega menus to configure the
remote switch or run diagnostics.
The only option that is not available is
remote system
same is true if you used Telnet).
4. Select
Quit
when you are done.
It is important that you select
Otherwise, you may block other sessions or software downloads via
the network to the remote switch. See also Setting Time Out
Protection on page 4-21.
from the
Quit
Connect to a
Administration
Note
menu (the
after the Omega session.
4-3
Page 34

Pinging a Remote System
3LQJLQJ#D#5HPRWH#6\VWHP
To ping a remote system, use the PING facility to test the reachability
of receiving systems by sending them an Internet Control Message
Protocol (ICMP) echo request and by then waiting for a reply.
0HQX1#
1. Select
2. Enter one o f the fol lowing:
Administration> Ping a remote system
Administration> Ping a remote system
Please enter station to ping:
The system may be identified by name (‘name’),
by IP address (128.2.3.4), or by Ethernet address
(0000F4 123456).
Note: Ping will repeat until a key is hit
->
system name, IP address, or
Ethernet address
Pinging: [Host 149.35.18.3, delay 1.000]
Ping 149.35.18.3 #1 ok RTT 0.111 seconds
Ping 149.35.18.3 #2 ok RTT 0.009 seconds
Ping 149.35.18.3 #3 ok RTT 0.001 seconds
. The following screen displays.
Ping in Progress
.
4-4
Note
When using browser management, 19 pings are sent and then stop.
Page 35

(QDEOLQJ#RU#'LVDEOLQJ#D#3RUW
Port 1
Link State: Online
Port State: Enabled
Transmission Mode: Half Duplex
Please select an option:
>Enable this port
Disable (partition) this port
Port Status
Port Link Status Mode
1:Finance Online Disabled Half duplex
2:Sales Online Enabled Full duplex
Disabled port
AT-S20 User’s Guide
0HQX1#
Port status and configuration> <Port
Number>
Ports are enabled as a default.
Disable a port if you suspect there is a problem and you want to
isolate the problem to that port, therefore preventing error
proliferation. You may also want to temporarily disable a port that is
not in use (an unoccupied office, for example) for security reasons.
1. Select
Port Status and configuration
to display the
list of ports.
2. Select a port number, for example, 1, from the list. The port configuration screen appears here partially shown.
3. Select the option to enable or disable the selected port.
4. Select
Return to Port Status Menu...
list of ports with the updated information. For example, a
disabled
Port 1 displays.
to display the
4-5
Page 36

Configuring IP Parameters
&RQILJXULQJ#,3#3DUDPHWHUV
0HQX1#
System Configuration> IP parameters
This option applies to TCP/IP based networks only. Some IP
parameters are required and others have default values you may
keep. There are also optional parameters for information purposes
only.
Note
If you have a BootP server and you have mapped the switch’s MAC
address to IP parameters, the switch will obtain its IP parameters from
the server.
1. Select
Ip address: 141.00.01.00
Subnet mask: 255.255.0.0
Gateway address:
Domain Name Server
Default Domain Name
Manager address: Null (not configured)
Manager address: Null (not configured)
Manager address: Null (not configured)
Manager address: Null (not configured)
System Configuration,
IP parameters
then
.
Download Password: *****
Get community string: public
Set community string: private
Trap community string: public
Location: Null (not configured)
Contact: Null (not configured)
Return to System Administrator Menu ...
2. Select the parameter you want to configure from the following
list. Then select
Return to Main Menu
Note
.
If you have a generic (dumb) terminal configuration, enter the letter corresponding to your choice.
4-6
Page 37

AT-S20 User’s Guide
IP address - This address is required.
Subnet mask - This is required.
Gateway address - This address is required if you need to send
packets from one IP network to another via a router.
Domain Name Server - This address is configurable and if
enabled, the DNS server will resolve names for IP commands,
such as Connect (Telnet), Ping, and TFTP downloads. When
entering an ASCII name at the Connect command, the switch
issues a DNS name lookup request to that particular DNS
configured server.
Default Domain Name - None. Optional parameter used in
resolution of DNS entities.
Manager address - You may enter IP addresses for a maximum
of four network management servers that will receive SNMP
traps. This parameter is optional.
Download Password - ATS20 (default, uppercase)
The download process requires this password to send
software from one switch to other switches in the network,
provided that the switches belong to the same product series
and that the download password is the same throughout the
switches. You can keep the default or change it. If you change
the download password of the source switch, the receiving
switches cannot accept software downloads from this switch.
Note
The software automatically searches for this password during
downloads without user input. This password is different from the
optional system password you configured to protect the switch from
unauthorized use.
SNMP community strings - The default community strings are
provided:
Get=public
Set=private, Trap=public
,
.
You have the option to keep or change them.
Location - You may enter a text string to indicate the physical
location of the switch. For example, enter
Lab
. This parameter is optional and is used for SNMP
First Floor,
management.
4-7
Page 38

Naming the Switch
1DPLQJ#WKH#6ZLWFK
Contact - You may enter a text string to indicate the name,
phone number, and other useful information to help identify
the person responsible for the switch. This parameter is
optional and is used for SNMP management.
0HQX1#
System configuration> System name
The switch has several possible unique identifiers:
❑
A factory-designated MAC address
❑
An IP address that you assign, if you have TCP/IP
❑
A unique name that you assign for easy management
❑
An assigned DNS name in the software of the DNS server for
use with IP communication
Allied Telesyn recommends assigning unique names to switches to
avoid unwanted or accidental software downloads.
1. Select
System configuration System name
System name
Null (not configured)
.
2. Enter a name of up to 20 characters at the prompt, for example,
Accounting Switch
.
4-8
Page 39

AT-S20 User’s Guide
System Configuration Menu
Accounting
System Name
Default VLAN Aging Time
Accounting
Omega Options
IP parameters
Security/Source Address Table
Terminal configuration
Update software in another system
Broadcast updated software to all systems
Xmodem software update to this system
Connect to a remote system
Ping a remote system
Activity monitor
Diagnostics
Reset and restart the system
Return to Main Menu ...
The system administration menu displays with the switch’s
name displayed at the top of the screen.
3. Select
The assigned switch name will display at the top of most of the
screens.
Return to Main Menu
.
4-9
Page 40

Naming the Switch
&KDQJH2'HOHWH
WKH#6ZLWFK#1DPH
1. Select
System configuration> System name
to display
the switch’s current name.
System name Accounting
2. Remove or change the current name.
3. Select the current name; press RETURN. The greater-than arrow key displays indicating that the system
is ready to either accept a new name or delete the existing
name.
4. Press the space bar until the name has been deleted. Press
RETURN.
Null (not configured)
displays.
5. Return to the Main Menu. The top of the screen no longer displays the switch’s name.
6. If you want to confirm the deletion, select
System Name
the System configuration menu.
from
System name Null (not configured)
4-10
Page 41

1DPLQJ#WKH#3RUW
AT-S20 User’s Guide
0HQX1#
Port status and configuration> <Port
Number>
Depending on the model, the switch has the following ports,
identified numerically, as listed in Table 4-1.
Table 4-1
Switch Port # Port Type
AT-3726XL,
AT-3726
AT-3716XL 1-16 10Base-T
1-24 10Base-T
25 Remote management port for Omega
26 (Uplink port A) 10/100Base-TX
27 (Uplink port B) Optional MDA (TX or FX)
17 Remote management port for Omega
18 (Uplink port A) 10/100Base-TX
19 (Uplink port B) Optional MDA (TX or FX)
Port Numbering
AT-3714FXL,
AT-3714F
1-12 10Base-FL
13 Remote management port for Omega
14 (Uplink port A) 100Base-FX
15 (Uplink port B) Optional MDA (TX or FX)
Because of the number of ports, you may find it more convenient to
manage the ports if you assign a unique name to each port. You can
associate a port number with a specific user or a location (for
example,
1. Select
Port 1 to Room 1147
).
Port status and configuration
to display the list
of ports.
2. Select a port number from the list.
4-11
Page 42

Naming the Port
The port configuration screen is partially shown.
>Transmit Pacing Enabled
No Transmit Pacing
Port name
Return to Port Status Menu ...
3. Enter a
port name
. Then press RETURN.
Note
Enter a name of up to 20 characters, for example,
Port naming option
Room 1147
The system updates the port configuration screen by
displaying the name you entered at the top of the screen, as
shown in the following example.
Port 1 - Room 1147
Link State: Online
Port State: Enabled
Transmission Mode: Half duplex
Please select an option:
>Enable this port
Disable this port
.
4-12
4. Select
Return to previous menu...
A current list of newly named ports displays.
Port Status
Port Link Status Mode
1:Finance Online Disabled Half duplex
2:Sales Online Enabled Full duplex
Page 43

AT-S20 User’s Guide
Transmit pacing enabled
>No transmit pacing
Port name Saturn
&KDQJLQJ#RU
'HOHWLQJ#D#3RUW
1DPH
1. Select
Port status and configuration
to display the
list of ports.
2. Select a port number, for example, 1, from the list to display the port configuration screen.
3. Select
Port name
and press RETURN. Type a new port name or
delete the existing one. (Screen partially shown.) Press RETURN.
4. If deleting the port name, the system also erases the name from the top of the screen.
5. Return to the Main Menu and select
Port Configuration
to
see the name deletion or change for the specified port.
The system displays an updated port list.
4-13
Page 44

Assigning a Password to the Switch
$VVLJQLQJ#D#3DVVZRUG#WR#WKH#6ZLWFK
0HQX 1#
System configuration> Omega options>
Password
Assigning a password protects the switch management software
from unauthorized configuration changes. Once you configure a
password, you need to enter it at the start of an Omega session.
1. Select
Password
Password: ->
Null (not configured)
Timeout: 5
2. Highlight
System configuration> Omega options>
.
Null (not configured)
, press RETURN, then
enter a password (maximum 20 characters). Press RETURN again.
See Setting Time Ou t Protection on page 4-21 for additional
information.
3. Select
Return to Main Menu
.
)RUJHWWLQJ#<RXU
3DVVZRUG
If you forget or lose your password, either reset the switch to factory
defaults (see Setting Switch Defaults on page 1-5) or con t act Allied
Telesyn’s Technical Support.
4-14
Page 45

AT-S20 User’s Guide
>Store-and-forward
Cut-through (fragment-free)
A: Port options if the switch uses store-and-forward method
Store-and-forward
>C
ut-through (fragment-free)
B: Port options if the switch uses fragment free method
(QDEOLQJ#6WRUH0DQG0IRUZDUG#RU#&XW0WKURXJK#+)UDJPHQW0)UHH,
0HQX1#
Port Status and configuration<PortNumber>
Forwarding method determines how the port handles packets. The
options you see on the port configuration screen is related to how
the switch is configured to forward packets as a whole. The default
setting for the switch is
1. Select
Port status and configuration
Store-and-Forward
.
to display the
list of ports.
2. Select a port number from the list. The port configuration screen appears. Depending on the
switch’s forwarding method, your options for the port can be:
3. Select the forwarding method you want for the port. Store-and-forward. In this default mode, the switch stores the
incoming packet until it has the entire packet, then forwards it
onto its destination.
The switch software checks for a valid CRC before forwarding the
packet and allows the switch to store the packet until network
resources, for example, an unused link, are available for
forwarding. This allows complete error checking. Store-andforward ensures data integrity and prevents packet errors from
being propagated in the network. On the other hand, every storeand-forward device in the path from the sender to the receiver
adds a small delay due to the time spent in storing and checking
the packet before forwarding it.
Select this forwarding method if you are running applications
where data integrity is more important than small delays.
4-15
Page 46

Enabling Store-and-forward or Cut-through (Fragment-Free)
Cut-through (fragment-free). This option is available for non-XL
versions only. In this method, the switch starts to forward the
incoming packet to its destination while the packet is still being
received.
Cut-through (fragment-free) provides low latency for forwarding
frames and also filtering fragment frames by not transmitting a
frame until 64 bytes have been received by the switch. In cutthrough (fragment-free) mode, fragment frames or runts (frames
less than 64 bytes) are filtered, thus providing some network error
protection.
Select the cut-through (fragment-free) method if you are running
time-sensitive applications.
4-16
Page 47

(QDEOLQJ#$XWR01HJRWLDWH2+DOI0'XSOH[2)XOO0'XSOH[
Link State: Online
Port State: Enabled
Transmission Mode: Full duplex
Please select an option:
>Enable this port
Disable (partition) this port
>Auto negotiate
Full duplex
Half duplex
Transmission mode options
AT-S20 User’s Guide
0HQX1#
Port status and configuration> <Port
Number>
The port’s transmission mode defines the direction that data can
move. The switch provides the following port transmission modes:
❑
Auto-negotiate (AT-3726XL, AT-3716XL, AT-3726 default)
❑
Full-duplex
❑
Half-duplex (AT-3714FXL, AT-3714F default)
1. Select
Port Status and configuration
to display the
list of ports.
2. Select a port number from the list of ports. The port configuration screen appears (partial screen shown
only).
3. Select the transmission mode you want for the port. If you select
Auto-negotiate
, the switch detects the speed
and duplex settings of the connected device.
If the switch and end device are not set to the same setting, a high
collision rate could occur which may degrade network
performance.
4-17
Page 48

Enabling Transmit Pacing
Make sure that both ends of the connect are set to the same mode. If
only one end of the connection is capable of auto-negotiation, then
both ends of the connection must be manually set for speed and halfor full-duplex.
(QDEOLQJ#7UDQVPLW#3DFLQJ
Transmit Pacing is the switch’s capability to inject transmit delays
and is selectable on a per port basis. Transmit pacing introduces
delays into the normal transmission of packets, which delays
transmission attempts between stations thereby reducing the
probability of collisions during heavy traffic (as indicated by packet
deferrals and collisions). This situation applies in cases where
congestion exists within the switch. For example, all ports on the
switch are queueing up to send traffic out through only one uplink
port. When the congestion clears, the switch stops sending the
delays so that devices can begin retransmitting. This mode then
increases the chances of successful transmission.
Note
1. Select
Port status and configuration
to display the
list of ports.
2. Select a port number from the list. The port configuration screen displays. (Partial screen is shown
here.)
Transmit pacing enabled
>No transmit pacing
3. Select
Transmit pacing enabled
.
4-18
Page 49

6HWWLQJ#8S#D#97433
>
VT100-compatible / ANSI
Generic “dumb” terminal
>
8 data bits
7 data bits
>
1 stop bit
2 stop bits
>
No parity
Odd parity
Even parity
>
Full duplex (echo)
Half duplex (no echo)
Data rate (“baud rate”) ...
AT-S20 User’s Guide
0HQX1#S
ystem configuration> Terminal
configuration>VT100-compatible/ANSI
The system displays the default terminal configuration settings.
6HWWLQJ#8S#D
*HQHULF#+'XPE,
7HU PL QDO
)XOO0'XSOH[2
6HWWLQJ
+DOI0'XSOH[
0RGH
To make your terminal selections, simply select the setting of you
choice, then select
Return to Main Menu
0HQX1#
System configuration> Terminal
Configuration> Generic
0HQX1#S
ystem configuration> Terminal
Configuration> Generic
Return to previous menu... or
.
dumb
terminal
dumb
terminal Full duplex
4-19
Page 50

Setting Up a VT100
6HWWLQJ#%DXG
5DWHV
0HQX1#
Configuration> Generic
baud
System configuration> Terminal
dumb
terminal> (Data rate
rate)...
Note
The default is automatic baud rate detection.
You can also select from the following fixed baud rates. Allied
Telesyn recommends 9600 bps.
Table 4-2
19200 bps 600 bps
9600 bps 300 bps
4800 bps 150 bps
2400 bps 75 bps
1200 bps
Fixed Baud Rates
4-20
Page 51

6HWWLQJ#7LPH#2XW#3URWHFWLRQ
Omega Options menu
Password: Null (not configured)
Timeout: 5
AT-S20 User’s Guide
0HQX1#
A timeout value is one way to protect the switch from unauthorized
use in case you forget to exit from Omega and then leave the switch
unattended. If you configure a timeout value, the software clocks the
elapsed time between the last time any key was pressed during an
Omega session and the current time. If the elapsed time exceeds the
timeout value, the software automatically terminates the session.
1. Select
2. Enter a timeout value from 0 to 32,767 minutes. Press RETURN. If the timeout value is set to zero, you must always quit after a
management session. Otherwise, subsequent Telnet sessions and
software uploads will be blocked to the switch. To avoid blocking
any Telnet sessions or software uploads, you must manually enter
Quit
System configuration> Omega Options
System administration> Omega Options
.
.
'HOHWLQJ#D
3UHYLRXVO\
&RQILJXUHG
7LPHRXW#9DO XH
If you want to delete a previously configured timeout value, repeat
the above procedure and enter 0 (zero) as the new value.
4-21
Page 52

Enabling/Disabl ing Omega Access
(QDEOLQJ2'LVDEOLQJ#2PHJD#$FFHVV
/RFDO#2PHJD
5HPRWH#2PHJD
:HE0EDVHG
2PHJD
The default for Local Omega is
Enabled
. This means you can access
the Omega menus from a terminal or PC connected to the switch’s
RS232 port.
The default for Remote Omega is
Enabled.
You still can use SNMP to manage the hub remotely. To change the
setting again, use Local Omega.
The default for Web-based Omega is
0HQX1#
System configuration> Omega Options
Omega Options Menu
Brandy
Password: Null (not configured)
Timeout: 5
> Local Omega Enabled
Disable Local Omega
Enabled
.
> Remote Omega Enabled
No Remote Omega
> Web-based Omega Enabled
Exclude Web-based Omega
Return to System Configuration Menu ...
Figure 4-1
Enabling/Disabling Omega
4-22
Page 53

(QDEOLQJ2'LVDEOLQJ#%DFNSUHVVXUH
This feature is available for the XL versions only. For backpressure to
be implemented, the ports must be in half-duplex mode.
Backpressure is useful when a port’s input buffer is running low on of
memory resources. For example, outbound packets are traversing a
single uplink port. When backpressure is enabled, the switch
simulates a collision when its input buffers are nearly filled so that
sending devices will defer transmissions. These sending devices will
retry transmissions according to the Ethernet back-off algorithm.
Once switch resources are available again, the switch stops sending
the collision signals and devices can freely transmit again. Figure 4-2
shows backpressure enabled.
AT-S20 User’s Guide
Figure4-2
Enabling Backpressure
4-23
Page 54

Performing Software Upgrades Via TFTP
3HUIRUPLQJ#6RIWZDUH#8SJUDGHV#9LD#7)73
You can download software upgrades from a switch to one or more
switches on the network, or download onto a switch via Trivial File
Transfer Protocol (TFTP) from a TFTP server.
The switches initially use a factory-configured default download
password, ATS20 to authorize software downloads. You do not need
to manually enter this password to download software successfully.
This download password can be changed to prevent unauthorized changes to the switch firmware.
Note
&RQGLWLRQV#IRU
1HWZRUN
'RZQORDGV#YLD
7)73
8VLQJ#7)73
The switch uses TFTP of the TCP/IP protocol suite to download
software to other switches whether or not your network uses TCP/IP.
TFTP is transparent to other devices on the network.
The switch can download software within the following conditions:
❑
The switches must be directly connected to the same
network cable or joined by switches or bridges and routers,
if the gateway addresses in both switches are properly
configured.
❑
All switches receiving the same software must use the same
download password (ATS20). See Configuring IP
Parameters on page 4-6).
If you have TFTP, you can use it to download an image file from the
switch with the upgraded software. When issuing the TFTP get or put
command, take note of the following variables:
Image file name. Get the latest from Allied Telesyn’s website at
www.alliedtelesyn.com.
4-24
IP address. This is the IP address of the switch that is the source
or destination of the file.
Download password. The default download password is
ATS20 in uppercase.
File type. The file type is octet or binary.
Note
TFTP platforms vary. Some have graphical user interfaces while other
platforms require you to type the commands.
Page 55

AT-S20 User’s Guide
Please specify the system to be downloaded:
The system may be identified by name (‘name’),
by IP address (128.2.3.4), or by Ethernet
address (0000F4 123455).
Activity monitor
load request received from Second Floor Computer
Room
loading... 000287-02A8C
completed.
'RZQORDGLQJ
IURP#2QH#6ZLWFK
WR#$QRWKHU
0HQX1#
Administration> Update software in
another system
Follow this procedure:
❑
To download software to another switch on the network
without physically being at the destination switch
❑
To ensure that all the switches on the network you intend to
upgrade will be upgraded, since you will be manually
upgrading one switch at a time
1. Select
Update software in another system
.
2. Enter either the destination switch’s name, its IP address, or its
MAC address (also known as the Ethernet address printed above
the switch’s RS232 management port). Then press RETURN.
3. Select the Return to Main Menu icon to see a confirmation similar to the following screen.
Repeat this procedure to download software to every switch on the
network.
4-25
Page 56

Performing Software Upgrades Via TFTP
%URDGFDVW
8SGDWHG#6RIWZDUH
WR#$OO#6\VWHPV
0HQX1#
Administration> Broadcast Updated
Software to All Systems
Note
Plan a software broadcast during times when your network is not busy.
1. Select
Administration> Broadcast updated
software to All systems.
The switch announces the availability of the software to all
switches; in turn, the switches that need the upgrade respond
with a request message.
The screen immediately turns on the Activity Monitor screen and
displays the information as switches on the network request and
then receive the software.
Activity monitor
Broadcast notification sent
Broadcast notification sent
Broadcast notification sent
Note
You cannot undo this command once executed.
2. Select
Return to Main Menu...
without interrupting the
software download.
If you have many switches requesting the download, not all of them
may receive the download, especially if the network is busy. Repeat
the procedure to ensure that all switches receive the software
upgrade.
Note
Switches on your network with different download passwords will not receive the software upgrades.
4-26
Page 57

AT-S20 User’s Guide
Accounting
Ready to receive software upgrade via XModem.
Warning: During software update Management activity
is disabled.
Do XModem update now? (Yes or No):
The System host is now ready for download.Please
start your XMODEM transfer.
CCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCC
CCCCCCCCCCCCCCCCCCCCCCCCC
Stop Sending: ATS20 Retries: 0
8VLQJ#;0RGHP
WR#'RZQORDG
1. Select
this system
2. Enter
Adminstration<XModem software update to
.
Yes
.
The above screen displays the downloading progress and that there
were no retries.
4-27
Page 58

Configurin g for Bridging
&RQILJXULQJ#IRU#%ULGJLQJ
0HQX1#
Bridging
The options under the Bridging Menu item are for configuring and
enabling spanning tree.
As a bridge, the switch:
❑
Learns source and destination MAC addresses of incoming
packets by storing the information in a forwarding table (see
also Activity Monitor on page 6-2).
❑
Forwards the packet to the destination’s network segment if
the source is from a different network segment; or discards
the packet if the source and destination address are on the
same segment because all stations on the segment have
already received the packet.
❑
Ages out the addresses (deletes the information from the
table) if undetected by any port within a user-defined or a
default elapsed time.
❑
Updates the MAC address table automatically as you add,
remove, or relocate devices on the network.
❑
Prevents loops with spanning tree.
❑
Updates other bridges with topology information by
periodically sending bridge protocol data units (BPDUs).
When you select
Bridging
from the Main Menu, the following
screen displays:
Spanning tree parameters
Port spanning tree confirmation
Return to Main Menu ...
Figure 4-3
Bridging Submenu
You are now ready to configure or disable spanning tree. Note that
Spanning Tree is on by default. See Configuring Spanning Tree
Parameters.
If you want an overview of the Spanning Tree Protocol (STP) before
proceeding, go to AppendixA, Spanning Tree Protocol.
4-28
Page 59

AT-S20 User’s Guide
Note
Although defaults are adequate for most installations, changing
defaults should be done only if the network administrator
understands the IEEE 802.1d standard.
&RQILJXULQJ
6SDQQLQJ#7UHH
3DUDPHWHUV
0HQX1#
Default spanning tree parameters are provided; you do not need to
change them.
1. Select
Bridging Spanning tree parameters
Bridging, spanning tree parameters
the bridging options, as shown in the following screen.
Bridge configuration Menu
Bridge Identifier (Mac Address: Priority) f32c20 5474b5: 32768
Root Bridge Identifier (Mac Address: Priority) f32c00 535b97: 32768
Cost to the root 0
Port closest to the root 1
Max Age 20
Forwarding Delay 15
Bridge Priority: 32768
Max age time: 20
Hello time: 2
Forwarding delay: 15
Return to bridge Menu ...
to display
Spanning Tree Screen
and enter a priority number.
2. Select
Figure 4-4
Bridge Priority
The number can be from 0 to 65,535 with 0 being the highest
priority. The number consists of a 2-byte bridge priority number
and a 6-byte MAC address. Bridges use this number to determine
the root bridge for a loop-free implementation. If bridges happen
to have equal priority values, the bridge with the numerically
lowest MAC address becomes the root bridge.
When the root bridge malfunctions, the bridge with the next
priority number (the next lowest MAC address) automatically
takes over as root bridge.
4-29
Page 60

Configurin g for Bridging
3. Enter
Max age time
to get the next screen and enter the aging
time in seconds at the prompt.
The aging time can be from 6-40 seconds, with 20 seconds as a
default. All bridges in a bridged LAN use this aging time to test the
age of stored configuration messages called bridge protocol data
units (BPDUs).
For example, if you use the default 20, all bridges delete current
configuration messages after 20 seconds.
Note
Aging time for BPDUs are different from aging time in the MAC address table.
4. Enter
Hello time
and enter the time in seconds at the prompt.
Hello time can be from 1-10 seconds, with 2 seconds as the
default. Bridges use this parameter to determine the time interval
between generating and sending configuration messages.
5. Enter
Forwarding delay
value and enter the time in seconds.
The default is 15 seconds. The time indicates the waiting period
before a bridge changes to a new state, for example, becomes the
new root bridge after the topology changes. If the bridge
transitions too soon, not all links may have yet adapted to the
change; therefore, loops may result.
6. Select
Return to Main Menu
and repeat the procedure if you
want to reconfigure the spanning tree parameters for
Administration.
4-30
Page 61

AT-S20 User’s Guide
Charlie
Port Priority Cost
1: 128 100
2: 128 100
3: 128 100
4: 128 100
5: 128 100
6: 128 100
7: 128 100
8: 128 100
9: 128 100
10: 128 100
11: 128 100
12: 128 100
More...
Enable Spanning Tree for All Ports
Disable Spanning Tree for All Ports
Return to Bridge Menu ...
Bridge Menu
Port 1 - Finance
>Enable Spanning Tree
Disable Spanning Tree
Priority:128
Cost: 100
Return to previous menu ...
'HVLJQDWLQJ#WKH
5RRW#3RUW
0HQX1#
Bridging> Port spanning tree
configuration
In this procedure, you identify the root port and the path cost for the
spanning tree. Default values will work for the majority of the users;
but for purposes of illustration, Port 1 will be the root. All ports have
priority 128 and cost values are 100 by default.
1. Select
Port spanning tree configuration
from the
Bridging Menu to get a similar list shown on the screen.
2. Select a port number, for exam ple, 1, to get a screen similar to the following.
4-31
Page 62

Configurin g for Bridging
3. Select
Priority
to get the next screen and enter 0 as the
priority number at the prompt to make Port 1 the root port.
The range is 0-255. When the designated root port is disabled or
the cable connection breaks, the STP algorithm reconfigures an
alternate path to the LAN by identifying the port with the next
lowest priority number.
4. Select
Cost
to get the next screen and enter a cost parameter
ranging from 1-65,535; or keep the default value.
The spanning tree algorithm uses the cost parameter in
combination with the priority to decide which bridges provide
the lowest cost path to the root bridge for that LAN.
Higher port costs are associated with ports of lower bandwidth,
and vice versa. For example, 100 is the cost for a 10 Mbps port, 10
for a 100 Mbps port, and 1 for a 1 Gbps port.
You are done with spanning tree configuration. Now that the
required parameters have been configured, bridges can make a
determination on the best single path to a destination.
A formula determines the amount of time it takes for the topology to
reconfigure, depending upon the spanning tree values you use.
Refer to the IEEE specification for details.
4-32
Page 63

6HOHFWLQJ#*OREDO#&RQILJXUDWLRQ
AT-S20 User’s Guide
0HQX1#
Port Status and configuration> <Port
Number> >Global Config
Selecting this option copies the displayed port configuration
(enable, auto-negotiate, etc.) to all regular (non-uplink) ports on the
switch without changing the port names or VLAN assignments. Port
names and VLAN assignments remain as originally defined.
1. Select
Port Status and configuration
to display the list
of ports.
2. Select a port number, for example, 1 , from the list.
3. Select the
Global Config
option.
4. Confirm your action.
5. Select
Return to Port Status Menu...
to display the
list of ports with the updated information.
4-33
Page 64

Enabling/Disabling Port Trunking
(QDEOLQJ2'LVDEOLQJ#3RUW#7UXQNLQJ
Port Trunking configures Ports A and B to function as a single uplink
port to increase the bandwidth of the connection. Communication
streams between two devices across the trunked uplink port will
always be passed on the same physical port. If one trunk port
becomes inactive, the other continues to operate and handle all
uplink traffic. When the inactive port recovers, the switch
automatically resumes its operation; no reset is required.
This option displays only when both uplink ports are installed.
Port Trunking requires that both uplink ports be of the same type and operate in the same mo de.
When enabled, this option copies the port configuration parameters
and the port VLAN assignments of Port A to Port B. All changes to
Port A parameters or VLANs assignments also change Port B. Both
ports operate as a single uplink until this option is disabled.
Note
The Port name field in the Port Status and Configuration menu
displays the ports as “Trunk #1/active” or “Trunk #1/inactive” for each
of the ports, according to their status.
1. Select
Trunking
2. Select
then select
System configuration > Enable Port
.
Return to System Configuration Menu…
Port Status and configuration Menu...
,
to display the list of ports with the updated information.
4-34
Page 65

&KDSWHU 8
9LUWXDO#/$1#&RQILJXUDWLRQ
This chapter introduces VLAN configuration as it applies to Allied
Telesyn’s implementation of VLANs. VLAN features are provided only
on the XL versions of the switches. The XL versions support portbased VLANs and 802.1Q (draft 8) VLAN tagging.
0HQX1
By default, the switch has one port-based VLAN (all ports’ VLAN
assignment showing as Default VLAN) and one spanning tree
domain. In most situations, users find the defaults acceptable and do
not require further configuration; however, your network may
require assigning end stations into logical groupings, regardless of
their physical location.
Virtual LANs
Figure 5-1
.
Virtual LANs Menu
5-1
Page 66

Virtual LAN Configuration
#2
You can group your end stations logically through VLANs.
Information exchange is confined within the members of a given
VLAN. A VLAN constitutes one broadcast domain; therefore,
broadcast packets from an end station only go to other stations
within the same VLAN.
Port-based VLANs cannot communicate with each other through the
switch; they require a router to do this (Figure5-2).
AT-3714FXL
#11
#12
#4
#6
#8
#10
VLAN 1
Router
Figure5-2
Advantages of Usin g VLA Ns
❑
You have the flexibility of grouping workstations logically or
functionally, regardless of their physical location on the
network.
❑
You can change VLAN memberships anytime by software
configuration without moving the workstations physically, or
change group memberships by simply moving a cable from
one port to another.
❑
With VLAN tagging, the ability to group workstations into
logical work groups is more ver satile. Yo u can assign a port to
be an uplink to another 802.1Q-compatible switch and enable
it to carry all VLAN traffic instead of using one uplink port per
each VLAN port configured.
VLAN 2
VLAN Example
5-2
The VLAN ID used to tag incoming packets without a tag is called the
Port Virtual LAN (PVID) for the specified port.
Page 67

AT-S20 User’s Guide
When a port is a member of a port-based VLAN, it is internally
assigned a unique Port VLAN ID or PVID. This PVID is added as a VLAN
tag as frames enter this port. This PVID is used to route the frame
through the switch and through 802.1Q-based switches. This
enables legacy (non-802.1Q compliant) devices connected to the
switch to take advantage of the VLAN capabilities of the switch.
Note
The manager is a legacy device. It cannot interpret VLAN tags. The
management agent responds only to pings from any device that is
located within the same VLAN, defined by the management port’s
PVID.
Figure5-3 shows how VLANs are used across uplink ports and
between two different manufacturer’ s equipment. The switches hav e
the following VLAN configurations:
AT-3714FXL Configuration
❑
Port 1 is a member of the “Default VLAN”
❑
Ports 2 and 14 are members of VLAN #2
The AT-3714FXL is configured as follows:
❑
The AT-3714FXL will have a VLAN named “Default VLAN”. Port
1 will be both tagged and a port-based member of “Default
VLAN” with a PVID and a VLAN ID of 1. Port 15 is added as a tag
member so that “Default VLAN” will have access to the uplink
between switches.
❑
The AT-3714FXL will have a VLAN named “VLAN 2”. Ports 2 and
14 will be both a tagged and a port-based member of VLAN #2
with a PVID and a VLAN ID of 2. Port 15 is added as a tag
member so that “VLAN 2” will have access to the uplink
between switches.
❑
The AT-3714F XL will have a VLAN named “Uplink ”. Port 15 will
be both tagged and a port-based member of VLAN “Uplink”
with a PVID and a VLAN ID of 3. See Figure 5-3.
AT-8518 Configuration
❑
Ports 1 and 3 are members of the “Default VLAN”
❑
Ports 2 is a member of VLAN #2
5-3
Page 68

Virtual LAN Configuration
The AT-8518 is configured as follows:
❑
The AT-8518 will have a VLAN named “Default VLAN”. Ports 1
and 3 will be both tagged and a port-based member of
“Default VLAN” with a PVID and a VLAN ID of 1. Port 10 is
added as a tag member so that “Default VLAN” will have
access to the uplink between switches.
❑
The AT-8518 will have a VLAN named “VLAN 2”. Port 2 will be
tagged and a port-based member of VLAN # 2 with a PVID and
VLAN ID of 2. Port 10 is added as a tag member so that “VLAN
2” will have access to the uplink between switches.
❑
The AT-8518 will have a VLAN named “Uplink”. Port 10 will be
tagged and a port-based member of VLAN “Uplink” with a
PVID and a VLAN ID of 3. See Figure 5-3.
Workstation #1
Default VLAN
Default VLAN
Workstation #3
Workstation #2
Port 2
VLAN #2
Port 1
Port 1
VLAN 2
Workstation #4
AT-8518
1234
9101112
Port 2
Switch
5678
13 14 15 16
AT-3714FXL
LINK/ACTIVITY
12345678
18 17R 17
ACTIVITY
910111213141516
LINK
LINKACTIVITY DISABLED
1000BASE-X NETWORK PORTS10/100BASE-TX MDI-X NETWORK PORTS
17R 17
802.1Q Compliant Server “A”
Port 14
VLAN #2
PVID = 3
Port 15
10/100BASE-T ETHERNET SWITCH
WITH GIGABIT ETHERNET
18
POWER
DIAG
“Uplink” VLAN
Port 10
PVID = 3
Default VLAN
Port 3
Legacy Sever B
5-4
Figure5-3
Typical Configuration
Note
The PVIDs must match on the trunk or uplink port between the
AT-8518 switch and the AT-3714FXL switch. For example, they both
must have IDs of 1.
Page 69

AT-S20 User’s Guide
Uplink ports (15 and 10 on both switches) are used to connect the
two switches. To allow VLANs to span across switches, these uplink
ports are output enabled for every configured VLAN on the switch.
Therefore, when a broadcast packet is received on any port
(representing a packet on any VLAN), it is transmitted through the
uplink port. Note that since the uplink port on the AT-3714FXL has
PVID of “3”, packets transmitted on the uplink port from VLAN 2 or
the “Default VLAN” will be transmitted with their VLAN tag in place.
This scheme preserves the VLAN information across the uplink port.
In this example, Workstation #4 can talk with Server A because its
VLAN information is preserved across the uplink. In turn, Workstation
#1 can talk with Server B for the same reason. Workstation #2 is
precluded from talking to Server B since Server B has a different
VLAN, and any packets generated from Workstation #2 that traverse
the uplink port will continue to be associated with VLAN 2.
&RQILJXUDWLRQ
,QIRUPDWLRQ
3RUW#,QIRUPDWLRQ
By default, only one VLAN is defined in a 3700XL switch. Up to 32
VLANs can be defined in the unit. A VLAN is defined when the
following occurs:
❑
Name the VLAN
❑
Assign a VLAN ID number
❑
Define a port configuration to be used for that VLAN
By default, the VLAN named “Default VLAN” is assigned and given a
VLAN ID and PVID of 1, and all ports receive packets for this VLAN.
Each port must be assigned a PVID. The VLAN can be chosen from
one of the VLANS defined in the VLAN configuration. By default, all
ports belong to the “Default VLAN” which has a PVID of 1.
5-5
Page 70

Virtual LAN Configuration
The following Omega configuration screens show VLAN and port to
VLAN definitions.
Figure5-4
Figure 5-5
Virtual LAN Main Menu
Default VLAN Menu
5-6
Page 71

AT-S20 User’s Guide
$GGLQJ#D#1HZ
9/$1
0HQX1
new table entry>
1. Select
Virtual LANs><Virtual LAN definitions><Add
Add new table entry>
The following screen displays.
.
Figure5-6
Adding New VLAN Descriptors
2. Enter the following VLAN descriptors:
❑
New VLAN name (in this example Lindsey)
When you enter a new VLAN name, for example Lindsey, the
ID number automatically increments to the next VLAN ID
number, for example from 1 to 2. See following screen.
❑
VLAN ports (in this example 14, 15)
By default, the uplink ports are included in the VLAN ports. A
port can belong to any number of VLANs, maximum of 32
VLANs.
5-7
Page 72

Virtual LAN Configuration
3. Select
Return to VLAN Definition Menu
screen displays showing the new VLAN descriptors.
automatically increments
Figure5-7
New VLAN Descriptors
. The following
5-8
Note
Allied Telesyn highly recommends that you use the VLAN ID (default)
supplied by the system. Although you can change VLAN IDs to suit
your specific needs, changing them requires a more advanced
understanding of VLAN tagging.
Page 73

AT-S20 User’s Guide
3RUW#WR#9/$1
&RQILJXUDWLRQ
0HQX1
Virtual LANs><Port to VLAN configuration>
1. Select
Port to VLAN configuration
Figure 5-8
Virtual LAN Menu
.
Figure5-9
Port-T o-VLAN Configuration
If you select Port 6 for example, the screen will show that Port 6 is
now associated with the Default VLAN.
5-9
Page 74

Virtual LAN Configuration
'HOHWLQJ#D#3RUW
IURP#D#9/$1#RU
&KDQJLQJ#3RUW·V
9/$1
$VVLJQPHQW
1. Select
LANs
2. Select the port number you want to delete or change. The screen displays the port’s VLAN configuration and a list of
available VLANs).
3. Do one of the following:
❑
❑
The screen displays the list of ports with the updated VLAN
assignment.
Port VLAN configuration
menu to display the port list with VLAN assignments.
To reassign the port to another VLAN, select the new VLAN
name from the list.
To delete the port from a VLAN, select Default VLAN from the
list.
from the
Virtual
5-10
Page 75

&KDSWHU 9
0RQLWRULQJ
This chapter describes the tasks related to monitoring the switch.
The tasks are shown in the following order:
❑
Activity Monitor on page 6-2
❑
MAC Address Table on page 6-3
❑
Static MAC Addresses on page 6-6
❑
Security/Source Address Table on page 6-12
❑
Mirror Port on page 6-23
❑
Port Status on page 6-25
❑
Port Numbering on page 6-26
❑
Statistics: Received and Transmitted Ethernet Frames on
page 6-28
For illustration purposes, the procedures throughout this chapter are
based on a switch named Accounting. Some of the ports have
names.
6-1
Page 76

Activity Monito r
$FWLYLW\#0RQLWRU
0HQX1#
Administration> Activity Monitor
The Activity Monitor option is useful in troubleshooting or in
monitoring software broadcasts. You can observe ongoing system
activity, if any.
The following screen displays when you select
Administration>
Activity monitor.
Accounting
Activity monitor
Broadcast notification sent.
Broadcast notification sent.
The activity monitor also automatically activates when you
download software to switches on the network (
System
administration, Broadcast updated software to
all systems
). The system displays the MAC address of a switch as
software downloads to it.
Accounting
Activity monitor
load request received from Second Floor Computer
Room
loading... 000f4-02A8CE
completed.
load request received from Third Floor
Administration
loading... 0000F4 D0D070
completed.
load request received from Third Floor SysLab
loading... 0000F4 C00520
completed.
Figure6-1
Activity Monitor During Software Downloads
6-2
Page 77

0$&#$GGUHVV#7DEOH
MAC Address Menu
Accounting
Show all MAC addresses
By port MAC addresses
Get port from MAC Address
---Static addresses display and configuration--All static MAC address
Per port static MAC address
Get Port from MAC Address
Multicast addresses
Clear static MAC table
Return to Main Menu...
AT-S20 User’s Guide
The MAC address table (also referred to as the forwarding table) is a
snapshot of source MAC addresses that the switch has learned and
static MAC addresses which have been stored in the switch’s volatile
memory until the addresses have aged. The information on the table
dynamically changes as packets appear on any port.
The software deletes a MAC address from the table after the aging
time of 300 seconds (5 minutes). If you reset the switch or remove
power, the table clears the learned addresses but gets updated as
soon as the switch is operational and the ports start to detect
packets.
0HQX1#
MAC Address Table
Figure6-2
Sample MAC Address Table
6-3
Page 78

MAC Address Table
6KRZ#$OO#0$&
$GGUHVVHV
6KRZ#%\#3RUW
0$&#$GGUHVVHV
Select
0HQX1#
1. Select
MAC Address Table> Show all MAC addresses
MAC Address Table
Accounting
MAC Addresses - Page 1
MAC Address Port MAC Address Port
0000F4 010001 2 0000F4 010010 2
0000F4 010003 2 0000F4 010011 2
0000F4 010004 2 0000F4 010011 2
0000F4 010005 2 0000F4 010013 2
0000F4 010006 2 0000F4 010014 2
0000F4 010007 2 0000F4 010015 2
Next page
Return to MAC Address Menu ...
Figure6-3
Show All MAC Addresses
By port MAC addresses
MAC Address Table
from the main menu. The MAC
address menu displays.
.
2. To learn the MAC address of a specific port, select
addresses
.
By port MAC
3. Select a specific port number to learn the MAC addresses for that
port. The following screen displays as an example, Port 5’s MAC
addresses.
MAC Address Table
Port 5
MAC Addresses - Page 1
MAC Address MAC Address MAC Address MAC Address
0000F4 010203 0000F4 010205 0000F4 010211 0000F4 010209
0000F4 010212 0000F4 010206 0000F4 010235 0000F4 010208
0000F4 010211 0000F4 010207 0000F4 010245 0000F4 010207
0000F4 010214 0000F4 010208 0000F4 010255 0000F4 010206
0000F4 010214 0000F4 010209 0000F4 010265 0000F4 010205
0000F4 010216 0000F4 010201 0000F4 010275 0000F4 010204
Next page
Return to Port Selection Menu...
6-4
Figure6-4
By Port MAC Address (Port 5)
Page 79

AT-S20 User’s Guide
*HW#3RUW#IURP
0$&#$GGUHVV
Users can enter a MAC address and the program returns the port
number associated with the MAC address.
0HQX1#
1. Select
Get Port from MAC Address
MAC Address Table
from the main menu. The MAC
address menu displays.
2. Select
Get Port from MAC Address.
3. In the MAC Address field, using the Up Arrow key, enter the MAC
Address, for example 0000F4 010203. Then press RETURN.
The following screen shows that the MAC Address of 0000F4
010203 is associated with Port 5.
Figure6-5
Get Port from MAC Address (Port 5)
6-5
Page 80

Static MAC Addresses
6WDWLF#0$&#$GGUHVVHV
Static MAC addresses are associated with only one port, the port
assigned to the device with that MAC address. Static addresses
remain in the table and are not aged in 5 minutes like other learned
MAC addresses.
6KRZ#$OO#6WDWLF
0$&#$GGUHVVHV
0HQX1#
MAC Address Table> All static MAC
addresses
Static Address Configuration Menu
Accounting
MAC Addresses - Page 1
MAC Address Port MAC Address Port
0000F4 010001 2 0000F4 000010 2
0000F4 01000F 2
0000F4 01001F 2 01A0D2 02F01C
0000F4 01002D 2
Next page
Return to MAC Address Menu ...
Figure6-6
00A0D2 56002C 2
Show All Static MAC Addresses
6-6
Page 81

AT-S20 User’s Guide
Port Selection Menu
Accounting
Port 1 Port 2
Port 3 Port 4
Port 5 Port 6
Port 7 Port 8
Port 9 Port 10
Port 11 Port 12
Port 13 Port 14
Port 15 Port 16
Port 17 Port 18
Port 19 Port 20
Port 21 Port 22
Port 23 Port 24
Port 26 - Uplink Port A Port 27 - Uplink Port B
Return to MAC Address Menu ...
6KRZ#3HU#3RUW
6WDWLF#0$&
$GGUHVVHV
0HQX1#
MAC Address Table>Per Port Static MAC
Addresses> Port number
See Figure6-7 and Figure6-8.
Figure6-7
The static MAC addresses for Port 2 display, as shown in Figure6-8.
Add MAC Address Menu
Accounting
MAC Addresses MAC Address MAC Address MAC Address
0000F4 010203 0000F4 010205 0000F4 010211 0000F4 010209
0000F4 010212 0000F4 010206 0000F4 010235 0000F4 010208
0000F4 010211 0000F4 010207 0000F4 010245 0000F4 010207
0000F4 010214 0000F4 010208 0000F4 010255 0000F4 010206
0000F4 010214 0000F4 010209 0000F4 010265 0000F4 010205
0000F4 010216 0000F4 010201 0000F4 010275 0000F4 010204
Add MAC address Null (not configured)
Delete MAC address Null (not configured)
Next page
Return to Port Selection Menu...
Figure 6-8
Per Static MAC Addresses
Port 2
Per Port Static MAC Address (Port 2)
6-7
Page 82

Static MAC Addresses
'HOHWH2$GG#6WDWLF
0$&#$GGUHVV
0HQX1#
MAC Address Table> Per port static MAC
addresses> Port number> Add MAC address
1. Select
<Port Number>.
Per port static MAC address screen
, then
2. Enter your six digit static MAC address. Figure 6-9 shows that the
static MAC address table has been added to Port 19 (Randy)
Static Address Configuration Menu
Accounting
MAC Addresses - Page 1
MAC Address Port MAC Address Port
000010 000001 2 0000F4 00001013
000002 00000B Port 19 - Randy
0000D2 56001F 2
0000D2 56002D 7
Please select an option:
Next page
Add Mac Address 000002 00000B
Delete this entry
00A0D2 56002C17
.
Figure6-9
Add Static MAC Address (Port 19)
6-8
Page 83

AT-S20 User’s Guide
Add Static MAC Address Menu
Accounting
MAC Addresses
MAC Address Ports for Multicast Packets
0100F4 010243 14,15
0100F4 397492 all
0100F4 070697 7,8
0100F4 643476 2,3
0100F4 365454 4,5
Add MAC address
Null (not configured)
Ports for multicast
Null (not configured)
(Example: 1, 3, 8, or all)
Delete MAC address Null (not configured)
Next page
$GG2'HOHWH#6WDWLF
0$&#$GGUHVVHV
DQG#6HOHFWLQJ
3RUWV#IRU
0XOWLFDVWV
0HQX1#
Multicast addresses> Add MAC address>
Ports for Multicasts
Multicast addresses are a type of static address. When you clear the
static address table, all multicast addresses are discarded. However, if
you add a multicast address, this address appears in the static
address table.
Note
You add or delete a MAC address from the Muticast Addresses menu.
Figure6-10
1. Select
Multicast addresses, Add MAC address
Muticast Addresses (Add/Delete MAC Addresses)
Prior to MAC addresses being added, you must enter both the MAC
address and ports to receive multicast packets.
.
Note
6-9
Page 84

Static MAC Addresses
2. As an example, enter the six digit multicast MAC address (010002
00000B) and the ports (5,10,12) that you want to receive multicast
packets from that device. See Figure 6-11.
Add Static MAC Address Menu
Accounting
MAC Addresses
MAC Address Ports for Multicast Packets
0100F4 010243 14,15
0100F4 397492 all
0100F4 070697 7,8
0100F4 643476 2,3
0100F4 365454 4,5
Add MAC address
Ports for multicast
(Example: 1, 3, 8, or all)
Delete MAC address Null (not configured)
Next page
Return to MAC Address Menu ...
010002 00000B
5,10,12
Figure6-11
Add MAC Ad dress and Muticast for Ports 5, 10, and 12
3. To see your newly added MAC address and ports that are to
receive multicast packets, press RETURN. This simply refreshes
the screen.
Note
If you want to change any of the ports that have already been
assigned a multicast, you must re-add the new ports designated to
receive multicast packets.
6-10
Page 85

AT-S20 User’s Guide
Clear Static MAC table now? (Yes or No):
&OHDULQJ#6WDWLF
0$DE OH
/RFDWLQJ#<RXU
6ZLWFK·V#0$&
$GGUHVV
When you clear the static address table, all multicast addresses are
discarded. However, if you add a multicast address, this address
appears in the static address table.
0HQX1#
MAC Address Table Clear> Clear static MAC
table
1. Select
static MAC table
MAC Address Table, then select Clear
.
2. Enter y to clear the MAC address table.
❑
Look at the MAC address label directly above the RS232
management port on the switch’s front panel, or
❑
Select
Diagnostics
from the System Administration Menu
to read the address from the screen.
6-11
Page 86

Security/Source Address Table
6HFXULW\26RXUFH#$GGUHVV#7DEOH#
The Security/Source Address Table menu defines two options:
❑
Source Address Learning Mode (Secure or Automatic)
❑
Intruder Protection Action (SNMP Trap/No Trap; Port
Disabled/Not Disabled
❑
Threshold Security
Figure6-12 shows the Security/Source Address Table menu and
defaults.
Figure 6-12
Security/Source Address Table
6-12
Page 87

AT-S20 User’s Guide
Table 6-1 briefly lists the options in the Security/Source Address
Table menu. For complete definitions of this options, see the
sections that follow this table.
Table 6-1
Security/Source Address Table
Options S tates Definition
Source Address
Automatic
Learning Mode
Secure
Threshold
Intruder Protection Send Trap
No Trap
Disable Port
Source address learning is
enabled, and the intruder
protection is disabled.
The source address table is
locked, and the intruder
protection is enabled.
Learning is enabled. Intruder
protection is enabled if
threshold is exceeded.
Trap is transmitted.
Trap is not transmitted when
an intruder is detected.
The port is disabled when an
intruder is detected.
6RXUFH#$GGUHVV
/HDUQLQJ#0RGH
Port State
Unchanged
The port remains ON when an
intruder is detected.
The Source Address Table (SAT or MAC forwarding table) is a
database of MAC addresses and their associated port of entry
learned by the switch. The Source Address Learning Mode allows you
to control it is as a “secure” or “automatic” state.
Secure: Learning Off/Security On
In the “secure” mode, the learning feature is disabled and the source
address table is in a “locked” state. This setting is used when the MAC
address learning is completed and when any new MAC address
entries are to be entered manually. When the SAT is locked, no new
addresses will be learned. If a packet is received with an address that
is not already in the SAT, the packet is dropped and the new MAC
address is not learned.
6-13
Page 88

Security/Source Address Table
Automatic: Learning On/Security Off
The automatic mode is the default setting. When in “automatic”
mode, the SAT is in an “unlocked” state and is updated each time a
port receives a packet from a new source address. The SAT address
table can store 2K of MAC addresses.
When the switch is in a learning mode, the software:
❑
Monitors the MAC source address as frames come into each
port
❑
Compares the incoming source addresses to entries in the SAT
table
❑
Updates the SAT table by storing the new MAC address
Note
If you do not lock the SAT table, it will not be saved when the switch is reset.
Most users typically keep the source address learning mode ON to
continuously update the MAC address table. Information in the table
is useful for inventory control, based on MAC addresses of the
devices connected to the module. As an option, you can manually
turn learning OFF and go to a secure mode if you want to restrict the
module only to specific MAC addresses. Once this process is
complete, all MAC addresses become static addresses and will stay in
the MAC address table until the table is cleared or until the address is
deleted.
6-14
Page 89

AT-S20 User’s Guide
6HFXULW\
7KUHVKROG
Security Threshold allows the user to limit or set the number of MAC
addresses for any port or all ports. In addition, when threshold is
enabled; intruder protection also is enabled. The port continues to
learn new MAC addresses until it is disabled. In a busy network, the
port may accumulate more MAC addresses than the specified limit if
MAC addresses are learned between the time the threshold is
exceeded and the time the port is disabled. See Figure6-13.
Figure6-13
Security Threshold
To set the number of MAC addresses associated for a specified port
or for all ports, use the
port
command.
Figure 6-14
Config MAC address limit per
Configure MAC Address Li mit
6-15
Page 90

Security/Source Address Table
Figure 6-15
Figure6-16
MAC Address Limit on Port 5
MAC Address Limit on All Ports
All ports
the limit
with
of three MA C
Addresses
6-16
Page 91

AT-S20 User’s Guide
,QWUX GHU
3URWHFWLRQ
The Intruder Protection feature resides in the lower-half of the
Security/Source Address Table menu and is shown in Figure 6-12.
This screen does not appear until you first enable
Secure:
source address table locked; intruder protection
enabled
option.
Figure6-17
Intruder Prot ection Screen Section
The Intruder Protection option determines how the switch handles
transmissions from MAC addresses not found in the SAT. These
options are available when the switch is set to the “secure” mode.
The switch detects intruders by comparing incoming source MAC
addresses to entries in the SAT table. Intruders are transmissions
from addresses not found in the table. There are several possibilities
for configuring a port in relationship to intruders:
❑
Transmit SNMP trap message (port state unchanged)
❑
Disable the port (no SNMP trap)
❑
Transmit SNMP trap and disable the port
❑
No action (default)--(No trap; port state unchanged)
Transmit SNMP Trap Message (port status unchanged)
Use this configuration to send an SNMP trap message to the SNMP
manager when an intruder is detected. (See Configuring IP
Parameters on page 4-6. The IP parameters is a submenu of the
System Configuration menu.)
The message contains enough SNMP MIB information to help you
identify the port where the intrusion took place. Regardless of the
mode you select for Transmit SNMP Trap, SNMP statistics gathering
continues.
6-17
Page 92

Security/Source Address Table
Disable the Port (no SNMP trap)
Use this configuration when you want the switch to automatically
disable the port when an intruder is detected. Once the switch
software disables a port because of an intruder, no source address
can use that port. The port remains disabled until you manually
enable it.
Note
When the Security feature is used to disable a port, the MAC
addresses are not deleted until the port is re-enabled. This allows the
user to check the MAC address display to see which MAC addresses
came in on the specified port.
Transmit SNMP Trap and Disable port
Use this configuration if you want to send an SNMP trap message
and disable the port at the same time during an intrusion. Once the
switch software disables a port because of an intruder, no source
address can use that port. Note that when the port becomes
disabled by enabling the securing feature, the MAC addresses
associated with the specified port are not removed immediately
from the table. However, the addresses will be removed from the
table as the MAC addresses age out.
No Action (default) (No trap; port state unchanged)
In this default setting, an SNMP trap is not sent and the port state
remains unchanged when an intruder is detected.
6-18
Page 93

6HWWLQJ#6HFXULW\26RXUFH#$GGUHVV#7DEOH#2SWLRQV#
Security options are enabled or disabled on a system-wide basis.
To set any of the options within the Source Address Learning Mode
menu, simply select the desired option using the UP and DOWN
arrow keys and then press Enter. Options on the menu that are in
bold print are the defaults.
AT-S20 User’s Guide
6HWWLQJ#6RXUFH
$GGUHVV#/HDUQLQJ
0RGH
0HQX1#
Address Table>
1. Select <
System configuration<Security/Source
Figure6-18
intruder protection disabled
Address Learning Enabled screen displays
Security/Source Address Table Screen (defaults)
Secure: source address learning enabled;
>. The Secure: Source
.
Figure6-19
Secure: Source Address Learning Enabled
6-19
Page 94

Setting Security/Source Address Table Options
6HWWLQJ#6HFXULW\
7KUHVKROG
6HWWLQJ#1XPEHU
RI#0$&#$GGUHVV
1. Select <
Threshold:intruder protection when port
MAC address limit exceeded>
When enabled, this feature displays in bold print on your screen.
Select <
Config MAC address limit per port>
The
following screen displays.
Figure6-20
Five MAC Addresses Assigned to Port 1
2. Select the specified port and enter the maximum number of MAC
addresses assigned to that port, for example three MAC addresses
for Port 5.
Figure 6-21
MAC Address Limit on Port 5
6-20
Page 95

AT-S20 User’s Guide
All ports
with the limit
of three MAC
Addresses
3. To apply the same number of MAC address limits to all ports,
select <
Apply this limit to all ports
>. The following
screen displays.
6HWWLQJ#,QWUXGHU
3URWHFWLRQ
Figure6-22
MAC Address Limit on All Ports
Setting a port(s) to 0 (default) indicates that there is no limit of MAC
addresses for the specified port(s). In threshold mode, the port
disable option must be enabled to stop intruder traffic since the
switch is in learning mode.
When a packet with an unknown address is received, the port on
which the packet is received is disabled. This feature can be enabled
or disabled.
When a packet with an unknown address is received, an SNMP trap is
generated to notify the network administrator of such event. This
feature can be enabled or disabled.
Figure6-23
Intruder Protection
6-21
Page 96

Setting Security/Source Address Table Options
The defaults for Intruder Protection are:
❑
No SNMP Trap if an intruder is detected
❑
Port state unchanged if an intruder is detected
1. Select <
Transmit an SNMP Trap if an intruder is
detected>
2. Select <
Disable the port if an intruder is
detected>
For detailed MAC address information, see MAC Ad dr e ss Ta bl e on
page 6-3. All other related MAC address information follows the MAC
Address Table section.
6-22
Page 97

0LUURU#3RUW#
Port mirroring state:
>Enabled
Disabled
Note: Both transmit and receive activity will be
mirrored.
AT-S20 User’s Guide
0HQX1#
Traffic/Port Mirroring
The Mirror Port allows you to monitor traffic on any port with the use
of a monitoring device.
Traditionally, users had to sacrifice one other port to mirror another;
for example, to monitor traffic on Port 2 (the source port), you had to
configure another port (for example, Port 3), as the destination port
to mirror it. Port 3 therefore could not perform its primary function,
switching packets, while it is mirroring Port 2. The Mirror Port is an
extra port designated as the fixed destination port. It can mirror any
source port you identify.
The mirror port will mirror both receive and transmit activity on the
mirrored port.
For the non-XL versions of the switch, the receive and transmit
activities can be monitored selectively. For the XL versions, both
receive and transmit activities are monitored simultaneously.
When you physically connect a monitoring device to the Mirror Port,
the Mirror Port LINK LED lights green. Make sure you also refer to the
monitoring device’s manual.
1. Select
Traffic/Port Mirroring
Port Mirroring screen is displayed.
2. Select
Enabled
to display additional options on the same
screen.
3. Select a source port number.
from the main menu. The
6-23
Page 98

Mirror Po rt
The software displays a list of ports, similar to the following
screen (some ports have been named in the example):
Please select a port:
Port 1-Room 1148 Port 2-Room 1149
Port 3-Room 1150 Port 4-Room 1151
Port 5 Port 6
Port 7 Port 8
Port 9 Port 10
Port 11 Port 12
Port 13 Port 14
Port 15 Port 16
Port 17 Port 18
Port 19 Port 20
Port 21 Port 22
Port 23 Port 24
Port 26-Uplink Port A Port 27-Uplink Port B
Return to Port Mirroring Configuration...
4. Select
Return to Main Menu...
5. Go to your monitoring device to see the traffic.
6-24
Page 99

3RUW#6WDWXV
Accounting
Port Link Status Mode
1: Online Enabled Half duplex
2: Online Enabled Half duplex
3: Online Enabled Autonegotiate
4: Online Enabled Half duplex
5: Online Enabled Autonegotiate
6: Online Enabled Autonegotiate
7: Online Enabled
8: Online Enabled
9: Online Enabled
10: Online Enabled
11: Online Enabled
12: Online Enabled
More ...
Return to Main
Standard uplink
port
Optional uplink
port (MDA)
Accounting
Port Link Status Mode
13: Online Enabled Half duplex
14: Online Enabled Half duplex
15: Online Enabled Half duplex
16: Online Enabled Half duplex
17: Online Enabled Half duplex
18: Online Enabled Half duplex
19: Online Enabled Half duplex
20: Online Enabled Half duplex
21: Online Enabled Half duplex
22: Online Enabled Half duplex
23: Online Enabled Half duplex
24: Online Enabled Half duplex
25: Online Enabled Half duplex
26: Uplink Port A Online Enabled Half duplex
27: Uplink Port B Online Enabled Half duplex
More...
AT-S20 User’s Guide
0HQX1#
Selecting
Port status and configuration
Port Status and configuration
from the Main
Menu for the first time displays the list of ports similar to the
following screens.
Note
For the AT-3714FXL and AT-3714F, Ports 14 and 15 are the uplink ports (Port A and Port B).
Figure6-24
Port List from Port Status (for AT-3726XL, AT-3726)
6-25
Page 100

Port Numbering
3RUW#1XPEHULQJ
Table 6-2 shows the port numbers for the switch.
Table 6-2
Port Numbering
Switch Port # Port Type
AT-3726XL,
1-24 10Base-T
AT-3726
25 Remote management port for
Omega
26 (Uplink port A) 10/100Base-TX
27 (Uplink port B) Optional MDA (TX or FX)
AT-3716XL 1-16 10Base-T
17 Remote management port for
Omega
18 (Uplink port A) 10/100Base-TX
19 (Uplink port B) Optional MDA (TX or FX)
AT-3714FXL,
1-12 10Base-FL
AT-3714F
13 Remote management port for
Omega
14 (Uplink port A) 100Base-FX
15 (Uplink port B) Optional MDA (TX or FX)
6-26
 Loading...
Loading...