Page 1
EKI-7657C
7+3G port Industrial Managed
Redundant Gigabit Ethernet
Switch
User Manual
Page 2

Copyright
The documentation and the software included with this product are copyrighted 2007 by
Advantech Co., Ltd. All rights are reserved. Advantech Co., Ltd. reserves the right to make
improvements in the products described in this manual at any time without notice. No part of
this manual may be reproduced, copied, translated or transmitted in any form or by any
means without the prior written permission of Advantech Co., Ltd. Information provided in this
manual is intended to be accurate and reliable. However, Advantech Co., Ltd. assumes no
responsibility for its use, nor for any infringements of the rights of third parties, which may
result from its use.
Acknowledgements
Intel and Pentium are trademarks of Intel Corporation.
Microsoft Windows and MS-DOS are registered trademarks of Microsoft Corp.
All other product names or trademarks are properties of their respective owners.
Part No.
Printed in China
EKI-7657C _Manual_ed1 ii
1st Edition
April 2008
Page 3

Product Warranty (2 years)
Advantech warrants to you, the original purchaser, that each of its products will be free from
defects in materials and workmanship for two years from the date of purchase.
This warranty does not apply to any products which have been repaired or altered by persons
other than repair personnel authorized by Advantech, or which have been subject to misuse,
abuse, accident or improper installation. Advantech assumes no liability under the terms of
this warranty as a consequence of such events.
Because of Advantech′s high quality-control standards and rigorous testing, most of our
customers never need to use our repair service. If an Advantech product is defective, it will be
repaired or replaced at no charge during the warranty period. For out-of-warranty repairs, you
will be billed according to the cost of replacement materials, service time and freight. Please
consult your dealer for more details.
If you think you have a defective product, follow these steps:
1. Collect all the information about the problem encountered. (For example, CPU speed,
Advantech products used, other hardware and software used, etc.) Note anything
abnormal and list any onscreen messages you get when the problem occurs.
2. Call your dealer and describe the problem. Please have your manual, product, and any
helpful information readily available.
3. If your product is diagnosed as defective, obtain an RMA (return merchandize
authorization) number from your dealer. This allows us to process your return more
quickly.
4. Carefully pack the defective product, a fully-completed Repair and Replacement Order
Card and a photocopy proof of purchase date (such as your sales receipt) in a shippable
container. A product returned without proof of the purchase date is not eligible for
warranty service.
5. Write the RMA number visibly on the outside of the package and ship it prepaid to your
dealer.
iii
Page 4

Declaration of Conformity
CE
This product has passed the CE test for environmental specifications. Test conditions for
passing included the equipment being operated within an industrial enclosure. In order to
protect the product from being damaged by ESD (Electrostatic Discharge) and EMI leakage,
we strongly recommend the use of CE-compliant industrial enclosure products.
FCC Class A
This equipment has been tested and found to comply with the limits for a Class A digital
device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide
reasonable protection against harmful interference when the equipment is operated in a
commercial environment. This equipment generates, uses and can radiate radio frequency
energy and, if not installed and used in accordance with the instruction manual, may cause
harmful interference to radio communications. Operation of this equipment in a residential
area is likely to cause harmful interference in which case the user will be required to correct
the interference at his own expense.
Technical Support and Assistance
Step 1. Visit the Advantech web site at www.advantech.com/support where you can find
the latest information about the product.
Step 2. Contact your distributor, sales representative, or Advantech’s customer service
center for technical support if you need additional assistance. Please have the
following information ready before you call:
- Product name and serial number
- Description of your peripheral attachments
- Description of your software (operating system, version, application software,
etc.)
- A complete description of the problem
- The exact wording of any error messages
EKI-7657C _Manual_ed1 iv
Page 5

Safety Instructions
1. Read these safety instructions carefully.
2. Keep this User's Manual for later reference.
3. Disconnect this equipment from any AC outlet before cleaning. Use a damp cloth. Do not
use liquid or spray detergents for cleaning.
4. For plug-in equipment, the power outlet socket must be located near the equipment and
must be easily accessible.
5. Keep this equipment away from humidity.
6. Put this equipment on a reliable surface during installation. Dropping it or letting it fall may
cause damage.
7. The openings on the enclosure are for air convection. Protect the equipment from
overheating. DO NOT COVER THE OPENINGS.
8. Make sure the voltage of the power source is correct before connecting the equipment to
the power outlet.
9. Position the power cord so that people cannot step on it. Do not place anything over the
power cord.
10. All cautions and warnings on the equipment should be noted.
11. If the equipment is not used for a long time, disconnect it from the power source to avoid
damage by transient overvoltage.
12. Never pour any liquid into an opening. This may cause fire or electrical shock.
13. Never open the equipment. For safety reasons, the equipment should be opened only by
qualified service personnel.
14. If one of the following situations arises, get the equipment checked by service personnel:
a. The power cord or plug is damaged.
b. Liquid has penetrated into the equipment.
c. The equipment has been exposed to moisture.
d. The equipment does not work well, or you cannot get it to work according to the user's
manual.
e. The equipment has been dropped and damaged.
f. The equipment has obvious signs of breakage.
15. DO NOT LEAVE THIS EQUIPMENT IN AN ENVIRONMENT WHERE THE STORAGE
TEMPERATURE MAY GO BELOW -40℃ (-40℉) OR ABOVE 85 ℃ (185℉). THIS
COULD DAMAGE THE EQUIPMENT. THE EQUIPMENT SHOULD BE IN A
CONTROLLED ENVIRONMENT.
v
Page 6

Safety Precaution - Static Electricity
Follow these simple precautions to protect yourself from harm and the products from damage.
1. To avoid electrical shock, always disconnect the power from your PC chassis before you
work on it. Don't touch any components on the CPU card or other cards while the PC is
on.
2. Disconnect power before making any configuration changes. The sudden rush of power
as you connect a jumper or install a card may damage sensitive electronic components.
EKI-7657C _Manual_ed1 vi
Page 7

Contents
Chapter 1 Overview...........................................2
1.1 Introduction.........................................................2
1.1.1 The SFP Advantage .................................. 2
1.1.2 High-Speed Transmissions .......................2
1.1.3 Dual Power Input ....................................... 2
1.1.4 DIDO.......................................................... 2
1.1.5 Flexible Mounting ......................................3
1.1.6 Advanced Protection .................................3
1.1.7 Wide Operating Temperature .................... 3
1.1.8 Easy Troubleshooting................................ 3
1.2 Features.............................................................. 4
1.3 Specification ....................................................... 5
1.4 Packing List ........................................................ 7
1.5 Safety Precaution ............................................... 7
Chapter 2 Installation......................................10
2.1 LED Indicators .................................................. 10
Table 2.1: EKI-7657C LED Definition.......................10
2.2 Dimensions (units: mm) .................................... 11
Figure 2.1: Front View of EKI-7657C ........................11
Figure 2.2: Side View of EKI-7657C..........................12
Figure 2.3: Rear View of EKI-7657C .........................13
Figure 2.4: Top View of EKI-7657C...........................14
2.3 Mounting........................................................... 15
2.3.1 Wall mounting.......................................... 15
Figure 2.5: Combine the Metal Mounting Kit (units:
mm)..............................................................................15
2.3.2 DIN-rail Mounting..................................... 16
Figure 2.6: Installation to DIN-rail Step 1...................16
Figure 2.7: Installation to DIN-rail Step 2...................17
2.4 Network Connection .........................................18
2.5 Connection to a Fiber Optic Network................ 18
Figure 2.8: Transceiver to the SFP module.................18
Figure 2.9: Transceiver Inserted..................................19
Figure 2.10: LC connector to the transceiver..............19
Figure 2.11: Remove LC connector ............................20
Figure 2.12: Pull out from the transceiver...................20
2.6 Power Connection ............................................ 21
Figure 2.13: Pin Assignment of the Power Connector 21
2.7 Wiring the Digital Inputs/Outputs ...................... 22
Figure 2.14: Pin Assignment of the DIDO Connector 22
Chapter 3 Configuration.................................25
3.1 RS-232 Console ............................................... 25
Figure 3.1: Open Hyper Terminal ...............................25
vii Contents
Page 8

Figure 3.2: COM Port Properties Setting ....................26
Figure 3.3: Login Screen: RS-232 Configuration .......26
Figure 3.4: Command Line Interface ..........................27
3.1.1 Commands Level..................................... 27
Table 3.1: Command Level.........................................27
3.1.2 Commands Set List ................................. 28
Table 3.2: Commands Set List ....................................28
3.1.3 System Commands Set........................... 28
Table 3.3: System Commands Set...............................28
3.1.4 Port Commands Set ................................ 29
Table 3.4: Port Commands Set...................................29
3.1.5 Trunk Commands Set.............................. 30
Table 3.5: Trunk Commands Set................................30
3.1.6 VLAN Commands Set .............................31
Table 3.6: VLAN Commands Set...............................31
3.1.7 Spanning Tree Commands Set ............... 32
Table 3.7: Spanning Tree Commands Set..................32
3.1.8 QOS Commands Set............................... 33
Table 3.8: QOS Commands Set..................................33
3.1.9 IGMP Commands Set.............................. 33
Table 3.9: QOS Commands Set..................................33
3.1.10 Mac/Filter Table Commands Set........... 33
Table 3.10: Mac/Filter Table Commands Set..............34
3.1.11 SNMP Commands Set .......................... 34
Table 3.11: SNMP Commands Set..............................34
3.1.12 Port Mirroring Commands Set............... 35
Table 3.12: Port Mirroring Commands Set.................35
3.1.13 802.1x Commands Set.......................... 35
Table 3.13: 802.1x Commands Set.............................35
3.1.14 TFTP Commands Set............................ 36
Table 3.14: TFTP Commands Set ..............................36
3.1.15 SystemLog, SMTP and Event ............... 36
Table 3.15: SysLog,SMTP,Event Commands Set......36
3.1.16 SNTP Commands Set ........................... 37
Table 3.16: SNTP Commands Set...............................37
3.1.17 X-ring Commands Set ........................... 38
Table 3.17: X-ring Commands Set..............................38
3.2 Web Browser .................................................... 39
Figure 3.5: Type the address in the URL.....................39
Figure 3.6: Web Login Window..................................39
Figure 3.7: Main page..................................................40
3.2.1 System..................................................... 41
Figure 3.8: System Information...................................41
Figure 3.9: IP Configuration........................................42
Figure 3.10: DHCP Server – System Configuration ...43
Figure 3.11: DHCP Server – Client Entries ................44
Figure 3.12: DHCP Server – Port and IP Binding.......44
EKI-7657C _Manual_ed1 viii
Page 9

Figure 3.13: TFTP – Update Firmware.......................45
Figure 3.14: TFTP – Restore Configuration................46
Figure 3.15: TFTP – Backup Configuration................46
Figure 3.16: Syslog Configuration ..............................47
Figure 3.17: SMTP Configuration...............................48
Figure 3.18: Event Configuration................................49
Figure 3.19: Fault Relay Alarm...................................50
Table 3.18: UTC Timezone.........................................51
Figure 3.20: SNTP Configuration ...............................52
Figure 3.21: IP Security...............................................53
Figure 3.22: User Authentication ................................54
Figure 3.23: Digital Input/Output interface.................56
3.2.2 Port..........................................................57
Figure 3.24: Port Statistics...........................................57
Figure 3.25: Port Control.............................................58
Figure 3.26: 2 work ports with LACP enabled............60
Figure 3.27: 2 work ports with LACP disabled...........60
Figure 3.28: Static trunking group of 2 ports on single
switch...........................................................................61
Figure 3.29: Aggregator Information ..........................61
Figure 3.30: State Activity...........................................62
Figure 3.31: Port Mirroring.........................................63
Figure 3.32: Rate Limiting ..........................................64
3.2.3 Protocol ................................................... 65
Figure 3.33: VLAN Configuration..............................65
Figure 3.34: Port based mode......................................66
Figure 3.35: Port based mode-Add interface...............67
Figure 3.36: Port Based Edit/Delete interface.............68
Figure 3.37: 802.1Q VLAN Configuration.................69
Figure 3.38: Edit Group Configuration interface ........70
Figure 3.39: 802.1Q Group Configuration-Edit..........70
Figure 3.40: RSTP System Configuration interface....72
Figure 3.41: RSTP Port Configuration interface.........73
Figure 3.42: SNMP System Configuration interface...74
Figure 3.43: Trap Configuration interface...................75
Figure 3.44: SNMP V3 Configuration interface .........76
Figure 3.45: QoS Configuration interface...................78
Table 3.19: IGMP types...............................................80
Figure 3.46: IGMP Configuration interface................80
Figure 3.47: X-ring interface.......................................82
Figure 3.48: LLDP Configuration interface................83
3.2.4 Security.................................................... 84
Figure 3.49: 802.1x/Radius System Configuration
interface.......................................................................84
Figure 3.50: 802.1x/Radius - Port Setting interface....85
Figure 3.51: 802.1x/Radius - Misc Configuration
interface.......................................................................86
Figure 3.52: Static MAC Addresses interface.............87
Figure 3.53: MAC Filtering interface..........................88
Figure 3.54: All MAC Address interface ....................88
ix Contents
Page 10

Figure 3.55: All MAC Address interface ....................89
Figure 3.56: Factory Default interface ........................90
Figure 3.57: Save Configuration interface ..................91
Figure 3.58: System Reboot interface .........................92
Chapter 4 Troubleshooting ............................94
Appendix A Pin Assignment & Wiring...........96
Figure A.1: RJ-45 Pin Assignment..............................96
Figure A.2: EIA/TIA-568B .........................................96
Figure A.3: EIA/TIA-568A.........................................96
Figure A.4: DB 9-pin female connector......................97
Appendix B Compatible SFP Modules.........100
EKI-7657C _Manual_ed1 x
Page 11

Overview
Sections include:
z Introduction
z Features
z Specifications
z Packing List
CHAPTER
z Safety Precaution
1 Chapter1
Page 12

Chapter 1 Overview
1.1 Introduction
To create reliability in your network, the EKI-7657C comes equipped with a proprietary
redundant network protocol—X-Ring that was developed by Advantech, which
provides users with an easy way to establish a redundant Ethernet network with ultra
high-speed recovery time less than 10 ms.
Aside from 7 x 10/100Base-TX fast Ethernet ports, the EKI-7657C comes equipped
with 3 combo 10/100/1000 Mbps RJ-45 copper ports or mini-GBIC expansion ports.
Traditional RJ-45 ports can be used for uplinking wide-band paths in short distance (<
100 m), or the appropriate replaceable SFP module can be used for the application of
wideband uploading and long distance transmissions to fit the field request flexibility.
Also, the long MTBF (Mean Time Between Failures) ensures that the EKI-7657C will
continue to operate until a Gigabit network infrastructure has been established, without
requiring any extra upgrade costs.
1.1.1 The SFP Advantage
The EKI-7657C’s three SFP fiber slots provide a lot of flexibility when planning and
implementing a network. The slots can accept any SFP-type fiber module and these
modules are designed for transmitting over distances of either 500m (multi-mode),
10km, 30km, 50km, 70km or 110km (single-mode)—and the slots support SFP
modules for WDM single-fiber transmissions. This means that you can easily change
the transmission mode and distance of the switch by simply pulling out the SFP
module and plugging in a different module. The SFP modules are hot-swappable and
plug-and-play! Also, the fact that the switch has three of these slots, means that the
network manager can, for example, have one 10km module in one slot and one 110km
in the other.
1.1.2 High-Speed Transmissions
The EKI-7657C includes a switch controller that can automatically sense transmission
speeds (10/100 Mbps). The RJ-45 interface can also be auto-detected, so MDI or MDIX is automatically selected and a crossover cable is not required. All Ethernet ports
have memory buffers that support the store-and-forward mechanism. This assures that
data is properly transmitted.
1.1.3 Dual Power Input
To reduce the risk of power failure, the EKI-7657C provides +12 ~ 48 V
inputs. If there is power failure, EKI-7657C will automatically switch to the secondary
power input.
1.1.4 DIDO
EKI-7657C provides 2 digital inputs and 2 digital outputs. When disconnection of the
specific port was detected, the digital output will activate the connected warning device
to alarm the user. As for the digital inputs, they can integrate sensors into the system
to issue alarms by sending Syslog, SMTP, or SNMP Trap.
dual power
DC
EKI-7657C _Manual_ed1 2
Page 13

1.1.5 Flexible Mounting
EKI-7657C is compact and can be mounted on a DIN-rail or panel, so it is suitable for
any space-constrained environment.
1.1.6 Advanced Protection
The power line of EKI-7657C supports up to 3,000 V
equipment against unregulated voltage and make systems safer and more reliable.
Meanwhile, 4,000 V
suitable for harsh environments.
ESD protections for Ethernet ports make EKI-7657C more
DC
EFT protection, which secure
DC
1.1.7 Wide Operating Temperature
The operating temperature of the EKI-7657C is between -10 ~ 60 ℃. With such a wide
range, you can use the EKI-7657C in some of the harshest industrial environments that
exist.
1.1.8 Easy Troubleshooting
LED indicators make troubleshooting quick and easy. Each 10/100 Base-TX port has 2
LEDs that display the link status, transmission speed and collision status. Also the
three power indicators P1, P2 and P-Fail help you diagnose immediately.
3 Chapter1
Page 14

1.2 Features
• 3 Gigabit Copper/SFP combo ports, plus 7 Fast Ethernet ports
• SFP socket for Easy and Flexible Fiber Expansion
• Redundancy: Gigabit X-Ring (ultra high-speed recovery time<10ms), RSTP/STP
(802.1w/1D)
• Management: Web, Telnet, Serial Console, Windows Utility and SNMP
• Control: VLAN/GVRP, QOS, IGMP Snooping, LACP, and Rate Limit
• Security: IP/MAC and port binding, DHCP Server, IP access list, 802.1x, SNMPv3
• Diagnostic: Port Statistic, Port Mirroring, RMON, Trap, SNMP Alert, and Syslog
• Dual 12 ~ 48 V
• Robust mechanism and special heat spreader design
• Supports DIDO function (2 digital inputs/2 digital outputs)
power input and 1 Relay Output
DC
EKI-7657C _Manual_ed1 4
Page 15

1.3 Specification
Communications
Standard
LAN
Transmission Distance
Transmission Speed
Interface
Connectors
1 x 6-pin removable terminal (power & Relay)
1 x 6-pin removable terminal (DIDO)
LED Indicators
Console
Power
Power Consumption
Power Input
Overload Current Protection
Fault Output
Mechanism
Dimensions (WxHxD)
Enclosure
Mounting
Protection
IEEE 802.3, 802.3ab, 802.3ad, 802.3u, 802.3x,
802.3z
IEEE 802.1ab, 802.1D, 802.1w, 802.1p, 802.1Q,
802.1X
10/100/1000Base-TX, Optional 100Base-FX,
1000Base-SX/LX/LHX/XD/ZX/EZX
Ethernet: Up to 100m (4-wire Cat.5e, Cat.6 RJ-45
cable suggested for Gigabit port)
SFP: Up to 110km (depends on SFP type)
Ethernet: 10/100Mbps, Auto-Negotiation
Gigabit Copper: Up to 1000 Mbps
Gigabit Fiber: Up to 1000Mbps
7 x RJ-45 (Ethernet)
3 x RJ-45/SFP (mini-GBIC) combo ports
System: PWR, PWR1, PWR2, R.M., P-Fail
10/100TX: Link/Activity, Duplex/Collision
Gigabit Copper: Link/Activity, Speed (1000Mbps)
SFP: Link/Activity
RS-232 (RJ-45)
Max. 10 W
2 x Unregulated +12 ~ 48 V
3.5A@12VDC (Re-settable Fuse)
1 Relay Output
79 x 152 x 105 mm
IP30, metal shell with solid mounting
DIN-rail, wall
(0.85A max.)
DC
kits
5 Chapter1
Page 16

ESD (Ethernet)
Surge (EFT for power)
Reverse Polarity
Environment
Operating Temperature
Operating Humidity
Storage Temperature
Storage Humidity
MTBF
Certifications
Safety
EMC
EN55022, Class A,
EN61000-3-2/3
EN55024
IEC61000-4-2/3/4/5/6/8
EN61000-6-2
Freefall
Shock
Vibration
4,000 V
3,000 V
Present
-10 ~ 60
5 ~ 95% (non-condensing)
-40 ~ 85
0 ~ 95% (non-condensing)
260,818 hours
UL, 60950-1, CAN/CSA-C22.2 No.60950
EU: EN55011, EN61000-6-4
IEC60068-2-32
IEC60068-2-27
IEC60068-2-6
DC
DC
o
C (14 ~ 140oF)
o
C (-40 ~ 185oF)
EKI-7657C _Manual_ed1 6
Page 17

1.4 Packing List
• 1 x EKI-7657C Industrial Managed Gigabit Ethernet Switch
• 1 x eAutomation Industrial Communication CD-ROM with software, and User manual
• 2 x Wall Mounting Bracket and Screws
• 1 x DIN-rail Mounting Bracket and Screws
• 1 x 8-pin RJ-45 to RS-232 serial cable
• 1 x DC Jack Cable φ2.0/150mm
• 1 x EKI-7657C Startup Manual
1.5 Safety Precaution
Attention IF DC voltage is supplied by an external circuit, please use a protection device
on the power supply input.
7 Chapter1
Page 18

EKI-7657C _Manual_ed1 8
Page 19

Installation
Sections include:
z LED Indicators
z Dimensions
z Mounting
z Network Connection
CHAPTER
z Connection to a Fiber Optic Network
z Power Connection
9 Chapter2
Page 20

Chapter 2 Installation
In this chapter, you will be given an overview of the EKI-7657C hardware installation
procedures.
2.1 LED Indicators
There are few LEDs display the power status and network status located on the front
panel of EKI-7657C, each of them has its own specific meaning shown as below.
Table 2.1: EKI-7657C LED Definition
LED Color Description
PWR Green
R.M. Green
PWR1 Green
PWR2 Green
P-Fail Red
Link/Active
(G7, G9, G10 SFP)
Green
Green
(Upper LED)
On System power on
Off No power input
On The industrial switch is the master of the X-ring group
Off The industrial switch is not the master of the X-ring group
On Power input 1 is active
Off Power input 1 is inactive
On Power input 2 is active
Off Power input 2 is inactive
On
Off Power input 1 and 2 are both active, or no power input
On SFP port is linking
Flashing Data is transmitting or receiving
Off Not connected to network
On The port is operating at speed of 1000M
Off The port is disconnected or not operating at speed of 1000M
Power input 1 or 2 is inactive or port link down
(depends on Fault Relay Alarm configuration)
G7, G9, G10 (RJ-45)
Link/Active
(1 ~ 6 & 8)
Duplex/Collision
(1 ~ 6 & 8)
Green
(Lower LED)
Green
Orange
On Connected to network
Flashing Networking is active
Off Not connected to network
On Connected to network
Flashing Networking is active
Off Not connected to network
On Ethernet port full duplex
Flashing Collision of packets occurs
Off Ethernet port half duplex or not connected to network
EKI-7657C _Manual_ed1 10
Page 21
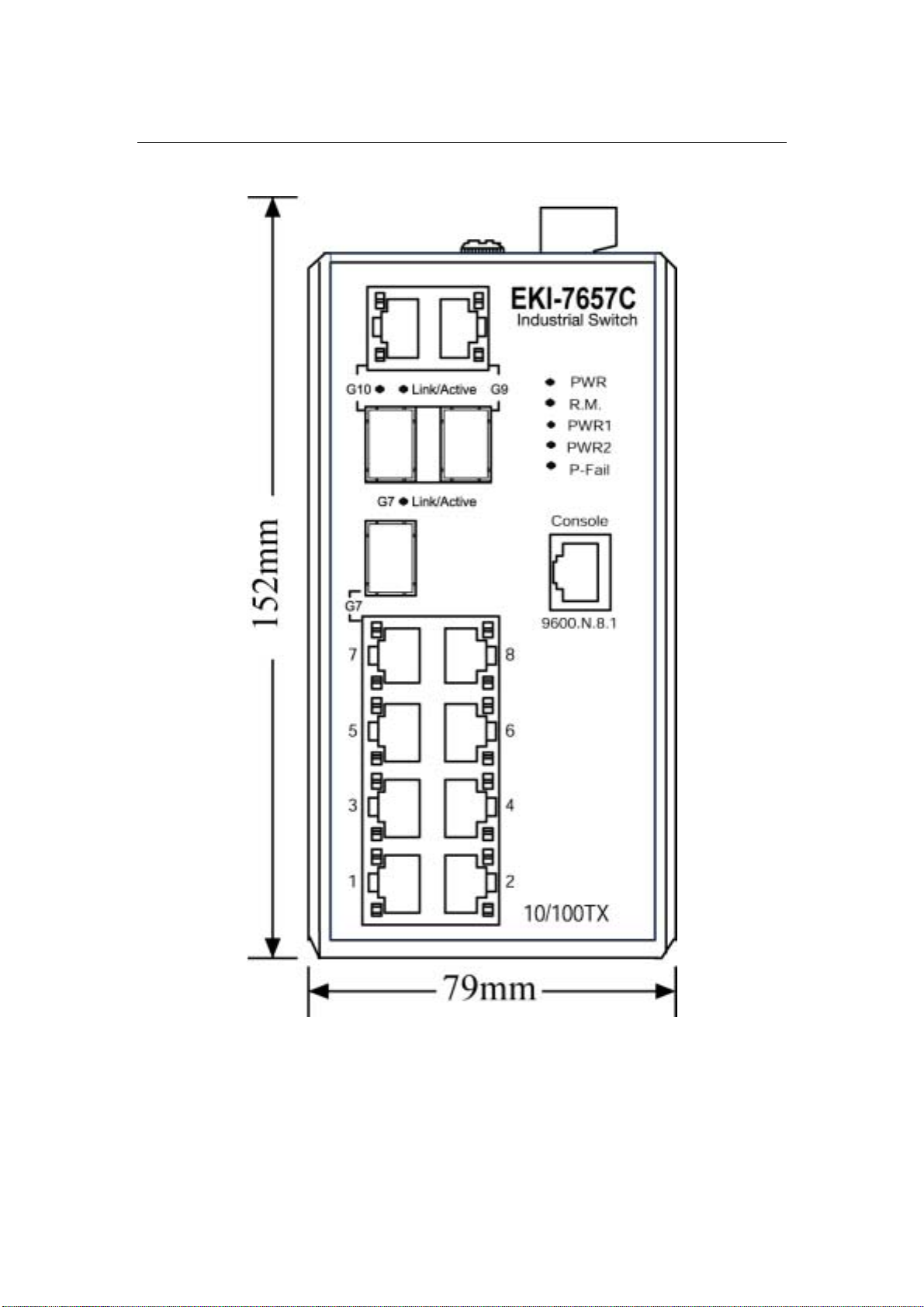
2.2 Dimensions (units: mm)
Figure 2.1: Front View of EKI-7657C
11 Chapter2
Page 22
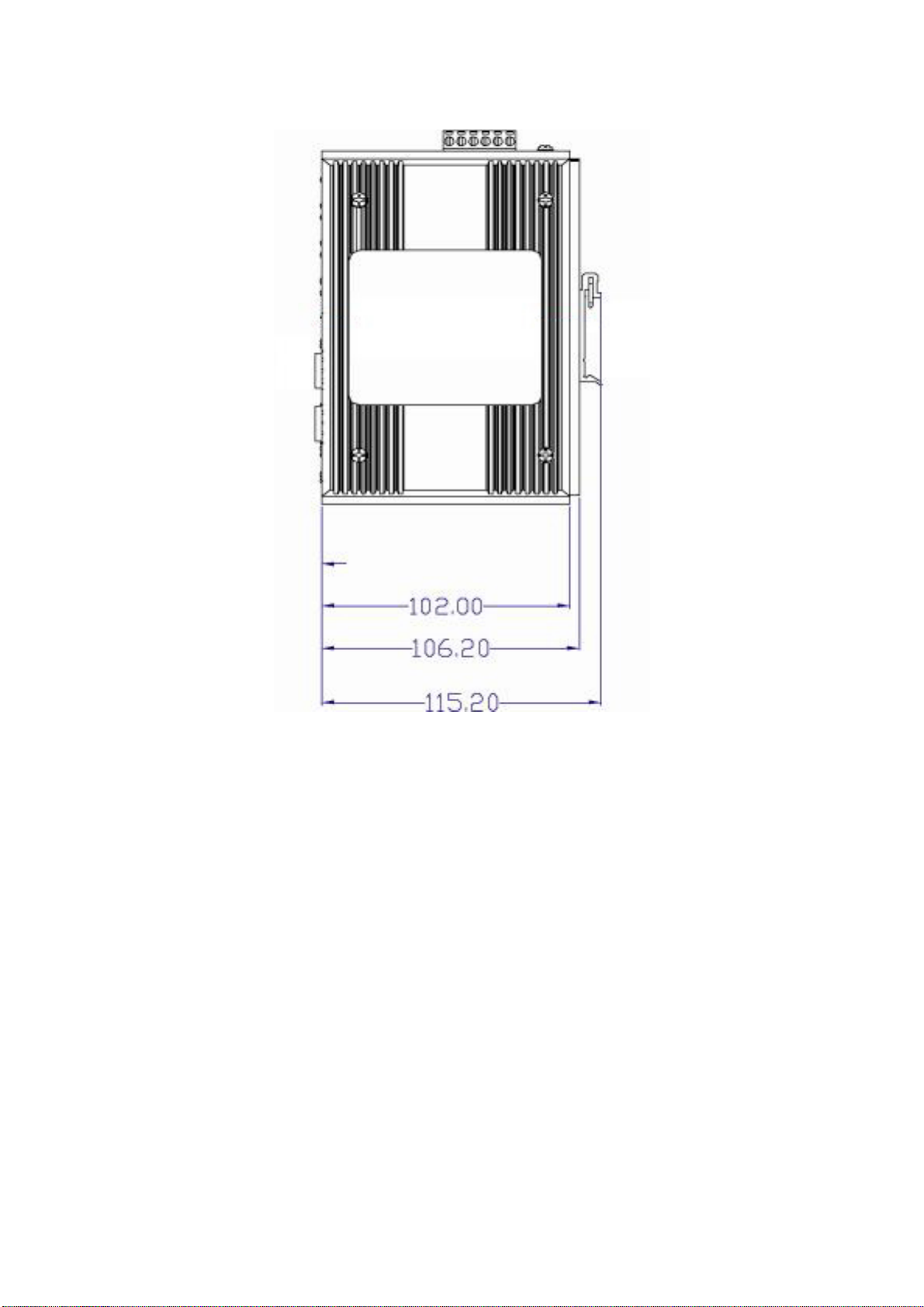
Figure 2.2: Side View of EKI-7657C
EKI-7657C _Manual_ed1 12
Page 23
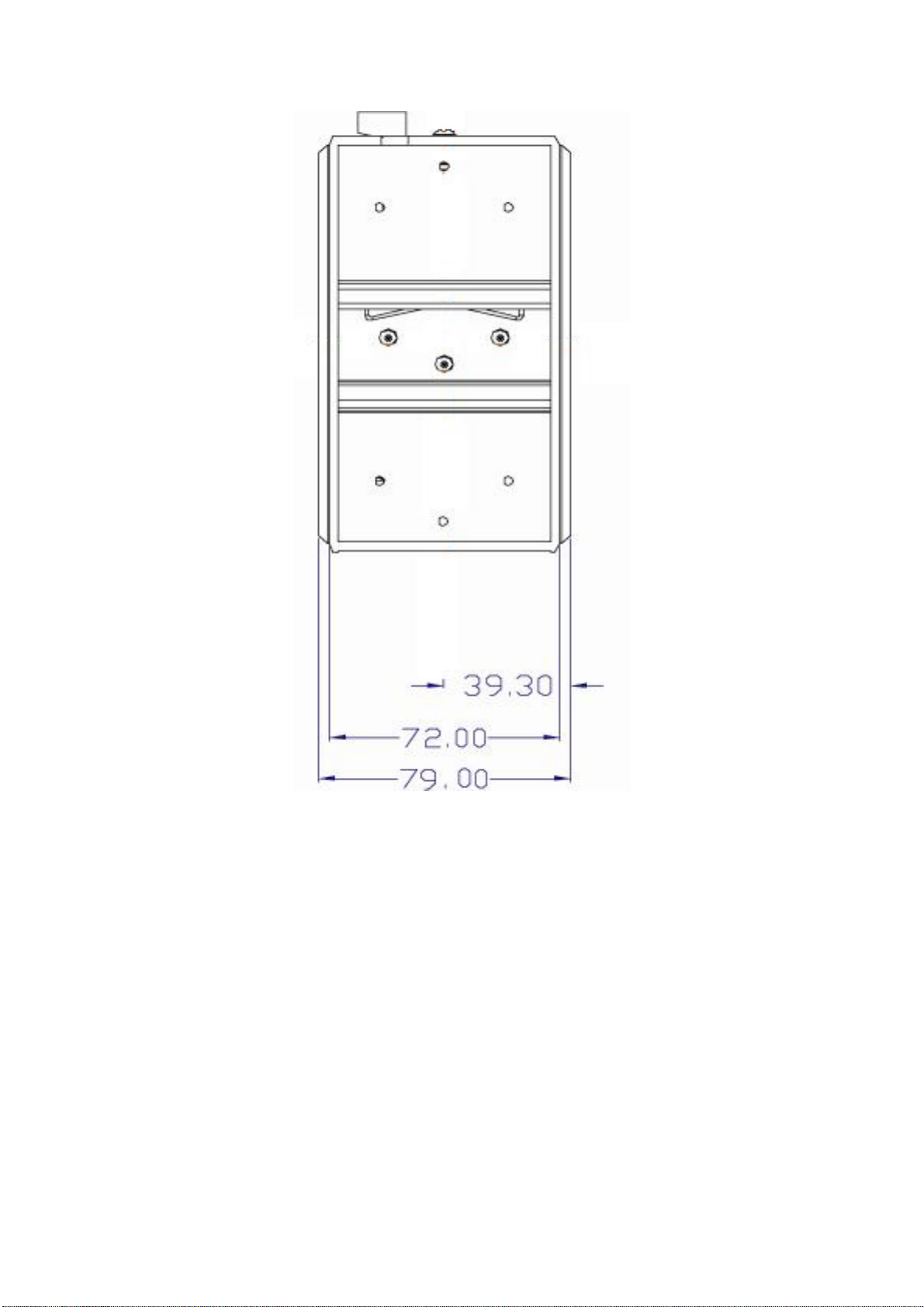
Figure 2.3: Rear View of EKI-7657C
13 Chapter2
Page 24

Figure 2.4: Top View of EKI-7657C
EKI-7657C _Manual_ed1 14
Page 25

2.3 Mounting
The EKI-7657C supports two mounting methods: DIN-rail & Wall.
2.3.1 Wall mounting
EKI-7657C can be wall-mounted by using the included mounting kit. Then, hang on the
EKI-7657C to the nails on the wall.
First, use the screws included in the package to combine the EKI-7657C and metal
mounting kit. And then you can install the device firmly via the components, please see
Figure 2.5 as below.
Figure 2.5: Combine the Metal Mounting Kit (units: mm)
15 Chapter2
Page 26

2.3.2 DIN-rail Mounting
You can also mount EKI-7657C on a standard DIN-rail by steps below.
The DIN-rail kit is screwed on the industrial switch when out of factory. If the DIN-rail kit
is not screwed on the industrial switch, please screw the DIN-rail kit on the switch first.
First, hang the EKI-7657C to the DIN-rail with angle of inclination. See Figure 2.6.
Figure 2.6: Installation to DIN-rail Step 1
EKI-7657C _Manual_ed1 16
Page 27

Then, let the device down straight to slide over the rail smoothly. See Figure 2.7.
Figure 2.7: Installation to DIN-rail Step 2
17 Chapter2
Page 28

2.4 Network Connection
The EKI-7657C has 7 x RJ-45 ports that support connection to 10 Mbps Ethernet, or
100 Mbps Fast Ethernet, and half or full duplex operation. EKI-7657C can be
connected to other hubs or switches via a twisted-pair straight-through or crossover
cable up to 100m long. The connection can be made from any TX port of the EKI7657C (MDI-X) to another hub or switch either MDI-X or uplink MDI port.
The EKI-7657C supports auto-crossover to make networking more easy and flexible.
You can connect any RJ-45 (MDI-X) station port on the switch to any device such as a
switch, bridge or router.
2.5 Connection to a Fiber Optic Network
EKI-7657C has three SFP slots for connecting to the network segment with single or
multi-mode fiber. You can choose appropriate SFP transceiver to plug into the slot.
Make sure the transceiver is aligned correctly and then slide the transceiver into the
SFP slot until a click is heard. You can use proper multi-mode or single-mode fiber
according to the used SFP transceiver. With fiber optic, it transmits speed up to 1000
Mbps and you can prevent noise interference from the system and transmission
distance up to 110 km, depending on the SFP transceiver.
The small form-factor pluggable (SFP) is a compact optical transceiver used in optical
communications for both telecommunication and data communications applications.
Note
The SFP/Copper Combo port can’t be both used at the same time. The SFP port has the
higher priority than the copper port; if you insert the 1000M SFP transceiver (which is
being connected to the remote device) into the SFP port, the connection of the
accompanying copper port will link down.
If you insert the 100M SFP transceiver into the SFP port even without a fiber connection
to the remote, the connection of the accompanying copper port will link down
immediately.
To connect the transceiver and LC cable, please follow the steps shown below:
First, insert the transceiver into the SFP module. Notice that the triangle mark is the
bottom of the module.
Figure 2.8: Transceiver to the SFP module
EKI-7657C _Manual_ed1 18
Page 29
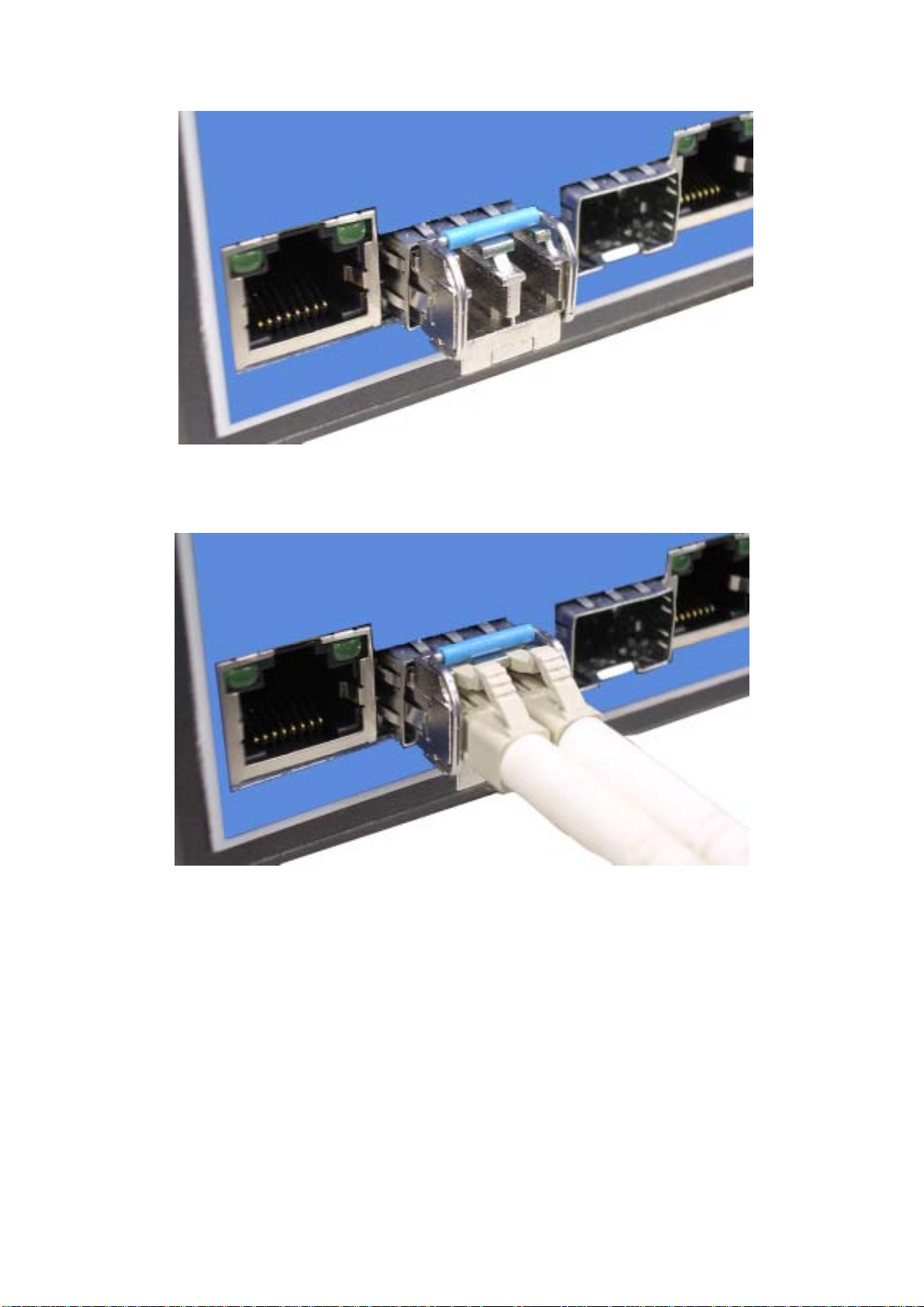
Figure 2.9: Transceiver Inserted
Second, insert the fiber cable of LC connector into the transceiver.
Figure 2.10: LC connector to the transceiver
19 Chapter2
Page 30
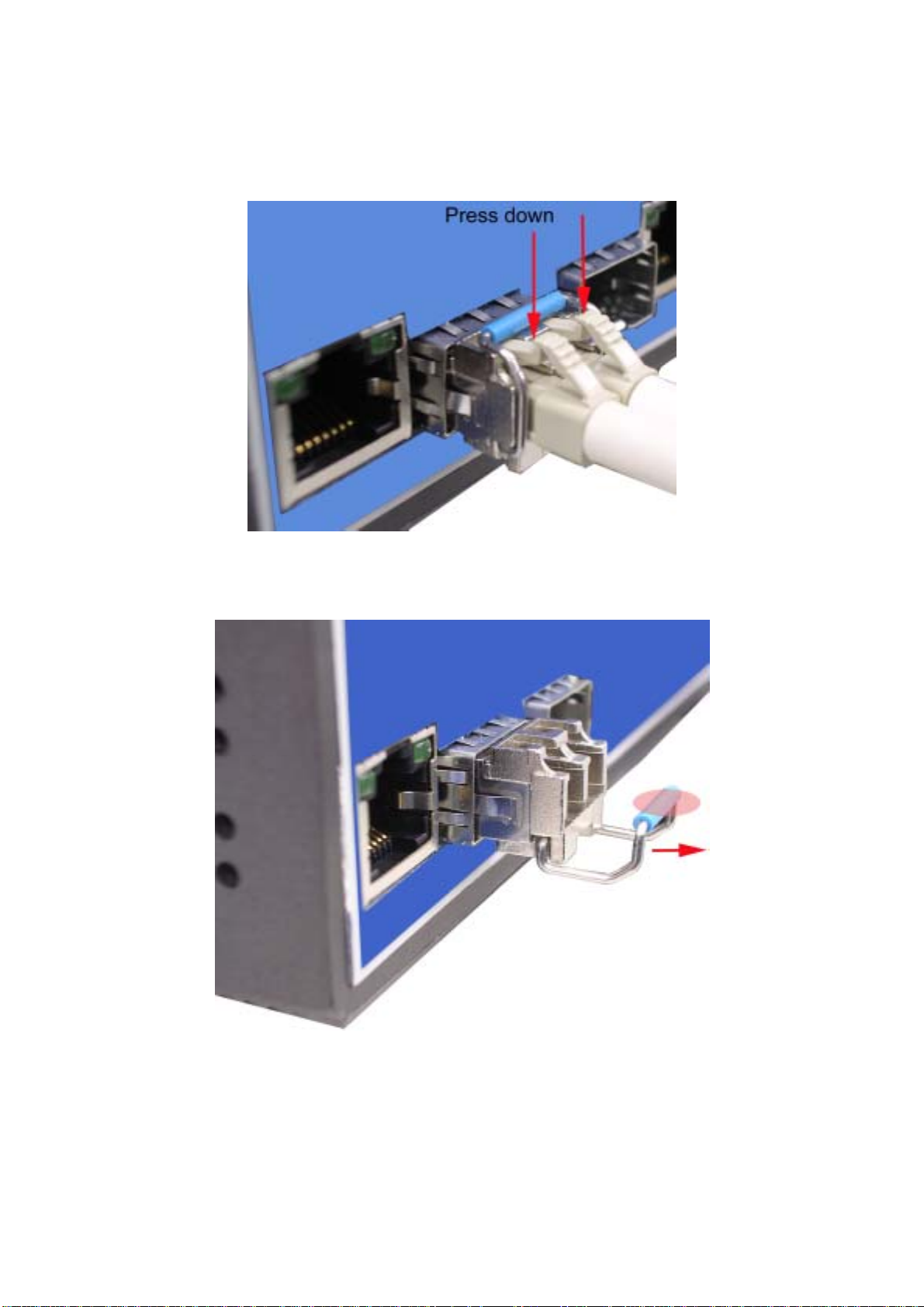
To remove the LC connector from the transceiver, please follow the steps shown below:
First, press the upper side of the LC connector to release from the transceiver and pull
it out.
Figure 2.11: Remove LC connector
Second, push down the metal loop and pull the transceiver out by the plastic handle.
Figure 2.12: Pull out from the transceiver
EKI-7657C _Manual_ed1 20
Page 31

2.6 Power Connection
The EKI-7657C supports dual +12 ~ 48 V
power inputs and power-fail relay output.
DC
Figure 2.13: Pin Assignment of the Power Connector
You can connect an alarm indicator, buzzer or other signaling equipment through the
relay output. The relay opens if power input 1, 2 fails or port link down/break (″Open″
means if you connect relay output with an LED, the light would be off).
21 Chapter2
Page 32

2.7 Wiring the Digital Inputs/Outputs
EKI-7657C is equipped with two sets of digital input/output contacts of the terminal
block connector. Connect the wires to DI0, DI1, DO0, DO1, and GND respectively.
GND is the common ground for DI0, DI1, DO0, and DO1. Don’t connect DO0/DO1 to
the external device using power higher than 40V/200mA.
Figure 2.14: Pin Assignment of the DIDO Connector
EKI-7657C _Manual_ed1 22
Page 33

23 Chapter2
Page 34

Configuration
Sections include:
z RS-232 Console
z Web Browser
z Mounting
z Self Diagnosis
CHAPTER
EKI-7657C _Manual_ed1 24
Page 35

Chapter 3 Configuration
The EKI-7657C can be configured in two ways: via RS-232 Console or a web browser.
3.1 RS-232 Console
EKI-7657C’s RS-232 console is designed for rapidly configuring which provides the console
management—CLI command.
Attach the supplied cable, which one end is RJ-45 and the other end is female DB9, to connect EKI7657C and your host PC or terminal. The connected PC or terminal must support the terminal emulation
program.
From the Windows desktop, click Start/Programs/Accessories/Communications/HyperTerminal to
open Hyper Terminal program.
Figure 3.1: Open Hyper Terminal
25 Chapter3
Page 36

Select the appropriate COM port, and set the parameter as Fig.3.2 (9600 for Baud Rate, 8 for Data Bits,
None for Parity, 1 for Stop Bits, and None for Flow Control).
Figure 3.2: COM Port Properties Setting
Press Enter for login screen (If you can not find the login screen, press Enter one more time). The
default user name and password are both “admin”. Key-in the user name and password to enter the
command line interface.
Figure 3.3: Login Screen: RS-232 Configuration
EKI-7657C _Manual_ed1 26
Page 37

After you have logged in to the system, you will see a command prompt. To enter CLI management interface,
type in the “enable” command.
Figure 3.4: Command Line Interface
The following table lists the CLI commands and description.
3.1.1 Commands Level
Table 3.1: Command Level
Modes Access Method Prompt Exit Method About This Model
User EXEC
Privileged
EXEC
Global
configuration
VLAN database
Interface
configuration
Begin a session with
your switch.
Enter the enable
command while in
user EXEC mode.
Enter the configure
command while in
privileged EXEC
mode.
Enter the vlan
database command
while in privileged
EXEC mode.
Enter the interface
command (with a
specific interface)
while in global
configuration mode
switch>
switch#
switch(config)#
switch(vlan)#
switch(config-if)#
Enter logout or quit. The user commands available
Enter disable to exit. The privileged command is the
To exit to privileged
EXEC mode, enter
exit or end
To exit to user EXEC
mode, enter exit.
To exit to global
configuration mode,
enter exit.
To exist to privileged
EXEC mode, enter
exit or end.
at the user level are a subset
of those available at the
privileged level.
Use this mode to
• Perform basic tests.
• Display system information.
advanced mode
Use this mode to
• Display advanced function
status
• Save configuration
Use this mode to configure the
parameters that are going to
be applied to your switch
Use this mode to configure
VLAN-specific parameters.
Use this mode to configure the
parameters for the switch and
Ethernet ports.
27 Chapter3
Page 38

3.1.2 Commands Set List
Table 3.2: Commands Set List
User EXEC E
Privileged EXEC P
Global configuration G
VLAN database V
Interface configuration I
3.1.3 System Commands Set
Command Code Word
Table 3.3: System Commands Set
Netstar Commands Level Description Example
show config E Show switch configuration switch>show config
show terminal P Show console information switch#show terminal
write memory
system name
[System Name]
system location
[System Location]
system description
[System Description]
system contact
[System Contact]
show system-info E Show system information switch>show system-info
ip address
[Ip-address] [Subnet-mask]
[Gateway]
ip dhcp
show ip P Show IP information of switch switch#show ip
no ip dhcp
reload G Halt and perform a cold restart switch(config)#reload
default G Restore to default switch(config)#default
admin username
[Username]
admin password
[Password]
show admin P Show administrator information switch#show admin
dhcpserver enable
Dhcpserver disable
dhcpserver lowip
[Low IP]
dhcpserver highip
[High IP]
Save user configuration into
P
permanent memory (flash rom)
Configure system name switch(config)#system name xxx
G
Set switch system location string switch(config)#system location xxx
G
Set switch system description string switch(config)#system description xxx
G
Set switch system contact window
G
string
Configure the IP address of switch switch(config)#ip address 192.168.1.1
G
Enable DHCP client function of
G
switch
Disable DHCP client function of
G
switch
Changes a login username.
G
(maximum 10 words)
Specifies a password
G
(maximum 10 words)
Enable DHCP Server switch(config)#dhcpserver enable
G
Disable DHCP Server switch(config)#no dhcpserver
G
Configure low IP address for IP pool switch(config)#dhcpserver lowip 192.168.1.100
G
Configure high IP address for IP
G
pool
switch#write memory
switch(config)#system contact xxx
255.255.255.0 192.168.1.254
switch(config)#ip dhcp
switch(config)#no ip dhcp
switch(config)#admin username xxxxxx
switch(config)#admin password xxxxxx
switch(config)#dhcpserver highip 192.168.1.200
EKI-7657C _Manual_ed1 28
Page 39

dhcpserver subnetmask
[Subnet mask]
dhcpserver gateway
[Gateway]
dhcpserver dnsip
[DNS IP]
dhcpserver leasetime
[Hours]
dhcpserver ipbinding
[IP address]
show dhcpserver configuration P Show configuration of DHCP server switch#show dhcpserver configuration
show dhcpserver clients P Show client entries of DHCP server switch#show dhcpserver clients
show dhcpserver ip-binding
no dhcpserver
security enable
security http
security telnet
security ip
[Index(1..10)] [IP Address]
show security
no security
no security http
no security telnet
Configure subnet mask for DHCP
G
clients
Configure gateway for DHCP clients switch(config)#dhcpserver gateway 192.168.1.254
G
Configure DNS IP for DHCP clients switch(config)#dhcpserver dnsip 192.168.1.1
G
Configure lease time (in hour) switch(config)#dhcpserver leasetime 1
G
Set static IP for DHCP clients by port switch(config)#interface fastEthernet 2
I
Show IP-Binding information of
P
DHCP server
Disable DHCP server function switch(config)#no dhcpserver
G
Enable IP security function switch(config)#security enable
G
Enable IP security of HTTP server switch(config)#security http
G
Enable IP security of telnet server switch(config)#security telnet
G
Set the IP security list switch(config)#security ip 1 192.168.1.55
G
Show the information of IP security switch#show security
P
Disable IP security function switch(config)#no security
G
Disable IP security of HTTP server switch(config)#no security http
G
Disable IP security of telnet server switch(config)#no security telnet
G
switch(config)#dhcpserver subnetmask
255.255.255.0
switch(config)#dhcpserver ipbinding 192.168.1.1
switch#show dhcpserver ip-binding
3.1.4 Port Commands Set
Table 3.4: Port Commands Set
Netstar Commands Level Description Example
interface fastEthernet
[Portid]
duplex
[full | half]
speed
[10|100|1000|auto]
no flowcontrol
security enable
no security
Choose the port for modification. switch(config)#interface fastEthe rnet 2
G
Use the duplex configuration
command to specify the duplex
I
mode of operation for Fast
Ethernet.
Use the speed configuration
command to specify the speed
mode of operation for Fast
I
Ethernet., the speed can’t be set to
1000 if the port isn’t a giga port..
Disable flow control of interface switch(config-if)#no flowcontrol
I
Enable security of interface switch(config)#interface fastEthernet 2
I
Disable security of interface switch(config)#interface fastEthernet 2
I
switch(config)#interface fastEthernet 2
switch(config-if)#duplex full
switch(config)#interface fastEthernet 2
switch(config-if)#speed 100
switch(config-if)#security enable
switch(config-if)#no security
29 Chapter3
Page 40

bandwidth type all
bandwidth type broadcast-multicastflooded-unicast
bandwidth type broadcast-multicast
bandwidth type broadcast-only
bandwidth in
[Value]
bandwidth out
[Value]
show bandwidth
state
[Enable | Disable]
show interface configuration
show interface status
show interface accounting
no accounting
Set interface ingress limit frame
type to “accept all frame”
I
Set interface ingress limit frame
type to “accept broadcast,
I
multicast, and flooded unicast
frame”
Set interface ingress limit frame
type to “accept broadcast and
I
multicast frame”
Set interface ingress limit frame
type to “only accept broadcast
I
frame”
Set interface input bandwidth. Rate
Range is from 100 kbps to 102400
I
kbps or to 256000 kbps for giga
ports,
and zero means no limit.
Set interface output bandwidth.
Rate Range is from 100 kbps to
102400 kbps or to 256000 kbps for
giga ports,
and zero means no limit.
Show interfaces bandwidth control switch(config)#interface fastEthernet 2
I
Use the state interface
configuration command to specify
the state mode of operation for
I
Ethernet ports. Use the disable
form of this command to disable
the port.
show interface configuration status switch(config)#interface fastEthernet 2
I
show interface actual status switch(config)#interface fastEthernet 2
I
show interface statistic counter switch(config)#interface fastEthe rnet 2
I
Clear interface accounting
I
information
switch(config)#interface fastEthernet 2
switch(config-if)#bandwidth type all
switch(config)#interface fastEthernet 2
switch(config-if)#bandwidth type broadcast-
multicast-flooded-unicast
switch(config)#interface fastEthernet 2
switch(config-if)#bandwidth type broadcast-
multicast
switch(config)#interface fastEthernet 2
switch(config-if)#bandwidth type broadcast-only
switch(config)#interface fastEthernet 2
switch(config-if)#bandwidth in 100
switch(config)#interface fastEthernet 2
switch(config-if)#bandwidth out 100
switch(config-if)#show bandwidth
switch(config)#interface fastEthernet 2
switch(config-if)#state Disable
switch(config-if)#show interface configuration
switch(config-if)#show interface status
switch(config-if)#show interface accounting
switch(config)#interface fastEthernet 2
switch(config-if)#no accounting
3.1.5 Trunk Commands Set
Table 3.5: Trunk Commands Set
Netstar Commands Level Description Example
aggregator priority
[1~65535]
aggregator activityport
[Group ID]
[Port Numbers]
aggregator group
[GroupID] [Port-list]
lacp
workp
[Workport]
Set port group system priority switch(config)#aggregator priority 22
G
Set activity port switch(config)#aggregator activityport 2
G
Assign a trunk group with LACP
active.
[GroupID] :1~3
[Port-list]:Member port list, This
parameter could be a port
G
range(ex.1-4) or a port list separate
by a comma(ex.2, 3, 6)
[Workport]: The amount of work
ports, this value could not be less
than zero or be large than the
amount of member ports.
switch(config)#aggregator group 1 1-4 lacp workp
2
or
switch(config)#aggregator group 2 1,4,3 lacp
workp 3
EKI-7657C _Manual_ed1 30
Page 41

aggregator group
[GroupID] [Port-list]
nolacp
show aggregator
no aggregator lacp
[GroupID]
no aggregator group
[GroupID]
3.1.6 VLAN Commands Set
Table 3.6: VLAN Commands Set
Netstar Commands Level Description Example
Assign a static trunk group.
[GroupID] :1~3
[Port-list]:Member port list, This
G
parameter could be a port
range(ex.1-4) or a port list separate
by a comma(ex.2, 3, 6)
Show the information of trunk group switch#show aggregator 1
P
Disable the LACP function of trunk
group
G
Remove a trunk group switch(config)#no aggreator group 2
G
switch(config)#aggregator group 1 2-4 nolacp
or
switch(config)#aggregator group 1 3,1,2 nolacp
or
switch#show aggregator 2
or
switch#show aggregator 3
switch(config)#no aggreator lacp 1
vlan database P Enter VLAN configure mode switch#vlan database
Vlanmode
[portbase| 802.1q | gvrp]
V
no vlan V No VLAN Switch(vlan)#no vlan
Ported based VLAN configuration
vlan port-based grpname
[Group Name]
grpid
[GroupID]
port
[PortNumbers]
show vlan [GroupID]
or
show vlan
no vlan group
[GroupID]
IEEE 802.1Q VLAN
vlan 8021q name
[GroupName]
vid
[VID]
vlan 8021q port
[PortNumber]
access-link untag
[UntaggedVID]
vlan 8021q port
[PortNumber]
trunk-link tag
[TaggedVID List]
vlan 8021q port
[PortNumber]
hybrid-link untag
[UntaggedVID]
tag
[TaggedVID List]
To set switch VLAN mode. switch(vlan)#vlanmode portbase
Add new port based VALN switch(vlan)#vlan port-based grpname test grpid
V
Show VLAN information switch(vlan)#show vlan 23
V
Delete port base group ID switch(vlan)#no vlan group 2
V
Change the name of VLAN group, if
the group didn’t exist, this command
V
can’t be applied.
Assign a access link for VLAN by
port, if the port belong to a trunk
V
group, this command can’t be
applied.
Assign a trunk link for VLAN by port,
if the port belong to a trunk group,
V
this command can’t be applied.
Assign a hybrid link for VLAN by
port, if the port belong to a trunk
group, this command can’t be
V
applied.
or
switch(vlan)#vlanmode 802.1q
or
switch(vlan)#vlanmode gvrp
2 port 2-4
or
switch(vlan)#vlan port-based grpname test grpid
2 port 2,3,4
switch(vlan)#vlan 8021q name test vid 22
switch(vlan)#vlan 8021q port 3 access-link untag
33
switch(vlan)#vlan 8021q port 3 trunk-link tag
2,3,6,99
or
switch(vlan)#vlan 8021q port 3 trunk-link tag 3-20
switch(vlan)#vlan 8021q port 3 hybrid-link untag 4
tag 3,6,8
or
switch(vlan)#vlan 8021q port 3 hybrid-link untag 5
tag 6-8
31 Chapter3
Page 42

vlan 8021q trunk
[PortNumber]
access-link untag
[UntaggedVID]
vlan 8021q trunk
[PortNumber]
trunk-link tag
[TaggedVID List]
vlan 8021q trunk
[PortNumber]
hybrid-link untag
[UntaggedVID]
tag
[TaggedVID List]
show vlan [GroupID]
or
show vlan
no vlan group
[GroupID]
Assign a access link for VLAN by
trunk group
V
Assign a trunk link for VLAN by trunk
group
V
Assign a hybrid link for VLAN by
trunk group
V
Show VLAN information switch(vlan)#show vlan 23
V
Delete port base group ID switch(vlan)#no vlan group 2
V
switch(vlan)#vlan 8021q trunk 3 access-link untag
33
switch(vlan)#vlan 8021q trunk 3 trunk-link tag
2,3,6,99
or
switch(vlan)#vlan 8021q trunk 3 trunk-link tag 3-
20
switch(vlan)#vlan 8021q trunk 3 hybrid-link untag
4 tag 3,6,8
or
switch(vlan)#vlan 8021q trunk 3 hybrid-link untag
5 tag 6-8
3.1.7 Spanning Tree Commands Set
Table 3.7: Spanning Tree Commands Set
Netstar Commands Level Description Example
spanning-tree enable G Enable spanning tree switch(config)#spanning-tree enable
spanning-tree priority [0~61440]
spanning-tree max-age [seconds]
spanning-tree hello-time [seconds]
spanning-tree forward-time [seconds]
stp-path-cost
[1~200000000]
stp-path-priority
[Port Priority]
Configure spanning tree priority
G
parameter
Use the spanning-tree max-age
global configuration command to
change the interval between
messages the spanning tree
receives from the root switch. If a
G
switch does not receive a bridge
protocol data unit (BPDU)
message from the root switch
within this interval, it recomputed
the Spanning Tree Protocol (STP)
topology.
Use the spanning-tree hello-time
global configuration command to
specify the interval between hello
G
bridge protocol data units
(BPDUs).
Use the spanning-tree forwardtime global configuration command
to set the forwarding-time for the
specified spanning-tree instances.
G
The forwarding time determines
how long each of the listening and
learning states last before the port
begins forwarding.
Use the spanning-tree cost
interface configuration command
to set the path cost for Spanning
Tree
Protocol (STP) calculations. In the
I
event of a loop, spanning tree
considers the path cost when
selecting
an interface to place into the
forwarding state.
Use the spanning-tree port-priority
interface configuration command
I
to configure a port priority that
is used when two switches tie for
switch(config)#spanning-tree priority 32768
switch(config)#spanning-tree max-age 15
switch(config)#spanning-tree hello-time 3
switch(config)#spanning-tree forward-time 20
switch(config)#interface fastEthernet 2
switch(config-if)#stp-path-cost 20
switch(config)#interface fastEthernet 2
switch(config-if)#stp-path-priority 128
EKI-7657C _Manual_ed1 32
Page 43

stp-admin-p2p
[Auto|True|False]
stp-admin-edge
[True|False]
stp-admin-non-stp
[True|False]
show spanning-tree
no spanning-tree G Disable spanning-tree. switch(config)#no spanning-tree
position as the root switch.
Admin P2P of STP priority on this
I
interface.
Admin Edge of STP priority on this
I
interface.
Admin NonSTP of STP priority on
I
this interface.
Displays a summary of the
E
spanning-tree states.
switch(config)#interface fastEthernet 2
switch(config-if)#stp-admin-p2p Auto
switch(config)#interface fastEthernet 2
switch(config-if)#stp-admin-edge True
switch(config)#interface fastEthernet 2
switch(config-if)#stp-admin-non-stp False
switch>show spanning-tree
3.1.8 QOS Commands Set
Table 3.8: QOS Commands Set
Netstar Commands Level Description Example
qos policy
[weighted-fair|strict]
qos prioritytype
[port-based|cos-only|tos-only|cosfirst|tos-first]
qos priority portbased
[Port] [lowest|low|middle|high]
qos priority cos
[Priority][lowest|low|middle|high]
qos priority tos
[Priority][lowest|low|middle|high]
show qos
no qos
Select QOS policy scheduling switch(config)#qos policy weighted-fair
G
Setting of QOS priority type switch(config)#qos prioritytype
G
Configure Port-based Priority switch(config)#qos priority portbased 1 low
G
Configure COS Priority switch(config)#qos priority cos 0 middle
G
Configure TOS Priority switch(config)#qos priority tos 3 high
G
Displays the information of QoS
P
configuration
Disable QoS function switch(config)#no qos
G
Switch#show qos
3.1.9 IGMP Commands Set
Table 3.9: QOS Commands Set
Netstar Commands Level Description Example
igmp enable
Igmp-query auto
Igmp-query force
show igmp configuration
show igmp multi
no igmp
no igmp-query
Enable IGMP snooping function switch(config)#igmp enable
G
Set IGMP query to auto mode switch(config)#Igmp- query auto
G
Set IGMP query to force mode switch(config)#Igmp-query force
G
Displays the details of an IGMP
P
configuration.
Displays the details of an IGMP
P
snooping entries.
Disable IGMP snooping function switch(config)#no igmp
G
Disable IGMP query switch#no igmp-query
G
3.1.10 Mac/Filter Table Commands Set
switch#show igmp configuration
switch#show igmp multi
33 Chapter3
Page 44

Table 3.10: Mac/Filter Table Commands Set
Netstar Commands Level Description Example
mac-address-table static hwaddr
[MAC]
mac-address-table filter hwaddr
[MAC]
show mac-address-table P Show all MAC address table switch#show mac-address-table
show mac-address-table static P Show static MAC address table switch#show mac-address-table static
show mac-address-table filter P Show filter MAC address table. switch#show mac-address-table filter
no mac-address-table static hwaddr
[MAC] I
no mac-address-table filter hwaddr
[MAC]
no mac-address-table
Configure MAC address table of
I
interface (static).
Configure MAC address
G
table(filter)
Remove an entry of MAC address
table of interface (static)
Remove an entry of MAC address
G
table (filter)
Remove dynamic entry of MAC
G
address table
switch(config)#interface fastEthernet 2
switch(config-if)#mac-address-table static hwaddr
000012345678
switch(config)#mac-address-table filter hwaddr
000012348678
switch(config)#interface fastEthernet 2
switch(config-if)#no mac-address-table static
hwaddr 000012345678
switch(config)#no mac-address-table filter hwaddr
000012348678
switch(config)#no mac-address-table
3.1.11 SNMP Commands Set
Table 3.11: SNMP Commands Set
Netstar Commands Level Description Example
snmp system-name
[System Name]
snmp system-location
[System Location]
snmp system-contact
[System Contact]
snmp agent-mode
[v1v2c|v3|v1v2cv3]
snmp community-strings [Community]
right
[RO/RW]
snmp-server host
[IP address]
community
[Community-string]
trap-version
[v1|v2c]
snmpv3 context-name
[Context Name ]
snmpv3 user
[User Name]
group
[Group Name]
password
[Authentication Password] [Privacy
Password]
snmpv3 access context-name
[Context Name ]
group
[Group Name ]
security-level
[NoAuthNoPriv|AuthNoPriv|AuthPriv]
match-rule
[Exact|Prifix]
views
[Read View Name] [Write View Name]
[Notify View Name]
snmpv3 mibview view
[View Name]
type
[Excluded|Included]
Set SNMP agent system name switch(config)#snmp system-name l2switch
G
Set SNMP agent system location switch(config)#snmp system-location lab
G
Set SNMP agent system contact switch(config)#snmp system-contact where
G
Select the agent mode of SNMP switch(config)#snmp agent-mode v1v2cv3
G
Add SNMP community string. switch(config)#snmp community-strings public
G
Configure SNMP server host
information and community string
G
Configure the context name switch(config)#snmpv3 context-name Test
G
Configure the userprofile for
SNMPV3 agent. Privacy password
could be empty.
G
Configure the access table of
SNMPV3 agent
G
Configure the mibview table of
SNMPV3 agent
G
right rw
switch(config)#snmp-server host 192.168.1.50
community public trap-version v1
(remove)
Switch(config)#
no snmp-server host
192.168.1.50
switch(config)#snmpv3 user test01 group G1
password AuthPW PrivPW
switch(config)#snmpv3 access context-name Test
group G1 security-level AuthPriv
match-rule Exact views V1 V1 V1
switch(config)#snmpv3 mibview view V1 type
Excluded sub-oid 1.3.6.1
EKI-7657C _Manual_ed1 34
Page 45

sub-oid
[OID]
show snmp P Show SNMP configuration switch#show snmp
no snmp community-strings
[Community]
no snmp-server host
[Host-address]
no snmpv3 user
[User Name]
no snmpv3 access context-name
[Context Name ]
group
[Group Name ]
security-level
[NoAuthNoPriv|AuthNoPriv|AuthPriv]
match-rule
[Exact|Prifix]
views
[Read View Name] [Write View Name]
[Notify View Name]
no snmpv3 mibview view
[View Name]
type
[Excluded|Included]
sub-oid
[OID]
Remove the specified community. switch(config)#no snmp community-strings public
G
Remove the SNMP server host. switch(config)#no snmp-server host 192.168.1.50
G
Remove specified user of SNMPv3
G
agent.
Remove specified access table of
SNMPv3 agent.
G
Remove specified mibview table of
SNMPV3 agent.
G
switch(config)#no snmpv3 user Test
switch(config)#no snmpv3 access context-name
Test group G1 security-level AuthPr
iv match-rule Exact views V1 V1 V1
switch(config)#no snmpv3 mibview view V1 type
Excluded sub-oid 1.3.6.1
3.1.12 Port Mirroring Commands Set
Table 3.12: Port Mirroring Commands Set
Netstar Commands Level Description Example
monitor rx
monitor tx
show monitor
monitor
[RX|TX|Both]
show monitor
no monitor
Set RX destination port of monitor
G
function
Set TX destination port of monitor
G
function
Show port monitor information switch#show monitor
P
Configure source port of monitor
I
function
Show port monitor information switch(config)#interface fastEthernet 2
I
Disable source port of monitor
I
function
3.1.13 802.1x Commands Set
Table 3.13: 802.1x Commands Set
Netstar Commands Level Description Example
8021x enable
8021x system radiusip
[IP address]
8021x system serverport
[port ID]
Use the 802.1x global
G
configuration command to enable
802.1x protocols.
Use the 802.1x system radius IP
G
global configuration command to
change the radius server IP.
Use the 802.1x system server port
G
global configuration command to
switch(config)#monitor rx
switch(config)#monitor tx
switch(config)#interface fastEthernet 2
switch(config-if)#monitor RX
switch(config-if)#show monitor
switch(config)#interface fastEthernet 2
switch(config-if)#no monitor
switch(config)# 8021x enable
switch(config)# 8021x system radiusip 192.168.1.1
switch(config)# 8021x system serverport 1812
35 Chapter3
Page 46

change the radius server port
8021x system accountport
[port ID]
8021x system sharedkey
[ID]
8021x system nasid
[words]
8021x misc quietperiod
[sec.]
8021x misc txperiod
[sec.]
8021x misc supptimeout [sec.]
G
8021x misc servertimeout [sec.]
8021x misc maxrequest [number]
G
8021x misc reauthperiod [sec.]
8021x portstate
[disable | reject | accept | authorize] I
show 8021x
no 8021x G Disable 802.1x function switch(config)#no 8021x
Use the 802.1x system account
G
port global configuration command
to change the accounting port
Use the 802.1x system share key
G
global configuration command to
change the shared key value.
Use the 802.1x system nasid
G
global configuration command to
change the NAS ID
Use the 802.1x misc quiet period
global configuration command to
G
specify the quiet period value of
the switch.
Use the 802.1x misc TX period
G
global configuration command to
set the TX period.
Use the 802.1x misc supp timeout
global configuration command to
set the supplicant timeout.
Use the 802.1x misc server
timeout global configuration
G
command to set the server
timeout.
Use the 802.1x misc max request
global configuration command to
set the MAX requests.
Use the 802.1x misc reauth period
G
global configuration command to
set the reauth period.
Use the 802.1x port state interface
configuration command to set the
state of the selected port.
Displays a summary of the 802.1x
E
properties and also the port sates.
switch(config)# 8021x system accountport 1813
switch(config)# 8021x system sharedkey 123456
switch(config)# 8021x system nasid test1
switch(config)# 8021x misc quietperiod 10
switch(config)# 8021x misc txperiod 5
switch(config)# 8021x misc supptimeout 20
switch(config)#8021x misc servertimeout 20
switch(config)# 8021x misc maxrequest 3
switch(config)# 8021x misc reauthperiod 3000
switch(config)#interface fastethernet 3
switch(config-if)#8021x portstate accept
switch>show 8021x
3.1.14 TFTP Commands Set
Table 3.14: TFTP Commands Set
Netstar Commands Level Description Defaults Example
backup flash:backup_cfg
restore flash:restore_cfg
upgrade flash:upgrade_fw
Save configuration to TFTP and need
to specify the IP of TFTP server and
G
the file name of image.
Get configuration from TFTP server
and need to specify the IP of TFTP
G
server and the file name of image.
Upgrade firmware by TFTP and need
to specify the IP of TFTP server and
G
the file name of image.
3.1.15 SystemLog, SMTP and Event
Table 3.15: SysLog,SMTP,Event Commands Set
Netstar Commands Level Description Example
systemlog ip
[IP address]
Set System log server IP address. switch(config)# systemlog ip 192.168.1.100
G
switch(config)#backup flash:backup_cfg
switch(config)#restore flash:restore_cfg
switch(config)#upgrade flash:upgrade_fw
EKI-7657C _Manual_ed1 36
Page 47

systemlog mode
[client|server|both]
show systemlog E Displays system log. Switch>show systemlog
show systemlog
no systemlog G Disable systemlog functon switch(config)#no systemlog
smtp enable G Enable SMTP function switch(config)#smtp enable
smtp serverip
[IP address]
smtp authentication G Enable SMTP authentication switch(config)#smtp authentication
smtp account
[account]
smtp password
[password]
smtp rcptemail
[Index] [Email address]
show smtp P Show the information of SMTP switch#show smtp
no smtp G Disable SMTP function switch(config)#no smtp
event device-cold-start
[Systemlog|SMTP|Both]
event authentication-failure
[Systemlog|SMTP|Both]
event ring-topology-change
[Systemlog|SMTP|Both]
event systemlog
[Link-UP|Link-Down|Both]
event smtp
[Link-UP|Link-Down|Both]
show event P Show event selection switch#show event
no event device-cold-start G Disable cold start event type switch(config)#no event device-cold-start
no event authentication-failure
no event ring-topology-change
no event systemlog
no event smpt
show systemlog
Specified the log mode switch(config)# systemlog mode both
G
Show system log client & server
P
information
Configure SMTP server IP switch(config)#smtp serverip 192.168.1.5
G
Configure authentication account switch(config)#smtp account User
G
Configure authentication password switch(config)#smtp password
G
Configure Rcpt e-mail Address switch(config)#smtp rcptemail 1 Alert@test.com
G
Set cold start event type switch(config)#event device-cold-start both
G
Set Authentication failure event
G
type
Set X - ring topology changed
G
event type
Set port event for system log switch(config)#interface fastethernet 3
I
Set port event for SMTP switch(config)#interface fastethernet 3
I
Disable Authentication failure
G
event type
Disable X - ring topology changed
G
event type
Disable port event for system log switch(config)#interface fastethernet 3
I
Disable port event for SMTP switch(config)#interface fastethernet 3
I
Show system log client & server
P
information
switch#show systemlog
switch(config)#event authentication-failure both
switch(config)#event ring-topology-change both
switch(config-if)#event systemlog both
switch(config-if)#event smtp both
switch(config)#no event authentication-failure
switch(config)#no event ring-topology-change
switch(config-if)#no event systemlog
switch(config-if)#no event smtp
switch#show systemlog
3.1.16 SNTP Commands Set
Table 3.16: SNTP Commands Set
Netstar Commands Level Description Example
sntp enable
sntp daylight
sntp daylight-period
[Start time] [End time]
sntp daylight-offset
[Minute]
sntp ip
[IP]
sntp timezone
[Timezone] G
show sntp P Show SNTP information switch#show sntp
Enable SNTP function switch(config)#sntp enable
G
Enable daylight saving time, if
SNTP function is inactive, this
G
command can’t be applied.
Set period of daylight saving time,
if SNTP function is inactive, this
command can’t be applied.
G
Parameter format:
[yyyymmdd-hh:mm]
Set offset of daylight saving time, if
SNTP function is inactive, this
G
command can’t be applied.
Set SNTP server IP, if SNTP
function is inactive, this command
G
can’t be applied.
Set timezone index, use “show
sntp timzezone” command to get
more information of index number
switch(config)#sntp daylight
switch(config)# sntp daylight-period 20060101-
01:01 20060202-01-01
switch(config)#sntp daylight-offset 3
switch(config)#sntp ip 192.169.1.1
switch(config)#sntp timezone 22
37 Chapter3
Page 48

show sntp timezone
no sntp
no sntp daylight
3.1.17 X-ring Commands Set
Table 3.17: X-ring Commands Set
Netstar Commands Level Description Example
ring enable
ring master
ring couplering
ring dualhoming
ring ringport
[1st Ring Port] [2nd Ring Port]
ring couplingport
[Coupling Port]
ring controlport
[Control Port]
ring homingport
[Dual Homing Port]
show ring
no ring
no ring master
no ring couplering
no ring dualhoming
Show index number of time zone
P
list
Disable SNTP function switch(config)#no sntp
G
Disable daylight saving time switch(config)#no sntp daylight
G
Enable X-ring switch(config)#ring enable
G
Enable ring master switch(config)#ring master
G
Enable couple ring switch(config)#ring couplering
G
Enable dual homing switch(config)#ring dualhoming
G
Configure 1st/2nd Ring Port switch(config)#ring ringport 7 8
G
Configure Coupling Port switch(config)#ring couplingport 1
G
Configure Control Port switch(config)#ring controlport 2
G
Configure Dual Homing Port switch(config)#ring homingport 3
G
Show the information of X - Ring switch#show ring
P
Disable X-ring switch(config)#no ring
G
Disable ring master switch(config)# no ring master
G
Disable couple ring switch(config)# no ring couplering
G
Disable dual homing switch(config)# no ring dualhoming
G
switch#show sntp timezone
EKI-7657C _Manual_ed1 38
Page 49

3.2 Web Browser
EKI-7657C provides a convenient configuring way via web browser. You can follow the steps below to
access EKI-7657C.
EKI-7657C’s default IP is 192.168.1.1. Make sure your host PC and EKI-7657C are on the same logical
sub-network.
Warning Your host PC should be in the same VLAN setting with EKI-7657C, or the
management will not be configured.
Connect EKI-7657C to the Ethernet then your host PC could be configured via Ethernet. Or you can
directly connect EKI-7657C to your host PC with a straight-through or cross over Ethernet cable.
Before to use web management, install the industrial switch on the network and make sure that any one
of PCs on the network can connect with the industrial switch through the web browser. The industrial
switch default value of IP, subnet mask, username and password are as below:
• IP Address: 192.168.1.1
• Subnet Mask: 255.255.255.0
• Default Gateway: 192.168.1.254
• User Name: admin
• Password: admin
Open Internet Explorer and type EKI-7657C’s IP in the Address field then press Enter to open the web
login page.
Figure 3.5: Type the address in the URL
Figure 3.6: Web Login Window
The default user name and password are both admin, fill in the user name and password then press OK
to enter the configuration. You can change the password in the system setting.
In the main page, you can find the tree menu structure of the EKI-7657C in the left side. Click the “+”
symbol to unroll the hiding hyperlink, and click the hyperlink to open the function page you want to
configure.
39 Chapter3
Page 50

Figure 3.7: Main page
EKI-7657C _Manual_ed1 40
Page 51

3.2.1 System
System Information
Here you can view the system information and assign the system name and location to make this switch
more easily to be identified on your network.
• System Name: Assign the name of the switch. The maximum length is 64 bytes.
• System Description: Displays the description of switch. Read only cannot be modified.
• System Location: Assign the switch physical location. The maximum length is 64 bytes.
• System Contact: Enter the name of contact person or organization.
• Firmware Version: Displays the switch’s firmware version.
• Kernel Version: Displays the kernel software version.
• MAC Address: Displays the unique hardware address assigned by manufacturer (default).
Warning Don’t set “0” for the first segment of the subnet mask and default gateway
(000.xxx.xxx.xxx).
Refresh the web screen if the web could not be displayed while you change
the setting.
Figure 3.8: System Information
41 Chapter3
Page 52

IP Configuration
User can configure the IP Settings and DHCP client function here.
• DHCP Client: Enable or disable the DHCP client function. When DHCP client function is enabled, the
industrial switch will be assigned an IP address from the network DHCP server. The default IP address
will be replaced by the assigned IP address on DHCP server. After user click Apply, a popup dialog
shows up. It is to inform the user that when the DHCP client is enabled, the current IP will lose and
user should find the new IP on the DHCP server.
• IP Address: Assign the IP address that the network is using. If DHCP client function is enabled, and
then the user doesn’t need to assign the IP address. And, the network DHCP server will assign the IP
address displaying in this column for the industrial switch. The default IP is 192.168.16.1.
• Subnet Mask: Assign the subnet mask to the IP address. If DHCP client function is enabled, and then
the user does not need to assign the subnet mask.
• Gateway: Assign the network gateway for the industrial switch. The default gateway is 192.168.16.254.
• DNS1: The abbreviation of Domain Name Server—an Internet service that translate domain name into
IP addresses. Domain name are alphabetic which are easy to be remembered. Because the Internet is
based on IP address; every time you use a domain name, therefore, a DNS service must translate the
name into the corresponding IP address. For example, the domain name www.net.com might
translate to 192.168.1.1
• DNS2: The backup for DNS1. When DNS1 cannot function, DNS2 will then replace DNS1 immediately.
Apply
And then, click
•
Figure 3.9: IP Configuration
EKI-7657C _Manual_ed1 42
Page 53

DHCP Server—System configuration
DHCP is the abbreviation of Dynamic Host Configuration Protocol that is a protocol for assigning
dynamic IP addresses to devices on a network. With dynamic addressing, a device can have a different
IP address every time it connects to the network. In some systems, the device's IP address can even
change while it is still connected. DHCP also supports a mix of static and dynamic IP addresses.
Dynamic addressing simplifies network administration because the software keeps track of IP addresses
rather than requiring an administrator to manage the task. This means that a new computer can be
added to a network without the hassle of manually assigning it a unique IP address.
The system provides the DHCP server function. The system provides the DHCP server function. Having
enabled the DHCP server function, the switch system can be a DHCP server.
• DHCP Server: Enable or Disable the DHCP Server function. Enable—the switch will be the DHCP
server on your local network.
• Low IP Address: Type in an IP address. Low IP address is the beginning of the dynamic IP range. For
example, dynamic IP is in the range between 192.168.1.100 ~ 192.168.1.200. In contrast,
192.168.1.100 is the Low IP address.
• High IP Address: Type in an IP address. High IP address is the end of the dynamic IP range. For
example, dynamic IP is in the range between 192.168.1.100 ~ 192.168.1.200. In contrast,
192.168.1.200 is the High IP address.
• Subnet Mask: Type in the subnet mask of the IP configuration.
• Gateway: Type in the IP address of the gateway in your network.
• DNS: Type in the Domain Name Server IP Address in your network.
• Lease Time (sec): It is the time period that system will reset the dynamic IP assignment to ensure the
dynamic IP will not been occupied for a long time or the server doesn’t know that the dynamic IP is idle.
Apply
And then, click
•
.
Figure 3.10: DHCP Server – System Configuration
DHCP Client—System Configuration
When the DHCP server function is active, the system will collect the DHCP client information and
displays it here.
43 Chapter3
Page 54

Figure 3.11: DHCP Server – Client Entries
DHCP Server—Port and IP Bindings
Assign the dynamic IP address to the port. When the device is connecting to the port and asks for IP
assigning, the system will assign the IP address that has been assigned before to the connected device.
Figure 3.12: DHCP Server – Port and IP Binding
EKI-7657C _Manual_ed1 44
Page 55

TFTP—Update Firmware
Trivial File Transfer Protocol (TFTP) is a very simple file transfer protocol, with the functionality of a very
basic form of FTP. It provides the functions to allow the user to update the switch firmware. Before
updating, make sure you have your TFTP server ready and the firmware image is on the TFTP server.
• TFTP Server IP Address: Fill in your TFTP server IP.
• Firmware File Name: Type in the name of firmware image.
Apply
And then, click
•
.
Figure 3.13: TFTP – Update Firmware
TFTP—Restore Configuration
You can restore the configuration from TFTP server. Before doing that, you must put the image file on
TFTP server first and the switch will download back the flash image.
• TFTP Server IP Address: Fill in the TFTP server IP.
• Restore File Name: Fill in the correct restore file name.
Click
•
Apply
45 Chapter3
Page 56

Figure 3.14: TFTP – Restore Configuration
TFTP—Backup Configuration
You can save current Flash ROM value from the switch to TFTP server for restoring later.
• TFTP Server IP Address: Fill in the TFTP server IP
• Backup File Name: Fill in the file name
Apply
Click
•
.
Figure 3.15: TFTP – Backup Configuration
EKI-7657C _Manual_ed1 46
Page 57

System Event Log—Syslog Configuration
Configure the system event mode to collect system log.
• Syslog Client Mode: Select the system log mode—Client Only, Server Only, or Both.
• System Log Server IP Address: Assign the system log server IP.
When Syslog Client Mode is set as
•
switch’s RAM until next reboot. When Syslog Client Mode is set as
only be sent to the syslog server and you have to type the IP address in the Sysylog Server IP Address
column. If the Syslog Client Mode is set as
and sent to server.
Click
•
Reload
to refresh the events log.
Client Only
, the system event log will only be reserved in the
Server Only
, the system log will be reserved in the switch’s RAM
Both
, the system log will
Click
•
After configuring, click
•
Clear
to clear all current events log.
Apply
.
Figure 3.16: Syslog Configuration
System Event Log—SMTP Configuration
You can set up the mail server IP, mail account, password, and forwarded email account for receiving the
event alert.
• Email Alert: Enable or disable the email alert function.
• SMTP Server IP: Set up the mail server IP address (when Email Alert enabled, this function will then
be available).
47 Chapter3
Page 58

• Sender: Type in an alias of the switch in complete email address format, e.g. switch01@123.com
identify where the event log comes from.
• Authentication: Tick the checkbox to enable this function, configuring the email account and
password for authentication (when Email Alert enabled, this function will then be available).
• Mail Account: Set up the email account, e.g. Tomadmin
email account on the mail server, which you had set up in SMTP Server IP Address column.
• Passw ord: Type in the password to the email account.
• Confirm Password: Reconfirm the password.
• Rcpt e-mail Address 1 ~ 6: You can also assign up to 6 e-mail accounts to receive the alert.
Apply
Click
•
.
, to receive the alert. It must be an existing
, to
Figure 3.17: SMTP Configuration
System Event Log—Event Configuration
When the
Also, per port log (link up, link down, and both) events can be sent to the system log server/SMTP server
with the respective checkbox ticked. After configuring, click ‘Apply’ to have the setting taken effect.
• System event selection: There are 4 event types—Device cold start, Device warm start,
Authentication Failure, and X-ring topology change. Before you can tick the checkbox of each event
type, the Syslog Client Mode column on the Syslog Configuration tab/E-mail Alert column on the SMTP
Configuration tab must be enabled first.
Syslog/SMTP
¾ Device cold start: When the device executes cold start action, the system will issue a log
event.
¾ Device warm start: When the device executes warm start, the system will issue a log event.
¾ Authentication Failure: When the SNMP authentication fails, the system will issue a log event.
¾ X-ring topology change: When the X-ring topology has changed, the system will issue a log
event.
checkbox is ticked, the event log will be sent to system log server/SMTP server.
EKI-7657C _Manual_ed1 48
Page 59

• Port event selection: Also, before the drop-down menu items are available, the Syslog Client Mode
column on the Syslog Configuration tab/E-mail Alert column on the SMTP Configuration tab must be
enabled first. Those drop-down menu items have 3 selections—Link UP, Link Down, and Link UP &
Link Down. Disable means no event will be sent to the system log server/SMTP server.
¾ Link UP: The system will issue a log message when port connection links up only.
¾ Link Down: The system will issue a log message when port connection links down only.
¾ Link UP & Link Down: The system will issue a log message when port connection is up and
down.
Figure 3.18: Event Configuration
Fault Relay Alarm
• Pow er Failure: Tick the checkbox to enable the function of lighting up the FAULT LED on the panel
when power fails.
• Port Link Dow n/Broken: Tick the checkbox to enable the function of lighting up FAULT LED on the
panel when ports’ states are link-down or broken.
49 Chapter3
Page 60

Figure 3.19: Fault Relay Alarm
EKI-7657C _Manual_ed1 50
Page 61

A
A
A
A
SNTP Configuration
You can configure the SNTP (Simple Network Time Protocol) settings which allow you to synchronize
switch clocks on the Internet.
• SNTP Client: Enable/disable SNTP function to get the time from the SNTP server.
• Daylight Saving Time: Enable/disable daylight saving time function. When daylight saving time is
enabled, you need to configure the daylight saving time period.
• UTC Timezone: Set the switch location time zone. The following table lists the different location time
zone for your reference.
Table 3.18: UTC Timezone
Local Time Zone Conversion from UTC Time at 12:00 UTC
November Time Zone - 1 hour 11am
Oscar Time Zone -2 hours 10 am
DT - Atlantic Daylight -3 hours 9 am
ST - Atlantic Standard
EDT - Eastern Daylight
EST - Eastern Standard
CDT - Central Daylight
CST - Central Standard
MDT - Mountain Daylight
MST - Mountain Standard
PDT - Pacific Daylight
PST - Pacific Standard
DT - Alaskan Daylight
LA - Alaskan Standard -9 hours 3 am
HAW - Hawaiian Standard -10 hours 2 am
Nome, Alaska -11 hours 1 am
CET - Central European
FWT - French Winter
MET - Middle European
MEWT - Middle European Winter
SWT - Swedish Winter
-4 hours 8 am
-5 hours 7 am
-6 hours 6 am
-7 hours 5 am
-8 hours 4 am
+1 hour 1 pm
EET - Eastern European, USSR Zone 1 +2 hours 2 pm
BT - Baghdad, USSR Zone 2 +3 hours 3 pm
ZP4 - USSR Zone 3 +4 hours 4 pm
51 Chapter3
Page 62

ZP5 - USSR Zone 4 +5 hours 5 pm
ZP6 - USSR Zone 5 +6 hours 6 pm
WAST - West Australian Standard +7 hours 7 pm
CCT - China Coast, USSR Zone 7 +8 hours 8 pm
JST - Japan Standard, USSR Zone 8 +9 hours 9 pm
EAST - East Australian Standard GST
Guam Standard, USSR Zone 9
IDLE - International Date Line
NZST - New Zealand Standard
NZT - New Zealand
+10 hours 10 pm
+12 hours Midnight
• SNTP Sever URL: Set the SNTP server IP address.
• Switch Timer: Displays the current time of the switch.
• Da ylight Saving Period: Set up the Daylight Saving beginning time and Daylight Saving ending time.
Both will be different in every year.
• Da ylight Saving Offset (mins): For non-US and European countries, specify the amount of time for
day light savings.
Apply
Click
•
.
Figure 3.20: SNTP Configuration
EKI-7657C _Manual_ed1 52
Page 63

IP Security
IP security function allows the user to assign 10 specific IP addresses that have permission to access the
switch through the web browser for the securing switch management.
• IP Securit y Mode: When this option is in Enable mode, the Enable HTTP Server and Enable Telnet
Server checkboxes will then be available.
• Enable HTTP Ser ver: When this checkbox is ticked, the IP addresses among Security IP1 ~ IP10 will
be allowed to access this switch via HTTP service.
• Enable Telnet Server: When this checkbox is ticked, the IP addresses among Security IP1 ~ IP10 will
be allowed to access this switch via telnet service.
• Securit y IP 1 ~ 10: The system allows the user to assign up to 10 specific IP addresses for access
security. Only these 10 IP addresses can access and manage the switch through the HTTP/Telnet
service.
Apply
And then, click
•
to apply the configuration.
Note Remember to execute the “Save Configuration” action, otherwise the new
configuration will lose when switch power off.
Figure 3.21: IP Security
53 Chapter3
Page 64

User Authentication
Change web management login user name and password for the management security issue.
• User name: Key in the new user name (The default is “admin”).
• Passw ord: Key in the new password (The default is “admin”).
• Confirm password: Re-type the new password.
Apply
And then, click
•
to apply the configuration.
Figure 3.22: User Authentication
EKI-7657C _Manual_ed1 54
Page 65

Digital Input/Output
The EKI-7657C contains two digital inputs and two digital outputs. The digital inputs may be used to
receive the voltage-changing signal of the remote equipment to sense the state of the remote equipment
like heater, pump, and other electrical equipment. Therefore the switch can be configured to send system
log, SMTP and SNMP traps to syslog server, SMTP server and SNMP trap station respectively (please
refer to System Event Log and SNMP configuration section). Outputs are open-collector transistor
switches used to connect to the external device like alarm buzzer or LED to inform the user of the
port/power status.
Digital Input
When First/Second Digital Input function is enabled, their
•
Action
Digital Input:
•
setting items will then be available respectively.
Choose the transition type to trigger DI0/DI1.
Digital Input, Event Description
¾ LowÆHigh: Having focused this radio button, DI0/DI1 will only report the status when the
external device’s voltage changes from low to high.
¾ HighÆLow: Having focused this radio button, DI0/DI1 will only report the status when the
external device’s voltage changes from high to low.
Event description:
•
Action:
•
Trap.
Tick the check boxes to decide whether or not to send the events via Syslog, SMTP, or SNMP
Please fill in the description for the event.
Digital Output
When First/Second Digital Output function is enabled, their
•
Condition
and
Action
setting items will
then be available respectively.
Condition:
•
(DO0)/Second Digital Output (DO1) when the condition of ticked checkbox is met.
The system will send an electrical Low-to-High or High-to-Low signal to First Digital Output
¾ Port Fail: Having ticked this checkbox, DO0/DO1 will output an electrical Low-to-High or High-
to-Low signal when port failure occurs.
¾ Power Fail: Having ticked this checkbox, DO0/DO1 will output an electrical Low-to-High or
High-to-Low signal when power failure occurs.
Action: Choose the output type of electrical signal.
•
¾ LowÆHigh: Having focused this radio button, DO0/DO1 will output an electrical signal of Low-
to-High when the condition of the ticked checkbox is met (port/power failure occurs).
¾ HighÆLow: Having focused this radio button, DO0/DO1 will output an electrical signal of Low-
to-High when the condition of the ticked checkbox is met (port/power failure occurs).
Note Besides ticking the checkboxes in the Condition column field, the power/port failure
checkboxes of Fault Relay Alarm have to be ticked as the precondition. Please refer to
Fault Relay Alarm section. Also, please notice that the digital output can’t connect to
the external device using power higher than 40V/200mA.
and
55 Chapter3
Page 66

Figure 3.23: Digital Input/Output interface
EKI-7657C _Manual_ed1 56
Page 67

3.2.2 Port
Port setting includes Port Statistics, Port Control, Port Trunk, Port Mirroring, and Rate Limiting. The user
can use this interface to set the parameters and control the packet flow among the ports.
Port Statistics
The following information provides the current port statistic information.
• Port: Displays the port number.
•
• Link: The status of linking—‘Up’ or ‘Down’.
• State: The user can set the state of the port as ‘Enable’ or ‘Disable’ via Port Control. When the state is
• Tx Good Packet: The counts of transmitting good packets via this port.
• Tx Bad Packet: The counts of transmitting bad packets (including undersize [less than 64 bytes],
• Rx Good Packet: The counts of receiving good packets via this port.
• Rx Bad Packet: The counts of receiving bad packets (including undersize [less than 64 bytes],
• Tx Abort Packet: The aborted packet while transmitting.
• Packet Collision: The counts of collision packet.
• Packet Dropped: The counts of dropped packet.
• Rx Bcast Packet: The counts of broadcast packet.
• Rx Mcast Packet: The counts of multicast packet.
Click
•
Displays the media type of the port.
Type:
disabled, the port will not transmit or receive any packet.
oversize, CRC Align errors, fragments and jabbers packets) via this port.
oversize, CRC error, fragments and jabbers) via this port.
Clear
to clean all counts.
Figure 3.24: Port Statistics
57 Chapter3
Page 68

Port Control
In Port Control, you can pull down the selection items to set the parameters of each port to control the
transmitting/receiving packets.
• Port: Select the port that you want to configure.
• State: Current port status. The port can be set to disable or enable mode. If the port state is set as
‘Disable’, it will not receive or transmit any packet.
• Negotiation: Auto and Force. Being set as Auto, the speed and duplex mode are negotiated
automatically. When you set it as Force, you have to assign the speed and duplex mode manually.
• Speed: It is available for selecting when the Negotiation column is set as Force. When the Negotiation
column is set as Auto, this column is read only.
• Duplex: It is available for selecting when the Negotiation column is set as Force. When the Negotiation
column is set as Auto, this column is read only.
• Flow Control: Set flow control function as Enable or Disable. When enabled, once the device exceed
the input data rate of another device as a result the receiving device will send a PAUSE frame which
halts the transmission of the sender for a specified period of time. When disabled, the receiving device
will drop the packet if too much to process.
• Security: Once the Security selection is set as ‘On’, any access from the device which connects to this
port will be blocked unless the MAC address of the device is included in the static MAC address table.
See the segment of Static MAC Table.
Apply
Click
•
to make the configuration effective.
Figure 3.25: Port Control
EKI-7657C _Manual_ed1 58
Page 69

Port Trunk
The Link Aggregation Control Protocol (LACP) provides a standardized means for exchanging
information between Partner Systems on a link to allow their Link Aggregation Control instances to reach
agreement on the identity of the Link Aggregation Group to which the link belongs, move the link to that
Link Aggregation Group, and enable its transmission and reception functions in an orderly manner. Link
aggregation lets you group up to 4 ports into one dedicated connections. This feature can expand
bandwidth to a device on the network. LACP operation requires full-duplex mode, more detail
information refers to IEEE 802.3ad.
Aggregator setting
• System Priority: A value which is used to identify the active LACP. The switch with the lowest value
has the highest priority and is selected as the active LACP.
Group ID:
•
There are four trunk groups to be selected. Choose the ‘
Group ID
’ and click
Select
• LACP: When enabled, the trunk group is using LACP. A port which joins an LACP trunk group has to
make an agreement with its member ports first. When disabled, the trunk group is a static trunk group.
The advantage of having the LACP disabled is that a port joins the trunk group without any
handshaking with its member ports. But member ports won’t know that they should be aggregated
together to form a logic trunk group.
• Work ports: This column field allows the user to type in the total number of active port up to four. With
LACP trunk group, you create a trunk group by connecting two or more switches (e.g. you assign four
ports to be the members of a trunk group whose work ports column field is set as two). The exceed
ports are standby (the Aggregator Information tab will show standby status on the exceed ports) and
can be aggregated if work ports fail. If it is a static trunk group, the number of work ports must equal
the total number of group member ports.
Select the ports to join the trunk group. The system allows four ports maximum to be aggregated in a
•
Add
trunk group. Click
to add the port which is focused to the left field. To remove unwanted ports,
.
select the port and click
When LACP enabled, you can configure LACP Active/Passive status for each port on State Activity
•
Remove
.
page.
Click
•
Use
•
Apply
.
Apply
to delete Trunk Group. Select the Group ID and click
Delete
.
59 Chapter3
Page 70

Figure 3.26: 2 work ports with LACP enabled
Aggregator Information
When you have set up the aggregator setting with LACP disabled, you will see the local static trunk group
information as below.
Figure 3.27: 2 work ports with LACP disabled
EKI-7657C _Manual_ed1 60
Page 71

Figure 3.28: Static trunking group of 2 ports on single switch
When you have set up the aggregator setting of two interconnected switches with LACP enabled, you will
see the respective LACP trunk group information as below. ‘Actor’ means the switch which is connecting
to the host computer.
Figure 3.29: Aggregator Information
State Activity
Having set up the LACP aggregator on the tab of Aggregator Setting, you can configure the state activity
for the members of the LACP trunk group. You can tick or cancel the checkbox beside the state display.
When you remove the tick mark to the port and click
Passive
.
Apply
, the port state activity will change to
• Active: The port automatically sends LACP protocol packets.
• Passive: The port does not automatically send LACP protocol packets, and responds only if it receives
LACP protocol packets from the opposite device.
Note A link having either two active LACP nodes or one active node can perform
dynamic LACP trunk.
A link having two passive LACP nodes will not perform dynamic LACP trunk
61 Chapter3
Page 72

because both ports are waiting for an LACP protocol packet from the opposite
device.
Figure 3.30: State Activity
EKI-7657C _Manual_ed1 62
Page 73

Port Mirroring
The Port mirroring is a method for monitoring traffic in switched networks. Traffic through ports can be
monitored by one specific port which means traffic goes in or out monitored (source) ports will be
duplicated into mirroring (destination) port.
• Destination Port: There is only one port can be selected to be the destination (mirroring) port for
monitoring both RX and TX traffic which come from the source port. Or, use one of two ports for
monitoring RX traffic only and the other one for TX traffic only. The user can connect the mirroring port
to LAN analyzer or Netxray.
• Source Port: The ports that the user wants to monitor. All monitored port traffic will be copied to
mirroring (destination) port. The user can select multiple source ports by ticking the RX or TX
checkboxes to be monitored.
And then, click
•
Apply
.
Figure 3.31: Port Mirroring
63 Chapter3
Page 74

Rate Limiting
Here you can set up every port’s frame limitation type and bandwidth rate.
• Ingress Limit Frame type: Select the frame type you want to filter. The frame types have 4 options for
selecting: All, Broadcast/Multicast/Flooded Unicast, Broadcast/Multicast, and Broadcast only.
The four frame type options are for ingress frames limitation. The egress rate only supports ‘All’ type.
All ports support port ingress and egress rate control. For example, assume port 1 is 10Mbps; the user
can set the effective egress rate of port 1 as 1Mbps, ingress rate 500Kbps. The switch performs the
ingress rate by packet counter to meet the specified rate
• Ingress: Enter the port effective ingress rate (The default value is “0”)
• Egress: Enter the port effective egress rate (The default value is “0”)
Apply
And then, click
•
to make the settings taken effect.
Figure 3.32: Rate Limiting
EKI-7657C _Manual_ed1 64
Page 75

3.2.3 Protocol
The user can set the layer 2 protocol setting via this interface.
VLAN configuration
A Virtual LAN (VLAN) is a logical network grouping that limits the broadcast domain, which would allow
you to isolate network traffic, so only the members of the same VLAN will receive traffic from the ones of
the same VLAN. Basically, creating a VLAN from a switch is logically equivalent of reconnecting a group
of network devices to another Layer 2 switch. However, all the network devices are still plugged into the
same switch physically.
The switch supports
operation mode is “
Port-based
Disable
”.
and
802.1Q
(tagged-based) VLAN. The default configuration of VLAN
Figure 3.33: VLAN Configuration
VLAN configuration - Port-based VLAN
Packets can go among only members of the same VLAN group. Note all unselected ports are treated as
belonging to another single VLAN. If the port-based VLAN enabled, the VLAN-tagging is ignored.
In order for an end station to send packets to different VLAN groups, it itself has to be either capable of
tagging packets it sends with VLAN tags or attached to a VLAN-aware bridge that is capable of
classifying and tagging the packet with different VLAN ID based on not only default PVID but also other
information about the packet, such as the protocol.
65 Chapter3
Page 76

Figure 3.34: Port based mode
Pull down the selection item and focus on
•
Mode in
Click
•
Port Based
to add a new VLAN group.
Add
mode.
Port Based
then press
Apply
to set the VLAN Operation
EKI-7657C _Manual_ed1 66
Page 77

Apply
Figure 3.35: Port based mode-Add interface
Enter the group name and VLAN ID. Add the port number having selected into the right field to group
•
these members to be a VLAN group or remove any of them listed in the right field from the VLAN.
And then, click
•
You will see the VLAN displays.
•
to have the settings taken effect.
67 Chapter3
Page 78

Figure 3.36: Port Based Edit/Delete interface
Use
•
Use
•
Delete
to delete the VLAN.
Edit
to modify group name, VLAN ID, or add/remove the members of the existing VLAN group.
Note Remember to execute the “Save Configuration” action, otherwise the new
configuration will lose when switch power off.
802.1Q VLAN
Tagged-based VLAN is an IEEE 802.1Q specification standard. Therefore, it is possible to create a VLAN
across devices from different switch venders. IEEE 802.1Q VLAN uses a technique to insert a “tag” into
the Ethernet frames. Tag contains a VLAN Identifier (VID) that indicates the VLAN numbers.
You can create Tag-based VLAN, and enable or disable GVRP protocol. There are 256 VLAN groups to
provide configuration. Enable 802.1Q VLAN, all ports on the switch belong to default VLAN of VID 1. The
default VLAN can’t be deleted.
GVRP (GARP VLAN Registration Protocol) is a protocol that facilitates control of virtual local area
networks (VLANs) within a larger network. GVRP conforms to the IEEE 802.1Q specification, which
defines a method of tagging frames with VLAN configuration data. This allows network devices to
dynamically exchange VLAN configuration information with other devices.
GVRP is based on GARP (Generic Attribute Registration Protocol), a protocol that defines procedures by
which end stations and switches in a local area network (LAN) can register and de-register attributes,
such as identifiers or addresses, with each other.
Every end station and switch thus has a current record of all the other end stations and switches that can
be reached.
802.1Q Configuration
EKI-7657C _Manual_ed1 68
Page 79

Apply
Pull down the selection item and focus on
•
Mode in
Enable GVRP Protocol:
•
802.1Q
the VLAN Operation Mode is in
Management VLAN ID:
•
mode.
Tick the checkbox to enable GVRP protocol. This checkbox is available while
802.1Q
mode.
The default value is ‘0’ which means VLAN function in 802.1Q mode is not
802.1Q
then press
to set the VLAN Operation
available. While this column field is filled with a value from 1 to 4096, the member ports of this VLAN
can access the management interface.
Select the port you want to configure.
•
Link Type:
•
there are 3 types of link type.
¾ Access Link: Single switch only, it allows the user to group ports by assigning the same
Untagged VID. While this link type is set, the Untagged VID column field is available but the
Tagged VID column field is disabled.
¾ Trunk Link: The extended application of Access Link. It allows the tagged frames go across
two or more switches by assigning the tag with VID to the frames. Having set this link type, the
Tagged VID column field is available but the Untagged VID column field is disabled.
¾ Hybrid Link: Both Access Link and Trunk Link are available.
Untagged VID:
•
Tagged VID:
•
Click
•
Apply
Assign the untagged frame VID.
Assign the tagged frame VID.
to have the settings taken effect.
Figure 3.37: 802.1Q VLAN Configuration
Group Configuration
Edit the existing VLAN Group.
Select the VLAN group in the table list.
•
69 Chapter3
Page 80

Edit
Click
•
.
You can Change the VLAN group name and VLAN ID.
•
Click
•
Rapid Spanning Tree
Apply
Figure 3.38: Edit Group Configuration interface
Figure 3.39: 802.1Q Group Configuration-Edit
.
EKI-7657C _Manual_ed1 70
Page 81

The Rapid Spanning Tree Protocol (RSTP) is an evolution of the Spanning Tree Protocol and provides for
faster spanning tree convergence after a topology change. The system also supports STP and the
system will auto-detect the connected device that is running STP or RSTP protocol.
71 Chapter3
Page 82

y
RSTP—System Configuration
The user can view spanning tree information of the Root Bridge.
•
The user can modify RSTP state. After modification, click
•
¾ RSTP mode: The user must enable the RSTP function first before configuring the related
parameters.
¾ Priority (0-61440): The switch with the lowest value has the highest priority and is selected as
the root. If the value is changed, the user must reboot the switch. The value must be a multiple
of 4096 according to the protocol standard rule.
¾ Max Age (6-40): The number of seconds a switch waits without receiving Spanning-tree
Protocol configuration messages before attempting a reconfiguration. Enter a value between 6
through 40.
¾ Hello Time (1-10): The time that controls the switch to send out the BPDU packet to check
RSTP current status. Enter a value between 1 through 10.
¾ Forward Delay Time (4-30): The number of seconds a port waits before changing from its
Rapid Spanning-Tree Protocol learning and listening states to the forwarding state. Enter a
value between 4 through 30.
Appl
.
Note Follow the rule to configure the MAX Age, Hello Time, and Forward Delay
Time.
2 x (Forward Delay Time value –1) > = Max Age value >= 2 x (Hello Time
value +1)
Figure 3.40: RSTP System Configuration interface
RSTP—Port Configuration
Here you can configure the path cost and priority of each port.
Select the port in the port column field.
•
Path Cost:
•
Enter a number 1 through 200,000,000.
Priority:
•
port of the highest value will be blocked). The value of priority must be the multiple of 16.
EKI-7657C _Manual_ed1 72
The cost of the path to the other bridge from this transmitting bridge at the specified port.
Decide which port should be blocked by priority in LAN. Enter a number 0 through 240 (the
Page 83

Apply
Admin P2P:
•
whether the port concerned can only be connected to exactly one other bridge (i.e. it is served by a
point-to-point LAN segment), or can be connected to two or more bridges (i.e. it is served by a shared
medium LAN segment). This function allows the P2P status of the link to be manipulated
administratively. True is P2P enabling. False is P2P disabling.
Admin Edge:
•
configure the port as an edge port, set the port to “
Admin Non Stp:
•
mathematic calculation.
Click
•
Some of the rapid state transactions that are possible within RSTP are dependent upon
The port directly connected to end stations won’t create bridging loop in the network. To
” status.
True
The port includes the STP mathematic calculation.
is including the STP mathematic calculation.
False
.
is not including STP
True
Figure 3.41: RSTP Port Configuration interface
73 Chapter3
Page 84

A
SNMP Configuration
Simple Network Management Protocol (SNMP) is the protocol developed to manage nodes (servers,
workstations, routers, switches and hubs etc.) on an IP network. SNMP enables network administrators to
manage network performance, find and solve network problems, and plan for network growth. Network
management systems learn of problems by receiving traps or change notices from network devices
implementing SNMP.
System Configuration
Community Strings
Here you can define the new community string set and remove the unwanted community string.
String:
•
RO:
•
information.
RW:
•
information and to set MIB objects.
Click
•
To remove the community string, select the community string that you have defined and click
•
Fill the name string.
Read only. Enables requests accompanied by this community string to display MIB-object
Read write. Enables requests accompanied by this community string to display MIB-object
dd
.
Remove
. You cannot edit the name of the default community string set.
Agent Mode
Select the SNMP version that you want to use and then click
Change
to switch to the selected SNMP
version mode. The default value is ‘SNMP v1/v2c only’
Figure 3.42: SNMP System Configuration interface
Trap Configuration
EKI-7657C _Manual_ed1 74
Page 85

A
A trap manager is a management station that receives the trap messages generated by the switch. If no
trap manager is defined, no traps will be issued. Create a trap manager by entering the IP address of the
station and a community string. To define a management station as a trap manager, assign an IP
address, enter the SNMP community strings, and select the SNMP trap version.
IP Address:
•
Community:
•
Trap Version:
•
Click
•
To remove the community string, select the community string listed in the current managers field and
•
Remove
click
Enter the IP address of the trap manager.
Enter the community string.
Select the SNMP trap version type—v1 or v2c.
dd
.
.
Figure 3.43: Trap Configuration interface
SNMPV3 Configuration
Configure the SNMP V3 function.
Context Table
Configure SNMP v3 context table. Assign the context name of context table. Click
name. Click
Remove
to remove unwanted context name.
User Profile
Configure SNMP v3 user table.
User ID:
•
Authentication Password:
•
Privacy Password:
•
Click
•
Click
•
Set up the user name.
Set up the private password.
Add
to add context name.
Remove
to remove unwanted context name.
Set up the authentication password.
Add
to add context
75 Chapter3
Page 86

Figure 3.44: SNMP V3 Configuration interface
Group Table
Configure SNMP v3 group table.
Security Name (User ID):
•
Group Name:
•
Click
•
Click
•
Add
Remove
Set up the group name.
to add context name.
to remove the unwanted context name.
Assign the user name that you have set up in user table.
EKI-7657C _Manual_ed1 76
Page 87

Access Table
Configure SNMP v3 access table.
Context Prefix:
•
Group Name:
•
Security Level:
•
Context Match Rule:
•
Read View Name:
•
Write View Name:
•
Notify View Name:
•
Click
•
Add
Set up the context name.
Set up the group.
Set up the access level.
to add context name.
Select the context match rule.
Set up the read view.
Set up the write view.
Set up the notify view.
Click
•
Remove
to remove unwanted context name.
MIBview Table
Configure MIB view table.
ViewName:
•
Sub-Oid Tree:
•
Type:
•
Click
•
Click
•
Set up the name.
Fill the Sub OID.
Select the type—excluded or included.
Add
to add context name.
Remove
to remove unwanted context name.
77 Chapter3
Page 88

QoS Configuration
Here you can configure Qos policy and priority setting, per port priority setting, COS and TOS setting.
QoS Policy and Priority Type
Qos Policy:
•
Select the QoS policy rule.
¾ Use an 8,4,2,1 weighted fair queuing scheme: The switch will follow 8:4:2:1 rate to process
priority queue from High to lowest queue. For example, while the system processing, 1 frame of
the lowest queue, 2 frames of the low queue, 4 frames of the middle queue, and 8 frames of the
high queue will be processed at the same time in accordance with the 8,4,2,1 policy rule.
¾ Use a strict priority scheme: Always the higher queue will be processed first, except the
higher queue is empty.
Click
•
¾
Priority Type:
only, TOS first
Apply
to make the settings effective.
There are 5 priority type selections available—
, and
COS first
. Disable means no priority type is selected.
Port-based, TOS only, COS
Figure 3.45: QoS Configuration interface
EKI-7657C _Manual_ed1 78
Page 89

Port Base Priority
Configure the priority level for each port. With the drop-down selection item of Priority Type above being
selected as Port-based, this control item will then be available to set the queuing policy for each port.
Port x:
•
Click
•
Each port has 4 priority levels—High, Middle, Low, and Lowest—to be chosen.
Apply
to have the settings taken effect.
COS Configuration
Set up the COS priority level. With the drop-down selection item of Priority Type above being selected
as COS only/COS first, this control item will then be available to set the queuing policy for each port.
COS priority:
•
Click
•
Apply
Set up the COS priority level 0~7—High, Middle, Low, Lowest.
.
TOS Configuration
Set up the TOS priority. With the drop-down selection item of Priority Type above being selected as TOS
only/TOS first, this control item will then be available to set the queuing policy for each port.
TOS priority:
•
The system provides 0~63 TOS priority level. Each level has 4 types of priority—High,
Middle, Low, and Lowest. The default value is ‘Lowest’ priority for each level. When the IP packet is
received, the system will check the TOS level value in the IP packet that has received. For example,
the user sets the TOS level 25 as high, the system will check the TOS value of the received IP packet.
If the TOS value of received IP packet is 25 (priority = high), and then the packet priority will have
highest priority.
Click
•
Apply
to make the settings taken effect.
79 Chapter3
Page 90

IGMP Configuration
The Internet Group Management Protocol (IGMP) is an internal protocol of the Internet Protocol (IP) suite.
IP manages multicast traffic by using switches, routers, and hosts that support IGMP. Enabling IGMP
allows the ports to detect IGMP queries, report packets, and manage IP multicast traffic through the
switch. IGMP have three fundamental types of message shown as follows:
Table 3.19: IGMP types
Message Description
Query
Report
Leave Group
A message sent from the querier (IGMP router or switch) asking for a response from each host
belonging to the multicast group.
A message sent by a host to the querier to indicate that the host wants to be or is a member of a
given group indicated in the report message.
A message sent by a host to the querier to indicate that the host has quit being a member of a
specific multicast group.
The switch supports IP multicast. You can enable IGMP protocol via setting the IGMP Configuration page
to see the IGMP snooping information. IP multicast addresses are in the range of 224.0.0.0 through
239.255.255.255.
IGMP Protocol:
•
IGMP Query:
•
IGMP version 2 multicast networks.
Click
•
Apply
Enable or disable the IGMP protocol.
Select the IGMP query function as Enable or Auto to set the switch as a querier for
.
Figure 3.46: IGMP Configuration interface
EKI-7657C _Manual_ed1 80
Page 91

X-Ring
X-Ring provides a faster redundant recovery than Spanning Tree topology. The action is similar to STP or
RSTP, but the algorithms between them are not the same.
In the X-Ring topology, every switch should be enabled with X-Ring function and two ports should be
assigned as the member ports in the ring. Only one switch in the X-Ring group would be set as the
master switch that one of its two member ports would be blocked, called backup port, and another port is
called working port. Other switches in the X-Ring group are called working switches and their two
member ports are called working ports. When the failure of network connection occurs, the backup port of
the master switch (Ring Master) will automatically become a working port to recover from the failure.
The switch supports the function and interface for setting the switch as the ring master or not. The ring
master can negotiate and place command to other switches in the X-Ring group. If there are 2 or more
switches in master mode, the software will select the switch with lowest MAC address number as the ring
master. The X-Ring master ring mode can be enabled by setting the X-Ring configuration interface. Also,
the user can identify whether the switch is the ring master by checking the R.M. LED indicator on the
panel of the switch.
The system also supports the Couple Ring that can connect 2 or more X-Ring group for the redundant
backup function; Dual Homing function that can prevent connection lose between X-Ring group and
upper level/core switch. Apart from the advantages, Central Ring can handle up to 4 rings in the system
and has the ability to recover from failure within 10 milliseconds.
Enable Ring
•
: To enable the X-Ring function, tick the checkbox beside the
Enable Ring
string label. If
this checkbox is not ticked, all the ring functions are unavailable.
¾
Enable Ring Master
¾
1st & 2nd Ring Ports
1
Ring Port
st
the system will automatically upgrade the
Enable Couple Ring
•
string label.
Ring
¾
Couple port
¾
Control port
is the working port and
: Assign the member port which is connected to the other ring group.
: When the
: Tick the checkbox to enable this switch to be the ring master.
: Pull down the selection menu to assign the ports as the member ports.
Ring Port
2
nd
2
nd
is the backup port. When
Ring Port
to be the working port.
1
: To enable the coupe ring function, tick the checkbox beside the
Enable Couple Ring
checkbox is ticked, you have to assign the
Ring Port
st
Enable Couple
control port to form a couple-ring group between the two X-rings.
Enable Dual Homing
•
: Set up one of the ports on the switch to be the Dual Homing port. For a switch,
there is only one Dual Homing port. Dual Homing function only works when the X-Ring function
enabled.
Enable Dual Ring
•
: When this check box is ticked, the ‘
Enable Ring Master
’ check box will then also
be enabled by the system which means this equipment is assigned as the Ring Master. The Dual Ring
differs from the Couple Ring in that it only needs a unit to form a redundant linking system of two rings.
And then, click
•
Apply
to apply the configuration.
fails,
81 Chapter3
Page 92

Figure 3.47: X-ring interface
Note When the X-Ring function enable, user must disable the RSTP. The X-Ring
function and RSTP function cannot exist at the same time.
Remember to execute the “Save Configuration” action, otherwise the new
configuration will lose when switch power off.
EKI-7657C _Manual_ed1 82
Page 93

LLDP Configuration
LLDP (Link Layer Discovery Protocol) function allows the switch to advertise its information to other
nodes on the network and store the information it discovers.
LLDP Protocol:
•
LLDP Interval:
•
Click
•
Apply
Disable or enable LLDP function.
Set the interval of learning the information time in second.
.
Figure 3.48: LLDP Configuration interface
83 Chapter3
Page 94

3.2.4 Security
In this section, you can configure 802.1x and MAC address table.
802.1X/Radius Configuration
802.1x is an IEEE authentication specification which prevents the client from connecting to a wireless
access point or wired switch until it provides authority, like the user name and password that are verified
by an authentication server (such as RADIUS server).
802.1X/Radius - System Configuration
After enabling the IEEE 802.1X function, you can configure the parameters of this function.
IEEE 802.1x Protocol:
•
Radius Server IP:
•
Server Port:
•
Accounting Port:
•
Server.
Shared Key:
•
RADIUS server. This key must match the encryption key used on the RADIUS Server.
NAS, Identifier:
•
Click
•
Set the UDP destination port for authentication requests to the specified RADIUS Server.
Set an encryption key for using during authentication sessions with the specified
Apply
.
Enable or disable 802.1x protocol.
Assign the RADIUS Server IP address.
Set the UDP destination port for accounting requests to the specified RADIUS
Set the identifier for the RADIUS client.
Figure 3.49: 802.1x/Radius System Configuration interface
802.1x/Radius—Port Configuration
You can configure the 802.1x authentication state for each port. The state provides Disable, Accept,
Reject, and Authorize.
Reject:
•
Accept:
•
Authorized:
•
outcome of an authentication exchange between the Supplicant and the authentication server.
Disable:
•
Click
•
The specified port is required to be held in the unauthorized state.
The specified port is required to be held in the Authorized state.
The specified port is set to the Authorized or Unauthorized state in accordance with the
When disabled, the specified port works without complying with 802.1x protocol.
Apply
.
EKI-7657C _Manual_ed1 84
Page 95

802.1X/Radius—Misc Configuration
Quiet Period:
•
TX Period:
•
Set the period which the port doesn’t try to acquire a supplicant.
Set the period the port waits for retransmit next EAPOL PDU during an authentication
session.
Supplicant Timeout:
•
request.
Server Timeout:
•
Set the period of time the switch waits for a server response to an authentication
request.
Max Requests:
•
Set the number of authentication that must time-out before authentication fails and the
authentication session ends.
Reauth period:
•
Click
•
Apply
Set the period of time which clients connected must be re-authenticated.
.
Figure 3.50: 802.1x/Radius - Port Setting interface
Set the period of time the switch waits for a supplicant response to an EAP
85 Chapter3
Page 96

Figure 3.51: 802.1x/Radius - Misc Configuration interface
EKI-7657C _Manual_ed1 86
Page 97

MAC Address Table
Use the MAC address table to ensure the port security.
You can add a static MAC address; it remains in the switch's address table, regardless of whether the
device is physically connected to the switch. This saves the switch from having to re-learn a device's
MAC address when the disconnected or powered-off device is active on the network again. You can add /
modify / delete a static MAC address.
MAC Address Table—Static MAC Address
You can add static MAC address in the switch MAC table here.
MAC Address:
•
of the device network activity.
Port No.:
•
Click
•
Add
Enter the MAC address of the port that should permanently forward traffic, regardless
Pull down the selection menu to select the port number.
.
If you want to delete the MAC address from filtering table, select the MAC address and click
•
Figure 3.52: Static MAC Addresses interface
MAC Address Table—MAC Filtering
By filtering MAC address, the switch can easily filter the pre-configured MAC address and reduce the unsafety. You can add and delete filtering MAC address.
Delete
.
87 Chapter3
Page 98

Figure 3.53: MAC Filtering interface
MAC Address
•
Click
•
If you want to delete the MAC address from filtering table, select the MAC address and click
•
Add
: Enter the MAC address that you want to filter.
.
MAC Address Table—All MAC Addresses
You can view the port that connected device’s MAC address and the related devices’ MAC address.
Select the port.
•
The selected port of static & dynamic MAC address information will be displayed in here.
•
Click
•
Clear MAC Table
to clear the current port static MAC address information on screen.
Delete
.
Figure 3.54: All MAC Address interface
EKI-7657C _Manual_ed1 88
Page 99

MAC Address Table—Multicast Filtering
Multicasts are similar to broadcasts, they are sent to all end stations on a LAN or VLAN. Multicast filtering
is the system by which end stations only receive multicast traffic if they register to join specific multicast
groups. With multicast filtering, network devices only forward multicast traffic to the ports that are
connected to registered end stations.
IP Address
•
Member Ports
•
: Assign a multicast group IP address in the range of 224.0.0.0 ~ 239.255.255.255.
: Tick the check box beside the port number to include them as the member ports in the
specific multicast group IP address.
Click
•
Clear MAC Table
to clear the current port static MAC address information on screen.
Figure 3.55: All MAC Address interface
89 Chapter3
Page 100

Factory Default
Reset switch to default configuration. Click
Reset
to reset all configurations to the default value.
Figure 3.56: Factory Default interface
EKI-7657C _Manual_ed1 90
 Loading...
Loading...