Page 1

R2 Extender
User Manual
V 1.1.0 January 2009
Page 2
Copyright
Copyright © 2008 all rights reserved. No part of this publication may be reproduced, adapted, stored in a
retrieval system, translated into any language, or transmitted in any form or by any means without the
written permission of the supplier.
About This Manual
This user manual is intended to guide professional installer to install the R2 Extender and how to build the
infrastructure centered on it. It includes procedures to assist you in avoiding unforeseen problems.
Conventions
For your attention on important parts, special characters and patterns are used in this manual:
This indicates an important note that you must pay attention to.
This indicates a warning or caution that you have to abide.
Bold: Indicates the function, important words, and so on.
Warning:
Note:
Page 3

Federal Communication Commission Interference Statement
This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant
to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful
interference in a residential installation. This equipment generates uses and can radiate radio frequency
energy and, if not installed and used in accordance with the instructions, may cause harmful interference
to radio communications. However, there is no guarantee that interference will not occur in a particular
installation. If this equipment does cause harmful interference to radio or television reception, which can
be determined by turning the equipment off and on, the user is encouraged to try to correct the interference
by one of the following measures:
- Reorient or relocate the receiving antenna.
- Increase the separation between the equipment and receiver.
- Connect the equipment into an outlet on a circuit different from that to which the receiver is connected.
- Consult the dealer or an experienced radio/TV technician for help.
This device complies with Part 15 of the FCC Rules. Operation is subject to the following two conditions: (1)
This device may not cause harmful interference, and (2) this device must accept any interference received,
including interference that may cause undesired operation.
FCC Caution: Any changes or modifications not expressly approved by the party responsible for
compliance could void the user's authority to operate this equipment.
Page 4

FCC Radiation Exposure Statement:
This equipment complies with FCC radiation exposure limits set forth for an uncontrolled environment. To
avoid the possibility of exceeding radio frequency exposure limits, you shall beep a distance of at least
100cm between you and the antenna of the installed equipment. This transmitter must not be co-located
or operating in conjunction with any other antenna or transmitter.
The availability of some specific channels and/or operational frequency bands are country
dependent and are firmware programmed at the factory to match the intended destination. The
firmware setting is not accessible by the end user.
Page 5

Content
CHAPTER 1 INTRODUCTION............................................................................................................................. 11
INTRODUCTION ........................................................................................................................................................ 11
APPEARANCE ...........................................................................................................................................................12
KEY FEATURES.........................................................................................................................................................12
TYPICAL APPLICATIONS ...........................................................................................................................................13
Telemedicine Broadband Wireless Application ...................................................................................................13
Education Broadband Wir eless Application........................................................................................................14
CHAPTER 2 HARDWARE INSTALLATION.......................................................................................................15
PREPARATION BEFORE INSTALLATION ......................................................................................................................15
Professional Installation Required......................................................................................................................15
Safety Precautions...............................................................................................................................................16
Product Package................................................................................................................................................. 16
HARDWARE INSTALLATION ......................................................................................................................................18
Assemble the Mounting Bracket..........................................................................................................................18
Pole Mounting.....................................................................................................................................................18
Interface Definition.............................................................................................................................................20
Connect Up..........................................................................................................................................................23
Grounding...........................................................................................................................................................24
Power On ............................................................................................................................................................ 24
CHAPTER 3 BASIC SETTINGS............................................................................................................................ 26
FACTORY DEFAULT SETTINGS ..................................................................................................................................26
SYSTEM REQUIREMENTS..........................................................................................................................................27
HOW TO LOGIN THE WEB-BASED INTERFACE...........................................................................................................28
BASIC SYSTEM SETUP.............................................................................................................................................. 30
BASIC WIRELESS SETTINGS .....................................................................................................................................31
Page 6

CHAPTER 4 ADVANCED SETTINGS..................................................................................................................34
ADVANCED WIRELESS SETTINGS ............................................................................................................................. 34
PEER-TO-PEER LINKS...............................................................................................................................................36
Antenna Alignment Tool......................................................................................................................................37
LINK TEST................................................................................................................................................................38
LINK AGGREGATION.................................................................................................................................................40
SUPER MODE ........................................................................................................................................................... 41
WIRELESS SECURITY SETTINGS ...............................................................................................................................42
Security Profile Configuration............................................................................................................................ 42
Access Control.....................................................................................................................................................44
RADIUS SETTINGS..................................................................................................................................................45
CHAPTER 5 MANAGEMENT...............................................................................................................................47
VIEW R2 EXTENDER BASIC INFORMATION...............................................................................................................47
VIEW ETHERNET STATISTICS ....................................................................................................................................47
VIEW WIRELESS STATISTICS ....................................................................................................................................48
CONNECTION ...........................................................................................................................................................49
PASSWORD ...............................................................................................................................................................50
REMOTE MANAGEMENT...........................................................................................................................................51
Remote Console...................................................................................................................................................52
SNMP..................................................................................................................................................................55
TIME SETTINGS ........................................................................................................................................................56
UPGRADE FIRMWARE............................................................................................................................................... 57
BACKUP/RETRIEVE SETTINGS.................................................................................................................................. 58
RESTORE FACTORY DEFAUL T SETTINGS ...................................................................................................................59
EVENT LOG..............................................................................................................................................................60
REBOOT ................................................................................................................................................................... 61
CHAPTER 6 TROUBLESHOOTING.................................................................................................................... 62
Page 7

APPENDIX A. CHANNEL – FREQUENCY TABLE............................................................................................64
APPENDIX B. ASCII ...............................................................................................................................................66
APPENDIX C. SSH SETTINGS..............................................................................................................................67
APPENDIX D. SERVICE SUPPORT..................................................................................................................... 73
Page 8

Figure
FIGURE 1 R2 EXTENDER ..............................................................................................................................................12
FIGURE 2 TELEMEDICINE WIRELESS BROADBAND....................................................................................................... 13
FIGURE 3 CAMPUS WIRELESS BROADBAND .................................................................................................................14
FIGURE 4 BRACKET MOUNTING – STEP 1.....................................................................................................................18
FIGURE 5 BRACKET MOUNTING – STEP 2.....................................................................................................................18
FIGURE 6 POLE MOUNTING –STEP 1.............................................................................................................................19
FIGURE 7 POLE MOUNTING – STEP 2............................................................................................................................ 19
FIGURE 8 POLE MOUNTING – STEP 3............................................................................................................................ 19
FIGURE 9 INTERFACE DEFINITION ................................................................................................................................ 20
FIGURE 10 DETAILED VIEW OF RS-232 PORT...............................................................................................................21
FIGURE 11 WARNING LABEL ........................................................................................................................................21
FIGURE 12 VENT.......................................................................................................................................................... 22
FIGURE 13 CONNECT UP – STEP 1................................................................................................................................23
FIGURE 14 CONNECT UP – STEP 2................................................................................................................................23
FIGURE 15 CONNECT UP – STEP 3................................................................................................................................23
FIGURE 16 CONNECT UP – STEP 4................................................................................................................................24
FIGURE 17 GROUNDING ............................................................................................................................................... 24
FIGURE 18 POE CONNECTION ......................................................................................................................................25
FIGURE 19 SECURITY ALERT........................................................................................................................................ 28
FIGURE 20 LOGIN......................................................................................................................................................... 28
FIGURE 21 MAIN PAGE.................................................................................................................................................29
FIGURE 22 BASIC SETUP ..............................................................................................................................................30
FIGURE 23 BASIC WIRELESS SETTINGS........................................................................................................................31
FIGURE 24 ADVANCED PARAMETERS ........................................................................................................................... 34
FIGURE 25 PEER-TO-PEER LINKS ................................................................................................................................. 36
FIGURE 26 ANTENNA ALIGNMENT TOOL......................................................................................................................37
Page 9

FIGURE 27 LINK TEST ..................................................................................................................................................39
FIGURE 28 LINK AGGREGATION...................................................................................................................................40
FIGURE 29 SUPER MODE..............................................................................................................................................41
FIGURE 30 SECURITY ...................................................................................................................................................42
FIGURE 31 ACCESS CONTROL ......................................................................................................................................44
FIGURE 32 RADIUS SETTINGS.................................................................................................................................... 45
FIGURE 33 BASIC INFORMATION ..................................................................................................................................47
FIGURE 34 ETHERNET STATISTICS ................................................................................................................................ 48
FIGURE 35 WIRELESS STATISTICS................................................................................................................................. 49
FIGURE 36 CONNECTION..............................................................................................................................................50
FIGURE 37 PASSWORD..................................................................................................................................................51
FIGURE 38 REMOTE MANAGEMENT............................................................................................................................. 52
FIGURE 39 PUTTY CONFIGURATION 1......................................................................................................................... 53
FIGURE 40 PUTTY CONFIGURATION 2......................................................................................................................... 54
FIGURE 41 SSH............................................................................................................................................................ 54
FIGURE 42 OBTAIN MIB FILE.......................................................................................................................................55
FIGURE 43 TIME SETTINGS...........................................................................................................................................56
FIGURE 44 UPGRADE FIRMWARE .................................................................................................................................57
FIGURE 45 BACKUP/RESTORE SETTINGS......................................................................................................................58
FIGURE 46 RESTORE SETTINGS ....................................................................................................................................59
FIGURE 47 EVENT LOG ................................................................................................................................................60
FIGURE 48 REBOOT......................................................................................................................................................61
Page 10

Table
TABLE 1 PIN DEFINITION.............................................................................................................................................21
TABLE 2 R2 EXTENDER FACTORY DEFAULT SETTINGS................................................................................................. 26
TABLE 3 RSSI-BEEP FREQUENCY ................................................................................................................................ 38
TABLE 4 CHANNELS IN 5MHZ CENTRE FREQUENCY.................................................................................................... 64
TABLE 5 CHANNELS IN 10MHZ CENTRE FREQUENCY..................................................................................................64
TABLE 6 CHANNELS IN 20MHZ CENTRE FREQUENCY..................................................................................................65
TABLE 7 CHANNELS IN 40MHZ CENTRE FREQUENCY..................................................................................................65
TABLE 8 ACSII............................................................................................................................................................66
TABLE 9 SSH SETTINGS ...............................................................................................................................................67
Page 11

Chapter 1 Introduction Page 11
Chapter 1 Introduction
Introduction
The R2 extender is a high-performance outdoor-deployable wireless bridge that provides wireless
connectivity among multiple network locations. The R2 Extender has a built-in 23dBi planar antenna that
can deliver up to a 40Km connection. An external antenna may also be used to improve signal quality
and improve distance. The R2 Extender allows for link aggregation by combining multiple links into one
link with greater transmission rate.
The R2 Extender is a multi function communication device that supports Base Station, CPE, PTP and
PTMP connectivity. It allows for local area network (LANs) in different locations (buildings) to be easily
interconnected. The R2 Extender delivers “last mile” broadband connectivity through its PTP and PTMP
capabilities.
The R2 Extender allows to be operated on PTP mode in one card and on bridge in another. And with an
external omni antenna for bridge side may provide users with flexibility in various local coverage
applications.
With high throughput and long-distance transmission, the R2 Extender is an ideal backhaul solution for
Carriers, Service Providers and Enterprises!
Page 12

Chapter 1 Introduction Page 12
Appearance
Figure 1 R2 Extender
Key Features
Provide easy installation and high performance wireless connectivity of up to 40km
IP67 waterproof housing endures almost any harsh environments
Multiple operating modes including Base station, CPE, PTP and PTMP
Support 64/128-bit WEP and 802.1X, WPA-PSK, WPA2-PSK and WPA-PSK&WPA2-PSK, etc
Support WMM and Quality of service (QoS) for enhanced performance
Proprietary Antenna Alignment Tool helps identify the antenna orientation with the best signal
strength
Link aggregation combines multiple links into one with greater transmission rate
Buzzer design helps to determine the device power initial condition
Super mode to boost the data rate up to 108Mbps
Advanced management tools like SNMP and Secure Shell (SSH)
User-friendly Web, SSH and SNMP-based management interface
Page 13
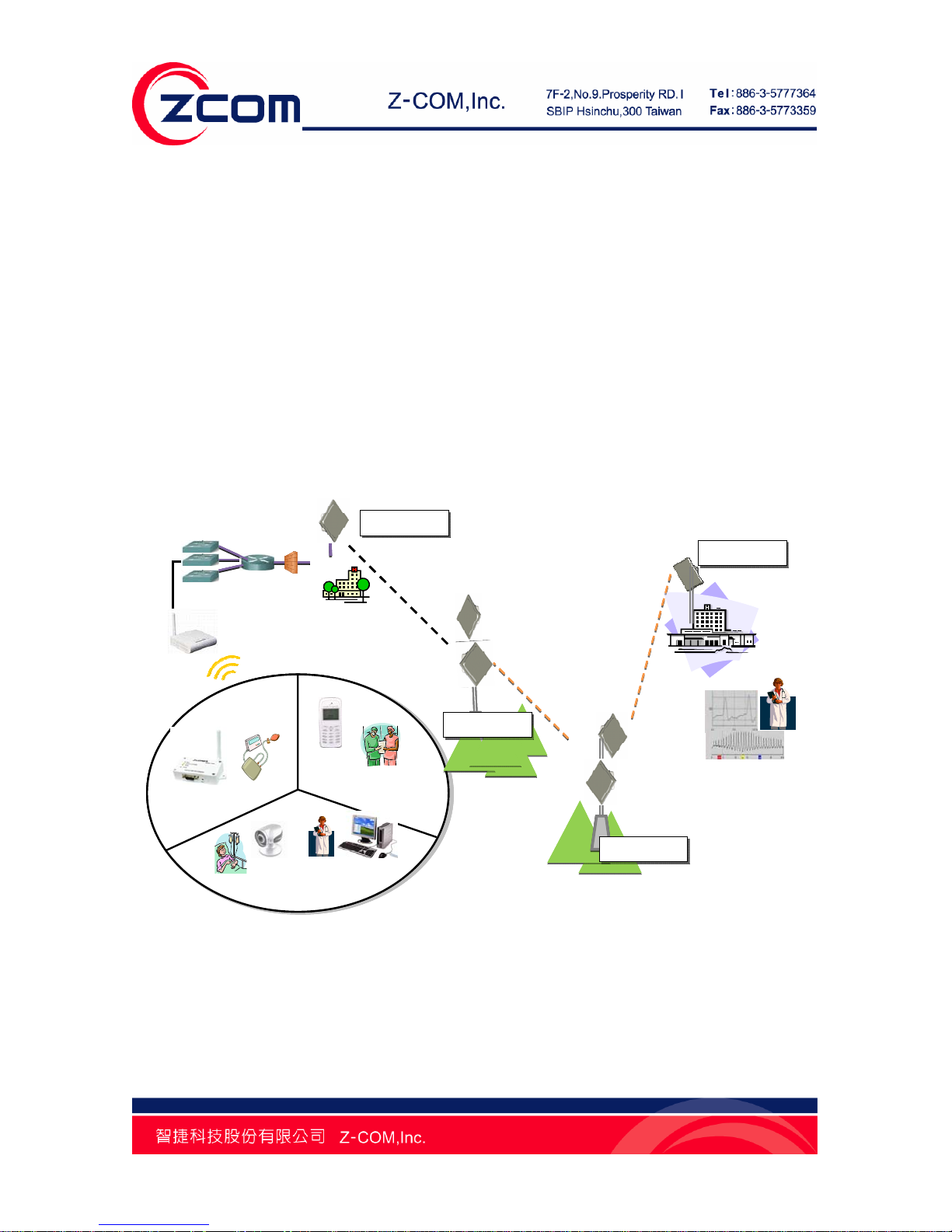
Chapter 1 Introduction Page 13
T ypical Applications
This section describes typical applications of the R2 Extender.
Telemedicine Broadband Wireless Application
The R2 Extender primary usage is as a relay or bridging technology that may be combined with cost
effective solar power solution allowing for telemedicine application in remote and rural environments. The
R2 Extender is able to deliver stable and high performance broadband connectivity for typical telemedicine
applications in a Line-of-Sight environment.
Health Center
Health Center
Telemedicine
Telemedicine
Wireless Application
Wireless Ap p lication
Relay
Relay
Rural Clinics
Rural Clinics
WIWI--FI AP
FI AP
for indoor
for indoor
coverage
coverage
Relay
Relay
RS-232
Wi-Fi adaptor
Wi-Fi
phone
Video Surveillance
Video S urveillance
Communication
Communication
Data transmission
Data transmission
Long distance
Long distance
Diagnosis
Diagnosis
L ow balance R outer
F ire wall
Swit ch
R2 Ext ender
R2 Ext ender
R1 Ext ender
R1 Ext ender
R2 Ext ender
R2 Ext ender
R1 Ext ender
R1 Ext ender
Health Center
Health Center
Telemedicine
Telemedicine
Wireless Application
Wireless Ap p lication
Relay
Relay
Rural Clinics
Rural Clinics
WIWI--FI AP
FI AP
for indoor
for indoor
coverage
coverage
Relay
Relay
RS-232
Wi-Fi adaptor
RS-232
Wi-Fi adaptor
Wi-Fi
phone
Wi-Fi
phone
Video Surveillance
Video S urveillance
Communication
Communication
Data transmission
Data transmission
Long distance
Long distance
Diagnosis
Diagnosis
L ow balance R outer
F ire wall
Swit ch
F ire wall
Swit ch
R2 Ext ender
R2 Ext ender
R1 Ext ender
R1 Ext ender
R2 Ext ender
R2 Ext ender
R1 Ext ender
R1 Ext ender
Figure 2 T ele medicine Wireless Broadband
Page 14
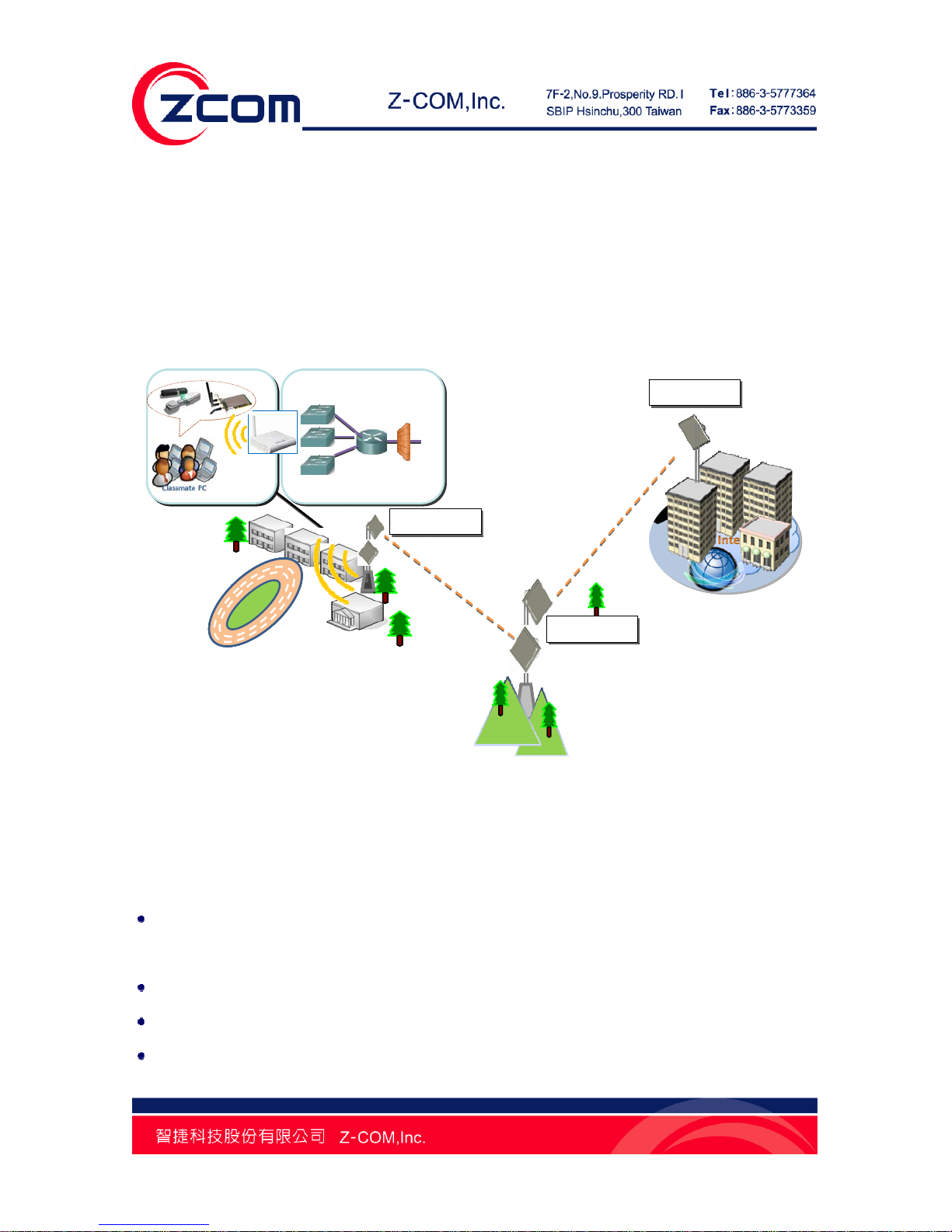
Chapter 1 Introduction Page 14
Education Broadband Wireless Application
School in remote area or rural areas can be provided with broadband connectivity via local Internet service
providers The relay ability of the R2 Extender allows for multiple hops to be made thus allowing the R2
Extender to reach more remote LOS locations beyond 40Kms or to circumvent natural obstructions like
mountains..
Relay
Relay
Firewall
L ow balance R outer
Swit ch
Z-Com Wi-Fi clients
School
School
In terne t
In terne t
Provider
Provider
R2 Ext ender
R2 Ext ender
R2 Ext ender
R2 Ext ender
R1 Ext ender
R1 Ext ender
Relay
Relay
Firewall
L ow balance R outer
Swit ch
Z-Com Wi-Fi clients
Firewall
L ow balance R outer
Swit ch
Firewall
L ow balance R outer
Swit ch
Z-Com Wi-Fi clients
School
School
School
School
In terne t
In terne t
Provider
Provider
R2 Ext ender
R2 Ext ender
R2 Ext ender
R2 Ext ender
R1 Ext ender
R1 Ext ender
Figure 3 Campus Wireless Broadband
Besides, the R2 extender can also be applied into the following environments:
Cost-effectively provide long distance backhaul for remote areas (like village, oil well, island,
mountain and etc.)
Establish local backhaul for campus, farm and factory
Provide and access for video streaming or surveillance for industrial and mining enterprises
Plays as a relay connecting different networks
Page 15

Chapter 2 Hardware Installation Page 15
Chapter 2 Hardware Installation
This chapter describes safety precautions and product information you have to know and check before
installing R2 Extender.
Preparation before Installation
Professional Installation Required
1. Please seek assistance from a professional installer who is well trained in the RF installation and
knowledgeable in the local regulations.
2. The R2 Extender is distributed through distributor and system installer with professional
technicians and will not be sold directly through retail store.
3. The equipment shall be installed in RESTRICTED ACCESS LOCATIONS. Access can only be
gained by service persons or by users who have been instructed about the reasons for the
restrictions applied to the location and about any precautions that shall be taken. Furthermore,
access is through the use of a tool or lock and key, or other means of security, and is controlled b
the authority responsible for the location.
4. If you are intended to use an external antenna with the R2 Extender, please contact your
supplier/installer to ensure that your unit is set for you have fulfilled all the local regulatory
requirements. It is the responsibility of the installer/user to check that the equipment as deployed
meets local regulatory requirements.
Page 16
Chapter 2 Hardware Installation Page 16
Safety Precautions
For your safety and proper installation, please read and follow the instructions below:
ONLY qualified service personnel should service or disassemble this device;
When installing the device, note the followings:
- Do NOT use a metal ladder;
- Do NOT work on a windy or raining day;
- Do NOT install, use or service the device during a thunderstorm, as this may cause a remote
risk of electric shock from lightning;
- Wear shoes with rubber soles and heels, rubber gloves, long sleeved shirt or jacket.
- When the system is operational, avoid standing directly in front of the antenna. Strong RF
fields are present when the transmitter is on.
Ground the device properly with grounding wire to protect against lightening;
Use ONLY appropriate accessories for the device.
If the temperatures of the unit surface exceeds the limit, be precautious not to continuous held or
touch the device for a certain period of time.
Product Package
The product package you have received should contain the following items. If any of them are not
included or damaged, please contact your local vendor for support.
R2 Extender with integrated 23dBi antenna ×1
Mounting Kit ×1
PoE Injector & Power cord ×1
Grounding Wire w/ screw ×1
Waterproof RJ-45 Connector Kit ×1
Page 17

Chapter 2 Hardware Installation Page 17
Quick Installation Guide ×1
Product CD ×1
Product CD contains Management Tool, Quick Installation Guide and User Manual!
Mounting Kit
Wall/Pole Mounting Bracket
1. T-Form Bracket ×1
2. Articulation Pole ×1
3. Pole Mount Bar ×1
Fasteners
4. M8×80 Screw ×2
M8×90 Screw ×1
5. M8 Washer ×3
6. M8 Spring Washer ×3
7. M8 Nut ×1
8. M5×16 Screw ×4
9. M5 Washer ×4
10. Wood Screw ×4 (for Wall Mount)
11. Wall/Gyprock Plug ×4 (for Wall Mount)
Waterproof RJ-45 Connector Kit
1. Gland ×1
2. Sealing Nut ×1
3. Sealing ×1
Note:
Page 18
Chapter 2 Hardware Installation Page 18
Hardware Installation
Assemble the Mounting Bracket
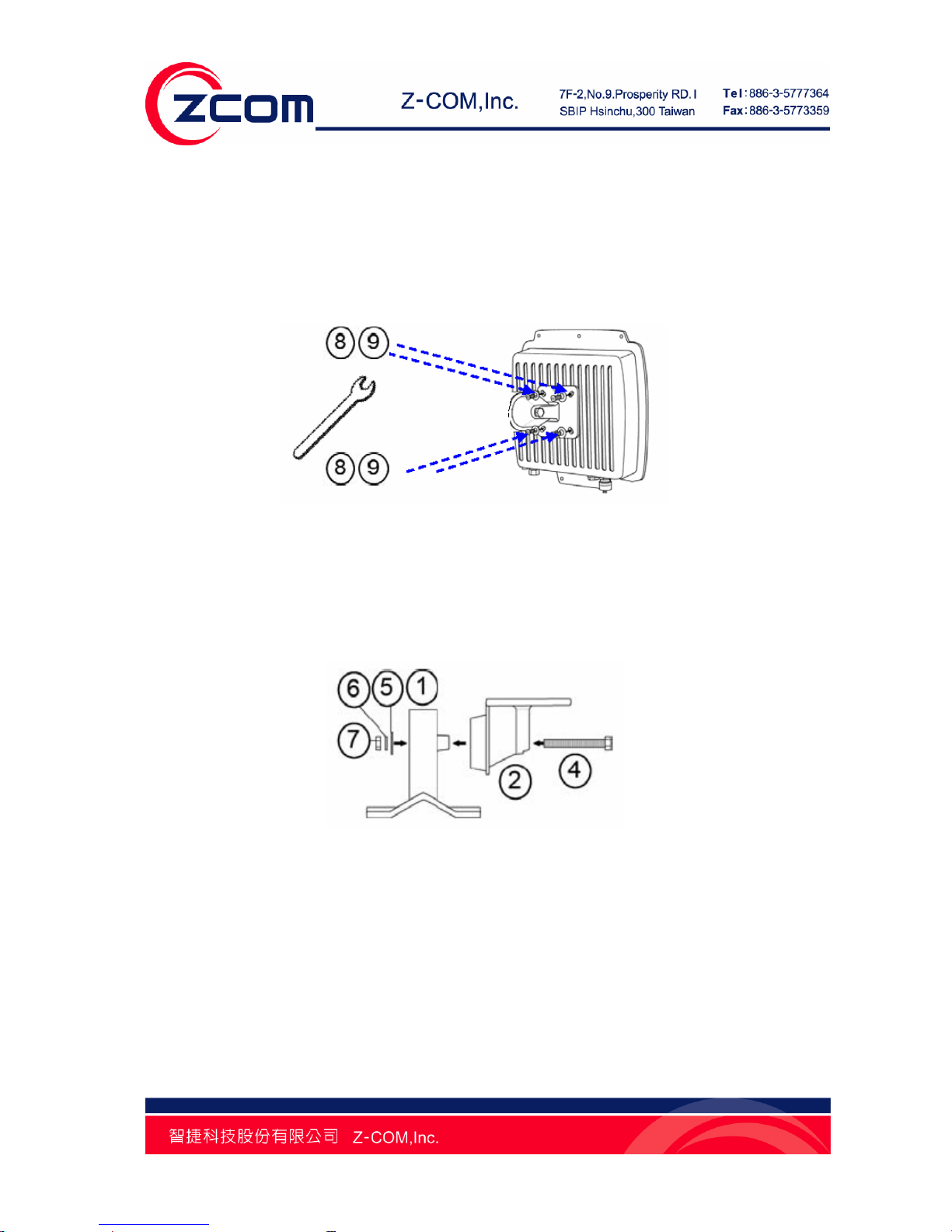
1. Place the main bracket into the seating and use a spanner to fasten the bracket to the R2
Extender with M5×16 screws ⑧ and M5 washers ⑨ provided in the hardware packets;
Figure 4 Bracket Mounting – Step 1
2. Assemble the main bracket by placing articulation pole ② to the T-form bracket ① via a
M8×90 ④ screw through the insertion axe and fix with the M8 washer ⑤ , spring washer ⑥
and M8 nut⑦;
Figure 5 Bracket Mounting – Step 2
Pole Mounting
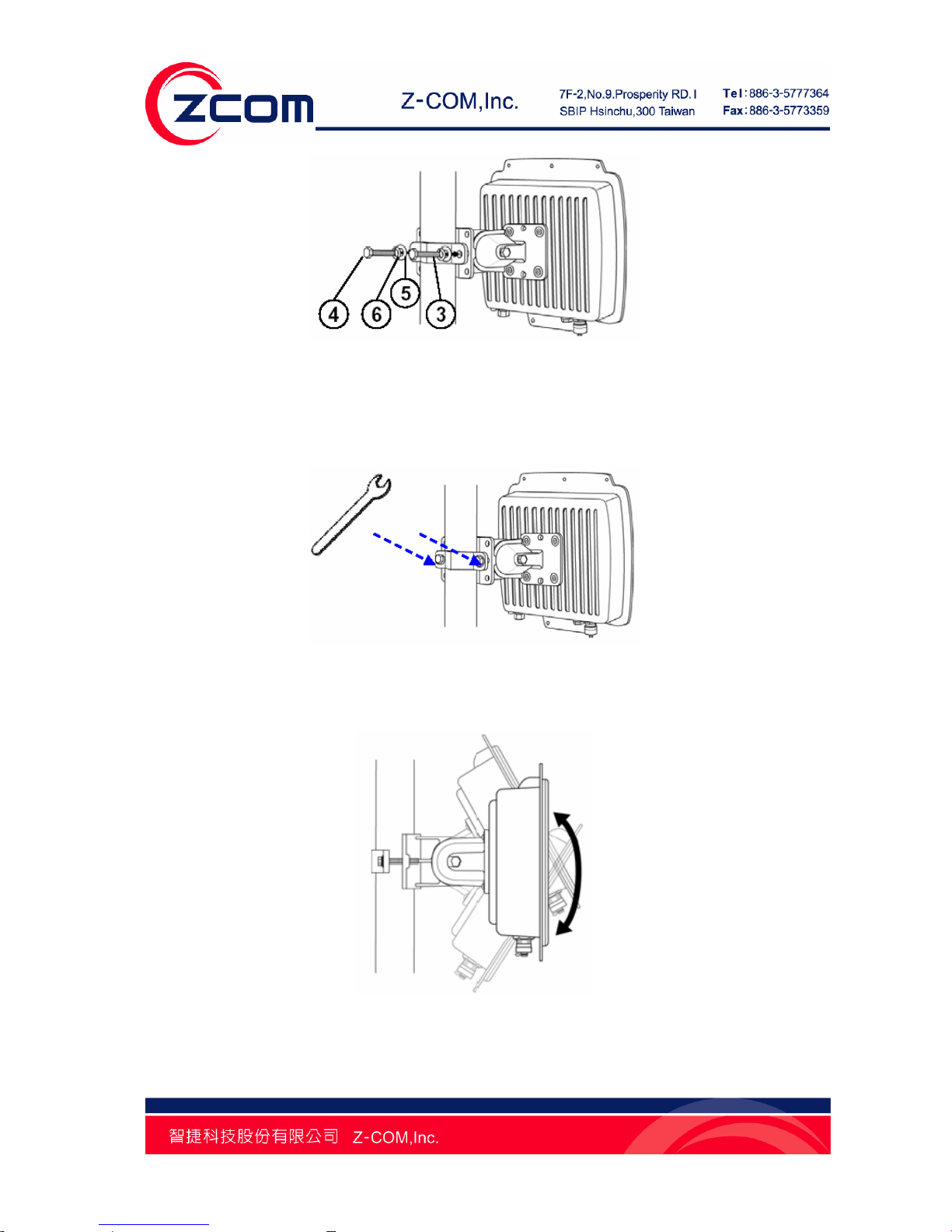
1. Install the main bracket and the pole mount bar ③ over the top of the pole by securing the
drill holes of the pole mount bar to the main bracket ones and insert two M8×80 ④ screws,
spring washers ⑥ and washers ⑤ through the drill holes and main bracket;
Page 19
Chapter 2 Hardware Installation Page 19
Figure 6 Pole Mounting –Step 1
2. Fasten two M8×80 screws ④ and washers ⑤ through the drill holes and main bracket with
a spanner;
Figure 7 Pole Mounting – Step 2
3. Adjust the antenna for appropriate tilt / vertical orientation.
Figure 8 Pole Mounting – Step 3
Page 20

Chapter 2 Hardware Installation Page 20
The horizontal and vertical beamwidth of R2 default antenna is about 10 degree
respectively.
Interface Definition
The R2 Extender currently provides two interfaces at the bottom, which are PoE & Data with a black
plastic cover and RS-232 with a light gray cover that labed “WARNING! No PoE”. Among which, a
black RJ45 waterproof connector will be provided for the PoE + Data interface.
Figure 9 Interface Definition
RS-232
RS-232, which is labeled COM/RESET, is used for debugging purposes as well as for hard reset of the
R2 Extender. Below you may find the pin definition of the RS-232.
Note:
Page 21

Chapter 2 Hardware Installation Page 21
T able 1 PIN Definition
Pin Assignment Name Description
P1 TXD0 Data Transmit 0
P2 DSR0 Data Set Ready 0
P3 RXD0 Data Receive 0
P4 TXD1 Data Transmit 1
P5 RXD1 Data Receive 1
P6 DTR1 Data Terminal Ready
P7 Hard Reset Hard reset the unit
P8 GND Ground
To reset the device, short P7 (Hard Reset) to P8 (GND) for less than 1 second and the system will
reset. If P7 (Hard Reset) is shorted to P8 (GND) for over 5 seconds, the R2 Extender will be reset to
the factory default settings.
Figure 10 Detailed View of RS-232 Port
Below are the views of RS-232 cover and RJ-45 port respectively, please note the label covered on
and DO strictly follow the instructions to avoid damaging your equipment!
Figure 11 Warning Label
Page 22

Chapter 2 Hardware Installation Page 22
Do NOT connect PoE powered Ethernet cable to the RS-232 port; otherwise the port
may burnout!
If RS-232 cable is used outdoor, please DO add a surge protector to protect the
equipment circuit!
Strongly recommend to add a lightning arrestor on the RS-232 port to prevent from
lightning attack!
Vent
The vent is designed to exclude vapors and moisture out of the unit as well as repel water, dust, and
dirt by the specially designed membrane, thereby preventing the R2 Extender from electric
malfunctioning.
Figure 12 Vent
Warning:
Vent
Page 23

Chapter 2 Hardware Installation Page 23
Connect Up
Before installing the Ethernet cable with a waterproof RJ-45 connector, it is recommended that the
Cat-5 RJ-45 coaxial cable be used for the R2 Extender to power PoE connector.
1. To connect to the hole labeled PoE+Data, open the black cover in advance by using a coin or a
slotted screwdriver and then screw in the body of the gland and tighten.
Figure 13 Connect Up – Step 1
2. Slide the sealing nut to the RJ-45 cable from its middle breach and then insert the sealing into the
cable.
Figure 14 Connect Up – Step 2
3. Insert the RJ-45 connector and make sure that the locking tab snaps home.
Figure 15 Connect Up – Step 3
4. Screw the sealing on the gland and tighten.
Slide the Sealing Nut from its Breach
R2 Extender RJ-45 Port
Page 24

Chapter 2 Hardware Installation Page 24
Figure 16 Connect Up – Step 4
Grounding
The R2 Extender is shipped with a grounding wire. The unit must be properly grounded to protect
against power surges. The R2 Extender grounding point can be found on the bottom of the unit. It is
supplied with an appropriate grounding lug for attachment to the ODU.
Figure 17 Grounding
Power On
To power up the R2 Extender, follow the steps bellow:
1. Plug a user-supplied Cat-5 Ethernet cable from your wired LAN (or a computer) into the power
injector RJ-45 jack (DATA IN);
2. Plug a user-supplied Cat-5 Ethernet cable from the R2 Extender into the power injector RJ-45 jack
(P+DATA OUT);
3. Connect the power module to the power injector and plug the AC cord into an AC power
Page 25

Chapter 2 Hardware Installation Page 25
receptacle;
4. After being powered on, the device will send out the beep sound lasting about 1.5 seconds,
informing you that the R2 Extender is powered up! Wait for about 60 seconds the system will be
initialized and start working!
Figure 18 PoE Connection
Make sure PoE is correctly connected to the RJ-45 port on the R2 Extender labeled
PoE+Data, otherwise the extender will be severely damaged!
Warning:
Page 26
Chapter 3 Basic Settings Page 26
Chapter 3 Basic Settings
Factory Default Settings
We’ll elaborate the R2 Extender factory default settings. You can re-acquire these parameters by
default. If necessary, please refer to the “Restore Factory Default Settings
”.
T able 2 R2 Extender Factory Default Settings
Features Factory Default Settings
Username admin
Password password
Wireless Device Name DEVICEXXXXXX (X represents the
last 6 digits of Ethernet MAC
address)
Operating Mode Peer-to-Peer (CSMA)
Country/Region United States (Country dependent
and software programmed)
Ethernet Data Rate Automatic
IP Address 192.168.1.1
Subnet Mask 255.255.255.0
Gateway 0.0.0.0
Primary DNS Server 0.0.0.0
LAN
Secondary DNS Server 0.0.0.0
DHCP Client Disable
Spanning Tree Enable
Link Aggregation Disable
Wireless Mode 802.11a
Channel/Frequency 149/5.745GHz
BSSID wireless
Transmit Rate Best
Output Power 100% (Full)
Bandwidth 20MHz
TDM Coordination Disable
WMM Disable
Page 27

Chapter 3 Basic Settings Page 27
Super Mode Fast Frame
RTS Threshold (byte) 2346
Fragmentation Length (byte) 2346
Beacon Interval 100
Distance in Meters 10000
VQoS Time Slice 4
Security Open System
Encryption None
Wireless Client Isolation Disable
Access Control Disable
SSH (Secure Shell) Enable
Enable/Disable Enable
Read Community Name Public
Write Community Name Private
SNMP
IP Address 0.0.0.0
System Requirements
Before configuration, please make sure your system meets the following requirements:
A computer coupled with 10/ 100 Base-TX adapter;
Configure the computer with a static IP address of 192.168.1.x, as the default IP address of R2
Extender is 192.168.1.1, X can not be 0, 1, nor 255;
A Web browser on PC for configuration such as Microsoft Internet Explorer 6.0 or above,
Netscape or Firefox.
Page 28

Chapter 3 Basic Settings Page 28
How to Login the Web-based Interface
The R2 Extender provides you with user-friendly Web-based management tool.
Open IE and enter the default IP address (Default: 192.168.1.1) of R2 Extender into the address field.
A Security Alert window may popup as below, due to browser’s security trusted sites. You may
choose to continue to the login webpage.
Figure 19 Security Alert
Click “Yes” will usher you into the login page:
Figure 20 Login
Page 29
Chapter 3 Basic Settings Page 29
Enter the username (Default: admin) and password (Default: password) respectively and click
“Login Now” to login the main page of R2 Extender. As you can see, this management interface
provides four main options in the black bar above, which are System, Wireless, Status and
Management.
Figure 21 Main Page
The username and password are case-sensitive, and the password is no more than 19
characters!
Note:
Page 30

Chapter 3 Basic Settings Page 30
Basic System Setup
For users who use the R2 Extender for the first time, it is recommended that you begin configuration from
“Basic” in “System” shown below:
Figure 22 Basic Setup
Wireless Device Name
Specify the device name, which is composed of no more than 15 characters with (0-9), (A-Z), (a-z) or
(-).
Country/Region
For the available radio bands vary from country to country, the working channels used are different.
Ethernet Data rate
Specify the transmission rate of data.
IP Address
If you select “Manual”, you have to specify a static IP address, subnet mask, default gateway and
DNS server for your local area network which connects to the LAN port of R2 Extender. Make sure
the specified IP address is unique on your network in order to prevent IP conflict.
Page 31
Chapter 3 Basic Settings Page 31
DHCP Client
Enable DHCP client to allow the DHCP server within your local area network to assign an IP address
automatically.
Spanning Tree Protocol (STP)
The Spanning Tree Protocol allows redundant connections to be created between different LAN
segments for purposes of fault tolerance.
Link Aggregation
Link Aggregation combines two physical network links into a single logical link for increased
bandwidth. Besides, it provides load balancing.
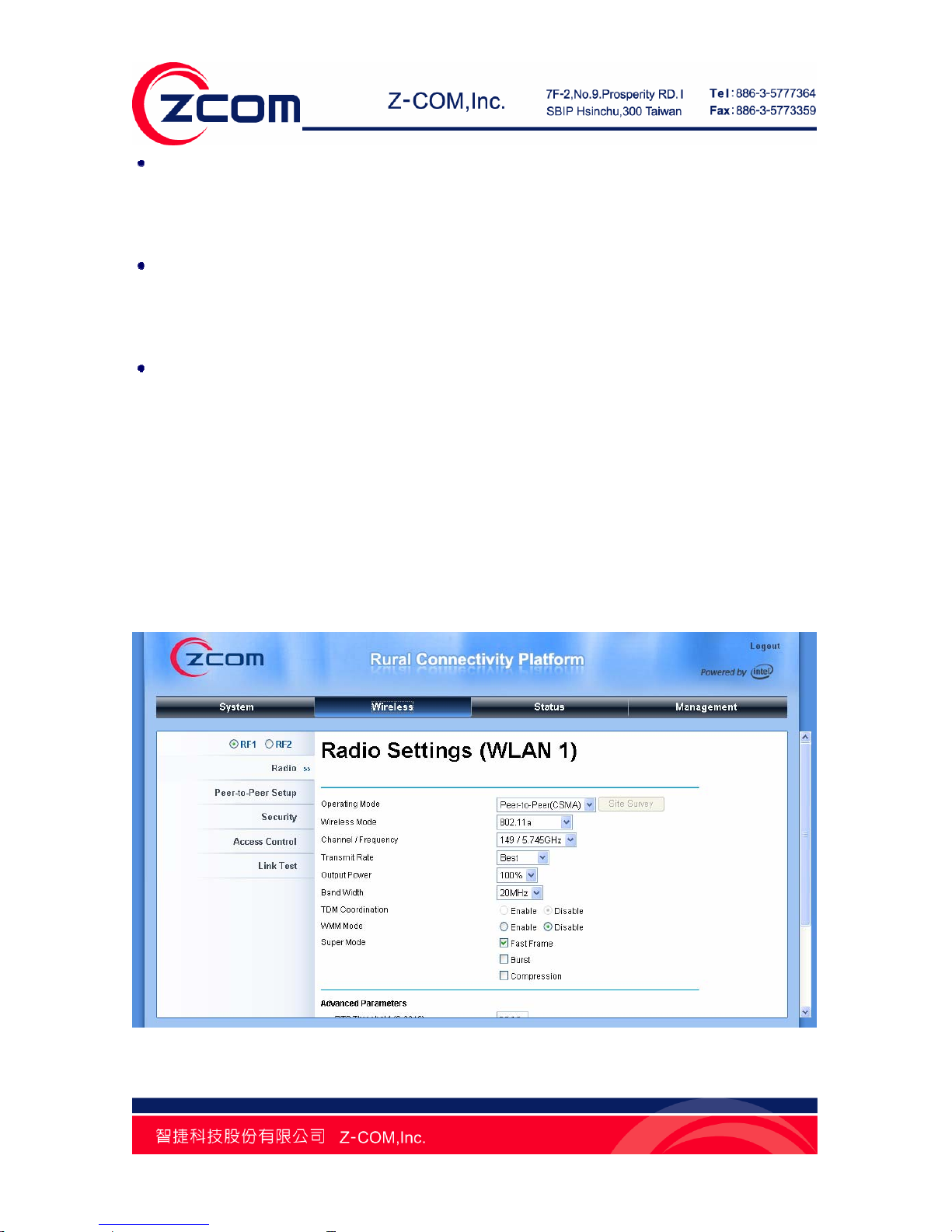
Basic Wireless Settings
Open “Radio” in “Wireless” as below and select “RF1” or “RF2” to make basic wireless configuration on
radio card 1 and 2.
Figure 23 Basic Wireless Settings
Page 32

Chapter 3 Basic Settings Page 32
Operating Mode
Four operating modes are available on the R2 Extender. In a point to point environment where there
are only two radios, Peer-to-Peer is recommended as it works more efficiently.
Base Station
: The R2 Extender connects directly to the main Ethernet LAN and receives
connectivity from other wireless devices.
CPE
: The R2 Extender connects to a remote LAN and the Base Station in it.
Peer-to-Peer (CSMA)
: The R2 Extender connects to another wireless device within the same
networking program using CSMA protocol. CSMA ensures that only one node is transmitting on the
network at any one time. Under this mode, both PTP and PTMP are available. It is highly
recommended to use this mode when the distance between two nodes is less than 20KM.
Peer-to-Peer (TDMA)
: The R2 Extender connects to another wireless device within the same
networking program using TDMA protocol. TDMA divides each cellular channel into multiple time
slots to increase the amount of data that can be carried, hence increase the throughput. Under this
mode, only PTP is available and is suggested to use when the distance between the two R2
Extender is greater than 20KM.
Base Station ID (SSID)
For Base Station mode, it requires SSID for CPU clients to associate with. This wireless network
name is shared among all associated devices in your wireless network. Keep it identical on all those
devices. Note that the SSID is case-sensitive and can not exceed 32 characters.
Wireless Mode
The R2 Extender can only communicate with wireless devices of 802.11a.
Channel/Frequency
Channel varies much as the available band differs from country to country. Select a proper operating
channel in the drop-down list according to your situation. To avoid adjacent channel interference, it
is highly suggested to set separate of the 2 RF links as far as possible.
Transmit Rate
Usually “Best” is preferred. Under this rate, the R2 Extender will automatically select the highest
available rate to transmit. In some cases, however, like where there is no great demand for speed,
Page 33

Chapter 3 Basic Settings Page 33
you can have a relatively-low transmit rate for compromise of a long distance.
Output Power
Specify the signal transmission power. The higher the output power is, the wider the signal can cover,
but the power consumption will be greater accordingly then. Usually “100%” is preferred.
Band Width
Four levels are available: 5MHz, 10MHz, 20MHz and 40MHz. Among them, 40MHz can enhance
the data rate more effectively, but will take more bandwidth, thus cause possible interference.
TDM Coordination
Stands for “Time-Division Multiplexing technique”, this resource reservation control mechanisms can
avoid packet collisions and send the packets much more efficiently allowing for higher effective
throughput rates.
WMM
WMM (Wi-Fi Multimedia) is a subset of 802.11e. It allows wireless communication to define a priority
limit on the basis of data type, thus those time-sensitive data, like video/audio data, may own a
higher priority than common one. To enable WMM, the wireless client should support it.
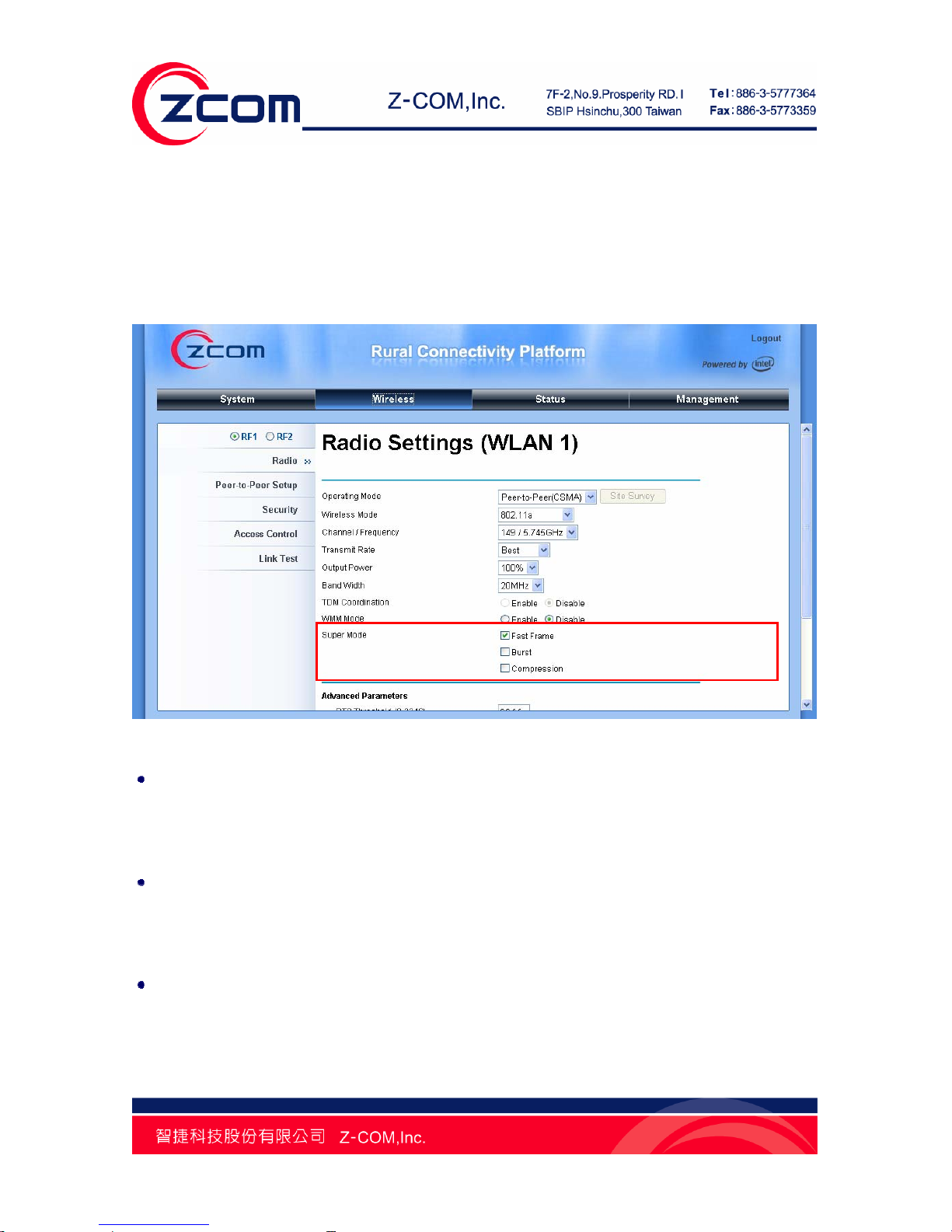
Super Mode
Super mode is an effective way to enhance performance. It can boost the transmission data rate
up to 108Mbps. R2 Extender provides you with three kinds of Super mode, which are Fast Frame,
Burst and Compression. To enable Super Mode, the remote R2 Extender should enable the
function as well. For more information you may refer to Super Mode in Chapter 4 Advance Settings
.
Page 34

Chapter 4 Advanced Settings Page 34
Chapter 4 Advanced Settings
Advanced Wireless Settings
Open “Radio” in “Wireless” and turn to “Advanced Parameters” at the bottom to make advanced
wireless settings.
Figure 24 Advanced Parameters
CPE Download Speed
Specify fractional data rates (× 64Kbps). It allows the administrator to control the amount of data rate
each user is receiving. This is only available in CPE mode.
RTS Threshold
The R2 Extender sends RTS (Request to Send) frames to certain receiving station and negotiates
the sending of a data frame. After receiving an RTS, that STA responds with a CTS (Clear to Send)
frame to acknowledge the right to start transmission. The setting range is 0-2346 in byte.
Page 35

Chapter 4 Advanced Settings Page 35
Fragmentation Length
Specify the maximum size in byte for a packet before data is fragmented into multiple packets.
Setting it too low may result in poor network performance. Leave it at its default of 2346 is
recommended.
Beacon Interval
Specify the frequency interval to broadcast packets. Enter a value between 20 and 1000.
Distance in Meters
To decrease the chances of data retransmission at long distance, R2 Extender can auto adjust
proper ACK timeout value by specifying distance of the two nodes. Default distance is 10km. This
will be only usefully in CSMA mode.
TDM Coordination Time Slice
Specify the time slice of TDM Coordination. It allows a certain amount of time (in ms) that data will
transmit to each other before it moves to the next user. This is a repetitive cycle.
We strongly recommended you leave most advanced settings at their defaults except
Distance in Meters; any modification on them may negatively impact the performance of
your wireless network.
Note:
Page 36

Chapter 4 Advanced Settings Page 36
Peer-to-Peer Links
Open “Peer-to-Peer Setup” in “Wireless”. Peer-to-Peer Links allow establishing PTP or PTMP
connectivity with as most four remote wireless devices, this feature only available under Peer-to-Peer
(CSMA) mode and only devices with the same SSID can communicate. Select “RF1” or “RF2”, and input
the MAC addresses of radio cards from remote unit respectively.
Figure 25 Peer-to-Peer Links
Page 37

Chapter 4 Advanced Settings Page 37
Antenna Alignment Tool
Under Peer-to-Peer (CSMA) mode, Antenna Alignment Tool is available. This function helps to point in the
approximate direction of the remote R2 Extender antenna and assist user easily align the local antenna to
reach maximum signal strength.
Figure 26 Antenna Alignment Tool
To use Antenna Alignment Tool, follow the steps bellow:
Open “Peer-to-Peer Setup” and select “RF1” or “RF2”. By clicking “Align Antenna” button,
“Antenna Alignment Tool ” window will popup.
Set the target RSSI (e.g. -70dBm) and click “Start” button.
Wait about 5 seconds, the antenna alignment starts and performs alignment every one second.
Fix the local antenna and adjust the remote antenna elevation and horizontal direction. During the
adjustment, observe “Current RSSI” in local R2 Extender. The value will refresh every 1 second. Fix
the remote antenna when it reaches your expectation. Usually, RSSI between -60 and -70dBm
indicates rather good signal strength.
Adjust the local antenna after fixing the remote one. During the adjustment, observe “Current RSSI”
in the remote R2 Extender. Fix the local antenna when it reaches your expectation.
Page 38

Chapter 4 Advanced Settings Page 38
When the antenna alignment tool starts, the R2 Extender will issue beep sound to indicate current
RSSI. Once the tool is closed the R2 Extender will stop beeping. Frequency of beep indicate the
following RSSI:
T able 3 RSSI-Beep Frequency
RSSI Beep Frequency
>-50 100 /sec
-50~-60 50 /sec
-60~-70 5 /sec
-70~-80 2 / sec
-80~-90 1 /sec
< -90 No beep sound
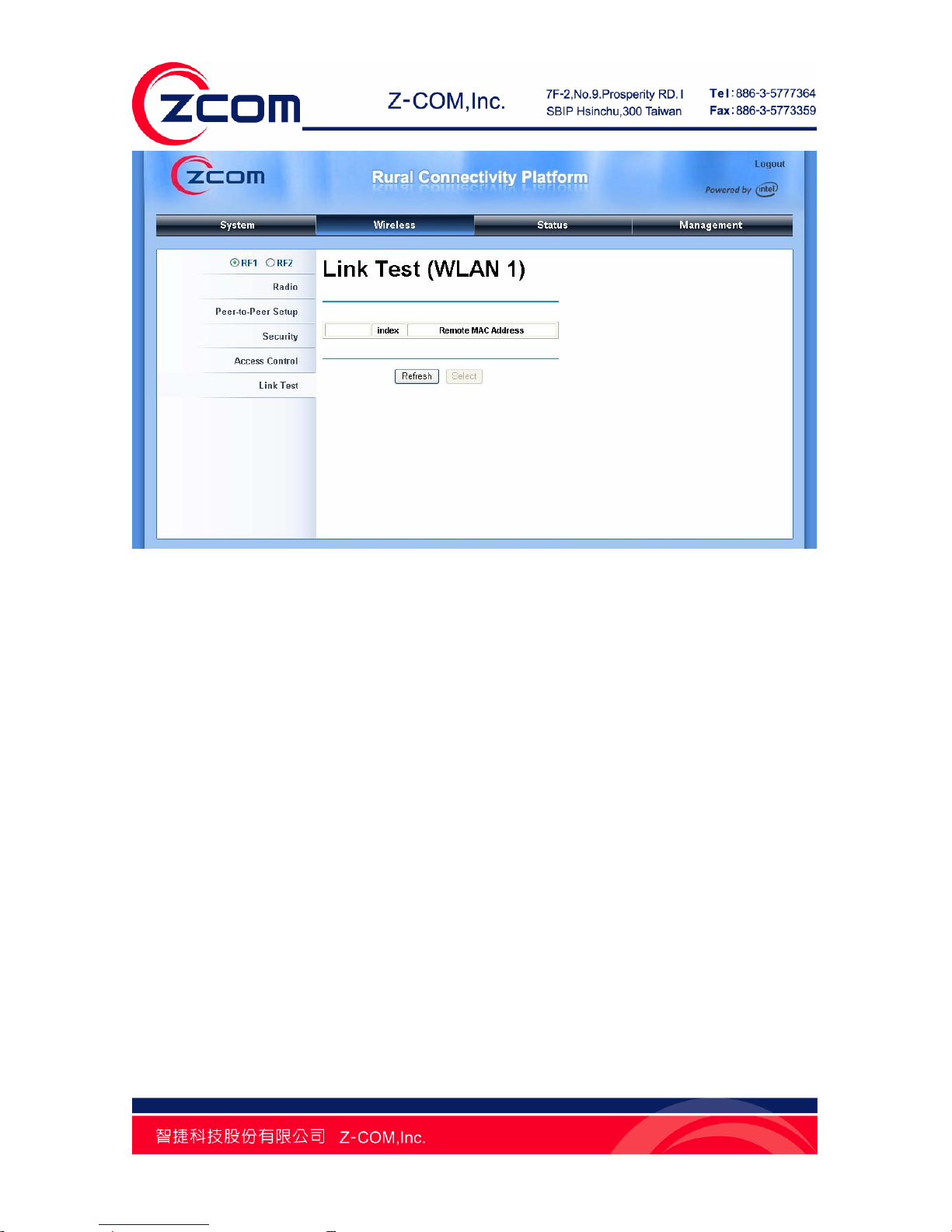
Link Test
Under Base Station, CPE or Peer-to-Peer (TDMA) mode when Antenna Alignment Tool is not available,
Link Test provides another option to check the signal strength towards the connecting device. Open “Link
Test” in “Wireless” as below, and click “Refresh” to view the current signal strength of wireless
connectivity. The table will be updated every 3 seconds. If the signal is not so good, align the antenna
manually.
Page 39
Chapter 4 Advanced Settings Page 39
Figure 27 Link Test
Page 40
Chapter 4 Advanced Settings Page 40
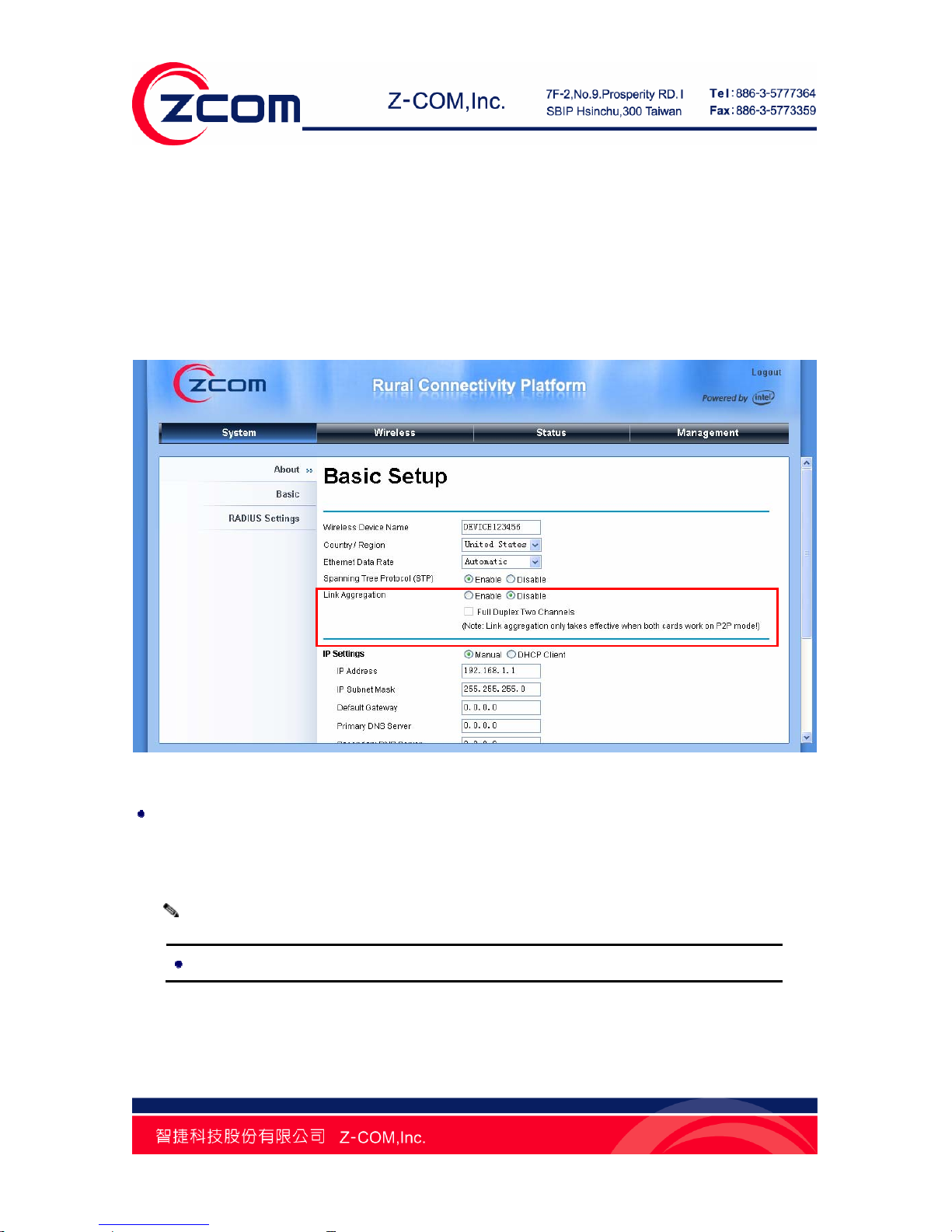
Link Aggregation
Link Aggregation combines two physical network links into a single logical link for increased bandwidth.
With it enabled, users can increase the capacity and availability of the communications channel between
devices (both switches and end stations). Besides, link aggregation also provides load balancing.
Open “Basic” in “System”, Link Aggregation is as below:
Figure 28 Link Aggregation
Full Duplex Two Channels: Normally, the wireless module in R2 Extender receives and transmits
wireless packets concurrently; if check this box, it only transmits wireless packets on WLAN but stops
receiving. Thus the wireless performance could be enhanced further more.
Link aggregation takes effect only when both cards work on peer-to-peer mode!
Note:
Page 41
Chapter 4 Advanced Settings Page 41
Super Mode
Super mode is an effective way to enhance the Wi-Fi performance; it can boost the transmission data rate.
R2 Extender provides you with three kinds of Super mode, which are Fast Frame, Burst and Compression.
Open “Radio” in “Wireless”, Super Mode is as below:
Figure 29 Super Mode
Fast Frame
By utilizing frame aggregation and timing modifications, it increases throughput via transmitting more
data per frame and removing inter-frame pauses.
Burst
By allowing more data frames per given period of time, it increases throughput via overhead
reduction.
Compression
By performing real-time hardware data compression, it increases throughput via using
pre-compressed frames with no impact on host processor.
Page 42

Chapter 4 Advanced Settings Page 42
Only all the wireless devices share the same wireless connectivity support Super mode,
can this function be available!
The throughput may vary depending on the actually environment and data traffic flow.
Wireless Security Settings
To prevent unauthorized radios from accessing data transmitting over the connectivity, R2 Extender
provides you with rock solid security settings.
Security Profile Configuration
Open “Security” in “Wireless” as below:
Figure 30 Security
Broadcast SSID
Hiding network name is necessary when you are in a wireless environment that may have potential
Note:
Page 43

Chapter 4 Advanced Settings Page 43
risk. By using this function, the STA can not scan and find R2 Extender, so that malicious attack by
some illegal STA could be avoided.
Network Authentication
Open
: It allows any device to join the network without performing any security check.
Shared Key
: Data encryption and key are required for wireless authentication.
WPA-PSK
: It is a simplified WPA mode with no need for specific authentication server. In this
so-called WPA Pre-Shared Key, all you have to do is just pre-enter a key in each WLAN node and
this is the common way to be adopted in large and middle enterprise as well as residential network.
WPA2-PSK
: As a new version of WPA, only all the clients support WPA2, can it be available. If it is
selected, the data encryption can only be AES and the passphrase is required.
WPA-PSK&WPA2-PSK
: It provides options of WPA (TKIP) or WPA2 (AES) encryption for the client.
If it is selected, the data encryption can only be TKIP + AES and the passphrase is required.
Data Encryption
If data encryption is enabled, the key is required and only sharing the same key with other wireless
devices can the communication be established.
None
: Available only when the authentication type is open system.
64 bits WEP
: It is made up of 10 hexadecimal numbers.
128 bits WEP
: It is made up of 26 hexadecimal numbers.
TKIP
: Temporal Key Integrity Protocol, which is a kind of dynamic encryption, is co-used with
WPA-PSK, etc.
AES
: Advanced Encryption Standard, it is usually co-used with WPA2-PSK, WPA, WPA2, etc.
TKIP + AES
: It allows for backwards compatibility with devices using TKIP.
Wireless Client Isolation Mode
Enable this mode can prevent the communication between connected wireless clients.
We strongly recommend you enable wireless security on your network!
Note:
Page 44

Chapter 4 Advanced Settings Page 44
Only setting the same Authentication, Data Encryption and Key in the R2 Extender and
other wireless devices that connecting with it, can the communication be established!
Access Control
The Access Control appoints the authority to STA on accessing R2 Extender, thus a further security
mechanism is provided. This function is available only under Base Station and Peer-to-Peer (TDMA)
modes.
Open “Access Control” in “Wireless” as below, check “Turn Access Control On” to enable this function.
Figure 31 Access Control
Available CPEs
In this table lists the CPEs connecting with R2 Extender currently. Check the box before each MAC
address, click “Add” to add one or more available CPE(s) into the “Trusted CPEs” and click “Apply”
to save settings.
Add New CPE Manually
Enter the MAC address of the CPE that you would like to list into the access control list, click “Add”
Page 45

Chapter 4 Advanced Settings Page 45
then the CPE will be added into the “Trusted CPEs”.
Trusted CPEs
Check the box before one or more MAC addresses of CPEs that you would like to cancel, and click
“Delete” to cancel that access control rule.
RADIUS Settings
RADIUS (Remote Authentication Dial-In User Service) is a server for remote user authentication and
accounting; playing a central role in the network in providing the capabilities of authenticating, authorizing,
accounting, auditing, alarming and etc. It allows an organization to maintain user profiles in a central
database that all remote servers can share.
Open “RADIUS Settings” in “System” to make RADIUS configuration.
Figure 32 RADIUS Settings
Authentication/Access Control RADIUS Server Login
This is for RADIUS authentication. It can communicate with RADIUS through IP Address, Port
Number and Shared Secret. If the Primary RADIUS fails to work, the Secondary RADIUS Server is
Page 46

Chapter 4 Advanced Settings Page 46
an option.
IP Address
: Enter the IP address of the Radius Server;
Port Number
: Enter the port number of the Radius Server;
Shared Secret
: This secret, which is composed of no more than 31 characters, is shared by the R2
Extender and RADIUS during authentication.
Advanced WPA/802.1X Parameters
Re-authentication Time
: Set the time interval between two authentications.
Global-Key Update
: Check this option and specify the time interval between two global-key
updates.
Page 47

Chapter 5 Management Page 47
Chapter 5 Management
View R2 Extender Basic Information
Open “About” in “System” to check the basic information of R2 Extender, which is read only.
Figure 33 Basic Information
View Ethernet Statistics
Open “Ethernet Status” in “Status” to check the data packets received on and transmitted from the
Ethernet port in LAN. Click “Refresh” to view current statistics. All is read only.
Page 48

Chapter 5 Management Page 48
Figure 34 Ethernet Statistics
View Wireless Statistics
Open “Wireless Status” in “Status” to check the data packets received on and transmitted via wireless
network. Click “Refresh” to view current statistics. All is read only.
Page 49

Chapter 5 Management Page 49
Figure 35 Wireless Statistics
Connection
Open “Connection” in “Status” to check the information of remote CPEs connected with the R2 Extender,
these values also help determine whether the antenna is aligned in an appropriate direction. The table will
be updated every 30 seconds. All is read only.
Page 50

Chapter 5 Management Page 50
Figure 36 Connection
Password
From “Change Password” in “Management”, you can change or default the password to manage your R2
Extender.
Page 51

Chapter 5 Management Page 51
Figure 37 Password
Change Password
For security concern, you have to enter the current password first and then enter the new one twice
respectively in “New Password” and “Repeat New Password” fields.
Restore Default Password
If you would like to restore the default password, enter the current password first and then check
“Yes” and click “Apply” to default the password.
The password is case-sensitive and its length can not exceed 19 characters!
Remote Management
The R2 Extender provides you with two more options for device management, which are SSH (Secure
Shell) and SNMP.
Note:
Page 52

Chapter 5 Management Page 52
Open “Remote Management” in “Management” to configure the remote management of R2 Extender.
Figure 38 Remote Management
Remote Console
The R2 Extender supports CLI management, which could be accessed by Secure Shell (SSH). It is
recommended PuTTY be used to login. Download it from http://www.putty.org/
for free. The minimum
system requirement for using PuTTY is Windows 95, 98, ME, NT, 2000, XP and Vista on Intel x86.
Follow the steps below to implement:
Once the program is downloaded, open up by double-clicking ; Note that before using
PuTTY, be sure you are able to connect to the R2 Extender.
Enter IP Address of R2 Extender (Default: 192.168.1.1), Port (22) and check SSH as connection
type;
Page 53

Chapter 5 Management Page 53
Figure 39 PuTTY Configuration 1
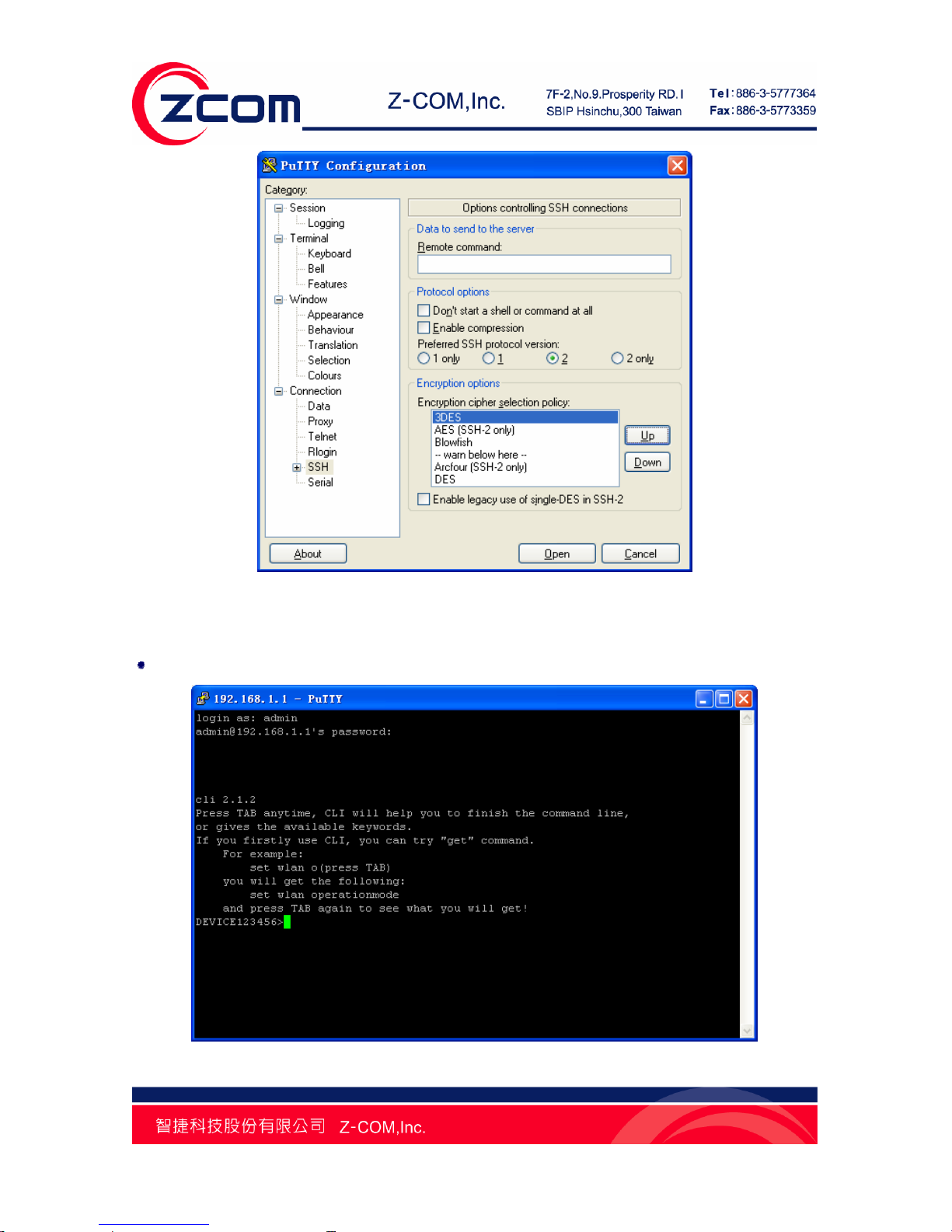
From “Connection” in the left menu bar, click “SSH”; select “2” as “Preferred SSH protocol
version”; make “3DES” the top position in “Encryption cipher selection policy”;
Page 54
Chapter 5 Management Page 54
Figure 40 PuTTY Configuration 2
Click “Open”, a window as below will popup:
Figure 41 SSH
Page 55

Chapter 5 Management Page 55
Enter the user name and password (Default user name/ password: admin/password) respectively,
you will see “DEVICE123456>”, which is the name of R2 Extender;
Enter “help” command to get setting information; alternatively, you can refer to Appendix C. SSH
Settings for details.
SNMP
The R2 Extender supports SNMP management. Set the SNMP parameters and obtain MIB file before
remote management.
From “Remote Management” in “Management”, set the parameters for SNMP:
- Enable SNMP by checking “Enable”;
- Specify the “Read Community Name”, “Write Com munity Name” and “IP Address to Receive
Traps”
- Hit “Apply” to save settings.
Obtain MIB file via FTP:
- Enter ftp 192.168.1.1 , username (Default: admin) and password (Default: password);
-
After successful login, enter command “get bridge.mib”, the information will as below and then
bridge.mib file is obtained.
Figure 42 Obtain MIB File
Page 56

Chapter 5 Management Page 56
Time Settings
Compliant with NTP, the R2 Extender is capable of keeping its time in complete accord with the Internet
time. Make configuration in “Basic” from “System”:
Figure 43 Time Settings
Enter the time server IP address and port respectively in “Time Serve r” and “Time Server Port”
fields;
Select your desired time zone from the drop-down list, check “Adjust for Daylight Saving Time” if
necessary;
Hit “Apply” to save settings.
Page 57

Chapter 5 Management Page 57
Upgrade Firmware
Open “Upgrade Firmware” in “Management” and follow the steps below to upgrade firmware locally or
remotely through R2 Extender’s Web:
Figure 44 Upgrade Firmware
Click “Browse” to select the firmware file.
Click “Upload” to load the file into the R2 Extender.
Wait a moment, the system will reboot after successfully upgrade.
Do NOT cut the power off during upgrade, otherwise the system may crash!
Note:
Page 58
Chapter 5 Management Page 58
Backup/Retrieve Settings
It is strongly recommended to back up configuration information in case of something unexpected. If
tragedy hits your device, you may have an access to restore the important files by the backup. All these
can be done by the local or remote computer.
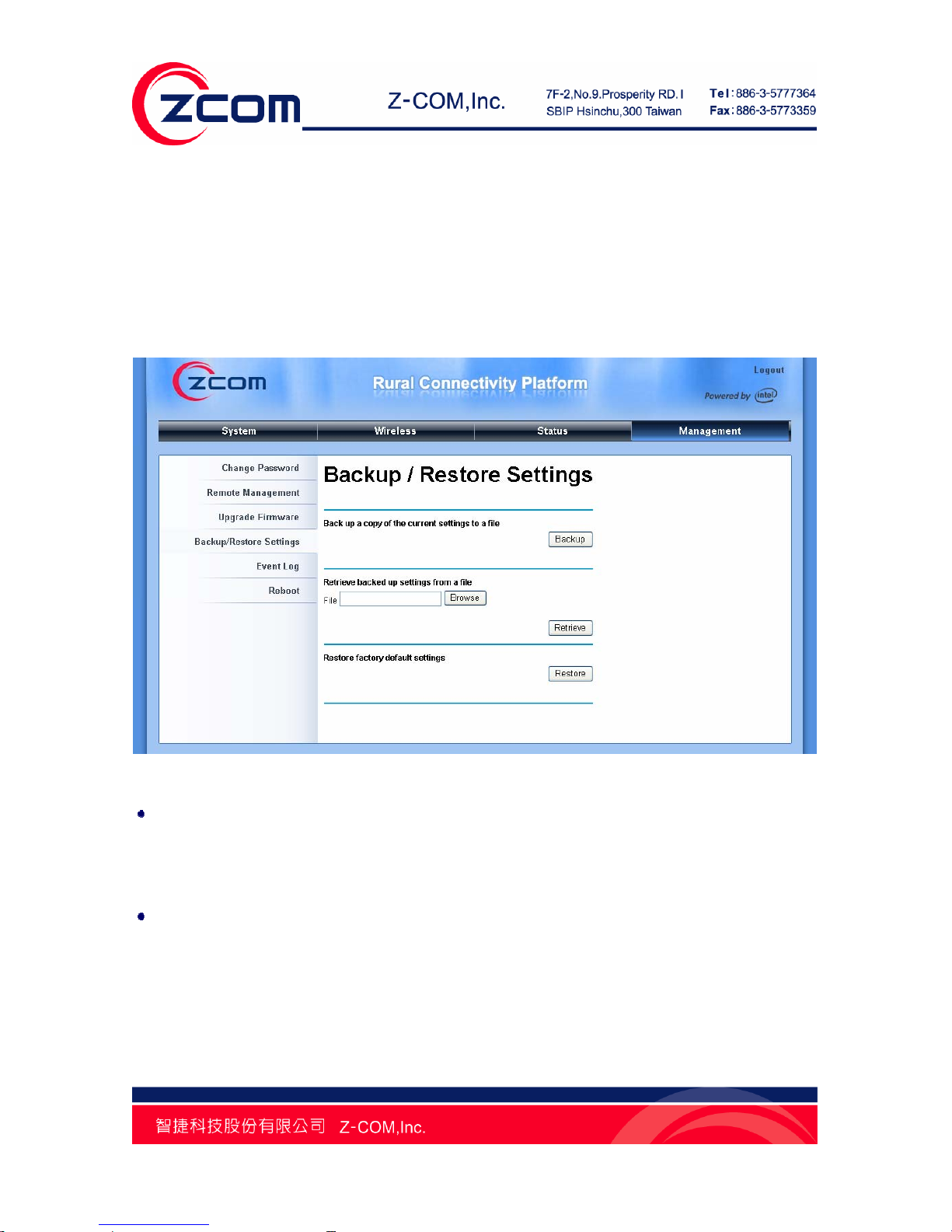
Open “Backup/Restore Settings” in “Management” as below:
Figure 45 Backup/Restore Settings
Backup Settings
By clicking “Backup” a dialog box will popup. Save it, then the configuration file is saved to your
local computer.
Retrieve Settings
By clicking “Browse” a file selection menu will appear, select the file you want to load, like bridge.cfg;
Click “Retrieve” to load the file. After automatically rebooting, new settings are applied.
Page 59

Chapter 5 Management Page 59
Restore Factory Default Settings
The R2 Extender provides two ways to restore the factory default settings:
Restore factory default settings via Web
From “Backup/Restore Settings”, clicking “Restore” will eliminate all current settings and reboot
your device, then default settings are applied.
Figure 46 Restore Settings
Restore factory default settings via RS-232
If software in R2 Extender is unexpectedly crashed and no longer reset the unit via WEB, you may do
hardware reset via RS-232. For detailed instructions please refer to Chapter 2 RS-232 section.
Page 60

Chapter 5 Management Page 60
Event Log
Event log is used for recording events occurred on the R2 Extender, including station connection,
disconnection, system reboot and etc.
Open “Event Log” in “Management” as below.
Figure 47 Event Log
Enable Log: Enable System log or not;
Syslog Server IP Address: Specify the IP address of the server;
Syslog Server Port Number: Specify the port number of the server;
Hit “Apply” to save settings;
Event Log Window: Lists all occurred events in this field.
Page 61

Chapter 5 Management Page 61
Reboot
You can reboot your device from “Reboot” in “Management” as below:
Figure 48 Reboot
Check “Yes” and click “Apply” to reboot the R2 Extender. This takes a few minutes, during which the
device will send out the buzzing sound, informing you the system is rebooting.
Page 62

Chapter 6 Troubleshooting Page 62
Chapter 6 Troubleshooting
This chapter provides troubleshooting procedures for basic problems with the R2 Extender.
Q 1. What if my R2 Extender fails to connect to the remote one?
• Ethernet Link: Check the availability of power to the bridge by observing the LED status on the
power injector or on top of the RJ-45 Jack of the unit.
- Green: The R2 Extender is connecting to the backhaul network.
- Off: The R2 Extender disconnects from the wired network, check whether the power cord and
Ethernet cables to the network and bridge are correctly connected.
• Basic Configurations: Mismatched basic settings among bridges are the most common cause
of connectivity fail. If the bridge does not associate with a remote bridge, check whether in each
device are identical.
• Security Settings: Remote bridges attempting to authenticate to your R2 Extender must support
the same security options configured in your bridge, such as WEP and WPA (2)-PSK. If your
bridge fails to associate with others, check whether the security settings are the same as your
bridge settings.
• Antenna Alignment: If the methods above are all checked to be correct, you can observe and
verify antenna alignment with RSSI value.
Q 2. What if I would like to reset the unit to default settings?
You may restore factory default settings in “Backup/Restore Settings” from “Management”
Q 3. What if I would like to backup and restore my configuration settings?
You may do the backup by generating a configuration file or retrieve the settings you have backed up
previously in “Backup/Restore Settings” from “Management”.
Page 63

Chapter 6 Troubleshooting Page 63
Q 4. What if I can not open the Web-based management interface?
Please check the followings:
• Check whether the power supply is OK; Try to power on the unit again.
• Check whether the IP address of PC is correct (in the same network segment as the unit);
• Login the unit via other browser such as Firefox.
• Hard reset the unit.
Q 5. What if the signal quality is poor or not so good?
• Check whether there is obstacle between units. Obstacle may lead to poor signal.
• Check the antenna height. Place the unit in a high position can help to get a better
communication in long distance transmission.
• Check the polarization direction of antenna. Keep the polarization direction of antennas on two
associating units the same; if not (one is horizontal, another is vertical), the signal quality may
reduce dramatically.
• Check the antenna angle. Align the antenna to the remote one if using directional antenna. Big
angle shift may lead to poor signal.
• Check the feeder length. Too long feeder may increase the signal loss and affect the unit
performance
Page 64

Appendix A. Channel – Frequency Table Page 64
Appendix A. Channel – Frequency Table
The R2 Extender can be operated in four different band widths, which are 5MHz, 10MHz, 20MHz and
40MHz. The following tables illustrate the channel with corresponding frequency in each band width.
T able 4 Channels in 5MHz Centre Frequency
Channel Frequency
149 5.745 GHz
150 5.750 GHz
151 5.755 GHz
152 5.760 GHz
153 5.765 GHz
154 5.770 GHz
155 5.775 GHz
156 5.780 GHz
157 5.785 GHz
158 5.790 GHz
159 5.795 GHz
160 5.800 GHz
161 5.805 GHz
162 5.810 GHz
163 5.815 GHz
164 5.820 GHz
165 5.825 GHz
T able 5 Channels in 10MHz Centre Frequency
Channel Frequency
149 5.745 GHz
151 5.755 GHz
153 5.765 GHz
155 5.775 GHz
157 5.785 GHz
159 5.795 GHz
161 5.805 GHz
163 5.815 GHz
165 5.825 GHz
Page 65

Appendix A. Channel – Frequency Table Page 65
T able 6 Channels in 20MHz Centre Frequency
Channel Frequency
149 5.745 GHz
153 5.765 GHz
157 5.785 GHz
161 5.805 GHz
165 5.825 GHz
T able 7 Channels in 40MHz Centre Frequency
Channel Frequency
149 5.745GHz
157 5.785GHz
165 5.825GHz
The availability of some specific channels and/or operational frequency bands are country
dependent and are firmware programmed at the factory to match the intended destination. The
firmware setting is not accessible by the end user.
Page 66

Appendix B. ASCII Page 66
Appendix B. ASCII
WEP can be configured with a 64-bit or 128-bit Shared Key (hexadecimal number or ACSII). As defined,
hexadecimal number is represented by 0-9, A-F or a-f; ACSII is represented by 0-9, A-F, a-f or punctuation.
Each one consists of two-digit hexadecimal.
T able 8 ACSII
ASCII
Character
Hex
Equivalent
ASCII
Character
Hex
Equivalent
ASCII
Character
Hex
Equivalent
ASCII
Character
Hex
Equivalent
! 21 9 39 Q 51 i 69
" 22 : 3A R 52 j 6A
# 23 ; 3B S 53 k 6B
$ 24 < 3C T 54 l 6C
% 25 = 3D U 55 m 6D
& 26 > 3E V 56 n 6E
‘ 27 ? 3F W 57 o 6F
( 28 @ 40 X 58 p 70
) 29 A 41 Y 59 q 71
* 2A B 42 Z 5A r 72
+ 2B C 43 [ 5B s 73
, 2C D 44 \ 5C t 74
- 2D E 45 ] 5D u 75
. 2E F 46 ^ 5E v 76
/ 2F G 47 _ 5F w 77
0 30 H 48 ` 60 x 78
1 31 I 49 a 61 y 79
2 32 J 4A b 62 z 7A
3 33 K 4B c 63 { 7B
4 34 L 4C d 64 | 7C
5 35 M 4D e 65 } 7D
6 36 N 4E f 66 ~ 7E
7 37 O 4F g 67
8 38 P 50 h 68
Page 67

Appendix C. SSH Settings Page 67
Appendix C. SSH Settings
T able 9 SSH Settings
get set del Keyword Descriptions
√ √ time --time setting
√ -now --current system time
√ √ -zone --time zone
√ √ -daylight saving -- daylight saving
√ √ -server --time server setting
√ √ -name
--time server (domain
name or IP address)
√ √ -port --time server port
√ √ system --system setting
√ -version --system firmware version
√ √ -devicename --system name
√ -macaddr --system MAC address
√ √ -country --country/region
√
-restoreFactory
Default
-- restore factory default
√ √ -iptype --system dhcp client
√ √ -ipaddr --system IP address
√ √ -netmask --system network mask
√ √ -gateway --system gateway
√ √ -dns --system dns
√ √ -primary
-- primary system DNS
server
√ √ -secondary
-- secondary system DNS
server
√ √ -stp
--enable spanning tree
protocol
√ √ -linkaggr --enable link aggregation
√ √
-linkaggrfixtrans
mit
--fix transmit on a wlan
√ √ -ethrate --ethernet data rate
√ -ethstats --ethernet statistics
√ √ radius --radius settig
√ √ -auth
--authentication radius
setting
Page 68

Appendix C. SSH Settings Page 68
get set del Keyword Descriptions
√ √ -primary -- primary
√ √ -ipaddr -- radius IP address
√ √ -port -- radius port number
√ √ -secret -- radius secret string
√ √ -secondary -- secondary
√ √ -ipaddr -- radius IP address
√ √ -port -- radius port number
√ √ -secret -- radius secret string
√ √ √ -wpa --wireless WPA setting
√ √ -reauthtime
-- wireless WPA re-auth
period(in seconds)
√ √ -keyupdate
-- enable wireless WPA
global update condition
√ √ -mode
-- wireless WPA global
key update condition
√ √ -interval
-- wireless WPA global
key update interval
√ √ -account --account radius setting
√ √ -primary -- primary
√ √ -ipaddr -- radius IP address
√ √ -port -- radius port number
√ √ -secret -- radius secret string
√ √ -secondary -- secondary
√ √ -ipaddr -- radius IP address
√ √ -port -- radius port number
√ √ -secret -- radius secret string
√ √ ssh
--enable remote SSH
access
√ √ snmp --SNMP setting
√ √ -server --enable SNMP agent
√ √
-trap server
--SNMP TrapServer IP
address
√ √
-read
community
--SNMP ReadCommunity
√ √
-write
community
--SNMP WriteCommunity
√ √ log --syslog setting
√ √ -client --enable syslog client
√ √ -ipaddr --syslog server IP address
Page 69

Appendix C. SSH Settings Page 69
get set del Keyword Descriptions
√ √ -port
--syslog server port
number
√ √ wlan --wireless setting
√ √ -wirelessmode --wireless mode
√ √ -channel
--wireless
channel(depends on
country and wireless
mode)
√ √ -txrate
--wireless transmission
data rate
√ √ -bandwidth -- wireless bandwidth
√ √ -cpe mode --use multicli or lan-to-lan
√ √
-cpedownflowwi
dth
-- wireless down flow
width for CPE mode
√ √ -OutputPower --wireless transmit power
√ √ -VQoS/TDM
--enable TDM mode or
not
√ √ -tdm timeslice --station’s timeslice value
√ √
-fragmentationt
hreshold
--wireless fragmentation
threshold(even only)
√ √ -rtsthreshold
--wireless RTS/CTS
threshold
√ √ -beaconinterval
-- wireless beacon period
in TU (1024us)
√ √
-operating
mode
-- wireless operation
mode
√ √ √ -remotebs
--wireless remote
AP(s)(depends on
operation mode)
√ √ √ -pxp
--remote AP address for
pxp mode
√ √
-wirelessisola
te
--pxp wirelessisolate
√ √ √ -1
--1
st
remote AP for pxp
mode
√ √ √ -macaddress
-- remote AP mac address
for pxp mode
√ √ -bandwidth
--down flow width for pxp
mode
√ -status --remote AP status or
Page 70

Appendix C. SSH Settings Page 70
active for pxp mode
get set del Keyword Descriptions
√ -ipaddr -- remote AP ipaddr
√ -rssi -- remote AP rssi
√ √ √ -2
--2
nd
remote AP for pxp
mode
√ √ √ -macaddress
-- remote AP mac address
for pxp mode
√ √ -bandwidth
--down flow width for pxp
mode
√ -status
--remote AP status or
active for pxp mode
√ -ipaddr -- remote AP ipaddr
√ -rssi -- remote AP rssi
√ √ √ -3
--3
rd
remote AP for pxp
mode
√ √ √ -macaddress
-- remote AP mac address
for pxp mode
√ √ -bandwidth
--down flow width for pxp
mode
√ -status
--remote AP status or
active for pxp mode
√ -ipaddr -- remote AP ipaddr
√ -rssi -- remote AP rssi
√ √ √ -4
--4
th
remote AP for pxp
mode
√ √ √ -macaddress
-- remote AP mac address
for pxp mode
√ √ -bandwidth
--down flow width for pxp
mode
√ -status
--remote AP status or
active for pxp mode
√ -ipaddr -- remote AP ipaddr
√ -rssi -- remote AP rssi
√ √ √ -acl --wireless access control
√ √ -mode
--enable wireless access
control(ACL)
√ √ √ -list --display trusted CPEs
√ -all
--(delete only)all local
ACL address
Page 71

Appendix C. SSH Settings Page 71
get set del Keyword Descriptions
√ √ √ -(null) --edit local ACL address
√ -association
--list of associated
wireless clients
√ -wlanstats --wlan statistics
√ √ √ -key --wireless wep key setting
√ √ -type -- wireless wep key type
√ √ √ -1 -- wireless wep key 1
√ √ √ -2 -- wireless wep key 2
√ √ √ -3 -- wireless wep key 3
√ √ √ -4 -- wireless wep key 4
√ √ -spaceinmeter --wireless space in meter
√ √ √ -remotebssid
--wireless remote bssid in
cpe mode
√ √ -remotessid
-- wireless remote ssid in
cpe mode
√ -network-status --wireless network status
√ -bsscanlist --bs list
√ -signal level -- signal level(dBm)
√ -remoterssi --remote bs and rssi
√ √ -wmm --wmm settngs
√ √ -super_audio --Fast_Frame settings
√ √ -super_video --super burst settings
√ √ -super_picture --compression settings
√ √ √ -bs --<null>
√ √ -ssid
--network name of this
bs(1-32 chars)
√ √ -hiddenssid
--bs ssid broadcast
suppress
√ √
-wirelessisola
te
-- bs isolate
communication between
clients
√ √
-authenticatio
n
--bs authentication type
√ √ -encryption --bs data encryption
√ √ -default --bs wep default key index
√ √ √ -psk
--bs pre-shared key(PSK)
for WPA-PSK or
WPA2-PSK
√ √ -autowdsenable --auto wds settings
√ √ -wdsgroupid --wds group id name
Page 72
Appendix C. SSH Settings Page 72
get set del Keyword Descriptions
password --system password
reboot --reboot system
exit --logout from CLI
quit --quit CLI
Page 73

Appendix D. Service Support Page 73
Appendix D. Service Support
If you have any further trouble using the R2 Extender or you would like to require additional support, you
may visit our website at www.zcom.com.tw/rcp
or you may contact us as below for support:
Z-Com, Inc.
Taiwan
Business
Center
7F-2, No.9. Prosperity
RD. I Science-Based
Industrial Park
Hsinchu ,300 Taiwan
Tel: +886-3-5777364
Fax:+886-3-5773359
Sales Contact
info@zcom.com.tw
FAE Support
support@zcom.com.tw
Zcomax Technologies, Inc.
California
Business
Center
14545 Valley View Ave.,
Suite "S"
Santa Fe Springs, CA
90670
Tel: +1-562-926-4588
Fax:+1-562-926-7885
New
Jersey
Business
Center
98 Ford Road, Suite 3-F,
Denville, NJ 07834, USA
Tel: +1-973-664-0310
Fax:+1-973-664-0313
Sales/Product Inquiries:
sales@zcomax.com
Tech Support/Questions:
support@zcomax.com
ZCOMAX - United Kingdom Limited
European
Business
Centre
19 Colindale Avenue
London NW9 5DS UK
Tel:+44-(0)-20-8982-8200
Fax:+44-(0)-20-8201-3232
Sales Contact
sales@zcomax.co.uk
FAE Support
support@zcomax.co.uk
Z-Dotcom, Inc
China
Business
Centre
168 Long Pan Zhong
Road, Jiangsu Software
Park, Suite 118 Nanjing,
China 210002
Tel: +86-25-84661300
Fax:+86-25-84661313
Sales Contact
sales@zcom.com.cn
FAE Support
support@zcom.com.cn
For warranty assistance, contact your service provider or distributor for the process.
 Loading...
Loading...