Page 1

ZyWALL 5/35/70 Series
Internet Security Appliance
User’s Guide
Version 4.04
03/2008
Edition 1
DEFAULT LOGIN
IP Address http://192.168.1.1
Password 1234
www.zyxel.com
Page 2

Page 3

About This User's Guide
About This User's Guide
Intended Audience
This manual is intended for people who want to configure the ZyWALL using the web
configurator or System Management Terminal (SMT). You should have at least a basic
knowledge of TCP/IP networking concepts and topology.
Related Documentation
• Quick Start Guide
The Quick Start Guide is designed to help you get up and running right away. It contains
information on setting up your network and configuring for Internet access.
• Web Configurator Online Help
Embedded web help for descriptions of individual screens and supplementary
information.
• CLI Reference Guide
The CLI Reference Guide explains how to use the Command-Line Interface (CLI) to
configure the ZyWALL.
• Supporting Disk
Refer to the included CD for support documents.
• ZyXEL Web Site
Please refer to www.zyxel.com
certifications.
for additional support documentation and product
User Guide Feedback
Help us help you. Send all User Guide-related comments, questions or suggestions for
improvement to the following address, or use e-mail instead. Thank you!
The Technical Writing Team,
ZyXEL Communications Corp.,
6 Innovation Road II,
Science-Based Industrial Park,
Hsinchu, 300, Taiwan.
E-mail: techwriters@zyxel.com.tw
ZyWALL 5/35/70 Series User’s Guide
3
Page 4

Document Conventions
Document Conventions
Warnings and Notes
These are how warnings and notes are shown in this User’s Guide.
1 Warnings tell you about things that could harm you or your device.
" Notes tell you other important information (for example, other things you may
need to configure or helpful tips) or recommendations.
Syntax Conventions
• The ZyWALL 5/35/70 series may be referred to as the “ZyWALL”, the “devic e” or the
“system” in this User’s Guide.
• Product labels, screen names, field labels and field choices are all in bold font.
• A key stroke is denoted by square brackets and uppercase text, for example, [ENTER]
means the “enter” or “return” key on your keyboard.
• “Enter” means for you to type one or more characters and then press the [ENTER] key.
“Select” or “choose” means for you to use one of the predefined choices.
• A right angle bracket ( > ) within a screen name denotes a mouse click. For example,
Maintenance > Log > Log Setting means you first click Maintenance in the navigation
panel, then the Log sub menu and finally the Log Setting tab to get to that screen.
• Units of measurement may denote the “metric” value or the “scientific” value. For
example, “k” for kilo may denote “1000” or “1024”, “M” for mega may denote “1000000”
or “1048576” and so on.
• “e.g.,” is a shorthand for “for instance”, and “i.e.,” means “that is” or “in other words”.
4
ZyWALL 5/35/70 Series User’s Guide
Page 5
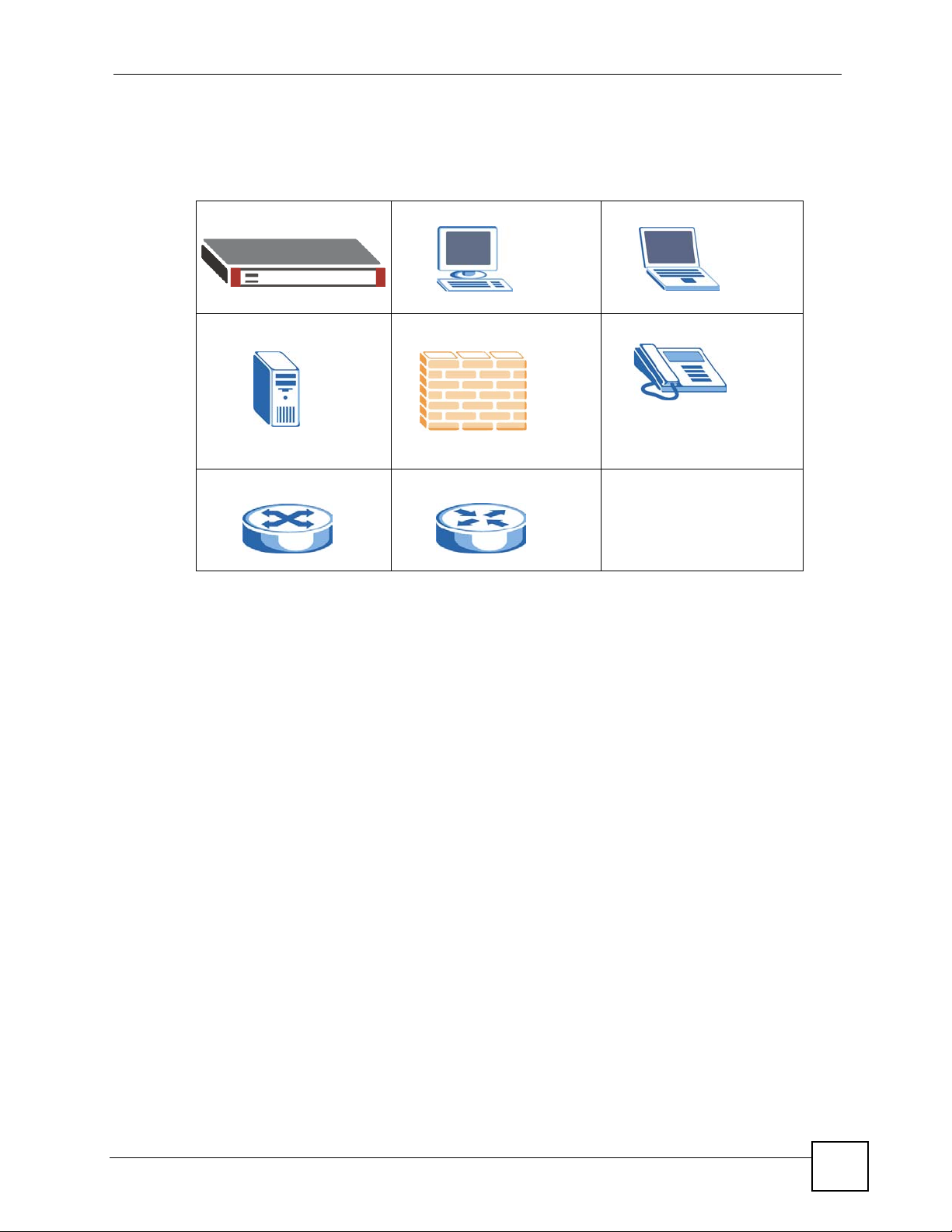
Document Conventions
Icons Used in Figures
Figures in this User’s Guide may use the following generic icons. The ZyWALL icon is not an
exact representation of your device.
ZyWALL Computer Notebook computer
Server Firewall Telephone
Switch Router
ZyWALL 5/35/70 Series User’s Guide
5
Page 6

Safety Warnings
Safety Warnings
1 For your safety, be sure to read and follow all warning notices and instructions.
• Do NOT use this product near water, for example, in a wet basement or near a swimming
pool.
• Do NOT expose your device to dampness, dust or corrosive liquids.
• Do NOT store things on the device.
• Do NOT install, use, or service this device during a thunderstorm. There is a remote risk
of electric shock from lightning.
• Connect ONLY suitable accessories to the device.
• Do NOT open the device or unit. Opening or removing covers can expose you to
dangerous high voltage points or other risks. ONLY qualified service personnel should
service or disassemble this device. Please contact your vendor for further information.
• Make sure to connect the cables to the correct ports.
• Place connecting cables carefully so that no one will step on them or stumble over them.
• Always disconnect all cables from this device before servicing or disassembling.
• Use ONLY an appropriate power adaptor or cord for your device.
• Connect the power adaptor or cord to the right supply voltage (for example, 110V AC in
North America or 230V AC in Europe).
• Do NOT remove the plug and connect it to a power outlet by itself; always attach the plug
to the power adaptor first before connecting it to a power outlet.
• Do NOT allow anything to rest on the power adaptor or cord and do NOT place the
product where anyone can walk on the power adaptor or cord.
• Do NOT use the device if the power adaptor or cord is damaged as it might cause
electrocution.
• If the power adaptor or cord is damaged, remove it from the power outlet.
• Do NOT attempt to repair the power adaptor or cord. Contact your local vendor to order a
new one.
• Do not use the device outside, and make sure all the connections are indoors. There is a
remote risk of electric shock from lightning.
• CAUTION: RISK OF EXPLOSION IF BATTERY (on the motherboard) IS REPLACED
BY AN INCORRECT TYPE. DISPOSE OF USED BATTERIES ACCORDING TO
THE INSTRUCTIONS. Dispose them at the applicable collection point for the recycling
of electrical and electronic equipment. For detailed information about recycling of this
product, please contact your local city offi ce, your household waste disposal service or the
store where you purchased the product.
• Do NOT obstruct the device ventilation slots, as insufficient airflow may harm your
device.
• Fuse Warning! Replace a fuse only with a fuse of the same type and rating.
6
ZyWALL 5/35/70 Series User’s Guide
Page 7

This product is recyclable. Dispose of it properly.
Safety Warnings
ZyWALL 5/35/70 Series User’s Guide
7
Page 8

Safety Warnings
8
ZyWALL 5/35/70 Series User’s Guide
Page 9

Contents Overview
Contents Overview
Introduction ............................................................................................................................49
Getting to Know Your ZyWALL .................................................................................................. 51
Hardware Installation .......................................... .......................................................... .............55
Introducing the Web Configurator .............................................................................................. 61
Wizard Setup ............................................................................................................................. 87
Tutorials ...................................................................................................................................109
Registration Screens ............................................................................................................... 141
Network .................................................................................................................................147
LAN Screens ........................................................................................................................... 149
Bridge Screens ............ ... .... ... .......................................................... ... ... .... ... ... ... .... ... ... ...........161
WAN Screens ........ ... ... ... ........................................................... ... ... ... ... .... ..............................169
DMZ Screens ........................................................................................................................... 207
WLAN Screens ........................................................................................................................ 219
Wireless Screens ................ ... .......................................................... ... ... .... ... ... ... .... ... ... ...........229
Security .................................................................................................................................249
Firewall Screens ...................................................................................................................... 251
Intrusion Detection and Prevention (IDP) Screens ................................................................. 277
Anti-Virus Screens ...................................................................................................................299
Anti-Spam Screens .................................................................................................................. 313
Content Filtering Screens ........................................................................................................ 327
Content Filtering Reports ............. .... ... ... ... ... .... ... ... ... ............................................................... 349
IPSec VPN ................... ... ........................................................... ... ... ... ... .................................. 357
Certificates ................................... ....................... ....................... ...................... ........................ 399
Authentication Server Screens ........... ... ... ... .... ... ... ... .... ........................................................... 427
Advanced ..............................................................................................................................433
Network Address Translation (NAT) ........................................................................................ 435
Static Route Screens ...............................................................................................................451
Policy Route Screens .............................................................................................................. 457
Bandwidth Management Screens .................... ... .....................................................................465
DNS Screens ............................................ ... .... ... ... ... .... ... ... ..................................................... 479
Remote Management Screens ................................................................................................491
UPnP Screens ......................................................................................................................... 519
Custom Application Screen ..................................................................................................... 529
ALG Screen ............................................................................................................................. 531
ZyWALL 5/35/70 Series User’s Guide
9
Page 10

Contents Overview
Reports, Logs and Maintenance .........................................................................................537
Reports Screens ......................................................................................................................539
Logs Screens .......................................................................................................................... 555
Maintenance Screens ..............................................................................................................585
SMT .......................................................................................................................................603
Introducing the SMT ................................................................................................................ 605
SMT Menu 1 - General Setup ................... ... .... ... ... ... .... ... ... ... .................................................. 613
WAN and Dial Backup Setup ................................................................................................... 619
LAN Setup ............................................................................................................................... 633
Internet Access ........................................................................................................................ 639
DMZ Setup ..............................................................................................................................645
Route Setup .............. ... ... .... .......................................................... ... ... ... .... ... ...........................649
Wireless Setup ............................................ .... ... ... ... .... ... ... ... .... .............................................. 653
Remote Node Setup ................................................................................................................ 659
IP Static Route Setup .............................................................................................................. 669
Network Address Translation (NAT) ........................................................................................ 673
Introducing the ZyWALL Firewall ............................................................................................. 693
Filter Configuration .................................................................................................................. 695
SNMP Configuration .................................................................................................................711
System Information & Diagnosis .............................................................................................713
Firmware and Configuration File Maintenance ........................................................................ 725
System Maintenance Menus 8 to 10 ............................................................................ ... ... .... . 739
Remote Management ..............................................................................................................745
IP Policy Routing ................... ... ... .... ... ... ... ... ........................................................... ... ... ...........749
Call Scheduling ........................................................................................................................ 757
Troubleshooting and Product Specifications ...................................................................761
Troubleshooting ..................................................... .................................................................. 763
Product Specifications ............................................................................................................. 769
Appendices and Index .........................................................................................................779
10
ZyWALL 5/35/70 Series User’s Guide
Page 11

Table of Contents
Table of Contents
About This User's Guide..........................................................................................................3
Document Conventions............................................................................................................4
Safety Warnings ........................................................................................................................6
Contents Overview ...................................................................................................................9
Table of Contents....................................................................................................................11
List of Figures.........................................................................................................................29
List of Tables...........................................................................................................................41
Part I: Introduction................................................................................. 49
Chapter 1
Getting to Know Your ZyWALL..............................................................................................51
1.1 ZyWALL Internet Security Appliance Overview ............... .... ... ... ... ....................................... 51
1.2 ZyWALL Features ......... ... .......................................................... ... ... .... ... ... ..........................51
1.3 Applications for the ZyWALL ...............................................................................................52
1.3.1 Secure Broadband Internet Access via Cable or DSL Modem .................................. 52
1.3.2 VPN Application ........................ ... .... ... ... ... .......................................................... .... ... 53
1.3.3 3G WAN Application (ZyWALL 5 Only) ...................................................................... 53
1.4 Ways to Manage the ZyWALL ............................ .... ... ... ....................................................... 54
1.5 Good Habits for Managing the ZyWALL .............................................................................. 54
Chapter 2
Hardware Installation..............................................................................................................55
2.1 General Installation Instructions ...... ... ... .... ... ... ... .... ... ... .......................................................55
2.2 Desktop Installation ............................................................................................................ 55
2.3 Rack-mounted Installation Requirements ........................................ .................................... 56
2.4 Rack-Mounted Installation ................................................................................................... 57
2.5 3G Card, WLAN Card and ZyWALL Turbo Card Installation ...............................................58
2.6 Front Panel Lights .............................................. .... ... ... ... .... ... ............................................. 59
Chapter 3
Introducing the Web Configurator ........................................................................................61
3.1 Web Configurator Overview .................................................................................................61
ZyWALL 5/35/70 Series User’s Guide
11
Page 12

Table of Contents
3.2 Accessing the ZyWALL Web Configurator ............. ... ... ... .................................................... 61
3.3 Resetting the ZyWALL ........ ... .... ... ... .......................................................... ... .... ... ... ... ... ....... 63
3.3.1 Procedure To Use The Reset Button ......................................................................... 63
3.3.2 Uploading a Configuration File Via Console Port ....................................................... 63
3.4 Navigating the ZyWALL Web Configurator .......................................................................... 64
3.4.1 Title Bar ............................................ ... ... ... .... ... ... ... .................................................... 64
3.4.2 Main Window .......................... ... .......................................................... .... ... ... ... ... .......65
3.4.3 HOME Screen: Router Mode ...................................................................................65
3.4.4 HOME Screen: Bridge Mode .......................... ... ... .... ... ... ... ... .... ................................ 71
3.4.5 Navigation Panel ....................... ... .... ..........................................................................74
3.4.6 Port Statistics ............................................................................................................ 80
3.4.7 Show Statistics: Line Chart ................. ... ... .......................................................... .... ... 81
3.4.8 DHCP Table ...........................................................................................................82
3.4.9 VPN Status ................... .... ... ... ... ... ........................................................... ... ................83
3.4.10 Bandwidth Monitor .................................................................................................. 84
Chapter 4
Wizard Setup...........................................................................................................................87
4.1 Wizard Setup Overview ......................................................................................................87
4.2 Internet Access ................................................................................................................... 88
4.2.1 ISP Parameters ................................................ ... ... .... ................................................ 88
4.2.2 Internet Access Wizard: Second Screen ....................................................................92
4.2.3 Internet Access Wizard: Registration ......................................................................... 93
4.2.4 Internet Access Wizard: Status .................................................................................. 94
4.2.5 Internet Access Wizard: Service Activation ...............................................................95
4.3 VPN Wizard Gateway Setting .............................................................................................. 96
4.4 VPN Wizard Network Setting ............................................................................................... 97
4.5 VPN Wizard IKE Tunnel Setting (IKE Phase 1) ...................................................................99
4.6 VPN Wizard IPSec Setting (IKE Phase 2) ......................................................................... 100
4.7 VPN Wizard Status Summary ............................................................................................102
4.8 VPN Wizard Setup Complete ............................................................................................ 104
4.9 Anti-Spam Wizard: Email Server Location Setting ............................................................104
4.10 Anti-Spam Wizard: Direction Recommendations ............................................................ . 105
4.11 Anti-Spam Wizard: Direction Configuration ...................................................................... 106
4.12 Anti-Spam Wizard: Setup Complete ................................................................................ 108
Chapter 5
Tutorials.................................................................................................................................109
12
5.1 Dynamic VPN Rule Configuration ............................................. ... ..................................... 1 09
5.1.1 Configure Bob’s User Account ..................................................................................110
5.1.2 VPN Gateway and Network Policy Configuration .....................................................110
5.1.3 Configure Zero Configuration Mode on ZyWALL B ...................................................116
5.1.4 Testing Your VPN Configuration ................................. ... ... ... ... .... ... ... ... .... ... ... ... ... ......117
ZyWALL 5/35/70 Series User’s Guide
Page 13

Table of Contents
5.1.5 Using the Dynamic VPN Rule for More VPN Tunnels ............................. ... ... ... ... .... ..119
5.2 Security Settings for VPN Traffic ..................................... .... ... ... ... ... ...................................119
5.2.1 IDP for From VPN Traffic Example ..........................................................................120
5.2.2 IDP for To VPN Traffic Example ................................. ... ... ... ... .... .............................. 121
5.3 Firewall Rule for VPN Example ............. .... ... ... ... .... ... ... ... .... ... ........................................... 122
5.3.1 Configuring the VPN Rule ........................................................................................123
5.3.2 Configuring the Firewall Rules ............... ..................................................................127
5.4 How to Set up a 3G WAN Connection ............................................................................... 130
5.4.1 Inserting a 3G Card ............................................. ... .................................................. 130
5.4.2 Configuring 3G WAN Settings ................... .... ... ... ... .................................................. 131
5.4.3 Checking WAN Connections .................................................................................... 132
5.5 Configuring Load Balancing ...................................... ... ... .... ... ... ........................................ 132
5.6 Configuring Content Filtering ........................... .................................................... ..............133
5.6.1 Enable Content Filtering ............................ .... ... ... ... .... ... ... ... ..................................... 1 33
5.6.2 Block Categories of Web Content ............................................................................ 134
5.6.3 Assign Bob’s Computer a Specific IP Address .........................................................136
5.6.4 Create a Content Filter Policy for Bob ......................................................................136
5.6.5 Set the Content Filter Schedule ...............................................................................137
5.6.6 Block Categories of Web Content for Bob ............................................................... 138
Chapter 6
Registration Screens............................................................................................................141
6.1 Overview ............. .......................................................... ... .... ... ... ........................................ 141
6.1.1 What You Can Do in the Registration Screens ........................................................ 141
6.1.2 What You Need to Know About Registration ....... ... .................................................. 141
6.2 The Registration Screen ....................................................................................................142
6.3 The Service Screen ...... .......................................................... ... ... ... .... ... ...........................144
Part II: Network..................................................................................... 147
Chapter 7
LAN Screens..........................................................................................................................149
7.1 Overview ............. .......................................................... ... .... ... ... ........................................ 149
7.1.1 What You Can Do in The LAN Screens ...................................................................149
7.1.2 What You Need to Know About LAN .......................................... ... ... ... .... ... ... ... ... .... . 150
7.2 The LAN Screen ................................................................................................................ 152
7.3 The LAN Static DHCP Screen ...........................................................................................155
7.4 The LAN IP Alias Screen ..................................................................................................156
7.5 The LAN Port Roles Screen .............................................................................................. 158
Chapter 8
Bridge Screens......................................................................................................................161
ZyWALL 5/35/70 Series User’s Guide
13
Page 14

Table of Contents
8.1 Overview ............. .......................................................... ... .... ... ... ........................................ 161
8.1.1 What You Can Do in the Bridge Screens ................................................................. 161
8.1.2 What You Need To Know About Bridging ............................... .................................. 162
8.2 The Bridge Screen ................. .... ... ... .......................................................... ... .... ... ... ... ... ..... 163
8.3 The Bridge Port Roles Screen ............................................... ........................................... 164
8.4 Bridge Technical Reference ............................................................................................... 166
Chapter 9
WAN Screens.........................................................................................................................169
9.1 Overview ............. .......................................................... ... .... ... ... ........................................ 169
9.1.1 What Yo u Can Do in the WAN Screens ...................................................................170
9.1.2 What You Need to Know About WAN ........................................ ... ... ... .... ... ..............170
9.1.3 Before You Begin ............................................. ........................................................ 172
9.2 The General Screen ..........................................................................................................172
9.2.1 Configuring the General Screen ...............................................................................173
9.2.2 Configuring Load Balancing ................ ... ... .... ... ... ... .................................................. 177
9.2.3 Least Load First .......................................................................................................177
9.2.4 Weighted Round Robin .................... ... ... ... .... ... ... ... .................................................. 179
9.2.5 Spillover .................................................. ... .... ... ... ... .... ... ........................................... 180
9.3 The WAN1 and WAN2 Screen .......................................................................................... 182
9.3.1 WAN Ethernet Encapsulation ................................................................................... 183
9.3.2 PPPoE Encapsulation ..............................................................................................186
9.3.3 PPTP Encapsulation ........................ ... ... ... .... ... ... ... .... .............................................. 189
9.4 The 3G (WAN2) Screen ................................................... .... ... ... ... ... .... ... ... ... .... ... ... ... ... .... . 192
9.5 The Traffic Redirect Screen ............................................................................................... 197
9.6 Configuring the Traffic Redirect Screen ............................................................................. 198
9.7 The Dial Backup Screen ....................................................................................................199
9.7.1 The Advanced Modem Setup Screen ......................................................................201
9.7.2 Configuring the Advanced Modem Setup Screen ............................ ... .... ... ... ... ... .... . 202
9.8 WAN Technical Reference ................................................................................................. 204
Chapter 10
DMZ Screens.........................................................................................................................207
10.1 Overview .......................................................................................................................... 207
10.1.1 What You Can Do in the DMZ Screens .................................................................. 207
10.1.2 What You Need To Know About DMZ .................................................................... 208
10.1.3 DMZ Public IP Address Example ...........................................................................208
10.1.4 DMZ Private and Public IP Address Example .......................... .............................. 209
10.2 The DMZ Screen ..................... ... ... ... ... .... ... ... ... .......................................................... ..... 210
10.3 The Static DHCP Screen ................................................................................................213
10.4 The IP Alias Screen ........................................................................................................ 214
10.5 The DMZ Port Roles Screen .......................................................................................... 216
14
ZyWALL 5/35/70 Series User’s Guide
Page 15

Table of Contents
Chapter 11
WLAN Screens......................................................................................................................219
11.1 Overview ..........................................................................................................................219
11.1.1 What You Can Do in the WLAN Screens ............................................................... 219
11.1.2 What You Need to Know About WLAN ...................................................................220
11.2 The WLAN Screen ...........................................................................................................220
11.3 WLAN Static DHCP .........................................................................................................223
11.4 WLAN IP Alias ................................................................................................................ 224
11.5 WLAN Port Roles ............................................................................................................. 226
Chapter 12
Wireless Screens..................................................................................................................229
12.1 Overview .......................................................................................................................... 229
12.1.1 What You Can Do in the Wireless Screens ............................................................ 229
12.1.2 What You Need to Know ........................................................................................ 229
12.2 Wireless Card ..................................................................................................................232
12.2.1 Static WEP ............................................................................................................. 234
12.2.2 WPA-PSK ....................................... ........................................................................235
12.2.3 WPA .......................................................................................................................237
12.2.4 IEEE 802.1x + Dynamic WEP ................................................................................ 238
12.2.5 IEEE 802.1x + Static WEP .....................................................................................239
12.2.6 IEEE 802.1x + No WEP .........................................................................................240
12.2.7 No Access 802.1x + Static WEP ............................................................................241
12.2.8 No Access 802.1x + No WEP ................................................................................ 242
12.3 MAC Filter ....................................................................................................................... 243
12.4 Technical Reference ........................................................................................................244
Part III: Security.................................................................................... 249
Chapter 13
Firewall Screens....................................................................................................................251
13.1 Overview .......................................................................................................................... 251
13.1.1 What You Can Do Using the Firewall Screens .................................. .... ... ... ... ... .... . 252
13.1.2 What You Need To Know About the ZyWALL Firewall ................ ... ... .... ... ... ... ... .....252
13.1.3 Before You Begin ...................................................................................................252
13.2 Firewall Rules Example ................................................................................................... 252
13.3 The Firewall Default Rule Screen .................................................................................... 254
13.4 The Firewall Default Rule (Bridge Mode) Screen ............................................................ 256
13.5 The Firewall Rule Summary Screen ...............................................................................259
13.5.1 The Firewall Edit Rule Screen ............................................................................... 260
13.6 The Anti-Probing Screen .................... .... ... ... ... .... ... ... ... .... ... ... ... ... .... ... ........................... 263
ZyWALL 5/35/70 Series User’s Guide
15
Page 16

Table of Contents
13.7 The Firewall Thresholds Screen ..................................................................................... 264
13.8 The Firewall Services Screen ........................................... ... ... ... ... .... .............................. 266
13.8.1 The Firewall Edit Custom Service Screen ............................................................. 267
13.8.2 My Service Firewall Rule Example .........................................................................268
13.9 Technical Reference ........................................................................................................271
Chapter 14
Intrusion Detection and Prevention (IDP) Screens ...........................................................277
14.1 Overview .......................................................................................................................... 277
14.1.1 What You Can Do Using the IDP Screens ........... .... ... ... ........................................ 277
14.1.2 What You Need To Know About the ZyWALL IDP ............... .... ... ... ... .... ... ..............278
14.1.3 Before You Begin ...................................................................................................279
14.2 The General Setup Screen ..............................................................................................279
14.3 The Signatures Screen ....................................................................................................281
14.3.1 Attack Types ...........................................................................................................281
14.3.2 Intrusion Severity ................................................................................................... 282
14.3.3 Signature Actions ................................................................................................... 282
14.3.4 Configuring The IDP Signatures Screen ................................................................ 283
14.3.5 The Query View Screen ........................................................................................ 284
14.4 The Anomaly Screen ....................................................................................................... 289
14.5 The Update Screen ........................................................................................................291
14.5.1 mySecurityZone .....................................................................................................291
14.5.2 Configuring The IDP Update Screen ...................................................................... 292
14.6 The Backup and Restore Screen ....................................................................................293
14.7 Technical Reference ........................................................................................................294
Chapter 15
Anti-Virus Screens................................................................................................................299
15.1 Overview .......................................................................................................................... 299
15.1.1 What You Can Do in the Antivirus Screens ............................................................ 299
15.1.2 What You Need to Know About Antivirus ...............................................................300
15.2 The General Screen ........................................................................................................301
15.3 The Signature Screen .....................................................................................................303
15.3.1 Signature Search Example .. ... ... .... ... ... ............................................................. .... . 305
15.4 The Update Screen ........................................................................................................306
15.4.1 mySecurityZone .....................................................................................................307
15.4.2 Configuring Anti-virus Update ................................................................................ 307
15.5 The Backup and Restore Screen ................................................................................... 309
15.6 Technical Reference ........................................................................................................310
Chapter 16
Anti-Spam Screens...............................................................................................................313
16.1 Overview .......................................................................................................................... 313
16
ZyWALL 5/35/70 Series User’s Guide
Page 17

Table of Contents
16.1.1 What You Can Do in the Antispam Screens ................... .......... ......... .......... .......... . 313
16.1.2 What You Need to Know About Antispam .............................................................. 314
16.2 The General Screen ........................................................................................................315
16.3 The External DB Screen .............................................................................................318
16.4 The Lists Screen .............................................................................................................. 320
16.5 Anti-Spam Lists Edit Screen ..........................................................................................322
16.6 Technical Reference ........................................................................................................324
Chapter 17
Content Filtering Screens....................................................................................................327
17.1 Overview .......................................................................................................................... 327
17.1.1 What You Can Do in the Content Filtering Screens ............................................... 327
17.1.2 What You Need to Know About Content Filtering .................................................. 327
17.2 General Screen ...............................................................................................................328
17.3 The Policy Screen ........................................................................................................331
17.4 Content Filter Policy: General ......................................................................................... 332
17.5 Content Filter Policy: External Database .......................... .............................................. 334
17.6 Content Filter Policy: Customization ............................................................................... 341
17.7 Content Filter Policy: Schedule ...................................................................................... 342
17.8 Content Filter Object ....................................................................................................... 343
17.9 Content Filtering Cache ..................................................................................................346
Chapter 18
Content Filtering Reports.....................................................................................................349
18.1 Overview .......................................................................................................................... 349
18.2 Checking Content Filtering Activation ......................... .......................... .......................... . 349
18.3 Viewing Content Filtering Reports ................................................................................... 349
18.4 Web Site Submission .......................................................................................................354
Chapter 19
IPSec VPN..............................................................................................................................357
19.1 Overview .......................................................................................................................... 357
19.1.1 What You Can Do in the IPSec VPN Screens ........................................................ 357
19.1.2 What You Need to Know About IPSec VPN ........................................................... 358
19.2 The VPN Rules (IKE) Screen .......................................................................................... 360
19.3 The VPN Rules (IKE) Gateway Policy Edit Screen ......................................................... 361
19.4 The Network Policy Edit Screen ....................................................................................367
19.5 The Network Policy Edit: Port Forwarding Screen .......................................................... 372
19.6 The Network Policy Move Screen ................................................................................... 374
19.7 The VPN Rules (Manual) Screen .................................................................................... 375
19.8 The VPN Rules (Manual): Edit Screen ................................. ... ... ..................................... 3 76
19.9 The VPN SA Monitor Screen ...........................................................................................379
19.10 The VPN Global Setting Screen .................................................................................... 379
ZyWALL 5/35/70 Series User’s Guide
17
Page 18

Table of Contents
19.11 Telecommuter VPN/IPSec Examples ........................................... .... ... ... ... .... ... ..............382
19.11. 1 Telecommuters Sharing One VPN Rule Example ................................................ 383
19.11.2 Telecommuters Using Unique VPN Rules Example .............................................383
19.12 VPN and Remote Management .....................................................................................385
19.13 Hub-and-spoke VPN ...................................................................................................... 385
19.13.1 Hub-and-spoke VPN Example ............................................................................. 386
19.13.2 Hub-and-spoke Example VPN Rule Addresses ..................... .............................. 387
19.13.3 Hub-and-spoke VPN Requirements and Suggestions ......................................... 387
19.14 IPSec VPN Background Information ............................................................................. 388
Chapter 20
Certificates ............................................................................................................................399
20.1 Overview .......................................................................................................................... 399
20.1.1 What You Can Do in the Certificate Screens ......................................................... 399
20.1.2 What You Need to Know About Certificates ........................................................... 399
20.1.3 Verifying a Certificate ............................................................................................. 400
20.2 The My Certificates Screen ............................................................................................. 401
20.2.1 The My Certificate Details Screen ..........................................................................403
20.3 The My Certificate Export Screen ....................................................................................406
20.4 The My Certificate Import Screen ....................................................................................407
20.4.1 Using the My Certificate Import Screen ................................................................. 407
20.5 The My Certificate Create Screen ................................................................................... 409
20.6 The Trusted CAs Screen .................................................................................................413
20.7 The Trusted CA Details Screen ....................................................................................... 415
20.8 The Trusted CA Import Screen ........................................................................................ 418
20.9 The Trusted Remote Hosts Screen .................................................................................419
20.10 The Trusted Remote Hosts Import Screen .................................................................... 421
20.11 The Trusted Remote Host Certificate Details Screen .................................................... 422
20.12 The Directory Servers Screen ....................................................................................... 424
20.13 The Directory Server Add or Edit Screen ......................................................................425
Chapter 21
Authentication Server Screens...................................................................................... ......427
21.1 Overview .......................................................................................................................... 427
21.1.1 What You Can Do in the Authentication Server Screens ....................................... 427
21.1.2 What You Need To Know About Authentication Server .......................................... 427
21.2 The Local User Database Screen .................................................................................... 428
21.3 The RADIUS Screen .......................................................................................................430
Part IV: Advanced ................................................................................ 433
18
ZyWALL 5/35/70 Series User’s Guide
Page 19

Table of Contents
Chapter 22
Network Address Translation (NAT)....................................................................................435
22.1 Overview .......................................................................................................................... 435
22.1.1 What You Can Do Using the NAT Screens . ... ... ... .... ... ... ... ..................................... 435
22.1.2 What You Need To Know About NAT .....................................................................435
22.1.3 Before You Begin ...................................................................................................436
22.2 The NAT Overview Screen .............................................................................................. 436
22.3 The NAT Address Mapping Screen ................................................................................. 438
22.3.1 NAT Address Mapping Edit ................................................................................... 440
22.4 The Port Forwarding Screen ........................................................................................... 441
22.4.1 Default Server IP Address ......................................................................................441
22.4.2 Port Forwarding: Services and Port Numbers ...................... ................. ................ . 442
22.4.3 Configuring Servers Behind Port Forwarding (Example) ....................................... 442
22.4.4 NAT and Multiple WAN ........................................................................................... 442
22.4.5 Port Translation ......................................................................................................443
22.4.6 Configuring The Port Forwarding Screen ............................................................... 443
22.5 The Port Triggering Screen ............................................................................................. 445
22.5.1 Configuring Port Triggering ....................................................................................446
22.6 Technical Reference ........................................................................................................447
Chapter 23
Static Route Screens............................................................................................................451
23.1 Overview .......................................................................................................................... 451
23.1.1 What You Can Do in the Static Route Screens ...................................................... 451
23.2 The IP Static Route Screen .............................................................................................452
23.2.1 The IP Static Route Edit Screen ............................................................................. 454
Chapter 24
Policy Route Screens...........................................................................................................457
24.1 Overview .......................................................................................................................... 457
24.1.1 What You Can Do in the Policy Route Screens ..................................................... 457
24.1.2 What You Need To Know About Policy Route ....................................................... . 457
24.2 The Policy Route Summary Screen ................................................................................ 458
24.2.1 The Policy Route Edit Screen ................................................................................ 460
Chapter 25
Bandwidth Management Screens........................................................................................465
25.1 Overview .......................................................................................................................... 465
25.1.1 What You Can Do in the Bandwidth Management Screens ................................... 465
25.1.2 What You Need to Know About Bandwidth Management ...................................... 465
25.1.3 Application and Subnet-based Bandwidth Management Example ........................ 466
25.1.4 Over Allotment of Bandwidth Example ................................................................... 467
25.1.5 Maximize Bandwidth Usage With Bandwidth Borrowing Example .........................467
ZyWALL 5/35/70 Series User’s Guide
19
Page 20

Table of Contents
25.2 The Summary Screen ................. ... ... ... .... ............................................................. ... ... .....467
25.2.1 Maximize Bandwidth Usage Example .................................................................... 470
25.2.2 Reserving Bandwidth for Non-Bandwidth Class Traff ic .................................. ... .... . 471
25.3 The Class Setup Screen ................................................................................................. 471
25.4 Bandwidth Manager Class Configuration ......................................................................473
25.4.1 Bandwidth Borrowing Example .............................................................................. 476
25.5 Bandwidth Management Statistics ................................................................................. 477
25.6 The Monitor Screen ......................................................................................................478
Chapter 26
DNS Screens .........................................................................................................................479
26.1 Overview .......................................................................................................................... 479
26.1.1 What You Can Do in the DNS Screens ..................................................................479
26.1.2 What You Need To Know About DNS .................................................................... 479
26.2 The System Screen .........................................................................................................481
26.2.1 The Add Address Record Screen ..... .....................................................................483
26.2.2 The Insert Name Server Record Screen ........................ ........................................ 484
26.3 The DNS Cache Screen .................................................................................................. 485
26.4 The DHCP Screen ...........................................................................................................487
26.5 The DDNS Screen ..........................................................................................................488
26.6 Configuring the Dynamic DNS Screen ............................................................................489
Chapter 27
Remote Management Screens.............................................................................................491
27.1 Overview .......................................................................................................................... 491
27.1.1 What You Can Do in the Remote Management Screens .......................................491
27.1.2 What You Need To Know About Remote Management .........................................492
27.2 HTTPS Example ..............................................................................................................493
27.2.1 Internet Explorer Warning Messages ..................................................................... 493
27.2.2 Netscape Navigator Warning Messages ................................................................493
27.2.3 Avoiding the Browser Warning Messages ......................................... .... ... ..............494
27.2.4 Login Screen .......................................................................................................... 495
27.2.5 Enrolling and Importing SSL Client Certificates (Example) ....................................496
27.2.6 Installing the CA’s Certificate (Example) ................................................................497
27.2.7 Installing Your Personal Certificate(s) (Example) ................................................... 498
27.2.8 Using a Certificate When Accessing the ZyWALL (Example) ................................ 501
27.2.9 Secure Telnet Using SSH Examples ...................................................................... 502
27.3 The WWW Screen .........................................................................................................504
27.4 Configuring the WWW Screen .......................... .......................... .......................... ........... 505
27.5 The SSH Screen ............................................................................................................. 507
27.6 Configuring the SSH Screen ........................................................................................... 507
27.7 The Telnet Screen ........................................................................................................... 508
27.8 The FTP Screen ....................................................................................... .... .................509
20
ZyWALL 5/35/70 Series User’s Guide
Page 21

Table of Contents
27.9 The SNMP Screen .........................................................................................................510
27.9.1 Configuring the SNMP Screen ...............................................................................512
27.10 The DNS Screen ..........................................................................................................513
27.11 The CNM Screen ...... ... ... ... .... ... ............................................................. ... .....................514
27.12 Configuring the CNM Screen .........................................................................................514
27.13 Remote Management Technical Reference ................ .... ... ... ... ... .... ... ... ... .....................516
Chapter 28
UPnP Screens .......................................................................................................................519
28.1 Overview .......................................................................................................................... 519
28.1.1 What You Can Do in the UPnP Screens ................................................................ 519
28.1.2 What You Need To Know About UPnP ...................................................................519
28.2 UPnP Examples ..............................................................................................................520
28.2.1 Installing UPnP in Windows Example .................................................................... 520
28.2.2 Using UPnP in Windows XP Example ...................................................................522
28.3 The UPnP Screen ............................................................................................................ 526
28.4 The Ports Screen .......................................................................................................... 527
Chapter 29
Custom Application Screen.................................................................................................529
29.1 Overview .......................................................................................................................... 529
29.1.1 What You Can Do in the Custom Application Screen .................................... ... .... . 529
29.1.2 What You Need to Know About Custom Application .............................................. 529
29.2 The Custom Application Screen ...................................................................................... 529
Chapter 30
ALG Screen ...........................................................................................................................531
30.1 Overview .......................................................................................................................... 531
30.1.1 What You Need to Know About ALG .....................................................................531
30.2 The ALG Screen ..............................................................................................................535
Part V: Reports, Logs and Maintenance ............................................ 537
Chapter 31
Reports Screens ...................................................................................................................539
31.1 Overview .......................................................................................................................... 539
31.1.1 What You Can Do in the Reports Screens ..................... ........................................ 539
31.2 The Traffic Statistics Screen ............................................................................................ 539
31.2.1 Viewing Web Site Hits ............................................................................................ 541
31.2.2 Viewing Host IP Address ................................................ ....................... ................. 542
31.2.3 Viewing Protocol/Port ............................................................................................. 543
ZyWALL 5/35/70 Series User’s Guide
21
Page 22

Table of Contents
31.2.4 System Reports Specifications .......................................................... ................ ..... 545
31.3 The IDP Screen ..................... ... ... ... ... .... ... ... ... ............................................................... 545
31.4 The Anti-Virus Screen ...................................................................................................547
31.5 The Anti-Spam Screen ................................................................................................... 549
31.6 The E-mail Report Screen .............................................................................................551
Chapter 32
Logs Screens .......................................................................................................................555
32.1 Overview .......................................................................................................................... 555
32.1.1 What You Can Do in the Log Screens .................................................................... 555
32.1.2 What You Need To Know About Logs .................................................................... 555
32.2 The View Log Screen ...................................................................................................... 555
32.2.1 Log Description Example .......................................................................................556
32.2.2 About the Certificate Not Trusted Log .................................................................... 557
32.3 The Log Settings Screen ................................................................................................ 558
32.4 Technical Reference ........................................................................................................561
Chapter 33
Maintenance Screens...........................................................................................................585
33.1 Overview .......................................................................................................................... 585
33.1.1 What You Can Do in the Maintenance Screens .....................................................585
33.2 The General Setup Screen ..............................................................................................585
33.3 The Password Screen .................................................................................................... 586
33.4 The Time and Date Screen ............................................ ............. ............. ............. ........... 587
33.4.1 Time Server Synchronization Example ... .... ... ... ... .... ... ... ... ... .... ... ... ... .... .................590
33.5 The Device Mode Screen ................................................................................................ 591
33.6 Configuring the Device Mode Screen (Router) ............. .... .............................................. 592
33.7 Configuring the Device Mode Screen (Bridge) ............. .... ... ... ... ... .................................. 593
33.8 The F/W Upload Screen .................................................................................................595
33.9 The Backup and Restore Screen ....................................................................................597
33.10 The Restart Screen .......................................................................................................599
33.11 The Diagnostics Screen ................................................................................................. 599
Part VI: SMT.......................................................................................... 603
Chapter 34
Introducing the SMT.............................................................................................................605
22
34.1 Introduction to the SMT ...................................................................................................605
34.2 Accessing the SMT via the Console Port ........................................................................ 605
34.2.1 Initial Screen ..........................................................................................................605
34.2.2 Entering the Password ................................ ........................................................... 606
ZyWALL 5/35/70 Series User’s Guide
Page 23

Table of Contents
34.3 Navigating the SMT Interface .......................................................................................... 606
34.3.1 Main Menu ............................................................................................................. 607
34.3.2 SMT Menus Overview ............................................................................................ 609
34.4 Changing the System Password .....................................................................................610
34.5 Resetting the ZyWALL ......................................................................................................611
Chapter 35
SMT Menu 1 - General Setup ...............................................................................................613
35.1 Introduction to General Setup .......................................................................................... 613
35.2 Configuring General Setup ..............................................................................................613
35.2.1 Configuring Dynamic DNS ..................................................................................... 615
Chapter 36
WAN and Dial Backup Setup................................................................................................619
36.1 Introduction to WAN and Dial Backup Setup ................................................................... 619
36.2 WAN Setup ......................................................................................................................619
36.3 Dial Backup ..................................................................................................................... 620
36.3.1 Configuring Dial Backup in Menu 2 ........................................................................ 620
36.3.2 Advanced WAN Setup ........................................................................................... 621
36.3.3 Remote Node Profile (Backup ISP) ................... ... .... ... ... ... ... .... ... ... ... .....................623
36.3.4 Editing TCP/IP Options ..........................................................................................625
36.3.5 Editing Login Script ................................................................................................626
36.3.6 Remote Node Filter ................................................................................................ 628
36.3.7 3G Modem Setup ................................................................................................... 629
36.3.8 Remote Node Profile (3G WAN) ................. ... ........................................................ 630
Chapter 37
LAN Setup..............................................................................................................................633
37.1 Introduction to LAN Setup ............................................................................................... 633
37.2 Accessing the LAN Menus .............................................................................................. 633
37.3 LAN Port Filter Setup ....................................................................................................... 633
37.4 TCP/IP and DHCP Ethernet Setup Menu ........................................................................ 634
37.4.1 IP Alias Setup .........................................................................................................636
Chapter 38
Internet Access.....................................................................................................................639
38.1 Introduction to Internet Access Setup ..............................................................................639
38.2 Ethernet Encapsulation ...................................................................................................639
38.3 Configuring the PPTP Client ............................................................................................ 641
38.4 Configuring the PPPoE Client .........................................................................................642
38.5 Basic Setup Complete ..................................................................................................... 643
Chapter 39
DMZ Setup.............................................................................................................................645
ZyWALL 5/35/70 Series User’s Guide
23
Page 24

Table of Contents
39.1 Configuring DMZ Setup ...................................................................................................645
39.2 DMZ Port Filter Setup ......................................................................................................645
39.3 TCP/IP Setup ................................................................................................................... 646
39.3.1 IP Address ..............................................................................................................646
39.3.2 IP Alias Setup .........................................................................................................647
Chapter 40
Route Setup................................................................ .......... ........... ........... ...........................649
40.1 Configuring Route Setup ................................................................................................. 649
40.2 Route Assessment ..........................................................................................................649
40.3 Traffic Redirect ................................................................................................................ 650
40.4 Route Failover ................................................................................................................. 651
Chapter 41
Wireless Setup......................................................................................................................653
41.1 Wireless LAN Setup ........................................................................................................653
41.1.1 MAC Address Filter Setup ......................................................................................655
41.2 TCP/IP Setup ................................................................................................................... 656
41.2.1 IP Address ..............................................................................................................656
41.2.2 IP Alias Setup .........................................................................................................657
Chapter 42
Remote Node Setup..............................................................................................................659
42.1 Introduction to Remote Node Setup ................................................................................659
42.2 Remote Node Setup ........................................................................................................ 659
42.3 Remote Node Profile Setup .................................. .......................................................... . 660
42.3.1 Ethernet Encapsulation ..........................................................................................660
42.3.2 PPPoE Encapsulation ............................................................................................ 661
42.3.3 PPTP Encapsulation ..............................................................................................663
42.4 Edit IP .............................................................................................................................. 664
42.5 Remote Node Filter .........................................................................................................666
Chapter 43
IP Static Route Setup............................................................................................................669
43.1 IP Static Route Setup ......................................................................................................669
Chapter 44
Network Address Translation (NAT)....................................................................................673
44.1 Using NAT ........................................................................................................................ 673
44.1.1 SUA (Single User Account) Versus NAT ................................................................ 673
44.1.2 Applying NAT ......................................................................................................... 673
44.2 NAT Setup ....................................................................................................................... 675
44.2.1 Address Mapping Sets ...........................................................................................676
24
ZyWALL 5/35/70 Series User’s Guide
Page 25

Table of Contents
44.3 Configuring a Server behind NAT ........ .... ... .......................................................... ... ... .....681
44.4 General NAT Examples ...................................................................................................683
44.4.1 Internet Access Only .............................................................................................. 683
44.4.2 Example 2: Internet Access with a Default Server ............ ... .... ... ... ... .... .................685
44.4.3 Example 3: Multiple Public IP Addresses With Inside Servers .............................. 685
44.4.4 Example 4: NAT Unfriendly Application Programs ................................................. 689
44.5 Trigger Port Forwarding ...................................................................................................690
44.5.1 Two Points To Remember About Trigger Ports ...................................................... 690
Chapter 45
Introducing the ZyWALL Firewall........................................................................................693
45.1 Using ZyWALL SMT Menus ............................................................................................ 693
45.1.1 Activating the Firewall ............................................................................................693
Chapter 46
Filter Configuration...............................................................................................................695
46.1 Introduction to Filters ....................................................................................................... 695
46.1.1 The Filter Structure of the ZyWALL ........................................................................ 696
46.2 Configuring a Filter Set ....................................................................................................698
46.2.1 Configuring a Filter Rule ........................................................................................699
46.2.2 Configuring a TCP/IP Filter Rule ............................................................................ 700
46.2.3 Configuring a Generic Filter Rule ........................................................................... 702
46.3 Example Filter .................................................................................................................. 704
46.4 Filter Types and NAT .......................................................................................................706
46.5 Firewall Versus Filters ..................................................................................................... 706
46.5.1 Packet Filtering: ..................................................................................................... 706
46.5.2 Firewall ...................................................................................................................707
46.6 Applying a Filter ..............................................................................................................707
46.6.1 Applying LAN Filters ............................................................................................... 708
46.6.2 Applying DMZ Filters .............................................................................................. 708
46.6.3 Applying Remote Node Filters ............................................................................... 709
Chapter 47
SNMP Configuration.............................................................................................................711
47.1 SNMP Configuration .........................................................................................................711
47.2 SNMP Traps ....................................................................................................................712
Chapter 48
System Information & Diagnosis.........................................................................................713
48.1 Introduction to System Status .......................................................................................... 713
48.2 System Status ..................................................................................................................713
48.3 System Information and Console Port Speed .................................... ... ........................... 715
48.3.1 System Information ................................................................................................ 715
ZyWALL 5/35/70 Series User’s Guide
25
Page 26

Table of Contents
48.3.2 Console Port Speed ............................................................................................... 716
48.4 Log and Trace ..................................................................................................................717
48.4.1 Viewing Error Log ...................................................................................................717
48.4.2 Syslog Logging .......................................................................................................718
48.4.3 Call-Triggering Packet ............................................................................................ 721
48.5 Diagnostic ........................................................................................................................722
48.5.1 WAN DHCP ............................................................................................................ 723
Chapter 49
Firmware and Configuration File Maintenance..................................................................725
49.1 Introduction ......................................................................................................................725
49.2 Filename Conventions .....................................................................................................725
49.3 Backup Configuration ......................................................................................................726
49.3.1 Backup Configuration ........................ ....................................... .............................. 726
49.3.2 Using the FTP Command from the Command Line ................. ... ... ... .... ... ... ... ... .... . 727
49.3.3 Example of FTP Commands from the Command Line .......................................... 727
49.3.4 GUI-based FTP Clients ..........................................................................................728
49.3.5 File Maintenance Over WAN ..................................................................................728
49.3.6 Backup Configuration Using TFTP ......................................................................... 728
49.3.7 TFTP Command Example ...................................................................................... 729
49.3.8 GUI-based TFTP Clients ........................................................................................ 729
49.3.9 Backup Via Console Port .......................................................................................729
49.4 Restore Configuration ...................................................................................................... 730
49.4.1 Restore Using FTP ................................................................................................. 731
49.4.2 Restore Using FTP Session Example .................................................................... 732
49.4.3 Restore Via Console Port .......................................................................................732
49.5 Uploading Firmware and Configuration Files .................................................................. 733
49.5.1 Firmware File Upload .............................. ............................................................... 733
49.5.2 Configuration File Upload .......................................................................................734
49.5.3 FTP File Upload Command from the DOS Prompt Example ................................. 735
49.5.4 FTP Session Example of Firmware File Upload .................................................... 735
49.5.5 TFTP File Upload ................................................................................................... 735
49.5.6 TFTP Upload Command Example ......................................................................... 736
49.5.7 Uploading Via Console Port ................................................................................... 736
49.5.8 Uploading Firmware File Via Console Port ............................................................736
49.5.9 Example Xmodem Firmware Upload Using HyperTerminal ................................... 737
49.5.10 Uploading Configuration File Via Console Port ............................................... .... . 737
49.5.11 Example Xmodem Configuration Upload Using HyperTerminal ........................... 738
Chapter 50
System Maintenance Menus 8 to 10....................................................................................739
50.1 Command Interpreter Mode ............................................................................................739
50.2 Call Control Support ........................................................................................................ 740
26
ZyWALL 5/35/70 Series User’s Guide
Page 27

Table of Contents
50.2.1 Budget Management .............................................................................................. 740
50.2.2 Call History .............................................................................................................741
50.3 Time and Date Setting .......................................................... ...........................................742
Chapter 51
Remote Management............................................................................................................745
51.1 Remote Management ...................................................................................................... 745
51.1.1 Remote Management Limitations ..........................................................................747
Chapter 52
IP Policy Routing ..................................................................................................................749
52.1 IP Routing Policy Summary .............................................................................................749
52.2 IP Routing Policy Setup ...................................................................................................750
52.2.1 Applying Policy to Packets ..................................................................................... 752
52.3 IP Policy Routing Example .............................................................................................. 753
Chapter 53
Call Scheduling.....................................................................................................................757
53.1 Introduction to Call Scheduling ........................................................................................ 757
Part VII: Troubleshooting and Product Specifications..................... 761
Chapter 54
Troubleshooting....................................................................................................................763
54.1 Power, Hardware Connections, and LEDs .... ... .... ... ... ... .... ... ........................................... 763
54.2 ZyWALL Access and Login ..............................................................................................764
54.3 Internet Access ................................................................................................................766
54.4 Wireless Router/AP Troubleshooting ............................................................................... 767
54.5 UPnP ............................................................................................................................... 768
Chapter 55
Product Specifications.........................................................................................................769
55.1 Compatible 3G Cards ......................................................................................................773
55.2 Power Adaptor Specifications .......................................................................................... 775
Part VIII: Appendices and Index ......................................................... 779
Appendix A Removing and Installing a Fuse .......................................................................781
Appendix B Common Services.............................................................................................783
ZyWALL 5/35/70 Series User’s Guide
27
Page 28

Table of Contents
Appendix C Wireless LANs ..................................................................................................787
Appendix D Windows 98 SE/Me Requirements for Anti-Virus Message Display.................801
Appendix E Legal Information ..............................................................................................805
Appendix F Customer Support.............................................................................................809
Index.......................................................................................................................................815
28
ZyWALL 5/35/70 Series User’s Guide
Page 29

List of Figures
List of Figures
Figure 1 Secure Internet Access via Cable, DSL or Wireless Modem ................................................... 52
Figure 2 VPN Application .......................................................................................................................53
Figure 3 3G WAN Application ................................................................................................................. 53
Figure 4 Attaching Rubber Feet ............................................................................................................ 56
Figure 5 Attaching Mounting Brackets and Screws ................................................................................57
Figure 6 Rack Mounting .........................................................................................................................57
Figure 7 WLAN Card Installation ............................................................................................................58
Figure 8 ZyWALL 70 Front Panel ........................................................................................................... 59
Figure 9 ZyWALL 35 Front Panel ........................................................................................................... 59
Figure 10 ZyWALL 5 Front Panel ....................... .................................................................................... 59
Figure 11 Change Password Screen ...................................................................................................... 62
Figure 12 Replace Certificate Screen ..................................................................................................... 62
Figure 13 Example Xmodem Upload ......................................................................................................63
Figure 14 HOME Screen .............................. ............................................................. ... ..........................64
Figure 15 Web Configurator HOME Screen in Router Mode (ZyWALL 5) ............................................ 65
Figure 16 Web Configurator HOME Screen in Bridge Mode .................................................................. 71
Figure 17 HOME > Port Statistics ........................................................................................................... 80
Figure 18 HOME > Show Statistics > Line Chart .................................................................................... 81
Figure 19 HOME > Show DHCP Table ...................................................................................................82
Figure 20 HOME > VPN Status .............................................................................................................. 83
Figure 21 Home > Bandwidth Monitor ................................... ................................................................. 84
Figure 22 Wizard Setup Welcome ..........................................................................................................87
Figure 23 ISP Parameters: Ethernet Encapsulation ...............................................................................88
Figure 24 ISP Parameters: PPPoE Encapsulation ................................................................................. 89
Figure 25 ISP Parameters: PPTP Encapsulation ...................................................................................91
Figure 26 Internet Access Wizard: Second Screen ................................................................................92
Figure 27 Internet Access Setup Complete .................................. ... ... .... ... ... ... ... .................................... 93
Figure 28 Internet Access Wizard: Registration .....................................................................................93
Figure 29 Internet Access Wizard: Registration in Progress .................................................................. 94
Figure 30 Internet Access Wizard: Status .............................................................................................. 95
Figure 31 Internet Access Wizard: Registration Failed ..........................................................................95
Figure 32 Internet Access Wizard: Registered Device ........................................................................... 95
Figure 33 Internet Access Wizard: Activated Services ...........................................................................96
Figure 34 VPN Wizard: Gateway Setting ............................................................................................... 96
Figure 35 VPN Wizard: Network Setting ................................................................................................ 98
Figure 36 VPN Wizard: IKE Tunnel Setting ............................................................................................99
Figure 37 VPN Wizard: IPSec Setting ..................................................................................................101
Figure 38 VPN Wizard: VPN Status ..................................................................................................... 102
ZyWALL 5/35/70 Series User’s Guide
29
Page 30

List of Figures
Figure 39 VPN Wizard Setup Complete ................... .... ... ... ... .......................................................... ..... 104
Figure 40 Anti-Spam Wizard: Email Server Location Setting .............................................................. 105
Figure 41 Anti-Spam Wizard: Direction Recommendations ...... ... ... ... .... ... ... ... ... .... ... ... ... .... ... ... ... ........106
Figure 42 Anti-Spam Wizard: Direction Configuration .......................................................................... 107
Figure 43 Anti-Spam Wizard: Setup Complete ...... ... .... ... ... ... .... ... ... ... ..................................................108
Figure 44 Dynamic VPN Rule Example ........................... ... ... .... ... ... ... .... ... ... ... ... .... ... ... ... .... ... ... ... ... .....109
Figure 45 VPN Gateway Policy Edit Screens ............................................... ... ... .... ... ... ... ......................112
Figure 46 SECURITY > VPN > Add Network Policy (ZyWALL A) .........................................................113
Figure 47 VPN Network Policy Edit Screens ................................................ ... ... .... ... ... ... .... ... ... ... ... ......114
Figure 48 Activate VPN Rule (ZyWALL B) ...........................................................................................115
Figure 49 Tutorial: VPN Summary Screens Comparison Example .............. ... ... .... ... ... ... .... ... ...............116
Figure 50 Check The Telecommuter's Computer IP Address ...............................................................117
Figure 51 Telecommuter Pinging a Network X IP Address Example .....................................................118
Figure 52 Additional Dynamic VPN Rules Example ........................ ... .... ... ... ... ... .... ... ... ... .... ... ... ... ... .... ..119
Figure 53 IDP for From VPN Traffic ......................................................................................................120
Figure 54 IDP Configuration for Traffic From VPN ...............................................................................121
Figure 55 IDP for To VPN Traffic ..... ............................................................. ... ... .................................. 121
Figure 56 IDP Configuration for To VPN Traffic .. ..................................................................................122
Figure 57 Firewall Rule for VPN ...................... ... ... ... .... ... ... ..................................................................123
Figure 58 SECURITY > VPN > VPN Rules (IKE) ................................................................................. 123
Figure 59 SECURITY > VPN > VPN Rules (IKE)> Add Gateway Policy ........................................... 124
Figure 60 SECURITY > VPN > VPN Rules (IKE): With Gateway Policy Example ...............................125
Figure 61 SECURITY > VPN > VPN Rules (IKE)> Add Network Policy ............................................. 126
Figure 62 SECURITY > FIREWALL > Rule Summary .........................................................................127
Figure 63 SECURITY > FIREWALL > Rule Summary > Edit: Allow ..................................... ... ... ........128
Figure 64 SECURITY > FIREWALL > Rule Summary: Allow ............................. .................................. 129
Figure 65 SECURITY > FIREWALL > Default Rule: Block From VPN To LAN ....................................130
Figure 66 Tutorial: NETWORK > WAN > 3G (WAN2) ....................................................................... 131
Figure 67 Tutorial: Home .....................................................................................................................132
Figure 68 Tutorial: NETWORK > WAN > General ............................................................................. 133
Figure 69 SECURITY > CONTENT FILTER > General ........................................................................ 134
Figure 70 SECURITY > CONTENT FILTER > Policy ........................................................................... 135
Figure 71 SECURITY > CONTENT FILTER > Policy > External Database (Default) .......................... 135
Figure 72 HOME > Show DHCP Table .................................................................................................136
Figure 73 SECURITY > CONTENT FILTER > Policy ........................................................................... 136
Figure 74 SECURITY > CONTENT FILTER > Policy > Insert ............................................. ................. 137
Figure 75 SECURITY > CONTENT FILTER > Policy ........................................................................... 137
Figure 76 SECURITY > CONTENT FILTER > Policy > Schedule (Bob) ..............................................138
Figure 77 SECURITY > CONTENT FILTER > Policy ........................................................................... 138
Figure 78 SECURITY > CONTENT FILTER > Policy > External Database (Bob) ............................... 139
Figure 79 REGISTRATION > Registration ...........................................................................................143
Figure 80 REGISTRATION > Registration: Registered Device ............................................................ 144
Figure 81 REGISTRATION > Service ................................................................................................... 145
30
ZyWALL 5/35/70 Series User’s Guide
Page 31

List of Figures
Figure 82 LAN and WAN ..................................................................................................................... 149
Figure 83 NETWORK > LAN ................................................................................................................ 153
Figure 84 NETWORK > LAN > Static DHCP ........................................................................................ 156
Figure 85 Physical Network & Partitioned Logical Networks ................................................................ 157
Figure 86 NETWORK > LAN > IP Alias ................................................................................................ 157
Figure 87 NETWORK > LAN > Port Roles ...........................................................................................159
Figure 88 Port Roles Change Complete ....................................... ................... .................... ................. 159
Figure 89 Bridge Mode ......................................................................................................................... 161
Figure 90 Router Mode ......................................................................................................................... 161
Figure 91 Bridge Loop: Bridge Connected to Wired LAN ..................................................................... 162
Figure 92 NETWORK > Bridge .............................................................................................................163
Figure 93 NETWORK > Bridge > Port Roles ........................................................................................165
Figure 94 Port Roles Change Complete ....................................... ................... .................... ................. 165
Figure 95 LAN and WAN (Multiple) ...................................................................................................... 169
Figure 96 LAN and WAN (Multiple) ...................................................................................................... 169
Figure 97 Incorrect WAN IP .................................................................................................................. 173
Figure 98 NETWORK > WAN > General .............................................................................................174
Figure 99 Least Load First Example .................................................................................................... 177
Figure 100 Load Balancing: Least Load First ....................................................................................... 178
Figure 101 Weighted Round Robin Algorithm Example ....................................................................... 180
Figure 102 Load Balancing: Weighted Round Robin ........................................................................... 180
Figure 103 Spillover Algorithm Example .......................................................... ................ ..................... 181
Figure 104 Load Balancing: Spillover ................................................................................................... 181
Figure 105 NETWORK > WAN > WAN (Ethernet Encapsulation) ..................................................... 184
Figure 106 NETWORK > WAN > WAN (PPPoE Encapsulation) ......................................................... 187
Figure 107 NETWORK > WAN > WAN (PPTP Encapsulation) ...........................................................190
Figure 108 NETWORK > WAN > 3G (WAN 2) ..................................................................................194
Figure 109 Traffic Redirect WAN Setup ................................................................................................ 197
Figure 110 Traffic Redirect LAN Setup ................................................................................................. 198
Figure 111 NETWORK > WAN > Traffic Redirect .................................................................................198
Figure 112 NETWORK > WAN > Dial Backup .....................................................................................199
Figure 113 NETWORK > WAN > Dial Backup > Edit ..........................................................................203
Figure 114 DMZ Overview .................................................................................................................... 207
Figure 115 DMZ Public Address Example .................................................... ........................................ 209
Figure 116 DMZ Private and Public Address Example ......................................................................... 210
Figure 117 NETWORK > DMZ .............................................................................................................211
Figure 118 NETWORK > DMZ > Static DHCP .................................................................................... 214
Figure 119 NETWORK > DMZ > IP Alias ............................................................................................215
Figure 120 NETWORK > DMZ > Port Roles ....................................................................................... 216
Figure 121 WLAN Overview ................................................................................................................. 219
Figure 122 NETWORK > WLAN ..........................................................................................................221
Figure 123 NETWORK > WLAN > Static DHCP ................................................................................. 224
Figure 124 NETWORK > WLAN > IP Alias ......................................................................................... 225
ZyWALL 5/35/70 Series User’s Guide
31
Page 32

List of Figures
Figure 125 WLAN Port Role Example ................................................................................................. 226
Figure 126 NETWORK > WLAN > Port Roles ..................................................................................... 227
Figure 127 NETWORK > WLAN > Port Roles: Change Complete .. ... .... ... ... ... ... .... ... ........................... 227
Figure 128 WLAN Overview ................................................................................................................. 229
Figure 129 ZyWALL Wireless Security Levels ...................................................................................... 230
Figure 130 WIRELESS > Wi-Fi > Wireless Card: No Security ............................................................. 232
Figure 131 WIRELESS > Wi-Fi > Wireless Card: Static WEP .............................................................. 235
Figure 132 WIRELESS > Wi-Fi > Wireless Card: WPA-PSK ...............................................................236
Figure 133 WIRELESS > Wi-Fi > Wireless Card: WPA ........................................................................ 237
Figure 134 WIRELESS > Wi-Fi > Wireless Card: 802.1x + Dynamic WEP .......................................... 238
Figure 135 WIRELESS > Wi-Fi > Wireless Card: 802.1x + Static WEP ............................................... 239
Figure 136 WIRELESS > Wi-Fi > Wireless Card: 802.1x + No WEP ................................................... 241
Figure 137 WIRELESS > Wi-Fi > Wireless Card: No Access 802.1x + Static WEP .............................242
Figure 138 WIRELESS > Wi-Fi > MAC Filter .......................................................................................243
Figure 139 EAP Authentication ............................................................................................................ 245
Figure 140 WPA-PSK Authentication ................................................................................................... 246
Figure 141 WPA with RADIUS Application Example ............................................................................ 247
Figure 142 Default Firewall Action ........................................................................................................ 251
Figure 143 Blocking All LAN to WAN IRC Traffic Example ..................................................................253
Figure 144 Limited LAN to WAN IRC Traffic Example .......................................................................... 254
Figure 145 SECURITY > FIREWALL > Default Rule (Router Mode) ................................................... 255
Figure 146 SECURITY > FIREWALL > Default Rule (Bridge Mode) .................................................... 257
Figure 147 SECURITY > FIREWALL > Rule Summary .......................................................................259
Figure 148 SECURITY > FIREWALL > Rule Summary > Edit ............................................................ 261
Figure 149 SECURITY > FIREWALL > Anti-Probing ........................................................................... 263
Figure 150 SECURITY > FIREWALL > Threshold ............................................................................ 264
Figure 151 SECURITY > FIREWALL > Service ................................................................................... 266
Figure 152 SECURITY > FIREWALL > Service > Add .........................................................................267
Figure 153 My Service Firewall Rule Example: Service ...................................................................... 268
Figure 154 My Service Firewall Rule Example: Edit Custom Service ................................................. 268
Figure 155 My Service Firewall Rule Example: Rule Summary ...................................... .... .................269
Figure 156 My Service Firewall Rule Example: Rule Edit ...................................................................269
Figure 157 My Service Firewall Rule Example: Rule Configuration ....................................... ... ... ... .... . 270
Figure 158 My Service Firewall Rule Example: Rule Summary ...................................... .... .................271
Figure 159 From LAN to VPN Example ...............................................................................................273
Figure 160 From VPN to LAN Example ...............................................................................................273
Figure 161 From VPN to VPN Example .............................................................................................. 274
Figure 162 Using IP Alias to Solve the Triangle Route Problem ..... ..................................................... 275
Figure 163 Three-Way Handshake ....................................................................................................... 275
Figure 164 Network Intrusions ............................................................................................................. 277
Figure 165 Applying IDP to Interfaces .................................................................................................. 278
Figure 166 SECURITY > IDP > General .............................................................................................. 279
Figure 167 SECURITY > IDP > Signature: Group View ....................................................................... 283
32
ZyWALL 5/35/70 Series User’s Guide
Page 33

List of Figures
Figure 168 SECURITY > IDP > Signature: Query View ....................................................................... 285
Figure 169 SECURITY > IDP > Signature: Query by Partial Name .....................................................287
Figure 170 SECURITY > IDP > Signature: Query by Complete ID ......................................................288
Figure 171 Signature Query by Attribute. .............................................................................................289
Figure 172 SECURITY > IDP > Anomaly ............................................................................................. 290
Figure 173 SECURITY > IDP > Update ...............................................................................................292
Figure 174 SECURITY > IDP > Backup & Restore .............................................................................. 294
Figure 175 ZyWALL Anti-virus Overview ........................................................................................... 299
Figure 176 SECURITY > ANTI-VIRUS > General ...............................................................................302
Figure 177 SECURITY > ANTI-VIRUS > Signature: Query View .........................................................304
Figure 178 Query Example Search Criteria .......................................................................................... 305
Figure 179 Query Example Search Results .........................................................................................306
Figure 180 SECURITY > ANTI-VIRUS > Update ................................................................................. 307
Figure 181 SECURITY > ANTI-VIRUS > Backup and Restore ............................................................ 309
Figure 182 Anti-spam Overview ........................................................................................................... 313
Figure 183 SECURITY > ANTI-SPAM > General ................................................................................. 316
Figure 184 SECURITY > ANTI-SPAM > External DB ..........................................................................319
Figure 185 SECURITY > ANTI-SPAM > Lists ...................................................................................... 321
Figure 186 SECURITY > ANTI-SPAM > Lists > Edit ........................................................................... 322
Figure 187 Content Filtering Lookup Procedure ...................................................................................328
Figure 188 SECURITY > CONTENT FILTER > General ...................................................................... 329
Figure 189 SECURITY > CONTENT FILTER > Policy ......................................................................... 331
Figure 190 SECURITY > CONTENT FILTER > Policy > General ........................................................ 333
Figure 191 SECURITY > CONTENT FILTER > Policy > External Database ....................................... 334
Figure 192 SECURITY > CONTENT FILTER > Policy > Customization .............................................. 341
Figure 193 SECURITY > CONTENT FILTER > Policy > Schedule ...................................................... 343
Figure 194 SECURITY > CONTENT FILTER > Object ........................................................................344
Figure 195 SECURITY > CONTENT FILTER > Cache ........................................................................ 346
Figure 196 myZyXEL.com: Login ......................................................................................................... 350
Figure 197 myZyXEL.com: Welcome ................................................................................................... 350
Figure 198 myZyXEL.com: Service Management ................................................................................ 351
Figure 199 Blue Coat: Login ................................................................................................................. 351
Figure 200 Content Filtering Reports Main Screen ..............................................................................352
Figure 201 Blue Coat: Report Home ....................................................................................................352
Figure 202 Global Report Screen Example .......................................................................................... 353
Figure 203 Requested URLs Example ................................................................................................. 354
Figure 204 Web Page Review Process Screen ................................................................................... 355
Figure 205 VPN: Example .................................................................................................................... 357
Figure 206 VPN: IKE SA and IPSec SA .............................................................................................. 358
Figure 207 Gateway and Network Policies ........... ... .... ... ... ... .... ... ........................................................ 359
Figure 208 IPSec Fields Summary ......................................................................................................359
Figure 209 SECURITY > VPN > VPN Rules (IKE) ..............................................................................360
Figure 210 SECURITY > VPN > VPN Rules (IKE) > Edit Gateway Policy .................................... .... . 362
ZyWALL 5/35/70 Series User’s Guide
33
Page 34

List of Figures
Figure 211 SECURITY > VPN > VPN Rules (IKE) > Edit Network Policy ........................................... 368
Figure 212 SECURITY > VPN > VPN Rules (IKE) > Edit Network Polic y > Port Forwarding ............. 373
Figure 213 SECURITY > VPN > VPN Rules (IKE) > Move Network Policy ... ... .... ... ... ... .... ... ... ... ... .... . 374
Figure 214 SECURITY > VPN > VPN Rules (Manual) ........................................................................ 375
Figure 215 SECURITY > VPN > VPN Rules (Manual) > Edit ..............................................................376
Figure 216 SECURITY > VPN > SA Monitor ....................................................................................... 379
Figure 217 Overlap in a Dynamic VPN Rule ........................................................................................380
Figure 218 Overlap in IP Alias and VPN Remote Networks ................... .............................................. 381
Figure 219 SECURITY > VPN > Global Setting .................................................................................. 381
Figure 220 Telecommuters Sharing One VPN Rule Example .............................................................. 383
Figure 221 Telecommuters Using Unique VPN Rules Example ........................................................... 384
Figure 222 VPN for Remote Management Example ............................................................................385
Figure 223 VPN Topologies .................................................................................................................. 386
Figure 224 Hub-and-spoke VPN Example ...........................................................................................387
Figure 225 IKE SA: Main Negotiation Mode, Steps 1 - 2: IKE SA Proposal ......................................... 388
Figure 226 IKE SA: Main Negotiation Mode, Steps 3 - 4: DH Key Exchange ......................................389
Figure 227 IKE SA: Main Negotiation Mode, Steps 5 - 6: Authentication ............................................. 389
Figure 228 VPN/NAT Example .............................................................................................................392
Figure 229 Virtual Mapping of Local and Remote Network IP Addresses ........................... ................. 394
Figure 230 VPN: Transport and Tunnel Mode Encapsulation .............................................................. 394
Figure 231 IPSec High Availability ....................................................................................................... 397
Figure 232 Certificates on Your Computer ...........................................................................................400
Figure 233 Certificate Details .............................................................................................................. 401
Figure 234 SECURITY > CERTIFICATES > My Certificates ...............................................................402
Figure 235 SECURITY > CERTIFICATES > My Certificates > Details ................................................. 404
Figure 236 SECURITY > CERTIFICATES > My Certificates > Export ................................................. 406
Figure 237 SECURITY > CERTIFICATES > My Certificates > Import ................................................. 408
Figure 238 SECURITY > CERTIFICATES > My Certificates > Import: PKCS#12 ............................... 408
Figure 239 SECURITY > CERTIFICATES > My Certificates > Create (Basic) .................................... 409
Figure 240 SECURITY > CERTIFICATES > My Certificates > Create (Advanced) ............................. 410
Figure 241 SECURITY > CERTIFICATES > Trusted CAs ...................................................................414
Figure 242 SECURITY > CERTIFICATES > Trusted CAs > Details .................................................... 416
Figure 243 SECURITY > CERTIFICATES > Trusted CAs > Import ..................................................... 419
Figure 244 SECURITY > CERTIFICATES > Trusted Remote Hosts .................................................... 420
Figure 245 SECURITY > CERTIFICATES > Trusted Remote Hosts > Import ..................................... 421
Figure 246 SECURITY > CERTIFICATES > Trusted Remote Hosts > Details ..................................... 422
Figure 247 SECURITY > CERTIFICATES > Directory Servers ....................................................... ..... 424
Figure 248 SECURITY > CERTIFICATES > Directory Server > Add ................................................... 425
Figure 249 SECURITY > AUTH SERVER > Local User Database ...................................................... 429
Figure 250 SECURITY > AUTH SERVER > RADIUS .......................................................................... 430
Figure 251 ADVANCED > NAT > NAT Overview .................................................................................. 437
Figure 252 ADVANCED > NAT > Address Mapping .............................................................................439
Figure 253 ADVANCED > NAT > Address Mapping > Edit .................................................................. 440
34
ZyWALL 5/35/70 Series User’s Guide
Page 35

List of Figures
Figure 254 Multiple Servers Behind NAT Example .............................................................................. 4 42
Figure 255 Port Translation Example ................................................................................................... 443
Figure 256 ADVANCED > NAT > Port Forwarding ...............................................................................444
Figure 257 Trigger Port Forwarding Process: Example ............................................. .......... ......... ........ 445
Figure 258 ADVANCED > NAT > Port Triggering ................................................................................. 446
Figure 259 NAT Overview .................................................................................................................... 448
Figure 260 NAT Application With IP Alias ............................................................................................ 449
Figure 261 Port Restricted Cone NAT Example ................................................................................... 450
Figure 262 Example of Static Routing Topology ...................................................................................451
Figure 263 ADVANCED > STATIC ROUTE > IP Static Route .............................................................. 453
Figure 264 ADVANCED > STATIC ROUTE > IP Static Route > Edit ............ ... ... .... ... ... ........................ 454
Figure 265 ADVANCED > POLICY ROUTE > Policy Route Summary ................................................ 459
Figure 266 ADVANCED > POLICY ROUTE > Edit ..............................................................................461
Figure 267 Subnet-based Bandwidth Management Example ......................... ... .... ... ... ... .... ... ... ... ... .... . 466
Figure 268 ADVANCED > BW MGMT > Summary .............................................................................. 468
Figure 269 ADVANCED > BW MGMT > Class Setup .......................................................................... 472
Figure 270 ADVANCED > BW MGMT > Class Setup > Add Sub-Class ................................... ... ... .... . 474
Figure 271 ADVANCED > BW MGMT > Class Setup > Statistics ........................................................ 477
Figure 272 ADVANCED > BW MGMT > Monitor ................................................................................. 478
Figure 273 Private DNS Server Example .............................................................................................481
Figure 274 ADVANCED > DNS > System DNS ................................................................................... 482
Figure 275 ADVANCED > DNS > Add (Address Record) .................................................................... 483
Figure 276 ADVANCED > DNS > Insert (Name Server Record) ............................................... ........... 484
Figure 277 ADVANCED > DNS > Cache ............................................................................................. 486
Figure 278 ADVANCED > DNS > DHCP ..............................................................................................487
Figure 279 ADVANCED > DNS > DDNS ..............................................................................................489
Figure 280 Secure and Insecure Remote Management From the WAN ..............................................491
Figure 281 Security Alert Dialog Box (Internet Explorer) ......................................................................493
Figure 282 Security Certificate 1 (Netscape) ........................................................................................494
Figure 283 Security Certificate 2 (Netscape) ........................................................................................494
Figure 284 Example: Lock Denoting a Secure Connection ............................. ..................................... 495
Figure 285 Replace Certificate ............................................................................................................. 495
Figure 286 Device-specific Certificate ..................................................................................................496
Figure 287 Common ZyWALL Certificate ............................................................................................. 496
Figure 288 ZyWALL Trusted CA Screen .............................................................................................. 497
Figure 289 CA Certificate Example ...................................................................................................... 498
Figure 290 Personal Certificate Import Wizard 1 ....................... ... ... ..................................................... 499
Figure 291 Personal Certificate Import Wizard 2 ....................... ... ... ..................................................... 499
Figure 292 Personal Certificate Import Wizard 3 ....................... ... ... ..................................................... 500
Figure 293 Personal Certificate Import Wizard 4 ....................... ... ... ..................................................... 500
Figure 294 Personal Certificate Import Wizard 5 ....................... ... ... ..................................................... 501
Figure 295 Personal Certificate Import Wizard 6 ....................... ... ... ..................................................... 501
Figure 296 Access the ZyWALL Via HTTPS ........................................................................................ 501
ZyWALL 5/35/70 Series User’s Guide
35
Page 36

List of Figures
Figure 297 SSL Client Authentication ................................................................................................... 502
Figure 298 Secure Web Configurator Login Screen .............................................................................502
Figure 299 SSH Example 1: Store Host Key ........................................................................................ 503
Figure 300 SSH Example 2: Test ........................................................................................................503
Figure 301 SSH Example 2: Log in ...................................................................................................... 503
Figure 302 Secure FTP: Firmware Upload Example ............................................................................ 504
Figure 303 HTTPS Implementation ...................................................................................................... 505
Figure 304 ADVANCED > REMOTE MGMT > WWW ..........................................................................506
Figure 305 SSH Communication Over the WAN Example ............................. ... .... .............................. 507
Figure 306 ADVANCED > REMOTE MGMT > SSH ............................................................................. 508
Figure 307 ADVANCED > REMOTE MGMT > Telnet ..........................................................................509
Figure 308 ADVANCED > REMOTE MGMT > FTP ............................................................................. 510
Figure 309 SNMP Management Model .................................................................................................511
Figure 310 ADVANCED > REMOTE MGMT > SNMP .......................................................................... 512
Figure 311 ADVANCED > REMOTE MGMT > DNS ............................................................................. 514
Figure 312 ADVANCED > REMOTE MGMT > CNM ............................................................................515
Figure 313 How SSH Works ................................................................................................................. 516
Figure 314 ADVANCED > UPnP .......................................................................................................... 526
Figure 315 ADVANCED > UPnP > Ports ..............................................................................................527
Figure 316 ADV ANCED > Custom APP ..............................................................................................530
Figure 317 H.323 ALG Example ..........................................................................................................533
Figure 318 H.323 with Multiple WAN IP Addresses
Figure 319 H.323 Calls from the WAN
Figure 320 SIP ALG Example ............................................................................................................. 535
Figure 321 ADVANCED > ALG ........................................................................................................... 536
Figure 322 REPORTS > Traffic Statistics .............................................................................................540
Figure 323 REPORTS > Traffic Statistics: Web Site Hits Example ......................................................542
Figure 324 REPORTS > Traffic Statistics: Host IP Address Example ..................................................543
Figure 325 REPORTS > Traffic Statistics: Protocol/Port Example .......................................................544
Figure 326 REPORTS > IDP ............................................................................................................... 545
Figure 327 REPORTS > IDP > Source ...............................................................................................547
Figure 328 REPORTS > IDP > Destination .........................................................................................547
Figure 329 REPORTS > Anti-Virus ..................................................................................................... 547
Figure 330 REPORTS > Anti-Virus > Source ......................................................................................548
Figure 331 REPORTS > Anti-Virus > Destination ...............................................................................549
Figure 332 REPORTS > Anti-Spam ....................................................................................................549
Figure 333 REPORTS > Anti-Spam > Source ..................................................................................... 551
Figure 334 REPORTS > Anti-Spam > Score Distribution ....................................................................551
Figure 335 REPORTS > E-mail Report ...............................................................................................552
Figure 336 LOGS > View Log ...........................................................................................................556
Figure 337 myZyXEL.com: Download Center ...................................................................................... 558
Figure 338 myZyXEL.com: Certificate Download ................................................................................. 558
Figure 339 LOGS > Log Settings ......................................................................................................... 559
with Multiple Outgoing Calls .................................................... 534
............................................................................ 533
36
ZyWALL 5/35/70 Series User’s Guide
Page 37

List of Figures
Figure 340 MAINTENANCE > General Setup ......................................................................................586
Figure 341 MAINTENANCE > Password ............................................................................................ 587
Figure 342 MAINTENANCE > Time and Date ......................................................................................588
Figure 343 Synchronization in Process ................................................................................................590
Figure 344 Synchronization is Successful ................ .................................................... ........................ 590
Figure 345 Synchronization Fail ........................................................................................................... 591
Figure 346 MAINTENANCE > Device Mode (Router Mode) .................. .............................................. 593
Figure 347 MAINTENANCE > Device Mode (Bridge Mode) ................................................................ 594
Figure 348 MAINTENANCE > Firmware Upload .................................................................................. 595
Figure 349 Firmware Upload In Process .............................................................................................. 596
Figure 350 Network Temporarily Disconnected ....................................................................................596
Figure 351 Firmware Upload Error ....................................................................................................... 596
Figure 352 MAINTENANCE > Backup and Restore ............................................................................. 597
Figure 353 Configuration Upload Successful .......................................................................................598
Figure 354 Network Temporarily Disconnected ....................................................................................598
Figure 355 Configuration Upload Error .................................................................................................598
Figure 356 Reset Warning Message .................................................................................................... 599
Figure 357 MAINTENANCE > Restart .................................................................................................599
Figure 358 MAINTENANCE > Diagnostics .........................................................................................600
Figure 359 Initial Screen ....................................................................................................................... 606
Figure 360 Password Screen .............................................................................................................. 606
Figure 361 Main Menu (Router Mode) ................................................................................................. 607
Figure 362 Main Menu (Bridge Mode) .................................................................................................. 608
Figure 363 Menu 23: System Password ............................. .................... ................... ................... .........611
Figure 364 Menu 1: General Setup (Router Mode) ..............................................................................613
Figure 365 Menu 1: General Setup (Bridge Mode) .............................................................................. 614
Figure 366 Menu 1.1: Configure Dynamic DNS ...................................................................................615
Figure 367 Menu 1.1.1: DDNS Host Summary .................................................................................... 616
Figure 368 Menu 1.1.1: DDNS Edit Host .............................................................................................. 617
Figure 369 MAC Address Cloning in WAN Setup ................................................................................. 619
Figure 370 Menu 2: Dial Backup Setup ............................................................................................... 621
Figure 371 Menu 2.1: Advanced WAN Setup .......................................................................................622
Figure 372 Menu 11.3: Remote Node Profile (Backup ISP) ................................................................. 623
Figure 373 Menu 11.3.2: Remote Node Network Layer Options ......................................... ... ... ... ... .... . 625
Figure 374 Menu 11.3.3: Remote Node Script .....................................................................................627
Figure 375 Menu 11.3.4: Remote Node Filter ...................................................................................... 628
Figure 376 3G Modem Setup in WAN Setup (ZyWALL 5) ................................................................... 629
Figure 377 Menu 11.2: Remote Node Profile (3G WAN) ......................................................................630
Figure 378 Menu 3: LAN Setup ............................................................................................................ 633
Figure 379 Menu 3.1: LAN Port Filter Setup ........................................................................................ 634
Figure 380 Menu 3: TCP/IP and DHCP Setup .................................................................................... 634
Figure 381 Menu 3.2: TCP/IP and DHCP Ethernet Setup ....................................................................635
Figure 382 Menu 3.2.1: IP Alias Setup ................................................................................................. 636
ZyWALL 5/35/70 Series User’s Guide
37
Page 38

List of Figures
Figure 383 Menu 4: Internet Access Setup (Ethernet) .........................................................................640
Figure 384 Internet Access Setup (PPTP) ........................................................................................... 642
Figure 385 Internet Access Setup (PPPoE) ......................................................................................... 643
Figure 386 Menu 5: DMZ Setup ........................................................................................................... 645
Figure 387 Menu 5.1: DMZ Port Filter Setup ........................................................................................645
Figure 388 Menu 5: DMZ Setup ........................................................................................................... 646
Figure 389 Menu 5.2: TCP/IP and DHCP Ethernet Setup ....................................................................646
Figure 390 Menu 5.2.1: IP Alias Setup ................................................................................................. 647
Figure 391 Menu 6: Route Setup ......................................................................................................... 649
Figure 392 Menu 6.1: Route Assessment ............................................................................................ 649
Figure 393 Menu 6.2: Traffic Redirect .................................................................................................. 650
Figure 394 Menu 6.3: Route Failover ...................................................................................................651
Figure 395 Menu 7.1: Wireless Setup ..................................................................................................653
Figure 396 Menu 7.1.1: WLAN MAC Address Filter ............................................................................. 655
Figure 397 Menu 7: WLAN Setup .......................... .................... ................... ................... ..................... 656
Figure 398 Menu 7.2: TCP/IP and DHCP Ethernet Setup ....................................................................657
Figure 399 Menu 7.2.1: IP Alias Setup ................................................................................................. 658
Figure 400 Menu 11: Remote Node Setup ............................ .... ... ... ... .... ... ... ... ... ..................................659
Figure 401 Menu 11.1: Remote Node Profile for Ethernet Encapsulation ............................................ 660
Figure 402 Menu 11.1: Remote Node Profile for PPPoE Encapsulation ..............................................662
Figure 403 Menu 11.1: Remote Node Profile for PPTP Encapsulation ................................................ 664
Figure 404 Menu 11.1.2: Remote Node Network Layer Options for Ethernet Encapsulation ............... 665
Figure 405 Menu 11.1.4: Remote Node Filter (Ethernet Encapsulation) .............................................. 667
Figure 406 Menu 11.1.4: Remote Node Filter (PPPoE or PPTP Encapsulation) .................................667
Figure 407 Menu 12: IP Static Route Setup ........................................................................................670
Figure 408 Menu 12. 1: Edit IP Static Route ........................................................................................670
Figure 409 Menu 4: Applying NAT for Internet Access ....................................... .... ... ... ........................ 674
Figure 410 Menu 11.1.2: Applying NAT to the Remote Node .... ... ... ... .... .............................................. 674
Figure 411 Menu 15: NAT Setup .......................................................................................................... 675
Figure 412 Menu 15.1: Address Mapping Sets ...................................................................... ... ... ... .... . 676
Figure 413 Menu 15.1.255: SUA Address Mapping Rules ................................................................... 676
Figure 414 Menu 15.1.1: First Set ........................................................................................................ 678
Figure 415 Menu 15.1.1.1: Editing/Configuring an Individual Rule in a Set ......................................... 680
Figure 416 Menu 15.2: NAT Server Sets .............................................................................................. 681
Figure 417 Menu 15.2.x: NAT Server Sets ........................................................................................... 681
Figure 418 15.2.x.x: NAT Server Configuration ....................................................................................682
Figure 419 Menu 15.2.1: NAT Server Setup .......................................................................................683
Figure 420 Server Behind NAT Example ...................................................... ............................. ........... 683
Figure 421 NAT Example 1 .................................................................................................................. 684
Figure 422 Menu 4: Internet Access & NAT Example .......................................................................... 684
Figure 423 NAT Example 2 .................................................................................................................. 685
Figure 424 Menu 15.2.1: Specifying an Inside Server .......................................................................... 685
Figure 425 NAT Example 3 .................................................................................................................. 686
38
ZyWALL 5/35/70 Series User’s Guide
Page 39

List of Figures
Figure 426 Example 3: Menu 11.1.2 ..................................................................................................... 687
Figure 427 Example 3: Menu 15.1.1.1 .................................................................................................687
Figure 428 Example 3: Final Menu 15.1.1 ............................................................................................ 688
Figure 429 Example 3: Menu 15.2.1 ....................................................................................................688
Figure 430 NAT Example 4 .................................................................................................................. 689
Figure 431 Example 4: Menu 15.1.1.1: Address Mapping Rule ........................................................... 689
Figure 432 Example 4: Menu 15.1.1: Address Mapping Rules ............................................................690
Figure 433 Menu 15.3.1: Trigger Port Setup ........................................................................................ 691
Figure 434 Menu 21: Filter and Firewall Setup ......... .... ... ... ... .... ... ... ... .... ... ........................................... 693
Figure 435 Menu 21.2: Firewall Setup ................................ .................... ................... ...........................694
Figure 436 Outgoing Packet Filtering Process ..................................................................................... 695
Figure 437 Filter Rule Process .............................................................................................................697
Figure 438 Menu 21: Filter and Firewall Setup ......... .... ... ... ... .... ... ... ... .... ... ........................................... 698
Figure 439 Menu 21.1: Filter Set Configuration ....................................................................................698
Figure 440 Menu 21.1.1.1: TCP/IP Filter Rule ..................................................................................... 700
Figure 441 Executing an IP Filter ......................................................................................................... 702
Figure 442 Menu 21.1.1.1: Generic Filter Rule .................................................................................... 703
Figure 443 Telnet Filter Example ..........................................................................................................704
Figure 444 Example Filter: Menu 21.1.3.1 ........................................................................................... 705
Figure 445 Example Filter Rules Summary: Menu 21.1.3 .................................................................... 705
Figure 446 Protocol and Device Filter Sets .......................................................................................... 706
Figure 447 Filtering LAN Traffic ............................................................................................................ 708
Figure 448 Filtering DMZ Traffic ........................................................................................................... 708
Figure 449 Filtering Remote Node Traffic ............................................................................................. 709
Figure 450 Menu 22: SNMP Configuration ............................ .................... ................... ................... ......711
Figure 451 Menu 24: System Maintenance .......................................................................................... 713
Figure 452 Menu 24.1: System Maintenance: Status ..........................................................................714
Figure 453 Menu 24.2: System Information and Console Port Speed ................................................. 715
Figure 454 Menu 24.2.1: System Maintenance: Information .................... ........................................... 716
Figure 455 Menu 24.2.2: System Maintenance: Change Console Port Speed .................................... 717
Figure 456 Menu 24.3: System Maintenance: Log and Trace .............................................................. 717
Figure 457 Examples of Error and Information Messages ................................................................... 718
Figure 458 Menu 24.3.2: System Maintenance: Syslog Logging .........................................................718
Figure 459 Call-Triggering Packet Example .........................................................................................722
Figure 460 Menu 24.4: System Maintenance: Diagnostic (ZyWALL 5) ............................................... 723
Figure 461 WAN & LAN DHCP .............................................................................................................723
Figure 462 Telnet into Menu 24.5 .........................................................................................................727
Figure 463 FTP Session Example ........................................................................................................ 727
Figure 464 System Maintenance: Backup Configuration ..................................................................... 730
Figure 465 System Maintenance: Starting Xmodem Download Screen ............................................... 730
Figure 466 Backup Configuration Example ..........................................................................................730
Figure 467 Successful Backup Confirmation Screen ...........................................................................730
Figure 468 Telnet into Menu 24.6 .........................................................................................................731
ZyWALL 5/35/70 Series User’s Guide
39
Page 40

List of Figures
Figure 469 Restore Using FTP Session Example ................................................................................732
Figure 470 System Maintenance: Restore Configuration ..................................................................... 732
Figure 471 System Maintenance: Starting Xmodem Download Screen ............................................... 732
Figure 472 Restore Configuration Example ......................................................................................... 732
Figure 473 Successful Restoration Confirmation Screen ....................... .............................................. 733
Figure 474 Telnet Into Menu 24.7.1: Upload System Firmware ................................... ... .... ... ... ... ... .... . 734
Figure 475 Telnet Into Menu 24.7.2: System Maintenance ......................................................... ... .... . 734
Figure 476 FTP Session Example of Firmware File Upload .................................................................735
Figure 477 Menu 24.7.1 As Seen Using the Console Port ..................................... ... ... ... .... ... ... ...........737
Figure 478 Example Xmodem Upload ............................. ................... .................... ................... ........... 737
Figure 479 Menu 24.7.2 As Seen Using the Console Port ....................................... ... ... .... ... ... ... ........738
Figure 480 Example Xmodem Upload ............................. ................... .................... ................... ........... 738
Figure 481 Command Mode in Menu 24 ..............................................................................................739
Figure 482 Call Control ......................................................................................................................... 740
Figure 483 Budget Management .......................................................................................................... 740
Figure 484 Call History ......................................................................................................................... 741
Figure 485 Menu 24: System Maintenance .......................................................................................... 742
Figure 486 Menu 24.10 System Maintenance: Time and Date Setting ................................................ 743
Figure 487 Menu 24.11 – Remote Management Control .....................................................................746
Figure 488 Menu 25: Sample IP Routing Policy Summary .................................................................. 749
Figure 489 Menu 25.1: IP Routing Policy Setup ...................................................................................751
Figure 490 Menu 25.1.1: IP Routing Policy Setup ................................................................................753
Figure 491 Example of IP Policy Routing ............................................................................................. 754
Figure 492 IP Routing Policy Example 1 .............................................................................................. 754
Figure 493 IP Routing Policy Example 2 .............................................................................................. 755
Figure 494 Schedule Setup .................................................................................................................. 757
Figure 495 Schedule Set Setup ............................................................................................................ 758
Figure 496 Applying Schedule Set(s) to a Remote Node (PPPoE) ...................................................... 759
Figure 497 Applying Schedule Set(s) to a Remote Node (PPTP) ........................................................ 760
Figure 498 Console/Dial Backup Port Pin Layout ................................................................................ 776
Figure 499 Peer-to-Peer Communication in an Ad-hoc Network ......................................................... 787
Figure 500 Basic Service Set ............................................................................................................... 788
Figure 501 Infrastructure WLAN ............................... ................................................. ........................... 789
Figure 502 RTS/CTS ............................................................................................................................ 790
Figure 503 WPA(2) with RADIUS Application Example ....................................................................... 797
Figure 504 WPA(2)-PSK Authentication ...............................................................................................798
Figure 505 Windows 98 SE: WinPopup .............................................................................................. 801
Figure 506 WIndows 98 SE: Program Task Bar ................................................................................. 802
Figure 507 Windows 98 SE: Task Bar Properties .............................................. .............................. 802
Figure 508 Windows 98 SE: StartUp ...................................................................................................803
Figure 509 Windows 98 SE: Startup: Create Shortcut ......................................................................803
Figure 510 Windows 98 SE: Startup: Select a Title for the Program ................................................ . 804
Figure 511 Windows 98 SE: Startup: Shortcut ....................................................................................804
40
ZyWALL 5/35/70 Series User’s Guide
Page 41

List of Tables
List of Tables
Table 1 ZyWALL Model Specific Features ............................................................................................. 52
Table 2 Front Panel Lights ..................................................................................................................... 59
Table 3 Title Bar: Web Configurator Icons .............................................................................................64
Table 4 Web Configurator HOME Screen in Router Mode .................................................................... 65
Table 5 Web Configurator HOME Screen in Bridge Mode .................................................................... 71
Table 6 Bridge and Router Mode Features Comparison .......... .......................................................... ... 74
Table 7 Screens Summary .................................................................................................................... 75
Table 8 HOME > Port Statistics ............................................................................................................. 80
Table 9 HOME > Show Statistics > Line Chart ......................................................................................82
Table 10 HOME > Show DHCP Table ...................................................................................................82
Table 11 HOME > VPN Status ............................................................................................................... 83
Table 12 ADVANCED > BW MGMT > Monitor ......................................................................................84
Table 13 ISP Parameters: Ethernet Encapsulation ...............................................................................88
Table 14 ISP Parameters: PPPoE Encapsulation ................................................................................. 90
Table 15 ISP Parameters: PPTP Encapsulation ...... .... ... ... ... .... ... ... ... .... ... ... ... ... .... ... ... ... .... ... ... ... ... .... ... 91
Table 16 Internet Access Wizard: Registration ......................................................................................94
Table 17 VPN Wizard: Gateway Setting ................................................................................................96
Table 18 VPN Wizard: Network Setting ....................................... ... ... .... ... ... ... ... .... ... ... ... .... ... ................98
Table 19 VPN Wizard: IKE Tunnel Setting ........................................................................................... 100
Table 20 VPN Wizard: IPSec Setting ................................................................................................... 101
Table 21 VPN Wizard: VPN Status ...................................................................................................... 103
Table 22 Anti-Spam Wizard: Email Server Location Setting ................................................................105
Table 23 Anti-Spam Wizard: Direction Configuration ............................. ... ... ... ... .... .............................. 107
Table 24 Dynamic VPN Rule Tutorial Settings .................................................................................... 109
Table 25 REGISTRATION > Registration ............................................................................................143
Table 26 REGISTRATION > Service ...................................................................................................145
Table 27 NETWORK > LAN ................................................................................................................. 153
Table 28 NETWORK > LAN > Static DHCP ........................................................................................ 156
Table 29 NETWORK > LAN > IP Alias ................................................................................................ 158
Table 30 NETWORK > LAN > Port Roles ............................................................................................ 159
Table 31 NETWORK > Bridge ............................................................................................................. 163
Table 32 NETWORK > Bridge > Port Roles ........................................................................................165
Table 33 STP Path Costs ....................................................................................................................166
Table 34 STP Port States .................................................................................................................... 167
Table 35 NETWORK > WAN > General ..............................................................................................175
Table 36 Least Load First: Example 1 ................................................................................................. 178
Table 37 Least Load First: Example 2 ................................................................................................. 178
Table 38 Load Balancing: Least Load First .........................................................................................179
ZyWALL 5/35/70 Series User’s Guide
41
Page 42

List of Tables
Table 39 Load Balancing: Weighted Round Robin ...... ... ... ... .... ... ... ... .... ... ... ... ... .... ... ... ... .... ... ... ... ... .... . 180
Table 40 Load Balancing: Spillover ........................................... ... ........................................................ 181
Table 41 Private IP Address Ranges ................................. ... .... ... ... ... .... ... ... ... ... .... ... ........................... 182
Table 42 NETWORK > WAN > WAN (Ethernet Encapsulation) .......................................................... 184
Table 43 NETWORK > WAN > WAN (PPPoE Encapsulation) ............................................................ 187
Table 44 NETWORK > WAN > WAN (PPTP Encapsulation) ...............................................................190
Table 45 NETWORK > WAN > 3G (WAN 2) ........................................................................................ 194
Table 46 NETWORK > WAN > Traffic Redirect ................................................................................... 198
Table 47 NETWORK > WAN > Dial Backup ........................................................................................ 200
Table 48 NETWORK > WAN > Dial Backup > Edit .............................................................................. 203
Table 49 2G, 2.5G, 2.75G, 3G and 3.5G Wireless Technologies .........................................................204
Table 50 NETWORK > DMZ .................................................................................................................211
Table 51 NETWORK > DMZ > Static DHCP ........................................................................................214
Table 52 NETWORK > DMZ > IP Alias ...............................................................................................215
Table 53 NETWORK > DMZ > Port Roles ...........................................................................................216
Table 54 NETWORK > WLAN ............................................................................................................. 221
Table 55 NETWORK > WLAN > Static DHCP .....................................................................................224
Table 56 NETWORK > WLAN > IP Alias .............................................................................................225
Table 57 NETWORK > WLAN > Port Roles ........................................................................................ 227
Table 58 WIRELESS > Wi-Fi > Wireless Card: No Security .................................. ... ... ... .... ... ... ...........233
Table 59 WIRELESS > Wi-Fi > Wireless Card: Static WEP ........... ... .... ... ... ... ..................................... 235
Table 60 WIRELESS > Wi-Fi > Wireless Card: WPA-PSK .................................................................. 236
Table 61 WIRELESS > Wi-Fi > Wireless Card: WPA .......................................................................... 237
Table 62 WIRELESS > Wi-Fi > Wireless Card: 802.1x + Dynamic WEP ............................................ 238
Table 63 WIRELESS > Wi-Fi > Wireless Card: 802.1x + Static WEP ................................................. 239
Table 64 WIRELESS > Wi-Fi > Wireless Card: 802.1x + No WEP ......................................................241
Table 65 WIRELESS > Wi-Fi > Wireless Card: No Access 802.1x + Static WEP ............................... 242
Table 66 WIRELESS > Wi-Fi > MAC Filter ..........................................................................................243
Table 67 Blocking All LAN to WAN IRC Traffic Example ..................................................................... 253
Table 68 Limited LAN to WAN IRC Traffic Example ............................................................................ 254
Table 69 SECURITY > FIREWALL > Default Rule (Router Mode) ......................................................255
Table 70 SECURITY > FIREWALL > Default Rule (Bridge Mode) .................... .... .............................. 257
Table 71 SECURITY > FIREWALL > Rule Summary ..........................................................................259
Table 72 SECURITY > FIREWALL > Rule Summary > Edit ................................................................262
Table 73 SECURITY > FIREWALL > Anti-Probing ..............................................................................264
Table 74 SECURITY > FIREWALL > Threshold .................................................................................. 265
Table 75 SECURITY > FIREWALL > Service ...................................................................................... 266
Table 76 SECURITY > FIREWALL > Service > Add ........................................................................... 267
Table 77 SECURITY > IDP > General Setup ......................................................................................280
Table 78 SECURITY > IDP > Signature: Attack Types ........................................................................ 281
Table 79 SECURITY > IDP > Signature: Intrusion Severity ................................................................282
Table 80 SECURITY > IDP > Signature: Actions ................................................................................282
Table 81 SECURITY > IDP > Signature: Group View .........................................................................283
42
ZyWALL 5/35/70 Series User’s Guide
Page 43

List of Tables
Table 82 SECURITY > IDP > Signature: Query View .......................................................................... 285
Table 83 SECURITY > IDP > Anomaly ................................................................................................ 290
Table 84 SECURITY > IDP > Update ..................................................................................................292
Table 85 SECURITY > ANTI-VIRUS > General ..................................................................................302
Table 86 SECURITY > ANTI-VIRUS > Signature: Query View ...........................................................304
Table 87 Common Computer Virus Types ........................................................................................... 310
Table 88 SECURITY > ANTI-SPAM > General ................................................................................... 316
Table 89 SECURITY > ANTI-SPAM > External DB .............................................................................319
Table 90 SECURITY > ANTI-SPAM > Lists .........................................................................................321
Table 91 SECURITY > ANTI-SPAM > Lists > Edit ............................................................................... 323
Table 92 SECURITY > CONTENT FILTER > General ........................................................................329
Table 93 SECURITY > CONTENT FILTER > Policy ........................................................................... 332
Table 94 SECURITY > CONTENT FILTER > Policy > General ........................................................... 333
Table 95 SECURITY > CONTENT FILTER > Policy > External Database .......................................... 335
Table 96 SECURITY > CONTENT FILTER > Policy > Customization ............................ .....................342
Table 97 SECURITY > CONTENT FILTER > Policy > Schedule ........................................................343
Table 98 SECURITY > CONTENT FILTER > Object ...........................................................................345
Table 99 SECURITY > CONTENT FILTER > Cache ...........................................................................346
Table 100 SECURITY > VPN > VPN Rules (IKE) ...............................................................................360
Table 101 SECURITY > VPN > VPN Rules (IKE) > Edit Gateway Policy ............................. ... ... ... .... . 363
Table 102 SECURITY > VPN > VPN Rules (IKE) > Edit Network Policy ............................................ 369
Table 103 SECURITY > VPN > VPN Rules (IKE) > Edit Network Policy > Port Forwarding ...............373
Table 104 SECURITY > VPN > VPN Rules (IKE) > Move Network Policy .......................................... 374
Table 105 SECURITY > VPN > VPN Rules (Manual) .........................................................................375
Table 106 SECURITY > VPN > VPN Rules (Manual) > Edit ............................................................... 377
Table 107 SECURITY > VPN > SA Monitor ........................................................................................379
Table 108 SECURITY > VPN > Global Setting .................................................................................... 381
Table 109 Telecommuters Sharing One VPN Rule Example ............................................................... 383
Table 110 Telecommuters Using Unique VPN Rules Example ............................................................384
Table 111 VPN Example: Matching ID Type and Content .................................................................... 390
Table 112 VPN Example: Mismatching ID T ype and Content ..............................................................390
Table 113 SECURITY > CERTIFICATES > My Certificates ................................................................ 402
Table 114 SECURITY > CERTIFICATES > My Certificates > Details ................................................. 404
Table 115 SECURITY > CERTIFICATES > My Certificates > Export ..................................................406
Table 116 SECURITY > CERTIFICATES > My Certificates > Import .................................................. 408
Table 117 SECURITY > CERTIFICATES > My Certificates > Import: PKCS#12 ................................408
Table 118 SECURITY > CERTIFICATES > My Certificates > Create .................................................. 410
Table 119 SECURITY > CERTIFICATES > Trusted CAs ....................................................................414
Table 120 SECURITY > CERTIFICATES > Trusted CAs > Details .....................................................416
Table 121 SECURITY > CERTIFICATES > Trusted CAs Import ......................................................... 419
Table 122 SECURITY > CERTIFICATES > Trusted Remote Hosts ....................................................420
Table 123 SECURITY > CERTIFICATES > Trusted Remote Hosts > Import ...................................... 421
Table 124 SECURITY > CERTIFICATES > Trusted Remote Hosts > Details ..................................... 423
ZyWALL 5/35/70 Series User’s Guide
43
Page 44

List of Tables
Table 125 SECURITY > CERTIFICATES > Directory Servers ............................................................425
Table 126 SECURITY > CERTIFICATES > Directory Server > Add ................................................... 426
Table 127 SECURITY > AUTH SERVER > Local User Database ....................................................... 430
Table 128 SECURITY > AUTH SERVER > RADIUS ..........................................................................430
Table 129 NAT Mapping Types ............................................................................................................436
Table 130 ADVANCED > NAT > NAT Overview ..................................................................................437
Table 131 ADVANCED > NAT > Address Mapping .............................................................................439
Table 132 ADVANCED > NAT > Address Mapping > Edit ...................................................................441
Table 133 ADVANCED > NAT > Port Forwarding ................................................................................ 444
Table 134 ADVANCED > NAT > Port Triggering ................................................................................. 446
Table 135 ADVANCED > STATIC ROUTE > IP Static Route .............................................................. 453
Table 136 ADVANCED > STATIC ROUTE > IP Static Route > Edit .................................................... 454
Table 137 ADVANCED > POLICY ROUTE > Policy Route Summary ................................................. 459
Table 138 ADVANCED > POLICY ROUTE > Edit ............................................................................... 461
Table 139 Application and Subnet-based Bandwidth Management Example ..................................... 466
Table 140 Over Allotment of Bandwidth Example ............................................................................... 467
Table 141 ADVANCED > BW MGMT > Summary ............................................................................... 469
Table 142 Maximize Bandwidth Usage Example ................................................................................. 470
Table 143 Priority-based Allotment of Unused and Unbudgeted Bandwidth Example ........................ 470
Table 144 Fairness-based Allotment of Unused and Unbudgeted Bandwidth Example ..................... 471
Table 145 ADVANCED > BW MGMT > Class Setup ........................................................................... 472
Table 146 ADVANCED > BW MGMT > Class Setup > Add Sub-Class ...............................................474
Table 147 Bandwidth Borrowing Example ...........................................................................................476
Table 148 ADVANCED > DNS > Add (Address Record) ..................................................................... 484
Table 149 ADVANCED > REMOTE MGMT > WWW ........................................................................... 506
Table 150 ADVANCED > REMOTE MGMT > SSH .............................................................................508
Table 151 ADVANCED > REMOTE MGMT > Telnet ........................................................................... 509
Table 152 ADVANCED > REMOTE MGMT > FTP .............................................................................. 510
Table 153 SNMP Traps ........................................................................................................................ 512
Table 154 ADVANCED > REMOTE MGMT > SNMP ..........................................................................513
Table 155 ADVANCED > REMOTE MGMT > DNS .............................................................................514
Table 156 ADVANCED > REMOTE MGMT > CNM ............................................................................. 515
Table 157 ADVANCED > UPnP ........................................................................................................... 526
Table 158 ADVANCED > UPnP > Ports ..............................................................................................527
Table 159 ADVANCED > Custom APP ................................................................................................ 530
Table 160 ADVANCED > ALG .............................................................................................................536
Table 161 REPORTS > Traffic Statistics .............................................................................................. 540
Table 162 REPORTS > Traffic Statistics: Web Site Hits Report .......................................................... 542
Table 163 REPORTS > Traffic Statistics: Host IP Address .................................................................. 543
Table 164 REPORTS > Traffic Statistics: Protocol/ Port ......................................................................544
Table 165 Report Specifications ..........................................................................................................545
Table 166 REPORTS > IDP ................................................................................................................. 546
Table 167 REPORTS > Anti-Virus .......................................................................................................548
44
ZyWALL 5/35/70 Series User’s Guide
Page 45

List of Tables
Table 168 REPORTS > Anti-Spam ......................................................................................................549
Table 169 REPORTS > E-mail Report ................................................................................................. 552
Table 170 LOGS > View Log ............................................................................................................... 556
Table 171 Log Description Example ....................................................................................................557
Table 172 LOGS > Log Settings .......................................................................................................... 559
Table 173 System Maintenance Logs .................................................................................................. 561
Table 174 System Error Logs .............................................................................................................. 563
Table 175 Access Control Logs ...........................................................................................................563
Table 176 TCP Reset Logs .................................................................................................................. 564
Table 177 Packet Filter Logs ............................................................................................................... 565
Table 178 ICMP Logs .......................................................................................................................... 565
Table 179 CDR Logs ........................................................................................................................... 566
Table 180 PPP Logs ............................................................................................................................ 566
Table 181 3G Logs .............................................................................................................................. 566
Table 182 UPnP Logs .......................................................................................................................... 567
Table 183 Content Filtering Logs .........................................................................................................568
Table 184 Attack Logs ......................................................................................................................... 568
Table 185 Remote Management Logs ................................................................................................. 570
Table 186 Wireless Logs ..................................................................................................................... 570
Table 187 IPSec Logs .......................................................................................................................... 571
Table 188 IKE Logs ............................................................................................................................. 571
Table 189 PKI Logs ............................................................................................................................. 574
Table 190 802.1X Logs ........................................................................................................................ 576
Table 191 ACL Setting Notes .............................................................................................................. 577
Table 192 ICMP Notes ......................................................................................................................... 578
Table 193 IDP Logs ............................................................................................................................. 579
Table 194 AV Logs ............................................................................................................................... 579
Table 195 AS Logs .............................................................................................................................. 581
Table 196 Syslog Logs ........................................................................................................................ 583
Table 197 RFC-2408 ISAKMP Payload Types ....................................................................................584
Table 198 MAINTENANCE > General Setup ....................................................................................... 586
Table 199 MAINTENANCE > Password ..............................................................................................587
Table 200 MAINTENANCE > Time and Date ......................................................................................588
Table 201 MAC-address-to-port Mapping Table ..................................................................................591
Table 202 MAINTENANCE > Device Mode (Router Mode) .................................................................593
Table 203 MAINTENANCE > Device Mode (Bridge Mode) .. .... ... ... ... .................................................. 594
Table 204 MAINTENANCE > Firmware Upload .................................................................................. 595
Table 205 Restore Configuration .........................................................................................................597
Table 206 MAINTENANCE > Diagnostics ...........................................................................................600
Table 207 Main Menu Commands ............................................ ... ... ... .... ... ... ... ... .... ... ... ... .... ... ... ... ........606
Table 208 Main Menu Summary ........................................... .... ... ... ... .... ... ... ... ... .... ... ... ... .... ... ... ...........608
Table 209 SMT Menus Overview ......................................................................................................... 609
Table 210 Menu 1: General Setup (Router Mode) ............................................................................... 613
ZyWALL 5/35/70 Series User’s Guide
45
Page 46

List of Tables
Table 211 Menu 1: General Setup (Bridge Mode) ............................................................................... 614
Table 212 Menu 1.1: Configure Dynamic DNS ....................................................................................615
Table 213 Menu 1.1.1: DDNS Host Summary ..................................................................................... 616
Table 214 Menu 1.1.1: DDNS Edit Host .............................................................................................. 617
Table 215 MAC Address Cloning in WAN Setup .................................................................................620
Table 216 Menu 2: Dial Backup Setup ................................................................................................621
Table 217 Advanced WAN Port Setup: AT Commands Fields ............................................................ 622
Table 218 Advanced WAN Port Setup: Call Control Parameters ................................................... .... . 623
Table 219 Menu 11.3: Remote Node Profile (Backup ISP) .................................................................. 624
Table 220 Menu 11.3.2: Remote Node Network Layer Options ..... ... .... ... ... ... ... .... ... ... ... .... ... ..............625
Table 221 Menu 11.3.3: Remote Node Script ...................................................................................... 628
Table 222 3G Modem Setup in WAN Setup (ZyWALL 5) .................................................................... 629
Table 223 Menu 11.2: Remote Node Profile (3G WAN) ...................................................................... 630
Table 224 Menu 3.2: DHCP Ethernet Setup Fields .............................................................................635
Table 225 Menu 3.2: LAN TCP/IP Setup Fields ..................................................................................635
Table 226 Menu 3.2.1: IP Alias Setup .................................................................................................637
Table 227 Menu 4: Internet Access Setup (Ethernet) .......................................................................... 640
Table 228 New Fields in Menu 4 (PPTP) Screen ................................................................................ 642
Table 229 New Fields in Menu 4 (PPPoE) screen ...............................................................................643
Table 230 Menu 6.1: Route Assessment .............................................................................................650
Table 231 Menu 6.2: Traffic Redirect ................................................................................................... 650
Table 232 Menu 6.3: Route Failover .................................................................................................... 651
Table 233 Menu 7.1: Wireless Setup ...................................................................................................654
Table 234 Menu 7.1.1: WLAN MAC Address Filter .............................................................................656
Table 235 Menu 11.1: Remote Node Profile for Ethernet Encapsulation ............................................. 660
Table 236 Fields in Menu 11.1 (PPPoE Encapsulation Specific) .........................................................663
Table 237 Menu 11.1: Remote Node Profile for PPTP Encapsulation ................................................. 664
Table 238 Remote Node Network Layer Options Menu Fields ............................................................665
Table 239 Menu 12. 1: Edit IP Static Route .........................................................................................670
Table 240 Applying NAT in Menus 4 & 11.1.2 ...................................................................................... 675
Table 241 SUA Address Mapping Rules .............................................................................................677
Table 242 Fields in Menu 15.1.1 .......................................................................................................... 679
Table 243 Menu 15.1.1.1: Editing/Configuring an Individual Rule in a Set .......................................... 680
Table 244 15.2.x.x: NAT Server Configuration .................................................................................... 682
Table 245 Menu 15.3.1: Trigger Port Setup ......................................................................................... 691
Table 246 Abbreviations Used in the Filter Rules Summary Menu ..................................................... 699
Table 247 Rule Abbreviations Used ....................................................................................................699
Table 248 Menu 21.1.1.1: TCP/IP Filter Rule ...................................................................................... 700
Table 249 Generic Filter Rule Menu Fields .........................................................................................703
Table 250 SNMP Configuration Menu Fields ........................................................................................711
Table 251 SNMP Traps ........................................................................................................................ 712
Table 252 System Maintenance: Status Menu Fields ..........................................................................714
Table 253 Fields in System Maintenance: Information ........................................................................716
46
ZyWALL 5/35/70 Series User’s Guide
Page 47

List of Tables
Table 254 System Maintenance Menu Syslog Parameters ................................................................. 718
Table 255 System Maintenance Menu Diagnostic ...............................................................................724
Table 256 Filename Conventions ........................................................................................................ 726
Table 257 General Commands for GUI-based FTP Clients ................................................................ 728
Table 258 General Commands for GUI-based TFTP Clients ..............................................................729
Table 259 Budget Management ........................................................................................................... 741
Table 260 Call History ..........................................................................................................................741
Table 261 Menu 24.10 System Maintenance: Time and Date Setting ................................................. 743
Table 262 Menu 24.11 – Remote Management Control ...................................................................... 746
Table 263 Menu 25: Sample IP Routing Policy Summary ................................................................... 749
Table 264 IP Routing Policy Setup ...................................................................................................... 750
Table 265 Menu 25.1: IP Routing Policy Setup ...................................................................................751
Table 266 Menu 25.1.1: IP Routing Policy Setup ................................................................................753
Table 267 Schedule Set Setup ............................................................................................................ 758
Table 268 Hardware Specifications ..................................................................................................... 769
Table 269 Firmware Specifications ......................................................................................................770
Table 270 Feature and Performance Specifications ............................................................................ 771
Table 271 Compatible ZyXEL WLAN Cards and Security Features .................................................... 772
Table 272 3G Features Supported By Compatible 3G Cards ..............................................................773
Table 273 3G Features Supported By Additional Compatible 3G Cards .............................................773
Table 274 3G Features Supported By Additional Compatible 3G Cards .............................................774
Table 275 North American Plug Standards ..........................................................................................775
Table 276 European Plug Standards ...................................................................................................775
Table 277 United Kingdom Plug Standards .........................................................................................775
Table 278 Australia And New Zealand Plug Standards .......................................................................775
Table 279 Japan Plug Standards ......................................................................................................... 775
Table 280 China Plug Standards .........................................................................................................776
Table 281 Console/Dial Backup Port Pin Assignments .......................................................................776
Table 282 Ethernet Cable Pin Assignments ........................................................................................ 777
Table 283 Commonly Used Services ....... .... ... ... ... ... .... ... ... ... .... ... ... ... .... ... ... ... ..................................... 783
Table 284 IEEE 802.11g ...................................................................................................................... 791
Table 285 Wireless Security Levels ..................................................................................................... 792
Table 286 Comparison of EAP Authentication Types .......................................................................... 795
Table 287 Wireless Security Relational Matrix ....................................................................................798
ZyWALL 5/35/70 Series User’s Guide
47
Page 48

List of Tables
48
ZyWALL 5/35/70 Series User’s Guide
Page 49

PART I
Introduction
Getting to Know Your ZyWALL (51)
Hardware Installation (55)
Introducing the Web Configurator (61)
Wizard Setup (87)
Tutorials (109)
Registration Screens (141)
49
Page 50

50
Page 51

CHAPTER 1
Getting to Know Your ZyWALL
This chapter introduces the main features and applications of the ZyWALL.
1.1 ZyWALL Internet Security Appliance Overview
The ZyWALL is loaded with security features including VPN, firewall, content filtering, antispam, IDP (Intrusion Detection and Prevention), anti-virus and certificates. The ZyWALL’s
De-Militarized Zone (DMZ) increases LAN security by providing separate ports for
connecting publicly accessible servers. The ZyWALL is designed for small and medium sized
business that need the increased throughput and reliability of dual WAN interfaces and load
balancing. The ZyWALL 35 and ZyWALL 5 provide the option to change port roles from
LAN to DMZ.
You can also deploy the ZyWALL as a transparent firewall in an existing network with
minimal configuration.
The ZyWALL provides bandwidth management, NAT, port forwarding , policy routing,
DHCP server and many other powerful features.
You can add an IEEE 802.11b/g-compliant wireless LAN by either inserting a wireless LAN
card into the PCMCIA/CardBus slot or connecting an access point (AP) to an Ethernet port in
a WLAN port role. If you insert a wireless LAN card to add a WLAN, the ZyWALL offers
highly secured wireless connectivity to your wired network with IEEE 802.1x, WEP data
encryption, WPA (Wi-Fi Protected Access) and MAC address filtering. You can use the
wireless card as part of the LAN, DMZ or WLAN.
1.2 ZyWALL Features
The following table lists model specific features.
ZyWALL 5/35/70 Series User’s Guide
51
Page 52

Chapter 1 Getting to Know Your ZyWALL
" See Chapter 55 on page 769 for a complete list of features.
Table 1 ZyWALL Model Specific Features
MODEL #
FEATURE
Two WAN Ports Y Y
3G Card Supported Y
Load Balancing Y Y Y
Changing Port Roles between LAN and DMZ Y Y
Changing Port Roles between LAN and WLAN Y Y Y
Table Key: A Y in a model’s column shows that the model has the specified feature. The
information in this table was correct at the time of writing, although it may be subject to
change.
70 35 5
1.3 Applications for the ZyWALL
Here are some examples of what you can do with your ZyWALL.
1.3.1 Secure Broadband Internet Access via Cable or DSL Modem
You can connect a cable modem, DSL or wireless modem to the ZyWALL for broadband
Internet access via an Ethernet or wireless port on the modem. The ZyWALL guarantees not
only high speed Internet access, but secure internal network protection and traffic management
as well.
Figure 1 Secure Internet Access via Cable, DSL or Wireless Modem
DMZ
WAN
LAN
52
ZyWALL 5/35/70 Series User’s Guide
Page 53

1.3.2 VPN Application
ZyWALL VPN is an ideal cost-effective way to securely connect branch offices, business
partners and telecommuters over the Internet without the need (and expense) for leased lines
between sites.
Figure 2 VPN Application
1.3.3 3G WAN Application (ZyWALL 5 Only)
Chapter 1 Getting to Know Your ZyWALL
Insert a 3G card to have the ZyWALL (in router mode) wirelessly access the Internet via a 3G
base station.
" At the time of writing, only ZyWALL 5 supports 3G, so all 3G descriptions
relate to ZyWALL 5 only. See Section 9.4 on page 192 for more information
about 3G.
With both the primary WAN (physical WAN port) and 3G WAN connections enabled, you
can use load balancing to improve quality of service and maximize bandwidth utilization or set
one of the WAN connections as a backup.
Figure 3 3G WAN Application
ZyWALL 5/35/70 Series User’s Guide
53
Page 54

Chapter 1 Getting to Know Your ZyWALL
1.4 Ways to Manage the ZyWALL
Use any of the following methods to manage the ZyWALL.
• Web Configurator. This is recommended for everyday management of the ZyWALL
using a (supported) web browser.
• Command Line Interface. Line commands are mostly used for troubleshooting by service
engineers. See the Command Reference Guide for more information about the CLI.
• SMT. System Management Terminal is a text-based configuration menu that you can use
to configure your device.
• FTP for firmware upgrades and configuration backup/restore.
• SNMP. The device can be monitored by an SNMP manager . See the SNMP chapter in this
User’s Guide.
• Vantage CNM (Centralized Network Management). The device can be remotely managed
using a Vantage CNM server.
1.5 Good Habits for Managing the ZyWALL
Do the following things regularly to make the ZyWALL more secure and to manage the
ZyWALL more effectively.
• Change the password. Use a password that’s not easy to guess and that consists of
different types of characters, such as numbers and letters.
• Write down the password and put it in a safe place.
• Back up the configuration (and make sure you know how to restore it). Restoring an
earlier working configuration may be useful if the device becomes unstable or even
crashes. If you forget your password, you will have to reset the ZyWALL to its factory
default settings. If you backed up an earlier configuration file, you would not have to
totally re-configure the ZyWALL. You could simply restore your last configuration.
54
ZyWALL 5/35/70 Series User’s Guide
Page 55

CHAPTER 2
Hardware Installation
The ZyWALL can be placed on a desktop or rack-mounted on a standard EIA rack. Use the
brackets in a rack-mounted installation.
2.1 General Installation Instructions
Read all the safety warnings in the beginning of this User's Guide before you begin and make
sure you follow them.
Perform the installation as follows:
1 Make sure the ZyWALL is off.
2 Install the hardware first.
3 See the Quick Start Guide for instructions on making power and panel connections and
turning on the ZyWALL.
" For proper ventilation, allow at least 4 inches (10 cm) of clearance at the front
and two sides and 3.4 inches (8 cm) at the back of the ZyWALL. This is
especially important for enclosed rack installations.
2.2 Desktop Installation
1 Make sure the ZyWALL is clean and dry.
2 Set the ZyWALL on a smooth, level surface strong enough to support the weight of the
ZyWALL and the connected cables. Make sure there is a power outlet nearby.
3 Make sure there is enough clearance around the ZyWALL to allow air circulation and
the attachment of cables and the power cord or power adaptor.
4 Remove the adhesive backing from the rubber feet.
5 Attach the rubber feet to each corner on the bottom of the ZyWALL. These rubber feet
help protect the ZyWALL from shock or vibration and ensure space between devices
when stacking.
ZyWALL 5/35/70 Series User’s Guide
55
Page 56

Chapter 2 Hardware Installation
Figure 4 Attaching Rubber Feet
" Do not block the ventilation holes. Leave space between ZyWALLs when
stacking.
2.3 Rack-mounted Installation Requirements
The ZyWALL can be mounted on an EIA standard size, 19-inch rack or in a wiring closet with
other equipment. Follow the steps below to mount your ZyWALL on a standard EIA rack
using a rack-mounting kit.
" Make sure the rack will safely support the combined weight of all the
equipment it contains.
Make sure the position of the ZyWALL does not make the rack unstable or topheavy. Take all necessary precautions to anchor the rack securely before
installing the unit.
Use a #2 Phillips screwdriver to install the screws.
" Failure to use the proper screws may damage the unit.
56
ZyWALL 5/35/70 Series User’s Guide
Page 57

2.4 Rack-Mounted Installation
1 Align one bracket with the holes on one side of the ZyWALL and secure it with the
bracket screws (smaller than the rack-mounting screws).
2 Attach the other bracket in a similar fashion.
Figure 5 Attaching Mounting Brackets and Screws
3 After attaching both mounting brackets, position the ZyWALL in the rack by lining up
the holes in the brackets with the appropriate holes on the rack. Secure the ZyWALL to
the rack with the rack-mounting screws.
Chapter 2 Hardware Installation
Figure 6 Rack Mounting
ZyWALL 5/35/70 Series User’s Guide
57
Page 58

Chapter 2 Hardware Installation
2.5 3G Card, WLAN Card and ZyWALL Turbo Card Installation
" Do not insert or remove a card with the ZyWALL turned on.
Make sure the ZyWALL is off before inserting or removing an 802.11b/g-compliant wireless
LAN PCMCIA or CardBus card, 3G card or ZyWALL Turbo Card (to avoid damage). Slide
the connector end of the card into the slot as shown next.
" Only certain ZyXEL wireless LAN cards or 3G card are compatible with the
ZyWALL. Only the ZyWALL 5 can use a 3G card.
Do not force, bend or twist the wireless LAN card, 3G card or ZyWALL Turbo
Card.
Figure 7 WLAN Card Installation
58
ZyWALL 5/35/70 Series User’s Guide
Page 59

2.6 Front Panel Lights
Figure 8 ZyWALL 70 Front Panel
Figure 9 ZyWALL 35 Front Panel
Figure 10 ZyWALL 5 Front Panel
Chapter 2 Hardware Installation
The following table describes the lights.
Table 2 Front Panel Lights
LED COLOR STATUS DESCRIPTION
PWR Off The ZyWALL is turned off.
Green On The ZyWALL is turned on.
Red On The power to the ZyWALL is too low.
SYS Green Off The ZyWALL is not ready or has failed.
On The ZyWALL is ready and running.
Flashing The ZyWALL is restarting.
ACT Green Off The backup port is not connected.
Flashing The backup port is sending or receiving packets.
CARD Green Off The wireless LAN or 3G card is not ready, or has failed.
On The wireless LAN or 3G card is ready.
Flashing The wireless LAN or 3G card is sending or receiving
packets.
LAN 10/100
(ZyWALL 70
only)
Green On The ZyWALL has a successful 10 Mbps Ethernet
Orange On The ZyWALL has a successful 100 Mbps Ethernet
Off The LAN is not connected.
connection.
Flashing The 10 M LAN is sending or receiving packets.
connection.
Flashing The 100 M LAN is sending or receiving packets.
ZyWALL 5/35/70 Series User’s Guide
59
Page 60

Chapter 2 Hardware Installation
Table 2 Front Panel Lights (continued)
LED COLOR STATUS DESCRIPTION
WAN1/2 10/
100
or
WAN 10/100
DMZ 10/100
(ZyWALL 70
only)
LAN/DMZ 10/
100
(ZyWALL 35
and ZyWALL 5)
Green On The ZyWALL has a successful 10 Mbps WAN connection.
Orange On The ZyWALL has a successful 100 Mbps WAN connection.
Green On The ZyWALL has a successful 10 Mbps Ethernet
Orange On The ZyWALL has a successful 100 Mbps Ethernet
Green On The ZyWALL has a successful 10 Mbps Ethernet
Orange On The ZyWALL has a successful 100 Mbps Ethernet
Off The WAN connection is not ready, or has failed.
Flashing The 10M WAN is sending or receiving packets.
Flashing The 100M WAN is sending or receiving packets.
Off The LAN/DMZ is not connected.
connection.
Flashing The 10M DMZ is sending or receiving packets.
connection.
Flashing The 100M /DMZ is sending or receiving packets.
Off The LAN/DMZ is not connected.
connection.
Flashing The 10 M LAN/DMZ is sendi n g or re cei v i n g packets.
connection.
Flashing The 100 M LAN/DMZ is sending or receiving packets.
60
ZyWALL 5/35/70 Series User’s Guide
Page 61

CHAPTER 3
Introducing the Web
Configurator
This chapter describes how to access the ZyWALL web configurator and provides an
overview of its screens.
3.1 Web Configurator Overview
The web configurator is an HTML-based management interface that allows easy ZyWALL
setup and management via Internet browser. Use Internet Explorer 6.0 and later or Netscape
Navigator 7.0 and later versions. The recommended screen resolution is 1024 by 768 pixels.
In order to use the web configurator you need to allow:
• Web browser pop-up windows from your device. Web pop-up blocking is enabled by
default in Windows XP SP (Service Pack) 2.
• JavaScripts (enabled by default).
• Java permissions (enabled by default).
See Appendix B on page 785 if you want to make sure these functions are allowed in Internet
Explorer or Netscape Navigator.
3.2 Accessing the ZyWALL Web Configurator
" By default, the packets from WLAN to WLAN/ZyWALL are dropped and users
cannot configure the ZyWALL wirelessly.
1 Make sure your ZyWALL hardware is properly connected and prepare your computer/
computer network to connect to the ZyWA LL (refer to the Quick Start Guide).
2 Launch your web browser.
3 Type "192.168.1.1" as the URL.
4 Type "1234" (default) as the password and click Login. In some versions, the default
password appears automatically - if this is the case, click Login.
ZyWALL 5/35/70 Series User’s Guide
61
Page 62

Chapter 3 Introducing the Web Configurator
5 You should see a screen asking you to change your password (highly recommended) as
shown next. Type a new password (and retype it to confirm) and click Apply or click
Ignore.
Figure 11 Change Password Screen
6 Click Apply in the Replace Certificate screen to create a certificate using your
ZyWALL’s MAC address that will be specific to this device.
" If you do not replace the default certificate here or in the CERTIFICATES
screen, this screen displays every time you access the web configurator.
Figure 12 Replace Certificate Screen
7 You should now see the HOME screen (see Figure 15 on page 65).
" The management session automatically times out when the time period set in
the Administrator Inactivity Timer field expires (default five minutes). Simply
log back into the ZyWALL if this happens to you.
62
ZyWALL 5/35/70 Series User’s Guide
Page 63

3.3 Resetting the ZyWALL
If you forget your password or cannot access the web configurator , you will need to reload the
factory-default configuration file or use the RESET button on the back of the ZyWALL.
Uploading this configuration file replaces the current configuration file with the factorydefault configuration file. This means that you will lose all configurations that you had
previously and the speed of the console port will be reset to the default of 9600bps with 8 data
bit, no parity, one stop bit and flow control set to none. The password will be reset to 1234,
also.
3.3.1 Procedure To Use The Reset Button
Make sure the SYS LED is on (not blinking) before you begin this procedure.
1 Press the RESET button for ten seconds, and then release it. If the SYS LED begins to
blink, the defaults have been restored and the ZyWALL restarts. Otherwise, go to step 2.
2 Turn the ZyWALL off.
3 While pressing the RESET button, turn the ZyWALL on.
4 Continue to hold the RESET button. The SYS LED will begin to blink and flicker very
quickly after about 20 seconds. This indicates that the defaults have been restored and
the ZyWALL is now restarting.
5 Release the RESET button and wait for the ZyWALL to finish restarting.
Chapter 3 Introducing the Web Configurator
3.3.2 Uploading a Configuration File Via Console Port
1 Download the default configuration file from the ZyXEL FTP site, unzip it and save it in
a folder.
2 Turn off the ZyWALL, begin a terminal emulation software session and turn on the
ZyWALL again. When you see the message "Press Any key to enter Debug Mode within
3 seconds", press any key to enter debug mode.
3 Enter "y" at the prompt below to go into debug mode.
4 Enter "atlc" after "Enter Debug Mode" message.
5 Wait for "Starting XMODEM upload" message before activating Xmodem upload on
your terminal. This is an example Xmodem configuration upload using HyperTerminal.
Figure 13 Example Xmodem Upload
Type the configuration file’s location,
or click Browse to search for it.
Choose the Xmodem protocol.
Then click Send.
6 After successful firmware upload, enter "atgo" to restart the router.
ZyWALL 5/35/70 Series User’s Guide
63
Page 64

Chapter 3 Introducing the Web Configurator
3.4 Navigating the ZyWALL Web Configurator
The following summarizes how to navigate the web configurator from the HOME screen.
This guide uses the ZyWALL 70 screenshots as an example. The screens may vary slightly for
different ZyWALL models.
Figure 14 HOME Screen
A
C
B
D
As illustrated above, the main screen is divided into these parts:
• A - title bar
• B - navigation panel
• C - main window
• D - status bar
3.4.1 Title Bar
The title bar provides some icons in the upper right corner.
The icons provide the following functions.
Table 3 Title Bar: Web Configurator Icons
ICON DESCRIPTION
Wizards: Click this icon to open one of the web configurator wizards. See Chapter 4
on page 87 for more information.
Help: Click this icon to open the help page for the current screen.
64
ZyWALL 5/35/70 Series User’s Guide
Page 65

3.4.2 Main Window
The main window shows the screen you select in the navigation panel. It is discussed in more
detail in the rest of this document.
Right after you log in, the HOME screen is displayed. The screen varies according to the
device mode you select in the MAINTENANCE > Device Mode screen.
3.4.3 HOME Screen: Router Mode
The following screen displays when the ZyWALL is set to router mode. This screen displays
general status information about the ZyWALL. The ZyWALL is set to router mode by default.
Not all fields are available on all models.
WAN 2 refers to either the physical WAN 2 port on a ZyWALL with multiple WAN ports or
the 3G card on a single WAN ZyWALL in router mode.
Figure 15 Web Configurator HOME Screen in Router Mode (ZyWALL 5)
Chapter 3 Introducing the Web Configurator
The following table describes the labels in this screen.
Table 4 Web Configurator HOME Screen in Router Mode
LABEL DESCRIPTION
Automatic Refresh
Interval
Refresh Click this button to update the status screen statistics immediately.
System
Information
ZyWALL 5/35/70 Series User’s Guide
Select a number of seconds or None from the drop-down list box to update all
screen statistics automatically at the end of every time interval or to not update
the screen statistics.
65
Page 66

Chapter 3 Introducing the Web Configurator
Table 4 Web Configurator HOME Screen in Router Mode (continued)
LABEL DESCRIPTION
System Name This is the System Name you enter in the MAINTENANCE > General screen. It
is for identification purposes. Click the field label to go to the screen where you
can specify a name for this ZyWALL.
Model This is the model name of your ZyWALL.
Bootbase Version This is the bootbase version and the date created.
Firmware Version This is the ZyNOS Firmware version and the date created. ZyNOS is ZyXEL's
Up Time This field displays how long the ZyWALL has been running since it last started up.
System Time This field displays your ZyWALL’s present date (in yyyy-mm-dd format) and time
Device Mode This displays whether the ZyWALL is functioning as a router or a bridge. Click the
Firewall This displays whether or not the ZyWALL’s firewall is activated. Click the field
System Resources
Flash The first number shows how many megabytes of the flash the ZyWALL is using.
Memory The first number shows how many megabytes of the heap memory the ZyWALL
Sessions The first number shows how many sessions are currently open on the ZyWALL.
CPU This field displays what percentage of the ZyWALL’s processing ability is
Interfaces This is the port type.
proprietary Network Operating System design. Click the field label to go to the
screen where you can upload a new firmware file.
The ZyWALL starts up when you turn it on, when you restart it (MAINTENANCE >
Restart), or when you reset it (see Section 3.3 on page 63).
(in hh:mm:ss format) along with the difference from the Greenwich Mean Time
(GMT) zone. The difference from GMT is based on the time zone. It is also
adjusted for Daylight Saving Time if you set the ZyWALL to use it. Click the field
label to go to the screen where you can modify the ZyWALL’s date and time
settings.
field label to go to the screen where you can configure the ZyWALL as a router or
a bridge.
label to go to the screen where you can turn the firewall on or off.
is using. Heap memory refers to the memory that is not used by ZyNOS (ZyXEL
Network Operating System) and is thus available for running processes like NAT,
VPN and the firewall.
The second number shows the ZyWALL's total heap memory (in megabytes).
The bar displays what percent of the ZyWALL's heap memory is in use. The bar
turns from green to red when the maximum is being approached.
This includes all sessions that are currently traversing the ZyWALL, terminating at
the ZyWALL or Initiated from the ZyWALL
The second number is the maximum number of sessions that can be open at one
time.
The bar displays what percent of the maximum number of sessions is in use. The
bar turns from green to red when the maximum is being approached.
currently used. When this percentage is close to 100%, the ZyWALL is running at
full load, and the throughput is not going to improve anymore. If you want some
applications to have more throughput, you should turn off other applications (for
example, using bandwidth management.
Click "+" to expand or "-" to collapse the IP alias drop-down lists.
Hold your cursor over an interface’s label to display the interface’s MAC Address.
Click an interface’s label to go to the screen where you can configure settings for
that interface.
66
ZyWALL 5/35/70 Series User’s Guide
Page 67

Chapter 3 Introducing the Web Configurator
Table 4 Web Configurator HOME Screen in Router Mode (continued)
LABEL DESCRIPTION
Status For the LAN, DMZ and WLAN ports, this displays the port speed and duplex
setting. Ethernet port connections can be in half-duplex or full-du plex mode. Full-
duplex refers to a device's ability to send and receive simultaneously, while half-
duplex indicates that traffic can flow in only one direction at a time. The Ethernet
port must use the same speed or duplex mode setting as the peer Ethernet port in
order to connect.
For the WAN interface(s) and the Dial Backup port, it displays the port speed and
duplex setting if you’re using Ethernet encapsulation or the remote node name
(configured through the SMT) for a PPP connection and Down (line is down or
not connected), Idle (line (ppp) idle), Dial (starting to trigger a call) or Drop
(dropping a call) if you’re using PPPoE encapsulation.
IP/Netmask Th is shows the port’s IP address and subnet mask.
IP Assignment For the WAN, if the ZyWALL gets its IP address automatically from an ISP, this
Renew If you are using Ethernet encapsulation and the WAN port is configured to get the
Security Services
Turbo Card This field displays whether or not a ZyWALL Turbo Card is installed.
displays DHCP client when you’re using Ethernet encaps ulation and IPCP Client
when you’re using PPPoE or PPTP encapsulation. Static displays if the WAN
port is using a manually entered static (fixed) IP address.
For the LAN, WLAN or DMZ, DHCP server displays when the ZyWALL is set to
automatically give IP address information to the computers connected to the LAN.
DHCP relay displays when the ZyWALL is set to forward IP address assignment
requests to another DHCP server. Static displays if the LAN port is using a
manually entered static (fixed) IP address. In this case, you must have another
DHCP server on your LAN, or else the computers must be manually configured.
For the dial backup port, this shows N/A when dial backup is disabled and IPCP
client when dial backup is enabled.
IP address automatically from the ISP, click Renew to release the WAN port’s
dynamically assigned IP address and get the IP address afresh. Click Dial to dial
up the PPTP, PPPoE or dial backup connection. Click Drop to disconnect the
PPTP, PPPoE, 3G WAN or dial backup connection.
Note: The ZyWALL must have a Turbo Card installed and a valid
IDP/Anti-Virus
Definitions
IDP/Anti-Virus
Expiration Date
Anti-Spam
Expiration Date
Content Filter
Expiration Date
Intrusion Detected This displays how many intrusions the ZyWALL has detected since it last started
ZyWALL 5/35/70 Series User’s Guide
This is the version number of the signatures set that the ZyWALL is using and the
date and time that the set was released. Click the field label to go to the screen
where you can update the signatures. N/A displays when there is no Turbo Card
installed or the service subscription has expired.
This is the date the IDP/anti-virus service subscription expires. Click the field label
to go to the screen where you can update your service subscription.
This is the date the anti-spam service subscription expires. Click the fie l d l a be l to
go to the screen where you can update your service subscription.
This is the date the category-based cont ent filtering service subscription expires.
Click the field label to go to the screen where you can update your service
subscription.
up. N/A displays when the ZyWALL has never had an IDP subscription or there is
no Turbo Card installed. Disable displays when IDP threat statistics collection is
disabled.
Click the field label to go to the related screen.
service subscription to use the IDP and anti-virus features.
67
Page 68

Chapter 3 Introducing the Web Configurator
Table 4 Web Configurator HOME Screen in Router Mode (continued)
LABEL DESCRIPTION
Virus Detected This displays how many virus-infected files the ZyWALL has detected sinc e it last
started up. It also displays the percentage of virus-infected files out of the total
number of files that the ZyWALL has scanned (since it last started up). N/A
displays when the ZyWALL has never had an anti-virus subscription or there is no
Turbo Card installed. Disable displays when anti-virus threat statistics collection
is disabled.
Click the field label to go to the related screen.
Spam Mail
Detected
Web Site Blocked This displays how many web site hits the ZyWALL has blocked since it last
Top 5 Intrusion &
Virus Detections
Rank This is the ranking number of an intrusion or virus. This is an intrusion’s or virus’s
Intrusion Detected This is the name of a signature for which the ZyWALL has detected matching
Virus Detected This is the name of the virus that the ZyWALL has detected.
3G WAN Interface
Status
show detail / hide
detail
3G Connection
Status
Service Provider This displays the name of your network service provider or Limited Service when
Signal Strength This displays the strength of the signal. The signal strength mainly depends on
This displays how many spam e-mails the ZyWALL has detected since it last
started up. It also displays the percentage of spam e-mail out of the total number
of e-mails that the ZyWALL has scanned (since it last started up). Disable
displays when anti-spam threat statistics collection is disabled.
Click the field label to go to the related screen.
started up. N/A displays when the ZyWALL has never had an external database
content filtering service subscription. Disable (collect statistics) displays when the
ZyWALL has been subscribed to the external database content filtering service,
but content filtering is not active.
Click the field label to go to the related screen.
The following is a list of the five intrusions or viruses that the ZyWALL has most
frequently detected since it last started up.
place in the list of most common intrusions or viruses.
packets. The number in brackets indicates how many times the signature has
been matched.
Click the hyperlink for more detailed information on the intrusion.
These fields display when a 3G card is inserted and the 3G connection is
enabled.
Click show detail to see more information about the 3G connection. Click hide
detail to
WAN2 (the remote node name configured through the SMT) displays when the
3G connection is up.
Ready to Connect displays when the 3G card is inserted and enabled.
Connecting displays when the ZyWALL is trying to bring the 3G connection up.
Connected displays when the 3G connection is up.
Down displays when the 3G connection is down or not activated.
Idle displays when the 3G connection is idle.
Init displays when the ZyWALL is initializing the 3G card.
Drop displays when the ZyWALL is dropping a call.
This field also displays the type of the network to which the ZyWALL is
connected. The network type varies depending on the 3G card you inserted and
could be UMTS, HSDPA, GPRS or EDGE when you insert a GSM 3G card, or
1xRTT, EVDO Rev.0 or EVDO Rev.A when you insert a CDMA 3G card.
the signal strength is too low.
the antenna output power and the distance between your ZyWALL and the
service provider’s base station. You can see a signal strength indication even
when the ZyWALL does not have a 3G connection (because the signal is still
there even when the ZyWALL is not using it).
68
ZyWALL 5/35/70 Series User’s Guide
Page 69

Chapter 3 Introducing the Web Configurator
Table 4 Web Configurator HOME Screen in Router Mode (continued)
LABEL DESCRIPTION
Last Connection
Up Time
Tx Bytes This displays the total number of data frames transmitted.
Rx Bytes This displays the total number of data frames received.
3G Card
Manufacturer
3G Card Model This displays the model name of your 3G card.
3G Card Firmware
Revision
3G Card IMEI This displays the International Mobile Equipment Number (IMEI) which is the
SIM Card IMSI This displays the International Mobile Subscriber Identity (IMSI) stored in the SIM
3G Card ESN This field is available only when you insert a CDMA (Code Division Multiple
Enter PIN code
again
Apply Click Apply to save the correct PIN code and replace the one you specified in the
PUK Code If you enter the PIN code incorrectly three times, the SIM card will be blocked by
New PIN Code Configure a PIN code for the SIM card. You can specify any four to eight digits to
Confirm New PIN
Code
Apply Click Apply to save your changes in this section.
Reset budget
counters, resume
budget control
Resume budget
control
This displays how long the 3G connection has been up.
This displays the manufacturer of your 3G card.
This displays the version of the firmware currently used in the 3G card.
serial number of the 3G wireless card. IMEI is a unique 15-digit number used to
identify a mobile device.
(Subscriber Identity Module) card. The SIM card is installed in a mobile device
and used for authenticating a customer to the carrier network. IMSI is a unique
15-digit number used to identify a user on a network.
Access) 3G card.
This shows the ESN (Electronic Serial Number) of the inserted CDMA 3G card.
The ESN is the serial number of a CDMA 3G card and is similar to the IMEI on a
GSM or UMTS 3G card.
If the PIN code you specified in the 3G (WAN 2) screen is not the right one for the
card you inserted, this field displays allowing you to enter the correct PIN code.
Enter the PIN code (four to eight digits) for the inserted 3G card.
3G (WAN 2) screen.
your ISP and you cannot use the account to access the Internet. You should get
the PUK (Personal Unblocking Key) code (four to eight digits) from your ISP.
Enter the PUK code to enable the SIM card. If an incorrect PUK code is entered
10 times, the SIM card will be disabled permanently. You then need to contact
your ISP for a new SIM card.
have a new PIN code or enter the previous PIN code.
Enter the PIN code again for confirmation.
This field displays if you have enabled budget control but insert a 3G card with a
different user account from the one for which you configured budget control.
Select this option to have the ZyWALL do budget calculation starting from 0 but
use the previous settings.
This field displays if you have enabled budget control but insert a 3G card with a
different user account from the one for which you configured budget control.
Select this option to have the ZyWALL keep the existing statistics and continue
counting.
ZyWALL 5/35/70 Series User’s Guide
69
Page 70

Chapter 3 Introducing the Web Configurator
Table 4 Web Configurator HOME Screen in Router Mode (continued)
LABEL DESCRIPTION
Disable budget
control
Apply Click Apply to save your changes in this section.
Enter modem
unlock code
Apply Click Apply to save your changes in this section.
Remaining Time
Budget
Remaining Data
Budget
This field displays if you have enabled budget control but insert a 3G card with a
different user account from the one for which you configured budget control.
Select this option to disable budget control.
If you want to enable and configure new budget control settings for the new user
account, go to the 3G (WAN 2) screen.
The ZyWALL keeps the existing statistics if you do not change the budget control
settings. You could reinsert the original card and enable budget control to have
the ZyWALL continue counting the budget control statistics.
This field only displays when you insert a 3G card and the internal modem on the
3G card is blocked.
Enter a key to enable the internal modem on your 3G card. By default, the key is
the last four digits of your phone number used to dial up the 3G connection.
Otherwise, you need to get the key from your service provider.
This displays when you enable budget control in the 3G (WAN 2) screen.
This shows the amount of time the 3G connection can still be used before the
ZyWALL takes the actions you specified in the 3G (WAN 2) screen.
This displays when you enable budget control in the 3G (WAN 2) screen.
This shows how much data (in bytes) can still be transmitted through the 3G
connection before the ZyWALL takes the actions you specified in the 3G (WAN 2)
screen.
Note: The budget counters will not be reset when you restore the
factory defaults. The budget counters are saved to the flash
every hour or when the 3G connection is dropped. If you
restart the ZyWALL within one hour, any change in the
counters will not be saved.
Reset time and
data budget
counters
Latest Alerts This table displays the five most recent alerts recorded by the ZyWALL. You can
Date/Time This is the date and time the alert was recorded.
Message This is the reason for the alert.
System Status
Port Statistics Click Port Statistics to see router performance statistics such as the number of
DHCP Table Click DHCP Table to show current DHCP client information.
VPN Click VPN to display the active VPN connections.
Bandwidth Click Bandwidth to view the ZyWALL’s bandwidth usage and allotments.
This displays when you enable budget control in the Network > WAN > 3G (WAN
2) screen.
Click this button to reset the time and data budgets immediately. The count starts
over with the 3G connection’s full configured monthly time and data budgets. This
does not affect the normal monthly budget restart.
see more information in the View Log screen, such as the source and destination
IP addresses and port numbers of the incoming packets.
packets sent and number of packets received for each port.
70
ZyWALL 5/35/70 Series User’s Guide
Page 71

3.4.4 HOME Screen: Bridge Mode
The following screen displays when the ZyWALL is set to bridge mode. In bridge mode, the
ZyWALL functions as a transparent firewall (also known as a bridge firewall). The ZyWA LL
bridges traffic traveling between the ZyWALL's interfaces and still filters and inspects
packets. You do not need to change the configuration of your existing network.
In bridge mode, the ZyWALL cannot get an IP address from a DHCP server. The LAN, W AN,
DMZ and WLAN interfaces all have the same (static) IP address and subnet mask. You can
configure the ZyWALL's IP address in order to access the ZyWALL for management. If you
connect your computer directly to the ZyWALL, you also need to assign your computer a
static IP address in the same subnet as the ZyWALL's IP address in order to access the
ZyWALL.
You can use the firewall and VPN in bridge mode. See the user’s guide for a list of other
features that are available in bridge mode.
Figure 16 Web Configurator HOME Screen in Bridge Mode
Chapter 3 Introducing the Web Configurator
The following table describes the labels in this screen.
Table 5 Web Configurator HOME Screen in Bridge Mode
LABEL DESCRIPTION
Automatic
Refresh Interval
Refresh Click this button to update the screen’s statistics immediately.
System
Information
System Name This is the System Name you enter in the MAINTENANCE > General screen. It is
Model This is the model name of your ZyWALL.
ZyWALL 5/35/70 Series User’s Guide
Select a number of seconds or None from the drop-down list box to update all
screen statistics automatically at the end of every time interval or to not update the
screen statistics.
for identification purposes. Click the field label to go to the screen where you can
specify a name for this ZyWALL.
71
Page 72

Chapter 3 Introducing the Web Configurator
Table 5 Web Configurator HOME Screen in Bridge Mode (continued)
LABEL DESCRIPTION
Bootbase
Version
Firmware
Version
Up Time This field displays how long the ZyWALL has been running since it last started up.
System Time This field displays your ZyWALL’s present date (in yyyy-mm-dd format) and time
Device Mode This displays whether the ZyWALL is functioning as a router or a bridge. Click the
Firewall This displays whether or not the ZyWALL’ s firewall is activated. Click the field label
System
Resources
Flash The first number shows how many megabytes of the flash the ZyWALL is using.
Memory The first number shows how many megabytes of the heap memory the ZyWALL is
Sessions The first number shows how many sessions are currently open on the ZyWALL.
CPU This field displays what percentage of the ZyWALL’s processing ability is currently
Network Status Click more to display information about the individual interfaces.
IP/Netmask
Address
Gateway IP
Address
Rapid Spanning
Tree Protocol
Bridge Priority This is the bridge priority of the ZyWALL. The bridge (or switch) with the lowest
This is the bootbase version and the date created.
This is the ZyNOS Firmware version and the date created. ZyNOS is ZyXEL's
proprietary Network Operating System design. Click the field label to go to the
screen where you can upload a new firmware file.
The ZyWALL starts up when you turn it on, when you restart it (MAINTENANCE >
Restart), or when you reset it (see Section 3.3 on page 63).
(in hh:mm:ss format) along with the difference from the Greenwich Mean Time
(GMT) zone. The difference from GMT is based on the time zone. It is also
adjusted for Daylight Saving Time if you set the ZyWALL to use it. Click the field
label to go to the screen where you can modify the ZyWALL’s date and time
settings.
field label to go to the screen where you can configure the ZyWALL as a router or a
bridge.
to go to the screen where you can turn the firewall on or off.
using. Heap memory refers to the memory that is not used by ZyNOS (ZyXEL
Network Operating System) and is thus available for running processes like NAT,
VPN and the firewall.
The second number shows the ZyWALL's total heap memory (in megabytes).
The bar displays what percent of the ZyWALL's heap memory is in use. The bar
turns from green to red when the maximum is being approached.
This includes all sessions that are currently traversing the ZyWALL, terminating at
the ZyWALL or initiated from the ZyWALL
The second number is the maximum number of sessions that can be open at one
time.
The bar displays what percent of the maximum number of sessions is in use. The
bar turns from green to red when the maximum is being approached.
used. When this percentage is close to 100%, the ZyWALL is running at full load,
and the throughput is not going to improve anymore. If you want some applications
to have more throughput, you should turn off other applications (for example, using
bandwidth management.
This is the IP address and subnet mask of your ZyWALL in dotted decimal
notation.
This is the gateway IP address.
This shows whether RSTP (Rapid Spanning Tree Protocol) is active or not. The
following labels or values relative to RSTP do not apply when RSTP is disabled.
bridge priority value in the network is the root bridge (the base of the spanning
tree).
72
ZyWALL 5/35/70 Series User’s Guide
Page 73

Chapter 3 Introducing the Web Configurator
Table 5 Web Configurator HOME Screen in Bridge Mode (continued)
LABEL DESCRIPTION
Bridge Hello
Time
Bridge Max Age This is the predefined interval that a bridge waits to get a Hello message (BPDU)
Forward Delay This is the forward delay interval.
Bridge Port This is the port type. Port types are: WAN (or WAN1, WAN2), LAN, Wireless
Port Status For the WAN, LAN, DMZ, and WLAN Interfaces, this displays the port speed and
RSTP Status This is the RSTP status of the corresponding port.
RSTP Active This shows whether or not RSTP is active on the corresponding port.
RSTP Priority This is the RSTP priority of the corresponding port.
RSTP Path Cost This is the cost of transmitting a frame from the root bridge to the corresponding
Security Services
Turbo Card This field displays whether or not a ZyWALL Turbo Card is installed.
This is the interval of BPDUs (Bridge Protocol Data Units) from the root bridge.
from the root bridge.
Card, DMZ and WLAN Interface.
duplex setting. For the WAN port, it displays Down when the link is not ready or
has failed. For the wireless card, it displays the transmission rate when a wireless
LAN card is inserted and WLAN is enabled or Down when a wireless LAN is not
inserted or WLAN is disabled.
port.
Note: The ZyWALL must have a Turbo Card installed and a valid
service subscription to use the IDP and anti-virus features.
IDP/Anti-Virus
Definitions
IDP/Anti-Virus
Expiration Date
Anti-Spam
Expiration Date
Content Filter
Expiration Date
Intrusion
Detected
Virus Detected This displays how many virus-infected files the ZyWALL has detected since it last
This is the version number of the signatures set that the ZyWALL is using and the
date and time that the set was released. Click the field label to go to the screen
where you can update the signatures. N/A displays when there is no Turbo Card
installed or the service subscription has expired.
This is the date the IDP/anti-virus service subscription expires. Click the field label
to go to the screen where you can update your service subscription.
This is the date the anti-spam service subscription expires. Click the field label to
go to the screen where you can update your service subscription.
This is the date the category-based content filtering service subscription expires.
Click the field label to go to the screen where you can update your service
subscription.
This displays how many intrusions the ZyWALL has detected since it last started
up.
N/A displays when there is no valid license or there is no Turbo Card installed.
Disable displays when the IDP threat statistics collection is disabled.
Click the field label to go to the screen where you can turn the statistics collection
on or off.
started up. It also displays the percentage of virus-infected files out of the total
number of files that the ZyWALL has scanned (since it last started up).
N/A displays when there is no valid license or there is no Turbo Card installed.
Disable displays when the anti-virus threat statistics collection is disabled.
Click the field label to go to the screen where you can turn the statistics collection
on or off.
ZyWALL 5/35/70 Series User’s Guide
73
Page 74

Chapter 3 Introducing the Web Configurator
Table 5 Web Configurator HOME Screen in Bridge Mode (continued)
LABEL DESCRIPTION
Spam Mail
Detected
Web Site
Blocked
Top 5 Intrusion &
Virus Detections
Rank This is the ranking number of an intrusion or virus. This is an intrusion’s or virus’s
Intrusion
Detected
Virus Detected This is the name of the virus that the ZyWALL has detected.
Latest Alerts This table displays the five most recent alerts recorded by the ZyWALL. You can
Date/Time This is the date and time the alert was recorded.
Message This is the reason for the alert.
System Status
Port Statistics Click Port Statistics to see router performance statistics such as the number of
VPN Click VPN to display the active VPN connections.
Bandwidth Click Bandwidth to view the ZyWALL’s bandwidth usage and allotments.
This displays how many spam e-mails the ZyWAL L has detected since it last
started up. It also displays the percentage of spam e-mail out of the total number of
e-mails that the ZyWALL has scanned (since it last started up).
Disable displays when the anti-spam threat statistics collection is disabled.
Click the field label to go to the screen where you can turn the statistics collection
on or off.
This displays how many web site hits the ZyWALL has blocked since it last started
up.
N/A displays when there is no valid license.
Disable (collect statistics) displays when the content filtering feature is disab l ed .
Click the field label to go to the screen where you can turn content filtering on or off.
The following is a list of the five intrusions or viruses that the ZyWALL has most
frequently detected since it last started up.
place in the list of most common intrusions or viruses.
This is the name of a signature for which the ZyWALL has detected matching
packets. The number in brackets indicates how many times the signature has been
matched.
Click the hyperlink for more detailed information on the intrusion.
see more information in the View Log screen, such as the source and destination
IP addresses and port numbers of the incoming packets.
packets sent and number of packets received for each port.
3.4.5 Navigation Panel
After you enter the password, use the sub-menus on the navigation panel to configure
ZyWALL features.
The following table lists the features available for each device mode. Not all ZyWALLs have
all features listed in this table.
Table 6 Bridge and Router Mode Features Comparison
FEATURE BRIDGE MODE ROUTER MODE
Internet Access Wizard Y
VPN Wizard Y Y
DHCP Table Y
System Statistics Y Y
Registration Y Y
LAN Y
74
ZyWALL 5/35/70 Series User’s Guide
Page 75

Chapter 3 Introducing the Web Configurator
Table 6 Bridge and Router Mode Features Comparison
FEATURE BRIDGE MODE ROUTER MODE
WAN Y
DMZ Y
Bridge Y
WLAN Y
Wireless Card Y Y
Firewall Y Y
IDP Y Y
Anti-Virus Y Y
Anti-Spam Y Y
Content Filter Y Y
VPN Y Y
Certificates Y Y
Authentication Server Y Y
NAT Y
Static Route Y
Policy Route Y
Bandwidth Management Y Y
DNS Y
Remote Management Y Y
UPnP Y
Custom Application Y Y
ALG Y Y
Reports Y Y
Logs Y Y
Maintenance Y Y
T able Key: A Y in a mode’s column shows that the device mode has the specified feature. The
information in this table was correct at the time of writing, although it may be subject to
change.
The following table describes the sub-menus.
Table 7 Screens Summary
LINK TAB FUNCTION
HOME This screen shows the ZyWALL’s general device and network
REGISTRATIONRegistration Use this screen to register your ZyWALL and activate the trial
Service Use this to manage and update the service status and license
NETWORK
ZyWALL 5/35/70 Series User’s Guide
status information. Use this screen to access the wizards,
statistics and DHCP table.
service subscriptions.
information.
75
Page 76

Chapter 3 Introducing the Web Configurator
Table 7 Screens Summary (continued)
LINK TAB FUNCTION
LAN LAN Use this screen to configure LAN DHCP and TCP/IP settings.
Static DHCP Use this screen to assign fixed IP addresses on the LAN.
IP Alias Use this screen to partition your LAN interface into subnets.
Port Roles
(ZyWALL 5
and ZyWALL
35)
BRIDGE Bridge Use this screen to change the bridge settings on the ZyWALL.
Port Roles Use this screen to change the DMZ/WLAN port roles on the
WAN General This screen allows you to configure load balancing, route priority
WAN1 Use this screen to configure the WAN1 connection for Internet
WAN2 Use this screen to configure the WAN2 connection for Internet
3G (WAN2) Use this screen to configure the 3G WAN2 connection for Internet
Traffic
Redirect
Dial Backup Use this screen to configure the backup WAN dial-up connection.
DMZ DMZ Use this screen to configure your DMZ connection.
Static DHCP Use this screen to assign fixed IP addresses on the DMZ.
IP Alias Use this screen to partition your DMZ interface into subnets.
Port Roles Use this screen to change the DMZ/WLAN port roles on the
WLAN WLAN Use this screen to configure your WLAN connection.
Static DHCP Use this screen to assign fixed IP addresses on the WLAN.
IP Alias Use this screen to partition your WLAN interface into subnets.
Port Roles Use this screen to change the DMZ/WLAN port roles on the
WIRELESS
3G (WAN2) This is the same as WAN > 3G (WAN2).
Wi-Fi Wireless Card Use this screen to configure the wireless LAN settings and WLAN
MAC Filter Use this screen to change MAC filter settings on the ZyWALL
SECURITY
Use this screen to change the LAN/DMZ/WLAN port roles.
ZyWALL 70 or the LAN/DMZ/WLAN port roles on the ZyWALL 5 or
ZyWALL 35.
and traffic redirect properties.
access.
access.
access (ZyWALL 5 only).
Use this screen to configure your traffic redirect properties and
parameters.
ZyWALL 70 or the LAN/DMZ/WLAN port roles on the ZyWALL 5 or
ZyWALL 35.
ZyWALL 70 or the LAN/DMZ/WLAN port roles on the ZyWALL 5 or
ZyWALL 35.
authentication/security settings.
76
ZyWALL 5/35/70 Series User’s Guide
Page 77

Chapter 3 Introducing the Web Configurator
Table 7 Screens Summary (continued)
LINK TAB FUNCTION
FIREWALL Default Rule Use this screen to activate/deactivate the firewall and the direction
of network traffic to which to apply the rule
Rule Summary This screen shows a summary of the firewall rules, and allows you
to edit/add a firewall rule.
Anti-Probing Use this screen to change your anti-probing settings.
Threshold Use this screen to configure the threshold for DoS attacks.
Service Use this screen to configure custom services.
IDP General Use this screen to enable IDP on the ZyWALL and choose what
interface(s) you want to protect from intrusions.
Signature Use these screens to view signatures by attack type or search for
signatures by signature name, ID, severity, target operating
system, action etc. You can also configure signature actions here.
Anomaly Use this screen to configure anomaly detection settings.
Update Use this screen to download new signature downloads. It is
important to do this as new intrusions evolve.
Backup &
Restore
ANTI-VIRUS General Use this screen to activate AV scanning on the interface(s) and
Signature Use these screens to search for signatures by signature name or
Update Use this screen to view the version number of the current
Backup &
Restore
ANTI-SPAM General Use this screen to turn the anti-spam feature on or off and set how
External DB Use this screen to enable or disable the use of the anti-spam
Lists Use this screen to configure the whitelist to identify legitimate e-
CONTENT
FILTER
VPN VPN Rules
General This screen allows you to enable content filtering and block certain
Policy Use these screens to configure content filtering policies for
Object Use this screen to configure a master list of trusted web sites,
Cache Use this screen to view and configure the ZyWALL’s URL caching.
(IKE)
VPN Rules
(Manual)
SA Monitor Use this screen to display and manage active VPN connections.
Global Setting Use this screen to configure the IPSec timer settings.
Use this screen to back up, restore or revert to the default
signatures’ actions.
specify actions when a virus is detected.
attributes and configure how the ZyWALL uses them.
signatures and configure the signature update schedule.
Use this screen to back up, restore or revert to the default
signatures’ actions.
the ZyWALL treats spam.
external database.
mail and configure the blacklist to identify spam e-mail.
web features.
particular source IP addresses or ranges of IP addresses. Select
web features and categories of web pages to block. You can also
configure schedules for applying the content filtering.
forbidden web sites, and keywords. Then you can use the objects
in individual policies.
Use this screen to configure VPN connections using IKE key
management and view the rule summary.
Use this screen to configure VPN connections using manual key
management and view the rule summary.
ZyWALL 5/35/70 Series User’s Guide
77
Page 78

Chapter 3 Introducing the Web Configurator
Table 7 Screens Summary (continued)
LINK TAB FUNCTION
CERTIFICATES My Certificates Use this screen to view a summary list of certificates and manage
Trusted CAs Use this screen to view and manage the list of the trusted CAs.
Trusted
Remote Hosts
Directory
Servers
AUTH SERVER Local User
Database
RADIUS Configure this screen to use an external server to authenticate
ADVANCED
NAT NAT Overview Use this screen to enable NAT.
Address
Mapping
Port
Forwarding
Port Triggering Use this screen to change your ZyWALL’s port triggering settings.
STATIC ROUTE IP Static Route Use this screen to configure IP static routes.
POLICY ROUTE Policy Route
Summary
BW MGMT Summary Use this screen to enable bandwidth management on an interface.
Class Setup Use this screen to set up the bandwidth classes.
Monitor Use this screen to view the ZyWALL’s bandwidth usage and
DNS System Use this screen to configure the address and name server
Cache Use this screen to configure the DNS resolution cache.
DHCP Use this screen to configure LAN/DMZ/WLAN DNS informati on.
DDNS Use this screen to set up dynamic DNS.
certificates and certification requests.
Use this screen to view and manage the certificates belonging to
the trusted remote hosts.
Use this screen to view and manage the list of the directory
servers.
Use this screen to configure the local user account(s) on the
ZyWALL.
wireless and/or VPN users.
Use this screen to configure network address translation mapping
rules.
Use this screen to configure servers behind the ZyWALL.
Use this screen to view a summary list of all the policies and
configure policies for use in IP policy routing.
allotments.
records.
78
ZyWALL 5/35/70 Series User’s Guide
Page 79

Chapter 3 Introducing the Web Configurator
Table 7 Screens Summary (continued)
LINK TAB FUNCTION
REMOTE
MGMT
UPnP UPnP Use this screen to enable UPnP on the ZyWALL.
Custom APP Custom APP Use this screen to specify port numbers for the ZyWALL to monitor
ALG ALG Use this screen to allow certain applications to pass through the
REPORTS
WWW Use this screen to configure through which interface(s) and from
which IP address(es) users can use HTTPS or HTTP to manage
the ZyWALL.
SSH Use this screen to configure through which interface(s) and from
which IP address(es) users can use Secure Shell to manage the
ZyWALL.
TELNET Use this screen to configure through which interface(s) and from
which IP address(es) users can use Telnet to manage the
ZyWALL.
FTP Use this screen to confi gure through which interface(s) and from
which IP address(es) users can use FTP to access the ZyWALL.
SNMP Use this screen to configure your ZyWALL’s settings for Simple
Network Management Protocol management.
DNS Use this screen to configure through which interface(s) and from
which IP address(es) users can send DNS queries to the ZyWALL.
CNM Use this scre en to configure and allow your ZyWALL to be
managed by the Vantage CNM server.
Ports Use this screen to view the NAT port mapping rules that UPnP
creates on the ZyWALL.
for FTP, HTTP, SMTP, POP3, H323, and SIP traffic.
ZyWALL.
Reports Use this screen to have the ZyWALL record and display network
usage reports.
IDP Use this screen to collect and display statistics on the intrusions
that the ZyWALL has detected.
Anti-Virus Use this screen to collect and display statistics on the viruses that
Anti-Spam Use this screen to collect and display statistics on spam mail that
E-mail Report Use this screen to have reports emailed in a single file.
LOGS View Log Use this screen to view the logs for the categories that you
Log Settings Use this screen to change your ZyWALL’s log settings.
the ZyWALL has detected.
the ZyWALL has detected.
selected.
ZyWALL 5/35/70 Series User’s Guide
79
Page 80

Chapter 3 Introducing the Web Configurator
Table 7 Screens Summary (continued)
LINK TAB FUNCTION
MAINTENANCE General This screen contains administrative.
Password Use this screen to change your password.
Time and Date Use this screen to change your ZyWALL’s time and date.
Device Mode Use this screen to configure and have your ZyWALL work as a
F/W Upload Use this screen to upload firmware to your ZyWALL
Backup &
Restore
Restart This screen allows you to reboot the ZyWALL without turning the
Diagnosis Use this screen to have the ZyWALL generate and send
LOGOUT Click this label to exit the web configurator.
3.4.6 Port Statistics
router or a bridge.
Use this screen to backup and restore the configuration or reset
the factory defaults to your ZyWALL.
power off.
diagnostic files by e-mail and/or the console port.
Click Port Statistics in the HOME screen. Read-only information here includes port status
and packet specific statistics. The Poll Interval(s) field is configurable. Not all items
described are available on all models.
Figure 17 HOME > Port Statistics
The following table describes the labels in this screen.
Table 8 HOME > Port Statistics
LABEL DESCRIPTION
Click the icon to display the chart of throughput statistics.
80
Port These are the ZyWALL’s interfaces.
ZyWALL 5/35/70 Series User’s Guide
Page 81

Chapter 3 Introducing the Web Configurator
Table 8 HOME > Port Statistics (continued)
LABEL DESCRIPTION
Status For the WAN interface(s) and the Dial Backup port, this displays the port speed and
duplex setting if you’re using Ethernet encapsulation or the remote node name for a
PPP connection and Down (line is down or not connected), Idle (line (ppp) idle),
Dial (starting to trigger a call) or Drop (dropping a call) if you’re using PPPoE
encapsulation. Dial backup is not available in bridge mode.
For the LAN, DMZ and WLAN ports, this displays the port speed and duplex setting.
For the WLAN card, this displays the transmission rate when a wireless LAN card is
inserted and WLAN is enabled or Down when a wireless LAN is not inserted or
WLAN is disabled.
TxPkts This is the number of transmitted packets on this port.
RxPkts This is the number of received packets on this port.
Tx B/s This displays the transmission speed in bytes per second on this port.
Rx B/s This displays the reception speed in bytes per second on this port.
Up Time This is the total amount of time the line has been up.
System Up Time This is the total time the ZyWALL has been on.
Automatic
Refresh Interval
Refresh Click this button to update the screen’s statistics immediately.
Select a number of seconds or None from the drop-down list box to update all
screen statistics automatically at the end of every time interval or to not update the
screen statistics.
3.4.7 Show Statistics: Line Chart
Click the icon in the Show Statistics screen. This screen shows you a line chart of each port’s
throughput statistics.
Figure 18 HOME > Show Statistics > Line Chart
ZyWALL 5/35/70 Series User’s Guide
81
Page 82

Chapter 3 Introducing the Web Configurator
The following table describes the labels in this screen.
Table 9 HOME > Show Statistics > Line Chart
LABEL DESCRIPTION
Click the icon to go back to the Show Statistics screen.
Port Select the check box(es) to display the throughput statistics of the corresponding
interface(s).
B/s Specify the direction of the traffic for which you want to show throughput statistics in
this table.
Select Tx to display transmitted traffic throughput statistics and the amount of traffic
(in bytes). Select Rx to display received traffic throughput statistics and the amount
of traffic (in bytes).
Throughput
Range
Set the range of the throughput (in B/s, KB/s or MB/s) to display.
Click Set Range to save this setting back to the ZyWALL.
3.4.8 DHCP Table
DHCP (Dynamic Host Configuration Protocol, RFC 2131 and RFC 2132) allows individual
clients to obtain TCP/IP configuration at start-up from a server. You can configure the
ZyWALL as a DHCP server or disable it. When configured as a server, the ZyWALL provides
the TCP/IP configuration for the clients. If DHCP service is disabled, you must have another
DHCP server on your LAN, or else the computer must be manually configured.
Click Show DHCP Table in the HOME screen when the ZyWALL is set to router mode.
Read-only information here relates to your DHCP status. The DHCP table shows current
DHCP client information (including IP Address, Host Name and MAC Address) of all
network clients using the ZyWALL’s DHCP server.
Figure 19 HOME > Show DHCP Table
The following table describes the labels in this screen.
Table 10 HOME > Show DHCP Table
LABEL DESCRIPTION
Interface Select LAN, DMZ or WLAN to show the current DHCP client information for the
specified interface.
# This is the index number of the host computer.
IP Address This field displays the IP address relative to the # field listed above.
Host Name This field displays the computer host name.
82
ZyWALL 5/35/70 Series User’s Guide
Page 83

Table 10 HOME > Show DHCP Table (continued)
LABEL DESCRIPTION
MAC Address The MAC (Media Access Control) or Ethernet address on a LAN (Local Area
Reserve Select the check box in the heading row to automatically select all check boxes or
Refresh Click Refresh to reload the DHCP table.
3.4.9 VPN Status
Click VPN in the HOME screen. This screen displays read-only information about the active
VPN connections. The Poll Interval(s) field is configurable. A Security Association (SA) is
the group of security settings related to a specific VPN tunnel.
Chapter 3 Introducing the Web Configurator
Network) is unique to your computer (six pairs of hexadecimal notation).
A network interface card such as an Ethernet adapter has a hardwired address that is
assigned at the factory. This address follows an industry standard that ensures no
other adapter has a similar address.
select the check box(es) in each entry to have the ZyWALL always assign the
selected entry(ies)’s IP address(es) to the corresponding MAC address(es) (and host
name(s)). You can select up to 128 entries in this table. After you click Apply, the
MAC address and IP address also display in the corresponding LAN, DMZ or WLAN
Static DHCP screen (where you can edit them).
Figure 20 HOME > VPN Status
The following table describes the labels in this screen.
Table 11 HOME > VPN Status
LABEL DESCRIPTION
# This is the security association index number.
Name This field displays the identification name for this VPN policy.
Local Network This field displays the IP address of the computer using the VPN IPSec feature of
your ZyWALL.
Remote Network This field displays IP address (in a range) of computers on the remote network
behind the remote IPSec router.
Encapsulation This field displays Tunnel or Transport mode.
ZyWALL 5/35/70 Series User’s Guide
83
Page 84

Chapter 3 Introducing the Web Configurator
Table 11 HOME > VPN Status
LABEL DESCRIPTION
IPSec Algorithm This field displays the security protocols used for an SA.
Both AH and ESP increase ZyWALL processing requirements and communications
latency (delay).
Automatic
Refresh Interval
Refresh Click this button to update the screen’s statistics immediately.
Select a number of seconds or None from the drop-down list box to update all
screen statistics automatically at the end of every time interval or to not update the
screen statistics.
3.4.10 Bandwidth Monitor
Click Bandwidth in the HOME screen to display the bandwidth monitor. This screen displays
the device’s bandwidth usage and allotments.
Figure 21 Home > Bandwidth Monitor
84
The following table describes the labels in this screen.
Table 12 ADVANCED > BW MGMT > Monitor
LABEL DESCRIPTION
Interface Select an interface from the drop-down list box to view the bandwidth usage
Class This field displays the name of the bandwidth class.
Budget (kbps) This field displays the amount of bandwidth allocated to the bandwidth class.
Current Usage (kbps) This field displays the amount of bandwidth that each bandwidth class is
of its bandwidth classes.
A Default Class automatically displays for all the bandwidth in the Root
Class that is not allocated to bandwidth classes. If you do not enable
maximize bandwidth usage on an interface, the ZyWALL uses the bandwidth
in this default class to send traffic that does not match any of the bandwidth
classes.
using.
A
ZyWALL 5/35/70 Series User’s Guide
Page 85

Chapter 3 Introducing the Web Configurator
Table 12 ADVANCED > BW MGMT > Monitor
LABEL DESCRIPTION
Automatic Refresh
Interval
Refresh Click this button to update the screen’s statistics immediately.
A. If you allocate all the root class’s bandwidth to the bandwidth classes, the default class still displays a budget of 2
kbps (the minimum amount of bandwidth that can be assigned to a bandwidth class).
Select a number of seconds or None from the drop-down list box to update all
screen statistics automatically at the end of every time interval or to not
update the screen statistics.
ZyWALL 5/35/70 Series User’s Guide
85
Page 86

Chapter 3 Introducing the Web Configurator
86
ZyWALL 5/35/70 Series User’s Guide
Page 87

CHAPTER 4
Wizard Setup
This chapter provides information on the Wizard Setup screens in the web configurator. The
Internet access wizard is only applicable when the ZyWALL is in router mode.
4.1 Wizard Setup Overview
The web configurator's setup wizards help you co nfig ure Intern et and VPN co nn ection
settings.
In the HOME screen, click the Wizard icon
The following summarizes the wizards you can select:
• Internet Access Setup
Click this link to open a wizard to set up an Internet connection for WAN1 on a ZyWALL
with multiple WAN ports or the WAN port on a ZyWALL with a single WAN port.
• VPN Setup
Use VPN Setup to configure a VPN connection that uses a pre-shared key. If you want to
set the rule to use a certificate, please go to the VPN screens for configuration. See Section
4.3 on page 96.
• Anti-Spam Setup
Use Anti-Spam Setup to select which traffic directions the anti-spam feature checks for
unsolicited commercial or junk e-mail (spam). See Section 4.3 on page 96.
Figure 22 Wizard Setup Welcome
to open the Wizard Setup Welcome screen.
ZyWALL 5/35/70 Series User’s Guide
87
Page 88

Chapter 4 Wizard Setup
4.2 Internet Access
The Internet access wizard screen has three variations depending on what encapsulation type
you use. Refer to information provided by your ISP to know what to enter in each field. Leave
a field blank if you don’t have that information.
4.2.1 ISP Parameters
The ZyWALL offers three choices of encapsulation. They are Ethernet, PPTP or PPPoE.
The wizard screen varies according to the type of encapsulation that you select in the
Encapsulation field.
4.2.1.1 Ethernet
For ISPs (such as Telstra) that send UDP heartbeat packets to verify that the customer is still
online, please create a WAN-to-WAN/ZyWALL firewall rule for those packets. Con ta ct your
ISP to find the correct port number.
Choose Ethernet when the WAN port is used as a regular Ethernet.
Figure 23 ISP Parameters: Ethernet Encapsulation
88
The following table describes the labels in this screen.
Table 13 ISP Parameters: Ethernet Encapsulation
LABEL DESCRIPTION
ISP Parameters
for Internet
Access
Encapsulation You must choose the Ethernet option when the WAN port is used as a regular
Ethernet. Otherwise, choose PPPoE or PPTP for a dial-up connection.
WAN IP Address
Assignment
ZyWALL 5/35/70 Series User’s Guide
Page 89

Table 13 ISP Parameters: Ethernet Encapsulation
LABEL DESCRIPTION
IP Address
Assignment
My WAN IP
Address
My WAN IP
Subnet Mask
Gateway IP
Address
First DNS Server
Second DNS
Server
Back Click Back to return to the previous wizard screen.
Apply Click Apply to save your changes and go to the next screen.
Select Dynamic If your ISP did not assign you a fixed IP address. This is the
default selection.
Select Static If the ISP assigned a fixed IP address.
The fields below are available only wh e n yo u sel e ct Static.
Enter your WAN IP address in this field.
Enter the IP subnet mask in this field.
Enter the gateway IP address in this field.
Enter the DNS server's IP address(es) in the field(s) to the right.
Leave the field as 0.0.0.0 if you do not want to configure DNS servers. If you do not
configure a DNS server, you must know the IP address of a machine in order to
access it.
4.2.1.2 PPPoE Encapsulation
Point-to-Point Protocol over Ethernet (PPPoE) functions as a dial-up connection. PPPoE is an
IETF (Internet Engineering Task Force) standard specifying how a host personal computer
interacts with a broadband modem (for example DSL, cable, wireless, etc.) to achieve access
to high-speed data networks.
Chapter 4 Wizard Setup
Figure 24 ISP Parameters: PPPoE Encapsulation
ZyWALL 5/35/70 Series User’s Guide
89
Page 90

Chapter 4 Wizard Setup
The following table describes the labels in this screen.
Table 14 ISP Parameters: PPPoE Encapsulation
LABEL DESCRIPTION
ISP Parameter
for Internet
Access
Encapsulation Choose an encapsulation method from the pull-down list box. PPP over Ethernet
Service Name Type the name of your service provider.
User Name Type the user name given to you by your ISP.
Password Type the password associated with the user name above.
Retype to
Confirm
Nailed-Up Select Nailed-Up if you do not want the connection to time out.
Idle Timeout Type the time in seconds that elapses before the router automatically disconnects
WAN IP Address
Assignment
IP Address
Assignment
My WAN IP
Address
First DNS Server
Second DNS
Server
Back Click Back to return to the previous wizard screen.
Apply Click Apply to save your changes and go to the next screen.
forms a dial-up connection.
Type your password again for confirmation.
from the PPPoE server. The default time is 100 seconds.
Select Dynamic If your ISP did not assign you a fixed IP address. This is the
default selection.
Select Static If the ISP assigned a fixed IP address.
The fields below are available only when you select Static.
Enter your WAN IP address in this field.
Enter the DNS server's IP address(es) in the field(s) to the right.
Leave the field as 0.0.0.0 if you do not want to configure DNS servers. If you do not
configure a DNS server, you must know the IP address of a machine in order to
access it.
4.2.1.3 PPTP Encapsulation
Point-to-Point Tunneling Protocol (PPTP) is a network protocol that enables transfers of data
from a remote client to a private server, creating a Virtual Private Network (VPN) using TCP/
IP-based networks.
PPTP supports on-demand, multi-protocol, and virtual private networking over public
networks, such as the Internet.
" The ZyWALL supports one PPTP server connection at any given time.
90
ZyWALL 5/35/70 Series User’s Guide
Page 91

Figure 25 ISP Parameters: PPTP Encapsulation
Chapter 4 Wizard Setup
The following table describes the labels in this screen.
Table 15 ISP Parameters: PPTP Encapsulation
LABEL DESCRIPTION
ISP Parameters for
Internet Access
Encapsulation Select PPTP from the drop-down list box. To configure a PPTP client, you must
User Name Type the user name given to you by your ISP.
Password Type the password associated with the User Name above.
Retype to Confirm Type your password again for confirmation.
Nailed-Up Select Nailed-Up if you do not want the connection to time out.
Idle Timeout Type the time in seconds that elapses before the router automatically
PPTP
Configuration
My IP Address Type the (static) IP address assigned to you by your ISP.
My IP Subnet Mask Type the subnet mask assigned to you by your ISP (if given).
Server IP Address Type the IP address of the PPTP server.
Connection ID/
Name
configure the User Name and Password fields for a PPP connection and the
PPTP parameters for a PPTP connection.
disconnects from the PPTP server.
Enter the connection ID or connection name in this field. It must follow the "c:id"
and "n:name" format. For example, C:12 or N:My ISP.
This field is optional and depends on the requirements of your xDSL modem.
ZyWALL 5/35/70 Series User’s Guide
91
Page 92

Chapter 4 Wizard Setup
Table 15 ISP Parameters: PPTP Encapsulation
LABEL DESCRIPTION
WAN IP Address
Assignment
IP Address
Assignment
My WAN IP
Address
First DNS Server
Second DNS
Server
Back Click Back to return to the previous wizard screen.
Apply Click Apply to save your changes and go to the next screen.
Select Dynamic If your ISP did not assign you a fixed IP address. This is the
default selection.
Select Static If the ISP assigned a fixed IP address.
The fields below are available only when you select Static.
Enter your WAN IP address in this field.
Enter the DNS server's IP address(es) in the field(s) to the right.
Leave the field as 0.0.0.0 if you do not want to configure DNS servers. If you do
not configure a DNS server, you must know the IP address of a machine in order
to access it.
4.2.2 Internet Access Wizard: Second Screen
Click Next to go to the screen where you can register your ZyWALL and activate the free
content filtering, anti-spam, anti-virus and IDP trial applications. Otherwise, click Skip to
display the congratulations screen and click Close to complete the Internet access setup.
" Make sure you have installed the ZyWALL Turbo Card before you activate the
IDP and anti-virus subscription services.
Turn the ZyWALL off before you install or remove the ZyWALL Turbo Card.
Figure 26 Internet Access Wizard: Second Screen
92
ZyWALL 5/35/70 Series User’s Guide
Page 93

Figure 27 Internet Access Setup Complete
4.2.3 Internet Access Wizard: Registration
Chapter 4 Wizard Setup
If you clicked Next in the previous screen (see Figure 26 on page 92), the following screen
displays.
Use this screen to register the ZyWALL with myZyXEL.com. You must register your
ZyWALL before you can activate trial applications of services like content filtering, antispam, anti-virus and IDP.
" If you want to activate a standard service with your iCard’s PIN number
(license key), use the REGISTRATION > Service screen.
Figure 28 Internet Access Wizard: Registration
ZyWALL 5/35/70 Series User’s Guide
93
Page 94

Chapter 4 Wizard Setup
The following table describes the labels in this screen.
Table 16 Internet Access Wizard: Registration
LABEL DESCRIPTION
Device Registration If you select Existing myZyXEL.com account, only the User Name and
New myZyXEL.com
account
Existing myZyXEL.com
account
User Name Enter a user name for your myZyXEL.com account. The name should be
Check Click this button to check with the myZyXEL.com database to verify the user
Password Enter a password of between six and 20 alphanumeric characters (and the
Confirm Password Enter the password again for confirmation.
E-Mail Address Enter your e-mail address. You can use up to 80 alphanumeric characters
Country Select your country from the drop-down box list.
Back Click Back to return to the previous screen.
Next Click Next to continue.
Password fields are available.
If you haven’t created an account at myZyXEL.com, select this option and
configure the following fields to create an account and register your
ZyWALL.
If you already have an account at myZyXEL.com, select this option and enter
your user name and password in the fields below to register your ZyWALL.
from six to 20 alphanumeric characters (and the underscore). Spaces are
not allowed.
name you entered has not been used.
underscore). Spaces are not allowed.
(periods and the underscore are also allowed) without spaces.
After you fill in the fields and click Next, the following screen shows indicating the
registration is in progress. Wait for the registration progress to finish.
Figure 29 Internet Access Wizard: Registration in Progress
4.2.4 Internet Access Wizard: Status
This screen shows your device registration and service subscription status. Click Close to
leave the wizard screen when the registration and activation are done.
94
ZyWALL 5/35/70 Series User’s Guide
Page 95

Chapter 4 Wizard Setup
Figure 30 Internet Access Wizard: Status
A screen similar to the following appears if the registration was not successful. Click Return
to go back to the Device Registration screen and check your settings.
Figure 31 Internet Access Wizard: Registration Failed
4.2.5 Internet Access Wizard: Service Activation
If the ZyWALL has been registered, the Device Registration screen is read-only and the
Service Activation screen appears indicating what trial applications are activated after you
click Next.
Figure 32 Internet Access Wizard: Registered Device
ZyWALL 5/35/70 Series User’s Guide
95
Page 96

Chapter 4 Wizard Setup
Figure 33 Internet Access Wizard: Activated Services
4.3 VPN Wizard Gateway Setting
Use this screen to name the VPN gateway policy (IKE SA) and identify the IPSec routers at
either end of the VPN tunnel.
Click VPN Setup in the Wizard Setup Welcome screen (Figure 22 on page 87) to open the
VPN configuration wizard. The first screen displays as shown next.
Figure 34 VPN Wizard: Gateway Setting
The following table describes the labels in this screen.
Table 17 VPN Wizard: Gateway Setting
LABEL DESCRIPTION
Gateway Policy
Property
Name Type up to 32 charac ters to identify this VPN gateway policy. You may use any
character, including spaces, but the ZyWALL drops trailing spaces.
96
ZyWALL 5/35/70 Series User’s Guide
Page 97

Chapter 4 Wizard Setup
Table 17 VPN Wizard: Gateway Setting
LABEL DESCRIPTION
My ZyWALL When the ZyWALL is in router mode, enter the WAN IP address or the domain name
of your ZyWALL or leave the field set to 0.0.0.0.
The following applies if the My ZyWALL field is configured as 0.0.0.0:
When the WAN interface operation mode is set to Active/Passive, the ZyW ALL uses
the IP address (static or dynamic) of the WAN interface that is in use.
When the WAN interface operation mode is set to Active/Active, the ZyWALL uses
the IP address (static or dynamic) of the primary (highest priority) WAN interface to
set up the VPN tunnel as long as the corresponding WAN1 or WAN2 connection is
up. If the corresponding WAN1 or WAN2 connection goes down, the ZyWALL uses
the IP address of the other WAN port.
If both WAN connections go down, the ZyWALL uses the dial backup IP address for
the VPN tunnel when using dial backup or the LAN IP address when using traffic
redirect. See the chapter on WAN for details on dial backup and traffic redirect.
When the ZyWALL is in bridge mode, this field is read-only and displays the
ZyWALL’s IP address.
Remote
Gateway
Address
Back Click Back to return to the previous screen.
Next Click Next to continue.
Enter the WAN IP address or domain name of the remote IPSec router (secure
gateway) in the field below to identify the remote IPSec router by its IP address or a
domain name. Set this field to 0.0.0.0 if the remote IPSec router has a dynamic WAN
IP address.
4.4 VPN Wizard Network Setting
Use this screen to name the VPN network policy (IPSec SA) and identify the devices behind
the IPSec routers at either end of a VPN tunnel.
Two active SAs cannot have the local and remote IP address(es) both the same. Two active
SAs can have the same local or remote IP address, but not both. You can configure multiple
SAs between the same local and remote IP addresses, as long as only one is active at any time.
ZyWALL 5/35/70 Series User’s Guide
97
Page 98

Chapter 4 Wizard Setup
Figure 35 VPN Wizard: Network Setting
The following table describes the labels in this screen.
Table 18 VPN Wizard: Network Setting
LABEL DESCRIPTION
Network Policy
Property
Active If the Active check box is sel ected, p acket s for the tunnel tri gger the Z yW AL L to build
Name Type up to 32 characters to identify this VPN network policy. You may use any
Network Policy
Setting
Local Network Local IP addresses must be static and correspond to the remote IPSec router's
Starting IP
Address
Ending IP
Address/
Subnet Mask
Remote
Network
the tunnel.
Clear the Active check box to turn the network policy off. The ZyWALL does not
apply the policy. Packets for the tunnel do not trigger the tunnel.
character, including spaces, but the ZyWALL drops trailing spaces.
configured remote IP addresses.
Select Single for a single IP address. Select Range IP for a specific range of IP
addresses. Select Subnet to specify IP addresses on a network by their subnet
mask.
When the Local Network field is configured to Single, enter a (static) IP address on
the LAN behind your ZyWALL. When the Local Network field is configured to Range
IP, enter the beginning (static) IP address, in a range of computers on the LAN behind
your ZyWALL. When the Local Network field is configured to Subnet, this is a
(static) IP address on the LAN behind your ZyWALL.
When the Local Network field is configured to Single, this field is N/A. When the
Local Network field is configured to Range IP, enter the end (static) IP address, in a
range of computers on the LAN behind your ZyWALL. When the Local Network field
is configured to Subnet, this is a subnet mask on the LAN behind your ZyWALL.
Remote IP addresses must be static and correspond to the remote IPSec router's
configured local IP addresses.
Select Single for a single IP address. Select Range IP for a specific range of IP
addresses. Select Subnet to specify IP addresses on a network by their subnet
mask.
98
ZyWALL 5/35/70 Series User’s Guide
Page 99

Chapter 4 Wizard Setup
Table 18 VPN Wizard: Network Setting
LABEL DESCRIPTION
Starting IP
Address
Ending IP
Address/
Subnet Mask
Back Click Back to return to the previous screen.
Next Click Next to continue.
When the Remote Network field is configured to Single, enter a (static) IP address
on the network behind the remote IPSec router. When the Remote Network field is
configured to Range IP, enter the beginning (static) IP address, in a range of
computers on the network behind the remote IPSec router. When the Remote
Network field is configured to Subnet, enter a (static) IP address on the network
behind the remote IPSec router
When the Remote Network field is configured to Single, this field is N/A. When the
Remote Network field is configured to Range IP , enter the end (static) IP address, in
a range of computers on the network behind the remote IPSec router. When the
Remote Network field is configured to Subnet, enter a subnet mask on the network
behind the remote IPSec router.
4.5 VPN Wizard IKE Tunnel Setting (IKE Phase 1)
Use this screen to specify the authentication, encryption and other settings needed to negotiate
a phase 1 IKE SA.
Figure 36 VPN Wizard: IKE Tunnel Setting
ZyWALL 5/35/70 Series User’s Guide
99
Page 100

Chapter 4 Wizard Setup
The following table describes the labels in this screen.
Table 19 VPN Wizard: IKE Tunnel Setting
LABEL DESCRIPTION
Negotiation Mode Select Main Mode for identity protection. Select Aggressive Mode to allow
Encryption
Algorithm
Authentication
Algorithm
Key Group You must choose a key group for phase 1 IKE setup. DH1 (default) refers to
SA Life Time
(Seconds)
Pre-Shared Key Type your pre-sh a re d ke y in this field. A pre-shared key identifies a
Back Click Back to return to the previous screen.
Next Click Next to continue.
more incoming connections from dynamic IP addresses to use separate
passwords.
Note: Multiple SAs (security associations) connecting through a
secure gateway must have the same negotiation mode.
When DES is used for data communications, both sender and receiver must
know the same secret key, which can be used to encrypt and decrypt the
message or to generate and verify a message authentication code. The DES
encryption algorithm uses a 56-bit key. T riple DES (3DES) is a variation on DES
that uses a 168-bit key. As a result, 3DES is more secure than DES. It also
requires more processing power, resulting in increased latency and decreased
throughput. This implementation of AES uses a 128-bit key. AES is faster than
3DES.
MD5 (Message Digest 5) and SHA1 (Secure Hash Algorithm) are hash
algorithms used to authenticate packet data. The SHA1 algorithm is generally
considered stronger than MD5, but is slower. Select MD5 for minimal security
and SHA-1 for maximum security.
Diffie-Hellman Group 1 a 768 bit random number. DH2 refers to Diffie-Hellman
Group 2 a 1024 bit (1 Kb) random number. DH5 refers to Diffie-Hellman Group
5 a 1536-bit random number.
Define the length of time before an IKE SA automatically renegotiates in this
field. The minimum value is 180 seconds.
A short SA Life Time increases security by forcing the two VPN gateways to
update the encryption and authentication keys. However, every time the VPN
tunnel renegotiates, all users accessing remote resources are temporarily
disconnected.
communicating party during a phase 1 IKE negotiation. It is called "pre-shared"
because you have to share it with another party before you can communicate
with them over a secure connection.
Type from 8 to 31 case-sensitive ASCII characters or from 16 to 62
hexadecimal ("0-9", "A-F") characters. You must precede a hexadecimal key
with a "0x (zero x), which is not counted as part of the 16 to 62 character range
for the key. For example, in "0x0123456789ABCDEF", 0x denotes that the key
is hexadecimal and 0123456789ABCDEF is the key itself.
Both ends of the VPN tunnel must use the same pre-shared key. You will
receive a PYLD_MALFORMED (payload malformed) packet if the same preshared key is not used on both ends.
4.6 VPN Wizard IPSec Setting (IKE Phase 2)
Use this screen to specify the authentication, encryption and other settings needed to negotiate
a phase 2 IPSec SA.
100
ZyWALL 5/35/70 Series User’s Guide
 Loading...
Loading...